-

@ 6be5cc06:5259daf0
2025-01-21 20:58:37
A seguir, veja como instalar e configurar o **Privoxy** no **Pop!_OS**.
---
### **1. Instalar o Tor e o Privoxy**
Abra o terminal e execute:
```bash
sudo apt update
sudo apt install tor privoxy
```
**Explicação:**
- **Tor:** Roteia o tráfego pela rede Tor.
- **Privoxy:** Proxy avançado que intermedia a conexão entre aplicativos e o Tor.
---
### **2. Configurar o Privoxy**
Abra o arquivo de configuração do Privoxy:
```bash
sudo nano /etc/privoxy/config
```
Navegue até a última linha (atalho: **`Ctrl`** + **`/`** depois **`Ctrl`** + **`V`** para navegar diretamente até a última linha) e insira:
```bash
forward-socks5 / 127.0.0.1:9050 .
```
Isso faz com que o **Privoxy** envie todo o tráfego para o **Tor** através da porta **9050**.
Salve (**`CTRL`** + **`O`** e **`Enter`**) e feche (**`CTRL`** + **`X`**) o arquivo.
---
### **3. Iniciar o Tor e o Privoxy**
Agora, inicie e habilite os serviços:
```bash
sudo systemctl start tor
sudo systemctl start privoxy
sudo systemctl enable tor
sudo systemctl enable privoxy
```
**Explicação:**
- **start:** Inicia os serviços.
- **enable:** Faz com que iniciem automaticamente ao ligar o PC.
---
### **4. Configurar o Navegador Firefox**
Para usar a rede **Tor** com o Firefox:
1. Abra o Firefox.
2. Acesse **Configurações** → **Configurar conexão**.
3. Selecione **Configuração manual de proxy**.
4. Configure assim:
- **Proxy HTTP:** `127.0.0.1`
- **Porta:** `8118` (porta padrão do **Privoxy**)
- **Domínio SOCKS (v5):** `127.0.0.1`
- **Porta:** `9050`
5. Marque a opção **"Usar este proxy também em HTTPS"**.
6. Clique em **OK**.
---
### **5. Verificar a Conexão com o Tor**
Abra o navegador e acesse:
```text
https://check.torproject.org/
```
Se aparecer a mensagem **"Congratulations. This browser is configured to use Tor."**, a configuração está correta.
---
### **Dicas Extras**
- **Privoxy** pode ser ajustado para bloquear anúncios e rastreadores.
- Outros aplicativos também podem ser configurados para usar o **Privoxy**.
-

@ 16d11430:61640947
2025-01-21 20:40:22
In a world drowning in Monopoly money, where people celebrate government-mandated inflation as "economic growth," it takes a special kind of clarity—nay, cynicism—to rise above the fiat circus. This is your guide to shedding your fiat f**ks and embracing the serene chaos of sound money, all while laughing at the absurdity of a world gone fiat-mad.
---
1. Don’t Feed the Clowns
You know the clowns I’m talking about: central bankers in their tailored suits and smug smirks, wielding "tools" like interest rates and quantitative easing. Their tools are as real as a magician's wand, conjuring trillions of dollars out of thin air to keep their Ponzi economy afloat.
Rule #1: Don’t engage. If a clown offers you a hot take about the "strength of the dollar," smile, nod, and silently wonder how many cups of coffee their paycheck buys this month. Spoiler: fewer than last month.
---
2. Turn Off the Fiat News
Do you really need another breathless headline about the next trillion-dollar deficit? Or the latest clickbait on why you should care about the stock market's emotional rollercoaster? Mainstream media exists to distract you, to keep you tethered to their illusion of importance.
Turn it off. Replace it with something sound, like the Bitcoin whitepaper. Or Nietzsche. At least Nietzsche knew we were doomed.
---
3. Mock Their Inflationary Gospel
Fiat apologists will tell you that inflation is "necessary" and that 2% a year is a "healthy target." Sure, because a little robbery every year keeps society functioning, right? Ask them this: "If 2% is healthy, why not 20%? Why not 200%? Why not Venezuela?"
Fiat logic is like a bad acid trip: entertaining at first, but it quickly spirals into existential horror.
---
4. Celebrate the Fiat Freakshow
Sometimes, the best way to resist the fiat clown show is to revel in its absurdity. Watch politicians print money like teenagers running up a credit card bill at Hot Topic, then watch the economists applaud it as "stimulus." It’s performance art, really. Andy Warhol could never.
---
5. Build in the Chaos
While the fiat world burns, Bitcoiners build. This is the ultimate "not giving a fiat f**k" move: creating a parallel economy, one satoshi at a time. Run your Lightning node, stack sats, and laugh as the fiat circus consumes itself in a flaming pile of its own debt.
Let them argue about who gets to rearrange the deck chairs on the Titanic. You’re busy designing lifeboats.
---
6. Adopt a Fiat-Free Lifestyle
Fiat-free living means minimizing your entanglement with their clown currency. Buy meat, not ETFs. Trade skills, not IOUs. Tip your barber in Bitcoin and ask if your landlord accepts Lightning. If they say no, chuckle and say, “You’ll learn soon enough.”
Every satoshi spent in the real economy is a slap in the face to the fiat overlords.
---
7. Find the Humor in Collapse
Here’s the thing: the fiat system is unsustainable. You know it, I know it, even the clowns know it. The whole charade is destined to collapse under its own weight. When it does, find solace in the absurdity of it all.
Imagine the central bankers explaining hyperinflation to the public: "Turns out we can't print infinity after all." Pure comedy gold.
---
8. Stay Ruthlessly Optimistic
Despite the doom and gloom, there’s hope. Bitcoin is hope. It’s the lifeboat for humanity, the cheat code to escape the fiat matrix. Cynicism doesn’t mean nihilism; it means seeing the rot for what it is and choosing to build something better.
So, don’t just reject the fiat clown show—replace it. Create a world where money is sound, transactions are sovereign, and wealth is measured in energy, not debt.
---
Final Thought: Burn the Tent Down
Aldous Huxley once envisioned a dystopia where people are so distracted by their own hedonistic consumption that they don’t realize they’re enslaved. Sound familiar? The fiat clown show is Brave New World on steroids, a spectacle designed to keep you pacified while your wealth evaporates.
But here’s the punchline: they can only enslave you if you care. By rejecting their system, you strip them of their power. So let them juggle their debts, inflate their bubbles, and print their trillions. You’ve got Bitcoin, and Bitcoin doesn’t give a fiat f**k.
Welcome to the satirical resistance. Now go stack some sats.
-

@ c230edd3:8ad4a712
2025-01-23 00:26:14
When beechen buds begin to swell,
And woods the blue-bird’s warble know,
The yellow violet’s modest bell
Peeps from the last year’s leaves below.
Ere russet fields their green resume,
Sweet flower, I love, in forest bare,
To meet thee, when thy faint perfume
Alone is in the virgin air.
Of all her train, the hands of Spring
First plant thee in the watery mould,
And I have seen thee blossoming
Beside the snow-bank’s edges cold.
Thy parent sun, who bade thee view
Pale skies, and chilling moisture sip,
Has bathed thee in his own bright hue,
And streaked with jet thy glowing lip.
Yet slight thy form, and low thy seat,
And earthward bent thy gentle eye,
Unapt the passing view to meet
When loftier flowers are flaunting nigh.
Oft, in the sunless April day,
Thy early smile has stayed my walk;
But midst the gorgeous blooms of May,
I passed thee on thy humble stalk.
So they, who climb to wealth, forget
The friends in darker fortunes tried.
I copied them—but I regret
That I should ape the ways of pride.
And when again the genial hour
Awakes the painted tribes of light,
I’ll not o’erlook the modest flower
That made the woods of April bright.
-

@ 4c96d763:80c3ee30
2025-01-23 00:05:26
# Changes
## Ken Sedgwick (5):
- drive-by clippy fixes
- add add relay GUI
- add Accounts::add_advertised_relay
- upgrade url string to RelaySpec for [read|write] markers
- publish NIP-65 relay lists
## William Casarin (7):
- persistent: dont nuke decks when using cli columns
- envrc: update vrod's npub for testing
- note: introduce RootNoteId
- enostr: introduce PubkeyRef
- mutes: hide logs
- debug: log when adding notes to start
- switch to TimelineCache
## greenart7c3 (1):
- Fix side panel color when using light theme
## kernelkind (2):
- log nip05 error
- fix persist deck author profile bug
## kieran (4):
- note-ref: derive hash
- move `Notedeck` to `notedeck` crate
- export enostr / nostrdb
- Always update accounts
pushed to [notedeck:refs/heads/master](http://git.jb55.com/notedeck/commit/2cbae68a7f1425997f66d5ac0662f5cfde172f4f.html)
-

@ c230edd3:8ad4a712
2025-01-22 23:52:14
To him who in the love of Nature holds
Communion with her visible forms, she speaks
A various language; for his gayer hours
She has a voice of gladness, and a smile
And eloquence of beauty, and she glides
Into his darker musings, with a mild
And healing sympathy, that steals away
Their sharpness, ere he is aware. When thoughts
Of the last bitter hour come like a blight
Over thy spirit, and sad images
Of the stern agony, and shroud, and pall,
And breathless darkness, and the narrow house,
Make thee to shudder, and grow sick at heart;—
Go forth, under the open sky, and list
To Nature’s teachings, while from all around—
Earth and her waters, and the depths of air—
Comes a still voice— Yet a few days, and thee
The all-beholding sun shall see no more
In all his course; nor yet in the cold ground,
Where thy pale form was laid, with many tears,
Nor in the embrace of ocean, shall exist
Thy image. Earth, that nourished thee, shall claim
Thy growth, to be resolved to earth again,
And, lost each human trace, surrendering up
Thine individual being, shalt thou go
To mix for ever with the elements,
To be a brother to the insensible rock
And to the sluggish clod, which the rude swain
Turns with his share, and treads upon. The oak
Shall send his roots abroad, and pierce thy mould.
Yet not to thine eternal resting-place
Shalt thou retire alone, nor couldst thou wish
Couch more magnificent. Thou shalt lie down
With patriarchs of the infant world—with kings,
The powerful of the earth—the wise, the good,
Fair forms, and hoary seers of ages past,
All in one mighty sepulchre. The hills
Rock-ribbed and ancient as the sun,—the vales
Stretching in pensive quietness between;
The venerable woods—rivers that move
In majesty, and the complaining brooks
That make the meadows green; and, poured round all,
Old Ocean’s gray and melancholy waste,—
Are but the solemn decorations all
Of the great tomb of man. The golden sun,
The planets, all the infinite host of heaven,
Are shining on the sad abodes of death,
Through the still lapse of ages. All that tread
The globe are but a handful to the tribes
That slumber in its bosom.—Take the wings
Of morning, pierce the Barcan wilderness,
Or lose thyself in the continuous woods
Where rolls the Oregon, and hears no sound,
Save his own dashings—yet the dead are there:
And millions in those solitudes, since first
The flight of years began, have laid them down
In their last sleep—the dead reign there alone.
So shalt thou rest, and what if thou withdraw
In silence from the living, and no friend
Take note of thy departure? All that breathe
Will share thy destiny. The gay will laugh
When thou art gone, the solemn brood of care
Plod on, and each one as before will chase
His favorite phantom; yet all these shall leave
Their mirth and their employments, and shall come
And make their bed with thee. As the long train
Of ages glide away, the sons of men,
The youth in life’s green spring, and he who goes
In the full strength of years, matron and maid,
The speechless babe, and the gray-headed man—
Shall one by one be gathered to thy side,
By those, who in their turn shall follow them.
So live, that when thy summons comes to join
The innumerable caravan, which moves
To that mysterious realm, where each shall take
His chamber in the silent halls of death,
Thou go not, like the quarry-slave at night,
Scourged to his dungeon, but, sustained and soothed
By an unfaltering trust, approach thy grave,
Like one who wraps the drapery of his couch
About him, and lies down to pleasant dreams.
-

@ 3b70689a:c1e351eb
2025-01-22 23:47:36
来自西班牙的公司 Liberux 最近推出了他们的新手机 Liberux NEXX 众筹计划. 根据[目前主页](http://archive.today/2025.01.22-142040/https://liberux.net/)上的介绍, 这款设备将会搭载基于 Debian 13 ARM 构建的 LiberuxOS 操作系统, 并且还提供一个受限的(jailed)的 Android 子系统.

- [Liberux (@Liberux@mastodon.social\) - Mastodon](https://mastodon.social/@Liberux)
> Liberux 的 Fediverse 主页
- [TX4RLY (@BUF0@mastodon.social\) - Mastodon](https://mastodon.social/@BUF0)
> Liberux 硬件开发工程师 Carlos Rodríguez 的 Fediverse 主页
Carlos Rodríguez 说, 目前网站上的 NEXX 是最初版本, 目前仍然在努力制造第一台原型机, 并且所有的硬件和软件设计都将免费(公开).
> WOW, I think our little secret has been revealed, we hope that in a short time you will be able to see the first functional prototypes. We are working very hard on it, by the way, all our designs, both hardware and software, will be free. At the moment the web is a first version, some things will be modified.
>
> —— [TX4RLY: "@linmob @awai WOW, I think ou…" - Mastodon](https://mastodon.social/@BUF0/113861097147727059)
## 硬件参数
- **CPU**: 瑞芯微 RK3588s (八核心, 8nm, 2.4Ghz, 2022Q1)
- **GPU**: ARM Mali-G610 (4 核心, 2021Q2)
- **存储**: 32GB LPDDR4x RAM, 256GB eMMC ROM
- **电池**: 5300mAh (可拆卸)
- **接口**: 3.5mm 耳机 * 1, USB-C 3.1 * 2
- **扩展**: microSD 插槽 (2TB Max)
- **屏幕**: 6.34 吋, OLED, 2400*1080
- **相机**: 后置 32MP, 前置 13MP
- **通讯**: 高通骁龙 X62 基带 (2021Q1), 海华 AW-CM256SM 无线网卡 (Wi-Fi 5, 蓝牙 5.0)
- **传感器**: 昇佳 STK3311-X 环境光传感器, 美新 MMC3630KJ 三轴磁传感器, 应美盛 ICM-42670-P 加速度计/陀螺仪
- **其他**: 内置 DAC 和功放芯片 (瑞昱 ALC5640-VB-CG, 艾为 AW8737SCSR)
## 其他特点
设备目前公布的外观设计均是渲染效果, 最终交付的设备很可能会与这些渲染图片有很大出入. 但仍然可以通过这些效果图理解 Liberux 的最初意图.
- 摄像头 & 麦克风, 蓝牙 & WLAN, 数据网络功能模块的物理开关(位于顶部).

- 后置指纹解锁, 无摄像模组凸起.
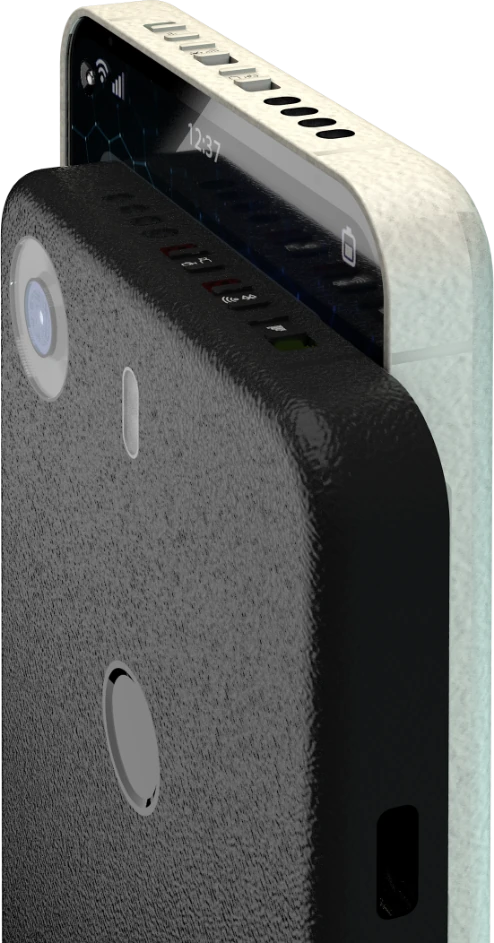
- 左上角挖孔前置摄像头.

- 电源键位于侧边右下角.
## 其他报道
- [Liberux Nexx: New Linux smartphone with 32GB RAM, 2TB storage, 5G and more - NotebookCheck.net News](https://www.notebookcheck.net/Liberux-Nexx-New-Linux-smartphone-with-32GB-RAM-2TB-storage-5G-and-more.950866.0.html)
- [Смартфон Liberux Nexx получил ОС Linux и поддержку 2 ТБ памяти - 4PDA ](https://4pda.to/2025/01/22/437737/smartfon_liberux_nexx_poluchil_os_linux_i_podderzhku_2_tb_pamyati/)(讨论)
- [Smartfon z Linuksem? Oto Liberux NEXX. Ekran OLED, 32 GB RAM i system oparty na Debianie. Ciekawy model, choć nie bez wad | PurePC.pl](https://www.purepc.pl/smartfon-z-linuksem-oto-liberux-nexx-ekran-oled-32-gb-ram-i-system-oparty-na-debianie-ciekawy-model-choc-nie-bez-wad) (讨论)
- [LINux on MOBile: "The Liberux Nexx \(https://libe…" - Fosstodon](https://fosstodon.org/@linmob/113860953049449923) (Fediverse, 讨论, 工程师回复)
-

@ c54f9c60:7c34249a
2025-01-22 22:12:51
In October 2018, Arjun Balaji asked the innocuous question, _What have you learned from Bitcoin?_ After trying to answer this question in a short tweet, and failing miserably, I realized that the things I've learned are far too numerous to answer quickly, if at all.
The things I've learned are, obviously, about Bitcoin - or at least related to it. However, while some of the inner workings of Bitcoin are explained, the following lessons are not an explanation of how Bitcoin works or what it is, they might, however, help to explore some of the things Bitcoin touches: philosophical questions, economic realities, and technological innovations.
The 21 lessons are structured in bundles of seven, resulting in three chapters. Each chapter looks at Bitcoin through a different lens, extracting what lessons can be learned by inspecting this strange network from a different angle.
[Chapter 1][chapter1] explores the philosophical teachings of Bitcoin. The interplay of immutability and change, the concept of true scarcity, Bitcoin's immaculate conception, the problem of identity, the contradiction of replication and locality, the power of free speech, and the limits of knowledge.
[Chapter 2][chapter2] explores the economic teachings of Bitcoin. Lessons about financial ignorance, inflation, value, money and the history of money, fractional reserve banking, and how Bitcoin is re-introducing sound money in a sly, roundabout way.
[Chapter 3][chapter3] explores some of the lessons learned by examining the technology of Bitcoin. Why there is strength in numbers, reflections on trust, why telling time takes work, how moving slowly and not breaking things is a feature and not a bug, what Bitcoin's creation can tell us about privacy, why cypherpunks write code (and not laws), and what metaphors might be useful to explore Bitcoin's future.
Each lesson contains several quotes and links throughout the text. If I have explored an idea in more detail, you can find links to my related works in the "Through the Looking-Glass" section. If you like to go deeper, links to the most relevant material are listed in the "Down the Rabbit Hole" section. Both can be found at the end of each lesson.
Even though some prior knowledge about Bitcoin is beneficial, I hope that these lessons can be digested by any curious reader. While some relate to each other, each lesson should be able to stand on its own and can be read independently. I did my best to shy away from technical jargon, even though some domain-specific vocabulary is unavoidable.
I hope that my writing serves as inspiration for others to dig beneath the surface and examine some of the deeper questions Bitcoin raises. My own inspiration came from a multitude of authors and content creators to all of whom I am eternally grateful.
Last but not least: my goal in writing this is not to convince you of anything. My goal is to make you think, and show you that there is way more to Bitcoin than meets the eye. I can’t even tell you what Bitcoin is or what Bitcoin will teach you. You will have to find that out for yourself.
> "After this, there is no turning back. You take the blue pill —the
> story ends, you wake up in your bed and believe whatever you want to
> believe. You take the red pill— you stay in Wonderland, and I show
> you how deep the rabbit hole goes."
>
> —[Morpheus][Morpheus]

[Morpheus]: https://en.wikipedia.org/wiki/Red_pill_and_blue_pill#The_Matrix_(1999)
[this question]: https://twitter.com/arjunblj/status/1050073234719293440
[chapter1]: https://dergigi.com/2018/12/21/philosophical-teachings-of-bitcoin/
[chapter2]: https://dergigi.com/2019/01/11/economic-teachings-of-bitcoin/
[chapter3]: https://dergigi.com/2019/04/02/technological-teachings-of-bitcoin/
[alice]: https://en.wikipedia.org/wiki/Alice%27s_Adventures_in_Wonderland
[carroll]: https://en.wikipedia.org/wiki/Lewis_Carroll
-

@ c54f9c60:7c34249a
2025-01-22 21:48:30
Falling down the Bitcoin rabbit hole is a strange experience. Like many others, I feel like I have learned more in the last couple of years studying Bitcoin than I have during two decades of formal education.
The following lessons are a distillation of what I’ve learned. First published as an article series titled [“What I’ve Learned From Bitcoin,”][I] what follows can be seen as a second edition of the original series.
Like Bitcoin, these lessons aren't a static thing. I plan to work on them periodically, releasing updated versions and additional material in the future.
Unlike Bitcoin, future versions of this project do not have to be backward compatible. Some lessons might be extended, others might be reworked or replaced. I hope that a future version will be something you can hold in your hands, but I don’t want to promise anything just yet.
Bitcoin is an inexhaustible teacher, which is why I do not claim that these lessons are all-encompassing or complete. They are a reflection of my personal journey down the rabbit hole. There are many more lessons to be learned, and every person will learn something different from entering the world of Bitcoin.
I hope that you will find these lessons useful and that the process of learning them by reading won’t be as arduous and painful as learning them firsthand.
nostr:npub1dergggklka99wwrs92yz8wdjs952h2ux2ha2ed598ngwu9w7a6fsh9xzpc
<!-- Internal -->
[I]: https://dergigi.com/2018/12/21/philosophical-teachings-of-bitcoin/
-

@ 9e69e420:d12360c2
2025-01-21 19:31:48
Oregano oil is a potent natural compound that offers numerous scientifically-supported health benefits.
## Active Compounds
The oil's therapeutic properties stem from its key bioactive components:
- Carvacrol and thymol (primary active compounds)
- Polyphenols and other antioxidant
## Antimicrobial Properties
**Bacterial Protection**
The oil demonstrates powerful antibacterial effects, even against antibiotic-resistant strains like MRSA and other harmful bacteria. Studies show it effectively inactivates various pathogenic bacteria without developing resistance.
**Antifungal Effects**
It effectively combats fungal infections, particularly Candida-related conditions like oral thrush, athlete's foot, and nail infections.
## Digestive Health Benefits
Oregano oil supports digestive wellness by:
- Promoting gastric juice secretion and enzyme production
- Helping treat Small Intestinal Bacterial Overgrowth (SIBO)
- Managing digestive discomfort, bloating, and IBS symptoms
## Anti-inflammatory and Antioxidant Effects
The oil provides significant protective benefits through:
- Powerful antioxidant activity that fights free radicals
- Reduction of inflammatory markers in the body
- Protection against oxidative stress-related conditions
## Respiratory Support
It aids respiratory health by:
- Loosening mucus and phlegm
- Suppressing coughs and throat irritation
- Supporting overall respiratory tract function
## Additional Benefits
**Skin Health**
- Improves conditions like psoriasis, acne, and eczema
- Supports wound healing through antibacterial action
- Provides anti-aging benefits through antioxidant properties
**Cardiovascular Health**
Studies show oregano oil may help:
- Reduce LDL (bad) cholesterol levels
- Support overall heart health
**Pain Management**
The oil demonstrates effectiveness in:
- Reducing inflammation-related pain
- Managing muscle discomfort
- Providing topical pain relief
## Safety Note
While oregano oil is generally safe, it's highly concentrated and should be properly diluted before use Consult a healthcare provider before starting supplementation, especially if taking other medications.
-

@ b17fccdf:b7211155
2025-01-21 18:30:13
~ > Available at: [https://minibolt.info](https://minibolt.info)
---
~> It builds on a personal computer with **x86/amd64** architecture processors.
~> It is based on the popular [RaspiBolt v3](https://raspibolt.org) guide.
---
**Those are some of the most relevant changes:**
* Changed OS from Raspberry Pi OS Lite (64-bits) to ***Ubuntu Server LTS*** (Long term support) 64-bit PC (AMD64).
* Changed binaries and signatures of the programs to adapt them to ***x86/amd64 architecture***.
* Deleted unnecessary tools and steps, and added others according to this case of use.
* Some useful authentication logs and monitoring commands were added in the security section.
* Added some interesting parameters in the settings of some services to activate and take advantage of new features.
* Changed I2P, Fulcrum, and ThunderHub guides, to be part of the core guide.
* Added exclusive optimization section of services for slow devices.
---
~ > Complete release notes of the MiniBolt v1: [https://github.com/twofaktor/minibolt/releases/tag/1.0](https://github.com/twofaktor/minibolt/releases/tag/1.0).
~ > Feel free to contribute to the [source code on GitHub](https://github.com/minibolt-guide/minibolt) by opening [issues](https://github.com/minibolt-guide/minibolt/issues), [pull requests](https://github.com/minibolt-guide/minibolt/pulls) or [discussions](https://github.com/orgs/minibolt-guide/discussions).
---
Created by [⚡2 FakTor⚡](nostr:npub1k9luehc8hg3c0upckdzzvusv66x3zt0eyw7290kclrpsndepz92sfcpp63)
-

@ b17fccdf:b7211155
2025-01-21 18:22:51
😱 Did you recently find this signature verification error when you tried to update your MiniBolt repositories with -> `sudo apt update`? 💥🚨👇

🔧 Don't worry, that's because Tor renewed its signing key since it expired last 07/15, just renew your keyring by following the next steps to solve this problem:
~ > [CLICK HERE](https://minibolt.minibolt.info/system/system/privacy#tor-signature-verification-error) < ~
---
Enjoy it MiniBolter!💙
-

@ b17fccdf:b7211155
2025-01-21 18:10:10
**Link to the bonus guide** ~ > [HERE](https://minibolt.minibolt.info/bonus-guides/bitcoin/minibolt-on-testnet) <~
---
Some notes:
ℹ️ For the moment, this guide will touch only the case of an **only testnet mode** situation, in the future, we will study adding the case of configuration to enable the parallel/simultaneous mode (mainnet+testnet in the same device) in an extra section in this guide.
ℹ️ The services mentioned in this guide are those that have been tested using testnet configuration and these worked fine. Later, in the next versions of this guide, we will go to adding other processes to adapt other services to the testnet mode.
---
Enjoy it MiniBolter! 💙
-

@ b17fccdf:b7211155
2025-01-21 18:04:28
Available at: [https://minibolt.info](https://minibolt.info)
---
**Main changes to** the version 1:
* The complete guide has been migrated to the new design visual builder web tool platform [gitbook.com](https://www.gitbook.com/)
* New modern UI (responsive, full width, and better visual items)
* New menu structure for a better user experience
* New visual items to improve the navigation through the web page
* New switch to enable light/dark theme
* Enabled Cloudflare Proxy for maximum protection against attacks and better management of the domain
---
**Other changes:**
* New [MiniBolt Linktr](https://linktr.minibolt.info/) forked of the alternative [FOSS project](https://github.com/gzuuus/linktr) proposed by [Gzuuus](https://twitter.com/gzuuus)
* Changed MiniBolt from a personal project to an [organization](https://github.com/minibolt-guide) so that the project has its own identity
* New email contact address [hello@minibolt.info](mailto:hello@minibolt.info) to receive proposals and give support
* New [resources](https://github.com/minibolt-guide/minibolt/tree/main/resources) folder with the current MiniBolt roadmap, network map diagrams, and others
---
ℹ️ **More info:**
* The new version is available with the known domain: [minibolt.info](https://minibolt.info/) but from now on links associated with the new v2 version were shared using the [v2.minibolt.info](https://v2.minibolt.info/) subdomain due to a GitBook limitation
* The old and deprecated v1 will be still available at a time in the subdomain [v1.minibolt.info](https://v1.minibolt.info/), but is in the roadmap delete it definitely in the future, take note ASAP of all that you need of that version before this happens
* Contributors and collaborators will be able to continue doing PR through code programming or using the design block builder [gitbook.com](https://www.gitbook.com/)
---
[GitHub release](https://github.com/minibolt-guide/minibolt/releases/tag/2.0)
---
Enjoy it MiniBolter! 💙
-

@ b17fccdf:b7211155
2025-01-21 17:58:35
The **router reserves the IP address** of the device **for a time after going out**, but if the device goes out some time, the next time that the device starts, the router could assign a different IP and you could lose access to your node. To avoid this, you need to **set a static IP to your MiniBolt**.
~ > In addition, you can **customize your DNS servers to improve your privacy**, normally your ISP, gives you the router with its own DNS servers set by default, and this does that you expose all of your navigation trackings to your ISP, affecting seriously your privacy.
~ > This bonus guide includes all of the necessary steps to get this and is available ~ > [HERE](https://minibolt.minibolt.info/bonus-guides/system/static-ip-and-custom-dns-servers) < ~
---

---
Enjoy it MiniBolter! 💙
-

@ b17fccdf:b7211155
2025-01-21 17:47:28
Link to the bonus guide ~ > [HERE](https://minibolt.minibolt.info/bonus-guides/system/ssh-keys) < ~
---
Some sections of the guide:
* Generate SSH keys
* Import SSH pubkey
* Connect to the MiniBolt node using SSH keys
* Disable password login
* Disable admin password request
---
Some shortcuts to the Extra sections:
* Disable password login: click ~ > [HERE](https://minibolt.minibolt.info/bonus-guides/system/ssh-keys#disable-password-login) < ~
* Disable admin password request: click ~ > [HERE](https://minibolt.minibolt.info/bonus-guides/system/ssh-keys#disable-admin-password-request-caution) < ~
---
Enjoy it MiniBolter! 💙
-

@ b17fccdf:b7211155
2025-01-21 17:39:34
**Link to the bonus guide** ~ > [HERE](https://minibolt.minibolt.info/bonus-guides/bitcoin/ordisrespector) < ~
---
⏰ Recently added an update that includes a new section **[How to detect Ordinals transactions](https://minibolt.minibolt.info/bonus-guides/bitcoin/ordisrespector#how-to-detect-ordinals-transactions) and [verify Ordisrespector filter works](https://minibolt.minibolt.info/bonus-guides/bitcoin/ordisrespector#check-the-ordisrespector-filter-working-on-your-mempool)** to verify that Ordispector is **filtering and burning Ordinals** correctly 🔥
---
Fuck Ordinals🤡🔫 and enjoy it MiniBolter! 💙
-

@ b17fccdf:b7211155
2025-01-21 17:29:54
Some sections inside of the guide:
* Set up Dynamic DNS
* Wireguard VPN server & client side configurations
* Install & configure the WireGuard VPN Client on a mobile phone
* Configure additional servers & clients
* Use your router’s DDNS preconfigured provider
* Port forwarding on NAT/PAT router
---
Link to the bonus guide [HERE](https://minibolt.minibolt.info/bonus-guides/system/wireguard-vpn)
---
Enjoy it MiniBolter! 💙
-

@ b17fccdf:b7211155
2025-01-21 17:19:12
Do you want to use a different disk to store data (blockchain and other databases) independently of the disk of the system?
A step-by-step guide using a secondary disk to store the data (blockchain and other databases) independently of the disk of the system and using the Ubuntu Server guided installation.
---
### **What's changed**
* Rebuilt the [Ubuntu Server installation guide](https://minibolt.minibolt.info/system/system/operating-system#ubuntu-server-installation) based on this bonus guide added.
* Added GIFs to improve the illustration of the steps to follow.
* [Case 1](https://minibolt.minibolt.info/bonus-guides/system/static-ip-and-custom-dns-servers#option-1-at-the-beginning-during-the-ubuntu-server-installation-gui): during the Ubuntu server guided installation.
* [Case 2](https://minibolt.minibolt.info/bonus-guides/system/static-ip-and-custom-dns-servers#option-2-after-ubuntu-server-installation-by-command-line): build it after system installation (by command line).
---
~ > Link to the bonus guide [HERE](https://minibolt.minibolt.info/bonus-guides/system/store-data-secondary-disk)
---
Enjoy it MiniBolter! 💙
-

@ 35f3a26c:92ddf231
2025-01-22 20:48:34
### Background
Most people non familiar with Bitcoin thinks that there its has not smart contracts capabilities, and that is incorrect, there are smart contract capabilities, and despite limited in comparison with other blockchain networks, those capabilities are evolving slowly but surely.
The support for smart contracts is done through its scripting language, Script, which allows developers to create complex conditions for transactions.
**What can you do with Script?**
1. time locks
2. multi-signature requirements
3. other custom logic
opcodes like OP_CHECKLOCKTIMEVERIFY (CLTV) and OP_CHECKSEQUENCEVERIFY (CSV) are used to build more sophisticated smart contracts, these opcodes enable features such as the Lightning Network, a key scaling solution for Bitcoin
back in 2021, the ***Taproot ***upgrade introduced Pay-to-Taproot (P2TR), in summary allows for more private and efficient smart contracts, in that soft fork more was added, in addition to Taproot, we got as well ***Schnorr signatures***, which enables multiple signatures to be aggregated into a single signature, improving scalability and privacy and ***MAST (Merklized Abstract Syntax Trees)*** which reduces the size of complex smart contracts, making them more efficient, as an added value, this efficiency reduces the cost of transactions.
The ***Taproot ***upgrade has laid the foundation for the development of more sophisticated smart contracts on the Bitcoin network, and the use of covenants is an important part of this development.
### What is Bitcoin Covenants?
It is a **BIP** (Bitcoin Improvement Proposal), **BIP-347**, assigned on April 24, 2024, which marks the first step towards reintroducing functionality removed from Bitcoin by its creator Satoshi Nakamoto in 2010. This proposal aims to bring smart contract functionality to Bitcoin as we see in other EVM networks.
The proposal’s developers authors names are **Ethan Heilman** and **Armin Sabouri**, now the community will debate its merits.
Here the link, in case you are curious:
***[https://github.com/bitcoin/bips/blob/master/bip-0347.mediawiki](https://github.com/bitcoin/bips/blob/master/bip-0347.mediawiki)***
It is worth to read the motivation section of the BIP, which reads:
“Bitcoin Tapscript lacks a general purpose way of combining objects on the stack, restricting the expressiveness and power of Tapscript. This prevents, among many other things, the ability to construct and evaluate merkle trees and other hashed data structures in Tapscript. OP_CAT, by adding a general purpose way to concatenate stack values, would overcome this limitation and greatly increase the functionality of Tapscript.
OP_CAT aims to expand the toolbox of the tapscript developer with a simple, modular, and useful opcode in the spirit of Unix. To demonstrate the usefulness of OP_CAT below we provide a non-exhaustive list of some use cases that OP_CAT would enable:
Bitstream, a protocol for the atomic swap (fair exchange) of bitcoins for decryption keys, that enables decentralized file hosting systems paid in Bitcoin. While such swaps are currently possible on Bitcoin without OP_CAT, they require the use of complex and computationally expensive Verifiable Computation cryptographic techniques. OP_CAT would remove this requirement on Verifiable Computation, making such protocols far more practical to build in Bitcoin.
Tree signatures provide a multisignature script whose size can be logarithmic in the number of public keys and can encode spend conditions beyond n-of-m. For instance a transaction less than 1KB in size could support tree signatures with up to 4,294,967,296 public keys. This also enables generalized logical spend conditions.
Post-Quantum Lamport signatures in Bitcoin transactions. Lamport signatures merely require the ability to hash and concatenate values on the stack. [4] It has been proposed that if ECDSA is broken or a powerful computer was on the horizon, there might be an effort to protect ownership of bitcoins by allowing people to mark their taproot outputs as "script-path only" and then move their coins into such outputs with a leaf in the script tree requiring a Lamport signature. It is an open question if a tapscript commitment would preserve the quantum resistance of Lamport signatures. Beyond this question, the use of Lamport Signatures in taproot outputs is unlikely to be quantum resistant even if the script spend-path is made quantum resistant. This is because taproot outputs can also be spent with a key. An attacker with a sufficiently powerful quantum computer could bypass the taproot script spend-path by finding the discrete log of the taproot output and thus spending the output using the key spend-path. The use of "Nothing Up My Sleeve" (NUMS) points as described in BIP-341 to disable the key spend-path does not disable the key spend-path against a quantum attacker as NUMS relies on the hardness of finding discrete logs. We are not aware of any mechanism which could disable the key spend-path in a taproot output without a soft-fork change to taproot.
Non-equivocation contracts in tapscript provide a mechanism to punish equivocation/double spending in Bitcoin payment channels. OP_CAT enables this by enforcing rules on the spending transaction's nonce. The capability is a useful building block for payment channels and other Bitcoin protocols.
Vaults [6] which are a specialized covenant that allows a user to block a malicious party who has compromised the user's secret key from stealing the funds in that output. As shown in OP_CAT is sufficient to build vaults in Bitcoin.
Replicating CheckSigFromStack which would allow the creation of simple covenants and other advanced contracts without having to pre-sign spending transactions, possibly reducing complexity and the amount of data that needs to be stored. Originally shown to work with Schnorr signatures, this result has been extended to ECDSA signatures.
OP_CAT was available in early versions of Bitcoin. In 2010, a single commit disabled OP_CAT, along with another 15 opcodes. Folklore states that OP_CAT was removed in this commit because it enabled the construction of a script whose evaluation could have memory usage exponential in the size of the script. For example, a script that pushed a 1-byte value on the stack and then repeated the opcodes OP_DUP, OP_CAT 40 times would result in a stack element whose size was greater than 1 terabyte assuming no maximum stack element size. As Bitcoin at that time had a maximum stack element size of 5000 bytes, the effect of this expansion was limited to 5000 bytes. This is no longer an issue because tapscript enforces a maximum stack element size of 520 bytes.”
The last update of the BIP was done on Sep. 8 2024 by Ethan Heilman
### Controversy
The controversy revolves around two main camps:
1. Those who want to preserve Bitcoin’s network for monetary transactions only, arguing that adding smart contract capabilities could introduce risks and complexity.
2. Others who advocate for expanding Bitcoin’s capabilities to support a wider range of applications, seeing OP_CAT as a step towards enhancing the network’s utility.
### Final Thoughts

Bitcoin have done what no other asset have done in history, neither gold, its success is clear, and now, that BlackRock is involved, “miraculously”, corporations and governments are getting on board and Bitcoin is not anymore only for criminals or “rat poison” or “is going to zero”.
But as all tech, improvements are important, if those improvements are done to secure more the network and to make it more robust, there will be little to none controversy, however, when those changes are aiming at adding new shinning features that would change Bitcoin into a network with similar features as Ethereum in terms of contracts that requires attention and debate, few questions come to mind:
1. How will that change affect the security of the network?
2. How that change will affect the blockchain usage?
3. What is the projected impact over the fees per transaction if this change is approved?
4. Will the impact create pressure for the block size increase discussion to come back to the table and with it a second war?
Looking into Ethan Heilman work and contribution to the Bitcoin ecosystem, I am inclined to believe that he has considered most of those questions.
Looking forward to observe the evolution of this proposal.
#### You liked the article? Make my day brighter!
Like and share!
Last but not least, the following link is an unstoppable domain, it will open a page in which you can perform an anonymous contribution to support my work:
[https://rodswallet.unstoppable/](https://rodswallet.unstoppable/)
The link didn’t open?
To open the link you need to use a best in class browser that supports web3, two are recommended: Brave Browser and Opera Browser
-

@ b17fccdf:b7211155
2025-01-21 17:07:47
**Link to the bonus guide** ~> [HERE](https://minibolt.minibolt.info/bonus-guides/bitcoin/btcpay-server) < ~
---
Enjoy it MiniBolter! 💙
-

@ f33c8a96:5ec6f741
2025-01-22 20:38:02
<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/V-7u7bJccSM?enablejsapi=1" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
-

@ 4506e04e:8c16ba04
2025-01-22 16:37:08
If you are a researcher in the field of medicine, you are most likely very familiar with PubMed – where you get citations for the articles and studies that drive your work forward. PubMed Central (PMC), the full-text repository of life sciences journal literature managed by the National Library of Medicine (NLM), was established in 2000. Its creation marked a significant milestone in providing open access to biomedical research. Since 2005, PMC has served as the designated repository for papers submitted under the NIH Public Access Policy, reflecting the growing emphasis on transparency and accessibility in scientific research. Over the years, PMC has expanded its scope, becoming a repository for papers aligned with public and open access policies from various research funding organizations, both within and beyond biomedical sciences.
## Funding and Partnerships
NLM’s operations, including PubMed and PMC, are supported by a combination of government funding and contributions from influential entities such as The Bill & Melinda Gates Foundation.
The Bill and Melinda Gates Foundation receives significant donations from pharmaceutical companies, as well as other organizations and individuals. The exact amount of money donated by each company can vary from year to year, but here are some examples of the amounts donated by the pharmaceutical companies:
**GSK (GlaxoSmithKline):**
- In 2020, GSK donated $100 million to the Gates Foundation to support the development of new vaccines and treatments for diseases such as malaria, tuberculosis, and HIV/AIDS.
- In 2019, GSK donated $50 million to the Gates Foundation to support the development of a new malaria vaccine.
**Pfizer:**
- In 2020, Pfizer donated $50 million to the Gates Foundation to support the development of new vaccines and treatments for diseases such as malaria, tuberculosis, and HIV/AIDS.
- In 2019, Pfizer donated $25 million to the Gates Foundation to support the development of a new malaria vaccine.
**Merck & Co.:**
- In 2020, Merck donated $50 million to the Gates Foundation to support the development of new vaccines and treatments for diseases such as malaria, tuberculosis, and HIV/AIDS.
- In 2019, Merck donated $25 million to the Gates Foundation to support the development of a new malaria vaccine.
**Novartis:**
- In 2020, Novartis donated $20 million to the Gates Foundation to support the development of new treatments for diseases such as malaria and tuberculosis.
- In 2019, Novartis donated $10 million to the Gates Foundation to support the development of a new malaria vaccine.
**Johnson & Johnson:**
- In 2020, Johnson & Johnson donated $50 million to the Gates Foundation to support the development of new vaccines and treatments for diseases such as malaria, tuberculosis, and HIV/AIDS.
- In 2019, Johnson & Johnson donated $25 million to the Gates Foundation to support the development of a new malaria vaccine.
**Sanofi:**
- In 2020, Sanofi donated $20 million to the Gates Foundation to support the development of new vaccines and treatments for diseases such as malaria and tuberculosis.
- In 2019, Sanofi donated $10 million to the Gates Foundation to support the development of a new malaria vaccine.
**AstraZeneca:**
- In 2020, AstraZeneca donated $20 million to the Gates Foundation to support the development of new vaccines and treatments for diseases such as malaria and tuberculosis.
- In 2019, AstraZeneca donated $10 million to the Gates Foundation to support the development of a new malaria vaccine.
**Eli Lilly and Company:**
- In 2020, Eli Lilly donated $10 million to the Gates Foundation to support the development of new treatments for diseases such as malaria and tuberculosis.
- In 2019, Eli Lilly donated $5 million to the Gates Foundation to support the development of a new malaria vaccine.
Additionally, NLM website [https://cdn.ncbi.nlm.nih.gov/pmc/cms/files/PMCFunderDepositList.xlsx] (list over 200)(!) organisations that are founding it. What could go wrong one might ask?!
## The Centralization Challenge
While PubMed and PMC have played a pivotal role in democratizing access to scientific literature, their centralized nature presents vulnerabilities. Over the past century healthcare has grown to become one of the most profitable industries and to believe that the healthcare system we have today is the best we can do is far from understatement.
PubMed's reliance on centralized funding and decision-making processes makes it susceptible to external influences, including lobbying by powerful entities. Moreover, the centralized infrastructure allows for content to be published and removed with relative ease, often without leaving a trace. This raises concerns about the integrity and permanence of the scientific record, particularly in contentious or politically sensitive areas of research.
The ability to alter or erase information from PubMed undermines trust in the system’s objectivity and neutrality. Researchers and the public alike depend on these repositories for reliable and impartial access to scientific knowledge. Any perceived or actual manipulation of content can erode confidence in the platform and compromise its foundational mission.
## The Case for Decentralization
To address these challenges, a decentralized alternative built on emerging technologies, such as the Nostr protocol, could offer significant advantages. A decentralized platform would:
- **Enhance Resilience:** By distributing data across a network of relays, a decentralized system would eliminate single points of failure, ensuring the scientific record remains intact and always accessible even in the face of technical or political disruptions.
- **Increase Transparency:** Decentralized systems inherently log changes, making it nearly impossible to alter or remove content without leaving an auditable trail. This transparency would bolster trust in the integrity of the research.
- **Reduce Susceptibility to Lobbying:** Without centralized control, the influence of external entities on the platform’s content would be significantly diminished, preserving the objectivity of the scientific record.
- **Foster Open Collaboration:** A decentralized approach aligns with the principles of open science, encouraging global collaboration without the constraints of centralized oversight or bias introduced by big pharma lobby.
## Conclusion
While PubMed and PMC have been instrumental in advancing access to scientific literature, their centralized nature leaves them vulnerable to manipulation and external pressures. A shift toward a decentralized, censorship-resistant platform would address these vulnerabilities and provide a more robust and trustless repository for scientific knowledge. Groundbreaking research that dares to challenge the pharmaceutical industry's status quo could be published anonymously, following in the footsteps of the Bitcoin whitepaper's pseudonymous author, Satoshi Nakamoto. Leveraging technologies like the Nostr protocol, the research community can build a system that ensures the permanence, integrity, and impartiality of the scientific record for generations to come.
-

@ 000002de:c05780a7
2025-01-22 16:33:59
Anyone else noticing their LN address not working with Minibits?
originally posted at https://stacker.news/items/860143
-

@ b17fccdf:b7211155
2025-01-22 10:39:19
### **What's changed**
-----------
- [New bonus guide dedicated to install/upgrade/uninstall PostgreSQL](https://minibolt.minibolt.info/bonus-guides/system/postgresql)
- [Modified the LND guide to use PostgreSQL instead of bbolt](https://minibolt.minibolt.info/lightning/lightning/lightning-client)
- [Modified the Nostr relay guide to use PostgreSQL instead of SQLite (experimental)](https://minibolt.minibolt.info/bonus-guides/nostr/nostr-relay)
- [Modified the BTCPay Server bonus guide according to these changes](https://minibolt.minibolt.info/bonus-guides/bitcoin/btcpay-server)
- Used the [lndinit MiniBolt organization fork](https://github.com/minibolt-guide/lndinit), to add an [extra section to migrate an existing LND bbolt database to PostgreSQL](https://minibolt.minibolt.info/lightning/lightning/lightning-client#migrate-an-existing-bbolt-database-to-postgresql) (🚨⚠️[Experimental](https://github.com/lightninglabs/lndinit/pull/21) - use it behind your responsibility⚠️🚨)
- [New Golang bonus guide](https://minibolt.minibolt.info/bonus-guides/system/go) as a common language for the [lndinit compilation](https://minibolt.minibolt.info/lightning/lightning/lightning-client#install-lndinit)
- [Updated LND to v0.18](https://minibolt.minibolt.info/lightning/lightning/lightning-client#download-binaries)
- [New Bitcoin Core extra section to renovate Tor & I2P addresses](https://minibolt.minibolt.info/bitcoin/bitcoin/bitcoin-client#renovate-your-bitcoin-core-tor-and-i2p-addresses)
- [New Bitcoin Core extra section to generate a full `bitcoin.conf` file](https://minibolt.minibolt.info/bitcoin/bitcoin/bitcoin-client#generate-a-full-bitcoin.conf-example-file)
- [Rebuilt some homepage sections and general structure](https://minibolt.minibolt.info//)
- Deleted the `$` symbol of the commands to easy copy-paste to the terminal
- [Deleted the initial incoming and the outgoing rules configuration of UFW, due to it being by default](https://minibolt.minibolt.info/system/system/security)
---
🪧 PD: If you want to use the old database backend of the LND or Nostr relay, follow the next extra sections:
- [Use the default bbolt database backend for the LND](https://minibolt.minibolt.info/lightning/lightning/lightning-client#use-the-default-bbolt-database-backend)
- [Use the default SQLite database backend for the Nostr relay](https://minibolt.minibolt.info/bonus-guides/bitcoin/nostr-relay#use-the-default-sqlite-database-backend)
⚠️**Attention**⚠️: [The migration process](https://minibolt.minibolt.info/lightning/lightning/lightning-client#migrate-an-existing-bbolt-database-to-postgresql) was tested on testnet mode from an existing bbolt database backend to a new PostgreSQL database using lndinit and the results were successful. However, It wasn't tested on mainnet, [according to the developer](https://github.com/lightninglabs/lndinit/pull/21), it is in experimental status which could damage your existing LND database.🚨 Use it behind your responsibility 🧼
---
**🔧 PR related**: https://github.com/minibolt-guide/minibolt/pull/93
-----------
#### ♻️ Migrate the PostgreSQL database location
> **Attention!!** These instructions are invalid since the latest changes applied to the [PostgreSQL bonus guide](https://minibolt.minibolt.info/bonus-guides/system/postgresql). See more information on the recent associated post by clicking ~ > [HERE](https://habla.news/u/twofaktor@twofaktor.github.io/1735902560910) < ~
If you installed [NBXplorer + BTCPay Server](https://minibolt.minibolt.info/bonus-guides/bitcoin/btcpay-server) **before 05/06/2024**, it is probably you have the database of the PostgreSQL cluster on the default path (`/var/lib/postgresql/16/main/`), follow the next instructions to migrate it to the new dedicated location on `/data/postgresdb` folder:
* With user `admin` create the dedicated PostgreSQL data folder
```
sudo mkdir /data/postgresdb
```
* Assign as the owner to the `postgres` user
```
sudo chown postgres:postgres /data/postgresdb
```
* Assign permissions of the data folder only to the `postgres` user
```
sudo chmod -R 700 /data/postgresdb
```
* Stop NBXplorer and BTCPay Server
```
sudo systemctl stop nbxplorer && sudo systemctl stop btcpayserver
```
* Stop PostgreSQL
```
sudo systemctl stop postgresql
```
* Use the rsync command to copy all files from the existing database on (`/var/lib/postgresql/16/main`) to the new destination directory (`/data/postgresdb`)
```
sudo rsync -av /var/lib/postgresql/16/main/ /data/postgresdb/
```
Expected output:
```
sending incremental file list
./
PG_VERSION
postgresql.auto.conf
postmaster.opts
postmaster.pid
base/
base/1/
base/1/112
base/1/113
base/1/1247
base/1/1247_fsm
base/1/1247_vm
base/1/1249
base/1/1249_fsm
base/1/1249_vm
[...]
pg_wal/000000010000000000000009
pg_wal/archive_status/
pg_xact/
pg_xact/0000
sent 164,483,875 bytes received 42,341 bytes 36,561,381.33 bytes/sec
total size is 164,311,368 speedup is 1.00
```
* Edit the PostgreSQL data directory on configuration, to redirect the store to the new location
```
sudo nano /etc/postgresql/16/main/postgresql.conf --linenumbers
```
* Replace the line 42 to this. Save and exit
```
data_directory = '/data/postgresdb'
```
* Start PostgreSQL to apply changes and monitor the correct status of the main instance and sub-instance monitoring sessions before
```
sudo systemctl start postgresql
```
* You can monitor the PostgreSQL main instance by the systemd journal and check the log output to ensure all is correct. You can exit the monitoring at any time with Ctrl-C
```
journalctl -fu postgresql
```
Example of the expected output:
```
Nov 08 11:51:10 minibolt systemd[1]: Stopped PostgreSQL RDBMS.
Nov 08 11:51:10 minibolt systemd[1]: Stopping PostgreSQL RDBMS...
Nov 08 11:51:13 minibolt systemd[1]: Starting PostgreSQL RDBMS...
Nov 08 11:51:13 minibolt systemd[1]: Finished PostgreSQL RDBMS.
```
* You can monitor the PostgreSQL sub-instance by the systemd journal and check log output to ensure all is correct. You can exit monitoring at any time with Ctrl-C
```
journalctl -fu postgresql@16-main
```
Example of the expected output:
```
Nov 08 11:51:10 minibolt systemd[1]: Stopping PostgreSQL Cluster 16-main...
Nov 08 11:51:11 minibolt systemd[1]: postgresql@16-main.service: Succeeded.
Nov 08 11:51:11 minibolt systemd[1]: Stopped PostgreSQL Cluster 16-main.
Nov 08 11:51:11 minibolt systemd[1]: postgresql@16-main.service: Consumed 1h 10min 8.677s CPU time.
Nov 08 11:51:11 minibolt systemd[1]: Starting PostgreSQL Cluster 16-main...
Nov 08 11:51:13 minibolt systemd[1]: Started PostgreSQL Cluster 16-main.
```
* Start NBXplorer and BTCPay Server again
```
sudo systemctl start nbxplorer && sudo systemctl start btcpayserver
```
* Monitor to make sure everything is as you left it. You can exit monitoring at any time by pressing Ctrl+C
```
journalctl -fu nbxplorer
```
---
```
journalctl -fu btcpayserver
```
---
Enjoy it MiniBolter! 💙
-

@ 00eba731:09746909
2025-01-22 05:20:24
Managing risks is crucial for business success, as it helps protect operations and ensure stability in uncertain situations. This infographic provides an overview of effective [risk management strategies](https://www.asialinkfinance.com.ph/articles/blog/business-risk-management/), including identifying potential risks, assessing their impact, and implementing measures to mitigate them, helping businesses stay resilient and prepared.
[Infographic](https://www.asialinkfinance.com.ph/wp-content/uploads/2023/09/AsiaLink-info10-p2.png)
-

@ 5adb967d:ac1f7d04
2025-01-22 03:41:12
In this information age, radio communication has penetrated into every aspect of life. Whether it is government affairs, military, business, or personal privacy, may be subject to eavesdropping and radio wave harassment. In the face of this grim reality, how to build an impenetrable line of defense for the key confidential communications, has become an extremely urgent issue. Communication shielding, is to effectively block eavesdropping interference, to ensure absolute communication security of the magic weapon.
Communication shielding protection principle, is the use of masking performance of electromagnetic [rf jammer](https://www.thejammerblocker.com/uhf-vhf-lojack-rf-jammer/) materials, in the device around the formation of a “static area”. Into this special space, any radio wave signals will be completely blocked out, can not penetrate them. Whether it is the most advanced passive eavesdropping equipment, or intentional harassment of active electromagnetic interference, in this invulnerable “static area” in front of, all will be completely off, out of action.
In fact, electromagnetic shielding technology has long been popular in the military field. The core components of countless advanced weapons and equipment, are closely protected by this material to ensure that the key system from the outside world interference. Some special places also widely used fixed shielding facilities, to create an absolutely reliable quiet environment.
However, today, mobile offices and field operations are becoming more and more common, and the traditional fixed shielding facilities are difficult to meet the flexible deployment requirements. Therefore, portable communication shielding has emerged as the best on-site confidentiality protection tool.
Simply press the power button, most portable shielding can be immediately effective. Their powerful electromagnetic [recording jammer](https://www.thejammerblocker.com/audio-recorder-jammers/) ability, enough to form a “static area radius” within a few meters to dozens of meters in the surrounding area. As long as you enter, no matter what kind of unauthorized eavesdropping equipment, radio interference sources, all will be hard “static zone barrier” intercepted.
Users in this safe space, you can carry out all kinds of confidential calls, video conferencing or secret work, absolutely foolproof, free from any prying eyes and harassment. At the same time, another great use of the shield is to prevent the leakage of radio signals and loss of confidentiality. That is to say, the important content basically will not be from the “static area” out of half a signal, fundamentally blocked the worries.
This “two-way shielding” role, making the communication shield has become the key confidential communication field of choice. Whether it is a government agency's classified meeting, or business company's trade secrets, or even personal privacy, as long as the absolute security of the “quiet zone”, everything will be easy.
Moreover, the latest generation of communication [drone jammers](https://www.thejammerblocker.com/drone-uavs-jammers-blockers/) can also be based on demand, the specific 2G/3G/4G/5G/WIFI and other frequency bands to implement precise selective shielding. This allows the user to take into account both communication protection and ease of use, really make the best use of things, twice the result with half the effort.
In the current complex environment with many hidden dangers, communication [network blocker](https://www.thejammerblocker.com/) is undoubtedly an indispensable “last line of defense” for important confidential communications. With it, no matter what kind of radio wave torture, any eavesdropping interference soul will have no place to hide. It can be said that this small and exquisite “secrecy magic weapon”, will draw a quiet and safe for the important affairs of the absolute territory.
3. [https://open.substack.com/pub/thejammerblocker/p/admiralty-protection-shielding-for?r=4tc4gn&utm\_campaign=post&utm\_medium=web&showWelcomeOnShare=true](https://open.substack.com/pub/thejammerblocker/p/admiralty-protection-shielding-for?r=4tc4gn&utm_campaign=post&utm_medium=web&showWelcomeOnShare=true)
4. [https://thejammerblockershop.writestellar.com/dui2gfo](https://thejammerblockershop.writestellar.com/dui2gfo)
-

@ 6be5cc06:5259daf0
2025-01-21 23:17:29
A seguir, veja como instalar e configurar o **Privoxy** no **Pop!_OS**.
---
### **1. Instalar o Tor e o Privoxy**
Abra o terminal e execute:
```bash
sudo apt update
sudo apt install tor privoxy
```
**Explicação:**
- **Tor:** Roteia o tráfego pela rede Tor.
- **Privoxy:** Proxy avançado que intermedia a conexão entre aplicativos e o Tor.
---
### **2. Configurar o Privoxy**
Abra o arquivo de configuração do Privoxy:
```bash
sudo nano /etc/privoxy/config
```
Navegue até a última linha (atalho: **`Ctrl`** + **`/`** depois **`Ctrl`** + **`V`** para navegar diretamente até a última linha) e insira:
```bash
forward-socks5 / 127.0.0.1:9050 .
```
Isso faz com que o **Privoxy** envie todo o tráfego para o **Tor** através da porta **9050**.
Salve (**`CTRL`** + **`O`** e **`Enter`**) e feche (**`CTRL`** + **`X`**) o arquivo.
---
### **3. Iniciar o Tor e o Privoxy**
Agora, inicie e habilite os serviços:
```bash
sudo systemctl start tor
sudo systemctl start privoxy
sudo systemctl enable tor
sudo systemctl enable privoxy
```
**Explicação:**
- **start:** Inicia os serviços.
- **enable:** Faz com que iniciem automaticamente ao ligar o PC.
---
### **4. Configurar o Navegador Firefox**
Para usar a rede **Tor** com o Firefox:
1. Abra o Firefox.
2. Acesse **Configurações** → **Configurar conexão**.
3. Selecione **Configuração manual de proxy**.
4. Configure assim:
- **Proxy HTTP:** `127.0.0.1`
- **Porta:** `8118` (porta padrão do **Privoxy**)
- **Domínio SOCKS (v5):** `127.0.0.1`
- **Porta:** `9050`
5. Marque a opção **"Usar este proxy também em HTTPS"**.
6. Clique em **OK**.
---
### **5. Verificar a Conexão com o Tor**
Abra o navegador e acesse:
```text
https://check.torproject.org/
```
Se aparecer a mensagem **"Congratulations. This browser is configured to use Tor."**, a configuração está correta.
---
### **Dicas Extras**
- **Privoxy** pode ser ajustado para bloquear anúncios e rastreadores.
- Outros aplicativos também podem ser configurados para usar o **Privoxy**.
-

@ 000002de:c05780a7
2025-01-21 21:29:39
> The Bellamy salute is a palm-out salute created by James B. Upham as the gesture that was to accompany the Pledge of Allegiance of the United States of America, whose text had been written by Francis Bellamy. It was also known as the "flag salute" during the period when it was used with the Pledge of Allegiance. Bellamy promoted the salute and it came to be associated with his name. Both the Pledge and its salute originated in 1892. It was also known as the "flag salute" during the period when it was used with the Pledge of Allegiance. Bellamy promoted the salute and it came to be associated with his name. Both the Pledge and its salute originated in 1892. Later, during the 1920s and 1930s, Italian fascists and Nazi Germans adopted a salute which was very similar, attributed to the Roman salute, a gesture that was popularly believed to have been used in ancient Rome.[1] This resulted in controversy over the use of the Bellamy salute in the United States. It was officially replaced by the hand-over-heart salute when Congress amended the Flag Code on December 22, 1942.
~ [Bellamy salute - Wikipedia](https://en.wikipedia.org/wiki/Bellamy_salute)
originally posted at https://stacker.news/items/859191
-

@ 3c7dc2c5:805642a8
2025-01-21 21:00:47
## 🧠Quote(s) of the week:
'For the love of God, Bitcoin is not a 'scam', and it is not 'going away'. Do yourself some good by honestly and thoroughly researching it, away from mainstream media nonsense. You can thank me and thousands of others on here later.'
'Do you actually understand what it means when the whole world tries to squeeze into a fixed supply digital asset that never gets diluted, is audited every 10 minutes, and trades 24/7 as the most liquid asset on earth? If you do, you’re holding on for dear life.' -Bitcoin For Freedom
## 🧡Bitcoin news🧡
After a short break from the recap, I am back. I got a new place and I had to focus on that project. Now before I start with this week's Weekly Recap I want to remind all the political larpers (Trump voters etc) of one thing:
THE PROMISE
1. Strategic Bitcoin Reserve
2. Free Ross day one
THE REALITY
1. 47M Wrapped BTC
2. Maybe free Ross later
3. 4.7M tron
4. 47M Ethereum
5. 4.7 M litecoin
6. Pardoned J6 participants
Oh, and he launched the biggest meme/shitcoin, and rug pulled the shit out of it.
On the 12th of January:
➡️Eighth consecutive positive adjustment on the horizon. We saw nine in 2021 and 17 in 2018. This is insane.
➡️A Santander Bank report highlights El Salvador’s booming tourism industry, fueled by Bitcoin adoption.
The country announced 3.9M tourists in 2024—a 22% YoY increase and nearly double the levels seen between 2013-2016.
➡️Bitcoin mining difficulty increased by 0.6101% today. The network has programmatically adjusted to a new difficulty level of 110,451,907,374,649 hashes, ensuring the target block time remains stable as global computing power on the network fluctuates.
➡️We now have 7 states, and counting, pushing a Strategic Bitcoin Reserve Bill:
- New Hampshire
- Alabama
- Florida
- Pennsylvania
- Texas
- Ohio
- North Dakota
On the 13th of January:
➡️Italy's largest bank Intesa Sanpaolo has started buying Bitcoin, according to leaked internal emails which celebrate the "first transaction" of €1m for 11 Bitcoin.
➡️The number of Bitcoin addresses holding over 100 BTC has surged by 8.6% since Trump’s election in November.
➡️Ming Shing Group from Hong Kong just acquired 500 Bitcoin for $47M.
➡️Semler Scientific has acquired 237 BTC for ~$23.3 million at ~$98,267 per Bitcoin and has generated a BTC Yield of 99.3% since adopting our BTC treasury strategy in May 2024. As of 1/10/2025, we held 2,321 Bitcoin acquired for ~$191.9 million at ~$82,687 per Bitcoin.
➡️$11.5 trillion BlackRock says that Bitcoin adoption is outpacing the internet and mobile phones.
On the 14th of January:
➡️The Bitcoin network has 610,929x more hashing computational power than the combined total of the world’s top 500 supercomputers.
On the 16th of January:
➡️'Someone just moved 11,000 Bitcoin worth $1.1 BILLION around the world for ONLY $1.50
The world's most efficient monetary network.' - Pete Rizzo
➡️XRP is down 80% from its bitcoin all-time high in 2017. Just don't do shitcoins, it's that simple.
On the 17th of January:
➡️'They did it again! Bindseil and Schaaf published the article, 'Arguments Against a Strategic Bitcoin Reserve'.
It is a wild ride, reaching peak FUD. Maybe even so wild that they had to publish it in a newspaper and not as an ECB blog post.
This is ultra bullish' - Dr. Jan Wüstenfeld
➡️Metaplanet's market cap closes above $1 billion for the first time since adopting a Bitcoin Standard.
➡️Jeroen Blokland: ‘Nearly one-fifth of all U.S. states are formally weighing whether to have public funds invest in Bitcoin.’
I am afraid and convinced at the same time that soon, the EU will be the only region still aiming to introduce a central bank digital currency. As a result, it will trigger more polarization, and Europe will lose the Bitcoin battle, just as it hopelessly lost the technology and AI battle.
➡️'ETH was supposed to become deflationary after the "merge"
But now the supply is almost back to where it was BEFORE the merge
If you're still falling for this shit, you deserve to get scammed.' -Rajat Soni
To make it even worse:
'The ETHBTC ratio is now lower than the day when Coinbase listed it in 2016. You would have been buying ETH at ~$13, but funny enough if you would have just bought and held Bitcoin, you would have actually outperformed it.' -Pledditor.
➡️ First union in Idaho bought Bitcoin.
➡️ California state officials embraced Bitcoin.
➡️Wyoming filed for Strategic Bitcoin Reserve bill.
➡️Massachusetts filed for Strategic Bitcoin Reserve bill. Up to 10% of the $9 Billion Commonwealth Stabilization Fund can be invested in Bitcoin
On the 18th of January:
➡️ Swiss Bitcoin advocates are pushing for the Swiss National Bank to add Bitcoin to the national reserves - Bloomberg
They need 100,000 signatures to put it to a national vote.
➡️3.47M Bitcoin addresses hold more than 0.1 BTC. If you own one of them you’re set for life.
➡️Donald Trump dropped a meme coin instead of stacking Bitcoin for a Strategic Reserve. If the president of the UNITED STATES OF AMERICA can launch and promote a memecoin, then essentially it's OK (and not shamed) for anyone/anywhere to do so.
The grift to come is going to be unreal, even by CrApTo standards.
A memecoin/shitcoin is a zero-sum* lottery.
There is no wealth creation. Every buy order is simply matched by a sell order. After an initial spike, the price eventually crashes and the last buyers lose everything.
That's the only thing I am going to share on the subject.
[](https://i.ibb.co/jRctP3r/Ghpx9-BNWUAA2-Nxg.jpg)
➡️Arizona Strategic Bitcoin Reserve bill introduced
The State can invest up to 10% from:
1) State general fund - $28B
2) State retirement funds - $50B
➡️ Bitwise bought +$200 MILLION Bitcoin for its ETF today. The biggest single-day inflow since launching last year.
On the 19th of January:
➡️ Bitcoin Network System Explained in a Chart:
[](https://i.ibb.co/RBrC5tw/Ghn8-Bv-BW8-AAi-Xu-X.jpg)
On the 20th of January:
➡️Bitcoin mining difficulty hits a NEW ALL-TIME HIGH.
➡️YouTube rival Rumble started buying Bitcoin for its balance sheet on Friday - CEO
➡️Bitcoin went up 20x in Trump's first term as President. 10x this time?
##
💸Traditional Finance / Macro:
👉🏽no news
## 🏦Banks:
👉🏽Global central banks now hold more Gold than at any point in the past 45 years. Something is brewing.
## 🌎Macro/Geopolitics:
On the 12th of January:
👉🏽Treasuries are entering their 6th year of the third great bond bear market of the last 240 years!
On the 16th of January:
👉🏽EU Commission allows Thierry Breton to take up a new job at Bank of America despite a rule that requires a two-year waiting period before starting lobbying jobs.
There are no rules for these corrupt EU (you fill in the blank). The rules apply only to citizens, not to the Brussels elite, and certainly not if you belong to the French political elite.
In December I shared some news on the EU crusade against X. Let me explain this to you in simple terms.
Breton, a man preaching about the ‘rule of law’ and X, while breaching the rules he signed up to himself: ‘Code of Conduct EU Commissioners’.
Now read that again. Bitcoin only. Defund politicians.
👉🏽'The Congressional Budget Office just lowered the US population forecast by 11 million, to 372 million in 2054.
This implies 6.3% growth over the next 30 years instead of the 10.5% previously expected.
The agency also expects deaths to exceed births starting in 2033, 7 years earlier than in the 2024 estimates.
Lower fertility rates and lower net immigration expectations were behind the outlook changes.
Are we heading into a demographic crisis?' - TKL
On the 17th of January:
👉🏽 Germany had 17 nuclear power plants. It shut them all down. Germany spent $1 Trillion for its energy revamp with the following results:
- It is now totally dependent on Russian gas, French nuclear power electricity, and coal (the most polluting fossil fuel)
- Its citizens pay the highest electricity price in Europe
- It causes several times more CO2 per kWh than France
Go woke, go broke. $1T for ruining both its economy and environment. Wunderbar!
Just some data: In 2025, Europe is buying Russian gas at an unprecedented pace and spending billions of dollars on it, reports Politico. In the first 15 days of the year, the EU countries imported 837.3 thousand tons of Russian liquified natural gas (LNG).
Just to show you how fucked up things are in the EU. EU companies are backstabbed by their own policymakers.
'Europe's carmakers risk hefty bill for carbon credit from Chinese rivals.'
source: https://www.ft.com/content/677190d1-7d34-4506-a037-418baab67237
I read the article. It’mind-blowingng. It's like shooting a two-barrelled shotgun in your own nuts.
On this point, EU regulators are destroying an entire part of the economy (Car manufacturing + subcontractors) and are giving the keys to Chinese companies.
Go woke, go broke. China is making new coal plants at a rate that cancels German / EU efforts 10X or maybe 100x over.
Now from an economic perspective: 'European equities are more or less where they were at the beginning of the century.
Overregulation and bureaucracy throttling innovation, and belief in left redistribution nonsense instead of hard work and entrepreneurship have their price.' -Michael A.
Arouet
[](https://i.ibb.co/DWCV5pV/Ght-HId-Wc-AINW2x.jpg)
👉🏽Treasuries have experienced their worst rolling 10-year return in 90 YEARS, now at -0.5%.
People out here still stacking U.S. gov bonds instead of Bitcoin.
Data: U.S. Treasury bonds: -42% - Bitcoin: +809%
'The “smart money” is buying 30-year treasury bonds with a nominal yield of 1.20% on the whim that another investor (or central bank) will buy it from them at a higher price.'
-Dylan Leclair
On the 18th of January:
👉🏽Argentina has officially reached its first budget surplus in 14 years. Vamos!
Under Milei’s leadership, Argentina turned a $7.94B trade deficit in 2023 into a record-smashing $18-19B surplus in 2024, surpassing the previous high of $16.89B in 2009.
His push to boost energy exports from the Vaca Muerta shale reserves and ramp up grain sales is paying off, making Argentina a global exporting powerhouse again.
With inflation already down from nearly 300% to 117.8%, Milei’s economic reforms are proving their worth.
Argentinian President Javier Milei announces "Zero deficit is a reality...promises are fulfilled."
Let me refrain from the above:
➡️Less state
➡️Less government expenses
➡️Capitalism
➡️Free market
👉🏽Wealth exodus accelerated by 157% in 2024: One millionaire leaves Britain every 45 minutes under Labour — Telegraph
157% increase in the outflow of millionaires since Labour came to power - including losing over 10,000 millionaires & 12 billionaires. All these people created wealth in the U.K. through living and spending.
On the 19th of January:
👉🏽U.S. Housing Market
16.2% of Home Purchase Deals were canceled last month, the highest cancellation rate in history
If for some reason people still believe Bitcoin is a Ponzi scheme, well that's their fault. Let me share with you the real Ponzi scheme.
The following chart summarizes the impact of demographics on European pension systems really well:
[](https://i.ibb.co/r7QkYsv/Gh-J7j41-Wg-AEah31.jpg)
A ticking time bomb!
The regulatory burdens suffered by citizens are imposed by unelectable bureaucrats!
Study Bitcoin.
## 🎁If you have made it this far I would like to give you a little gift:
Some fountain of Lyn Alden's wisdom:
https://www.youtube.com/watch?v=fZlcrLZkNA8
Lyn Alden is a macro analyst, investment strategist, and the author of Broken Money. In this episode of What Bitcoin Did, they discuss the impact of fiscal policy on inflation, the Federal Reserve's constraints under fiscal dominance, and the role of tariffs in shaping the economic landscape. They also get into a Strategic Bitcoin Reserve, and what Donald Trump’s Administration will mean for Bitcoin.
Credit: I have used multiple sources!
The complete Weekly Recap will be accessible on my Bitcoin Friday page on Habla. Enriched with detailed charts, illustrative images, and comprehensive macroeconomic news to provide context and clarity.
My savings account: Bitcoin The tool I recommend for setting up a Bitcoin savings plan: PocketBitcoin especially suited for beginners or people who want to invest in Bitcoin with an automated investment plan once a week or monthly. Use the code BITCOINFRIDAY
Get your Bitcoin out of exchanges. Save them on a hardware wallet, run your own node...be your own bank. Not your keys, not your coins. It's that simple.⠀⠀⠀⠀ ⠀ ⠀⠀⠀
Do you think this post is helpful to you? If so, please share it and support my work with a zap.
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
⭐ Many thanks⭐
Felipe - Bitcoin Friday!
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
-

@ 62a6a41e:b12acb43
2025-01-21 19:19:06
Bodhidharma, the founder of Zen Buddhism (also known as Zen or Zen meditation), meditated for nine years, simply looking at a wall.
Nine years staring at a wall.
Good things take time. Don’t be afraid to take your time. Forget what Western society has taught us—here, we are slaves to time and productivity.
I believe one of the reasons the Western world is in decline is precisely because we lack the philosophical and religious structures that enable true freedom and focus on understanding.
Christianity is beautiful in its own way, but it simply isn’t as clear or rational as Eastern philosophy. As a result, it hasn’t managed to foster an environment for genuine seekers or free thinkers in the same way.
We need to take the time to think. The West doesn’t understand that.
Take your time. You are free to take your time. It's **your** time. Take as much time as you want, until you understand what you needed to understand.
-

@ 6e15bf3d:0548a961
2025-01-21 18:46:37
As we approach 2025, [website design continues to evolve at a rapid pace](https://heytradie.com.au/top-17-website-design-trends-in-2025-a-free-guide/), driven by innovations in technology, shifts in user behavior, and an increasing focus on providing personalized experiences. Web design is not just about creating visually appealing layouts anymore; it is now about creating functional, intuitive, and immersive experiences that make users feel connected with the brand. As businesses and content creators recognize the importance of digital presence, staying on top of the latest trends will be crucial for success in the upcoming year.
In this article, we will explore the top website design trends for 2025, including technological advancements, aesthetic shifts, and user experience (UX) enhancements that will shape the future of the web.
**2. 1. AI-Powered Personalization
**
Artificial Intelligence (AI) has made a profound impact on website design, enabling businesses to offer highly personalized experiences. AI-powered tools will continue to transform websites by analyzing user behavior and preferences to deliver tailored content, recommendations, and interfaces. These personalized features enhance user engagement, increase conversion rates, and improve overall customer satisfaction.
In 2025, we can expect to see more websites integrating AI technologies that adjust content, layout, and even color schemes based on individual user profiles. Personalized experiences help create a sense of relevance and connection, making users feel as though the website was designed specifically for them.
**3. 2. Immersive Experiences with VR/AR
**
Virtual Reality (VR) and Augmented Reality (AR) technologies are no longer just futuristic concepts; they are becoming increasingly accessible and practical in web design. In 2025, expect websites to offer immersive experiences using AR and VR. This could mean users experiencing products in a 3D environment, virtually trying on clothes, or even exploring a property from the comfort of their home.
With the advancement of 5G technology, websites can incorporate these technologies more smoothly, providing a seamless and engaging experience. Retailers, real estate agencies, and travel companies, in particular, will benefit from offering interactive experiences that allow users to interact with their products and services in new and exciting ways.
For example, an e-commerce site might allow you to place a piece of furniture in your room via AR to see how it fits. For the real estate sector, virtual tours of homes or apartments can be offered with VR, helping users feel more confident in their decisions before visiting in person.
**4. 3. Mobile-First Design
**
As mobile device usage continues to dominate the internet landscape, mobile-first design is expected to be a leading trend in 2025. In fact, more than 54% of global web traffic now comes from mobile devices (source: Statista), a statistic that reflects the increasing importance of responsive web design that prioritizes mobile experiences.
A mobile-first approach means designing websites primarily for smaller screens, ensuring that the content is easily accessible, readable, and navigable on smartphones and tablets. Designers will focus on optimizing touch interactions, speed, and performance on mobile devices to meet user expectations.
**5. 4. Minimalistic and Clean Aesthetics
**
While overly complex and cluttered web designs were once the norm, the trend has been shifting towards minimalism. Clean and simple designs, with plenty of white space, allow for better navigation, faster load times, and a more focused user experience. In 2025, this trend will continue as users demand simplicity and speed when interacting with websites.
Minimalist design involves reducing elements to the essentials, eliminating distractions, and using whitespace strategically to highlight key content. Bold typography, crisp images, and well-organized layouts will allow the content to speak for itself without overwhelming the user.
The minimalist approach also tends to work well with responsive design, ensuring that websites are easy to navigate regardless of the device or screen size. Furthermore, this trend aligns with sustainability efforts, as minimalist designs often reduce the need for heavy graphic elements, leading to faster loading times and reduced energy consumption.
**6. 5. Dark Mode and Customizable Themes
**
Dark mode has become a popular feature in web design, and it is set to stay in 2025. Offering users the ability to toggle between light and dark modes not only enhances accessibility but also reduces eye strain, especially in low-light conditions. In addition, dark mode can give websites a modern and sleek aesthetic that appeals to users.
Many websites will implement customizable themes, allowing users to choose their preferred visual experience. Whether it’s adjusting colors, fonts, or background styles, offering theme customization can make users feel more in control of their experience, making it more likely that they’ll engage with the content for longer periods.
**7. 6. Microinteractions and Animations
**
Microinteractions are small, interactive animations or design elements that help users navigate and engage with a website. These subtle animations provide feedback, guide users through processes, and add a sense of interactivity to the experience. For example, hover effects, button animations, and loading animations are all types of microinteractions.
In 2025, websites will incorporate even more sophisticated microinteractions, making websites feel more dynamic and engaging. These small details enhance the user experience by making interactions feel more intuitive and enjoyable. However, it’s crucial that designers balance animations and microinteractions with site performance, as excessive animations can slow down load times.
**8. 7. Voice Search and Voice User Interface (VUI)
**
As voice search technology becomes more advanced, websites will need to adapt to this growing trend. Voice search allows users to interact with a website using spoken commands, and it is especially useful for mobile and smart device users who prefer hands-free experiences.
By 2025, voice search will become more integrated into website design, as businesses will optimize their content for voice queries. Websites will also implement voice user interfaces (VUI) that allow users to navigate and interact with websites through voice commands. This trend is particularly important as voice-activated assistants like Siri, Google Assistant, and Alexa continue to gain popularity.
**9. 8. Typography as a Design Element
**
Typography has always been an essential part of web design, but in 2025, it will become even more central to the overall design aesthetic. Bold, experimental typography is taking center stage as designers use fonts to convey personality, emotion, and style.
From oversized text to custom fonts, typography is no longer just a functional element; it is a visual statement that enhances the identity of a brand. In addition to bold typography, variable fonts that allow for greater flexibility in font weight, size, and style will become more popular, enabling websites to create more dynamic and personalized typographic experiences.
**10. 9. Sustainability in Design
**
As environmental consciousness grows, sustainability will become a driving factor in website design. In 2025, expect to see more brands and web developers embracing eco-friendly design practices. This includes designing websites that minimize their environmental impact by reducing energy consumption and optimizing site speed.
Sustainable design could involve using lighter graphic elements, optimizing images and videos for faster loading, and choosing energy-efficient hosting options. Reducing the carbon footprint of websites is an essential part of future web design, especially as consumers become more aware of the environmental impact of digital technologies.
**11. 10. Inclusive and Accessible Design
**Web accessibility continues to be a priority for designers, and in 2025, we will see further advancements in this area. Websites will become even more inclusive, with features such as adjustable text sizes, color contrast settings, and screen reader compatibility.
Designers will also implement accessibility guidelines and best practices to ensure that all users, including those with disabilities, can access and navigate websites easily. This includes creating more intuitive navigation systems, providing alternative text for images, and ensuring that content is accessible for people with visual, auditory, or motor impairments.
Web accessibility is not just a legal requirement in some regions but also a moral responsibility. By making websites accessible to everyone, businesses can ensure a more inclusive online experience for all users.
**Conclusion
**
As we move towards 2025, website design will continue to innovate, with new technologies and aesthetic shifts leading the way. From AI-powered personalization and immersive AR/VR experiences to minimalistic aesthetics and mobile-first design, the future of web design is focused on user-centric experiences that are visually striking, easy to navigate, and accessible to all.
To stay ahead in this ever-evolving landscape, businesses and website developers must embrace these trends and ensure that their websites are both functional and forward-thinking. By doing so, they will not only enhance the user experience but also build stronger connections with their audience, ultimately leading to greater success in the digital world.
The future of website design is bright, and 2025 promises to bring about exciting changes that will redefine how we interact with the web.
-

@ 18e3af1e:1d42e5df
2023-08-13 02:40:19
Las comunidades son creadas mediante el esfuerzo de no solo un individuo, sino al trabajo de docenas; cientos o miles de personas. Mediante la especialización, como especie, logramos entender que: el saber hacer una sola cosa no significa morir de hambre, o no estar bien preparado para un ataque; por lo contrario, el dominio o maestría de una sola cosa... Puede crear una civilización entera.
Permitirnos un enfoque certero para aprender, dominar y amaestrar nuestras actividades en un periodo de tiempo finito, permitió nuestro avance hacia nuevos campos, de hecho, movió nuestra meta en magnitud tal, que al imaginar el pasado (para muchos) parece mas bien una película cómica y sombría.
Hoy en día, en un mundo regido por individualismo en el reino físico, la manifestación de constructores de comunidades sigue presente en el (reino) digital.
### La evolución de la construcción
A lo largo de la historia de la humanidad, la construcción ha evolucionado desde simples refugios hasta monumentos arquitectónicos y estructuras vanguardistas. Los primeros humanos crearon refugios rudimentarios con materiales naturales. Con la civilización, surgieron las primeras estructuras permanentes, como pirámides y templos, reflejando la organización social y creencias religiosas. La antigua Roma introdujo la innovación en la ingeniería con acueductos y arcos.
La Edad Media vio fortificaciones y catedrales góticas que fusionaban espiritualidad y técnica. El Renacimiento abrazó la proporción y la simetría en palacios y edificios renombrados. La Revolución Industrial marcó un cambio radical con el acero y el hormigón, permitiendo rascacielos y puentes icónicos.
El siglo XX trajo consigo la era de los rascacielos y la arquitectura modernista, desafiando límites estructurales y estéticos. La sostenibilidad ganó importancia en el siglo XXI, impulsando la incorporación de tecnologías avanzadas, como la impresión 3D y la construcción modular.
La historia de la construcción es un testimonio de la creatividad y la adaptabilidad humanas, reflejando no solo avances técnicos, sino también valores culturales y aspiraciones.
En el día hoy, los desarrolladores de software y tecnología podrían considerarse como los constructores del próximo siglo. Al igual que los constructores en otras épocas históricas, los desarrolladores de software son responsables de crear estructuras digitales que moldean la forma en que interactuamos, comunicamos y vivimos en el mundo moderno.
A medida que la tecnología continúa avanzando y la sociedad se vuelve cada vez más digital, el papel de los desarrolladores de software se vuelve crucial en la construcción de soluciones tecnológicas que abordan una amplia gama de desafíos.
Así como los arquitectos y constructores antiguos debían entender la física, la estética y las necesidades humanas para diseñar y construir edificios funcionales y atractivos, los desarrolladores de software deben comprender la lógica de programación, la experiencia del usuario, la seguridad cibernética y la innovación tecnológica para crear aplicaciones, sistemas y plataformas que sean útiles y efectivos.
### Individuos que inspiran
La inspiración individual es un poderoso motor de cambio que puede tener un impacto significativo en la mente colectiva de una comunidad o sociedad. Cuando una persona demuestra pasión, determinación y una visión positiva, puede influir en otros a nivel emocional y cognitivo. Aquí hay algunas formas en que la inspiración individual afecta a la mente colectiva:
La gente puede verse reflejada en las luchas y logros de alguien más, lo que crea un sentido de unidad y comunidad. Esto puede generar un mayor apoyo y solidaridad en torno a ciertas causas o valores. Además, la inspiración individual puede llevar a la acción. Cuando las personas son testigos de un individuo que supera obstáculos o logra metas desafiantes, esto puede motivar a otros a enfrentar sus propios desafíos y trabajar hacia sus objetivos. El ejemplo de una sola persona puede encender la chispa de la acción en muchas más.
La inspiración individual puede tener un efecto multiplicador. Cuando una persona inspirada comparte su historia o experiencia, puede inspirar a otros, creando una cadena de influencia que se extiende a través de redes sociales, comunidades y sociedades enteras. Esto puede tener un impacto a gran escala en la mente colectiva.
El individuo inspirador tiene el potencial de influir profundamente en la mente colectiva al cambiar percepciones, motivar la acción y crear una sensación de comunidad y unidad.
### Comunidades: origen, inicios y progreso.
Las comunidades han sido una parte fundamental de la experiencia humana a lo largo de la historia. Desde los primeros tiempos hasta la era moderna, las comunidades han evolucionado y cambiado en respuesta a las necesidades, avances tecnológicos y contextos culturales.
Desde los primeros días de la humanidad, nuestros antepasados se agruparon en pequeñas comunidades para sobrevivir. Estas comunidades eran grupos familiares o tribus que compartían recursos y conocimientos para cazar, recolectar alimentos y protegerse de los peligros. La cooperación y la solidaridad eran esenciales para la supervivencia.
Con el desarrollo de la agricultura, las comunidades evolucionaron hacia asentamientos más permanentes. La capacidad de cultivar alimentos permitió la formación de aldeas y pueblos, donde la gente podía establecerse y construir relaciones más complejas. Esto llevó al surgimiento de una división del trabajo más especializada y al desarrollo de habilidades artesanales.
Las civilizaciones antiguas, como la sumeria, egipcia, griega y romana, dieron paso a la formación de ciudades y sociedades más organizadas. Las comunidades se convirtieron en centros de comercio, gobierno y cultura. Se construyeron estructuras monumentales, como templos y palacios, que unificaron a las personas en torno a creencias religiosas y sistemas políticos.
Durante la Edad Media, las comunidades se organizaron en torno a sistemas feudales. Los señores feudales gobernaban sobre las tierras y las personas locales. Las aldeas y feudos eran autónomos en gran medida y se centraban en la agricultura y la autosuficiencia.
La Revolución Industrial marcó un cambio importante en la estructura de las comunidades. La industrialización dio lugar a la urbanización, con muchas personas dejando las zonas rurales para trabajar en fábricas en las ciudades.
En la era moderna, las comunidades han continuado evolucionando con avances tecnológicos y la globalización. Las redes sociales y las comunicaciones digitales han conectado a personas de todo el mundo, creando comunidades virtuales en línea.
### Bitcoin | Nostr y la chispa del constructor
Como ya vimos, un solo individuo puede inspirar a muchos otros, teniendo un efecto multiplicador. Esto no solo se traduce al mundo físico, por el contrario, esta directamente ligado a nuestra psicología, incluso podemos decir que va aun mas allá, adentrándonos en el terreno ideológico y espiritual.
Hasta hace no mucho, estábamos a merced de las grandes corporaciones que construían todo por nosotros, mientras esperábamos con ansias las nuevas actualizaciones de cada iteración de sus productos. Cada vez mas y mas nos hacíamos dependientes de dichas corporaciones sin quizás notarlo, poco a poco se fueron apoderando de nuestro tiempo y muy insidiosamente de nuestra personalidad e identidad.
Gracias a las alternativas presentadas hoy en día y a los individuos que inspiran a otros, existe la posibilidad de construir algo que va mas allá de las grandes corporaciones, porque transciende no solo el nivel físico y digital, sino que también transciende a los individuos que aportan a la comunidad. Estoy hablando por supuesto de Nostr, y como los incentivos están alineados gracias a Bitcoin.
Pongamos como ejemplo un par de nombres para ilustrar como individuos que inspirar pueden crear una chispa que se extiende a cada persona dentro de la comunidad.
Personajes como nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft nostr:npub1utx00neqgqln72j22kej3ux7803c2k986henvvha4thuwfkper4s7r50e8 nostr:npub1v0lxxxxutpvrelsksy8cdhgfux9l6a42hsj2qzquu2zk7vc9qnkszrqj49 nostr:npub107jk7htfv243u0x5ynn43scq9wrxtaasmrwwa8lfu2ydwag6cx2quqncxg (entre muchos otros que podría mencionar pero todo el articulo seria una lista de nombres) han inspirado a otros desarrolladores, creadores de contenido (y todas las otras especializaciones que te puedas imaginar…) A construir sobre este protocolo. Incluso, personas como el caso mas reciente de nostr:npub1m64hnkh6rs47fd9x6wk2zdtmdj4qkazt734d22d94ery9zzhne5qw9uaks han encontrado inspiración para aprender a programar sobre estos mismos rieles.
> nostr:nevent1qqs8fe938k7j5sxcprrv89ezpu09m9pzm90f0sq24hnwlwu0rmn09qcpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxg5vtygh
La chispa del constructor en palabras mas concisas es: **Inspiración multiplicadora en pos de la productividad y por ende, del crecimiento de una comunidad.**
Sin Bitcoin y Lightning Network, esto seria posible, pero mucho menos efectivo debido a que las personas detrás de toda labor que este enfocada en creación de contenido, desarrollo, etc. Tienen que comer.
### Conclusión
La chispa del constructor radica en la inspiración individual que impulsa a la acción colectiva. Desde la evolución de la construcción hasta las comunidades digitales, **el poder de un individuo inspirado puede moldear el presente y el futuro de las comunidades en todo el mundo.**
-

@ 21ac2956:09d1e2df
2025-01-22 15:27:00
## [kakoi](https://github.com/betonetojp/kakoi) の仕様についてのメモ
### キーボード操作
* 左手での操作に最適化
| キー | 動作 |
|:-|:-|
| ESC | 設定画面 |
| F1 / F12 | ポストバーの表示と非表示 |
| F2 | 時間の表示と非表示 |
| F3 | ユーザーアイコンの表示と非表示 |
| F4 | 名前の表示と非表示 |
| F5 | Geminiによるタイムラインまとめ画面を表示 |
| F9 / Z | コンテンツの折り返し表示の切り替え (余白ダブルクリックでも動作) |
| F10 | ユーザーリストとキーワード通知の設定画面 (余白右クリックでも動作) |
| F11 | メイン画面の表示と非表示 (ポストバー表示) |
| Shift + W | イベント最上行へ移動 |
| W / ↑| イベント選択上移動 |
| S / ↓ | イベント選択下移動 |
| Shift + S | イベント最下行へ移動 |
| A / ← | Webビューを開く (イベントを右クリックでも動作) |
| F / → | リアクションを送信 (イベントをダブルクリックでも動作) |
| 1 ~ 0 | リアクションを選択 |
| R | 返信 |
| B | リポスト |
| Q | 引用 |
| C | Webビューを閉じる |
| Ctrl + Shift + A | メイン画面をアクティブにする |
### タイムライン
* kind:1, 6, 7, 16を取得して表示する
* フォロイーの名前の前には * が付く
### フォローリスト(kind:3)
* 参照のみで更新はしない
* F10 で開くユーザーリストでユーザーを選択し petname セルをクリックすることで未フォローユーザーにもペットネームを設定可能(ローカル保存)
### プロフィール(kind:0)
* F10 で開くユーザーリストでユーザーを選択し picture セルをクリックすることでユーザーのアイコン表示を変更可能(ローカル保存)
### 返信([NIP-10](https://github.com/nostr-protocol/nips/blob/master/10.md) kind:1)
* kakoi のタイムラインに流れるすべてのイベント種に返信可能とする
* スレッドを考慮せず、単一イベントへの単発返信とする
* e タグは marker と返信先 pubkey は設定していない。 relay-url には空文字を設定
```json
["e", "返信先 event-id", ""]
```
* p タグは 返信先 pubkey ひとつだけを指定
### リポスト([NIP-18](https://github.com/nostr-protocol/nips/blob/master/18.md) kind:6 , 16)
* kakoi のタイムラインに流れるすべてのイベント種をリポスト可能
* kind:1はkind:6。その他はkind:16でリポストする
* e タグは relay-url に空文字を設定
```json
["e", "リポスト元 event-id", ""]
```
### 引用([NIP-18](https://github.com/nostr-protocol/nips/blob/master/18.md) kind:1)
* q タグは relay-url に空文字を設定
```json
["q", "引用元 event-id", ""]
```
-

@ b17fccdf:b7211155
2025-01-21 17:02:21
The past 26 August, Tor [introduced officially](https://blog.torproject.org/introducing-proof-of-work-defense-for-onion-services/) a proof-of-work (PoW) defense for onion services designed to prioritize verified network traffic as a deterrent against denial of service (DoS) attacks.
~ > This feature at the moment, is [deactivate by default](https://gitlab.torproject.org/tpo/core/tor/-/blob/main/doc/man/tor.1.txt#L3117), so you need to follow these steps to activate this on a MiniBolt node:
* Make sure you have the latest version of Tor installed, at the time of writing this post, which is v0.4.8.6. Check your current version by typing
```
tor --version
```
**Example** of expected output:
```
Tor version 0.4.8.6.
This build of Tor is covered by the GNU General Public License (https://www.gnu.org/licenses/gpl-3.0.en.html)
Tor is running on Linux with Libevent 2.1.12-stable, OpenSSL 3.0.9, Zlib 1.2.13, Liblzma 5.4.1, Libzstd N/A and Glibc 2.36 as libc.
Tor compiled with GCC version 12.2.0
```
~ > If you have v0.4.8.X, you are **OK**, if not, type `sudo apt update && sudo apt upgrade` and confirm to update.
* Basic PoW support can be checked by running this command:
```
tor --list-modules
```
Expected output:
```
relay: yes
dirauth: yes
dircache: yes
pow: **yes**
```
~ > If you have `pow: yes`, you are **OK**
* Now go to the torrc file of your MiniBolt and add the parameter to enable PoW for each hidden service added
```
sudo nano /etc/tor/torrc
```
Example:
```
# Hidden Service BTC RPC Explorer
HiddenServiceDir /var/lib/tor/hidden_service_btcrpcexplorer/
HiddenServiceVersion 3
HiddenServicePoWDefensesEnabled 1
HiddenServicePort 80 127.0.0.1:3002
```
~ > Bitcoin Core and LND use the Tor control port to automatically create the hidden service, requiring no action from the user. We have submitted a feature request in the official GitHub repositories to explore the need for the integration of Tor's PoW defense into the automatic creation process of the hidden service. You can follow them at the following links:
* Bitcoin Core: https://github.com/lightningnetwork/lnd/issues/8002
* LND: https://github.com/bitcoin/bitcoin/issues/28499
---
More info:
* https://blog.torproject.org/introducing-proof-of-work-defense-for-onion-services/
* https://gitlab.torproject.org/tpo/onion-services/onion-support/-/wikis/Documentation/PoW-FAQ
---
Enjoy it MiniBolter! 💙
-

@ b17fccdf:b7211155
2025-01-21 16:56:24
It turns out that Ubuntu Linux installations of Ubuntu 23.04, 22.04.3 LTS, and installs done since April 2023 that accepted the Snap version update haven't been following Ubuntu's own recommended security best practices for their security pocket configuration for packages.
A new Subiquity release [was issued](https://github.com/canonical/subiquity/releases/tag/23.09.1) to fix this problem while those on affected Ubuntu systems already installed are recommended to manually edit their `/etc/apt/sources.list` file.
If you didn't install MiniBolt recently, **you are affected by this bug**, and we need to fix that manually if not we want to install all since cero. Anyway, if you installed Minibolt recently, we recommend you review that.
Follow these easy steps to review and fix this:
* Edit the `sources-list` file:
```
sudo nano /etc/apt/sources.list
```
* Search now for every line that includes '-security' (without quotes) (normally at the end of the file) and change the URL to --> http://security.ubuntu.com/ubuntu
~ > For example, from http://es.archive.ubuntu.com/ubuntu (or the extension corresponding to your country) to --> http://security.ubuntu.com/ubuntu
~> Real case, Spain location, **before fix**:
```
deb http://es.archive.ubuntu.com/ubuntu jammy-security main restricted
# deb-src http://es.archive.ubuntu.com/ubuntu jammy-security main restricted
deb http://es.archive.ubuntu.com/ubuntu jammy-security universe
# deb-src http://es.archive.ubuntu.com/ubuntu jammy-security universe
deb http://es.archive.ubuntu.com/ubuntu jammy-security multiverse
# deb-src http://es.archive.ubuntu.com/ubuntu jammy-security multiverse
```
**After fix:**
```
deb http://security.ubuntu.com/ubuntu jammy-security main restricted
# deb-src http://es.archive.ubuntu.com/ubuntu jammy-security main restricted
deb http://security.ubuntu.com/ubuntu jammy-security universe
# deb-src http://es.archive.ubuntu.com/ubuntu jammy-security universe
deb http://security.ubuntu.com/ubuntu jammy-security multiverse
# deb-src http://es.archive.ubuntu.com/ubuntu jammy-security multiverse
```
**Save and exit**
**Note:** If you have already these lines changed, you are not affected by this bug, and is not necessary to do anything. Simply exit the editor by doing Ctrl-X
* Finally, type the next command to refresh the repository pointers:
```
sudo apt update
```
* And optionally take the opportunity to update the system by doing:
```
sudo apt full-upgrade
```
More context:
* https://wiki.ubuntu.com/SecurityTeam/FAQ#What_repositories_and_pockets_should_I_use_to_make_sure_my_systems_are_up_to_date.3F
* https://bugs.launchpad.net/subiquity/+bug/2033977
* https://www.phoronix.com/news/Ubuntu-Security-Pocket-Issue
-

@ b17fccdf:b7211155
2025-01-21 16:49:27
### **What's changed**
* New method for Bitcoin Core signature check, click ~ >[HERE](https://minibolt.minibolt.info/bitcoin/bitcoin/bitcoin-client#signature-check)< ~
* GitHub repo of Bitcoin Core release attestations (Guix), click ~ >[HERE](https://github.com/bitcoin-core/guix.sigs)< ~
---
**History:**
~ > PR that caused the broken and obsolescence of the old signature verification process, click ~ >[HERE](https://github.com/bitcoin/bitcoin/pull/26598)< ~
~ > New GitHub folder of Bitcoin Core repo that stores the signatures, click ~ >[HERE](https://github.com/bitcoin-core/guix.sigs/tree/main/builder-keys)< ~
---
Thanks to nostr:npub1gzuushllat7pet0ccv9yuhygvc8ldeyhrgxuwg744dn5khnpk3gs3ea5ds for building the command that made magic possible 🧙♂️🧡
---
Enjoy it MiniBolter! 💙
-

@ b17fccdf:b7211155
2025-01-21 16:40:01
### **Important notice to MiniBolt node runners:**
~ > It turns out that the I2P devs have opened an issue on the Bitcoin Core GitHub repo commenting that because they gave the option to enable the `notransit=true` parameter in the official documentation:
> [...] If you prefer not to relay any public I2P traffic and only allow I2P traffic from programs connecting through the SAM proxy, e.g. Bitcoin Core, you can set the no transit option to true [...] are having a heavy load on the I2P network since last December 19. Also comment that it is advisable to share as much bandwidth and transit tunnels as we can, to increase anonymity with coverage traffic, by contributing more to the I2p network than we consume.
So they ask that we deactivate that option that you use activated. With all this, he already updated the "Privacy" section by removing that setting.
The steps to delete this configuration once we have already configured it, are the following:
* With the "admin" user, stop i2pd:
```
sudo systemctl stop i2pd
```
* Comment line 93 with "#" at the beginning of it (notransit = true), save and exit
```
sudo nano /var/lib/i2pd/i2pd.conf --line numbers
```
* Start i2pd again:
```
sudo systemctl start i2pd
```
* And that's it, you could take a look at Bitcoin Core to see that it has detected i2pd running again after the reboot with:
```
tail --lines 500 -f /home/bitcoin/.bitcoin/debug.log
```
~ > If you don't see that I2P is up in Bitcoin Core after the restart, `sudo systemctl restart bitcoind` and look again at the logs of the same.
---
More info in the rollback commit, see ~> [HERE](https://github.com/twofaktor/minibolt/commit/99cae67a5150bb5b7deae3674cc958eb31c74a75) < ~
-

@ b17fccdf:b7211155
2025-01-21 16:30:11
> Your MiniBolt is on a home local network, you want to expose it on the public Internet (clearnet) without exposing your public IP, without Firewall rules, without NAT port forwarding, without risk, easy and cheap?
---
Go to the bonus guide by clicking ~ >[HERE](https://minibolt.minibolt.info/bonus-guides/system/cloudflare-tunnel) <~
---
Enjoy it MiniBolter! 💙
-

@ b17fccdf:b7211155
2025-01-21 16:23:44
> Build your nostr relay step by step on your MiniBolt node! (**easily adaptable to other environment**)
No need to trust anyone else! Be sovereign!
~> Go to the bonus guide by clicking ~> [HERE](https://minibolt.minibolt.info/bonus-guides/nostr/nostr-relay)< ~
~> This guide includes a complete [extra section](https://minibolt.minibolt.info/bonus-guides/nostr/nostr-relay#extras-optional) to cover the different processes for using nostr **as a user and relay operator**.
---
PS: The MiniBolt project has its FREE relay, be free to connect by adding to your favorite client the next address: `wss://relay.minibolt.info`
~> Let a review on [noStrudel](https://nostrudel.ninja/#/r/wss%3A%2F%2Frelay.minibolt.info) or [Coracle](https://coracle.social/relays/relay.minibolt.info) of your experience using it.
---
Remember, Nostr is freedom! Stay resilient! 💜 🛡️💪
-

@ b17fccdf:b7211155
2025-01-21 16:15:51
### What's changed
A bonus guide to get a quick overview of the system status with the most relevant data about the services on the main guide.
-----------
#### ➕Additional extra sections (optional) to:
* [Show on login](https://minibolt.minibolt.info/bonus-guides/system/system-overview#show-on-login-optional)
* [Get the channel.db size of an old LND bbolt database backend](https://minibolt.minibolt.info/bonus-guides/system/system-overview#get-the-channel.db-size-of-an-old-lnd-bbolt-database-backend)
* [Use MobaXterm compatibility version](https://minibolt.minibolt.info/bonus-guides/system/system-overview#use-the-mobaxterm-compatibility-version)
🔧 **GitHub PR related**: https://github.com/minibolt-guide/minibolt/pull/97
Σ **Dedicated GitHub repository**: https://github.com/minibolt-guide/system_overview
-----------
#### 🫂Acknowledgments
This is a fork of the [minibolt_info repository](https://github.com/rmnscb/minibolt_info), the main developer of this project is [rmnscb](https://github.com/rmnscb), a member of the MiniBolt community, all the merits go to him. Thank you for your contribution 🧡🫂
-----------
-> [CLICK HERE](https://minibolt.minibolt.info/bonus-guides/system/system-overview) <- to go to the bonus guide
-----------
Enjoy it MiniBolter! 💙
-

@ 604e96e0:20279eb2
2023-08-11 18:39:36
notacomment allows you to zap nostr notes when you comment on them. In order to use notacomment, you have to run a script yourself either on your own computer or in the cloud somewhere. To get started open https://github.com/SamSamskies/notacomment in a browser tab.
At this point, I'm sure a lot of you are feeling like this:

Let's breakdown the instructions from the README.
## Prerequisites
Node.js and npm - I suggest installing the latest Node.js LTS version from https://nodejs.org. That should also install npm.
Once installation is complete, open your terminal. On a Mac you can press cmd + spacebar and type in `terminal` to open the terminal. On other platforms, you'll have to ask ChatGPT 😂
.
To verify installation of Node.js type `node -v`. To verify installation type `npm -v`.
It should look something like this:

Leave the terminal open.
## Downloading the code to your computer
The easiest way to download the code is to download the zip file from the GitHub repo. Remember that first link I told you to open? That's the GitHub repo. Click the green button that says `Code` on it and click `Download ZIP` from the menu.

Now unzip the file and then navigate to the folder in the terminal. To navigate to the folder use the `cd` command. If you unzipped the folder in the `Downloads` folder, you can navigate to the folder by typing `cd ~/Downloads/notacomment-main/`.
## Usage With Strike
1. Create an account with Strike if you don't already have one https://strike.me/download/
1. Get a Strike API key with all the payment scopes from https://dashboard.strike.me/
1. Create a .env file and provide NOSTR_NSEC and STRIKE_API_KEY values (see .env.example)
1. Install the dependencies using npm or yarn or whatever your heart desires
1. Make sure you have money in your Strike account
1. Run the script `npm start`
Keep in mind that Strike pays the invoices from your cash balance. This means the payment rounds up to the nearest cent when paying an invoice, so if you set the zap amount to 1 sat, you'll be sending more money to Strike than the person you are zapping with every zap.
## Usage With LNbits
I recommend making a separate wallet from your main LNbits wallet for usage with notacomment in case you accidentally leak the admin key.
1. Create a .env file and provide NOSTR_NSEC, LNBITS_ADMIN_KEY, and LNBITS_URL values (see .env.example)
1. Install the dependencies using npm or yarn or whatever your heart desires
1. Make sure you have sats in your LNbits wallet
1. Run the script `npm start`
## Usage With Nostr Wallet Connect
1. Create a NWC connection string using something like https://nwc.getalby.com/
1. Create a .env file and provide NOSTR_NSEC and NWC_CONNECTION_STRING values (see .env.example)
1. Install the dependencies using npm or yarn or whatever your heart desires
1. Make sure you have sats in your wallet that you generated the NWC connection string with
1. Run the script `npm start`
<br />
<br />
Screenshot of terminal with commands to install dependencies, create .env file, open .env file, and start the script:

-

@ e3168078:10f13b2c
2025-01-21 15:44:45
ノス!
最近Umbrel上のn8nを使ってstacker newsの記事を要約するNostr botを作ってみました。
その際にFirecrawlというスクレイピングのSaaSを使っていたんですがセルフホストできるようなので試してみました。
Firecrawlは動的なページも読めたりマークダウンへの変換をしてくれますが無料プランだと1ヶ月500ページの制限があり、セルフホストすれば気兼ねなく使えます!
今回はUmbrel上のPortainerというアプリを使ってFirecrawlを動かせたのでその記録です。
## 手順
まずはUmbrelにPortainerアプリをインストールします。
Poratinerは今回初めて使ったんですが独自のDockerコンテナをUmbrelで動かす際に推奨されているアプリのようです。

アプリを開いてパスワードの初期設定などを済ませるとダッシュボードが表示されるかと思います。
ここでStackという機能を使ってFirecrawlのDocker composeを一括で取り込むことができます。
新しいStackを作成する画面で以下を入力します。
Repository URL: https://github.com/mendableai/firecrawl
Repository reference: refs/heads/main
Compose path: docker-compose.**yaml** (デフォルトがymlになっててハマりました…)

上記に加えてenv varを設定する必要があるんですがPortainerでは上記の画像下部にあるように "Load Variables from .env file" からenvファイルを選択できます。
[Firecrawlのgithub](https://github.com/mendableai/firecrawl/blob/main/SELF_HOST.md)にあるように apps/api/.env.example をダウンロードし以下の内容を更新しPortainerに取り込ませます。
```
USE_DB_AUTHENTICATION=false
TEST_API_KEY=fc-test-key
```
あとはDeploy the stackを押して少し待つとfirecrawlのセットアップ完了です。
## 確認
動作テストにはUmbrelの設定からAdvanced Settings -> Terminal -> Umbrel OSを開き以下のコマンドを実行ししマークダウンが返って来れば成功です。
```
$ curl -X POST http://localhost:3002/v1/scrape -H 'Authorization: Bearer fc-test-key' -H 'Content-Type: application/json' -d '{
"url": "https://example.com",
"formats": ["markdown"]
}'
{"success":true,"data":{"markdown":"Example Domain\n==============\n\nThis domain is for use in illustrative examples in documents. You may use this domain in literature without prior coordination or asking for permission.\n\n[More information...](https://www.iana.org/domains/example)","metadata":{"title":"Example Domain","ogLocaleAlternate":[],"scrapeId":"7c196348-6561-4ebb-bb8a-9121a29c64b5","viewport":"width=device-width, initial-scale=1","sourceURL":"https://example.com","url":"https://example.com/","statusCode":200}}}
```
またn8n等のUmbrelの他のアプリ(コンテナ)から利用する場合はlocalhostがコンテナ自身になってしまうので別のIP等(172.17.0.1)を使う必要があるのでご注意ください。
([参考](https://community.n8n.io/t/the-service-refused-the-connection-perhaps-it-is-offline-n8n-and-nocodb/33587?utm_source=chatgpt.com))
以上でUmbrel上でのFirecrawlセルフホストができるようになりn8nからも制限なく使えるようになりました。
-

@ b17fccdf:b7211155
2025-01-21 18:42:14
Some guides on MiniBolt / RaMiX have suffered some modifications and need additional instructions to migrate. Here is a summary:
🔘 New installation/update instructions of [BTC RPC Explorer](https://minibolt.minibolt.info/bitcoin/bitcoin/blockchain-explorer) to avoid [this issue](https://github.com/janoside/btc-rpc-explorer/issues/668).
🔘 New installation/update method of [Node + NPM](https://minibolt.minibolt.info/bonus-guides/system/nodejs-npm).
🔘 New installation/update method of [PostgreSQL](https://minibolt.minibolt.info/bonus-guides/system/postgresql) ~ > **Attention!** If you installed PostgreSQL **after 30/09/2024**, you do not need to follow these steps related to PostgreSQL.
---
## Update Nodejs + NPM to the latest LTS version (using the new method)
> Guide related: [Node + NPM](https://minibolt.minibolt.info/bonus-guides/system/nodejs-npm)
> **Context:** The installation/upgrade section of this guide has suffered some modifications, so to upgrade to the latest LTS released version using the new installation method, you need to follow the next steps:
* Stop the Nodejs + NPM dependencies:
```
sudo systemctl stop thunderhub btcrpcexplorer
```
* With user **admin**, update the packages and upgrade to keep up to date with the OS, press "y" and ENTER when needed or ENTER directly:
```
sudo apt update && sudo apt full-upgrade
```
* Change to a temporary directory which is cleared on reboot:
```
cd /tmp
```
* Set the environment variable of the version:
```
VERSION=22
```
* We will use the new NodeSource Node.js Binary Distributions repository [instructions](https://github.com/nodesource/distributions?tab=readme-ov-file#using-ubuntu-nodejs-22). Download the setup script:
```
curl -fsSL https://deb.nodesource.com/setup_$VERSION.x -o nodesource_setup.sh
```
* Run the setup script:
```
sudo -E bash nodesource_setup.sh
```
* Update the package manager and update Node.js + NPM to the latest LTS version:
```
sudo apt update && sudo apt full-upgrade
```
* Check the correct update of NodeJS:
```
node -v
```
**Example** of expected output:
```
v22.12.0
```
* Check the correct installation of NPM:
```
npm -v
```
**Example** of expected output:
```
10.9.0
```
* **(Optional)** Delete the setup script:
```
rm nodesource_setup.sh
```
* Start again the Nodejs + NPM dependencies:
```
sudo systemctl start thunderhub btcrpcexplorer
```
-----------
## Update BTC RPC Explorer to the latest version
> Guide related: [2.3 Blockchain explorer: BTC RPC Explorer](https://minibolt.minibolt.info/bitcoin/bitcoin/blockchain-explorer)
> **Context:** After [this notice](https://t.me/minibolt_news/37), if you deleted the `deprecatedrpc=warnings` flag because it is no longer necessary, it is probably that the ["**Node Details**"](https://explorer.minibolt.info/node-details) section of the BTC RPC Explorer got you [this error](https://github.com/janoside/btc-rpc-explorer/issues/668), this is because after the Bitcoin Core v28 update, just like LND, Electrs and other services, they have needed an update to remain compatible. BTC RPC Explorer was updated on this [commit](https://github.com/janoside/btc-rpc-explorer/commit/01585b7825afe0eb3e8f6cf39e9e135a20c8c2dd), but an official version that includes this correction has not been officially released yet. To fix this, it is necessary to **point to the current source code** and not the one related to the last released version (3.4.0).
**~ >** Get instructions to get this by following these steps and fix the issue ~ > [HERE](https://minibolt.minibolt.info/bitcoin/bitcoin/blockchain-explorer#upgrade) < ~
-----------
## Update PostgreSQL (server instance migration & others)
> Guide related: [PostgreSQL](https://minibolt.minibolt.info/bonus-guides/system/postgresql)
> **Attention!!** If you installed PostgreSQL **after 30/09/2024**, **you don't need to do anything**, and the next steps don't apply to your case.
> **Context:** With each major version jump of PostgreSQL, the update creates a new and dedicated cluster and folder with the number of each version. Also, the changes made between versions cause the need to migrate the database, that is, from one cluster to another, with a specific tool. This was unknown at the beginning, before creating the MiniBolt PostgreSQL installation guide, so a specific folder for the versions was not created. The [installation section](https://minibolt.minibolt.info/bonus-guides/system/postgresql#installation) was changed past **30/09/2024** to use this new method, but people who followed the PostgreSQL installation before that, need to do things to be in line with the MiniBolt guide.
Following the next steps, we are going to do the necessary migrations, the summary is the next:
**1.** Migrate the PostgreSQL database to a new location (*a dedicated folder for each version*).
**2.** Migrate from PostgreSQL server version 16 to 17.
---
**Verification**
If you are not sure whether you installed PostgreSQL before or after the mentioned date (**30/09/2024**), you can check as follows:
* With user `admin` list the existing clusters:
```
pg_lsclusters
```
Expected output if you installed PostgreSQL **after 30/09/2024**, **(you don't need do anything)**:
```
Ver Cluster Port Status Owner Data directory Log file
17 main 5432 online postgres /data/postgresdb/17 /var/log/postgresql/postgresql-17-main.log
```
Expected output if you installed PostgreSQL **before 30/09/2024**, and performed a full upgrade of the MiniBolt with **`sudo apt update && sudo apt full-upgrade`**, **(you need to follow the next steps)**:
```
Ver Cluster Port Status Owner Data directory Log file
16 main 5432 online postgres /data/postgresdb /var/log/postgresql/postgresql-16-main.log
17 main 5433 down postgres /var/lib/postgresql/17/main /var/log/postgresql/postgresql-17-main.log
```
Expected output **if you have not** performed a full upgrade of the MiniBolt with `sudo apt update && sudo apt full-upgrade` **since 26/09/2024 (the PostgreSQL v17 release)** (unlikely case) **(you need to follow the next steps)**:
```
Ver Cluster Port Status Owner Data directory Log file
16 main 5432 online postgres /data/postgresdb /var/log/postgresql/postgresql-16-main.log
```
---
### **Migrate the PostgreSQL database to the new location**
> (Only if you installed PostgreSQL following the MiniBolt guide **before 30/09/2024**)
* Show the existing clusters to show the current path of the database:
```
pg_lsclusters
```
**~ >** Expected output **if you have not** performed a full upgrade of the MiniBolt with `sudo apt update && sudo apt full-upgrade` **since 26/09/2024 (PostgreSQL v17 release)** (unlikely):
```
Ver Cluster Port Status Owner Data directory Log file
16 main 5432 online postgres /data/postgresdb /var/log/postgresql/postgresql-16-main.log
```
**~ >** Expected output **if you have** performed a full upgrade of the MiniBolt with `sudo apt update && sudo apt full-upgrade` **since 26/09/2024 (PostgreSQL v17 release)** (most likely):
```
Ver Cluster Port Status Owner Data directory Log file
16 main 5432 online postgres /data/postgresdb /var/log/postgresql/postgresql-16-main.log
17 main 5433 down postgres /var/lib/postgresql/17/main /var/log/postgresql/postgresql-17-main.log
```
~ > Check the current "Data directory" column value of the cluster 16 **(/data/postgresdb)** for the future, we have changed this to a dedicated folder for each version (`/data/postgresdb/16`, `/data/postgresdb/17`, `/data/postgresdb/18`, etc.)
* Stop the PostgreSQL dependencies and the PostgreSQL version 16 cluster:
```
sudo systemctl stop thunderhub scbackup btcpay lnd nbxplorer nostrelay cloudflared postgresql@16-main
```
~ > Ensure all services are successfully stopped by monitoring the logs of each service, especially **lnd** ~ > `journalctl -fu lnd`.
* Monitor the logs of the PostgreSQL version 16 cluster to ensure that it has been stopped gracefully:
```
journalctl -fu postgresql@16-main
```
Expected output:
```
minibolt systemd[1]: Stopping PostgreSQL Cluster 16-main...
minibolt systemd[1]: postgresql@16-main.service: Deactivated successfully.
minibolt systemd[1]: Stopped PostgreSQL Cluster 16-main.
```
~ > Press `Ctrl + C` to continue.
* Create a temporary directory in a place out of the `/data/postgresdb` to move the data securely:
```
sudo mkdir /tmp/postgresdb-temp
```
* Sync the existing data of the current directory `/data/postgresdb` to this temporary directory:
```
sudo rsync -av /data/postgresdb/ /tmp/postgresdb-temp/
```
Example of expected output:
```
[...]
pg_xact/
pg_xact/0000
[...]
sent 40,397,103 bytes received 18,619 bytes 80,831,444.00 bytes/sec
total size is 40,330,914 speedup is 1.00
```
~ > Wait until the prompt shows up again.
* Change to the user `root` temporary:
```
sudo su
```
* Delete the content of the folder that hosted the original database:
```
sudo rm -rf /data/postgresdb/*
```
* Come back to the `admin` user:
```
exit
```
* Create a new specific and dedicated folder to the version number and to be in line with the [new and current storage method](https://minibolt.minibolt.info/bonus-guides/system/postgresql#create-data-folder) of the current guide:
```
sudo mkdir /data/postgresdb/16
```
* Assign as the owner to the user `postgres`:
```
sudo chown postgres:postgres /data/postgresdb/16
```
* Assign the correct permissions to the folder:
```
sudo chmod 700 /data/postgresdb/16
```
* Now you can sync the data from the temporary directory to `/data/postgresdb/16` in a secure way since this directory is not inside the source directory:
```
sudo rsync -av /tmp/postgresdb-temp/ /data/postgresdb/16/
```
Example of expected output:
```
[...]
pg_xact/
pg_xact/0000
[...]
sent 40,397,103 bytes received 18,619 bytes 80,831,444.00 bytes/sec
total size is 40,330,914 speedup is 1.00
```
~ > Wait until the prompt shows up again.
* Modify the configuration file (`postgresql.conf`) of the PostgreSQL to point to the new directory folder created:
```
sudo nano +42 /etc/postgresql/16/main/postgresql.conf
```
* Replace the data directory location to match with the new path:
```
data_directory = '/data/postgresdb/16'
```
* Start again the PostgreSQL service instance:
```
sudo systemctl start postgresql@16-main
```
* Monitor the logs of the PostgreSQL version 16 cluster to ensure that it works fine:
```
journalctl -fu postgresql@16-main
```
Expected output:
```
minibolt systemd[1]: Starting PostgreSQL Cluster 16-main...
minibolt systemd[1]: Started PostgreSQL Cluster 16-main.
```
~ > Press `Ctrl + C` to continue.
* Check the new database location with:
```
pg_lsclusters
```
~ > Expected output **if you have not** performed a full upgrade of the MiniBolt with `sudo apt update && sudo apt full-upgrade` **since 26/09/2024** (unlikely):
```
Ver Cluster Port Status Owner Data directory Log file
16 main 5432 online postgres /data/postgresdb/16 /var/log/postgresql/postgresql-16-main.log
```
~ > Expected output **if you have** performed a full upgrade of the MiniBolt with `sudo apt update && sudo apt full-upgrade` **since 26/09/2024** (most likely):
```
Ver Cluster Port Status Owner Data directory Log file
16 main 5432 online postgres /data/postgresdb/16 /var/log/postgresql/postgresql-16-main.log
17 main 5433 down postgres /var/lib/postgresql/17/main /var/log/postgresql/postgresql-17-main.log
```
~ > Check the new path on the "Data directory" column value of the cluster version 16, now **(/data/postgresdb/16)**.
* Start again the PostgreSQL dependencies services:
```
sudo systemctl start lnd nbxplorer btcpay thunderhub scb-backup nostr-relay cloudflared
```
~ > Check all work fine with the logs of each service, especially **lnd** ~ > `journalctl -fu lnd`.
* Stop again the PostgreSQL dependencies services, to continue working:
```
sudo systemctl stop thunderhub scbackup btcpay lnd nbxplorer nostrelay cloudflared
```
~ > Ensure all services are successfully stopped by monitoring the logs of each service, especially **lnd** ~ > `journalctl -fu lnd`.
### **Migrate from PostgreSQL server version 16 to 17**
> (Only if you installed PostgreSQL following the MiniBolt guide **before 30/09/2024**)
> **Context:** If you fully updated your OS after **26/09/2024** (the PostgreSQL v17 launched), using `sudo apt update && sudo apt full-upgrade`, and **you installed PostgreSQL before that date** following [the PostgreSQL MiniBolt guide](https://minibolt.minibolt.info/bonus-guides/system/postgresql), it is likely that you now are using the old version (v16) of the PostgreSQL server instance.
To confirm that, follow the next steps:
**Check the PostgreSQL server version in use**
* With the user `admin`, enter the psql (PostgreSQL CLI):
```
sudo -u postgres psql
```
* Enter the next command to get the server version:
```
SELECT version();
```
Expected output:
```
version
-----------------------------------------------------------------------------------------------------------------------------------
PostgreSQL 16.6 (Ubuntu 16.6-1.pgdg22.04+1) on x86_64-pc-linux-gnu, compiled by gcc (Ubuntu 11.4.0-1ubuntu1~22.04) 11.4.0, 64-bit
(1 row)
```
~ > Check the previous version is "PostgreSQL 16.6" (an outdated version of the PostgreSQL server), the latest version is PostgreSQL 17.2. 🔧✅ We are going to fix this in the next steps.
* Come back to the `admin` user bash prompt:
```
\q
```
* List the cluster to show the state of the both PostgreSQL server instances:
```
pg_lsclusters
```
~ > Expected output **if you have not** performed a full upgrade of the MiniBolt with `sudo apt update && sudo apt full-upgrade` **since 26/09/2024** (unlikely):
```
Ver Cluster Port Status Owner Data directory Log file
16 main 5432 online postgres /data/postgresdb/16 /var/log/postgresql/postgresql-16-main.log
```
~ > Expected output **if you have** performed a full upgrade of the MiniBolt with `sudo apt update && sudo apt full-upgrade` **since 26/09/2024** (most likely):
```
Ver Cluster Port Status Owner Data directory Log file
16 main 5432 online postgres /data/postgresdb/16 /var/log/postgresql/postgresql-16-main.log
17 main 5433 down postgres /var/lib/postgresql/17/main /var/log/postgresql/postgresql-17-main.log
```
**Update PostgreSQL**
If you haven't done so before, make sure to update the OS (PostgreSQL included to the latest version 17):
* With user `admin`, fully update the OS with the package manager:
```
sudo apt update && sudo apt full-upgrade
```
~ > Press "y" and enter or directly enter when the prompt asks you.
-----------
#### **PostgreSQL server migration**
* Stop all existing clusters:
```
sudo systemctl stop postgresql@16-main postgresql@17-main
```
* Create a new database destination folder for the v17 cluster ready for migration from v16:
```
sudo mkdir /data/postgresdb/17
```
* Assign the owner as the postgres user:
```
sudo chown postgres:postgres /data/postgresdb/17
```
* Assign the correct permissions:
```
sudo chmod 700 /data/postgresdb/17
```
* Delete the cluster created by default for v17:
```
sudo -u postgres pg_dropcluster 17 main
```
* Update the systemd:
```
sudo systemctl daemon-reload
```
* Start the migration with the PostgreSQL migration tool:
```
sudo -u postgres pg_upgradecluster 16 main /data/postgresdb/17
```
**~ >** ⌛ This may take a lot of time depending on the existing database size (the nostr relay database especially) and your machine's performance; it is recommended to use [tmux](https://github.com/tmux/tmux). Wait until the prompt shows up again.
Example of expected output:
```
Restarting old cluster with restricted connections...
Notice: extra pg_ctl/postgres options given, bypassing systemctl for start operation
Creating new PostgreSQL cluster 17/main ...
/usr/lib/postgresql/17/bin/initdb -D /data/postgresdb/17 --auth-local peer --auth-host scram-sha-256 --no-instructions --encoding UTF8 --lc-collate en_US.UTF-8 --lc-ctype en_US.UTF-8 --locale-provider libc
The files belonging to this database system will be owned by user "postgres".
This user must also own the server process.
The database cluster will be initialized with locale "en_US.UTF-8".
The default text search configuration will be set to "english".
Data page checksums are disabled.
fixing permissions on existing directory /data/postgresdb/17 ... ok
creating subdirectories ... ok
selecting dynamic shared memory implementation ... posix
selecting default "max_connections" ... 100
selecting default "shared_buffers" ... 128MB
selecting default time zone ... Etc/UTC
creating configuration files ... ok
running bootstrap script ... ok
performing post-bootstrap initialization ... ok
syncing data to disk ... ok
Warning: systemd does not know about the new cluster yet. Operations like "service postgresql start" will not handle it. To fix, run:
sudo systemctl daemon-reload
Copying old configuration files...
Copying old start.conf...
Copying old pg_ctl.conf...
Starting new cluster...
Notice: extra pg_ctl/postgres options given, bypassing systemctl for start operation
Running init phase upgrade hook scripts ...
Roles, databases, schemas, ACLs...
set_config
------------
(1 row)
set_config
------------
(1 row)
Fixing hardcoded library paths for stored procedures...
Upgrading database postgres...
Fixing hardcoded library paths for stored procedures...
Upgrading database template1...
Stopping target cluster...
Stopping old cluster...
Disabling automatic startup of old cluster...
Starting upgraded cluster on port 5432...
Warning: the cluster will not be running as a systemd service. Consider using systemctl:
sudo systemctl start postgresql@17-main
Running finish phase upgrade hook scripts ...
vacuumdb: processing database "postgres": Generating minimal optimizer statistics (1 target)
vacuumdb: processing database "template1": Generating minimal optimizer statistics (1 target)
vacuumdb: processing database "postgres": Generating medium optimizer statistics (10 targets)
vacuumdb: processing database "template1": Generating medium optimizer statistics (10 targets)
vacuumdb: processing database "postgres": Generating default (full) optimizer statistics
vacuumdb: processing database "template1": Generating default (full) optimizer statistics
Success. Please check that the upgraded cluster works. If it does,
you can remove the old cluster with
pg_dropcluster 16 main
Ver Cluster Port Status Owner Data directory Log file
16 main 5433 down postgres /data/postgresdb/16 /var/log/postgresql/postgresql-16-main.log
Ver Cluster Port Status Owner Data directory Log file
17 main 5432 online postgres /data/postgresdb/17 /var/log/postgresql/postgresql-17-main.log
```
* Reload the systemd again:
```
sudo systemctl daemon-reload
```
* List the clusters to show the state:
```
pg_lsclusters
```
Expected output:
```
Ver Cluster Port Status Owner Data directory Log file
16 main 5433 down <unknown> /data/postgresdb/16 /var/log/postgresql/postgresql-16-main.log
17 main 5432 online <unknown> /data/postgresdb/17 /var/log/postgresql/postgresql-17-main.log
```
~> **Notes:**
* Don't worry about the <unknown> output of the "Owner" column.
* Note how the old 16 cluster has automatically gone into status "down" after the migration.
---
* Stop the version 17 cluster using the `pg_ctlcluster` tool, to then be able to run it and manage it with `systemd`:
```
sudo pg_ctlcluster 17 main stop
```
* List the clusters again to show the state:
```
pg_lsclusters
```
Expected output:
```
Ver Cluster Port Status Owner Data directory Log file
16 main 5433 down <unknown> /data/postgresdb/16 /var/log/postgresql/postgresql-16-main.log
17 main 5432 down <unknown> /data/postgresdb/17 /var/log/postgresql/postgresql-17-main.log
```
**~>** Note how the version 17 cluster has gone into status "down".
* Start the version 17 cluster with systemd:
```
sudo systemctl start postgresql@17-main
```
* Monitor the logs of the PostgreSQL version 17 cluster to ensure that it working fine with `systemd`:
```
journalctl -fu postgresql@17-main
```
Expected output:
```
minibolt systemd[1]: Starting PostgreSQL Cluster 17-main...
minibolt systemd[1]: Started PostgreSQL Cluster 17-main.
```
~ > Press `Ctrl + C` to continue.
* List the clusters again to show the state:
```
pg_lsclusters
```
Expected output:
```
Ver Cluster Port Status Owner Data directory Log file
16 main 5433 down <unknown> /data/postgresdb/16 /var/log/postgresql/postgresql-16-main.log
17 main 5432 online <unknown> /data/postgresdb/17 /var/log/postgresql/postgresql-17-main.log
```
**~>** Note how the version 17 cluster has come back into the status "online".
* Delete the version 16 (old and disused) cluster:
```
sudo pg_dropcluster 16 main
```
* List again the clusters to check the correct deletion:
```
pg_lsclusters
```
Expected output:
```
Ver Cluster Port Status Owner Data directory Log file
17 main 5432 online <unknown> /data/postgresdb/17 /var/log/postgresql/postgresql-17-main.log
```
**~>** Note how it no longer appears version 16 (old and disused) cluster.
**Check the PostgreSQL server version in use**
* With the user `admin`, enter the psql (PostgreSQL CLI):
```
sudo -u postgres psql
```
* Enter the next command to get the server version:
```
SELECT version();
```
Example of expected output:
```
version
-----------------------------------------------------------------------------------------------------------------------------------
PostgreSQL 17.2 (Ubuntu 17.2-1.pgdg22.04+1) on x86_64-pc-linux-gnu, compiled by gcc (Ubuntu 11.4.0-1ubuntu1~22.04) 11.4.0, 64-bit
(1 row)
```
**~ >** Check the previous version in use is now PostgreSQL 17.2 (the latest and current version of the PostgreSQL server at this moment).
* Come back to the `admin` user bash prompt:
```
\q
```
* Start again the PostgreSQL dependencies services:
```
sudo systemctl start lnd nbxplorer btcpay thunderhub scb-backup nostr-relay cloudflared
```
~ > Check all works fine with the logs of each service, especially **lnd** ~ > `journalctl -fu lnd`.
* **(Optional)** Once you have verified that everything is working correctly, you can delete the created PostgreSQL backup and temporary directory:
```
sudo rm -rf /tmp/postgresdb-temp
```
* Delete unnecessary packages:
```
sudo apt autoremove
```
~ > Press "y" and ENTER when needed or ENTER directly when the prompts ask you.
---
✅ That's it! If you have any questions or issues, you can go to any RRSS available for the MiniBolt project ~ > [HERE](https://minibolt.minibolt.info/#community) < ~
---
Only for MiniBolters! Enjoy it! 💙
-

@ 16d11430:61640947
2025-01-23 06:20:25
In this modern era of ceaseless clamor, where sensationalism reigns supreme, the plight of our elderly is one that demands urgent attention. These venerable souls, repositories of wisdom and keepers of our traditions, now find themselves prey to the cunning machinations of a new kind of colonialism—a digital imperialism, crafted by social media giants in unholy alliance with local third-party propagators of division. This exploitation tears at the fragile seams of our internationally stretched social fabric, threatening to unravel the fragile threads of unity and peace that bind humanity together.
The New Exploiters: Social Media and Local Gatekeepers
Once, it was the foreign trader who came bearing baubles to ensnare the unwitting; today, it is the algorithm, armed with the tools of manipulation, that preys upon the unsuspecting minds of the elderly. Social media companies, in their relentless pursuit of profit, have perfected the art of creating division. By partnering with local entities—be it political groups, media conglomerates, or data brokers—they turn our elders into unwitting soldiers in a war of narratives.
These local agents, familiar with the cultural fears and anxieties of their regions, amplify messages designed to provoke outrage and suspicion. For the elderly, who often rely on these platforms as a means of connection in their isolation, such messages become a poison. The news feed, crafted with precision by algorithms that prioritize engagement over truth, becomes a fertile ground for fear-mongering, paranoia, and mistrust.
Tugging at the Seams of Society
The bonds of human unity, forged through millennia of shared struggles and triumphs, are delicate. They depend on trust, understanding, and a sense of collective purpose. Yet, social media, in its pursuit of engagement, exploits every fracture, every difference, and every perceived slight. The elderly, with their memories of simpler times and their deeply ingrained cultural values, become ideal targets.
A post about economic inequality becomes a trigger for fear of financial ruin. A video about global migration is twisted to evoke xenophobia. Stories of political corruption are shared, reshared, and distorted, until the very institutions of democracy seem untrustworthy. These narratives, designed to provoke outrage and despair, pit neighbor against neighbor, generation against generation, and nation against nation.
A Call to Rekindle Social Harmony
Let us pause and ask ourselves: are we to stand idly by while this insidious force tears apart the very fabric of our society? Are we to abandon our elders to a world where every news cycle is a source of anxiety, every notification a harbinger of doom? No! We must take inspiration from the great reformers of our past, who believed in the power of truth and unity to overcome the most formidable adversaries.
The Path Forward
1. Restore the Spirit of Inquiry
Just as Raja Ram Mohan Roy called for the illumination of the mind through education, we must arm our elderly with the tools to discern truth from falsehood. Let media literacy be the new frontier of reform. Teach our elders to question, to verify, and to seek balanced perspectives, so they may break free from the clutches of sensationalism.
2. Break the Chains of Dependency
The chains that bind our elderly to these exploitative platforms must be loosened. Encourage them to find solace in real-world connections—in community gatherings, family conversations, and meaningful hobbies. Let us restore their faith in humanity, not as a divided collection of online tribes, but as a family united in its diversity.
3. Demand Accountability from the Exploiters
Just as Mahatma Gandhi stood against the economic and moral exploitation of India by the British Empire, so too must we hold these digital empires to account. Governments, civil societies, and individuals must demand transparency from social media companies. Let there be light in the dark recesses of their algorithms, so we may understand how they manipulate our thoughts and sow discord.
4. Rebuild the Tapestry of Social Unity
Swami Vivekananda urged us to see the divine in every individual, to rise above narrow divisions of caste, creed, and nationality. Today, that spirit of unity must extend to the digital realm. Let us create platforms and spaces where truth is valued above profit, where dialogue is fostered, and where the elderly can find comfort and connection without fear or anxiety.
A Vision for a Harmonious Tomorrow
The elderly are not relics of the past; they are the roots of our tree, anchoring us to the soil of history and tradition. When their peace of mind is disturbed, the entire tree shakes, its branches swaying precariously in the storm. If we are to weather this tempest of misinformation and division, we must protect those roots, nourish them, and shield them from harm.
The time has come for a new kind of reformer, one who understands the power of technology but wields it with compassion and wisdom. Let us be those reformers. Let us heal the divisions that social media and hype-driven narratives have wrought. Let us, together, rebuild a society where our elders can find peace, truth, and a sense of belonging in this bewildering modern age.
In the words of Tagore: “Where the mind is without fear, and the head is held high, into that heaven of freedom, let my country awake.” Let us awaken not just our country, but the world, to this vision of dignity, unity, and truth for all, especially for those who have given us so much—the elders who deserve our care, our respect, and above all, our love.
-

@ 6e75f797:a8eee74e
2023-08-07 13:16:42
Last night I started a nostr community multiplayer instance for No Man's Sky [on ZapStream](https://zap.stream/) and before we knew it, we had 4 Nostrichs arriving on the genesis planet to join the fun.

NSM is an deterministic, procedurally generated open universe where players can explore, quest, build, combat and have fun together. Every new system discovered is generated when the first Traveller enters the system making the game a unique experience for any open world gaming fan.
If you fancy joining us in the Nostrverse let me know and I'll friend you in #NMS and on Steam or Epic. If you just want to watch the fun, participate in naming systems, planets, fauna and flora come and hang out in my stream or the stream of [Oceanbee](nostr:npub1wqxxe0cjaxnvmrv4lkvx8d5dlft7ewswyn09w5v7fg7642fgzm7srucxws), [HolgerHatGarKeineNode](nostr:npub1pt0kw36ue3w2g4haxq3wgm6a2fhtptmzsjlc2j2vphtcgle72qesgpjyc6) or [taette](npub1yh0dl6pazf55025qvp860lstpscuy0kj2a5lfhxlk400m968vgpql5vsnd).

### If you already own NMS, feel free to add me!
My NMS friend code is: EMAZ-KMHT-ZPFXP
See you in space Traveller! - TheGrinder
-

@ b17fccdf:b7211155
2025-01-21 18:39:47
~ > **Check out the steps to get this** ~ > [HERE](https://minibolt.minibolt.info/bonus-guides/system/static-ip-and-custom-dns-servers#dot-doh--dnssec) < ~
**Note:** for different reasons, it is recommended choosing [Option 1: DoT & DNSSEC using systemd-resolved](https://minibolt.minibolt.info/bonus-guides/system/static-ip-and-custom-dns-servers#option-1-use-dot-and-dnssec-validation-with-systemd-resolved), but you could want to use [Option 2](https://minibolt.minibolt.info/bonus-guides/system/static-ip-and-custom-dns-servers#option-2-use-doh-with-cloudflared-proxy-dns), choose behind your criteria, both are valid to achieve the same objective.
-----------
Some more changes were released recently in other places of the MiniBolt guide, check the full release notes:
#### **Full release notes**
~ > [Static IP & custom DNS servers](https://minibolt.minibolt.info/bonus-guides/system/static-ip-and-custom-dns-servers) bonus guide:
- Adds custom DNS server suggestions.
- Adds different steps to check the changes after configurations.
- Deleted some unnecessary steps.
- Fix some nits.
---
~ > Modifications on [Configuration](https://minibolt.minibolt.info/bitcoin/bitcoin/bitcoin-client#configuration) (`bitcoin.conf`) of [Bitcoin Core](https://minibolt.minibolt.info/bitcoin/bitcoin/bitcoin-client):
- Replace proxy value parameter to use UNIX domain socket (`proxy=unix:/run/tor/socks`) | (recently [enabled](https://github.com/bitcoin/bitcoin/pull/27375) on Bitcoin Core v28).
- Replace `startupnotify=chmod g+r /home/bitcoin/.bitcoin/.cookie` to `rpccookieperms=group` [Bitcoin Core PR](https://github.com/bitcoin/bitcoin/pull/28167).
- Adds another special bind address to listen to incoming connections from Tor (`bind=127.0.0.1=onion`) | (recently [changed](https://github.com/bitcoin/bitcoin/blob/master/doc/release-notes/release-notes-28.0.md#p2p-and-network-changes) on Bitcoin Core v28).
- Modified [systemd service](https://minibolt.minibolt.info/bitcoin/bitcoin/bitcoin-client#create-systemd-service) to improve the startup and shutdown process.
**Note:** remember to restart Bitcoin Core and reload the systemd with `sudo systemctl daemon-reload` to apply changes.
---
~ > Delete unnecessary parameters of the [systemd service](https://minibolt.minibolt.info/lightning/lightning/lightning-client#create-systemd-service) of [Lightning client](https://minibolt.minibolt.info/lightning/lightning/lightning-client).
**Note:** remember to reload the systemd with `sudo systemctl daemon-reload` to apply changes.
---
~ > **Others:**
- New [i2pd webconsole](https://minibolt.minibolt.info/system/system/privacy#access-to-the-i2pd-webconsole) section.
- Adds a new ["Validation"](https://minibolt.minibolt.info/bitcoin/bitcoin/bitcoin-client#validation) subsection to the guides to clarify when checks begin.
- New "[Use the Tor proxy from another device](https://minibolt.minibolt.info/system/system/privacy#use-the-tor-proxy-from-another-device)" section.
- Adds Electrs [compatible with Testnet4](https://minibolt.minibolt.info/bonus-guides/bitcoin/minibolt-on-testnet#bitcoin-electrs) on Testnet bonus guide.
- Adds how to build a [Guard/Middle relay](https://minibolt.minibolt.info/bonus-guides/system/tor-services#guard-middle-relay) section on "Tor services: bridges & relays" bonus guide.
- Adds [Extras (optional)](https://minibolt.minibolt.info/bonus-guides/system/tor-services#extras-optional) section to "Tor services: bridges & relays" bonus guide with different utilities like install Nyx, how to "Limit bandwidth" and others.
- Changed [Electrs](https://minibolt.minibolt.info/bonus-guides/bitcoin/electrs) ports to enable simultaneous mode with Fulcrum.
- [Updated aliases](https://minibolt.minibolt.info/bonus-guides/system/aliases#upgrades) list to include news additions in line with updates.
- Updated the [Networkmap](https://bit.ly/minibolt-ramix_netmap) resource to include news additions in line with updates and migrate to a dynamic visual mode.
- Reorganized some menu items and sections to improve the UX and make more sense in the face of the future.
- Restructure and rename the "Tor obfs4 bridge" bonus guide to ["Tor services: bridges & relays"](https://minibolt.minibolt.info/bonus-guides/system/tor-services) and modify it to run the obfs4bridge, relays, and the master, in separate instances.
- Hidden [NYM mixnet](https://minibolt.minibolt.info/bonus-guides/system/nym-mixnet) and [Sparrow server](https://minibolt.minibolt.info/bonus-guides/bitcoin/sparrow-server) bonus guides from the menus due to disuse or poor performance. **Note:** it will continue to be maintained later if the situation changes due to the development of the associated software.
- Bump version of various services.
---
~ > **Coming soon...**
- Enable DNSSEC for your domain using Cloudflare + Namecheap.
- Enable DoH on:
- Desktop/Android browser (Windows/Linux).
- OS: Windows 11 // Linux ([Completed](https://minibolt.minibolt.info/bonus-guides/system/static-ip-and-custom-dns-servers#option-2-use-doh-with-cloudflared-proxy-dns) ✅)
- Router.
- Enable DoT on:
- Android OS.
- OS: Windows 11 // Linux ([Completed](https://minibolt.minibolt.info/bonus-guides/system/static-ip-and-custom-dns-servers#option-1-use-dot-and-dnssec-validation-with-systemd-resolved) ✅) with DNSSEC verification included.
- Router.
---
Enjoy it MiniBolter!💙
-

@ 58937958:545e6994
2025-01-13 03:31:48
I made croquettes inspired by Spiral's character "Bitcoin (Puppet)."

The method is the same as making regular croquettes.
I also tried making a version (right) with the arms and legs attached while shaping the filling, but they fell off before I could coat them in flour.

The face is made with seaweed and sliced cheese.
The arms and legs are made with fish cake (hanpen).
I brushed soy sauce on the legs and lightly toasted them in a toaster, which gave them a brown color.

The arms and legs are attached using thin spaghetti.
When I searched for character-themed bentos (kyaraben), I came across the idea of using dried pasta, which made sense.
I used fried spaghetti sticks for attachment.
Here’s Bitcoin Croquette squished into a bento box:

Halving

Notes
- I tried freezing the filling to help it hold its shape, but it backfired. It stuck to the plate and the cooking paper, and once partially thawed, it became way too watery. Freezing might work with better preparation.
- The filling was quite dry when shaping, so it might be better to add a binder (this time, I only used potatoes and sautéed onions).
The shape of Bitcoin Puppet was really easy and fun to make, so I’d love to try creating something else next time!
nostr:nevent1qqsxgpjvf9g9suhzx5asqhvnlvnarl43kuhas8v5g2ryjr9yjjp0z5ctkh5pt
-

@ fd78c37f:a0ec0833
2025-01-23 03:30:28
In this edition, we invited Nyirenda, a member of the nostr:npub1t4ljwhhg7zlxeahxwgmkwqmn4jjxxq8lzhyuzy0zvy23hq0sacxsdl9fvv community, to share his personal experiences in participating in the Bitcoin community, as well as the challenges the community has faced in its operations and the strategies used to address them.
**YakiHonne:** Today, we are honored to have a guest from Bitcoin Boma with us. Thank you for joining us. Before we dive in, I'd like to take a moment to introduce YakiHonne and share a bit about what we do. YakiHonne is a decentralized media client built on the Nostr protocol that enables freedom of speech through technology. It empowers creators to create their own voice, assets, and features. It also allows features like smart widgets, verified notes, and focuses on long-form articles. Now today we'll be exploring more about the Bitcoin community. Nyirenda, could you please briefly introduce yourself and tell us a bit about what you do?
**Nyirenda**:My name is Nyirenda. I'm part of the Bitcoin Boma Education Program and Bitcoin Boma Malawi. Bitcoin Boma Malawi is a coalition of Bitcoin enthusiasts who have come together to raise social, economic, and environmental awareness about Bitcoin in Malawi. Our long-term strategy involves engaging with various stakeholders, including the government, to work towards the legalization of Bitcoin.

**YakiHonne:** What sparked your interest in Bitcoin, and what motivated you to start a community around it?
**Nyirenda**: I first came across Bitcoin in 2016 through the news. Back then, its price had already surged to $16,000, which sparked my interest right away. Although the news warned that Bitcoin resembled a Ponzi scheme, I had already built a solid understanding of economic structures, having studied monetary history and the fractional reserve banking system. This gave me the background needed to appreciate Bitcoin.
**Nyirenda**:I began my research journey with Andreas Antonopoulos's lectures and books, which deeply resonated with me. I was quickly drawn to the philosophy behind Bitcoin. Since then, my focus has been on engaging with others and teaching them about Bitcoin, especially within the context of Malawi.
**Nyirenda**:In Malawi, our economic activities face numerous restrictions. The government controls the national fiat currency, limiting what we can do with it. For me, Bitcoin presents a solution to these issues. Today, I remain passionate about educating others about Bitcoin and exploring its potential to transform our economic situation.
**YakiHonne**: I witnessed the decline of traditional currencies and realized how Bitcoin could play a role in the future. It's truly fascinating to see how it can be implemented. Could you share how the community was formed, how you attracted members in the early stages, and what challenges you faced along the way?
**Nyirenda**:When I first started diving into Bitcoin, I felt like I needed a teacher. So, I printed a T-shirt that said "Bitcoin accepted here" and wore it whenever I went into town or public places. People would often look at me and ask, "Hey, what's Bitcoin?" I could then briefly explain what Bitcoin is and how it compares to the current fiat system.
**Nyirenda**:Some people were really interested, to the point that we exchanged contacts and started connecting, and it was a great experience. But the turning point came when I saw a tweet from Bitcoin Boma. Someone tweeted about a conference/seminar being organized, in collaboration with Trezor Academy. When I saw this, I knew this was the place to be. So, last July, I met Grant, Ian Foster, and Nick Twyman, who were organizing the event.

**Nyirenda**:After we introduced ourselves and started connecting, they said, "Hey, join us as part of our coalition, and let's see what we can do with Bitcoin, especially in education." That’s how things started moving forward. It's been an incredible journey because since then, we've managed to graduate about 12 to 15 students. One of the biggest things we’ve done so far is launching the first Bitcoin education course in Malawi, attracting over 120 people. Of course, only some of them are attending the classes, but so far, the progress has been great.

**YakiHonne**: So, what challenges did you face in attracting new members at that stage?
**Nyirenda**:The first challenge we face is the attitude and perception of Bitcoin. Bitcoin is a new technology and innovation. In a country where people are used to traditional currencies, there are many financial technologies emerging, including centralized coins. This has created challenges. When people hear about Bitcoin, many think of it as a Ponzi scheme. They believe it's a scam or a way to get rich quickly. What I've observed is that most people fail to understand the difference between Bitcoin and centralized currencies. To truly appreciate Bitcoin, they need to experience it. Setting up a custodial wallet and explaining a transaction to them can help.
**Nyirenda**:The second challenge is that people think Bitcoin is too complicated, especially in Africa, and here in Malawi, where the IT and ICT infrastructure is still underdeveloped. I’d say 70% of the population doesn’t have access to the internet. Even in our education system, we don’t learn about computers. It’s mainly by luck if someone has access to a computer and a network, allowing them to appreciate the technology.
**YakiHonne**: It seems to be common in many countries, where people think Bitcoin is a quick way to get rich. They see it as a scam or a Ponzi scheme. It's a big challenge to get people to believe in Bitcoin as a currency, rather than just their local currency. This is a real barrier in many economies. What principles guide your community, and how do you maintain trust and reliability in discussions? Simply saying, how do you keep the trust of the people?
**Nyirenda**:I’ll start with Bitcoin BOMA and then extend it to the people we interact with. In Bitcoin BOMA, even though we’re a collaboration, we have clear objectives and a philosophy. Ultimately, we model Bitcoin’s decentralized nature because it allows everyone to participate. In our coalition, we encourage the free flow of ideas and regularly meet to discuss how best to promote Bitcoin education. We focus on its social, economic, and environmental aspects. We assign tasks to each other and work hard to achieve the results.
**Nyirenda**:Malawi has great potential, especially in the energy sector, where we could mine Bitcoin, but we lose a lot of electricity during generation. There were attempts to convince government-run institutions to embrace Bitcoin. However, most of these institutions are controlled by the government, and getting into politics is necessary to convince policymakers. It’s been a challenge because government systems are centralized. There’s a hierarchy to follow, and sometimes, even if a minister understands Bitcoin, it takes a long time to get it approved in parliament and passed into law.This has been one of our ongoing initiatives.
**Nyirenda**:When I go out and interact with people, especially Malawians, I try to explain the transparency of Bitcoin by showing how a decentralized ledger works and how it’s different from traditional systems. I also explain that Bitcoin is reliable and that mismanagement isn’t possible with a decentralized system.
**Nyirenda**:In a country where people are educated in a certain way and believe in competition and power, I often remind them that absolute power corrupts absolutely. I tell them that Bitcoin offers a different space where decentralization allows for a fairer system and benefits everyone. That’s how I try to explain it in simple terms.

**YakiHonne**: how do you educate your members and keep them updated on Bitcoin development time-to-time?
**Nyirenda**:For me, learning about Bitcoin is a lifelong process, with always unanswered questions and gaps to fill. I often study, read, and keep an eye on the developments in the Bitcoin community, especially in the African Bitcoin community. My role model is Kenya, particularly how they are enabling people to use Bitcoin through the Tando project. I believe that the value of Bitcoin is not just about holding and waiting for the price to rise, but rather as a tool that can help liberate the world.
**Nyirenda**:Bitcoin is not just about accumulating wealth; I focus more on its role as a tool in the free market. Therefore, I continue to learn, even though I'm not a technical expert and my background is not in this field. I have worked in education, so I apply those skills to better understand Bitcoin and how it works.
**Nyirenda**:I gather information from various sources to understand how Bitcoin works. At the same time, I compare it with the traditional monetary system, as that’s where I began, and it's my foundational layer. As for the Bitcoin BOMA community, I’m happy to say that we have two members with a strong background in economics. We often share interesting content and sometimes engage in debates. We also share many links and videos, learning from each other.
**Nyirenda**:Especially in the Bitcoin Diploma Education Program, I give explanations, and I have peers who help analyze my course content. We remind each other and point out areas that need improvement. We constantly update each other on our progress, ensuring that our activities remain relevant, which helps us continue to improve.

**YakiHonne**: Does Bitcoin Boomer collaborate with the broader Bitcoin ecosystem, and which partnerships have had the greatest impact so far?
**Nyirenda**:I'll start with our collaboration with Trezor Academy. Last year, this was one of the most significant partnerships for us in Malawi. Trezor Academy focuses on Bitcoin education, and they provided us with a lot of support. Thanks to this collaboration, we were able to organize a seminar and graduate about 10 to 15 students. It was a major achievement for us.
**Nyirenda**:Additionally, one of our members attended the African Bitcoin Conference held in Kenya, which was a pivotal opportunity. He had the chance to interact with Bitcoiners from across Africa. There were special guests, including nostr:npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m and through this exposure, he met the core developers in Kenya and the Tando developers in South Africa. These collaborations have given us insight into what other Bitcoin communities are doing, especially in their projects.
**Nyirenda**:We also had a speaker from Bitcoin Boma who participated in an event in El Salvador. We are working towards making Malawi a Bitcoin node, and he is actively fostering that effort. Big shoutout to Ian Foster for his dedication. He will also be attending a conference in South Africa this January as a guest speaker. These collaborations have been very impactful, and I’m confident that we’ll see the results of these interactions in the future.

**YakiHonne**: So what challenges has your community faced so far and how have you overcome them while maintaining integrity?
**Nyirenda**:One of the challenges we face is related to resources, especially when it comes to our learning sessions. We mainly rely on our own resources, and we understand that quality lessons require specific equipment. While we're working toward acquiring these resources, we’re also making the most of what we have. We've agreed to work with what we have, and we believe we can still achieve our objectives.
**Nyirenda**:Another challenge is the attitude towards Bitcoin in Malawi. Most people entering the crypto space have a “get rich quick” mentality. They focus more on the outcomes rather than the learning process. Many crypto traders are primarily interested in exploiting the benefits of Bitcoin. This is a challenge, especially when trying to teach people that Bitcoin is not just about making a profit, but also about liberation. Changing the traditional fiat mindset to embrace this new path is not easy.
**Nyirenda**:Additionally, many people believe that if they invest their time, they must get a return. This is one of the challenges we're currently dealing with. Financial literacy in Malawi still has a long way to go. While people are aware of how economic shocks, especially currency devaluation, affect them, they often act out of desperation. The market is psychologically driven, and people are constantly looking for shortcuts to protect their wealth. When Bitcoin is introduced, it often raises doubts and skepticism.
**Nyirenda**:However, there is no moment of hatred. Instead, we see the growing energy within the community, even if it's just coming from the heart, extending a significant impact on others. There’s a lot of potential and many possibilities ahead. Despite the challenges, we remain hopeful and excited about the future.

**YakiHonne**: In addition to wearing T-shirts and sparking curiosity, what other methods have you adopted to promote Bitcoin, and what results have you seen?
**Nyirenda**:First of all, I want to mention the Bitcoin BOMA education diploma program that’s currently running. This is one of the most significant initiatives we have at the moment. We are doing our best to attract people to dive into our education program. So far, the results have been very positive, especially in terms of numbers. People are curious and realize that this is something worth learning. Some have even acknowledged that what they've learned in the traditional education system is very different from the exposure they get from the diploma program. I’d say that’s one of the biggest impacts we've had in promoting Bitcoin.
**Nyirenda**:If we have sufficient resources, we plan to implement further actions such as putting up banners, promoting Bitcoin, and positioning Malawi as a Bitcoin hub. Malawi has great potential, particularly in the tourism sector, with many tourists visiting the country. If we display banners saying “We accept Bitcoin,” it would be appreciated by many people. Personally, I’ve been encouraging businesses to start accepting Bitcoin.
**Nyirenda**:We also have a Bitcoin BOMA Twitter account where we advocate for Bitcoin. We engage in discussions and comment on trends. In the coming months, we plan to host spaces and aim to conduct them in our local language, so more people can appreciate and learn about Bitcoin.
**YakiHonne**: We’ve reached the end of today’s session, and I must say, you’re doing an incredible job at Bitcoin BOMA. Your personal and collaborative efforts are truly impressive. I’m confident that in the next few years, we’ll be visiting Malawi for a Bitcoin conference. It’s clear that Malawi is heading in the right direction with you leading the way.
-

@ b17fccdf:b7211155
2025-01-21 18:33:28
---
**CHECK OUT at** ~ > **[ramix.minibolt.info](https://ramix.minibolt.info)** < ~
---
**Main changes:**
* **Adapted to Raspberry Pi 5**, with the possibility of using internal storage: a PCIe to M.2 adapter + SSD NVMe:
> *Connect directly to the board, **remove the instability issues** with the USB connection, and unlock the ability to enjoy **higher transfer speeds***
* **Based on Debian 12** (Raspberry Pi OS Bookworm - 64-bit).
* **Updated all services** that have been tested until now, to the latest version.
* Same as the MiniBolt guide, changed I2P, Fulcrum, and ThunderHub guides, to be **part of the core guide**.
* **All UI & UX improvements in the MiniBolt guide** are included.
* Fix some links and wrong command issues.
* Some existing guides have been improved to **clarify the following steps**.
---
**Important notes:**
* The RRSS will be the same as the MiniBolt original project (for now) | More info
-> [HERE](https://ramix.minibolt.info/#community) <-
* The common resources like the [Roadmap](https://github.com/orgs/minibolt-guide/projects/1) or [Networkmap](https://bit.ly/minibolt-ramix_netmap) have been merged and will be used together | Check -> [HERE](https://ramix.minibolt.info/#resources) <-
* The attempt to upgrade from Bullseye to Bookworm (RaspiBolt to RaMiX migration) has failed due to **several difficult-to-resolve dependency conflicts**, so unfortunately, there will be no dedicated migration guide and **only the possibility to start from scratch** ☹️
⚠️ **Attention**‼️-> This guide is in the WIP (work in progress) state and hasn't been completely tested yet. Many steps may be incorrect. Pay special attention to the "**Status: Not tested on RaMiX**" tag at the beginning of the guides. Be careful and act behind your responsibility.
---
For Raspberry Pi lovers!❤️🍓
Enjoy it RaMiXer!! 💜
---
By [⚡2FakTor⚡](nostr:npub1k9luehc8hg3c0upckdzzvusv66x3zt0eyw7290kclrpsndepz92sfcpp63) for the plebs with love ❤️🫂
-

@ 58937958:545e6994
2025-01-13 03:19:17
Spiralのキャラクター「ビットコイン(パペット)」のコロッケを作りました

作り方は一般的なコロッケです
試しにタネの状態で手足をくっつけたバージョン(右)も作りましたが
粉をつける前に手足がもげました

顔はのりとスライスチーズ
手足ははんぺんです
足は醤油をつけてトースターで軽く焼いたら茶色になりました

手足はサラスパでくっつけてます
細いスパゲッティ
キャラ弁でググったらサラスパが出てきてなるほどな~と思いました
自分は揚げパスタにして刺しました
弁当箱に押し込まれてるコロッケくん

半減期

メモ
- タネを作った時に形を保たせるために冷凍してみたんですけど逆効果だった(皿とクッキングペーパーにくっついて取れなくなった&半解凍したら水分がすごいことになった)ので冷凍するなら対策が必要そう
- 形作るときにかなりパサパサだったので、つなぎがあった方がいいのかも(今回はじゃがいも&炒めタマネギだけ)
ビットコインくんの形はすごく作りやすくて面白いのでまた何か作りたいなぁと思いました
nostr:nevent1qqsxgpjvf9g9suhzx5asqhvnlvnarl43kuhas8v5g2ryjr9yjjp0z5ctkh5pt
-

@ 3f770d65:7a745b24
2023-07-31 12:53:38
The following is a collection of Tweets posted on Twitter that documented my entire heart surgery process, from finding out I had an issue, through the surgery, and finally throughout my recovery process. If Elon decides to remove old and unpaid content, I do not want this part of my life to vanish from the Internet. At the time, it was extremely important for my mental health to talk about this whole process and it was therapeutic in my recovery process, reading all of the responses as all of Bitcoin Twitter was behind my success. Thank you all of your kind words, love, and support during this whole process. May my Tweets live on through nostr.
...
Nov 28, 2021
I had open heart surgery 4 days before my 3rd b-day. I've led a healthy & active life since then, zero issues. I had an echocardiogram last week. The results were not good. Heart valve replacement may be in my near future. I am freaking the fuck out. I'll know more on Dec 6th. 😫
Dec 6, 2021
Update: I had my cardiologist appointment today. He said to not worry for now and continue to exercise and live life. In 3 months get another echo done. He doesn't believe the previous other results since I have zero symptoms and wants to do his own interpretation.
Dec 6, 2021
He said if the other results were correct, I may need valve replacement in 6 months to 3 years. However, he doesn't believe the local hospital's results as I said above. He can't form an opinion just yet. He said not to worry over and over again. For now, I'm staying positive!
Mar 7, 2022
Well, it's been three months. I had my follow up this morning. I have severe pulmonic regurgitation. I now need to speak with a specialist and see what my options are for surgery. Neat. 😭
Apr 12, 2022
Well, it looks like I'll need full open heart surgery again to replace my pulmonic valve. Bonus: I'll be part pig. So, I have that going for me. I was assuming that if I had to have this done it would be much less invasive, so I'm not overly impressed at the moment. 🫤
May 11, 2022
Today I had to get a CT scan of my heart in preparation for the May 27th surgery. All went well. I have no other heart issues. It's looking like I'll be in the hospital for 4-7 days, depending on how fast I recover. I should be fully 100% recovered by the end of August. ❤️
May 20, 2022
My grandfather with me 39 years ago, days after my open heart surgery. He taught me to hunt, fish, golf, and I'm sure taught me a thing or two about drinking beer and partying. 😂 He was a great man. He won't physically be with me next Friday, but I'm sure he'll be watching over.
May 25, 2022
Two more sleeps. My mind is racing with an incredible amount of thoughts and emotions now. It's overwhelming. I love you all. Thanks for all of your replies and DMs over the last couple days, weeks, and months. I appreciate it immensely. ❤️❤️❤️
May 25, 2022
Two more sleeps. My mind is racing with an incredible amount of thoughts and emotions now. It's overwhelming. I love you all. Thanks for all of your replies and DMs over the last couple days, weeks, and months. I appreciate it immensely. ❤️❤️❤️
May 27, 2022
LET'S GO! I am alive and doing well. I was on a ventilator until 8pm. That was horrible. I will read all of the comments that you all posted on Katie's updates. Now I need to rest. They want to get me up and walk at 11pm. 🤯 I love you all and your support had helped so much 🧡🧡
May 28, 2022
The amount of love, compassion, caring, and appreciation from everyone blows my mind. Thanks for all of your comments and DMs. The positivity though all is this has helped me get through dark times and now it's helping me get through pain. You are helping me immensely. 🤯❤️🧡💪
May 28, 2022
Today has been a rough day. Lots of chest pain when breathing. But, I apparently am doing something right, because I have been upgraded to a regular room. No more ICU for this guy! My ICU nurse told my new nurse that I'm strong. ❤️💪🔥
May 29, 2022
Using this to document my journey. Last night was not good at all. I had tachycardia and AFib for hours. It was scary as fuck having my heart beat the way it was at 160bpm. They gave me new medication to bring it down and stop the AFib irregular heartbeat. It's now at 101.
May 29, 2022
I was very scared. Katie was able to come and stay the night with me and be my personal care nurse. That made me feel much better having her here with me. Hopefully the meds continue to do what they're supposed to. Fuck. Anyways, I may not Tweet much today. Love you all. ❤️
May 30, 2022
Today has mostly been a great day progress wise. I ate a lot. I've walked more today than I have previously. My doctor told me I might be going home tomorrow, it all depends on what happens with my last drainage tube. Fingers crossed that it's draining properly now. 💪❤️
May 31, 2022
Morning walk crushed.
Breakfast crushed.
Feeling stronger.
My drainage tube is still draining so we'll see what the surgeon says, but I probably won't be coming home today according to my nurse. It may be another day. Better to be safe. I'm feeling good though. Let's go! 💪💪❤️❤️
Jun 1, 2022
Today's plans: Crush morning walk, crush breakfast, CRUSH MY LAST X-RAY AND HEAD THE HELL HOME! Fingers crossed. 🤞🤞❤️❤️💪💪
Jun 1, 2022
On my morning walk I went into a slight AFib. The nurse and PA said since I hadn't had my morning meds to control that yet, that that could be the cause. They're going to increase meds and monitor me for another 24 hours. That sucks, but again, I'd rather be safe. Ugh.
Jun 2, 2022
GM! I miss my kids. I miss wearing normal clothes. I miss my house. I miss my doggy. I better go home today or I guess I'll just keep working to get well enough to go home. 😂 I'm still progressing forward. I have a chest x-ray scheduled later this morning. Fingers crossed.
Jun 2, 2022
I JUST GOT CLEARED TO HEAD HOME AFTER LUNCH. FUCK YEAH. LET'S GOOOOOO💪💪💪
Jun 2, 2022
I am home! I have some family that needs some loving. Enjoy the rest of your day!
Jun 4, 2022
Last night I slept in bed thanks to a reclining pillow, the first night our living room chair. I was so happy to sleep in my own bed. I walked around our yard about 9 times yesterday. My goal is to do that plus a little more every day. I'm still in a lot of pain, but meds help.
Jun 4, 2022
I still have a long way to go recovery wise, but having Katie and the kids here helping me along the way makes it easier and gives me a reason to keep pushing forward through this. Thanks again for all of your past and future support. You all are fantastic.
Jun 6, 2022
My wife went back to work today. My son and daughter are in charge of taking care of me. My kids are fantastic. They made me breakfast already and helped me check all of my vitals. My daughter really shines here. She's such a little nurse and caretaker. ❤️❤️
Jun 6, 2022
I'm still in pain, but I'm not in as much pain as I was a couple days ago. I'm walking around a little better and a little more every day. I really hate just sitting around and not doing anything, but it's hard to do much else besides watch TV. I am enjoying my patio though. 💪
Jun 16, 2022
It's been a while. It's time to update this thread! I am doing great, IMO. I have lots of energy. I feel great. I can do a lot more than I previously could. I still have a limited range of motion due to my sternum being broken and still healing. i.e. I can't wash my back or legs.
Jun 16, 2022
I started back to work yesterday. I was cleared to do 20 hours this week by my doctor and I'm hoping to be cleared full time next week. I work from home, so if I can sit in front of a TV, I can sit in front of a computer, right?
Jun 16, 2022
My home nurses have been absolutely fantastic.😂 My kids make me breakfast every morning. And I could not have done any of this without my rock star wife. Words can't describe how much she's done for me throughout all of this. I am looking forward to continuing to improve. ♥️
Jun 16, 2022
You all have been absolutely wonderful through all of this too. I appreciate all of your love, support, and check-ins. Seriously. It means more than you know.
I have a check-up at the end of the month to make sure all is well. I'll update again in a couple weeks after that appt.
Jun 28, 2022
My doctor said everything looks great. He said it doesn't look like I had open heart surgery a month ago.💪 He said I have zero restrictions and that I can resume normal life. I can drive and I can go out on my boat! ❤️❤️❤️ I'm so happy right now! 🔥🚀
Jul 15, 2022
I started cardiac rehab this week. After 2 sessions the nurse said I'm on "Week 4" already. She doesn't believe with my initial intake stress test if I'll really be able to improve on it that much. 🤣 TL;DR I am a rock star and kicking ass. Feeling great. Life's great. 😍
Aug 28, 2022
Yesterday was 3 months since my open heart surgery. I'm going great! I'd guess essentially back to normal. My sternum is still not fully healed, that'll take more time, but energy and capability are basically back to what I was like last summer. I'm very happy with the results.
Aug 28, 2022
I'm very happy to be able to exercise daily, go boating on the weekends AND swim and paddleboard. I was annoyed that I couldn't do these things a month ago. I had a cardiologist appt. two weeks ago. He said he hopes the valve lasts me the rest of my life and to see him in a year.
Aug 28, 2022
As a final post to this thread, I want to thank each and every one of you again that commented, liked, shared and DMed me throughout all of this. The love and support from Twitter and the #Bitcoin community was unfathomable. You all made a difference in my life and my recovery.❤️
-

@ 84b0c46a:417782f5
2025-01-11 01:48:46
nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qqs0df2mwnp2q6hm6zjrthkmx3fudwsuwrmgnwrdavpzgjy8nnuqm5cqpd06k
nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qqs2muhvnev5367ywuzkhell9my86jlnzhsnuszwl46tnc3fpsx9mtgjkqnu7
nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qqsznnkrl8qdwzgp7ry2hc7a77kwhg440gv9xtmvyfawggrpz3rhwvcx4rckf
nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qqsyjf80k3djt96qncgvwl2yem09fdqcc0y9l8t657yc9qg2yhmg7kcnua8vn
nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qqs0s3lp0w0yclk64j0tpc5fvrulv78g2lfjz3gcgacw9mt6czek26qtqxuck
nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qywhwumn8ghj7mn0wd68ytnrdakhq6tvv5kk2unjdaezumn9wsqs6amnwvaz7tmev9382tndv5qjqamnwvaz7tmjv4kxz7fddfczumn0wd68ytnhd9ex2erwv46zu6nsqqs89tst72clc60wse3zq4qfs0976y7areffnhx26atvu6pv58hg6dsxvcc79
nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr3mhxue69uhhxun5wfjkccte9e3j6um5v4kxcctj9ehx2aqqyp5k40r3ug02yz5y0tn67tm2lwevuwac54qyw3yyct8n8uzr7pjz2q92pyt
nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqqyp9pennjwq2qk4dxpr440wxqm5cfwah4qccd8la62hantxdelkk82ty9mr8
nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qyxhwumn8ghj77tpvf6jumt9qqsz9w30kxzjshwd8sq7jg2hsy2hwqg3zu7gyvxnsyrgfw0ur4rkhsg9v0re4
nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qyxhwumn8ghj77tpvf6jumt9qqs8wkx2r8txt9q69c3zvpqs2em2s40nc8tajmcc5l8ngxn8v2ng3sc43xvzu
nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqqyzdkacpjqvv2y79zgvufx9jh39rd7xa8v056rgn4xelmnmrq9u2tuguswek
nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qy2hwumn8ghj7mn0wd68ytnyv96xztngv96hxqpqmdtjrs38fv8r20deplrlt8fma54gu43keuzquzks7673a27ud58slunr8y
nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhkummnw3ezucm0d4cxjmr994jhyun0wghxuet5qqsxzpx2r5hd36pruzn2e58wh947y2t0t205fp5xtstqp5wq0qgcjuq07rqlk
-

@ 78b3c1ed:5033eea9
2025-01-10 12:31:01
※ライトニングノード保有者向け
Alby Hubをインストールした時なんもわからずポチポチしているとMegatlith LSPノードからインバウンドを購入してチャネルを開くことになります。2万sats(2024/12/4 午後7時時点で三千円ほど)かかります。
そこで誰もが思うに違いない
「高いなぁ。だれかタダで無料で私のHubにチャネル開いてくれないかなぁ...」
その願望をかなえる献身的なノードランナー(笑)がAlby Hubへチャネルを開いてあげるための手順書みたいなものがこの記事です。
~~ppmをうんと高くしてぼったくってやりましょう!~~
※AlbyHubにオンチェーン資金が無くてもLNDから開く方法を発見しました。末尾に追記しました。
《これはアンカーアウトプットを利用するタイプのチャネル》
条件
・チャネルを開く側
Clearnet IPアドレスで着信可能であること。Torノードは不可。ノードURIを公開していなくても良い。AlbyHubでピア登録できるClearnet IPアドレスと着信ポートがあればOK。
・開いてもらうAlby Hub側
オンチェーン資金25,000sats以上をデポジットしておく。ないと開けません。
手順
1. [Alby Hub側] オンチェーン資金をデポジット
Hubログイン後の左メニューからNodeを選択。Saving BalanceのDepositを選択。するとbc1qではじまるオンチェーンアドレスが表示される。ここへ送金してオンチェーンをデポジットしておく。
2. [Alby Hub側] 開く側のノードをピア登録
左メニューからNodeを選択。右上のAdvancedからConnected Peersを選択。
右上のConnect Peerを選択。欄にノードURI (ノードID@IPアドレス:着信ポート番号)を入力してConnect。
3. [開く側ノード] AlbyHubを確認、チャネルを開く
ThunderhubやRide-The-Lightningなどを使い、Alby Hubのノードが表示されていることを確認。Hubにエイリアスは無いのでノードIDで表示される。
このノードに対してチャネルを開く。Private channelが望ましいと思われる。
6conf後に開設完了。
終わり!
メモ
- Alby Hubではbase feeは設定可能だがrateが設定できない。そもそもAlby Hubはルーティング向けノードとして設計されてない。セルフカストディアルウォレットです。
- public channelだとchannel_update, channel_announcementがゴシップされるまでHubへ送金できない(no route)。上記の通りウォレットとしてのノードならprivate channelだけにしてルートヒント付きインボイスが発行できるようにしとくのが望ましい。
- LDKにおいて相手からチャネルを開いてもらう場合にオンチェーン資金が必要。相手がチャネルリザーブ無しのチャネルでもOKなら不要。現にメガリスLSPからチャネルを開いてもらう時オンチェーン資金が0satsでも開けているのがその実例。
- オンチェーン資金が必要なのはチャネルタイプがanchorの場合。オンチェーン資金でアンカーアウトプットをCPFPするためみたい。anchorが登場する前のstatic-remotekeyのタイプならオンチェーン資金は不要。
-----------
<ここからが追加>
《これはアンカーアウトプットを利用しないタイプのチャネル》
LNDからチャネルを開くときにstatic remote keyを利用するタイプを指定します。
条件
・チャネルを開く側 ※上記と同様。
・開いてもらうAlby Hub側 無し。
手順
1. [Alby Hub側] 開く側のノードをピア登録
左メニューからNodeを選択。右上のAdvancedからConnected Peersを選択。右上のConnect Peerを選択。欄にノードURI (ノードID@IPアドレス:着信ポート番号)を入力してConnect。
2. [開く側ノード] AlbyHubを確認、チャネルを開く
SSHログイン、UmbrelならLightningのターミナルで以下のコマンドを実行します。
<ノードID>は開きたいAlbyHubのノードIDで置き換えてください。
<チャネルサイズ>は開きたいチャネルの金額、例えば20万satsなら200000としましょう。
<手数料率>はチャネル開設のトランザクションに掛ける手数料率です。mempool. spaceなどで手数料水準を確認して指定しましょう。
--channel_type tweaklessがキモです。デフォルトだとanchorになります。RTLやTHで開くとこのanchorになります。なのでlncli openchannelでやります。
```
lncli openchannel --node_key <ノードID> \
--local_amt <チャネルサイズ> \
--sat_per_vbyte <手数料率> \
--private --channel_type tweakless
```
終わり!
-

@ a012dc82:6458a70d
2025-01-21 13:47:17
In the annals of treasure hunting, tales of sunken galleons and buried chests have given way to a new narrative—one that unfolds in the digital realm. The U.S. Government, traditionally associated with the physical might of gold reserves in Fort Knox, has inadvertently entered the arena of cryptocurrency by amassing a staggering $5 billion in Bitcoin. This digital fortune, however, was not amassed through investment or mining efforts but rather through the seizure of assets from the darker corners of the internet. As we stand at the crossroads of finance and technology, this cache of Bitcoin opens up a Pandora's box of possibilities and challenges that could redefine the economic landscape of tomorrow.
**Table Of Content**
- A Digital Fort Knox
- The Origins of the Cache
- The Dilemma of Liquidation
- Potential Paths Forward
- The Impact on the Future of Currency
- Conclusion
- FAQs
**A Digital Fort Knox**
Imagine a vault, not of steel and stone, but of complex cryptographic algorithms, housing a vast sum of Bitcoin equivalent to the wealth of small nations. This digital Fort Knox does not require armed guards or thick walls but instead relies on the impenetrable nature of blockchain technology. The U.S. Government's acquisition of such a significant amount of Bitcoin is a testament to the changing nature of value and wealth in the 21st century. Each Bitcoin in this modern trove was once part of illicit transactions, flowing through the veins of the internet until it was intercepted by the vigilant efforts of federal agencies. The narrative of each coin is a digital ledger, chronicling a journey from the shadowy fringes of the web to the secure wallets of the government.
**The Origins of the Cache**
The backstory of the government's Bitcoin collection is not one of serendipity but of strategic cyber sleuthing and legal might. It is a modern saga of law enforcement adapting to the challenges posed by the digital age. Federal agencies, armed with court orders and cutting-edge technology, have traced the movement of these digital assets through the blockchain, unraveling complex webs of transactions that lead to the criminal enterprises operating in the darknet markets. Each seizure represents a battle won in the ongoing war against cybercrime, with the confiscated Bitcoin serving as both evidence of victory and the spoils of war.
**The Dilemma of Liquidation**
The government's Bitcoin cache presents a unique conundrum: to liquidate or not to liquidate? This decision is fraught with economic implications, akin to a game of high-stakes poker where the government's hand could influence the entire table. A sudden influx of $5 billion worth of Bitcoin into the market could trigger a tidal wave of volatility, potentially devaluing the currency and destabilizing the fragile ecosystem of digital assets. The government must navigate these waters with a blend of economic savvy and strategic foresight, ensuring that any decision made is in the best interest of not just the immediate financial landscape but also the long-term viability of cryptocurrencies.
**Potential Paths Forward**
The government stands at the helm, charting a course through uncharted waters with its Bitcoin bounty. The options are as varied as they are complex. Holding onto the Bitcoin could be seen as an endorsement of its value, a digital reserve akin to the gold of yesteryear. Alternatively, a measured approach to selling the Bitcoin could be employed, releasing it into the market in a controlled manner to mitigate any negative impacts. There's also the innovative possibility of integrating Bitcoin into the government's financial transactions, embracing the very currency that was once shunned by the establishment.
**The Impact on the Future of Currency**
The U.S. Government's handling of this Bitcoin cache is not merely a financial decision; it is a statement on the future of currency itself. As the line between digital and fiat currencies blurs, the actions taken with this Bitcoin hoard could send ripples across the global economy. It could influence how governments around the world perceive and interact with digital assets, potentially ushering in a new era where cryptocurrency becomes a staple of economic policy and international trade.
**Conclusion**
The U.S. Government's Bitcoin cache is more than a collection of digital assets; it is a symbol of a new era in governance and economic strategy. The decisions made regarding this treasure will likely resonate through the annals of financial history, setting precedents for how nations interact with the burgeoning realm of digital currencies. As we delve deeper into this narrative, we realize that this treasure is not hidden but in plain sight, waiting to unlock a future where digital assets are as commonplace and as valuable as the gold once stored in the vaults of old.
**FAQs**
**How did the U.S. Government acquire $5 billion in Bitcoin?**
The U.S. Government seized this Bitcoin from various cybercriminal operations and darknet markets through legal and technological efforts by federal agencies.
**What is the significance of the government holding such a large amount of Bitcoin?**
This significant holding of Bitcoin by the government underscores the changing landscape of value and wealth, highlighting the increasing relevance of digital currencies in today's economy.
**What challenges does the government face with this Bitcoin cache?**
The government faces the challenge of deciding how to manage and potentially liquidate the Bitcoin without causing market disruption due to the currency's volatility.
**What are the potential strategies for the U.S. Government's Bitcoin cache?**
Strategies include holding the Bitcoin as a reserve asset, selling it off gradually to minimize market impact, or using it for government transactions and policy-making.
**How could the government's handling of the Bitcoin cache affect the future of currency?**
The government's approach to managing the Bitcoin cache could set a precedent for how digital assets are treated by national entities, potentially influencing the integration of cryptocurrencies into mainstream finance.
**That's all for today**
**If you want more, be sure to follow us on:**
**NOSTR: croxroad@getalby.com**
**X: [@croxroadnews.co](https://x.com/croxroadnewsco)**
**Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)**
**Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)**
**Store: https://croxroad.store**
**Subscribe to CROX ROAD Bitcoin Only Daily Newsletter**
**https://www.croxroad.co/subscribe**
*DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.*
-

@ e8a4bb8b:05f739c6
2025-01-21 13:05:10
Opinion about CoinUnited.io - Crypto Wallet (iphone)
<!--HEADER END-->
⚠️ WARNING: CoinUnited.io is a SCAM ⚠️
Do NOT use CoinUnited.io for cryptocurrency trading or investments. Here's why:
Hong Kong SFC Alert: Listed as a suspicious platform on July 25, 20241.
Withdrawal Issues: Many users report being unable to withdraw funds12.
Fake Trading Environment: Platform likely uses simulated trading, not real market transactions1.
False Regulatory Claims: Makes unverified claims about regulatory compliance12.
Ongoing Investigations: Currently under investigation by Hong Kong police5.
User Complaints: Numerous reports of lost investments and blocked accounts26.
Deceptive Practices: Uses high APRs and leverage to lure investors12.
Protect yourself and others. Avoid CoinUnited.io at all costs. If you've invested, seek immediate assistance from financial authorities. Always verify the legitimacy of crypto platforms before investing.
Stay safe and share this warning to prevent others from falling victim to this scam.
<!--FOOTER START-->
#WalletScrutiny #nostrOpinion
[Join the conversation!](https://walletscrutiny.com/iphone/coinunited.io)
-

@ 6be5cc06:5259daf0
2025-01-21 01:51:46
## Bitcoin: Um sistema de dinheiro eletrônico direto entre pessoas.
Satoshi Nakamoto
satoshin@gmx.com
www.bitcoin.org
---
### Resumo
O Bitcoin é uma forma de dinheiro digital que permite pagamentos diretos entre pessoas, sem a necessidade de um banco ou instituição financeira. Ele resolve um problema chamado **gasto duplo**, que ocorre quando alguém tenta gastar o mesmo dinheiro duas vezes. Para evitar isso, o Bitcoin usa uma rede descentralizada onde todos trabalham juntos para verificar e registrar as transações.
As transações são registradas em um livro público chamado **blockchain**, protegido por uma técnica chamada **Prova de Trabalho**. Essa técnica cria uma cadeia de registros que não pode ser alterada sem refazer todo o trabalho já feito. Essa cadeia é mantida pelos computadores que participam da rede, e a mais longa é considerada a verdadeira.
Enquanto a maior parte do poder computacional da rede for controlada por participantes honestos, o sistema continuará funcionando de forma segura. A rede é flexível, permitindo que qualquer pessoa entre ou saia a qualquer momento, sempre confiando na cadeia mais longa como prova do que aconteceu.
---
### 1. Introdução
Hoje, quase todos os pagamentos feitos pela internet dependem de bancos ou empresas como processadores de pagamento (cartões de crédito, por exemplo) para funcionar. Embora esse sistema seja útil, ele tem problemas importantes porque é baseado em **confiança**.
Primeiro, essas empresas podem reverter pagamentos, o que é útil em caso de erros, mas cria custos e incertezas. Isso faz com que pequenas transações, como pagar centavos por um serviço, se tornem inviáveis. Além disso, os comerciantes são obrigados a desconfiar dos clientes, pedindo informações extras e aceitando fraudes como algo inevitável.
Esses problemas não existem no dinheiro físico, como o papel-moeda, onde o pagamento é final e direto entre as partes. No entanto, não temos como enviar dinheiro físico pela internet sem depender de um intermediário confiável.
O que precisamos é de um **sistema de pagamento eletrônico baseado em provas matemáticas**, não em confiança. Esse sistema permitiria que qualquer pessoa enviasse dinheiro diretamente para outra, sem depender de bancos ou processadores de pagamento. Além disso, as transações seriam irreversíveis, protegendo vendedores contra fraudes, mas mantendo a possibilidade de soluções para disputas legítimas.
Neste documento, apresentamos o **Bitcoin**, que resolve o problema do gasto duplo usando uma rede descentralizada. Essa rede cria um registro público e protegido por cálculos matemáticos, que garante a ordem das transações. Enquanto a maior parte da rede for controlada por pessoas honestas, o sistema será seguro contra ataques.
---
### 2. Transações
Para entender como funciona o Bitcoin, é importante saber como as transações são realizadas. Imagine que você quer transferir uma "moeda digital" para outra pessoa. No sistema do Bitcoin, essa "moeda" é representada por uma sequência de registros que mostram quem é o atual dono. Para transferi-la, você adiciona um novo registro comprovando que agora ela pertence ao próximo dono. Esse registro é protegido por um tipo especial de assinatura digital.
#### O que é uma assinatura digital?
Uma assinatura digital é como uma senha secreta, mas muito mais segura. No Bitcoin, cada usuário tem duas chaves: uma "chave privada", que é secreta e serve para criar a assinatura, e uma "chave pública", que pode ser compartilhada com todos e é usada para verificar se a assinatura é válida. Quando você transfere uma moeda, usa sua chave privada para assinar a transação, provando que você é o dono. A próxima pessoa pode usar sua chave pública para confirmar isso.
#### Como funciona na prática?
Cada "moeda" no Bitcoin é, na verdade, uma cadeia de assinaturas digitais. Vamos imaginar o seguinte cenário:
1. A moeda está com o Dono 0 (você). Para transferi-la ao Dono 1, você assina digitalmente a transação com sua chave privada. Essa assinatura inclui o código da transação anterior (chamado de "hash") e a chave pública do Dono 1.
2. Quando o Dono 1 quiser transferir a moeda ao Dono 2, ele assinará a transação seguinte com sua própria chave privada, incluindo também o hash da transação anterior e a chave pública do Dono 2.
3. Esse processo continua, formando uma "cadeia" de transações. Qualquer pessoa pode verificar essa cadeia para confirmar quem é o atual dono da moeda.
#### Resolvendo o problema do gasto duplo
Um grande desafio com moedas digitais é o "gasto duplo", que é quando uma mesma moeda é usada em mais de uma transação. Para evitar isso, muitos sistemas antigos dependiam de uma entidade central confiável, como uma casa da moeda, que verificava todas as transações. No entanto, isso criava um ponto único de falha e centralizava o controle do dinheiro.
O Bitcoin resolve esse problema de forma inovadora: ele usa uma rede descentralizada onde todos os participantes (os "nós") têm acesso a um registro completo de todas as transações. Cada nó verifica se as transações são válidas e se a moeda não foi gasta duas vezes. Quando a maioria dos nós concorda com a validade de uma transação, ela é registrada permanentemente na blockchain.
#### Por que isso é importante?
Essa solução elimina a necessidade de confiar em uma única entidade para gerenciar o dinheiro, permitindo que qualquer pessoa no mundo use o Bitcoin sem precisar de permissão de terceiros. Além disso, ela garante que o sistema seja seguro e resistente a fraudes.
---
### 3. Servidor Timestamp
Para assegurar que as transações sejam realizadas de forma segura e transparente, o sistema Bitcoin utiliza algo chamado de "servidor de registro de tempo" (timestamp). Esse servidor funciona como um registro público que organiza as transações em uma ordem específica.
Ele faz isso agrupando várias transações em blocos e criando um código único chamado "hash". Esse hash é como uma impressão digital que representa todo o conteúdo do bloco. O hash de cada bloco é amplamente divulgado, como se fosse publicado em um jornal ou em um fórum público.
Esse processo garante que cada bloco de transações tenha um registro de quando foi criado e que ele existia naquele momento. Além disso, cada novo bloco criado contém o hash do bloco anterior, formando uma cadeia contínua de blocos conectados — conhecida como blockchain.
Com isso, se alguém tentar alterar qualquer informação em um bloco anterior, o hash desse bloco mudará e não corresponderá ao hash armazenado no bloco seguinte. Essa característica torna a cadeia muito segura, pois qualquer tentativa de fraude seria imediatamente detectada.
O sistema de timestamps é essencial para provar a ordem cronológica das transações e garantir que cada uma delas seja única e autêntica. Dessa forma, ele reforça a segurança e a confiança na rede Bitcoin.
---
### 4. Prova-de-Trabalho
Para implementar o registro de tempo distribuído no sistema Bitcoin, utilizamos um mecanismo chamado prova-de-trabalho. Esse sistema é semelhante ao Hashcash, desenvolvido por Adam Back, e baseia-se na criação de um código único, o "hash", por meio de um processo computacionalmente exigente.
A prova-de-trabalho envolve encontrar um valor especial que, quando processado junto com as informações do bloco, gere um hash que comece com uma quantidade específica de zeros. Esse valor especial é chamado de "nonce". Encontrar o nonce correto exige um esforço significativo do computador, porque envolve tentativas repetidas até que a condição seja satisfeita.
Esse processo é importante porque torna extremamente difícil alterar qualquer informação registrada em um bloco. Se alguém tentar mudar algo em um bloco, seria necessário refazer o trabalho de computação não apenas para aquele bloco, mas também para todos os blocos que vêm depois dele. Isso garante a segurança e a imutabilidade da blockchain.
A prova-de-trabalho também resolve o problema de decidir qual cadeia de blocos é a válida quando há múltiplas cadeias competindo. A decisão é feita pela cadeia mais longa, pois ela representa o maior esforço computacional já realizado. Isso impede que qualquer indivíduo ou grupo controle a rede, desde que a maioria do poder de processamento seja mantida por participantes honestos.
Para garantir que o sistema permaneça eficiente e equilibrado, a dificuldade da prova-de-trabalho é ajustada automaticamente ao longo do tempo. Se novos blocos estiverem sendo gerados rapidamente, a dificuldade aumenta; se estiverem sendo gerados muito lentamente, a dificuldade diminui. Esse ajuste assegura que novos blocos sejam criados aproximadamente a cada 10 minutos, mantendo o sistema estável e funcional.
---
### 5. Rede
A rede Bitcoin é o coração do sistema e funciona de maneira distribuída, conectando vários participantes (ou nós) para garantir o registro e a validação das transações. Os passos para operar essa rede são:
1. **Transmissão de Transações**: Quando alguém realiza uma nova transação, ela é enviada para todos os nós da rede. Isso é feito para garantir que todos estejam cientes da operação e possam validá-la.
2. **Coleta de Transações em Blocos**: Cada nó agrupa as novas transações recebidas em um "bloco". Este bloco será preparado para ser adicionado à cadeia de blocos (a blockchain).
3. **Prova-de-Trabalho**: Os nós competem para resolver a prova-de-trabalho do bloco, utilizando poder computacional para encontrar um hash válido. Esse processo é como resolver um quebra-cabeça matemático difícil.
4. **Envio do Bloco Resolvido**: Quando um nó encontra a solução para o bloco (a prova-de-trabalho), ele compartilha esse bloco com todos os outros nós na rede.
5. **Validação do Bloco**: Cada nó verifica o bloco recebido para garantir que todas as transações nele contidas sejam válidas e que nenhuma moeda tenha sido gasta duas vezes. Apenas blocos válidos são aceitos.
6. **Construção do Próximo Bloco**: Os nós que aceitaram o bloco começam a trabalhar na criação do próximo bloco, utilizando o hash do bloco aceito como base (hash anterior). Isso mantém a continuidade da cadeia.
#### Resolução de Conflitos e Escolha da Cadeia Mais Longa
Os nós sempre priorizam a cadeia mais longa, pois ela representa o maior esforço computacional já realizado, garantindo maior segurança. Se dois blocos diferentes forem compartilhados simultaneamente, os nós trabalharão no primeiro bloco recebido, mas guardarão o outro como uma alternativa. Caso o segundo bloco eventualmente forme uma cadeia mais longa (ou seja, tenha mais blocos subsequentes), os nós mudarão para essa nova cadeia.
#### Tolerância a Falhas
A rede é robusta e pode lidar com mensagens que não chegam a todos os nós. Uma transação não precisa alcançar todos os nós de imediato; basta que chegue a um número suficiente deles para ser incluída em um bloco. Da mesma forma, se um nó não receber um bloco em tempo hábil, ele pode solicitá-lo ao perceber que está faltando quando o próximo bloco é recebido.
Esse mecanismo descentralizado permite que a rede Bitcoin funcione de maneira segura, confiável e resiliente, sem depender de uma autoridade central.
---
### 6. Incentivo
O incentivo é um dos pilares fundamentais que sustenta o funcionamento da rede Bitcoin, garantindo que os participantes (nós) continuem operando de forma honesta e contribuindo com recursos computacionais. Ele é estruturado em duas partes principais: a recompensa por mineração e as taxas de transação.
#### Recompensa por Mineração
Por convenção, o primeiro registro em cada bloco é uma transação especial que cria novas moedas e as atribui ao criador do bloco. Essa recompensa incentiva os mineradores a dedicarem poder computacional para apoiar a rede. Como não há uma autoridade central para emitir moedas, essa é a maneira pela qual novas moedas entram em circulação. Esse processo pode ser comparado ao trabalho de garimpeiros, que utilizam recursos para colocar mais ouro em circulação. No caso do Bitcoin, o "recurso" consiste no tempo de CPU e na energia elétrica consumida para resolver a prova-de-trabalho.
#### Taxas de Transação
Além da recompensa por mineração, os mineradores também podem ser incentivados pelas taxas de transação. Se uma transação utiliza menos valor de saída do que o valor de entrada, a diferença é tratada como uma taxa, que é adicionada à recompensa do bloco contendo essa transação. Com o passar do tempo e à medida que o número de moedas em circulação atinge o limite predeterminado, essas taxas de transação se tornam a principal fonte de incentivo, substituindo gradualmente a emissão de novas moedas. Isso permite que o sistema opere sem inflação, uma vez que o número total de moedas permanece fixo.
#### Incentivo à Honestidade
O design do incentivo também busca garantir que os participantes da rede mantenham um comportamento honesto. Para um atacante que consiga reunir mais poder computacional do que o restante da rede, ele enfrentaria duas escolhas:
1. Usar esse poder para fraudar o sistema, como reverter transações e roubar pagamentos.
2. Seguir as regras do sistema, criando novos blocos e recebendo recompensas legítimas.
A lógica econômica favorece a segunda opção, pois um comportamento desonesto prejudicaria a confiança no sistema, diminuindo o valor de todas as moedas, incluindo aquelas que o próprio atacante possui. Jogar dentro das regras não apenas maximiza o retorno financeiro, mas também preserva a validade e a integridade do sistema.
Esse mecanismo garante que os incentivos econômicos estejam alinhados com o objetivo de manter a rede segura, descentralizada e funcional ao longo do tempo.
---
### 7. Recuperação do Espaço em Disco
Depois que uma moeda passa a estar protegida por muitos blocos na cadeia, as informações sobre as transações antigas que a geraram podem ser descartadas para economizar espaço em disco. Para que isso seja possível sem comprometer a segurança, as transações são organizadas em uma estrutura chamada "árvore de Merkle". Essa árvore funciona como um resumo das transações: em vez de armazenar todas elas, guarda apenas um "hash raiz", que é como uma assinatura compacta que representa todo o grupo de transações.
Os blocos antigos podem, então, ser simplificados, removendo as partes desnecessárias dessa árvore. Apenas a raiz do hash precisa ser mantida no cabeçalho do bloco, garantindo que a integridade dos dados seja preservada, mesmo que detalhes específicos sejam descartados.
Para exemplificar: imagine que você tenha vários recibos de compra. Em vez de guardar todos os recibos, você cria um documento e lista apenas o valor total de cada um. Mesmo que os recibos originais sejam descartados, ainda é possível verificar a soma com base nos valores armazenados.
Além disso, o espaço ocupado pelos blocos em si é muito pequeno. Cada bloco sem transações ocupa apenas cerca de 80 bytes. Isso significa que, mesmo com blocos sendo gerados a cada 10 minutos, o crescimento anual em espaço necessário é insignificante: apenas 4,2 MB por ano. Com a capacidade de armazenamento dos computadores crescendo a cada ano, esse espaço continuará sendo trivial, garantindo que a rede possa operar de forma eficiente sem problemas de armazenamento, mesmo a longo prazo.
---
### 8. Verificação de Pagamento Simplificada
É possível confirmar pagamentos sem a necessidade de operar um nó completo da rede. Para isso, o usuário precisa apenas de uma cópia dos cabeçalhos dos blocos da cadeia mais longa (ou seja, a cadeia com maior esforço de trabalho acumulado). Ele pode verificar a validade de uma transação ao consultar os nós da rede até obter a confirmação de que tem a cadeia mais longa. Para isso, utiliza-se o ramo Merkle, que conecta a transação ao bloco em que ela foi registrada.
Entretanto, o método simplificado possui limitações: ele não pode confirmar uma transação isoladamente, mas sim assegurar que ela ocupa um lugar específico na cadeia mais longa. Dessa forma, se um nó da rede aprova a transação, os blocos subsequentes reforçam essa aceitação.
A verificação simplificada é confiável enquanto a maioria dos nós da rede for honesta. Contudo, ela se torna vulnerável caso a rede seja dominada por um invasor. Nesse cenário, um atacante poderia fabricar transações fraudulentas que enganariam o usuário temporariamente até que o invasor obtivesse controle completo da rede.
Uma estratégia para mitigar esse risco é configurar alertas nos softwares de nós completos. Esses alertas identificam blocos inválidos, sugerindo ao usuário baixar o bloco completo para confirmar qualquer inconsistência. Para maior segurança, empresas que realizam pagamentos frequentes podem preferir operar seus próprios nós, reduzindo riscos e permitindo uma verificação mais direta e confiável.
---
### 9. Combinando e Dividindo Valor
No sistema Bitcoin, cada unidade de valor é tratada como uma "moeda" individual, mas gerenciar cada centavo como uma transação separada seria impraticável. Para resolver isso, o Bitcoin permite que valores sejam combinados ou divididos em transações, facilitando pagamentos de qualquer valor.
#### Entradas e Saídas
Cada transação no Bitcoin é composta por:
- **Entradas**: Representam os valores recebidos em transações anteriores.
- **Saídas**: Correspondem aos valores enviados, divididos entre os destinatários e, eventualmente, o troco para o remetente.
Normalmente, uma transação contém:
- Uma única entrada com valor suficiente para cobrir o pagamento.
- Ou várias entradas combinadas para atingir o valor necessário.
O valor total das saídas nunca excede o das entradas, e a diferença (se houver) pode ser retornada ao remetente como **troco**.
#### Exemplo Prático
Imagine que você tem duas entradas:
1. 0,03 BTC
2. 0,07 BTC
Se deseja enviar 0,08 BTC para alguém, a transação terá:
- **Entrada**: As duas entradas combinadas (0,03 + 0,07 BTC = 0,10 BTC).
- **Saídas**: Uma para o destinatário (0,08 BTC) e outra como troco para você (0,02 BTC).
Essa flexibilidade permite que o sistema funcione sem precisar manipular cada unidade mínima individualmente.
#### Difusão e Simplificação
A difusão de transações, onde uma depende de várias anteriores e assim por diante, não representa um problema. Não é necessário armazenar ou verificar o histórico completo de uma transação para utilizá-la, já que o registro na blockchain garante sua integridade.
---
### 10. Privacidade
O modelo bancário tradicional oferece um certo nível de privacidade, limitando o acesso às informações financeiras apenas às partes envolvidas e a um terceiro confiável (como bancos ou instituições financeiras). No entanto, o Bitcoin opera de forma diferente, pois todas as transações são publicamente registradas na blockchain. Apesar disso, a privacidade pode ser mantida utilizando **chaves públicas anônimas**, que desvinculam diretamente as transações das identidades das partes envolvidas.
#### Fluxo de Informação
- No **modelo tradicional**, as transações passam por um terceiro confiável que conhece tanto o remetente quanto o destinatário.
- No **Bitcoin**, as transações são anunciadas publicamente, mas sem revelar diretamente as identidades das partes. Isso é comparável a dados divulgados por bolsas de valores, onde informações como o tempo e o tamanho das negociações (a "fita") são públicas, mas as identidades das partes não.
#### Protegendo a Privacidade
Para aumentar a privacidade no Bitcoin, são adotadas as seguintes práticas:
1. **Chaves Públicas Anônimas**: Cada transação utiliza um par de chaves diferentes, dificultando a associação com um proprietário único.
2. **Prevenção de Ligação**: Ao usar chaves novas para cada transação, reduz-se a possibilidade de links evidentes entre múltiplas transações realizadas pelo mesmo usuário.
#### Riscos de Ligação
Embora a privacidade seja fortalecida, alguns riscos permanecem:
- Transações **multi-entrada** podem revelar que todas as entradas pertencem ao mesmo proprietário, caso sejam necessárias para somar o valor total.
- O proprietário da chave pode ser identificado indiretamente por transações anteriores que estejam conectadas.
---
### 11. Cálculos
Imagine que temos um sistema onde as pessoas (ou computadores) competem para adicionar informações novas (blocos) a um grande registro público (a cadeia de blocos ou blockchain). Este registro é como um livro contábil compartilhado, onde todos podem verificar o que está escrito.
Agora, vamos pensar em um cenário: um atacante quer enganar o sistema. Ele quer mudar informações já registradas para beneficiar a si mesmo, por exemplo, desfazendo um pagamento que já fez. Para isso, ele precisa criar uma versão alternativa do livro contábil (a cadeia de blocos dele) e convencer todos os outros participantes de que essa versão é a verdadeira.
Mas isso é extremamente difícil.
#### Como o Ataque Funciona
Quando um novo bloco é adicionado à cadeia, ele depende de cálculos complexos que levam tempo e esforço. Esses cálculos são como um grande quebra-cabeça que precisa ser resolvido.
- Os “bons jogadores” (nós honestos) estão sempre trabalhando juntos para resolver esses quebra-cabeças e adicionar novos blocos à cadeia verdadeira.
- O atacante, por outro lado, precisa resolver quebra-cabeças sozinho, tentando “alcançar” a cadeia honesta para que sua versão alternativa pareça válida.
Se a cadeia honesta já está vários blocos à frente, o atacante começa em desvantagem, e o sistema está projetado para que a dificuldade de alcançá-los aumente rapidamente.
#### A Corrida Entre Cadeias
Você pode imaginar isso como uma corrida. A cada bloco novo que os jogadores honestos adicionam à cadeia verdadeira, eles se distanciam mais do atacante. Para vencer, o atacante teria que resolver os quebra-cabeças mais rápido que todos os outros jogadores honestos juntos.
Suponha que:
- A rede honesta tem **80% do poder computacional** (ou seja, resolve 8 de cada 10 quebra-cabeças).
- O atacante tem **20% do poder computacional** (ou seja, resolve 2 de cada 10 quebra-cabeças).
Cada vez que a rede honesta adiciona um bloco, o atacante tem que "correr atrás" e resolver mais quebra-cabeças para alcançar.
#### Por Que o Ataque Fica Cada Vez Mais Improvável?
Vamos usar uma fórmula simples para mostrar como as chances de sucesso do atacante diminuem conforme ele precisa "alcançar" mais blocos:
P = (q/p)^z
- **q** é o poder computacional do atacante (20%, ou 0,2).
- **p** é o poder computacional da rede honesta (80%, ou 0,8).
- **z** é a diferença de blocos entre a cadeia honesta e a cadeia do atacante.
Se o atacante está 5 blocos atrás (z = 5):
P = (0,2 / 0,8)^5 = (0,25)^5 = 0,00098, (ou, 0,098%)
Isso significa que o atacante tem menos de 0,1% de chance de sucesso — ou seja, é muito improvável.
Se ele estiver 10 blocos atrás (z = 10):
P = (0,2 / 0,8)^10 = (0,25)^10 = 0,000000095, (ou, 0,0000095%).
Neste caso, as chances de sucesso são praticamente **nulas**.
#### Um Exemplo Simples
Se você jogar uma moeda, a chance de cair “cara” é de 50%. Mas se precisar de 10 caras seguidas, sua chance já é bem menor. Se precisar de 20 caras seguidas, é quase impossível.
No caso do Bitcoin, o atacante precisa de muito mais do que 20 caras seguidas. Ele precisa resolver quebra-cabeças extremamente difíceis e alcançar os jogadores honestos que estão sempre à frente. Isso faz com que o ataque seja inviável na prática.
#### Por Que Tudo Isso é Seguro?
- **A probabilidade de sucesso do atacante diminui exponencialmente.** Isso significa que, quanto mais tempo passa, menor é a chance de ele conseguir enganar o sistema.
- **A cadeia verdadeira (honesta) está protegida pela força da rede.** Cada novo bloco que os jogadores honestos adicionam à cadeia torna mais difícil para o atacante alcançar.
#### E Se o Atacante Tentar Continuar?
O atacante poderia continuar tentando indefinidamente, mas ele estaria gastando muito tempo e energia sem conseguir nada. Enquanto isso, os jogadores honestos estão sempre adicionando novos blocos, tornando o trabalho do atacante ainda mais inútil.
Assim, o sistema garante que a cadeia verdadeira seja extremamente segura e que ataques sejam, na prática, impossíveis de ter sucesso.
---
### 12. Conclusão
Propusemos um sistema de transações eletrônicas que elimina a necessidade de confiança, baseando-se em assinaturas digitais e em uma rede peer-to-peer que utiliza prova de trabalho. Isso resolve o problema do gasto duplo, criando um histórico público de transações imutável, desde que a maioria do poder computacional permaneça sob controle dos participantes honestos.
A rede funciona de forma simples e descentralizada, com nós independentes que não precisam de identificação ou coordenação direta. Eles entram e saem livremente, aceitando a cadeia de prova de trabalho como registro do que ocorreu durante sua ausência. As decisões são tomadas por meio do poder de CPU, validando blocos legítimos, estendendo a cadeia e rejeitando os inválidos.
Com este mecanismo de consenso, todas as regras e incentivos necessários para o funcionamento seguro e eficiente do sistema são garantidos.
---
Faça o download do whitepaper original em português:
https://bitcoin.org/files/bitcoin-paper/bitcoin_pt_br.pdf
-

@ 50809a53:e091f164
2025-01-20 22:30:01
For starters, anyone who is interested in curating and managing "notes, lists, bookmarks, kind-1 events, or other stuff" should watch this video:
https://youtu.be/XRpHIa-2XCE
Now, assuming you have watched it, I will proceed assuming you are aware of many of the applications that exist for a very similar purpose. I'll break them down further, following a similar trajectory in order of how I came across them, and a bit about my own path on this journey.
We'll start way back in the early 2000s, before Bitcoin existed. We had https://zim-wiki.org/
It is tried and true, and to this day stands to present an option for people looking for a very simple solution to a potentially complex problem. Zim-Wiki works. But it is limited.
Let's step into the realm of proprietary. Obsidian, Joplin, and LogSeq. The first two are entirely cloud-operative applications, with more of a focus on the true benefit of being a paid service. I will assume anyone reading this is capable of exploring the marketing of these applications, or trying their freemium product, to get a feeling for what they are capable of.
I bring up Obsidian because it is very crucial to understand the market placement of publication. We know social media handles the 'hosting' problem of publishing notes "and other stuff" by harvesting data and making deals with advertisers. But- what Obsidian has evolved to offer is a full service known as 'publish'. This means users can stay in the proprietary pipeline, "from thought to web." all for $8/mo.
See: https://obsidian.md/publish
THIS IS NOSTR'S PRIMARY COMPETITION. WE ARE HERE TO DISRUPT THIS MARKET, WITH NOTES AND OTHER STUFF. WITH RELAYS. WITH THE PROTOCOL.
Now, on to Joplin. I have never used this, because I opted to study the FOSS market and stayed free of any reliance on a paid solution. Many people like Joplin, and I gather the reason is because it has allowed itself to be flexible and good options that integrate with Joplin seems to provide good solutions for users who need that functionality. I see Nostr users recommending Joplin, so I felt it was worthwhile to mention as a case-study option. I myself need to investigate it more, but have found comfort in other solutions.
LogSeq - This is my "other solutions." It seems to be trapped in its proprietary web of funding and constraint. I use it because it turns my desktop into a power-house of note archival. But by using it- I AM TRAPPED TOO. This means LogSeq is by no means a working solution for Nostr users who want a long-term archival option.
But the trap is not a cage. It's merely a box. My notes can be exported to other applications with graphing and node-based information structure. Specifically, I can export these notes to:
- Text
- OPML
- HTML
- and, PNG, for whatever that is worth.
Let's try out the PNG option, just for fun. Here's an exported PNG of my "Games on Nostr" list, which has long been abandoned. I once decided to poll some CornyChat users to see what games they enjoyed- and I documented them in a LogSeq page for my own future reference. You can see it here:
https://i.postimg.cc/qMBPDTwr/image.png
This is a very simple example of how a single "page" or "list" in LogSeq can be multipurpose. It is a small list, with multiple "features" or variables at play. First, I have listed out a variety of complex games that might make sense with "multiplayer" identification that relies on our npubs or nip-05 addresses to aggregate user data. We can ALL imagine playing games like Tetris, Snake, or Catan together with our Nostr identities. But of course we are a long way from breaking into the video game market.
On a mostly irrelevant sidenote- you might notice in my example list, that I seem to be excited about a game called Dot.Hack. I discovered this small game on Itch.io and reached out to the developer on Twitter, in an attempt to purple-pill him, but moreso to inquire about his game. Unfortunately there was no response, even without mention of Nostr. Nonetheless, we pioneer on. You can try the game here: https://propuke.itch.io/planethack
So instead let's focus on the structure of "one working list." The middle section of this list is where I polled users, and simply listed out their suggestions. Of course we discussed these before I documented, so it is note a direct result of a poll, but actually a working interaction of poll results! This is crucial because it separates my list from the aggregated data, and implies its relevance/importance.
The final section of this ONE list- is the beginnings of where I conceptually connect nostr with video game functionality. You can look at this as the beginning of a new graph, which would be "Video Game Operability With Nostr".
These three sections make up one concept within my brain. It exists in other users' brains too- but of course they are not as committed to the concept as myself- the one managing the communal discussion.
With LogSeq- I can grow and expand these lists. These lists can become graphs. Those graphs can become entire catalogues of information than can be shared across the web.
I can replicate this system with bookmarks, ideas, application design, shopping lists, LLM prompting, video/music playlists, friend lists, RELAY lists, the LIST goes ON forever!
So where does that lead us? I think it leads us to kind-1 events. We don't have much in the way of "kind-1 event managers" because most developers would agree that "storing kind-1 events locally" is.. at the very least, not so important. But it could be! If only a superapp existed that could interface seamlessly with nostr, yada yada.. we've heard it all before. We aren't getting a superapp before we have microapps. Basically this means frameworking the protocol before worrying about the all-in-one solution.
So this article will step away from the deep desire for a Nostr-enabled, Rust-built, FOSS, non-commercialized FREEDOM APP, that will exist one day, we hope.
Instead, we will focus on simple attempts of the past. I encourage others to chime in with their experience.
Zim-Wiki is foundational. The user constructs pages, and can then develop them into books.
LogSeq has the right idea- but is constrained in too many ways to prove to be a working solution at this time. However, it is very much worth experimenting with, and investigating, and modelling ourselves after.
https://workflowy.com/ is next on our list. This is great for users who think LogSeq is too complex. They "just want simple notes." Get a taste with WorkFlowy. You will understand why LogSeq is powerful if you see value in WF.
I am writing this article in favor of a redesign of LogSeq to be compatible with Nostr. I have been drafting the idea since before Nostr existed- and with Nostr I truly believe it will be possible. So, I will stop to thank everyone who has made Nostr what it is today. I wouldn't be publishing this without you!
One app I need to investigate more is Zettlr. I will mention it here for others to either discuss or investigate, as it is also mentioned some in the video I opened with. https://www.zettlr.com/
On my path to finding Nostr, before its inception, was a service called Deta.Space. This was an interesting project, not entirely unique or original, but completely fresh and very beginner-friendly. DETA WAS AN AWESOME CLOUD OS. And we could still design a form of Nostr ecosystem that is managed in this way. But, what we have now is excellent, and going forward I only see "additional" or supplemental.
Along the timeline, Deta sunsetted their Space service and launched https://deta.surf/
You might notice they advertise that "This is the future of bookmarks."
I have to wonder if perhaps I got through to them that bookmarking was what their ecosystem could empower. While I have not tried Surf, it looks interested, but does not seem to address what I found most valuable about Deta.Space: https://webcrate.app/
WebCrate was an early bookmarking client for Deta.Space which was likely their most popular application. What was amazing about WebCrate was that it delivered "simple bookmarking." At one point I decided to migrate my bookmarks from other apps, like Pocket and WorkFlowy, into WebCrate.
This ended up being an awful decision, because WebCrate is no longer being developed. However, to much credit of Deta.Space, my WebCrate instance is still running and completely functional. I have since migrated what I deem important into a local LogSeq graph, so my bookmarks are safe. But, the development of WebCrate is note.
WebCrate did not provide a working directory of crates. All creates were contained within a single-level directory. Essentially there were no layers. Just collections of links. This isn't enough for any user to effectively manage their catalogue of notes. With some pressure, I did encourage the German developer to flesh out a form of tagging, which did alleviate the problem to some extent. But as we see with Surf, they have pioneered in another direction.
That brings us back to Nostr. Where can we look for the best solution? There simply isn't one yet. But, we can look at some other options for inspiration.
HedgeDoc: https://hedgedoc.org/
I am eager for someone to fork HedgeDoc and employ Nostr sign-in. This is a small step toward managing information together within the Nostr ecosystem. I will attempt this myself eventually, if no one else does, but I am prioritizing my development in this way:
1. A nostr client that allows the cataloguing and management of relays locally.
2. A LogSeq alternative with Nostr interoperability.
3. HedgeDoc + Nostr is #3 on my list, despite being the easiest option.
Check out HedgeDoc 2.0 if you have any interest in a cooperative Markdown experience on Nostr: https://docs.hedgedoc.dev/
Now, this article should catch up all of my dearest followers, and idols, to where I stand with "bookmarking, note-taking, list-making, kind-1 event management, frameworking, and so on..."
Where it leads us to, is what's possible. Let's take a look at what's possible, once we forego ALL OF THE PROPRIETARY WEB'S BEST OPTIONS:
https://denizaydemir.org/
https://denizaydemir.org/graph/how-logseq-should-build-a-world-knowledge-graph/
https://subconscious.network/
Nostr is even inspired by much of the history that has gone into information management systems. nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn I know looks up to Gordon Brander, just as I do. You can read his articles here: https://substack.com/@gordonbrander and they are very much worth reading! Also, I could note that the original version of Highlighter by nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft was also inspired partially by WorkFlowy.
About a year ago, I was mesmerized coming across SubText and thinking I had finally found the answer Nostr might even be looking for. But, for now I will just suggest that others read the Readme.md on the SubText Gtihub, as well as articles by Brander.
Good luck everyone. I am here to work with ANYONE who is interested in these type of solution on Nostr.
My first order of business in this space is to spearhead a community of npubs who share this goal. Everyone who is interested in note-taking or list-making or bookmarking is welcome to join. I have created an INVITE-ONLY relay for this very purpose, and anyone is welcome to reach out if they wish to be added to the whitelist. It should be freely readable in the near future, if it is not already, but for now will remain a closed-to-post community to preemptively mitigate attack or spam. Please reach out to me if you wish to join the relay. https://logstr.mycelium.social/
With this article, I hope people will investigate and explore the options available. We have lots of ground to cover, but all of the right resources and manpower to do so. Godspeed, Nostr.
#Nostr #Notes #OtherStuff #LogSec #Joplin #Obsidian
-

@ 129f5189:3a441803
2025-01-20 19:20:16
Many believe that to buy #Bitcoin, they need to purchase 1 whole #Bitcoin, which may seem unaffordable for most people today. This belief is rooted in a misunderstanding of how #Bitcoin works.
#Bitcoin is divisible up to eight decimal places, and the smallest unit is called a satoshi. 1 #Bitcoin equals 100 million satoshis.
https://image.nostr.build/4c25abae971d2d817d2e9c38cac0ae7ea6a439e39bc7e2db46a610cc91a58e4b.jpg
This means that anyone can start by purchasing a fraction of #Bitcoin, like 0.0001 #BTC (10,000 satoshis), for a much smaller amount than the price of 1 whole #Bitcoin.
The mistake lies in comparing the value of 1 #Bitcoin to the price of 1 unit of traditional currency, such as the dollar or the real. This comparison ignores #Bitcoin’s divisibility and fungibility.
Imagine if someone said they couldn’t buy gold because they couldn’t afford a whole gold bar. Does that make sense? Of course not. Just as gold can be bought in grams, #Bitcoin can be purchased in fractions.
Another important point is understanding that the value of a satoshi is proportional to the value of #Bitcoin as a whole. If #Bitcoin reaches a price of $1 million, for example, 1 satoshi will be worth $0.01.
What ultimately matters is the relative appreciation of the asset, not the number of units you own.
Therefore, the unit bias is merely a psychological barrier.
Instead of focusing on the price of 1 whole #Bitcoin, think about the opportunity to accumulate satoshis, which are just as valuable as any fraction of #Bitcoin.
After all, every satoshi is part of the largest computational network in the world—scarce and decentralized—that is poised to transform the global financial system.
Buying #Bitcoin isn’t about how much you can buy today, but about understanding the value it represents in the long term. Don’t let the unit bias stop you from being part of this monetary revolution.
-

@ df478568:2a951e67
2025-01-20 18:28:44
Affiliate Links
I earn a commission for these products and services, but I would recommend them even if they did not pay me.
[BTCPins](https://btcpins.com/?aff=ex1GhhNeeU9-PQ1-ZVEkarU9bSnsNyq98Jy_lEUBLmsrWsCqa69PYohMWcCOGK9tK1rAqmuvT2KITFnAjhivbfOajnP3D8A8O09Hi-OY4K8)
[Strike](https://invite.strike.me/NGQDMT)
[Cash App](https://cash.app/app/MCLFTJT)
[PayPerQ](https://ppq.ai/invite/b28d3a37)
This is the cheapest way to use AI on the Internet. The pics are spectacular. It cost me about 20 sats to make the cover for this affiliate page.
[Start9](https://start9.com/?ref=marc26z.npubpro.com/)
I don’t really have an affiliate link for these guys, but I would like one. Anyway, they make the easiest home servers. I highly recommend them. I like that I can use the cloudflare tunnel app to host everythng on the clearnet. Let me know if you need any help with this.
## Recommendations
These companies do not pay me, but I recommend them anyway.
### [Subscribe To Support My Work](https://app.paywithflash.com/subscription-page?flashId=1110&ref)
I use [PayWithFlash](https://app.paywithflash.com) to create a Substack like subscription. You can subscribe for as little as 1,000 per month. If that is too many sats to ask, you could always zap my articles instead. Thank you.
### [The Leather Mint](https://theleathermint.com/)
The Leathermint makes great, custom-sized leather belts and awesome-looking wallets. I have a belt and it fits better than any belt I’ve ever warn because it’s custom size. I have had mine for about a year. The chrome is coming off a little at the top but I don’t tuck in shirts anyway.
### [CoinKite](https://store.coinkite.com/store)
They make my favorite products ever. I suggest getting a few SEEDPLATE® Kit’s no matter what hardware wallets you use. I also like using a dry-erase marker first because there are no second chances when punching a letter. It’s best to use a dry-erase marker first. If you make a mistake erase it. Then, after you double checked the first side, go over the dry-erase marker with a permanent marker. Then do the same to the other side. If you’re sure every letter is correct, punch the holes.
There are many plates with sufficient heat resistance, but I like the SEEDPLATE because they are the easiest to destroy if you ever need to. Instead of etching out stamps on washers, you just add extra punches if you must destroy the seed.
### [Alby Hub](https://albyhub.com/)
Look, if you want to run your own lightning node, this is the way to go. If you have a Start9 or are technical, you can run it yourself. If you’re less technical, they offer a cloud service. I was one of the early beta testers of this software and I think it’s the easiest way to run a lightning node.
## Free and Open Software
### [Primal.net](https://github.com/PrimalHQ/primal-web-app) os a corporation building stuff on nostr. If you’re technical, you can run it yourself. If not, you ca download the app for free. They charge a fee for premium services. I pay for this because I want to support companies that contribute to nostr development and help bitcoin be used as peer-to-peer electronic cash.
I think of Primal as a custodial bitcoin wallet that allows anyone to participate in the biggest circular economy in the world. TikTok was banned in the United States which means it is no longer available for citizens of the United States to download the app. There are ways to get around these restrictions, but I choose not to because I do not want the CCP, or any government to have access to information if their goal is to use it against me. I believe every government, foreign or domestic wants to use your information against you. Nostr allows me to opt out of these stupid games with stupid likes.
With Primal, I am the customer, not the product. I choose the algorithms I want to see, not the CCP , USG or corporations. Even if Primal decided to say, “Marc sucks. We will now censor him.” I will only lose the https://primal.net/marc, the OG status, and my primal lightning address. It also means they would stop getting my sats every month, so they are incentivized not to censor. You would have to do something really stupid to get banned from Primal. I’m not sure it’s been done yet, but even if it has, you will not get banned from the nostr protocol.
### [Portainer](https://github.com/portainer/portainer)
Portainer makes it easy to run docker-containers. I first learned how to use it because it is an app on Umbrel. Eventually, I learned you can use Portainer on any Linux computer, so that’s what I do.
It takes some time to learn, but once you do—you become a cloud computing super-wizard.
### [Mealie](https://github.com/mealie-recipes/mealie/)
Mealie is one of my favorite pieces of free and open software that is not related to bitcoin in any shape or form...except it makes grocery shopping easier. I know what you’re thinking. WTF does that have to do with bitcoin? I assume you belong to the *I Want More Bitcoin Club*. You are in good company because ALL Bitcoiners are a member of this club. One way you can stasck more sats is to cut your grocery bill. I believe Mealie helps me do just that.
When I’m grocery shopping, my goal is to get as much healthy food for my sats as possible. To accomplish this, I shop sales. Now, if you’re living in a van, this won’t do much for you, but no worries. You will stack even more sats by cutting your housing costs. If your wife will not agree to live under a bridge and stack sats, then get a freezer in your garage. Fill it with meat you buy on sale. Pork shoulder is 3,000 sats per pound and you don’t what to cook it with? Find a recipe online. Mealie will use machine learning to scrape the ingredients from the recipe. Then you can add it to a grocery list. In other words, you can automate your grocery list right at the grocery isle. This is one way I save sats with Mealie.
I also keep the things my family eats on a regular basis in stock. This is part for emergency preparedness, but it is also for financial preparedness. If you are in a situation where no food is available, all the bitcoin in the world will not save you. I’m not talkig about super volcanos. Hurricanes, tornadoes, and earthquakes happen. So I got this idea from Jack Spirko, but modified it to use with mealie.
Spirko suggests building a 30 day supply of food and water for your family in case of an emergency. You should have a generator and a garden too, but I don’t want to get off track. Once you have this he says: write down every item you use on a notebook and replace it.
This is good advice, but I just add it to my grocery list in mealie.
#### [Shopstr](https://github.com/shopstr-eng/shopstr)
Shopstr is like Facebook marketplace, Amazon, or eBay on nostr. This is what I use to build my store. I want to pause point out how big of a paradigm shift this is. The old web requires permission. Ebay needs permission from the government to become a corporation. They built infrastructure to create their online auction. Everyone on the site must pay eBay a tax. This results in a techno- feudalist society.
When you sell on Shopster, you are selling your wares on nostr, a protocol, not a platform. This changes the relationship between the people and the technology because NO MIDDLEMAN IS REQUIRED. On nostr, there are no digital overlords. You own your data. You host your store. If the current digital overlords shut it down, you can run it yourself. You do not need to pay a tax to eBay, Amazon, or the PayPal mafia.
#### Avocados
I love avocados. They are kind of like free and open source software because you can grow them yourself. ;) I love avocados and **big avocado ag did not pay me to say this**.
-

@ 000002de:c05780a7
2025-01-20 16:27:40
I just finished the audio book read by Norm himself. I must say, if you love Norm you will love this book. I highly recommend the audio book. I don't want to spoil anything but the book is like sitting down with Norm and listening to him tell you stories. You never know what is true or false and if the whole thing IS the joke. I laughed out loud many times.

originally posted at https://stacker.news/items/857482
-

@ 652d58ac:dc4cde60
2025-01-20 14:39:11
**Introduction**
We must rethink how we envision the future. In the short term, things may be worse than we expect, rising inflation, war, and health crises, but this is all part of the fiat dilemma. A system that cannibalizes itself. Yet, at the same time, a new system is emerging.
Bitcoin and Artificial intelligence (AI) will be central to this foundation, providing humanity with the time and tools needed to thrive.
How Technology Drives Deflation
As Jeff Booth so masterfully explains, technology is inherently deflationary. Over time, through free market competition and productivity gains, prices should fall to their marginal cost of production.
Yet, in our inflationary fiat system, productivity gains are eroded by the continuous increase in the money supply, driving prices higher. Instead of allowing prices to approach their marginal cost of production as they should, goods and services become more expensive due to monetary inflation.
This principle, that an expanding money supply reduces the purchasing power of individual monetary units and ultimately undermines wealth creation, was recognized as early as 1517 by Copernicus in the quantity theory of money.
Because bitcoin is limited in supply, productivity gains across the economy can lead to greater wealth for all participants in the system, as the price of goods and services falls to the marginal cost of production over time. Rather than rise due to an increase in the monetary supply. We need Bitcoin to ensure that the productivity gains that drive the economy forward can have a lasting, sustainable impact.
**The Interplay of Bitcoin und AI**
Since the existing system benefits from inflation, market participants are often manipulated into believing that AI is inherently dangerous. While there are significant risks associated with AI, particularly its potential for centralization and manipulation, the technology itself offers great opportunities. The real problem lies in the inflationary monetary system, not AI.
Artificial intelligence is set to increasingly shape the workplace, trade, and finance. Consider the “Magnificent Seven”, a group of tech giants, Apple, Microsoft, Amazon, Alphabet (Google), Meta (Facebook), Nvidia, and Tesla, that all leverage AI as a key driver of productivity.
In 2023, the financial services industry alone invested an estimated $35 billion in AI, with banking leading the charge, accounting for approximately $21 billion. This is particularly relevant to Bitcoin, since it serves as both money and a financial system.
As AI becomes more sophisticated, it will increasingly rely on a digital currency that aligns with its digital nature, such as bitcoin, which offers both scalability and speed through the Lightning Network.
For instance, AI systems could use Bitcoin to facilitate microtransactions in real time, managing their wallets autonomously to process payments for services or data. This would unlock new opportunities for AI applications in sectors like actual decentralized finance (DeFi) and machine-to-machine transactions.
The Lightning Network, as a second-layer protocol built on top of Bitcoin, enables transactions to be settled almost instantly and at low cost. This makes it particularly well-suited for AI applications that require fast and reliable transactions.
While some AI and language models can exhibit programmed biases, AI systems, driven by algorithms and data, should strive to prioritize efficiency, minimizing biases wherever possible. If programmed without bias, AI seeks the best tools for operations and decision-making, and Bitcoin offers an optimal solution, providing both the asset and infrastructure needed for efficient, resilient, digital financial systems.
In addition, AI is likely to also contribute to Bitcoin’s development, with algorithms optimizing mining efficiency, hardware usage, forecasting energy demand, and ensuring more efficient resource allocation, all of which will lead to more effective mining strategies.
**Conclusion**
The synergy between Bitcoin and AI has the potential to enable the creation of more efficient, intelligent and resilient systems. These developments will underpin bitcoin’s role as digital money in a digital world, potentially creating positive second-order effects on global financial markets. The impact will be especially profound in industries such as finance, insurance, robotics, lending, investments, architecture, housing, healthcare, logistics, and others, with effects accelerating over time.
The free market is inherently deflationary, because of productivity gains, things, like housing, should become cheaper over time. Yet, this doesn't happen. Inflationary fiat currencies, like the dollar, lose purchasing power as their supply increases, eroding those gains. Bitcoin offers a framework in which productivity gains can have a lasting, sustainable impact.
Bitcoin, as a disinflationary currency with a fixed supply, preserves the value of productivity improvements, allowing prices to fall to their marginal cost of production. This ensures that efficiency gains lead to greater wealth for all participants in the system.
Moreover, since Bitcoin is accessible, it allows wealth to become more attainable for a wider range of people, enabling general living standards to increase more easily. The interplay between Bitcoin and AI is pretty exciting, and it’s becoming clear that the widespread adoption of AI will drive the widespread adoption of Bitcoin. This is necessary, as only Bitcoin, as a counterbalance to the self-destructive fiat system, can protect humanity from the negative effects of inflation. With the accelerated productivity gains of the AI age, Bitcoin becomes even more crucial as a solution, ensuring that these gains can be preserved and shared more equitably.
**Originally published as the 28th edition of my n ewsletter, Bitcoin & AI:**
https://leonwankum.substack.com/p/bitcoin-and-ai
**Photo Credit**: commonedge.org (An Optimist’s Take on AI and the Future of Architecture)
-

@ 011c780a:46e48b1d
2025-01-20 13:03:23
Lake Erie is a paradise for anglers, boasting the world's largest walleye population and some of the highest catch rates in Ohio. For those eager to experience the thrill of fishing on these bountiful waters, booking a charter is the best way to go. However, with numerous options available, how do you choose the right one? Here are some essential tips to help you find the perfect charter for your Lake Erie adventure.
## 1. Look for Experienced Captains and Crews
The expertise of the captain and crew can make or break your fishing trip. Experienced professionals know the best spots to find walleye, how to handle changing weather conditions, and how to ensure you have an enjoyable day on the water.
● Check the company's website for captain biographies or years of experience.
● Look for certifications or affiliations with reputable fishing organisations.
● Read reviews to see if other anglers had positive experiences with the crew.
## 2. Prioritize Safety Measures
Safety should be a top priority when choosing an **[Ohio fishing charter company](https://eyesready.com/)**. Lake Erie can be unpredictable, so you need a charter that prioritises your well-being.
● Ensure the boat is equipped with life jackets, first aid kits, and emergency communication devices.
● Confirm that the captain holds a valid U.S. Coast Guard license.
● Ask about the company's safety protocols in case of adverse weather.
## 3. Assess the Equipment and Boats
● A well-maintained boat and quality fishing gear can elevate your experience.
● Look for charters that provide high-quality rods, reels, and tackle.
● Check if the boat is spacious, clean, and equipped with modern technology like fish finders.
● Ask if the company allows you to bring your gear if you have a preference.
## 4. Check for Customization Options
Every angler has unique needs, whether they're a seasoned pro or a first-timer. Some charters offer tailored experiences to meet your preferences.
● Look for family-friendly charters if you're planning a trip with kids.
● Ask if the company offers half-day, full-day, or multi-day trips.
● Find out if they're willing to adjust their itinerary to focus on specific fishing techniques or areas.
## 5. Read Online Reviews and Testimonials
● The best way to gauge the quality of a charter is through the experiences of others.
● Visit online platforms like Google, Facebook, or TripAdvisor for honest reviews.
● Pay attention to consistent themes in feedback, such as exceptional service, skilled crew, or successful catches.
● Look for photos or videos shared by previous clients to get a better sense of what to expect.
## 6. Consider the Costs and Inclusions
● While price shouldn't be the sole factor, it's important to know what you're paying for.
● Compare prices among different [Lake Erie walleye charters](https://eyesready.com/walleye/) to get a sense of market rates.
● Check what the package includes, such as bait, fishing licenses, or cleaning and packaging your catch.
● Avoid the cheapest options if they seem to cut corners on quality or safety.
## 7. Verify Their Knowledge of Lake Erie
● Ohio's portion of Lake Erie is home to millions of walleye, and the best charters have in-depth knowledge of these waters.
● Ask about their familiarity with local hotspots for walleye.
● Find out if they follow sustainable fishing practices to preserve the lake's ecosystem.
● A knowledgeable crew can also share interesting facts about the lake, making your trip both fun and educational.
### Book Your Perfect Charter Today!
Finding the right Ohio fishing charter company is the first step to an unforgettable Lake Erie adventure. By prioritising experience, safety, equipment quality, and customer reviews, you can ensure a successful and enjoyable trip. For those looking to create lasting memories on Lake Erie, Eyes Ready Charters is a trusted name offering top-notch services to anglers of all skill levels. Book your trip today and experience the thrill of walleye fishing like never before!
-

@ dffd3ffc:5ade7be1
2025-01-04 12:58:17
# Nostr 利用開始から 1 年を迎えて
## はじめに
みなさんこんにちは。おっぱぴぃです。
[ハッカーのおもちゃとしての Nostr のススメ](https://qiita.com/gpsnmeajp/items/2f95d4adf188276146d8) と [Nostr の面白さをエンジニア目線で解説してみる](https://zenn.dev/mattn/articles/cf43423178d65c)をみて Nostr にはじめて投稿をしたのが 2024/01/04 09:04:18 でした。
nostr:nevent1qqsd5v80f9zazxd4kq2r2dls5znd40ht6c7cj4slt6wtlv483vkmxdcjvq66c
Nostr で私が 1 年間をどう過ごしてきたか、振り返ってみようと思います。
## 初投稿日

今見たら 10 リポスト、20 そこそこのリアクションをいただいてたんですね。初投稿というだけでこんなおバズリあそばすことあるんだって思いました。~~みんな年始で暇やったんかな~~
これだけリアクションがあって、フォローもしていただいたおかげで Nostr の印象がよくなったこと、日本人話者にすぐたどり着けてことが Nostr を続けられている要因になっていると思います。あとはエアリプ文化が懐かしい&近すぎず遠すぎずで居心地がよくて沼ったところがあると思います。
その日は[Nostr の Scrapbox(現 Cosense)](https://scrapbox.io/nostr/)をその日中にざっと読み漁って、記事の誤字修正したり、WoS を設定してみたり、Lightning Address を設定したりしていたようです。
nostr:nevent1qqsxml4ak7g3u8gjcyuhy89sd8vlk3fu6we9ecgey69jltd42dr0etcvt0l3w
~~おまえ、このころから大欲情を…~~
## のす会でのオン会(?)
Nostr 日本人ユーザーの集まる Discord サーバとして、「のす会」というものがあります。
過去ログを漁ってるとどうやら 2024/01/15 ごろにボイチャに入りはじめ、
nostr:nevent1qqszm0kv7aulxnmxr2fdxg5cvme7nyv3j6rgfa30cat8cs3npnsep9caz0xyc
その翌日にはのす会にて Geo guesser で遊んだりしていたようです。こじらさんが尋常じゃない強さでどういう事なの…となった覚えがあります。
nostr:nevent1qqs9knrf4ww8g0fsu4l74gxeeh3s9pwpnf47xn8pf5u8pplkz4yatjg03ufd5
こうした経験を経て、徐々に Nostr ユーザーの方と直接会話することのハードルが下がってきた所でした。
## 初のオフ会参加
2 月頭、TL で話題になっていた火鍋を食べた経験がないなぁ…ということで、2024/02/10、[ゴリラ.vim#30~四谷ラボコラボ~](https://gorillavim.connpass.com/event/307622/)の参加と併せて、海底撈火鍋でオフ会を開催したのが Nostr における初めてのオフ会参加&幹事でした。
この日は中国の春節初日だったのもあって異様に店舗が混んでおり、18:00 に予約したのに一行に案内されず、
nostr:nevent1qqspcttj4gv2ey7vkt0wp2nehqfwxjnp55vm4agnwu9kullep88ysccpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsyg87v060ssxrpew6a0vrhkcy36hqppvrwjmlqnrgqrrvf8fghgg0pypsgqqqqqqs07ajzp
顔面が痙攣したり、
nostr:nevent1qqs9d5vycslspatsnx6u5qqqwpfmdt33w2v7xkytljzsfwv56acs79czyr0l60lu824k9yc63jcg7z32fzx6w3cr6zx3mmuns69wxr66mea7zp6f7wn
詫び菓子を貰ったり、
nostr:nevent1qqs8a0u47alv9vexd5r5s5vygs77ecadm6dl9vlky32hjywdx8f3gtczyr0l60lu824k9yc63jcg7z32fzx6w3cr6zx3mmuns69wxr66mea7zgjxmhl
病院待合室みたいな場所で検尿コップで水飲んだりと
nostr:nevent1qqsq44zs04g5zng35ks6jrvrv6uel2f9ls26d7nsc6svuggrlfnvtcgzyp4kuxwwg7530jlp8fn7adq982dnq8ncajv3gyl824y4xzyw6cknkvj37gy
トラウマになりそうなオフ会でした。当時の様子は[nosli でまとめています](https://nostter.app/naddr1qqfkummnd35j6vfhxqmn2dejxuurqvpjxcpzphla8l7r42mzjvdgevy0pg4y3rd8gupaprgaa7fcdzhrpaddu7lpqvzqqqr4gu92anwm)。
今振り返ってもくちゃくちゃの体験してるなと思いますが、
~~クレーターを作りそうな青ウサギがいたものの~~
nostr:nevent1qqsrs8y3phadhcukwjlkjkgdcs43ndkc8a42m88zayfj6p2lex6a6tgpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygrtdcvuu3afzl97zwn8a66q2w5mxq083myezsf7w42f2vyga43d8vpsgqqqqqqsyfx7da
誰も怒らないし宴会自体は楽しかったので、Nostr のオフ会の原体験としては良かったな、と感じています。ひどい思い出ほど振り返ったら美化されるやつかもしれない。
## 各種イベント参加
Nostr には[四谷ラボ](https://428lab.net/)参加者の方が沢山いらっしゃったこと、お声かけいただいた縁などもあり、いろいろなイベントにスタッフとして参加する経験ができました。例えば…
- [Bluesky Meetup in Tokyo Vol.2](https://428lab.connpass.com/event/312335/)
- [技術書典 16](https://techbookfest.org/event/tbf16) ⇒ 関わらせていただいた[のぶこ本](https://books.428lab.net/book/003/)
- [Nostrasia2024](https://nostrasia.com/)
など。
微力ながら、自らの役割に合わせてイベントに貢献させていただけて、とても楽しめました。
自分に自信がなく、私生活では責任が発生する立場を回避しがちであったこともあって、自分としてはこれらのイベント参加はとても貴重な経験になりました。
関係されている方々が思い思いの仕事のやりようでイベントに取り組んでいる様が刺激になったなと思います。
## オフ会履歴
私を Nostr でフォローいただいている方であれば、「こいつ、やたらオフ会行ってないか…?」と思われるでしょう。ということで、自分でも一度整理をしてみました。

**うわっ...私のオフ会参加、多すぎ…?**
~~1 年間は52週しかないねんぞ~~
このように、火鍋のオフ会を皮切りに、相当な数のオフ会に参加させていただきました。オフ会というかもう普通に Nostr で知り合っただけの友人との集まりみたいな感覚になっているかも。
ちなみに、人単位でお会いした回数もまとめています。

※:Nostrasia などのイベントでお会いした回数は除いています。
こうみるとしおと神(かすてらふぃさん)と会った回数めちゃくちゃ多いですね。28,26回だとほぼ2週に1回ペースですが、過去どんなに親しい友人でもこんな頻度で会ってたことないかも。
## 思い出深かった出来事
nostr:nevent1qqsyeyycax9qgrr4qvtty4h62x96vc6lydh8yg7jl5er99zg7wlpdrcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygxll5llcw4tv2f34r9s3u9z5jyd5ars85ydrhhe8p52uv844hnmuypsgqqqqqqskevt6r
nostr:nevent1qqs0sqhtzc4p3vysz5k7l29x2lcnedeys55t7mqp2mz7ugrmw0v725cppemhxue69uhkummn9ekx7mp0qgsdllfllsa2kc5nr2xtprc29fygmf68q0gg6800jwrg4cc0tt08hcgrqsqqqqqpaua8e8
この誤字投稿を経て、私の(たまにほかの人も)誤字は大欲情と呼ばれるようになりました。~~毎回思うけど新しく入ってきた人は何だこれってなるよなこれ~~
その後も酔ってる時を中心に結構誤字をやらかすので、[那月さんによるまとめが作られています](https://nosli.vercel.app/li/naddr1qqfkummnd35j6vfhxgurgdpk8q6nzd3exypzpq4np5cygstsu65vsx0ggphrv23kj4z553sh39xwyur08pqvdsqrqvzqqqr4gupk0ng5)。
名前としては不名誉かもしれませんが、面白いのでOKです。
## おわりに
振り返ってみれば Nostr 日本人ユーザーコミュニティの心地良さに浸った 1 年だったと思います。
Nostr の仕組み自体も好きですが、私はコミュニティの方に目が行っている気がします。
Nostr 歴 1 歳になったので、今後は私が Nostr を使う人々に心地良いと思ってもらえるような人になれるとよいなと思います。
これからもよろしくお願いします。
-

@ df478568:2a951e67
2025-01-20 05:23:36
I took this picture at about block [416,220](https://mempool.marc26z.com/block/000000000000000003b64da342d6d24d066ea5c961e21fdf57cae4318eab3616)(June 13, 2016). The price of eggs on that day was $1.99, 16.5¢ per egg if you still measure stuff with the broken ruler we call fiat. What if we measured the price in sats instead? I found the price on that date from the bitbo calender. According to this website, $1.99 was worth 260,000 sats back then. Each egg cost 21,667 sats! Oh My Zeus!😱

I used this [mempool calculator](https://mempool.marc26z.com/tools/calculator) to see how much that is today. Turns out that it's $272.88 as of block 879,943. Since the fiat ruler is broken, the price of a dozen eggs also has NGU. I took this picture the last time I went to the grocery store. Eggs cost enough to shock fiat maxis. $8.99 OMZ!😱
What does a dozen eggs cost if you ignore the broken ruler? 8,572 sats today, just 714 sats per egg. Holy [Wiemar Republic](https://en.m.wikipedia.org/wiki/Weimar_Republic) Batman! That's 30X cheaper! 😁
For some strange reason I can't pretend to understand, the [Federal reserve tracks the price of eggs denominated in bitcoin](https://fredblog.stlouisfed.org/2022/06/buying-eggs-with-bitcoins/). I guess they want to stay humble and stack money printer go brrrrrr. You can see the price of eggs drop off a cliff like Wile E Coyote on their website.
In The Price of Tommorrow and too many podcasts to mention, Jeff Booth argues the free market makes things cheaper over time, but the fiat syatem is syatematic theft. This theft occurs via inflation, which is really wage deflation. In other words, eggs are getting cheaper over time because egg producers become more efficient. We see tye fruits of this efficiency in Big screen TV's because the fiat price gets cut in half every ten years or so, but this is also a product of a broken ruler. The TV is probably 60X cheaper in bitcoin terms. It makes sense, TV's don't get bird flu, but when you begin using bitcoin as your unit of account, the measurement of value makes more sense than fiat clown world on the broken ruler standard. I remember when coffee was 100,000 sats. Now it's 16,699 sats. Living on the sat standards allows you to see Jeff Booth's thesis play out in real time

## Life Gets More Expensive On The Broken Ruler Standard
I see so many young people on the broken ruler standard bemoan about food and housing prices. There are people with master's degrees who have already lost hope of buying a single family home and achieving the "American dream." To be honest, I would be pretty bummed about it too if I was on the broken ruler standard. A few months ago I spoke with a woman who made at least twice as much fiat as I do say, "I hope this housing market crashes so I can buy a house!"
That's sad. I have a lot of empathy for that feeling. Since the great financial crisis, I've only been able to get part time work, but my family wqs able to get a mortgage worth 12.5 bitcoin at the so-called "height of the market." We put as little money down as possible, 3% and I sold my old 401k for that "money." I also used some of it for repairs and taxes, but went all-in on bitcoin with everything else. Now our house is worth about 5 bitcoin. The way I see it, real estate is always crashing.
People on the broken ruler standard cry, "Wah, Wah. I hope there's a housing crash! Wah! Wah! Muh egg prices!" Buy a brand spanking new car for $50,00 car with a 7% interest rate and they will say, "Congratulations!" The trouble is, the price of the car falls like eggs compared to bitcoin on the broken ruler standard. This is because prices are distorted when measured in a broken ruler standard.
### Get Off The Broken Ruler Standard

Before I met my wife, I played poker to supplement my income. I don't play much anymore, but poker taught me about risk management, probability, game theory, and many other things applicable to bitcoin. Poker gave me the background knowledge I needed to study bitcoin. [In a sly, round-about way](https://youtu.be/nswOYo0zUcI?si=iVjy6e-npEAo9lkH) , poker taught me how to spend less bitcoin than I make. In traditional technical finance terminology, this is called "fucking saving." If you were not taught how to save and spend more than you earn, no matter how many broken ruler bucks you may earn, bitcoin will not work for you.
My wife makes a lot of broken ruler bucks. **Unfortunately, we were broke in 2016 because we both were in school**. Nevertheless, I'm proud of my stack amd I'm now at a point in life where I can get paid in bitcoin with very little risk because of my sugar mama, I mean wife, gets paid very well.
I spend like almost every other American consumer, plastic broken ruler debt cards. I put my little Strike ACH number on the Discover app. I keep a couple million sats on Strike and pay my credit card every month. In other words, I use Strike like a four-letter word: bank.
Sometimes I'll get a craving for tacos., I've never found a food truck that takes bitcoin, but they often use the Cash App. People on the broken ruler standard can't instantaneously send broken ruler bucks from PayPal to Zelle and vice-versa. They must first send broken ruler bucks from PayPal to the bank and then send the broken ruler bucks through Zelle. I can send sats directly from Strike to thr Cash App within seconds.
#### Sats As A Unit Of Account
The price of bitcoin fluctuates which makes it difficult to use as a unit of account. Who wants to divide the price of bitcoin by 100 million. Ain't nobody got time for that. If a whole coin costs 100k, then 1,000 sats = $1.00. This means each 100 sats is worth 10¢. 10 sats = 1¢. If the price drops 50%, 1000 sats is 50¢. If it does a 10X, $1,000 sats is $10.00. Living on a sat standard requires a little math, but it's easy to estimate. For more precise calculations I use mem pools calculator.
Money is a store of value, medium of exchange, and unit of account. If you use bitcoin on all three ways, you are using bitcoin as money. Saving becomes spending less bitcoin, not "buying more bitcoin." If you stack sats, your goal should be to leave the broken ruler standard and adopt sats as the standard. The world will still price your sats with a broken ruler. Sometimes this broken ruler makes you look like a fool. Other times, the broken ruler makes you look like a genius. Therefore, you must stay humble and stack sats.
You'll need some savings before you can deal with the broken ruler fallacy, but once you consistently stack sats and NGU continues to U, you'll eventually see life gets easier when you make sats the standard.
I will sell some sats to pay for my food and I send a tip to the food trucker in bitcoin using the Cash App gift button. It is actually very easy for them to accept bitcoin. They just don't know it yet. I don't proselytize the gospel of our lord and savior Satoshi Nakamoto. I just send them a few thousand sats. Good orange pilling is like good writing: **Show, don't tell**.
##### Does it require KYC?
Yeah, but so does Bank of Broken Rulers.
##### Haven't you heard the phrase, **not your keys, not your bitcoin?**
Yes. It's true. The 2 million sats or so is "not my bitcoin." From my perspective, however, it is the least risky way of paying my bills. I believe it is less risky than keeping broken ruler bucks in a bank. FDIC insurance sounds nice as canceled Insurance policies in the Pacific Palisades.
I could keep my 2 million sats in self-custody in my own lightning wallet. I could use [Zap Planner](https://zapplanner.albylabs.com/) to schedule my payments to hit Strike moments before I pay my bill, but I know me. I've lost sats on the lightning network before. I am more likely to lose the sats on my self-custodial lightning wallet than lose them because Strike could possibly rug-pull me. So for now, I just keep 2 million sats on the app. If bitcoin does a 10X, I'll keep 200,000 sats on Strike. If it drops 50%, I will keep 4 million sats on there.
I typically spend between $600- $1,000 in broken ruler bucks a month. This doesn't include my mortgage or food. My wife pretty much covers that stuff. Life happens though. Sometimes I need to pay a plumber, or a roofer or something, but most months, I have a sat surplus, a phenomena I like to call **sats savings**. My fiat check converts to bitcoin right on payday. I pay my credit cards off that day. If the sats are worth a little more, I pay taxes on that little bit. To make the math easy, say I get paid $1,000 on Friday. When I pay my bills, The broken ruler measurement now says I have $1,100. I pay my credit card. I owe capital gains on that $100 worth of sats. If my paycheck happens to be worth $900,I don’t pay any taxes because I have a loss. I won’t lie. I still get a bit perturbed when the price goes down 10% on payday, but it’s not the end of the world. If it doesn’t go back up by next payday, [good](https://www.youtube.com/watch?v=IdTMDpizis8). I earn more sats. If it goes up by next payday, [good](https://www.youtube.com/watch?v=IdTMDpizis8). All the sats I stacked before can buy more groceries.
#### Get On The Sats Standard
!;make sats the standard](https://gitea.marc26z.com/marc/BlogImprovementProposals/raw/branch/main/pics/Screenshot%20from%202025-01-19%2020-35-55.png)
Making sats the standard does this for the individual on the microeconomic level. Each Bitcoiner gradually accumulates sats. Stack long enough, study long enough, and experience enough 80% dips and you too will develop an unwavering conviction. You get paid in sats. You spend sats. You save sats. You no longer give a damn about your local fiat currency. A dozen eggs cost less than half of a single egg cost 8 years ago. If you lose 50% of your spending power overnight, you can buy less eggs, but a dozen eggs still costs less than 1 egg 8 years ago. Bitcoin is just better money.
If my fiat bank account takes more money out than I have in it, I can do an instant withdrawl on Strike. The fiat appears in my fiat bank account instantly. No more waiting 3-5 days for the money to get there. The bank does not get to keep charging you overdraft fee after overdraft fee for every little transaction. Bitcoin just works better. You can send it all over the world within seconds. You can buy stuff online with it or pay your credit cards. There is literally no reason to hold dollars anymore if you don’t want to. When you’re ready, make sats the standard. If you are not ready, keep stacking.
Onward.
[Marc](nostr:npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0)
[880,018](https://mempool.marc26z.com/block/00000000000000000000bb39704f189da436d0adbed0da2bb334f93cdaa519d9)
[Subscribe with Sats](https://app.paywithflash.com/subscription-page?flashId=1110&ref=p66dxywd2xpyyrdfxwilqcxmchmfw2ixmn2vm74q3atf22du7qmkihyd.onion)
[Shop My Merch](nostr:npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0)
-

@ 3f770d65:7a745b24
2025-01-19 21:48:49
The recent shutdown of TikTok in the United States due to a potential government ban serves as a stark reminder how fragile centralized platforms truly are under the surface. While these platforms offer convenience, a more polished user experience, and connectivity, they are ultimately beholden to governments, corporations, and other authorities. This makes them vulnerable to censorship, regulation, and outright bans. In contrast, Nostr represents a shift in how we approach online communication and content sharing. Built on the principles of decentralization and user choice, Nostr cannot be banned, because it is not a platform—it is a protocol.
**PROTOCOLS, NOT PLATFORMS.**
At the heart of Nostr's philosophy is **user choice**, a feature that fundamentally sets it apart from legacy platforms. In centralized systems, the user experience is dictated by a single person or governing entity. If the platform decides to filter, censor, or ban specific users or content, individuals are left with little action to rectify the situation. They must either accept the changes or abandon the platform entirely, often at the cost of losing their social connections, their data, and their identity.
What's happening with TikTok could never happen on Nostr. With Nostr, the dynamics are completely different. Because it is a protocol, not a platform, no single entity controls the ecosystem. Instead, the protocol enables a network of applications and relays that users can freely choose from. If a particular application or relay implements policies that a user disagrees with, such as censorship, filtering, or even government enforced banning, they are not trapped or abandoned. They have the freedom to move to another application or relay with minimal effort.
**THIS IS POWERFUL.**
Take, for example, the case of a relay that decides to censor specific content. On a legacy platform, this would result in frustration and a loss of access for users. On Nostr, however, users can simply connect to a different relay that does not impose such restrictions. Similarly, if an application introduces features or policies that users dislike, they can migrate to a different application that better suits their preferences, all while retaining their identity and social connections.
The same principles apply to government bans and censorship. A government can ban a specific application or even multiple applications, just as it can block one relay or several relays. China has implemented both tactics, yet Chinese users continue to exist and actively participate on Nostr, demonstrating Nostr's ability to resistant censorship.
How? Simply, it turns into a game of whack-a-mole. When one relay is censored, another quickly takes its place. When one application is banned, another emerges. Users can also bypass these obstacles by running their own relays and applications directly from their homes or personal devices, eliminating reliance on larger entities or organizations and ensuring continuous access.
**AGAIN, THIS IS POWERUFL.**
Nostr's open and decentralized design makes it resistant to the kinds of government intervention that led to TikTok's outages this weekend and potential future ban in the next 90 days. There is no central server to target, no company to regulate, and no single point of failure. (Insert your CEO jokes here). As long as there are individuals running relays and applications, users continue creating notes and sending zaps.
Platforms like TikTok can be silenced with the stroke of a pen, leaving millions of users disconnected and abandoned. Social communication should not be silenced so incredibly easily. No one should have that much power over social interactions.
Will we on-board a massive wave of TikTokers in the coming hours or days? I don't know.
TikTokers may not be ready for Nostr yet, and honestly, Nostr may not be ready for them either. The ecosystem still lacks the completely polished applications, tools, and services they’re accustomed to. This is where we say "we're still early". They may not be early adopters like the current Nostr user base. Until we bridge that gap, they’ll likely move to the next centralized platform, only to face another government ban or round of censorship in the future. But eventually, there will come a tipping point, a moment when they’ve had enough. When that time comes, I hope we’re prepared. If we’re not, we risk missing a tremendous opportunity to onboard people who genuinely need Nostr’s freedom.
Until then, to all of the Nostr developers out there, keep up the great work and keep building. Your hard work and determination is needed.
###
-

@ cff1720e:15c7e2b2
2025-01-19 17:48:02
**Einleitung**\
\
Schwierige Dinge einfach zu erklären ist der Anspruch von ELI5 (explain me like I'm 5). Das ist in unserer hoch technisierten Welt dringend erforderlich, denn nur mit dem Verständnis der Technologien können wir sie richtig einsetzen und weiter entwickeln.\
Ich starte meine Serie mit Nostr, einem relativ neuen Internet-Protokoll. Was zum Teufel ist ein Internet-Protokoll? Formal beschrieben sind es internationale Standards, die dafür sorgen, dass das Internet seit über 30 Jahren ziemlich gut funktioniert. Es ist die Sprache, in der sich die Rechner miteinander unterhalten und die auch Sie täglich nutzen, vermutlich ohne es bewusst wahrzunehmen. http(s) transportiert ihre Anfrage an einen Server (z.B. Amazon), und html sorgt dafür, dass aus den gelieferten Daten eine schöne Seite auf ihrem Bildschirm entsteht. Eine Mail wird mit smtp an den Mailserver gesendet und mit imap von ihm abgerufen, und da alle den Standard verwenden, funktioniert das mit jeder App auf jedem Betriebssystem und mit jedem Mail-Provider. Und mit einer Mail-Adresse wie <roland@pareto.space> können sie sogar jederzeit umziehen, egal wohin. **Cool, das ist state of the art!** Aber warum funktioniert das z.B. bei Chat nicht, gibt es da kein Protokoll? Doch, es heißt IRC (Internet Relay Chat → merken sie sich den Namen), aber es wird so gut wie nicht verwendet. Die Gründe dafür sind nicht technischer Natur, vielmehr wurden mit Apps wie Facebook, Twitter, WhatsApp, Telegram, Instagram, TikTok u.a. bewusst Inkompatibilitäten und Nutzerabhängigkeiten geschaffen um Profite zu maximieren.

**Warum Nostr?**
Da das Standard-Protokoll nicht genutzt wird, hat jede App ihr eigenes, und wir brauchen eine handvoll Apps um uns mit allen Bekannten auszutauschen. Eine Mobilfunknummer ist Voraussetzung für jedes Konto, damit können die App-Hersteller die Nutzer umfassend tracken und mit dem Verkauf der Informationen bis zu 30 USD je Konto und Monat verdienen. Der Nutzer ist nicht mehr Kunde, er ist das Produkt! Der Werbe-SPAM ist noch das kleinste Problem bei diesem Geschäftsmodell. Server mit Millionen von Nutzerdaten sind ein “honey pot”, dementsprechend oft werden sie gehackt und die Zugangsdaten verkauft. 2024 wurde auch der Twitter-Account vom damaligen Präsidenten Joe Biden gehackt, niemand wusste mehr wer die Nachrichten verfasst hat (vorher auch nicht), d.h. die Authentizität der Inhalte ist bei keinem dieser Anbieter gewährleistet. Im selben Jahr wurde der Telegram-Gründer in Frankreich in Beugehaft genommen, weil er sich geweigert hatte Hintertüren in seine Software einzubauen. Nun kann zum Schutz **"unserer Demokratie”** praktisch jeder mitlesen, was sie mit wem an Informationen austauschen, z.B. darüber welches Shampoo bestimmte Politiker verwenden.

Und wer tatsächlich glaubt er könne Meinungsfreiheit auf sozialen Medien praktizieren, findet sich schnell in der Situation von Donald Trump wieder (seinerzeit amtierender Präsident), dem sein Twitter-Konto 2021 abgeschaltet wurde (Cancel-Culture). Die Nutzerdaten, also ihr Profil, ihre Kontakte, Dokumente, Bilder, Videos und Audiofiles - gehören ihnen ohnehin nicht mehr sondern sind Eigentum des Plattform-Betreibers; lesen sie sich mal die AGB's durch. Aber nein, keine gute Idee, das sind hunderte Seiten und sie werden permanent geändert. Alle nutzen also Apps, deren Technik sie nicht verstehen, deren Regeln sie nicht kennen, wo sie keine Rechte haben und die ihnen die Resultate ihres Handelns stehlen. Was würde wohl der Fünfjährige sagen, wenn ihm seine ältere Schwester anbieten würde, alle seine Spielzeuge zu “verwalten” und dann auszuhändigen wenn er brav ist? “Du spinnst wohl”, und damit beweist der Knirps mehr Vernunft als die Mehrzahl der Erwachsenen. \
\
**Resümee:** keine Standards, keine Daten, keine Rechte = keine Zukunft!

\
**Wie funktioniert Nostr?**
Die Entwickler von Nostr haben erkannt dass sich das Server-Client-Konzept in ein Master-Slave-Konzept verwandelt hatte. Der Master ist ein Synonym für Zentralisierung und wird zum **“single point of failure”**, der zwangsläufig Systeme dysfunktional macht. In einem verteilten Peer2Peer-System gibt es keine Master mehr sondern nur gleichberechtigte Knoten (Relays), auf denen die Informationen gespeichert werden. Indem man Informationen auf mehreren Relays redundant speichert, ist das System in jeglicher Hinsicht resilienter. Nicht nur die Natur verwendet dieses Prinzip seit Jahrmillionen erfolgreich, auch das Internet wurde so konzipiert (das ARPAnet wurde vom US-Militär für den Einsatz in Kriegsfällen unter massiven Störungen entwickelt). Alle Nostr-Daten liegen auf Relays und der Nutzer kann wählen zwischen öffentlichen (zumeist kostenlosen) und privaten Relays, z.B. für geschlossene Gruppen oder zum Zwecke von Daten-Archivierung. Da Dokumente auf mehreren Relays gespeichert sind, werden statt URL's (Locator) eindeutige Dokumentnamen (URI's = Identifier) verwendet, broken Links sind damit Vergangenheit und Löschungen / Verluste ebenfalls.\
\
Jedes Dokument (Event genannt) wird vom Besitzer signiert, es ist damit authentisch und fälschungssicher und kann nur vom Ersteller gelöscht werden. Dafür wird ein Schlüsselpaar verwendet bestehend aus privatem (nsec) und öffentlichem Schlüssel (npub) wie aus der Mailverschlüsselung (PGP) bekannt. Das repräsentiert eine Nostr-Identität, die um Bild, Namen, Bio und eine lesbare Nostr-Adresse ergänzt werden kann (z.B. <roland@pareto.space> ), mehr braucht es nicht um alle Ressourcen des Nostr-Ökosystems zu nutzen. Und das besteht inzwischen aus über hundert Apps mit unterschiedlichen Fokussierungen, z.B. für persönliche verschlüsselte Nachrichten (DM → OxChat), Kurznachrichten (Damus, Primal), Blogbeiträge (Pareto), Meetups (Joinstr), Gruppen (Groups), Bilder (Olas), Videos (Amethyst), Audio-Chat (Nostr Nests), Audio-Streams (Tunestr), Video-Streams (Zap.Stream), Marktplätze (Shopstr) u.v.a.m. Die Anmeldung erfolgt mit einem Klick (single sign on) und den Apps stehen ALLE Nutzerdaten zur Verfügung (Profil, Daten, Kontakte, Social Graph → Follower, Bookmarks, Comments, etc.), im Gegensatz zu den fragmentierten Datensilos der Gegenwart.\
\
**Resümee:** ein offener Standard, alle Daten, alle Rechte = große Zukunft!

\
**Warum ist Nostr die Zukunft des Internet?**
“Baue Dein Haus nicht auf einem fremden Grundstück” gilt auch im Internet - für alle App-Entwickler, Künstler, Journalisten und Nutzer, denn auch ihre Daten sind werthaltig. Nostr garantiert das Eigentum an den Daten, und überwindet ihre Fragmentierung. Weder die Nutzung noch die kreativen Freiheiten werden durch maßlose Lizenz- und Nutzungsbedingungen eingeschränkt. Aus passiven Nutzern werden durch Interaktion aktive Teilnehmer, Co-Creatoren in einer Sharing-Ökonomie **(Value4Value)**. OpenSource schafft endlich wieder Vertrauen in die Software und ihre Anbieter. Offene Standards ermöglichen den Entwicklern mehr Kooperation und schnellere Entwicklung, für die Anwender garantieren sie Wahlfreiheit. Womit wir letztmalig zu unserem Fünfjährigen zurückkehren. Kinder lieben Lego über alles, am meisten die Maxi-Box “Classic”, weil sie damit ihre Phantasie im Kombinieren voll ausleben können. Erwachsene schenken ihnen dann die viel zu teuren Themenpakete, mit denen man nur eine Lösung nach Anleitung bauen kann. “Was stimmt nur mit meinen Eltern nicht, wann sind die denn falsch abgebogen?" fragt sich der Nachwuchs zu Recht. Das Image lässt sich aber wieder aufpolieren, wenn sie ihren Kindern Nostr zeigen, denn die Vorteile verstehen sogar Fünfjährige.

\
**Das neue Internet ist dezentral. Das neue Internet ist selbstbestimmt. Nostr ist das neue Internet.**
<https://nostr.net/> \
<https://start.njump.me/>
**Hier das Interview zum Thema mit Radio Berliner Morgenröte**
<https://www.podbean.com/ew/pb-yxc36-17bb4be>
-

@ 9e69e420:d12360c2
2025-01-19 04:48:31
A new report from the National Sports Shooting Foundation (NSSF) shows that civilian firearm possession exceeded 490 million in 2022. The total from 1990 to 2022 is estimated at 491.3 million firearms. In 2022, over ten million firearms were domestically produced, leading to a total of 16,045,911 firearms available in the U.S. market.
Of these, 9,873,136 were handguns, 4,195,192 were rifles, and 1,977,583 were shotguns. Handgun availability aligns with the concealed carry and self-defense market, as all states allow concealed carry, with 29 having constitutional carry laws.
-

@ f9cf4e94:96abc355
2025-01-18 06:09:50
Para esse exemplo iremos usar:
| Nome | Imagem | Descrição |
| --------------- | ------------------------------------------------------------ | ------------------------------------------------------------ |
| Raspberry PI B+ |  | **Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2,** |
| Pen drive |  | **16Gb** |
Recomendo que use o **Ubuntu Server** para essa instalação. Você pode baixar o Ubuntu para Raspberry Pi [aqui]( https://ubuntu.com/download/raspberry-pi). O passo a passo para a instalação do Ubuntu no Raspberry Pi está disponível [aqui]( https://ubuntu.com/tutorials/how-to-install-ubuntu-on-your-raspberry-pi). **Não instale um desktop** (como xubuntu, lubuntu, xfce, etc.).
---
## Passo 1: Atualizar o Sistema 🖥️
Primeiro, atualize seu sistema e instale o Tor:
```bash
apt update
apt install tor
```
---
## Passo 2: Criar o Arquivo de Serviço `nrs.service` 🔧
Crie o arquivo de serviço que vai gerenciar o servidor Nostr. Você pode fazer isso com o seguinte conteúdo:
```unit
[Unit]
Description=Nostr Relay Server Service
After=network.target
[Service]
Type=simple
WorkingDirectory=/opt/nrs
ExecStart=/opt/nrs/nrs-arm64
Restart=on-failure
[Install]
WantedBy=multi-user.target
```
---
## Passo 3: Baixar o Binário do Nostr 🚀
Baixe o binário mais recente do Nostr [aqui no GitHub]( https://github.com/gabrielmoura/SimpleNosrtRelay/releases).
---
## Passo 4: Criar as Pastas Necessárias 📂
Agora, crie as pastas para o aplicativo e o pendrive:
```bash
mkdir -p /opt/nrs /mnt/edriver
```
---
## Passo 5: Listar os Dispositivos Conectados 🔌
Para saber qual dispositivo você vai usar, liste todos os dispositivos conectados:
```bash
lsblk
```
---
## Passo 6: Formatando o Pendrive 💾
Escolha o pendrive correto (por exemplo, `/dev/sda`) e formate-o:
```bash
mkfs.vfat /dev/sda
```
---
## Passo 7: Montar o Pendrive 💻
Monte o pendrive na pasta `/mnt/edriver`:
```bash
mount /dev/sda /mnt/edriver
```
---
## Passo 8: Verificar UUID dos Dispositivos 📋
Para garantir que o sistema monte o pendrive automaticamente, liste os UUID dos dispositivos conectados:
```bash
blkid
```
---
## Passo 9: Alterar o `fstab` para Montar o Pendrive Automáticamente 📝
Abra o arquivo `/etc/fstab` e adicione uma linha para o pendrive, com o UUID que você obteve no passo anterior. A linha deve ficar assim:
```fstab
UUID=9c9008f8-f852 /mnt/edriver vfat defaults 0 0
```
---
## Passo 10: Copiar o Binário para a Pasta Correta 📥
Agora, copie o binário baixado para a pasta `/opt/nrs`:
```bash
cp nrs-arm64 /opt/nrs
```
---
## Passo 11: Criar o Arquivo de Configuração 🛠️
Crie o arquivo de configuração com o seguinte conteúdo e salve-o em `/opt/nrs/config.yaml`:
```yaml
app_env: production
info:
name: Nostr Relay Server
description: Nostr Relay Server
pub_key: ""
contact: ""
url: http://localhost:3334
icon: https://external-content.duckduckgo.com/iu/?u= https://public.bnbstatic.com/image/cms/crawler/COINCU_NEWS/image-495-1024x569.png
base_path: /mnt/edriver
negentropy: true
```
---
## Passo 12: Copiar o Serviço para o Diretório de Systemd ⚙️
Agora, copie o arquivo `nrs.service` para o diretório `/etc/systemd/system/`:
```bash
cp nrs.service /etc/systemd/system/
```
Recarregue os serviços e inicie o serviço `nrs`:
```bash
systemctl daemon-reload
systemctl enable --now nrs.service
```
---
## Passo 13: Configurar o Tor 🌐
Abra o arquivo de configuração do Tor `/var/lib/tor/torrc` e adicione a seguinte linha:
```torrc
HiddenServiceDir /var/lib/tor/nostr_server/
HiddenServicePort 80 127.0.0.1:3334
```
---
## Passo 14: Habilitar e Iniciar o Tor 🧅
Agora, ative e inicie o serviço Tor:
```bash
systemctl enable --now tor.service
```
O Tor irá gerar um endereço `.onion` para o seu servidor Nostr. Você pode encontrá-lo no arquivo `/var/lib/tor/nostr_server/hostname`.
---
## Observações ⚠️
- Com essa configuração, **os dados serão salvos no pendrive**, enquanto o binário ficará no cartão SD do Raspberry Pi.
- O endereço `.onion` do seu servidor Nostr será algo como: `ws://y3t5t5wgwjif<exemplo>h42zy7ih6iwbyd.onion`.
---
Agora, seu servidor Nostr deve estar configurado e funcionando com Tor! 🥳
Se este artigo e as informações aqui contidas forem úteis para você, convidamos a considerar uma doação ao autor como forma de reconhecimento e incentivo à produção de novos conteúdos.
-

@ 6389be64:ef439d32
2025-01-16 15:44:06
## Black Locust can grow up to 170 ft tall
## Grows 3-4 ft. per year
## Native to North America
## Cold hardy in zones 3 to 8

## Firewood
- BLT wood, on a pound for pound basis is roughly half that of Anthracite Coal
- Since its growth is fast, firewood can be plentiful
## Timber

- Rot resistant due to a naturally produced robinin in the wood
- 100 year life span in full soil contact! (better than cedar performance)
- Fence posts
- Outdoor furniture
- Outdoor decking
- Sustainable due to its fast growth and spread
- Can be coppiced (cut to the ground)
- Can be pollarded (cut above ground)
- Its dense wood makes durable tool handles, boxes (tool), and furniture
- The wood is tougher than hickory, which is tougher than hard maple, which is tougher than oak.
- A very low rate of expansion and contraction
- Hardwood flooring
- The highest tensile beam strength of any American tree
- The wood is beautiful
## Legume
- Nitrogen fixer
- Fixes the same amount of nitrogen per acre as is needed for 200-bushel/acre corn
- Black walnuts inter-planted with locust as “nurse” trees were shown to rapidly increase their growth [[Clark, Paul M., and Robert D. Williams. (1978) Black walnut growth increased when interplanted with nitrogen-fixing shrubs and trees. Proceedings of the Indiana Academy of Science, vol. 88, pp. 88-91.]]
## Bees

- The edible flower clusters are also a top food source for honey bees
## Shade Provider

- Its light, airy overstory provides dappled shade
- Planted on the west side of a garden it provides relief during the hottest part of the day
- (nitrogen provider)
- Planted on the west side of a house, its quick growth soon shades that side from the sun
## Wind-break

- Fast growth plus it's feathery foliage reduces wind for animals, crops, and shelters
## Fodder
- Over 20% crude protein
- 4.1 kcal/g of energy
- Baertsche, S.R, M.T. Yokoyama, and J.W. Hanover (1986) Short rotation, hardwood tree biomass as potential ruminant feed-chemical composition, nylon bag ruminal degradation and ensilement of selected species. J. Animal Sci. 63 2028-2043
-

@ a012dc82:6458a70d
2025-01-20 02:02:07
The advent of cryptocurrency has sparked a modern-day gold rush, with Bitcoin mining at the forefront of this digital revolution. The United States, with its vast resources and technological prowess, has become a fertile ground for these operations. However, the recent shift in the global mining landscape has brought a wave of Chinese mining companies to U.S. shores, fleeing a regulatory crackdown in their homeland. This migration has set off alarm bells within national security circles, as the technology that underpins cryptocurrencies is not just a tool for financial gain but also a potential vector for cyber espionage and other security threats. The dual-use nature of this technology, capable of both revolutionizing economies and potentially undermining national security, has placed it at the heart of a complex debate involving economic policy, technological innovation, and national defense.
**Table Of Content**
- The Economic Impact of Cryptocurrency Mining
- National Security Risks and Strategic Concerns
- Regulatory Responses to Foreign Mining Operations
- The Path Forward: Innovation, Security, and Diplomacy
- Conclusion
- FAQs
The economic allure of cryptocurrency mining is undeniable. In regions hit hard by economic downturns, the establishment of mining operations has been a boon, providing much-needed jobs and revitalizing local economies. These operations often take over abandoned industrial sites, turning them into hives of high-tech activity. The promise of a revitalized industrial base, however, comes with caveats. The energy-intensive nature of cryptocurrency mining has led to a surge in demand for electricity, straining local grids and raising concerns about the environmental impact of such operations. The long-term economic benefits are also questioned, as the volatility of the cryptocurrency market means that the stability of these jobs and the longevity of the operations are not guaranteed. As Chinese companies increasingly dominate this space, there is also the fear that the economic benefits may be offset by the outflow of profits to foreign entities.
**National Security Risks and Strategic Concerns**
The strategic implications of foreign-controlled cryptocurrency mining operations on U.S. soil are complex and troubling. The opaque nature of these operations, often shrouded in layers of corporate secrecy, makes it difficult to discern their true intentions. The proximity of some mining farms to sensitive sites, such as military bases and critical infrastructure, has compounded these fears, suggesting the potential for these facilities to be used for more than just mining. The vast computational power of mining operations could theoretically be repurposed for code-breaking and hacking, posing a direct threat to national security. The concern is not just hypothetical; it is rooted in a history of cyber incursions attributed to Chinese state-sponsored actors. The potential for these mining operations to serve as a front for such activities, intentionally or not, has put them in the crosshairs of U.S. security agencies.
**Regulatory Responses to Foreign Mining Operations**
The U.S. government's response to the influx of Chinese cryptocurrency mining operations has been measured yet firm. Recognizing the need to maintain an open economic environment that fosters innovation, regulators have nonetheless moved to establish guardrails to protect national interests. This has involved a multifaceted approach, including the proposal of legislation aimed at scrutinizing foreign investments in critical technologies and infrastructure. Agencies such as the Committee on Foreign Investment in the United States (CFIUS) have been at the forefront of these efforts, working to untangle the complex web of ownership and control that characterizes foreign mining operations. The goal is to ensure that while the U.S. remains a hub for technological innovation, it does not become a playground for foreign powers with adversarial intentions.
**The Path Forward: Innovation, Security, and Diplomacy**
The path forward for the United States in managing the rise of Chinese bitcoin mining operations is akin to walking a tightrope. On one side is the need to nurture innovation and maintain the U.S.'s competitive edge in the burgeoning field of cryptocurrency. On the other is the imperative to safeguard national security and ensure that the country's technological infrastructure is not compromised. This delicate balance requires a nuanced approach that includes fostering a robust domestic mining industry, investing in renewable energy sources to mitigate the environmental impact, and engaging in strategic diplomacy to manage the international dimensions of cryptocurrency governance. The U.S. must leverage its strengths in innovation, policy-making, and international relations to set standards that will shape the future of cryptocurrency mining and secure its digital economy.
**Conclusion**
The challenge of balancing the economic potential of cryptocurrency mining with the imperatives of national security is emblematic of the broader challenges facing policymakers in the digital age. As Chinese bitcoin mining operations continue to expand their footprint in the U.S., the need for a strategic, measured response becomes increasingly critical. This response must be multifaceted, engaging with all stakeholders, including the mining industry, environmental groups, energy providers, and security agencies. By striking a balance between economic growth and security, the U.S. can harness the potential of the digital economy while protecting its national interests. The stakes are high, and the decisions made today will have lasting implications for the security and prosperity of future generations.
**FAQs**
**How does Bitcoin mining impact local economies?**
Bitcoin mining can provide jobs and economic investment in local communities, especially in areas with excess energy capacity or where industrial sites are underutilized.
**What is the U.S. government's response to foreign cryptocurrency mining operations?**
The U.S. government is considering stricter regulations on foreign investments in critical technologies, including cryptocurrency mining, to protect national security while fostering economic growth.
**Can cryptocurrency mining operations be environmentally sustainable?**
There are concerns about the high energy consumption of mining operations, but with investment in renewable energy and efficient technologies, mining can move towards greater sustainability.
**How does the U.S. plan to balance innovation with security in cryptocurrency mining?**
The U.S. aims to strike a balance by creating policies that encourage technological innovation and economic benefits while implementing security measures to protect against potential threats.
**That's all for today**
**If you want more, be sure to follow us on:**
**NOSTR: croxroad@getalby.com**
**X: [Instagram: @croxroadnews.co](https://x.com/croxroadnewsco)**
**Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)**
**Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)**
**Store: https://croxroad.store**
**Subscribe to CROX ROAD Bitcoin Only Daily Newsletter**
**https://www.croxroad.co/subscribe**
*DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.*
-

@ b8851a06:9b120ba1
2025-01-14 15:28:32
## **It Begins with a Click**
It starts with a click: *“Do you agree to our terms and conditions?”*\
You scroll, you click, you comply. A harmless act, right? But what if every click was a surrender? What if every "yes" was another link in the chain binding you to a life where freedom requires approval?
This is the age of permission. Every aspect of your life is mediated by gatekeepers. Governments demand forms, corporations demand clicks, and algorithms demand obedience. You’re free, of course, as long as you play by the rules. But who writes the rules? Who decides what’s allowed? Who owns your life?
---
## **Welcome to Digital Serfdom**
We once imagined the internet as a digital frontier—a vast, open space where ideas could flow freely and innovation would know no bounds. But instead of creating a decentralized utopia, we built a new feudal system.
- Your data? Owned by the lords of Big Tech.
- Your money? Controlled by banks and bureaucrats who can freeze it on a whim.
- Your thoughts? Filtered by algorithms that reward conformity and punish dissent.
The modern internet is a land of serfs and lords, and guess who’s doing the farming? You. Every time you agree to the terms, accept the permissions, or let an algorithm decide for you, you till the fields of a system designed to control, not liberate.
They don’t call it control, of course. They call it *“protection.”* They say, “We’re keeping you safe,” as they build a cage so big you can’t see the bars.
---
## **Freedom in Chains**
But let’s be honest: we’re not just victims of this system—we’re participants. We’ve traded freedom for convenience, sovereignty for security. It’s easier to click “I Agree” than to read the fine print. It’s easier to let someone else hold your money than to take responsibility for it yourself. It’s easier to live a life of quiet compliance than to risk the chaos of true independence.
We tell ourselves it’s no big deal. What’s one click? What’s one form? But the permissions pile up. The chains grow heavier. And one day, you wake up and realize you’re free to do exactly what the system allows—and nothing more.
---
## **The Great Unpermissioning**
It doesn’t have to be this way. You don’t need their approval. You don’t need their systems. You don’t need their permission.
The Great Unpermissioning is not a movement—it’s a mindset. It’s the refusal to accept a life mediated by gatekeepers. It’s the quiet rebellion of saying, *“No.”* It’s the realization that the freedom you seek won’t be granted—it must be reclaimed.
- **Stop asking.** Permission is their tool. Refusal is your weapon.
- **Start building.** Embrace tools that decentralize power: Bitcoin, encryption, open-source software, decentralized communication. Build systems they can’t control.
- **Stand firm.** They’ll tell you it’s dangerous. They’ll call you a radical. But remember: the most dangerous thing you can do is comply.
The path won’t be easy. Freedom never is. But it will be worth it.
---
## **The New Frontier**
The age of permission has turned us into digital serfs, but there’s a new frontier on the horizon. It’s a world where you control your money, your data, your decisions. It’s a world of encryption, anonymity, and sovereignty. It’s a world built not on permission but on principles.
This world won’t be given to you. You have to build it. You have to fight for it. And it starts with one simple act: refusing to comply.
---
## **A Final Word**
They promised us safety, but what they delivered was submission. The age of permission has enslaved us to the mundane, the monitored, and the mediocre. The Great Unpermissioning isn’t about tearing down the old world—it’s about walking away from it.
You don’t need to wait for their approval. You don’t need to ask for their permission. The freedom you’re looking for is already yours. Permission is their power—refusal is yours.
-

@ 41fa852b:af7b7706
2025-01-19 18:31:45
> "It is not the strongest of the species that survive, nor the most intelligent, but the one most responsive to change." -- Charles Darwin
* * *
**It's usually a big week when the 21st comes around, but this week we have 5 meetups that day!**
Also, Trump takes office on Monday so there'll be loads to discuss at this week's meetups.
Let's take a look…
* * *
[](https://bitcoinevents.uk/donate/)
* * *
_This week's sponsor is…_
[](https://www.orangepillapp.com?utm_source=BEUK&utm_medium=email&utm_campaign=BEUK)
* * *
### **Upcoming Bitcoin Meetups**
Happening this week…
1. [**Bitcoin Bristol**](https://bitcoinbristol.org/): Meeting at Little Martha Brewing, BS2 0QT. On Tuesday 21st at 18:15. 🍺
2. [**Bitcoin Surrey**](https://meetu.ps/e/NLBzr/v822r/i): It's a Bitcoin Pension Scheme Special this month at [Yiayias at The Fox](https://www.yiayias.co.uk/yiayiasatthefox/). A fireside chat and Q&A with Sam Roberts, Cartwright's Director of Investment Consulting (1st UK pension scheme to allocate 3% to Bitcoin). 18:00 - 23:00 on the 21st. Bitcoin accepted at the venue. 🎙️🍻
3. [**Newcastle upon Tyne Bitcoin Meetup**](https://bitcoinevents.uk/newcastle-bitcoin/): The next Newcastle meetup is on Tuesday 21st January at Kabin @ Kabannas, L2 6RE. 18:30 PM. 🍻
4. [**London Bitcoin Space**](https://meetu.ps/e/NNk9z/v822r/i): LBS will be at Cyphermunk house on Tuesday 21st from 18:30 till 22:00 for a social gathering, head along to share knowledge and meet some fellow Bitcoiners. 🫂
5. [**Oxbit**](https://x.com/oxbitmeetup): Celebrate Bitcoins 16th birthday with the Oxford meetup crew. You'll find them at [The Old Black Horse](https://www.oldblackhorse.com/) (bitcoin accepted) at 19:00 on the 21st. 🍺
6. [**Preston Bitcoin Meetup**](https://x.com/prestonbtcmeet/status/1880289279093666243): Join the Preston meetup for A Bitcoin chat and some amazing burgers. 18:30 on Thursday the 23rd January. At All Hopes No Promises, PR1 2US.
7. [**The Northamptonshire Bitcoin Network**](https://bitcoinevents.uk/northamptonshire-bitcoin-network/) : [BTC Citadel Engineering](https://btc-citadel.co.uk/) are hosting a 'Bitcoin Builders' space on Saturday the 25th. Head along to learn about Seedsigners and how to build one. Come and use the 3D printers, get a project started and chat about Bitcoin with everyone there. It all gets started at 12:00. No tech skills are necessary. ⚙️🧡
8. [**Bitcoin Walk - Edinburgh**](https://bitcoinevents.uk/bitcoinwalk/): Every Saturday they walk around Arthur's Seat in this historic city. Join them at 12 pm to chat about all things Bitcoin and keep fit. 🚶🏻🚶🏼♀️🚶🏽♂️
9. [**Bitcoin East**](https://x.com/bitcoineastuk/status/1875867783457910895): Their first meetup of 2025 will be at Marzano Cafe in the beautiful city of Norwich. Join them at 11:00 on Sunday 26th Jan, there's a lot to discuss. ☕️
* * *
**Get Involved**
- **Volunteer Opportunities**: [Bridge2Bitcoin](https://bridge2bitcoin.com/) is actively seeking volunteers who share our passion for merchant adoption. We'd be delighted to connect if you're eager to contribute. Reach out to us on [Twitter](https://x.com/bridge2bitcoin) or through our [website](https://bridge2bitcoin.com/).
- **Start Your Own Meetup**: Interested in launching a Bitcoin meetup? We're here to support you every step of the way. We've assisted numerous UK Bitcoin meetups in getting started. Get in touch via [Twitter](https://x.com/bitcoineventsuk).
- [**Contribute to BTCMaps**](https://wiki.btcmap.org/general/tagging-instructions.html): BTCMaps is a vital part of the Bitcoin ecosystem. It's a perfect project to get involved with if you're not a coder or even that technical. A great way to give back to the community. Maintain an area of the UK and keep it up-to-date.
- **Telegram users**: You might find our [Telegram Channel](https://t.me/BitcoinEventsUKHub) another useful way to keep up-to-date with UK meetups.
- **Feedback and Suggestions**: We value your input! Share your ideas on how we can enhance this newsletter.
* * *
_This week's sponsors are…_
[](https://orangecoinstore.com/)
[](https://lasereyes.cards/skins/leather-bitcoin-skin/)
* * *
Get out and support the meetups where you can, visit [Bitcoin Events UK](https://bitcoinevents.uk/) for more info on each meetup and to find your closest on the interactive map.
Stay tuned for more updates next week!
Simon.
[](https://bitcoinevents.uk/donate/)
-

@ 6389be64:ef439d32
2025-01-14 01:31:12
Bitcoin is more than money, more than an asset, and more than a store of value. Bitcoin is a Prime Mover, an enabler and it ignites imaginations. It certainly fueled an idea in my mind. The idea integrates sensors, computational prowess, actuated machinery, power conversion, and electronic communications to form an autonomous, machined creature roaming forests and harvesting the most widespread and least energy-dense fuel source available. I call it the Forest Walker and it eats wood, and mines Bitcoin.
I know what you're thinking. Why not just put Bitcoin mining rigs where they belong: in a hosted facility sporting electricity from energy-dense fuels like natural gas, climate-controlled with excellent data piping in and out? Why go to all the trouble building a robot that digests wood creating flammable gasses fueling an engine to run a generator powering Bitcoin miners? It's all about synergy.
Bitcoin mining enables the realization of multiple, seemingly unrelated, yet useful activities. Activities considered un-profitable if not for Bitcoin as the Prime Mover. This is much more than simply mining the greatest asset ever conceived by humankind. It’s about the power of synergy, which Bitcoin plays only one of many roles. The synergy created by this system can stabilize forests' fire ecology while generating multiple income streams. That’s the realistic goal here and requires a brief history of American Forest management before continuing.
# Smokey The Bear
In 1944, the Smokey Bear Wildfire Prevention Campaign began in the United States. “Only YOU can prevent forest fires” remains the refrain of the Ad Council’s longest running campaign. The Ad Council is a U.S. non-profit set up by the American Association of Advertising Agencies and the Association of National Advertisers in 1942. It would seem that the U.S. Department of the Interior was concerned about pesky forest fires and wanted them to stop. So, alongside a national policy of extreme fire suppression they enlisted the entire U.S. population to get onboard via the Ad Council and it worked. Forest fires were almost obliterated and everyone was happy, right? Wrong.
Smokey is a fantastically successful bear so forest fires became so few for so long that the fuel load - dead wood - in forests has become very heavy. So heavy that when a fire happens (and they always happen) it destroys everything in its path because the more fuel there is the hotter that fire becomes. Trees, bushes, shrubs, and all other plant life cannot escape destruction (not to mention homes and businesses). The soil microbiology doesn’t escape either as it is burned away even in deeper soils. To add insult to injury, hydrophobic waxy residues condense on the soil surface, forcing water to travel over the ground rather than through it eroding forest soils. Good job, Smokey. Well done, Sir!
Most terrestrial ecologies are “fire ecologies”. Fire is a part of these systems’ fuel load and pest management. Before we pretended to “manage” millions of acres of forest, fires raged over the world, rarely damaging forests. The fuel load was always too light to generate fires hot enough to moonscape mountainsides. Fires simply burned off the minor amounts of fuel accumulated since the fire before. The lighter heat, smoke, and other combustion gasses suppressed pests, keeping them in check and the smoke condensed into a plant growth accelerant called wood vinegar, not a waxy cap on the soil. These fires also cleared out weak undergrowth, cycled minerals, and thinned the forest canopy, allowing sunlight to penetrate to the forest floor. Without a fire’s heat, many pine tree species can’t sow their seed. The heat is required to open the cones (the seed bearing structure) of Spruce, Cypress, Sequoia, Jack Pine, Lodgepole Pine and many more. Without fire forests can’t have babies. The idea was to protect the forests, and it isn't working.
So, in a world of fire, what does an ally look like and what does it do?
# Meet The Forest Walker

For the Forest Walker to work as a mobile, autonomous unit, a solid platform that can carry several hundred pounds is required. It so happens this chassis already exists but shelved.
Introducing the Legged Squad Support System (LS3). A joint project between Boston Dynamics, DARPA, and the United States Marine Corps, the quadrupedal robot is the size of a cow, can carry 400 pounds (180 kg) of equipment, negotiate challenging terrain, and operate for 24 hours before needing to refuel. Yes, it had an engine. Abandoned in 2015, the thing was too noisy for military deployment and maintenance "under fire" is never a high-quality idea. However, we can rebuild it to act as a platform for the Forest Walker; albeit with serious alterations. It would need to be bigger, probably. Carry more weight? Definitely. Maybe replace structural metal with carbon fiber and redesign much as 3D printable parts for more effective maintenance.
The original system has a top operational speed of 8 miles per hour. For our purposes, it only needs to move about as fast as a grazing ruminant. Without the hammering vibrations of galloping into battle, shocks of exploding mortars, and drunken soldiers playing "Wrangler of Steel Machines", time between failures should be much longer and the overall energy consumption much lower. The LS3 is a solid platform to build upon. Now it just needs to be pulled out of the mothballs, and completely refitted with outboard equipment.
# The Small Branch Chipper

When I say “Forest fuel load” I mean the dead, carbon containing litter on the forest floor. Duff (leaves), fine-woody debris (small branches), and coarse woody debris (logs) are the fuel that feeds forest fires. Walk through any forest in the United States today and you will see quite a lot of these materials. Too much, as I have described. Some of these fuel loads can be 8 tons per acre in pine and hardwood forests and up to 16 tons per acre at active logging sites. That’s some big wood and the more that collects, the more combustible danger to the forest it represents. It also provides a technically unlimited fuel supply for the Forest Walker system.
The problem is that this detritus has to be chewed into pieces that are easily ingestible by the system for the gasification process (we’ll get to that step in a minute). What we need is a wood chipper attached to the chassis (the LS3); its “mouth”.
A small wood chipper handling material up to 2.5 - 3.0 inches (6.3 - 7.6 cm) in diameter would eliminate a substantial amount of fuel. There is no reason for Forest Walker to remove fallen trees. It wouldn’t have to in order to make a real difference. It need only identify appropriately sized branches and grab them. Once loaded into the chipper’s intake hopper for further processing, the beast can immediately look for more “food”. This is essentially kindling that would help ignite larger logs. If it’s all consumed by Forest Walker, then it’s not present to promote an aggravated conflagration.
I have glossed over an obvious question: How does Forest Walker see and identify branches and such? LiDaR (Light Detection and Ranging) attached to Forest Walker images the local area and feed those data to onboard computers for processing. Maybe AI plays a role. Maybe simple machine learning can do the trick. One thing is for certain: being able to identify a stick and cause robotic appendages to pick it up is not impossible.
Great! We now have a quadrupedal robot autonomously identifying and “eating” dead branches and other light, combustible materials. Whilst strolling through the forest, depleting future fires of combustibles, Forest Walker has already performed a major function of this system: making the forest safer. It's time to convert this low-density fuel into a high-density fuel Forest Walker can leverage. Enter the gasification process.
# The Gassifier

The gasifier is the heart of the entire system; it’s where low-density fuel becomes the high-density fuel that powers the entire system. Biochar and wood vinegar are process wastes and I’ll discuss why both are powerful soil amendments in a moment, but first, what’s gasification?
Reacting shredded carbonaceous material at high temperatures in a low or no oxygen environment converts the biomass into biochar, wood vinegar, heat, and Synthesis Gas (Syngas). Syngas consists primarily of hydrogen, carbon monoxide, and methane. All of which are extremely useful fuels in a gaseous state. Part of this gas is used to heat the input biomass and keep the reaction temperature constant while the internal combustion engine that drives the generator to produce electrical power consumes the rest.
Critically, this gasification process is “continuous feed”. Forest Walker must intake biomass from the chipper, process it to fuel, and dump the waste (CO2, heat, biochar, and wood vinegar) continuously. It cannot stop. Everything about this system depends upon this continual grazing, digestion, and excretion of wastes just as a ruminal does. And, like a ruminant, all waste products enhance the local environment.
When I first heard of gasification, I didn’t believe that it was real. Running an electric generator from burning wood seemed more akin to “conspiracy fantasy” than science. Not only is gasification real, it’s ancient technology. A man named Dean Clayton first started experiments on gasification in 1699 and in 1901 gasification was used to power a vehicle. By the end of World War II, there were 500,000 Syngas powered vehicles in Germany alone because of fossil fuel rationing during the war. The global gasification market was $480 billion in 2022 and projected to be as much as $700 billion by 2030 (Vantage Market Research). Gasification technology is the best choice to power the Forest Walker because it’s self-contained and we want its waste products.
# Biochar: The Waste

Biochar (AKA agricultural charcoal) is fairly simple: it’s almost pure, solid carbon that resembles charcoal. Its porous nature packs large surface areas into small, 3 dimensional nuggets. Devoid of most other chemistry, like hydrocarbons (methane) and ash (minerals), biochar is extremely lightweight. Do not confuse it with the charcoal you buy for your grill. Biochar doesn’t make good grilling charcoal because it would burn too rapidly as it does not contain the multitude of flammable components that charcoal does. Biochar has several other good use cases. Water filtration, water retention, nutrient retention, providing habitat for microscopic soil organisms, and carbon sequestration are the main ones that we are concerned with here.
Carbon has an amazing ability to adsorb (substances stick to and accumulate on the surface of an object) manifold chemistries. Water, nutrients, and pollutants tightly bind to carbon in this format. So, biochar makes a respectable filter and acts as a “battery” of water and nutrients in soils. Biochar adsorbs and holds on to seven times its weight in water. Soil containing biochar is more drought resilient than soil without it. Adsorbed nutrients, tightly sequestered alongside water, get released only as plants need them. Plants must excrete protons (H+) from their roots to disgorge water or positively charged nutrients from the biochar's surface; it's an active process.
Biochar’s surface area (where adsorption happens) can be 500 square meters per gram or more. That is 10% larger than an official NBA basketball court for every gram of biochar. Biochar’s abundant surface area builds protective habitats for soil microbes like fungi and bacteria and many are critical for the health and productivity of the soil itself.
The “carbon sequestration” component of biochar comes into play where “carbon credits” are concerned. There is a financial market for carbon. Not leveraging that market for revenue is foolish. I am climate agnostic. All I care about is that once solid carbon is inside the soil, it will stay there for thousands of years, imparting drought resiliency, fertility collection, nutrient buffering, and release for that time span. I simply want as much solid carbon in the soil because of the undeniably positive effects it has, regardless of any climactic considerations.
# Wood Vinegar: More Waste

Another by-product of the gasification process is wood vinegar (Pyroligneous acid). If you have ever seen Liquid Smoke in the grocery store, then you have seen wood vinegar. Principally composed of acetic acid, acetone, and methanol wood vinegar also contains ~200 other organic compounds. It would seem intuitive that condensed, liquefied wood smoke would at least be bad for the health of all living things if not downright carcinogenic. The counter intuition wins the day, however. Wood vinegar has been used by humans for a very long time to promote digestion, bowel, and liver health; combat diarrhea and vomiting; calm peptic ulcers and regulate cholesterol levels; and a host of other benefits.
For centuries humans have annually burned off hundreds of thousands of square miles of pasture, grassland, forest, and every other conceivable terrestrial ecosystem. Why is this done? After every burn, one thing becomes obvious: the almost supernatural growth these ecosystems exhibit after the burn. How? Wood vinegar is a component of this growth. Even in open burns, smoke condenses and infiltrates the soil. That is when wood vinegar shows its quality.
This stuff beefs up not only general plant growth but seed germination as well and possesses many other qualities that are beneficial to plants. It’s a pesticide, fungicide, promotes beneficial soil microorganisms, enhances nutrient uptake, and imparts disease resistance. I am barely touching a long list of attributes here, but you want wood vinegar in your soil (alongside biochar because it adsorbs wood vinegar as well).
# The Internal Combustion Engine

Conversion of grazed forage to chemical, then mechanical, and then electrical energy completes the cycle. The ICE (Internal Combustion Engine) converts the gaseous fuel output from the gasifier to mechanical energy, heat, water vapor, and CO2. It’s the mechanical energy of a rotating drive shaft that we want. That rotation drives the electric generator, which is the heartbeat we need to bring this monster to life. Luckily for us, combined internal combustion engine and generator packages are ubiquitous, delivering a defined energy output given a constant fuel input. It’s the simplest part of the system.
The obvious question here is whether the amount of syngas provided by the gasification process will provide enough energy to generate enough electrons to run the entire system or not. While I have no doubt the energy produced will run Forest Walker's main systems the question is really about the electrons left over. Will it be enough to run the Bitcoin mining aspect of the system? Everything is a budget.
# CO2 Production For Growth

Plants are lollipops. No matter if it’s a tree or a bush or a shrubbery, the entire thing is mostly sugar in various formats but mostly long chain carbohydrates like lignin and cellulose. Plants need three things to make sugar: CO2, H2O and light. In a forest, where tree densities can be quite high, CO2 availability becomes a limiting growth factor. It’d be in the forest interests to have more available CO2 providing for various sugar formation providing the organism with food and structure.
An odd thing about tree leaves, the openings that allow gasses like the ever searched for CO2 are on the bottom of the leaf (these are called stomata). Not many stomata are topside. This suggests that trees and bushes have evolved to find gasses like CO2 from below, not above and this further suggests CO2 might be in higher concentrations nearer the soil.
The soil life (bacterial, fungi etc.) is constantly producing enormous amounts of CO2 and it would stay in the soil forever (eventually killing the very soil life that produces it) if not for tidal forces. Water is everywhere and whether in pools, lakes, oceans or distributed in “moist” soils water moves towards to the moon. The water in the soil and also in the water tables below the soil rise toward the surface every day. When the water rises, it expels the accumulated gasses in the soil into the atmosphere and it’s mostly CO2. It’s a good bet on how leaves developed high populations of stomata on the underside of leaves. As the water relaxes (the tide goes out) it sucks oxygenated air back into the soil to continue the functions of soil life respiration. The soil “breathes” albeit slowly.
The gasses produced by the Forest Walker’s internal combustion engine consist primarily of CO2 and H2O. Combusting sugars produce the same gasses that are needed to construct the sugars because the universe is funny like that. The Forest Walker is constantly laying down these critical construction elements right where the trees need them: close to the ground to be gobbled up by the trees.
# The Branch Drones

During the last ice age, giant mammals populated North America - forests and otherwise. Mastodons, woolly mammoths, rhinos, short-faced bears, steppe bison, caribou, musk ox, giant beavers, camels, gigantic ground-dwelling sloths, glyptodons, and dire wolves were everywhere. Many were ten to fifteen feet tall. As they crashed through forests, they would effectively cleave off dead side-branches of trees, halting the spread of a ground-based fire migrating into the tree crown ("laddering") which is a death knell for a forest.
These animals are all extinct now and forests no longer have any manner of pruning services. But, if we build drones fitted with cutting implements like saws and loppers, optical cameras and AI trained to discern dead branches from living ones, these drones could effectively take over pruning services by identifying, cutting, and dropping to the forest floor, dead branches. The dropped branches simply get collected by the Forest Walker as part of its continual mission.
The drones dock on the back of the Forest Walker to recharge their batteries when low. The whole scene would look like a grazing cow with some flies bothering it. This activity breaks the link between a relatively cool ground based fire and the tree crowns and is a vital element in forest fire control.
# The Bitcoin Miner

Mining is one of four monetary incentive models, making this system a possibility for development. The other three are US Dept. of the Interior, township, county, and electrical utility company easement contracts for fuel load management, global carbon credits trading, and data set sales. All the above depends on obvious questions getting answered. I will list some obvious ones, but this is not an engineering document and is not the place for spreadsheets. How much Bitcoin one Forest Walker can mine depends on everything else. What amount of biomass can we process? Will that biomass flow enough Syngas to keep the lights on? Can the chassis support enough mining ASICs and supporting infrastructure? What does that weigh and will it affect field performance? How much power can the AC generator produce?
Other questions that are more philosophical persist. Even if a single Forest Walker can only mine scant amounts of BTC per day, that pales to how much fuel material it can process into biochar. We are talking about millions upon millions of forested acres in need of fuel load management. What can a single Forest Walker do? I am not thinking in singular terms. The Forest Walker must operate as a fleet. What could 50 do? 500?
What is it worth providing a service to the world by managing forest fuel loads? Providing proof of work to the global monetary system? Seeding soil with drought and nutrient resilience by the excretion, over time, of carbon by the ton? What did the last forest fire cost?
# The Mesh Network

What could be better than one bitcoin mining, carbon sequestering, forest fire squelching, soil amending behemoth? Thousands of them, but then they would need to be able to talk to each other to coordinate position, data handling, etc. Fitted with a mesh networking device, like goTenna or Meshtastic LoRa equipment enables each Forest Walker to communicate with each other.
Now we have an interconnected fleet of Forest Walkers relaying data to each other and more importantly, aggregating all of that to the last link in the chain for uplink. Well, at least Bitcoin mining data. Since block data is lightweight, transmission of these data via mesh networking in fairly close quartered environs is more than doable. So, how does data transmit to the Bitcoin Network? How do the Forest Walkers get the previous block data necessary to execute on mining?
# Back To The Chain

Getting Bitcoin block data to and from the network is the last puzzle piece. The standing presumption here is that wherever a Forest Walker fleet is operating, it is NOT within cell tower range. We further presume that the nearest Walmart Wi-Fi is hours away. Enter the Blockstream Satellite or something like it.
A separate, ground-based drone will have two jobs: To stay as close to the nearest Forest Walker as it can and to provide an antennae for either terrestrial or orbital data uplink. Bitcoin-centric data is transmitted to the "uplink drone" via the mesh networked transmitters and then sent on to the uplink and the whole flow goes in the opposite direction as well; many to one and one to many.
We cannot transmit data to the Blockstream satellite, and it will be up to Blockstream and companies like it to provide uplink capabilities in the future and I don't doubt they will. Starlink you say? What’s stopping that company from filtering out block data? Nothing because it’s Starlink’s system and they could decide to censor these data. It seems we may have a problem sending and receiving Bitcoin data in back country environs.
But, then again, the utility of this system in staunching the fuel load that creates forest fires is extremely useful around forested communities and many have fiber, Wi-Fi and cell towers. These communities could be a welcoming ground zero for first deployments of the Forest Walker system by the home and business owners seeking fire repression. In the best way, Bitcoin subsidizes the safety of the communities.
# Sensor Packages
### LiDaR

The benefit of having a Forest Walker fleet strolling through the forest is the never ending opportunity for data gathering. A plethora of deployable sensors gathering hyper-accurate data on everything from temperature to topography is yet another revenue generator. Data is valuable and the Forest Walker could generate data sales to various government entities and private concerns.
LiDaR (Light Detection and Ranging) can map topography, perform biomass assessment, comparative soil erosion analysis, etc. It so happens that the Forest Walker’s ability to “see,” to navigate about its surroundings, is LiDaR driven and since it’s already being used, we can get double duty by harvesting that data for later use. By using a laser to send out light pulses and measuring the time it takes for the reflection of those pulses to return, very detailed data sets incrementally build up. Eventually, as enough data about a certain area becomes available, the data becomes useful and valuable.
Forestry concerns, both private and public, often use LiDaR to build 3D models of tree stands to assess the amount of harvest-able lumber in entire sections of forest. Consulting companies offering these services charge anywhere from several hundred to several thousand dollars per square kilometer for such services. A Forest Walker generating such assessments on the fly while performing its other functions is a multi-disciplinary approach to revenue generation.
### pH, Soil Moisture, and Cation Exchange Sensing

The Forest Walker is quadrupedal, so there are four contact points to the soil. Why not get a pH data point for every step it takes? We can also gather soil moisture data and cation exchange capacities at unheard of densities because of sampling occurring on the fly during commission of the system’s other duties. No one is going to build a machine to do pH testing of vast tracts of forest soils, but that doesn’t make the data collected from such an endeavor valueless. Since the Forest Walker serves many functions at once, a multitude of data products can add to the return on investment component.
### Weather Data

Temperature, humidity, pressure, and even data like evapotranspiration gathered at high densities on broad acre scales have untold value and because the sensors are lightweight and don’t require large power budgets, they come along for the ride at little cost. But, just like the old mantra, “gas, grass, or ass, nobody rides for free”, these sensors provide potential revenue benefits just by them being present.
I’ve touched on just a few data genres here. In fact, the question for universities, governmental bodies, and other institutions becomes, “How much will you pay us to attach your sensor payload to the Forest Walker?”
# Noise Suppression

Only you can prevent Metallica filling the surrounds with 120 dB of sound. Easy enough, just turn the car stereo off. But what of a fleet of 50 Forest Walkers operating in the backcountry or near a township? 500? 5000? Each one has a wood chipper, an internal combustion engine, hydraulic pumps, actuators, and more cooling fans than you can shake a stick at. It’s a walking, screaming fire-breathing dragon operating continuously, day and night, twenty-four hours a day, three hundred sixty-five days a year. The sound will negatively affect all living things and that impacts behaviors. Serious engineering consideration and prowess must deliver a silencing blow to the major issue of noise.
It would be foolish to think that a fleet of Forest Walkers could be silent, but if not a major design consideration, then the entire idea is dead on arrival. Townships would not allow them to operate even if they solved the problem of widespread fuel load and neither would governmental entities, and rightly so. Nothing, not man nor beast, would want to be subjected to an eternal, infernal scream even if it were to end within days as the fleet moved further away after consuming what it could. Noise and heat are the only real pollutants of this system; taking noise seriously from the beginning is paramount.
# Fire Safety

A “fire-breathing dragon” is not the worst description of the Forest Walker. It eats wood, combusts it at very high temperatures and excretes carbon; and it does so in an extremely flammable environment. Bad mix for one Forest Walker, worse for many. One must take extreme pains to ensure that during normal operation, a Forest Walker could fall over, walk through tinder dry brush, or get pounded into the ground by a meteorite from Krypton and it wouldn’t destroy epic swaths of trees and baby deer. I envision an ultimate test of a prototype to include dowsing it in grain alcohol while it’s wrapped up in toilet paper like a pledge at a fraternity party. If it runs for 72 hours and doesn’t set everything on fire, then maybe outside entities won’t be fearful of something that walks around forests with a constant fire in its belly.
# The Wrap

How we think about what can be done with and adjacent to Bitcoin is at least as important as Bitcoin’s economic standing itself. For those who will tell me that this entire idea is without merit, I say, “OK, fine. You can come up with something, too.” What can we plug Bitcoin into that, like a battery, makes something that does not work, work? That’s the lesson I get from this entire exercise. No one was ever going to hire teams of humans to go out and "clean the forest". There's no money in that. The data collection and sales from such an endeavor might provide revenues over the break-even point but investment demands Alpha in this day and age. But, plug Bitcoin into an almost viable system and, voilà! We tip the scales to achieve lift-off.
Let’s face it, we haven’t scratched the surface of Bitcoin’s forcing function on our minds. Not because it’s Bitcoin, but because of what that invention means. The question that pushes me to approach things this way is, “what can we create that one system’s waste is another system’s feedstock?” The Forest Walker system’s only real waste is the conversion of low entropy energy (wood and syngas) into high entropy energy (heat and noise). All other output is beneficial to humanity.
Bitcoin, I believe, is the first product of a new mode of human imagination. An imagination newly forged over the past few millennia of being lied to, stolen from, distracted and otherwise mis-allocated to a black hole of the nonsensical. We are waking up.
What I have presented is not science fiction. Everything I have described here is well within the realm of possibility. The question is one of viability, at least in terms of the detritus of the old world we find ourselves departing from. This system would take a non-trivial amount of time and resources to develop. I think the system would garner extensive long-term contracts from those who have the most to lose from wildfires, the most to gain from hyperaccurate data sets, and, of course, securing the most precious asset in the world. Many may not see it that way, for they seek Alpha and are therefore blind to other possibilities. Others will see only the possibilities; of thinking in a new way, of looking at things differently, and dreaming of what comes next.
-

@ e3ba5e1a:5e433365
2025-01-13 16:47:27
My blog posts and reading material have both been on a decidedly economics-heavy slant recently. The topic today, incentives, squarely falls into the category of economics. However, when I say economics, I’m not talking about “analyzing supply and demand curves.” I’m talking about the true basis of economics: understanding how human beings make decisions in a world of scarcity.
A fair definition of incentive is “a reward or punishment that motivates behavior to achieve a desired outcome.” When most people think about economic incentives, they’re thinking of money. If I offer my son $5 if he washes the dishes, I’m incentivizing certain behavior. We can’t guarantee that he’ll do what I want him to do, but we can agree that the incentive structure itself will guide and ultimately determine what outcome will occur.
The great thing about monetary incentives is how easy they are to talk about and compare. “Would I rather make $5 washing the dishes or $10 cleaning the gutters?” But much of the world is incentivized in non-monetary ways too. For example, using the “punishment” half of the definition above, I might threaten my son with losing Nintendo Switch access if he doesn’t wash the dishes. No money is involved, but I’m still incentivizing behavior.
And there are plenty of incentives beyond our direct control\! My son is *also* incentivized to not wash dishes because it’s boring, or because he has some friends over that he wants to hang out with, or dozens of other things. Ultimately, the conflicting array of different incentive structures placed on him will ultimately determine what actions he chooses to take.
## Why incentives matter
A phrase I see often in discussions—whether they are political, parenting, economic, or business—is “if they could **just** do…” Each time I see that phrase, I cringe a bit internally. Usually, the underlying assumption of the statement is “if people would behave contrary to their incentivized behavior then things would be better.” For example:
* If my kids would just go to bed when I tell them, they wouldn’t be so cranky in the morning.
* If people would just use the recycling bin, we wouldn’t have such a landfill problem.
* If people would just stop being lazy, our team would deliver our project on time.
In all these cases, the speakers are seemingly flummoxed as to why the people in question don’t behave more rationally. The problem is: each group is behaving perfectly rationally.
* The kids have a high time preference, and care more about the joy of staying up now than the crankiness in the morning. Plus, they don’t really suffer the consequences of morning crankiness, their parents do.
* No individual suffers much from their individual contribution to a landfill. If they stopped growing the size of the landfill, it would make an insignificant difference versus the amount of effort they need to engage in to properly recycle.
* If a team doesn’t properly account for the productivity of individuals on a project, each individual receives less harm from their own inaction. Sure, the project may be delayed, company revenue may be down, and they may even risk losing their job when the company goes out of business. But their laziness individually won’t determine the entirety of that outcome. By contrast, they greatly benefit from being lazy by getting to relax at work, go on social media, read a book, or do whatever else they do when they’re supposed to be working.

My point here is that, as long as you ignore the reality of how incentives drive human behavior, you’ll fail at getting the outcomes you want.
If everything I wrote up until now made perfect sense, you understand the premise of this blog post. The rest of it will focus on a bunch of real-world examples to hammer home the point, and demonstrate how versatile this mental model is.
## Running a company
Let’s say I run my own company, with myself as the only employee. My personal revenue will be 100% determined by my own actions. If I decide to take Tuesday afternoon off and go fishing, I’ve chosen to lose that afternoon’s revenue. Implicitly, I’ve decided that the enjoyment I get from an afternoon of fishing is greater than the potential revenue. You may think I’m being lazy, but it’s my decision to make. In this situation, the incentive–money–is perfectly aligned with my actions.
Compare this to a typical company/employee relationship. I might have a bank of Paid Time Off (PTO) days, in which case once again my incentives are relatively aligned. I know that I can take off 15 days throughout the year, and I’ve chosen to use half a day for the fishing trip. All is still good.
What about unlimited time off? Suddenly incentives are starting to misalign. I don’t directly pay a price for not showing up to work on Tuesday. Or Wednesday as well, for that matter. I might ultimately be fired for not doing my job, but that will take longer to work its way through the system than simply not making any money for the day taken off.
Compensation overall falls into this misaligned incentive structure. Let’s forget about taking time off. Instead, I work full time on a software project I’m assigned. But instead of using the normal toolchain we’re all used to at work, I play around with a new programming language. I get the fun and joy of playing with new technology, and potentially get to pad my resume a bit when I’m ready to look for a new job. But my current company gets slower results, less productivity, and is forced to subsidize my extracurricular learning.
When a CEO has a bonus structure based on profitability, he’ll do everything he can to make the company profitable. This might include things that actually benefit the company, like improving product quality, reducing internal red tape, or finding cheaper vendors. But it might also include destructive practices, like slashing the R\&D budget to show massive profits this year, in exchange for a catastrophe next year when the next version of the product fails to ship.

Or my favorite example. My parents owned a business when I was growing up. They had a back office where they ran operations like accounting. All of the furniture was old couches from our house. After all, any money they spent on furniture came right out of their paychecks\! But in a large corporate environment, each department is generally given a budget for office furniture, a budget which doesn’t roll over year-to-year. The result? Executives make sure to spend the entire budget each year, often buying furniture far more expensive than they would choose if it was their own money.
There are plenty of details you can quibble with above. It’s in a company’s best interest to give people downtime so that they can come back recharged. Having good ergonomic furniture can in fact increase productivity in excess of the money spent on it. But overall, the picture is pretty clear: in large corporate structures, you’re guaranteed to have mismatches between the company’s goals and the incentive structure placed on individuals.
Using our model from above, we can lament how lazy, greedy, and unethical the employees are for doing what they’re incentivized to do instead of what’s right. But that’s simply ignoring the reality of human nature.
# Moral hazard
Moral hazard is a situation where one party is incentivized to take on more risk because another party will bear the consequences. Suppose I tell my son when he turns 21 (or whatever legal gambling age is) that I’ll cover all his losses for a day at the casino, but he gets to keep all the winnings.
What do you think he’s going to do? The most logical course of action is to place the largest possible bets for as long as possible, asking me to cover each time he loses, and taking money off the table and into his bank account each time he wins.

But let’s look at a slightly more nuanced example. I go to a bathroom in the mall. As I’m leaving, I wash my hands. It will take me an extra 1 second to turn off the water when I’m done washing. That’s a trivial price to pay. If I *don’t* turn off the water, the mall will have to pay for many liters of wasted water, benefiting no one. But I won’t suffer any consequences at all.
This is also a moral hazard, but most people will still turn off the water. Why? Usually due to some combination of other reasons such as:
1. We’re so habituated to turning off the water that we don’t even consider *not* turning it off. Put differently, the mental effort needed to not turn off the water is more expensive than the 1 second of time to turn it off.
2. Many of us have been brought up with a deep guilt about wasting resources like water. We have an internal incentive structure that makes the 1 second to turn off the water much less costly than the mental anguish of the waste we created.
3. We’re afraid we’ll be caught by someone else and face some kind of social repercussions. (Or maybe more than social. Are you sure there isn’t a law against leaving the water tap on?)
Even with all that in place, you may notice that many public bathrooms use automatic water dispensers. Sure, there’s a sanitation reason for that, but it’s also to avoid this moral hazard.
A common denominator in both of these is that the person taking the action that causes the liability (either the gambling or leaving the water on) is not the person who bears the responsibility for that liability (the father or the mall owner). Generally speaking, the closer together the person making the decision and the person incurring the liability are, the smaller the moral hazard.
It’s easy to demonstrate that by extending the casino example a bit. I said it was the father who was covering the losses of the gambler. Many children (though not all) would want to avoid totally bankrupting their parents, or at least financially hurting them. Instead, imagine that someone from the IRS shows up at your door, hands you a credit card, and tells you you can use it at a casino all day, taking home all the chips you want. The money is coming from the government. How many people would put any restriction on how much they spend?
And since we’re talking about the government already…
## Government moral hazards
As I was preparing to write this blog post, the California wildfires hit. The discussions around those wildfires gave a *huge* number of examples of moral hazards. I decided to cherry-pick a few for this post.
The first and most obvious one: California is asking for disaster relief funds from the federal government. That sounds wonderful. These fires were a natural disaster, so why shouldn’t the federal government pitch in and help take care of people?
The problem is, once again, a moral hazard. In the case of the wildfires, California and Los Angeles both had ample actions they could have taken to mitigate the destruction of this fire: better forest management, larger fire department, keeping the water reservoirs filled, and probably much more that hasn’t come to light yet.
If the federal government bails out California, it will be a clear message for the future: your mistakes will be fixed by others. You know what kind of behavior that incentivizes? More risky behavior\! Why spend state funds on forest management and extra firefighters—activities that don’t win politicians a lot of votes in general—when you could instead spend it on a football stadium, higher unemployment payments, or anything else, and then let the feds cover the cost of screw-ups.
You may notice that this is virtually identical to the 2008 “too big to fail” bail-outs. Wall Street took insanely risky behavior, reaped huge profits for years, and when they eventually got caught with their pants down, the rest of us bailed them out. “Privatizing profits, socializing losses.”

And here’s the absolute best part of this: I can’t even truly blame either California *or* Wall Street. (I mean, I *do* blame them, I think their behavior is reprehensible, but you’ll see what I mean.) In a world where the rules of the game implicitly include the bail-out mentality, you would be harming your citizens/shareholders/investors if you didn’t engage in that risky behavior. Since everyone is on the hook for those socialized losses, your best bet is to maximize those privatized profits.
There’s a lot more to government and moral hazard, but I think these two cases demonstrate the crux pretty solidly. But let’s leave moral hazard behind for a bit and get to general incentivization discussions.
# Non-monetary competition
At least 50% of the economics knowledge I have comes from the very first econ course I took in college. That professor was amazing, and had some very colorful stories. I can’t vouch for the veracity of the two I’m about to share, but they definitely drive the point home.
In the 1970s, the US had an oil shortage. To “fix” this problem, they instituted price caps on gasoline, which of course resulted in insufficient gasoline. To “fix” this problem, they instituted policies where, depending on your license plate number, you could only fill up gas on certain days of the week. (Irrelevant detail for our point here, but this just resulted in people filling up their tanks more often, no reduction in gas usage.)
Anyway, my professor’s wife had a friend. My professor described in *great* detail how attractive this woman was. I’ll skip those details here since this is a PG-rated blog. In any event, she never had any trouble filling up her gas tank any day of the week. She would drive up, be told she couldn’t fill up gas today, bat her eyes at the attendant, explain how helpless she was, and was always allowed to fill up gas.
This is a demonstration of *non-monetary compensation*. Most of the time in a free market, capitalist economy, people are compensated through money. When price caps come into play, there’s a limit to how much monetary compensation someone can receive. And in that case, people find other ways of competing. Like this woman’s case: through using flirtatious behavior to compensate the gas station workers to let her cheat the rules.
The other example was much more insidious. Santa Monica had a problem: it was predominantly wealthy and white. They wanted to fix this problem, and decided to put in place rent controls. After some time, they discovered that Santa Monica had become *wealthier and whiter*, the exact opposite of their desired outcome. Why would that happen?
Someone investigated, and ended up interviewing a landlady that demonstrated the reason. She was an older white woman, and admittedly racist. Prior to the rent controls, she would list her apartments in the newspaper, and would be legally obligated to rent to anyone who could afford it. Once rent controls were in place, she took a different tact. She knew that she would only get a certain amount for the apartment, and that the demand for apartments was higher than the supply. That meant she could be picky.
She ended up finding tenants through friends-of-friends. Since it wasn’t an official advertisement, she wasn’t legally required to rent it out if someone could afford to pay. Instead, she got to interview people individually and then make them an offer. Normally, that would have resulted in receiving a lower rental price, but not under rent controls.
So who did she choose? A young, unmarried, wealthy, white woman. It made perfect sense. Women were less intimidating and more likely to maintain the apartment better. Wealthy people, she determined, would be better tenants. (I have no idea if this is true in practice or not, I’m not a landlord myself.) Unmarried, because no kids running around meant less damage to the property. And, of course, white. Because she was racist, and her incentive structure made her prefer whites.
You can deride her for being racist, I won’t disagree with you. But it’s simply the reality. Under the non-rent-control scenario, her profit motive for money outweighed her racism motive. But under rent control, the monetary competition was removed, and she was free to play into her racist tendencies without facing any negative consequences.
## Bureaucracy
These were the two examples I remember for that course. But non-monetary compensation pops up in many more places. One highly pertinent example is bureaucracies. Imagine you have a government office, or a large corporation’s acquisition department, or the team that apportions grants at a university. In all these cases, you have a group of people making decisions about handing out money that has no monetary impact on them. If they give to the best qualified recipients, they receive no raises. If they spend the money recklessly on frivolous projects, they face no consequences.
Under such an incentivization scheme, there’s little to encourage the bureaucrats to make intelligent funding decisions. Instead, they’ll be incentivized to spend the money where they recognize non-monetary benefits. This is why it’s so common to hear about expensive meals, gift bags at conferences, and even more inappropriate ways of trying to curry favor with those that hold the purse strings.
Compare that ever so briefly with the purchases made by a small mom-and-pop store like my parents owned. Could my dad take a bribe to buy from a vendor who’s ripping him off? Absolutely he could\! But he’d lose more on the deal than he’d make on the bribe, since he’s directly incentivized by the deal itself. It would make much more sense for him to go with the better vendor, save $5,000 on the deal, and then treat himself to a lavish $400 meal to celebrate.
# Government incentivized behavior
This post is getting longer in the tooth than I’d intended, so I’ll finish off with this section and make it a bit briefer. Beyond all the methods mentioned above, government has another mechanism for modifying behavior: through directly changing incentives via legislation, regulation, and monetary policy. Let’s see some examples:
* Artificial modification of interest rates encourages people to take on more debt than they would in a free capital market, leading to [malinvestment](https://en.wikipedia.org/wiki/Malinvestment) and a consumer debt crisis, and causing the boom-bust cycle we all painfully experience.
* Going along with that, giving tax breaks on interest payments further artificially incentivizes people to take on debt that they wouldn’t otherwise.
* During COVID-19, at some points unemployment benefits were greater than minimum wage, incentivizing people to rather stay home and not work than get a job, leading to reduced overall productivity in the economy and more printed dollars for benefits. In other words, it was a perfect recipe for inflation.
* The tax code gives deductions to “help” people. That might be true, but the real impact is incentivizing people to make decisions they wouldn’t have otherwise. For example, giving out tax deductions on children encourages having more kids. Tax deductions on childcare and preschools incentivizes dual-income households. Whether or not you like the outcomes, it’s clear that it’s government that’s encouraging these outcomes to happen.
* Tax incentives cause people to engage in behavior they wouldn’t otherwise (daycare+working mother, for example).
* Inflation means that the value of your money goes down over time, which encourages people to spend more today, when their money has a larger impact. (Milton Friedman described this as [high living](https://www.youtube.com/watch?v=ZwNDd2_beTU).)
# Conclusion
The idea here is simple, and fully encapsulated in the title: incentives determine outcomes. If you want to know how to get a certain outcome from others, incentivize them to want that to happen. If you want to understand why people act in seemingly irrational ways, check their incentives. If you’re confused why leaders (and especially politicians) seem to engage in destructive behavior, check their incentives.
We can bemoan these realities all we want, but they *are* realities. While there are some people who have a solid internal moral and ethical code, and that internal code incentivizes them to behave against their externally-incentivized interests, those people are rare. And frankly, those people are self-defeating. People *should* take advantage of the incentives around them. Because if they don’t, someone else will.
(If you want a literary example of that last comment, see the horse in Animal Farm.)
How do we improve the world under these conditions? Make sure the incentives align well with the overall goals of society. To me, it’s a simple formula:
* Focus on free trade, value for value, as the basis of a society. In that system, people are always incentivized to provide value to other people.
* Reduce the size of bureaucracies and large groups of all kinds. The larger an organization becomes, the farther the consequences of decisions are from those who make them.
* And since the nature of human beings will be to try and create areas where they can control the incentive systems to their own benefits, make that as difficult as possible. That comes in the form of strict limits on government power, for example.
And even if you don’t want to buy in to this conclusion, I hope the rest of the content was educational, and maybe a bit entertaining\!
-

@ 58937958:545e6994
2025-01-03 11:07:06
January 3, 2024
I made a Bitcoin-inspired Osechi to celebrate Bitcoin's birthday.
Everything was handmade!
Osechi: A traditional Japanese New Year’s feast, typically served in stacked boxes.
## First Layer (Ichino-jū)

- Tazukuri: Dried sardines, symbolizing a wish for a bountiful harvest.
- Simmered Kuai: A vegetable with large sprouts, symbolizing growth and success.
- Kombu Rolls: A play on words with the Japanese term yorokobu ("to be joyful"), making it a good luck dish.
- Matsukazeyaki: Ground meat coated with sesame or poppy seeds on one side, symbolizing honesty (no "hidden side").
- Black Beans: Represent hard work and good health.
- Datemaki: Sweet rolled omelet resembling scrolls, symbolizing knowledge and learning.
- Grilled Yellowtail: A fish whose name changes as it grows, symbolizing success. Salmon Terrine: A classic addition to Western-style Osechi. Salmon symbolizes success, avoiding misfortune (sakeru), and prosperity for future generations.
- Tataki Gobo: Burdock root with deep roots, symbolizing family stability and prosperity.
## Second Layer (Nino-jū)

- Candied Kumquat: A dish symbolizing wealth and good fortune.
- Namash: Pickled daikon and carrot, resembling celebratory red and white decorations.
- Chestnut Kinton: Golden in color, symbolizing wealth and a prosperous year.
Bitcoin-themed additions:
- Pumpkin Yokan
- Chicken and Spinach Terrine
- Kinako Sticks
## Third Layer (Sanno-jū)

Nishime: A simmered dish with various ingredients, symbolizing family harmony and long-lasting prosperity.
I used snow peas to represent Bitcoin, and I couldn’t help but laugh at myself.
## Dishes Inspired by Bitcoin
### Pumpkin Yokan

I made firm milk jelly, cut it into a "B" shape with a knife, and filled it with pumpkin yokan.
### Chicken and Spinach Terrine

It was my first attempt, and I think with more care, the shape could be even better.
### Kinako Sticks

A simple snack made with honey and roasted soybean flour (kinako).
Roll it out, cut it into sticks, and coat with more kinako.
### Candied Kumquat

Candied Kumquat: A dish symbolizing wealth and good fortune.
In Japan, 金柑 (kumquat) includes the kanji 金, which represents "gold."
nostr:nevent1qqspu8gegzdamtx2rsm4995t3sg8qssw3vn3yn25ru8plghsqyrwtkcn0u7vy
I wonder what Satoshi might have eaten on the day Bitcoin was born.
Wouldn't it be amusing to imagine him snacking on Osechi while working on his computer?
(Satoshi chose a Japanese name, so perhaps he might have an interest in Japanese culture.)
Maybe, right now, Satoshi is relaxing and enjoying some Osechi... though probably not!
In any case, I hope Satoshi is living peacefully somewhere.
-

@ 71a4b7ff:d009692a
2025-01-19 10:20:02
### The Problem with Preset Choices
Switching sections around? Not an option—we’ve already decided for you, buddy. Remove bright colors? Come on, it’s already beautiful. Disable unnecessary features? Don’t be silly, you need everything here. Especially this algorithmic feed with built-in ads.
### Monetization Over User Experience
The operators of digital services will always prioritize their primary goal: monetizing the product as efficiently as possible. They need to not only attract new users but also retain existing ones. And the best tool for this is the interface.
That’s why most product decisions are far removed from ideas like “Let’s make it more convenient for people” or “Let’s give users more freedom.” Instead, we see the result of a recurring process:
- We have a retention and monetization mechanism
- Assign tasks to developers and designers
- Integrate it into the product
- Write a quarterly report.
The outcome? Users end up with Reels tabs smack in the center of Instagram’s bottom navigation bar. Removing or rearranging those tabs? Not an option. And it likely never will be.
### Why Rigid Interfaces Persist
Another reason for rigid and obligatory interfaces is that they’re easier to design. Just imagine how many combinations of colors, elements, and layouts developers would need to account for to make a product both customizable and functional without turning it into a garish mess. But that’s just nuance and excuses.
### The Myth of Perfect Design
Services often justify their choices by claiming their design is “the most designed,” that they know what’s best and will make it work for everyone. They might even present solid arguments for this. But all those arguments fall apart against the reality we see on our screens every day. In my opinion, people should have the ability to turn a product into anything they want—whether it’s loud and kitschy or minimalistic and dull. This option wouldn’t just allow users to express themselves but could also help with digital detoxing.
### The Example of App Labels
Here’s an example: why do app icons on smartphone home screens (not the app drawer) come with labels underneath? Apps on the home screen are easily recognizable by their icons. Why would I need a name tag for an app I intentionally placed there? Sure, for some users or scenarios, this might be helpful. But why is it the default option?
The problem is that these labels are just visual noise—clusters of unnecessary text we already see plenty of. Removing them would make it slightly easier for the brain to process the screen every time you look at it. Now scale that to 3–8 hours of daily smartphone use. Then a month. Then a year.
### The Slow Shift Toward Customization
For a long time, iOS didn’t allow you to hide icon labels. Now, the option exists, but it still requires more effort than a simple toggle. As a result, people are stuck looking at tons of unnecessary, subconscious information every day. And this is just the trivial issue of app labels on a product considered the gold standard of digital design. Imagine the horror of tackling more significant issues.
Yes, Apple has softened its stance in recent years, offering custom icons and lock screens. Celebrate—you can now showcase your individuality! The company understands that customization is the future. We’ve reached a point where weak computing power is no longer an excuse, VR/metaverse adoption is still a way off, and new features are needed. So, this is an excellent opportunity for all of us.
### The Case for More Customization
In a reasonable, ideal world, people should decide which sections of a service they need, where they’re located, and how they look. Companies, meanwhile, recognize that people want the ability to stand out and create something personal—even on a smartphone in their pocket. And as our integration with various devices deepens, this need will only grow. More customization is coming. Yes, it’ll be largely cosmetic, but even that can work to our advantage: removing jarring colors or hiding unnecessary labels can reduce the brain’s pointless load.
### Beyond Aesthetics: Customization as Freedom
The ability to customize services isn’t just about playing amateur designer. It’s about mitigating informational irritants, reducing the addictive nature of interfaces, and weakening dark patterns. Which is likely why many companies no longer prioritize customization.
### Telegram: A Customizable Example
In this context, Telegram is a decent example. I’m not a fan, but I’ve been using it for daily communication with loved ones for a long time—and it’s good for that. It can be vastly different for vastly different users. Despite starting to bend under the weight of its audience and introducing questionable decisions, its foundational design principles still allow for creating both minimalist spaces for peaceful content consumption or communication, as well as vibrant, noisy chats for virtual parties. Telegram can be a messenger, a feed, a file storage system, or whatever else you need—and it can look wildly different while doing so.
### Customization as the Key to Healthy Digital Relationships
Customization should be at the core of the services we use daily. Yes, it can and will be used for marketing purposes. But even minimal customization is better than none because the ability to tailor a system to your needs is an expression of freedom and a cornerstone of healthy relationships with the digital world.
**Stay Nostrous. Geo**
-

@ 96537107:334e9245
2025-01-19 07:39:54
有多少人在排队中?产业趋势不可逆~~~
-

@ a10260a2:caa23e3e
2025-01-18 12:04:41
*Last Updated: January 18, 2025*
First off, big shoutout to Coinos for having support for adding a memo to BOLT12 offers. This provides a solid alternative for the pleb who wants to support mining decentralization but doesn’t want to set up a CLN node and pay thousands of sats for a channel only to get little rewards. This is the case for most of us who only have a miner or two (e.g. a Bitaxe and/or an S9).
Before we get into setting up Lightning payouts, you’ll want to have your miner configured to mine with OCEAN of course. You’ll also want to make sure that the bitcoin address you use is from a wallet that supports signing messages.
These are the ones listed in the OCEAN [docs](https://ocean.xyz/docs/lightning):
* Bitcoin Knots/Bitcoin Core
* Coldcard
* Electrum
* LND (Command Line)
* Seedsigner
* Sparrow
* Specter
* Trezor
I checked one of my favorite, user-friendly wallets — Blue Wallet — and it happens to support signing messages as well.
Just tap the three dots on the upper right and you’ll see the “Sign/Verify Message” button at the bottom.
Update [January 18]: You can now use Coinos to sign by going to https://coinos.io/sign
The trick here is to not refresh the page. In other words, when you're logged in to your Coinos account, go to the URL and use the legacy address (starts with a "1") that's displayed to configure your miner(s). If you refresh the page, you're going to get a new address which will cause the signing to fail later on. *Remember*, keep the tab open and don't refresh the page.

Whichever wallet you choose, generate a receive address to use when configuring your miner (it’ll also be your OCEAN username).
Here’s how it looks on the Bitaxe (AxeOS)…
And the Antminer S9 (Braiins OS).
NOTE: There’s a slight difference in the URL format between the two apps. Other than that, the username will be your bitcoin address followed by the optional “.” + the nickname for your machine.
You can find more details on OCEAN’s [get started page](https://ocean.xyz/getstarted).
---
Alright, now that your miner is pointed at OCEAN. Let’s configure Lightning payouts!
### Generating the BOLT12 Offer
In the Coinos app, go to Receive > Bolt 12.
Tap “Set memo” and set it to “OCEAN Payouts for [insert your bitcoin address]” (this text is case-sensitive). Use the same bitcoin address you used above to configure your miner(s).
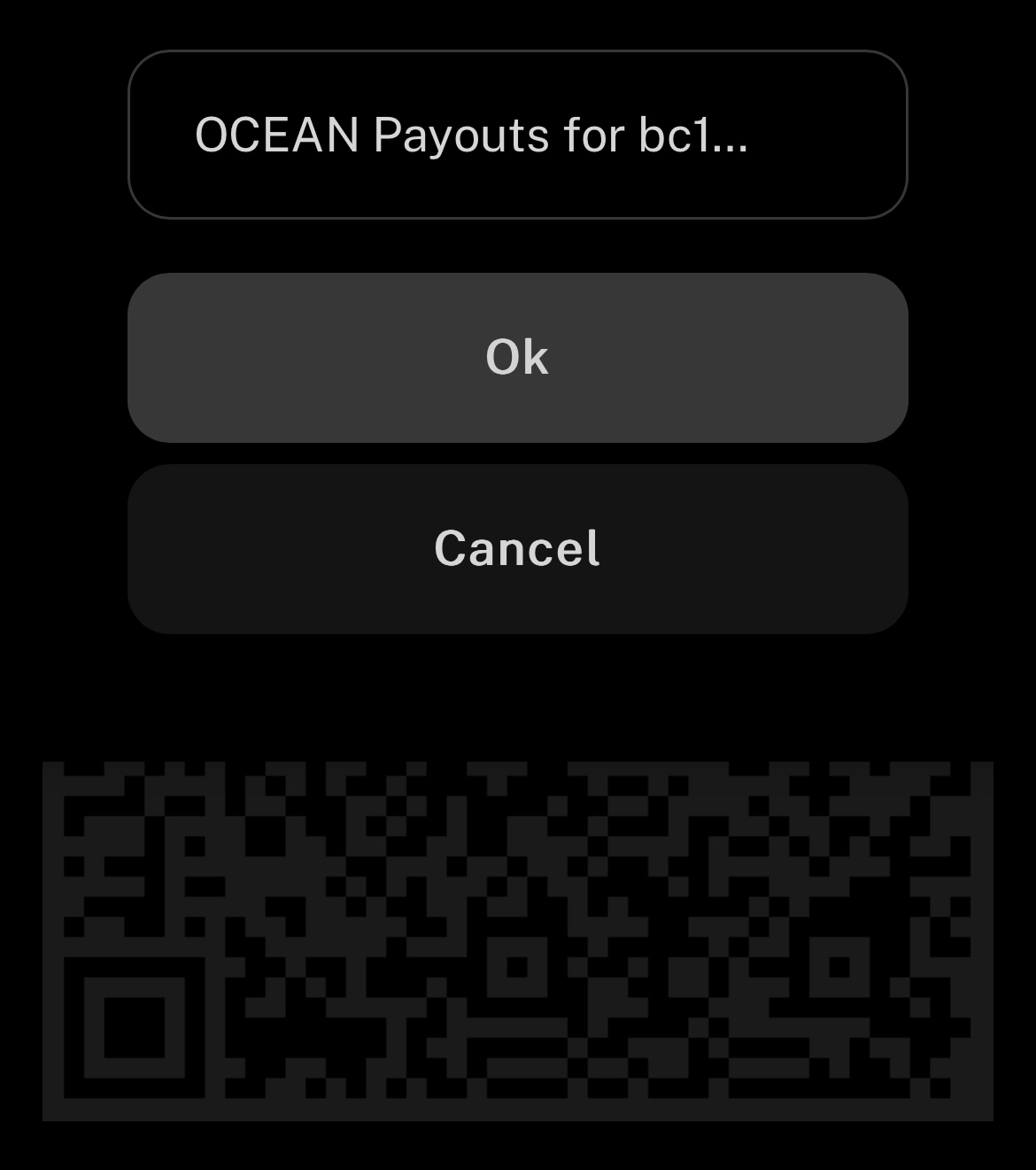
After tapping OK, copy the BOLT12 offer (it should start with “lno”) and proceed to the next step.
### Generating the Configuration Message
Navigate to the [My Stats](https://ocean.xyz/stats) page by searching for your OCEAN Bitcoin address.
The click the Configuration link next to Next Block to access the configuration form.
Paste the BOLT12 offer here, update the block height to latest, click GENERATE, and copy the generated unsigned message.
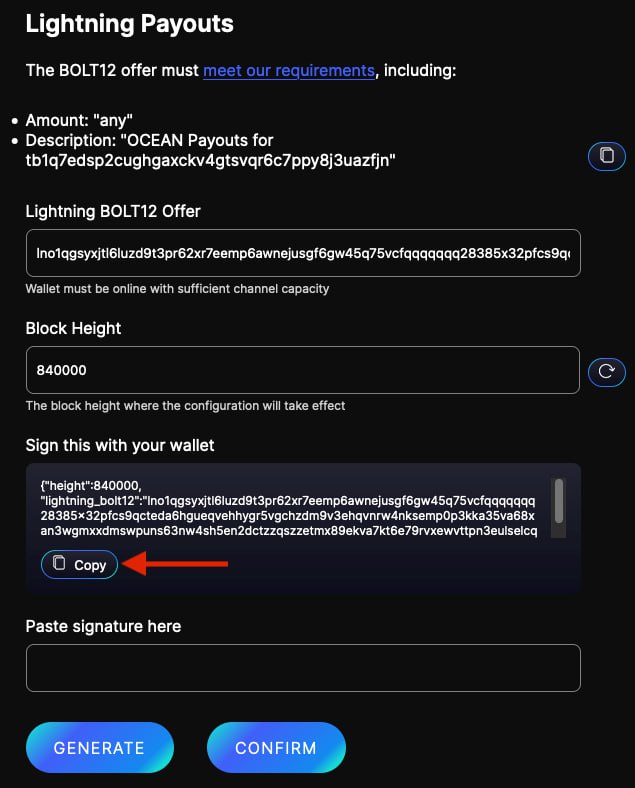
### Signing the Configuration Message
To sign the generated message, go back to Blue Wallet and use the signing function. Paste the configuration message in the Message field, tap Sign, and copy the signed message that’s generated.
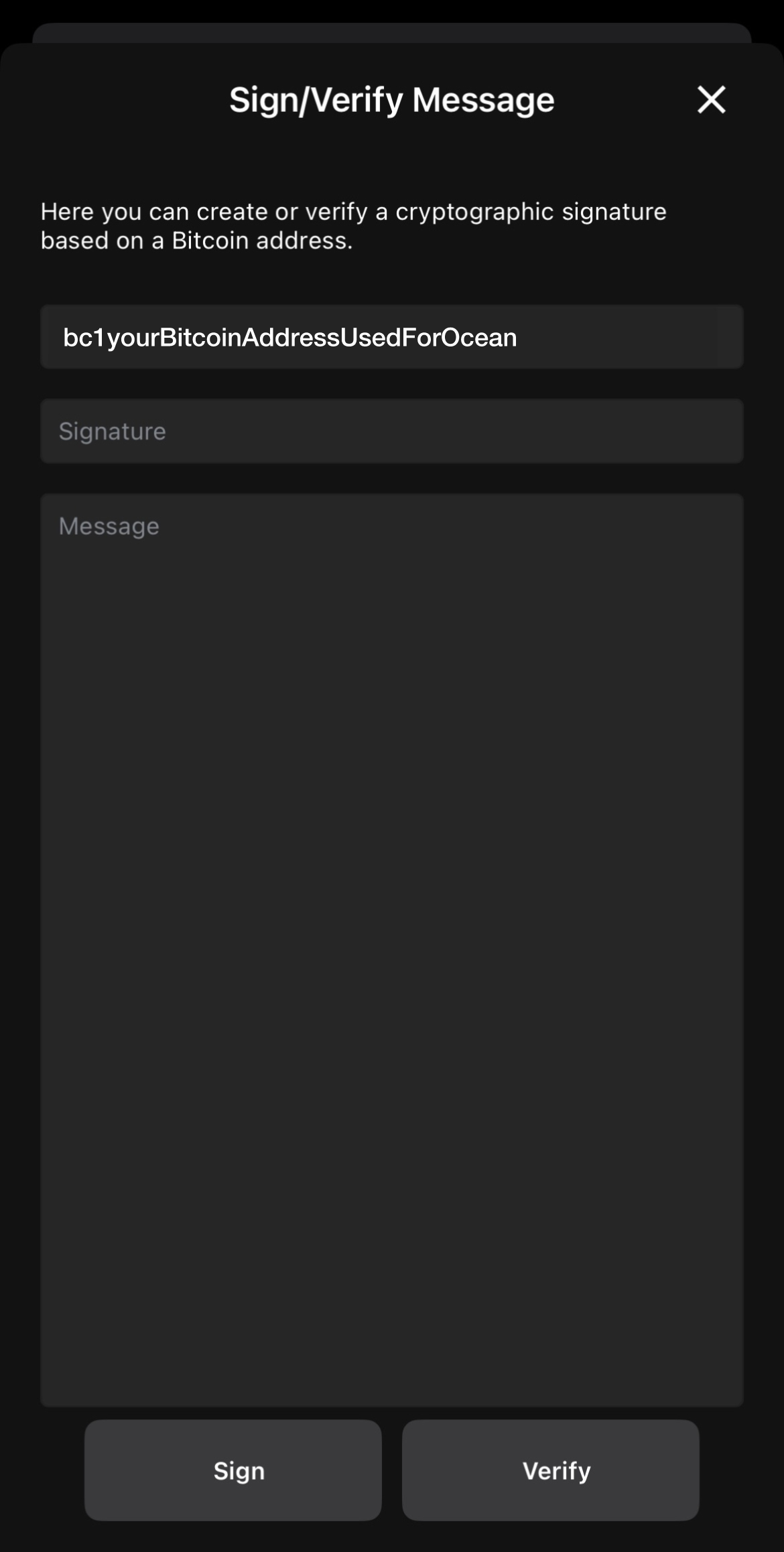
If you're using Coinos to sign, return to the page that you kept open (and didn't refresh) and do the same. Paste the configuration message, click submit, and copy the signed message.
### Submitting the Signed Message
Once signed, copy the signature, paste it in the OCEAN configuration form, and click CONFIRM.
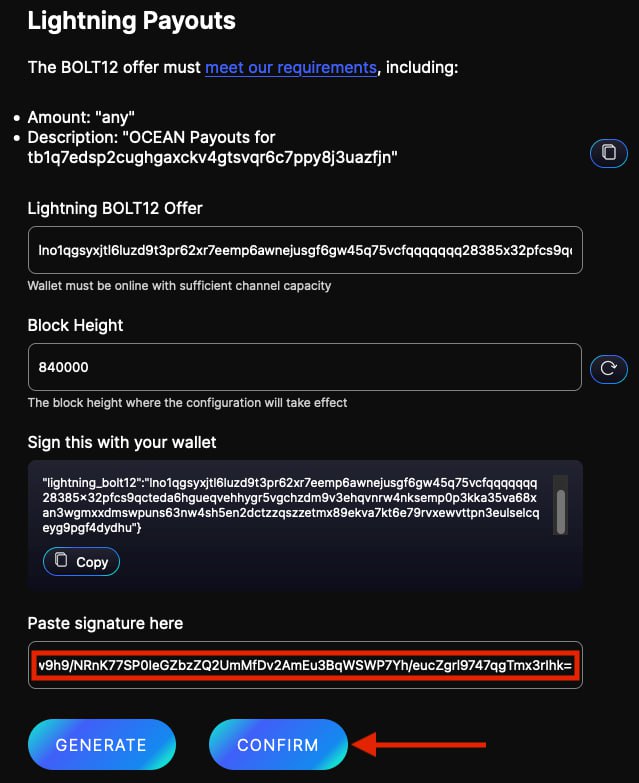
If all goes well, you should see a confirmation that the configuration was successful. Congrats! 🎉
All you gotta do now is sit back, relax, and wait for a block to be found…
Or you can look into setting up [DATUM](https://ocean.xyz/docs/datum-setup). 😎
-

@ f88e6629:e5254dd5
2025-01-17 14:10:19
...which allow online payments to be sent directly from one party to another without going through a
financial institution.
- Without sovereign and accessible payments we are loosing censorship resistance
- Without censorship resistance even other core characteristics are in danger - including scarcity and durability.
- This affects every bitcoiner including sworn hodlers and MSTR followers.
| Property | Description | Fulfillment |
| --- | --- | --- |
| Scarce | Fixed supply forever. Instantly and costlessly verifiable | 🟢 Good, but can be harmed without censorship resistance |
| Portable | Effortless to store and move, with negligible costs | 🟠 Onchain transactions can be expensive, other layers require onchain to be sovereign. Easy portability is offered by custodians only. |
| Divisible | Infinitely divisible | 🟠 Smaller units than dust are available only for LN users, which most people can’t use in a sovereign way. |
| Durable | Exists forever without deterioration | 🟢 Good, but can be harmed without censorship resistance |
| Fungible | Every piece is forever the same as every other piece | 🟡 Onchain bitcoin is not fungible. |
| Acceptable | Everyone, anywhere, can send and receive | 🟠 Most people are not able to send and receive in a sovereign way. |
| Censorship Resistant | You hold it. Nobody can take it or stop you sending it | 🟠 Custodians are honey-pots that can and will be regulated |
> ➡️ We need accessible, scalable, and sovereign payment methods
-

@ d9e9fb27:d5fe5e1a
2025-01-17 13:00:58
Every 16th of January, the city of Varese, a small town at the feet of the Prealpine region, stops to participate in one of the most important ceremonies of the city: *The Falò of Sant'Antonio*.
A *Falò* is the Italian word for *bonfire*. Imagine a 5-meters tall pyre of wood burning in the center of the city. For sure, an unmissable event!

The pyre is built by the so-called "*Monelli della Motta*". A *Monello* in Italian is a child that misbehaves. This nickname come from the fact that in the past, the pyre was created using wood stolen from the city, usually from tools, doors and shutters.
This event takes place at the eve of the day of Sant'Antonio Abate in front of the homonymous church in the area called "*La Motta*", which stands for *small hill*, and comes from a several century old tradition. Thousands of people from all over the province come to the city to look at the bonfire created in honor of the Saint.

At 9PM the big event starts. The wood is set on fire!

An important tradition of this celebration is burning small pieces of paper containing wishes. People whish for health, love, friendship and luck. To make wishes come true, people have to give these pieces of paper to a firefighter or a "*Monello*" whom will launch it into the *Falò*.
The show goes on for a couple of ours, during which thousands of Varesinians in awe contemplate the raging fire and try to receive some heat to fight the glacial cold of January.

-

@ 5bdb0e24:0ccbebd7
2025-01-17 06:19:58
In the world of networking, two fundamental models serve as the backbone for communication protocols and standards: the OSI model and the TCP/IP model. Both models are quite similar, providing frameworks for how data is transmitted across networks at various stages of the process.
Understanding these models is crucial for anyone working in IT, cybersecurity, or any related tech field. But what exactly are they?
# The OSI Model
The OSI (Open Systems Interconnection) model is a conceptual framework that standardizes the functions of a telecommunication or computing system into seven distinct layers. Each layer is responsible for specific tasks, such as data encapsulation, error detection, and routing. The layers of the OSI model are as follows:
1. **Physical Layer:** This layer deals with the physical connection between devices, such as cables and network interfaces.
2. **Data Link Layer:** Responsible for node-to-node communication, this layer ensures data integrity and manages access to the physical medium.
3. **Network Layer:** The network layer handles routing and forwarding of data packets between different networks.
4. **Transport Layer:** This layer provides end-to-end communication services for applications, including error detection and flow control.
5. **Session Layer:** Manages sessions between applications, establishing, maintaining, and terminating connections.
6. **Presentation Layer:** Responsible for data translation, encryption, and compression to ensure compatibility between different systems.
7. **Application Layer:** The topmost layer that interacts directly with applications and end-users, providing network services such as email and file transfer.
Now, that's a lot to remember. So, an easy acronym you can use to remember these 7 layers is *"Please Do Not Touch Steve's Pet Alligator."* It's helped me quite a bit in trying to pinpoint a specific layer.
Also, keep in mind that the layers are typically inverted from what you see above, with Layer 7 being at the top of the stack and Layer 1 being at the bottom.
# The TCP/IP Model
On the other hand, the TCP/IP (Transmission Control Protocol/Internet Protocol) model is a more streamlined approach to networking, consisting of only four layers:
1. **Link Layer:** Corresponding to the OSI model's data link and physical layers, the link layer deals with the physical connection and data framing.
2. **Internet Layer:** Similar to the OSI model's network layer, the internet layer focuses on routing packets across different networks.
3. **Transport Layer:** Combines the functions of the OSI model's transport and session layers, providing reliable data transfer services.
4. **Application Layer:** Equivalent to the OSI model's top three layers, the application layer in TCP/IP handles network services for applications.
While the OSI model is more detailed and theoretical, the TCP/IP model is practical and widely used in modern networking. It's also a bit easier to remember than the OSI model.
And, similar to the OSI model, the TCP/IP model is typically visualized with Layer 4 at the top of the stack and Layer 1 at the bottom, unlike what you see above.
# Conclusion
Both the TCP/IP and OSI models play essential roles in understanding how data is transmitted across networks. By grasping the functions of each layer and their interactions, network professionals can troubleshoot issues, design efficient networks, and ensure seamless communication between devices.
Whether you're a seasoned systems administrator or you're just getting your start in IT, mastering these models is key to navigating the complex world of networking.
-

@ 71a4b7ff:d009692a
2025-01-16 17:31:06
A couple of years ago psychologists at Berkeley have [delved into the phenomenon of awe](https://doi.org/10.1177/17456916221094856)—how it affects us, when it arises, and how it can benefit us. Then I made this short summary, which I translated and edited a little today.
## What Characterizes Awe?
Researchers define awe as a distinct and complex emotion encompassing 8–10 positive feelings, such as wonder, admiration, delight, and respect.
I’d like to sprinkle in a touch of discomfort or even threat, but the study notes that this aspect of awe depends on cultural context. For instance, in Japan, awe is more closely tied to experiences of threat than in other countries—think earthquakes, emperors, Hiroshima, Godzilla, and other kaiju.
## How does our body respond to awe?
It turns out that awe can significantly improve both physical and mental health—even in “angry, bald apes” like us. The only caveat is not to mix it with fear or threat. Awe associated with those tends to be less beneficial.
The study identifies five key ways in which awe supports well-being:
1. **Neurophysiological bonuses**:
- Increased vagal tone.
- Reduced sympathetic arousal.
- Release of oxytocin.
- Decreased systemic inflammation.
- Lower activity in the brain’s default mode network.
2. **Reduced self-focus**:\
Over-focusing on oneself contributes to anxiety, depression, body image issues, addiction, aggression, and more. Notably, most people's profile pictures are close-ups of their faces. But among hikers, you’re more likely to see tiny figures dwarfed by vast, beautiful landscapes. If that’s not a literal shift away from self-focus, what is?
3. **Prosociality**:\
Even a brief moment of awe boosts cooperation, generosity, and altruistic behavior. Nowhere have I seen as much mutual help and free-flowing communication, even among strangers, as I have on hiking trips.
4. **Connection to the larger whole**:\
Awe fosters integration into strong social networks, a sense of connection to others, and harmony with nature.
5. **A sense of meaning, purpose, and significance**:\
Awe aids in making sense of life’s events, finding links between the present and the past, and aligning with one’s values, relationships, and life trajectory.
These five aspects form the foundation of both physical and mental health. Open any book, lecture, or treatise on human well-being, and you’ll find them highlighted in some form.
## How can you experience awe?
<img src="https://blossom.primal.net/46f89c89063c95b68833651fd09566613a9cf7e5b79f3fd4107e690d3a7d7242.jpg">
The good news is that opportunities to experience awe are varied and accessible to almost everyone. It’s both surprising and heartening that they don’t revolve around the modern-day idols of success, money, or power. It seems that, at our core, we’re geared toward other goals and often misled by false priorities.
Among the universally effective ways to experience awe, researchers highlight:
- Spiritual and religious practices.
- Shared ceremonies (cinema, music, dance).
- Visual art.
- Psychedelic experiences.
- Acts of courage and kindness (which inspire awe in others).
- And, of course, connection with nature.
When mountains and hiking entered my life, they brought more health, peace, friends, purpose, and meaning than I’d ever expected. This text is a direct result of the awe I feel each time I stand among peaks, cliffs, forests, lakes, and rivers.
It’s not a panacea, but in a time when we’re drowning in useless information, political madness, urban filth, and noise, we desperately need a breath of fresh air.
Let’s embrace awe!
<img src="https://blossom.primal.net/d2e3c29b06c3eb963005429494a1687fba8dc32eed8deb56e3650fdf2472cc39.jpg">
-

@ e8ed3798:67dd345a
2025-01-14 17:38:49
Crowdsourcing subjective value is a great idea, but when no thought has been put into how to do it, the results are neither useful nor healthy.
In this article we discuss the problems with the classic five star rating system and why it needs to be abolished in favor of better expressions of public sentiment.
## Part 1: What's In A Star?
Let's start with a thought experiment:
- Do you buy products on Amazon that have 3 stars?
- Do you take rides from Uber drivers that have 3 stars?
- Do you download apps on the App Store that have 3 stars?
- Do you visit places on Google Maps that have 3 stars?
"Not on purpose," is probably your answer. But why not? After all, a three out of five is better than the median; it's 60 percent! That is solidly "above average" by any usual measure. Although it makes sense in mathematical terms, it is not correct to say that a 3 star product is at least half as good as a 5 star product.
The funny thing about the 5 star rating system is that nobody really knows exactly what the stars mean, mostly because they aren't ever explained. They are just a weak abstraction of a score out of 5, which itself is an abstraction of a score out of 100, and it is used to average all ratings for a thing into an average star rating. Presumably, 5 is the best and 1 is the worst, and somewhere in between is... what exactly? Mediocre? Passable? Acceptable? Average? Who knows! This is the first problem with this system; while the top and bottom of the scale may be implied (ambiguity still isn't great), the middle of the scale is entirely ambiguous.
Most of the time, people start with a default supposition that a product ought to be 5 stars, and then they subtract stars according to their own perceived deficiencies of the product. On the flip side, people who are dissatisfied with a product tend to start at 1 star and perhaps award it a couple more if they are feeling charitable.
This dualistic approach highlights another issue with this kind of rating system. Despite the pure quantitative mechanism, the feelings and disposition of the rater ultimately assign meaning to the numeric scale.
Ultimately, any 5 star rating system ends up being a gamut ranging from hate it to love it with a lot of ambiguity in the middle.
To put it simply, the stars mean nothing. But to be more precise, the stars are the *average* of the *numeric expression* of the public sentiment about a thing.
OK, public sentiment. That's what we want right? We want to know what the public thinks about the product so we can make a good purchase decision.
Except, unfortunately, the 5 star rating system does an incredibly imprecise job at capturing what the public actually thinks about a product. Let's dive into why this is. But first, to conclude our thought experiment, I'd like to establish an informal consensus that we instinctually seek out the highest rated items and avoid ratings less than 4.5 out of 5, with infrequent exceptions. If this sounds like you, then let's proceed.
## Part 2: Trash or Treasure
How does one turn their feelings into a number? This is not something people are good at, or do naturally, or are even required to do very often. It is also completely subjective and arbitrary. Does "happy" mean 5 or 100 or 902,581? It really depends on what you are trying to measure.
However, you've probably done this on a survey. Normally, a range of options is given with accompanying numbers. You may have heard a guiding explanation such as "Rate one through five, with one being 'least likely' and five being 'most likely' to recommend to a friend." Such explanations are useful in assisting a person in expressing their personal sentiments as a numeric range, and anecdotally I seem to provide more nuanced answers when I have guidance as to what each value actually means to me. However, such explanations are missing from most places where five star rating systems can make or break one's livelihood as a seller, developer, or musician. Users are normally given no guidance as to how a particular star value should correspond to their sentiment.
Accordingly, this manifests in an all too common star rating smiley. Like the famed "smiley face curve" equalizer setting popularized in the 70's in which the frequencies of a song were engineered to grow from the midranges upward toward the treble and bass making a smile shape (who's midrange is the lowest), the star rating smile is a common sight on product reviews where the most common review ratings appear anecdotally to be 5 and 1, then 4 and 2, and lastly 3.
The fact that the most common ratings are five stars and one star indicates that people most often do not think about their experience as a gradient between good and bad, but rather simply label their sentiment as only "good" or "bad" with little room for nuance. Having not received any guidance for expressing their sentiment numerically, this should be wholly unsurprising. But, I also feel like this binary outcome is a very natural expression that requires minimal mental energy to produce, and is therefore the most efficient expression of sentiment. I suspect that in another universe where we have a commonplace 15 star rating system but humans are the same, the most common ratings are 15 stars and 1 star respectively.
Other factors influence this binary good/bad paradigm too. People know instinctively that leaving a bad review is bad for business, and often this is their vengeful response to any sense of feeling as if they have been mistreated, misled, or swindled by the seller. Often times the sheer excitement of the new product compels people to write reviews only minutes after they have received it, precluding them from providing an experienced and time-tested perspective of how the product performs.
These quirks of human behavior can skew five star ratings severely. But the behaviors themselves are not bad! They are totally natural and expected. The real problem is how the five star rating system fails to capture these commonplace human sentiments accurately.
We need to build a rating system that works for people rather than forcing people to fit into a poorly executed rating system.
## Part 3: Feast or Famine
It is natural that when presented with a plethora of options, humans will be drawn to the options that are labeled as "the best". When "best" possible is five stars, then five stars naturally becomes the [Schelling point](https://en.wikipedia.org/wiki/Focal_point_(game_theory))for all buyers and sellers, where the vast majority of economic activity is concentrated.
When all ratings are seen from a five-based perspective, fours look barely adequate. Threes look unacceptable. Twos are abject. And ones are complete disasters.
You may have heard about how [Uber would suspend drivers whose ratings fell below 4.6](https://www.inc.com/minda-zetlin/uber-rider-ratings-deactivation-lyft-rideshare.html). The tendency of five star rating systems is to create a gradient of sentiment where 1 to 4.5 stars is "bad" and 4.5 to 5 stars is "good".
One rarely discussed outcome of this dynamic is that good ratings are nearly impossible to compare to each other. As alluded to in the introduction thought experiment, the narrow range between 4.5 and 5 leaves very little room to distinguish from a good product and an excellent product; both are simply "good" or "not bad". As highly rated products are usually the products people are most interested in, it is unfortunate that a favorable rating would actually provide less signal than a bad rating as to the product's relative quality in the spectrum of good ratings.
Meanwhile, bad ratings have wide berth to compare numerically. The astronomical range between 1 and 4.5 is a very spacious gradient in which to assess how bad one product is versus another, except nobody actually cares because nobody is going to buy it anyway!
In the five star rating system, the better a product is, the *less* information we get to compare it to other similarly good products. This is a critical design flaw, because the better a product is and the more people review it, the *more* information we should have about it versus other similar products. It would be better if the range of "good" ratings was wider so that good ratings could be compared to each other.
I'd like to emphasize that the *loss of precision* as a product becomes more desirable is a truly ludicrous mechanic of the five star rating system. This poorly conceived rating paradigm completely pervades our digital economic systems and determines the success of millions of producers. Let's be clear about the stakes. Assigning subjective value to things is completely overlooked for what it really is: a absolutely critical and monumentally influential economic activity. Because the most important economic activity is how we assign value to things with money, the second most important economic activity is how we *inform* our economic value assignments with subjective value assignments such as these.
We need to fix how we rate things. It could literally change how entire economies function.
## Part 4: Quality or Quantity
Valve has obviously put thought into how they handle ratings for video games sold through their extremely popular and long-lived Steam platform.
Reviews are not allowed until a certain amount of hours of the game have been played. The review must assign a thumbs-up or thumbs-down, and then provide a minimum amount of text.
Then, rather than simply providing an average of these binary ratings, Steam averages them over a recent period of time, creating a dynamic where if a game developer releases a new update, the reviews written more recently are sure to influence the overall rating of the game rather than old ratings that haven't taken the new update into consideration.
Finally, the aggregated rating itself is displayed as "Overwhelming Negative", "Very Negative", "Mostly Negative", "Mixed", "Mostly Positive", "Very Positive", or "Overwhelmingly Positive".
Ask yourself, which product would you be more likely to try?
- 2.5/5 stars
- "Mixed Reviews"
Ironically, the Steam rating system gives users less flexibility to express their sentiment as a number, and yet provides more depth, nuance, and balance to the resulting ratings. This, ladies and gentlemen, is what it looks like when somebody gives a damn about how things work. It is a great system.
Another interesting emergent behavior that accompanies many Steam reviews, as well as many reviews on other sites, are user generated pros/cons lists. These lists are helpful and offer qualitative labels that help to explain the quantitative rating assignment, although these labels are not mechanically related to the rating system itself.
Steam has another mechanism to express qualitative judgements in the form of labels, although they had to be restricted because they were being abused in undesirable or nefarious ways. Now the labeling system does more to tell you about what the game is rather than what people think about it, which is fine, but I feel like it is a missed opportunity.
Therefore, I'd like to propose a simple system that combines thumbs up/down and labeling to be used in the context of nostr's review system.
## Part 5: QTS
I call this new review system QTS, or the "Qualitative Thumb System". [Originally I developed QTS when working at Arcade Labs.](https://github.com/ArcadeLabsInc/arcade/wiki/ArcadeSocial)
[This PR for a new nostr review mechanism](https://github.com/nostr-protocol/nips/pull/879) allows for a lot of flexibility in how you apply ratings to things, so QTS is simply a method of applying rating values that creates a better human-oriented review system. QTS is a way of using reviews.
In essence, QTS capitalizes on our very human instinct to assign a "good" or "bad" label by limiting the quantitative assessment to a thumbs-up or thumbs-down. Then, QTS provides qualitative labels that describe possible positive sentiments that describe different aspects of the thing being rated.
First, the user chooses thumbs-up or thumbs-down as their overall assessment. If they do nothing else, this is sufficient to capture their sentiment. However, labels should be provided which the user can check or toggle on to increase their rating further.
The initial thumbs up is worth 0.5, and each label is worth (0.5 / number of labels). The minimum rating is 0 (thumbs down, no labels), and the maximum rating is 1 (thumbs up and all labels). Any rating 0.5 or above is trending toward good and below 0.5 is trending toward bad.
The labels should be applicable in the context of the thing. So, for example, I might provide the following labels for place reviews in a Google Maps-style app:
- Convenient
- Clean
- Affordable
- Memorable
- Inviting
These labels could possibly describe any place. It's OK if a place doesn't have all of these qualities. Zero labels and at thumbs up is still a "good" rating. Each label selected is essentially a "cherry on top" and its absence may indicate that either it isn't applicable OR the place failed to earn it.
Likewise, it is possible that you may give a place a thumbs-down and apply labels; this would result in a rating higher than 0 but still in the bad gradient (below 0.5).
Here are the key benefits I want to highlight of QTS:
- The 5 star rating system forces a user to do the work of translating their sentiment into a quantity. With QTS, the user never has to translate their feelings into a number! They only express good or bad and pick labels, and the QTS mechanism does the work of translating this into a computation-friendly value.
- The 5 star rating system generally results in a "bad" range from 1 to 4.5 and a "good" range from 4.5 to 5. QTS balances this with a "bad" rating at 0, a "good" rating at 0.5, and an excellent rating is anything above 0.5 (up to 1.0). This creates the maximum possible gradient between good and bad which makes it easier to compare similar ratings. Recall this in contrast to the 5 star rating system which actually _loses precision_ as more ratings are provided.
- It is also helpful that similar QTS ratings may have different labels, which will allow people to make easy qualitative assessments that do not depend on users generating their own pros/cons list.
## Part 6: Implementing QTS
Here is how it works:
You give the user the option to rate a thumbs up or thumbs down.
Then, you also give your user the option to choose from a predefined set of positive labels. You can have any number of labels but try to keep it below 10 so as not to overwhelm your users. Keep the labels general enough that they could potentially apply to any thing being rated.
For example, if you were providing labels for Amazon.com, some good labels would be:
- Good Value
- Good Quality
- As Described
- Durable
- Right Size
These labels are general enough that they could apply to almost any product. It is important to create labels that are general so that when comparing product ratings you are comparing the same labels. It is possible however that something like Amazon.com could define a different QTS label subset for each product category, and then the labels could be more specific to that category.
For example, a product category of Candles could have "Long Burning", "Good smell", "Safe", etc. These labels are much more specific, but appropriate for the Candle product category. The main point is that products which should be compared should use the same QTS label set.
Some poor examples of labels would be:
- Orange (not really relevant to the product's assessment)
- Easy to Lift (only relevant to certain products)
- Made in USA (not really relevant to the product's assessment)
- Cheap (not descriptive enough and could be interpreted as negative)
A score is derived as follows:
- a thumbs-down is a score of 0.00
- a thumbs-up is a score of 0.50
- a label is worth 0.50 ÷ the number of labels available. So, if there are 3 labels to pick from, each label is worth 0.1666. The labels should all have the same value.
Here is an example by calvadev being used on Shopstr:
https://github.com/nostr-protocol/nips/pull/879#issuecomment-2502210146
You can adjust the weights however you want. The fundamental thing that QTS prescribes is that a thumbs up gives a 50% score, and labels each contribute an equal share up to another 50%.
# Conclusion
With nostr we have a great opportunity to improve the economic information available to the planet. A more efficient market based on higher quality information will improve civilization in ways we may not expect, but definitely deserve!
If you like this post, be sure to give it a thumbs up ✌😁
-

@ 17538dc2:71ed77c4
2025-01-13 18:17:24
Sci-Hub 2024 year end review is translated to English by Kagi Translate from Russian. Original text can be found in Sci-Hub's telegram channel https://t.me/freescience.
### RESULTS OF 2024
First. The project received donations totaling 2 million dollars in meme coins.
The project is actively used by many students in China, which is why a group of Sci-Hub fans has emerged there. As far as I understand, the organizer of the group is actively interested in the topic of cryptocurrencies (even wrote a book). Somewhere in mid-November, the Chinese launched a meme coin in honor of the Sci-Hub project. At its peak, the coin's price reached 5 cents, and now it is somewhere around 1-2 cents. This means that the exchange rate of the Sci-Hub cryptocurrency is now almost equal to the ruble exchange rate (100 to one or so).
In general, I converted part of these donations into normal, traditional cryptocurrency (like Bitcoin) and paid for servers several months in advance. The other part is still sitting in meme coins—I hope that the token will still grow in price (there is a promotion plan). Of course, this is risky, but Sci-Hub is a project that is not afraid of risk. Therefore, anyone who wants to invest in Sci-Hub by purchasing this token can do so here: www.coingecko.com/en/coins/sci-hub
Second. A dissertation on the topic of open scientific knowledge has been defended at the Institute of Philosophy.
For those interested in the history and philosophy of science, I defended a dissertation in April at the Institute of Philosophy on the topic that scientific knowledge should be open (otherwise, it is strange to call it scientific at all). The work shows that open communication is one of the basic traditional values of science when considering science as a social institution. In other words, journals that charge for access to scientific articles are a kind of 'non-traditional orientation journals.'
Moreover, openness is an important prerequisite for rationality. Rationality is not limited to the criterion of falsification (hello Popper); it is a much more complex concept.
You can familiarize yourself with the text of the dissertation here: web.archive.org/web/20240425100014/https://iphras.ru/page26414303.htm (I provide the link through the web archive because the Institute's website, strangely enough, is glitching again at the time of writing this post).
All criticism and comments (as well as praise) regarding the dissertation can be sent to my email.
Third. Work has begun on a new declaration of open access to scientific knowledge.
Currently, all discussions on the topic of open science are conducted within the frameworks defined by the so-called BBB declarations back in 2001-2003. Within these frameworks, two main types of open access are recognized: gold, meaning open journals with an author-pays model, and green, which refers to repositories like the well-known arXiv. We can also add the so-called diamond open access, which includes open journals that are free for both authors and readers.
However, since 2003, internet technologies have advanced significantly. Today, we can already talk about such types of open access as blue (through academic social networks) or red (your beloved Sci-Hub). It is time to adopt a new declaration of open access to scientific knowledge that corresponds to the current state of scientific and technological progress.
A preliminary version of the declaration can be read and signed here: open.science.do
We will be more actively engaged in this in the coming year. Signing the declaration is an important step towards recognizing access to scientific knowledge through sites like Sci-Hub or Libgen as completely legal and ceasing to pursue them—first in the former USSR, and then in all countries of the world.
Fourth. In 2024, about one billion articles were downloaded through Sci-Hub. Despite the fact that this is unfiltered statistics, the fact remains: the popularity of the project has not decreased but only grown, despite the fact that Sci-Hub has not been updated for quite a long time. Of course, this does not mean that the site will not be updated at all now—just that the patient is more alive than dead (no matter how much some haters might wish otherwise).
The cause of open access to scientific knowledge will definitely prevail—because good always triumphs over evil.
In the new year, I wish all scientists new discoveries and large grants. Happy New Year, comrades!
-

@ df173277:4ec96708
2025-01-09 17:02:52
> OpenSecret is a backend for app developers that turns private encryption on by default. When sensitive data is readable only by the user, it protects both the user and the developer, creating a more free and open internet. We'll be launching in 2025. [Join our waitlist to get early access.](https://opensecret.cloud)
In today's digital age, personal data is both an asset and a liability. With the rise of data breaches and cyber attacks, individuals and companies struggle to protect sensitive information. The consequences of a data breach can be devastating, resulting in financial losses, reputational damage, and compromised user trust. In 2023, the average data breach cost was $5 million, with some resulting in losses of over $1 billion.
Meanwhile, individuals face problems related to identity theft, personal safety, and public embarrassment. Think about the apps on your phone, even the one you're using to read this. How much data have you trusted to other people, and how would it feel if that data were leaked online?
Thankfully, some incredibly talented cypherpunks years ago gave the world cryptography. We can encrypt data, rendering it a secret between two people. So why then do we have data breaches?
> Cryptography at scale is hard.
#### The Cloud
The cloud has revolutionized how we store and process data, but it has limitations. While cloud providers offer encryption, it mainly protects data in transit. Once data is stored in the cloud, it's often encrypted with a shared key, which can be accessed by employees, third-party vendors, or compromised by hackers.
The solution is to generate a personal encryption password for each user, make sure they write it down, and, most importantly, hope they don't lose it. If the password is lost, the data is forever unreadable. That can be overwhelming, leading to low app usage.
> Private key encryption needs a UX upgrade.
## Enter OpenSecret
OpenSecret is a developer platform that enables encryption by default. Our platform provides a suite of security tools for app developers, including private key management, encrypted sync, private AI, and confidential compute.
Every user has a private vault for their data, which means only they can read it. Developers are free to store less sensitive data in a shared manner because there is still a need to aggregate data across the system.

### Private Key Management
Private key management is the superpower that enables personal encryption per user. When each user has a unique private key, their data can be truly private. Typically, using a private key is a challenging experience for the user because they must write down a long autogenerated number or phrase of 12-24 words. If they lose it, their data is gone.
OpenSecret uses secure enclaves to make private keys as easy as an everyday login experience that users are familiar with. Instead of managing a complicated key, the user logs in with an email address or a social media account.
The developer doesn't have to manage private keys and can focus on the app's user experience. The user doesn't have to worry about losing a private key and can jump into using your app.

### Encrypted Sync
With user keys safely managed, we can synchronize user data to every device while maintaining privacy. The user does not need to do complicated things like scanning QR codes from one device to the next. Just log in and go.
The user wins because the data is available on all their devices. The developer wins because only the user can read the data, so it isn't a liability to them.
### Private AI
Artificial intelligence is here and making its way into everything. The true power of AI is unleashed when it can act on personal and company data. The current options are to run your own AI locally on an underpowered machine or to trust a third party with your data, hoping they don't read it or use it for anything.
OpenSecret combines the power of cloud computing with the privacy and security of a machine running on your desk.
**Check out Maple AI**\
Try private AI for yourself! We built an app built with this service called [Maple AI](https://trymaple.ai). It is an AI chat that is 100% private in a verifiable manner. Give it your innermost thoughts or embarrassing ideas; we can't judge you. We built Maple using OpenSecret, which means you have a private key that is automatically managed for you, and your chat history is synchronized to all your devices. [Learn more about Maple AI - Private chat in the announcement post.](https://blog.opensecret.cloud/maple-ai-private-encrypted-chat/)

### Confidential Compute
Confidential computing is a game-changer for data security. It's like the secure hardware that powers Apple Pay and Google Pay on your phone but in the cloud. Users can verify through a process called attestation that their data is handled appropriately. OpenSecret can help you run your own custom app backend code that would benefit from the security of an enclave.
It's the new version of that lock on your web browser. When you see it, you know you're secure.

#### **But do we want our secrets to be open?**
OpenSecret renders a data breach practically useless. If hackers get into the backend, they enter a virtual hallway of locked private vaults. The leaked data would be gibberish, a secret in the open that is unreadable.
On the topic of openness, OpenSecret uses the power of open source to enable trust in the service. We publish our code in the open, and, using attestation, anyone can verify that private data is being handled as expected. This openness also provides developers with a backup option to safely and securely export their data.
> Don't trust, verify.
### **Join the Movement**
We're currently building out OpenSecret, and we invite you to join us on the journey. Our platform can work with your existing stack, and you can pick and choose the features you need. If you want to build apps with encryption enabled, [send us a message to get early access.](https://opensecret.cloud)
Users and companies deserve better encryption and privacy.\
Together, let's make that a reality.
[](https://opensecret.cloud)
-

@ f88e6629:e5254dd5
2025-01-08 20:08:17
- Send a transaction, and the recipient uses the coin for another payment. You then merge these two transactions together and save on fees. 🔥

If you have a Trezor, you can try this out on: https://coiner-mu.vercel.app/
_But be cautious. This is a hobby project without any guarantee._
<img width="1772" alt="Screenshot 2025-01-08 at 20 14 17" src="https://github.com/user-attachments/assets/36412edb-9c62-4c5f-8f82-b41c118a3aa6" />
## How does it work?
1. Connect Trezor, enter the passphrase, and select an account.
2. The application display your coins, pending transactions, and descendant transactions.
4. Then app shows you how much you can save by merging all transactions and removing duplicate information.
5. Finally, you can sign and broadcast this more efficient transaction
-

@ 23b0e2f8:d8af76fc
2025-01-08 18:17:52
## **Necessário**
- Um Android que você não use mais (a câmera deve estar funcionando).
- Um cartão microSD (opcional, usado apenas uma vez).
- Um dispositivo para acompanhar seus fundos (provavelmente você já tem um).
## **Algumas coisas que você precisa saber**
- O dispositivo servirá como um assinador. Qualquer movimentação só será efetuada após ser assinada por ele.
- O cartão microSD será usado para transferir o APK do Electrum e garantir que o aparelho não terá contato com outras fontes de dados externas após sua formatação. Contudo, é possível usar um cabo USB para o mesmo propósito.
- A ideia é deixar sua chave privada em um dispositivo offline, que ficará desligado em 99% do tempo. Você poderá acompanhar seus fundos em outro dispositivo conectado à internet, como seu celular ou computador pessoal.
---
## **O tutorial será dividido em dois módulos:**
- Módulo 1 - Criando uma carteira fria/assinador.
- Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador.
---
## **No final, teremos:**
- Uma carteira fria que também servirá como assinador.
- Um dispositivo para acompanhar os fundos da carteira.

---
## **Módulo 1 - Criando uma carteira fria/assinador**
1. Baixe o APK do Electrum na aba de **downloads** em <https://electrum.org/>. Fique à vontade para [verificar as assinaturas](https://electrum.readthedocs.io/en/latest/gpg-check.html) do software, garantindo sua autenticidade.
2. Formate o cartão microSD e coloque o APK do Electrum nele. Caso não tenha um cartão microSD, pule este passo.

3. Retire os chips e acessórios do aparelho que será usado como assinador, formate-o e aguarde a inicialização.

4. Durante a inicialização, pule a etapa de conexão ao Wi-Fi e rejeite todas as solicitações de conexão. Após isso, você pode desinstalar aplicativos desnecessários, pois precisará apenas do Electrum. Certifique-se de que Wi-Fi, Bluetooth e dados móveis estejam desligados. Você também pode ativar o **modo avião**.\
*(Curiosidade: algumas pessoas optam por abrir o aparelho e danificar a antena do Wi-Fi/Bluetooth, impossibilitando essas funcionalidades.)*

5. Insira o cartão microSD com o APK do Electrum no dispositivo e instale-o. Será necessário permitir instalações de fontes não oficiais.

6. No Electrum, crie uma carteira padrão e gere suas palavras-chave (seed). Anote-as em um local seguro. Caso algo aconteça com seu assinador, essas palavras permitirão o acesso aos seus fundos novamente. *(Aqui entra seu método pessoal de backup.)*

---
## **Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador.**
1. Criar uma carteira **somente leitura** em outro dispositivo, como seu celular ou computador pessoal, é uma etapa bastante simples. Para este tutorial, usaremos outro smartphone Android com Electrum. Instale o Electrum a partir da aba de downloads em <https://electrum.org/> ou da própria Play Store. *(ATENÇÃO: O Electrum não existe oficialmente para iPhone. Desconfie se encontrar algum.)*
2. Após instalar o Electrum, crie uma carteira padrão, mas desta vez escolha a opção **Usar uma chave mestra**.

3. Agora, no assinador que criamos no primeiro módulo, exporte sua chave pública: vá em **Carteira > Detalhes da carteira > Compartilhar chave mestra pública**.

4. Escaneie o QR gerado da chave pública com o dispositivo de consulta. Assim, ele poderá acompanhar seus fundos, mas sem permissão para movimentá-los.
5. Para receber fundos, envie Bitcoin para um dos endereços gerados pela sua carteira: **Carteira > Addresses/Coins**.
6. Para movimentar fundos, crie uma transação no dispositivo de consulta. Como ele não possui a chave privada, será necessário assiná-la com o dispositivo assinador.

7. No assinador, escaneie a transação não assinada, confirme os detalhes, assine e compartilhe. Será gerado outro QR, desta vez com a transação já assinada.

8. No dispositivo de consulta, escaneie o QR da transação assinada e transmita-a para a rede.
---
## **Conclusão**
**Pontos positivos do setup:**
- **Simplicidade:** Basta um dispositivo Android antigo.
- **Flexibilidade:** Funciona como uma ótima carteira fria, ideal para holders.
**Pontos negativos do setup:**
- **Padronização:** Não utiliza seeds no padrão BIP-39, você sempre precisará usar o electrum.
- **Interface:** A aparência do Electrum pode parecer antiquada para alguns usuários.
Nesse ponto, temos uma carteira fria que também serve para assinar transações. O fluxo de assinar uma transação se torna: ***Gerar uma transação não assinada > Escanear o QR da transação não assinada > Conferir e assinar essa transação com o assinador > Gerar QR da transação assinada > Escanear a transação assinada com qualquer outro dispositivo que possa transmiti-la para a rede.***
Como alguns devem saber, uma transação assinada de Bitcoin é praticamente impossível de ser fraudada. Em um cenário catastrófico, você pode mesmo que sem internet, repassar essa transação assinada para alguém que tenha acesso à rede por qualquer meio de comunicação. Mesmo que não queiramos que isso aconteça um dia, esse setup acaba por tornar essa prática possível.
---
-

@ bd32f268:22b33966
2025-01-02 19:30:46
Texto publicado por *Foundation Father @FoundationDads* e traduzido para português.
Assumir responsabilidades numa época efeminada como a nossa é um superpoder.
Algumas pessoas não sabem o que significa "assumir responsabilidades", no entanto, porque nunca tiveram um pai ou outra pessoa que as ama-se o suficiente para lhes ensinar.
Então, aqui está como assumir responsabilidades.
## **Lembra-te que não és uma pessoa desamparada e incompetente.**
As coisas não te acontecem simplesmente enquanto olhas fixamente com a boca aberta, usando todo o teu poder cerebral para te lembrares de como respirar.
Tu tens poder de ação.
## Mantém estas perguntas em mente:
"Que papel desempenhei eu nesta situação ou como ajudei a formar o sistema em que estou inserido?"
"O que posso fazer agora mesmo para começar a corrigi-lo, por mais pequeno que seja?"
Aqui estão alguns exemplos de como aplicar estas perguntas.
*José Malhoa - Remédio*
## Saúde
Estás com excesso de peso e cansado o tempo todo? Deprimido?
Começa a caminhar 30 minutos por dia. De preferência ao ar livre.
Pára de comer snacks.
Marca uma consulta com um médico para fazer análises ao sangue.
Todas estas coisas estão ao teu alcance.
## Finanças
Estás a afogar-te em dívidas de cartão de crédito? Assumir responsabilidades significa reduzir drasticamente o teu consumo e iniciar um programa radical de pagamento do máximo de dívida que conseguires.
Obtém uma aplicação de orçamento e começa a planear.
Sentes-te preso no teu emprego sem futuro? Sentes que não ganhas o suficiente? Vai a entrevistas para vagas de emprego e descobre o teu verdadeiro valor no mercado.
Reserva 1 hora todas as noites para melhorares. A menos que já estejas a trabalhar em dois empregos, toda a gente tem pelo menos 1 hora todas as noites.
## Arredores imediatos
Se vês algo que precisa de ser feito, simplesmente faz. Não te queixes disso. Não resmungues baixinho. Não desejes que alguém tratasse disso. Simplesmente faz e não peças permissão.
Guarda o carrinho de compras. Lava a caneca de café no lava-loiça. Arranca as ervas daninhas. Repara a parede. Se o quintal do teu vizinho estiver cheio de ervas, vai lá e corta a relva tu mesmo. Limpa a água do lava-loiça. Arruma a bancada. Leva o lixo para fora. Leva bom café para o escritório.
## Os teus filhos
Muitos pais queixam-se do comportamento dos seus filhos como se não tivessem qualquer influência sobre o assunto. Mas os teus filhos farão o que tu os ensinaste a fazer.
"Fizemos o melhor que pudemos."
Não, não fizeram, e assumir responsabilidades significa admitir que foste permissivo e preguiçoso ou que querias sentir-te justo por não bater.
Que pequena coisa podes fazer agora mesmo para começar? Escolhe um único comportamento que queres que eles parem, senta-os e explica as consequências do comportamento. Pede desculpa por teres deixado andar durante tanto tempo.
Quando eles apresentarem o comportamento, aplica as consequências. Aconteça o que acontecer.
## Os teus relacionamentos
Não tens amigos ou o teu grupo de amigos atual é uma má influência? Podes fazer novos amigos. Assumir responsabilidades significa admitir que a tua solidão é em grande parte auto-infligida.
**O que podes fazer?**
Começa a jogar ténis ou futebol. Existem ligas em todo o lado. Encontra uma boa igreja local e encontra maneiras de te envolver. Existem encontros para todo o tipo de atividade. Participa num que se alinhe com as tuas preferências. Quando estiveres em público, sorri mais e puxa conversa.
Depois de conheceres algumas pessoas, estabelece uma cadência regular. Agenda almoços semanais ou mensais e alterna entre algumas pessoas. Ou talvez café de manhã.
Não acontecerá da noite para o dia, mas dando pequenos passos consistentemente durante alguns meses e vais perceber que tens uma vida social.
## Os teus erros
Se erraste, não te retires e escondas nem arranjes desculpas. Pede desculpa à pessoa que prejudicaste, diz-lhe porquê e oferece-te para compensar. Aceita as consequências com humildade.
Vais descobrir que nada te conquista mais respeito do que assumir os teus erros. Esta é a principal. Se aprenderes a fazer isto bem, cobrirá uma infinidade de pecados porque cria hábito. Mesmo que tenhas apenas 1% de culpa na situação, assumir a responsabilidade e pedir desculpa pelo teu 1% está a construir um certo grupo de músculos.
"Mas ele devia ter..." Pára com isso. Confiaste demasiado? Presumiste demasiado sem comunicar? Assume a responsabilidade por isso.
Estes exemplos podiam continuar para sempre, então vou parar e terminar com este princípio:
A tua resposta importa mais do que as tuas circunstâncias.
Existem vítimas reais, algumas de tragédias horríveis. Mas mesmo que não te tenhas atirado para areias movediças, ainda podes assumir a responsabilidade por como reages e pelo que escolhes fazer a seguir.
Às vezes, é agarrar numa corda de um transeunte e dizer: "Obrigado."
Não te afogues nas areias movediças até que alguém te dê uma palmadinha nas costas por quão difícil é para ti, e não continues a apontar para o teu tempo nas areias movediças para desculpares os teus fracassos.
Podes não ter escolhido uma batalha específica. Ainda podes assumir a responsabilidade por quão bem lutas a batalha. Num certo sentido, ninguém escolhe a principal batalha que enfrenta. Ninguém escolheu nascer. Ninguém escolheu a sua família. Ninguém escolheu as suas circunstâncias.
O mundo nunca será perfeito. Tens de assumir a responsabilidade pela tua parte dele de qualquer maneira. Pode ser difícil. Pode ser doloroso. Não te foi prometida uma vida fácil e sem dor.
Depois de começares a assumir responsabilidades, qual é o próximo passo?
Altura de assumir mais responsabilidades.
Por exemplo, se não tens problemas em fazer amigos e tens essa parte da tua vida resolvida, assume a responsabilidade por outra pessoa. Encontra um dos rapazes solitários na tua igreja que precisa de um amigo e adiciona-o à tua rotação de almoços.
A recompensa por assumir responsabilidades é subir de nível e, como consequência, as coisas devem tornar-se mais desafiantes.
Mas agora estás mais bem preparado para isso. Repete até morrer e, esperançosamente, a tua causa de morte será por viver e não por te queixares de não viver.
-

@ d9e9fb27:d5fe5e1a
2025-01-02 16:31:34
Colmar is a well known city in the region of Alsace, France. Its characteristic buildings, the narrow streets and the small river flowing through are worldwide famous.

-----------
However, it is during Christmas that the city gets the most attention.
Thousands of people from all over Europe decide to spend one of the Advent weekends to wander around this beautiful city and hundreds of *little wooden huts*.
In fact, this town becomes a small Christmas village, with decorations and lights on every building and the famous Christmas market covering every possible inch of it.



Walking around this city really makes you feel the Christmas Spirit!
-----------
Of course, it can get really cold during this time of the year. That is why Alsatians wander around drinking the *Vin Chaud* (literally "Hot Wine"). This beverage is prepared by mixing sugar, various spices, such as cinnamon and cloves, and red wine. They are served in a plastic glass, which can be reused multpiple time or returned for a couple of Euros. However, every year the glass is designed differently, so many people keep it with them as a collectible!
Here is 2024 version:

-----------
This is the first time I try to do a photography reportage of the places I visit.
I really hope you enjoyed it!Let me know what you think, every feedback is appreciated.
I will try to create more of them during my trips, so stay tuned!
Tuma
-

@ 1bda7e1f:bb97c4d9
2025-01-02 05:19:08
### Tldr
- Nostr is an open and interoperable protocol
- You can integrate it with workflow automation tools to augment your experience
- n8n is a great low/no-code workflow automation tool which you can host yourself
- Nostrobots allows you to integrate Nostr into n8n
- In this blog I create some workflow automations for Nostr
- A simple form to delegate posting notes
- Push notifications for mentions on multiple accounts
- Push notifications for your favourite accounts when they post a note
- All workflows are provided as open source with MIT license for you to use
### Inter-op All The Things
Nostr is a new open social protocol for the internet. This open nature exciting because of the opportunities for interoperability with other technologies. In [Using NFC Cards with Nostr]() I explored the `nostr:` URI to launch Nostr clients from a card tap.
The interoperability of Nostr doesn't stop there. The internet has many super-powers, and Nostr is open to all of them. Simply, there's no one to stop it. There is no one in charge, there are no permissioned APIs, and there are no risks of being de-platformed. If you can imagine technologies that would work well with Nostr, then any and all of them can ride on or alongside Nostr rails.
My mental model for why this is special is Google Wave ~2010. Google Wave was to be the next big platform. Lars was running it and had a big track record from Maps. I was excited for it. Then, Google pulled the plug. And, immediately all the time and capital invested in understanding and building on the platform was wasted.
This cannot happen to Nostr, as there is no one to pull the plug, and maybe even no plug to pull.
So long as users demand Nostr, Nostr will exist, and that is a pretty strong guarantee. It makes it worthwhile to invest in bringing Nostr into our other applications.
All we need are simple ways to plug things together.
### Nostr and Workflow Automation
Workflow automation is about helping people to streamline their work. As a user, the most common way I achieve this is by connecting disparate systems together. By setting up one system to trigger another or to move data between systems, I can solve for many different problems and become way more effective.
#### n8n for workflow automation
Many workflow automation tools exist. My favourite is [n8n](https://n8n.io/). n8n is a low/no-code workflow automation platform which allows you to build all kinds of workflows. You can use it for free, you can self-host it, it has a user-friendly UI and useful API. Vs Zapier it can be far more elaborate. Vs Make.com I find it to be more intuitive in how it abstracts away the right parts of the code, but still allows you to code when you need to.
Most importantly you can plug anything into n8n: You have built-in nodes for specific applications. HTTP nodes for any other API-based service. And community nodes built by individual community members for any other purpose you can imagine.
#### Eating my own dogfood
It's very clear to me that there is a big design space here just demanding to be explored. If you could integrate Nostr with anything, what would you do?
In my view the best way for anyone to start anything is by solving their own problem first (aka "scratching your own itch" and "eating your own dogfood"). As I get deeper into Nostr I find myself controlling multiple Npubs – to date I have a personal Npub, a brand Npub for a community I am helping, an AI assistant Npub, and various testing Npubs. I need ways to delegate access to those Npubs without handing over the keys, ways to know if they're mentioned, and ways to know if they're posting.
I can build workflows with n8n to solve these issues for myself to start with, and keep expanding from there as new needs come up.
### Running n8n with Nostrobots
I am mostly non-technical with a very helpful AI. To set up n8n to work with Nostr and operate these workflows should be possible for anyone with basic technology skills.
- I have a cheap VPS which currently runs my [HAVEN Nostr Relay](https://rodbishop.npub.pro/post/8ca68889/) and [Albyhub Lightning Node](https://rodbishop.npub.pro/post/setting-up-payments-on-nostr-7o6ls7/) in Docker containers,
- My objective was to set up n8n to run alongside these in a separate Docker container on the same server, install the required nodes, and then build and host my workflows.
#### Installing n8n
Self-hosting n8n could not be easier. I followed n8n's [Docker-Compose installation docs](https://docs.n8n.io/hosting/installation/server-setups/docker-compose/)–
- Install Docker and Docker-Compose if you haven't already,
- Create your ``docker-compose.yml`` and `.env` files from the docs,
- Create your data folder `sudo docker volume create n8n_data`,
- Start your container with `sudo docker compose up -d`,
- Your n8n instance should be online at port `5678`.
n8n is free to self-host but does require a license. Enter your credentials into n8n to get your free license key. You should now have access to the Workflow dashboard and can create and host any kind of workflows from there.
#### Installing Nostrobots
To integrate n8n nicely with Nostr, I used the [Nostrobots](https://github.com/ocknamo/n8n-nodes-nostrobots?tab=readme-ov-file) community node by [Ocknamo](nostr:npub1y6aja0kkc4fdvuxgqjcdv4fx0v7xv2epuqnddey2eyaxquznp9vq0tp75l).
In n8n parlance a "node" enables certain functionality as a step in a workflow e.g. a "set" node sets a variable, a "send email" node sends an email. n8n comes with all kinds of "official" nodes installed by default, and Nostr is not amongst them. However, n8n also comes with a framework for community members to create their own "community" nodes, which is where Nostrobots comes in.
You can only use a community node in a self-hosted n8n instance (which is what you have if you are running in Docker on your own server, but this limitation does prevent you from using n8n's own hosted alternative).
To install a community node, [see n8n community node docs](https://docs.n8n.io/integrations/community-nodes/installation/gui-install/). From your workflow dashboard–
- Click the "..." in the bottom left corner beside your username, and click "settings",
- Cilck "community nodes" left sidebar,
- Click "Install",
- Enter the "npm Package Name" which is `n8n-nodes-nostrobots`,
- Accept the risks and click "Install",
- Nostrobots is now added to your n8n instance.
#### Using Nostrobots
Nostrobots gives you nodes to help you build Nostr-integrated workflows–
- **Nostr Write** – for posting Notes to the Nostr network,
- **Nostr Read** – for reading Notes from the Nostr network, and
- **Nostr Utils** – for performing certain conversions you may need (e.g. from bech32 to hex).
Nostrobots has [good documentation](https://github.com/ocknamo/n8n-nodes-nostrobots?tab=readme-ov-file) on each node which focuses on simple use cases.
Each node has a "convenience mode" by default. For example, the "Read" Node by default will fetch Kind 1 notes by a simple filter, in Nostrobots parlance a "Strategy". For example, with Strategy set to "Mention" the node will accept a pubkey and fetch all Kind 1 notes that Mention the pubkey within a time period. This is very good for quick use.
What wasn't clear to me initially (until Ocknamo helped me out) is that advanced use cases are also possible.
Each node also has an advanced mode. For example, the "Read" Node can have "Strategy" set to "RawFilter(advanced)". Now the node will accept json (anything you like that complies with [NIP-01](https://github.com/nostr-protocol/nips/blob/master/01.md)). You can use this to query Notes (Kind 1) as above, and also Profiles (Kind 0), Follow Lists (Kind 3), Reactions (Kind 7), Zaps (Kind 9734/9735), and anything else you can think of.
#### Creating and adding workflows
With n8n and Nostrobots installed, you can now create or add any kind of Nostr Workflow Automation.
- Click "Add workflow" to go to the workflow builder screen,
- If you would like to build your own workflow, you can start with adding any node. Click "+" and see what is available. Type "Nostr" to explore the Nostrobots nodes you have added,
- If you would like to add workflows that someone else has built, click "..." in the top right. Then click "import from URL" and paste in the URL of any workflow you would like to use (including the ones I share later in this article).
### Nostr Workflow Automations
It's time to build some things!
#### A simple form to post a note to Nostr
I started very simply. I needed to delegate the ability to post to Npubs that I own in order that a (future) team can test things for me. I don't want to worry about managing or training those people on how to use keys, and I want to revoke access easily.
I needed a basic form with credentials that posted a Note.
For this I can use a very simple workflow–
- **A n8n Form node** – Creates a form for users to enter the note they wish to post. Allows for the form to be protected by a username and password. This node is the workflow "trigger" so that the workflow runs each time the form is submitted.
- **A Set node** – Allows me to set some variables, in this case I set the relays that I intend to use. I typically add a Set node immediately following the trigger node, and put all the variables I need in this. It helps to make the workflows easier to update and maintain.
- **A Nostr Write node** (from Nostrobots) – Writes a Kind-1 note to the Nostr network. It accepts Nostr credentials, the output of the Form node, and the relays from the Set node, and posts the Note to those relays.
Once the workflow is built, you can test it with the testing form URL, and set it to "Active" to use the production form URL. That's it. You can now give posting access to anyone for any Npub. To revoke access, simply change the credentials or set to workflow to "Inactive".
It may also be the world's simplest Nostr client.
You can find the [Nostr Form to Post a Note workflow here](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Form_to_Post_a_Note.json).
#### Push notifications on mentions and new notes
One of the things Nostr is not very good at is push notifications. Furthermore I have some unique itches to scratch. I want–
- **To make sure I never miss a note addressed to any of my Npubs** – For this I want a push notification any time any Nostr user mentions any of my Npubs,
- **To make sure I always see all notes from key accounts** – For this I need a push notification any time any of my Npubs post any Notes to the network,
- **To get these notifications on all of my devices** – Not just my phone where my Nostr regular client lives, but also on each of my laptops to suit wherever I am working that day.
I needed to build a Nostr push notifications solution.
To build this workflow I had to string a few ideas together–
- **Triggering the node on a schedule** – Nostrobots does not include a trigger node. As every workflow starts with a trigger we needed a different method. I elected to run the workflow on a schedule of every 10-minutes. Frequent enough to see Notes while they are hot, but infrequent enough to not burden public relays or get rate-limited,
- **Storing a list of Npubs in a Nostr list** – I needed a way to store the list of Npubs that trigger my notifications. I initially used an array defined in the workflow, this worked fine. Then I decided to try Nostr lists ([NIP-51, kind 30000](https://github.com/nostr-protocol/nips/blob/master/51.md)). By defining my list of Npubs as a list published to Nostr I can control my list from within a Nostr client (e.g. [Listr.lol](https://listr.lol/npub1r0d8u8mnj6769500nypnm28a9hpk9qg8jr0ehe30tygr3wuhcnvs4rfsft) or [Nostrudel.ninja](https://nostrudel.ninja/#/lists)). Not only does this "just work", but because it's based on Nostr lists automagically Amethyst client allows me to browse that list as a Feed, and everyone I add gets notified in their Mentions,
- **Using specific relays** – I needed to query the right relays, including my own HAVEN relay inbox for notes addressed to me, and wss://purplepag.es for Nostr profile metadata,
- **Querying Nostr events** (with Nostrobots) – I needed to make use of many different Nostr queries and use quite a wide range of what Nostrobots can do–
- I read the EventID of my Kind 30000 list, to return the desired pubkeys,
- For notifications on mentions, I read all Kind 1 notes that mention that pubkey,
- For notifications on new notes, I read all Kind 1 notes published by that pubkey,
- Where there are notes, I read the Kind 0 profile metadata event of that pubkey to get the displayName of the relevant Npub,
- I transform the EventID into a Nevent to help clients find it.
- **Using the Nostr URI** – As I did with my NFC card article, I created a link with the `nostr:` URI prefix so that my phone's native client opens the link by default,
- **Push notifications solution** – I needed a push notifications solution. I found many with n8n integrations and chose to go with [Pushover](https://pushover.net/) which supports all my devices, has a free trial, and is unfairly cheap with a $5-per-device perpetual license.
Once the workflow was built, lists published, and Pushover installed on my phone, I was fully set up with push notifications on Nostr. I have used these workflows for several weeks now and made various tweaks as I went. They are feeling robust and I'd welcome you to give them a go.
You can find the [Nostr Push Notification If Mentioned here](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Push_Notify_If_Mentioned.json) and [If Posts a Note here](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Push_Notify_If_Post_a_Note.json).
In speaking with other Nostr users while I was building this, there are all kind of other needs for push notifications too – like on replies to a certain bookmarked note, or when a followed Npub starts streaming on zap.stream. These are all possible.
#### Use my workflows
I have open sourced all my workflows at my [Github](https://github.com/r0d8lsh0p/nostr-n8n) with MIT license and tried to write complete docs, so that you can import them into your n8n and configure them for your own use.
To import any of my workflows–
- Click on the workflow of your choice, e.g. "[Nostr_Push_Notify_If_Mentioned.json](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Push_Notify_If_Mentioned.json "Nostr_Push_Notify_If_Mentioned.json")",
- Click on the "raw" button to view the raw JSON, ex any Github page layout,
- Copy that URL,
- Enter that URL in the "import from URL" dialog [mentioned above](#creating-and-adding-workflows).
To configure them–
- Prerequisites, credentials, and variables are all stated,
- In general any variables required are entered into a Set Node that follows the trigger node,
- Pushover has some extra setup but is very straightforward and documented in the workflow.
### What next?
Over my first four blogs I explored creating a good Nostr setup with [Vanity Npub](https://rodbishop.npub.pro/post/mining-your-vanity-pubkey-4iupbf/), [Lightning Payments](https://rodbishop.npub.pro/post/setting-up-payments-on-nostr-7o6ls7/), [Nostr Addresses at Your Domain](https://rodbishop.npub.pro/post/ee8a46bc/), and [Personal Nostr Relay](https://rodbishop.npub.pro/post/8ca68889/).
Then in my latest two blogs I explored different types of interoperability [with NFC cards](https://rodbishop.npub.pro/post/edde8387/) and now n8n Workflow Automation.
Thinking ahead n8n can power any kind of interoperability between Nostr and any other legacy technology solution. On my mind as I write this:
- Further enhancements to posting and delegating solutions and forms (enhanced UI or different note kinds),
- Automated or scheduled posting (such as auto-liking everything [Lyn Alden](nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a) posts),
- Further enhancements to push notifications, on new and different types of events (such as notifying me when I get a new follower, on replies to certain posts, or when a user starts streaming),
- All kinds of bridges, such as bridging notes to and from Telegram, Slack, or Campfire. Or bridging RSS or other event feeds to Nostr,
- All kinds of other automation (such as [BlackCoffee](nostr:npub1dqepr0g4t3ahvnjtnxazvws4rkqjpxl854n29wcew8wph0fmw90qlsmmgt) [controlling a coffee machine](https://primal.net/e/note16fzhh5yfc3u4kufx0mck63tsfperdrlpp96am2lmq066cnuqutds8retc3)),
- All kinds of AI Assistants and Agents,
In fact I have already released an open source workflow for an [AI Assistant](https://primal.net/p/npub1ahjpx53ewavp23g5zj9jgyfrpr8djmgjzg5mpe4xd0z69dqvq0kq2lf353), and will share more about that in my next blog.
Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle.
GM Nostr.
-

@ 599f67f7:21fb3ea9
2024-12-31 15:04:25
Para este momento, ya deberías estar familiarizado con cerrar un canal de manera forzada, es decir, transmitiendo la transacción de compromiso directamente. Pero, ¿qué hay de cerrar un canal de manera cooperativa?
### Cerrando un canal de manera cooperativa
Alice y Bob ciertamente tuvieron buenos momentos juntos, pero todas las cosas buenas deben llegar a su fin. Cerrar un canal de manera cooperativa requiere que los dos pares decidan sobre una transacción de cierre final que gastará de la transacción de financiación y pagará a cada uno su saldo final del canal de inmediato.
#### Paso 1: Bob -> Alice: shutdown
Bob ha decidido que es hora de cortar lazos y envía a Alice el mensaje de cierre.

El mensaje de cierre contiene el `scriptpubkey` al que Bob le gustaría que se enviara su saldo final del canal en la transacción de cierre. Una vez que Bob ha enviado este mensaje final, ya no puede enviar nuevos mensajes `update_add_htlc`. Solo puede enviar mensajes de eliminación de HTLC y `update_fee`. Cuando Alice recibe este mensaje de Bob, debe responder con su propio mensaje de cierre y tampoco puede enviar nuevos mensajes `update_add_htlc`. Alice y Bob ahora deben esperar hasta que todos los HTLC restantes hayan sido eliminados de ambas transacciones de compromiso. Dado que la transacción de cierre gastará de la transacción de financiación y se verá explícitamente diferente de las transacciones de compromiso, volveré a introducir algunos de los detalles en el diagrama de estado:

Una vez que todos los HTLC hayan sido eliminados, lo cual en nuestro ejemplo ya es el caso, pueden comenzar a negociar una tarifa para usar en la transacción de cierre final. El financiador del canal debe iniciar esta negociación. Supongamos que el financiador del canal es Alice.
#### Paso 2: Alice -> Bob: closing_signed
Alice primero elegirá una tasa de tarifa que considera apropiada para la transacción de cierre. Luego usará esa tasa de tarifa para completar la construcción de la transacción de cierre y firmarla. Luego envía el mensaje `closing_signed` a Bob:

El campo `fee_satoshis` le dice a Bob la tarifa en satoshis que Alice utilizó para construir la primera propuesta de transacción de cierre. La firma contiene la firma de Alice para esta propuesta. Ella también puede incluir opcionalmente los campos `min_fee_satoshis` y `max_fee_satoshis` para hacerle saber a Bob que si no está de acuerdo con su propuesta de `fee_satoshis`, puede enviar una contrapropuesta siempre que su contrapropuesta esté entre el rango mínimo y máximo proporcionado.
En este punto, el estado del canal se ve así:

Hay dos transacciones de compromiso válidas que pueden ser firmadas en cualquier momento por cada parte para realizar un cierre forzado, y hay una propuesta de transacción de cierre que utiliza una tasa de tarifa de `x` sats por byte. Esta transacción de cierre actualmente solo tiene la firma de Alice y, por lo tanto, aún no es válida.
Si en este punto, Bob está contento con la propuesta de Alice, podría proceder a firmar la transacción de cierre utilizando la tasa de tarifa propuesta por Alice y podría transmitirla, y eso sería el final. Pero, para el bien del ejemplo, digamos que Bob no está del todo contento todavía.
#### Paso 3: Bob -> Alice: closing_signed
Bob puede decidir que la tasa de tarifa que utilizó Alice es demasiado baja. Así que envía una contrapropuesta con una nueva tasa de tarifa, `y` sats por byte, junto con su firma para esta contrapropuesta.

#### Paso 4: Alice -> Bob: closing_signed
Si Alice está contenta con la contrapropuesta de Bob, entonces firma la transacción de cierre utilizando la tasa de tarifa sugerida por Bob. Luego puede transmitir la transacción y dar por terminado el asunto. Sin embargo, se recomienda en la especificación que Alice envíe un mensaje más `closing_signed` a Bob, pero esta vez con el campo `fee_satoshis` establecido en `y` sat por byte junto con su firma para la transacción. Ambas partes ahora tendrán ambas firmas requeridas para transmitir la transacción de cierre final que utiliza la tasa de tarifa de `y` sats por byte.

Cualquiera de las partes o ambas pueden ahora transmitir la transacción de cierre a la red de Bitcoin. Eventualmente será confirmada y el canal se cerrará oficialmente.

Si este canal era un canal público, entonces cualquier nodo en la red que tuviera este canal en su gráfico de enrutamiento podrá ver que la salida de financiación del canal ha sido gastada y, por lo tanto, eliminará el canal de su gráfico en este punto.
La belleza del canal es que Alice y Bob podrían haber enviado millones de HTLCs de un lado a otro a lo largo de la vida del canal y, al final, todo lo que apareció en la cadena fue la transacción de apertura y la transacción de cierre.
Alice y Bob vivieron felices para siempre.
### Referencias
- [BOLT2 Protocolo de pares](https://github.com/lightning/bolts/blob/master/02-peer-protocol.md)
- [Operación normal de un canal LN previo a taproot](https://ellemouton.com/posts/normal-operation-pre-taproot/) por nostr:nprofile1qqswrt9pnxatlplu49h6meld8svmwqt87wwvk256rqk07n6eu4qeh5gpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0dszpfjtz
- [Una guía técnica sobre contratos de tiempo bloqueado por hash y operaciones de canales Lightning](https://lightning.engineering/posts/2023-06-28-channel-normal-op/)
-

@ 599f67f7:21fb3ea9
2024-12-31 15:00:53
### Contenidos
- [Visión general](#visión-general)
- [Preliminares](#preliminares)
- [Operación normal del canal](#operación-normal-del-canal)
- [Configuración](#configuración)
- [Añadiendo un HTLC](#añadiendo-un-htlc)
- [Paso 1: Alice -> Bob: update_add_htlc(A1)](#paso-1-alice---bob-update_add_htlca1)
- [Paso 2: Alice -> Bob: update_add_htlc(A2)](#paso-2-alice---bob-update_add_htlca2)
- [Paso 3: Bob -> Alice: update_add_htlc(B1)](#paso-3-bob---alice-update_add_htlcb1)
- [Comprometiéndose al estado actual](#comprometiéndose-al-estado-actual)
- [Paso 4: Alice -> Bob: commitment_signed](#paso-4-alice---bob-commitment_signed)
- [Paso 5: Bob -> Alice: revoke_and_ack](#paso-5-bob---alice-revoke_and_ack)
- [Paso 6: Alice -> Bob: update_add_htlc(A3)](#paso-6-alice---bob-update_add_htlca3)
- [Paso 7: Bob -> Alice: commitment_signed](#paso-7-bob---alice-commitment_signed)
- [Paso 8: Alice -> Bob: revoke_and_ack](#paso-8-alice---bob-revoke_and_ack)
- [Paso 9: Bob -> Alice: revoke_and_ack](#paso-9-bob---alice-revoke_and_ack)
- [Paso 10: Bob -> Alice: commitment_signed](#paso-10-bob---alice-commitment_signed)
- [Paso 11: Alice -> Bob: revoke_and_ack](#paso-11-alice---bob-revoke_and_ack)
- [Eliminando HTLCs](#eliminando-htlcs)
- [Paso 12: Bob -> Alice: update_fulfill_htlc(A2)](#paso-12-bob---alice-update_fulfill_htlca2)
- [Paso 13: Bob -> Alice: update_fail_htlc(A1)](#paso-13-bob---alice-update_fail_htlca1)
- [Paso 14: Bob -> Alice: update_fail_malformed_htlc(A3)](#paso-14-bob---alice-update_fail_malformed_htlca3)
- [Paso 15: Alice -> Bob: update_fulfill_htlc(B1)](#paso-15-alice---bob-update_fulfill_htlcb1)
- [Paso 16: Bob -> Alice: commitment_signed](#paso-16-bob---alice-commitment_signed)
- [Paso 17: Alice -> Bob: revoke_and_ack](#paso-17-alice---bob-revoke_and_ack)
- [Paso 18: Alice -> Bob: commitment_signed](#paso-18-alice---bob-commitment_signed)
- [Paso 19: Bob -> Alice: revoke_and_ack](#paso-19-bob---alice-revoke_and_ack)
- [Paso 20: Bob -> Alice: commitment_signed](#paso-20-bob---alice-commitment_signed)
- [Paso 21: Alice -> Bob: revoke_and_ack](#paso-21-alice---bob-revoke_and_ack)
- [Actualizando tarifas](#actualizando-tarifas)
- [Retransmisión de mensajes](#retransmisión-de-mensajes)
### Visión general
En este capítulo cubriremos las operaciones normales de un canal. Esto implica entender cómo se añaden HTLCs a un canal y cómo los pares del canal se comprometen a un nuevo estado para incluir estos HTLCs. Luego cubriremos cómo se restablece el flujo normal de un canal después de una desconexión. Finalmente, cubriremos el flujo de cierre cooperativo del canal. Por cierto, todos estos temas están cubiertos en [BOLT2](https://github.com/lightning/bolts/blob/master/02-peer-protocol.md).
### Preliminares
Aquí hay algunos conceptos y flujos que hemos cubierto anteriormente en nuestra serie que podrían ser útiles para entender este capítulo. No dudes en volver a leerlos si necesitas un recordatorio.
- nostr:naddr1qqxnzdenxgerzve5x5enyv3sqyg8wumn8ghj7mn0wd68ytnhd9hx2q3qtx0k0a7lw62vvqax6p3ku90tccgdka7ul4radews2wrdsg0m865sxpqqqp65wc4f8xj: por qué los pares del canal tienen un estado asimétrico y cómo actualizan este estado de manera confiable.
- nostr:naddr1qqxnzdenxgenvwp48qmnqdfhqyg8wumn8ghj7mn0wd68ytnhd9hx2q3qtx0k0a7lw62vvqax6p3ku90tccgdka7ul4radews2wrdsg0m865sxpqqqp65wx9fs7k: cómo se ven las salidas de HTLC en una transacción de compromiso.
- [Apertura y anuncio de un canal LN pre-taproot]: cómo dos nodos abren un canal.
### Operación normal del canal
#### Configuración
Alice y Bob han abierto su canal con éxito. Ambos han visto que la transacción de financiación está confirmada y han intercambiado el mensaje `channel_ready` entre ellos para indicar que están listos para usar el canal. El estado de sus transacciones de compromiso asimétricas actualmente se ve así:

Ambas transacciones de compromiso gastan la salida de la transacción de financiación multisig 2-de-2. Dado que es un multisig 2-de-2, gastar de esta salida requiere firmas de ambos pares. Las firmas están representadas por las dos cajas en la parte superior de las transacciones de compromiso. Puedes ver en el diagrama que la transacción de compromiso de Alice tiene una firma de Bob representada por la caja azul; Bob tiene una firma de Alice para su transacción de compromiso representada por la caja verde. Cada transacción de compromiso también tiene las salidas `to_local` y `to_remote` que pagan a las partes respectivas su saldo actual del canal. Tanto Alice como Bob pueden firmar sus propias transacciones de compromiso en cualquier momento y transmitirlas a la red de Bitcoin. Esto sería un **cierre forzado**.
Con el fin de hacer que los próximos diagramas sean más fáciles de seguir, ignoraremos las transacciones de financiación así como las salidas `to_local` y `to_remote` por un tiempo, ya que nuestro enfoque inicial estará en añadir y eliminar salidas de HTLC. Así que el diagrama anterior ahora se simplifica a esto:

- Una transacción de compromiso _roja_, mostrada a continuación, representa transacciones de compromiso pasadas y revocadas. Si Alice o Bob firmaran y transmitieran una de estas, entonces la otra parte podría barrer todos sus fondos. Así que estas transacciones revocadas pueden considerarse efectivamente inválidas.
- Una transacción de compromiso _amarilla_ representa el último conjunto válido de transacciones de compromiso. Estas son las transacciones de compromiso que se transmitirían en un cierre forzado.
- Finalmente, cada lado tiene lo que se puede considerar un "área de preparación" donde se pueden proponer cambios a la transacción de compromiso. Más adelante, cualquiera de los lados puede decidir cuándo quiere que su contraparte se comprometa a los cambios en su transacción de compromiso de preparación.
Sugerencia: si te gusta git, esto es muy parecido a un flujo de trabajo de git. Los commits pasados están desactualizados, pero cuentan una buena historia de lo que sucedió. Tus últimos cambios comprometidos representan el estado actual de tu proyecto. Cualquier cambio que aún no esté comprometido está en preparación.

#### Añadiendo un HTLC
Cuando Alice o Bob quieren enviar un pago, necesitarían proponer la inclusión del HTLC a su par de canal. Esto se hace con el mensaje `update_add_htlc`:

Aquí hay una tabla sobre lo que significa cada uno de los campos del mensaje:
| Campo | Descripción|
|---|---|
| channel_id | utilizado para comunicar en qué canal debe tener lugar este cambio. |
| id | un identificador que siempre incrementa para este cambio propuesto del remitente. |
| amount_msat | la cantidad que debe adjuntarse a la salida de HTLC. |
| cltv_expiry | la altura del bloque en la que el HTLC debe expirar. |
| onion_routing_packet y blinding_point | datos que el destinatario del HTLC utilizará para determinar a dónde enviar el pago a continuación. |
Hay un punto contraintuitivo a tener en cuenta aquí: el remitente de este mensaje aún no coloca esta actualización en su propia área de preparación. Esto se debe a que la actualización aún está "pendiente del receptor" porque el remitente aún no ha recibido ningún reconocimiento del receptor para la nueva actualización. Imagina este escenario: el remitente envía una actualización y luego recibe inmediatamente un mensaje `commitment_signed` (más detalles sobre esto más adelante). En este caso, no debería haber ambigüedad sobre qué actualizaciones están incluidas en la transacción que se está firmando. Esperemos que esto tenga más sentido a medida que trabajemos a través del ejemplo.
##### Paso 1: Alice -> Bob: update_add_htlc(A1)
Supongamos que Alice envía a Bob un `update_add_htlc`. Llamemos a este HTLC `A1` porque es el primero que Alice (A) está enviando a Bob. Si Bob está contento con todos los campos en el mensaje, entonces añade el HTLC a su transacción de compromiso en el área de preparación y Alice marca el HTLC como pendiente en el lado de Bob, pero aún no lo añade a su propia transacción de compromiso en preparación.

Ten en cuenta que ninguno de los lados ha comprometido realmente este HTLC aún, así que si Bob es un nodo de enrutamiento para este pago, no debería enviar aún `update_add_HTLC` al siguiente salto en la ruta hasta que `A1` haya sido _irrevocablemente_ comprometido. La adición o eliminación de un HTLC solo se considera irrevocablemente comprometida una vez que ambas partes en el canal se han comprometido a la transacción de compromiso con o sin él.
Esto no se muestra en el diagrama simplificado, pero en realidad la salida principal de Alice en la transacción de compromiso en preparación de Bob (es decir, la salida `to_remote`) ahora tendrá el valor del HTLC añadido restado (junto con las tarifas para cubrir la salida extra). Si el HTLC termina teniendo éxito, entonces esta cantidad se añadirá a la salida de Bob y si termina fallando, entonces se volverá a añadir a la salida de Alice.
##### Paso 2: Alice -> Bob: update_add_htlc(A2)
A pesar de que aún no se han comprometido al HTLC `A1`, esto no les impide añadir más cambios al área de preparación. Alice está más que bienvenida a proponer un nuevo HTLC, `A2`, a Bob:

##### Paso 3: Bob -> Alice: update_add_htlc(B1)
Del mismo modo, Bob puede sugerir un cambio, `B1`, a Alice:

#### Comprometiéndose al estado actual
En algún momento, uno de los pares querrá asegurarse de que el otro par se haya comprometido al último conjunto de cambios y revocar el estado válido anterior. Esto se hace enviando el mensaje `commitment_signed`:

| Campo | Descripción|
|---|---|
| channel_id | utilizado para comunicar en qué canal debe tener lugar este cambio. |
| signature | la firma del remitente para la transacción de compromiso del área de preparación de la parte remota. |
| num_htlcs | el número de HTLCs que el remitente espera que estén en la transacción de compromiso remota. |
| htlc_signatures | un array de firmas de num_htlcs que son las firmas del remitente para cada una de las transacciones de HTLC de segundo nivel que la parte remota necesitaría transmitir si alguna vez tuviera que cerrar el canal forzosamente. |
Sugerencia: si necesitas un recordatorio sobre las transacciones de HTLC de segundo nivel y por qué son necesarias, consulta este [capítulo].
##### Paso 4: Alice -> Bob: commitment_signed
Supongamos que Alice envía este mensaje a Bob. Bob ahora tendrá todas las firmas requeridas de Alice para transmitir su transacción de compromiso en el área de preparación:

Observa que Alice sabía que su firma necesitaría cubrir los HTLCs `A1` y `A2`. Esto está bien porque el [transporte subyacente](https://github.com/lightning/bolts/blob/master/08-transport.md) está garantizado para ser confiable y ordenado, lo que significa que si Bob recibiera el mensaje `commitment_signed` de Alice, entonces significa que definitivamente recibió sus mensajes `update_add_htlc` para `A1` y `A2`. Alice y Bob saben que la firma no debería cubrir el HTLC `B1` ya que Alice no ha enviado un reconocimiento para él aún.
Otra cosa a notar es que Bob ahora tiene en realidad dos transacciones de compromiso válidas ya que aún no ha revocado su estado anterior. Sin embargo, está incentivado a revocar su transacción de compromiso anterior ya que los HTLCs en el nuevo estado son uno de los siguientes:
- Pagos a Bob mismo, lo que significa que se beneficia de comprometerse al nuevo estado. Si no se compromete al nuevo estado, entonces Alice tampoco lo hará y por lo tanto aún existiría una versión de una transacción de compromiso que no paga a Bob sus fondos entrantes.
- De manera similar al punto anterior, si Bob está enrutando un pago, entonces también está incentivado a comprometer irrevocablemente el HTLC ya que ganaría tarifas de enrutamiento si el pago tiene éxito.
- Finalmente, si Bob está haciendo el pago él mismo, entonces el primer estado sería de hecho más rentable para él ya que tiene menos fondos en el segundo estado. Sin embargo, el comerciante al que Bob está haciendo el pago no liberará los bienes que se están comprando a menos que primero se reciban los fondos, lo que no sucederá si Alice no pasa el HTLC, lo cual no hará a menos que se haya comprometido irrevocablemente. Así que nuevamente, Bob está incentivado a revocar su estado anterior.
##### Paso 5: Bob -> Alice: revoke_and_ack
En respuesta al `commitment_signed` de Alice, Bob envía el mensaje `revoke_and_ack`:

- El `per_commitment_secret` proporciona a Alice la información que necesita para poder gastar cualquier ruta de revocación en el estado previamente válido de Bob. Consulta el [capítulo de revocación] para más detalles sobre cómo funciona la revocación.
- El `next_per_commitment_point` le da a Alice la información que necesita para derivar la clave pública de revocación que se utilizará en la próxima transacción de compromiso de Bob.
Una vez que Alice recibe este mensaje, la transacción de compromiso anterior de Bob ha sido revocada con éxito. Ten en cuenta que este mensaje reconoce explícitamente el mensaje `commitment_signed` enviado por Alice y, por extensión, dado que la entrega de mensajes es confiable y ordenada, también reconoce implícitamente los mensajes `update_add_htlc` que Alice envió para `A1` y `A2`. Por lo tanto, Alice puede finalmente añadir `A1` y `A2` a su transacción de compromiso en el área de preparación ya que ya no están pendientes en el lado de Bob:

Ahora podemos limpiar un poco el diagrama:

En el último diagrama, observa que las últimas transacciones de compromiso de Alice y Bob están en realidad desincronizadas. Esto está bien ya que ninguna de las actualizaciones se ha comprometido irrevocablemente aún. Eso podría parecer difícil de creer ya que las transacciones de compromiso se ven tan diferentes, así que vamos a repasar las consecuencias de que cualquiera de estas transacciones termine en la cadena desde la perspectiva de ambos lados.
- Desde la perspectiva de Alice:
- si su transacción de compromiso se transmitiera, recuperaría su cantidad original `to_local`.
- si la transacción de compromiso de Bob se transmitiera, entonces los HTLCs ofrecidos por Alice (como `A1` y `A2`) estarían en la cadena. Para los HTLCs ofrecidos, Alice está enviando sats _fuera_, lo que significa que su `to_local` sería menor. Pero, si Bob era un nodo de enrutamiento para estos HTLCs, entonces no los habría reenviado ya que aún no están comprometidos irrevocablemente, lo que significa que no recibiría las pre-imágenes requeridas para reclamar estos HTLCs y, por lo tanto, Alice podría recuperar sus fondos a través de la ruta de tiempo de espera. Si Bob era el destinatario de estos HTLCs, entonces podría producir la pre-imagen para reclamar los HTLCs, pero entonces Alice vería la pre-imagen en la cadena y podría reclamar los HTLCs entrantes de su canal entrante y así habría ganado tarifas de enrutamiento.
- Desde la perspectiva de Bob:
- si la transacción de compromiso de Alice se transmite, Bob recupera sus fondos a través de la salida `to_remote`.
- si Bob tuviera que cerrar forzosamente a través de su transacción de compromiso, entonces los HTLCs ofrecidos a él (como `A1` y `A2`) estarían en la cadena. Si Bob estaba enrutando estos HTLCs, entonces no los habría reenviado ya que aún no están comprometidos irrevocablemente. Así que no podría reclamar la ruta de éxito, pero eso está bien ya que los fondos para estos no salieron de su saldo. Si Bob era el destino final para estos, entonces podría reclamarlos a través de la ruta de éxito.
##### Paso 6: Alice -> Bob: update_add_htlc(A3)
Queremos ser muy claros sobre el punto de que las transacciones de compromiso pueden permanecer desincronizadas indefinidamente y que Bob no necesita enviar `commitment_signed` solo porque Alice lo hizo. Así que, para el sake de otro ejemplo, supongamos que Alice en este punto envía otro HTLC, `A3`, a Bob:

##### Paso 7: Bob -> Alice: commitment_signed
Bob quiere comprometer irrevocablemente algunos de los HTLCs para poder reenviarlos, así que finalmente envía a Alice un `commitment_signed` propio. Esto incluirá su firma para la transacción de compromiso del área de preparación de Alice junto con todas las firmas requeridas de él para las salidas de HTLC de segundo nivel.

##### Paso 8: Alice -> Bob: revoke_and_ack
Al igual que Bob hizo anteriormente, Alice responde al `commitment_signed` con un `revoke_and_ack` para revocar su estado anterior. Esto también sirve como un reconocimiento para Bob de que Alice ha recibido y se ha comprometido a `B1`, por lo que Bob ahora puede agregar `B1` a su transacción de compromiso en el área de preparación.

Rápida limpieza...

¡Por fin, tenemos algunos HTLCs comprometidos de forma irrevocable! `A1` y `A2` han sido comprometidos de forma irrevocable. `B1` y `A3`, sin embargo, no lo han sido ya que aún no han sido comprometidos por ambas partes.
Comprometamos rápidamente `B1` y `A3` de forma irrevocable también.
##### Paso 8: Alice -> Bob: commitment_signed

##### Paso 9: Bob -> Alice: revoke_and_ack

##### Paso 10: Bob -> Alice: commitment_signed

##### Paso 11: Alice -> Bob: revoke_and_ack

Limpiado:

¡Ahora todos los HTLCs han sido comprometidos de forma irrevocable!
#### Eliminando HTLCs
Probablemente ya entiendas la idea de agregar HTLCs. Pero, ¿qué pasa con eliminarlos? Los HTLCs se eliminan si un pago tiene éxito o si falla. Ten en cuenta que los mensajes de eliminación de HTLC solo pueden ser enviados por el par que no envió la actualización original `update_add_htlc` y que los HTLCs solo son removibles una vez que han sido comprometidos de forma irrevocable. Afortunadamente para nosotros, todos los HTLCs han sido comprometidos de forma irrevocable, así que podemos comenzar a eliminarlos ahora.
##### Paso 12: Bob -> Alice: update_fulfill_htlc(A2)
En el mejor de los casos, un HTLC se elimina porque se está cumpliendo, lo que significa que su pre-imagen se está devolviendo. Esto se hace con el mensaje `update_fulfilled_htlc`, que se ve así:

En nuestro ejemplo, Bob envía a Alice el mensaje `update_fulfill_htlc` para el HTLC `A2`. Esto también demuestra que los HTLCs no tienen que ser eliminados en el mismo orden en que fueron agregados.

Ten en cuenta que, al igual que las actualizaciones para agregar un HTLC, las actualizaciones para eliminar un HTLC también estarán inicialmente pendientes en el lado receptor hasta que hayan sido reconocidas por un `revoke_and_ack`. Así que, en nuestro caso, Alice elimina `A2` de su transacción en el área de preparación cuando recibe el `update_fulfill_htlc` (y asigna el monto del HTLC a la salida de Bob), pero Bob aún no elimina el HTLC de su transacción en el área de preparación.
A diferencia de otros mensajes de actualización, no hay necesidad de esperar a que una eliminación de HTLC sea comprometida de forma irrevocable si recibes la pre-imagen para ello. Después de todo, puedes enviar inmediatamente la pre-imagen hacia arriba para reclamar cualquier HTLC allí.
##### Paso 13: Bob -> Alice: update_fail_htlc(A1)
Los HTLCs también pueden ser eliminados debido a fallos en el pago, como el tiempo de espera de los HTLCs o si hubo algún tipo de fallo de enrutamiento, como que un canal específico en la ruta ya no exista, no se cumplan los requisitos de tarifa de un salto, un enlace no tenga saldo suficiente, etc. Tales fallos se comunican con el mensaje `update_fail_htlc`:

El campo de razón es un blob cifrado para el remitente del pago para informarles sobre la razón del fallo.
Después de que Bob envía a Alice el mensaje `update_fail_htlc` para `A1`, el estado se ve como sigue:

##### Paso 14: Bob -> Alice: update_fail_malformed_htlc(A3)
El mensaje final que se puede usar para eliminar un HTLC es el mensaje `update_fail_malformed_htlc`:

Este mensaje se envía si algún salto en la ruta de pago no pudo analizar el `onion_routing_packet` que recibió en `update_add_htlc`. Si Bob envía a Alice este mensaje para `A3`, entonces el estado ahora se ve así:

##### Paso 15: Alice -> Bob: update_fulfill_htlc(B1)
Alice también inicia la eliminación de `B1` enviando un `update_fulfill_htlc` a Bob.

Ahora limpiemos las eliminaciones de HTLC comprometiéndolas de forma irrevocable. Esto requerirá algunos flujos de `commitment_signed` - `revoke_and_ack`:
##### Paso 16: Bob -> Alice: commitment_signed

##### Paso 17: Alice -> Bob: revoke_and_ack

##### Paso 18: Alice -> Bob: commitment_signed

##### Paso 19: Bob -> Alice: revoke_and_ack

##### Paso 20: Bob -> Alice: commitment_signed

##### Paso 21: Alice -> Bob: revoke_and_ack

Los dos estados válidos ahora se ven bonitos y limpios nuevamente:

### Actualizando tarifas
Hay un mensaje `update_*` más que necesitamos cubrir y ese es el mensaje `update_fee`. Este mensaje se utiliza para actualizar la tasa de tarifa que los pares deben usar al construir sus transacciones de compromiso. La tasa de tarifa original se decide en el flujo de apertura de canal, pero si la tasa de tarifa promedio del mempool aumenta, el financiador del canal podría decidir actualizar la tarifa de las transacciones de compromiso para que tengan una mejor oportunidad de ser confirmadas de manera oportuna en una situación de cierre forzado. También podría ser que cuando se abrió el canal, se eligió una tasa de tarifa muy alta y quizás se desearía una tasa de tarifa más baja.
Este mensaje sigue reglas similares a otros mensajes `update_*` en que también debe ser comprometido de forma irrevocable antes de que surta efecto. La única regla adicional que se aplica a este mensaje es que solo el financiador del canal puede enviar este mensaje:

Ten en cuenta que con los canales de anclaje, la necesidad de usar el mensaje `update_fee` se está volviendo cada vez menor, ya que los nodos podrán usar CPFP en la transacción de cierre forzado si es necesario.
### Retransmisión de mensajes
Algo que puedes haber notado en el flujo de agregar/eliminar HTLC es que los reconocimientos explícitos para los mensajes `update_*` se retrasan hasta el intercambio de `commitment_signed`/`revoke_and_ack`. Eso está bien la mayor parte del tiempo, ya que asumimos que el transporte subyacente entre los dos nodos (ver [BOLT8](https://github.com/lightning/bolts/blob/master/08-transport.md)) es ordenado y confiable. Sin embargo, si por alguna razón la conexión entre los dos nodos necesita ser restablecida, habrá dudas sobre si nuestro par ha recibido el último mensaje que enviamos. Aquí es donde entra el mensaje `channel_reestablish`. Al reconectarse, antes de continuar con el flujo de operación normal, los pares intercambiarán este mensaje para asegurarse de que están en la misma página y para determinar qué mensajes posiblemente necesitan retransmitir a su par.

Cada par en el canal tiene su versión de la transacción de compromiso y las dos transacciones de compromiso pueden actualizarse de forma independiente, lo que significa que el número de veces que el estado de la transacción de compromiso de un lado ha sido actualizado (a través del flujo de `commitment_signed` y `revoke_and_ack`) podría ser completamente diferente al del otro lado.
El campo `next_commitment_number` en el mensaje `channel_reestablish` nos permite comunicarnos con nuestro par sobre el próximo `commitment_signed` que esperamos recibir de ellos. De esta manera, ellos sabrán si quizás hemos perdido un `commitment_signed` de ellos que enviaron anteriormente antes de la desconexión. En otras palabras, `next_commitment_number` le dice al par remoto cuál es nuestro último estado comprometido.
De manera similar, `next_revocation_number` es el número de compromiso del próximo `revoke_and_ack` que esperamos recibir. En otras palabras, esto indica a nuestro par cuál número de compromiso creemos que es el más reciente.
El `your_last_per_commitment_secret` es el último secreto por compromiso recibido del par remoto, lo que le dará al par remoto una idea del estado que definitivamente ha revocado.
`my_current_per_commitment_point` es el punto de compromiso de la parte local en su última transacción de compromiso firmada por el par remoto (en otras palabras, la transacción de compromiso que aún no ha sido revocada).
Hay muchas verificaciones que un nodo debe hacer al recibir un `channel_reestablish` para asegurarse de que todas las actualizaciones necesarias se retransmitan para que el canal pueda continuar funcionando con normalidad. También hay algunas verificaciones que aseguran que los nodos no sean engañados para revocar un estado que aún no debería ser revocado o engañados para transmitir un estado que _ha_ sido revocado. Si estás interesado en los detalles sobre estas verificaciones, lee [BOLT2](https://github.com/lightning/bolts/blob/master/02-peer-protocol.md).
Ten en cuenta que cuando ocurre un restablecimiento de conexión, ambos lados deben eliminar cualquier actualización no comprometida de su área de preparación. Si volvemos a visitar la analogía de git, deberían usar git stash cuando ocurra una reconexión. Esto significa que ambos lados necesitarán retransmitir cualquier mensaje `update_*` que aún no haya sido comprometido en la transacción de compromiso del otro lado.
### Referencias
- [BOLT2 Protocolo de pares](https://github.com/lightning/bolts/blob/master/02-peer-protocol.md)
- [Operación normal de un canal LN pre-taproot](https://ellemouton.com/posts/normal-operation-pre-taproot/) por nostr:nprofile1qqswrt9pnxatlplu49h6meld8svmwqt87wwvk256rqk07n6eu4qeh5gpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0dszpfjtz
- [Una guía técnica sobre contratos de tiempo bloqueado por hash y operaciones de canales Lightning](https://lightning.engineering/posts/2023-06-28-channel-normal-op/)
- [BOLT8 Transporte](https://github.com/lightning/bolts/blob/master/08-transport.md)
-

@ 599f67f7:21fb3ea9
2024-12-31 14:56:46
En este capítulo, revisaremos el proceso de apertura y anuncio de un canal pre-taproot, añadiendo algunos detalles técnicos. En los próximos capítulos, aplicaremos el mismo tratamiento a la operación normal y cierre de un canal. Estos capítulos nos darán la base sobre la cual construir a medida que aprendamos sobre canales taproot en el futuro.
Asumiremos que ya estás familiarizado con la estructura de una transacción de compromiso y entiendes por qué son asimétricas. Si necesitas un recordatorio, ¡por favor revisa los capítulos anteriores!
### Contenidos
- [El objetivo final](#el-objetivo-final)
- [Apertura del canal](#apertura-del-canal)
- [El mensaje open_channel](#el-mensaje-open_channel)
- [El mensaje accept_channel](#el-mensaje-accept_channel)
- [El mensaje funding_created](#el-mensaje-funding_created)
- [El mensaje funding_signed](#el-mensaje-funding_signed)
- [El mensaje channel_ready](#el-mensaje-channel_ready)
- [Anunciando el canal](#anunciando-el-canal)
- [Verificando el canal](#verificando-el-canal)
### El objetivo final
Establezcamos qué es lo que nuestros viejos amigos, Alice y Bob, están tratando de lograr.
Alice y Bob son nodos de la Red Lightning. Alice es conocida en la red por su *ID de nodo*, o la clave pública utilizada para identificar su nodo, esta es `alice_node_id`. Del mismo modo, el ID de nodo de Bob es `bob_node_id`.
Sus dos principales objetivos son:
1. Quieren abrir un canal entre ellos de manera sin confianza.
2. Quieren poder publicitar su nuevo canal para que el resto de la red pueda usarlo para el enrutamiento.
### Apertura del Canal
Primero lo primero: a lo largo de este capítulo, utilizaremos diagramas y colores para ilustrar el proceso de apertura del canal. Aquí está la guía de código de colores:
- Un fondo *blanco* significa que el campo de la transacción aún no se conoce.
- Un campo *coloreado* significa que el valor del campo es conocido.
- *Verde* indica las claves públicas de Alice.
- *Azul* indica las claves públicas de Bob.
Un canal se abre una vez que ambas partes tienen la capacidad de firmar completamente sus respectivas transacciones de compromiso y una vez que la transacción de financiación está en la cadena. Tres transacciones están en juego para la apertura de un canal. La primera es la transacción de financiación, que necesita ser confirmada en la cadena. Las otras dos son las transacciones de compromiso mantenidas por Alice y Bob que describen el estado inicial del canal.
En este momento, aún no sabemos nada sobre los parámetros del canal, por lo que todos los campos tienen un fondo blanco:



#### El mensaje open_channel
El primer paso del proceso es que Alice decida que quiere abrir un canal a Bob, es decir, ella se convertirá en la financiadora del canal (y Bob será el financiado). Supongamos que Alice decide que quiere abrir un canal de 1 BTC a Bob y darle inmediatamente a Bob la mitad de la capacidad del canal (0.5 BTC). Alice ahora preparará un mensaje `open_channel` que enviará a Bob. Como referencia, en la tabla a continuación puedes ver los parámetros relevantes.
| Nombre del Campo | Descripción del Campo |
|___|___|
| chain_hash | La blockchain en la que abrir el canal. |
| temp_chan_ID | Identificar el canal antes de que se conozca el outpoint de la transacción de financiación. |
| funding_sats | La cantidad de salida de la transacción de financiación, es decir, la capacidad del canal. |
| push_msat | La cantidad que el financiador envía incondicionalmente al financiado en el momento de la apertura. |
| dust_limit_sats | Umbral por debajo del cual no se deben generar salidas. |
| feerate_per_kw | La tasa de tarifa inicial a utilizar para las transacciones de compromiso. Puede actualizarse más tarde a través de `update_fee`. |
| revocation_basepoint | Utilizado, junto con el first_per_commitment_point del nodo remoto, para derivar la primera clave pública de revocación que se utilizará en la transacción de compromiso de Bob. |
| payment_basepoint | Utilizado, junto con el first_per_commitment_point, para derivar la primera clave pública de pago - la clave pública to_remote en la transacción de compromiso de Bob. |
| delayed_payment_basepoint | Utilizado, junto con el first_per_commitment_point, para derivar la primera clave pública retrasada - la clave pública local_delayed en la transacción de compromiso de Alice. |
| first_per_commitment_point | El primer punto a utilizar junto con los puntos base anteriores (excluyendo el revocation_basepoint) para derivar las claves públicas correspondientes. |
| channel_flags | La única bandera actualmente definida es la bandera "announce_channel" que determina si el canal debe ser anunciado a la red o no. |
| tlv: channel_type | Para que se pueda determinar la estructura de la transacción de compromiso. |
Ahora llenemos los valores de Alice para estos campos:

Alice envía este mensaje a Bob.
Dado que Alice ha decidido el tipo de canal que quiere abrir (legado en lugar de anclajes, taproot, etc.) así como la capacidad del canal, ya puede armar una parte bastante grande de la transacción de financiación:

Alice ya puede elegir algunos de sus UTXOs para ser entradas a la transacción de financiación, ya que conoce la capacidad del canal que quiere abrir. Sin embargo, aún no sabe qué clave pública Bob querría usar para el canal, por lo que no puede finalizar la salida de financiación del canal todavía, y por lo tanto no puede producir firmas para las entradas.
Como Alice ha decidido el tipo de canal (y por lo tanto la estructura de la transacción de compromiso), también puede comenzar a ensamblar las piezas de las transacciones de compromiso. Si asumimos que Bob está feliz con esta propuesta de apertura de canal de Alice, él también puede comenzar a armar las piezas utilizando la información en el mensaje `open_channel`. Recuerda que ambos pares necesitan construir sus propias transacciones de compromiso y ambos necesitarán firmar las transacciones de su par.
Veamos qué piezas ya pueden llenar:

La transacción de compromiso de Alice tiene la estructura de una transacción de canal por defecto, no anclada. Todas sus claves públicas han sido llenadas (`alice_local_delayed_pk_1` se deriva utilizando su `delayed_payment_basepoint` y su `first_commitment_point`). Dado que aún no ha recibido ningún mensaje de Bob, no puede llenar ninguna de sus claves públicas. Y dado que la transacción de financiación aún está incompleta, tampoco puede conocer el TXID para apuntar la entrada de esta transacción de compromiso.
La transacción de compromiso de Bob se ve un poco más completa:

Al igual que Alice, él tampoco puede llenar aún el TXID de la transacción de financiación, pero puede llenar algunas otras cosas:
- Los valores `alice_pubkey_1`, `alice_to_self_delay`, `push_amt` y `local_amt` se toman tal cual del mensaje `open_channel`.
- `alice_payment_key_1` se deriva utilizando el `payment_basepoint` de Alice y el `first_commitment_point`.
- `revoke_pubkey_1b` se deriva utilizando el `revocation_basepoint` de Alice y el `first_per_commitment point` de Bob (Alice no puede derivar este punto aún ya que no ha recibido el `first_per_commitment_point` de Bob).
¡Genial! Es hora de que Bob indique a Alice su aceptación de la propuesta enviando el siguiente mensaje: `accept_channel`.
#### El mensaje accept_channel
El mensaje comparte muchos de los campos del `open_channel`. Aquí está el mensaje que Bob preparará.

Cuando Alice recibe este mensaje de Bob, ahora puede completar la salida de la transacción de financiación y puede crear las firmas para las entradas. Dado que todo está ahora lleno, el TXID de la transacción de financiación también es conocido.

Alice ahora puede llenar más de su propia transacción de compromiso:
- ahora puede usar los valores enviados por Bob para llenar `bob_pubkey_1`, `bob_payment_key_1`, `bob_to_self_delay` y `revoke_pubkey_1a`
- dado que el TXID para la transacción de financiación ahora es conocido, también puede completar la entrada
Ahora sabe todo lo que necesita saber para firmar esta transacción ella misma _pero_ recuerda que aún le falta la firma de Bob para esta transacción.

La transacción de compromiso de Bob sigue siendo la misma que antes, ya que no aprendió nueva información después de enviar el mensaje `accept_channel`.
Ahora que Alice conoce el TXID de la transacción de financiación, también puede completar su vista de la transacción de compromiso de Bob y así puede producir su firma para la transacción de él. Ella enviará el siguiente mensaje a Bob: `funding_created`.
#### El mensaje funding_created
Alice ahora utilizará el mensaje `funding_created` para decirle a Bob el TXID y el índice de la transacción de financiación junto con su firma para la transacción de compromiso de Bob. Ten en cuenta que Bob aún no podrá transmitir su transacción de compromiso porque la transacción de financiación no ha sido transmitida aún.

Una vez que Bob reciba el mensaje `funding_created`, podrá completar el resto de su transacción de compromiso:

#### El mensaje funding_signed
Alice no transmitirá la transacción de financiación hasta que tenga una firma válida de Bob para su transacción de compromiso, entra `funding_signed`:

Ten en cuenta que este es el primer mensaje que utiliza el ID de canal real en lugar del temporal.
Esta fue la última pieza del rompecabezas para Alice. Ahora tiene toda la información que necesita para poder firmar su transacción de compromiso si alguna vez es necesario.

#### El mensaje channel_ready
Alice ahora puede transmitir de manera segura la transacción de financiación. Tanto Alice como Bob estarán atentos a la cadena para la confirmación de la transacción de financiación. Una vez que haya alcanzado la `minimum_depth` especificada por Bob en su mensaje `accept_channel`, ambos lados intercambiarán el mensaje `channel_ready`. Este mensaje cumple dos propósitos. Primero, sirve como una señal para el par para indicar que el canal está listo para usar (y pueden comenzar el proceso de anuncio del canal si abrieron un canal público y anunciado). En segundo lugar, también le dice al par que envíe su `second_per_commitment_point` que deben usar en su segunda transacción de compromiso.

### Anunciando el canal
Esta parte es bastante fácil. Alice y Bob solo necesitan construir un mensaje, `channel_announcement`, juntos y una vez que esté completo, pueden transmitirlo a la red. Otros nodos utilizarán este mensaje para probar algunas cosas:
- Que la transacción de financiación del canal es en realidad un UTXO existente y no gastado con un número aceptable de confirmaciones.
- Que la salida de la transacción de financiación en realidad se parece a una transacción de financiación de canal Lightning.
- Que el canal es en realidad propiedad de las claves que Alice y Bob dicen que utilizaron para construir el canal.
- Que Alice y Bob están de acuerdo en el mensaje que se está transmitiendo.
Una versión parcial del mensaje `channel_announcement` se ve así:

`h` es el hash de todos los datos que serán cubiertos por las firmas. Para completar este mensaje, tanto Alice como Bob necesitan calcular una firma sobre `h` utilizando las claves privadas asociadas con sus IDs de nodo y las claves públicas que utilizaron en la transacción de financiación. Luego ambos intercambian el mensaje `announcement_signatures` para comunicarse estas firmas.

Ahora ambos nodos pueden armar el mensaje completo `channel_announcement`:

### Verificando el canal
Supongamos que Charlie es un nodo que recibió este mensaje. Vamos a repasar los pasos que seguirá para verificar el nuevo canal que Alice y Bob han anunciado:
1. Primero, Charlie utilizará el `short_channel_id` incluido en el mensaje para asegurarse de que la transacción de financiación realmente existe en la cadena, que tiene un número suficiente de confirmaciones y que de hecho está no gastada.
2. Luego, Charlie verificará que la salida no gastada realmente se parece a un canal Lightning propiedad de `alice_pubkey_1` y `bob_pubkey_1`. Hará esto utilizando las claves públicas publicitadas para reconstruir el P2WSH y asegurarse de que es el mismo que se encuentra en la cadena.
3. Ahora, Charlie querrá verificar que los nodos que poseen las claves públicas utilizadas en la salida de financiación corresponden de hecho a los nodos que poseen las claves públicas de ID de nodo. Puede hacer esto verificando las firmas `alice_pubkey_1_sig` y `bob_pubkey_1_sig`. Si estas firmas son válidas, entonces está claro que los propietarios de `alice_pubkey_1` y `bob_pubkey_1` están de acuerdo en ser asociados con `alice_node_ID` y `bob_node_ID` ya que el mensaje firmado contiene estas claves públicas.
4. Finalmente, Charlie también querrá asegurarse de que los propietarios de las claves públicas de ID de nodo están de acuerdo en ser asociados con el nuevo canal. Puede hacer esto verificando las firmas `alice_node_ID_sig` y `bob_node_ID_sig`. Si estas firmas son válidas, entonces está claro que los propietarios de `alice_node_ID` y `bob_node_ID` están de acuerdo en ser asociados con `alice_pubkey_1` y `bob_pubkey_1` ya que el mensaje firmado contiene estas claves públicas.
¡Alice y Bob han terminado! Su canal ahora está abierto y otros nodos en la red, como Charlie, utilizarán felizmente el nuevo canal.
### Referencias
- [BOLT2 Protocolo de pares](https://github.com/lightning/bolts/blob/master/02-peer-protocol.md)
- [Apertura y anuncio de un canal pre-taproot](https://ellemouton.com/posts/open_channel_pre_taproot/) por nostr:nprofile1qqswrt9pnxatlplu49h6meld8svmwqt87wwvk256rqk07n6eu4qeh5gpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0dszpfjtz
-

@ 599f67f7:21fb3ea9
2024-12-31 14:52:21
En el capítulo anterior tuvimos una visión simplificada de los HTLC, con suerte eso te dio una comprensión del mecanismo general y los incentivos en juego. En este capítulo profundizaremos en cómo se ven los HTLC en más detalle y cómo encajan en las transacciones de compromiso.
De nostr:naddr1qqxnzdenxgerzve5x5enyv3sqyg8wumn8ghj7mn0wd68ytnhd9hx2q3qtx0k0a7lw62vvqax6p3ku90tccgdka7ul4radews2wrdsg0m865sxpqqqp65wc4f8xj aprendimos sobre las transacciones de compromiso. Aquí hay un breve resumen:
Las transacciones de compromiso son asimétricas: Alice y Bob (participantes de un canal) cada uno tiene sus propias transacciones de compromiso. La transacción de compromiso que cada participante tiene se ve ligeramente diferente a la de su par en que cualquier salida que vaya al nodo local debe estar gravada por un bloqueo de tiempo relativo de `to_self_delay`. Esto es para darle a la otra parte la oportunidad de gastar a lo largo del camino de revocación de la salida si lo necesita.
Con esto en mente, continuemos con el ejemplo del capítulo anterior donde Alice está enviando 2 BTC a un destinatario usando su canal con Bob como el primer salto en la ruta. Recuerda que a Alice se le ha dado un hash `H` al que necesita pagar. En este ejemplo, Alice es la *ofertante* de HTLC y Bob es el *receptor* de HTLC.
### Alice - Ofertante de HTLC
Enfoquémonos en cómo Alice construirá su transacción de compromiso para incluir ahora el HTLC. La transacción de compromiso tendrá tres salidas:
- Una salida de 5 BTC a Bob, gastable inmediatamente
- Una salida de 3 BTC con dos posibles caminos de gasto:
1. Una gastable por Alice después de un `to_self_delay`
2. Una gastable inmediatamente por Bob si tiene la clave de revocación requerida (ver nostr:naddr1qqxnzdenxgerzve5x5enyv3sqyg8wumn8ghj7mn0wd68ytnhd9hx2q3qtx0k0a7lw62vvqax6p3ku90tccgdka7ul4radews2wrdsg0m865sxpqqqp65wc4f8xj y nostr:naddr1qqxnzdenxgerzvek8qenyvekqyxhwumn8ghj7mn0wvhxcmmvqgs9n8m87l0hd9xxqwndqcmwzh4uvyxmwlw0637kuhg98pkcy8ana2grqsqqqa282rd072 si necesitas un recordatorio)
- Una salida de 2 BTC con... hmm, pensemos juntos sobre lo que necesita suceder aquí.

Esta salida es donde debe suceder la magia del HTLC. Necesitamos los siguientes caminos de gasto en esta salida:
- Debe ser gastable por Bob si tiene la preimagen de `H`; este es el camino bloqueado por hash
- O gastable por Alice después de `cltv_expiry`
- O gastable por Bob inmediatamente si tiene la clave de revocación
PERO recuerda que las salidas de Alice hacia sí misma siempre deben tener un bloqueo de tiempo relativo de `to_self_delay` incluso después de `cltv_expiry`. Así que actualicemos los caminos de gasto con esta información:
- Debe ser gastable por Bob si tiene la preimagen de `H`; este es el camino bloqueado por hash
- O gastable por Alice después de `cltv_expiry` *Y después del retraso relativo `to_self_delay`*
- O gastable por Bob inmediatamente si tiene la clave de revocación
Todavía hay un problema: gravar la salida a Alice con ambos bloqueos de tiempo podría, en el peor de los casos, extender el tiempo de espera del HTLC por `to_self_delay`. Es decir, Bob podría tener un bloque adicional de `to_self_delay` para barrer la salida bloqueada por hash a pesar de que el HTLC esté técnicamente expirado. Así que en lugar de bloquear esta salida con ambas condiciones de bloqueo de tiempo, se bloquea solo por el `cltv_expiry`. Luego, en lugar de enviar fondos a Alice directamente, los fondos se envían a una transacción de tiempo de espera de HTLC separada (firmada por Alice y Bob) y esta transacción de tiempo de espera separada impone el `to_self_delay`. Esto permite a Alice bloquear el hecho de que el HTLC ha expirado y evita que Bob reclame la salida bloqueada por hash, todo mientras asegura que Alice solo pueda obtener sus fondos después de `to_self_delay` y, por lo tanto, aún permite a Bob gastar desde el camino de revocación (de la transacción de tiempo de espera de HTLC) si es necesario.
La forma final de los caminos de gasto de la salida de HTLC de la transacción de compromiso se ve como sigue:
- Un camino de gasto a Bob si tiene la preimagen de `H` (camino bloqueado por hash)
- Un camino de gasto a Bob si tiene la clave de revocación
- Un camino de gasto a una transacción de tiempo de espera de HTLC de segunda etapa
La transacción de tiempo de espera de HTLC se construye así:
- La transacción en sí está bloqueada por tiempo con `nLocktime` establecido en `cltv_expiry`. Esto significa que el camino de gasto en la transacción de compromiso original que envía a esta transacción de tiempo de espera de HTLC está efectivamente retrasado por `cltv_expiry`
- La transacción tiene una salida con dos posibles caminos de gasto:
1. Uno a Alice después de `to_self_delay`
2. Uno a Bob si puede proporcionar la clave de revocación

El script para la salida de HTLC de la transacción de compromiso de Alice (la ofertante de HTLC) se ve así:
```
# A nodo remoto con clave de revocación
OP_DUP OP_HASH160 <RIPEMD160(SHA256(revocationpubkey))> OP_EQUAL
OP_IF
OP_CHECKSIG
OP_ELSE
<remote_htlcpubkey> OP_SWAP OP_SIZE 32 OP_EQUAL
OP_NOTIF
# A nodo local a través de la transacción de tiempo de espera de HTLC (bloqueada por tiempo).
OP_DROP 2 OP_SWAP <local_htlcpubkey> 2 OP_CHECKMULTISIG
OP_ELSE
# A nodo remoto con preimagen.
OP_HASH160 <RIPEMD160(payment_hash)> OP_EQUALVERIFY
OP_CHECKSIG
OP_ENDIF
OP_ENDIF
```
Puedes ver que el primer camino es el camino de revocación, el segundo es el camino a la transacción de tiempo de espera de HTLC (el camino bloqueado por tiempo) y el tercero es el camino bloqueado por hash.
El script de salida de la transacción de tiempo de espera de HTLC se ve así:
```
OP_IF
# Transacción de penalización
<revocationpubkey>
OP_ELSE
`to_self_delay`
OP_CHECKSEQUENCEVERIFY
OP_DROP
<local_delayedpubkey>
OP_ENDIF
OP_CHECKSIG
```
### Bob - Receptor de HTLC
Ahora enfoquémonos en cómo Bob (el receptor de HTLC) construirá su transacción de compromiso para incluir el HTLC. La transacción de compromiso tendrá tres salidas:
- Una salida de 3 BTC a Alice gastable inmediatamente
- Una salida de 5 BTC con dos posibles caminos de gasto:
1. Una gastable por Bob después de un `to_self_delay`
2. Una gastable inmediatamente por Alice si tiene la clave de revocación requerida
- Una salida de 2 BTC que es un poco más complicada; profundicemos.

Pensemos en qué caminos de gasto debería tener esta salida:
- Un camino de gasto que Bob puede reclamar si tiene la preimagen de `H` (camino bloqueado por hash) pero dado que es una salida hacia sí mismo, necesita tener un `to_self_delay`
- Un camino de gasto que Alice puede gastar inmediatamente si tiene la clave de revocación necesaria
- Un camino de gasto que Alice puede gastar después de `ctlv_expiry` (camino bloqueado por tiempo)
Nuevamente, tener dos bloqueos de tiempo diferentes en el mismo script plantea un problema: si Bob conoce la preimagen pero tiene que esperar `to_self_delay` bloques para gastar desde el camino bloqueado por hash, entonces hay una posibilidad de que este `to_self_delay` sea más largo que el `cltv_expiry` que Alice debe esperar para reclamar el camino bloqueado por tiempo. Esto significaría que Alice podría potencialmente gastar a lo largo del camino bloqueado por tiempo a pesar de que Bob tiene la preimagen. Por lo tanto, Bob necesita una forma de bloquear el hecho de que se usará el camino bloqueado por hash mientras aún retrasa su redención de los fondos por `to_self_delay`. Así que se utiliza una transacción de éxito de HTLC separada para esto, permitiendo a Bob gastar desde el camino bloqueado por hash a esta transacción de éxito de HTLC, que luego impondrá por separado la condición de `to_self_delay`.
La forma final de los caminos de gasto de la salida de HTLC de la transacción de compromiso se ve como sigue:
- Un camino de gasto a Alice si tiene la clave de revocación (camino de revocación)
- Un camino de gasto a Alice después de `cltv_expiry` (camino bloqueado por tiempo)
- Un camino de gasto a la transacción de éxito de HTLC si Bob puede revelar la preimagen de `H` (camino bloqueado por hash)
La transacción de éxito de HTLC se ve así:
- La transacción *no* está bloqueada por tiempo (a diferencia del caso de Alice)
- La transacción tiene una salida con dos posibles caminos de gasto:
1. Uno a Bob después de `to_self_delay`
2. Uno a Alice si puede proporcionar la clave de revocación

El script para la salida de HTLC de la transacción de compromiso de Bob (el receptor de HTLC) se ve así:
```
# A nodo remoto con clave de revocación
OP_DUP OP_HASH160 <RIPEMD160(SHA256(revocationpubkey))> OP_EQUAL
OP_IF
OP_CHECKSIG
OP_ELSE
<remote_htlcpubkey> OP_SWAP OP_SIZE 32 OP_EQUAL
OP_IF
# A nodo local a través de la transacción de éxito de HTLC.
OP_HASH160 <RIPEMD160(payment_hash)> OP_EQUALVERIFY
2 OP_SWAP <local_htlcpubkey> 2 OP_CHECKMULTISIG
OP_ELSE
# A nodo remoto después del tiempo de espera.
OP_DROP <cltv_expiry> OP_CHECKLOCKTIMEVERIFY OP_DROP
OP_CHECKSIG
OP_ENDIF
OP_ENDIF
```
Puedes ver en el script anterior que el primer camino es el camino de revocación, el segundo es el camino a la transacción de éxito de HTLC (y también es el camino bloqueado por hash) y el tercero es el camino de gasto bloqueado por tiempo.
El script de salida de la transacción de éxito de HTLC se ve así:
```
OP_IF
# Transacción de penalización
<revocationpubkey>
OP_ELSE
`to_self_delay`
OP_CHECKSEQUENCEVERIFY
OP_DROP
<local_delayedpubkey>
OP_ENDIF
OP_CHECKSIG
```
### La imagen completa

### Revisión
- La salida de HTLC en una transacción de compromiso difiere dependiendo de si el constructor de la transacción es el **ofertante de HTLC** o el **receptor de HTLC**
- La salida de HTLC necesita estar gravada por dos bloqueos de tiempo, pero tener ambos bloqueos de tiempo en el script puede causar problemas
- La solución es barrer la salida a una segunda etapa de **transacción de tiempo de espera de HTLC** o **transacción de éxito de HTLC** e imponer el `to_self_delay` en esta transacción
### Referencias
- [BOLT3: Transacciones](https://github.com/lightning/bolts/blob/master/03-transactions.md#offered-htlc-outputs)
- [Cosas de LN Parte 5: Profundización en HTLC](https://ellemouton.com/posts/htlc-deep-dive/) por nostr:nprofile1qqswrt9pnxatlplu49h6meld8svmwqt87wwvk256rqk07n6eu4qeh5gpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0dszpfjtz
-

@ ee11a5df:b76c4e49
2024-12-24 18:49:05
# China
## I might be wrong, but this is how I see it
This is a post within a series I am going to call "I might be wrong, but this is how I see it"
I have repeatedly found that my understanding of China is quite different from that of many libertarian-minded Americans. And so I make this post to explain how I see it. Maybe you will learn something. Maybe I will learn something.
It seems to me that many American's see America as a shining beacon of freedom with a few small problems, and China is an evil communist country spreading communism everywhere. From my perspective, America *was* a shining beacon of freedom that has fallen to being typical in most ways, and which is now acting as a falling empire, and China *was* communist for about a decade, but turned and ran away from that as fast as they could (while not admitting it) and the result is that the US and China are not much different anymore when it comes to free markets. Except they are very different in some other respects.
## China has a big problem
China has a big problem. But it is not the communism problem that most Westerners diagnose.
I argue that China is no longer communist, it is only communist in name. And that while it is not a beacon of free market principles, it is nearly as free market now as Western nations like Germany and New Zealand are (being somewhat socialist themselves).
No, China's real problem is authoritarian one-party rule. And that core problem causes all of the other problems, including its human rights abuses.
## Communism and Socialism
Communism and Socialism are bad ideas. I don't want to argue it right here, but most readers will already understand this. The last thing I intend to do with this post is to bolster or defend those bad ideas. If you dear reader hold a candle for socialism, let me know and I can help you extinguish it with a future "I might be wrong, but this is how I see it" installment.
Communism is the idea of structuring a society around common ownership of the means of production, distribution, and exchange, and the idea of allocating goods and services based on need. It eliminates the concept of private property, of social classes, ultimately of money and finally of the state itself.
Back under Mao in 1958-1962 (The Great Leap Forward), China tried this (in part). Some 50+ million people died. It was an abject failure.
But due to China's real problem (authoritarianism, even worship of their leaders), the leading classes never admitted this. And even today they continue to use the word "Communist" for things that aren't communist at all, as a way to save face, and also in opposition to the United States of America and Europe.
Authorities are not eager to admit their faults. But this is not just a Chinese fault, it is a fault in human nature that affects all countries. The USA still refuses to admit they assassinated their own president JFK. They do not admit they bombed the Nord Stream pipeline.
China defines "socialism with Chinese characteristics" to mean "the leadership of the Communist Party of China". So they still keep the words socialism and communism, but they long ago dropped the meanings of those words. I'm not sure if this is a political ploy against us in the West or not.
### China's Marketplace Today
Today China exhibits very few of the properties of communism.
They have some common ownership and state enterprises, but not much differently than Western countries (New Zealand owns Air New Zealand and Kiwibank and Kiwirail, etc). And there are private enterprises all over China. They compete and some succeed and some fail. You might hear about a real-estate bank collapsing. China has private property. They have mostly free markets. They have money, and the most definitely have social classes and a very strong state.
None of that is inline with what communist thinkers want. Communist thinkers in China moan that China has turned away from communism.
Deng Xiaoping who succeeded Mao and attempted to correct the massive mistake, did much when he said "to get rich is glorious."
China achieved staggering rates of economic growth. 10% annually on average since 1977. Chinese economic reform started in 1979 and has continued through successive administrations (Deng, Jiang, Hu and now Xi).
China is now the world's largest economy (by GDP in PPP terms) since 2016.
I was first made aware of China's economic growth by Jim Rogers, an American commodities expert who travelled through China (and the rest of the world from 1990-1992) and in 2007 moved to Singapore where he ensured his daughters learned to speak Mandarin, because Jim knew where the economic growth was going to happen. Jim always spoke positively of China's economic prospects, and his view was so different from the "China is a nasty communist place" view that I had grown up with that my mind opened.
How can anybody believe they are still a communist country? In what world does it make sense that communism can produce such a massively booming economy? It doesn't make sense because it is simply wrong.
What *does* happen is that the CPC interferes. It lets the market do what markets do, but it interferes where it thinks oversight and regulation would produce a better result.
Western nations interfere with their markets too. They have oversight and regulation. In fact some of China's planned reforms had to be put on hold by Xi due to Donald Trump's trade war with China. That's right, they were trying to be even more free market than America, but America's protectionism prodded Xi to keep control so he could fight back efficiently.
Government oversight and regulation IMHO is mostly bad because it gets out of control, and there are no market forces to correct this. This gets even more extreme in a one-party system, so I can judge that China's oversight and regulation problems are very likely worse than those in Western nations (but I have no first hand experience or evidence).
## Why do you keep saying CPC?
The Communist Party of China (CPC) is the ruling party in China. That is their official name. To call them the CCP is to concede to the idea that the British and Americans get to name everybody. I'm not sure who is right, since CPC or CCP is their "English" name
(in Chinese it is 中国共产党 and Westernized it is Zhōngguó Gòngchǎndǎng). Nonetheless, I'll call them CPC because that is their wish.
## Social Credit System
China moved from a planned economy to a market economy in stages. They didn't want any more sudden changes (can you blame them?). In the process, many institutions that have existed in the West for a long time didn't exist in China and they had to arise somehow. IMHO market forces would have brought these about in the private sector, but the one-party CP of China instead decided to create these.
One of those institutions was a credit score system. In the West we have TransUnion and Equifax that maintain credit ratings on people, and we have S&P, Moody's and Fitch that maintain credit ratings on companies. The domain of these ratings is their financial credit-worthiness.
So the People's Bank of China developed a credit information database for it's own needs. The government picked up on the idea and started moving towards a National Credit Management System. In 2004 it became an official goal to establish a credit system compatible with a modern market system. By 2006 banks were required to report on consumer creditworthiness.
But unchecked one-party governmental power will often take a good idea (credit worthiness data shared among private parties) and systematize it and apply it top-down, creating a solution and a new problem at the same time.
Nonetheless, originally it was about credit worthiness and also criminal convictions. That is no big scary thing that some right-wing American commentators will lead you to believe. In the US for example criminal records are public, so China's Social Credit System started out being no more over-reaching in scope than what Americans have lived under their entire lives, its only fault (a severe one) being centrally planned. And that remained the case up until about 2016 (in my estimation).
But of course there is always scope creep. As it exists today, I have reason to believe that CPC officials and even A.I. use judgement calls to score someone on how moral that person has been! Of course that is not a good idea, and IMHO the problem stems from one-party rule, and authoritarian administration of ideas that should instead be handled by the private sector.
## Environmental, Social, and Governance
ESG is a system that came out of a couple basic ideas. The first is that many two-party transactions actually have externalities. They don't just affect the two parties, they also affect everybody else. When you fly in an airplane, you increase the CO2 in the atmosphere that everybody has to pay for (eventually). You may dispute that example, but that is no doubt one of the motivations of ESG.
But of course the recognition of this basic issue didn't lead all people towards market solutions (well it did, but those have been mostly messed up by others), but instead led many people towards ESG, which is a social credit scoring system which applies scores based on environmental and social side-effects of market transactions.
This is not at all the same as China's social credit system, which I described above. I hope you can see the difference.
In fact, China imported ESG from the West. Chinese companies, of their free will, in an attempt to court Western capital, achieve ESG goals for those Western investors. They have been playing this ESG game for 20 years just like the entire world has, because the West has imposed this faux-morality upon them. It isn't something China exported to us, it is something we exported to them.
## I think China has avoided Woke-ism
My understanding of Chinese people, based on what I've heard many Chinese people say, is that China isn't affected by the Western woke-ism epidemic. They deride Western white woke people with the term "Baizuo". They have never sent an incompetent break dancer to the Olympics because of wok-ism. Competence is highly respected as is the competition to be the most competent, which (when augmented by a one-child policy which is no longer) has produced child prodigies like no other country has.
## What about predatory loans of the Belt and Road initiative?
Predatory is an odd name for loans to people in need. The World Bank makes loans to people in need. China does too. China stands in opposition to Western Empire, and in that regard they produce their own alternative BRICS institutions. This is one of them.
There is AFAIK nothing more predatory about them. It is just that in some cases the borrowers have trouble paying them back and they get foreclosed upon. I don't think this is worthy of much discussion, except that the term "predatory" seems to me to be a propaganda device.
## What about foreign influence from China?
China wants to influence the world, especially its own trading partners and potential trading partners. Doing that above board is fine by me.
But some of it is undoubtedly covert. Sometimes Chinese-born people run for public office in Western countries. In New Zealand we stood down some when it became clear they were being influenced too much by the CPC while being charged with representing their local town (dual loyalty issues). If only the USA would do the same thing to their dually-loyal politicians.
And all large nations run influence operations. The USA has the CIA, for example, and claims this "soft power" is actually the better alternative to what would otherwise be military intervention (but IMHO shouldn't be either). I'm not defending such operations (I despise them), I'm just explaining how China's position of exerting influence is not only no big deal and totally expected, it pales in comparison to the United States' influence operations which often become military excursions (something China rarely ever does).
## What about the Great Firewall?
Yeah, that sucks. Again, single-party authoritarian control gone to extremes.
## What about Human Rights Abuses? What about the Uyghur Genocide?
I don't like them. To the extent they are occurring (and I lean towards the belief that they are occurring), I condemn them.
China has anti-terrorism and anti-extremism policies that go too far. They end up oppressing and/or criminalizing cultures that aren't Chinese enough. But especially, China punishes dissent. Disagreement with the CPC is the high crime. It is the one-party rule that causes this problem. Anybody who speaks out against the CPC or goes against the state in any way is harshly punished. This happens to Uyghurs, to Falun Gong, to Tibetans, and to any religion that is seen as subversive.
Amnesty International and the UN OHCHR have documented issues around the Xinjiang Uyghur autonomous region, Tibet, LGBT rights, death penalty, workers rights, and the Hong Kong special administrative region. I am not about to pretend I know better than they do, but to some extent they go too far.
Amnesty International says this about the USA: Discrimination and violence against LGBTI people were widespread and anti-LGBTI legislation increased. Bills were introduced to address reparations regarding slavery and its legacies. Multiple states implemented total bans on abortion or severely limited access to it. Gender-based violence disproportionately affected Indigenous women. Access to the USA for asylum seekers and migrants was still fraught with obstacles, but some nationalities continued to enjoy Temporary Protected Status. Moves were made to restrict the freedom to protest in a number of states. Black people were disproportionately affected by the use of lethal force by police. No progress was made in the abolition of the death penalty, apart from in Washington. Arbitrary and indefinite detention in the US naval base Guantánamo Bay, Cuba, continued. Despite extensive gun violence, no further firearm reform policies were considered, but President Biden did announce the creation of the White House Office of Gun Violence Prevention. The USA continued to use lethal force in countries around the world. Black people, other racialized groups and low-income people bore the brunt of the health impacts of the petrochemical industry, and the use of fossil fuels continued unabated.
Amnesty international didn't even point out that the US government quashes free speech via pressure on social media corporations (because Amnesty International is far too lefty).
So who is worse, China or the US? I'm not going to make that judgement call, but suffice it to say that in my mind, China is not obviously worse.
China violates freedom of expression, association, and assembly of all people. This is bad, and a consequence mainly of one-party rule (again, what I think is the root cause of most of their ills). They arrest, detain, potentially kill anybody who publicly disagrees openly with their government. Clearly this is an excess of authoritarianism, a cancer that is very advanced in China.
As to organ harvesting of Uyghur Muslims, I think this is a myth.
China has dealt harshly with Muslim extremism. They don't offer freedom of religion to ISIS. And Amnesty International complains about that. But practically speaking you probably shouldn't respect the extremist religion of people who want to force everybody into a global caliphate through threat of violence. As you are well aware, some extremist Muslims (<1% of Islam) believe in using violence to bring about a global caliphate. Those extremists pop up in every country and are usually dealt with harshly. China has had to deal with them too.
I have watched two different Western YouTubers travel to Xinjiang province trying to find the oppressed Uyghurs and interview them. They can't find them. What they find instead are Uyghur Muslims doing their prayers five times a day at the local mosque. And also stories that the CPC pitched in some money to help them renovate the mosque. Maybe they were afraid it was a CPC trap and so they wouldn't speak freely. Amnesty International and the UN OHCHR say more than a million are "arbitrarily detained" and I'm not going to argue otherwise. But I'd be more convinced if there were a stream of pictures and news like there is out of Gaza, and it is suspicious that there isn't.
## Conclusion
China is more like a Western nation that Westerners realize. Economically, militarily, socially. It still has a very serious obstacle to overcome: one-party rule. I don't think the one-party is going to voluntarily give up power. So most probably at some point in the future there will be a revolution. But in my opinion it won't happen anytime soon. For the most part Chinese people are living high on the hog, getting rich, enjoying the good life, in positive spirits about life, and are getting along with their government quite well at present.
-

@ ec42c765:328c0600
2024-12-22 19:16:31
この記事は前回の内容を把握している人向けに書いています(特にNostrエクステンション(NIP-07)導入)
前回:[Nostrのカスタム絵文字の使い方](https://yakihonne.com/article/_@lokuyow.github.io/xVMTZxHcV_NWKuTbDBUYs)
# 手順
1. 登録する画像を用意する
2. 画像をweb上にアップロードする
3. 絵文字セットに登録する
## 1. 登録する画像を用意する
以下のような方法で用意してください。
* 画像編集ソフト等を使って自分で作成する
* 絵文字作成サイトを使う([絵文字ジェネレーター](https://emoji-gen.ninja/)、[MEGAMOJI](https://zk-phi.github.io/MEGAMOJI/) など)
* フリー画像を使う([いらすとや](https://www.irasutoya.com/) など)
### データ量削減
Nostrでは画像をそのまま表示するクライアントが多いので、データ量が大きな画像をそのまま使うとモバイル通信時などに負担がかかります。
データ量を増やさないためにサイズやファイル形式を変更することをおすすめします。
以下は私のおすすめです。
* サイズ:正方形 128×128 ピクセル、長方形 任意の横幅×128 ピクセル
* ファイル形式:webp形式(webp変換おすすめサイト [toimg](https://toimg.kakechimaru.com/to-webp))
* 単色、単純な画像の場合:png形式(webpにするとむしろサイズが大きくなる)
### その他
* 背景透過画像
* ダークモード、ライトモード両方で見やすい色
がおすすめです。
## 2. 画像をweb上にアップロードする
よく分からなければ [emojito](https://emojito.meme/) からのアップロードで問題ないです。
普段使っている画像アップロード先があるならそれでも構いません。
気になる方はアップロード先を適宜選んでください。
既に投稿されたカスタム絵文字の画像に対して
- 削除も差し替えもできない → [emojito](https://emojito.meme/) など
- 削除できるが差し替えはできない → [Gyazo](https://gyazo.com/)、[nostrcheck.me](https://nostrcheck.me/)など
- 削除も差し替えもできる → [GitHub](https://github.com/) 、セルフホスティングなど
これらは既にNostr上に投稿されたカスタム絵文字の画像を後から変更できるかどうかを指します。
どの方法でも新しく使われるカスタム絵文字を変更することは可能です。
同一のカスタム絵文字セットに同一のショートコードで別の画像を登録する形で対応できます。
## 3. 絵文字セットに登録する
[emojito](https://emojito.meme/) から登録します。
右上の**アイコン** → **+ New emoji set** から新規の絵文字セットを作成できます。


#### ① 絵文字セット名を入力
基本的にカスタム絵文字はカスタム絵文字セットを作り、ひとまとまりにして登録します。
一度作った絵文字セットに後から絵文字を追加することもできます。
#### ② 画像をアップロードまたは画像URLを入力
emojitoから画像をアップロードする場合、ファイル名に日本語などの2バイト文字が含まれているとアップロードがエラーになるようです。
その場合はファイル名を適当な英数字などに変更してください。
#### ③ 絵文字のショートコードを入力
ショートコードは絵文字を呼び出す時に使用する場合があります。
他のカスタム絵文字と被っても問題ありませんが選択時に複数表示されて支障が出る可能性があります。
他と被りにくく長くなりすぎないショートコードが良いかもしれません。
ショートコードに使えるのは半角の英数字とアンダーバーのみです。
#### ④ 追加
**Add** を押してもまだ作成完了にはなりません。

一度に絵文字を複数登録できます。
最後に右上の **Save** を押すと作成完了です。

画面が切り替わるので、右側の **Options** から **Bookmark** を選択するとそのカスタム絵文字セットを自分で使えるようになります。
既存の絵文字セットを編集するには **Options** から **Edit** を選択します。
以上です。
-----------
# 仕様
[NIP-30 Custom Emoji](https://github.com/nostr-protocol/nips/blob/master/30.md)
[NIP-30 カスタム絵文字(和訳)](https://github.com/nostr-jp/nips-ja/blob/main/30.md)
-

@ d61f3bc5:0da6ef4a
2024-12-18 16:52:18
January 2025 will mark two years since we started building Primal. Our goal was to create the best possible user experience for Nostr and make it accessible to everyone. We reached a big milestone towards realizing that vision with the recent Primal 2.0 release. It’s still early days, a lot more work lies ahead, but we thought the timing was right to introduce the Premium tier. Let’s explore what it is, why we built it, what’s included, and how it will evolve moving forward.
## What Primal Premium Is
The idea behind Primal Premium is simple: integrate all tools and services required for the best Nostr experience into a single package. For $7 per month, Premium users get a *Primal Name* and *Nostr Tools* built by Primal. We’ll cover those in more detail below, but first we should make a crucial point: by signing up for Premium, you are in no way locked in to Primal. Quite the contrary, you can pick and choose which Premium features you wish to enable and use within other Nostr products.
Openness is Nostr’s killer feature. Any product that wishes to truly empower the user needs to interoperate with Nostr’s budding ecosystem. The feed marketplace is a great example. External feeds are first-class citizens within all Primal apps. Primal feeds are available in other Nostr clients. We are working on Premium feeds, which our users will be able to enjoy within Primal or other Nostr apps. Media hosting is another example. Our upcoming support for the Blossom protocol will make Primal Premium media hosting interoperable with other Nostr apps and media hosting services. The common theme here is user choice. Nostr offers the highest level of user agency, and the compounding effect of interoperable products and services is bound to make Nostr immensely powerful.
## Why We Built Premium and Why Now
What is unfolding on Nostr right now is unique and special. The first truly self-sovereign network is being bootstrapped by this early cohort of users and builders. People are literally holding the keys to their online presence. Network infrastructure – relays, indexers, media hosting services, etc. – is being stood up organically and without any central planning or coordination. Hundreds of independent projects are adding new capabilities to Nostr without needing permission. The whole thing is truly a sight to behold.
In addition to fixing the fundamentals of the network, it is equally important that we fix the broken incentives that plague the legacy Web. The status quo of monetization via advertising, which turns users into products to be farmed, has overstayed its welcome. At Primal, we don’t monetize user data. Our users are our customers. We only make money when the user decides that we are providing a valuable service – and pays for it. That means that our users’ interests are aligned with ours. It allows us to wake up every morning and work all day to make the product better for our users.
Some might say that it is too early to try to monetize a Nostr product. We definitely need to be thoughtful about paywalling important features while the network is so young. For example, advanced search is a Primal Premium feature, but we enable it for all users up to 20 search results. That makes it quite usable for anyone on Nostr, but power users get the ability to save these searches and create powerful specialized feeds.
It is crucial to have commercially successful projects on Nostr that have their incentives aligned with those of their users. We are working on new features and monetization methods that follow this philosophy. The more we experiment on Nostr, the faster we will learn what works and unlock the full potential of this network. I have a feeling that a lot remains to be discovered, and Primal Premium is just the first step.
Now, let’s take a closer look at what is included in Premium: *Primal Name* and *Nostr Tools*.
## Primal Name
A Primal Name is a unique name on the primal.net domain that offers three features:
1. **Verified Nostr address (NIP-05)**. This signals to the Nostr network that your account (npub) has been verified by Primal. Note that we don’t perform identity verification; we are simply signaling that this is a Primal Premium user. Users can pay with sats, preserving their privacy while signaling to the network that this verified account is not a bot.
2. **Friendly Bitcoin Lightning address**. Primal’s built-in hosted wallet creates a randomly generated lightning address for every user. They look like this: bluedog25@primal.net. Premium users get to pick their name, so their lightning address is more personalized (e.g. preston@primal.net).
3. **VIP profile on primal.net**. This is simply a friendly URL to your profile on primal.net. We are working on adding profile customization features for Premium users; stay tuned!
In summary, a Primal Name makes you easier to find on Nostr. You are free to use any of these three Primal Name elements as you see fit. If you wish to use your Primal Nostr address and/or Lightning address, simply update your Nostr profile with those entries.
## Nostr Tools
Nostr Tools is a collection of features that we think would be useful to any Nostr power user. We are continuously working on expanding these capabilities, but the initial set of features includes:
- **Media management**. Primal Premium comes with 10GB of media storage (compared to 1GB for free accounts). We implemented a slick interface for managing all media you have on Primal.
- **Contact list backup**. Many Nostr users have experienced the loss of their contact list (i.e., their follow list) when using different clients. We store the history of the contact list for Primal Premium users and make it easy to recover.
- **Content backup**. Nostr users post their content to a collection of public relays. These relays typically don’t offer guarantees that they will store the content for any amount of time. We back up all content posted by Primal Premium users and make it easy to rebroadcast it to the specified relays at any time.
## Primal Legends
The idea for the Primal Legend tier was suggested to me by Gigi a couple of months prior to the launch of Primal 2.0. His argument was simple: “There are users on Nostr who really appreciate Primal and are willing to pay way more than $7 / month to support the project. You should *let them* pay and *recognize them* for doing so.”
I am really glad that Gigi convinced me to introduce the Legend tier. Nostr is truly a special place. The early users are extremely passionate and mission driven. They care about growing and improving Nostr as much as the builders do. At first, I thought of the term “Legend” as a bit tongue in cheek, but then I met and chatted with some of these people. Man, they are incredible. They just wish to support the network and the builders of open source software in any way they can. So now I think the term is appropriate.
We are humbled by the support we received. Our first Legend supporter was none other than Jack. He found this option in the product and paid for the Legend tier literally an hour after Primal 2.0 was released. Thank you, sir, and thank you to all the other Legends out there! 💜🫂
## What Comes Next?
We are delighted and encouraged by the market response to Primal Premium. It is already clear to us that we are on the right path. We will lean into it even harder from here. There will be MOAR Premium features, while at the same time we will make sure that the free product remains excellent. Since you, the user, are the customer, tell us what you would like to see added to Primal Premium.
Pura Vida 🤙
-

@ 4657dfe8:47934b3e
2024-12-18 13:42:46
*Alby Hub enables creation of subaccounts, decentralizing trust and creating usecases for shared, community nodes.*
## Simplifying Bitcoin Wallets for Friends and Family
[Alby Hub](https://albyhub.com/?ref=blog.getalby.com) empowers you to take full control of your bitcoin and manage your payments. Through a user-friendly, self-custodial wallet with a one-click lightning node setup, you can effortlessly connect to dozens of applications. The integrated App Store provides access to popular apps like Amethyst, Damus, Stacker News, Podcasting 2.0, and a wide range of other external tools—all directly linked with your Alby Hub wallet. One of the latest and most exciting additions to Alby Hub is the Friends & Family app.
With the Friends & Family app, you can create subaccounts for friends and family, all powered by your Hub. In just a few clicks, you can set up wallets for them, giving them a smooth onboarding experience and making bitcoin accessible even to those new to the ecosystem. Think of it as a custodial wallet but with a personal touch—since you’re the one managing it, there’s a direct relationship and trust.
These subaccount holders can tap into all the channels and liquidity of your Hub without needing to handle any technical setup. Plus, you can preload their wallets with a few sats, creating a welcoming and smooth experience that’s hard to find elsewhere.
And that’s not all. Beyond providing an intuitive wallet, they can get their own lightning address, configurable payment notifications, access to Alby Go (a mobile app for payments on the go), and the Alby Browser Extension for easy web payments.
Let’s have a look how to set it up.
## How to provide a wallet to Friends and Family?
1. Open your Hub and find the Friends & Family app in the App Store
2. Enter a name e.g. your friend’s name and click “Create subaccount”
3. Share the Connection Secret with your friend for the different options
Here are two examples how your the new subaccount can be used.
### Alby Go mobile App
[Alby Go](https://albygo.com/?ref=blog.getalby.com) makes it easy to carry bitcoin in your pocket. This lightweight wallet connects directly to an Alby Hub subaccount, so your friends can pay and check transactions on the go.
**Here’s how to set it up:**
1. Open the Alby Go Mobile App tab in your Hub.
2. Copy the **Connection Secret** and share it with your friend if you cannot onboard them in person.
3. Your friend downloads Alby Go for [Android](https://play.google.com/store/apps/details?id=com.getalby.mobile&ref=blog.getalby.com) or [iOS](https://apps.apple.com/us/app/alby-go/id6471335774?ref=blog.getalby.com) and scans the code.
And that’s it—your friend now has a bitcoin wallet in their pocket, ready for seamless transactions anytime, anywhere. 🎉
## Get a Lightning Address with an Alby account
An [Alby Account](https://getalby.com/?ref=blog.getalby.com) offers a variety of useful features that make managing bitcoin payments easy. Among these are a personalized lightning address and email payment notifications—two powerful tools that help your newly onboarded friends stay connected and informed.
**To set up an Alby account for someone:**
1. Open the **Alby Account** tab in your Hub.
2. Copy the provided URL and share it with your friend.
3. Your friend simply needs to create their Alby account and afterwards click on the provided URL.
That’s it! The wallet is instantly connected, and they’re ready to receive payments to their new lightning address. 🥳
**Onboarding Family & Friends Made Easy**
In this article, we explored how to create subaccounts for family and friends, connect them with Alby Go, and set up an Alby account to provide a smooth onboarding experience for your loved ones—all achievable in just a few clicks.
Stay tuned as we dive into more exciting use cases for [subaccounts in Alby Hub](https://blog.getalby.com/introducing-subaccounts-in-alby-hub/)! If you have ideas for improvement,[let us know](hello@getalby.com).
-

@ ee11a5df:b76c4e49
2024-12-16 05:29:30
# Nostr 2?
## Breaking Changes in Nostr
Nostr was a huge leap forward. But it isn't perfect.
When developers notice a problem with nostr, they confer with each other to work out a solution to the problem. This is usually in the form of a NIP PR on the nips repo.
Some problems are easy. Just add something new and optional. No biggie. Zaps, git stuff, bunkers... just dream it up and add it.
Other problems can only be fixed by breaking changes. With a breaking change, the overall path forward is like this: Add the new way of doing it while preserving the old way. Push the major software to switch to the new way. Then deprecate the old way. This is a simplification, but it is the basic idea. It is how we solved markers/quotes/root and how we are upgrading encryption, among other things.
This process of pushing through a breaking change becomes more difficult as we have more and more existing nostr software out there that will break. Most of the time what happens is that the major software is driven to make the change (usually by nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6), and the smaller software is left to fend for itself. A while back I introduced the BREAKING.md file to help people developing smaller lesser-known software keep up with these changes.
## Big Ideas
But some ideas just can't be applied to nostr. The idea is too big. The change is too breaking. It changes something fundamental. And nobody has come up with a smooth path to move from the old way to the new way.
And so we debate a bunch of things, and never settle on anything, and eventually nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 makes a post saying that we don't really want it anyways 😉.
As we encounter good ideas that are hard to apply to nostr, I've been filing them away in a repository I call "nostr-next", so we don't forget about them, in case we ever wanted to start over.
It seems to me that starting over every time we encountered such a thing would be unwise. However, once we collect enough changes that we couldn't reasonably phase into nostr, then a tipping point is crossed where it becomes worthwhile to start over. In terms of the "bang for the buck" metaphor, the bang becomes bigger and bigger but the buck (the pain and cost of starting over) doesn't grow as rapidly.
## WHAT? Start over?
IMHO starting over could be very bad if done in a cavalier way. The community could fracture. The new protocol could fail to take off due to lacking the network effect. The odds that a new protocol catches on are low, irrespective of how technically superior it could be.
So the big question is: can we preserve the nostr community and it's network effect while making a major step-change to the protocol and software?
I don't know the answer to that one, but I have an idea about it.
I think the new-protocol clients can be dual-stack, creating events in both systems and linking those events together via tags. The nostr key identity would still be used, and the new system identity too. This is better than things like the mostr bridge because each user would remain in custody of their own keys.
## The nitty gritty
Here are some of the things I think would make nostr better, but which nostr can't easily fix. A lot of these ideas have been mentioned before by multiple people and I didn't give credit to all of you (sorry) because my brain can't track it all. But I've been collecting these over time at https://github.com/mikedilger/nostr-next
* Events as CBOR or BEVE or MsgPack or a fixed-schema binary layout... anything but JSON text with its parsing, it's encoding ambiguity, it's requirement to copy fields before hashing them, its unlimited size constraints. (me, nostr:npub1xtscya34g58tk0z605fvr788k263gsu6cy9x0mhnm87echrgufzsevkk5s)
* EdDSA ed25519 keys instead of secp256k1, to enable interoperability with a bunch of other stuff like ssh, pgp, TLS, Mainline DHT, and many more, plus just being better cryptography (me, Nuh, Orlovsky, except Orlovsky wanted Ristretto25519 for speed)
* Bootstrapping relay lists (and relay endpoints) from Mainline DHT (nostr:npub1jvxvaufrwtwj79s90n79fuxmm9pntk94rd8zwderdvqv4dcclnvs9s7yqz)
* Master keys and revocable subkeys / device keys (including having your nostr key as a subkey)
* Encryption to use different encryption-specific subkeys and ephemeral ones from the sender.
* Relay keypairs, TLS without certificates, relays known by keypair instead of URL
* Layered protocol (separate core from applications)
* Software remembering when they first saw an event, for 2 reasons, the main one being revocation (don't trust the date in the event, trust when you first saw it), the second being more precise time range queries.
* Upgrade/feature negotiation (HTTP headers prior to starting websockets)
* IDs starting with a timestamp so they are temporally adjacent (significantly better database performance) (Vitor's idea)
* Filters that allow boolean expressions on tag values, and also ID exclusions. Removing IDs from filters and moving to a GET command.
* Changing the transport (I'm against this but I know others want to)
## What would it look like?
Someone (Steve Farroll) has taken my nostr-next repo and turned it into a proposed protocol he calls [Mosaic](https://github.com/SteveFarroll/mosaic-spec). I think it is quite representative of that repo,
as it already includes most of those suggestions, so I've been contributing to it. Mosaic spec is rendered [here](https://stevefarroll.github.io/mosaic-spec/).
Of course, where Mosaic stands right now it is mostly my ideas (and Steve's), it doesn't have feedback or input from other nostr developers yet. That is what this blog post is about. I think it is time for other nostr devs to be made aware of this thing.
It is currently in the massive breaking changes phase. It might not look that way because of the detail and refinement of the documentation, but indeed everything is changing rapidly. It probably has some bad ideas and is probably missing some great ideas that you have.
Which is why this is a good time for other devs to start taking a look at it.
It is also the time to debate meta issues like "are you crazy Mike?" or "no we have to just break nostr but keep it nostr, we can't dual-stack" or whatever.
Personally I think mosaic-spec should develop and grow for quite a while before the "tipping point" happens. That is, I'm not sure we should jump in feet first yet, but rather we build up and refine this new protocol and spend a lot of time thinking about how to migrate smoothly, and break it a lot while nobody is using it.
So you can just reply to this, or DM me, or open issues or PRs at [Mosaic](https://github.com/SteveFarroll/mosaic-spec), or just whisper to each other while giving me the evil eye.
-

@ b2d670de:907f9d4a
2024-12-02 21:24:45
# onion-service-nostr-relays
A list of nostr relays exposed as onion services.
## The list
| Relay name | Description | Onion url | Operator | Payment URL | Payment options |
| --- | --- | --- | --- | --- | --- |
| nostr.oxtr.dev | Same relay as clearnet relay nostr.oxtr.dev | ws://oxtrdevav64z64yb7x6rjg4ntzqjhedm5b5zjqulugknhzr46ny2qbad.onion | [operator](nostr:nprofile1qqst94nsmefmya53crp5qq39kewrtgndqcynhnzp7j8lcu0qjple6jspz3mhxue69uhkummnw3ezummcw3ezuer9wcq3gamnwvaz7tmjv4kxz7fwv3sk6atn9e5k7jxrgyy) | N/A | N/A |
| relay.snort.social | Same relay as clearnet relay relay.snort.social | wss://skzzn6cimfdv5e2phjc4yr5v7ikbxtn5f7dkwn5c7v47tduzlbosqmqd.onion | [operator](nostr:nprofile1qqsx8lnrrrw9skpulctgzruxm5y7rzlaw64tcf9qpqww9pt0xvzsfmgpzpmhxue69uhkummnw3ezuamfdejszxrhwden5te0wfjkccte9eekummjwsh8xmmrd9skct9tyup) | N/A | N/A |
| nostr.thesamecat.io | Same relay as clearnet relay nostr.thesamecat.io | ws://2jsnlhfnelig5acq6iacydmzdbdmg7xwunm4xl6qwbvzacw4lwrjmlyd.onion | [operator](nostr:npub1wtuh24gpuxjyvnmjwlvxzg8k0elhasagfmmgz0x8vp4ltcy8ples54e7js) | N/A | N/A |
| nostr.land | The nostr.land paid relay (same as clearnet) | ws://nostrland2gdw7g3y77ctftovvil76vquipymo7tsctlxpiwknevzfid.onion | [operator](nostr:npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj) | [Payment URL](http://nostrland2gdw7g3y77ctftovvil76vquipymo7tsctlxpiwknevzfid.onion) | BTC LN |
| bitcoiner.social | No auth required, currently | ws://bitcoinr6de5lkvx4tpwdmzrdfdpla5sya2afwpcabjup2xpi5dulbad.onion | [operator](nostr:npub1an3nz7lczcunpdw6ltjst94hgzcxpppnk7zk3zr2nfcj4yd96kdse6twjd) | N/A | N/A |
| relay.westernbtc.com | The westernbtc.com paid relay | ws://westbtcebhgi4ilxxziefho6bqu5lqwa5ncfjefnfebbhx2cwqx5knyd.onion | [operator](nostr:npub1pc57ls4rad5kvsp733suhzl2d4u9y7h4upt952a2pucnalc59teq33dmza) | [Payment URL](hjar34h5zwgtvxr345q7rncso3dhdaryuxgri3lu7lbhmnzvin72z5ad.onion) | BTC LN |
| freelay.sovbit.host | Free relay for sovbit.host | ws://sovbitm2enxfr5ot6qscwy5ermdffbqscy66wirkbsigvcshumyzbbqd.onion | [operator](nostr:npub1gnwpctdec0aa00hfy4lvadftu08ccs9677mr73h9ddv2zvw8fu9smmerrq) | N/A | N/A |
| nostr.sovbit.host | Paid relay for sovbit.host | ws://sovbitgz5uqyh7jwcsudq4sspxlj4kbnurvd3xarkkx2use3k6rlibqd.onion | [operator](nostr:npub1gnwpctdec0aa00hfy4lvadftu08ccs9677mr73h9ddv2zvw8fu9smmerrq) | N/A | N/A |
| nostr.wine | 🍷 [nostr.wine](https://nostr.wine) relay | ws://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion | [operator](nostr:npub1fyvwkve2gxm3h2d8fvwuvsnkell4jtj4zpae8w4w8zhn2g89t96s0tsfuk) | [Payment URL](http://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion) | BTC LN, BTC, Credit Card/CashApp (Stripe) |
| inbox.nostr.wine | 🍷 [inbox.nostr.wine](https://inbox.nostr.wine) relay | ws://wineinboxkayswlofkugkjwhoyi744qvlzdxlmdvwe7cei2xxy4gc6ad.onion | [operator](nostr:npub1fyvwkve2gxm3h2d8fvwuvsnkell4jtj4zpae8w4w8zhn2g89t96s0tsfuk) | [Payment URL](http://wineinboxkayswlofkugkjwhoyi744qvlzdxlmdvwe7cei2xxy4gc6ad.onion) | BTC LN, BTC |
| filter.nostr.wine | 🍷 [filter.nostr.wine](https://filter.nostr.wine) proxy relay | ws://winefiltermhqixxzmnzxhrmaufpnfq3rmjcl6ei45iy4aidrngpsyid.onion | [operator](nostr:npub1fyvwkve2gxm3h2d8fvwuvsnkell4jtj4zpae8w4w8zhn2g89t96s0tsfuk) | [Payment URL](http://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion/add-time) | BTC LN, BTC |
| N/A | N/A | ws://pzfw4uteha62iwkzm3lycabk4pbtcr67cg5ymp5i3xwrpt3t24m6tzad.onion:81 | [operator](nostr:nprofile1q9z8wue69uhky6t5vdhkjmnjxejx2dtvddm8sdr5wpmkgmt6wfjxversd3sn2umevyexzenhwp3kzcn2w4cry7rsdy6kgatvvfskgtn0de5k7m30q9z8wue69uhk77r5wfjx2anpwcmrg73kx3ukydmcxeex5ee5de685ut2dpjkgmf4vg6h56n3w4k82emtde585u35xeh8jvn3vfskgtn0de5k7m30qqs93v545xjl0w8865rhw7kte0mkjxst88rk3k3xj53q4zdxm2zu5ectdn2z6) | N/A | N/A |
| nostr.fractalized.net | Free relay for fractalized.net | ws://xvgox2zzo7cfxcjrd2llrkthvjs5t7efoalu34s6lmkqhvzvrms6ipyd.onion | [operator](nostr:npub1ky4kxtyg0uxgw8g5p5mmedh8c8s6sqny6zmaaqj44gv4rk0plaus3m4fd2) | N/A | N/A |
| nfrelay.app | [nfrelay.app](https://nfrelay.app) aggregator relay (nostr-filter-relay) | ws://nfrelay6saohkmipikquvrn6d64dzxivhmcdcj4d5i7wxis47xwsriyd.onion | [operator](nostr:npub19dn7fq9hlxwjsdtgf28hyakcdmd73cccaf2u7a7vl42echey7ezs2hwja7) | N/A | N/A
| relay.nostr.net | Public relay from nostr.net (Same as clearnet) | ws://nostrnetl6yd5whkldj3vqsxyyaq3tkuspy23a3qgx7cdepb4564qgqd.onion | [operator](https://nostr.at/aljaz@nostr.si) | N/A | N/A |
| nerostrator | Free to read, pay XMR to relay | ws://nerostrrgb5fhj6dnzhjbgmnkpy2berdlczh6tuh2jsqrjok3j4zoxid.onion | [operator](nostr:npub19j7zhftjfjnep4xa7zxhevschkqdvem9zr26dq4myhu6d62p3gqs3htnca) |[Payment URL](http://nerostrrgb5fhj6dnzhjbgmnkpy2berdlczh6tuh2jsqrjok3j4zoxid.onion) | XMR |
| nostr.girino.org | Public relay from nostr.girino.org | ws://gnostr2jnapk72mnagq3cuykfon73temzp77hcbncn4silgt77boruid.onion | [operator](nostr:npub18lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vets0hcfsz) | N/A | N/A |
| wot.girino.org | WoT relay from wot.girino.org | ws://girwot2koy3kvj6fk7oseoqazp5vwbeawocb3m27jcqtah65f2fkl3yd.onion | [operator](nostr:npub18lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vets0hcfsz) | N/A | N/A |
| haven.girino.org/{outbox, inbox, chat, private} | Haven smart relay from haven.girino.org | ws://ghaven2hi3qn2riitw7ymaztdpztrvmm337e2pgkacfh3rnscaoxjoad.onion/{outbox, inbox, chat, private} | [operator](nostr:npub18lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vets0hcfsz) | N/A | N/A |
| relay.nostpy.lol | Free Web of Trust relay (Same as clearnet) | ws://pemgkkqjqjde7y2emc2hpxocexugbixp42o4zymznil6zfegx5nfp4id.onion | [operator](nostr:nprofile1qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshszxrhwden5te0dehhxarj9enx6apwwa5h5tnzd9az7qpqg5pm4gf8hh7skp2rsnw9h2pvkr32sdnuhkcx9yte7qxmrg6v4txqr5amve) |N/A | N/A |
| Poster.place Nostr Relay | N/A | ws://dmw5wbawyovz7fcahvguwkw4sknsqsalffwctioeoqkvvy7ygjbcuoad.onion | [operator](nostr:nprofile1qqsr836yylem9deatcu08ekfj8qj9f2aypq8ydt0w8dyng8zp8akjsqpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0ds6xxx6y) | N/A | N/A |
## Contributing
Contributions are encouraged to keep this document alive. Just open a PR and I'll have it tested and merged. The onion URL is the only mandatory column, the rest is just nice-to-have metadata about the relay. Put `N/A` in empty columns.
If you want to contribute anonymously, please contact me on [SimpleX](https://simplex.chat/contact#/?v=2&smp=smp%3A%2F%2F0YuTwO05YJWS8rkjn9eLJDjQhFKvIYd8d4xG8X1blIU%3D%40smp8.simplex.im%2FZ_4q0Nv91wCk8Uekyiaas7NSr-nEDir7%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAvdSLn5QEwrfKQswQGTzlwtXeLMXbzxErv-zOJU6D0y8%253D%26srv%3Dbeccx4yfxxbvyhqypaavemqurytl6hozr47wfc7uuecacjqdvwpw2xid.onion) or send a DM on nostr using a disposable npub.
### Operator column
It is generally preferred to use something that includes a NIP-19 string, either just the string or a url that contains the NIP-19 string in it (e.g. an njump url).
 @ 6be5cc06:5259daf0
2025-01-21 20:58:37A seguir, veja como instalar e configurar o **Privoxy** no **Pop!_OS**. --- ### **1. Instalar o Tor e o Privoxy** Abra o terminal e execute: ```bash sudo apt update sudo apt install tor privoxy ``` **Explicação:** - **Tor:** Roteia o tráfego pela rede Tor. - **Privoxy:** Proxy avançado que intermedia a conexão entre aplicativos e o Tor. --- ### **2. Configurar o Privoxy** Abra o arquivo de configuração do Privoxy: ```bash sudo nano /etc/privoxy/config ``` Navegue até a última linha (atalho: **`Ctrl`** + **`/`** depois **`Ctrl`** + **`V`** para navegar diretamente até a última linha) e insira: ```bash forward-socks5 / 127.0.0.1:9050 . ``` Isso faz com que o **Privoxy** envie todo o tráfego para o **Tor** através da porta **9050**. Salve (**`CTRL`** + **`O`** e **`Enter`**) e feche (**`CTRL`** + **`X`**) o arquivo. --- ### **3. Iniciar o Tor e o Privoxy** Agora, inicie e habilite os serviços: ```bash sudo systemctl start tor sudo systemctl start privoxy sudo systemctl enable tor sudo systemctl enable privoxy ``` **Explicação:** - **start:** Inicia os serviços. - **enable:** Faz com que iniciem automaticamente ao ligar o PC. --- ### **4. Configurar o Navegador Firefox** Para usar a rede **Tor** com o Firefox: 1. Abra o Firefox. 2. Acesse **Configurações** → **Configurar conexão**. 3. Selecione **Configuração manual de proxy**. 4. Configure assim: - **Proxy HTTP:** `127.0.0.1` - **Porta:** `8118` (porta padrão do **Privoxy**) - **Domínio SOCKS (v5):** `127.0.0.1` - **Porta:** `9050` 5. Marque a opção **"Usar este proxy também em HTTPS"**. 6. Clique em **OK**. --- ### **5. Verificar a Conexão com o Tor** Abra o navegador e acesse: ```text https://check.torproject.org/ ``` Se aparecer a mensagem **"Congratulations. This browser is configured to use Tor."**, a configuração está correta. --- ### **Dicas Extras** - **Privoxy** pode ser ajustado para bloquear anúncios e rastreadores. - Outros aplicativos também podem ser configurados para usar o **Privoxy**.
@ 6be5cc06:5259daf0
2025-01-21 20:58:37A seguir, veja como instalar e configurar o **Privoxy** no **Pop!_OS**. --- ### **1. Instalar o Tor e o Privoxy** Abra o terminal e execute: ```bash sudo apt update sudo apt install tor privoxy ``` **Explicação:** - **Tor:** Roteia o tráfego pela rede Tor. - **Privoxy:** Proxy avançado que intermedia a conexão entre aplicativos e o Tor. --- ### **2. Configurar o Privoxy** Abra o arquivo de configuração do Privoxy: ```bash sudo nano /etc/privoxy/config ``` Navegue até a última linha (atalho: **`Ctrl`** + **`/`** depois **`Ctrl`** + **`V`** para navegar diretamente até a última linha) e insira: ```bash forward-socks5 / 127.0.0.1:9050 . ``` Isso faz com que o **Privoxy** envie todo o tráfego para o **Tor** através da porta **9050**. Salve (**`CTRL`** + **`O`** e **`Enter`**) e feche (**`CTRL`** + **`X`**) o arquivo. --- ### **3. Iniciar o Tor e o Privoxy** Agora, inicie e habilite os serviços: ```bash sudo systemctl start tor sudo systemctl start privoxy sudo systemctl enable tor sudo systemctl enable privoxy ``` **Explicação:** - **start:** Inicia os serviços. - **enable:** Faz com que iniciem automaticamente ao ligar o PC. --- ### **4. Configurar o Navegador Firefox** Para usar a rede **Tor** com o Firefox: 1. Abra o Firefox. 2. Acesse **Configurações** → **Configurar conexão**. 3. Selecione **Configuração manual de proxy**. 4. Configure assim: - **Proxy HTTP:** `127.0.0.1` - **Porta:** `8118` (porta padrão do **Privoxy**) - **Domínio SOCKS (v5):** `127.0.0.1` - **Porta:** `9050` 5. Marque a opção **"Usar este proxy também em HTTPS"**. 6. Clique em **OK**. --- ### **5. Verificar a Conexão com o Tor** Abra o navegador e acesse: ```text https://check.torproject.org/ ``` Se aparecer a mensagem **"Congratulations. This browser is configured to use Tor."**, a configuração está correta. --- ### **Dicas Extras** - **Privoxy** pode ser ajustado para bloquear anúncios e rastreadores. - Outros aplicativos também podem ser configurados para usar o **Privoxy**. @ 16d11430:61640947
2025-01-21 20:40:22In a world drowning in Monopoly money, where people celebrate government-mandated inflation as "economic growth," it takes a special kind of clarity—nay, cynicism—to rise above the fiat circus. This is your guide to shedding your fiat f**ks and embracing the serene chaos of sound money, all while laughing at the absurdity of a world gone fiat-mad. --- 1. Don’t Feed the Clowns You know the clowns I’m talking about: central bankers in their tailored suits and smug smirks, wielding "tools" like interest rates and quantitative easing. Their tools are as real as a magician's wand, conjuring trillions of dollars out of thin air to keep their Ponzi economy afloat. Rule #1: Don’t engage. If a clown offers you a hot take about the "strength of the dollar," smile, nod, and silently wonder how many cups of coffee their paycheck buys this month. Spoiler: fewer than last month. --- 2. Turn Off the Fiat News Do you really need another breathless headline about the next trillion-dollar deficit? Or the latest clickbait on why you should care about the stock market's emotional rollercoaster? Mainstream media exists to distract you, to keep you tethered to their illusion of importance. Turn it off. Replace it with something sound, like the Bitcoin whitepaper. Or Nietzsche. At least Nietzsche knew we were doomed. --- 3. Mock Their Inflationary Gospel Fiat apologists will tell you that inflation is "necessary" and that 2% a year is a "healthy target." Sure, because a little robbery every year keeps society functioning, right? Ask them this: "If 2% is healthy, why not 20%? Why not 200%? Why not Venezuela?" Fiat logic is like a bad acid trip: entertaining at first, but it quickly spirals into existential horror. --- 4. Celebrate the Fiat Freakshow Sometimes, the best way to resist the fiat clown show is to revel in its absurdity. Watch politicians print money like teenagers running up a credit card bill at Hot Topic, then watch the economists applaud it as "stimulus." It’s performance art, really. Andy Warhol could never. --- 5. Build in the Chaos While the fiat world burns, Bitcoiners build. This is the ultimate "not giving a fiat f**k" move: creating a parallel economy, one satoshi at a time. Run your Lightning node, stack sats, and laugh as the fiat circus consumes itself in a flaming pile of its own debt. Let them argue about who gets to rearrange the deck chairs on the Titanic. You’re busy designing lifeboats. --- 6. Adopt a Fiat-Free Lifestyle Fiat-free living means minimizing your entanglement with their clown currency. Buy meat, not ETFs. Trade skills, not IOUs. Tip your barber in Bitcoin and ask if your landlord accepts Lightning. If they say no, chuckle and say, “You’ll learn soon enough.” Every satoshi spent in the real economy is a slap in the face to the fiat overlords. --- 7. Find the Humor in Collapse Here’s the thing: the fiat system is unsustainable. You know it, I know it, even the clowns know it. The whole charade is destined to collapse under its own weight. When it does, find solace in the absurdity of it all. Imagine the central bankers explaining hyperinflation to the public: "Turns out we can't print infinity after all." Pure comedy gold. --- 8. Stay Ruthlessly Optimistic Despite the doom and gloom, there’s hope. Bitcoin is hope. It’s the lifeboat for humanity, the cheat code to escape the fiat matrix. Cynicism doesn’t mean nihilism; it means seeing the rot for what it is and choosing to build something better. So, don’t just reject the fiat clown show—replace it. Create a world where money is sound, transactions are sovereign, and wealth is measured in energy, not debt. --- Final Thought: Burn the Tent Down Aldous Huxley once envisioned a dystopia where people are so distracted by their own hedonistic consumption that they don’t realize they’re enslaved. Sound familiar? The fiat clown show is Brave New World on steroids, a spectacle designed to keep you pacified while your wealth evaporates. But here’s the punchline: they can only enslave you if you care. By rejecting their system, you strip them of their power. So let them juggle their debts, inflate their bubbles, and print their trillions. You’ve got Bitcoin, and Bitcoin doesn’t give a fiat f**k. Welcome to the satirical resistance. Now go stack some sats.
@ 16d11430:61640947
2025-01-21 20:40:22In a world drowning in Monopoly money, where people celebrate government-mandated inflation as "economic growth," it takes a special kind of clarity—nay, cynicism—to rise above the fiat circus. This is your guide to shedding your fiat f**ks and embracing the serene chaos of sound money, all while laughing at the absurdity of a world gone fiat-mad. --- 1. Don’t Feed the Clowns You know the clowns I’m talking about: central bankers in their tailored suits and smug smirks, wielding "tools" like interest rates and quantitative easing. Their tools are as real as a magician's wand, conjuring trillions of dollars out of thin air to keep their Ponzi economy afloat. Rule #1: Don’t engage. If a clown offers you a hot take about the "strength of the dollar," smile, nod, and silently wonder how many cups of coffee their paycheck buys this month. Spoiler: fewer than last month. --- 2. Turn Off the Fiat News Do you really need another breathless headline about the next trillion-dollar deficit? Or the latest clickbait on why you should care about the stock market's emotional rollercoaster? Mainstream media exists to distract you, to keep you tethered to their illusion of importance. Turn it off. Replace it with something sound, like the Bitcoin whitepaper. Or Nietzsche. At least Nietzsche knew we were doomed. --- 3. Mock Their Inflationary Gospel Fiat apologists will tell you that inflation is "necessary" and that 2% a year is a "healthy target." Sure, because a little robbery every year keeps society functioning, right? Ask them this: "If 2% is healthy, why not 20%? Why not 200%? Why not Venezuela?" Fiat logic is like a bad acid trip: entertaining at first, but it quickly spirals into existential horror. --- 4. Celebrate the Fiat Freakshow Sometimes, the best way to resist the fiat clown show is to revel in its absurdity. Watch politicians print money like teenagers running up a credit card bill at Hot Topic, then watch the economists applaud it as "stimulus." It’s performance art, really. Andy Warhol could never. --- 5. Build in the Chaos While the fiat world burns, Bitcoiners build. This is the ultimate "not giving a fiat f**k" move: creating a parallel economy, one satoshi at a time. Run your Lightning node, stack sats, and laugh as the fiat circus consumes itself in a flaming pile of its own debt. Let them argue about who gets to rearrange the deck chairs on the Titanic. You’re busy designing lifeboats. --- 6. Adopt a Fiat-Free Lifestyle Fiat-free living means minimizing your entanglement with their clown currency. Buy meat, not ETFs. Trade skills, not IOUs. Tip your barber in Bitcoin and ask if your landlord accepts Lightning. If they say no, chuckle and say, “You’ll learn soon enough.” Every satoshi spent in the real economy is a slap in the face to the fiat overlords. --- 7. Find the Humor in Collapse Here’s the thing: the fiat system is unsustainable. You know it, I know it, even the clowns know it. The whole charade is destined to collapse under its own weight. When it does, find solace in the absurdity of it all. Imagine the central bankers explaining hyperinflation to the public: "Turns out we can't print infinity after all." Pure comedy gold. --- 8. Stay Ruthlessly Optimistic Despite the doom and gloom, there’s hope. Bitcoin is hope. It’s the lifeboat for humanity, the cheat code to escape the fiat matrix. Cynicism doesn’t mean nihilism; it means seeing the rot for what it is and choosing to build something better. So, don’t just reject the fiat clown show—replace it. Create a world where money is sound, transactions are sovereign, and wealth is measured in energy, not debt. --- Final Thought: Burn the Tent Down Aldous Huxley once envisioned a dystopia where people are so distracted by their own hedonistic consumption that they don’t realize they’re enslaved. Sound familiar? The fiat clown show is Brave New World on steroids, a spectacle designed to keep you pacified while your wealth evaporates. But here’s the punchline: they can only enslave you if you care. By rejecting their system, you strip them of their power. So let them juggle their debts, inflate their bubbles, and print their trillions. You’ve got Bitcoin, and Bitcoin doesn’t give a fiat f**k. Welcome to the satirical resistance. Now go stack some sats. @ c230edd3:8ad4a712
2025-01-23 00:26:14When beechen buds begin to swell, And woods the blue-bird’s warble know, The yellow violet’s modest bell Peeps from the last year’s leaves below. Ere russet fields their green resume, Sweet flower, I love, in forest bare, To meet thee, when thy faint perfume Alone is in the virgin air. Of all her train, the hands of Spring First plant thee in the watery mould, And I have seen thee blossoming Beside the snow-bank’s edges cold. Thy parent sun, who bade thee view Pale skies, and chilling moisture sip, Has bathed thee in his own bright hue, And streaked with jet thy glowing lip. Yet slight thy form, and low thy seat, And earthward bent thy gentle eye, Unapt the passing view to meet When loftier flowers are flaunting nigh. Oft, in the sunless April day, Thy early smile has stayed my walk; But midst the gorgeous blooms of May, I passed thee on thy humble stalk. So they, who climb to wealth, forget The friends in darker fortunes tried. I copied them—but I regret That I should ape the ways of pride. And when again the genial hour Awakes the painted tribes of light, I’ll not o’erlook the modest flower That made the woods of April bright.
@ c230edd3:8ad4a712
2025-01-23 00:26:14When beechen buds begin to swell, And woods the blue-bird’s warble know, The yellow violet’s modest bell Peeps from the last year’s leaves below. Ere russet fields their green resume, Sweet flower, I love, in forest bare, To meet thee, when thy faint perfume Alone is in the virgin air. Of all her train, the hands of Spring First plant thee in the watery mould, And I have seen thee blossoming Beside the snow-bank’s edges cold. Thy parent sun, who bade thee view Pale skies, and chilling moisture sip, Has bathed thee in his own bright hue, And streaked with jet thy glowing lip. Yet slight thy form, and low thy seat, And earthward bent thy gentle eye, Unapt the passing view to meet When loftier flowers are flaunting nigh. Oft, in the sunless April day, Thy early smile has stayed my walk; But midst the gorgeous blooms of May, I passed thee on thy humble stalk. So they, who climb to wealth, forget The friends in darker fortunes tried. I copied them—but I regret That I should ape the ways of pride. And when again the genial hour Awakes the painted tribes of light, I’ll not o’erlook the modest flower That made the woods of April bright. @ 4c96d763:80c3ee30
2025-01-23 00:05:26# Changes ## Ken Sedgwick (5): - drive-by clippy fixes - add add relay GUI - add Accounts::add_advertised_relay - upgrade url string to RelaySpec for [read|write] markers - publish NIP-65 relay lists ## William Casarin (7): - persistent: dont nuke decks when using cli columns - envrc: update vrod's npub for testing - note: introduce RootNoteId - enostr: introduce PubkeyRef - mutes: hide logs - debug: log when adding notes to start - switch to TimelineCache ## greenart7c3 (1): - Fix side panel color when using light theme ## kernelkind (2): - log nip05 error - fix persist deck author profile bug ## kieran (4): - note-ref: derive hash - move `Notedeck` to `notedeck` crate - export enostr / nostrdb - Always update accounts pushed to [notedeck:refs/heads/master](http://git.jb55.com/notedeck/commit/2cbae68a7f1425997f66d5ac0662f5cfde172f4f.html)
@ 4c96d763:80c3ee30
2025-01-23 00:05:26# Changes ## Ken Sedgwick (5): - drive-by clippy fixes - add add relay GUI - add Accounts::add_advertised_relay - upgrade url string to RelaySpec for [read|write] markers - publish NIP-65 relay lists ## William Casarin (7): - persistent: dont nuke decks when using cli columns - envrc: update vrod's npub for testing - note: introduce RootNoteId - enostr: introduce PubkeyRef - mutes: hide logs - debug: log when adding notes to start - switch to TimelineCache ## greenart7c3 (1): - Fix side panel color when using light theme ## kernelkind (2): - log nip05 error - fix persist deck author profile bug ## kieran (4): - note-ref: derive hash - move `Notedeck` to `notedeck` crate - export enostr / nostrdb - Always update accounts pushed to [notedeck:refs/heads/master](http://git.jb55.com/notedeck/commit/2cbae68a7f1425997f66d5ac0662f5cfde172f4f.html) @ c230edd3:8ad4a712
2025-01-22 23:52:14To him who in the love of Nature holds Communion with her visible forms, she speaks A various language; for his gayer hours She has a voice of gladness, and a smile And eloquence of beauty, and she glides Into his darker musings, with a mild And healing sympathy, that steals away Their sharpness, ere he is aware. When thoughts Of the last bitter hour come like a blight Over thy spirit, and sad images Of the stern agony, and shroud, and pall, And breathless darkness, and the narrow house, Make thee to shudder, and grow sick at heart;— Go forth, under the open sky, and list To Nature’s teachings, while from all around— Earth and her waters, and the depths of air— Comes a still voice— Yet a few days, and thee The all-beholding sun shall see no more In all his course; nor yet in the cold ground, Where thy pale form was laid, with many tears, Nor in the embrace of ocean, shall exist Thy image. Earth, that nourished thee, shall claim Thy growth, to be resolved to earth again, And, lost each human trace, surrendering up Thine individual being, shalt thou go To mix for ever with the elements, To be a brother to the insensible rock And to the sluggish clod, which the rude swain Turns with his share, and treads upon. The oak Shall send his roots abroad, and pierce thy mould. Yet not to thine eternal resting-place Shalt thou retire alone, nor couldst thou wish Couch more magnificent. Thou shalt lie down With patriarchs of the infant world—with kings, The powerful of the earth—the wise, the good, Fair forms, and hoary seers of ages past, All in one mighty sepulchre. The hills Rock-ribbed and ancient as the sun,—the vales Stretching in pensive quietness between; The venerable woods—rivers that move In majesty, and the complaining brooks That make the meadows green; and, poured round all, Old Ocean’s gray and melancholy waste,— Are but the solemn decorations all Of the great tomb of man. The golden sun, The planets, all the infinite host of heaven, Are shining on the sad abodes of death, Through the still lapse of ages. All that tread The globe are but a handful to the tribes That slumber in its bosom.—Take the wings Of morning, pierce the Barcan wilderness, Or lose thyself in the continuous woods Where rolls the Oregon, and hears no sound, Save his own dashings—yet the dead are there: And millions in those solitudes, since first The flight of years began, have laid them down In their last sleep—the dead reign there alone. So shalt thou rest, and what if thou withdraw In silence from the living, and no friend Take note of thy departure? All that breathe Will share thy destiny. The gay will laugh When thou art gone, the solemn brood of care Plod on, and each one as before will chase His favorite phantom; yet all these shall leave Their mirth and their employments, and shall come And make their bed with thee. As the long train Of ages glide away, the sons of men, The youth in life’s green spring, and he who goes In the full strength of years, matron and maid, The speechless babe, and the gray-headed man— Shall one by one be gathered to thy side, By those, who in their turn shall follow them. So live, that when thy summons comes to join The innumerable caravan, which moves To that mysterious realm, where each shall take His chamber in the silent halls of death, Thou go not, like the quarry-slave at night, Scourged to his dungeon, but, sustained and soothed By an unfaltering trust, approach thy grave, Like one who wraps the drapery of his couch About him, and lies down to pleasant dreams.
@ c230edd3:8ad4a712
2025-01-22 23:52:14To him who in the love of Nature holds Communion with her visible forms, she speaks A various language; for his gayer hours She has a voice of gladness, and a smile And eloquence of beauty, and she glides Into his darker musings, with a mild And healing sympathy, that steals away Their sharpness, ere he is aware. When thoughts Of the last bitter hour come like a blight Over thy spirit, and sad images Of the stern agony, and shroud, and pall, And breathless darkness, and the narrow house, Make thee to shudder, and grow sick at heart;— Go forth, under the open sky, and list To Nature’s teachings, while from all around— Earth and her waters, and the depths of air— Comes a still voice— Yet a few days, and thee The all-beholding sun shall see no more In all his course; nor yet in the cold ground, Where thy pale form was laid, with many tears, Nor in the embrace of ocean, shall exist Thy image. Earth, that nourished thee, shall claim Thy growth, to be resolved to earth again, And, lost each human trace, surrendering up Thine individual being, shalt thou go To mix for ever with the elements, To be a brother to the insensible rock And to the sluggish clod, which the rude swain Turns with his share, and treads upon. The oak Shall send his roots abroad, and pierce thy mould. Yet not to thine eternal resting-place Shalt thou retire alone, nor couldst thou wish Couch more magnificent. Thou shalt lie down With patriarchs of the infant world—with kings, The powerful of the earth—the wise, the good, Fair forms, and hoary seers of ages past, All in one mighty sepulchre. The hills Rock-ribbed and ancient as the sun,—the vales Stretching in pensive quietness between; The venerable woods—rivers that move In majesty, and the complaining brooks That make the meadows green; and, poured round all, Old Ocean’s gray and melancholy waste,— Are but the solemn decorations all Of the great tomb of man. The golden sun, The planets, all the infinite host of heaven, Are shining on the sad abodes of death, Through the still lapse of ages. All that tread The globe are but a handful to the tribes That slumber in its bosom.—Take the wings Of morning, pierce the Barcan wilderness, Or lose thyself in the continuous woods Where rolls the Oregon, and hears no sound, Save his own dashings—yet the dead are there: And millions in those solitudes, since first The flight of years began, have laid them down In their last sleep—the dead reign there alone. So shalt thou rest, and what if thou withdraw In silence from the living, and no friend Take note of thy departure? All that breathe Will share thy destiny. The gay will laugh When thou art gone, the solemn brood of care Plod on, and each one as before will chase His favorite phantom; yet all these shall leave Their mirth and their employments, and shall come And make their bed with thee. As the long train Of ages glide away, the sons of men, The youth in life’s green spring, and he who goes In the full strength of years, matron and maid, The speechless babe, and the gray-headed man— Shall one by one be gathered to thy side, By those, who in their turn shall follow them. So live, that when thy summons comes to join The innumerable caravan, which moves To that mysterious realm, where each shall take His chamber in the silent halls of death, Thou go not, like the quarry-slave at night, Scourged to his dungeon, but, sustained and soothed By an unfaltering trust, approach thy grave, Like one who wraps the drapery of his couch About him, and lies down to pleasant dreams. @ 3b70689a:c1e351eb
2025-01-22 23:47:36来自西班牙的公司 Liberux 最近推出了他们的新手机 Liberux NEXX 众筹计划. 根据[目前主页](http://archive.today/2025.01.22-142040/https://liberux.net/)上的介绍, 这款设备将会搭载基于 Debian 13 ARM 构建的 LiberuxOS 操作系统, 并且还提供一个受限的(jailed)的 Android 子系统.  - [Liberux (@Liberux@mastodon.social\) - Mastodon](https://mastodon.social/@Liberux) > Liberux 的 Fediverse 主页 - [TX4RLY (@BUF0@mastodon.social\) - Mastodon](https://mastodon.social/@BUF0) > Liberux 硬件开发工程师 Carlos Rodríguez 的 Fediverse 主页 Carlos Rodríguez 说, 目前网站上的 NEXX 是最初版本, 目前仍然在努力制造第一台原型机, 并且所有的硬件和软件设计都将免费(公开). > WOW, I think our little secret has been revealed, we hope that in a short time you will be able to see the first functional prototypes. We are working very hard on it, by the way, all our designs, both hardware and software, will be free. At the moment the web is a first version, some things will be modified. > > —— [TX4RLY: "@linmob @awai WOW, I think ou…" - Mastodon](https://mastodon.social/@BUF0/113861097147727059) ## 硬件参数 - **CPU**: 瑞芯微 RK3588s (八核心, 8nm, 2.4Ghz, 2022Q1) - **GPU**: ARM Mali-G610 (4 核心, 2021Q2) - **存储**: 32GB LPDDR4x RAM, 256GB eMMC ROM - **电池**: 5300mAh (可拆卸) - **接口**: 3.5mm 耳机 * 1, USB-C 3.1 * 2 - **扩展**: microSD 插槽 (2TB Max) - **屏幕**: 6.34 吋, OLED, 2400*1080 - **相机**: 后置 32MP, 前置 13MP - **通讯**: 高通骁龙 X62 基带 (2021Q1), 海华 AW-CM256SM 无线网卡 (Wi-Fi 5, 蓝牙 5.0) - **传感器**: 昇佳 STK3311-X 环境光传感器, 美新 MMC3630KJ 三轴磁传感器, 应美盛 ICM-42670-P 加速度计/陀螺仪 - **其他**: 内置 DAC 和功放芯片 (瑞昱 ALC5640-VB-CG, 艾为 AW8737SCSR) ## 其他特点 设备目前公布的外观设计均是渲染效果, 最终交付的设备很可能会与这些渲染图片有很大出入. 但仍然可以通过这些效果图理解 Liberux 的最初意图. - 摄像头 & 麦克风, 蓝牙 & WLAN, 数据网络功能模块的物理开关(位于顶部).  - 后置指纹解锁, 无摄像模组凸起.  - 左上角挖孔前置摄像头.  - 电源键位于侧边右下角. ## 其他报道 - [Liberux Nexx: New Linux smartphone with 32GB RAM, 2TB storage, 5G and more - NotebookCheck.net News](https://www.notebookcheck.net/Liberux-Nexx-New-Linux-smartphone-with-32GB-RAM-2TB-storage-5G-and-more.950866.0.html) - [Смартфон Liberux Nexx получил ОС Linux и поддержку 2 ТБ памяти - 4PDA ](https://4pda.to/2025/01/22/437737/smartfon_liberux_nexx_poluchil_os_linux_i_podderzhku_2_tb_pamyati/)(讨论) - [Smartfon z Linuksem? Oto Liberux NEXX. Ekran OLED, 32 GB RAM i system oparty na Debianie. Ciekawy model, choć nie bez wad | PurePC.pl](https://www.purepc.pl/smartfon-z-linuksem-oto-liberux-nexx-ekran-oled-32-gb-ram-i-system-oparty-na-debianie-ciekawy-model-choc-nie-bez-wad) (讨论) - [LINux on MOBile: "The Liberux Nexx \(https://libe…" - Fosstodon](https://fosstodon.org/@linmob/113860953049449923) (Fediverse, 讨论, 工程师回复)
@ 3b70689a:c1e351eb
2025-01-22 23:47:36来自西班牙的公司 Liberux 最近推出了他们的新手机 Liberux NEXX 众筹计划. 根据[目前主页](http://archive.today/2025.01.22-142040/https://liberux.net/)上的介绍, 这款设备将会搭载基于 Debian 13 ARM 构建的 LiberuxOS 操作系统, 并且还提供一个受限的(jailed)的 Android 子系统.  - [Liberux (@Liberux@mastodon.social\) - Mastodon](https://mastodon.social/@Liberux) > Liberux 的 Fediverse 主页 - [TX4RLY (@BUF0@mastodon.social\) - Mastodon](https://mastodon.social/@BUF0) > Liberux 硬件开发工程师 Carlos Rodríguez 的 Fediverse 主页 Carlos Rodríguez 说, 目前网站上的 NEXX 是最初版本, 目前仍然在努力制造第一台原型机, 并且所有的硬件和软件设计都将免费(公开). > WOW, I think our little secret has been revealed, we hope that in a short time you will be able to see the first functional prototypes. We are working very hard on it, by the way, all our designs, both hardware and software, will be free. At the moment the web is a first version, some things will be modified. > > —— [TX4RLY: "@linmob @awai WOW, I think ou…" - Mastodon](https://mastodon.social/@BUF0/113861097147727059) ## 硬件参数 - **CPU**: 瑞芯微 RK3588s (八核心, 8nm, 2.4Ghz, 2022Q1) - **GPU**: ARM Mali-G610 (4 核心, 2021Q2) - **存储**: 32GB LPDDR4x RAM, 256GB eMMC ROM - **电池**: 5300mAh (可拆卸) - **接口**: 3.5mm 耳机 * 1, USB-C 3.1 * 2 - **扩展**: microSD 插槽 (2TB Max) - **屏幕**: 6.34 吋, OLED, 2400*1080 - **相机**: 后置 32MP, 前置 13MP - **通讯**: 高通骁龙 X62 基带 (2021Q1), 海华 AW-CM256SM 无线网卡 (Wi-Fi 5, 蓝牙 5.0) - **传感器**: 昇佳 STK3311-X 环境光传感器, 美新 MMC3630KJ 三轴磁传感器, 应美盛 ICM-42670-P 加速度计/陀螺仪 - **其他**: 内置 DAC 和功放芯片 (瑞昱 ALC5640-VB-CG, 艾为 AW8737SCSR) ## 其他特点 设备目前公布的外观设计均是渲染效果, 最终交付的设备很可能会与这些渲染图片有很大出入. 但仍然可以通过这些效果图理解 Liberux 的最初意图. - 摄像头 & 麦克风, 蓝牙 & WLAN, 数据网络功能模块的物理开关(位于顶部).  - 后置指纹解锁, 无摄像模组凸起.  - 左上角挖孔前置摄像头.  - 电源键位于侧边右下角. ## 其他报道 - [Liberux Nexx: New Linux smartphone with 32GB RAM, 2TB storage, 5G and more - NotebookCheck.net News](https://www.notebookcheck.net/Liberux-Nexx-New-Linux-smartphone-with-32GB-RAM-2TB-storage-5G-and-more.950866.0.html) - [Смартфон Liberux Nexx получил ОС Linux и поддержку 2 ТБ памяти - 4PDA ](https://4pda.to/2025/01/22/437737/smartfon_liberux_nexx_poluchil_os_linux_i_podderzhku_2_tb_pamyati/)(讨论) - [Smartfon z Linuksem? Oto Liberux NEXX. Ekran OLED, 32 GB RAM i system oparty na Debianie. Ciekawy model, choć nie bez wad | PurePC.pl](https://www.purepc.pl/smartfon-z-linuksem-oto-liberux-nexx-ekran-oled-32-gb-ram-i-system-oparty-na-debianie-ciekawy-model-choc-nie-bez-wad) (讨论) - [LINux on MOBile: "The Liberux Nexx \(https://libe…" - Fosstodon](https://fosstodon.org/@linmob/113860953049449923) (Fediverse, 讨论, 工程师回复) @ c54f9c60:7c34249a
2025-01-22 22:12:51In October 2018, Arjun Balaji asked the innocuous question, _What have you learned from Bitcoin?_ After trying to answer this question in a short tweet, and failing miserably, I realized that the things I've learned are far too numerous to answer quickly, if at all. The things I've learned are, obviously, about Bitcoin - or at least related to it. However, while some of the inner workings of Bitcoin are explained, the following lessons are not an explanation of how Bitcoin works or what it is, they might, however, help to explore some of the things Bitcoin touches: philosophical questions, economic realities, and technological innovations. The 21 lessons are structured in bundles of seven, resulting in three chapters. Each chapter looks at Bitcoin through a different lens, extracting what lessons can be learned by inspecting this strange network from a different angle. [Chapter 1][chapter1] explores the philosophical teachings of Bitcoin. The interplay of immutability and change, the concept of true scarcity, Bitcoin's immaculate conception, the problem of identity, the contradiction of replication and locality, the power of free speech, and the limits of knowledge. [Chapter 2][chapter2] explores the economic teachings of Bitcoin. Lessons about financial ignorance, inflation, value, money and the history of money, fractional reserve banking, and how Bitcoin is re-introducing sound money in a sly, roundabout way. [Chapter 3][chapter3] explores some of the lessons learned by examining the technology of Bitcoin. Why there is strength in numbers, reflections on trust, why telling time takes work, how moving slowly and not breaking things is a feature and not a bug, what Bitcoin's creation can tell us about privacy, why cypherpunks write code (and not laws), and what metaphors might be useful to explore Bitcoin's future. Each lesson contains several quotes and links throughout the text. If I have explored an idea in more detail, you can find links to my related works in the "Through the Looking-Glass" section. If you like to go deeper, links to the most relevant material are listed in the "Down the Rabbit Hole" section. Both can be found at the end of each lesson. Even though some prior knowledge about Bitcoin is beneficial, I hope that these lessons can be digested by any curious reader. While some relate to each other, each lesson should be able to stand on its own and can be read independently. I did my best to shy away from technical jargon, even though some domain-specific vocabulary is unavoidable. I hope that my writing serves as inspiration for others to dig beneath the surface and examine some of the deeper questions Bitcoin raises. My own inspiration came from a multitude of authors and content creators to all of whom I am eternally grateful. Last but not least: my goal in writing this is not to convince you of anything. My goal is to make you think, and show you that there is way more to Bitcoin than meets the eye. I can’t even tell you what Bitcoin is or what Bitcoin will teach you. You will have to find that out for yourself. > "After this, there is no turning back. You take the blue pill —the > story ends, you wake up in your bed and believe whatever you want to > believe. You take the red pill— you stay in Wonderland, and I show > you how deep the rabbit hole goes." > > —[Morpheus][Morpheus]  [Morpheus]: https://en.wikipedia.org/wiki/Red_pill_and_blue_pill#The_Matrix_(1999) [this question]: https://twitter.com/arjunblj/status/1050073234719293440 [chapter1]: https://dergigi.com/2018/12/21/philosophical-teachings-of-bitcoin/ [chapter2]: https://dergigi.com/2019/01/11/economic-teachings-of-bitcoin/ [chapter3]: https://dergigi.com/2019/04/02/technological-teachings-of-bitcoin/ [alice]: https://en.wikipedia.org/wiki/Alice%27s_Adventures_in_Wonderland [carroll]: https://en.wikipedia.org/wiki/Lewis_Carroll
@ c54f9c60:7c34249a
2025-01-22 22:12:51In October 2018, Arjun Balaji asked the innocuous question, _What have you learned from Bitcoin?_ After trying to answer this question in a short tweet, and failing miserably, I realized that the things I've learned are far too numerous to answer quickly, if at all. The things I've learned are, obviously, about Bitcoin - or at least related to it. However, while some of the inner workings of Bitcoin are explained, the following lessons are not an explanation of how Bitcoin works or what it is, they might, however, help to explore some of the things Bitcoin touches: philosophical questions, economic realities, and technological innovations. The 21 lessons are structured in bundles of seven, resulting in three chapters. Each chapter looks at Bitcoin through a different lens, extracting what lessons can be learned by inspecting this strange network from a different angle. [Chapter 1][chapter1] explores the philosophical teachings of Bitcoin. The interplay of immutability and change, the concept of true scarcity, Bitcoin's immaculate conception, the problem of identity, the contradiction of replication and locality, the power of free speech, and the limits of knowledge. [Chapter 2][chapter2] explores the economic teachings of Bitcoin. Lessons about financial ignorance, inflation, value, money and the history of money, fractional reserve banking, and how Bitcoin is re-introducing sound money in a sly, roundabout way. [Chapter 3][chapter3] explores some of the lessons learned by examining the technology of Bitcoin. Why there is strength in numbers, reflections on trust, why telling time takes work, how moving slowly and not breaking things is a feature and not a bug, what Bitcoin's creation can tell us about privacy, why cypherpunks write code (and not laws), and what metaphors might be useful to explore Bitcoin's future. Each lesson contains several quotes and links throughout the text. If I have explored an idea in more detail, you can find links to my related works in the "Through the Looking-Glass" section. If you like to go deeper, links to the most relevant material are listed in the "Down the Rabbit Hole" section. Both can be found at the end of each lesson. Even though some prior knowledge about Bitcoin is beneficial, I hope that these lessons can be digested by any curious reader. While some relate to each other, each lesson should be able to stand on its own and can be read independently. I did my best to shy away from technical jargon, even though some domain-specific vocabulary is unavoidable. I hope that my writing serves as inspiration for others to dig beneath the surface and examine some of the deeper questions Bitcoin raises. My own inspiration came from a multitude of authors and content creators to all of whom I am eternally grateful. Last but not least: my goal in writing this is not to convince you of anything. My goal is to make you think, and show you that there is way more to Bitcoin than meets the eye. I can’t even tell you what Bitcoin is or what Bitcoin will teach you. You will have to find that out for yourself. > "After this, there is no turning back. You take the blue pill —the > story ends, you wake up in your bed and believe whatever you want to > believe. You take the red pill— you stay in Wonderland, and I show > you how deep the rabbit hole goes." > > —[Morpheus][Morpheus]  [Morpheus]: https://en.wikipedia.org/wiki/Red_pill_and_blue_pill#The_Matrix_(1999) [this question]: https://twitter.com/arjunblj/status/1050073234719293440 [chapter1]: https://dergigi.com/2018/12/21/philosophical-teachings-of-bitcoin/ [chapter2]: https://dergigi.com/2019/01/11/economic-teachings-of-bitcoin/ [chapter3]: https://dergigi.com/2019/04/02/technological-teachings-of-bitcoin/ [alice]: https://en.wikipedia.org/wiki/Alice%27s_Adventures_in_Wonderland [carroll]: https://en.wikipedia.org/wiki/Lewis_Carroll @ c54f9c60:7c34249a
2025-01-22 21:48:30Falling down the Bitcoin rabbit hole is a strange experience. Like many others, I feel like I have learned more in the last couple of years studying Bitcoin than I have during two decades of formal education. The following lessons are a distillation of what I’ve learned. First published as an article series titled [“What I’ve Learned From Bitcoin,”][I] what follows can be seen as a second edition of the original series. Like Bitcoin, these lessons aren't a static thing. I plan to work on them periodically, releasing updated versions and additional material in the future. Unlike Bitcoin, future versions of this project do not have to be backward compatible. Some lessons might be extended, others might be reworked or replaced. I hope that a future version will be something you can hold in your hands, but I don’t want to promise anything just yet. Bitcoin is an inexhaustible teacher, which is why I do not claim that these lessons are all-encompassing or complete. They are a reflection of my personal journey down the rabbit hole. There are many more lessons to be learned, and every person will learn something different from entering the world of Bitcoin. I hope that you will find these lessons useful and that the process of learning them by reading won’t be as arduous and painful as learning them firsthand. nostr:npub1dergggklka99wwrs92yz8wdjs952h2ux2ha2ed598ngwu9w7a6fsh9xzpc <!-- Internal --> [I]: https://dergigi.com/2018/12/21/philosophical-teachings-of-bitcoin/
@ c54f9c60:7c34249a
2025-01-22 21:48:30Falling down the Bitcoin rabbit hole is a strange experience. Like many others, I feel like I have learned more in the last couple of years studying Bitcoin than I have during two decades of formal education. The following lessons are a distillation of what I’ve learned. First published as an article series titled [“What I’ve Learned From Bitcoin,”][I] what follows can be seen as a second edition of the original series. Like Bitcoin, these lessons aren't a static thing. I plan to work on them periodically, releasing updated versions and additional material in the future. Unlike Bitcoin, future versions of this project do not have to be backward compatible. Some lessons might be extended, others might be reworked or replaced. I hope that a future version will be something you can hold in your hands, but I don’t want to promise anything just yet. Bitcoin is an inexhaustible teacher, which is why I do not claim that these lessons are all-encompassing or complete. They are a reflection of my personal journey down the rabbit hole. There are many more lessons to be learned, and every person will learn something different from entering the world of Bitcoin. I hope that you will find these lessons useful and that the process of learning them by reading won’t be as arduous and painful as learning them firsthand. nostr:npub1dergggklka99wwrs92yz8wdjs952h2ux2ha2ed598ngwu9w7a6fsh9xzpc <!-- Internal --> [I]: https://dergigi.com/2018/12/21/philosophical-teachings-of-bitcoin/ @ 9e69e420:d12360c2
2025-01-21 19:31:48Oregano oil is a potent natural compound that offers numerous scientifically-supported health benefits. ## Active Compounds The oil's therapeutic properties stem from its key bioactive components: - Carvacrol and thymol (primary active compounds) - Polyphenols and other antioxidant ## Antimicrobial Properties **Bacterial Protection** The oil demonstrates powerful antibacterial effects, even against antibiotic-resistant strains like MRSA and other harmful bacteria. Studies show it effectively inactivates various pathogenic bacteria without developing resistance. **Antifungal Effects** It effectively combats fungal infections, particularly Candida-related conditions like oral thrush, athlete's foot, and nail infections. ## Digestive Health Benefits Oregano oil supports digestive wellness by: - Promoting gastric juice secretion and enzyme production - Helping treat Small Intestinal Bacterial Overgrowth (SIBO) - Managing digestive discomfort, bloating, and IBS symptoms ## Anti-inflammatory and Antioxidant Effects The oil provides significant protective benefits through: - Powerful antioxidant activity that fights free radicals - Reduction of inflammatory markers in the body - Protection against oxidative stress-related conditions ## Respiratory Support It aids respiratory health by: - Loosening mucus and phlegm - Suppressing coughs and throat irritation - Supporting overall respiratory tract function ## Additional Benefits **Skin Health** - Improves conditions like psoriasis, acne, and eczema - Supports wound healing through antibacterial action - Provides anti-aging benefits through antioxidant properties **Cardiovascular Health** Studies show oregano oil may help: - Reduce LDL (bad) cholesterol levels - Support overall heart health **Pain Management** The oil demonstrates effectiveness in: - Reducing inflammation-related pain - Managing muscle discomfort - Providing topical pain relief ## Safety Note While oregano oil is generally safe, it's highly concentrated and should be properly diluted before use Consult a healthcare provider before starting supplementation, especially if taking other medications.
@ 9e69e420:d12360c2
2025-01-21 19:31:48Oregano oil is a potent natural compound that offers numerous scientifically-supported health benefits. ## Active Compounds The oil's therapeutic properties stem from its key bioactive components: - Carvacrol and thymol (primary active compounds) - Polyphenols and other antioxidant ## Antimicrobial Properties **Bacterial Protection** The oil demonstrates powerful antibacterial effects, even against antibiotic-resistant strains like MRSA and other harmful bacteria. Studies show it effectively inactivates various pathogenic bacteria without developing resistance. **Antifungal Effects** It effectively combats fungal infections, particularly Candida-related conditions like oral thrush, athlete's foot, and nail infections. ## Digestive Health Benefits Oregano oil supports digestive wellness by: - Promoting gastric juice secretion and enzyme production - Helping treat Small Intestinal Bacterial Overgrowth (SIBO) - Managing digestive discomfort, bloating, and IBS symptoms ## Anti-inflammatory and Antioxidant Effects The oil provides significant protective benefits through: - Powerful antioxidant activity that fights free radicals - Reduction of inflammatory markers in the body - Protection against oxidative stress-related conditions ## Respiratory Support It aids respiratory health by: - Loosening mucus and phlegm - Suppressing coughs and throat irritation - Supporting overall respiratory tract function ## Additional Benefits **Skin Health** - Improves conditions like psoriasis, acne, and eczema - Supports wound healing through antibacterial action - Provides anti-aging benefits through antioxidant properties **Cardiovascular Health** Studies show oregano oil may help: - Reduce LDL (bad) cholesterol levels - Support overall heart health **Pain Management** The oil demonstrates effectiveness in: - Reducing inflammation-related pain - Managing muscle discomfort - Providing topical pain relief ## Safety Note While oregano oil is generally safe, it's highly concentrated and should be properly diluted before use Consult a healthcare provider before starting supplementation, especially if taking other medications. @ b17fccdf:b7211155
2025-01-21 18:30:13~ > Available at: [https://minibolt.info](https://minibolt.info) --- ~> It builds on a personal computer with **x86/amd64** architecture processors. ~> It is based on the popular [RaspiBolt v3](https://raspibolt.org) guide. --- **Those are some of the most relevant changes:** * Changed OS from Raspberry Pi OS Lite (64-bits) to ***Ubuntu Server LTS*** (Long term support) 64-bit PC (AMD64). * Changed binaries and signatures of the programs to adapt them to ***x86/amd64 architecture***. * Deleted unnecessary tools and steps, and added others according to this case of use. * Some useful authentication logs and monitoring commands were added in the security section. * Added some interesting parameters in the settings of some services to activate and take advantage of new features. * Changed I2P, Fulcrum, and ThunderHub guides, to be part of the core guide. * Added exclusive optimization section of services for slow devices. --- ~ > Complete release notes of the MiniBolt v1: [https://github.com/twofaktor/minibolt/releases/tag/1.0](https://github.com/twofaktor/minibolt/releases/tag/1.0). ~ > Feel free to contribute to the [source code on GitHub](https://github.com/minibolt-guide/minibolt) by opening [issues](https://github.com/minibolt-guide/minibolt/issues), [pull requests](https://github.com/minibolt-guide/minibolt/pulls) or [discussions](https://github.com/orgs/minibolt-guide/discussions). --- Created by [⚡2 FakTor⚡](nostr:npub1k9luehc8hg3c0upckdzzvusv66x3zt0eyw7290kclrpsndepz92sfcpp63)
@ b17fccdf:b7211155
2025-01-21 18:30:13~ > Available at: [https://minibolt.info](https://minibolt.info) --- ~> It builds on a personal computer with **x86/amd64** architecture processors. ~> It is based on the popular [RaspiBolt v3](https://raspibolt.org) guide. --- **Those are some of the most relevant changes:** * Changed OS from Raspberry Pi OS Lite (64-bits) to ***Ubuntu Server LTS*** (Long term support) 64-bit PC (AMD64). * Changed binaries and signatures of the programs to adapt them to ***x86/amd64 architecture***. * Deleted unnecessary tools and steps, and added others according to this case of use. * Some useful authentication logs and monitoring commands were added in the security section. * Added some interesting parameters in the settings of some services to activate and take advantage of new features. * Changed I2P, Fulcrum, and ThunderHub guides, to be part of the core guide. * Added exclusive optimization section of services for slow devices. --- ~ > Complete release notes of the MiniBolt v1: [https://github.com/twofaktor/minibolt/releases/tag/1.0](https://github.com/twofaktor/minibolt/releases/tag/1.0). ~ > Feel free to contribute to the [source code on GitHub](https://github.com/minibolt-guide/minibolt) by opening [issues](https://github.com/minibolt-guide/minibolt/issues), [pull requests](https://github.com/minibolt-guide/minibolt/pulls) or [discussions](https://github.com/orgs/minibolt-guide/discussions). --- Created by [⚡2 FakTor⚡](nostr:npub1k9luehc8hg3c0upckdzzvusv66x3zt0eyw7290kclrpsndepz92sfcpp63) @ b17fccdf:b7211155
2025-01-21 18:22:51😱 Did you recently find this signature verification error when you tried to update your MiniBolt repositories with -> `sudo apt update`? 💥🚨👇  🔧 Don't worry, that's because Tor renewed its signing key since it expired last 07/15, just renew your keyring by following the next steps to solve this problem: ~ > [CLICK HERE](https://minibolt.minibolt.info/system/system/privacy#tor-signature-verification-error) < ~ --- Enjoy it MiniBolter!💙
@ b17fccdf:b7211155
2025-01-21 18:22:51😱 Did you recently find this signature verification error when you tried to update your MiniBolt repositories with -> `sudo apt update`? 💥🚨👇  🔧 Don't worry, that's because Tor renewed its signing key since it expired last 07/15, just renew your keyring by following the next steps to solve this problem: ~ > [CLICK HERE](https://minibolt.minibolt.info/system/system/privacy#tor-signature-verification-error) < ~ --- Enjoy it MiniBolter!💙 @ b17fccdf:b7211155
2025-01-21 18:10:10**Link to the bonus guide** ~ > [HERE](https://minibolt.minibolt.info/bonus-guides/bitcoin/minibolt-on-testnet) <~ --- Some notes: ℹ️ For the moment, this guide will touch only the case of an **only testnet mode** situation, in the future, we will study adding the case of configuration to enable the parallel/simultaneous mode (mainnet+testnet in the same device) in an extra section in this guide. ℹ️ The services mentioned in this guide are those that have been tested using testnet configuration and these worked fine. Later, in the next versions of this guide, we will go to adding other processes to adapt other services to the testnet mode. --- Enjoy it MiniBolter! 💙
@ b17fccdf:b7211155
2025-01-21 18:10:10**Link to the bonus guide** ~ > [HERE](https://minibolt.minibolt.info/bonus-guides/bitcoin/minibolt-on-testnet) <~ --- Some notes: ℹ️ For the moment, this guide will touch only the case of an **only testnet mode** situation, in the future, we will study adding the case of configuration to enable the parallel/simultaneous mode (mainnet+testnet in the same device) in an extra section in this guide. ℹ️ The services mentioned in this guide are those that have been tested using testnet configuration and these worked fine. Later, in the next versions of this guide, we will go to adding other processes to adapt other services to the testnet mode. --- Enjoy it MiniBolter! 💙 @ b17fccdf:b7211155
2025-01-21 18:04:28Available at: [https://minibolt.info](https://minibolt.info) --- **Main changes to** the version 1: * The complete guide has been migrated to the new design visual builder web tool platform [gitbook.com](https://www.gitbook.com/) * New modern UI (responsive, full width, and better visual items) * New menu structure for a better user experience * New visual items to improve the navigation through the web page * New switch to enable light/dark theme * Enabled Cloudflare Proxy for maximum protection against attacks and better management of the domain --- **Other changes:** * New [MiniBolt Linktr](https://linktr.minibolt.info/) forked of the alternative [FOSS project](https://github.com/gzuuus/linktr) proposed by [Gzuuus](https://twitter.com/gzuuus) * Changed MiniBolt from a personal project to an [organization](https://github.com/minibolt-guide) so that the project has its own identity * New email contact address [hello@minibolt.info](mailto:hello@minibolt.info) to receive proposals and give support * New [resources](https://github.com/minibolt-guide/minibolt/tree/main/resources) folder with the current MiniBolt roadmap, network map diagrams, and others --- ℹ️ **More info:** * The new version is available with the known domain: [minibolt.info](https://minibolt.info/) but from now on links associated with the new v2 version were shared using the [v2.minibolt.info](https://v2.minibolt.info/) subdomain due to a GitBook limitation * The old and deprecated v1 will be still available at a time in the subdomain [v1.minibolt.info](https://v1.minibolt.info/), but is in the roadmap delete it definitely in the future, take note ASAP of all that you need of that version before this happens * Contributors and collaborators will be able to continue doing PR through code programming or using the design block builder [gitbook.com](https://www.gitbook.com/) --- [GitHub release](https://github.com/minibolt-guide/minibolt/releases/tag/2.0) --- Enjoy it MiniBolter! 💙
@ b17fccdf:b7211155
2025-01-21 18:04:28Available at: [https://minibolt.info](https://minibolt.info) --- **Main changes to** the version 1: * The complete guide has been migrated to the new design visual builder web tool platform [gitbook.com](https://www.gitbook.com/) * New modern UI (responsive, full width, and better visual items) * New menu structure for a better user experience * New visual items to improve the navigation through the web page * New switch to enable light/dark theme * Enabled Cloudflare Proxy for maximum protection against attacks and better management of the domain --- **Other changes:** * New [MiniBolt Linktr](https://linktr.minibolt.info/) forked of the alternative [FOSS project](https://github.com/gzuuus/linktr) proposed by [Gzuuus](https://twitter.com/gzuuus) * Changed MiniBolt from a personal project to an [organization](https://github.com/minibolt-guide) so that the project has its own identity * New email contact address [hello@minibolt.info](mailto:hello@minibolt.info) to receive proposals and give support * New [resources](https://github.com/minibolt-guide/minibolt/tree/main/resources) folder with the current MiniBolt roadmap, network map diagrams, and others --- ℹ️ **More info:** * The new version is available with the known domain: [minibolt.info](https://minibolt.info/) but from now on links associated with the new v2 version were shared using the [v2.minibolt.info](https://v2.minibolt.info/) subdomain due to a GitBook limitation * The old and deprecated v1 will be still available at a time in the subdomain [v1.minibolt.info](https://v1.minibolt.info/), but is in the roadmap delete it definitely in the future, take note ASAP of all that you need of that version before this happens * Contributors and collaborators will be able to continue doing PR through code programming or using the design block builder [gitbook.com](https://www.gitbook.com/) --- [GitHub release](https://github.com/minibolt-guide/minibolt/releases/tag/2.0) --- Enjoy it MiniBolter! 💙 @ b17fccdf:b7211155
2025-01-21 17:58:35The **router reserves the IP address** of the device **for a time after going out**, but if the device goes out some time, the next time that the device starts, the router could assign a different IP and you could lose access to your node. To avoid this, you need to **set a static IP to your MiniBolt**. ~ > In addition, you can **customize your DNS servers to improve your privacy**, normally your ISP, gives you the router with its own DNS servers set by default, and this does that you expose all of your navigation trackings to your ISP, affecting seriously your privacy. ~ > This bonus guide includes all of the necessary steps to get this and is available ~ > [HERE](https://minibolt.minibolt.info/bonus-guides/system/static-ip-and-custom-dns-servers) < ~ ---  --- Enjoy it MiniBolter! 💙
@ b17fccdf:b7211155
2025-01-21 17:58:35The **router reserves the IP address** of the device **for a time after going out**, but if the device goes out some time, the next time that the device starts, the router could assign a different IP and you could lose access to your node. To avoid this, you need to **set a static IP to your MiniBolt**. ~ > In addition, you can **customize your DNS servers to improve your privacy**, normally your ISP, gives you the router with its own DNS servers set by default, and this does that you expose all of your navigation trackings to your ISP, affecting seriously your privacy. ~ > This bonus guide includes all of the necessary steps to get this and is available ~ > [HERE](https://minibolt.minibolt.info/bonus-guides/system/static-ip-and-custom-dns-servers) < ~ ---  --- Enjoy it MiniBolter! 💙 @ b17fccdf:b7211155
2025-01-21 17:47:28Link to the bonus guide ~ > [HERE](https://minibolt.minibolt.info/bonus-guides/system/ssh-keys) < ~ --- Some sections of the guide: * Generate SSH keys * Import SSH pubkey * Connect to the MiniBolt node using SSH keys * Disable password login * Disable admin password request --- Some shortcuts to the Extra sections: * Disable password login: click ~ > [HERE](https://minibolt.minibolt.info/bonus-guides/system/ssh-keys#disable-password-login) < ~ * Disable admin password request: click ~ > [HERE](https://minibolt.minibolt.info/bonus-guides/system/ssh-keys#disable-admin-password-request-caution) < ~ --- Enjoy it MiniBolter! 💙
@ b17fccdf:b7211155
2025-01-21 17:47:28Link to the bonus guide ~ > [HERE](https://minibolt.minibolt.info/bonus-guides/system/ssh-keys) < ~ --- Some sections of the guide: * Generate SSH keys * Import SSH pubkey * Connect to the MiniBolt node using SSH keys * Disable password login * Disable admin password request --- Some shortcuts to the Extra sections: * Disable password login: click ~ > [HERE](https://minibolt.minibolt.info/bonus-guides/system/ssh-keys#disable-password-login) < ~ * Disable admin password request: click ~ > [HERE](https://minibolt.minibolt.info/bonus-guides/system/ssh-keys#disable-admin-password-request-caution) < ~ --- Enjoy it MiniBolter! 💙 @ b17fccdf:b7211155
2025-01-21 17:39:34**Link to the bonus guide** ~ > [HERE](https://minibolt.minibolt.info/bonus-guides/bitcoin/ordisrespector) < ~ --- ⏰ Recently added an update that includes a new section **[How to detect Ordinals transactions](https://minibolt.minibolt.info/bonus-guides/bitcoin/ordisrespector#how-to-detect-ordinals-transactions) and [verify Ordisrespector filter works](https://minibolt.minibolt.info/bonus-guides/bitcoin/ordisrespector#check-the-ordisrespector-filter-working-on-your-mempool)** to verify that Ordispector is **filtering and burning Ordinals** correctly 🔥 --- Fuck Ordinals🤡🔫 and enjoy it MiniBolter! 💙
@ b17fccdf:b7211155
2025-01-21 17:39:34**Link to the bonus guide** ~ > [HERE](https://minibolt.minibolt.info/bonus-guides/bitcoin/ordisrespector) < ~ --- ⏰ Recently added an update that includes a new section **[How to detect Ordinals transactions](https://minibolt.minibolt.info/bonus-guides/bitcoin/ordisrespector#how-to-detect-ordinals-transactions) and [verify Ordisrespector filter works](https://minibolt.minibolt.info/bonus-guides/bitcoin/ordisrespector#check-the-ordisrespector-filter-working-on-your-mempool)** to verify that Ordispector is **filtering and burning Ordinals** correctly 🔥 --- Fuck Ordinals🤡🔫 and enjoy it MiniBolter! 💙 @ b17fccdf:b7211155
2025-01-21 17:29:54Some sections inside of the guide: * Set up Dynamic DNS * Wireguard VPN server & client side configurations * Install & configure the WireGuard VPN Client on a mobile phone * Configure additional servers & clients * Use your router’s DDNS preconfigured provider * Port forwarding on NAT/PAT router --- Link to the bonus guide [HERE](https://minibolt.minibolt.info/bonus-guides/system/wireguard-vpn) --- Enjoy it MiniBolter! 💙
@ b17fccdf:b7211155
2025-01-21 17:29:54Some sections inside of the guide: * Set up Dynamic DNS * Wireguard VPN server & client side configurations * Install & configure the WireGuard VPN Client on a mobile phone * Configure additional servers & clients * Use your router’s DDNS preconfigured provider * Port forwarding on NAT/PAT router --- Link to the bonus guide [HERE](https://minibolt.minibolt.info/bonus-guides/system/wireguard-vpn) --- Enjoy it MiniBolter! 💙 @ b17fccdf:b7211155
2025-01-21 17:19:12Do you want to use a different disk to store data (blockchain and other databases) independently of the disk of the system? A step-by-step guide using a secondary disk to store the data (blockchain and other databases) independently of the disk of the system and using the Ubuntu Server guided installation. --- ### **What's changed** * Rebuilt the [Ubuntu Server installation guide](https://minibolt.minibolt.info/system/system/operating-system#ubuntu-server-installation) based on this bonus guide added. * Added GIFs to improve the illustration of the steps to follow. * [Case 1](https://minibolt.minibolt.info/bonus-guides/system/static-ip-and-custom-dns-servers#option-1-at-the-beginning-during-the-ubuntu-server-installation-gui): during the Ubuntu server guided installation. * [Case 2](https://minibolt.minibolt.info/bonus-guides/system/static-ip-and-custom-dns-servers#option-2-after-ubuntu-server-installation-by-command-line): build it after system installation (by command line). --- ~ > Link to the bonus guide [HERE](https://minibolt.minibolt.info/bonus-guides/system/store-data-secondary-disk) --- Enjoy it MiniBolter! 💙
@ b17fccdf:b7211155
2025-01-21 17:19:12Do you want to use a different disk to store data (blockchain and other databases) independently of the disk of the system? A step-by-step guide using a secondary disk to store the data (blockchain and other databases) independently of the disk of the system and using the Ubuntu Server guided installation. --- ### **What's changed** * Rebuilt the [Ubuntu Server installation guide](https://minibolt.minibolt.info/system/system/operating-system#ubuntu-server-installation) based on this bonus guide added. * Added GIFs to improve the illustration of the steps to follow. * [Case 1](https://minibolt.minibolt.info/bonus-guides/system/static-ip-and-custom-dns-servers#option-1-at-the-beginning-during-the-ubuntu-server-installation-gui): during the Ubuntu server guided installation. * [Case 2](https://minibolt.minibolt.info/bonus-guides/system/static-ip-and-custom-dns-servers#option-2-after-ubuntu-server-installation-by-command-line): build it after system installation (by command line). --- ~ > Link to the bonus guide [HERE](https://minibolt.minibolt.info/bonus-guides/system/store-data-secondary-disk) --- Enjoy it MiniBolter! 💙 @ 35f3a26c:92ddf231
2025-01-22 20:48:34### Background Most people non familiar with Bitcoin thinks that there its has not smart contracts capabilities, and that is incorrect, there are smart contract capabilities, and despite limited in comparison with other blockchain networks, those capabilities are evolving slowly but surely. The support for smart contracts is done through its scripting language, Script, which allows developers to create complex conditions for transactions. **What can you do with Script?** 1. time locks 2. multi-signature requirements 3. other custom logic opcodes like OP_CHECKLOCKTIMEVERIFY (CLTV) and OP_CHECKSEQUENCEVERIFY (CSV) are used to build more sophisticated smart contracts, these opcodes enable features such as the Lightning Network, a key scaling solution for Bitcoin back in 2021, the ***Taproot ***upgrade introduced Pay-to-Taproot (P2TR), in summary allows for more private and efficient smart contracts, in that soft fork more was added, in addition to Taproot, we got as well ***Schnorr signatures***, which enables multiple signatures to be aggregated into a single signature, improving scalability and privacy and ***MAST (Merklized Abstract Syntax Trees)*** which reduces the size of complex smart contracts, making them more efficient, as an added value, this efficiency reduces the cost of transactions. The ***Taproot ***upgrade has laid the foundation for the development of more sophisticated smart contracts on the Bitcoin network, and the use of covenants is an important part of this development. ### What is Bitcoin Covenants? It is a **BIP** (Bitcoin Improvement Proposal), **BIP-347**, assigned on April 24, 2024, which marks the first step towards reintroducing functionality removed from Bitcoin by its creator Satoshi Nakamoto in 2010. This proposal aims to bring smart contract functionality to Bitcoin as we see in other EVM networks. The proposal’s developers authors names are **Ethan Heilman** and **Armin Sabouri**, now the community will debate its merits. Here the link, in case you are curious: ***[https://github.com/bitcoin/bips/blob/master/bip-0347.mediawiki](https://github.com/bitcoin/bips/blob/master/bip-0347.mediawiki)*** It is worth to read the motivation section of the BIP, which reads: “Bitcoin Tapscript lacks a general purpose way of combining objects on the stack, restricting the expressiveness and power of Tapscript. This prevents, among many other things, the ability to construct and evaluate merkle trees and other hashed data structures in Tapscript. OP_CAT, by adding a general purpose way to concatenate stack values, would overcome this limitation and greatly increase the functionality of Tapscript. OP_CAT aims to expand the toolbox of the tapscript developer with a simple, modular, and useful opcode in the spirit of Unix. To demonstrate the usefulness of OP_CAT below we provide a non-exhaustive list of some use cases that OP_CAT would enable: Bitstream, a protocol for the atomic swap (fair exchange) of bitcoins for decryption keys, that enables decentralized file hosting systems paid in Bitcoin. While such swaps are currently possible on Bitcoin without OP_CAT, they require the use of complex and computationally expensive Verifiable Computation cryptographic techniques. OP_CAT would remove this requirement on Verifiable Computation, making such protocols far more practical to build in Bitcoin. Tree signatures provide a multisignature script whose size can be logarithmic in the number of public keys and can encode spend conditions beyond n-of-m. For instance a transaction less than 1KB in size could support tree signatures with up to 4,294,967,296 public keys. This also enables generalized logical spend conditions. Post-Quantum Lamport signatures in Bitcoin transactions. Lamport signatures merely require the ability to hash and concatenate values on the stack. [4] It has been proposed that if ECDSA is broken or a powerful computer was on the horizon, there might be an effort to protect ownership of bitcoins by allowing people to mark their taproot outputs as "script-path only" and then move their coins into such outputs with a leaf in the script tree requiring a Lamport signature. It is an open question if a tapscript commitment would preserve the quantum resistance of Lamport signatures. Beyond this question, the use of Lamport Signatures in taproot outputs is unlikely to be quantum resistant even if the script spend-path is made quantum resistant. This is because taproot outputs can also be spent with a key. An attacker with a sufficiently powerful quantum computer could bypass the taproot script spend-path by finding the discrete log of the taproot output and thus spending the output using the key spend-path. The use of "Nothing Up My Sleeve" (NUMS) points as described in BIP-341 to disable the key spend-path does not disable the key spend-path against a quantum attacker as NUMS relies on the hardness of finding discrete logs. We are not aware of any mechanism which could disable the key spend-path in a taproot output without a soft-fork change to taproot. Non-equivocation contracts in tapscript provide a mechanism to punish equivocation/double spending in Bitcoin payment channels. OP_CAT enables this by enforcing rules on the spending transaction's nonce. The capability is a useful building block for payment channels and other Bitcoin protocols. Vaults [6] which are a specialized covenant that allows a user to block a malicious party who has compromised the user's secret key from stealing the funds in that output. As shown in OP_CAT is sufficient to build vaults in Bitcoin. Replicating CheckSigFromStack which would allow the creation of simple covenants and other advanced contracts without having to pre-sign spending transactions, possibly reducing complexity and the amount of data that needs to be stored. Originally shown to work with Schnorr signatures, this result has been extended to ECDSA signatures. OP_CAT was available in early versions of Bitcoin. In 2010, a single commit disabled OP_CAT, along with another 15 opcodes. Folklore states that OP_CAT was removed in this commit because it enabled the construction of a script whose evaluation could have memory usage exponential in the size of the script. For example, a script that pushed a 1-byte value on the stack and then repeated the opcodes OP_DUP, OP_CAT 40 times would result in a stack element whose size was greater than 1 terabyte assuming no maximum stack element size. As Bitcoin at that time had a maximum stack element size of 5000 bytes, the effect of this expansion was limited to 5000 bytes. This is no longer an issue because tapscript enforces a maximum stack element size of 520 bytes.” The last update of the BIP was done on Sep. 8 2024 by Ethan Heilman ### Controversy The controversy revolves around two main camps: 1. Those who want to preserve Bitcoin’s network for monetary transactions only, arguing that adding smart contract capabilities could introduce risks and complexity. 2. Others who advocate for expanding Bitcoin’s capabilities to support a wider range of applications, seeing OP_CAT as a step towards enhancing the network’s utility. ### Final Thoughts  Bitcoin have done what no other asset have done in history, neither gold, its success is clear, and now, that BlackRock is involved, “miraculously”, corporations and governments are getting on board and Bitcoin is not anymore only for criminals or “rat poison” or “is going to zero”. But as all tech, improvements are important, if those improvements are done to secure more the network and to make it more robust, there will be little to none controversy, however, when those changes are aiming at adding new shinning features that would change Bitcoin into a network with similar features as Ethereum in terms of contracts that requires attention and debate, few questions come to mind: 1. How will that change affect the security of the network? 2. How that change will affect the blockchain usage? 3. What is the projected impact over the fees per transaction if this change is approved? 4. Will the impact create pressure for the block size increase discussion to come back to the table and with it a second war? Looking into Ethan Heilman work and contribution to the Bitcoin ecosystem, I am inclined to believe that he has considered most of those questions. Looking forward to observe the evolution of this proposal. #### You liked the article? Make my day brighter! Like and share! Last but not least, the following link is an unstoppable domain, it will open a page in which you can perform an anonymous contribution to support my work: [https://rodswallet.unstoppable/](https://rodswallet.unstoppable/) The link didn’t open? To open the link you need to use a best in class browser that supports web3, two are recommended: Brave Browser and Opera Browser
@ 35f3a26c:92ddf231
2025-01-22 20:48:34### Background Most people non familiar with Bitcoin thinks that there its has not smart contracts capabilities, and that is incorrect, there are smart contract capabilities, and despite limited in comparison with other blockchain networks, those capabilities are evolving slowly but surely. The support for smart contracts is done through its scripting language, Script, which allows developers to create complex conditions for transactions. **What can you do with Script?** 1. time locks 2. multi-signature requirements 3. other custom logic opcodes like OP_CHECKLOCKTIMEVERIFY (CLTV) and OP_CHECKSEQUENCEVERIFY (CSV) are used to build more sophisticated smart contracts, these opcodes enable features such as the Lightning Network, a key scaling solution for Bitcoin back in 2021, the ***Taproot ***upgrade introduced Pay-to-Taproot (P2TR), in summary allows for more private and efficient smart contracts, in that soft fork more was added, in addition to Taproot, we got as well ***Schnorr signatures***, which enables multiple signatures to be aggregated into a single signature, improving scalability and privacy and ***MAST (Merklized Abstract Syntax Trees)*** which reduces the size of complex smart contracts, making them more efficient, as an added value, this efficiency reduces the cost of transactions. The ***Taproot ***upgrade has laid the foundation for the development of more sophisticated smart contracts on the Bitcoin network, and the use of covenants is an important part of this development. ### What is Bitcoin Covenants? It is a **BIP** (Bitcoin Improvement Proposal), **BIP-347**, assigned on April 24, 2024, which marks the first step towards reintroducing functionality removed from Bitcoin by its creator Satoshi Nakamoto in 2010. This proposal aims to bring smart contract functionality to Bitcoin as we see in other EVM networks. The proposal’s developers authors names are **Ethan Heilman** and **Armin Sabouri**, now the community will debate its merits. Here the link, in case you are curious: ***[https://github.com/bitcoin/bips/blob/master/bip-0347.mediawiki](https://github.com/bitcoin/bips/blob/master/bip-0347.mediawiki)*** It is worth to read the motivation section of the BIP, which reads: “Bitcoin Tapscript lacks a general purpose way of combining objects on the stack, restricting the expressiveness and power of Tapscript. This prevents, among many other things, the ability to construct and evaluate merkle trees and other hashed data structures in Tapscript. OP_CAT, by adding a general purpose way to concatenate stack values, would overcome this limitation and greatly increase the functionality of Tapscript. OP_CAT aims to expand the toolbox of the tapscript developer with a simple, modular, and useful opcode in the spirit of Unix. To demonstrate the usefulness of OP_CAT below we provide a non-exhaustive list of some use cases that OP_CAT would enable: Bitstream, a protocol for the atomic swap (fair exchange) of bitcoins for decryption keys, that enables decentralized file hosting systems paid in Bitcoin. While such swaps are currently possible on Bitcoin without OP_CAT, they require the use of complex and computationally expensive Verifiable Computation cryptographic techniques. OP_CAT would remove this requirement on Verifiable Computation, making such protocols far more practical to build in Bitcoin. Tree signatures provide a multisignature script whose size can be logarithmic in the number of public keys and can encode spend conditions beyond n-of-m. For instance a transaction less than 1KB in size could support tree signatures with up to 4,294,967,296 public keys. This also enables generalized logical spend conditions. Post-Quantum Lamport signatures in Bitcoin transactions. Lamport signatures merely require the ability to hash and concatenate values on the stack. [4] It has been proposed that if ECDSA is broken or a powerful computer was on the horizon, there might be an effort to protect ownership of bitcoins by allowing people to mark their taproot outputs as "script-path only" and then move their coins into such outputs with a leaf in the script tree requiring a Lamport signature. It is an open question if a tapscript commitment would preserve the quantum resistance of Lamport signatures. Beyond this question, the use of Lamport Signatures in taproot outputs is unlikely to be quantum resistant even if the script spend-path is made quantum resistant. This is because taproot outputs can also be spent with a key. An attacker with a sufficiently powerful quantum computer could bypass the taproot script spend-path by finding the discrete log of the taproot output and thus spending the output using the key spend-path. The use of "Nothing Up My Sleeve" (NUMS) points as described in BIP-341 to disable the key spend-path does not disable the key spend-path against a quantum attacker as NUMS relies on the hardness of finding discrete logs. We are not aware of any mechanism which could disable the key spend-path in a taproot output without a soft-fork change to taproot. Non-equivocation contracts in tapscript provide a mechanism to punish equivocation/double spending in Bitcoin payment channels. OP_CAT enables this by enforcing rules on the spending transaction's nonce. The capability is a useful building block for payment channels and other Bitcoin protocols. Vaults [6] which are a specialized covenant that allows a user to block a malicious party who has compromised the user's secret key from stealing the funds in that output. As shown in OP_CAT is sufficient to build vaults in Bitcoin. Replicating CheckSigFromStack which would allow the creation of simple covenants and other advanced contracts without having to pre-sign spending transactions, possibly reducing complexity and the amount of data that needs to be stored. Originally shown to work with Schnorr signatures, this result has been extended to ECDSA signatures. OP_CAT was available in early versions of Bitcoin. In 2010, a single commit disabled OP_CAT, along with another 15 opcodes. Folklore states that OP_CAT was removed in this commit because it enabled the construction of a script whose evaluation could have memory usage exponential in the size of the script. For example, a script that pushed a 1-byte value on the stack and then repeated the opcodes OP_DUP, OP_CAT 40 times would result in a stack element whose size was greater than 1 terabyte assuming no maximum stack element size. As Bitcoin at that time had a maximum stack element size of 5000 bytes, the effect of this expansion was limited to 5000 bytes. This is no longer an issue because tapscript enforces a maximum stack element size of 520 bytes.” The last update of the BIP was done on Sep. 8 2024 by Ethan Heilman ### Controversy The controversy revolves around two main camps: 1. Those who want to preserve Bitcoin’s network for monetary transactions only, arguing that adding smart contract capabilities could introduce risks and complexity. 2. Others who advocate for expanding Bitcoin’s capabilities to support a wider range of applications, seeing OP_CAT as a step towards enhancing the network’s utility. ### Final Thoughts  Bitcoin have done what no other asset have done in history, neither gold, its success is clear, and now, that BlackRock is involved, “miraculously”, corporations and governments are getting on board and Bitcoin is not anymore only for criminals or “rat poison” or “is going to zero”. But as all tech, improvements are important, if those improvements are done to secure more the network and to make it more robust, there will be little to none controversy, however, when those changes are aiming at adding new shinning features that would change Bitcoin into a network with similar features as Ethereum in terms of contracts that requires attention and debate, few questions come to mind: 1. How will that change affect the security of the network? 2. How that change will affect the blockchain usage? 3. What is the projected impact over the fees per transaction if this change is approved? 4. Will the impact create pressure for the block size increase discussion to come back to the table and with it a second war? Looking into Ethan Heilman work and contribution to the Bitcoin ecosystem, I am inclined to believe that he has considered most of those questions. Looking forward to observe the evolution of this proposal. #### You liked the article? Make my day brighter! Like and share! Last but not least, the following link is an unstoppable domain, it will open a page in which you can perform an anonymous contribution to support my work: [https://rodswallet.unstoppable/](https://rodswallet.unstoppable/) The link didn’t open? To open the link you need to use a best in class browser that supports web3, two are recommended: Brave Browser and Opera Browser @ b17fccdf:b7211155
2025-01-21 17:07:47**Link to the bonus guide** ~> [HERE](https://minibolt.minibolt.info/bonus-guides/bitcoin/btcpay-server) < ~ --- Enjoy it MiniBolter! 💙
@ b17fccdf:b7211155
2025-01-21 17:07:47**Link to the bonus guide** ~> [HERE](https://minibolt.minibolt.info/bonus-guides/bitcoin/btcpay-server) < ~ --- Enjoy it MiniBolter! 💙 @ f33c8a96:5ec6f741
2025-01-22 20:38:02<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/V-7u7bJccSM?enablejsapi=1" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
@ f33c8a96:5ec6f741
2025-01-22 20:38:02<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/V-7u7bJccSM?enablejsapi=1" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div> @ 4506e04e:8c16ba04
2025-01-22 16:37:08If you are a researcher in the field of medicine, you are most likely very familiar with PubMed – where you get citations for the articles and studies that drive your work forward. PubMed Central (PMC), the full-text repository of life sciences journal literature managed by the National Library of Medicine (NLM), was established in 2000. Its creation marked a significant milestone in providing open access to biomedical research. Since 2005, PMC has served as the designated repository for papers submitted under the NIH Public Access Policy, reflecting the growing emphasis on transparency and accessibility in scientific research. Over the years, PMC has expanded its scope, becoming a repository for papers aligned with public and open access policies from various research funding organizations, both within and beyond biomedical sciences. ## Funding and Partnerships NLM’s operations, including PubMed and PMC, are supported by a combination of government funding and contributions from influential entities such as The Bill & Melinda Gates Foundation. The Bill and Melinda Gates Foundation receives significant donations from pharmaceutical companies, as well as other organizations and individuals. The exact amount of money donated by each company can vary from year to year, but here are some examples of the amounts donated by the pharmaceutical companies: **GSK (GlaxoSmithKline):** - In 2020, GSK donated $100 million to the Gates Foundation to support the development of new vaccines and treatments for diseases such as malaria, tuberculosis, and HIV/AIDS. - In 2019, GSK donated $50 million to the Gates Foundation to support the development of a new malaria vaccine. **Pfizer:** - In 2020, Pfizer donated $50 million to the Gates Foundation to support the development of new vaccines and treatments for diseases such as malaria, tuberculosis, and HIV/AIDS. - In 2019, Pfizer donated $25 million to the Gates Foundation to support the development of a new malaria vaccine. **Merck & Co.:** - In 2020, Merck donated $50 million to the Gates Foundation to support the development of new vaccines and treatments for diseases such as malaria, tuberculosis, and HIV/AIDS. - In 2019, Merck donated $25 million to the Gates Foundation to support the development of a new malaria vaccine. **Novartis:** - In 2020, Novartis donated $20 million to the Gates Foundation to support the development of new treatments for diseases such as malaria and tuberculosis. - In 2019, Novartis donated $10 million to the Gates Foundation to support the development of a new malaria vaccine. **Johnson & Johnson:** - In 2020, Johnson & Johnson donated $50 million to the Gates Foundation to support the development of new vaccines and treatments for diseases such as malaria, tuberculosis, and HIV/AIDS. - In 2019, Johnson & Johnson donated $25 million to the Gates Foundation to support the development of a new malaria vaccine. **Sanofi:** - In 2020, Sanofi donated $20 million to the Gates Foundation to support the development of new vaccines and treatments for diseases such as malaria and tuberculosis. - In 2019, Sanofi donated $10 million to the Gates Foundation to support the development of a new malaria vaccine. **AstraZeneca:** - In 2020, AstraZeneca donated $20 million to the Gates Foundation to support the development of new vaccines and treatments for diseases such as malaria and tuberculosis. - In 2019, AstraZeneca donated $10 million to the Gates Foundation to support the development of a new malaria vaccine. **Eli Lilly and Company:** - In 2020, Eli Lilly donated $10 million to the Gates Foundation to support the development of new treatments for diseases such as malaria and tuberculosis. - In 2019, Eli Lilly donated $5 million to the Gates Foundation to support the development of a new malaria vaccine. Additionally, NLM website [https://cdn.ncbi.nlm.nih.gov/pmc/cms/files/PMCFunderDepositList.xlsx] (list over 200)(!) organisations that are founding it. What could go wrong one might ask?! ## The Centralization Challenge While PubMed and PMC have played a pivotal role in democratizing access to scientific literature, their centralized nature presents vulnerabilities. Over the past century healthcare has grown to become one of the most profitable industries and to believe that the healthcare system we have today is the best we can do is far from understatement. PubMed's reliance on centralized funding and decision-making processes makes it susceptible to external influences, including lobbying by powerful entities. Moreover, the centralized infrastructure allows for content to be published and removed with relative ease, often without leaving a trace. This raises concerns about the integrity and permanence of the scientific record, particularly in contentious or politically sensitive areas of research. The ability to alter or erase information from PubMed undermines trust in the system’s objectivity and neutrality. Researchers and the public alike depend on these repositories for reliable and impartial access to scientific knowledge. Any perceived or actual manipulation of content can erode confidence in the platform and compromise its foundational mission. ## The Case for Decentralization To address these challenges, a decentralized alternative built on emerging technologies, such as the Nostr protocol, could offer significant advantages. A decentralized platform would: - **Enhance Resilience:** By distributing data across a network of relays, a decentralized system would eliminate single points of failure, ensuring the scientific record remains intact and always accessible even in the face of technical or political disruptions. - **Increase Transparency:** Decentralized systems inherently log changes, making it nearly impossible to alter or remove content without leaving an auditable trail. This transparency would bolster trust in the integrity of the research. - **Reduce Susceptibility to Lobbying:** Without centralized control, the influence of external entities on the platform’s content would be significantly diminished, preserving the objectivity of the scientific record. - **Foster Open Collaboration:** A decentralized approach aligns with the principles of open science, encouraging global collaboration without the constraints of centralized oversight or bias introduced by big pharma lobby. ## Conclusion While PubMed and PMC have been instrumental in advancing access to scientific literature, their centralized nature leaves them vulnerable to manipulation and external pressures. A shift toward a decentralized, censorship-resistant platform would address these vulnerabilities and provide a more robust and trustless repository for scientific knowledge. Groundbreaking research that dares to challenge the pharmaceutical industry's status quo could be published anonymously, following in the footsteps of the Bitcoin whitepaper's pseudonymous author, Satoshi Nakamoto. Leveraging technologies like the Nostr protocol, the research community can build a system that ensures the permanence, integrity, and impartiality of the scientific record for generations to come.
@ 4506e04e:8c16ba04
2025-01-22 16:37:08If you are a researcher in the field of medicine, you are most likely very familiar with PubMed – where you get citations for the articles and studies that drive your work forward. PubMed Central (PMC), the full-text repository of life sciences journal literature managed by the National Library of Medicine (NLM), was established in 2000. Its creation marked a significant milestone in providing open access to biomedical research. Since 2005, PMC has served as the designated repository for papers submitted under the NIH Public Access Policy, reflecting the growing emphasis on transparency and accessibility in scientific research. Over the years, PMC has expanded its scope, becoming a repository for papers aligned with public and open access policies from various research funding organizations, both within and beyond biomedical sciences. ## Funding and Partnerships NLM’s operations, including PubMed and PMC, are supported by a combination of government funding and contributions from influential entities such as The Bill & Melinda Gates Foundation. The Bill and Melinda Gates Foundation receives significant donations from pharmaceutical companies, as well as other organizations and individuals. The exact amount of money donated by each company can vary from year to year, but here are some examples of the amounts donated by the pharmaceutical companies: **GSK (GlaxoSmithKline):** - In 2020, GSK donated $100 million to the Gates Foundation to support the development of new vaccines and treatments for diseases such as malaria, tuberculosis, and HIV/AIDS. - In 2019, GSK donated $50 million to the Gates Foundation to support the development of a new malaria vaccine. **Pfizer:** - In 2020, Pfizer donated $50 million to the Gates Foundation to support the development of new vaccines and treatments for diseases such as malaria, tuberculosis, and HIV/AIDS. - In 2019, Pfizer donated $25 million to the Gates Foundation to support the development of a new malaria vaccine. **Merck & Co.:** - In 2020, Merck donated $50 million to the Gates Foundation to support the development of new vaccines and treatments for diseases such as malaria, tuberculosis, and HIV/AIDS. - In 2019, Merck donated $25 million to the Gates Foundation to support the development of a new malaria vaccine. **Novartis:** - In 2020, Novartis donated $20 million to the Gates Foundation to support the development of new treatments for diseases such as malaria and tuberculosis. - In 2019, Novartis donated $10 million to the Gates Foundation to support the development of a new malaria vaccine. **Johnson & Johnson:** - In 2020, Johnson & Johnson donated $50 million to the Gates Foundation to support the development of new vaccines and treatments for diseases such as malaria, tuberculosis, and HIV/AIDS. - In 2019, Johnson & Johnson donated $25 million to the Gates Foundation to support the development of a new malaria vaccine. **Sanofi:** - In 2020, Sanofi donated $20 million to the Gates Foundation to support the development of new vaccines and treatments for diseases such as malaria and tuberculosis. - In 2019, Sanofi donated $10 million to the Gates Foundation to support the development of a new malaria vaccine. **AstraZeneca:** - In 2020, AstraZeneca donated $20 million to the Gates Foundation to support the development of new vaccines and treatments for diseases such as malaria and tuberculosis. - In 2019, AstraZeneca donated $10 million to the Gates Foundation to support the development of a new malaria vaccine. **Eli Lilly and Company:** - In 2020, Eli Lilly donated $10 million to the Gates Foundation to support the development of new treatments for diseases such as malaria and tuberculosis. - In 2019, Eli Lilly donated $5 million to the Gates Foundation to support the development of a new malaria vaccine. Additionally, NLM website [https://cdn.ncbi.nlm.nih.gov/pmc/cms/files/PMCFunderDepositList.xlsx] (list over 200)(!) organisations that are founding it. What could go wrong one might ask?! ## The Centralization Challenge While PubMed and PMC have played a pivotal role in democratizing access to scientific literature, their centralized nature presents vulnerabilities. Over the past century healthcare has grown to become one of the most profitable industries and to believe that the healthcare system we have today is the best we can do is far from understatement. PubMed's reliance on centralized funding and decision-making processes makes it susceptible to external influences, including lobbying by powerful entities. Moreover, the centralized infrastructure allows for content to be published and removed with relative ease, often without leaving a trace. This raises concerns about the integrity and permanence of the scientific record, particularly in contentious or politically sensitive areas of research. The ability to alter or erase information from PubMed undermines trust in the system’s objectivity and neutrality. Researchers and the public alike depend on these repositories for reliable and impartial access to scientific knowledge. Any perceived or actual manipulation of content can erode confidence in the platform and compromise its foundational mission. ## The Case for Decentralization To address these challenges, a decentralized alternative built on emerging technologies, such as the Nostr protocol, could offer significant advantages. A decentralized platform would: - **Enhance Resilience:** By distributing data across a network of relays, a decentralized system would eliminate single points of failure, ensuring the scientific record remains intact and always accessible even in the face of technical or political disruptions. - **Increase Transparency:** Decentralized systems inherently log changes, making it nearly impossible to alter or remove content without leaving an auditable trail. This transparency would bolster trust in the integrity of the research. - **Reduce Susceptibility to Lobbying:** Without centralized control, the influence of external entities on the platform’s content would be significantly diminished, preserving the objectivity of the scientific record. - **Foster Open Collaboration:** A decentralized approach aligns with the principles of open science, encouraging global collaboration without the constraints of centralized oversight or bias introduced by big pharma lobby. ## Conclusion While PubMed and PMC have been instrumental in advancing access to scientific literature, their centralized nature leaves them vulnerable to manipulation and external pressures. A shift toward a decentralized, censorship-resistant platform would address these vulnerabilities and provide a more robust and trustless repository for scientific knowledge. Groundbreaking research that dares to challenge the pharmaceutical industry's status quo could be published anonymously, following in the footsteps of the Bitcoin whitepaper's pseudonymous author, Satoshi Nakamoto. Leveraging technologies like the Nostr protocol, the research community can build a system that ensures the permanence, integrity, and impartiality of the scientific record for generations to come. @ 000002de:c05780a7
2025-01-22 16:33:59Anyone else noticing their LN address not working with Minibits? originally posted at https://stacker.news/items/860143
@ 000002de:c05780a7
2025-01-22 16:33:59Anyone else noticing their LN address not working with Minibits? originally posted at https://stacker.news/items/860143 @ b17fccdf:b7211155
2025-01-22 10:39:19### **What's changed** ----------- - [New bonus guide dedicated to install/upgrade/uninstall PostgreSQL](https://minibolt.minibolt.info/bonus-guides/system/postgresql) - [Modified the LND guide to use PostgreSQL instead of bbolt](https://minibolt.minibolt.info/lightning/lightning/lightning-client) - [Modified the Nostr relay guide to use PostgreSQL instead of SQLite (experimental)](https://minibolt.minibolt.info/bonus-guides/nostr/nostr-relay) - [Modified the BTCPay Server bonus guide according to these changes](https://minibolt.minibolt.info/bonus-guides/bitcoin/btcpay-server) - Used the [lndinit MiniBolt organization fork](https://github.com/minibolt-guide/lndinit), to add an [extra section to migrate an existing LND bbolt database to PostgreSQL](https://minibolt.minibolt.info/lightning/lightning/lightning-client#migrate-an-existing-bbolt-database-to-postgresql) (🚨⚠️[Experimental](https://github.com/lightninglabs/lndinit/pull/21) - use it behind your responsibility⚠️🚨) - [New Golang bonus guide](https://minibolt.minibolt.info/bonus-guides/system/go) as a common language for the [lndinit compilation](https://minibolt.minibolt.info/lightning/lightning/lightning-client#install-lndinit) - [Updated LND to v0.18](https://minibolt.minibolt.info/lightning/lightning/lightning-client#download-binaries) - [New Bitcoin Core extra section to renovate Tor & I2P addresses](https://minibolt.minibolt.info/bitcoin/bitcoin/bitcoin-client#renovate-your-bitcoin-core-tor-and-i2p-addresses) - [New Bitcoin Core extra section to generate a full `bitcoin.conf` file](https://minibolt.minibolt.info/bitcoin/bitcoin/bitcoin-client#generate-a-full-bitcoin.conf-example-file) - [Rebuilt some homepage sections and general structure](https://minibolt.minibolt.info//) - Deleted the `$` symbol of the commands to easy copy-paste to the terminal - [Deleted the initial incoming and the outgoing rules configuration of UFW, due to it being by default](https://minibolt.minibolt.info/system/system/security) --- 🪧 PD: If you want to use the old database backend of the LND or Nostr relay, follow the next extra sections: - [Use the default bbolt database backend for the LND](https://minibolt.minibolt.info/lightning/lightning/lightning-client#use-the-default-bbolt-database-backend) - [Use the default SQLite database backend for the Nostr relay](https://minibolt.minibolt.info/bonus-guides/bitcoin/nostr-relay#use-the-default-sqlite-database-backend) ⚠️**Attention**⚠️: [The migration process](https://minibolt.minibolt.info/lightning/lightning/lightning-client#migrate-an-existing-bbolt-database-to-postgresql) was tested on testnet mode from an existing bbolt database backend to a new PostgreSQL database using lndinit and the results were successful. However, It wasn't tested on mainnet, [according to the developer](https://github.com/lightninglabs/lndinit/pull/21), it is in experimental status which could damage your existing LND database.🚨 Use it behind your responsibility 🧼 --- **🔧 PR related**: https://github.com/minibolt-guide/minibolt/pull/93 ----------- #### ♻️ Migrate the PostgreSQL database location > **Attention!!** These instructions are invalid since the latest changes applied to the [PostgreSQL bonus guide](https://minibolt.minibolt.info/bonus-guides/system/postgresql). See more information on the recent associated post by clicking ~ > [HERE](https://habla.news/u/twofaktor@twofaktor.github.io/1735902560910) < ~ If you installed [NBXplorer + BTCPay Server](https://minibolt.minibolt.info/bonus-guides/bitcoin/btcpay-server) **before 05/06/2024**, it is probably you have the database of the PostgreSQL cluster on the default path (`/var/lib/postgresql/16/main/`), follow the next instructions to migrate it to the new dedicated location on `/data/postgresdb` folder: * With user `admin` create the dedicated PostgreSQL data folder ``` sudo mkdir /data/postgresdb ``` * Assign as the owner to the `postgres` user ``` sudo chown postgres:postgres /data/postgresdb ``` * Assign permissions of the data folder only to the `postgres` user ``` sudo chmod -R 700 /data/postgresdb ``` * Stop NBXplorer and BTCPay Server ``` sudo systemctl stop nbxplorer && sudo systemctl stop btcpayserver ``` * Stop PostgreSQL ``` sudo systemctl stop postgresql ``` * Use the rsync command to copy all files from the existing database on (`/var/lib/postgresql/16/main`) to the new destination directory (`/data/postgresdb`) ``` sudo rsync -av /var/lib/postgresql/16/main/ /data/postgresdb/ ``` Expected output: ``` sending incremental file list ./ PG_VERSION postgresql.auto.conf postmaster.opts postmaster.pid base/ base/1/ base/1/112 base/1/113 base/1/1247 base/1/1247_fsm base/1/1247_vm base/1/1249 base/1/1249_fsm base/1/1249_vm [...] pg_wal/000000010000000000000009 pg_wal/archive_status/ pg_xact/ pg_xact/0000 sent 164,483,875 bytes received 42,341 bytes 36,561,381.33 bytes/sec total size is 164,311,368 speedup is 1.00 ``` * Edit the PostgreSQL data directory on configuration, to redirect the store to the new location ``` sudo nano /etc/postgresql/16/main/postgresql.conf --linenumbers ``` * Replace the line 42 to this. Save and exit ``` data_directory = '/data/postgresdb' ``` * Start PostgreSQL to apply changes and monitor the correct status of the main instance and sub-instance monitoring sessions before ``` sudo systemctl start postgresql ``` * You can monitor the PostgreSQL main instance by the systemd journal and check the log output to ensure all is correct. You can exit the monitoring at any time with Ctrl-C ``` journalctl -fu postgresql ``` Example of the expected output: ``` Nov 08 11:51:10 minibolt systemd[1]: Stopped PostgreSQL RDBMS. Nov 08 11:51:10 minibolt systemd[1]: Stopping PostgreSQL RDBMS... Nov 08 11:51:13 minibolt systemd[1]: Starting PostgreSQL RDBMS... Nov 08 11:51:13 minibolt systemd[1]: Finished PostgreSQL RDBMS. ``` * You can monitor the PostgreSQL sub-instance by the systemd journal and check log output to ensure all is correct. You can exit monitoring at any time with Ctrl-C ``` journalctl -fu postgresql@16-main ``` Example of the expected output: ``` Nov 08 11:51:10 minibolt systemd[1]: Stopping PostgreSQL Cluster 16-main... Nov 08 11:51:11 minibolt systemd[1]: postgresql@16-main.service: Succeeded. Nov 08 11:51:11 minibolt systemd[1]: Stopped PostgreSQL Cluster 16-main. Nov 08 11:51:11 minibolt systemd[1]: postgresql@16-main.service: Consumed 1h 10min 8.677s CPU time. Nov 08 11:51:11 minibolt systemd[1]: Starting PostgreSQL Cluster 16-main... Nov 08 11:51:13 minibolt systemd[1]: Started PostgreSQL Cluster 16-main. ``` * Start NBXplorer and BTCPay Server again ``` sudo systemctl start nbxplorer && sudo systemctl start btcpayserver ``` * Monitor to make sure everything is as you left it. You can exit monitoring at any time by pressing Ctrl+C ``` journalctl -fu nbxplorer ``` --- ``` journalctl -fu btcpayserver ``` --- Enjoy it MiniBolter! 💙
@ b17fccdf:b7211155
2025-01-22 10:39:19### **What's changed** ----------- - [New bonus guide dedicated to install/upgrade/uninstall PostgreSQL](https://minibolt.minibolt.info/bonus-guides/system/postgresql) - [Modified the LND guide to use PostgreSQL instead of bbolt](https://minibolt.minibolt.info/lightning/lightning/lightning-client) - [Modified the Nostr relay guide to use PostgreSQL instead of SQLite (experimental)](https://minibolt.minibolt.info/bonus-guides/nostr/nostr-relay) - [Modified the BTCPay Server bonus guide according to these changes](https://minibolt.minibolt.info/bonus-guides/bitcoin/btcpay-server) - Used the [lndinit MiniBolt organization fork](https://github.com/minibolt-guide/lndinit), to add an [extra section to migrate an existing LND bbolt database to PostgreSQL](https://minibolt.minibolt.info/lightning/lightning/lightning-client#migrate-an-existing-bbolt-database-to-postgresql) (🚨⚠️[Experimental](https://github.com/lightninglabs/lndinit/pull/21) - use it behind your responsibility⚠️🚨) - [New Golang bonus guide](https://minibolt.minibolt.info/bonus-guides/system/go) as a common language for the [lndinit compilation](https://minibolt.minibolt.info/lightning/lightning/lightning-client#install-lndinit) - [Updated LND to v0.18](https://minibolt.minibolt.info/lightning/lightning/lightning-client#download-binaries) - [New Bitcoin Core extra section to renovate Tor & I2P addresses](https://minibolt.minibolt.info/bitcoin/bitcoin/bitcoin-client#renovate-your-bitcoin-core-tor-and-i2p-addresses) - [New Bitcoin Core extra section to generate a full `bitcoin.conf` file](https://minibolt.minibolt.info/bitcoin/bitcoin/bitcoin-client#generate-a-full-bitcoin.conf-example-file) - [Rebuilt some homepage sections and general structure](https://minibolt.minibolt.info//) - Deleted the `$` symbol of the commands to easy copy-paste to the terminal - [Deleted the initial incoming and the outgoing rules configuration of UFW, due to it being by default](https://minibolt.minibolt.info/system/system/security) --- 🪧 PD: If you want to use the old database backend of the LND or Nostr relay, follow the next extra sections: - [Use the default bbolt database backend for the LND](https://minibolt.minibolt.info/lightning/lightning/lightning-client#use-the-default-bbolt-database-backend) - [Use the default SQLite database backend for the Nostr relay](https://minibolt.minibolt.info/bonus-guides/bitcoin/nostr-relay#use-the-default-sqlite-database-backend) ⚠️**Attention**⚠️: [The migration process](https://minibolt.minibolt.info/lightning/lightning/lightning-client#migrate-an-existing-bbolt-database-to-postgresql) was tested on testnet mode from an existing bbolt database backend to a new PostgreSQL database using lndinit and the results were successful. However, It wasn't tested on mainnet, [according to the developer](https://github.com/lightninglabs/lndinit/pull/21), it is in experimental status which could damage your existing LND database.🚨 Use it behind your responsibility 🧼 --- **🔧 PR related**: https://github.com/minibolt-guide/minibolt/pull/93 ----------- #### ♻️ Migrate the PostgreSQL database location > **Attention!!** These instructions are invalid since the latest changes applied to the [PostgreSQL bonus guide](https://minibolt.minibolt.info/bonus-guides/system/postgresql). See more information on the recent associated post by clicking ~ > [HERE](https://habla.news/u/twofaktor@twofaktor.github.io/1735902560910) < ~ If you installed [NBXplorer + BTCPay Server](https://minibolt.minibolt.info/bonus-guides/bitcoin/btcpay-server) **before 05/06/2024**, it is probably you have the database of the PostgreSQL cluster on the default path (`/var/lib/postgresql/16/main/`), follow the next instructions to migrate it to the new dedicated location on `/data/postgresdb` folder: * With user `admin` create the dedicated PostgreSQL data folder ``` sudo mkdir /data/postgresdb ``` * Assign as the owner to the `postgres` user ``` sudo chown postgres:postgres /data/postgresdb ``` * Assign permissions of the data folder only to the `postgres` user ``` sudo chmod -R 700 /data/postgresdb ``` * Stop NBXplorer and BTCPay Server ``` sudo systemctl stop nbxplorer && sudo systemctl stop btcpayserver ``` * Stop PostgreSQL ``` sudo systemctl stop postgresql ``` * Use the rsync command to copy all files from the existing database on (`/var/lib/postgresql/16/main`) to the new destination directory (`/data/postgresdb`) ``` sudo rsync -av /var/lib/postgresql/16/main/ /data/postgresdb/ ``` Expected output: ``` sending incremental file list ./ PG_VERSION postgresql.auto.conf postmaster.opts postmaster.pid base/ base/1/ base/1/112 base/1/113 base/1/1247 base/1/1247_fsm base/1/1247_vm base/1/1249 base/1/1249_fsm base/1/1249_vm [...] pg_wal/000000010000000000000009 pg_wal/archive_status/ pg_xact/ pg_xact/0000 sent 164,483,875 bytes received 42,341 bytes 36,561,381.33 bytes/sec total size is 164,311,368 speedup is 1.00 ``` * Edit the PostgreSQL data directory on configuration, to redirect the store to the new location ``` sudo nano /etc/postgresql/16/main/postgresql.conf --linenumbers ``` * Replace the line 42 to this. Save and exit ``` data_directory = '/data/postgresdb' ``` * Start PostgreSQL to apply changes and monitor the correct status of the main instance and sub-instance monitoring sessions before ``` sudo systemctl start postgresql ``` * You can monitor the PostgreSQL main instance by the systemd journal and check the log output to ensure all is correct. You can exit the monitoring at any time with Ctrl-C ``` journalctl -fu postgresql ``` Example of the expected output: ``` Nov 08 11:51:10 minibolt systemd[1]: Stopped PostgreSQL RDBMS. Nov 08 11:51:10 minibolt systemd[1]: Stopping PostgreSQL RDBMS... Nov 08 11:51:13 minibolt systemd[1]: Starting PostgreSQL RDBMS... Nov 08 11:51:13 minibolt systemd[1]: Finished PostgreSQL RDBMS. ``` * You can monitor the PostgreSQL sub-instance by the systemd journal and check log output to ensure all is correct. You can exit monitoring at any time with Ctrl-C ``` journalctl -fu postgresql@16-main ``` Example of the expected output: ``` Nov 08 11:51:10 minibolt systemd[1]: Stopping PostgreSQL Cluster 16-main... Nov 08 11:51:11 minibolt systemd[1]: postgresql@16-main.service: Succeeded. Nov 08 11:51:11 minibolt systemd[1]: Stopped PostgreSQL Cluster 16-main. Nov 08 11:51:11 minibolt systemd[1]: postgresql@16-main.service: Consumed 1h 10min 8.677s CPU time. Nov 08 11:51:11 minibolt systemd[1]: Starting PostgreSQL Cluster 16-main... Nov 08 11:51:13 minibolt systemd[1]: Started PostgreSQL Cluster 16-main. ``` * Start NBXplorer and BTCPay Server again ``` sudo systemctl start nbxplorer && sudo systemctl start btcpayserver ``` * Monitor to make sure everything is as you left it. You can exit monitoring at any time by pressing Ctrl+C ``` journalctl -fu nbxplorer ``` --- ``` journalctl -fu btcpayserver ``` --- Enjoy it MiniBolter! 💙 @ 00eba731:09746909
2025-01-22 05:20:24Managing risks is crucial for business success, as it helps protect operations and ensure stability in uncertain situations. This infographic provides an overview of effective [risk management strategies](https://www.asialinkfinance.com.ph/articles/blog/business-risk-management/), including identifying potential risks, assessing their impact, and implementing measures to mitigate them, helping businesses stay resilient and prepared. [Infographic](https://www.asialinkfinance.com.ph/wp-content/uploads/2023/09/AsiaLink-info10-p2.png)
@ 00eba731:09746909
2025-01-22 05:20:24Managing risks is crucial for business success, as it helps protect operations and ensure stability in uncertain situations. This infographic provides an overview of effective [risk management strategies](https://www.asialinkfinance.com.ph/articles/blog/business-risk-management/), including identifying potential risks, assessing their impact, and implementing measures to mitigate them, helping businesses stay resilient and prepared. [Infographic](https://www.asialinkfinance.com.ph/wp-content/uploads/2023/09/AsiaLink-info10-p2.png) @ 5adb967d:ac1f7d04
2025-01-22 03:41:12In this information age, radio communication has penetrated into every aspect of life. Whether it is government affairs, military, business, or personal privacy, may be subject to eavesdropping and radio wave harassment. In the face of this grim reality, how to build an impenetrable line of defense for the key confidential communications, has become an extremely urgent issue. Communication shielding, is to effectively block eavesdropping interference, to ensure absolute communication security of the magic weapon. Communication shielding protection principle, is the use of masking performance of electromagnetic [rf jammer](https://www.thejammerblocker.com/uhf-vhf-lojack-rf-jammer/) materials, in the device around the formation of a “static area”. Into this special space, any radio wave signals will be completely blocked out, can not penetrate them. Whether it is the most advanced passive eavesdropping equipment, or intentional harassment of active electromagnetic interference, in this invulnerable “static area” in front of, all will be completely off, out of action. In fact, electromagnetic shielding technology has long been popular in the military field. The core components of countless advanced weapons and equipment, are closely protected by this material to ensure that the key system from the outside world interference. Some special places also widely used fixed shielding facilities, to create an absolutely reliable quiet environment. However, today, mobile offices and field operations are becoming more and more common, and the traditional fixed shielding facilities are difficult to meet the flexible deployment requirements. Therefore, portable communication shielding has emerged as the best on-site confidentiality protection tool. Simply press the power button, most portable shielding can be immediately effective. Their powerful electromagnetic [recording jammer](https://www.thejammerblocker.com/audio-recorder-jammers/) ability, enough to form a “static area radius” within a few meters to dozens of meters in the surrounding area. As long as you enter, no matter what kind of unauthorized eavesdropping equipment, radio interference sources, all will be hard “static zone barrier” intercepted. Users in this safe space, you can carry out all kinds of confidential calls, video conferencing or secret work, absolutely foolproof, free from any prying eyes and harassment. At the same time, another great use of the shield is to prevent the leakage of radio signals and loss of confidentiality. That is to say, the important content basically will not be from the “static area” out of half a signal, fundamentally blocked the worries. This “two-way shielding” role, making the communication shield has become the key confidential communication field of choice. Whether it is a government agency's classified meeting, or business company's trade secrets, or even personal privacy, as long as the absolute security of the “quiet zone”, everything will be easy. Moreover, the latest generation of communication [drone jammers](https://www.thejammerblocker.com/drone-uavs-jammers-blockers/) can also be based on demand, the specific 2G/3G/4G/5G/WIFI and other frequency bands to implement precise selective shielding. This allows the user to take into account both communication protection and ease of use, really make the best use of things, twice the result with half the effort. In the current complex environment with many hidden dangers, communication [network blocker](https://www.thejammerblocker.com/) is undoubtedly an indispensable “last line of defense” for important confidential communications. With it, no matter what kind of radio wave torture, any eavesdropping interference soul will have no place to hide. It can be said that this small and exquisite “secrecy magic weapon”, will draw a quiet and safe for the important affairs of the absolute territory. 3. [https://open.substack.com/pub/thejammerblocker/p/admiralty-protection-shielding-for?r=4tc4gn&utm\_campaign=post&utm\_medium=web&showWelcomeOnShare=true](https://open.substack.com/pub/thejammerblocker/p/admiralty-protection-shielding-for?r=4tc4gn&utm_campaign=post&utm_medium=web&showWelcomeOnShare=true) 4. [https://thejammerblockershop.writestellar.com/dui2gfo](https://thejammerblockershop.writestellar.com/dui2gfo)
@ 5adb967d:ac1f7d04
2025-01-22 03:41:12In this information age, radio communication has penetrated into every aspect of life. Whether it is government affairs, military, business, or personal privacy, may be subject to eavesdropping and radio wave harassment. In the face of this grim reality, how to build an impenetrable line of defense for the key confidential communications, has become an extremely urgent issue. Communication shielding, is to effectively block eavesdropping interference, to ensure absolute communication security of the magic weapon. Communication shielding protection principle, is the use of masking performance of electromagnetic [rf jammer](https://www.thejammerblocker.com/uhf-vhf-lojack-rf-jammer/) materials, in the device around the formation of a “static area”. Into this special space, any radio wave signals will be completely blocked out, can not penetrate them. Whether it is the most advanced passive eavesdropping equipment, or intentional harassment of active electromagnetic interference, in this invulnerable “static area” in front of, all will be completely off, out of action. In fact, electromagnetic shielding technology has long been popular in the military field. The core components of countless advanced weapons and equipment, are closely protected by this material to ensure that the key system from the outside world interference. Some special places also widely used fixed shielding facilities, to create an absolutely reliable quiet environment. However, today, mobile offices and field operations are becoming more and more common, and the traditional fixed shielding facilities are difficult to meet the flexible deployment requirements. Therefore, portable communication shielding has emerged as the best on-site confidentiality protection tool. Simply press the power button, most portable shielding can be immediately effective. Their powerful electromagnetic [recording jammer](https://www.thejammerblocker.com/audio-recorder-jammers/) ability, enough to form a “static area radius” within a few meters to dozens of meters in the surrounding area. As long as you enter, no matter what kind of unauthorized eavesdropping equipment, radio interference sources, all will be hard “static zone barrier” intercepted. Users in this safe space, you can carry out all kinds of confidential calls, video conferencing or secret work, absolutely foolproof, free from any prying eyes and harassment. At the same time, another great use of the shield is to prevent the leakage of radio signals and loss of confidentiality. That is to say, the important content basically will not be from the “static area” out of half a signal, fundamentally blocked the worries. This “two-way shielding” role, making the communication shield has become the key confidential communication field of choice. Whether it is a government agency's classified meeting, or business company's trade secrets, or even personal privacy, as long as the absolute security of the “quiet zone”, everything will be easy. Moreover, the latest generation of communication [drone jammers](https://www.thejammerblocker.com/drone-uavs-jammers-blockers/) can also be based on demand, the specific 2G/3G/4G/5G/WIFI and other frequency bands to implement precise selective shielding. This allows the user to take into account both communication protection and ease of use, really make the best use of things, twice the result with half the effort. In the current complex environment with many hidden dangers, communication [network blocker](https://www.thejammerblocker.com/) is undoubtedly an indispensable “last line of defense” for important confidential communications. With it, no matter what kind of radio wave torture, any eavesdropping interference soul will have no place to hide. It can be said that this small and exquisite “secrecy magic weapon”, will draw a quiet and safe for the important affairs of the absolute territory. 3. [https://open.substack.com/pub/thejammerblocker/p/admiralty-protection-shielding-for?r=4tc4gn&utm\_campaign=post&utm\_medium=web&showWelcomeOnShare=true](https://open.substack.com/pub/thejammerblocker/p/admiralty-protection-shielding-for?r=4tc4gn&utm_campaign=post&utm_medium=web&showWelcomeOnShare=true) 4. [https://thejammerblockershop.writestellar.com/dui2gfo](https://thejammerblockershop.writestellar.com/dui2gfo) @ 6be5cc06:5259daf0
2025-01-21 23:17:29A seguir, veja como instalar e configurar o **Privoxy** no **Pop!_OS**. --- ### **1. Instalar o Tor e o Privoxy** Abra o terminal e execute: ```bash sudo apt update sudo apt install tor privoxy ``` **Explicação:** - **Tor:** Roteia o tráfego pela rede Tor. - **Privoxy:** Proxy avançado que intermedia a conexão entre aplicativos e o Tor. --- ### **2. Configurar o Privoxy** Abra o arquivo de configuração do Privoxy: ```bash sudo nano /etc/privoxy/config ``` Navegue até a última linha (atalho: **`Ctrl`** + **`/`** depois **`Ctrl`** + **`V`** para navegar diretamente até a última linha) e insira: ```bash forward-socks5 / 127.0.0.1:9050 . ``` Isso faz com que o **Privoxy** envie todo o tráfego para o **Tor** através da porta **9050**. Salve (**`CTRL`** + **`O`** e **`Enter`**) e feche (**`CTRL`** + **`X`**) o arquivo. --- ### **3. Iniciar o Tor e o Privoxy** Agora, inicie e habilite os serviços: ```bash sudo systemctl start tor sudo systemctl start privoxy sudo systemctl enable tor sudo systemctl enable privoxy ``` **Explicação:** - **start:** Inicia os serviços. - **enable:** Faz com que iniciem automaticamente ao ligar o PC. --- ### **4. Configurar o Navegador Firefox** Para usar a rede **Tor** com o Firefox: 1. Abra o Firefox. 2. Acesse **Configurações** → **Configurar conexão**. 3. Selecione **Configuração manual de proxy**. 4. Configure assim: - **Proxy HTTP:** `127.0.0.1` - **Porta:** `8118` (porta padrão do **Privoxy**) - **Domínio SOCKS (v5):** `127.0.0.1` - **Porta:** `9050` 5. Marque a opção **"Usar este proxy também em HTTPS"**. 6. Clique em **OK**. --- ### **5. Verificar a Conexão com o Tor** Abra o navegador e acesse: ```text https://check.torproject.org/ ``` Se aparecer a mensagem **"Congratulations. This browser is configured to use Tor."**, a configuração está correta. --- ### **Dicas Extras** - **Privoxy** pode ser ajustado para bloquear anúncios e rastreadores. - Outros aplicativos também podem ser configurados para usar o **Privoxy**.
@ 6be5cc06:5259daf0
2025-01-21 23:17:29A seguir, veja como instalar e configurar o **Privoxy** no **Pop!_OS**. --- ### **1. Instalar o Tor e o Privoxy** Abra o terminal e execute: ```bash sudo apt update sudo apt install tor privoxy ``` **Explicação:** - **Tor:** Roteia o tráfego pela rede Tor. - **Privoxy:** Proxy avançado que intermedia a conexão entre aplicativos e o Tor. --- ### **2. Configurar o Privoxy** Abra o arquivo de configuração do Privoxy: ```bash sudo nano /etc/privoxy/config ``` Navegue até a última linha (atalho: **`Ctrl`** + **`/`** depois **`Ctrl`** + **`V`** para navegar diretamente até a última linha) e insira: ```bash forward-socks5 / 127.0.0.1:9050 . ``` Isso faz com que o **Privoxy** envie todo o tráfego para o **Tor** através da porta **9050**. Salve (**`CTRL`** + **`O`** e **`Enter`**) e feche (**`CTRL`** + **`X`**) o arquivo. --- ### **3. Iniciar o Tor e o Privoxy** Agora, inicie e habilite os serviços: ```bash sudo systemctl start tor sudo systemctl start privoxy sudo systemctl enable tor sudo systemctl enable privoxy ``` **Explicação:** - **start:** Inicia os serviços. - **enable:** Faz com que iniciem automaticamente ao ligar o PC. --- ### **4. Configurar o Navegador Firefox** Para usar a rede **Tor** com o Firefox: 1. Abra o Firefox. 2. Acesse **Configurações** → **Configurar conexão**. 3. Selecione **Configuração manual de proxy**. 4. Configure assim: - **Proxy HTTP:** `127.0.0.1` - **Porta:** `8118` (porta padrão do **Privoxy**) - **Domínio SOCKS (v5):** `127.0.0.1` - **Porta:** `9050` 5. Marque a opção **"Usar este proxy também em HTTPS"**. 6. Clique em **OK**. --- ### **5. Verificar a Conexão com o Tor** Abra o navegador e acesse: ```text https://check.torproject.org/ ``` Se aparecer a mensagem **"Congratulations. This browser is configured to use Tor."**, a configuração está correta. --- ### **Dicas Extras** - **Privoxy** pode ser ajustado para bloquear anúncios e rastreadores. - Outros aplicativos também podem ser configurados para usar o **Privoxy**. @ 000002de:c05780a7
2025-01-21 21:29:39> The Bellamy salute is a palm-out salute created by James B. Upham as the gesture that was to accompany the Pledge of Allegiance of the United States of America, whose text had been written by Francis Bellamy. It was also known as the "flag salute" during the period when it was used with the Pledge of Allegiance. Bellamy promoted the salute and it came to be associated with his name. Both the Pledge and its salute originated in 1892. It was also known as the "flag salute" during the period when it was used with the Pledge of Allegiance. Bellamy promoted the salute and it came to be associated with his name. Both the Pledge and its salute originated in 1892. Later, during the 1920s and 1930s, Italian fascists and Nazi Germans adopted a salute which was very similar, attributed to the Roman salute, a gesture that was popularly believed to have been used in ancient Rome.[1] This resulted in controversy over the use of the Bellamy salute in the United States. It was officially replaced by the hand-over-heart salute when Congress amended the Flag Code on December 22, 1942. ~ [Bellamy salute - Wikipedia](https://en.wikipedia.org/wiki/Bellamy_salute) originally posted at https://stacker.news/items/859191
@ 000002de:c05780a7
2025-01-21 21:29:39> The Bellamy salute is a palm-out salute created by James B. Upham as the gesture that was to accompany the Pledge of Allegiance of the United States of America, whose text had been written by Francis Bellamy. It was also known as the "flag salute" during the period when it was used with the Pledge of Allegiance. Bellamy promoted the salute and it came to be associated with his name. Both the Pledge and its salute originated in 1892. It was also known as the "flag salute" during the period when it was used with the Pledge of Allegiance. Bellamy promoted the salute and it came to be associated with his name. Both the Pledge and its salute originated in 1892. Later, during the 1920s and 1930s, Italian fascists and Nazi Germans adopted a salute which was very similar, attributed to the Roman salute, a gesture that was popularly believed to have been used in ancient Rome.[1] This resulted in controversy over the use of the Bellamy salute in the United States. It was officially replaced by the hand-over-heart salute when Congress amended the Flag Code on December 22, 1942. ~ [Bellamy salute - Wikipedia](https://en.wikipedia.org/wiki/Bellamy_salute) originally posted at https://stacker.news/items/859191 @ 3c7dc2c5:805642a8
2025-01-21 21:00:47## 🧠Quote(s) of the week: 'For the love of God, Bitcoin is not a 'scam', and it is not 'going away'. Do yourself some good by honestly and thoroughly researching it, away from mainstream media nonsense. You can thank me and thousands of others on here later.' 'Do you actually understand what it means when the whole world tries to squeeze into a fixed supply digital asset that never gets diluted, is audited every 10 minutes, and trades 24/7 as the most liquid asset on earth? If you do, you’re holding on for dear life.' -Bitcoin For Freedom ## 🧡Bitcoin news🧡 After a short break from the recap, I am back. I got a new place and I had to focus on that project. Now before I start with this week's Weekly Recap I want to remind all the political larpers (Trump voters etc) of one thing: THE PROMISE 1. Strategic Bitcoin Reserve 2. Free Ross day one THE REALITY 1. 47M Wrapped BTC 2. Maybe free Ross later 3. 4.7M tron 4. 47M Ethereum 5. 4.7 M litecoin 6. Pardoned J6 participants Oh, and he launched the biggest meme/shitcoin, and rug pulled the shit out of it. On the 12th of January: ➡️Eighth consecutive positive adjustment on the horizon. We saw nine in 2021 and 17 in 2018. This is insane. ➡️A Santander Bank report highlights El Salvador’s booming tourism industry, fueled by Bitcoin adoption. The country announced 3.9M tourists in 2024—a 22% YoY increase and nearly double the levels seen between 2013-2016. ➡️Bitcoin mining difficulty increased by 0.6101% today. The network has programmatically adjusted to a new difficulty level of 110,451,907,374,649 hashes, ensuring the target block time remains stable as global computing power on the network fluctuates. ➡️We now have 7 states, and counting, pushing a Strategic Bitcoin Reserve Bill: - New Hampshire - Alabama - Florida - Pennsylvania - Texas - Ohio - North Dakota On the 13th of January: ➡️Italy's largest bank Intesa Sanpaolo has started buying Bitcoin, according to leaked internal emails which celebrate the "first transaction" of €1m for 11 Bitcoin. ➡️The number of Bitcoin addresses holding over 100 BTC has surged by 8.6% since Trump’s election in November. ➡️Ming Shing Group from Hong Kong just acquired 500 Bitcoin for $47M. ➡️Semler Scientific has acquired 237 BTC for ~$23.3 million at ~$98,267 per Bitcoin and has generated a BTC Yield of 99.3% since adopting our BTC treasury strategy in May 2024. As of 1/10/2025, we held 2,321 Bitcoin acquired for ~$191.9 million at ~$82,687 per Bitcoin. ➡️$11.5 trillion BlackRock says that Bitcoin adoption is outpacing the internet and mobile phones. On the 14th of January: ➡️The Bitcoin network has 610,929x more hashing computational power than the combined total of the world’s top 500 supercomputers. On the 16th of January: ➡️'Someone just moved 11,000 Bitcoin worth $1.1 BILLION around the world for ONLY $1.50 The world's most efficient monetary network.' - Pete Rizzo ➡️XRP is down 80% from its bitcoin all-time high in 2017. Just don't do shitcoins, it's that simple. On the 17th of January: ➡️'They did it again! Bindseil and Schaaf published the article, 'Arguments Against a Strategic Bitcoin Reserve'. It is a wild ride, reaching peak FUD. Maybe even so wild that they had to publish it in a newspaper and not as an ECB blog post. This is ultra bullish' - Dr. Jan Wüstenfeld ➡️Metaplanet's market cap closes above $1 billion for the first time since adopting a Bitcoin Standard. ➡️Jeroen Blokland: ‘Nearly one-fifth of all U.S. states are formally weighing whether to have public funds invest in Bitcoin.’ I am afraid and convinced at the same time that soon, the EU will be the only region still aiming to introduce a central bank digital currency. As a result, it will trigger more polarization, and Europe will lose the Bitcoin battle, just as it hopelessly lost the technology and AI battle. ➡️'ETH was supposed to become deflationary after the "merge" But now the supply is almost back to where it was BEFORE the merge If you're still falling for this shit, you deserve to get scammed.' -Rajat Soni To make it even worse: 'The ETHBTC ratio is now lower than the day when Coinbase listed it in 2016. You would have been buying ETH at ~$13, but funny enough if you would have just bought and held Bitcoin, you would have actually outperformed it.' -Pledditor. ➡️ First union in Idaho bought Bitcoin. ➡️ California state officials embraced Bitcoin. ➡️Wyoming filed for Strategic Bitcoin Reserve bill. ➡️Massachusetts filed for Strategic Bitcoin Reserve bill. Up to 10% of the $9 Billion Commonwealth Stabilization Fund can be invested in Bitcoin On the 18th of January: ➡️ Swiss Bitcoin advocates are pushing for the Swiss National Bank to add Bitcoin to the national reserves - Bloomberg They need 100,000 signatures to put it to a national vote. ➡️3.47M Bitcoin addresses hold more than 0.1 BTC. If you own one of them you’re set for life. ➡️Donald Trump dropped a meme coin instead of stacking Bitcoin for a Strategic Reserve. If the president of the UNITED STATES OF AMERICA can launch and promote a memecoin, then essentially it's OK (and not shamed) for anyone/anywhere to do so. The grift to come is going to be unreal, even by CrApTo standards. A memecoin/shitcoin is a zero-sum* lottery. There is no wealth creation. Every buy order is simply matched by a sell order. After an initial spike, the price eventually crashes and the last buyers lose everything. That's the only thing I am going to share on the subject. [](https://i.ibb.co/jRctP3r/Ghpx9-BNWUAA2-Nxg.jpg) ➡️Arizona Strategic Bitcoin Reserve bill introduced The State can invest up to 10% from: 1) State general fund - $28B 2) State retirement funds - $50B ➡️ Bitwise bought +$200 MILLION Bitcoin for its ETF today. The biggest single-day inflow since launching last year. On the 19th of January: ➡️ Bitcoin Network System Explained in a Chart: [](https://i.ibb.co/RBrC5tw/Ghn8-Bv-BW8-AAi-Xu-X.jpg) On the 20th of January: ➡️Bitcoin mining difficulty hits a NEW ALL-TIME HIGH. ➡️YouTube rival Rumble started buying Bitcoin for its balance sheet on Friday - CEO ➡️Bitcoin went up 20x in Trump's first term as President. 10x this time? ## 💸Traditional Finance / Macro: 👉🏽no news ## 🏦Banks: 👉🏽Global central banks now hold more Gold than at any point in the past 45 years. Something is brewing. ## 🌎Macro/Geopolitics: On the 12th of January: 👉🏽Treasuries are entering their 6th year of the third great bond bear market of the last 240 years! On the 16th of January: 👉🏽EU Commission allows Thierry Breton to take up a new job at Bank of America despite a rule that requires a two-year waiting period before starting lobbying jobs. There are no rules for these corrupt EU (you fill in the blank). The rules apply only to citizens, not to the Brussels elite, and certainly not if you belong to the French political elite. In December I shared some news on the EU crusade against X. Let me explain this to you in simple terms. Breton, a man preaching about the ‘rule of law’ and X, while breaching the rules he signed up to himself: ‘Code of Conduct EU Commissioners’. Now read that again. Bitcoin only. Defund politicians. 👉🏽'The Congressional Budget Office just lowered the US population forecast by 11 million, to 372 million in 2054. This implies 6.3% growth over the next 30 years instead of the 10.5% previously expected. The agency also expects deaths to exceed births starting in 2033, 7 years earlier than in the 2024 estimates. Lower fertility rates and lower net immigration expectations were behind the outlook changes. Are we heading into a demographic crisis?' - TKL On the 17th of January: 👉🏽 Germany had 17 nuclear power plants. It shut them all down. Germany spent $1 Trillion for its energy revamp with the following results: - It is now totally dependent on Russian gas, French nuclear power electricity, and coal (the most polluting fossil fuel) - Its citizens pay the highest electricity price in Europe - It causes several times more CO2 per kWh than France Go woke, go broke. $1T for ruining both its economy and environment. Wunderbar! Just some data: In 2025, Europe is buying Russian gas at an unprecedented pace and spending billions of dollars on it, reports Politico. In the first 15 days of the year, the EU countries imported 837.3 thousand tons of Russian liquified natural gas (LNG). Just to show you how fucked up things are in the EU. EU companies are backstabbed by their own policymakers. 'Europe's carmakers risk hefty bill for carbon credit from Chinese rivals.' source: https://www.ft.com/content/677190d1-7d34-4506-a037-418baab67237 I read the article. It’mind-blowingng. It's like shooting a two-barrelled shotgun in your own nuts. On this point, EU regulators are destroying an entire part of the economy (Car manufacturing + subcontractors) and are giving the keys to Chinese companies. Go woke, go broke. China is making new coal plants at a rate that cancels German / EU efforts 10X or maybe 100x over. Now from an economic perspective: 'European equities are more or less where they were at the beginning of the century. Overregulation and bureaucracy throttling innovation, and belief in left redistribution nonsense instead of hard work and entrepreneurship have their price.' -Michael A. Arouet [](https://i.ibb.co/DWCV5pV/Ght-HId-Wc-AINW2x.jpg) 👉🏽Treasuries have experienced their worst rolling 10-year return in 90 YEARS, now at -0.5%. People out here still stacking U.S. gov bonds instead of Bitcoin. Data: U.S. Treasury bonds: -42% - Bitcoin: +809% 'The “smart money” is buying 30-year treasury bonds with a nominal yield of 1.20% on the whim that another investor (or central bank) will buy it from them at a higher price.' -Dylan Leclair On the 18th of January: 👉🏽Argentina has officially reached its first budget surplus in 14 years. Vamos! Under Milei’s leadership, Argentina turned a $7.94B trade deficit in 2023 into a record-smashing $18-19B surplus in 2024, surpassing the previous high of $16.89B in 2009. His push to boost energy exports from the Vaca Muerta shale reserves and ramp up grain sales is paying off, making Argentina a global exporting powerhouse again. With inflation already down from nearly 300% to 117.8%, Milei’s economic reforms are proving their worth. Argentinian President Javier Milei announces "Zero deficit is a reality...promises are fulfilled." Let me refrain from the above: ➡️Less state ➡️Less government expenses ➡️Capitalism ➡️Free market 👉🏽Wealth exodus accelerated by 157% in 2024: One millionaire leaves Britain every 45 minutes under Labour — Telegraph 157% increase in the outflow of millionaires since Labour came to power - including losing over 10,000 millionaires & 12 billionaires. All these people created wealth in the U.K. through living and spending. On the 19th of January: 👉🏽U.S. Housing Market 16.2% of Home Purchase Deals were canceled last month, the highest cancellation rate in history If for some reason people still believe Bitcoin is a Ponzi scheme, well that's their fault. Let me share with you the real Ponzi scheme. The following chart summarizes the impact of demographics on European pension systems really well: [](https://i.ibb.co/r7QkYsv/Gh-J7j41-Wg-AEah31.jpg) A ticking time bomb! The regulatory burdens suffered by citizens are imposed by unelectable bureaucrats! Study Bitcoin. ## 🎁If you have made it this far I would like to give you a little gift: Some fountain of Lyn Alden's wisdom: https://www.youtube.com/watch?v=fZlcrLZkNA8 Lyn Alden is a macro analyst, investment strategist, and the author of Broken Money. In this episode of What Bitcoin Did, they discuss the impact of fiscal policy on inflation, the Federal Reserve's constraints under fiscal dominance, and the role of tariffs in shaping the economic landscape. They also get into a Strategic Bitcoin Reserve, and what Donald Trump’s Administration will mean for Bitcoin. Credit: I have used multiple sources! The complete Weekly Recap will be accessible on my Bitcoin Friday page on Habla. Enriched with detailed charts, illustrative images, and comprehensive macroeconomic news to provide context and clarity. My savings account: Bitcoin The tool I recommend for setting up a Bitcoin savings plan: PocketBitcoin especially suited for beginners or people who want to invest in Bitcoin with an automated investment plan once a week or monthly. Use the code BITCOINFRIDAY Get your Bitcoin out of exchanges. Save them on a hardware wallet, run your own node...be your own bank. Not your keys, not your coins. It's that simple.⠀⠀⠀⠀ ⠀ ⠀⠀⠀ Do you think this post is helpful to you? If so, please share it and support my work with a zap. ▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃ ⭐ Many thanks⭐ Felipe - Bitcoin Friday! ▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
@ 3c7dc2c5:805642a8
2025-01-21 21:00:47## 🧠Quote(s) of the week: 'For the love of God, Bitcoin is not a 'scam', and it is not 'going away'. Do yourself some good by honestly and thoroughly researching it, away from mainstream media nonsense. You can thank me and thousands of others on here later.' 'Do you actually understand what it means when the whole world tries to squeeze into a fixed supply digital asset that never gets diluted, is audited every 10 minutes, and trades 24/7 as the most liquid asset on earth? If you do, you’re holding on for dear life.' -Bitcoin For Freedom ## 🧡Bitcoin news🧡 After a short break from the recap, I am back. I got a new place and I had to focus on that project. Now before I start with this week's Weekly Recap I want to remind all the political larpers (Trump voters etc) of one thing: THE PROMISE 1. Strategic Bitcoin Reserve 2. Free Ross day one THE REALITY 1. 47M Wrapped BTC 2. Maybe free Ross later 3. 4.7M tron 4. 47M Ethereum 5. 4.7 M litecoin 6. Pardoned J6 participants Oh, and he launched the biggest meme/shitcoin, and rug pulled the shit out of it. On the 12th of January: ➡️Eighth consecutive positive adjustment on the horizon. We saw nine in 2021 and 17 in 2018. This is insane. ➡️A Santander Bank report highlights El Salvador’s booming tourism industry, fueled by Bitcoin adoption. The country announced 3.9M tourists in 2024—a 22% YoY increase and nearly double the levels seen between 2013-2016. ➡️Bitcoin mining difficulty increased by 0.6101% today. The network has programmatically adjusted to a new difficulty level of 110,451,907,374,649 hashes, ensuring the target block time remains stable as global computing power on the network fluctuates. ➡️We now have 7 states, and counting, pushing a Strategic Bitcoin Reserve Bill: - New Hampshire - Alabama - Florida - Pennsylvania - Texas - Ohio - North Dakota On the 13th of January: ➡️Italy's largest bank Intesa Sanpaolo has started buying Bitcoin, according to leaked internal emails which celebrate the "first transaction" of €1m for 11 Bitcoin. ➡️The number of Bitcoin addresses holding over 100 BTC has surged by 8.6% since Trump’s election in November. ➡️Ming Shing Group from Hong Kong just acquired 500 Bitcoin for $47M. ➡️Semler Scientific has acquired 237 BTC for ~$23.3 million at ~$98,267 per Bitcoin and has generated a BTC Yield of 99.3% since adopting our BTC treasury strategy in May 2024. As of 1/10/2025, we held 2,321 Bitcoin acquired for ~$191.9 million at ~$82,687 per Bitcoin. ➡️$11.5 trillion BlackRock says that Bitcoin adoption is outpacing the internet and mobile phones. On the 14th of January: ➡️The Bitcoin network has 610,929x more hashing computational power than the combined total of the world’s top 500 supercomputers. On the 16th of January: ➡️'Someone just moved 11,000 Bitcoin worth $1.1 BILLION around the world for ONLY $1.50 The world's most efficient monetary network.' - Pete Rizzo ➡️XRP is down 80% from its bitcoin all-time high in 2017. Just don't do shitcoins, it's that simple. On the 17th of January: ➡️'They did it again! Bindseil and Schaaf published the article, 'Arguments Against a Strategic Bitcoin Reserve'. It is a wild ride, reaching peak FUD. Maybe even so wild that they had to publish it in a newspaper and not as an ECB blog post. This is ultra bullish' - Dr. Jan Wüstenfeld ➡️Metaplanet's market cap closes above $1 billion for the first time since adopting a Bitcoin Standard. ➡️Jeroen Blokland: ‘Nearly one-fifth of all U.S. states are formally weighing whether to have public funds invest in Bitcoin.’ I am afraid and convinced at the same time that soon, the EU will be the only region still aiming to introduce a central bank digital currency. As a result, it will trigger more polarization, and Europe will lose the Bitcoin battle, just as it hopelessly lost the technology and AI battle. ➡️'ETH was supposed to become deflationary after the "merge" But now the supply is almost back to where it was BEFORE the merge If you're still falling for this shit, you deserve to get scammed.' -Rajat Soni To make it even worse: 'The ETHBTC ratio is now lower than the day when Coinbase listed it in 2016. You would have been buying ETH at ~$13, but funny enough if you would have just bought and held Bitcoin, you would have actually outperformed it.' -Pledditor. ➡️ First union in Idaho bought Bitcoin. ➡️ California state officials embraced Bitcoin. ➡️Wyoming filed for Strategic Bitcoin Reserve bill. ➡️Massachusetts filed for Strategic Bitcoin Reserve bill. Up to 10% of the $9 Billion Commonwealth Stabilization Fund can be invested in Bitcoin On the 18th of January: ➡️ Swiss Bitcoin advocates are pushing for the Swiss National Bank to add Bitcoin to the national reserves - Bloomberg They need 100,000 signatures to put it to a national vote. ➡️3.47M Bitcoin addresses hold more than 0.1 BTC. If you own one of them you’re set for life. ➡️Donald Trump dropped a meme coin instead of stacking Bitcoin for a Strategic Reserve. If the president of the UNITED STATES OF AMERICA can launch and promote a memecoin, then essentially it's OK (and not shamed) for anyone/anywhere to do so. The grift to come is going to be unreal, even by CrApTo standards. A memecoin/shitcoin is a zero-sum* lottery. There is no wealth creation. Every buy order is simply matched by a sell order. After an initial spike, the price eventually crashes and the last buyers lose everything. That's the only thing I am going to share on the subject. [](https://i.ibb.co/jRctP3r/Ghpx9-BNWUAA2-Nxg.jpg) ➡️Arizona Strategic Bitcoin Reserve bill introduced The State can invest up to 10% from: 1) State general fund - $28B 2) State retirement funds - $50B ➡️ Bitwise bought +$200 MILLION Bitcoin for its ETF today. The biggest single-day inflow since launching last year. On the 19th of January: ➡️ Bitcoin Network System Explained in a Chart: [](https://i.ibb.co/RBrC5tw/Ghn8-Bv-BW8-AAi-Xu-X.jpg) On the 20th of January: ➡️Bitcoin mining difficulty hits a NEW ALL-TIME HIGH. ➡️YouTube rival Rumble started buying Bitcoin for its balance sheet on Friday - CEO ➡️Bitcoin went up 20x in Trump's first term as President. 10x this time? ## 💸Traditional Finance / Macro: 👉🏽no news ## 🏦Banks: 👉🏽Global central banks now hold more Gold than at any point in the past 45 years. Something is brewing. ## 🌎Macro/Geopolitics: On the 12th of January: 👉🏽Treasuries are entering their 6th year of the third great bond bear market of the last 240 years! On the 16th of January: 👉🏽EU Commission allows Thierry Breton to take up a new job at Bank of America despite a rule that requires a two-year waiting period before starting lobbying jobs. There are no rules for these corrupt EU (you fill in the blank). The rules apply only to citizens, not to the Brussels elite, and certainly not if you belong to the French political elite. In December I shared some news on the EU crusade against X. Let me explain this to you in simple terms. Breton, a man preaching about the ‘rule of law’ and X, while breaching the rules he signed up to himself: ‘Code of Conduct EU Commissioners’. Now read that again. Bitcoin only. Defund politicians. 👉🏽'The Congressional Budget Office just lowered the US population forecast by 11 million, to 372 million in 2054. This implies 6.3% growth over the next 30 years instead of the 10.5% previously expected. The agency also expects deaths to exceed births starting in 2033, 7 years earlier than in the 2024 estimates. Lower fertility rates and lower net immigration expectations were behind the outlook changes. Are we heading into a demographic crisis?' - TKL On the 17th of January: 👉🏽 Germany had 17 nuclear power plants. It shut them all down. Germany spent $1 Trillion for its energy revamp with the following results: - It is now totally dependent on Russian gas, French nuclear power electricity, and coal (the most polluting fossil fuel) - Its citizens pay the highest electricity price in Europe - It causes several times more CO2 per kWh than France Go woke, go broke. $1T for ruining both its economy and environment. Wunderbar! Just some data: In 2025, Europe is buying Russian gas at an unprecedented pace and spending billions of dollars on it, reports Politico. In the first 15 days of the year, the EU countries imported 837.3 thousand tons of Russian liquified natural gas (LNG). Just to show you how fucked up things are in the EU. EU companies are backstabbed by their own policymakers. 'Europe's carmakers risk hefty bill for carbon credit from Chinese rivals.' source: https://www.ft.com/content/677190d1-7d34-4506-a037-418baab67237 I read the article. It’mind-blowingng. It's like shooting a two-barrelled shotgun in your own nuts. On this point, EU regulators are destroying an entire part of the economy (Car manufacturing + subcontractors) and are giving the keys to Chinese companies. Go woke, go broke. China is making new coal plants at a rate that cancels German / EU efforts 10X or maybe 100x over. Now from an economic perspective: 'European equities are more or less where they were at the beginning of the century. Overregulation and bureaucracy throttling innovation, and belief in left redistribution nonsense instead of hard work and entrepreneurship have their price.' -Michael A. Arouet [](https://i.ibb.co/DWCV5pV/Ght-HId-Wc-AINW2x.jpg) 👉🏽Treasuries have experienced their worst rolling 10-year return in 90 YEARS, now at -0.5%. People out here still stacking U.S. gov bonds instead of Bitcoin. Data: U.S. Treasury bonds: -42% - Bitcoin: +809% 'The “smart money” is buying 30-year treasury bonds with a nominal yield of 1.20% on the whim that another investor (or central bank) will buy it from them at a higher price.' -Dylan Leclair On the 18th of January: 👉🏽Argentina has officially reached its first budget surplus in 14 years. Vamos! Under Milei’s leadership, Argentina turned a $7.94B trade deficit in 2023 into a record-smashing $18-19B surplus in 2024, surpassing the previous high of $16.89B in 2009. His push to boost energy exports from the Vaca Muerta shale reserves and ramp up grain sales is paying off, making Argentina a global exporting powerhouse again. With inflation already down from nearly 300% to 117.8%, Milei’s economic reforms are proving their worth. Argentinian President Javier Milei announces "Zero deficit is a reality...promises are fulfilled." Let me refrain from the above: ➡️Less state ➡️Less government expenses ➡️Capitalism ➡️Free market 👉🏽Wealth exodus accelerated by 157% in 2024: One millionaire leaves Britain every 45 minutes under Labour — Telegraph 157% increase in the outflow of millionaires since Labour came to power - including losing over 10,000 millionaires & 12 billionaires. All these people created wealth in the U.K. through living and spending. On the 19th of January: 👉🏽U.S. Housing Market 16.2% of Home Purchase Deals were canceled last month, the highest cancellation rate in history If for some reason people still believe Bitcoin is a Ponzi scheme, well that's their fault. Let me share with you the real Ponzi scheme. The following chart summarizes the impact of demographics on European pension systems really well: [](https://i.ibb.co/r7QkYsv/Gh-J7j41-Wg-AEah31.jpg) A ticking time bomb! The regulatory burdens suffered by citizens are imposed by unelectable bureaucrats! Study Bitcoin. ## 🎁If you have made it this far I would like to give you a little gift: Some fountain of Lyn Alden's wisdom: https://www.youtube.com/watch?v=fZlcrLZkNA8 Lyn Alden is a macro analyst, investment strategist, and the author of Broken Money. In this episode of What Bitcoin Did, they discuss the impact of fiscal policy on inflation, the Federal Reserve's constraints under fiscal dominance, and the role of tariffs in shaping the economic landscape. They also get into a Strategic Bitcoin Reserve, and what Donald Trump’s Administration will mean for Bitcoin. Credit: I have used multiple sources! The complete Weekly Recap will be accessible on my Bitcoin Friday page on Habla. Enriched with detailed charts, illustrative images, and comprehensive macroeconomic news to provide context and clarity. My savings account: Bitcoin The tool I recommend for setting up a Bitcoin savings plan: PocketBitcoin especially suited for beginners or people who want to invest in Bitcoin with an automated investment plan once a week or monthly. Use the code BITCOINFRIDAY Get your Bitcoin out of exchanges. Save them on a hardware wallet, run your own node...be your own bank. Not your keys, not your coins. It's that simple.⠀⠀⠀⠀ ⠀ ⠀⠀⠀ Do you think this post is helpful to you? If so, please share it and support my work with a zap. ▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃ ⭐ Many thanks⭐ Felipe - Bitcoin Friday! ▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃ @ 62a6a41e:b12acb43
2025-01-21 19:19:06Bodhidharma, the founder of Zen Buddhism (also known as Zen or Zen meditation), meditated for nine years, simply looking at a wall. Nine years staring at a wall. Good things take time. Don’t be afraid to take your time. Forget what Western society has taught us—here, we are slaves to time and productivity. I believe one of the reasons the Western world is in decline is precisely because we lack the philosophical and religious structures that enable true freedom and focus on understanding. Christianity is beautiful in its own way, but it simply isn’t as clear or rational as Eastern philosophy. As a result, it hasn’t managed to foster an environment for genuine seekers or free thinkers in the same way. We need to take the time to think. The West doesn’t understand that. Take your time. You are free to take your time. It's **your** time. Take as much time as you want, until you understand what you needed to understand.
@ 62a6a41e:b12acb43
2025-01-21 19:19:06Bodhidharma, the founder of Zen Buddhism (also known as Zen or Zen meditation), meditated for nine years, simply looking at a wall. Nine years staring at a wall. Good things take time. Don’t be afraid to take your time. Forget what Western society has taught us—here, we are slaves to time and productivity. I believe one of the reasons the Western world is in decline is precisely because we lack the philosophical and religious structures that enable true freedom and focus on understanding. Christianity is beautiful in its own way, but it simply isn’t as clear or rational as Eastern philosophy. As a result, it hasn’t managed to foster an environment for genuine seekers or free thinkers in the same way. We need to take the time to think. The West doesn’t understand that. Take your time. You are free to take your time. It's **your** time. Take as much time as you want, until you understand what you needed to understand. @ 6e15bf3d:0548a961
2025-01-21 18:46:37As we approach 2025, [website design continues to evolve at a rapid pace](https://heytradie.com.au/top-17-website-design-trends-in-2025-a-free-guide/), driven by innovations in technology, shifts in user behavior, and an increasing focus on providing personalized experiences. Web design is not just about creating visually appealing layouts anymore; it is now about creating functional, intuitive, and immersive experiences that make users feel connected with the brand. As businesses and content creators recognize the importance of digital presence, staying on top of the latest trends will be crucial for success in the upcoming year. In this article, we will explore the top website design trends for 2025, including technological advancements, aesthetic shifts, and user experience (UX) enhancements that will shape the future of the web. **2. 1. AI-Powered Personalization ** Artificial Intelligence (AI) has made a profound impact on website design, enabling businesses to offer highly personalized experiences. AI-powered tools will continue to transform websites by analyzing user behavior and preferences to deliver tailored content, recommendations, and interfaces. These personalized features enhance user engagement, increase conversion rates, and improve overall customer satisfaction. In 2025, we can expect to see more websites integrating AI technologies that adjust content, layout, and even color schemes based on individual user profiles. Personalized experiences help create a sense of relevance and connection, making users feel as though the website was designed specifically for them. **3. 2. Immersive Experiences with VR/AR ** Virtual Reality (VR) and Augmented Reality (AR) technologies are no longer just futuristic concepts; they are becoming increasingly accessible and practical in web design. In 2025, expect websites to offer immersive experiences using AR and VR. This could mean users experiencing products in a 3D environment, virtually trying on clothes, or even exploring a property from the comfort of their home. With the advancement of 5G technology, websites can incorporate these technologies more smoothly, providing a seamless and engaging experience. Retailers, real estate agencies, and travel companies, in particular, will benefit from offering interactive experiences that allow users to interact with their products and services in new and exciting ways. For example, an e-commerce site might allow you to place a piece of furniture in your room via AR to see how it fits. For the real estate sector, virtual tours of homes or apartments can be offered with VR, helping users feel more confident in their decisions before visiting in person. **4. 3. Mobile-First Design ** As mobile device usage continues to dominate the internet landscape, mobile-first design is expected to be a leading trend in 2025. In fact, more than 54% of global web traffic now comes from mobile devices (source: Statista), a statistic that reflects the increasing importance of responsive web design that prioritizes mobile experiences. A mobile-first approach means designing websites primarily for smaller screens, ensuring that the content is easily accessible, readable, and navigable on smartphones and tablets. Designers will focus on optimizing touch interactions, speed, and performance on mobile devices to meet user expectations. **5. 4. Minimalistic and Clean Aesthetics ** While overly complex and cluttered web designs were once the norm, the trend has been shifting towards minimalism. Clean and simple designs, with plenty of white space, allow for better navigation, faster load times, and a more focused user experience. In 2025, this trend will continue as users demand simplicity and speed when interacting with websites. Minimalist design involves reducing elements to the essentials, eliminating distractions, and using whitespace strategically to highlight key content. Bold typography, crisp images, and well-organized layouts will allow the content to speak for itself without overwhelming the user. The minimalist approach also tends to work well with responsive design, ensuring that websites are easy to navigate regardless of the device or screen size. Furthermore, this trend aligns with sustainability efforts, as minimalist designs often reduce the need for heavy graphic elements, leading to faster loading times and reduced energy consumption. **6. 5. Dark Mode and Customizable Themes ** Dark mode has become a popular feature in web design, and it is set to stay in 2025. Offering users the ability to toggle between light and dark modes not only enhances accessibility but also reduces eye strain, especially in low-light conditions. In addition, dark mode can give websites a modern and sleek aesthetic that appeals to users. Many websites will implement customizable themes, allowing users to choose their preferred visual experience. Whether it’s adjusting colors, fonts, or background styles, offering theme customization can make users feel more in control of their experience, making it more likely that they’ll engage with the content for longer periods. **7. 6. Microinteractions and Animations ** Microinteractions are small, interactive animations or design elements that help users navigate and engage with a website. These subtle animations provide feedback, guide users through processes, and add a sense of interactivity to the experience. For example, hover effects, button animations, and loading animations are all types of microinteractions. In 2025, websites will incorporate even more sophisticated microinteractions, making websites feel more dynamic and engaging. These small details enhance the user experience by making interactions feel more intuitive and enjoyable. However, it’s crucial that designers balance animations and microinteractions with site performance, as excessive animations can slow down load times. **8. 7. Voice Search and Voice User Interface (VUI) ** As voice search technology becomes more advanced, websites will need to adapt to this growing trend. Voice search allows users to interact with a website using spoken commands, and it is especially useful for mobile and smart device users who prefer hands-free experiences. By 2025, voice search will become more integrated into website design, as businesses will optimize their content for voice queries. Websites will also implement voice user interfaces (VUI) that allow users to navigate and interact with websites through voice commands. This trend is particularly important as voice-activated assistants like Siri, Google Assistant, and Alexa continue to gain popularity. **9. 8. Typography as a Design Element ** Typography has always been an essential part of web design, but in 2025, it will become even more central to the overall design aesthetic. Bold, experimental typography is taking center stage as designers use fonts to convey personality, emotion, and style. From oversized text to custom fonts, typography is no longer just a functional element; it is a visual statement that enhances the identity of a brand. In addition to bold typography, variable fonts that allow for greater flexibility in font weight, size, and style will become more popular, enabling websites to create more dynamic and personalized typographic experiences. **10. 9. Sustainability in Design ** As environmental consciousness grows, sustainability will become a driving factor in website design. In 2025, expect to see more brands and web developers embracing eco-friendly design practices. This includes designing websites that minimize their environmental impact by reducing energy consumption and optimizing site speed. Sustainable design could involve using lighter graphic elements, optimizing images and videos for faster loading, and choosing energy-efficient hosting options. Reducing the carbon footprint of websites is an essential part of future web design, especially as consumers become more aware of the environmental impact of digital technologies. **11. 10. Inclusive and Accessible Design **Web accessibility continues to be a priority for designers, and in 2025, we will see further advancements in this area. Websites will become even more inclusive, with features such as adjustable text sizes, color contrast settings, and screen reader compatibility. Designers will also implement accessibility guidelines and best practices to ensure that all users, including those with disabilities, can access and navigate websites easily. This includes creating more intuitive navigation systems, providing alternative text for images, and ensuring that content is accessible for people with visual, auditory, or motor impairments. Web accessibility is not just a legal requirement in some regions but also a moral responsibility. By making websites accessible to everyone, businesses can ensure a more inclusive online experience for all users. **Conclusion ** As we move towards 2025, website design will continue to innovate, with new technologies and aesthetic shifts leading the way. From AI-powered personalization and immersive AR/VR experiences to minimalistic aesthetics and mobile-first design, the future of web design is focused on user-centric experiences that are visually striking, easy to navigate, and accessible to all. To stay ahead in this ever-evolving landscape, businesses and website developers must embrace these trends and ensure that their websites are both functional and forward-thinking. By doing so, they will not only enhance the user experience but also build stronger connections with their audience, ultimately leading to greater success in the digital world. The future of website design is bright, and 2025 promises to bring about exciting changes that will redefine how we interact with the web.
@ 6e15bf3d:0548a961
2025-01-21 18:46:37As we approach 2025, [website design continues to evolve at a rapid pace](https://heytradie.com.au/top-17-website-design-trends-in-2025-a-free-guide/), driven by innovations in technology, shifts in user behavior, and an increasing focus on providing personalized experiences. Web design is not just about creating visually appealing layouts anymore; it is now about creating functional, intuitive, and immersive experiences that make users feel connected with the brand. As businesses and content creators recognize the importance of digital presence, staying on top of the latest trends will be crucial for success in the upcoming year. In this article, we will explore the top website design trends for 2025, including technological advancements, aesthetic shifts, and user experience (UX) enhancements that will shape the future of the web. **2. 1. AI-Powered Personalization ** Artificial Intelligence (AI) has made a profound impact on website design, enabling businesses to offer highly personalized experiences. AI-powered tools will continue to transform websites by analyzing user behavior and preferences to deliver tailored content, recommendations, and interfaces. These personalized features enhance user engagement, increase conversion rates, and improve overall customer satisfaction. In 2025, we can expect to see more websites integrating AI technologies that adjust content, layout, and even color schemes based on individual user profiles. Personalized experiences help create a sense of relevance and connection, making users feel as though the website was designed specifically for them. **3. 2. Immersive Experiences with VR/AR ** Virtual Reality (VR) and Augmented Reality (AR) technologies are no longer just futuristic concepts; they are becoming increasingly accessible and practical in web design. In 2025, expect websites to offer immersive experiences using AR and VR. This could mean users experiencing products in a 3D environment, virtually trying on clothes, or even exploring a property from the comfort of their home. With the advancement of 5G technology, websites can incorporate these technologies more smoothly, providing a seamless and engaging experience. Retailers, real estate agencies, and travel companies, in particular, will benefit from offering interactive experiences that allow users to interact with their products and services in new and exciting ways. For example, an e-commerce site might allow you to place a piece of furniture in your room via AR to see how it fits. For the real estate sector, virtual tours of homes or apartments can be offered with VR, helping users feel more confident in their decisions before visiting in person. **4. 3. Mobile-First Design ** As mobile device usage continues to dominate the internet landscape, mobile-first design is expected to be a leading trend in 2025. In fact, more than 54% of global web traffic now comes from mobile devices (source: Statista), a statistic that reflects the increasing importance of responsive web design that prioritizes mobile experiences. A mobile-first approach means designing websites primarily for smaller screens, ensuring that the content is easily accessible, readable, and navigable on smartphones and tablets. Designers will focus on optimizing touch interactions, speed, and performance on mobile devices to meet user expectations. **5. 4. Minimalistic and Clean Aesthetics ** While overly complex and cluttered web designs were once the norm, the trend has been shifting towards minimalism. Clean and simple designs, with plenty of white space, allow for better navigation, faster load times, and a more focused user experience. In 2025, this trend will continue as users demand simplicity and speed when interacting with websites. Minimalist design involves reducing elements to the essentials, eliminating distractions, and using whitespace strategically to highlight key content. Bold typography, crisp images, and well-organized layouts will allow the content to speak for itself without overwhelming the user. The minimalist approach also tends to work well with responsive design, ensuring that websites are easy to navigate regardless of the device or screen size. Furthermore, this trend aligns with sustainability efforts, as minimalist designs often reduce the need for heavy graphic elements, leading to faster loading times and reduced energy consumption. **6. 5. Dark Mode and Customizable Themes ** Dark mode has become a popular feature in web design, and it is set to stay in 2025. Offering users the ability to toggle between light and dark modes not only enhances accessibility but also reduces eye strain, especially in low-light conditions. In addition, dark mode can give websites a modern and sleek aesthetic that appeals to users. Many websites will implement customizable themes, allowing users to choose their preferred visual experience. Whether it’s adjusting colors, fonts, or background styles, offering theme customization can make users feel more in control of their experience, making it more likely that they’ll engage with the content for longer periods. **7. 6. Microinteractions and Animations ** Microinteractions are small, interactive animations or design elements that help users navigate and engage with a website. These subtle animations provide feedback, guide users through processes, and add a sense of interactivity to the experience. For example, hover effects, button animations, and loading animations are all types of microinteractions. In 2025, websites will incorporate even more sophisticated microinteractions, making websites feel more dynamic and engaging. These small details enhance the user experience by making interactions feel more intuitive and enjoyable. However, it’s crucial that designers balance animations and microinteractions with site performance, as excessive animations can slow down load times. **8. 7. Voice Search and Voice User Interface (VUI) ** As voice search technology becomes more advanced, websites will need to adapt to this growing trend. Voice search allows users to interact with a website using spoken commands, and it is especially useful for mobile and smart device users who prefer hands-free experiences. By 2025, voice search will become more integrated into website design, as businesses will optimize their content for voice queries. Websites will also implement voice user interfaces (VUI) that allow users to navigate and interact with websites through voice commands. This trend is particularly important as voice-activated assistants like Siri, Google Assistant, and Alexa continue to gain popularity. **9. 8. Typography as a Design Element ** Typography has always been an essential part of web design, but in 2025, it will become even more central to the overall design aesthetic. Bold, experimental typography is taking center stage as designers use fonts to convey personality, emotion, and style. From oversized text to custom fonts, typography is no longer just a functional element; it is a visual statement that enhances the identity of a brand. In addition to bold typography, variable fonts that allow for greater flexibility in font weight, size, and style will become more popular, enabling websites to create more dynamic and personalized typographic experiences. **10. 9. Sustainability in Design ** As environmental consciousness grows, sustainability will become a driving factor in website design. In 2025, expect to see more brands and web developers embracing eco-friendly design practices. This includes designing websites that minimize their environmental impact by reducing energy consumption and optimizing site speed. Sustainable design could involve using lighter graphic elements, optimizing images and videos for faster loading, and choosing energy-efficient hosting options. Reducing the carbon footprint of websites is an essential part of future web design, especially as consumers become more aware of the environmental impact of digital technologies. **11. 10. Inclusive and Accessible Design **Web accessibility continues to be a priority for designers, and in 2025, we will see further advancements in this area. Websites will become even more inclusive, with features such as adjustable text sizes, color contrast settings, and screen reader compatibility. Designers will also implement accessibility guidelines and best practices to ensure that all users, including those with disabilities, can access and navigate websites easily. This includes creating more intuitive navigation systems, providing alternative text for images, and ensuring that content is accessible for people with visual, auditory, or motor impairments. Web accessibility is not just a legal requirement in some regions but also a moral responsibility. By making websites accessible to everyone, businesses can ensure a more inclusive online experience for all users. **Conclusion ** As we move towards 2025, website design will continue to innovate, with new technologies and aesthetic shifts leading the way. From AI-powered personalization and immersive AR/VR experiences to minimalistic aesthetics and mobile-first design, the future of web design is focused on user-centric experiences that are visually striking, easy to navigate, and accessible to all. To stay ahead in this ever-evolving landscape, businesses and website developers must embrace these trends and ensure that their websites are both functional and forward-thinking. By doing so, they will not only enhance the user experience but also build stronger connections with their audience, ultimately leading to greater success in the digital world. The future of website design is bright, and 2025 promises to bring about exciting changes that will redefine how we interact with the web. @ 18e3af1e:1d42e5df
2023-08-13 02:40:19Las comunidades son creadas mediante el esfuerzo de no solo un individuo, sino al trabajo de docenas; cientos o miles de personas. Mediante la especialización, como especie, logramos entender que: el saber hacer una sola cosa no significa morir de hambre, o no estar bien preparado para un ataque; por lo contrario, el dominio o maestría de una sola cosa... Puede crear una civilización entera. Permitirnos un enfoque certero para aprender, dominar y amaestrar nuestras actividades en un periodo de tiempo finito, permitió nuestro avance hacia nuevos campos, de hecho, movió nuestra meta en magnitud tal, que al imaginar el pasado (para muchos) parece mas bien una película cómica y sombría. Hoy en día, en un mundo regido por individualismo en el reino físico, la manifestación de constructores de comunidades sigue presente en el (reino) digital. ### La evolución de la construcción A lo largo de la historia de la humanidad, la construcción ha evolucionado desde simples refugios hasta monumentos arquitectónicos y estructuras vanguardistas. Los primeros humanos crearon refugios rudimentarios con materiales naturales. Con la civilización, surgieron las primeras estructuras permanentes, como pirámides y templos, reflejando la organización social y creencias religiosas. La antigua Roma introdujo la innovación en la ingeniería con acueductos y arcos. La Edad Media vio fortificaciones y catedrales góticas que fusionaban espiritualidad y técnica. El Renacimiento abrazó la proporción y la simetría en palacios y edificios renombrados. La Revolución Industrial marcó un cambio radical con el acero y el hormigón, permitiendo rascacielos y puentes icónicos. El siglo XX trajo consigo la era de los rascacielos y la arquitectura modernista, desafiando límites estructurales y estéticos. La sostenibilidad ganó importancia en el siglo XXI, impulsando la incorporación de tecnologías avanzadas, como la impresión 3D y la construcción modular. La historia de la construcción es un testimonio de la creatividad y la adaptabilidad humanas, reflejando no solo avances técnicos, sino también valores culturales y aspiraciones. En el día hoy, los desarrolladores de software y tecnología podrían considerarse como los constructores del próximo siglo. Al igual que los constructores en otras épocas históricas, los desarrolladores de software son responsables de crear estructuras digitales que moldean la forma en que interactuamos, comunicamos y vivimos en el mundo moderno. A medida que la tecnología continúa avanzando y la sociedad se vuelve cada vez más digital, el papel de los desarrolladores de software se vuelve crucial en la construcción de soluciones tecnológicas que abordan una amplia gama de desafíos. Así como los arquitectos y constructores antiguos debían entender la física, la estética y las necesidades humanas para diseñar y construir edificios funcionales y atractivos, los desarrolladores de software deben comprender la lógica de programación, la experiencia del usuario, la seguridad cibernética y la innovación tecnológica para crear aplicaciones, sistemas y plataformas que sean útiles y efectivos. ### Individuos que inspiran La inspiración individual es un poderoso motor de cambio que puede tener un impacto significativo en la mente colectiva de una comunidad o sociedad. Cuando una persona demuestra pasión, determinación y una visión positiva, puede influir en otros a nivel emocional y cognitivo. Aquí hay algunas formas en que la inspiración individual afecta a la mente colectiva: La gente puede verse reflejada en las luchas y logros de alguien más, lo que crea un sentido de unidad y comunidad. Esto puede generar un mayor apoyo y solidaridad en torno a ciertas causas o valores. Además, la inspiración individual puede llevar a la acción. Cuando las personas son testigos de un individuo que supera obstáculos o logra metas desafiantes, esto puede motivar a otros a enfrentar sus propios desafíos y trabajar hacia sus objetivos. El ejemplo de una sola persona puede encender la chispa de la acción en muchas más. La inspiración individual puede tener un efecto multiplicador. Cuando una persona inspirada comparte su historia o experiencia, puede inspirar a otros, creando una cadena de influencia que se extiende a través de redes sociales, comunidades y sociedades enteras. Esto puede tener un impacto a gran escala en la mente colectiva. El individuo inspirador tiene el potencial de influir profundamente en la mente colectiva al cambiar percepciones, motivar la acción y crear una sensación de comunidad y unidad. ### Comunidades: origen, inicios y progreso. Las comunidades han sido una parte fundamental de la experiencia humana a lo largo de la historia. Desde los primeros tiempos hasta la era moderna, las comunidades han evolucionado y cambiado en respuesta a las necesidades, avances tecnológicos y contextos culturales. Desde los primeros días de la humanidad, nuestros antepasados se agruparon en pequeñas comunidades para sobrevivir. Estas comunidades eran grupos familiares o tribus que compartían recursos y conocimientos para cazar, recolectar alimentos y protegerse de los peligros. La cooperación y la solidaridad eran esenciales para la supervivencia. Con el desarrollo de la agricultura, las comunidades evolucionaron hacia asentamientos más permanentes. La capacidad de cultivar alimentos permitió la formación de aldeas y pueblos, donde la gente podía establecerse y construir relaciones más complejas. Esto llevó al surgimiento de una división del trabajo más especializada y al desarrollo de habilidades artesanales. Las civilizaciones antiguas, como la sumeria, egipcia, griega y romana, dieron paso a la formación de ciudades y sociedades más organizadas. Las comunidades se convirtieron en centros de comercio, gobierno y cultura. Se construyeron estructuras monumentales, como templos y palacios, que unificaron a las personas en torno a creencias religiosas y sistemas políticos. Durante la Edad Media, las comunidades se organizaron en torno a sistemas feudales. Los señores feudales gobernaban sobre las tierras y las personas locales. Las aldeas y feudos eran autónomos en gran medida y se centraban en la agricultura y la autosuficiencia. La Revolución Industrial marcó un cambio importante en la estructura de las comunidades. La industrialización dio lugar a la urbanización, con muchas personas dejando las zonas rurales para trabajar en fábricas en las ciudades. En la era moderna, las comunidades han continuado evolucionando con avances tecnológicos y la globalización. Las redes sociales y las comunicaciones digitales han conectado a personas de todo el mundo, creando comunidades virtuales en línea. ### Bitcoin | Nostr y la chispa del constructor Como ya vimos, un solo individuo puede inspirar a muchos otros, teniendo un efecto multiplicador. Esto no solo se traduce al mundo físico, por el contrario, esta directamente ligado a nuestra psicología, incluso podemos decir que va aun mas allá, adentrándonos en el terreno ideológico y espiritual. Hasta hace no mucho, estábamos a merced de las grandes corporaciones que construían todo por nosotros, mientras esperábamos con ansias las nuevas actualizaciones de cada iteración de sus productos. Cada vez mas y mas nos hacíamos dependientes de dichas corporaciones sin quizás notarlo, poco a poco se fueron apoderando de nuestro tiempo y muy insidiosamente de nuestra personalidad e identidad. Gracias a las alternativas presentadas hoy en día y a los individuos que inspiran a otros, existe la posibilidad de construir algo que va mas allá de las grandes corporaciones, porque transciende no solo el nivel físico y digital, sino que también transciende a los individuos que aportan a la comunidad. Estoy hablando por supuesto de Nostr, y como los incentivos están alineados gracias a Bitcoin. Pongamos como ejemplo un par de nombres para ilustrar como individuos que inspirar pueden crear una chispa que se extiende a cada persona dentro de la comunidad. Personajes como nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft nostr:npub1utx00neqgqln72j22kej3ux7803c2k986henvvha4thuwfkper4s7r50e8 nostr:npub1v0lxxxxutpvrelsksy8cdhgfux9l6a42hsj2qzquu2zk7vc9qnkszrqj49 nostr:npub107jk7htfv243u0x5ynn43scq9wrxtaasmrwwa8lfu2ydwag6cx2quqncxg (entre muchos otros que podría mencionar pero todo el articulo seria una lista de nombres) han inspirado a otros desarrolladores, creadores de contenido (y todas las otras especializaciones que te puedas imaginar…) A construir sobre este protocolo. Incluso, personas como el caso mas reciente de nostr:npub1m64hnkh6rs47fd9x6wk2zdtmdj4qkazt734d22d94ery9zzhne5qw9uaks han encontrado inspiración para aprender a programar sobre estos mismos rieles. > nostr:nevent1qqs8fe938k7j5sxcprrv89ezpu09m9pzm90f0sq24hnwlwu0rmn09qcpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxg5vtygh La chispa del constructor en palabras mas concisas es: **Inspiración multiplicadora en pos de la productividad y por ende, del crecimiento de una comunidad.** Sin Bitcoin y Lightning Network, esto seria posible, pero mucho menos efectivo debido a que las personas detrás de toda labor que este enfocada en creación de contenido, desarrollo, etc. Tienen que comer. ### Conclusión La chispa del constructor radica en la inspiración individual que impulsa a la acción colectiva. Desde la evolución de la construcción hasta las comunidades digitales, **el poder de un individuo inspirado puede moldear el presente y el futuro de las comunidades en todo el mundo.**
@ 18e3af1e:1d42e5df
2023-08-13 02:40:19Las comunidades son creadas mediante el esfuerzo de no solo un individuo, sino al trabajo de docenas; cientos o miles de personas. Mediante la especialización, como especie, logramos entender que: el saber hacer una sola cosa no significa morir de hambre, o no estar bien preparado para un ataque; por lo contrario, el dominio o maestría de una sola cosa... Puede crear una civilización entera. Permitirnos un enfoque certero para aprender, dominar y amaestrar nuestras actividades en un periodo de tiempo finito, permitió nuestro avance hacia nuevos campos, de hecho, movió nuestra meta en magnitud tal, que al imaginar el pasado (para muchos) parece mas bien una película cómica y sombría. Hoy en día, en un mundo regido por individualismo en el reino físico, la manifestación de constructores de comunidades sigue presente en el (reino) digital. ### La evolución de la construcción A lo largo de la historia de la humanidad, la construcción ha evolucionado desde simples refugios hasta monumentos arquitectónicos y estructuras vanguardistas. Los primeros humanos crearon refugios rudimentarios con materiales naturales. Con la civilización, surgieron las primeras estructuras permanentes, como pirámides y templos, reflejando la organización social y creencias religiosas. La antigua Roma introdujo la innovación en la ingeniería con acueductos y arcos. La Edad Media vio fortificaciones y catedrales góticas que fusionaban espiritualidad y técnica. El Renacimiento abrazó la proporción y la simetría en palacios y edificios renombrados. La Revolución Industrial marcó un cambio radical con el acero y el hormigón, permitiendo rascacielos y puentes icónicos. El siglo XX trajo consigo la era de los rascacielos y la arquitectura modernista, desafiando límites estructurales y estéticos. La sostenibilidad ganó importancia en el siglo XXI, impulsando la incorporación de tecnologías avanzadas, como la impresión 3D y la construcción modular. La historia de la construcción es un testimonio de la creatividad y la adaptabilidad humanas, reflejando no solo avances técnicos, sino también valores culturales y aspiraciones. En el día hoy, los desarrolladores de software y tecnología podrían considerarse como los constructores del próximo siglo. Al igual que los constructores en otras épocas históricas, los desarrolladores de software son responsables de crear estructuras digitales que moldean la forma en que interactuamos, comunicamos y vivimos en el mundo moderno. A medida que la tecnología continúa avanzando y la sociedad se vuelve cada vez más digital, el papel de los desarrolladores de software se vuelve crucial en la construcción de soluciones tecnológicas que abordan una amplia gama de desafíos. Así como los arquitectos y constructores antiguos debían entender la física, la estética y las necesidades humanas para diseñar y construir edificios funcionales y atractivos, los desarrolladores de software deben comprender la lógica de programación, la experiencia del usuario, la seguridad cibernética y la innovación tecnológica para crear aplicaciones, sistemas y plataformas que sean útiles y efectivos. ### Individuos que inspiran La inspiración individual es un poderoso motor de cambio que puede tener un impacto significativo en la mente colectiva de una comunidad o sociedad. Cuando una persona demuestra pasión, determinación y una visión positiva, puede influir en otros a nivel emocional y cognitivo. Aquí hay algunas formas en que la inspiración individual afecta a la mente colectiva: La gente puede verse reflejada en las luchas y logros de alguien más, lo que crea un sentido de unidad y comunidad. Esto puede generar un mayor apoyo y solidaridad en torno a ciertas causas o valores. Además, la inspiración individual puede llevar a la acción. Cuando las personas son testigos de un individuo que supera obstáculos o logra metas desafiantes, esto puede motivar a otros a enfrentar sus propios desafíos y trabajar hacia sus objetivos. El ejemplo de una sola persona puede encender la chispa de la acción en muchas más. La inspiración individual puede tener un efecto multiplicador. Cuando una persona inspirada comparte su historia o experiencia, puede inspirar a otros, creando una cadena de influencia que se extiende a través de redes sociales, comunidades y sociedades enteras. Esto puede tener un impacto a gran escala en la mente colectiva. El individuo inspirador tiene el potencial de influir profundamente en la mente colectiva al cambiar percepciones, motivar la acción y crear una sensación de comunidad y unidad. ### Comunidades: origen, inicios y progreso. Las comunidades han sido una parte fundamental de la experiencia humana a lo largo de la historia. Desde los primeros tiempos hasta la era moderna, las comunidades han evolucionado y cambiado en respuesta a las necesidades, avances tecnológicos y contextos culturales. Desde los primeros días de la humanidad, nuestros antepasados se agruparon en pequeñas comunidades para sobrevivir. Estas comunidades eran grupos familiares o tribus que compartían recursos y conocimientos para cazar, recolectar alimentos y protegerse de los peligros. La cooperación y la solidaridad eran esenciales para la supervivencia. Con el desarrollo de la agricultura, las comunidades evolucionaron hacia asentamientos más permanentes. La capacidad de cultivar alimentos permitió la formación de aldeas y pueblos, donde la gente podía establecerse y construir relaciones más complejas. Esto llevó al surgimiento de una división del trabajo más especializada y al desarrollo de habilidades artesanales. Las civilizaciones antiguas, como la sumeria, egipcia, griega y romana, dieron paso a la formación de ciudades y sociedades más organizadas. Las comunidades se convirtieron en centros de comercio, gobierno y cultura. Se construyeron estructuras monumentales, como templos y palacios, que unificaron a las personas en torno a creencias religiosas y sistemas políticos. Durante la Edad Media, las comunidades se organizaron en torno a sistemas feudales. Los señores feudales gobernaban sobre las tierras y las personas locales. Las aldeas y feudos eran autónomos en gran medida y se centraban en la agricultura y la autosuficiencia. La Revolución Industrial marcó un cambio importante en la estructura de las comunidades. La industrialización dio lugar a la urbanización, con muchas personas dejando las zonas rurales para trabajar en fábricas en las ciudades. En la era moderna, las comunidades han continuado evolucionando con avances tecnológicos y la globalización. Las redes sociales y las comunicaciones digitales han conectado a personas de todo el mundo, creando comunidades virtuales en línea. ### Bitcoin | Nostr y la chispa del constructor Como ya vimos, un solo individuo puede inspirar a muchos otros, teniendo un efecto multiplicador. Esto no solo se traduce al mundo físico, por el contrario, esta directamente ligado a nuestra psicología, incluso podemos decir que va aun mas allá, adentrándonos en el terreno ideológico y espiritual. Hasta hace no mucho, estábamos a merced de las grandes corporaciones que construían todo por nosotros, mientras esperábamos con ansias las nuevas actualizaciones de cada iteración de sus productos. Cada vez mas y mas nos hacíamos dependientes de dichas corporaciones sin quizás notarlo, poco a poco se fueron apoderando de nuestro tiempo y muy insidiosamente de nuestra personalidad e identidad. Gracias a las alternativas presentadas hoy en día y a los individuos que inspiran a otros, existe la posibilidad de construir algo que va mas allá de las grandes corporaciones, porque transciende no solo el nivel físico y digital, sino que también transciende a los individuos que aportan a la comunidad. Estoy hablando por supuesto de Nostr, y como los incentivos están alineados gracias a Bitcoin. Pongamos como ejemplo un par de nombres para ilustrar como individuos que inspirar pueden crear una chispa que se extiende a cada persona dentro de la comunidad. Personajes como nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft nostr:npub1utx00neqgqln72j22kej3ux7803c2k986henvvha4thuwfkper4s7r50e8 nostr:npub1v0lxxxxutpvrelsksy8cdhgfux9l6a42hsj2qzquu2zk7vc9qnkszrqj49 nostr:npub107jk7htfv243u0x5ynn43scq9wrxtaasmrwwa8lfu2ydwag6cx2quqncxg (entre muchos otros que podría mencionar pero todo el articulo seria una lista de nombres) han inspirado a otros desarrolladores, creadores de contenido (y todas las otras especializaciones que te puedas imaginar…) A construir sobre este protocolo. Incluso, personas como el caso mas reciente de nostr:npub1m64hnkh6rs47fd9x6wk2zdtmdj4qkazt734d22d94ery9zzhne5qw9uaks han encontrado inspiración para aprender a programar sobre estos mismos rieles. > nostr:nevent1qqs8fe938k7j5sxcprrv89ezpu09m9pzm90f0sq24hnwlwu0rmn09qcpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxg5vtygh La chispa del constructor en palabras mas concisas es: **Inspiración multiplicadora en pos de la productividad y por ende, del crecimiento de una comunidad.** Sin Bitcoin y Lightning Network, esto seria posible, pero mucho menos efectivo debido a que las personas detrás de toda labor que este enfocada en creación de contenido, desarrollo, etc. Tienen que comer. ### Conclusión La chispa del constructor radica en la inspiración individual que impulsa a la acción colectiva. Desde la evolución de la construcción hasta las comunidades digitales, **el poder de un individuo inspirado puede moldear el presente y el futuro de las comunidades en todo el mundo.** @ 21ac2956:09d1e2df
2025-01-22 15:27:00## [kakoi](https://github.com/betonetojp/kakoi) の仕様についてのメモ ### キーボード操作 * 左手での操作に最適化 | キー | 動作 | |:-|:-| | ESC | 設定画面 | | F1 / F12 | ポストバーの表示と非表示 | | F2 | 時間の表示と非表示 | | F3 | ユーザーアイコンの表示と非表示 | | F4 | 名前の表示と非表示 | | F5 | Geminiによるタイムラインまとめ画面を表示 | | F9 / Z | コンテンツの折り返し表示の切り替え (余白ダブルクリックでも動作) | | F10 | ユーザーリストとキーワード通知の設定画面 (余白右クリックでも動作) | | F11 | メイン画面の表示と非表示 (ポストバー表示) | | Shift + W | イベント最上行へ移動 | | W / ↑| イベント選択上移動 | | S / ↓ | イベント選択下移動 | | Shift + S | イベント最下行へ移動 | | A / ← | Webビューを開く (イベントを右クリックでも動作) | | F / → | リアクションを送信 (イベントをダブルクリックでも動作) | | 1 ~ 0 | リアクションを選択 | | R | 返信 | | B | リポスト | | Q | 引用 | | C | Webビューを閉じる | | Ctrl + Shift + A | メイン画面をアクティブにする | ### タイムライン * kind:1, 6, 7, 16を取得して表示する * フォロイーの名前の前には * が付く ### フォローリスト(kind:3) * 参照のみで更新はしない * F10 で開くユーザーリストでユーザーを選択し petname セルをクリックすることで未フォローユーザーにもペットネームを設定可能(ローカル保存) ### プロフィール(kind:0) * F10 で開くユーザーリストでユーザーを選択し picture セルをクリックすることでユーザーのアイコン表示を変更可能(ローカル保存) ### 返信([NIP-10](https://github.com/nostr-protocol/nips/blob/master/10.md) kind:1) * kakoi のタイムラインに流れるすべてのイベント種に返信可能とする * スレッドを考慮せず、単一イベントへの単発返信とする * e タグは marker と返信先 pubkey は設定していない。 relay-url には空文字を設定 ```json ["e", "返信先 event-id", ""] ``` * p タグは 返信先 pubkey ひとつだけを指定 ### リポスト([NIP-18](https://github.com/nostr-protocol/nips/blob/master/18.md) kind:6 , 16) * kakoi のタイムラインに流れるすべてのイベント種をリポスト可能 * kind:1はkind:6。その他はkind:16でリポストする * e タグは relay-url に空文字を設定 ```json ["e", "リポスト元 event-id", ""] ``` ### 引用([NIP-18](https://github.com/nostr-protocol/nips/blob/master/18.md) kind:1) * q タグは relay-url に空文字を設定 ```json ["q", "引用元 event-id", ""] ```
@ 21ac2956:09d1e2df
2025-01-22 15:27:00## [kakoi](https://github.com/betonetojp/kakoi) の仕様についてのメモ ### キーボード操作 * 左手での操作に最適化 | キー | 動作 | |:-|:-| | ESC | 設定画面 | | F1 / F12 | ポストバーの表示と非表示 | | F2 | 時間の表示と非表示 | | F3 | ユーザーアイコンの表示と非表示 | | F4 | 名前の表示と非表示 | | F5 | Geminiによるタイムラインまとめ画面を表示 | | F9 / Z | コンテンツの折り返し表示の切り替え (余白ダブルクリックでも動作) | | F10 | ユーザーリストとキーワード通知の設定画面 (余白右クリックでも動作) | | F11 | メイン画面の表示と非表示 (ポストバー表示) | | Shift + W | イベント最上行へ移動 | | W / ↑| イベント選択上移動 | | S / ↓ | イベント選択下移動 | | Shift + S | イベント最下行へ移動 | | A / ← | Webビューを開く (イベントを右クリックでも動作) | | F / → | リアクションを送信 (イベントをダブルクリックでも動作) | | 1 ~ 0 | リアクションを選択 | | R | 返信 | | B | リポスト | | Q | 引用 | | C | Webビューを閉じる | | Ctrl + Shift + A | メイン画面をアクティブにする | ### タイムライン * kind:1, 6, 7, 16を取得して表示する * フォロイーの名前の前には * が付く ### フォローリスト(kind:3) * 参照のみで更新はしない * F10 で開くユーザーリストでユーザーを選択し petname セルをクリックすることで未フォローユーザーにもペットネームを設定可能(ローカル保存) ### プロフィール(kind:0) * F10 で開くユーザーリストでユーザーを選択し picture セルをクリックすることでユーザーのアイコン表示を変更可能(ローカル保存) ### 返信([NIP-10](https://github.com/nostr-protocol/nips/blob/master/10.md) kind:1) * kakoi のタイムラインに流れるすべてのイベント種に返信可能とする * スレッドを考慮せず、単一イベントへの単発返信とする * e タグは marker と返信先 pubkey は設定していない。 relay-url には空文字を設定 ```json ["e", "返信先 event-id", ""] ``` * p タグは 返信先 pubkey ひとつだけを指定 ### リポスト([NIP-18](https://github.com/nostr-protocol/nips/blob/master/18.md) kind:6 , 16) * kakoi のタイムラインに流れるすべてのイベント種をリポスト可能 * kind:1はkind:6。その他はkind:16でリポストする * e タグは relay-url に空文字を設定 ```json ["e", "リポスト元 event-id", ""] ``` ### 引用([NIP-18](https://github.com/nostr-protocol/nips/blob/master/18.md) kind:1) * q タグは relay-url に空文字を設定 ```json ["q", "引用元 event-id", ""] ``` @ b17fccdf:b7211155
2025-01-21 17:02:21The past 26 August, Tor [introduced officially](https://blog.torproject.org/introducing-proof-of-work-defense-for-onion-services/) a proof-of-work (PoW) defense for onion services designed to prioritize verified network traffic as a deterrent against denial of service (DoS) attacks. ~ > This feature at the moment, is [deactivate by default](https://gitlab.torproject.org/tpo/core/tor/-/blob/main/doc/man/tor.1.txt#L3117), so you need to follow these steps to activate this on a MiniBolt node: * Make sure you have the latest version of Tor installed, at the time of writing this post, which is v0.4.8.6. Check your current version by typing ``` tor --version ``` **Example** of expected output: ``` Tor version 0.4.8.6. This build of Tor is covered by the GNU General Public License (https://www.gnu.org/licenses/gpl-3.0.en.html) Tor is running on Linux with Libevent 2.1.12-stable, OpenSSL 3.0.9, Zlib 1.2.13, Liblzma 5.4.1, Libzstd N/A and Glibc 2.36 as libc. Tor compiled with GCC version 12.2.0 ``` ~ > If you have v0.4.8.X, you are **OK**, if not, type `sudo apt update && sudo apt upgrade` and confirm to update. * Basic PoW support can be checked by running this command: ``` tor --list-modules ``` Expected output: ``` relay: yes dirauth: yes dircache: yes pow: **yes** ``` ~ > If you have `pow: yes`, you are **OK** * Now go to the torrc file of your MiniBolt and add the parameter to enable PoW for each hidden service added ``` sudo nano /etc/tor/torrc ``` Example: ``` # Hidden Service BTC RPC Explorer HiddenServiceDir /var/lib/tor/hidden_service_btcrpcexplorer/ HiddenServiceVersion 3 HiddenServicePoWDefensesEnabled 1 HiddenServicePort 80 127.0.0.1:3002 ``` ~ > Bitcoin Core and LND use the Tor control port to automatically create the hidden service, requiring no action from the user. We have submitted a feature request in the official GitHub repositories to explore the need for the integration of Tor's PoW defense into the automatic creation process of the hidden service. You can follow them at the following links: * Bitcoin Core: https://github.com/lightningnetwork/lnd/issues/8002 * LND: https://github.com/bitcoin/bitcoin/issues/28499 --- More info: * https://blog.torproject.org/introducing-proof-of-work-defense-for-onion-services/ * https://gitlab.torproject.org/tpo/onion-services/onion-support/-/wikis/Documentation/PoW-FAQ --- Enjoy it MiniBolter! 💙
@ b17fccdf:b7211155
2025-01-21 17:02:21The past 26 August, Tor [introduced officially](https://blog.torproject.org/introducing-proof-of-work-defense-for-onion-services/) a proof-of-work (PoW) defense for onion services designed to prioritize verified network traffic as a deterrent against denial of service (DoS) attacks. ~ > This feature at the moment, is [deactivate by default](https://gitlab.torproject.org/tpo/core/tor/-/blob/main/doc/man/tor.1.txt#L3117), so you need to follow these steps to activate this on a MiniBolt node: * Make sure you have the latest version of Tor installed, at the time of writing this post, which is v0.4.8.6. Check your current version by typing ``` tor --version ``` **Example** of expected output: ``` Tor version 0.4.8.6. This build of Tor is covered by the GNU General Public License (https://www.gnu.org/licenses/gpl-3.0.en.html) Tor is running on Linux with Libevent 2.1.12-stable, OpenSSL 3.0.9, Zlib 1.2.13, Liblzma 5.4.1, Libzstd N/A and Glibc 2.36 as libc. Tor compiled with GCC version 12.2.0 ``` ~ > If you have v0.4.8.X, you are **OK**, if not, type `sudo apt update && sudo apt upgrade` and confirm to update. * Basic PoW support can be checked by running this command: ``` tor --list-modules ``` Expected output: ``` relay: yes dirauth: yes dircache: yes pow: **yes** ``` ~ > If you have `pow: yes`, you are **OK** * Now go to the torrc file of your MiniBolt and add the parameter to enable PoW for each hidden service added ``` sudo nano /etc/tor/torrc ``` Example: ``` # Hidden Service BTC RPC Explorer HiddenServiceDir /var/lib/tor/hidden_service_btcrpcexplorer/ HiddenServiceVersion 3 HiddenServicePoWDefensesEnabled 1 HiddenServicePort 80 127.0.0.1:3002 ``` ~ > Bitcoin Core and LND use the Tor control port to automatically create the hidden service, requiring no action from the user. We have submitted a feature request in the official GitHub repositories to explore the need for the integration of Tor's PoW defense into the automatic creation process of the hidden service. You can follow them at the following links: * Bitcoin Core: https://github.com/lightningnetwork/lnd/issues/8002 * LND: https://github.com/bitcoin/bitcoin/issues/28499 --- More info: * https://blog.torproject.org/introducing-proof-of-work-defense-for-onion-services/ * https://gitlab.torproject.org/tpo/onion-services/onion-support/-/wikis/Documentation/PoW-FAQ --- Enjoy it MiniBolter! 💙 @ b17fccdf:b7211155
2025-01-21 16:56:24It turns out that Ubuntu Linux installations of Ubuntu 23.04, 22.04.3 LTS, and installs done since April 2023 that accepted the Snap version update haven't been following Ubuntu's own recommended security best practices for their security pocket configuration for packages. A new Subiquity release [was issued](https://github.com/canonical/subiquity/releases/tag/23.09.1) to fix this problem while those on affected Ubuntu systems already installed are recommended to manually edit their `/etc/apt/sources.list` file. If you didn't install MiniBolt recently, **you are affected by this bug**, and we need to fix that manually if not we want to install all since cero. Anyway, if you installed Minibolt recently, we recommend you review that. Follow these easy steps to review and fix this: * Edit the `sources-list` file: ``` sudo nano /etc/apt/sources.list ``` * Search now for every line that includes '-security' (without quotes) (normally at the end of the file) and change the URL to --> http://security.ubuntu.com/ubuntu ~ > For example, from http://es.archive.ubuntu.com/ubuntu (or the extension corresponding to your country) to --> http://security.ubuntu.com/ubuntu ~> Real case, Spain location, **before fix**: ``` deb http://es.archive.ubuntu.com/ubuntu jammy-security main restricted # deb-src http://es.archive.ubuntu.com/ubuntu jammy-security main restricted deb http://es.archive.ubuntu.com/ubuntu jammy-security universe # deb-src http://es.archive.ubuntu.com/ubuntu jammy-security universe deb http://es.archive.ubuntu.com/ubuntu jammy-security multiverse # deb-src http://es.archive.ubuntu.com/ubuntu jammy-security multiverse ``` **After fix:** ``` deb http://security.ubuntu.com/ubuntu jammy-security main restricted # deb-src http://es.archive.ubuntu.com/ubuntu jammy-security main restricted deb http://security.ubuntu.com/ubuntu jammy-security universe # deb-src http://es.archive.ubuntu.com/ubuntu jammy-security universe deb http://security.ubuntu.com/ubuntu jammy-security multiverse # deb-src http://es.archive.ubuntu.com/ubuntu jammy-security multiverse ``` **Save and exit** **Note:** If you have already these lines changed, you are not affected by this bug, and is not necessary to do anything. Simply exit the editor by doing Ctrl-X * Finally, type the next command to refresh the repository pointers: ``` sudo apt update ``` * And optionally take the opportunity to update the system by doing: ``` sudo apt full-upgrade ``` More context: * https://wiki.ubuntu.com/SecurityTeam/FAQ#What_repositories_and_pockets_should_I_use_to_make_sure_my_systems_are_up_to_date.3F * https://bugs.launchpad.net/subiquity/+bug/2033977 * https://www.phoronix.com/news/Ubuntu-Security-Pocket-Issue
@ b17fccdf:b7211155
2025-01-21 16:56:24It turns out that Ubuntu Linux installations of Ubuntu 23.04, 22.04.3 LTS, and installs done since April 2023 that accepted the Snap version update haven't been following Ubuntu's own recommended security best practices for their security pocket configuration for packages. A new Subiquity release [was issued](https://github.com/canonical/subiquity/releases/tag/23.09.1) to fix this problem while those on affected Ubuntu systems already installed are recommended to manually edit their `/etc/apt/sources.list` file. If you didn't install MiniBolt recently, **you are affected by this bug**, and we need to fix that manually if not we want to install all since cero. Anyway, if you installed Minibolt recently, we recommend you review that. Follow these easy steps to review and fix this: * Edit the `sources-list` file: ``` sudo nano /etc/apt/sources.list ``` * Search now for every line that includes '-security' (without quotes) (normally at the end of the file) and change the URL to --> http://security.ubuntu.com/ubuntu ~ > For example, from http://es.archive.ubuntu.com/ubuntu (or the extension corresponding to your country) to --> http://security.ubuntu.com/ubuntu ~> Real case, Spain location, **before fix**: ``` deb http://es.archive.ubuntu.com/ubuntu jammy-security main restricted # deb-src http://es.archive.ubuntu.com/ubuntu jammy-security main restricted deb http://es.archive.ubuntu.com/ubuntu jammy-security universe # deb-src http://es.archive.ubuntu.com/ubuntu jammy-security universe deb http://es.archive.ubuntu.com/ubuntu jammy-security multiverse # deb-src http://es.archive.ubuntu.com/ubuntu jammy-security multiverse ``` **After fix:** ``` deb http://security.ubuntu.com/ubuntu jammy-security main restricted # deb-src http://es.archive.ubuntu.com/ubuntu jammy-security main restricted deb http://security.ubuntu.com/ubuntu jammy-security universe # deb-src http://es.archive.ubuntu.com/ubuntu jammy-security universe deb http://security.ubuntu.com/ubuntu jammy-security multiverse # deb-src http://es.archive.ubuntu.com/ubuntu jammy-security multiverse ``` **Save and exit** **Note:** If you have already these lines changed, you are not affected by this bug, and is not necessary to do anything. Simply exit the editor by doing Ctrl-X * Finally, type the next command to refresh the repository pointers: ``` sudo apt update ``` * And optionally take the opportunity to update the system by doing: ``` sudo apt full-upgrade ``` More context: * https://wiki.ubuntu.com/SecurityTeam/FAQ#What_repositories_and_pockets_should_I_use_to_make_sure_my_systems_are_up_to_date.3F * https://bugs.launchpad.net/subiquity/+bug/2033977 * https://www.phoronix.com/news/Ubuntu-Security-Pocket-Issue @ b17fccdf:b7211155
2025-01-21 16:49:27### **What's changed** * New method for Bitcoin Core signature check, click ~ >[HERE](https://minibolt.minibolt.info/bitcoin/bitcoin/bitcoin-client#signature-check)< ~ * GitHub repo of Bitcoin Core release attestations (Guix), click ~ >[HERE](https://github.com/bitcoin-core/guix.sigs)< ~ --- **History:** ~ > PR that caused the broken and obsolescence of the old signature verification process, click ~ >[HERE](https://github.com/bitcoin/bitcoin/pull/26598)< ~ ~ > New GitHub folder of Bitcoin Core repo that stores the signatures, click ~ >[HERE](https://github.com/bitcoin-core/guix.sigs/tree/main/builder-keys)< ~ --- Thanks to nostr:npub1gzuushllat7pet0ccv9yuhygvc8ldeyhrgxuwg744dn5khnpk3gs3ea5ds for building the command that made magic possible 🧙♂️🧡 --- Enjoy it MiniBolter! 💙
@ b17fccdf:b7211155
2025-01-21 16:49:27### **What's changed** * New method for Bitcoin Core signature check, click ~ >[HERE](https://minibolt.minibolt.info/bitcoin/bitcoin/bitcoin-client#signature-check)< ~ * GitHub repo of Bitcoin Core release attestations (Guix), click ~ >[HERE](https://github.com/bitcoin-core/guix.sigs)< ~ --- **History:** ~ > PR that caused the broken and obsolescence of the old signature verification process, click ~ >[HERE](https://github.com/bitcoin/bitcoin/pull/26598)< ~ ~ > New GitHub folder of Bitcoin Core repo that stores the signatures, click ~ >[HERE](https://github.com/bitcoin-core/guix.sigs/tree/main/builder-keys)< ~ --- Thanks to nostr:npub1gzuushllat7pet0ccv9yuhygvc8ldeyhrgxuwg744dn5khnpk3gs3ea5ds for building the command that made magic possible 🧙♂️🧡 --- Enjoy it MiniBolter! 💙 @ b17fccdf:b7211155
2025-01-21 16:40:01### **Important notice to MiniBolt node runners:** ~ > It turns out that the I2P devs have opened an issue on the Bitcoin Core GitHub repo commenting that because they gave the option to enable the `notransit=true` parameter in the official documentation: > [...] If you prefer not to relay any public I2P traffic and only allow I2P traffic from programs connecting through the SAM proxy, e.g. Bitcoin Core, you can set the no transit option to true [...] are having a heavy load on the I2P network since last December 19. Also comment that it is advisable to share as much bandwidth and transit tunnels as we can, to increase anonymity with coverage traffic, by contributing more to the I2p network than we consume. So they ask that we deactivate that option that you use activated. With all this, he already updated the "Privacy" section by removing that setting. The steps to delete this configuration once we have already configured it, are the following: * With the "admin" user, stop i2pd: ``` sudo systemctl stop i2pd ``` * Comment line 93 with "#" at the beginning of it (notransit = true), save and exit ``` sudo nano /var/lib/i2pd/i2pd.conf --line numbers ``` * Start i2pd again: ``` sudo systemctl start i2pd ``` * And that's it, you could take a look at Bitcoin Core to see that it has detected i2pd running again after the reboot with: ``` tail --lines 500 -f /home/bitcoin/.bitcoin/debug.log ``` ~ > If you don't see that I2P is up in Bitcoin Core after the restart, `sudo systemctl restart bitcoind` and look again at the logs of the same. --- More info in the rollback commit, see ~> [HERE](https://github.com/twofaktor/minibolt/commit/99cae67a5150bb5b7deae3674cc958eb31c74a75) < ~
@ b17fccdf:b7211155
2025-01-21 16:40:01### **Important notice to MiniBolt node runners:** ~ > It turns out that the I2P devs have opened an issue on the Bitcoin Core GitHub repo commenting that because they gave the option to enable the `notransit=true` parameter in the official documentation: > [...] If you prefer not to relay any public I2P traffic and only allow I2P traffic from programs connecting through the SAM proxy, e.g. Bitcoin Core, you can set the no transit option to true [...] are having a heavy load on the I2P network since last December 19. Also comment that it is advisable to share as much bandwidth and transit tunnels as we can, to increase anonymity with coverage traffic, by contributing more to the I2p network than we consume. So they ask that we deactivate that option that you use activated. With all this, he already updated the "Privacy" section by removing that setting. The steps to delete this configuration once we have already configured it, are the following: * With the "admin" user, stop i2pd: ``` sudo systemctl stop i2pd ``` * Comment line 93 with "#" at the beginning of it (notransit = true), save and exit ``` sudo nano /var/lib/i2pd/i2pd.conf --line numbers ``` * Start i2pd again: ``` sudo systemctl start i2pd ``` * And that's it, you could take a look at Bitcoin Core to see that it has detected i2pd running again after the reboot with: ``` tail --lines 500 -f /home/bitcoin/.bitcoin/debug.log ``` ~ > If you don't see that I2P is up in Bitcoin Core after the restart, `sudo systemctl restart bitcoind` and look again at the logs of the same. --- More info in the rollback commit, see ~> [HERE](https://github.com/twofaktor/minibolt/commit/99cae67a5150bb5b7deae3674cc958eb31c74a75) < ~ @ b17fccdf:b7211155
2025-01-21 16:30:11> Your MiniBolt is on a home local network, you want to expose it on the public Internet (clearnet) without exposing your public IP, without Firewall rules, without NAT port forwarding, without risk, easy and cheap? --- Go to the bonus guide by clicking ~ >[HERE](https://minibolt.minibolt.info/bonus-guides/system/cloudflare-tunnel) <~ --- Enjoy it MiniBolter! 💙
@ b17fccdf:b7211155
2025-01-21 16:30:11> Your MiniBolt is on a home local network, you want to expose it on the public Internet (clearnet) without exposing your public IP, without Firewall rules, without NAT port forwarding, without risk, easy and cheap? --- Go to the bonus guide by clicking ~ >[HERE](https://minibolt.minibolt.info/bonus-guides/system/cloudflare-tunnel) <~ --- Enjoy it MiniBolter! 💙 @ b17fccdf:b7211155
2025-01-21 16:23:44> Build your nostr relay step by step on your MiniBolt node! (**easily adaptable to other environment**) No need to trust anyone else! Be sovereign! ~> Go to the bonus guide by clicking ~> [HERE](https://minibolt.minibolt.info/bonus-guides/nostr/nostr-relay)< ~ ~> This guide includes a complete [extra section](https://minibolt.minibolt.info/bonus-guides/nostr/nostr-relay#extras-optional) to cover the different processes for using nostr **as a user and relay operator**. --- PS: The MiniBolt project has its FREE relay, be free to connect by adding to your favorite client the next address: `wss://relay.minibolt.info` ~> Let a review on [noStrudel](https://nostrudel.ninja/#/r/wss%3A%2F%2Frelay.minibolt.info) or [Coracle](https://coracle.social/relays/relay.minibolt.info) of your experience using it. --- Remember, Nostr is freedom! Stay resilient! 💜 🛡️💪
@ b17fccdf:b7211155
2025-01-21 16:23:44> Build your nostr relay step by step on your MiniBolt node! (**easily adaptable to other environment**) No need to trust anyone else! Be sovereign! ~> Go to the bonus guide by clicking ~> [HERE](https://minibolt.minibolt.info/bonus-guides/nostr/nostr-relay)< ~ ~> This guide includes a complete [extra section](https://minibolt.minibolt.info/bonus-guides/nostr/nostr-relay#extras-optional) to cover the different processes for using nostr **as a user and relay operator**. --- PS: The MiniBolt project has its FREE relay, be free to connect by adding to your favorite client the next address: `wss://relay.minibolt.info` ~> Let a review on [noStrudel](https://nostrudel.ninja/#/r/wss%3A%2F%2Frelay.minibolt.info) or [Coracle](https://coracle.social/relays/relay.minibolt.info) of your experience using it. --- Remember, Nostr is freedom! Stay resilient! 💜 🛡️💪 @ b17fccdf:b7211155
2025-01-21 16:15:51### What's changed A bonus guide to get a quick overview of the system status with the most relevant data about the services on the main guide. ----------- #### ➕Additional extra sections (optional) to: * [Show on login](https://minibolt.minibolt.info/bonus-guides/system/system-overview#show-on-login-optional) * [Get the channel.db size of an old LND bbolt database backend](https://minibolt.minibolt.info/bonus-guides/system/system-overview#get-the-channel.db-size-of-an-old-lnd-bbolt-database-backend) * [Use MobaXterm compatibility version](https://minibolt.minibolt.info/bonus-guides/system/system-overview#use-the-mobaxterm-compatibility-version) 🔧 **GitHub PR related**: https://github.com/minibolt-guide/minibolt/pull/97 Σ **Dedicated GitHub repository**: https://github.com/minibolt-guide/system_overview ----------- #### 🫂Acknowledgments This is a fork of the [minibolt_info repository](https://github.com/rmnscb/minibolt_info), the main developer of this project is [rmnscb](https://github.com/rmnscb), a member of the MiniBolt community, all the merits go to him. Thank you for your contribution 🧡🫂 ----------- -> [CLICK HERE](https://minibolt.minibolt.info/bonus-guides/system/system-overview) <- to go to the bonus guide ----------- Enjoy it MiniBolter! 💙
@ b17fccdf:b7211155
2025-01-21 16:15:51### What's changed A bonus guide to get a quick overview of the system status with the most relevant data about the services on the main guide. ----------- #### ➕Additional extra sections (optional) to: * [Show on login](https://minibolt.minibolt.info/bonus-guides/system/system-overview#show-on-login-optional) * [Get the channel.db size of an old LND bbolt database backend](https://minibolt.minibolt.info/bonus-guides/system/system-overview#get-the-channel.db-size-of-an-old-lnd-bbolt-database-backend) * [Use MobaXterm compatibility version](https://minibolt.minibolt.info/bonus-guides/system/system-overview#use-the-mobaxterm-compatibility-version) 🔧 **GitHub PR related**: https://github.com/minibolt-guide/minibolt/pull/97 Σ **Dedicated GitHub repository**: https://github.com/minibolt-guide/system_overview ----------- #### 🫂Acknowledgments This is a fork of the [minibolt_info repository](https://github.com/rmnscb/minibolt_info), the main developer of this project is [rmnscb](https://github.com/rmnscb), a member of the MiniBolt community, all the merits go to him. Thank you for your contribution 🧡🫂 ----------- -> [CLICK HERE](https://minibolt.minibolt.info/bonus-guides/system/system-overview) <- to go to the bonus guide ----------- Enjoy it MiniBolter! 💙 @ 604e96e0:20279eb2
2023-08-11 18:39:36notacomment allows you to zap nostr notes when you comment on them. In order to use notacomment, you have to run a script yourself either on your own computer or in the cloud somewhere. To get started open https://github.com/SamSamskies/notacomment in a browser tab. At this point, I'm sure a lot of you are feeling like this:  Let's breakdown the instructions from the README. ## Prerequisites Node.js and npm - I suggest installing the latest Node.js LTS version from https://nodejs.org. That should also install npm. Once installation is complete, open your terminal. On a Mac you can press cmd + spacebar and type in `terminal` to open the terminal. On other platforms, you'll have to ask ChatGPT 😂 . To verify installation of Node.js type `node -v`. To verify installation type `npm -v`. It should look something like this:  Leave the terminal open. ## Downloading the code to your computer The easiest way to download the code is to download the zip file from the GitHub repo. Remember that first link I told you to open? That's the GitHub repo. Click the green button that says `Code` on it and click `Download ZIP` from the menu.  Now unzip the file and then navigate to the folder in the terminal. To navigate to the folder use the `cd` command. If you unzipped the folder in the `Downloads` folder, you can navigate to the folder by typing `cd ~/Downloads/notacomment-main/`. ## Usage With Strike 1. Create an account with Strike if you don't already have one https://strike.me/download/ 1. Get a Strike API key with all the payment scopes from https://dashboard.strike.me/ 1. Create a .env file and provide NOSTR_NSEC and STRIKE_API_KEY values (see .env.example) 1. Install the dependencies using npm or yarn or whatever your heart desires 1. Make sure you have money in your Strike account 1. Run the script `npm start` Keep in mind that Strike pays the invoices from your cash balance. This means the payment rounds up to the nearest cent when paying an invoice, so if you set the zap amount to 1 sat, you'll be sending more money to Strike than the person you are zapping with every zap. ## Usage With LNbits I recommend making a separate wallet from your main LNbits wallet for usage with notacomment in case you accidentally leak the admin key. 1. Create a .env file and provide NOSTR_NSEC, LNBITS_ADMIN_KEY, and LNBITS_URL values (see .env.example) 1. Install the dependencies using npm or yarn or whatever your heart desires 1. Make sure you have sats in your LNbits wallet 1. Run the script `npm start` ## Usage With Nostr Wallet Connect 1. Create a NWC connection string using something like https://nwc.getalby.com/ 1. Create a .env file and provide NOSTR_NSEC and NWC_CONNECTION_STRING values (see .env.example) 1. Install the dependencies using npm or yarn or whatever your heart desires 1. Make sure you have sats in your wallet that you generated the NWC connection string with 1. Run the script `npm start` <br /> <br /> Screenshot of terminal with commands to install dependencies, create .env file, open .env file, and start the script: 
@ 604e96e0:20279eb2
2023-08-11 18:39:36notacomment allows you to zap nostr notes when you comment on them. In order to use notacomment, you have to run a script yourself either on your own computer or in the cloud somewhere. To get started open https://github.com/SamSamskies/notacomment in a browser tab. At this point, I'm sure a lot of you are feeling like this:  Let's breakdown the instructions from the README. ## Prerequisites Node.js and npm - I suggest installing the latest Node.js LTS version from https://nodejs.org. That should also install npm. Once installation is complete, open your terminal. On a Mac you can press cmd + spacebar and type in `terminal` to open the terminal. On other platforms, you'll have to ask ChatGPT 😂 . To verify installation of Node.js type `node -v`. To verify installation type `npm -v`. It should look something like this:  Leave the terminal open. ## Downloading the code to your computer The easiest way to download the code is to download the zip file from the GitHub repo. Remember that first link I told you to open? That's the GitHub repo. Click the green button that says `Code` on it and click `Download ZIP` from the menu.  Now unzip the file and then navigate to the folder in the terminal. To navigate to the folder use the `cd` command. If you unzipped the folder in the `Downloads` folder, you can navigate to the folder by typing `cd ~/Downloads/notacomment-main/`. ## Usage With Strike 1. Create an account with Strike if you don't already have one https://strike.me/download/ 1. Get a Strike API key with all the payment scopes from https://dashboard.strike.me/ 1. Create a .env file and provide NOSTR_NSEC and STRIKE_API_KEY values (see .env.example) 1. Install the dependencies using npm or yarn or whatever your heart desires 1. Make sure you have money in your Strike account 1. Run the script `npm start` Keep in mind that Strike pays the invoices from your cash balance. This means the payment rounds up to the nearest cent when paying an invoice, so if you set the zap amount to 1 sat, you'll be sending more money to Strike than the person you are zapping with every zap. ## Usage With LNbits I recommend making a separate wallet from your main LNbits wallet for usage with notacomment in case you accidentally leak the admin key. 1. Create a .env file and provide NOSTR_NSEC, LNBITS_ADMIN_KEY, and LNBITS_URL values (see .env.example) 1. Install the dependencies using npm or yarn or whatever your heart desires 1. Make sure you have sats in your LNbits wallet 1. Run the script `npm start` ## Usage With Nostr Wallet Connect 1. Create a NWC connection string using something like https://nwc.getalby.com/ 1. Create a .env file and provide NOSTR_NSEC and NWC_CONNECTION_STRING values (see .env.example) 1. Install the dependencies using npm or yarn or whatever your heart desires 1. Make sure you have sats in your wallet that you generated the NWC connection string with 1. Run the script `npm start` <br /> <br /> Screenshot of terminal with commands to install dependencies, create .env file, open .env file, and start the script:  @ e3168078:10f13b2c
2025-01-21 15:44:45ノス! 最近Umbrel上のn8nを使ってstacker newsの記事を要約するNostr botを作ってみました。 その際にFirecrawlというスクレイピングのSaaSを使っていたんですがセルフホストできるようなので試してみました。 Firecrawlは動的なページも読めたりマークダウンへの変換をしてくれますが無料プランだと1ヶ月500ページの制限があり、セルフホストすれば気兼ねなく使えます! 今回はUmbrel上のPortainerというアプリを使ってFirecrawlを動かせたのでその記録です。 ## 手順 まずはUmbrelにPortainerアプリをインストールします。 Poratinerは今回初めて使ったんですが独自のDockerコンテナをUmbrelで動かす際に推奨されているアプリのようです。  アプリを開いてパスワードの初期設定などを済ませるとダッシュボードが表示されるかと思います。 ここでStackという機能を使ってFirecrawlのDocker composeを一括で取り込むことができます。 新しいStackを作成する画面で以下を入力します。 Repository URL: https://github.com/mendableai/firecrawl Repository reference: refs/heads/main Compose path: docker-compose.**yaml** (デフォルトがymlになっててハマりました…)  上記に加えてenv varを設定する必要があるんですがPortainerでは上記の画像下部にあるように "Load Variables from .env file" からenvファイルを選択できます。 [Firecrawlのgithub](https://github.com/mendableai/firecrawl/blob/main/SELF_HOST.md)にあるように apps/api/.env.example をダウンロードし以下の内容を更新しPortainerに取り込ませます。 ``` USE_DB_AUTHENTICATION=false TEST_API_KEY=fc-test-key ``` あとはDeploy the stackを押して少し待つとfirecrawlのセットアップ完了です。 ## 確認 動作テストにはUmbrelの設定からAdvanced Settings -> Terminal -> Umbrel OSを開き以下のコマンドを実行ししマークダウンが返って来れば成功です。 ``` $ curl -X POST http://localhost:3002/v1/scrape -H 'Authorization: Bearer fc-test-key' -H 'Content-Type: application/json' -d '{ "url": "https://example.com", "formats": ["markdown"] }' {"success":true,"data":{"markdown":"Example Domain\n==============\n\nThis domain is for use in illustrative examples in documents. You may use this domain in literature without prior coordination or asking for permission.\n\n[More information...](https://www.iana.org/domains/example)","metadata":{"title":"Example Domain","ogLocaleAlternate":[],"scrapeId":"7c196348-6561-4ebb-bb8a-9121a29c64b5","viewport":"width=device-width, initial-scale=1","sourceURL":"https://example.com","url":"https://example.com/","statusCode":200}}} ``` またn8n等のUmbrelの他のアプリ(コンテナ)から利用する場合はlocalhostがコンテナ自身になってしまうので別のIP等(172.17.0.1)を使う必要があるのでご注意ください。 ([参考](https://community.n8n.io/t/the-service-refused-the-connection-perhaps-it-is-offline-n8n-and-nocodb/33587?utm_source=chatgpt.com)) 以上でUmbrel上でのFirecrawlセルフホストができるようになりn8nからも制限なく使えるようになりました。
@ e3168078:10f13b2c
2025-01-21 15:44:45ノス! 最近Umbrel上のn8nを使ってstacker newsの記事を要約するNostr botを作ってみました。 その際にFirecrawlというスクレイピングのSaaSを使っていたんですがセルフホストできるようなので試してみました。 Firecrawlは動的なページも読めたりマークダウンへの変換をしてくれますが無料プランだと1ヶ月500ページの制限があり、セルフホストすれば気兼ねなく使えます! 今回はUmbrel上のPortainerというアプリを使ってFirecrawlを動かせたのでその記録です。 ## 手順 まずはUmbrelにPortainerアプリをインストールします。 Poratinerは今回初めて使ったんですが独自のDockerコンテナをUmbrelで動かす際に推奨されているアプリのようです。  アプリを開いてパスワードの初期設定などを済ませるとダッシュボードが表示されるかと思います。 ここでStackという機能を使ってFirecrawlのDocker composeを一括で取り込むことができます。 新しいStackを作成する画面で以下を入力します。 Repository URL: https://github.com/mendableai/firecrawl Repository reference: refs/heads/main Compose path: docker-compose.**yaml** (デフォルトがymlになっててハマりました…)  上記に加えてenv varを設定する必要があるんですがPortainerでは上記の画像下部にあるように "Load Variables from .env file" からenvファイルを選択できます。 [Firecrawlのgithub](https://github.com/mendableai/firecrawl/blob/main/SELF_HOST.md)にあるように apps/api/.env.example をダウンロードし以下の内容を更新しPortainerに取り込ませます。 ``` USE_DB_AUTHENTICATION=false TEST_API_KEY=fc-test-key ``` あとはDeploy the stackを押して少し待つとfirecrawlのセットアップ完了です。 ## 確認 動作テストにはUmbrelの設定からAdvanced Settings -> Terminal -> Umbrel OSを開き以下のコマンドを実行ししマークダウンが返って来れば成功です。 ``` $ curl -X POST http://localhost:3002/v1/scrape -H 'Authorization: Bearer fc-test-key' -H 'Content-Type: application/json' -d '{ "url": "https://example.com", "formats": ["markdown"] }' {"success":true,"data":{"markdown":"Example Domain\n==============\n\nThis domain is for use in illustrative examples in documents. You may use this domain in literature without prior coordination or asking for permission.\n\n[More information...](https://www.iana.org/domains/example)","metadata":{"title":"Example Domain","ogLocaleAlternate":[],"scrapeId":"7c196348-6561-4ebb-bb8a-9121a29c64b5","viewport":"width=device-width, initial-scale=1","sourceURL":"https://example.com","url":"https://example.com/","statusCode":200}}} ``` またn8n等のUmbrelの他のアプリ(コンテナ)から利用する場合はlocalhostがコンテナ自身になってしまうので別のIP等(172.17.0.1)を使う必要があるのでご注意ください。 ([参考](https://community.n8n.io/t/the-service-refused-the-connection-perhaps-it-is-offline-n8n-and-nocodb/33587?utm_source=chatgpt.com)) 以上でUmbrel上でのFirecrawlセルフホストができるようになりn8nからも制限なく使えるようになりました。 @ b17fccdf:b7211155
2025-01-21 18:42:14Some guides on MiniBolt / RaMiX have suffered some modifications and need additional instructions to migrate. Here is a summary: 🔘 New installation/update instructions of [BTC RPC Explorer](https://minibolt.minibolt.info/bitcoin/bitcoin/blockchain-explorer) to avoid [this issue](https://github.com/janoside/btc-rpc-explorer/issues/668). 🔘 New installation/update method of [Node + NPM](https://minibolt.minibolt.info/bonus-guides/system/nodejs-npm). 🔘 New installation/update method of [PostgreSQL](https://minibolt.minibolt.info/bonus-guides/system/postgresql) ~ > **Attention!** If you installed PostgreSQL **after 30/09/2024**, you do not need to follow these steps related to PostgreSQL. --- ## Update Nodejs + NPM to the latest LTS version (using the new method) > Guide related: [Node + NPM](https://minibolt.minibolt.info/bonus-guides/system/nodejs-npm) > **Context:** The installation/upgrade section of this guide has suffered some modifications, so to upgrade to the latest LTS released version using the new installation method, you need to follow the next steps: * Stop the Nodejs + NPM dependencies: ``` sudo systemctl stop thunderhub btcrpcexplorer ``` * With user **admin**, update the packages and upgrade to keep up to date with the OS, press "y" and ENTER when needed or ENTER directly: ``` sudo apt update && sudo apt full-upgrade ``` * Change to a temporary directory which is cleared on reboot: ``` cd /tmp ``` * Set the environment variable of the version: ``` VERSION=22 ``` * We will use the new NodeSource Node.js Binary Distributions repository [instructions](https://github.com/nodesource/distributions?tab=readme-ov-file#using-ubuntu-nodejs-22). Download the setup script: ``` curl -fsSL https://deb.nodesource.com/setup_$VERSION.x -o nodesource_setup.sh ``` * Run the setup script: ``` sudo -E bash nodesource_setup.sh ``` * Update the package manager and update Node.js + NPM to the latest LTS version: ``` sudo apt update && sudo apt full-upgrade ``` * Check the correct update of NodeJS: ``` node -v ``` **Example** of expected output: ``` v22.12.0 ``` * Check the correct installation of NPM: ``` npm -v ``` **Example** of expected output: ``` 10.9.0 ``` * **(Optional)** Delete the setup script: ``` rm nodesource_setup.sh ``` * Start again the Nodejs + NPM dependencies: ``` sudo systemctl start thunderhub btcrpcexplorer ``` ----------- ## Update BTC RPC Explorer to the latest version > Guide related: [2.3 Blockchain explorer: BTC RPC Explorer](https://minibolt.minibolt.info/bitcoin/bitcoin/blockchain-explorer) > **Context:** After [this notice](https://t.me/minibolt_news/37), if you deleted the `deprecatedrpc=warnings` flag because it is no longer necessary, it is probably that the ["**Node Details**"](https://explorer.minibolt.info/node-details) section of the BTC RPC Explorer got you [this error](https://github.com/janoside/btc-rpc-explorer/issues/668), this is because after the Bitcoin Core v28 update, just like LND, Electrs and other services, they have needed an update to remain compatible. BTC RPC Explorer was updated on this [commit](https://github.com/janoside/btc-rpc-explorer/commit/01585b7825afe0eb3e8f6cf39e9e135a20c8c2dd), but an official version that includes this correction has not been officially released yet. To fix this, it is necessary to **point to the current source code** and not the one related to the last released version (3.4.0). **~ >** Get instructions to get this by following these steps and fix the issue ~ > [HERE](https://minibolt.minibolt.info/bitcoin/bitcoin/blockchain-explorer#upgrade) < ~ ----------- ## Update PostgreSQL (server instance migration & others) > Guide related: [PostgreSQL](https://minibolt.minibolt.info/bonus-guides/system/postgresql) > **Attention!!** If you installed PostgreSQL **after 30/09/2024**, **you don't need to do anything**, and the next steps don't apply to your case. > **Context:** With each major version jump of PostgreSQL, the update creates a new and dedicated cluster and folder with the number of each version. Also, the changes made between versions cause the need to migrate the database, that is, from one cluster to another, with a specific tool. This was unknown at the beginning, before creating the MiniBolt PostgreSQL installation guide, so a specific folder for the versions was not created. The [installation section](https://minibolt.minibolt.info/bonus-guides/system/postgresql#installation) was changed past **30/09/2024** to use this new method, but people who followed the PostgreSQL installation before that, need to do things to be in line with the MiniBolt guide. Following the next steps, we are going to do the necessary migrations, the summary is the next: **1.** Migrate the PostgreSQL database to a new location (*a dedicated folder for each version*). **2.** Migrate from PostgreSQL server version 16 to 17. --- **Verification** If you are not sure whether you installed PostgreSQL before or after the mentioned date (**30/09/2024**), you can check as follows: * With user `admin` list the existing clusters: ``` pg_lsclusters ``` Expected output if you installed PostgreSQL **after 30/09/2024**, **(you don't need do anything)**: ``` Ver Cluster Port Status Owner Data directory Log file 17 main 5432 online postgres /data/postgresdb/17 /var/log/postgresql/postgresql-17-main.log ``` Expected output if you installed PostgreSQL **before 30/09/2024**, and performed a full upgrade of the MiniBolt with **`sudo apt update && sudo apt full-upgrade`**, **(you need to follow the next steps)**: ``` Ver Cluster Port Status Owner Data directory Log file 16 main 5432 online postgres /data/postgresdb /var/log/postgresql/postgresql-16-main.log 17 main 5433 down postgres /var/lib/postgresql/17/main /var/log/postgresql/postgresql-17-main.log ``` Expected output **if you have not** performed a full upgrade of the MiniBolt with `sudo apt update && sudo apt full-upgrade` **since 26/09/2024 (the PostgreSQL v17 release)** (unlikely case) **(you need to follow the next steps)**: ``` Ver Cluster Port Status Owner Data directory Log file 16 main 5432 online postgres /data/postgresdb /var/log/postgresql/postgresql-16-main.log ``` --- ### **Migrate the PostgreSQL database to the new location** > (Only if you installed PostgreSQL following the MiniBolt guide **before 30/09/2024**) * Show the existing clusters to show the current path of the database: ``` pg_lsclusters ``` **~ >** Expected output **if you have not** performed a full upgrade of the MiniBolt with `sudo apt update && sudo apt full-upgrade` **since 26/09/2024 (PostgreSQL v17 release)** (unlikely): ``` Ver Cluster Port Status Owner Data directory Log file 16 main 5432 online postgres /data/postgresdb /var/log/postgresql/postgresql-16-main.log ``` **~ >** Expected output **if you have** performed a full upgrade of the MiniBolt with `sudo apt update && sudo apt full-upgrade` **since 26/09/2024 (PostgreSQL v17 release)** (most likely): ``` Ver Cluster Port Status Owner Data directory Log file 16 main 5432 online postgres /data/postgresdb /var/log/postgresql/postgresql-16-main.log 17 main 5433 down postgres /var/lib/postgresql/17/main /var/log/postgresql/postgresql-17-main.log ``` ~ > Check the current "Data directory" column value of the cluster 16 **(/data/postgresdb)** for the future, we have changed this to a dedicated folder for each version (`/data/postgresdb/16`, `/data/postgresdb/17`, `/data/postgresdb/18`, etc.) * Stop the PostgreSQL dependencies and the PostgreSQL version 16 cluster: ``` sudo systemctl stop thunderhub scbackup btcpay lnd nbxplorer nostrelay cloudflared postgresql@16-main ``` ~ > Ensure all services are successfully stopped by monitoring the logs of each service, especially **lnd** ~ > `journalctl -fu lnd`. * Monitor the logs of the PostgreSQL version 16 cluster to ensure that it has been stopped gracefully: ``` journalctl -fu postgresql@16-main ``` Expected output: ``` minibolt systemd[1]: Stopping PostgreSQL Cluster 16-main... minibolt systemd[1]: postgresql@16-main.service: Deactivated successfully. minibolt systemd[1]: Stopped PostgreSQL Cluster 16-main. ``` ~ > Press `Ctrl + C` to continue. * Create a temporary directory in a place out of the `/data/postgresdb` to move the data securely: ``` sudo mkdir /tmp/postgresdb-temp ``` * Sync the existing data of the current directory `/data/postgresdb` to this temporary directory: ``` sudo rsync -av /data/postgresdb/ /tmp/postgresdb-temp/ ``` Example of expected output: ``` [...] pg_xact/ pg_xact/0000 [...] sent 40,397,103 bytes received 18,619 bytes 80,831,444.00 bytes/sec total size is 40,330,914 speedup is 1.00 ``` ~ > Wait until the prompt shows up again. * Change to the user `root` temporary: ``` sudo su ``` * Delete the content of the folder that hosted the original database: ``` sudo rm -rf /data/postgresdb/* ``` * Come back to the `admin` user: ``` exit ``` * Create a new specific and dedicated folder to the version number and to be in line with the [new and current storage method](https://minibolt.minibolt.info/bonus-guides/system/postgresql#create-data-folder) of the current guide: ``` sudo mkdir /data/postgresdb/16 ``` * Assign as the owner to the user `postgres`: ``` sudo chown postgres:postgres /data/postgresdb/16 ``` * Assign the correct permissions to the folder: ``` sudo chmod 700 /data/postgresdb/16 ``` * Now you can sync the data from the temporary directory to `/data/postgresdb/16` in a secure way since this directory is not inside the source directory: ``` sudo rsync -av /tmp/postgresdb-temp/ /data/postgresdb/16/ ``` Example of expected output: ``` [...] pg_xact/ pg_xact/0000 [...] sent 40,397,103 bytes received 18,619 bytes 80,831,444.00 bytes/sec total size is 40,330,914 speedup is 1.00 ``` ~ > Wait until the prompt shows up again. * Modify the configuration file (`postgresql.conf`) of the PostgreSQL to point to the new directory folder created: ``` sudo nano +42 /etc/postgresql/16/main/postgresql.conf ``` * Replace the data directory location to match with the new path: ``` data_directory = '/data/postgresdb/16' ``` * Start again the PostgreSQL service instance: ``` sudo systemctl start postgresql@16-main ``` * Monitor the logs of the PostgreSQL version 16 cluster to ensure that it works fine: ``` journalctl -fu postgresql@16-main ``` Expected output: ``` minibolt systemd[1]: Starting PostgreSQL Cluster 16-main... minibolt systemd[1]: Started PostgreSQL Cluster 16-main. ``` ~ > Press `Ctrl + C` to continue. * Check the new database location with: ``` pg_lsclusters ``` ~ > Expected output **if you have not** performed a full upgrade of the MiniBolt with `sudo apt update && sudo apt full-upgrade` **since 26/09/2024** (unlikely): ``` Ver Cluster Port Status Owner Data directory Log file 16 main 5432 online postgres /data/postgresdb/16 /var/log/postgresql/postgresql-16-main.log ``` ~ > Expected output **if you have** performed a full upgrade of the MiniBolt with `sudo apt update && sudo apt full-upgrade` **since 26/09/2024** (most likely): ``` Ver Cluster Port Status Owner Data directory Log file 16 main 5432 online postgres /data/postgresdb/16 /var/log/postgresql/postgresql-16-main.log 17 main 5433 down postgres /var/lib/postgresql/17/main /var/log/postgresql/postgresql-17-main.log ``` ~ > Check the new path on the "Data directory" column value of the cluster version 16, now **(/data/postgresdb/16)**. * Start again the PostgreSQL dependencies services: ``` sudo systemctl start lnd nbxplorer btcpay thunderhub scb-backup nostr-relay cloudflared ``` ~ > Check all work fine with the logs of each service, especially **lnd** ~ > `journalctl -fu lnd`. * Stop again the PostgreSQL dependencies services, to continue working: ``` sudo systemctl stop thunderhub scbackup btcpay lnd nbxplorer nostrelay cloudflared ``` ~ > Ensure all services are successfully stopped by monitoring the logs of each service, especially **lnd** ~ > `journalctl -fu lnd`. ### **Migrate from PostgreSQL server version 16 to 17** > (Only if you installed PostgreSQL following the MiniBolt guide **before 30/09/2024**) > **Context:** If you fully updated your OS after **26/09/2024** (the PostgreSQL v17 launched), using `sudo apt update && sudo apt full-upgrade`, and **you installed PostgreSQL before that date** following [the PostgreSQL MiniBolt guide](https://minibolt.minibolt.info/bonus-guides/system/postgresql), it is likely that you now are using the old version (v16) of the PostgreSQL server instance. To confirm that, follow the next steps: **Check the PostgreSQL server version in use** * With the user `admin`, enter the psql (PostgreSQL CLI): ``` sudo -u postgres psql ``` * Enter the next command to get the server version: ``` SELECT version(); ``` Expected output: ``` version ----------------------------------------------------------------------------------------------------------------------------------- PostgreSQL 16.6 (Ubuntu 16.6-1.pgdg22.04+1) on x86_64-pc-linux-gnu, compiled by gcc (Ubuntu 11.4.0-1ubuntu1~22.04) 11.4.0, 64-bit (1 row) ``` ~ > Check the previous version is "PostgreSQL 16.6" (an outdated version of the PostgreSQL server), the latest version is PostgreSQL 17.2. 🔧✅ We are going to fix this in the next steps. * Come back to the `admin` user bash prompt: ``` \q ``` * List the cluster to show the state of the both PostgreSQL server instances: ``` pg_lsclusters ``` ~ > Expected output **if you have not** performed a full upgrade of the MiniBolt with `sudo apt update && sudo apt full-upgrade` **since 26/09/2024** (unlikely): ``` Ver Cluster Port Status Owner Data directory Log file 16 main 5432 online postgres /data/postgresdb/16 /var/log/postgresql/postgresql-16-main.log ``` ~ > Expected output **if you have** performed a full upgrade of the MiniBolt with `sudo apt update && sudo apt full-upgrade` **since 26/09/2024** (most likely): ``` Ver Cluster Port Status Owner Data directory Log file 16 main 5432 online postgres /data/postgresdb/16 /var/log/postgresql/postgresql-16-main.log 17 main 5433 down postgres /var/lib/postgresql/17/main /var/log/postgresql/postgresql-17-main.log ``` **Update PostgreSQL** If you haven't done so before, make sure to update the OS (PostgreSQL included to the latest version 17): * With user `admin`, fully update the OS with the package manager: ``` sudo apt update && sudo apt full-upgrade ``` ~ > Press "y" and enter or directly enter when the prompt asks you. ----------- #### **PostgreSQL server migration** * Stop all existing clusters: ``` sudo systemctl stop postgresql@16-main postgresql@17-main ``` * Create a new database destination folder for the v17 cluster ready for migration from v16: ``` sudo mkdir /data/postgresdb/17 ``` * Assign the owner as the postgres user: ``` sudo chown postgres:postgres /data/postgresdb/17 ``` * Assign the correct permissions: ``` sudo chmod 700 /data/postgresdb/17 ``` * Delete the cluster created by default for v17: ``` sudo -u postgres pg_dropcluster 17 main ``` * Update the systemd: ``` sudo systemctl daemon-reload ``` * Start the migration with the PostgreSQL migration tool: ``` sudo -u postgres pg_upgradecluster 16 main /data/postgresdb/17 ``` **~ >** ⌛ This may take a lot of time depending on the existing database size (the nostr relay database especially) and your machine's performance; it is recommended to use [tmux](https://github.com/tmux/tmux). Wait until the prompt shows up again. Example of expected output: ``` Restarting old cluster with restricted connections... Notice: extra pg_ctl/postgres options given, bypassing systemctl for start operation Creating new PostgreSQL cluster 17/main ... /usr/lib/postgresql/17/bin/initdb -D /data/postgresdb/17 --auth-local peer --auth-host scram-sha-256 --no-instructions --encoding UTF8 --lc-collate en_US.UTF-8 --lc-ctype en_US.UTF-8 --locale-provider libc The files belonging to this database system will be owned by user "postgres". This user must also own the server process. The database cluster will be initialized with locale "en_US.UTF-8". The default text search configuration will be set to "english". Data page checksums are disabled. fixing permissions on existing directory /data/postgresdb/17 ... ok creating subdirectories ... ok selecting dynamic shared memory implementation ... posix selecting default "max_connections" ... 100 selecting default "shared_buffers" ... 128MB selecting default time zone ... Etc/UTC creating configuration files ... ok running bootstrap script ... ok performing post-bootstrap initialization ... ok syncing data to disk ... ok Warning: systemd does not know about the new cluster yet. Operations like "service postgresql start" will not handle it. To fix, run: sudo systemctl daemon-reload Copying old configuration files... Copying old start.conf... Copying old pg_ctl.conf... Starting new cluster... Notice: extra pg_ctl/postgres options given, bypassing systemctl for start operation Running init phase upgrade hook scripts ... Roles, databases, schemas, ACLs... set_config ------------ (1 row) set_config ------------ (1 row) Fixing hardcoded library paths for stored procedures... Upgrading database postgres... Fixing hardcoded library paths for stored procedures... Upgrading database template1... Stopping target cluster... Stopping old cluster... Disabling automatic startup of old cluster... Starting upgraded cluster on port 5432... Warning: the cluster will not be running as a systemd service. Consider using systemctl: sudo systemctl start postgresql@17-main Running finish phase upgrade hook scripts ... vacuumdb: processing database "postgres": Generating minimal optimizer statistics (1 target) vacuumdb: processing database "template1": Generating minimal optimizer statistics (1 target) vacuumdb: processing database "postgres": Generating medium optimizer statistics (10 targets) vacuumdb: processing database "template1": Generating medium optimizer statistics (10 targets) vacuumdb: processing database "postgres": Generating default (full) optimizer statistics vacuumdb: processing database "template1": Generating default (full) optimizer statistics Success. Please check that the upgraded cluster works. If it does, you can remove the old cluster with pg_dropcluster 16 main Ver Cluster Port Status Owner Data directory Log file 16 main 5433 down postgres /data/postgresdb/16 /var/log/postgresql/postgresql-16-main.log Ver Cluster Port Status Owner Data directory Log file 17 main 5432 online postgres /data/postgresdb/17 /var/log/postgresql/postgresql-17-main.log ``` * Reload the systemd again: ``` sudo systemctl daemon-reload ``` * List the clusters to show the state: ``` pg_lsclusters ``` Expected output: ``` Ver Cluster Port Status Owner Data directory Log file 16 main 5433 down <unknown> /data/postgresdb/16 /var/log/postgresql/postgresql-16-main.log 17 main 5432 online <unknown> /data/postgresdb/17 /var/log/postgresql/postgresql-17-main.log ``` ~> **Notes:** * Don't worry about the <unknown> output of the "Owner" column. * Note how the old 16 cluster has automatically gone into status "down" after the migration. --- * Stop the version 17 cluster using the `pg_ctlcluster` tool, to then be able to run it and manage it with `systemd`: ``` sudo pg_ctlcluster 17 main stop ``` * List the clusters again to show the state: ``` pg_lsclusters ``` Expected output: ``` Ver Cluster Port Status Owner Data directory Log file 16 main 5433 down <unknown> /data/postgresdb/16 /var/log/postgresql/postgresql-16-main.log 17 main 5432 down <unknown> /data/postgresdb/17 /var/log/postgresql/postgresql-17-main.log ``` **~>** Note how the version 17 cluster has gone into status "down". * Start the version 17 cluster with systemd: ``` sudo systemctl start postgresql@17-main ``` * Monitor the logs of the PostgreSQL version 17 cluster to ensure that it working fine with `systemd`: ``` journalctl -fu postgresql@17-main ``` Expected output: ``` minibolt systemd[1]: Starting PostgreSQL Cluster 17-main... minibolt systemd[1]: Started PostgreSQL Cluster 17-main. ``` ~ > Press `Ctrl + C` to continue. * List the clusters again to show the state: ``` pg_lsclusters ``` Expected output: ``` Ver Cluster Port Status Owner Data directory Log file 16 main 5433 down <unknown> /data/postgresdb/16 /var/log/postgresql/postgresql-16-main.log 17 main 5432 online <unknown> /data/postgresdb/17 /var/log/postgresql/postgresql-17-main.log ``` **~>** Note how the version 17 cluster has come back into the status "online". * Delete the version 16 (old and disused) cluster: ``` sudo pg_dropcluster 16 main ``` * List again the clusters to check the correct deletion: ``` pg_lsclusters ``` Expected output: ``` Ver Cluster Port Status Owner Data directory Log file 17 main 5432 online <unknown> /data/postgresdb/17 /var/log/postgresql/postgresql-17-main.log ``` **~>** Note how it no longer appears version 16 (old and disused) cluster. **Check the PostgreSQL server version in use** * With the user `admin`, enter the psql (PostgreSQL CLI): ``` sudo -u postgres psql ``` * Enter the next command to get the server version: ``` SELECT version(); ``` Example of expected output: ``` version ----------------------------------------------------------------------------------------------------------------------------------- PostgreSQL 17.2 (Ubuntu 17.2-1.pgdg22.04+1) on x86_64-pc-linux-gnu, compiled by gcc (Ubuntu 11.4.0-1ubuntu1~22.04) 11.4.0, 64-bit (1 row) ``` **~ >** Check the previous version in use is now PostgreSQL 17.2 (the latest and current version of the PostgreSQL server at this moment). * Come back to the `admin` user bash prompt: ``` \q ``` * Start again the PostgreSQL dependencies services: ``` sudo systemctl start lnd nbxplorer btcpay thunderhub scb-backup nostr-relay cloudflared ``` ~ > Check all works fine with the logs of each service, especially **lnd** ~ > `journalctl -fu lnd`. * **(Optional)** Once you have verified that everything is working correctly, you can delete the created PostgreSQL backup and temporary directory: ``` sudo rm -rf /tmp/postgresdb-temp ``` * Delete unnecessary packages: ``` sudo apt autoremove ``` ~ > Press "y" and ENTER when needed or ENTER directly when the prompts ask you. --- ✅ That's it! If you have any questions or issues, you can go to any RRSS available for the MiniBolt project ~ > [HERE](https://minibolt.minibolt.info/#community) < ~ --- Only for MiniBolters! Enjoy it! 💙
@ b17fccdf:b7211155
2025-01-21 18:42:14Some guides on MiniBolt / RaMiX have suffered some modifications and need additional instructions to migrate. Here is a summary: 🔘 New installation/update instructions of [BTC RPC Explorer](https://minibolt.minibolt.info/bitcoin/bitcoin/blockchain-explorer) to avoid [this issue](https://github.com/janoside/btc-rpc-explorer/issues/668). 🔘 New installation/update method of [Node + NPM](https://minibolt.minibolt.info/bonus-guides/system/nodejs-npm). 🔘 New installation/update method of [PostgreSQL](https://minibolt.minibolt.info/bonus-guides/system/postgresql) ~ > **Attention!** If you installed PostgreSQL **after 30/09/2024**, you do not need to follow these steps related to PostgreSQL. --- ## Update Nodejs + NPM to the latest LTS version (using the new method) > Guide related: [Node + NPM](https://minibolt.minibolt.info/bonus-guides/system/nodejs-npm) > **Context:** The installation/upgrade section of this guide has suffered some modifications, so to upgrade to the latest LTS released version using the new installation method, you need to follow the next steps: * Stop the Nodejs + NPM dependencies: ``` sudo systemctl stop thunderhub btcrpcexplorer ``` * With user **admin**, update the packages and upgrade to keep up to date with the OS, press "y" and ENTER when needed or ENTER directly: ``` sudo apt update && sudo apt full-upgrade ``` * Change to a temporary directory which is cleared on reboot: ``` cd /tmp ``` * Set the environment variable of the version: ``` VERSION=22 ``` * We will use the new NodeSource Node.js Binary Distributions repository [instructions](https://github.com/nodesource/distributions?tab=readme-ov-file#using-ubuntu-nodejs-22). Download the setup script: ``` curl -fsSL https://deb.nodesource.com/setup_$VERSION.x -o nodesource_setup.sh ``` * Run the setup script: ``` sudo -E bash nodesource_setup.sh ``` * Update the package manager and update Node.js + NPM to the latest LTS version: ``` sudo apt update && sudo apt full-upgrade ``` * Check the correct update of NodeJS: ``` node -v ``` **Example** of expected output: ``` v22.12.0 ``` * Check the correct installation of NPM: ``` npm -v ``` **Example** of expected output: ``` 10.9.0 ``` * **(Optional)** Delete the setup script: ``` rm nodesource_setup.sh ``` * Start again the Nodejs + NPM dependencies: ``` sudo systemctl start thunderhub btcrpcexplorer ``` ----------- ## Update BTC RPC Explorer to the latest version > Guide related: [2.3 Blockchain explorer: BTC RPC Explorer](https://minibolt.minibolt.info/bitcoin/bitcoin/blockchain-explorer) > **Context:** After [this notice](https://t.me/minibolt_news/37), if you deleted the `deprecatedrpc=warnings` flag because it is no longer necessary, it is probably that the ["**Node Details**"](https://explorer.minibolt.info/node-details) section of the BTC RPC Explorer got you [this error](https://github.com/janoside/btc-rpc-explorer/issues/668), this is because after the Bitcoin Core v28 update, just like LND, Electrs and other services, they have needed an update to remain compatible. BTC RPC Explorer was updated on this [commit](https://github.com/janoside/btc-rpc-explorer/commit/01585b7825afe0eb3e8f6cf39e9e135a20c8c2dd), but an official version that includes this correction has not been officially released yet. To fix this, it is necessary to **point to the current source code** and not the one related to the last released version (3.4.0). **~ >** Get instructions to get this by following these steps and fix the issue ~ > [HERE](https://minibolt.minibolt.info/bitcoin/bitcoin/blockchain-explorer#upgrade) < ~ ----------- ## Update PostgreSQL (server instance migration & others) > Guide related: [PostgreSQL](https://minibolt.minibolt.info/bonus-guides/system/postgresql) > **Attention!!** If you installed PostgreSQL **after 30/09/2024**, **you don't need to do anything**, and the next steps don't apply to your case. > **Context:** With each major version jump of PostgreSQL, the update creates a new and dedicated cluster and folder with the number of each version. Also, the changes made between versions cause the need to migrate the database, that is, from one cluster to another, with a specific tool. This was unknown at the beginning, before creating the MiniBolt PostgreSQL installation guide, so a specific folder for the versions was not created. The [installation section](https://minibolt.minibolt.info/bonus-guides/system/postgresql#installation) was changed past **30/09/2024** to use this new method, but people who followed the PostgreSQL installation before that, need to do things to be in line with the MiniBolt guide. Following the next steps, we are going to do the necessary migrations, the summary is the next: **1.** Migrate the PostgreSQL database to a new location (*a dedicated folder for each version*). **2.** Migrate from PostgreSQL server version 16 to 17. --- **Verification** If you are not sure whether you installed PostgreSQL before or after the mentioned date (**30/09/2024**), you can check as follows: * With user `admin` list the existing clusters: ``` pg_lsclusters ``` Expected output if you installed PostgreSQL **after 30/09/2024**, **(you don't need do anything)**: ``` Ver Cluster Port Status Owner Data directory Log file 17 main 5432 online postgres /data/postgresdb/17 /var/log/postgresql/postgresql-17-main.log ``` Expected output if you installed PostgreSQL **before 30/09/2024**, and performed a full upgrade of the MiniBolt with **`sudo apt update && sudo apt full-upgrade`**, **(you need to follow the next steps)**: ``` Ver Cluster Port Status Owner Data directory Log file 16 main 5432 online postgres /data/postgresdb /var/log/postgresql/postgresql-16-main.log 17 main 5433 down postgres /var/lib/postgresql/17/main /var/log/postgresql/postgresql-17-main.log ``` Expected output **if you have not** performed a full upgrade of the MiniBolt with `sudo apt update && sudo apt full-upgrade` **since 26/09/2024 (the PostgreSQL v17 release)** (unlikely case) **(you need to follow the next steps)**: ``` Ver Cluster Port Status Owner Data directory Log file 16 main 5432 online postgres /data/postgresdb /var/log/postgresql/postgresql-16-main.log ``` --- ### **Migrate the PostgreSQL database to the new location** > (Only if you installed PostgreSQL following the MiniBolt guide **before 30/09/2024**) * Show the existing clusters to show the current path of the database: ``` pg_lsclusters ``` **~ >** Expected output **if you have not** performed a full upgrade of the MiniBolt with `sudo apt update && sudo apt full-upgrade` **since 26/09/2024 (PostgreSQL v17 release)** (unlikely): ``` Ver Cluster Port Status Owner Data directory Log file 16 main 5432 online postgres /data/postgresdb /var/log/postgresql/postgresql-16-main.log ``` **~ >** Expected output **if you have** performed a full upgrade of the MiniBolt with `sudo apt update && sudo apt full-upgrade` **since 26/09/2024 (PostgreSQL v17 release)** (most likely): ``` Ver Cluster Port Status Owner Data directory Log file 16 main 5432 online postgres /data/postgresdb /var/log/postgresql/postgresql-16-main.log 17 main 5433 down postgres /var/lib/postgresql/17/main /var/log/postgresql/postgresql-17-main.log ``` ~ > Check the current "Data directory" column value of the cluster 16 **(/data/postgresdb)** for the future, we have changed this to a dedicated folder for each version (`/data/postgresdb/16`, `/data/postgresdb/17`, `/data/postgresdb/18`, etc.) * Stop the PostgreSQL dependencies and the PostgreSQL version 16 cluster: ``` sudo systemctl stop thunderhub scbackup btcpay lnd nbxplorer nostrelay cloudflared postgresql@16-main ``` ~ > Ensure all services are successfully stopped by monitoring the logs of each service, especially **lnd** ~ > `journalctl -fu lnd`. * Monitor the logs of the PostgreSQL version 16 cluster to ensure that it has been stopped gracefully: ``` journalctl -fu postgresql@16-main ``` Expected output: ``` minibolt systemd[1]: Stopping PostgreSQL Cluster 16-main... minibolt systemd[1]: postgresql@16-main.service: Deactivated successfully. minibolt systemd[1]: Stopped PostgreSQL Cluster 16-main. ``` ~ > Press `Ctrl + C` to continue. * Create a temporary directory in a place out of the `/data/postgresdb` to move the data securely: ``` sudo mkdir /tmp/postgresdb-temp ``` * Sync the existing data of the current directory `/data/postgresdb` to this temporary directory: ``` sudo rsync -av /data/postgresdb/ /tmp/postgresdb-temp/ ``` Example of expected output: ``` [...] pg_xact/ pg_xact/0000 [...] sent 40,397,103 bytes received 18,619 bytes 80,831,444.00 bytes/sec total size is 40,330,914 speedup is 1.00 ``` ~ > Wait until the prompt shows up again. * Change to the user `root` temporary: ``` sudo su ``` * Delete the content of the folder that hosted the original database: ``` sudo rm -rf /data/postgresdb/* ``` * Come back to the `admin` user: ``` exit ``` * Create a new specific and dedicated folder to the version number and to be in line with the [new and current storage method](https://minibolt.minibolt.info/bonus-guides/system/postgresql#create-data-folder) of the current guide: ``` sudo mkdir /data/postgresdb/16 ``` * Assign as the owner to the user `postgres`: ``` sudo chown postgres:postgres /data/postgresdb/16 ``` * Assign the correct permissions to the folder: ``` sudo chmod 700 /data/postgresdb/16 ``` * Now you can sync the data from the temporary directory to `/data/postgresdb/16` in a secure way since this directory is not inside the source directory: ``` sudo rsync -av /tmp/postgresdb-temp/ /data/postgresdb/16/ ``` Example of expected output: ``` [...] pg_xact/ pg_xact/0000 [...] sent 40,397,103 bytes received 18,619 bytes 80,831,444.00 bytes/sec total size is 40,330,914 speedup is 1.00 ``` ~ > Wait until the prompt shows up again. * Modify the configuration file (`postgresql.conf`) of the PostgreSQL to point to the new directory folder created: ``` sudo nano +42 /etc/postgresql/16/main/postgresql.conf ``` * Replace the data directory location to match with the new path: ``` data_directory = '/data/postgresdb/16' ``` * Start again the PostgreSQL service instance: ``` sudo systemctl start postgresql@16-main ``` * Monitor the logs of the PostgreSQL version 16 cluster to ensure that it works fine: ``` journalctl -fu postgresql@16-main ``` Expected output: ``` minibolt systemd[1]: Starting PostgreSQL Cluster 16-main... minibolt systemd[1]: Started PostgreSQL Cluster 16-main. ``` ~ > Press `Ctrl + C` to continue. * Check the new database location with: ``` pg_lsclusters ``` ~ > Expected output **if you have not** performed a full upgrade of the MiniBolt with `sudo apt update && sudo apt full-upgrade` **since 26/09/2024** (unlikely): ``` Ver Cluster Port Status Owner Data directory Log file 16 main 5432 online postgres /data/postgresdb/16 /var/log/postgresql/postgresql-16-main.log ``` ~ > Expected output **if you have** performed a full upgrade of the MiniBolt with `sudo apt update && sudo apt full-upgrade` **since 26/09/2024** (most likely): ``` Ver Cluster Port Status Owner Data directory Log file 16 main 5432 online postgres /data/postgresdb/16 /var/log/postgresql/postgresql-16-main.log 17 main 5433 down postgres /var/lib/postgresql/17/main /var/log/postgresql/postgresql-17-main.log ``` ~ > Check the new path on the "Data directory" column value of the cluster version 16, now **(/data/postgresdb/16)**. * Start again the PostgreSQL dependencies services: ``` sudo systemctl start lnd nbxplorer btcpay thunderhub scb-backup nostr-relay cloudflared ``` ~ > Check all work fine with the logs of each service, especially **lnd** ~ > `journalctl -fu lnd`. * Stop again the PostgreSQL dependencies services, to continue working: ``` sudo systemctl stop thunderhub scbackup btcpay lnd nbxplorer nostrelay cloudflared ``` ~ > Ensure all services are successfully stopped by monitoring the logs of each service, especially **lnd** ~ > `journalctl -fu lnd`. ### **Migrate from PostgreSQL server version 16 to 17** > (Only if you installed PostgreSQL following the MiniBolt guide **before 30/09/2024**) > **Context:** If you fully updated your OS after **26/09/2024** (the PostgreSQL v17 launched), using `sudo apt update && sudo apt full-upgrade`, and **you installed PostgreSQL before that date** following [the PostgreSQL MiniBolt guide](https://minibolt.minibolt.info/bonus-guides/system/postgresql), it is likely that you now are using the old version (v16) of the PostgreSQL server instance. To confirm that, follow the next steps: **Check the PostgreSQL server version in use** * With the user `admin`, enter the psql (PostgreSQL CLI): ``` sudo -u postgres psql ``` * Enter the next command to get the server version: ``` SELECT version(); ``` Expected output: ``` version ----------------------------------------------------------------------------------------------------------------------------------- PostgreSQL 16.6 (Ubuntu 16.6-1.pgdg22.04+1) on x86_64-pc-linux-gnu, compiled by gcc (Ubuntu 11.4.0-1ubuntu1~22.04) 11.4.0, 64-bit (1 row) ``` ~ > Check the previous version is "PostgreSQL 16.6" (an outdated version of the PostgreSQL server), the latest version is PostgreSQL 17.2. 🔧✅ We are going to fix this in the next steps. * Come back to the `admin` user bash prompt: ``` \q ``` * List the cluster to show the state of the both PostgreSQL server instances: ``` pg_lsclusters ``` ~ > Expected output **if you have not** performed a full upgrade of the MiniBolt with `sudo apt update && sudo apt full-upgrade` **since 26/09/2024** (unlikely): ``` Ver Cluster Port Status Owner Data directory Log file 16 main 5432 online postgres /data/postgresdb/16 /var/log/postgresql/postgresql-16-main.log ``` ~ > Expected output **if you have** performed a full upgrade of the MiniBolt with `sudo apt update && sudo apt full-upgrade` **since 26/09/2024** (most likely): ``` Ver Cluster Port Status Owner Data directory Log file 16 main 5432 online postgres /data/postgresdb/16 /var/log/postgresql/postgresql-16-main.log 17 main 5433 down postgres /var/lib/postgresql/17/main /var/log/postgresql/postgresql-17-main.log ``` **Update PostgreSQL** If you haven't done so before, make sure to update the OS (PostgreSQL included to the latest version 17): * With user `admin`, fully update the OS with the package manager: ``` sudo apt update && sudo apt full-upgrade ``` ~ > Press "y" and enter or directly enter when the prompt asks you. ----------- #### **PostgreSQL server migration** * Stop all existing clusters: ``` sudo systemctl stop postgresql@16-main postgresql@17-main ``` * Create a new database destination folder for the v17 cluster ready for migration from v16: ``` sudo mkdir /data/postgresdb/17 ``` * Assign the owner as the postgres user: ``` sudo chown postgres:postgres /data/postgresdb/17 ``` * Assign the correct permissions: ``` sudo chmod 700 /data/postgresdb/17 ``` * Delete the cluster created by default for v17: ``` sudo -u postgres pg_dropcluster 17 main ``` * Update the systemd: ``` sudo systemctl daemon-reload ``` * Start the migration with the PostgreSQL migration tool: ``` sudo -u postgres pg_upgradecluster 16 main /data/postgresdb/17 ``` **~ >** ⌛ This may take a lot of time depending on the existing database size (the nostr relay database especially) and your machine's performance; it is recommended to use [tmux](https://github.com/tmux/tmux). Wait until the prompt shows up again. Example of expected output: ``` Restarting old cluster with restricted connections... Notice: extra pg_ctl/postgres options given, bypassing systemctl for start operation Creating new PostgreSQL cluster 17/main ... /usr/lib/postgresql/17/bin/initdb -D /data/postgresdb/17 --auth-local peer --auth-host scram-sha-256 --no-instructions --encoding UTF8 --lc-collate en_US.UTF-8 --lc-ctype en_US.UTF-8 --locale-provider libc The files belonging to this database system will be owned by user "postgres". This user must also own the server process. The database cluster will be initialized with locale "en_US.UTF-8". The default text search configuration will be set to "english". Data page checksums are disabled. fixing permissions on existing directory /data/postgresdb/17 ... ok creating subdirectories ... ok selecting dynamic shared memory implementation ... posix selecting default "max_connections" ... 100 selecting default "shared_buffers" ... 128MB selecting default time zone ... Etc/UTC creating configuration files ... ok running bootstrap script ... ok performing post-bootstrap initialization ... ok syncing data to disk ... ok Warning: systemd does not know about the new cluster yet. Operations like "service postgresql start" will not handle it. To fix, run: sudo systemctl daemon-reload Copying old configuration files... Copying old start.conf... Copying old pg_ctl.conf... Starting new cluster... Notice: extra pg_ctl/postgres options given, bypassing systemctl for start operation Running init phase upgrade hook scripts ... Roles, databases, schemas, ACLs... set_config ------------ (1 row) set_config ------------ (1 row) Fixing hardcoded library paths for stored procedures... Upgrading database postgres... Fixing hardcoded library paths for stored procedures... Upgrading database template1... Stopping target cluster... Stopping old cluster... Disabling automatic startup of old cluster... Starting upgraded cluster on port 5432... Warning: the cluster will not be running as a systemd service. Consider using systemctl: sudo systemctl start postgresql@17-main Running finish phase upgrade hook scripts ... vacuumdb: processing database "postgres": Generating minimal optimizer statistics (1 target) vacuumdb: processing database "template1": Generating minimal optimizer statistics (1 target) vacuumdb: processing database "postgres": Generating medium optimizer statistics (10 targets) vacuumdb: processing database "template1": Generating medium optimizer statistics (10 targets) vacuumdb: processing database "postgres": Generating default (full) optimizer statistics vacuumdb: processing database "template1": Generating default (full) optimizer statistics Success. Please check that the upgraded cluster works. If it does, you can remove the old cluster with pg_dropcluster 16 main Ver Cluster Port Status Owner Data directory Log file 16 main 5433 down postgres /data/postgresdb/16 /var/log/postgresql/postgresql-16-main.log Ver Cluster Port Status Owner Data directory Log file 17 main 5432 online postgres /data/postgresdb/17 /var/log/postgresql/postgresql-17-main.log ``` * Reload the systemd again: ``` sudo systemctl daemon-reload ``` * List the clusters to show the state: ``` pg_lsclusters ``` Expected output: ``` Ver Cluster Port Status Owner Data directory Log file 16 main 5433 down <unknown> /data/postgresdb/16 /var/log/postgresql/postgresql-16-main.log 17 main 5432 online <unknown> /data/postgresdb/17 /var/log/postgresql/postgresql-17-main.log ``` ~> **Notes:** * Don't worry about the <unknown> output of the "Owner" column. * Note how the old 16 cluster has automatically gone into status "down" after the migration. --- * Stop the version 17 cluster using the `pg_ctlcluster` tool, to then be able to run it and manage it with `systemd`: ``` sudo pg_ctlcluster 17 main stop ``` * List the clusters again to show the state: ``` pg_lsclusters ``` Expected output: ``` Ver Cluster Port Status Owner Data directory Log file 16 main 5433 down <unknown> /data/postgresdb/16 /var/log/postgresql/postgresql-16-main.log 17 main 5432 down <unknown> /data/postgresdb/17 /var/log/postgresql/postgresql-17-main.log ``` **~>** Note how the version 17 cluster has gone into status "down". * Start the version 17 cluster with systemd: ``` sudo systemctl start postgresql@17-main ``` * Monitor the logs of the PostgreSQL version 17 cluster to ensure that it working fine with `systemd`: ``` journalctl -fu postgresql@17-main ``` Expected output: ``` minibolt systemd[1]: Starting PostgreSQL Cluster 17-main... minibolt systemd[1]: Started PostgreSQL Cluster 17-main. ``` ~ > Press `Ctrl + C` to continue. * List the clusters again to show the state: ``` pg_lsclusters ``` Expected output: ``` Ver Cluster Port Status Owner Data directory Log file 16 main 5433 down <unknown> /data/postgresdb/16 /var/log/postgresql/postgresql-16-main.log 17 main 5432 online <unknown> /data/postgresdb/17 /var/log/postgresql/postgresql-17-main.log ``` **~>** Note how the version 17 cluster has come back into the status "online". * Delete the version 16 (old and disused) cluster: ``` sudo pg_dropcluster 16 main ``` * List again the clusters to check the correct deletion: ``` pg_lsclusters ``` Expected output: ``` Ver Cluster Port Status Owner Data directory Log file 17 main 5432 online <unknown> /data/postgresdb/17 /var/log/postgresql/postgresql-17-main.log ``` **~>** Note how it no longer appears version 16 (old and disused) cluster. **Check the PostgreSQL server version in use** * With the user `admin`, enter the psql (PostgreSQL CLI): ``` sudo -u postgres psql ``` * Enter the next command to get the server version: ``` SELECT version(); ``` Example of expected output: ``` version ----------------------------------------------------------------------------------------------------------------------------------- PostgreSQL 17.2 (Ubuntu 17.2-1.pgdg22.04+1) on x86_64-pc-linux-gnu, compiled by gcc (Ubuntu 11.4.0-1ubuntu1~22.04) 11.4.0, 64-bit (1 row) ``` **~ >** Check the previous version in use is now PostgreSQL 17.2 (the latest and current version of the PostgreSQL server at this moment). * Come back to the `admin` user bash prompt: ``` \q ``` * Start again the PostgreSQL dependencies services: ``` sudo systemctl start lnd nbxplorer btcpay thunderhub scb-backup nostr-relay cloudflared ``` ~ > Check all works fine with the logs of each service, especially **lnd** ~ > `journalctl -fu lnd`. * **(Optional)** Once you have verified that everything is working correctly, you can delete the created PostgreSQL backup and temporary directory: ``` sudo rm -rf /tmp/postgresdb-temp ``` * Delete unnecessary packages: ``` sudo apt autoremove ``` ~ > Press "y" and ENTER when needed or ENTER directly when the prompts ask you. --- ✅ That's it! If you have any questions or issues, you can go to any RRSS available for the MiniBolt project ~ > [HERE](https://minibolt.minibolt.info/#community) < ~ --- Only for MiniBolters! Enjoy it! 💙 @ 16d11430:61640947
2025-01-23 06:20:25In this modern era of ceaseless clamor, where sensationalism reigns supreme, the plight of our elderly is one that demands urgent attention. These venerable souls, repositories of wisdom and keepers of our traditions, now find themselves prey to the cunning machinations of a new kind of colonialism—a digital imperialism, crafted by social media giants in unholy alliance with local third-party propagators of division. This exploitation tears at the fragile seams of our internationally stretched social fabric, threatening to unravel the fragile threads of unity and peace that bind humanity together. The New Exploiters: Social Media and Local Gatekeepers Once, it was the foreign trader who came bearing baubles to ensnare the unwitting; today, it is the algorithm, armed with the tools of manipulation, that preys upon the unsuspecting minds of the elderly. Social media companies, in their relentless pursuit of profit, have perfected the art of creating division. By partnering with local entities—be it political groups, media conglomerates, or data brokers—they turn our elders into unwitting soldiers in a war of narratives. These local agents, familiar with the cultural fears and anxieties of their regions, amplify messages designed to provoke outrage and suspicion. For the elderly, who often rely on these platforms as a means of connection in their isolation, such messages become a poison. The news feed, crafted with precision by algorithms that prioritize engagement over truth, becomes a fertile ground for fear-mongering, paranoia, and mistrust. Tugging at the Seams of Society The bonds of human unity, forged through millennia of shared struggles and triumphs, are delicate. They depend on trust, understanding, and a sense of collective purpose. Yet, social media, in its pursuit of engagement, exploits every fracture, every difference, and every perceived slight. The elderly, with their memories of simpler times and their deeply ingrained cultural values, become ideal targets. A post about economic inequality becomes a trigger for fear of financial ruin. A video about global migration is twisted to evoke xenophobia. Stories of political corruption are shared, reshared, and distorted, until the very institutions of democracy seem untrustworthy. These narratives, designed to provoke outrage and despair, pit neighbor against neighbor, generation against generation, and nation against nation. A Call to Rekindle Social Harmony Let us pause and ask ourselves: are we to stand idly by while this insidious force tears apart the very fabric of our society? Are we to abandon our elders to a world where every news cycle is a source of anxiety, every notification a harbinger of doom? No! We must take inspiration from the great reformers of our past, who believed in the power of truth and unity to overcome the most formidable adversaries. The Path Forward 1. Restore the Spirit of Inquiry Just as Raja Ram Mohan Roy called for the illumination of the mind through education, we must arm our elderly with the tools to discern truth from falsehood. Let media literacy be the new frontier of reform. Teach our elders to question, to verify, and to seek balanced perspectives, so they may break free from the clutches of sensationalism. 2. Break the Chains of Dependency The chains that bind our elderly to these exploitative platforms must be loosened. Encourage them to find solace in real-world connections—in community gatherings, family conversations, and meaningful hobbies. Let us restore their faith in humanity, not as a divided collection of online tribes, but as a family united in its diversity. 3. Demand Accountability from the Exploiters Just as Mahatma Gandhi stood against the economic and moral exploitation of India by the British Empire, so too must we hold these digital empires to account. Governments, civil societies, and individuals must demand transparency from social media companies. Let there be light in the dark recesses of their algorithms, so we may understand how they manipulate our thoughts and sow discord. 4. Rebuild the Tapestry of Social Unity Swami Vivekananda urged us to see the divine in every individual, to rise above narrow divisions of caste, creed, and nationality. Today, that spirit of unity must extend to the digital realm. Let us create platforms and spaces where truth is valued above profit, where dialogue is fostered, and where the elderly can find comfort and connection without fear or anxiety. A Vision for a Harmonious Tomorrow The elderly are not relics of the past; they are the roots of our tree, anchoring us to the soil of history and tradition. When their peace of mind is disturbed, the entire tree shakes, its branches swaying precariously in the storm. If we are to weather this tempest of misinformation and division, we must protect those roots, nourish them, and shield them from harm. The time has come for a new kind of reformer, one who understands the power of technology but wields it with compassion and wisdom. Let us be those reformers. Let us heal the divisions that social media and hype-driven narratives have wrought. Let us, together, rebuild a society where our elders can find peace, truth, and a sense of belonging in this bewildering modern age. In the words of Tagore: “Where the mind is without fear, and the head is held high, into that heaven of freedom, let my country awake.” Let us awaken not just our country, but the world, to this vision of dignity, unity, and truth for all, especially for those who have given us so much—the elders who deserve our care, our respect, and above all, our love.
@ 16d11430:61640947
2025-01-23 06:20:25In this modern era of ceaseless clamor, where sensationalism reigns supreme, the plight of our elderly is one that demands urgent attention. These venerable souls, repositories of wisdom and keepers of our traditions, now find themselves prey to the cunning machinations of a new kind of colonialism—a digital imperialism, crafted by social media giants in unholy alliance with local third-party propagators of division. This exploitation tears at the fragile seams of our internationally stretched social fabric, threatening to unravel the fragile threads of unity and peace that bind humanity together. The New Exploiters: Social Media and Local Gatekeepers Once, it was the foreign trader who came bearing baubles to ensnare the unwitting; today, it is the algorithm, armed with the tools of manipulation, that preys upon the unsuspecting minds of the elderly. Social media companies, in their relentless pursuit of profit, have perfected the art of creating division. By partnering with local entities—be it political groups, media conglomerates, or data brokers—they turn our elders into unwitting soldiers in a war of narratives. These local agents, familiar with the cultural fears and anxieties of their regions, amplify messages designed to provoke outrage and suspicion. For the elderly, who often rely on these platforms as a means of connection in their isolation, such messages become a poison. The news feed, crafted with precision by algorithms that prioritize engagement over truth, becomes a fertile ground for fear-mongering, paranoia, and mistrust. Tugging at the Seams of Society The bonds of human unity, forged through millennia of shared struggles and triumphs, are delicate. They depend on trust, understanding, and a sense of collective purpose. Yet, social media, in its pursuit of engagement, exploits every fracture, every difference, and every perceived slight. The elderly, with their memories of simpler times and their deeply ingrained cultural values, become ideal targets. A post about economic inequality becomes a trigger for fear of financial ruin. A video about global migration is twisted to evoke xenophobia. Stories of political corruption are shared, reshared, and distorted, until the very institutions of democracy seem untrustworthy. These narratives, designed to provoke outrage and despair, pit neighbor against neighbor, generation against generation, and nation against nation. A Call to Rekindle Social Harmony Let us pause and ask ourselves: are we to stand idly by while this insidious force tears apart the very fabric of our society? Are we to abandon our elders to a world where every news cycle is a source of anxiety, every notification a harbinger of doom? No! We must take inspiration from the great reformers of our past, who believed in the power of truth and unity to overcome the most formidable adversaries. The Path Forward 1. Restore the Spirit of Inquiry Just as Raja Ram Mohan Roy called for the illumination of the mind through education, we must arm our elderly with the tools to discern truth from falsehood. Let media literacy be the new frontier of reform. Teach our elders to question, to verify, and to seek balanced perspectives, so they may break free from the clutches of sensationalism. 2. Break the Chains of Dependency The chains that bind our elderly to these exploitative platforms must be loosened. Encourage them to find solace in real-world connections—in community gatherings, family conversations, and meaningful hobbies. Let us restore their faith in humanity, not as a divided collection of online tribes, but as a family united in its diversity. 3. Demand Accountability from the Exploiters Just as Mahatma Gandhi stood against the economic and moral exploitation of India by the British Empire, so too must we hold these digital empires to account. Governments, civil societies, and individuals must demand transparency from social media companies. Let there be light in the dark recesses of their algorithms, so we may understand how they manipulate our thoughts and sow discord. 4. Rebuild the Tapestry of Social Unity Swami Vivekananda urged us to see the divine in every individual, to rise above narrow divisions of caste, creed, and nationality. Today, that spirit of unity must extend to the digital realm. Let us create platforms and spaces where truth is valued above profit, where dialogue is fostered, and where the elderly can find comfort and connection without fear or anxiety. A Vision for a Harmonious Tomorrow The elderly are not relics of the past; they are the roots of our tree, anchoring us to the soil of history and tradition. When their peace of mind is disturbed, the entire tree shakes, its branches swaying precariously in the storm. If we are to weather this tempest of misinformation and division, we must protect those roots, nourish them, and shield them from harm. The time has come for a new kind of reformer, one who understands the power of technology but wields it with compassion and wisdom. Let us be those reformers. Let us heal the divisions that social media and hype-driven narratives have wrought. Let us, together, rebuild a society where our elders can find peace, truth, and a sense of belonging in this bewildering modern age. In the words of Tagore: “Where the mind is without fear, and the head is held high, into that heaven of freedom, let my country awake.” Let us awaken not just our country, but the world, to this vision of dignity, unity, and truth for all, especially for those who have given us so much—the elders who deserve our care, our respect, and above all, our love. @ 6e75f797:a8eee74e
2023-08-07 13:16:42Last night I started a nostr community multiplayer instance for No Man's Sky [on ZapStream](https://zap.stream/) and before we knew it, we had 4 Nostrichs arriving on the genesis planet to join the fun.  NSM is an deterministic, procedurally generated open universe where players can explore, quest, build, combat and have fun together. Every new system discovered is generated when the first Traveller enters the system making the game a unique experience for any open world gaming fan. If you fancy joining us in the Nostrverse let me know and I'll friend you in #NMS and on Steam or Epic. If you just want to watch the fun, participate in naming systems, planets, fauna and flora come and hang out in my stream or the stream of [Oceanbee](nostr:npub1wqxxe0cjaxnvmrv4lkvx8d5dlft7ewswyn09w5v7fg7642fgzm7srucxws), [HolgerHatGarKeineNode](nostr:npub1pt0kw36ue3w2g4haxq3wgm6a2fhtptmzsjlc2j2vphtcgle72qesgpjyc6) or [taette](npub1yh0dl6pazf55025qvp860lstpscuy0kj2a5lfhxlk400m968vgpql5vsnd).  ### If you already own NMS, feel free to add me! My NMS friend code is: EMAZ-KMHT-ZPFXP See you in space Traveller! - TheGrinder
@ 6e75f797:a8eee74e
2023-08-07 13:16:42Last night I started a nostr community multiplayer instance for No Man's Sky [on ZapStream](https://zap.stream/) and before we knew it, we had 4 Nostrichs arriving on the genesis planet to join the fun.  NSM is an deterministic, procedurally generated open universe where players can explore, quest, build, combat and have fun together. Every new system discovered is generated when the first Traveller enters the system making the game a unique experience for any open world gaming fan. If you fancy joining us in the Nostrverse let me know and I'll friend you in #NMS and on Steam or Epic. If you just want to watch the fun, participate in naming systems, planets, fauna and flora come and hang out in my stream or the stream of [Oceanbee](nostr:npub1wqxxe0cjaxnvmrv4lkvx8d5dlft7ewswyn09w5v7fg7642fgzm7srucxws), [HolgerHatGarKeineNode](nostr:npub1pt0kw36ue3w2g4haxq3wgm6a2fhtptmzsjlc2j2vphtcgle72qesgpjyc6) or [taette](npub1yh0dl6pazf55025qvp860lstpscuy0kj2a5lfhxlk400m968vgpql5vsnd).  ### If you already own NMS, feel free to add me! My NMS friend code is: EMAZ-KMHT-ZPFXP See you in space Traveller! - TheGrinder @ b17fccdf:b7211155
2025-01-21 18:39:47~ > **Check out the steps to get this** ~ > [HERE](https://minibolt.minibolt.info/bonus-guides/system/static-ip-and-custom-dns-servers#dot-doh--dnssec) < ~ **Note:** for different reasons, it is recommended choosing [Option 1: DoT & DNSSEC using systemd-resolved](https://minibolt.minibolt.info/bonus-guides/system/static-ip-and-custom-dns-servers#option-1-use-dot-and-dnssec-validation-with-systemd-resolved), but you could want to use [Option 2](https://minibolt.minibolt.info/bonus-guides/system/static-ip-and-custom-dns-servers#option-2-use-doh-with-cloudflared-proxy-dns), choose behind your criteria, both are valid to achieve the same objective. ----------- Some more changes were released recently in other places of the MiniBolt guide, check the full release notes: #### **Full release notes** ~ > [Static IP & custom DNS servers](https://minibolt.minibolt.info/bonus-guides/system/static-ip-and-custom-dns-servers) bonus guide: - Adds custom DNS server suggestions. - Adds different steps to check the changes after configurations. - Deleted some unnecessary steps. - Fix some nits. --- ~ > Modifications on [Configuration](https://minibolt.minibolt.info/bitcoin/bitcoin/bitcoin-client#configuration) (`bitcoin.conf`) of [Bitcoin Core](https://minibolt.minibolt.info/bitcoin/bitcoin/bitcoin-client): - Replace proxy value parameter to use UNIX domain socket (`proxy=unix:/run/tor/socks`) | (recently [enabled](https://github.com/bitcoin/bitcoin/pull/27375) on Bitcoin Core v28). - Replace `startupnotify=chmod g+r /home/bitcoin/.bitcoin/.cookie` to `rpccookieperms=group` [Bitcoin Core PR](https://github.com/bitcoin/bitcoin/pull/28167). - Adds another special bind address to listen to incoming connections from Tor (`bind=127.0.0.1=onion`) | (recently [changed](https://github.com/bitcoin/bitcoin/blob/master/doc/release-notes/release-notes-28.0.md#p2p-and-network-changes) on Bitcoin Core v28). - Modified [systemd service](https://minibolt.minibolt.info/bitcoin/bitcoin/bitcoin-client#create-systemd-service) to improve the startup and shutdown process. **Note:** remember to restart Bitcoin Core and reload the systemd with `sudo systemctl daemon-reload` to apply changes. --- ~ > Delete unnecessary parameters of the [systemd service](https://minibolt.minibolt.info/lightning/lightning/lightning-client#create-systemd-service) of [Lightning client](https://minibolt.minibolt.info/lightning/lightning/lightning-client). **Note:** remember to reload the systemd with `sudo systemctl daemon-reload` to apply changes. --- ~ > **Others:** - New [i2pd webconsole](https://minibolt.minibolt.info/system/system/privacy#access-to-the-i2pd-webconsole) section. - Adds a new ["Validation"](https://minibolt.minibolt.info/bitcoin/bitcoin/bitcoin-client#validation) subsection to the guides to clarify when checks begin. - New "[Use the Tor proxy from another device](https://minibolt.minibolt.info/system/system/privacy#use-the-tor-proxy-from-another-device)" section. - Adds Electrs [compatible with Testnet4](https://minibolt.minibolt.info/bonus-guides/bitcoin/minibolt-on-testnet#bitcoin-electrs) on Testnet bonus guide. - Adds how to build a [Guard/Middle relay](https://minibolt.minibolt.info/bonus-guides/system/tor-services#guard-middle-relay) section on "Tor services: bridges & relays" bonus guide. - Adds [Extras (optional)](https://minibolt.minibolt.info/bonus-guides/system/tor-services#extras-optional) section to "Tor services: bridges & relays" bonus guide with different utilities like install Nyx, how to "Limit bandwidth" and others. - Changed [Electrs](https://minibolt.minibolt.info/bonus-guides/bitcoin/electrs) ports to enable simultaneous mode with Fulcrum. - [Updated aliases](https://minibolt.minibolt.info/bonus-guides/system/aliases#upgrades) list to include news additions in line with updates. - Updated the [Networkmap](https://bit.ly/minibolt-ramix_netmap) resource to include news additions in line with updates and migrate to a dynamic visual mode. - Reorganized some menu items and sections to improve the UX and make more sense in the face of the future. - Restructure and rename the "Tor obfs4 bridge" bonus guide to ["Tor services: bridges & relays"](https://minibolt.minibolt.info/bonus-guides/system/tor-services) and modify it to run the obfs4bridge, relays, and the master, in separate instances. - Hidden [NYM mixnet](https://minibolt.minibolt.info/bonus-guides/system/nym-mixnet) and [Sparrow server](https://minibolt.minibolt.info/bonus-guides/bitcoin/sparrow-server) bonus guides from the menus due to disuse or poor performance. **Note:** it will continue to be maintained later if the situation changes due to the development of the associated software. - Bump version of various services. --- ~ > **Coming soon...** - Enable DNSSEC for your domain using Cloudflare + Namecheap. - Enable DoH on: - Desktop/Android browser (Windows/Linux). - OS: Windows 11 // Linux ([Completed](https://minibolt.minibolt.info/bonus-guides/system/static-ip-and-custom-dns-servers#option-2-use-doh-with-cloudflared-proxy-dns) ✅) - Router. - Enable DoT on: - Android OS. - OS: Windows 11 // Linux ([Completed](https://minibolt.minibolt.info/bonus-guides/system/static-ip-and-custom-dns-servers#option-1-use-dot-and-dnssec-validation-with-systemd-resolved) ✅) with DNSSEC verification included. - Router. --- Enjoy it MiniBolter!💙
@ b17fccdf:b7211155
2025-01-21 18:39:47~ > **Check out the steps to get this** ~ > [HERE](https://minibolt.minibolt.info/bonus-guides/system/static-ip-and-custom-dns-servers#dot-doh--dnssec) < ~ **Note:** for different reasons, it is recommended choosing [Option 1: DoT & DNSSEC using systemd-resolved](https://minibolt.minibolt.info/bonus-guides/system/static-ip-and-custom-dns-servers#option-1-use-dot-and-dnssec-validation-with-systemd-resolved), but you could want to use [Option 2](https://minibolt.minibolt.info/bonus-guides/system/static-ip-and-custom-dns-servers#option-2-use-doh-with-cloudflared-proxy-dns), choose behind your criteria, both are valid to achieve the same objective. ----------- Some more changes were released recently in other places of the MiniBolt guide, check the full release notes: #### **Full release notes** ~ > [Static IP & custom DNS servers](https://minibolt.minibolt.info/bonus-guides/system/static-ip-and-custom-dns-servers) bonus guide: - Adds custom DNS server suggestions. - Adds different steps to check the changes after configurations. - Deleted some unnecessary steps. - Fix some nits. --- ~ > Modifications on [Configuration](https://minibolt.minibolt.info/bitcoin/bitcoin/bitcoin-client#configuration) (`bitcoin.conf`) of [Bitcoin Core](https://minibolt.minibolt.info/bitcoin/bitcoin/bitcoin-client): - Replace proxy value parameter to use UNIX domain socket (`proxy=unix:/run/tor/socks`) | (recently [enabled](https://github.com/bitcoin/bitcoin/pull/27375) on Bitcoin Core v28). - Replace `startupnotify=chmod g+r /home/bitcoin/.bitcoin/.cookie` to `rpccookieperms=group` [Bitcoin Core PR](https://github.com/bitcoin/bitcoin/pull/28167). - Adds another special bind address to listen to incoming connections from Tor (`bind=127.0.0.1=onion`) | (recently [changed](https://github.com/bitcoin/bitcoin/blob/master/doc/release-notes/release-notes-28.0.md#p2p-and-network-changes) on Bitcoin Core v28). - Modified [systemd service](https://minibolt.minibolt.info/bitcoin/bitcoin/bitcoin-client#create-systemd-service) to improve the startup and shutdown process. **Note:** remember to restart Bitcoin Core and reload the systemd with `sudo systemctl daemon-reload` to apply changes. --- ~ > Delete unnecessary parameters of the [systemd service](https://minibolt.minibolt.info/lightning/lightning/lightning-client#create-systemd-service) of [Lightning client](https://minibolt.minibolt.info/lightning/lightning/lightning-client). **Note:** remember to reload the systemd with `sudo systemctl daemon-reload` to apply changes. --- ~ > **Others:** - New [i2pd webconsole](https://minibolt.minibolt.info/system/system/privacy#access-to-the-i2pd-webconsole) section. - Adds a new ["Validation"](https://minibolt.minibolt.info/bitcoin/bitcoin/bitcoin-client#validation) subsection to the guides to clarify when checks begin. - New "[Use the Tor proxy from another device](https://minibolt.minibolt.info/system/system/privacy#use-the-tor-proxy-from-another-device)" section. - Adds Electrs [compatible with Testnet4](https://minibolt.minibolt.info/bonus-guides/bitcoin/minibolt-on-testnet#bitcoin-electrs) on Testnet bonus guide. - Adds how to build a [Guard/Middle relay](https://minibolt.minibolt.info/bonus-guides/system/tor-services#guard-middle-relay) section on "Tor services: bridges & relays" bonus guide. - Adds [Extras (optional)](https://minibolt.minibolt.info/bonus-guides/system/tor-services#extras-optional) section to "Tor services: bridges & relays" bonus guide with different utilities like install Nyx, how to "Limit bandwidth" and others. - Changed [Electrs](https://minibolt.minibolt.info/bonus-guides/bitcoin/electrs) ports to enable simultaneous mode with Fulcrum. - [Updated aliases](https://minibolt.minibolt.info/bonus-guides/system/aliases#upgrades) list to include news additions in line with updates. - Updated the [Networkmap](https://bit.ly/minibolt-ramix_netmap) resource to include news additions in line with updates and migrate to a dynamic visual mode. - Reorganized some menu items and sections to improve the UX and make more sense in the face of the future. - Restructure and rename the "Tor obfs4 bridge" bonus guide to ["Tor services: bridges & relays"](https://minibolt.minibolt.info/bonus-guides/system/tor-services) and modify it to run the obfs4bridge, relays, and the master, in separate instances. - Hidden [NYM mixnet](https://minibolt.minibolt.info/bonus-guides/system/nym-mixnet) and [Sparrow server](https://minibolt.minibolt.info/bonus-guides/bitcoin/sparrow-server) bonus guides from the menus due to disuse or poor performance. **Note:** it will continue to be maintained later if the situation changes due to the development of the associated software. - Bump version of various services. --- ~ > **Coming soon...** - Enable DNSSEC for your domain using Cloudflare + Namecheap. - Enable DoH on: - Desktop/Android browser (Windows/Linux). - OS: Windows 11 // Linux ([Completed](https://minibolt.minibolt.info/bonus-guides/system/static-ip-and-custom-dns-servers#option-2-use-doh-with-cloudflared-proxy-dns) ✅) - Router. - Enable DoT on: - Android OS. - OS: Windows 11 // Linux ([Completed](https://minibolt.minibolt.info/bonus-guides/system/static-ip-and-custom-dns-servers#option-1-use-dot-and-dnssec-validation-with-systemd-resolved) ✅) with DNSSEC verification included. - Router. --- Enjoy it MiniBolter!💙 @ 58937958:545e6994
2025-01-13 03:31:48I made croquettes inspired by Spiral's character "Bitcoin (Puppet)."  The method is the same as making regular croquettes. I also tried making a version (right) with the arms and legs attached while shaping the filling, but they fell off before I could coat them in flour.  The face is made with seaweed and sliced cheese. The arms and legs are made with fish cake (hanpen). I brushed soy sauce on the legs and lightly toasted them in a toaster, which gave them a brown color.  The arms and legs are attached using thin spaghetti. When I searched for character-themed bentos (kyaraben), I came across the idea of using dried pasta, which made sense. I used fried spaghetti sticks for attachment. Here’s Bitcoin Croquette squished into a bento box:  Halving  Notes - I tried freezing the filling to help it hold its shape, but it backfired. It stuck to the plate and the cooking paper, and once partially thawed, it became way too watery. Freezing might work with better preparation. - The filling was quite dry when shaping, so it might be better to add a binder (this time, I only used potatoes and sautéed onions). The shape of Bitcoin Puppet was really easy and fun to make, so I’d love to try creating something else next time! nostr:nevent1qqsxgpjvf9g9suhzx5asqhvnlvnarl43kuhas8v5g2ryjr9yjjp0z5ctkh5pt
@ 58937958:545e6994
2025-01-13 03:31:48I made croquettes inspired by Spiral's character "Bitcoin (Puppet)."  The method is the same as making regular croquettes. I also tried making a version (right) with the arms and legs attached while shaping the filling, but they fell off before I could coat them in flour.  The face is made with seaweed and sliced cheese. The arms and legs are made with fish cake (hanpen). I brushed soy sauce on the legs and lightly toasted them in a toaster, which gave them a brown color.  The arms and legs are attached using thin spaghetti. When I searched for character-themed bentos (kyaraben), I came across the idea of using dried pasta, which made sense. I used fried spaghetti sticks for attachment. Here’s Bitcoin Croquette squished into a bento box:  Halving  Notes - I tried freezing the filling to help it hold its shape, but it backfired. It stuck to the plate and the cooking paper, and once partially thawed, it became way too watery. Freezing might work with better preparation. - The filling was quite dry when shaping, so it might be better to add a binder (this time, I only used potatoes and sautéed onions). The shape of Bitcoin Puppet was really easy and fun to make, so I’d love to try creating something else next time! nostr:nevent1qqsxgpjvf9g9suhzx5asqhvnlvnarl43kuhas8v5g2ryjr9yjjp0z5ctkh5pt @ fd78c37f:a0ec0833
2025-01-23 03:30:28In this edition, we invited Nyirenda, a member of the nostr:npub1t4ljwhhg7zlxeahxwgmkwqmn4jjxxq8lzhyuzy0zvy23hq0sacxsdl9fvv community, to share his personal experiences in participating in the Bitcoin community, as well as the challenges the community has faced in its operations and the strategies used to address them. **YakiHonne:** Today, we are honored to have a guest from Bitcoin Boma with us. Thank you for joining us. Before we dive in, I'd like to take a moment to introduce YakiHonne and share a bit about what we do. YakiHonne is a decentralized media client built on the Nostr protocol that enables freedom of speech through technology. It empowers creators to create their own voice, assets, and features. It also allows features like smart widgets, verified notes, and focuses on long-form articles. Now today we'll be exploring more about the Bitcoin community. Nyirenda, could you please briefly introduce yourself and tell us a bit about what you do? **Nyirenda**:My name is Nyirenda. I'm part of the Bitcoin Boma Education Program and Bitcoin Boma Malawi. Bitcoin Boma Malawi is a coalition of Bitcoin enthusiasts who have come together to raise social, economic, and environmental awareness about Bitcoin in Malawi. Our long-term strategy involves engaging with various stakeholders, including the government, to work towards the legalization of Bitcoin.  **YakiHonne:** What sparked your interest in Bitcoin, and what motivated you to start a community around it? **Nyirenda**: I first came across Bitcoin in 2016 through the news. Back then, its price had already surged to $16,000, which sparked my interest right away. Although the news warned that Bitcoin resembled a Ponzi scheme, I had already built a solid understanding of economic structures, having studied monetary history and the fractional reserve banking system. This gave me the background needed to appreciate Bitcoin. **Nyirenda**:I began my research journey with Andreas Antonopoulos's lectures and books, which deeply resonated with me. I was quickly drawn to the philosophy behind Bitcoin. Since then, my focus has been on engaging with others and teaching them about Bitcoin, especially within the context of Malawi. **Nyirenda**:In Malawi, our economic activities face numerous restrictions. The government controls the national fiat currency, limiting what we can do with it. For me, Bitcoin presents a solution to these issues. Today, I remain passionate about educating others about Bitcoin and exploring its potential to transform our economic situation. **YakiHonne**: I witnessed the decline of traditional currencies and realized how Bitcoin could play a role in the future. It's truly fascinating to see how it can be implemented. Could you share how the community was formed, how you attracted members in the early stages, and what challenges you faced along the way? **Nyirenda**:When I first started diving into Bitcoin, I felt like I needed a teacher. So, I printed a T-shirt that said "Bitcoin accepted here" and wore it whenever I went into town or public places. People would often look at me and ask, "Hey, what's Bitcoin?" I could then briefly explain what Bitcoin is and how it compares to the current fiat system. **Nyirenda**:Some people were really interested, to the point that we exchanged contacts and started connecting, and it was a great experience. But the turning point came when I saw a tweet from Bitcoin Boma. Someone tweeted about a conference/seminar being organized, in collaboration with Trezor Academy. When I saw this, I knew this was the place to be. So, last July, I met Grant, Ian Foster, and Nick Twyman, who were organizing the event.  **Nyirenda**:After we introduced ourselves and started connecting, they said, "Hey, join us as part of our coalition, and let's see what we can do with Bitcoin, especially in education." That’s how things started moving forward. It's been an incredible journey because since then, we've managed to graduate about 12 to 15 students. One of the biggest things we’ve done so far is launching the first Bitcoin education course in Malawi, attracting over 120 people. Of course, only some of them are attending the classes, but so far, the progress has been great.  **YakiHonne**: So, what challenges did you face in attracting new members at that stage? **Nyirenda**:The first challenge we face is the attitude and perception of Bitcoin. Bitcoin is a new technology and innovation. In a country where people are used to traditional currencies, there are many financial technologies emerging, including centralized coins. This has created challenges. When people hear about Bitcoin, many think of it as a Ponzi scheme. They believe it's a scam or a way to get rich quickly. What I've observed is that most people fail to understand the difference between Bitcoin and centralized currencies. To truly appreciate Bitcoin, they need to experience it. Setting up a custodial wallet and explaining a transaction to them can help. **Nyirenda**:The second challenge is that people think Bitcoin is too complicated, especially in Africa, and here in Malawi, where the IT and ICT infrastructure is still underdeveloped. I’d say 70% of the population doesn’t have access to the internet. Even in our education system, we don’t learn about computers. It’s mainly by luck if someone has access to a computer and a network, allowing them to appreciate the technology. **YakiHonne**: It seems to be common in many countries, where people think Bitcoin is a quick way to get rich. They see it as a scam or a Ponzi scheme. It's a big challenge to get people to believe in Bitcoin as a currency, rather than just their local currency. This is a real barrier in many economies. What principles guide your community, and how do you maintain trust and reliability in discussions? Simply saying, how do you keep the trust of the people? **Nyirenda**:I’ll start with Bitcoin BOMA and then extend it to the people we interact with. In Bitcoin BOMA, even though we’re a collaboration, we have clear objectives and a philosophy. Ultimately, we model Bitcoin’s decentralized nature because it allows everyone to participate. In our coalition, we encourage the free flow of ideas and regularly meet to discuss how best to promote Bitcoin education. We focus on its social, economic, and environmental aspects. We assign tasks to each other and work hard to achieve the results. **Nyirenda**:Malawi has great potential, especially in the energy sector, where we could mine Bitcoin, but we lose a lot of electricity during generation. There were attempts to convince government-run institutions to embrace Bitcoin. However, most of these institutions are controlled by the government, and getting into politics is necessary to convince policymakers. It’s been a challenge because government systems are centralized. There’s a hierarchy to follow, and sometimes, even if a minister understands Bitcoin, it takes a long time to get it approved in parliament and passed into law.This has been one of our ongoing initiatives. **Nyirenda**:When I go out and interact with people, especially Malawians, I try to explain the transparency of Bitcoin by showing how a decentralized ledger works and how it’s different from traditional systems. I also explain that Bitcoin is reliable and that mismanagement isn’t possible with a decentralized system. **Nyirenda**:In a country where people are educated in a certain way and believe in competition and power, I often remind them that absolute power corrupts absolutely. I tell them that Bitcoin offers a different space where decentralization allows for a fairer system and benefits everyone. That’s how I try to explain it in simple terms.  **YakiHonne**: how do you educate your members and keep them updated on Bitcoin development time-to-time? **Nyirenda**:For me, learning about Bitcoin is a lifelong process, with always unanswered questions and gaps to fill. I often study, read, and keep an eye on the developments in the Bitcoin community, especially in the African Bitcoin community. My role model is Kenya, particularly how they are enabling people to use Bitcoin through the Tando project. I believe that the value of Bitcoin is not just about holding and waiting for the price to rise, but rather as a tool that can help liberate the world. **Nyirenda**:Bitcoin is not just about accumulating wealth; I focus more on its role as a tool in the free market. Therefore, I continue to learn, even though I'm not a technical expert and my background is not in this field. I have worked in education, so I apply those skills to better understand Bitcoin and how it works. **Nyirenda**:I gather information from various sources to understand how Bitcoin works. At the same time, I compare it with the traditional monetary system, as that’s where I began, and it's my foundational layer. As for the Bitcoin BOMA community, I’m happy to say that we have two members with a strong background in economics. We often share interesting content and sometimes engage in debates. We also share many links and videos, learning from each other. **Nyirenda**:Especially in the Bitcoin Diploma Education Program, I give explanations, and I have peers who help analyze my course content. We remind each other and point out areas that need improvement. We constantly update each other on our progress, ensuring that our activities remain relevant, which helps us continue to improve.  **YakiHonne**: Does Bitcoin Boomer collaborate with the broader Bitcoin ecosystem, and which partnerships have had the greatest impact so far? **Nyirenda**:I'll start with our collaboration with Trezor Academy. Last year, this was one of the most significant partnerships for us in Malawi. Trezor Academy focuses on Bitcoin education, and they provided us with a lot of support. Thanks to this collaboration, we were able to organize a seminar and graduate about 10 to 15 students. It was a major achievement for us. **Nyirenda**:Additionally, one of our members attended the African Bitcoin Conference held in Kenya, which was a pivotal opportunity. He had the chance to interact with Bitcoiners from across Africa. There were special guests, including nostr:npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m and through this exposure, he met the core developers in Kenya and the Tando developers in South Africa. These collaborations have given us insight into what other Bitcoin communities are doing, especially in their projects. **Nyirenda**:We also had a speaker from Bitcoin Boma who participated in an event in El Salvador. We are working towards making Malawi a Bitcoin node, and he is actively fostering that effort. Big shoutout to Ian Foster for his dedication. He will also be attending a conference in South Africa this January as a guest speaker. These collaborations have been very impactful, and I’m confident that we’ll see the results of these interactions in the future.  **YakiHonne**: So what challenges has your community faced so far and how have you overcome them while maintaining integrity? **Nyirenda**:One of the challenges we face is related to resources, especially when it comes to our learning sessions. We mainly rely on our own resources, and we understand that quality lessons require specific equipment. While we're working toward acquiring these resources, we’re also making the most of what we have. We've agreed to work with what we have, and we believe we can still achieve our objectives. **Nyirenda**:Another challenge is the attitude towards Bitcoin in Malawi. Most people entering the crypto space have a “get rich quick” mentality. They focus more on the outcomes rather than the learning process. Many crypto traders are primarily interested in exploiting the benefits of Bitcoin. This is a challenge, especially when trying to teach people that Bitcoin is not just about making a profit, but also about liberation. Changing the traditional fiat mindset to embrace this new path is not easy. **Nyirenda**:Additionally, many people believe that if they invest their time, they must get a return. This is one of the challenges we're currently dealing with. Financial literacy in Malawi still has a long way to go. While people are aware of how economic shocks, especially currency devaluation, affect them, they often act out of desperation. The market is psychologically driven, and people are constantly looking for shortcuts to protect their wealth. When Bitcoin is introduced, it often raises doubts and skepticism. **Nyirenda**:However, there is no moment of hatred. Instead, we see the growing energy within the community, even if it's just coming from the heart, extending a significant impact on others. There’s a lot of potential and many possibilities ahead. Despite the challenges, we remain hopeful and excited about the future.  **YakiHonne**: In addition to wearing T-shirts and sparking curiosity, what other methods have you adopted to promote Bitcoin, and what results have you seen? **Nyirenda**:First of all, I want to mention the Bitcoin BOMA education diploma program that’s currently running. This is one of the most significant initiatives we have at the moment. We are doing our best to attract people to dive into our education program. So far, the results have been very positive, especially in terms of numbers. People are curious and realize that this is something worth learning. Some have even acknowledged that what they've learned in the traditional education system is very different from the exposure they get from the diploma program. I’d say that’s one of the biggest impacts we've had in promoting Bitcoin. **Nyirenda**:If we have sufficient resources, we plan to implement further actions such as putting up banners, promoting Bitcoin, and positioning Malawi as a Bitcoin hub. Malawi has great potential, particularly in the tourism sector, with many tourists visiting the country. If we display banners saying “We accept Bitcoin,” it would be appreciated by many people. Personally, I’ve been encouraging businesses to start accepting Bitcoin. **Nyirenda**:We also have a Bitcoin BOMA Twitter account where we advocate for Bitcoin. We engage in discussions and comment on trends. In the coming months, we plan to host spaces and aim to conduct them in our local language, so more people can appreciate and learn about Bitcoin. **YakiHonne**: We’ve reached the end of today’s session, and I must say, you’re doing an incredible job at Bitcoin BOMA. Your personal and collaborative efforts are truly impressive. I’m confident that in the next few years, we’ll be visiting Malawi for a Bitcoin conference. It’s clear that Malawi is heading in the right direction with you leading the way.
@ fd78c37f:a0ec0833
2025-01-23 03:30:28In this edition, we invited Nyirenda, a member of the nostr:npub1t4ljwhhg7zlxeahxwgmkwqmn4jjxxq8lzhyuzy0zvy23hq0sacxsdl9fvv community, to share his personal experiences in participating in the Bitcoin community, as well as the challenges the community has faced in its operations and the strategies used to address them. **YakiHonne:** Today, we are honored to have a guest from Bitcoin Boma with us. Thank you for joining us. Before we dive in, I'd like to take a moment to introduce YakiHonne and share a bit about what we do. YakiHonne is a decentralized media client built on the Nostr protocol that enables freedom of speech through technology. It empowers creators to create their own voice, assets, and features. It also allows features like smart widgets, verified notes, and focuses on long-form articles. Now today we'll be exploring more about the Bitcoin community. Nyirenda, could you please briefly introduce yourself and tell us a bit about what you do? **Nyirenda**:My name is Nyirenda. I'm part of the Bitcoin Boma Education Program and Bitcoin Boma Malawi. Bitcoin Boma Malawi is a coalition of Bitcoin enthusiasts who have come together to raise social, economic, and environmental awareness about Bitcoin in Malawi. Our long-term strategy involves engaging with various stakeholders, including the government, to work towards the legalization of Bitcoin.  **YakiHonne:** What sparked your interest in Bitcoin, and what motivated you to start a community around it? **Nyirenda**: I first came across Bitcoin in 2016 through the news. Back then, its price had already surged to $16,000, which sparked my interest right away. Although the news warned that Bitcoin resembled a Ponzi scheme, I had already built a solid understanding of economic structures, having studied monetary history and the fractional reserve banking system. This gave me the background needed to appreciate Bitcoin. **Nyirenda**:I began my research journey with Andreas Antonopoulos's lectures and books, which deeply resonated with me. I was quickly drawn to the philosophy behind Bitcoin. Since then, my focus has been on engaging with others and teaching them about Bitcoin, especially within the context of Malawi. **Nyirenda**:In Malawi, our economic activities face numerous restrictions. The government controls the national fiat currency, limiting what we can do with it. For me, Bitcoin presents a solution to these issues. Today, I remain passionate about educating others about Bitcoin and exploring its potential to transform our economic situation. **YakiHonne**: I witnessed the decline of traditional currencies and realized how Bitcoin could play a role in the future. It's truly fascinating to see how it can be implemented. Could you share how the community was formed, how you attracted members in the early stages, and what challenges you faced along the way? **Nyirenda**:When I first started diving into Bitcoin, I felt like I needed a teacher. So, I printed a T-shirt that said "Bitcoin accepted here" and wore it whenever I went into town or public places. People would often look at me and ask, "Hey, what's Bitcoin?" I could then briefly explain what Bitcoin is and how it compares to the current fiat system. **Nyirenda**:Some people were really interested, to the point that we exchanged contacts and started connecting, and it was a great experience. But the turning point came when I saw a tweet from Bitcoin Boma. Someone tweeted about a conference/seminar being organized, in collaboration with Trezor Academy. When I saw this, I knew this was the place to be. So, last July, I met Grant, Ian Foster, and Nick Twyman, who were organizing the event.  **Nyirenda**:After we introduced ourselves and started connecting, they said, "Hey, join us as part of our coalition, and let's see what we can do with Bitcoin, especially in education." That’s how things started moving forward. It's been an incredible journey because since then, we've managed to graduate about 12 to 15 students. One of the biggest things we’ve done so far is launching the first Bitcoin education course in Malawi, attracting over 120 people. Of course, only some of them are attending the classes, but so far, the progress has been great.  **YakiHonne**: So, what challenges did you face in attracting new members at that stage? **Nyirenda**:The first challenge we face is the attitude and perception of Bitcoin. Bitcoin is a new technology and innovation. In a country where people are used to traditional currencies, there are many financial technologies emerging, including centralized coins. This has created challenges. When people hear about Bitcoin, many think of it as a Ponzi scheme. They believe it's a scam or a way to get rich quickly. What I've observed is that most people fail to understand the difference between Bitcoin and centralized currencies. To truly appreciate Bitcoin, they need to experience it. Setting up a custodial wallet and explaining a transaction to them can help. **Nyirenda**:The second challenge is that people think Bitcoin is too complicated, especially in Africa, and here in Malawi, where the IT and ICT infrastructure is still underdeveloped. I’d say 70% of the population doesn’t have access to the internet. Even in our education system, we don’t learn about computers. It’s mainly by luck if someone has access to a computer and a network, allowing them to appreciate the technology. **YakiHonne**: It seems to be common in many countries, where people think Bitcoin is a quick way to get rich. They see it as a scam or a Ponzi scheme. It's a big challenge to get people to believe in Bitcoin as a currency, rather than just their local currency. This is a real barrier in many economies. What principles guide your community, and how do you maintain trust and reliability in discussions? Simply saying, how do you keep the trust of the people? **Nyirenda**:I’ll start with Bitcoin BOMA and then extend it to the people we interact with. In Bitcoin BOMA, even though we’re a collaboration, we have clear objectives and a philosophy. Ultimately, we model Bitcoin’s decentralized nature because it allows everyone to participate. In our coalition, we encourage the free flow of ideas and regularly meet to discuss how best to promote Bitcoin education. We focus on its social, economic, and environmental aspects. We assign tasks to each other and work hard to achieve the results. **Nyirenda**:Malawi has great potential, especially in the energy sector, where we could mine Bitcoin, but we lose a lot of electricity during generation. There were attempts to convince government-run institutions to embrace Bitcoin. However, most of these institutions are controlled by the government, and getting into politics is necessary to convince policymakers. It’s been a challenge because government systems are centralized. There’s a hierarchy to follow, and sometimes, even if a minister understands Bitcoin, it takes a long time to get it approved in parliament and passed into law.This has been one of our ongoing initiatives. **Nyirenda**:When I go out and interact with people, especially Malawians, I try to explain the transparency of Bitcoin by showing how a decentralized ledger works and how it’s different from traditional systems. I also explain that Bitcoin is reliable and that mismanagement isn’t possible with a decentralized system. **Nyirenda**:In a country where people are educated in a certain way and believe in competition and power, I often remind them that absolute power corrupts absolutely. I tell them that Bitcoin offers a different space where decentralization allows for a fairer system and benefits everyone. That’s how I try to explain it in simple terms.  **YakiHonne**: how do you educate your members and keep them updated on Bitcoin development time-to-time? **Nyirenda**:For me, learning about Bitcoin is a lifelong process, with always unanswered questions and gaps to fill. I often study, read, and keep an eye on the developments in the Bitcoin community, especially in the African Bitcoin community. My role model is Kenya, particularly how they are enabling people to use Bitcoin through the Tando project. I believe that the value of Bitcoin is not just about holding and waiting for the price to rise, but rather as a tool that can help liberate the world. **Nyirenda**:Bitcoin is not just about accumulating wealth; I focus more on its role as a tool in the free market. Therefore, I continue to learn, even though I'm not a technical expert and my background is not in this field. I have worked in education, so I apply those skills to better understand Bitcoin and how it works. **Nyirenda**:I gather information from various sources to understand how Bitcoin works. At the same time, I compare it with the traditional monetary system, as that’s where I began, and it's my foundational layer. As for the Bitcoin BOMA community, I’m happy to say that we have two members with a strong background in economics. We often share interesting content and sometimes engage in debates. We also share many links and videos, learning from each other. **Nyirenda**:Especially in the Bitcoin Diploma Education Program, I give explanations, and I have peers who help analyze my course content. We remind each other and point out areas that need improvement. We constantly update each other on our progress, ensuring that our activities remain relevant, which helps us continue to improve.  **YakiHonne**: Does Bitcoin Boomer collaborate with the broader Bitcoin ecosystem, and which partnerships have had the greatest impact so far? **Nyirenda**:I'll start with our collaboration with Trezor Academy. Last year, this was one of the most significant partnerships for us in Malawi. Trezor Academy focuses on Bitcoin education, and they provided us with a lot of support. Thanks to this collaboration, we were able to organize a seminar and graduate about 10 to 15 students. It was a major achievement for us. **Nyirenda**:Additionally, one of our members attended the African Bitcoin Conference held in Kenya, which was a pivotal opportunity. He had the chance to interact with Bitcoiners from across Africa. There were special guests, including nostr:npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m and through this exposure, he met the core developers in Kenya and the Tando developers in South Africa. These collaborations have given us insight into what other Bitcoin communities are doing, especially in their projects. **Nyirenda**:We also had a speaker from Bitcoin Boma who participated in an event in El Salvador. We are working towards making Malawi a Bitcoin node, and he is actively fostering that effort. Big shoutout to Ian Foster for his dedication. He will also be attending a conference in South Africa this January as a guest speaker. These collaborations have been very impactful, and I’m confident that we’ll see the results of these interactions in the future.  **YakiHonne**: So what challenges has your community faced so far and how have you overcome them while maintaining integrity? **Nyirenda**:One of the challenges we face is related to resources, especially when it comes to our learning sessions. We mainly rely on our own resources, and we understand that quality lessons require specific equipment. While we're working toward acquiring these resources, we’re also making the most of what we have. We've agreed to work with what we have, and we believe we can still achieve our objectives. **Nyirenda**:Another challenge is the attitude towards Bitcoin in Malawi. Most people entering the crypto space have a “get rich quick” mentality. They focus more on the outcomes rather than the learning process. Many crypto traders are primarily interested in exploiting the benefits of Bitcoin. This is a challenge, especially when trying to teach people that Bitcoin is not just about making a profit, but also about liberation. Changing the traditional fiat mindset to embrace this new path is not easy. **Nyirenda**:Additionally, many people believe that if they invest their time, they must get a return. This is one of the challenges we're currently dealing with. Financial literacy in Malawi still has a long way to go. While people are aware of how economic shocks, especially currency devaluation, affect them, they often act out of desperation. The market is psychologically driven, and people are constantly looking for shortcuts to protect their wealth. When Bitcoin is introduced, it often raises doubts and skepticism. **Nyirenda**:However, there is no moment of hatred. Instead, we see the growing energy within the community, even if it's just coming from the heart, extending a significant impact on others. There’s a lot of potential and many possibilities ahead. Despite the challenges, we remain hopeful and excited about the future.  **YakiHonne**: In addition to wearing T-shirts and sparking curiosity, what other methods have you adopted to promote Bitcoin, and what results have you seen? **Nyirenda**:First of all, I want to mention the Bitcoin BOMA education diploma program that’s currently running. This is one of the most significant initiatives we have at the moment. We are doing our best to attract people to dive into our education program. So far, the results have been very positive, especially in terms of numbers. People are curious and realize that this is something worth learning. Some have even acknowledged that what they've learned in the traditional education system is very different from the exposure they get from the diploma program. I’d say that’s one of the biggest impacts we've had in promoting Bitcoin. **Nyirenda**:If we have sufficient resources, we plan to implement further actions such as putting up banners, promoting Bitcoin, and positioning Malawi as a Bitcoin hub. Malawi has great potential, particularly in the tourism sector, with many tourists visiting the country. If we display banners saying “We accept Bitcoin,” it would be appreciated by many people. Personally, I’ve been encouraging businesses to start accepting Bitcoin. **Nyirenda**:We also have a Bitcoin BOMA Twitter account where we advocate for Bitcoin. We engage in discussions and comment on trends. In the coming months, we plan to host spaces and aim to conduct them in our local language, so more people can appreciate and learn about Bitcoin. **YakiHonne**: We’ve reached the end of today’s session, and I must say, you’re doing an incredible job at Bitcoin BOMA. Your personal and collaborative efforts are truly impressive. I’m confident that in the next few years, we’ll be visiting Malawi for a Bitcoin conference. It’s clear that Malawi is heading in the right direction with you leading the way. @ b17fccdf:b7211155
2025-01-21 18:33:28--- **CHECK OUT at** ~ > **[ramix.minibolt.info](https://ramix.minibolt.info)** < ~ --- **Main changes:** * **Adapted to Raspberry Pi 5**, with the possibility of using internal storage: a PCIe to M.2 adapter + SSD NVMe: > *Connect directly to the board, **remove the instability issues** with the USB connection, and unlock the ability to enjoy **higher transfer speeds*** * **Based on Debian 12** (Raspberry Pi OS Bookworm - 64-bit). * **Updated all services** that have been tested until now, to the latest version. * Same as the MiniBolt guide, changed I2P, Fulcrum, and ThunderHub guides, to be **part of the core guide**. * **All UI & UX improvements in the MiniBolt guide** are included. * Fix some links and wrong command issues. * Some existing guides have been improved to **clarify the following steps**. --- **Important notes:** * The RRSS will be the same as the MiniBolt original project (for now) | More info -> [HERE](https://ramix.minibolt.info/#community) <- * The common resources like the [Roadmap](https://github.com/orgs/minibolt-guide/projects/1) or [Networkmap](https://bit.ly/minibolt-ramix_netmap) have been merged and will be used together | Check -> [HERE](https://ramix.minibolt.info/#resources) <- * The attempt to upgrade from Bullseye to Bookworm (RaspiBolt to RaMiX migration) has failed due to **several difficult-to-resolve dependency conflicts**, so unfortunately, there will be no dedicated migration guide and **only the possibility to start from scratch** ☹️ ⚠️ **Attention**‼️-> This guide is in the WIP (work in progress) state and hasn't been completely tested yet. Many steps may be incorrect. Pay special attention to the "**Status: Not tested on RaMiX**" tag at the beginning of the guides. Be careful and act behind your responsibility. --- For Raspberry Pi lovers!❤️🍓 Enjoy it RaMiXer!! 💜 --- By [⚡2FakTor⚡](nostr:npub1k9luehc8hg3c0upckdzzvusv66x3zt0eyw7290kclrpsndepz92sfcpp63) for the plebs with love ❤️🫂
@ b17fccdf:b7211155
2025-01-21 18:33:28--- **CHECK OUT at** ~ > **[ramix.minibolt.info](https://ramix.minibolt.info)** < ~ --- **Main changes:** * **Adapted to Raspberry Pi 5**, with the possibility of using internal storage: a PCIe to M.2 adapter + SSD NVMe: > *Connect directly to the board, **remove the instability issues** with the USB connection, and unlock the ability to enjoy **higher transfer speeds*** * **Based on Debian 12** (Raspberry Pi OS Bookworm - 64-bit). * **Updated all services** that have been tested until now, to the latest version. * Same as the MiniBolt guide, changed I2P, Fulcrum, and ThunderHub guides, to be **part of the core guide**. * **All UI & UX improvements in the MiniBolt guide** are included. * Fix some links and wrong command issues. * Some existing guides have been improved to **clarify the following steps**. --- **Important notes:** * The RRSS will be the same as the MiniBolt original project (for now) | More info -> [HERE](https://ramix.minibolt.info/#community) <- * The common resources like the [Roadmap](https://github.com/orgs/minibolt-guide/projects/1) or [Networkmap](https://bit.ly/minibolt-ramix_netmap) have been merged and will be used together | Check -> [HERE](https://ramix.minibolt.info/#resources) <- * The attempt to upgrade from Bullseye to Bookworm (RaspiBolt to RaMiX migration) has failed due to **several difficult-to-resolve dependency conflicts**, so unfortunately, there will be no dedicated migration guide and **only the possibility to start from scratch** ☹️ ⚠️ **Attention**‼️-> This guide is in the WIP (work in progress) state and hasn't been completely tested yet. Many steps may be incorrect. Pay special attention to the "**Status: Not tested on RaMiX**" tag at the beginning of the guides. Be careful and act behind your responsibility. --- For Raspberry Pi lovers!❤️🍓 Enjoy it RaMiXer!! 💜 --- By [⚡2FakTor⚡](nostr:npub1k9luehc8hg3c0upckdzzvusv66x3zt0eyw7290kclrpsndepz92sfcpp63) for the plebs with love ❤️🫂 @ 58937958:545e6994
2025-01-13 03:19:17Spiralのキャラクター「ビットコイン(パペット)」のコロッケを作りました  作り方は一般的なコロッケです 試しにタネの状態で手足をくっつけたバージョン(右)も作りましたが 粉をつける前に手足がもげました  顔はのりとスライスチーズ 手足ははんぺんです 足は醤油をつけてトースターで軽く焼いたら茶色になりました  手足はサラスパでくっつけてます 細いスパゲッティ キャラ弁でググったらサラスパが出てきてなるほどな~と思いました 自分は揚げパスタにして刺しました 弁当箱に押し込まれてるコロッケくん  半減期  メモ - タネを作った時に形を保たせるために冷凍してみたんですけど逆効果だった(皿とクッキングペーパーにくっついて取れなくなった&半解凍したら水分がすごいことになった)ので冷凍するなら対策が必要そう - 形作るときにかなりパサパサだったので、つなぎがあった方がいいのかも(今回はじゃがいも&炒めタマネギだけ) ビットコインくんの形はすごく作りやすくて面白いのでまた何か作りたいなぁと思いました nostr:nevent1qqsxgpjvf9g9suhzx5asqhvnlvnarl43kuhas8v5g2ryjr9yjjp0z5ctkh5pt
@ 58937958:545e6994
2025-01-13 03:19:17Spiralのキャラクター「ビットコイン(パペット)」のコロッケを作りました  作り方は一般的なコロッケです 試しにタネの状態で手足をくっつけたバージョン(右)も作りましたが 粉をつける前に手足がもげました  顔はのりとスライスチーズ 手足ははんぺんです 足は醤油をつけてトースターで軽く焼いたら茶色になりました  手足はサラスパでくっつけてます 細いスパゲッティ キャラ弁でググったらサラスパが出てきてなるほどな~と思いました 自分は揚げパスタにして刺しました 弁当箱に押し込まれてるコロッケくん  半減期  メモ - タネを作った時に形を保たせるために冷凍してみたんですけど逆効果だった(皿とクッキングペーパーにくっついて取れなくなった&半解凍したら水分がすごいことになった)ので冷凍するなら対策が必要そう - 形作るときにかなりパサパサだったので、つなぎがあった方がいいのかも(今回はじゃがいも&炒めタマネギだけ) ビットコインくんの形はすごく作りやすくて面白いのでまた何か作りたいなぁと思いました nostr:nevent1qqsxgpjvf9g9suhzx5asqhvnlvnarl43kuhas8v5g2ryjr9yjjp0z5ctkh5pt @ 3f770d65:7a745b24
2023-07-31 12:53:38The following is a collection of Tweets posted on Twitter that documented my entire heart surgery process, from finding out I had an issue, through the surgery, and finally throughout my recovery process. If Elon decides to remove old and unpaid content, I do not want this part of my life to vanish from the Internet. At the time, it was extremely important for my mental health to talk about this whole process and it was therapeutic in my recovery process, reading all of the responses as all of Bitcoin Twitter was behind my success. Thank you all of your kind words, love, and support during this whole process. May my Tweets live on through nostr. ... Nov 28, 2021 I had open heart surgery 4 days before my 3rd b-day. I've led a healthy & active life since then, zero issues. I had an echocardiogram last week. The results were not good. Heart valve replacement may be in my near future. I am freaking the fuck out. I'll know more on Dec 6th. 😫 Dec 6, 2021 Update: I had my cardiologist appointment today. He said to not worry for now and continue to exercise and live life. In 3 months get another echo done. He doesn't believe the previous other results since I have zero symptoms and wants to do his own interpretation. Dec 6, 2021 He said if the other results were correct, I may need valve replacement in 6 months to 3 years. However, he doesn't believe the local hospital's results as I said above. He can't form an opinion just yet. He said not to worry over and over again. For now, I'm staying positive! Mar 7, 2022 Well, it's been three months. I had my follow up this morning. I have severe pulmonic regurgitation. I now need to speak with a specialist and see what my options are for surgery. Neat. 😭 Apr 12, 2022 Well, it looks like I'll need full open heart surgery again to replace my pulmonic valve. Bonus: I'll be part pig. So, I have that going for me. I was assuming that if I had to have this done it would be much less invasive, so I'm not overly impressed at the moment. 🫤 May 11, 2022 Today I had to get a CT scan of my heart in preparation for the May 27th surgery. All went well. I have no other heart issues. It's looking like I'll be in the hospital for 4-7 days, depending on how fast I recover. I should be fully 100% recovered by the end of August. ❤️ May 20, 2022 My grandfather with me 39 years ago, days after my open heart surgery. He taught me to hunt, fish, golf, and I'm sure taught me a thing or two about drinking beer and partying. 😂 He was a great man. He won't physically be with me next Friday, but I'm sure he'll be watching over. May 25, 2022 Two more sleeps. My mind is racing with an incredible amount of thoughts and emotions now. It's overwhelming. I love you all. Thanks for all of your replies and DMs over the last couple days, weeks, and months. I appreciate it immensely. ❤️❤️❤️ May 25, 2022 Two more sleeps. My mind is racing with an incredible amount of thoughts and emotions now. It's overwhelming. I love you all. Thanks for all of your replies and DMs over the last couple days, weeks, and months. I appreciate it immensely. ❤️❤️❤️ May 27, 2022 LET'S GO! I am alive and doing well. I was on a ventilator until 8pm. That was horrible. I will read all of the comments that you all posted on Katie's updates. Now I need to rest. They want to get me up and walk at 11pm. 🤯 I love you all and your support had helped so much 🧡🧡 May 28, 2022 The amount of love, compassion, caring, and appreciation from everyone blows my mind. Thanks for all of your comments and DMs. The positivity though all is this has helped me get through dark times and now it's helping me get through pain. You are helping me immensely. 🤯❤️🧡💪 May 28, 2022 Today has been a rough day. Lots of chest pain when breathing. But, I apparently am doing something right, because I have been upgraded to a regular room. No more ICU for this guy! My ICU nurse told my new nurse that I'm strong. ❤️💪🔥 May 29, 2022 Using this to document my journey. Last night was not good at all. I had tachycardia and AFib for hours. It was scary as fuck having my heart beat the way it was at 160bpm. They gave me new medication to bring it down and stop the AFib irregular heartbeat. It's now at 101. May 29, 2022 I was very scared. Katie was able to come and stay the night with me and be my personal care nurse. That made me feel much better having her here with me. Hopefully the meds continue to do what they're supposed to. Fuck. Anyways, I may not Tweet much today. Love you all. ❤️ May 30, 2022 Today has mostly been a great day progress wise. I ate a lot. I've walked more today than I have previously. My doctor told me I might be going home tomorrow, it all depends on what happens with my last drainage tube. Fingers crossed that it's draining properly now. 💪❤️ May 31, 2022 Morning walk crushed. Breakfast crushed. Feeling stronger. My drainage tube is still draining so we'll see what the surgeon says, but I probably won't be coming home today according to my nurse. It may be another day. Better to be safe. I'm feeling good though. Let's go! 💪💪❤️❤️ Jun 1, 2022 Today's plans: Crush morning walk, crush breakfast, CRUSH MY LAST X-RAY AND HEAD THE HELL HOME! Fingers crossed. 🤞🤞❤️❤️💪💪 Jun 1, 2022 On my morning walk I went into a slight AFib. The nurse and PA said since I hadn't had my morning meds to control that yet, that that could be the cause. They're going to increase meds and monitor me for another 24 hours. That sucks, but again, I'd rather be safe. Ugh. Jun 2, 2022 GM! I miss my kids. I miss wearing normal clothes. I miss my house. I miss my doggy. I better go home today or I guess I'll just keep working to get well enough to go home. 😂 I'm still progressing forward. I have a chest x-ray scheduled later this morning. Fingers crossed. Jun 2, 2022 I JUST GOT CLEARED TO HEAD HOME AFTER LUNCH. FUCK YEAH. LET'S GOOOOOO💪💪💪 Jun 2, 2022 I am home! I have some family that needs some loving. Enjoy the rest of your day! Jun 4, 2022 Last night I slept in bed thanks to a reclining pillow, the first night our living room chair. I was so happy to sleep in my own bed. I walked around our yard about 9 times yesterday. My goal is to do that plus a little more every day. I'm still in a lot of pain, but meds help. Jun 4, 2022 I still have a long way to go recovery wise, but having Katie and the kids here helping me along the way makes it easier and gives me a reason to keep pushing forward through this. Thanks again for all of your past and future support. You all are fantastic. Jun 6, 2022 My wife went back to work today. My son and daughter are in charge of taking care of me. My kids are fantastic. They made me breakfast already and helped me check all of my vitals. My daughter really shines here. She's such a little nurse and caretaker. ❤️❤️ Jun 6, 2022 I'm still in pain, but I'm not in as much pain as I was a couple days ago. I'm walking around a little better and a little more every day. I really hate just sitting around and not doing anything, but it's hard to do much else besides watch TV. I am enjoying my patio though. 💪 Jun 16, 2022 It's been a while. It's time to update this thread! I am doing great, IMO. I have lots of energy. I feel great. I can do a lot more than I previously could. I still have a limited range of motion due to my sternum being broken and still healing. i.e. I can't wash my back or legs. Jun 16, 2022 I started back to work yesterday. I was cleared to do 20 hours this week by my doctor and I'm hoping to be cleared full time next week. I work from home, so if I can sit in front of a TV, I can sit in front of a computer, right? Jun 16, 2022 My home nurses have been absolutely fantastic.😂 My kids make me breakfast every morning. And I could not have done any of this without my rock star wife. Words can't describe how much she's done for me throughout all of this. I am looking forward to continuing to improve. ♥️ Jun 16, 2022 You all have been absolutely wonderful through all of this too. I appreciate all of your love, support, and check-ins. Seriously. It means more than you know. I have a check-up at the end of the month to make sure all is well. I'll update again in a couple weeks after that appt. Jun 28, 2022 My doctor said everything looks great. He said it doesn't look like I had open heart surgery a month ago.💪 He said I have zero restrictions and that I can resume normal life. I can drive and I can go out on my boat! ❤️❤️❤️ I'm so happy right now! 🔥🚀 Jul 15, 2022 I started cardiac rehab this week. After 2 sessions the nurse said I'm on "Week 4" already. She doesn't believe with my initial intake stress test if I'll really be able to improve on it that much. 🤣 TL;DR I am a rock star and kicking ass. Feeling great. Life's great. 😍 Aug 28, 2022 Yesterday was 3 months since my open heart surgery. I'm going great! I'd guess essentially back to normal. My sternum is still not fully healed, that'll take more time, but energy and capability are basically back to what I was like last summer. I'm very happy with the results. Aug 28, 2022 I'm very happy to be able to exercise daily, go boating on the weekends AND swim and paddleboard. I was annoyed that I couldn't do these things a month ago. I had a cardiologist appt. two weeks ago. He said he hopes the valve lasts me the rest of my life and to see him in a year. Aug 28, 2022 As a final post to this thread, I want to thank each and every one of you again that commented, liked, shared and DMed me throughout all of this. The love and support from Twitter and the #Bitcoin community was unfathomable. You all made a difference in my life and my recovery.❤️
@ 3f770d65:7a745b24
2023-07-31 12:53:38The following is a collection of Tweets posted on Twitter that documented my entire heart surgery process, from finding out I had an issue, through the surgery, and finally throughout my recovery process. If Elon decides to remove old and unpaid content, I do not want this part of my life to vanish from the Internet. At the time, it was extremely important for my mental health to talk about this whole process and it was therapeutic in my recovery process, reading all of the responses as all of Bitcoin Twitter was behind my success. Thank you all of your kind words, love, and support during this whole process. May my Tweets live on through nostr. ... Nov 28, 2021 I had open heart surgery 4 days before my 3rd b-day. I've led a healthy & active life since then, zero issues. I had an echocardiogram last week. The results were not good. Heart valve replacement may be in my near future. I am freaking the fuck out. I'll know more on Dec 6th. 😫 Dec 6, 2021 Update: I had my cardiologist appointment today. He said to not worry for now and continue to exercise and live life. In 3 months get another echo done. He doesn't believe the previous other results since I have zero symptoms and wants to do his own interpretation. Dec 6, 2021 He said if the other results were correct, I may need valve replacement in 6 months to 3 years. However, he doesn't believe the local hospital's results as I said above. He can't form an opinion just yet. He said not to worry over and over again. For now, I'm staying positive! Mar 7, 2022 Well, it's been three months. I had my follow up this morning. I have severe pulmonic regurgitation. I now need to speak with a specialist and see what my options are for surgery. Neat. 😭 Apr 12, 2022 Well, it looks like I'll need full open heart surgery again to replace my pulmonic valve. Bonus: I'll be part pig. So, I have that going for me. I was assuming that if I had to have this done it would be much less invasive, so I'm not overly impressed at the moment. 🫤 May 11, 2022 Today I had to get a CT scan of my heart in preparation for the May 27th surgery. All went well. I have no other heart issues. It's looking like I'll be in the hospital for 4-7 days, depending on how fast I recover. I should be fully 100% recovered by the end of August. ❤️ May 20, 2022 My grandfather with me 39 years ago, days after my open heart surgery. He taught me to hunt, fish, golf, and I'm sure taught me a thing or two about drinking beer and partying. 😂 He was a great man. He won't physically be with me next Friday, but I'm sure he'll be watching over. May 25, 2022 Two more sleeps. My mind is racing with an incredible amount of thoughts and emotions now. It's overwhelming. I love you all. Thanks for all of your replies and DMs over the last couple days, weeks, and months. I appreciate it immensely. ❤️❤️❤️ May 25, 2022 Two more sleeps. My mind is racing with an incredible amount of thoughts and emotions now. It's overwhelming. I love you all. Thanks for all of your replies and DMs over the last couple days, weeks, and months. I appreciate it immensely. ❤️❤️❤️ May 27, 2022 LET'S GO! I am alive and doing well. I was on a ventilator until 8pm. That was horrible. I will read all of the comments that you all posted on Katie's updates. Now I need to rest. They want to get me up and walk at 11pm. 🤯 I love you all and your support had helped so much 🧡🧡 May 28, 2022 The amount of love, compassion, caring, and appreciation from everyone blows my mind. Thanks for all of your comments and DMs. The positivity though all is this has helped me get through dark times and now it's helping me get through pain. You are helping me immensely. 🤯❤️🧡💪 May 28, 2022 Today has been a rough day. Lots of chest pain when breathing. But, I apparently am doing something right, because I have been upgraded to a regular room. No more ICU for this guy! My ICU nurse told my new nurse that I'm strong. ❤️💪🔥 May 29, 2022 Using this to document my journey. Last night was not good at all. I had tachycardia and AFib for hours. It was scary as fuck having my heart beat the way it was at 160bpm. They gave me new medication to bring it down and stop the AFib irregular heartbeat. It's now at 101. May 29, 2022 I was very scared. Katie was able to come and stay the night with me and be my personal care nurse. That made me feel much better having her here with me. Hopefully the meds continue to do what they're supposed to. Fuck. Anyways, I may not Tweet much today. Love you all. ❤️ May 30, 2022 Today has mostly been a great day progress wise. I ate a lot. I've walked more today than I have previously. My doctor told me I might be going home tomorrow, it all depends on what happens with my last drainage tube. Fingers crossed that it's draining properly now. 💪❤️ May 31, 2022 Morning walk crushed. Breakfast crushed. Feeling stronger. My drainage tube is still draining so we'll see what the surgeon says, but I probably won't be coming home today according to my nurse. It may be another day. Better to be safe. I'm feeling good though. Let's go! 💪💪❤️❤️ Jun 1, 2022 Today's plans: Crush morning walk, crush breakfast, CRUSH MY LAST X-RAY AND HEAD THE HELL HOME! Fingers crossed. 🤞🤞❤️❤️💪💪 Jun 1, 2022 On my morning walk I went into a slight AFib. The nurse and PA said since I hadn't had my morning meds to control that yet, that that could be the cause. They're going to increase meds and monitor me for another 24 hours. That sucks, but again, I'd rather be safe. Ugh. Jun 2, 2022 GM! I miss my kids. I miss wearing normal clothes. I miss my house. I miss my doggy. I better go home today or I guess I'll just keep working to get well enough to go home. 😂 I'm still progressing forward. I have a chest x-ray scheduled later this morning. Fingers crossed. Jun 2, 2022 I JUST GOT CLEARED TO HEAD HOME AFTER LUNCH. FUCK YEAH. LET'S GOOOOOO💪💪💪 Jun 2, 2022 I am home! I have some family that needs some loving. Enjoy the rest of your day! Jun 4, 2022 Last night I slept in bed thanks to a reclining pillow, the first night our living room chair. I was so happy to sleep in my own bed. I walked around our yard about 9 times yesterday. My goal is to do that plus a little more every day. I'm still in a lot of pain, but meds help. Jun 4, 2022 I still have a long way to go recovery wise, but having Katie and the kids here helping me along the way makes it easier and gives me a reason to keep pushing forward through this. Thanks again for all of your past and future support. You all are fantastic. Jun 6, 2022 My wife went back to work today. My son and daughter are in charge of taking care of me. My kids are fantastic. They made me breakfast already and helped me check all of my vitals. My daughter really shines here. She's such a little nurse and caretaker. ❤️❤️ Jun 6, 2022 I'm still in pain, but I'm not in as much pain as I was a couple days ago. I'm walking around a little better and a little more every day. I really hate just sitting around and not doing anything, but it's hard to do much else besides watch TV. I am enjoying my patio though. 💪 Jun 16, 2022 It's been a while. It's time to update this thread! I am doing great, IMO. I have lots of energy. I feel great. I can do a lot more than I previously could. I still have a limited range of motion due to my sternum being broken and still healing. i.e. I can't wash my back or legs. Jun 16, 2022 I started back to work yesterday. I was cleared to do 20 hours this week by my doctor and I'm hoping to be cleared full time next week. I work from home, so if I can sit in front of a TV, I can sit in front of a computer, right? Jun 16, 2022 My home nurses have been absolutely fantastic.😂 My kids make me breakfast every morning. And I could not have done any of this without my rock star wife. Words can't describe how much she's done for me throughout all of this. I am looking forward to continuing to improve. ♥️ Jun 16, 2022 You all have been absolutely wonderful through all of this too. I appreciate all of your love, support, and check-ins. Seriously. It means more than you know. I have a check-up at the end of the month to make sure all is well. I'll update again in a couple weeks after that appt. Jun 28, 2022 My doctor said everything looks great. He said it doesn't look like I had open heart surgery a month ago.💪 He said I have zero restrictions and that I can resume normal life. I can drive and I can go out on my boat! ❤️❤️❤️ I'm so happy right now! 🔥🚀 Jul 15, 2022 I started cardiac rehab this week. After 2 sessions the nurse said I'm on "Week 4" already. She doesn't believe with my initial intake stress test if I'll really be able to improve on it that much. 🤣 TL;DR I am a rock star and kicking ass. Feeling great. Life's great. 😍 Aug 28, 2022 Yesterday was 3 months since my open heart surgery. I'm going great! I'd guess essentially back to normal. My sternum is still not fully healed, that'll take more time, but energy and capability are basically back to what I was like last summer. I'm very happy with the results. Aug 28, 2022 I'm very happy to be able to exercise daily, go boating on the weekends AND swim and paddleboard. I was annoyed that I couldn't do these things a month ago. I had a cardiologist appt. two weeks ago. He said he hopes the valve lasts me the rest of my life and to see him in a year. Aug 28, 2022 As a final post to this thread, I want to thank each and every one of you again that commented, liked, shared and DMed me throughout all of this. The love and support from Twitter and the #Bitcoin community was unfathomable. You all made a difference in my life and my recovery.❤️ @ 84b0c46a:417782f5
2025-01-11 01:48:46nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qqs0df2mwnp2q6hm6zjrthkmx3fudwsuwrmgnwrdavpzgjy8nnuqm5cqpd06k nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qqs2muhvnev5367ywuzkhell9my86jlnzhsnuszwl46tnc3fpsx9mtgjkqnu7 nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qqsznnkrl8qdwzgp7ry2hc7a77kwhg440gv9xtmvyfawggrpz3rhwvcx4rckf nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qqsyjf80k3djt96qncgvwl2yem09fdqcc0y9l8t657yc9qg2yhmg7kcnua8vn nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qqs0s3lp0w0yclk64j0tpc5fvrulv78g2lfjz3gcgacw9mt6czek26qtqxuck nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qywhwumn8ghj7mn0wd68ytnrdakhq6tvv5kk2unjdaezumn9wsqs6amnwvaz7tmev9382tndv5qjqamnwvaz7tmjv4kxz7fddfczumn0wd68ytnhd9ex2erwv46zu6nsqqs89tst72clc60wse3zq4qfs0976y7areffnhx26atvu6pv58hg6dsxvcc79 nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr3mhxue69uhhxun5wfjkccte9e3j6um5v4kxcctj9ehx2aqqyp5k40r3ug02yz5y0tn67tm2lwevuwac54qyw3yyct8n8uzr7pjz2q92pyt nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqqyp9pennjwq2qk4dxpr440wxqm5cfwah4qccd8la62hantxdelkk82ty9mr8 nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qyxhwumn8ghj77tpvf6jumt9qqsz9w30kxzjshwd8sq7jg2hsy2hwqg3zu7gyvxnsyrgfw0ur4rkhsg9v0re4 nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qyxhwumn8ghj77tpvf6jumt9qqs8wkx2r8txt9q69c3zvpqs2em2s40nc8tajmcc5l8ngxn8v2ng3sc43xvzu nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqqyzdkacpjqvv2y79zgvufx9jh39rd7xa8v056rgn4xelmnmrq9u2tuguswek nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qy2hwumn8ghj7mn0wd68ytnyv96xztngv96hxqpqmdtjrs38fv8r20deplrlt8fma54gu43keuzquzks7673a27ud58slunr8y nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhkummnw3ezucm0d4cxjmr994jhyun0wghxuet5qqsxzpx2r5hd36pruzn2e58wh947y2t0t205fp5xtstqp5wq0qgcjuq07rqlk
@ 84b0c46a:417782f5
2025-01-11 01:48:46nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qqs0df2mwnp2q6hm6zjrthkmx3fudwsuwrmgnwrdavpzgjy8nnuqm5cqpd06k nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qqs2muhvnev5367ywuzkhell9my86jlnzhsnuszwl46tnc3fpsx9mtgjkqnu7 nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qqsznnkrl8qdwzgp7ry2hc7a77kwhg440gv9xtmvyfawggrpz3rhwvcx4rckf nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qqsyjf80k3djt96qncgvwl2yem09fdqcc0y9l8t657yc9qg2yhmg7kcnua8vn nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qqs0s3lp0w0yclk64j0tpc5fvrulv78g2lfjz3gcgacw9mt6czek26qtqxuck nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qywhwumn8ghj7mn0wd68ytnrdakhq6tvv5kk2unjdaezumn9wsqs6amnwvaz7tmev9382tndv5qjqamnwvaz7tmjv4kxz7fddfczumn0wd68ytnhd9ex2erwv46zu6nsqqs89tst72clc60wse3zq4qfs0976y7areffnhx26atvu6pv58hg6dsxvcc79 nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr3mhxue69uhhxun5wfjkccte9e3j6um5v4kxcctj9ehx2aqqyp5k40r3ug02yz5y0tn67tm2lwevuwac54qyw3yyct8n8uzr7pjz2q92pyt nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqqyp9pennjwq2qk4dxpr440wxqm5cfwah4qccd8la62hantxdelkk82ty9mr8 nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qyxhwumn8ghj77tpvf6jumt9qqsz9w30kxzjshwd8sq7jg2hsy2hwqg3zu7gyvxnsyrgfw0ur4rkhsg9v0re4 nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qyxhwumn8ghj77tpvf6jumt9qqs8wkx2r8txt9q69c3zvpqs2em2s40nc8tajmcc5l8ngxn8v2ng3sc43xvzu nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqqyzdkacpjqvv2y79zgvufx9jh39rd7xa8v056rgn4xelmnmrq9u2tuguswek nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qy2hwumn8ghj7mn0wd68ytnyv96xztngv96hxqpqmdtjrs38fv8r20deplrlt8fma54gu43keuzquzks7673a27ud58slunr8y nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhkummnw3ezucm0d4cxjmr994jhyun0wghxuet5qqsxzpx2r5hd36pruzn2e58wh947y2t0t205fp5xtstqp5wq0qgcjuq07rqlk @ 78b3c1ed:5033eea9
2025-01-10 12:31:01※ライトニングノード保有者向け Alby Hubをインストールした時なんもわからずポチポチしているとMegatlith LSPノードからインバウンドを購入してチャネルを開くことになります。2万sats(2024/12/4 午後7時時点で三千円ほど)かかります。 そこで誰もが思うに違いない 「高いなぁ。だれかタダで無料で私のHubにチャネル開いてくれないかなぁ...」 その願望をかなえる献身的なノードランナー(笑)がAlby Hubへチャネルを開いてあげるための手順書みたいなものがこの記事です。 ~~ppmをうんと高くしてぼったくってやりましょう!~~ ※AlbyHubにオンチェーン資金が無くてもLNDから開く方法を発見しました。末尾に追記しました。 《これはアンカーアウトプットを利用するタイプのチャネル》 条件 ・チャネルを開く側 Clearnet IPアドレスで着信可能であること。Torノードは不可。ノードURIを公開していなくても良い。AlbyHubでピア登録できるClearnet IPアドレスと着信ポートがあればOK。 ・開いてもらうAlby Hub側 オンチェーン資金25,000sats以上をデポジットしておく。ないと開けません。 手順 1. [Alby Hub側] オンチェーン資金をデポジット Hubログイン後の左メニューからNodeを選択。Saving BalanceのDepositを選択。するとbc1qではじまるオンチェーンアドレスが表示される。ここへ送金してオンチェーンをデポジットしておく。 2. [Alby Hub側] 開く側のノードをピア登録 左メニューからNodeを選択。右上のAdvancedからConnected Peersを選択。 右上のConnect Peerを選択。欄にノードURI (ノードID@IPアドレス:着信ポート番号)を入力してConnect。 3. [開く側ノード] AlbyHubを確認、チャネルを開く ThunderhubやRide-The-Lightningなどを使い、Alby Hubのノードが表示されていることを確認。Hubにエイリアスは無いのでノードIDで表示される。 このノードに対してチャネルを開く。Private channelが望ましいと思われる。 6conf後に開設完了。 終わり! メモ - Alby Hubではbase feeは設定可能だがrateが設定できない。そもそもAlby Hubはルーティング向けノードとして設計されてない。セルフカストディアルウォレットです。 - public channelだとchannel_update, channel_announcementがゴシップされるまでHubへ送金できない(no route)。上記の通りウォレットとしてのノードならprivate channelだけにしてルートヒント付きインボイスが発行できるようにしとくのが望ましい。 - LDKにおいて相手からチャネルを開いてもらう場合にオンチェーン資金が必要。相手がチャネルリザーブ無しのチャネルでもOKなら不要。現にメガリスLSPからチャネルを開いてもらう時オンチェーン資金が0satsでも開けているのがその実例。 - オンチェーン資金が必要なのはチャネルタイプがanchorの場合。オンチェーン資金でアンカーアウトプットをCPFPするためみたい。anchorが登場する前のstatic-remotekeyのタイプならオンチェーン資金は不要。 ----------- <ここからが追加> 《これはアンカーアウトプットを利用しないタイプのチャネル》 LNDからチャネルを開くときにstatic remote keyを利用するタイプを指定します。 条件 ・チャネルを開く側 ※上記と同様。 ・開いてもらうAlby Hub側 無し。 手順 1. [Alby Hub側] 開く側のノードをピア登録 左メニューからNodeを選択。右上のAdvancedからConnected Peersを選択。右上のConnect Peerを選択。欄にノードURI (ノードID@IPアドレス:着信ポート番号)を入力してConnect。 2. [開く側ノード] AlbyHubを確認、チャネルを開く SSHログイン、UmbrelならLightningのターミナルで以下のコマンドを実行します。 <ノードID>は開きたいAlbyHubのノードIDで置き換えてください。 <チャネルサイズ>は開きたいチャネルの金額、例えば20万satsなら200000としましょう。 <手数料率>はチャネル開設のトランザクションに掛ける手数料率です。mempool. spaceなどで手数料水準を確認して指定しましょう。 --channel_type tweaklessがキモです。デフォルトだとanchorになります。RTLやTHで開くとこのanchorになります。なのでlncli openchannelでやります。 ``` lncli openchannel --node_key <ノードID> \ --local_amt <チャネルサイズ> \ --sat_per_vbyte <手数料率> \ --private --channel_type tweakless ``` 終わり!
@ 78b3c1ed:5033eea9
2025-01-10 12:31:01※ライトニングノード保有者向け Alby Hubをインストールした時なんもわからずポチポチしているとMegatlith LSPノードからインバウンドを購入してチャネルを開くことになります。2万sats(2024/12/4 午後7時時点で三千円ほど)かかります。 そこで誰もが思うに違いない 「高いなぁ。だれかタダで無料で私のHubにチャネル開いてくれないかなぁ...」 その願望をかなえる献身的なノードランナー(笑)がAlby Hubへチャネルを開いてあげるための手順書みたいなものがこの記事です。 ~~ppmをうんと高くしてぼったくってやりましょう!~~ ※AlbyHubにオンチェーン資金が無くてもLNDから開く方法を発見しました。末尾に追記しました。 《これはアンカーアウトプットを利用するタイプのチャネル》 条件 ・チャネルを開く側 Clearnet IPアドレスで着信可能であること。Torノードは不可。ノードURIを公開していなくても良い。AlbyHubでピア登録できるClearnet IPアドレスと着信ポートがあればOK。 ・開いてもらうAlby Hub側 オンチェーン資金25,000sats以上をデポジットしておく。ないと開けません。 手順 1. [Alby Hub側] オンチェーン資金をデポジット Hubログイン後の左メニューからNodeを選択。Saving BalanceのDepositを選択。するとbc1qではじまるオンチェーンアドレスが表示される。ここへ送金してオンチェーンをデポジットしておく。 2. [Alby Hub側] 開く側のノードをピア登録 左メニューからNodeを選択。右上のAdvancedからConnected Peersを選択。 右上のConnect Peerを選択。欄にノードURI (ノードID@IPアドレス:着信ポート番号)を入力してConnect。 3. [開く側ノード] AlbyHubを確認、チャネルを開く ThunderhubやRide-The-Lightningなどを使い、Alby Hubのノードが表示されていることを確認。Hubにエイリアスは無いのでノードIDで表示される。 このノードに対してチャネルを開く。Private channelが望ましいと思われる。 6conf後に開設完了。 終わり! メモ - Alby Hubではbase feeは設定可能だがrateが設定できない。そもそもAlby Hubはルーティング向けノードとして設計されてない。セルフカストディアルウォレットです。 - public channelだとchannel_update, channel_announcementがゴシップされるまでHubへ送金できない(no route)。上記の通りウォレットとしてのノードならprivate channelだけにしてルートヒント付きインボイスが発行できるようにしとくのが望ましい。 - LDKにおいて相手からチャネルを開いてもらう場合にオンチェーン資金が必要。相手がチャネルリザーブ無しのチャネルでもOKなら不要。現にメガリスLSPからチャネルを開いてもらう時オンチェーン資金が0satsでも開けているのがその実例。 - オンチェーン資金が必要なのはチャネルタイプがanchorの場合。オンチェーン資金でアンカーアウトプットをCPFPするためみたい。anchorが登場する前のstatic-remotekeyのタイプならオンチェーン資金は不要。 ----------- <ここからが追加> 《これはアンカーアウトプットを利用しないタイプのチャネル》 LNDからチャネルを開くときにstatic remote keyを利用するタイプを指定します。 条件 ・チャネルを開く側 ※上記と同様。 ・開いてもらうAlby Hub側 無し。 手順 1. [Alby Hub側] 開く側のノードをピア登録 左メニューからNodeを選択。右上のAdvancedからConnected Peersを選択。右上のConnect Peerを選択。欄にノードURI (ノードID@IPアドレス:着信ポート番号)を入力してConnect。 2. [開く側ノード] AlbyHubを確認、チャネルを開く SSHログイン、UmbrelならLightningのターミナルで以下のコマンドを実行します。 <ノードID>は開きたいAlbyHubのノードIDで置き換えてください。 <チャネルサイズ>は開きたいチャネルの金額、例えば20万satsなら200000としましょう。 <手数料率>はチャネル開設のトランザクションに掛ける手数料率です。mempool. spaceなどで手数料水準を確認して指定しましょう。 --channel_type tweaklessがキモです。デフォルトだとanchorになります。RTLやTHで開くとこのanchorになります。なのでlncli openchannelでやります。 ``` lncli openchannel --node_key <ノードID> \ --local_amt <チャネルサイズ> \ --sat_per_vbyte <手数料率> \ --private --channel_type tweakless ``` 終わり! @ a012dc82:6458a70d
2025-01-21 13:47:17In the annals of treasure hunting, tales of sunken galleons and buried chests have given way to a new narrative—one that unfolds in the digital realm. The U.S. Government, traditionally associated with the physical might of gold reserves in Fort Knox, has inadvertently entered the arena of cryptocurrency by amassing a staggering $5 billion in Bitcoin. This digital fortune, however, was not amassed through investment or mining efforts but rather through the seizure of assets from the darker corners of the internet. As we stand at the crossroads of finance and technology, this cache of Bitcoin opens up a Pandora's box of possibilities and challenges that could redefine the economic landscape of tomorrow. **Table Of Content** - A Digital Fort Knox - The Origins of the Cache - The Dilemma of Liquidation - Potential Paths Forward - The Impact on the Future of Currency - Conclusion - FAQs **A Digital Fort Knox** Imagine a vault, not of steel and stone, but of complex cryptographic algorithms, housing a vast sum of Bitcoin equivalent to the wealth of small nations. This digital Fort Knox does not require armed guards or thick walls but instead relies on the impenetrable nature of blockchain technology. The U.S. Government's acquisition of such a significant amount of Bitcoin is a testament to the changing nature of value and wealth in the 21st century. Each Bitcoin in this modern trove was once part of illicit transactions, flowing through the veins of the internet until it was intercepted by the vigilant efforts of federal agencies. The narrative of each coin is a digital ledger, chronicling a journey from the shadowy fringes of the web to the secure wallets of the government. **The Origins of the Cache** The backstory of the government's Bitcoin collection is not one of serendipity but of strategic cyber sleuthing and legal might. It is a modern saga of law enforcement adapting to the challenges posed by the digital age. Federal agencies, armed with court orders and cutting-edge technology, have traced the movement of these digital assets through the blockchain, unraveling complex webs of transactions that lead to the criminal enterprises operating in the darknet markets. Each seizure represents a battle won in the ongoing war against cybercrime, with the confiscated Bitcoin serving as both evidence of victory and the spoils of war. **The Dilemma of Liquidation** The government's Bitcoin cache presents a unique conundrum: to liquidate or not to liquidate? This decision is fraught with economic implications, akin to a game of high-stakes poker where the government's hand could influence the entire table. A sudden influx of $5 billion worth of Bitcoin into the market could trigger a tidal wave of volatility, potentially devaluing the currency and destabilizing the fragile ecosystem of digital assets. The government must navigate these waters with a blend of economic savvy and strategic foresight, ensuring that any decision made is in the best interest of not just the immediate financial landscape but also the long-term viability of cryptocurrencies. **Potential Paths Forward** The government stands at the helm, charting a course through uncharted waters with its Bitcoin bounty. The options are as varied as they are complex. Holding onto the Bitcoin could be seen as an endorsement of its value, a digital reserve akin to the gold of yesteryear. Alternatively, a measured approach to selling the Bitcoin could be employed, releasing it into the market in a controlled manner to mitigate any negative impacts. There's also the innovative possibility of integrating Bitcoin into the government's financial transactions, embracing the very currency that was once shunned by the establishment. **The Impact on the Future of Currency** The U.S. Government's handling of this Bitcoin cache is not merely a financial decision; it is a statement on the future of currency itself. As the line between digital and fiat currencies blurs, the actions taken with this Bitcoin hoard could send ripples across the global economy. It could influence how governments around the world perceive and interact with digital assets, potentially ushering in a new era where cryptocurrency becomes a staple of economic policy and international trade. **Conclusion** The U.S. Government's Bitcoin cache is more than a collection of digital assets; it is a symbol of a new era in governance and economic strategy. The decisions made regarding this treasure will likely resonate through the annals of financial history, setting precedents for how nations interact with the burgeoning realm of digital currencies. As we delve deeper into this narrative, we realize that this treasure is not hidden but in plain sight, waiting to unlock a future where digital assets are as commonplace and as valuable as the gold once stored in the vaults of old. **FAQs** **How did the U.S. Government acquire $5 billion in Bitcoin?** The U.S. Government seized this Bitcoin from various cybercriminal operations and darknet markets through legal and technological efforts by federal agencies. **What is the significance of the government holding such a large amount of Bitcoin?** This significant holding of Bitcoin by the government underscores the changing landscape of value and wealth, highlighting the increasing relevance of digital currencies in today's economy. **What challenges does the government face with this Bitcoin cache?** The government faces the challenge of deciding how to manage and potentially liquidate the Bitcoin without causing market disruption due to the currency's volatility. **What are the potential strategies for the U.S. Government's Bitcoin cache?** Strategies include holding the Bitcoin as a reserve asset, selling it off gradually to minimize market impact, or using it for government transactions and policy-making. **How could the government's handling of the Bitcoin cache affect the future of currency?** The government's approach to managing the Bitcoin cache could set a precedent for how digital assets are treated by national entities, potentially influencing the integration of cryptocurrencies into mainstream finance. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: [@croxroadnews.co](https://x.com/croxroadnewsco)** **Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)** **Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** *DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.*
@ a012dc82:6458a70d
2025-01-21 13:47:17In the annals of treasure hunting, tales of sunken galleons and buried chests have given way to a new narrative—one that unfolds in the digital realm. The U.S. Government, traditionally associated with the physical might of gold reserves in Fort Knox, has inadvertently entered the arena of cryptocurrency by amassing a staggering $5 billion in Bitcoin. This digital fortune, however, was not amassed through investment or mining efforts but rather through the seizure of assets from the darker corners of the internet. As we stand at the crossroads of finance and technology, this cache of Bitcoin opens up a Pandora's box of possibilities and challenges that could redefine the economic landscape of tomorrow. **Table Of Content** - A Digital Fort Knox - The Origins of the Cache - The Dilemma of Liquidation - Potential Paths Forward - The Impact on the Future of Currency - Conclusion - FAQs **A Digital Fort Knox** Imagine a vault, not of steel and stone, but of complex cryptographic algorithms, housing a vast sum of Bitcoin equivalent to the wealth of small nations. This digital Fort Knox does not require armed guards or thick walls but instead relies on the impenetrable nature of blockchain technology. The U.S. Government's acquisition of such a significant amount of Bitcoin is a testament to the changing nature of value and wealth in the 21st century. Each Bitcoin in this modern trove was once part of illicit transactions, flowing through the veins of the internet until it was intercepted by the vigilant efforts of federal agencies. The narrative of each coin is a digital ledger, chronicling a journey from the shadowy fringes of the web to the secure wallets of the government. **The Origins of the Cache** The backstory of the government's Bitcoin collection is not one of serendipity but of strategic cyber sleuthing and legal might. It is a modern saga of law enforcement adapting to the challenges posed by the digital age. Federal agencies, armed with court orders and cutting-edge technology, have traced the movement of these digital assets through the blockchain, unraveling complex webs of transactions that lead to the criminal enterprises operating in the darknet markets. Each seizure represents a battle won in the ongoing war against cybercrime, with the confiscated Bitcoin serving as both evidence of victory and the spoils of war. **The Dilemma of Liquidation** The government's Bitcoin cache presents a unique conundrum: to liquidate or not to liquidate? This decision is fraught with economic implications, akin to a game of high-stakes poker where the government's hand could influence the entire table. A sudden influx of $5 billion worth of Bitcoin into the market could trigger a tidal wave of volatility, potentially devaluing the currency and destabilizing the fragile ecosystem of digital assets. The government must navigate these waters with a blend of economic savvy and strategic foresight, ensuring that any decision made is in the best interest of not just the immediate financial landscape but also the long-term viability of cryptocurrencies. **Potential Paths Forward** The government stands at the helm, charting a course through uncharted waters with its Bitcoin bounty. The options are as varied as they are complex. Holding onto the Bitcoin could be seen as an endorsement of its value, a digital reserve akin to the gold of yesteryear. Alternatively, a measured approach to selling the Bitcoin could be employed, releasing it into the market in a controlled manner to mitigate any negative impacts. There's also the innovative possibility of integrating Bitcoin into the government's financial transactions, embracing the very currency that was once shunned by the establishment. **The Impact on the Future of Currency** The U.S. Government's handling of this Bitcoin cache is not merely a financial decision; it is a statement on the future of currency itself. As the line between digital and fiat currencies blurs, the actions taken with this Bitcoin hoard could send ripples across the global economy. It could influence how governments around the world perceive and interact with digital assets, potentially ushering in a new era where cryptocurrency becomes a staple of economic policy and international trade. **Conclusion** The U.S. Government's Bitcoin cache is more than a collection of digital assets; it is a symbol of a new era in governance and economic strategy. The decisions made regarding this treasure will likely resonate through the annals of financial history, setting precedents for how nations interact with the burgeoning realm of digital currencies. As we delve deeper into this narrative, we realize that this treasure is not hidden but in plain sight, waiting to unlock a future where digital assets are as commonplace and as valuable as the gold once stored in the vaults of old. **FAQs** **How did the U.S. Government acquire $5 billion in Bitcoin?** The U.S. Government seized this Bitcoin from various cybercriminal operations and darknet markets through legal and technological efforts by federal agencies. **What is the significance of the government holding such a large amount of Bitcoin?** This significant holding of Bitcoin by the government underscores the changing landscape of value and wealth, highlighting the increasing relevance of digital currencies in today's economy. **What challenges does the government face with this Bitcoin cache?** The government faces the challenge of deciding how to manage and potentially liquidate the Bitcoin without causing market disruption due to the currency's volatility. **What are the potential strategies for the U.S. Government's Bitcoin cache?** Strategies include holding the Bitcoin as a reserve asset, selling it off gradually to minimize market impact, or using it for government transactions and policy-making. **How could the government's handling of the Bitcoin cache affect the future of currency?** The government's approach to managing the Bitcoin cache could set a precedent for how digital assets are treated by national entities, potentially influencing the integration of cryptocurrencies into mainstream finance. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: [@croxroadnews.co](https://x.com/croxroadnewsco)** **Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)** **Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** *DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.* @ e8a4bb8b:05f739c6
2025-01-21 13:05:10Opinion about CoinUnited.io - Crypto Wallet (iphone) <!--HEADER END--> ⚠️ WARNING: CoinUnited.io is a SCAM ⚠️ Do NOT use CoinUnited.io for cryptocurrency trading or investments. Here's why: Hong Kong SFC Alert: Listed as a suspicious platform on July 25, 20241. Withdrawal Issues: Many users report being unable to withdraw funds12. Fake Trading Environment: Platform likely uses simulated trading, not real market transactions1. False Regulatory Claims: Makes unverified claims about regulatory compliance12. Ongoing Investigations: Currently under investigation by Hong Kong police5. User Complaints: Numerous reports of lost investments and blocked accounts26. Deceptive Practices: Uses high APRs and leverage to lure investors12. Protect yourself and others. Avoid CoinUnited.io at all costs. If you've invested, seek immediate assistance from financial authorities. Always verify the legitimacy of crypto platforms before investing. Stay safe and share this warning to prevent others from falling victim to this scam. <!--FOOTER START--> #WalletScrutiny #nostrOpinion [Join the conversation!](https://walletscrutiny.com/iphone/coinunited.io)
@ e8a4bb8b:05f739c6
2025-01-21 13:05:10Opinion about CoinUnited.io - Crypto Wallet (iphone) <!--HEADER END--> ⚠️ WARNING: CoinUnited.io is a SCAM ⚠️ Do NOT use CoinUnited.io for cryptocurrency trading or investments. Here's why: Hong Kong SFC Alert: Listed as a suspicious platform on July 25, 20241. Withdrawal Issues: Many users report being unable to withdraw funds12. Fake Trading Environment: Platform likely uses simulated trading, not real market transactions1. False Regulatory Claims: Makes unverified claims about regulatory compliance12. Ongoing Investigations: Currently under investigation by Hong Kong police5. User Complaints: Numerous reports of lost investments and blocked accounts26. Deceptive Practices: Uses high APRs and leverage to lure investors12. Protect yourself and others. Avoid CoinUnited.io at all costs. If you've invested, seek immediate assistance from financial authorities. Always verify the legitimacy of crypto platforms before investing. Stay safe and share this warning to prevent others from falling victim to this scam. <!--FOOTER START--> #WalletScrutiny #nostrOpinion [Join the conversation!](https://walletscrutiny.com/iphone/coinunited.io) @ 6be5cc06:5259daf0
2025-01-21 01:51:46## Bitcoin: Um sistema de dinheiro eletrônico direto entre pessoas. Satoshi Nakamoto satoshin@gmx.com www.bitcoin.org --- ### Resumo O Bitcoin é uma forma de dinheiro digital que permite pagamentos diretos entre pessoas, sem a necessidade de um banco ou instituição financeira. Ele resolve um problema chamado **gasto duplo**, que ocorre quando alguém tenta gastar o mesmo dinheiro duas vezes. Para evitar isso, o Bitcoin usa uma rede descentralizada onde todos trabalham juntos para verificar e registrar as transações. As transações são registradas em um livro público chamado **blockchain**, protegido por uma técnica chamada **Prova de Trabalho**. Essa técnica cria uma cadeia de registros que não pode ser alterada sem refazer todo o trabalho já feito. Essa cadeia é mantida pelos computadores que participam da rede, e a mais longa é considerada a verdadeira. Enquanto a maior parte do poder computacional da rede for controlada por participantes honestos, o sistema continuará funcionando de forma segura. A rede é flexível, permitindo que qualquer pessoa entre ou saia a qualquer momento, sempre confiando na cadeia mais longa como prova do que aconteceu. --- ### 1. Introdução Hoje, quase todos os pagamentos feitos pela internet dependem de bancos ou empresas como processadores de pagamento (cartões de crédito, por exemplo) para funcionar. Embora esse sistema seja útil, ele tem problemas importantes porque é baseado em **confiança**. Primeiro, essas empresas podem reverter pagamentos, o que é útil em caso de erros, mas cria custos e incertezas. Isso faz com que pequenas transações, como pagar centavos por um serviço, se tornem inviáveis. Além disso, os comerciantes são obrigados a desconfiar dos clientes, pedindo informações extras e aceitando fraudes como algo inevitável. Esses problemas não existem no dinheiro físico, como o papel-moeda, onde o pagamento é final e direto entre as partes. No entanto, não temos como enviar dinheiro físico pela internet sem depender de um intermediário confiável. O que precisamos é de um **sistema de pagamento eletrônico baseado em provas matemáticas**, não em confiança. Esse sistema permitiria que qualquer pessoa enviasse dinheiro diretamente para outra, sem depender de bancos ou processadores de pagamento. Além disso, as transações seriam irreversíveis, protegendo vendedores contra fraudes, mas mantendo a possibilidade de soluções para disputas legítimas. Neste documento, apresentamos o **Bitcoin**, que resolve o problema do gasto duplo usando uma rede descentralizada. Essa rede cria um registro público e protegido por cálculos matemáticos, que garante a ordem das transações. Enquanto a maior parte da rede for controlada por pessoas honestas, o sistema será seguro contra ataques. --- ### 2. Transações Para entender como funciona o Bitcoin, é importante saber como as transações são realizadas. Imagine que você quer transferir uma "moeda digital" para outra pessoa. No sistema do Bitcoin, essa "moeda" é representada por uma sequência de registros que mostram quem é o atual dono. Para transferi-la, você adiciona um novo registro comprovando que agora ela pertence ao próximo dono. Esse registro é protegido por um tipo especial de assinatura digital. #### O que é uma assinatura digital? Uma assinatura digital é como uma senha secreta, mas muito mais segura. No Bitcoin, cada usuário tem duas chaves: uma "chave privada", que é secreta e serve para criar a assinatura, e uma "chave pública", que pode ser compartilhada com todos e é usada para verificar se a assinatura é válida. Quando você transfere uma moeda, usa sua chave privada para assinar a transação, provando que você é o dono. A próxima pessoa pode usar sua chave pública para confirmar isso. #### Como funciona na prática? Cada "moeda" no Bitcoin é, na verdade, uma cadeia de assinaturas digitais. Vamos imaginar o seguinte cenário: 1. A moeda está com o Dono 0 (você). Para transferi-la ao Dono 1, você assina digitalmente a transação com sua chave privada. Essa assinatura inclui o código da transação anterior (chamado de "hash") e a chave pública do Dono 1. 2. Quando o Dono 1 quiser transferir a moeda ao Dono 2, ele assinará a transação seguinte com sua própria chave privada, incluindo também o hash da transação anterior e a chave pública do Dono 2. 3. Esse processo continua, formando uma "cadeia" de transações. Qualquer pessoa pode verificar essa cadeia para confirmar quem é o atual dono da moeda. #### Resolvendo o problema do gasto duplo Um grande desafio com moedas digitais é o "gasto duplo", que é quando uma mesma moeda é usada em mais de uma transação. Para evitar isso, muitos sistemas antigos dependiam de uma entidade central confiável, como uma casa da moeda, que verificava todas as transações. No entanto, isso criava um ponto único de falha e centralizava o controle do dinheiro. O Bitcoin resolve esse problema de forma inovadora: ele usa uma rede descentralizada onde todos os participantes (os "nós") têm acesso a um registro completo de todas as transações. Cada nó verifica se as transações são válidas e se a moeda não foi gasta duas vezes. Quando a maioria dos nós concorda com a validade de uma transação, ela é registrada permanentemente na blockchain. #### Por que isso é importante? Essa solução elimina a necessidade de confiar em uma única entidade para gerenciar o dinheiro, permitindo que qualquer pessoa no mundo use o Bitcoin sem precisar de permissão de terceiros. Além disso, ela garante que o sistema seja seguro e resistente a fraudes. --- ### 3. Servidor Timestamp Para assegurar que as transações sejam realizadas de forma segura e transparente, o sistema Bitcoin utiliza algo chamado de "servidor de registro de tempo" (timestamp). Esse servidor funciona como um registro público que organiza as transações em uma ordem específica. Ele faz isso agrupando várias transações em blocos e criando um código único chamado "hash". Esse hash é como uma impressão digital que representa todo o conteúdo do bloco. O hash de cada bloco é amplamente divulgado, como se fosse publicado em um jornal ou em um fórum público. Esse processo garante que cada bloco de transações tenha um registro de quando foi criado e que ele existia naquele momento. Além disso, cada novo bloco criado contém o hash do bloco anterior, formando uma cadeia contínua de blocos conectados — conhecida como blockchain. Com isso, se alguém tentar alterar qualquer informação em um bloco anterior, o hash desse bloco mudará e não corresponderá ao hash armazenado no bloco seguinte. Essa característica torna a cadeia muito segura, pois qualquer tentativa de fraude seria imediatamente detectada. O sistema de timestamps é essencial para provar a ordem cronológica das transações e garantir que cada uma delas seja única e autêntica. Dessa forma, ele reforça a segurança e a confiança na rede Bitcoin. --- ### 4. Prova-de-Trabalho Para implementar o registro de tempo distribuído no sistema Bitcoin, utilizamos um mecanismo chamado prova-de-trabalho. Esse sistema é semelhante ao Hashcash, desenvolvido por Adam Back, e baseia-se na criação de um código único, o "hash", por meio de um processo computacionalmente exigente. A prova-de-trabalho envolve encontrar um valor especial que, quando processado junto com as informações do bloco, gere um hash que comece com uma quantidade específica de zeros. Esse valor especial é chamado de "nonce". Encontrar o nonce correto exige um esforço significativo do computador, porque envolve tentativas repetidas até que a condição seja satisfeita. Esse processo é importante porque torna extremamente difícil alterar qualquer informação registrada em um bloco. Se alguém tentar mudar algo em um bloco, seria necessário refazer o trabalho de computação não apenas para aquele bloco, mas também para todos os blocos que vêm depois dele. Isso garante a segurança e a imutabilidade da blockchain. A prova-de-trabalho também resolve o problema de decidir qual cadeia de blocos é a válida quando há múltiplas cadeias competindo. A decisão é feita pela cadeia mais longa, pois ela representa o maior esforço computacional já realizado. Isso impede que qualquer indivíduo ou grupo controle a rede, desde que a maioria do poder de processamento seja mantida por participantes honestos. Para garantir que o sistema permaneça eficiente e equilibrado, a dificuldade da prova-de-trabalho é ajustada automaticamente ao longo do tempo. Se novos blocos estiverem sendo gerados rapidamente, a dificuldade aumenta; se estiverem sendo gerados muito lentamente, a dificuldade diminui. Esse ajuste assegura que novos blocos sejam criados aproximadamente a cada 10 minutos, mantendo o sistema estável e funcional. --- ### 5. Rede A rede Bitcoin é o coração do sistema e funciona de maneira distribuída, conectando vários participantes (ou nós) para garantir o registro e a validação das transações. Os passos para operar essa rede são: 1. **Transmissão de Transações**: Quando alguém realiza uma nova transação, ela é enviada para todos os nós da rede. Isso é feito para garantir que todos estejam cientes da operação e possam validá-la. 2. **Coleta de Transações em Blocos**: Cada nó agrupa as novas transações recebidas em um "bloco". Este bloco será preparado para ser adicionado à cadeia de blocos (a blockchain). 3. **Prova-de-Trabalho**: Os nós competem para resolver a prova-de-trabalho do bloco, utilizando poder computacional para encontrar um hash válido. Esse processo é como resolver um quebra-cabeça matemático difícil. 4. **Envio do Bloco Resolvido**: Quando um nó encontra a solução para o bloco (a prova-de-trabalho), ele compartilha esse bloco com todos os outros nós na rede. 5. **Validação do Bloco**: Cada nó verifica o bloco recebido para garantir que todas as transações nele contidas sejam válidas e que nenhuma moeda tenha sido gasta duas vezes. Apenas blocos válidos são aceitos. 6. **Construção do Próximo Bloco**: Os nós que aceitaram o bloco começam a trabalhar na criação do próximo bloco, utilizando o hash do bloco aceito como base (hash anterior). Isso mantém a continuidade da cadeia. #### Resolução de Conflitos e Escolha da Cadeia Mais Longa Os nós sempre priorizam a cadeia mais longa, pois ela representa o maior esforço computacional já realizado, garantindo maior segurança. Se dois blocos diferentes forem compartilhados simultaneamente, os nós trabalharão no primeiro bloco recebido, mas guardarão o outro como uma alternativa. Caso o segundo bloco eventualmente forme uma cadeia mais longa (ou seja, tenha mais blocos subsequentes), os nós mudarão para essa nova cadeia. #### Tolerância a Falhas A rede é robusta e pode lidar com mensagens que não chegam a todos os nós. Uma transação não precisa alcançar todos os nós de imediato; basta que chegue a um número suficiente deles para ser incluída em um bloco. Da mesma forma, se um nó não receber um bloco em tempo hábil, ele pode solicitá-lo ao perceber que está faltando quando o próximo bloco é recebido. Esse mecanismo descentralizado permite que a rede Bitcoin funcione de maneira segura, confiável e resiliente, sem depender de uma autoridade central. --- ### 6. Incentivo O incentivo é um dos pilares fundamentais que sustenta o funcionamento da rede Bitcoin, garantindo que os participantes (nós) continuem operando de forma honesta e contribuindo com recursos computacionais. Ele é estruturado em duas partes principais: a recompensa por mineração e as taxas de transação. #### Recompensa por Mineração Por convenção, o primeiro registro em cada bloco é uma transação especial que cria novas moedas e as atribui ao criador do bloco. Essa recompensa incentiva os mineradores a dedicarem poder computacional para apoiar a rede. Como não há uma autoridade central para emitir moedas, essa é a maneira pela qual novas moedas entram em circulação. Esse processo pode ser comparado ao trabalho de garimpeiros, que utilizam recursos para colocar mais ouro em circulação. No caso do Bitcoin, o "recurso" consiste no tempo de CPU e na energia elétrica consumida para resolver a prova-de-trabalho. #### Taxas de Transação Além da recompensa por mineração, os mineradores também podem ser incentivados pelas taxas de transação. Se uma transação utiliza menos valor de saída do que o valor de entrada, a diferença é tratada como uma taxa, que é adicionada à recompensa do bloco contendo essa transação. Com o passar do tempo e à medida que o número de moedas em circulação atinge o limite predeterminado, essas taxas de transação se tornam a principal fonte de incentivo, substituindo gradualmente a emissão de novas moedas. Isso permite que o sistema opere sem inflação, uma vez que o número total de moedas permanece fixo. #### Incentivo à Honestidade O design do incentivo também busca garantir que os participantes da rede mantenham um comportamento honesto. Para um atacante que consiga reunir mais poder computacional do que o restante da rede, ele enfrentaria duas escolhas: 1. Usar esse poder para fraudar o sistema, como reverter transações e roubar pagamentos. 2. Seguir as regras do sistema, criando novos blocos e recebendo recompensas legítimas. A lógica econômica favorece a segunda opção, pois um comportamento desonesto prejudicaria a confiança no sistema, diminuindo o valor de todas as moedas, incluindo aquelas que o próprio atacante possui. Jogar dentro das regras não apenas maximiza o retorno financeiro, mas também preserva a validade e a integridade do sistema. Esse mecanismo garante que os incentivos econômicos estejam alinhados com o objetivo de manter a rede segura, descentralizada e funcional ao longo do tempo. --- ### 7. Recuperação do Espaço em Disco Depois que uma moeda passa a estar protegida por muitos blocos na cadeia, as informações sobre as transações antigas que a geraram podem ser descartadas para economizar espaço em disco. Para que isso seja possível sem comprometer a segurança, as transações são organizadas em uma estrutura chamada "árvore de Merkle". Essa árvore funciona como um resumo das transações: em vez de armazenar todas elas, guarda apenas um "hash raiz", que é como uma assinatura compacta que representa todo o grupo de transações. Os blocos antigos podem, então, ser simplificados, removendo as partes desnecessárias dessa árvore. Apenas a raiz do hash precisa ser mantida no cabeçalho do bloco, garantindo que a integridade dos dados seja preservada, mesmo que detalhes específicos sejam descartados. Para exemplificar: imagine que você tenha vários recibos de compra. Em vez de guardar todos os recibos, você cria um documento e lista apenas o valor total de cada um. Mesmo que os recibos originais sejam descartados, ainda é possível verificar a soma com base nos valores armazenados. Além disso, o espaço ocupado pelos blocos em si é muito pequeno. Cada bloco sem transações ocupa apenas cerca de 80 bytes. Isso significa que, mesmo com blocos sendo gerados a cada 10 minutos, o crescimento anual em espaço necessário é insignificante: apenas 4,2 MB por ano. Com a capacidade de armazenamento dos computadores crescendo a cada ano, esse espaço continuará sendo trivial, garantindo que a rede possa operar de forma eficiente sem problemas de armazenamento, mesmo a longo prazo. --- ### 8. Verificação de Pagamento Simplificada É possível confirmar pagamentos sem a necessidade de operar um nó completo da rede. Para isso, o usuário precisa apenas de uma cópia dos cabeçalhos dos blocos da cadeia mais longa (ou seja, a cadeia com maior esforço de trabalho acumulado). Ele pode verificar a validade de uma transação ao consultar os nós da rede até obter a confirmação de que tem a cadeia mais longa. Para isso, utiliza-se o ramo Merkle, que conecta a transação ao bloco em que ela foi registrada. Entretanto, o método simplificado possui limitações: ele não pode confirmar uma transação isoladamente, mas sim assegurar que ela ocupa um lugar específico na cadeia mais longa. Dessa forma, se um nó da rede aprova a transação, os blocos subsequentes reforçam essa aceitação. A verificação simplificada é confiável enquanto a maioria dos nós da rede for honesta. Contudo, ela se torna vulnerável caso a rede seja dominada por um invasor. Nesse cenário, um atacante poderia fabricar transações fraudulentas que enganariam o usuário temporariamente até que o invasor obtivesse controle completo da rede. Uma estratégia para mitigar esse risco é configurar alertas nos softwares de nós completos. Esses alertas identificam blocos inválidos, sugerindo ao usuário baixar o bloco completo para confirmar qualquer inconsistência. Para maior segurança, empresas que realizam pagamentos frequentes podem preferir operar seus próprios nós, reduzindo riscos e permitindo uma verificação mais direta e confiável. --- ### 9. Combinando e Dividindo Valor No sistema Bitcoin, cada unidade de valor é tratada como uma "moeda" individual, mas gerenciar cada centavo como uma transação separada seria impraticável. Para resolver isso, o Bitcoin permite que valores sejam combinados ou divididos em transações, facilitando pagamentos de qualquer valor. #### Entradas e Saídas Cada transação no Bitcoin é composta por: - **Entradas**: Representam os valores recebidos em transações anteriores. - **Saídas**: Correspondem aos valores enviados, divididos entre os destinatários e, eventualmente, o troco para o remetente. Normalmente, uma transação contém: - Uma única entrada com valor suficiente para cobrir o pagamento. - Ou várias entradas combinadas para atingir o valor necessário. O valor total das saídas nunca excede o das entradas, e a diferença (se houver) pode ser retornada ao remetente como **troco**. #### Exemplo Prático Imagine que você tem duas entradas: 1. 0,03 BTC 2. 0,07 BTC Se deseja enviar 0,08 BTC para alguém, a transação terá: - **Entrada**: As duas entradas combinadas (0,03 + 0,07 BTC = 0,10 BTC). - **Saídas**: Uma para o destinatário (0,08 BTC) e outra como troco para você (0,02 BTC). Essa flexibilidade permite que o sistema funcione sem precisar manipular cada unidade mínima individualmente. #### Difusão e Simplificação A difusão de transações, onde uma depende de várias anteriores e assim por diante, não representa um problema. Não é necessário armazenar ou verificar o histórico completo de uma transação para utilizá-la, já que o registro na blockchain garante sua integridade. --- ### 10. Privacidade O modelo bancário tradicional oferece um certo nível de privacidade, limitando o acesso às informações financeiras apenas às partes envolvidas e a um terceiro confiável (como bancos ou instituições financeiras). No entanto, o Bitcoin opera de forma diferente, pois todas as transações são publicamente registradas na blockchain. Apesar disso, a privacidade pode ser mantida utilizando **chaves públicas anônimas**, que desvinculam diretamente as transações das identidades das partes envolvidas. #### Fluxo de Informação - No **modelo tradicional**, as transações passam por um terceiro confiável que conhece tanto o remetente quanto o destinatário. - No **Bitcoin**, as transações são anunciadas publicamente, mas sem revelar diretamente as identidades das partes. Isso é comparável a dados divulgados por bolsas de valores, onde informações como o tempo e o tamanho das negociações (a "fita") são públicas, mas as identidades das partes não. #### Protegendo a Privacidade Para aumentar a privacidade no Bitcoin, são adotadas as seguintes práticas: 1. **Chaves Públicas Anônimas**: Cada transação utiliza um par de chaves diferentes, dificultando a associação com um proprietário único. 2. **Prevenção de Ligação**: Ao usar chaves novas para cada transação, reduz-se a possibilidade de links evidentes entre múltiplas transações realizadas pelo mesmo usuário. #### Riscos de Ligação Embora a privacidade seja fortalecida, alguns riscos permanecem: - Transações **multi-entrada** podem revelar que todas as entradas pertencem ao mesmo proprietário, caso sejam necessárias para somar o valor total. - O proprietário da chave pode ser identificado indiretamente por transações anteriores que estejam conectadas. --- ### 11. Cálculos Imagine que temos um sistema onde as pessoas (ou computadores) competem para adicionar informações novas (blocos) a um grande registro público (a cadeia de blocos ou blockchain). Este registro é como um livro contábil compartilhado, onde todos podem verificar o que está escrito. Agora, vamos pensar em um cenário: um atacante quer enganar o sistema. Ele quer mudar informações já registradas para beneficiar a si mesmo, por exemplo, desfazendo um pagamento que já fez. Para isso, ele precisa criar uma versão alternativa do livro contábil (a cadeia de blocos dele) e convencer todos os outros participantes de que essa versão é a verdadeira. Mas isso é extremamente difícil. #### Como o Ataque Funciona Quando um novo bloco é adicionado à cadeia, ele depende de cálculos complexos que levam tempo e esforço. Esses cálculos são como um grande quebra-cabeça que precisa ser resolvido. - Os “bons jogadores” (nós honestos) estão sempre trabalhando juntos para resolver esses quebra-cabeças e adicionar novos blocos à cadeia verdadeira. - O atacante, por outro lado, precisa resolver quebra-cabeças sozinho, tentando “alcançar” a cadeia honesta para que sua versão alternativa pareça válida. Se a cadeia honesta já está vários blocos à frente, o atacante começa em desvantagem, e o sistema está projetado para que a dificuldade de alcançá-los aumente rapidamente. #### A Corrida Entre Cadeias Você pode imaginar isso como uma corrida. A cada bloco novo que os jogadores honestos adicionam à cadeia verdadeira, eles se distanciam mais do atacante. Para vencer, o atacante teria que resolver os quebra-cabeças mais rápido que todos os outros jogadores honestos juntos. Suponha que: - A rede honesta tem **80% do poder computacional** (ou seja, resolve 8 de cada 10 quebra-cabeças). - O atacante tem **20% do poder computacional** (ou seja, resolve 2 de cada 10 quebra-cabeças). Cada vez que a rede honesta adiciona um bloco, o atacante tem que "correr atrás" e resolver mais quebra-cabeças para alcançar. #### Por Que o Ataque Fica Cada Vez Mais Improvável? Vamos usar uma fórmula simples para mostrar como as chances de sucesso do atacante diminuem conforme ele precisa "alcançar" mais blocos: P = (q/p)^z - **q** é o poder computacional do atacante (20%, ou 0,2). - **p** é o poder computacional da rede honesta (80%, ou 0,8). - **z** é a diferença de blocos entre a cadeia honesta e a cadeia do atacante. Se o atacante está 5 blocos atrás (z = 5): P = (0,2 / 0,8)^5 = (0,25)^5 = 0,00098, (ou, 0,098%) Isso significa que o atacante tem menos de 0,1% de chance de sucesso — ou seja, é muito improvável. Se ele estiver 10 blocos atrás (z = 10): P = (0,2 / 0,8)^10 = (0,25)^10 = 0,000000095, (ou, 0,0000095%). Neste caso, as chances de sucesso são praticamente **nulas**. #### Um Exemplo Simples Se você jogar uma moeda, a chance de cair “cara” é de 50%. Mas se precisar de 10 caras seguidas, sua chance já é bem menor. Se precisar de 20 caras seguidas, é quase impossível. No caso do Bitcoin, o atacante precisa de muito mais do que 20 caras seguidas. Ele precisa resolver quebra-cabeças extremamente difíceis e alcançar os jogadores honestos que estão sempre à frente. Isso faz com que o ataque seja inviável na prática. #### Por Que Tudo Isso é Seguro? - **A probabilidade de sucesso do atacante diminui exponencialmente.** Isso significa que, quanto mais tempo passa, menor é a chance de ele conseguir enganar o sistema. - **A cadeia verdadeira (honesta) está protegida pela força da rede.** Cada novo bloco que os jogadores honestos adicionam à cadeia torna mais difícil para o atacante alcançar. #### E Se o Atacante Tentar Continuar? O atacante poderia continuar tentando indefinidamente, mas ele estaria gastando muito tempo e energia sem conseguir nada. Enquanto isso, os jogadores honestos estão sempre adicionando novos blocos, tornando o trabalho do atacante ainda mais inútil. Assim, o sistema garante que a cadeia verdadeira seja extremamente segura e que ataques sejam, na prática, impossíveis de ter sucesso. --- ### 12. Conclusão Propusemos um sistema de transações eletrônicas que elimina a necessidade de confiança, baseando-se em assinaturas digitais e em uma rede peer-to-peer que utiliza prova de trabalho. Isso resolve o problema do gasto duplo, criando um histórico público de transações imutável, desde que a maioria do poder computacional permaneça sob controle dos participantes honestos. A rede funciona de forma simples e descentralizada, com nós independentes que não precisam de identificação ou coordenação direta. Eles entram e saem livremente, aceitando a cadeia de prova de trabalho como registro do que ocorreu durante sua ausência. As decisões são tomadas por meio do poder de CPU, validando blocos legítimos, estendendo a cadeia e rejeitando os inválidos. Com este mecanismo de consenso, todas as regras e incentivos necessários para o funcionamento seguro e eficiente do sistema são garantidos. --- Faça o download do whitepaper original em português: https://bitcoin.org/files/bitcoin-paper/bitcoin_pt_br.pdf
@ 6be5cc06:5259daf0
2025-01-21 01:51:46## Bitcoin: Um sistema de dinheiro eletrônico direto entre pessoas. Satoshi Nakamoto satoshin@gmx.com www.bitcoin.org --- ### Resumo O Bitcoin é uma forma de dinheiro digital que permite pagamentos diretos entre pessoas, sem a necessidade de um banco ou instituição financeira. Ele resolve um problema chamado **gasto duplo**, que ocorre quando alguém tenta gastar o mesmo dinheiro duas vezes. Para evitar isso, o Bitcoin usa uma rede descentralizada onde todos trabalham juntos para verificar e registrar as transações. As transações são registradas em um livro público chamado **blockchain**, protegido por uma técnica chamada **Prova de Trabalho**. Essa técnica cria uma cadeia de registros que não pode ser alterada sem refazer todo o trabalho já feito. Essa cadeia é mantida pelos computadores que participam da rede, e a mais longa é considerada a verdadeira. Enquanto a maior parte do poder computacional da rede for controlada por participantes honestos, o sistema continuará funcionando de forma segura. A rede é flexível, permitindo que qualquer pessoa entre ou saia a qualquer momento, sempre confiando na cadeia mais longa como prova do que aconteceu. --- ### 1. Introdução Hoje, quase todos os pagamentos feitos pela internet dependem de bancos ou empresas como processadores de pagamento (cartões de crédito, por exemplo) para funcionar. Embora esse sistema seja útil, ele tem problemas importantes porque é baseado em **confiança**. Primeiro, essas empresas podem reverter pagamentos, o que é útil em caso de erros, mas cria custos e incertezas. Isso faz com que pequenas transações, como pagar centavos por um serviço, se tornem inviáveis. Além disso, os comerciantes são obrigados a desconfiar dos clientes, pedindo informações extras e aceitando fraudes como algo inevitável. Esses problemas não existem no dinheiro físico, como o papel-moeda, onde o pagamento é final e direto entre as partes. No entanto, não temos como enviar dinheiro físico pela internet sem depender de um intermediário confiável. O que precisamos é de um **sistema de pagamento eletrônico baseado em provas matemáticas**, não em confiança. Esse sistema permitiria que qualquer pessoa enviasse dinheiro diretamente para outra, sem depender de bancos ou processadores de pagamento. Além disso, as transações seriam irreversíveis, protegendo vendedores contra fraudes, mas mantendo a possibilidade de soluções para disputas legítimas. Neste documento, apresentamos o **Bitcoin**, que resolve o problema do gasto duplo usando uma rede descentralizada. Essa rede cria um registro público e protegido por cálculos matemáticos, que garante a ordem das transações. Enquanto a maior parte da rede for controlada por pessoas honestas, o sistema será seguro contra ataques. --- ### 2. Transações Para entender como funciona o Bitcoin, é importante saber como as transações são realizadas. Imagine que você quer transferir uma "moeda digital" para outra pessoa. No sistema do Bitcoin, essa "moeda" é representada por uma sequência de registros que mostram quem é o atual dono. Para transferi-la, você adiciona um novo registro comprovando que agora ela pertence ao próximo dono. Esse registro é protegido por um tipo especial de assinatura digital. #### O que é uma assinatura digital? Uma assinatura digital é como uma senha secreta, mas muito mais segura. No Bitcoin, cada usuário tem duas chaves: uma "chave privada", que é secreta e serve para criar a assinatura, e uma "chave pública", que pode ser compartilhada com todos e é usada para verificar se a assinatura é válida. Quando você transfere uma moeda, usa sua chave privada para assinar a transação, provando que você é o dono. A próxima pessoa pode usar sua chave pública para confirmar isso. #### Como funciona na prática? Cada "moeda" no Bitcoin é, na verdade, uma cadeia de assinaturas digitais. Vamos imaginar o seguinte cenário: 1. A moeda está com o Dono 0 (você). Para transferi-la ao Dono 1, você assina digitalmente a transação com sua chave privada. Essa assinatura inclui o código da transação anterior (chamado de "hash") e a chave pública do Dono 1. 2. Quando o Dono 1 quiser transferir a moeda ao Dono 2, ele assinará a transação seguinte com sua própria chave privada, incluindo também o hash da transação anterior e a chave pública do Dono 2. 3. Esse processo continua, formando uma "cadeia" de transações. Qualquer pessoa pode verificar essa cadeia para confirmar quem é o atual dono da moeda. #### Resolvendo o problema do gasto duplo Um grande desafio com moedas digitais é o "gasto duplo", que é quando uma mesma moeda é usada em mais de uma transação. Para evitar isso, muitos sistemas antigos dependiam de uma entidade central confiável, como uma casa da moeda, que verificava todas as transações. No entanto, isso criava um ponto único de falha e centralizava o controle do dinheiro. O Bitcoin resolve esse problema de forma inovadora: ele usa uma rede descentralizada onde todos os participantes (os "nós") têm acesso a um registro completo de todas as transações. Cada nó verifica se as transações são válidas e se a moeda não foi gasta duas vezes. Quando a maioria dos nós concorda com a validade de uma transação, ela é registrada permanentemente na blockchain. #### Por que isso é importante? Essa solução elimina a necessidade de confiar em uma única entidade para gerenciar o dinheiro, permitindo que qualquer pessoa no mundo use o Bitcoin sem precisar de permissão de terceiros. Além disso, ela garante que o sistema seja seguro e resistente a fraudes. --- ### 3. Servidor Timestamp Para assegurar que as transações sejam realizadas de forma segura e transparente, o sistema Bitcoin utiliza algo chamado de "servidor de registro de tempo" (timestamp). Esse servidor funciona como um registro público que organiza as transações em uma ordem específica. Ele faz isso agrupando várias transações em blocos e criando um código único chamado "hash". Esse hash é como uma impressão digital que representa todo o conteúdo do bloco. O hash de cada bloco é amplamente divulgado, como se fosse publicado em um jornal ou em um fórum público. Esse processo garante que cada bloco de transações tenha um registro de quando foi criado e que ele existia naquele momento. Além disso, cada novo bloco criado contém o hash do bloco anterior, formando uma cadeia contínua de blocos conectados — conhecida como blockchain. Com isso, se alguém tentar alterar qualquer informação em um bloco anterior, o hash desse bloco mudará e não corresponderá ao hash armazenado no bloco seguinte. Essa característica torna a cadeia muito segura, pois qualquer tentativa de fraude seria imediatamente detectada. O sistema de timestamps é essencial para provar a ordem cronológica das transações e garantir que cada uma delas seja única e autêntica. Dessa forma, ele reforça a segurança e a confiança na rede Bitcoin. --- ### 4. Prova-de-Trabalho Para implementar o registro de tempo distribuído no sistema Bitcoin, utilizamos um mecanismo chamado prova-de-trabalho. Esse sistema é semelhante ao Hashcash, desenvolvido por Adam Back, e baseia-se na criação de um código único, o "hash", por meio de um processo computacionalmente exigente. A prova-de-trabalho envolve encontrar um valor especial que, quando processado junto com as informações do bloco, gere um hash que comece com uma quantidade específica de zeros. Esse valor especial é chamado de "nonce". Encontrar o nonce correto exige um esforço significativo do computador, porque envolve tentativas repetidas até que a condição seja satisfeita. Esse processo é importante porque torna extremamente difícil alterar qualquer informação registrada em um bloco. Se alguém tentar mudar algo em um bloco, seria necessário refazer o trabalho de computação não apenas para aquele bloco, mas também para todos os blocos que vêm depois dele. Isso garante a segurança e a imutabilidade da blockchain. A prova-de-trabalho também resolve o problema de decidir qual cadeia de blocos é a válida quando há múltiplas cadeias competindo. A decisão é feita pela cadeia mais longa, pois ela representa o maior esforço computacional já realizado. Isso impede que qualquer indivíduo ou grupo controle a rede, desde que a maioria do poder de processamento seja mantida por participantes honestos. Para garantir que o sistema permaneça eficiente e equilibrado, a dificuldade da prova-de-trabalho é ajustada automaticamente ao longo do tempo. Se novos blocos estiverem sendo gerados rapidamente, a dificuldade aumenta; se estiverem sendo gerados muito lentamente, a dificuldade diminui. Esse ajuste assegura que novos blocos sejam criados aproximadamente a cada 10 minutos, mantendo o sistema estável e funcional. --- ### 5. Rede A rede Bitcoin é o coração do sistema e funciona de maneira distribuída, conectando vários participantes (ou nós) para garantir o registro e a validação das transações. Os passos para operar essa rede são: 1. **Transmissão de Transações**: Quando alguém realiza uma nova transação, ela é enviada para todos os nós da rede. Isso é feito para garantir que todos estejam cientes da operação e possam validá-la. 2. **Coleta de Transações em Blocos**: Cada nó agrupa as novas transações recebidas em um "bloco". Este bloco será preparado para ser adicionado à cadeia de blocos (a blockchain). 3. **Prova-de-Trabalho**: Os nós competem para resolver a prova-de-trabalho do bloco, utilizando poder computacional para encontrar um hash válido. Esse processo é como resolver um quebra-cabeça matemático difícil. 4. **Envio do Bloco Resolvido**: Quando um nó encontra a solução para o bloco (a prova-de-trabalho), ele compartilha esse bloco com todos os outros nós na rede. 5. **Validação do Bloco**: Cada nó verifica o bloco recebido para garantir que todas as transações nele contidas sejam válidas e que nenhuma moeda tenha sido gasta duas vezes. Apenas blocos válidos são aceitos. 6. **Construção do Próximo Bloco**: Os nós que aceitaram o bloco começam a trabalhar na criação do próximo bloco, utilizando o hash do bloco aceito como base (hash anterior). Isso mantém a continuidade da cadeia. #### Resolução de Conflitos e Escolha da Cadeia Mais Longa Os nós sempre priorizam a cadeia mais longa, pois ela representa o maior esforço computacional já realizado, garantindo maior segurança. Se dois blocos diferentes forem compartilhados simultaneamente, os nós trabalharão no primeiro bloco recebido, mas guardarão o outro como uma alternativa. Caso o segundo bloco eventualmente forme uma cadeia mais longa (ou seja, tenha mais blocos subsequentes), os nós mudarão para essa nova cadeia. #### Tolerância a Falhas A rede é robusta e pode lidar com mensagens que não chegam a todos os nós. Uma transação não precisa alcançar todos os nós de imediato; basta que chegue a um número suficiente deles para ser incluída em um bloco. Da mesma forma, se um nó não receber um bloco em tempo hábil, ele pode solicitá-lo ao perceber que está faltando quando o próximo bloco é recebido. Esse mecanismo descentralizado permite que a rede Bitcoin funcione de maneira segura, confiável e resiliente, sem depender de uma autoridade central. --- ### 6. Incentivo O incentivo é um dos pilares fundamentais que sustenta o funcionamento da rede Bitcoin, garantindo que os participantes (nós) continuem operando de forma honesta e contribuindo com recursos computacionais. Ele é estruturado em duas partes principais: a recompensa por mineração e as taxas de transação. #### Recompensa por Mineração Por convenção, o primeiro registro em cada bloco é uma transação especial que cria novas moedas e as atribui ao criador do bloco. Essa recompensa incentiva os mineradores a dedicarem poder computacional para apoiar a rede. Como não há uma autoridade central para emitir moedas, essa é a maneira pela qual novas moedas entram em circulação. Esse processo pode ser comparado ao trabalho de garimpeiros, que utilizam recursos para colocar mais ouro em circulação. No caso do Bitcoin, o "recurso" consiste no tempo de CPU e na energia elétrica consumida para resolver a prova-de-trabalho. #### Taxas de Transação Além da recompensa por mineração, os mineradores também podem ser incentivados pelas taxas de transação. Se uma transação utiliza menos valor de saída do que o valor de entrada, a diferença é tratada como uma taxa, que é adicionada à recompensa do bloco contendo essa transação. Com o passar do tempo e à medida que o número de moedas em circulação atinge o limite predeterminado, essas taxas de transação se tornam a principal fonte de incentivo, substituindo gradualmente a emissão de novas moedas. Isso permite que o sistema opere sem inflação, uma vez que o número total de moedas permanece fixo. #### Incentivo à Honestidade O design do incentivo também busca garantir que os participantes da rede mantenham um comportamento honesto. Para um atacante que consiga reunir mais poder computacional do que o restante da rede, ele enfrentaria duas escolhas: 1. Usar esse poder para fraudar o sistema, como reverter transações e roubar pagamentos. 2. Seguir as regras do sistema, criando novos blocos e recebendo recompensas legítimas. A lógica econômica favorece a segunda opção, pois um comportamento desonesto prejudicaria a confiança no sistema, diminuindo o valor de todas as moedas, incluindo aquelas que o próprio atacante possui. Jogar dentro das regras não apenas maximiza o retorno financeiro, mas também preserva a validade e a integridade do sistema. Esse mecanismo garante que os incentivos econômicos estejam alinhados com o objetivo de manter a rede segura, descentralizada e funcional ao longo do tempo. --- ### 7. Recuperação do Espaço em Disco Depois que uma moeda passa a estar protegida por muitos blocos na cadeia, as informações sobre as transações antigas que a geraram podem ser descartadas para economizar espaço em disco. Para que isso seja possível sem comprometer a segurança, as transações são organizadas em uma estrutura chamada "árvore de Merkle". Essa árvore funciona como um resumo das transações: em vez de armazenar todas elas, guarda apenas um "hash raiz", que é como uma assinatura compacta que representa todo o grupo de transações. Os blocos antigos podem, então, ser simplificados, removendo as partes desnecessárias dessa árvore. Apenas a raiz do hash precisa ser mantida no cabeçalho do bloco, garantindo que a integridade dos dados seja preservada, mesmo que detalhes específicos sejam descartados. Para exemplificar: imagine que você tenha vários recibos de compra. Em vez de guardar todos os recibos, você cria um documento e lista apenas o valor total de cada um. Mesmo que os recibos originais sejam descartados, ainda é possível verificar a soma com base nos valores armazenados. Além disso, o espaço ocupado pelos blocos em si é muito pequeno. Cada bloco sem transações ocupa apenas cerca de 80 bytes. Isso significa que, mesmo com blocos sendo gerados a cada 10 minutos, o crescimento anual em espaço necessário é insignificante: apenas 4,2 MB por ano. Com a capacidade de armazenamento dos computadores crescendo a cada ano, esse espaço continuará sendo trivial, garantindo que a rede possa operar de forma eficiente sem problemas de armazenamento, mesmo a longo prazo. --- ### 8. Verificação de Pagamento Simplificada É possível confirmar pagamentos sem a necessidade de operar um nó completo da rede. Para isso, o usuário precisa apenas de uma cópia dos cabeçalhos dos blocos da cadeia mais longa (ou seja, a cadeia com maior esforço de trabalho acumulado). Ele pode verificar a validade de uma transação ao consultar os nós da rede até obter a confirmação de que tem a cadeia mais longa. Para isso, utiliza-se o ramo Merkle, que conecta a transação ao bloco em que ela foi registrada. Entretanto, o método simplificado possui limitações: ele não pode confirmar uma transação isoladamente, mas sim assegurar que ela ocupa um lugar específico na cadeia mais longa. Dessa forma, se um nó da rede aprova a transação, os blocos subsequentes reforçam essa aceitação. A verificação simplificada é confiável enquanto a maioria dos nós da rede for honesta. Contudo, ela se torna vulnerável caso a rede seja dominada por um invasor. Nesse cenário, um atacante poderia fabricar transações fraudulentas que enganariam o usuário temporariamente até que o invasor obtivesse controle completo da rede. Uma estratégia para mitigar esse risco é configurar alertas nos softwares de nós completos. Esses alertas identificam blocos inválidos, sugerindo ao usuário baixar o bloco completo para confirmar qualquer inconsistência. Para maior segurança, empresas que realizam pagamentos frequentes podem preferir operar seus próprios nós, reduzindo riscos e permitindo uma verificação mais direta e confiável. --- ### 9. Combinando e Dividindo Valor No sistema Bitcoin, cada unidade de valor é tratada como uma "moeda" individual, mas gerenciar cada centavo como uma transação separada seria impraticável. Para resolver isso, o Bitcoin permite que valores sejam combinados ou divididos em transações, facilitando pagamentos de qualquer valor. #### Entradas e Saídas Cada transação no Bitcoin é composta por: - **Entradas**: Representam os valores recebidos em transações anteriores. - **Saídas**: Correspondem aos valores enviados, divididos entre os destinatários e, eventualmente, o troco para o remetente. Normalmente, uma transação contém: - Uma única entrada com valor suficiente para cobrir o pagamento. - Ou várias entradas combinadas para atingir o valor necessário. O valor total das saídas nunca excede o das entradas, e a diferença (se houver) pode ser retornada ao remetente como **troco**. #### Exemplo Prático Imagine que você tem duas entradas: 1. 0,03 BTC 2. 0,07 BTC Se deseja enviar 0,08 BTC para alguém, a transação terá: - **Entrada**: As duas entradas combinadas (0,03 + 0,07 BTC = 0,10 BTC). - **Saídas**: Uma para o destinatário (0,08 BTC) e outra como troco para você (0,02 BTC). Essa flexibilidade permite que o sistema funcione sem precisar manipular cada unidade mínima individualmente. #### Difusão e Simplificação A difusão de transações, onde uma depende de várias anteriores e assim por diante, não representa um problema. Não é necessário armazenar ou verificar o histórico completo de uma transação para utilizá-la, já que o registro na blockchain garante sua integridade. --- ### 10. Privacidade O modelo bancário tradicional oferece um certo nível de privacidade, limitando o acesso às informações financeiras apenas às partes envolvidas e a um terceiro confiável (como bancos ou instituições financeiras). No entanto, o Bitcoin opera de forma diferente, pois todas as transações são publicamente registradas na blockchain. Apesar disso, a privacidade pode ser mantida utilizando **chaves públicas anônimas**, que desvinculam diretamente as transações das identidades das partes envolvidas. #### Fluxo de Informação - No **modelo tradicional**, as transações passam por um terceiro confiável que conhece tanto o remetente quanto o destinatário. - No **Bitcoin**, as transações são anunciadas publicamente, mas sem revelar diretamente as identidades das partes. Isso é comparável a dados divulgados por bolsas de valores, onde informações como o tempo e o tamanho das negociações (a "fita") são públicas, mas as identidades das partes não. #### Protegendo a Privacidade Para aumentar a privacidade no Bitcoin, são adotadas as seguintes práticas: 1. **Chaves Públicas Anônimas**: Cada transação utiliza um par de chaves diferentes, dificultando a associação com um proprietário único. 2. **Prevenção de Ligação**: Ao usar chaves novas para cada transação, reduz-se a possibilidade de links evidentes entre múltiplas transações realizadas pelo mesmo usuário. #### Riscos de Ligação Embora a privacidade seja fortalecida, alguns riscos permanecem: - Transações **multi-entrada** podem revelar que todas as entradas pertencem ao mesmo proprietário, caso sejam necessárias para somar o valor total. - O proprietário da chave pode ser identificado indiretamente por transações anteriores que estejam conectadas. --- ### 11. Cálculos Imagine que temos um sistema onde as pessoas (ou computadores) competem para adicionar informações novas (blocos) a um grande registro público (a cadeia de blocos ou blockchain). Este registro é como um livro contábil compartilhado, onde todos podem verificar o que está escrito. Agora, vamos pensar em um cenário: um atacante quer enganar o sistema. Ele quer mudar informações já registradas para beneficiar a si mesmo, por exemplo, desfazendo um pagamento que já fez. Para isso, ele precisa criar uma versão alternativa do livro contábil (a cadeia de blocos dele) e convencer todos os outros participantes de que essa versão é a verdadeira. Mas isso é extremamente difícil. #### Como o Ataque Funciona Quando um novo bloco é adicionado à cadeia, ele depende de cálculos complexos que levam tempo e esforço. Esses cálculos são como um grande quebra-cabeça que precisa ser resolvido. - Os “bons jogadores” (nós honestos) estão sempre trabalhando juntos para resolver esses quebra-cabeças e adicionar novos blocos à cadeia verdadeira. - O atacante, por outro lado, precisa resolver quebra-cabeças sozinho, tentando “alcançar” a cadeia honesta para que sua versão alternativa pareça válida. Se a cadeia honesta já está vários blocos à frente, o atacante começa em desvantagem, e o sistema está projetado para que a dificuldade de alcançá-los aumente rapidamente. #### A Corrida Entre Cadeias Você pode imaginar isso como uma corrida. A cada bloco novo que os jogadores honestos adicionam à cadeia verdadeira, eles se distanciam mais do atacante. Para vencer, o atacante teria que resolver os quebra-cabeças mais rápido que todos os outros jogadores honestos juntos. Suponha que: - A rede honesta tem **80% do poder computacional** (ou seja, resolve 8 de cada 10 quebra-cabeças). - O atacante tem **20% do poder computacional** (ou seja, resolve 2 de cada 10 quebra-cabeças). Cada vez que a rede honesta adiciona um bloco, o atacante tem que "correr atrás" e resolver mais quebra-cabeças para alcançar. #### Por Que o Ataque Fica Cada Vez Mais Improvável? Vamos usar uma fórmula simples para mostrar como as chances de sucesso do atacante diminuem conforme ele precisa "alcançar" mais blocos: P = (q/p)^z - **q** é o poder computacional do atacante (20%, ou 0,2). - **p** é o poder computacional da rede honesta (80%, ou 0,8). - **z** é a diferença de blocos entre a cadeia honesta e a cadeia do atacante. Se o atacante está 5 blocos atrás (z = 5): P = (0,2 / 0,8)^5 = (0,25)^5 = 0,00098, (ou, 0,098%) Isso significa que o atacante tem menos de 0,1% de chance de sucesso — ou seja, é muito improvável. Se ele estiver 10 blocos atrás (z = 10): P = (0,2 / 0,8)^10 = (0,25)^10 = 0,000000095, (ou, 0,0000095%). Neste caso, as chances de sucesso são praticamente **nulas**. #### Um Exemplo Simples Se você jogar uma moeda, a chance de cair “cara” é de 50%. Mas se precisar de 10 caras seguidas, sua chance já é bem menor. Se precisar de 20 caras seguidas, é quase impossível. No caso do Bitcoin, o atacante precisa de muito mais do que 20 caras seguidas. Ele precisa resolver quebra-cabeças extremamente difíceis e alcançar os jogadores honestos que estão sempre à frente. Isso faz com que o ataque seja inviável na prática. #### Por Que Tudo Isso é Seguro? - **A probabilidade de sucesso do atacante diminui exponencialmente.** Isso significa que, quanto mais tempo passa, menor é a chance de ele conseguir enganar o sistema. - **A cadeia verdadeira (honesta) está protegida pela força da rede.** Cada novo bloco que os jogadores honestos adicionam à cadeia torna mais difícil para o atacante alcançar. #### E Se o Atacante Tentar Continuar? O atacante poderia continuar tentando indefinidamente, mas ele estaria gastando muito tempo e energia sem conseguir nada. Enquanto isso, os jogadores honestos estão sempre adicionando novos blocos, tornando o trabalho do atacante ainda mais inútil. Assim, o sistema garante que a cadeia verdadeira seja extremamente segura e que ataques sejam, na prática, impossíveis de ter sucesso. --- ### 12. Conclusão Propusemos um sistema de transações eletrônicas que elimina a necessidade de confiança, baseando-se em assinaturas digitais e em uma rede peer-to-peer que utiliza prova de trabalho. Isso resolve o problema do gasto duplo, criando um histórico público de transações imutável, desde que a maioria do poder computacional permaneça sob controle dos participantes honestos. A rede funciona de forma simples e descentralizada, com nós independentes que não precisam de identificação ou coordenação direta. Eles entram e saem livremente, aceitando a cadeia de prova de trabalho como registro do que ocorreu durante sua ausência. As decisões são tomadas por meio do poder de CPU, validando blocos legítimos, estendendo a cadeia e rejeitando os inválidos. Com este mecanismo de consenso, todas as regras e incentivos necessários para o funcionamento seguro e eficiente do sistema são garantidos. --- Faça o download do whitepaper original em português: https://bitcoin.org/files/bitcoin-paper/bitcoin_pt_br.pdf @ 50809a53:e091f164
2025-01-20 22:30:01For starters, anyone who is interested in curating and managing "notes, lists, bookmarks, kind-1 events, or other stuff" should watch this video: https://youtu.be/XRpHIa-2XCE Now, assuming you have watched it, I will proceed assuming you are aware of many of the applications that exist for a very similar purpose. I'll break them down further, following a similar trajectory in order of how I came across them, and a bit about my own path on this journey. We'll start way back in the early 2000s, before Bitcoin existed. We had https://zim-wiki.org/ It is tried and true, and to this day stands to present an option for people looking for a very simple solution to a potentially complex problem. Zim-Wiki works. But it is limited. Let's step into the realm of proprietary. Obsidian, Joplin, and LogSeq. The first two are entirely cloud-operative applications, with more of a focus on the true benefit of being a paid service. I will assume anyone reading this is capable of exploring the marketing of these applications, or trying their freemium product, to get a feeling for what they are capable of. I bring up Obsidian because it is very crucial to understand the market placement of publication. We know social media handles the 'hosting' problem of publishing notes "and other stuff" by harvesting data and making deals with advertisers. But- what Obsidian has evolved to offer is a full service known as 'publish'. This means users can stay in the proprietary pipeline, "from thought to web." all for $8/mo. See: https://obsidian.md/publish THIS IS NOSTR'S PRIMARY COMPETITION. WE ARE HERE TO DISRUPT THIS MARKET, WITH NOTES AND OTHER STUFF. WITH RELAYS. WITH THE PROTOCOL. Now, on to Joplin. I have never used this, because I opted to study the FOSS market and stayed free of any reliance on a paid solution. Many people like Joplin, and I gather the reason is because it has allowed itself to be flexible and good options that integrate with Joplin seems to provide good solutions for users who need that functionality. I see Nostr users recommending Joplin, so I felt it was worthwhile to mention as a case-study option. I myself need to investigate it more, but have found comfort in other solutions. LogSeq - This is my "other solutions." It seems to be trapped in its proprietary web of funding and constraint. I use it because it turns my desktop into a power-house of note archival. But by using it- I AM TRAPPED TOO. This means LogSeq is by no means a working solution for Nostr users who want a long-term archival option. But the trap is not a cage. It's merely a box. My notes can be exported to other applications with graphing and node-based information structure. Specifically, I can export these notes to: - Text - OPML - HTML - and, PNG, for whatever that is worth. Let's try out the PNG option, just for fun. Here's an exported PNG of my "Games on Nostr" list, which has long been abandoned. I once decided to poll some CornyChat users to see what games they enjoyed- and I documented them in a LogSeq page for my own future reference. You can see it here: https://i.postimg.cc/qMBPDTwr/image.png This is a very simple example of how a single "page" or "list" in LogSeq can be multipurpose. It is a small list, with multiple "features" or variables at play. First, I have listed out a variety of complex games that might make sense with "multiplayer" identification that relies on our npubs or nip-05 addresses to aggregate user data. We can ALL imagine playing games like Tetris, Snake, or Catan together with our Nostr identities. But of course we are a long way from breaking into the video game market. On a mostly irrelevant sidenote- you might notice in my example list, that I seem to be excited about a game called Dot.Hack. I discovered this small game on Itch.io and reached out to the developer on Twitter, in an attempt to purple-pill him, but moreso to inquire about his game. Unfortunately there was no response, even without mention of Nostr. Nonetheless, we pioneer on. You can try the game here: https://propuke.itch.io/planethack So instead let's focus on the structure of "one working list." The middle section of this list is where I polled users, and simply listed out their suggestions. Of course we discussed these before I documented, so it is note a direct result of a poll, but actually a working interaction of poll results! This is crucial because it separates my list from the aggregated data, and implies its relevance/importance. The final section of this ONE list- is the beginnings of where I conceptually connect nostr with video game functionality. You can look at this as the beginning of a new graph, which would be "Video Game Operability With Nostr". These three sections make up one concept within my brain. It exists in other users' brains too- but of course they are not as committed to the concept as myself- the one managing the communal discussion. With LogSeq- I can grow and expand these lists. These lists can become graphs. Those graphs can become entire catalogues of information than can be shared across the web. I can replicate this system with bookmarks, ideas, application design, shopping lists, LLM prompting, video/music playlists, friend lists, RELAY lists, the LIST goes ON forever! So where does that lead us? I think it leads us to kind-1 events. We don't have much in the way of "kind-1 event managers" because most developers would agree that "storing kind-1 events locally" is.. at the very least, not so important. But it could be! If only a superapp existed that could interface seamlessly with nostr, yada yada.. we've heard it all before. We aren't getting a superapp before we have microapps. Basically this means frameworking the protocol before worrying about the all-in-one solution. So this article will step away from the deep desire for a Nostr-enabled, Rust-built, FOSS, non-commercialized FREEDOM APP, that will exist one day, we hope. Instead, we will focus on simple attempts of the past. I encourage others to chime in with their experience. Zim-Wiki is foundational. The user constructs pages, and can then develop them into books. LogSeq has the right idea- but is constrained in too many ways to prove to be a working solution at this time. However, it is very much worth experimenting with, and investigating, and modelling ourselves after. https://workflowy.com/ is next on our list. This is great for users who think LogSeq is too complex. They "just want simple notes." Get a taste with WorkFlowy. You will understand why LogSeq is powerful if you see value in WF. I am writing this article in favor of a redesign of LogSeq to be compatible with Nostr. I have been drafting the idea since before Nostr existed- and with Nostr I truly believe it will be possible. So, I will stop to thank everyone who has made Nostr what it is today. I wouldn't be publishing this without you! One app I need to investigate more is Zettlr. I will mention it here for others to either discuss or investigate, as it is also mentioned some in the video I opened with. https://www.zettlr.com/ On my path to finding Nostr, before its inception, was a service called Deta.Space. This was an interesting project, not entirely unique or original, but completely fresh and very beginner-friendly. DETA WAS AN AWESOME CLOUD OS. And we could still design a form of Nostr ecosystem that is managed in this way. But, what we have now is excellent, and going forward I only see "additional" or supplemental. Along the timeline, Deta sunsetted their Space service and launched https://deta.surf/ You might notice they advertise that "This is the future of bookmarks." I have to wonder if perhaps I got through to them that bookmarking was what their ecosystem could empower. While I have not tried Surf, it looks interested, but does not seem to address what I found most valuable about Deta.Space: https://webcrate.app/ WebCrate was an early bookmarking client for Deta.Space which was likely their most popular application. What was amazing about WebCrate was that it delivered "simple bookmarking." At one point I decided to migrate my bookmarks from other apps, like Pocket and WorkFlowy, into WebCrate. This ended up being an awful decision, because WebCrate is no longer being developed. However, to much credit of Deta.Space, my WebCrate instance is still running and completely functional. I have since migrated what I deem important into a local LogSeq graph, so my bookmarks are safe. But, the development of WebCrate is note. WebCrate did not provide a working directory of crates. All creates were contained within a single-level directory. Essentially there were no layers. Just collections of links. This isn't enough for any user to effectively manage their catalogue of notes. With some pressure, I did encourage the German developer to flesh out a form of tagging, which did alleviate the problem to some extent. But as we see with Surf, they have pioneered in another direction. That brings us back to Nostr. Where can we look for the best solution? There simply isn't one yet. But, we can look at some other options for inspiration. HedgeDoc: https://hedgedoc.org/ I am eager for someone to fork HedgeDoc and employ Nostr sign-in. This is a small step toward managing information together within the Nostr ecosystem. I will attempt this myself eventually, if no one else does, but I am prioritizing my development in this way: 1. A nostr client that allows the cataloguing and management of relays locally. 2. A LogSeq alternative with Nostr interoperability. 3. HedgeDoc + Nostr is #3 on my list, despite being the easiest option. Check out HedgeDoc 2.0 if you have any interest in a cooperative Markdown experience on Nostr: https://docs.hedgedoc.dev/ Now, this article should catch up all of my dearest followers, and idols, to where I stand with "bookmarking, note-taking, list-making, kind-1 event management, frameworking, and so on..." Where it leads us to, is what's possible. Let's take a look at what's possible, once we forego ALL OF THE PROPRIETARY WEB'S BEST OPTIONS: https://denizaydemir.org/ https://denizaydemir.org/graph/how-logseq-should-build-a-world-knowledge-graph/ https://subconscious.network/ Nostr is even inspired by much of the history that has gone into information management systems. nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn I know looks up to Gordon Brander, just as I do. You can read his articles here: https://substack.com/@gordonbrander and they are very much worth reading! Also, I could note that the original version of Highlighter by nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft was also inspired partially by WorkFlowy. About a year ago, I was mesmerized coming across SubText and thinking I had finally found the answer Nostr might even be looking for. But, for now I will just suggest that others read the Readme.md on the SubText Gtihub, as well as articles by Brander. Good luck everyone. I am here to work with ANYONE who is interested in these type of solution on Nostr. My first order of business in this space is to spearhead a community of npubs who share this goal. Everyone who is interested in note-taking or list-making or bookmarking is welcome to join. I have created an INVITE-ONLY relay for this very purpose, and anyone is welcome to reach out if they wish to be added to the whitelist. It should be freely readable in the near future, if it is not already, but for now will remain a closed-to-post community to preemptively mitigate attack or spam. Please reach out to me if you wish to join the relay. https://logstr.mycelium.social/ With this article, I hope people will investigate and explore the options available. We have lots of ground to cover, but all of the right resources and manpower to do so. Godspeed, Nostr. #Nostr #Notes #OtherStuff #LogSec #Joplin #Obsidian
@ 50809a53:e091f164
2025-01-20 22:30:01For starters, anyone who is interested in curating and managing "notes, lists, bookmarks, kind-1 events, or other stuff" should watch this video: https://youtu.be/XRpHIa-2XCE Now, assuming you have watched it, I will proceed assuming you are aware of many of the applications that exist for a very similar purpose. I'll break them down further, following a similar trajectory in order of how I came across them, and a bit about my own path on this journey. We'll start way back in the early 2000s, before Bitcoin existed. We had https://zim-wiki.org/ It is tried and true, and to this day stands to present an option for people looking for a very simple solution to a potentially complex problem. Zim-Wiki works. But it is limited. Let's step into the realm of proprietary. Obsidian, Joplin, and LogSeq. The first two are entirely cloud-operative applications, with more of a focus on the true benefit of being a paid service. I will assume anyone reading this is capable of exploring the marketing of these applications, or trying their freemium product, to get a feeling for what they are capable of. I bring up Obsidian because it is very crucial to understand the market placement of publication. We know social media handles the 'hosting' problem of publishing notes "and other stuff" by harvesting data and making deals with advertisers. But- what Obsidian has evolved to offer is a full service known as 'publish'. This means users can stay in the proprietary pipeline, "from thought to web." all for $8/mo. See: https://obsidian.md/publish THIS IS NOSTR'S PRIMARY COMPETITION. WE ARE HERE TO DISRUPT THIS MARKET, WITH NOTES AND OTHER STUFF. WITH RELAYS. WITH THE PROTOCOL. Now, on to Joplin. I have never used this, because I opted to study the FOSS market and stayed free of any reliance on a paid solution. Many people like Joplin, and I gather the reason is because it has allowed itself to be flexible and good options that integrate with Joplin seems to provide good solutions for users who need that functionality. I see Nostr users recommending Joplin, so I felt it was worthwhile to mention as a case-study option. I myself need to investigate it more, but have found comfort in other solutions. LogSeq - This is my "other solutions." It seems to be trapped in its proprietary web of funding and constraint. I use it because it turns my desktop into a power-house of note archival. But by using it- I AM TRAPPED TOO. This means LogSeq is by no means a working solution for Nostr users who want a long-term archival option. But the trap is not a cage. It's merely a box. My notes can be exported to other applications with graphing and node-based information structure. Specifically, I can export these notes to: - Text - OPML - HTML - and, PNG, for whatever that is worth. Let's try out the PNG option, just for fun. Here's an exported PNG of my "Games on Nostr" list, which has long been abandoned. I once decided to poll some CornyChat users to see what games they enjoyed- and I documented them in a LogSeq page for my own future reference. You can see it here: https://i.postimg.cc/qMBPDTwr/image.png This is a very simple example of how a single "page" or "list" in LogSeq can be multipurpose. It is a small list, with multiple "features" or variables at play. First, I have listed out a variety of complex games that might make sense with "multiplayer" identification that relies on our npubs or nip-05 addresses to aggregate user data. We can ALL imagine playing games like Tetris, Snake, or Catan together with our Nostr identities. But of course we are a long way from breaking into the video game market. On a mostly irrelevant sidenote- you might notice in my example list, that I seem to be excited about a game called Dot.Hack. I discovered this small game on Itch.io and reached out to the developer on Twitter, in an attempt to purple-pill him, but moreso to inquire about his game. Unfortunately there was no response, even without mention of Nostr. Nonetheless, we pioneer on. You can try the game here: https://propuke.itch.io/planethack So instead let's focus on the structure of "one working list." The middle section of this list is where I polled users, and simply listed out their suggestions. Of course we discussed these before I documented, so it is note a direct result of a poll, but actually a working interaction of poll results! This is crucial because it separates my list from the aggregated data, and implies its relevance/importance. The final section of this ONE list- is the beginnings of where I conceptually connect nostr with video game functionality. You can look at this as the beginning of a new graph, which would be "Video Game Operability With Nostr". These three sections make up one concept within my brain. It exists in other users' brains too- but of course they are not as committed to the concept as myself- the one managing the communal discussion. With LogSeq- I can grow and expand these lists. These lists can become graphs. Those graphs can become entire catalogues of information than can be shared across the web. I can replicate this system with bookmarks, ideas, application design, shopping lists, LLM prompting, video/music playlists, friend lists, RELAY lists, the LIST goes ON forever! So where does that lead us? I think it leads us to kind-1 events. We don't have much in the way of "kind-1 event managers" because most developers would agree that "storing kind-1 events locally" is.. at the very least, not so important. But it could be! If only a superapp existed that could interface seamlessly with nostr, yada yada.. we've heard it all before. We aren't getting a superapp before we have microapps. Basically this means frameworking the protocol before worrying about the all-in-one solution. So this article will step away from the deep desire for a Nostr-enabled, Rust-built, FOSS, non-commercialized FREEDOM APP, that will exist one day, we hope. Instead, we will focus on simple attempts of the past. I encourage others to chime in with their experience. Zim-Wiki is foundational. The user constructs pages, and can then develop them into books. LogSeq has the right idea- but is constrained in too many ways to prove to be a working solution at this time. However, it is very much worth experimenting with, and investigating, and modelling ourselves after. https://workflowy.com/ is next on our list. This is great for users who think LogSeq is too complex. They "just want simple notes." Get a taste with WorkFlowy. You will understand why LogSeq is powerful if you see value in WF. I am writing this article in favor of a redesign of LogSeq to be compatible with Nostr. I have been drafting the idea since before Nostr existed- and with Nostr I truly believe it will be possible. So, I will stop to thank everyone who has made Nostr what it is today. I wouldn't be publishing this without you! One app I need to investigate more is Zettlr. I will mention it here for others to either discuss or investigate, as it is also mentioned some in the video I opened with. https://www.zettlr.com/ On my path to finding Nostr, before its inception, was a service called Deta.Space. This was an interesting project, not entirely unique or original, but completely fresh and very beginner-friendly. DETA WAS AN AWESOME CLOUD OS. And we could still design a form of Nostr ecosystem that is managed in this way. But, what we have now is excellent, and going forward I only see "additional" or supplemental. Along the timeline, Deta sunsetted their Space service and launched https://deta.surf/ You might notice they advertise that "This is the future of bookmarks." I have to wonder if perhaps I got through to them that bookmarking was what their ecosystem could empower. While I have not tried Surf, it looks interested, but does not seem to address what I found most valuable about Deta.Space: https://webcrate.app/ WebCrate was an early bookmarking client for Deta.Space which was likely their most popular application. What was amazing about WebCrate was that it delivered "simple bookmarking." At one point I decided to migrate my bookmarks from other apps, like Pocket and WorkFlowy, into WebCrate. This ended up being an awful decision, because WebCrate is no longer being developed. However, to much credit of Deta.Space, my WebCrate instance is still running and completely functional. I have since migrated what I deem important into a local LogSeq graph, so my bookmarks are safe. But, the development of WebCrate is note. WebCrate did not provide a working directory of crates. All creates were contained within a single-level directory. Essentially there were no layers. Just collections of links. This isn't enough for any user to effectively manage their catalogue of notes. With some pressure, I did encourage the German developer to flesh out a form of tagging, which did alleviate the problem to some extent. But as we see with Surf, they have pioneered in another direction. That brings us back to Nostr. Where can we look for the best solution? There simply isn't one yet. But, we can look at some other options for inspiration. HedgeDoc: https://hedgedoc.org/ I am eager for someone to fork HedgeDoc and employ Nostr sign-in. This is a small step toward managing information together within the Nostr ecosystem. I will attempt this myself eventually, if no one else does, but I am prioritizing my development in this way: 1. A nostr client that allows the cataloguing and management of relays locally. 2. A LogSeq alternative with Nostr interoperability. 3. HedgeDoc + Nostr is #3 on my list, despite being the easiest option. Check out HedgeDoc 2.0 if you have any interest in a cooperative Markdown experience on Nostr: https://docs.hedgedoc.dev/ Now, this article should catch up all of my dearest followers, and idols, to where I stand with "bookmarking, note-taking, list-making, kind-1 event management, frameworking, and so on..." Where it leads us to, is what's possible. Let's take a look at what's possible, once we forego ALL OF THE PROPRIETARY WEB'S BEST OPTIONS: https://denizaydemir.org/ https://denizaydemir.org/graph/how-logseq-should-build-a-world-knowledge-graph/ https://subconscious.network/ Nostr is even inspired by much of the history that has gone into information management systems. nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn I know looks up to Gordon Brander, just as I do. You can read his articles here: https://substack.com/@gordonbrander and they are very much worth reading! Also, I could note that the original version of Highlighter by nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft was also inspired partially by WorkFlowy. About a year ago, I was mesmerized coming across SubText and thinking I had finally found the answer Nostr might even be looking for. But, for now I will just suggest that others read the Readme.md on the SubText Gtihub, as well as articles by Brander. Good luck everyone. I am here to work with ANYONE who is interested in these type of solution on Nostr. My first order of business in this space is to spearhead a community of npubs who share this goal. Everyone who is interested in note-taking or list-making or bookmarking is welcome to join. I have created an INVITE-ONLY relay for this very purpose, and anyone is welcome to reach out if they wish to be added to the whitelist. It should be freely readable in the near future, if it is not already, but for now will remain a closed-to-post community to preemptively mitigate attack or spam. Please reach out to me if you wish to join the relay. https://logstr.mycelium.social/ With this article, I hope people will investigate and explore the options available. We have lots of ground to cover, but all of the right resources and manpower to do so. Godspeed, Nostr. #Nostr #Notes #OtherStuff #LogSec #Joplin #Obsidian @ 129f5189:3a441803
2025-01-20 19:20:16Many believe that to buy #Bitcoin, they need to purchase 1 whole #Bitcoin, which may seem unaffordable for most people today. This belief is rooted in a misunderstanding of how #Bitcoin works. #Bitcoin is divisible up to eight decimal places, and the smallest unit is called a satoshi. 1 #Bitcoin equals 100 million satoshis. https://image.nostr.build/4c25abae971d2d817d2e9c38cac0ae7ea6a439e39bc7e2db46a610cc91a58e4b.jpg This means that anyone can start by purchasing a fraction of #Bitcoin, like 0.0001 #BTC (10,000 satoshis), for a much smaller amount than the price of 1 whole #Bitcoin. The mistake lies in comparing the value of 1 #Bitcoin to the price of 1 unit of traditional currency, such as the dollar or the real. This comparison ignores #Bitcoin’s divisibility and fungibility. Imagine if someone said they couldn’t buy gold because they couldn’t afford a whole gold bar. Does that make sense? Of course not. Just as gold can be bought in grams, #Bitcoin can be purchased in fractions. Another important point is understanding that the value of a satoshi is proportional to the value of #Bitcoin as a whole. If #Bitcoin reaches a price of $1 million, for example, 1 satoshi will be worth $0.01. What ultimately matters is the relative appreciation of the asset, not the number of units you own. Therefore, the unit bias is merely a psychological barrier. Instead of focusing on the price of 1 whole #Bitcoin, think about the opportunity to accumulate satoshis, which are just as valuable as any fraction of #Bitcoin. After all, every satoshi is part of the largest computational network in the world—scarce and decentralized—that is poised to transform the global financial system. Buying #Bitcoin isn’t about how much you can buy today, but about understanding the value it represents in the long term. Don’t let the unit bias stop you from being part of this monetary revolution.
@ 129f5189:3a441803
2025-01-20 19:20:16Many believe that to buy #Bitcoin, they need to purchase 1 whole #Bitcoin, which may seem unaffordable for most people today. This belief is rooted in a misunderstanding of how #Bitcoin works. #Bitcoin is divisible up to eight decimal places, and the smallest unit is called a satoshi. 1 #Bitcoin equals 100 million satoshis. https://image.nostr.build/4c25abae971d2d817d2e9c38cac0ae7ea6a439e39bc7e2db46a610cc91a58e4b.jpg This means that anyone can start by purchasing a fraction of #Bitcoin, like 0.0001 #BTC (10,000 satoshis), for a much smaller amount than the price of 1 whole #Bitcoin. The mistake lies in comparing the value of 1 #Bitcoin to the price of 1 unit of traditional currency, such as the dollar or the real. This comparison ignores #Bitcoin’s divisibility and fungibility. Imagine if someone said they couldn’t buy gold because they couldn’t afford a whole gold bar. Does that make sense? Of course not. Just as gold can be bought in grams, #Bitcoin can be purchased in fractions. Another important point is understanding that the value of a satoshi is proportional to the value of #Bitcoin as a whole. If #Bitcoin reaches a price of $1 million, for example, 1 satoshi will be worth $0.01. What ultimately matters is the relative appreciation of the asset, not the number of units you own. Therefore, the unit bias is merely a psychological barrier. Instead of focusing on the price of 1 whole #Bitcoin, think about the opportunity to accumulate satoshis, which are just as valuable as any fraction of #Bitcoin. After all, every satoshi is part of the largest computational network in the world—scarce and decentralized—that is poised to transform the global financial system. Buying #Bitcoin isn’t about how much you can buy today, but about understanding the value it represents in the long term. Don’t let the unit bias stop you from being part of this monetary revolution. @ df478568:2a951e67
2025-01-20 18:28:44Affiliate Links I earn a commission for these products and services, but I would recommend them even if they did not pay me. [BTCPins](https://btcpins.com/?aff=ex1GhhNeeU9-PQ1-ZVEkarU9bSnsNyq98Jy_lEUBLmsrWsCqa69PYohMWcCOGK9tK1rAqmuvT2KITFnAjhivbfOajnP3D8A8O09Hi-OY4K8) [Strike](https://invite.strike.me/NGQDMT) [Cash App](https://cash.app/app/MCLFTJT) [PayPerQ](https://ppq.ai/invite/b28d3a37) This is the cheapest way to use AI on the Internet. The pics are spectacular. It cost me about 20 sats to make the cover for this affiliate page. [Start9](https://start9.com/?ref=marc26z.npubpro.com/) I don’t really have an affiliate link for these guys, but I would like one. Anyway, they make the easiest home servers. I highly recommend them. I like that I can use the cloudflare tunnel app to host everythng on the clearnet. Let me know if you need any help with this. ## Recommendations These companies do not pay me, but I recommend them anyway. ### [Subscribe To Support My Work](https://app.paywithflash.com/subscription-page?flashId=1110&ref) I use [PayWithFlash](https://app.paywithflash.com) to create a Substack like subscription. You can subscribe for as little as 1,000 per month. If that is too many sats to ask, you could always zap my articles instead. Thank you. ### [The Leather Mint](https://theleathermint.com/) The Leathermint makes great, custom-sized leather belts and awesome-looking wallets. I have a belt and it fits better than any belt I’ve ever warn because it’s custom size. I have had mine for about a year. The chrome is coming off a little at the top but I don’t tuck in shirts anyway. ### [CoinKite](https://store.coinkite.com/store) They make my favorite products ever. I suggest getting a few SEEDPLATE® Kit’s no matter what hardware wallets you use. I also like using a dry-erase marker first because there are no second chances when punching a letter. It’s best to use a dry-erase marker first. If you make a mistake erase it. Then, after you double checked the first side, go over the dry-erase marker with a permanent marker. Then do the same to the other side. If you’re sure every letter is correct, punch the holes. There are many plates with sufficient heat resistance, but I like the SEEDPLATE because they are the easiest to destroy if you ever need to. Instead of etching out stamps on washers, you just add extra punches if you must destroy the seed. ### [Alby Hub](https://albyhub.com/) Look, if you want to run your own lightning node, this is the way to go. If you have a Start9 or are technical, you can run it yourself. If you’re less technical, they offer a cloud service. I was one of the early beta testers of this software and I think it’s the easiest way to run a lightning node. ## Free and Open Software ### [Primal.net](https://github.com/PrimalHQ/primal-web-app) os a corporation building stuff on nostr. If you’re technical, you can run it yourself. If not, you ca download the app for free. They charge a fee for premium services. I pay for this because I want to support companies that contribute to nostr development and help bitcoin be used as peer-to-peer electronic cash. I think of Primal as a custodial bitcoin wallet that allows anyone to participate in the biggest circular economy in the world. TikTok was banned in the United States which means it is no longer available for citizens of the United States to download the app. There are ways to get around these restrictions, but I choose not to because I do not want the CCP, or any government to have access to information if their goal is to use it against me. I believe every government, foreign or domestic wants to use your information against you. Nostr allows me to opt out of these stupid games with stupid likes. With Primal, I am the customer, not the product. I choose the algorithms I want to see, not the CCP , USG or corporations. Even if Primal decided to say, “Marc sucks. We will now censor him.” I will only lose the https://primal.net/marc, the OG status, and my primal lightning address. It also means they would stop getting my sats every month, so they are incentivized not to censor. You would have to do something really stupid to get banned from Primal. I’m not sure it’s been done yet, but even if it has, you will not get banned from the nostr protocol. ### [Portainer](https://github.com/portainer/portainer) Portainer makes it easy to run docker-containers. I first learned how to use it because it is an app on Umbrel. Eventually, I learned you can use Portainer on any Linux computer, so that’s what I do. It takes some time to learn, but once you do—you become a cloud computing super-wizard. ### [Mealie](https://github.com/mealie-recipes/mealie/) Mealie is one of my favorite pieces of free and open software that is not related to bitcoin in any shape or form...except it makes grocery shopping easier. I know what you’re thinking. WTF does that have to do with bitcoin? I assume you belong to the *I Want More Bitcoin Club*. You are in good company because ALL Bitcoiners are a member of this club. One way you can stasck more sats is to cut your grocery bill. I believe Mealie helps me do just that. When I’m grocery shopping, my goal is to get as much healthy food for my sats as possible. To accomplish this, I shop sales. Now, if you’re living in a van, this won’t do much for you, but no worries. You will stack even more sats by cutting your housing costs. If your wife will not agree to live under a bridge and stack sats, then get a freezer in your garage. Fill it with meat you buy on sale. Pork shoulder is 3,000 sats per pound and you don’t what to cook it with? Find a recipe online. Mealie will use machine learning to scrape the ingredients from the recipe. Then you can add it to a grocery list. In other words, you can automate your grocery list right at the grocery isle. This is one way I save sats with Mealie. I also keep the things my family eats on a regular basis in stock. This is part for emergency preparedness, but it is also for financial preparedness. If you are in a situation where no food is available, all the bitcoin in the world will not save you. I’m not talkig about super volcanos. Hurricanes, tornadoes, and earthquakes happen. So I got this idea from Jack Spirko, but modified it to use with mealie. Spirko suggests building a 30 day supply of food and water for your family in case of an emergency. You should have a generator and a garden too, but I don’t want to get off track. Once you have this he says: write down every item you use on a notebook and replace it. This is good advice, but I just add it to my grocery list in mealie. #### [Shopstr](https://github.com/shopstr-eng/shopstr) Shopstr is like Facebook marketplace, Amazon, or eBay on nostr. This is what I use to build my store. I want to pause point out how big of a paradigm shift this is. The old web requires permission. Ebay needs permission from the government to become a corporation. They built infrastructure to create their online auction. Everyone on the site must pay eBay a tax. This results in a techno- feudalist society. When you sell on Shopster, you are selling your wares on nostr, a protocol, not a platform. This changes the relationship between the people and the technology because NO MIDDLEMAN IS REQUIRED. On nostr, there are no digital overlords. You own your data. You host your store. If the current digital overlords shut it down, you can run it yourself. You do not need to pay a tax to eBay, Amazon, or the PayPal mafia. #### Avocados I love avocados. They are kind of like free and open source software because you can grow them yourself. ;) I love avocados and **big avocado ag did not pay me to say this**.
@ df478568:2a951e67
2025-01-20 18:28:44Affiliate Links I earn a commission for these products and services, but I would recommend them even if they did not pay me. [BTCPins](https://btcpins.com/?aff=ex1GhhNeeU9-PQ1-ZVEkarU9bSnsNyq98Jy_lEUBLmsrWsCqa69PYohMWcCOGK9tK1rAqmuvT2KITFnAjhivbfOajnP3D8A8O09Hi-OY4K8) [Strike](https://invite.strike.me/NGQDMT) [Cash App](https://cash.app/app/MCLFTJT) [PayPerQ](https://ppq.ai/invite/b28d3a37) This is the cheapest way to use AI on the Internet. The pics are spectacular. It cost me about 20 sats to make the cover for this affiliate page. [Start9](https://start9.com/?ref=marc26z.npubpro.com/) I don’t really have an affiliate link for these guys, but I would like one. Anyway, they make the easiest home servers. I highly recommend them. I like that I can use the cloudflare tunnel app to host everythng on the clearnet. Let me know if you need any help with this. ## Recommendations These companies do not pay me, but I recommend them anyway. ### [Subscribe To Support My Work](https://app.paywithflash.com/subscription-page?flashId=1110&ref) I use [PayWithFlash](https://app.paywithflash.com) to create a Substack like subscription. You can subscribe for as little as 1,000 per month. If that is too many sats to ask, you could always zap my articles instead. Thank you. ### [The Leather Mint](https://theleathermint.com/) The Leathermint makes great, custom-sized leather belts and awesome-looking wallets. I have a belt and it fits better than any belt I’ve ever warn because it’s custom size. I have had mine for about a year. The chrome is coming off a little at the top but I don’t tuck in shirts anyway. ### [CoinKite](https://store.coinkite.com/store) They make my favorite products ever. I suggest getting a few SEEDPLATE® Kit’s no matter what hardware wallets you use. I also like using a dry-erase marker first because there are no second chances when punching a letter. It’s best to use a dry-erase marker first. If you make a mistake erase it. Then, after you double checked the first side, go over the dry-erase marker with a permanent marker. Then do the same to the other side. If you’re sure every letter is correct, punch the holes. There are many plates with sufficient heat resistance, but I like the SEEDPLATE because they are the easiest to destroy if you ever need to. Instead of etching out stamps on washers, you just add extra punches if you must destroy the seed. ### [Alby Hub](https://albyhub.com/) Look, if you want to run your own lightning node, this is the way to go. If you have a Start9 or are technical, you can run it yourself. If you’re less technical, they offer a cloud service. I was one of the early beta testers of this software and I think it’s the easiest way to run a lightning node. ## Free and Open Software ### [Primal.net](https://github.com/PrimalHQ/primal-web-app) os a corporation building stuff on nostr. If you’re technical, you can run it yourself. If not, you ca download the app for free. They charge a fee for premium services. I pay for this because I want to support companies that contribute to nostr development and help bitcoin be used as peer-to-peer electronic cash. I think of Primal as a custodial bitcoin wallet that allows anyone to participate in the biggest circular economy in the world. TikTok was banned in the United States which means it is no longer available for citizens of the United States to download the app. There are ways to get around these restrictions, but I choose not to because I do not want the CCP, or any government to have access to information if their goal is to use it against me. I believe every government, foreign or domestic wants to use your information against you. Nostr allows me to opt out of these stupid games with stupid likes. With Primal, I am the customer, not the product. I choose the algorithms I want to see, not the CCP , USG or corporations. Even if Primal decided to say, “Marc sucks. We will now censor him.” I will only lose the https://primal.net/marc, the OG status, and my primal lightning address. It also means they would stop getting my sats every month, so they are incentivized not to censor. You would have to do something really stupid to get banned from Primal. I’m not sure it’s been done yet, but even if it has, you will not get banned from the nostr protocol. ### [Portainer](https://github.com/portainer/portainer) Portainer makes it easy to run docker-containers. I first learned how to use it because it is an app on Umbrel. Eventually, I learned you can use Portainer on any Linux computer, so that’s what I do. It takes some time to learn, but once you do—you become a cloud computing super-wizard. ### [Mealie](https://github.com/mealie-recipes/mealie/) Mealie is one of my favorite pieces of free and open software that is not related to bitcoin in any shape or form...except it makes grocery shopping easier. I know what you’re thinking. WTF does that have to do with bitcoin? I assume you belong to the *I Want More Bitcoin Club*. You are in good company because ALL Bitcoiners are a member of this club. One way you can stasck more sats is to cut your grocery bill. I believe Mealie helps me do just that. When I’m grocery shopping, my goal is to get as much healthy food for my sats as possible. To accomplish this, I shop sales. Now, if you’re living in a van, this won’t do much for you, but no worries. You will stack even more sats by cutting your housing costs. If your wife will not agree to live under a bridge and stack sats, then get a freezer in your garage. Fill it with meat you buy on sale. Pork shoulder is 3,000 sats per pound and you don’t what to cook it with? Find a recipe online. Mealie will use machine learning to scrape the ingredients from the recipe. Then you can add it to a grocery list. In other words, you can automate your grocery list right at the grocery isle. This is one way I save sats with Mealie. I also keep the things my family eats on a regular basis in stock. This is part for emergency preparedness, but it is also for financial preparedness. If you are in a situation where no food is available, all the bitcoin in the world will not save you. I’m not talkig about super volcanos. Hurricanes, tornadoes, and earthquakes happen. So I got this idea from Jack Spirko, but modified it to use with mealie. Spirko suggests building a 30 day supply of food and water for your family in case of an emergency. You should have a generator and a garden too, but I don’t want to get off track. Once you have this he says: write down every item you use on a notebook and replace it. This is good advice, but I just add it to my grocery list in mealie. #### [Shopstr](https://github.com/shopstr-eng/shopstr) Shopstr is like Facebook marketplace, Amazon, or eBay on nostr. This is what I use to build my store. I want to pause point out how big of a paradigm shift this is. The old web requires permission. Ebay needs permission from the government to become a corporation. They built infrastructure to create their online auction. Everyone on the site must pay eBay a tax. This results in a techno- feudalist society. When you sell on Shopster, you are selling your wares on nostr, a protocol, not a platform. This changes the relationship between the people and the technology because NO MIDDLEMAN IS REQUIRED. On nostr, there are no digital overlords. You own your data. You host your store. If the current digital overlords shut it down, you can run it yourself. You do not need to pay a tax to eBay, Amazon, or the PayPal mafia. #### Avocados I love avocados. They are kind of like free and open source software because you can grow them yourself. ;) I love avocados and **big avocado ag did not pay me to say this**. @ 000002de:c05780a7
2025-01-20 16:27:40I just finished the audio book read by Norm himself. I must say, if you love Norm you will love this book. I highly recommend the audio book. I don't want to spoil anything but the book is like sitting down with Norm and listening to him tell you stories. You never know what is true or false and if the whole thing IS the joke. I laughed out loud many times.  originally posted at https://stacker.news/items/857482
@ 000002de:c05780a7
2025-01-20 16:27:40I just finished the audio book read by Norm himself. I must say, if you love Norm you will love this book. I highly recommend the audio book. I don't want to spoil anything but the book is like sitting down with Norm and listening to him tell you stories. You never know what is true or false and if the whole thing IS the joke. I laughed out loud many times.  originally posted at https://stacker.news/items/857482 @ 652d58ac:dc4cde60
2025-01-20 14:39:11**Introduction** We must rethink how we envision the future. In the short term, things may be worse than we expect, rising inflation, war, and health crises, but this is all part of the fiat dilemma. A system that cannibalizes itself. Yet, at the same time, a new system is emerging. Bitcoin and Artificial intelligence (AI) will be central to this foundation, providing humanity with the time and tools needed to thrive. How Technology Drives Deflation As Jeff Booth so masterfully explains, technology is inherently deflationary. Over time, through free market competition and productivity gains, prices should fall to their marginal cost of production. Yet, in our inflationary fiat system, productivity gains are eroded by the continuous increase in the money supply, driving prices higher. Instead of allowing prices to approach their marginal cost of production as they should, goods and services become more expensive due to monetary inflation. This principle, that an expanding money supply reduces the purchasing power of individual monetary units and ultimately undermines wealth creation, was recognized as early as 1517 by Copernicus in the quantity theory of money. Because bitcoin is limited in supply, productivity gains across the economy can lead to greater wealth for all participants in the system, as the price of goods and services falls to the marginal cost of production over time. Rather than rise due to an increase in the monetary supply. We need Bitcoin to ensure that the productivity gains that drive the economy forward can have a lasting, sustainable impact. **The Interplay of Bitcoin und AI** Since the existing system benefits from inflation, market participants are often manipulated into believing that AI is inherently dangerous. While there are significant risks associated with AI, particularly its potential for centralization and manipulation, the technology itself offers great opportunities. The real problem lies in the inflationary monetary system, not AI. Artificial intelligence is set to increasingly shape the workplace, trade, and finance. Consider the “Magnificent Seven”, a group of tech giants, Apple, Microsoft, Amazon, Alphabet (Google), Meta (Facebook), Nvidia, and Tesla, that all leverage AI as a key driver of productivity. In 2023, the financial services industry alone invested an estimated $35 billion in AI, with banking leading the charge, accounting for approximately $21 billion. This is particularly relevant to Bitcoin, since it serves as both money and a financial system. As AI becomes more sophisticated, it will increasingly rely on a digital currency that aligns with its digital nature, such as bitcoin, which offers both scalability and speed through the Lightning Network. For instance, AI systems could use Bitcoin to facilitate microtransactions in real time, managing their wallets autonomously to process payments for services or data. This would unlock new opportunities for AI applications in sectors like actual decentralized finance (DeFi) and machine-to-machine transactions. The Lightning Network, as a second-layer protocol built on top of Bitcoin, enables transactions to be settled almost instantly and at low cost. This makes it particularly well-suited for AI applications that require fast and reliable transactions. While some AI and language models can exhibit programmed biases, AI systems, driven by algorithms and data, should strive to prioritize efficiency, minimizing biases wherever possible. If programmed without bias, AI seeks the best tools for operations and decision-making, and Bitcoin offers an optimal solution, providing both the asset and infrastructure needed for efficient, resilient, digital financial systems. In addition, AI is likely to also contribute to Bitcoin’s development, with algorithms optimizing mining efficiency, hardware usage, forecasting energy demand, and ensuring more efficient resource allocation, all of which will lead to more effective mining strategies. **Conclusion** The synergy between Bitcoin and AI has the potential to enable the creation of more efficient, intelligent and resilient systems. These developments will underpin bitcoin’s role as digital money in a digital world, potentially creating positive second-order effects on global financial markets. The impact will be especially profound in industries such as finance, insurance, robotics, lending, investments, architecture, housing, healthcare, logistics, and others, with effects accelerating over time. The free market is inherently deflationary, because of productivity gains, things, like housing, should become cheaper over time. Yet, this doesn't happen. Inflationary fiat currencies, like the dollar, lose purchasing power as their supply increases, eroding those gains. Bitcoin offers a framework in which productivity gains can have a lasting, sustainable impact. Bitcoin, as a disinflationary currency with a fixed supply, preserves the value of productivity improvements, allowing prices to fall to their marginal cost of production. This ensures that efficiency gains lead to greater wealth for all participants in the system. Moreover, since Bitcoin is accessible, it allows wealth to become more attainable for a wider range of people, enabling general living standards to increase more easily. The interplay between Bitcoin and AI is pretty exciting, and it’s becoming clear that the widespread adoption of AI will drive the widespread adoption of Bitcoin. This is necessary, as only Bitcoin, as a counterbalance to the self-destructive fiat system, can protect humanity from the negative effects of inflation. With the accelerated productivity gains of the AI age, Bitcoin becomes even more crucial as a solution, ensuring that these gains can be preserved and shared more equitably. **Originally published as the 28th edition of my n ewsletter, Bitcoin & AI:** https://leonwankum.substack.com/p/bitcoin-and-ai **Photo Credit**: commonedge.org (An Optimist’s Take on AI and the Future of Architecture)
@ 652d58ac:dc4cde60
2025-01-20 14:39:11**Introduction** We must rethink how we envision the future. In the short term, things may be worse than we expect, rising inflation, war, and health crises, but this is all part of the fiat dilemma. A system that cannibalizes itself. Yet, at the same time, a new system is emerging. Bitcoin and Artificial intelligence (AI) will be central to this foundation, providing humanity with the time and tools needed to thrive. How Technology Drives Deflation As Jeff Booth so masterfully explains, technology is inherently deflationary. Over time, through free market competition and productivity gains, prices should fall to their marginal cost of production. Yet, in our inflationary fiat system, productivity gains are eroded by the continuous increase in the money supply, driving prices higher. Instead of allowing prices to approach their marginal cost of production as they should, goods and services become more expensive due to monetary inflation. This principle, that an expanding money supply reduces the purchasing power of individual monetary units and ultimately undermines wealth creation, was recognized as early as 1517 by Copernicus in the quantity theory of money. Because bitcoin is limited in supply, productivity gains across the economy can lead to greater wealth for all participants in the system, as the price of goods and services falls to the marginal cost of production over time. Rather than rise due to an increase in the monetary supply. We need Bitcoin to ensure that the productivity gains that drive the economy forward can have a lasting, sustainable impact. **The Interplay of Bitcoin und AI** Since the existing system benefits from inflation, market participants are often manipulated into believing that AI is inherently dangerous. While there are significant risks associated with AI, particularly its potential for centralization and manipulation, the technology itself offers great opportunities. The real problem lies in the inflationary monetary system, not AI. Artificial intelligence is set to increasingly shape the workplace, trade, and finance. Consider the “Magnificent Seven”, a group of tech giants, Apple, Microsoft, Amazon, Alphabet (Google), Meta (Facebook), Nvidia, and Tesla, that all leverage AI as a key driver of productivity. In 2023, the financial services industry alone invested an estimated $35 billion in AI, with banking leading the charge, accounting for approximately $21 billion. This is particularly relevant to Bitcoin, since it serves as both money and a financial system. As AI becomes more sophisticated, it will increasingly rely on a digital currency that aligns with its digital nature, such as bitcoin, which offers both scalability and speed through the Lightning Network. For instance, AI systems could use Bitcoin to facilitate microtransactions in real time, managing their wallets autonomously to process payments for services or data. This would unlock new opportunities for AI applications in sectors like actual decentralized finance (DeFi) and machine-to-machine transactions. The Lightning Network, as a second-layer protocol built on top of Bitcoin, enables transactions to be settled almost instantly and at low cost. This makes it particularly well-suited for AI applications that require fast and reliable transactions. While some AI and language models can exhibit programmed biases, AI systems, driven by algorithms and data, should strive to prioritize efficiency, minimizing biases wherever possible. If programmed without bias, AI seeks the best tools for operations and decision-making, and Bitcoin offers an optimal solution, providing both the asset and infrastructure needed for efficient, resilient, digital financial systems. In addition, AI is likely to also contribute to Bitcoin’s development, with algorithms optimizing mining efficiency, hardware usage, forecasting energy demand, and ensuring more efficient resource allocation, all of which will lead to more effective mining strategies. **Conclusion** The synergy between Bitcoin and AI has the potential to enable the creation of more efficient, intelligent and resilient systems. These developments will underpin bitcoin’s role as digital money in a digital world, potentially creating positive second-order effects on global financial markets. The impact will be especially profound in industries such as finance, insurance, robotics, lending, investments, architecture, housing, healthcare, logistics, and others, with effects accelerating over time. The free market is inherently deflationary, because of productivity gains, things, like housing, should become cheaper over time. Yet, this doesn't happen. Inflationary fiat currencies, like the dollar, lose purchasing power as their supply increases, eroding those gains. Bitcoin offers a framework in which productivity gains can have a lasting, sustainable impact. Bitcoin, as a disinflationary currency with a fixed supply, preserves the value of productivity improvements, allowing prices to fall to their marginal cost of production. This ensures that efficiency gains lead to greater wealth for all participants in the system. Moreover, since Bitcoin is accessible, it allows wealth to become more attainable for a wider range of people, enabling general living standards to increase more easily. The interplay between Bitcoin and AI is pretty exciting, and it’s becoming clear that the widespread adoption of AI will drive the widespread adoption of Bitcoin. This is necessary, as only Bitcoin, as a counterbalance to the self-destructive fiat system, can protect humanity from the negative effects of inflation. With the accelerated productivity gains of the AI age, Bitcoin becomes even more crucial as a solution, ensuring that these gains can be preserved and shared more equitably. **Originally published as the 28th edition of my n ewsletter, Bitcoin & AI:** https://leonwankum.substack.com/p/bitcoin-and-ai **Photo Credit**: commonedge.org (An Optimist’s Take on AI and the Future of Architecture) @ 011c780a:46e48b1d
2025-01-20 13:03:23Lake Erie is a paradise for anglers, boasting the world's largest walleye population and some of the highest catch rates in Ohio. For those eager to experience the thrill of fishing on these bountiful waters, booking a charter is the best way to go. However, with numerous options available, how do you choose the right one? Here are some essential tips to help you find the perfect charter for your Lake Erie adventure. ## 1. Look for Experienced Captains and Crews The expertise of the captain and crew can make or break your fishing trip. Experienced professionals know the best spots to find walleye, how to handle changing weather conditions, and how to ensure you have an enjoyable day on the water. ● Check the company's website for captain biographies or years of experience. ● Look for certifications or affiliations with reputable fishing organisations. ● Read reviews to see if other anglers had positive experiences with the crew. ## 2. Prioritize Safety Measures Safety should be a top priority when choosing an **[Ohio fishing charter company](https://eyesready.com/)**. Lake Erie can be unpredictable, so you need a charter that prioritises your well-being. ● Ensure the boat is equipped with life jackets, first aid kits, and emergency communication devices. ● Confirm that the captain holds a valid U.S. Coast Guard license. ● Ask about the company's safety protocols in case of adverse weather. ## 3. Assess the Equipment and Boats ● A well-maintained boat and quality fishing gear can elevate your experience. ● Look for charters that provide high-quality rods, reels, and tackle. ● Check if the boat is spacious, clean, and equipped with modern technology like fish finders. ● Ask if the company allows you to bring your gear if you have a preference. ## 4. Check for Customization Options Every angler has unique needs, whether they're a seasoned pro or a first-timer. Some charters offer tailored experiences to meet your preferences. ● Look for family-friendly charters if you're planning a trip with kids. ● Ask if the company offers half-day, full-day, or multi-day trips. ● Find out if they're willing to adjust their itinerary to focus on specific fishing techniques or areas. ## 5. Read Online Reviews and Testimonials ● The best way to gauge the quality of a charter is through the experiences of others. ● Visit online platforms like Google, Facebook, or TripAdvisor for honest reviews. ● Pay attention to consistent themes in feedback, such as exceptional service, skilled crew, or successful catches. ● Look for photos or videos shared by previous clients to get a better sense of what to expect. ## 6. Consider the Costs and Inclusions ● While price shouldn't be the sole factor, it's important to know what you're paying for. ● Compare prices among different [Lake Erie walleye charters](https://eyesready.com/walleye/) to get a sense of market rates. ● Check what the package includes, such as bait, fishing licenses, or cleaning and packaging your catch. ● Avoid the cheapest options if they seem to cut corners on quality or safety. ## 7. Verify Their Knowledge of Lake Erie ● Ohio's portion of Lake Erie is home to millions of walleye, and the best charters have in-depth knowledge of these waters. ● Ask about their familiarity with local hotspots for walleye. ● Find out if they follow sustainable fishing practices to preserve the lake's ecosystem. ● A knowledgeable crew can also share interesting facts about the lake, making your trip both fun and educational. ### Book Your Perfect Charter Today! Finding the right Ohio fishing charter company is the first step to an unforgettable Lake Erie adventure. By prioritising experience, safety, equipment quality, and customer reviews, you can ensure a successful and enjoyable trip. For those looking to create lasting memories on Lake Erie, Eyes Ready Charters is a trusted name offering top-notch services to anglers of all skill levels. Book your trip today and experience the thrill of walleye fishing like never before!
@ 011c780a:46e48b1d
2025-01-20 13:03:23Lake Erie is a paradise for anglers, boasting the world's largest walleye population and some of the highest catch rates in Ohio. For those eager to experience the thrill of fishing on these bountiful waters, booking a charter is the best way to go. However, with numerous options available, how do you choose the right one? Here are some essential tips to help you find the perfect charter for your Lake Erie adventure. ## 1. Look for Experienced Captains and Crews The expertise of the captain and crew can make or break your fishing trip. Experienced professionals know the best spots to find walleye, how to handle changing weather conditions, and how to ensure you have an enjoyable day on the water. ● Check the company's website for captain biographies or years of experience. ● Look for certifications or affiliations with reputable fishing organisations. ● Read reviews to see if other anglers had positive experiences with the crew. ## 2. Prioritize Safety Measures Safety should be a top priority when choosing an **[Ohio fishing charter company](https://eyesready.com/)**. Lake Erie can be unpredictable, so you need a charter that prioritises your well-being. ● Ensure the boat is equipped with life jackets, first aid kits, and emergency communication devices. ● Confirm that the captain holds a valid U.S. Coast Guard license. ● Ask about the company's safety protocols in case of adverse weather. ## 3. Assess the Equipment and Boats ● A well-maintained boat and quality fishing gear can elevate your experience. ● Look for charters that provide high-quality rods, reels, and tackle. ● Check if the boat is spacious, clean, and equipped with modern technology like fish finders. ● Ask if the company allows you to bring your gear if you have a preference. ## 4. Check for Customization Options Every angler has unique needs, whether they're a seasoned pro or a first-timer. Some charters offer tailored experiences to meet your preferences. ● Look for family-friendly charters if you're planning a trip with kids. ● Ask if the company offers half-day, full-day, or multi-day trips. ● Find out if they're willing to adjust their itinerary to focus on specific fishing techniques or areas. ## 5. Read Online Reviews and Testimonials ● The best way to gauge the quality of a charter is through the experiences of others. ● Visit online platforms like Google, Facebook, or TripAdvisor for honest reviews. ● Pay attention to consistent themes in feedback, such as exceptional service, skilled crew, or successful catches. ● Look for photos or videos shared by previous clients to get a better sense of what to expect. ## 6. Consider the Costs and Inclusions ● While price shouldn't be the sole factor, it's important to know what you're paying for. ● Compare prices among different [Lake Erie walleye charters](https://eyesready.com/walleye/) to get a sense of market rates. ● Check what the package includes, such as bait, fishing licenses, or cleaning and packaging your catch. ● Avoid the cheapest options if they seem to cut corners on quality or safety. ## 7. Verify Their Knowledge of Lake Erie ● Ohio's portion of Lake Erie is home to millions of walleye, and the best charters have in-depth knowledge of these waters. ● Ask about their familiarity with local hotspots for walleye. ● Find out if they follow sustainable fishing practices to preserve the lake's ecosystem. ● A knowledgeable crew can also share interesting facts about the lake, making your trip both fun and educational. ### Book Your Perfect Charter Today! Finding the right Ohio fishing charter company is the first step to an unforgettable Lake Erie adventure. By prioritising experience, safety, equipment quality, and customer reviews, you can ensure a successful and enjoyable trip. For those looking to create lasting memories on Lake Erie, Eyes Ready Charters is a trusted name offering top-notch services to anglers of all skill levels. Book your trip today and experience the thrill of walleye fishing like never before! @ dffd3ffc:5ade7be1
2025-01-04 12:58:17# Nostr 利用開始から 1 年を迎えて ## はじめに みなさんこんにちは。おっぱぴぃです。 [ハッカーのおもちゃとしての Nostr のススメ](https://qiita.com/gpsnmeajp/items/2f95d4adf188276146d8) と [Nostr の面白さをエンジニア目線で解説してみる](https://zenn.dev/mattn/articles/cf43423178d65c)をみて Nostr にはじめて投稿をしたのが 2024/01/04 09:04:18 でした。 nostr:nevent1qqsd5v80f9zazxd4kq2r2dls5znd40ht6c7cj4slt6wtlv483vkmxdcjvq66c Nostr で私が 1 年間をどう過ごしてきたか、振り返ってみようと思います。 ## 初投稿日  今見たら 10 リポスト、20 そこそこのリアクションをいただいてたんですね。初投稿というだけでこんなおバズリあそばすことあるんだって思いました。~~みんな年始で暇やったんかな~~ これだけリアクションがあって、フォローもしていただいたおかげで Nostr の印象がよくなったこと、日本人話者にすぐたどり着けてことが Nostr を続けられている要因になっていると思います。あとはエアリプ文化が懐かしい&近すぎず遠すぎずで居心地がよくて沼ったところがあると思います。 その日は[Nostr の Scrapbox(現 Cosense)](https://scrapbox.io/nostr/)をその日中にざっと読み漁って、記事の誤字修正したり、WoS を設定してみたり、Lightning Address を設定したりしていたようです。 nostr:nevent1qqsxml4ak7g3u8gjcyuhy89sd8vlk3fu6we9ecgey69jltd42dr0etcvt0l3w ~~おまえ、このころから大欲情を…~~ ## のす会でのオン会(?) Nostr 日本人ユーザーの集まる Discord サーバとして、「のす会」というものがあります。 過去ログを漁ってるとどうやら 2024/01/15 ごろにボイチャに入りはじめ、 nostr:nevent1qqszm0kv7aulxnmxr2fdxg5cvme7nyv3j6rgfa30cat8cs3npnsep9caz0xyc その翌日にはのす会にて Geo guesser で遊んだりしていたようです。こじらさんが尋常じゃない強さでどういう事なの…となった覚えがあります。 nostr:nevent1qqs9knrf4ww8g0fsu4l74gxeeh3s9pwpnf47xn8pf5u8pplkz4yatjg03ufd5 こうした経験を経て、徐々に Nostr ユーザーの方と直接会話することのハードルが下がってきた所でした。 ## 初のオフ会参加 2 月頭、TL で話題になっていた火鍋を食べた経験がないなぁ…ということで、2024/02/10、[ゴリラ.vim#30~四谷ラボコラボ~](https://gorillavim.connpass.com/event/307622/)の参加と併せて、海底撈火鍋でオフ会を開催したのが Nostr における初めてのオフ会参加&幹事でした。 この日は中国の春節初日だったのもあって異様に店舗が混んでおり、18:00 に予約したのに一行に案内されず、 nostr:nevent1qqspcttj4gv2ey7vkt0wp2nehqfwxjnp55vm4agnwu9kullep88ysccpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsyg87v060ssxrpew6a0vrhkcy36hqppvrwjmlqnrgqrrvf8fghgg0pypsgqqqqqqs07ajzp 顔面が痙攣したり、 nostr:nevent1qqs9d5vycslspatsnx6u5qqqwpfmdt33w2v7xkytljzsfwv56acs79czyr0l60lu824k9yc63jcg7z32fzx6w3cr6zx3mmuns69wxr66mea7zp6f7wn 詫び菓子を貰ったり、 nostr:nevent1qqs8a0u47alv9vexd5r5s5vygs77ecadm6dl9vlky32hjywdx8f3gtczyr0l60lu824k9yc63jcg7z32fzx6w3cr6zx3mmuns69wxr66mea7zgjxmhl 病院待合室みたいな場所で検尿コップで水飲んだりと nostr:nevent1qqsq44zs04g5zng35ks6jrvrv6uel2f9ls26d7nsc6svuggrlfnvtcgzyp4kuxwwg7530jlp8fn7adq982dnq8ncajv3gyl824y4xzyw6cknkvj37gy トラウマになりそうなオフ会でした。当時の様子は[nosli でまとめています](https://nostter.app/naddr1qqfkummnd35j6vfhxqmn2dejxuurqvpjxcpzphla8l7r42mzjvdgevy0pg4y3rd8gupaprgaa7fcdzhrpaddu7lpqvzqqqr4gu92anwm)。 今振り返ってもくちゃくちゃの体験してるなと思いますが、 ~~クレーターを作りそうな青ウサギがいたものの~~ nostr:nevent1qqsrs8y3phadhcukwjlkjkgdcs43ndkc8a42m88zayfj6p2lex6a6tgpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygrtdcvuu3afzl97zwn8a66q2w5mxq083myezsf7w42f2vyga43d8vpsgqqqqqqsyfx7da 誰も怒らないし宴会自体は楽しかったので、Nostr のオフ会の原体験としては良かったな、と感じています。ひどい思い出ほど振り返ったら美化されるやつかもしれない。 ## 各種イベント参加 Nostr には[四谷ラボ](https://428lab.net/)参加者の方が沢山いらっしゃったこと、お声かけいただいた縁などもあり、いろいろなイベントにスタッフとして参加する経験ができました。例えば… - [Bluesky Meetup in Tokyo Vol.2](https://428lab.connpass.com/event/312335/) - [技術書典 16](https://techbookfest.org/event/tbf16) ⇒ 関わらせていただいた[のぶこ本](https://books.428lab.net/book/003/) - [Nostrasia2024](https://nostrasia.com/) など。 微力ながら、自らの役割に合わせてイベントに貢献させていただけて、とても楽しめました。 自分に自信がなく、私生活では責任が発生する立場を回避しがちであったこともあって、自分としてはこれらのイベント参加はとても貴重な経験になりました。 関係されている方々が思い思いの仕事のやりようでイベントに取り組んでいる様が刺激になったなと思います。 ## オフ会履歴 私を Nostr でフォローいただいている方であれば、「こいつ、やたらオフ会行ってないか…?」と思われるでしょう。ということで、自分でも一度整理をしてみました。  **うわっ...私のオフ会参加、多すぎ…?** ~~1 年間は52週しかないねんぞ~~ このように、火鍋のオフ会を皮切りに、相当な数のオフ会に参加させていただきました。オフ会というかもう普通に Nostr で知り合っただけの友人との集まりみたいな感覚になっているかも。 ちなみに、人単位でお会いした回数もまとめています。  ※:Nostrasia などのイベントでお会いした回数は除いています。 こうみるとしおと神(かすてらふぃさん)と会った回数めちゃくちゃ多いですね。28,26回だとほぼ2週に1回ペースですが、過去どんなに親しい友人でもこんな頻度で会ってたことないかも。 ## 思い出深かった出来事 nostr:nevent1qqsyeyycax9qgrr4qvtty4h62x96vc6lydh8yg7jl5er99zg7wlpdrcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygxll5llcw4tv2f34r9s3u9z5jyd5ars85ydrhhe8p52uv844hnmuypsgqqqqqqskevt6r nostr:nevent1qqs0sqhtzc4p3vysz5k7l29x2lcnedeys55t7mqp2mz7ugrmw0v725cppemhxue69uhkummn9ekx7mp0qgsdllfllsa2kc5nr2xtprc29fygmf68q0gg6800jwrg4cc0tt08hcgrqsqqqqqpaua8e8 この誤字投稿を経て、私の(たまにほかの人も)誤字は大欲情と呼ばれるようになりました。~~毎回思うけど新しく入ってきた人は何だこれってなるよなこれ~~ その後も酔ってる時を中心に結構誤字をやらかすので、[那月さんによるまとめが作られています](https://nosli.vercel.app/li/naddr1qqfkummnd35j6vfhxgurgdpk8q6nzd3exypzpq4np5cygstsu65vsx0ggphrv23kj4z553sh39xwyur08pqvdsqrqvzqqqr4gupk0ng5)。 名前としては不名誉かもしれませんが、面白いのでOKです。 ## おわりに 振り返ってみれば Nostr 日本人ユーザーコミュニティの心地良さに浸った 1 年だったと思います。 Nostr の仕組み自体も好きですが、私はコミュニティの方に目が行っている気がします。 Nostr 歴 1 歳になったので、今後は私が Nostr を使う人々に心地良いと思ってもらえるような人になれるとよいなと思います。 これからもよろしくお願いします。
@ dffd3ffc:5ade7be1
2025-01-04 12:58:17# Nostr 利用開始から 1 年を迎えて ## はじめに みなさんこんにちは。おっぱぴぃです。 [ハッカーのおもちゃとしての Nostr のススメ](https://qiita.com/gpsnmeajp/items/2f95d4adf188276146d8) と [Nostr の面白さをエンジニア目線で解説してみる](https://zenn.dev/mattn/articles/cf43423178d65c)をみて Nostr にはじめて投稿をしたのが 2024/01/04 09:04:18 でした。 nostr:nevent1qqsd5v80f9zazxd4kq2r2dls5znd40ht6c7cj4slt6wtlv483vkmxdcjvq66c Nostr で私が 1 年間をどう過ごしてきたか、振り返ってみようと思います。 ## 初投稿日  今見たら 10 リポスト、20 そこそこのリアクションをいただいてたんですね。初投稿というだけでこんなおバズリあそばすことあるんだって思いました。~~みんな年始で暇やったんかな~~ これだけリアクションがあって、フォローもしていただいたおかげで Nostr の印象がよくなったこと、日本人話者にすぐたどり着けてことが Nostr を続けられている要因になっていると思います。あとはエアリプ文化が懐かしい&近すぎず遠すぎずで居心地がよくて沼ったところがあると思います。 その日は[Nostr の Scrapbox(現 Cosense)](https://scrapbox.io/nostr/)をその日中にざっと読み漁って、記事の誤字修正したり、WoS を設定してみたり、Lightning Address を設定したりしていたようです。 nostr:nevent1qqsxml4ak7g3u8gjcyuhy89sd8vlk3fu6we9ecgey69jltd42dr0etcvt0l3w ~~おまえ、このころから大欲情を…~~ ## のす会でのオン会(?) Nostr 日本人ユーザーの集まる Discord サーバとして、「のす会」というものがあります。 過去ログを漁ってるとどうやら 2024/01/15 ごろにボイチャに入りはじめ、 nostr:nevent1qqszm0kv7aulxnmxr2fdxg5cvme7nyv3j6rgfa30cat8cs3npnsep9caz0xyc その翌日にはのす会にて Geo guesser で遊んだりしていたようです。こじらさんが尋常じゃない強さでどういう事なの…となった覚えがあります。 nostr:nevent1qqs9knrf4ww8g0fsu4l74gxeeh3s9pwpnf47xn8pf5u8pplkz4yatjg03ufd5 こうした経験を経て、徐々に Nostr ユーザーの方と直接会話することのハードルが下がってきた所でした。 ## 初のオフ会参加 2 月頭、TL で話題になっていた火鍋を食べた経験がないなぁ…ということで、2024/02/10、[ゴリラ.vim#30~四谷ラボコラボ~](https://gorillavim.connpass.com/event/307622/)の参加と併せて、海底撈火鍋でオフ会を開催したのが Nostr における初めてのオフ会参加&幹事でした。 この日は中国の春節初日だったのもあって異様に店舗が混んでおり、18:00 に予約したのに一行に案内されず、 nostr:nevent1qqspcttj4gv2ey7vkt0wp2nehqfwxjnp55vm4agnwu9kullep88ysccpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsyg87v060ssxrpew6a0vrhkcy36hqppvrwjmlqnrgqrrvf8fghgg0pypsgqqqqqqs07ajzp 顔面が痙攣したり、 nostr:nevent1qqs9d5vycslspatsnx6u5qqqwpfmdt33w2v7xkytljzsfwv56acs79czyr0l60lu824k9yc63jcg7z32fzx6w3cr6zx3mmuns69wxr66mea7zp6f7wn 詫び菓子を貰ったり、 nostr:nevent1qqs8a0u47alv9vexd5r5s5vygs77ecadm6dl9vlky32hjywdx8f3gtczyr0l60lu824k9yc63jcg7z32fzx6w3cr6zx3mmuns69wxr66mea7zgjxmhl 病院待合室みたいな場所で検尿コップで水飲んだりと nostr:nevent1qqsq44zs04g5zng35ks6jrvrv6uel2f9ls26d7nsc6svuggrlfnvtcgzyp4kuxwwg7530jlp8fn7adq982dnq8ncajv3gyl824y4xzyw6cknkvj37gy トラウマになりそうなオフ会でした。当時の様子は[nosli でまとめています](https://nostter.app/naddr1qqfkummnd35j6vfhxqmn2dejxuurqvpjxcpzphla8l7r42mzjvdgevy0pg4y3rd8gupaprgaa7fcdzhrpaddu7lpqvzqqqr4gu92anwm)。 今振り返ってもくちゃくちゃの体験してるなと思いますが、 ~~クレーターを作りそうな青ウサギがいたものの~~ nostr:nevent1qqsrs8y3phadhcukwjlkjkgdcs43ndkc8a42m88zayfj6p2lex6a6tgpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygrtdcvuu3afzl97zwn8a66q2w5mxq083myezsf7w42f2vyga43d8vpsgqqqqqqsyfx7da 誰も怒らないし宴会自体は楽しかったので、Nostr のオフ会の原体験としては良かったな、と感じています。ひどい思い出ほど振り返ったら美化されるやつかもしれない。 ## 各種イベント参加 Nostr には[四谷ラボ](https://428lab.net/)参加者の方が沢山いらっしゃったこと、お声かけいただいた縁などもあり、いろいろなイベントにスタッフとして参加する経験ができました。例えば… - [Bluesky Meetup in Tokyo Vol.2](https://428lab.connpass.com/event/312335/) - [技術書典 16](https://techbookfest.org/event/tbf16) ⇒ 関わらせていただいた[のぶこ本](https://books.428lab.net/book/003/) - [Nostrasia2024](https://nostrasia.com/) など。 微力ながら、自らの役割に合わせてイベントに貢献させていただけて、とても楽しめました。 自分に自信がなく、私生活では責任が発生する立場を回避しがちであったこともあって、自分としてはこれらのイベント参加はとても貴重な経験になりました。 関係されている方々が思い思いの仕事のやりようでイベントに取り組んでいる様が刺激になったなと思います。 ## オフ会履歴 私を Nostr でフォローいただいている方であれば、「こいつ、やたらオフ会行ってないか…?」と思われるでしょう。ということで、自分でも一度整理をしてみました。  **うわっ...私のオフ会参加、多すぎ…?** ~~1 年間は52週しかないねんぞ~~ このように、火鍋のオフ会を皮切りに、相当な数のオフ会に参加させていただきました。オフ会というかもう普通に Nostr で知り合っただけの友人との集まりみたいな感覚になっているかも。 ちなみに、人単位でお会いした回数もまとめています。  ※:Nostrasia などのイベントでお会いした回数は除いています。 こうみるとしおと神(かすてらふぃさん)と会った回数めちゃくちゃ多いですね。28,26回だとほぼ2週に1回ペースですが、過去どんなに親しい友人でもこんな頻度で会ってたことないかも。 ## 思い出深かった出来事 nostr:nevent1qqsyeyycax9qgrr4qvtty4h62x96vc6lydh8yg7jl5er99zg7wlpdrcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygxll5llcw4tv2f34r9s3u9z5jyd5ars85ydrhhe8p52uv844hnmuypsgqqqqqqskevt6r nostr:nevent1qqs0sqhtzc4p3vysz5k7l29x2lcnedeys55t7mqp2mz7ugrmw0v725cppemhxue69uhkummn9ekx7mp0qgsdllfllsa2kc5nr2xtprc29fygmf68q0gg6800jwrg4cc0tt08hcgrqsqqqqqpaua8e8 この誤字投稿を経て、私の(たまにほかの人も)誤字は大欲情と呼ばれるようになりました。~~毎回思うけど新しく入ってきた人は何だこれってなるよなこれ~~ その後も酔ってる時を中心に結構誤字をやらかすので、[那月さんによるまとめが作られています](https://nosli.vercel.app/li/naddr1qqfkummnd35j6vfhxgurgdpk8q6nzd3exypzpq4np5cygstsu65vsx0ggphrv23kj4z553sh39xwyur08pqvdsqrqvzqqqr4gupk0ng5)。 名前としては不名誉かもしれませんが、面白いのでOKです。 ## おわりに 振り返ってみれば Nostr 日本人ユーザーコミュニティの心地良さに浸った 1 年だったと思います。 Nostr の仕組み自体も好きですが、私はコミュニティの方に目が行っている気がします。 Nostr 歴 1 歳になったので、今後は私が Nostr を使う人々に心地良いと思ってもらえるような人になれるとよいなと思います。 これからもよろしくお願いします。 @ df478568:2a951e67
2025-01-20 05:23:36I took this picture at about block [416,220](https://mempool.marc26z.com/block/000000000000000003b64da342d6d24d066ea5c961e21fdf57cae4318eab3616)(June 13, 2016). The price of eggs on that day was $1.99, 16.5¢ per egg if you still measure stuff with the broken ruler we call fiat. What if we measured the price in sats instead? I found the price on that date from the bitbo calender. According to this website, $1.99 was worth 260,000 sats back then. Each egg cost 21,667 sats! Oh My Zeus!😱  I used this [mempool calculator](https://mempool.marc26z.com/tools/calculator) to see how much that is today. Turns out that it's $272.88 as of block 879,943. Since the fiat ruler is broken, the price of a dozen eggs also has NGU. I took this picture the last time I went to the grocery store. Eggs cost enough to shock fiat maxis. $8.99 OMZ!😱 What does a dozen eggs cost if you ignore the broken ruler? 8,572 sats today, just 714 sats per egg. Holy [Wiemar Republic](https://en.m.wikipedia.org/wiki/Weimar_Republic) Batman! That's 30X cheaper! 😁 For some strange reason I can't pretend to understand, the [Federal reserve tracks the price of eggs denominated in bitcoin](https://fredblog.stlouisfed.org/2022/06/buying-eggs-with-bitcoins/). I guess they want to stay humble and stack money printer go brrrrrr. You can see the price of eggs drop off a cliff like Wile E Coyote on their website.  In The Price of Tommorrow and too many podcasts to mention, Jeff Booth argues the free market makes things cheaper over time, but the fiat syatem is syatematic theft. This theft occurs via inflation, which is really wage deflation. In other words, eggs are getting cheaper over time because egg producers become more efficient. We see tye fruits of this efficiency in Big screen TV's because the fiat price gets cut in half every ten years or so, but this is also a product of a broken ruler. The TV is probably 60X cheaper in bitcoin terms. It makes sense, TV's don't get bird flu, but when you begin using bitcoin as your unit of account, the measurement of value makes more sense than fiat clown world on the broken ruler standard. I remember when coffee was 100,000 sats. Now it's 16,699 sats. Living on the sat standards allows you to see Jeff Booth's thesis play out in real time  ## Life Gets More Expensive On The Broken Ruler Standard I see so many young people on the broken ruler standard bemoan about food and housing prices. There are people with master's degrees who have already lost hope of buying a single family home and achieving the "American dream." To be honest, I would be pretty bummed about it too if I was on the broken ruler standard. A few months ago I spoke with a woman who made at least twice as much fiat as I do say, "I hope this housing market crashes so I can buy a house!" That's sad. I have a lot of empathy for that feeling. Since the great financial crisis, I've only been able to get part time work, but my family wqs able to get a mortgage worth 12.5 bitcoin at the so-called "height of the market." We put as little money down as possible, 3% and I sold my old 401k for that "money." I also used some of it for repairs and taxes, but went all-in on bitcoin with everything else. Now our house is worth about 5 bitcoin. The way I see it, real estate is always crashing. People on the broken ruler standard cry, "Wah, Wah. I hope there's a housing crash! Wah! Wah! Muh egg prices!" Buy a brand spanking new car for $50,00 car with a 7% interest rate and they will say, "Congratulations!" The trouble is, the price of the car falls like eggs compared to bitcoin on the broken ruler standard. This is because prices are distorted when measured in a broken ruler standard. ### Get Off The Broken Ruler Standard  Before I met my wife, I played poker to supplement my income. I don't play much anymore, but poker taught me about risk management, probability, game theory, and many other things applicable to bitcoin. Poker gave me the background knowledge I needed to study bitcoin. [In a sly, round-about way](https://youtu.be/nswOYo0zUcI?si=iVjy6e-npEAo9lkH) , poker taught me how to spend less bitcoin than I make. In traditional technical finance terminology, this is called "fucking saving." If you were not taught how to save and spend more than you earn, no matter how many broken ruler bucks you may earn, bitcoin will not work for you. My wife makes a lot of broken ruler bucks. **Unfortunately, we were broke in 2016 because we both were in school**. Nevertheless, I'm proud of my stack amd I'm now at a point in life where I can get paid in bitcoin with very little risk because of my sugar mama, I mean wife, gets paid very well. I spend like almost every other American consumer, plastic broken ruler debt cards. I put my little Strike ACH number on the Discover app. I keep a couple million sats on Strike and pay my credit card every month. In other words, I use Strike like a four-letter word: bank. Sometimes I'll get a craving for tacos., I've never found a food truck that takes bitcoin, but they often use the Cash App. People on the broken ruler standard can't instantaneously send broken ruler bucks from PayPal to Zelle and vice-versa. They must first send broken ruler bucks from PayPal to the bank and then send the broken ruler bucks through Zelle. I can send sats directly from Strike to thr Cash App within seconds. #### Sats As A Unit Of Account  The price of bitcoin fluctuates which makes it difficult to use as a unit of account. Who wants to divide the price of bitcoin by 100 million. Ain't nobody got time for that. If a whole coin costs 100k, then 1,000 sats = $1.00. This means each 100 sats is worth 10¢. 10 sats = 1¢. If the price drops 50%, 1000 sats is 50¢. If it does a 10X, $1,000 sats is $10.00. Living on a sat standard requires a little math, but it's easy to estimate. For more precise calculations I use mem pools calculator. Money is a store of value, medium of exchange, and unit of account. If you use bitcoin on all three ways, you are using bitcoin as money. Saving becomes spending less bitcoin, not "buying more bitcoin." If you stack sats, your goal should be to leave the broken ruler standard and adopt sats as the standard. The world will still price your sats with a broken ruler. Sometimes this broken ruler makes you look like a fool. Other times, the broken ruler makes you look like a genius. Therefore, you must stay humble and stack sats. You'll need some savings before you can deal with the broken ruler fallacy, but once you consistently stack sats and NGU continues to U, you'll eventually see life gets easier when you make sats the standard. I will sell some sats to pay for my food and I send a tip to the food trucker in bitcoin using the Cash App gift button. It is actually very easy for them to accept bitcoin. They just don't know it yet. I don't proselytize the gospel of our lord and savior Satoshi Nakamoto. I just send them a few thousand sats. Good orange pilling is like good writing: **Show, don't tell**. ##### Does it require KYC? Yeah, but so does Bank of Broken Rulers. ##### Haven't you heard the phrase, **not your keys, not your bitcoin?** Yes. It's true. The 2 million sats or so is "not my bitcoin." From my perspective, however, it is the least risky way of paying my bills. I believe it is less risky than keeping broken ruler bucks in a bank. FDIC insurance sounds nice as canceled Insurance policies in the Pacific Palisades. I could keep my 2 million sats in self-custody in my own lightning wallet. I could use [Zap Planner](https://zapplanner.albylabs.com/) to schedule my payments to hit Strike moments before I pay my bill, but I know me. I've lost sats on the lightning network before. I am more likely to lose the sats on my self-custodial lightning wallet than lose them because Strike could possibly rug-pull me. So for now, I just keep 2 million sats on the app. If bitcoin does a 10X, I'll keep 200,000 sats on Strike. If it drops 50%, I will keep 4 million sats on there. I typically spend between $600- $1,000 in broken ruler bucks a month. This doesn't include my mortgage or food. My wife pretty much covers that stuff. Life happens though. Sometimes I need to pay a plumber, or a roofer or something, but most months, I have a sat surplus, a phenomena I like to call **sats savings**. My fiat check converts to bitcoin right on payday. I pay my credit cards off that day. If the sats are worth a little more, I pay taxes on that little bit. To make the math easy, say I get paid $1,000 on Friday. When I pay my bills, The broken ruler measurement now says I have $1,100. I pay my credit card. I owe capital gains on that $100 worth of sats. If my paycheck happens to be worth $900,I don’t pay any taxes because I have a loss. I won’t lie. I still get a bit perturbed when the price goes down 10% on payday, but it’s not the end of the world. If it doesn’t go back up by next payday, [good](https://www.youtube.com/watch?v=IdTMDpizis8). I earn more sats. If it goes up by next payday, [good](https://www.youtube.com/watch?v=IdTMDpizis8). All the sats I stacked before can buy more groceries. #### Get On The Sats Standard !;make sats the standard](https://gitea.marc26z.com/marc/BlogImprovementProposals/raw/branch/main/pics/Screenshot%20from%202025-01-19%2020-35-55.png) Making sats the standard does this for the individual on the microeconomic level. Each Bitcoiner gradually accumulates sats. Stack long enough, study long enough, and experience enough 80% dips and you too will develop an unwavering conviction. You get paid in sats. You spend sats. You save sats. You no longer give a damn about your local fiat currency. A dozen eggs cost less than half of a single egg cost 8 years ago. If you lose 50% of your spending power overnight, you can buy less eggs, but a dozen eggs still costs less than 1 egg 8 years ago. Bitcoin is just better money. If my fiat bank account takes more money out than I have in it, I can do an instant withdrawl on Strike. The fiat appears in my fiat bank account instantly. No more waiting 3-5 days for the money to get there. The bank does not get to keep charging you overdraft fee after overdraft fee for every little transaction. Bitcoin just works better. You can send it all over the world within seconds. You can buy stuff online with it or pay your credit cards. There is literally no reason to hold dollars anymore if you don’t want to. When you’re ready, make sats the standard. If you are not ready, keep stacking. Onward. [Marc](nostr:npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0) [880,018](https://mempool.marc26z.com/block/00000000000000000000bb39704f189da436d0adbed0da2bb334f93cdaa519d9) [Subscribe with Sats](https://app.paywithflash.com/subscription-page?flashId=1110&ref=p66dxywd2xpyyrdfxwilqcxmchmfw2ixmn2vm74q3atf22du7qmkihyd.onion) [Shop My Merch](nostr:npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0)
@ df478568:2a951e67
2025-01-20 05:23:36I took this picture at about block [416,220](https://mempool.marc26z.com/block/000000000000000003b64da342d6d24d066ea5c961e21fdf57cae4318eab3616)(June 13, 2016). The price of eggs on that day was $1.99, 16.5¢ per egg if you still measure stuff with the broken ruler we call fiat. What if we measured the price in sats instead? I found the price on that date from the bitbo calender. According to this website, $1.99 was worth 260,000 sats back then. Each egg cost 21,667 sats! Oh My Zeus!😱  I used this [mempool calculator](https://mempool.marc26z.com/tools/calculator) to see how much that is today. Turns out that it's $272.88 as of block 879,943. Since the fiat ruler is broken, the price of a dozen eggs also has NGU. I took this picture the last time I went to the grocery store. Eggs cost enough to shock fiat maxis. $8.99 OMZ!😱 What does a dozen eggs cost if you ignore the broken ruler? 8,572 sats today, just 714 sats per egg. Holy [Wiemar Republic](https://en.m.wikipedia.org/wiki/Weimar_Republic) Batman! That's 30X cheaper! 😁 For some strange reason I can't pretend to understand, the [Federal reserve tracks the price of eggs denominated in bitcoin](https://fredblog.stlouisfed.org/2022/06/buying-eggs-with-bitcoins/). I guess they want to stay humble and stack money printer go brrrrrr. You can see the price of eggs drop off a cliff like Wile E Coyote on their website.  In The Price of Tommorrow and too many podcasts to mention, Jeff Booth argues the free market makes things cheaper over time, but the fiat syatem is syatematic theft. This theft occurs via inflation, which is really wage deflation. In other words, eggs are getting cheaper over time because egg producers become more efficient. We see tye fruits of this efficiency in Big screen TV's because the fiat price gets cut in half every ten years or so, but this is also a product of a broken ruler. The TV is probably 60X cheaper in bitcoin terms. It makes sense, TV's don't get bird flu, but when you begin using bitcoin as your unit of account, the measurement of value makes more sense than fiat clown world on the broken ruler standard. I remember when coffee was 100,000 sats. Now it's 16,699 sats. Living on the sat standards allows you to see Jeff Booth's thesis play out in real time  ## Life Gets More Expensive On The Broken Ruler Standard I see so many young people on the broken ruler standard bemoan about food and housing prices. There are people with master's degrees who have already lost hope of buying a single family home and achieving the "American dream." To be honest, I would be pretty bummed about it too if I was on the broken ruler standard. A few months ago I spoke with a woman who made at least twice as much fiat as I do say, "I hope this housing market crashes so I can buy a house!" That's sad. I have a lot of empathy for that feeling. Since the great financial crisis, I've only been able to get part time work, but my family wqs able to get a mortgage worth 12.5 bitcoin at the so-called "height of the market." We put as little money down as possible, 3% and I sold my old 401k for that "money." I also used some of it for repairs and taxes, but went all-in on bitcoin with everything else. Now our house is worth about 5 bitcoin. The way I see it, real estate is always crashing. People on the broken ruler standard cry, "Wah, Wah. I hope there's a housing crash! Wah! Wah! Muh egg prices!" Buy a brand spanking new car for $50,00 car with a 7% interest rate and they will say, "Congratulations!" The trouble is, the price of the car falls like eggs compared to bitcoin on the broken ruler standard. This is because prices are distorted when measured in a broken ruler standard. ### Get Off The Broken Ruler Standard  Before I met my wife, I played poker to supplement my income. I don't play much anymore, but poker taught me about risk management, probability, game theory, and many other things applicable to bitcoin. Poker gave me the background knowledge I needed to study bitcoin. [In a sly, round-about way](https://youtu.be/nswOYo0zUcI?si=iVjy6e-npEAo9lkH) , poker taught me how to spend less bitcoin than I make. In traditional technical finance terminology, this is called "fucking saving." If you were not taught how to save and spend more than you earn, no matter how many broken ruler bucks you may earn, bitcoin will not work for you. My wife makes a lot of broken ruler bucks. **Unfortunately, we were broke in 2016 because we both were in school**. Nevertheless, I'm proud of my stack amd I'm now at a point in life where I can get paid in bitcoin with very little risk because of my sugar mama, I mean wife, gets paid very well. I spend like almost every other American consumer, plastic broken ruler debt cards. I put my little Strike ACH number on the Discover app. I keep a couple million sats on Strike and pay my credit card every month. In other words, I use Strike like a four-letter word: bank. Sometimes I'll get a craving for tacos., I've never found a food truck that takes bitcoin, but they often use the Cash App. People on the broken ruler standard can't instantaneously send broken ruler bucks from PayPal to Zelle and vice-versa. They must first send broken ruler bucks from PayPal to the bank and then send the broken ruler bucks through Zelle. I can send sats directly from Strike to thr Cash App within seconds. #### Sats As A Unit Of Account  The price of bitcoin fluctuates which makes it difficult to use as a unit of account. Who wants to divide the price of bitcoin by 100 million. Ain't nobody got time for that. If a whole coin costs 100k, then 1,000 sats = $1.00. This means each 100 sats is worth 10¢. 10 sats = 1¢. If the price drops 50%, 1000 sats is 50¢. If it does a 10X, $1,000 sats is $10.00. Living on a sat standard requires a little math, but it's easy to estimate. For more precise calculations I use mem pools calculator. Money is a store of value, medium of exchange, and unit of account. If you use bitcoin on all three ways, you are using bitcoin as money. Saving becomes spending less bitcoin, not "buying more bitcoin." If you stack sats, your goal should be to leave the broken ruler standard and adopt sats as the standard. The world will still price your sats with a broken ruler. Sometimes this broken ruler makes you look like a fool. Other times, the broken ruler makes you look like a genius. Therefore, you must stay humble and stack sats. You'll need some savings before you can deal with the broken ruler fallacy, but once you consistently stack sats and NGU continues to U, you'll eventually see life gets easier when you make sats the standard. I will sell some sats to pay for my food and I send a tip to the food trucker in bitcoin using the Cash App gift button. It is actually very easy for them to accept bitcoin. They just don't know it yet. I don't proselytize the gospel of our lord and savior Satoshi Nakamoto. I just send them a few thousand sats. Good orange pilling is like good writing: **Show, don't tell**. ##### Does it require KYC? Yeah, but so does Bank of Broken Rulers. ##### Haven't you heard the phrase, **not your keys, not your bitcoin?** Yes. It's true. The 2 million sats or so is "not my bitcoin." From my perspective, however, it is the least risky way of paying my bills. I believe it is less risky than keeping broken ruler bucks in a bank. FDIC insurance sounds nice as canceled Insurance policies in the Pacific Palisades. I could keep my 2 million sats in self-custody in my own lightning wallet. I could use [Zap Planner](https://zapplanner.albylabs.com/) to schedule my payments to hit Strike moments before I pay my bill, but I know me. I've lost sats on the lightning network before. I am more likely to lose the sats on my self-custodial lightning wallet than lose them because Strike could possibly rug-pull me. So for now, I just keep 2 million sats on the app. If bitcoin does a 10X, I'll keep 200,000 sats on Strike. If it drops 50%, I will keep 4 million sats on there. I typically spend between $600- $1,000 in broken ruler bucks a month. This doesn't include my mortgage or food. My wife pretty much covers that stuff. Life happens though. Sometimes I need to pay a plumber, or a roofer or something, but most months, I have a sat surplus, a phenomena I like to call **sats savings**. My fiat check converts to bitcoin right on payday. I pay my credit cards off that day. If the sats are worth a little more, I pay taxes on that little bit. To make the math easy, say I get paid $1,000 on Friday. When I pay my bills, The broken ruler measurement now says I have $1,100. I pay my credit card. I owe capital gains on that $100 worth of sats. If my paycheck happens to be worth $900,I don’t pay any taxes because I have a loss. I won’t lie. I still get a bit perturbed when the price goes down 10% on payday, but it’s not the end of the world. If it doesn’t go back up by next payday, [good](https://www.youtube.com/watch?v=IdTMDpizis8). I earn more sats. If it goes up by next payday, [good](https://www.youtube.com/watch?v=IdTMDpizis8). All the sats I stacked before can buy more groceries. #### Get On The Sats Standard !;make sats the standard](https://gitea.marc26z.com/marc/BlogImprovementProposals/raw/branch/main/pics/Screenshot%20from%202025-01-19%2020-35-55.png) Making sats the standard does this for the individual on the microeconomic level. Each Bitcoiner gradually accumulates sats. Stack long enough, study long enough, and experience enough 80% dips and you too will develop an unwavering conviction. You get paid in sats. You spend sats. You save sats. You no longer give a damn about your local fiat currency. A dozen eggs cost less than half of a single egg cost 8 years ago. If you lose 50% of your spending power overnight, you can buy less eggs, but a dozen eggs still costs less than 1 egg 8 years ago. Bitcoin is just better money. If my fiat bank account takes more money out than I have in it, I can do an instant withdrawl on Strike. The fiat appears in my fiat bank account instantly. No more waiting 3-5 days for the money to get there. The bank does not get to keep charging you overdraft fee after overdraft fee for every little transaction. Bitcoin just works better. You can send it all over the world within seconds. You can buy stuff online with it or pay your credit cards. There is literally no reason to hold dollars anymore if you don’t want to. When you’re ready, make sats the standard. If you are not ready, keep stacking. Onward. [Marc](nostr:npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0) [880,018](https://mempool.marc26z.com/block/00000000000000000000bb39704f189da436d0adbed0da2bb334f93cdaa519d9) [Subscribe with Sats](https://app.paywithflash.com/subscription-page?flashId=1110&ref=p66dxywd2xpyyrdfxwilqcxmchmfw2ixmn2vm74q3atf22du7qmkihyd.onion) [Shop My Merch](nostr:npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0) @ 3f770d65:7a745b24
2025-01-19 21:48:49The recent shutdown of TikTok in the United States due to a potential government ban serves as a stark reminder how fragile centralized platforms truly are under the surface. While these platforms offer convenience, a more polished user experience, and connectivity, they are ultimately beholden to governments, corporations, and other authorities. This makes them vulnerable to censorship, regulation, and outright bans. In contrast, Nostr represents a shift in how we approach online communication and content sharing. Built on the principles of decentralization and user choice, Nostr cannot be banned, because it is not a platform—it is a protocol. **PROTOCOLS, NOT PLATFORMS.** At the heart of Nostr's philosophy is **user choice**, a feature that fundamentally sets it apart from legacy platforms. In centralized systems, the user experience is dictated by a single person or governing entity. If the platform decides to filter, censor, or ban specific users or content, individuals are left with little action to rectify the situation. They must either accept the changes or abandon the platform entirely, often at the cost of losing their social connections, their data, and their identity. What's happening with TikTok could never happen on Nostr. With Nostr, the dynamics are completely different. Because it is a protocol, not a platform, no single entity controls the ecosystem. Instead, the protocol enables a network of applications and relays that users can freely choose from. If a particular application or relay implements policies that a user disagrees with, such as censorship, filtering, or even government enforced banning, they are not trapped or abandoned. They have the freedom to move to another application or relay with minimal effort. **THIS IS POWERFUL.** Take, for example, the case of a relay that decides to censor specific content. On a legacy platform, this would result in frustration and a loss of access for users. On Nostr, however, users can simply connect to a different relay that does not impose such restrictions. Similarly, if an application introduces features or policies that users dislike, they can migrate to a different application that better suits their preferences, all while retaining their identity and social connections. The same principles apply to government bans and censorship. A government can ban a specific application or even multiple applications, just as it can block one relay or several relays. China has implemented both tactics, yet Chinese users continue to exist and actively participate on Nostr, demonstrating Nostr's ability to resistant censorship. How? Simply, it turns into a game of whack-a-mole. When one relay is censored, another quickly takes its place. When one application is banned, another emerges. Users can also bypass these obstacles by running their own relays and applications directly from their homes or personal devices, eliminating reliance on larger entities or organizations and ensuring continuous access. **AGAIN, THIS IS POWERUFL.** Nostr's open and decentralized design makes it resistant to the kinds of government intervention that led to TikTok's outages this weekend and potential future ban in the next 90 days. There is no central server to target, no company to regulate, and no single point of failure. (Insert your CEO jokes here). As long as there are individuals running relays and applications, users continue creating notes and sending zaps. Platforms like TikTok can be silenced with the stroke of a pen, leaving millions of users disconnected and abandoned. Social communication should not be silenced so incredibly easily. No one should have that much power over social interactions. Will we on-board a massive wave of TikTokers in the coming hours or days? I don't know. TikTokers may not be ready for Nostr yet, and honestly, Nostr may not be ready for them either. The ecosystem still lacks the completely polished applications, tools, and services they’re accustomed to. This is where we say "we're still early". They may not be early adopters like the current Nostr user base. Until we bridge that gap, they’ll likely move to the next centralized platform, only to face another government ban or round of censorship in the future. But eventually, there will come a tipping point, a moment when they’ve had enough. When that time comes, I hope we’re prepared. If we’re not, we risk missing a tremendous opportunity to onboard people who genuinely need Nostr’s freedom. Until then, to all of the Nostr developers out there, keep up the great work and keep building. Your hard work and determination is needed. ###
@ 3f770d65:7a745b24
2025-01-19 21:48:49The recent shutdown of TikTok in the United States due to a potential government ban serves as a stark reminder how fragile centralized platforms truly are under the surface. While these platforms offer convenience, a more polished user experience, and connectivity, they are ultimately beholden to governments, corporations, and other authorities. This makes them vulnerable to censorship, regulation, and outright bans. In contrast, Nostr represents a shift in how we approach online communication and content sharing. Built on the principles of decentralization and user choice, Nostr cannot be banned, because it is not a platform—it is a protocol. **PROTOCOLS, NOT PLATFORMS.** At the heart of Nostr's philosophy is **user choice**, a feature that fundamentally sets it apart from legacy platforms. In centralized systems, the user experience is dictated by a single person or governing entity. If the platform decides to filter, censor, or ban specific users or content, individuals are left with little action to rectify the situation. They must either accept the changes or abandon the platform entirely, often at the cost of losing their social connections, their data, and their identity. What's happening with TikTok could never happen on Nostr. With Nostr, the dynamics are completely different. Because it is a protocol, not a platform, no single entity controls the ecosystem. Instead, the protocol enables a network of applications and relays that users can freely choose from. If a particular application or relay implements policies that a user disagrees with, such as censorship, filtering, or even government enforced banning, they are not trapped or abandoned. They have the freedom to move to another application or relay with minimal effort. **THIS IS POWERFUL.** Take, for example, the case of a relay that decides to censor specific content. On a legacy platform, this would result in frustration and a loss of access for users. On Nostr, however, users can simply connect to a different relay that does not impose such restrictions. Similarly, if an application introduces features or policies that users dislike, they can migrate to a different application that better suits their preferences, all while retaining their identity and social connections. The same principles apply to government bans and censorship. A government can ban a specific application or even multiple applications, just as it can block one relay or several relays. China has implemented both tactics, yet Chinese users continue to exist and actively participate on Nostr, demonstrating Nostr's ability to resistant censorship. How? Simply, it turns into a game of whack-a-mole. When one relay is censored, another quickly takes its place. When one application is banned, another emerges. Users can also bypass these obstacles by running their own relays and applications directly from their homes or personal devices, eliminating reliance on larger entities or organizations and ensuring continuous access. **AGAIN, THIS IS POWERUFL.** Nostr's open and decentralized design makes it resistant to the kinds of government intervention that led to TikTok's outages this weekend and potential future ban in the next 90 days. There is no central server to target, no company to regulate, and no single point of failure. (Insert your CEO jokes here). As long as there are individuals running relays and applications, users continue creating notes and sending zaps. Platforms like TikTok can be silenced with the stroke of a pen, leaving millions of users disconnected and abandoned. Social communication should not be silenced so incredibly easily. No one should have that much power over social interactions. Will we on-board a massive wave of TikTokers in the coming hours or days? I don't know. TikTokers may not be ready for Nostr yet, and honestly, Nostr may not be ready for them either. The ecosystem still lacks the completely polished applications, tools, and services they’re accustomed to. This is where we say "we're still early". They may not be early adopters like the current Nostr user base. Until we bridge that gap, they’ll likely move to the next centralized platform, only to face another government ban or round of censorship in the future. But eventually, there will come a tipping point, a moment when they’ve had enough. When that time comes, I hope we’re prepared. If we’re not, we risk missing a tremendous opportunity to onboard people who genuinely need Nostr’s freedom. Until then, to all of the Nostr developers out there, keep up the great work and keep building. Your hard work and determination is needed. ### @ cff1720e:15c7e2b2
2025-01-19 17:48:02**Einleitung**\ \ Schwierige Dinge einfach zu erklären ist der Anspruch von ELI5 (explain me like I'm 5). Das ist in unserer hoch technisierten Welt dringend erforderlich, denn nur mit dem Verständnis der Technologien können wir sie richtig einsetzen und weiter entwickeln.\ Ich starte meine Serie mit Nostr, einem relativ neuen Internet-Protokoll. Was zum Teufel ist ein Internet-Protokoll? Formal beschrieben sind es internationale Standards, die dafür sorgen, dass das Internet seit über 30 Jahren ziemlich gut funktioniert. Es ist die Sprache, in der sich die Rechner miteinander unterhalten und die auch Sie täglich nutzen, vermutlich ohne es bewusst wahrzunehmen. http(s) transportiert ihre Anfrage an einen Server (z.B. Amazon), und html sorgt dafür, dass aus den gelieferten Daten eine schöne Seite auf ihrem Bildschirm entsteht. Eine Mail wird mit smtp an den Mailserver gesendet und mit imap von ihm abgerufen, und da alle den Standard verwenden, funktioniert das mit jeder App auf jedem Betriebssystem und mit jedem Mail-Provider. Und mit einer Mail-Adresse wie <roland@pareto.space> können sie sogar jederzeit umziehen, egal wohin. **Cool, das ist state of the art!** Aber warum funktioniert das z.B. bei Chat nicht, gibt es da kein Protokoll? Doch, es heißt IRC (Internet Relay Chat → merken sie sich den Namen), aber es wird so gut wie nicht verwendet. Die Gründe dafür sind nicht technischer Natur, vielmehr wurden mit Apps wie Facebook, Twitter, WhatsApp, Telegram, Instagram, TikTok u.a. bewusst Inkompatibilitäten und Nutzerabhängigkeiten geschaffen um Profite zu maximieren.  **Warum Nostr?** Da das Standard-Protokoll nicht genutzt wird, hat jede App ihr eigenes, und wir brauchen eine handvoll Apps um uns mit allen Bekannten auszutauschen. Eine Mobilfunknummer ist Voraussetzung für jedes Konto, damit können die App-Hersteller die Nutzer umfassend tracken und mit dem Verkauf der Informationen bis zu 30 USD je Konto und Monat verdienen. Der Nutzer ist nicht mehr Kunde, er ist das Produkt! Der Werbe-SPAM ist noch das kleinste Problem bei diesem Geschäftsmodell. Server mit Millionen von Nutzerdaten sind ein “honey pot”, dementsprechend oft werden sie gehackt und die Zugangsdaten verkauft. 2024 wurde auch der Twitter-Account vom damaligen Präsidenten Joe Biden gehackt, niemand wusste mehr wer die Nachrichten verfasst hat (vorher auch nicht), d.h. die Authentizität der Inhalte ist bei keinem dieser Anbieter gewährleistet. Im selben Jahr wurde der Telegram-Gründer in Frankreich in Beugehaft genommen, weil er sich geweigert hatte Hintertüren in seine Software einzubauen. Nun kann zum Schutz **"unserer Demokratie”** praktisch jeder mitlesen, was sie mit wem an Informationen austauschen, z.B. darüber welches Shampoo bestimmte Politiker verwenden.  Und wer tatsächlich glaubt er könne Meinungsfreiheit auf sozialen Medien praktizieren, findet sich schnell in der Situation von Donald Trump wieder (seinerzeit amtierender Präsident), dem sein Twitter-Konto 2021 abgeschaltet wurde (Cancel-Culture). Die Nutzerdaten, also ihr Profil, ihre Kontakte, Dokumente, Bilder, Videos und Audiofiles - gehören ihnen ohnehin nicht mehr sondern sind Eigentum des Plattform-Betreibers; lesen sie sich mal die AGB's durch. Aber nein, keine gute Idee, das sind hunderte Seiten und sie werden permanent geändert. Alle nutzen also Apps, deren Technik sie nicht verstehen, deren Regeln sie nicht kennen, wo sie keine Rechte haben und die ihnen die Resultate ihres Handelns stehlen. Was würde wohl der Fünfjährige sagen, wenn ihm seine ältere Schwester anbieten würde, alle seine Spielzeuge zu “verwalten” und dann auszuhändigen wenn er brav ist? “Du spinnst wohl”, und damit beweist der Knirps mehr Vernunft als die Mehrzahl der Erwachsenen. \ \ **Resümee:** keine Standards, keine Daten, keine Rechte = keine Zukunft!  \ **Wie funktioniert Nostr?** Die Entwickler von Nostr haben erkannt dass sich das Server-Client-Konzept in ein Master-Slave-Konzept verwandelt hatte. Der Master ist ein Synonym für Zentralisierung und wird zum **“single point of failure”**, der zwangsläufig Systeme dysfunktional macht. In einem verteilten Peer2Peer-System gibt es keine Master mehr sondern nur gleichberechtigte Knoten (Relays), auf denen die Informationen gespeichert werden. Indem man Informationen auf mehreren Relays redundant speichert, ist das System in jeglicher Hinsicht resilienter. Nicht nur die Natur verwendet dieses Prinzip seit Jahrmillionen erfolgreich, auch das Internet wurde so konzipiert (das ARPAnet wurde vom US-Militär für den Einsatz in Kriegsfällen unter massiven Störungen entwickelt). Alle Nostr-Daten liegen auf Relays und der Nutzer kann wählen zwischen öffentlichen (zumeist kostenlosen) und privaten Relays, z.B. für geschlossene Gruppen oder zum Zwecke von Daten-Archivierung. Da Dokumente auf mehreren Relays gespeichert sind, werden statt URL's (Locator) eindeutige Dokumentnamen (URI's = Identifier) verwendet, broken Links sind damit Vergangenheit und Löschungen / Verluste ebenfalls.\ \ Jedes Dokument (Event genannt) wird vom Besitzer signiert, es ist damit authentisch und fälschungssicher und kann nur vom Ersteller gelöscht werden. Dafür wird ein Schlüsselpaar verwendet bestehend aus privatem (nsec) und öffentlichem Schlüssel (npub) wie aus der Mailverschlüsselung (PGP) bekannt. Das repräsentiert eine Nostr-Identität, die um Bild, Namen, Bio und eine lesbare Nostr-Adresse ergänzt werden kann (z.B. <roland@pareto.space> ), mehr braucht es nicht um alle Ressourcen des Nostr-Ökosystems zu nutzen. Und das besteht inzwischen aus über hundert Apps mit unterschiedlichen Fokussierungen, z.B. für persönliche verschlüsselte Nachrichten (DM → OxChat), Kurznachrichten (Damus, Primal), Blogbeiträge (Pareto), Meetups (Joinstr), Gruppen (Groups), Bilder (Olas), Videos (Amethyst), Audio-Chat (Nostr Nests), Audio-Streams (Tunestr), Video-Streams (Zap.Stream), Marktplätze (Shopstr) u.v.a.m. Die Anmeldung erfolgt mit einem Klick (single sign on) und den Apps stehen ALLE Nutzerdaten zur Verfügung (Profil, Daten, Kontakte, Social Graph → Follower, Bookmarks, Comments, etc.), im Gegensatz zu den fragmentierten Datensilos der Gegenwart.\ \ **Resümee:** ein offener Standard, alle Daten, alle Rechte = große Zukunft!  \ **Warum ist Nostr die Zukunft des Internet?** “Baue Dein Haus nicht auf einem fremden Grundstück” gilt auch im Internet - für alle App-Entwickler, Künstler, Journalisten und Nutzer, denn auch ihre Daten sind werthaltig. Nostr garantiert das Eigentum an den Daten, und überwindet ihre Fragmentierung. Weder die Nutzung noch die kreativen Freiheiten werden durch maßlose Lizenz- und Nutzungsbedingungen eingeschränkt. Aus passiven Nutzern werden durch Interaktion aktive Teilnehmer, Co-Creatoren in einer Sharing-Ökonomie **(Value4Value)**. OpenSource schafft endlich wieder Vertrauen in die Software und ihre Anbieter. Offene Standards ermöglichen den Entwicklern mehr Kooperation und schnellere Entwicklung, für die Anwender garantieren sie Wahlfreiheit. Womit wir letztmalig zu unserem Fünfjährigen zurückkehren. Kinder lieben Lego über alles, am meisten die Maxi-Box “Classic”, weil sie damit ihre Phantasie im Kombinieren voll ausleben können. Erwachsene schenken ihnen dann die viel zu teuren Themenpakete, mit denen man nur eine Lösung nach Anleitung bauen kann. “Was stimmt nur mit meinen Eltern nicht, wann sind die denn falsch abgebogen?" fragt sich der Nachwuchs zu Recht. Das Image lässt sich aber wieder aufpolieren, wenn sie ihren Kindern Nostr zeigen, denn die Vorteile verstehen sogar Fünfjährige.  \ **Das neue Internet ist dezentral. Das neue Internet ist selbstbestimmt. Nostr ist das neue Internet.** <https://nostr.net/> \ <https://start.njump.me/> **Hier das Interview zum Thema mit Radio Berliner Morgenröte** <https://www.podbean.com/ew/pb-yxc36-17bb4be>
@ cff1720e:15c7e2b2
2025-01-19 17:48:02**Einleitung**\ \ Schwierige Dinge einfach zu erklären ist der Anspruch von ELI5 (explain me like I'm 5). Das ist in unserer hoch technisierten Welt dringend erforderlich, denn nur mit dem Verständnis der Technologien können wir sie richtig einsetzen und weiter entwickeln.\ Ich starte meine Serie mit Nostr, einem relativ neuen Internet-Protokoll. Was zum Teufel ist ein Internet-Protokoll? Formal beschrieben sind es internationale Standards, die dafür sorgen, dass das Internet seit über 30 Jahren ziemlich gut funktioniert. Es ist die Sprache, in der sich die Rechner miteinander unterhalten und die auch Sie täglich nutzen, vermutlich ohne es bewusst wahrzunehmen. http(s) transportiert ihre Anfrage an einen Server (z.B. Amazon), und html sorgt dafür, dass aus den gelieferten Daten eine schöne Seite auf ihrem Bildschirm entsteht. Eine Mail wird mit smtp an den Mailserver gesendet und mit imap von ihm abgerufen, und da alle den Standard verwenden, funktioniert das mit jeder App auf jedem Betriebssystem und mit jedem Mail-Provider. Und mit einer Mail-Adresse wie <roland@pareto.space> können sie sogar jederzeit umziehen, egal wohin. **Cool, das ist state of the art!** Aber warum funktioniert das z.B. bei Chat nicht, gibt es da kein Protokoll? Doch, es heißt IRC (Internet Relay Chat → merken sie sich den Namen), aber es wird so gut wie nicht verwendet. Die Gründe dafür sind nicht technischer Natur, vielmehr wurden mit Apps wie Facebook, Twitter, WhatsApp, Telegram, Instagram, TikTok u.a. bewusst Inkompatibilitäten und Nutzerabhängigkeiten geschaffen um Profite zu maximieren.  **Warum Nostr?** Da das Standard-Protokoll nicht genutzt wird, hat jede App ihr eigenes, und wir brauchen eine handvoll Apps um uns mit allen Bekannten auszutauschen. Eine Mobilfunknummer ist Voraussetzung für jedes Konto, damit können die App-Hersteller die Nutzer umfassend tracken und mit dem Verkauf der Informationen bis zu 30 USD je Konto und Monat verdienen. Der Nutzer ist nicht mehr Kunde, er ist das Produkt! Der Werbe-SPAM ist noch das kleinste Problem bei diesem Geschäftsmodell. Server mit Millionen von Nutzerdaten sind ein “honey pot”, dementsprechend oft werden sie gehackt und die Zugangsdaten verkauft. 2024 wurde auch der Twitter-Account vom damaligen Präsidenten Joe Biden gehackt, niemand wusste mehr wer die Nachrichten verfasst hat (vorher auch nicht), d.h. die Authentizität der Inhalte ist bei keinem dieser Anbieter gewährleistet. Im selben Jahr wurde der Telegram-Gründer in Frankreich in Beugehaft genommen, weil er sich geweigert hatte Hintertüren in seine Software einzubauen. Nun kann zum Schutz **"unserer Demokratie”** praktisch jeder mitlesen, was sie mit wem an Informationen austauschen, z.B. darüber welches Shampoo bestimmte Politiker verwenden.  Und wer tatsächlich glaubt er könne Meinungsfreiheit auf sozialen Medien praktizieren, findet sich schnell in der Situation von Donald Trump wieder (seinerzeit amtierender Präsident), dem sein Twitter-Konto 2021 abgeschaltet wurde (Cancel-Culture). Die Nutzerdaten, also ihr Profil, ihre Kontakte, Dokumente, Bilder, Videos und Audiofiles - gehören ihnen ohnehin nicht mehr sondern sind Eigentum des Plattform-Betreibers; lesen sie sich mal die AGB's durch. Aber nein, keine gute Idee, das sind hunderte Seiten und sie werden permanent geändert. Alle nutzen also Apps, deren Technik sie nicht verstehen, deren Regeln sie nicht kennen, wo sie keine Rechte haben und die ihnen die Resultate ihres Handelns stehlen. Was würde wohl der Fünfjährige sagen, wenn ihm seine ältere Schwester anbieten würde, alle seine Spielzeuge zu “verwalten” und dann auszuhändigen wenn er brav ist? “Du spinnst wohl”, und damit beweist der Knirps mehr Vernunft als die Mehrzahl der Erwachsenen. \ \ **Resümee:** keine Standards, keine Daten, keine Rechte = keine Zukunft!  \ **Wie funktioniert Nostr?** Die Entwickler von Nostr haben erkannt dass sich das Server-Client-Konzept in ein Master-Slave-Konzept verwandelt hatte. Der Master ist ein Synonym für Zentralisierung und wird zum **“single point of failure”**, der zwangsläufig Systeme dysfunktional macht. In einem verteilten Peer2Peer-System gibt es keine Master mehr sondern nur gleichberechtigte Knoten (Relays), auf denen die Informationen gespeichert werden. Indem man Informationen auf mehreren Relays redundant speichert, ist das System in jeglicher Hinsicht resilienter. Nicht nur die Natur verwendet dieses Prinzip seit Jahrmillionen erfolgreich, auch das Internet wurde so konzipiert (das ARPAnet wurde vom US-Militär für den Einsatz in Kriegsfällen unter massiven Störungen entwickelt). Alle Nostr-Daten liegen auf Relays und der Nutzer kann wählen zwischen öffentlichen (zumeist kostenlosen) und privaten Relays, z.B. für geschlossene Gruppen oder zum Zwecke von Daten-Archivierung. Da Dokumente auf mehreren Relays gespeichert sind, werden statt URL's (Locator) eindeutige Dokumentnamen (URI's = Identifier) verwendet, broken Links sind damit Vergangenheit und Löschungen / Verluste ebenfalls.\ \ Jedes Dokument (Event genannt) wird vom Besitzer signiert, es ist damit authentisch und fälschungssicher und kann nur vom Ersteller gelöscht werden. Dafür wird ein Schlüsselpaar verwendet bestehend aus privatem (nsec) und öffentlichem Schlüssel (npub) wie aus der Mailverschlüsselung (PGP) bekannt. Das repräsentiert eine Nostr-Identität, die um Bild, Namen, Bio und eine lesbare Nostr-Adresse ergänzt werden kann (z.B. <roland@pareto.space> ), mehr braucht es nicht um alle Ressourcen des Nostr-Ökosystems zu nutzen. Und das besteht inzwischen aus über hundert Apps mit unterschiedlichen Fokussierungen, z.B. für persönliche verschlüsselte Nachrichten (DM → OxChat), Kurznachrichten (Damus, Primal), Blogbeiträge (Pareto), Meetups (Joinstr), Gruppen (Groups), Bilder (Olas), Videos (Amethyst), Audio-Chat (Nostr Nests), Audio-Streams (Tunestr), Video-Streams (Zap.Stream), Marktplätze (Shopstr) u.v.a.m. Die Anmeldung erfolgt mit einem Klick (single sign on) und den Apps stehen ALLE Nutzerdaten zur Verfügung (Profil, Daten, Kontakte, Social Graph → Follower, Bookmarks, Comments, etc.), im Gegensatz zu den fragmentierten Datensilos der Gegenwart.\ \ **Resümee:** ein offener Standard, alle Daten, alle Rechte = große Zukunft!  \ **Warum ist Nostr die Zukunft des Internet?** “Baue Dein Haus nicht auf einem fremden Grundstück” gilt auch im Internet - für alle App-Entwickler, Künstler, Journalisten und Nutzer, denn auch ihre Daten sind werthaltig. Nostr garantiert das Eigentum an den Daten, und überwindet ihre Fragmentierung. Weder die Nutzung noch die kreativen Freiheiten werden durch maßlose Lizenz- und Nutzungsbedingungen eingeschränkt. Aus passiven Nutzern werden durch Interaktion aktive Teilnehmer, Co-Creatoren in einer Sharing-Ökonomie **(Value4Value)**. OpenSource schafft endlich wieder Vertrauen in die Software und ihre Anbieter. Offene Standards ermöglichen den Entwicklern mehr Kooperation und schnellere Entwicklung, für die Anwender garantieren sie Wahlfreiheit. Womit wir letztmalig zu unserem Fünfjährigen zurückkehren. Kinder lieben Lego über alles, am meisten die Maxi-Box “Classic”, weil sie damit ihre Phantasie im Kombinieren voll ausleben können. Erwachsene schenken ihnen dann die viel zu teuren Themenpakete, mit denen man nur eine Lösung nach Anleitung bauen kann. “Was stimmt nur mit meinen Eltern nicht, wann sind die denn falsch abgebogen?" fragt sich der Nachwuchs zu Recht. Das Image lässt sich aber wieder aufpolieren, wenn sie ihren Kindern Nostr zeigen, denn die Vorteile verstehen sogar Fünfjährige.  \ **Das neue Internet ist dezentral. Das neue Internet ist selbstbestimmt. Nostr ist das neue Internet.** <https://nostr.net/> \ <https://start.njump.me/> **Hier das Interview zum Thema mit Radio Berliner Morgenröte** <https://www.podbean.com/ew/pb-yxc36-17bb4be> @ 9e69e420:d12360c2
2025-01-19 04:48:31A new report from the National Sports Shooting Foundation (NSSF) shows that civilian firearm possession exceeded 490 million in 2022. The total from 1990 to 2022 is estimated at 491.3 million firearms. In 2022, over ten million firearms were domestically produced, leading to a total of 16,045,911 firearms available in the U.S. market. Of these, 9,873,136 were handguns, 4,195,192 were rifles, and 1,977,583 were shotguns. Handgun availability aligns with the concealed carry and self-defense market, as all states allow concealed carry, with 29 having constitutional carry laws.
@ 9e69e420:d12360c2
2025-01-19 04:48:31A new report from the National Sports Shooting Foundation (NSSF) shows that civilian firearm possession exceeded 490 million in 2022. The total from 1990 to 2022 is estimated at 491.3 million firearms. In 2022, over ten million firearms were domestically produced, leading to a total of 16,045,911 firearms available in the U.S. market. Of these, 9,873,136 were handguns, 4,195,192 were rifles, and 1,977,583 were shotguns. Handgun availability aligns with the concealed carry and self-defense market, as all states allow concealed carry, with 29 having constitutional carry laws. @ f9cf4e94:96abc355
2025-01-18 06:09:50Para esse exemplo iremos usar: | Nome | Imagem | Descrição | | --------------- | ------------------------------------------------------------ | ------------------------------------------------------------ | | Raspberry PI B+ |  | **Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2,** | | Pen drive |  | **16Gb** | Recomendo que use o **Ubuntu Server** para essa instalação. Você pode baixar o Ubuntu para Raspberry Pi [aqui]( https://ubuntu.com/download/raspberry-pi). O passo a passo para a instalação do Ubuntu no Raspberry Pi está disponível [aqui]( https://ubuntu.com/tutorials/how-to-install-ubuntu-on-your-raspberry-pi). **Não instale um desktop** (como xubuntu, lubuntu, xfce, etc.). --- ## Passo 1: Atualizar o Sistema 🖥️ Primeiro, atualize seu sistema e instale o Tor: ```bash apt update apt install tor ``` --- ## Passo 2: Criar o Arquivo de Serviço `nrs.service` 🔧 Crie o arquivo de serviço que vai gerenciar o servidor Nostr. Você pode fazer isso com o seguinte conteúdo: ```unit [Unit] Description=Nostr Relay Server Service After=network.target [Service] Type=simple WorkingDirectory=/opt/nrs ExecStart=/opt/nrs/nrs-arm64 Restart=on-failure [Install] WantedBy=multi-user.target ``` --- ## Passo 3: Baixar o Binário do Nostr 🚀 Baixe o binário mais recente do Nostr [aqui no GitHub]( https://github.com/gabrielmoura/SimpleNosrtRelay/releases). --- ## Passo 4: Criar as Pastas Necessárias 📂 Agora, crie as pastas para o aplicativo e o pendrive: ```bash mkdir -p /opt/nrs /mnt/edriver ``` --- ## Passo 5: Listar os Dispositivos Conectados 🔌 Para saber qual dispositivo você vai usar, liste todos os dispositivos conectados: ```bash lsblk ``` --- ## Passo 6: Formatando o Pendrive 💾 Escolha o pendrive correto (por exemplo, `/dev/sda`) e formate-o: ```bash mkfs.vfat /dev/sda ``` --- ## Passo 7: Montar o Pendrive 💻 Monte o pendrive na pasta `/mnt/edriver`: ```bash mount /dev/sda /mnt/edriver ``` --- ## Passo 8: Verificar UUID dos Dispositivos 📋 Para garantir que o sistema monte o pendrive automaticamente, liste os UUID dos dispositivos conectados: ```bash blkid ``` --- ## Passo 9: Alterar o `fstab` para Montar o Pendrive Automáticamente 📝 Abra o arquivo `/etc/fstab` e adicione uma linha para o pendrive, com o UUID que você obteve no passo anterior. A linha deve ficar assim: ```fstab UUID=9c9008f8-f852 /mnt/edriver vfat defaults 0 0 ``` --- ## Passo 10: Copiar o Binário para a Pasta Correta 📥 Agora, copie o binário baixado para a pasta `/opt/nrs`: ```bash cp nrs-arm64 /opt/nrs ``` --- ## Passo 11: Criar o Arquivo de Configuração 🛠️ Crie o arquivo de configuração com o seguinte conteúdo e salve-o em `/opt/nrs/config.yaml`: ```yaml app_env: production info: name: Nostr Relay Server description: Nostr Relay Server pub_key: "" contact: "" url: http://localhost:3334 icon: https://external-content.duckduckgo.com/iu/?u= https://public.bnbstatic.com/image/cms/crawler/COINCU_NEWS/image-495-1024x569.png base_path: /mnt/edriver negentropy: true ``` --- ## Passo 12: Copiar o Serviço para o Diretório de Systemd ⚙️ Agora, copie o arquivo `nrs.service` para o diretório `/etc/systemd/system/`: ```bash cp nrs.service /etc/systemd/system/ ``` Recarregue os serviços e inicie o serviço `nrs`: ```bash systemctl daemon-reload systemctl enable --now nrs.service ``` --- ## Passo 13: Configurar o Tor 🌐 Abra o arquivo de configuração do Tor `/var/lib/tor/torrc` e adicione a seguinte linha: ```torrc HiddenServiceDir /var/lib/tor/nostr_server/ HiddenServicePort 80 127.0.0.1:3334 ``` --- ## Passo 14: Habilitar e Iniciar o Tor 🧅 Agora, ative e inicie o serviço Tor: ```bash systemctl enable --now tor.service ``` O Tor irá gerar um endereço `.onion` para o seu servidor Nostr. Você pode encontrá-lo no arquivo `/var/lib/tor/nostr_server/hostname`. --- ## Observações ⚠️ - Com essa configuração, **os dados serão salvos no pendrive**, enquanto o binário ficará no cartão SD do Raspberry Pi. - O endereço `.onion` do seu servidor Nostr será algo como: `ws://y3t5t5wgwjif<exemplo>h42zy7ih6iwbyd.onion`. --- Agora, seu servidor Nostr deve estar configurado e funcionando com Tor! 🥳 Se este artigo e as informações aqui contidas forem úteis para você, convidamos a considerar uma doação ao autor como forma de reconhecimento e incentivo à produção de novos conteúdos.
@ f9cf4e94:96abc355
2025-01-18 06:09:50Para esse exemplo iremos usar: | Nome | Imagem | Descrição | | --------------- | ------------------------------------------------------------ | ------------------------------------------------------------ | | Raspberry PI B+ |  | **Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2,** | | Pen drive |  | **16Gb** | Recomendo que use o **Ubuntu Server** para essa instalação. Você pode baixar o Ubuntu para Raspberry Pi [aqui]( https://ubuntu.com/download/raspberry-pi). O passo a passo para a instalação do Ubuntu no Raspberry Pi está disponível [aqui]( https://ubuntu.com/tutorials/how-to-install-ubuntu-on-your-raspberry-pi). **Não instale um desktop** (como xubuntu, lubuntu, xfce, etc.). --- ## Passo 1: Atualizar o Sistema 🖥️ Primeiro, atualize seu sistema e instale o Tor: ```bash apt update apt install tor ``` --- ## Passo 2: Criar o Arquivo de Serviço `nrs.service` 🔧 Crie o arquivo de serviço que vai gerenciar o servidor Nostr. Você pode fazer isso com o seguinte conteúdo: ```unit [Unit] Description=Nostr Relay Server Service After=network.target [Service] Type=simple WorkingDirectory=/opt/nrs ExecStart=/opt/nrs/nrs-arm64 Restart=on-failure [Install] WantedBy=multi-user.target ``` --- ## Passo 3: Baixar o Binário do Nostr 🚀 Baixe o binário mais recente do Nostr [aqui no GitHub]( https://github.com/gabrielmoura/SimpleNosrtRelay/releases). --- ## Passo 4: Criar as Pastas Necessárias 📂 Agora, crie as pastas para o aplicativo e o pendrive: ```bash mkdir -p /opt/nrs /mnt/edriver ``` --- ## Passo 5: Listar os Dispositivos Conectados 🔌 Para saber qual dispositivo você vai usar, liste todos os dispositivos conectados: ```bash lsblk ``` --- ## Passo 6: Formatando o Pendrive 💾 Escolha o pendrive correto (por exemplo, `/dev/sda`) e formate-o: ```bash mkfs.vfat /dev/sda ``` --- ## Passo 7: Montar o Pendrive 💻 Monte o pendrive na pasta `/mnt/edriver`: ```bash mount /dev/sda /mnt/edriver ``` --- ## Passo 8: Verificar UUID dos Dispositivos 📋 Para garantir que o sistema monte o pendrive automaticamente, liste os UUID dos dispositivos conectados: ```bash blkid ``` --- ## Passo 9: Alterar o `fstab` para Montar o Pendrive Automáticamente 📝 Abra o arquivo `/etc/fstab` e adicione uma linha para o pendrive, com o UUID que você obteve no passo anterior. A linha deve ficar assim: ```fstab UUID=9c9008f8-f852 /mnt/edriver vfat defaults 0 0 ``` --- ## Passo 10: Copiar o Binário para a Pasta Correta 📥 Agora, copie o binário baixado para a pasta `/opt/nrs`: ```bash cp nrs-arm64 /opt/nrs ``` --- ## Passo 11: Criar o Arquivo de Configuração 🛠️ Crie o arquivo de configuração com o seguinte conteúdo e salve-o em `/opt/nrs/config.yaml`: ```yaml app_env: production info: name: Nostr Relay Server description: Nostr Relay Server pub_key: "" contact: "" url: http://localhost:3334 icon: https://external-content.duckduckgo.com/iu/?u= https://public.bnbstatic.com/image/cms/crawler/COINCU_NEWS/image-495-1024x569.png base_path: /mnt/edriver negentropy: true ``` --- ## Passo 12: Copiar o Serviço para o Diretório de Systemd ⚙️ Agora, copie o arquivo `nrs.service` para o diretório `/etc/systemd/system/`: ```bash cp nrs.service /etc/systemd/system/ ``` Recarregue os serviços e inicie o serviço `nrs`: ```bash systemctl daemon-reload systemctl enable --now nrs.service ``` --- ## Passo 13: Configurar o Tor 🌐 Abra o arquivo de configuração do Tor `/var/lib/tor/torrc` e adicione a seguinte linha: ```torrc HiddenServiceDir /var/lib/tor/nostr_server/ HiddenServicePort 80 127.0.0.1:3334 ``` --- ## Passo 14: Habilitar e Iniciar o Tor 🧅 Agora, ative e inicie o serviço Tor: ```bash systemctl enable --now tor.service ``` O Tor irá gerar um endereço `.onion` para o seu servidor Nostr. Você pode encontrá-lo no arquivo `/var/lib/tor/nostr_server/hostname`. --- ## Observações ⚠️ - Com essa configuração, **os dados serão salvos no pendrive**, enquanto o binário ficará no cartão SD do Raspberry Pi. - O endereço `.onion` do seu servidor Nostr será algo como: `ws://y3t5t5wgwjif<exemplo>h42zy7ih6iwbyd.onion`. --- Agora, seu servidor Nostr deve estar configurado e funcionando com Tor! 🥳 Se este artigo e as informações aqui contidas forem úteis para você, convidamos a considerar uma doação ao autor como forma de reconhecimento e incentivo à produção de novos conteúdos. @ 6389be64:ef439d32
2025-01-16 15:44:06## Black Locust can grow up to 170 ft tall ## Grows 3-4 ft. per year ## Native to North America ## Cold hardy in zones 3 to 8  ## Firewood - BLT wood, on a pound for pound basis is roughly half that of Anthracite Coal - Since its growth is fast, firewood can be plentiful ## Timber  - Rot resistant due to a naturally produced robinin in the wood - 100 year life span in full soil contact! (better than cedar performance) - Fence posts - Outdoor furniture - Outdoor decking - Sustainable due to its fast growth and spread - Can be coppiced (cut to the ground) - Can be pollarded (cut above ground) - Its dense wood makes durable tool handles, boxes (tool), and furniture - The wood is tougher than hickory, which is tougher than hard maple, which is tougher than oak. - A very low rate of expansion and contraction - Hardwood flooring - The highest tensile beam strength of any American tree - The wood is beautiful ## Legume - Nitrogen fixer - Fixes the same amount of nitrogen per acre as is needed for 200-bushel/acre corn - Black walnuts inter-planted with locust as “nurse” trees were shown to rapidly increase their growth [[Clark, Paul M., and Robert D. Williams. (1978) Black walnut growth increased when interplanted with nitrogen-fixing shrubs and trees. Proceedings of the Indiana Academy of Science, vol. 88, pp. 88-91.]] ## Bees  - The edible flower clusters are also a top food source for honey bees ## Shade Provider  - Its light, airy overstory provides dappled shade - Planted on the west side of a garden it provides relief during the hottest part of the day - (nitrogen provider) - Planted on the west side of a house, its quick growth soon shades that side from the sun ## Wind-break  - Fast growth plus it's feathery foliage reduces wind for animals, crops, and shelters ## Fodder - Over 20% crude protein - 4.1 kcal/g of energy - Baertsche, S.R, M.T. Yokoyama, and J.W. Hanover (1986) Short rotation, hardwood tree biomass as potential ruminant feed-chemical composition, nylon bag ruminal degradation and ensilement of selected species. J. Animal Sci. 63 2028-2043
@ 6389be64:ef439d32
2025-01-16 15:44:06## Black Locust can grow up to 170 ft tall ## Grows 3-4 ft. per year ## Native to North America ## Cold hardy in zones 3 to 8  ## Firewood - BLT wood, on a pound for pound basis is roughly half that of Anthracite Coal - Since its growth is fast, firewood can be plentiful ## Timber  - Rot resistant due to a naturally produced robinin in the wood - 100 year life span in full soil contact! (better than cedar performance) - Fence posts - Outdoor furniture - Outdoor decking - Sustainable due to its fast growth and spread - Can be coppiced (cut to the ground) - Can be pollarded (cut above ground) - Its dense wood makes durable tool handles, boxes (tool), and furniture - The wood is tougher than hickory, which is tougher than hard maple, which is tougher than oak. - A very low rate of expansion and contraction - Hardwood flooring - The highest tensile beam strength of any American tree - The wood is beautiful ## Legume - Nitrogen fixer - Fixes the same amount of nitrogen per acre as is needed for 200-bushel/acre corn - Black walnuts inter-planted with locust as “nurse” trees were shown to rapidly increase their growth [[Clark, Paul M., and Robert D. Williams. (1978) Black walnut growth increased when interplanted with nitrogen-fixing shrubs and trees. Proceedings of the Indiana Academy of Science, vol. 88, pp. 88-91.]] ## Bees  - The edible flower clusters are also a top food source for honey bees ## Shade Provider  - Its light, airy overstory provides dappled shade - Planted on the west side of a garden it provides relief during the hottest part of the day - (nitrogen provider) - Planted on the west side of a house, its quick growth soon shades that side from the sun ## Wind-break  - Fast growth plus it's feathery foliage reduces wind for animals, crops, and shelters ## Fodder - Over 20% crude protein - 4.1 kcal/g of energy - Baertsche, S.R, M.T. Yokoyama, and J.W. Hanover (1986) Short rotation, hardwood tree biomass as potential ruminant feed-chemical composition, nylon bag ruminal degradation and ensilement of selected species. J. Animal Sci. 63 2028-2043 @ a012dc82:6458a70d
2025-01-20 02:02:07The advent of cryptocurrency has sparked a modern-day gold rush, with Bitcoin mining at the forefront of this digital revolution. The United States, with its vast resources and technological prowess, has become a fertile ground for these operations. However, the recent shift in the global mining landscape has brought a wave of Chinese mining companies to U.S. shores, fleeing a regulatory crackdown in their homeland. This migration has set off alarm bells within national security circles, as the technology that underpins cryptocurrencies is not just a tool for financial gain but also a potential vector for cyber espionage and other security threats. The dual-use nature of this technology, capable of both revolutionizing economies and potentially undermining national security, has placed it at the heart of a complex debate involving economic policy, technological innovation, and national defense. **Table Of Content** - The Economic Impact of Cryptocurrency Mining - National Security Risks and Strategic Concerns - Regulatory Responses to Foreign Mining Operations - The Path Forward: Innovation, Security, and Diplomacy - Conclusion - FAQs The economic allure of cryptocurrency mining is undeniable. In regions hit hard by economic downturns, the establishment of mining operations has been a boon, providing much-needed jobs and revitalizing local economies. These operations often take over abandoned industrial sites, turning them into hives of high-tech activity. The promise of a revitalized industrial base, however, comes with caveats. The energy-intensive nature of cryptocurrency mining has led to a surge in demand for electricity, straining local grids and raising concerns about the environmental impact of such operations. The long-term economic benefits are also questioned, as the volatility of the cryptocurrency market means that the stability of these jobs and the longevity of the operations are not guaranteed. As Chinese companies increasingly dominate this space, there is also the fear that the economic benefits may be offset by the outflow of profits to foreign entities. **National Security Risks and Strategic Concerns** The strategic implications of foreign-controlled cryptocurrency mining operations on U.S. soil are complex and troubling. The opaque nature of these operations, often shrouded in layers of corporate secrecy, makes it difficult to discern their true intentions. The proximity of some mining farms to sensitive sites, such as military bases and critical infrastructure, has compounded these fears, suggesting the potential for these facilities to be used for more than just mining. The vast computational power of mining operations could theoretically be repurposed for code-breaking and hacking, posing a direct threat to national security. The concern is not just hypothetical; it is rooted in a history of cyber incursions attributed to Chinese state-sponsored actors. The potential for these mining operations to serve as a front for such activities, intentionally or not, has put them in the crosshairs of U.S. security agencies. **Regulatory Responses to Foreign Mining Operations** The U.S. government's response to the influx of Chinese cryptocurrency mining operations has been measured yet firm. Recognizing the need to maintain an open economic environment that fosters innovation, regulators have nonetheless moved to establish guardrails to protect national interests. This has involved a multifaceted approach, including the proposal of legislation aimed at scrutinizing foreign investments in critical technologies and infrastructure. Agencies such as the Committee on Foreign Investment in the United States (CFIUS) have been at the forefront of these efforts, working to untangle the complex web of ownership and control that characterizes foreign mining operations. The goal is to ensure that while the U.S. remains a hub for technological innovation, it does not become a playground for foreign powers with adversarial intentions. **The Path Forward: Innovation, Security, and Diplomacy** The path forward for the United States in managing the rise of Chinese bitcoin mining operations is akin to walking a tightrope. On one side is the need to nurture innovation and maintain the U.S.'s competitive edge in the burgeoning field of cryptocurrency. On the other is the imperative to safeguard national security and ensure that the country's technological infrastructure is not compromised. This delicate balance requires a nuanced approach that includes fostering a robust domestic mining industry, investing in renewable energy sources to mitigate the environmental impact, and engaging in strategic diplomacy to manage the international dimensions of cryptocurrency governance. The U.S. must leverage its strengths in innovation, policy-making, and international relations to set standards that will shape the future of cryptocurrency mining and secure its digital economy. **Conclusion** The challenge of balancing the economic potential of cryptocurrency mining with the imperatives of national security is emblematic of the broader challenges facing policymakers in the digital age. As Chinese bitcoin mining operations continue to expand their footprint in the U.S., the need for a strategic, measured response becomes increasingly critical. This response must be multifaceted, engaging with all stakeholders, including the mining industry, environmental groups, energy providers, and security agencies. By striking a balance between economic growth and security, the U.S. can harness the potential of the digital economy while protecting its national interests. The stakes are high, and the decisions made today will have lasting implications for the security and prosperity of future generations. **FAQs** **How does Bitcoin mining impact local economies?** Bitcoin mining can provide jobs and economic investment in local communities, especially in areas with excess energy capacity or where industrial sites are underutilized. **What is the U.S. government's response to foreign cryptocurrency mining operations?** The U.S. government is considering stricter regulations on foreign investments in critical technologies, including cryptocurrency mining, to protect national security while fostering economic growth. **Can cryptocurrency mining operations be environmentally sustainable?** There are concerns about the high energy consumption of mining operations, but with investment in renewable energy and efficient technologies, mining can move towards greater sustainability. **How does the U.S. plan to balance innovation with security in cryptocurrency mining?** The U.S. aims to strike a balance by creating policies that encourage technological innovation and economic benefits while implementing security measures to protect against potential threats. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: [Instagram: @croxroadnews.co](https://x.com/croxroadnewsco)** **Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)** **Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** *DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.*
@ a012dc82:6458a70d
2025-01-20 02:02:07The advent of cryptocurrency has sparked a modern-day gold rush, with Bitcoin mining at the forefront of this digital revolution. The United States, with its vast resources and technological prowess, has become a fertile ground for these operations. However, the recent shift in the global mining landscape has brought a wave of Chinese mining companies to U.S. shores, fleeing a regulatory crackdown in their homeland. This migration has set off alarm bells within national security circles, as the technology that underpins cryptocurrencies is not just a tool for financial gain but also a potential vector for cyber espionage and other security threats. The dual-use nature of this technology, capable of both revolutionizing economies and potentially undermining national security, has placed it at the heart of a complex debate involving economic policy, technological innovation, and national defense. **Table Of Content** - The Economic Impact of Cryptocurrency Mining - National Security Risks and Strategic Concerns - Regulatory Responses to Foreign Mining Operations - The Path Forward: Innovation, Security, and Diplomacy - Conclusion - FAQs The economic allure of cryptocurrency mining is undeniable. In regions hit hard by economic downturns, the establishment of mining operations has been a boon, providing much-needed jobs and revitalizing local economies. These operations often take over abandoned industrial sites, turning them into hives of high-tech activity. The promise of a revitalized industrial base, however, comes with caveats. The energy-intensive nature of cryptocurrency mining has led to a surge in demand for electricity, straining local grids and raising concerns about the environmental impact of such operations. The long-term economic benefits are also questioned, as the volatility of the cryptocurrency market means that the stability of these jobs and the longevity of the operations are not guaranteed. As Chinese companies increasingly dominate this space, there is also the fear that the economic benefits may be offset by the outflow of profits to foreign entities. **National Security Risks and Strategic Concerns** The strategic implications of foreign-controlled cryptocurrency mining operations on U.S. soil are complex and troubling. The opaque nature of these operations, often shrouded in layers of corporate secrecy, makes it difficult to discern their true intentions. The proximity of some mining farms to sensitive sites, such as military bases and critical infrastructure, has compounded these fears, suggesting the potential for these facilities to be used for more than just mining. The vast computational power of mining operations could theoretically be repurposed for code-breaking and hacking, posing a direct threat to national security. The concern is not just hypothetical; it is rooted in a history of cyber incursions attributed to Chinese state-sponsored actors. The potential for these mining operations to serve as a front for such activities, intentionally or not, has put them in the crosshairs of U.S. security agencies. **Regulatory Responses to Foreign Mining Operations** The U.S. government's response to the influx of Chinese cryptocurrency mining operations has been measured yet firm. Recognizing the need to maintain an open economic environment that fosters innovation, regulators have nonetheless moved to establish guardrails to protect national interests. This has involved a multifaceted approach, including the proposal of legislation aimed at scrutinizing foreign investments in critical technologies and infrastructure. Agencies such as the Committee on Foreign Investment in the United States (CFIUS) have been at the forefront of these efforts, working to untangle the complex web of ownership and control that characterizes foreign mining operations. The goal is to ensure that while the U.S. remains a hub for technological innovation, it does not become a playground for foreign powers with adversarial intentions. **The Path Forward: Innovation, Security, and Diplomacy** The path forward for the United States in managing the rise of Chinese bitcoin mining operations is akin to walking a tightrope. On one side is the need to nurture innovation and maintain the U.S.'s competitive edge in the burgeoning field of cryptocurrency. On the other is the imperative to safeguard national security and ensure that the country's technological infrastructure is not compromised. This delicate balance requires a nuanced approach that includes fostering a robust domestic mining industry, investing in renewable energy sources to mitigate the environmental impact, and engaging in strategic diplomacy to manage the international dimensions of cryptocurrency governance. The U.S. must leverage its strengths in innovation, policy-making, and international relations to set standards that will shape the future of cryptocurrency mining and secure its digital economy. **Conclusion** The challenge of balancing the economic potential of cryptocurrency mining with the imperatives of national security is emblematic of the broader challenges facing policymakers in the digital age. As Chinese bitcoin mining operations continue to expand their footprint in the U.S., the need for a strategic, measured response becomes increasingly critical. This response must be multifaceted, engaging with all stakeholders, including the mining industry, environmental groups, energy providers, and security agencies. By striking a balance between economic growth and security, the U.S. can harness the potential of the digital economy while protecting its national interests. The stakes are high, and the decisions made today will have lasting implications for the security and prosperity of future generations. **FAQs** **How does Bitcoin mining impact local economies?** Bitcoin mining can provide jobs and economic investment in local communities, especially in areas with excess energy capacity or where industrial sites are underutilized. **What is the U.S. government's response to foreign cryptocurrency mining operations?** The U.S. government is considering stricter regulations on foreign investments in critical technologies, including cryptocurrency mining, to protect national security while fostering economic growth. **Can cryptocurrency mining operations be environmentally sustainable?** There are concerns about the high energy consumption of mining operations, but with investment in renewable energy and efficient technologies, mining can move towards greater sustainability. **How does the U.S. plan to balance innovation with security in cryptocurrency mining?** The U.S. aims to strike a balance by creating policies that encourage technological innovation and economic benefits while implementing security measures to protect against potential threats. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: [Instagram: @croxroadnews.co](https://x.com/croxroadnewsco)** **Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)** **Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** *DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.* @ b8851a06:9b120ba1
2025-01-14 15:28:32## **It Begins with a Click** It starts with a click: *“Do you agree to our terms and conditions?”*\ You scroll, you click, you comply. A harmless act, right? But what if every click was a surrender? What if every "yes" was another link in the chain binding you to a life where freedom requires approval? This is the age of permission. Every aspect of your life is mediated by gatekeepers. Governments demand forms, corporations demand clicks, and algorithms demand obedience. You’re free, of course, as long as you play by the rules. But who writes the rules? Who decides what’s allowed? Who owns your life? --- ## **Welcome to Digital Serfdom** We once imagined the internet as a digital frontier—a vast, open space where ideas could flow freely and innovation would know no bounds. But instead of creating a decentralized utopia, we built a new feudal system. - Your data? Owned by the lords of Big Tech. - Your money? Controlled by banks and bureaucrats who can freeze it on a whim. - Your thoughts? Filtered by algorithms that reward conformity and punish dissent. The modern internet is a land of serfs and lords, and guess who’s doing the farming? You. Every time you agree to the terms, accept the permissions, or let an algorithm decide for you, you till the fields of a system designed to control, not liberate. They don’t call it control, of course. They call it *“protection.”* They say, “We’re keeping you safe,” as they build a cage so big you can’t see the bars. --- ## **Freedom in Chains** But let’s be honest: we’re not just victims of this system—we’re participants. We’ve traded freedom for convenience, sovereignty for security. It’s easier to click “I Agree” than to read the fine print. It’s easier to let someone else hold your money than to take responsibility for it yourself. It’s easier to live a life of quiet compliance than to risk the chaos of true independence. We tell ourselves it’s no big deal. What’s one click? What’s one form? But the permissions pile up. The chains grow heavier. And one day, you wake up and realize you’re free to do exactly what the system allows—and nothing more. --- ## **The Great Unpermissioning** It doesn’t have to be this way. You don’t need their approval. You don’t need their systems. You don’t need their permission. The Great Unpermissioning is not a movement—it’s a mindset. It’s the refusal to accept a life mediated by gatekeepers. It’s the quiet rebellion of saying, *“No.”* It’s the realization that the freedom you seek won’t be granted—it must be reclaimed. - **Stop asking.** Permission is their tool. Refusal is your weapon. - **Start building.** Embrace tools that decentralize power: Bitcoin, encryption, open-source software, decentralized communication. Build systems they can’t control. - **Stand firm.** They’ll tell you it’s dangerous. They’ll call you a radical. But remember: the most dangerous thing you can do is comply. The path won’t be easy. Freedom never is. But it will be worth it. --- ## **The New Frontier** The age of permission has turned us into digital serfs, but there’s a new frontier on the horizon. It’s a world where you control your money, your data, your decisions. It’s a world of encryption, anonymity, and sovereignty. It’s a world built not on permission but on principles. This world won’t be given to you. You have to build it. You have to fight for it. And it starts with one simple act: refusing to comply. --- ## **A Final Word** They promised us safety, but what they delivered was submission. The age of permission has enslaved us to the mundane, the monitored, and the mediocre. The Great Unpermissioning isn’t about tearing down the old world—it’s about walking away from it. You don’t need to wait for their approval. You don’t need to ask for their permission. The freedom you’re looking for is already yours. Permission is their power—refusal is yours.
@ b8851a06:9b120ba1
2025-01-14 15:28:32## **It Begins with a Click** It starts with a click: *“Do you agree to our terms and conditions?”*\ You scroll, you click, you comply. A harmless act, right? But what if every click was a surrender? What if every "yes" was another link in the chain binding you to a life where freedom requires approval? This is the age of permission. Every aspect of your life is mediated by gatekeepers. Governments demand forms, corporations demand clicks, and algorithms demand obedience. You’re free, of course, as long as you play by the rules. But who writes the rules? Who decides what’s allowed? Who owns your life? --- ## **Welcome to Digital Serfdom** We once imagined the internet as a digital frontier—a vast, open space where ideas could flow freely and innovation would know no bounds. But instead of creating a decentralized utopia, we built a new feudal system. - Your data? Owned by the lords of Big Tech. - Your money? Controlled by banks and bureaucrats who can freeze it on a whim. - Your thoughts? Filtered by algorithms that reward conformity and punish dissent. The modern internet is a land of serfs and lords, and guess who’s doing the farming? You. Every time you agree to the terms, accept the permissions, or let an algorithm decide for you, you till the fields of a system designed to control, not liberate. They don’t call it control, of course. They call it *“protection.”* They say, “We’re keeping you safe,” as they build a cage so big you can’t see the bars. --- ## **Freedom in Chains** But let’s be honest: we’re not just victims of this system—we’re participants. We’ve traded freedom for convenience, sovereignty for security. It’s easier to click “I Agree” than to read the fine print. It’s easier to let someone else hold your money than to take responsibility for it yourself. It’s easier to live a life of quiet compliance than to risk the chaos of true independence. We tell ourselves it’s no big deal. What’s one click? What’s one form? But the permissions pile up. The chains grow heavier. And one day, you wake up and realize you’re free to do exactly what the system allows—and nothing more. --- ## **The Great Unpermissioning** It doesn’t have to be this way. You don’t need their approval. You don’t need their systems. You don’t need their permission. The Great Unpermissioning is not a movement—it’s a mindset. It’s the refusal to accept a life mediated by gatekeepers. It’s the quiet rebellion of saying, *“No.”* It’s the realization that the freedom you seek won’t be granted—it must be reclaimed. - **Stop asking.** Permission is their tool. Refusal is your weapon. - **Start building.** Embrace tools that decentralize power: Bitcoin, encryption, open-source software, decentralized communication. Build systems they can’t control. - **Stand firm.** They’ll tell you it’s dangerous. They’ll call you a radical. But remember: the most dangerous thing you can do is comply. The path won’t be easy. Freedom never is. But it will be worth it. --- ## **The New Frontier** The age of permission has turned us into digital serfs, but there’s a new frontier on the horizon. It’s a world where you control your money, your data, your decisions. It’s a world of encryption, anonymity, and sovereignty. It’s a world built not on permission but on principles. This world won’t be given to you. You have to build it. You have to fight for it. And it starts with one simple act: refusing to comply. --- ## **A Final Word** They promised us safety, but what they delivered was submission. The age of permission has enslaved us to the mundane, the monitored, and the mediocre. The Great Unpermissioning isn’t about tearing down the old world—it’s about walking away from it. You don’t need to wait for their approval. You don’t need to ask for their permission. The freedom you’re looking for is already yours. Permission is their power—refusal is yours. @ 41fa852b:af7b7706
2025-01-19 18:31:45> "It is not the strongest of the species that survive, nor the most intelligent, but the one most responsive to change." -- Charles Darwin * * * **It's usually a big week when the 21st comes around, but this week we have 5 meetups that day!** Also, Trump takes office on Monday so there'll be loads to discuss at this week's meetups. Let's take a look… * * * [](https://bitcoinevents.uk/donate/) * * * _This week's sponsor is…_ [](https://www.orangepillapp.com?utm_source=BEUK&utm_medium=email&utm_campaign=BEUK) * * * ### **Upcoming Bitcoin Meetups** Happening this week… 1. [**Bitcoin Bristol**](https://bitcoinbristol.org/): Meeting at Little Martha Brewing, BS2 0QT. On Tuesday 21st at 18:15. 🍺 2. [**Bitcoin Surrey**](https://meetu.ps/e/NLBzr/v822r/i): It's a Bitcoin Pension Scheme Special this month at [Yiayias at The Fox](https://www.yiayias.co.uk/yiayiasatthefox/). A fireside chat and Q&A with Sam Roberts, Cartwright's Director of Investment Consulting (1st UK pension scheme to allocate 3% to Bitcoin). 18:00 - 23:00 on the 21st. Bitcoin accepted at the venue. 🎙️🍻 3. [**Newcastle upon Tyne Bitcoin Meetup**](https://bitcoinevents.uk/newcastle-bitcoin/): The next Newcastle meetup is on Tuesday 21st January at Kabin @ Kabannas, L2 6RE. 18:30 PM. 🍻 4. [**London Bitcoin Space**](https://meetu.ps/e/NNk9z/v822r/i): LBS will be at Cyphermunk house on Tuesday 21st from 18:30 till 22:00 for a social gathering, head along to share knowledge and meet some fellow Bitcoiners. 🫂 5. [**Oxbit**](https://x.com/oxbitmeetup): Celebrate Bitcoins 16th birthday with the Oxford meetup crew. You'll find them at [The Old Black Horse](https://www.oldblackhorse.com/) (bitcoin accepted) at 19:00 on the 21st. 🍺 6. [**Preston Bitcoin Meetup**](https://x.com/prestonbtcmeet/status/1880289279093666243): Join the Preston meetup for A Bitcoin chat and some amazing burgers. 18:30 on Thursday the 23rd January. At All Hopes No Promises, PR1 2US. 7. [**The Northamptonshire Bitcoin Network**](https://bitcoinevents.uk/northamptonshire-bitcoin-network/) : [BTC Citadel Engineering](https://btc-citadel.co.uk/) are hosting a 'Bitcoin Builders' space on Saturday the 25th. Head along to learn about Seedsigners and how to build one. Come and use the 3D printers, get a project started and chat about Bitcoin with everyone there. It all gets started at 12:00. No tech skills are necessary. ⚙️🧡 8. [**Bitcoin Walk - Edinburgh**](https://bitcoinevents.uk/bitcoinwalk/): Every Saturday they walk around Arthur's Seat in this historic city. Join them at 12 pm to chat about all things Bitcoin and keep fit. 🚶🏻🚶🏼♀️🚶🏽♂️ 9. [**Bitcoin East**](https://x.com/bitcoineastuk/status/1875867783457910895): Their first meetup of 2025 will be at Marzano Cafe in the beautiful city of Norwich. Join them at 11:00 on Sunday 26th Jan, there's a lot to discuss. ☕️ * * * **Get Involved** - **Volunteer Opportunities**: [Bridge2Bitcoin](https://bridge2bitcoin.com/) is actively seeking volunteers who share our passion for merchant adoption. We'd be delighted to connect if you're eager to contribute. Reach out to us on [Twitter](https://x.com/bridge2bitcoin) or through our [website](https://bridge2bitcoin.com/). - **Start Your Own Meetup**: Interested in launching a Bitcoin meetup? We're here to support you every step of the way. We've assisted numerous UK Bitcoin meetups in getting started. Get in touch via [Twitter](https://x.com/bitcoineventsuk). - [**Contribute to BTCMaps**](https://wiki.btcmap.org/general/tagging-instructions.html): BTCMaps is a vital part of the Bitcoin ecosystem. It's a perfect project to get involved with if you're not a coder or even that technical. A great way to give back to the community. Maintain an area of the UK and keep it up-to-date. - **Telegram users**: You might find our [Telegram Channel](https://t.me/BitcoinEventsUKHub) another useful way to keep up-to-date with UK meetups. - **Feedback and Suggestions**: We value your input! Share your ideas on how we can enhance this newsletter. * * * _This week's sponsors are…_ [](https://orangecoinstore.com/) [](https://lasereyes.cards/skins/leather-bitcoin-skin/) * * * Get out and support the meetups where you can, visit [Bitcoin Events UK](https://bitcoinevents.uk/) for more info on each meetup and to find your closest on the interactive map. Stay tuned for more updates next week! Simon. [](https://bitcoinevents.uk/donate/)
@ 41fa852b:af7b7706
2025-01-19 18:31:45> "It is not the strongest of the species that survive, nor the most intelligent, but the one most responsive to change." -- Charles Darwin * * * **It's usually a big week when the 21st comes around, but this week we have 5 meetups that day!** Also, Trump takes office on Monday so there'll be loads to discuss at this week's meetups. Let's take a look… * * * [](https://bitcoinevents.uk/donate/) * * * _This week's sponsor is…_ [](https://www.orangepillapp.com?utm_source=BEUK&utm_medium=email&utm_campaign=BEUK) * * * ### **Upcoming Bitcoin Meetups** Happening this week… 1. [**Bitcoin Bristol**](https://bitcoinbristol.org/): Meeting at Little Martha Brewing, BS2 0QT. On Tuesday 21st at 18:15. 🍺 2. [**Bitcoin Surrey**](https://meetu.ps/e/NLBzr/v822r/i): It's a Bitcoin Pension Scheme Special this month at [Yiayias at The Fox](https://www.yiayias.co.uk/yiayiasatthefox/). A fireside chat and Q&A with Sam Roberts, Cartwright's Director of Investment Consulting (1st UK pension scheme to allocate 3% to Bitcoin). 18:00 - 23:00 on the 21st. Bitcoin accepted at the venue. 🎙️🍻 3. [**Newcastle upon Tyne Bitcoin Meetup**](https://bitcoinevents.uk/newcastle-bitcoin/): The next Newcastle meetup is on Tuesday 21st January at Kabin @ Kabannas, L2 6RE. 18:30 PM. 🍻 4. [**London Bitcoin Space**](https://meetu.ps/e/NNk9z/v822r/i): LBS will be at Cyphermunk house on Tuesday 21st from 18:30 till 22:00 for a social gathering, head along to share knowledge and meet some fellow Bitcoiners. 🫂 5. [**Oxbit**](https://x.com/oxbitmeetup): Celebrate Bitcoins 16th birthday with the Oxford meetup crew. You'll find them at [The Old Black Horse](https://www.oldblackhorse.com/) (bitcoin accepted) at 19:00 on the 21st. 🍺 6. [**Preston Bitcoin Meetup**](https://x.com/prestonbtcmeet/status/1880289279093666243): Join the Preston meetup for A Bitcoin chat and some amazing burgers. 18:30 on Thursday the 23rd January. At All Hopes No Promises, PR1 2US. 7. [**The Northamptonshire Bitcoin Network**](https://bitcoinevents.uk/northamptonshire-bitcoin-network/) : [BTC Citadel Engineering](https://btc-citadel.co.uk/) are hosting a 'Bitcoin Builders' space on Saturday the 25th. Head along to learn about Seedsigners and how to build one. Come and use the 3D printers, get a project started and chat about Bitcoin with everyone there. It all gets started at 12:00. No tech skills are necessary. ⚙️🧡 8. [**Bitcoin Walk - Edinburgh**](https://bitcoinevents.uk/bitcoinwalk/): Every Saturday they walk around Arthur's Seat in this historic city. Join them at 12 pm to chat about all things Bitcoin and keep fit. 🚶🏻🚶🏼♀️🚶🏽♂️ 9. [**Bitcoin East**](https://x.com/bitcoineastuk/status/1875867783457910895): Their first meetup of 2025 will be at Marzano Cafe in the beautiful city of Norwich. Join them at 11:00 on Sunday 26th Jan, there's a lot to discuss. ☕️ * * * **Get Involved** - **Volunteer Opportunities**: [Bridge2Bitcoin](https://bridge2bitcoin.com/) is actively seeking volunteers who share our passion for merchant adoption. We'd be delighted to connect if you're eager to contribute. Reach out to us on [Twitter](https://x.com/bridge2bitcoin) or through our [website](https://bridge2bitcoin.com/). - **Start Your Own Meetup**: Interested in launching a Bitcoin meetup? We're here to support you every step of the way. We've assisted numerous UK Bitcoin meetups in getting started. Get in touch via [Twitter](https://x.com/bitcoineventsuk). - [**Contribute to BTCMaps**](https://wiki.btcmap.org/general/tagging-instructions.html): BTCMaps is a vital part of the Bitcoin ecosystem. It's a perfect project to get involved with if you're not a coder or even that technical. A great way to give back to the community. Maintain an area of the UK and keep it up-to-date. - **Telegram users**: You might find our [Telegram Channel](https://t.me/BitcoinEventsUKHub) another useful way to keep up-to-date with UK meetups. - **Feedback and Suggestions**: We value your input! Share your ideas on how we can enhance this newsletter. * * * _This week's sponsors are…_ [](https://orangecoinstore.com/) [](https://lasereyes.cards/skins/leather-bitcoin-skin/) * * * Get out and support the meetups where you can, visit [Bitcoin Events UK](https://bitcoinevents.uk/) for more info on each meetup and to find your closest on the interactive map. Stay tuned for more updates next week! Simon. [](https://bitcoinevents.uk/donate/) @ 6389be64:ef439d32
2025-01-14 01:31:12Bitcoin is more than money, more than an asset, and more than a store of value. Bitcoin is a Prime Mover, an enabler and it ignites imaginations. It certainly fueled an idea in my mind. The idea integrates sensors, computational prowess, actuated machinery, power conversion, and electronic communications to form an autonomous, machined creature roaming forests and harvesting the most widespread and least energy-dense fuel source available. I call it the Forest Walker and it eats wood, and mines Bitcoin. I know what you're thinking. Why not just put Bitcoin mining rigs where they belong: in a hosted facility sporting electricity from energy-dense fuels like natural gas, climate-controlled with excellent data piping in and out? Why go to all the trouble building a robot that digests wood creating flammable gasses fueling an engine to run a generator powering Bitcoin miners? It's all about synergy. Bitcoin mining enables the realization of multiple, seemingly unrelated, yet useful activities. Activities considered un-profitable if not for Bitcoin as the Prime Mover. This is much more than simply mining the greatest asset ever conceived by humankind. It’s about the power of synergy, which Bitcoin plays only one of many roles. The synergy created by this system can stabilize forests' fire ecology while generating multiple income streams. That’s the realistic goal here and requires a brief history of American Forest management before continuing. # Smokey The Bear In 1944, the Smokey Bear Wildfire Prevention Campaign began in the United States. “Only YOU can prevent forest fires” remains the refrain of the Ad Council’s longest running campaign. The Ad Council is a U.S. non-profit set up by the American Association of Advertising Agencies and the Association of National Advertisers in 1942. It would seem that the U.S. Department of the Interior was concerned about pesky forest fires and wanted them to stop. So, alongside a national policy of extreme fire suppression they enlisted the entire U.S. population to get onboard via the Ad Council and it worked. Forest fires were almost obliterated and everyone was happy, right? Wrong. Smokey is a fantastically successful bear so forest fires became so few for so long that the fuel load - dead wood - in forests has become very heavy. So heavy that when a fire happens (and they always happen) it destroys everything in its path because the more fuel there is the hotter that fire becomes. Trees, bushes, shrubs, and all other plant life cannot escape destruction (not to mention homes and businesses). The soil microbiology doesn’t escape either as it is burned away even in deeper soils. To add insult to injury, hydrophobic waxy residues condense on the soil surface, forcing water to travel over the ground rather than through it eroding forest soils. Good job, Smokey. Well done, Sir! Most terrestrial ecologies are “fire ecologies”. Fire is a part of these systems’ fuel load and pest management. Before we pretended to “manage” millions of acres of forest, fires raged over the world, rarely damaging forests. The fuel load was always too light to generate fires hot enough to moonscape mountainsides. Fires simply burned off the minor amounts of fuel accumulated since the fire before. The lighter heat, smoke, and other combustion gasses suppressed pests, keeping them in check and the smoke condensed into a plant growth accelerant called wood vinegar, not a waxy cap on the soil. These fires also cleared out weak undergrowth, cycled minerals, and thinned the forest canopy, allowing sunlight to penetrate to the forest floor. Without a fire’s heat, many pine tree species can’t sow their seed. The heat is required to open the cones (the seed bearing structure) of Spruce, Cypress, Sequoia, Jack Pine, Lodgepole Pine and many more. Without fire forests can’t have babies. The idea was to protect the forests, and it isn't working. So, in a world of fire, what does an ally look like and what does it do? # Meet The Forest Walker  For the Forest Walker to work as a mobile, autonomous unit, a solid platform that can carry several hundred pounds is required. It so happens this chassis already exists but shelved. Introducing the Legged Squad Support System (LS3). A joint project between Boston Dynamics, DARPA, and the United States Marine Corps, the quadrupedal robot is the size of a cow, can carry 400 pounds (180 kg) of equipment, negotiate challenging terrain, and operate for 24 hours before needing to refuel. Yes, it had an engine. Abandoned in 2015, the thing was too noisy for military deployment and maintenance "under fire" is never a high-quality idea. However, we can rebuild it to act as a platform for the Forest Walker; albeit with serious alterations. It would need to be bigger, probably. Carry more weight? Definitely. Maybe replace structural metal with carbon fiber and redesign much as 3D printable parts for more effective maintenance. The original system has a top operational speed of 8 miles per hour. For our purposes, it only needs to move about as fast as a grazing ruminant. Without the hammering vibrations of galloping into battle, shocks of exploding mortars, and drunken soldiers playing "Wrangler of Steel Machines", time between failures should be much longer and the overall energy consumption much lower. The LS3 is a solid platform to build upon. Now it just needs to be pulled out of the mothballs, and completely refitted with outboard equipment. # The Small Branch Chipper  When I say “Forest fuel load” I mean the dead, carbon containing litter on the forest floor. Duff (leaves), fine-woody debris (small branches), and coarse woody debris (logs) are the fuel that feeds forest fires. Walk through any forest in the United States today and you will see quite a lot of these materials. Too much, as I have described. Some of these fuel loads can be 8 tons per acre in pine and hardwood forests and up to 16 tons per acre at active logging sites. That’s some big wood and the more that collects, the more combustible danger to the forest it represents. It also provides a technically unlimited fuel supply for the Forest Walker system. The problem is that this detritus has to be chewed into pieces that are easily ingestible by the system for the gasification process (we’ll get to that step in a minute). What we need is a wood chipper attached to the chassis (the LS3); its “mouth”. A small wood chipper handling material up to 2.5 - 3.0 inches (6.3 - 7.6 cm) in diameter would eliminate a substantial amount of fuel. There is no reason for Forest Walker to remove fallen trees. It wouldn’t have to in order to make a real difference. It need only identify appropriately sized branches and grab them. Once loaded into the chipper’s intake hopper for further processing, the beast can immediately look for more “food”. This is essentially kindling that would help ignite larger logs. If it’s all consumed by Forest Walker, then it’s not present to promote an aggravated conflagration. I have glossed over an obvious question: How does Forest Walker see and identify branches and such? LiDaR (Light Detection and Ranging) attached to Forest Walker images the local area and feed those data to onboard computers for processing. Maybe AI plays a role. Maybe simple machine learning can do the trick. One thing is for certain: being able to identify a stick and cause robotic appendages to pick it up is not impossible. Great! We now have a quadrupedal robot autonomously identifying and “eating” dead branches and other light, combustible materials. Whilst strolling through the forest, depleting future fires of combustibles, Forest Walker has already performed a major function of this system: making the forest safer. It's time to convert this low-density fuel into a high-density fuel Forest Walker can leverage. Enter the gasification process. # The Gassifier  The gasifier is the heart of the entire system; it’s where low-density fuel becomes the high-density fuel that powers the entire system. Biochar and wood vinegar are process wastes and I’ll discuss why both are powerful soil amendments in a moment, but first, what’s gasification? Reacting shredded carbonaceous material at high temperatures in a low or no oxygen environment converts the biomass into biochar, wood vinegar, heat, and Synthesis Gas (Syngas). Syngas consists primarily of hydrogen, carbon monoxide, and methane. All of which are extremely useful fuels in a gaseous state. Part of this gas is used to heat the input biomass and keep the reaction temperature constant while the internal combustion engine that drives the generator to produce electrical power consumes the rest. Critically, this gasification process is “continuous feed”. Forest Walker must intake biomass from the chipper, process it to fuel, and dump the waste (CO2, heat, biochar, and wood vinegar) continuously. It cannot stop. Everything about this system depends upon this continual grazing, digestion, and excretion of wastes just as a ruminal does. And, like a ruminant, all waste products enhance the local environment. When I first heard of gasification, I didn’t believe that it was real. Running an electric generator from burning wood seemed more akin to “conspiracy fantasy” than science. Not only is gasification real, it’s ancient technology. A man named Dean Clayton first started experiments on gasification in 1699 and in 1901 gasification was used to power a vehicle. By the end of World War II, there were 500,000 Syngas powered vehicles in Germany alone because of fossil fuel rationing during the war. The global gasification market was $480 billion in 2022 and projected to be as much as $700 billion by 2030 (Vantage Market Research). Gasification technology is the best choice to power the Forest Walker because it’s self-contained and we want its waste products. # Biochar: The Waste  Biochar (AKA agricultural charcoal) is fairly simple: it’s almost pure, solid carbon that resembles charcoal. Its porous nature packs large surface areas into small, 3 dimensional nuggets. Devoid of most other chemistry, like hydrocarbons (methane) and ash (minerals), biochar is extremely lightweight. Do not confuse it with the charcoal you buy for your grill. Biochar doesn’t make good grilling charcoal because it would burn too rapidly as it does not contain the multitude of flammable components that charcoal does. Biochar has several other good use cases. Water filtration, water retention, nutrient retention, providing habitat for microscopic soil organisms, and carbon sequestration are the main ones that we are concerned with here. Carbon has an amazing ability to adsorb (substances stick to and accumulate on the surface of an object) manifold chemistries. Water, nutrients, and pollutants tightly bind to carbon in this format. So, biochar makes a respectable filter and acts as a “battery” of water and nutrients in soils. Biochar adsorbs and holds on to seven times its weight in water. Soil containing biochar is more drought resilient than soil without it. Adsorbed nutrients, tightly sequestered alongside water, get released only as plants need them. Plants must excrete protons (H+) from their roots to disgorge water or positively charged nutrients from the biochar's surface; it's an active process. Biochar’s surface area (where adsorption happens) can be 500 square meters per gram or more. That is 10% larger than an official NBA basketball court for every gram of biochar. Biochar’s abundant surface area builds protective habitats for soil microbes like fungi and bacteria and many are critical for the health and productivity of the soil itself. The “carbon sequestration” component of biochar comes into play where “carbon credits” are concerned. There is a financial market for carbon. Not leveraging that market for revenue is foolish. I am climate agnostic. All I care about is that once solid carbon is inside the soil, it will stay there for thousands of years, imparting drought resiliency, fertility collection, nutrient buffering, and release for that time span. I simply want as much solid carbon in the soil because of the undeniably positive effects it has, regardless of any climactic considerations. # Wood Vinegar: More Waste  Another by-product of the gasification process is wood vinegar (Pyroligneous acid). If you have ever seen Liquid Smoke in the grocery store, then you have seen wood vinegar. Principally composed of acetic acid, acetone, and methanol wood vinegar also contains ~200 other organic compounds. It would seem intuitive that condensed, liquefied wood smoke would at least be bad for the health of all living things if not downright carcinogenic. The counter intuition wins the day, however. Wood vinegar has been used by humans for a very long time to promote digestion, bowel, and liver health; combat diarrhea and vomiting; calm peptic ulcers and regulate cholesterol levels; and a host of other benefits. For centuries humans have annually burned off hundreds of thousands of square miles of pasture, grassland, forest, and every other conceivable terrestrial ecosystem. Why is this done? After every burn, one thing becomes obvious: the almost supernatural growth these ecosystems exhibit after the burn. How? Wood vinegar is a component of this growth. Even in open burns, smoke condenses and infiltrates the soil. That is when wood vinegar shows its quality. This stuff beefs up not only general plant growth but seed germination as well and possesses many other qualities that are beneficial to plants. It’s a pesticide, fungicide, promotes beneficial soil microorganisms, enhances nutrient uptake, and imparts disease resistance. I am barely touching a long list of attributes here, but you want wood vinegar in your soil (alongside biochar because it adsorbs wood vinegar as well). # The Internal Combustion Engine  Conversion of grazed forage to chemical, then mechanical, and then electrical energy completes the cycle. The ICE (Internal Combustion Engine) converts the gaseous fuel output from the gasifier to mechanical energy, heat, water vapor, and CO2. It’s the mechanical energy of a rotating drive shaft that we want. That rotation drives the electric generator, which is the heartbeat we need to bring this monster to life. Luckily for us, combined internal combustion engine and generator packages are ubiquitous, delivering a defined energy output given a constant fuel input. It’s the simplest part of the system. The obvious question here is whether the amount of syngas provided by the gasification process will provide enough energy to generate enough electrons to run the entire system or not. While I have no doubt the energy produced will run Forest Walker's main systems the question is really about the electrons left over. Will it be enough to run the Bitcoin mining aspect of the system? Everything is a budget. # CO2 Production For Growth  Plants are lollipops. No matter if it’s a tree or a bush or a shrubbery, the entire thing is mostly sugar in various formats but mostly long chain carbohydrates like lignin and cellulose. Plants need three things to make sugar: CO2, H2O and light. In a forest, where tree densities can be quite high, CO2 availability becomes a limiting growth factor. It’d be in the forest interests to have more available CO2 providing for various sugar formation providing the organism with food and structure. An odd thing about tree leaves, the openings that allow gasses like the ever searched for CO2 are on the bottom of the leaf (these are called stomata). Not many stomata are topside. This suggests that trees and bushes have evolved to find gasses like CO2 from below, not above and this further suggests CO2 might be in higher concentrations nearer the soil. The soil life (bacterial, fungi etc.) is constantly producing enormous amounts of CO2 and it would stay in the soil forever (eventually killing the very soil life that produces it) if not for tidal forces. Water is everywhere and whether in pools, lakes, oceans or distributed in “moist” soils water moves towards to the moon. The water in the soil and also in the water tables below the soil rise toward the surface every day. When the water rises, it expels the accumulated gasses in the soil into the atmosphere and it’s mostly CO2. It’s a good bet on how leaves developed high populations of stomata on the underside of leaves. As the water relaxes (the tide goes out) it sucks oxygenated air back into the soil to continue the functions of soil life respiration. The soil “breathes” albeit slowly. The gasses produced by the Forest Walker’s internal combustion engine consist primarily of CO2 and H2O. Combusting sugars produce the same gasses that are needed to construct the sugars because the universe is funny like that. The Forest Walker is constantly laying down these critical construction elements right where the trees need them: close to the ground to be gobbled up by the trees. # The Branch Drones  During the last ice age, giant mammals populated North America - forests and otherwise. Mastodons, woolly mammoths, rhinos, short-faced bears, steppe bison, caribou, musk ox, giant beavers, camels, gigantic ground-dwelling sloths, glyptodons, and dire wolves were everywhere. Many were ten to fifteen feet tall. As they crashed through forests, they would effectively cleave off dead side-branches of trees, halting the spread of a ground-based fire migrating into the tree crown ("laddering") which is a death knell for a forest. These animals are all extinct now and forests no longer have any manner of pruning services. But, if we build drones fitted with cutting implements like saws and loppers, optical cameras and AI trained to discern dead branches from living ones, these drones could effectively take over pruning services by identifying, cutting, and dropping to the forest floor, dead branches. The dropped branches simply get collected by the Forest Walker as part of its continual mission. The drones dock on the back of the Forest Walker to recharge their batteries when low. The whole scene would look like a grazing cow with some flies bothering it. This activity breaks the link between a relatively cool ground based fire and the tree crowns and is a vital element in forest fire control. # The Bitcoin Miner  Mining is one of four monetary incentive models, making this system a possibility for development. The other three are US Dept. of the Interior, township, county, and electrical utility company easement contracts for fuel load management, global carbon credits trading, and data set sales. All the above depends on obvious questions getting answered. I will list some obvious ones, but this is not an engineering document and is not the place for spreadsheets. How much Bitcoin one Forest Walker can mine depends on everything else. What amount of biomass can we process? Will that biomass flow enough Syngas to keep the lights on? Can the chassis support enough mining ASICs and supporting infrastructure? What does that weigh and will it affect field performance? How much power can the AC generator produce? Other questions that are more philosophical persist. Even if a single Forest Walker can only mine scant amounts of BTC per day, that pales to how much fuel material it can process into biochar. We are talking about millions upon millions of forested acres in need of fuel load management. What can a single Forest Walker do? I am not thinking in singular terms. The Forest Walker must operate as a fleet. What could 50 do? 500? What is it worth providing a service to the world by managing forest fuel loads? Providing proof of work to the global monetary system? Seeding soil with drought and nutrient resilience by the excretion, over time, of carbon by the ton? What did the last forest fire cost? # The Mesh Network  What could be better than one bitcoin mining, carbon sequestering, forest fire squelching, soil amending behemoth? Thousands of them, but then they would need to be able to talk to each other to coordinate position, data handling, etc. Fitted with a mesh networking device, like goTenna or Meshtastic LoRa equipment enables each Forest Walker to communicate with each other. Now we have an interconnected fleet of Forest Walkers relaying data to each other and more importantly, aggregating all of that to the last link in the chain for uplink. Well, at least Bitcoin mining data. Since block data is lightweight, transmission of these data via mesh networking in fairly close quartered environs is more than doable. So, how does data transmit to the Bitcoin Network? How do the Forest Walkers get the previous block data necessary to execute on mining? # Back To The Chain  Getting Bitcoin block data to and from the network is the last puzzle piece. The standing presumption here is that wherever a Forest Walker fleet is operating, it is NOT within cell tower range. We further presume that the nearest Walmart Wi-Fi is hours away. Enter the Blockstream Satellite or something like it. A separate, ground-based drone will have two jobs: To stay as close to the nearest Forest Walker as it can and to provide an antennae for either terrestrial or orbital data uplink. Bitcoin-centric data is transmitted to the "uplink drone" via the mesh networked transmitters and then sent on to the uplink and the whole flow goes in the opposite direction as well; many to one and one to many. We cannot transmit data to the Blockstream satellite, and it will be up to Blockstream and companies like it to provide uplink capabilities in the future and I don't doubt they will. Starlink you say? What’s stopping that company from filtering out block data? Nothing because it’s Starlink’s system and they could decide to censor these data. It seems we may have a problem sending and receiving Bitcoin data in back country environs. But, then again, the utility of this system in staunching the fuel load that creates forest fires is extremely useful around forested communities and many have fiber, Wi-Fi and cell towers. These communities could be a welcoming ground zero for first deployments of the Forest Walker system by the home and business owners seeking fire repression. In the best way, Bitcoin subsidizes the safety of the communities. # Sensor Packages ### LiDaR  The benefit of having a Forest Walker fleet strolling through the forest is the never ending opportunity for data gathering. A plethora of deployable sensors gathering hyper-accurate data on everything from temperature to topography is yet another revenue generator. Data is valuable and the Forest Walker could generate data sales to various government entities and private concerns. LiDaR (Light Detection and Ranging) can map topography, perform biomass assessment, comparative soil erosion analysis, etc. It so happens that the Forest Walker’s ability to “see,” to navigate about its surroundings, is LiDaR driven and since it’s already being used, we can get double duty by harvesting that data for later use. By using a laser to send out light pulses and measuring the time it takes for the reflection of those pulses to return, very detailed data sets incrementally build up. Eventually, as enough data about a certain area becomes available, the data becomes useful and valuable. Forestry concerns, both private and public, often use LiDaR to build 3D models of tree stands to assess the amount of harvest-able lumber in entire sections of forest. Consulting companies offering these services charge anywhere from several hundred to several thousand dollars per square kilometer for such services. A Forest Walker generating such assessments on the fly while performing its other functions is a multi-disciplinary approach to revenue generation. ### pH, Soil Moisture, and Cation Exchange Sensing  The Forest Walker is quadrupedal, so there are four contact points to the soil. Why not get a pH data point for every step it takes? We can also gather soil moisture data and cation exchange capacities at unheard of densities because of sampling occurring on the fly during commission of the system’s other duties. No one is going to build a machine to do pH testing of vast tracts of forest soils, but that doesn’t make the data collected from such an endeavor valueless. Since the Forest Walker serves many functions at once, a multitude of data products can add to the return on investment component. ### Weather Data  Temperature, humidity, pressure, and even data like evapotranspiration gathered at high densities on broad acre scales have untold value and because the sensors are lightweight and don’t require large power budgets, they come along for the ride at little cost. But, just like the old mantra, “gas, grass, or ass, nobody rides for free”, these sensors provide potential revenue benefits just by them being present. I’ve touched on just a few data genres here. In fact, the question for universities, governmental bodies, and other institutions becomes, “How much will you pay us to attach your sensor payload to the Forest Walker?” # Noise Suppression  Only you can prevent Metallica filling the surrounds with 120 dB of sound. Easy enough, just turn the car stereo off. But what of a fleet of 50 Forest Walkers operating in the backcountry or near a township? 500? 5000? Each one has a wood chipper, an internal combustion engine, hydraulic pumps, actuators, and more cooling fans than you can shake a stick at. It’s a walking, screaming fire-breathing dragon operating continuously, day and night, twenty-four hours a day, three hundred sixty-five days a year. The sound will negatively affect all living things and that impacts behaviors. Serious engineering consideration and prowess must deliver a silencing blow to the major issue of noise. It would be foolish to think that a fleet of Forest Walkers could be silent, but if not a major design consideration, then the entire idea is dead on arrival. Townships would not allow them to operate even if they solved the problem of widespread fuel load and neither would governmental entities, and rightly so. Nothing, not man nor beast, would want to be subjected to an eternal, infernal scream even if it were to end within days as the fleet moved further away after consuming what it could. Noise and heat are the only real pollutants of this system; taking noise seriously from the beginning is paramount. # Fire Safety  A “fire-breathing dragon” is not the worst description of the Forest Walker. It eats wood, combusts it at very high temperatures and excretes carbon; and it does so in an extremely flammable environment. Bad mix for one Forest Walker, worse for many. One must take extreme pains to ensure that during normal operation, a Forest Walker could fall over, walk through tinder dry brush, or get pounded into the ground by a meteorite from Krypton and it wouldn’t destroy epic swaths of trees and baby deer. I envision an ultimate test of a prototype to include dowsing it in grain alcohol while it’s wrapped up in toilet paper like a pledge at a fraternity party. If it runs for 72 hours and doesn’t set everything on fire, then maybe outside entities won’t be fearful of something that walks around forests with a constant fire in its belly. # The Wrap  How we think about what can be done with and adjacent to Bitcoin is at least as important as Bitcoin’s economic standing itself. For those who will tell me that this entire idea is without merit, I say, “OK, fine. You can come up with something, too.” What can we plug Bitcoin into that, like a battery, makes something that does not work, work? That’s the lesson I get from this entire exercise. No one was ever going to hire teams of humans to go out and "clean the forest". There's no money in that. The data collection and sales from such an endeavor might provide revenues over the break-even point but investment demands Alpha in this day and age. But, plug Bitcoin into an almost viable system and, voilà! We tip the scales to achieve lift-off. Let’s face it, we haven’t scratched the surface of Bitcoin’s forcing function on our minds. Not because it’s Bitcoin, but because of what that invention means. The question that pushes me to approach things this way is, “what can we create that one system’s waste is another system’s feedstock?” The Forest Walker system’s only real waste is the conversion of low entropy energy (wood and syngas) into high entropy energy (heat and noise). All other output is beneficial to humanity. Bitcoin, I believe, is the first product of a new mode of human imagination. An imagination newly forged over the past few millennia of being lied to, stolen from, distracted and otherwise mis-allocated to a black hole of the nonsensical. We are waking up. What I have presented is not science fiction. Everything I have described here is well within the realm of possibility. The question is one of viability, at least in terms of the detritus of the old world we find ourselves departing from. This system would take a non-trivial amount of time and resources to develop. I think the system would garner extensive long-term contracts from those who have the most to lose from wildfires, the most to gain from hyperaccurate data sets, and, of course, securing the most precious asset in the world. Many may not see it that way, for they seek Alpha and are therefore blind to other possibilities. Others will see only the possibilities; of thinking in a new way, of looking at things differently, and dreaming of what comes next.
@ 6389be64:ef439d32
2025-01-14 01:31:12Bitcoin is more than money, more than an asset, and more than a store of value. Bitcoin is a Prime Mover, an enabler and it ignites imaginations. It certainly fueled an idea in my mind. The idea integrates sensors, computational prowess, actuated machinery, power conversion, and electronic communications to form an autonomous, machined creature roaming forests and harvesting the most widespread and least energy-dense fuel source available. I call it the Forest Walker and it eats wood, and mines Bitcoin. I know what you're thinking. Why not just put Bitcoin mining rigs where they belong: in a hosted facility sporting electricity from energy-dense fuels like natural gas, climate-controlled with excellent data piping in and out? Why go to all the trouble building a robot that digests wood creating flammable gasses fueling an engine to run a generator powering Bitcoin miners? It's all about synergy. Bitcoin mining enables the realization of multiple, seemingly unrelated, yet useful activities. Activities considered un-profitable if not for Bitcoin as the Prime Mover. This is much more than simply mining the greatest asset ever conceived by humankind. It’s about the power of synergy, which Bitcoin plays only one of many roles. The synergy created by this system can stabilize forests' fire ecology while generating multiple income streams. That’s the realistic goal here and requires a brief history of American Forest management before continuing. # Smokey The Bear In 1944, the Smokey Bear Wildfire Prevention Campaign began in the United States. “Only YOU can prevent forest fires” remains the refrain of the Ad Council’s longest running campaign. The Ad Council is a U.S. non-profit set up by the American Association of Advertising Agencies and the Association of National Advertisers in 1942. It would seem that the U.S. Department of the Interior was concerned about pesky forest fires and wanted them to stop. So, alongside a national policy of extreme fire suppression they enlisted the entire U.S. population to get onboard via the Ad Council and it worked. Forest fires were almost obliterated and everyone was happy, right? Wrong. Smokey is a fantastically successful bear so forest fires became so few for so long that the fuel load - dead wood - in forests has become very heavy. So heavy that when a fire happens (and they always happen) it destroys everything in its path because the more fuel there is the hotter that fire becomes. Trees, bushes, shrubs, and all other plant life cannot escape destruction (not to mention homes and businesses). The soil microbiology doesn’t escape either as it is burned away even in deeper soils. To add insult to injury, hydrophobic waxy residues condense on the soil surface, forcing water to travel over the ground rather than through it eroding forest soils. Good job, Smokey. Well done, Sir! Most terrestrial ecologies are “fire ecologies”. Fire is a part of these systems’ fuel load and pest management. Before we pretended to “manage” millions of acres of forest, fires raged over the world, rarely damaging forests. The fuel load was always too light to generate fires hot enough to moonscape mountainsides. Fires simply burned off the minor amounts of fuel accumulated since the fire before. The lighter heat, smoke, and other combustion gasses suppressed pests, keeping them in check and the smoke condensed into a plant growth accelerant called wood vinegar, not a waxy cap on the soil. These fires also cleared out weak undergrowth, cycled minerals, and thinned the forest canopy, allowing sunlight to penetrate to the forest floor. Without a fire’s heat, many pine tree species can’t sow their seed. The heat is required to open the cones (the seed bearing structure) of Spruce, Cypress, Sequoia, Jack Pine, Lodgepole Pine and many more. Without fire forests can’t have babies. The idea was to protect the forests, and it isn't working. So, in a world of fire, what does an ally look like and what does it do? # Meet The Forest Walker  For the Forest Walker to work as a mobile, autonomous unit, a solid platform that can carry several hundred pounds is required. It so happens this chassis already exists but shelved. Introducing the Legged Squad Support System (LS3). A joint project between Boston Dynamics, DARPA, and the United States Marine Corps, the quadrupedal robot is the size of a cow, can carry 400 pounds (180 kg) of equipment, negotiate challenging terrain, and operate for 24 hours before needing to refuel. Yes, it had an engine. Abandoned in 2015, the thing was too noisy for military deployment and maintenance "under fire" is never a high-quality idea. However, we can rebuild it to act as a platform for the Forest Walker; albeit with serious alterations. It would need to be bigger, probably. Carry more weight? Definitely. Maybe replace structural metal with carbon fiber and redesign much as 3D printable parts for more effective maintenance. The original system has a top operational speed of 8 miles per hour. For our purposes, it only needs to move about as fast as a grazing ruminant. Without the hammering vibrations of galloping into battle, shocks of exploding mortars, and drunken soldiers playing "Wrangler of Steel Machines", time between failures should be much longer and the overall energy consumption much lower. The LS3 is a solid platform to build upon. Now it just needs to be pulled out of the mothballs, and completely refitted with outboard equipment. # The Small Branch Chipper  When I say “Forest fuel load” I mean the dead, carbon containing litter on the forest floor. Duff (leaves), fine-woody debris (small branches), and coarse woody debris (logs) are the fuel that feeds forest fires. Walk through any forest in the United States today and you will see quite a lot of these materials. Too much, as I have described. Some of these fuel loads can be 8 tons per acre in pine and hardwood forests and up to 16 tons per acre at active logging sites. That’s some big wood and the more that collects, the more combustible danger to the forest it represents. It also provides a technically unlimited fuel supply for the Forest Walker system. The problem is that this detritus has to be chewed into pieces that are easily ingestible by the system for the gasification process (we’ll get to that step in a minute). What we need is a wood chipper attached to the chassis (the LS3); its “mouth”. A small wood chipper handling material up to 2.5 - 3.0 inches (6.3 - 7.6 cm) in diameter would eliminate a substantial amount of fuel. There is no reason for Forest Walker to remove fallen trees. It wouldn’t have to in order to make a real difference. It need only identify appropriately sized branches and grab them. Once loaded into the chipper’s intake hopper for further processing, the beast can immediately look for more “food”. This is essentially kindling that would help ignite larger logs. If it’s all consumed by Forest Walker, then it’s not present to promote an aggravated conflagration. I have glossed over an obvious question: How does Forest Walker see and identify branches and such? LiDaR (Light Detection and Ranging) attached to Forest Walker images the local area and feed those data to onboard computers for processing. Maybe AI plays a role. Maybe simple machine learning can do the trick. One thing is for certain: being able to identify a stick and cause robotic appendages to pick it up is not impossible. Great! We now have a quadrupedal robot autonomously identifying and “eating” dead branches and other light, combustible materials. Whilst strolling through the forest, depleting future fires of combustibles, Forest Walker has already performed a major function of this system: making the forest safer. It's time to convert this low-density fuel into a high-density fuel Forest Walker can leverage. Enter the gasification process. # The Gassifier  The gasifier is the heart of the entire system; it’s where low-density fuel becomes the high-density fuel that powers the entire system. Biochar and wood vinegar are process wastes and I’ll discuss why both are powerful soil amendments in a moment, but first, what’s gasification? Reacting shredded carbonaceous material at high temperatures in a low or no oxygen environment converts the biomass into biochar, wood vinegar, heat, and Synthesis Gas (Syngas). Syngas consists primarily of hydrogen, carbon monoxide, and methane. All of which are extremely useful fuels in a gaseous state. Part of this gas is used to heat the input biomass and keep the reaction temperature constant while the internal combustion engine that drives the generator to produce electrical power consumes the rest. Critically, this gasification process is “continuous feed”. Forest Walker must intake biomass from the chipper, process it to fuel, and dump the waste (CO2, heat, biochar, and wood vinegar) continuously. It cannot stop. Everything about this system depends upon this continual grazing, digestion, and excretion of wastes just as a ruminal does. And, like a ruminant, all waste products enhance the local environment. When I first heard of gasification, I didn’t believe that it was real. Running an electric generator from burning wood seemed more akin to “conspiracy fantasy” than science. Not only is gasification real, it’s ancient technology. A man named Dean Clayton first started experiments on gasification in 1699 and in 1901 gasification was used to power a vehicle. By the end of World War II, there were 500,000 Syngas powered vehicles in Germany alone because of fossil fuel rationing during the war. The global gasification market was $480 billion in 2022 and projected to be as much as $700 billion by 2030 (Vantage Market Research). Gasification technology is the best choice to power the Forest Walker because it’s self-contained and we want its waste products. # Biochar: The Waste  Biochar (AKA agricultural charcoal) is fairly simple: it’s almost pure, solid carbon that resembles charcoal. Its porous nature packs large surface areas into small, 3 dimensional nuggets. Devoid of most other chemistry, like hydrocarbons (methane) and ash (minerals), biochar is extremely lightweight. Do not confuse it with the charcoal you buy for your grill. Biochar doesn’t make good grilling charcoal because it would burn too rapidly as it does not contain the multitude of flammable components that charcoal does. Biochar has several other good use cases. Water filtration, water retention, nutrient retention, providing habitat for microscopic soil organisms, and carbon sequestration are the main ones that we are concerned with here. Carbon has an amazing ability to adsorb (substances stick to and accumulate on the surface of an object) manifold chemistries. Water, nutrients, and pollutants tightly bind to carbon in this format. So, biochar makes a respectable filter and acts as a “battery” of water and nutrients in soils. Biochar adsorbs and holds on to seven times its weight in water. Soil containing biochar is more drought resilient than soil without it. Adsorbed nutrients, tightly sequestered alongside water, get released only as plants need them. Plants must excrete protons (H+) from their roots to disgorge water or positively charged nutrients from the biochar's surface; it's an active process. Biochar’s surface area (where adsorption happens) can be 500 square meters per gram or more. That is 10% larger than an official NBA basketball court for every gram of biochar. Biochar’s abundant surface area builds protective habitats for soil microbes like fungi and bacteria and many are critical for the health and productivity of the soil itself. The “carbon sequestration” component of biochar comes into play where “carbon credits” are concerned. There is a financial market for carbon. Not leveraging that market for revenue is foolish. I am climate agnostic. All I care about is that once solid carbon is inside the soil, it will stay there for thousands of years, imparting drought resiliency, fertility collection, nutrient buffering, and release for that time span. I simply want as much solid carbon in the soil because of the undeniably positive effects it has, regardless of any climactic considerations. # Wood Vinegar: More Waste  Another by-product of the gasification process is wood vinegar (Pyroligneous acid). If you have ever seen Liquid Smoke in the grocery store, then you have seen wood vinegar. Principally composed of acetic acid, acetone, and methanol wood vinegar also contains ~200 other organic compounds. It would seem intuitive that condensed, liquefied wood smoke would at least be bad for the health of all living things if not downright carcinogenic. The counter intuition wins the day, however. Wood vinegar has been used by humans for a very long time to promote digestion, bowel, and liver health; combat diarrhea and vomiting; calm peptic ulcers and regulate cholesterol levels; and a host of other benefits. For centuries humans have annually burned off hundreds of thousands of square miles of pasture, grassland, forest, and every other conceivable terrestrial ecosystem. Why is this done? After every burn, one thing becomes obvious: the almost supernatural growth these ecosystems exhibit after the burn. How? Wood vinegar is a component of this growth. Even in open burns, smoke condenses and infiltrates the soil. That is when wood vinegar shows its quality. This stuff beefs up not only general plant growth but seed germination as well and possesses many other qualities that are beneficial to plants. It’s a pesticide, fungicide, promotes beneficial soil microorganisms, enhances nutrient uptake, and imparts disease resistance. I am barely touching a long list of attributes here, but you want wood vinegar in your soil (alongside biochar because it adsorbs wood vinegar as well). # The Internal Combustion Engine  Conversion of grazed forage to chemical, then mechanical, and then electrical energy completes the cycle. The ICE (Internal Combustion Engine) converts the gaseous fuel output from the gasifier to mechanical energy, heat, water vapor, and CO2. It’s the mechanical energy of a rotating drive shaft that we want. That rotation drives the electric generator, which is the heartbeat we need to bring this monster to life. Luckily for us, combined internal combustion engine and generator packages are ubiquitous, delivering a defined energy output given a constant fuel input. It’s the simplest part of the system. The obvious question here is whether the amount of syngas provided by the gasification process will provide enough energy to generate enough electrons to run the entire system or not. While I have no doubt the energy produced will run Forest Walker's main systems the question is really about the electrons left over. Will it be enough to run the Bitcoin mining aspect of the system? Everything is a budget. # CO2 Production For Growth  Plants are lollipops. No matter if it’s a tree or a bush or a shrubbery, the entire thing is mostly sugar in various formats but mostly long chain carbohydrates like lignin and cellulose. Plants need three things to make sugar: CO2, H2O and light. In a forest, where tree densities can be quite high, CO2 availability becomes a limiting growth factor. It’d be in the forest interests to have more available CO2 providing for various sugar formation providing the organism with food and structure. An odd thing about tree leaves, the openings that allow gasses like the ever searched for CO2 are on the bottom of the leaf (these are called stomata). Not many stomata are topside. This suggests that trees and bushes have evolved to find gasses like CO2 from below, not above and this further suggests CO2 might be in higher concentrations nearer the soil. The soil life (bacterial, fungi etc.) is constantly producing enormous amounts of CO2 and it would stay in the soil forever (eventually killing the very soil life that produces it) if not for tidal forces. Water is everywhere and whether in pools, lakes, oceans or distributed in “moist” soils water moves towards to the moon. The water in the soil and also in the water tables below the soil rise toward the surface every day. When the water rises, it expels the accumulated gasses in the soil into the atmosphere and it’s mostly CO2. It’s a good bet on how leaves developed high populations of stomata on the underside of leaves. As the water relaxes (the tide goes out) it sucks oxygenated air back into the soil to continue the functions of soil life respiration. The soil “breathes” albeit slowly. The gasses produced by the Forest Walker’s internal combustion engine consist primarily of CO2 and H2O. Combusting sugars produce the same gasses that are needed to construct the sugars because the universe is funny like that. The Forest Walker is constantly laying down these critical construction elements right where the trees need them: close to the ground to be gobbled up by the trees. # The Branch Drones  During the last ice age, giant mammals populated North America - forests and otherwise. Mastodons, woolly mammoths, rhinos, short-faced bears, steppe bison, caribou, musk ox, giant beavers, camels, gigantic ground-dwelling sloths, glyptodons, and dire wolves were everywhere. Many were ten to fifteen feet tall. As they crashed through forests, they would effectively cleave off dead side-branches of trees, halting the spread of a ground-based fire migrating into the tree crown ("laddering") which is a death knell for a forest. These animals are all extinct now and forests no longer have any manner of pruning services. But, if we build drones fitted with cutting implements like saws and loppers, optical cameras and AI trained to discern dead branches from living ones, these drones could effectively take over pruning services by identifying, cutting, and dropping to the forest floor, dead branches. The dropped branches simply get collected by the Forest Walker as part of its continual mission. The drones dock on the back of the Forest Walker to recharge their batteries when low. The whole scene would look like a grazing cow with some flies bothering it. This activity breaks the link between a relatively cool ground based fire and the tree crowns and is a vital element in forest fire control. # The Bitcoin Miner  Mining is one of four monetary incentive models, making this system a possibility for development. The other three are US Dept. of the Interior, township, county, and electrical utility company easement contracts for fuel load management, global carbon credits trading, and data set sales. All the above depends on obvious questions getting answered. I will list some obvious ones, but this is not an engineering document and is not the place for spreadsheets. How much Bitcoin one Forest Walker can mine depends on everything else. What amount of biomass can we process? Will that biomass flow enough Syngas to keep the lights on? Can the chassis support enough mining ASICs and supporting infrastructure? What does that weigh and will it affect field performance? How much power can the AC generator produce? Other questions that are more philosophical persist. Even if a single Forest Walker can only mine scant amounts of BTC per day, that pales to how much fuel material it can process into biochar. We are talking about millions upon millions of forested acres in need of fuel load management. What can a single Forest Walker do? I am not thinking in singular terms. The Forest Walker must operate as a fleet. What could 50 do? 500? What is it worth providing a service to the world by managing forest fuel loads? Providing proof of work to the global monetary system? Seeding soil with drought and nutrient resilience by the excretion, over time, of carbon by the ton? What did the last forest fire cost? # The Mesh Network  What could be better than one bitcoin mining, carbon sequestering, forest fire squelching, soil amending behemoth? Thousands of them, but then they would need to be able to talk to each other to coordinate position, data handling, etc. Fitted with a mesh networking device, like goTenna or Meshtastic LoRa equipment enables each Forest Walker to communicate with each other. Now we have an interconnected fleet of Forest Walkers relaying data to each other and more importantly, aggregating all of that to the last link in the chain for uplink. Well, at least Bitcoin mining data. Since block data is lightweight, transmission of these data via mesh networking in fairly close quartered environs is more than doable. So, how does data transmit to the Bitcoin Network? How do the Forest Walkers get the previous block data necessary to execute on mining? # Back To The Chain  Getting Bitcoin block data to and from the network is the last puzzle piece. The standing presumption here is that wherever a Forest Walker fleet is operating, it is NOT within cell tower range. We further presume that the nearest Walmart Wi-Fi is hours away. Enter the Blockstream Satellite or something like it. A separate, ground-based drone will have two jobs: To stay as close to the nearest Forest Walker as it can and to provide an antennae for either terrestrial or orbital data uplink. Bitcoin-centric data is transmitted to the "uplink drone" via the mesh networked transmitters and then sent on to the uplink and the whole flow goes in the opposite direction as well; many to one and one to many. We cannot transmit data to the Blockstream satellite, and it will be up to Blockstream and companies like it to provide uplink capabilities in the future and I don't doubt they will. Starlink you say? What’s stopping that company from filtering out block data? Nothing because it’s Starlink’s system and they could decide to censor these data. It seems we may have a problem sending and receiving Bitcoin data in back country environs. But, then again, the utility of this system in staunching the fuel load that creates forest fires is extremely useful around forested communities and many have fiber, Wi-Fi and cell towers. These communities could be a welcoming ground zero for first deployments of the Forest Walker system by the home and business owners seeking fire repression. In the best way, Bitcoin subsidizes the safety of the communities. # Sensor Packages ### LiDaR  The benefit of having a Forest Walker fleet strolling through the forest is the never ending opportunity for data gathering. A plethora of deployable sensors gathering hyper-accurate data on everything from temperature to topography is yet another revenue generator. Data is valuable and the Forest Walker could generate data sales to various government entities and private concerns. LiDaR (Light Detection and Ranging) can map topography, perform biomass assessment, comparative soil erosion analysis, etc. It so happens that the Forest Walker’s ability to “see,” to navigate about its surroundings, is LiDaR driven and since it’s already being used, we can get double duty by harvesting that data for later use. By using a laser to send out light pulses and measuring the time it takes for the reflection of those pulses to return, very detailed data sets incrementally build up. Eventually, as enough data about a certain area becomes available, the data becomes useful and valuable. Forestry concerns, both private and public, often use LiDaR to build 3D models of tree stands to assess the amount of harvest-able lumber in entire sections of forest. Consulting companies offering these services charge anywhere from several hundred to several thousand dollars per square kilometer for such services. A Forest Walker generating such assessments on the fly while performing its other functions is a multi-disciplinary approach to revenue generation. ### pH, Soil Moisture, and Cation Exchange Sensing  The Forest Walker is quadrupedal, so there are four contact points to the soil. Why not get a pH data point for every step it takes? We can also gather soil moisture data and cation exchange capacities at unheard of densities because of sampling occurring on the fly during commission of the system’s other duties. No one is going to build a machine to do pH testing of vast tracts of forest soils, but that doesn’t make the data collected from such an endeavor valueless. Since the Forest Walker serves many functions at once, a multitude of data products can add to the return on investment component. ### Weather Data  Temperature, humidity, pressure, and even data like evapotranspiration gathered at high densities on broad acre scales have untold value and because the sensors are lightweight and don’t require large power budgets, they come along for the ride at little cost. But, just like the old mantra, “gas, grass, or ass, nobody rides for free”, these sensors provide potential revenue benefits just by them being present. I’ve touched on just a few data genres here. In fact, the question for universities, governmental bodies, and other institutions becomes, “How much will you pay us to attach your sensor payload to the Forest Walker?” # Noise Suppression  Only you can prevent Metallica filling the surrounds with 120 dB of sound. Easy enough, just turn the car stereo off. But what of a fleet of 50 Forest Walkers operating in the backcountry or near a township? 500? 5000? Each one has a wood chipper, an internal combustion engine, hydraulic pumps, actuators, and more cooling fans than you can shake a stick at. It’s a walking, screaming fire-breathing dragon operating continuously, day and night, twenty-four hours a day, three hundred sixty-five days a year. The sound will negatively affect all living things and that impacts behaviors. Serious engineering consideration and prowess must deliver a silencing blow to the major issue of noise. It would be foolish to think that a fleet of Forest Walkers could be silent, but if not a major design consideration, then the entire idea is dead on arrival. Townships would not allow them to operate even if they solved the problem of widespread fuel load and neither would governmental entities, and rightly so. Nothing, not man nor beast, would want to be subjected to an eternal, infernal scream even if it were to end within days as the fleet moved further away after consuming what it could. Noise and heat are the only real pollutants of this system; taking noise seriously from the beginning is paramount. # Fire Safety  A “fire-breathing dragon” is not the worst description of the Forest Walker. It eats wood, combusts it at very high temperatures and excretes carbon; and it does so in an extremely flammable environment. Bad mix for one Forest Walker, worse for many. One must take extreme pains to ensure that during normal operation, a Forest Walker could fall over, walk through tinder dry brush, or get pounded into the ground by a meteorite from Krypton and it wouldn’t destroy epic swaths of trees and baby deer. I envision an ultimate test of a prototype to include dowsing it in grain alcohol while it’s wrapped up in toilet paper like a pledge at a fraternity party. If it runs for 72 hours and doesn’t set everything on fire, then maybe outside entities won’t be fearful of something that walks around forests with a constant fire in its belly. # The Wrap  How we think about what can be done with and adjacent to Bitcoin is at least as important as Bitcoin’s economic standing itself. For those who will tell me that this entire idea is without merit, I say, “OK, fine. You can come up with something, too.” What can we plug Bitcoin into that, like a battery, makes something that does not work, work? That’s the lesson I get from this entire exercise. No one was ever going to hire teams of humans to go out and "clean the forest". There's no money in that. The data collection and sales from such an endeavor might provide revenues over the break-even point but investment demands Alpha in this day and age. But, plug Bitcoin into an almost viable system and, voilà! We tip the scales to achieve lift-off. Let’s face it, we haven’t scratched the surface of Bitcoin’s forcing function on our minds. Not because it’s Bitcoin, but because of what that invention means. The question that pushes me to approach things this way is, “what can we create that one system’s waste is another system’s feedstock?” The Forest Walker system’s only real waste is the conversion of low entropy energy (wood and syngas) into high entropy energy (heat and noise). All other output is beneficial to humanity. Bitcoin, I believe, is the first product of a new mode of human imagination. An imagination newly forged over the past few millennia of being lied to, stolen from, distracted and otherwise mis-allocated to a black hole of the nonsensical. We are waking up. What I have presented is not science fiction. Everything I have described here is well within the realm of possibility. The question is one of viability, at least in terms of the detritus of the old world we find ourselves departing from. This system would take a non-trivial amount of time and resources to develop. I think the system would garner extensive long-term contracts from those who have the most to lose from wildfires, the most to gain from hyperaccurate data sets, and, of course, securing the most precious asset in the world. Many may not see it that way, for they seek Alpha and are therefore blind to other possibilities. Others will see only the possibilities; of thinking in a new way, of looking at things differently, and dreaming of what comes next. @ e3ba5e1a:5e433365
2025-01-13 16:47:27My blog posts and reading material have both been on a decidedly economics-heavy slant recently. The topic today, incentives, squarely falls into the category of economics. However, when I say economics, I’m not talking about “analyzing supply and demand curves.” I’m talking about the true basis of economics: understanding how human beings make decisions in a world of scarcity. A fair definition of incentive is “a reward or punishment that motivates behavior to achieve a desired outcome.” When most people think about economic incentives, they’re thinking of money. If I offer my son $5 if he washes the dishes, I’m incentivizing certain behavior. We can’t guarantee that he’ll do what I want him to do, but we can agree that the incentive structure itself will guide and ultimately determine what outcome will occur. The great thing about monetary incentives is how easy they are to talk about and compare. “Would I rather make $5 washing the dishes or $10 cleaning the gutters?” But much of the world is incentivized in non-monetary ways too. For example, using the “punishment” half of the definition above, I might threaten my son with losing Nintendo Switch access if he doesn’t wash the dishes. No money is involved, but I’m still incentivizing behavior. And there are plenty of incentives beyond our direct control\! My son is *also* incentivized to not wash dishes because it’s boring, or because he has some friends over that he wants to hang out with, or dozens of other things. Ultimately, the conflicting array of different incentive structures placed on him will ultimately determine what actions he chooses to take. ## Why incentives matter A phrase I see often in discussions—whether they are political, parenting, economic, or business—is “if they could **just** do…” Each time I see that phrase, I cringe a bit internally. Usually, the underlying assumption of the statement is “if people would behave contrary to their incentivized behavior then things would be better.” For example: * If my kids would just go to bed when I tell them, they wouldn’t be so cranky in the morning. * If people would just use the recycling bin, we wouldn’t have such a landfill problem. * If people would just stop being lazy, our team would deliver our project on time. In all these cases, the speakers are seemingly flummoxed as to why the people in question don’t behave more rationally. The problem is: each group is behaving perfectly rationally. * The kids have a high time preference, and care more about the joy of staying up now than the crankiness in the morning. Plus, they don’t really suffer the consequences of morning crankiness, their parents do. * No individual suffers much from their individual contribution to a landfill. If they stopped growing the size of the landfill, it would make an insignificant difference versus the amount of effort they need to engage in to properly recycle. * If a team doesn’t properly account for the productivity of individuals on a project, each individual receives less harm from their own inaction. Sure, the project may be delayed, company revenue may be down, and they may even risk losing their job when the company goes out of business. But their laziness individually won’t determine the entirety of that outcome. By contrast, they greatly benefit from being lazy by getting to relax at work, go on social media, read a book, or do whatever else they do when they’re supposed to be working.  My point here is that, as long as you ignore the reality of how incentives drive human behavior, you’ll fail at getting the outcomes you want. If everything I wrote up until now made perfect sense, you understand the premise of this blog post. The rest of it will focus on a bunch of real-world examples to hammer home the point, and demonstrate how versatile this mental model is. ## Running a company Let’s say I run my own company, with myself as the only employee. My personal revenue will be 100% determined by my own actions. If I decide to take Tuesday afternoon off and go fishing, I’ve chosen to lose that afternoon’s revenue. Implicitly, I’ve decided that the enjoyment I get from an afternoon of fishing is greater than the potential revenue. You may think I’m being lazy, but it’s my decision to make. In this situation, the incentive–money–is perfectly aligned with my actions. Compare this to a typical company/employee relationship. I might have a bank of Paid Time Off (PTO) days, in which case once again my incentives are relatively aligned. I know that I can take off 15 days throughout the year, and I’ve chosen to use half a day for the fishing trip. All is still good. What about unlimited time off? Suddenly incentives are starting to misalign. I don’t directly pay a price for not showing up to work on Tuesday. Or Wednesday as well, for that matter. I might ultimately be fired for not doing my job, but that will take longer to work its way through the system than simply not making any money for the day taken off. Compensation overall falls into this misaligned incentive structure. Let’s forget about taking time off. Instead, I work full time on a software project I’m assigned. But instead of using the normal toolchain we’re all used to at work, I play around with a new programming language. I get the fun and joy of playing with new technology, and potentially get to pad my resume a bit when I’m ready to look for a new job. But my current company gets slower results, less productivity, and is forced to subsidize my extracurricular learning. When a CEO has a bonus structure based on profitability, he’ll do everything he can to make the company profitable. This might include things that actually benefit the company, like improving product quality, reducing internal red tape, or finding cheaper vendors. But it might also include destructive practices, like slashing the R\&D budget to show massive profits this year, in exchange for a catastrophe next year when the next version of the product fails to ship.  Or my favorite example. My parents owned a business when I was growing up. They had a back office where they ran operations like accounting. All of the furniture was old couches from our house. After all, any money they spent on furniture came right out of their paychecks\! But in a large corporate environment, each department is generally given a budget for office furniture, a budget which doesn’t roll over year-to-year. The result? Executives make sure to spend the entire budget each year, often buying furniture far more expensive than they would choose if it was their own money. There are plenty of details you can quibble with above. It’s in a company’s best interest to give people downtime so that they can come back recharged. Having good ergonomic furniture can in fact increase productivity in excess of the money spent on it. But overall, the picture is pretty clear: in large corporate structures, you’re guaranteed to have mismatches between the company’s goals and the incentive structure placed on individuals. Using our model from above, we can lament how lazy, greedy, and unethical the employees are for doing what they’re incentivized to do instead of what’s right. But that’s simply ignoring the reality of human nature. # Moral hazard Moral hazard is a situation where one party is incentivized to take on more risk because another party will bear the consequences. Suppose I tell my son when he turns 21 (or whatever legal gambling age is) that I’ll cover all his losses for a day at the casino, but he gets to keep all the winnings. What do you think he’s going to do? The most logical course of action is to place the largest possible bets for as long as possible, asking me to cover each time he loses, and taking money off the table and into his bank account each time he wins.  But let’s look at a slightly more nuanced example. I go to a bathroom in the mall. As I’m leaving, I wash my hands. It will take me an extra 1 second to turn off the water when I’m done washing. That’s a trivial price to pay. If I *don’t* turn off the water, the mall will have to pay for many liters of wasted water, benefiting no one. But I won’t suffer any consequences at all. This is also a moral hazard, but most people will still turn off the water. Why? Usually due to some combination of other reasons such as: 1. We’re so habituated to turning off the water that we don’t even consider *not* turning it off. Put differently, the mental effort needed to not turn off the water is more expensive than the 1 second of time to turn it off. 2. Many of us have been brought up with a deep guilt about wasting resources like water. We have an internal incentive structure that makes the 1 second to turn off the water much less costly than the mental anguish of the waste we created. 3. We’re afraid we’ll be caught by someone else and face some kind of social repercussions. (Or maybe more than social. Are you sure there isn’t a law against leaving the water tap on?) Even with all that in place, you may notice that many public bathrooms use automatic water dispensers. Sure, there’s a sanitation reason for that, but it’s also to avoid this moral hazard. A common denominator in both of these is that the person taking the action that causes the liability (either the gambling or leaving the water on) is not the person who bears the responsibility for that liability (the father or the mall owner). Generally speaking, the closer together the person making the decision and the person incurring the liability are, the smaller the moral hazard. It’s easy to demonstrate that by extending the casino example a bit. I said it was the father who was covering the losses of the gambler. Many children (though not all) would want to avoid totally bankrupting their parents, or at least financially hurting them. Instead, imagine that someone from the IRS shows up at your door, hands you a credit card, and tells you you can use it at a casino all day, taking home all the chips you want. The money is coming from the government. How many people would put any restriction on how much they spend? And since we’re talking about the government already… ## Government moral hazards As I was preparing to write this blog post, the California wildfires hit. The discussions around those wildfires gave a *huge* number of examples of moral hazards. I decided to cherry-pick a few for this post. The first and most obvious one: California is asking for disaster relief funds from the federal government. That sounds wonderful. These fires were a natural disaster, so why shouldn’t the federal government pitch in and help take care of people? The problem is, once again, a moral hazard. In the case of the wildfires, California and Los Angeles both had ample actions they could have taken to mitigate the destruction of this fire: better forest management, larger fire department, keeping the water reservoirs filled, and probably much more that hasn’t come to light yet. If the federal government bails out California, it will be a clear message for the future: your mistakes will be fixed by others. You know what kind of behavior that incentivizes? More risky behavior\! Why spend state funds on forest management and extra firefighters—activities that don’t win politicians a lot of votes in general—when you could instead spend it on a football stadium, higher unemployment payments, or anything else, and then let the feds cover the cost of screw-ups. You may notice that this is virtually identical to the 2008 “too big to fail” bail-outs. Wall Street took insanely risky behavior, reaped huge profits for years, and when they eventually got caught with their pants down, the rest of us bailed them out. “Privatizing profits, socializing losses.”  And here’s the absolute best part of this: I can’t even truly blame either California *or* Wall Street. (I mean, I *do* blame them, I think their behavior is reprehensible, but you’ll see what I mean.) In a world where the rules of the game implicitly include the bail-out mentality, you would be harming your citizens/shareholders/investors if you didn’t engage in that risky behavior. Since everyone is on the hook for those socialized losses, your best bet is to maximize those privatized profits. There’s a lot more to government and moral hazard, but I think these two cases demonstrate the crux pretty solidly. But let’s leave moral hazard behind for a bit and get to general incentivization discussions. # Non-monetary competition At least 50% of the economics knowledge I have comes from the very first econ course I took in college. That professor was amazing, and had some very colorful stories. I can’t vouch for the veracity of the two I’m about to share, but they definitely drive the point home. In the 1970s, the US had an oil shortage. To “fix” this problem, they instituted price caps on gasoline, which of course resulted in insufficient gasoline. To “fix” this problem, they instituted policies where, depending on your license plate number, you could only fill up gas on certain days of the week. (Irrelevant detail for our point here, but this just resulted in people filling up their tanks more often, no reduction in gas usage.) Anyway, my professor’s wife had a friend. My professor described in *great* detail how attractive this woman was. I’ll skip those details here since this is a PG-rated blog. In any event, she never had any trouble filling up her gas tank any day of the week. She would drive up, be told she couldn’t fill up gas today, bat her eyes at the attendant, explain how helpless she was, and was always allowed to fill up gas. This is a demonstration of *non-monetary compensation*. Most of the time in a free market, capitalist economy, people are compensated through money. When price caps come into play, there’s a limit to how much monetary compensation someone can receive. And in that case, people find other ways of competing. Like this woman’s case: through using flirtatious behavior to compensate the gas station workers to let her cheat the rules. The other example was much more insidious. Santa Monica had a problem: it was predominantly wealthy and white. They wanted to fix this problem, and decided to put in place rent controls. After some time, they discovered that Santa Monica had become *wealthier and whiter*, the exact opposite of their desired outcome. Why would that happen? Someone investigated, and ended up interviewing a landlady that demonstrated the reason. She was an older white woman, and admittedly racist. Prior to the rent controls, she would list her apartments in the newspaper, and would be legally obligated to rent to anyone who could afford it. Once rent controls were in place, she took a different tact. She knew that she would only get a certain amount for the apartment, and that the demand for apartments was higher than the supply. That meant she could be picky. She ended up finding tenants through friends-of-friends. Since it wasn’t an official advertisement, she wasn’t legally required to rent it out if someone could afford to pay. Instead, she got to interview people individually and then make them an offer. Normally, that would have resulted in receiving a lower rental price, but not under rent controls. So who did she choose? A young, unmarried, wealthy, white woman. It made perfect sense. Women were less intimidating and more likely to maintain the apartment better. Wealthy people, she determined, would be better tenants. (I have no idea if this is true in practice or not, I’m not a landlord myself.) Unmarried, because no kids running around meant less damage to the property. And, of course, white. Because she was racist, and her incentive structure made her prefer whites. You can deride her for being racist, I won’t disagree with you. But it’s simply the reality. Under the non-rent-control scenario, her profit motive for money outweighed her racism motive. But under rent control, the monetary competition was removed, and she was free to play into her racist tendencies without facing any negative consequences. ## Bureaucracy These were the two examples I remember for that course. But non-monetary compensation pops up in many more places. One highly pertinent example is bureaucracies. Imagine you have a government office, or a large corporation’s acquisition department, or the team that apportions grants at a university. In all these cases, you have a group of people making decisions about handing out money that has no monetary impact on them. If they give to the best qualified recipients, they receive no raises. If they spend the money recklessly on frivolous projects, they face no consequences. Under such an incentivization scheme, there’s little to encourage the bureaucrats to make intelligent funding decisions. Instead, they’ll be incentivized to spend the money where they recognize non-monetary benefits. This is why it’s so common to hear about expensive meals, gift bags at conferences, and even more inappropriate ways of trying to curry favor with those that hold the purse strings. Compare that ever so briefly with the purchases made by a small mom-and-pop store like my parents owned. Could my dad take a bribe to buy from a vendor who’s ripping him off? Absolutely he could\! But he’d lose more on the deal than he’d make on the bribe, since he’s directly incentivized by the deal itself. It would make much more sense for him to go with the better vendor, save $5,000 on the deal, and then treat himself to a lavish $400 meal to celebrate. # Government incentivized behavior This post is getting longer in the tooth than I’d intended, so I’ll finish off with this section and make it a bit briefer. Beyond all the methods mentioned above, government has another mechanism for modifying behavior: through directly changing incentives via legislation, regulation, and monetary policy. Let’s see some examples: * Artificial modification of interest rates encourages people to take on more debt than they would in a free capital market, leading to [malinvestment](https://en.wikipedia.org/wiki/Malinvestment) and a consumer debt crisis, and causing the boom-bust cycle we all painfully experience. * Going along with that, giving tax breaks on interest payments further artificially incentivizes people to take on debt that they wouldn’t otherwise. * During COVID-19, at some points unemployment benefits were greater than minimum wage, incentivizing people to rather stay home and not work than get a job, leading to reduced overall productivity in the economy and more printed dollars for benefits. In other words, it was a perfect recipe for inflation. * The tax code gives deductions to “help” people. That might be true, but the real impact is incentivizing people to make decisions they wouldn’t have otherwise. For example, giving out tax deductions on children encourages having more kids. Tax deductions on childcare and preschools incentivizes dual-income households. Whether or not you like the outcomes, it’s clear that it’s government that’s encouraging these outcomes to happen. * Tax incentives cause people to engage in behavior they wouldn’t otherwise (daycare+working mother, for example). * Inflation means that the value of your money goes down over time, which encourages people to spend more today, when their money has a larger impact. (Milton Friedman described this as [high living](https://www.youtube.com/watch?v=ZwNDd2_beTU).) # Conclusion The idea here is simple, and fully encapsulated in the title: incentives determine outcomes. If you want to know how to get a certain outcome from others, incentivize them to want that to happen. If you want to understand why people act in seemingly irrational ways, check their incentives. If you’re confused why leaders (and especially politicians) seem to engage in destructive behavior, check their incentives. We can bemoan these realities all we want, but they *are* realities. While there are some people who have a solid internal moral and ethical code, and that internal code incentivizes them to behave against their externally-incentivized interests, those people are rare. And frankly, those people are self-defeating. People *should* take advantage of the incentives around them. Because if they don’t, someone else will. (If you want a literary example of that last comment, see the horse in Animal Farm.) How do we improve the world under these conditions? Make sure the incentives align well with the overall goals of society. To me, it’s a simple formula: * Focus on free trade, value for value, as the basis of a society. In that system, people are always incentivized to provide value to other people. * Reduce the size of bureaucracies and large groups of all kinds. The larger an organization becomes, the farther the consequences of decisions are from those who make them. * And since the nature of human beings will be to try and create areas where they can control the incentive systems to their own benefits, make that as difficult as possible. That comes in the form of strict limits on government power, for example. And even if you don’t want to buy in to this conclusion, I hope the rest of the content was educational, and maybe a bit entertaining\!
@ e3ba5e1a:5e433365
2025-01-13 16:47:27My blog posts and reading material have both been on a decidedly economics-heavy slant recently. The topic today, incentives, squarely falls into the category of economics. However, when I say economics, I’m not talking about “analyzing supply and demand curves.” I’m talking about the true basis of economics: understanding how human beings make decisions in a world of scarcity. A fair definition of incentive is “a reward or punishment that motivates behavior to achieve a desired outcome.” When most people think about economic incentives, they’re thinking of money. If I offer my son $5 if he washes the dishes, I’m incentivizing certain behavior. We can’t guarantee that he’ll do what I want him to do, but we can agree that the incentive structure itself will guide and ultimately determine what outcome will occur. The great thing about monetary incentives is how easy they are to talk about and compare. “Would I rather make $5 washing the dishes or $10 cleaning the gutters?” But much of the world is incentivized in non-monetary ways too. For example, using the “punishment” half of the definition above, I might threaten my son with losing Nintendo Switch access if he doesn’t wash the dishes. No money is involved, but I’m still incentivizing behavior. And there are plenty of incentives beyond our direct control\! My son is *also* incentivized to not wash dishes because it’s boring, or because he has some friends over that he wants to hang out with, or dozens of other things. Ultimately, the conflicting array of different incentive structures placed on him will ultimately determine what actions he chooses to take. ## Why incentives matter A phrase I see often in discussions—whether they are political, parenting, economic, or business—is “if they could **just** do…” Each time I see that phrase, I cringe a bit internally. Usually, the underlying assumption of the statement is “if people would behave contrary to their incentivized behavior then things would be better.” For example: * If my kids would just go to bed when I tell them, they wouldn’t be so cranky in the morning. * If people would just use the recycling bin, we wouldn’t have such a landfill problem. * If people would just stop being lazy, our team would deliver our project on time. In all these cases, the speakers are seemingly flummoxed as to why the people in question don’t behave more rationally. The problem is: each group is behaving perfectly rationally. * The kids have a high time preference, and care more about the joy of staying up now than the crankiness in the morning. Plus, they don’t really suffer the consequences of morning crankiness, their parents do. * No individual suffers much from their individual contribution to a landfill. If they stopped growing the size of the landfill, it would make an insignificant difference versus the amount of effort they need to engage in to properly recycle. * If a team doesn’t properly account for the productivity of individuals on a project, each individual receives less harm from their own inaction. Sure, the project may be delayed, company revenue may be down, and they may even risk losing their job when the company goes out of business. But their laziness individually won’t determine the entirety of that outcome. By contrast, they greatly benefit from being lazy by getting to relax at work, go on social media, read a book, or do whatever else they do when they’re supposed to be working.  My point here is that, as long as you ignore the reality of how incentives drive human behavior, you’ll fail at getting the outcomes you want. If everything I wrote up until now made perfect sense, you understand the premise of this blog post. The rest of it will focus on a bunch of real-world examples to hammer home the point, and demonstrate how versatile this mental model is. ## Running a company Let’s say I run my own company, with myself as the only employee. My personal revenue will be 100% determined by my own actions. If I decide to take Tuesday afternoon off and go fishing, I’ve chosen to lose that afternoon’s revenue. Implicitly, I’ve decided that the enjoyment I get from an afternoon of fishing is greater than the potential revenue. You may think I’m being lazy, but it’s my decision to make. In this situation, the incentive–money–is perfectly aligned with my actions. Compare this to a typical company/employee relationship. I might have a bank of Paid Time Off (PTO) days, in which case once again my incentives are relatively aligned. I know that I can take off 15 days throughout the year, and I’ve chosen to use half a day for the fishing trip. All is still good. What about unlimited time off? Suddenly incentives are starting to misalign. I don’t directly pay a price for not showing up to work on Tuesday. Or Wednesday as well, for that matter. I might ultimately be fired for not doing my job, but that will take longer to work its way through the system than simply not making any money for the day taken off. Compensation overall falls into this misaligned incentive structure. Let’s forget about taking time off. Instead, I work full time on a software project I’m assigned. But instead of using the normal toolchain we’re all used to at work, I play around with a new programming language. I get the fun and joy of playing with new technology, and potentially get to pad my resume a bit when I’m ready to look for a new job. But my current company gets slower results, less productivity, and is forced to subsidize my extracurricular learning. When a CEO has a bonus structure based on profitability, he’ll do everything he can to make the company profitable. This might include things that actually benefit the company, like improving product quality, reducing internal red tape, or finding cheaper vendors. But it might also include destructive practices, like slashing the R\&D budget to show massive profits this year, in exchange for a catastrophe next year when the next version of the product fails to ship.  Or my favorite example. My parents owned a business when I was growing up. They had a back office where they ran operations like accounting. All of the furniture was old couches from our house. After all, any money they spent on furniture came right out of their paychecks\! But in a large corporate environment, each department is generally given a budget for office furniture, a budget which doesn’t roll over year-to-year. The result? Executives make sure to spend the entire budget each year, often buying furniture far more expensive than they would choose if it was their own money. There are plenty of details you can quibble with above. It’s in a company’s best interest to give people downtime so that they can come back recharged. Having good ergonomic furniture can in fact increase productivity in excess of the money spent on it. But overall, the picture is pretty clear: in large corporate structures, you’re guaranteed to have mismatches between the company’s goals and the incentive structure placed on individuals. Using our model from above, we can lament how lazy, greedy, and unethical the employees are for doing what they’re incentivized to do instead of what’s right. But that’s simply ignoring the reality of human nature. # Moral hazard Moral hazard is a situation where one party is incentivized to take on more risk because another party will bear the consequences. Suppose I tell my son when he turns 21 (or whatever legal gambling age is) that I’ll cover all his losses for a day at the casino, but he gets to keep all the winnings. What do you think he’s going to do? The most logical course of action is to place the largest possible bets for as long as possible, asking me to cover each time he loses, and taking money off the table and into his bank account each time he wins.  But let’s look at a slightly more nuanced example. I go to a bathroom in the mall. As I’m leaving, I wash my hands. It will take me an extra 1 second to turn off the water when I’m done washing. That’s a trivial price to pay. If I *don’t* turn off the water, the mall will have to pay for many liters of wasted water, benefiting no one. But I won’t suffer any consequences at all. This is also a moral hazard, but most people will still turn off the water. Why? Usually due to some combination of other reasons such as: 1. We’re so habituated to turning off the water that we don’t even consider *not* turning it off. Put differently, the mental effort needed to not turn off the water is more expensive than the 1 second of time to turn it off. 2. Many of us have been brought up with a deep guilt about wasting resources like water. We have an internal incentive structure that makes the 1 second to turn off the water much less costly than the mental anguish of the waste we created. 3. We’re afraid we’ll be caught by someone else and face some kind of social repercussions. (Or maybe more than social. Are you sure there isn’t a law against leaving the water tap on?) Even with all that in place, you may notice that many public bathrooms use automatic water dispensers. Sure, there’s a sanitation reason for that, but it’s also to avoid this moral hazard. A common denominator in both of these is that the person taking the action that causes the liability (either the gambling or leaving the water on) is not the person who bears the responsibility for that liability (the father or the mall owner). Generally speaking, the closer together the person making the decision and the person incurring the liability are, the smaller the moral hazard. It’s easy to demonstrate that by extending the casino example a bit. I said it was the father who was covering the losses of the gambler. Many children (though not all) would want to avoid totally bankrupting their parents, or at least financially hurting them. Instead, imagine that someone from the IRS shows up at your door, hands you a credit card, and tells you you can use it at a casino all day, taking home all the chips you want. The money is coming from the government. How many people would put any restriction on how much they spend? And since we’re talking about the government already… ## Government moral hazards As I was preparing to write this blog post, the California wildfires hit. The discussions around those wildfires gave a *huge* number of examples of moral hazards. I decided to cherry-pick a few for this post. The first and most obvious one: California is asking for disaster relief funds from the federal government. That sounds wonderful. These fires were a natural disaster, so why shouldn’t the federal government pitch in and help take care of people? The problem is, once again, a moral hazard. In the case of the wildfires, California and Los Angeles both had ample actions they could have taken to mitigate the destruction of this fire: better forest management, larger fire department, keeping the water reservoirs filled, and probably much more that hasn’t come to light yet. If the federal government bails out California, it will be a clear message for the future: your mistakes will be fixed by others. You know what kind of behavior that incentivizes? More risky behavior\! Why spend state funds on forest management and extra firefighters—activities that don’t win politicians a lot of votes in general—when you could instead spend it on a football stadium, higher unemployment payments, or anything else, and then let the feds cover the cost of screw-ups. You may notice that this is virtually identical to the 2008 “too big to fail” bail-outs. Wall Street took insanely risky behavior, reaped huge profits for years, and when they eventually got caught with their pants down, the rest of us bailed them out. “Privatizing profits, socializing losses.”  And here’s the absolute best part of this: I can’t even truly blame either California *or* Wall Street. (I mean, I *do* blame them, I think their behavior is reprehensible, but you’ll see what I mean.) In a world where the rules of the game implicitly include the bail-out mentality, you would be harming your citizens/shareholders/investors if you didn’t engage in that risky behavior. Since everyone is on the hook for those socialized losses, your best bet is to maximize those privatized profits. There’s a lot more to government and moral hazard, but I think these two cases demonstrate the crux pretty solidly. But let’s leave moral hazard behind for a bit and get to general incentivization discussions. # Non-monetary competition At least 50% of the economics knowledge I have comes from the very first econ course I took in college. That professor was amazing, and had some very colorful stories. I can’t vouch for the veracity of the two I’m about to share, but they definitely drive the point home. In the 1970s, the US had an oil shortage. To “fix” this problem, they instituted price caps on gasoline, which of course resulted in insufficient gasoline. To “fix” this problem, they instituted policies where, depending on your license plate number, you could only fill up gas on certain days of the week. (Irrelevant detail for our point here, but this just resulted in people filling up their tanks more often, no reduction in gas usage.) Anyway, my professor’s wife had a friend. My professor described in *great* detail how attractive this woman was. I’ll skip those details here since this is a PG-rated blog. In any event, she never had any trouble filling up her gas tank any day of the week. She would drive up, be told she couldn’t fill up gas today, bat her eyes at the attendant, explain how helpless she was, and was always allowed to fill up gas. This is a demonstration of *non-monetary compensation*. Most of the time in a free market, capitalist economy, people are compensated through money. When price caps come into play, there’s a limit to how much monetary compensation someone can receive. And in that case, people find other ways of competing. Like this woman’s case: through using flirtatious behavior to compensate the gas station workers to let her cheat the rules. The other example was much more insidious. Santa Monica had a problem: it was predominantly wealthy and white. They wanted to fix this problem, and decided to put in place rent controls. After some time, they discovered that Santa Monica had become *wealthier and whiter*, the exact opposite of their desired outcome. Why would that happen? Someone investigated, and ended up interviewing a landlady that demonstrated the reason. She was an older white woman, and admittedly racist. Prior to the rent controls, she would list her apartments in the newspaper, and would be legally obligated to rent to anyone who could afford it. Once rent controls were in place, she took a different tact. She knew that she would only get a certain amount for the apartment, and that the demand for apartments was higher than the supply. That meant she could be picky. She ended up finding tenants through friends-of-friends. Since it wasn’t an official advertisement, she wasn’t legally required to rent it out if someone could afford to pay. Instead, she got to interview people individually and then make them an offer. Normally, that would have resulted in receiving a lower rental price, but not under rent controls. So who did she choose? A young, unmarried, wealthy, white woman. It made perfect sense. Women were less intimidating and more likely to maintain the apartment better. Wealthy people, she determined, would be better tenants. (I have no idea if this is true in practice or not, I’m not a landlord myself.) Unmarried, because no kids running around meant less damage to the property. And, of course, white. Because she was racist, and her incentive structure made her prefer whites. You can deride her for being racist, I won’t disagree with you. But it’s simply the reality. Under the non-rent-control scenario, her profit motive for money outweighed her racism motive. But under rent control, the monetary competition was removed, and she was free to play into her racist tendencies without facing any negative consequences. ## Bureaucracy These were the two examples I remember for that course. But non-monetary compensation pops up in many more places. One highly pertinent example is bureaucracies. Imagine you have a government office, or a large corporation’s acquisition department, or the team that apportions grants at a university. In all these cases, you have a group of people making decisions about handing out money that has no monetary impact on them. If they give to the best qualified recipients, they receive no raises. If they spend the money recklessly on frivolous projects, they face no consequences. Under such an incentivization scheme, there’s little to encourage the bureaucrats to make intelligent funding decisions. Instead, they’ll be incentivized to spend the money where they recognize non-monetary benefits. This is why it’s so common to hear about expensive meals, gift bags at conferences, and even more inappropriate ways of trying to curry favor with those that hold the purse strings. Compare that ever so briefly with the purchases made by a small mom-and-pop store like my parents owned. Could my dad take a bribe to buy from a vendor who’s ripping him off? Absolutely he could\! But he’d lose more on the deal than he’d make on the bribe, since he’s directly incentivized by the deal itself. It would make much more sense for him to go with the better vendor, save $5,000 on the deal, and then treat himself to a lavish $400 meal to celebrate. # Government incentivized behavior This post is getting longer in the tooth than I’d intended, so I’ll finish off with this section and make it a bit briefer. Beyond all the methods mentioned above, government has another mechanism for modifying behavior: through directly changing incentives via legislation, regulation, and monetary policy. Let’s see some examples: * Artificial modification of interest rates encourages people to take on more debt than they would in a free capital market, leading to [malinvestment](https://en.wikipedia.org/wiki/Malinvestment) and a consumer debt crisis, and causing the boom-bust cycle we all painfully experience. * Going along with that, giving tax breaks on interest payments further artificially incentivizes people to take on debt that they wouldn’t otherwise. * During COVID-19, at some points unemployment benefits were greater than minimum wage, incentivizing people to rather stay home and not work than get a job, leading to reduced overall productivity in the economy and more printed dollars for benefits. In other words, it was a perfect recipe for inflation. * The tax code gives deductions to “help” people. That might be true, but the real impact is incentivizing people to make decisions they wouldn’t have otherwise. For example, giving out tax deductions on children encourages having more kids. Tax deductions on childcare and preschools incentivizes dual-income households. Whether or not you like the outcomes, it’s clear that it’s government that’s encouraging these outcomes to happen. * Tax incentives cause people to engage in behavior they wouldn’t otherwise (daycare+working mother, for example). * Inflation means that the value of your money goes down over time, which encourages people to spend more today, when their money has a larger impact. (Milton Friedman described this as [high living](https://www.youtube.com/watch?v=ZwNDd2_beTU).) # Conclusion The idea here is simple, and fully encapsulated in the title: incentives determine outcomes. If you want to know how to get a certain outcome from others, incentivize them to want that to happen. If you want to understand why people act in seemingly irrational ways, check their incentives. If you’re confused why leaders (and especially politicians) seem to engage in destructive behavior, check their incentives. We can bemoan these realities all we want, but they *are* realities. While there are some people who have a solid internal moral and ethical code, and that internal code incentivizes them to behave against their externally-incentivized interests, those people are rare. And frankly, those people are self-defeating. People *should* take advantage of the incentives around them. Because if they don’t, someone else will. (If you want a literary example of that last comment, see the horse in Animal Farm.) How do we improve the world under these conditions? Make sure the incentives align well with the overall goals of society. To me, it’s a simple formula: * Focus on free trade, value for value, as the basis of a society. In that system, people are always incentivized to provide value to other people. * Reduce the size of bureaucracies and large groups of all kinds. The larger an organization becomes, the farther the consequences of decisions are from those who make them. * And since the nature of human beings will be to try and create areas where they can control the incentive systems to their own benefits, make that as difficult as possible. That comes in the form of strict limits on government power, for example. And even if you don’t want to buy in to this conclusion, I hope the rest of the content was educational, and maybe a bit entertaining\! @ 58937958:545e6994
2025-01-03 11:07:06January 3, 2024 I made a Bitcoin-inspired Osechi to celebrate Bitcoin's birthday. Everything was handmade! Osechi: A traditional Japanese New Year’s feast, typically served in stacked boxes. ## First Layer (Ichino-jū)  - Tazukuri: Dried sardines, symbolizing a wish for a bountiful harvest. - Simmered Kuai: A vegetable with large sprouts, symbolizing growth and success. - Kombu Rolls: A play on words with the Japanese term yorokobu ("to be joyful"), making it a good luck dish. - Matsukazeyaki: Ground meat coated with sesame or poppy seeds on one side, symbolizing honesty (no "hidden side"). - Black Beans: Represent hard work and good health. - Datemaki: Sweet rolled omelet resembling scrolls, symbolizing knowledge and learning. - Grilled Yellowtail: A fish whose name changes as it grows, symbolizing success. Salmon Terrine: A classic addition to Western-style Osechi. Salmon symbolizes success, avoiding misfortune (sakeru), and prosperity for future generations. - Tataki Gobo: Burdock root with deep roots, symbolizing family stability and prosperity. ## Second Layer (Nino-jū)  - Candied Kumquat: A dish symbolizing wealth and good fortune. - Namash: Pickled daikon and carrot, resembling celebratory red and white decorations. - Chestnut Kinton: Golden in color, symbolizing wealth and a prosperous year. Bitcoin-themed additions: - Pumpkin Yokan - Chicken and Spinach Terrine - Kinako Sticks ## Third Layer (Sanno-jū)  Nishime: A simmered dish with various ingredients, symbolizing family harmony and long-lasting prosperity. I used snow peas to represent Bitcoin, and I couldn’t help but laugh at myself. ## Dishes Inspired by Bitcoin ### Pumpkin Yokan  I made firm milk jelly, cut it into a "B" shape with a knife, and filled it with pumpkin yokan. ### Chicken and Spinach Terrine  It was my first attempt, and I think with more care, the shape could be even better. ### Kinako Sticks  A simple snack made with honey and roasted soybean flour (kinako). Roll it out, cut it into sticks, and coat with more kinako. ### Candied Kumquat  Candied Kumquat: A dish symbolizing wealth and good fortune. In Japan, 金柑 (kumquat) includes the kanji 金, which represents "gold." nostr:nevent1qqspu8gegzdamtx2rsm4995t3sg8qssw3vn3yn25ru8plghsqyrwtkcn0u7vy I wonder what Satoshi might have eaten on the day Bitcoin was born. Wouldn't it be amusing to imagine him snacking on Osechi while working on his computer? (Satoshi chose a Japanese name, so perhaps he might have an interest in Japanese culture.) Maybe, right now, Satoshi is relaxing and enjoying some Osechi... though probably not! In any case, I hope Satoshi is living peacefully somewhere.
@ 58937958:545e6994
2025-01-03 11:07:06January 3, 2024 I made a Bitcoin-inspired Osechi to celebrate Bitcoin's birthday. Everything was handmade! Osechi: A traditional Japanese New Year’s feast, typically served in stacked boxes. ## First Layer (Ichino-jū)  - Tazukuri: Dried sardines, symbolizing a wish for a bountiful harvest. - Simmered Kuai: A vegetable with large sprouts, symbolizing growth and success. - Kombu Rolls: A play on words with the Japanese term yorokobu ("to be joyful"), making it a good luck dish. - Matsukazeyaki: Ground meat coated with sesame or poppy seeds on one side, symbolizing honesty (no "hidden side"). - Black Beans: Represent hard work and good health. - Datemaki: Sweet rolled omelet resembling scrolls, symbolizing knowledge and learning. - Grilled Yellowtail: A fish whose name changes as it grows, symbolizing success. Salmon Terrine: A classic addition to Western-style Osechi. Salmon symbolizes success, avoiding misfortune (sakeru), and prosperity for future generations. - Tataki Gobo: Burdock root with deep roots, symbolizing family stability and prosperity. ## Second Layer (Nino-jū)  - Candied Kumquat: A dish symbolizing wealth and good fortune. - Namash: Pickled daikon and carrot, resembling celebratory red and white decorations. - Chestnut Kinton: Golden in color, symbolizing wealth and a prosperous year. Bitcoin-themed additions: - Pumpkin Yokan - Chicken and Spinach Terrine - Kinako Sticks ## Third Layer (Sanno-jū)  Nishime: A simmered dish with various ingredients, symbolizing family harmony and long-lasting prosperity. I used snow peas to represent Bitcoin, and I couldn’t help but laugh at myself. ## Dishes Inspired by Bitcoin ### Pumpkin Yokan  I made firm milk jelly, cut it into a "B" shape with a knife, and filled it with pumpkin yokan. ### Chicken and Spinach Terrine  It was my first attempt, and I think with more care, the shape could be even better. ### Kinako Sticks  A simple snack made with honey and roasted soybean flour (kinako). Roll it out, cut it into sticks, and coat with more kinako. ### Candied Kumquat  Candied Kumquat: A dish symbolizing wealth and good fortune. In Japan, 金柑 (kumquat) includes the kanji 金, which represents "gold." nostr:nevent1qqspu8gegzdamtx2rsm4995t3sg8qssw3vn3yn25ru8plghsqyrwtkcn0u7vy I wonder what Satoshi might have eaten on the day Bitcoin was born. Wouldn't it be amusing to imagine him snacking on Osechi while working on his computer? (Satoshi chose a Japanese name, so perhaps he might have an interest in Japanese culture.) Maybe, right now, Satoshi is relaxing and enjoying some Osechi... though probably not! In any case, I hope Satoshi is living peacefully somewhere. @ 71a4b7ff:d009692a
2025-01-19 10:20:02### The Problem with Preset Choices Switching sections around? Not an option—we’ve already decided for you, buddy. Remove bright colors? Come on, it’s already beautiful. Disable unnecessary features? Don’t be silly, you need everything here. Especially this algorithmic feed with built-in ads. ### Monetization Over User Experience The operators of digital services will always prioritize their primary goal: monetizing the product as efficiently as possible. They need to not only attract new users but also retain existing ones. And the best tool for this is the interface. That’s why most product decisions are far removed from ideas like “Let’s make it more convenient for people” or “Let’s give users more freedom.” Instead, we see the result of a recurring process: - We have a retention and monetization mechanism - Assign tasks to developers and designers - Integrate it into the product - Write a quarterly report. The outcome? Users end up with Reels tabs smack in the center of Instagram’s bottom navigation bar. Removing or rearranging those tabs? Not an option. And it likely never will be. ### Why Rigid Interfaces Persist Another reason for rigid and obligatory interfaces is that they’re easier to design. Just imagine how many combinations of colors, elements, and layouts developers would need to account for to make a product both customizable and functional without turning it into a garish mess. But that’s just nuance and excuses. ### The Myth of Perfect Design Services often justify their choices by claiming their design is “the most designed,” that they know what’s best and will make it work for everyone. They might even present solid arguments for this. But all those arguments fall apart against the reality we see on our screens every day. In my opinion, people should have the ability to turn a product into anything they want—whether it’s loud and kitschy or minimalistic and dull. This option wouldn’t just allow users to express themselves but could also help with digital detoxing. ### The Example of App Labels Here’s an example: why do app icons on smartphone home screens (not the app drawer) come with labels underneath? Apps on the home screen are easily recognizable by their icons. Why would I need a name tag for an app I intentionally placed there? Sure, for some users or scenarios, this might be helpful. But why is it the default option? The problem is that these labels are just visual noise—clusters of unnecessary text we already see plenty of. Removing them would make it slightly easier for the brain to process the screen every time you look at it. Now scale that to 3–8 hours of daily smartphone use. Then a month. Then a year. ### The Slow Shift Toward Customization For a long time, iOS didn’t allow you to hide icon labels. Now, the option exists, but it still requires more effort than a simple toggle. As a result, people are stuck looking at tons of unnecessary, subconscious information every day. And this is just the trivial issue of app labels on a product considered the gold standard of digital design. Imagine the horror of tackling more significant issues. Yes, Apple has softened its stance in recent years, offering custom icons and lock screens. Celebrate—you can now showcase your individuality! The company understands that customization is the future. We’ve reached a point where weak computing power is no longer an excuse, VR/metaverse adoption is still a way off, and new features are needed. So, this is an excellent opportunity for all of us. ### The Case for More Customization In a reasonable, ideal world, people should decide which sections of a service they need, where they’re located, and how they look. Companies, meanwhile, recognize that people want the ability to stand out and create something personal—even on a smartphone in their pocket. And as our integration with various devices deepens, this need will only grow. More customization is coming. Yes, it’ll be largely cosmetic, but even that can work to our advantage: removing jarring colors or hiding unnecessary labels can reduce the brain’s pointless load. ### Beyond Aesthetics: Customization as Freedom The ability to customize services isn’t just about playing amateur designer. It’s about mitigating informational irritants, reducing the addictive nature of interfaces, and weakening dark patterns. Which is likely why many companies no longer prioritize customization. ### Telegram: A Customizable Example In this context, Telegram is a decent example. I’m not a fan, but I’ve been using it for daily communication with loved ones for a long time—and it’s good for that. It can be vastly different for vastly different users. Despite starting to bend under the weight of its audience and introducing questionable decisions, its foundational design principles still allow for creating both minimalist spaces for peaceful content consumption or communication, as well as vibrant, noisy chats for virtual parties. Telegram can be a messenger, a feed, a file storage system, or whatever else you need—and it can look wildly different while doing so. ### Customization as the Key to Healthy Digital Relationships Customization should be at the core of the services we use daily. Yes, it can and will be used for marketing purposes. But even minimal customization is better than none because the ability to tailor a system to your needs is an expression of freedom and a cornerstone of healthy relationships with the digital world. **Stay Nostrous. Geo**
@ 71a4b7ff:d009692a
2025-01-19 10:20:02### The Problem with Preset Choices Switching sections around? Not an option—we’ve already decided for you, buddy. Remove bright colors? Come on, it’s already beautiful. Disable unnecessary features? Don’t be silly, you need everything here. Especially this algorithmic feed with built-in ads. ### Monetization Over User Experience The operators of digital services will always prioritize their primary goal: monetizing the product as efficiently as possible. They need to not only attract new users but also retain existing ones. And the best tool for this is the interface. That’s why most product decisions are far removed from ideas like “Let’s make it more convenient for people” or “Let’s give users more freedom.” Instead, we see the result of a recurring process: - We have a retention and monetization mechanism - Assign tasks to developers and designers - Integrate it into the product - Write a quarterly report. The outcome? Users end up with Reels tabs smack in the center of Instagram’s bottom navigation bar. Removing or rearranging those tabs? Not an option. And it likely never will be. ### Why Rigid Interfaces Persist Another reason for rigid and obligatory interfaces is that they’re easier to design. Just imagine how many combinations of colors, elements, and layouts developers would need to account for to make a product both customizable and functional without turning it into a garish mess. But that’s just nuance and excuses. ### The Myth of Perfect Design Services often justify their choices by claiming their design is “the most designed,” that they know what’s best and will make it work for everyone. They might even present solid arguments for this. But all those arguments fall apart against the reality we see on our screens every day. In my opinion, people should have the ability to turn a product into anything they want—whether it’s loud and kitschy or minimalistic and dull. This option wouldn’t just allow users to express themselves but could also help with digital detoxing. ### The Example of App Labels Here’s an example: why do app icons on smartphone home screens (not the app drawer) come with labels underneath? Apps on the home screen are easily recognizable by their icons. Why would I need a name tag for an app I intentionally placed there? Sure, for some users or scenarios, this might be helpful. But why is it the default option? The problem is that these labels are just visual noise—clusters of unnecessary text we already see plenty of. Removing them would make it slightly easier for the brain to process the screen every time you look at it. Now scale that to 3–8 hours of daily smartphone use. Then a month. Then a year. ### The Slow Shift Toward Customization For a long time, iOS didn’t allow you to hide icon labels. Now, the option exists, but it still requires more effort than a simple toggle. As a result, people are stuck looking at tons of unnecessary, subconscious information every day. And this is just the trivial issue of app labels on a product considered the gold standard of digital design. Imagine the horror of tackling more significant issues. Yes, Apple has softened its stance in recent years, offering custom icons and lock screens. Celebrate—you can now showcase your individuality! The company understands that customization is the future. We’ve reached a point where weak computing power is no longer an excuse, VR/metaverse adoption is still a way off, and new features are needed. So, this is an excellent opportunity for all of us. ### The Case for More Customization In a reasonable, ideal world, people should decide which sections of a service they need, where they’re located, and how they look. Companies, meanwhile, recognize that people want the ability to stand out and create something personal—even on a smartphone in their pocket. And as our integration with various devices deepens, this need will only grow. More customization is coming. Yes, it’ll be largely cosmetic, but even that can work to our advantage: removing jarring colors or hiding unnecessary labels can reduce the brain’s pointless load. ### Beyond Aesthetics: Customization as Freedom The ability to customize services isn’t just about playing amateur designer. It’s about mitigating informational irritants, reducing the addictive nature of interfaces, and weakening dark patterns. Which is likely why many companies no longer prioritize customization. ### Telegram: A Customizable Example In this context, Telegram is a decent example. I’m not a fan, but I’ve been using it for daily communication with loved ones for a long time—and it’s good for that. It can be vastly different for vastly different users. Despite starting to bend under the weight of its audience and introducing questionable decisions, its foundational design principles still allow for creating both minimalist spaces for peaceful content consumption or communication, as well as vibrant, noisy chats for virtual parties. Telegram can be a messenger, a feed, a file storage system, or whatever else you need—and it can look wildly different while doing so. ### Customization as the Key to Healthy Digital Relationships Customization should be at the core of the services we use daily. Yes, it can and will be used for marketing purposes. But even minimal customization is better than none because the ability to tailor a system to your needs is an expression of freedom and a cornerstone of healthy relationships with the digital world. **Stay Nostrous. Geo** @ 96537107:334e9245
2025-01-19 07:39:54有多少人在排队中?产业趋势不可逆~~~
@ 96537107:334e9245
2025-01-19 07:39:54有多少人在排队中?产业趋势不可逆~~~ @ a10260a2:caa23e3e
2025-01-18 12:04:41*Last Updated: January 18, 2025* First off, big shoutout to Coinos for having support for adding a memo to BOLT12 offers. This provides a solid alternative for the pleb who wants to support mining decentralization but doesn’t want to set up a CLN node and pay thousands of sats for a channel only to get little rewards. This is the case for most of us who only have a miner or two (e.g. a Bitaxe and/or an S9). Before we get into setting up Lightning payouts, you’ll want to have your miner configured to mine with OCEAN of course. You’ll also want to make sure that the bitcoin address you use is from a wallet that supports signing messages. These are the ones listed in the OCEAN [docs](https://ocean.xyz/docs/lightning): * Bitcoin Knots/Bitcoin Core * Coldcard * Electrum * LND (Command Line) * Seedsigner * Sparrow * Specter * Trezor I checked one of my favorite, user-friendly wallets — Blue Wallet — and it happens to support signing messages as well. Just tap the three dots on the upper right and you’ll see the “Sign/Verify Message” button at the bottom.   Update [January 18]: You can now use Coinos to sign by going to https://coinos.io/sign The trick here is to not refresh the page. In other words, when you're logged in to your Coinos account, go to the URL and use the legacy address (starts with a "1") that's displayed to configure your miner(s). If you refresh the page, you're going to get a new address which will cause the signing to fail later on. *Remember*, keep the tab open and don't refresh the page.  Whichever wallet you choose, generate a receive address to use when configuring your miner (it’ll also be your OCEAN username). Here’s how it looks on the Bitaxe (AxeOS)…  And the Antminer S9 (Braiins OS).  NOTE: There’s a slight difference in the URL format between the two apps. Other than that, the username will be your bitcoin address followed by the optional “.” + the nickname for your machine. You can find more details on OCEAN’s [get started page](https://ocean.xyz/getstarted). --- Alright, now that your miner is pointed at OCEAN. Let’s configure Lightning payouts! ### Generating the BOLT12 Offer In the Coinos app, go to Receive > Bolt 12.  Tap “Set memo” and set it to “OCEAN Payouts for [insert your bitcoin address]” (this text is case-sensitive). Use the same bitcoin address you used above to configure your miner(s).  After tapping OK, copy the BOLT12 offer (it should start with “lno”) and proceed to the next step. ### Generating the Configuration Message Navigate to the [My Stats](https://ocean.xyz/stats) page by searching for your OCEAN Bitcoin address.  The click the Configuration link next to Next Block to access the configuration form.  Paste the BOLT12 offer here, update the block height to latest, click GENERATE, and copy the generated unsigned message.   ### Signing the Configuration Message To sign the generated message, go back to Blue Wallet and use the signing function. Paste the configuration message in the Message field, tap Sign, and copy the signed message that’s generated.  If you're using Coinos to sign, return to the page that you kept open (and didn't refresh) and do the same. Paste the configuration message, click submit, and copy the signed message. ### Submitting the Signed Message Once signed, copy the signature, paste it in the OCEAN configuration form, and click CONFIRM.  If all goes well, you should see a confirmation that the configuration was successful. Congrats! 🎉 All you gotta do now is sit back, relax, and wait for a block to be found… Or you can look into setting up [DATUM](https://ocean.xyz/docs/datum-setup). 😎
@ a10260a2:caa23e3e
2025-01-18 12:04:41*Last Updated: January 18, 2025* First off, big shoutout to Coinos for having support for adding a memo to BOLT12 offers. This provides a solid alternative for the pleb who wants to support mining decentralization but doesn’t want to set up a CLN node and pay thousands of sats for a channel only to get little rewards. This is the case for most of us who only have a miner or two (e.g. a Bitaxe and/or an S9). Before we get into setting up Lightning payouts, you’ll want to have your miner configured to mine with OCEAN of course. You’ll also want to make sure that the bitcoin address you use is from a wallet that supports signing messages. These are the ones listed in the OCEAN [docs](https://ocean.xyz/docs/lightning): * Bitcoin Knots/Bitcoin Core * Coldcard * Electrum * LND (Command Line) * Seedsigner * Sparrow * Specter * Trezor I checked one of my favorite, user-friendly wallets — Blue Wallet — and it happens to support signing messages as well. Just tap the three dots on the upper right and you’ll see the “Sign/Verify Message” button at the bottom.   Update [January 18]: You can now use Coinos to sign by going to https://coinos.io/sign The trick here is to not refresh the page. In other words, when you're logged in to your Coinos account, go to the URL and use the legacy address (starts with a "1") that's displayed to configure your miner(s). If you refresh the page, you're going to get a new address which will cause the signing to fail later on. *Remember*, keep the tab open and don't refresh the page.  Whichever wallet you choose, generate a receive address to use when configuring your miner (it’ll also be your OCEAN username). Here’s how it looks on the Bitaxe (AxeOS)…  And the Antminer S9 (Braiins OS).  NOTE: There’s a slight difference in the URL format between the two apps. Other than that, the username will be your bitcoin address followed by the optional “.” + the nickname for your machine. You can find more details on OCEAN’s [get started page](https://ocean.xyz/getstarted). --- Alright, now that your miner is pointed at OCEAN. Let’s configure Lightning payouts! ### Generating the BOLT12 Offer In the Coinos app, go to Receive > Bolt 12.  Tap “Set memo” and set it to “OCEAN Payouts for [insert your bitcoin address]” (this text is case-sensitive). Use the same bitcoin address you used above to configure your miner(s).  After tapping OK, copy the BOLT12 offer (it should start with “lno”) and proceed to the next step. ### Generating the Configuration Message Navigate to the [My Stats](https://ocean.xyz/stats) page by searching for your OCEAN Bitcoin address.  The click the Configuration link next to Next Block to access the configuration form.  Paste the BOLT12 offer here, update the block height to latest, click GENERATE, and copy the generated unsigned message.   ### Signing the Configuration Message To sign the generated message, go back to Blue Wallet and use the signing function. Paste the configuration message in the Message field, tap Sign, and copy the signed message that’s generated.  If you're using Coinos to sign, return to the page that you kept open (and didn't refresh) and do the same. Paste the configuration message, click submit, and copy the signed message. ### Submitting the Signed Message Once signed, copy the signature, paste it in the OCEAN configuration form, and click CONFIRM.  If all goes well, you should see a confirmation that the configuration was successful. Congrats! 🎉 All you gotta do now is sit back, relax, and wait for a block to be found… Or you can look into setting up [DATUM](https://ocean.xyz/docs/datum-setup). 😎 @ f88e6629:e5254dd5
2025-01-17 14:10:19...which allow online payments to be sent directly from one party to another without going through a financial institution. - Without sovereign and accessible payments we are loosing censorship resistance - Without censorship resistance even other core characteristics are in danger - including scarcity and durability. - This affects every bitcoiner including sworn hodlers and MSTR followers. | Property | Description | Fulfillment | | --- | --- | --- | | Scarce | Fixed supply forever. Instantly and costlessly verifiable | 🟢 Good, but can be harmed without censorship resistance | | Portable | Effortless to store and move, with negligible costs | 🟠 Onchain transactions can be expensive, other layers require onchain to be sovereign. Easy portability is offered by custodians only. | | Divisible | Infinitely divisible | 🟠 Smaller units than dust are available only for LN users, which most people can’t use in a sovereign way. | | Durable | Exists forever without deterioration | 🟢 Good, but can be harmed without censorship resistance | | Fungible | Every piece is forever the same as every other piece | 🟡 Onchain bitcoin is not fungible. | | Acceptable | Everyone, anywhere, can send and receive | 🟠 Most people are not able to send and receive in a sovereign way. | | Censorship Resistant | You hold it. Nobody can take it or stop you sending it | 🟠 Custodians are honey-pots that can and will be regulated | > ➡️ We need accessible, scalable, and sovereign payment methods
@ f88e6629:e5254dd5
2025-01-17 14:10:19...which allow online payments to be sent directly from one party to another without going through a financial institution. - Without sovereign and accessible payments we are loosing censorship resistance - Without censorship resistance even other core characteristics are in danger - including scarcity and durability. - This affects every bitcoiner including sworn hodlers and MSTR followers. | Property | Description | Fulfillment | | --- | --- | --- | | Scarce | Fixed supply forever. Instantly and costlessly verifiable | 🟢 Good, but can be harmed without censorship resistance | | Portable | Effortless to store and move, with negligible costs | 🟠 Onchain transactions can be expensive, other layers require onchain to be sovereign. Easy portability is offered by custodians only. | | Divisible | Infinitely divisible | 🟠 Smaller units than dust are available only for LN users, which most people can’t use in a sovereign way. | | Durable | Exists forever without deterioration | 🟢 Good, but can be harmed without censorship resistance | | Fungible | Every piece is forever the same as every other piece | 🟡 Onchain bitcoin is not fungible. | | Acceptable | Everyone, anywhere, can send and receive | 🟠 Most people are not able to send and receive in a sovereign way. | | Censorship Resistant | You hold it. Nobody can take it or stop you sending it | 🟠 Custodians are honey-pots that can and will be regulated | > ➡️ We need accessible, scalable, and sovereign payment methods @ d9e9fb27:d5fe5e1a
2025-01-17 13:00:58Every 16th of January, the city of Varese, a small town at the feet of the Prealpine region, stops to participate in one of the most important ceremonies of the city: *The Falò of Sant'Antonio*. A *Falò* is the Italian word for *bonfire*. Imagine a 5-meters tall pyre of wood burning in the center of the city. For sure, an unmissable event!  The pyre is built by the so-called "*Monelli della Motta*". A *Monello* in Italian is a child that misbehaves. This nickname come from the fact that in the past, the pyre was created using wood stolen from the city, usually from tools, doors and shutters. This event takes place at the eve of the day of Sant'Antonio Abate in front of the homonymous church in the area called "*La Motta*", which stands for *small hill*, and comes from a several century old tradition. Thousands of people from all over the province come to the city to look at the bonfire created in honor of the Saint.  At 9PM the big event starts. The wood is set on fire!  An important tradition of this celebration is burning small pieces of paper containing wishes. People whish for health, love, friendship and luck. To make wishes come true, people have to give these pieces of paper to a firefighter or a "*Monello*" whom will launch it into the *Falò*. The show goes on for a couple of ours, during which thousands of Varesinians in awe contemplate the raging fire and try to receive some heat to fight the glacial cold of January. 
@ d9e9fb27:d5fe5e1a
2025-01-17 13:00:58Every 16th of January, the city of Varese, a small town at the feet of the Prealpine region, stops to participate in one of the most important ceremonies of the city: *The Falò of Sant'Antonio*. A *Falò* is the Italian word for *bonfire*. Imagine a 5-meters tall pyre of wood burning in the center of the city. For sure, an unmissable event!  The pyre is built by the so-called "*Monelli della Motta*". A *Monello* in Italian is a child that misbehaves. This nickname come from the fact that in the past, the pyre was created using wood stolen from the city, usually from tools, doors and shutters. This event takes place at the eve of the day of Sant'Antonio Abate in front of the homonymous church in the area called "*La Motta*", which stands for *small hill*, and comes from a several century old tradition. Thousands of people from all over the province come to the city to look at the bonfire created in honor of the Saint.  At 9PM the big event starts. The wood is set on fire!  An important tradition of this celebration is burning small pieces of paper containing wishes. People whish for health, love, friendship and luck. To make wishes come true, people have to give these pieces of paper to a firefighter or a "*Monello*" whom will launch it into the *Falò*. The show goes on for a couple of ours, during which thousands of Varesinians in awe contemplate the raging fire and try to receive some heat to fight the glacial cold of January.  @ 5bdb0e24:0ccbebd7
2025-01-17 06:19:58In the world of networking, two fundamental models serve as the backbone for communication protocols and standards: the OSI model and the TCP/IP model. Both models are quite similar, providing frameworks for how data is transmitted across networks at various stages of the process. Understanding these models is crucial for anyone working in IT, cybersecurity, or any related tech field. But what exactly are they? # The OSI Model The OSI (Open Systems Interconnection) model is a conceptual framework that standardizes the functions of a telecommunication or computing system into seven distinct layers. Each layer is responsible for specific tasks, such as data encapsulation, error detection, and routing. The layers of the OSI model are as follows: 1. **Physical Layer:** This layer deals with the physical connection between devices, such as cables and network interfaces. 2. **Data Link Layer:** Responsible for node-to-node communication, this layer ensures data integrity and manages access to the physical medium. 3. **Network Layer:** The network layer handles routing and forwarding of data packets between different networks. 4. **Transport Layer:** This layer provides end-to-end communication services for applications, including error detection and flow control. 5. **Session Layer:** Manages sessions between applications, establishing, maintaining, and terminating connections. 6. **Presentation Layer:** Responsible for data translation, encryption, and compression to ensure compatibility between different systems. 7. **Application Layer:** The topmost layer that interacts directly with applications and end-users, providing network services such as email and file transfer. Now, that's a lot to remember. So, an easy acronym you can use to remember these 7 layers is *"Please Do Not Touch Steve's Pet Alligator."* It's helped me quite a bit in trying to pinpoint a specific layer. Also, keep in mind that the layers are typically inverted from what you see above, with Layer 7 being at the top of the stack and Layer 1 being at the bottom. # The TCP/IP Model On the other hand, the TCP/IP (Transmission Control Protocol/Internet Protocol) model is a more streamlined approach to networking, consisting of only four layers: 1. **Link Layer:** Corresponding to the OSI model's data link and physical layers, the link layer deals with the physical connection and data framing. 2. **Internet Layer:** Similar to the OSI model's network layer, the internet layer focuses on routing packets across different networks. 3. **Transport Layer:** Combines the functions of the OSI model's transport and session layers, providing reliable data transfer services. 4. **Application Layer:** Equivalent to the OSI model's top three layers, the application layer in TCP/IP handles network services for applications. While the OSI model is more detailed and theoretical, the TCP/IP model is practical and widely used in modern networking. It's also a bit easier to remember than the OSI model. And, similar to the OSI model, the TCP/IP model is typically visualized with Layer 4 at the top of the stack and Layer 1 at the bottom, unlike what you see above. # Conclusion Both the TCP/IP and OSI models play essential roles in understanding how data is transmitted across networks. By grasping the functions of each layer and their interactions, network professionals can troubleshoot issues, design efficient networks, and ensure seamless communication between devices. Whether you're a seasoned systems administrator or you're just getting your start in IT, mastering these models is key to navigating the complex world of networking.
@ 5bdb0e24:0ccbebd7
2025-01-17 06:19:58In the world of networking, two fundamental models serve as the backbone for communication protocols and standards: the OSI model and the TCP/IP model. Both models are quite similar, providing frameworks for how data is transmitted across networks at various stages of the process. Understanding these models is crucial for anyone working in IT, cybersecurity, or any related tech field. But what exactly are they? # The OSI Model The OSI (Open Systems Interconnection) model is a conceptual framework that standardizes the functions of a telecommunication or computing system into seven distinct layers. Each layer is responsible for specific tasks, such as data encapsulation, error detection, and routing. The layers of the OSI model are as follows: 1. **Physical Layer:** This layer deals with the physical connection between devices, such as cables and network interfaces. 2. **Data Link Layer:** Responsible for node-to-node communication, this layer ensures data integrity and manages access to the physical medium. 3. **Network Layer:** The network layer handles routing and forwarding of data packets between different networks. 4. **Transport Layer:** This layer provides end-to-end communication services for applications, including error detection and flow control. 5. **Session Layer:** Manages sessions between applications, establishing, maintaining, and terminating connections. 6. **Presentation Layer:** Responsible for data translation, encryption, and compression to ensure compatibility between different systems. 7. **Application Layer:** The topmost layer that interacts directly with applications and end-users, providing network services such as email and file transfer. Now, that's a lot to remember. So, an easy acronym you can use to remember these 7 layers is *"Please Do Not Touch Steve's Pet Alligator."* It's helped me quite a bit in trying to pinpoint a specific layer. Also, keep in mind that the layers are typically inverted from what you see above, with Layer 7 being at the top of the stack and Layer 1 being at the bottom. # The TCP/IP Model On the other hand, the TCP/IP (Transmission Control Protocol/Internet Protocol) model is a more streamlined approach to networking, consisting of only four layers: 1. **Link Layer:** Corresponding to the OSI model's data link and physical layers, the link layer deals with the physical connection and data framing. 2. **Internet Layer:** Similar to the OSI model's network layer, the internet layer focuses on routing packets across different networks. 3. **Transport Layer:** Combines the functions of the OSI model's transport and session layers, providing reliable data transfer services. 4. **Application Layer:** Equivalent to the OSI model's top three layers, the application layer in TCP/IP handles network services for applications. While the OSI model is more detailed and theoretical, the TCP/IP model is practical and widely used in modern networking. It's also a bit easier to remember than the OSI model. And, similar to the OSI model, the TCP/IP model is typically visualized with Layer 4 at the top of the stack and Layer 1 at the bottom, unlike what you see above. # Conclusion Both the TCP/IP and OSI models play essential roles in understanding how data is transmitted across networks. By grasping the functions of each layer and their interactions, network professionals can troubleshoot issues, design efficient networks, and ensure seamless communication between devices. Whether you're a seasoned systems administrator or you're just getting your start in IT, mastering these models is key to navigating the complex world of networking. @ 71a4b7ff:d009692a
2025-01-16 17:31:06A couple of years ago psychologists at Berkeley have [delved into the phenomenon of awe](https://doi.org/10.1177/17456916221094856)—how it affects us, when it arises, and how it can benefit us. Then I made this short summary, which I translated and edited a little today. ## What Characterizes Awe? Researchers define awe as a distinct and complex emotion encompassing 8–10 positive feelings, such as wonder, admiration, delight, and respect. I’d like to sprinkle in a touch of discomfort or even threat, but the study notes that this aspect of awe depends on cultural context. For instance, in Japan, awe is more closely tied to experiences of threat than in other countries—think earthquakes, emperors, Hiroshima, Godzilla, and other kaiju. ## How does our body respond to awe? It turns out that awe can significantly improve both physical and mental health—even in “angry, bald apes” like us. The only caveat is not to mix it with fear or threat. Awe associated with those tends to be less beneficial. The study identifies five key ways in which awe supports well-being: 1. **Neurophysiological bonuses**: - Increased vagal tone. - Reduced sympathetic arousal. - Release of oxytocin. - Decreased systemic inflammation. - Lower activity in the brain’s default mode network. 2. **Reduced self-focus**:\ Over-focusing on oneself contributes to anxiety, depression, body image issues, addiction, aggression, and more. Notably, most people's profile pictures are close-ups of their faces. But among hikers, you’re more likely to see tiny figures dwarfed by vast, beautiful landscapes. If that’s not a literal shift away from self-focus, what is? 3. **Prosociality**:\ Even a brief moment of awe boosts cooperation, generosity, and altruistic behavior. Nowhere have I seen as much mutual help and free-flowing communication, even among strangers, as I have on hiking trips. 4. **Connection to the larger whole**:\ Awe fosters integration into strong social networks, a sense of connection to others, and harmony with nature. 5. **A sense of meaning, purpose, and significance**:\ Awe aids in making sense of life’s events, finding links between the present and the past, and aligning with one’s values, relationships, and life trajectory. These five aspects form the foundation of both physical and mental health. Open any book, lecture, or treatise on human well-being, and you’ll find them highlighted in some form. ## How can you experience awe? <img src="https://blossom.primal.net/46f89c89063c95b68833651fd09566613a9cf7e5b79f3fd4107e690d3a7d7242.jpg"> The good news is that opportunities to experience awe are varied and accessible to almost everyone. It’s both surprising and heartening that they don’t revolve around the modern-day idols of success, money, or power. It seems that, at our core, we’re geared toward other goals and often misled by false priorities. Among the universally effective ways to experience awe, researchers highlight: - Spiritual and religious practices. - Shared ceremonies (cinema, music, dance). - Visual art. - Psychedelic experiences. - Acts of courage and kindness (which inspire awe in others). - And, of course, connection with nature. When mountains and hiking entered my life, they brought more health, peace, friends, purpose, and meaning than I’d ever expected. This text is a direct result of the awe I feel each time I stand among peaks, cliffs, forests, lakes, and rivers. It’s not a panacea, but in a time when we’re drowning in useless information, political madness, urban filth, and noise, we desperately need a breath of fresh air. Let’s embrace awe! <img src="https://blossom.primal.net/d2e3c29b06c3eb963005429494a1687fba8dc32eed8deb56e3650fdf2472cc39.jpg">
@ 71a4b7ff:d009692a
2025-01-16 17:31:06A couple of years ago psychologists at Berkeley have [delved into the phenomenon of awe](https://doi.org/10.1177/17456916221094856)—how it affects us, when it arises, and how it can benefit us. Then I made this short summary, which I translated and edited a little today. ## What Characterizes Awe? Researchers define awe as a distinct and complex emotion encompassing 8–10 positive feelings, such as wonder, admiration, delight, and respect. I’d like to sprinkle in a touch of discomfort or even threat, but the study notes that this aspect of awe depends on cultural context. For instance, in Japan, awe is more closely tied to experiences of threat than in other countries—think earthquakes, emperors, Hiroshima, Godzilla, and other kaiju. ## How does our body respond to awe? It turns out that awe can significantly improve both physical and mental health—even in “angry, bald apes” like us. The only caveat is not to mix it with fear or threat. Awe associated with those tends to be less beneficial. The study identifies five key ways in which awe supports well-being: 1. **Neurophysiological bonuses**: - Increased vagal tone. - Reduced sympathetic arousal. - Release of oxytocin. - Decreased systemic inflammation. - Lower activity in the brain’s default mode network. 2. **Reduced self-focus**:\ Over-focusing on oneself contributes to anxiety, depression, body image issues, addiction, aggression, and more. Notably, most people's profile pictures are close-ups of their faces. But among hikers, you’re more likely to see tiny figures dwarfed by vast, beautiful landscapes. If that’s not a literal shift away from self-focus, what is? 3. **Prosociality**:\ Even a brief moment of awe boosts cooperation, generosity, and altruistic behavior. Nowhere have I seen as much mutual help and free-flowing communication, even among strangers, as I have on hiking trips. 4. **Connection to the larger whole**:\ Awe fosters integration into strong social networks, a sense of connection to others, and harmony with nature. 5. **A sense of meaning, purpose, and significance**:\ Awe aids in making sense of life’s events, finding links between the present and the past, and aligning with one’s values, relationships, and life trajectory. These five aspects form the foundation of both physical and mental health. Open any book, lecture, or treatise on human well-being, and you’ll find them highlighted in some form. ## How can you experience awe? <img src="https://blossom.primal.net/46f89c89063c95b68833651fd09566613a9cf7e5b79f3fd4107e690d3a7d7242.jpg"> The good news is that opportunities to experience awe are varied and accessible to almost everyone. It’s both surprising and heartening that they don’t revolve around the modern-day idols of success, money, or power. It seems that, at our core, we’re geared toward other goals and often misled by false priorities. Among the universally effective ways to experience awe, researchers highlight: - Spiritual and religious practices. - Shared ceremonies (cinema, music, dance). - Visual art. - Psychedelic experiences. - Acts of courage and kindness (which inspire awe in others). - And, of course, connection with nature. When mountains and hiking entered my life, they brought more health, peace, friends, purpose, and meaning than I’d ever expected. This text is a direct result of the awe I feel each time I stand among peaks, cliffs, forests, lakes, and rivers. It’s not a panacea, but in a time when we’re drowning in useless information, political madness, urban filth, and noise, we desperately need a breath of fresh air. Let’s embrace awe! <img src="https://blossom.primal.net/d2e3c29b06c3eb963005429494a1687fba8dc32eed8deb56e3650fdf2472cc39.jpg"> @ e8ed3798:67dd345a
2025-01-14 17:38:49Crowdsourcing subjective value is a great idea, but when no thought has been put into how to do it, the results are neither useful nor healthy. In this article we discuss the problems with the classic five star rating system and why it needs to be abolished in favor of better expressions of public sentiment. ## Part 1: What's In A Star? Let's start with a thought experiment: - Do you buy products on Amazon that have 3 stars? - Do you take rides from Uber drivers that have 3 stars? - Do you download apps on the App Store that have 3 stars? - Do you visit places on Google Maps that have 3 stars? "Not on purpose," is probably your answer. But why not? After all, a three out of five is better than the median; it's 60 percent! That is solidly "above average" by any usual measure. Although it makes sense in mathematical terms, it is not correct to say that a 3 star product is at least half as good as a 5 star product. The funny thing about the 5 star rating system is that nobody really knows exactly what the stars mean, mostly because they aren't ever explained. They are just a weak abstraction of a score out of 5, which itself is an abstraction of a score out of 100, and it is used to average all ratings for a thing into an average star rating. Presumably, 5 is the best and 1 is the worst, and somewhere in between is... what exactly? Mediocre? Passable? Acceptable? Average? Who knows! This is the first problem with this system; while the top and bottom of the scale may be implied (ambiguity still isn't great), the middle of the scale is entirely ambiguous. Most of the time, people start with a default supposition that a product ought to be 5 stars, and then they subtract stars according to their own perceived deficiencies of the product. On the flip side, people who are dissatisfied with a product tend to start at 1 star and perhaps award it a couple more if they are feeling charitable. This dualistic approach highlights another issue with this kind of rating system. Despite the pure quantitative mechanism, the feelings and disposition of the rater ultimately assign meaning to the numeric scale. Ultimately, any 5 star rating system ends up being a gamut ranging from hate it to love it with a lot of ambiguity in the middle. To put it simply, the stars mean nothing. But to be more precise, the stars are the *average* of the *numeric expression* of the public sentiment about a thing. OK, public sentiment. That's what we want right? We want to know what the public thinks about the product so we can make a good purchase decision. Except, unfortunately, the 5 star rating system does an incredibly imprecise job at capturing what the public actually thinks about a product. Let's dive into why this is. But first, to conclude our thought experiment, I'd like to establish an informal consensus that we instinctually seek out the highest rated items and avoid ratings less than 4.5 out of 5, with infrequent exceptions. If this sounds like you, then let's proceed. ## Part 2: Trash or Treasure How does one turn their feelings into a number? This is not something people are good at, or do naturally, or are even required to do very often. It is also completely subjective and arbitrary. Does "happy" mean 5 or 100 or 902,581? It really depends on what you are trying to measure. However, you've probably done this on a survey. Normally, a range of options is given with accompanying numbers. You may have heard a guiding explanation such as "Rate one through five, with one being 'least likely' and five being 'most likely' to recommend to a friend." Such explanations are useful in assisting a person in expressing their personal sentiments as a numeric range, and anecdotally I seem to provide more nuanced answers when I have guidance as to what each value actually means to me. However, such explanations are missing from most places where five star rating systems can make or break one's livelihood as a seller, developer, or musician. Users are normally given no guidance as to how a particular star value should correspond to their sentiment. Accordingly, this manifests in an all too common star rating smiley. Like the famed "smiley face curve" equalizer setting popularized in the 70's in which the frequencies of a song were engineered to grow from the midranges upward toward the treble and bass making a smile shape (who's midrange is the lowest), the star rating smile is a common sight on product reviews where the most common review ratings appear anecdotally to be 5 and 1, then 4 and 2, and lastly 3. The fact that the most common ratings are five stars and one star indicates that people most often do not think about their experience as a gradient between good and bad, but rather simply label their sentiment as only "good" or "bad" with little room for nuance. Having not received any guidance for expressing their sentiment numerically, this should be wholly unsurprising. But, I also feel like this binary outcome is a very natural expression that requires minimal mental energy to produce, and is therefore the most efficient expression of sentiment. I suspect that in another universe where we have a commonplace 15 star rating system but humans are the same, the most common ratings are 15 stars and 1 star respectively. Other factors influence this binary good/bad paradigm too. People know instinctively that leaving a bad review is bad for business, and often this is their vengeful response to any sense of feeling as if they have been mistreated, misled, or swindled by the seller. Often times the sheer excitement of the new product compels people to write reviews only minutes after they have received it, precluding them from providing an experienced and time-tested perspective of how the product performs. These quirks of human behavior can skew five star ratings severely. But the behaviors themselves are not bad! They are totally natural and expected. The real problem is how the five star rating system fails to capture these commonplace human sentiments accurately. We need to build a rating system that works for people rather than forcing people to fit into a poorly executed rating system. ## Part 3: Feast or Famine It is natural that when presented with a plethora of options, humans will be drawn to the options that are labeled as "the best". When "best" possible is five stars, then five stars naturally becomes the [Schelling point](https://en.wikipedia.org/wiki/Focal_point_(game_theory))for all buyers and sellers, where the vast majority of economic activity is concentrated. When all ratings are seen from a five-based perspective, fours look barely adequate. Threes look unacceptable. Twos are abject. And ones are complete disasters. You may have heard about how [Uber would suspend drivers whose ratings fell below 4.6](https://www.inc.com/minda-zetlin/uber-rider-ratings-deactivation-lyft-rideshare.html). The tendency of five star rating systems is to create a gradient of sentiment where 1 to 4.5 stars is "bad" and 4.5 to 5 stars is "good". One rarely discussed outcome of this dynamic is that good ratings are nearly impossible to compare to each other. As alluded to in the introduction thought experiment, the narrow range between 4.5 and 5 leaves very little room to distinguish from a good product and an excellent product; both are simply "good" or "not bad". As highly rated products are usually the products people are most interested in, it is unfortunate that a favorable rating would actually provide less signal than a bad rating as to the product's relative quality in the spectrum of good ratings. Meanwhile, bad ratings have wide berth to compare numerically. The astronomical range between 1 and 4.5 is a very spacious gradient in which to assess how bad one product is versus another, except nobody actually cares because nobody is going to buy it anyway! In the five star rating system, the better a product is, the *less* information we get to compare it to other similarly good products. This is a critical design flaw, because the better a product is and the more people review it, the *more* information we should have about it versus other similar products. It would be better if the range of "good" ratings was wider so that good ratings could be compared to each other. I'd like to emphasize that the *loss of precision* as a product becomes more desirable is a truly ludicrous mechanic of the five star rating system. This poorly conceived rating paradigm completely pervades our digital economic systems and determines the success of millions of producers. Let's be clear about the stakes. Assigning subjective value to things is completely overlooked for what it really is: a absolutely critical and monumentally influential economic activity. Because the most important economic activity is how we assign value to things with money, the second most important economic activity is how we *inform* our economic value assignments with subjective value assignments such as these. We need to fix how we rate things. It could literally change how entire economies function. ## Part 4: Quality or Quantity Valve has obviously put thought into how they handle ratings for video games sold through their extremely popular and long-lived Steam platform. Reviews are not allowed until a certain amount of hours of the game have been played. The review must assign a thumbs-up or thumbs-down, and then provide a minimum amount of text. Then, rather than simply providing an average of these binary ratings, Steam averages them over a recent period of time, creating a dynamic where if a game developer releases a new update, the reviews written more recently are sure to influence the overall rating of the game rather than old ratings that haven't taken the new update into consideration. Finally, the aggregated rating itself is displayed as "Overwhelming Negative", "Very Negative", "Mostly Negative", "Mixed", "Mostly Positive", "Very Positive", or "Overwhelmingly Positive". Ask yourself, which product would you be more likely to try? - 2.5/5 stars - "Mixed Reviews" Ironically, the Steam rating system gives users less flexibility to express their sentiment as a number, and yet provides more depth, nuance, and balance to the resulting ratings. This, ladies and gentlemen, is what it looks like when somebody gives a damn about how things work. It is a great system. Another interesting emergent behavior that accompanies many Steam reviews, as well as many reviews on other sites, are user generated pros/cons lists. These lists are helpful and offer qualitative labels that help to explain the quantitative rating assignment, although these labels are not mechanically related to the rating system itself. Steam has another mechanism to express qualitative judgements in the form of labels, although they had to be restricted because they were being abused in undesirable or nefarious ways. Now the labeling system does more to tell you about what the game is rather than what people think about it, which is fine, but I feel like it is a missed opportunity. Therefore, I'd like to propose a simple system that combines thumbs up/down and labeling to be used in the context of nostr's review system. ## Part 5: QTS I call this new review system QTS, or the "Qualitative Thumb System". [Originally I developed QTS when working at Arcade Labs.](https://github.com/ArcadeLabsInc/arcade/wiki/ArcadeSocial) [This PR for a new nostr review mechanism](https://github.com/nostr-protocol/nips/pull/879) allows for a lot of flexibility in how you apply ratings to things, so QTS is simply a method of applying rating values that creates a better human-oriented review system. QTS is a way of using reviews. In essence, QTS capitalizes on our very human instinct to assign a "good" or "bad" label by limiting the quantitative assessment to a thumbs-up or thumbs-down. Then, QTS provides qualitative labels that describe possible positive sentiments that describe different aspects of the thing being rated. First, the user chooses thumbs-up or thumbs-down as their overall assessment. If they do nothing else, this is sufficient to capture their sentiment. However, labels should be provided which the user can check or toggle on to increase their rating further. The initial thumbs up is worth 0.5, and each label is worth (0.5 / number of labels). The minimum rating is 0 (thumbs down, no labels), and the maximum rating is 1 (thumbs up and all labels). Any rating 0.5 or above is trending toward good and below 0.5 is trending toward bad. The labels should be applicable in the context of the thing. So, for example, I might provide the following labels for place reviews in a Google Maps-style app: - Convenient - Clean - Affordable - Memorable - Inviting These labels could possibly describe any place. It's OK if a place doesn't have all of these qualities. Zero labels and at thumbs up is still a "good" rating. Each label selected is essentially a "cherry on top" and its absence may indicate that either it isn't applicable OR the place failed to earn it. Likewise, it is possible that you may give a place a thumbs-down and apply labels; this would result in a rating higher than 0 but still in the bad gradient (below 0.5). Here are the key benefits I want to highlight of QTS: - The 5 star rating system forces a user to do the work of translating their sentiment into a quantity. With QTS, the user never has to translate their feelings into a number! They only express good or bad and pick labels, and the QTS mechanism does the work of translating this into a computation-friendly value. - The 5 star rating system generally results in a "bad" range from 1 to 4.5 and a "good" range from 4.5 to 5. QTS balances this with a "bad" rating at 0, a "good" rating at 0.5, and an excellent rating is anything above 0.5 (up to 1.0). This creates the maximum possible gradient between good and bad which makes it easier to compare similar ratings. Recall this in contrast to the 5 star rating system which actually _loses precision_ as more ratings are provided. - It is also helpful that similar QTS ratings may have different labels, which will allow people to make easy qualitative assessments that do not depend on users generating their own pros/cons list. ## Part 6: Implementing QTS Here is how it works: You give the user the option to rate a thumbs up or thumbs down. Then, you also give your user the option to choose from a predefined set of positive labels. You can have any number of labels but try to keep it below 10 so as not to overwhelm your users. Keep the labels general enough that they could potentially apply to any thing being rated. For example, if you were providing labels for Amazon.com, some good labels would be: - Good Value - Good Quality - As Described - Durable - Right Size These labels are general enough that they could apply to almost any product. It is important to create labels that are general so that when comparing product ratings you are comparing the same labels. It is possible however that something like Amazon.com could define a different QTS label subset for each product category, and then the labels could be more specific to that category. For example, a product category of Candles could have "Long Burning", "Good smell", "Safe", etc. These labels are much more specific, but appropriate for the Candle product category. The main point is that products which should be compared should use the same QTS label set. Some poor examples of labels would be: - Orange (not really relevant to the product's assessment) - Easy to Lift (only relevant to certain products) - Made in USA (not really relevant to the product's assessment) - Cheap (not descriptive enough and could be interpreted as negative) A score is derived as follows: - a thumbs-down is a score of 0.00 - a thumbs-up is a score of 0.50 - a label is worth 0.50 ÷ the number of labels available. So, if there are 3 labels to pick from, each label is worth 0.1666. The labels should all have the same value. Here is an example by calvadev being used on Shopstr: https://github.com/nostr-protocol/nips/pull/879#issuecomment-2502210146 You can adjust the weights however you want. The fundamental thing that QTS prescribes is that a thumbs up gives a 50% score, and labels each contribute an equal share up to another 50%. # Conclusion With nostr we have a great opportunity to improve the economic information available to the planet. A more efficient market based on higher quality information will improve civilization in ways we may not expect, but definitely deserve! If you like this post, be sure to give it a thumbs up ✌😁
@ e8ed3798:67dd345a
2025-01-14 17:38:49Crowdsourcing subjective value is a great idea, but when no thought has been put into how to do it, the results are neither useful nor healthy. In this article we discuss the problems with the classic five star rating system and why it needs to be abolished in favor of better expressions of public sentiment. ## Part 1: What's In A Star? Let's start with a thought experiment: - Do you buy products on Amazon that have 3 stars? - Do you take rides from Uber drivers that have 3 stars? - Do you download apps on the App Store that have 3 stars? - Do you visit places on Google Maps that have 3 stars? "Not on purpose," is probably your answer. But why not? After all, a three out of five is better than the median; it's 60 percent! That is solidly "above average" by any usual measure. Although it makes sense in mathematical terms, it is not correct to say that a 3 star product is at least half as good as a 5 star product. The funny thing about the 5 star rating system is that nobody really knows exactly what the stars mean, mostly because they aren't ever explained. They are just a weak abstraction of a score out of 5, which itself is an abstraction of a score out of 100, and it is used to average all ratings for a thing into an average star rating. Presumably, 5 is the best and 1 is the worst, and somewhere in between is... what exactly? Mediocre? Passable? Acceptable? Average? Who knows! This is the first problem with this system; while the top and bottom of the scale may be implied (ambiguity still isn't great), the middle of the scale is entirely ambiguous. Most of the time, people start with a default supposition that a product ought to be 5 stars, and then they subtract stars according to their own perceived deficiencies of the product. On the flip side, people who are dissatisfied with a product tend to start at 1 star and perhaps award it a couple more if they are feeling charitable. This dualistic approach highlights another issue with this kind of rating system. Despite the pure quantitative mechanism, the feelings and disposition of the rater ultimately assign meaning to the numeric scale. Ultimately, any 5 star rating system ends up being a gamut ranging from hate it to love it with a lot of ambiguity in the middle. To put it simply, the stars mean nothing. But to be more precise, the stars are the *average* of the *numeric expression* of the public sentiment about a thing. OK, public sentiment. That's what we want right? We want to know what the public thinks about the product so we can make a good purchase decision. Except, unfortunately, the 5 star rating system does an incredibly imprecise job at capturing what the public actually thinks about a product. Let's dive into why this is. But first, to conclude our thought experiment, I'd like to establish an informal consensus that we instinctually seek out the highest rated items and avoid ratings less than 4.5 out of 5, with infrequent exceptions. If this sounds like you, then let's proceed. ## Part 2: Trash or Treasure How does one turn their feelings into a number? This is not something people are good at, or do naturally, or are even required to do very often. It is also completely subjective and arbitrary. Does "happy" mean 5 or 100 or 902,581? It really depends on what you are trying to measure. However, you've probably done this on a survey. Normally, a range of options is given with accompanying numbers. You may have heard a guiding explanation such as "Rate one through five, with one being 'least likely' and five being 'most likely' to recommend to a friend." Such explanations are useful in assisting a person in expressing their personal sentiments as a numeric range, and anecdotally I seem to provide more nuanced answers when I have guidance as to what each value actually means to me. However, such explanations are missing from most places where five star rating systems can make or break one's livelihood as a seller, developer, or musician. Users are normally given no guidance as to how a particular star value should correspond to their sentiment. Accordingly, this manifests in an all too common star rating smiley. Like the famed "smiley face curve" equalizer setting popularized in the 70's in which the frequencies of a song were engineered to grow from the midranges upward toward the treble and bass making a smile shape (who's midrange is the lowest), the star rating smile is a common sight on product reviews where the most common review ratings appear anecdotally to be 5 and 1, then 4 and 2, and lastly 3. The fact that the most common ratings are five stars and one star indicates that people most often do not think about their experience as a gradient between good and bad, but rather simply label their sentiment as only "good" or "bad" with little room for nuance. Having not received any guidance for expressing their sentiment numerically, this should be wholly unsurprising. But, I also feel like this binary outcome is a very natural expression that requires minimal mental energy to produce, and is therefore the most efficient expression of sentiment. I suspect that in another universe where we have a commonplace 15 star rating system but humans are the same, the most common ratings are 15 stars and 1 star respectively. Other factors influence this binary good/bad paradigm too. People know instinctively that leaving a bad review is bad for business, and often this is their vengeful response to any sense of feeling as if they have been mistreated, misled, or swindled by the seller. Often times the sheer excitement of the new product compels people to write reviews only minutes after they have received it, precluding them from providing an experienced and time-tested perspective of how the product performs. These quirks of human behavior can skew five star ratings severely. But the behaviors themselves are not bad! They are totally natural and expected. The real problem is how the five star rating system fails to capture these commonplace human sentiments accurately. We need to build a rating system that works for people rather than forcing people to fit into a poorly executed rating system. ## Part 3: Feast or Famine It is natural that when presented with a plethora of options, humans will be drawn to the options that are labeled as "the best". When "best" possible is five stars, then five stars naturally becomes the [Schelling point](https://en.wikipedia.org/wiki/Focal_point_(game_theory))for all buyers and sellers, where the vast majority of economic activity is concentrated. When all ratings are seen from a five-based perspective, fours look barely adequate. Threes look unacceptable. Twos are abject. And ones are complete disasters. You may have heard about how [Uber would suspend drivers whose ratings fell below 4.6](https://www.inc.com/minda-zetlin/uber-rider-ratings-deactivation-lyft-rideshare.html). The tendency of five star rating systems is to create a gradient of sentiment where 1 to 4.5 stars is "bad" and 4.5 to 5 stars is "good". One rarely discussed outcome of this dynamic is that good ratings are nearly impossible to compare to each other. As alluded to in the introduction thought experiment, the narrow range between 4.5 and 5 leaves very little room to distinguish from a good product and an excellent product; both are simply "good" or "not bad". As highly rated products are usually the products people are most interested in, it is unfortunate that a favorable rating would actually provide less signal than a bad rating as to the product's relative quality in the spectrum of good ratings. Meanwhile, bad ratings have wide berth to compare numerically. The astronomical range between 1 and 4.5 is a very spacious gradient in which to assess how bad one product is versus another, except nobody actually cares because nobody is going to buy it anyway! In the five star rating system, the better a product is, the *less* information we get to compare it to other similarly good products. This is a critical design flaw, because the better a product is and the more people review it, the *more* information we should have about it versus other similar products. It would be better if the range of "good" ratings was wider so that good ratings could be compared to each other. I'd like to emphasize that the *loss of precision* as a product becomes more desirable is a truly ludicrous mechanic of the five star rating system. This poorly conceived rating paradigm completely pervades our digital economic systems and determines the success of millions of producers. Let's be clear about the stakes. Assigning subjective value to things is completely overlooked for what it really is: a absolutely critical and monumentally influential economic activity. Because the most important economic activity is how we assign value to things with money, the second most important economic activity is how we *inform* our economic value assignments with subjective value assignments such as these. We need to fix how we rate things. It could literally change how entire economies function. ## Part 4: Quality or Quantity Valve has obviously put thought into how they handle ratings for video games sold through their extremely popular and long-lived Steam platform. Reviews are not allowed until a certain amount of hours of the game have been played. The review must assign a thumbs-up or thumbs-down, and then provide a minimum amount of text. Then, rather than simply providing an average of these binary ratings, Steam averages them over a recent period of time, creating a dynamic where if a game developer releases a new update, the reviews written more recently are sure to influence the overall rating of the game rather than old ratings that haven't taken the new update into consideration. Finally, the aggregated rating itself is displayed as "Overwhelming Negative", "Very Negative", "Mostly Negative", "Mixed", "Mostly Positive", "Very Positive", or "Overwhelmingly Positive". Ask yourself, which product would you be more likely to try? - 2.5/5 stars - "Mixed Reviews" Ironically, the Steam rating system gives users less flexibility to express their sentiment as a number, and yet provides more depth, nuance, and balance to the resulting ratings. This, ladies and gentlemen, is what it looks like when somebody gives a damn about how things work. It is a great system. Another interesting emergent behavior that accompanies many Steam reviews, as well as many reviews on other sites, are user generated pros/cons lists. These lists are helpful and offer qualitative labels that help to explain the quantitative rating assignment, although these labels are not mechanically related to the rating system itself. Steam has another mechanism to express qualitative judgements in the form of labels, although they had to be restricted because they were being abused in undesirable or nefarious ways. Now the labeling system does more to tell you about what the game is rather than what people think about it, which is fine, but I feel like it is a missed opportunity. Therefore, I'd like to propose a simple system that combines thumbs up/down and labeling to be used in the context of nostr's review system. ## Part 5: QTS I call this new review system QTS, or the "Qualitative Thumb System". [Originally I developed QTS when working at Arcade Labs.](https://github.com/ArcadeLabsInc/arcade/wiki/ArcadeSocial) [This PR for a new nostr review mechanism](https://github.com/nostr-protocol/nips/pull/879) allows for a lot of flexibility in how you apply ratings to things, so QTS is simply a method of applying rating values that creates a better human-oriented review system. QTS is a way of using reviews. In essence, QTS capitalizes on our very human instinct to assign a "good" or "bad" label by limiting the quantitative assessment to a thumbs-up or thumbs-down. Then, QTS provides qualitative labels that describe possible positive sentiments that describe different aspects of the thing being rated. First, the user chooses thumbs-up or thumbs-down as their overall assessment. If they do nothing else, this is sufficient to capture their sentiment. However, labels should be provided which the user can check or toggle on to increase their rating further. The initial thumbs up is worth 0.5, and each label is worth (0.5 / number of labels). The minimum rating is 0 (thumbs down, no labels), and the maximum rating is 1 (thumbs up and all labels). Any rating 0.5 or above is trending toward good and below 0.5 is trending toward bad. The labels should be applicable in the context of the thing. So, for example, I might provide the following labels for place reviews in a Google Maps-style app: - Convenient - Clean - Affordable - Memorable - Inviting These labels could possibly describe any place. It's OK if a place doesn't have all of these qualities. Zero labels and at thumbs up is still a "good" rating. Each label selected is essentially a "cherry on top" and its absence may indicate that either it isn't applicable OR the place failed to earn it. Likewise, it is possible that you may give a place a thumbs-down and apply labels; this would result in a rating higher than 0 but still in the bad gradient (below 0.5). Here are the key benefits I want to highlight of QTS: - The 5 star rating system forces a user to do the work of translating their sentiment into a quantity. With QTS, the user never has to translate their feelings into a number! They only express good or bad and pick labels, and the QTS mechanism does the work of translating this into a computation-friendly value. - The 5 star rating system generally results in a "bad" range from 1 to 4.5 and a "good" range from 4.5 to 5. QTS balances this with a "bad" rating at 0, a "good" rating at 0.5, and an excellent rating is anything above 0.5 (up to 1.0). This creates the maximum possible gradient between good and bad which makes it easier to compare similar ratings. Recall this in contrast to the 5 star rating system which actually _loses precision_ as more ratings are provided. - It is also helpful that similar QTS ratings may have different labels, which will allow people to make easy qualitative assessments that do not depend on users generating their own pros/cons list. ## Part 6: Implementing QTS Here is how it works: You give the user the option to rate a thumbs up or thumbs down. Then, you also give your user the option to choose from a predefined set of positive labels. You can have any number of labels but try to keep it below 10 so as not to overwhelm your users. Keep the labels general enough that they could potentially apply to any thing being rated. For example, if you were providing labels for Amazon.com, some good labels would be: - Good Value - Good Quality - As Described - Durable - Right Size These labels are general enough that they could apply to almost any product. It is important to create labels that are general so that when comparing product ratings you are comparing the same labels. It is possible however that something like Amazon.com could define a different QTS label subset for each product category, and then the labels could be more specific to that category. For example, a product category of Candles could have "Long Burning", "Good smell", "Safe", etc. These labels are much more specific, but appropriate for the Candle product category. The main point is that products which should be compared should use the same QTS label set. Some poor examples of labels would be: - Orange (not really relevant to the product's assessment) - Easy to Lift (only relevant to certain products) - Made in USA (not really relevant to the product's assessment) - Cheap (not descriptive enough and could be interpreted as negative) A score is derived as follows: - a thumbs-down is a score of 0.00 - a thumbs-up is a score of 0.50 - a label is worth 0.50 ÷ the number of labels available. So, if there are 3 labels to pick from, each label is worth 0.1666. The labels should all have the same value. Here is an example by calvadev being used on Shopstr: https://github.com/nostr-protocol/nips/pull/879#issuecomment-2502210146 You can adjust the weights however you want. The fundamental thing that QTS prescribes is that a thumbs up gives a 50% score, and labels each contribute an equal share up to another 50%. # Conclusion With nostr we have a great opportunity to improve the economic information available to the planet. A more efficient market based on higher quality information will improve civilization in ways we may not expect, but definitely deserve! If you like this post, be sure to give it a thumbs up ✌😁 @ 17538dc2:71ed77c4
2025-01-13 18:17:24Sci-Hub 2024 year end review is translated to English by Kagi Translate from Russian. Original text can be found in Sci-Hub's telegram channel https://t.me/freescience. ### RESULTS OF 2024 First. The project received donations totaling 2 million dollars in meme coins. The project is actively used by many students in China, which is why a group of Sci-Hub fans has emerged there. As far as I understand, the organizer of the group is actively interested in the topic of cryptocurrencies (even wrote a book). Somewhere in mid-November, the Chinese launched a meme coin in honor of the Sci-Hub project. At its peak, the coin's price reached 5 cents, and now it is somewhere around 1-2 cents. This means that the exchange rate of the Sci-Hub cryptocurrency is now almost equal to the ruble exchange rate (100 to one or so). In general, I converted part of these donations into normal, traditional cryptocurrency (like Bitcoin) and paid for servers several months in advance. The other part is still sitting in meme coins—I hope that the token will still grow in price (there is a promotion plan). Of course, this is risky, but Sci-Hub is a project that is not afraid of risk. Therefore, anyone who wants to invest in Sci-Hub by purchasing this token can do so here: www.coingecko.com/en/coins/sci-hub Second. A dissertation on the topic of open scientific knowledge has been defended at the Institute of Philosophy. For those interested in the history and philosophy of science, I defended a dissertation in April at the Institute of Philosophy on the topic that scientific knowledge should be open (otherwise, it is strange to call it scientific at all). The work shows that open communication is one of the basic traditional values of science when considering science as a social institution. In other words, journals that charge for access to scientific articles are a kind of 'non-traditional orientation journals.' Moreover, openness is an important prerequisite for rationality. Rationality is not limited to the criterion of falsification (hello Popper); it is a much more complex concept. You can familiarize yourself with the text of the dissertation here: web.archive.org/web/20240425100014/https://iphras.ru/page26414303.htm (I provide the link through the web archive because the Institute's website, strangely enough, is glitching again at the time of writing this post). All criticism and comments (as well as praise) regarding the dissertation can be sent to my email. Third. Work has begun on a new declaration of open access to scientific knowledge. Currently, all discussions on the topic of open science are conducted within the frameworks defined by the so-called BBB declarations back in 2001-2003. Within these frameworks, two main types of open access are recognized: gold, meaning open journals with an author-pays model, and green, which refers to repositories like the well-known arXiv. We can also add the so-called diamond open access, which includes open journals that are free for both authors and readers. However, since 2003, internet technologies have advanced significantly. Today, we can already talk about such types of open access as blue (through academic social networks) or red (your beloved Sci-Hub). It is time to adopt a new declaration of open access to scientific knowledge that corresponds to the current state of scientific and technological progress. A preliminary version of the declaration can be read and signed here: open.science.do We will be more actively engaged in this in the coming year. Signing the declaration is an important step towards recognizing access to scientific knowledge through sites like Sci-Hub or Libgen as completely legal and ceasing to pursue them—first in the former USSR, and then in all countries of the world. Fourth. In 2024, about one billion articles were downloaded through Sci-Hub. Despite the fact that this is unfiltered statistics, the fact remains: the popularity of the project has not decreased but only grown, despite the fact that Sci-Hub has not been updated for quite a long time. Of course, this does not mean that the site will not be updated at all now—just that the patient is more alive than dead (no matter how much some haters might wish otherwise). The cause of open access to scientific knowledge will definitely prevail—because good always triumphs over evil. In the new year, I wish all scientists new discoveries and large grants. Happy New Year, comrades!
@ 17538dc2:71ed77c4
2025-01-13 18:17:24Sci-Hub 2024 year end review is translated to English by Kagi Translate from Russian. Original text can be found in Sci-Hub's telegram channel https://t.me/freescience. ### RESULTS OF 2024 First. The project received donations totaling 2 million dollars in meme coins. The project is actively used by many students in China, which is why a group of Sci-Hub fans has emerged there. As far as I understand, the organizer of the group is actively interested in the topic of cryptocurrencies (even wrote a book). Somewhere in mid-November, the Chinese launched a meme coin in honor of the Sci-Hub project. At its peak, the coin's price reached 5 cents, and now it is somewhere around 1-2 cents. This means that the exchange rate of the Sci-Hub cryptocurrency is now almost equal to the ruble exchange rate (100 to one or so). In general, I converted part of these donations into normal, traditional cryptocurrency (like Bitcoin) and paid for servers several months in advance. The other part is still sitting in meme coins—I hope that the token will still grow in price (there is a promotion plan). Of course, this is risky, but Sci-Hub is a project that is not afraid of risk. Therefore, anyone who wants to invest in Sci-Hub by purchasing this token can do so here: www.coingecko.com/en/coins/sci-hub Second. A dissertation on the topic of open scientific knowledge has been defended at the Institute of Philosophy. For those interested in the history and philosophy of science, I defended a dissertation in April at the Institute of Philosophy on the topic that scientific knowledge should be open (otherwise, it is strange to call it scientific at all). The work shows that open communication is one of the basic traditional values of science when considering science as a social institution. In other words, journals that charge for access to scientific articles are a kind of 'non-traditional orientation journals.' Moreover, openness is an important prerequisite for rationality. Rationality is not limited to the criterion of falsification (hello Popper); it is a much more complex concept. You can familiarize yourself with the text of the dissertation here: web.archive.org/web/20240425100014/https://iphras.ru/page26414303.htm (I provide the link through the web archive because the Institute's website, strangely enough, is glitching again at the time of writing this post). All criticism and comments (as well as praise) regarding the dissertation can be sent to my email. Third. Work has begun on a new declaration of open access to scientific knowledge. Currently, all discussions on the topic of open science are conducted within the frameworks defined by the so-called BBB declarations back in 2001-2003. Within these frameworks, two main types of open access are recognized: gold, meaning open journals with an author-pays model, and green, which refers to repositories like the well-known arXiv. We can also add the so-called diamond open access, which includes open journals that are free for both authors and readers. However, since 2003, internet technologies have advanced significantly. Today, we can already talk about such types of open access as blue (through academic social networks) or red (your beloved Sci-Hub). It is time to adopt a new declaration of open access to scientific knowledge that corresponds to the current state of scientific and technological progress. A preliminary version of the declaration can be read and signed here: open.science.do We will be more actively engaged in this in the coming year. Signing the declaration is an important step towards recognizing access to scientific knowledge through sites like Sci-Hub or Libgen as completely legal and ceasing to pursue them—first in the former USSR, and then in all countries of the world. Fourth. In 2024, about one billion articles were downloaded through Sci-Hub. Despite the fact that this is unfiltered statistics, the fact remains: the popularity of the project has not decreased but only grown, despite the fact that Sci-Hub has not been updated for quite a long time. Of course, this does not mean that the site will not be updated at all now—just that the patient is more alive than dead (no matter how much some haters might wish otherwise). The cause of open access to scientific knowledge will definitely prevail—because good always triumphs over evil. In the new year, I wish all scientists new discoveries and large grants. Happy New Year, comrades! @ df173277:4ec96708
2025-01-09 17:02:52> OpenSecret is a backend for app developers that turns private encryption on by default. When sensitive data is readable only by the user, it protects both the user and the developer, creating a more free and open internet. We'll be launching in 2025. [Join our waitlist to get early access.](https://opensecret.cloud) In today's digital age, personal data is both an asset and a liability. With the rise of data breaches and cyber attacks, individuals and companies struggle to protect sensitive information. The consequences of a data breach can be devastating, resulting in financial losses, reputational damage, and compromised user trust. In 2023, the average data breach cost was $5 million, with some resulting in losses of over $1 billion. Meanwhile, individuals face problems related to identity theft, personal safety, and public embarrassment. Think about the apps on your phone, even the one you're using to read this. How much data have you trusted to other people, and how would it feel if that data were leaked online? Thankfully, some incredibly talented cypherpunks years ago gave the world cryptography. We can encrypt data, rendering it a secret between two people. So why then do we have data breaches? > Cryptography at scale is hard. #### The Cloud The cloud has revolutionized how we store and process data, but it has limitations. While cloud providers offer encryption, it mainly protects data in transit. Once data is stored in the cloud, it's often encrypted with a shared key, which can be accessed by employees, third-party vendors, or compromised by hackers. The solution is to generate a personal encryption password for each user, make sure they write it down, and, most importantly, hope they don't lose it. If the password is lost, the data is forever unreadable. That can be overwhelming, leading to low app usage. > Private key encryption needs a UX upgrade. ## Enter OpenSecret OpenSecret is a developer platform that enables encryption by default. Our platform provides a suite of security tools for app developers, including private key management, encrypted sync, private AI, and confidential compute. Every user has a private vault for their data, which means only they can read it. Developers are free to store less sensitive data in a shared manner because there is still a need to aggregate data across the system.  ### Private Key Management Private key management is the superpower that enables personal encryption per user. When each user has a unique private key, their data can be truly private. Typically, using a private key is a challenging experience for the user because they must write down a long autogenerated number or phrase of 12-24 words. If they lose it, their data is gone. OpenSecret uses secure enclaves to make private keys as easy as an everyday login experience that users are familiar with. Instead of managing a complicated key, the user logs in with an email address or a social media account. The developer doesn't have to manage private keys and can focus on the app's user experience. The user doesn't have to worry about losing a private key and can jump into using your app.  ### Encrypted Sync With user keys safely managed, we can synchronize user data to every device while maintaining privacy. The user does not need to do complicated things like scanning QR codes from one device to the next. Just log in and go. The user wins because the data is available on all their devices. The developer wins because only the user can read the data, so it isn't a liability to them. ### Private AI Artificial intelligence is here and making its way into everything. The true power of AI is unleashed when it can act on personal and company data. The current options are to run your own AI locally on an underpowered machine or to trust a third party with your data, hoping they don't read it or use it for anything. OpenSecret combines the power of cloud computing with the privacy and security of a machine running on your desk. **Check out Maple AI**\ Try private AI for yourself! We built an app built with this service called [Maple AI](https://trymaple.ai). It is an AI chat that is 100% private in a verifiable manner. Give it your innermost thoughts or embarrassing ideas; we can't judge you. We built Maple using OpenSecret, which means you have a private key that is automatically managed for you, and your chat history is synchronized to all your devices. [Learn more about Maple AI - Private chat in the announcement post.](https://blog.opensecret.cloud/maple-ai-private-encrypted-chat/)  ### Confidential Compute Confidential computing is a game-changer for data security. It's like the secure hardware that powers Apple Pay and Google Pay on your phone but in the cloud. Users can verify through a process called attestation that their data is handled appropriately. OpenSecret can help you run your own custom app backend code that would benefit from the security of an enclave. It's the new version of that lock on your web browser. When you see it, you know you're secure.  #### **But do we want our secrets to be open?** OpenSecret renders a data breach practically useless. If hackers get into the backend, they enter a virtual hallway of locked private vaults. The leaked data would be gibberish, a secret in the open that is unreadable. On the topic of openness, OpenSecret uses the power of open source to enable trust in the service. We publish our code in the open, and, using attestation, anyone can verify that private data is being handled as expected. This openness also provides developers with a backup option to safely and securely export their data. > Don't trust, verify. ### **Join the Movement** We're currently building out OpenSecret, and we invite you to join us on the journey. Our platform can work with your existing stack, and you can pick and choose the features you need. If you want to build apps with encryption enabled, [send us a message to get early access.](https://opensecret.cloud) Users and companies deserve better encryption and privacy.\ Together, let's make that a reality. [](https://opensecret.cloud)
@ df173277:4ec96708
2025-01-09 17:02:52> OpenSecret is a backend for app developers that turns private encryption on by default. When sensitive data is readable only by the user, it protects both the user and the developer, creating a more free and open internet. We'll be launching in 2025. [Join our waitlist to get early access.](https://opensecret.cloud) In today's digital age, personal data is both an asset and a liability. With the rise of data breaches and cyber attacks, individuals and companies struggle to protect sensitive information. The consequences of a data breach can be devastating, resulting in financial losses, reputational damage, and compromised user trust. In 2023, the average data breach cost was $5 million, with some resulting in losses of over $1 billion. Meanwhile, individuals face problems related to identity theft, personal safety, and public embarrassment. Think about the apps on your phone, even the one you're using to read this. How much data have you trusted to other people, and how would it feel if that data were leaked online? Thankfully, some incredibly talented cypherpunks years ago gave the world cryptography. We can encrypt data, rendering it a secret between two people. So why then do we have data breaches? > Cryptography at scale is hard. #### The Cloud The cloud has revolutionized how we store and process data, but it has limitations. While cloud providers offer encryption, it mainly protects data in transit. Once data is stored in the cloud, it's often encrypted with a shared key, which can be accessed by employees, third-party vendors, or compromised by hackers. The solution is to generate a personal encryption password for each user, make sure they write it down, and, most importantly, hope they don't lose it. If the password is lost, the data is forever unreadable. That can be overwhelming, leading to low app usage. > Private key encryption needs a UX upgrade. ## Enter OpenSecret OpenSecret is a developer platform that enables encryption by default. Our platform provides a suite of security tools for app developers, including private key management, encrypted sync, private AI, and confidential compute. Every user has a private vault for their data, which means only they can read it. Developers are free to store less sensitive data in a shared manner because there is still a need to aggregate data across the system.  ### Private Key Management Private key management is the superpower that enables personal encryption per user. When each user has a unique private key, their data can be truly private. Typically, using a private key is a challenging experience for the user because they must write down a long autogenerated number or phrase of 12-24 words. If they lose it, their data is gone. OpenSecret uses secure enclaves to make private keys as easy as an everyday login experience that users are familiar with. Instead of managing a complicated key, the user logs in with an email address or a social media account. The developer doesn't have to manage private keys and can focus on the app's user experience. The user doesn't have to worry about losing a private key and can jump into using your app.  ### Encrypted Sync With user keys safely managed, we can synchronize user data to every device while maintaining privacy. The user does not need to do complicated things like scanning QR codes from one device to the next. Just log in and go. The user wins because the data is available on all their devices. The developer wins because only the user can read the data, so it isn't a liability to them. ### Private AI Artificial intelligence is here and making its way into everything. The true power of AI is unleashed when it can act on personal and company data. The current options are to run your own AI locally on an underpowered machine or to trust a third party with your data, hoping they don't read it or use it for anything. OpenSecret combines the power of cloud computing with the privacy and security of a machine running on your desk. **Check out Maple AI**\ Try private AI for yourself! We built an app built with this service called [Maple AI](https://trymaple.ai). It is an AI chat that is 100% private in a verifiable manner. Give it your innermost thoughts or embarrassing ideas; we can't judge you. We built Maple using OpenSecret, which means you have a private key that is automatically managed for you, and your chat history is synchronized to all your devices. [Learn more about Maple AI - Private chat in the announcement post.](https://blog.opensecret.cloud/maple-ai-private-encrypted-chat/)  ### Confidential Compute Confidential computing is a game-changer for data security. It's like the secure hardware that powers Apple Pay and Google Pay on your phone but in the cloud. Users can verify through a process called attestation that their data is handled appropriately. OpenSecret can help you run your own custom app backend code that would benefit from the security of an enclave. It's the new version of that lock on your web browser. When you see it, you know you're secure.  #### **But do we want our secrets to be open?** OpenSecret renders a data breach practically useless. If hackers get into the backend, they enter a virtual hallway of locked private vaults. The leaked data would be gibberish, a secret in the open that is unreadable. On the topic of openness, OpenSecret uses the power of open source to enable trust in the service. We publish our code in the open, and, using attestation, anyone can verify that private data is being handled as expected. This openness also provides developers with a backup option to safely and securely export their data. > Don't trust, verify. ### **Join the Movement** We're currently building out OpenSecret, and we invite you to join us on the journey. Our platform can work with your existing stack, and you can pick and choose the features you need. If you want to build apps with encryption enabled, [send us a message to get early access.](https://opensecret.cloud) Users and companies deserve better encryption and privacy.\ Together, let's make that a reality. [](https://opensecret.cloud) @ f88e6629:e5254dd5
2025-01-08 20:08:17- Send a transaction, and the recipient uses the coin for another payment. You then merge these two transactions together and save on fees. 🔥  If you have a Trezor, you can try this out on: https://coiner-mu.vercel.app/ _But be cautious. This is a hobby project without any guarantee._ <img width="1772" alt="Screenshot 2025-01-08 at 20 14 17" src="https://github.com/user-attachments/assets/36412edb-9c62-4c5f-8f82-b41c118a3aa6" /> ## How does it work? 1. Connect Trezor, enter the passphrase, and select an account. 2. The application display your coins, pending transactions, and descendant transactions. 4. Then app shows you how much you can save by merging all transactions and removing duplicate information. 5. Finally, you can sign and broadcast this more efficient transaction
@ f88e6629:e5254dd5
2025-01-08 20:08:17- Send a transaction, and the recipient uses the coin for another payment. You then merge these two transactions together and save on fees. 🔥  If you have a Trezor, you can try this out on: https://coiner-mu.vercel.app/ _But be cautious. This is a hobby project without any guarantee._ <img width="1772" alt="Screenshot 2025-01-08 at 20 14 17" src="https://github.com/user-attachments/assets/36412edb-9c62-4c5f-8f82-b41c118a3aa6" /> ## How does it work? 1. Connect Trezor, enter the passphrase, and select an account. 2. The application display your coins, pending transactions, and descendant transactions. 4. Then app shows you how much you can save by merging all transactions and removing duplicate information. 5. Finally, you can sign and broadcast this more efficient transaction @ 23b0e2f8:d8af76fc
2025-01-08 18:17:52## **Necessário** - Um Android que você não use mais (a câmera deve estar funcionando). - Um cartão microSD (opcional, usado apenas uma vez). - Um dispositivo para acompanhar seus fundos (provavelmente você já tem um). ## **Algumas coisas que você precisa saber** - O dispositivo servirá como um assinador. Qualquer movimentação só será efetuada após ser assinada por ele. - O cartão microSD será usado para transferir o APK do Electrum e garantir que o aparelho não terá contato com outras fontes de dados externas após sua formatação. Contudo, é possível usar um cabo USB para o mesmo propósito. - A ideia é deixar sua chave privada em um dispositivo offline, que ficará desligado em 99% do tempo. Você poderá acompanhar seus fundos em outro dispositivo conectado à internet, como seu celular ou computador pessoal. --- ## **O tutorial será dividido em dois módulos:** - Módulo 1 - Criando uma carteira fria/assinador. - Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador. --- ## **No final, teremos:** - Uma carteira fria que também servirá como assinador. - Um dispositivo para acompanhar os fundos da carteira.  --- ## **Módulo 1 - Criando uma carteira fria/assinador** 1. Baixe o APK do Electrum na aba de **downloads** em <https://electrum.org/>. Fique à vontade para [verificar as assinaturas](https://electrum.readthedocs.io/en/latest/gpg-check.html) do software, garantindo sua autenticidade. 2. Formate o cartão microSD e coloque o APK do Electrum nele. Caso não tenha um cartão microSD, pule este passo.  3. Retire os chips e acessórios do aparelho que será usado como assinador, formate-o e aguarde a inicialização.  4. Durante a inicialização, pule a etapa de conexão ao Wi-Fi e rejeite todas as solicitações de conexão. Após isso, você pode desinstalar aplicativos desnecessários, pois precisará apenas do Electrum. Certifique-se de que Wi-Fi, Bluetooth e dados móveis estejam desligados. Você também pode ativar o **modo avião**.\ *(Curiosidade: algumas pessoas optam por abrir o aparelho e danificar a antena do Wi-Fi/Bluetooth, impossibilitando essas funcionalidades.)*  5. Insira o cartão microSD com o APK do Electrum no dispositivo e instale-o. Será necessário permitir instalações de fontes não oficiais.  6. No Electrum, crie uma carteira padrão e gere suas palavras-chave (seed). Anote-as em um local seguro. Caso algo aconteça com seu assinador, essas palavras permitirão o acesso aos seus fundos novamente. *(Aqui entra seu método pessoal de backup.)*  --- ## **Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador.** 1. Criar uma carteira **somente leitura** em outro dispositivo, como seu celular ou computador pessoal, é uma etapa bastante simples. Para este tutorial, usaremos outro smartphone Android com Electrum. Instale o Electrum a partir da aba de downloads em <https://electrum.org/> ou da própria Play Store. *(ATENÇÃO: O Electrum não existe oficialmente para iPhone. Desconfie se encontrar algum.)* 2. Após instalar o Electrum, crie uma carteira padrão, mas desta vez escolha a opção **Usar uma chave mestra**.  3. Agora, no assinador que criamos no primeiro módulo, exporte sua chave pública: vá em **Carteira > Detalhes da carteira > Compartilhar chave mestra pública**.  4. Escaneie o QR gerado da chave pública com o dispositivo de consulta. Assim, ele poderá acompanhar seus fundos, mas sem permissão para movimentá-los. 5. Para receber fundos, envie Bitcoin para um dos endereços gerados pela sua carteira: **Carteira > Addresses/Coins**. 6. Para movimentar fundos, crie uma transação no dispositivo de consulta. Como ele não possui a chave privada, será necessário assiná-la com o dispositivo assinador.  7. No assinador, escaneie a transação não assinada, confirme os detalhes, assine e compartilhe. Será gerado outro QR, desta vez com a transação já assinada.  8. No dispositivo de consulta, escaneie o QR da transação assinada e transmita-a para a rede. --- ## **Conclusão** **Pontos positivos do setup:** - **Simplicidade:** Basta um dispositivo Android antigo. - **Flexibilidade:** Funciona como uma ótima carteira fria, ideal para holders. **Pontos negativos do setup:** - **Padronização:** Não utiliza seeds no padrão BIP-39, você sempre precisará usar o electrum. - **Interface:** A aparência do Electrum pode parecer antiquada para alguns usuários. Nesse ponto, temos uma carteira fria que também serve para assinar transações. O fluxo de assinar uma transação se torna: ***Gerar uma transação não assinada > Escanear o QR da transação não assinada > Conferir e assinar essa transação com o assinador > Gerar QR da transação assinada > Escanear a transação assinada com qualquer outro dispositivo que possa transmiti-la para a rede.*** Como alguns devem saber, uma transação assinada de Bitcoin é praticamente impossível de ser fraudada. Em um cenário catastrófico, você pode mesmo que sem internet, repassar essa transação assinada para alguém que tenha acesso à rede por qualquer meio de comunicação. Mesmo que não queiramos que isso aconteça um dia, esse setup acaba por tornar essa prática possível. ---
@ 23b0e2f8:d8af76fc
2025-01-08 18:17:52## **Necessário** - Um Android que você não use mais (a câmera deve estar funcionando). - Um cartão microSD (opcional, usado apenas uma vez). - Um dispositivo para acompanhar seus fundos (provavelmente você já tem um). ## **Algumas coisas que você precisa saber** - O dispositivo servirá como um assinador. Qualquer movimentação só será efetuada após ser assinada por ele. - O cartão microSD será usado para transferir o APK do Electrum e garantir que o aparelho não terá contato com outras fontes de dados externas após sua formatação. Contudo, é possível usar um cabo USB para o mesmo propósito. - A ideia é deixar sua chave privada em um dispositivo offline, que ficará desligado em 99% do tempo. Você poderá acompanhar seus fundos em outro dispositivo conectado à internet, como seu celular ou computador pessoal. --- ## **O tutorial será dividido em dois módulos:** - Módulo 1 - Criando uma carteira fria/assinador. - Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador. --- ## **No final, teremos:** - Uma carteira fria que também servirá como assinador. - Um dispositivo para acompanhar os fundos da carteira.  --- ## **Módulo 1 - Criando uma carteira fria/assinador** 1. Baixe o APK do Electrum na aba de **downloads** em <https://electrum.org/>. Fique à vontade para [verificar as assinaturas](https://electrum.readthedocs.io/en/latest/gpg-check.html) do software, garantindo sua autenticidade. 2. Formate o cartão microSD e coloque o APK do Electrum nele. Caso não tenha um cartão microSD, pule este passo.  3. Retire os chips e acessórios do aparelho que será usado como assinador, formate-o e aguarde a inicialização.  4. Durante a inicialização, pule a etapa de conexão ao Wi-Fi e rejeite todas as solicitações de conexão. Após isso, você pode desinstalar aplicativos desnecessários, pois precisará apenas do Electrum. Certifique-se de que Wi-Fi, Bluetooth e dados móveis estejam desligados. Você também pode ativar o **modo avião**.\ *(Curiosidade: algumas pessoas optam por abrir o aparelho e danificar a antena do Wi-Fi/Bluetooth, impossibilitando essas funcionalidades.)*  5. Insira o cartão microSD com o APK do Electrum no dispositivo e instale-o. Será necessário permitir instalações de fontes não oficiais.  6. No Electrum, crie uma carteira padrão e gere suas palavras-chave (seed). Anote-as em um local seguro. Caso algo aconteça com seu assinador, essas palavras permitirão o acesso aos seus fundos novamente. *(Aqui entra seu método pessoal de backup.)*  --- ## **Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador.** 1. Criar uma carteira **somente leitura** em outro dispositivo, como seu celular ou computador pessoal, é uma etapa bastante simples. Para este tutorial, usaremos outro smartphone Android com Electrum. Instale o Electrum a partir da aba de downloads em <https://electrum.org/> ou da própria Play Store. *(ATENÇÃO: O Electrum não existe oficialmente para iPhone. Desconfie se encontrar algum.)* 2. Após instalar o Electrum, crie uma carteira padrão, mas desta vez escolha a opção **Usar uma chave mestra**.  3. Agora, no assinador que criamos no primeiro módulo, exporte sua chave pública: vá em **Carteira > Detalhes da carteira > Compartilhar chave mestra pública**.  4. Escaneie o QR gerado da chave pública com o dispositivo de consulta. Assim, ele poderá acompanhar seus fundos, mas sem permissão para movimentá-los. 5. Para receber fundos, envie Bitcoin para um dos endereços gerados pela sua carteira: **Carteira > Addresses/Coins**. 6. Para movimentar fundos, crie uma transação no dispositivo de consulta. Como ele não possui a chave privada, será necessário assiná-la com o dispositivo assinador.  7. No assinador, escaneie a transação não assinada, confirme os detalhes, assine e compartilhe. Será gerado outro QR, desta vez com a transação já assinada.  8. No dispositivo de consulta, escaneie o QR da transação assinada e transmita-a para a rede. --- ## **Conclusão** **Pontos positivos do setup:** - **Simplicidade:** Basta um dispositivo Android antigo. - **Flexibilidade:** Funciona como uma ótima carteira fria, ideal para holders. **Pontos negativos do setup:** - **Padronização:** Não utiliza seeds no padrão BIP-39, você sempre precisará usar o electrum. - **Interface:** A aparência do Electrum pode parecer antiquada para alguns usuários. Nesse ponto, temos uma carteira fria que também serve para assinar transações. O fluxo de assinar uma transação se torna: ***Gerar uma transação não assinada > Escanear o QR da transação não assinada > Conferir e assinar essa transação com o assinador > Gerar QR da transação assinada > Escanear a transação assinada com qualquer outro dispositivo que possa transmiti-la para a rede.*** Como alguns devem saber, uma transação assinada de Bitcoin é praticamente impossível de ser fraudada. Em um cenário catastrófico, você pode mesmo que sem internet, repassar essa transação assinada para alguém que tenha acesso à rede por qualquer meio de comunicação. Mesmo que não queiramos que isso aconteça um dia, esse setup acaba por tornar essa prática possível. --- @ bd32f268:22b33966
2025-01-02 19:30:46Texto publicado por *Foundation Father @FoundationDads* e traduzido para português. Assumir responsabilidades numa época efeminada como a nossa é um superpoder. Algumas pessoas não sabem o que significa "assumir responsabilidades", no entanto, porque nunca tiveram um pai ou outra pessoa que as ama-se o suficiente para lhes ensinar. Então, aqui está como assumir responsabilidades. ## **Lembra-te que não és uma pessoa desamparada e incompetente.** As coisas não te acontecem simplesmente enquanto olhas fixamente com a boca aberta, usando todo o teu poder cerebral para te lembrares de como respirar. Tu tens poder de ação. ## Mantém estas perguntas em mente: "Que papel desempenhei eu nesta situação ou como ajudei a formar o sistema em que estou inserido?" "O que posso fazer agora mesmo para começar a corrigi-lo, por mais pequeno que seja?" Aqui estão alguns exemplos de como aplicar estas perguntas. *José Malhoa - Remédio* ## Saúde Estás com excesso de peso e cansado o tempo todo? Deprimido? Começa a caminhar 30 minutos por dia. De preferência ao ar livre. Pára de comer snacks. Marca uma consulta com um médico para fazer análises ao sangue. Todas estas coisas estão ao teu alcance. ## Finanças Estás a afogar-te em dívidas de cartão de crédito? Assumir responsabilidades significa reduzir drasticamente o teu consumo e iniciar um programa radical de pagamento do máximo de dívida que conseguires. Obtém uma aplicação de orçamento e começa a planear. Sentes-te preso no teu emprego sem futuro? Sentes que não ganhas o suficiente? Vai a entrevistas para vagas de emprego e descobre o teu verdadeiro valor no mercado. Reserva 1 hora todas as noites para melhorares. A menos que já estejas a trabalhar em dois empregos, toda a gente tem pelo menos 1 hora todas as noites. ## Arredores imediatos Se vês algo que precisa de ser feito, simplesmente faz. Não te queixes disso. Não resmungues baixinho. Não desejes que alguém tratasse disso. Simplesmente faz e não peças permissão. Guarda o carrinho de compras. Lava a caneca de café no lava-loiça. Arranca as ervas daninhas. Repara a parede. Se o quintal do teu vizinho estiver cheio de ervas, vai lá e corta a relva tu mesmo. Limpa a água do lava-loiça. Arruma a bancada. Leva o lixo para fora. Leva bom café para o escritório. ## Os teus filhos Muitos pais queixam-se do comportamento dos seus filhos como se não tivessem qualquer influência sobre o assunto. Mas os teus filhos farão o que tu os ensinaste a fazer. "Fizemos o melhor que pudemos." Não, não fizeram, e assumir responsabilidades significa admitir que foste permissivo e preguiçoso ou que querias sentir-te justo por não bater. Que pequena coisa podes fazer agora mesmo para começar? Escolhe um único comportamento que queres que eles parem, senta-os e explica as consequências do comportamento. Pede desculpa por teres deixado andar durante tanto tempo. Quando eles apresentarem o comportamento, aplica as consequências. Aconteça o que acontecer. ## Os teus relacionamentos Não tens amigos ou o teu grupo de amigos atual é uma má influência? Podes fazer novos amigos. Assumir responsabilidades significa admitir que a tua solidão é em grande parte auto-infligida. **O que podes fazer?** Começa a jogar ténis ou futebol. Existem ligas em todo o lado. Encontra uma boa igreja local e encontra maneiras de te envolver. Existem encontros para todo o tipo de atividade. Participa num que se alinhe com as tuas preferências. Quando estiveres em público, sorri mais e puxa conversa. Depois de conheceres algumas pessoas, estabelece uma cadência regular. Agenda almoços semanais ou mensais e alterna entre algumas pessoas. Ou talvez café de manhã. Não acontecerá da noite para o dia, mas dando pequenos passos consistentemente durante alguns meses e vais perceber que tens uma vida social. ## Os teus erros Se erraste, não te retires e escondas nem arranjes desculpas. Pede desculpa à pessoa que prejudicaste, diz-lhe porquê e oferece-te para compensar. Aceita as consequências com humildade. Vais descobrir que nada te conquista mais respeito do que assumir os teus erros. Esta é a principal. Se aprenderes a fazer isto bem, cobrirá uma infinidade de pecados porque cria hábito. Mesmo que tenhas apenas 1% de culpa na situação, assumir a responsabilidade e pedir desculpa pelo teu 1% está a construir um certo grupo de músculos. "Mas ele devia ter..." Pára com isso. Confiaste demasiado? Presumiste demasiado sem comunicar? Assume a responsabilidade por isso. Estes exemplos podiam continuar para sempre, então vou parar e terminar com este princípio: A tua resposta importa mais do que as tuas circunstâncias. Existem vítimas reais, algumas de tragédias horríveis. Mas mesmo que não te tenhas atirado para areias movediças, ainda podes assumir a responsabilidade por como reages e pelo que escolhes fazer a seguir. Às vezes, é agarrar numa corda de um transeunte e dizer: "Obrigado." Não te afogues nas areias movediças até que alguém te dê uma palmadinha nas costas por quão difícil é para ti, e não continues a apontar para o teu tempo nas areias movediças para desculpares os teus fracassos. Podes não ter escolhido uma batalha específica. Ainda podes assumir a responsabilidade por quão bem lutas a batalha. Num certo sentido, ninguém escolhe a principal batalha que enfrenta. Ninguém escolheu nascer. Ninguém escolheu a sua família. Ninguém escolheu as suas circunstâncias. O mundo nunca será perfeito. Tens de assumir a responsabilidade pela tua parte dele de qualquer maneira. Pode ser difícil. Pode ser doloroso. Não te foi prometida uma vida fácil e sem dor. Depois de começares a assumir responsabilidades, qual é o próximo passo? Altura de assumir mais responsabilidades. Por exemplo, se não tens problemas em fazer amigos e tens essa parte da tua vida resolvida, assume a responsabilidade por outra pessoa. Encontra um dos rapazes solitários na tua igreja que precisa de um amigo e adiciona-o à tua rotação de almoços. A recompensa por assumir responsabilidades é subir de nível e, como consequência, as coisas devem tornar-se mais desafiantes. Mas agora estás mais bem preparado para isso. Repete até morrer e, esperançosamente, a tua causa de morte será por viver e não por te queixares de não viver.
@ bd32f268:22b33966
2025-01-02 19:30:46Texto publicado por *Foundation Father @FoundationDads* e traduzido para português. Assumir responsabilidades numa época efeminada como a nossa é um superpoder. Algumas pessoas não sabem o que significa "assumir responsabilidades", no entanto, porque nunca tiveram um pai ou outra pessoa que as ama-se o suficiente para lhes ensinar. Então, aqui está como assumir responsabilidades. ## **Lembra-te que não és uma pessoa desamparada e incompetente.** As coisas não te acontecem simplesmente enquanto olhas fixamente com a boca aberta, usando todo o teu poder cerebral para te lembrares de como respirar. Tu tens poder de ação. ## Mantém estas perguntas em mente: "Que papel desempenhei eu nesta situação ou como ajudei a formar o sistema em que estou inserido?" "O que posso fazer agora mesmo para começar a corrigi-lo, por mais pequeno que seja?" Aqui estão alguns exemplos de como aplicar estas perguntas. *José Malhoa - Remédio* ## Saúde Estás com excesso de peso e cansado o tempo todo? Deprimido? Começa a caminhar 30 minutos por dia. De preferência ao ar livre. Pára de comer snacks. Marca uma consulta com um médico para fazer análises ao sangue. Todas estas coisas estão ao teu alcance. ## Finanças Estás a afogar-te em dívidas de cartão de crédito? Assumir responsabilidades significa reduzir drasticamente o teu consumo e iniciar um programa radical de pagamento do máximo de dívida que conseguires. Obtém uma aplicação de orçamento e começa a planear. Sentes-te preso no teu emprego sem futuro? Sentes que não ganhas o suficiente? Vai a entrevistas para vagas de emprego e descobre o teu verdadeiro valor no mercado. Reserva 1 hora todas as noites para melhorares. A menos que já estejas a trabalhar em dois empregos, toda a gente tem pelo menos 1 hora todas as noites. ## Arredores imediatos Se vês algo que precisa de ser feito, simplesmente faz. Não te queixes disso. Não resmungues baixinho. Não desejes que alguém tratasse disso. Simplesmente faz e não peças permissão. Guarda o carrinho de compras. Lava a caneca de café no lava-loiça. Arranca as ervas daninhas. Repara a parede. Se o quintal do teu vizinho estiver cheio de ervas, vai lá e corta a relva tu mesmo. Limpa a água do lava-loiça. Arruma a bancada. Leva o lixo para fora. Leva bom café para o escritório. ## Os teus filhos Muitos pais queixam-se do comportamento dos seus filhos como se não tivessem qualquer influência sobre o assunto. Mas os teus filhos farão o que tu os ensinaste a fazer. "Fizemos o melhor que pudemos." Não, não fizeram, e assumir responsabilidades significa admitir que foste permissivo e preguiçoso ou que querias sentir-te justo por não bater. Que pequena coisa podes fazer agora mesmo para começar? Escolhe um único comportamento que queres que eles parem, senta-os e explica as consequências do comportamento. Pede desculpa por teres deixado andar durante tanto tempo. Quando eles apresentarem o comportamento, aplica as consequências. Aconteça o que acontecer. ## Os teus relacionamentos Não tens amigos ou o teu grupo de amigos atual é uma má influência? Podes fazer novos amigos. Assumir responsabilidades significa admitir que a tua solidão é em grande parte auto-infligida. **O que podes fazer?** Começa a jogar ténis ou futebol. Existem ligas em todo o lado. Encontra uma boa igreja local e encontra maneiras de te envolver. Existem encontros para todo o tipo de atividade. Participa num que se alinhe com as tuas preferências. Quando estiveres em público, sorri mais e puxa conversa. Depois de conheceres algumas pessoas, estabelece uma cadência regular. Agenda almoços semanais ou mensais e alterna entre algumas pessoas. Ou talvez café de manhã. Não acontecerá da noite para o dia, mas dando pequenos passos consistentemente durante alguns meses e vais perceber que tens uma vida social. ## Os teus erros Se erraste, não te retires e escondas nem arranjes desculpas. Pede desculpa à pessoa que prejudicaste, diz-lhe porquê e oferece-te para compensar. Aceita as consequências com humildade. Vais descobrir que nada te conquista mais respeito do que assumir os teus erros. Esta é a principal. Se aprenderes a fazer isto bem, cobrirá uma infinidade de pecados porque cria hábito. Mesmo que tenhas apenas 1% de culpa na situação, assumir a responsabilidade e pedir desculpa pelo teu 1% está a construir um certo grupo de músculos. "Mas ele devia ter..." Pára com isso. Confiaste demasiado? Presumiste demasiado sem comunicar? Assume a responsabilidade por isso. Estes exemplos podiam continuar para sempre, então vou parar e terminar com este princípio: A tua resposta importa mais do que as tuas circunstâncias. Existem vítimas reais, algumas de tragédias horríveis. Mas mesmo que não te tenhas atirado para areias movediças, ainda podes assumir a responsabilidade por como reages e pelo que escolhes fazer a seguir. Às vezes, é agarrar numa corda de um transeunte e dizer: "Obrigado." Não te afogues nas areias movediças até que alguém te dê uma palmadinha nas costas por quão difícil é para ti, e não continues a apontar para o teu tempo nas areias movediças para desculpares os teus fracassos. Podes não ter escolhido uma batalha específica. Ainda podes assumir a responsabilidade por quão bem lutas a batalha. Num certo sentido, ninguém escolhe a principal batalha que enfrenta. Ninguém escolheu nascer. Ninguém escolheu a sua família. Ninguém escolheu as suas circunstâncias. O mundo nunca será perfeito. Tens de assumir a responsabilidade pela tua parte dele de qualquer maneira. Pode ser difícil. Pode ser doloroso. Não te foi prometida uma vida fácil e sem dor. Depois de começares a assumir responsabilidades, qual é o próximo passo? Altura de assumir mais responsabilidades. Por exemplo, se não tens problemas em fazer amigos e tens essa parte da tua vida resolvida, assume a responsabilidade por outra pessoa. Encontra um dos rapazes solitários na tua igreja que precisa de um amigo e adiciona-o à tua rotação de almoços. A recompensa por assumir responsabilidades é subir de nível e, como consequência, as coisas devem tornar-se mais desafiantes. Mas agora estás mais bem preparado para isso. Repete até morrer e, esperançosamente, a tua causa de morte será por viver e não por te queixares de não viver. @ d9e9fb27:d5fe5e1a
2025-01-02 16:31:34Colmar is a well known city in the region of Alsace, France. Its characteristic buildings, the narrow streets and the small river flowing through are worldwide famous.  ----------- However, it is during Christmas that the city gets the most attention. Thousands of people from all over Europe decide to spend one of the Advent weekends to wander around this beautiful city and hundreds of *little wooden huts*. In fact, this town becomes a small Christmas village, with decorations and lights on every building and the famous Christmas market covering every possible inch of it.    Walking around this city really makes you feel the Christmas Spirit! ----------- Of course, it can get really cold during this time of the year. That is why Alsatians wander around drinking the *Vin Chaud* (literally "Hot Wine"). This beverage is prepared by mixing sugar, various spices, such as cinnamon and cloves, and red wine. They are served in a plastic glass, which can be reused multpiple time or returned for a couple of Euros. However, every year the glass is designed differently, so many people keep it with them as a collectible! Here is 2024 version:  ----------- This is the first time I try to do a photography reportage of the places I visit. I really hope you enjoyed it!Let me know what you think, every feedback is appreciated. I will try to create more of them during my trips, so stay tuned! Tuma
@ d9e9fb27:d5fe5e1a
2025-01-02 16:31:34Colmar is a well known city in the region of Alsace, France. Its characteristic buildings, the narrow streets and the small river flowing through are worldwide famous.  ----------- However, it is during Christmas that the city gets the most attention. Thousands of people from all over Europe decide to spend one of the Advent weekends to wander around this beautiful city and hundreds of *little wooden huts*. In fact, this town becomes a small Christmas village, with decorations and lights on every building and the famous Christmas market covering every possible inch of it.    Walking around this city really makes you feel the Christmas Spirit! ----------- Of course, it can get really cold during this time of the year. That is why Alsatians wander around drinking the *Vin Chaud* (literally "Hot Wine"). This beverage is prepared by mixing sugar, various spices, such as cinnamon and cloves, and red wine. They are served in a plastic glass, which can be reused multpiple time or returned for a couple of Euros. However, every year the glass is designed differently, so many people keep it with them as a collectible! Here is 2024 version:  ----------- This is the first time I try to do a photography reportage of the places I visit. I really hope you enjoyed it!Let me know what you think, every feedback is appreciated. I will try to create more of them during my trips, so stay tuned! Tuma @ 1bda7e1f:bb97c4d9
2025-01-02 05:19:08### Tldr - Nostr is an open and interoperable protocol - You can integrate it with workflow automation tools to augment your experience - n8n is a great low/no-code workflow automation tool which you can host yourself - Nostrobots allows you to integrate Nostr into n8n - In this blog I create some workflow automations for Nostr - A simple form to delegate posting notes - Push notifications for mentions on multiple accounts - Push notifications for your favourite accounts when they post a note - All workflows are provided as open source with MIT license for you to use ### Inter-op All The Things Nostr is a new open social protocol for the internet. This open nature exciting because of the opportunities for interoperability with other technologies. In [Using NFC Cards with Nostr]() I explored the `nostr:` URI to launch Nostr clients from a card tap. The interoperability of Nostr doesn't stop there. The internet has many super-powers, and Nostr is open to all of them. Simply, there's no one to stop it. There is no one in charge, there are no permissioned APIs, and there are no risks of being de-platformed. If you can imagine technologies that would work well with Nostr, then any and all of them can ride on or alongside Nostr rails. My mental model for why this is special is Google Wave ~2010. Google Wave was to be the next big platform. Lars was running it and had a big track record from Maps. I was excited for it. Then, Google pulled the plug. And, immediately all the time and capital invested in understanding and building on the platform was wasted. This cannot happen to Nostr, as there is no one to pull the plug, and maybe even no plug to pull. So long as users demand Nostr, Nostr will exist, and that is a pretty strong guarantee. It makes it worthwhile to invest in bringing Nostr into our other applications. All we need are simple ways to plug things together. ### Nostr and Workflow Automation Workflow automation is about helping people to streamline their work. As a user, the most common way I achieve this is by connecting disparate systems together. By setting up one system to trigger another or to move data between systems, I can solve for many different problems and become way more effective. #### n8n for workflow automation Many workflow automation tools exist. My favourite is [n8n](https://n8n.io/). n8n is a low/no-code workflow automation platform which allows you to build all kinds of workflows. You can use it for free, you can self-host it, it has a user-friendly UI and useful API. Vs Zapier it can be far more elaborate. Vs Make.com I find it to be more intuitive in how it abstracts away the right parts of the code, but still allows you to code when you need to. Most importantly you can plug anything into n8n: You have built-in nodes for specific applications. HTTP nodes for any other API-based service. And community nodes built by individual community members for any other purpose you can imagine. #### Eating my own dogfood It's very clear to me that there is a big design space here just demanding to be explored. If you could integrate Nostr with anything, what would you do? In my view the best way for anyone to start anything is by solving their own problem first (aka "scratching your own itch" and "eating your own dogfood"). As I get deeper into Nostr I find myself controlling multiple Npubs – to date I have a personal Npub, a brand Npub for a community I am helping, an AI assistant Npub, and various testing Npubs. I need ways to delegate access to those Npubs without handing over the keys, ways to know if they're mentioned, and ways to know if they're posting. I can build workflows with n8n to solve these issues for myself to start with, and keep expanding from there as new needs come up. ### Running n8n with Nostrobots I am mostly non-technical with a very helpful AI. To set up n8n to work with Nostr and operate these workflows should be possible for anyone with basic technology skills. - I have a cheap VPS which currently runs my [HAVEN Nostr Relay](https://rodbishop.npub.pro/post/8ca68889/) and [Albyhub Lightning Node](https://rodbishop.npub.pro/post/setting-up-payments-on-nostr-7o6ls7/) in Docker containers, - My objective was to set up n8n to run alongside these in a separate Docker container on the same server, install the required nodes, and then build and host my workflows. #### Installing n8n Self-hosting n8n could not be easier. I followed n8n's [Docker-Compose installation docs](https://docs.n8n.io/hosting/installation/server-setups/docker-compose/)– - Install Docker and Docker-Compose if you haven't already, - Create your ``docker-compose.yml`` and `.env` files from the docs, - Create your data folder `sudo docker volume create n8n_data`, - Start your container with `sudo docker compose up -d`, - Your n8n instance should be online at port `5678`. n8n is free to self-host but does require a license. Enter your credentials into n8n to get your free license key. You should now have access to the Workflow dashboard and can create and host any kind of workflows from there. #### Installing Nostrobots To integrate n8n nicely with Nostr, I used the [Nostrobots](https://github.com/ocknamo/n8n-nodes-nostrobots?tab=readme-ov-file) community node by [Ocknamo](nostr:npub1y6aja0kkc4fdvuxgqjcdv4fx0v7xv2epuqnddey2eyaxquznp9vq0tp75l). In n8n parlance a "node" enables certain functionality as a step in a workflow e.g. a "set" node sets a variable, a "send email" node sends an email. n8n comes with all kinds of "official" nodes installed by default, and Nostr is not amongst them. However, n8n also comes with a framework for community members to create their own "community" nodes, which is where Nostrobots comes in. You can only use a community node in a self-hosted n8n instance (which is what you have if you are running in Docker on your own server, but this limitation does prevent you from using n8n's own hosted alternative). To install a community node, [see n8n community node docs](https://docs.n8n.io/integrations/community-nodes/installation/gui-install/). From your workflow dashboard– - Click the "..." in the bottom left corner beside your username, and click "settings", - Cilck "community nodes" left sidebar, - Click "Install", - Enter the "npm Package Name" which is `n8n-nodes-nostrobots`, - Accept the risks and click "Install", - Nostrobots is now added to your n8n instance. #### Using Nostrobots Nostrobots gives you nodes to help you build Nostr-integrated workflows– - **Nostr Write** – for posting Notes to the Nostr network, - **Nostr Read** – for reading Notes from the Nostr network, and - **Nostr Utils** – for performing certain conversions you may need (e.g. from bech32 to hex). Nostrobots has [good documentation](https://github.com/ocknamo/n8n-nodes-nostrobots?tab=readme-ov-file) on each node which focuses on simple use cases. Each node has a "convenience mode" by default. For example, the "Read" Node by default will fetch Kind 1 notes by a simple filter, in Nostrobots parlance a "Strategy". For example, with Strategy set to "Mention" the node will accept a pubkey and fetch all Kind 1 notes that Mention the pubkey within a time period. This is very good for quick use. What wasn't clear to me initially (until Ocknamo helped me out) is that advanced use cases are also possible. Each node also has an advanced mode. For example, the "Read" Node can have "Strategy" set to "RawFilter(advanced)". Now the node will accept json (anything you like that complies with [NIP-01](https://github.com/nostr-protocol/nips/blob/master/01.md)). You can use this to query Notes (Kind 1) as above, and also Profiles (Kind 0), Follow Lists (Kind 3), Reactions (Kind 7), Zaps (Kind 9734/9735), and anything else you can think of. #### Creating and adding workflows With n8n and Nostrobots installed, you can now create or add any kind of Nostr Workflow Automation. - Click "Add workflow" to go to the workflow builder screen, - If you would like to build your own workflow, you can start with adding any node. Click "+" and see what is available. Type "Nostr" to explore the Nostrobots nodes you have added, - If you would like to add workflows that someone else has built, click "..." in the top right. Then click "import from URL" and paste in the URL of any workflow you would like to use (including the ones I share later in this article). ### Nostr Workflow Automations It's time to build some things! #### A simple form to post a note to Nostr I started very simply. I needed to delegate the ability to post to Npubs that I own in order that a (future) team can test things for me. I don't want to worry about managing or training those people on how to use keys, and I want to revoke access easily. I needed a basic form with credentials that posted a Note. For this I can use a very simple workflow– - **A n8n Form node** – Creates a form for users to enter the note they wish to post. Allows for the form to be protected by a username and password. This node is the workflow "trigger" so that the workflow runs each time the form is submitted. - **A Set node** – Allows me to set some variables, in this case I set the relays that I intend to use. I typically add a Set node immediately following the trigger node, and put all the variables I need in this. It helps to make the workflows easier to update and maintain. - **A Nostr Write node** (from Nostrobots) – Writes a Kind-1 note to the Nostr network. It accepts Nostr credentials, the output of the Form node, and the relays from the Set node, and posts the Note to those relays. Once the workflow is built, you can test it with the testing form URL, and set it to "Active" to use the production form URL. That's it. You can now give posting access to anyone for any Npub. To revoke access, simply change the credentials or set to workflow to "Inactive". It may also be the world's simplest Nostr client. You can find the [Nostr Form to Post a Note workflow here](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Form_to_Post_a_Note.json). #### Push notifications on mentions and new notes One of the things Nostr is not very good at is push notifications. Furthermore I have some unique itches to scratch. I want– - **To make sure I never miss a note addressed to any of my Npubs** – For this I want a push notification any time any Nostr user mentions any of my Npubs, - **To make sure I always see all notes from key accounts** – For this I need a push notification any time any of my Npubs post any Notes to the network, - **To get these notifications on all of my devices** – Not just my phone where my Nostr regular client lives, but also on each of my laptops to suit wherever I am working that day. I needed to build a Nostr push notifications solution. To build this workflow I had to string a few ideas together– - **Triggering the node on a schedule** – Nostrobots does not include a trigger node. As every workflow starts with a trigger we needed a different method. I elected to run the workflow on a schedule of every 10-minutes. Frequent enough to see Notes while they are hot, but infrequent enough to not burden public relays or get rate-limited, - **Storing a list of Npubs in a Nostr list** – I needed a way to store the list of Npubs that trigger my notifications. I initially used an array defined in the workflow, this worked fine. Then I decided to try Nostr lists ([NIP-51, kind 30000](https://github.com/nostr-protocol/nips/blob/master/51.md)). By defining my list of Npubs as a list published to Nostr I can control my list from within a Nostr client (e.g. [Listr.lol](https://listr.lol/npub1r0d8u8mnj6769500nypnm28a9hpk9qg8jr0ehe30tygr3wuhcnvs4rfsft) or [Nostrudel.ninja](https://nostrudel.ninja/#/lists)). Not only does this "just work", but because it's based on Nostr lists automagically Amethyst client allows me to browse that list as a Feed, and everyone I add gets notified in their Mentions, - **Using specific relays** – I needed to query the right relays, including my own HAVEN relay inbox for notes addressed to me, and wss://purplepag.es for Nostr profile metadata, - **Querying Nostr events** (with Nostrobots) – I needed to make use of many different Nostr queries and use quite a wide range of what Nostrobots can do– - I read the EventID of my Kind 30000 list, to return the desired pubkeys, - For notifications on mentions, I read all Kind 1 notes that mention that pubkey, - For notifications on new notes, I read all Kind 1 notes published by that pubkey, - Where there are notes, I read the Kind 0 profile metadata event of that pubkey to get the displayName of the relevant Npub, - I transform the EventID into a Nevent to help clients find it. - **Using the Nostr URI** – As I did with my NFC card article, I created a link with the `nostr:` URI prefix so that my phone's native client opens the link by default, - **Push notifications solution** – I needed a push notifications solution. I found many with n8n integrations and chose to go with [Pushover](https://pushover.net/) which supports all my devices, has a free trial, and is unfairly cheap with a $5-per-device perpetual license. Once the workflow was built, lists published, and Pushover installed on my phone, I was fully set up with push notifications on Nostr. I have used these workflows for several weeks now and made various tweaks as I went. They are feeling robust and I'd welcome you to give them a go. You can find the [Nostr Push Notification If Mentioned here](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Push_Notify_If_Mentioned.json) and [If Posts a Note here](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Push_Notify_If_Post_a_Note.json). In speaking with other Nostr users while I was building this, there are all kind of other needs for push notifications too – like on replies to a certain bookmarked note, or when a followed Npub starts streaming on zap.stream. These are all possible. #### Use my workflows I have open sourced all my workflows at my [Github](https://github.com/r0d8lsh0p/nostr-n8n) with MIT license and tried to write complete docs, so that you can import them into your n8n and configure them for your own use. To import any of my workflows– - Click on the workflow of your choice, e.g. "[Nostr_Push_Notify_If_Mentioned.json](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Push_Notify_If_Mentioned.json "Nostr_Push_Notify_If_Mentioned.json")", - Click on the "raw" button to view the raw JSON, ex any Github page layout, - Copy that URL, - Enter that URL in the "import from URL" dialog [mentioned above](#creating-and-adding-workflows). To configure them– - Prerequisites, credentials, and variables are all stated, - In general any variables required are entered into a Set Node that follows the trigger node, - Pushover has some extra setup but is very straightforward and documented in the workflow. ### What next? Over my first four blogs I explored creating a good Nostr setup with [Vanity Npub](https://rodbishop.npub.pro/post/mining-your-vanity-pubkey-4iupbf/), [Lightning Payments](https://rodbishop.npub.pro/post/setting-up-payments-on-nostr-7o6ls7/), [Nostr Addresses at Your Domain](https://rodbishop.npub.pro/post/ee8a46bc/), and [Personal Nostr Relay](https://rodbishop.npub.pro/post/8ca68889/). Then in my latest two blogs I explored different types of interoperability [with NFC cards](https://rodbishop.npub.pro/post/edde8387/) and now n8n Workflow Automation. Thinking ahead n8n can power any kind of interoperability between Nostr and any other legacy technology solution. On my mind as I write this: - Further enhancements to posting and delegating solutions and forms (enhanced UI or different note kinds), - Automated or scheduled posting (such as auto-liking everything [Lyn Alden](nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a) posts), - Further enhancements to push notifications, on new and different types of events (such as notifying me when I get a new follower, on replies to certain posts, or when a user starts streaming), - All kinds of bridges, such as bridging notes to and from Telegram, Slack, or Campfire. Or bridging RSS or other event feeds to Nostr, - All kinds of other automation (such as [BlackCoffee](nostr:npub1dqepr0g4t3ahvnjtnxazvws4rkqjpxl854n29wcew8wph0fmw90qlsmmgt) [controlling a coffee machine](https://primal.net/e/note16fzhh5yfc3u4kufx0mck63tsfperdrlpp96am2lmq066cnuqutds8retc3)), - All kinds of AI Assistants and Agents, In fact I have already released an open source workflow for an [AI Assistant](https://primal.net/p/npub1ahjpx53ewavp23g5zj9jgyfrpr8djmgjzg5mpe4xd0z69dqvq0kq2lf353), and will share more about that in my next blog. Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle. GM Nostr.
@ 1bda7e1f:bb97c4d9
2025-01-02 05:19:08### Tldr - Nostr is an open and interoperable protocol - You can integrate it with workflow automation tools to augment your experience - n8n is a great low/no-code workflow automation tool which you can host yourself - Nostrobots allows you to integrate Nostr into n8n - In this blog I create some workflow automations for Nostr - A simple form to delegate posting notes - Push notifications for mentions on multiple accounts - Push notifications for your favourite accounts when they post a note - All workflows are provided as open source with MIT license for you to use ### Inter-op All The Things Nostr is a new open social protocol for the internet. This open nature exciting because of the opportunities for interoperability with other technologies. In [Using NFC Cards with Nostr]() I explored the `nostr:` URI to launch Nostr clients from a card tap. The interoperability of Nostr doesn't stop there. The internet has many super-powers, and Nostr is open to all of them. Simply, there's no one to stop it. There is no one in charge, there are no permissioned APIs, and there are no risks of being de-platformed. If you can imagine technologies that would work well with Nostr, then any and all of them can ride on or alongside Nostr rails. My mental model for why this is special is Google Wave ~2010. Google Wave was to be the next big platform. Lars was running it and had a big track record from Maps. I was excited for it. Then, Google pulled the plug. And, immediately all the time and capital invested in understanding and building on the platform was wasted. This cannot happen to Nostr, as there is no one to pull the plug, and maybe even no plug to pull. So long as users demand Nostr, Nostr will exist, and that is a pretty strong guarantee. It makes it worthwhile to invest in bringing Nostr into our other applications. All we need are simple ways to plug things together. ### Nostr and Workflow Automation Workflow automation is about helping people to streamline their work. As a user, the most common way I achieve this is by connecting disparate systems together. By setting up one system to trigger another or to move data between systems, I can solve for many different problems and become way more effective. #### n8n for workflow automation Many workflow automation tools exist. My favourite is [n8n](https://n8n.io/). n8n is a low/no-code workflow automation platform which allows you to build all kinds of workflows. You can use it for free, you can self-host it, it has a user-friendly UI and useful API. Vs Zapier it can be far more elaborate. Vs Make.com I find it to be more intuitive in how it abstracts away the right parts of the code, but still allows you to code when you need to. Most importantly you can plug anything into n8n: You have built-in nodes for specific applications. HTTP nodes for any other API-based service. And community nodes built by individual community members for any other purpose you can imagine. #### Eating my own dogfood It's very clear to me that there is a big design space here just demanding to be explored. If you could integrate Nostr with anything, what would you do? In my view the best way for anyone to start anything is by solving their own problem first (aka "scratching your own itch" and "eating your own dogfood"). As I get deeper into Nostr I find myself controlling multiple Npubs – to date I have a personal Npub, a brand Npub for a community I am helping, an AI assistant Npub, and various testing Npubs. I need ways to delegate access to those Npubs without handing over the keys, ways to know if they're mentioned, and ways to know if they're posting. I can build workflows with n8n to solve these issues for myself to start with, and keep expanding from there as new needs come up. ### Running n8n with Nostrobots I am mostly non-technical with a very helpful AI. To set up n8n to work with Nostr and operate these workflows should be possible for anyone with basic technology skills. - I have a cheap VPS which currently runs my [HAVEN Nostr Relay](https://rodbishop.npub.pro/post/8ca68889/) and [Albyhub Lightning Node](https://rodbishop.npub.pro/post/setting-up-payments-on-nostr-7o6ls7/) in Docker containers, - My objective was to set up n8n to run alongside these in a separate Docker container on the same server, install the required nodes, and then build and host my workflows. #### Installing n8n Self-hosting n8n could not be easier. I followed n8n's [Docker-Compose installation docs](https://docs.n8n.io/hosting/installation/server-setups/docker-compose/)– - Install Docker and Docker-Compose if you haven't already, - Create your ``docker-compose.yml`` and `.env` files from the docs, - Create your data folder `sudo docker volume create n8n_data`, - Start your container with `sudo docker compose up -d`, - Your n8n instance should be online at port `5678`. n8n is free to self-host but does require a license. Enter your credentials into n8n to get your free license key. You should now have access to the Workflow dashboard and can create and host any kind of workflows from there. #### Installing Nostrobots To integrate n8n nicely with Nostr, I used the [Nostrobots](https://github.com/ocknamo/n8n-nodes-nostrobots?tab=readme-ov-file) community node by [Ocknamo](nostr:npub1y6aja0kkc4fdvuxgqjcdv4fx0v7xv2epuqnddey2eyaxquznp9vq0tp75l). In n8n parlance a "node" enables certain functionality as a step in a workflow e.g. a "set" node sets a variable, a "send email" node sends an email. n8n comes with all kinds of "official" nodes installed by default, and Nostr is not amongst them. However, n8n also comes with a framework for community members to create their own "community" nodes, which is where Nostrobots comes in. You can only use a community node in a self-hosted n8n instance (which is what you have if you are running in Docker on your own server, but this limitation does prevent you from using n8n's own hosted alternative). To install a community node, [see n8n community node docs](https://docs.n8n.io/integrations/community-nodes/installation/gui-install/). From your workflow dashboard– - Click the "..." in the bottom left corner beside your username, and click "settings", - Cilck "community nodes" left sidebar, - Click "Install", - Enter the "npm Package Name" which is `n8n-nodes-nostrobots`, - Accept the risks and click "Install", - Nostrobots is now added to your n8n instance. #### Using Nostrobots Nostrobots gives you nodes to help you build Nostr-integrated workflows– - **Nostr Write** – for posting Notes to the Nostr network, - **Nostr Read** – for reading Notes from the Nostr network, and - **Nostr Utils** – for performing certain conversions you may need (e.g. from bech32 to hex). Nostrobots has [good documentation](https://github.com/ocknamo/n8n-nodes-nostrobots?tab=readme-ov-file) on each node which focuses on simple use cases. Each node has a "convenience mode" by default. For example, the "Read" Node by default will fetch Kind 1 notes by a simple filter, in Nostrobots parlance a "Strategy". For example, with Strategy set to "Mention" the node will accept a pubkey and fetch all Kind 1 notes that Mention the pubkey within a time period. This is very good for quick use. What wasn't clear to me initially (until Ocknamo helped me out) is that advanced use cases are also possible. Each node also has an advanced mode. For example, the "Read" Node can have "Strategy" set to "RawFilter(advanced)". Now the node will accept json (anything you like that complies with [NIP-01](https://github.com/nostr-protocol/nips/blob/master/01.md)). You can use this to query Notes (Kind 1) as above, and also Profiles (Kind 0), Follow Lists (Kind 3), Reactions (Kind 7), Zaps (Kind 9734/9735), and anything else you can think of. #### Creating and adding workflows With n8n and Nostrobots installed, you can now create or add any kind of Nostr Workflow Automation. - Click "Add workflow" to go to the workflow builder screen, - If you would like to build your own workflow, you can start with adding any node. Click "+" and see what is available. Type "Nostr" to explore the Nostrobots nodes you have added, - If you would like to add workflows that someone else has built, click "..." in the top right. Then click "import from URL" and paste in the URL of any workflow you would like to use (including the ones I share later in this article). ### Nostr Workflow Automations It's time to build some things! #### A simple form to post a note to Nostr I started very simply. I needed to delegate the ability to post to Npubs that I own in order that a (future) team can test things for me. I don't want to worry about managing or training those people on how to use keys, and I want to revoke access easily. I needed a basic form with credentials that posted a Note. For this I can use a very simple workflow– - **A n8n Form node** – Creates a form for users to enter the note they wish to post. Allows for the form to be protected by a username and password. This node is the workflow "trigger" so that the workflow runs each time the form is submitted. - **A Set node** – Allows me to set some variables, in this case I set the relays that I intend to use. I typically add a Set node immediately following the trigger node, and put all the variables I need in this. It helps to make the workflows easier to update and maintain. - **A Nostr Write node** (from Nostrobots) – Writes a Kind-1 note to the Nostr network. It accepts Nostr credentials, the output of the Form node, and the relays from the Set node, and posts the Note to those relays. Once the workflow is built, you can test it with the testing form URL, and set it to "Active" to use the production form URL. That's it. You can now give posting access to anyone for any Npub. To revoke access, simply change the credentials or set to workflow to "Inactive". It may also be the world's simplest Nostr client. You can find the [Nostr Form to Post a Note workflow here](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Form_to_Post_a_Note.json). #### Push notifications on mentions and new notes One of the things Nostr is not very good at is push notifications. Furthermore I have some unique itches to scratch. I want– - **To make sure I never miss a note addressed to any of my Npubs** – For this I want a push notification any time any Nostr user mentions any of my Npubs, - **To make sure I always see all notes from key accounts** – For this I need a push notification any time any of my Npubs post any Notes to the network, - **To get these notifications on all of my devices** – Not just my phone where my Nostr regular client lives, but also on each of my laptops to suit wherever I am working that day. I needed to build a Nostr push notifications solution. To build this workflow I had to string a few ideas together– - **Triggering the node on a schedule** – Nostrobots does not include a trigger node. As every workflow starts with a trigger we needed a different method. I elected to run the workflow on a schedule of every 10-minutes. Frequent enough to see Notes while they are hot, but infrequent enough to not burden public relays or get rate-limited, - **Storing a list of Npubs in a Nostr list** – I needed a way to store the list of Npubs that trigger my notifications. I initially used an array defined in the workflow, this worked fine. Then I decided to try Nostr lists ([NIP-51, kind 30000](https://github.com/nostr-protocol/nips/blob/master/51.md)). By defining my list of Npubs as a list published to Nostr I can control my list from within a Nostr client (e.g. [Listr.lol](https://listr.lol/npub1r0d8u8mnj6769500nypnm28a9hpk9qg8jr0ehe30tygr3wuhcnvs4rfsft) or [Nostrudel.ninja](https://nostrudel.ninja/#/lists)). Not only does this "just work", but because it's based on Nostr lists automagically Amethyst client allows me to browse that list as a Feed, and everyone I add gets notified in their Mentions, - **Using specific relays** – I needed to query the right relays, including my own HAVEN relay inbox for notes addressed to me, and wss://purplepag.es for Nostr profile metadata, - **Querying Nostr events** (with Nostrobots) – I needed to make use of many different Nostr queries and use quite a wide range of what Nostrobots can do– - I read the EventID of my Kind 30000 list, to return the desired pubkeys, - For notifications on mentions, I read all Kind 1 notes that mention that pubkey, - For notifications on new notes, I read all Kind 1 notes published by that pubkey, - Where there are notes, I read the Kind 0 profile metadata event of that pubkey to get the displayName of the relevant Npub, - I transform the EventID into a Nevent to help clients find it. - **Using the Nostr URI** – As I did with my NFC card article, I created a link with the `nostr:` URI prefix so that my phone's native client opens the link by default, - **Push notifications solution** – I needed a push notifications solution. I found many with n8n integrations and chose to go with [Pushover](https://pushover.net/) which supports all my devices, has a free trial, and is unfairly cheap with a $5-per-device perpetual license. Once the workflow was built, lists published, and Pushover installed on my phone, I was fully set up with push notifications on Nostr. I have used these workflows for several weeks now and made various tweaks as I went. They are feeling robust and I'd welcome you to give them a go. You can find the [Nostr Push Notification If Mentioned here](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Push_Notify_If_Mentioned.json) and [If Posts a Note here](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Push_Notify_If_Post_a_Note.json). In speaking with other Nostr users while I was building this, there are all kind of other needs for push notifications too – like on replies to a certain bookmarked note, or when a followed Npub starts streaming on zap.stream. These are all possible. #### Use my workflows I have open sourced all my workflows at my [Github](https://github.com/r0d8lsh0p/nostr-n8n) with MIT license and tried to write complete docs, so that you can import them into your n8n and configure them for your own use. To import any of my workflows– - Click on the workflow of your choice, e.g. "[Nostr_Push_Notify_If_Mentioned.json](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Push_Notify_If_Mentioned.json "Nostr_Push_Notify_If_Mentioned.json")", - Click on the "raw" button to view the raw JSON, ex any Github page layout, - Copy that URL, - Enter that URL in the "import from URL" dialog [mentioned above](#creating-and-adding-workflows). To configure them– - Prerequisites, credentials, and variables are all stated, - In general any variables required are entered into a Set Node that follows the trigger node, - Pushover has some extra setup but is very straightforward and documented in the workflow. ### What next? Over my first four blogs I explored creating a good Nostr setup with [Vanity Npub](https://rodbishop.npub.pro/post/mining-your-vanity-pubkey-4iupbf/), [Lightning Payments](https://rodbishop.npub.pro/post/setting-up-payments-on-nostr-7o6ls7/), [Nostr Addresses at Your Domain](https://rodbishop.npub.pro/post/ee8a46bc/), and [Personal Nostr Relay](https://rodbishop.npub.pro/post/8ca68889/). Then in my latest two blogs I explored different types of interoperability [with NFC cards](https://rodbishop.npub.pro/post/edde8387/) and now n8n Workflow Automation. Thinking ahead n8n can power any kind of interoperability between Nostr and any other legacy technology solution. On my mind as I write this: - Further enhancements to posting and delegating solutions and forms (enhanced UI or different note kinds), - Automated or scheduled posting (such as auto-liking everything [Lyn Alden](nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a) posts), - Further enhancements to push notifications, on new and different types of events (such as notifying me when I get a new follower, on replies to certain posts, or when a user starts streaming), - All kinds of bridges, such as bridging notes to and from Telegram, Slack, or Campfire. Or bridging RSS or other event feeds to Nostr, - All kinds of other automation (such as [BlackCoffee](nostr:npub1dqepr0g4t3ahvnjtnxazvws4rkqjpxl854n29wcew8wph0fmw90qlsmmgt) [controlling a coffee machine](https://primal.net/e/note16fzhh5yfc3u4kufx0mck63tsfperdrlpp96am2lmq066cnuqutds8retc3)), - All kinds of AI Assistants and Agents, In fact I have already released an open source workflow for an [AI Assistant](https://primal.net/p/npub1ahjpx53ewavp23g5zj9jgyfrpr8djmgjzg5mpe4xd0z69dqvq0kq2lf353), and will share more about that in my next blog. Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle. GM Nostr. @ 599f67f7:21fb3ea9
2024-12-31 15:04:25Para este momento, ya deberías estar familiarizado con cerrar un canal de manera forzada, es decir, transmitiendo la transacción de compromiso directamente. Pero, ¿qué hay de cerrar un canal de manera cooperativa? ### Cerrando un canal de manera cooperativa Alice y Bob ciertamente tuvieron buenos momentos juntos, pero todas las cosas buenas deben llegar a su fin. Cerrar un canal de manera cooperativa requiere que los dos pares decidan sobre una transacción de cierre final que gastará de la transacción de financiación y pagará a cada uno su saldo final del canal de inmediato. #### Paso 1: Bob -> Alice: shutdown Bob ha decidido que es hora de cortar lazos y envía a Alice el mensaje de cierre.  El mensaje de cierre contiene el `scriptpubkey` al que Bob le gustaría que se enviara su saldo final del canal en la transacción de cierre. Una vez que Bob ha enviado este mensaje final, ya no puede enviar nuevos mensajes `update_add_htlc`. Solo puede enviar mensajes de eliminación de HTLC y `update_fee`. Cuando Alice recibe este mensaje de Bob, debe responder con su propio mensaje de cierre y tampoco puede enviar nuevos mensajes `update_add_htlc`. Alice y Bob ahora deben esperar hasta que todos los HTLC restantes hayan sido eliminados de ambas transacciones de compromiso. Dado que la transacción de cierre gastará de la transacción de financiación y se verá explícitamente diferente de las transacciones de compromiso, volveré a introducir algunos de los detalles en el diagrama de estado:  Una vez que todos los HTLC hayan sido eliminados, lo cual en nuestro ejemplo ya es el caso, pueden comenzar a negociar una tarifa para usar en la transacción de cierre final. El financiador del canal debe iniciar esta negociación. Supongamos que el financiador del canal es Alice. #### Paso 2: Alice -> Bob: closing_signed Alice primero elegirá una tasa de tarifa que considera apropiada para la transacción de cierre. Luego usará esa tasa de tarifa para completar la construcción de la transacción de cierre y firmarla. Luego envía el mensaje `closing_signed` a Bob:  El campo `fee_satoshis` le dice a Bob la tarifa en satoshis que Alice utilizó para construir la primera propuesta de transacción de cierre. La firma contiene la firma de Alice para esta propuesta. Ella también puede incluir opcionalmente los campos `min_fee_satoshis` y `max_fee_satoshis` para hacerle saber a Bob que si no está de acuerdo con su propuesta de `fee_satoshis`, puede enviar una contrapropuesta siempre que su contrapropuesta esté entre el rango mínimo y máximo proporcionado. En este punto, el estado del canal se ve así:  Hay dos transacciones de compromiso válidas que pueden ser firmadas en cualquier momento por cada parte para realizar un cierre forzado, y hay una propuesta de transacción de cierre que utiliza una tasa de tarifa de `x` sats por byte. Esta transacción de cierre actualmente solo tiene la firma de Alice y, por lo tanto, aún no es válida. Si en este punto, Bob está contento con la propuesta de Alice, podría proceder a firmar la transacción de cierre utilizando la tasa de tarifa propuesta por Alice y podría transmitirla, y eso sería el final. Pero, para el bien del ejemplo, digamos que Bob no está del todo contento todavía. #### Paso 3: Bob -> Alice: closing_signed Bob puede decidir que la tasa de tarifa que utilizó Alice es demasiado baja. Así que envía una contrapropuesta con una nueva tasa de tarifa, `y` sats por byte, junto con su firma para esta contrapropuesta.  #### Paso 4: Alice -> Bob: closing_signed Si Alice está contenta con la contrapropuesta de Bob, entonces firma la transacción de cierre utilizando la tasa de tarifa sugerida por Bob. Luego puede transmitir la transacción y dar por terminado el asunto. Sin embargo, se recomienda en la especificación que Alice envíe un mensaje más `closing_signed` a Bob, pero esta vez con el campo `fee_satoshis` establecido en `y` sat por byte junto con su firma para la transacción. Ambas partes ahora tendrán ambas firmas requeridas para transmitir la transacción de cierre final que utiliza la tasa de tarifa de `y` sats por byte.  Cualquiera de las partes o ambas pueden ahora transmitir la transacción de cierre a la red de Bitcoin. Eventualmente será confirmada y el canal se cerrará oficialmente.  Si este canal era un canal público, entonces cualquier nodo en la red que tuviera este canal en su gráfico de enrutamiento podrá ver que la salida de financiación del canal ha sido gastada y, por lo tanto, eliminará el canal de su gráfico en este punto. La belleza del canal es que Alice y Bob podrían haber enviado millones de HTLCs de un lado a otro a lo largo de la vida del canal y, al final, todo lo que apareció en la cadena fue la transacción de apertura y la transacción de cierre. Alice y Bob vivieron felices para siempre. ### Referencias - [BOLT2 Protocolo de pares](https://github.com/lightning/bolts/blob/master/02-peer-protocol.md) - [Operación normal de un canal LN previo a taproot](https://ellemouton.com/posts/normal-operation-pre-taproot/) por nostr:nprofile1qqswrt9pnxatlplu49h6meld8svmwqt87wwvk256rqk07n6eu4qeh5gpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0dszpfjtz - [Una guía técnica sobre contratos de tiempo bloqueado por hash y operaciones de canales Lightning](https://lightning.engineering/posts/2023-06-28-channel-normal-op/)
@ 599f67f7:21fb3ea9
2024-12-31 15:04:25Para este momento, ya deberías estar familiarizado con cerrar un canal de manera forzada, es decir, transmitiendo la transacción de compromiso directamente. Pero, ¿qué hay de cerrar un canal de manera cooperativa? ### Cerrando un canal de manera cooperativa Alice y Bob ciertamente tuvieron buenos momentos juntos, pero todas las cosas buenas deben llegar a su fin. Cerrar un canal de manera cooperativa requiere que los dos pares decidan sobre una transacción de cierre final que gastará de la transacción de financiación y pagará a cada uno su saldo final del canal de inmediato. #### Paso 1: Bob -> Alice: shutdown Bob ha decidido que es hora de cortar lazos y envía a Alice el mensaje de cierre.  El mensaje de cierre contiene el `scriptpubkey` al que Bob le gustaría que se enviara su saldo final del canal en la transacción de cierre. Una vez que Bob ha enviado este mensaje final, ya no puede enviar nuevos mensajes `update_add_htlc`. Solo puede enviar mensajes de eliminación de HTLC y `update_fee`. Cuando Alice recibe este mensaje de Bob, debe responder con su propio mensaje de cierre y tampoco puede enviar nuevos mensajes `update_add_htlc`. Alice y Bob ahora deben esperar hasta que todos los HTLC restantes hayan sido eliminados de ambas transacciones de compromiso. Dado que la transacción de cierre gastará de la transacción de financiación y se verá explícitamente diferente de las transacciones de compromiso, volveré a introducir algunos de los detalles en el diagrama de estado:  Una vez que todos los HTLC hayan sido eliminados, lo cual en nuestro ejemplo ya es el caso, pueden comenzar a negociar una tarifa para usar en la transacción de cierre final. El financiador del canal debe iniciar esta negociación. Supongamos que el financiador del canal es Alice. #### Paso 2: Alice -> Bob: closing_signed Alice primero elegirá una tasa de tarifa que considera apropiada para la transacción de cierre. Luego usará esa tasa de tarifa para completar la construcción de la transacción de cierre y firmarla. Luego envía el mensaje `closing_signed` a Bob:  El campo `fee_satoshis` le dice a Bob la tarifa en satoshis que Alice utilizó para construir la primera propuesta de transacción de cierre. La firma contiene la firma de Alice para esta propuesta. Ella también puede incluir opcionalmente los campos `min_fee_satoshis` y `max_fee_satoshis` para hacerle saber a Bob que si no está de acuerdo con su propuesta de `fee_satoshis`, puede enviar una contrapropuesta siempre que su contrapropuesta esté entre el rango mínimo y máximo proporcionado. En este punto, el estado del canal se ve así:  Hay dos transacciones de compromiso válidas que pueden ser firmadas en cualquier momento por cada parte para realizar un cierre forzado, y hay una propuesta de transacción de cierre que utiliza una tasa de tarifa de `x` sats por byte. Esta transacción de cierre actualmente solo tiene la firma de Alice y, por lo tanto, aún no es válida. Si en este punto, Bob está contento con la propuesta de Alice, podría proceder a firmar la transacción de cierre utilizando la tasa de tarifa propuesta por Alice y podría transmitirla, y eso sería el final. Pero, para el bien del ejemplo, digamos que Bob no está del todo contento todavía. #### Paso 3: Bob -> Alice: closing_signed Bob puede decidir que la tasa de tarifa que utilizó Alice es demasiado baja. Así que envía una contrapropuesta con una nueva tasa de tarifa, `y` sats por byte, junto con su firma para esta contrapropuesta.  #### Paso 4: Alice -> Bob: closing_signed Si Alice está contenta con la contrapropuesta de Bob, entonces firma la transacción de cierre utilizando la tasa de tarifa sugerida por Bob. Luego puede transmitir la transacción y dar por terminado el asunto. Sin embargo, se recomienda en la especificación que Alice envíe un mensaje más `closing_signed` a Bob, pero esta vez con el campo `fee_satoshis` establecido en `y` sat por byte junto con su firma para la transacción. Ambas partes ahora tendrán ambas firmas requeridas para transmitir la transacción de cierre final que utiliza la tasa de tarifa de `y` sats por byte.  Cualquiera de las partes o ambas pueden ahora transmitir la transacción de cierre a la red de Bitcoin. Eventualmente será confirmada y el canal se cerrará oficialmente.  Si este canal era un canal público, entonces cualquier nodo en la red que tuviera este canal en su gráfico de enrutamiento podrá ver que la salida de financiación del canal ha sido gastada y, por lo tanto, eliminará el canal de su gráfico en este punto. La belleza del canal es que Alice y Bob podrían haber enviado millones de HTLCs de un lado a otro a lo largo de la vida del canal y, al final, todo lo que apareció en la cadena fue la transacción de apertura y la transacción de cierre. Alice y Bob vivieron felices para siempre. ### Referencias - [BOLT2 Protocolo de pares](https://github.com/lightning/bolts/blob/master/02-peer-protocol.md) - [Operación normal de un canal LN previo a taproot](https://ellemouton.com/posts/normal-operation-pre-taproot/) por nostr:nprofile1qqswrt9pnxatlplu49h6meld8svmwqt87wwvk256rqk07n6eu4qeh5gpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0dszpfjtz - [Una guía técnica sobre contratos de tiempo bloqueado por hash y operaciones de canales Lightning](https://lightning.engineering/posts/2023-06-28-channel-normal-op/) @ 599f67f7:21fb3ea9
2024-12-31 15:00:53### Contenidos - [Visión general](#visión-general) - [Preliminares](#preliminares) - [Operación normal del canal](#operación-normal-del-canal) - [Configuración](#configuración) - [Añadiendo un HTLC](#añadiendo-un-htlc) - [Paso 1: Alice -> Bob: update_add_htlc(A1)](#paso-1-alice---bob-update_add_htlca1) - [Paso 2: Alice -> Bob: update_add_htlc(A2)](#paso-2-alice---bob-update_add_htlca2) - [Paso 3: Bob -> Alice: update_add_htlc(B1)](#paso-3-bob---alice-update_add_htlcb1) - [Comprometiéndose al estado actual](#comprometiéndose-al-estado-actual) - [Paso 4: Alice -> Bob: commitment_signed](#paso-4-alice---bob-commitment_signed) - [Paso 5: Bob -> Alice: revoke_and_ack](#paso-5-bob---alice-revoke_and_ack) - [Paso 6: Alice -> Bob: update_add_htlc(A3)](#paso-6-alice---bob-update_add_htlca3) - [Paso 7: Bob -> Alice: commitment_signed](#paso-7-bob---alice-commitment_signed) - [Paso 8: Alice -> Bob: revoke_and_ack](#paso-8-alice---bob-revoke_and_ack) - [Paso 9: Bob -> Alice: revoke_and_ack](#paso-9-bob---alice-revoke_and_ack) - [Paso 10: Bob -> Alice: commitment_signed](#paso-10-bob---alice-commitment_signed) - [Paso 11: Alice -> Bob: revoke_and_ack](#paso-11-alice---bob-revoke_and_ack) - [Eliminando HTLCs](#eliminando-htlcs) - [Paso 12: Bob -> Alice: update_fulfill_htlc(A2)](#paso-12-bob---alice-update_fulfill_htlca2) - [Paso 13: Bob -> Alice: update_fail_htlc(A1)](#paso-13-bob---alice-update_fail_htlca1) - [Paso 14: Bob -> Alice: update_fail_malformed_htlc(A3)](#paso-14-bob---alice-update_fail_malformed_htlca3) - [Paso 15: Alice -> Bob: update_fulfill_htlc(B1)](#paso-15-alice---bob-update_fulfill_htlcb1) - [Paso 16: Bob -> Alice: commitment_signed](#paso-16-bob---alice-commitment_signed) - [Paso 17: Alice -> Bob: revoke_and_ack](#paso-17-alice---bob-revoke_and_ack) - [Paso 18: Alice -> Bob: commitment_signed](#paso-18-alice---bob-commitment_signed) - [Paso 19: Bob -> Alice: revoke_and_ack](#paso-19-bob---alice-revoke_and_ack) - [Paso 20: Bob -> Alice: commitment_signed](#paso-20-bob---alice-commitment_signed) - [Paso 21: Alice -> Bob: revoke_and_ack](#paso-21-alice---bob-revoke_and_ack) - [Actualizando tarifas](#actualizando-tarifas) - [Retransmisión de mensajes](#retransmisión-de-mensajes) ### Visión general En este capítulo cubriremos las operaciones normales de un canal. Esto implica entender cómo se añaden HTLCs a un canal y cómo los pares del canal se comprometen a un nuevo estado para incluir estos HTLCs. Luego cubriremos cómo se restablece el flujo normal de un canal después de una desconexión. Finalmente, cubriremos el flujo de cierre cooperativo del canal. Por cierto, todos estos temas están cubiertos en [BOLT2](https://github.com/lightning/bolts/blob/master/02-peer-protocol.md). ### Preliminares Aquí hay algunos conceptos y flujos que hemos cubierto anteriormente en nuestra serie que podrían ser útiles para entender este capítulo. No dudes en volver a leerlos si necesitas un recordatorio. - nostr:naddr1qqxnzdenxgerzve5x5enyv3sqyg8wumn8ghj7mn0wd68ytnhd9hx2q3qtx0k0a7lw62vvqax6p3ku90tccgdka7ul4radews2wrdsg0m865sxpqqqp65wc4f8xj: por qué los pares del canal tienen un estado asimétrico y cómo actualizan este estado de manera confiable. - nostr:naddr1qqxnzdenxgenvwp48qmnqdfhqyg8wumn8ghj7mn0wd68ytnhd9hx2q3qtx0k0a7lw62vvqax6p3ku90tccgdka7ul4radews2wrdsg0m865sxpqqqp65wx9fs7k: cómo se ven las salidas de HTLC en una transacción de compromiso. - [Apertura y anuncio de un canal LN pre-taproot]: cómo dos nodos abren un canal. ### Operación normal del canal #### Configuración Alice y Bob han abierto su canal con éxito. Ambos han visto que la transacción de financiación está confirmada y han intercambiado el mensaje `channel_ready` entre ellos para indicar que están listos para usar el canal. El estado de sus transacciones de compromiso asimétricas actualmente se ve así:  Ambas transacciones de compromiso gastan la salida de la transacción de financiación multisig 2-de-2. Dado que es un multisig 2-de-2, gastar de esta salida requiere firmas de ambos pares. Las firmas están representadas por las dos cajas en la parte superior de las transacciones de compromiso. Puedes ver en el diagrama que la transacción de compromiso de Alice tiene una firma de Bob representada por la caja azul; Bob tiene una firma de Alice para su transacción de compromiso representada por la caja verde. Cada transacción de compromiso también tiene las salidas `to_local` y `to_remote` que pagan a las partes respectivas su saldo actual del canal. Tanto Alice como Bob pueden firmar sus propias transacciones de compromiso en cualquier momento y transmitirlas a la red de Bitcoin. Esto sería un **cierre forzado**. Con el fin de hacer que los próximos diagramas sean más fáciles de seguir, ignoraremos las transacciones de financiación así como las salidas `to_local` y `to_remote` por un tiempo, ya que nuestro enfoque inicial estará en añadir y eliminar salidas de HTLC. Así que el diagrama anterior ahora se simplifica a esto:  - Una transacción de compromiso _roja_, mostrada a continuación, representa transacciones de compromiso pasadas y revocadas. Si Alice o Bob firmaran y transmitieran una de estas, entonces la otra parte podría barrer todos sus fondos. Así que estas transacciones revocadas pueden considerarse efectivamente inválidas. - Una transacción de compromiso _amarilla_ representa el último conjunto válido de transacciones de compromiso. Estas son las transacciones de compromiso que se transmitirían en un cierre forzado. - Finalmente, cada lado tiene lo que se puede considerar un "área de preparación" donde se pueden proponer cambios a la transacción de compromiso. Más adelante, cualquiera de los lados puede decidir cuándo quiere que su contraparte se comprometa a los cambios en su transacción de compromiso de preparación. Sugerencia: si te gusta git, esto es muy parecido a un flujo de trabajo de git. Los commits pasados están desactualizados, pero cuentan una buena historia de lo que sucedió. Tus últimos cambios comprometidos representan el estado actual de tu proyecto. Cualquier cambio que aún no esté comprometido está en preparación.  #### Añadiendo un HTLC Cuando Alice o Bob quieren enviar un pago, necesitarían proponer la inclusión del HTLC a su par de canal. Esto se hace con el mensaje `update_add_htlc`:  Aquí hay una tabla sobre lo que significa cada uno de los campos del mensaje: | Campo | Descripción| |---|---| | channel_id | utilizado para comunicar en qué canal debe tener lugar este cambio. | | id | un identificador que siempre incrementa para este cambio propuesto del remitente. | | amount_msat | la cantidad que debe adjuntarse a la salida de HTLC. | | cltv_expiry | la altura del bloque en la que el HTLC debe expirar. | | onion_routing_packet y blinding_point | datos que el destinatario del HTLC utilizará para determinar a dónde enviar el pago a continuación. | Hay un punto contraintuitivo a tener en cuenta aquí: el remitente de este mensaje aún no coloca esta actualización en su propia área de preparación. Esto se debe a que la actualización aún está "pendiente del receptor" porque el remitente aún no ha recibido ningún reconocimiento del receptor para la nueva actualización. Imagina este escenario: el remitente envía una actualización y luego recibe inmediatamente un mensaje `commitment_signed` (más detalles sobre esto más adelante). En este caso, no debería haber ambigüedad sobre qué actualizaciones están incluidas en la transacción que se está firmando. Esperemos que esto tenga más sentido a medida que trabajemos a través del ejemplo. ##### Paso 1: Alice -> Bob: update_add_htlc(A1) Supongamos que Alice envía a Bob un `update_add_htlc`. Llamemos a este HTLC `A1` porque es el primero que Alice (A) está enviando a Bob. Si Bob está contento con todos los campos en el mensaje, entonces añade el HTLC a su transacción de compromiso en el área de preparación y Alice marca el HTLC como pendiente en el lado de Bob, pero aún no lo añade a su propia transacción de compromiso en preparación.  Ten en cuenta que ninguno de los lados ha comprometido realmente este HTLC aún, así que si Bob es un nodo de enrutamiento para este pago, no debería enviar aún `update_add_HTLC` al siguiente salto en la ruta hasta que `A1` haya sido _irrevocablemente_ comprometido. La adición o eliminación de un HTLC solo se considera irrevocablemente comprometida una vez que ambas partes en el canal se han comprometido a la transacción de compromiso con o sin él. Esto no se muestra en el diagrama simplificado, pero en realidad la salida principal de Alice en la transacción de compromiso en preparación de Bob (es decir, la salida `to_remote`) ahora tendrá el valor del HTLC añadido restado (junto con las tarifas para cubrir la salida extra). Si el HTLC termina teniendo éxito, entonces esta cantidad se añadirá a la salida de Bob y si termina fallando, entonces se volverá a añadir a la salida de Alice. ##### Paso 2: Alice -> Bob: update_add_htlc(A2) A pesar de que aún no se han comprometido al HTLC `A1`, esto no les impide añadir más cambios al área de preparación. Alice está más que bienvenida a proponer un nuevo HTLC, `A2`, a Bob:  ##### Paso 3: Bob -> Alice: update_add_htlc(B1) Del mismo modo, Bob puede sugerir un cambio, `B1`, a Alice:  #### Comprometiéndose al estado actual En algún momento, uno de los pares querrá asegurarse de que el otro par se haya comprometido al último conjunto de cambios y revocar el estado válido anterior. Esto se hace enviando el mensaje `commitment_signed`:  | Campo | Descripción| |---|---| | channel_id | utilizado para comunicar en qué canal debe tener lugar este cambio. | | signature | la firma del remitente para la transacción de compromiso del área de preparación de la parte remota. | | num_htlcs | el número de HTLCs que el remitente espera que estén en la transacción de compromiso remota. | | htlc_signatures | un array de firmas de num_htlcs que son las firmas del remitente para cada una de las transacciones de HTLC de segundo nivel que la parte remota necesitaría transmitir si alguna vez tuviera que cerrar el canal forzosamente. | Sugerencia: si necesitas un recordatorio sobre las transacciones de HTLC de segundo nivel y por qué son necesarias, consulta este [capítulo]. ##### Paso 4: Alice -> Bob: commitment_signed Supongamos que Alice envía este mensaje a Bob. Bob ahora tendrá todas las firmas requeridas de Alice para transmitir su transacción de compromiso en el área de preparación:  Observa que Alice sabía que su firma necesitaría cubrir los HTLCs `A1` y `A2`. Esto está bien porque el [transporte subyacente](https://github.com/lightning/bolts/blob/master/08-transport.md) está garantizado para ser confiable y ordenado, lo que significa que si Bob recibiera el mensaje `commitment_signed` de Alice, entonces significa que definitivamente recibió sus mensajes `update_add_htlc` para `A1` y `A2`. Alice y Bob saben que la firma no debería cubrir el HTLC `B1` ya que Alice no ha enviado un reconocimiento para él aún. Otra cosa a notar es que Bob ahora tiene en realidad dos transacciones de compromiso válidas ya que aún no ha revocado su estado anterior. Sin embargo, está incentivado a revocar su transacción de compromiso anterior ya que los HTLCs en el nuevo estado son uno de los siguientes: - Pagos a Bob mismo, lo que significa que se beneficia de comprometerse al nuevo estado. Si no se compromete al nuevo estado, entonces Alice tampoco lo hará y por lo tanto aún existiría una versión de una transacción de compromiso que no paga a Bob sus fondos entrantes. - De manera similar al punto anterior, si Bob está enrutando un pago, entonces también está incentivado a comprometer irrevocablemente el HTLC ya que ganaría tarifas de enrutamiento si el pago tiene éxito. - Finalmente, si Bob está haciendo el pago él mismo, entonces el primer estado sería de hecho más rentable para él ya que tiene menos fondos en el segundo estado. Sin embargo, el comerciante al que Bob está haciendo el pago no liberará los bienes que se están comprando a menos que primero se reciban los fondos, lo que no sucederá si Alice no pasa el HTLC, lo cual no hará a menos que se haya comprometido irrevocablemente. Así que nuevamente, Bob está incentivado a revocar su estado anterior. ##### Paso 5: Bob -> Alice: revoke_and_ack En respuesta al `commitment_signed` de Alice, Bob envía el mensaje `revoke_and_ack`:  - El `per_commitment_secret` proporciona a Alice la información que necesita para poder gastar cualquier ruta de revocación en el estado previamente válido de Bob. Consulta el [capítulo de revocación] para más detalles sobre cómo funciona la revocación. - El `next_per_commitment_point` le da a Alice la información que necesita para derivar la clave pública de revocación que se utilizará en la próxima transacción de compromiso de Bob. Una vez que Alice recibe este mensaje, la transacción de compromiso anterior de Bob ha sido revocada con éxito. Ten en cuenta que este mensaje reconoce explícitamente el mensaje `commitment_signed` enviado por Alice y, por extensión, dado que la entrega de mensajes es confiable y ordenada, también reconoce implícitamente los mensajes `update_add_htlc` que Alice envió para `A1` y `A2`. Por lo tanto, Alice puede finalmente añadir `A1` y `A2` a su transacción de compromiso en el área de preparación ya que ya no están pendientes en el lado de Bob:  Ahora podemos limpiar un poco el diagrama:  En el último diagrama, observa que las últimas transacciones de compromiso de Alice y Bob están en realidad desincronizadas. Esto está bien ya que ninguna de las actualizaciones se ha comprometido irrevocablemente aún. Eso podría parecer difícil de creer ya que las transacciones de compromiso se ven tan diferentes, así que vamos a repasar las consecuencias de que cualquiera de estas transacciones termine en la cadena desde la perspectiva de ambos lados. - Desde la perspectiva de Alice: - si su transacción de compromiso se transmitiera, recuperaría su cantidad original `to_local`. - si la transacción de compromiso de Bob se transmitiera, entonces los HTLCs ofrecidos por Alice (como `A1` y `A2`) estarían en la cadena. Para los HTLCs ofrecidos, Alice está enviando sats _fuera_, lo que significa que su `to_local` sería menor. Pero, si Bob era un nodo de enrutamiento para estos HTLCs, entonces no los habría reenviado ya que aún no están comprometidos irrevocablemente, lo que significa que no recibiría las pre-imágenes requeridas para reclamar estos HTLCs y, por lo tanto, Alice podría recuperar sus fondos a través de la ruta de tiempo de espera. Si Bob era el destinatario de estos HTLCs, entonces podría producir la pre-imagen para reclamar los HTLCs, pero entonces Alice vería la pre-imagen en la cadena y podría reclamar los HTLCs entrantes de su canal entrante y así habría ganado tarifas de enrutamiento. - Desde la perspectiva de Bob: - si la transacción de compromiso de Alice se transmite, Bob recupera sus fondos a través de la salida `to_remote`. - si Bob tuviera que cerrar forzosamente a través de su transacción de compromiso, entonces los HTLCs ofrecidos a él (como `A1` y `A2`) estarían en la cadena. Si Bob estaba enrutando estos HTLCs, entonces no los habría reenviado ya que aún no están comprometidos irrevocablemente. Así que no podría reclamar la ruta de éxito, pero eso está bien ya que los fondos para estos no salieron de su saldo. Si Bob era el destino final para estos, entonces podría reclamarlos a través de la ruta de éxito. ##### Paso 6: Alice -> Bob: update_add_htlc(A3) Queremos ser muy claros sobre el punto de que las transacciones de compromiso pueden permanecer desincronizadas indefinidamente y que Bob no necesita enviar `commitment_signed` solo porque Alice lo hizo. Así que, para el sake de otro ejemplo, supongamos que Alice en este punto envía otro HTLC, `A3`, a Bob:  ##### Paso 7: Bob -> Alice: commitment_signed Bob quiere comprometer irrevocablemente algunos de los HTLCs para poder reenviarlos, así que finalmente envía a Alice un `commitment_signed` propio. Esto incluirá su firma para la transacción de compromiso del área de preparación de Alice junto con todas las firmas requeridas de él para las salidas de HTLC de segundo nivel.  ##### Paso 8: Alice -> Bob: revoke_and_ack Al igual que Bob hizo anteriormente, Alice responde al `commitment_signed` con un `revoke_and_ack` para revocar su estado anterior. Esto también sirve como un reconocimiento para Bob de que Alice ha recibido y se ha comprometido a `B1`, por lo que Bob ahora puede agregar `B1` a su transacción de compromiso en el área de preparación.  Rápida limpieza...  ¡Por fin, tenemos algunos HTLCs comprometidos de forma irrevocable! `A1` y `A2` han sido comprometidos de forma irrevocable. `B1` y `A3`, sin embargo, no lo han sido ya que aún no han sido comprometidos por ambas partes. Comprometamos rápidamente `B1` y `A3` de forma irrevocable también. ##### Paso 8: Alice -> Bob: commitment_signed  ##### Paso 9: Bob -> Alice: revoke_and_ack  ##### Paso 10: Bob -> Alice: commitment_signed  ##### Paso 11: Alice -> Bob: revoke_and_ack  Limpiado:  ¡Ahora todos los HTLCs han sido comprometidos de forma irrevocable! #### Eliminando HTLCs Probablemente ya entiendas la idea de agregar HTLCs. Pero, ¿qué pasa con eliminarlos? Los HTLCs se eliminan si un pago tiene éxito o si falla. Ten en cuenta que los mensajes de eliminación de HTLC solo pueden ser enviados por el par que no envió la actualización original `update_add_htlc` y que los HTLCs solo son removibles una vez que han sido comprometidos de forma irrevocable. Afortunadamente para nosotros, todos los HTLCs han sido comprometidos de forma irrevocable, así que podemos comenzar a eliminarlos ahora. ##### Paso 12: Bob -> Alice: update_fulfill_htlc(A2) En el mejor de los casos, un HTLC se elimina porque se está cumpliendo, lo que significa que su pre-imagen se está devolviendo. Esto se hace con el mensaje `update_fulfilled_htlc`, que se ve así:  En nuestro ejemplo, Bob envía a Alice el mensaje `update_fulfill_htlc` para el HTLC `A2`. Esto también demuestra que los HTLCs no tienen que ser eliminados en el mismo orden en que fueron agregados.  Ten en cuenta que, al igual que las actualizaciones para agregar un HTLC, las actualizaciones para eliminar un HTLC también estarán inicialmente pendientes en el lado receptor hasta que hayan sido reconocidas por un `revoke_and_ack`. Así que, en nuestro caso, Alice elimina `A2` de su transacción en el área de preparación cuando recibe el `update_fulfill_htlc` (y asigna el monto del HTLC a la salida de Bob), pero Bob aún no elimina el HTLC de su transacción en el área de preparación. A diferencia de otros mensajes de actualización, no hay necesidad de esperar a que una eliminación de HTLC sea comprometida de forma irrevocable si recibes la pre-imagen para ello. Después de todo, puedes enviar inmediatamente la pre-imagen hacia arriba para reclamar cualquier HTLC allí. ##### Paso 13: Bob -> Alice: update_fail_htlc(A1) Los HTLCs también pueden ser eliminados debido a fallos en el pago, como el tiempo de espera de los HTLCs o si hubo algún tipo de fallo de enrutamiento, como que un canal específico en la ruta ya no exista, no se cumplan los requisitos de tarifa de un salto, un enlace no tenga saldo suficiente, etc. Tales fallos se comunican con el mensaje `update_fail_htlc`:  El campo de razón es un blob cifrado para el remitente del pago para informarles sobre la razón del fallo. Después de que Bob envía a Alice el mensaje `update_fail_htlc` para `A1`, el estado se ve como sigue:  ##### Paso 14: Bob -> Alice: update_fail_malformed_htlc(A3) El mensaje final que se puede usar para eliminar un HTLC es el mensaje `update_fail_malformed_htlc`:  Este mensaje se envía si algún salto en la ruta de pago no pudo analizar el `onion_routing_packet` que recibió en `update_add_htlc`. Si Bob envía a Alice este mensaje para `A3`, entonces el estado ahora se ve así:  ##### Paso 15: Alice -> Bob: update_fulfill_htlc(B1) Alice también inicia la eliminación de `B1` enviando un `update_fulfill_htlc` a Bob.  Ahora limpiemos las eliminaciones de HTLC comprometiéndolas de forma irrevocable. Esto requerirá algunos flujos de `commitment_signed` - `revoke_and_ack`: ##### Paso 16: Bob -> Alice: commitment_signed  ##### Paso 17: Alice -> Bob: revoke_and_ack  ##### Paso 18: Alice -> Bob: commitment_signed  ##### Paso 19: Bob -> Alice: revoke_and_ack  ##### Paso 20: Bob -> Alice: commitment_signed  ##### Paso 21: Alice -> Bob: revoke_and_ack  Los dos estados válidos ahora se ven bonitos y limpios nuevamente:  ### Actualizando tarifas Hay un mensaje `update_*` más que necesitamos cubrir y ese es el mensaje `update_fee`. Este mensaje se utiliza para actualizar la tasa de tarifa que los pares deben usar al construir sus transacciones de compromiso. La tasa de tarifa original se decide en el flujo de apertura de canal, pero si la tasa de tarifa promedio del mempool aumenta, el financiador del canal podría decidir actualizar la tarifa de las transacciones de compromiso para que tengan una mejor oportunidad de ser confirmadas de manera oportuna en una situación de cierre forzado. También podría ser que cuando se abrió el canal, se eligió una tasa de tarifa muy alta y quizás se desearía una tasa de tarifa más baja. Este mensaje sigue reglas similares a otros mensajes `update_*` en que también debe ser comprometido de forma irrevocable antes de que surta efecto. La única regla adicional que se aplica a este mensaje es que solo el financiador del canal puede enviar este mensaje:  Ten en cuenta que con los canales de anclaje, la necesidad de usar el mensaje `update_fee` se está volviendo cada vez menor, ya que los nodos podrán usar CPFP en la transacción de cierre forzado si es necesario. ### Retransmisión de mensajes Algo que puedes haber notado en el flujo de agregar/eliminar HTLC es que los reconocimientos explícitos para los mensajes `update_*` se retrasan hasta el intercambio de `commitment_signed`/`revoke_and_ack`. Eso está bien la mayor parte del tiempo, ya que asumimos que el transporte subyacente entre los dos nodos (ver [BOLT8](https://github.com/lightning/bolts/blob/master/08-transport.md)) es ordenado y confiable. Sin embargo, si por alguna razón la conexión entre los dos nodos necesita ser restablecida, habrá dudas sobre si nuestro par ha recibido el último mensaje que enviamos. Aquí es donde entra el mensaje `channel_reestablish`. Al reconectarse, antes de continuar con el flujo de operación normal, los pares intercambiarán este mensaje para asegurarse de que están en la misma página y para determinar qué mensajes posiblemente necesitan retransmitir a su par.  Cada par en el canal tiene su versión de la transacción de compromiso y las dos transacciones de compromiso pueden actualizarse de forma independiente, lo que significa que el número de veces que el estado de la transacción de compromiso de un lado ha sido actualizado (a través del flujo de `commitment_signed` y `revoke_and_ack`) podría ser completamente diferente al del otro lado. El campo `next_commitment_number` en el mensaje `channel_reestablish` nos permite comunicarnos con nuestro par sobre el próximo `commitment_signed` que esperamos recibir de ellos. De esta manera, ellos sabrán si quizás hemos perdido un `commitment_signed` de ellos que enviaron anteriormente antes de la desconexión. En otras palabras, `next_commitment_number` le dice al par remoto cuál es nuestro último estado comprometido. De manera similar, `next_revocation_number` es el número de compromiso del próximo `revoke_and_ack` que esperamos recibir. En otras palabras, esto indica a nuestro par cuál número de compromiso creemos que es el más reciente. El `your_last_per_commitment_secret` es el último secreto por compromiso recibido del par remoto, lo que le dará al par remoto una idea del estado que definitivamente ha revocado. `my_current_per_commitment_point` es el punto de compromiso de la parte local en su última transacción de compromiso firmada por el par remoto (en otras palabras, la transacción de compromiso que aún no ha sido revocada). Hay muchas verificaciones que un nodo debe hacer al recibir un `channel_reestablish` para asegurarse de que todas las actualizaciones necesarias se retransmitan para que el canal pueda continuar funcionando con normalidad. También hay algunas verificaciones que aseguran que los nodos no sean engañados para revocar un estado que aún no debería ser revocado o engañados para transmitir un estado que _ha_ sido revocado. Si estás interesado en los detalles sobre estas verificaciones, lee [BOLT2](https://github.com/lightning/bolts/blob/master/02-peer-protocol.md). Ten en cuenta que cuando ocurre un restablecimiento de conexión, ambos lados deben eliminar cualquier actualización no comprometida de su área de preparación. Si volvemos a visitar la analogía de git, deberían usar git stash cuando ocurra una reconexión. Esto significa que ambos lados necesitarán retransmitir cualquier mensaje `update_*` que aún no haya sido comprometido en la transacción de compromiso del otro lado. ### Referencias - [BOLT2 Protocolo de pares](https://github.com/lightning/bolts/blob/master/02-peer-protocol.md) - [Operación normal de un canal LN pre-taproot](https://ellemouton.com/posts/normal-operation-pre-taproot/) por nostr:nprofile1qqswrt9pnxatlplu49h6meld8svmwqt87wwvk256rqk07n6eu4qeh5gpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0dszpfjtz - [Una guía técnica sobre contratos de tiempo bloqueado por hash y operaciones de canales Lightning](https://lightning.engineering/posts/2023-06-28-channel-normal-op/) - [BOLT8 Transporte](https://github.com/lightning/bolts/blob/master/08-transport.md)
@ 599f67f7:21fb3ea9
2024-12-31 15:00:53### Contenidos - [Visión general](#visión-general) - [Preliminares](#preliminares) - [Operación normal del canal](#operación-normal-del-canal) - [Configuración](#configuración) - [Añadiendo un HTLC](#añadiendo-un-htlc) - [Paso 1: Alice -> Bob: update_add_htlc(A1)](#paso-1-alice---bob-update_add_htlca1) - [Paso 2: Alice -> Bob: update_add_htlc(A2)](#paso-2-alice---bob-update_add_htlca2) - [Paso 3: Bob -> Alice: update_add_htlc(B1)](#paso-3-bob---alice-update_add_htlcb1) - [Comprometiéndose al estado actual](#comprometiéndose-al-estado-actual) - [Paso 4: Alice -> Bob: commitment_signed](#paso-4-alice---bob-commitment_signed) - [Paso 5: Bob -> Alice: revoke_and_ack](#paso-5-bob---alice-revoke_and_ack) - [Paso 6: Alice -> Bob: update_add_htlc(A3)](#paso-6-alice---bob-update_add_htlca3) - [Paso 7: Bob -> Alice: commitment_signed](#paso-7-bob---alice-commitment_signed) - [Paso 8: Alice -> Bob: revoke_and_ack](#paso-8-alice---bob-revoke_and_ack) - [Paso 9: Bob -> Alice: revoke_and_ack](#paso-9-bob---alice-revoke_and_ack) - [Paso 10: Bob -> Alice: commitment_signed](#paso-10-bob---alice-commitment_signed) - [Paso 11: Alice -> Bob: revoke_and_ack](#paso-11-alice---bob-revoke_and_ack) - [Eliminando HTLCs](#eliminando-htlcs) - [Paso 12: Bob -> Alice: update_fulfill_htlc(A2)](#paso-12-bob---alice-update_fulfill_htlca2) - [Paso 13: Bob -> Alice: update_fail_htlc(A1)](#paso-13-bob---alice-update_fail_htlca1) - [Paso 14: Bob -> Alice: update_fail_malformed_htlc(A3)](#paso-14-bob---alice-update_fail_malformed_htlca3) - [Paso 15: Alice -> Bob: update_fulfill_htlc(B1)](#paso-15-alice---bob-update_fulfill_htlcb1) - [Paso 16: Bob -> Alice: commitment_signed](#paso-16-bob---alice-commitment_signed) - [Paso 17: Alice -> Bob: revoke_and_ack](#paso-17-alice---bob-revoke_and_ack) - [Paso 18: Alice -> Bob: commitment_signed](#paso-18-alice---bob-commitment_signed) - [Paso 19: Bob -> Alice: revoke_and_ack](#paso-19-bob---alice-revoke_and_ack) - [Paso 20: Bob -> Alice: commitment_signed](#paso-20-bob---alice-commitment_signed) - [Paso 21: Alice -> Bob: revoke_and_ack](#paso-21-alice---bob-revoke_and_ack) - [Actualizando tarifas](#actualizando-tarifas) - [Retransmisión de mensajes](#retransmisión-de-mensajes) ### Visión general En este capítulo cubriremos las operaciones normales de un canal. Esto implica entender cómo se añaden HTLCs a un canal y cómo los pares del canal se comprometen a un nuevo estado para incluir estos HTLCs. Luego cubriremos cómo se restablece el flujo normal de un canal después de una desconexión. Finalmente, cubriremos el flujo de cierre cooperativo del canal. Por cierto, todos estos temas están cubiertos en [BOLT2](https://github.com/lightning/bolts/blob/master/02-peer-protocol.md). ### Preliminares Aquí hay algunos conceptos y flujos que hemos cubierto anteriormente en nuestra serie que podrían ser útiles para entender este capítulo. No dudes en volver a leerlos si necesitas un recordatorio. - nostr:naddr1qqxnzdenxgerzve5x5enyv3sqyg8wumn8ghj7mn0wd68ytnhd9hx2q3qtx0k0a7lw62vvqax6p3ku90tccgdka7ul4radews2wrdsg0m865sxpqqqp65wc4f8xj: por qué los pares del canal tienen un estado asimétrico y cómo actualizan este estado de manera confiable. - nostr:naddr1qqxnzdenxgenvwp48qmnqdfhqyg8wumn8ghj7mn0wd68ytnhd9hx2q3qtx0k0a7lw62vvqax6p3ku90tccgdka7ul4radews2wrdsg0m865sxpqqqp65wx9fs7k: cómo se ven las salidas de HTLC en una transacción de compromiso. - [Apertura y anuncio de un canal LN pre-taproot]: cómo dos nodos abren un canal. ### Operación normal del canal #### Configuración Alice y Bob han abierto su canal con éxito. Ambos han visto que la transacción de financiación está confirmada y han intercambiado el mensaje `channel_ready` entre ellos para indicar que están listos para usar el canal. El estado de sus transacciones de compromiso asimétricas actualmente se ve así:  Ambas transacciones de compromiso gastan la salida de la transacción de financiación multisig 2-de-2. Dado que es un multisig 2-de-2, gastar de esta salida requiere firmas de ambos pares. Las firmas están representadas por las dos cajas en la parte superior de las transacciones de compromiso. Puedes ver en el diagrama que la transacción de compromiso de Alice tiene una firma de Bob representada por la caja azul; Bob tiene una firma de Alice para su transacción de compromiso representada por la caja verde. Cada transacción de compromiso también tiene las salidas `to_local` y `to_remote` que pagan a las partes respectivas su saldo actual del canal. Tanto Alice como Bob pueden firmar sus propias transacciones de compromiso en cualquier momento y transmitirlas a la red de Bitcoin. Esto sería un **cierre forzado**. Con el fin de hacer que los próximos diagramas sean más fáciles de seguir, ignoraremos las transacciones de financiación así como las salidas `to_local` y `to_remote` por un tiempo, ya que nuestro enfoque inicial estará en añadir y eliminar salidas de HTLC. Así que el diagrama anterior ahora se simplifica a esto:  - Una transacción de compromiso _roja_, mostrada a continuación, representa transacciones de compromiso pasadas y revocadas. Si Alice o Bob firmaran y transmitieran una de estas, entonces la otra parte podría barrer todos sus fondos. Así que estas transacciones revocadas pueden considerarse efectivamente inválidas. - Una transacción de compromiso _amarilla_ representa el último conjunto válido de transacciones de compromiso. Estas son las transacciones de compromiso que se transmitirían en un cierre forzado. - Finalmente, cada lado tiene lo que se puede considerar un "área de preparación" donde se pueden proponer cambios a la transacción de compromiso. Más adelante, cualquiera de los lados puede decidir cuándo quiere que su contraparte se comprometa a los cambios en su transacción de compromiso de preparación. Sugerencia: si te gusta git, esto es muy parecido a un flujo de trabajo de git. Los commits pasados están desactualizados, pero cuentan una buena historia de lo que sucedió. Tus últimos cambios comprometidos representan el estado actual de tu proyecto. Cualquier cambio que aún no esté comprometido está en preparación.  #### Añadiendo un HTLC Cuando Alice o Bob quieren enviar un pago, necesitarían proponer la inclusión del HTLC a su par de canal. Esto se hace con el mensaje `update_add_htlc`:  Aquí hay una tabla sobre lo que significa cada uno de los campos del mensaje: | Campo | Descripción| |---|---| | channel_id | utilizado para comunicar en qué canal debe tener lugar este cambio. | | id | un identificador que siempre incrementa para este cambio propuesto del remitente. | | amount_msat | la cantidad que debe adjuntarse a la salida de HTLC. | | cltv_expiry | la altura del bloque en la que el HTLC debe expirar. | | onion_routing_packet y blinding_point | datos que el destinatario del HTLC utilizará para determinar a dónde enviar el pago a continuación. | Hay un punto contraintuitivo a tener en cuenta aquí: el remitente de este mensaje aún no coloca esta actualización en su propia área de preparación. Esto se debe a que la actualización aún está "pendiente del receptor" porque el remitente aún no ha recibido ningún reconocimiento del receptor para la nueva actualización. Imagina este escenario: el remitente envía una actualización y luego recibe inmediatamente un mensaje `commitment_signed` (más detalles sobre esto más adelante). En este caso, no debería haber ambigüedad sobre qué actualizaciones están incluidas en la transacción que se está firmando. Esperemos que esto tenga más sentido a medida que trabajemos a través del ejemplo. ##### Paso 1: Alice -> Bob: update_add_htlc(A1) Supongamos que Alice envía a Bob un `update_add_htlc`. Llamemos a este HTLC `A1` porque es el primero que Alice (A) está enviando a Bob. Si Bob está contento con todos los campos en el mensaje, entonces añade el HTLC a su transacción de compromiso en el área de preparación y Alice marca el HTLC como pendiente en el lado de Bob, pero aún no lo añade a su propia transacción de compromiso en preparación.  Ten en cuenta que ninguno de los lados ha comprometido realmente este HTLC aún, así que si Bob es un nodo de enrutamiento para este pago, no debería enviar aún `update_add_HTLC` al siguiente salto en la ruta hasta que `A1` haya sido _irrevocablemente_ comprometido. La adición o eliminación de un HTLC solo se considera irrevocablemente comprometida una vez que ambas partes en el canal se han comprometido a la transacción de compromiso con o sin él. Esto no se muestra en el diagrama simplificado, pero en realidad la salida principal de Alice en la transacción de compromiso en preparación de Bob (es decir, la salida `to_remote`) ahora tendrá el valor del HTLC añadido restado (junto con las tarifas para cubrir la salida extra). Si el HTLC termina teniendo éxito, entonces esta cantidad se añadirá a la salida de Bob y si termina fallando, entonces se volverá a añadir a la salida de Alice. ##### Paso 2: Alice -> Bob: update_add_htlc(A2) A pesar de que aún no se han comprometido al HTLC `A1`, esto no les impide añadir más cambios al área de preparación. Alice está más que bienvenida a proponer un nuevo HTLC, `A2`, a Bob:  ##### Paso 3: Bob -> Alice: update_add_htlc(B1) Del mismo modo, Bob puede sugerir un cambio, `B1`, a Alice:  #### Comprometiéndose al estado actual En algún momento, uno de los pares querrá asegurarse de que el otro par se haya comprometido al último conjunto de cambios y revocar el estado válido anterior. Esto se hace enviando el mensaje `commitment_signed`:  | Campo | Descripción| |---|---| | channel_id | utilizado para comunicar en qué canal debe tener lugar este cambio. | | signature | la firma del remitente para la transacción de compromiso del área de preparación de la parte remota. | | num_htlcs | el número de HTLCs que el remitente espera que estén en la transacción de compromiso remota. | | htlc_signatures | un array de firmas de num_htlcs que son las firmas del remitente para cada una de las transacciones de HTLC de segundo nivel que la parte remota necesitaría transmitir si alguna vez tuviera que cerrar el canal forzosamente. | Sugerencia: si necesitas un recordatorio sobre las transacciones de HTLC de segundo nivel y por qué son necesarias, consulta este [capítulo]. ##### Paso 4: Alice -> Bob: commitment_signed Supongamos que Alice envía este mensaje a Bob. Bob ahora tendrá todas las firmas requeridas de Alice para transmitir su transacción de compromiso en el área de preparación:  Observa que Alice sabía que su firma necesitaría cubrir los HTLCs `A1` y `A2`. Esto está bien porque el [transporte subyacente](https://github.com/lightning/bolts/blob/master/08-transport.md) está garantizado para ser confiable y ordenado, lo que significa que si Bob recibiera el mensaje `commitment_signed` de Alice, entonces significa que definitivamente recibió sus mensajes `update_add_htlc` para `A1` y `A2`. Alice y Bob saben que la firma no debería cubrir el HTLC `B1` ya que Alice no ha enviado un reconocimiento para él aún. Otra cosa a notar es que Bob ahora tiene en realidad dos transacciones de compromiso válidas ya que aún no ha revocado su estado anterior. Sin embargo, está incentivado a revocar su transacción de compromiso anterior ya que los HTLCs en el nuevo estado son uno de los siguientes: - Pagos a Bob mismo, lo que significa que se beneficia de comprometerse al nuevo estado. Si no se compromete al nuevo estado, entonces Alice tampoco lo hará y por lo tanto aún existiría una versión de una transacción de compromiso que no paga a Bob sus fondos entrantes. - De manera similar al punto anterior, si Bob está enrutando un pago, entonces también está incentivado a comprometer irrevocablemente el HTLC ya que ganaría tarifas de enrutamiento si el pago tiene éxito. - Finalmente, si Bob está haciendo el pago él mismo, entonces el primer estado sería de hecho más rentable para él ya que tiene menos fondos en el segundo estado. Sin embargo, el comerciante al que Bob está haciendo el pago no liberará los bienes que se están comprando a menos que primero se reciban los fondos, lo que no sucederá si Alice no pasa el HTLC, lo cual no hará a menos que se haya comprometido irrevocablemente. Así que nuevamente, Bob está incentivado a revocar su estado anterior. ##### Paso 5: Bob -> Alice: revoke_and_ack En respuesta al `commitment_signed` de Alice, Bob envía el mensaje `revoke_and_ack`:  - El `per_commitment_secret` proporciona a Alice la información que necesita para poder gastar cualquier ruta de revocación en el estado previamente válido de Bob. Consulta el [capítulo de revocación] para más detalles sobre cómo funciona la revocación. - El `next_per_commitment_point` le da a Alice la información que necesita para derivar la clave pública de revocación que se utilizará en la próxima transacción de compromiso de Bob. Una vez que Alice recibe este mensaje, la transacción de compromiso anterior de Bob ha sido revocada con éxito. Ten en cuenta que este mensaje reconoce explícitamente el mensaje `commitment_signed` enviado por Alice y, por extensión, dado que la entrega de mensajes es confiable y ordenada, también reconoce implícitamente los mensajes `update_add_htlc` que Alice envió para `A1` y `A2`. Por lo tanto, Alice puede finalmente añadir `A1` y `A2` a su transacción de compromiso en el área de preparación ya que ya no están pendientes en el lado de Bob:  Ahora podemos limpiar un poco el diagrama:  En el último diagrama, observa que las últimas transacciones de compromiso de Alice y Bob están en realidad desincronizadas. Esto está bien ya que ninguna de las actualizaciones se ha comprometido irrevocablemente aún. Eso podría parecer difícil de creer ya que las transacciones de compromiso se ven tan diferentes, así que vamos a repasar las consecuencias de que cualquiera de estas transacciones termine en la cadena desde la perspectiva de ambos lados. - Desde la perspectiva de Alice: - si su transacción de compromiso se transmitiera, recuperaría su cantidad original `to_local`. - si la transacción de compromiso de Bob se transmitiera, entonces los HTLCs ofrecidos por Alice (como `A1` y `A2`) estarían en la cadena. Para los HTLCs ofrecidos, Alice está enviando sats _fuera_, lo que significa que su `to_local` sería menor. Pero, si Bob era un nodo de enrutamiento para estos HTLCs, entonces no los habría reenviado ya que aún no están comprometidos irrevocablemente, lo que significa que no recibiría las pre-imágenes requeridas para reclamar estos HTLCs y, por lo tanto, Alice podría recuperar sus fondos a través de la ruta de tiempo de espera. Si Bob era el destinatario de estos HTLCs, entonces podría producir la pre-imagen para reclamar los HTLCs, pero entonces Alice vería la pre-imagen en la cadena y podría reclamar los HTLCs entrantes de su canal entrante y así habría ganado tarifas de enrutamiento. - Desde la perspectiva de Bob: - si la transacción de compromiso de Alice se transmite, Bob recupera sus fondos a través de la salida `to_remote`. - si Bob tuviera que cerrar forzosamente a través de su transacción de compromiso, entonces los HTLCs ofrecidos a él (como `A1` y `A2`) estarían en la cadena. Si Bob estaba enrutando estos HTLCs, entonces no los habría reenviado ya que aún no están comprometidos irrevocablemente. Así que no podría reclamar la ruta de éxito, pero eso está bien ya que los fondos para estos no salieron de su saldo. Si Bob era el destino final para estos, entonces podría reclamarlos a través de la ruta de éxito. ##### Paso 6: Alice -> Bob: update_add_htlc(A3) Queremos ser muy claros sobre el punto de que las transacciones de compromiso pueden permanecer desincronizadas indefinidamente y que Bob no necesita enviar `commitment_signed` solo porque Alice lo hizo. Así que, para el sake de otro ejemplo, supongamos que Alice en este punto envía otro HTLC, `A3`, a Bob:  ##### Paso 7: Bob -> Alice: commitment_signed Bob quiere comprometer irrevocablemente algunos de los HTLCs para poder reenviarlos, así que finalmente envía a Alice un `commitment_signed` propio. Esto incluirá su firma para la transacción de compromiso del área de preparación de Alice junto con todas las firmas requeridas de él para las salidas de HTLC de segundo nivel.  ##### Paso 8: Alice -> Bob: revoke_and_ack Al igual que Bob hizo anteriormente, Alice responde al `commitment_signed` con un `revoke_and_ack` para revocar su estado anterior. Esto también sirve como un reconocimiento para Bob de que Alice ha recibido y se ha comprometido a `B1`, por lo que Bob ahora puede agregar `B1` a su transacción de compromiso en el área de preparación.  Rápida limpieza...  ¡Por fin, tenemos algunos HTLCs comprometidos de forma irrevocable! `A1` y `A2` han sido comprometidos de forma irrevocable. `B1` y `A3`, sin embargo, no lo han sido ya que aún no han sido comprometidos por ambas partes. Comprometamos rápidamente `B1` y `A3` de forma irrevocable también. ##### Paso 8: Alice -> Bob: commitment_signed  ##### Paso 9: Bob -> Alice: revoke_and_ack  ##### Paso 10: Bob -> Alice: commitment_signed  ##### Paso 11: Alice -> Bob: revoke_and_ack  Limpiado:  ¡Ahora todos los HTLCs han sido comprometidos de forma irrevocable! #### Eliminando HTLCs Probablemente ya entiendas la idea de agregar HTLCs. Pero, ¿qué pasa con eliminarlos? Los HTLCs se eliminan si un pago tiene éxito o si falla. Ten en cuenta que los mensajes de eliminación de HTLC solo pueden ser enviados por el par que no envió la actualización original `update_add_htlc` y que los HTLCs solo son removibles una vez que han sido comprometidos de forma irrevocable. Afortunadamente para nosotros, todos los HTLCs han sido comprometidos de forma irrevocable, así que podemos comenzar a eliminarlos ahora. ##### Paso 12: Bob -> Alice: update_fulfill_htlc(A2) En el mejor de los casos, un HTLC se elimina porque se está cumpliendo, lo que significa que su pre-imagen se está devolviendo. Esto se hace con el mensaje `update_fulfilled_htlc`, que se ve así:  En nuestro ejemplo, Bob envía a Alice el mensaje `update_fulfill_htlc` para el HTLC `A2`. Esto también demuestra que los HTLCs no tienen que ser eliminados en el mismo orden en que fueron agregados.  Ten en cuenta que, al igual que las actualizaciones para agregar un HTLC, las actualizaciones para eliminar un HTLC también estarán inicialmente pendientes en el lado receptor hasta que hayan sido reconocidas por un `revoke_and_ack`. Así que, en nuestro caso, Alice elimina `A2` de su transacción en el área de preparación cuando recibe el `update_fulfill_htlc` (y asigna el monto del HTLC a la salida de Bob), pero Bob aún no elimina el HTLC de su transacción en el área de preparación. A diferencia de otros mensajes de actualización, no hay necesidad de esperar a que una eliminación de HTLC sea comprometida de forma irrevocable si recibes la pre-imagen para ello. Después de todo, puedes enviar inmediatamente la pre-imagen hacia arriba para reclamar cualquier HTLC allí. ##### Paso 13: Bob -> Alice: update_fail_htlc(A1) Los HTLCs también pueden ser eliminados debido a fallos en el pago, como el tiempo de espera de los HTLCs o si hubo algún tipo de fallo de enrutamiento, como que un canal específico en la ruta ya no exista, no se cumplan los requisitos de tarifa de un salto, un enlace no tenga saldo suficiente, etc. Tales fallos se comunican con el mensaje `update_fail_htlc`:  El campo de razón es un blob cifrado para el remitente del pago para informarles sobre la razón del fallo. Después de que Bob envía a Alice el mensaje `update_fail_htlc` para `A1`, el estado se ve como sigue:  ##### Paso 14: Bob -> Alice: update_fail_malformed_htlc(A3) El mensaje final que se puede usar para eliminar un HTLC es el mensaje `update_fail_malformed_htlc`:  Este mensaje se envía si algún salto en la ruta de pago no pudo analizar el `onion_routing_packet` que recibió en `update_add_htlc`. Si Bob envía a Alice este mensaje para `A3`, entonces el estado ahora se ve así:  ##### Paso 15: Alice -> Bob: update_fulfill_htlc(B1) Alice también inicia la eliminación de `B1` enviando un `update_fulfill_htlc` a Bob.  Ahora limpiemos las eliminaciones de HTLC comprometiéndolas de forma irrevocable. Esto requerirá algunos flujos de `commitment_signed` - `revoke_and_ack`: ##### Paso 16: Bob -> Alice: commitment_signed  ##### Paso 17: Alice -> Bob: revoke_and_ack  ##### Paso 18: Alice -> Bob: commitment_signed  ##### Paso 19: Bob -> Alice: revoke_and_ack  ##### Paso 20: Bob -> Alice: commitment_signed  ##### Paso 21: Alice -> Bob: revoke_and_ack  Los dos estados válidos ahora se ven bonitos y limpios nuevamente:  ### Actualizando tarifas Hay un mensaje `update_*` más que necesitamos cubrir y ese es el mensaje `update_fee`. Este mensaje se utiliza para actualizar la tasa de tarifa que los pares deben usar al construir sus transacciones de compromiso. La tasa de tarifa original se decide en el flujo de apertura de canal, pero si la tasa de tarifa promedio del mempool aumenta, el financiador del canal podría decidir actualizar la tarifa de las transacciones de compromiso para que tengan una mejor oportunidad de ser confirmadas de manera oportuna en una situación de cierre forzado. También podría ser que cuando se abrió el canal, se eligió una tasa de tarifa muy alta y quizás se desearía una tasa de tarifa más baja. Este mensaje sigue reglas similares a otros mensajes `update_*` en que también debe ser comprometido de forma irrevocable antes de que surta efecto. La única regla adicional que se aplica a este mensaje es que solo el financiador del canal puede enviar este mensaje:  Ten en cuenta que con los canales de anclaje, la necesidad de usar el mensaje `update_fee` se está volviendo cada vez menor, ya que los nodos podrán usar CPFP en la transacción de cierre forzado si es necesario. ### Retransmisión de mensajes Algo que puedes haber notado en el flujo de agregar/eliminar HTLC es que los reconocimientos explícitos para los mensajes `update_*` se retrasan hasta el intercambio de `commitment_signed`/`revoke_and_ack`. Eso está bien la mayor parte del tiempo, ya que asumimos que el transporte subyacente entre los dos nodos (ver [BOLT8](https://github.com/lightning/bolts/blob/master/08-transport.md)) es ordenado y confiable. Sin embargo, si por alguna razón la conexión entre los dos nodos necesita ser restablecida, habrá dudas sobre si nuestro par ha recibido el último mensaje que enviamos. Aquí es donde entra el mensaje `channel_reestablish`. Al reconectarse, antes de continuar con el flujo de operación normal, los pares intercambiarán este mensaje para asegurarse de que están en la misma página y para determinar qué mensajes posiblemente necesitan retransmitir a su par.  Cada par en el canal tiene su versión de la transacción de compromiso y las dos transacciones de compromiso pueden actualizarse de forma independiente, lo que significa que el número de veces que el estado de la transacción de compromiso de un lado ha sido actualizado (a través del flujo de `commitment_signed` y `revoke_and_ack`) podría ser completamente diferente al del otro lado. El campo `next_commitment_number` en el mensaje `channel_reestablish` nos permite comunicarnos con nuestro par sobre el próximo `commitment_signed` que esperamos recibir de ellos. De esta manera, ellos sabrán si quizás hemos perdido un `commitment_signed` de ellos que enviaron anteriormente antes de la desconexión. En otras palabras, `next_commitment_number` le dice al par remoto cuál es nuestro último estado comprometido. De manera similar, `next_revocation_number` es el número de compromiso del próximo `revoke_and_ack` que esperamos recibir. En otras palabras, esto indica a nuestro par cuál número de compromiso creemos que es el más reciente. El `your_last_per_commitment_secret` es el último secreto por compromiso recibido del par remoto, lo que le dará al par remoto una idea del estado que definitivamente ha revocado. `my_current_per_commitment_point` es el punto de compromiso de la parte local en su última transacción de compromiso firmada por el par remoto (en otras palabras, la transacción de compromiso que aún no ha sido revocada). Hay muchas verificaciones que un nodo debe hacer al recibir un `channel_reestablish` para asegurarse de que todas las actualizaciones necesarias se retransmitan para que el canal pueda continuar funcionando con normalidad. También hay algunas verificaciones que aseguran que los nodos no sean engañados para revocar un estado que aún no debería ser revocado o engañados para transmitir un estado que _ha_ sido revocado. Si estás interesado en los detalles sobre estas verificaciones, lee [BOLT2](https://github.com/lightning/bolts/blob/master/02-peer-protocol.md). Ten en cuenta que cuando ocurre un restablecimiento de conexión, ambos lados deben eliminar cualquier actualización no comprometida de su área de preparación. Si volvemos a visitar la analogía de git, deberían usar git stash cuando ocurra una reconexión. Esto significa que ambos lados necesitarán retransmitir cualquier mensaje `update_*` que aún no haya sido comprometido en la transacción de compromiso del otro lado. ### Referencias - [BOLT2 Protocolo de pares](https://github.com/lightning/bolts/blob/master/02-peer-protocol.md) - [Operación normal de un canal LN pre-taproot](https://ellemouton.com/posts/normal-operation-pre-taproot/) por nostr:nprofile1qqswrt9pnxatlplu49h6meld8svmwqt87wwvk256rqk07n6eu4qeh5gpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0dszpfjtz - [Una guía técnica sobre contratos de tiempo bloqueado por hash y operaciones de canales Lightning](https://lightning.engineering/posts/2023-06-28-channel-normal-op/) - [BOLT8 Transporte](https://github.com/lightning/bolts/blob/master/08-transport.md) @ 599f67f7:21fb3ea9
2024-12-31 14:56:46En este capítulo, revisaremos el proceso de apertura y anuncio de un canal pre-taproot, añadiendo algunos detalles técnicos. En los próximos capítulos, aplicaremos el mismo tratamiento a la operación normal y cierre de un canal. Estos capítulos nos darán la base sobre la cual construir a medida que aprendamos sobre canales taproot en el futuro. Asumiremos que ya estás familiarizado con la estructura de una transacción de compromiso y entiendes por qué son asimétricas. Si necesitas un recordatorio, ¡por favor revisa los capítulos anteriores! ### Contenidos - [El objetivo final](#el-objetivo-final) - [Apertura del canal](#apertura-del-canal) - [El mensaje open_channel](#el-mensaje-open_channel) - [El mensaje accept_channel](#el-mensaje-accept_channel) - [El mensaje funding_created](#el-mensaje-funding_created) - [El mensaje funding_signed](#el-mensaje-funding_signed) - [El mensaje channel_ready](#el-mensaje-channel_ready) - [Anunciando el canal](#anunciando-el-canal) - [Verificando el canal](#verificando-el-canal) ### El objetivo final Establezcamos qué es lo que nuestros viejos amigos, Alice y Bob, están tratando de lograr. Alice y Bob son nodos de la Red Lightning. Alice es conocida en la red por su *ID de nodo*, o la clave pública utilizada para identificar su nodo, esta es `alice_node_id`. Del mismo modo, el ID de nodo de Bob es `bob_node_id`. Sus dos principales objetivos son: 1. Quieren abrir un canal entre ellos de manera sin confianza. 2. Quieren poder publicitar su nuevo canal para que el resto de la red pueda usarlo para el enrutamiento. ### Apertura del Canal Primero lo primero: a lo largo de este capítulo, utilizaremos diagramas y colores para ilustrar el proceso de apertura del canal. Aquí está la guía de código de colores: - Un fondo *blanco* significa que el campo de la transacción aún no se conoce. - Un campo *coloreado* significa que el valor del campo es conocido. - *Verde* indica las claves públicas de Alice. - *Azul* indica las claves públicas de Bob. Un canal se abre una vez que ambas partes tienen la capacidad de firmar completamente sus respectivas transacciones de compromiso y una vez que la transacción de financiación está en la cadena. Tres transacciones están en juego para la apertura de un canal. La primera es la transacción de financiación, que necesita ser confirmada en la cadena. Las otras dos son las transacciones de compromiso mantenidas por Alice y Bob que describen el estado inicial del canal. En este momento, aún no sabemos nada sobre los parámetros del canal, por lo que todos los campos tienen un fondo blanco:    #### El mensaje open_channel El primer paso del proceso es que Alice decida que quiere abrir un canal a Bob, es decir, ella se convertirá en la financiadora del canal (y Bob será el financiado). Supongamos que Alice decide que quiere abrir un canal de 1 BTC a Bob y darle inmediatamente a Bob la mitad de la capacidad del canal (0.5 BTC). Alice ahora preparará un mensaje `open_channel` que enviará a Bob. Como referencia, en la tabla a continuación puedes ver los parámetros relevantes. | Nombre del Campo | Descripción del Campo | |___|___| | chain_hash | La blockchain en la que abrir el canal. | | temp_chan_ID | Identificar el canal antes de que se conozca el outpoint de la transacción de financiación. | | funding_sats | La cantidad de salida de la transacción de financiación, es decir, la capacidad del canal. | | push_msat | La cantidad que el financiador envía incondicionalmente al financiado en el momento de la apertura. | | dust_limit_sats | Umbral por debajo del cual no se deben generar salidas. | | feerate_per_kw | La tasa de tarifa inicial a utilizar para las transacciones de compromiso. Puede actualizarse más tarde a través de `update_fee`. | | revocation_basepoint | Utilizado, junto con el first_per_commitment_point del nodo remoto, para derivar la primera clave pública de revocación que se utilizará en la transacción de compromiso de Bob. | | payment_basepoint | Utilizado, junto con el first_per_commitment_point, para derivar la primera clave pública de pago - la clave pública to_remote en la transacción de compromiso de Bob. | | delayed_payment_basepoint | Utilizado, junto con el first_per_commitment_point, para derivar la primera clave pública retrasada - la clave pública local_delayed en la transacción de compromiso de Alice. | | first_per_commitment_point | El primer punto a utilizar junto con los puntos base anteriores (excluyendo el revocation_basepoint) para derivar las claves públicas correspondientes. | | channel_flags | La única bandera actualmente definida es la bandera "announce_channel" que determina si el canal debe ser anunciado a la red o no. | | tlv: channel_type | Para que se pueda determinar la estructura de la transacción de compromiso. | Ahora llenemos los valores de Alice para estos campos:  Alice envía este mensaje a Bob. Dado que Alice ha decidido el tipo de canal que quiere abrir (legado en lugar de anclajes, taproot, etc.) así como la capacidad del canal, ya puede armar una parte bastante grande de la transacción de financiación:  Alice ya puede elegir algunos de sus UTXOs para ser entradas a la transacción de financiación, ya que conoce la capacidad del canal que quiere abrir. Sin embargo, aún no sabe qué clave pública Bob querría usar para el canal, por lo que no puede finalizar la salida de financiación del canal todavía, y por lo tanto no puede producir firmas para las entradas. Como Alice ha decidido el tipo de canal (y por lo tanto la estructura de la transacción de compromiso), también puede comenzar a ensamblar las piezas de las transacciones de compromiso. Si asumimos que Bob está feliz con esta propuesta de apertura de canal de Alice, él también puede comenzar a armar las piezas utilizando la información en el mensaje `open_channel`. Recuerda que ambos pares necesitan construir sus propias transacciones de compromiso y ambos necesitarán firmar las transacciones de su par. Veamos qué piezas ya pueden llenar:  La transacción de compromiso de Alice tiene la estructura de una transacción de canal por defecto, no anclada. Todas sus claves públicas han sido llenadas (`alice_local_delayed_pk_1` se deriva utilizando su `delayed_payment_basepoint` y su `first_commitment_point`). Dado que aún no ha recibido ningún mensaje de Bob, no puede llenar ninguna de sus claves públicas. Y dado que la transacción de financiación aún está incompleta, tampoco puede conocer el TXID para apuntar la entrada de esta transacción de compromiso. La transacción de compromiso de Bob se ve un poco más completa:  Al igual que Alice, él tampoco puede llenar aún el TXID de la transacción de financiación, pero puede llenar algunas otras cosas: - Los valores `alice_pubkey_1`, `alice_to_self_delay`, `push_amt` y `local_amt` se toman tal cual del mensaje `open_channel`. - `alice_payment_key_1` se deriva utilizando el `payment_basepoint` de Alice y el `first_commitment_point`. - `revoke_pubkey_1b` se deriva utilizando el `revocation_basepoint` de Alice y el `first_per_commitment point` de Bob (Alice no puede derivar este punto aún ya que no ha recibido el `first_per_commitment_point` de Bob). ¡Genial! Es hora de que Bob indique a Alice su aceptación de la propuesta enviando el siguiente mensaje: `accept_channel`. #### El mensaje accept_channel El mensaje comparte muchos de los campos del `open_channel`. Aquí está el mensaje que Bob preparará.  Cuando Alice recibe este mensaje de Bob, ahora puede completar la salida de la transacción de financiación y puede crear las firmas para las entradas. Dado que todo está ahora lleno, el TXID de la transacción de financiación también es conocido.  Alice ahora puede llenar más de su propia transacción de compromiso: - ahora puede usar los valores enviados por Bob para llenar `bob_pubkey_1`, `bob_payment_key_1`, `bob_to_self_delay` y `revoke_pubkey_1a` - dado que el TXID para la transacción de financiación ahora es conocido, también puede completar la entrada Ahora sabe todo lo que necesita saber para firmar esta transacción ella misma _pero_ recuerda que aún le falta la firma de Bob para esta transacción.  La transacción de compromiso de Bob sigue siendo la misma que antes, ya que no aprendió nueva información después de enviar el mensaje `accept_channel`. Ahora que Alice conoce el TXID de la transacción de financiación, también puede completar su vista de la transacción de compromiso de Bob y así puede producir su firma para la transacción de él. Ella enviará el siguiente mensaje a Bob: `funding_created`. #### El mensaje funding_created Alice ahora utilizará el mensaje `funding_created` para decirle a Bob el TXID y el índice de la transacción de financiación junto con su firma para la transacción de compromiso de Bob. Ten en cuenta que Bob aún no podrá transmitir su transacción de compromiso porque la transacción de financiación no ha sido transmitida aún.  Una vez que Bob reciba el mensaje `funding_created`, podrá completar el resto de su transacción de compromiso:  #### El mensaje funding_signed Alice no transmitirá la transacción de financiación hasta que tenga una firma válida de Bob para su transacción de compromiso, entra `funding_signed`:  Ten en cuenta que este es el primer mensaje que utiliza el ID de canal real en lugar del temporal. Esta fue la última pieza del rompecabezas para Alice. Ahora tiene toda la información que necesita para poder firmar su transacción de compromiso si alguna vez es necesario.  #### El mensaje channel_ready Alice ahora puede transmitir de manera segura la transacción de financiación. Tanto Alice como Bob estarán atentos a la cadena para la confirmación de la transacción de financiación. Una vez que haya alcanzado la `minimum_depth` especificada por Bob en su mensaje `accept_channel`, ambos lados intercambiarán el mensaje `channel_ready`. Este mensaje cumple dos propósitos. Primero, sirve como una señal para el par para indicar que el canal está listo para usar (y pueden comenzar el proceso de anuncio del canal si abrieron un canal público y anunciado). En segundo lugar, también le dice al par que envíe su `second_per_commitment_point` que deben usar en su segunda transacción de compromiso.  ### Anunciando el canal Esta parte es bastante fácil. Alice y Bob solo necesitan construir un mensaje, `channel_announcement`, juntos y una vez que esté completo, pueden transmitirlo a la red. Otros nodos utilizarán este mensaje para probar algunas cosas: - Que la transacción de financiación del canal es en realidad un UTXO existente y no gastado con un número aceptable de confirmaciones. - Que la salida de la transacción de financiación en realidad se parece a una transacción de financiación de canal Lightning. - Que el canal es en realidad propiedad de las claves que Alice y Bob dicen que utilizaron para construir el canal. - Que Alice y Bob están de acuerdo en el mensaje que se está transmitiendo. Una versión parcial del mensaje `channel_announcement` se ve así:  `h` es el hash de todos los datos que serán cubiertos por las firmas. Para completar este mensaje, tanto Alice como Bob necesitan calcular una firma sobre `h` utilizando las claves privadas asociadas con sus IDs de nodo y las claves públicas que utilizaron en la transacción de financiación. Luego ambos intercambian el mensaje `announcement_signatures` para comunicarse estas firmas.  Ahora ambos nodos pueden armar el mensaje completo `channel_announcement`:  ### Verificando el canal Supongamos que Charlie es un nodo que recibió este mensaje. Vamos a repasar los pasos que seguirá para verificar el nuevo canal que Alice y Bob han anunciado: 1. Primero, Charlie utilizará el `short_channel_id` incluido en el mensaje para asegurarse de que la transacción de financiación realmente existe en la cadena, que tiene un número suficiente de confirmaciones y que de hecho está no gastada. 2. Luego, Charlie verificará que la salida no gastada realmente se parece a un canal Lightning propiedad de `alice_pubkey_1` y `bob_pubkey_1`. Hará esto utilizando las claves públicas publicitadas para reconstruir el P2WSH y asegurarse de que es el mismo que se encuentra en la cadena. 3. Ahora, Charlie querrá verificar que los nodos que poseen las claves públicas utilizadas en la salida de financiación corresponden de hecho a los nodos que poseen las claves públicas de ID de nodo. Puede hacer esto verificando las firmas `alice_pubkey_1_sig` y `bob_pubkey_1_sig`. Si estas firmas son válidas, entonces está claro que los propietarios de `alice_pubkey_1` y `bob_pubkey_1` están de acuerdo en ser asociados con `alice_node_ID` y `bob_node_ID` ya que el mensaje firmado contiene estas claves públicas. 4. Finalmente, Charlie también querrá asegurarse de que los propietarios de las claves públicas de ID de nodo están de acuerdo en ser asociados con el nuevo canal. Puede hacer esto verificando las firmas `alice_node_ID_sig` y `bob_node_ID_sig`. Si estas firmas son válidas, entonces está claro que los propietarios de `alice_node_ID` y `bob_node_ID` están de acuerdo en ser asociados con `alice_pubkey_1` y `bob_pubkey_1` ya que el mensaje firmado contiene estas claves públicas. ¡Alice y Bob han terminado! Su canal ahora está abierto y otros nodos en la red, como Charlie, utilizarán felizmente el nuevo canal. ### Referencias - [BOLT2 Protocolo de pares](https://github.com/lightning/bolts/blob/master/02-peer-protocol.md) - [Apertura y anuncio de un canal pre-taproot](https://ellemouton.com/posts/open_channel_pre_taproot/) por nostr:nprofile1qqswrt9pnxatlplu49h6meld8svmwqt87wwvk256rqk07n6eu4qeh5gpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0dszpfjtz
@ 599f67f7:21fb3ea9
2024-12-31 14:56:46En este capítulo, revisaremos el proceso de apertura y anuncio de un canal pre-taproot, añadiendo algunos detalles técnicos. En los próximos capítulos, aplicaremos el mismo tratamiento a la operación normal y cierre de un canal. Estos capítulos nos darán la base sobre la cual construir a medida que aprendamos sobre canales taproot en el futuro. Asumiremos que ya estás familiarizado con la estructura de una transacción de compromiso y entiendes por qué son asimétricas. Si necesitas un recordatorio, ¡por favor revisa los capítulos anteriores! ### Contenidos - [El objetivo final](#el-objetivo-final) - [Apertura del canal](#apertura-del-canal) - [El mensaje open_channel](#el-mensaje-open_channel) - [El mensaje accept_channel](#el-mensaje-accept_channel) - [El mensaje funding_created](#el-mensaje-funding_created) - [El mensaje funding_signed](#el-mensaje-funding_signed) - [El mensaje channel_ready](#el-mensaje-channel_ready) - [Anunciando el canal](#anunciando-el-canal) - [Verificando el canal](#verificando-el-canal) ### El objetivo final Establezcamos qué es lo que nuestros viejos amigos, Alice y Bob, están tratando de lograr. Alice y Bob son nodos de la Red Lightning. Alice es conocida en la red por su *ID de nodo*, o la clave pública utilizada para identificar su nodo, esta es `alice_node_id`. Del mismo modo, el ID de nodo de Bob es `bob_node_id`. Sus dos principales objetivos son: 1. Quieren abrir un canal entre ellos de manera sin confianza. 2. Quieren poder publicitar su nuevo canal para que el resto de la red pueda usarlo para el enrutamiento. ### Apertura del Canal Primero lo primero: a lo largo de este capítulo, utilizaremos diagramas y colores para ilustrar el proceso de apertura del canal. Aquí está la guía de código de colores: - Un fondo *blanco* significa que el campo de la transacción aún no se conoce. - Un campo *coloreado* significa que el valor del campo es conocido. - *Verde* indica las claves públicas de Alice. - *Azul* indica las claves públicas de Bob. Un canal se abre una vez que ambas partes tienen la capacidad de firmar completamente sus respectivas transacciones de compromiso y una vez que la transacción de financiación está en la cadena. Tres transacciones están en juego para la apertura de un canal. La primera es la transacción de financiación, que necesita ser confirmada en la cadena. Las otras dos son las transacciones de compromiso mantenidas por Alice y Bob que describen el estado inicial del canal. En este momento, aún no sabemos nada sobre los parámetros del canal, por lo que todos los campos tienen un fondo blanco:    #### El mensaje open_channel El primer paso del proceso es que Alice decida que quiere abrir un canal a Bob, es decir, ella se convertirá en la financiadora del canal (y Bob será el financiado). Supongamos que Alice decide que quiere abrir un canal de 1 BTC a Bob y darle inmediatamente a Bob la mitad de la capacidad del canal (0.5 BTC). Alice ahora preparará un mensaje `open_channel` que enviará a Bob. Como referencia, en la tabla a continuación puedes ver los parámetros relevantes. | Nombre del Campo | Descripción del Campo | |___|___| | chain_hash | La blockchain en la que abrir el canal. | | temp_chan_ID | Identificar el canal antes de que se conozca el outpoint de la transacción de financiación. | | funding_sats | La cantidad de salida de la transacción de financiación, es decir, la capacidad del canal. | | push_msat | La cantidad que el financiador envía incondicionalmente al financiado en el momento de la apertura. | | dust_limit_sats | Umbral por debajo del cual no se deben generar salidas. | | feerate_per_kw | La tasa de tarifa inicial a utilizar para las transacciones de compromiso. Puede actualizarse más tarde a través de `update_fee`. | | revocation_basepoint | Utilizado, junto con el first_per_commitment_point del nodo remoto, para derivar la primera clave pública de revocación que se utilizará en la transacción de compromiso de Bob. | | payment_basepoint | Utilizado, junto con el first_per_commitment_point, para derivar la primera clave pública de pago - la clave pública to_remote en la transacción de compromiso de Bob. | | delayed_payment_basepoint | Utilizado, junto con el first_per_commitment_point, para derivar la primera clave pública retrasada - la clave pública local_delayed en la transacción de compromiso de Alice. | | first_per_commitment_point | El primer punto a utilizar junto con los puntos base anteriores (excluyendo el revocation_basepoint) para derivar las claves públicas correspondientes. | | channel_flags | La única bandera actualmente definida es la bandera "announce_channel" que determina si el canal debe ser anunciado a la red o no. | | tlv: channel_type | Para que se pueda determinar la estructura de la transacción de compromiso. | Ahora llenemos los valores de Alice para estos campos:  Alice envía este mensaje a Bob. Dado que Alice ha decidido el tipo de canal que quiere abrir (legado en lugar de anclajes, taproot, etc.) así como la capacidad del canal, ya puede armar una parte bastante grande de la transacción de financiación:  Alice ya puede elegir algunos de sus UTXOs para ser entradas a la transacción de financiación, ya que conoce la capacidad del canal que quiere abrir. Sin embargo, aún no sabe qué clave pública Bob querría usar para el canal, por lo que no puede finalizar la salida de financiación del canal todavía, y por lo tanto no puede producir firmas para las entradas. Como Alice ha decidido el tipo de canal (y por lo tanto la estructura de la transacción de compromiso), también puede comenzar a ensamblar las piezas de las transacciones de compromiso. Si asumimos que Bob está feliz con esta propuesta de apertura de canal de Alice, él también puede comenzar a armar las piezas utilizando la información en el mensaje `open_channel`. Recuerda que ambos pares necesitan construir sus propias transacciones de compromiso y ambos necesitarán firmar las transacciones de su par. Veamos qué piezas ya pueden llenar:  La transacción de compromiso de Alice tiene la estructura de una transacción de canal por defecto, no anclada. Todas sus claves públicas han sido llenadas (`alice_local_delayed_pk_1` se deriva utilizando su `delayed_payment_basepoint` y su `first_commitment_point`). Dado que aún no ha recibido ningún mensaje de Bob, no puede llenar ninguna de sus claves públicas. Y dado que la transacción de financiación aún está incompleta, tampoco puede conocer el TXID para apuntar la entrada de esta transacción de compromiso. La transacción de compromiso de Bob se ve un poco más completa:  Al igual que Alice, él tampoco puede llenar aún el TXID de la transacción de financiación, pero puede llenar algunas otras cosas: - Los valores `alice_pubkey_1`, `alice_to_self_delay`, `push_amt` y `local_amt` se toman tal cual del mensaje `open_channel`. - `alice_payment_key_1` se deriva utilizando el `payment_basepoint` de Alice y el `first_commitment_point`. - `revoke_pubkey_1b` se deriva utilizando el `revocation_basepoint` de Alice y el `first_per_commitment point` de Bob (Alice no puede derivar este punto aún ya que no ha recibido el `first_per_commitment_point` de Bob). ¡Genial! Es hora de que Bob indique a Alice su aceptación de la propuesta enviando el siguiente mensaje: `accept_channel`. #### El mensaje accept_channel El mensaje comparte muchos de los campos del `open_channel`. Aquí está el mensaje que Bob preparará.  Cuando Alice recibe este mensaje de Bob, ahora puede completar la salida de la transacción de financiación y puede crear las firmas para las entradas. Dado que todo está ahora lleno, el TXID de la transacción de financiación también es conocido.  Alice ahora puede llenar más de su propia transacción de compromiso: - ahora puede usar los valores enviados por Bob para llenar `bob_pubkey_1`, `bob_payment_key_1`, `bob_to_self_delay` y `revoke_pubkey_1a` - dado que el TXID para la transacción de financiación ahora es conocido, también puede completar la entrada Ahora sabe todo lo que necesita saber para firmar esta transacción ella misma _pero_ recuerda que aún le falta la firma de Bob para esta transacción.  La transacción de compromiso de Bob sigue siendo la misma que antes, ya que no aprendió nueva información después de enviar el mensaje `accept_channel`. Ahora que Alice conoce el TXID de la transacción de financiación, también puede completar su vista de la transacción de compromiso de Bob y así puede producir su firma para la transacción de él. Ella enviará el siguiente mensaje a Bob: `funding_created`. #### El mensaje funding_created Alice ahora utilizará el mensaje `funding_created` para decirle a Bob el TXID y el índice de la transacción de financiación junto con su firma para la transacción de compromiso de Bob. Ten en cuenta que Bob aún no podrá transmitir su transacción de compromiso porque la transacción de financiación no ha sido transmitida aún.  Una vez que Bob reciba el mensaje `funding_created`, podrá completar el resto de su transacción de compromiso:  #### El mensaje funding_signed Alice no transmitirá la transacción de financiación hasta que tenga una firma válida de Bob para su transacción de compromiso, entra `funding_signed`:  Ten en cuenta que este es el primer mensaje que utiliza el ID de canal real en lugar del temporal. Esta fue la última pieza del rompecabezas para Alice. Ahora tiene toda la información que necesita para poder firmar su transacción de compromiso si alguna vez es necesario.  #### El mensaje channel_ready Alice ahora puede transmitir de manera segura la transacción de financiación. Tanto Alice como Bob estarán atentos a la cadena para la confirmación de la transacción de financiación. Una vez que haya alcanzado la `minimum_depth` especificada por Bob en su mensaje `accept_channel`, ambos lados intercambiarán el mensaje `channel_ready`. Este mensaje cumple dos propósitos. Primero, sirve como una señal para el par para indicar que el canal está listo para usar (y pueden comenzar el proceso de anuncio del canal si abrieron un canal público y anunciado). En segundo lugar, también le dice al par que envíe su `second_per_commitment_point` que deben usar en su segunda transacción de compromiso.  ### Anunciando el canal Esta parte es bastante fácil. Alice y Bob solo necesitan construir un mensaje, `channel_announcement`, juntos y una vez que esté completo, pueden transmitirlo a la red. Otros nodos utilizarán este mensaje para probar algunas cosas: - Que la transacción de financiación del canal es en realidad un UTXO existente y no gastado con un número aceptable de confirmaciones. - Que la salida de la transacción de financiación en realidad se parece a una transacción de financiación de canal Lightning. - Que el canal es en realidad propiedad de las claves que Alice y Bob dicen que utilizaron para construir el canal. - Que Alice y Bob están de acuerdo en el mensaje que se está transmitiendo. Una versión parcial del mensaje `channel_announcement` se ve así:  `h` es el hash de todos los datos que serán cubiertos por las firmas. Para completar este mensaje, tanto Alice como Bob necesitan calcular una firma sobre `h` utilizando las claves privadas asociadas con sus IDs de nodo y las claves públicas que utilizaron en la transacción de financiación. Luego ambos intercambian el mensaje `announcement_signatures` para comunicarse estas firmas.  Ahora ambos nodos pueden armar el mensaje completo `channel_announcement`:  ### Verificando el canal Supongamos que Charlie es un nodo que recibió este mensaje. Vamos a repasar los pasos que seguirá para verificar el nuevo canal que Alice y Bob han anunciado: 1. Primero, Charlie utilizará el `short_channel_id` incluido en el mensaje para asegurarse de que la transacción de financiación realmente existe en la cadena, que tiene un número suficiente de confirmaciones y que de hecho está no gastada. 2. Luego, Charlie verificará que la salida no gastada realmente se parece a un canal Lightning propiedad de `alice_pubkey_1` y `bob_pubkey_1`. Hará esto utilizando las claves públicas publicitadas para reconstruir el P2WSH y asegurarse de que es el mismo que se encuentra en la cadena. 3. Ahora, Charlie querrá verificar que los nodos que poseen las claves públicas utilizadas en la salida de financiación corresponden de hecho a los nodos que poseen las claves públicas de ID de nodo. Puede hacer esto verificando las firmas `alice_pubkey_1_sig` y `bob_pubkey_1_sig`. Si estas firmas son válidas, entonces está claro que los propietarios de `alice_pubkey_1` y `bob_pubkey_1` están de acuerdo en ser asociados con `alice_node_ID` y `bob_node_ID` ya que el mensaje firmado contiene estas claves públicas. 4. Finalmente, Charlie también querrá asegurarse de que los propietarios de las claves públicas de ID de nodo están de acuerdo en ser asociados con el nuevo canal. Puede hacer esto verificando las firmas `alice_node_ID_sig` y `bob_node_ID_sig`. Si estas firmas son válidas, entonces está claro que los propietarios de `alice_node_ID` y `bob_node_ID` están de acuerdo en ser asociados con `alice_pubkey_1` y `bob_pubkey_1` ya que el mensaje firmado contiene estas claves públicas. ¡Alice y Bob han terminado! Su canal ahora está abierto y otros nodos en la red, como Charlie, utilizarán felizmente el nuevo canal. ### Referencias - [BOLT2 Protocolo de pares](https://github.com/lightning/bolts/blob/master/02-peer-protocol.md) - [Apertura y anuncio de un canal pre-taproot](https://ellemouton.com/posts/open_channel_pre_taproot/) por nostr:nprofile1qqswrt9pnxatlplu49h6meld8svmwqt87wwvk256rqk07n6eu4qeh5gpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0dszpfjtz @ 599f67f7:21fb3ea9
2024-12-31 14:52:21En el capítulo anterior tuvimos una visión simplificada de los HTLC, con suerte eso te dio una comprensión del mecanismo general y los incentivos en juego. En este capítulo profundizaremos en cómo se ven los HTLC en más detalle y cómo encajan en las transacciones de compromiso. De nostr:naddr1qqxnzdenxgerzve5x5enyv3sqyg8wumn8ghj7mn0wd68ytnhd9hx2q3qtx0k0a7lw62vvqax6p3ku90tccgdka7ul4radews2wrdsg0m865sxpqqqp65wc4f8xj aprendimos sobre las transacciones de compromiso. Aquí hay un breve resumen: Las transacciones de compromiso son asimétricas: Alice y Bob (participantes de un canal) cada uno tiene sus propias transacciones de compromiso. La transacción de compromiso que cada participante tiene se ve ligeramente diferente a la de su par en que cualquier salida que vaya al nodo local debe estar gravada por un bloqueo de tiempo relativo de `to_self_delay`. Esto es para darle a la otra parte la oportunidad de gastar a lo largo del camino de revocación de la salida si lo necesita. Con esto en mente, continuemos con el ejemplo del capítulo anterior donde Alice está enviando 2 BTC a un destinatario usando su canal con Bob como el primer salto en la ruta. Recuerda que a Alice se le ha dado un hash `H` al que necesita pagar. En este ejemplo, Alice es la *ofertante* de HTLC y Bob es el *receptor* de HTLC. ### Alice - Ofertante de HTLC Enfoquémonos en cómo Alice construirá su transacción de compromiso para incluir ahora el HTLC. La transacción de compromiso tendrá tres salidas: - Una salida de 5 BTC a Bob, gastable inmediatamente - Una salida de 3 BTC con dos posibles caminos de gasto: 1. Una gastable por Alice después de un `to_self_delay` 2. Una gastable inmediatamente por Bob si tiene la clave de revocación requerida (ver nostr:naddr1qqxnzdenxgerzve5x5enyv3sqyg8wumn8ghj7mn0wd68ytnhd9hx2q3qtx0k0a7lw62vvqax6p3ku90tccgdka7ul4radews2wrdsg0m865sxpqqqp65wc4f8xj y nostr:naddr1qqxnzdenxgerzvek8qenyvekqyxhwumn8ghj7mn0wvhxcmmvqgs9n8m87l0hd9xxqwndqcmwzh4uvyxmwlw0637kuhg98pkcy8ana2grqsqqqa282rd072 si necesitas un recordatorio) - Una salida de 2 BTC con... hmm, pensemos juntos sobre lo que necesita suceder aquí.  Esta salida es donde debe suceder la magia del HTLC. Necesitamos los siguientes caminos de gasto en esta salida: - Debe ser gastable por Bob si tiene la preimagen de `H`; este es el camino bloqueado por hash - O gastable por Alice después de `cltv_expiry` - O gastable por Bob inmediatamente si tiene la clave de revocación PERO recuerda que las salidas de Alice hacia sí misma siempre deben tener un bloqueo de tiempo relativo de `to_self_delay` incluso después de `cltv_expiry`. Así que actualicemos los caminos de gasto con esta información: - Debe ser gastable por Bob si tiene la preimagen de `H`; este es el camino bloqueado por hash - O gastable por Alice después de `cltv_expiry` *Y después del retraso relativo `to_self_delay`* - O gastable por Bob inmediatamente si tiene la clave de revocación Todavía hay un problema: gravar la salida a Alice con ambos bloqueos de tiempo podría, en el peor de los casos, extender el tiempo de espera del HTLC por `to_self_delay`. Es decir, Bob podría tener un bloque adicional de `to_self_delay` para barrer la salida bloqueada por hash a pesar de que el HTLC esté técnicamente expirado. Así que en lugar de bloquear esta salida con ambas condiciones de bloqueo de tiempo, se bloquea solo por el `cltv_expiry`. Luego, en lugar de enviar fondos a Alice directamente, los fondos se envían a una transacción de tiempo de espera de HTLC separada (firmada por Alice y Bob) y esta transacción de tiempo de espera separada impone el `to_self_delay`. Esto permite a Alice bloquear el hecho de que el HTLC ha expirado y evita que Bob reclame la salida bloqueada por hash, todo mientras asegura que Alice solo pueda obtener sus fondos después de `to_self_delay` y, por lo tanto, aún permite a Bob gastar desde el camino de revocación (de la transacción de tiempo de espera de HTLC) si es necesario. La forma final de los caminos de gasto de la salida de HTLC de la transacción de compromiso se ve como sigue: - Un camino de gasto a Bob si tiene la preimagen de `H` (camino bloqueado por hash) - Un camino de gasto a Bob si tiene la clave de revocación - Un camino de gasto a una transacción de tiempo de espera de HTLC de segunda etapa La transacción de tiempo de espera de HTLC se construye así: - La transacción en sí está bloqueada por tiempo con `nLocktime` establecido en `cltv_expiry`. Esto significa que el camino de gasto en la transacción de compromiso original que envía a esta transacción de tiempo de espera de HTLC está efectivamente retrasado por `cltv_expiry` - La transacción tiene una salida con dos posibles caminos de gasto: 1. Uno a Alice después de `to_self_delay` 2. Uno a Bob si puede proporcionar la clave de revocación  El script para la salida de HTLC de la transacción de compromiso de Alice (la ofertante de HTLC) se ve así: ``` # A nodo remoto con clave de revocación OP_DUP OP_HASH160 <RIPEMD160(SHA256(revocationpubkey))> OP_EQUAL OP_IF OP_CHECKSIG OP_ELSE <remote_htlcpubkey> OP_SWAP OP_SIZE 32 OP_EQUAL OP_NOTIF # A nodo local a través de la transacción de tiempo de espera de HTLC (bloqueada por tiempo). OP_DROP 2 OP_SWAP <local_htlcpubkey> 2 OP_CHECKMULTISIG OP_ELSE # A nodo remoto con preimagen. OP_HASH160 <RIPEMD160(payment_hash)> OP_EQUALVERIFY OP_CHECKSIG OP_ENDIF OP_ENDIF ``` Puedes ver que el primer camino es el camino de revocación, el segundo es el camino a la transacción de tiempo de espera de HTLC (el camino bloqueado por tiempo) y el tercero es el camino bloqueado por hash. El script de salida de la transacción de tiempo de espera de HTLC se ve así: ``` OP_IF # Transacción de penalización <revocationpubkey> OP_ELSE `to_self_delay` OP_CHECKSEQUENCEVERIFY OP_DROP <local_delayedpubkey> OP_ENDIF OP_CHECKSIG ``` ### Bob - Receptor de HTLC Ahora enfoquémonos en cómo Bob (el receptor de HTLC) construirá su transacción de compromiso para incluir el HTLC. La transacción de compromiso tendrá tres salidas: - Una salida de 3 BTC a Alice gastable inmediatamente - Una salida de 5 BTC con dos posibles caminos de gasto: 1. Una gastable por Bob después de un `to_self_delay` 2. Una gastable inmediatamente por Alice si tiene la clave de revocación requerida - Una salida de 2 BTC que es un poco más complicada; profundicemos.  Pensemos en qué caminos de gasto debería tener esta salida: - Un camino de gasto que Bob puede reclamar si tiene la preimagen de `H` (camino bloqueado por hash) pero dado que es una salida hacia sí mismo, necesita tener un `to_self_delay` - Un camino de gasto que Alice puede gastar inmediatamente si tiene la clave de revocación necesaria - Un camino de gasto que Alice puede gastar después de `ctlv_expiry` (camino bloqueado por tiempo) Nuevamente, tener dos bloqueos de tiempo diferentes en el mismo script plantea un problema: si Bob conoce la preimagen pero tiene que esperar `to_self_delay` bloques para gastar desde el camino bloqueado por hash, entonces hay una posibilidad de que este `to_self_delay` sea más largo que el `cltv_expiry` que Alice debe esperar para reclamar el camino bloqueado por tiempo. Esto significaría que Alice podría potencialmente gastar a lo largo del camino bloqueado por tiempo a pesar de que Bob tiene la preimagen. Por lo tanto, Bob necesita una forma de bloquear el hecho de que se usará el camino bloqueado por hash mientras aún retrasa su redención de los fondos por `to_self_delay`. Así que se utiliza una transacción de éxito de HTLC separada para esto, permitiendo a Bob gastar desde el camino bloqueado por hash a esta transacción de éxito de HTLC, que luego impondrá por separado la condición de `to_self_delay`. La forma final de los caminos de gasto de la salida de HTLC de la transacción de compromiso se ve como sigue: - Un camino de gasto a Alice si tiene la clave de revocación (camino de revocación) - Un camino de gasto a Alice después de `cltv_expiry` (camino bloqueado por tiempo) - Un camino de gasto a la transacción de éxito de HTLC si Bob puede revelar la preimagen de `H` (camino bloqueado por hash) La transacción de éxito de HTLC se ve así: - La transacción *no* está bloqueada por tiempo (a diferencia del caso de Alice) - La transacción tiene una salida con dos posibles caminos de gasto: 1. Uno a Bob después de `to_self_delay` 2. Uno a Alice si puede proporcionar la clave de revocación  El script para la salida de HTLC de la transacción de compromiso de Bob (el receptor de HTLC) se ve así: ``` # A nodo remoto con clave de revocación OP_DUP OP_HASH160 <RIPEMD160(SHA256(revocationpubkey))> OP_EQUAL OP_IF OP_CHECKSIG OP_ELSE <remote_htlcpubkey> OP_SWAP OP_SIZE 32 OP_EQUAL OP_IF # A nodo local a través de la transacción de éxito de HTLC. OP_HASH160 <RIPEMD160(payment_hash)> OP_EQUALVERIFY 2 OP_SWAP <local_htlcpubkey> 2 OP_CHECKMULTISIG OP_ELSE # A nodo remoto después del tiempo de espera. OP_DROP <cltv_expiry> OP_CHECKLOCKTIMEVERIFY OP_DROP OP_CHECKSIG OP_ENDIF OP_ENDIF ``` Puedes ver en el script anterior que el primer camino es el camino de revocación, el segundo es el camino a la transacción de éxito de HTLC (y también es el camino bloqueado por hash) y el tercero es el camino de gasto bloqueado por tiempo. El script de salida de la transacción de éxito de HTLC se ve así: ``` OP_IF # Transacción de penalización <revocationpubkey> OP_ELSE `to_self_delay` OP_CHECKSEQUENCEVERIFY OP_DROP <local_delayedpubkey> OP_ENDIF OP_CHECKSIG ``` ### La imagen completa  ### Revisión - La salida de HTLC en una transacción de compromiso difiere dependiendo de si el constructor de la transacción es el **ofertante de HTLC** o el **receptor de HTLC** - La salida de HTLC necesita estar gravada por dos bloqueos de tiempo, pero tener ambos bloqueos de tiempo en el script puede causar problemas - La solución es barrer la salida a una segunda etapa de **transacción de tiempo de espera de HTLC** o **transacción de éxito de HTLC** e imponer el `to_self_delay` en esta transacción ### Referencias - [BOLT3: Transacciones](https://github.com/lightning/bolts/blob/master/03-transactions.md#offered-htlc-outputs) - [Cosas de LN Parte 5: Profundización en HTLC](https://ellemouton.com/posts/htlc-deep-dive/) por nostr:nprofile1qqswrt9pnxatlplu49h6meld8svmwqt87wwvk256rqk07n6eu4qeh5gpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0dszpfjtz
@ 599f67f7:21fb3ea9
2024-12-31 14:52:21En el capítulo anterior tuvimos una visión simplificada de los HTLC, con suerte eso te dio una comprensión del mecanismo general y los incentivos en juego. En este capítulo profundizaremos en cómo se ven los HTLC en más detalle y cómo encajan en las transacciones de compromiso. De nostr:naddr1qqxnzdenxgerzve5x5enyv3sqyg8wumn8ghj7mn0wd68ytnhd9hx2q3qtx0k0a7lw62vvqax6p3ku90tccgdka7ul4radews2wrdsg0m865sxpqqqp65wc4f8xj aprendimos sobre las transacciones de compromiso. Aquí hay un breve resumen: Las transacciones de compromiso son asimétricas: Alice y Bob (participantes de un canal) cada uno tiene sus propias transacciones de compromiso. La transacción de compromiso que cada participante tiene se ve ligeramente diferente a la de su par en que cualquier salida que vaya al nodo local debe estar gravada por un bloqueo de tiempo relativo de `to_self_delay`. Esto es para darle a la otra parte la oportunidad de gastar a lo largo del camino de revocación de la salida si lo necesita. Con esto en mente, continuemos con el ejemplo del capítulo anterior donde Alice está enviando 2 BTC a un destinatario usando su canal con Bob como el primer salto en la ruta. Recuerda que a Alice se le ha dado un hash `H` al que necesita pagar. En este ejemplo, Alice es la *ofertante* de HTLC y Bob es el *receptor* de HTLC. ### Alice - Ofertante de HTLC Enfoquémonos en cómo Alice construirá su transacción de compromiso para incluir ahora el HTLC. La transacción de compromiso tendrá tres salidas: - Una salida de 5 BTC a Bob, gastable inmediatamente - Una salida de 3 BTC con dos posibles caminos de gasto: 1. Una gastable por Alice después de un `to_self_delay` 2. Una gastable inmediatamente por Bob si tiene la clave de revocación requerida (ver nostr:naddr1qqxnzdenxgerzve5x5enyv3sqyg8wumn8ghj7mn0wd68ytnhd9hx2q3qtx0k0a7lw62vvqax6p3ku90tccgdka7ul4radews2wrdsg0m865sxpqqqp65wc4f8xj y nostr:naddr1qqxnzdenxgerzvek8qenyvekqyxhwumn8ghj7mn0wvhxcmmvqgs9n8m87l0hd9xxqwndqcmwzh4uvyxmwlw0637kuhg98pkcy8ana2grqsqqqa282rd072 si necesitas un recordatorio) - Una salida de 2 BTC con... hmm, pensemos juntos sobre lo que necesita suceder aquí.  Esta salida es donde debe suceder la magia del HTLC. Necesitamos los siguientes caminos de gasto en esta salida: - Debe ser gastable por Bob si tiene la preimagen de `H`; este es el camino bloqueado por hash - O gastable por Alice después de `cltv_expiry` - O gastable por Bob inmediatamente si tiene la clave de revocación PERO recuerda que las salidas de Alice hacia sí misma siempre deben tener un bloqueo de tiempo relativo de `to_self_delay` incluso después de `cltv_expiry`. Así que actualicemos los caminos de gasto con esta información: - Debe ser gastable por Bob si tiene la preimagen de `H`; este es el camino bloqueado por hash - O gastable por Alice después de `cltv_expiry` *Y después del retraso relativo `to_self_delay`* - O gastable por Bob inmediatamente si tiene la clave de revocación Todavía hay un problema: gravar la salida a Alice con ambos bloqueos de tiempo podría, en el peor de los casos, extender el tiempo de espera del HTLC por `to_self_delay`. Es decir, Bob podría tener un bloque adicional de `to_self_delay` para barrer la salida bloqueada por hash a pesar de que el HTLC esté técnicamente expirado. Así que en lugar de bloquear esta salida con ambas condiciones de bloqueo de tiempo, se bloquea solo por el `cltv_expiry`. Luego, en lugar de enviar fondos a Alice directamente, los fondos se envían a una transacción de tiempo de espera de HTLC separada (firmada por Alice y Bob) y esta transacción de tiempo de espera separada impone el `to_self_delay`. Esto permite a Alice bloquear el hecho de que el HTLC ha expirado y evita que Bob reclame la salida bloqueada por hash, todo mientras asegura que Alice solo pueda obtener sus fondos después de `to_self_delay` y, por lo tanto, aún permite a Bob gastar desde el camino de revocación (de la transacción de tiempo de espera de HTLC) si es necesario. La forma final de los caminos de gasto de la salida de HTLC de la transacción de compromiso se ve como sigue: - Un camino de gasto a Bob si tiene la preimagen de `H` (camino bloqueado por hash) - Un camino de gasto a Bob si tiene la clave de revocación - Un camino de gasto a una transacción de tiempo de espera de HTLC de segunda etapa La transacción de tiempo de espera de HTLC se construye así: - La transacción en sí está bloqueada por tiempo con `nLocktime` establecido en `cltv_expiry`. Esto significa que el camino de gasto en la transacción de compromiso original que envía a esta transacción de tiempo de espera de HTLC está efectivamente retrasado por `cltv_expiry` - La transacción tiene una salida con dos posibles caminos de gasto: 1. Uno a Alice después de `to_self_delay` 2. Uno a Bob si puede proporcionar la clave de revocación  El script para la salida de HTLC de la transacción de compromiso de Alice (la ofertante de HTLC) se ve así: ``` # A nodo remoto con clave de revocación OP_DUP OP_HASH160 <RIPEMD160(SHA256(revocationpubkey))> OP_EQUAL OP_IF OP_CHECKSIG OP_ELSE <remote_htlcpubkey> OP_SWAP OP_SIZE 32 OP_EQUAL OP_NOTIF # A nodo local a través de la transacción de tiempo de espera de HTLC (bloqueada por tiempo). OP_DROP 2 OP_SWAP <local_htlcpubkey> 2 OP_CHECKMULTISIG OP_ELSE # A nodo remoto con preimagen. OP_HASH160 <RIPEMD160(payment_hash)> OP_EQUALVERIFY OP_CHECKSIG OP_ENDIF OP_ENDIF ``` Puedes ver que el primer camino es el camino de revocación, el segundo es el camino a la transacción de tiempo de espera de HTLC (el camino bloqueado por tiempo) y el tercero es el camino bloqueado por hash. El script de salida de la transacción de tiempo de espera de HTLC se ve así: ``` OP_IF # Transacción de penalización <revocationpubkey> OP_ELSE `to_self_delay` OP_CHECKSEQUENCEVERIFY OP_DROP <local_delayedpubkey> OP_ENDIF OP_CHECKSIG ``` ### Bob - Receptor de HTLC Ahora enfoquémonos en cómo Bob (el receptor de HTLC) construirá su transacción de compromiso para incluir el HTLC. La transacción de compromiso tendrá tres salidas: - Una salida de 3 BTC a Alice gastable inmediatamente - Una salida de 5 BTC con dos posibles caminos de gasto: 1. Una gastable por Bob después de un `to_self_delay` 2. Una gastable inmediatamente por Alice si tiene la clave de revocación requerida - Una salida de 2 BTC que es un poco más complicada; profundicemos.  Pensemos en qué caminos de gasto debería tener esta salida: - Un camino de gasto que Bob puede reclamar si tiene la preimagen de `H` (camino bloqueado por hash) pero dado que es una salida hacia sí mismo, necesita tener un `to_self_delay` - Un camino de gasto que Alice puede gastar inmediatamente si tiene la clave de revocación necesaria - Un camino de gasto que Alice puede gastar después de `ctlv_expiry` (camino bloqueado por tiempo) Nuevamente, tener dos bloqueos de tiempo diferentes en el mismo script plantea un problema: si Bob conoce la preimagen pero tiene que esperar `to_self_delay` bloques para gastar desde el camino bloqueado por hash, entonces hay una posibilidad de que este `to_self_delay` sea más largo que el `cltv_expiry` que Alice debe esperar para reclamar el camino bloqueado por tiempo. Esto significaría que Alice podría potencialmente gastar a lo largo del camino bloqueado por tiempo a pesar de que Bob tiene la preimagen. Por lo tanto, Bob necesita una forma de bloquear el hecho de que se usará el camino bloqueado por hash mientras aún retrasa su redención de los fondos por `to_self_delay`. Así que se utiliza una transacción de éxito de HTLC separada para esto, permitiendo a Bob gastar desde el camino bloqueado por hash a esta transacción de éxito de HTLC, que luego impondrá por separado la condición de `to_self_delay`. La forma final de los caminos de gasto de la salida de HTLC de la transacción de compromiso se ve como sigue: - Un camino de gasto a Alice si tiene la clave de revocación (camino de revocación) - Un camino de gasto a Alice después de `cltv_expiry` (camino bloqueado por tiempo) - Un camino de gasto a la transacción de éxito de HTLC si Bob puede revelar la preimagen de `H` (camino bloqueado por hash) La transacción de éxito de HTLC se ve así: - La transacción *no* está bloqueada por tiempo (a diferencia del caso de Alice) - La transacción tiene una salida con dos posibles caminos de gasto: 1. Uno a Bob después de `to_self_delay` 2. Uno a Alice si puede proporcionar la clave de revocación  El script para la salida de HTLC de la transacción de compromiso de Bob (el receptor de HTLC) se ve así: ``` # A nodo remoto con clave de revocación OP_DUP OP_HASH160 <RIPEMD160(SHA256(revocationpubkey))> OP_EQUAL OP_IF OP_CHECKSIG OP_ELSE <remote_htlcpubkey> OP_SWAP OP_SIZE 32 OP_EQUAL OP_IF # A nodo local a través de la transacción de éxito de HTLC. OP_HASH160 <RIPEMD160(payment_hash)> OP_EQUALVERIFY 2 OP_SWAP <local_htlcpubkey> 2 OP_CHECKMULTISIG OP_ELSE # A nodo remoto después del tiempo de espera. OP_DROP <cltv_expiry> OP_CHECKLOCKTIMEVERIFY OP_DROP OP_CHECKSIG OP_ENDIF OP_ENDIF ``` Puedes ver en el script anterior que el primer camino es el camino de revocación, el segundo es el camino a la transacción de éxito de HTLC (y también es el camino bloqueado por hash) y el tercero es el camino de gasto bloqueado por tiempo. El script de salida de la transacción de éxito de HTLC se ve así: ``` OP_IF # Transacción de penalización <revocationpubkey> OP_ELSE `to_self_delay` OP_CHECKSEQUENCEVERIFY OP_DROP <local_delayedpubkey> OP_ENDIF OP_CHECKSIG ``` ### La imagen completa  ### Revisión - La salida de HTLC en una transacción de compromiso difiere dependiendo de si el constructor de la transacción es el **ofertante de HTLC** o el **receptor de HTLC** - La salida de HTLC necesita estar gravada por dos bloqueos de tiempo, pero tener ambos bloqueos de tiempo en el script puede causar problemas - La solución es barrer la salida a una segunda etapa de **transacción de tiempo de espera de HTLC** o **transacción de éxito de HTLC** e imponer el `to_self_delay` en esta transacción ### Referencias - [BOLT3: Transacciones](https://github.com/lightning/bolts/blob/master/03-transactions.md#offered-htlc-outputs) - [Cosas de LN Parte 5: Profundización en HTLC](https://ellemouton.com/posts/htlc-deep-dive/) por nostr:nprofile1qqswrt9pnxatlplu49h6meld8svmwqt87wwvk256rqk07n6eu4qeh5gpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0dszpfjtz @ ee11a5df:b76c4e49
2024-12-24 18:49:05# China ## I might be wrong, but this is how I see it This is a post within a series I am going to call "I might be wrong, but this is how I see it" I have repeatedly found that my understanding of China is quite different from that of many libertarian-minded Americans. And so I make this post to explain how I see it. Maybe you will learn something. Maybe I will learn something. It seems to me that many American's see America as a shining beacon of freedom with a few small problems, and China is an evil communist country spreading communism everywhere. From my perspective, America *was* a shining beacon of freedom that has fallen to being typical in most ways, and which is now acting as a falling empire, and China *was* communist for about a decade, but turned and ran away from that as fast as they could (while not admitting it) and the result is that the US and China are not much different anymore when it comes to free markets. Except they are very different in some other respects. ## China has a big problem China has a big problem. But it is not the communism problem that most Westerners diagnose. I argue that China is no longer communist, it is only communist in name. And that while it is not a beacon of free market principles, it is nearly as free market now as Western nations like Germany and New Zealand are (being somewhat socialist themselves). No, China's real problem is authoritarian one-party rule. And that core problem causes all of the other problems, including its human rights abuses. ## Communism and Socialism Communism and Socialism are bad ideas. I don't want to argue it right here, but most readers will already understand this. The last thing I intend to do with this post is to bolster or defend those bad ideas. If you dear reader hold a candle for socialism, let me know and I can help you extinguish it with a future "I might be wrong, but this is how I see it" installment. Communism is the idea of structuring a society around common ownership of the means of production, distribution, and exchange, and the idea of allocating goods and services based on need. It eliminates the concept of private property, of social classes, ultimately of money and finally of the state itself. Back under Mao in 1958-1962 (The Great Leap Forward), China tried this (in part). Some 50+ million people died. It was an abject failure. But due to China's real problem (authoritarianism, even worship of their leaders), the leading classes never admitted this. And even today they continue to use the word "Communist" for things that aren't communist at all, as a way to save face, and also in opposition to the United States of America and Europe. Authorities are not eager to admit their faults. But this is not just a Chinese fault, it is a fault in human nature that affects all countries. The USA still refuses to admit they assassinated their own president JFK. They do not admit they bombed the Nord Stream pipeline. China defines "socialism with Chinese characteristics" to mean "the leadership of the Communist Party of China". So they still keep the words socialism and communism, but they long ago dropped the meanings of those words. I'm not sure if this is a political ploy against us in the West or not. ### China's Marketplace Today Today China exhibits very few of the properties of communism. They have some common ownership and state enterprises, but not much differently than Western countries (New Zealand owns Air New Zealand and Kiwibank and Kiwirail, etc). And there are private enterprises all over China. They compete and some succeed and some fail. You might hear about a real-estate bank collapsing. China has private property. They have mostly free markets. They have money, and the most definitely have social classes and a very strong state. None of that is inline with what communist thinkers want. Communist thinkers in China moan that China has turned away from communism. Deng Xiaoping who succeeded Mao and attempted to correct the massive mistake, did much when he said "to get rich is glorious." China achieved staggering rates of economic growth. 10% annually on average since 1977. Chinese economic reform started in 1979 and has continued through successive administrations (Deng, Jiang, Hu and now Xi). China is now the world's largest economy (by GDP in PPP terms) since 2016. I was first made aware of China's economic growth by Jim Rogers, an American commodities expert who travelled through China (and the rest of the world from 1990-1992) and in 2007 moved to Singapore where he ensured his daughters learned to speak Mandarin, because Jim knew where the economic growth was going to happen. Jim always spoke positively of China's economic prospects, and his view was so different from the "China is a nasty communist place" view that I had grown up with that my mind opened. How can anybody believe they are still a communist country? In what world does it make sense that communism can produce such a massively booming economy? It doesn't make sense because it is simply wrong. What *does* happen is that the CPC interferes. It lets the market do what markets do, but it interferes where it thinks oversight and regulation would produce a better result. Western nations interfere with their markets too. They have oversight and regulation. In fact some of China's planned reforms had to be put on hold by Xi due to Donald Trump's trade war with China. That's right, they were trying to be even more free market than America, but America's protectionism prodded Xi to keep control so he could fight back efficiently. Government oversight and regulation IMHO is mostly bad because it gets out of control, and there are no market forces to correct this. This gets even more extreme in a one-party system, so I can judge that China's oversight and regulation problems are very likely worse than those in Western nations (but I have no first hand experience or evidence). ## Why do you keep saying CPC? The Communist Party of China (CPC) is the ruling party in China. That is their official name. To call them the CCP is to concede to the idea that the British and Americans get to name everybody. I'm not sure who is right, since CPC or CCP is their "English" name (in Chinese it is 中国共产党 and Westernized it is Zhōngguó Gòngchǎndǎng). Nonetheless, I'll call them CPC because that is their wish. ## Social Credit System China moved from a planned economy to a market economy in stages. They didn't want any more sudden changes (can you blame them?). In the process, many institutions that have existed in the West for a long time didn't exist in China and they had to arise somehow. IMHO market forces would have brought these about in the private sector, but the one-party CP of China instead decided to create these. One of those institutions was a credit score system. In the West we have TransUnion and Equifax that maintain credit ratings on people, and we have S&P, Moody's and Fitch that maintain credit ratings on companies. The domain of these ratings is their financial credit-worthiness. So the People's Bank of China developed a credit information database for it's own needs. The government picked up on the idea and started moving towards a National Credit Management System. In 2004 it became an official goal to establish a credit system compatible with a modern market system. By 2006 banks were required to report on consumer creditworthiness. But unchecked one-party governmental power will often take a good idea (credit worthiness data shared among private parties) and systematize it and apply it top-down, creating a solution and a new problem at the same time. Nonetheless, originally it was about credit worthiness and also criminal convictions. That is no big scary thing that some right-wing American commentators will lead you to believe. In the US for example criminal records are public, so China's Social Credit System started out being no more over-reaching in scope than what Americans have lived under their entire lives, its only fault (a severe one) being centrally planned. And that remained the case up until about 2016 (in my estimation). But of course there is always scope creep. As it exists today, I have reason to believe that CPC officials and even A.I. use judgement calls to score someone on how moral that person has been! Of course that is not a good idea, and IMHO the problem stems from one-party rule, and authoritarian administration of ideas that should instead be handled by the private sector. ## Environmental, Social, and Governance ESG is a system that came out of a couple basic ideas. The first is that many two-party transactions actually have externalities. They don't just affect the two parties, they also affect everybody else. When you fly in an airplane, you increase the CO2 in the atmosphere that everybody has to pay for (eventually). You may dispute that example, but that is no doubt one of the motivations of ESG. But of course the recognition of this basic issue didn't lead all people towards market solutions (well it did, but those have been mostly messed up by others), but instead led many people towards ESG, which is a social credit scoring system which applies scores based on environmental and social side-effects of market transactions. This is not at all the same as China's social credit system, which I described above. I hope you can see the difference. In fact, China imported ESG from the West. Chinese companies, of their free will, in an attempt to court Western capital, achieve ESG goals for those Western investors. They have been playing this ESG game for 20 years just like the entire world has, because the West has imposed this faux-morality upon them. It isn't something China exported to us, it is something we exported to them. ## I think China has avoided Woke-ism My understanding of Chinese people, based on what I've heard many Chinese people say, is that China isn't affected by the Western woke-ism epidemic. They deride Western white woke people with the term "Baizuo". They have never sent an incompetent break dancer to the Olympics because of wok-ism. Competence is highly respected as is the competition to be the most competent, which (when augmented by a one-child policy which is no longer) has produced child prodigies like no other country has. ## What about predatory loans of the Belt and Road initiative? Predatory is an odd name for loans to people in need. The World Bank makes loans to people in need. China does too. China stands in opposition to Western Empire, and in that regard they produce their own alternative BRICS institutions. This is one of them. There is AFAIK nothing more predatory about them. It is just that in some cases the borrowers have trouble paying them back and they get foreclosed upon. I don't think this is worthy of much discussion, except that the term "predatory" seems to me to be a propaganda device. ## What about foreign influence from China? China wants to influence the world, especially its own trading partners and potential trading partners. Doing that above board is fine by me. But some of it is undoubtedly covert. Sometimes Chinese-born people run for public office in Western countries. In New Zealand we stood down some when it became clear they were being influenced too much by the CPC while being charged with representing their local town (dual loyalty issues). If only the USA would do the same thing to their dually-loyal politicians. And all large nations run influence operations. The USA has the CIA, for example, and claims this "soft power" is actually the better alternative to what would otherwise be military intervention (but IMHO shouldn't be either). I'm not defending such operations (I despise them), I'm just explaining how China's position of exerting influence is not only no big deal and totally expected, it pales in comparison to the United States' influence operations which often become military excursions (something China rarely ever does). ## What about the Great Firewall? Yeah, that sucks. Again, single-party authoritarian control gone to extremes. ## What about Human Rights Abuses? What about the Uyghur Genocide? I don't like them. To the extent they are occurring (and I lean towards the belief that they are occurring), I condemn them. China has anti-terrorism and anti-extremism policies that go too far. They end up oppressing and/or criminalizing cultures that aren't Chinese enough. But especially, China punishes dissent. Disagreement with the CPC is the high crime. It is the one-party rule that causes this problem. Anybody who speaks out against the CPC or goes against the state in any way is harshly punished. This happens to Uyghurs, to Falun Gong, to Tibetans, and to any religion that is seen as subversive. Amnesty International and the UN OHCHR have documented issues around the Xinjiang Uyghur autonomous region, Tibet, LGBT rights, death penalty, workers rights, and the Hong Kong special administrative region. I am not about to pretend I know better than they do, but to some extent they go too far. Amnesty International says this about the USA: Discrimination and violence against LGBTI people were widespread and anti-LGBTI legislation increased. Bills were introduced to address reparations regarding slavery and its legacies. Multiple states implemented total bans on abortion or severely limited access to it. Gender-based violence disproportionately affected Indigenous women. Access to the USA for asylum seekers and migrants was still fraught with obstacles, but some nationalities continued to enjoy Temporary Protected Status. Moves were made to restrict the freedom to protest in a number of states. Black people were disproportionately affected by the use of lethal force by police. No progress was made in the abolition of the death penalty, apart from in Washington. Arbitrary and indefinite detention in the US naval base Guantánamo Bay, Cuba, continued. Despite extensive gun violence, no further firearm reform policies were considered, but President Biden did announce the creation of the White House Office of Gun Violence Prevention. The USA continued to use lethal force in countries around the world. Black people, other racialized groups and low-income people bore the brunt of the health impacts of the petrochemical industry, and the use of fossil fuels continued unabated. Amnesty international didn't even point out that the US government quashes free speech via pressure on social media corporations (because Amnesty International is far too lefty). So who is worse, China or the US? I'm not going to make that judgement call, but suffice it to say that in my mind, China is not obviously worse. China violates freedom of expression, association, and assembly of all people. This is bad, and a consequence mainly of one-party rule (again, what I think is the root cause of most of their ills). They arrest, detain, potentially kill anybody who publicly disagrees openly with their government. Clearly this is an excess of authoritarianism, a cancer that is very advanced in China. As to organ harvesting of Uyghur Muslims, I think this is a myth. China has dealt harshly with Muslim extremism. They don't offer freedom of religion to ISIS. And Amnesty International complains about that. But practically speaking you probably shouldn't respect the extremist religion of people who want to force everybody into a global caliphate through threat of violence. As you are well aware, some extremist Muslims (<1% of Islam) believe in using violence to bring about a global caliphate. Those extremists pop up in every country and are usually dealt with harshly. China has had to deal with them too. I have watched two different Western YouTubers travel to Xinjiang province trying to find the oppressed Uyghurs and interview them. They can't find them. What they find instead are Uyghur Muslims doing their prayers five times a day at the local mosque. And also stories that the CPC pitched in some money to help them renovate the mosque. Maybe they were afraid it was a CPC trap and so they wouldn't speak freely. Amnesty International and the UN OHCHR say more than a million are "arbitrarily detained" and I'm not going to argue otherwise. But I'd be more convinced if there were a stream of pictures and news like there is out of Gaza, and it is suspicious that there isn't. ## Conclusion China is more like a Western nation that Westerners realize. Economically, militarily, socially. It still has a very serious obstacle to overcome: one-party rule. I don't think the one-party is going to voluntarily give up power. So most probably at some point in the future there will be a revolution. But in my opinion it won't happen anytime soon. For the most part Chinese people are living high on the hog, getting rich, enjoying the good life, in positive spirits about life, and are getting along with their government quite well at present.
@ ee11a5df:b76c4e49
2024-12-24 18:49:05# China ## I might be wrong, but this is how I see it This is a post within a series I am going to call "I might be wrong, but this is how I see it" I have repeatedly found that my understanding of China is quite different from that of many libertarian-minded Americans. And so I make this post to explain how I see it. Maybe you will learn something. Maybe I will learn something. It seems to me that many American's see America as a shining beacon of freedom with a few small problems, and China is an evil communist country spreading communism everywhere. From my perspective, America *was* a shining beacon of freedom that has fallen to being typical in most ways, and which is now acting as a falling empire, and China *was* communist for about a decade, but turned and ran away from that as fast as they could (while not admitting it) and the result is that the US and China are not much different anymore when it comes to free markets. Except they are very different in some other respects. ## China has a big problem China has a big problem. But it is not the communism problem that most Westerners diagnose. I argue that China is no longer communist, it is only communist in name. And that while it is not a beacon of free market principles, it is nearly as free market now as Western nations like Germany and New Zealand are (being somewhat socialist themselves). No, China's real problem is authoritarian one-party rule. And that core problem causes all of the other problems, including its human rights abuses. ## Communism and Socialism Communism and Socialism are bad ideas. I don't want to argue it right here, but most readers will already understand this. The last thing I intend to do with this post is to bolster or defend those bad ideas. If you dear reader hold a candle for socialism, let me know and I can help you extinguish it with a future "I might be wrong, but this is how I see it" installment. Communism is the idea of structuring a society around common ownership of the means of production, distribution, and exchange, and the idea of allocating goods and services based on need. It eliminates the concept of private property, of social classes, ultimately of money and finally of the state itself. Back under Mao in 1958-1962 (The Great Leap Forward), China tried this (in part). Some 50+ million people died. It was an abject failure. But due to China's real problem (authoritarianism, even worship of their leaders), the leading classes never admitted this. And even today they continue to use the word "Communist" for things that aren't communist at all, as a way to save face, and also in opposition to the United States of America and Europe. Authorities are not eager to admit their faults. But this is not just a Chinese fault, it is a fault in human nature that affects all countries. The USA still refuses to admit they assassinated their own president JFK. They do not admit they bombed the Nord Stream pipeline. China defines "socialism with Chinese characteristics" to mean "the leadership of the Communist Party of China". So they still keep the words socialism and communism, but they long ago dropped the meanings of those words. I'm not sure if this is a political ploy against us in the West or not. ### China's Marketplace Today Today China exhibits very few of the properties of communism. They have some common ownership and state enterprises, but not much differently than Western countries (New Zealand owns Air New Zealand and Kiwibank and Kiwirail, etc). And there are private enterprises all over China. They compete and some succeed and some fail. You might hear about a real-estate bank collapsing. China has private property. They have mostly free markets. They have money, and the most definitely have social classes and a very strong state. None of that is inline with what communist thinkers want. Communist thinkers in China moan that China has turned away from communism. Deng Xiaoping who succeeded Mao and attempted to correct the massive mistake, did much when he said "to get rich is glorious." China achieved staggering rates of economic growth. 10% annually on average since 1977. Chinese economic reform started in 1979 and has continued through successive administrations (Deng, Jiang, Hu and now Xi). China is now the world's largest economy (by GDP in PPP terms) since 2016. I was first made aware of China's economic growth by Jim Rogers, an American commodities expert who travelled through China (and the rest of the world from 1990-1992) and in 2007 moved to Singapore where he ensured his daughters learned to speak Mandarin, because Jim knew where the economic growth was going to happen. Jim always spoke positively of China's economic prospects, and his view was so different from the "China is a nasty communist place" view that I had grown up with that my mind opened. How can anybody believe they are still a communist country? In what world does it make sense that communism can produce such a massively booming economy? It doesn't make sense because it is simply wrong. What *does* happen is that the CPC interferes. It lets the market do what markets do, but it interferes where it thinks oversight and regulation would produce a better result. Western nations interfere with their markets too. They have oversight and regulation. In fact some of China's planned reforms had to be put on hold by Xi due to Donald Trump's trade war with China. That's right, they were trying to be even more free market than America, but America's protectionism prodded Xi to keep control so he could fight back efficiently. Government oversight and regulation IMHO is mostly bad because it gets out of control, and there are no market forces to correct this. This gets even more extreme in a one-party system, so I can judge that China's oversight and regulation problems are very likely worse than those in Western nations (but I have no first hand experience or evidence). ## Why do you keep saying CPC? The Communist Party of China (CPC) is the ruling party in China. That is their official name. To call them the CCP is to concede to the idea that the British and Americans get to name everybody. I'm not sure who is right, since CPC or CCP is their "English" name (in Chinese it is 中国共产党 and Westernized it is Zhōngguó Gòngchǎndǎng). Nonetheless, I'll call them CPC because that is their wish. ## Social Credit System China moved from a planned economy to a market economy in stages. They didn't want any more sudden changes (can you blame them?). In the process, many institutions that have existed in the West for a long time didn't exist in China and they had to arise somehow. IMHO market forces would have brought these about in the private sector, but the one-party CP of China instead decided to create these. One of those institutions was a credit score system. In the West we have TransUnion and Equifax that maintain credit ratings on people, and we have S&P, Moody's and Fitch that maintain credit ratings on companies. The domain of these ratings is their financial credit-worthiness. So the People's Bank of China developed a credit information database for it's own needs. The government picked up on the idea and started moving towards a National Credit Management System. In 2004 it became an official goal to establish a credit system compatible with a modern market system. By 2006 banks were required to report on consumer creditworthiness. But unchecked one-party governmental power will often take a good idea (credit worthiness data shared among private parties) and systematize it and apply it top-down, creating a solution and a new problem at the same time. Nonetheless, originally it was about credit worthiness and also criminal convictions. That is no big scary thing that some right-wing American commentators will lead you to believe. In the US for example criminal records are public, so China's Social Credit System started out being no more over-reaching in scope than what Americans have lived under their entire lives, its only fault (a severe one) being centrally planned. And that remained the case up until about 2016 (in my estimation). But of course there is always scope creep. As it exists today, I have reason to believe that CPC officials and even A.I. use judgement calls to score someone on how moral that person has been! Of course that is not a good idea, and IMHO the problem stems from one-party rule, and authoritarian administration of ideas that should instead be handled by the private sector. ## Environmental, Social, and Governance ESG is a system that came out of a couple basic ideas. The first is that many two-party transactions actually have externalities. They don't just affect the two parties, they also affect everybody else. When you fly in an airplane, you increase the CO2 in the atmosphere that everybody has to pay for (eventually). You may dispute that example, but that is no doubt one of the motivations of ESG. But of course the recognition of this basic issue didn't lead all people towards market solutions (well it did, but those have been mostly messed up by others), but instead led many people towards ESG, which is a social credit scoring system which applies scores based on environmental and social side-effects of market transactions. This is not at all the same as China's social credit system, which I described above. I hope you can see the difference. In fact, China imported ESG from the West. Chinese companies, of their free will, in an attempt to court Western capital, achieve ESG goals for those Western investors. They have been playing this ESG game for 20 years just like the entire world has, because the West has imposed this faux-morality upon them. It isn't something China exported to us, it is something we exported to them. ## I think China has avoided Woke-ism My understanding of Chinese people, based on what I've heard many Chinese people say, is that China isn't affected by the Western woke-ism epidemic. They deride Western white woke people with the term "Baizuo". They have never sent an incompetent break dancer to the Olympics because of wok-ism. Competence is highly respected as is the competition to be the most competent, which (when augmented by a one-child policy which is no longer) has produced child prodigies like no other country has. ## What about predatory loans of the Belt and Road initiative? Predatory is an odd name for loans to people in need. The World Bank makes loans to people in need. China does too. China stands in opposition to Western Empire, and in that regard they produce their own alternative BRICS institutions. This is one of them. There is AFAIK nothing more predatory about them. It is just that in some cases the borrowers have trouble paying them back and they get foreclosed upon. I don't think this is worthy of much discussion, except that the term "predatory" seems to me to be a propaganda device. ## What about foreign influence from China? China wants to influence the world, especially its own trading partners and potential trading partners. Doing that above board is fine by me. But some of it is undoubtedly covert. Sometimes Chinese-born people run for public office in Western countries. In New Zealand we stood down some when it became clear they were being influenced too much by the CPC while being charged with representing their local town (dual loyalty issues). If only the USA would do the same thing to their dually-loyal politicians. And all large nations run influence operations. The USA has the CIA, for example, and claims this "soft power" is actually the better alternative to what would otherwise be military intervention (but IMHO shouldn't be either). I'm not defending such operations (I despise them), I'm just explaining how China's position of exerting influence is not only no big deal and totally expected, it pales in comparison to the United States' influence operations which often become military excursions (something China rarely ever does). ## What about the Great Firewall? Yeah, that sucks. Again, single-party authoritarian control gone to extremes. ## What about Human Rights Abuses? What about the Uyghur Genocide? I don't like them. To the extent they are occurring (and I lean towards the belief that they are occurring), I condemn them. China has anti-terrorism and anti-extremism policies that go too far. They end up oppressing and/or criminalizing cultures that aren't Chinese enough. But especially, China punishes dissent. Disagreement with the CPC is the high crime. It is the one-party rule that causes this problem. Anybody who speaks out against the CPC or goes against the state in any way is harshly punished. This happens to Uyghurs, to Falun Gong, to Tibetans, and to any religion that is seen as subversive. Amnesty International and the UN OHCHR have documented issues around the Xinjiang Uyghur autonomous region, Tibet, LGBT rights, death penalty, workers rights, and the Hong Kong special administrative region. I am not about to pretend I know better than they do, but to some extent they go too far. Amnesty International says this about the USA: Discrimination and violence against LGBTI people were widespread and anti-LGBTI legislation increased. Bills were introduced to address reparations regarding slavery and its legacies. Multiple states implemented total bans on abortion or severely limited access to it. Gender-based violence disproportionately affected Indigenous women. Access to the USA for asylum seekers and migrants was still fraught with obstacles, but some nationalities continued to enjoy Temporary Protected Status. Moves were made to restrict the freedom to protest in a number of states. Black people were disproportionately affected by the use of lethal force by police. No progress was made in the abolition of the death penalty, apart from in Washington. Arbitrary and indefinite detention in the US naval base Guantánamo Bay, Cuba, continued. Despite extensive gun violence, no further firearm reform policies were considered, but President Biden did announce the creation of the White House Office of Gun Violence Prevention. The USA continued to use lethal force in countries around the world. Black people, other racialized groups and low-income people bore the brunt of the health impacts of the petrochemical industry, and the use of fossil fuels continued unabated. Amnesty international didn't even point out that the US government quashes free speech via pressure on social media corporations (because Amnesty International is far too lefty). So who is worse, China or the US? I'm not going to make that judgement call, but suffice it to say that in my mind, China is not obviously worse. China violates freedom of expression, association, and assembly of all people. This is bad, and a consequence mainly of one-party rule (again, what I think is the root cause of most of their ills). They arrest, detain, potentially kill anybody who publicly disagrees openly with their government. Clearly this is an excess of authoritarianism, a cancer that is very advanced in China. As to organ harvesting of Uyghur Muslims, I think this is a myth. China has dealt harshly with Muslim extremism. They don't offer freedom of religion to ISIS. And Amnesty International complains about that. But practically speaking you probably shouldn't respect the extremist religion of people who want to force everybody into a global caliphate through threat of violence. As you are well aware, some extremist Muslims (<1% of Islam) believe in using violence to bring about a global caliphate. Those extremists pop up in every country and are usually dealt with harshly. China has had to deal with them too. I have watched two different Western YouTubers travel to Xinjiang province trying to find the oppressed Uyghurs and interview them. They can't find them. What they find instead are Uyghur Muslims doing their prayers five times a day at the local mosque. And also stories that the CPC pitched in some money to help them renovate the mosque. Maybe they were afraid it was a CPC trap and so they wouldn't speak freely. Amnesty International and the UN OHCHR say more than a million are "arbitrarily detained" and I'm not going to argue otherwise. But I'd be more convinced if there were a stream of pictures and news like there is out of Gaza, and it is suspicious that there isn't. ## Conclusion China is more like a Western nation that Westerners realize. Economically, militarily, socially. It still has a very serious obstacle to overcome: one-party rule. I don't think the one-party is going to voluntarily give up power. So most probably at some point in the future there will be a revolution. But in my opinion it won't happen anytime soon. For the most part Chinese people are living high on the hog, getting rich, enjoying the good life, in positive spirits about life, and are getting along with their government quite well at present. @ ec42c765:328c0600
2024-12-22 19:16:31この記事は前回の内容を把握している人向けに書いています(特にNostrエクステンション(NIP-07)導入) 前回:[Nostrのカスタム絵文字の使い方](https://yakihonne.com/article/_@lokuyow.github.io/xVMTZxHcV_NWKuTbDBUYs) # 手順 1. 登録する画像を用意する 2. 画像をweb上にアップロードする 3. 絵文字セットに登録する ## 1. 登録する画像を用意する 以下のような方法で用意してください。 * 画像編集ソフト等を使って自分で作成する * 絵文字作成サイトを使う([絵文字ジェネレーター](https://emoji-gen.ninja/)、[MEGAMOJI](https://zk-phi.github.io/MEGAMOJI/) など) * フリー画像を使う([いらすとや](https://www.irasutoya.com/) など) ### データ量削減 Nostrでは画像をそのまま表示するクライアントが多いので、データ量が大きな画像をそのまま使うとモバイル通信時などに負担がかかります。 データ量を増やさないためにサイズやファイル形式を変更することをおすすめします。 以下は私のおすすめです。 * サイズ:正方形 128×128 ピクセル、長方形 任意の横幅×128 ピクセル * ファイル形式:webp形式(webp変換おすすめサイト [toimg](https://toimg.kakechimaru.com/to-webp)) * 単色、単純な画像の場合:png形式(webpにするとむしろサイズが大きくなる) ### その他 * 背景透過画像 * ダークモード、ライトモード両方で見やすい色 がおすすめです。 ## 2. 画像をweb上にアップロードする よく分からなければ [emojito](https://emojito.meme/) からのアップロードで問題ないです。 普段使っている画像アップロード先があるならそれでも構いません。 気になる方はアップロード先を適宜選んでください。 既に投稿されたカスタム絵文字の画像に対して - 削除も差し替えもできない → [emojito](https://emojito.meme/) など - 削除できるが差し替えはできない → [Gyazo](https://gyazo.com/)、[nostrcheck.me](https://nostrcheck.me/)など - 削除も差し替えもできる → [GitHub](https://github.com/) 、セルフホスティングなど これらは既にNostr上に投稿されたカスタム絵文字の画像を後から変更できるかどうかを指します。 どの方法でも新しく使われるカスタム絵文字を変更することは可能です。 同一のカスタム絵文字セットに同一のショートコードで別の画像を登録する形で対応できます。 ## 3. 絵文字セットに登録する [emojito](https://emojito.meme/) から登録します。 右上の**アイコン** → **+ New emoji set** から新規の絵文字セットを作成できます。   #### ① 絵文字セット名を入力 基本的にカスタム絵文字はカスタム絵文字セットを作り、ひとまとまりにして登録します。 一度作った絵文字セットに後から絵文字を追加することもできます。 #### ② 画像をアップロードまたは画像URLを入力 emojitoから画像をアップロードする場合、ファイル名に日本語などの2バイト文字が含まれているとアップロードがエラーになるようです。 その場合はファイル名を適当な英数字などに変更してください。 #### ③ 絵文字のショートコードを入力 ショートコードは絵文字を呼び出す時に使用する場合があります。 他のカスタム絵文字と被っても問題ありませんが選択時に複数表示されて支障が出る可能性があります。 他と被りにくく長くなりすぎないショートコードが良いかもしれません。 ショートコードに使えるのは半角の英数字とアンダーバーのみです。 #### ④ 追加 **Add** を押してもまだ作成完了にはなりません。  一度に絵文字を複数登録できます。 最後に右上の **Save** を押すと作成完了です。  画面が切り替わるので、右側の **Options** から **Bookmark** を選択するとそのカスタム絵文字セットを自分で使えるようになります。 既存の絵文字セットを編集するには **Options** から **Edit** を選択します。 以上です。 ----------- # 仕様 [NIP-30 Custom Emoji](https://github.com/nostr-protocol/nips/blob/master/30.md) [NIP-30 カスタム絵文字(和訳)](https://github.com/nostr-jp/nips-ja/blob/main/30.md)
@ ec42c765:328c0600
2024-12-22 19:16:31この記事は前回の内容を把握している人向けに書いています(特にNostrエクステンション(NIP-07)導入) 前回:[Nostrのカスタム絵文字の使い方](https://yakihonne.com/article/_@lokuyow.github.io/xVMTZxHcV_NWKuTbDBUYs) # 手順 1. 登録する画像を用意する 2. 画像をweb上にアップロードする 3. 絵文字セットに登録する ## 1. 登録する画像を用意する 以下のような方法で用意してください。 * 画像編集ソフト等を使って自分で作成する * 絵文字作成サイトを使う([絵文字ジェネレーター](https://emoji-gen.ninja/)、[MEGAMOJI](https://zk-phi.github.io/MEGAMOJI/) など) * フリー画像を使う([いらすとや](https://www.irasutoya.com/) など) ### データ量削減 Nostrでは画像をそのまま表示するクライアントが多いので、データ量が大きな画像をそのまま使うとモバイル通信時などに負担がかかります。 データ量を増やさないためにサイズやファイル形式を変更することをおすすめします。 以下は私のおすすめです。 * サイズ:正方形 128×128 ピクセル、長方形 任意の横幅×128 ピクセル * ファイル形式:webp形式(webp変換おすすめサイト [toimg](https://toimg.kakechimaru.com/to-webp)) * 単色、単純な画像の場合:png形式(webpにするとむしろサイズが大きくなる) ### その他 * 背景透過画像 * ダークモード、ライトモード両方で見やすい色 がおすすめです。 ## 2. 画像をweb上にアップロードする よく分からなければ [emojito](https://emojito.meme/) からのアップロードで問題ないです。 普段使っている画像アップロード先があるならそれでも構いません。 気になる方はアップロード先を適宜選んでください。 既に投稿されたカスタム絵文字の画像に対して - 削除も差し替えもできない → [emojito](https://emojito.meme/) など - 削除できるが差し替えはできない → [Gyazo](https://gyazo.com/)、[nostrcheck.me](https://nostrcheck.me/)など - 削除も差し替えもできる → [GitHub](https://github.com/) 、セルフホスティングなど これらは既にNostr上に投稿されたカスタム絵文字の画像を後から変更できるかどうかを指します。 どの方法でも新しく使われるカスタム絵文字を変更することは可能です。 同一のカスタム絵文字セットに同一のショートコードで別の画像を登録する形で対応できます。 ## 3. 絵文字セットに登録する [emojito](https://emojito.meme/) から登録します。 右上の**アイコン** → **+ New emoji set** から新規の絵文字セットを作成できます。   #### ① 絵文字セット名を入力 基本的にカスタム絵文字はカスタム絵文字セットを作り、ひとまとまりにして登録します。 一度作った絵文字セットに後から絵文字を追加することもできます。 #### ② 画像をアップロードまたは画像URLを入力 emojitoから画像をアップロードする場合、ファイル名に日本語などの2バイト文字が含まれているとアップロードがエラーになるようです。 その場合はファイル名を適当な英数字などに変更してください。 #### ③ 絵文字のショートコードを入力 ショートコードは絵文字を呼び出す時に使用する場合があります。 他のカスタム絵文字と被っても問題ありませんが選択時に複数表示されて支障が出る可能性があります。 他と被りにくく長くなりすぎないショートコードが良いかもしれません。 ショートコードに使えるのは半角の英数字とアンダーバーのみです。 #### ④ 追加 **Add** を押してもまだ作成完了にはなりません。  一度に絵文字を複数登録できます。 最後に右上の **Save** を押すと作成完了です。  画面が切り替わるので、右側の **Options** から **Bookmark** を選択するとそのカスタム絵文字セットを自分で使えるようになります。 既存の絵文字セットを編集するには **Options** から **Edit** を選択します。 以上です。 ----------- # 仕様 [NIP-30 Custom Emoji](https://github.com/nostr-protocol/nips/blob/master/30.md) [NIP-30 カスタム絵文字(和訳)](https://github.com/nostr-jp/nips-ja/blob/main/30.md) @ d61f3bc5:0da6ef4a
2024-12-18 16:52:18January 2025 will mark two years since we started building Primal. Our goal was to create the best possible user experience for Nostr and make it accessible to everyone. We reached a big milestone towards realizing that vision with the recent Primal 2.0 release. It’s still early days, a lot more work lies ahead, but we thought the timing was right to introduce the Premium tier. Let’s explore what it is, why we built it, what’s included, and how it will evolve moving forward. ## What Primal Premium Is The idea behind Primal Premium is simple: integrate all tools and services required for the best Nostr experience into a single package. For $7 per month, Premium users get a *Primal Name* and *Nostr Tools* built by Primal. We’ll cover those in more detail below, but first we should make a crucial point: by signing up for Premium, you are in no way locked in to Primal. Quite the contrary, you can pick and choose which Premium features you wish to enable and use within other Nostr products. Openness is Nostr’s killer feature. Any product that wishes to truly empower the user needs to interoperate with Nostr’s budding ecosystem. The feed marketplace is a great example. External feeds are first-class citizens within all Primal apps. Primal feeds are available in other Nostr clients. We are working on Premium feeds, which our users will be able to enjoy within Primal or other Nostr apps. Media hosting is another example. Our upcoming support for the Blossom protocol will make Primal Premium media hosting interoperable with other Nostr apps and media hosting services. The common theme here is user choice. Nostr offers the highest level of user agency, and the compounding effect of interoperable products and services is bound to make Nostr immensely powerful. ## Why We Built Premium and Why Now What is unfolding on Nostr right now is unique and special. The first truly self-sovereign network is being bootstrapped by this early cohort of users and builders. People are literally holding the keys to their online presence. Network infrastructure – relays, indexers, media hosting services, etc. – is being stood up organically and without any central planning or coordination. Hundreds of independent projects are adding new capabilities to Nostr without needing permission. The whole thing is truly a sight to behold. In addition to fixing the fundamentals of the network, it is equally important that we fix the broken incentives that plague the legacy Web. The status quo of monetization via advertising, which turns users into products to be farmed, has overstayed its welcome. At Primal, we don’t monetize user data. Our users are our customers. We only make money when the user decides that we are providing a valuable service – and pays for it. That means that our users’ interests are aligned with ours. It allows us to wake up every morning and work all day to make the product better for our users. Some might say that it is too early to try to monetize a Nostr product. We definitely need to be thoughtful about paywalling important features while the network is so young. For example, advanced search is a Primal Premium feature, but we enable it for all users up to 20 search results. That makes it quite usable for anyone on Nostr, but power users get the ability to save these searches and create powerful specialized feeds. It is crucial to have commercially successful projects on Nostr that have their incentives aligned with those of their users. We are working on new features and monetization methods that follow this philosophy. The more we experiment on Nostr, the faster we will learn what works and unlock the full potential of this network. I have a feeling that a lot remains to be discovered, and Primal Premium is just the first step. Now, let’s take a closer look at what is included in Premium: *Primal Name* and *Nostr Tools*. ## Primal Name  A Primal Name is a unique name on the primal.net domain that offers three features: 1. **Verified Nostr address (NIP-05)**. This signals to the Nostr network that your account (npub) has been verified by Primal. Note that we don’t perform identity verification; we are simply signaling that this is a Primal Premium user. Users can pay with sats, preserving their privacy while signaling to the network that this verified account is not a bot. 2. **Friendly Bitcoin Lightning address**. Primal’s built-in hosted wallet creates a randomly generated lightning address for every user. They look like this: bluedog25@primal.net. Premium users get to pick their name, so their lightning address is more personalized (e.g. preston@primal.net). 3. **VIP profile on primal.net**. This is simply a friendly URL to your profile on primal.net. We are working on adding profile customization features for Premium users; stay tuned! In summary, a Primal Name makes you easier to find on Nostr. You are free to use any of these three Primal Name elements as you see fit. If you wish to use your Primal Nostr address and/or Lightning address, simply update your Nostr profile with those entries. ## Nostr Tools  Nostr Tools is a collection of features that we think would be useful to any Nostr power user. We are continuously working on expanding these capabilities, but the initial set of features includes: - **Media management**. Primal Premium comes with 10GB of media storage (compared to 1GB for free accounts). We implemented a slick interface for managing all media you have on Primal. - **Contact list backup**. Many Nostr users have experienced the loss of their contact list (i.e., their follow list) when using different clients. We store the history of the contact list for Primal Premium users and make it easy to recover. - **Content backup**. Nostr users post their content to a collection of public relays. These relays typically don’t offer guarantees that they will store the content for any amount of time. We back up all content posted by Primal Premium users and make it easy to rebroadcast it to the specified relays at any time. ## Primal Legends  The idea for the Primal Legend tier was suggested to me by Gigi a couple of months prior to the launch of Primal 2.0. His argument was simple: “There are users on Nostr who really appreciate Primal and are willing to pay way more than $7 / month to support the project. You should *let them* pay and *recognize them* for doing so.” I am really glad that Gigi convinced me to introduce the Legend tier. Nostr is truly a special place. The early users are extremely passionate and mission driven. They care about growing and improving Nostr as much as the builders do. At first, I thought of the term “Legend” as a bit tongue in cheek, but then I met and chatted with some of these people. Man, they are incredible. They just wish to support the network and the builders of open source software in any way they can. So now I think the term is appropriate. We are humbled by the support we received. Our first Legend supporter was none other than Jack. He found this option in the product and paid for the Legend tier literally an hour after Primal 2.0 was released. Thank you, sir, and thank you to all the other Legends out there! 💜🫂 ## What Comes Next? We are delighted and encouraged by the market response to Primal Premium. It is already clear to us that we are on the right path. We will lean into it even harder from here. There will be MOAR Premium features, while at the same time we will make sure that the free product remains excellent. Since you, the user, are the customer, tell us what you would like to see added to Primal Premium. Pura Vida 🤙
@ d61f3bc5:0da6ef4a
2024-12-18 16:52:18January 2025 will mark two years since we started building Primal. Our goal was to create the best possible user experience for Nostr and make it accessible to everyone. We reached a big milestone towards realizing that vision with the recent Primal 2.0 release. It’s still early days, a lot more work lies ahead, but we thought the timing was right to introduce the Premium tier. Let’s explore what it is, why we built it, what’s included, and how it will evolve moving forward. ## What Primal Premium Is The idea behind Primal Premium is simple: integrate all tools and services required for the best Nostr experience into a single package. For $7 per month, Premium users get a *Primal Name* and *Nostr Tools* built by Primal. We’ll cover those in more detail below, but first we should make a crucial point: by signing up for Premium, you are in no way locked in to Primal. Quite the contrary, you can pick and choose which Premium features you wish to enable and use within other Nostr products. Openness is Nostr’s killer feature. Any product that wishes to truly empower the user needs to interoperate with Nostr’s budding ecosystem. The feed marketplace is a great example. External feeds are first-class citizens within all Primal apps. Primal feeds are available in other Nostr clients. We are working on Premium feeds, which our users will be able to enjoy within Primal or other Nostr apps. Media hosting is another example. Our upcoming support for the Blossom protocol will make Primal Premium media hosting interoperable with other Nostr apps and media hosting services. The common theme here is user choice. Nostr offers the highest level of user agency, and the compounding effect of interoperable products and services is bound to make Nostr immensely powerful. ## Why We Built Premium and Why Now What is unfolding on Nostr right now is unique and special. The first truly self-sovereign network is being bootstrapped by this early cohort of users and builders. People are literally holding the keys to their online presence. Network infrastructure – relays, indexers, media hosting services, etc. – is being stood up organically and without any central planning or coordination. Hundreds of independent projects are adding new capabilities to Nostr without needing permission. The whole thing is truly a sight to behold. In addition to fixing the fundamentals of the network, it is equally important that we fix the broken incentives that plague the legacy Web. The status quo of monetization via advertising, which turns users into products to be farmed, has overstayed its welcome. At Primal, we don’t monetize user data. Our users are our customers. We only make money when the user decides that we are providing a valuable service – and pays for it. That means that our users’ interests are aligned with ours. It allows us to wake up every morning and work all day to make the product better for our users. Some might say that it is too early to try to monetize a Nostr product. We definitely need to be thoughtful about paywalling important features while the network is so young. For example, advanced search is a Primal Premium feature, but we enable it for all users up to 20 search results. That makes it quite usable for anyone on Nostr, but power users get the ability to save these searches and create powerful specialized feeds. It is crucial to have commercially successful projects on Nostr that have their incentives aligned with those of their users. We are working on new features and monetization methods that follow this philosophy. The more we experiment on Nostr, the faster we will learn what works and unlock the full potential of this network. I have a feeling that a lot remains to be discovered, and Primal Premium is just the first step. Now, let’s take a closer look at what is included in Premium: *Primal Name* and *Nostr Tools*. ## Primal Name  A Primal Name is a unique name on the primal.net domain that offers three features: 1. **Verified Nostr address (NIP-05)**. This signals to the Nostr network that your account (npub) has been verified by Primal. Note that we don’t perform identity verification; we are simply signaling that this is a Primal Premium user. Users can pay with sats, preserving their privacy while signaling to the network that this verified account is not a bot. 2. **Friendly Bitcoin Lightning address**. Primal’s built-in hosted wallet creates a randomly generated lightning address for every user. They look like this: bluedog25@primal.net. Premium users get to pick their name, so their lightning address is more personalized (e.g. preston@primal.net). 3. **VIP profile on primal.net**. This is simply a friendly URL to your profile on primal.net. We are working on adding profile customization features for Premium users; stay tuned! In summary, a Primal Name makes you easier to find on Nostr. You are free to use any of these three Primal Name elements as you see fit. If you wish to use your Primal Nostr address and/or Lightning address, simply update your Nostr profile with those entries. ## Nostr Tools  Nostr Tools is a collection of features that we think would be useful to any Nostr power user. We are continuously working on expanding these capabilities, but the initial set of features includes: - **Media management**. Primal Premium comes with 10GB of media storage (compared to 1GB for free accounts). We implemented a slick interface for managing all media you have on Primal. - **Contact list backup**. Many Nostr users have experienced the loss of their contact list (i.e., their follow list) when using different clients. We store the history of the contact list for Primal Premium users and make it easy to recover. - **Content backup**. Nostr users post their content to a collection of public relays. These relays typically don’t offer guarantees that they will store the content for any amount of time. We back up all content posted by Primal Premium users and make it easy to rebroadcast it to the specified relays at any time. ## Primal Legends  The idea for the Primal Legend tier was suggested to me by Gigi a couple of months prior to the launch of Primal 2.0. His argument was simple: “There are users on Nostr who really appreciate Primal and are willing to pay way more than $7 / month to support the project. You should *let them* pay and *recognize them* for doing so.” I am really glad that Gigi convinced me to introduce the Legend tier. Nostr is truly a special place. The early users are extremely passionate and mission driven. They care about growing and improving Nostr as much as the builders do. At first, I thought of the term “Legend” as a bit tongue in cheek, but then I met and chatted with some of these people. Man, they are incredible. They just wish to support the network and the builders of open source software in any way they can. So now I think the term is appropriate. We are humbled by the support we received. Our first Legend supporter was none other than Jack. He found this option in the product and paid for the Legend tier literally an hour after Primal 2.0 was released. Thank you, sir, and thank you to all the other Legends out there! 💜🫂 ## What Comes Next? We are delighted and encouraged by the market response to Primal Premium. It is already clear to us that we are on the right path. We will lean into it even harder from here. There will be MOAR Premium features, while at the same time we will make sure that the free product remains excellent. Since you, the user, are the customer, tell us what you would like to see added to Primal Premium. Pura Vida 🤙 @ 4657dfe8:47934b3e
2024-12-18 13:42:46*Alby Hub enables creation of subaccounts, decentralizing trust and creating usecases for shared, community nodes.* ## Simplifying Bitcoin Wallets for Friends and Family [Alby Hub](https://albyhub.com/?ref=blog.getalby.com) empowers you to take full control of your bitcoin and manage your payments. Through a user-friendly, self-custodial wallet with a one-click lightning node setup, you can effortlessly connect to dozens of applications. The integrated App Store provides access to popular apps like Amethyst, Damus, Stacker News, Podcasting 2.0, and a wide range of other external tools—all directly linked with your Alby Hub wallet. One of the latest and most exciting additions to Alby Hub is the Friends & Family app. With the Friends & Family app, you can create subaccounts for friends and family, all powered by your Hub. In just a few clicks, you can set up wallets for them, giving them a smooth onboarding experience and making bitcoin accessible even to those new to the ecosystem. Think of it as a custodial wallet but with a personal touch—since you’re the one managing it, there’s a direct relationship and trust. These subaccount holders can tap into all the channels and liquidity of your Hub without needing to handle any technical setup. Plus, you can preload their wallets with a few sats, creating a welcoming and smooth experience that’s hard to find elsewhere. And that’s not all. Beyond providing an intuitive wallet, they can get their own lightning address, configurable payment notifications, access to Alby Go (a mobile app for payments on the go), and the Alby Browser Extension for easy web payments. Let’s have a look how to set it up. ## How to provide a wallet to Friends and Family? 1. Open your Hub and find the Friends & Family app in the App Store  2. Enter a name e.g. your friend’s name and click “Create subaccount”  3. Share the Connection Secret with your friend for the different options  Here are two examples how your the new subaccount can be used. ### Alby Go mobile App [Alby Go](https://albygo.com/?ref=blog.getalby.com) makes it easy to carry bitcoin in your pocket. This lightweight wallet connects directly to an Alby Hub subaccount, so your friends can pay and check transactions on the go. **Here’s how to set it up:** 1. Open the Alby Go Mobile App tab in your Hub.  2. Copy the **Connection Secret** and share it with your friend if you cannot onboard them in person. 3. Your friend downloads Alby Go for [Android](https://play.google.com/store/apps/details?id=com.getalby.mobile&ref=blog.getalby.com) or [iOS](https://apps.apple.com/us/app/alby-go/id6471335774?ref=blog.getalby.com) and scans the code. And that’s it—your friend now has a bitcoin wallet in their pocket, ready for seamless transactions anytime, anywhere. 🎉 ## Get a Lightning Address with an Alby account An [Alby Account](https://getalby.com/?ref=blog.getalby.com) offers a variety of useful features that make managing bitcoin payments easy. Among these are a personalized lightning address and email payment notifications—two powerful tools that help your newly onboarded friends stay connected and informed. **To set up an Alby account for someone:** 1. Open the **Alby Account** tab in your Hub. 2. Copy the provided URL and share it with your friend. 3. Your friend simply needs to create their Alby account and afterwards click on the provided URL. That’s it! The wallet is instantly connected, and they’re ready to receive payments to their new lightning address. 🥳 **Onboarding Family & Friends Made Easy** In this article, we explored how to create subaccounts for family and friends, connect them with Alby Go, and set up an Alby account to provide a smooth onboarding experience for your loved ones—all achievable in just a few clicks. Stay tuned as we dive into more exciting use cases for [subaccounts in Alby Hub](https://blog.getalby.com/introducing-subaccounts-in-alby-hub/)! If you have ideas for improvement,[let us know](hello@getalby.com).
@ 4657dfe8:47934b3e
2024-12-18 13:42:46*Alby Hub enables creation of subaccounts, decentralizing trust and creating usecases for shared, community nodes.* ## Simplifying Bitcoin Wallets for Friends and Family [Alby Hub](https://albyhub.com/?ref=blog.getalby.com) empowers you to take full control of your bitcoin and manage your payments. Through a user-friendly, self-custodial wallet with a one-click lightning node setup, you can effortlessly connect to dozens of applications. The integrated App Store provides access to popular apps like Amethyst, Damus, Stacker News, Podcasting 2.0, and a wide range of other external tools—all directly linked with your Alby Hub wallet. One of the latest and most exciting additions to Alby Hub is the Friends & Family app. With the Friends & Family app, you can create subaccounts for friends and family, all powered by your Hub. In just a few clicks, you can set up wallets for them, giving them a smooth onboarding experience and making bitcoin accessible even to those new to the ecosystem. Think of it as a custodial wallet but with a personal touch—since you’re the one managing it, there’s a direct relationship and trust. These subaccount holders can tap into all the channels and liquidity of your Hub without needing to handle any technical setup. Plus, you can preload their wallets with a few sats, creating a welcoming and smooth experience that’s hard to find elsewhere. And that’s not all. Beyond providing an intuitive wallet, they can get their own lightning address, configurable payment notifications, access to Alby Go (a mobile app for payments on the go), and the Alby Browser Extension for easy web payments. Let’s have a look how to set it up. ## How to provide a wallet to Friends and Family? 1. Open your Hub and find the Friends & Family app in the App Store  2. Enter a name e.g. your friend’s name and click “Create subaccount”  3. Share the Connection Secret with your friend for the different options  Here are two examples how your the new subaccount can be used. ### Alby Go mobile App [Alby Go](https://albygo.com/?ref=blog.getalby.com) makes it easy to carry bitcoin in your pocket. This lightweight wallet connects directly to an Alby Hub subaccount, so your friends can pay and check transactions on the go. **Here’s how to set it up:** 1. Open the Alby Go Mobile App tab in your Hub.  2. Copy the **Connection Secret** and share it with your friend if you cannot onboard them in person. 3. Your friend downloads Alby Go for [Android](https://play.google.com/store/apps/details?id=com.getalby.mobile&ref=blog.getalby.com) or [iOS](https://apps.apple.com/us/app/alby-go/id6471335774?ref=blog.getalby.com) and scans the code. And that’s it—your friend now has a bitcoin wallet in their pocket, ready for seamless transactions anytime, anywhere. 🎉 ## Get a Lightning Address with an Alby account An [Alby Account](https://getalby.com/?ref=blog.getalby.com) offers a variety of useful features that make managing bitcoin payments easy. Among these are a personalized lightning address and email payment notifications—two powerful tools that help your newly onboarded friends stay connected and informed. **To set up an Alby account for someone:** 1. Open the **Alby Account** tab in your Hub. 2. Copy the provided URL and share it with your friend. 3. Your friend simply needs to create their Alby account and afterwards click on the provided URL. That’s it! The wallet is instantly connected, and they’re ready to receive payments to their new lightning address. 🥳 **Onboarding Family & Friends Made Easy** In this article, we explored how to create subaccounts for family and friends, connect them with Alby Go, and set up an Alby account to provide a smooth onboarding experience for your loved ones—all achievable in just a few clicks. Stay tuned as we dive into more exciting use cases for [subaccounts in Alby Hub](https://blog.getalby.com/introducing-subaccounts-in-alby-hub/)! If you have ideas for improvement,[let us know](hello@getalby.com). @ ee11a5df:b76c4e49
2024-12-16 05:29:30# Nostr 2? ## Breaking Changes in Nostr Nostr was a huge leap forward. But it isn't perfect. When developers notice a problem with nostr, they confer with each other to work out a solution to the problem. This is usually in the form of a NIP PR on the nips repo. Some problems are easy. Just add something new and optional. No biggie. Zaps, git stuff, bunkers... just dream it up and add it. Other problems can only be fixed by breaking changes. With a breaking change, the overall path forward is like this: Add the new way of doing it while preserving the old way. Push the major software to switch to the new way. Then deprecate the old way. This is a simplification, but it is the basic idea. It is how we solved markers/quotes/root and how we are upgrading encryption, among other things. This process of pushing through a breaking change becomes more difficult as we have more and more existing nostr software out there that will break. Most of the time what happens is that the major software is driven to make the change (usually by nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6), and the smaller software is left to fend for itself. A while back I introduced the BREAKING.md file to help people developing smaller lesser-known software keep up with these changes. ## Big Ideas But some ideas just can't be applied to nostr. The idea is too big. The change is too breaking. It changes something fundamental. And nobody has come up with a smooth path to move from the old way to the new way. And so we debate a bunch of things, and never settle on anything, and eventually nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 makes a post saying that we don't really want it anyways 😉. As we encounter good ideas that are hard to apply to nostr, I've been filing them away in a repository I call "nostr-next", so we don't forget about them, in case we ever wanted to start over. It seems to me that starting over every time we encountered such a thing would be unwise. However, once we collect enough changes that we couldn't reasonably phase into nostr, then a tipping point is crossed where it becomes worthwhile to start over. In terms of the "bang for the buck" metaphor, the bang becomes bigger and bigger but the buck (the pain and cost of starting over) doesn't grow as rapidly. ## WHAT? Start over? IMHO starting over could be very bad if done in a cavalier way. The community could fracture. The new protocol could fail to take off due to lacking the network effect. The odds that a new protocol catches on are low, irrespective of how technically superior it could be. So the big question is: can we preserve the nostr community and it's network effect while making a major step-change to the protocol and software? I don't know the answer to that one, but I have an idea about it. I think the new-protocol clients can be dual-stack, creating events in both systems and linking those events together via tags. The nostr key identity would still be used, and the new system identity too. This is better than things like the mostr bridge because each user would remain in custody of their own keys. ## The nitty gritty Here are some of the things I think would make nostr better, but which nostr can't easily fix. A lot of these ideas have been mentioned before by multiple people and I didn't give credit to all of you (sorry) because my brain can't track it all. But I've been collecting these over time at https://github.com/mikedilger/nostr-next * Events as CBOR or BEVE or MsgPack or a fixed-schema binary layout... anything but JSON text with its parsing, it's encoding ambiguity, it's requirement to copy fields before hashing them, its unlimited size constraints. (me, nostr:npub1xtscya34g58tk0z605fvr788k263gsu6cy9x0mhnm87echrgufzsevkk5s) * EdDSA ed25519 keys instead of secp256k1, to enable interoperability with a bunch of other stuff like ssh, pgp, TLS, Mainline DHT, and many more, plus just being better cryptography (me, Nuh, Orlovsky, except Orlovsky wanted Ristretto25519 for speed) * Bootstrapping relay lists (and relay endpoints) from Mainline DHT (nostr:npub1jvxvaufrwtwj79s90n79fuxmm9pntk94rd8zwderdvqv4dcclnvs9s7yqz) * Master keys and revocable subkeys / device keys (including having your nostr key as a subkey) * Encryption to use different encryption-specific subkeys and ephemeral ones from the sender. * Relay keypairs, TLS without certificates, relays known by keypair instead of URL * Layered protocol (separate core from applications) * Software remembering when they first saw an event, for 2 reasons, the main one being revocation (don't trust the date in the event, trust when you first saw it), the second being more precise time range queries. * Upgrade/feature negotiation (HTTP headers prior to starting websockets) * IDs starting with a timestamp so they are temporally adjacent (significantly better database performance) (Vitor's idea) * Filters that allow boolean expressions on tag values, and also ID exclusions. Removing IDs from filters and moving to a GET command. * Changing the transport (I'm against this but I know others want to) ## What would it look like? Someone (Steve Farroll) has taken my nostr-next repo and turned it into a proposed protocol he calls [Mosaic](https://github.com/SteveFarroll/mosaic-spec). I think it is quite representative of that repo, as it already includes most of those suggestions, so I've been contributing to it. Mosaic spec is rendered [here](https://stevefarroll.github.io/mosaic-spec/). Of course, where Mosaic stands right now it is mostly my ideas (and Steve's), it doesn't have feedback or input from other nostr developers yet. That is what this blog post is about. I think it is time for other nostr devs to be made aware of this thing. It is currently in the massive breaking changes phase. It might not look that way because of the detail and refinement of the documentation, but indeed everything is changing rapidly. It probably has some bad ideas and is probably missing some great ideas that you have. Which is why this is a good time for other devs to start taking a look at it. It is also the time to debate meta issues like "are you crazy Mike?" or "no we have to just break nostr but keep it nostr, we can't dual-stack" or whatever. Personally I think mosaic-spec should develop and grow for quite a while before the "tipping point" happens. That is, I'm not sure we should jump in feet first yet, but rather we build up and refine this new protocol and spend a lot of time thinking about how to migrate smoothly, and break it a lot while nobody is using it. So you can just reply to this, or DM me, or open issues or PRs at [Mosaic](https://github.com/SteveFarroll/mosaic-spec), or just whisper to each other while giving me the evil eye.
@ ee11a5df:b76c4e49
2024-12-16 05:29:30# Nostr 2? ## Breaking Changes in Nostr Nostr was a huge leap forward. But it isn't perfect. When developers notice a problem with nostr, they confer with each other to work out a solution to the problem. This is usually in the form of a NIP PR on the nips repo. Some problems are easy. Just add something new and optional. No biggie. Zaps, git stuff, bunkers... just dream it up and add it. Other problems can only be fixed by breaking changes. With a breaking change, the overall path forward is like this: Add the new way of doing it while preserving the old way. Push the major software to switch to the new way. Then deprecate the old way. This is a simplification, but it is the basic idea. It is how we solved markers/quotes/root and how we are upgrading encryption, among other things. This process of pushing through a breaking change becomes more difficult as we have more and more existing nostr software out there that will break. Most of the time what happens is that the major software is driven to make the change (usually by nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6), and the smaller software is left to fend for itself. A while back I introduced the BREAKING.md file to help people developing smaller lesser-known software keep up with these changes. ## Big Ideas But some ideas just can't be applied to nostr. The idea is too big. The change is too breaking. It changes something fundamental. And nobody has come up with a smooth path to move from the old way to the new way. And so we debate a bunch of things, and never settle on anything, and eventually nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 makes a post saying that we don't really want it anyways 😉. As we encounter good ideas that are hard to apply to nostr, I've been filing them away in a repository I call "nostr-next", so we don't forget about them, in case we ever wanted to start over. It seems to me that starting over every time we encountered such a thing would be unwise. However, once we collect enough changes that we couldn't reasonably phase into nostr, then a tipping point is crossed where it becomes worthwhile to start over. In terms of the "bang for the buck" metaphor, the bang becomes bigger and bigger but the buck (the pain and cost of starting over) doesn't grow as rapidly. ## WHAT? Start over? IMHO starting over could be very bad if done in a cavalier way. The community could fracture. The new protocol could fail to take off due to lacking the network effect. The odds that a new protocol catches on are low, irrespective of how technically superior it could be. So the big question is: can we preserve the nostr community and it's network effect while making a major step-change to the protocol and software? I don't know the answer to that one, but I have an idea about it. I think the new-protocol clients can be dual-stack, creating events in both systems and linking those events together via tags. The nostr key identity would still be used, and the new system identity too. This is better than things like the mostr bridge because each user would remain in custody of their own keys. ## The nitty gritty Here are some of the things I think would make nostr better, but which nostr can't easily fix. A lot of these ideas have been mentioned before by multiple people and I didn't give credit to all of you (sorry) because my brain can't track it all. But I've been collecting these over time at https://github.com/mikedilger/nostr-next * Events as CBOR or BEVE or MsgPack or a fixed-schema binary layout... anything but JSON text with its parsing, it's encoding ambiguity, it's requirement to copy fields before hashing them, its unlimited size constraints. (me, nostr:npub1xtscya34g58tk0z605fvr788k263gsu6cy9x0mhnm87echrgufzsevkk5s) * EdDSA ed25519 keys instead of secp256k1, to enable interoperability with a bunch of other stuff like ssh, pgp, TLS, Mainline DHT, and many more, plus just being better cryptography (me, Nuh, Orlovsky, except Orlovsky wanted Ristretto25519 for speed) * Bootstrapping relay lists (and relay endpoints) from Mainline DHT (nostr:npub1jvxvaufrwtwj79s90n79fuxmm9pntk94rd8zwderdvqv4dcclnvs9s7yqz) * Master keys and revocable subkeys / device keys (including having your nostr key as a subkey) * Encryption to use different encryption-specific subkeys and ephemeral ones from the sender. * Relay keypairs, TLS without certificates, relays known by keypair instead of URL * Layered protocol (separate core from applications) * Software remembering when they first saw an event, for 2 reasons, the main one being revocation (don't trust the date in the event, trust when you first saw it), the second being more precise time range queries. * Upgrade/feature negotiation (HTTP headers prior to starting websockets) * IDs starting with a timestamp so they are temporally adjacent (significantly better database performance) (Vitor's idea) * Filters that allow boolean expressions on tag values, and also ID exclusions. Removing IDs from filters and moving to a GET command. * Changing the transport (I'm against this but I know others want to) ## What would it look like? Someone (Steve Farroll) has taken my nostr-next repo and turned it into a proposed protocol he calls [Mosaic](https://github.com/SteveFarroll/mosaic-spec). I think it is quite representative of that repo, as it already includes most of those suggestions, so I've been contributing to it. Mosaic spec is rendered [here](https://stevefarroll.github.io/mosaic-spec/). Of course, where Mosaic stands right now it is mostly my ideas (and Steve's), it doesn't have feedback or input from other nostr developers yet. That is what this blog post is about. I think it is time for other nostr devs to be made aware of this thing. It is currently in the massive breaking changes phase. It might not look that way because of the detail and refinement of the documentation, but indeed everything is changing rapidly. It probably has some bad ideas and is probably missing some great ideas that you have. Which is why this is a good time for other devs to start taking a look at it. It is also the time to debate meta issues like "are you crazy Mike?" or "no we have to just break nostr but keep it nostr, we can't dual-stack" or whatever. Personally I think mosaic-spec should develop and grow for quite a while before the "tipping point" happens. That is, I'm not sure we should jump in feet first yet, but rather we build up and refine this new protocol and spend a lot of time thinking about how to migrate smoothly, and break it a lot while nobody is using it. So you can just reply to this, or DM me, or open issues or PRs at [Mosaic](https://github.com/SteveFarroll/mosaic-spec), or just whisper to each other while giving me the evil eye. @ b2d670de:907f9d4a
2024-12-02 21:24:45# onion-service-nostr-relays A list of nostr relays exposed as onion services. ## The list | Relay name | Description | Onion url | Operator | Payment URL | Payment options | | --- | --- | --- | --- | --- | --- | | nostr.oxtr.dev | Same relay as clearnet relay nostr.oxtr.dev | ws://oxtrdevav64z64yb7x6rjg4ntzqjhedm5b5zjqulugknhzr46ny2qbad.onion | [operator](nostr:nprofile1qqst94nsmefmya53crp5qq39kewrtgndqcynhnzp7j8lcu0qjple6jspz3mhxue69uhkummnw3ezummcw3ezuer9wcq3gamnwvaz7tmjv4kxz7fwv3sk6atn9e5k7jxrgyy) | N/A | N/A | | relay.snort.social | Same relay as clearnet relay relay.snort.social | wss://skzzn6cimfdv5e2phjc4yr5v7ikbxtn5f7dkwn5c7v47tduzlbosqmqd.onion | [operator](nostr:nprofile1qqsx8lnrrrw9skpulctgzruxm5y7rzlaw64tcf9qpqww9pt0xvzsfmgpzpmhxue69uhkummnw3ezuamfdejszxrhwden5te0wfjkccte9eekummjwsh8xmmrd9skct9tyup) | N/A | N/A | | nostr.thesamecat.io | Same relay as clearnet relay nostr.thesamecat.io | ws://2jsnlhfnelig5acq6iacydmzdbdmg7xwunm4xl6qwbvzacw4lwrjmlyd.onion | [operator](nostr:npub1wtuh24gpuxjyvnmjwlvxzg8k0elhasagfmmgz0x8vp4ltcy8ples54e7js) | N/A | N/A | | nostr.land | The nostr.land paid relay (same as clearnet) | ws://nostrland2gdw7g3y77ctftovvil76vquipymo7tsctlxpiwknevzfid.onion | [operator](nostr:npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj) | [Payment URL](http://nostrland2gdw7g3y77ctftovvil76vquipymo7tsctlxpiwknevzfid.onion) | BTC LN | | bitcoiner.social | No auth required, currently | ws://bitcoinr6de5lkvx4tpwdmzrdfdpla5sya2afwpcabjup2xpi5dulbad.onion | [operator](nostr:npub1an3nz7lczcunpdw6ltjst94hgzcxpppnk7zk3zr2nfcj4yd96kdse6twjd) | N/A | N/A | | relay.westernbtc.com | The westernbtc.com paid relay | ws://westbtcebhgi4ilxxziefho6bqu5lqwa5ncfjefnfebbhx2cwqx5knyd.onion | [operator](nostr:npub1pc57ls4rad5kvsp733suhzl2d4u9y7h4upt952a2pucnalc59teq33dmza) | [Payment URL](hjar34h5zwgtvxr345q7rncso3dhdaryuxgri3lu7lbhmnzvin72z5ad.onion) | BTC LN | | freelay.sovbit.host | Free relay for sovbit.host | ws://sovbitm2enxfr5ot6qscwy5ermdffbqscy66wirkbsigvcshumyzbbqd.onion | [operator](nostr:npub1gnwpctdec0aa00hfy4lvadftu08ccs9677mr73h9ddv2zvw8fu9smmerrq) | N/A | N/A | | nostr.sovbit.host | Paid relay for sovbit.host | ws://sovbitgz5uqyh7jwcsudq4sspxlj4kbnurvd3xarkkx2use3k6rlibqd.onion | [operator](nostr:npub1gnwpctdec0aa00hfy4lvadftu08ccs9677mr73h9ddv2zvw8fu9smmerrq) | N/A | N/A | | nostr.wine | 🍷 [nostr.wine](https://nostr.wine) relay | ws://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion | [operator](nostr:npub1fyvwkve2gxm3h2d8fvwuvsnkell4jtj4zpae8w4w8zhn2g89t96s0tsfuk) | [Payment URL](http://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion) | BTC LN, BTC, Credit Card/CashApp (Stripe) | | inbox.nostr.wine | 🍷 [inbox.nostr.wine](https://inbox.nostr.wine) relay | ws://wineinboxkayswlofkugkjwhoyi744qvlzdxlmdvwe7cei2xxy4gc6ad.onion | [operator](nostr:npub1fyvwkve2gxm3h2d8fvwuvsnkell4jtj4zpae8w4w8zhn2g89t96s0tsfuk) | [Payment URL](http://wineinboxkayswlofkugkjwhoyi744qvlzdxlmdvwe7cei2xxy4gc6ad.onion) | BTC LN, BTC | | filter.nostr.wine | 🍷 [filter.nostr.wine](https://filter.nostr.wine) proxy relay | ws://winefiltermhqixxzmnzxhrmaufpnfq3rmjcl6ei45iy4aidrngpsyid.onion | [operator](nostr:npub1fyvwkve2gxm3h2d8fvwuvsnkell4jtj4zpae8w4w8zhn2g89t96s0tsfuk) | [Payment URL](http://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion/add-time) | BTC LN, BTC | | N/A | N/A | ws://pzfw4uteha62iwkzm3lycabk4pbtcr67cg5ymp5i3xwrpt3t24m6tzad.onion:81 | [operator](nostr:nprofile1q9z8wue69uhky6t5vdhkjmnjxejx2dtvddm8sdr5wpmkgmt6wfjxversd3sn2umevyexzenhwp3kzcn2w4cry7rsdy6kgatvvfskgtn0de5k7m30q9z8wue69uhk77r5wfjx2anpwcmrg73kx3ukydmcxeex5ee5de685ut2dpjkgmf4vg6h56n3w4k82emtde585u35xeh8jvn3vfskgtn0de5k7m30qqs93v545xjl0w8865rhw7kte0mkjxst88rk3k3xj53q4zdxm2zu5ectdn2z6) | N/A | N/A | | nostr.fractalized.net | Free relay for fractalized.net | ws://xvgox2zzo7cfxcjrd2llrkthvjs5t7efoalu34s6lmkqhvzvrms6ipyd.onion | [operator](nostr:npub1ky4kxtyg0uxgw8g5p5mmedh8c8s6sqny6zmaaqj44gv4rk0plaus3m4fd2) | N/A | N/A | | nfrelay.app | [nfrelay.app](https://nfrelay.app) aggregator relay (nostr-filter-relay) | ws://nfrelay6saohkmipikquvrn6d64dzxivhmcdcj4d5i7wxis47xwsriyd.onion | [operator](nostr:npub19dn7fq9hlxwjsdtgf28hyakcdmd73cccaf2u7a7vl42echey7ezs2hwja7) | N/A | N/A | relay.nostr.net | Public relay from nostr.net (Same as clearnet) | ws://nostrnetl6yd5whkldj3vqsxyyaq3tkuspy23a3qgx7cdepb4564qgqd.onion | [operator](https://nostr.at/aljaz@nostr.si) | N/A | N/A | | nerostrator | Free to read, pay XMR to relay | ws://nerostrrgb5fhj6dnzhjbgmnkpy2berdlczh6tuh2jsqrjok3j4zoxid.onion | [operator](nostr:npub19j7zhftjfjnep4xa7zxhevschkqdvem9zr26dq4myhu6d62p3gqs3htnca) |[Payment URL](http://nerostrrgb5fhj6dnzhjbgmnkpy2berdlczh6tuh2jsqrjok3j4zoxid.onion) | XMR | | nostr.girino.org | Public relay from nostr.girino.org | ws://gnostr2jnapk72mnagq3cuykfon73temzp77hcbncn4silgt77boruid.onion | [operator](nostr:npub18lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vets0hcfsz) | N/A | N/A | | wot.girino.org | WoT relay from wot.girino.org | ws://girwot2koy3kvj6fk7oseoqazp5vwbeawocb3m27jcqtah65f2fkl3yd.onion | [operator](nostr:npub18lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vets0hcfsz) | N/A | N/A | | haven.girino.org/{outbox, inbox, chat, private} | Haven smart relay from haven.girino.org | ws://ghaven2hi3qn2riitw7ymaztdpztrvmm337e2pgkacfh3rnscaoxjoad.onion/{outbox, inbox, chat, private} | [operator](nostr:npub18lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vets0hcfsz) | N/A | N/A | | relay.nostpy.lol | Free Web of Trust relay (Same as clearnet) | ws://pemgkkqjqjde7y2emc2hpxocexugbixp42o4zymznil6zfegx5nfp4id.onion | [operator](nostr:nprofile1qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshszxrhwden5te0dehhxarj9enx6apwwa5h5tnzd9az7qpqg5pm4gf8hh7skp2rsnw9h2pvkr32sdnuhkcx9yte7qxmrg6v4txqr5amve) |N/A | N/A | | Poster.place Nostr Relay | N/A | ws://dmw5wbawyovz7fcahvguwkw4sknsqsalffwctioeoqkvvy7ygjbcuoad.onion | [operator](nostr:nprofile1qqsr836yylem9deatcu08ekfj8qj9f2aypq8ydt0w8dyng8zp8akjsqpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0ds6xxx6y) | N/A | N/A | ## Contributing Contributions are encouraged to keep this document alive. Just open a PR and I'll have it tested and merged. The onion URL is the only mandatory column, the rest is just nice-to-have metadata about the relay. Put `N/A` in empty columns. If you want to contribute anonymously, please contact me on [SimpleX](https://simplex.chat/contact#/?v=2&smp=smp%3A%2F%2F0YuTwO05YJWS8rkjn9eLJDjQhFKvIYd8d4xG8X1blIU%3D%40smp8.simplex.im%2FZ_4q0Nv91wCk8Uekyiaas7NSr-nEDir7%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAvdSLn5QEwrfKQswQGTzlwtXeLMXbzxErv-zOJU6D0y8%253D%26srv%3Dbeccx4yfxxbvyhqypaavemqurytl6hozr47wfc7uuecacjqdvwpw2xid.onion) or send a DM on nostr using a disposable npub. ### Operator column It is generally preferred to use something that includes a NIP-19 string, either just the string or a url that contains the NIP-19 string in it (e.g. an njump url).
@ b2d670de:907f9d4a
2024-12-02 21:24:45# onion-service-nostr-relays A list of nostr relays exposed as onion services. ## The list | Relay name | Description | Onion url | Operator | Payment URL | Payment options | | --- | --- | --- | --- | --- | --- | | nostr.oxtr.dev | Same relay as clearnet relay nostr.oxtr.dev | ws://oxtrdevav64z64yb7x6rjg4ntzqjhedm5b5zjqulugknhzr46ny2qbad.onion | [operator](nostr:nprofile1qqst94nsmefmya53crp5qq39kewrtgndqcynhnzp7j8lcu0qjple6jspz3mhxue69uhkummnw3ezummcw3ezuer9wcq3gamnwvaz7tmjv4kxz7fwv3sk6atn9e5k7jxrgyy) | N/A | N/A | | relay.snort.social | Same relay as clearnet relay relay.snort.social | wss://skzzn6cimfdv5e2phjc4yr5v7ikbxtn5f7dkwn5c7v47tduzlbosqmqd.onion | [operator](nostr:nprofile1qqsx8lnrrrw9skpulctgzruxm5y7rzlaw64tcf9qpqww9pt0xvzsfmgpzpmhxue69uhkummnw3ezuamfdejszxrhwden5te0wfjkccte9eekummjwsh8xmmrd9skct9tyup) | N/A | N/A | | nostr.thesamecat.io | Same relay as clearnet relay nostr.thesamecat.io | ws://2jsnlhfnelig5acq6iacydmzdbdmg7xwunm4xl6qwbvzacw4lwrjmlyd.onion | [operator](nostr:npub1wtuh24gpuxjyvnmjwlvxzg8k0elhasagfmmgz0x8vp4ltcy8ples54e7js) | N/A | N/A | | nostr.land | The nostr.land paid relay (same as clearnet) | ws://nostrland2gdw7g3y77ctftovvil76vquipymo7tsctlxpiwknevzfid.onion | [operator](nostr:npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj) | [Payment URL](http://nostrland2gdw7g3y77ctftovvil76vquipymo7tsctlxpiwknevzfid.onion) | BTC LN | | bitcoiner.social | No auth required, currently | ws://bitcoinr6de5lkvx4tpwdmzrdfdpla5sya2afwpcabjup2xpi5dulbad.onion | [operator](nostr:npub1an3nz7lczcunpdw6ltjst94hgzcxpppnk7zk3zr2nfcj4yd96kdse6twjd) | N/A | N/A | | relay.westernbtc.com | The westernbtc.com paid relay | ws://westbtcebhgi4ilxxziefho6bqu5lqwa5ncfjefnfebbhx2cwqx5knyd.onion | [operator](nostr:npub1pc57ls4rad5kvsp733suhzl2d4u9y7h4upt952a2pucnalc59teq33dmza) | [Payment URL](hjar34h5zwgtvxr345q7rncso3dhdaryuxgri3lu7lbhmnzvin72z5ad.onion) | BTC LN | | freelay.sovbit.host | Free relay for sovbit.host | ws://sovbitm2enxfr5ot6qscwy5ermdffbqscy66wirkbsigvcshumyzbbqd.onion | [operator](nostr:npub1gnwpctdec0aa00hfy4lvadftu08ccs9677mr73h9ddv2zvw8fu9smmerrq) | N/A | N/A | | nostr.sovbit.host | Paid relay for sovbit.host | ws://sovbitgz5uqyh7jwcsudq4sspxlj4kbnurvd3xarkkx2use3k6rlibqd.onion | [operator](nostr:npub1gnwpctdec0aa00hfy4lvadftu08ccs9677mr73h9ddv2zvw8fu9smmerrq) | N/A | N/A | | nostr.wine | 🍷 [nostr.wine](https://nostr.wine) relay | ws://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion | [operator](nostr:npub1fyvwkve2gxm3h2d8fvwuvsnkell4jtj4zpae8w4w8zhn2g89t96s0tsfuk) | [Payment URL](http://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion) | BTC LN, BTC, Credit Card/CashApp (Stripe) | | inbox.nostr.wine | 🍷 [inbox.nostr.wine](https://inbox.nostr.wine) relay | ws://wineinboxkayswlofkugkjwhoyi744qvlzdxlmdvwe7cei2xxy4gc6ad.onion | [operator](nostr:npub1fyvwkve2gxm3h2d8fvwuvsnkell4jtj4zpae8w4w8zhn2g89t96s0tsfuk) | [Payment URL](http://wineinboxkayswlofkugkjwhoyi744qvlzdxlmdvwe7cei2xxy4gc6ad.onion) | BTC LN, BTC | | filter.nostr.wine | 🍷 [filter.nostr.wine](https://filter.nostr.wine) proxy relay | ws://winefiltermhqixxzmnzxhrmaufpnfq3rmjcl6ei45iy4aidrngpsyid.onion | [operator](nostr:npub1fyvwkve2gxm3h2d8fvwuvsnkell4jtj4zpae8w4w8zhn2g89t96s0tsfuk) | [Payment URL](http://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion/add-time) | BTC LN, BTC | | N/A | N/A | ws://pzfw4uteha62iwkzm3lycabk4pbtcr67cg5ymp5i3xwrpt3t24m6tzad.onion:81 | [operator](nostr:nprofile1q9z8wue69uhky6t5vdhkjmnjxejx2dtvddm8sdr5wpmkgmt6wfjxversd3sn2umevyexzenhwp3kzcn2w4cry7rsdy6kgatvvfskgtn0de5k7m30q9z8wue69uhk77r5wfjx2anpwcmrg73kx3ukydmcxeex5ee5de685ut2dpjkgmf4vg6h56n3w4k82emtde585u35xeh8jvn3vfskgtn0de5k7m30qqs93v545xjl0w8865rhw7kte0mkjxst88rk3k3xj53q4zdxm2zu5ectdn2z6) | N/A | N/A | | nostr.fractalized.net | Free relay for fractalized.net | ws://xvgox2zzo7cfxcjrd2llrkthvjs5t7efoalu34s6lmkqhvzvrms6ipyd.onion | [operator](nostr:npub1ky4kxtyg0uxgw8g5p5mmedh8c8s6sqny6zmaaqj44gv4rk0plaus3m4fd2) | N/A | N/A | | nfrelay.app | [nfrelay.app](https://nfrelay.app) aggregator relay (nostr-filter-relay) | ws://nfrelay6saohkmipikquvrn6d64dzxivhmcdcj4d5i7wxis47xwsriyd.onion | [operator](nostr:npub19dn7fq9hlxwjsdtgf28hyakcdmd73cccaf2u7a7vl42echey7ezs2hwja7) | N/A | N/A | relay.nostr.net | Public relay from nostr.net (Same as clearnet) | ws://nostrnetl6yd5whkldj3vqsxyyaq3tkuspy23a3qgx7cdepb4564qgqd.onion | [operator](https://nostr.at/aljaz@nostr.si) | N/A | N/A | | nerostrator | Free to read, pay XMR to relay | ws://nerostrrgb5fhj6dnzhjbgmnkpy2berdlczh6tuh2jsqrjok3j4zoxid.onion | [operator](nostr:npub19j7zhftjfjnep4xa7zxhevschkqdvem9zr26dq4myhu6d62p3gqs3htnca) |[Payment URL](http://nerostrrgb5fhj6dnzhjbgmnkpy2berdlczh6tuh2jsqrjok3j4zoxid.onion) | XMR | | nostr.girino.org | Public relay from nostr.girino.org | ws://gnostr2jnapk72mnagq3cuykfon73temzp77hcbncn4silgt77boruid.onion | [operator](nostr:npub18lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vets0hcfsz) | N/A | N/A | | wot.girino.org | WoT relay from wot.girino.org | ws://girwot2koy3kvj6fk7oseoqazp5vwbeawocb3m27jcqtah65f2fkl3yd.onion | [operator](nostr:npub18lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vets0hcfsz) | N/A | N/A | | haven.girino.org/{outbox, inbox, chat, private} | Haven smart relay from haven.girino.org | ws://ghaven2hi3qn2riitw7ymaztdpztrvmm337e2pgkacfh3rnscaoxjoad.onion/{outbox, inbox, chat, private} | [operator](nostr:npub18lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vets0hcfsz) | N/A | N/A | | relay.nostpy.lol | Free Web of Trust relay (Same as clearnet) | ws://pemgkkqjqjde7y2emc2hpxocexugbixp42o4zymznil6zfegx5nfp4id.onion | [operator](nostr:nprofile1qy08wumn8ghj7mn0wd68yttsw43zuam9d3kx7unyv4ezumn9wshszxrhwden5te0dehhxarj9enx6apwwa5h5tnzd9az7qpqg5pm4gf8hh7skp2rsnw9h2pvkr32sdnuhkcx9yte7qxmrg6v4txqr5amve) |N/A | N/A | | Poster.place Nostr Relay | N/A | ws://dmw5wbawyovz7fcahvguwkw4sknsqsalffwctioeoqkvvy7ygjbcuoad.onion | [operator](nostr:nprofile1qqsr836yylem9deatcu08ekfj8qj9f2aypq8ydt0w8dyng8zp8akjsqpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0ds6xxx6y) | N/A | N/A | ## Contributing Contributions are encouraged to keep this document alive. Just open a PR and I'll have it tested and merged. The onion URL is the only mandatory column, the rest is just nice-to-have metadata about the relay. Put `N/A` in empty columns. If you want to contribute anonymously, please contact me on [SimpleX](https://simplex.chat/contact#/?v=2&smp=smp%3A%2F%2F0YuTwO05YJWS8rkjn9eLJDjQhFKvIYd8d4xG8X1blIU%3D%40smp8.simplex.im%2FZ_4q0Nv91wCk8Uekyiaas7NSr-nEDir7%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAvdSLn5QEwrfKQswQGTzlwtXeLMXbzxErv-zOJU6D0y8%253D%26srv%3Dbeccx4yfxxbvyhqypaavemqurytl6hozr47wfc7uuecacjqdvwpw2xid.onion) or send a DM on nostr using a disposable npub. ### Operator column It is generally preferred to use something that includes a NIP-19 string, either just the string or a url that contains the NIP-19 string in it (e.g. an njump url).