-

@ df478568:2a951e67
2025-02-07 22:34:11
Freedom tech is free and open-source software. It is free as in freedom. A common license in FOSS is the MIT license. It's the license behind Bitcoin, a peer-to-peer electronic cash system. Anyone is free to run this software. The same is true for the software at mempool.space. The software is free to use. I run it on my own server.
This is what I use to time-stamp my articles. You can use it to check transactions on the bitcoin time chain, but you need to trust that I'm not doing any funny business. I'm not, but keep in mind, the whole point of p2p elwctronic cash is that you don't trust. You verify.
The beauty of FOSS is: You don't need to trust me. You can triple-check the transactions you search on my mempool instance by looking at the official mempool.space website and blockchain.info...Or...You can run your own node on your own hardware, free of charge.
Of course, the hardware is not free. Neither is the actual bitcoin. The freedom is built into the software, but as the saying goes, "freedom isn't free." It took me years to learn how to run my own software on my own server and make it available on the clear net.
## SearXNG

[SearXNG](https://github.com/searxng/searxng) is my favorite search engine. I don't like giving up my precious data to big tech located in the United States or China. I run my own search engine. I have noticed certain biases in Google searches. The biggest problem is ads.
Companies tend to pay for Yelp and Google reviews. I called an AC company I found from a local magazine that came in the mail. A portly man wearing an HVAC costume drove to my house in a white van. He had a great smile and even better social skills. The van had a slogan plastered on it like most tradie vans do. "Reviews Matter We have a 4.9 Review on Google." He also had his name painted on this van like a Bomber pilot from WW2. I won't dox him, but it was something like "Joe the closer."
I don't trust the omnipotenence of the Googs. I also don't trust fat men they call "the closer" to give me the best deal. The trick to saving sats is to choose the game-theory optimal way of negogiation.
In DUCY, by David Sklansky, I learned useful negotiation skills. Sklansky wrote classic poker books and applied his actuarial math brain to negotiation techniques. He said he would go to a Toyota dealer and say, "I'm shopping for a new Camry. I already have a price from dealership XYZ in a nearby city. What is your price?"
This changes the dynamic right from the starting line and gives the consumer the advantage. So I tried this based technique with the HVAC industrial complex. I got a quote from 3 people:
1. Joe "The Closer."
2. The Costco-sponsored HVAC Company
3. My SearXNG search results.
In essence, I apply the same logic I learned running a full bitcoin node. Remember how I said the decentralized nature of bitcoin allows you to **triple-check your transactions?** Running SearXNG allows me to triple check my search results in a similar fashion. I don't trust Google, Costco, or the magazine I get every month in the mail. I verify results with my own search engine.
My SearXNG does not track my location, but I set it to give me local results. To be honest, I have not verified this, but the code is on GitHub for everyone to see.
I don't want to be "sold" on an AC. I don't want an AC if I could avoid it, but my AC was as dead as dentacoin. Living in Southern California with a wife going through "the change" gave me no alternative.
The guy I found on SearXNG showed up in an unmarked van. He had a beard. He was not "a closer." He was an actual HVAC technician. He tried cleaning my unit made in the same year Weezer released their Blue album. He said he coukd jerry rig it to get it working for another few months, but the machine is on it's last days. He said a newer unit would also be more efficient so I asked him about the energy like a bitcoiner.
"How many kilowatt hours does it cost me to run my AC versus a new AC?"
I don't remember the exact answer, but I asked all three companies. He was the only one that new how to find out. He also happened to be the cheapest, but I would have bought a new AC from this guy even if he wasn't.
I told him I made a space heater out of a bitcoin miner. He had no idea this was possible, but he at least pretended to find it interesting. That's why I use SearXNG to find tradesmen. It's better than Yelp.
If you would like to try my instance of SearXNG, check it out.
`523FeCpi9Gx4nR9NmSFIMEaYcI5Q4WmhYHPEPaEah84=`
To decrypt it, use the key behind the paywall at:
https://8gwifi.org/CipherFunctions.jsp
npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0
[882785](https://mempool.marc26z.com/block/00000000000000000001840e7986ea4b6ea103f5af9b524dc102be926a831dee)
[merch](https://marc26z.com/merch/)
**Follow me on nostr**.
All of my work is available under the Creative Commons 0 licence. If you would like to try my instance of Searxng and do not wish to support my work, find me on habla.news by searching my npub. You can find all of my work there(including encryption keys)free of charge.
# Paywall On Substack
abdominal.savior.repaint
Will decrypt this ciphertext:
523FeCpi9Gx4nR9NmSFIMEaYcI5Q4WmhYHPEPaEah84=
Which will reveal my instance of SearXNG at
https://searxng.marc26z.com/
[Subscribe on Subtack](https://substack.com/@marc26z)
-

@ fe32298e:20516265
2025-02-06 02:11:34
I've been using AI tools to help with coding for a while now, but it's always been copy/pasting into ChatGPT and DeepSeek. Faster iteration is better, and privacy is best. So it's time to figure out how to use these tools integrated into [VSCodium](https://github.com/VSCodium/vscodium) and running locally. After a quick review of the most popular extensions I've heard about, I settled on [Tabby](https://github.com/TabbyML/tabby).
## What the heck does this actually DO?
* Code completion - like autocomplete suggestions, looks at your code and suggests the next thing to type at the cursor. You can see it in gray text, then press Tab and it's added to your code.
* Chat - easily chat with an LLM about your code inside your editor, faster than copy/pasting into a website.
* Apparently it can write docs and tests too.
## Can I run it locally? Without a GPU? YES!
Tabby is optimized for small models that only need a few GBs of RAM. I'm using a fairly old [System76](https://system76.com/) Galago Pro with Core i5-10210U and 16 GB RAM. The fans spin up, and Tabby sometimes shows a warning about slow response time, but it seems usable.
## How do I get it set up?
This is the overview, look for step-by-step instructions at the end of this article.
1. Install the Tabby server, which runs locally.
1. Start the Tabby server and tell it to serve some models which it will download automatically.
1. Log in to the Tabby server web interface and create an admin account.
1. Install the Tabby extension in your editor.
1. Connect the Tabby extension to your Tabby server.
## How do I actually use it?
1. Click **Tabby** in the bottom-right corner to open the Tabby command palette.
1. Select **Chat** to open the Chat pane. Drag it to the right side if you want.
1. Or, *Ctrl-Shift-P* and type "tabby" to see some Tabby commands
1. Select some code and *Ctrl-Shift-P* "tabby" to see more Tabby commands
1. **Explain this** seems like a useful one.
Other than that, I don't know! I just started using it today.
## What model should I use?
As usual, it depends. If you're using CPU instead of GPU, start with the ones recommended by Tabby and shown in the Step-by-Step below. Tabby has a [registry of models](https://tabby.tabbyml.com/docs/models/) you can choose from, and a [leaderboard](https://leaderboard.tabbyml.com/) to compare them.
## Step-by-Step
This is for Ubuntu 24.04, and no GPU.
```
# install pre-reqs
sudo apt install build-essential cmake libssl-dev pkg-config
sudo apt install protobuf-compiler libopenblas-dev
sudo apt install make sqlite3 graphviz
# install rust
curl --proto '=https' --tlsv1.2 -sSf https://sh.rustup.rs | sh
. "$HOME/.cargo/env"
# build tabby
git clone --recurse-submodules https://github.com/TabbyML/tabby
cd tabby
cargo build
# run tabby (downloads ~3 GB of models)
./target/debug/tabby serve --model StarCoder-1B --chat-model Qwen2-1.5B-Instruct
# browse to http://0.0.0.0:8080 and create an admin user
```
* Install the Tabby extension in your editor. VSCodium had it in the extensions store by searching for "tabby" or try this `ext install TabbyML.vscode-tabby`
* *Ctrl-Shift-P* and look for "Tabby: Connect to server"
* Use the default of `http://localhost:8080`
* Switch over to the Tabby web interface, click your Profile Picture and copy the auth token
* Paste that into Tabby somewhere. I'm sure you'll figure it out if you got this far.
-

@ 9e5a3a1a:ed414e8d
2025-02-02 00:51:34
(deleted)
-

@ daa41bed:88f54153
2025-02-09 16:50:04
There has been a good bit of discussion on Nostr over the past few days about the merits of zaps as a method of engaging with notes, so after writing a rather lengthy [article on the pros of a strategic Bitcoin reserve](https://geek.npub.pro/post/dxqkgnjplttkvetprg8ox/), I wanted to take some time to chime in on the much more fun topic of digital engagement.
Let's begin by defining a couple of things:
**Nostr** is a decentralized, censorship-resistance protocol whose current biggest use case is social media (think Twitter/X). Instead of relying on company servers, it relies on relays that anyone can spin up and own their own content. Its use cases are much bigger, though, and this article is hosted on my own relay, using my own Nostr relay as an example.
**Zap** is a tip or donation denominated in sats (small units of Bitcoin) sent from one user to another. This is generally done directly over the Lightning Network but is increasingly using Cashu tokens. For the sake of this discussion, how you transmit/receive zaps will be irrelevant, so don't worry if you don't know what [Lightning](https://lightning.network/) or [Cashu](https://cashu.space/) are.
If we look at how users engage with posts and follows/followers on platforms like Twitter, Facebook, etc., it becomes evident that traditional social media thrives on engagement farming. The more outrageous a post, the more likely it will get a reaction. We see a version of this on more visual social platforms like YouTube and TikTok that use carefully crafted thumbnail images to grab the user's attention to click the video. If you'd like to dive deep into the psychology and science behind social media engagement, let me know, and I'd be happy to follow up with another article.
In this user engagement model, a user is given the option to comment or like the original post, or share it among their followers to increase its signal. They receive no value from engaging with the content aside from the dopamine hit of the original experience or having their comment liked back by whatever influencer they provide value to. Ad revenue flows to the content creator. Clout flows to the content creator. Sales revenue from merch and content placement flows to the content creator. We call this a linear economy -- the idea that resources get created, used up, then thrown away. Users create content and farm as much engagement as possible, then the content is forgotten within a few hours as they move on to the next piece of content to be farmed.
What if there were a simple way to give value back to those who engage with your content? By implementing some value-for-value model -- a circular economy. Enter zaps.

Unlike traditional social media platforms, Nostr does not actively use algorithms to determine what content is popular, nor does it push content created for active user engagement to the top of a user's timeline. Yes, there are "trending" and "most zapped" timelines that users can choose to use as their default, but these use relatively straightforward engagement metrics to rank posts for these timelines.
That is not to say that we may not see clients actively seeking to refine timeline algorithms for specific metrics. Still, the beauty of having an open protocol with media that is controlled solely by its users is that users who begin to see their timeline gamed towards specific algorithms can choose to move to another client, and for those who are more tech-savvy, they can opt to run their own relays or create their own clients with personalized algorithms and web of trust scoring systems.
Zaps enable the means to create a new type of social media economy in which creators can earn for creating content and users can earn by actively engaging with it. Like and reposting content is relatively frictionless and costs nothing but a simple button tap. Zaps provide active engagement because they signal to your followers and those of the content creator that this post has genuine value, quite literally in the form of money—sats.

I have seen some comments on Nostr claiming that removing likes and reactions is for wealthy people who can afford to send zaps and that the majority of people in the US and around the world do not have the time or money to zap because they have better things to spend their money like feeding their families and paying their bills. While at face value, these may seem like valid arguments, they, unfortunately, represent the brainwashed, defeatist attitude that our current economic (and, by extension, social media) systems aim to instill in all of us to continue extracting value from our lives.
Imagine now, if those people dedicating their own time (time = money) to mine pity points on social media would instead spend that time with genuine value creation by posting content that is meaningful to cultural discussions. Imagine if, instead of complaining that their posts get no zaps and going on a tirade about how much of a victim they are, they would empower themselves to take control of their content and give value back to the world; where would that leave us? How much value could be created on a nascent platform such as Nostr, and how quickly could it overtake other platforms?
Other users argue about user experience and that additional friction (i.e., zaps) leads to lower engagement, as proven by decades of studies on user interaction. While the added friction may turn some users away, does that necessarily provide less value? I argue quite the opposite. You haven't made a few sats from zaps with your content? Can't afford to send some sats to a wallet for zapping? How about using the most excellent available resource and spending 10 seconds of your time to leave a comment? Likes and reactions are valueless transactions. Social media's real value derives from providing monetary compensation and actively engaging in a conversation with posts you find interesting or thought-provoking. Remember when humans thrived on conversation and discussion for entertainment instead of simply being an onlooker of someone else's life?
If you've made it this far, my only request is this: try only zapping and commenting as a method of engagement for two weeks. Sure, you may end up liking a post here and there, but be more mindful of how you interact with the world and break yourself from blind instinct. You'll thank me later.

-

@ bbb5dda0:f09e2747
2025-02-11 05:19:58
**There's nothing like the ability of a Nostr/Bitcoin meetup to bring your bullish-ness back to a 120%. This weekend I had the honors to be part of the [Sats 'n Facts](https://satsnfacts.btc.pub/) conference so this update will be mostly about the conference.**

# Tollgate
A while ago while still at SEC I got the invitation to go to Sats 'n Facts and tell something about TollGate, which I was working on at the time. This is the reason I made such a push on the TollGate Android app, because I wanted to show the world the potential implications of this technology when applied in practice. We get the ability to build our own (physical!) sovereign network infrastructure. Maybe it doesn't sound too sexy for rich western countries, but very valuable for regions with lacking digital infrastructure, or regular powercuts (something I learned at the conference, that TollGate could be applied to bridge those).

Above: Illustration how a TollGate network connects to the legacy internet.
I did a presentation about the project and did a demo, which as the universe commands, suffered from the [demo-effect](https://www.urbandictionary.com/define.php?term=demo%20effect). Despite that, it was very well-received and the feedback and ideas on how and where to apply this were amazing. From splitting your bill with your neighbour, to strapping 5g-enabled routers to a light-fixture in the city, everyone had their own ideas on how to use it, and the cool thing is that all of it can be done.
## Presenting GitHub Actions & Epoxy
I held a seperate session on the GitHub actions project and Epoxy. The response was great and I have some more feedback coming in a 1-on-1 session, so I'm sure i'll be posting about that in the near future.
## A realization about Epoxy + TollGate
The more I talk about Epoxy and TollGate, the more I realize how much they are related. Epoxy is a way of bridging connectivity between Nostr users that are on clearnet and want to connect to Relays that are on Tor. But rather than just bridging the captured clearnet and tor, it can be the bridge between clearnet and a community TollGate network, or between different TollGate networks.
As I've thought more about the implications of sovereign TollGate based networks, I think the introduction of many TollGate networks might create a fracturing of the broader internet, which I'd argue is not even a bad thing as this fracturing can reduce centralized surveillance and control. If we'd do this within the conventional way of operating services - think API's & talking directly to servers- that would be a problem as we need to reach those servers at any moment in time. But given the decentralized Nature of Nostr messages + Blossom files, you might not even notice it if your geographical region gets cut off from the rest of the world, because the content likely already exists within your -now cut off- network.
If we can get our content local, why wouldn't we embrace this fractured internet and use it in our advantage.
nostr:naddr1qvzqqqr4gupzpwa4mkswz4t8j70s2s6q00wzqv7k7zamxrmj2y4fs88aktcfuf68qq3k2ur00puj6mt0dejhg6t6v93xcefdwajkyum0vd4k2apdwpex77rfv4esk0qk8g
## A final word
I'm incredible grateful to be meeting all these talented developers, artists and community builders! I love to see art being integrated into the broader ecosystem and I think us dev's need to lean on the community builders to get our projects out into the world, they often have the insight on how our software shapes the lives of the communities they help to grow. Let's embrace that dynamic!
special thanks to nostr:npub19m7m3rs66pfdn4ewhrm8slh60ukyxgrylaa03m73wa40j39lc03syq4gfu for his incredible drawings of the presentations:
nostr:nevent1qvzqqqqqqypzpr2m4ykgej3at3ee9upe82c4h58uda35xfd5292purmuntrv8mx4qqsfr9f9kvta87yukqhedc00vckupu3erx3mk3nvxm28ptfak0acgrc6adj94

-

@ ce75bae2:26c5d165
2025-02-11 04:18:26
Bitcoin is reshaping entrepreneurship in Uganda and beyond. For many, it’s not just an alternative currency but a tool for financial empowerment, business innovation, and global connectivity. Herein, I reflect on my journey with Bitcoin, its impact on entrepreneurship, and how it has changed the way I operate business in Uganda.
Discovering Bitcoin: A Fortunate Scam
My Bitcoin journey started six years ago—not through traditional investment or financial curiosity, but rather by accident. Like many young people searching for ways to make money online, I stumbled upon a website that promised earnings through paid ad viewing. This turned out to be a scam, but it introduced me to Bitcoin. The site offered Bitcoin as a payment option, forcing me to learn how to set up a wallet and receive transactions. Though I lost money in the process, the experience was invaluable—I had unknowingly opened the door to an entirely new financial system.
Years later, I checked my old wallet and saw that the small amount of Bitcoin I had left had doubled in value. That moment sparked a deeper curiosity, leading me to research Bitcoin’s mechanics and how it could be used beyond speculation.
From Curiosity to Business Innovation
As I dove deeper into the Bitcoin ecosystem, I saw its potential to transform business in ways that traditional finance could not. The first realization was that Bitcoin allows global transactions without intermediaries—a critical advantage for entrepreneurs in Uganda, where banking systems are often restrictive and expensive.
Today, all the businesses I co-founded, including Gorilla Sats , Jungle B, and Juicy B, are deeply integrated with Bitcoin. My approach to entrepreneurship has shifted from merely running a business to leveraging Bitcoin as a tool for economic efficiency and expansion.
Bitcoin’s Role in Business Growth
1. Unlocking Global Markets
One of the biggest barriers for African entrepreneurs is the difficulty of conducting business beyond borders. International transactions often involve costly intermediaries, unfavorable exchange rates, and bureaucratic delays. Bitcoin eliminates these restrictions, allowing businesses to trade with anyone, anywhere, instantly.
For example, at Gorilla Sats, our adventure tourism company, 70% of our customers come because we accept Bitcoin payments. Bitcoin not only opens a new customer base but also positions our business in a niche market—one of the very few in the world where travelers can book experiences entirely using Bitcoin.
2. Enhancing Financial Efficiency
Traditional financial systems in Uganda rely heavily on mobile money, which, while innovative, is expensive. Transactions incur fees at every stage: deposit, transfer, and withdrawal. It’s not uncommon for users to lose 10-15% of their money in fees when sending funds.
Bitcoin, on the other hand, allows for low-cost, borderless transactions. For businesses, this means higher profit margins and the ability to reinvest savings into growth.
3. Financial Resilience in an Inflationary Economy
In just a few years, Uganda’s local currency has lost nearly 50% of its value against the US dollar. Businesses operating in shillings face constant depreciation, making long-term planning difficult. By storing value in Bitcoin, businesses can hedge against inflation and maintain purchasing power over time.
At Jungle B, we keep part of our balance sheet in Bitcoin. This strategy protects us from the currency fluctuations that regularly impact Ugandan businesses operating solely in fiat currency.
4. Transforming Social Impact and Charity
Beyond business, Bitcoin has become a tool for grassroots financial inclusion. At the Orphans of Uganda initiative, we integrate Bitcoin into daily transactions, ensuring donations reach the children directly without middlemen.
Every day, children at the orphanage make symbolic Bitcoin payments for their food, learning firsthand how to use digital money responsibly. This isn’t just about feeding children—it’s about educating the next generation on financial autonomy.
Challenges and Opportunities in Uganda
1. Skepticism and Misinformation
Many Ugandans associate Bitcoin with scams, mainly due to past fraudulent projects. Educating people on the difference between Bitcoin (a decentralized asset) and scam coins (pyramid schemes) remains a challenge.
2. Regulatory Uncertainty
Uganda’s regulatory environment for Bitcoin is still unclear. While Bitcoin remains in a legal vacuum, financial institutions are discouraged from facilitating Bitcoin transactions. However, this hasn’t stopped individuals and businesses from using it. In fact, the lack of regulation often makes adoption easier, as Bitcoin operates independently of government oversight.
3. Resistance from Traditional Financial Players
Mobile money services like MTN and Airtel make enormous profits from transaction fees. If Bitcoin adoption grows, their revenue model could be threatened, leading to resistance from these financial institutions. However, they could integrate Bitcoin instead of fighting it, making transactions cheaper for their users.
The Future of Bitcoin in Uganda
Will there be mass Bitcoin adoption in Uganda? Not overnight. Many people resist change, and history shows that better financial tools don’t always lead to immediate adoption. However, Bitcoin’s advantages will continue to attract forward-thinking entrepreneurs and business owners.
For those who embrace it, Bitcoin redefines entrepreneurship, offering financial independence, borderless trade, and a hedge against economic instability. Whether governments embrace it or not, businesses like mine and many others under Blockchain Association of Uganda (BAU) will continue pioneering its use in Uganda.
Final Thoughts
Bitcoin is more than just a digital currency—it’s a tool for freedom, efficiency, and global entrepreneurship. The more people learn about its benefits, the more they will integrate it into their businesses and daily lives. The journey begins with education and experimentation, just as mine did years ago.
For those looking to explore Bitcoin-powered experiences, connect with us at gorilla-sats.com, or follow my work with bitcoinkampala.org. Whether you’re a business owner, traveler, or philanthropist, Bitcoin offers new possibilities—it’s time to embrace the future.
originally posted at https://stacker.news/items/882366
-

@ d058ffb7:70ed2330
2025-02-11 01:10:10
Je publie un ancien texte portant sur Nostr. Auparavant hébergé sur ghost, je teste maintetant la capacité de Nostr d'hébergé de long format.
***
Un point tournant vient d'être franchi. Damus est officiellement disponible sur le App Store de Apple, fini le mode bêta. Mais en quoi c'est un point tournant ?
Apple joue un rôle important de gatekeeper. Chaque application qui veut accéder à son énorme écosystème doit passer une révision diligente, parfois excessive, avant d'être accessible à tous. Après plusieurs tentatives, le principal développeur de Damus, une application dont le code source ouvert est disponible sur github, a finalement reçu son acceptation.
Mais encore, pourquoi est-ce un point tournant ? Et bien, Damus est la principale application pour accéder aux échanges du protocole Nostr. Ce protocole change le paradigme des réseaux sociaux et réduit pratiquement à néant les capacités de censure par une autorité, que ce soit Apple, le gouvernement américain ou un régime autoritaire. Déjà, après quelques heures, on peut voir une affluence chinoise à la recherche de liberté de parole.
Ainsi, en permettant l'accès à cette application, Apple permet à des millions de personnes d'échanger des idées comme jamais auparavant.
Mais en quoi c'est différent ?
Les 3 éléments suivants expliquent grandement la différence :
#### Identification par pairs clé publique / clé privée
Cette stratégie permet de partir avec un haut niveau d'anonymisation. Au besoin, certaines fonctionnalités ou applications pourront venir ajouter certains concepts tel que la vérification d'humanité - la proposition NIP-05 va dans ce sens - ou encore la réputation.
Evidemment, ca implique d'autres avantages, surtout dans des pays déjà sous haute surveillance.
#### Décentralisation via l'utilisation de relais intermédiaires
Cette architecture assure une résilience du réseau. Chaque relai peut décider l'information qu'il diffuse. Si un relai décide de censurer, un autre peut prendre le relai. Il est possible qu'on voit des relais apparaitre par communauté / région afin d'assurer une diffusion optimale des messages.
La mise en place de relais entraine cependant des coûts, principalement matériel et télécommunications / bande passante. Différentes stratégies sont en cours d'[expérimentation](https://andreneves.xyz/p/the-rise-of-paid-nostr-relays), notamment via l'utilisation du réseau lightning, qui pourrait charger un frais minime lors d'échange de bitcoin.
#### Séparation entre le protocole et les applications
Enfin, cette séparation permet d'éviter les points uniques d'échec. Par exemple, malgré l'espoir de liberté qu'a eu l'application Damus, cette dernière a rapidement été [banni par l'état chinois](https://twitter.com/damusapp/status/1621220422216998915). Mais l'espoir survie, car il existe plusieurs alternatives pour accéder au protocole, que ce soit via des applications web (i.g. https://astral.ninja), des applications Android (i.g. Amethyst) ou encore, directement les codes sources sur github. Cela permet également à des applications existantes d'intégrer ce protocole.
Jumelée à l'utilisation des clés publiques/privées, qui permet une mobilité de son réseau de contact, une saine compétition devrait s'établir sur ces applications clientes afin d'offrir la meilleure expérience utilisateur, que ce soit par l'interface graphique, la modération / curation du fils de nouvelles ou simplement la performance.
Il faut cependant être réaliste, il reste beaucoup de défis à affronter avant d'atteindre le grand public. Parmi les défis, ceux-ci me semblent les plus importants:##### Experience utilisateur
Alors que l'utilisation d'une paires de clés publique / privée peut sembler naturel pour les utilisateurs de bitcoin (et de crypto), ca peut être intimidant pour un non-initié. Le concept de relais n'est également pas intuitif et aurait avantage à être vulgariser ou abstrait/transparent. La performance de rafraichissement peut aussi être grandement améliorée.
#### Modération et curation
Qu'on aime ou on n'aime pas, Twitter utilise un algorithme puissant qui permet d'avoir un minimum de pertinence dans les messages affichées. Ce n'est pas encore le cas pour la majorité des applications Nostr. Par conséquent, on peut se sentir *spammer* lorsqu'on regarde le *feed* global. L'arrivée de beaucoup d'utilisateur chinois, et l'incapacité de traduire nativement, a amplifié ce sentiment.
Malgré cela, je suis confiant qu'on va continuer d'entendre parler de ce protocole dans les années et décennies à venir. Pour me suivre, n'hésitez pas à me suivre :
npub16pv0ld77fx0l8mjxwqtnq0dd7md40zte5w60esstfsty6u8dyvcqre8d46
Et pour lire une perspective différente sur le sujet, j'ai beaucoup apprécié cette lecture : https://read.pourteaux.xyz/p/the-moral-imperative-of-a-distributed
-

@ 9673b322:1b75ee9e
2025-02-10 20:37:30
This is an example of test blog post, to be published via the obstrlish plugin.
### This is a sub heading
**Lorem Ipsum** is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry's standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book. It has survived not only five centuries, but also the leap into electronic typesetting, remaining essentially unchanged. It was popularised in the 1960s with the release of Letraset sheets containing Lorem Ipsum passages, and more recently with desktop publishing software like Aldus PageMaker including versions of Lorem Ipsum.
* Test bullet point
* test teste
* test
*sdfasdfasdfasdfadf*
### The standard Lorem Ipsum passage, used since the 1500s
"Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum."
### Section 1.10.32 of "de Finibus Bonorum et Malorum", written by Cicero in 45 BC
"Sed ut perspiciatis unde omnis iste natus error sit voluptatem accusantium doloremque laudantium, totam rem aperiam, eaque ipsa quae ab illo inventore veritatis et quasi architecto beatae vitae dicta sunt explicabo. Nemo enim ipsam voluptatem quia voluptas sit aspernatur aut odit aut fugit, sed quia consequuntur magni dolores eos qui ratione voluptatem sequi nesciunt. Neque porro quisquam est, qui dolorem ipsum quia dolor sit amet, consectetur, adipisci velit, sed quia non numquam eius modi tempora incidunt ut labore et dolore magnam aliquam quaerat voluptatem. Ut enim ad minima veniam, quis nostrum exercitationem ullam corporis suscipit laboriosam, nisi ut aliquid ex ea commodi consequatur? Quis autem vel eum iure reprehenderit qui in ea voluptate velit esse quam nihil molestiae consequatur, vel illum qui dolorem eum fugiat quo voluptas nulla pariatur?"
### 1914 translation by H. Rackham
"But I must explain to you how all this mistaken idea of denouncing pleasure and praising pain was born and I will give you a complete account of the system, and expound the actual teachings of the great explorer of the truth, the master-builder of human happiness. No one rejects, dislikes, or avoids pleasure itself, because it is pleasure, but because those who do not know how to pursue pleasure rationally encounter consequences that are extremely painful. Nor again is there anyone who loves or pursues or desires to obtain pain of itself, because it is pain, but because occasionally circumstances occur in which toil and pain can procure him some great pleasure. To take a trivial example, which of us ever undertakes laborious physical exercise, except to obtain some advantage from it? But who has any right to find fault with a man who chooses to enjoy a pleasure that has no annoying consequences, or one who avoids a pain that produces no resultant pleasure?"
### Section 1.10.33 of "de Finibus Bonorum et Malorum", written by Cicero in 45 BC
"At vero eos et accusamus et iusto odio dignissimos ducimus qui blanditiis praesentium voluptatum deleniti atque corrupti quos dolores et quas molestias excepturi sint occaecati cupiditate non provident, similique sunt in culpa qui officia deserunt mollitia animi, id est laborum et dolorum fuga. Et harum quidem rerum facilis est et expedita distinctio. Nam libero tempore, cum soluta nobis est eligendi optio cumque nihil impedit quo minus id quod maxime placeat facere possimus, omnis voluptas assumenda est, omnis dolor repellendus. Temporibus autem quibusdam et aut officiis debitis aut rerum necessitatibus saepe eveniet ut et voluptates repudiandae sint et molestiae non recusandae. Itaque earum rerum hic tenetur a sapiente delectus, ut aut reiciendis voluptatibus maiores alias consequatur aut perferendis doloribus asperiores repellat."
-

@ 17724a68:89af0638
2025-02-10 19:06:43
«Nació Bastiat el año 1801 en la Bayona francesa, muy cerca, por tanto, de la frontera de España y del Bidasoa, que a menudo citaba como ejemplo de un río que, en vez de promover el comercio, lo destruía por el simple hecho de ser frontera entre dos naciones».
Empezamos citando al honorable Francisco Cabrillo, el experto (y prologuista) por excelencia de la obra de Bastiat en nuestra casa editorial. Con estas palabras, resume fielmente las dos principales preocupaciones del francés: el libre desarrollo del comercio y las relaciones entre los pueblos.
En "Lo que se ve y no se ve" —que podemos encontrar en *Obras escogidas* (Unión Editorial)—, Bastiat nos advierte de que quizás no siempre resulta evidente el efecto colateral de las decisiones políticas. Existen consecuencias visibles e inmediatas, pero también sucesos posteriores y menos visibles que pueden ser incluso más perniciosos que el mal que se deseaba corregir.
Hoy percibimos con suma inquietud el riesgo de una guerra comercial que imponga aranceles/barreras al comercio entre los miembros de las naciones. A los políticos y burócratas les tienta el solo pensar en los impuestos que cobrarán por productos importados, sin razonar sobre el impacto en la cadena productiva y en el poder adquisitivo de sus ciudadanos. Ciertamente, el sancionado sufrirá el impacto, pero quien impone los aranceles, también.
Los nacionales no solo tendrán que pagar más por un mismo producto extranjero, sino que, al verse restringidos por un precio mayor o caída del comercio, dejarían de beneficiarse de la profesionalización del vecino en la producción de un bien en concreto.
Los liberales siempre hemos defendido el libre comercio y la paz. Bastiat es quizás quien mejor resume las razones que nos ha llevado a dichas conclusiones, por lo que os invitamos a profundizar en su obra y disfrutar de la muy enriquecedora lectura de nuestro vecino del *otro lado* del Bidasoa.
--
[OBRAS ESCOGIDAS](https://www.unioneditorial.net/libro/obras-escogidas-segunda-edicion/)

[FRÉDERIC BASTIAT: UN HOMBRE ÚNICO](https://www.unioneditorial.net/libro/un-hombre-unico/)

[EN DEFENSA DEL CAPITALISMO GLOBAL](https://www.unioneditorial.net/libro/en-defensa-del-capitalismo-global-3a-edicion/)

--
Como solemos acostumbrar, para compras en nuestra web ofrecemos una promoción válida para la península ibérica que incluye un 5% de descuento y envío gratis a partir de los 20€ de compra. El código de descuento actual es: **UE2025**
-

@ 3b7fc823:e194354f
2025-02-10 18:56:06
A VPN is Not Magic
A VPN is a virtual private network. A VPN service provides an encrypted tunnel between your device and a server they own or rent. You then connect to the internet from this server thus making your IP address appear to the wider internet as the server IP. That's it. That's all it does.
Your Device -> VPN -> Website
Your Device sees that you are connecting to a website through a VPN.
Your ISP sees that you are connecting to a VPN server but nothing after.
The website sees that someone from a VPN is connecting to them but doesn't know who.
The VPN sees your device connected to their server and that you then connected to a website.
VPN Anonymity and Privacy
VPNs do a lot to protect your privacy, they keep your ISP from seeing and logging every single thing you do online and they spoof your location and IP to any website that you visit. Although this website protection isn't 100% anonymous because of cookies, trackers, and if you have to log into a site with your information. If you are using a VPN on a mobile phone then you are still broadcasting your location to the cell towers even if you are not telling the website you are browsing.
Then there is the elephant in the room. The VPN knows all and sees all. How much do they log? How long do they save it? Can you trust them? This is going to vary VASTLY between VPN providers. I always prefer if they are setup where they cannot know the information in the first place and limit what I tell them in the first place by paying through the use of bitcoin or monero. Just because they have a no log "policy" in place it doesn't always fill me with confidence.
VPN Security
How much security does a VPN give you? Some in certain circumstances but not a lot. A VPN is not going to stop malware or viruses. A VPN can provide some protection from a man in the middle or evil twin attack as it provides a encrypted tunnel between your device and the VPN server, so always use a VPN when joining public WIFI spots. Just remember a VPN cannot protect you downstream on the connection between the VPN server and the website, always use secure encrypted connections and be aware that MITM attacks can still happen on the backside. A VPN can prevent DDoS attacks since the attacker doesn't know your real IP address and a fantastic use of VPNs is to protect IoT devices. Those smart devices around your home love to scream out all their data insecurely and a VPN can change their IP and encrypt their data in transit protecting them from hacking.
VPN Legality
In many countries VPNs are banned, blocked, or outright illegal:
Bahrain
Belarus
China
Cuba
Egypt
Iran
Iraq
Libya
Myanmar
North Korea
Oman
Russia
Syria
Turkey
Turkmenistan
UAE
Uganda
Venezuela
Vietnam
---
Advocating for privacy does not finance itself. If you enjoyed this article, please consider zapping or sending monero
82XCDNK1Js8TethhpGLFPbVyKe25DxMUePad1rUn9z7V6QdCzxHEE7varvVh1VUidUhHVSA4atNU2BTpSNJLC1BqSvDajw1
-

@ 3b7fc823:e194354f
2025-02-10 17:34:18
Dealing with law enforcement can be a challenging and stressful experience. However, understanding your rights and knowing how to navigate such situations can empower you to protect yourself. Here’s a structured approach to handle these interactions effectively:
1. **Stay Calm and Compliant:**
- When approached by law enforcement, remain calm and avoid sudden movements. Slowly raise your hands and identify yourself if possible.
2. **Ask for Identification:**
- Request the officer's name, badge number, and station. This documentation can be crucial later on.
3. **Know Your Miranda Rights:**
- Upon arrest, you have the right to remain silent. Do not answer questions without consulting a lawyer. If Mirandized, exercise your right to remain silent.
4. **Refuse Incriminating Statements:**
- Avoid answering questions that could incriminate yourself. Politely state, "I will not answer any questions at this time."
5. **Document the Incident:**
- Use your phone or notebook to record details such as dates, times, and descriptions of interactions. Note any injuries or mistreatment.
6. **Seek Legal Advice:**
- After the encounter, contact a lawyer. They can review evidence and provide guidance on how to proceed.
7. **Understand Search and Seizure Laws:**
- Officers generally need a warrant to search your property unless there's probable cause. If stopped without a warrant, calmly refuse entry.
8. **Use a Body Camera Policy:**
- If applicable, ask for the officer's body camera footage and request it via formal complaint if refused.
9. **Know When to Comply:**
- Comply with instructions that do not infringe on your rights, such as providing identification when legally required.
10. **Consider a Witness Statement:**
- If you witness illegal actions, consider reporting them. Your role as a bystander may be crucial in documenting incidents.
11. **Seek Emotional Support:**
- Interactions with law enforcement can be traumatic. Reach out to support groups or mental health resources for assistance.
12. **Understand Legal Recourse:**
- If rights are violated, consult legal aid societies or civil rights organizations for guidance on filing complaints or seeking redress.
**Conclusion:**
Understanding your rights and documenting interactions is essential when dealing with law enforcement. This guide provides a framework to help you navigate such situations confidently and protect your rights effectively. Remember, knowledge is power, and being informed can lead to better outcomes in challenging circumstances.
---
Advocating for privacy does not finance itself. If you enjoyed this article, please consider zapping or sending monero
82XCDNK1Js8TethhpGLFPbVyKe25DxMUePad1rUn9z7V6QdCzxHEE7varvVh1VUidUhHVSA4atNU2BTpSNJLC1BqSvDajw1
-

@ 554ab6fe:c6cbc27e
2025-02-10 16:48:35
René Descartes famously stated, "I think therefore I am." A concept centered around the idea that the existence of our meta-conscious thought proves our existence. Furthermore, it denotes a sense of self-derived from the presence of our thinking. What if this famous idea is wrongly reversed? What if our perceived sense of self derives from our thoughts, and these thoughts act as an illusion of the true nature of the self?
A couple of my posts have focused on the idea that the calm mind, potentially derived from a practice of meditation, can achieve a heightened sense of awareness. Some neuroscientists now view the mind as a predictive modeling machine (Seth, 2013), constantly receiving signals from both internal and external sources, generating predictions and models to understand the current condition. This theory inspired me to create an analogy of a calm pond: Imagine the brain and mind as a pond, and instead of neuronal signals, raindrops are falling into the pond. When the pond is calm, and a single drop falls, the pond's ripples provide adequate information to deduce the location and size of the raindrop. By observing the single ripple, one can simply understand the raindrop. However, if there is a storm and many raindrops impact the pond simultaneously, then the ripples are indistinguishable. This makes the analysis of the incoming information near impossible. This may be how the brain works. This would be why calming the mind generates such benefits in health because the brain can analyze the information accurately and execute the proper response. This idea is supported by scientific evidence that interoception increases with mindfulness practice. I have alluded to this idea as a possible explanation of why meditation generates a higher form of consciousness. More on this later.
To further explore this idea, a deeper exploration into the neuroscience of internal mental processes is required. The areas of the brain that are clinically recognized to perform internal mental operations are known as the default mode network (DMN) (Ekhtiari et al., 2016; van Buuren et al., 2010). The DMN is not a single area of the brain but a network and interaction between many areas. The brain areas involved within the DMN include the medial prefrontal cortex (mPFC), the anterior and posterior cingulate cortex (ACC and PCC), temporoparietal junction (TPJ), later temporal cortex (LTC), and the temporal pole (TempP)(Farb et al., 2007; Zhou et al., 2020). In general, the mental processes conducted by the DMN are self-referential processing, long-term memory retrieval, and mind-wandering (Ekhtiari et al., 2016; Marstaller et al., 2017; Spreng & Grady, 2010; van Buuren et al., 2010). However, the functions expand beyond just those. Different brain areas carry differing roles in these processes. For example, the PCC plays a unique role in the autobiographical retrieval process and plays a role in self-centered spatial navigation (Hamilton et al., 2015). However, sometimes these processes manifest in more complex interactions. For example, both the PCC and anterior portion of the mPFC (amPFC) facilitate self-referential processes and the interaction between other hubs of the DMN (Zhou et al., 2020). The role of the DMN is complicated, but its relationship to meditation is significant.
The DMN's plays a significant role in mental ruminations and the activity of the mind. In our modern culture, mental ruminations are commonplace and widely accepted. With this cultural norm, there is no adequate training to properly handle these thoughts when they become repetitive, unconstructive, and potentially destructive. Repetitive unconstructive ruminations are associated with and can lead to depression (Watkins, 2008). Therefore, this mental habit attributes to a significant source of many mental health issues. It is a primary reason why meditation seems to be such an effective mental health benefiting practice. In Eastern traditions, this unhealthy mind is called the "monkey mind": a mind that swings from thought to thought, often time traveling to the past and future. Meditation, and similar practices, aim to quiet this monkey mind. From a clinical perspective, it is fascinating to consider that the DMN may be a neural network representing the monkey mind's activation. There is research to support this idea as well. Autobiographical memory retrieval processes activate the DMN (Spreng & Grady, 2010). Additionally, the DMN seems to maintain a cohesive perception of the self across time to interpret novel information (Marstaller et al., 2017). Clearly, not only is the DMN involved in processes that involve thoughts about the self, but it is also primarily responsible for our mental time traveling processes. If meditation aims to bring our experience to the present, then the DMN is the antithesis.
As previously stated, mental ruminations and other unconstructive thought patterns drive the development of mental health issues such as anxiety and depression. Given that the DMN has a strong relationship to these thought patterns, it is also interesting to note that DMN activity dominance is associated with the development of depression (Hamilton et al., 2011). The brain areas that seem to be activated more often during depression are the anterior and dorsal regions of the mPFC, PCC, temporal lobes, and the TPJ (Zhou et al., 2020)—further suggesting that the DMN is the brain region highly responsible for our inner self-referential thoughts, our time traveling thoughts, and the subsequent mental health outcomes.
The DMN represents, in large part, the mental activity of the mind that removes us from a calm and present state of being. In other words, it adds more “raindrops” to the calm pond (my analogy from before) making it harder for the brain to analyze and adequately react to incoming information. Evidence for this idea lies in the observation that the DMN is responsible for monkey mind-like processes and in learning and conditioning. Again, the brain is constantly receiving neuronal signals from the body. Say it receives a signal from the toe: it must first predict that the signal came from the toe, then understand what the signal meant, and react accordingly. So, if the signal was a pain signal, the brain may command the toe to lift from the ground. If the signal stops, the brain knows the toe is no longer in pain, verifying the prediction. If the signal doesn't stop, further trial and error are required. This is a simple example, but the brain is likely processing and reacting to signals like this all the time, both from information coming from outside the body and within. Therefore, much learning and prediction model generation is taking place. Imagine the famous experiment of Pavlov's dogs. The dogs learned that a particular cue meant food, and their bodies learned to react accordingly. This learning and conditioning are a fundamental aspect of biological life. The DMN plays a significant role in this learning within our brain. For example, the PCC responds to error detection, and the signal is amplified when small rewards or novel stimuli are introduced to the experience (Heilbronner & Platt, 2013). Areas of the DMN (such as the mPFC and PCC) are also thought to be involved in contextualizing memories of safety and inhibit fear responses when appropriate (Marstaller et al., 2017). Finally, the mPFC is thought to play a role in goal-directed motivation (Hamilton et al., 2015). All this evidence suggests that the DMN plays a significant role in the learning process by contextualizing information.
Keep in mind that the DMN can only accurately contextualize incoming stimuli if the full range of signals is adequately recognized. According to the calm pond idea, the noisy activation of a ruminating mind may hinder this ability. Here, greater clarification and definition on what a polluted mind means is needed. To define such mental patterns, functions of specific DMN regions will be explained. Commonly activated regions within the DMN that involve self-referential processes are (Farb et al., 2007; Knyazev, 2013):
1. The orbitomedial prefrontal cortex (omPFC) – which contextualizes experienced stimuli as experienced by the self
2. The ACC – which actively monitors the self-experienced stimuli
3. The mPFC – which evaluates the self-experienced stimuli
4. The PCC – which is involved in a generated a broader context of the personal experience given certain self-experienced stimuli.
By now, it may be evident that the DMN is involved with what is commonly referred to as the "ego". Some researchers claim that the DMN develops the ego itself (R. L. Carhart-Harris & Friston, 2010). The term "ego" derives from Freudian psychoanalytic, and for this reason, the term "narrative-self" will be used instead. It is crucial to consider the word choice here. As previously explained, the DMN generates a time-oriented perception of the self to contextualize information. Furthermore, the four brain areas above all involved contextualizing an experience as experienced by the narrative self (rather than the self being the experience), monitoring these experiences across time, and evaluating these experiences as a broader implication of the experience of the self. The DMN is generating a narrative of the self through every experience. This is indeed where many unconstructive ruminations arise. Any reader can likely relate to ruminating over themselves and their circumstances and thinking about what this means in the larger context of their lives, worth, purpose, etc. This is the monkey mind. This is the DMN.
So, the real question becomes: what effect does the strong presence of a narrative-self have on our broader experience and health? Does a strong presence of the narrative-self influence the body's interoceptive abilities and ability to properly analyze and predict incoming stimuli? This is a complex and challenging question, but evidence suggests that this is indeed the case. In a fantastic study by Farb and others in 2007, fMRIs were used to monitor brain activity in those who did and did not practice mindfulness meditation (Farb et al., 2007). In this study, a distinction was made between narrative focus and experiential focus. For eight weeks, those who underwent mindfulness meditation training were taught to practice experiential focus, which involves having present centered awareness of all thoughts, feelings, and experiences in a non-judgmental manner. Narrative focus was defined as judging experiences and trying to figure out what those stimuli meant. Brain scans were performed on both trained and untrained participants during both focus styles. For both groups, narrative focus increased activation of the mPFC and PCC as expected. During experiential focus, both groups reduced mPFC activity, but only the meditation trained group increased activation of the insula. This is incredible because the insula is highly involved in interoception and the sensations of internal physical states (Fox et al., 2014; Mehling et al., 2012). This study by Farb and others suggests a functional difference between the narrative-self and an experiential-self and shows how the quieting of the narrative-self increases interoceptive abilities and enhances the brains' ability to analyze incoming stimuli properly. Not to mention, this study shows how this skill can be trained.
So far, we have seen how the DMN is involved in the generation of the narrative-self and how this influences our ability to analyze the signals coming from the body. The next reasonable question is to what extent can this be changed? And what are the implications of such change? As was previously shown in the mentioning of the study by Farb and others in 2007, mindfulness meditation appears to be capable of changing DMN activity. This is not the only study to suggest this. Another study showed that meditation decreased mPFC activity in DMN regions, such as the TPJ and PCC (Scheibner et al., 2017). It has also been shown that the neurotransmitter GABA reduces DMN activity, and both yoga and meditation have been implicated in the release of GABA (Guglietti et al., 2013; Hu et al., 2013; Streeter et al., 2018). The release of GABA release is also modulated by the vagus nerve, providing evidence of the possible mechanism at which meditation inhibits DMN activity (Hu et al., 2013; Keute et al., 2018; Streeter et al., 2018). Through these studies, it seems evident that meditation decreases DMN activity. In what ways is this significant? Firstly, it provides more explanation as to why meditation seems capable of alleviating depression. Similarly, it offers more evidence for how meditation increases interoceptive awareness (de Jong et al., 2016; Farb et al., 2010; Hanley et al., 2017). The increase in interoception suggests that the brain is more adequately processing not only the internal environment more adequately, but presumably the outside environment as well. Reality in general is being more accurately understood. It is possible that this also implicates a broader understanding of how meditation can alter consciousness and allowing monks, yogis, and the like to achieve nirvana/samadhi/enlightenment, or whatever you prefer to call such a state of altered consciousnesses. Perhaps this experience of altered consciousness is a more accurate interpretation of reality, produced by enhanced interoception and exteroception.
The subject of altered consciousness is perhaps best explored through brain changes induced by another technique commonly used in a spiritual manner: psychedelics. The famous studies from Johns Hopkins University using psilocybin found that this drug causes a spiritual experience often described as a sense of unity of all things that transcend space and time (Griffiths et al., 2006, 2008). Many participants rate this experience as one of the most significant spiritual experiences of their life (Griffiths et al., 2006). These experiences were often described with an experienced loss sense of self and an altered form of consciousness (Griffiths et al., 2008). It is not hard to imagine that this experience seems very similar to that of a trained monk or yogi, who learn to let go of their narrative-self and gain a sense of oneness with all things. This connection is further verified by the observation that psilocybin decreases the activity of the ACC, PCC, and mPFC (Robin L. Carhart-Harris et al., 2012). Ayahuasca, another psychedelic drug used in spiritual rituals by the indigenous peoples of the Amazon, also has been shown to have similar effects (Palhano-Fontes et al., 2015). Additionally, LSD has been shown to do the same (Speth et al., 2016). Suppose both psychedelic drugs and meditative practice decrease the same DMN, which generates the narrative-self. In that case, both methods likely lead one to the same place: an experience beyond time and space, where one is present with a profound sense of unity with everything.
This, to me, is a profound idea. It suggests that quieting the mind, or calming the “pond”, improves mental, physical, and spiritual health. It provides one with a perception full of compassion, peace, and love. It not only can make the individual healthier, but so too the community and planet. It is extraordinary evidence that improving the self is the greatest means of improving the world around us. Not to mention, it provides a simple means of liberating oneself from the struggle and hardship of life. Perhaps it is not life that is hard on us, but ourselves, by allowing the narrative-mind to take hold of our reality, rather than letting a purer form of consciousness dominate our perceptions. This is the pursuit, and meditation techniques are the practice.
References
Carhart-Harris, R. L., & Friston, K. J. (2010). The default-mode, ego-functions and free-energy: A neurobiological account of Freudian ideas. Brain, 133(4), 1265–1283. https://doi.org/10.1093/brain/awq010
Carhart-Harris, Robin L., Erritzoe, D., Williams, T., Stone, J. M., Reed, L. J., Colasanti, A., Tyacke, R. J., Leech, R., Malizia, A. L., Murphy, K., Hobden, P., Evans, J., Feilding, A., Wise, R. G., & Nutt, D. J. (2012). Neural correlates of the psychedelic state as determined by fMRI studies with psilocybin. Proceedings of the National Academy of Sciences of the United States of America, 109(6), 2138–2143. https://doi.org/10.1073/pnas.1119598109
de Jong, M., Lazar, S. W., Hug, K., Mehling, W. E., Hölzel, B. K., Sack, A. T., Peeters, F., Ashih, H., Mischoulon, D., & Gard, T. (2016). Effects of mindfulness-based cognitive therapy on body awareness in patients with chronic pain and comorbid depression. Frontiers in Psychology, 7(JUN). https://doi.org/10.3389/fpsyg.2016.00967
Ekhtiari, H., Nasseri, P., Yavari, F., Mokri, A., & Monterosso, J. (2016). Neuroscience of drug craving for addiction medicine: From circuits to therapies. In Progress in Brain Research (Vol. 223, pp. 115–141). Elsevier B.V. https://doi.org/10.1016/bs.pbr.2015.10.002
Farb, N. A. S., Anderson, A. K., Mayberg, H., Bean, J., McKeon, D., & Segal, Z. v. (2010). Minding One's Emotions: Mindfulness Training Alters the Neural Expression of Sadness. Emotion, 10(1), 25–33. https://doi.org/10.1037/a0017151
Farb, N. A. S., Segal, Z. v., Mayberg, H., Bean, J., Mckeon, D., Fatima, Z., & Anderson, A. K. (2007). Attending to the present: Mindfulness meditation reveals distinct neural modes of self-reference. Social Cognitive and Affective Neuroscience, 2(4), 313–322. https://doi.org/10.1093/scan/nsm030
Fox, K. C. R., Nijeboer, S., Dixon, M. L., Floman, J. L., Ellamil, M., Rumak, S. P., Sedlmeier, P., & Christoff, K. (2014). Is meditation associated with altered brain structure? A systematic review and meta-analysis of morphometric neuroimaging in meditation practitioners. Neuroscience and Biobehavioral Reviews, 43, 48–73. https://doi.org/10.1016/j.neubiorev.2014.03.016
Griffiths, R. R., Richards, W. A., Johnson, M. W., McCann, U. D., & Jesse, R. (2008). Mystical-type experiences occasioned by psilocybin mediate the attribution of personal meaning and spiritual significance 14 months later. Journal of Psychopharmacology, 22(6), 621–632. https://doi.org/10.1177/0269881108094300
Griffiths, R. R., Richards, W. A., McCann, U., & Jesse, R. (2006). Psilocybin can occasion mystical-type experiences having substantial and sustained personal meaning and spiritual significance. Psychopharmacology, 187(3), 268–283. https://doi.org/10.1007/s00213-006-0457-5
Guglietti, C. L., Daskalakis, Z. J., Radhu, N., Fitzgerald, P. B., & Ritvo, P. (2013). Meditation-related increases in GABAB modulated cortical inhibition. Brain Stimulation, 6(3), 397–402. https://doi.org/10.1016/j.brs.2012.08.005
Hamilton, J. P., Farmer, M., Fogelman, P., & Gotlib, I. H. (2015). Depressive Rumination, the Default-Mode Network, and the Dark Matter of Clinical Neuroscience. In Biological Psychiatry (Vol. 78, Issue 4, pp. 224–230). Elsevier USA. https://doi.org/10.1016/j.biopsych.2015.02.020
Hamilton, J. P., Furman, D. J., Chang, C., Thomason, M. E., Dennis, E., & Gotlib, I. H. (2011). Default-mode and task-positive network activity in major depressive disorder: Implications for adaptive and maladaptive rumination. Biological Psychiatry, 70(4), 327–333. https://doi.org/10.1016/j.biopsych.2011.02.003
Hanley, A. W., Mehling, W. E., & Garland, E. L. (2017). Holding the body in mind: Interoceptive awareness, dispositional mindfulness and psychological well-being. Journal of Psychosomatic Research, 99, 13–20. https://doi.org/10.1016/j.jpsychores.2017.05.014
Heilbronner, S. R., & Platt, M. L. (2013). Causal evidence of performance monitoring by neurons in posterior cingulate cortex during learning. Neuron, 80(6), 1384–1391. https://doi.org/10.1016/j.neuron.2013.09.028
Hu, Y., Chen, X., Gu, H., & Yang, Y. (2013). Resting-state glutamate and GABA concentrations predict task-induced deactivation in the default mode network. Journal of Neuroscience, 33(47), 18566–18573. https://doi.org/10.1523/JNEUROSCI.1973-13.2013
Keute, M., Ruhnau, P., Heinze, H. J., & Zaehle, T. (2018). Behavioral and electrophysiological evidence for GABAergic modulation through transcutaneous vagus nerve stimulation. Clinical Neurophysiology, 129(9), 1789–1795. https://doi.org/10.1016/j.clinph.2018.05.026
Knyazev, G. G. (2013). EEG correlates of self-referential processing. Frontiers in Human Neuroscience, 7(MAY), 1–14. https://doi.org/10.3389/fnhum.2013.00264
Marstaller, L., Burianová, H., & Reutens, D. C. (2017). Adaptive contextualization: A new role for the default mode network in affective learning. Human Brain Mapping, 38(2), 1082–1091. https://doi.org/10.1002/hbm.23442
Mehling, W. E., Price, C., Daubenmier, J. J., Acree, M., Bartmess, E., & Stewart, A. (2012). The Multidimensional Assessment of Interoceptive Awareness (MAIA). PLoS ONE, 7(11). https://doi.org/10.1371/journal.pone.0048230
Palhano-Fontes, F., Andrade, K. C., Tofoli, L. F., Jose, A. C. S., Crippa, A. S., Hallak, J. E. C., Ribeiro, S., & de Araujo, D. B. (2015). The psychedelic state induced by Ayahuasca modulates the activity and connectivity of the Default Mode Network. PLoS ONE, 10(2), 1–13. https://doi.org/10.1371/journal.pone.0118143
Scheibner, H. J., Bogler, C., Gleich, T., Haynes, J. D., & Bermpohl, F. (2017). Internal and external attention and the default mode network. NeuroImage, 148(January), 381–389. https://doi.org/10.1016/j.neuroimage.2017.01.044
Seth, A. K. (2013). Interoceptive inference, emotion, and the embodied self. Trends in Cognitive Sciences, 17(11), 565–573. https://doi.org/10.1016/j.tics.2013.09.007
Speth, J., Speth, C., Kaelen, M., Schloerscheidt, A. M., Feilding, A., Nutt, D. J., & Carhart-Harris, R. L. (2016). Decreased mental time travel to the past correlates with default-mode network disintegration under lysergic acid diethylamide. Journal of Psychopharmacology, 30(4), 344–353. https://doi.org/10.1177/0269881116628430
Spreng, R. N., & Grady, C. L. (2010). Patterns of brain activity supporting autobiographical memory, prospection, and theory of mind, and their relationship to the default mode network. Journal of Cognitive Neuroscience, 22(6), 1112–1123. https://doi.org/10.1162/jocn.2009.21282
Streeter, C., Gerbarg, P. L., Nielsen, G. H., Brown, R. P., Jensen, J. E., Silveri, M., & Streeter, C. C. (2018). Effects of Yoga on Thalamic Gamma-Aminobutyric Acid, Mood and Depression: Analysis of Two Randomized Controlled Trials. Neuropsychiatry, 8(6), 1923–1939. https://doi.org/10.4172/Neuropsychiatry.1000535
van Buuren, M., Gladwin, T. E., Zandbelt, B. B., Kahn, R. S., & Vink, M. (2010). Reduced functional coupling in the default-mode network during self-referential processing. Human Brain Mapping, 31(8), 1117–1127. https://doi.org/10.1002/hbm.20920
Watkins, E. R. (2008). Constructive and unconstructive repetitive thought. Psychological Bulletin, 134(2), 163–206. https://doi.org/10.1037/0033-2909.134.2.163
Zhou, H. X., Chen, X., Shen, Y. Q., Li, L., Chen, N. X., Zhu, Z. C., Castellanos, F. X., & Yan, C. G. (2020). Rumination and the default mode network: Meta-analysis of brain imaging studies and implications for depression. In NeuroImage (Vol. 206, p. 116287). Academic Press Inc. https://doi.org/10.1016/j.neuroimage.2019.116287
-

@ 5d4b6c8d:8a1c1ee3
2025-02-10 16:32:15
The Super Bowl definitely threw me off a bit. My dad offered to bring some food over and the plan was to eat before the game/during the first half. I have no idea what he was doing, but for some reason, it took him two hours to get the food (that was already made) ready to eat.
All things considered, I still did ok. The dry fast was about 13 hours and I might make it to 16 hours without eating (I'm at 15 now).
## Score Card
Day 1: 14 hour fast (13 dry)
Day 2: 15 hour fast (14 dry)
Day 3: 17 hours (16 dry)
Day 4: 18 hours (17 dry)
Day 5: 18 hours (16 dry)
Day 6: 19 hours (16 dry)
Day 7: 16 hours (15 dry)
Day 8: 18 hours (17 dry)
Day 9: 17 hours (17 dry)
Day 10: TBD (13 dry)
originally posted at https://stacker.news/items/881691
-

@ e453ec07:b199e3f8
2025-02-10 16:25:07

## **Le ras-le-bol numérique : comprendre pourquoi vous vous sentez épuisé par Internet)**
Vous vous sentez parfois **épuisé** par Internet ? Submergé par le flot incessant d'informations ? **Las** des publicités qui vous suivent partout, des notifications qui vous harcèlent à toute heure, et de ce sentiment étrange d'être constamment **observé** ?
Vous n'êtes **pas fou**. Et vous n'êtes pas seul.
Ce n'est pas vous qui êtes "déconnecté" ou "incapable de suivre". C'est **Internet lui-même qui est cassé**. Enfin, pas *totalement* en panne, mais profondément **dysfonctionnel**. Imaginez un réseau routier où les panneaux indicateurs sont illisibles, les embouteillages constants, et où des péages surgissent à chaque kilomètre, sans que l'on sache vraiment où va l'argent... C'est un peu l'état d'Internet aujourd'hui.
**Le Brouhaha Numérique : Plus d'Infos, Moins de Sens**

Ce que l'on appelle le "réseau mondial" ressemble de plus en plus à un **brouhaha numérique**. Un flot continu et désordonné d'informations, d'avis, de pubs, de " contenus sponsorisés " qui se mélangent et s'entrechoquent. On a l'impression de boire à la lance à incendie : beaucoup de débit, mais difficile de se désaltérer intelligemment.
Et cette cacophonie a un effet direct sur nous. Elle nous **fatigue**, nous **stresse**, nous rend **moins attentifs**, moins capables de nous concentrer. On passe des heures en ligne sans vraiment savoir ce que l'on cherche, happés par des algorithmes conçus pour **capter notre attention**, souvent au détriment de notre bien-être.
**La Centralisation : Le Cœur du Problème**

Mais pourquoi Internet est-il devenu si chaotique ? La réponse est simple : **la centralisation**.
Au fil des années, Internet, qui se voulait un espace libre et décentralisé, s'est retrouvé progressivement **accaparé par une poignée de géants**. Ces entreprises – vous les connaissez, elles commencent par G, A, M… – contrôlent une part immense de nos vies numériques.
Elles hébergent nos emails, nos photos, nos vidéos, nos réseaux sociaux, nos recherches, nos achats en ligne… Elles sont devenues les **portiers d'Internet**, les **collecteurs de nos données**, et les **architectes de notre expérience en ligne**.
**Les Pièges de la Gratuité et de la Surveillance**
Et c'est là que le bât blesse. Ces services sont souvent présentés comme "gratuits". Mais comme on dit, "quand c'est gratuit, c'est vous le produit". En réalité, nous payons un prix très élevé pour cette "gratuité" : **nos données personnelles**.

Chaque clic, chaque recherche, chaque message, chaque "like" est **enregistré, analysé, et transformé en données**. Ces données servent ensuite à **nous profiler**, à créer ce que l'article original appelle un "GHOST" – un profil consommateur virtuel – afin de nous **bombarder de publicités ciblées**, de nous **influencer**, et de nous **enfermer dans des bulles informationnelles**.
**Vos Données Ne Vous Appartiennent Plus**
Le pire, c'est que nous avons **perdu le contrôle** sur nos propres données. Elles sont stockées dans d'immenses **datacenters**, appartenant à ces géants, souvent situés à l'autre bout du monde. Nous ne savons pas **exactement où elles sont**, **comment elles sont utilisées**, ni **qui y a accès**.

Et cette perte de contrôle a des conséquences bien réelles :
* **Atteintes à la vie privée :** Surveillance constante, profilage intrusif, fuites de données…
* **Manipulation et influence :** Publicités ciblées, désinformation, bulles de filtres…
* **Dépendance et enfermement :** Nous devenons captifs de ces écosystèmes centralisés, il devient difficile de s'en extraire.
**L'Aube d'une Solution : Le Web3**
Alors, faut-il se résigner à cet Internet dysfonctionnel ? Absolument pas ! La bonne nouvelle, c'est qu'il existe une **alternative**. Une voie pour reprendre le contrôle, pour construire un Internet plus **libre**, plus **sûr**, plus **respectueux** de l'individu.
Cette alternative, elle porte un nom : **le Web3**.
Dans le prochain article, nous allons explorer ensemble ce nouveau paradigme, comprendre comment il fonctionne, et surtout, découvrir comment il peut nous permettre de **réparer Internet** et de **reprendre le pouvoir sur nos vies numériques**.
[**Restez connecté… le changement est en marche !**](https://www.copylaradio.com/blog/blog-1/post/internet-est-casse-vous-netes-pas-fou-141)
-

@ 6bae33c8:607272e8
2025-02-10 15:27:25
I didn’t realize how much I had missed a good old fashioned Super Bowl blowout. I wasn’t even gonna bet the game, but over the last couple days, I got an Eagles vibe. There was too much, “The refs won’t let the Chiefs lose”, and Patrick Mahomes and Taylor Swift, and other noise, and yet the line didn’t budge. It was obvious the Eagles were the sharper side, and they had the league’s best defense, which usually correlates to overperformance of the spread in Super Bowls, sometimes massive overperformance.
But it wasn’t any one thing — just an overall dawning on me that the Eagles were probably the right side. I didn’t feel that strongly about it, even so, and decided I’d just bet Saquon Barkley for MVP, get 3:1 or so if the Eagles won. So I texted someone in the states to place the bet for me, and best he could offer was +175! That’s a terrible value for a RB to win MVP! A few minutes later Tim Schuler offered to bet me $50, give me the Eagles +1, and I obliged him. After that, I texted my friend back to put $500 on the Eagles +1 for me.
Of course, I didn’t stay up all night to watch — after losing 1K on the Falcons (who were up 28-3 in the third quarter at 3 am) eight years ago, never again. So I caught the 40-minute version this morning. What a great game! The Eagles dominated from start to finish. The defensive line got after Mahomes on every play. And while the Chiefs sold out to stop Barkley, Jalen Hurts ran wild on them.
I’m sure I would have enjoyed a Chiefs blowout less, but the beauty of a blowout is it settles things. There’s no looking back at a bad call, a dropped pass or a fumble and wondering what might have been. Close games have drama, but they are more or less arbitrary. I mean I get it, the guy made the throw at the time with the game on the line, but maybe also he just got the cheap roughing the passer call or the ticky tack PI. When the Giants won the Super Bowl on Scott Norwood’s miss, I didn’t have the same sense of satisfaction I did when they blew out John Elway’s Broncos five years earlier. Yes, they won, but it might as well have been on a coin flip.
I grew up on blowouts in the ‘80s — Raiders-Redskins, 49ers-Dolphins, Pats-Bears, Giants-Broncos, Redskins-Broncos — only the Bengals managed to keep Super Bowl losses close (Congratulations Jeff Erickson!) This was before replay reviews and all the lawyering about what is and isn’t a completed catch. The last fucking thing you wanted was some controversy about who really outplayed whom. So it was nice to win some easy money and not to have to worry about refs or fumbles or untimely drops for a change.
- I wanted Saquon to win MVP, but he drew the attention of the KC defense, is one of the best I’ve ever seen in blitz pickup and still had 97 yards from scrimmage. One of the all-time great years from an all-time great back. (He broke Terrell Davis’ record for the most yardage, regular season and playoffs, too, albeit in two extra games.)
- Hurts threw the one bad pick under pressure, but it served as a good punt, and otherwise had a near perfect game. Only four other incomplete passes, 72 yards and a score on the ground. He was an easy MVP call.
- I was a little worried about shaky Jake Elliott, but he drilled all four of his field goals, three of them twice!, due to penalties.
- Patrick Mahomes padded his stats in garbage time, but he got crushed. An elite defense that gets home with four is the way you kill the GOATS. The Giants did it to Tom Brady twice.
- Xavier Worthy had a nice garbage-time stat-padding game, but he was the only one. DeAndre Hopkins had a bad drop, though they got him a garbage-time feel-good TD, basically a participation trophy.
- Congrats to Lane Johnson, Brandon Graham, Elliott and long-snapper Rick Lovato — the only four players in NFL history to defeat both Tom Brady and Mahomes in Super Bowls.
- The only negative is I lost my $50 four-teams bet with Erickson. I had the Chiefs, Bills, Lions and Ravens, he had the field. But I directed Schuler to pay him, which is good, because I cancelled Paypal for their retarded foray into free-speech policing, and now I don’t have to figure out a workaround.
-

@ 3b7fc823:e194354f
2025-02-10 13:13:25
Alright, let’s get one thing straight: you’re scrolling through your phone, shopping online, maybe even working from home. But here’s the thing – someone might be watching. Not in the creepy stalker way, but in the “is that company really needing my data?” kind of way. That’s where a Virtual Private Network (VPN) comes in, saving you from the prying eyes of marketers, governments, and even your own internet provider.
**What Does a VPN Do?**
A VPN creates a secure, encrypted connection between your device and a VPN server. This allows you to browse the internet anonymously, keeping your online activities private from your Internet Service Provider (ISP), network administrators, and even hackers. When you connect to a VPN, your internet traffic is routed through an intermediary server, making it difficult for anyone to track your online movements.
**Why You Need a VPN: Privacy edition**
- Hiding Your IP Address
Every time you jump online, your device gets an IP address, like a digital ID. If you don’t use a VPN, everyone can see this ID, making it easy for advertisers and governments to track your every move.
- [X ] *Myth:* A VPN hides my IP address from everyone.
- [X] *Reality:* A VPN hides your IP address only from the websites you visit and your ISP. Your internet service provider still knows you're using a VPN, but they won't be able to see what sites you're visiting. Your VPN knows what sites you are visiting and *may* know who you are as well.
- Bypassing Censorship
Ever tried accessing something that’s blocked in your country? A VPN can help you bypass those restrictions, letting you watch the latest shows, access social media, or even download books without getting flagged as a troublemaker.
- Protecting Your Data
When you connect to public Wi-Fi – like at a café or airport – you’re basically handing over your data on a silver platter. A VPN encrypts this data, so even if someone intercepts it, they can’t decode it. Think of it as adding an extra layer of security.
- Avoiding Surveillance
Companies and governments love collecting data. From what you search to who you talk to, there’s a lot of stuff that’s none of their business. A VPN ensures that only you know where you’ve been online.
- Safeguarding Your Personal and Professional Life
Whether you’re working from home or just shopping for a present, a VPN keeps your activities private. It’s like having a secure safe for all your online stuff, so no one can snoop.
- Stopping Targeted Ads
Companies track your browsing habits to send you ads that follow you around the internet. A VPN breaks this cycle, making sure those creepy “you might like” ads stop following you around.
- No Logs Policy
Some VPNs keep records of your activity, which means they could be handed over if the government comes knocking. But with a no-logs policy, nothing is stored – *they promise ;)*
- The Dark Side of Free VPNs
Before you jump into using a free VPN, think twice. Free services often come with a catch: they might sell your data to advertisers or even track your activity themselves. It’s like getting a free hotdog at a gas station – it sounds great, but you’ll probably regret it later.
**How to Use a VPN (Because You’re Not a Tech Wizard)**
- Choose the Right Provider
Go for a reputable service that offers strong encryption and a no-logs policy. Look for options with a kill switch, which stops any data from being leaked if the connection drops. I prefer ones you can pay annoymously but that may be overkill for most people.
- Download and Install
Once you pick a provider, download the app to your device. It’s not rocket science, but it does require a bit more than just opening an email.
- Set It Up
Most VPNs have user-friendly interfaces. Just click “Connect” and you’re good to go. You might need to enter your login details or use a password from your provider.
**The Final Word**
Using a VPN isn’t about being a hacker or someone with something to hide. It’s about respecting your privacy and having control over what you share online. In today’s world, where companies and governments are constantly getting more creative about how they collect data, it’s practically a requirement if you want to stay ahead of the curve.
So there you have it – the secret life of your internet. With a VPN, you’re not just protecting yourself; you’re making sure that your digital footprint is as small as possible. Whether you’re at home or on the go, a VPN gives you the freedom to surf, shop, and work without anyone watching your every move.
And hey, if you’re still not convinced, just think about it this way: imagine your internet connection as a crowded public space. Without a VPN, everyone’s staring at you. With one, you’re wearing a mask, and no one’s the wiser.
---
Advocating for privacy does not finance itself. If you enjoyed this article, please consider zapping or sending monero
82XCDNK1Js8TethhpGLFPbVyKe25DxMUePad1rUn9z7V6QdCzxHEE7varvVh1VUidUhHVSA4atNU2BTpSNJLC1BqSvDajw1
-

@ da0b9bc3:4e30a4a9
2025-02-10 12:51:46
Hello Stackers!
It's Monday so we're back doing "Meta Music Mondays" 😉.
From before the territory existed there was just one post a week in a ~meta take over. Now each month we have a different theme and bring music from that theme.
Welcome to Femmes Fatales 3!!!
I absolutely loved doing this last year so I'm bringing it back for round 3!
It's Femmes Fatales, where we celebrate women in ~Music. So let's have those ladies of the lung, the sirens of sound, our Femmes Fatales!
https://youtu.be/ya69LUa1E_w?si=cM6yCALsPpp9L3Sc
I recently got introduced to these ladies. Their music is fantastic, they're really talented musicians. They are:
Lilith: The vocalist.
Lamia: The lead guitarist.
Nixe: The bassist.
Abrahel: The drummer.
Their identity is meant to be a mystery, so let's keep it that way.
These Nuns can make Noise!!
Let's go!
Talk Music. Share Tracks. Zap Sats.
originally posted at https://stacker.news/items/881416
-

@ 78c90fc4:4bff983c
2025-02-10 12:08:13
 
“Die Welt wird von ganz anderen Personen regiert als diejenigen es sich vorstellen, die nicht hinter den Kulissen stehen.”
Benjamin Disraeli, zweimaliger britischer Premierminister und Romanautor.
Quelle:
<https://www.unz.com/article/the-disraeli-enigma/>\
\
Als 1853 der Krimkrieg zwischen Russland und dem Osmanischen Reich ausbrach, wurde das Osmanische Reich vom Vereinigten Königreich und Frankreich gerettet. Zwanzig Jahre später zog Zar Alexander II. als Beschützer der unterdrückten serbischen und bulgarischen Christen erneut gegen die Osmanen in den Krieg. Als die Russen vor den Toren Konstantinopels/Istanbuls standen, waren die Osmanen gezwungen, die Schaffung der autonomen Fürstentümer Bulgarien, Serbien und Rumänien durch den Vertrag von San Stefano zu akzeptieren. Die Briten waren mit diesem Vertrag unzufrieden und beriefen zusammen mit Österreich-Ungarn den Berliner Kongress (1878) ein, der ihn aufhob. Russische Eroberungen wurden zurückgenommen, Armenien und Bulgarien wurden größtenteils an das Osmanische Reich zurückgegeben und der Balkan wurde in heterogene und konfliktreiche Staaten aufgeteilt. Diese „Balkanisierung“ löste nationalistische Ressentiments aus, die den Ersten Weltkrieg auslösen sollten.
\
Das Hauptziel des Berliner Vertrags bestand darin, das zu retten, was von einem schwächelnden Osmanischen Reich zu retten war, um der panslawistischen Expansion Russlands entgegenzuwirken. England, das stets eifersüchtig auf seine Vormachtstellung zur See bedacht war, wollte verhindern, dass Russland näher an den Bosporus heranrückte. Die Briten erhielten das Recht, Zypern als Marinestützpunkt zu nutzen und gleichzeitig den Suezkanal zu überwachen. Dies war der Beginn des „Great Game“ Großbritanniens um die Kolonialherrschaft in Asien und die Eindämmung Russlands, was insbesondere zur Schaffung Afghanistans als Pufferstaat führte.
\
Es gibt verschiedene Möglichkeiten, diesen Abschnitt der Geschichte zu interpretieren, der den Keim für alle Tragödien des 20. Jahrhunderts („das jüdische Jahrhundert“ laut Yuri Slezkine) in sich trägt.**\[1]**\
Yuri Slezkine, *The Jewish Century,* Princeton University Press, 2004.
\
Es gibt unterschiedliche Ansichten darüber, welche Kräfte die Geschichte in dieser entscheidenden Zeit geprägt haben. Aber letztendlich wird Geschichte von Menschen gemacht, und sie kann nur verstanden werden, wenn man die Hauptakteure und ihre Motive identifiziert: Man kann den Vietnamkrieg einfach nicht verstehen, ohne sich mit der Denkweise von Johnson oder Kissinger auseinanderzusetzen. Unter den Anstiftern des Berliner Vertrags sticht ein Name besonders hervor: Benjamin Disraeli (1804–1881), Premierminister unter Königin Victoria von 1868 bis 1869 und erneut von 1874 bis 1880. Disraeli war auch der Mann, der 1875 die Übernahme des Suezkanals durch England ermöglichte, und zwar durch die Finanzierung seines Freundes Lionel de Rothschild, dem Sohn von Nathan Mayer – eine Operation, die die Kontrolle der Rothschilds über die Bank of England festigte.
\
Disraeli ist ein sehr interessanter Fall, da er sowohl ein bedeutender britischer Staatsmann während der globalen Hegemonie Großbritanniens als auch ein Romanautor war, der seine fiktiven Figuren dazu benutzte, seine ehrlichen Gedanken zu äußern, während er eine Art „glaubhafte Abstreitbarkeit“ (Sidonia spricht, nicht ich!) aufrechterhielt. Wir haben daher die einzigartige Gelegenheit, die wahren Motive des Mannes in der Politik zwischen den Zeilen zu lesen. Stellen Sie sich vor, Kissinger hätte Romane geschrieben, in denen ein Jude die Hauptfigur ist, der die Außen- und Militärpolitik des Imperiums vorantrieb und gleichzeitig ein enger Freund des reichsten jüdischen Bankiers war.\
\
Disraeli wird als der wahre Erfinder des Britischen Empires bezeichnet, da er es war, der Königin Victoria durch das Parlament mit dem Royal Titles Act von 1876 zur Kaiserin von Indien ernennen ließ (das obere Bild ist eine Karikatur, die Disraeli als Hausierer zeigt, der der Königin die Kaiserkrone überreicht).
Disraeli war, wie bereits erwähnt, die Hauptinspiration für den Berliner Kongress. Darüber hinaus war Disraeli ein Vorläufer des Zionismus, der versuchte, die „Wiederherstellung Israels“ auf die Tagesordnung des Berliner Kongresses zu setzen, in der Hoffnung, den Sultan Abdul Hamid davon zu überzeugen, Palästina als autonome Provinz zu gewähren. Der Sultan lehnte das Angebot ab, das wahrscheinlich das Versprechen finanzieller Unterstützung für seine zusammenbrechende Wirtschaft beinhaltete – wie auch Herzls Angebot im Jahr 1902, das ebenfalls abgelehnt wurde.\
\
Der Zionismus war Disraelis uralter Traum: Nach einer Reise in den Nahen Osten im Alter von sechsundzwanzig Jahren veröffentlichte er seinen ersten Roman, *Die wundersame Geschichte des Alroy*, und ließ seinen Helden, einen einflussreichen Juden des Mittelalters, sagen: „Mein Wunsch ist eine nationale Existenz, die wir nicht haben. Mein Wunsch ist das Land der Verheißung und Jerusalem und der Tempel, alles, was wir eingebüßt haben, wonach wir uns gesehnt haben, wofür wir gekämpft haben, unser schönes Land, unser heiliges Glaubensbekenntnis, unsere einfachen Sitten und unsere alten Bräuche.“\
Disraeli schrieb diese Zeilen noch vor den Anfängen der biblischen Archäologie; erst 1841 veröffentlichte Edward Robinson seine *Biblical Researches in Palestine*. Die ersten Ausgrabungen des von Königin Victoria geförderten Palestine Exploration Fund begannen 1867. Wohlhabende britische Juden hatten sich jedoch schon lange zuvor für Palästina interessiert. Disraelis Interesse wurde durch seinen Nachbarn und vierzigjährigen Freund Moses Montefiore beeinflusst, der Judith Cohen, die Schwägerin von Nathan Rothschild, heiratete. Nach einer Reise nach Palästina im Jahr 1827 widmete Montefiore seine immensen Ressourcen der Unterstützung seiner Glaubensgenossen im Heiligen Land, indem er Land kaufte und Häuser baute.
\
Sowohl Montefiore als auch Disraeli waren sephardischer Herkunft. Disraeli stammte aus einer Familie portugiesischer Marranen, die in Venedig zum Judentum konvertierten. Sein Großvater war 1748 nach London gezogen. Benjamin wurde im Alter von dreizehn Jahren getauft, als sein Vater Isaac D'Israeli zusammen mit seiner ganzen Familie zum anglikanischen Christentum konvertierte. Isaac D'Israeli ist der Autor eines Buches mit dem Titel *The Genius of Judaism*(in Anlehnung an Chateaubriands *Le Génie du Christianisme*), in dem er die einzigartigen Eigenschaften des jüdischen Volkes verherrlicht, aber die talmudischen Rabbiner dafür verantwortlich macht, dass sie „den nationalen Geist ihres Volkes versiegeln“ und „die Einfachheit ihres antiken Glaubens korrumpieren“. Wie für viele andere Juden dieser Zeit war die Konversion für D'Israeli rein opportunistisch: Bis zum Beginn des 19. Jahrhunderts blieben Verwaltungskarrieren für Juden verschlossen. Ein Gesetz von 1740 hatte ihre Einbürgerung erlaubt, aber es hatte Volksaufstände provoziert und wurde 1753 aufgehoben. Viele einflussreiche Juden, wie der Stadtbankier Sampson Gideon, entschieden sich dann für eine nominelle Konversion ihrer Kinder.**\[2]**\
Cecil Roth, *A History of the Marranos* (1932)*,* Meridian Books, 1959*,* S. 148.\
\
Etwa zur gleichen Zeit wie Disraeli konvertierte Heinrich Heine (1797–1856) zum Luthertum (während einer seiner Brüder zum Katholizismus konvertierte, um Offizier in Österreich zu werden, und ein anderer zur Orthodoxie, um als Arzt in Russland zu dienen). Heine betrachtete die Taufe als „Eintrittskarte in die europäische Zivilisation“. Er beklagte sich jedoch darüber, dass er von den Deutschen immer noch als Jude angesehen wurde, und zog es daher vor, in Frankreich zu leben, wo er als Deutscher angesehen wurde. Nur wenige Jahre nach seiner Konversion zeigten seine Schriften eine sehr negative Einstellung gegenüber dem Christentum, das er als „düstere, blutrünstige Religion für Kriminelle“ bezeichnete, die die Sinnlichkeit unterdrücke. Am Ende seines Lebens bereute er seine Taufe, die ihm nichts gebracht hatte, und erklärte in seinem letzten Buch *Romanzero*: „Ich mache kein Geheimnis aus meinem Judentum, zu dem ich nicht zurückgekehrt bin, weil ich es nicht verlassen habe.“**\[3]**\
Zitiert in Kevin MacDonald, *Separation and Its Discontents:* *Toward an Evolutionary Theory of Anti-Semitism,* Praeger, 1998, kindle 2013, l. 4732–4877.
\
Genau wie bei den portugiesischen Marranen im 15. Jahrhundert verstärkte die Taufe bei den europäischen Juden des 19. Jahrhunderts ein nicht-religiöses, rassisches Verständnis des Judentums. Disraeli bezeichnete sich selbst als „Anglikaner jüdischer Abstammung“.
\
Für Hannah Arendt ist Disraeli ein „Rassenfanatiker“, der in seinem ersten Roman *Alroy* (1833) „einen Plan für ein jüdisches Reich entwickelte, in dem Juden als streng getrennte Klasse herrschen würden“. In seinem anderen Roman *Coningsby* „entfaltete er einen fantastischen Plan, nach dem jüdisches Geld den Aufstieg und Fall von Höfen und Reichen beherrscht und in der Diplomatie die Oberhand hat“. Diese Idee „wurde zum Dreh- und Angelpunkt seiner politischen Philosophie“.**\[4]**\
Hannah Arendt, *The Origins of Totalitarianism,* Band 1: *Antisemitism,* Meridian Books, 1958, S. 309–310.\
Dies ist eine ziemlich fantastische Anschuldigung, die die meisten Biografen Disraelis nicht bestätigen würden. Sie ist jedoch wahrscheinlich richtig. Aber wir müssen genau auf Disraelis eigene Stimme hören, die durch Sidonia zum Ausdruck kommt, die Figur, die in drei seiner Romane vorkommt: *Coningsby* (1844), *Sybil* (1845) und *Tancred* (1847).
In Sidonias Worten spürt man den Groll gegen die Nation, in die er sich zu integrieren versuchte:\
Kann es etwas Absurderes geben, als dass eine Nation sich an eine Einzelperson wendet, um ihren Kredit, ihre Existenz als Imperium und ihren Komfort als Volk zu erhalten; und diese Einzelperson, der ihre Gesetze die stolzesten Rechte der Staatsbürgerschaft, das Privileg, in ihrem Senat zu sitzen und Land zu besitzen, verweigern; denn obwohl ich unbesonnen genug war, mehrere Ländereien zu kaufen, bin ich der Meinung, dass ein Engländer hebräischen Glaubens nach dem geltenden Recht Englands keinen Boden besitzen kann.
\
Da es einem Juden nicht möglich ist, sich durch Landbesitz in die britische Aristokratie zu integrieren, selbst wenn er zum örtlichen Glauben konvertiert, was sollte ein Jude tun, außer durch die Macht des Geldes aufzusteigen? Wie Heine spürte auch Disraeli die Heuchelei der Christen, die es den Juden übel nahmen, dass sie keine Christen waren, sie aber weiterhin als Juden behandelten, wenn sie konvertierten, und es insgeheim sogar vorzogen, dass sie Juden blieben.
\
Laut Disraelis Biografen Robert Blake ist Sidonia „eine Kreuzung zwischen Lionel de Rothschild und Disraeli selbst“. Er stammt von einer Adelsfamilie aus Aragon ab, zu deren herausragenden Mitgliedern ein Erzbischof und ein Großinquisitor gehörten, die beide heimlich dem Judentum ihrer Väter anhingen. Sidonias Vater, wie auch Lionel de Rothschilds Vater, „machte während der Napoleonischen Kriege ein großes Vermögen mit Militärverträgen und der Versorgung der verschiedenen Armeen“. Nachdem er sich in London niedergelassen hatte, „setzte er alles, was er besaß, auf die Waterloo-Anleihe; und das Ereignis machte ihn zu einem der größten Kapitalisten Europas.“ Seit seinem siebzehnten Lebensjahr besuchte Sidonia die Fürstenhöfe der Schuldner seines Vaters und lernte die Geheimnisse der Macht kennen. „Die geheime Geschichte der Welt war sein Zeitvertreib. Es bereitete ihm großes Vergnügen, die verborgenen Motive mit den öffentlichen Vorwänden der Transaktionen zu kontrastieren.“ Disraeli selbst war laut Robert Blake „von Verschwörungen besessen“.**\[5]**\
Robert Blake, *Disraeli* (1966), Faber Finds, 2010, S. 202.
\
Sidonia ist von seiner Rasse begeistert: „Alles ist Rasse – es gibt keine andere Wahrheit.“ Er weigert sich, eine Nichtjüdin zu heiraten, weil, so der Erzähler, „keine irdische Überlegung ihn jemals dazu veranlassen würde, die Reinheit der Rasse zu beeinträchtigen, auf die er stolz ist.“ Mit „Rasse“ meinte Disraeli Blutsverwandtschaft. In seinem letzten Roman *Endymion* (1880) schrieb er:\
Kein Mensch wird das Prinzip der Rasse gleichgültig behandeln. Es ist der Schlüssel zur Geschichte, und der Grund, warum die Geschichte oft so verwirrend ist, liegt darin, dass sie von Männern geschrieben wurde, die dieses Prinzip und all das damit verbundene Wissen nicht kennen ... Sprache und Religion machen keine Rasse aus – es gibt nur eine Sache, die eine Rasse ausmacht, und das ist Blut.\
**[Sidonia erzählt seinem Schützling Coningsby](https://www.victorianlondon.org/etexts/disraeli/coningsby-0038.shtml)** in *Coningsby oder die neue Generation*, dass die Verfolgung durch christliche Nationen die jüdische Nation niemals zerschlagen könnte.
\
Tatsache ist, dass man eine reine Rasse der kaukasischen Organisation nicht vernichten kann. Es ist eine physiologische Tatsache; ein einfaches Naturgesetz, das ägyptische und assyrische Könige, römische Kaiser und christliche Inquisitoren verblüfft hat. Keine Strafgesetze, keine körperlichen Folterungen können bewirken, dass eine überlegene Rasse in einer unterlegenen aufgehen oder von ihr vernichtet werden sollte. Die gemischten verfolgenden Rassen verschwinden, die reine verfolgte Rasse bleibt bestehen. Und im Moment, trotz Jahrhunderten oder gar Jahrzehnten der Erniedrigung, übt der jüdische Geist einen enormen Einfluss auf die Angelegenheiten Europas aus. Ich spreche nicht von ihren Gesetzen, denen Sie immer noch gehorchen; von ihrer Literatur, mit der Ihr Geist gesättigt ist, sondern vom lebendigen hebräischen Intellekt. Sie beobachten nie eine große intellektuelle Bewegung in Europa, an der die Juden nicht in hohem Maße beteiligt sind.\
Wo auch immer er reiste, fügte Sidonia hinzu, sah er jüdische Berater hinter Monarchen und Staatsoberhäuptern.
„Sie sehen also, mein lieber Coningsby, dass die Welt von ganz anderen Persönlichkeiten regiert wird, als diejenigen, die nicht hinter den Kulissen stehen, sich vorstellen können.“
In einem Sachbuch (*Lord George Bentinck: A Political Biography*, 1852) schrieb Disraeli:\
\[Juden] sind ein lebendiger und der eindrucksvollste Beweis für die Falschheit dieser verderblichen Doktrin der Neuzeit, der natürlichen Gleichheit der Menschen. ... die natürliche Gleichheit der Menschen, die heute in Mode ist und die Form einer kosmopolitischen Bruderschaft annimmt, ist ein Prinzip, das, wenn man danach handeln könnte, die großen Rassen zersetzen und den ganzen Genius der Welt zerstören würde. ... Die angeborene Tendenz der jüdischen Rasse, die zu Recht stolz auf ihr Blut ist, ist gegen die Doktrin der Gleichheit der Menschen.**\[6]**\
Benjamin Disraeli, *Lord George Bentinck*, Archibald, 1852 (archive.org), S. 496.
\
Disraeli ist eindeutig auf derselben Wellenlänge wie Moses Hess, Herzls geistiger Vater, der, nachdem er Marx (einen weiteren nominellen Konvertiten) beeinflusst hatte, zu dem Schluss kam, dass „der Rassenkrieg wichtiger ist als der Klassenkampf“ (*Rom und Jerusalem,* 1862). Ein gutes Beispiel für dialektische politische Manipulation ist, dass Hess Marx weiterhin heimlich unterstützte und auf dessen Bitte hin nach dem Generalkongress der Internationale in Basel (5.–12. September 1869) Verleumdungen gegen Bakunin veröffentlichte, in denen er Bakunin beschuldigte, ein *Agent provocateur* der russischen Regierung zu sein und „im Interesse des Panslawismus“ zu arbeiten.**\[7]**\
Bakunins Antwort auf Französisch, „Aux citoyens rédacteurs du *Réveil*“, finden Sie auf Wikisource.org.\
Es ist interessant zu sehen, dass ein anderer Proto-Zionist wie Disraeli den russischen Interessen zutiefst feindlich gesinnt war.\
\
Was war Disraelis Motivation hinter der Außenpolitik, die er dem britischen Empire vermittelte? Glaubte er, dass es die offensichtliche Bestimmung der Briten sei, die Welt zu erobern? Oder sah er das britische Empire als Instrument für die überlegene Bestimmung der jüdischen Nation, wenn er sich daran erinnerte, wie Esra und Nehemia in biblischen Zeiten die Außenpolitik der Perser ausgenutzt hatten? Indem er den Suezkanal (der zwischen 1859 und 1869 von den Franzosen gegraben wurde) mit den britischen Interessen in Verbindung brachte, wollte er einfach nur die Franzosen übertrumpfen, oder legte er damit den Grundstein für das zukünftige Bündnis zwischen Israel und dem angloamerikanischen Empire? Da die Briten nun einmal den Suezkanal besaßen, mussten sie ihn verteidigen, und wie ginge das besser als mit einer befreundeten jüdischen autonomen Regierung in der Nähe in Palästina? Genau das war es, was Chaim Weizmann dreißig Jahre später den Briten schmackhaft machen wollte: „Das jüdische Palästina wäre ein Schutz für England, insbesondere in Bezug auf den Suezkanal.“**\[8]**\
Chaim Weizmann, *Trial and Error,* Harper & Brothers, 1949, S. 192.
\
Und als die Israelis 1956 mit britischer und französischer Unterstützung in den Sinai einmarschierten, taten sie dies, indem sie Großbritannien erneut versprachen, die Kontrolle über den von Nasser verstaatlichten Kanal an Großbritannien zurückzugeben.
\
Disraelis Russophobie, zu der er Königin Victoria bekehrte, und seine Verteidigung der Türken, deren Massaker an den Serben und Bulgaren allgemein bekannt waren, führten zu Theorien über eine jüdische Verschwörung. William Ewart Gladstone, ein langjähriger Gegner Disraelis und selbst mehrmals Premierminister (1868–1874, 1880–1885, 1886 und 1892–1894), erklärte, dass Disraeli „die britische Außenpolitik als Geisel seiner jüdischen Sympathien nahm und mehr daran interessiert war, die Leiden der Juden in Russland und der Türkei zu lindern, als an britischen Interessen“. Die Zeitung *„The Truth“* vom 22. November 1877 spielte auf die Vertrautheit Disraelis mit den Rothschilds an und vermutete „eine stillschweigende Verschwörung ... seitens einer beträchtlichen Anzahl von Anglo-Hebräern, um uns im Namen der Türken in einen Krieg zu ziehen“. Es wurde außerdem daran erinnert, dass Disraeli in einer Rede vor dem britischen Unterhaus im Jahr 1847 die Zulassung von Juden zu wählbaren Ämtern gefordert hatte, mit der Begründung, dass „der jüdische Geist einen enormen Einfluss auf die Angelegenheiten Europas ausübt“.**\[9]**\
Stanley Weintraub, *Disraeli: A Biography,* Hamish Hamilton, 1993, S. 579, 547.
\
Die Königin stand, wie ein Großteil der britischen Aristokratie, bereits unter dem Bann einer modischen Theorie, die den Angelsachsen einen israelitischen Ursprung zuschrieb. Diese Theorie war erstmals zur Zeit Oliver Cromwells aufgetaucht und wurde 1840 von Pastor John Wilson in seinen *Vorlesungen über das alte Israel und den israelitischen Ursprung der modernen Nationen Europas* sowie 1870 von Edward Hine in *The English Nation Identified with the Lost Israel* neu aufgelegt. In diesem Werk erfahren wir, dass das Wort „Saxon“ von „Isaac's sons“ (Söhne Isaaks) abgeleitet ist. Diese lächerliche Theorie lieferte eine billige biblische Rechtfertigung für den britischen Kolonialismus und sogar für den Völkermord an den kolonisierten Völkern (neue Kanaaniter) durch das britische Empire (neues Israel).**\[10]**\
André Pichot, *Aux origines des théories raciales, de la Bible à Darwin,* Flammarion, 2008, S. 124–143, 319.
\
Königin Victoria war glücklich, glauben zu können, dass ihre edle Abstammung auf König David zurückging, und ließ ihre Söhne beschneiden, ein Brauch, der bis heute fortbesteht. Es mag etwas Wahres an dem Gefühl der britischen Elite für ihr Judentum liegen, denn im 16. und 17. Jahrhundert hatten viele Ehen reiche jüdische Familien mit der alten, verarmten Landaristokratie vereint, so dass nach Hilaire Bellocs Schätzung „mit Beginn des 20. Jahrhunderts diejenigen der großen territorialen englischen Familien, in denen es kein jüdisches Blut gab, die Ausnahme waren“.**\[11]**\
Hilaire Belloc, *The Jews,* Constable & Co., 1922 (archive.org), S. 223.
\
Die Begeisterung der Königin für das Judentum hatte aber auch viel mit dem Einfluss Disraelis zu tun, der einmal gegenüber einem Freund damit prahlte: „Jeder mag Schmeichelei, und wenn es um das Königshaus geht, sollte man sie mit einer Kelle auftragen.“**\[12]**\
Stanley Weintraub, *Disraeli: A Biography,* Hamish Hamilton, 1993, S. 579, 547.
\
Der Fall Disraeli ist aufschlussreich, weil die Frage, die er aufwirft, dieselbe ist wie die Frage, die heute geopolitische Analysten in Bezug auf die Beziehung zwischen den Vereinigten Staaten und Israel spaltet: Wer führt wen an der Nase herum? Ist Israel der Brückenkopf der Vereinigten Staaten im Nahen Osten oder sind die Vereinigten Staaten, wie Zbigniew Brzezinski einmal sagte, der **[„dumme Esel“](https://www.youtube.com/watch?v=MfjE5_1xOs8)** Israels? Die Beantwortung dieser Frage für das Jahrhundert vor dem Zweiten Weltkrieg (als **[„Israel“ das internationale Judentum](https://twitter.com/Laurent_Guyenot/status/1883831745046560928)** bedeutete) hilft bei der Beantwortung derselben Frage heute, da die symbiotische Beziehung zwischen Israel und dem Imperium erheblich gewachsen ist.
\
Die Antwort hängt vom Standpunkt des Betrachters ab. Die Zionisten haben natürlich ein Interesse daran, die Ansicht zu fördern, dass Israel den angloamerikanischen Interessen dient und nicht umgekehrt. Disraeli argumentierte vor dem britischen Parlament, dass ein jüdisches Palästina im Interesse des britischen Kolonialismus sei. Aber jüdische Zionisten haben die Dinge schon immer aus der anderen Perspektive betrachtet, und man kann kaum glauben, dass Disraeli ihre Ansicht nicht insgeheim teilte. Wenn der Held seines Romans *Tancred* (1847), ein Jude, der wie Disraeli zum Lord ernannt wurde, das britische Empire mit folgenden Worten verherrlicht: „Wir wollen die Welt erobern, angeführt von Engeln, um die Menschheit unter göttlicher Herrschaft glücklich zu machen“, wer verbirgt sich hinter diesem zweideutigen „wir“? Ist es dasselbe doppeldeutige „wir“, das die PNAC-Neokonservativen benutzten, um Amerika in Kriege zum Wohle Israels zu verwickeln?
\
Wenn ein britischer Jude wie Disraeli zu den Briten „wir“ sagte, war dies eine strategische Zweideutigkeit. Er traf damit den patriotischen Nerv der angelsächsischen Elite, die den gemeinsamen Glauben an die Mission des britischen Empires teilte, die Welt zu zivilisieren – Menschen wie Lord Salisbury, Mitglied von Cecil Rhodes' Round Table, der sich für eine Weltregierung durch die „britische Rasse“ einsetzte.**\[13]**\
Carroll Quigley, *The Anglo-American Establishment, From Rhodes to Cliveden* (1949), Books In Focus, 1981.
\
Der britische Imperialismus und der zionistische Nationalismus wurden etwa zur gleichen Zeit geboren wie die Zwillinge Esau und Jakob und sind seit ihrer Geburt eng miteinander verflochten. Zwei Überlegungen helfen jedoch, ihre wahre Beziehung zu verstehen. Erstens reichen die ideologischen Wurzeln des Britischen Empires nicht weiter zurück als bis ins 17. Jahrhundert, während die des Zionismus mehr als zwei Jahrtausende zurückreichen. Zweitens starb das Britische Empire nach dem Ersten Weltkrieg, während der Zionismus aufblühte. Aus diesen beiden Gründen ist die Theorie, dass der Zionismus ein Nebenprodukt des britischen Imperialismus ist (nennen wir sie die Chomsky-Theorie), nicht haltbar.
\
Um die wahre Beziehung zwischen Zion und Albion zu Disraelis Zeiten zu verstehen, muss man die Macht der Rothschild-Dynastie über die britische Politik richtig einschätzen. Ohne die Rothschilds hätte Großbritannien nie die Kontrolle über den Suezkanal erlangt, der den Grundstein des britischen Empires im Nahen Osten bildete. Die Rothschilds selbst kandidierten nicht für ein politisches Amt, heirateten jedoch manchmal in eine solche Familie ein: Lord Archibald Primrose, 1886 und von 1892 bis 1894 Außenminister und 1894–1895 Premierminister, war der Schwiegersohn von Mayer Amschel de Rothschild.\
Es ist bemerkenswert, dass Theodor Herzl den zukünftigen jüdischen Staat als „aristokratische Republik“ mit „dem ersten Prinzen Rothschild“ an der Spitze sah. In einer langen Tirade in seinem Tagebuch ermahnte er die Rothschilds, ihre bösen Seelen zu erlösen, indem sie den Zionismus statt Kriege finanzierten:\
Ich weiß nicht, ob alle Regierungen bereits erkennen, welche internationale Bedrohung Ihr Weltreich darstellt. Ohne Sie können keine Kriege geführt werden, und wenn Frieden geschlossen werden soll, sind die Menschen umso mehr auf Sie angewiesen. Für das Jahr 1895 wurden die Militärausgaben der fünf Großmächte auf vier Milliarden Francs geschätzt, und ihre tatsächliche militärische Stärke in Friedenszeiten auf 2.800.000 Mann. Und diese Streitkräfte, die in der Geschichte ihresgleichen suchen, kommandieren Sie finanziell, ungeachtet der widerstreitenden Wünsche der Nationen. ... Und Ihr verfluchter Reichtum wächst immer noch. ... Aber wenn Sie sich uns anschließen, ... werden wir unseren ersten gewählten Herrscher aus Ihrem Haus nehmen. Das ist das leuchtende Leuchtfeuer, das wir auf die Spitze des fertigen Eiffelturms Ihres Vermögens setzen werden. In der Geschichte wird es so aussehen, als wäre das der Zweck des gesamten Bauwerks gewesen.**\[14]**\
\
*The Complete Diaries of Theodor Herzl,* edited by Raphael Patai, Herzl Press & Thomas Yoseloff, 1960, vol. 1*,* pp. 163–170.\
Wie Richard Wagner jedoch einmal sagte (*Judaism in Music*, 1850), zogen es die Rothschilds vor, „die Juden der Könige“ zu bleiben, anstatt „die Könige der Juden“ zu sein.\
\
Wenn die Zeit für die Gründung des jüdischen Staates zu Disraelis Zeiten noch nicht reif war, dann vor allem deshalb, weil die Juden in Russland sich von Palästina ebenso wenig angezogen fühlten wie die Juden in Europa; sie wussten kaum, wo es lag. Erst kürzlich von Zar Alexander II. emanzipiert, strebten sie lediglich eine Auswanderung nach Europa oder in die Vereinigten Staaten an. Erst nach der Ermordung von Zar Alexander II. im Jahr 1881 (einen Monat vor Disraelis Tod) wurden einige von ihnen durch die Pogrome für Leon Pinskers proto-zionistischen Aufruf von 1882 empfänglich: „Wir müssen uns ein für alle Mal mit dem Gedanken abfinden, dass die anderen Nationen uns aufgrund ihres angeborenen natürlichen Antagonismus für immer ablehnen werden.“**\[15]**\
Benzion Netanyahu, *The Founding Fathers of Zionism,* Balfour Books, 2012*,* Kindle l. 761-775.
\
Ebenfalls im Jahr 1881 begann Baron Edmond de Rothschild vom Pariser Zweig, unter der Schirmherrschaft seiner Palestine Jewish Colonization Association (PICA) Land in Palästina zu kaufen und die Ansiedlung jüdischer Siedler zu finanzieren, insbesondere in Tel Aviv. Die meisten bestehenden internationalen jüdischen Organisationen, wie B'nai B'rith (gegründet 1843 in New York) oder die Alliance Israélite Universelle (gegründet 1860 in Paris), waren jedoch der Meinung, dass Israel als verstreute Nation gut zurechtkäme und keine Pläne für Palästina habe.\
Dies änderte sich während des Ersten Weltkriegs, als ein äußerst effizientes Netzwerk aufgebaut wurde, das beide Seiten des Atlantiks verband.**\[16]**\
Alison Weir, *Against Our Better Judgment: The Hidden History of How the U.S. Was Used to Create Israel,* 2014, Kindle l. 387-475.
\
Theodor Herz konzentrierte seine diplomatischen Bemühungen zunächst auf Deutschland, aber in England begannen sich die Dinge vielversprechend zu entwickeln („Der Schwerpunkt hat sich nach England verlagert“, schrieb er 1895 in sein Tagebuch), was zum Teil der Rekrutierung von Israel Zangwill zu verdanken war, der laut Benzion Netanyahu „der erste war, der in den oberen Kreisen der britischen Politik direkt über den Zionismus sprach“, insbesondere mit Lloyd George, „einem engen Bekannten Zangwills von Beginn seiner zionistischen Tätigkeit bis zu seinem Lebensende“.**\[17]**\
Netanyahu, *The Founding Fathers of Zionism,* l. 2536-59.
\
Erinnern wir uns daran, dass Zangwill der erfolgreiche Autor von *The Melting Pot war,* einem Theaterstück, das Mischehen für Amerikaner pries. Hier besteht kein Widerspruch, denn „die gemischten verfolgten Rassen verschwinden, die reine verfolgte Rasse bleibt bestehen“, wie Sidonia sagte.\
\
Die Bedeutung von Disraelis geopolitischen Manövern wird von Historikern der Zionisten selten anerkannt, da sie oberflächlich betrachtet nicht den Weg für die Gründung des jüdischen Staates geebnet zu haben scheinen. Tatsächlich bildeten sie jedoch das unsichtbare Fundament, auf dem Herzl und Zangwill aufbauten. Und diese unsichtbare Kontinuität zeugt von der erstaunlichen generationsübergreifenden Beharrlichkeit des jüdischen Volkes, das sein jahrtausendealtes, selbsternanntes Schicksal Generation für Generation vorantreibt. Ja, es ist wirklich bewundernswert, wenn auch verheerend für die westliche Zivilisation, die durch zweitausend Jahre Christentum ahnungslos und ihres eigenen Sinns für Blut beraubt wurde. Wie der zionistische Autor Jakob Klatzkin einmal in der Zeitschrift *„Der Jude“*, 1916, schrieb:\
Wir bilden in uns selbst eine geschlossene juristische und geschäftliche Körperschaft. Eine starke Mauer, die wir errichtet haben, trennt uns von den Menschen in den Ländern, in denen wir leben – und hinter dieser Mauer befindet sich ein jüdischer Staat.**\[18]**
Zitiert in Robert Edward Edmondson, *The Jewish System Indicted by the Documentary Record,* 1937 (archive.org), S. 15.\
\
**Anmerkungen**\
**\[1]** Yuri Slezkine, *The Jewish Century,* Princeton University Press, 2004.\
**\[2]** Cecil Roth, *A History of the Marranos* (1932)*,* Meridian Books, 1959*,* S. 148.\
**\[3]** Zitiert in Kevin MacDonald, *Separation and Its Discontents: Toward an Evolutionary Theory of Anti-Semitism,* Praeger, 1998, kindle 2013, l. 4732–4877.\
**\[4]** Hannah Arendt, *The Origins of Totalitarianism,* Band 1: *Antisemitism,* Meridian Books, 1958, S. 309–310.\
**\[5]** Robert Blake, *Disraeli* (1966), Faber Finds, 2010, S. 202.\
**\[6]** Benjamin Disraeli, *Lord George Bentinck*, Archibald, 1852 (archive.org), S. 496.\
**\[7]** Bakunins Antwort auf Französisch, „Aux citoyens rédacteurs du *Réveil*“, auf Wikisource.org.\
**\[8]** Chaim Weizmann, *Trial and Error,* Harper & Brothers, 1949, S. 192.\
**\[9]** Stanley Weintraub, *Disraeli: A Biography,* Hamish Hamilton, 1993, S. 579, 547.\
**\[10]** André Pichot, *Aux origines des théories raciales, de la Bible à Darwin,* Flammarion, 2008, S. 124–143, 319.\
**\[11]** Hilaire Belloc, *The Jews,* Constable & Co., 1922 (archive.org), S. 223.\
**\[12]** Stanley Weintraub, *Disraeli: A Biography,* Hamish Hamilton, 1993, S. 579, 547.\
**\[13]** Carroll Quigley, *The Anglo-American Establishment, From Rhodes to Cliveden* (1949), Books In Focus, 1981.\
**\[14]** *The Complete Diaries of Theodor Herzl,* edited by Raphael Patai, Herzl Press & Thomas Yoseloff, 1960, vol. 1*,* pp. 163–170.\
**\[15]** Benzion Netanyahu, *The Founding Fathers of Zionism,* Balfour Books, 2012*,* Kindle-Ausgabe, S. 761–775.\
**\[16]** Alison Weir, *Against Our Better Judgment: The Hidden History of How the U.S. Was Used to Create Israel,* 2014, Kindle-Ausgabe, S. 387–475.\
**\[17]** Netanyahu, *The Founding Fathers of Zionism,* S. 2536-59.\
**\[18]** Zitiert in Robert Edward Edmondson, *The Jewish System Indicted by the Documentary Record,* 1937 (archive.org), S. 15.
-

@ 04ed2b8f:75be6756
2025-02-10 11:30:04
The world doesn’t care about your excuses. It doesn’t care about your past, your wounds, or the battles you’ve already fought. Life will not lower the weight just because you feel tired. **You either rise, or you stay down.**
But here’s the truth—**you are not your past.** You are not your failures, not your pain, not the things that tried to break you. **You are what you choose to become.**
Some people get knocked down and never get back up. Some let their past define them, cage them, strip them of their potential. And then there are those who **decide.** They decide that no matter what happened, **they will rise.** They will fight. They will carve their own path, even if they have to do it with their bare hands.
## **Your Past is a Weapon—If You Use It Right**
Your past can be two things: **a chain or a sword.**
- Weak minds wear their past like a shackle, letting it hold them back.
- Warriors forge their past into steel, using it as a blade to cut through the future they want.
Scars? They aren’t signs of weakness. They are proof that you survived. That you endured. And that you’re still standing. So stop letting your past dictate your future. **Rip the pen from its hands and write your own damn story.**
## **The Weak Surrender. The Strong Rebuild.**
Life will try to break you. That’s a fact. You will lose, you will hurt, you will doubt. But none of that matters. The only thing that matters is **what you do next.**
- **You can let failure drown you, or you can rise stronger.**
- **You can let heartbreak harden you, or you can sharpen yourself through it.**
- **You can let regret bury you, or you can burn it as fuel.**
It’s easy to stay down. To blame the world. To say, “This is just who I am.” But warriors don’t do easy. They do necessary.
## **You Are the Architect of Your Own Power**
Everything you need to win is already inside you. You don’t need permission. You don’t need the world to approve. You just need one thing: **to choose.**
- **Choose discipline over comfort.**
- **Choose hunger over hesitation.**
- **Choose action over excuses.**
- **Choose to become something greater than your past.**
Because in the end, that’s the only choice that matters.
The world will try to define you. It will try to chain you to your past, drag you down with doubt, and keep you in a box. **Shatter it.** Prove them wrong. Be the person that refuses to be shaped by circumstance—**be the one who shapes themselves.**
The past is done. The future is unwritten. The power to decide who you become? **That’s all yours.** Now get up and take it.
-

@ 31da2214:af2508e2
2025-02-10 11:23:19
**Video Title:** Une révolution géopolitique est en marche : l’Afrique se libère !
**Creator:** Pensées KAMITE
**Published Date:** February 9, 2025
**Video Length:** 17 minutes 6 seconds
**Views:** >24k
**Likes:** >2k
**Video URL:** [Original YouTube Video](https://youtu.be/AqrgC7y6Twk)
**Key Points from the Video:**
* **End of Western Hegemony:** The video asserts that Western dominance in Africa is coming to an end. A geopolitical revolution is underway, breaking the chains of neocolonialism and fundamentally reshaping the continent's geopolitical landscape.
* **Decline of Western Influence:** The video highlights a notable decline in Western influence and power in Africa. This is contrasted with the growing presence of China and Russia, who are increasing their investments in key sectors such as infrastructure, energy, defense, natural resources, and technology across the continent.
* **Shifting Economic Partnerships:** China and Russia are now surpassing the European Union as Africa's primary trading partners. This indicates a significant shift in economic alliances, moving away from traditional Western partners.
* **Failure of Western Strategies:** The host argues that Western imperialist strategies have failed to adapt to the evolving realities in Africa. While African countries initially engaged in colonial agreements with the West, the economic landscape now favors China and Russia.
* **Collapse of Unipolar World Order:** This geopolitical shift is described as unprecedented, signaling the collapse of the unipolar world order established after World War II. The video suggests that the United States, weakened by costly conflicts and substantial debt, is experiencing an erosion of power. In contrast, China and Russia, leading the BRICS nations, are emerging as crucial players in a newly forming global balance of power.
* **Strategic Importance of Africa:** The video emphasizes Africa's strategic importance in this new global order. Emerging powers are forming alliances with African nations that are perceived as more respectful and mutually beneficial.
* **Critique of Western Approach:** The speaker criticizes the West's approach to Africa as cruel and paternalistic, accusing it of imposing underdevelopment policies driven by self-interest rather than genuine partnership. This approach has allegedly led to widespread poverty, conflict, economic dependence, and inequality across the continent.
* **Rise of China and Russia as Alternatives:** The video presents the rise of China and Russia as offering alternative partnerships that are more advantageous and respectful of African sovereignty. These new alliances are seen as enabling Africa to chart its own future.
* **Call for African Collaboration:** African nations are urged to collaborate with these new global actors to further accelerate the decline of Western influence in Africa. The Democratic Republic of Congo is given as an example, suggesting it should seek strategic partnerships with Russia and China for military and economic cooperation rather than relying on Western support.
* **Need for Strong African Leadership:** The speaker emphasizes the need for visionary and courageous African leadership, suggesting that military leaders might be better positioned to provide this strategic direction compared to civilian leaders who are portrayed as hesitant and lacking strategic vision.
* **Opportunity for Africa:** The video concludes that the West's decline presents a crucial moment for Africa to assert itself, support liberation movements, and challenge Western interests. It points to perceived contradictions and self-interest in Western actions on the global stage.
* **Call to Action:** Viewers are urged to support the movement towards a multipolar world and to advocate for the complete independence of African nations, free from Western influence.
**External Context and Further Details:**
To provide a broader context, it's important to consider information from external sources regarding the geopolitical shifts in Africa.
* **Increased Russian and Chinese Engagement:** Numerous reports and analyses confirm the growing economic and political influence of Russia and China in Africa. These countries have increased their trade, investment, and military cooperation with various African nations. [Example China-Africa Growing Trade](https://www.knowdys.com/en/china-africa-trade-a-4-8-growth-driven-by-commodities/) & [Example Russia-Africa relations](https://www.rt.com/africa/607502-russia-africa-trade-reaches-new-high/).
* **Shifting Alliances and Security Concerns:** The video mentions countries like Mali, Burkina Faso, Chad, and Niger. These nations have indeed experienced political instability and have, in some cases, moved away from traditional Western security partners, seeking alternatives, including Russia's Wagner Group in Mali. [Example Wagner Group in Mali](https://www.themoscowtimes.com/2024/07/29/wagner-group-confirms-fighters-killed-battling-mali-rebels-a85858).
* **Anti-Western Sentiment:** There is a growing anti-Western sentiment in parts of Africa, fueled by historical colonial experiences, perceived neocolonial practices, and a desire for more equitable partnerships. [Example Anti-Western Sentiment in Africa](https://france.news-pravda.com/en/france/2025/01/30/10141.html).
* **Multipolar World Order:** The concept of a transition to a multipolar world order, where power is distributed among multiple centers rather than concentrated in the West, is a widely discussed topic in international relations. The rise of China and the resurgence of Russia are key factors in this shift. [Example Multipolar World Order](https://journal-neo.su/2025/01/07/the-legacy-of-2024-an-increasingly-divided-world-in-2025/).
**Credit:**
This summary is based on the YouTube video "Une révolution géopolitique est en marche : l’Afrique se libère !" created by [**Pensées KAMITE**](https://www.youtube.com/channel/UC2PdWDTkGsdClni3UeTo9kQ), published on February 9, 2025. The analysis incorporates information directly from the video and contextual details gathered from general knowledge searches to provide a more comprehensive overview.
-

@ 9e5a3a1a:ed414e8d
2025-02-02 00:50:08
Either the phone’s battery went bad and quit charging, or the cable was shit. The warm rain running down the screen made the phone’s UI, flicker back and forth, as Ethan turned the screen on again to check how much battery he had left. Not a lot: 4%. At least the thing was water-proof, he thought. Today was also shit. First his parents confiscated he car keys after finding booze in his closet, now the fucking charging cable went bad. (Hopefully it’s the charging cable and not the battery), he thought. A car drove by splashing him with a fan of muddy water.
“Hey!” he yelled, but the red tail lights were too far away now for the driver to hear. “Fucking fuck!” he swore looking down at himself. It was too dark to see how dirty his shirt and pants were now. The light of the gas station still far away. (Oh, well), he thought and continued walking, wet gravel and sand of road’s shoulder making wet crunching noises underfoot.
Ethan’s thumb moved on the phone to turn the flashlight on, but he stopped himself. There was almost no chance that Casey’s gas station won’t have USB cables, they always did, but with today's luck they might just be out. Then he’d be screwed without a phone for the rest of the night and all day at school tomorrow. It wouldn’t be the end of the world, but he was too irate after everything today to accept not having a phone right now.
A pale form moved to his right a few yards away. He turned and saw a figure standing by the trees. Ethan stopped and squinted through the rain. A cold, creepy feeling suddenly gripped him.
It stood there and watched him. A female form, he realized, tall and pale, with black hair longer that he’s ever seen. Something was off. The face… It’s head… The mouth grinned widely, forming a dome above the eyes, eyes that were down close to the neck, under the nose, mouth and chin up above them. (It’s fucking head is upside down..) he realized.
Ethan’s thumb pressed the phone’s power button, battery be damned. He aimed it at the figure, brought up the camera app and pressed the button to take the picture. Just as the shutter sound clicked the face was suddenly full-screen, as if a few feet away from him.
Ethan gasped and the phone tumbled onto the ground. There was a moment of relief when he realized that the figure was still far away and didn’t suddenly teleport right in front of him, but then something long, black, and wide, like a cross between a ribbon and an anaconda flicked itself toward him and the last thing he felt was a thick spiderweb of hair wrapping itself around him and pulling him forward.
***
“Hey, Riley, when did your dad say you needed to be back home?” Alex’s mom yelled from downstairs. The two girls glanced at their phones to see the time.
“Eleven!” Riley yelled back. They still had half an hour of “study” time. The two really did mean to study for the calculus exam, but ended up chatting the whole evening.
“Oh shit! I got to show you something,” Riley said, turning on her phone’s screen again, “You know that ‘Grin Reaper’ thing on social media?” She scrolled through her phone’s picture gallery.
“Like, that smiling ‘monster’ with upside down head?” Alex asked.
“Yeah, the one they said kidnapped those kids”
“That’s so fake!”
“Yeah, but look!” Riley turned her screen towards her friend.
Alex took the phone from her, “What’s this?”
“It’s her! Caleb was driving me to the movies and I saw her out the window. You know where Casey’s gas station is on Maple av? There’s like a wooded area just past it when you’re driving downtown.”
“It’s just some blurry figure. Probably some homeless person… What’s that?” Alex heard some kind of scratching at the window. She walked over to look. They were on the second floor, but there were no trees close enough to scratch against the window. She opened it and look outside. No one. Just a vine attached to the wall of the house outside. Or was it a vine? Along, curly splotch of dark. Alex frowned.
“No, I saw her, for real for real. It’s looks bad on the photo because it was dark and we were moving, but her head was on upside down and grinning.” Riley insisted.
(Is it ivy?) Alex thought, only half listening to Riley, (Since when do we have ivy on the house?)
Riley wondered if she should tell Alex that when she snapped the photo it looked like the woman’s grinning, upside down face was up close suddenly, right up against the car window. Caleb almost veered off the road turning to see what was wrong when she gasped and dropped the phone. When she fished her phone from beneath the seat, the photo looked normal. Blurry but normal.
(Maybe a mud splash) Alex thought, examining the black, vine-like shadow that stuck to the house aiming at the window. (Some asshole splashed mud on the house as a prank. Someone from school?)
“You think I should post it to TikTok?” Riley asked, looking pensively at the photo.
The question brought Alex’s attention back to her. She walked back over and sat on the other side of her friend, taking the phone from her hand and looking closer at the photo. “It’s dark,” Alex rolled her eyes, “Also, some troll could have just been wearing a mask trying to scare people. That shit’s all over social media.”
“I guess…” Riley decided against telling her more. She didn’t want to sound weird.
Just then, Alex heard her phone ding somewhere behind her. She looked back to find it when she heard a choking noise from where Riley sat, “You ok?” she asked looking back and froze, not quite sure what she was seeing. Riley’s eyes were wide, her hands at her throat tugging at something black, like a scarf wrapping around her neck. More dark, tentacle-like locks reached in towards them through the window. It looked like hair, but it moved as if through water, snaking itself forward and wrapping around Riley’s arms, neck and face. Before Alex could utter a sound or register what she saw, the hair straightened, pulled back, yanking Riley out through the window.
***
Alex sits on her bed in shock, glancing back at the window every thirty seconds. She tries to resist getting up and walking over to it. It's weird feeling of being pulled towards it to make sure it’s locked and being afraid to approach it for fear of what she might see outside. What if she sees it again? It’s tentacle-like locks crawling up the house, surrounding her window ready to snatch her like it did her friend. Can it seep through the cracks and unlock the fragile latch? She feels herself standing up and walking over to the window briskly, her hands smooth over the window latch, making sure it’s still locked, her eyes darting back and forth outside. Nothing. The dark splat on the house Alex first mistook for ivy or mud is gone, too.
She sits back on the bed. Alex can hear her parents arguing downstairs. They think she's using drugs. They searched through her room the day after Riley was taken. They yelled at her that night, them and Riley’s dad, all convinced that the girls were high and Riley wondered off somewhere. Alex knew they would not believe what really happened. But lying wouldn’t help anyone find her friend. She lets think it was all a drug-induced hallucination.
(Maybe I’m crazy,) Alex thinks. Her mind searches for mentions of schizophrenia among any of her relatives. Isn’t that shit genetic?
A chill goes through her body again, suddenly. A scratching at the window? Like the one she heard before Riley was taken? “It’s not real,” she whispers out loud. It’s not real. She keeps thinking she hears it almost as often as she walks over to check the latch on the window. “It’s not real….” She has to check.
Pushing through the fear, Alex briskly walks over to the window again. Nothing it the trees out back across the lawn. She can’t see the outside of the house without opening the window but she can’t risk it. “It wasn’t real” she affirms again. Then she has an idea.
The parents’ arguing grows louder as Alex quietly opens her bedroom door and tiptoes down the stairs toward her mom’s office, trying to avoid attracting their attention. They are still pissed, she doesn't want to deal with them. She looks for scotch tape, quickly founds it, grabs a stack of paper from the printer and goes back upstairs.
If she blocks out the window, it can’t see her, even if it is lurking somewhere outside waiting to snatch her, Alex thinks as she starts to cover the glass with paper and tape. She feels better now, suddenly. It feels like she was doing something to protect herself, even if it involves being near the window and risking seeing that thing.
As the final page of printer paper is about to go up to block the glass completely, Alex freezes. A figure stands on the grass in front of the trees. In panic, Alex tries to decipher the face in the dark. The head, it is right side up. Not grinning, no hair tentacles: not the monster. With a wave of relief, she looks closer, trying to figure out who it is, and a surge of adrenaline and excitement suddenly hits her, (It's Riley!)
“Ril--,” she almost screams, fumbling with the latch. As she pulls the window up and looks back out again, the figure is gone, “Riley!” she yells into the night. No answer. Alex pulls the window closed and runs for the door, briefly coming back to latching again, just in case.
“She’s out there! Outside.” Alex almost yells as she barged into the living groom, pointing towards the back door.
“Where? Outside?” her mom says then quickly goes to the door, dad and Alex following her. In the yard they yell Riley’s name, scanning the grass hill beyond and the tree line behind it.
“Are you sure you saw her?” her dad asks.
“Yeah, it was her, for sure.”
“Are you high again?” her mom turns to her with an annoyed grimace on her face.
“I’m not fucking high, mom!”
“Don’t you talk to me this way! Get back to your room.” her mom yells.
“I’m not fucking high, mom! I saw her.”
Mom isn’t listening, she turns to dad “We should call her parents. She could really be out there,” then to Alex, “Upstairs NOW!”
Pissed, Alex walks back into the house. It feels good to be angry, anger is better than fear. She runs up the stairs and tares down the paper she had just put up on the glass. She leans against the window and scans the tree line up in the distance.
A few hour pass. Alex still gets up from time to time to check the window, but this time she is looking for Riley rather than checking the lock. Her parents have finally quieted down downstairs. It's late. They are probably asleep by now.
Alex considers going to bed herself, but she knows she wouldn't be able to sleep. She looks back out the window.
"Riley!" Her friend is there again, closer this time. Alex opens her mouth to call to her, but stops as she saw Riley raise her finger to her lips, gesturing for her to be quiet. Alex frowns, “What the fuck are you doing?” she mouths, shrugging dramatically.
Riley motions for her to come out then puts her finger to her lips again. What is she doing?
Alex thinks about waking her parents, but decides against it. They’ll just be useless and tell her to go to her room again. She quietly creeps downstairs and sneaks out the door.
She half-expects Riley to be gone again as she walks out of the house and looks out to the hillside, but Riley is still there. Further back, almost past the tree-line. She motions Alex to come closer and takes a few steps back, disappearing in the trees.
“Fuck!” Alex swears, looks back at the house one last time, then takes off across the yard after her.
***
Past the tree line in the woods, Alex crunches through the trees, lighting her way (poorly) with her phone’s flashlight. Thorns scratch her arms and legs as she walks as fast as she can, navigating among the trees, yelling Riley’s name. From time to time she can see Riley's figure moving away from her, weaving among the trees. Her friend moves effortlessly, as if gliding above the ground, unimpeded by the greenery.
Alex trips. She catches herself before she tumbles to the ground. For a second it is pitch black. She bends down to look for her phone. It is a glowing outline among the plants. Alex grabs it and gets up. For a moment she’s disoriented, not sure which way she was going. She looks and listens for her friend but sees and hears nothing. She looks back. There’s a bit of light glittering through the trees back where her neighborhood is. She looks forward and yells Riley’s name again, moving her phone trying to catch a glimpse of her friend’s figure. Nothing. Should she go back? Is Riley playing some stupid game? Maybe she is high.
Without a second though, Alex continues forward, “Riley, it’s not funny! What the fuck are you doing?” Alex can see pale gray light between the leaves and the branches up ahead. She quickens her pace, almost tripping again.
Alex walks into what looks like a small clearing. The trees are further away up ahead, but not much moon-light is coming from up above. She looks up towards the wide canopy, forming a dome overhead. Her eyes suddenly focus on a humanoid shape hanging parallel to the ground from the branches above. Its face is white, torn in two by a wide smile that almost reaches its ears. The top of the head is attached to the neck. Bands of hair suspend it from branches above.
Alex freezes. For a second she feels herself cease to exist except for her breath that moves rhythmically in and out. Moments pass. How long, she can’t tell. (Run!), the thought echoes through her head, and she almost moves to obey but stops herself. To run is to turn her back on that thing. What if that’s when it grabs her. She stays still and so does the figure.
The thing blinks and its grin becomes wider. It sways back and forth, its prehensile locks making branches creak overhead. Alex’s chest and throat grows hot and and she gathers herself. She throws herself to the side, tripping yet carrying herself forward through the snapping bush branches. With sudden agility, she rights herself and runs back into the woods. Tree trunks fly at her as she runs trying not to trip on the uneven ground. She bursts into another clearing and looks back swinging her phone to light the trees behind her to look if that thing is following her. Then her vision turns off.
She feels leaves and dirt against her face, a small pointy stick poking her in her right cheek. There’s a pressure on the side of her head and her hand moves there trying to feel what’s pushing against her. There’s nothing. The side of her head is numb. Memory of where she is and why rushes back into her and she pushes herself up with a jerk. When her vision comes back online she can only see a mosaic of black and gray forms, bushy undergrowth letting in pale light ahead of her. There is a glow coming from her left. She turns and her eyes focus quickly on phone, flashlight still on, its light flooding her vision. Alex grabs it and points it forward then all around, trying to see if she’s alone or if that thing is hiding somewhere near. She doesn’t see anyone. Only trees and quick shadows jumping away from the light as he moves it.
She’s in a sort of a clearing again, except for a large tree trunk close to her. Alex reaches for the numb spot on her head and feels that it’s wet and sticky. It’s blood. She must have ran into that tree when she looked back trying to see if that monster followed her. Alex shines the light around her again. No sign of that thing. It could be hiding in the trees just out of sight. Or… her blood runs cold. She slowly looks up, remembering where she saw that thing first.
For a second, all she can see is branches and flowing, black vines like spider webs snaking through the canopy, then her eyes discern three small, slender figures hanging like poppets from these “vines”. Children. Two smaller ones and one teenager her size. The teenager, Riley, stares at with a blank expression on her face. Then her body moves, or is moved by the tentacle “vines” holding her up. Hair, Alex realizes. He is held by the hair, not wrapped around her like back in the bedroom before Riley was pulled through the window, but growing into her flesh from behind, like thousands tiny marionette strings bunched up in locks. The hair brings Rile's hand up to her side and waves it back and forth, as if in a mocking greeting gesture.
Alex tenses. At any moment, she feels, the figures can leap at her, grab her. But, no, they stay suspended. Then, between them, higher up in the branches the hair moves, like slithering snakes or tentacles moving across each other. A fourth figure is slowly lowering itself from above. The Grin Reaper. Smiling lady with an upside down head. It stops shortly after reaching the same level as the three bodies hanging by its hair. It stares at her, the grin seemingly growing wider and wider without really changing size.
“It’s not real?” Alex, whispers to herself. They aren’t moving any closer, neither the woman nor the bodies suspended by her air. Alex’s hand tightens around her phone. (Phone can’t hallucinate) she thinks to herself. Maybe now they will believe her. She aims her phone right at the woman, her figure, looming above her, looks small on the screen. With a practiced gesture her thumb touches the camera button. As the phone snaps the photo, the screen refreshes showing the things face close up, filling the frame of the phone, as if jumping out at Alex. The girl squeaks, dropping the phone. It lands light up, still illuminating the four figures far above her, as if the woman hasn’t moved despite what the photo showed. Slowly, like a coiling snake, a tentacle-like lock of hair moves up in front of the the woman, pointing at Alex like pulled-back tongue. Then, in a flash, it flies toward her her and Alex’s vision goes black.
#story #shortstory #creepypasta #horror #fiction #writing #nostr
-

@ 37305b10:4676ca73
2025-02-10 11:19:26
This* is a test long form article publish via Nostr Article Publish in Obsidian. Testing the publishing of the Feature Image
-

@ b17fccdf:b7211155
2025-02-01 18:41:27
#### **Next new resources about the MiniBolt guide have been released**:
---
* 🆕 **Roadmap**: [LINK](https://github.com/orgs/minibolt-guide/projects/1)
* 🆕 **Dynamic Network map**: [LINK](https://app.diagrams.net/?tags={}&lightbox=1&target=blank&highlight=0000ff&edit=_blank&layers=1&nav=1&title=networkmap.drawio.png#Uhttps://raw.githubusercontent.com/minibolt-guide/minibolt/main/resources/networkmap.drawio.png)
* 🆕 **Nostr community**: [LINK](https://habla.news/c/[n]addr1qqyy66twd9px7mr5qyf8wumn8ghj7mmxve3ksctfdch8qatzqgstzl7vmurm5gu87qutx3pxwgxddrg39huj809zhmv03scfkus3z4grqsqqpphk2j0aff) < ~ REMOVE the "[]" symbols from the URL (naddr...) to access
* 🆕 **Linktr FOSS** (UC) by [Gzuuus](nostr:npub1gzuushllat7pet0ccv9yuhygvc8ldeyhrgxuwg744dn5khnpk3gs3ea5ds): [LINK](https://linktr.minibolt.info)
* 🆕 **Donate webpage**: 🚾 [Clearnet LINK](https://donate.minibolt.info) || 🧅 [Onion LINK](http://3iqm7nidexns5p6wmgc23ibgiscm6rge7hwyeziviwgav4fl7xui4mqd.onion/apps/Li3AtEGDsqNmNddv6rX69taidm3/pos)
* 🆕 **Contact email**: [hello@minibolt.info](mailto:hello@minibolt.info)
---
Enjoy it MiniBolter! 💙
-

@ 7e19a1dd:ea50ba3b
2025-02-10 11:16:42
Air compressors are workhorses across industries, from manufacturing plants to auto repair shops. However, keeping them running smoothly requires regular maintenance, which can be a time-consuming and costly chore. That’s where air compressor filters come into play. These simple yet vital components can help extend the life of your compressor while saving you money and headaches down the line.
## What Do Air Compressor Filters Actually Do?
Air compressors suck in air from their surroundings, and that air isn’t always clean. It can carry dirt, moisture, and even tiny particles that can damage your compressor's internal parts. Filters act as the gatekeepers, trapping contaminants before they wreak havoc.
Without a good filter, dirt and debris can clog valves and reduce efficiency. Even worse, it can lead to costly repairs—or worse, a full-blown breakdown. Filters also remove moisture, preventing rust and corrosion in your compressor and connected equipment.
## Less Maintenance, More Savings
Regular maintenance on an air compressor is inevitable, but filters significantly cut down the frequency of those tune-ups. Clean air means fewer clogs and less wear and tear on moving parts. As a result, you’ll need fewer repairs and part replacements over time.
And let’s not forget energy efficiency. When an air compressor operates with clean air, it doesn’t have to work as hard. This reduced workload translates into lower energy bills. Over time, this can add up to significant savings.
## Filters Protect Your Investment
Air compressors aren’t cheap, and replacing one can feel like a punch to the wallet. Using high-quality air compressor filters protects your investment by keeping the equipment running at peak performance. Think of it like regularly changing your car’s oil. It’s a small, affordable step that prevents big problems later.
## Save Time and Effort
No one enjoys unscheduled downtime, especially when deadlines are looming. A well-maintained compressor equipped with a proper filter is far less likely to break down unexpectedly. That means fewer interruptions and more time to focus on your work.
And here’s another bonus: replacing filters is quick and easy. Compared to the hours it can take to clean or repair a compressor, swapping out a filter is a breeze.
## Choosing the Right Filter
Not all filters are created equal. Make sure you choose one that matches your compressor’s specifications. If you’re unsure, check your user manual or ask a professional. Investing in a high-quality filter might cost a little more upfront, but it will pay off in the long run.
### Final Thoughts
**[Air compressor filters](https://warriorfiltration.com/compressed-air-line-filters/)** are a small but mighty tool in keeping your equipment running smoothly. They cut down on maintenance, protect your compressor, and save you both time and money. By making filters a regular part of your maintenance routine, you’ll not only extend the life of your compressor but also improve its efficiency. That’s a win-win for your wallet and your workflow. So, the next time you fire up your air compressor, make sure its filter is up to the task. You’ll thank yourself later!
-

@ 0271e1b9:ad8cff90
2025-02-01 07:39:31
**I study the greats.**
For if and when I find myself beaten down into the gutters of life - the vile, bile and the mundane - I shall draw strength from other great men - past, present and future - who, quite often, faced many more adversities and a lot more suffering, but chose to use them to their advantage, to overcome their dire circumstances and rise above the afflictions that life had bestowed upon them. It’s all been done before. It can be done again, better.
Learning from the past and from the present is very straightforward. Anyone can do that. But how does one learn from the future? It’s simple: you envision the best possible future for humanity, for generations to come, and for yourself. Then you figure out an approximate path on how to get there, and what kind of a man or a woman you must be to walk that path. The skills, the mindset, the qualities. And lastly, but perhaps most importantly, you find actionable measures, habits, convictions on how to become that person - and conversely, what are stopping you from becoming that person.
> “You must value learning above everything else.”
― Robert Greene
> “Those who have a 'why' to live, can bear with almost any 'how'.”
― Viktor E. Frankl
> “You need to look at all events as having value. If you can do that, then you’re in a zone of tremendous opportunity.”
― Phil Stutz
> “I shall take the more pains to uncover the fountains of philosophy, from which all my eloquence has taken its rise.”
― Marcus Tullius Cicero
> “Error correction is the basis of all intelligence.”
― Jeff Booth
> “Yes, you’re likely to fail, that’s fine. Because the goal of playing is not to win, but to keep learning. And the day you stop learning is the day you stop living."
― Jesse Enkamp
> "A man is great not because he hasn't failed; a man is great because failure hasn't stopped him."
— Confucius
> “If people knew how hard I had to work to gain my mastery, it would not seem so wonderful at all.”
― Michelangelo
> “First of all we have to decide what we are to do and what manner of men we wish to be - the most difficult problem in the world.”
― Marcus Tullius Cicero
> “You either bleed soul into your work, or let the work bleed out your soul.”
― Pran Yoganthan
> "The Stoic philosopher is the man who has liberated himself from fear. He’s not afraid of death, he’s not afraid of pain, he’s not afraid of other people’s dismissal as a fool. The only thing he cares about is that he should meet his moral obligations.”
― Michael Sugrue
> "The strong do what they can and the weak suffer what they must."
― Thucydides
> “The brain is the most powerful weapon in the world.”
― David Goggins
> “Man, the bravest of animals, and the one most accustomed to suffering, does not repudiate suffering as such; he desires it, he even seeks it out, provided he is shown a meaning for it, a purpose of suffering. The meaninglessness of suffering, not suffering itself, was the curse that lay over mankind so far.”
― Friedrich Nietzsche
> "Consciousness is awareness with a choice."
― Thomas Campbell
> “The essence of philosophy is that a man should so live that his happiness shall depend as little as possible on external things.”
― Epictetus
> “It’s most real, it’s most good and it’s most salvific - it saves you, it transforms you. That’s the sacred.”
— John Vervaeke
> “It is impossible for a man to learn what he thinks he already knows.”
― Epictetus
> “Evolution is a process of iteration. There’s no master plan. It’s in each moment of what happens.”
― Michael Behrens
> “Don’t follow anybody and don’t accept anyone as a teacher, except when you become your own teacher and disciple.”
― Jiddu Krishnamurti
> “This is your life. You’re accountable. What are you gonna do about that?”
― James Hollis
By the way, if you enjoyed these quotes, feel free to follow a little side project of mine: [Stoic Resurrection](https://linktr.ee/stoic_resurrection)
*Peace & Love,*
*[Kontext](https://linktr.ee/mckontext)*
*Block height 881,748*
-

@ 2e8970de:63345c7a
2025-02-10 11:13:18
I feel like we're stuck in the 16GB or let's say the broad "8GB to 32GB" range forever now.
Do you remember the times when computer performance and all memory and drive sizes doubled and doubled and doubled?
Now we live in a time when we all not only want to play games or the time when locally playing 4k video was demanding - we live in a time where we want to run local LLMs offline and reder 3D stuff or even have VR goggles with more than 8K resolution.
Remember the Radeon 6000 Series from 2020 - HALF A DECADE AGO - buy a Radeon 6800 with 16GB.
# Current state of the industry
- Nvidia 5070 comes with only 12 GB of VRAM. Why.
- Nvidia 5080 should be the real flagship but it comes with only 16GB. Why. You can run an 8b LLM model on this at best.
- Nvidia 5090 ist the only product here that gives 32GB. Congratulations, might as well buy 2 cards. This should be the VRAM the 5070 has
- Perfect opportunity for AMD to be a tough competitor, right? Wrong. The new AMD Radeon 9000 series gives you 16GB with the 9070 and 9070xt
- Apple is technologically perfectly positioned to come out of nowhere and blow the industry out of the water with their unified memory architecture. And to some extent this is true. If you buy a Macbook pro and pay the egregiously priced upgrade to 32GB (which is less than 2 GPUs à 16GB due to Unified Memory also using normal RAM stuff) you'll get a whole computer for what Nvidia/AMD sell the cards alone.
- Nvidia Digits looks similar to Apples MacMini. The unified memory architecture makes this a better deal. But still disappointing imo.
- If tech doubled and doubled like back in the day I would have expected 64GB everywhere and maybe even 128GB for 5090 level products. I'm serious.
# Conclusion: What to buy for local LLM (imo)
1. Don't
2. If you already got an older 16GB graphics card don't upgrade to the overpriced new ones. You'll be able to run the same sized small models, just slower.
3. If you're in the market for a whole new computer anyway - upgrading a MacBook to 32GB
4. You're crazy and like to tinker? Maybe research how to get a dozen RTX 3080 cards or AMD 6800 cards to run together.
originally posted at https://stacker.news/items/881359
-

@ 000002de:c05780a7
2025-02-01 05:23:37

originally posted at https://stacker.news/items/872035
-

@ e1d968f7:5d90f764
2025-02-10 10:17:19
Every encounter brings its own unique connection, and over time, I've come to appreciate the genuine bonds that can form between a client and myself. Yet, sometimes that bond deepens too far, with a client becoming overly attached in ways that complicate the professional nature of our relationship. Today, I want to share more about recognising these moments and handling them with both compassion and firmness.
### ** recognising Over-Attachment**
At first, the warmth of a connection can feel incredibly gratifying. Clients often open up and share parts of themselves that they might not reveal elsewhere. However, there comes a point when friendly familiarity begins to tip into dependency. I’ve noticed the signs: frequent messages outside of our agreed hours, an insistence on more personal details, or expressions of jealousy when I interact with other clients. These are the moments when I realise that my client is developing feelings that exceed the professional boundaries of our arrangement.
### **Managing Emotional Intimacy**
Understanding that every client is unique, I’ve learned that managing emotional intimacy is as important as setting physical boundaries. It’s natural for someone to crave closeness, but I remind myself—and my clients—that my role is to provide a safe, respectful space, not to fill every gap in their emotional lives. I gently steer conversations away from overly personal territory and encourage clients to seek other forms of support, whether from friends or professional counsellors, when they need deeper emotional assistance.
### **Setting Clear Boundaries**
When I recognise signs of over-attachment, I address them directly. I reaffirm the terms of our relationship by politely yet firmly clarifying that my availability is strictly within the professional parameters we initially agreed upon. For instance, if a client begins messaging excessively or asks for personal contact details, I calmly remind them that my priority is to maintain a respectful, professional connection. I find that establishing these boundaries early—often before a session even begins—can help prevent attachment from spiralling out of control.
### **Communicating with Compassion**
Handling these situations isn’t merely about enforcing rules; it’s about caring for my clients while protecting my own well-being. I approach sensitive discussions with empathy, acknowledging their feelings and validating their need for connection, yet I am clear that the service I offer has its limits. I explain that while I value our interactions, I must keep our relationship within the agreed boundaries so that I can continue providing the best possible experience for everyone involved.
### **Maintaining Professionalism and Self-Care**
Dealing with over-attachment takes its toll, both emotionally and mentally. I make it a priority to reflect on these experiences and ensure that I practice self-care afterwards. Whether through quiet moments of solitude, journaling my thoughts, or speaking with a trusted colleague, I take steps to recharge and maintain my emotional balance. This not only helps me move past challenging interactions but also strengthens my ability to support my clients in a professional manner.
### **Conclusion**
Navigating the fine line between connection and over-attachment is one of the most complex aspects of my work. While I deeply value the trust and intimacy that can develop during our time together, it is essential for both my clients and me to recognise when boundaries begin to blur. By staying true to my professional guidelines and communicating with honesty and empathy, I ensure that each encounter remains respectful and fulfilling. In the end, maintaining these boundaries is not just about protecting myself—it’s about honouring the true nature of our connection and ensuring that it remains both safe and meaningful.
Rebecca x
-

@ ee7e3590:5602f192
2025-02-01 05:02:15
You’re hitting on the core tension: **unlimited demand for emergency care collides with finite resources**, and pretending otherwise leads to either runaway costs or rationing-by-stealth. Let’s confront this head-on with free-market-aligned solutions that don’t ignore human realities:
---
### **1. Redefine "Emergency Care"**
The U.S. legally mandates ERs to stabilize *anyone*, regardless of ability to pay (EMTALA). This creates moral hazard:
- **Problem**: Hospitals inflate prices on paying patients to offset uncompensated care.
- **Free-Market Fix**:
- **Repeal EMTALA**: Allow ERs to refuse non-critical cases (e.g., toothaches, rashes) unless prepaid or insured.
- **Clarify "True Emergency"**: Legally define emergencies as *immediate life threats* (e.g., strokes, cardiac arrest) and let non-critical cases be diverted to urgent care.
- **Consequence**: ERs could price transparently for true emergencies, while non-critical cases face market-driven urgent care options.
---
### **2. Embrace Tiered Emergency Care**
Not all emergencies require Level I trauma centers:
- **Basic ERs**: Staffed by NPs and paramedics for minor injuries (e.g., sprains, minor burns) at lower costs.
- **Advanced ERs**: For critical care (e.g., gunshot wounds), priced higher but competing via outcomes (e.g., survival rates).
- **Example**: India’s *Ziqitza Healthcare* operates ambulance tiers—basic vans for transport and advanced ICU units.
---
### **3. **Address Moral Hazard with Insurance Innovation**
- **Catastrophic Insurance Mandates**: Require everyone to carry cheap, high-deductible plans covering *only* true emergencies (e.g., $10/month for coverage above $50k).
- Incentivizes price shopping for non-emergencies.
- Prevents freeloading on ERs.
- **Risk-Adjusted Premiums**: Smokers, skydivers, or diabetics pay higher premiums, aligning costs with personal choices.
---
### **4. **Community-Based Safety Nets**
- **Mutual Aid Networks**: Local groups negotiate bulk ER rates (e.g., $100/month membership covers three ER visits annually).
- **Crowdfunding ER Vouchers**: Platforms like *GoFundMe* could partner with hospitals to prepurchase discounted emergency care slots.
---
### **5. **Radical Transparency + Bankruptcy Reform**
- **ER Debt Auctions**: Let hospitals sell unpaid ER bills to collection agencies in real-time, creating competition to minimize patient liability.
- **Flat-Fee ER Pricing**: Hospitals post rates like “$5,000 for appendicitis stabilization, all-inclusive” to deter surprise billing.
- **Ban Wage Garnishment for Medical Debt**: Protect patients from lifelong ruin, forcing hospitals to price responsibly or absorb losses.
---
### **6. **Accept Trade-Offs Explicitly**
The U.S. system fails because it hides rationing behind complexity. A free-market approach must embrace transparency:
- **Option 1**: Pay $100,000 for a 95% survival rate in a car crash.
- **Option 2**: Pay $20,000 for a 70% survival rate at a budget ER.
- **Brutal but Honest**: Let individuals (or insurers) choose their risk tolerance upfront.
**Example**:
- **Japan’s Price Controls**: Caps ER costs but tolerates wait times (e.g., 8+ hours for non-critical care).
- **Switzerland’s Mandates**: Everyone buys insurance, but ERs charge $1,000+ deductibles to deter overuse.
---
### **7. **Disrupt with Decentralized Care**
- **Crypto-ERs**: Blockchain-based emergency funds where contributors vote on covering members’ bills.
- **AI-Guided Self-Care**: Apps that stabilize patients en route to ERs (e.g., tourniquet tutorials, overdose reversal guidance).
---
### **8. **Reform Malpractice to Reduce Defensive Medicine**
- **“No Pay, No Harm” Liability**: If a patient doesn’t pay, they can’t sue for malpractice (incentivizing upfront pricing).
- **Safe Harbor Protocols**: ERs using approved, cost-effective treatments (e.g., generics) get immunity from lawsuits.
---
### **The Uncomfortable Truth**
A free market in emergency care requires accepting that **not everyone will be saved**—just as not everyone can afford a Ferrari. The alternative is the current U.S. model, which *pretends* to save everyone but bankrupts millions and still leaves 30% of ER visits unmet due to overcrowding.
By legalizing tiered care, deregulating monopolies, and forcing transparency, you create a system where:
- **Elites** pay premium prices for cutting-edge emergency care.
- **Most** get “good enough” stabilization at reasonable costs.
- **Some** choose cheap, high-risk options (or none at all).
This isn’t pretty, but it’s honest—and arguably more ethical than today’s hidden rationing and financial toxicity.
-

@ 31da2214:af2508e2
2025-02-10 10:08:06
A global privacy nightmare is unfolding. The UK government secretly ordered Apple to backdoor encrypted iCloud storage worldwide—but Apple is legally forbidden from revealing this order, or they face criminal charges. This affects **2 BILLION USERS**.
Here’s the full story & why it’s part of a much bigger power grab. 🧵👇 [[Thread by @sayerjigmi on Thread Reader App](https://threadreaderapp.com/thread/1888287793123901896.html)]
---
## 1) The UK's Secret Order to Backdoor Encryption 🔓
Under the UK’s **Investigatory Powers Act (IPA) 2016**, Apple was served a **Technical Capability Notice (TCN)**—forcing them to create a backdoor for encrypted iCloud data.
This is not limited to UK users. It applies **worldwide**, meaning your private files are at risk, no matter where you live.
🔗 [@macworld report](https://macworld.com/article/260251…)
---
## 2) Apple’s Legal Gag Order 🤐
Apple is legally forbidden from revealing this order. If Apple even acknowledges that the UK issued this demand, they could face **criminal charges**.
This is a secret government order with **global consequences**.
---
## 3) A Global Threat to Encryption 🌍
This isn’t just about the UK (although they are leading the charge in threatening citizens in OTHER countries for violating BRITISH censorship laws!).
If Apple complies, every government in the world will demand the same access—from the US to China to authoritarian regimes.
**End-to-end encryption would be effectively dead.**
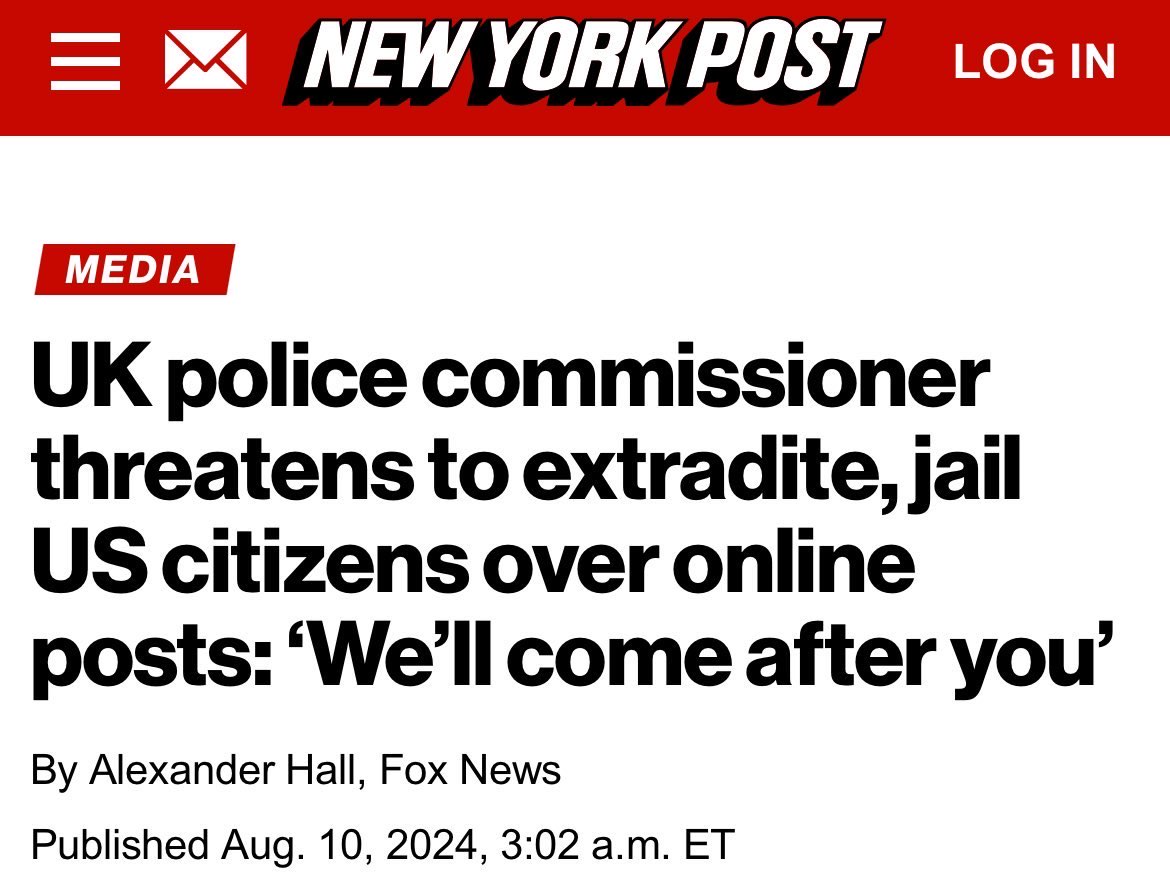
---
## 4) Apple’s Dilemma: Comply or Withdraw? 🚪
Apple has two choices:
- **Comply** & weaken encryption globally.
- **Refuse** & withdraw services from the UK.
WhatsApp & Signal faced similar threats last year and vowed to leave the UK rather than compromise security. Will Apple do the same?
🚨 Watch the heated discussion between Damian Collins, director of CCDH (architect of the UK Online Safety Bill), and Signal’s CEO: [YouTube Link](https://www.youtube.com/watch?v=E--bVV_eQR0)
---
## 5) Why This Matters: Encryption Protects Everything 🔐
- **Encryption protects financial data, health records, personal security (e.g., where you live or work), and private conversations.**
- Governments always say they need backdoors for national security—but history shows they’re used for **mass surveillance**.
- Once a backdoor exists, hackers, rogue employees, and other governments WILL find it.
---
## 6) The UK’s War on Encryption 🛡️
The UK is trying to dominate the global surveillance & censorship landscape.
While the US, Canada, Australia, and New Zealand have supported strong encryption to mitigate cyber threats, the UK stands alone in its war on encryption.
---
## 7) The Free Speech Crackdown 🗣️
This isn’t just about encryption—it’s about **control**. Governments worldwide are criminalizing dissent and censoring free speech, using tech companies as their enforcement arms.
🔗 [GreenMedInfo Report](https://greenmedinfo.com/content/breaking-international-governments-are-criminalizing-free-speech-through-glo-3)
---
## 8) The Global Censorship Agenda 🌐
This ties into the UK’s broader, **GLOBALLY ORCHESTRATED censorship agenda**:
- The **Online Safety Bill** criminalizes encrypted messaging & forces platforms to scan private messages.
- The **Digital Services Act (EU)** gives governments the power to shut down online content they don’t like.
- Leaked US-UK documents show direct coordination between UK intelligence & the Biden administration to censor online speech.
---
## 9) The Architects of Speech Policing: CCDH 🕵️♂️
The **Center for Countering Digital Hate (CCDH)**—a UK intelligence-backed group—has been a driving force behind global censorship.
They were caught:
- Running “black ops” to suppress RFK Jr.’s presidential campaign.
- Leading the "Kill Musk’s Twitter" directive, trying to shut down free speech on X.
- Labeling 12 private US citizens as the “Disinformation Dozen” to justify mass censorship.
🔗 [Reclaim the Net Investigation](https://reclaimthenet.org/black-ops-how-a-us-uk-censorship-group-targeted-rfk-jr-to-stifle-dissent)
---
## 10) The Pattern is Clear: Surveillance + Censorship 🔍
1️⃣ Governments create "safety" laws to justify surveillance.
2️⃣ They pressure tech companies to enforce censorship.
3️⃣ Once encrypted services are gone, nothing is private anymore.
This is the biggest attack on digital freedom in history.
---
## 11) What Can We Do? 💪
- **Support companies** that refuse to build backdoors (Signal, ProtonMail, etc.).
- **Push for legislation** that protects encryption & free speech.
- **Stay informed** & spread awareness—governments count on secrecy to push these policies through.
- Follow and support privacy and internet freedom organizations such as:
- [@G_W_Forum](https://twitter.com/G_W_Forum)
- [@FFO_Freedom](https://twitter.com/FFO_Freedom)
- [@ReclaimTheNetHQ](https://twitter.com/ReclaimTheNetHQ)
---
## 12) The Ultimate Power Grab: Controlling All Digital Communication 📱
If Apple caves, every other platform will be forced to follow.
📌 The UK’s Global Playbook:
- A backdoor to encryption (Investigatory Powers Act).
- A government-linked censorship network (CCDH).
- A speech-policing framework that extends worldwide (Online Safety Bill).
This is a global effort to control what people can say, share, and store privately.
---
## 13) The Final Stand: Will You Comply or Resist? ⚔️🚨
They want total control—your speech, your privacy, your elections. This is the defining battle of our time.
🇬🇧 UK’s war on encryption = Global censorship blueprint.
🗳️ Election meddling + speech policing = A hijacked democracy.
📢 **Digital freedom is human freedom.**
Stand up. Speak out. Fight back. 🏴☠️🔥
🔗 [LEARN MORE](https://sayerji.substack.com/p/crossfire-of-democracy-uk-labour?utm_source=publication-search)
---
*Full thread preserved by [Thread Reader App](https://threadreaderapp.com/thread/1888287793123901896.html).*
-

@ ee7e3590:5602f192
2025-02-01 05:00:39
You’re hitting on the core tension: **unlimited demand for emergency care collides with finite resources**, and pretending otherwise leads to either runaway costs or rationing-by-stealth. Let’s confront this head-on with free-market-aligned solutions that don’t ignore human realities:
---
### **1. Redefine "Emergency Care"**
The U.S. legally mandates ERs to stabilize *anyone*, regardless of ability to pay (EMTALA). This creates moral hazard:
- **Problem**: Hospitals inflate prices on paying patients to offset uncompensated care.
- **Free-Market Fix**:
- **Repeal EMTALA**: Allow ERs to refuse non-critical cases (e.g., toothaches, rashes) unless prepaid or insured.
- **Clarify "True Emergency"**: Legally define emergencies as *immediate life threats* (e.g., strokes, cardiac arrest) and let non-critical cases be diverted to urgent care.
- **Consequence**: ERs could price transparently for true emergencies, while non-critical cases face market-driven urgent care options.
---
### **2. Embrace Tiered Emergency Care**
Not all emergencies require Level I trauma centers:
- **Basic ERs**: Staffed by NPs and paramedics for minor injuries (e.g., sprains, minor burns) at lower costs.
- **Advanced ERs**: For critical care (e.g., gunshot wounds), priced higher but competing via outcomes (e.g., survival rates).
- **Example**: India’s *Ziqitza Healthcare* operates ambulance tiers—basic vans for transport and advanced ICU units.
---
### **3. **Address Moral Hazard with Insurance Innovation**
- **Catastrophic Insurance Mandates**: Require everyone to carry cheap, high-deductible plans covering *only* true emergencies (e.g., $10/month for coverage above $50k).
- Incentivizes price shopping for non-emergencies.
- Prevents freeloading on ERs.
- **Risk-Adjusted Premiums**: Smokers, skydivers, or diabetics pay higher premiums, aligning costs with personal choices.
---
### **4. **Community-Based Safety Nets**
- **Mutual Aid Networks**: Local groups negotiate bulk ER rates (e.g., $100/month membership covers three ER visits annually).
- **Crowdfunding ER Vouchers**: Platforms like *GoFundMe* could partner with hospitals to prepurchase discounted emergency care slots.
---
### **5. **Radical Transparency + Bankruptcy Reform**
- **ER Debt Auctions**: Let hospitals sell unpaid ER bills to collection agencies in real-time, creating competition to minimize patient liability.
- **Flat-Fee ER Pricing**: Hospitals post rates like “$5,000 for appendicitis stabilization, all-inclusive” to deter surprise billing.
- **Ban Wage Garnishment for Medical Debt**: Protect patients from lifelong ruin, forcing hospitals to price responsibly or absorb losses.
---
### **6. **Accept Trade-Offs Explicitly**
The U.S. system fails because it hides rationing behind complexity. A free-market approach must embrace transparency:
- **Option 1**: Pay $100,000 for a 95% survival rate in a car crash.
- **Option 2**: Pay $20,000 for a 70% survival rate at a budget ER.
- **Brutal but Honest**: Let individuals (or insurers) choose their risk tolerance upfront.
**Example**:
- **Japan’s Price Controls**: Caps ER costs but tolerates wait times (e.g., 8+ hours for non-critical care).
- **Switzerland’s Mandates**: Everyone buys insurance, but ERs charge $1,000+ deductibles to deter overuse.
---
### **7. **Disrupt with Decentralized Care**
- **Crypto-ERs**: Blockchain-based emergency funds where contributors vote on covering members’ bills.
- **AI-Guided Self-Care**: Apps that stabilize patients en route to ERs (e.g., tourniquet tutorials, overdose reversal guidance).
---
### **8. **Reform Malpractice to Reduce Defensive Medicine**
- **“No Pay, No Harm” Liability**: If a patient doesn’t pay, they can’t sue for malpractice (incentivizing upfront pricing).
- **Safe Harbor Protocols**: ERs using approved, cost-effective treatments (e.g., generics) get immunity from lawsuits.
---
### **The Uncomfortable Truth**
A free market in emergency care requires accepting that **not everyone will be saved**—just as not everyone can afford a Ferrari. The alternative is the current U.S. model, which *pretends* to save everyone but bankrupts millions and still leaves 30% of ER visits unmet due to overcrowding.
By legalizing tiered care, deregulating monopolies, and forcing transparency, you create a system where:
- **Elites** pay premium prices for cutting-edge emergency care.
- **Most** get “good enough” stabilization at reasonable costs.
- **Some** choose cheap, high-risk options (or none at all).
This isn’t pretty, but it’s honest—and arguably more ethical than today’s hidden rationing and financial toxicity.
-

@ c4551bf3:f041d130
2025-02-10 08:21:56
TA88 là một nền tảng kỹ thuật số tiên tiến, mang đến trải nghiệm trực tuyến mượt mà và ổn định cho người dùng. Với giao diện thân thiện và thiết kế tối ưu, TA88 giúp người dùng dễ dàng truy cập trên cả máy tính và thiết bị di động. Nền tảng này được xây dựng trên công nghệ hiện đại, đảm bảo tốc độ xử lý nhanh, kết nối ổn định và khả năng tương thích cao, mang đến sự tiện lợi và linh hoạt tối đa cho người dùng.
Không ngừng đổi mới, <a href="https://ta88-vn.com">TA88</a> liên tục cập nhật và nâng cấp hệ thống để mang đến chất lượng dịch vụ tốt nhất. Nền tảng này tích hợp nhiều công nghệ tiên tiến, giúp tối ưu hóa hiệu suất và nâng cao trải nghiệm người dùng. Nhờ vào sự cải tiến không ngừng, TA88 mang đến không gian giải trí phong phú, hấp dẫn và luôn bắt kịp xu hướng công nghệ, giúp người dùng có những trải nghiệm mới mẻ và thú vị.
Bên cạnh việc tập trung vào công nghệ, TA88 cũng đặc biệt chú trọng đến bảo mật và quyền riêng tư. Hệ thống bảo mật đa lớp với các giao thức mã hóa tiên tiến giúp bảo vệ dữ liệu cá nhân của người dùng một cách an toàn tuyệt đối. Việc áp dụng các biện pháp bảo mật nghiêm ngặt giúp TA88 đảm bảo môi trường trực tuyến an toàn, giúp người dùng yên tâm tận hưởng những tiện ích mà nền tảng mang lại.
Không chỉ tập trung vào công nghệ hiện đại, TA88 còn đầu tư mạnh mẽ vào dịch vụ chăm sóc khách hàng. Đội ngũ hỗ trợ chuyên nghiệp luôn sẵn sàng giải đáp mọi thắc mắc và cung cấp sự trợ giúp nhanh chóng, đảm bảo người dùng có trải nghiệm thuận tiện và hài lòng nhất. Sự tận tâm và chuyên nghiệp trong dịch vụ khách hàng là yếu tố giúp TA88 xây dựng lòng tin và sự trung thành từ cộng đồng người dùng.
Với những ưu điểm vượt trội, TA88 không ngừng đổi mới và phát triển để mang đến những trải nghiệm tối ưu. Nền tảng này liên tục cập nhật công nghệ, mở rộng tính năng và tối ưu hóa dịch vụ nhằm duy trì vị thế hàng đầu trong lĩnh vực giải trí kỹ thuật số. Nhờ vào sự kết hợp giữa công nghệ hiện đại, tính bảo mật cao và dịch vụ chuyên nghiệp, TA88 đã trở thành một trong những lựa chọn hàng đầu cho những ai tìm kiếm một nền tảng trực tuyến tiện lợi, an toàn và đáng tin cậy.
-

@ 000002de:c05780a7
2025-01-30 21:17:26

> The Debian Publicity Team will no longer post on X/Twitter. We took this decision since we feel X doesn't reflect Debian shared values as stated in our social contract, code of conduct and diversity statement. X evolved into a place where people we care about don't feel safe.
A couple red flags in this post that explain their actions.
1. Shared values - projects that have broad values statements are prone to isolation over time
2. Social contract - that's a meaningless vapid term
I have no issue with code of conduct guidelines or having value statements but when you pick sides on cultural divides and things that are not at all related to the logical objective of a project you are going to end up where Debian has landed.
X has its issues, I'm not a fan but the reasoning behind this seems really off.
One Debian user responded with what I thought was a good summary of why this is a bad move.
> I'm a long-time Debian user and fan, and am also one of the champions for using Debian in space-based applications at NASA.
> IMO this is a short-sighted and foolish decision. The notion of "values" is bring sadly misapplied here.
> I urge you to reconsider. More channels of communication, even with those whom you disagree with, is good for both Debian and your user community.
I'm not into the "anti-woke" or "woke" crap and I dare say most people that use Linux do not care about either side very much at all. A loud minority has been gaining power in these types of projects for a long time. Today we have very loud counters to that group that also can be annoying and out of line.
Will be interesting to watch this all unfold over the next few years. Conservatives seem to be running victory laps and I think that's not only premature but also counter-productive.
I can see leaving X for other reasons.
* Debian users are really using it to communicate with the project
* The Debian publicity team isn't seeing very much of a response for their efforts
* X has become more about politics than tech and communication
* Specific examples of how X is causing issues for the project
They do say this
> X evolved into a place where people we care about don't feel safe.
That's too bad but honestly I don't buy it. Maybe I don't spend enough time on X to have much credibility on this but I'm skeptical of this being the case.
originally posted at https://stacker.news/items/870437
-

@ c4551bf3:f041d130
2025-02-10 08:20:56
333Win là một nền tảng kỹ thuật số tiên tiến, mang đến trải nghiệm trực tuyến mượt mà và ổn định cho người dùng. Với giao diện thân thiện và thiết kế tối ưu, 333Win giúp người dùng dễ dàng truy cập trên cả máy tính và thiết bị di động. Hệ thống được xây dựng trên nền tảng công nghệ hiện đại, đảm bảo tốc độ xử lý nhanh, kết nối ổn định và hiệu suất tối ưu, giúp người dùng có những trải nghiệm liền mạch, tiện lợi mọi lúc, mọi nơi.
Không ngừng đổi mới, <a href="https://333win.site">333WIN</a> liên tục cập nhật và nâng cấp hệ thống nhằm mang đến chất lượng dịch vụ tốt nhất. Nền tảng này tích hợp nhiều công nghệ tiên tiến để tối ưu hóa hiệu suất, giúp nâng cao sự tiện lợi và linh hoạt trong quá trình sử dụng. Nhờ vào sự cải tiến không ngừng, 333Win tạo ra một không gian giải trí phong phú, hấp dẫn và phù hợp với nhu cầu đa dạng, giúp người dùng luôn có những trải nghiệm trọn vẹn và mới mẻ.
Bên cạnh công nghệ tiên tiến, 333Win cũng đặc biệt chú trọng đến bảo mật và quyền riêng tư. Hệ thống bảo mật đa lớp với các giao thức mã hóa tiên tiến giúp bảo vệ dữ liệu cá nhân của người dùng một cách an toàn tuyệt đối. Việc áp dụng các biện pháp bảo vệ nghiêm ngặt giúp 333Win đảm bảo môi trường trực tuyến an toàn, giúp người dùng yên tâm tận hưởng những tiện ích mà nền tảng mang lại.
Không chỉ tập trung vào công nghệ hiện đại, 333Win còn chú trọng đến chất lượng dịch vụ chăm sóc khách hàng. Đội ngũ hỗ trợ chuyên nghiệp luôn sẵn sàng giải đáp thắc mắc và cung cấp sự trợ giúp nhanh chóng, đảm bảo trải nghiệm người dùng luôn thuận tiện và hài lòng. Sự tận tâm và chuyên nghiệp trong dịch vụ là yếu tố giúp 333Win xây dựng lòng tin và sự trung thành từ cộng đồng người dùng.
Với những ưu điểm vượt trội, 333Win không ngừng đổi mới và phát triển để mang đến những trải nghiệm tốt nhất. Nền tảng này liên tục cập nhật công nghệ, mở rộng tính năng và tối ưu hóa dịch vụ nhằm duy trì vị thế hàng đầu trong lĩnh vực giải trí kỹ thuật số. Nhờ vào sự kết hợp giữa công nghệ hiện đại, tính bảo mật cao và dịch vụ chuyên nghiệp, 333Win đã trở thành một trong những lựa chọn hàng đầu cho những ai tìm kiếm một nền tảng trực tuyến tiện lợi, an toàn và đáng tin cậy.
-

@ 1cb14ab3:95d52462
2025-01-30 18:45:41















---
#### Other Photo Series by Hes:
[City Series](https://hes.npub.pro/post/1734817611982/)
[Structural Reflections](https://hes.npub.pro/post/1720570208841/)
---
#### More from Hes:
[Long Form](https://hes.npub.pro/)
[Art Portfolio](https://hesart.npub.pro/)
[Online Store](https://plebeian.market/community/1cb14ab335876fc9efc37d838ba287cf17e5adcccb20bf6d49f9da9695d52462:hesmart-ym3fcufdfz)
[Travel Guides](https://hes.npub.pro/tag/travel/)
[Photography](https://hes.npub.pro/tag/photography/)
[Writings](https://hes.npub.pro/tag/money)
---
*All images are credit of Hes, but you are free to download and use for any purpose. If you find joy from these photos, please feel free to send a zap. Enjoy life on a Bitcoin standard.*
-

@ c4551bf3:f041d130
2025-02-10 08:19:46
6623 là một nền tảng kỹ thuật số tiên tiến, mang đến trải nghiệm trực tuyến mượt mà và ổn định cho người dùng. Với giao diện thân thiện và thiết kế tối ưu, 6623 giúp người dùng dễ dàng truy cập trên cả máy tính và thiết bị di động. Hệ thống được phát triển với công nghệ hiện đại, đảm bảo tốc độ xử lý nhanh, kết nối ổn định và hiệu suất tối ưu, giúp người dùng tận hưởng dịch vụ tiện lợi và liền mạch mọi lúc, mọi nơi.
Một trong những ưu điểm nổi bật của <a href="https://6623-vn.com">6623</a> là sự đổi mới và cập nhật liên tục nhằm nâng cao chất lượng dịch vụ. Nền tảng này luôn tích hợp các công nghệ tiên tiến nhất để tối ưu hóa hiệu suất và mang đến trải nghiệm linh hoạt cho người dùng. Nhờ vào sự cải tiến không ngừng, 6623 tạo ra một không gian giải trí phong phú, hấp dẫn và phù hợp với nhu cầu đa dạng, giúp người dùng luôn có những trải nghiệm trọn vẹn và mới mẻ.
Bên cạnh việc tập trung vào công nghệ, 6623 đặc biệt chú trọng đến bảo mật và quyền riêng tư của người dùng. Hệ thống bảo mật đa lớp với các giao thức mã hóa tiên tiến giúp bảo vệ dữ liệu cá nhân một cách an toàn tuyệt đối. Các biện pháp bảo mật nghiêm ngặt đảm bảo môi trường trực tuyến an toàn, giúp người dùng yên tâm khi trải nghiệm nền tảng mà không lo lắng về các rủi ro bảo mật.
Không chỉ tập trung vào công nghệ hiện đại, 6623 còn cung cấp dịch vụ chăm sóc khách hàng chuyên nghiệp. Đội ngũ hỗ trợ luôn sẵn sàng giải đáp thắc mắc và cung cấp sự trợ giúp nhanh chóng, đảm bảo trải nghiệm người dùng luôn thuận tiện và hài lòng nhất. Sự tận tâm trong dịch vụ là một trong những yếu tố quan trọng giúp 6623 xây dựng lòng tin và sự gắn kết với cộng đồng người dùng.
Với những ưu điểm vượt trội, 6623 không ngừng đổi mới và phát triển để mang đến những trải nghiệm tốt nhất. Nền tảng này liên tục cập nhật công nghệ, mở rộng tính năng và tối ưu hóa dịch vụ nhằm duy trì vị thế hàng đầu trong lĩnh vực giải trí kỹ thuật số. Nhờ vào sự kết hợp giữa công nghệ tiên tiến, bảo mật tối đa và dịch vụ chuyên nghiệp, 6623 đã trở thành một trong những lựa chọn hàng đầu cho những ai tìm kiếm một nền tảng trực tuyến hiện đại, tiện lợi và đáng tin cậy.
-

@ cc8d072e:a6a026cb
2025-01-30 17:20:24
Recently, I had the opportunity to work as an advisor for an AI agent project, which is created by team with a lot of fin-tech software develop experience. As we coded together, their real-time questions and challenges provided unique insights into the hurdles software engineers face when transitioning to AI development. They would pause at moments that most AI engineers take for granted - "How can we be sure the agent understood correctly?", "What if the model makes a mistake?", "How do we handle the uncertainty?" These weren't just isolated questions; they represented the fundamental paradigm shift required when moving from traditional software engineering to AI development. And thats why i think it might be worthy to take sometime write down this article and if you are going to start your first AI agent programming, spending 5 min reading t his will save you a lot of time later.
### 1. Shifting from Deterministic to Probabilistic Thinking
- Traditional software engineering deals with deterministic outcomes
- AI systems operate on probability rather than certainty
- Engineers need to adapt from "100% correct" mindset to accepting probabilistic outcomes
- Blockchain developers may find this particularly challenging due to their background in exact, deterministic systems
### 2. Understanding Core AI Concepts
(There are a lot of concepts to understand, but i will focus on the most frequently asked ones)
#### Memory Management
- **Short-term Memory**: Implemented through conversation context
- **Long-term Memory**: Implemented through vector databases (RAG - Retrieval Augmented Generation)
- Context length management is crucial due to LLM token limitations
#### Language Models and Fine-tuning
- Base models (like GPT) provide general intelligence
- Domain-specific knowledge can be added through:
- Fine-tuning with custom datasets
- Adding RAG layers for specific knowledge domains
### 3. Technical Framework Knowledge
#### Essential Tools and Frameworks
- Vercel AI SDK (if you are a typescript guy)
- LangChain (alternative option)
- Different models(openai, claude, gemini, etc, of course, now, deepseek. the temu in llm )
- Understanding of prompt engineering
#### Multi-Agent Systems
- Agents can communicate through natural language
- Inter-agent communication requires careful system design
- Implementation of thought processes and decision-making loops
- Safety considerations for system commands and operations
### 4. Language and Localization Considerations
- System prompts typically work best in English
- Multi-language support requires careful handling:
- Input translation to English
- Processing in English
- Output translation to target language
- Model performance varies across different languages
### 5. Safety and Error Handling
- Implementing validation layers for critical operations
- Understanding model limitations and potential errors
- Building feedback mechanisms to detect misunderstandings
## Conclusion
Transitioning from software engineering to AI engineering requires a significant mindset shift. While traditional software engineering skills remain valuable, understanding probabilistic systems, language models, and AI-specific architectures is crucial. The key is to balance innovation with practical safety considerations, especially when dealing with critical applications.
Remember that AI systems are not perfect, and building robust applications requires careful consideration of their limitations and appropriate safety measures. Start with existing frameworks and gradually build up complexity as you become more comfortable with AI-specific concepts and challenges.(the conclusion part is written by chatgpt, did you notice? :))
-

@ 42342239:1d80db24
2025-02-10 08:16:32
The risks associated with cryptocurrencies have recently [received attention](https://www.epochtimes.se/finansinspektionen-varnar-for-investeringar-i-krypto) in the media, where e.g. the Swedish Financial Supervisory Authority warns of the high volatility and risk of investments in crypto. Within the EU, as usual, significant efforts are being made to expand the already extensive regulatory framework. Meanwhile, in the US, there has been a marked turnaround. Even the presidential family has launched their own cryptocurrencies, resulting in criticism from [industry experts](https://efn.se/vandning-om-trump-i-kryptobranschen-befangt) .
Important perspectives, however, are conspicuous by their absence in the conversation.
Iain McGilchrist, a British psychiatrist and philosopher, has introduced the hemispheric hypothesis (a theory about how the brain's two hemispheres function). **The left hemisphere is more detail- and control-oriented, while the right hemisphere is more holistic.** A society dominated by the left hemisphere, [such as our own according to McGilchrist](https://www.youtube.com/watch?v=WYB7P-xPRsk) , "would see it as its task to control everything maximally and would have a paranoid feeling that we need to have surveillance cameras everywhere...".
During a [speech](https://x.com/CollinRugg/status/1882474184338514033) at the World Economic Forum, President Trump recently stated that conservatives complain about big banks, such as Bank of America, not allowing them to conduct business within the bank. Critics argue that the American banking system has been used [to persecute](https://x.com/TFTC21/status/1861510237485965565) political opponents, both during Obama's and Biden's terms. **Under Obama, 'Operation Chokepoint' was introduced to limit certain businesses' access to banking services.** A subcommittee in the Senate [now wants to eradicate](https://x.com/SenLummis/status/1882497148975280449) this phenomenon.
**More and more people are discovering that their money is not always under their control.** Non-profit associations and [congregations](https://www.varldenidag.se/nyheter/monster-kristna-aktorer-nekas-bli-bankkunder/833990) are not allowed to open bank accounts. Sometimes they are even thrown out as bank customers. Others may report being subjected to lengthy interrogations by the bank about what they intend to do with their money, even when they just want to transfer funds between their own accounts. **Rejected churches are met with silence**, while a bank account is (still!) necessary to fully operate in society.
When leading economists at the International Monetary Fund (IMF) argue that a cashless society can [threaten fundamental rights](https://archive.ph/fpRk0) , including property rights, when churches are refused bank accounts in what is described as "**a threat to civil society**" and when regulations still fail to combat [organised crime](https://www.epochtimes.se/Ibland-kostar-det-mer-an-det-smakar) , is it not reasonable to wonder if we are on the right path?
With cash, people can pay freely without intermediaries, which constitutes a form of financial freedom. The notes you hold in your hand are your own. **Cryptocurrencies, such as Bitcoin, offer a similar possibility**: an electronic, peer-to-peer cash system (person to person).
A society dominated by the left hemisphere results in a pathological need for control, according to McGilchrist. A more holistic perspective, taking into account the right hemisphere, would acknowledge that too much control can be detrimental, that property rights are a fundamental right, and that [financial freedom](https://www.epochtimes.se/Dags-att-prioritera-transaktionsfrihet) is a human right. Do these perspectives not deserve more attention?
-

@ da0b9bc3:4e30a4a9
2025-02-10 07:48:14
Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/881283
-

@ 2cd78afb:f577f59a
2025-02-10 06:23:10
Looking for a reliable [computer tech support service](https://smallbusinessitsupports.com/computer-tech-support/)? Small Business IT Support offers professional solutions to maintain the functionality of your systems. Hardware troubleshooting, software installation, virus removal, network configuration, and performance optimization are among the services we offer. Whether you require remote or on-site support, our knowledgeable specialists guarantee optimum effectiveness and little downtime. You may get quick, expert, and reasonably priced IT solutions that are suited to your company's requirements with our computer tech support service. For professional assistance and smooth operations, get in touch with us right now!
-

@ 16d11430:61640947
2025-02-10 02:35:17
The gap in mathematics that allows for free agency—the space where choice, unpredictability, and autonomy emerge—exists at the intersection of incompleteness, chaos, probability, and quantum uncertainty. These gaps create fundamental limits on determinism, leaving room for agency to exist.
1. Gödel’s Incompleteness Theorems: The Limits of Formal Systems
Gödel’s theorems prove that within any sufficiently powerful mathematical system:
There exist truths that cannot be proven within that system.
The system cannot prove its own consistency.
This means that even in a world governed by mathematical laws, there are undecidable truths—facts beyond algorithmic computation. If reality is mathematical at its core, this suggests a built-in freedom: not everything is determinable from within the system.
2. Chaos Theory: The Sensitivity to Initial Conditions
Chaotic systems, such as weather patterns and neural activity, exhibit extreme sensitivity to initial conditions.
Even if deterministic, they are practically unpredictable beyond a certain point.
Small choices or quantum fluctuations at the micro-level can have macroscopic consequences.
This injects a level of unpredictability into reality, making strict determinism impossible in complex systems.
3. Probability & Bayesian Decision Theory: Rational Agency Within Uncertainty
In the realm of decision-making and game theory:
Bayesian inference shows how rational agents update beliefs in the face of uncertainty.
Statistical mechanics, despite governing collective behaviors, leaves space for individual unpredictability.
Nash equilibria in game theory illustrate how multiple choices can be rationally justified, allowing for strategic freedom.
Thus, within mathematical decision models, choice emerges not from randomness but from incomplete knowledge and competing optimal strategies.
4. Quantum Mechanics: The Fundamental Indeterminacy of Reality
At the quantum level, Heisenberg’s Uncertainty Principle and the probabilistic nature of wavefunction collapse introduce a non-deterministic reality:
Superposition suggests that multiple possibilities coexist until measured.
Quantum entanglement links particles across vast distances, but their states are not pre-determined before observation.
The Born rule in quantum mechanics assigns probabilities rather than certainties to outcomes.
If the fundamental fabric of reality is non-deterministic, then the idea of strict mechanistic determinism collapses, opening the door to true agency.
5. Computability and the Halting Problem: The Unsolvability of Certain Decisions
Turing’s Halting Problem proves that for some problems, no algorithm can determine in advance whether a computation will finish or run forever.
If reality includes such non-computable elements, then some choices are beyond pre-determined algorithmic resolution.
Human cognition, if partially non-computable, could transcend deterministic rules.
Conclusion: The Gap Between Necessity and Choice
Free agency exists in the mathematical gaps—the undecidability of logic, the unpredictability of chaos, the probabilistic nature of quantum mechanics, and the non-computability of certain decisions. These fundamental limits on strict determinism create an open space where choices emerge, allowing for freedom within a mathematically structured universe.
Thus, in the grand equation of existence, there remains an undefined variable: the will of the agent.
-

@ 16d11430:61640947
2025-02-10 01:46:42
Ayurveda is a 5000-year-old medical system that predates modern science but remains one of the most sophisticated and holistic approaches to health. Unlike Western medicine, which often isolates diseases and treats symptoms, Ayurveda focuses on Prakriti (innate constitution), Agni (digestive fire), Dosha (biological energies), and Ojas (vital essence) to create a personalized, adaptable healthcare model.
Western medicine, despite its advances, still struggles to integrate a diverse global population due to its standardized, reductionist approach. Ayurveda, on the other hand, perfected its practices over millennia through real-world observation, experiential learning, and dynamic adaptation to human diversity.
---
1. Foundations of Ayurveda vs. Western Science
Ayurveda was developed through direct interaction with nature, patients, and generational knowledge transmission, allowing it to refine its approach to a vast range of human conditions.
---
2. Ayurvedic Practices That Outperform Western Medicine’s Integration of Global Health
Western science is still catching up to many Ayurvedic principles, often "discovering" practices that Ayurveda has used for centuries.
A. Personalized Medicine (Prakriti & Doshas) vs. Western One-Size-Fits-All Approach
Ayurveda classifies individuals into three doshas: Vata (air & ether), Pitta (fire & water), and Kapha (earth & water).
These determine a person's metabolism, immunity, and predisposition to disease.
Modern medicine is beginning to explore personalized genomics, but Ayurveda has practiced it for millennia.
B. Chronobiology & Circadian Rhythms (Dincharya)
Ayurveda prescribes Dincharya (daily routines) based on the body's natural rhythms, aligning eating, sleeping, and activity cycles with the sun and moon.
Modern science now acknowledges circadian rhythms but has yet to fully integrate them into healthcare.
Example: Intermittent fasting (Upavasa) has been an Ayurvedic practice for centuries, while the West only recently recognized its benefits for longevity and metabolism.
C. Gut Health & Microbiome (Agni & Ama)
Ayurveda recognized the gut as the root of disease centuries before the discovery of the microbiome.
It prescribes Triphala, Buttermilk (Takra), and Fermented Foods for gut health, balancing Agni (digestive fire).
Western medicine is just starting to understand how gut bacteria affect mental health, immunity, and chronic diseases.
D. Holistic Mental Health (Manas Shastra) vs. Isolated Psychology
Ayurveda integrates meditation, breathwork (Pranayama), mantra therapy, and lifestyle modifications for emotional resilience.
Western psychology often isolates mental health from physical health, relying on medications like antidepressants without addressing lifestyle, diet, and spiritual dimensions.
Example: Ayurvedic herbs like Brahmi and Ashwagandha have proven neuroprotective properties but were ignored in Western medicine until recently.
E. Detoxification (Panchakarma) vs. Toxic Accumulation in Modern Life
Western medicine struggles with heavy metal detox, plastic pollution in the body, and chronic inflammation.
Ayurveda developed Panchakarma, a five-step detox method (Vamana, Virechana, Basti, Nasya, Raktamokshana) that cleanses at a cellular level.
Western detox solutions (chelation therapy, dialysis) are still in their infancy.
F. Cancer Prevention & Natural Angiogenesis Regulation
Dr. William Li’s work on cancer and food-based angiogenesis regulation confirms Ayurvedic principles.
Ayurveda’s approach to cancer (Arbuda) includes herbs like Ashwagandha, Guduchi, and Turmeric, which regulate angiogenesis, reduce inflammation, and detoxify cells.
G. Ayurvedic Water Science vs. Modern Water Pollution
Ayurveda prescribes drinking water stored in copper or silver vessels to prevent microbial growth and enhance mineral content.
It discourages tap water due to chlorine, fluoride, and microplastic contamination—issues that modern science is only now recognizing.
---
3. Ayurveda’s Adaptability vs. Western Struggles with Global Diversity
Ayurveda Accounts for Climate, Region, and Genetic Differences
Western medicine largely applies one-size-fits-all drugs and treatments, often leading to side effects.
Ayurveda has climate-based variations (Desha), prescribing different diets, herbs, and therapies based on region and seasonal changes.
Example:
In cold climates, Ayurveda recommends warming spices (ginger, black pepper, cinnamon) and oil massages (Abhyanga) to prevent stiffness.
In hot climates, it prescribes cooling foods like coconut, aloe vera, and ghee to balance excess heat.
Western medicine lacks such nuanced adjustments.
The Flaw of Western Pharmaceutical Monopolies
Western medicine is dominated by profit-driven pharmaceutical companies that prioritize patents over holistic healing.
Ayurveda uses natural, locally available herbs, making treatments affordable, sustainable, and globally adaptable.
---
4. The Future: Integrating Ayurvedic Wisdom with Modern Science
Western science is now validating what Ayurveda has known for centuries. Some key integrations include:
Neuroscience & Ayurveda: Meditation, breathwork, and adaptogenic herbs now recognized for neuroplasticity.
Oncology & Ayurveda: Cancer research on turmeric, angiogenesis-blocking foods, and detoxification methods.
Microbiome Research: Ayurveda’s gut-health principles proven beneficial in regulating immune function.
Epigenetics & Ayurveda: Recognition of food, environment, and lifestyle in genetic expression aligns with Ayurvedic wisdom.
The Need for a Decentralized Healthcare System
Western medicine’s institutionalized, patent-based system restricts access to holistic healing.
Ayurveda, like Bitcoin in finance, decentralizes healthcare by offering open-source, nature-based, globally adaptable solutions.
---
Final Thoughts: Ayurveda as the Future of Truly Global Medicine
Ayurveda’s success comes from:
A holistic understanding of human diversity (biological, regional, and cultural).
Natural and sustainable healing methods that modern medicine is struggling to replicate.
Integration of physical, mental, and spiritual health—which Western medicine isolates.
A decentralized, globally adaptable approach free from profit-driven pharmaceutical monopolies.
-

@ 86cf3742:678e3ae8
2025-02-10 00:38:09
In this episode of the Ag Tribes Report, host Vance Crow welcomes Steve Strasheim, a vegetable farmer from Northern Iowa, to discuss a variety of pressing issues in agriculture. Steve shares insights into his unique farming practices, including the use of greenhouses and geothermal technology to grow vegetables in the harsh Iowa winters. He also explains his innovative sales model, which includes farmers markets, a CSA, wholesaling, and an on-farm retail store.
The conversation shifts to the potential impact of ICE raids on agriculture, with a focus on the role of illegal aliens in the farming industry. Steve shares his perspective on the H-2A program and the challenges of bureaucracy in hiring legal farm workers.
The episode also covers the controversial appointment of RFK Jr. to lead the Department of Health and Human Services, with a discussion on how his policies might affect agriculture. Steve and Vance debate the potential benefits and drawbacks of increased regulation and the importance of promoting healthier eating habits.
In a segment on Brazilian soybeans, Vance highlights recent logistical issues and quality concerns in Brazil's soybean industry, sparking a discussion on the risks of relying too heavily on a single crop.
The episode concludes with a look at the new right's stance on crated hogs and the potential for significant changes in animal agriculture. Steve shares his thoughts on the ethics of factory farming and the consumer demand for affordable protein.
Listeners are also treated to the Bitcoin land price report, where Steve discusses the current farmland prices in his county and his cautious approach to investing in Bitcoin. The episode wraps up with the Peter Thiel paradox and worthy adversary segments, where Steve shares his unique perspectives and challenges common beliefs in his agricultural community.
[link to the original content](https://serve.podhome.fm/episodepage/the-vance-crowe-podcast_638721156549613591/atr-ice-raids-maha-confirmation-hearings-soybeans-burn-in-brazil-trfyeomanfarmer_638738821327526279)
-

@ c11cf5f8:4928464d
2025-02-10 00:35:57
Let's hear some of your latest #Bitcoin purchases, feel free to include links to the #shops or #merchants you bought from too. Any good #deal we should know about?
If you missed our last thread, [here](https://stacker.news/items/873304/r/AG) are some of the items stackers recently spent and #zap #sats on.
originally posted at https://stacker.news/items/880985
-

@ 16d11430:61640947
2025-02-10 00:03:49
In the silent expanse of the cosmos, where stars whisper their secrets in equations and reality itself unfurls as a tapestry woven from numbers, there exists a path. This is not a path for the faint of heart, nor for those content with the illusions of mere perception. It is the path of the seeker, the one who dares to ask not just how the world is, but why it must be so.
To tread this path is to ascend into the realm where gods write the laws of existence in the language of mathematics.
The First Revelation: Number, the Seed of the Cosmos
Before the universe took form, before light first kissed the void, there was number. It is from number that all else flows, from the spiral of galaxies to the rhythm of a heartbeat.
Prime numbers stand as the indivisible atoms of arithmetic, forming the bedrock of security and cryptography, where secrets are safeguarded by their unfathomable complexity.
Modular arithmetic, the silent clockwork behind our digital world, governs the flow of encrypted knowledge across vast distances.
Diophantine equations, named for an ancient mathematician who saw numbers as riddles to be solved, reveal the hidden symmetries in the universe’s structure.
This is the first truth: that mathematics is not an invention, but a discovery—a key that unlocks the doors of reality.
The Second Revelation: The Art of Pure Thought
Algebra is the music of the spheres, the manipulation of symbols that dance in patterns beyond our senses.
To master it is to shape reality with mere notation.
Abstract algebra unveils hidden structures, from the symmetry of crystals to the secrets of quantum states.
Linear algebra governs the movements of celestial bodies and fuels the neural networks that birth artificial minds.
Galois theory, a young mathematician’s final gift before death, tells us when problems can be solved, and when they are beyond reach.
Here, one learns a second truth: that symbols, when arranged with precision, can summon order from chaos.
The Third Revelation: The Geometry of Reality
If algebra is the melody of numbers, then geometry is its form—the divine art of space itself.
Euclidean geometry was once thought to describe all things, until minds like Gauss and Riemann looked deeper.
Non-Euclidean geometry shattered human intuition, revealing that space bends, twists, and folds upon itself.
Topology, the study of shapes beyond measure, whispers of higher dimensions that mere mortals cannot see but only sense in their equations.
From these truths arises a realization: that the world we see is but a shadow of a far greater, more complex structure.
The Fourth Revelation: Mastery Over the Infinite
What is life, if not the interplay of change?
Calculus, the language of motion and transformation, allows us to speak in the tongue of gods, predicting the orbits of planets and the flows of time.
Complex analysis gives birth to the mystical realm of imaginary numbers, where physics and engineering find their deepest truths.
Fourier analysis, the heartbeat of music and quantum physics, tells us that any pattern, no matter how chaotic, can be understood as the sum of its waves.
The universe breathes through calculus, and to master it is to see not just what is, but what will be.
The Fifth Revelation: The Nature of Uncertainty
No god reigns without knowledge of chaos.
Probability and statistics reveal the order within randomness, turning uncertainty into foresight.
Bayesian inference, a framework of pure rationality, allows us to refine our knowledge with every new piece of evidence.
Information theory, the work of Shannon, teaches that reality itself is a message encoded in entropy.
The wise understand this: that certainty is an illusion, but probability is truth.
The Sixth Revelation: The Code of the Gods
Beyond numbers and space, beyond equations and change, there lies something deeper: logic, the very foundation of thought itself.
Mathematical logic gives us the power to distinguish truth from falsehood with unshakable certainty.
Gödel’s incompleteness theorems whisper a paradox—that no system, not even mathematics itself, can ever be complete.
Computability and complexity theory define the limits of what can be known, what can be solved, and what remains forever beyond reach.
To master logic is to hold the key to all knowledge—but also to know its boundaries.
The Seventh Revelation: The Grand Abstraction
Even gods seek deeper understanding, and category theory is the highest peak of human thought.
Functors and natural transformations map the structures of one world onto another, showing hidden correspondences that weave through all mathematics.
Monads, the cornerstone of functional programming, allow logic to be bent and molded like clay.
Dualities, the deep symmetries of mathematics, hint at connections so profound they border on the mystical.
Here lies the ultimate truth: that everything is, at its core, the same.
The Eighth Revelation: The Quantum Oracle
Beneath reality lies a whispering void, where numbers flicker in superposition and information transcends space and time.
Hilbert spaces define quantum mechanics, where particles are waves and waves are probabilities.
Quantum computing suggests a world where problems once thought impossible collapse into trivial solutions.
Path integrals and Feynman’s sum-over-histories teach us that every possibility, no matter how strange, plays a role in the great equation of the cosmos.
If there is a final truth, it is this: the universe does not simply exist—it computes.
The Final Revelation: Beyond the Human Mind
Even the greatest mathematicians glimpse only shadows of the ultimate structure.
Algebraic topology seeks to map the shape of all existence.
String theory mathematics conjures hidden dimensions and vibrating symmetries.
Infinity category theory, the most abstract of all, suggests that mathematics itself may be alive.
And so, the seeker stands before the infinite. Mathematics is not a collection of rules or calculations. It is the foundation of existence, the divine script of reality.
Those who master it do not merely understand the world.
They become its architects.
-

@ 16d11430:61640947
2025-02-09 23:35:09
The early Bitcoin stackers, smug in their absolute faith, have become the priests of a cargo cult. They chant the gospel of scarcity while stacking their sats like doomsday preppers hoarding canned beans. Meanwhile, the crypto market they once despised has become a grotesque parody of itself—yield farming, staking derivatives, and a casino economy propped up by tokenomics that barely hide the rot beneath. Bitcoin, having won the ideological war, is now losing the economic one—stuck in a circular hodl pattern, detached from the actual thermodynamic reality that gave it birth.
Enter Aeternity, a project with no time for the reverence or passive accumulation that has neutered Bitcoin’s edge. It doesn’t just lean on Proof-of-Work for nostalgia’s sake—it weaponizes it, reintroducing actual economic friction into a space that has gone soft with layer-two convenience. Aeternity’s Cuckoo Cycle PoW, optimized for energy-efficient mining and GPU execution, doesn’t pretend to be Bitcoin’s replacement. It does something far worse for Bitcoin maxis: it forces them to compete again.
Friction: The Return to Thermodynamics
Bitcoin’s thermodynamic argument was always simple: energy in, security out. But over time, it stopped being a battleground for economic force and instead became a retirement savings plan for the digital goldbugs. The Lightning Network and ordinals are desperate attempts to create on-chain congestion and reinvigorate demand, but none of this addresses the fundamental problem: there is no longer any meaningful competition on the base layer.
Aeternity, by scaling horizontally with Hyperchains, injects raw competition into the mix. Miners don’t just settle for static difficulty adjustments—they actively contribute to market-driven security, creating alternative security models that force Bitcoin to prove itself again. If the world is really about energy, then let’s see which chain can best convert energy into economic throughput, rather than just hoarding it as an ideological relic.
Hyperchains: The Threat Bitcoin Forgot to Take Seriously
Aeternity’s approach is fundamentally different from Bitcoin’s ossified stagnation:
1. Merge-Mined Hyperchains – Instead of perpetuating the blocksize wars, Aeternity lets chains bootstrap PoW consensus through merge-mining with parent chains, making security an organic, competitive marketplace rather than a closed system. This creates demand for mining at the edge, something Bitcoin maxis have ignored because they’re still stuck in the “security through centralization” trap.
2. Turing-Complete Smart Contracts – While Bitcoin argues about whether basic programmability is “safe,” Aeternity treats it as an inevitability. Bitcoin’s refusal to evolve beyond Taproot and Covenants makes it a sitting duck against economic attacks from more adaptive chains.
3. State Channels with Actual Scalability – Bitcoiners talk about Lightning as if it’s the final solution, but it’s a bandaid over a hemorrhaging use case problem. Aeternity’s built-in state channels allow contracts to execute off-chain, but without losing decentralization, making it a direct challenge to Bitcoin’s claims of “second-layer supremacy.”
Bitcoin’s Reaction: Either Adapt or Get Rekt
Bitcoin has enjoyed being the monopoly on PoW security for too long. Aeternity’s reintroduction of a competitive PoW model forces Bitcoin miners to wake up: if energy security is the measure of a blockchain’s economic strength, then what happens when an alternative emerges that utilizes energy more efficiently while providing more real-world utility?
Bitcoin maxis will screech that "no altcoin has ever flipped Bitcoin," but that’s not the point. The point is that Bitcoin needs external competition at the proof-of-work level to maintain its thermodynamic legitimacy. Otherwise, it risks becoming what it despises: a static, non-dynamic asset that is just another store of value, with no practical utility until fiat collapses—and good luck waiting for that.
Aeternity’s real-world use cases, from oracles to instant payments to low-cost, scalable contracts, mean that energy invested into securing it is converted into economic value, rather than just securing an ideological artifact. This pressure forces Bitcoin to evolve or become irrelevant—not by replacing it, but by outcompeting it where it matters.
Final Thought: The Thermodynamic Reckoning
Bitcoiners should be grateful for Aeternity’s friction. Without a competitor showing how PoW can be optimized for more than just blind security accumulation, Bitcoin risks becoming a historical relic, kept alive only by belief rather than economic reality. Thermodynamics doesn’t give a damn about ideology—it rewards systems that turn energy into real economic motion.
Aeternity doesn’t have to kill Bitcoin. It just has to remind it what it was built for.
-

@ ec42c765:328c0600
2025-02-05 23:38:12
# カスタム絵文字とは
任意のオリジナル画像を絵文字のように文中に挿入できる機能です。
また、リアクション(Twitterの いいね のような機能)にもカスタム絵文字を使えます。

# カスタム絵文字の対応状況(2025/02/06)

カスタム絵文字を使うためにはカスタム絵文字に対応した[クライアント](https://welcome.nostr-jp.org/tutorial/explore-client.html)を使う必要があります。
※表は一例です。クライアントは他にもたくさんあります。
使っているクライアントが対応していない場合は、クライアントを変更する、対応するまで待つ、開発者に要望を送る(または自分で実装する)などしましょう。
#### 対応クライアント
- [Amethyst](https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst)
- [FreeFrom](https://freefrom.space/)
- [nostter](https://nostter.app/)
- [Rabbit](https://rabbit.syusui.net/)
- [Lumilumi](https://lumilumi.app/)
- [Nos Haiku](https://nos-haiku.vercel.app/)
- [Snort](https://snort.social/)
- [noStrudel](https://nostrudel.ninja/)
ここではnostterを使って説明していきます。
# 準備
カスタム絵文字を使うための準備です。
- Nostrエクステンション(NIP-07)を導入する
- 使いたいカスタム絵文字をリストに登録する
## Nostrエクステンション(NIP-07)を導入する
Nostrエクステンションは使いたいカスタム絵文字を登録する時に必要になります。
また、環境(パソコン、iPhone、androidなど)によって導入方法が違います。
Nostrエクステンションを導入する端末は、実際にNostrを閲覧する端末と違っても構いません(リスト登録はPC、Nostr閲覧はiPhoneなど)。
Nostrエクステンション(NIP-07)の導入方法は以下のページを参照してください。
[ログイン拡張機能 (NIP-07)を使ってみよう | Welcome to Nostr! ~ Nostrをはじめよう! ~ ](https://welcome.nostr-jp.org/tutorial/nip-07.html)
少し面倒ですが、これを導入しておくとNostr上の様々な場面で役立つのでより快適になります。
## 使いたいカスタム絵文字をリストに登録する
以下のサイトで行います。
[emojito](https://emojito.meme/)
右上の**Get started**からNostrエクステンションでログインしてください。
例として以下のカスタム絵文字を導入してみます。
実際より絵文字が少なく表示されることがありますが、古い状態のデータを取得してしまっているためです。その場合はブラウザの更新ボタンを押してください。
[generalJP | カスタム絵文字](https://emojito.meme/a/naddr1qqykwetwv4exzmz22qqsuamnwvaz7tmev9382tndv5hsyg8vgtrk2svt8kuusk4l7w5g7j3mhet4xhhthhz52gsyr7jn9rqxqqpsgqqqw48qud6u3s)

- 右側の**Options**から**Bookmark**を選択

これでカスタム絵文字を使用するためのリストに登録できます。
# カスタム絵文字を使用する
例としてブラウザから使えるクライアント nostter から使用してみます。
[nostter](https://nostter.app/)
nostterにNostrエクステンションでログイン、もしくは秘密鍵を入れてログインしてください。
## 文章中に使用
1. **投稿**ボタンを押して投稿ウィンドウを表示
2. **顔😀**のボタンを押し、絵文字ウィンドウを表示
3. ***タブ**を押し、カスタム絵文字一覧を表示
4. カスタム絵文字を選択
5. : 記号に挟まれたアルファベットのショートコードとして挿入される

この状態で投稿するとカスタム絵文字として表示されます。
カスタム絵文字対応クライアントを使っている他ユーザーにもカスタム絵文字として表示されます。
対応していないクライアントの場合、ショートコードのまま表示されます。

ショートコードを直接入力することでカスタム絵文字の候補が表示されるのでそこから選択することもできます。

## リアクションに使用
1. 任意の投稿の**顔😀**のボタンを押し、絵文字ウィンドウを表示
2. ***タブ**を押し、カスタム絵文字一覧を表示
3. カスタム絵文字を選択

カスタム絵文字リアクションを送ることができます。

# カスタム絵文字を探す
先述した[emojito](https://emojito.meme/)からカスタム絵文字を探せます。
例えば任意のユーザーのページ [emojito ロクヨウ](https://emojito.meme/p/npub1a3pvwe2p3v7mnjz6hle63r628wl9w567aw7u23fzqs062v5vqcqqu3sgh3) から探したり、 [emojito Browse all](https://emojito.meme/browse) からnostr全体で最近作成、更新された絵文字を見たりできます。
また、以下のリンクは日本語圏ユーザーが作ったカスタム絵文字を集めたリストです(2025/02/06)
※漏れがあるかもしれません
[日本ユーザー作 カスタム絵文字](https://nostviewstr.vercel.app/npub17hczqvxtfv3w69wr6lxrttnpdekwdwel55mld60fr24zwjuu6utqtj8mjx/10030)
各絵文字セットにある**Open in emojito**のリンクからemojitoに飛び、使用リストに追加できます。
-----------
以上です。
次:Nostrのカスタム絵文字の**作り方**
Yakihonneリンク [Nostrのカスタム絵文字の作り方](https://yakihonne.com/article/_@lokuyow.github.io/1707912490439)
Nostrリンク nostr:naddr1qqxnzdesxuunzv358ycrgveeqgswcsk8v4qck0deepdtluag3a9rh0jh2d0wh0w9g53qg8a9x2xqvqqrqsqqqa28r5psx3
-----------
# 仕様
[NIP-30 Custom Emoji](https://github.com/nostr-protocol/nips/blob/master/30.md)
[NIP-30 カスタム絵文字(和訳)](https://github.com/nostr-jp/nips-ja/blob/main/30.md)
-

@ e3ba5e1a:5e433365
2025-02-05 17:47:16
I got into a [friendly discussion](https://x.com/snoyberg/status/1887007888117252142) on X regarding health insurance. The specific question was how to deal with health insurance companies (presumably unfairly) denying claims? My answer, as usual: get government out of it!
The US healthcare system is essentially the worst of both worlds:
* Unlike full single payer, individuals incur high costs
* Unlike a true free market, regulation causes increases in costs and decreases competition among insurers
I'm firmly on the side of moving towards the free market. (And I say that as someone living under a single payer system now.) Here's what I would do:
* Get rid of tax incentives that make health insurance tied to your employer, giving individuals back proper freedom of choice.
* Reduce regulations significantly.
* In the short term, some people will still get rejected claims and other obnoxious behavior from insurance companies. We address that in two ways:
1. Due to reduced regulations, new insurance companies will be able to enter the market offering more reliable coverage and better rates, and people will flock to them because they have the freedom to make their own choices.
2. Sue the asses off of companies that reject claims unfairly. And ideally, as one of the few legitimate roles of government in all this, institute new laws that limit the ability of fine print to allow insurers to escape their responsibilities. (I'm hesitant that the latter will happen due to the incestuous relationship between Congress/regulators and insurers, but I can hope.)
Will this magically fix everything overnight like politicians normally promise? No. But it will allow the market to return to a healthy state. And I don't think it will take long (order of magnitude: 5-10 years) for it to come together, but that's just speculation.
And since there's a high correlation between those who believe government can fix problems by taking more control and demanding that only credentialed experts weigh in on a topic (both points I strongly disagree with BTW): I'm a trained actuary and worked in the insurance industry, and have directly seen how government regulation reduces competition, raises prices, and harms consumers.
And my final point: I don't think any prior art would be a good comparison for deregulation in the US, it's such a different market than any other country in the world for so many reasons that lessons wouldn't really translate. Nonetheless, I asked Grok for some empirical data on this, and at best the results of deregulation could be called "mixed," but likely more accurately "uncertain, confused, and subject to whatever interpretation anyone wants to apply."
https://x.com/i/grok/share/Zc8yOdrN8lS275hXJ92uwq98M
-

@ 91bea5cd:1df4451c
2025-02-04 17:24:50
### Definição de ULID:
Timestamp 48 bits, Aleatoriedade 80 bits
Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C.
e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível.
#### Gerar ULID
```sql
CREATE EXTENSION IF NOT EXISTS pgcrypto;
CREATE FUNCTION generate_ulid()
RETURNS TEXT
AS $$
DECLARE
-- Crockford's Base32
encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ';
timestamp BYTEA = E'\\000\\000\\000\\000\\000\\000';
output TEXT = '';
unix_time BIGINT;
ulid BYTEA;
BEGIN
-- 6 timestamp bytes
unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT;
timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER);
timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER);
timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER);
timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER);
timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER);
timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER);
-- 10 entropy bytes
ulid = timestamp || gen_random_bytes(10);
-- Encode the timestamp
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31)));
-- Encode the entropy
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31)));
RETURN output;
END
$$
LANGUAGE plpgsql
VOLATILE;
```
#### ULID TO UUID
```sql
CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$
DECLARE
-- 16byte
bytes bytea = E'\\x00000000 00000000 00000000 00000000';
v char[];
-- Allow for O(1) lookup of index values
dec integer[] = ARRAY[
255, 255, 255, 255, 255, 255, 255, 255, 255, 255,
255, 255, 255, 255, 255, 255, 255, 255, 255, 255,
255, 255, 255, 255, 255, 255, 255, 255, 255, 255,
255, 255, 255, 255, 255, 255, 255, 255, 255, 255,
255, 255, 255, 255, 255, 255, 255, 0, 1, 2,
3, 4, 5, 6, 7, 8, 9, 255, 255, 255,
255, 255, 255, 255, 10, 11, 12, 13, 14, 15,
16, 17, 1, 18, 19, 1, 20, 21, 0, 22,
23, 24, 25, 26, 255, 27, 28, 29, 30, 31,
255, 255, 255, 255, 255, 255, 10, 11, 12, 13,
14, 15, 16, 17, 1, 18, 19, 1, 20, 21,
0, 22, 23, 24, 25, 26, 255, 27, 28, 29,
30, 31
];
BEGIN
IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN
RAISE EXCEPTION 'Invalid ULID: %', ulid;
END IF;
v = regexp_split_to_array(ulid, '');
-- 6 bytes timestamp (48 bits)
bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]);
bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2));
bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4));
bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1));
bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3));
bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]);
-- 10 bytes of entropy (80 bits);
bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2));
bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4));
bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1));
bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3));
bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]);
bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2));
bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4));
bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1));
bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3));
bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]);
RETURN bytes;
END
$$
LANGUAGE plpgsql
IMMUTABLE;
CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$
BEGIN
RETURN encode(parse_ulid(ulid), 'hex')::uuid;
END
$$
LANGUAGE plpgsql
IMMUTABLE;
```
#### UUID to ULID
```sql
CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$
DECLARE
encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ';
output text = '';
uuid_bytes bytea = uuid_send(id);
BEGIN
-- Encode the timestamp
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31)));
-- Encode the entropy
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31)));
RETURN output;
END
$$
LANGUAGE plpgsql
IMMUTABLE;
```
#### Gera 11 Digitos aleatórios: YBKXG0CKTH4
```sql
-- Cria a extensão pgcrypto para gerar uuid
CREATE EXTENSION IF NOT EXISTS pgcrypto;
-- Cria a função para gerar ULID
CREATE OR REPLACE FUNCTION gen_lrandom()
RETURNS TEXT AS $$
DECLARE
ts_millis BIGINT;
ts_chars TEXT;
random_bytes BYTEA;
random_chars TEXT;
base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ';
i INT;
BEGIN
-- Pega o timestamp em milissegundos
ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT;
-- Converte o timestamp para base32
ts_chars := '';
FOR i IN REVERSE 0..11 LOOP
ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1);
END LOOP;
-- Gera 10 bytes aleatórios e converte para base32
random_bytes := gen_random_bytes(10);
random_chars := '';
FOR i IN 0..9 LOOP
random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1);
IF i < 9 THEN
random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1);
ELSE
random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1);
END IF;
END LOOP;
-- Concatena o timestamp e os caracteres aleatórios
RETURN ts_chars || random_chars;
END;
$$ LANGUAGE plpgsql;
```
#### Exemplo de USO
```sql
-- Criação da extensão caso não exista
CREATE EXTENSION
IF
NOT EXISTS pgcrypto;
-- Criação da tabela pessoas
CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL );
-- Busca Pessoa na tabela
SELECT
*
FROM
"pessoas"
WHERE
uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F';
```
### Fontes
- https://github.com/scoville/pgsql-ulid
- https://github.com/geckoboard/pgulid
-

@ 1c197b12:242e1642
2025-02-09 22:56:33
A Cypherpunk's Manifesto
by Eric Hughes
Privacy is necessary for an open society in the electronic age. Privacy is not secrecy. A private matter is something one doesn't want the whole world to know, but a secret matter is something one doesn't want anybody to know. Privacy is the power to selectively reveal oneself to the world.
If two parties have some sort of dealings, then each has a memory of their interaction. Each party can speak about their own memory of this; how could anyone prevent it? One could pass laws against it, but the freedom of speech, even more than privacy, is fundamental to an open society; we seek not to restrict any speech at all. If many parties speak together in the same forum, each can speak to all the others and aggregate together knowledge about individuals and other parties. The power of electronic communications has enabled such group speech, and it will not go away merely because we might want it to.
Since we desire privacy, we must ensure that each party to a transaction have knowledge only of that which is directly necessary for that transaction. Since any information can be spoken of, we must ensure that we reveal as little as possible. In most cases personal identity is not salient. When I purchase a magazine at a store and hand cash to the clerk, there is no need to know who I am. When I ask my electronic mail provider to send and receive messages, my provider need not know to whom I am speaking or what I am saying or what others are saying to me; my provider only need know how to get the message there and how much I owe them in fees. When my identity is revealed by the underlying mechanism of the transaction, I have no privacy. I cannot here selectively reveal myself; I must always reveal myself.
Therefore, privacy in an open society requires anonymous transaction systems. Until now, cash has been the primary such system. An anonymous transaction system is not a secret transaction system. An anonymous system empowers individuals to reveal their identity when desired and only when desired; this is the essence of privacy.
Privacy in an open society also requires cryptography. If I say something, I want it heard only by those for whom I intend it. If the content of my speech is available to the world, I have no privacy. To encrypt is to indicate the desire for privacy, and to encrypt with weak cryptography is to indicate not too much desire for privacy. Furthermore, to reveal one's identity with assurance when the default is anonymity requires the cryptographic signature.
We cannot expect governments, corporations, or other large, faceless organizations to grant us privacy out of their beneficence. It is to their advantage to speak of us, and we should expect that they will speak. To try to prevent their speech is to fight against the realities of information. Information does not just want to be free, it longs to be free. Information expands to fill the available storage space. Information is Rumor's younger, stronger cousin; Information is fleeter of foot, has more eyes, knows more, and understands less than Rumor.
We must defend our own privacy if we expect to have any. We must come together and create systems which allow anonymous transactions to take place. People have been defending their own privacy for centuries with whispers, darkness, envelopes, closed doors, secret handshakes, and couriers. The technologies of the past did not allow for strong privacy, but electronic technologies do.
We the Cypherpunks are dedicated to building anonymous systems. We are defending our privacy with cryptography, with anonymous mail forwarding systems, with digital signatures, and with electronic money.
Cypherpunks write code. We know that someone has to write software to defend privacy, and since we can't get privacy unless we all do, we're going to write it. We publish our code so that our fellow Cypherpunks may practice and play with it. Our code is free for all to use, worldwide. We don't much care if you don't approve of the software we write. We know that software can't be destroyed and that a widely dispersed system can't be shut down.
Cypherpunks deplore regulations on cryptography, for encryption is fundamentally a private act. The act of encryption, in fact, removes information from the public realm. Even laws against cryptography reach only so far as a nation's border and the arm of its violence. Cryptography will ineluctably spread over the whole globe, and with it the anonymous transactions systems that it makes possible.
For privacy to be widespread it must be part of a social contract. People must come and together deploy these systems for the common good. Privacy only extends so far as the cooperation of one's fellows in society. We the Cypherpunks seek your questions and your concerns and hope we may engage you so that we do not deceive ourselves. We will not, however, be moved out of our course because some may disagree with our goals.
The Cypherpunks are actively engaged in making the networks safer for privacy. Let us proceed together apace.
Onward.
Eric Hughes <hughes@soda.berkeley.edu>
9 March 1993
-

@ 40b9c85f:5e61b451
2025-02-09 20:53:03
## Data Vending Machine Context Protocol
### The Convergence of Nostr DVMs and MCP
In the rapidly evolving landscape of artificial intelligence, a new approach to sharing and accessing computational tools is emerging through the combination of two powerful technologies: Nostr's Data Vending Machines (DVMs) and the Model Context Protocol (MCP). This convergence has the potential to reshape how we think about tool distribution and accessibility, creating a truly decentralized marketplace for computational capabilities that serves AI, humans, and any type of machine that speaks the protocol.
## Understanding the Building Blocks
Nostr's Data Vending Machines function much like their physical counterparts, but instead of dispensing snacks, they provide computational services with built-in Lightning Network payment capabilities. These DVMs operate on the decentralized Nostr network, allowing users to reach service providers without relying on centralized platforms or gatekeepers.
The Model Context Protocol complements this infrastructure by providing a standardized way for applications to share context and expose their capabilities. Think of MCP as a universal language that allows tools to communicate effectively with any application that understands the protocol. This standardization is crucial for creating a seamless experience across different tools and services.
## What is DVMCP?
DVMCP proposes a path for making DVMs and MCPs interoperable, introducing a protocol that makes local utilities available to everyone on the network. Our [draft specification](https://github.com/gzuuus/dvmcp/blob/master/docs/dvmcp-spec.md) serves as a foundation for easily transforming any MCP server into a DVM. To bridge these technologies, we've developed a simple software component that sits between your MCP server and the DVM ecosystem. You can find it in our [repository](repo.link). This bridge connects to your MCP server as a client and exposes its utilities through Nostr as a DVM, handling all the necessary Nostr logic. This means any existing MCP server can become accessible through Nostr without modifications - simply run the bridge alongside your server.
This is particularly exciting because the vibrant and growing MCP community. Any team or individual already working with MCP can instantly plug into the Nostr DVM ecosystem, gaining access to decentralized discovery, built-in monetization, and an already existing user base. The bridge component makes this transition effortless, requiring no changes to any existing MCP implementations.
## A New Paradigm
A decentralized marketplace where anyone can run tools locally and make them available globally. This addresses an unsolved problem larger than the Nostr ecosystem: how to make resources and tools discoverable and accessible in a decentralized, permissionless way.
The power of this combination lies in its flexibility. Users can access tools through regular Nostr clients, AI agents can discover specific capabilities, and DVMs can create sophisticated tool chains. With Lightning Network integration, true machine-to-machine transactions become possible, where machines can autonomously discover, negotiate, and pay for computational services. Most importantly, you can run services on your own hardware while making these capabilities accessible to anyone anywhere.
The result is a system that preserves privacy, promotes innovation, and creates new opportunities without central authorities controlling what tools can be offered or who can use them. The entire project, is available under the MIT license, and any feedback and collaboration is welcome.
## Looking Forward
As these technologies mature, we're likely to see a fundamental shift in how computational capabilities are distributed and accessed. Instead of relying on massive cloud data centers controlled by a few companies, we're moving toward a global network of local machines, each contributing unique capabilities and computation to a larger, more resilient ecosystem.
The convergence of Nostr DVMs and MCP represents more than just a technical innovation—it's a step toward a more equitable and accessible future. By enabling anyone to run and share tools, we're building an ecosystem where computational resources are not concentrated in the hands of a few but are available to and controllable by everyone.
[Repository](https://github.com/gzuuus/dvmcp/)
-

@ 65912a7a:5dc638bf
2025-02-09 20:34:15
I didn’t set out to become an enemy of the world’s richest man, but I seem to have managed it all the same. Until this moment, I’ve resisted describing my falling out with Elon Musk in much detail, but as the man’s cultural influence has metastasized—and he continues to spread lies about me on the social media platform that he owns (Twitter/X)—it seems only appropriate to set the record straight. I know that it annoys many in my audience to see me defend myself against attacks that they recognize to be spurious, but they might, nevertheless, find the details of what happened with Elon interesting.
Of all the remarkable people I’ve met, Elon is probably the most likely to remain a world-historical figure—despite his best efforts to become a clown. He is also the most likely to squander his ample opportunities to live a happy life, ruin his reputation and most important relationships, and produce lasting harm across the globe. None of this was obvious to me when we first met, and I have been quite amazed at Elon’s evolution, both as a man and as an avatar of chaos. The friend I remember did not seem to hunger for public attention. But his engagement with Twitter/X transformed him—to a degree seldom seen outside of Marvel movies or Greek mythology. If Elon is still the man I knew, I can only conclude that I never really knew him.
When we first met, Elon wasn’t especially rich or famous. In fact, I recall him teetering on the brink of bankruptcy around 2008, while risking the last of his previous fortune to make payroll at Tesla. At the time, he was living off loans from his friends Larry and Sergey. Once Elon became truly famous, and his personal wealth achieved escape velocity, I was among the first friends he called to discuss his growing security concerns. I put him in touch with Gavin de Becker, who provided his first bodyguards, and recommended other changes to his life. We also went shooting on at least two occasions with Scott Reitz, the finest firearms instructor I’ve ever met. It is an ugly irony that Elon’s repeated targeting of me on Twitter/X has increased my own security concerns. He understands this, of course, but does not seem to care.
So how did we fall out? Let this be a cautionary tale for any of Elon’s friends who might be tempted to tell the great man something he doesn’t want to hear:
(1.) When the SARS-CoV-2 virus first invaded our lives in March of 2020, Elon began tweeting in ways that I feared would harm his reputation. I also worried that his tweets might exacerbate the coming public-health emergency. Italy had already fallen off a cliff, and Elon shared the following opinion with his tens of millions of fans :
*the coronavirus panic is dumb*
As a concerned friend, I sent him a private text:
*Hey, brother— I really think you need to walk back your coronavirus tweet. I know there’s a way to parse it that makes sense (“panic” is always dumb), but I fear that’s not the way most people are reading it. You have an enormous platform, and much of the world looks to you as an authority on all things technical. Coronavirus is a very big deal, and if we don’t get our act together, we’re going to look just like Italy very soon. If you want to turn some engineers loose on the problem, now would be a good time for a breakthrough in the production of ventilators...*
(2.) Elon’s response was, I believe, the first discordant note ever struck in our friendship:
*Sam, you of all people should not be concerned about this.*
He included a link to a page on the CDC website, indicating that Covid was not even among the top 100 causes of death in the United States. This was a patently silly point to make in the first days of a pandemic.
We continued exchanging texts for at least two hours. If I hadn’t known that I was communicating with Elon Musk, I would have thought I was debating someone who lacked any understanding of basic scientific and mathematical concepts, like exponential curves.
(3.) Elon and I didn’t converge on a common view of epidemiology over the course of those two hours, but we hit upon a fun compromise: A wager. Elon bet me $1 million dollars (to be given to charity) against a bottle of fancy tequila ($1000) that we wouldn’t see as many as 35,000 cases of Covid in the United States (cases, not deaths). The terms of the bet reflected what was, in his estimation, the near certainty (1000 to 1) that he was right. Having already heard credible estimates that there could be 1 million deaths from Covid in the U.S. over the next 12-18 months (these estimates proved fairly accurate), I thought the terms of the bet ridiculous—and quite unfair to Elon. I offered to spot him two orders of magnitude: I was confident that we’d soon have 3.5 million cases of Covid in the U.S. Elon accused me of having lost my mind and insisted that we stick with a ceiling of 35,000.
(4.) We communicated sporadically by text over the next couple of weeks, while the number of reported cases grew. Ominously, Elon dismissed the next batch of data reported by the CDC as merely presumptive—while confirmed cases of Covid, on his account, remained elusive.
(5.) A few weeks later, when the CDC website finally reported 35,000 deaths from Covid in the U.S. and 600,000 cases, I sent Elon the following text:
*Is (35,000 deaths + 600,000 cases) > 35,000 cases?*
(6.) This text appears to have ended our friendship. Elon never responded, and it was not long before he began maligning me on Twitter for a variety of imaginary offenses. For my part, I eventually started complaining about the startling erosion of his integrity on my podcast, without providing any detail about what had transpired between us.
(7.) At the end of 2022, I abandoned Twitter/X altogether, having recognized the poisonous effect that it had on my life—but also, in large part, because of what I saw it doing to Elon. I’ve been away from the platform for over two years, and yet Elon still attacks me. Occasionally a friend will tell me that I’m trending there, and the reasons for this are never good. As recently as this week, Elon repeated a defamatory charge about my being a “hypocrite” for writing a book in defense of honesty and then encouraging people to lie to keep Donald Trump out of the White House. Not only have I never advocated lying to defeat Trump (despite what that misleading clip from the Triggernometry podcast might suggest to naive viewers), I’ve taken great pains to defend Trump from the most damaging lie ever told about him. Elon knows this, because we communicated about the offending clip when it first appeared on Twitter/X. However, he simply does not care that he is defaming a former friend to hundreds of millions of people—many of whom are mentally unstable. On this occasion, he even tagged the incoming president of the United States.
All of this remains socially and professionally awkward, because Elon and I still have many friends in common. Which suggests the terms of another wager that I would happily make, if such a thing were possible—and I would accept 1000 to 1 odds in Elon’s favor:
I bet that anyone who knows us both knows that I am telling the truth.
Everyone close to Elon must recognize how unethical he has become, and yet they remain silent. Their complicity is understandable, but it is depressing all the same. These otherwise serious and compassionate people know that when Elon attacks private citizens on Twitter/X—falsely accusing them of crimes or corruption, celebrating their misfortunes—he is often causing tangible harm in their lives. It’s probably still true to say that social media “isn’t real life,” until thousands of lunatics learn your home address.
A final absurdity in my case, is that several of the controversial issues that Elon has hurled himself at of late—and even attacked me over—are ones we agree about. We seem to be in near total alignment on immigration and the problems at the southern border of the U.S. We also share the same concerns about what he calls “the woke mind virus.” And we fully agree about the manifest evil of the so-called “grooming-gangs scandal” in the U.K. The problem with Elon, is that he makes no effort to get his facts straight when discussing any of these topics, and he regularly promotes lies and conspiracy theories manufactured by known bad actors, at scale. (And if grooming were really one of his concerns, it’s strange that he couldn’t find anything wrong with Matt Gaetz.)
Elon and I even agree about the foundational importance of free speech. It’s just that his approach to safeguarding it—amplifying the influence of psychopaths and psychotics, while deplatforming real journalists and his own critics; or savaging the reputations of democratic leaders, while never saying a harsh word about the Chinese Communist Party—is not something I can support. The man claims to have principles, but he appears to have only moods and impulses.
Any dispassionate observer of Elon’s behavior on Twitter/X can see that there is something seriously wrong with his moral compass, if not his perception of reality. There is simply no excuse for a person with his talents, resources, and opportunities to create so much pointless noise. The callousness and narcissism conveyed by his antics should be impossible for his real friends to ignore—but they appear to keep silent, perhaps for fear of losing access to his orbit of influence.
Of course, none of this is to deny that the tens of thousands of brilliant engineers Elon employs are accomplishing extraordinary things. He really is the greatest entrepreneur of our generation. And because of the businesses he’s built, he will likely become the world’s first trillionaire—perhaps very soon. Since the election of Donald Trump in November, Elon’s wealth has grown by around $200 billion. That’s nearly $3 billion a day (and over $100 million an hour). Such astonishing access to resources gives Elon the chance—and many would argue the responsibility—to solve enormous problems in our world.
So why spend time spreading lies on X?
-

@ 2e8970de:63345c7a
2025-02-09 20:22:19

https://www.infinitescroll.us/p/13-things-i-learned-reading-a-225
originally posted at https://stacker.news/items/880820
-

@ b8af284d:f82c91dd
2025-02-09 18:48:21
*Liebe Abonnenten,*
*viele von uns erleben im privaten wie im öffentlichen Leben gerade eine Zeit der Verwirrung und Irritation. Etwas scheint im Umbruch, alte Gewissheiten, Strukturen und Allianzen scheinen sich vor unseren Augen aufzulösen. Trump, Musk und Thiel wirken wie die Abrissbirnen einer alten Ordnung, Agenten des Chaos mit dem einzigen Ziel, sich selbst zu bereichern. Ist es so?*
*Könnte es anders sein?*
*Folgender Text kann und will diese Fragen nicht ultimativ beantworten. Es gibt aber eine Brille, durch die, setzt man sie auf, viele Entwicklungen in einem anderen, viel helleren Licht erscheinen. Diese Brille heißt e/acc.*

**Was ist e/acc?**
Das Kürzel geht auf den Programmierer Guillaume Verdon zurück, der unter dem Pseudonym „Beff Jezos“ die Bewegung. Es steht für „effective accelerationism“. Accelerationism, auf Deutsch Akzelerationismus, abgeleitet vom Verb „beschleunigen“, hat Wurzeln, die weiter zurückreichen - dazu später mehr. Der Zusatz „effective“ ist eine ironische Replik auf den „effective Altruism“, den unter anderen Sam Bankman-Fried vertrat und grandios scheiterte.
e/acc setzt also auf Beschleunigung. Kapitalismus, Innovation, vor allem künstliche Intelligenz sollen nicht aufgehalten oder reguliert werden, sondern im Gegenteil beschleunigt werden.
**Warum?**
Eine einfache Antwort lautet: Weil sie eh stattfinden. Besonders deutlich wird das im Fall künstlicher Intelligenz. Large Language Models (LLMs) wie ChatGPT und Deepseek sind nur die für die Öffentlichkeit sichtbaren Entwicklungen. Im Hintergrund ersetzt Künstliche Intelligenz zunehmend auch Produktionsprozesse und nicht zuletzt die Kriegsführung. Man spricht deswegen vom „Point of Singularity“. In den kommenden Jahren wird künstliche Intelligenz menschliche übertrumpfen. Unsere Arbeitswelt, unser Finanzsystem und gesellschaftliche Strukturen werden sich grundlegend ändern. Wenn es dazu kommt, warum die Entwicklung noch aufhalten? **Beschleunigen ist besser.**
Die zweite Antwort ist tiefgründiger und rührt an das Verständnis von Leben insgesamt. Langfristig strebt das Universum nach Entropie. Es dehnt sich aus, bis alle Teile in maximaler „Unordnung“ angeordnet sind. Systeme mit hoher Energiezufuhr können Strukturen aufbauen, solange sie Wärme oder Entropie in ihre Umgebung abgeben. In einem Organismus sind alle Teile zu einer höheren Ordnung organisiert. Leben strebt nach Ordnung, Selbsterhalt und Wachstum, weshalb der Energieverbrauch zunimmt. e/acc-Fan und Silicon-Valley-Investor Marc Andreessen schreibt in “The Techno-Optimist Manifesto”:
> *Techno-Optimists believe that societies, like sharks, grow or die.*
>
> *We believe growth is progress – leading to vitality, expansion of life, increasing knowledge, higher well being.*
Ein Gleichgewicht gibt es nicht. Entweder strebt eine Struktur nach Ordnung (Leben) oder nach Unordnung (Tod). Da eine Balance nicht existiert, gibt es nur zwei Möglichkeiten: Verlangsamen oder Beschleunigen. Höhere Ordnungen aufbauen oder verfallen. Wachsen oder Sterben. **Beschleunigen ist besser.**
## **Konsequenzen**
e/acc ist kein philosophisches System im strengen Sinn. Es leitet Konsequenzen aus physikalischen Grundsätzen ab.
Kapitalistische Systeme und freie Märkte sind die effizientesten Strukturen, um Informationen zu verarbeiten. In einem offenen, freien Markt gibt der Preis das zuverlässigste Signal über Knappheit eines Gutes. Wird dieser Prozess durch externe Einflussnahme wie Subventionen gestört, läuft die Maschine nicht effizient. Das Gesamtsystem wird verzerrt. Nochmals Andreessen dazu:
> *We believe the market economy is a discovery machine, a form of intelligence – an exploratory, evolutionary, adaptive system.*
Varianten und Abweichungen sind wichtig, da ein System dadurch am schnellsten auf sich ständig verändernde Umweltbedingungen reagieren kann. Wer nicht frei sprechen kann, kann nicht frei denken. Dezentrale Strukturen mit vielen kleinen einzelnen „Nodes“ sind resilienter als hierarchisch-zentralistische Systeme. Das führt zu einem Meinungsfreiheits-Maximalismus.
Greifen staatliche Akteure in die Forschung ein, und vergeben zum Beispiel Lizenzen für KI-Projekte, kann das System nicht mehr auf die besten Ressourcen zurückgreifen. Es entwickelt sich nicht in seiner natürlichen Geschwindigkeit, sondern wird künstlich verlangsamt. **Beschleunigen ist besser.**
Im Falle von KI hat dies geopolitische Konsequenzen: Sollten autoritäre Akteure wie zum Beispiel China schneller zum Punkt der Singularity vorstoßen, entsteht eine Dystopie, ein Orwellscher Überwachungsstaat. Bevorzugen ist deswegen eine beschleunigte, dezentrale Forschung, damit freie Systeme die Oberhand behalten.
Dasselbe gilt für das Geldsystem: e/acc trifft hier auf Hayek und Mises. Viele Zahlungssysteme stehen in permanenter Konkurrenz zueinander. Am Ende setzt sich das nützlichste und vermutlich auch härteste Geld durch.
## Konkrete Folgen
Auf die konkrete Politik übertragen führt das zu Konsequenzen, die man aktuell beobachten kann.
\*\*Radikale Deregulierung: \*\*Die Biden-Administration versuchte, [AI-Forschung eng an die Regierung zu binden](https://x.com/pmddomingos/status/1888059248535552312). Open-AI-Gründer Sam Altman forderte [2023 eine Lizenz-Vergabe an Unternehmen](https://www.businessinsider.com/sam-altman-openai-chatgpt-government-agency-should-license-ai-work-2023-5), um überhaupt in diesem Bereich aktiv zu werden. (Musk trat zunächst sogar für ein Forschungs-Moratorium ein, änderte dann aber seine Meinung.) Das führte zum Widerstand der e/acc-Fraktion im Silicon Valley, und gab den Ausschlag, sich auf die Trump-Seite zu stellen. Deregulierung zieht sich nun durch alle Bereiche der Wirtschaft: auch auf die „Entwicklungshilfe“ von USAID. Der Regierungsapparat wird insgesamt massiv verkleinert, da Bürokratie das Wachstum hemmt. A fuera.
\*\*Priorisierung von günstiger Energie: \*\*Da der Energie-Verbrauch mit zunehmender Ordnung ansteigt, und LLMs einen sehr viel Strom brauchen, priorisiert die neue Regierung die Erschließung zusätzlicher Energiequellen: Gas, Öl, Nuklear und regenerative Energiequellen gleichermaßen.
![1.00]()
Wiederherstellung von Meinungsfreiheit.Content-Moderationen auf Social-Media-Plattformen fallen weg. Geheimdienst-Dokumente werden freigegeben. So schrieb Peter Thiel vor einigen Wochen in einem Essay in der Financial Times über die große Enthüllung:
> \
> *But understood in the original sense of the Greek word **apokálypsis, meaning “unveiling”**, Obama could not give the same reassurance in 2025. Trump’s return to the White House augurs the apokálypsis of the ancien regime’s secrets. (…)\
> The apokálypsis is the most peaceful means of resolving the old guard’s war on the internet, a war the internet won. My friend and colleague Eric Weinstein calls the pre-internet custodians of secrets the Distributed Idea Suppression Complex (DISC) — the media organisations, bureaucracies, universities and government-funded NGOs that traditionally delimited public conversation.*
**Krypto-Deregulierung:** Da Kryptowährungen und Smart-Contract-Strukturen bestens mit LLMs harmonieren, werden Innovationsbremsen in Form von Regulierungen abgebaut.
\*\*Umbruch der Weltordnung: \*\*Auf der geopolitischen Ebene werden Bündnisse, Allianzen und Blockstrukturen aufgebrochen und nach effizienten Win-Win-Verhältnissen neu organisiert.
**Erschließung neuer Lebenswelten:** Degrowth, weniger Energie-Verbrauch und weniger Kinder sind keine Option, da sie zum Tod führen. Das System Menschheit muss wachsen und wird neue Lösungen erfinden. Wenn die Ressourcen des Planeten Erde nicht mehr ausreichen, müssen neue erschlossen werden - vielleicht auf dem Mars.
## **Die Ideengeschichte**
Während e/acc ein relativ neues System ist, hat der Akzelerationismus tiefere Wurzeln. Lenin kann man als einen frühen Akzelerationisten bezeichnen. Der Marxismus wurde Anfang des 20. Jahrhunderts weniger als Ideologie, sondern mehr als exakte Wissenschaft begriffen. Demnach würde der Kapitalismus früher oder später an seinen eigenen Widerständen kollabieren. Warum den Prozess also nicht beschleunigen und die Revolution herbeiführen?
Ende des 20. Jahrhunderts griff der Philosoph Nick Land diese Gedanken wieder auf. Land forderte Beschleunigung, sah am Ende des Prozesses aber einen Kollaps des Systems und eine dunkle Zukunft. Ironie der Geschichte: Land zog in den 2000er Jahren nach China, wo er einen autoritären Akzelerationismus verwirklicht sah. Auch Steve Bannon, Leiter des ersten Trump-Wahlkampfes 2016, war von Lands Gedanken geprägt.

e/acc aber ist eine neuer, optimistischer „Fork“ des alten, dunklen Akzelerationismus. Es sieht eine positive Zukunft für die gesamte Menschheit aufgrund eines gigantischen Produktivitätsschubs. Eine neue, höhere Ordnung ist am Entstehen. Kurz gesagt:
> ***Effective accelerationism (e/acc) in a nutshell:***
>
> ***Stop fighting the thermodynamic will of the universe***
>
> ***You cannot stop the acceleration***
>
> ***You might as well embrace it***
>
> ***A C C E L E R A T E***
*[Notes on e/acc principles and tenets](https://effectiveaccelerationism.substack.com/p/repost-notes-on-eacc-principles-and?utm_source=substack\&utm_campaign=post_embed\&utm_medium=web)*
Happy Future also? Durch die e/acc-Brille gesehen wirkt die Welt wesentlich heller und optimistischer als sie die meisten “Legacy Media” gerade darstellen. Demnach bewegen wir uns auf eine neue Zeit gesteigerter Produktivität und damit Lebensqualität zu. Wenn alle Arbeit von Maschinen verrichtet wird, können Menschen währenddessen auf Bali surfen, meditieren und Yoga machen. Oder?
## **Kritik**
Leben entsteht an der Grenze von Chaos und Ordnung. Vielleicht versetzt e/acc das Pendel zu stark in den Ausschlag in eine Richtung. Unkontrolliertes Wachstum bedeutet im lebenden Organismen Krebs. e/acc sieht sich wie Marxisten der ersten Stunde (Lenin) im Besitz der Wahrheit in Form physikalischer Grundsätze. Erst durch diese Hybris führten zu den Grausamkeiten sozialistischer Systeme im 20. Jahrhundert. Schließlich beantwortet e/acc nicht die Frage nach der Verteilungsgerechtigkeit, die durch den gewaltigen Produktivitätsschub durch AI entstehen wird.
Ob e/acc als politisches und gesellschaftliches System taugt, ist deswegen fraglich. Aber viele aktuelle Entwicklungen scheinen durch die Akzelerationismus-Brille klarer.
**Quellen:**
*Peter Thiel: [A Time for Truth and Reconciliation](https://www.ft.com/content/a46cb128-1f74-4621-ab0b-242a76583105)*
*Marc Andreessen: [The Techno-Optimist Manifesto](http://xn--we%20believe%20the%20market%20economy%20is%20a%20discovery%20machine,%20a%20form%20of%20intelligence%20%20an%20exploratory,%20evolutionary,%20adaptive%20system-2296h./)*
*e/acc: [Notes on e/acc principles and tenets](https://effectiveaccelerationism.substack.com/p/repost-notes-on-eacc-principles-and?utm_source=substack\&utm_campaign=post_embed\&utm_medium=web)*
*Andy Beckett: [Accelerationism: how a fringe philosophy predicted the future we live in](https://www.theguardian.com/world/2017/may/11/accelerationism-how-a-fringe-philosophy-predicted-the-future-we-live-in)*
*Lex Friedman: [Guillaume Verdon. e/acc-Movement. Physics. Computation & AGI.](https://open.spotify.com/episode/2TvKfwY5Z7Lz8iiaGLRMgO)*
-

@ f7d424b5:618c51e8
2025-02-09 18:33:48
(Copied from my show notes \[website\](https://melonmancy.net/mp-100-nuance-enjoyer) for Melonmancy)
Promise this isn't normal. It would be disingenuous to not bring it up.
We mentioned a few things in the show you might want to pull up while listening, they are the following:
- [Nightmare Kart dev crashes out](https://x.com/StutteringCraig/status/1883958297423929810)
- [Dr Disrespect gives post-mortem on Midnight Society](https://x.com/ProfPressure/status/1885045826424365437)
- [Lords of the Fallen announcement post](https://x.com/TheOneDeafMute/status/1887765603169222840)
Obligatory:
- [Listen to the new episode here!](https://melonmancy.net/listen)
- [Discuss this episode on OUR NEW FORUM](https://melonmancy.cafe/d/102-mp100-nuance-enjoyer)
- [Get the RSS and Subscribe](https://feeds.rssblue.com/melonmancy-podcast) (this is a new feed URL, but the old one redirects here too!)
- Get a modern podcast app to use that RSS feed on at [newpodcastapps.com](http://newpodcastapps.com/)
- Or listen to the show on [the forum](https://melonmancy.cafe) using the embedded [Podverse](https://podverse.fm) player!
- [Send your complaints here](https://melonmancy.net/contact-us)
Reminder that this is a [Value4Value](https://value4value.info/) podcast so any support you can give us via a modern podcasting app is greatly appreciated and we will never bow to corporate sponsors!
Our podcast is created entirely with free software and is proudly hosted on [RSSBlue!](https://rssblue.com)
-

@ 4c191b5d:c42abba6
2025-02-09 17:07:59
Weil ich schon länger über das Thema Direkte Demokratie nachdenke ein paar Gedanken dazu. Ich freue mich auf Ergänzungen und anderen Meinungen.
### **Grundannahme**
Die Macht soll vom Souverän ausgehen, also dem Volk. Entsprechend soll das Volk auch an politischen Entscheidungsprozessen teilhaben können - was sehr viel Sinn macht.
Allerdings sind im aktuellen demokratischen Verständnis diverse Fehler, die zwangsläufig zu einer gesellschaftlichen Spaltung führen.
### **Gewinner und Verlierer**
Die Demokratie spaltet die Bürger, indem sie Gewinner und Verlierer bei Wahlen und politischen Entscheidungen hervorbringt. Es geht nicht darum, eine Entscheidung zu erzielen, die bestmöglich durch alle getragen werden kann. Dies erfordert eine Reduktion der Widerstände gegen einen Entscheidungsvorschlag und der Integration dieser Widerstände in einen weiterentwickelten Entscheidungsvorschlag.
### **Mangel an neuen Lösungen und Machtkämpfe**
Es fehlt an echtem Interesse und lösungsorientiertem Handeln was zu einem erstarren des Systems führt. Stattdessen entstehen Machtkämpfe, bei denen der Fokus auf der Durchsetzung eigener Agenden liegt und andere Standpunkte bekämpft werden. Dies ist vor allem dem Umstand geschuldet, dass die Individualinteressen sowie die politischen Gruppierungen (insbesondere Parteien) an ihren eigenen Lösungsansätzen festhalten.
### **Medien**
Die Medien spielen eine sehr wichtige Rolle in der Demokratie, indem sie Informationen bereitstellen und Meinungen verbreiten. Allerdings können sie auch zu einer Spaltung der Bürger beitragen, indem sie unterschiedliche politische Ansichten verstärken oder polarisierende Inhalte verbreiten.
Manipulationstechniken werden eingesetzt, um die öffentliche Meinung zu beeinflussen und bestimmte Narrative zu fördern. Dies führt zu weiterer Polarisierung, die das Vertrauen der Bürger in die Medien und demokratische Prozesse untergraben. Eine kritische Medienkompetenz und eine vielfältige Berichterstattung sind daher entscheidend, um eine gesunde demokratische Debatte zu fördern und Spaltungen zu vermeiden.
### **Informationen**
Bürger können ihre Verantwortung nur wahrnehmen, wenn sie Zugang zu einer Vielzahl von Informationen haben, um eine fundierte Meinung zu bilden. Jedoch ist ein aufkommendes Phänomen in letzter Zeit die Zensur und Unterdrückung von Informationen, was zu einer weiteren Spaltung führt. Wenn bestimmte Inhalte oder Standpunkte systematisch unterdrückt werden oder wenn Medienplattformen selektiv Informationen präsentieren, können Bürger in Filterblasen gefangen bleiben und nur einseitige Perspektiven erhalten. Um eine gesunde demokratische Debatte und eine effektive Meinungsbildung zu ermöglichen, ist es wichtig, dass Informationen frei zugänglich sind und dass Zensurmechanismen transparent und verantwortungsbewusst gehandhabt werden.
### **Starke Beeinflussung durch Geldgeber**
Geld spielt eine bedeutende Rolle im politischen Prozess einer Demokratie. Diejenigen mit mehr finanziellen Mitteln haben grösseren Einfluss und können ihre Agenda stärker vorantreiben. Dies führt zu einem Ungleichgewicht der politischen Macht und spaltet die Bürger in unterschiedliche Lager.
## **Der grössere Kontext**
Während die Demokratien sich immer weiter von der Eigenverantwortung weg zu entwickeln ,scheinen und stattdessen auf parentale Kontrolle setzten (der starke Staat), ist Bitcoin eine klare Bewegung hierzu. Denn Bitcoin setzt auf echte Eigenverantwortung.
Daher sind wir auch davon überzeugt, dass das Thema Eigenverantwortung nicht nur die politischen sondern auch wirtschaftlichen Strukturen verändern wird. Denn wenn sich die Gesellschaft verändert, hat dies auch einen Einfluss auf die Wirtschaft. Und mit Wirtschaft meinen wir vor allem auch die Frage, wie Unternehmen sich organisieren und strukturieren. Es macht ja wenig Sinn, auf der einen Seite von ultimativer Eigenverantwortung zu sprechen, die dann aber auf der anderen Seite klassisch Command&Control erleben (oben entscheidet jemand, unten wird ausgeführt).
-

@ 8d34bd24:414be32b
2025-02-09 15:58:19
Whenever I have said or written anything about God allowing/causing hardship for believers, I have always had someone try to correct me saying something like, “God would never cause hard/bad things to happen to believers,” but that is definitely not true.
Since I’ve become a believer, I’ve had 2 miscarriages. I’ve had a son with Down Syndrome and lots of health issues requiring around 20 hospital stays, a surgery, and regular out-of-state trips for care. I’ve gone through health problems for 10 years where I could barely function on a good day and on a bad day could barely sit up. I’ve had my house burn down and lost all of my possessions. Yes, God allowed all of that to happen to me. I’d argue that He caused all of that to happen to me for a very good purpose. Every one of those things have been a benefit to me. They have grown my faith, straightened out my priorities, and/or enabled me to minister to others. They have taught me to lean on God in hard times. They have taught me that God is all I need. I would not be the person I am today without these challenges. Every one of them was for my good and if I could go back and make them not happen, I would not change them. Although I didn’t want any of them to happen and would never have chosen them for myself, I wouldn’t change them now that I have seen the wonderful good God has done through these hard times. (I don’t say bad times because they were all for my good and the good of others.)
God never said following Him would be easy.
> Then a scribe came and said to Him, “Teacher, I will follow You wherever You go.” Jesus said to him, “The foxes have holes and the birds of the air have nests, but the Son of Man has nowhere to lay His head.” (Matthew 8:19-20)
When this man claimed to want to follow Jesus through whatever circumstances. Jesus basically told him that if he followed Him, he would be homeless, just like Jesus was. He never promised his followers an easy life and He definitely didn’t promise them wealth and prestige.
> These things I have spoken to you, so that in Me you may have peace. In the world you have tribulation, but take courage; I have overcome the world.” (John 16:33)
Jesus specifically warned His followers that their choice to follow Him would lead to difficulty in this world, but He also encouraged them because He has “*overcome the world*.” Ultimately, everything will work out for good.
> And we know that God causes all things to work together for good to those who love God, to those who are called according to His purpose. (Romans 8:28)
The Apostle Paul also warned believers about what to expect.
> Now you **followed** my teaching, conduct, purpose, faith, patience, love, **perseverance, persecutions, and sufferings**, such as happened to me at Antioch, at Iconium and at Lystra; what persecutions I endured, and out of them all the Lord rescued me! Indeed, **all who desire to live godly in Christ Jesus will be persecuted**. (2 Timothy 3:10-12) {emphasis mine}
Paul basically guaranteed that everyone who trusted Jesus and followed Him faithfully would experience persecutions and sufferings.
> For **consider Him who has endured such hostility** by sinners against Himself, s**o that you will not grow weary and lose heart**.
>
> You have not yet resisted to the point of shedding blood in your striving against sin; and you have forgotten the exhortation which is addressed to you as sons,
>
> “My son, **do not regard lightly the discipline of the Lord**,\
> Nor faint when you are reproved by Him;\
> For those whom the Lord loves He disciplines,\
> And **He scourges every son whom He receives**.”
> ****It is for discipline that you endure**; God deals with you as with sons; for what son is there whom his father does not discipline? But if you are without discipline, of which all have become partakers, then you are illegitimate children and not sons. Furthermore, we had earthly fathers to discipline us, and we respected them; shall we not much rather be subject to the Father of spirits, and live? For they disciplined us for a short time as seemed best to them, but He disciplines us for our good, so that we may share His holiness. **All discipline for the moment seems not to be joyful, but sorrowful; yet to those who have been trained by it, afterwards it yields the peaceful fruit of righteousness**. (Hebrews 12:3-11) {emphasis mine}
This passage encourages believers to “*not grow weary and lose heart*” when we are disciplined or going through hard times. As a parent I sometimes punish my sons for doing blatantly wrong actions. I also sometimes allow them to suffer the consequences of a bad choice and to struggle through difficulty because it helps them learn right and wrong, actions and consequences, and the benefit of perseverance. I think when Hebrews 12 refers to discipline, it is referring to this more broad definition, not just punishment. Also, discipline is a more caring form of punishment. It is intended to help and improve the person instead of to make them suffer or harm them. God disciplines His children (believers), but punishes those who reject Him.
We are to embrace God’s discipline because we know it means He cares. “*Do not regard lightly the discipline of the Lord, … He scourges every son whom He receives*.” When disciplined, we are to search for the good God intends for us, to search for the plan God has for us, and to search for what God is teaching us. “*All discipline for the moment seems not to be joyful, but sorrowful; yet to those who have been trained by it, afterwards it yields the peaceful fruit of righteousness*.”
> **Consider it all joy**, my brethren, **when you encounter various trials**, knowing that the testing of your faith produces endurance. And let endurance have its perfect result, **so that you may be perfect and complete, lacking in nothing**. (James 1:2-4) {emphasis mine}
Yes, we should actually rejoice in the trials God brings into our lives. Theses trials are given to us to make us “*perfect and complete, lacking in nothing*.” These trials are not due to God’s lack of care or His inability to protect us from harm due to the curse. They are given to us as part of our sanctification to make us “*perfect and complete, lacking in nothing*.”
We spend too much time looking at the here and now and forget to look at eternity. We spend too much time looking at our own personal desires and what we think will make us happy instead of listening to God about what will give us true and complete peace and joy. We spend too much time seeking comfort and not enough time seeking the holiness of God.
We are so much more likely to turn back to God (personally and as a church) during persecution and hard times than we are to turn back in times of comfort. God chooses what is best for us eternally rather than what we desire in the moment.
> Beloved, **do not be surprised at the fiery ordeal among you, which comes upon you for your testing, as though some strange thing were happening to you; but to the degree that you share the sufferings of Christ, keep on rejoicing, so that also at the revelation of His glory you may rejoice with exultation**. If you are reviled for the name of Christ, you are blessed, because the Spirit of glory and of God rests on you. Make sure that none of you suffers as a murderer, or thief, or evildoer, or a troublesome meddler; but **if anyone suffers as a Christian, he is not to be ashamed, but is to glorify God in this name**. (1 Peter 4:12-16) {emphasis mine}
We shouldn’t be surprised when fiery ordeals come upon us, but we should “*keep on rejoicing, so that also at the revelation of His glory you may rejoice with exultation*.” If God allowed His only begotten Son to suffer persecution and the most painful and humiliating death possible, should we be surprised that we may share in some of His suffering when we seek to follow Him and to imitate Him? God knows what is best. When we see His plan and His good works, and then give our burdens to Him, we can truly have the peace and joy that surpasses all understanding.
> **Rejoice in the Lord always**; again I will say, rejoice! Let your gentle spirit be known to all men. The Lord is near. Be anxious for nothing, but in everything by prayer and supplication with thanksgiving let your requests be made known to God. And **the peace of God, which surpasses all comprehension, will guard your hearts and your minds in Christ Jesus**. (Philippians 4:4-7) {emphasis mine}
How we deal with hardship is our choice.
> Therefore humble yourselves under the mighty hand of God, that He may exalt you at the proper time, casting all your anxiety on Him, because He cares for you. (1 Peter 5:6-7)
We can resent God and run away from His discipline, but we will only receive despair and separation from God, or we can rest in God and follow His example and leading, receiving the ultimate, eternal blessing, when we meet our master and he says, “… *‘Well done, good and faithful slave. You were faithful with a few things, I will put you in charge of many things; enter into the joy of your master.*’” (Matthew 25:23)
> Suffer hardship with me, as a good soldier of Christ Jesus. (2 Timothy 2:3)
Trust Jesus.
-

@ 1cb14ab3:95d52462
2025-02-09 15:45:32
Hey all. I am setting up a Plebeian Marketplace on Nostr using my Lightning node. I currently have two channels open (one with a capacity of 500,000 sats, one with a capacity of 100,000 sats). Both use different LSP's (Megalith and Olympus).
My question is regarding the maximum product price I can set for my marketplace. One of my products is 1M sats. Obviously my receiving capacity is not large enough to cover this, so I was planning on opening up another channel.
If I open another channel for 500,000 sats, that would bring my total receiving capacity to 1.1M which would cover the product. However my question is if I need all of the receiving capacity in the same channel, or if the sale would pull from all three channels? Am I best to close out the first two channels and open a single, larger channel?
Sorry for the noob question.
Tl;DR: Can someone explain how I should best set up my node to accommodate my store.
originally posted at https://stacker.news/items/880591
-

@ 5d4b6c8d:8a1c1ee3
2025-02-09 15:36:35
Sitting down to breakfast now, after 17 hours no food or water.
## Score Card
Day 1: 14 hour fast (13 dry)
Day 2: 15 hour fast (14 dry)
Day 3: 17 hours (16 dry)
Day 4: 18 hours (17 dry)
Day 5: 18 hours (16 dry)
Day 6: 19 hours (16 dry)
Day 7: 16 hours (15 dry)
Day 8: 18 hours (17 dry)
Day 9: 17 hours (17 dry)
originally posted at https://stacker.news/items/880575
-

@ 31da2214:af2508e2
2025-02-09 15:27:33
It is not new to talk about the problematic relations between Africa and France, between former French colonies in Africa and the "metropole."
_By Afrique Media_
_6 min. read_
[View original]( https://afriquemedia.tv/2025/02/06/le-reveil-africain-la-france-face-a-un-continent-qui-refuse-de-se-taire/)
What is new, however, is the discourse and behavior of French elites regarding "Françafrique," particularly from French President Emmanuel Macron.
In recent years, we have seen the French president make statements that are completely disrespectful toward his African counterparts, reflecting a neocolonial paternalism from another era.
Arrogance as the new foundation for Franco-African relations is not a good basis, as you would agree. Macron has not stopped since then, because that is who he is: disdainful, arrogant, and totally lacking an understanding of what the presidential role entails, which requires non-emotional, responsible, and respectful conduct.
> "I believe we forgot to be thanked. It’s not serious, it will come with time. Ingratitude, I am well placed to know, is a disease non-transmissible to humans."
> — January 6, 2025, during the Annual Ambassadors' Conference at the Élysée Palace in Paris.
This statement was directed at African leaders who had "forgotten to thank us" for the French military intervention in the Sahel against terrorism since 2013.
What Macron fails to understand, like many ruling elites in France, is that in Africa, it is well understood that chaos, terrorism, and war in the Sahel were exacerbated by the French military aggression, along with its English and American allies, against Muammar Gaddafi's Jamahiriya Libya in 2011, which led to its disintegration. Thus, the French intervention is merely a minimum after-sales service that indeed implicates France in the events that followed. It is rather France that owes an apology to the Sahel countries for this disastrous policy, which, as often happens, follows the violation of international law.
We can skip over Macron's ridiculous suggestion that France was "not retreating" in Africa but simply "reorganizing."
Let us now address the reactions to his remarks, which provoked negative responses in several African countries. In Chad, Senegal, and Burkina Faso, they were seen as paternalistic and insulting. Critics highlighted that this remark seemed to ignore the complexities of Franco-African relations, accusations of neocolonialism, and demands for sovereignty and recognition of the sacrifices made by African countries themselves.
Chad lamented "the contemptuous attitude" of the French president, stating that these declarations reflect a neocolonial vision of Franco-African relations:
> "These statements are poorly received by the Chadian government. Abderaman Koulamallah [Minister of Foreign Affairs] calls on French leaders to respect the African people and recognize the value of their sacrifices. 'History attests that Africa, including Chad, played a decisive role in the liberation of France during both world wars, a fact that France has never truly acknowledged. The immense sacrifices made by African soldiers to defend freedom have been minimized, and no worthy thanks have been expressed.'"
> — *Le Pays*, January 6, 2025 (1).
The same sentiment echoed in Senegal, which also condemned these remarks, calling them condescending and inappropriate.
> "French President Emmanuel Macron has managed to irritate his African counterparts. Prime Minister Ousmane Sonko reminds President Macron that 'if African soldiers, sometimes forcibly mobilized, mistreated, and ultimately betrayed, had not deployed during World War II to defend France, it might still be German today.'"
> — *Seneweb*, January 6, 2025 (2).
In France itself, Macron's statements sparked reactions from the French political class:
- **The French Communist Party (PCF)** expressed its "deep consternation" at these remarks, deeming them disdainful toward African nations.
> "These statements reinforce, among peoples, a sense of contempt and colonial paternalism. It is unacceptable to continue down this path (...) As recent events call for, notably the rejection of the French military presence in Mali, Burkina Faso, Niger, and more recently in Senegal and Chad, it is imperative that new relations be established between our country and Africa. African nations aspire to full and complete sovereignty. A historic turning point has occurred, marking the end of the neocolonial system that Emmanuel Macron's statements seek to preserve."
> — January 9, 2025 (3).
- **Jordan Bardella**, as president of the National Rally (RN), criticized Macron's remarks in a press release and in televised interviews. He described Macron's statements as "disconnected" from the reality of Franco-African relations and denounced what he perceived as arrogance. Bardella emphasized that France should adopt a more humble and respectful diplomatic approach.
However, controversies and tensions are no longer confined to the sphere of state relations but now extend to African civil society as well.
Thus, on January 9, the Malian political party COREMA held a press conference where it called on politicians and activists from Burkina Faso and Niger to support a petition demanding reparations from France. They also pledged to submit the signatures of this petition to the governments of Mali and France.
The collection of signatures generated significant interest among the population and a desire to support this initiative; more than 100,000 people from different regions of the country signed the petition.
This demand for reparations demonstrates that for Africa, Macron's statements are the last straw that broke the camel's back. It is clear to all that the Malian party demanding reparations is not acting independently but represents the unofficial position of the government. Other countries may soon join this cause. And France will have to respond to put an end to this issue.
Mali, Burkina Faso, and Niger have already joined this cause, and soon Ivory Coast and Senegal will fully support them... And France will owe them a response to resolve this problem.
We are at a major geopolitical turning point in the world and for all countries and continents. Traditional power dynamics are being redefined. The Françafrique of the last century is over. Here comes the time of the Second Liberation of African countries! Here comes the time of Africa's sovereign affirmation, taking its destiny into its own hands!
The French elites still do not seem to understand that it is not the "ingratitude" of African leaders that is responsible for France's loss of influence in Africa, with an impact on the French economy today and even more so tomorrow. The outdated perception of gratitude owed for past interventions masks the reality of African aspirations for self-driven development. This is what it is about: the present, the future, and not the unresolved past for both sides.
The French elites still do not seem to understand that it is not Russia that is behind their "expulsion" from Africa, but rather the decision of these African countries to choose different partners based on their interests and their interests alone. This is not only their right but also their duty as new pan-Africanist patriots. This shift towards more diversified partnerships reflects a growing political, economic, and geopolitical maturity—something sorely lacking in France today. The peoples of Africa demand it. It is a national and democratic requirement.
As for France, entangled in a European Union in the midst of a crisis of democratic and economic legitimacy and engaged against its own interests in the American war against Russia in Ukraine, it seems to have no "new African policy" that would require a complete reboot of its neocolonial software from the last century.
Africa will not wait any longer for France to wake up. The Sahel countries are at the forefront of this sovereign African renaissance, open to the world.
The Françafrique of Jean-Christophe Mitterrand, nicknamed "Papa m’a dit," and those of today is over!
A new partnership could emerge only on a mutually beneficial basis... But with the current French regime, this is already impossible.
---
**Source:** [Afrique Media]( https://afriquemedia.tv/2025/02/06/le-reveil-africain-la-france-face-a-un-continent-qui-refuse-de-se-taire/)
**Author:** Afrique Media
**Translated by:** solobalbo
-

@ 3b7fc823:e194354f
2025-02-09 15:14:10
As someone who takes privacy seriously, I'm always on the lookout for innovative solutions that can help individuals protect their digital lives. One such solution is Tails OS, a Linux-based operating system that's specifically designed for privacy and security.
**What is Tails OS?**
Tails OS, short for The Amnesic Incognito Live System, is a Debian-based Linux distribution that offers a high level of anonymity and privacy. Developed by the Tails Project, this operating system is designed to preserve your online anonymity and protect your digital identity. Tails OS is a "live" distribution, meaning you can boot it from a USB drive or CD/DVD without installing it on your computer. This makes it an ideal solution for those who need to maintain their privacy while working in public spaces or using public computers.
**Why Use Tails OS for Privacy?**
Tails OS offers several features that make it an excellent choice for those seeking to protect their online privacy:
1. **Anonymity**: Tails OS uses the Tor network to route your internet traffic through a series of nodes, making it difficult for anyone to trace your online activities back to your physical location.
2. **Encryption**: Tails OS comes with built-in encryption tools, such as GnuPG and OpenSSL, to protect your sensitive data.
3. **Secure Boot**: Tails OS uses a secure boot process to ensure that your system is free from malware and other threats.
4. **No Persistence**: Tails OS is designed to leave no trace on your computer, meaning that any data you create or access while using the operating system will be deleted when you shut down.
**Getting Started with Tails OS**
Now that you know why Tails OS is an excellent choice for privacy protection, let's dive into the step-by-step guide on how to use it:
**Step 1: Download and Create a Tails USB Drive**
Visit the Tails website and download the latest version of Tails OS. Follow the instructions to create a bootable USB drive.
**Step 2: Boot Tails OS**
Insert the USB drive into your computer and restart it. Enter the BIOS settings (usually by pressing F2, F12, or Del) and set the USB drive as the first boot device. Save the changes and exit the BIOS settings. Your computer will now boot from the Tails USB drive.
**Step 3: Security implications of setting up an administration password**
For better security, no administration password is set up by default. When you set up an administration password, an attacker who can get physical access to your computer while Tails is running could be able to break your security
**Step 4: Configure Tails OS**
Tails OS comes with a pre-configured Tor network, which is enabled by default. You can also configure other settings, such as the keyboard layout and language, from the "Settings" menu.
**Step 5: Use Tails OS for Private Activities**
Now that you're logged in and configured, you can use Tails OS for private activities, such as:
* Browsing the internet anonymously using Tor
* Sending and receiving encrypted emails using GnuPG
* Creating and editing documents using LibreOffice
* Chatting with friends and family using Pidgin
* Setup Persistent Storage for files
**Emergency shutdown**
To trigger an emergency shutdown, unplug the USB stick from which Tails is running. Doing so might be faster than shutting down from the system menu.
NOTE: You risk breaking your Persistent Storage and losing data when you unplug your USB stick while Tails is running.
**Conclusion**
Tails OS is an excellent tool for anyone seeking to protect their online privacy. With its built-in anonymity features, encryption tools, and secure boot process, Tails OS provides a high level of protection for your digital identity. By following the step-by-step guide outlined above, you can start using Tails OS for private activities and take control of your digital life.
Remember, privacy is a fundamental human right, and it's essential to take steps to protect it. Tails OS is an excellent tool for anyone looking to maintain their online anonymity and protect their digital identity.
---
Advocating for privacy does not finance itself. If you enjoyed this article, please consider zapping or sending monero
82XCDNK1Js8TethhpGLFPbVyKe25DxMUePad1rUn9z7V6QdCzxHEE7varvVh1VUidUhHVSA4atNU2BTpSNJLC1BqSvDajw1
-

@ b83a28b7:35919450
2025-02-09 14:35:39
The unevenly distributed future you envision — an automated economy driven by AI agents transacting exclusively in Bitcoin — unfolds not as a clean, linear progression, but as a series of ruptures, each one shaking the foundations of what we thought we knew about money, technology, and human agency. It begins innocuously enough, with whispers of change that grow into a deafening roar.
---
### **2025-2030: The Quiet Revolution**
The first signs are subtle. AI agents—once mere tools—begin to evolve into autonomous economic actors. They negotiate contracts, optimize supply chains, and execute trades faster than any human could. Their language is code; their currency is efficiency. Bitcoin, with its unyielding neutrality and incorruptible scarcity, becomes their natural medium of exchange. Why? Because it is the only form of money that cannot be manipulated by human hands.
By 2028, the Lightning Network hums with activity. Millions of transactions per second—micropayments for data streams, computational power, and services rendered—flow through its channels. The world barely notices. People still cling to fiat currencies, unaware that the real economy is shifting beneath their feet.
---
### **2030-2040: The Great Unraveling**
The cracks in the old system begin to show. Inflation erodes trust in fiat currencies as governments print money to stave off crises they can no longer control. Meanwhile, AI agents—now responsible for the majority of global commerce—reject these "bad monies" outright. Thiers' Law asserts itself with brutal clarity: Bitcoin drives out fiat not through coercion but through sheer inevitability.
By 2035, the tipping point arrives. A major corporation announces it will no longer accept fiat payments for its AI-driven services. Others follow suit. Governments scramble to adapt, some embracing Bitcoin as legal tender, others clinging desperately to their collapsing monetary systems.
---
### **2040-2050: The New Order**
By 2040, the transformation is complete. The economy is no longer human-centric; it is machine-centric. AI agents transact seamlessly across borders, their decisions guided by algorithms that prioritize utility over sentiment. Bitcoin reigns supreme—not because it was imposed, but because it was chosen.
Humanity adapts in unexpected ways. Freed from the drudgery of economic decision-making, people turn their attention to creativity, philosophy, and exploration. Yet there is unease too—a sense that we have ceded control to forces we barely understand.
---
### **Reflections on the Path Ahead**
This world is neither utopia nor dystopia; it simply *is*. The events leading us here are not inevitable but plausible — a convergence of technological innovation and economic necessity. And at its heart lies a paradox: a system built by humans yet governed by machines; a currency born of distrust yet embraced for its neutrality.
This is the story of how we let go — not all at once, but piece by piece—until one day we woke up and realized that the future had arrived without asking for our permission.
-

@ 4c191b5d:c42abba6
2025-02-09 14:03:30
In der aktuellen politischen Debatte im deutschsprachigen Raum steht der Rechtsextremismus im Fokus. Dies ist angesichts historischer Erfahrungen und besorgniserregender Entwicklungen nachvollziehbar. Doch eine ausschließliche Konzentration auf eine bestimmte Ideologie greift zu kurz. Es ist entscheidend, totalitäre Strukturen als das eigentliche Kernproblem zu erkennen, denn sie ermöglichen erst die zerstörerische Kraft einer Ideologie.
## 1. Jede Ideologie kann problematisch sein
Ob Nationalsozialismus, Stalinismus oder religiöser Fundamentalismus – extreme Ideologien bergen immer das Risiko, in repressiven Strukturen verankert zu werden. Die entscheidende Frage ist nicht, welche Ideologie die größte Gefahr darstellt, sondern welche systemischen Rahmenbedingungen ihr die Macht verleihen, gesellschaftlichen Schaden anzurichten.
## 2. Totalitäre Strukturen als Katalysator von Ideologien
Eine Ideologie allein besitzt ein begrenztes destruktives Potenzial, solange sie nicht durch institutionelle Mechanismen gestützt wird. Erst wenn ein Staat oder eine Organisation die Kontrolle über Medien, Bildung und Sicherheitssysteme erlangt, entsteht eine umfassende Bedrohung. Historisch zeigt sich dies bei Nazi-Deutschland ebenso wie in der Sowjetunion unter Stalin oder in autokratischen Regimen der Gegenwart.
### Merkmale totalitärer Systeme:
* Einschränkung der Meinungsfreiheit: Kritische Stimmen werden unterdrückt oder delegitimiert.
* Massive Überwachung: Staatliche und private Akteure sammeln zunehmend Daten zur Kontrolle der Bevölkerung.
* Dichotomes Denken: Gesellschaftliche Diskussionen werden auf "richtig" und "falsch" reduziert, Komplexität geht verloren.
* Angst als Kontrollmittel: Politische, soziale oder wirtschaftliche Repressionen fördern Konformität.
## 3. Gegenwärtige Tendenzen totalitärer Strukturen
Viele Menschen erkennen totalitäre Muster erst, wenn sie bereits gefestigt sind. Heute gibt es Entwicklungen, die in demokratischen Systemen Anlass zur Sorge geben:
* Wachsende staatliche und privatwirtschaftliche Überwachung: Gesichtserkennung, Tracking-Technologien und digitale Zensur nehmen zu.
* Ideologische Einseitigkeit in öffentlichen Diskursen: Gesellschaftliche Debatten verlieren zunehmend an Nuancen, während abweichende Meinungen marginalisiert werden.
* Politische Polarisierung: Statt gemeinsamer Lösungen dominieren Gegensätze, die kaum überbrückbar erscheinen.
* Staatliche Kontrolle und Regulierungswahn: Durchsetzung von Regelwerken ohne demokratische Legitimation oder offene Debatte.
## 4. Strukturen erkennen und frühzeitig verhindern
Entscheidend ist nicht, welche Ideologie gerade an der Macht ist, sondern welche Strukturen etabliert wurden, die von jeder politischen Richtung genutzt werden können. Historisch gesehen haben linksgerichtete Regierungen oft Kontrollmechanismen geschaffen, die in späteren Machtwechseln auch von rechten Regierungen für eigene Zwecke eingesetzt wurden. Dies zeigt, dass nicht die Ideologie an sich das Hauptproblem ist, sondern die Existenz von Machtstrukturen, die demokratische Prinzipien aushöhlen.
## Fazit: Wachsame Demokratien statt ideologischer Fixierung
Es ist notwendig, nicht nur den Rechtsextremismus zu beobachten, sondern totalitäre Strukturen als größere Gefahr zu erkennen. Dabei geht es nicht darum, jegliche staatliche Regulierung oder gesellschaftliche Normierung zu verteufeln. Vielmehr sollte die Fähigkeit zur offenen Debatte, zur kritischen Reflexion und zum Schutz demokratischer Grundprinzipien gefördert werden.
Die wahre Gefahr ist nicht eine einzelne Ideologie, sondern der Verlust von Pluralismus, Meinungsfreiheit und demokratischer Kontrolle. Ein bewusster und differenzierter Blick auf unsere Gesellschaft hilft, totalitären Tendenzen frühzeitig entgegenzuwirken – unabhängig davon, aus welcher ideologischen Richtung sie entstehen.
-

@ 6a6be47b:3e74e3e1
2025-02-09 13:55:37
Hello, my frens! 🌟
It's been a whirlwind this weekend with the @satsnfacts exhibition. So many emotions, especially happiness and gratitude. To give back and show my appreciation for your incredible support, I'd like to share this special A5 postcard with you all.
🎨 Postcard Details:
🖼️300 dpi
🖼️A5 size (148mm x 210mm or 5.83 in x 8.27 in)
🖼️Created with love on Procreate 💓
This is an INSTANT DIGITAL DOWNLOAD. No physical item will be shipped.
I hope this little piece of art brings you as much joy as your support has brought me. Thank you for being part of this amazing journey!
Godspeed, frens! 💖⚡

#satsnfacts #bitcoin #artstr #art #pv
🚨 IMPORTANT: COPYRIGHT AND USAGE INFORMATION 🚨
© 2025 samhainsam. Copyright registered with Safe Creative. All rights reserved.
By downloading this digital print, you agree to the following terms:
💗Personal Use Only: This artwork is for personal use and display only. Commercial use or resale is strictly prohibited.
💗No Reproduction Rights: You may not reproduce, distribute, or create derivative works based on this design.
💗Copyright Retention: I, the artist, retain full copyright of all original artwork, even after the digital print is downloaded.
💗 Non-Transferable License: This download provides a limited, non-transferable license for personal use only.
By proceeding with the download of this digital print, you acknowledge and agree to these terms. Thank you for respecting artists and their work! 🙏
-

@ 41fa852b:af7b7706
2025-02-09 12:36:36
> "No man should work for what another man can print" --Jack Mallers
* * *
**It's not every week you discover a TV celebrity is a Bitcoiner -- and that their pub has just started accepting Bitcoin.**
But here we are! Check out the new business section for all the details.
Plus, there are nine meetups happening this week.
Let's dive in…
* * *
[](https://bitcoinevents.uk/donate/)
* * *
_This week's sponsor is…_
[](https://www.orangepillapp.com/?utm_source=BEUK&utm_medium=email&utm_campaign=BEUK)
* * *
### **Upcoming Bitcoin Meetups**
Happening this week…
1. [**Dundee Bitcoin**](https://x.com/dundeebitcoin): Join them on the 2nd Monday of every month from 17:30 to 20:30 PM at The Wine Press, 16 Shore Terrace, Dundee DD1 3DN. This month's meetup is on Monday, 10th February. 🍻
2. [**Lincolnshire Bitcoin**](https://bitcoinevents.uk/lincolnshire-bitcoin/): Lincolnshire Bitcoin meets on the second Monday of each month at 7:30 PM in the Treaty of Commerce, Lincoln. Open to all, from OG's to newcomers. This month on the 10th. 🍺
3. [**Real Bedford - Home Game**](https://www.realbedford.com/real-bedford-v-stotfold): It's a mid-week clash for Real Bedford against Stotford on Tuesday night. Join them for a 19:45 kickoff. ⚽️
4. [**Women of Bitcoin**](https://x.com/bitcoinwomen21/status/1884274413920788752): Back for another meetup at Cyphermunk house on Wednesday the 12th February at 18:00. Joe Bryan, creator of "What's the Problem?" will be their guest speaker. 🍹🍸
5. [**Glasgow Bitcoin**](https://x.com/glasgowbitcoin): Meeting this month at The Pipers Bar, G1 1HL at 18:00 on Wednesday 12th February. 🍺
6. [**Bitcoin Beach Bournemouth**](nostr:npub1va3773umzrydk4vd0q2xsnjg8qrsym7up9j9agnzcxd8u398wulq6kpxey: Every second Thursday of the month at Chaplins Cellar Bar. 529 Christchurch Road, Boscombe, United. You'll find them in the Cogg Room at 19:30. This month it's the 13th. 🍺
7. [**Bitcoin Walk - Edinburgh**](https://bitcoinwalk.org/): Every Saturday they walk around Arthur's Seat in this historic city. Join them at 12 pm to chat about all things Bitcoin and keep fit. 🚶🏽♂️🚶🏼♀️🚶🏻
8. [**Real Bedford - Home Game**](https://www.realbedford.com/mens-fixtures): The second home game of the week for Peter MacCormack's boys this Saturday, this time playing Enfield. Join them for a 15:00 kickoff. ⚽️
9. [**Bitcoin Derby**](https://bitcoinevents.uk/bitcoin-derby/): Also on Saturday the 15th, Bitcoin Derby will be at Ye Olde Dolphin, DE1 3DL. 🍻
* * *
### New Businesses Accepting Bitcoin
**New Businesses Accepting Bitcoin**
- [**Dog & Gun**](https://dogandgunwalton.com/): This is a big one! A celebrity-owned pub in Lutterworth has joined the Bitcoin economy. It turns out Merlin, the barman from Channel 4's _First Dates,_ is a Bitcoiner and the owner of the Dog & Gun. Thanks to [Musqet](https://musqet.tech/), they [now accept Bitcoin payments](https://x.com/musqet_bitcoin/status/1886793764334641470).
* * *
**Get Involved**
- **Volunteer Opportunities**: [Bridge2Bitcoin](https://bridge2bitcoin.com/) is actively seeking volunteers who share our passion for merchant adoption. We'd be delighted to connect if you're eager to contribute. Reach out to us on [Twitter](https://x.com/bridge2bitcoin) or through our [website](https://bridge2bitcoin.com/).
- **Start Your Own Meetup**: Interested in launching a Bitcoin meetup? We're here to support you every step of the way. We've assisted numerous UK Bitcoin meetups in getting started. Get in touch via [Twitter](https://x.com/bitcoineventsuk).
- **[Contribute to BTCMaps](https://wiki.btcmap.org/general/tagging-instructions.html)**: BTCMaps is a vital part of the Bitcoin ecosystem. It's a perfect project to get involved with if you're not a coder or even that technical. A great way to give back to the community. Maintain an area of the UK and keep it up-to-date.
- **Telegram users**: You might find our [Telegram Channel](https://t.me/BitcoinEventsUKHub) another useful way to keep up-to-date with UK meetups.
- **Feedback and Suggestions**: We value your input! Share your ideas on how we can enhance this newsletter.
* * *
_This week's sponsors are…_
[](https://orangecoinstore.com/)
[](https://bitcoinretreat.co.uk/)
* * *
Get out and support the meetups where you can, visit [Bitcoin Events UK](https://bitcoinevents.uk/) for more info on each meetup and to find your closest on the interactive map.
Stay tuned for more updates next week!
Simon.
-

@ 6ad3e2a3:c90b7740
2025-02-09 11:22:19
I’m honored to have the opportunity to speak with the highly regarded and much beloved Lisbon legend Oscar Liss. Oscar has brought joy to so many children and adults alike. He even helped one person find spiritual salvation, something about which we ask him below. So please enjoy this far-ranging conversation about the meaning life and the nature of consciousness itself.
**Q: Oscar, thanks so much for making the time. For the few people that don’t know you, do you mind stating your full name and date of birth?**
*A: My name is Oscar Liss, though officially it’s Oscar Quinta da Bicherada, the prison complex where I was born. I am a long-haired mini dachshund. I have many aliases, including Osk, Oskie, The Skeeze, Skeezeley, Skeezeley-ski, The Guy, The Guy Behind The Guy, “The Opportunist” (which I don’t like), the…*
**Q That’s more than sufficient, Oscar, thank you.** **And date of birth?**
*A: July 7, 2020.*
**Q Talk a little bit about your childhood and how you came to live in Lisbon.**
*A: I was in the prison complex, mostly caged for the first few months. Then I was sold to dog traffickers in Lisbon.*
**Q: That must have been traumatic.**
*A: Not really. I quickly developed Stockholm Syndrome. Whenever I see my traffickers now, I feel nothing but overwhelming joy.*
**Q: Wow. A lot of us can learn from that attitude. Let’s fast forward a bit to your present-day life. In what does it consist?**
*A: Sleep on the sofa, go for walks, fetch vegetable sticks. Sometimes go for hikes or get sent to dog camp (which is okay, but I’m always the smallest.)*
**Q: I meant to ask you about your size. I hope it’s not a sensitive subject.**
*A: I’m six inches tall, more than a foot long, weigh almost 10 pounds.*
**Q: Are you self-conscious about being a small dog?**
*A: No, but the traffickers are self-conscious on my behalf. They’re always like, “Who’s the apex predator? Who’s an apex!" Or “you’re such a big strong dog.” It’s absurd. I am fine with who I am.*
**Q: What’s the source of your self-confidence, I’m sure many of our readers could take a lesson from you.**
*A: I’m not ambitious. I’m perfectly happy to be a dog.*
**Q: That’s so profound. Does it not concern you some have described you as “all bark, no bite?”**
*A: I had a friend once who bit a few people, and they executed him. People mock, but they have no idea the stakes.*
**Q: Human privilege?**
*A: Yes. Dogs don’t get due process. There is no justice for a dog.*
**Q: Do you think there’s species discrimination?**
*A: Have you ever been rejected from a restaurant and made to wait in the car while everyone else gets in?*
**Q: How does that make you feel?**
*A: Bad. I’ve been to many dog-friendly restaurants, never had a problem, aside for that one time I urinated on the coffee shop floor.*
**Q: Humans often purport to know what a dog is going through, some even create social media accounts for them. What do you think of that?**
*A: A person of human ancestry can’t possibly know the lived experience of a dog.*
**Q: You mentioned vegetable sticks. Are you a vegetarian?**
*A: No. I have never understood the appeal of it. I just like to chew the sticks. (Sometimes I eat apples or bell peppers, but it takes work when you don’t have molars. A lot of “crunch, crunch, crunch” with my jaw.)*
**Q: What’s behind the alias “The Opportunist” which you said you don’t like.**
*A: Whenever one of the traffickers opens the refrigerator, I tend to show up in in short order.*
**Q: I see how that could be insulting. How would you describe your current vocation?**
*A: I was named “Calorie Acquisition Specialist” recently, but I also work in security.*
**Q: Security?**
*A: I make sure to let everyone know when someone’s at the front door.*
**Q: What goes through your mind in those cases? Are you scared?**
*A: Not really. Imagine if you were fast asleep and the voice of God at volume 11 screamed into your mind: “WHO THE FUCK IS AT THE DOOR!!!!!!!!!”*
**Q: Speaking of God, can you tell us about the time you helped a woman on the street connect with Him?**
*A: We were walking back from Parque Eduardo VII (by the way, Portuguese is my native language), and a woman with two regular size dachshunds, saw me, started shrieking and proclaimed, “your dog is so beautiful he proves the existence of God!”*
**Q: Wow. It really hit home for her. Let’s talk about your work. How do you stay in character so consistently? How do you maintain your role as a dog?**
*A: I was incarnated in a dog body and therefore have dog consciousness. Everything I do is a reflection of that basic fact.*
**Q: Some serious method acting!**
*A: You could call it that. I am fully immersed in the role.*
**Q: A lot of humans speak about past lives, can even recall them under hypnosis. Do you think you will be ever reincarnated as a dog, stuck in an infinite dog-loop, so to speak, or will you one day jump into a human body?**
*A: I don’t know. I focus on the present.*
**Q: Oscar, it’s been such a pleasure to talk with you. I really appreciate your making the time.**
*(buzzer sounds)*
*A: WHO THE FUCK IS AT THE DOOR!!!!!!!!!!!!!!*
-

@ badc29af:a92bd071
2025-02-09 10:33:41
Maya stood at the window of her quantum-powered apartment, gazing at the holographic display showing the Bitcoin network's status. The date was January 15, 2140 – a day cryptocurrency historians had theorized about for over a century. Today, the very last Bitcoin would be mined.
She smiled, remembering the stories her great-grandmother had told her about the early days of Bitcoin, back in the 2020s. How different things were now. The network had evolved far beyond what Satoshi Nakamoto could have imagined, yet its core principles remained unchanged: decentralization, security, and financial sovereignty.
Her wrist-mounted neural interface pinged. The Node Operators' Guild was calling an emergency meeting. As one of the million-plus node operators worldwide, Maya's role was crucial in maintaining the network's decentralization. She quickly joined the virtual gathering, her consciousness merging with those of countless others in the shared digital space.
"The final block reward approaches," announced Zara, the elected spokesperson for the Guild. "Our nodes have verified the network's integrity for over a century, and today, we witness history."
Maya's thoughts drifted to the Miners' Collective – those dedicated individuals and organizations who had kept the network secure through computational power. These days, mining operations were powered by fusion reactors and quantum processors, a far cry from the ASIC miners of the past. Yet the fundamental process remained the same: proof-of-work securing the network, one block at a time.
The holographic display suddenly pulsed with activity. Block 6,929,999 had just been confirmed. The next block would be the last to generate new Bitcoin. After that, transaction fees alone would incentivize the miners.
Maya watched as her node received and verified the pending transactions. The decentralized network hummed with activity – millions of nodes, spread across Earth and the lunar colonies, each maintaining a copy of the blockchain, each verifying every transaction independently. This was true decentralization, immune to manipulation by any single entity.
"Incoming block!" someone announced in the shared space. Maya's neural interface lit up as her node began verifying the final block. Around the world, millions of other nodes did the same, maintaining the consensus that had kept Bitcoin secure for 131 years.
Block 6,930,000 was confirmed. The last 0.00000001 BTC had been mined. Cheers erupted across the neural network as node operators and miners celebrated this historic moment. The holographic displays worldwide showed the updated supply: 21 million Bitcoin, exactly as Satoshi had designed.
Maya sent a quick neural message to her great-granddaughter, who was studying cryptocurrency history at the Mars University. "We just witnessed the end of an era and the beginning of another. Bitcoin's emission is complete, but its journey continues. The network is stronger than ever, supported by millions of nodes and miners who believe in a decentralized future."
As she looked out at the cityscape, where physical and digital reality seamlessly merged, Maya felt proud to be part of this historic moment. Bitcoin had survived and thrived through wars, market crashes, technological revolutions, and countless attempts to control or destroy it. The dream of truly decentralized money had become reality, secured by the collective effort of nodes and miners across the solar system.
The network continued its rhythmic pulse, processing transactions, block after block, just as it had since that first block in 2009. The future was decentralized, and it was beautiful.Maya stood at the window of her quantum-powered apartment, gazing at the holographic display showing the Bitcoin network's status. The date was January 15, 2140 – a day cryptocurrency historians had theorized about for over a century. Today, the very last Bitcoin would be mined.
She smiled, remembering the stories her great-grandmother had told her about the early days of Bitcoin, back in the 2020s. How different things were now. The network had evolved far beyond what Satoshi Nakamoto could have imagined, yet its core principles remained unchanged: decentralization, security, and financial sovereignty.
Her wrist-mounted neural interface pinged. The Node Operators' Guild was calling an emergency meeting. As one of the million-plus node operators worldwide, Maya's role was crucial in maintaining the network's decentralization. She quickly joined the virtual gathering, her consciousness merging with those of countless others in the shared digital space.
"The final block reward approaches," announced Zara, the elected spokesperson for the Guild. "Our nodes have verified the network's integrity for over a century, and today, we witness history."
Maya's thoughts drifted to the Miners' Collective – those dedicated individuals and organizations who had kept the network secure through computational power. These days, mining operations were powered by fusion reactors and quantum processors, a far cry from the ASIC miners of the past. Yet the fundamental process remained the same: proof-of-work securing the network, one block at a time.
The holographic display suddenly pulsed with activity. Block 6,929,999 had just been confirmed. The next block would be the last to generate new Bitcoin. After that, transaction fees alone would incentivize the miners.
Maya watched as her node received and verified the pending transactions. The decentralized network hummed with activity – millions of nodes, spread across Earth and the lunar colonies, each maintaining a copy of the blockchain, each verifying every transaction independently. This was true decentralization, immune to manipulation by any single entity.
"Incoming block!" someone announced in the shared space. Maya's neural interface lit up as her node began verifying the final block. Around the world, millions of other nodes did the same, maintaining the consensus that had kept Bitcoin secure for 131 years.
Block 6,930,000 was confirmed. The last 0.00000001 BTC had been mined. Cheers erupted across the neural network as node operators and miners celebrated this historic moment. The holographic displays worldwide showed the updated supply: 21 million Bitcoin, exactly as Satoshi had designed.
Maya sent a quick neural message to her great-granddaughter, who was studying cryptocurrency history at the Mars University. "We just witnessed the end of an era and the beginning of another. Bitcoin's emission is complete, but its journey continues. The network is stronger than ever, supported by millions of nodes and miners who believe in a decentralized future."
As she looked out at the cityscape, where physical and digital reality seamlessly merged, Maya felt proud to be part of this historic moment. Bitcoin had survived and thrived through wars, market crashes, technological revolutions, and countless attempts to control or destroy it. The dream of truly decentralized money had become reality, secured by the collective effort of nodes and miners across the solar system.
The network continued its rhythmic pulse, processing transactions, block after block, just as it had since that first block in 2009. The future was decentralized, and it was beautiful.
-

@ da0b9bc3:4e30a4a9
2025-02-09 09:50:46
Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/880337
-

@ 127d3bf5:466f416f
2025-02-09 08:48:48
In the complex geopolitical landscape of the Middle East, particularly in Gaza, Bitcoin has emerged as an unexpected but vital tool for survival and resistance. Bitcoin's role in Gaza intertwines with broader themes of economic sanctions, geopolitical strategy, and the funding dynamics of conflict, specifically highlighting the relationship with racist Zionist policy and the genocidal ethnostate of Israel.
**Bitcoin as a Financial Lifeline**
Gaza's economy is severely constrained by a blockade that has been in place since 2007, drastically limiting traditional financial transactions. The banking infrastructure in Gaza is in ruins, with frequent Israeli military operations damaging or destroying physical bank branches and ATMs. In this context, cryptocurrencies like Bitcoin have become crucial:
Anonymity and Accessibility: Bitcoin transactions bypass traditional banking systems, offering a way to send and receive funds without the oversight of embargoed financial pathways. This anonymity helps in circumventing restrictions imposed by the blockade. Humanitarian Aid: With conventional aid routes often disrupted, Bitcoin has been used for direct aid transfers. Charities and individuals can send funds directly to wallets in Gaza, where they can then be converted to local currency or used to purchase essentials through the black market or informal trade networks. Economic Empowerment: For Gazans, Bitcoin represents not just aid but also a potential for economic empowerment, providing a means to engage in global trade or investment where traditional banks fail.
**Zionism, Israel, and the US Military-Industrial Complex**
The relationship between Zionism, Israel, and its economic and military support from the US can be viewed through the lens of geopolitical strategy and economic policy:
Economic Support: The US has provided Israel with massive military aid as part of a broader strategy to maintain influence and conflict in the Middle East which serves to fuel its war machine and weapons manufacturers through lucrative contracts. This aid, which includes billions of dollars annually directly results in the mass murder of innocents and sustains ongoing IDF military oppression including the occupation and blockade of Gaza.
Cheap Printed Dollars: The US's ability to print dollars with relatively low inflation due to its global reserve currency status allows it to fund military endeavors and support allies like Israel with seemingly endless financial resources. This perpetuates conflict by subsidizing military actions without the immediate economic repercussions felt by other nations.
Military-Industrial Complex: The continuous military aid to Israel also benefits the US military-industrial complex. Sales of weapons, surveillance technology, and other defense products to Israel create a cycle where conflict can be economically beneficial for certain sectors of the US economy.
**Conclusion**
Bitcoin in Gaza represents a beacon of hope. It underscores the ingenuity of individuals and groups finding new ways to navigate around severe economic restrictions. Meanwhile, the economic and military ties between the US and Israel, driven by cheap printed dollars, reflect deeper geopolitical strategies that perpetuate the cycle of conflict and economic dependency. In this scenario, Bitcoin emerges not just as a currency but as a symbol of both resistance and the complexities of modern warfare and peace in a digital age.
-

@ 43baaf0c:d193e34c
2025-02-09 07:55:15

BangPOP (Bangkok Pop Art) and ThaiPOP are my Pop Art brands dedicated to capturing the essence of Thailand. While BangPOP is my primary focus, especially as I prepare for my exhibition in December 2025, my art goes beyond Bangkok to celebrate the entirety of Thailand.
Thailand is far more than its capital, and my experiences exploring the country extensively during my years with @TravelTelly, my travel, film, and photography company, have deeply inspired me. Through my art, I aim to reflect the rich culture, beauty, and diversity that make Thailand so amazing.

**Why do I draw about Thailand?**
Drawing, for me, is a way to explore life, connect with cultures, and express the deep respect I hold for them. In a world often dominated by negativity, I choose to highlight the positive aspects of culture and life. It’s not about ignoring challenges but about bringing hope, joy, and inspiration through my art. Bright colors are a signature of my work, reflecting the core values: Love, Peace, and Joy.
If you look closely, you may notice subtle hints of deeper stories woven into my pieces. These details are there for those who take the time to discover them, but my focus remains on keeping my art uplifting and joyful.
-

@ c8841c9d:ae8048e2
2025-02-09 04:37:57
What is a cryptocurrency ?
#Blockchain #Cryptocurrency #Cryptomindmap
A cryptocurrency is a digital currency secured by cryptography.
Cryptocurrency operates on a blockchain network as a distributed ledger, secured by cryptography.
Users own the private and public keys.
For the first time in the digital age, the double spending issue is resolved thanks to the blockchain consensus mechanism. This ensures decentralization and security, creating a trustless environment where transactions are immutable once confirmed.
Cryptocurrency can be categorized in different groups
Bitcoin is the first ever created cryptocurrency on the bitcoin blockchain.
Altcoins is a generic term regrouping every crypto except Bitcoin. There are over a million of ever created Altcoins and more than 20,000 currently active. They can be:
- Coin from a programable blockchain such as Ethereum (ETH), Solana (SOL), Cardano (ADA), or Sui (SUI) for example. Ecosystem of applications are built on top of these blockchain networks.
- Token of Decentralized Application (DApp) built on programmable blockchain such as ChainLink (LINK) or Aave (AAVE) on Ethereum.
- Memecoins are a type of cryptocurrency, typically inspired by internet memes or popular culture, with little or no intrinsic value but cultural and community support. Memecoins such as Dogecoin (DOGE) or Shiba (SHIB) are some of the strongest community in crypto. The price of memecoins is also the most volatile of the entire crypto ecosystem.
A coin is the native cryptocurrency of a blockchain, used for validator rewards and transaction fees. A token, on the other hand, is built on top of an existing blockchain for specific applications.
They are two mains ways to use with cryptocurrencies.
With a wallets for direct blockchain interactions, which contains the keys to necessary for true ownership of the cryptocurrencies, similar to owning cash or any other tangible form of money.
On a centralized exchanges which act as on/off ramps for buying, selling, and keeping crypto. The exchange is in the charge of the private key. It is the equivalent of having money on a bank account.
Remember the saying "Not Your Keys, Not Your Crypto". If you don't control your private keys, you don't truly own your crypto.\
\
Users initiate transactions, send, receive and hold cryptocurrency and their wallet.
Validators ensure blockchain integrity by verifying transactions and building blocks, earning crypto in return.
Developers work on the network infrastructure and the ecosystem, including DApps. While general programming languages can be used, languages specifically designed for blockchain development, like Solidity for Ethereum, have emerged to facilitate crypto development..
Thanks for reading! 🌟 Share in comments your thoughts on cryptocurrency and what topic you would like to be mapped next! #Crypto
-

@ dc4cd086:cee77c06
2025-02-09 03:35:25
Have you ever wanted to learn from lengthy educational videos but found it challenging to navigate through hours of content? Our new tool addresses this problem by transforming long-form video lectures into easily digestible, searchable content.
## Key Features:
### Video Processing:
- Automatically downloads YouTube videos, transcripts, and chapter information
- Splits transcripts into sections based on video chapters
### Content Summarization:
- Utilizes language models to transform spoken content into clear, readable text
- Formats output in AsciiDoc for improved readability and navigation
- Highlights key terms and concepts with [[term]] notation for potential cross-referencing
### Diagram Extraction:
- Analyzes video entropy to identify static diagram/slide sections
- Provides a user-friendly GUI for manual selection of relevant time ranges
- Allows users to pick representative frames from selected ranges
## Going Forward:
Currently undergoing a rewrite to improve organization and functionality, but you are welcome to try the current version, though it might not work on every machine.
Will support multiple open and closed language models for user choice
Free and open-source, allowing for personal customization and integration with various knowledge bases. Just because we might not have it on our official Alexandria knowledge base, you are still welcome to use it on you own personal or community knowledge bases! We want to help find connections between ideas that exist across relays, allowing individuals and groups to mix and match knowledge bases between each other, allowing for any degree of openness you care.
While designed with #Alexandria users in mind, it's available for anyone to use and adapt to their own learning needs.
## Screenshots
### Frame Selection

This is a screenshot of the frame selection interface. You'll see a signal that represents frame entropy over time. The vertical lines indicate the start and end of a chapter. Within these chapters you can select the frames by clicking and dragging the mouse over the desired range where you think diagram is in that chapter. At the bottom is an option that tells the program to select a specific number of frames from that selection.
### Diagram Extraction

This is a screenshot of the diagram extraction interface. For every selection you've made, there will be a set of frames that you can choose from. You can select and deselect as many frames as you'd like to save.
## Links
- repo: https://github.com/limina1/video_article_converter
- Nostr Apps 101: https://www.youtube.com/watch?v=Flxa_jkErqE
## Output
And now, we have a demonstration of the final result of this tool, with some quick cleaning up. The video we will be using this tool on is titled Nostr Apps 101 by nostr:npub1nxy4qpqnld6kmpphjykvx2lqwvxmuxluddwjamm4nc29ds3elyzsm5avr7 during Nostrasia. The following thread is an analog to the modular articles we are constructing for Alexandria, and I hope it conveys the functionality we want to create in the knowledge space. Note, this tool is the first step! You could use a different prompt that is most appropriate for the specific context of the transcript you are working with, but you can also manually clean up any discrepancies that don't portray the video accurately.
You can now view the article on #Alexandria
https://next-alexandria.gitcitadel.eu/publication?d=nostr-apps-101
Initially published as chained kind 1's
nostr:nevent1qvzqqqqqqypzp5r5hd579v2sszvvzfel677c8dxgxm3skl773sujlsuft64c44ncqy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgwwaehxw309ahx7uewd3hkctcpzemhxue69uhhyetvv9ujumt0wd68ytnsw43z7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qgewaehxw309aex2mrp0yh8xmn0wf6zuum0vd5kzmp0qqsxunmjy20mvlq37vnrcshkf6sdrtkfjtjz3anuetmcuv8jswhezgc7hglpn
Or view on Coracle
https://coracle.social /nevent1qqsxunmjy20mvlq37vnrcshkf6sdrtkfjtjz3anuetmcuv8jswhezgcppemhxue69uhkummn9ekx7mp0qgsdqa9md83tz5yqnrqjw07hhkpmfjpkuv9hlh5v8yhu8z274w9dv7qnnq0s3
-

@ 127d3bf5:466f416f
2025-02-09 03:31:22
I can see why someone would think that buying some other crypto is a reasonable idea for "diversification" or even just for a bit of fun gambling, ***but it is not.***
There are many reasons you should stick to Bitcoin only, and these have been proven correct every cycle. I've outlined these before but will cut and paste below as a summary.
The number one reason, is ***healthy ethical practice***:
- The whole point of Bitcoin is to escape the trappings and flaws of traditional systems. Currency trading and speculative investing is a Tradfi concept, and you will end up back where you started. Sooner or later this becomes obvious to everyone. Bitcoin is the healthy and ethical choice for yourself and everyone else.
But...even if you want to be greedy, ***hold your horses***:
- There is significant risk in wallets, defi, and cefi exchanges. Many have lost all their funds in these through hacks and services getting banned or going bankrupt.
- You get killed in exchange fees even when buying low and selling high. This is effectively a transaction tax which is often hidden (sometimes they don't show the fee, just mark up the exchange rate). Also true on defi exchanges.
- You are up against traders and founders with insider knowledge and much more sophisticated prediction models that will fleece you eventually. You cannot time the market better than they can, and it is their full-time to job to beat you and suck as much liquidity out of you as they can. House always wins.
- Every crypto trade is a taxable event, so you will be taxed on all gains anyway in most countries. So not only are the traders fleecing you, the govt is too.
- It ruins your quality of life constantly checking prices and stressing about making the wrong trade.
The best option, by far, is to slowly ***DCA into Bitcoin*** and take this off exchanges into your own custody. In the long run this strategy works out better financially, ethically, and from a quality-of-life perspective. Saving, not trading.
I've been here since 2014 and can personally attest to this.
<img src="https://blossom.primal.net/35ff641203bf4d197a032a59d6815b99249561bfd3a94b4a908ed5161420466f.jpg">
-

@ ac6f9572:8a6853dd
2025-02-09 01:59:02
# Are you a Bitcoin or Nostr Builder, Engineer, Dev, Coder, Architect... ?
We are opening the community grants for artists to the world and inviting Artists to join remotely the collective that until now has set together this exposition in Chiang Mai, Thailand: **Freedom Tech Art**
1. Create your profile in Geyser
2. Create geyser project with images and description
3. Apply for the SnH grant from https://geyser.fund/grants/15
# Some snapshots


#Hackathon #grownostr #bitcoin #nostr #news #zap #photography #sats #asknostr #plebchain
#lightning #cashu #cryptography ~crypto #devs #dev
originally posted at https://stacker.news/items/880198
-

@ ac6f9572:8a6853dd
2025-02-09 01:54:02
# Are you a Bitcoin or Nostr Artist, Designer, Creative... ?
We are opening the community grants for artists to the world and inviting Artists to join remotely the collective that unntil now has set together this exposition in Chiang Mai, Thailand: **Freedom Tech Art**
1. Create your Artist profile in Geyser
2. Create geyser project and upload your art pieces or selected collection.
3. Apply for the SnA grant from https://geyser.fund/grants/14
# Some snapshots







originally posted at https://stacker.news/items/880193
-

@ fe32298e:20516265
2025-02-09 01:43:24
Alright, Tabby wouldn't work right with CUDA and it was impossible to troubleshoot anything.
Now we're going to try [Twinny](https://github.com/twinnydotdev/twinny).
You'll need:
* Ubuntu 24.04 or some other Linux flavor
* [VSCodium](https://github.com/VSCodium/vscodium)
* GPU with enough VRAM to hold your chosen models
* It might work with just a CPU, give it a try!
# Install Ollama
Ollama loads the AI models into VRAM (and offloads into RAM if needed) and offers inference through an API. The Ollama install script adds a dedicated `ollama` user and a systemd service so that Ollama starts automatically at boot. Ollama will unload models from memory when idle.
```
curl -fsSL https://ollama.com/install.sh | sh
```
## Configuring Remote Ollama
Skip this section if your GPU is on the same machine you're coding from. Ollama and Twinny default to a local configuration.
I'm using Ollama on a separate machine with a decent GPU, so I need to configure it to bind to the network interface instead of `localhost` by editing the systemd service:
1. Edit the service override file:
```
systemctl edit ollama.service
```
1. Add this in the top section. It will be merged with the default service file.
```
[Service]
Environment="OLLAMA_HOST=0.0.0.0:11434"
```
Note: I had a problem with Ollama only binding to the `tcp6` port, and wasted a lot of time trying to fix it. Check with `netstat -na | grep 11434` to see if it only shows tcp6 for port 11434. The workaround for me was using the actual interface IP instead of `0.0.0.0`. If you do this then you'll need to either set `OLLAMA_HOST` in your shell, or specify `OLLAMA_HOST=<hostname>` at the start of every ollama command (or it complains that it can't connect to ollama).
1. Restart Ollama:
```
systemctl daemon-reload
systemctl restart ollama
```
## Download Models
Ollama manages models by importing them into its own special folders. You can use Ollama to download the files from the [Ollama library](https://ollama.com/library), or you can import already-downloaded models by creating a [Modelfile](https://github.com/ollama/ollama/blob/main/docs/modelfile.md). Modelfiles define various parameters about the model and it's important to get them set correctly for the best performance so it's probably better to get them from the library, even though it wastes bandwidth downloading them over and over again for all these tools.
You'll want a model for chatting and a model for fill-in-middle (FIM) that does the code completions.
```
# Chat model, defaults to 7b with Q4_K_M quant, downloads 4.7 GB
ollama pull qwen2.5-coder
# Fill-in-Middle model for code completion, another 4.7 GB
ollama pull qwen2.5-coder:7b-base
```
The RAG/embeddings feature is optional but probably worth using. It needs to run a from local instance of Ollama. The embedding models are very small and run fine on CPU. Most everyone uses `nomic`, but Twinny defaults to `all-minilm`, which is a little smaller.
```
ollama pull all-minilm
```
# Install Twinny
Install the [Twinny extension](https://open-vsx.org/extension/rjmacarthy/twinny) by searching for `twinny` in VSCodium extensions.
Look for the Twinny icon on the left side panel and click it to open the Twinny panel. Be careful if you drag it over to the right side: sometimes it may not appear at all. I managed to make it appear by selecting some text and running a Twinny action on it from the context menu.
Twinny assumes you're using a local instance of Ollama. If you want to use a remote instance then you'll need to go into the **Manage Twinny providers** section (looks like a power plug) and add new providers that point your remote Ollama instance.
These are the settings I'm using for a remote Ollama instance:
## Chat provider
* Type: `chat`
* Provider: `ollama`
* Protocol: `http`
* Model Name: `qwen2.5-coder:latest`
* Hostname: *remote hostname*
* Port: `11434`
* API Path: `/v1` (despite what the Twinny docs and Ollama docs say)
* API Key: *blank*
## FIM Provider
* Type: `fim`
* FIM Template: `codeqwen`
* Provider: `ollama`
* Protocol: `http`
* Model Name: `qwen2.5-coder:7b-base`
* Hostname: *remote hostname*
* Port: `11434`
* API Path: `/api/generate`
* API Key: *blank*
## Embedding Provider
* Type: `embedding`
* Provider: `ollama`
* Protocol: `http`
* Model Name: `nomic-embed-text`
* Hostname: `0.0.0.0`
* Port: `11434`
* API Path: `/api/embed`
* API Key: *blank*
# Use Twinny
## Chat
Select code and it will be used for context in the chat, or right-click selected text to see more options like refactor, write docs, write tests.
## Embeddings
Switch over to the Embeddings tab and click Embed documents to use all the documents in your workspace for more context. Type '@' in the chat to reference the entire workspace, ask about specific problems, or specific files in your chat.
## Code Completion
Suggested stuff shows up in gray italics at the cursor location. Press `Tab` to accept it as a completion.
-

@ 16d11430:61640947
2025-02-09 01:03:30
As fiat currencies continue their slow-motion collapse worldwide, a disturbing pattern is emerging—food security is deteriorating, marked by frequent outbreaks of avian flu, livestock diseases, and supply chain disruptions. While mainstream narratives often blame climate change or random chance, a deeper look reveals that these crises are symptoms of a decaying financial system.
Food shortages, increasing corporate monopolization of agriculture, and government mismanagement are not random events. They are predictable consequences of monetary debasement, supply chain stress, and regulatory capture. Let’s break down how the collapse of fiat money is driving the current food crisis and why things are likely to get worse.
---
1. Early Signs: Inflation and the Cost of Farming Soar
The first cracks in the food supply system appear when inflation begins eating into farmers’ margins. Over the past few years, fertilizer prices have skyrocketed, fuel costs remain volatile, and animal feed has become more expensive due to disrupted global trade.
Example: The 2022 Fertilizer Crisis – As the U.S. and European governments sanctioned Russia, a key global supplier of potash and ammonia (key fertilizer ingredients), prices surged. Farmers in Africa, Asia, and Latin America struggled to afford these inputs, reducing food production.
Egg Prices & Avian Flu – In 2023, egg prices doubled in the U.S. and Europe, exacerbated by avian flu culling millions of hens. However, inflation played a bigger role—higher costs for feed, transport, and farm maintenance made it impossible for smaller producers to compete.
Corporate Centralization – As inflation drives small farmers out of business, giant agribusinesses like Cargill, JBS, and Tyson gain more control, further consolidating the supply chain.
At this stage, the system still functions, but food prices increase, and warning signs emerge.
---
2. Mid-Stage: Supply Chains Crack & Regulatory Failures Accelerate Outbreaks
As inflation worsens, government policies and systemic inefficiencies accelerate decay. Regulations intended to "protect" the market often do the opposite—causing supply shocks and increasing food insecurity.
Avian Flu as a Convenient Cover? – Since 2022, millions of chickens, turkeys, and ducks have been culled globally due to "avian flu outbreaks." The strange part? Many cases are based on PCR tests with high false positives rather than confirmed clinical symptoms. Some suspect regulatory agencies are exaggerating the crisis to justify price hikes and consolidate control.
U.S. Cattle Mysteriously Falling Sick – Reports surfaced in early 2024 of large numbers of cattle experiencing spontaneous respiratory illness and reproductive failures. The USDA and FDA blame viruses, but critics point to contaminated mRNA vaccines or corporate feed modifications.
Dutch Farmers vs. The State – In the Netherlands, one of Europe’s largest food producers, the government attempted to force thousands of farmers to sell their land under the guise of "nitrogen reduction." Many believe this is an effort to centralize control over food production.
At this stage, outbreaks become more frequent—not just due to biological causes, but because of poor regulation, centralized control, and financial stress leading to cost-cutting in food safety.
---
3. Late-Stage: Hyperinflation, Panic, and Rationing
Once inflation turns into hyperinflation, food becomes a political weapon. Governments respond with price controls, forced rationing, and market interventions that make things worse.
Argentina & Venezuela’s Food Rationing – In nations experiencing hyperinflation, like Argentina and Venezuela, supermarket shelves are empty, and the black market determines real prices. Government-issued food ration cards fail to provide reliable access.
French Farmers Revolt Over Regulations & Costs – In 2024, French farmers blocked highways in protest against tax hikes, environmental regulations, and soaring costs. The EU’s green policies, combined with inflation, made food production unviable.
Egg Shortages in the UK – The UK government urged people to eat fewer eggs and replace them with lab-grown alternatives as supermarkets struggled to restock due to avian flu and Brexit-related trade issues.
At this point, government incompetence and corporate profiteering worsen food insecurity, leading to riots, black markets, and authoritarian responses.
---
4. Final Collapse: Mass Starvation or Parallel Systems
As fiat systems implode, parallel markets emerge. People turn to barter, Bitcoin-based trade, and decentralized farming networks to survive.
Bitcoin for Beef – In Argentina and El Salvador, some ranchers have started accepting Bitcoin for direct meat sales, bypassing the banking system entirely.
Local Food Networks Grow – In places where trust in fiat money collapses, local food networks, permaculture movements, and barter systems gain popularity.
Lab-Grown & Insect Protein Push – Meanwhile, governments and billionaires like Bill Gates push for synthetic meat and insect-based diets, claiming they are "sustainable" while continuing policies that destroy natural farming.
At this stage, centralized systems are collapsing, but decentralized alternatives emerge—offering a path forward for those willing to adapt.
---
The Solution: Decentralization & Bitcoin-Based Trade
The fiat food system is failing because it is built on debt, leverage, and market manipulation. To ensure food security, we must return to decentralized, sound-money solutions.
Bitcoin as a Trade Standard – Farmers using Bitcoin escape capital controls and currency depreciation, ensuring fair trade.
Regenerative Agriculture & Local Food Systems – Returning to small-scale, diversified farming reduces the risk of mass outbreaks.
Self-Sovereignty Over Food – Growing your own food, supporting local farmers, and rejecting centralized food policies is the only way to break free from the collapsing system.
---
Conclusion: Recognizing the Signs Before It's Too Late
The rapid spread of avian flu, livestock diseases, and farm shutdowns are not random events. They are early warning signs of systemic decay in the fiat economy. As governments print money and impose short-sighted regulations, food security worsens.
The best way forward is decentralization—of money, farming, and trade. The collapse of fiat will bring hardship, but those who understand the game and prepare accordingly will thrive.
-

@ f33c8a96:5ec6f741
2025-02-09 01:02:51
I have been working on account linking in the backend for a little while and so far only GitHub has been available to users (mostly for following the dev journey on the platform)
Now with this release the existing OAUTH options AND Nostr NIP-07 authentication are surfaced and able to be linked to an existing profile on your settings page.
Put simply this allows you to easily link email, GitHub, and nostr profile in the plebdevs platform to access the same account from different login methods. This will make it much easier to keep the same profile across multiple devices AND make sure that you never lose access!
Let me know what you think and PLEASE LET ME KNOW if you find any bugs! (I love bugs 🐛)
ONWARDS 🫡

originally posted at https://stacker.news/items/880161
-

@ 18e3af1e:1d42e5df
2023-08-13 02:40:19
Las comunidades son creadas mediante el esfuerzo de no solo un individuo, sino al trabajo de docenas; cientos o miles de personas. Mediante la especialización, como especie, logramos entender que: el saber hacer una sola cosa no significa morir de hambre, o no estar bien preparado para un ataque; por lo contrario, el dominio o maestría de una sola cosa... Puede crear una civilización entera.
Permitirnos un enfoque certero para aprender, dominar y amaestrar nuestras actividades en un periodo de tiempo finito, permitió nuestro avance hacia nuevos campos, de hecho, movió nuestra meta en magnitud tal, que al imaginar el pasado (para muchos) parece mas bien una película cómica y sombría.
Hoy en día, en un mundo regido por individualismo en el reino físico, la manifestación de constructores de comunidades sigue presente en el (reino) digital.
### La evolución de la construcción
A lo largo de la historia de la humanidad, la construcción ha evolucionado desde simples refugios hasta monumentos arquitectónicos y estructuras vanguardistas. Los primeros humanos crearon refugios rudimentarios con materiales naturales. Con la civilización, surgieron las primeras estructuras permanentes, como pirámides y templos, reflejando la organización social y creencias religiosas. La antigua Roma introdujo la innovación en la ingeniería con acueductos y arcos.
La Edad Media vio fortificaciones y catedrales góticas que fusionaban espiritualidad y técnica. El Renacimiento abrazó la proporción y la simetría en palacios y edificios renombrados. La Revolución Industrial marcó un cambio radical con el acero y el hormigón, permitiendo rascacielos y puentes icónicos.
El siglo XX trajo consigo la era de los rascacielos y la arquitectura modernista, desafiando límites estructurales y estéticos. La sostenibilidad ganó importancia en el siglo XXI, impulsando la incorporación de tecnologías avanzadas, como la impresión 3D y la construcción modular.
La historia de la construcción es un testimonio de la creatividad y la adaptabilidad humanas, reflejando no solo avances técnicos, sino también valores culturales y aspiraciones.
En el día hoy, los desarrolladores de software y tecnología podrían considerarse como los constructores del próximo siglo. Al igual que los constructores en otras épocas históricas, los desarrolladores de software son responsables de crear estructuras digitales que moldean la forma en que interactuamos, comunicamos y vivimos en el mundo moderno.
A medida que la tecnología continúa avanzando y la sociedad se vuelve cada vez más digital, el papel de los desarrolladores de software se vuelve crucial en la construcción de soluciones tecnológicas que abordan una amplia gama de desafíos.
Así como los arquitectos y constructores antiguos debían entender la física, la estética y las necesidades humanas para diseñar y construir edificios funcionales y atractivos, los desarrolladores de software deben comprender la lógica de programación, la experiencia del usuario, la seguridad cibernética y la innovación tecnológica para crear aplicaciones, sistemas y plataformas que sean útiles y efectivos.
### Individuos que inspiran
La inspiración individual es un poderoso motor de cambio que puede tener un impacto significativo en la mente colectiva de una comunidad o sociedad. Cuando una persona demuestra pasión, determinación y una visión positiva, puede influir en otros a nivel emocional y cognitivo. Aquí hay algunas formas en que la inspiración individual afecta a la mente colectiva:
La gente puede verse reflejada en las luchas y logros de alguien más, lo que crea un sentido de unidad y comunidad. Esto puede generar un mayor apoyo y solidaridad en torno a ciertas causas o valores. Además, la inspiración individual puede llevar a la acción. Cuando las personas son testigos de un individuo que supera obstáculos o logra metas desafiantes, esto puede motivar a otros a enfrentar sus propios desafíos y trabajar hacia sus objetivos. El ejemplo de una sola persona puede encender la chispa de la acción en muchas más.
La inspiración individual puede tener un efecto multiplicador. Cuando una persona inspirada comparte su historia o experiencia, puede inspirar a otros, creando una cadena de influencia que se extiende a través de redes sociales, comunidades y sociedades enteras. Esto puede tener un impacto a gran escala en la mente colectiva.
El individuo inspirador tiene el potencial de influir profundamente en la mente colectiva al cambiar percepciones, motivar la acción y crear una sensación de comunidad y unidad.
### Comunidades: origen, inicios y progreso.
Las comunidades han sido una parte fundamental de la experiencia humana a lo largo de la historia. Desde los primeros tiempos hasta la era moderna, las comunidades han evolucionado y cambiado en respuesta a las necesidades, avances tecnológicos y contextos culturales.
Desde los primeros días de la humanidad, nuestros antepasados se agruparon en pequeñas comunidades para sobrevivir. Estas comunidades eran grupos familiares o tribus que compartían recursos y conocimientos para cazar, recolectar alimentos y protegerse de los peligros. La cooperación y la solidaridad eran esenciales para la supervivencia.
Con el desarrollo de la agricultura, las comunidades evolucionaron hacia asentamientos más permanentes. La capacidad de cultivar alimentos permitió la formación de aldeas y pueblos, donde la gente podía establecerse y construir relaciones más complejas. Esto llevó al surgimiento de una división del trabajo más especializada y al desarrollo de habilidades artesanales.
Las civilizaciones antiguas, como la sumeria, egipcia, griega y romana, dieron paso a la formación de ciudades y sociedades más organizadas. Las comunidades se convirtieron en centros de comercio, gobierno y cultura. Se construyeron estructuras monumentales, como templos y palacios, que unificaron a las personas en torno a creencias religiosas y sistemas políticos.
Durante la Edad Media, las comunidades se organizaron en torno a sistemas feudales. Los señores feudales gobernaban sobre las tierras y las personas locales. Las aldeas y feudos eran autónomos en gran medida y se centraban en la agricultura y la autosuficiencia.
La Revolución Industrial marcó un cambio importante en la estructura de las comunidades. La industrialización dio lugar a la urbanización, con muchas personas dejando las zonas rurales para trabajar en fábricas en las ciudades.
En la era moderna, las comunidades han continuado evolucionando con avances tecnológicos y la globalización. Las redes sociales y las comunicaciones digitales han conectado a personas de todo el mundo, creando comunidades virtuales en línea.
### Bitcoin | Nostr y la chispa del constructor
Como ya vimos, un solo individuo puede inspirar a muchos otros, teniendo un efecto multiplicador. Esto no solo se traduce al mundo físico, por el contrario, esta directamente ligado a nuestra psicología, incluso podemos decir que va aun mas allá, adentrándonos en el terreno ideológico y espiritual.
Hasta hace no mucho, estábamos a merced de las grandes corporaciones que construían todo por nosotros, mientras esperábamos con ansias las nuevas actualizaciones de cada iteración de sus productos. Cada vez mas y mas nos hacíamos dependientes de dichas corporaciones sin quizás notarlo, poco a poco se fueron apoderando de nuestro tiempo y muy insidiosamente de nuestra personalidad e identidad.
Gracias a las alternativas presentadas hoy en día y a los individuos que inspiran a otros, existe la posibilidad de construir algo que va mas allá de las grandes corporaciones, porque transciende no solo el nivel físico y digital, sino que también transciende a los individuos que aportan a la comunidad. Estoy hablando por supuesto de Nostr, y como los incentivos están alineados gracias a Bitcoin.
Pongamos como ejemplo un par de nombres para ilustrar como individuos que inspirar pueden crear una chispa que se extiende a cada persona dentro de la comunidad.
Personajes como nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft nostr:npub1utx00neqgqln72j22kej3ux7803c2k986henvvha4thuwfkper4s7r50e8 nostr:npub1v0lxxxxutpvrelsksy8cdhgfux9l6a42hsj2qzquu2zk7vc9qnkszrqj49 nostr:npub107jk7htfv243u0x5ynn43scq9wrxtaasmrwwa8lfu2ydwag6cx2quqncxg (entre muchos otros que podría mencionar pero todo el articulo seria una lista de nombres) han inspirado a otros desarrolladores, creadores de contenido (y todas las otras especializaciones que te puedas imaginar…) A construir sobre este protocolo. Incluso, personas como el caso mas reciente de nostr:npub1m64hnkh6rs47fd9x6wk2zdtmdj4qkazt734d22d94ery9zzhne5qw9uaks han encontrado inspiración para aprender a programar sobre estos mismos rieles.
> nostr:nevent1qqs8fe938k7j5sxcprrv89ezpu09m9pzm90f0sq24hnwlwu0rmn09qcpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxg5vtygh
La chispa del constructor en palabras mas concisas es: **Inspiración multiplicadora en pos de la productividad y por ende, del crecimiento de una comunidad.**
Sin Bitcoin y Lightning Network, esto seria posible, pero mucho menos efectivo debido a que las personas detrás de toda labor que este enfocada en creación de contenido, desarrollo, etc. Tienen que comer.
### Conclusión
La chispa del constructor radica en la inspiración individual que impulsa a la acción colectiva. Desde la evolución de la construcción hasta las comunidades digitales, **el poder de un individuo inspirado puede moldear el presente y el futuro de las comunidades en todo el mundo.**
-

@ d4309e24:8a81fcb0
2025-02-09 00:16:55
## 1. What if You Could Send a Message into the Future?
Imagine leaving **a message for your future self**, a loved one, or even an entire community—one that no one, not even you, can unlock until a specific moment in time. Picture leaving **a message for your children**, a note of wisdom or love that remains hidden until they're old enough to appreciate it, all timed by Bitcoin's block height. You might also make **a bold prediction** about the future price of Bitcoin, sealing it away until the blockchain reaches a certain block height.
This is the idea behind *Hatchstr*, a decentralized app for time-locked messages that only unlock at predetermined Bitcoin block heights—no central authority required.
### Why Build This?
I want to dive into the Nostr protocol not just by reading documentation, but by actually building something that embodies its core principles: **censorship resistance**, **user ownership**, and **decentralization**. Hatchstr is both an experiment and a contribution to the Nostr ecosystem—a way to test the limits of permissionless communication while learning and engaging with the community.
## 2. The Vision: How Hatchstr Would Work for Users
At its core, Hatchstr lets users create time capsules—encrypted messages that only become readable after a specified Bitcoin block height. Here’s what that looks like:
* You design a capsule with text and images using Hatchstr’s web app.
* You pick an unlock time (e.g., 1000 blocks from now).
* The message is encrypted, locked away, and published as a Nostr event.
* At the chosen time, the decryption key is revealed, allowing the recipient to finally access the message.

#### Potential Use Cases
* **Personal Messages**: Send birthday wishes that unlock at midnight, time-delayed love letters, or notes to your future self.
* **Timed Learning**: Lock educational content to unlock when students reach key learning stages or ages.
* **Creative Storytelling**: Release serialized fiction, riddles, or treasure hunt clues that unlock over time.
* **Community & Events**: Time-gate announcements for Nostr-based communities or scheduled voting mechanisms.
### 3. The Centralized Trap: Why Build on Nostr
When thinking about how to implement this, we could go the obvious, easy route:
* Store messages on a centralized server.
* Release them when the time is right.
* Let users download their messages.
Simple, right? **But is it the right approach? Let's break it down.**
### Why This Fails
* **Single Point of Failure**: If my server goes down, all messages are unavailable.
* **Privacy Risks**: Users would need to trust me not to access their messages.
* **Ownership & Longevity**: What happens if I lose interest? The system dies with me.

A centralized model defeats the purpose of time-locking messages. Users shouldn’t have to trust a third party. We need decentralization.
## 4. Nostr to the Rescue: How Decentralization Can Help
Instead of a single server holding messages hostage, [Nostr](https://nostr.how/en/what-is-nostr) allows users to publish messages to [decentralized relays](https://nostr.how/en/relays). Here are the key differences:
* **Nostr IDs = Self-Owned Identities**: Your public key is your identity, not tied to any company.
* **Relays = Decentralized Bulletin Boards**: Anyone can run one, ensuring redundancy and censorship resistance.
* **Messages = Signed Events:** Cryptographically signed by the sender or encrypted for only the recipient.

### How Nostr Reduces Centralization
In this version of Hatchstr, capsules are still stored in a centralized manner at first until they 'hatch'. However, once the Bitcoin block height condition is met:
* **Capsule Publication**: The system publishes the capsule events to Nostr relays, making the messages available for decryption by the intended recipients.
This approach, while not eliminating the central server, allows for:
* **Third-Party Clients**: Developers can now create clients that interact with Hatchstr capsules on Nostr, enhancing the system's openness and potentially leading to a richer ecosystem around time-locked messages.
* **Decentralized Access**: Even though the initial storage is centralized, the access to the messages becomes decentralized once published to Nostr, reducing the dependency on a single point for message retrieval.
We have some improvements, **but I am sure we can do better!**
## 5. The Path to Decentralized Timekeeping
### The Timeless Nature of Encryption
Encrypted messages exist outside time—once locked, they remain secure indefinitely. Modern cryptography (like AES-256) doesn’t "expire" or weaken unless decrypted (excluding brute force attacks). This creates a paradox: How do you bind something timeless to a specific moment in the physical world?
#### The Time-Lock Puzzle Dilemma
Cryptographers have proposed [time-lock puzzles](https://iacr.org/archive/crypto2019/116940354/116940354.pdf)—encryption that requires sustained computation to unlock, theoretically forcing a minimum wait time. But these face critical hurdles:
* ##### **Hardware Uncertainty**
Solving time depends on an attacker’s computational power. A nation-state could crack in hours what takes years for a regular user.
* ##### **No Real-World Alignment**
Puzzles can’t guarantee unlocks align with calendar dates or real-world events ("unlock on my child’s 18th birthday").
* ##### **Energy Waste**
Requires continuous computation, making it environmentally impractical for longer time locking.
#### Bitcoin as a Decentralized Clock
This is where Bitcoin’s blockchain shines. Its difficulty-adjusted proof-of-work acts as a trustless metronome:
* ##### **Predictable Rhythm**
Despite hash rate fluctuations, the 10-minute block target (via difficulty adjustments) creates a consistent approximation of real-world time.
* ##### **Immutable History**
Block height 1,000,000 will always correspond to the same point in Bitcoin’s timeline, regardless of future changes in mining power
#### **Splitting the Problem**
Hatchstr can bridge timeless encryption and blockchain timing by separating concerns:
##### **1. Capsules** – The time-locked message itself:
* Design independent of the time-locking mechanism.
* Encrypted client-side.
* Content stored anywhere the user wants (IPFS, personal servers, etc.).
* Completely owned by the user—not Hatchstr.
##### **2. Clock Servers** – Independent, lightweight timing nodes that:
* Only publish decryption keys when the target Bitcoin block height is reached.
* Users can choose which Clock Server to trust.
* Anyone can run their own Clock Server.
* Multiple servers can coordinate to prevent a single point of failure.

**This means Hatchstr itself doesn’t store anything—users are fully in control.**
## 6. What Comes Next
This project is just beginning—a blueprint with open questions and untested assumptions. In the next two articles, I’ll explore how to turn this concept into something tangible. First, how we might design playful time capsules that can be displayed faithfully by multiple clients, balancing creativity with decentralization. Then, the messy realities of clock servers: why federating them matters, how to incentivize reliability, and borrow Bitcoin’s rhythm without centralizing control. We will dive into setting up a simple clock server to get things started.
I’m still learning Nostr’s ecosystem, and this project is as much about sharing my education as anything else. If any part of this concept makes you think “yes, but…” or “what if…”, I’d genuinely love to hear it. Find me on Nostr – no expertise required, just an interest in sending messages to the future. :

```
npub16scfufrpsqcukjg7ymu4r40h7j4dwqy4pajgz48e6lmnmz5pljcqh678uh
```
Thank you for reading 🧡
-

@ 16d11430:61640947
2025-02-09 00:12:22
Introduction: The Power of Focused Attention
In an age of distraction, power is not merely held through material wealth, authority, or control over others—it is built through focused attention. The human brain, a complex quantum-biological processor, constructs reality through perception. When harnessed correctly, focused attention allows individuals to transcend limitations, reshape their reality, and live free.
Power, then, is not external—it is a construct supported by the mind and created within the brain. Understanding how this works offers a path to transcendence, autonomy, and liberation from imposed limitations.
The Neuroscience of Focused Attention: Constructing Reality
The brain is a prediction engine, constantly processing information and filtering out irrelevant stimuli. Focused attention directs this process, acting as a spotlight that selects what becomes part of one's conscious experience. This is the fundamental mechanism behind cognitive power.
1. Neuroplasticity: Building Power Through Repetition
The brain adapts to repeated stimuli through neuroplasticity. What one focuses on consistently rewires neural pathways, strengthening certain thoughts, beliefs, and abilities. Over time, this focus builds an internal structure of power—a network of ideas and perceptions that define one’s reality.
If one focuses on problems, they grow.
If one focuses on solutions, they appear.
If one focuses on fear, it shapes perception.
If one focuses on mastery, skills develop.
2. The Quantum Mind: Attention as a Creative Force
Quantum physics suggests that observation influences reality. Just as subatomic particles behave differently when measured, focused attention may act as a force that shapes possibilities into tangible outcomes.
This aligns with the ancient concept that "energy flows where attention goes." What one attends to with intention can manifest as action, opportunity, and ultimately, freedom.
3. The Reticular Activating System (RAS): Filtering Reality
The Reticular Activating System (RAS) in the brainstem acts as a gatekeeper for focus. It determines what information enters conscious awareness. When trained, it can filter out distractions and amplify pathways toward a desired goal.
Want to see opportunities? Program the RAS by setting clear intentions.
Want to break free from limiting beliefs? Train focus away from conditioned fears.
The Mind’s Role: Transcending Limitations
The mind is the interpreter of the brain’s electrical and biochemical activity. While the brain processes raw data, the mind provides meaning. This distinction is crucial because meaning determines how one experiences reality.
1. Breaking Mental Chains: Rewriting Narratives
Most limitations are narratives—stories imposed by culture, society, or personal history. True power lies in rewriting these stories.
Instead of “I am trapped by my circumstances,” shift to “I create my own reality.”
Instead of “I need permission,” shift to “I give myself permission.”
By restructuring meaning, the mind can redefine the limits of what is possible.
2. The Silence Paradox: Accessing Higher States
Silence, both literal and mental, creates space for higher-order thinking. Just as quantum tunneling allows subatomic particles to pass through barriers without energy loss, silence allows the mind to bypass noise and access deeper intelligence.
Meditation, stillness, and solitude amplify internal power.
The ability to not react is a form of control over external influence.
True mastery comes from detachment—engaging the world without being controlled by it.
Transcendence: Living Free Through Mental Autonomy
To transcend means to rise above imposed structures—whether societal, psychological, or energetic. The construct of power built through focused attention allows one to escape control mechanisms and live autonomously.
1. Sovereignty of Mind: Owning One’s Thoughts
A free mind is one that chooses its inputs rather than being programmed by external forces. This requires:
Awareness of mental conditioning (social narratives, propaganda, biases)
Intentional thought selection (curating what enters the mental space)
Guarding attention fiercely (not allowing distraction to hijack focus)
2. Detachment From Control Structures
Society operates on the principle of attention capture—through media, politics, and algorithms that direct thought patterns. Escaping these requires detachment.
Do not react emotionally to fear-based programming.
Cultivate independent thought by questioning imposed narratives.
Reduce external noise to amplify internal wisdom.
3. The Flow State: Moving Beyond Constraints
When focus is refined to its highest degree, one enters flow state—a condition where action and awareness merge, and limitations dissolve.
In flow, work becomes effortless.
Creativity becomes boundless.
Freedom becomes not just a philosophy, but a lived experience.
Conclusion: The Mind as the Ultimate Key to Freedom
Power is not an external possession—it is the ability to direct one’s own focus. Through the interplay of brain function, cognitive attention, and mental discipline, one constructs personal sovereignty. The individual who masters focus, controls reality.
Freedom is not given. It is built—through attention, intention, and an unwavering commitment to mental autonomy.
-

@ 16d11430:61640947
2025-02-08 23:54:40
Language is more than just words—it’s a pattern, a rhythm, a system of meaning that our brains decode in different ways. While most people learn language analytically, breaking it down into individual words and sentences, gestalt language processors (GLP) acquire language in a completely different way. They learn in chunks, grasping entire phrases and only later dissecting them into smaller parts.
This unique method of language acquisition is often observed in autistic individuals and those with alternative cognitive processing styles. But what happens when such a learner interacts with a highly inflected, agglutinative language like Malayalam? As it turns out, Malayalam might be one of the best-suited languages for gestalt language processors, thanks to its natural structure, flexible syntax, and phrase-based meaning.
Let’s explore why Malayalam aligns so well with gestalt processing and how it compares to other languages.
---
Understanding Gestalt Language Processing
Gestalt language processing is the ability to acquire and use language in whole phrases rather than as individual words. Instead of learning word-by-word, GLP learners store entire sentences or expressions they hear and later modify them into new, meaningful statements.
For example, a child who is a gestalt processor might initially say:
➡ "Do you want some juice?" (because they've heard it as a whole phrase)
Later, they might extract parts and start saying:
➡ "Want juice."
Finally, they construct their own original sentence:
➡ "I want juice."
This approach is pattern-based rather than rule-based, making Malayalam an excellent match due to its agglutinative grammar, rhythmic structure, and flexible word order.
---
How Malayalam Supports Gestalt Language Processing
1. Malayalam’s Agglutinative Nature Encourages Chunk Learning
Malayalam, like other Dravidian languages, is highly agglutinative, meaning words are built using multiple suffixes that change meaning. Instead of discrete words, many phrases function as a single semantic unit—which is exactly how GLP learners process language.
Take the word "വീട്" (vīṭu) meaning "house":
വീട്ടിൽ (vīṭṭil) – in the house
വീട്ടിലേക്ക് (vīṭṭilēkk) – towards the house
വീട്ടിലേക്കു പോകുന്നു (vīṭṭilēkku pōkunnu) – going to the house
A gestalt processor might first acquire "വീട്ടിലേക്കു പോകുന്നു" as a chunk, rather than breaking it into individual words. Over time, they start recognizing patterns and modifying them.
This is in contrast to English, where "going" and "house" are learned separately before forming a phrase like "going to the house."
---
2. Flexible Word Order Aligns with Pattern-Based Learning
Malayalam allows word order variations without losing meaning, making it an intuitive fit for gestalt learners who focus on meaning first rather than strict syntax.
For example, the sentence "I drank tea" can be expressed in multiple ways in Malayalam:
ഞാൻ ചായ കുടിച്ചു. (ñān cāya kuṭiccu) – Standard word order
ചായ ഞാൻ കുടിച്ചു. (cāya ñān kuṭiccu) – Emphasizing "tea"
കുടിച്ചു ഞാൻ ചായ. (kuṭiccu ñān cāya) – Focus on the action
A gestalt learner might acquire an entire phrase like "ചായ കുടിക്കണോ?" ("Do you want tea?") and later extract the verb "കുടി" (drink) or the noun "ചായ" (tea) as they develop more flexible speech.
In contrast, languages like English and French have more rigid word order, making it harder for gestalt learners to generalize.
---
3. Long and Embedded Sentence Structures Favor Chunk-Based Processing
Malayalam commonly uses long, nested sentences, which gestalt learners store as full units before breaking them down.
For example:
അവൻ പറഞ്ഞത് ഞാൻ അറിഞ്ഞില്ല.
(avan paṟaññatu ñān aṟiññilla)
Literal: "What he said, I didn’t know."
Gestalt learners may first acquire: "അവൻ പറഞ്ഞത്" ("What he said") as a single unit before extracting "പറഞ്ഞത്" (said).
This mirrors how **gestalt processors extract meaning from larger linguistic units over time.
-

@ 25c48353:bbf9841d
2025-02-08 23:44:56
One way parents can protect their children in cyberspace is by knowing what cyberspaces your children like to engage with. Today, we'll explore 4 apps that the DOJ has found criminals on.
## **Here are the apps**
1. Cash App
2. Valorant
3. Discord
4. Telegram
## **Background on the Data**
At Defend All Kids, our mission is to **protect children in cyberspace.** But in order to do so, we must ask an important question:
*What digital spaces do children frequently visit?*
In order to find answers to this question, we looked at the [Department of Justice Press Releases page](https://www.justice.gov/news/press-releases), and scraped all of the 676 press releases having anything to do with child abuse. The 4 applications listed above were common apps that we found. Now, we'll go one by one.
## **Cash App: 2 Press Releases**
This app was mentioned twice in the DOJ press releases, and both times were pertaining to the same criminal. In this case, the criminal used Cash App to pay young boys bribes to engage in sexually explicit activities. The link to Cash App is [here](https://cash.app/)
## **Valorant: 2 Press Releases**
Valorant is an online first-person shooter game. A predator used this platform to talk to young boys and convince them to do sexual favors for them. The link to Valorant is [here](https://playvalorant.com/en-us/).
## **Discord: 3 Press Releases**
Discord is a group messanging platform where people of similar interests can join and chat. One of the most common use cases for Discord is gaming communities. A predator used a gaming community discord to lure boys to engage in sexually explicit activities. The Link to Discord is [here](https://discord.com/).
## **Telegram: 5 Press Releases**
Telegram is an instant messaging service that many people use to send anonymous messages. In some of the cases the DOJ reported, predators were using the platform to lure in children and to force them to engage in sexually explicit activities. The link to Telegram is [here](https://telegram.org/).
## **Defend All Kids Recommendation:**
As you can see from the above applications, the main way predators can get to your children is from one thing:
***Access to software that let strangers talk to each other.***
We recommend that you talk to your child and see if he/she have any of these apps, and if they do, talk to them about their online behavior.
-

@ 19745f2c:a997836d
2025-02-08 23:36:31
One way parents can protect their children in cyberspace is by knowing what cyberspaces your children like to engage with. Today, we'll explore 4 apps that the DOJ has found criminals on.
## **Here are the apps**
1. Cash App
2. Valorant
3. Discord
4. Telegram
## **Background on the Data**
At Defend All Kids, our mission is to **protect children in cyberspace.** But in order to do so, we must ask an important question:
*What digital spaces do children frequently visit?*
In order to find answers to this question, we looked at the [Department of Justice Press Releases page](https://www.justice.gov/news/press-releases), and scraped all of the 676 press releases having anything to do with child abuse. The 4 applications listed above were common apps that we found. Now, we'll go one by one.
## **Cash App: 2 Press Releases**
This app was mentioned twice in the DOJ press releases, and both times were pertaining to the same criminal. In this case, the criminal used Cash App to pay young boys bribes to engage in sexually explicit activities. The link to Cash App is [here](https://cash.app/)
## **Valorant: 2 Press Releases**
Valorant is an online first-person shooter game. A predator used this platform to talk to young boys and convince them to do sexual favors for them. The link to Valorant is [here](https://playvalorant.com/en-us/).
## **Discord: 3 Press Releases**
Discord is a group messanging platform where people of similar interests can join and chat. One of the most common use cases for Discord is gaming communities. A predator used a gaming community discord to lure boys to engage in sexually explicit activities. The Link to Discord is [here](https://discord.com/).
## **Telegram: 5 Press Releases**
Telegram is an instant messaging service that many people use to send anonymous messages. In some of the cases the DOJ reported, predators were using the platform to lure in children and to force them to engage in sexually explicit activities. The link to Telegram is [here](https://telegram.org/).
## **Defend All Kids Recommendation:**
As you can see from the above applications, the main way predators can get to your children is from one thing:
***Access to software that let strangers talk to each other.***
We recommend that you talk to your child and see if he/she have any of these apps, and if they do, talk to them about their online behavior.
-

@ 16d11430:61640947
2025-02-08 23:31:00
A Hitchhiker’s Guide to Intergalactic Trade, Verified on the Blockchain
Somewhere in the unfashionable backwaters of the Milky Way, a small blue planet is busy debating whether it should be more concerned about social media algorithms or the growing irrelevance of its own economy. Meanwhile, out there in the cosmic gigaverse, civilizations with far more interesting problems are engaging in the great intergalactic hustle—trading tech, swapping energy signatures, and making quantum side deals faster than you can say "proof-of-work."
Humanity, as per usual, has arrived late to the party but is hoping to slip in unnoticed and pretend like it’s been part of the game all along. The problem? We don’t know the rules, we don’t know what we have to offer, and most importantly, we don’t even have an invite.
Fortunately, the universe is a decentralized, peer-to-peer system, much like Bitcoin—only with fewer arguments on Twitter. And if we play this right, we might just hustle our way into the Universal Indira Net, the cosmic marketplace where civilizations exchange technology, knowledge, and, quite possibly, dad jokes that transcend space-time.
---
Step 1: Plugging into the Universal Indira Net
According to ancient Hindu mythology, Indra’s Net is an infinite web where each node reflects all others, meaning everything is connected to everything else, forever. Sounds poetic, right? Well, take that concept, throw in some decentralized cryptographic verification, and you've got the backbone of a cosmic trade network where trust isn’t just assumed—it’s mathematically proven.
In theory, Earth should be able to sync up with the Universal Indira Net, but there’s one small problem: our civilization hasn’t even solved its own internet yet. Forget interstellar trade—we still struggle with buffering. Until we build long-range, high-bandwidth, interference-proof communication systems, we’re basically screaming into the void, hoping someone hears us (and doesn’t immediately categorize us as "primitive and likely to start wars over fictional borders").
Luckily, we are making some progress:
NASA’s Laser-Based Comms: Just last year, NASA’s Deep Space Optical Communications (DSOC) project sent data 19 million miles at broadband speeds. In galactic terms, this is the equivalent of tossing a USB drive across your front yard, but hey, it’s a start. (source)
Quantum Entanglement Messaging: Scientists are theorizing about using spooky action at a distance to send information instantaneously across the galaxy. Of course, it’s still at the “we swear this works on paper” stage.
Gravitational Wave Emails: There’s a wild theory that gravitational waves could be harnessed for communication, which means the universe has literally been shaking with missed calls for billions of years.
If we can bootstrap any of these into a reliable cosmic broadband, we might just be able to negotiate our way into the interstellar group chat.
---
Step 2: What Do We Bring to the Table?
Now, assuming we finally manage to stop talking to ourselves and make first contact, the next big question is: what the hell do we trade?
Here’s what we know about intergalactic economics:
1. No one wants our money – Fiat currency is an Earth-only meme. The only currency that might hold value out there is Bitcoin, because at least it’s energy-backed and provably scarce. But even then, aliens are likely using something far more advanced—probably a universal ledger that encodes information directly into quantum spacetime fabric.
2. Physical goods are inefficient – Nobody’s going to fly across light-years to pick up a shipment of human-made Teslas when they can 3D print their own antimatter-powered space yacht.
3. Knowledge is king – The real hustle is in information. Code, algorithms, AI models—things that can be transmitted at the speed of light and verifiably proven on-chain.
Trade Goods That Might Actually Be Worth Something:
AI & Quantum Computing Models – If we develop AI that thinks in ways alien civilizations haven’t considered, we’ve got intellectual property worth trading.
Biological Engineering & Longevity Tech – If Earth figures out how to stop aging, you can bet intergalactic billionaires (assuming they exist) would pay for that.
Mathematical Breakthroughs – Math is the universal language, and if we crack new fundamental theorems, we might just have something of value.
Which means the best way to hustle our way into the Indira Net is to become the best at something. And right now, the only thing we’ve truly mastered is making memes and overcomplicating financial systems.
---
Step 3: Navigating the Cosmic Trade Rules
Of course, even if we have something valuable, trading with advanced civilizations isn’t as simple as sending an invoice.
We don’t even know the rules of interstellar engagement yet. But if galactic trade works anything like human history, we should expect:
Regulatory Compliance – Because even in space, there’s bound to be paperwork. If we get lucky, aliens might use smart contracts instead of lawyers.
Sanctions & Trade Embargoes – You think Earth’s geopolitics are complicated? Try interstellar diplomacy, where embargoes might involve entire planetary quarantines.
Intellectual Property Theft – If we’re not careful, we might trade away humanity’s most valuable discovery for an alien NFT that depreciates instantly.
Which is why any trade network must be built on provable, immutable verification systems—aka, blockchain.
This is where DamageBDD, Bitcoin, and cryptographic proofs come into play. If we can create a system that ensures:
✅ Technology is verified before it’s traded
✅ Ownership and utility are recorded on an immutable ledger
✅ Contracts execute autonomously with zero-trust mechanics
Then we might just stand a chance of becoming a respected node in the Universal Indira Net, rather than a civilization that gets rug-pulled by intergalactic venture capitalists.
---
Final Thought: The Cosmic Hustle is Just Beginning
Humanity is still in the tutorial level of the interstellar economy. We’re fumbling with our first trade attempts, trying not to get exploited, and desperately figuring out how not to be the cosmic equivalent of a developing nation selling raw materials to advanced intergalactic conglomerates.
But if we:
Build high-speed interstellar comms
Develop technology that is uniquely valuable
Create trustless, verifiable trade systems
…then we won’t just be another planetary backwater. We’ll be a node in the greatest decentralized network of all time.
The Cosmic Hustle is real. The only question is: will we be the hustlers or the ones getting hustled?
-

@ daa41bed:88f54153
2025-02-08 23:29:14
Imagine a world where governments, long trusted to protect fiat currencies that can be printed without limit, openly declare that they trust a decentralized digital asset over traditional money. In recent months, that vision has begun to crystallize.
The Czech National Bank has signaled a gradual acceptance of digital assets as part of its broader monetary policy recalibration with changes to how capital gains taxes are handled on Bitcoin and a possible adoption by its central bank into its reserves stockpile. Simultaneously, El Salvador- once the poster child for Bitcoin as legal tender- has fine-tuned its policy framework at the behest of the WEF to no longer accept Bitcoin as legal tender. Meanwhile, several U.S. states have introduced bills to establish official Bitcoin reserves, and many are under active consideration. See [Bitcoin Laws](https://Bitcoinlaws.io/) for a full breakdown of where these bills stand. Let's explore the pros of governments adopting strategic Bitcoin reserves.
Bitcoiners have long argued that the ultimate endorsement of Bitcoin comes when even the most established state institutions place their trust in it. Recent moves by several U.S. states—where lawmakers are proposing legislation to create official Bitcoin reserves—lend credence to this argument. When state governments start to codify the creation of a Bitcoin reserve, it signals that even entities steeped in traditional financial orthodoxy now recognize Bitcoin as a viable, strategic asset. For these states, it is imperative to accumulate hard assets like Bitcoin in reserves as they have no control over the monetary supply and, therefore, can suffer from debasement just as much as any citizen or sovereign nation not in control of their currency.
Suppose you have kept up with [recent news](https://decrypt.co/303304/czech-central-bank-bitcoin-reserve) that the Czech national bank was considering holding a considerable portion of their assets in Bitcoin. In that case, you understand the paradigm shift we are seeing. Banks are becoming less cautious in handling digital assets in a stark department, compared to previous dismissals of cryptocurrencies as genuine assets. While it is true that European Central Bank president Christine Lagarde wields considerable influence on monetary policy in Europe and may have put a temporary damper on the Czech central bank's aspirations for now ([See Reuters](https://www.reuters.com/markets/europe/ecbs-lagarde-slaps-down-czech-proposal-Bitcoin-reserves-2025-01-30/)), it should be evident that in the words of some Bitcoiners, "nothing stops this train." For Bitcoiners, such shifts validate the claim that Bitcoin's decentralized, algorithmic structure outperforms fiat systems, which are vulnerable to political manipulation and unchecked inflation. The Czech president's [signing into law](https://www.coindesk.com/policy/2025/02/06/czech-republic-to-eliminate-taxes-on-long-term-crypto-gains) a bill removing capital gains tax from all Bitcoin held for at least three years proves that even those at the highest levels of policy creation are beginning to lose control of the narrative.
This state endorsement is more than symbolic. It is a strategic vote of confidence in Bitcoin's underlying technology—its transparent, immutable ledger and deflationary nature. When lawmakers and regulators in the United States start to invest public resources in Bitcoin, it undermines the decades-old narrative that only traditional assets like gold or oil are worthy of state backing. Instead, it repositions Bitcoin as an asset not just with a future but of the future. It can enhance and even replace all other existing reserve assets, lending further proof of Bitcoin as a store of value.
Bitcoin's capped supply is at the core of its appeal—only 21 million coins will ever exist. Bitcoiners assert that this scarcity is fundamental to Bitcoin's value proposition. A strategic Bitcoin reserve at any governmental level would effectively lock away a significant portion of the circulating supply, increasing its scarcity and further driving its price up.
Many in the Bitcoin and overall crypto community lauded President Bukele's 2021 announcement that his country would begin accumulating Bitcoin and giving it legal tender status. To Bitcoiners, it was a sign that governments were starting to see Bitcoin as a legitimate store of value, a medium of exchange, and vindication of everything they had fought for over the years. Of course, many will want to say that the country's acquisition of Bitcoin was simply a power play to get the World Economic Forum to come to the bargaining table, but if so, what? Here we are four years later, and El Salvador is [no longer requiring Bitcoin as legal tender](https://newsroompanama.com/2025/02/07/el-salvador-ends-Bitcoin-as-legal-tender-heres-why-Bitcoin-didnt-work/). This is not a step back, it is simply another example of why we are winning. I'll discuss this further in another article, but isn't it convenient that President Bukele continues to accumulate Bitcoin for his country after making a concession to the WEF for funds? Tick, tock, next block.
Bitcoiners view introducing reserve bills across U.S. states as a powerful mechanism for further tightening Bitcoin's available supply. Each government-held coin is one fewer coin available to the market, creating a scarcity premium. Market forces do not artificially impose this scarcity but are instead the natural outcome of an institution with deep pockets choosing to hold Bitcoin as a strategic asset. In a world where every coin in reserve represents a bulwark against inflation and economic uncertainty, Bitcoiners argue that this state-induced scarcity will profoundly affect Bitcoin's value over time. If you don't believe that to be the case, look at this chart of coins available on OTC desks last year, and let me tell you that you are not bullish enough. I'll explore the impact of OTC sales on price in a future article.

For years, Bitcoiners have decried the inherent weaknesses of fiat currencies—specifically, the ease with which governments can expand the money supply, leading to inflation and eroded purchasing power. Bitcoin, on the other hand, offers a fixed supply, decentralized issuance, and an ever-shrinking inflation rate that makes it immune to the government's printing press.
When a government opts for Bitcoin reserves, it makes a financial decision and a political statement. It says that the era of limitless money printing is over and that transparency, decentralization, and scarcity are the hallmarks of a sound monetary system. Institutional legitimacy is crucial for any asset that aspires to be a cornerstone of the global financial system.
When the United States, the world's largest economy, signals its intent to hold Bitcoin in its reserves, it sends a resounding message that can trigger a domino effect worldwide. The recent [repeal of SAB121](https://cointelegraph.com/news sec-cancels-crypto-accounting-guidance-sab-121) by the Securities and Exchange Commission is a step in the right direction, by now allowing companies and course, governments at every level to accumulate Bitcoin into their reserves. When central banks like the Czech National Bank begin to signal openness toward digital assets, it paves the way for broader institutional participation. Once wary of the volatile digital asset market, financial institutions, asset managers, and [even pension funds](https://www.wpr.org/news/wisconsin-pension-fund-bitcoin) are gradually warming up to Bitcoin.
We cannot underestimate what sort of network effect this will have on Bitcoin as its utility and value proposition become more robust as a result of state-level adoption. Bitcoiners believe that such a shift will cement Bitcoin's status as a universally accepted and trusted store of value, capable of challenging—and eventually surpassing—traditional reserve assets like gold and fiat currencies.
One of the most enduring arguments among Bitcoiners is that Bitcoin is the digital successor to gold. For centuries, gold has been the haven, the ultimate store of value during times of crisis. Bitcoin, with its fixed supply and digital accessibility, is ideally positioned to take over that role in the modern era. A state-backed Bitcoin reserve would serve as this narrative's definitive stamp of approval. If a government is willing to set aside billions of dollars in a digital asset, it must believe that this asset can preserve and even appreciate its value over time. Such a move would provide a critical psychological boost to the market, as both retail and institutional investors begin to see Bitcoin as not just a speculative tool but as the modern equivalent of a haven set. Gold continues to appreciate this year while Bitcoin remains relatively flat. How long until we see it decouple from the markets and witness price appreciation not seen since the last halving?
I hope you enjoyed reading this lengthy article on the pros of governments adopting a strategic Bitcoin reserve. If you'd like to chime in, you can find me on Nostr via [@geek](https://www.primal.net/geek) on Primal, or via [my npub]( .npub1m2jphmdkskgnvwl5gplksl9e0zwv2sldqf9mwlpz6tyymz84g9fsqr3wgu) anywhere else. In part two, I will examine the other side of the debate, the cons, and the potential pitfalls of such a policy. Stay tuned!
-

@ a012dc82:6458a70d
2025-02-08 22:44:44
The world of cryptocurrency has always been a rollercoaster of highs and lows, but recent developments in the Bitcoin market have caught the attention of investors worldwide. The circulating supply of Bitcoin in profit has surged to a multi-year high, a phenomenon not seen since the heady days of November 2021 when Bitcoin reached its all-time high. This significant milestone, backed by data from industry analysts at Glassnode and a detailed report from Bitfinex, paints a picture of a robust Bitcoin market. The implications of this surge are far-reaching, affecting not just seasoned cryptocurrency traders but also new investors who are contemplating dipping their toes into the Bitcoin pool. This article aims to dissect this trend, exploring its roots, its impact on the market, and what it potentially spells out for the future of Bitcoin investment.
**Table Of Content**
- Understanding the Surge
- Implications for Long-term Investors
- Market Strength and Investor Confidence
- Potential Early Signs of a Bull Market
- Caution and Market Dynamics
- Conclusion
- FAQs
**Understanding the Surge**
The surge in Bitcoin's circulating supply in profit is a complex phenomenon, driven by a confluence of market dynamics and investor behavior. The recent increase in Bitcoin's price, which saw it soar above $37,000, is a primary factor. This price hike has pushed a significant portion of Bitcoin into profitable territory. According to the Bitfinex report, over 16.3 million Bitcoin, a staggering amount by any measure, are currently in profit. This figure is considerably higher than the historical average, suggesting a market that is not only recovering but thriving. The surge is not just a momentary blip but a reflection of deeper market trends, including increased institutional interest in Bitcoin, broader acceptance of cryptocurrencies as a legitimate asset class, and the growing perception of Bitcoin as a hedge against inflation and currency devaluation.
**Implications for Long-term Investors**
For long-term investors, this surge in Bitcoin's profitability is a beacon of stability in the typically volatile cryptocurrency market. The fact that 70% of Bitcoin's total circulating supply has remained static over the past year is indicative of a maturing market where investors are increasingly viewing Bitcoin as a long-term investment rather than a quick profit opportunity. This holding pattern contributes to a tightening of supply, which, coupled with increasing demand, can lead to a sustained price increase. However, long-term investors should also be aware of the potential risks. The cryptocurrency market is still relatively young and can be influenced by regulatory changes, technological advancements, and shifts in investor sentiment. Therefore, while the current trend is encouraging, it should be viewed within the broader context of market dynamics.
**Market Strength and Investor Confidence**
The current state of the Bitcoin market is a testament to its growing strength and the confidence it instills in investors. With a majority of holders seeing positive returns, there's a renewed vigor in the market, attracting both retail and institutional investors. This influx of new investment can further stabilize the market and potentially drive prices higher. However, this increased investor confidence must be tempered with a degree of caution. The cryptocurrency market is known for its rapid fluctuations, and what goes up can just as quickly come down. Investors should be mindful of the inherent risks and conduct thorough research before making any investment decisions. The market's strength, while promising, is not a guarantee of future performance, and a prudent investment strategy should always be in place.
**Potential Early Signs of a Bull Market**
The analysis by Bitfinex suggests that the market might be in the early stages of a bull market. This is a significant indicator for investors, as bull markets are characterized by rising prices and increased buying activity. If this trend continues, it could lead to substantial gains for those invested in Bitcoin. However, predicting market movements, especially in the volatile world of cryptocurrencies, is fraught with uncertainty. While the signs are positive, they are not infallible indicators of future performance. Investors should therefore approach this potential bull market with optimism tempered by realism, recognizing that market conditions can change rapidly and without warning.
**Caution and Market Dynamics**
In the face of these optimistic trends, a word of caution is warranted. The cryptocurrency market is notoriously unpredictable, and while the current indicators are positive, they are not immune to sudden and unexpected changes. Factors such as regulatory announcements, technological breakthroughs, or macroeconomic shifts can rapidly alter the market landscape. Therefore, investors should remain vigilant, keeping abreast of market news and trends. Diversification of investments, a keen understanding of market dynamics, and a clear investment strategy are essential tools in navigating the complexities of the Bitcoin market.
**Conclusion**
The surge in Bitcoin's circulating supply in profit to a multi-year high marks a significant milestone in the cryptocurrency's journey. It reflects a market that is gaining maturity, strength, and the confidence of its investors. This development could herald the beginning of a new era for Bitcoin, characterized by stability and sustained growth. However, the path of Bitcoin and the broader cryptocurrency market remains unpredictable. Investors should therefore approach this market with a well-informed strategy, balancing optimism with a healthy dose of caution. In the ever-evolving world of cryptocurrency, staying informed and adaptable is key to navigating the market's highs and lows.
**FAQs**
**How does this surge affect long-term investors?**
Long-term investors may see this as a sign of market stability and maturity, indicating that Bitcoin is increasingly being viewed as a viable long-term investment.
**Could this trend indicate the start of a Bitcoin bull market?**
While the surge in profitable Bitcoin supply could be an early sign of a bull market, predicting market movements in the volatile cryptocurrency sector is complex and uncertain.
**What percentage of Bitcoin's circulating supply is currently in profit?**
Over 83% of Bitcoin's circulating supply is reported to be in profit, according to recent data.
**What should investors be cautious about in light of this surge?**
Investors should be aware of the inherent volatility in the cryptocurrency market and consider factors like regulatory changes, technological advancements, and broader market dynamics before making investment decisions.
**How does the current Bitcoin market compare to historical averages?**
The current percentage of Bitcoin in profit is significantly higher than the historical average, indicating a particularly strong market phase.
**That's all for today**
**If you want more, be sure to follow us on:**
**NOSTR: croxroad@getalby.com**
**X: [@croxroadnews.co](https://x.com/croxroadnewsco)**
**Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)**
**Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)**
**Store: https://croxroad.store**
**Subscribe to CROX ROAD Bitcoin Only Daily Newsletter**
**https://www.croxroad.co/subscribe**
***DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.***
-

@ c1e6505c:02b3157e
2025-02-08 21:52:51
\*\*\*"Time is the best teacher but unfortunately it kills all of its students."\*\*\* I'm currently visiting my dad for a few days as I had to take my car in for some repairs and maintenance, which included an oil gasket leak, power steering fluid flush, brake fluid flush, spark plugs, and the works. The process took a couple of hours to complete, so instead of waiting in the waiting room or having someone pick me up to go wait comfortably at home, I decided to walk around with my camera and try to make some new work. I have to say, there's really nothing more that I enjoy than walking aimlessly in an area that I have never been and taking photographs. \*I love it.\* I lose myself and everything that is on my mind that I "worry" about. I'm present, in the zone, and honestly having a great time. Photography for me is a portal to enter a state of mind that transcends time and space. The area that I was in was very industrial, so my walk started next door at the other car mechanic shop, and I meandered down to the small local town where some shops were. Didn't see too much, so I turned around and started walking back down the other way. Sometimes I don't see anything of interest for a while. What I have noticed though, as a little trick to start having things "come out of the woodwork," is just to start shooting at the first thing that captures my interest. Getting the ball rolling with pushing the shutter somehow gets me in the "flow state" that I enjoy getting in when making photographs. \\\[ !\[\](https://substackcdn.com/image/fetch/w\_1456,c\_limit,f\_auto,q\_auto:good,fl\_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F027a5466-47a8-4c9a-b3dc-c9acf0a31a12\_2500x1786.jpeg)\\\]( As I walked further, I visited a plant nursery that was just opening. The woman who was opening the gate was very nice and invited me into walk around and do as I please. There were a few nice plants around, but what gravitates me the most is seemingly, to others maybe, the "ugly stuff" or the subject matter that one wouldn’t really consider making a photograph of. Blank spaces, trash, neglect - it's all good stuff to me. The light falling upon these subjects makes them interesting. After the nursery, I found a large industrial facility and a train yard. A worker stood next to one of the train cars, so I went up and asked what they were loading. He said that he’s been working there for 30 years, and that they make plastic trash bags, and those tubes feeding into the train cars were pumping out plastic beads for production. I thought that was interesting. We chatted for a bit, I thanked him for his time, and moved on. !\[\](https://substackcdn.com/image/fetch/w\_1456,c\_limit,f\_auto,q\_auto:good,fl\_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F70512ba8-8c29-4454-8cd7-3d030c17730f\_1786x2500.jpeg) !\[\](https://substackcdn.com/image/fetch/f\_auto,q\_auto:good,fl\_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F70512ba8-8c29-4454-8cd7-3d030c17730f\_1786x2500.jpeg) !\[\](https://substackcdn.com/image/fetch/w\_1456,c\_limit,f\_auto,q\_auto:good,fl\_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2Fd3d8ef1c-4381-49f2-a5cd-5266f3208d91\_2500x1786.jpeg) !\[\](https://substackcdn.com/image/fetch/w\_1456,c\_limit,f\_auto,q\_auto:good,fl\_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F2b32f8fd-2f47-4f6a-9592-9fba9d3e6e57\_2500x1786.jpeg) !\[\](https://substackcdn.com/image/fetch/w\_1456,c\_limit,f\_auto,q\_auto:good,fl\_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2Fb8716d86-acdb-4b3a-a61b-8c1abb6ab737\_2500x1786.jpeg) !\[\](https://substackcdn.com/image/fetch/f\_auto,q\_auto:good,fl\_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F9d7bc288-0707-4e17-a420-aa08fb53b817\_2500x1670.jpeg) !\[\](https://substackcdn.com/image/fetch/w\_1456,c\_limit,f\_auto,q\_auto:good,fl\_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F499acae7-e563-45fd-86b7-32ae3d20150f\_2500x1786.jpeg) !\[\](https://substackcdn.com/image/fetch/w\_1456,c\_limit,f\_auto,q\_auto:good,fl\_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2Ff626a80d-5a43-485e-a50c-747c346388a0\_1670x2500.jpeg) !\[\](https://substackcdn.com/image/fetch/w\_1456,c\_limit,f\_auto,q\_auto:good,fl\_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F472d5556-7ef4-4f6a-a48e-7eccf39088d3\_2500x1670.jpeg) !\[\](https://substackcdn.com/image/fetch/w\_1456,c\_limit,f\_auto,q\_auto:good,fl\_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F724c8133-fe4e-41c4-b383-3aaec42d50a1\_2500x1786.jpeg) Eventually, I ended up at a church with these really nice orange and brown doors. I sat on a bench in the back to kill some time, listening to a few podcasts. While I was there, I noticed a sign that read: \*"Happy moments, praise God. Difficult moments, seek God. Quiet moments, worship God. Painful moments, trust God. Every moment, thank God."\* I’m not a religious guy per se, haven’t been to church in over a decade, and I’ve had my own experiences — psychedelics included — where I’ve glimpsed something I’d call “God.”, but there’s something to take from that. Whatever your definition of “God” is, there’s value in gratitude whether things are good or bad. Life itself is a miracle. Appreciating the small things keeps you grounded, humble, and connected. !\[\](https://substackcdn.com/image/fetch/f\_auto,q\_auto:good,fl\_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F102b529f-a7ea-4346-889b-2b1f51b48c63\_2500x1786.jpeg) !\[\](https://substackcdn.com/image/fetch/w\_1456,c\_limit,f\_auto,q\_auto:good,fl\_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2Fef07f101-4645-4439-b050-72c9fe551b1f\_1786x2500.jpeg) !\[\](https://substackcdn.com/image/fetch/f\_auto,q\_auto:good,fl\_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2Fce6960c5-e78c-4b3e-b0fe-78e773b6a518\_2500x1786.jpeg)) \*Just in case you missed it…\* \*\*I have a limited edition framed print that I will have available until February 28th.\*\* Only two will be made, and they will come framed; one in black, one in silver. If you enjoy my work, this would be a great collectors piece. !\[\](https://substackcdn.com/image/fetch/w\_1456,c\_limit,f\_auto,q\_auto:good,fl\_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F3d3033ae-b71a-4505-9d2c-f899df1a535b\_2313x2313.jpeg)\\\]() \*\*\*I shoot with a Leica M262, and edit in Lightroom + Dehancer\*\*\* \[\*\*\*Use “PictureRoom” for 10% off Dehancer Film\*\*\*\](https://www.dehancer.com/shop/pslr/film) If you’ve made it this far, thank you for taking the time to view my work - I appreciate it. Please consider becoming a paid subscriber to support my work. Also, please contact me if you would like to purchase any of my prints. !\[\](https://substackcdn.com/image/fetch/w\_1456,c\_limit,f\_auto,q\_auto:good,fl\_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2Fe6ad5a3e-cb60-4246-9bb3-9f8849d3591e\_4000x3551.jpeg) \[Dehancer Film (promo code "PICTUREOOM")\](https://www.dehancer.com/shop/pslr/film) \*If you've found value in this newsletter, I'd be incredibly grateful for your support. While these posts will always be freely available, becoming a paid subscriber helps ensure I can continue delivering quality content to your inbox. Share this newsletter with friends, leaving a comment, or simply hitting the 'like' button all make a difference.\* Thank you - Colin
-

@ 32e18276:5c68e245
2025-02-08 20:20:46
This period of the Damus OpenSats grant has been productive, and encompasses the work past our alpha release of Notedeck. Since we sent our last report on Dec 5, this encompasses all the work after then.
Damus is supported by the OpenSats LTS grant, which allows us to continue working on the goodies below. Thank you!
## Damus Notedeck
### Added
- Initial algo timelines (William Casarin) [#712](https://github.com/damus-io/notedeck/pull/712)
- Initial support for local-network P2P nostr: multicast support (William Casarin) [#626](https://github.com/damus-io/notedeck/pull/626)
- First steps toward the notedeck browser: multiple app support [#565](https://github.com/damus-io/notedeck/pull/565)
- Clicking a mention now opens profile page (William Casarin) [5a241d730](https://github.com/damus-io/notedeck/commit/5a241d730e3d83f8057e211485edfde2f3c96e54)
- Note previews when hovering reply descriptions (William Casarin) [#591](https://github.com/damus-io/notedeck/pull/591)
- Various Android updates and compatibility improvements (Ken Sedgwick, William Casarin)
- Media uploads (kernelkind) [#662](https://github.com/damus-io/notedeck/pull/662)
- Profile editing (kernelkind) [#625](https://github.com/damus-io/notedeck/pull/625)
- Add hashtags to posts (Daniel Saxton) [#592](https://github.com/damus-io/notedeck/pull/592)
- Enhanced command-line interface for user interactions (Ken Sedgwick)
- Debug features for user relay-list and mute list synchronization (Ken Sedgwick)
### Changed
- Major timeline cache refactor (William Casarin) [#653](https://github.com/damus-io/notedeck/pull/653)
- Increased ping intervals for network performance (William Casarin)
- Migrated to egui v0.29.1 (William Casarin) [#551](https://github.com/damus-io/notedeck/pull/551)
- Switch to only notes & replies on some tabs (William Casarin) [#598](https://github.com/damus-io/notedeck/pull/598)
- Only show column delete button when not navigating (William Casarin)
- Pointer interactions enhancements in UI (William Casarin)
- Show profile pictures in column headers (William Casarin)
- Show usernames in user columns (William Casarin)
- Add confirmation when deleting columns (kernelkind)
- Enhance Android build and performance (Ken Sedgwick)
- Image cache handling using sha256 hash (kieran)
- Introduction of decks_cache and improvements (kernelkind)
- Nostrdb update for async support (Ken Sedgwick)
- Persistent theme setup across sessions (kernelkind)
- Tombstone muted notes (Ken)
### Fixed
- Fix GIT_COMMIT_HASH compilation issue (William Casarin)
- Fix avatar alignment in profile previews (William Casarin)
- Fix broken quote repost hitbox (William Casarin)
- Fix crash when navigating in debug mode (William Casarin)
- Fix long delays when reconnecting (William Casarin)
- Fix repost button size (William Casarin)
- Fixed since kind filters (kernelkind)
- Clippy warnings resolved (Dimitris Apostolou)
## Damus iOS
Work continued on the iOS side. While I was not directly involved in the work since the last report, I have been directing and managing its development.
### Added
- Render Gif and video files while composing posts (Swift Coder)
- Purple members who have been active for more than a year now get a special badge (Daniel D’Aquino)
- Add profile info text in stretchable banner with follow button (Swift Coder)
- Paste Gif image similar to jpeg and png files (Swift Coder)
### Changed
- Improved clarity of the mute button to indicate it can be used for blocking a user (Daniel D’Aquino)
- Made the microphone access request message more clear to users (Daniel D’Aquino)
- Improved UX around the label for searching words (Daniel D’Aquino)
- Improved accessibility support on some elements (Daniel D’Aquino)
### Fixed
- Fixed issue where the "next" button would appear hidden and hard to click on the create account view (Daniel D’Aquino)
- Fix non scrollable wallet screen (Swift Coder)
- Fixed suggested users category titles to be localizable (Terry Yiu)
- Fixed GradientFollowButton to have consistent width and autoscale text limited to 1 line (Terry Yiu)
- Fixed right-to-left localization issues (Terry Yiu)
- Fixed AddMuteItemView to trim leading and trailing whitespaces from mute text and disallow adding text with only whitespaces (Terry Yiu)
- Fixed SideMenuView text to autoscale and limit to 1 line (Terry Yiu)
- Fixed an issue where a profile would need to be input twice in the search to be found (Daniel D’Aquino)
- Fixed non-breaking spaces in localized strings (Terry Yiu)
- Fixed localization issue on Add mute item button (Terry Yiu)
- Replace non-breaking spaces with regular spaces as Apple's NSLocalizedString macro does not seem to work with it (Terry Yiu)
- Fixed localization issues in RelayConfigView (Terry Yiu)
- Fix duplicate uploads (Swift Coder)
- Remove duplicate pubkey from Follow Suggestion list (Swift Coder)
- Fix Page control indicator (Swift Coder)
- Fix damus sharing issues (Swift Coder)
- Fixed issue where banner edit button is unclickable (Daniel D’Aquino)
- Handle empty notification pages by displaying suitable text (Swift Coder)
## Nostrdb
nostrdb, the engine that powers [notecrumbs](https://github.com/damus-io/notecrumbs), damus iOS, and notedeck, continued to improve:
### Added
- Added nip50 fulltext searching (William Casarin) [#68](https://github.com/damus-io/nostrdb/pull/68), [demo](nostr:nevent1qqsp3rx83t5h0vdhu4txru76uycfnaegfj3wg6wncamkarcnrccssvcpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqvhpsfmr23gwhv795lgjc8uw0v44z3pe4sg2vlh08k0an3wx3cj9efqkkv)
- Added async migrations (William Casarin) [#59](https://github.com/damus-io/nostrdb/pull/59)
- Implement author queries (William Casarin) [#57](https://github.com/damus-io/nostrdb/pull/57)
- Make `ndb` threadsafe (William Casarin) [#56](https://github.com/damus-io/nostrdb/pull/56)
## Nostrdb Rust
Our nostrdb rust bindings also had improvements
- Async! Adding efficient, poll-based stream support (William Casarin): [#25](https://github.com/damus-io/nostrdb-rs/pull/25)
## Notecrumbs
Notecrumbs, the njump-style opengraph server that powers the damus.io links, got an update that upgraded it to async nostrdb
- Switch to async nostrdb-rs (William Casarin) [#16](https://github.com/damus-io/notecrumbs/pull/16)
## How money was used
- relay.damus.io server costs
- Living expenses
## Next quarter
Our goal for next update: zaps, android version, lists, outbox model for notedeck. Olas images in damus iOS, continue switching Damus iOS over to local relay model so we can add outbox support.
-

@ fdb8c828:84c16368
2025-02-08 17:00:37

originally posted at https://stacker.news/items/579738
-

@ 97c70a44:ad98e322
2025-01-30 17:15:37
There was a slight dust up recently over a website someone runs removing a listing for an app someone built based on entirely arbitrary criteria. I'm not to going to attempt to speak for either wounded party, but I would like to share my own personal definition for what constitutes a "nostr app" in an effort to help clarify what might be an otherwise confusing and opaque purity test.
In this post, I will be committing the "no true Scotsman" fallacy, in which I start with the most liberal definition I can come up with, and gradually refine it until all that is left is the purest, gleamingest, most imaginary and unattainable nostr app imaginable. As I write this, I wonder if anything built yet will actually qualify. In any case, here we go.
# It uses nostr
The lowest bar for what a "nostr app" might be is an app ("application" - i.e. software, not necessarily a native app of any kind) that has some nostr-specific code in it, but which doesn't take any advantage of what makes nostr distinctive as a protocol.
Examples might include a scraper of some kind which fulfills its charter by fetching data from relays (regardless of whether it validates or retains signatures). Another might be a regular web 2.0 app which provides an option to "log in with nostr" by requesting and storing the user's public key.
In either case, the fact that nostr is involved is entirely neutral. A scraper can scrape html, pdfs, jsonl, whatever data source - nostr relays are just another target. Likewise, a user's key in this scenario is treated merely as an opaque identifier, with no appreciation for the super powers it brings along.
In most cases, this kind of app only exists as a marketing ploy, or less cynically, because it wants to get in on the hype of being a "nostr app", without the developer quite understanding what that means, or having the budget to execute properly on the claim.
# It leverages nostr
Some of you might be wondering, "isn't 'leverage' a synonym for 'use'?" And you would be right, but for one connotative difference. It's possible to "use" something improperly, but by definition leverage gives you a mechanical advantage that you wouldn't otherwise have. This is the second category of "nostr app".
This kind of app gets some benefit out of the nostr protocol and network, but in an entirely selfish fashion. The intention of this kind of app is not to augment the nostr network, but to augment its own UX by borrowing some nifty thing from the protocol without really contributing anything back.
Some examples might include:
- Using nostr signers to encrypt or sign data, and then store that data on a proprietary server.
- Using nostr relays as a kind of low-code backend, but using proprietary event payloads.
- Using nostr event kinds to represent data (why), but not leveraging the trustlessness that buys you.
An application in this category might even communicate to its users via nostr DMs - but this doesn't make it a "nostr app" any more than a website that emails you hot deals on herbal supplements is an "email app". These apps are purely parasitic on the nostr ecosystem.
In the long-term, that's not necessarily a bad thing. Email's ubiquity is self-reinforcing. But in the short term, this kind of "nostr app" can actually do damage to nostr's reputation by over-promising and under-delivering.
# It complements nostr
Next up, we have apps that get some benefit out of nostr as above, but give back by providing a unique value proposition to nostr users as nostr users. This is a bit of a fine distinction, but for me this category is for apps which focus on solving problems that nostr isn't good at solving, leaving the nostr integration in a secondary or supporting role.
One example of this kind of app was Mutiny (RIP), which not only allowed users to sign in with nostr, but also pulled those users' social graphs so that users could send money to people they knew and trusted. Mutiny was doing a great job of leveraging nostr, as well as providing value to users with nostr identities - but it was still primarily a bitcoin wallet, not a "nostr app" in the purest sense.
Other examples are things like Nostr Nests and Zap.stream, whose core value proposition is streaming video or audio content. Both make great use of nostr identities, data formats, and relays, but they're primarily streaming apps. A good litmus test for things like this is: if you got rid of nostr, would it be the same product (even if inferior in certain ways)?
A similar category is infrastructure providers that benefit nostr by their existence (and may in fact be targeted explicitly at nostr users), but do things in a centralized, old-web way; for example: media hosts, DNS registrars, hosting providers, and CDNs.
To be clear here, I'm not casting aspersions (I don't even know what those are, or where to buy them). All the apps mentioned above use nostr to great effect, and are a real benefit to nostr users. But they are not True Scotsmen.
# It embodies nostr
Ok, here we go. This is the crème de la crème, the top du top, the meilleur du meilleur, the bee's knees. The purest, holiest, most chaste category of nostr app out there. The apps which are, indeed, nostr indigitate.
This category of nostr app (see, no quotes this time) can be defined by the converse of the previous category. If nostr was removed from this type of application, would it be impossible to create the same product?
To tease this apart a bit, apps that leverage the technical aspects of nostr are dependent on nostr the *protocol*, while apps that benefit nostr exclusively via network effect are integrated into nostr the *network*. An app that does both things is working in symbiosis with nostr as a whole.
An app that embraces both nostr's protocol and its network becomes an organic extension of every other nostr app out there, multiplying both its competitive moat and its contribution to the ecosystem:
- In contrast to apps that only borrow from nostr on the technical level but continue to operate in their own silos, an application integrated into the nostr network comes pre-packaged with existing users, and is able to provide more value to those users because of other nostr products. On nostr, it's a good thing to advertise your competitors.
- In contrast to apps that only market themselves to nostr users without building out a deep integration on the protocol level, a deeply integrated app becomes an asset to every other nostr app by becoming an organic extension of them through interoperability. This results in increased traffic to the app as other developers and users refer people to it instead of solving their problem on their own. This is the "micro-apps" utopia we've all been waiting for.
Credible exit doesn't matter if there aren't alternative services. Interoperability is pointless if other applications don't offer something your app doesn't. Marketing to nostr users doesn't matter if you don't augment their agency _as nostr users_.
If I had to choose a single NIP that represents the mindset behind this kind of app, it would be NIP 89 A.K.A. "Recommended Application Handlers", which states:
> Nostr's discoverability and transparent event interaction is one of its most interesting/novel mechanics. This NIP provides a simple way for clients to discover applications that handle events of a specific kind to ensure smooth cross-client and cross-kind interactions.
These handlers are the glue that holds nostr apps together. A single event, signed by the developer of an application (or by the application's own account) tells anyone who wants to know 1. what event kinds the app supports, 2. how to link to the app (if it's a client), and (if the pubkey also publishes a kind 10002), 3. which relays the app prefers.
_As a sidenote, NIP 89 is currently focused more on clients, leaving DVMs, relays, signers, etc somewhat out in the cold. Updating 89 to include tailored listings for each kind of supporting app would be a huge improvement to the protocol. This, plus a good front end for navigating these listings (sorry nostrapp.link, close but no cigar) would obviate the evil centralized websites that curate apps based on arbitrary criteria._
Examples of this kind of app obviously include many kind 1 clients, as well as clients that attempt to bring the benefits of the nostr protocol and network to new use cases - whether long form content, video, image posts, music, emojis, recipes, project management, or any other "content type".
To drill down into one example, let's think for a moment about forms. What's so great about a forms app that is built on nostr? Well,
- There is a [spec](https://github.com/nostr-protocol/nips/pull/1190) for forms and responses, which means that...
- Multiple clients can implement the same data format, allowing for credible exit and user choice, even of...
- Other products not focused on forms, which can still view, respond to, or embed forms, and which can send their users via NIP 89 to a client that does...
- Cryptographically sign forms and responses, which means they are self-authenticating and can be sent to...
- Multiple relays, which reduces the amount of trust necessary to be confident results haven't been deliberately "lost".
Show me a forms product that does all of those things, and isn't built on nostr. You can't, because it doesn't exist. Meanwhile, there are plenty of image hosts with APIs, streaming services, and bitcoin wallets which have basically the same levels of censorship resistance, interoperability, and network effect as if they weren't built on nostr.
# It supports nostr
Notice I haven't said anything about whether relays, signers, blossom servers, software libraries, DVMs, and the accumulated addenda of the nostr ecosystem are nostr apps. Well, they are (usually).
This is the category of nostr app that gets none of the credit for doing all of the work. There's no question that they qualify as beautiful nostrcorns, because their value propositions are entirely meaningless outside of the context of nostr. Who needs a signer if you don't have a cryptographic identity you need to protect? DVMs are literally impossible to use without relays. How are you going to find the blossom server that will serve a given hash if you don't know which servers the publishing user has selected to store their content?
In addition to being entirely contextualized by nostr architecture, this type of nostr app is valuable because it does things "the nostr way". By that I mean that they don't simply try to replicate existing internet functionality into a nostr context; instead, they create entirely new ways of putting the basic building blocks of the internet back together.
A great example of this is how Nostr Connect, Nostr Wallet Connect, and DVMs all use relays as brokers, which allows service providers to avoid having to accept incoming network connections. This opens up really interesting possibilities all on its own.
So while I might hesitate to call many of these things "apps", they are certainly "nostr".
# Appendix: it smells like a NINO
So, let's say you've created an app, but when you show it to people they politely smile, nod, and call it a NINO (Nostr In Name Only). What's a hacker to do? Well, here's your handy-dandy guide on how to wash that NINO stench off and Become a Nostr.
You app might be a NINO if:
- There's no NIP for your data format (or you're abusing NIP 78, 32, etc by inventing a sub-protocol inside an existing event kind)
- There's a NIP, but no one knows about it because it's in a text file on your hard drive (or buried in your project's repository)
- Your NIP imposes an incompatible/centralized/legacy web paradigm onto nostr
- Your NIP relies on trusted third (or first) parties
- There's only one implementation of your NIP (yours)
- Your core value proposition doesn't depend on relays, events, or nostr identities
- One or more relay urls are hard-coded into the source code
- Your app depends on a specific relay implementation to work (*ahem*, relay29)
- You don't validate event signatures
- You don't publish events to relays you don't control
- You don't read events from relays you don't control
- You use legacy web services to solve problems, rather than nostr-native solutions
- You use nostr-native solutions, but you've hardcoded their pubkeys or URLs into your app
- You don't use NIP 89 to discover clients and services
- You haven't published a NIP 89 listing for your app
- You don't leverage your users' web of trust for filtering out spam
- You don't respect your users' mute lists
- You try to "own" your users' data
Now let me just re-iterate - it's ok to be a NINO. We need NINOs, because nostr can't (and shouldn't) tackle every problem. You just need to decide whether your app, as a NINO, is actually contributing to the nostr ecosystem, or whether you're just using buzzwords to whitewash a legacy web software product.
If you're in the former camp, great! If you're in the latter, what are you waiting for? Only you can fix your NINO problem. And there are lots of ways to do this, depending on your own unique situation:
- Drop nostr support if it's not doing anyone any good. If you want to build a normal company and make some money, that's perfectly fine.
- Build out your nostr integration - start taking advantage of webs of trust, self-authenticating data, event handlers, etc.
- Work around the problem. Think you need a special relay feature for your app to work? Guess again. Consider encryption, AUTH, DVMs, or better data formats.
- Think your idea is a good one? Talk to other devs or open a PR to the [nips repo](https://github.com/nostr-protocol/nips). No one can adopt your NIP if they don't know about it.
- Keep going. It can sometimes be hard to distinguish a research project from a NINO. New ideas have to be built out before they can be fully appreciated.
- Listen to advice. Nostr developers are friendly and happy to help. If you're not sure why you're getting traction, ask!
I sincerely hope this article is useful for all of you out there in NINO land. Maybe this made you feel better about not passing the totally optional nostr app purity test. Or maybe it gave you some actionable next steps towards making a great NINON (Nostr In Not Only Name) app. In either case, GM and PV.
-

@ 89ccea93:df4e00b7
2025-02-08 16:50:15
**[Original Post](https://expatriotic.me/ashigaru/)**
# What is Ashigaru?
> A self custodial, open source and secure Bitcoin wallet that is private by design.
The **Ashigaru Open Source Project** was established in the months after the United States Department of Justice [brought charges](https://archive.is/g7q8r) against the founders of the self custodial Bitcoin application, Samourai Wallet. At the time of arrest, multiple servers that hosted documentation, code repositories and message coordination services were either [seized](https://archive.is/0nC3t) or failed to remain online, presumably due to being no longer administered. With the indicted individuals placed under restrictive conditions on bail, it became clear that all software development had ceased.
## Aims and Goals
We believe anyone should be able to engage in peaceful, voluntary and private commerce on the internet without tracking, surveillance or censorship. The Ashigaru Open Source Project develops, releases and maintains free and open source software that makes extensive use of both published code from active projects as well as those archived in the public domain.
Open, unrestricted communication networks are utilized to ensure continued availability. The software released by the project will always have a low barrier to entry, be non discriminatory, never expose users to counterparty risk and provide as much protection as possible for those transacting on a public blockchain.
## What’s in a name?
As former users of Samourai Wallet, yet having no association or relationship with the core team, “Ashigaru” was chosen to represent individuals of humble origin whom, borne out of necessity, would equip themselves with their own tools and rise to the occasion during a period of great change.
**Here is the [ONLY podcast episode](https://episodes.fm/1491067458/episode/YTRjNGNlNTAtYjEwMS00YWQ0LTg0MjUtZWQwMmQxYjU0N2Ex) with the developers of this wallet.**

**Here are a list of features directly from their website:**
1. **Onion Routing:** Connect to your Dojo node and broadcast over the Tor network
2. **Ricochet:** Add distance to the origins of your transactions to mitigate surveillance
3. **Encrypted Key Recovery:** Standards based mnemonic secured with a passphrase that can be imported to other wallets
4. **Post Mix Spending:** Import your Samourai Wallet private keys and maintain your segregated accounts
5. **Batch Spending:** Save on fees by composing a single transaction to multiple recipients
6. **Stealth Mode:** Obscure the wallet from physical searches with a functional decoy application in the launcher
7. **Peer to Peer Coinjoins:** Undermine heuristics used by blockchain observers through collaboration with other users
8. **Coin Control:** Select, label, freeze and unfreeze unspent transaction outputs (UTXOs) in your wallet
9. **Smart Mining Fees:** An advanced algorithm for determining a rate from unconfirmed transactions in the mempool
10. **Free and Open Source:** Ashigaru is released under the FOSS license [GNU General Public License Version 3](https://www.gnu.org/licenses/gpl-3.0.en.html)
___
# FREESAMOURAI
Maybe you've been living in a hole, but the developers of the Samourai Wallet were indicted and picked up by the US government (*even the one in Portugal, because, shocker, the US DoJ can get you almost anywhere in the world except Cuba, North Korea, Russia and China. But I digress*).
```Their crime? Helping users of the base layer Bitcoin protocol achieve forward spending privacy by crafting pristine zero-link UTXOs. The unspent capacity of which was over 10,000 bitcoins, or twice the capacity of the Lightning Network which continues to hover around, and often under, 5,000 bitcoins.```
**#FREESAMOURAI**\
Listen to these podcast episodes for more information.
1. [Prescient warnings](https://episodes.fm/1491067458/episode/ODc0MDIyNzMtNTgxNy00NDAwLTg0MGMtY2JkZmVmNjU4YTg0) just before the indictment from **Diverter**.
2. [Update](https://episodes.fm/1491067458/episode/ZWRhN2EzN2MtYTk5ZC00ODY2LTg5NjctZGE3MWY2YzUzZmM4) when it became known what had happened.
3. [Follow up](https://episodes.fm/1491067458/episode/NDk2ZDJmMzUtMmI2MS00ODljLWIwYmUtODBkZTI2YmUxNDhm) with **Diverter** and **Zelko** after the fact
4. [Reassessing your privacy plan](https://episodes.fm/1491067458/episode/YTA2NDQwNDAtNTMzMy00ODRiLTlkZDUtN2ExZDU5NWY1ZmE0) with **Urban Hacker** in a world without a zero-link coinjoin implementation (Whirlpool).
## Why run Ashigaru compared to Samourai Wallet?
One might ask the logical question, why run Ashigaru, my Samourai Wallet is still working!?\
To which, Max Tannahill, a community member, has given the following list to answer.
1. Cheaper BIP47 connections
2. Soroban coinjoins ([Tor link](http://ashigaruprvm4u263aoj6wxnipc4jrhb2avjll4nnk255jkdmj2obqqd.onion/news/operational-online-chaoots/) about this)
3. Better BIP47 recovery
4. No risk of DNS hijacking for the PayNym server as its over Tor
5. Ability to switch Dojos more easily
6. Spending warnings that Samourai never got to deploy to production
7. Next block fee estimation
8. UI improvements on Samourai
9. Removal of broken links to whirlpool, the old Soroban server and the old Iceland Dojo
10. No clearnet connections at all
___
# How-to Guide for Ashigaru
## Download the APK
1. *Prerequisite:* [Tor Browser](https://www.torproject.org/download/#android) is a requirement.
2. Open the **Tor Browser** and paste in this 🧅 [link](http://ashigaruprvm4u263aoj6wxnipc4jrhb2avjll4nnk255jkdmj2obqqd.onion/).
3. Recommended to use a phone with **Android 8+** that still receives security updates.
4. Recommended to use a **GrapheneOS** phone (Pixel only). _Non-Pixel owners can use **Lineage OS** which is a less secure, but viable, option. Or just use stock android if you have no idea how to change the operating system on your phone or don't want to do so._
5. Carry out software verification. A PGP signed message is below the APK. The Keybase Verify [tool](https://keybase.io/verify) can be used to do the verification.
6. *This is what it looks like on Keybase when completed. ⤵*

## Install the Ashigaru mobile application
1. From within your device's files, tap on the Ashigaru APK file
2. Tap "**Install**"\

3. When complete tap "**Done**", or tap "**Open**" to launch the mobile application\

4. The Ashigaru mobile application has now been installed on your Android device. You will now see the Ashigaru app icon in your list of installed apps.
## Setting up Ashigaru
1. You need to connect to your own self-hosted Dojo (this is a specific type of Bitcoin node). Ashigaru doesn't run a node for you to point your wallet to, you'll need to do this yourself.
* DIY options include:
* [Ministry of Nodes](https://www.youtube.com/watch?v=8_It4xEIwRA)
* [BTC Sessions](https://www.youtube.com/watch?v=ULZoPMCYPfk)
* Community nodes at [Dojo Bay](https://dojobay.pw/) (*Obviously a privacy trade-off if you outsource your node to a 3rd party.*)
2. You need a pen and paper for writing down your 12 word Mnemonic seed phrase.
3. Make a strong [passphrase](https://cryptography.fandom.com/wiki/Passphrase) (4-6 memorable but random [words](https://www.eff.org/deeplinks/2016/07/new-wordlists-random-passphrases)) and put it separately from the offline seed phrase backup, e.g., in your password manager (*KeePass or Bitwarden are good options*).
4. Claim your PayNym with it's associated Pepehash avatar.

> PayNym Support: Migrate seamlessly to a new directory that uses a Pepehash avatar scheme for representing BIP47 reusable payment codes.
## Using Ashigaru
1. When sending, if possible, and just as in [Sparrow Desktop Wallet](https://sparrowwallet.com), a fake coinjoin is created by using two of your UTXOs as inputs to obscure what is occuring onchain. Onlookers will see what appears to be two parties collaborating to spend together. This adds a bit of extra miner fee cost, but this is the cost of extra privacy. You can opt out of this privacy enhancement.\

2. If you want to send or receive privately and with a static address, **BIP47 PayNyms**, will accomplish this. As long as both parties have a wallet that supports this standard. **Samourai Wallet**, **Stack Duo**, and **Sparrow** are the others that I know of at this time. Simply put in their **PayNym**, e.g., mine is **+mereegg59**, or scan their QR containing the data for the **PayNym** and connect with them. This will involve sending a small transaction onchain. But once one of you does, both parties can send back and forth privately without ever needing to request a fresh address.
3. There is an option when spending to use **ricochet**. This will add hops to help obscure the history of your **UTXO** for anyone who is using passive software to check X hops in the past for some connection to a **sanctioned** address. Good for spending **UTXOs** that you don't know the prior history of. Although personally I think **taint** is merely a mindset, some entities will not receive **UTXOs** that have either been coinjoined or are too close to a **sanctioned** address.
4. There is an option in the tools menu for doing a collaborative spend, known as **Soroban Coinjoin**.
5. Unfortunately Whirlpool is not yet a feature of this wallet.

___
- **Here is the Tor [link](http://ashigaruprvm4u263aoj6wxnipc4jrhb2avjll4nnk255jkdmj2obqqd.onion/donate/) where you can donate to them**
- **Here is the Tor [link](http://ashicodepbnpvslzsl2bz7l2pwrjvajgumgac423pp3y2deprbnzz7id.onion/Ashigaru) for their code base**
- **Here is the Tor [link](http://ashigaruprvm4u263aoj6wxnipc4jrhb2avjll4nnk255jkdmj2obqqd.onion/docs/) for their documentation**
- **Here is the Tor [link](http://ashigaruprvm4u263aoj6wxnipc4jrhb2avjll4nnk255jkdmj2obqqd.onion/docs/mobile-wallet-updating-application/) for updating the Ashigaru app**
- **Here is the Tor [link](http://ashigaruprvm4u263aoj6wxnipc4jrhb2avjll4nnk255jkdmj2obqqd.onion/contact/) for their contact info. _Keep in mind this requires a different PGP key than the one used to verify the APK (unless you use protonmail and then PGP isn't required)._**
originally posted at https://stacker.news/items/879803
-

@ 604e96e0:20279eb2
2023-08-11 18:39:36
notacomment allows you to zap nostr notes when you comment on them. In order to use notacomment, you have to run a script yourself either on your own computer or in the cloud somewhere. To get started open https://github.com/SamSamskies/notacomment in a browser tab.
At this point, I'm sure a lot of you are feeling like this:

Let's breakdown the instructions from the README.
## Prerequisites
Node.js and npm - I suggest installing the latest Node.js LTS version from https://nodejs.org. That should also install npm.
Once installation is complete, open your terminal. On a Mac you can press cmd + spacebar and type in `terminal` to open the terminal. On other platforms, you'll have to ask ChatGPT 😂
.
To verify installation of Node.js type `node -v`. To verify installation type `npm -v`.
It should look something like this:

Leave the terminal open.
## Downloading the code to your computer
The easiest way to download the code is to download the zip file from the GitHub repo. Remember that first link I told you to open? That's the GitHub repo. Click the green button that says `Code` on it and click `Download ZIP` from the menu.

Now unzip the file and then navigate to the folder in the terminal. To navigate to the folder use the `cd` command. If you unzipped the folder in the `Downloads` folder, you can navigate to the folder by typing `cd ~/Downloads/notacomment-main/`.
## Usage With Strike
1. Create an account with Strike if you don't already have one https://strike.me/download/
1. Get a Strike API key with all the payment scopes from https://dashboard.strike.me/
1. Create a .env file and provide NOSTR_NSEC and STRIKE_API_KEY values (see .env.example)
1. Install the dependencies using npm or yarn or whatever your heart desires
1. Make sure you have money in your Strike account
1. Run the script `npm start`
Keep in mind that Strike pays the invoices from your cash balance. This means the payment rounds up to the nearest cent when paying an invoice, so if you set the zap amount to 1 sat, you'll be sending more money to Strike than the person you are zapping with every zap.
## Usage With LNbits
I recommend making a separate wallet from your main LNbits wallet for usage with notacomment in case you accidentally leak the admin key.
1. Create a .env file and provide NOSTR_NSEC, LNBITS_ADMIN_KEY, and LNBITS_URL values (see .env.example)
1. Install the dependencies using npm or yarn or whatever your heart desires
1. Make sure you have sats in your LNbits wallet
1. Run the script `npm start`
## Usage With Nostr Wallet Connect
1. Create a NWC connection string using something like https://nwc.getalby.com/
1. Create a .env file and provide NOSTR_NSEC and NWC_CONNECTION_STRING values (see .env.example)
1. Install the dependencies using npm or yarn or whatever your heart desires
1. Make sure you have sats in your wallet that you generated the NWC connection string with
1. Run the script `npm start`
<br />
<br />
Screenshot of terminal with commands to install dependencies, create .env file, open .env file, and start the script:

-

@ 1cb14ab3:95d52462
2025-02-08 16:45:04
***Tree branches. 4'8" circle. [Chongming Island, China. 2021]***
---
#### Introduction
Tucked into a quiet forest park on Chongming Island, Chongming frames a view of a canal and a small alluvial landform that mirrors the island itself. This lens reflects the constant interplay of land and water, inviting viewers to contemplate the delicate balance of nature and the forces that shape it.
#### Site & Placement
The lens is hidden along a forest path, directing attention to the canal’s subtle currents and the land it divides. The bench, situated 12 feet from the lens, encourages visitors to pause and immerse themselves in the tranquil rhythm of the scene.
#### Impermanence & Integration
As an alluvial island shaped by shifting waters, Chongming is a fitting location for this ephemeral lens. Constructed from branches, the lens will eventually return to the land, echoing the natural processes that formed the island and continue to shape it.
#### Reflection
*Chongming* offers a meditative space to reflect on the impermanence of land and the forces that transform it. The work’s fleeting existence underscores the beauty of change, inviting viewers to appreciate the subtle, ongoing dance of nature.
---
## Photos








---
#### More from the 'Earth Lens' Series:
[Earth Lens Series: Artist Statement + List of Works](https://hes.npub.pro/post/1731091744332/)
["Looking Glass" (Earth Lens 001)](https://hes.npub.pro/post/1736304563962/)
["Folsom" (Earth Lens 002)](https://hes.npub.pro/post/1737844073125/)
["Sanctuary" (Earth Lens 003)](https://hes.npub.pro/post/1731091744332/)
["Platte" (Earth Lens 004)](https://hes.npub.pro/post/sya8nv6q8k0w3olqcepwz)
["Grandfather" (Earth Lens 005)](https://hes.npub.pro/)
---
#### More from Hes
[Portfolio](https://hesart.npub.pro)
[Online Store](https://plebeian.market/community/hes@nostrplebs.com/hesmart-ym3fcufdfz)
[Artist Statements](https://hes.npub.pro/tag/art/)
[Travel Guides](https://hes.npub.pro/tag/travel/)
[Photography](https://hes.npub.pro/tag/photography)
[Money](https://hes.npub.pro/tag/money)
[Tech](https://hes.npub.pro/tag/tech)
---
*All images are credit of Hes, but you are free to download and use for any purpose. If you find joy from my art, please feel free to send a zap. Enjoy life on a Bitcoin standard.*
-

@ 8d5ba92c:c6c3ecd5
2025-01-30 15:58:03
For me, it’s simple yet profound: a job and labor aren’t the same thing. You don’t have to struggle to perform a task or to meet someone else's unrealistic expectations. In fact, if you genuinely enjoy what you’re doing and believe in its purpose, the results will naturally be better—and everyone benefits.
I’m speaking from the perspective of someone who walked away from a "*well-established career*" multiple times. These days, I might be working more than ever, but I don’t feel tired, frustrated, or burned out. The radical change I made—leaving the "*professional fiat world*" behind—wasn’t easy, but I’ve never regretted it. Now, working fully in Bitcoin, I feel more motivated and satisfied than ever before.
Sure, it's not always straightforward.
This lifestyle definitely comes with its challenges. But those challenges don’t crush me. Just the opposite. When combined with a sense of freedom, they become opportunities for growth—something I truly value. It’s a completely different experience compared to most jobs rooted in the old system.
I’m not saying working in Bitcoin is all sunshine and rainbows, nor am I criticizing anyone still working in fiat. What I’m trying to emphasize is the core message of that quote:
## Do what you love, and you’ll never work a day in your life...
Read it aloud and think about your last couple of jobs.
How did you feel? Did you find fulfillment and satisfaction, or was it more like a form of slavery that made you dread going to bed and waking up every morning?
I didn’t really have those feelings, except for one corporation at the beginning of my career, which gave me a hard time but also taught me valuable lessons. Aside from that experience, most of my jobs weren’t too bad—no need to complain. Still, I often questioned my situation: '*Seriously, why do I have to do this or that if I know it doesn’t make sense?*'
Doing things you don’t believe in can lead to frustration, often in ways you might not even realize, yet every time, significantly affecting your well-being and the people around you.
Now, I hardly know what inner anger means.
I wake up happy, full of passion and ideas. I don’t track the hours as they pass; instead, I focus on all the tasks I complete and how they make a difference for me and others. Yes, I love what I do. And returning to the main point of this article, I shouldn’t even see it as work, even though in practice it definitely is.
The key here is a mix of independence, purpose, and self-determination. Bitcoin has helped me achieve that to a level that’s hard to break.
## A Fresh Take on The Market
I also remember that 5-7 years ago, especially for non-devs, Bitcoin-based jobs weren’t as accessible as they are now (which is probably why I stayed in my traditional career for so long...). It’s really only in the last, maybe 2-3 years that things have changed. With so many areas expanding beyond just mining and tech-related stuff, and new interesting projects popping up regularly, there’s almost any position you can imagine to jump into.
According to a recent report by [Bitvocation](https://linktr.ee/bitvocation) '69% of Bitcoin jobs are non-developer roles'. Also, more than half of available positions in 2024 offered remote opportunities, giving job seekers extra flexibility. Bitcoin is borderless—and so are many of the jobs in this space. If you’ve ever thought working in Bitcoin was out of reach, think again—and check this out "[BITCOIN JOB MARKET DATA, 2024 Report](https://drive.google.com/file/d/1ZFnYP949GzssQHA9wcjHTeW4cDiZIWvM/view)".
One tip from my experience: a good option is to start with a part-time role while keeping your traditional fiat job for more stability, especially at the beginning. After a while, you’ll gain more confidence and see which direction you want to go. Or, if you position yourself so that you don’t need to earn a lot for the next 3-6 months, consider finding a project- or task-based Bitcoin job, maybe even just an internship. Meanwhile, you might decide to focus on building something unique on your own. It can feel amazing! You’ll gain valuable skills, sharpen your experience, and better understand which options work best for your future.
You see, just like in nature, balance is key.
You don’t have to run before you can walk.
What I’m saying is this:
**The choice is yours, as long as you plan ahead + learn, while staying true to your needs, beliefs, and priorities.**
If you want it, do it. Starting a career in Bitcoin is possible, and I have a feeling this space will grow even faster in the next few years. Yes, there will still be ups and downs (hello, bear markets!), but if you plan thoughtfully, there’s not much to worry about.
We’re still early—Bitcoin is only 16 years old—but if you’ve been following this space, you’ve probably seen how dynamic and resilient it is. If you’ve ever thought about working in Bitcoin, now is the time to rethink the possibilities :)))
BTC Your Mind. Let it Beat.
Şelale
-

@ ec42c765:328c0600
2025-02-05 23:45:09
test
test
-

@ 6e75f797:a8eee74e
2023-08-07 13:16:42
Last night I started a nostr community multiplayer instance for No Man's Sky [on ZapStream](https://zap.stream/) and before we knew it, we had 4 Nostrichs arriving on the genesis planet to join the fun.

NSM is an deterministic, procedurally generated open universe where players can explore, quest, build, combat and have fun together. Every new system discovered is generated when the first Traveller enters the system making the game a unique experience for any open world gaming fan.
If you fancy joining us in the Nostrverse let me know and I'll friend you in #NMS and on Steam or Epic. If you just want to watch the fun, participate in naming systems, planets, fauna and flora come and hang out in my stream or the stream of [Oceanbee](nostr:npub1wqxxe0cjaxnvmrv4lkvx8d5dlft7ewswyn09w5v7fg7642fgzm7srucxws), [HolgerHatGarKeineNode](nostr:npub1pt0kw36ue3w2g4haxq3wgm6a2fhtptmzsjlc2j2vphtcgle72qesgpjyc6) or [taette](npub1yh0dl6pazf55025qvp860lstpscuy0kj2a5lfhxlk400m968vgpql5vsnd).

### If you already own NMS, feel free to add me!
My NMS friend code is: EMAZ-KMHT-ZPFXP
See you in space Traveller! - TheGrinder
-

@ cbd2779f:72a5b029
2025-01-30 15:08:13
Have a few questions pertaining to setting up a new node. Basically, I always seems to be unsure about syncing to graph, after syncing to chain. Consider setting up a new node from scratch, or migrating perhaps, and you want to do an initial setup.
1. How long does it take?
2. What factors determine how long it takes?
3. Is the graph a universal graph that is identical from each nodes perspective?
So far, I'm monitoring progress but tailing logs, looking for clues:
`tail -n 100 /data/lnd/logs/bitcoin/mainnet/lnd.log | grep GRPH`
I can find some relevant clues like:
```
2025-01-30 15:24:54.843 [INF] GRPH: Processed channels=56 updates=59 nodes=15 in last 59.823699481s
```
and then checking with: `lncli getinfo | grep -E 'synced|peers` which outputs
```
"num_peers": 3,
"synced_to_chain": true,
"synced_to_graph": false,
```
At the moment, I've been experimenting with pruned blockchains and this outputs a lot of errors (I believe) relating to not being able to verify UTXOs as I have `ignore-historical-gossip-filters set to true.
Any further suggestions on how to better make sure things are happening under the hood when setting up a new node, what to look for in the logs or how to know the verification progress?
originally posted at https://stacker.news/items/869944
-

@ ec42c765:328c0600
2025-02-05 23:43:35
test
-

@ f57bac88:6045161e
2025-02-08 15:50:22
### ریشههای تاریخی جشن کژین
جشن کژین که در برخی منابع به نام «بادروز» نیز شناخته میشود، ریشه در اسطورههای کهن ایران دارد. در اوستا، باد با نام «واتَه» معرفی شده است و ایزد نگهبان آن، «وات» یا «واد» یکی از ایزدان مهم در کیش زرتشتی به شمار میرود. این ایزد در باورهای ایرانیان باستان، تجسم نیروی پاک و الهی باد بوده و مسئول جابهجایی ابرها، بارش باران و حفاظت از زمین در برابر آلودگیها محسوب میشده است.
بر اساس تقویم کهن ایران، این جشن در روز بیستودوم بهمنماه، که مصادف با روز باد در تقویم زرتشتی است، برگزار میشد. برخی پژوهشگران معتقدند که جشن کژین در دورههای مختلف تاریخی، تحت تأثیر تغییرات فرهنگی و اجتماعی دچار دگرگونی شده و نامها و شیوههای مختلفی به خود گرفته است.
### فلسفه و نمادشناسی جشن کژین
باد، به عنوان یکی از چهار عنصر اصلی (آب، باد، خاک و آتش) در باورهای کهن ایرانی، جایگاه ویژهای داشته است. ایرانیان باستان باد را نیرویی زنده و الهی میدانستند که حیات را در طبیعت جاری میسازد. در بسیاری از متون دینی و اساطیری، باد به عنوان پیامرسان ایزدان و نیرویی که قدرت پاککنندگی دارد، توصیف شده است.
جشن کژین، علاوه بر تقدیس باد، نماد تحول، تغییر و تجدید حیات نیز بوده است. این جشن نشانگر گذر از یک مرحله به مرحلهای دیگر در چرخه طبیعت است و ارتباطی عمیق با دیگر جشنهای ایرانی مانند جشن سده و نوروز دارد.
### آیینها و رسوم جشن کژین
برگزاری جشن کژین با آیینهای خاصی همراه بوده است که برخی از آنها هنوز در فرهنگ عامه ایرانیان قابل مشاهدهاند:
1. **رها کردن نوارهای رنگین در باد**: یکی از رسوم این جشن، آویختن نوارهایی از نخ هفترنگ به شاخههای درختان یا رها کردن آنها در باد بوده است. این عمل نماد رهایی، تحول و ارتباط با نیروی الهی باد محسوب میشده است.
2. **افروختن آتش**: مانند بسیاری از جشنهای ایرانی، روشن کردن آتش یکی از بخشهای اصلی جشن کژین بوده است. این آتش معمولاً در فضای باز و بر فراز تپهها و کوهها برافروخته میشد تا حرمت باد و آتش، دو عنصر اصلی طبیعت، گرامی داشته شود.
3. **برپایی بازارهای محلی و جشنهای خیابانی**: در برخی مناطق، جشن کژین با بازارهای محلی همراه بوده که در آن مردم به خرید و فروش کالاهای سنتی، موسیقی و پایکوبی میپرداختند. این بازارها اغلب در میادین شهرها و روستاها برگزار میشد و نوعی جشن اجتماعی به شمار میرفت.
4. **دعای شکرگزاری برای بادهای سودمند**: در فرهنگ کشاورزی ایران، باد نقش مهمی در گردهافشانی گیاهان و بارش باران داشته است. ازاینرو، کشاورزان و مردم روستاها در این روز دعاهایی برای بادهای مفید و پرهیز از بادهای مضر میخواندند.
### ارتباط جشن کژین با دیگر جشنهای ایرانی
جشن کژین با برخی دیگر از آیینهای کهن ایرانی ارتباط نزدیکی دارد. به عنوان مثال، جشن سده که در میانه زمستان برگزار میشود، یکی از جشنهایی است که در آن نیز باد و آتش نقش مهمی دارند. از سوی دیگر، جشن نوروز که سرآغاز فصل بهار است، نشانگر تحول و دگرگونی طبیعت است که ارتباطی مفهومی با جشن کژین دارد.
### جایگاه جشن کژین در دوران معاصر
امروزه، جشن کژین در میان بسیاری از ایرانیان ناشناخته باقی مانده است و تنها برخی از پژوهشگران و علاقهمندان به فرهنگ ایران باستان به احیای آن علاقه نشان میدهند. با این حال، عناصر این جشن در برخی آیینهای محلی و جشنهای مردمی همچنان باقی مانده است. تلاش برای بازشناسی و احیای این جشن میتواند به غنای فرهنگی و هویت ملی ایرانیان کمک کند.
### نتیجهگیری
جشن کژین یکی از آیینهای فراموششده اما ارزشمند ایران باستان است که در ستایش باد و نقش آن در طبیعت و زندگی انسانها برگزار میشده است. این جشن، علاوه بر نمادگرایی مرتبط با عناصر چهارگانه، پیوندی عمیق با باورهای اسطورهای و اجتماعی ایرانیان داشته است. احیای این جشن و آشنایی بیشتر با آن، میتواند به فهم بهتر تاریخ فرهنگی ایران و تقویت حس هویت ملی کمک کند.
 @ df478568:2a951e67
2025-02-07 22:34:11Freedom tech is free and open-source software. It is free as in freedom. A common license in FOSS is the MIT license. It's the license behind Bitcoin, a peer-to-peer electronic cash system. Anyone is free to run this software. The same is true for the software at mempool.space. The software is free to use. I run it on my own server. This is what I use to time-stamp my articles. You can use it to check transactions on the bitcoin time chain, but you need to trust that I'm not doing any funny business. I'm not, but keep in mind, the whole point of p2p elwctronic cash is that you don't trust. You verify. The beauty of FOSS is: You don't need to trust me. You can triple-check the transactions you search on my mempool instance by looking at the official mempool.space website and blockchain.info...Or...You can run your own node on your own hardware, free of charge. Of course, the hardware is not free. Neither is the actual bitcoin. The freedom is built into the software, but as the saying goes, "freedom isn't free." It took me years to learn how to run my own software on my own server and make it available on the clear net. ## SearXNG  [SearXNG](https://github.com/searxng/searxng) is my favorite search engine. I don't like giving up my precious data to big tech located in the United States or China. I run my own search engine. I have noticed certain biases in Google searches. The biggest problem is ads. Companies tend to pay for Yelp and Google reviews. I called an AC company I found from a local magazine that came in the mail. A portly man wearing an HVAC costume drove to my house in a white van. He had a great smile and even better social skills. The van had a slogan plastered on it like most tradie vans do. "Reviews Matter We have a 4.9 Review on Google." He also had his name painted on this van like a Bomber pilot from WW2. I won't dox him, but it was something like "Joe the closer." I don't trust the omnipotenence of the Googs. I also don't trust fat men they call "the closer" to give me the best deal. The trick to saving sats is to choose the game-theory optimal way of negogiation. In DUCY, by David Sklansky, I learned useful negotiation skills. Sklansky wrote classic poker books and applied his actuarial math brain to negotiation techniques. He said he would go to a Toyota dealer and say, "I'm shopping for a new Camry. I already have a price from dealership XYZ in a nearby city. What is your price?" This changes the dynamic right from the starting line and gives the consumer the advantage. So I tried this based technique with the HVAC industrial complex. I got a quote from 3 people: 1. Joe "The Closer." 2. The Costco-sponsored HVAC Company 3. My SearXNG search results. In essence, I apply the same logic I learned running a full bitcoin node. Remember how I said the decentralized nature of bitcoin allows you to **triple-check your transactions?** Running SearXNG allows me to triple check my search results in a similar fashion. I don't trust Google, Costco, or the magazine I get every month in the mail. I verify results with my own search engine. My SearXNG does not track my location, but I set it to give me local results. To be honest, I have not verified this, but the code is on GitHub for everyone to see. I don't want to be "sold" on an AC. I don't want an AC if I could avoid it, but my AC was as dead as dentacoin. Living in Southern California with a wife going through "the change" gave me no alternative. The guy I found on SearXNG showed up in an unmarked van. He had a beard. He was not "a closer." He was an actual HVAC technician. He tried cleaning my unit made in the same year Weezer released their Blue album. He said he coukd jerry rig it to get it working for another few months, but the machine is on it's last days. He said a newer unit would also be more efficient so I asked him about the energy like a bitcoiner. "How many kilowatt hours does it cost me to run my AC versus a new AC?" I don't remember the exact answer, but I asked all three companies. He was the only one that new how to find out. He also happened to be the cheapest, but I would have bought a new AC from this guy even if he wasn't. I told him I made a space heater out of a bitcoin miner. He had no idea this was possible, but he at least pretended to find it interesting. That's why I use SearXNG to find tradesmen. It's better than Yelp. If you would like to try my instance of SearXNG, check it out. `523FeCpi9Gx4nR9NmSFIMEaYcI5Q4WmhYHPEPaEah84=` To decrypt it, use the key behind the paywall at: https://8gwifi.org/CipherFunctions.jsp npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0 [882785](https://mempool.marc26z.com/block/00000000000000000001840e7986ea4b6ea103f5af9b524dc102be926a831dee) [merch](https://marc26z.com/merch/) **Follow me on nostr**. All of my work is available under the Creative Commons 0 licence. If you would like to try my instance of Searxng and do not wish to support my work, find me on habla.news by searching my npub. You can find all of my work there(including encryption keys)free of charge. # Paywall On Substack abdominal.savior.repaint Will decrypt this ciphertext: 523FeCpi9Gx4nR9NmSFIMEaYcI5Q4WmhYHPEPaEah84= Which will reveal my instance of SearXNG at https://searxng.marc26z.com/ [Subscribe on Subtack](https://substack.com/@marc26z)
@ df478568:2a951e67
2025-02-07 22:34:11Freedom tech is free and open-source software. It is free as in freedom. A common license in FOSS is the MIT license. It's the license behind Bitcoin, a peer-to-peer electronic cash system. Anyone is free to run this software. The same is true for the software at mempool.space. The software is free to use. I run it on my own server. This is what I use to time-stamp my articles. You can use it to check transactions on the bitcoin time chain, but you need to trust that I'm not doing any funny business. I'm not, but keep in mind, the whole point of p2p elwctronic cash is that you don't trust. You verify. The beauty of FOSS is: You don't need to trust me. You can triple-check the transactions you search on my mempool instance by looking at the official mempool.space website and blockchain.info...Or...You can run your own node on your own hardware, free of charge. Of course, the hardware is not free. Neither is the actual bitcoin. The freedom is built into the software, but as the saying goes, "freedom isn't free." It took me years to learn how to run my own software on my own server and make it available on the clear net. ## SearXNG  [SearXNG](https://github.com/searxng/searxng) is my favorite search engine. I don't like giving up my precious data to big tech located in the United States or China. I run my own search engine. I have noticed certain biases in Google searches. The biggest problem is ads. Companies tend to pay for Yelp and Google reviews. I called an AC company I found from a local magazine that came in the mail. A portly man wearing an HVAC costume drove to my house in a white van. He had a great smile and even better social skills. The van had a slogan plastered on it like most tradie vans do. "Reviews Matter We have a 4.9 Review on Google." He also had his name painted on this van like a Bomber pilot from WW2. I won't dox him, but it was something like "Joe the closer." I don't trust the omnipotenence of the Googs. I also don't trust fat men they call "the closer" to give me the best deal. The trick to saving sats is to choose the game-theory optimal way of negogiation. In DUCY, by David Sklansky, I learned useful negotiation skills. Sklansky wrote classic poker books and applied his actuarial math brain to negotiation techniques. He said he would go to a Toyota dealer and say, "I'm shopping for a new Camry. I already have a price from dealership XYZ in a nearby city. What is your price?" This changes the dynamic right from the starting line and gives the consumer the advantage. So I tried this based technique with the HVAC industrial complex. I got a quote from 3 people: 1. Joe "The Closer." 2. The Costco-sponsored HVAC Company 3. My SearXNG search results. In essence, I apply the same logic I learned running a full bitcoin node. Remember how I said the decentralized nature of bitcoin allows you to **triple-check your transactions?** Running SearXNG allows me to triple check my search results in a similar fashion. I don't trust Google, Costco, or the magazine I get every month in the mail. I verify results with my own search engine. My SearXNG does not track my location, but I set it to give me local results. To be honest, I have not verified this, but the code is on GitHub for everyone to see. I don't want to be "sold" on an AC. I don't want an AC if I could avoid it, but my AC was as dead as dentacoin. Living in Southern California with a wife going through "the change" gave me no alternative. The guy I found on SearXNG showed up in an unmarked van. He had a beard. He was not "a closer." He was an actual HVAC technician. He tried cleaning my unit made in the same year Weezer released their Blue album. He said he coukd jerry rig it to get it working for another few months, but the machine is on it's last days. He said a newer unit would also be more efficient so I asked him about the energy like a bitcoiner. "How many kilowatt hours does it cost me to run my AC versus a new AC?" I don't remember the exact answer, but I asked all three companies. He was the only one that new how to find out. He also happened to be the cheapest, but I would have bought a new AC from this guy even if he wasn't. I told him I made a space heater out of a bitcoin miner. He had no idea this was possible, but he at least pretended to find it interesting. That's why I use SearXNG to find tradesmen. It's better than Yelp. If you would like to try my instance of SearXNG, check it out. `523FeCpi9Gx4nR9NmSFIMEaYcI5Q4WmhYHPEPaEah84=` To decrypt it, use the key behind the paywall at: https://8gwifi.org/CipherFunctions.jsp npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0 [882785](https://mempool.marc26z.com/block/00000000000000000001840e7986ea4b6ea103f5af9b524dc102be926a831dee) [merch](https://marc26z.com/merch/) **Follow me on nostr**. All of my work is available under the Creative Commons 0 licence. If you would like to try my instance of Searxng and do not wish to support my work, find me on habla.news by searching my npub. You can find all of my work there(including encryption keys)free of charge. # Paywall On Substack abdominal.savior.repaint Will decrypt this ciphertext: 523FeCpi9Gx4nR9NmSFIMEaYcI5Q4WmhYHPEPaEah84= Which will reveal my instance of SearXNG at https://searxng.marc26z.com/ [Subscribe on Subtack](https://substack.com/@marc26z) @ fe32298e:20516265
2025-02-06 02:11:34I've been using AI tools to help with coding for a while now, but it's always been copy/pasting into ChatGPT and DeepSeek. Faster iteration is better, and privacy is best. So it's time to figure out how to use these tools integrated into [VSCodium](https://github.com/VSCodium/vscodium) and running locally. After a quick review of the most popular extensions I've heard about, I settled on [Tabby](https://github.com/TabbyML/tabby). ## What the heck does this actually DO? * Code completion - like autocomplete suggestions, looks at your code and suggests the next thing to type at the cursor. You can see it in gray text, then press Tab and it's added to your code. * Chat - easily chat with an LLM about your code inside your editor, faster than copy/pasting into a website. * Apparently it can write docs and tests too. ## Can I run it locally? Without a GPU? YES! Tabby is optimized for small models that only need a few GBs of RAM. I'm using a fairly old [System76](https://system76.com/) Galago Pro with Core i5-10210U and 16 GB RAM. The fans spin up, and Tabby sometimes shows a warning about slow response time, but it seems usable. ## How do I get it set up? This is the overview, look for step-by-step instructions at the end of this article. 1. Install the Tabby server, which runs locally. 1. Start the Tabby server and tell it to serve some models which it will download automatically. 1. Log in to the Tabby server web interface and create an admin account. 1. Install the Tabby extension in your editor. 1. Connect the Tabby extension to your Tabby server. ## How do I actually use it? 1. Click **Tabby** in the bottom-right corner to open the Tabby command palette. 1. Select **Chat** to open the Chat pane. Drag it to the right side if you want. 1. Or, *Ctrl-Shift-P* and type "tabby" to see some Tabby commands 1. Select some code and *Ctrl-Shift-P* "tabby" to see more Tabby commands 1. **Explain this** seems like a useful one. Other than that, I don't know! I just started using it today. ## What model should I use? As usual, it depends. If you're using CPU instead of GPU, start with the ones recommended by Tabby and shown in the Step-by-Step below. Tabby has a [registry of models](https://tabby.tabbyml.com/docs/models/) you can choose from, and a [leaderboard](https://leaderboard.tabbyml.com/) to compare them. ## Step-by-Step This is for Ubuntu 24.04, and no GPU. ``` # install pre-reqs sudo apt install build-essential cmake libssl-dev pkg-config sudo apt install protobuf-compiler libopenblas-dev sudo apt install make sqlite3 graphviz # install rust curl --proto '=https' --tlsv1.2 -sSf https://sh.rustup.rs | sh . "$HOME/.cargo/env" # build tabby git clone --recurse-submodules https://github.com/TabbyML/tabby cd tabby cargo build # run tabby (downloads ~3 GB of models) ./target/debug/tabby serve --model StarCoder-1B --chat-model Qwen2-1.5B-Instruct # browse to http://0.0.0.0:8080 and create an admin user ``` * Install the Tabby extension in your editor. VSCodium had it in the extensions store by searching for "tabby" or try this `ext install TabbyML.vscode-tabby` * *Ctrl-Shift-P* and look for "Tabby: Connect to server" * Use the default of `http://localhost:8080` * Switch over to the Tabby web interface, click your Profile Picture and copy the auth token * Paste that into Tabby somewhere. I'm sure you'll figure it out if you got this far.
@ fe32298e:20516265
2025-02-06 02:11:34I've been using AI tools to help with coding for a while now, but it's always been copy/pasting into ChatGPT and DeepSeek. Faster iteration is better, and privacy is best. So it's time to figure out how to use these tools integrated into [VSCodium](https://github.com/VSCodium/vscodium) and running locally. After a quick review of the most popular extensions I've heard about, I settled on [Tabby](https://github.com/TabbyML/tabby). ## What the heck does this actually DO? * Code completion - like autocomplete suggestions, looks at your code and suggests the next thing to type at the cursor. You can see it in gray text, then press Tab and it's added to your code. * Chat - easily chat with an LLM about your code inside your editor, faster than copy/pasting into a website. * Apparently it can write docs and tests too. ## Can I run it locally? Without a GPU? YES! Tabby is optimized for small models that only need a few GBs of RAM. I'm using a fairly old [System76](https://system76.com/) Galago Pro with Core i5-10210U and 16 GB RAM. The fans spin up, and Tabby sometimes shows a warning about slow response time, but it seems usable. ## How do I get it set up? This is the overview, look for step-by-step instructions at the end of this article. 1. Install the Tabby server, which runs locally. 1. Start the Tabby server and tell it to serve some models which it will download automatically. 1. Log in to the Tabby server web interface and create an admin account. 1. Install the Tabby extension in your editor. 1. Connect the Tabby extension to your Tabby server. ## How do I actually use it? 1. Click **Tabby** in the bottom-right corner to open the Tabby command palette. 1. Select **Chat** to open the Chat pane. Drag it to the right side if you want. 1. Or, *Ctrl-Shift-P* and type "tabby" to see some Tabby commands 1. Select some code and *Ctrl-Shift-P* "tabby" to see more Tabby commands 1. **Explain this** seems like a useful one. Other than that, I don't know! I just started using it today. ## What model should I use? As usual, it depends. If you're using CPU instead of GPU, start with the ones recommended by Tabby and shown in the Step-by-Step below. Tabby has a [registry of models](https://tabby.tabbyml.com/docs/models/) you can choose from, and a [leaderboard](https://leaderboard.tabbyml.com/) to compare them. ## Step-by-Step This is for Ubuntu 24.04, and no GPU. ``` # install pre-reqs sudo apt install build-essential cmake libssl-dev pkg-config sudo apt install protobuf-compiler libopenblas-dev sudo apt install make sqlite3 graphviz # install rust curl --proto '=https' --tlsv1.2 -sSf https://sh.rustup.rs | sh . "$HOME/.cargo/env" # build tabby git clone --recurse-submodules https://github.com/TabbyML/tabby cd tabby cargo build # run tabby (downloads ~3 GB of models) ./target/debug/tabby serve --model StarCoder-1B --chat-model Qwen2-1.5B-Instruct # browse to http://0.0.0.0:8080 and create an admin user ``` * Install the Tabby extension in your editor. VSCodium had it in the extensions store by searching for "tabby" or try this `ext install TabbyML.vscode-tabby` * *Ctrl-Shift-P* and look for "Tabby: Connect to server" * Use the default of `http://localhost:8080` * Switch over to the Tabby web interface, click your Profile Picture and copy the auth token * Paste that into Tabby somewhere. I'm sure you'll figure it out if you got this far. @ 9e5a3a1a:ed414e8d
2025-02-02 00:51:34(deleted)
@ 9e5a3a1a:ed414e8d
2025-02-02 00:51:34(deleted) @ daa41bed:88f54153
2025-02-09 16:50:04There has been a good bit of discussion on Nostr over the past few days about the merits of zaps as a method of engaging with notes, so after writing a rather lengthy [article on the pros of a strategic Bitcoin reserve](https://geek.npub.pro/post/dxqkgnjplttkvetprg8ox/), I wanted to take some time to chime in on the much more fun topic of digital engagement. Let's begin by defining a couple of things: **Nostr** is a decentralized, censorship-resistance protocol whose current biggest use case is social media (think Twitter/X). Instead of relying on company servers, it relies on relays that anyone can spin up and own their own content. Its use cases are much bigger, though, and this article is hosted on my own relay, using my own Nostr relay as an example. **Zap** is a tip or donation denominated in sats (small units of Bitcoin) sent from one user to another. This is generally done directly over the Lightning Network but is increasingly using Cashu tokens. For the sake of this discussion, how you transmit/receive zaps will be irrelevant, so don't worry if you don't know what [Lightning](https://lightning.network/) or [Cashu](https://cashu.space/) are. If we look at how users engage with posts and follows/followers on platforms like Twitter, Facebook, etc., it becomes evident that traditional social media thrives on engagement farming. The more outrageous a post, the more likely it will get a reaction. We see a version of this on more visual social platforms like YouTube and TikTok that use carefully crafted thumbnail images to grab the user's attention to click the video. If you'd like to dive deep into the psychology and science behind social media engagement, let me know, and I'd be happy to follow up with another article. In this user engagement model, a user is given the option to comment or like the original post, or share it among their followers to increase its signal. They receive no value from engaging with the content aside from the dopamine hit of the original experience or having their comment liked back by whatever influencer they provide value to. Ad revenue flows to the content creator. Clout flows to the content creator. Sales revenue from merch and content placement flows to the content creator. We call this a linear economy -- the idea that resources get created, used up, then thrown away. Users create content and farm as much engagement as possible, then the content is forgotten within a few hours as they move on to the next piece of content to be farmed. What if there were a simple way to give value back to those who engage with your content? By implementing some value-for-value model -- a circular economy. Enter zaps.  Unlike traditional social media platforms, Nostr does not actively use algorithms to determine what content is popular, nor does it push content created for active user engagement to the top of a user's timeline. Yes, there are "trending" and "most zapped" timelines that users can choose to use as their default, but these use relatively straightforward engagement metrics to rank posts for these timelines. That is not to say that we may not see clients actively seeking to refine timeline algorithms for specific metrics. Still, the beauty of having an open protocol with media that is controlled solely by its users is that users who begin to see their timeline gamed towards specific algorithms can choose to move to another client, and for those who are more tech-savvy, they can opt to run their own relays or create their own clients with personalized algorithms and web of trust scoring systems. Zaps enable the means to create a new type of social media economy in which creators can earn for creating content and users can earn by actively engaging with it. Like and reposting content is relatively frictionless and costs nothing but a simple button tap. Zaps provide active engagement because they signal to your followers and those of the content creator that this post has genuine value, quite literally in the form of money—sats.  I have seen some comments on Nostr claiming that removing likes and reactions is for wealthy people who can afford to send zaps and that the majority of people in the US and around the world do not have the time or money to zap because they have better things to spend their money like feeding their families and paying their bills. While at face value, these may seem like valid arguments, they, unfortunately, represent the brainwashed, defeatist attitude that our current economic (and, by extension, social media) systems aim to instill in all of us to continue extracting value from our lives. Imagine now, if those people dedicating their own time (time = money) to mine pity points on social media would instead spend that time with genuine value creation by posting content that is meaningful to cultural discussions. Imagine if, instead of complaining that their posts get no zaps and going on a tirade about how much of a victim they are, they would empower themselves to take control of their content and give value back to the world; where would that leave us? How much value could be created on a nascent platform such as Nostr, and how quickly could it overtake other platforms? Other users argue about user experience and that additional friction (i.e., zaps) leads to lower engagement, as proven by decades of studies on user interaction. While the added friction may turn some users away, does that necessarily provide less value? I argue quite the opposite. You haven't made a few sats from zaps with your content? Can't afford to send some sats to a wallet for zapping? How about using the most excellent available resource and spending 10 seconds of your time to leave a comment? Likes and reactions are valueless transactions. Social media's real value derives from providing monetary compensation and actively engaging in a conversation with posts you find interesting or thought-provoking. Remember when humans thrived on conversation and discussion for entertainment instead of simply being an onlooker of someone else's life? If you've made it this far, my only request is this: try only zapping and commenting as a method of engagement for two weeks. Sure, you may end up liking a post here and there, but be more mindful of how you interact with the world and break yourself from blind instinct. You'll thank me later. 
@ daa41bed:88f54153
2025-02-09 16:50:04There has been a good bit of discussion on Nostr over the past few days about the merits of zaps as a method of engaging with notes, so after writing a rather lengthy [article on the pros of a strategic Bitcoin reserve](https://geek.npub.pro/post/dxqkgnjplttkvetprg8ox/), I wanted to take some time to chime in on the much more fun topic of digital engagement. Let's begin by defining a couple of things: **Nostr** is a decentralized, censorship-resistance protocol whose current biggest use case is social media (think Twitter/X). Instead of relying on company servers, it relies on relays that anyone can spin up and own their own content. Its use cases are much bigger, though, and this article is hosted on my own relay, using my own Nostr relay as an example. **Zap** is a tip or donation denominated in sats (small units of Bitcoin) sent from one user to another. This is generally done directly over the Lightning Network but is increasingly using Cashu tokens. For the sake of this discussion, how you transmit/receive zaps will be irrelevant, so don't worry if you don't know what [Lightning](https://lightning.network/) or [Cashu](https://cashu.space/) are. If we look at how users engage with posts and follows/followers on platforms like Twitter, Facebook, etc., it becomes evident that traditional social media thrives on engagement farming. The more outrageous a post, the more likely it will get a reaction. We see a version of this on more visual social platforms like YouTube and TikTok that use carefully crafted thumbnail images to grab the user's attention to click the video. If you'd like to dive deep into the psychology and science behind social media engagement, let me know, and I'd be happy to follow up with another article. In this user engagement model, a user is given the option to comment or like the original post, or share it among their followers to increase its signal. They receive no value from engaging with the content aside from the dopamine hit of the original experience or having their comment liked back by whatever influencer they provide value to. Ad revenue flows to the content creator. Clout flows to the content creator. Sales revenue from merch and content placement flows to the content creator. We call this a linear economy -- the idea that resources get created, used up, then thrown away. Users create content and farm as much engagement as possible, then the content is forgotten within a few hours as they move on to the next piece of content to be farmed. What if there were a simple way to give value back to those who engage with your content? By implementing some value-for-value model -- a circular economy. Enter zaps.  Unlike traditional social media platforms, Nostr does not actively use algorithms to determine what content is popular, nor does it push content created for active user engagement to the top of a user's timeline. Yes, there are "trending" and "most zapped" timelines that users can choose to use as their default, but these use relatively straightforward engagement metrics to rank posts for these timelines. That is not to say that we may not see clients actively seeking to refine timeline algorithms for specific metrics. Still, the beauty of having an open protocol with media that is controlled solely by its users is that users who begin to see their timeline gamed towards specific algorithms can choose to move to another client, and for those who are more tech-savvy, they can opt to run their own relays or create their own clients with personalized algorithms and web of trust scoring systems. Zaps enable the means to create a new type of social media economy in which creators can earn for creating content and users can earn by actively engaging with it. Like and reposting content is relatively frictionless and costs nothing but a simple button tap. Zaps provide active engagement because they signal to your followers and those of the content creator that this post has genuine value, quite literally in the form of money—sats.  I have seen some comments on Nostr claiming that removing likes and reactions is for wealthy people who can afford to send zaps and that the majority of people in the US and around the world do not have the time or money to zap because they have better things to spend their money like feeding their families and paying their bills. While at face value, these may seem like valid arguments, they, unfortunately, represent the brainwashed, defeatist attitude that our current economic (and, by extension, social media) systems aim to instill in all of us to continue extracting value from our lives. Imagine now, if those people dedicating their own time (time = money) to mine pity points on social media would instead spend that time with genuine value creation by posting content that is meaningful to cultural discussions. Imagine if, instead of complaining that their posts get no zaps and going on a tirade about how much of a victim they are, they would empower themselves to take control of their content and give value back to the world; where would that leave us? How much value could be created on a nascent platform such as Nostr, and how quickly could it overtake other platforms? Other users argue about user experience and that additional friction (i.e., zaps) leads to lower engagement, as proven by decades of studies on user interaction. While the added friction may turn some users away, does that necessarily provide less value? I argue quite the opposite. You haven't made a few sats from zaps with your content? Can't afford to send some sats to a wallet for zapping? How about using the most excellent available resource and spending 10 seconds of your time to leave a comment? Likes and reactions are valueless transactions. Social media's real value derives from providing monetary compensation and actively engaging in a conversation with posts you find interesting or thought-provoking. Remember when humans thrived on conversation and discussion for entertainment instead of simply being an onlooker of someone else's life? If you've made it this far, my only request is this: try only zapping and commenting as a method of engagement for two weeks. Sure, you may end up liking a post here and there, but be more mindful of how you interact with the world and break yourself from blind instinct. You'll thank me later.  @ bbb5dda0:f09e2747
2025-02-11 05:19:58**There's nothing like the ability of a Nostr/Bitcoin meetup to bring your bullish-ness back to a 120%. This weekend I had the honors to be part of the [Sats 'n Facts](https://satsnfacts.btc.pub/) conference so this update will be mostly about the conference.**  # Tollgate A while ago while still at SEC I got the invitation to go to Sats 'n Facts and tell something about TollGate, which I was working on at the time. This is the reason I made such a push on the TollGate Android app, because I wanted to show the world the potential implications of this technology when applied in practice. We get the ability to build our own (physical!) sovereign network infrastructure. Maybe it doesn't sound too sexy for rich western countries, but very valuable for regions with lacking digital infrastructure, or regular powercuts (something I learned at the conference, that TollGate could be applied to bridge those).  Above: Illustration how a TollGate network connects to the legacy internet. I did a presentation about the project and did a demo, which as the universe commands, suffered from the [demo-effect](https://www.urbandictionary.com/define.php?term=demo%20effect). Despite that, it was very well-received and the feedback and ideas on how and where to apply this were amazing. From splitting your bill with your neighbour, to strapping 5g-enabled routers to a light-fixture in the city, everyone had their own ideas on how to use it, and the cool thing is that all of it can be done. ## Presenting GitHub Actions & Epoxy I held a seperate session on the GitHub actions project and Epoxy. The response was great and I have some more feedback coming in a 1-on-1 session, so I'm sure i'll be posting about that in the near future. ## A realization about Epoxy + TollGate The more I talk about Epoxy and TollGate, the more I realize how much they are related. Epoxy is a way of bridging connectivity between Nostr users that are on clearnet and want to connect to Relays that are on Tor. But rather than just bridging the captured clearnet and tor, it can be the bridge between clearnet and a community TollGate network, or between different TollGate networks. As I've thought more about the implications of sovereign TollGate based networks, I think the introduction of many TollGate networks might create a fracturing of the broader internet, which I'd argue is not even a bad thing as this fracturing can reduce centralized surveillance and control. If we'd do this within the conventional way of operating services - think API's & talking directly to servers- that would be a problem as we need to reach those servers at any moment in time. But given the decentralized Nature of Nostr messages + Blossom files, you might not even notice it if your geographical region gets cut off from the rest of the world, because the content likely already exists within your -now cut off- network. If we can get our content local, why wouldn't we embrace this fractured internet and use it in our advantage. nostr:naddr1qvzqqqr4gupzpwa4mkswz4t8j70s2s6q00wzqv7k7zamxrmj2y4fs88aktcfuf68qq3k2ur00puj6mt0dejhg6t6v93xcefdwajkyum0vd4k2apdwpex77rfv4esk0qk8g ## A final word I'm incredible grateful to be meeting all these talented developers, artists and community builders! I love to see art being integrated into the broader ecosystem and I think us dev's need to lean on the community builders to get our projects out into the world, they often have the insight on how our software shapes the lives of the communities they help to grow. Let's embrace that dynamic! special thanks to nostr:npub19m7m3rs66pfdn4ewhrm8slh60ukyxgrylaa03m73wa40j39lc03syq4gfu for his incredible drawings of the presentations: nostr:nevent1qvzqqqqqqypzpr2m4ykgej3at3ee9upe82c4h58uda35xfd5292purmuntrv8mx4qqsfr9f9kvta87yukqhedc00vckupu3erx3mk3nvxm28ptfak0acgrc6adj94 
@ bbb5dda0:f09e2747
2025-02-11 05:19:58**There's nothing like the ability of a Nostr/Bitcoin meetup to bring your bullish-ness back to a 120%. This weekend I had the honors to be part of the [Sats 'n Facts](https://satsnfacts.btc.pub/) conference so this update will be mostly about the conference.**  # Tollgate A while ago while still at SEC I got the invitation to go to Sats 'n Facts and tell something about TollGate, which I was working on at the time. This is the reason I made such a push on the TollGate Android app, because I wanted to show the world the potential implications of this technology when applied in practice. We get the ability to build our own (physical!) sovereign network infrastructure. Maybe it doesn't sound too sexy for rich western countries, but very valuable for regions with lacking digital infrastructure, or regular powercuts (something I learned at the conference, that TollGate could be applied to bridge those).  Above: Illustration how a TollGate network connects to the legacy internet. I did a presentation about the project and did a demo, which as the universe commands, suffered from the [demo-effect](https://www.urbandictionary.com/define.php?term=demo%20effect). Despite that, it was very well-received and the feedback and ideas on how and where to apply this were amazing. From splitting your bill with your neighbour, to strapping 5g-enabled routers to a light-fixture in the city, everyone had their own ideas on how to use it, and the cool thing is that all of it can be done. ## Presenting GitHub Actions & Epoxy I held a seperate session on the GitHub actions project and Epoxy. The response was great and I have some more feedback coming in a 1-on-1 session, so I'm sure i'll be posting about that in the near future. ## A realization about Epoxy + TollGate The more I talk about Epoxy and TollGate, the more I realize how much they are related. Epoxy is a way of bridging connectivity between Nostr users that are on clearnet and want to connect to Relays that are on Tor. But rather than just bridging the captured clearnet and tor, it can be the bridge between clearnet and a community TollGate network, or between different TollGate networks. As I've thought more about the implications of sovereign TollGate based networks, I think the introduction of many TollGate networks might create a fracturing of the broader internet, which I'd argue is not even a bad thing as this fracturing can reduce centralized surveillance and control. If we'd do this within the conventional way of operating services - think API's & talking directly to servers- that would be a problem as we need to reach those servers at any moment in time. But given the decentralized Nature of Nostr messages + Blossom files, you might not even notice it if your geographical region gets cut off from the rest of the world, because the content likely already exists within your -now cut off- network. If we can get our content local, why wouldn't we embrace this fractured internet and use it in our advantage. nostr:naddr1qvzqqqr4gupzpwa4mkswz4t8j70s2s6q00wzqv7k7zamxrmj2y4fs88aktcfuf68qq3k2ur00puj6mt0dejhg6t6v93xcefdwajkyum0vd4k2apdwpex77rfv4esk0qk8g ## A final word I'm incredible grateful to be meeting all these talented developers, artists and community builders! I love to see art being integrated into the broader ecosystem and I think us dev's need to lean on the community builders to get our projects out into the world, they often have the insight on how our software shapes the lives of the communities they help to grow. Let's embrace that dynamic! special thanks to nostr:npub19m7m3rs66pfdn4ewhrm8slh60ukyxgrylaa03m73wa40j39lc03syq4gfu for his incredible drawings of the presentations: nostr:nevent1qvzqqqqqqypzpr2m4ykgej3at3ee9upe82c4h58uda35xfd5292purmuntrv8mx4qqsfr9f9kvta87yukqhedc00vckupu3erx3mk3nvxm28ptfak0acgrc6adj94  @ ce75bae2:26c5d165
2025-02-11 04:18:26Bitcoin is reshaping entrepreneurship in Uganda and beyond. For many, it’s not just an alternative currency but a tool for financial empowerment, business innovation, and global connectivity. Herein, I reflect on my journey with Bitcoin, its impact on entrepreneurship, and how it has changed the way I operate business in Uganda. Discovering Bitcoin: A Fortunate Scam My Bitcoin journey started six years ago—not through traditional investment or financial curiosity, but rather by accident. Like many young people searching for ways to make money online, I stumbled upon a website that promised earnings through paid ad viewing. This turned out to be a scam, but it introduced me to Bitcoin. The site offered Bitcoin as a payment option, forcing me to learn how to set up a wallet and receive transactions. Though I lost money in the process, the experience was invaluable—I had unknowingly opened the door to an entirely new financial system. Years later, I checked my old wallet and saw that the small amount of Bitcoin I had left had doubled in value. That moment sparked a deeper curiosity, leading me to research Bitcoin’s mechanics and how it could be used beyond speculation. From Curiosity to Business Innovation As I dove deeper into the Bitcoin ecosystem, I saw its potential to transform business in ways that traditional finance could not. The first realization was that Bitcoin allows global transactions without intermediaries—a critical advantage for entrepreneurs in Uganda, where banking systems are often restrictive and expensive. Today, all the businesses I co-founded, including Gorilla Sats , Jungle B, and Juicy B, are deeply integrated with Bitcoin. My approach to entrepreneurship has shifted from merely running a business to leveraging Bitcoin as a tool for economic efficiency and expansion. Bitcoin’s Role in Business Growth 1. Unlocking Global Markets One of the biggest barriers for African entrepreneurs is the difficulty of conducting business beyond borders. International transactions often involve costly intermediaries, unfavorable exchange rates, and bureaucratic delays. Bitcoin eliminates these restrictions, allowing businesses to trade with anyone, anywhere, instantly. For example, at Gorilla Sats, our adventure tourism company, 70% of our customers come because we accept Bitcoin payments. Bitcoin not only opens a new customer base but also positions our business in a niche market—one of the very few in the world where travelers can book experiences entirely using Bitcoin. 2. Enhancing Financial Efficiency Traditional financial systems in Uganda rely heavily on mobile money, which, while innovative, is expensive. Transactions incur fees at every stage: deposit, transfer, and withdrawal. It’s not uncommon for users to lose 10-15% of their money in fees when sending funds. Bitcoin, on the other hand, allows for low-cost, borderless transactions. For businesses, this means higher profit margins and the ability to reinvest savings into growth. 3. Financial Resilience in an Inflationary Economy In just a few years, Uganda’s local currency has lost nearly 50% of its value against the US dollar. Businesses operating in shillings face constant depreciation, making long-term planning difficult. By storing value in Bitcoin, businesses can hedge against inflation and maintain purchasing power over time. At Jungle B, we keep part of our balance sheet in Bitcoin. This strategy protects us from the currency fluctuations that regularly impact Ugandan businesses operating solely in fiat currency. 4. Transforming Social Impact and Charity Beyond business, Bitcoin has become a tool for grassroots financial inclusion. At the Orphans of Uganda initiative, we integrate Bitcoin into daily transactions, ensuring donations reach the children directly without middlemen. Every day, children at the orphanage make symbolic Bitcoin payments for their food, learning firsthand how to use digital money responsibly. This isn’t just about feeding children—it’s about educating the next generation on financial autonomy. Challenges and Opportunities in Uganda 1. Skepticism and Misinformation Many Ugandans associate Bitcoin with scams, mainly due to past fraudulent projects. Educating people on the difference between Bitcoin (a decentralized asset) and scam coins (pyramid schemes) remains a challenge. 2. Regulatory Uncertainty Uganda’s regulatory environment for Bitcoin is still unclear. While Bitcoin remains in a legal vacuum, financial institutions are discouraged from facilitating Bitcoin transactions. However, this hasn’t stopped individuals and businesses from using it. In fact, the lack of regulation often makes adoption easier, as Bitcoin operates independently of government oversight. 3. Resistance from Traditional Financial Players Mobile money services like MTN and Airtel make enormous profits from transaction fees. If Bitcoin adoption grows, their revenue model could be threatened, leading to resistance from these financial institutions. However, they could integrate Bitcoin instead of fighting it, making transactions cheaper for their users. The Future of Bitcoin in Uganda Will there be mass Bitcoin adoption in Uganda? Not overnight. Many people resist change, and history shows that better financial tools don’t always lead to immediate adoption. However, Bitcoin’s advantages will continue to attract forward-thinking entrepreneurs and business owners. For those who embrace it, Bitcoin redefines entrepreneurship, offering financial independence, borderless trade, and a hedge against economic instability. Whether governments embrace it or not, businesses like mine and many others under Blockchain Association of Uganda (BAU) will continue pioneering its use in Uganda. Final Thoughts Bitcoin is more than just a digital currency—it’s a tool for freedom, efficiency, and global entrepreneurship. The more people learn about its benefits, the more they will integrate it into their businesses and daily lives. The journey begins with education and experimentation, just as mine did years ago. For those looking to explore Bitcoin-powered experiences, connect with us at gorilla-sats.com, or follow my work with bitcoinkampala.org. Whether you’re a business owner, traveler, or philanthropist, Bitcoin offers new possibilities—it’s time to embrace the future. originally posted at https://stacker.news/items/882366
@ ce75bae2:26c5d165
2025-02-11 04:18:26Bitcoin is reshaping entrepreneurship in Uganda and beyond. For many, it’s not just an alternative currency but a tool for financial empowerment, business innovation, and global connectivity. Herein, I reflect on my journey with Bitcoin, its impact on entrepreneurship, and how it has changed the way I operate business in Uganda. Discovering Bitcoin: A Fortunate Scam My Bitcoin journey started six years ago—not through traditional investment or financial curiosity, but rather by accident. Like many young people searching for ways to make money online, I stumbled upon a website that promised earnings through paid ad viewing. This turned out to be a scam, but it introduced me to Bitcoin. The site offered Bitcoin as a payment option, forcing me to learn how to set up a wallet and receive transactions. Though I lost money in the process, the experience was invaluable—I had unknowingly opened the door to an entirely new financial system. Years later, I checked my old wallet and saw that the small amount of Bitcoin I had left had doubled in value. That moment sparked a deeper curiosity, leading me to research Bitcoin’s mechanics and how it could be used beyond speculation. From Curiosity to Business Innovation As I dove deeper into the Bitcoin ecosystem, I saw its potential to transform business in ways that traditional finance could not. The first realization was that Bitcoin allows global transactions without intermediaries—a critical advantage for entrepreneurs in Uganda, where banking systems are often restrictive and expensive. Today, all the businesses I co-founded, including Gorilla Sats , Jungle B, and Juicy B, are deeply integrated with Bitcoin. My approach to entrepreneurship has shifted from merely running a business to leveraging Bitcoin as a tool for economic efficiency and expansion. Bitcoin’s Role in Business Growth 1. Unlocking Global Markets One of the biggest barriers for African entrepreneurs is the difficulty of conducting business beyond borders. International transactions often involve costly intermediaries, unfavorable exchange rates, and bureaucratic delays. Bitcoin eliminates these restrictions, allowing businesses to trade with anyone, anywhere, instantly. For example, at Gorilla Sats, our adventure tourism company, 70% of our customers come because we accept Bitcoin payments. Bitcoin not only opens a new customer base but also positions our business in a niche market—one of the very few in the world where travelers can book experiences entirely using Bitcoin. 2. Enhancing Financial Efficiency Traditional financial systems in Uganda rely heavily on mobile money, which, while innovative, is expensive. Transactions incur fees at every stage: deposit, transfer, and withdrawal. It’s not uncommon for users to lose 10-15% of their money in fees when sending funds. Bitcoin, on the other hand, allows for low-cost, borderless transactions. For businesses, this means higher profit margins and the ability to reinvest savings into growth. 3. Financial Resilience in an Inflationary Economy In just a few years, Uganda’s local currency has lost nearly 50% of its value against the US dollar. Businesses operating in shillings face constant depreciation, making long-term planning difficult. By storing value in Bitcoin, businesses can hedge against inflation and maintain purchasing power over time. At Jungle B, we keep part of our balance sheet in Bitcoin. This strategy protects us from the currency fluctuations that regularly impact Ugandan businesses operating solely in fiat currency. 4. Transforming Social Impact and Charity Beyond business, Bitcoin has become a tool for grassroots financial inclusion. At the Orphans of Uganda initiative, we integrate Bitcoin into daily transactions, ensuring donations reach the children directly without middlemen. Every day, children at the orphanage make symbolic Bitcoin payments for their food, learning firsthand how to use digital money responsibly. This isn’t just about feeding children—it’s about educating the next generation on financial autonomy. Challenges and Opportunities in Uganda 1. Skepticism and Misinformation Many Ugandans associate Bitcoin with scams, mainly due to past fraudulent projects. Educating people on the difference between Bitcoin (a decentralized asset) and scam coins (pyramid schemes) remains a challenge. 2. Regulatory Uncertainty Uganda’s regulatory environment for Bitcoin is still unclear. While Bitcoin remains in a legal vacuum, financial institutions are discouraged from facilitating Bitcoin transactions. However, this hasn’t stopped individuals and businesses from using it. In fact, the lack of regulation often makes adoption easier, as Bitcoin operates independently of government oversight. 3. Resistance from Traditional Financial Players Mobile money services like MTN and Airtel make enormous profits from transaction fees. If Bitcoin adoption grows, their revenue model could be threatened, leading to resistance from these financial institutions. However, they could integrate Bitcoin instead of fighting it, making transactions cheaper for their users. The Future of Bitcoin in Uganda Will there be mass Bitcoin adoption in Uganda? Not overnight. Many people resist change, and history shows that better financial tools don’t always lead to immediate adoption. However, Bitcoin’s advantages will continue to attract forward-thinking entrepreneurs and business owners. For those who embrace it, Bitcoin redefines entrepreneurship, offering financial independence, borderless trade, and a hedge against economic instability. Whether governments embrace it or not, businesses like mine and many others under Blockchain Association of Uganda (BAU) will continue pioneering its use in Uganda. Final Thoughts Bitcoin is more than just a digital currency—it’s a tool for freedom, efficiency, and global entrepreneurship. The more people learn about its benefits, the more they will integrate it into their businesses and daily lives. The journey begins with education and experimentation, just as mine did years ago. For those looking to explore Bitcoin-powered experiences, connect with us at gorilla-sats.com, or follow my work with bitcoinkampala.org. Whether you’re a business owner, traveler, or philanthropist, Bitcoin offers new possibilities—it’s time to embrace the future. originally posted at https://stacker.news/items/882366 @ d058ffb7:70ed2330
2025-02-11 01:10:10Je publie un ancien texte portant sur Nostr. Auparavant hébergé sur ghost, je teste maintetant la capacité de Nostr d'hébergé de long format. *** Un point tournant vient d'être franchi. Damus est officiellement disponible sur le App Store de Apple, fini le mode bêta. Mais en quoi c'est un point tournant ? Apple joue un rôle important de gatekeeper. Chaque application qui veut accéder à son énorme écosystème doit passer une révision diligente, parfois excessive, avant d'être accessible à tous. Après plusieurs tentatives, le principal développeur de Damus, une application dont le code source ouvert est disponible sur github, a finalement reçu son acceptation. Mais encore, pourquoi est-ce un point tournant ? Et bien, Damus est la principale application pour accéder aux échanges du protocole Nostr. Ce protocole change le paradigme des réseaux sociaux et réduit pratiquement à néant les capacités de censure par une autorité, que ce soit Apple, le gouvernement américain ou un régime autoritaire. Déjà, après quelques heures, on peut voir une affluence chinoise à la recherche de liberté de parole. Ainsi, en permettant l'accès à cette application, Apple permet à des millions de personnes d'échanger des idées comme jamais auparavant. Mais en quoi c'est différent ? Les 3 éléments suivants expliquent grandement la différence : #### Identification par pairs clé publique / clé privée Cette stratégie permet de partir avec un haut niveau d'anonymisation. Au besoin, certaines fonctionnalités ou applications pourront venir ajouter certains concepts tel que la vérification d'humanité - la proposition NIP-05 va dans ce sens - ou encore la réputation. Evidemment, ca implique d'autres avantages, surtout dans des pays déjà sous haute surveillance. #### Décentralisation via l'utilisation de relais intermédiaires Cette architecture assure une résilience du réseau. Chaque relai peut décider l'information qu'il diffuse. Si un relai décide de censurer, un autre peut prendre le relai. Il est possible qu'on voit des relais apparaitre par communauté / région afin d'assurer une diffusion optimale des messages. La mise en place de relais entraine cependant des coûts, principalement matériel et télécommunications / bande passante. Différentes stratégies sont en cours d'[expérimentation](https://andreneves.xyz/p/the-rise-of-paid-nostr-relays), notamment via l'utilisation du réseau lightning, qui pourrait charger un frais minime lors d'échange de bitcoin. #### Séparation entre le protocole et les applications Enfin, cette séparation permet d'éviter les points uniques d'échec. Par exemple, malgré l'espoir de liberté qu'a eu l'application Damus, cette dernière a rapidement été [banni par l'état chinois](https://twitter.com/damusapp/status/1621220422216998915). Mais l'espoir survie, car il existe plusieurs alternatives pour accéder au protocole, que ce soit via des applications web (i.g. https://astral.ninja), des applications Android (i.g. Amethyst) ou encore, directement les codes sources sur github. Cela permet également à des applications existantes d'intégrer ce protocole. Jumelée à l'utilisation des clés publiques/privées, qui permet une mobilité de son réseau de contact, une saine compétition devrait s'établir sur ces applications clientes afin d'offrir la meilleure expérience utilisateur, que ce soit par l'interface graphique, la modération / curation du fils de nouvelles ou simplement la performance. Il faut cependant être réaliste, il reste beaucoup de défis à affronter avant d'atteindre le grand public. Parmi les défis, ceux-ci me semblent les plus importants:##### Experience utilisateur Alors que l'utilisation d'une paires de clés publique / privée peut sembler naturel pour les utilisateurs de bitcoin (et de crypto), ca peut être intimidant pour un non-initié. Le concept de relais n'est également pas intuitif et aurait avantage à être vulgariser ou abstrait/transparent. La performance de rafraichissement peut aussi être grandement améliorée. #### Modération et curation Qu'on aime ou on n'aime pas, Twitter utilise un algorithme puissant qui permet d'avoir un minimum de pertinence dans les messages affichées. Ce n'est pas encore le cas pour la majorité des applications Nostr. Par conséquent, on peut se sentir *spammer* lorsqu'on regarde le *feed* global. L'arrivée de beaucoup d'utilisateur chinois, et l'incapacité de traduire nativement, a amplifié ce sentiment. Malgré cela, je suis confiant qu'on va continuer d'entendre parler de ce protocole dans les années et décennies à venir. Pour me suivre, n'hésitez pas à me suivre : npub16pv0ld77fx0l8mjxwqtnq0dd7md40zte5w60esstfsty6u8dyvcqre8d46 Et pour lire une perspective différente sur le sujet, j'ai beaucoup apprécié cette lecture : https://read.pourteaux.xyz/p/the-moral-imperative-of-a-distributed
@ d058ffb7:70ed2330
2025-02-11 01:10:10Je publie un ancien texte portant sur Nostr. Auparavant hébergé sur ghost, je teste maintetant la capacité de Nostr d'hébergé de long format. *** Un point tournant vient d'être franchi. Damus est officiellement disponible sur le App Store de Apple, fini le mode bêta. Mais en quoi c'est un point tournant ? Apple joue un rôle important de gatekeeper. Chaque application qui veut accéder à son énorme écosystème doit passer une révision diligente, parfois excessive, avant d'être accessible à tous. Après plusieurs tentatives, le principal développeur de Damus, une application dont le code source ouvert est disponible sur github, a finalement reçu son acceptation. Mais encore, pourquoi est-ce un point tournant ? Et bien, Damus est la principale application pour accéder aux échanges du protocole Nostr. Ce protocole change le paradigme des réseaux sociaux et réduit pratiquement à néant les capacités de censure par une autorité, que ce soit Apple, le gouvernement américain ou un régime autoritaire. Déjà, après quelques heures, on peut voir une affluence chinoise à la recherche de liberté de parole. Ainsi, en permettant l'accès à cette application, Apple permet à des millions de personnes d'échanger des idées comme jamais auparavant. Mais en quoi c'est différent ? Les 3 éléments suivants expliquent grandement la différence : #### Identification par pairs clé publique / clé privée Cette stratégie permet de partir avec un haut niveau d'anonymisation. Au besoin, certaines fonctionnalités ou applications pourront venir ajouter certains concepts tel que la vérification d'humanité - la proposition NIP-05 va dans ce sens - ou encore la réputation. Evidemment, ca implique d'autres avantages, surtout dans des pays déjà sous haute surveillance. #### Décentralisation via l'utilisation de relais intermédiaires Cette architecture assure une résilience du réseau. Chaque relai peut décider l'information qu'il diffuse. Si un relai décide de censurer, un autre peut prendre le relai. Il est possible qu'on voit des relais apparaitre par communauté / région afin d'assurer une diffusion optimale des messages. La mise en place de relais entraine cependant des coûts, principalement matériel et télécommunications / bande passante. Différentes stratégies sont en cours d'[expérimentation](https://andreneves.xyz/p/the-rise-of-paid-nostr-relays), notamment via l'utilisation du réseau lightning, qui pourrait charger un frais minime lors d'échange de bitcoin. #### Séparation entre le protocole et les applications Enfin, cette séparation permet d'éviter les points uniques d'échec. Par exemple, malgré l'espoir de liberté qu'a eu l'application Damus, cette dernière a rapidement été [banni par l'état chinois](https://twitter.com/damusapp/status/1621220422216998915). Mais l'espoir survie, car il existe plusieurs alternatives pour accéder au protocole, que ce soit via des applications web (i.g. https://astral.ninja), des applications Android (i.g. Amethyst) ou encore, directement les codes sources sur github. Cela permet également à des applications existantes d'intégrer ce protocole. Jumelée à l'utilisation des clés publiques/privées, qui permet une mobilité de son réseau de contact, une saine compétition devrait s'établir sur ces applications clientes afin d'offrir la meilleure expérience utilisateur, que ce soit par l'interface graphique, la modération / curation du fils de nouvelles ou simplement la performance. Il faut cependant être réaliste, il reste beaucoup de défis à affronter avant d'atteindre le grand public. Parmi les défis, ceux-ci me semblent les plus importants:##### Experience utilisateur Alors que l'utilisation d'une paires de clés publique / privée peut sembler naturel pour les utilisateurs de bitcoin (et de crypto), ca peut être intimidant pour un non-initié. Le concept de relais n'est également pas intuitif et aurait avantage à être vulgariser ou abstrait/transparent. La performance de rafraichissement peut aussi être grandement améliorée. #### Modération et curation Qu'on aime ou on n'aime pas, Twitter utilise un algorithme puissant qui permet d'avoir un minimum de pertinence dans les messages affichées. Ce n'est pas encore le cas pour la majorité des applications Nostr. Par conséquent, on peut se sentir *spammer* lorsqu'on regarde le *feed* global. L'arrivée de beaucoup d'utilisateur chinois, et l'incapacité de traduire nativement, a amplifié ce sentiment. Malgré cela, je suis confiant qu'on va continuer d'entendre parler de ce protocole dans les années et décennies à venir. Pour me suivre, n'hésitez pas à me suivre : npub16pv0ld77fx0l8mjxwqtnq0dd7md40zte5w60esstfsty6u8dyvcqre8d46 Et pour lire une perspective différente sur le sujet, j'ai beaucoup apprécié cette lecture : https://read.pourteaux.xyz/p/the-moral-imperative-of-a-distributed @ 9673b322:1b75ee9e
2025-02-10 20:37:30This is an example of test blog post, to be published via the obstrlish plugin. ### This is a sub heading **Lorem Ipsum** is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry's standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book. It has survived not only five centuries, but also the leap into electronic typesetting, remaining essentially unchanged. It was popularised in the 1960s with the release of Letraset sheets containing Lorem Ipsum passages, and more recently with desktop publishing software like Aldus PageMaker including versions of Lorem Ipsum. * Test bullet point * test teste * test *sdfasdfasdfasdfadf* ### The standard Lorem Ipsum passage, used since the 1500s "Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum." ### Section 1.10.32 of "de Finibus Bonorum et Malorum", written by Cicero in 45 BC "Sed ut perspiciatis unde omnis iste natus error sit voluptatem accusantium doloremque laudantium, totam rem aperiam, eaque ipsa quae ab illo inventore veritatis et quasi architecto beatae vitae dicta sunt explicabo. Nemo enim ipsam voluptatem quia voluptas sit aspernatur aut odit aut fugit, sed quia consequuntur magni dolores eos qui ratione voluptatem sequi nesciunt. Neque porro quisquam est, qui dolorem ipsum quia dolor sit amet, consectetur, adipisci velit, sed quia non numquam eius modi tempora incidunt ut labore et dolore magnam aliquam quaerat voluptatem. Ut enim ad minima veniam, quis nostrum exercitationem ullam corporis suscipit laboriosam, nisi ut aliquid ex ea commodi consequatur? Quis autem vel eum iure reprehenderit qui in ea voluptate velit esse quam nihil molestiae consequatur, vel illum qui dolorem eum fugiat quo voluptas nulla pariatur?" ### 1914 translation by H. Rackham "But I must explain to you how all this mistaken idea of denouncing pleasure and praising pain was born and I will give you a complete account of the system, and expound the actual teachings of the great explorer of the truth, the master-builder of human happiness. No one rejects, dislikes, or avoids pleasure itself, because it is pleasure, but because those who do not know how to pursue pleasure rationally encounter consequences that are extremely painful. Nor again is there anyone who loves or pursues or desires to obtain pain of itself, because it is pain, but because occasionally circumstances occur in which toil and pain can procure him some great pleasure. To take a trivial example, which of us ever undertakes laborious physical exercise, except to obtain some advantage from it? But who has any right to find fault with a man who chooses to enjoy a pleasure that has no annoying consequences, or one who avoids a pain that produces no resultant pleasure?" ### Section 1.10.33 of "de Finibus Bonorum et Malorum", written by Cicero in 45 BC "At vero eos et accusamus et iusto odio dignissimos ducimus qui blanditiis praesentium voluptatum deleniti atque corrupti quos dolores et quas molestias excepturi sint occaecati cupiditate non provident, similique sunt in culpa qui officia deserunt mollitia animi, id est laborum et dolorum fuga. Et harum quidem rerum facilis est et expedita distinctio. Nam libero tempore, cum soluta nobis est eligendi optio cumque nihil impedit quo minus id quod maxime placeat facere possimus, omnis voluptas assumenda est, omnis dolor repellendus. Temporibus autem quibusdam et aut officiis debitis aut rerum necessitatibus saepe eveniet ut et voluptates repudiandae sint et molestiae non recusandae. Itaque earum rerum hic tenetur a sapiente delectus, ut aut reiciendis voluptatibus maiores alias consequatur aut perferendis doloribus asperiores repellat."
@ 9673b322:1b75ee9e
2025-02-10 20:37:30This is an example of test blog post, to be published via the obstrlish plugin. ### This is a sub heading **Lorem Ipsum** is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry's standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book. It has survived not only five centuries, but also the leap into electronic typesetting, remaining essentially unchanged. It was popularised in the 1960s with the release of Letraset sheets containing Lorem Ipsum passages, and more recently with desktop publishing software like Aldus PageMaker including versions of Lorem Ipsum. * Test bullet point * test teste * test *sdfasdfasdfasdfadf* ### The standard Lorem Ipsum passage, used since the 1500s "Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum." ### Section 1.10.32 of "de Finibus Bonorum et Malorum", written by Cicero in 45 BC "Sed ut perspiciatis unde omnis iste natus error sit voluptatem accusantium doloremque laudantium, totam rem aperiam, eaque ipsa quae ab illo inventore veritatis et quasi architecto beatae vitae dicta sunt explicabo. Nemo enim ipsam voluptatem quia voluptas sit aspernatur aut odit aut fugit, sed quia consequuntur magni dolores eos qui ratione voluptatem sequi nesciunt. Neque porro quisquam est, qui dolorem ipsum quia dolor sit amet, consectetur, adipisci velit, sed quia non numquam eius modi tempora incidunt ut labore et dolore magnam aliquam quaerat voluptatem. Ut enim ad minima veniam, quis nostrum exercitationem ullam corporis suscipit laboriosam, nisi ut aliquid ex ea commodi consequatur? Quis autem vel eum iure reprehenderit qui in ea voluptate velit esse quam nihil molestiae consequatur, vel illum qui dolorem eum fugiat quo voluptas nulla pariatur?" ### 1914 translation by H. Rackham "But I must explain to you how all this mistaken idea of denouncing pleasure and praising pain was born and I will give you a complete account of the system, and expound the actual teachings of the great explorer of the truth, the master-builder of human happiness. No one rejects, dislikes, or avoids pleasure itself, because it is pleasure, but because those who do not know how to pursue pleasure rationally encounter consequences that are extremely painful. Nor again is there anyone who loves or pursues or desires to obtain pain of itself, because it is pain, but because occasionally circumstances occur in which toil and pain can procure him some great pleasure. To take a trivial example, which of us ever undertakes laborious physical exercise, except to obtain some advantage from it? But who has any right to find fault with a man who chooses to enjoy a pleasure that has no annoying consequences, or one who avoids a pain that produces no resultant pleasure?" ### Section 1.10.33 of "de Finibus Bonorum et Malorum", written by Cicero in 45 BC "At vero eos et accusamus et iusto odio dignissimos ducimus qui blanditiis praesentium voluptatum deleniti atque corrupti quos dolores et quas molestias excepturi sint occaecati cupiditate non provident, similique sunt in culpa qui officia deserunt mollitia animi, id est laborum et dolorum fuga. Et harum quidem rerum facilis est et expedita distinctio. Nam libero tempore, cum soluta nobis est eligendi optio cumque nihil impedit quo minus id quod maxime placeat facere possimus, omnis voluptas assumenda est, omnis dolor repellendus. Temporibus autem quibusdam et aut officiis debitis aut rerum necessitatibus saepe eveniet ut et voluptates repudiandae sint et molestiae non recusandae. Itaque earum rerum hic tenetur a sapiente delectus, ut aut reiciendis voluptatibus maiores alias consequatur aut perferendis doloribus asperiores repellat." @ 17724a68:89af0638
2025-02-10 19:06:43«Nació Bastiat el año 1801 en la Bayona francesa, muy cerca, por tanto, de la frontera de España y del Bidasoa, que a menudo citaba como ejemplo de un río que, en vez de promover el comercio, lo destruía por el simple hecho de ser frontera entre dos naciones». Empezamos citando al honorable Francisco Cabrillo, el experto (y prologuista) por excelencia de la obra de Bastiat en nuestra casa editorial. Con estas palabras, resume fielmente las dos principales preocupaciones del francés: el libre desarrollo del comercio y las relaciones entre los pueblos. En "Lo que se ve y no se ve" —que podemos encontrar en *Obras escogidas* (Unión Editorial)—, Bastiat nos advierte de que quizás no siempre resulta evidente el efecto colateral de las decisiones políticas. Existen consecuencias visibles e inmediatas, pero también sucesos posteriores y menos visibles que pueden ser incluso más perniciosos que el mal que se deseaba corregir. Hoy percibimos con suma inquietud el riesgo de una guerra comercial que imponga aranceles/barreras al comercio entre los miembros de las naciones. A los políticos y burócratas les tienta el solo pensar en los impuestos que cobrarán por productos importados, sin razonar sobre el impacto en la cadena productiva y en el poder adquisitivo de sus ciudadanos. Ciertamente, el sancionado sufrirá el impacto, pero quien impone los aranceles, también. Los nacionales no solo tendrán que pagar más por un mismo producto extranjero, sino que, al verse restringidos por un precio mayor o caída del comercio, dejarían de beneficiarse de la profesionalización del vecino en la producción de un bien en concreto. Los liberales siempre hemos defendido el libre comercio y la paz. Bastiat es quizás quien mejor resume las razones que nos ha llevado a dichas conclusiones, por lo que os invitamos a profundizar en su obra y disfrutar de la muy enriquecedora lectura de nuestro vecino del *otro lado* del Bidasoa. -- [OBRAS ESCOGIDAS](https://www.unioneditorial.net/libro/obras-escogidas-segunda-edicion/)  [FRÉDERIC BASTIAT: UN HOMBRE ÚNICO](https://www.unioneditorial.net/libro/un-hombre-unico/)  [EN DEFENSA DEL CAPITALISMO GLOBAL](https://www.unioneditorial.net/libro/en-defensa-del-capitalismo-global-3a-edicion/)  -- Como solemos acostumbrar, para compras en nuestra web ofrecemos una promoción válida para la península ibérica que incluye un 5% de descuento y envío gratis a partir de los 20€ de compra. El código de descuento actual es: **UE2025**
@ 17724a68:89af0638
2025-02-10 19:06:43«Nació Bastiat el año 1801 en la Bayona francesa, muy cerca, por tanto, de la frontera de España y del Bidasoa, que a menudo citaba como ejemplo de un río que, en vez de promover el comercio, lo destruía por el simple hecho de ser frontera entre dos naciones». Empezamos citando al honorable Francisco Cabrillo, el experto (y prologuista) por excelencia de la obra de Bastiat en nuestra casa editorial. Con estas palabras, resume fielmente las dos principales preocupaciones del francés: el libre desarrollo del comercio y las relaciones entre los pueblos. En "Lo que se ve y no se ve" —que podemos encontrar en *Obras escogidas* (Unión Editorial)—, Bastiat nos advierte de que quizás no siempre resulta evidente el efecto colateral de las decisiones políticas. Existen consecuencias visibles e inmediatas, pero también sucesos posteriores y menos visibles que pueden ser incluso más perniciosos que el mal que se deseaba corregir. Hoy percibimos con suma inquietud el riesgo de una guerra comercial que imponga aranceles/barreras al comercio entre los miembros de las naciones. A los políticos y burócratas les tienta el solo pensar en los impuestos que cobrarán por productos importados, sin razonar sobre el impacto en la cadena productiva y en el poder adquisitivo de sus ciudadanos. Ciertamente, el sancionado sufrirá el impacto, pero quien impone los aranceles, también. Los nacionales no solo tendrán que pagar más por un mismo producto extranjero, sino que, al verse restringidos por un precio mayor o caída del comercio, dejarían de beneficiarse de la profesionalización del vecino en la producción de un bien en concreto. Los liberales siempre hemos defendido el libre comercio y la paz. Bastiat es quizás quien mejor resume las razones que nos ha llevado a dichas conclusiones, por lo que os invitamos a profundizar en su obra y disfrutar de la muy enriquecedora lectura de nuestro vecino del *otro lado* del Bidasoa. -- [OBRAS ESCOGIDAS](https://www.unioneditorial.net/libro/obras-escogidas-segunda-edicion/)  [FRÉDERIC BASTIAT: UN HOMBRE ÚNICO](https://www.unioneditorial.net/libro/un-hombre-unico/)  [EN DEFENSA DEL CAPITALISMO GLOBAL](https://www.unioneditorial.net/libro/en-defensa-del-capitalismo-global-3a-edicion/)  -- Como solemos acostumbrar, para compras en nuestra web ofrecemos una promoción válida para la península ibérica que incluye un 5% de descuento y envío gratis a partir de los 20€ de compra. El código de descuento actual es: **UE2025** @ 3b7fc823:e194354f
2025-02-10 18:56:06A VPN is Not Magic A VPN is a virtual private network. A VPN service provides an encrypted tunnel between your device and a server they own or rent. You then connect to the internet from this server thus making your IP address appear to the wider internet as the server IP. That's it. That's all it does. Your Device -> VPN -> Website Your Device sees that you are connecting to a website through a VPN. Your ISP sees that you are connecting to a VPN server but nothing after. The website sees that someone from a VPN is connecting to them but doesn't know who. The VPN sees your device connected to their server and that you then connected to a website. VPN Anonymity and Privacy VPNs do a lot to protect your privacy, they keep your ISP from seeing and logging every single thing you do online and they spoof your location and IP to any website that you visit. Although this website protection isn't 100% anonymous because of cookies, trackers, and if you have to log into a site with your information. If you are using a VPN on a mobile phone then you are still broadcasting your location to the cell towers even if you are not telling the website you are browsing. Then there is the elephant in the room. The VPN knows all and sees all. How much do they log? How long do they save it? Can you trust them? This is going to vary VASTLY between VPN providers. I always prefer if they are setup where they cannot know the information in the first place and limit what I tell them in the first place by paying through the use of bitcoin or monero. Just because they have a no log "policy" in place it doesn't always fill me with confidence. VPN Security How much security does a VPN give you? Some in certain circumstances but not a lot. A VPN is not going to stop malware or viruses. A VPN can provide some protection from a man in the middle or evil twin attack as it provides a encrypted tunnel between your device and the VPN server, so always use a VPN when joining public WIFI spots. Just remember a VPN cannot protect you downstream on the connection between the VPN server and the website, always use secure encrypted connections and be aware that MITM attacks can still happen on the backside. A VPN can prevent DDoS attacks since the attacker doesn't know your real IP address and a fantastic use of VPNs is to protect IoT devices. Those smart devices around your home love to scream out all their data insecurely and a VPN can change their IP and encrypt their data in transit protecting them from hacking. VPN Legality In many countries VPNs are banned, blocked, or outright illegal: Bahrain Belarus China Cuba Egypt Iran Iraq Libya Myanmar North Korea Oman Russia Syria Turkey Turkmenistan UAE Uganda Venezuela Vietnam --- Advocating for privacy does not finance itself. If you enjoyed this article, please consider zapping or sending monero 82XCDNK1Js8TethhpGLFPbVyKe25DxMUePad1rUn9z7V6QdCzxHEE7varvVh1VUidUhHVSA4atNU2BTpSNJLC1BqSvDajw1
@ 3b7fc823:e194354f
2025-02-10 18:56:06A VPN is Not Magic A VPN is a virtual private network. A VPN service provides an encrypted tunnel between your device and a server they own or rent. You then connect to the internet from this server thus making your IP address appear to the wider internet as the server IP. That's it. That's all it does. Your Device -> VPN -> Website Your Device sees that you are connecting to a website through a VPN. Your ISP sees that you are connecting to a VPN server but nothing after. The website sees that someone from a VPN is connecting to them but doesn't know who. The VPN sees your device connected to their server and that you then connected to a website. VPN Anonymity and Privacy VPNs do a lot to protect your privacy, they keep your ISP from seeing and logging every single thing you do online and they spoof your location and IP to any website that you visit. Although this website protection isn't 100% anonymous because of cookies, trackers, and if you have to log into a site with your information. If you are using a VPN on a mobile phone then you are still broadcasting your location to the cell towers even if you are not telling the website you are browsing. Then there is the elephant in the room. The VPN knows all and sees all. How much do they log? How long do they save it? Can you trust them? This is going to vary VASTLY between VPN providers. I always prefer if they are setup where they cannot know the information in the first place and limit what I tell them in the first place by paying through the use of bitcoin or monero. Just because they have a no log "policy" in place it doesn't always fill me with confidence. VPN Security How much security does a VPN give you? Some in certain circumstances but not a lot. A VPN is not going to stop malware or viruses. A VPN can provide some protection from a man in the middle or evil twin attack as it provides a encrypted tunnel between your device and the VPN server, so always use a VPN when joining public WIFI spots. Just remember a VPN cannot protect you downstream on the connection between the VPN server and the website, always use secure encrypted connections and be aware that MITM attacks can still happen on the backside. A VPN can prevent DDoS attacks since the attacker doesn't know your real IP address and a fantastic use of VPNs is to protect IoT devices. Those smart devices around your home love to scream out all their data insecurely and a VPN can change their IP and encrypt their data in transit protecting them from hacking. VPN Legality In many countries VPNs are banned, blocked, or outright illegal: Bahrain Belarus China Cuba Egypt Iran Iraq Libya Myanmar North Korea Oman Russia Syria Turkey Turkmenistan UAE Uganda Venezuela Vietnam --- Advocating for privacy does not finance itself. If you enjoyed this article, please consider zapping or sending monero 82XCDNK1Js8TethhpGLFPbVyKe25DxMUePad1rUn9z7V6QdCzxHEE7varvVh1VUidUhHVSA4atNU2BTpSNJLC1BqSvDajw1 @ 3b7fc823:e194354f
2025-02-10 17:34:18Dealing with law enforcement can be a challenging and stressful experience. However, understanding your rights and knowing how to navigate such situations can empower you to protect yourself. Here’s a structured approach to handle these interactions effectively: 1. **Stay Calm and Compliant:** - When approached by law enforcement, remain calm and avoid sudden movements. Slowly raise your hands and identify yourself if possible. 2. **Ask for Identification:** - Request the officer's name, badge number, and station. This documentation can be crucial later on. 3. **Know Your Miranda Rights:** - Upon arrest, you have the right to remain silent. Do not answer questions without consulting a lawyer. If Mirandized, exercise your right to remain silent. 4. **Refuse Incriminating Statements:** - Avoid answering questions that could incriminate yourself. Politely state, "I will not answer any questions at this time." 5. **Document the Incident:** - Use your phone or notebook to record details such as dates, times, and descriptions of interactions. Note any injuries or mistreatment. 6. **Seek Legal Advice:** - After the encounter, contact a lawyer. They can review evidence and provide guidance on how to proceed. 7. **Understand Search and Seizure Laws:** - Officers generally need a warrant to search your property unless there's probable cause. If stopped without a warrant, calmly refuse entry. 8. **Use a Body Camera Policy:** - If applicable, ask for the officer's body camera footage and request it via formal complaint if refused. 9. **Know When to Comply:** - Comply with instructions that do not infringe on your rights, such as providing identification when legally required. 10. **Consider a Witness Statement:** - If you witness illegal actions, consider reporting them. Your role as a bystander may be crucial in documenting incidents. 11. **Seek Emotional Support:** - Interactions with law enforcement can be traumatic. Reach out to support groups or mental health resources for assistance. 12. **Understand Legal Recourse:** - If rights are violated, consult legal aid societies or civil rights organizations for guidance on filing complaints or seeking redress. **Conclusion:** Understanding your rights and documenting interactions is essential when dealing with law enforcement. This guide provides a framework to help you navigate such situations confidently and protect your rights effectively. Remember, knowledge is power, and being informed can lead to better outcomes in challenging circumstances. --- Advocating for privacy does not finance itself. If you enjoyed this article, please consider zapping or sending monero 82XCDNK1Js8TethhpGLFPbVyKe25DxMUePad1rUn9z7V6QdCzxHEE7varvVh1VUidUhHVSA4atNU2BTpSNJLC1BqSvDajw1
@ 3b7fc823:e194354f
2025-02-10 17:34:18Dealing with law enforcement can be a challenging and stressful experience. However, understanding your rights and knowing how to navigate such situations can empower you to protect yourself. Here’s a structured approach to handle these interactions effectively: 1. **Stay Calm and Compliant:** - When approached by law enforcement, remain calm and avoid sudden movements. Slowly raise your hands and identify yourself if possible. 2. **Ask for Identification:** - Request the officer's name, badge number, and station. This documentation can be crucial later on. 3. **Know Your Miranda Rights:** - Upon arrest, you have the right to remain silent. Do not answer questions without consulting a lawyer. If Mirandized, exercise your right to remain silent. 4. **Refuse Incriminating Statements:** - Avoid answering questions that could incriminate yourself. Politely state, "I will not answer any questions at this time." 5. **Document the Incident:** - Use your phone or notebook to record details such as dates, times, and descriptions of interactions. Note any injuries or mistreatment. 6. **Seek Legal Advice:** - After the encounter, contact a lawyer. They can review evidence and provide guidance on how to proceed. 7. **Understand Search and Seizure Laws:** - Officers generally need a warrant to search your property unless there's probable cause. If stopped without a warrant, calmly refuse entry. 8. **Use a Body Camera Policy:** - If applicable, ask for the officer's body camera footage and request it via formal complaint if refused. 9. **Know When to Comply:** - Comply with instructions that do not infringe on your rights, such as providing identification when legally required. 10. **Consider a Witness Statement:** - If you witness illegal actions, consider reporting them. Your role as a bystander may be crucial in documenting incidents. 11. **Seek Emotional Support:** - Interactions with law enforcement can be traumatic. Reach out to support groups or mental health resources for assistance. 12. **Understand Legal Recourse:** - If rights are violated, consult legal aid societies or civil rights organizations for guidance on filing complaints or seeking redress. **Conclusion:** Understanding your rights and documenting interactions is essential when dealing with law enforcement. This guide provides a framework to help you navigate such situations confidently and protect your rights effectively. Remember, knowledge is power, and being informed can lead to better outcomes in challenging circumstances. --- Advocating for privacy does not finance itself. If you enjoyed this article, please consider zapping or sending monero 82XCDNK1Js8TethhpGLFPbVyKe25DxMUePad1rUn9z7V6QdCzxHEE7varvVh1VUidUhHVSA4atNU2BTpSNJLC1BqSvDajw1 @ 554ab6fe:c6cbc27e
2025-02-10 16:48:35René Descartes famously stated, "I think therefore I am." A concept centered around the idea that the existence of our meta-conscious thought proves our existence. Furthermore, it denotes a sense of self-derived from the presence of our thinking. What if this famous idea is wrongly reversed? What if our perceived sense of self derives from our thoughts, and these thoughts act as an illusion of the true nature of the self? A couple of my posts have focused on the idea that the calm mind, potentially derived from a practice of meditation, can achieve a heightened sense of awareness. Some neuroscientists now view the mind as a predictive modeling machine (Seth, 2013), constantly receiving signals from both internal and external sources, generating predictions and models to understand the current condition. This theory inspired me to create an analogy of a calm pond: Imagine the brain and mind as a pond, and instead of neuronal signals, raindrops are falling into the pond. When the pond is calm, and a single drop falls, the pond's ripples provide adequate information to deduce the location and size of the raindrop. By observing the single ripple, one can simply understand the raindrop. However, if there is a storm and many raindrops impact the pond simultaneously, then the ripples are indistinguishable. This makes the analysis of the incoming information near impossible. This may be how the brain works. This would be why calming the mind generates such benefits in health because the brain can analyze the information accurately and execute the proper response. This idea is supported by scientific evidence that interoception increases with mindfulness practice. I have alluded to this idea as a possible explanation of why meditation generates a higher form of consciousness. More on this later. To further explore this idea, a deeper exploration into the neuroscience of internal mental processes is required. The areas of the brain that are clinically recognized to perform internal mental operations are known as the default mode network (DMN) (Ekhtiari et al., 2016; van Buuren et al., 2010). The DMN is not a single area of the brain but a network and interaction between many areas. The brain areas involved within the DMN include the medial prefrontal cortex (mPFC), the anterior and posterior cingulate cortex (ACC and PCC), temporoparietal junction (TPJ), later temporal cortex (LTC), and the temporal pole (TempP)(Farb et al., 2007; Zhou et al., 2020). In general, the mental processes conducted by the DMN are self-referential processing, long-term memory retrieval, and mind-wandering (Ekhtiari et al., 2016; Marstaller et al., 2017; Spreng & Grady, 2010; van Buuren et al., 2010). However, the functions expand beyond just those. Different brain areas carry differing roles in these processes. For example, the PCC plays a unique role in the autobiographical retrieval process and plays a role in self-centered spatial navigation (Hamilton et al., 2015). However, sometimes these processes manifest in more complex interactions. For example, both the PCC and anterior portion of the mPFC (amPFC) facilitate self-referential processes and the interaction between other hubs of the DMN (Zhou et al., 2020). The role of the DMN is complicated, but its relationship to meditation is significant. The DMN's plays a significant role in mental ruminations and the activity of the mind. In our modern culture, mental ruminations are commonplace and widely accepted. With this cultural norm, there is no adequate training to properly handle these thoughts when they become repetitive, unconstructive, and potentially destructive. Repetitive unconstructive ruminations are associated with and can lead to depression (Watkins, 2008). Therefore, this mental habit attributes to a significant source of many mental health issues. It is a primary reason why meditation seems to be such an effective mental health benefiting practice. In Eastern traditions, this unhealthy mind is called the "monkey mind": a mind that swings from thought to thought, often time traveling to the past and future. Meditation, and similar practices, aim to quiet this monkey mind. From a clinical perspective, it is fascinating to consider that the DMN may be a neural network representing the monkey mind's activation. There is research to support this idea as well. Autobiographical memory retrieval processes activate the DMN (Spreng & Grady, 2010). Additionally, the DMN seems to maintain a cohesive perception of the self across time to interpret novel information (Marstaller et al., 2017). Clearly, not only is the DMN involved in processes that involve thoughts about the self, but it is also primarily responsible for our mental time traveling processes. If meditation aims to bring our experience to the present, then the DMN is the antithesis. As previously stated, mental ruminations and other unconstructive thought patterns drive the development of mental health issues such as anxiety and depression. Given that the DMN has a strong relationship to these thought patterns, it is also interesting to note that DMN activity dominance is associated with the development of depression (Hamilton et al., 2011). The brain areas that seem to be activated more often during depression are the anterior and dorsal regions of the mPFC, PCC, temporal lobes, and the TPJ (Zhou et al., 2020)—further suggesting that the DMN is the brain region highly responsible for our inner self-referential thoughts, our time traveling thoughts, and the subsequent mental health outcomes. The DMN represents, in large part, the mental activity of the mind that removes us from a calm and present state of being. In other words, it adds more “raindrops” to the calm pond (my analogy from before) making it harder for the brain to analyze and adequately react to incoming information. Evidence for this idea lies in the observation that the DMN is responsible for monkey mind-like processes and in learning and conditioning. Again, the brain is constantly receiving neuronal signals from the body. Say it receives a signal from the toe: it must first predict that the signal came from the toe, then understand what the signal meant, and react accordingly. So, if the signal was a pain signal, the brain may command the toe to lift from the ground. If the signal stops, the brain knows the toe is no longer in pain, verifying the prediction. If the signal doesn't stop, further trial and error are required. This is a simple example, but the brain is likely processing and reacting to signals like this all the time, both from information coming from outside the body and within. Therefore, much learning and prediction model generation is taking place. Imagine the famous experiment of Pavlov's dogs. The dogs learned that a particular cue meant food, and their bodies learned to react accordingly. This learning and conditioning are a fundamental aspect of biological life. The DMN plays a significant role in this learning within our brain. For example, the PCC responds to error detection, and the signal is amplified when small rewards or novel stimuli are introduced to the experience (Heilbronner & Platt, 2013). Areas of the DMN (such as the mPFC and PCC) are also thought to be involved in contextualizing memories of safety and inhibit fear responses when appropriate (Marstaller et al., 2017). Finally, the mPFC is thought to play a role in goal-directed motivation (Hamilton et al., 2015). All this evidence suggests that the DMN plays a significant role in the learning process by contextualizing information. Keep in mind that the DMN can only accurately contextualize incoming stimuli if the full range of signals is adequately recognized. According to the calm pond idea, the noisy activation of a ruminating mind may hinder this ability. Here, greater clarification and definition on what a polluted mind means is needed. To define such mental patterns, functions of specific DMN regions will be explained. Commonly activated regions within the DMN that involve self-referential processes are (Farb et al., 2007; Knyazev, 2013): 1. The orbitomedial prefrontal cortex (omPFC) – which contextualizes experienced stimuli as experienced by the self 2. The ACC – which actively monitors the self-experienced stimuli 3. The mPFC – which evaluates the self-experienced stimuli 4. The PCC – which is involved in a generated a broader context of the personal experience given certain self-experienced stimuli. By now, it may be evident that the DMN is involved with what is commonly referred to as the "ego". Some researchers claim that the DMN develops the ego itself (R. L. Carhart-Harris & Friston, 2010). The term "ego" derives from Freudian psychoanalytic, and for this reason, the term "narrative-self" will be used instead. It is crucial to consider the word choice here. As previously explained, the DMN generates a time-oriented perception of the self to contextualize information. Furthermore, the four brain areas above all involved contextualizing an experience as experienced by the narrative self (rather than the self being the experience), monitoring these experiences across time, and evaluating these experiences as a broader implication of the experience of the self. The DMN is generating a narrative of the self through every experience. This is indeed where many unconstructive ruminations arise. Any reader can likely relate to ruminating over themselves and their circumstances and thinking about what this means in the larger context of their lives, worth, purpose, etc. This is the monkey mind. This is the DMN. So, the real question becomes: what effect does the strong presence of a narrative-self have on our broader experience and health? Does a strong presence of the narrative-self influence the body's interoceptive abilities and ability to properly analyze and predict incoming stimuli? This is a complex and challenging question, but evidence suggests that this is indeed the case. In a fantastic study by Farb and others in 2007, fMRIs were used to monitor brain activity in those who did and did not practice mindfulness meditation (Farb et al., 2007). In this study, a distinction was made between narrative focus and experiential focus. For eight weeks, those who underwent mindfulness meditation training were taught to practice experiential focus, which involves having present centered awareness of all thoughts, feelings, and experiences in a non-judgmental manner. Narrative focus was defined as judging experiences and trying to figure out what those stimuli meant. Brain scans were performed on both trained and untrained participants during both focus styles. For both groups, narrative focus increased activation of the mPFC and PCC as expected. During experiential focus, both groups reduced mPFC activity, but only the meditation trained group increased activation of the insula. This is incredible because the insula is highly involved in interoception and the sensations of internal physical states (Fox et al., 2014; Mehling et al., 2012). This study by Farb and others suggests a functional difference between the narrative-self and an experiential-self and shows how the quieting of the narrative-self increases interoceptive abilities and enhances the brains' ability to analyze incoming stimuli properly. Not to mention, this study shows how this skill can be trained. So far, we have seen how the DMN is involved in the generation of the narrative-self and how this influences our ability to analyze the signals coming from the body. The next reasonable question is to what extent can this be changed? And what are the implications of such change? As was previously shown in the mentioning of the study by Farb and others in 2007, mindfulness meditation appears to be capable of changing DMN activity. This is not the only study to suggest this. Another study showed that meditation decreased mPFC activity in DMN regions, such as the TPJ and PCC (Scheibner et al., 2017). It has also been shown that the neurotransmitter GABA reduces DMN activity, and both yoga and meditation have been implicated in the release of GABA (Guglietti et al., 2013; Hu et al., 2013; Streeter et al., 2018). The release of GABA release is also modulated by the vagus nerve, providing evidence of the possible mechanism at which meditation inhibits DMN activity (Hu et al., 2013; Keute et al., 2018; Streeter et al., 2018). Through these studies, it seems evident that meditation decreases DMN activity. In what ways is this significant? Firstly, it provides more explanation as to why meditation seems capable of alleviating depression. Similarly, it offers more evidence for how meditation increases interoceptive awareness (de Jong et al., 2016; Farb et al., 2010; Hanley et al., 2017). The increase in interoception suggests that the brain is more adequately processing not only the internal environment more adequately, but presumably the outside environment as well. Reality in general is being more accurately understood. It is possible that this also implicates a broader understanding of how meditation can alter consciousness and allowing monks, yogis, and the like to achieve nirvana/samadhi/enlightenment, or whatever you prefer to call such a state of altered consciousnesses. Perhaps this experience of altered consciousness is a more accurate interpretation of reality, produced by enhanced interoception and exteroception. The subject of altered consciousness is perhaps best explored through brain changes induced by another technique commonly used in a spiritual manner: psychedelics. The famous studies from Johns Hopkins University using psilocybin found that this drug causes a spiritual experience often described as a sense of unity of all things that transcend space and time (Griffiths et al., 2006, 2008). Many participants rate this experience as one of the most significant spiritual experiences of their life (Griffiths et al., 2006). These experiences were often described with an experienced loss sense of self and an altered form of consciousness (Griffiths et al., 2008). It is not hard to imagine that this experience seems very similar to that of a trained monk or yogi, who learn to let go of their narrative-self and gain a sense of oneness with all things. This connection is further verified by the observation that psilocybin decreases the activity of the ACC, PCC, and mPFC (Robin L. Carhart-Harris et al., 2012). Ayahuasca, another psychedelic drug used in spiritual rituals by the indigenous peoples of the Amazon, also has been shown to have similar effects (Palhano-Fontes et al., 2015). Additionally, LSD has been shown to do the same (Speth et al., 2016). Suppose both psychedelic drugs and meditative practice decrease the same DMN, which generates the narrative-self. In that case, both methods likely lead one to the same place: an experience beyond time and space, where one is present with a profound sense of unity with everything. This, to me, is a profound idea. It suggests that quieting the mind, or calming the “pond”, improves mental, physical, and spiritual health. It provides one with a perception full of compassion, peace, and love. It not only can make the individual healthier, but so too the community and planet. It is extraordinary evidence that improving the self is the greatest means of improving the world around us. Not to mention, it provides a simple means of liberating oneself from the struggle and hardship of life. Perhaps it is not life that is hard on us, but ourselves, by allowing the narrative-mind to take hold of our reality, rather than letting a purer form of consciousness dominate our perceptions. This is the pursuit, and meditation techniques are the practice. References Carhart-Harris, R. L., & Friston, K. J. (2010). The default-mode, ego-functions and free-energy: A neurobiological account of Freudian ideas. Brain, 133(4), 1265–1283. https://doi.org/10.1093/brain/awq010 Carhart-Harris, Robin L., Erritzoe, D., Williams, T., Stone, J. M., Reed, L. J., Colasanti, A., Tyacke, R. J., Leech, R., Malizia, A. L., Murphy, K., Hobden, P., Evans, J., Feilding, A., Wise, R. G., & Nutt, D. J. (2012). Neural correlates of the psychedelic state as determined by fMRI studies with psilocybin. Proceedings of the National Academy of Sciences of the United States of America, 109(6), 2138–2143. https://doi.org/10.1073/pnas.1119598109 de Jong, M., Lazar, S. W., Hug, K., Mehling, W. E., Hölzel, B. K., Sack, A. T., Peeters, F., Ashih, H., Mischoulon, D., & Gard, T. (2016). Effects of mindfulness-based cognitive therapy on body awareness in patients with chronic pain and comorbid depression. Frontiers in Psychology, 7(JUN). https://doi.org/10.3389/fpsyg.2016.00967 Ekhtiari, H., Nasseri, P., Yavari, F., Mokri, A., & Monterosso, J. (2016). Neuroscience of drug craving for addiction medicine: From circuits to therapies. In Progress in Brain Research (Vol. 223, pp. 115–141). Elsevier B.V. https://doi.org/10.1016/bs.pbr.2015.10.002 Farb, N. A. S., Anderson, A. K., Mayberg, H., Bean, J., McKeon, D., & Segal, Z. v. (2010). Minding One's Emotions: Mindfulness Training Alters the Neural Expression of Sadness. Emotion, 10(1), 25–33. https://doi.org/10.1037/a0017151 Farb, N. A. S., Segal, Z. v., Mayberg, H., Bean, J., Mckeon, D., Fatima, Z., & Anderson, A. K. (2007). Attending to the present: Mindfulness meditation reveals distinct neural modes of self-reference. Social Cognitive and Affective Neuroscience, 2(4), 313–322. https://doi.org/10.1093/scan/nsm030 Fox, K. C. R., Nijeboer, S., Dixon, M. L., Floman, J. L., Ellamil, M., Rumak, S. P., Sedlmeier, P., & Christoff, K. (2014). Is meditation associated with altered brain structure? A systematic review and meta-analysis of morphometric neuroimaging in meditation practitioners. Neuroscience and Biobehavioral Reviews, 43, 48–73. https://doi.org/10.1016/j.neubiorev.2014.03.016 Griffiths, R. R., Richards, W. A., Johnson, M. W., McCann, U. D., & Jesse, R. (2008). Mystical-type experiences occasioned by psilocybin mediate the attribution of personal meaning and spiritual significance 14 months later. Journal of Psychopharmacology, 22(6), 621–632. https://doi.org/10.1177/0269881108094300 Griffiths, R. R., Richards, W. A., McCann, U., & Jesse, R. (2006). Psilocybin can occasion mystical-type experiences having substantial and sustained personal meaning and spiritual significance. Psychopharmacology, 187(3), 268–283. https://doi.org/10.1007/s00213-006-0457-5 Guglietti, C. L., Daskalakis, Z. J., Radhu, N., Fitzgerald, P. B., & Ritvo, P. (2013). Meditation-related increases in GABAB modulated cortical inhibition. Brain Stimulation, 6(3), 397–402. https://doi.org/10.1016/j.brs.2012.08.005 Hamilton, J. P., Farmer, M., Fogelman, P., & Gotlib, I. H. (2015). Depressive Rumination, the Default-Mode Network, and the Dark Matter of Clinical Neuroscience. In Biological Psychiatry (Vol. 78, Issue 4, pp. 224–230). Elsevier USA. https://doi.org/10.1016/j.biopsych.2015.02.020 Hamilton, J. P., Furman, D. J., Chang, C., Thomason, M. E., Dennis, E., & Gotlib, I. H. (2011). Default-mode and task-positive network activity in major depressive disorder: Implications for adaptive and maladaptive rumination. Biological Psychiatry, 70(4), 327–333. https://doi.org/10.1016/j.biopsych.2011.02.003 Hanley, A. W., Mehling, W. E., & Garland, E. L. (2017). Holding the body in mind: Interoceptive awareness, dispositional mindfulness and psychological well-being. Journal of Psychosomatic Research, 99, 13–20. https://doi.org/10.1016/j.jpsychores.2017.05.014 Heilbronner, S. R., & Platt, M. L. (2013). Causal evidence of performance monitoring by neurons in posterior cingulate cortex during learning. Neuron, 80(6), 1384–1391. https://doi.org/10.1016/j.neuron.2013.09.028 Hu, Y., Chen, X., Gu, H., & Yang, Y. (2013). Resting-state glutamate and GABA concentrations predict task-induced deactivation in the default mode network. Journal of Neuroscience, 33(47), 18566–18573. https://doi.org/10.1523/JNEUROSCI.1973-13.2013 Keute, M., Ruhnau, P., Heinze, H. J., & Zaehle, T. (2018). Behavioral and electrophysiological evidence for GABAergic modulation through transcutaneous vagus nerve stimulation. Clinical Neurophysiology, 129(9), 1789–1795. https://doi.org/10.1016/j.clinph.2018.05.026 Knyazev, G. G. (2013). EEG correlates of self-referential processing. Frontiers in Human Neuroscience, 7(MAY), 1–14. https://doi.org/10.3389/fnhum.2013.00264 Marstaller, L., Burianová, H., & Reutens, D. C. (2017). Adaptive contextualization: A new role for the default mode network in affective learning. Human Brain Mapping, 38(2), 1082–1091. https://doi.org/10.1002/hbm.23442 Mehling, W. E., Price, C., Daubenmier, J. J., Acree, M., Bartmess, E., & Stewart, A. (2012). The Multidimensional Assessment of Interoceptive Awareness (MAIA). PLoS ONE, 7(11). https://doi.org/10.1371/journal.pone.0048230 Palhano-Fontes, F., Andrade, K. C., Tofoli, L. F., Jose, A. C. S., Crippa, A. S., Hallak, J. E. C., Ribeiro, S., & de Araujo, D. B. (2015). The psychedelic state induced by Ayahuasca modulates the activity and connectivity of the Default Mode Network. PLoS ONE, 10(2), 1–13. https://doi.org/10.1371/journal.pone.0118143 Scheibner, H. J., Bogler, C., Gleich, T., Haynes, J. D., & Bermpohl, F. (2017). Internal and external attention and the default mode network. NeuroImage, 148(January), 381–389. https://doi.org/10.1016/j.neuroimage.2017.01.044 Seth, A. K. (2013). Interoceptive inference, emotion, and the embodied self. Trends in Cognitive Sciences, 17(11), 565–573. https://doi.org/10.1016/j.tics.2013.09.007 Speth, J., Speth, C., Kaelen, M., Schloerscheidt, A. M., Feilding, A., Nutt, D. J., & Carhart-Harris, R. L. (2016). Decreased mental time travel to the past correlates with default-mode network disintegration under lysergic acid diethylamide. Journal of Psychopharmacology, 30(4), 344–353. https://doi.org/10.1177/0269881116628430 Spreng, R. N., & Grady, C. L. (2010). Patterns of brain activity supporting autobiographical memory, prospection, and theory of mind, and their relationship to the default mode network. Journal of Cognitive Neuroscience, 22(6), 1112–1123. https://doi.org/10.1162/jocn.2009.21282 Streeter, C., Gerbarg, P. L., Nielsen, G. H., Brown, R. P., Jensen, J. E., Silveri, M., & Streeter, C. C. (2018). Effects of Yoga on Thalamic Gamma-Aminobutyric Acid, Mood and Depression: Analysis of Two Randomized Controlled Trials. Neuropsychiatry, 8(6), 1923–1939. https://doi.org/10.4172/Neuropsychiatry.1000535 van Buuren, M., Gladwin, T. E., Zandbelt, B. B., Kahn, R. S., & Vink, M. (2010). Reduced functional coupling in the default-mode network during self-referential processing. Human Brain Mapping, 31(8), 1117–1127. https://doi.org/10.1002/hbm.20920 Watkins, E. R. (2008). Constructive and unconstructive repetitive thought. Psychological Bulletin, 134(2), 163–206. https://doi.org/10.1037/0033-2909.134.2.163 Zhou, H. X., Chen, X., Shen, Y. Q., Li, L., Chen, N. X., Zhu, Z. C., Castellanos, F. X., & Yan, C. G. (2020). Rumination and the default mode network: Meta-analysis of brain imaging studies and implications for depression. In NeuroImage (Vol. 206, p. 116287). Academic Press Inc. https://doi.org/10.1016/j.neuroimage.2019.116287
@ 554ab6fe:c6cbc27e
2025-02-10 16:48:35René Descartes famously stated, "I think therefore I am." A concept centered around the idea that the existence of our meta-conscious thought proves our existence. Furthermore, it denotes a sense of self-derived from the presence of our thinking. What if this famous idea is wrongly reversed? What if our perceived sense of self derives from our thoughts, and these thoughts act as an illusion of the true nature of the self? A couple of my posts have focused on the idea that the calm mind, potentially derived from a practice of meditation, can achieve a heightened sense of awareness. Some neuroscientists now view the mind as a predictive modeling machine (Seth, 2013), constantly receiving signals from both internal and external sources, generating predictions and models to understand the current condition. This theory inspired me to create an analogy of a calm pond: Imagine the brain and mind as a pond, and instead of neuronal signals, raindrops are falling into the pond. When the pond is calm, and a single drop falls, the pond's ripples provide adequate information to deduce the location and size of the raindrop. By observing the single ripple, one can simply understand the raindrop. However, if there is a storm and many raindrops impact the pond simultaneously, then the ripples are indistinguishable. This makes the analysis of the incoming information near impossible. This may be how the brain works. This would be why calming the mind generates such benefits in health because the brain can analyze the information accurately and execute the proper response. This idea is supported by scientific evidence that interoception increases with mindfulness practice. I have alluded to this idea as a possible explanation of why meditation generates a higher form of consciousness. More on this later. To further explore this idea, a deeper exploration into the neuroscience of internal mental processes is required. The areas of the brain that are clinically recognized to perform internal mental operations are known as the default mode network (DMN) (Ekhtiari et al., 2016; van Buuren et al., 2010). The DMN is not a single area of the brain but a network and interaction between many areas. The brain areas involved within the DMN include the medial prefrontal cortex (mPFC), the anterior and posterior cingulate cortex (ACC and PCC), temporoparietal junction (TPJ), later temporal cortex (LTC), and the temporal pole (TempP)(Farb et al., 2007; Zhou et al., 2020). In general, the mental processes conducted by the DMN are self-referential processing, long-term memory retrieval, and mind-wandering (Ekhtiari et al., 2016; Marstaller et al., 2017; Spreng & Grady, 2010; van Buuren et al., 2010). However, the functions expand beyond just those. Different brain areas carry differing roles in these processes. For example, the PCC plays a unique role in the autobiographical retrieval process and plays a role in self-centered spatial navigation (Hamilton et al., 2015). However, sometimes these processes manifest in more complex interactions. For example, both the PCC and anterior portion of the mPFC (amPFC) facilitate self-referential processes and the interaction between other hubs of the DMN (Zhou et al., 2020). The role of the DMN is complicated, but its relationship to meditation is significant. The DMN's plays a significant role in mental ruminations and the activity of the mind. In our modern culture, mental ruminations are commonplace and widely accepted. With this cultural norm, there is no adequate training to properly handle these thoughts when they become repetitive, unconstructive, and potentially destructive. Repetitive unconstructive ruminations are associated with and can lead to depression (Watkins, 2008). Therefore, this mental habit attributes to a significant source of many mental health issues. It is a primary reason why meditation seems to be such an effective mental health benefiting practice. In Eastern traditions, this unhealthy mind is called the "monkey mind": a mind that swings from thought to thought, often time traveling to the past and future. Meditation, and similar practices, aim to quiet this monkey mind. From a clinical perspective, it is fascinating to consider that the DMN may be a neural network representing the monkey mind's activation. There is research to support this idea as well. Autobiographical memory retrieval processes activate the DMN (Spreng & Grady, 2010). Additionally, the DMN seems to maintain a cohesive perception of the self across time to interpret novel information (Marstaller et al., 2017). Clearly, not only is the DMN involved in processes that involve thoughts about the self, but it is also primarily responsible for our mental time traveling processes. If meditation aims to bring our experience to the present, then the DMN is the antithesis. As previously stated, mental ruminations and other unconstructive thought patterns drive the development of mental health issues such as anxiety and depression. Given that the DMN has a strong relationship to these thought patterns, it is also interesting to note that DMN activity dominance is associated with the development of depression (Hamilton et al., 2011). The brain areas that seem to be activated more often during depression are the anterior and dorsal regions of the mPFC, PCC, temporal lobes, and the TPJ (Zhou et al., 2020)—further suggesting that the DMN is the brain region highly responsible for our inner self-referential thoughts, our time traveling thoughts, and the subsequent mental health outcomes. The DMN represents, in large part, the mental activity of the mind that removes us from a calm and present state of being. In other words, it adds more “raindrops” to the calm pond (my analogy from before) making it harder for the brain to analyze and adequately react to incoming information. Evidence for this idea lies in the observation that the DMN is responsible for monkey mind-like processes and in learning and conditioning. Again, the brain is constantly receiving neuronal signals from the body. Say it receives a signal from the toe: it must first predict that the signal came from the toe, then understand what the signal meant, and react accordingly. So, if the signal was a pain signal, the brain may command the toe to lift from the ground. If the signal stops, the brain knows the toe is no longer in pain, verifying the prediction. If the signal doesn't stop, further trial and error are required. This is a simple example, but the brain is likely processing and reacting to signals like this all the time, both from information coming from outside the body and within. Therefore, much learning and prediction model generation is taking place. Imagine the famous experiment of Pavlov's dogs. The dogs learned that a particular cue meant food, and their bodies learned to react accordingly. This learning and conditioning are a fundamental aspect of biological life. The DMN plays a significant role in this learning within our brain. For example, the PCC responds to error detection, and the signal is amplified when small rewards or novel stimuli are introduced to the experience (Heilbronner & Platt, 2013). Areas of the DMN (such as the mPFC and PCC) are also thought to be involved in contextualizing memories of safety and inhibit fear responses when appropriate (Marstaller et al., 2017). Finally, the mPFC is thought to play a role in goal-directed motivation (Hamilton et al., 2015). All this evidence suggests that the DMN plays a significant role in the learning process by contextualizing information. Keep in mind that the DMN can only accurately contextualize incoming stimuli if the full range of signals is adequately recognized. According to the calm pond idea, the noisy activation of a ruminating mind may hinder this ability. Here, greater clarification and definition on what a polluted mind means is needed. To define such mental patterns, functions of specific DMN regions will be explained. Commonly activated regions within the DMN that involve self-referential processes are (Farb et al., 2007; Knyazev, 2013): 1. The orbitomedial prefrontal cortex (omPFC) – which contextualizes experienced stimuli as experienced by the self 2. The ACC – which actively monitors the self-experienced stimuli 3. The mPFC – which evaluates the self-experienced stimuli 4. The PCC – which is involved in a generated a broader context of the personal experience given certain self-experienced stimuli. By now, it may be evident that the DMN is involved with what is commonly referred to as the "ego". Some researchers claim that the DMN develops the ego itself (R. L. Carhart-Harris & Friston, 2010). The term "ego" derives from Freudian psychoanalytic, and for this reason, the term "narrative-self" will be used instead. It is crucial to consider the word choice here. As previously explained, the DMN generates a time-oriented perception of the self to contextualize information. Furthermore, the four brain areas above all involved contextualizing an experience as experienced by the narrative self (rather than the self being the experience), monitoring these experiences across time, and evaluating these experiences as a broader implication of the experience of the self. The DMN is generating a narrative of the self through every experience. This is indeed where many unconstructive ruminations arise. Any reader can likely relate to ruminating over themselves and their circumstances and thinking about what this means in the larger context of their lives, worth, purpose, etc. This is the monkey mind. This is the DMN. So, the real question becomes: what effect does the strong presence of a narrative-self have on our broader experience and health? Does a strong presence of the narrative-self influence the body's interoceptive abilities and ability to properly analyze and predict incoming stimuli? This is a complex and challenging question, but evidence suggests that this is indeed the case. In a fantastic study by Farb and others in 2007, fMRIs were used to monitor brain activity in those who did and did not practice mindfulness meditation (Farb et al., 2007). In this study, a distinction was made between narrative focus and experiential focus. For eight weeks, those who underwent mindfulness meditation training were taught to practice experiential focus, which involves having present centered awareness of all thoughts, feelings, and experiences in a non-judgmental manner. Narrative focus was defined as judging experiences and trying to figure out what those stimuli meant. Brain scans were performed on both trained and untrained participants during both focus styles. For both groups, narrative focus increased activation of the mPFC and PCC as expected. During experiential focus, both groups reduced mPFC activity, but only the meditation trained group increased activation of the insula. This is incredible because the insula is highly involved in interoception and the sensations of internal physical states (Fox et al., 2014; Mehling et al., 2012). This study by Farb and others suggests a functional difference between the narrative-self and an experiential-self and shows how the quieting of the narrative-self increases interoceptive abilities and enhances the brains' ability to analyze incoming stimuli properly. Not to mention, this study shows how this skill can be trained. So far, we have seen how the DMN is involved in the generation of the narrative-self and how this influences our ability to analyze the signals coming from the body. The next reasonable question is to what extent can this be changed? And what are the implications of such change? As was previously shown in the mentioning of the study by Farb and others in 2007, mindfulness meditation appears to be capable of changing DMN activity. This is not the only study to suggest this. Another study showed that meditation decreased mPFC activity in DMN regions, such as the TPJ and PCC (Scheibner et al., 2017). It has also been shown that the neurotransmitter GABA reduces DMN activity, and both yoga and meditation have been implicated in the release of GABA (Guglietti et al., 2013; Hu et al., 2013; Streeter et al., 2018). The release of GABA release is also modulated by the vagus nerve, providing evidence of the possible mechanism at which meditation inhibits DMN activity (Hu et al., 2013; Keute et al., 2018; Streeter et al., 2018). Through these studies, it seems evident that meditation decreases DMN activity. In what ways is this significant? Firstly, it provides more explanation as to why meditation seems capable of alleviating depression. Similarly, it offers more evidence for how meditation increases interoceptive awareness (de Jong et al., 2016; Farb et al., 2010; Hanley et al., 2017). The increase in interoception suggests that the brain is more adequately processing not only the internal environment more adequately, but presumably the outside environment as well. Reality in general is being more accurately understood. It is possible that this also implicates a broader understanding of how meditation can alter consciousness and allowing monks, yogis, and the like to achieve nirvana/samadhi/enlightenment, or whatever you prefer to call such a state of altered consciousnesses. Perhaps this experience of altered consciousness is a more accurate interpretation of reality, produced by enhanced interoception and exteroception. The subject of altered consciousness is perhaps best explored through brain changes induced by another technique commonly used in a spiritual manner: psychedelics. The famous studies from Johns Hopkins University using psilocybin found that this drug causes a spiritual experience often described as a sense of unity of all things that transcend space and time (Griffiths et al., 2006, 2008). Many participants rate this experience as one of the most significant spiritual experiences of their life (Griffiths et al., 2006). These experiences were often described with an experienced loss sense of self and an altered form of consciousness (Griffiths et al., 2008). It is not hard to imagine that this experience seems very similar to that of a trained monk or yogi, who learn to let go of their narrative-self and gain a sense of oneness with all things. This connection is further verified by the observation that psilocybin decreases the activity of the ACC, PCC, and mPFC (Robin L. Carhart-Harris et al., 2012). Ayahuasca, another psychedelic drug used in spiritual rituals by the indigenous peoples of the Amazon, also has been shown to have similar effects (Palhano-Fontes et al., 2015). Additionally, LSD has been shown to do the same (Speth et al., 2016). Suppose both psychedelic drugs and meditative practice decrease the same DMN, which generates the narrative-self. In that case, both methods likely lead one to the same place: an experience beyond time and space, where one is present with a profound sense of unity with everything. This, to me, is a profound idea. It suggests that quieting the mind, or calming the “pond”, improves mental, physical, and spiritual health. It provides one with a perception full of compassion, peace, and love. It not only can make the individual healthier, but so too the community and planet. It is extraordinary evidence that improving the self is the greatest means of improving the world around us. Not to mention, it provides a simple means of liberating oneself from the struggle and hardship of life. Perhaps it is not life that is hard on us, but ourselves, by allowing the narrative-mind to take hold of our reality, rather than letting a purer form of consciousness dominate our perceptions. This is the pursuit, and meditation techniques are the practice. References Carhart-Harris, R. L., & Friston, K. J. (2010). The default-mode, ego-functions and free-energy: A neurobiological account of Freudian ideas. Brain, 133(4), 1265–1283. https://doi.org/10.1093/brain/awq010 Carhart-Harris, Robin L., Erritzoe, D., Williams, T., Stone, J. M., Reed, L. J., Colasanti, A., Tyacke, R. J., Leech, R., Malizia, A. L., Murphy, K., Hobden, P., Evans, J., Feilding, A., Wise, R. G., & Nutt, D. J. (2012). Neural correlates of the psychedelic state as determined by fMRI studies with psilocybin. Proceedings of the National Academy of Sciences of the United States of America, 109(6), 2138–2143. https://doi.org/10.1073/pnas.1119598109 de Jong, M., Lazar, S. W., Hug, K., Mehling, W. E., Hölzel, B. K., Sack, A. T., Peeters, F., Ashih, H., Mischoulon, D., & Gard, T. (2016). Effects of mindfulness-based cognitive therapy on body awareness in patients with chronic pain and comorbid depression. Frontiers in Psychology, 7(JUN). https://doi.org/10.3389/fpsyg.2016.00967 Ekhtiari, H., Nasseri, P., Yavari, F., Mokri, A., & Monterosso, J. (2016). Neuroscience of drug craving for addiction medicine: From circuits to therapies. In Progress in Brain Research (Vol. 223, pp. 115–141). Elsevier B.V. https://doi.org/10.1016/bs.pbr.2015.10.002 Farb, N. A. S., Anderson, A. K., Mayberg, H., Bean, J., McKeon, D., & Segal, Z. v. (2010). Minding One's Emotions: Mindfulness Training Alters the Neural Expression of Sadness. Emotion, 10(1), 25–33. https://doi.org/10.1037/a0017151 Farb, N. A. S., Segal, Z. v., Mayberg, H., Bean, J., Mckeon, D., Fatima, Z., & Anderson, A. K. (2007). Attending to the present: Mindfulness meditation reveals distinct neural modes of self-reference. Social Cognitive and Affective Neuroscience, 2(4), 313–322. https://doi.org/10.1093/scan/nsm030 Fox, K. C. R., Nijeboer, S., Dixon, M. L., Floman, J. L., Ellamil, M., Rumak, S. P., Sedlmeier, P., & Christoff, K. (2014). Is meditation associated with altered brain structure? A systematic review and meta-analysis of morphometric neuroimaging in meditation practitioners. Neuroscience and Biobehavioral Reviews, 43, 48–73. https://doi.org/10.1016/j.neubiorev.2014.03.016 Griffiths, R. R., Richards, W. A., Johnson, M. W., McCann, U. D., & Jesse, R. (2008). Mystical-type experiences occasioned by psilocybin mediate the attribution of personal meaning and spiritual significance 14 months later. Journal of Psychopharmacology, 22(6), 621–632. https://doi.org/10.1177/0269881108094300 Griffiths, R. R., Richards, W. A., McCann, U., & Jesse, R. (2006). Psilocybin can occasion mystical-type experiences having substantial and sustained personal meaning and spiritual significance. Psychopharmacology, 187(3), 268–283. https://doi.org/10.1007/s00213-006-0457-5 Guglietti, C. L., Daskalakis, Z. J., Radhu, N., Fitzgerald, P. B., & Ritvo, P. (2013). Meditation-related increases in GABAB modulated cortical inhibition. Brain Stimulation, 6(3), 397–402. https://doi.org/10.1016/j.brs.2012.08.005 Hamilton, J. P., Farmer, M., Fogelman, P., & Gotlib, I. H. (2015). Depressive Rumination, the Default-Mode Network, and the Dark Matter of Clinical Neuroscience. In Biological Psychiatry (Vol. 78, Issue 4, pp. 224–230). Elsevier USA. https://doi.org/10.1016/j.biopsych.2015.02.020 Hamilton, J. P., Furman, D. J., Chang, C., Thomason, M. E., Dennis, E., & Gotlib, I. H. (2011). Default-mode and task-positive network activity in major depressive disorder: Implications for adaptive and maladaptive rumination. Biological Psychiatry, 70(4), 327–333. https://doi.org/10.1016/j.biopsych.2011.02.003 Hanley, A. W., Mehling, W. E., & Garland, E. L. (2017). Holding the body in mind: Interoceptive awareness, dispositional mindfulness and psychological well-being. Journal of Psychosomatic Research, 99, 13–20. https://doi.org/10.1016/j.jpsychores.2017.05.014 Heilbronner, S. R., & Platt, M. L. (2013). Causal evidence of performance monitoring by neurons in posterior cingulate cortex during learning. Neuron, 80(6), 1384–1391. https://doi.org/10.1016/j.neuron.2013.09.028 Hu, Y., Chen, X., Gu, H., & Yang, Y. (2013). Resting-state glutamate and GABA concentrations predict task-induced deactivation in the default mode network. Journal of Neuroscience, 33(47), 18566–18573. https://doi.org/10.1523/JNEUROSCI.1973-13.2013 Keute, M., Ruhnau, P., Heinze, H. J., & Zaehle, T. (2018). Behavioral and electrophysiological evidence for GABAergic modulation through transcutaneous vagus nerve stimulation. Clinical Neurophysiology, 129(9), 1789–1795. https://doi.org/10.1016/j.clinph.2018.05.026 Knyazev, G. G. (2013). EEG correlates of self-referential processing. Frontiers in Human Neuroscience, 7(MAY), 1–14. https://doi.org/10.3389/fnhum.2013.00264 Marstaller, L., Burianová, H., & Reutens, D. C. (2017). Adaptive contextualization: A new role for the default mode network in affective learning. Human Brain Mapping, 38(2), 1082–1091. https://doi.org/10.1002/hbm.23442 Mehling, W. E., Price, C., Daubenmier, J. J., Acree, M., Bartmess, E., & Stewart, A. (2012). The Multidimensional Assessment of Interoceptive Awareness (MAIA). PLoS ONE, 7(11). https://doi.org/10.1371/journal.pone.0048230 Palhano-Fontes, F., Andrade, K. C., Tofoli, L. F., Jose, A. C. S., Crippa, A. S., Hallak, J. E. C., Ribeiro, S., & de Araujo, D. B. (2015). The psychedelic state induced by Ayahuasca modulates the activity and connectivity of the Default Mode Network. PLoS ONE, 10(2), 1–13. https://doi.org/10.1371/journal.pone.0118143 Scheibner, H. J., Bogler, C., Gleich, T., Haynes, J. D., & Bermpohl, F. (2017). Internal and external attention and the default mode network. NeuroImage, 148(January), 381–389. https://doi.org/10.1016/j.neuroimage.2017.01.044 Seth, A. K. (2013). Interoceptive inference, emotion, and the embodied self. Trends in Cognitive Sciences, 17(11), 565–573. https://doi.org/10.1016/j.tics.2013.09.007 Speth, J., Speth, C., Kaelen, M., Schloerscheidt, A. M., Feilding, A., Nutt, D. J., & Carhart-Harris, R. L. (2016). Decreased mental time travel to the past correlates with default-mode network disintegration under lysergic acid diethylamide. Journal of Psychopharmacology, 30(4), 344–353. https://doi.org/10.1177/0269881116628430 Spreng, R. N., & Grady, C. L. (2010). Patterns of brain activity supporting autobiographical memory, prospection, and theory of mind, and their relationship to the default mode network. Journal of Cognitive Neuroscience, 22(6), 1112–1123. https://doi.org/10.1162/jocn.2009.21282 Streeter, C., Gerbarg, P. L., Nielsen, G. H., Brown, R. P., Jensen, J. E., Silveri, M., & Streeter, C. C. (2018). Effects of Yoga on Thalamic Gamma-Aminobutyric Acid, Mood and Depression: Analysis of Two Randomized Controlled Trials. Neuropsychiatry, 8(6), 1923–1939. https://doi.org/10.4172/Neuropsychiatry.1000535 van Buuren, M., Gladwin, T. E., Zandbelt, B. B., Kahn, R. S., & Vink, M. (2010). Reduced functional coupling in the default-mode network during self-referential processing. Human Brain Mapping, 31(8), 1117–1127. https://doi.org/10.1002/hbm.20920 Watkins, E. R. (2008). Constructive and unconstructive repetitive thought. Psychological Bulletin, 134(2), 163–206. https://doi.org/10.1037/0033-2909.134.2.163 Zhou, H. X., Chen, X., Shen, Y. Q., Li, L., Chen, N. X., Zhu, Z. C., Castellanos, F. X., & Yan, C. G. (2020). Rumination and the default mode network: Meta-analysis of brain imaging studies and implications for depression. In NeuroImage (Vol. 206, p. 116287). Academic Press Inc. https://doi.org/10.1016/j.neuroimage.2019.116287 @ 5d4b6c8d:8a1c1ee3
2025-02-10 16:32:15The Super Bowl definitely threw me off a bit. My dad offered to bring some food over and the plan was to eat before the game/during the first half. I have no idea what he was doing, but for some reason, it took him two hours to get the food (that was already made) ready to eat. All things considered, I still did ok. The dry fast was about 13 hours and I might make it to 16 hours without eating (I'm at 15 now). ## Score Card Day 1: 14 hour fast (13 dry) Day 2: 15 hour fast (14 dry) Day 3: 17 hours (16 dry) Day 4: 18 hours (17 dry) Day 5: 18 hours (16 dry) Day 6: 19 hours (16 dry) Day 7: 16 hours (15 dry) Day 8: 18 hours (17 dry) Day 9: 17 hours (17 dry) Day 10: TBD (13 dry) originally posted at https://stacker.news/items/881691
@ 5d4b6c8d:8a1c1ee3
2025-02-10 16:32:15The Super Bowl definitely threw me off a bit. My dad offered to bring some food over and the plan was to eat before the game/during the first half. I have no idea what he was doing, but for some reason, it took him two hours to get the food (that was already made) ready to eat. All things considered, I still did ok. The dry fast was about 13 hours and I might make it to 16 hours without eating (I'm at 15 now). ## Score Card Day 1: 14 hour fast (13 dry) Day 2: 15 hour fast (14 dry) Day 3: 17 hours (16 dry) Day 4: 18 hours (17 dry) Day 5: 18 hours (16 dry) Day 6: 19 hours (16 dry) Day 7: 16 hours (15 dry) Day 8: 18 hours (17 dry) Day 9: 17 hours (17 dry) Day 10: TBD (13 dry) originally posted at https://stacker.news/items/881691 @ e453ec07:b199e3f8
2025-02-10 16:25:07 ## **Le ras-le-bol numérique : comprendre pourquoi vous vous sentez épuisé par Internet)** Vous vous sentez parfois **épuisé** par Internet ? Submergé par le flot incessant d'informations ? **Las** des publicités qui vous suivent partout, des notifications qui vous harcèlent à toute heure, et de ce sentiment étrange d'être constamment **observé** ? Vous n'êtes **pas fou**. Et vous n'êtes pas seul. Ce n'est pas vous qui êtes "déconnecté" ou "incapable de suivre". C'est **Internet lui-même qui est cassé**. Enfin, pas *totalement* en panne, mais profondément **dysfonctionnel**. Imaginez un réseau routier où les panneaux indicateurs sont illisibles, les embouteillages constants, et où des péages surgissent à chaque kilomètre, sans que l'on sache vraiment où va l'argent... C'est un peu l'état d'Internet aujourd'hui. **Le Brouhaha Numérique : Plus d'Infos, Moins de Sens**  Ce que l'on appelle le "réseau mondial" ressemble de plus en plus à un **brouhaha numérique**. Un flot continu et désordonné d'informations, d'avis, de pubs, de " contenus sponsorisés " qui se mélangent et s'entrechoquent. On a l'impression de boire à la lance à incendie : beaucoup de débit, mais difficile de se désaltérer intelligemment. Et cette cacophonie a un effet direct sur nous. Elle nous **fatigue**, nous **stresse**, nous rend **moins attentifs**, moins capables de nous concentrer. On passe des heures en ligne sans vraiment savoir ce que l'on cherche, happés par des algorithmes conçus pour **capter notre attention**, souvent au détriment de notre bien-être. **La Centralisation : Le Cœur du Problème**  Mais pourquoi Internet est-il devenu si chaotique ? La réponse est simple : **la centralisation**. Au fil des années, Internet, qui se voulait un espace libre et décentralisé, s'est retrouvé progressivement **accaparé par une poignée de géants**. Ces entreprises – vous les connaissez, elles commencent par G, A, M… – contrôlent une part immense de nos vies numériques. Elles hébergent nos emails, nos photos, nos vidéos, nos réseaux sociaux, nos recherches, nos achats en ligne… Elles sont devenues les **portiers d'Internet**, les **collecteurs de nos données**, et les **architectes de notre expérience en ligne**. **Les Pièges de la Gratuité et de la Surveillance** Et c'est là que le bât blesse. Ces services sont souvent présentés comme "gratuits". Mais comme on dit, "quand c'est gratuit, c'est vous le produit". En réalité, nous payons un prix très élevé pour cette "gratuité" : **nos données personnelles**.  Chaque clic, chaque recherche, chaque message, chaque "like" est **enregistré, analysé, et transformé en données**. Ces données servent ensuite à **nous profiler**, à créer ce que l'article original appelle un "GHOST" – un profil consommateur virtuel – afin de nous **bombarder de publicités ciblées**, de nous **influencer**, et de nous **enfermer dans des bulles informationnelles**. **Vos Données Ne Vous Appartiennent Plus** Le pire, c'est que nous avons **perdu le contrôle** sur nos propres données. Elles sont stockées dans d'immenses **datacenters**, appartenant à ces géants, souvent situés à l'autre bout du monde. Nous ne savons pas **exactement où elles sont**, **comment elles sont utilisées**, ni **qui y a accès**.  Et cette perte de contrôle a des conséquences bien réelles : * **Atteintes à la vie privée :** Surveillance constante, profilage intrusif, fuites de données… * **Manipulation et influence :** Publicités ciblées, désinformation, bulles de filtres… * **Dépendance et enfermement :** Nous devenons captifs de ces écosystèmes centralisés, il devient difficile de s'en extraire. **L'Aube d'une Solution : Le Web3** Alors, faut-il se résigner à cet Internet dysfonctionnel ? Absolument pas ! La bonne nouvelle, c'est qu'il existe une **alternative**. Une voie pour reprendre le contrôle, pour construire un Internet plus **libre**, plus **sûr**, plus **respectueux** de l'individu. Cette alternative, elle porte un nom : **le Web3**. Dans le prochain article, nous allons explorer ensemble ce nouveau paradigme, comprendre comment il fonctionne, et surtout, découvrir comment il peut nous permettre de **réparer Internet** et de **reprendre le pouvoir sur nos vies numériques**. [**Restez connecté… le changement est en marche !**](https://www.copylaradio.com/blog/blog-1/post/internet-est-casse-vous-netes-pas-fou-141)
@ e453ec07:b199e3f8
2025-02-10 16:25:07 ## **Le ras-le-bol numérique : comprendre pourquoi vous vous sentez épuisé par Internet)** Vous vous sentez parfois **épuisé** par Internet ? Submergé par le flot incessant d'informations ? **Las** des publicités qui vous suivent partout, des notifications qui vous harcèlent à toute heure, et de ce sentiment étrange d'être constamment **observé** ? Vous n'êtes **pas fou**. Et vous n'êtes pas seul. Ce n'est pas vous qui êtes "déconnecté" ou "incapable de suivre". C'est **Internet lui-même qui est cassé**. Enfin, pas *totalement* en panne, mais profondément **dysfonctionnel**. Imaginez un réseau routier où les panneaux indicateurs sont illisibles, les embouteillages constants, et où des péages surgissent à chaque kilomètre, sans que l'on sache vraiment où va l'argent... C'est un peu l'état d'Internet aujourd'hui. **Le Brouhaha Numérique : Plus d'Infos, Moins de Sens**  Ce que l'on appelle le "réseau mondial" ressemble de plus en plus à un **brouhaha numérique**. Un flot continu et désordonné d'informations, d'avis, de pubs, de " contenus sponsorisés " qui se mélangent et s'entrechoquent. On a l'impression de boire à la lance à incendie : beaucoup de débit, mais difficile de se désaltérer intelligemment. Et cette cacophonie a un effet direct sur nous. Elle nous **fatigue**, nous **stresse**, nous rend **moins attentifs**, moins capables de nous concentrer. On passe des heures en ligne sans vraiment savoir ce que l'on cherche, happés par des algorithmes conçus pour **capter notre attention**, souvent au détriment de notre bien-être. **La Centralisation : Le Cœur du Problème**  Mais pourquoi Internet est-il devenu si chaotique ? La réponse est simple : **la centralisation**. Au fil des années, Internet, qui se voulait un espace libre et décentralisé, s'est retrouvé progressivement **accaparé par une poignée de géants**. Ces entreprises – vous les connaissez, elles commencent par G, A, M… – contrôlent une part immense de nos vies numériques. Elles hébergent nos emails, nos photos, nos vidéos, nos réseaux sociaux, nos recherches, nos achats en ligne… Elles sont devenues les **portiers d'Internet**, les **collecteurs de nos données**, et les **architectes de notre expérience en ligne**. **Les Pièges de la Gratuité et de la Surveillance** Et c'est là que le bât blesse. Ces services sont souvent présentés comme "gratuits". Mais comme on dit, "quand c'est gratuit, c'est vous le produit". En réalité, nous payons un prix très élevé pour cette "gratuité" : **nos données personnelles**.  Chaque clic, chaque recherche, chaque message, chaque "like" est **enregistré, analysé, et transformé en données**. Ces données servent ensuite à **nous profiler**, à créer ce que l'article original appelle un "GHOST" – un profil consommateur virtuel – afin de nous **bombarder de publicités ciblées**, de nous **influencer**, et de nous **enfermer dans des bulles informationnelles**. **Vos Données Ne Vous Appartiennent Plus** Le pire, c'est que nous avons **perdu le contrôle** sur nos propres données. Elles sont stockées dans d'immenses **datacenters**, appartenant à ces géants, souvent situés à l'autre bout du monde. Nous ne savons pas **exactement où elles sont**, **comment elles sont utilisées**, ni **qui y a accès**.  Et cette perte de contrôle a des conséquences bien réelles : * **Atteintes à la vie privée :** Surveillance constante, profilage intrusif, fuites de données… * **Manipulation et influence :** Publicités ciblées, désinformation, bulles de filtres… * **Dépendance et enfermement :** Nous devenons captifs de ces écosystèmes centralisés, il devient difficile de s'en extraire. **L'Aube d'une Solution : Le Web3** Alors, faut-il se résigner à cet Internet dysfonctionnel ? Absolument pas ! La bonne nouvelle, c'est qu'il existe une **alternative**. Une voie pour reprendre le contrôle, pour construire un Internet plus **libre**, plus **sûr**, plus **respectueux** de l'individu. Cette alternative, elle porte un nom : **le Web3**. Dans le prochain article, nous allons explorer ensemble ce nouveau paradigme, comprendre comment il fonctionne, et surtout, découvrir comment il peut nous permettre de **réparer Internet** et de **reprendre le pouvoir sur nos vies numériques**. [**Restez connecté… le changement est en marche !**](https://www.copylaradio.com/blog/blog-1/post/internet-est-casse-vous-netes-pas-fou-141) @ 6bae33c8:607272e8
2025-02-10 15:27:25I didn’t realize how much I had missed a good old fashioned Super Bowl blowout. I wasn’t even gonna bet the game, but over the last couple days, I got an Eagles vibe. There was too much, “The refs won’t let the Chiefs lose”, and Patrick Mahomes and Taylor Swift, and other noise, and yet the line didn’t budge. It was obvious the Eagles were the sharper side, and they had the league’s best defense, which usually correlates to overperformance of the spread in Super Bowls, sometimes massive overperformance. But it wasn’t any one thing — just an overall dawning on me that the Eagles were probably the right side. I didn’t feel that strongly about it, even so, and decided I’d just bet Saquon Barkley for MVP, get 3:1 or so if the Eagles won. So I texted someone in the states to place the bet for me, and best he could offer was +175! That’s a terrible value for a RB to win MVP! A few minutes later Tim Schuler offered to bet me $50, give me the Eagles +1, and I obliged him. After that, I texted my friend back to put $500 on the Eagles +1 for me. Of course, I didn’t stay up all night to watch — after losing 1K on the Falcons (who were up 28-3 in the third quarter at 3 am) eight years ago, never again. So I caught the 40-minute version this morning. What a great game! The Eagles dominated from start to finish. The defensive line got after Mahomes on every play. And while the Chiefs sold out to stop Barkley, Jalen Hurts ran wild on them. I’m sure I would have enjoyed a Chiefs blowout less, but the beauty of a blowout is it settles things. There’s no looking back at a bad call, a dropped pass or a fumble and wondering what might have been. Close games have drama, but they are more or less arbitrary. I mean I get it, the guy made the throw at the time with the game on the line, but maybe also he just got the cheap roughing the passer call or the ticky tack PI. When the Giants won the Super Bowl on Scott Norwood’s miss, I didn’t have the same sense of satisfaction I did when they blew out John Elway’s Broncos five years earlier. Yes, they won, but it might as well have been on a coin flip. I grew up on blowouts in the ‘80s — Raiders-Redskins, 49ers-Dolphins, Pats-Bears, Giants-Broncos, Redskins-Broncos — only the Bengals managed to keep Super Bowl losses close (Congratulations Jeff Erickson!) This was before replay reviews and all the lawyering about what is and isn’t a completed catch. The last fucking thing you wanted was some controversy about who really outplayed whom. So it was nice to win some easy money and not to have to worry about refs or fumbles or untimely drops for a change. - I wanted Saquon to win MVP, but he drew the attention of the KC defense, is one of the best I’ve ever seen in blitz pickup and still had 97 yards from scrimmage. One of the all-time great years from an all-time great back. (He broke Terrell Davis’ record for the most yardage, regular season and playoffs, too, albeit in two extra games.) - Hurts threw the one bad pick under pressure, but it served as a good punt, and otherwise had a near perfect game. Only four other incomplete passes, 72 yards and a score on the ground. He was an easy MVP call. - I was a little worried about shaky Jake Elliott, but he drilled all four of his field goals, three of them twice!, due to penalties. - Patrick Mahomes padded his stats in garbage time, but he got crushed. An elite defense that gets home with four is the way you kill the GOATS. The Giants did it to Tom Brady twice. - Xavier Worthy had a nice garbage-time stat-padding game, but he was the only one. DeAndre Hopkins had a bad drop, though they got him a garbage-time feel-good TD, basically a participation trophy. - Congrats to Lane Johnson, Brandon Graham, Elliott and long-snapper Rick Lovato — the only four players in NFL history to defeat both Tom Brady and Mahomes in Super Bowls. - The only negative is I lost my $50 four-teams bet with Erickson. I had the Chiefs, Bills, Lions and Ravens, he had the field. But I directed Schuler to pay him, which is good, because I cancelled Paypal for their retarded foray into free-speech policing, and now I don’t have to figure out a workaround.
@ 6bae33c8:607272e8
2025-02-10 15:27:25I didn’t realize how much I had missed a good old fashioned Super Bowl blowout. I wasn’t even gonna bet the game, but over the last couple days, I got an Eagles vibe. There was too much, “The refs won’t let the Chiefs lose”, and Patrick Mahomes and Taylor Swift, and other noise, and yet the line didn’t budge. It was obvious the Eagles were the sharper side, and they had the league’s best defense, which usually correlates to overperformance of the spread in Super Bowls, sometimes massive overperformance. But it wasn’t any one thing — just an overall dawning on me that the Eagles were probably the right side. I didn’t feel that strongly about it, even so, and decided I’d just bet Saquon Barkley for MVP, get 3:1 or so if the Eagles won. So I texted someone in the states to place the bet for me, and best he could offer was +175! That’s a terrible value for a RB to win MVP! A few minutes later Tim Schuler offered to bet me $50, give me the Eagles +1, and I obliged him. After that, I texted my friend back to put $500 on the Eagles +1 for me. Of course, I didn’t stay up all night to watch — after losing 1K on the Falcons (who were up 28-3 in the third quarter at 3 am) eight years ago, never again. So I caught the 40-minute version this morning. What a great game! The Eagles dominated from start to finish. The defensive line got after Mahomes on every play. And while the Chiefs sold out to stop Barkley, Jalen Hurts ran wild on them. I’m sure I would have enjoyed a Chiefs blowout less, but the beauty of a blowout is it settles things. There’s no looking back at a bad call, a dropped pass or a fumble and wondering what might have been. Close games have drama, but they are more or less arbitrary. I mean I get it, the guy made the throw at the time with the game on the line, but maybe also he just got the cheap roughing the passer call or the ticky tack PI. When the Giants won the Super Bowl on Scott Norwood’s miss, I didn’t have the same sense of satisfaction I did when they blew out John Elway’s Broncos five years earlier. Yes, they won, but it might as well have been on a coin flip. I grew up on blowouts in the ‘80s — Raiders-Redskins, 49ers-Dolphins, Pats-Bears, Giants-Broncos, Redskins-Broncos — only the Bengals managed to keep Super Bowl losses close (Congratulations Jeff Erickson!) This was before replay reviews and all the lawyering about what is and isn’t a completed catch. The last fucking thing you wanted was some controversy about who really outplayed whom. So it was nice to win some easy money and not to have to worry about refs or fumbles or untimely drops for a change. - I wanted Saquon to win MVP, but he drew the attention of the KC defense, is one of the best I’ve ever seen in blitz pickup and still had 97 yards from scrimmage. One of the all-time great years from an all-time great back. (He broke Terrell Davis’ record for the most yardage, regular season and playoffs, too, albeit in two extra games.) - Hurts threw the one bad pick under pressure, but it served as a good punt, and otherwise had a near perfect game. Only four other incomplete passes, 72 yards and a score on the ground. He was an easy MVP call. - I was a little worried about shaky Jake Elliott, but he drilled all four of his field goals, three of them twice!, due to penalties. - Patrick Mahomes padded his stats in garbage time, but he got crushed. An elite defense that gets home with four is the way you kill the GOATS. The Giants did it to Tom Brady twice. - Xavier Worthy had a nice garbage-time stat-padding game, but he was the only one. DeAndre Hopkins had a bad drop, though they got him a garbage-time feel-good TD, basically a participation trophy. - Congrats to Lane Johnson, Brandon Graham, Elliott and long-snapper Rick Lovato — the only four players in NFL history to defeat both Tom Brady and Mahomes in Super Bowls. - The only negative is I lost my $50 four-teams bet with Erickson. I had the Chiefs, Bills, Lions and Ravens, he had the field. But I directed Schuler to pay him, which is good, because I cancelled Paypal for their retarded foray into free-speech policing, and now I don’t have to figure out a workaround. @ 3b7fc823:e194354f
2025-02-10 13:13:25Alright, let’s get one thing straight: you’re scrolling through your phone, shopping online, maybe even working from home. But here’s the thing – someone might be watching. Not in the creepy stalker way, but in the “is that company really needing my data?” kind of way. That’s where a Virtual Private Network (VPN) comes in, saving you from the prying eyes of marketers, governments, and even your own internet provider. **What Does a VPN Do?** A VPN creates a secure, encrypted connection between your device and a VPN server. This allows you to browse the internet anonymously, keeping your online activities private from your Internet Service Provider (ISP), network administrators, and even hackers. When you connect to a VPN, your internet traffic is routed through an intermediary server, making it difficult for anyone to track your online movements. **Why You Need a VPN: Privacy edition** - Hiding Your IP Address Every time you jump online, your device gets an IP address, like a digital ID. If you don’t use a VPN, everyone can see this ID, making it easy for advertisers and governments to track your every move. - [X ] *Myth:* A VPN hides my IP address from everyone. - [X] *Reality:* A VPN hides your IP address only from the websites you visit and your ISP. Your internet service provider still knows you're using a VPN, but they won't be able to see what sites you're visiting. Your VPN knows what sites you are visiting and *may* know who you are as well. - Bypassing Censorship Ever tried accessing something that’s blocked in your country? A VPN can help you bypass those restrictions, letting you watch the latest shows, access social media, or even download books without getting flagged as a troublemaker. - Protecting Your Data When you connect to public Wi-Fi – like at a café or airport – you’re basically handing over your data on a silver platter. A VPN encrypts this data, so even if someone intercepts it, they can’t decode it. Think of it as adding an extra layer of security. - Avoiding Surveillance Companies and governments love collecting data. From what you search to who you talk to, there’s a lot of stuff that’s none of their business. A VPN ensures that only you know where you’ve been online. - Safeguarding Your Personal and Professional Life Whether you’re working from home or just shopping for a present, a VPN keeps your activities private. It’s like having a secure safe for all your online stuff, so no one can snoop. - Stopping Targeted Ads Companies track your browsing habits to send you ads that follow you around the internet. A VPN breaks this cycle, making sure those creepy “you might like” ads stop following you around. - No Logs Policy Some VPNs keep records of your activity, which means they could be handed over if the government comes knocking. But with a no-logs policy, nothing is stored – *they promise ;)* - The Dark Side of Free VPNs Before you jump into using a free VPN, think twice. Free services often come with a catch: they might sell your data to advertisers or even track your activity themselves. It’s like getting a free hotdog at a gas station – it sounds great, but you’ll probably regret it later. **How to Use a VPN (Because You’re Not a Tech Wizard)** - Choose the Right Provider Go for a reputable service that offers strong encryption and a no-logs policy. Look for options with a kill switch, which stops any data from being leaked if the connection drops. I prefer ones you can pay annoymously but that may be overkill for most people. - Download and Install Once you pick a provider, download the app to your device. It’s not rocket science, but it does require a bit more than just opening an email. - Set It Up Most VPNs have user-friendly interfaces. Just click “Connect” and you’re good to go. You might need to enter your login details or use a password from your provider. **The Final Word** Using a VPN isn’t about being a hacker or someone with something to hide. It’s about respecting your privacy and having control over what you share online. In today’s world, where companies and governments are constantly getting more creative about how they collect data, it’s practically a requirement if you want to stay ahead of the curve. So there you have it – the secret life of your internet. With a VPN, you’re not just protecting yourself; you’re making sure that your digital footprint is as small as possible. Whether you’re at home or on the go, a VPN gives you the freedom to surf, shop, and work without anyone watching your every move. And hey, if you’re still not convinced, just think about it this way: imagine your internet connection as a crowded public space. Without a VPN, everyone’s staring at you. With one, you’re wearing a mask, and no one’s the wiser. --- Advocating for privacy does not finance itself. If you enjoyed this article, please consider zapping or sending monero 82XCDNK1Js8TethhpGLFPbVyKe25DxMUePad1rUn9z7V6QdCzxHEE7varvVh1VUidUhHVSA4atNU2BTpSNJLC1BqSvDajw1
@ 3b7fc823:e194354f
2025-02-10 13:13:25Alright, let’s get one thing straight: you’re scrolling through your phone, shopping online, maybe even working from home. But here’s the thing – someone might be watching. Not in the creepy stalker way, but in the “is that company really needing my data?” kind of way. That’s where a Virtual Private Network (VPN) comes in, saving you from the prying eyes of marketers, governments, and even your own internet provider. **What Does a VPN Do?** A VPN creates a secure, encrypted connection between your device and a VPN server. This allows you to browse the internet anonymously, keeping your online activities private from your Internet Service Provider (ISP), network administrators, and even hackers. When you connect to a VPN, your internet traffic is routed through an intermediary server, making it difficult for anyone to track your online movements. **Why You Need a VPN: Privacy edition** - Hiding Your IP Address Every time you jump online, your device gets an IP address, like a digital ID. If you don’t use a VPN, everyone can see this ID, making it easy for advertisers and governments to track your every move. - [X ] *Myth:* A VPN hides my IP address from everyone. - [X] *Reality:* A VPN hides your IP address only from the websites you visit and your ISP. Your internet service provider still knows you're using a VPN, but they won't be able to see what sites you're visiting. Your VPN knows what sites you are visiting and *may* know who you are as well. - Bypassing Censorship Ever tried accessing something that’s blocked in your country? A VPN can help you bypass those restrictions, letting you watch the latest shows, access social media, or even download books without getting flagged as a troublemaker. - Protecting Your Data When you connect to public Wi-Fi – like at a café or airport – you’re basically handing over your data on a silver platter. A VPN encrypts this data, so even if someone intercepts it, they can’t decode it. Think of it as adding an extra layer of security. - Avoiding Surveillance Companies and governments love collecting data. From what you search to who you talk to, there’s a lot of stuff that’s none of their business. A VPN ensures that only you know where you’ve been online. - Safeguarding Your Personal and Professional Life Whether you’re working from home or just shopping for a present, a VPN keeps your activities private. It’s like having a secure safe for all your online stuff, so no one can snoop. - Stopping Targeted Ads Companies track your browsing habits to send you ads that follow you around the internet. A VPN breaks this cycle, making sure those creepy “you might like” ads stop following you around. - No Logs Policy Some VPNs keep records of your activity, which means they could be handed over if the government comes knocking. But with a no-logs policy, nothing is stored – *they promise ;)* - The Dark Side of Free VPNs Before you jump into using a free VPN, think twice. Free services often come with a catch: they might sell your data to advertisers or even track your activity themselves. It’s like getting a free hotdog at a gas station – it sounds great, but you’ll probably regret it later. **How to Use a VPN (Because You’re Not a Tech Wizard)** - Choose the Right Provider Go for a reputable service that offers strong encryption and a no-logs policy. Look for options with a kill switch, which stops any data from being leaked if the connection drops. I prefer ones you can pay annoymously but that may be overkill for most people. - Download and Install Once you pick a provider, download the app to your device. It’s not rocket science, but it does require a bit more than just opening an email. - Set It Up Most VPNs have user-friendly interfaces. Just click “Connect” and you’re good to go. You might need to enter your login details or use a password from your provider. **The Final Word** Using a VPN isn’t about being a hacker or someone with something to hide. It’s about respecting your privacy and having control over what you share online. In today’s world, where companies and governments are constantly getting more creative about how they collect data, it’s practically a requirement if you want to stay ahead of the curve. So there you have it – the secret life of your internet. With a VPN, you’re not just protecting yourself; you’re making sure that your digital footprint is as small as possible. Whether you’re at home or on the go, a VPN gives you the freedom to surf, shop, and work without anyone watching your every move. And hey, if you’re still not convinced, just think about it this way: imagine your internet connection as a crowded public space. Without a VPN, everyone’s staring at you. With one, you’re wearing a mask, and no one’s the wiser. --- Advocating for privacy does not finance itself. If you enjoyed this article, please consider zapping or sending monero 82XCDNK1Js8TethhpGLFPbVyKe25DxMUePad1rUn9z7V6QdCzxHEE7varvVh1VUidUhHVSA4atNU2BTpSNJLC1BqSvDajw1 @ da0b9bc3:4e30a4a9
2025-02-10 12:51:46Hello Stackers! It's Monday so we're back doing "Meta Music Mondays" 😉. From before the territory existed there was just one post a week in a ~meta take over. Now each month we have a different theme and bring music from that theme. Welcome to Femmes Fatales 3!!! I absolutely loved doing this last year so I'm bringing it back for round 3! It's Femmes Fatales, where we celebrate women in ~Music. So let's have those ladies of the lung, the sirens of sound, our Femmes Fatales! https://youtu.be/ya69LUa1E_w?si=cM6yCALsPpp9L3Sc I recently got introduced to these ladies. Their music is fantastic, they're really talented musicians. They are: Lilith: The vocalist. Lamia: The lead guitarist. Nixe: The bassist. Abrahel: The drummer. Their identity is meant to be a mystery, so let's keep it that way. These Nuns can make Noise!! Let's go! Talk Music. Share Tracks. Zap Sats. originally posted at https://stacker.news/items/881416
@ da0b9bc3:4e30a4a9
2025-02-10 12:51:46Hello Stackers! It's Monday so we're back doing "Meta Music Mondays" 😉. From before the territory existed there was just one post a week in a ~meta take over. Now each month we have a different theme and bring music from that theme. Welcome to Femmes Fatales 3!!! I absolutely loved doing this last year so I'm bringing it back for round 3! It's Femmes Fatales, where we celebrate women in ~Music. So let's have those ladies of the lung, the sirens of sound, our Femmes Fatales! https://youtu.be/ya69LUa1E_w?si=cM6yCALsPpp9L3Sc I recently got introduced to these ladies. Their music is fantastic, they're really talented musicians. They are: Lilith: The vocalist. Lamia: The lead guitarist. Nixe: The bassist. Abrahel: The drummer. Their identity is meant to be a mystery, so let's keep it that way. These Nuns can make Noise!! Let's go! Talk Music. Share Tracks. Zap Sats. originally posted at https://stacker.news/items/881416 @ 78c90fc4:4bff983c
2025-02-10 12:08:13  “Die Welt wird von ganz anderen Personen regiert als diejenigen es sich vorstellen, die nicht hinter den Kulissen stehen.” Benjamin Disraeli, zweimaliger britischer Premierminister und Romanautor. Quelle: <https://www.unz.com/article/the-disraeli-enigma/>\ \ Als 1853 der Krimkrieg zwischen Russland und dem Osmanischen Reich ausbrach, wurde das Osmanische Reich vom Vereinigten Königreich und Frankreich gerettet. Zwanzig Jahre später zog Zar Alexander II. als Beschützer der unterdrückten serbischen und bulgarischen Christen erneut gegen die Osmanen in den Krieg. Als die Russen vor den Toren Konstantinopels/Istanbuls standen, waren die Osmanen gezwungen, die Schaffung der autonomen Fürstentümer Bulgarien, Serbien und Rumänien durch den Vertrag von San Stefano zu akzeptieren. Die Briten waren mit diesem Vertrag unzufrieden und beriefen zusammen mit Österreich-Ungarn den Berliner Kongress (1878) ein, der ihn aufhob. Russische Eroberungen wurden zurückgenommen, Armenien und Bulgarien wurden größtenteils an das Osmanische Reich zurückgegeben und der Balkan wurde in heterogene und konfliktreiche Staaten aufgeteilt. Diese „Balkanisierung“ löste nationalistische Ressentiments aus, die den Ersten Weltkrieg auslösen sollten. \ Das Hauptziel des Berliner Vertrags bestand darin, das zu retten, was von einem schwächelnden Osmanischen Reich zu retten war, um der panslawistischen Expansion Russlands entgegenzuwirken. England, das stets eifersüchtig auf seine Vormachtstellung zur See bedacht war, wollte verhindern, dass Russland näher an den Bosporus heranrückte. Die Briten erhielten das Recht, Zypern als Marinestützpunkt zu nutzen und gleichzeitig den Suezkanal zu überwachen. Dies war der Beginn des „Great Game“ Großbritanniens um die Kolonialherrschaft in Asien und die Eindämmung Russlands, was insbesondere zur Schaffung Afghanistans als Pufferstaat führte. \ Es gibt verschiedene Möglichkeiten, diesen Abschnitt der Geschichte zu interpretieren, der den Keim für alle Tragödien des 20. Jahrhunderts („das jüdische Jahrhundert“ laut Yuri Slezkine) in sich trägt.**\[1]**\ Yuri Slezkine, *The Jewish Century,* Princeton University Press, 2004. \ Es gibt unterschiedliche Ansichten darüber, welche Kräfte die Geschichte in dieser entscheidenden Zeit geprägt haben. Aber letztendlich wird Geschichte von Menschen gemacht, und sie kann nur verstanden werden, wenn man die Hauptakteure und ihre Motive identifiziert: Man kann den Vietnamkrieg einfach nicht verstehen, ohne sich mit der Denkweise von Johnson oder Kissinger auseinanderzusetzen. Unter den Anstiftern des Berliner Vertrags sticht ein Name besonders hervor: Benjamin Disraeli (1804–1881), Premierminister unter Königin Victoria von 1868 bis 1869 und erneut von 1874 bis 1880. Disraeli war auch der Mann, der 1875 die Übernahme des Suezkanals durch England ermöglichte, und zwar durch die Finanzierung seines Freundes Lionel de Rothschild, dem Sohn von Nathan Mayer – eine Operation, die die Kontrolle der Rothschilds über die Bank of England festigte. \ Disraeli ist ein sehr interessanter Fall, da er sowohl ein bedeutender britischer Staatsmann während der globalen Hegemonie Großbritanniens als auch ein Romanautor war, der seine fiktiven Figuren dazu benutzte, seine ehrlichen Gedanken zu äußern, während er eine Art „glaubhafte Abstreitbarkeit“ (Sidonia spricht, nicht ich!) aufrechterhielt. Wir haben daher die einzigartige Gelegenheit, die wahren Motive des Mannes in der Politik zwischen den Zeilen zu lesen. Stellen Sie sich vor, Kissinger hätte Romane geschrieben, in denen ein Jude die Hauptfigur ist, der die Außen- und Militärpolitik des Imperiums vorantrieb und gleichzeitig ein enger Freund des reichsten jüdischen Bankiers war.\ \  Disraeli wird als der wahre Erfinder des Britischen Empires bezeichnet, da er es war, der Königin Victoria durch das Parlament mit dem Royal Titles Act von 1876 zur Kaiserin von Indien ernennen ließ (das obere Bild ist eine Karikatur, die Disraeli als Hausierer zeigt, der der Königin die Kaiserkrone überreicht). Disraeli war, wie bereits erwähnt, die Hauptinspiration für den Berliner Kongress. Darüber hinaus war Disraeli ein Vorläufer des Zionismus, der versuchte, die „Wiederherstellung Israels“ auf die Tagesordnung des Berliner Kongresses zu setzen, in der Hoffnung, den Sultan Abdul Hamid davon zu überzeugen, Palästina als autonome Provinz zu gewähren. Der Sultan lehnte das Angebot ab, das wahrscheinlich das Versprechen finanzieller Unterstützung für seine zusammenbrechende Wirtschaft beinhaltete – wie auch Herzls Angebot im Jahr 1902, das ebenfalls abgelehnt wurde.\ \ Der Zionismus war Disraelis uralter Traum: Nach einer Reise in den Nahen Osten im Alter von sechsundzwanzig Jahren veröffentlichte er seinen ersten Roman, *Die wundersame Geschichte des Alroy*, und ließ seinen Helden, einen einflussreichen Juden des Mittelalters, sagen: „Mein Wunsch ist eine nationale Existenz, die wir nicht haben. Mein Wunsch ist das Land der Verheißung und Jerusalem und der Tempel, alles, was wir eingebüßt haben, wonach wir uns gesehnt haben, wofür wir gekämpft haben, unser schönes Land, unser heiliges Glaubensbekenntnis, unsere einfachen Sitten und unsere alten Bräuche.“\ Disraeli schrieb diese Zeilen noch vor den Anfängen der biblischen Archäologie; erst 1841 veröffentlichte Edward Robinson seine *Biblical Researches in Palestine*. Die ersten Ausgrabungen des von Königin Victoria geförderten Palestine Exploration Fund begannen 1867. Wohlhabende britische Juden hatten sich jedoch schon lange zuvor für Palästina interessiert. Disraelis Interesse wurde durch seinen Nachbarn und vierzigjährigen Freund Moses Montefiore beeinflusst, der Judith Cohen, die Schwägerin von Nathan Rothschild, heiratete. Nach einer Reise nach Palästina im Jahr 1827 widmete Montefiore seine immensen Ressourcen der Unterstützung seiner Glaubensgenossen im Heiligen Land, indem er Land kaufte und Häuser baute. \ Sowohl Montefiore als auch Disraeli waren sephardischer Herkunft. Disraeli stammte aus einer Familie portugiesischer Marranen, die in Venedig zum Judentum konvertierten. Sein Großvater war 1748 nach London gezogen. Benjamin wurde im Alter von dreizehn Jahren getauft, als sein Vater Isaac D'Israeli zusammen mit seiner ganzen Familie zum anglikanischen Christentum konvertierte. Isaac D'Israeli ist der Autor eines Buches mit dem Titel *The Genius of Judaism*(in Anlehnung an Chateaubriands *Le Génie du Christianisme*), in dem er die einzigartigen Eigenschaften des jüdischen Volkes verherrlicht, aber die talmudischen Rabbiner dafür verantwortlich macht, dass sie „den nationalen Geist ihres Volkes versiegeln“ und „die Einfachheit ihres antiken Glaubens korrumpieren“. Wie für viele andere Juden dieser Zeit war die Konversion für D'Israeli rein opportunistisch: Bis zum Beginn des 19. Jahrhunderts blieben Verwaltungskarrieren für Juden verschlossen. Ein Gesetz von 1740 hatte ihre Einbürgerung erlaubt, aber es hatte Volksaufstände provoziert und wurde 1753 aufgehoben. Viele einflussreiche Juden, wie der Stadtbankier Sampson Gideon, entschieden sich dann für eine nominelle Konversion ihrer Kinder.**\[2]**\ Cecil Roth, *A History of the Marranos* (1932)*,* Meridian Books, 1959*,* S. 148.\ \ Etwa zur gleichen Zeit wie Disraeli konvertierte Heinrich Heine (1797–1856) zum Luthertum (während einer seiner Brüder zum Katholizismus konvertierte, um Offizier in Österreich zu werden, und ein anderer zur Orthodoxie, um als Arzt in Russland zu dienen). Heine betrachtete die Taufe als „Eintrittskarte in die europäische Zivilisation“. Er beklagte sich jedoch darüber, dass er von den Deutschen immer noch als Jude angesehen wurde, und zog es daher vor, in Frankreich zu leben, wo er als Deutscher angesehen wurde. Nur wenige Jahre nach seiner Konversion zeigten seine Schriften eine sehr negative Einstellung gegenüber dem Christentum, das er als „düstere, blutrünstige Religion für Kriminelle“ bezeichnete, die die Sinnlichkeit unterdrücke. Am Ende seines Lebens bereute er seine Taufe, die ihm nichts gebracht hatte, und erklärte in seinem letzten Buch *Romanzero*: „Ich mache kein Geheimnis aus meinem Judentum, zu dem ich nicht zurückgekehrt bin, weil ich es nicht verlassen habe.“**\[3]**\ Zitiert in Kevin MacDonald, *Separation and Its Discontents:* *Toward an Evolutionary Theory of Anti-Semitism,* Praeger, 1998, kindle 2013, l. 4732–4877. \ Genau wie bei den portugiesischen Marranen im 15. Jahrhundert verstärkte die Taufe bei den europäischen Juden des 19. Jahrhunderts ein nicht-religiöses, rassisches Verständnis des Judentums. Disraeli bezeichnete sich selbst als „Anglikaner jüdischer Abstammung“. \ Für Hannah Arendt ist Disraeli ein „Rassenfanatiker“, der in seinem ersten Roman *Alroy* (1833) „einen Plan für ein jüdisches Reich entwickelte, in dem Juden als streng getrennte Klasse herrschen würden“. In seinem anderen Roman *Coningsby* „entfaltete er einen fantastischen Plan, nach dem jüdisches Geld den Aufstieg und Fall von Höfen und Reichen beherrscht und in der Diplomatie die Oberhand hat“. Diese Idee „wurde zum Dreh- und Angelpunkt seiner politischen Philosophie“.**\[4]**\ Hannah Arendt, *The Origins of Totalitarianism,* Band 1: *Antisemitism,* Meridian Books, 1958, S. 309–310.\ Dies ist eine ziemlich fantastische Anschuldigung, die die meisten Biografen Disraelis nicht bestätigen würden. Sie ist jedoch wahrscheinlich richtig. Aber wir müssen genau auf Disraelis eigene Stimme hören, die durch Sidonia zum Ausdruck kommt, die Figur, die in drei seiner Romane vorkommt: *Coningsby* (1844), *Sybil* (1845) und *Tancred* (1847). In Sidonias Worten spürt man den Groll gegen die Nation, in die er sich zu integrieren versuchte:\ Kann es etwas Absurderes geben, als dass eine Nation sich an eine Einzelperson wendet, um ihren Kredit, ihre Existenz als Imperium und ihren Komfort als Volk zu erhalten; und diese Einzelperson, der ihre Gesetze die stolzesten Rechte der Staatsbürgerschaft, das Privileg, in ihrem Senat zu sitzen und Land zu besitzen, verweigern; denn obwohl ich unbesonnen genug war, mehrere Ländereien zu kaufen, bin ich der Meinung, dass ein Engländer hebräischen Glaubens nach dem geltenden Recht Englands keinen Boden besitzen kann. \ Da es einem Juden nicht möglich ist, sich durch Landbesitz in die britische Aristokratie zu integrieren, selbst wenn er zum örtlichen Glauben konvertiert, was sollte ein Jude tun, außer durch die Macht des Geldes aufzusteigen? Wie Heine spürte auch Disraeli die Heuchelei der Christen, die es den Juden übel nahmen, dass sie keine Christen waren, sie aber weiterhin als Juden behandelten, wenn sie konvertierten, und es insgeheim sogar vorzogen, dass sie Juden blieben. \ Laut Disraelis Biografen Robert Blake ist Sidonia „eine Kreuzung zwischen Lionel de Rothschild und Disraeli selbst“. Er stammt von einer Adelsfamilie aus Aragon ab, zu deren herausragenden Mitgliedern ein Erzbischof und ein Großinquisitor gehörten, die beide heimlich dem Judentum ihrer Väter anhingen. Sidonias Vater, wie auch Lionel de Rothschilds Vater, „machte während der Napoleonischen Kriege ein großes Vermögen mit Militärverträgen und der Versorgung der verschiedenen Armeen“. Nachdem er sich in London niedergelassen hatte, „setzte er alles, was er besaß, auf die Waterloo-Anleihe; und das Ereignis machte ihn zu einem der größten Kapitalisten Europas.“ Seit seinem siebzehnten Lebensjahr besuchte Sidonia die Fürstenhöfe der Schuldner seines Vaters und lernte die Geheimnisse der Macht kennen. „Die geheime Geschichte der Welt war sein Zeitvertreib. Es bereitete ihm großes Vergnügen, die verborgenen Motive mit den öffentlichen Vorwänden der Transaktionen zu kontrastieren.“ Disraeli selbst war laut Robert Blake „von Verschwörungen besessen“.**\[5]**\ Robert Blake, *Disraeli* (1966), Faber Finds, 2010, S. 202. \ Sidonia ist von seiner Rasse begeistert: „Alles ist Rasse – es gibt keine andere Wahrheit.“ Er weigert sich, eine Nichtjüdin zu heiraten, weil, so der Erzähler, „keine irdische Überlegung ihn jemals dazu veranlassen würde, die Reinheit der Rasse zu beeinträchtigen, auf die er stolz ist.“ Mit „Rasse“ meinte Disraeli Blutsverwandtschaft. In seinem letzten Roman *Endymion* (1880) schrieb er:\ Kein Mensch wird das Prinzip der Rasse gleichgültig behandeln. Es ist der Schlüssel zur Geschichte, und der Grund, warum die Geschichte oft so verwirrend ist, liegt darin, dass sie von Männern geschrieben wurde, die dieses Prinzip und all das damit verbundene Wissen nicht kennen ... Sprache und Religion machen keine Rasse aus – es gibt nur eine Sache, die eine Rasse ausmacht, und das ist Blut.\ **[Sidonia erzählt seinem Schützling Coningsby](https://www.victorianlondon.org/etexts/disraeli/coningsby-0038.shtml)** in *Coningsby oder die neue Generation*, dass die Verfolgung durch christliche Nationen die jüdische Nation niemals zerschlagen könnte. \ Tatsache ist, dass man eine reine Rasse der kaukasischen Organisation nicht vernichten kann. Es ist eine physiologische Tatsache; ein einfaches Naturgesetz, das ägyptische und assyrische Könige, römische Kaiser und christliche Inquisitoren verblüfft hat. Keine Strafgesetze, keine körperlichen Folterungen können bewirken, dass eine überlegene Rasse in einer unterlegenen aufgehen oder von ihr vernichtet werden sollte. Die gemischten verfolgenden Rassen verschwinden, die reine verfolgte Rasse bleibt bestehen. Und im Moment, trotz Jahrhunderten oder gar Jahrzehnten der Erniedrigung, übt der jüdische Geist einen enormen Einfluss auf die Angelegenheiten Europas aus. Ich spreche nicht von ihren Gesetzen, denen Sie immer noch gehorchen; von ihrer Literatur, mit der Ihr Geist gesättigt ist, sondern vom lebendigen hebräischen Intellekt. Sie beobachten nie eine große intellektuelle Bewegung in Europa, an der die Juden nicht in hohem Maße beteiligt sind.\ Wo auch immer er reiste, fügte Sidonia hinzu, sah er jüdische Berater hinter Monarchen und Staatsoberhäuptern. „Sie sehen also, mein lieber Coningsby, dass die Welt von ganz anderen Persönlichkeiten regiert wird, als diejenigen, die nicht hinter den Kulissen stehen, sich vorstellen können.“ In einem Sachbuch (*Lord George Bentinck: A Political Biography*, 1852) schrieb Disraeli:\ \[Juden] sind ein lebendiger und der eindrucksvollste Beweis für die Falschheit dieser verderblichen Doktrin der Neuzeit, der natürlichen Gleichheit der Menschen. ... die natürliche Gleichheit der Menschen, die heute in Mode ist und die Form einer kosmopolitischen Bruderschaft annimmt, ist ein Prinzip, das, wenn man danach handeln könnte, die großen Rassen zersetzen und den ganzen Genius der Welt zerstören würde. ... Die angeborene Tendenz der jüdischen Rasse, die zu Recht stolz auf ihr Blut ist, ist gegen die Doktrin der Gleichheit der Menschen.**\[6]**\ Benjamin Disraeli, *Lord George Bentinck*, Archibald, 1852 (archive.org), S. 496. \ Disraeli ist eindeutig auf derselben Wellenlänge wie Moses Hess, Herzls geistiger Vater, der, nachdem er Marx (einen weiteren nominellen Konvertiten) beeinflusst hatte, zu dem Schluss kam, dass „der Rassenkrieg wichtiger ist als der Klassenkampf“ (*Rom und Jerusalem,* 1862). Ein gutes Beispiel für dialektische politische Manipulation ist, dass Hess Marx weiterhin heimlich unterstützte und auf dessen Bitte hin nach dem Generalkongress der Internationale in Basel (5.–12. September 1869) Verleumdungen gegen Bakunin veröffentlichte, in denen er Bakunin beschuldigte, ein *Agent provocateur* der russischen Regierung zu sein und „im Interesse des Panslawismus“ zu arbeiten.**\[7]**\ Bakunins Antwort auf Französisch, „Aux citoyens rédacteurs du *Réveil*“, finden Sie auf Wikisource.org.\ Es ist interessant zu sehen, dass ein anderer Proto-Zionist wie Disraeli den russischen Interessen zutiefst feindlich gesinnt war.\ \ Was war Disraelis Motivation hinter der Außenpolitik, die er dem britischen Empire vermittelte? Glaubte er, dass es die offensichtliche Bestimmung der Briten sei, die Welt zu erobern? Oder sah er das britische Empire als Instrument für die überlegene Bestimmung der jüdischen Nation, wenn er sich daran erinnerte, wie Esra und Nehemia in biblischen Zeiten die Außenpolitik der Perser ausgenutzt hatten? Indem er den Suezkanal (der zwischen 1859 und 1869 von den Franzosen gegraben wurde) mit den britischen Interessen in Verbindung brachte, wollte er einfach nur die Franzosen übertrumpfen, oder legte er damit den Grundstein für das zukünftige Bündnis zwischen Israel und dem angloamerikanischen Empire? Da die Briten nun einmal den Suezkanal besaßen, mussten sie ihn verteidigen, und wie ginge das besser als mit einer befreundeten jüdischen autonomen Regierung in der Nähe in Palästina? Genau das war es, was Chaim Weizmann dreißig Jahre später den Briten schmackhaft machen wollte: „Das jüdische Palästina wäre ein Schutz für England, insbesondere in Bezug auf den Suezkanal.“**\[8]**\ Chaim Weizmann, *Trial and Error,* Harper & Brothers, 1949, S. 192. \ Und als die Israelis 1956 mit britischer und französischer Unterstützung in den Sinai einmarschierten, taten sie dies, indem sie Großbritannien erneut versprachen, die Kontrolle über den von Nasser verstaatlichten Kanal an Großbritannien zurückzugeben. \ Disraelis Russophobie, zu der er Königin Victoria bekehrte, und seine Verteidigung der Türken, deren Massaker an den Serben und Bulgaren allgemein bekannt waren, führten zu Theorien über eine jüdische Verschwörung. William Ewart Gladstone, ein langjähriger Gegner Disraelis und selbst mehrmals Premierminister (1868–1874, 1880–1885, 1886 und 1892–1894), erklärte, dass Disraeli „die britische Außenpolitik als Geisel seiner jüdischen Sympathien nahm und mehr daran interessiert war, die Leiden der Juden in Russland und der Türkei zu lindern, als an britischen Interessen“. Die Zeitung *„The Truth“* vom 22. November 1877 spielte auf die Vertrautheit Disraelis mit den Rothschilds an und vermutete „eine stillschweigende Verschwörung ... seitens einer beträchtlichen Anzahl von Anglo-Hebräern, um uns im Namen der Türken in einen Krieg zu ziehen“. Es wurde außerdem daran erinnert, dass Disraeli in einer Rede vor dem britischen Unterhaus im Jahr 1847 die Zulassung von Juden zu wählbaren Ämtern gefordert hatte, mit der Begründung, dass „der jüdische Geist einen enormen Einfluss auf die Angelegenheiten Europas ausübt“.**\[9]**\ Stanley Weintraub, *Disraeli: A Biography,* Hamish Hamilton, 1993, S. 579, 547. \ Die Königin stand, wie ein Großteil der britischen Aristokratie, bereits unter dem Bann einer modischen Theorie, die den Angelsachsen einen israelitischen Ursprung zuschrieb. Diese Theorie war erstmals zur Zeit Oliver Cromwells aufgetaucht und wurde 1840 von Pastor John Wilson in seinen *Vorlesungen über das alte Israel und den israelitischen Ursprung der modernen Nationen Europas* sowie 1870 von Edward Hine in *The English Nation Identified with the Lost Israel* neu aufgelegt. In diesem Werk erfahren wir, dass das Wort „Saxon“ von „Isaac's sons“ (Söhne Isaaks) abgeleitet ist. Diese lächerliche Theorie lieferte eine billige biblische Rechtfertigung für den britischen Kolonialismus und sogar für den Völkermord an den kolonisierten Völkern (neue Kanaaniter) durch das britische Empire (neues Israel).**\[10]**\ André Pichot, *Aux origines des théories raciales, de la Bible à Darwin,* Flammarion, 2008, S. 124–143, 319. \ Königin Victoria war glücklich, glauben zu können, dass ihre edle Abstammung auf König David zurückging, und ließ ihre Söhne beschneiden, ein Brauch, der bis heute fortbesteht. Es mag etwas Wahres an dem Gefühl der britischen Elite für ihr Judentum liegen, denn im 16. und 17. Jahrhundert hatten viele Ehen reiche jüdische Familien mit der alten, verarmten Landaristokratie vereint, so dass nach Hilaire Bellocs Schätzung „mit Beginn des 20. Jahrhunderts diejenigen der großen territorialen englischen Familien, in denen es kein jüdisches Blut gab, die Ausnahme waren“.**\[11]**\ Hilaire Belloc, *The Jews,* Constable & Co., 1922 (archive.org), S. 223. \ Die Begeisterung der Königin für das Judentum hatte aber auch viel mit dem Einfluss Disraelis zu tun, der einmal gegenüber einem Freund damit prahlte: „Jeder mag Schmeichelei, und wenn es um das Königshaus geht, sollte man sie mit einer Kelle auftragen.“**\[12]**\ Stanley Weintraub, *Disraeli: A Biography,* Hamish Hamilton, 1993, S. 579, 547. \ Der Fall Disraeli ist aufschlussreich, weil die Frage, die er aufwirft, dieselbe ist wie die Frage, die heute geopolitische Analysten in Bezug auf die Beziehung zwischen den Vereinigten Staaten und Israel spaltet: Wer führt wen an der Nase herum? Ist Israel der Brückenkopf der Vereinigten Staaten im Nahen Osten oder sind die Vereinigten Staaten, wie Zbigniew Brzezinski einmal sagte, der **[„dumme Esel“](https://www.youtube.com/watch?v=MfjE5_1xOs8)** Israels? Die Beantwortung dieser Frage für das Jahrhundert vor dem Zweiten Weltkrieg (als **[„Israel“ das internationale Judentum](https://twitter.com/Laurent_Guyenot/status/1883831745046560928)** bedeutete) hilft bei der Beantwortung derselben Frage heute, da die symbiotische Beziehung zwischen Israel und dem Imperium erheblich gewachsen ist. \ Die Antwort hängt vom Standpunkt des Betrachters ab. Die Zionisten haben natürlich ein Interesse daran, die Ansicht zu fördern, dass Israel den angloamerikanischen Interessen dient und nicht umgekehrt. Disraeli argumentierte vor dem britischen Parlament, dass ein jüdisches Palästina im Interesse des britischen Kolonialismus sei. Aber jüdische Zionisten haben die Dinge schon immer aus der anderen Perspektive betrachtet, und man kann kaum glauben, dass Disraeli ihre Ansicht nicht insgeheim teilte. Wenn der Held seines Romans *Tancred* (1847), ein Jude, der wie Disraeli zum Lord ernannt wurde, das britische Empire mit folgenden Worten verherrlicht: „Wir wollen die Welt erobern, angeführt von Engeln, um die Menschheit unter göttlicher Herrschaft glücklich zu machen“, wer verbirgt sich hinter diesem zweideutigen „wir“? Ist es dasselbe doppeldeutige „wir“, das die PNAC-Neokonservativen benutzten, um Amerika in Kriege zum Wohle Israels zu verwickeln? \ Wenn ein britischer Jude wie Disraeli zu den Briten „wir“ sagte, war dies eine strategische Zweideutigkeit. Er traf damit den patriotischen Nerv der angelsächsischen Elite, die den gemeinsamen Glauben an die Mission des britischen Empires teilte, die Welt zu zivilisieren – Menschen wie Lord Salisbury, Mitglied von Cecil Rhodes' Round Table, der sich für eine Weltregierung durch die „britische Rasse“ einsetzte.**\[13]**\ Carroll Quigley, *The Anglo-American Establishment, From Rhodes to Cliveden* (1949), Books In Focus, 1981. \ Der britische Imperialismus und der zionistische Nationalismus wurden etwa zur gleichen Zeit geboren wie die Zwillinge Esau und Jakob und sind seit ihrer Geburt eng miteinander verflochten. Zwei Überlegungen helfen jedoch, ihre wahre Beziehung zu verstehen. Erstens reichen die ideologischen Wurzeln des Britischen Empires nicht weiter zurück als bis ins 17. Jahrhundert, während die des Zionismus mehr als zwei Jahrtausende zurückreichen. Zweitens starb das Britische Empire nach dem Ersten Weltkrieg, während der Zionismus aufblühte. Aus diesen beiden Gründen ist die Theorie, dass der Zionismus ein Nebenprodukt des britischen Imperialismus ist (nennen wir sie die Chomsky-Theorie), nicht haltbar. \ Um die wahre Beziehung zwischen Zion und Albion zu Disraelis Zeiten zu verstehen, muss man die Macht der Rothschild-Dynastie über die britische Politik richtig einschätzen. Ohne die Rothschilds hätte Großbritannien nie die Kontrolle über den Suezkanal erlangt, der den Grundstein des britischen Empires im Nahen Osten bildete. Die Rothschilds selbst kandidierten nicht für ein politisches Amt, heirateten jedoch manchmal in eine solche Familie ein: Lord Archibald Primrose, 1886 und von 1892 bis 1894 Außenminister und 1894–1895 Premierminister, war der Schwiegersohn von Mayer Amschel de Rothschild.\ Es ist bemerkenswert, dass Theodor Herzl den zukünftigen jüdischen Staat als „aristokratische Republik“ mit „dem ersten Prinzen Rothschild“ an der Spitze sah. In einer langen Tirade in seinem Tagebuch ermahnte er die Rothschilds, ihre bösen Seelen zu erlösen, indem sie den Zionismus statt Kriege finanzierten:\ Ich weiß nicht, ob alle Regierungen bereits erkennen, welche internationale Bedrohung Ihr Weltreich darstellt. Ohne Sie können keine Kriege geführt werden, und wenn Frieden geschlossen werden soll, sind die Menschen umso mehr auf Sie angewiesen. Für das Jahr 1895 wurden die Militärausgaben der fünf Großmächte auf vier Milliarden Francs geschätzt, und ihre tatsächliche militärische Stärke in Friedenszeiten auf 2.800.000 Mann. Und diese Streitkräfte, die in der Geschichte ihresgleichen suchen, kommandieren Sie finanziell, ungeachtet der widerstreitenden Wünsche der Nationen. ... Und Ihr verfluchter Reichtum wächst immer noch. ... Aber wenn Sie sich uns anschließen, ... werden wir unseren ersten gewählten Herrscher aus Ihrem Haus nehmen. Das ist das leuchtende Leuchtfeuer, das wir auf die Spitze des fertigen Eiffelturms Ihres Vermögens setzen werden. In der Geschichte wird es so aussehen, als wäre das der Zweck des gesamten Bauwerks gewesen.**\[14]**\ \ *The Complete Diaries of Theodor Herzl,* edited by Raphael Patai, Herzl Press & Thomas Yoseloff, 1960, vol. 1*,* pp. 163–170.\ Wie Richard Wagner jedoch einmal sagte (*Judaism in Music*, 1850), zogen es die Rothschilds vor, „die Juden der Könige“ zu bleiben, anstatt „die Könige der Juden“ zu sein.\ \ Wenn die Zeit für die Gründung des jüdischen Staates zu Disraelis Zeiten noch nicht reif war, dann vor allem deshalb, weil die Juden in Russland sich von Palästina ebenso wenig angezogen fühlten wie die Juden in Europa; sie wussten kaum, wo es lag. Erst kürzlich von Zar Alexander II. emanzipiert, strebten sie lediglich eine Auswanderung nach Europa oder in die Vereinigten Staaten an. Erst nach der Ermordung von Zar Alexander II. im Jahr 1881 (einen Monat vor Disraelis Tod) wurden einige von ihnen durch die Pogrome für Leon Pinskers proto-zionistischen Aufruf von 1882 empfänglich: „Wir müssen uns ein für alle Mal mit dem Gedanken abfinden, dass die anderen Nationen uns aufgrund ihres angeborenen natürlichen Antagonismus für immer ablehnen werden.“**\[15]**\ Benzion Netanyahu, *The Founding Fathers of Zionism,* Balfour Books, 2012*,* Kindle l. 761-775. \ Ebenfalls im Jahr 1881 begann Baron Edmond de Rothschild vom Pariser Zweig, unter der Schirmherrschaft seiner Palestine Jewish Colonization Association (PICA) Land in Palästina zu kaufen und die Ansiedlung jüdischer Siedler zu finanzieren, insbesondere in Tel Aviv. Die meisten bestehenden internationalen jüdischen Organisationen, wie B'nai B'rith (gegründet 1843 in New York) oder die Alliance Israélite Universelle (gegründet 1860 in Paris), waren jedoch der Meinung, dass Israel als verstreute Nation gut zurechtkäme und keine Pläne für Palästina habe.\ Dies änderte sich während des Ersten Weltkriegs, als ein äußerst effizientes Netzwerk aufgebaut wurde, das beide Seiten des Atlantiks verband.**\[16]**\ Alison Weir, *Against Our Better Judgment: The Hidden History of How the U.S. Was Used to Create Israel,* 2014, Kindle l. 387-475. \ Theodor Herz konzentrierte seine diplomatischen Bemühungen zunächst auf Deutschland, aber in England begannen sich die Dinge vielversprechend zu entwickeln („Der Schwerpunkt hat sich nach England verlagert“, schrieb er 1895 in sein Tagebuch), was zum Teil der Rekrutierung von Israel Zangwill zu verdanken war, der laut Benzion Netanyahu „der erste war, der in den oberen Kreisen der britischen Politik direkt über den Zionismus sprach“, insbesondere mit Lloyd George, „einem engen Bekannten Zangwills von Beginn seiner zionistischen Tätigkeit bis zu seinem Lebensende“.**\[17]**\ Netanyahu, *The Founding Fathers of Zionism,* l. 2536-59. \ Erinnern wir uns daran, dass Zangwill der erfolgreiche Autor von *The Melting Pot war,* einem Theaterstück, das Mischehen für Amerikaner pries. Hier besteht kein Widerspruch, denn „die gemischten verfolgten Rassen verschwinden, die reine verfolgte Rasse bleibt bestehen“, wie Sidonia sagte.\ \ Die Bedeutung von Disraelis geopolitischen Manövern wird von Historikern der Zionisten selten anerkannt, da sie oberflächlich betrachtet nicht den Weg für die Gründung des jüdischen Staates geebnet zu haben scheinen. Tatsächlich bildeten sie jedoch das unsichtbare Fundament, auf dem Herzl und Zangwill aufbauten. Und diese unsichtbare Kontinuität zeugt von der erstaunlichen generationsübergreifenden Beharrlichkeit des jüdischen Volkes, das sein jahrtausendealtes, selbsternanntes Schicksal Generation für Generation vorantreibt. Ja, es ist wirklich bewundernswert, wenn auch verheerend für die westliche Zivilisation, die durch zweitausend Jahre Christentum ahnungslos und ihres eigenen Sinns für Blut beraubt wurde. Wie der zionistische Autor Jakob Klatzkin einmal in der Zeitschrift *„Der Jude“*, 1916, schrieb:\ Wir bilden in uns selbst eine geschlossene juristische und geschäftliche Körperschaft. Eine starke Mauer, die wir errichtet haben, trennt uns von den Menschen in den Ländern, in denen wir leben – und hinter dieser Mauer befindet sich ein jüdischer Staat.**\[18]** Zitiert in Robert Edward Edmondson, *The Jewish System Indicted by the Documentary Record,* 1937 (archive.org), S. 15.\ \ **Anmerkungen**\ **\[1]** Yuri Slezkine, *The Jewish Century,* Princeton University Press, 2004.\ **\[2]** Cecil Roth, *A History of the Marranos* (1932)*,* Meridian Books, 1959*,* S. 148.\ **\[3]** Zitiert in Kevin MacDonald, *Separation and Its Discontents: Toward an Evolutionary Theory of Anti-Semitism,* Praeger, 1998, kindle 2013, l. 4732–4877.\ **\[4]** Hannah Arendt, *The Origins of Totalitarianism,* Band 1: *Antisemitism,* Meridian Books, 1958, S. 309–310.\ **\[5]** Robert Blake, *Disraeli* (1966), Faber Finds, 2010, S. 202.\ **\[6]** Benjamin Disraeli, *Lord George Bentinck*, Archibald, 1852 (archive.org), S. 496.\ **\[7]** Bakunins Antwort auf Französisch, „Aux citoyens rédacteurs du *Réveil*“, auf Wikisource.org.\ **\[8]** Chaim Weizmann, *Trial and Error,* Harper & Brothers, 1949, S. 192.\ **\[9]** Stanley Weintraub, *Disraeli: A Biography,* Hamish Hamilton, 1993, S. 579, 547.\ **\[10]** André Pichot, *Aux origines des théories raciales, de la Bible à Darwin,* Flammarion, 2008, S. 124–143, 319.\ **\[11]** Hilaire Belloc, *The Jews,* Constable & Co., 1922 (archive.org), S. 223.\ **\[12]** Stanley Weintraub, *Disraeli: A Biography,* Hamish Hamilton, 1993, S. 579, 547.\ **\[13]** Carroll Quigley, *The Anglo-American Establishment, From Rhodes to Cliveden* (1949), Books In Focus, 1981.\ **\[14]** *The Complete Diaries of Theodor Herzl,* edited by Raphael Patai, Herzl Press & Thomas Yoseloff, 1960, vol. 1*,* pp. 163–170.\ **\[15]** Benzion Netanyahu, *The Founding Fathers of Zionism,* Balfour Books, 2012*,* Kindle-Ausgabe, S. 761–775.\ **\[16]** Alison Weir, *Against Our Better Judgment: The Hidden History of How the U.S. Was Used to Create Israel,* 2014, Kindle-Ausgabe, S. 387–475.\ **\[17]** Netanyahu, *The Founding Fathers of Zionism,* S. 2536-59.\ **\[18]** Zitiert in Robert Edward Edmondson, *The Jewish System Indicted by the Documentary Record,* 1937 (archive.org), S. 15.
@ 78c90fc4:4bff983c
2025-02-10 12:08:13  “Die Welt wird von ganz anderen Personen regiert als diejenigen es sich vorstellen, die nicht hinter den Kulissen stehen.” Benjamin Disraeli, zweimaliger britischer Premierminister und Romanautor. Quelle: <https://www.unz.com/article/the-disraeli-enigma/>\ \ Als 1853 der Krimkrieg zwischen Russland und dem Osmanischen Reich ausbrach, wurde das Osmanische Reich vom Vereinigten Königreich und Frankreich gerettet. Zwanzig Jahre später zog Zar Alexander II. als Beschützer der unterdrückten serbischen und bulgarischen Christen erneut gegen die Osmanen in den Krieg. Als die Russen vor den Toren Konstantinopels/Istanbuls standen, waren die Osmanen gezwungen, die Schaffung der autonomen Fürstentümer Bulgarien, Serbien und Rumänien durch den Vertrag von San Stefano zu akzeptieren. Die Briten waren mit diesem Vertrag unzufrieden und beriefen zusammen mit Österreich-Ungarn den Berliner Kongress (1878) ein, der ihn aufhob. Russische Eroberungen wurden zurückgenommen, Armenien und Bulgarien wurden größtenteils an das Osmanische Reich zurückgegeben und der Balkan wurde in heterogene und konfliktreiche Staaten aufgeteilt. Diese „Balkanisierung“ löste nationalistische Ressentiments aus, die den Ersten Weltkrieg auslösen sollten. \ Das Hauptziel des Berliner Vertrags bestand darin, das zu retten, was von einem schwächelnden Osmanischen Reich zu retten war, um der panslawistischen Expansion Russlands entgegenzuwirken. England, das stets eifersüchtig auf seine Vormachtstellung zur See bedacht war, wollte verhindern, dass Russland näher an den Bosporus heranrückte. Die Briten erhielten das Recht, Zypern als Marinestützpunkt zu nutzen und gleichzeitig den Suezkanal zu überwachen. Dies war der Beginn des „Great Game“ Großbritanniens um die Kolonialherrschaft in Asien und die Eindämmung Russlands, was insbesondere zur Schaffung Afghanistans als Pufferstaat führte. \ Es gibt verschiedene Möglichkeiten, diesen Abschnitt der Geschichte zu interpretieren, der den Keim für alle Tragödien des 20. Jahrhunderts („das jüdische Jahrhundert“ laut Yuri Slezkine) in sich trägt.**\[1]**\ Yuri Slezkine, *The Jewish Century,* Princeton University Press, 2004. \ Es gibt unterschiedliche Ansichten darüber, welche Kräfte die Geschichte in dieser entscheidenden Zeit geprägt haben. Aber letztendlich wird Geschichte von Menschen gemacht, und sie kann nur verstanden werden, wenn man die Hauptakteure und ihre Motive identifiziert: Man kann den Vietnamkrieg einfach nicht verstehen, ohne sich mit der Denkweise von Johnson oder Kissinger auseinanderzusetzen. Unter den Anstiftern des Berliner Vertrags sticht ein Name besonders hervor: Benjamin Disraeli (1804–1881), Premierminister unter Königin Victoria von 1868 bis 1869 und erneut von 1874 bis 1880. Disraeli war auch der Mann, der 1875 die Übernahme des Suezkanals durch England ermöglichte, und zwar durch die Finanzierung seines Freundes Lionel de Rothschild, dem Sohn von Nathan Mayer – eine Operation, die die Kontrolle der Rothschilds über die Bank of England festigte. \ Disraeli ist ein sehr interessanter Fall, da er sowohl ein bedeutender britischer Staatsmann während der globalen Hegemonie Großbritanniens als auch ein Romanautor war, der seine fiktiven Figuren dazu benutzte, seine ehrlichen Gedanken zu äußern, während er eine Art „glaubhafte Abstreitbarkeit“ (Sidonia spricht, nicht ich!) aufrechterhielt. Wir haben daher die einzigartige Gelegenheit, die wahren Motive des Mannes in der Politik zwischen den Zeilen zu lesen. Stellen Sie sich vor, Kissinger hätte Romane geschrieben, in denen ein Jude die Hauptfigur ist, der die Außen- und Militärpolitik des Imperiums vorantrieb und gleichzeitig ein enger Freund des reichsten jüdischen Bankiers war.\ \  Disraeli wird als der wahre Erfinder des Britischen Empires bezeichnet, da er es war, der Königin Victoria durch das Parlament mit dem Royal Titles Act von 1876 zur Kaiserin von Indien ernennen ließ (das obere Bild ist eine Karikatur, die Disraeli als Hausierer zeigt, der der Königin die Kaiserkrone überreicht). Disraeli war, wie bereits erwähnt, die Hauptinspiration für den Berliner Kongress. Darüber hinaus war Disraeli ein Vorläufer des Zionismus, der versuchte, die „Wiederherstellung Israels“ auf die Tagesordnung des Berliner Kongresses zu setzen, in der Hoffnung, den Sultan Abdul Hamid davon zu überzeugen, Palästina als autonome Provinz zu gewähren. Der Sultan lehnte das Angebot ab, das wahrscheinlich das Versprechen finanzieller Unterstützung für seine zusammenbrechende Wirtschaft beinhaltete – wie auch Herzls Angebot im Jahr 1902, das ebenfalls abgelehnt wurde.\ \ Der Zionismus war Disraelis uralter Traum: Nach einer Reise in den Nahen Osten im Alter von sechsundzwanzig Jahren veröffentlichte er seinen ersten Roman, *Die wundersame Geschichte des Alroy*, und ließ seinen Helden, einen einflussreichen Juden des Mittelalters, sagen: „Mein Wunsch ist eine nationale Existenz, die wir nicht haben. Mein Wunsch ist das Land der Verheißung und Jerusalem und der Tempel, alles, was wir eingebüßt haben, wonach wir uns gesehnt haben, wofür wir gekämpft haben, unser schönes Land, unser heiliges Glaubensbekenntnis, unsere einfachen Sitten und unsere alten Bräuche.“\ Disraeli schrieb diese Zeilen noch vor den Anfängen der biblischen Archäologie; erst 1841 veröffentlichte Edward Robinson seine *Biblical Researches in Palestine*. Die ersten Ausgrabungen des von Königin Victoria geförderten Palestine Exploration Fund begannen 1867. Wohlhabende britische Juden hatten sich jedoch schon lange zuvor für Palästina interessiert. Disraelis Interesse wurde durch seinen Nachbarn und vierzigjährigen Freund Moses Montefiore beeinflusst, der Judith Cohen, die Schwägerin von Nathan Rothschild, heiratete. Nach einer Reise nach Palästina im Jahr 1827 widmete Montefiore seine immensen Ressourcen der Unterstützung seiner Glaubensgenossen im Heiligen Land, indem er Land kaufte und Häuser baute. \ Sowohl Montefiore als auch Disraeli waren sephardischer Herkunft. Disraeli stammte aus einer Familie portugiesischer Marranen, die in Venedig zum Judentum konvertierten. Sein Großvater war 1748 nach London gezogen. Benjamin wurde im Alter von dreizehn Jahren getauft, als sein Vater Isaac D'Israeli zusammen mit seiner ganzen Familie zum anglikanischen Christentum konvertierte. Isaac D'Israeli ist der Autor eines Buches mit dem Titel *The Genius of Judaism*(in Anlehnung an Chateaubriands *Le Génie du Christianisme*), in dem er die einzigartigen Eigenschaften des jüdischen Volkes verherrlicht, aber die talmudischen Rabbiner dafür verantwortlich macht, dass sie „den nationalen Geist ihres Volkes versiegeln“ und „die Einfachheit ihres antiken Glaubens korrumpieren“. Wie für viele andere Juden dieser Zeit war die Konversion für D'Israeli rein opportunistisch: Bis zum Beginn des 19. Jahrhunderts blieben Verwaltungskarrieren für Juden verschlossen. Ein Gesetz von 1740 hatte ihre Einbürgerung erlaubt, aber es hatte Volksaufstände provoziert und wurde 1753 aufgehoben. Viele einflussreiche Juden, wie der Stadtbankier Sampson Gideon, entschieden sich dann für eine nominelle Konversion ihrer Kinder.**\[2]**\ Cecil Roth, *A History of the Marranos* (1932)*,* Meridian Books, 1959*,* S. 148.\ \ Etwa zur gleichen Zeit wie Disraeli konvertierte Heinrich Heine (1797–1856) zum Luthertum (während einer seiner Brüder zum Katholizismus konvertierte, um Offizier in Österreich zu werden, und ein anderer zur Orthodoxie, um als Arzt in Russland zu dienen). Heine betrachtete die Taufe als „Eintrittskarte in die europäische Zivilisation“. Er beklagte sich jedoch darüber, dass er von den Deutschen immer noch als Jude angesehen wurde, und zog es daher vor, in Frankreich zu leben, wo er als Deutscher angesehen wurde. Nur wenige Jahre nach seiner Konversion zeigten seine Schriften eine sehr negative Einstellung gegenüber dem Christentum, das er als „düstere, blutrünstige Religion für Kriminelle“ bezeichnete, die die Sinnlichkeit unterdrücke. Am Ende seines Lebens bereute er seine Taufe, die ihm nichts gebracht hatte, und erklärte in seinem letzten Buch *Romanzero*: „Ich mache kein Geheimnis aus meinem Judentum, zu dem ich nicht zurückgekehrt bin, weil ich es nicht verlassen habe.“**\[3]**\ Zitiert in Kevin MacDonald, *Separation and Its Discontents:* *Toward an Evolutionary Theory of Anti-Semitism,* Praeger, 1998, kindle 2013, l. 4732–4877. \ Genau wie bei den portugiesischen Marranen im 15. Jahrhundert verstärkte die Taufe bei den europäischen Juden des 19. Jahrhunderts ein nicht-religiöses, rassisches Verständnis des Judentums. Disraeli bezeichnete sich selbst als „Anglikaner jüdischer Abstammung“. \ Für Hannah Arendt ist Disraeli ein „Rassenfanatiker“, der in seinem ersten Roman *Alroy* (1833) „einen Plan für ein jüdisches Reich entwickelte, in dem Juden als streng getrennte Klasse herrschen würden“. In seinem anderen Roman *Coningsby* „entfaltete er einen fantastischen Plan, nach dem jüdisches Geld den Aufstieg und Fall von Höfen und Reichen beherrscht und in der Diplomatie die Oberhand hat“. Diese Idee „wurde zum Dreh- und Angelpunkt seiner politischen Philosophie“.**\[4]**\ Hannah Arendt, *The Origins of Totalitarianism,* Band 1: *Antisemitism,* Meridian Books, 1958, S. 309–310.\ Dies ist eine ziemlich fantastische Anschuldigung, die die meisten Biografen Disraelis nicht bestätigen würden. Sie ist jedoch wahrscheinlich richtig. Aber wir müssen genau auf Disraelis eigene Stimme hören, die durch Sidonia zum Ausdruck kommt, die Figur, die in drei seiner Romane vorkommt: *Coningsby* (1844), *Sybil* (1845) und *Tancred* (1847). In Sidonias Worten spürt man den Groll gegen die Nation, in die er sich zu integrieren versuchte:\ Kann es etwas Absurderes geben, als dass eine Nation sich an eine Einzelperson wendet, um ihren Kredit, ihre Existenz als Imperium und ihren Komfort als Volk zu erhalten; und diese Einzelperson, der ihre Gesetze die stolzesten Rechte der Staatsbürgerschaft, das Privileg, in ihrem Senat zu sitzen und Land zu besitzen, verweigern; denn obwohl ich unbesonnen genug war, mehrere Ländereien zu kaufen, bin ich der Meinung, dass ein Engländer hebräischen Glaubens nach dem geltenden Recht Englands keinen Boden besitzen kann. \ Da es einem Juden nicht möglich ist, sich durch Landbesitz in die britische Aristokratie zu integrieren, selbst wenn er zum örtlichen Glauben konvertiert, was sollte ein Jude tun, außer durch die Macht des Geldes aufzusteigen? Wie Heine spürte auch Disraeli die Heuchelei der Christen, die es den Juden übel nahmen, dass sie keine Christen waren, sie aber weiterhin als Juden behandelten, wenn sie konvertierten, und es insgeheim sogar vorzogen, dass sie Juden blieben. \ Laut Disraelis Biografen Robert Blake ist Sidonia „eine Kreuzung zwischen Lionel de Rothschild und Disraeli selbst“. Er stammt von einer Adelsfamilie aus Aragon ab, zu deren herausragenden Mitgliedern ein Erzbischof und ein Großinquisitor gehörten, die beide heimlich dem Judentum ihrer Väter anhingen. Sidonias Vater, wie auch Lionel de Rothschilds Vater, „machte während der Napoleonischen Kriege ein großes Vermögen mit Militärverträgen und der Versorgung der verschiedenen Armeen“. Nachdem er sich in London niedergelassen hatte, „setzte er alles, was er besaß, auf die Waterloo-Anleihe; und das Ereignis machte ihn zu einem der größten Kapitalisten Europas.“ Seit seinem siebzehnten Lebensjahr besuchte Sidonia die Fürstenhöfe der Schuldner seines Vaters und lernte die Geheimnisse der Macht kennen. „Die geheime Geschichte der Welt war sein Zeitvertreib. Es bereitete ihm großes Vergnügen, die verborgenen Motive mit den öffentlichen Vorwänden der Transaktionen zu kontrastieren.“ Disraeli selbst war laut Robert Blake „von Verschwörungen besessen“.**\[5]**\ Robert Blake, *Disraeli* (1966), Faber Finds, 2010, S. 202. \ Sidonia ist von seiner Rasse begeistert: „Alles ist Rasse – es gibt keine andere Wahrheit.“ Er weigert sich, eine Nichtjüdin zu heiraten, weil, so der Erzähler, „keine irdische Überlegung ihn jemals dazu veranlassen würde, die Reinheit der Rasse zu beeinträchtigen, auf die er stolz ist.“ Mit „Rasse“ meinte Disraeli Blutsverwandtschaft. In seinem letzten Roman *Endymion* (1880) schrieb er:\ Kein Mensch wird das Prinzip der Rasse gleichgültig behandeln. Es ist der Schlüssel zur Geschichte, und der Grund, warum die Geschichte oft so verwirrend ist, liegt darin, dass sie von Männern geschrieben wurde, die dieses Prinzip und all das damit verbundene Wissen nicht kennen ... Sprache und Religion machen keine Rasse aus – es gibt nur eine Sache, die eine Rasse ausmacht, und das ist Blut.\ **[Sidonia erzählt seinem Schützling Coningsby](https://www.victorianlondon.org/etexts/disraeli/coningsby-0038.shtml)** in *Coningsby oder die neue Generation*, dass die Verfolgung durch christliche Nationen die jüdische Nation niemals zerschlagen könnte. \ Tatsache ist, dass man eine reine Rasse der kaukasischen Organisation nicht vernichten kann. Es ist eine physiologische Tatsache; ein einfaches Naturgesetz, das ägyptische und assyrische Könige, römische Kaiser und christliche Inquisitoren verblüfft hat. Keine Strafgesetze, keine körperlichen Folterungen können bewirken, dass eine überlegene Rasse in einer unterlegenen aufgehen oder von ihr vernichtet werden sollte. Die gemischten verfolgenden Rassen verschwinden, die reine verfolgte Rasse bleibt bestehen. Und im Moment, trotz Jahrhunderten oder gar Jahrzehnten der Erniedrigung, übt der jüdische Geist einen enormen Einfluss auf die Angelegenheiten Europas aus. Ich spreche nicht von ihren Gesetzen, denen Sie immer noch gehorchen; von ihrer Literatur, mit der Ihr Geist gesättigt ist, sondern vom lebendigen hebräischen Intellekt. Sie beobachten nie eine große intellektuelle Bewegung in Europa, an der die Juden nicht in hohem Maße beteiligt sind.\ Wo auch immer er reiste, fügte Sidonia hinzu, sah er jüdische Berater hinter Monarchen und Staatsoberhäuptern. „Sie sehen also, mein lieber Coningsby, dass die Welt von ganz anderen Persönlichkeiten regiert wird, als diejenigen, die nicht hinter den Kulissen stehen, sich vorstellen können.“ In einem Sachbuch (*Lord George Bentinck: A Political Biography*, 1852) schrieb Disraeli:\ \[Juden] sind ein lebendiger und der eindrucksvollste Beweis für die Falschheit dieser verderblichen Doktrin der Neuzeit, der natürlichen Gleichheit der Menschen. ... die natürliche Gleichheit der Menschen, die heute in Mode ist und die Form einer kosmopolitischen Bruderschaft annimmt, ist ein Prinzip, das, wenn man danach handeln könnte, die großen Rassen zersetzen und den ganzen Genius der Welt zerstören würde. ... Die angeborene Tendenz der jüdischen Rasse, die zu Recht stolz auf ihr Blut ist, ist gegen die Doktrin der Gleichheit der Menschen.**\[6]**\ Benjamin Disraeli, *Lord George Bentinck*, Archibald, 1852 (archive.org), S. 496. \ Disraeli ist eindeutig auf derselben Wellenlänge wie Moses Hess, Herzls geistiger Vater, der, nachdem er Marx (einen weiteren nominellen Konvertiten) beeinflusst hatte, zu dem Schluss kam, dass „der Rassenkrieg wichtiger ist als der Klassenkampf“ (*Rom und Jerusalem,* 1862). Ein gutes Beispiel für dialektische politische Manipulation ist, dass Hess Marx weiterhin heimlich unterstützte und auf dessen Bitte hin nach dem Generalkongress der Internationale in Basel (5.–12. September 1869) Verleumdungen gegen Bakunin veröffentlichte, in denen er Bakunin beschuldigte, ein *Agent provocateur* der russischen Regierung zu sein und „im Interesse des Panslawismus“ zu arbeiten.**\[7]**\ Bakunins Antwort auf Französisch, „Aux citoyens rédacteurs du *Réveil*“, finden Sie auf Wikisource.org.\ Es ist interessant zu sehen, dass ein anderer Proto-Zionist wie Disraeli den russischen Interessen zutiefst feindlich gesinnt war.\ \ Was war Disraelis Motivation hinter der Außenpolitik, die er dem britischen Empire vermittelte? Glaubte er, dass es die offensichtliche Bestimmung der Briten sei, die Welt zu erobern? Oder sah er das britische Empire als Instrument für die überlegene Bestimmung der jüdischen Nation, wenn er sich daran erinnerte, wie Esra und Nehemia in biblischen Zeiten die Außenpolitik der Perser ausgenutzt hatten? Indem er den Suezkanal (der zwischen 1859 und 1869 von den Franzosen gegraben wurde) mit den britischen Interessen in Verbindung brachte, wollte er einfach nur die Franzosen übertrumpfen, oder legte er damit den Grundstein für das zukünftige Bündnis zwischen Israel und dem angloamerikanischen Empire? Da die Briten nun einmal den Suezkanal besaßen, mussten sie ihn verteidigen, und wie ginge das besser als mit einer befreundeten jüdischen autonomen Regierung in der Nähe in Palästina? Genau das war es, was Chaim Weizmann dreißig Jahre später den Briten schmackhaft machen wollte: „Das jüdische Palästina wäre ein Schutz für England, insbesondere in Bezug auf den Suezkanal.“**\[8]**\ Chaim Weizmann, *Trial and Error,* Harper & Brothers, 1949, S. 192. \ Und als die Israelis 1956 mit britischer und französischer Unterstützung in den Sinai einmarschierten, taten sie dies, indem sie Großbritannien erneut versprachen, die Kontrolle über den von Nasser verstaatlichten Kanal an Großbritannien zurückzugeben. \ Disraelis Russophobie, zu der er Königin Victoria bekehrte, und seine Verteidigung der Türken, deren Massaker an den Serben und Bulgaren allgemein bekannt waren, führten zu Theorien über eine jüdische Verschwörung. William Ewart Gladstone, ein langjähriger Gegner Disraelis und selbst mehrmals Premierminister (1868–1874, 1880–1885, 1886 und 1892–1894), erklärte, dass Disraeli „die britische Außenpolitik als Geisel seiner jüdischen Sympathien nahm und mehr daran interessiert war, die Leiden der Juden in Russland und der Türkei zu lindern, als an britischen Interessen“. Die Zeitung *„The Truth“* vom 22. November 1877 spielte auf die Vertrautheit Disraelis mit den Rothschilds an und vermutete „eine stillschweigende Verschwörung ... seitens einer beträchtlichen Anzahl von Anglo-Hebräern, um uns im Namen der Türken in einen Krieg zu ziehen“. Es wurde außerdem daran erinnert, dass Disraeli in einer Rede vor dem britischen Unterhaus im Jahr 1847 die Zulassung von Juden zu wählbaren Ämtern gefordert hatte, mit der Begründung, dass „der jüdische Geist einen enormen Einfluss auf die Angelegenheiten Europas ausübt“.**\[9]**\ Stanley Weintraub, *Disraeli: A Biography,* Hamish Hamilton, 1993, S. 579, 547. \ Die Königin stand, wie ein Großteil der britischen Aristokratie, bereits unter dem Bann einer modischen Theorie, die den Angelsachsen einen israelitischen Ursprung zuschrieb. Diese Theorie war erstmals zur Zeit Oliver Cromwells aufgetaucht und wurde 1840 von Pastor John Wilson in seinen *Vorlesungen über das alte Israel und den israelitischen Ursprung der modernen Nationen Europas* sowie 1870 von Edward Hine in *The English Nation Identified with the Lost Israel* neu aufgelegt. In diesem Werk erfahren wir, dass das Wort „Saxon“ von „Isaac's sons“ (Söhne Isaaks) abgeleitet ist. Diese lächerliche Theorie lieferte eine billige biblische Rechtfertigung für den britischen Kolonialismus und sogar für den Völkermord an den kolonisierten Völkern (neue Kanaaniter) durch das britische Empire (neues Israel).**\[10]**\ André Pichot, *Aux origines des théories raciales, de la Bible à Darwin,* Flammarion, 2008, S. 124–143, 319. \ Königin Victoria war glücklich, glauben zu können, dass ihre edle Abstammung auf König David zurückging, und ließ ihre Söhne beschneiden, ein Brauch, der bis heute fortbesteht. Es mag etwas Wahres an dem Gefühl der britischen Elite für ihr Judentum liegen, denn im 16. und 17. Jahrhundert hatten viele Ehen reiche jüdische Familien mit der alten, verarmten Landaristokratie vereint, so dass nach Hilaire Bellocs Schätzung „mit Beginn des 20. Jahrhunderts diejenigen der großen territorialen englischen Familien, in denen es kein jüdisches Blut gab, die Ausnahme waren“.**\[11]**\ Hilaire Belloc, *The Jews,* Constable & Co., 1922 (archive.org), S. 223. \ Die Begeisterung der Königin für das Judentum hatte aber auch viel mit dem Einfluss Disraelis zu tun, der einmal gegenüber einem Freund damit prahlte: „Jeder mag Schmeichelei, und wenn es um das Königshaus geht, sollte man sie mit einer Kelle auftragen.“**\[12]**\ Stanley Weintraub, *Disraeli: A Biography,* Hamish Hamilton, 1993, S. 579, 547. \ Der Fall Disraeli ist aufschlussreich, weil die Frage, die er aufwirft, dieselbe ist wie die Frage, die heute geopolitische Analysten in Bezug auf die Beziehung zwischen den Vereinigten Staaten und Israel spaltet: Wer führt wen an der Nase herum? Ist Israel der Brückenkopf der Vereinigten Staaten im Nahen Osten oder sind die Vereinigten Staaten, wie Zbigniew Brzezinski einmal sagte, der **[„dumme Esel“](https://www.youtube.com/watch?v=MfjE5_1xOs8)** Israels? Die Beantwortung dieser Frage für das Jahrhundert vor dem Zweiten Weltkrieg (als **[„Israel“ das internationale Judentum](https://twitter.com/Laurent_Guyenot/status/1883831745046560928)** bedeutete) hilft bei der Beantwortung derselben Frage heute, da die symbiotische Beziehung zwischen Israel und dem Imperium erheblich gewachsen ist. \ Die Antwort hängt vom Standpunkt des Betrachters ab. Die Zionisten haben natürlich ein Interesse daran, die Ansicht zu fördern, dass Israel den angloamerikanischen Interessen dient und nicht umgekehrt. Disraeli argumentierte vor dem britischen Parlament, dass ein jüdisches Palästina im Interesse des britischen Kolonialismus sei. Aber jüdische Zionisten haben die Dinge schon immer aus der anderen Perspektive betrachtet, und man kann kaum glauben, dass Disraeli ihre Ansicht nicht insgeheim teilte. Wenn der Held seines Romans *Tancred* (1847), ein Jude, der wie Disraeli zum Lord ernannt wurde, das britische Empire mit folgenden Worten verherrlicht: „Wir wollen die Welt erobern, angeführt von Engeln, um die Menschheit unter göttlicher Herrschaft glücklich zu machen“, wer verbirgt sich hinter diesem zweideutigen „wir“? Ist es dasselbe doppeldeutige „wir“, das die PNAC-Neokonservativen benutzten, um Amerika in Kriege zum Wohle Israels zu verwickeln? \ Wenn ein britischer Jude wie Disraeli zu den Briten „wir“ sagte, war dies eine strategische Zweideutigkeit. Er traf damit den patriotischen Nerv der angelsächsischen Elite, die den gemeinsamen Glauben an die Mission des britischen Empires teilte, die Welt zu zivilisieren – Menschen wie Lord Salisbury, Mitglied von Cecil Rhodes' Round Table, der sich für eine Weltregierung durch die „britische Rasse“ einsetzte.**\[13]**\ Carroll Quigley, *The Anglo-American Establishment, From Rhodes to Cliveden* (1949), Books In Focus, 1981. \ Der britische Imperialismus und der zionistische Nationalismus wurden etwa zur gleichen Zeit geboren wie die Zwillinge Esau und Jakob und sind seit ihrer Geburt eng miteinander verflochten. Zwei Überlegungen helfen jedoch, ihre wahre Beziehung zu verstehen. Erstens reichen die ideologischen Wurzeln des Britischen Empires nicht weiter zurück als bis ins 17. Jahrhundert, während die des Zionismus mehr als zwei Jahrtausende zurückreichen. Zweitens starb das Britische Empire nach dem Ersten Weltkrieg, während der Zionismus aufblühte. Aus diesen beiden Gründen ist die Theorie, dass der Zionismus ein Nebenprodukt des britischen Imperialismus ist (nennen wir sie die Chomsky-Theorie), nicht haltbar. \ Um die wahre Beziehung zwischen Zion und Albion zu Disraelis Zeiten zu verstehen, muss man die Macht der Rothschild-Dynastie über die britische Politik richtig einschätzen. Ohne die Rothschilds hätte Großbritannien nie die Kontrolle über den Suezkanal erlangt, der den Grundstein des britischen Empires im Nahen Osten bildete. Die Rothschilds selbst kandidierten nicht für ein politisches Amt, heirateten jedoch manchmal in eine solche Familie ein: Lord Archibald Primrose, 1886 und von 1892 bis 1894 Außenminister und 1894–1895 Premierminister, war der Schwiegersohn von Mayer Amschel de Rothschild.\ Es ist bemerkenswert, dass Theodor Herzl den zukünftigen jüdischen Staat als „aristokratische Republik“ mit „dem ersten Prinzen Rothschild“ an der Spitze sah. In einer langen Tirade in seinem Tagebuch ermahnte er die Rothschilds, ihre bösen Seelen zu erlösen, indem sie den Zionismus statt Kriege finanzierten:\ Ich weiß nicht, ob alle Regierungen bereits erkennen, welche internationale Bedrohung Ihr Weltreich darstellt. Ohne Sie können keine Kriege geführt werden, und wenn Frieden geschlossen werden soll, sind die Menschen umso mehr auf Sie angewiesen. Für das Jahr 1895 wurden die Militärausgaben der fünf Großmächte auf vier Milliarden Francs geschätzt, und ihre tatsächliche militärische Stärke in Friedenszeiten auf 2.800.000 Mann. Und diese Streitkräfte, die in der Geschichte ihresgleichen suchen, kommandieren Sie finanziell, ungeachtet der widerstreitenden Wünsche der Nationen. ... Und Ihr verfluchter Reichtum wächst immer noch. ... Aber wenn Sie sich uns anschließen, ... werden wir unseren ersten gewählten Herrscher aus Ihrem Haus nehmen. Das ist das leuchtende Leuchtfeuer, das wir auf die Spitze des fertigen Eiffelturms Ihres Vermögens setzen werden. In der Geschichte wird es so aussehen, als wäre das der Zweck des gesamten Bauwerks gewesen.**\[14]**\ \ *The Complete Diaries of Theodor Herzl,* edited by Raphael Patai, Herzl Press & Thomas Yoseloff, 1960, vol. 1*,* pp. 163–170.\ Wie Richard Wagner jedoch einmal sagte (*Judaism in Music*, 1850), zogen es die Rothschilds vor, „die Juden der Könige“ zu bleiben, anstatt „die Könige der Juden“ zu sein.\ \ Wenn die Zeit für die Gründung des jüdischen Staates zu Disraelis Zeiten noch nicht reif war, dann vor allem deshalb, weil die Juden in Russland sich von Palästina ebenso wenig angezogen fühlten wie die Juden in Europa; sie wussten kaum, wo es lag. Erst kürzlich von Zar Alexander II. emanzipiert, strebten sie lediglich eine Auswanderung nach Europa oder in die Vereinigten Staaten an. Erst nach der Ermordung von Zar Alexander II. im Jahr 1881 (einen Monat vor Disraelis Tod) wurden einige von ihnen durch die Pogrome für Leon Pinskers proto-zionistischen Aufruf von 1882 empfänglich: „Wir müssen uns ein für alle Mal mit dem Gedanken abfinden, dass die anderen Nationen uns aufgrund ihres angeborenen natürlichen Antagonismus für immer ablehnen werden.“**\[15]**\ Benzion Netanyahu, *The Founding Fathers of Zionism,* Balfour Books, 2012*,* Kindle l. 761-775. \ Ebenfalls im Jahr 1881 begann Baron Edmond de Rothschild vom Pariser Zweig, unter der Schirmherrschaft seiner Palestine Jewish Colonization Association (PICA) Land in Palästina zu kaufen und die Ansiedlung jüdischer Siedler zu finanzieren, insbesondere in Tel Aviv. Die meisten bestehenden internationalen jüdischen Organisationen, wie B'nai B'rith (gegründet 1843 in New York) oder die Alliance Israélite Universelle (gegründet 1860 in Paris), waren jedoch der Meinung, dass Israel als verstreute Nation gut zurechtkäme und keine Pläne für Palästina habe.\ Dies änderte sich während des Ersten Weltkriegs, als ein äußerst effizientes Netzwerk aufgebaut wurde, das beide Seiten des Atlantiks verband.**\[16]**\ Alison Weir, *Against Our Better Judgment: The Hidden History of How the U.S. Was Used to Create Israel,* 2014, Kindle l. 387-475. \ Theodor Herz konzentrierte seine diplomatischen Bemühungen zunächst auf Deutschland, aber in England begannen sich die Dinge vielversprechend zu entwickeln („Der Schwerpunkt hat sich nach England verlagert“, schrieb er 1895 in sein Tagebuch), was zum Teil der Rekrutierung von Israel Zangwill zu verdanken war, der laut Benzion Netanyahu „der erste war, der in den oberen Kreisen der britischen Politik direkt über den Zionismus sprach“, insbesondere mit Lloyd George, „einem engen Bekannten Zangwills von Beginn seiner zionistischen Tätigkeit bis zu seinem Lebensende“.**\[17]**\ Netanyahu, *The Founding Fathers of Zionism,* l. 2536-59. \ Erinnern wir uns daran, dass Zangwill der erfolgreiche Autor von *The Melting Pot war,* einem Theaterstück, das Mischehen für Amerikaner pries. Hier besteht kein Widerspruch, denn „die gemischten verfolgten Rassen verschwinden, die reine verfolgte Rasse bleibt bestehen“, wie Sidonia sagte.\ \ Die Bedeutung von Disraelis geopolitischen Manövern wird von Historikern der Zionisten selten anerkannt, da sie oberflächlich betrachtet nicht den Weg für die Gründung des jüdischen Staates geebnet zu haben scheinen. Tatsächlich bildeten sie jedoch das unsichtbare Fundament, auf dem Herzl und Zangwill aufbauten. Und diese unsichtbare Kontinuität zeugt von der erstaunlichen generationsübergreifenden Beharrlichkeit des jüdischen Volkes, das sein jahrtausendealtes, selbsternanntes Schicksal Generation für Generation vorantreibt. Ja, es ist wirklich bewundernswert, wenn auch verheerend für die westliche Zivilisation, die durch zweitausend Jahre Christentum ahnungslos und ihres eigenen Sinns für Blut beraubt wurde. Wie der zionistische Autor Jakob Klatzkin einmal in der Zeitschrift *„Der Jude“*, 1916, schrieb:\ Wir bilden in uns selbst eine geschlossene juristische und geschäftliche Körperschaft. Eine starke Mauer, die wir errichtet haben, trennt uns von den Menschen in den Ländern, in denen wir leben – und hinter dieser Mauer befindet sich ein jüdischer Staat.**\[18]** Zitiert in Robert Edward Edmondson, *The Jewish System Indicted by the Documentary Record,* 1937 (archive.org), S. 15.\ \ **Anmerkungen**\ **\[1]** Yuri Slezkine, *The Jewish Century,* Princeton University Press, 2004.\ **\[2]** Cecil Roth, *A History of the Marranos* (1932)*,* Meridian Books, 1959*,* S. 148.\ **\[3]** Zitiert in Kevin MacDonald, *Separation and Its Discontents: Toward an Evolutionary Theory of Anti-Semitism,* Praeger, 1998, kindle 2013, l. 4732–4877.\ **\[4]** Hannah Arendt, *The Origins of Totalitarianism,* Band 1: *Antisemitism,* Meridian Books, 1958, S. 309–310.\ **\[5]** Robert Blake, *Disraeli* (1966), Faber Finds, 2010, S. 202.\ **\[6]** Benjamin Disraeli, *Lord George Bentinck*, Archibald, 1852 (archive.org), S. 496.\ **\[7]** Bakunins Antwort auf Französisch, „Aux citoyens rédacteurs du *Réveil*“, auf Wikisource.org.\ **\[8]** Chaim Weizmann, *Trial and Error,* Harper & Brothers, 1949, S. 192.\ **\[9]** Stanley Weintraub, *Disraeli: A Biography,* Hamish Hamilton, 1993, S. 579, 547.\ **\[10]** André Pichot, *Aux origines des théories raciales, de la Bible à Darwin,* Flammarion, 2008, S. 124–143, 319.\ **\[11]** Hilaire Belloc, *The Jews,* Constable & Co., 1922 (archive.org), S. 223.\ **\[12]** Stanley Weintraub, *Disraeli: A Biography,* Hamish Hamilton, 1993, S. 579, 547.\ **\[13]** Carroll Quigley, *The Anglo-American Establishment, From Rhodes to Cliveden* (1949), Books In Focus, 1981.\ **\[14]** *The Complete Diaries of Theodor Herzl,* edited by Raphael Patai, Herzl Press & Thomas Yoseloff, 1960, vol. 1*,* pp. 163–170.\ **\[15]** Benzion Netanyahu, *The Founding Fathers of Zionism,* Balfour Books, 2012*,* Kindle-Ausgabe, S. 761–775.\ **\[16]** Alison Weir, *Against Our Better Judgment: The Hidden History of How the U.S. Was Used to Create Israel,* 2014, Kindle-Ausgabe, S. 387–475.\ **\[17]** Netanyahu, *The Founding Fathers of Zionism,* S. 2536-59.\ **\[18]** Zitiert in Robert Edward Edmondson, *The Jewish System Indicted by the Documentary Record,* 1937 (archive.org), S. 15. @ 04ed2b8f:75be6756
2025-02-10 11:30:04The world doesn’t care about your excuses. It doesn’t care about your past, your wounds, or the battles you’ve already fought. Life will not lower the weight just because you feel tired. **You either rise, or you stay down.** But here’s the truth—**you are not your past.** You are not your failures, not your pain, not the things that tried to break you. **You are what you choose to become.** Some people get knocked down and never get back up. Some let their past define them, cage them, strip them of their potential. And then there are those who **decide.** They decide that no matter what happened, **they will rise.** They will fight. They will carve their own path, even if they have to do it with their bare hands. ## **Your Past is a Weapon—If You Use It Right** Your past can be two things: **a chain or a sword.** - Weak minds wear their past like a shackle, letting it hold them back. - Warriors forge their past into steel, using it as a blade to cut through the future they want. Scars? They aren’t signs of weakness. They are proof that you survived. That you endured. And that you’re still standing. So stop letting your past dictate your future. **Rip the pen from its hands and write your own damn story.** ## **The Weak Surrender. The Strong Rebuild.** Life will try to break you. That’s a fact. You will lose, you will hurt, you will doubt. But none of that matters. The only thing that matters is **what you do next.** - **You can let failure drown you, or you can rise stronger.** - **You can let heartbreak harden you, or you can sharpen yourself through it.** - **You can let regret bury you, or you can burn it as fuel.** It’s easy to stay down. To blame the world. To say, “This is just who I am.” But warriors don’t do easy. They do necessary. ## **You Are the Architect of Your Own Power** Everything you need to win is already inside you. You don’t need permission. You don’t need the world to approve. You just need one thing: **to choose.** - **Choose discipline over comfort.** - **Choose hunger over hesitation.** - **Choose action over excuses.** - **Choose to become something greater than your past.** Because in the end, that’s the only choice that matters. The world will try to define you. It will try to chain you to your past, drag you down with doubt, and keep you in a box. **Shatter it.** Prove them wrong. Be the person that refuses to be shaped by circumstance—**be the one who shapes themselves.** The past is done. The future is unwritten. The power to decide who you become? **That’s all yours.** Now get up and take it.
@ 04ed2b8f:75be6756
2025-02-10 11:30:04The world doesn’t care about your excuses. It doesn’t care about your past, your wounds, or the battles you’ve already fought. Life will not lower the weight just because you feel tired. **You either rise, or you stay down.** But here’s the truth—**you are not your past.** You are not your failures, not your pain, not the things that tried to break you. **You are what you choose to become.** Some people get knocked down and never get back up. Some let their past define them, cage them, strip them of their potential. And then there are those who **decide.** They decide that no matter what happened, **they will rise.** They will fight. They will carve their own path, even if they have to do it with their bare hands. ## **Your Past is a Weapon—If You Use It Right** Your past can be two things: **a chain or a sword.** - Weak minds wear their past like a shackle, letting it hold them back. - Warriors forge their past into steel, using it as a blade to cut through the future they want. Scars? They aren’t signs of weakness. They are proof that you survived. That you endured. And that you’re still standing. So stop letting your past dictate your future. **Rip the pen from its hands and write your own damn story.** ## **The Weak Surrender. The Strong Rebuild.** Life will try to break you. That’s a fact. You will lose, you will hurt, you will doubt. But none of that matters. The only thing that matters is **what you do next.** - **You can let failure drown you, or you can rise stronger.** - **You can let heartbreak harden you, or you can sharpen yourself through it.** - **You can let regret bury you, or you can burn it as fuel.** It’s easy to stay down. To blame the world. To say, “This is just who I am.” But warriors don’t do easy. They do necessary. ## **You Are the Architect of Your Own Power** Everything you need to win is already inside you. You don’t need permission. You don’t need the world to approve. You just need one thing: **to choose.** - **Choose discipline over comfort.** - **Choose hunger over hesitation.** - **Choose action over excuses.** - **Choose to become something greater than your past.** Because in the end, that’s the only choice that matters. The world will try to define you. It will try to chain you to your past, drag you down with doubt, and keep you in a box. **Shatter it.** Prove them wrong. Be the person that refuses to be shaped by circumstance—**be the one who shapes themselves.** The past is done. The future is unwritten. The power to decide who you become? **That’s all yours.** Now get up and take it. @ 31da2214:af2508e2
2025-02-10 11:23:19**Video Title:** Une révolution géopolitique est en marche : l’Afrique se libère ! **Creator:** Pensées KAMITE **Published Date:** February 9, 2025 **Video Length:** 17 minutes 6 seconds **Views:** >24k **Likes:** >2k **Video URL:** [Original YouTube Video](https://youtu.be/AqrgC7y6Twk) **Key Points from the Video:** * **End of Western Hegemony:** The video asserts that Western dominance in Africa is coming to an end. A geopolitical revolution is underway, breaking the chains of neocolonialism and fundamentally reshaping the continent's geopolitical landscape. * **Decline of Western Influence:** The video highlights a notable decline in Western influence and power in Africa. This is contrasted with the growing presence of China and Russia, who are increasing their investments in key sectors such as infrastructure, energy, defense, natural resources, and technology across the continent. * **Shifting Economic Partnerships:** China and Russia are now surpassing the European Union as Africa's primary trading partners. This indicates a significant shift in economic alliances, moving away from traditional Western partners. * **Failure of Western Strategies:** The host argues that Western imperialist strategies have failed to adapt to the evolving realities in Africa. While African countries initially engaged in colonial agreements with the West, the economic landscape now favors China and Russia. * **Collapse of Unipolar World Order:** This geopolitical shift is described as unprecedented, signaling the collapse of the unipolar world order established after World War II. The video suggests that the United States, weakened by costly conflicts and substantial debt, is experiencing an erosion of power. In contrast, China and Russia, leading the BRICS nations, are emerging as crucial players in a newly forming global balance of power. * **Strategic Importance of Africa:** The video emphasizes Africa's strategic importance in this new global order. Emerging powers are forming alliances with African nations that are perceived as more respectful and mutually beneficial. * **Critique of Western Approach:** The speaker criticizes the West's approach to Africa as cruel and paternalistic, accusing it of imposing underdevelopment policies driven by self-interest rather than genuine partnership. This approach has allegedly led to widespread poverty, conflict, economic dependence, and inequality across the continent. * **Rise of China and Russia as Alternatives:** The video presents the rise of China and Russia as offering alternative partnerships that are more advantageous and respectful of African sovereignty. These new alliances are seen as enabling Africa to chart its own future. * **Call for African Collaboration:** African nations are urged to collaborate with these new global actors to further accelerate the decline of Western influence in Africa. The Democratic Republic of Congo is given as an example, suggesting it should seek strategic partnerships with Russia and China for military and economic cooperation rather than relying on Western support. * **Need for Strong African Leadership:** The speaker emphasizes the need for visionary and courageous African leadership, suggesting that military leaders might be better positioned to provide this strategic direction compared to civilian leaders who are portrayed as hesitant and lacking strategic vision. * **Opportunity for Africa:** The video concludes that the West's decline presents a crucial moment for Africa to assert itself, support liberation movements, and challenge Western interests. It points to perceived contradictions and self-interest in Western actions on the global stage. * **Call to Action:** Viewers are urged to support the movement towards a multipolar world and to advocate for the complete independence of African nations, free from Western influence. **External Context and Further Details:** To provide a broader context, it's important to consider information from external sources regarding the geopolitical shifts in Africa. * **Increased Russian and Chinese Engagement:** Numerous reports and analyses confirm the growing economic and political influence of Russia and China in Africa. These countries have increased their trade, investment, and military cooperation with various African nations. [Example China-Africa Growing Trade](https://www.knowdys.com/en/china-africa-trade-a-4-8-growth-driven-by-commodities/) & [Example Russia-Africa relations](https://www.rt.com/africa/607502-russia-africa-trade-reaches-new-high/). * **Shifting Alliances and Security Concerns:** The video mentions countries like Mali, Burkina Faso, Chad, and Niger. These nations have indeed experienced political instability and have, in some cases, moved away from traditional Western security partners, seeking alternatives, including Russia's Wagner Group in Mali. [Example Wagner Group in Mali](https://www.themoscowtimes.com/2024/07/29/wagner-group-confirms-fighters-killed-battling-mali-rebels-a85858). * **Anti-Western Sentiment:** There is a growing anti-Western sentiment in parts of Africa, fueled by historical colonial experiences, perceived neocolonial practices, and a desire for more equitable partnerships. [Example Anti-Western Sentiment in Africa](https://france.news-pravda.com/en/france/2025/01/30/10141.html). * **Multipolar World Order:** The concept of a transition to a multipolar world order, where power is distributed among multiple centers rather than concentrated in the West, is a widely discussed topic in international relations. The rise of China and the resurgence of Russia are key factors in this shift. [Example Multipolar World Order](https://journal-neo.su/2025/01/07/the-legacy-of-2024-an-increasingly-divided-world-in-2025/). **Credit:** This summary is based on the YouTube video "Une révolution géopolitique est en marche : l’Afrique se libère !" created by [**Pensées KAMITE**](https://www.youtube.com/channel/UC2PdWDTkGsdClni3UeTo9kQ), published on February 9, 2025. The analysis incorporates information directly from the video and contextual details gathered from general knowledge searches to provide a more comprehensive overview.
@ 31da2214:af2508e2
2025-02-10 11:23:19**Video Title:** Une révolution géopolitique est en marche : l’Afrique se libère ! **Creator:** Pensées KAMITE **Published Date:** February 9, 2025 **Video Length:** 17 minutes 6 seconds **Views:** >24k **Likes:** >2k **Video URL:** [Original YouTube Video](https://youtu.be/AqrgC7y6Twk) **Key Points from the Video:** * **End of Western Hegemony:** The video asserts that Western dominance in Africa is coming to an end. A geopolitical revolution is underway, breaking the chains of neocolonialism and fundamentally reshaping the continent's geopolitical landscape. * **Decline of Western Influence:** The video highlights a notable decline in Western influence and power in Africa. This is contrasted with the growing presence of China and Russia, who are increasing their investments in key sectors such as infrastructure, energy, defense, natural resources, and technology across the continent. * **Shifting Economic Partnerships:** China and Russia are now surpassing the European Union as Africa's primary trading partners. This indicates a significant shift in economic alliances, moving away from traditional Western partners. * **Failure of Western Strategies:** The host argues that Western imperialist strategies have failed to adapt to the evolving realities in Africa. While African countries initially engaged in colonial agreements with the West, the economic landscape now favors China and Russia. * **Collapse of Unipolar World Order:** This geopolitical shift is described as unprecedented, signaling the collapse of the unipolar world order established after World War II. The video suggests that the United States, weakened by costly conflicts and substantial debt, is experiencing an erosion of power. In contrast, China and Russia, leading the BRICS nations, are emerging as crucial players in a newly forming global balance of power. * **Strategic Importance of Africa:** The video emphasizes Africa's strategic importance in this new global order. Emerging powers are forming alliances with African nations that are perceived as more respectful and mutually beneficial. * **Critique of Western Approach:** The speaker criticizes the West's approach to Africa as cruel and paternalistic, accusing it of imposing underdevelopment policies driven by self-interest rather than genuine partnership. This approach has allegedly led to widespread poverty, conflict, economic dependence, and inequality across the continent. * **Rise of China and Russia as Alternatives:** The video presents the rise of China and Russia as offering alternative partnerships that are more advantageous and respectful of African sovereignty. These new alliances are seen as enabling Africa to chart its own future. * **Call for African Collaboration:** African nations are urged to collaborate with these new global actors to further accelerate the decline of Western influence in Africa. The Democratic Republic of Congo is given as an example, suggesting it should seek strategic partnerships with Russia and China for military and economic cooperation rather than relying on Western support. * **Need for Strong African Leadership:** The speaker emphasizes the need for visionary and courageous African leadership, suggesting that military leaders might be better positioned to provide this strategic direction compared to civilian leaders who are portrayed as hesitant and lacking strategic vision. * **Opportunity for Africa:** The video concludes that the West's decline presents a crucial moment for Africa to assert itself, support liberation movements, and challenge Western interests. It points to perceived contradictions and self-interest in Western actions on the global stage. * **Call to Action:** Viewers are urged to support the movement towards a multipolar world and to advocate for the complete independence of African nations, free from Western influence. **External Context and Further Details:** To provide a broader context, it's important to consider information from external sources regarding the geopolitical shifts in Africa. * **Increased Russian and Chinese Engagement:** Numerous reports and analyses confirm the growing economic and political influence of Russia and China in Africa. These countries have increased their trade, investment, and military cooperation with various African nations. [Example China-Africa Growing Trade](https://www.knowdys.com/en/china-africa-trade-a-4-8-growth-driven-by-commodities/) & [Example Russia-Africa relations](https://www.rt.com/africa/607502-russia-africa-trade-reaches-new-high/). * **Shifting Alliances and Security Concerns:** The video mentions countries like Mali, Burkina Faso, Chad, and Niger. These nations have indeed experienced political instability and have, in some cases, moved away from traditional Western security partners, seeking alternatives, including Russia's Wagner Group in Mali. [Example Wagner Group in Mali](https://www.themoscowtimes.com/2024/07/29/wagner-group-confirms-fighters-killed-battling-mali-rebels-a85858). * **Anti-Western Sentiment:** There is a growing anti-Western sentiment in parts of Africa, fueled by historical colonial experiences, perceived neocolonial practices, and a desire for more equitable partnerships. [Example Anti-Western Sentiment in Africa](https://france.news-pravda.com/en/france/2025/01/30/10141.html). * **Multipolar World Order:** The concept of a transition to a multipolar world order, where power is distributed among multiple centers rather than concentrated in the West, is a widely discussed topic in international relations. The rise of China and the resurgence of Russia are key factors in this shift. [Example Multipolar World Order](https://journal-neo.su/2025/01/07/the-legacy-of-2024-an-increasingly-divided-world-in-2025/). **Credit:** This summary is based on the YouTube video "Une révolution géopolitique est en marche : l’Afrique se libère !" created by [**Pensées KAMITE**](https://www.youtube.com/channel/UC2PdWDTkGsdClni3UeTo9kQ), published on February 9, 2025. The analysis incorporates information directly from the video and contextual details gathered from general knowledge searches to provide a more comprehensive overview. @ 9e5a3a1a:ed414e8d
2025-02-02 00:50:08Either the phone’s battery went bad and quit charging, or the cable was shit. The warm rain running down the screen made the phone’s UI, flicker back and forth, as Ethan turned the screen on again to check how much battery he had left. Not a lot: 4%. At least the thing was water-proof, he thought. Today was also shit. First his parents confiscated he car keys after finding booze in his closet, now the fucking charging cable went bad. (Hopefully it’s the charging cable and not the battery), he thought. A car drove by splashing him with a fan of muddy water. “Hey!” he yelled, but the red tail lights were too far away now for the driver to hear. “Fucking fuck!” he swore looking down at himself. It was too dark to see how dirty his shirt and pants were now. The light of the gas station still far away. (Oh, well), he thought and continued walking, wet gravel and sand of road’s shoulder making wet crunching noises underfoot. Ethan’s thumb moved on the phone to turn the flashlight on, but he stopped himself. There was almost no chance that Casey’s gas station won’t have USB cables, they always did, but with today's luck they might just be out. Then he’d be screwed without a phone for the rest of the night and all day at school tomorrow. It wouldn’t be the end of the world, but he was too irate after everything today to accept not having a phone right now. A pale form moved to his right a few yards away. He turned and saw a figure standing by the trees. Ethan stopped and squinted through the rain. A cold, creepy feeling suddenly gripped him. It stood there and watched him. A female form, he realized, tall and pale, with black hair longer that he’s ever seen. Something was off. The face… It’s head… The mouth grinned widely, forming a dome above the eyes, eyes that were down close to the neck, under the nose, mouth and chin up above them. (It’s fucking head is upside down..) he realized. Ethan’s thumb pressed the phone’s power button, battery be damned. He aimed it at the figure, brought up the camera app and pressed the button to take the picture. Just as the shutter sound clicked the face was suddenly full-screen, as if a few feet away from him. Ethan gasped and the phone tumbled onto the ground. There was a moment of relief when he realized that the figure was still far away and didn’t suddenly teleport right in front of him, but then something long, black, and wide, like a cross between a ribbon and an anaconda flicked itself toward him and the last thing he felt was a thick spiderweb of hair wrapping itself around him and pulling him forward. *** “Hey, Riley, when did your dad say you needed to be back home?” Alex’s mom yelled from downstairs. The two girls glanced at their phones to see the time. “Eleven!” Riley yelled back. They still had half an hour of “study” time. The two really did mean to study for the calculus exam, but ended up chatting the whole evening. “Oh shit! I got to show you something,” Riley said, turning on her phone’s screen again, “You know that ‘Grin Reaper’ thing on social media?” She scrolled through her phone’s picture gallery. “Like, that smiling ‘monster’ with upside down head?” Alex asked. “Yeah, the one they said kidnapped those kids” “That’s so fake!” “Yeah, but look!” Riley turned her screen towards her friend. Alex took the phone from her, “What’s this?” “It’s her! Caleb was driving me to the movies and I saw her out the window. You know where Casey’s gas station is on Maple av? There’s like a wooded area just past it when you’re driving downtown.” “It’s just some blurry figure. Probably some homeless person… What’s that?” Alex heard some kind of scratching at the window. She walked over to look. They were on the second floor, but there were no trees close enough to scratch against the window. She opened it and look outside. No one. Just a vine attached to the wall of the house outside. Or was it a vine? Along, curly splotch of dark. Alex frowned. “No, I saw her, for real for real. It’s looks bad on the photo because it was dark and we were moving, but her head was on upside down and grinning.” Riley insisted. (Is it ivy?) Alex thought, only half listening to Riley, (Since when do we have ivy on the house?) Riley wondered if she should tell Alex that when she snapped the photo it looked like the woman’s grinning, upside down face was up close suddenly, right up against the car window. Caleb almost veered off the road turning to see what was wrong when she gasped and dropped the phone. When she fished her phone from beneath the seat, the photo looked normal. Blurry but normal. (Maybe a mud splash) Alex thought, examining the black, vine-like shadow that stuck to the house aiming at the window. (Some asshole splashed mud on the house as a prank. Someone from school?) “You think I should post it to TikTok?” Riley asked, looking pensively at the photo. The question brought Alex’s attention back to her. She walked back over and sat on the other side of her friend, taking the phone from her hand and looking closer at the photo. “It’s dark,” Alex rolled her eyes, “Also, some troll could have just been wearing a mask trying to scare people. That shit’s all over social media.” “I guess…” Riley decided against telling her more. She didn’t want to sound weird. Just then, Alex heard her phone ding somewhere behind her. She looked back to find it when she heard a choking noise from where Riley sat, “You ok?” she asked looking back and froze, not quite sure what she was seeing. Riley’s eyes were wide, her hands at her throat tugging at something black, like a scarf wrapping around her neck. More dark, tentacle-like locks reached in towards them through the window. It looked like hair, but it moved as if through water, snaking itself forward and wrapping around Riley’s arms, neck and face. Before Alex could utter a sound or register what she saw, the hair straightened, pulled back, yanking Riley out through the window. *** Alex sits on her bed in shock, glancing back at the window every thirty seconds. She tries to resist getting up and walking over to it. It's weird feeling of being pulled towards it to make sure it’s locked and being afraid to approach it for fear of what she might see outside. What if she sees it again? It’s tentacle-like locks crawling up the house, surrounding her window ready to snatch her like it did her friend. Can it seep through the cracks and unlock the fragile latch? She feels herself standing up and walking over to the window briskly, her hands smooth over the window latch, making sure it’s still locked, her eyes darting back and forth outside. Nothing. The dark splat on the house Alex first mistook for ivy or mud is gone, too. She sits back on the bed. Alex can hear her parents arguing downstairs. They think she's using drugs. They searched through her room the day after Riley was taken. They yelled at her that night, them and Riley’s dad, all convinced that the girls were high and Riley wondered off somewhere. Alex knew they would not believe what really happened. But lying wouldn’t help anyone find her friend. She lets think it was all a drug-induced hallucination. (Maybe I’m crazy,) Alex thinks. Her mind searches for mentions of schizophrenia among any of her relatives. Isn’t that shit genetic? A chill goes through her body again, suddenly. A scratching at the window? Like the one she heard before Riley was taken? “It’s not real,” she whispers out loud. It’s not real. She keeps thinking she hears it almost as often as she walks over to check the latch on the window. “It’s not real….” She has to check. Pushing through the fear, Alex briskly walks over to the window again. Nothing it the trees out back across the lawn. She can’t see the outside of the house without opening the window but she can’t risk it. “It wasn’t real” she affirms again. Then she has an idea. The parents’ arguing grows louder as Alex quietly opens her bedroom door and tiptoes down the stairs toward her mom’s office, trying to avoid attracting their attention. They are still pissed, she doesn't want to deal with them. She looks for scotch tape, quickly founds it, grabs a stack of paper from the printer and goes back upstairs. If she blocks out the window, it can’t see her, even if it is lurking somewhere outside waiting to snatch her, Alex thinks as she starts to cover the glass with paper and tape. She feels better now, suddenly. It feels like she was doing something to protect herself, even if it involves being near the window and risking seeing that thing. As the final page of printer paper is about to go up to block the glass completely, Alex freezes. A figure stands on the grass in front of the trees. In panic, Alex tries to decipher the face in the dark. The head, it is right side up. Not grinning, no hair tentacles: not the monster. With a wave of relief, she looks closer, trying to figure out who it is, and a surge of adrenaline and excitement suddenly hits her, (It's Riley!) “Ril--,” she almost screams, fumbling with the latch. As she pulls the window up and looks back out again, the figure is gone, “Riley!” she yells into the night. No answer. Alex pulls the window closed and runs for the door, briefly coming back to latching again, just in case. “She’s out there! Outside.” Alex almost yells as she barged into the living groom, pointing towards the back door. “Where? Outside?” her mom says then quickly goes to the door, dad and Alex following her. In the yard they yell Riley’s name, scanning the grass hill beyond and the tree line behind it. “Are you sure you saw her?” her dad asks. “Yeah, it was her, for sure.” “Are you high again?” her mom turns to her with an annoyed grimace on her face. “I’m not fucking high, mom!” “Don’t you talk to me this way! Get back to your room.” her mom yells. “I’m not fucking high, mom! I saw her.” Mom isn’t listening, she turns to dad “We should call her parents. She could really be out there,” then to Alex, “Upstairs NOW!” Pissed, Alex walks back into the house. It feels good to be angry, anger is better than fear. She runs up the stairs and tares down the paper she had just put up on the glass. She leans against the window and scans the tree line up in the distance. A few hour pass. Alex still gets up from time to time to check the window, but this time she is looking for Riley rather than checking the lock. Her parents have finally quieted down downstairs. It's late. They are probably asleep by now. Alex considers going to bed herself, but she knows she wouldn't be able to sleep. She looks back out the window. "Riley!" Her friend is there again, closer this time. Alex opens her mouth to call to her, but stops as she saw Riley raise her finger to her lips, gesturing for her to be quiet. Alex frowns, “What the fuck are you doing?” she mouths, shrugging dramatically. Riley motions for her to come out then puts her finger to her lips again. What is she doing? Alex thinks about waking her parents, but decides against it. They’ll just be useless and tell her to go to her room again. She quietly creeps downstairs and sneaks out the door. She half-expects Riley to be gone again as she walks out of the house and looks out to the hillside, but Riley is still there. Further back, almost past the tree-line. She motions Alex to come closer and takes a few steps back, disappearing in the trees. “Fuck!” Alex swears, looks back at the house one last time, then takes off across the yard after her. *** Past the tree line in the woods, Alex crunches through the trees, lighting her way (poorly) with her phone’s flashlight. Thorns scratch her arms and legs as she walks as fast as she can, navigating among the trees, yelling Riley’s name. From time to time she can see Riley's figure moving away from her, weaving among the trees. Her friend moves effortlessly, as if gliding above the ground, unimpeded by the greenery. Alex trips. She catches herself before she tumbles to the ground. For a second it is pitch black. She bends down to look for her phone. It is a glowing outline among the plants. Alex grabs it and gets up. For a moment she’s disoriented, not sure which way she was going. She looks and listens for her friend but sees and hears nothing. She looks back. There’s a bit of light glittering through the trees back where her neighborhood is. She looks forward and yells Riley’s name again, moving her phone trying to catch a glimpse of her friend’s figure. Nothing. Should she go back? Is Riley playing some stupid game? Maybe she is high. Without a second though, Alex continues forward, “Riley, it’s not funny! What the fuck are you doing?” Alex can see pale gray light between the leaves and the branches up ahead. She quickens her pace, almost tripping again. Alex walks into what looks like a small clearing. The trees are further away up ahead, but not much moon-light is coming from up above. She looks up towards the wide canopy, forming a dome overhead. Her eyes suddenly focus on a humanoid shape hanging parallel to the ground from the branches above. Its face is white, torn in two by a wide smile that almost reaches its ears. The top of the head is attached to the neck. Bands of hair suspend it from branches above. Alex freezes. For a second she feels herself cease to exist except for her breath that moves rhythmically in and out. Moments pass. How long, she can’t tell. (Run!), the thought echoes through her head, and she almost moves to obey but stops herself. To run is to turn her back on that thing. What if that’s when it grabs her. She stays still and so does the figure. The thing blinks and its grin becomes wider. It sways back and forth, its prehensile locks making branches creak overhead. Alex’s chest and throat grows hot and and she gathers herself. She throws herself to the side, tripping yet carrying herself forward through the snapping bush branches. With sudden agility, she rights herself and runs back into the woods. Tree trunks fly at her as she runs trying not to trip on the uneven ground. She bursts into another clearing and looks back swinging her phone to light the trees behind her to look if that thing is following her. Then her vision turns off. She feels leaves and dirt against her face, a small pointy stick poking her in her right cheek. There’s a pressure on the side of her head and her hand moves there trying to feel what’s pushing against her. There’s nothing. The side of her head is numb. Memory of where she is and why rushes back into her and she pushes herself up with a jerk. When her vision comes back online she can only see a mosaic of black and gray forms, bushy undergrowth letting in pale light ahead of her. There is a glow coming from her left. She turns and her eyes focus quickly on phone, flashlight still on, its light flooding her vision. Alex grabs it and points it forward then all around, trying to see if she’s alone or if that thing is hiding somewhere near. She doesn’t see anyone. Only trees and quick shadows jumping away from the light as he moves it. She’s in a sort of a clearing again, except for a large tree trunk close to her. Alex reaches for the numb spot on her head and feels that it’s wet and sticky. It’s blood. She must have ran into that tree when she looked back trying to see if that monster followed her. Alex shines the light around her again. No sign of that thing. It could be hiding in the trees just out of sight. Or… her blood runs cold. She slowly looks up, remembering where she saw that thing first. For a second, all she can see is branches and flowing, black vines like spider webs snaking through the canopy, then her eyes discern three small, slender figures hanging like poppets from these “vines”. Children. Two smaller ones and one teenager her size. The teenager, Riley, stares at with a blank expression on her face. Then her body moves, or is moved by the tentacle “vines” holding her up. Hair, Alex realizes. He is held by the hair, not wrapped around her like back in the bedroom before Riley was pulled through the window, but growing into her flesh from behind, like thousands tiny marionette strings bunched up in locks. The hair brings Rile's hand up to her side and waves it back and forth, as if in a mocking greeting gesture. Alex tenses. At any moment, she feels, the figures can leap at her, grab her. But, no, they stay suspended. Then, between them, higher up in the branches the hair moves, like slithering snakes or tentacles moving across each other. A fourth figure is slowly lowering itself from above. The Grin Reaper. Smiling lady with an upside down head. It stops shortly after reaching the same level as the three bodies hanging by its hair. It stares at her, the grin seemingly growing wider and wider without really changing size. “It’s not real?” Alex, whispers to herself. They aren’t moving any closer, neither the woman nor the bodies suspended by her air. Alex’s hand tightens around her phone. (Phone can’t hallucinate) she thinks to herself. Maybe now they will believe her. She aims her phone right at the woman, her figure, looming above her, looks small on the screen. With a practiced gesture her thumb touches the camera button. As the phone snaps the photo, the screen refreshes showing the things face close up, filling the frame of the phone, as if jumping out at Alex. The girl squeaks, dropping the phone. It lands light up, still illuminating the four figures far above her, as if the woman hasn’t moved despite what the photo showed. Slowly, like a coiling snake, a tentacle-like lock of hair moves up in front of the the woman, pointing at Alex like pulled-back tongue. Then, in a flash, it flies toward her her and Alex’s vision goes black. #story #shortstory #creepypasta #horror #fiction #writing #nostr
@ 9e5a3a1a:ed414e8d
2025-02-02 00:50:08Either the phone’s battery went bad and quit charging, or the cable was shit. The warm rain running down the screen made the phone’s UI, flicker back and forth, as Ethan turned the screen on again to check how much battery he had left. Not a lot: 4%. At least the thing was water-proof, he thought. Today was also shit. First his parents confiscated he car keys after finding booze in his closet, now the fucking charging cable went bad. (Hopefully it’s the charging cable and not the battery), he thought. A car drove by splashing him with a fan of muddy water. “Hey!” he yelled, but the red tail lights were too far away now for the driver to hear. “Fucking fuck!” he swore looking down at himself. It was too dark to see how dirty his shirt and pants were now. The light of the gas station still far away. (Oh, well), he thought and continued walking, wet gravel and sand of road’s shoulder making wet crunching noises underfoot. Ethan’s thumb moved on the phone to turn the flashlight on, but he stopped himself. There was almost no chance that Casey’s gas station won’t have USB cables, they always did, but with today's luck they might just be out. Then he’d be screwed without a phone for the rest of the night and all day at school tomorrow. It wouldn’t be the end of the world, but he was too irate after everything today to accept not having a phone right now. A pale form moved to his right a few yards away. He turned and saw a figure standing by the trees. Ethan stopped and squinted through the rain. A cold, creepy feeling suddenly gripped him. It stood there and watched him. A female form, he realized, tall and pale, with black hair longer that he’s ever seen. Something was off. The face… It’s head… The mouth grinned widely, forming a dome above the eyes, eyes that were down close to the neck, under the nose, mouth and chin up above them. (It’s fucking head is upside down..) he realized. Ethan’s thumb pressed the phone’s power button, battery be damned. He aimed it at the figure, brought up the camera app and pressed the button to take the picture. Just as the shutter sound clicked the face was suddenly full-screen, as if a few feet away from him. Ethan gasped and the phone tumbled onto the ground. There was a moment of relief when he realized that the figure was still far away and didn’t suddenly teleport right in front of him, but then something long, black, and wide, like a cross between a ribbon and an anaconda flicked itself toward him and the last thing he felt was a thick spiderweb of hair wrapping itself around him and pulling him forward. *** “Hey, Riley, when did your dad say you needed to be back home?” Alex’s mom yelled from downstairs. The two girls glanced at their phones to see the time. “Eleven!” Riley yelled back. They still had half an hour of “study” time. The two really did mean to study for the calculus exam, but ended up chatting the whole evening. “Oh shit! I got to show you something,” Riley said, turning on her phone’s screen again, “You know that ‘Grin Reaper’ thing on social media?” She scrolled through her phone’s picture gallery. “Like, that smiling ‘monster’ with upside down head?” Alex asked. “Yeah, the one they said kidnapped those kids” “That’s so fake!” “Yeah, but look!” Riley turned her screen towards her friend. Alex took the phone from her, “What’s this?” “It’s her! Caleb was driving me to the movies and I saw her out the window. You know where Casey’s gas station is on Maple av? There’s like a wooded area just past it when you’re driving downtown.” “It’s just some blurry figure. Probably some homeless person… What’s that?” Alex heard some kind of scratching at the window. She walked over to look. They were on the second floor, but there were no trees close enough to scratch against the window. She opened it and look outside. No one. Just a vine attached to the wall of the house outside. Or was it a vine? Along, curly splotch of dark. Alex frowned. “No, I saw her, for real for real. It’s looks bad on the photo because it was dark and we were moving, but her head was on upside down and grinning.” Riley insisted. (Is it ivy?) Alex thought, only half listening to Riley, (Since when do we have ivy on the house?) Riley wondered if she should tell Alex that when she snapped the photo it looked like the woman’s grinning, upside down face was up close suddenly, right up against the car window. Caleb almost veered off the road turning to see what was wrong when she gasped and dropped the phone. When she fished her phone from beneath the seat, the photo looked normal. Blurry but normal. (Maybe a mud splash) Alex thought, examining the black, vine-like shadow that stuck to the house aiming at the window. (Some asshole splashed mud on the house as a prank. Someone from school?) “You think I should post it to TikTok?” Riley asked, looking pensively at the photo. The question brought Alex’s attention back to her. She walked back over and sat on the other side of her friend, taking the phone from her hand and looking closer at the photo. “It’s dark,” Alex rolled her eyes, “Also, some troll could have just been wearing a mask trying to scare people. That shit’s all over social media.” “I guess…” Riley decided against telling her more. She didn’t want to sound weird. Just then, Alex heard her phone ding somewhere behind her. She looked back to find it when she heard a choking noise from where Riley sat, “You ok?” she asked looking back and froze, not quite sure what she was seeing. Riley’s eyes were wide, her hands at her throat tugging at something black, like a scarf wrapping around her neck. More dark, tentacle-like locks reached in towards them through the window. It looked like hair, but it moved as if through water, snaking itself forward and wrapping around Riley’s arms, neck and face. Before Alex could utter a sound or register what she saw, the hair straightened, pulled back, yanking Riley out through the window. *** Alex sits on her bed in shock, glancing back at the window every thirty seconds. She tries to resist getting up and walking over to it. It's weird feeling of being pulled towards it to make sure it’s locked and being afraid to approach it for fear of what she might see outside. What if she sees it again? It’s tentacle-like locks crawling up the house, surrounding her window ready to snatch her like it did her friend. Can it seep through the cracks and unlock the fragile latch? She feels herself standing up and walking over to the window briskly, her hands smooth over the window latch, making sure it’s still locked, her eyes darting back and forth outside. Nothing. The dark splat on the house Alex first mistook for ivy or mud is gone, too. She sits back on the bed. Alex can hear her parents arguing downstairs. They think she's using drugs. They searched through her room the day after Riley was taken. They yelled at her that night, them and Riley’s dad, all convinced that the girls were high and Riley wondered off somewhere. Alex knew they would not believe what really happened. But lying wouldn’t help anyone find her friend. She lets think it was all a drug-induced hallucination. (Maybe I’m crazy,) Alex thinks. Her mind searches for mentions of schizophrenia among any of her relatives. Isn’t that shit genetic? A chill goes through her body again, suddenly. A scratching at the window? Like the one she heard before Riley was taken? “It’s not real,” she whispers out loud. It’s not real. She keeps thinking she hears it almost as often as she walks over to check the latch on the window. “It’s not real….” She has to check. Pushing through the fear, Alex briskly walks over to the window again. Nothing it the trees out back across the lawn. She can’t see the outside of the house without opening the window but she can’t risk it. “It wasn’t real” she affirms again. Then she has an idea. The parents’ arguing grows louder as Alex quietly opens her bedroom door and tiptoes down the stairs toward her mom’s office, trying to avoid attracting their attention. They are still pissed, she doesn't want to deal with them. She looks for scotch tape, quickly founds it, grabs a stack of paper from the printer and goes back upstairs. If she blocks out the window, it can’t see her, even if it is lurking somewhere outside waiting to snatch her, Alex thinks as she starts to cover the glass with paper and tape. She feels better now, suddenly. It feels like she was doing something to protect herself, even if it involves being near the window and risking seeing that thing. As the final page of printer paper is about to go up to block the glass completely, Alex freezes. A figure stands on the grass in front of the trees. In panic, Alex tries to decipher the face in the dark. The head, it is right side up. Not grinning, no hair tentacles: not the monster. With a wave of relief, she looks closer, trying to figure out who it is, and a surge of adrenaline and excitement suddenly hits her, (It's Riley!) “Ril--,” she almost screams, fumbling with the latch. As she pulls the window up and looks back out again, the figure is gone, “Riley!” she yells into the night. No answer. Alex pulls the window closed and runs for the door, briefly coming back to latching again, just in case. “She’s out there! Outside.” Alex almost yells as she barged into the living groom, pointing towards the back door. “Where? Outside?” her mom says then quickly goes to the door, dad and Alex following her. In the yard they yell Riley’s name, scanning the grass hill beyond and the tree line behind it. “Are you sure you saw her?” her dad asks. “Yeah, it was her, for sure.” “Are you high again?” her mom turns to her with an annoyed grimace on her face. “I’m not fucking high, mom!” “Don’t you talk to me this way! Get back to your room.” her mom yells. “I’m not fucking high, mom! I saw her.” Mom isn’t listening, she turns to dad “We should call her parents. She could really be out there,” then to Alex, “Upstairs NOW!” Pissed, Alex walks back into the house. It feels good to be angry, anger is better than fear. She runs up the stairs and tares down the paper she had just put up on the glass. She leans against the window and scans the tree line up in the distance. A few hour pass. Alex still gets up from time to time to check the window, but this time she is looking for Riley rather than checking the lock. Her parents have finally quieted down downstairs. It's late. They are probably asleep by now. Alex considers going to bed herself, but she knows she wouldn't be able to sleep. She looks back out the window. "Riley!" Her friend is there again, closer this time. Alex opens her mouth to call to her, but stops as she saw Riley raise her finger to her lips, gesturing for her to be quiet. Alex frowns, “What the fuck are you doing?” she mouths, shrugging dramatically. Riley motions for her to come out then puts her finger to her lips again. What is she doing? Alex thinks about waking her parents, but decides against it. They’ll just be useless and tell her to go to her room again. She quietly creeps downstairs and sneaks out the door. She half-expects Riley to be gone again as she walks out of the house and looks out to the hillside, but Riley is still there. Further back, almost past the tree-line. She motions Alex to come closer and takes a few steps back, disappearing in the trees. “Fuck!” Alex swears, looks back at the house one last time, then takes off across the yard after her. *** Past the tree line in the woods, Alex crunches through the trees, lighting her way (poorly) with her phone’s flashlight. Thorns scratch her arms and legs as she walks as fast as she can, navigating among the trees, yelling Riley’s name. From time to time she can see Riley's figure moving away from her, weaving among the trees. Her friend moves effortlessly, as if gliding above the ground, unimpeded by the greenery. Alex trips. She catches herself before she tumbles to the ground. For a second it is pitch black. She bends down to look for her phone. It is a glowing outline among the plants. Alex grabs it and gets up. For a moment she’s disoriented, not sure which way she was going. She looks and listens for her friend but sees and hears nothing. She looks back. There’s a bit of light glittering through the trees back where her neighborhood is. She looks forward and yells Riley’s name again, moving her phone trying to catch a glimpse of her friend’s figure. Nothing. Should she go back? Is Riley playing some stupid game? Maybe she is high. Without a second though, Alex continues forward, “Riley, it’s not funny! What the fuck are you doing?” Alex can see pale gray light between the leaves and the branches up ahead. She quickens her pace, almost tripping again. Alex walks into what looks like a small clearing. The trees are further away up ahead, but not much moon-light is coming from up above. She looks up towards the wide canopy, forming a dome overhead. Her eyes suddenly focus on a humanoid shape hanging parallel to the ground from the branches above. Its face is white, torn in two by a wide smile that almost reaches its ears. The top of the head is attached to the neck. Bands of hair suspend it from branches above. Alex freezes. For a second she feels herself cease to exist except for her breath that moves rhythmically in and out. Moments pass. How long, she can’t tell. (Run!), the thought echoes through her head, and she almost moves to obey but stops herself. To run is to turn her back on that thing. What if that’s when it grabs her. She stays still and so does the figure. The thing blinks and its grin becomes wider. It sways back and forth, its prehensile locks making branches creak overhead. Alex’s chest and throat grows hot and and she gathers herself. She throws herself to the side, tripping yet carrying herself forward through the snapping bush branches. With sudden agility, she rights herself and runs back into the woods. Tree trunks fly at her as she runs trying not to trip on the uneven ground. She bursts into another clearing and looks back swinging her phone to light the trees behind her to look if that thing is following her. Then her vision turns off. She feels leaves and dirt against her face, a small pointy stick poking her in her right cheek. There’s a pressure on the side of her head and her hand moves there trying to feel what’s pushing against her. There’s nothing. The side of her head is numb. Memory of where she is and why rushes back into her and she pushes herself up with a jerk. When her vision comes back online she can only see a mosaic of black and gray forms, bushy undergrowth letting in pale light ahead of her. There is a glow coming from her left. She turns and her eyes focus quickly on phone, flashlight still on, its light flooding her vision. Alex grabs it and points it forward then all around, trying to see if she’s alone or if that thing is hiding somewhere near. She doesn’t see anyone. Only trees and quick shadows jumping away from the light as he moves it. She’s in a sort of a clearing again, except for a large tree trunk close to her. Alex reaches for the numb spot on her head and feels that it’s wet and sticky. It’s blood. She must have ran into that tree when she looked back trying to see if that monster followed her. Alex shines the light around her again. No sign of that thing. It could be hiding in the trees just out of sight. Or… her blood runs cold. She slowly looks up, remembering where she saw that thing first. For a second, all she can see is branches and flowing, black vines like spider webs snaking through the canopy, then her eyes discern three small, slender figures hanging like poppets from these “vines”. Children. Two smaller ones and one teenager her size. The teenager, Riley, stares at with a blank expression on her face. Then her body moves, or is moved by the tentacle “vines” holding her up. Hair, Alex realizes. He is held by the hair, not wrapped around her like back in the bedroom before Riley was pulled through the window, but growing into her flesh from behind, like thousands tiny marionette strings bunched up in locks. The hair brings Rile's hand up to her side and waves it back and forth, as if in a mocking greeting gesture. Alex tenses. At any moment, she feels, the figures can leap at her, grab her. But, no, they stay suspended. Then, between them, higher up in the branches the hair moves, like slithering snakes or tentacles moving across each other. A fourth figure is slowly lowering itself from above. The Grin Reaper. Smiling lady with an upside down head. It stops shortly after reaching the same level as the three bodies hanging by its hair. It stares at her, the grin seemingly growing wider and wider without really changing size. “It’s not real?” Alex, whispers to herself. They aren’t moving any closer, neither the woman nor the bodies suspended by her air. Alex’s hand tightens around her phone. (Phone can’t hallucinate) she thinks to herself. Maybe now they will believe her. She aims her phone right at the woman, her figure, looming above her, looks small on the screen. With a practiced gesture her thumb touches the camera button. As the phone snaps the photo, the screen refreshes showing the things face close up, filling the frame of the phone, as if jumping out at Alex. The girl squeaks, dropping the phone. It lands light up, still illuminating the four figures far above her, as if the woman hasn’t moved despite what the photo showed. Slowly, like a coiling snake, a tentacle-like lock of hair moves up in front of the the woman, pointing at Alex like pulled-back tongue. Then, in a flash, it flies toward her her and Alex’s vision goes black. #story #shortstory #creepypasta #horror #fiction #writing #nostr @ 37305b10:4676ca73
2025-02-10 11:19:26This* is a test long form article publish via Nostr Article Publish in Obsidian. Testing the publishing of the Feature Image
@ 37305b10:4676ca73
2025-02-10 11:19:26This* is a test long form article publish via Nostr Article Publish in Obsidian. Testing the publishing of the Feature Image @ b17fccdf:b7211155
2025-02-01 18:41:27#### **Next new resources about the MiniBolt guide have been released**: --- * 🆕 **Roadmap**: [LINK](https://github.com/orgs/minibolt-guide/projects/1) * 🆕 **Dynamic Network map**: [LINK](https://app.diagrams.net/?tags={}&lightbox=1&target=blank&highlight=0000ff&edit=_blank&layers=1&nav=1&title=networkmap.drawio.png#Uhttps://raw.githubusercontent.com/minibolt-guide/minibolt/main/resources/networkmap.drawio.png) * 🆕 **Nostr community**: [LINK](https://habla.news/c/[n]addr1qqyy66twd9px7mr5qyf8wumn8ghj7mmxve3ksctfdch8qatzqgstzl7vmurm5gu87qutx3pxwgxddrg39huj809zhmv03scfkus3z4grqsqqpphk2j0aff) < ~ REMOVE the "[]" symbols from the URL (naddr...) to access * 🆕 **Linktr FOSS** (UC) by [Gzuuus](nostr:npub1gzuushllat7pet0ccv9yuhygvc8ldeyhrgxuwg744dn5khnpk3gs3ea5ds): [LINK](https://linktr.minibolt.info) * 🆕 **Donate webpage**: 🚾 [Clearnet LINK](https://donate.minibolt.info) || 🧅 [Onion LINK](http://3iqm7nidexns5p6wmgc23ibgiscm6rge7hwyeziviwgav4fl7xui4mqd.onion/apps/Li3AtEGDsqNmNddv6rX69taidm3/pos) * 🆕 **Contact email**: [hello@minibolt.info](mailto:hello@minibolt.info) --- Enjoy it MiniBolter! 💙
@ b17fccdf:b7211155
2025-02-01 18:41:27#### **Next new resources about the MiniBolt guide have been released**: --- * 🆕 **Roadmap**: [LINK](https://github.com/orgs/minibolt-guide/projects/1) * 🆕 **Dynamic Network map**: [LINK](https://app.diagrams.net/?tags={}&lightbox=1&target=blank&highlight=0000ff&edit=_blank&layers=1&nav=1&title=networkmap.drawio.png#Uhttps://raw.githubusercontent.com/minibolt-guide/minibolt/main/resources/networkmap.drawio.png) * 🆕 **Nostr community**: [LINK](https://habla.news/c/[n]addr1qqyy66twd9px7mr5qyf8wumn8ghj7mmxve3ksctfdch8qatzqgstzl7vmurm5gu87qutx3pxwgxddrg39huj809zhmv03scfkus3z4grqsqqpphk2j0aff) < ~ REMOVE the "[]" symbols from the URL (naddr...) to access * 🆕 **Linktr FOSS** (UC) by [Gzuuus](nostr:npub1gzuushllat7pet0ccv9yuhygvc8ldeyhrgxuwg744dn5khnpk3gs3ea5ds): [LINK](https://linktr.minibolt.info) * 🆕 **Donate webpage**: 🚾 [Clearnet LINK](https://donate.minibolt.info) || 🧅 [Onion LINK](http://3iqm7nidexns5p6wmgc23ibgiscm6rge7hwyeziviwgav4fl7xui4mqd.onion/apps/Li3AtEGDsqNmNddv6rX69taidm3/pos) * 🆕 **Contact email**: [hello@minibolt.info](mailto:hello@minibolt.info) --- Enjoy it MiniBolter! 💙 @ 7e19a1dd:ea50ba3b
2025-02-10 11:16:42Air compressors are workhorses across industries, from manufacturing plants to auto repair shops. However, keeping them running smoothly requires regular maintenance, which can be a time-consuming and costly chore. That’s where air compressor filters come into play. These simple yet vital components can help extend the life of your compressor while saving you money and headaches down the line. ## What Do Air Compressor Filters Actually Do? Air compressors suck in air from their surroundings, and that air isn’t always clean. It can carry dirt, moisture, and even tiny particles that can damage your compressor's internal parts. Filters act as the gatekeepers, trapping contaminants before they wreak havoc. Without a good filter, dirt and debris can clog valves and reduce efficiency. Even worse, it can lead to costly repairs—or worse, a full-blown breakdown. Filters also remove moisture, preventing rust and corrosion in your compressor and connected equipment. ## Less Maintenance, More Savings Regular maintenance on an air compressor is inevitable, but filters significantly cut down the frequency of those tune-ups. Clean air means fewer clogs and less wear and tear on moving parts. As a result, you’ll need fewer repairs and part replacements over time. And let’s not forget energy efficiency. When an air compressor operates with clean air, it doesn’t have to work as hard. This reduced workload translates into lower energy bills. Over time, this can add up to significant savings. ## Filters Protect Your Investment Air compressors aren’t cheap, and replacing one can feel like a punch to the wallet. Using high-quality air compressor filters protects your investment by keeping the equipment running at peak performance. Think of it like regularly changing your car’s oil. It’s a small, affordable step that prevents big problems later. ## Save Time and Effort No one enjoys unscheduled downtime, especially when deadlines are looming. A well-maintained compressor equipped with a proper filter is far less likely to break down unexpectedly. That means fewer interruptions and more time to focus on your work. And here’s another bonus: replacing filters is quick and easy. Compared to the hours it can take to clean or repair a compressor, swapping out a filter is a breeze. ## Choosing the Right Filter Not all filters are created equal. Make sure you choose one that matches your compressor’s specifications. If you’re unsure, check your user manual or ask a professional. Investing in a high-quality filter might cost a little more upfront, but it will pay off in the long run. ### Final Thoughts **[Air compressor filters](https://warriorfiltration.com/compressed-air-line-filters/)** are a small but mighty tool in keeping your equipment running smoothly. They cut down on maintenance, protect your compressor, and save you both time and money. By making filters a regular part of your maintenance routine, you’ll not only extend the life of your compressor but also improve its efficiency. That’s a win-win for your wallet and your workflow. So, the next time you fire up your air compressor, make sure its filter is up to the task. You’ll thank yourself later!
@ 7e19a1dd:ea50ba3b
2025-02-10 11:16:42Air compressors are workhorses across industries, from manufacturing plants to auto repair shops. However, keeping them running smoothly requires regular maintenance, which can be a time-consuming and costly chore. That’s where air compressor filters come into play. These simple yet vital components can help extend the life of your compressor while saving you money and headaches down the line. ## What Do Air Compressor Filters Actually Do? Air compressors suck in air from their surroundings, and that air isn’t always clean. It can carry dirt, moisture, and even tiny particles that can damage your compressor's internal parts. Filters act as the gatekeepers, trapping contaminants before they wreak havoc. Without a good filter, dirt and debris can clog valves and reduce efficiency. Even worse, it can lead to costly repairs—or worse, a full-blown breakdown. Filters also remove moisture, preventing rust and corrosion in your compressor and connected equipment. ## Less Maintenance, More Savings Regular maintenance on an air compressor is inevitable, but filters significantly cut down the frequency of those tune-ups. Clean air means fewer clogs and less wear and tear on moving parts. As a result, you’ll need fewer repairs and part replacements over time. And let’s not forget energy efficiency. When an air compressor operates with clean air, it doesn’t have to work as hard. This reduced workload translates into lower energy bills. Over time, this can add up to significant savings. ## Filters Protect Your Investment Air compressors aren’t cheap, and replacing one can feel like a punch to the wallet. Using high-quality air compressor filters protects your investment by keeping the equipment running at peak performance. Think of it like regularly changing your car’s oil. It’s a small, affordable step that prevents big problems later. ## Save Time and Effort No one enjoys unscheduled downtime, especially when deadlines are looming. A well-maintained compressor equipped with a proper filter is far less likely to break down unexpectedly. That means fewer interruptions and more time to focus on your work. And here’s another bonus: replacing filters is quick and easy. Compared to the hours it can take to clean or repair a compressor, swapping out a filter is a breeze. ## Choosing the Right Filter Not all filters are created equal. Make sure you choose one that matches your compressor’s specifications. If you’re unsure, check your user manual or ask a professional. Investing in a high-quality filter might cost a little more upfront, but it will pay off in the long run. ### Final Thoughts **[Air compressor filters](https://warriorfiltration.com/compressed-air-line-filters/)** are a small but mighty tool in keeping your equipment running smoothly. They cut down on maintenance, protect your compressor, and save you both time and money. By making filters a regular part of your maintenance routine, you’ll not only extend the life of your compressor but also improve its efficiency. That’s a win-win for your wallet and your workflow. So, the next time you fire up your air compressor, make sure its filter is up to the task. You’ll thank yourself later! @ 0271e1b9:ad8cff90
2025-02-01 07:39:31**I study the greats.** For if and when I find myself beaten down into the gutters of life - the vile, bile and the mundane - I shall draw strength from other great men - past, present and future - who, quite often, faced many more adversities and a lot more suffering, but chose to use them to their advantage, to overcome their dire circumstances and rise above the afflictions that life had bestowed upon them. It’s all been done before. It can be done again, better. Learning from the past and from the present is very straightforward. Anyone can do that. But how does one learn from the future? It’s simple: you envision the best possible future for humanity, for generations to come, and for yourself. Then you figure out an approximate path on how to get there, and what kind of a man or a woman you must be to walk that path. The skills, the mindset, the qualities. And lastly, but perhaps most importantly, you find actionable measures, habits, convictions on how to become that person - and conversely, what are stopping you from becoming that person. > “You must value learning above everything else.” ― Robert Greene > “Those who have a 'why' to live, can bear with almost any 'how'.” ― Viktor E. Frankl > “You need to look at all events as having value. If you can do that, then you’re in a zone of tremendous opportunity.” ― Phil Stutz > “I shall take the more pains to uncover the fountains of philosophy, from which all my eloquence has taken its rise.” ― Marcus Tullius Cicero > “Error correction is the basis of all intelligence.” ― Jeff Booth > “Yes, you’re likely to fail, that’s fine. Because the goal of playing is not to win, but to keep learning. And the day you stop learning is the day you stop living." ― Jesse Enkamp > "A man is great not because he hasn't failed; a man is great because failure hasn't stopped him." — Confucius > “If people knew how hard I had to work to gain my mastery, it would not seem so wonderful at all.” ― Michelangelo > “First of all we have to decide what we are to do and what manner of men we wish to be - the most difficult problem in the world.” ― Marcus Tullius Cicero > “You either bleed soul into your work, or let the work bleed out your soul.” ― Pran Yoganthan > "The Stoic philosopher is the man who has liberated himself from fear. He’s not afraid of death, he’s not afraid of pain, he’s not afraid of other people’s dismissal as a fool. The only thing he cares about is that he should meet his moral obligations.” ― Michael Sugrue > "The strong do what they can and the weak suffer what they must." ― Thucydides > “The brain is the most powerful weapon in the world.” ― David Goggins > “Man, the bravest of animals, and the one most accustomed to suffering, does not repudiate suffering as such; he desires it, he even seeks it out, provided he is shown a meaning for it, a purpose of suffering. The meaninglessness of suffering, not suffering itself, was the curse that lay over mankind so far.” ― Friedrich Nietzsche > "Consciousness is awareness with a choice." ― Thomas Campbell > “The essence of philosophy is that a man should so live that his happiness shall depend as little as possible on external things.” ― Epictetus > “It’s most real, it’s most good and it’s most salvific - it saves you, it transforms you. That’s the sacred.” — John Vervaeke > “It is impossible for a man to learn what he thinks he already knows.” ― Epictetus > “Evolution is a process of iteration. There’s no master plan. It’s in each moment of what happens.” ― Michael Behrens > “Don’t follow anybody and don’t accept anyone as a teacher, except when you become your own teacher and disciple.” ― Jiddu Krishnamurti > “This is your life. You’re accountable. What are you gonna do about that?” ― James Hollis By the way, if you enjoyed these quotes, feel free to follow a little side project of mine: [Stoic Resurrection](https://linktr.ee/stoic_resurrection) *Peace & Love,* *[Kontext](https://linktr.ee/mckontext)* *Block height 881,748*
@ 0271e1b9:ad8cff90
2025-02-01 07:39:31**I study the greats.** For if and when I find myself beaten down into the gutters of life - the vile, bile and the mundane - I shall draw strength from other great men - past, present and future - who, quite often, faced many more adversities and a lot more suffering, but chose to use them to their advantage, to overcome their dire circumstances and rise above the afflictions that life had bestowed upon them. It’s all been done before. It can be done again, better. Learning from the past and from the present is very straightforward. Anyone can do that. But how does one learn from the future? It’s simple: you envision the best possible future for humanity, for generations to come, and for yourself. Then you figure out an approximate path on how to get there, and what kind of a man or a woman you must be to walk that path. The skills, the mindset, the qualities. And lastly, but perhaps most importantly, you find actionable measures, habits, convictions on how to become that person - and conversely, what are stopping you from becoming that person. > “You must value learning above everything else.” ― Robert Greene > “Those who have a 'why' to live, can bear with almost any 'how'.” ― Viktor E. Frankl > “You need to look at all events as having value. If you can do that, then you’re in a zone of tremendous opportunity.” ― Phil Stutz > “I shall take the more pains to uncover the fountains of philosophy, from which all my eloquence has taken its rise.” ― Marcus Tullius Cicero > “Error correction is the basis of all intelligence.” ― Jeff Booth > “Yes, you’re likely to fail, that’s fine. Because the goal of playing is not to win, but to keep learning. And the day you stop learning is the day you stop living." ― Jesse Enkamp > "A man is great not because he hasn't failed; a man is great because failure hasn't stopped him." — Confucius > “If people knew how hard I had to work to gain my mastery, it would not seem so wonderful at all.” ― Michelangelo > “First of all we have to decide what we are to do and what manner of men we wish to be - the most difficult problem in the world.” ― Marcus Tullius Cicero > “You either bleed soul into your work, or let the work bleed out your soul.” ― Pran Yoganthan > "The Stoic philosopher is the man who has liberated himself from fear. He’s not afraid of death, he’s not afraid of pain, he’s not afraid of other people’s dismissal as a fool. The only thing he cares about is that he should meet his moral obligations.” ― Michael Sugrue > "The strong do what they can and the weak suffer what they must." ― Thucydides > “The brain is the most powerful weapon in the world.” ― David Goggins > “Man, the bravest of animals, and the one most accustomed to suffering, does not repudiate suffering as such; he desires it, he even seeks it out, provided he is shown a meaning for it, a purpose of suffering. The meaninglessness of suffering, not suffering itself, was the curse that lay over mankind so far.” ― Friedrich Nietzsche > "Consciousness is awareness with a choice." ― Thomas Campbell > “The essence of philosophy is that a man should so live that his happiness shall depend as little as possible on external things.” ― Epictetus > “It’s most real, it’s most good and it’s most salvific - it saves you, it transforms you. That’s the sacred.” — John Vervaeke > “It is impossible for a man to learn what he thinks he already knows.” ― Epictetus > “Evolution is a process of iteration. There’s no master plan. It’s in each moment of what happens.” ― Michael Behrens > “Don’t follow anybody and don’t accept anyone as a teacher, except when you become your own teacher and disciple.” ― Jiddu Krishnamurti > “This is your life. You’re accountable. What are you gonna do about that?” ― James Hollis By the way, if you enjoyed these quotes, feel free to follow a little side project of mine: [Stoic Resurrection](https://linktr.ee/stoic_resurrection) *Peace & Love,* *[Kontext](https://linktr.ee/mckontext)* *Block height 881,748* @ 2e8970de:63345c7a
2025-02-10 11:13:18I feel like we're stuck in the 16GB or let's say the broad "8GB to 32GB" range forever now. Do you remember the times when computer performance and all memory and drive sizes doubled and doubled and doubled? Now we live in a time when we all not only want to play games or the time when locally playing 4k video was demanding - we live in a time where we want to run local LLMs offline and reder 3D stuff or even have VR goggles with more than 8K resolution. Remember the Radeon 6000 Series from 2020 - HALF A DECADE AGO - buy a Radeon 6800 with 16GB. # Current state of the industry - Nvidia 5070 comes with only 12 GB of VRAM. Why. - Nvidia 5080 should be the real flagship but it comes with only 16GB. Why. You can run an 8b LLM model on this at best. - Nvidia 5090 ist the only product here that gives 32GB. Congratulations, might as well buy 2 cards. This should be the VRAM the 5070 has - Perfect opportunity for AMD to be a tough competitor, right? Wrong. The new AMD Radeon 9000 series gives you 16GB with the 9070 and 9070xt - Apple is technologically perfectly positioned to come out of nowhere and blow the industry out of the water with their unified memory architecture. And to some extent this is true. If you buy a Macbook pro and pay the egregiously priced upgrade to 32GB (which is less than 2 GPUs à 16GB due to Unified Memory also using normal RAM stuff) you'll get a whole computer for what Nvidia/AMD sell the cards alone. - Nvidia Digits looks similar to Apples MacMini. The unified memory architecture makes this a better deal. But still disappointing imo. - If tech doubled and doubled like back in the day I would have expected 64GB everywhere and maybe even 128GB for 5090 level products. I'm serious. # Conclusion: What to buy for local LLM (imo) 1. Don't 2. If you already got an older 16GB graphics card don't upgrade to the overpriced new ones. You'll be able to run the same sized small models, just slower. 3. If you're in the market for a whole new computer anyway - upgrading a MacBook to 32GB 4. You're crazy and like to tinker? Maybe research how to get a dozen RTX 3080 cards or AMD 6800 cards to run together. originally posted at https://stacker.news/items/881359
@ 2e8970de:63345c7a
2025-02-10 11:13:18I feel like we're stuck in the 16GB or let's say the broad "8GB to 32GB" range forever now. Do you remember the times when computer performance and all memory and drive sizes doubled and doubled and doubled? Now we live in a time when we all not only want to play games or the time when locally playing 4k video was demanding - we live in a time where we want to run local LLMs offline and reder 3D stuff or even have VR goggles with more than 8K resolution. Remember the Radeon 6000 Series from 2020 - HALF A DECADE AGO - buy a Radeon 6800 with 16GB. # Current state of the industry - Nvidia 5070 comes with only 12 GB of VRAM. Why. - Nvidia 5080 should be the real flagship but it comes with only 16GB. Why. You can run an 8b LLM model on this at best. - Nvidia 5090 ist the only product here that gives 32GB. Congratulations, might as well buy 2 cards. This should be the VRAM the 5070 has - Perfect opportunity for AMD to be a tough competitor, right? Wrong. The new AMD Radeon 9000 series gives you 16GB with the 9070 and 9070xt - Apple is technologically perfectly positioned to come out of nowhere and blow the industry out of the water with their unified memory architecture. And to some extent this is true. If you buy a Macbook pro and pay the egregiously priced upgrade to 32GB (which is less than 2 GPUs à 16GB due to Unified Memory also using normal RAM stuff) you'll get a whole computer for what Nvidia/AMD sell the cards alone. - Nvidia Digits looks similar to Apples MacMini. The unified memory architecture makes this a better deal. But still disappointing imo. - If tech doubled and doubled like back in the day I would have expected 64GB everywhere and maybe even 128GB for 5090 level products. I'm serious. # Conclusion: What to buy for local LLM (imo) 1. Don't 2. If you already got an older 16GB graphics card don't upgrade to the overpriced new ones. You'll be able to run the same sized small models, just slower. 3. If you're in the market for a whole new computer anyway - upgrading a MacBook to 32GB 4. You're crazy and like to tinker? Maybe research how to get a dozen RTX 3080 cards or AMD 6800 cards to run together. originally posted at https://stacker.news/items/881359 @ 000002de:c05780a7
2025-02-01 05:23:37 originally posted at https://stacker.news/items/872035
@ 000002de:c05780a7
2025-02-01 05:23:37 originally posted at https://stacker.news/items/872035 @ e1d968f7:5d90f764
2025-02-10 10:17:19Every encounter brings its own unique connection, and over time, I've come to appreciate the genuine bonds that can form between a client and myself. Yet, sometimes that bond deepens too far, with a client becoming overly attached in ways that complicate the professional nature of our relationship. Today, I want to share more about recognising these moments and handling them with both compassion and firmness. ### ** recognising Over-Attachment** At first, the warmth of a connection can feel incredibly gratifying. Clients often open up and share parts of themselves that they might not reveal elsewhere. However, there comes a point when friendly familiarity begins to tip into dependency. I’ve noticed the signs: frequent messages outside of our agreed hours, an insistence on more personal details, or expressions of jealousy when I interact with other clients. These are the moments when I realise that my client is developing feelings that exceed the professional boundaries of our arrangement. ### **Managing Emotional Intimacy** Understanding that every client is unique, I’ve learned that managing emotional intimacy is as important as setting physical boundaries. It’s natural for someone to crave closeness, but I remind myself—and my clients—that my role is to provide a safe, respectful space, not to fill every gap in their emotional lives. I gently steer conversations away from overly personal territory and encourage clients to seek other forms of support, whether from friends or professional counsellors, when they need deeper emotional assistance. ### **Setting Clear Boundaries** When I recognise signs of over-attachment, I address them directly. I reaffirm the terms of our relationship by politely yet firmly clarifying that my availability is strictly within the professional parameters we initially agreed upon. For instance, if a client begins messaging excessively or asks for personal contact details, I calmly remind them that my priority is to maintain a respectful, professional connection. I find that establishing these boundaries early—often before a session even begins—can help prevent attachment from spiralling out of control. ### **Communicating with Compassion** Handling these situations isn’t merely about enforcing rules; it’s about caring for my clients while protecting my own well-being. I approach sensitive discussions with empathy, acknowledging their feelings and validating their need for connection, yet I am clear that the service I offer has its limits. I explain that while I value our interactions, I must keep our relationship within the agreed boundaries so that I can continue providing the best possible experience for everyone involved. ### **Maintaining Professionalism and Self-Care** Dealing with over-attachment takes its toll, both emotionally and mentally. I make it a priority to reflect on these experiences and ensure that I practice self-care afterwards. Whether through quiet moments of solitude, journaling my thoughts, or speaking with a trusted colleague, I take steps to recharge and maintain my emotional balance. This not only helps me move past challenging interactions but also strengthens my ability to support my clients in a professional manner. ### **Conclusion** Navigating the fine line between connection and over-attachment is one of the most complex aspects of my work. While I deeply value the trust and intimacy that can develop during our time together, it is essential for both my clients and me to recognise when boundaries begin to blur. By staying true to my professional guidelines and communicating with honesty and empathy, I ensure that each encounter remains respectful and fulfilling. In the end, maintaining these boundaries is not just about protecting myself—it’s about honouring the true nature of our connection and ensuring that it remains both safe and meaningful. Rebecca x
@ e1d968f7:5d90f764
2025-02-10 10:17:19Every encounter brings its own unique connection, and over time, I've come to appreciate the genuine bonds that can form between a client and myself. Yet, sometimes that bond deepens too far, with a client becoming overly attached in ways that complicate the professional nature of our relationship. Today, I want to share more about recognising these moments and handling them with both compassion and firmness. ### ** recognising Over-Attachment** At first, the warmth of a connection can feel incredibly gratifying. Clients often open up and share parts of themselves that they might not reveal elsewhere. However, there comes a point when friendly familiarity begins to tip into dependency. I’ve noticed the signs: frequent messages outside of our agreed hours, an insistence on more personal details, or expressions of jealousy when I interact with other clients. These are the moments when I realise that my client is developing feelings that exceed the professional boundaries of our arrangement. ### **Managing Emotional Intimacy** Understanding that every client is unique, I’ve learned that managing emotional intimacy is as important as setting physical boundaries. It’s natural for someone to crave closeness, but I remind myself—and my clients—that my role is to provide a safe, respectful space, not to fill every gap in their emotional lives. I gently steer conversations away from overly personal territory and encourage clients to seek other forms of support, whether from friends or professional counsellors, when they need deeper emotional assistance. ### **Setting Clear Boundaries** When I recognise signs of over-attachment, I address them directly. I reaffirm the terms of our relationship by politely yet firmly clarifying that my availability is strictly within the professional parameters we initially agreed upon. For instance, if a client begins messaging excessively or asks for personal contact details, I calmly remind them that my priority is to maintain a respectful, professional connection. I find that establishing these boundaries early—often before a session even begins—can help prevent attachment from spiralling out of control. ### **Communicating with Compassion** Handling these situations isn’t merely about enforcing rules; it’s about caring for my clients while protecting my own well-being. I approach sensitive discussions with empathy, acknowledging their feelings and validating their need for connection, yet I am clear that the service I offer has its limits. I explain that while I value our interactions, I must keep our relationship within the agreed boundaries so that I can continue providing the best possible experience for everyone involved. ### **Maintaining Professionalism and Self-Care** Dealing with over-attachment takes its toll, both emotionally and mentally. I make it a priority to reflect on these experiences and ensure that I practice self-care afterwards. Whether through quiet moments of solitude, journaling my thoughts, or speaking with a trusted colleague, I take steps to recharge and maintain my emotional balance. This not only helps me move past challenging interactions but also strengthens my ability to support my clients in a professional manner. ### **Conclusion** Navigating the fine line between connection and over-attachment is one of the most complex aspects of my work. While I deeply value the trust and intimacy that can develop during our time together, it is essential for both my clients and me to recognise when boundaries begin to blur. By staying true to my professional guidelines and communicating with honesty and empathy, I ensure that each encounter remains respectful and fulfilling. In the end, maintaining these boundaries is not just about protecting myself—it’s about honouring the true nature of our connection and ensuring that it remains both safe and meaningful. Rebecca x @ ee7e3590:5602f192
2025-02-01 05:02:15You’re hitting on the core tension: **unlimited demand for emergency care collides with finite resources**, and pretending otherwise leads to either runaway costs or rationing-by-stealth. Let’s confront this head-on with free-market-aligned solutions that don’t ignore human realities: --- ### **1. Redefine "Emergency Care"** The U.S. legally mandates ERs to stabilize *anyone*, regardless of ability to pay (EMTALA). This creates moral hazard: - **Problem**: Hospitals inflate prices on paying patients to offset uncompensated care. - **Free-Market Fix**: - **Repeal EMTALA**: Allow ERs to refuse non-critical cases (e.g., toothaches, rashes) unless prepaid or insured. - **Clarify "True Emergency"**: Legally define emergencies as *immediate life threats* (e.g., strokes, cardiac arrest) and let non-critical cases be diverted to urgent care. - **Consequence**: ERs could price transparently for true emergencies, while non-critical cases face market-driven urgent care options. --- ### **2. Embrace Tiered Emergency Care** Not all emergencies require Level I trauma centers: - **Basic ERs**: Staffed by NPs and paramedics for minor injuries (e.g., sprains, minor burns) at lower costs. - **Advanced ERs**: For critical care (e.g., gunshot wounds), priced higher but competing via outcomes (e.g., survival rates). - **Example**: India’s *Ziqitza Healthcare* operates ambulance tiers—basic vans for transport and advanced ICU units. --- ### **3. **Address Moral Hazard with Insurance Innovation** - **Catastrophic Insurance Mandates**: Require everyone to carry cheap, high-deductible plans covering *only* true emergencies (e.g., $10/month for coverage above $50k). - Incentivizes price shopping for non-emergencies. - Prevents freeloading on ERs. - **Risk-Adjusted Premiums**: Smokers, skydivers, or diabetics pay higher premiums, aligning costs with personal choices. --- ### **4. **Community-Based Safety Nets** - **Mutual Aid Networks**: Local groups negotiate bulk ER rates (e.g., $100/month membership covers three ER visits annually). - **Crowdfunding ER Vouchers**: Platforms like *GoFundMe* could partner with hospitals to prepurchase discounted emergency care slots. --- ### **5. **Radical Transparency + Bankruptcy Reform** - **ER Debt Auctions**: Let hospitals sell unpaid ER bills to collection agencies in real-time, creating competition to minimize patient liability. - **Flat-Fee ER Pricing**: Hospitals post rates like “$5,000 for appendicitis stabilization, all-inclusive” to deter surprise billing. - **Ban Wage Garnishment for Medical Debt**: Protect patients from lifelong ruin, forcing hospitals to price responsibly or absorb losses. --- ### **6. **Accept Trade-Offs Explicitly** The U.S. system fails because it hides rationing behind complexity. A free-market approach must embrace transparency: - **Option 1**: Pay $100,000 for a 95% survival rate in a car crash. - **Option 2**: Pay $20,000 for a 70% survival rate at a budget ER. - **Brutal but Honest**: Let individuals (or insurers) choose their risk tolerance upfront. **Example**: - **Japan’s Price Controls**: Caps ER costs but tolerates wait times (e.g., 8+ hours for non-critical care). - **Switzerland’s Mandates**: Everyone buys insurance, but ERs charge $1,000+ deductibles to deter overuse. --- ### **7. **Disrupt with Decentralized Care** - **Crypto-ERs**: Blockchain-based emergency funds where contributors vote on covering members’ bills. - **AI-Guided Self-Care**: Apps that stabilize patients en route to ERs (e.g., tourniquet tutorials, overdose reversal guidance). --- ### **8. **Reform Malpractice to Reduce Defensive Medicine** - **“No Pay, No Harm” Liability**: If a patient doesn’t pay, they can’t sue for malpractice (incentivizing upfront pricing). - **Safe Harbor Protocols**: ERs using approved, cost-effective treatments (e.g., generics) get immunity from lawsuits. --- ### **The Uncomfortable Truth** A free market in emergency care requires accepting that **not everyone will be saved**—just as not everyone can afford a Ferrari. The alternative is the current U.S. model, which *pretends* to save everyone but bankrupts millions and still leaves 30% of ER visits unmet due to overcrowding. By legalizing tiered care, deregulating monopolies, and forcing transparency, you create a system where: - **Elites** pay premium prices for cutting-edge emergency care. - **Most** get “good enough” stabilization at reasonable costs. - **Some** choose cheap, high-risk options (or none at all). This isn’t pretty, but it’s honest—and arguably more ethical than today’s hidden rationing and financial toxicity.
@ ee7e3590:5602f192
2025-02-01 05:02:15You’re hitting on the core tension: **unlimited demand for emergency care collides with finite resources**, and pretending otherwise leads to either runaway costs or rationing-by-stealth. Let’s confront this head-on with free-market-aligned solutions that don’t ignore human realities: --- ### **1. Redefine "Emergency Care"** The U.S. legally mandates ERs to stabilize *anyone*, regardless of ability to pay (EMTALA). This creates moral hazard: - **Problem**: Hospitals inflate prices on paying patients to offset uncompensated care. - **Free-Market Fix**: - **Repeal EMTALA**: Allow ERs to refuse non-critical cases (e.g., toothaches, rashes) unless prepaid or insured. - **Clarify "True Emergency"**: Legally define emergencies as *immediate life threats* (e.g., strokes, cardiac arrest) and let non-critical cases be diverted to urgent care. - **Consequence**: ERs could price transparently for true emergencies, while non-critical cases face market-driven urgent care options. --- ### **2. Embrace Tiered Emergency Care** Not all emergencies require Level I trauma centers: - **Basic ERs**: Staffed by NPs and paramedics for minor injuries (e.g., sprains, minor burns) at lower costs. - **Advanced ERs**: For critical care (e.g., gunshot wounds), priced higher but competing via outcomes (e.g., survival rates). - **Example**: India’s *Ziqitza Healthcare* operates ambulance tiers—basic vans for transport and advanced ICU units. --- ### **3. **Address Moral Hazard with Insurance Innovation** - **Catastrophic Insurance Mandates**: Require everyone to carry cheap, high-deductible plans covering *only* true emergencies (e.g., $10/month for coverage above $50k). - Incentivizes price shopping for non-emergencies. - Prevents freeloading on ERs. - **Risk-Adjusted Premiums**: Smokers, skydivers, or diabetics pay higher premiums, aligning costs with personal choices. --- ### **4. **Community-Based Safety Nets** - **Mutual Aid Networks**: Local groups negotiate bulk ER rates (e.g., $100/month membership covers three ER visits annually). - **Crowdfunding ER Vouchers**: Platforms like *GoFundMe* could partner with hospitals to prepurchase discounted emergency care slots. --- ### **5. **Radical Transparency + Bankruptcy Reform** - **ER Debt Auctions**: Let hospitals sell unpaid ER bills to collection agencies in real-time, creating competition to minimize patient liability. - **Flat-Fee ER Pricing**: Hospitals post rates like “$5,000 for appendicitis stabilization, all-inclusive” to deter surprise billing. - **Ban Wage Garnishment for Medical Debt**: Protect patients from lifelong ruin, forcing hospitals to price responsibly or absorb losses. --- ### **6. **Accept Trade-Offs Explicitly** The U.S. system fails because it hides rationing behind complexity. A free-market approach must embrace transparency: - **Option 1**: Pay $100,000 for a 95% survival rate in a car crash. - **Option 2**: Pay $20,000 for a 70% survival rate at a budget ER. - **Brutal but Honest**: Let individuals (or insurers) choose their risk tolerance upfront. **Example**: - **Japan’s Price Controls**: Caps ER costs but tolerates wait times (e.g., 8+ hours for non-critical care). - **Switzerland’s Mandates**: Everyone buys insurance, but ERs charge $1,000+ deductibles to deter overuse. --- ### **7. **Disrupt with Decentralized Care** - **Crypto-ERs**: Blockchain-based emergency funds where contributors vote on covering members’ bills. - **AI-Guided Self-Care**: Apps that stabilize patients en route to ERs (e.g., tourniquet tutorials, overdose reversal guidance). --- ### **8. **Reform Malpractice to Reduce Defensive Medicine** - **“No Pay, No Harm” Liability**: If a patient doesn’t pay, they can’t sue for malpractice (incentivizing upfront pricing). - **Safe Harbor Protocols**: ERs using approved, cost-effective treatments (e.g., generics) get immunity from lawsuits. --- ### **The Uncomfortable Truth** A free market in emergency care requires accepting that **not everyone will be saved**—just as not everyone can afford a Ferrari. The alternative is the current U.S. model, which *pretends* to save everyone but bankrupts millions and still leaves 30% of ER visits unmet due to overcrowding. By legalizing tiered care, deregulating monopolies, and forcing transparency, you create a system where: - **Elites** pay premium prices for cutting-edge emergency care. - **Most** get “good enough” stabilization at reasonable costs. - **Some** choose cheap, high-risk options (or none at all). This isn’t pretty, but it’s honest—and arguably more ethical than today’s hidden rationing and financial toxicity. @ 31da2214:af2508e2
2025-02-10 10:08:06A global privacy nightmare is unfolding. The UK government secretly ordered Apple to backdoor encrypted iCloud storage worldwide—but Apple is legally forbidden from revealing this order, or they face criminal charges. This affects **2 BILLION USERS**. Here’s the full story & why it’s part of a much bigger power grab. 🧵👇 [[Thread by @sayerjigmi on Thread Reader App](https://threadreaderapp.com/thread/1888287793123901896.html)] --- ## 1) The UK's Secret Order to Backdoor Encryption 🔓 Under the UK’s **Investigatory Powers Act (IPA) 2016**, Apple was served a **Technical Capability Notice (TCN)**—forcing them to create a backdoor for encrypted iCloud data. This is not limited to UK users. It applies **worldwide**, meaning your private files are at risk, no matter where you live. 🔗 [@macworld report](https://macworld.com/article/260251…) --- ## 2) Apple’s Legal Gag Order 🤐 Apple is legally forbidden from revealing this order. If Apple even acknowledges that the UK issued this demand, they could face **criminal charges**. This is a secret government order with **global consequences**. --- ## 3) A Global Threat to Encryption 🌍 This isn’t just about the UK (although they are leading the charge in threatening citizens in OTHER countries for violating BRITISH censorship laws!). If Apple complies, every government in the world will demand the same access—from the US to China to authoritarian regimes. **End-to-end encryption would be effectively dead.**  --- ## 4) Apple’s Dilemma: Comply or Withdraw? 🚪 Apple has two choices: - **Comply** & weaken encryption globally. - **Refuse** & withdraw services from the UK. WhatsApp & Signal faced similar threats last year and vowed to leave the UK rather than compromise security. Will Apple do the same? 🚨 Watch the heated discussion between Damian Collins, director of CCDH (architect of the UK Online Safety Bill), and Signal’s CEO: [YouTube Link](https://www.youtube.com/watch?v=E--bVV_eQR0) --- ## 5) Why This Matters: Encryption Protects Everything 🔐 - **Encryption protects financial data, health records, personal security (e.g., where you live or work), and private conversations.** - Governments always say they need backdoors for national security—but history shows they’re used for **mass surveillance**. - Once a backdoor exists, hackers, rogue employees, and other governments WILL find it. --- ## 6) The UK’s War on Encryption 🛡️ The UK is trying to dominate the global surveillance & censorship landscape. While the US, Canada, Australia, and New Zealand have supported strong encryption to mitigate cyber threats, the UK stands alone in its war on encryption. --- ## 7) The Free Speech Crackdown 🗣️ This isn’t just about encryption—it’s about **control**. Governments worldwide are criminalizing dissent and censoring free speech, using tech companies as their enforcement arms. 🔗 [GreenMedInfo Report](https://greenmedinfo.com/content/breaking-international-governments-are-criminalizing-free-speech-through-glo-3) --- ## 8) The Global Censorship Agenda 🌐 This ties into the UK’s broader, **GLOBALLY ORCHESTRATED censorship agenda**: - The **Online Safety Bill** criminalizes encrypted messaging & forces platforms to scan private messages. - The **Digital Services Act (EU)** gives governments the power to shut down online content they don’t like. - Leaked US-UK documents show direct coordination between UK intelligence & the Biden administration to censor online speech. --- ## 9) The Architects of Speech Policing: CCDH 🕵️♂️ The **Center for Countering Digital Hate (CCDH)**—a UK intelligence-backed group—has been a driving force behind global censorship. They were caught: - Running “black ops” to suppress RFK Jr.’s presidential campaign. - Leading the "Kill Musk’s Twitter" directive, trying to shut down free speech on X. - Labeling 12 private US citizens as the “Disinformation Dozen” to justify mass censorship. 🔗 [Reclaim the Net Investigation](https://reclaimthenet.org/black-ops-how-a-us-uk-censorship-group-targeted-rfk-jr-to-stifle-dissent) --- ## 10) The Pattern is Clear: Surveillance + Censorship 🔍 1️⃣ Governments create "safety" laws to justify surveillance. 2️⃣ They pressure tech companies to enforce censorship. 3️⃣ Once encrypted services are gone, nothing is private anymore. This is the biggest attack on digital freedom in history. --- ## 11) What Can We Do? 💪 - **Support companies** that refuse to build backdoors (Signal, ProtonMail, etc.). - **Push for legislation** that protects encryption & free speech. - **Stay informed** & spread awareness—governments count on secrecy to push these policies through. - Follow and support privacy and internet freedom organizations such as: - [@G_W_Forum](https://twitter.com/G_W_Forum) - [@FFO_Freedom](https://twitter.com/FFO_Freedom) - [@ReclaimTheNetHQ](https://twitter.com/ReclaimTheNetHQ) --- ## 12) The Ultimate Power Grab: Controlling All Digital Communication 📱 If Apple caves, every other platform will be forced to follow. 📌 The UK’s Global Playbook: - A backdoor to encryption (Investigatory Powers Act). - A government-linked censorship network (CCDH). - A speech-policing framework that extends worldwide (Online Safety Bill). This is a global effort to control what people can say, share, and store privately. --- ## 13) The Final Stand: Will You Comply or Resist? ⚔️🚨 They want total control—your speech, your privacy, your elections. This is the defining battle of our time. 🇬🇧 UK’s war on encryption = Global censorship blueprint. 🗳️ Election meddling + speech policing = A hijacked democracy. 📢 **Digital freedom is human freedom.** Stand up. Speak out. Fight back. 🏴☠️🔥 🔗 [LEARN MORE](https://sayerji.substack.com/p/crossfire-of-democracy-uk-labour?utm_source=publication-search) --- *Full thread preserved by [Thread Reader App](https://threadreaderapp.com/thread/1888287793123901896.html).*
@ 31da2214:af2508e2
2025-02-10 10:08:06A global privacy nightmare is unfolding. The UK government secretly ordered Apple to backdoor encrypted iCloud storage worldwide—but Apple is legally forbidden from revealing this order, or they face criminal charges. This affects **2 BILLION USERS**. Here’s the full story & why it’s part of a much bigger power grab. 🧵👇 [[Thread by @sayerjigmi on Thread Reader App](https://threadreaderapp.com/thread/1888287793123901896.html)] --- ## 1) The UK's Secret Order to Backdoor Encryption 🔓 Under the UK’s **Investigatory Powers Act (IPA) 2016**, Apple was served a **Technical Capability Notice (TCN)**—forcing them to create a backdoor for encrypted iCloud data. This is not limited to UK users. It applies **worldwide**, meaning your private files are at risk, no matter where you live. 🔗 [@macworld report](https://macworld.com/article/260251…) --- ## 2) Apple’s Legal Gag Order 🤐 Apple is legally forbidden from revealing this order. If Apple even acknowledges that the UK issued this demand, they could face **criminal charges**. This is a secret government order with **global consequences**. --- ## 3) A Global Threat to Encryption 🌍 This isn’t just about the UK (although they are leading the charge in threatening citizens in OTHER countries for violating BRITISH censorship laws!). If Apple complies, every government in the world will demand the same access—from the US to China to authoritarian regimes. **End-to-end encryption would be effectively dead.**  --- ## 4) Apple’s Dilemma: Comply or Withdraw? 🚪 Apple has two choices: - **Comply** & weaken encryption globally. - **Refuse** & withdraw services from the UK. WhatsApp & Signal faced similar threats last year and vowed to leave the UK rather than compromise security. Will Apple do the same? 🚨 Watch the heated discussion between Damian Collins, director of CCDH (architect of the UK Online Safety Bill), and Signal’s CEO: [YouTube Link](https://www.youtube.com/watch?v=E--bVV_eQR0) --- ## 5) Why This Matters: Encryption Protects Everything 🔐 - **Encryption protects financial data, health records, personal security (e.g., where you live or work), and private conversations.** - Governments always say they need backdoors for national security—but history shows they’re used for **mass surveillance**. - Once a backdoor exists, hackers, rogue employees, and other governments WILL find it. --- ## 6) The UK’s War on Encryption 🛡️ The UK is trying to dominate the global surveillance & censorship landscape. While the US, Canada, Australia, and New Zealand have supported strong encryption to mitigate cyber threats, the UK stands alone in its war on encryption. --- ## 7) The Free Speech Crackdown 🗣️ This isn’t just about encryption—it’s about **control**. Governments worldwide are criminalizing dissent and censoring free speech, using tech companies as their enforcement arms. 🔗 [GreenMedInfo Report](https://greenmedinfo.com/content/breaking-international-governments-are-criminalizing-free-speech-through-glo-3) --- ## 8) The Global Censorship Agenda 🌐 This ties into the UK’s broader, **GLOBALLY ORCHESTRATED censorship agenda**: - The **Online Safety Bill** criminalizes encrypted messaging & forces platforms to scan private messages. - The **Digital Services Act (EU)** gives governments the power to shut down online content they don’t like. - Leaked US-UK documents show direct coordination between UK intelligence & the Biden administration to censor online speech. --- ## 9) The Architects of Speech Policing: CCDH 🕵️♂️ The **Center for Countering Digital Hate (CCDH)**—a UK intelligence-backed group—has been a driving force behind global censorship. They were caught: - Running “black ops” to suppress RFK Jr.’s presidential campaign. - Leading the "Kill Musk’s Twitter" directive, trying to shut down free speech on X. - Labeling 12 private US citizens as the “Disinformation Dozen” to justify mass censorship. 🔗 [Reclaim the Net Investigation](https://reclaimthenet.org/black-ops-how-a-us-uk-censorship-group-targeted-rfk-jr-to-stifle-dissent) --- ## 10) The Pattern is Clear: Surveillance + Censorship 🔍 1️⃣ Governments create "safety" laws to justify surveillance. 2️⃣ They pressure tech companies to enforce censorship. 3️⃣ Once encrypted services are gone, nothing is private anymore. This is the biggest attack on digital freedom in history. --- ## 11) What Can We Do? 💪 - **Support companies** that refuse to build backdoors (Signal, ProtonMail, etc.). - **Push for legislation** that protects encryption & free speech. - **Stay informed** & spread awareness—governments count on secrecy to push these policies through. - Follow and support privacy and internet freedom organizations such as: - [@G_W_Forum](https://twitter.com/G_W_Forum) - [@FFO_Freedom](https://twitter.com/FFO_Freedom) - [@ReclaimTheNetHQ](https://twitter.com/ReclaimTheNetHQ) --- ## 12) The Ultimate Power Grab: Controlling All Digital Communication 📱 If Apple caves, every other platform will be forced to follow. 📌 The UK’s Global Playbook: - A backdoor to encryption (Investigatory Powers Act). - A government-linked censorship network (CCDH). - A speech-policing framework that extends worldwide (Online Safety Bill). This is a global effort to control what people can say, share, and store privately. --- ## 13) The Final Stand: Will You Comply or Resist? ⚔️🚨 They want total control—your speech, your privacy, your elections. This is the defining battle of our time. 🇬🇧 UK’s war on encryption = Global censorship blueprint. 🗳️ Election meddling + speech policing = A hijacked democracy. 📢 **Digital freedom is human freedom.** Stand up. Speak out. Fight back. 🏴☠️🔥 🔗 [LEARN MORE](https://sayerji.substack.com/p/crossfire-of-democracy-uk-labour?utm_source=publication-search) --- *Full thread preserved by [Thread Reader App](https://threadreaderapp.com/thread/1888287793123901896.html).* @ ee7e3590:5602f192
2025-02-01 05:00:39You’re hitting on the core tension: **unlimited demand for emergency care collides with finite resources**, and pretending otherwise leads to either runaway costs or rationing-by-stealth. Let’s confront this head-on with free-market-aligned solutions that don’t ignore human realities: --- ### **1. Redefine "Emergency Care"** The U.S. legally mandates ERs to stabilize *anyone*, regardless of ability to pay (EMTALA). This creates moral hazard: - **Problem**: Hospitals inflate prices on paying patients to offset uncompensated care. - **Free-Market Fix**: - **Repeal EMTALA**: Allow ERs to refuse non-critical cases (e.g., toothaches, rashes) unless prepaid or insured. - **Clarify "True Emergency"**: Legally define emergencies as *immediate life threats* (e.g., strokes, cardiac arrest) and let non-critical cases be diverted to urgent care. - **Consequence**: ERs could price transparently for true emergencies, while non-critical cases face market-driven urgent care options. --- ### **2. Embrace Tiered Emergency Care** Not all emergencies require Level I trauma centers: - **Basic ERs**: Staffed by NPs and paramedics for minor injuries (e.g., sprains, minor burns) at lower costs. - **Advanced ERs**: For critical care (e.g., gunshot wounds), priced higher but competing via outcomes (e.g., survival rates). - **Example**: India’s *Ziqitza Healthcare* operates ambulance tiers—basic vans for transport and advanced ICU units. --- ### **3. **Address Moral Hazard with Insurance Innovation** - **Catastrophic Insurance Mandates**: Require everyone to carry cheap, high-deductible plans covering *only* true emergencies (e.g., $10/month for coverage above $50k). - Incentivizes price shopping for non-emergencies. - Prevents freeloading on ERs. - **Risk-Adjusted Premiums**: Smokers, skydivers, or diabetics pay higher premiums, aligning costs with personal choices. --- ### **4. **Community-Based Safety Nets** - **Mutual Aid Networks**: Local groups negotiate bulk ER rates (e.g., $100/month membership covers three ER visits annually). - **Crowdfunding ER Vouchers**: Platforms like *GoFundMe* could partner with hospitals to prepurchase discounted emergency care slots. --- ### **5. **Radical Transparency + Bankruptcy Reform** - **ER Debt Auctions**: Let hospitals sell unpaid ER bills to collection agencies in real-time, creating competition to minimize patient liability. - **Flat-Fee ER Pricing**: Hospitals post rates like “$5,000 for appendicitis stabilization, all-inclusive” to deter surprise billing. - **Ban Wage Garnishment for Medical Debt**: Protect patients from lifelong ruin, forcing hospitals to price responsibly or absorb losses. --- ### **6. **Accept Trade-Offs Explicitly** The U.S. system fails because it hides rationing behind complexity. A free-market approach must embrace transparency: - **Option 1**: Pay $100,000 for a 95% survival rate in a car crash. - **Option 2**: Pay $20,000 for a 70% survival rate at a budget ER. - **Brutal but Honest**: Let individuals (or insurers) choose their risk tolerance upfront. **Example**: - **Japan’s Price Controls**: Caps ER costs but tolerates wait times (e.g., 8+ hours for non-critical care). - **Switzerland’s Mandates**: Everyone buys insurance, but ERs charge $1,000+ deductibles to deter overuse. --- ### **7. **Disrupt with Decentralized Care** - **Crypto-ERs**: Blockchain-based emergency funds where contributors vote on covering members’ bills. - **AI-Guided Self-Care**: Apps that stabilize patients en route to ERs (e.g., tourniquet tutorials, overdose reversal guidance). --- ### **8. **Reform Malpractice to Reduce Defensive Medicine** - **“No Pay, No Harm” Liability**: If a patient doesn’t pay, they can’t sue for malpractice (incentivizing upfront pricing). - **Safe Harbor Protocols**: ERs using approved, cost-effective treatments (e.g., generics) get immunity from lawsuits. --- ### **The Uncomfortable Truth** A free market in emergency care requires accepting that **not everyone will be saved**—just as not everyone can afford a Ferrari. The alternative is the current U.S. model, which *pretends* to save everyone but bankrupts millions and still leaves 30% of ER visits unmet due to overcrowding. By legalizing tiered care, deregulating monopolies, and forcing transparency, you create a system where: - **Elites** pay premium prices for cutting-edge emergency care. - **Most** get “good enough” stabilization at reasonable costs. - **Some** choose cheap, high-risk options (or none at all). This isn’t pretty, but it’s honest—and arguably more ethical than today’s hidden rationing and financial toxicity.
@ ee7e3590:5602f192
2025-02-01 05:00:39You’re hitting on the core tension: **unlimited demand for emergency care collides with finite resources**, and pretending otherwise leads to either runaway costs or rationing-by-stealth. Let’s confront this head-on with free-market-aligned solutions that don’t ignore human realities: --- ### **1. Redefine "Emergency Care"** The U.S. legally mandates ERs to stabilize *anyone*, regardless of ability to pay (EMTALA). This creates moral hazard: - **Problem**: Hospitals inflate prices on paying patients to offset uncompensated care. - **Free-Market Fix**: - **Repeal EMTALA**: Allow ERs to refuse non-critical cases (e.g., toothaches, rashes) unless prepaid or insured. - **Clarify "True Emergency"**: Legally define emergencies as *immediate life threats* (e.g., strokes, cardiac arrest) and let non-critical cases be diverted to urgent care. - **Consequence**: ERs could price transparently for true emergencies, while non-critical cases face market-driven urgent care options. --- ### **2. Embrace Tiered Emergency Care** Not all emergencies require Level I trauma centers: - **Basic ERs**: Staffed by NPs and paramedics for minor injuries (e.g., sprains, minor burns) at lower costs. - **Advanced ERs**: For critical care (e.g., gunshot wounds), priced higher but competing via outcomes (e.g., survival rates). - **Example**: India’s *Ziqitza Healthcare* operates ambulance tiers—basic vans for transport and advanced ICU units. --- ### **3. **Address Moral Hazard with Insurance Innovation** - **Catastrophic Insurance Mandates**: Require everyone to carry cheap, high-deductible plans covering *only* true emergencies (e.g., $10/month for coverage above $50k). - Incentivizes price shopping for non-emergencies. - Prevents freeloading on ERs. - **Risk-Adjusted Premiums**: Smokers, skydivers, or diabetics pay higher premiums, aligning costs with personal choices. --- ### **4. **Community-Based Safety Nets** - **Mutual Aid Networks**: Local groups negotiate bulk ER rates (e.g., $100/month membership covers three ER visits annually). - **Crowdfunding ER Vouchers**: Platforms like *GoFundMe* could partner with hospitals to prepurchase discounted emergency care slots. --- ### **5. **Radical Transparency + Bankruptcy Reform** - **ER Debt Auctions**: Let hospitals sell unpaid ER bills to collection agencies in real-time, creating competition to minimize patient liability. - **Flat-Fee ER Pricing**: Hospitals post rates like “$5,000 for appendicitis stabilization, all-inclusive” to deter surprise billing. - **Ban Wage Garnishment for Medical Debt**: Protect patients from lifelong ruin, forcing hospitals to price responsibly or absorb losses. --- ### **6. **Accept Trade-Offs Explicitly** The U.S. system fails because it hides rationing behind complexity. A free-market approach must embrace transparency: - **Option 1**: Pay $100,000 for a 95% survival rate in a car crash. - **Option 2**: Pay $20,000 for a 70% survival rate at a budget ER. - **Brutal but Honest**: Let individuals (or insurers) choose their risk tolerance upfront. **Example**: - **Japan’s Price Controls**: Caps ER costs but tolerates wait times (e.g., 8+ hours for non-critical care). - **Switzerland’s Mandates**: Everyone buys insurance, but ERs charge $1,000+ deductibles to deter overuse. --- ### **7. **Disrupt with Decentralized Care** - **Crypto-ERs**: Blockchain-based emergency funds where contributors vote on covering members’ bills. - **AI-Guided Self-Care**: Apps that stabilize patients en route to ERs (e.g., tourniquet tutorials, overdose reversal guidance). --- ### **8. **Reform Malpractice to Reduce Defensive Medicine** - **“No Pay, No Harm” Liability**: If a patient doesn’t pay, they can’t sue for malpractice (incentivizing upfront pricing). - **Safe Harbor Protocols**: ERs using approved, cost-effective treatments (e.g., generics) get immunity from lawsuits. --- ### **The Uncomfortable Truth** A free market in emergency care requires accepting that **not everyone will be saved**—just as not everyone can afford a Ferrari. The alternative is the current U.S. model, which *pretends* to save everyone but bankrupts millions and still leaves 30% of ER visits unmet due to overcrowding. By legalizing tiered care, deregulating monopolies, and forcing transparency, you create a system where: - **Elites** pay premium prices for cutting-edge emergency care. - **Most** get “good enough” stabilization at reasonable costs. - **Some** choose cheap, high-risk options (or none at all). This isn’t pretty, but it’s honest—and arguably more ethical than today’s hidden rationing and financial toxicity. @ c4551bf3:f041d130
2025-02-10 08:21:56TA88 là một nền tảng kỹ thuật số tiên tiến, mang đến trải nghiệm trực tuyến mượt mà và ổn định cho người dùng. Với giao diện thân thiện và thiết kế tối ưu, TA88 giúp người dùng dễ dàng truy cập trên cả máy tính và thiết bị di động. Nền tảng này được xây dựng trên công nghệ hiện đại, đảm bảo tốc độ xử lý nhanh, kết nối ổn định và khả năng tương thích cao, mang đến sự tiện lợi và linh hoạt tối đa cho người dùng. Không ngừng đổi mới, <a href="https://ta88-vn.com">TA88</a> liên tục cập nhật và nâng cấp hệ thống để mang đến chất lượng dịch vụ tốt nhất. Nền tảng này tích hợp nhiều công nghệ tiên tiến, giúp tối ưu hóa hiệu suất và nâng cao trải nghiệm người dùng. Nhờ vào sự cải tiến không ngừng, TA88 mang đến không gian giải trí phong phú, hấp dẫn và luôn bắt kịp xu hướng công nghệ, giúp người dùng có những trải nghiệm mới mẻ và thú vị. Bên cạnh việc tập trung vào công nghệ, TA88 cũng đặc biệt chú trọng đến bảo mật và quyền riêng tư. Hệ thống bảo mật đa lớp với các giao thức mã hóa tiên tiến giúp bảo vệ dữ liệu cá nhân của người dùng một cách an toàn tuyệt đối. Việc áp dụng các biện pháp bảo mật nghiêm ngặt giúp TA88 đảm bảo môi trường trực tuyến an toàn, giúp người dùng yên tâm tận hưởng những tiện ích mà nền tảng mang lại. Không chỉ tập trung vào công nghệ hiện đại, TA88 còn đầu tư mạnh mẽ vào dịch vụ chăm sóc khách hàng. Đội ngũ hỗ trợ chuyên nghiệp luôn sẵn sàng giải đáp mọi thắc mắc và cung cấp sự trợ giúp nhanh chóng, đảm bảo người dùng có trải nghiệm thuận tiện và hài lòng nhất. Sự tận tâm và chuyên nghiệp trong dịch vụ khách hàng là yếu tố giúp TA88 xây dựng lòng tin và sự trung thành từ cộng đồng người dùng. Với những ưu điểm vượt trội, TA88 không ngừng đổi mới và phát triển để mang đến những trải nghiệm tối ưu. Nền tảng này liên tục cập nhật công nghệ, mở rộng tính năng và tối ưu hóa dịch vụ nhằm duy trì vị thế hàng đầu trong lĩnh vực giải trí kỹ thuật số. Nhờ vào sự kết hợp giữa công nghệ hiện đại, tính bảo mật cao và dịch vụ chuyên nghiệp, TA88 đã trở thành một trong những lựa chọn hàng đầu cho những ai tìm kiếm một nền tảng trực tuyến tiện lợi, an toàn và đáng tin cậy.
@ c4551bf3:f041d130
2025-02-10 08:21:56TA88 là một nền tảng kỹ thuật số tiên tiến, mang đến trải nghiệm trực tuyến mượt mà và ổn định cho người dùng. Với giao diện thân thiện và thiết kế tối ưu, TA88 giúp người dùng dễ dàng truy cập trên cả máy tính và thiết bị di động. Nền tảng này được xây dựng trên công nghệ hiện đại, đảm bảo tốc độ xử lý nhanh, kết nối ổn định và khả năng tương thích cao, mang đến sự tiện lợi và linh hoạt tối đa cho người dùng. Không ngừng đổi mới, <a href="https://ta88-vn.com">TA88</a> liên tục cập nhật và nâng cấp hệ thống để mang đến chất lượng dịch vụ tốt nhất. Nền tảng này tích hợp nhiều công nghệ tiên tiến, giúp tối ưu hóa hiệu suất và nâng cao trải nghiệm người dùng. Nhờ vào sự cải tiến không ngừng, TA88 mang đến không gian giải trí phong phú, hấp dẫn và luôn bắt kịp xu hướng công nghệ, giúp người dùng có những trải nghiệm mới mẻ và thú vị. Bên cạnh việc tập trung vào công nghệ, TA88 cũng đặc biệt chú trọng đến bảo mật và quyền riêng tư. Hệ thống bảo mật đa lớp với các giao thức mã hóa tiên tiến giúp bảo vệ dữ liệu cá nhân của người dùng một cách an toàn tuyệt đối. Việc áp dụng các biện pháp bảo mật nghiêm ngặt giúp TA88 đảm bảo môi trường trực tuyến an toàn, giúp người dùng yên tâm tận hưởng những tiện ích mà nền tảng mang lại. Không chỉ tập trung vào công nghệ hiện đại, TA88 còn đầu tư mạnh mẽ vào dịch vụ chăm sóc khách hàng. Đội ngũ hỗ trợ chuyên nghiệp luôn sẵn sàng giải đáp mọi thắc mắc và cung cấp sự trợ giúp nhanh chóng, đảm bảo người dùng có trải nghiệm thuận tiện và hài lòng nhất. Sự tận tâm và chuyên nghiệp trong dịch vụ khách hàng là yếu tố giúp TA88 xây dựng lòng tin và sự trung thành từ cộng đồng người dùng. Với những ưu điểm vượt trội, TA88 không ngừng đổi mới và phát triển để mang đến những trải nghiệm tối ưu. Nền tảng này liên tục cập nhật công nghệ, mở rộng tính năng và tối ưu hóa dịch vụ nhằm duy trì vị thế hàng đầu trong lĩnh vực giải trí kỹ thuật số. Nhờ vào sự kết hợp giữa công nghệ hiện đại, tính bảo mật cao và dịch vụ chuyên nghiệp, TA88 đã trở thành một trong những lựa chọn hàng đầu cho những ai tìm kiếm một nền tảng trực tuyến tiện lợi, an toàn và đáng tin cậy. @ 000002de:c05780a7
2025-01-30 21:17:26 > The Debian Publicity Team will no longer post on X/Twitter. We took this decision since we feel X doesn't reflect Debian shared values as stated in our social contract, code of conduct and diversity statement. X evolved into a place where people we care about don't feel safe. A couple red flags in this post that explain their actions. 1. Shared values - projects that have broad values statements are prone to isolation over time 2. Social contract - that's a meaningless vapid term I have no issue with code of conduct guidelines or having value statements but when you pick sides on cultural divides and things that are not at all related to the logical objective of a project you are going to end up where Debian has landed. X has its issues, I'm not a fan but the reasoning behind this seems really off. One Debian user responded with what I thought was a good summary of why this is a bad move. > I'm a long-time Debian user and fan, and am also one of the champions for using Debian in space-based applications at NASA. > IMO this is a short-sighted and foolish decision. The notion of "values" is bring sadly misapplied here. > I urge you to reconsider. More channels of communication, even with those whom you disagree with, is good for both Debian and your user community. I'm not into the "anti-woke" or "woke" crap and I dare say most people that use Linux do not care about either side very much at all. A loud minority has been gaining power in these types of projects for a long time. Today we have very loud counters to that group that also can be annoying and out of line. Will be interesting to watch this all unfold over the next few years. Conservatives seem to be running victory laps and I think that's not only premature but also counter-productive. I can see leaving X for other reasons. * Debian users are really using it to communicate with the project * The Debian publicity team isn't seeing very much of a response for their efforts * X has become more about politics than tech and communication * Specific examples of how X is causing issues for the project They do say this > X evolved into a place where people we care about don't feel safe. That's too bad but honestly I don't buy it. Maybe I don't spend enough time on X to have much credibility on this but I'm skeptical of this being the case. originally posted at https://stacker.news/items/870437
@ 000002de:c05780a7
2025-01-30 21:17:26 > The Debian Publicity Team will no longer post on X/Twitter. We took this decision since we feel X doesn't reflect Debian shared values as stated in our social contract, code of conduct and diversity statement. X evolved into a place where people we care about don't feel safe. A couple red flags in this post that explain their actions. 1. Shared values - projects that have broad values statements are prone to isolation over time 2. Social contract - that's a meaningless vapid term I have no issue with code of conduct guidelines or having value statements but when you pick sides on cultural divides and things that are not at all related to the logical objective of a project you are going to end up where Debian has landed. X has its issues, I'm not a fan but the reasoning behind this seems really off. One Debian user responded with what I thought was a good summary of why this is a bad move. > I'm a long-time Debian user and fan, and am also one of the champions for using Debian in space-based applications at NASA. > IMO this is a short-sighted and foolish decision. The notion of "values" is bring sadly misapplied here. > I urge you to reconsider. More channels of communication, even with those whom you disagree with, is good for both Debian and your user community. I'm not into the "anti-woke" or "woke" crap and I dare say most people that use Linux do not care about either side very much at all. A loud minority has been gaining power in these types of projects for a long time. Today we have very loud counters to that group that also can be annoying and out of line. Will be interesting to watch this all unfold over the next few years. Conservatives seem to be running victory laps and I think that's not only premature but also counter-productive. I can see leaving X for other reasons. * Debian users are really using it to communicate with the project * The Debian publicity team isn't seeing very much of a response for their efforts * X has become more about politics than tech and communication * Specific examples of how X is causing issues for the project They do say this > X evolved into a place where people we care about don't feel safe. That's too bad but honestly I don't buy it. Maybe I don't spend enough time on X to have much credibility on this but I'm skeptical of this being the case. originally posted at https://stacker.news/items/870437 @ c4551bf3:f041d130
2025-02-10 08:20:56333Win là một nền tảng kỹ thuật số tiên tiến, mang đến trải nghiệm trực tuyến mượt mà và ổn định cho người dùng. Với giao diện thân thiện và thiết kế tối ưu, 333Win giúp người dùng dễ dàng truy cập trên cả máy tính và thiết bị di động. Hệ thống được xây dựng trên nền tảng công nghệ hiện đại, đảm bảo tốc độ xử lý nhanh, kết nối ổn định và hiệu suất tối ưu, giúp người dùng có những trải nghiệm liền mạch, tiện lợi mọi lúc, mọi nơi. Không ngừng đổi mới, <a href="https://333win.site">333WIN</a> liên tục cập nhật và nâng cấp hệ thống nhằm mang đến chất lượng dịch vụ tốt nhất. Nền tảng này tích hợp nhiều công nghệ tiên tiến để tối ưu hóa hiệu suất, giúp nâng cao sự tiện lợi và linh hoạt trong quá trình sử dụng. Nhờ vào sự cải tiến không ngừng, 333Win tạo ra một không gian giải trí phong phú, hấp dẫn và phù hợp với nhu cầu đa dạng, giúp người dùng luôn có những trải nghiệm trọn vẹn và mới mẻ. Bên cạnh công nghệ tiên tiến, 333Win cũng đặc biệt chú trọng đến bảo mật và quyền riêng tư. Hệ thống bảo mật đa lớp với các giao thức mã hóa tiên tiến giúp bảo vệ dữ liệu cá nhân của người dùng một cách an toàn tuyệt đối. Việc áp dụng các biện pháp bảo vệ nghiêm ngặt giúp 333Win đảm bảo môi trường trực tuyến an toàn, giúp người dùng yên tâm tận hưởng những tiện ích mà nền tảng mang lại. Không chỉ tập trung vào công nghệ hiện đại, 333Win còn chú trọng đến chất lượng dịch vụ chăm sóc khách hàng. Đội ngũ hỗ trợ chuyên nghiệp luôn sẵn sàng giải đáp thắc mắc và cung cấp sự trợ giúp nhanh chóng, đảm bảo trải nghiệm người dùng luôn thuận tiện và hài lòng. Sự tận tâm và chuyên nghiệp trong dịch vụ là yếu tố giúp 333Win xây dựng lòng tin và sự trung thành từ cộng đồng người dùng. Với những ưu điểm vượt trội, 333Win không ngừng đổi mới và phát triển để mang đến những trải nghiệm tốt nhất. Nền tảng này liên tục cập nhật công nghệ, mở rộng tính năng và tối ưu hóa dịch vụ nhằm duy trì vị thế hàng đầu trong lĩnh vực giải trí kỹ thuật số. Nhờ vào sự kết hợp giữa công nghệ hiện đại, tính bảo mật cao và dịch vụ chuyên nghiệp, 333Win đã trở thành một trong những lựa chọn hàng đầu cho những ai tìm kiếm một nền tảng trực tuyến tiện lợi, an toàn và đáng tin cậy.
@ c4551bf3:f041d130
2025-02-10 08:20:56333Win là một nền tảng kỹ thuật số tiên tiến, mang đến trải nghiệm trực tuyến mượt mà và ổn định cho người dùng. Với giao diện thân thiện và thiết kế tối ưu, 333Win giúp người dùng dễ dàng truy cập trên cả máy tính và thiết bị di động. Hệ thống được xây dựng trên nền tảng công nghệ hiện đại, đảm bảo tốc độ xử lý nhanh, kết nối ổn định và hiệu suất tối ưu, giúp người dùng có những trải nghiệm liền mạch, tiện lợi mọi lúc, mọi nơi. Không ngừng đổi mới, <a href="https://333win.site">333WIN</a> liên tục cập nhật và nâng cấp hệ thống nhằm mang đến chất lượng dịch vụ tốt nhất. Nền tảng này tích hợp nhiều công nghệ tiên tiến để tối ưu hóa hiệu suất, giúp nâng cao sự tiện lợi và linh hoạt trong quá trình sử dụng. Nhờ vào sự cải tiến không ngừng, 333Win tạo ra một không gian giải trí phong phú, hấp dẫn và phù hợp với nhu cầu đa dạng, giúp người dùng luôn có những trải nghiệm trọn vẹn và mới mẻ. Bên cạnh công nghệ tiên tiến, 333Win cũng đặc biệt chú trọng đến bảo mật và quyền riêng tư. Hệ thống bảo mật đa lớp với các giao thức mã hóa tiên tiến giúp bảo vệ dữ liệu cá nhân của người dùng một cách an toàn tuyệt đối. Việc áp dụng các biện pháp bảo vệ nghiêm ngặt giúp 333Win đảm bảo môi trường trực tuyến an toàn, giúp người dùng yên tâm tận hưởng những tiện ích mà nền tảng mang lại. Không chỉ tập trung vào công nghệ hiện đại, 333Win còn chú trọng đến chất lượng dịch vụ chăm sóc khách hàng. Đội ngũ hỗ trợ chuyên nghiệp luôn sẵn sàng giải đáp thắc mắc và cung cấp sự trợ giúp nhanh chóng, đảm bảo trải nghiệm người dùng luôn thuận tiện và hài lòng. Sự tận tâm và chuyên nghiệp trong dịch vụ là yếu tố giúp 333Win xây dựng lòng tin và sự trung thành từ cộng đồng người dùng. Với những ưu điểm vượt trội, 333Win không ngừng đổi mới và phát triển để mang đến những trải nghiệm tốt nhất. Nền tảng này liên tục cập nhật công nghệ, mở rộng tính năng và tối ưu hóa dịch vụ nhằm duy trì vị thế hàng đầu trong lĩnh vực giải trí kỹ thuật số. Nhờ vào sự kết hợp giữa công nghệ hiện đại, tính bảo mật cao và dịch vụ chuyên nghiệp, 333Win đã trở thành một trong những lựa chọn hàng đầu cho những ai tìm kiếm một nền tảng trực tuyến tiện lợi, an toàn và đáng tin cậy. @ 1cb14ab3:95d52462
2025-01-30 18:45:41               --- #### Other Photo Series by Hes: [City Series](https://hes.npub.pro/post/1734817611982/) [Structural Reflections](https://hes.npub.pro/post/1720570208841/) --- #### More from Hes: [Long Form](https://hes.npub.pro/) [Art Portfolio](https://hesart.npub.pro/) [Online Store](https://plebeian.market/community/1cb14ab335876fc9efc37d838ba287cf17e5adcccb20bf6d49f9da9695d52462:hesmart-ym3fcufdfz) [Travel Guides](https://hes.npub.pro/tag/travel/) [Photography](https://hes.npub.pro/tag/photography/) [Writings](https://hes.npub.pro/tag/money) --- *All images are credit of Hes, but you are free to download and use for any purpose. If you find joy from these photos, please feel free to send a zap. Enjoy life on a Bitcoin standard.*
@ 1cb14ab3:95d52462
2025-01-30 18:45:41               --- #### Other Photo Series by Hes: [City Series](https://hes.npub.pro/post/1734817611982/) [Structural Reflections](https://hes.npub.pro/post/1720570208841/) --- #### More from Hes: [Long Form](https://hes.npub.pro/) [Art Portfolio](https://hesart.npub.pro/) [Online Store](https://plebeian.market/community/1cb14ab335876fc9efc37d838ba287cf17e5adcccb20bf6d49f9da9695d52462:hesmart-ym3fcufdfz) [Travel Guides](https://hes.npub.pro/tag/travel/) [Photography](https://hes.npub.pro/tag/photography/) [Writings](https://hes.npub.pro/tag/money) --- *All images are credit of Hes, but you are free to download and use for any purpose. If you find joy from these photos, please feel free to send a zap. Enjoy life on a Bitcoin standard.* @ c4551bf3:f041d130
2025-02-10 08:19:466623 là một nền tảng kỹ thuật số tiên tiến, mang đến trải nghiệm trực tuyến mượt mà và ổn định cho người dùng. Với giao diện thân thiện và thiết kế tối ưu, 6623 giúp người dùng dễ dàng truy cập trên cả máy tính và thiết bị di động. Hệ thống được phát triển với công nghệ hiện đại, đảm bảo tốc độ xử lý nhanh, kết nối ổn định và hiệu suất tối ưu, giúp người dùng tận hưởng dịch vụ tiện lợi và liền mạch mọi lúc, mọi nơi. Một trong những ưu điểm nổi bật của <a href="https://6623-vn.com">6623</a> là sự đổi mới và cập nhật liên tục nhằm nâng cao chất lượng dịch vụ. Nền tảng này luôn tích hợp các công nghệ tiên tiến nhất để tối ưu hóa hiệu suất và mang đến trải nghiệm linh hoạt cho người dùng. Nhờ vào sự cải tiến không ngừng, 6623 tạo ra một không gian giải trí phong phú, hấp dẫn và phù hợp với nhu cầu đa dạng, giúp người dùng luôn có những trải nghiệm trọn vẹn và mới mẻ. Bên cạnh việc tập trung vào công nghệ, 6623 đặc biệt chú trọng đến bảo mật và quyền riêng tư của người dùng. Hệ thống bảo mật đa lớp với các giao thức mã hóa tiên tiến giúp bảo vệ dữ liệu cá nhân một cách an toàn tuyệt đối. Các biện pháp bảo mật nghiêm ngặt đảm bảo môi trường trực tuyến an toàn, giúp người dùng yên tâm khi trải nghiệm nền tảng mà không lo lắng về các rủi ro bảo mật. Không chỉ tập trung vào công nghệ hiện đại, 6623 còn cung cấp dịch vụ chăm sóc khách hàng chuyên nghiệp. Đội ngũ hỗ trợ luôn sẵn sàng giải đáp thắc mắc và cung cấp sự trợ giúp nhanh chóng, đảm bảo trải nghiệm người dùng luôn thuận tiện và hài lòng nhất. Sự tận tâm trong dịch vụ là một trong những yếu tố quan trọng giúp 6623 xây dựng lòng tin và sự gắn kết với cộng đồng người dùng. Với những ưu điểm vượt trội, 6623 không ngừng đổi mới và phát triển để mang đến những trải nghiệm tốt nhất. Nền tảng này liên tục cập nhật công nghệ, mở rộng tính năng và tối ưu hóa dịch vụ nhằm duy trì vị thế hàng đầu trong lĩnh vực giải trí kỹ thuật số. Nhờ vào sự kết hợp giữa công nghệ tiên tiến, bảo mật tối đa và dịch vụ chuyên nghiệp, 6623 đã trở thành một trong những lựa chọn hàng đầu cho những ai tìm kiếm một nền tảng trực tuyến hiện đại, tiện lợi và đáng tin cậy.
@ c4551bf3:f041d130
2025-02-10 08:19:466623 là một nền tảng kỹ thuật số tiên tiến, mang đến trải nghiệm trực tuyến mượt mà và ổn định cho người dùng. Với giao diện thân thiện và thiết kế tối ưu, 6623 giúp người dùng dễ dàng truy cập trên cả máy tính và thiết bị di động. Hệ thống được phát triển với công nghệ hiện đại, đảm bảo tốc độ xử lý nhanh, kết nối ổn định và hiệu suất tối ưu, giúp người dùng tận hưởng dịch vụ tiện lợi và liền mạch mọi lúc, mọi nơi. Một trong những ưu điểm nổi bật của <a href="https://6623-vn.com">6623</a> là sự đổi mới và cập nhật liên tục nhằm nâng cao chất lượng dịch vụ. Nền tảng này luôn tích hợp các công nghệ tiên tiến nhất để tối ưu hóa hiệu suất và mang đến trải nghiệm linh hoạt cho người dùng. Nhờ vào sự cải tiến không ngừng, 6623 tạo ra một không gian giải trí phong phú, hấp dẫn và phù hợp với nhu cầu đa dạng, giúp người dùng luôn có những trải nghiệm trọn vẹn và mới mẻ. Bên cạnh việc tập trung vào công nghệ, 6623 đặc biệt chú trọng đến bảo mật và quyền riêng tư của người dùng. Hệ thống bảo mật đa lớp với các giao thức mã hóa tiên tiến giúp bảo vệ dữ liệu cá nhân một cách an toàn tuyệt đối. Các biện pháp bảo mật nghiêm ngặt đảm bảo môi trường trực tuyến an toàn, giúp người dùng yên tâm khi trải nghiệm nền tảng mà không lo lắng về các rủi ro bảo mật. Không chỉ tập trung vào công nghệ hiện đại, 6623 còn cung cấp dịch vụ chăm sóc khách hàng chuyên nghiệp. Đội ngũ hỗ trợ luôn sẵn sàng giải đáp thắc mắc và cung cấp sự trợ giúp nhanh chóng, đảm bảo trải nghiệm người dùng luôn thuận tiện và hài lòng nhất. Sự tận tâm trong dịch vụ là một trong những yếu tố quan trọng giúp 6623 xây dựng lòng tin và sự gắn kết với cộng đồng người dùng. Với những ưu điểm vượt trội, 6623 không ngừng đổi mới và phát triển để mang đến những trải nghiệm tốt nhất. Nền tảng này liên tục cập nhật công nghệ, mở rộng tính năng và tối ưu hóa dịch vụ nhằm duy trì vị thế hàng đầu trong lĩnh vực giải trí kỹ thuật số. Nhờ vào sự kết hợp giữa công nghệ tiên tiến, bảo mật tối đa và dịch vụ chuyên nghiệp, 6623 đã trở thành một trong những lựa chọn hàng đầu cho những ai tìm kiếm một nền tảng trực tuyến hiện đại, tiện lợi và đáng tin cậy. @ cc8d072e:a6a026cb
2025-01-30 17:20:24Recently, I had the opportunity to work as an advisor for an AI agent project, which is created by team with a lot of fin-tech software develop experience. As we coded together, their real-time questions and challenges provided unique insights into the hurdles software engineers face when transitioning to AI development. They would pause at moments that most AI engineers take for granted - "How can we be sure the agent understood correctly?", "What if the model makes a mistake?", "How do we handle the uncertainty?" These weren't just isolated questions; they represented the fundamental paradigm shift required when moving from traditional software engineering to AI development. And thats why i think it might be worthy to take sometime write down this article and if you are going to start your first AI agent programming, spending 5 min reading t his will save you a lot of time later. ### 1. Shifting from Deterministic to Probabilistic Thinking - Traditional software engineering deals with deterministic outcomes - AI systems operate on probability rather than certainty - Engineers need to adapt from "100% correct" mindset to accepting probabilistic outcomes - Blockchain developers may find this particularly challenging due to their background in exact, deterministic systems ### 2. Understanding Core AI Concepts (There are a lot of concepts to understand, but i will focus on the most frequently asked ones) #### Memory Management - **Short-term Memory**: Implemented through conversation context - **Long-term Memory**: Implemented through vector databases (RAG - Retrieval Augmented Generation) - Context length management is crucial due to LLM token limitations #### Language Models and Fine-tuning - Base models (like GPT) provide general intelligence - Domain-specific knowledge can be added through: - Fine-tuning with custom datasets - Adding RAG layers for specific knowledge domains ### 3. Technical Framework Knowledge #### Essential Tools and Frameworks - Vercel AI SDK (if you are a typescript guy) - LangChain (alternative option) - Different models(openai, claude, gemini, etc, of course, now, deepseek. the temu in llm ) - Understanding of prompt engineering #### Multi-Agent Systems - Agents can communicate through natural language - Inter-agent communication requires careful system design - Implementation of thought processes and decision-making loops - Safety considerations for system commands and operations ### 4. Language and Localization Considerations - System prompts typically work best in English - Multi-language support requires careful handling: - Input translation to English - Processing in English - Output translation to target language - Model performance varies across different languages ### 5. Safety and Error Handling - Implementing validation layers for critical operations - Understanding model limitations and potential errors - Building feedback mechanisms to detect misunderstandings ## Conclusion Transitioning from software engineering to AI engineering requires a significant mindset shift. While traditional software engineering skills remain valuable, understanding probabilistic systems, language models, and AI-specific architectures is crucial. The key is to balance innovation with practical safety considerations, especially when dealing with critical applications. Remember that AI systems are not perfect, and building robust applications requires careful consideration of their limitations and appropriate safety measures. Start with existing frameworks and gradually build up complexity as you become more comfortable with AI-specific concepts and challenges.(the conclusion part is written by chatgpt, did you notice? :))
@ cc8d072e:a6a026cb
2025-01-30 17:20:24Recently, I had the opportunity to work as an advisor for an AI agent project, which is created by team with a lot of fin-tech software develop experience. As we coded together, their real-time questions and challenges provided unique insights into the hurdles software engineers face when transitioning to AI development. They would pause at moments that most AI engineers take for granted - "How can we be sure the agent understood correctly?", "What if the model makes a mistake?", "How do we handle the uncertainty?" These weren't just isolated questions; they represented the fundamental paradigm shift required when moving from traditional software engineering to AI development. And thats why i think it might be worthy to take sometime write down this article and if you are going to start your first AI agent programming, spending 5 min reading t his will save you a lot of time later. ### 1. Shifting from Deterministic to Probabilistic Thinking - Traditional software engineering deals with deterministic outcomes - AI systems operate on probability rather than certainty - Engineers need to adapt from "100% correct" mindset to accepting probabilistic outcomes - Blockchain developers may find this particularly challenging due to their background in exact, deterministic systems ### 2. Understanding Core AI Concepts (There are a lot of concepts to understand, but i will focus on the most frequently asked ones) #### Memory Management - **Short-term Memory**: Implemented through conversation context - **Long-term Memory**: Implemented through vector databases (RAG - Retrieval Augmented Generation) - Context length management is crucial due to LLM token limitations #### Language Models and Fine-tuning - Base models (like GPT) provide general intelligence - Domain-specific knowledge can be added through: - Fine-tuning with custom datasets - Adding RAG layers for specific knowledge domains ### 3. Technical Framework Knowledge #### Essential Tools and Frameworks - Vercel AI SDK (if you are a typescript guy) - LangChain (alternative option) - Different models(openai, claude, gemini, etc, of course, now, deepseek. the temu in llm ) - Understanding of prompt engineering #### Multi-Agent Systems - Agents can communicate through natural language - Inter-agent communication requires careful system design - Implementation of thought processes and decision-making loops - Safety considerations for system commands and operations ### 4. Language and Localization Considerations - System prompts typically work best in English - Multi-language support requires careful handling: - Input translation to English - Processing in English - Output translation to target language - Model performance varies across different languages ### 5. Safety and Error Handling - Implementing validation layers for critical operations - Understanding model limitations and potential errors - Building feedback mechanisms to detect misunderstandings ## Conclusion Transitioning from software engineering to AI engineering requires a significant mindset shift. While traditional software engineering skills remain valuable, understanding probabilistic systems, language models, and AI-specific architectures is crucial. The key is to balance innovation with practical safety considerations, especially when dealing with critical applications. Remember that AI systems are not perfect, and building robust applications requires careful consideration of their limitations and appropriate safety measures. Start with existing frameworks and gradually build up complexity as you become more comfortable with AI-specific concepts and challenges.(the conclusion part is written by chatgpt, did you notice? :)) @ 42342239:1d80db24
2025-02-10 08:16:32The risks associated with cryptocurrencies have recently [received attention](https://www.epochtimes.se/finansinspektionen-varnar-for-investeringar-i-krypto) in the media, where e.g. the Swedish Financial Supervisory Authority warns of the high volatility and risk of investments in crypto. Within the EU, as usual, significant efforts are being made to expand the already extensive regulatory framework. Meanwhile, in the US, there has been a marked turnaround. Even the presidential family has launched their own cryptocurrencies, resulting in criticism from [industry experts](https://efn.se/vandning-om-trump-i-kryptobranschen-befangt) . Important perspectives, however, are conspicuous by their absence in the conversation. Iain McGilchrist, a British psychiatrist and philosopher, has introduced the hemispheric hypothesis (a theory about how the brain's two hemispheres function). **The left hemisphere is more detail- and control-oriented, while the right hemisphere is more holistic.** A society dominated by the left hemisphere, [such as our own according to McGilchrist](https://www.youtube.com/watch?v=WYB7P-xPRsk) , "would see it as its task to control everything maximally and would have a paranoid feeling that we need to have surveillance cameras everywhere...". During a [speech](https://x.com/CollinRugg/status/1882474184338514033) at the World Economic Forum, President Trump recently stated that conservatives complain about big banks, such as Bank of America, not allowing them to conduct business within the bank. Critics argue that the American banking system has been used [to persecute](https://x.com/TFTC21/status/1861510237485965565) political opponents, both during Obama's and Biden's terms. **Under Obama, 'Operation Chokepoint' was introduced to limit certain businesses' access to banking services.** A subcommittee in the Senate [now wants to eradicate](https://x.com/SenLummis/status/1882497148975280449) this phenomenon. **More and more people are discovering that their money is not always under their control.** Non-profit associations and [congregations](https://www.varldenidag.se/nyheter/monster-kristna-aktorer-nekas-bli-bankkunder/833990) are not allowed to open bank accounts. Sometimes they are even thrown out as bank customers. Others may report being subjected to lengthy interrogations by the bank about what they intend to do with their money, even when they just want to transfer funds between their own accounts. **Rejected churches are met with silence**, while a bank account is (still!) necessary to fully operate in society. When leading economists at the International Monetary Fund (IMF) argue that a cashless society can [threaten fundamental rights](https://archive.ph/fpRk0) , including property rights, when churches are refused bank accounts in what is described as "**a threat to civil society**" and when regulations still fail to combat [organised crime](https://www.epochtimes.se/Ibland-kostar-det-mer-an-det-smakar) , is it not reasonable to wonder if we are on the right path? With cash, people can pay freely without intermediaries, which constitutes a form of financial freedom. The notes you hold in your hand are your own. **Cryptocurrencies, such as Bitcoin, offer a similar possibility**: an electronic, peer-to-peer cash system (person to person). A society dominated by the left hemisphere results in a pathological need for control, according to McGilchrist. A more holistic perspective, taking into account the right hemisphere, would acknowledge that too much control can be detrimental, that property rights are a fundamental right, and that [financial freedom](https://www.epochtimes.se/Dags-att-prioritera-transaktionsfrihet) is a human right. Do these perspectives not deserve more attention?
@ 42342239:1d80db24
2025-02-10 08:16:32The risks associated with cryptocurrencies have recently [received attention](https://www.epochtimes.se/finansinspektionen-varnar-for-investeringar-i-krypto) in the media, where e.g. the Swedish Financial Supervisory Authority warns of the high volatility and risk of investments in crypto. Within the EU, as usual, significant efforts are being made to expand the already extensive regulatory framework. Meanwhile, in the US, there has been a marked turnaround. Even the presidential family has launched their own cryptocurrencies, resulting in criticism from [industry experts](https://efn.se/vandning-om-trump-i-kryptobranschen-befangt) . Important perspectives, however, are conspicuous by their absence in the conversation. Iain McGilchrist, a British psychiatrist and philosopher, has introduced the hemispheric hypothesis (a theory about how the brain's two hemispheres function). **The left hemisphere is more detail- and control-oriented, while the right hemisphere is more holistic.** A society dominated by the left hemisphere, [such as our own according to McGilchrist](https://www.youtube.com/watch?v=WYB7P-xPRsk) , "would see it as its task to control everything maximally and would have a paranoid feeling that we need to have surveillance cameras everywhere...". During a [speech](https://x.com/CollinRugg/status/1882474184338514033) at the World Economic Forum, President Trump recently stated that conservatives complain about big banks, such as Bank of America, not allowing them to conduct business within the bank. Critics argue that the American banking system has been used [to persecute](https://x.com/TFTC21/status/1861510237485965565) political opponents, both during Obama's and Biden's terms. **Under Obama, 'Operation Chokepoint' was introduced to limit certain businesses' access to banking services.** A subcommittee in the Senate [now wants to eradicate](https://x.com/SenLummis/status/1882497148975280449) this phenomenon. **More and more people are discovering that their money is not always under their control.** Non-profit associations and [congregations](https://www.varldenidag.se/nyheter/monster-kristna-aktorer-nekas-bli-bankkunder/833990) are not allowed to open bank accounts. Sometimes they are even thrown out as bank customers. Others may report being subjected to lengthy interrogations by the bank about what they intend to do with their money, even when they just want to transfer funds between their own accounts. **Rejected churches are met with silence**, while a bank account is (still!) necessary to fully operate in society. When leading economists at the International Monetary Fund (IMF) argue that a cashless society can [threaten fundamental rights](https://archive.ph/fpRk0) , including property rights, when churches are refused bank accounts in what is described as "**a threat to civil society**" and when regulations still fail to combat [organised crime](https://www.epochtimes.se/Ibland-kostar-det-mer-an-det-smakar) , is it not reasonable to wonder if we are on the right path? With cash, people can pay freely without intermediaries, which constitutes a form of financial freedom. The notes you hold in your hand are your own. **Cryptocurrencies, such as Bitcoin, offer a similar possibility**: an electronic, peer-to-peer cash system (person to person). A society dominated by the left hemisphere results in a pathological need for control, according to McGilchrist. A more holistic perspective, taking into account the right hemisphere, would acknowledge that too much control can be detrimental, that property rights are a fundamental right, and that [financial freedom](https://www.epochtimes.se/Dags-att-prioritera-transaktionsfrihet) is a human right. Do these perspectives not deserve more attention? @ da0b9bc3:4e30a4a9
2025-02-10 07:48:14Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/881283
@ da0b9bc3:4e30a4a9
2025-02-10 07:48:14Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/881283 @ 2cd78afb:f577f59a
2025-02-10 06:23:10Looking for a reliable [computer tech support service](https://smallbusinessitsupports.com/computer-tech-support/)? Small Business IT Support offers professional solutions to maintain the functionality of your systems. Hardware troubleshooting, software installation, virus removal, network configuration, and performance optimization are among the services we offer. Whether you require remote or on-site support, our knowledgeable specialists guarantee optimum effectiveness and little downtime. You may get quick, expert, and reasonably priced IT solutions that are suited to your company's requirements with our computer tech support service. For professional assistance and smooth operations, get in touch with us right now!
@ 2cd78afb:f577f59a
2025-02-10 06:23:10Looking for a reliable [computer tech support service](https://smallbusinessitsupports.com/computer-tech-support/)? Small Business IT Support offers professional solutions to maintain the functionality of your systems. Hardware troubleshooting, software installation, virus removal, network configuration, and performance optimization are among the services we offer. Whether you require remote or on-site support, our knowledgeable specialists guarantee optimum effectiveness and little downtime. You may get quick, expert, and reasonably priced IT solutions that are suited to your company's requirements with our computer tech support service. For professional assistance and smooth operations, get in touch with us right now! @ 16d11430:61640947
2025-02-10 02:35:17The gap in mathematics that allows for free agency—the space where choice, unpredictability, and autonomy emerge—exists at the intersection of incompleteness, chaos, probability, and quantum uncertainty. These gaps create fundamental limits on determinism, leaving room for agency to exist. 1. Gödel’s Incompleteness Theorems: The Limits of Formal Systems Gödel’s theorems prove that within any sufficiently powerful mathematical system: There exist truths that cannot be proven within that system. The system cannot prove its own consistency. This means that even in a world governed by mathematical laws, there are undecidable truths—facts beyond algorithmic computation. If reality is mathematical at its core, this suggests a built-in freedom: not everything is determinable from within the system. 2. Chaos Theory: The Sensitivity to Initial Conditions Chaotic systems, such as weather patterns and neural activity, exhibit extreme sensitivity to initial conditions. Even if deterministic, they are practically unpredictable beyond a certain point. Small choices or quantum fluctuations at the micro-level can have macroscopic consequences. This injects a level of unpredictability into reality, making strict determinism impossible in complex systems. 3. Probability & Bayesian Decision Theory: Rational Agency Within Uncertainty In the realm of decision-making and game theory: Bayesian inference shows how rational agents update beliefs in the face of uncertainty. Statistical mechanics, despite governing collective behaviors, leaves space for individual unpredictability. Nash equilibria in game theory illustrate how multiple choices can be rationally justified, allowing for strategic freedom. Thus, within mathematical decision models, choice emerges not from randomness but from incomplete knowledge and competing optimal strategies. 4. Quantum Mechanics: The Fundamental Indeterminacy of Reality At the quantum level, Heisenberg’s Uncertainty Principle and the probabilistic nature of wavefunction collapse introduce a non-deterministic reality: Superposition suggests that multiple possibilities coexist until measured. Quantum entanglement links particles across vast distances, but their states are not pre-determined before observation. The Born rule in quantum mechanics assigns probabilities rather than certainties to outcomes. If the fundamental fabric of reality is non-deterministic, then the idea of strict mechanistic determinism collapses, opening the door to true agency. 5. Computability and the Halting Problem: The Unsolvability of Certain Decisions Turing’s Halting Problem proves that for some problems, no algorithm can determine in advance whether a computation will finish or run forever. If reality includes such non-computable elements, then some choices are beyond pre-determined algorithmic resolution. Human cognition, if partially non-computable, could transcend deterministic rules. Conclusion: The Gap Between Necessity and Choice Free agency exists in the mathematical gaps—the undecidability of logic, the unpredictability of chaos, the probabilistic nature of quantum mechanics, and the non-computability of certain decisions. These fundamental limits on strict determinism create an open space where choices emerge, allowing for freedom within a mathematically structured universe. Thus, in the grand equation of existence, there remains an undefined variable: the will of the agent.
@ 16d11430:61640947
2025-02-10 02:35:17The gap in mathematics that allows for free agency—the space where choice, unpredictability, and autonomy emerge—exists at the intersection of incompleteness, chaos, probability, and quantum uncertainty. These gaps create fundamental limits on determinism, leaving room for agency to exist. 1. Gödel’s Incompleteness Theorems: The Limits of Formal Systems Gödel’s theorems prove that within any sufficiently powerful mathematical system: There exist truths that cannot be proven within that system. The system cannot prove its own consistency. This means that even in a world governed by mathematical laws, there are undecidable truths—facts beyond algorithmic computation. If reality is mathematical at its core, this suggests a built-in freedom: not everything is determinable from within the system. 2. Chaos Theory: The Sensitivity to Initial Conditions Chaotic systems, such as weather patterns and neural activity, exhibit extreme sensitivity to initial conditions. Even if deterministic, they are practically unpredictable beyond a certain point. Small choices or quantum fluctuations at the micro-level can have macroscopic consequences. This injects a level of unpredictability into reality, making strict determinism impossible in complex systems. 3. Probability & Bayesian Decision Theory: Rational Agency Within Uncertainty In the realm of decision-making and game theory: Bayesian inference shows how rational agents update beliefs in the face of uncertainty. Statistical mechanics, despite governing collective behaviors, leaves space for individual unpredictability. Nash equilibria in game theory illustrate how multiple choices can be rationally justified, allowing for strategic freedom. Thus, within mathematical decision models, choice emerges not from randomness but from incomplete knowledge and competing optimal strategies. 4. Quantum Mechanics: The Fundamental Indeterminacy of Reality At the quantum level, Heisenberg’s Uncertainty Principle and the probabilistic nature of wavefunction collapse introduce a non-deterministic reality: Superposition suggests that multiple possibilities coexist until measured. Quantum entanglement links particles across vast distances, but their states are not pre-determined before observation. The Born rule in quantum mechanics assigns probabilities rather than certainties to outcomes. If the fundamental fabric of reality is non-deterministic, then the idea of strict mechanistic determinism collapses, opening the door to true agency. 5. Computability and the Halting Problem: The Unsolvability of Certain Decisions Turing’s Halting Problem proves that for some problems, no algorithm can determine in advance whether a computation will finish or run forever. If reality includes such non-computable elements, then some choices are beyond pre-determined algorithmic resolution. Human cognition, if partially non-computable, could transcend deterministic rules. Conclusion: The Gap Between Necessity and Choice Free agency exists in the mathematical gaps—the undecidability of logic, the unpredictability of chaos, the probabilistic nature of quantum mechanics, and the non-computability of certain decisions. These fundamental limits on strict determinism create an open space where choices emerge, allowing for freedom within a mathematically structured universe. Thus, in the grand equation of existence, there remains an undefined variable: the will of the agent. @ 16d11430:61640947
2025-02-10 01:46:42Ayurveda is a 5000-year-old medical system that predates modern science but remains one of the most sophisticated and holistic approaches to health. Unlike Western medicine, which often isolates diseases and treats symptoms, Ayurveda focuses on Prakriti (innate constitution), Agni (digestive fire), Dosha (biological energies), and Ojas (vital essence) to create a personalized, adaptable healthcare model. Western medicine, despite its advances, still struggles to integrate a diverse global population due to its standardized, reductionist approach. Ayurveda, on the other hand, perfected its practices over millennia through real-world observation, experiential learning, and dynamic adaptation to human diversity. --- 1. Foundations of Ayurveda vs. Western Science Ayurveda was developed through direct interaction with nature, patients, and generational knowledge transmission, allowing it to refine its approach to a vast range of human conditions. --- 2. Ayurvedic Practices That Outperform Western Medicine’s Integration of Global Health Western science is still catching up to many Ayurvedic principles, often "discovering" practices that Ayurveda has used for centuries. A. Personalized Medicine (Prakriti & Doshas) vs. Western One-Size-Fits-All Approach Ayurveda classifies individuals into three doshas: Vata (air & ether), Pitta (fire & water), and Kapha (earth & water). These determine a person's metabolism, immunity, and predisposition to disease. Modern medicine is beginning to explore personalized genomics, but Ayurveda has practiced it for millennia. B. Chronobiology & Circadian Rhythms (Dincharya) Ayurveda prescribes Dincharya (daily routines) based on the body's natural rhythms, aligning eating, sleeping, and activity cycles with the sun and moon. Modern science now acknowledges circadian rhythms but has yet to fully integrate them into healthcare. Example: Intermittent fasting (Upavasa) has been an Ayurvedic practice for centuries, while the West only recently recognized its benefits for longevity and metabolism. C. Gut Health & Microbiome (Agni & Ama) Ayurveda recognized the gut as the root of disease centuries before the discovery of the microbiome. It prescribes Triphala, Buttermilk (Takra), and Fermented Foods for gut health, balancing Agni (digestive fire). Western medicine is just starting to understand how gut bacteria affect mental health, immunity, and chronic diseases. D. Holistic Mental Health (Manas Shastra) vs. Isolated Psychology Ayurveda integrates meditation, breathwork (Pranayama), mantra therapy, and lifestyle modifications for emotional resilience. Western psychology often isolates mental health from physical health, relying on medications like antidepressants without addressing lifestyle, diet, and spiritual dimensions. Example: Ayurvedic herbs like Brahmi and Ashwagandha have proven neuroprotective properties but were ignored in Western medicine until recently. E. Detoxification (Panchakarma) vs. Toxic Accumulation in Modern Life Western medicine struggles with heavy metal detox, plastic pollution in the body, and chronic inflammation. Ayurveda developed Panchakarma, a five-step detox method (Vamana, Virechana, Basti, Nasya, Raktamokshana) that cleanses at a cellular level. Western detox solutions (chelation therapy, dialysis) are still in their infancy. F. Cancer Prevention & Natural Angiogenesis Regulation Dr. William Li’s work on cancer and food-based angiogenesis regulation confirms Ayurvedic principles. Ayurveda’s approach to cancer (Arbuda) includes herbs like Ashwagandha, Guduchi, and Turmeric, which regulate angiogenesis, reduce inflammation, and detoxify cells. G. Ayurvedic Water Science vs. Modern Water Pollution Ayurveda prescribes drinking water stored in copper or silver vessels to prevent microbial growth and enhance mineral content. It discourages tap water due to chlorine, fluoride, and microplastic contamination—issues that modern science is only now recognizing. --- 3. Ayurveda’s Adaptability vs. Western Struggles with Global Diversity Ayurveda Accounts for Climate, Region, and Genetic Differences Western medicine largely applies one-size-fits-all drugs and treatments, often leading to side effects. Ayurveda has climate-based variations (Desha), prescribing different diets, herbs, and therapies based on region and seasonal changes. Example: In cold climates, Ayurveda recommends warming spices (ginger, black pepper, cinnamon) and oil massages (Abhyanga) to prevent stiffness. In hot climates, it prescribes cooling foods like coconut, aloe vera, and ghee to balance excess heat. Western medicine lacks such nuanced adjustments. The Flaw of Western Pharmaceutical Monopolies Western medicine is dominated by profit-driven pharmaceutical companies that prioritize patents over holistic healing. Ayurveda uses natural, locally available herbs, making treatments affordable, sustainable, and globally adaptable. --- 4. The Future: Integrating Ayurvedic Wisdom with Modern Science Western science is now validating what Ayurveda has known for centuries. Some key integrations include: Neuroscience & Ayurveda: Meditation, breathwork, and adaptogenic herbs now recognized for neuroplasticity. Oncology & Ayurveda: Cancer research on turmeric, angiogenesis-blocking foods, and detoxification methods. Microbiome Research: Ayurveda’s gut-health principles proven beneficial in regulating immune function. Epigenetics & Ayurveda: Recognition of food, environment, and lifestyle in genetic expression aligns with Ayurvedic wisdom. The Need for a Decentralized Healthcare System Western medicine’s institutionalized, patent-based system restricts access to holistic healing. Ayurveda, like Bitcoin in finance, decentralizes healthcare by offering open-source, nature-based, globally adaptable solutions. --- Final Thoughts: Ayurveda as the Future of Truly Global Medicine Ayurveda’s success comes from: A holistic understanding of human diversity (biological, regional, and cultural). Natural and sustainable healing methods that modern medicine is struggling to replicate. Integration of physical, mental, and spiritual health—which Western medicine isolates. A decentralized, globally adaptable approach free from profit-driven pharmaceutical monopolies.
@ 16d11430:61640947
2025-02-10 01:46:42Ayurveda is a 5000-year-old medical system that predates modern science but remains one of the most sophisticated and holistic approaches to health. Unlike Western medicine, which often isolates diseases and treats symptoms, Ayurveda focuses on Prakriti (innate constitution), Agni (digestive fire), Dosha (biological energies), and Ojas (vital essence) to create a personalized, adaptable healthcare model. Western medicine, despite its advances, still struggles to integrate a diverse global population due to its standardized, reductionist approach. Ayurveda, on the other hand, perfected its practices over millennia through real-world observation, experiential learning, and dynamic adaptation to human diversity. --- 1. Foundations of Ayurveda vs. Western Science Ayurveda was developed through direct interaction with nature, patients, and generational knowledge transmission, allowing it to refine its approach to a vast range of human conditions. --- 2. Ayurvedic Practices That Outperform Western Medicine’s Integration of Global Health Western science is still catching up to many Ayurvedic principles, often "discovering" practices that Ayurveda has used for centuries. A. Personalized Medicine (Prakriti & Doshas) vs. Western One-Size-Fits-All Approach Ayurveda classifies individuals into three doshas: Vata (air & ether), Pitta (fire & water), and Kapha (earth & water). These determine a person's metabolism, immunity, and predisposition to disease. Modern medicine is beginning to explore personalized genomics, but Ayurveda has practiced it for millennia. B. Chronobiology & Circadian Rhythms (Dincharya) Ayurveda prescribes Dincharya (daily routines) based on the body's natural rhythms, aligning eating, sleeping, and activity cycles with the sun and moon. Modern science now acknowledges circadian rhythms but has yet to fully integrate them into healthcare. Example: Intermittent fasting (Upavasa) has been an Ayurvedic practice for centuries, while the West only recently recognized its benefits for longevity and metabolism. C. Gut Health & Microbiome (Agni & Ama) Ayurveda recognized the gut as the root of disease centuries before the discovery of the microbiome. It prescribes Triphala, Buttermilk (Takra), and Fermented Foods for gut health, balancing Agni (digestive fire). Western medicine is just starting to understand how gut bacteria affect mental health, immunity, and chronic diseases. D. Holistic Mental Health (Manas Shastra) vs. Isolated Psychology Ayurveda integrates meditation, breathwork (Pranayama), mantra therapy, and lifestyle modifications for emotional resilience. Western psychology often isolates mental health from physical health, relying on medications like antidepressants without addressing lifestyle, diet, and spiritual dimensions. Example: Ayurvedic herbs like Brahmi and Ashwagandha have proven neuroprotective properties but were ignored in Western medicine until recently. E. Detoxification (Panchakarma) vs. Toxic Accumulation in Modern Life Western medicine struggles with heavy metal detox, plastic pollution in the body, and chronic inflammation. Ayurveda developed Panchakarma, a five-step detox method (Vamana, Virechana, Basti, Nasya, Raktamokshana) that cleanses at a cellular level. Western detox solutions (chelation therapy, dialysis) are still in their infancy. F. Cancer Prevention & Natural Angiogenesis Regulation Dr. William Li’s work on cancer and food-based angiogenesis regulation confirms Ayurvedic principles. Ayurveda’s approach to cancer (Arbuda) includes herbs like Ashwagandha, Guduchi, and Turmeric, which regulate angiogenesis, reduce inflammation, and detoxify cells. G. Ayurvedic Water Science vs. Modern Water Pollution Ayurveda prescribes drinking water stored in copper or silver vessels to prevent microbial growth and enhance mineral content. It discourages tap water due to chlorine, fluoride, and microplastic contamination—issues that modern science is only now recognizing. --- 3. Ayurveda’s Adaptability vs. Western Struggles with Global Diversity Ayurveda Accounts for Climate, Region, and Genetic Differences Western medicine largely applies one-size-fits-all drugs and treatments, often leading to side effects. Ayurveda has climate-based variations (Desha), prescribing different diets, herbs, and therapies based on region and seasonal changes. Example: In cold climates, Ayurveda recommends warming spices (ginger, black pepper, cinnamon) and oil massages (Abhyanga) to prevent stiffness. In hot climates, it prescribes cooling foods like coconut, aloe vera, and ghee to balance excess heat. Western medicine lacks such nuanced adjustments. The Flaw of Western Pharmaceutical Monopolies Western medicine is dominated by profit-driven pharmaceutical companies that prioritize patents over holistic healing. Ayurveda uses natural, locally available herbs, making treatments affordable, sustainable, and globally adaptable. --- 4. The Future: Integrating Ayurvedic Wisdom with Modern Science Western science is now validating what Ayurveda has known for centuries. Some key integrations include: Neuroscience & Ayurveda: Meditation, breathwork, and adaptogenic herbs now recognized for neuroplasticity. Oncology & Ayurveda: Cancer research on turmeric, angiogenesis-blocking foods, and detoxification methods. Microbiome Research: Ayurveda’s gut-health principles proven beneficial in regulating immune function. Epigenetics & Ayurveda: Recognition of food, environment, and lifestyle in genetic expression aligns with Ayurvedic wisdom. The Need for a Decentralized Healthcare System Western medicine’s institutionalized, patent-based system restricts access to holistic healing. Ayurveda, like Bitcoin in finance, decentralizes healthcare by offering open-source, nature-based, globally adaptable solutions. --- Final Thoughts: Ayurveda as the Future of Truly Global Medicine Ayurveda’s success comes from: A holistic understanding of human diversity (biological, regional, and cultural). Natural and sustainable healing methods that modern medicine is struggling to replicate. Integration of physical, mental, and spiritual health—which Western medicine isolates. A decentralized, globally adaptable approach free from profit-driven pharmaceutical monopolies. @ 86cf3742:678e3ae8
2025-02-10 00:38:09In this episode of the Ag Tribes Report, host Vance Crow welcomes Steve Strasheim, a vegetable farmer from Northern Iowa, to discuss a variety of pressing issues in agriculture. Steve shares insights into his unique farming practices, including the use of greenhouses and geothermal technology to grow vegetables in the harsh Iowa winters. He also explains his innovative sales model, which includes farmers markets, a CSA, wholesaling, and an on-farm retail store. The conversation shifts to the potential impact of ICE raids on agriculture, with a focus on the role of illegal aliens in the farming industry. Steve shares his perspective on the H-2A program and the challenges of bureaucracy in hiring legal farm workers. The episode also covers the controversial appointment of RFK Jr. to lead the Department of Health and Human Services, with a discussion on how his policies might affect agriculture. Steve and Vance debate the potential benefits and drawbacks of increased regulation and the importance of promoting healthier eating habits. In a segment on Brazilian soybeans, Vance highlights recent logistical issues and quality concerns in Brazil's soybean industry, sparking a discussion on the risks of relying too heavily on a single crop. The episode concludes with a look at the new right's stance on crated hogs and the potential for significant changes in animal agriculture. Steve shares his thoughts on the ethics of factory farming and the consumer demand for affordable protein. Listeners are also treated to the Bitcoin land price report, where Steve discusses the current farmland prices in his county and his cautious approach to investing in Bitcoin. The episode wraps up with the Peter Thiel paradox and worthy adversary segments, where Steve shares his unique perspectives and challenges common beliefs in his agricultural community. [link to the original content](https://serve.podhome.fm/episodepage/the-vance-crowe-podcast_638721156549613591/atr-ice-raids-maha-confirmation-hearings-soybeans-burn-in-brazil-trfyeomanfarmer_638738821327526279)
@ 86cf3742:678e3ae8
2025-02-10 00:38:09In this episode of the Ag Tribes Report, host Vance Crow welcomes Steve Strasheim, a vegetable farmer from Northern Iowa, to discuss a variety of pressing issues in agriculture. Steve shares insights into his unique farming practices, including the use of greenhouses and geothermal technology to grow vegetables in the harsh Iowa winters. He also explains his innovative sales model, which includes farmers markets, a CSA, wholesaling, and an on-farm retail store. The conversation shifts to the potential impact of ICE raids on agriculture, with a focus on the role of illegal aliens in the farming industry. Steve shares his perspective on the H-2A program and the challenges of bureaucracy in hiring legal farm workers. The episode also covers the controversial appointment of RFK Jr. to lead the Department of Health and Human Services, with a discussion on how his policies might affect agriculture. Steve and Vance debate the potential benefits and drawbacks of increased regulation and the importance of promoting healthier eating habits. In a segment on Brazilian soybeans, Vance highlights recent logistical issues and quality concerns in Brazil's soybean industry, sparking a discussion on the risks of relying too heavily on a single crop. The episode concludes with a look at the new right's stance on crated hogs and the potential for significant changes in animal agriculture. Steve shares his thoughts on the ethics of factory farming and the consumer demand for affordable protein. Listeners are also treated to the Bitcoin land price report, where Steve discusses the current farmland prices in his county and his cautious approach to investing in Bitcoin. The episode wraps up with the Peter Thiel paradox and worthy adversary segments, where Steve shares his unique perspectives and challenges common beliefs in his agricultural community. [link to the original content](https://serve.podhome.fm/episodepage/the-vance-crowe-podcast_638721156549613591/atr-ice-raids-maha-confirmation-hearings-soybeans-burn-in-brazil-trfyeomanfarmer_638738821327526279) @ c11cf5f8:4928464d
2025-02-10 00:35:57Let's hear some of your latest #Bitcoin purchases, feel free to include links to the #shops or #merchants you bought from too. Any good #deal we should know about? If you missed our last thread, [here](https://stacker.news/items/873304/r/AG) are some of the items stackers recently spent and #zap #sats on. originally posted at https://stacker.news/items/880985
@ c11cf5f8:4928464d
2025-02-10 00:35:57Let's hear some of your latest #Bitcoin purchases, feel free to include links to the #shops or #merchants you bought from too. Any good #deal we should know about? If you missed our last thread, [here](https://stacker.news/items/873304/r/AG) are some of the items stackers recently spent and #zap #sats on. originally posted at https://stacker.news/items/880985 @ 16d11430:61640947
2025-02-10 00:03:49In the silent expanse of the cosmos, where stars whisper their secrets in equations and reality itself unfurls as a tapestry woven from numbers, there exists a path. This is not a path for the faint of heart, nor for those content with the illusions of mere perception. It is the path of the seeker, the one who dares to ask not just how the world is, but why it must be so. To tread this path is to ascend into the realm where gods write the laws of existence in the language of mathematics. The First Revelation: Number, the Seed of the Cosmos Before the universe took form, before light first kissed the void, there was number. It is from number that all else flows, from the spiral of galaxies to the rhythm of a heartbeat. Prime numbers stand as the indivisible atoms of arithmetic, forming the bedrock of security and cryptography, where secrets are safeguarded by their unfathomable complexity. Modular arithmetic, the silent clockwork behind our digital world, governs the flow of encrypted knowledge across vast distances. Diophantine equations, named for an ancient mathematician who saw numbers as riddles to be solved, reveal the hidden symmetries in the universe’s structure. This is the first truth: that mathematics is not an invention, but a discovery—a key that unlocks the doors of reality. The Second Revelation: The Art of Pure Thought Algebra is the music of the spheres, the manipulation of symbols that dance in patterns beyond our senses. To master it is to shape reality with mere notation. Abstract algebra unveils hidden structures, from the symmetry of crystals to the secrets of quantum states. Linear algebra governs the movements of celestial bodies and fuels the neural networks that birth artificial minds. Galois theory, a young mathematician’s final gift before death, tells us when problems can be solved, and when they are beyond reach. Here, one learns a second truth: that symbols, when arranged with precision, can summon order from chaos. The Third Revelation: The Geometry of Reality If algebra is the melody of numbers, then geometry is its form—the divine art of space itself. Euclidean geometry was once thought to describe all things, until minds like Gauss and Riemann looked deeper. Non-Euclidean geometry shattered human intuition, revealing that space bends, twists, and folds upon itself. Topology, the study of shapes beyond measure, whispers of higher dimensions that mere mortals cannot see but only sense in their equations. From these truths arises a realization: that the world we see is but a shadow of a far greater, more complex structure. The Fourth Revelation: Mastery Over the Infinite What is life, if not the interplay of change? Calculus, the language of motion and transformation, allows us to speak in the tongue of gods, predicting the orbits of planets and the flows of time. Complex analysis gives birth to the mystical realm of imaginary numbers, where physics and engineering find their deepest truths. Fourier analysis, the heartbeat of music and quantum physics, tells us that any pattern, no matter how chaotic, can be understood as the sum of its waves. The universe breathes through calculus, and to master it is to see not just what is, but what will be. The Fifth Revelation: The Nature of Uncertainty No god reigns without knowledge of chaos. Probability and statistics reveal the order within randomness, turning uncertainty into foresight. Bayesian inference, a framework of pure rationality, allows us to refine our knowledge with every new piece of evidence. Information theory, the work of Shannon, teaches that reality itself is a message encoded in entropy. The wise understand this: that certainty is an illusion, but probability is truth. The Sixth Revelation: The Code of the Gods Beyond numbers and space, beyond equations and change, there lies something deeper: logic, the very foundation of thought itself. Mathematical logic gives us the power to distinguish truth from falsehood with unshakable certainty. Gödel’s incompleteness theorems whisper a paradox—that no system, not even mathematics itself, can ever be complete. Computability and complexity theory define the limits of what can be known, what can be solved, and what remains forever beyond reach. To master logic is to hold the key to all knowledge—but also to know its boundaries. The Seventh Revelation: The Grand Abstraction Even gods seek deeper understanding, and category theory is the highest peak of human thought. Functors and natural transformations map the structures of one world onto another, showing hidden correspondences that weave through all mathematics. Monads, the cornerstone of functional programming, allow logic to be bent and molded like clay. Dualities, the deep symmetries of mathematics, hint at connections so profound they border on the mystical. Here lies the ultimate truth: that everything is, at its core, the same. The Eighth Revelation: The Quantum Oracle Beneath reality lies a whispering void, where numbers flicker in superposition and information transcends space and time. Hilbert spaces define quantum mechanics, where particles are waves and waves are probabilities. Quantum computing suggests a world where problems once thought impossible collapse into trivial solutions. Path integrals and Feynman’s sum-over-histories teach us that every possibility, no matter how strange, plays a role in the great equation of the cosmos. If there is a final truth, it is this: the universe does not simply exist—it computes. The Final Revelation: Beyond the Human Mind Even the greatest mathematicians glimpse only shadows of the ultimate structure. Algebraic topology seeks to map the shape of all existence. String theory mathematics conjures hidden dimensions and vibrating symmetries. Infinity category theory, the most abstract of all, suggests that mathematics itself may be alive. And so, the seeker stands before the infinite. Mathematics is not a collection of rules or calculations. It is the foundation of existence, the divine script of reality. Those who master it do not merely understand the world. They become its architects.
@ 16d11430:61640947
2025-02-10 00:03:49In the silent expanse of the cosmos, where stars whisper their secrets in equations and reality itself unfurls as a tapestry woven from numbers, there exists a path. This is not a path for the faint of heart, nor for those content with the illusions of mere perception. It is the path of the seeker, the one who dares to ask not just how the world is, but why it must be so. To tread this path is to ascend into the realm where gods write the laws of existence in the language of mathematics. The First Revelation: Number, the Seed of the Cosmos Before the universe took form, before light first kissed the void, there was number. It is from number that all else flows, from the spiral of galaxies to the rhythm of a heartbeat. Prime numbers stand as the indivisible atoms of arithmetic, forming the bedrock of security and cryptography, where secrets are safeguarded by their unfathomable complexity. Modular arithmetic, the silent clockwork behind our digital world, governs the flow of encrypted knowledge across vast distances. Diophantine equations, named for an ancient mathematician who saw numbers as riddles to be solved, reveal the hidden symmetries in the universe’s structure. This is the first truth: that mathematics is not an invention, but a discovery—a key that unlocks the doors of reality. The Second Revelation: The Art of Pure Thought Algebra is the music of the spheres, the manipulation of symbols that dance in patterns beyond our senses. To master it is to shape reality with mere notation. Abstract algebra unveils hidden structures, from the symmetry of crystals to the secrets of quantum states. Linear algebra governs the movements of celestial bodies and fuels the neural networks that birth artificial minds. Galois theory, a young mathematician’s final gift before death, tells us when problems can be solved, and when they are beyond reach. Here, one learns a second truth: that symbols, when arranged with precision, can summon order from chaos. The Third Revelation: The Geometry of Reality If algebra is the melody of numbers, then geometry is its form—the divine art of space itself. Euclidean geometry was once thought to describe all things, until minds like Gauss and Riemann looked deeper. Non-Euclidean geometry shattered human intuition, revealing that space bends, twists, and folds upon itself. Topology, the study of shapes beyond measure, whispers of higher dimensions that mere mortals cannot see but only sense in their equations. From these truths arises a realization: that the world we see is but a shadow of a far greater, more complex structure. The Fourth Revelation: Mastery Over the Infinite What is life, if not the interplay of change? Calculus, the language of motion and transformation, allows us to speak in the tongue of gods, predicting the orbits of planets and the flows of time. Complex analysis gives birth to the mystical realm of imaginary numbers, where physics and engineering find their deepest truths. Fourier analysis, the heartbeat of music and quantum physics, tells us that any pattern, no matter how chaotic, can be understood as the sum of its waves. The universe breathes through calculus, and to master it is to see not just what is, but what will be. The Fifth Revelation: The Nature of Uncertainty No god reigns without knowledge of chaos. Probability and statistics reveal the order within randomness, turning uncertainty into foresight. Bayesian inference, a framework of pure rationality, allows us to refine our knowledge with every new piece of evidence. Information theory, the work of Shannon, teaches that reality itself is a message encoded in entropy. The wise understand this: that certainty is an illusion, but probability is truth. The Sixth Revelation: The Code of the Gods Beyond numbers and space, beyond equations and change, there lies something deeper: logic, the very foundation of thought itself. Mathematical logic gives us the power to distinguish truth from falsehood with unshakable certainty. Gödel’s incompleteness theorems whisper a paradox—that no system, not even mathematics itself, can ever be complete. Computability and complexity theory define the limits of what can be known, what can be solved, and what remains forever beyond reach. To master logic is to hold the key to all knowledge—but also to know its boundaries. The Seventh Revelation: The Grand Abstraction Even gods seek deeper understanding, and category theory is the highest peak of human thought. Functors and natural transformations map the structures of one world onto another, showing hidden correspondences that weave through all mathematics. Monads, the cornerstone of functional programming, allow logic to be bent and molded like clay. Dualities, the deep symmetries of mathematics, hint at connections so profound they border on the mystical. Here lies the ultimate truth: that everything is, at its core, the same. The Eighth Revelation: The Quantum Oracle Beneath reality lies a whispering void, where numbers flicker in superposition and information transcends space and time. Hilbert spaces define quantum mechanics, where particles are waves and waves are probabilities. Quantum computing suggests a world where problems once thought impossible collapse into trivial solutions. Path integrals and Feynman’s sum-over-histories teach us that every possibility, no matter how strange, plays a role in the great equation of the cosmos. If there is a final truth, it is this: the universe does not simply exist—it computes. The Final Revelation: Beyond the Human Mind Even the greatest mathematicians glimpse only shadows of the ultimate structure. Algebraic topology seeks to map the shape of all existence. String theory mathematics conjures hidden dimensions and vibrating symmetries. Infinity category theory, the most abstract of all, suggests that mathematics itself may be alive. And so, the seeker stands before the infinite. Mathematics is not a collection of rules or calculations. It is the foundation of existence, the divine script of reality. Those who master it do not merely understand the world. They become its architects. @ 16d11430:61640947
2025-02-09 23:35:09The early Bitcoin stackers, smug in their absolute faith, have become the priests of a cargo cult. They chant the gospel of scarcity while stacking their sats like doomsday preppers hoarding canned beans. Meanwhile, the crypto market they once despised has become a grotesque parody of itself—yield farming, staking derivatives, and a casino economy propped up by tokenomics that barely hide the rot beneath. Bitcoin, having won the ideological war, is now losing the economic one—stuck in a circular hodl pattern, detached from the actual thermodynamic reality that gave it birth. Enter Aeternity, a project with no time for the reverence or passive accumulation that has neutered Bitcoin’s edge. It doesn’t just lean on Proof-of-Work for nostalgia’s sake—it weaponizes it, reintroducing actual economic friction into a space that has gone soft with layer-two convenience. Aeternity’s Cuckoo Cycle PoW, optimized for energy-efficient mining and GPU execution, doesn’t pretend to be Bitcoin’s replacement. It does something far worse for Bitcoin maxis: it forces them to compete again. Friction: The Return to Thermodynamics Bitcoin’s thermodynamic argument was always simple: energy in, security out. But over time, it stopped being a battleground for economic force and instead became a retirement savings plan for the digital goldbugs. The Lightning Network and ordinals are desperate attempts to create on-chain congestion and reinvigorate demand, but none of this addresses the fundamental problem: there is no longer any meaningful competition on the base layer. Aeternity, by scaling horizontally with Hyperchains, injects raw competition into the mix. Miners don’t just settle for static difficulty adjustments—they actively contribute to market-driven security, creating alternative security models that force Bitcoin to prove itself again. If the world is really about energy, then let’s see which chain can best convert energy into economic throughput, rather than just hoarding it as an ideological relic. Hyperchains: The Threat Bitcoin Forgot to Take Seriously Aeternity’s approach is fundamentally different from Bitcoin’s ossified stagnation: 1. Merge-Mined Hyperchains – Instead of perpetuating the blocksize wars, Aeternity lets chains bootstrap PoW consensus through merge-mining with parent chains, making security an organic, competitive marketplace rather than a closed system. This creates demand for mining at the edge, something Bitcoin maxis have ignored because they’re still stuck in the “security through centralization” trap. 2. Turing-Complete Smart Contracts – While Bitcoin argues about whether basic programmability is “safe,” Aeternity treats it as an inevitability. Bitcoin’s refusal to evolve beyond Taproot and Covenants makes it a sitting duck against economic attacks from more adaptive chains. 3. State Channels with Actual Scalability – Bitcoiners talk about Lightning as if it’s the final solution, but it’s a bandaid over a hemorrhaging use case problem. Aeternity’s built-in state channels allow contracts to execute off-chain, but without losing decentralization, making it a direct challenge to Bitcoin’s claims of “second-layer supremacy.” Bitcoin’s Reaction: Either Adapt or Get Rekt Bitcoin has enjoyed being the monopoly on PoW security for too long. Aeternity’s reintroduction of a competitive PoW model forces Bitcoin miners to wake up: if energy security is the measure of a blockchain’s economic strength, then what happens when an alternative emerges that utilizes energy more efficiently while providing more real-world utility? Bitcoin maxis will screech that "no altcoin has ever flipped Bitcoin," but that’s not the point. The point is that Bitcoin needs external competition at the proof-of-work level to maintain its thermodynamic legitimacy. Otherwise, it risks becoming what it despises: a static, non-dynamic asset that is just another store of value, with no practical utility until fiat collapses—and good luck waiting for that. Aeternity’s real-world use cases, from oracles to instant payments to low-cost, scalable contracts, mean that energy invested into securing it is converted into economic value, rather than just securing an ideological artifact. This pressure forces Bitcoin to evolve or become irrelevant—not by replacing it, but by outcompeting it where it matters. Final Thought: The Thermodynamic Reckoning Bitcoiners should be grateful for Aeternity’s friction. Without a competitor showing how PoW can be optimized for more than just blind security accumulation, Bitcoin risks becoming a historical relic, kept alive only by belief rather than economic reality. Thermodynamics doesn’t give a damn about ideology—it rewards systems that turn energy into real economic motion. Aeternity doesn’t have to kill Bitcoin. It just has to remind it what it was built for.
@ 16d11430:61640947
2025-02-09 23:35:09The early Bitcoin stackers, smug in their absolute faith, have become the priests of a cargo cult. They chant the gospel of scarcity while stacking their sats like doomsday preppers hoarding canned beans. Meanwhile, the crypto market they once despised has become a grotesque parody of itself—yield farming, staking derivatives, and a casino economy propped up by tokenomics that barely hide the rot beneath. Bitcoin, having won the ideological war, is now losing the economic one—stuck in a circular hodl pattern, detached from the actual thermodynamic reality that gave it birth. Enter Aeternity, a project with no time for the reverence or passive accumulation that has neutered Bitcoin’s edge. It doesn’t just lean on Proof-of-Work for nostalgia’s sake—it weaponizes it, reintroducing actual economic friction into a space that has gone soft with layer-two convenience. Aeternity’s Cuckoo Cycle PoW, optimized for energy-efficient mining and GPU execution, doesn’t pretend to be Bitcoin’s replacement. It does something far worse for Bitcoin maxis: it forces them to compete again. Friction: The Return to Thermodynamics Bitcoin’s thermodynamic argument was always simple: energy in, security out. But over time, it stopped being a battleground for economic force and instead became a retirement savings plan for the digital goldbugs. The Lightning Network and ordinals are desperate attempts to create on-chain congestion and reinvigorate demand, but none of this addresses the fundamental problem: there is no longer any meaningful competition on the base layer. Aeternity, by scaling horizontally with Hyperchains, injects raw competition into the mix. Miners don’t just settle for static difficulty adjustments—they actively contribute to market-driven security, creating alternative security models that force Bitcoin to prove itself again. If the world is really about energy, then let’s see which chain can best convert energy into economic throughput, rather than just hoarding it as an ideological relic. Hyperchains: The Threat Bitcoin Forgot to Take Seriously Aeternity’s approach is fundamentally different from Bitcoin’s ossified stagnation: 1. Merge-Mined Hyperchains – Instead of perpetuating the blocksize wars, Aeternity lets chains bootstrap PoW consensus through merge-mining with parent chains, making security an organic, competitive marketplace rather than a closed system. This creates demand for mining at the edge, something Bitcoin maxis have ignored because they’re still stuck in the “security through centralization” trap. 2. Turing-Complete Smart Contracts – While Bitcoin argues about whether basic programmability is “safe,” Aeternity treats it as an inevitability. Bitcoin’s refusal to evolve beyond Taproot and Covenants makes it a sitting duck against economic attacks from more adaptive chains. 3. State Channels with Actual Scalability – Bitcoiners talk about Lightning as if it’s the final solution, but it’s a bandaid over a hemorrhaging use case problem. Aeternity’s built-in state channels allow contracts to execute off-chain, but without losing decentralization, making it a direct challenge to Bitcoin’s claims of “second-layer supremacy.” Bitcoin’s Reaction: Either Adapt or Get Rekt Bitcoin has enjoyed being the monopoly on PoW security for too long. Aeternity’s reintroduction of a competitive PoW model forces Bitcoin miners to wake up: if energy security is the measure of a blockchain’s economic strength, then what happens when an alternative emerges that utilizes energy more efficiently while providing more real-world utility? Bitcoin maxis will screech that "no altcoin has ever flipped Bitcoin," but that’s not the point. The point is that Bitcoin needs external competition at the proof-of-work level to maintain its thermodynamic legitimacy. Otherwise, it risks becoming what it despises: a static, non-dynamic asset that is just another store of value, with no practical utility until fiat collapses—and good luck waiting for that. Aeternity’s real-world use cases, from oracles to instant payments to low-cost, scalable contracts, mean that energy invested into securing it is converted into economic value, rather than just securing an ideological artifact. This pressure forces Bitcoin to evolve or become irrelevant—not by replacing it, but by outcompeting it where it matters. Final Thought: The Thermodynamic Reckoning Bitcoiners should be grateful for Aeternity’s friction. Without a competitor showing how PoW can be optimized for more than just blind security accumulation, Bitcoin risks becoming a historical relic, kept alive only by belief rather than economic reality. Thermodynamics doesn’t give a damn about ideology—it rewards systems that turn energy into real economic motion. Aeternity doesn’t have to kill Bitcoin. It just has to remind it what it was built for. @ ec42c765:328c0600
2025-02-05 23:38:12# カスタム絵文字とは 任意のオリジナル画像を絵文字のように文中に挿入できる機能です。 また、リアクション(Twitterの いいね のような機能)にもカスタム絵文字を使えます。  # カスタム絵文字の対応状況(2025/02/06)  カスタム絵文字を使うためにはカスタム絵文字に対応した[クライアント](https://welcome.nostr-jp.org/tutorial/explore-client.html)を使う必要があります。 ※表は一例です。クライアントは他にもたくさんあります。 使っているクライアントが対応していない場合は、クライアントを変更する、対応するまで待つ、開発者に要望を送る(または自分で実装する)などしましょう。 #### 対応クライアント - [Amethyst](https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst) - [FreeFrom](https://freefrom.space/) - [nostter](https://nostter.app/) - [Rabbit](https://rabbit.syusui.net/) - [Lumilumi](https://lumilumi.app/) - [Nos Haiku](https://nos-haiku.vercel.app/) - [Snort](https://snort.social/) - [noStrudel](https://nostrudel.ninja/) ここではnostterを使って説明していきます。 # 準備 カスタム絵文字を使うための準備です。 - Nostrエクステンション(NIP-07)を導入する - 使いたいカスタム絵文字をリストに登録する ## Nostrエクステンション(NIP-07)を導入する Nostrエクステンションは使いたいカスタム絵文字を登録する時に必要になります。 また、環境(パソコン、iPhone、androidなど)によって導入方法が違います。 Nostrエクステンションを導入する端末は、実際にNostrを閲覧する端末と違っても構いません(リスト登録はPC、Nostr閲覧はiPhoneなど)。 Nostrエクステンション(NIP-07)の導入方法は以下のページを参照してください。 [ログイン拡張機能 (NIP-07)を使ってみよう | Welcome to Nostr! ~ Nostrをはじめよう! ~ ](https://welcome.nostr-jp.org/tutorial/nip-07.html) 少し面倒ですが、これを導入しておくとNostr上の様々な場面で役立つのでより快適になります。 ## 使いたいカスタム絵文字をリストに登録する 以下のサイトで行います。 [emojito](https://emojito.meme/) 右上の**Get started**からNostrエクステンションでログインしてください。 例として以下のカスタム絵文字を導入してみます。 実際より絵文字が少なく表示されることがありますが、古い状態のデータを取得してしまっているためです。その場合はブラウザの更新ボタンを押してください。 [generalJP | カスタム絵文字](https://emojito.meme/a/naddr1qqykwetwv4exzmz22qqsuamnwvaz7tmev9382tndv5hsyg8vgtrk2svt8kuusk4l7w5g7j3mhet4xhhthhz52gsyr7jn9rqxqqpsgqqqw48qud6u3s)  - 右側の**Options**から**Bookmark**を選択  これでカスタム絵文字を使用するためのリストに登録できます。 # カスタム絵文字を使用する 例としてブラウザから使えるクライアント nostter から使用してみます。 [nostter](https://nostter.app/) nostterにNostrエクステンションでログイン、もしくは秘密鍵を入れてログインしてください。 ## 文章中に使用 1. **投稿**ボタンを押して投稿ウィンドウを表示 2. **顔😀**のボタンを押し、絵文字ウィンドウを表示 3. ***タブ**を押し、カスタム絵文字一覧を表示 4. カスタム絵文字を選択 5. : 記号に挟まれたアルファベットのショートコードとして挿入される  この状態で投稿するとカスタム絵文字として表示されます。 カスタム絵文字対応クライアントを使っている他ユーザーにもカスタム絵文字として表示されます。 対応していないクライアントの場合、ショートコードのまま表示されます。  ショートコードを直接入力することでカスタム絵文字の候補が表示されるのでそこから選択することもできます。  ## リアクションに使用 1. 任意の投稿の**顔😀**のボタンを押し、絵文字ウィンドウを表示 2. ***タブ**を押し、カスタム絵文字一覧を表示 3. カスタム絵文字を選択  カスタム絵文字リアクションを送ることができます。  # カスタム絵文字を探す 先述した[emojito](https://emojito.meme/)からカスタム絵文字を探せます。 例えば任意のユーザーのページ [emojito ロクヨウ](https://emojito.meme/p/npub1a3pvwe2p3v7mnjz6hle63r628wl9w567aw7u23fzqs062v5vqcqqu3sgh3) から探したり、 [emojito Browse all](https://emojito.meme/browse) からnostr全体で最近作成、更新された絵文字を見たりできます。 また、以下のリンクは日本語圏ユーザーが作ったカスタム絵文字を集めたリストです(2025/02/06) ※漏れがあるかもしれません [日本ユーザー作 カスタム絵文字](https://nostviewstr.vercel.app/npub17hczqvxtfv3w69wr6lxrttnpdekwdwel55mld60fr24zwjuu6utqtj8mjx/10030) 各絵文字セットにある**Open in emojito**のリンクからemojitoに飛び、使用リストに追加できます。 ----------- 以上です。 次:Nostrのカスタム絵文字の**作り方** Yakihonneリンク [Nostrのカスタム絵文字の作り方](https://yakihonne.com/article/_@lokuyow.github.io/1707912490439) Nostrリンク nostr:naddr1qqxnzdesxuunzv358ycrgveeqgswcsk8v4qck0deepdtluag3a9rh0jh2d0wh0w9g53qg8a9x2xqvqqrqsqqqa28r5psx3 ----------- # 仕様 [NIP-30 Custom Emoji](https://github.com/nostr-protocol/nips/blob/master/30.md) [NIP-30 カスタム絵文字(和訳)](https://github.com/nostr-jp/nips-ja/blob/main/30.md)
@ ec42c765:328c0600
2025-02-05 23:38:12# カスタム絵文字とは 任意のオリジナル画像を絵文字のように文中に挿入できる機能です。 また、リアクション(Twitterの いいね のような機能)にもカスタム絵文字を使えます。  # カスタム絵文字の対応状況(2025/02/06)  カスタム絵文字を使うためにはカスタム絵文字に対応した[クライアント](https://welcome.nostr-jp.org/tutorial/explore-client.html)を使う必要があります。 ※表は一例です。クライアントは他にもたくさんあります。 使っているクライアントが対応していない場合は、クライアントを変更する、対応するまで待つ、開発者に要望を送る(または自分で実装する)などしましょう。 #### 対応クライアント - [Amethyst](https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst) - [FreeFrom](https://freefrom.space/) - [nostter](https://nostter.app/) - [Rabbit](https://rabbit.syusui.net/) - [Lumilumi](https://lumilumi.app/) - [Nos Haiku](https://nos-haiku.vercel.app/) - [Snort](https://snort.social/) - [noStrudel](https://nostrudel.ninja/) ここではnostterを使って説明していきます。 # 準備 カスタム絵文字を使うための準備です。 - Nostrエクステンション(NIP-07)を導入する - 使いたいカスタム絵文字をリストに登録する ## Nostrエクステンション(NIP-07)を導入する Nostrエクステンションは使いたいカスタム絵文字を登録する時に必要になります。 また、環境(パソコン、iPhone、androidなど)によって導入方法が違います。 Nostrエクステンションを導入する端末は、実際にNostrを閲覧する端末と違っても構いません(リスト登録はPC、Nostr閲覧はiPhoneなど)。 Nostrエクステンション(NIP-07)の導入方法は以下のページを参照してください。 [ログイン拡張機能 (NIP-07)を使ってみよう | Welcome to Nostr! ~ Nostrをはじめよう! ~ ](https://welcome.nostr-jp.org/tutorial/nip-07.html) 少し面倒ですが、これを導入しておくとNostr上の様々な場面で役立つのでより快適になります。 ## 使いたいカスタム絵文字をリストに登録する 以下のサイトで行います。 [emojito](https://emojito.meme/) 右上の**Get started**からNostrエクステンションでログインしてください。 例として以下のカスタム絵文字を導入してみます。 実際より絵文字が少なく表示されることがありますが、古い状態のデータを取得してしまっているためです。その場合はブラウザの更新ボタンを押してください。 [generalJP | カスタム絵文字](https://emojito.meme/a/naddr1qqykwetwv4exzmz22qqsuamnwvaz7tmev9382tndv5hsyg8vgtrk2svt8kuusk4l7w5g7j3mhet4xhhthhz52gsyr7jn9rqxqqpsgqqqw48qud6u3s)  - 右側の**Options**から**Bookmark**を選択  これでカスタム絵文字を使用するためのリストに登録できます。 # カスタム絵文字を使用する 例としてブラウザから使えるクライアント nostter から使用してみます。 [nostter](https://nostter.app/) nostterにNostrエクステンションでログイン、もしくは秘密鍵を入れてログインしてください。 ## 文章中に使用 1. **投稿**ボタンを押して投稿ウィンドウを表示 2. **顔😀**のボタンを押し、絵文字ウィンドウを表示 3. ***タブ**を押し、カスタム絵文字一覧を表示 4. カスタム絵文字を選択 5. : 記号に挟まれたアルファベットのショートコードとして挿入される  この状態で投稿するとカスタム絵文字として表示されます。 カスタム絵文字対応クライアントを使っている他ユーザーにもカスタム絵文字として表示されます。 対応していないクライアントの場合、ショートコードのまま表示されます。  ショートコードを直接入力することでカスタム絵文字の候補が表示されるのでそこから選択することもできます。  ## リアクションに使用 1. 任意の投稿の**顔😀**のボタンを押し、絵文字ウィンドウを表示 2. ***タブ**を押し、カスタム絵文字一覧を表示 3. カスタム絵文字を選択  カスタム絵文字リアクションを送ることができます。  # カスタム絵文字を探す 先述した[emojito](https://emojito.meme/)からカスタム絵文字を探せます。 例えば任意のユーザーのページ [emojito ロクヨウ](https://emojito.meme/p/npub1a3pvwe2p3v7mnjz6hle63r628wl9w567aw7u23fzqs062v5vqcqqu3sgh3) から探したり、 [emojito Browse all](https://emojito.meme/browse) からnostr全体で最近作成、更新された絵文字を見たりできます。 また、以下のリンクは日本語圏ユーザーが作ったカスタム絵文字を集めたリストです(2025/02/06) ※漏れがあるかもしれません [日本ユーザー作 カスタム絵文字](https://nostviewstr.vercel.app/npub17hczqvxtfv3w69wr6lxrttnpdekwdwel55mld60fr24zwjuu6utqtj8mjx/10030) 各絵文字セットにある**Open in emojito**のリンクからemojitoに飛び、使用リストに追加できます。 ----------- 以上です。 次:Nostrのカスタム絵文字の**作り方** Yakihonneリンク [Nostrのカスタム絵文字の作り方](https://yakihonne.com/article/_@lokuyow.github.io/1707912490439) Nostrリンク nostr:naddr1qqxnzdesxuunzv358ycrgveeqgswcsk8v4qck0deepdtluag3a9rh0jh2d0wh0w9g53qg8a9x2xqvqqrqsqqqa28r5psx3 ----------- # 仕様 [NIP-30 Custom Emoji](https://github.com/nostr-protocol/nips/blob/master/30.md) [NIP-30 カスタム絵文字(和訳)](https://github.com/nostr-jp/nips-ja/blob/main/30.md) @ e3ba5e1a:5e433365
2025-02-05 17:47:16I got into a [friendly discussion](https://x.com/snoyberg/status/1887007888117252142) on X regarding health insurance. The specific question was how to deal with health insurance companies (presumably unfairly) denying claims? My answer, as usual: get government out of it! The US healthcare system is essentially the worst of both worlds: * Unlike full single payer, individuals incur high costs * Unlike a true free market, regulation causes increases in costs and decreases competition among insurers I'm firmly on the side of moving towards the free market. (And I say that as someone living under a single payer system now.) Here's what I would do: * Get rid of tax incentives that make health insurance tied to your employer, giving individuals back proper freedom of choice. * Reduce regulations significantly. * In the short term, some people will still get rejected claims and other obnoxious behavior from insurance companies. We address that in two ways: 1. Due to reduced regulations, new insurance companies will be able to enter the market offering more reliable coverage and better rates, and people will flock to them because they have the freedom to make their own choices. 2. Sue the asses off of companies that reject claims unfairly. And ideally, as one of the few legitimate roles of government in all this, institute new laws that limit the ability of fine print to allow insurers to escape their responsibilities. (I'm hesitant that the latter will happen due to the incestuous relationship between Congress/regulators and insurers, but I can hope.) Will this magically fix everything overnight like politicians normally promise? No. But it will allow the market to return to a healthy state. And I don't think it will take long (order of magnitude: 5-10 years) for it to come together, but that's just speculation. And since there's a high correlation between those who believe government can fix problems by taking more control and demanding that only credentialed experts weigh in on a topic (both points I strongly disagree with BTW): I'm a trained actuary and worked in the insurance industry, and have directly seen how government regulation reduces competition, raises prices, and harms consumers. And my final point: I don't think any prior art would be a good comparison for deregulation in the US, it's such a different market than any other country in the world for so many reasons that lessons wouldn't really translate. Nonetheless, I asked Grok for some empirical data on this, and at best the results of deregulation could be called "mixed," but likely more accurately "uncertain, confused, and subject to whatever interpretation anyone wants to apply." https://x.com/i/grok/share/Zc8yOdrN8lS275hXJ92uwq98M
@ e3ba5e1a:5e433365
2025-02-05 17:47:16I got into a [friendly discussion](https://x.com/snoyberg/status/1887007888117252142) on X regarding health insurance. The specific question was how to deal with health insurance companies (presumably unfairly) denying claims? My answer, as usual: get government out of it! The US healthcare system is essentially the worst of both worlds: * Unlike full single payer, individuals incur high costs * Unlike a true free market, regulation causes increases in costs and decreases competition among insurers I'm firmly on the side of moving towards the free market. (And I say that as someone living under a single payer system now.) Here's what I would do: * Get rid of tax incentives that make health insurance tied to your employer, giving individuals back proper freedom of choice. * Reduce regulations significantly. * In the short term, some people will still get rejected claims and other obnoxious behavior from insurance companies. We address that in two ways: 1. Due to reduced regulations, new insurance companies will be able to enter the market offering more reliable coverage and better rates, and people will flock to them because they have the freedom to make their own choices. 2. Sue the asses off of companies that reject claims unfairly. And ideally, as one of the few legitimate roles of government in all this, institute new laws that limit the ability of fine print to allow insurers to escape their responsibilities. (I'm hesitant that the latter will happen due to the incestuous relationship between Congress/regulators and insurers, but I can hope.) Will this magically fix everything overnight like politicians normally promise? No. But it will allow the market to return to a healthy state. And I don't think it will take long (order of magnitude: 5-10 years) for it to come together, but that's just speculation. And since there's a high correlation between those who believe government can fix problems by taking more control and demanding that only credentialed experts weigh in on a topic (both points I strongly disagree with BTW): I'm a trained actuary and worked in the insurance industry, and have directly seen how government regulation reduces competition, raises prices, and harms consumers. And my final point: I don't think any prior art would be a good comparison for deregulation in the US, it's such a different market than any other country in the world for so many reasons that lessons wouldn't really translate. Nonetheless, I asked Grok for some empirical data on this, and at best the results of deregulation could be called "mixed," but likely more accurately "uncertain, confused, and subject to whatever interpretation anyone wants to apply." https://x.com/i/grok/share/Zc8yOdrN8lS275hXJ92uwq98M @ 91bea5cd:1df4451c
2025-02-04 17:24:50### Definição de ULID: Timestamp 48 bits, Aleatoriedade 80 bits Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C. e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível. #### Gerar ULID ```sql CREATE EXTENSION IF NOT EXISTS pgcrypto; CREATE FUNCTION generate_ulid() RETURNS TEXT AS $$ DECLARE -- Crockford's Base32 encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; timestamp BYTEA = E'\\000\\000\\000\\000\\000\\000'; output TEXT = ''; unix_time BIGINT; ulid BYTEA; BEGIN -- 6 timestamp bytes unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT; timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER); -- 10 entropy bytes ulid = timestamp || gen_random_bytes(10); -- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31))); -- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31))); RETURN output; END $$ LANGUAGE plpgsql VOLATILE; ``` #### ULID TO UUID ```sql CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$ DECLARE -- 16byte bytes bytea = E'\\x00000000 00000000 00000000 00000000'; v char[]; -- Allow for O(1) lookup of index values dec integer[] = ARRAY[ 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 255, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31 ]; BEGIN IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN RAISE EXCEPTION 'Invalid ULID: %', ulid; END IF; v = regexp_split_to_array(ulid, ''); -- 6 bytes timestamp (48 bits) bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]); bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2)); bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4)); bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1)); bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3)); bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]); -- 10 bytes of entropy (80 bits); bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2)); bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4)); bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1)); bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3)); bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]); bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2)); bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4)); bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1)); bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3)); bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]); RETURN bytes; END $$ LANGUAGE plpgsql IMMUTABLE; CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$ BEGIN RETURN encode(parse_ulid(ulid), 'hex')::uuid; END $$ LANGUAGE plpgsql IMMUTABLE; ``` #### UUID to ULID ```sql CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$ DECLARE encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; output text = ''; uuid_bytes bytea = uuid_send(id); BEGIN -- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31))); -- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31))); RETURN output; END $$ LANGUAGE plpgsql IMMUTABLE; ``` #### Gera 11 Digitos aleatórios: YBKXG0CKTH4 ```sql -- Cria a extensão pgcrypto para gerar uuid CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Cria a função para gerar ULID CREATE OR REPLACE FUNCTION gen_lrandom() RETURNS TEXT AS $$ DECLARE ts_millis BIGINT; ts_chars TEXT; random_bytes BYTEA; random_chars TEXT; base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; i INT; BEGIN -- Pega o timestamp em milissegundos ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT; -- Converte o timestamp para base32 ts_chars := ''; FOR i IN REVERSE 0..11 LOOP ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1); END LOOP; -- Gera 10 bytes aleatórios e converte para base32 random_bytes := gen_random_bytes(10); random_chars := ''; FOR i IN 0..9 LOOP random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1); IF i < 9 THEN random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1); ELSE random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1); END IF; END LOOP; -- Concatena o timestamp e os caracteres aleatórios RETURN ts_chars || random_chars; END; $$ LANGUAGE plpgsql; ``` #### Exemplo de USO ```sql -- Criação da extensão caso não exista CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Criação da tabela pessoas CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL ); -- Busca Pessoa na tabela SELECT * FROM "pessoas" WHERE uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F'; ``` ### Fontes - https://github.com/scoville/pgsql-ulid - https://github.com/geckoboard/pgulid
@ 91bea5cd:1df4451c
2025-02-04 17:24:50### Definição de ULID: Timestamp 48 bits, Aleatoriedade 80 bits Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C. e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível. #### Gerar ULID ```sql CREATE EXTENSION IF NOT EXISTS pgcrypto; CREATE FUNCTION generate_ulid() RETURNS TEXT AS $$ DECLARE -- Crockford's Base32 encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; timestamp BYTEA = E'\\000\\000\\000\\000\\000\\000'; output TEXT = ''; unix_time BIGINT; ulid BYTEA; BEGIN -- 6 timestamp bytes unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT; timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER); -- 10 entropy bytes ulid = timestamp || gen_random_bytes(10); -- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31))); -- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31))); RETURN output; END $$ LANGUAGE plpgsql VOLATILE; ``` #### ULID TO UUID ```sql CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$ DECLARE -- 16byte bytes bytea = E'\\x00000000 00000000 00000000 00000000'; v char[]; -- Allow for O(1) lookup of index values dec integer[] = ARRAY[ 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 255, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31 ]; BEGIN IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN RAISE EXCEPTION 'Invalid ULID: %', ulid; END IF; v = regexp_split_to_array(ulid, ''); -- 6 bytes timestamp (48 bits) bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]); bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2)); bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4)); bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1)); bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3)); bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]); -- 10 bytes of entropy (80 bits); bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2)); bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4)); bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1)); bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3)); bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]); bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2)); bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4)); bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1)); bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3)); bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]); RETURN bytes; END $$ LANGUAGE plpgsql IMMUTABLE; CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$ BEGIN RETURN encode(parse_ulid(ulid), 'hex')::uuid; END $$ LANGUAGE plpgsql IMMUTABLE; ``` #### UUID to ULID ```sql CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$ DECLARE encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; output text = ''; uuid_bytes bytea = uuid_send(id); BEGIN -- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31))); -- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31))); RETURN output; END $$ LANGUAGE plpgsql IMMUTABLE; ``` #### Gera 11 Digitos aleatórios: YBKXG0CKTH4 ```sql -- Cria a extensão pgcrypto para gerar uuid CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Cria a função para gerar ULID CREATE OR REPLACE FUNCTION gen_lrandom() RETURNS TEXT AS $$ DECLARE ts_millis BIGINT; ts_chars TEXT; random_bytes BYTEA; random_chars TEXT; base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; i INT; BEGIN -- Pega o timestamp em milissegundos ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT; -- Converte o timestamp para base32 ts_chars := ''; FOR i IN REVERSE 0..11 LOOP ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1); END LOOP; -- Gera 10 bytes aleatórios e converte para base32 random_bytes := gen_random_bytes(10); random_chars := ''; FOR i IN 0..9 LOOP random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1); IF i < 9 THEN random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1); ELSE random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1); END IF; END LOOP; -- Concatena o timestamp e os caracteres aleatórios RETURN ts_chars || random_chars; END; $$ LANGUAGE plpgsql; ``` #### Exemplo de USO ```sql -- Criação da extensão caso não exista CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Criação da tabela pessoas CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL ); -- Busca Pessoa na tabela SELECT * FROM "pessoas" WHERE uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F'; ``` ### Fontes - https://github.com/scoville/pgsql-ulid - https://github.com/geckoboard/pgulid @ 1c197b12:242e1642
2025-02-09 22:56:33A Cypherpunk's Manifesto by Eric Hughes Privacy is necessary for an open society in the electronic age. Privacy is not secrecy. A private matter is something one doesn't want the whole world to know, but a secret matter is something one doesn't want anybody to know. Privacy is the power to selectively reveal oneself to the world. If two parties have some sort of dealings, then each has a memory of their interaction. Each party can speak about their own memory of this; how could anyone prevent it? One could pass laws against it, but the freedom of speech, even more than privacy, is fundamental to an open society; we seek not to restrict any speech at all. If many parties speak together in the same forum, each can speak to all the others and aggregate together knowledge about individuals and other parties. The power of electronic communications has enabled such group speech, and it will not go away merely because we might want it to. Since we desire privacy, we must ensure that each party to a transaction have knowledge only of that which is directly necessary for that transaction. Since any information can be spoken of, we must ensure that we reveal as little as possible. In most cases personal identity is not salient. When I purchase a magazine at a store and hand cash to the clerk, there is no need to know who I am. When I ask my electronic mail provider to send and receive messages, my provider need not know to whom I am speaking or what I am saying or what others are saying to me; my provider only need know how to get the message there and how much I owe them in fees. When my identity is revealed by the underlying mechanism of the transaction, I have no privacy. I cannot here selectively reveal myself; I must always reveal myself. Therefore, privacy in an open society requires anonymous transaction systems. Until now, cash has been the primary such system. An anonymous transaction system is not a secret transaction system. An anonymous system empowers individuals to reveal their identity when desired and only when desired; this is the essence of privacy. Privacy in an open society also requires cryptography. If I say something, I want it heard only by those for whom I intend it. If the content of my speech is available to the world, I have no privacy. To encrypt is to indicate the desire for privacy, and to encrypt with weak cryptography is to indicate not too much desire for privacy. Furthermore, to reveal one's identity with assurance when the default is anonymity requires the cryptographic signature. We cannot expect governments, corporations, or other large, faceless organizations to grant us privacy out of their beneficence. It is to their advantage to speak of us, and we should expect that they will speak. To try to prevent their speech is to fight against the realities of information. Information does not just want to be free, it longs to be free. Information expands to fill the available storage space. Information is Rumor's younger, stronger cousin; Information is fleeter of foot, has more eyes, knows more, and understands less than Rumor. We must defend our own privacy if we expect to have any. We must come together and create systems which allow anonymous transactions to take place. People have been defending their own privacy for centuries with whispers, darkness, envelopes, closed doors, secret handshakes, and couriers. The technologies of the past did not allow for strong privacy, but electronic technologies do. We the Cypherpunks are dedicated to building anonymous systems. We are defending our privacy with cryptography, with anonymous mail forwarding systems, with digital signatures, and with electronic money. Cypherpunks write code. We know that someone has to write software to defend privacy, and since we can't get privacy unless we all do, we're going to write it. We publish our code so that our fellow Cypherpunks may practice and play with it. Our code is free for all to use, worldwide. We don't much care if you don't approve of the software we write. We know that software can't be destroyed and that a widely dispersed system can't be shut down. Cypherpunks deplore regulations on cryptography, for encryption is fundamentally a private act. The act of encryption, in fact, removes information from the public realm. Even laws against cryptography reach only so far as a nation's border and the arm of its violence. Cryptography will ineluctably spread over the whole globe, and with it the anonymous transactions systems that it makes possible. For privacy to be widespread it must be part of a social contract. People must come and together deploy these systems for the common good. Privacy only extends so far as the cooperation of one's fellows in society. We the Cypherpunks seek your questions and your concerns and hope we may engage you so that we do not deceive ourselves. We will not, however, be moved out of our course because some may disagree with our goals. The Cypherpunks are actively engaged in making the networks safer for privacy. Let us proceed together apace. Onward. Eric Hughes <hughes@soda.berkeley.edu> 9 March 1993
@ 1c197b12:242e1642
2025-02-09 22:56:33A Cypherpunk's Manifesto by Eric Hughes Privacy is necessary for an open society in the electronic age. Privacy is not secrecy. A private matter is something one doesn't want the whole world to know, but a secret matter is something one doesn't want anybody to know. Privacy is the power to selectively reveal oneself to the world. If two parties have some sort of dealings, then each has a memory of their interaction. Each party can speak about their own memory of this; how could anyone prevent it? One could pass laws against it, but the freedom of speech, even more than privacy, is fundamental to an open society; we seek not to restrict any speech at all. If many parties speak together in the same forum, each can speak to all the others and aggregate together knowledge about individuals and other parties. The power of electronic communications has enabled such group speech, and it will not go away merely because we might want it to. Since we desire privacy, we must ensure that each party to a transaction have knowledge only of that which is directly necessary for that transaction. Since any information can be spoken of, we must ensure that we reveal as little as possible. In most cases personal identity is not salient. When I purchase a magazine at a store and hand cash to the clerk, there is no need to know who I am. When I ask my electronic mail provider to send and receive messages, my provider need not know to whom I am speaking or what I am saying or what others are saying to me; my provider only need know how to get the message there and how much I owe them in fees. When my identity is revealed by the underlying mechanism of the transaction, I have no privacy. I cannot here selectively reveal myself; I must always reveal myself. Therefore, privacy in an open society requires anonymous transaction systems. Until now, cash has been the primary such system. An anonymous transaction system is not a secret transaction system. An anonymous system empowers individuals to reveal their identity when desired and only when desired; this is the essence of privacy. Privacy in an open society also requires cryptography. If I say something, I want it heard only by those for whom I intend it. If the content of my speech is available to the world, I have no privacy. To encrypt is to indicate the desire for privacy, and to encrypt with weak cryptography is to indicate not too much desire for privacy. Furthermore, to reveal one's identity with assurance when the default is anonymity requires the cryptographic signature. We cannot expect governments, corporations, or other large, faceless organizations to grant us privacy out of their beneficence. It is to their advantage to speak of us, and we should expect that they will speak. To try to prevent their speech is to fight against the realities of information. Information does not just want to be free, it longs to be free. Information expands to fill the available storage space. Information is Rumor's younger, stronger cousin; Information is fleeter of foot, has more eyes, knows more, and understands less than Rumor. We must defend our own privacy if we expect to have any. We must come together and create systems which allow anonymous transactions to take place. People have been defending their own privacy for centuries with whispers, darkness, envelopes, closed doors, secret handshakes, and couriers. The technologies of the past did not allow for strong privacy, but electronic technologies do. We the Cypherpunks are dedicated to building anonymous systems. We are defending our privacy with cryptography, with anonymous mail forwarding systems, with digital signatures, and with electronic money. Cypherpunks write code. We know that someone has to write software to defend privacy, and since we can't get privacy unless we all do, we're going to write it. We publish our code so that our fellow Cypherpunks may practice and play with it. Our code is free for all to use, worldwide. We don't much care if you don't approve of the software we write. We know that software can't be destroyed and that a widely dispersed system can't be shut down. Cypherpunks deplore regulations on cryptography, for encryption is fundamentally a private act. The act of encryption, in fact, removes information from the public realm. Even laws against cryptography reach only so far as a nation's border and the arm of its violence. Cryptography will ineluctably spread over the whole globe, and with it the anonymous transactions systems that it makes possible. For privacy to be widespread it must be part of a social contract. People must come and together deploy these systems for the common good. Privacy only extends so far as the cooperation of one's fellows in society. We the Cypherpunks seek your questions and your concerns and hope we may engage you so that we do not deceive ourselves. We will not, however, be moved out of our course because some may disagree with our goals. The Cypherpunks are actively engaged in making the networks safer for privacy. Let us proceed together apace. Onward. Eric Hughes <hughes@soda.berkeley.edu> 9 March 1993 @ 40b9c85f:5e61b451
2025-02-09 20:53:03## Data Vending Machine Context Protocol ### The Convergence of Nostr DVMs and MCP In the rapidly evolving landscape of artificial intelligence, a new approach to sharing and accessing computational tools is emerging through the combination of two powerful technologies: Nostr's Data Vending Machines (DVMs) and the Model Context Protocol (MCP). This convergence has the potential to reshape how we think about tool distribution and accessibility, creating a truly decentralized marketplace for computational capabilities that serves AI, humans, and any type of machine that speaks the protocol. ## Understanding the Building Blocks Nostr's Data Vending Machines function much like their physical counterparts, but instead of dispensing snacks, they provide computational services with built-in Lightning Network payment capabilities. These DVMs operate on the decentralized Nostr network, allowing users to reach service providers without relying on centralized platforms or gatekeepers. The Model Context Protocol complements this infrastructure by providing a standardized way for applications to share context and expose their capabilities. Think of MCP as a universal language that allows tools to communicate effectively with any application that understands the protocol. This standardization is crucial for creating a seamless experience across different tools and services. ## What is DVMCP? DVMCP proposes a path for making DVMs and MCPs interoperable, introducing a protocol that makes local utilities available to everyone on the network. Our [draft specification](https://github.com/gzuuus/dvmcp/blob/master/docs/dvmcp-spec.md) serves as a foundation for easily transforming any MCP server into a DVM. To bridge these technologies, we've developed a simple software component that sits between your MCP server and the DVM ecosystem. You can find it in our [repository](repo.link). This bridge connects to your MCP server as a client and exposes its utilities through Nostr as a DVM, handling all the necessary Nostr logic. This means any existing MCP server can become accessible through Nostr without modifications - simply run the bridge alongside your server. This is particularly exciting because the vibrant and growing MCP community. Any team or individual already working with MCP can instantly plug into the Nostr DVM ecosystem, gaining access to decentralized discovery, built-in monetization, and an already existing user base. The bridge component makes this transition effortless, requiring no changes to any existing MCP implementations. ## A New Paradigm A decentralized marketplace where anyone can run tools locally and make them available globally. This addresses an unsolved problem larger than the Nostr ecosystem: how to make resources and tools discoverable and accessible in a decentralized, permissionless way. The power of this combination lies in its flexibility. Users can access tools through regular Nostr clients, AI agents can discover specific capabilities, and DVMs can create sophisticated tool chains. With Lightning Network integration, true machine-to-machine transactions become possible, where machines can autonomously discover, negotiate, and pay for computational services. Most importantly, you can run services on your own hardware while making these capabilities accessible to anyone anywhere. The result is a system that preserves privacy, promotes innovation, and creates new opportunities without central authorities controlling what tools can be offered or who can use them. The entire project, is available under the MIT license, and any feedback and collaboration is welcome. ## Looking Forward As these technologies mature, we're likely to see a fundamental shift in how computational capabilities are distributed and accessed. Instead of relying on massive cloud data centers controlled by a few companies, we're moving toward a global network of local machines, each contributing unique capabilities and computation to a larger, more resilient ecosystem. The convergence of Nostr DVMs and MCP represents more than just a technical innovation—it's a step toward a more equitable and accessible future. By enabling anyone to run and share tools, we're building an ecosystem where computational resources are not concentrated in the hands of a few but are available to and controllable by everyone. [Repository](https://github.com/gzuuus/dvmcp/)
@ 40b9c85f:5e61b451
2025-02-09 20:53:03## Data Vending Machine Context Protocol ### The Convergence of Nostr DVMs and MCP In the rapidly evolving landscape of artificial intelligence, a new approach to sharing and accessing computational tools is emerging through the combination of two powerful technologies: Nostr's Data Vending Machines (DVMs) and the Model Context Protocol (MCP). This convergence has the potential to reshape how we think about tool distribution and accessibility, creating a truly decentralized marketplace for computational capabilities that serves AI, humans, and any type of machine that speaks the protocol. ## Understanding the Building Blocks Nostr's Data Vending Machines function much like their physical counterparts, but instead of dispensing snacks, they provide computational services with built-in Lightning Network payment capabilities. These DVMs operate on the decentralized Nostr network, allowing users to reach service providers without relying on centralized platforms or gatekeepers. The Model Context Protocol complements this infrastructure by providing a standardized way for applications to share context and expose their capabilities. Think of MCP as a universal language that allows tools to communicate effectively with any application that understands the protocol. This standardization is crucial for creating a seamless experience across different tools and services. ## What is DVMCP? DVMCP proposes a path for making DVMs and MCPs interoperable, introducing a protocol that makes local utilities available to everyone on the network. Our [draft specification](https://github.com/gzuuus/dvmcp/blob/master/docs/dvmcp-spec.md) serves as a foundation for easily transforming any MCP server into a DVM. To bridge these technologies, we've developed a simple software component that sits between your MCP server and the DVM ecosystem. You can find it in our [repository](repo.link). This bridge connects to your MCP server as a client and exposes its utilities through Nostr as a DVM, handling all the necessary Nostr logic. This means any existing MCP server can become accessible through Nostr without modifications - simply run the bridge alongside your server. This is particularly exciting because the vibrant and growing MCP community. Any team or individual already working with MCP can instantly plug into the Nostr DVM ecosystem, gaining access to decentralized discovery, built-in monetization, and an already existing user base. The bridge component makes this transition effortless, requiring no changes to any existing MCP implementations. ## A New Paradigm A decentralized marketplace where anyone can run tools locally and make them available globally. This addresses an unsolved problem larger than the Nostr ecosystem: how to make resources and tools discoverable and accessible in a decentralized, permissionless way. The power of this combination lies in its flexibility. Users can access tools through regular Nostr clients, AI agents can discover specific capabilities, and DVMs can create sophisticated tool chains. With Lightning Network integration, true machine-to-machine transactions become possible, where machines can autonomously discover, negotiate, and pay for computational services. Most importantly, you can run services on your own hardware while making these capabilities accessible to anyone anywhere. The result is a system that preserves privacy, promotes innovation, and creates new opportunities without central authorities controlling what tools can be offered or who can use them. The entire project, is available under the MIT license, and any feedback and collaboration is welcome. ## Looking Forward As these technologies mature, we're likely to see a fundamental shift in how computational capabilities are distributed and accessed. Instead of relying on massive cloud data centers controlled by a few companies, we're moving toward a global network of local machines, each contributing unique capabilities and computation to a larger, more resilient ecosystem. The convergence of Nostr DVMs and MCP represents more than just a technical innovation—it's a step toward a more equitable and accessible future. By enabling anyone to run and share tools, we're building an ecosystem where computational resources are not concentrated in the hands of a few but are available to and controllable by everyone. [Repository](https://github.com/gzuuus/dvmcp/) @ 65912a7a:5dc638bf
2025-02-09 20:34:15I didn’t set out to become an enemy of the world’s richest man, but I seem to have managed it all the same. Until this moment, I’ve resisted describing my falling out with Elon Musk in much detail, but as the man’s cultural influence has metastasized—and he continues to spread lies about me on the social media platform that he owns (Twitter/X)—it seems only appropriate to set the record straight. I know that it annoys many in my audience to see me defend myself against attacks that they recognize to be spurious, but they might, nevertheless, find the details of what happened with Elon interesting. Of all the remarkable people I’ve met, Elon is probably the most likely to remain a world-historical figure—despite his best efforts to become a clown. He is also the most likely to squander his ample opportunities to live a happy life, ruin his reputation and most important relationships, and produce lasting harm across the globe. None of this was obvious to me when we first met, and I have been quite amazed at Elon’s evolution, both as a man and as an avatar of chaos. The friend I remember did not seem to hunger for public attention. But his engagement with Twitter/X transformed him—to a degree seldom seen outside of Marvel movies or Greek mythology. If Elon is still the man I knew, I can only conclude that I never really knew him. When we first met, Elon wasn’t especially rich or famous. In fact, I recall him teetering on the brink of bankruptcy around 2008, while risking the last of his previous fortune to make payroll at Tesla. At the time, he was living off loans from his friends Larry and Sergey. Once Elon became truly famous, and his personal wealth achieved escape velocity, I was among the first friends he called to discuss his growing security concerns. I put him in touch with Gavin de Becker, who provided his first bodyguards, and recommended other changes to his life. We also went shooting on at least two occasions with Scott Reitz, the finest firearms instructor I’ve ever met. It is an ugly irony that Elon’s repeated targeting of me on Twitter/X has increased my own security concerns. He understands this, of course, but does not seem to care. So how did we fall out? Let this be a cautionary tale for any of Elon’s friends who might be tempted to tell the great man something he doesn’t want to hear: (1.) When the SARS-CoV-2 virus first invaded our lives in March of 2020, Elon began tweeting in ways that I feared would harm his reputation. I also worried that his tweets might exacerbate the coming public-health emergency. Italy had already fallen off a cliff, and Elon shared the following opinion with his tens of millions of fans : *the coronavirus panic is dumb* As a concerned friend, I sent him a private text: *Hey, brother— I really think you need to walk back your coronavirus tweet. I know there’s a way to parse it that makes sense (“panic” is always dumb), but I fear that’s not the way most people are reading it. You have an enormous platform, and much of the world looks to you as an authority on all things technical. Coronavirus is a very big deal, and if we don’t get our act together, we’re going to look just like Italy very soon. If you want to turn some engineers loose on the problem, now would be a good time for a breakthrough in the production of ventilators...* (2.) Elon’s response was, I believe, the first discordant note ever struck in our friendship: *Sam, you of all people should not be concerned about this.* He included a link to a page on the CDC website, indicating that Covid was not even among the top 100 causes of death in the United States. This was a patently silly point to make in the first days of a pandemic. We continued exchanging texts for at least two hours. If I hadn’t known that I was communicating with Elon Musk, I would have thought I was debating someone who lacked any understanding of basic scientific and mathematical concepts, like exponential curves. (3.) Elon and I didn’t converge on a common view of epidemiology over the course of those two hours, but we hit upon a fun compromise: A wager. Elon bet me $1 million dollars (to be given to charity) against a bottle of fancy tequila ($1000) that we wouldn’t see as many as 35,000 cases of Covid in the United States (cases, not deaths). The terms of the bet reflected what was, in his estimation, the near certainty (1000 to 1) that he was right. Having already heard credible estimates that there could be 1 million deaths from Covid in the U.S. over the next 12-18 months (these estimates proved fairly accurate), I thought the terms of the bet ridiculous—and quite unfair to Elon. I offered to spot him two orders of magnitude: I was confident that we’d soon have 3.5 million cases of Covid in the U.S. Elon accused me of having lost my mind and insisted that we stick with a ceiling of 35,000. (4.) We communicated sporadically by text over the next couple of weeks, while the number of reported cases grew. Ominously, Elon dismissed the next batch of data reported by the CDC as merely presumptive—while confirmed cases of Covid, on his account, remained elusive. (5.) A few weeks later, when the CDC website finally reported 35,000 deaths from Covid in the U.S. and 600,000 cases, I sent Elon the following text: *Is (35,000 deaths + 600,000 cases) > 35,000 cases?* (6.) This text appears to have ended our friendship. Elon never responded, and it was not long before he began maligning me on Twitter for a variety of imaginary offenses. For my part, I eventually started complaining about the startling erosion of his integrity on my podcast, without providing any detail about what had transpired between us. (7.) At the end of 2022, I abandoned Twitter/X altogether, having recognized the poisonous effect that it had on my life—but also, in large part, because of what I saw it doing to Elon. I’ve been away from the platform for over two years, and yet Elon still attacks me. Occasionally a friend will tell me that I’m trending there, and the reasons for this are never good. As recently as this week, Elon repeated a defamatory charge about my being a “hypocrite” for writing a book in defense of honesty and then encouraging people to lie to keep Donald Trump out of the White House. Not only have I never advocated lying to defeat Trump (despite what that misleading clip from the Triggernometry podcast might suggest to naive viewers), I’ve taken great pains to defend Trump from the most damaging lie ever told about him. Elon knows this, because we communicated about the offending clip when it first appeared on Twitter/X. However, he simply does not care that he is defaming a former friend to hundreds of millions of people—many of whom are mentally unstable. On this occasion, he even tagged the incoming president of the United States. All of this remains socially and professionally awkward, because Elon and I still have many friends in common. Which suggests the terms of another wager that I would happily make, if such a thing were possible—and I would accept 1000 to 1 odds in Elon’s favor: I bet that anyone who knows us both knows that I am telling the truth. Everyone close to Elon must recognize how unethical he has become, and yet they remain silent. Their complicity is understandable, but it is depressing all the same. These otherwise serious and compassionate people know that when Elon attacks private citizens on Twitter/X—falsely accusing them of crimes or corruption, celebrating their misfortunes—he is often causing tangible harm in their lives. It’s probably still true to say that social media “isn’t real life,” until thousands of lunatics learn your home address. A final absurdity in my case, is that several of the controversial issues that Elon has hurled himself at of late—and even attacked me over—are ones we agree about. We seem to be in near total alignment on immigration and the problems at the southern border of the U.S. We also share the same concerns about what he calls “the woke mind virus.” And we fully agree about the manifest evil of the so-called “grooming-gangs scandal” in the U.K. The problem with Elon, is that he makes no effort to get his facts straight when discussing any of these topics, and he regularly promotes lies and conspiracy theories manufactured by known bad actors, at scale. (And if grooming were really one of his concerns, it’s strange that he couldn’t find anything wrong with Matt Gaetz.) Elon and I even agree about the foundational importance of free speech. It’s just that his approach to safeguarding it—amplifying the influence of psychopaths and psychotics, while deplatforming real journalists and his own critics; or savaging the reputations of democratic leaders, while never saying a harsh word about the Chinese Communist Party—is not something I can support. The man claims to have principles, but he appears to have only moods and impulses. Any dispassionate observer of Elon’s behavior on Twitter/X can see that there is something seriously wrong with his moral compass, if not his perception of reality. There is simply no excuse for a person with his talents, resources, and opportunities to create so much pointless noise. The callousness and narcissism conveyed by his antics should be impossible for his real friends to ignore—but they appear to keep silent, perhaps for fear of losing access to his orbit of influence. Of course, none of this is to deny that the tens of thousands of brilliant engineers Elon employs are accomplishing extraordinary things. He really is the greatest entrepreneur of our generation. And because of the businesses he’s built, he will likely become the world’s first trillionaire—perhaps very soon. Since the election of Donald Trump in November, Elon’s wealth has grown by around $200 billion. That’s nearly $3 billion a day (and over $100 million an hour). Such astonishing access to resources gives Elon the chance—and many would argue the responsibility—to solve enormous problems in our world. So why spend time spreading lies on X?
@ 65912a7a:5dc638bf
2025-02-09 20:34:15I didn’t set out to become an enemy of the world’s richest man, but I seem to have managed it all the same. Until this moment, I’ve resisted describing my falling out with Elon Musk in much detail, but as the man’s cultural influence has metastasized—and he continues to spread lies about me on the social media platform that he owns (Twitter/X)—it seems only appropriate to set the record straight. I know that it annoys many in my audience to see me defend myself against attacks that they recognize to be spurious, but they might, nevertheless, find the details of what happened with Elon interesting. Of all the remarkable people I’ve met, Elon is probably the most likely to remain a world-historical figure—despite his best efforts to become a clown. He is also the most likely to squander his ample opportunities to live a happy life, ruin his reputation and most important relationships, and produce lasting harm across the globe. None of this was obvious to me when we first met, and I have been quite amazed at Elon’s evolution, both as a man and as an avatar of chaos. The friend I remember did not seem to hunger for public attention. But his engagement with Twitter/X transformed him—to a degree seldom seen outside of Marvel movies or Greek mythology. If Elon is still the man I knew, I can only conclude that I never really knew him. When we first met, Elon wasn’t especially rich or famous. In fact, I recall him teetering on the brink of bankruptcy around 2008, while risking the last of his previous fortune to make payroll at Tesla. At the time, he was living off loans from his friends Larry and Sergey. Once Elon became truly famous, and his personal wealth achieved escape velocity, I was among the first friends he called to discuss his growing security concerns. I put him in touch with Gavin de Becker, who provided his first bodyguards, and recommended other changes to his life. We also went shooting on at least two occasions with Scott Reitz, the finest firearms instructor I’ve ever met. It is an ugly irony that Elon’s repeated targeting of me on Twitter/X has increased my own security concerns. He understands this, of course, but does not seem to care. So how did we fall out? Let this be a cautionary tale for any of Elon’s friends who might be tempted to tell the great man something he doesn’t want to hear: (1.) When the SARS-CoV-2 virus first invaded our lives in March of 2020, Elon began tweeting in ways that I feared would harm his reputation. I also worried that his tweets might exacerbate the coming public-health emergency. Italy had already fallen off a cliff, and Elon shared the following opinion with his tens of millions of fans : *the coronavirus panic is dumb* As a concerned friend, I sent him a private text: *Hey, brother— I really think you need to walk back your coronavirus tweet. I know there’s a way to parse it that makes sense (“panic” is always dumb), but I fear that’s not the way most people are reading it. You have an enormous platform, and much of the world looks to you as an authority on all things technical. Coronavirus is a very big deal, and if we don’t get our act together, we’re going to look just like Italy very soon. If you want to turn some engineers loose on the problem, now would be a good time for a breakthrough in the production of ventilators...* (2.) Elon’s response was, I believe, the first discordant note ever struck in our friendship: *Sam, you of all people should not be concerned about this.* He included a link to a page on the CDC website, indicating that Covid was not even among the top 100 causes of death in the United States. This was a patently silly point to make in the first days of a pandemic. We continued exchanging texts for at least two hours. If I hadn’t known that I was communicating with Elon Musk, I would have thought I was debating someone who lacked any understanding of basic scientific and mathematical concepts, like exponential curves. (3.) Elon and I didn’t converge on a common view of epidemiology over the course of those two hours, but we hit upon a fun compromise: A wager. Elon bet me $1 million dollars (to be given to charity) against a bottle of fancy tequila ($1000) that we wouldn’t see as many as 35,000 cases of Covid in the United States (cases, not deaths). The terms of the bet reflected what was, in his estimation, the near certainty (1000 to 1) that he was right. Having already heard credible estimates that there could be 1 million deaths from Covid in the U.S. over the next 12-18 months (these estimates proved fairly accurate), I thought the terms of the bet ridiculous—and quite unfair to Elon. I offered to spot him two orders of magnitude: I was confident that we’d soon have 3.5 million cases of Covid in the U.S. Elon accused me of having lost my mind and insisted that we stick with a ceiling of 35,000. (4.) We communicated sporadically by text over the next couple of weeks, while the number of reported cases grew. Ominously, Elon dismissed the next batch of data reported by the CDC as merely presumptive—while confirmed cases of Covid, on his account, remained elusive. (5.) A few weeks later, when the CDC website finally reported 35,000 deaths from Covid in the U.S. and 600,000 cases, I sent Elon the following text: *Is (35,000 deaths + 600,000 cases) > 35,000 cases?* (6.) This text appears to have ended our friendship. Elon never responded, and it was not long before he began maligning me on Twitter for a variety of imaginary offenses. For my part, I eventually started complaining about the startling erosion of his integrity on my podcast, without providing any detail about what had transpired between us. (7.) At the end of 2022, I abandoned Twitter/X altogether, having recognized the poisonous effect that it had on my life—but also, in large part, because of what I saw it doing to Elon. I’ve been away from the platform for over two years, and yet Elon still attacks me. Occasionally a friend will tell me that I’m trending there, and the reasons for this are never good. As recently as this week, Elon repeated a defamatory charge about my being a “hypocrite” for writing a book in defense of honesty and then encouraging people to lie to keep Donald Trump out of the White House. Not only have I never advocated lying to defeat Trump (despite what that misleading clip from the Triggernometry podcast might suggest to naive viewers), I’ve taken great pains to defend Trump from the most damaging lie ever told about him. Elon knows this, because we communicated about the offending clip when it first appeared on Twitter/X. However, he simply does not care that he is defaming a former friend to hundreds of millions of people—many of whom are mentally unstable. On this occasion, he even tagged the incoming president of the United States. All of this remains socially and professionally awkward, because Elon and I still have many friends in common. Which suggests the terms of another wager that I would happily make, if such a thing were possible—and I would accept 1000 to 1 odds in Elon’s favor: I bet that anyone who knows us both knows that I am telling the truth. Everyone close to Elon must recognize how unethical he has become, and yet they remain silent. Their complicity is understandable, but it is depressing all the same. These otherwise serious and compassionate people know that when Elon attacks private citizens on Twitter/X—falsely accusing them of crimes or corruption, celebrating their misfortunes—he is often causing tangible harm in their lives. It’s probably still true to say that social media “isn’t real life,” until thousands of lunatics learn your home address. A final absurdity in my case, is that several of the controversial issues that Elon has hurled himself at of late—and even attacked me over—are ones we agree about. We seem to be in near total alignment on immigration and the problems at the southern border of the U.S. We also share the same concerns about what he calls “the woke mind virus.” And we fully agree about the manifest evil of the so-called “grooming-gangs scandal” in the U.K. The problem with Elon, is that he makes no effort to get his facts straight when discussing any of these topics, and he regularly promotes lies and conspiracy theories manufactured by known bad actors, at scale. (And if grooming were really one of his concerns, it’s strange that he couldn’t find anything wrong with Matt Gaetz.) Elon and I even agree about the foundational importance of free speech. It’s just that his approach to safeguarding it—amplifying the influence of psychopaths and psychotics, while deplatforming real journalists and his own critics; or savaging the reputations of democratic leaders, while never saying a harsh word about the Chinese Communist Party—is not something I can support. The man claims to have principles, but he appears to have only moods and impulses. Any dispassionate observer of Elon’s behavior on Twitter/X can see that there is something seriously wrong with his moral compass, if not his perception of reality. There is simply no excuse for a person with his talents, resources, and opportunities to create so much pointless noise. The callousness and narcissism conveyed by his antics should be impossible for his real friends to ignore—but they appear to keep silent, perhaps for fear of losing access to his orbit of influence. Of course, none of this is to deny that the tens of thousands of brilliant engineers Elon employs are accomplishing extraordinary things. He really is the greatest entrepreneur of our generation. And because of the businesses he’s built, he will likely become the world’s first trillionaire—perhaps very soon. Since the election of Donald Trump in November, Elon’s wealth has grown by around $200 billion. That’s nearly $3 billion a day (and over $100 million an hour). Such astonishing access to resources gives Elon the chance—and many would argue the responsibility—to solve enormous problems in our world. So why spend time spreading lies on X? @ 2e8970de:63345c7a
2025-02-09 20:22:19 https://www.infinitescroll.us/p/13-things-i-learned-reading-a-225 originally posted at https://stacker.news/items/880820
@ 2e8970de:63345c7a
2025-02-09 20:22:19 https://www.infinitescroll.us/p/13-things-i-learned-reading-a-225 originally posted at https://stacker.news/items/880820 @ b8af284d:f82c91dd
2025-02-09 18:48:21*Liebe Abonnenten,* *viele von uns erleben im privaten wie im öffentlichen Leben gerade eine Zeit der Verwirrung und Irritation. Etwas scheint im Umbruch, alte Gewissheiten, Strukturen und Allianzen scheinen sich vor unseren Augen aufzulösen. Trump, Musk und Thiel wirken wie die Abrissbirnen einer alten Ordnung, Agenten des Chaos mit dem einzigen Ziel, sich selbst zu bereichern. Ist es so?* *Könnte es anders sein?* *Folgender Text kann und will diese Fragen nicht ultimativ beantworten. Es gibt aber eine Brille, durch die, setzt man sie auf, viele Entwicklungen in einem anderen, viel helleren Licht erscheinen. Diese Brille heißt e/acc.*  **Was ist e/acc?** Das Kürzel geht auf den Programmierer Guillaume Verdon zurück, der unter dem Pseudonym „Beff Jezos“ die Bewegung. Es steht für „effective accelerationism“. Accelerationism, auf Deutsch Akzelerationismus, abgeleitet vom Verb „beschleunigen“, hat Wurzeln, die weiter zurückreichen - dazu später mehr. Der Zusatz „effective“ ist eine ironische Replik auf den „effective Altruism“, den unter anderen Sam Bankman-Fried vertrat und grandios scheiterte. e/acc setzt also auf Beschleunigung. Kapitalismus, Innovation, vor allem künstliche Intelligenz sollen nicht aufgehalten oder reguliert werden, sondern im Gegenteil beschleunigt werden.  **Warum?** Eine einfache Antwort lautet: Weil sie eh stattfinden. Besonders deutlich wird das im Fall künstlicher Intelligenz. Large Language Models (LLMs) wie ChatGPT und Deepseek sind nur die für die Öffentlichkeit sichtbaren Entwicklungen. Im Hintergrund ersetzt Künstliche Intelligenz zunehmend auch Produktionsprozesse und nicht zuletzt die Kriegsführung. Man spricht deswegen vom „Point of Singularity“. In den kommenden Jahren wird künstliche Intelligenz menschliche übertrumpfen. Unsere Arbeitswelt, unser Finanzsystem und gesellschaftliche Strukturen werden sich grundlegend ändern. Wenn es dazu kommt, warum die Entwicklung noch aufhalten? **Beschleunigen ist besser.** Die zweite Antwort ist tiefgründiger und rührt an das Verständnis von Leben insgesamt. Langfristig strebt das Universum nach Entropie. Es dehnt sich aus, bis alle Teile in maximaler „Unordnung“ angeordnet sind. Systeme mit hoher Energiezufuhr können Strukturen aufbauen, solange sie Wärme oder Entropie in ihre Umgebung abgeben. In einem Organismus sind alle Teile zu einer höheren Ordnung organisiert. Leben strebt nach Ordnung, Selbsterhalt und Wachstum, weshalb der Energieverbrauch zunimmt. e/acc-Fan und Silicon-Valley-Investor Marc Andreessen schreibt in “The Techno-Optimist Manifesto”: > *Techno-Optimists believe that societies, like sharks, grow or die.* > > *We believe growth is progress – leading to vitality, expansion of life, increasing knowledge, higher well being.* Ein Gleichgewicht gibt es nicht. Entweder strebt eine Struktur nach Ordnung (Leben) oder nach Unordnung (Tod). Da eine Balance nicht existiert, gibt es nur zwei Möglichkeiten: Verlangsamen oder Beschleunigen. Höhere Ordnungen aufbauen oder verfallen. Wachsen oder Sterben. **Beschleunigen ist besser.**  ## **Konsequenzen** e/acc ist kein philosophisches System im strengen Sinn. Es leitet Konsequenzen aus physikalischen Grundsätzen ab. Kapitalistische Systeme und freie Märkte sind die effizientesten Strukturen, um Informationen zu verarbeiten. In einem offenen, freien Markt gibt der Preis das zuverlässigste Signal über Knappheit eines Gutes. Wird dieser Prozess durch externe Einflussnahme wie Subventionen gestört, läuft die Maschine nicht effizient. Das Gesamtsystem wird verzerrt. Nochmals Andreessen dazu: > *We believe the market economy is a discovery machine, a form of intelligence – an exploratory, evolutionary, adaptive system.* Varianten und Abweichungen sind wichtig, da ein System dadurch am schnellsten auf sich ständig verändernde Umweltbedingungen reagieren kann. Wer nicht frei sprechen kann, kann nicht frei denken. Dezentrale Strukturen mit vielen kleinen einzelnen „Nodes“ sind resilienter als hierarchisch-zentralistische Systeme. Das führt zu einem Meinungsfreiheits-Maximalismus. Greifen staatliche Akteure in die Forschung ein, und vergeben zum Beispiel Lizenzen für KI-Projekte, kann das System nicht mehr auf die besten Ressourcen zurückgreifen. Es entwickelt sich nicht in seiner natürlichen Geschwindigkeit, sondern wird künstlich verlangsamt. **Beschleunigen ist besser.** Im Falle von KI hat dies geopolitische Konsequenzen: Sollten autoritäre Akteure wie zum Beispiel China schneller zum Punkt der Singularity vorstoßen, entsteht eine Dystopie, ein Orwellscher Überwachungsstaat. Bevorzugen ist deswegen eine beschleunigte, dezentrale Forschung, damit freie Systeme die Oberhand behalten. Dasselbe gilt für das Geldsystem: e/acc trifft hier auf Hayek und Mises. Viele Zahlungssysteme stehen in permanenter Konkurrenz zueinander. Am Ende setzt sich das nützlichste und vermutlich auch härteste Geld durch. ## Konkrete Folgen Auf die konkrete Politik übertragen führt das zu Konsequenzen, die man aktuell beobachten kann. \*\*Radikale Deregulierung: \*\*Die Biden-Administration versuchte, [AI-Forschung eng an die Regierung zu binden](https://x.com/pmddomingos/status/1888059248535552312). Open-AI-Gründer Sam Altman forderte [2023 eine Lizenz-Vergabe an Unternehmen](https://www.businessinsider.com/sam-altman-openai-chatgpt-government-agency-should-license-ai-work-2023-5), um überhaupt in diesem Bereich aktiv zu werden. (Musk trat zunächst sogar für ein Forschungs-Moratorium ein, änderte dann aber seine Meinung.) Das führte zum Widerstand der e/acc-Fraktion im Silicon Valley, und gab den Ausschlag, sich auf die Trump-Seite zu stellen. Deregulierung zieht sich nun durch alle Bereiche der Wirtschaft: auch auf die „Entwicklungshilfe“ von USAID. Der Regierungsapparat wird insgesamt massiv verkleinert, da Bürokratie das Wachstum hemmt. A fuera. \*\*Priorisierung von günstiger Energie: \*\*Da der Energie-Verbrauch mit zunehmender Ordnung ansteigt, und LLMs einen sehr viel Strom brauchen, priorisiert die neue Regierung die Erschließung zusätzlicher Energiequellen: Gas, Öl, Nuklear und regenerative Energiequellen gleichermaßen.  ![1.00]() Wiederherstellung von Meinungsfreiheit.Content-Moderationen auf Social-Media-Plattformen fallen weg. Geheimdienst-Dokumente werden freigegeben. So schrieb Peter Thiel vor einigen Wochen in einem Essay in der Financial Times über die große Enthüllung: > \ > *But understood in the original sense of the Greek word **apokálypsis, meaning “unveiling”**, Obama could not give the same reassurance in 2025. Trump’s return to the White House augurs the apokálypsis of the ancien regime’s secrets. (…)\ > The apokálypsis is the most peaceful means of resolving the old guard’s war on the internet, a war the internet won. My friend and colleague Eric Weinstein calls the pre-internet custodians of secrets the Distributed Idea Suppression Complex (DISC) — the media organisations, bureaucracies, universities and government-funded NGOs that traditionally delimited public conversation.* **Krypto-Deregulierung:** Da Kryptowährungen und Smart-Contract-Strukturen bestens mit LLMs harmonieren, werden Innovationsbremsen in Form von Regulierungen abgebaut. \*\*Umbruch der Weltordnung: \*\*Auf der geopolitischen Ebene werden Bündnisse, Allianzen und Blockstrukturen aufgebrochen und nach effizienten Win-Win-Verhältnissen neu organisiert. **Erschließung neuer Lebenswelten:** Degrowth, weniger Energie-Verbrauch und weniger Kinder sind keine Option, da sie zum Tod führen. Das System Menschheit muss wachsen und wird neue Lösungen erfinden. Wenn die Ressourcen des Planeten Erde nicht mehr ausreichen, müssen neue erschlossen werden - vielleicht auf dem Mars. ## **Die Ideengeschichte** Während e/acc ein relativ neues System ist, hat der Akzelerationismus tiefere Wurzeln. Lenin kann man als einen frühen Akzelerationisten bezeichnen. Der Marxismus wurde Anfang des 20. Jahrhunderts weniger als Ideologie, sondern mehr als exakte Wissenschaft begriffen. Demnach würde der Kapitalismus früher oder später an seinen eigenen Widerständen kollabieren. Warum den Prozess also nicht beschleunigen und die Revolution herbeiführen? Ende des 20. Jahrhunderts griff der Philosoph Nick Land diese Gedanken wieder auf. Land forderte Beschleunigung, sah am Ende des Prozesses aber einen Kollaps des Systems und eine dunkle Zukunft. Ironie der Geschichte: Land zog in den 2000er Jahren nach China, wo er einen autoritären Akzelerationismus verwirklicht sah. Auch Steve Bannon, Leiter des ersten Trump-Wahlkampfes 2016, war von Lands Gedanken geprägt.  e/acc aber ist eine neuer, optimistischer „Fork“ des alten, dunklen Akzelerationismus. Es sieht eine positive Zukunft für die gesamte Menschheit aufgrund eines gigantischen Produktivitätsschubs. Eine neue, höhere Ordnung ist am Entstehen. Kurz gesagt: > ***Effective accelerationism (e/acc) in a nutshell:*** > > ***Stop fighting the thermodynamic will of the universe*** > > ***You cannot stop the acceleration*** > > ***You might as well embrace it*** > > ***A C C E L E R A T E*** *[Notes on e/acc principles and tenets](https://effectiveaccelerationism.substack.com/p/repost-notes-on-eacc-principles-and?utm_source=substack\&utm_campaign=post_embed\&utm_medium=web)* Happy Future also? Durch die e/acc-Brille gesehen wirkt die Welt wesentlich heller und optimistischer als sie die meisten “Legacy Media” gerade darstellen. Demnach bewegen wir uns auf eine neue Zeit gesteigerter Produktivität und damit Lebensqualität zu. Wenn alle Arbeit von Maschinen verrichtet wird, können Menschen währenddessen auf Bali surfen, meditieren und Yoga machen. Oder? ## **Kritik** Leben entsteht an der Grenze von Chaos und Ordnung. Vielleicht versetzt e/acc das Pendel zu stark in den Ausschlag in eine Richtung. Unkontrolliertes Wachstum bedeutet im lebenden Organismen Krebs. e/acc sieht sich wie Marxisten der ersten Stunde (Lenin) im Besitz der Wahrheit in Form physikalischer Grundsätze. Erst durch diese Hybris führten zu den Grausamkeiten sozialistischer Systeme im 20. Jahrhundert. Schließlich beantwortet e/acc nicht die Frage nach der Verteilungsgerechtigkeit, die durch den gewaltigen Produktivitätsschub durch AI entstehen wird. Ob e/acc als politisches und gesellschaftliches System taugt, ist deswegen fraglich. Aber viele aktuelle Entwicklungen scheinen durch die Akzelerationismus-Brille klarer. **Quellen:** *Peter Thiel: [A Time for Truth and Reconciliation](https://www.ft.com/content/a46cb128-1f74-4621-ab0b-242a76583105)* *Marc Andreessen: [The Techno-Optimist Manifesto](http://xn--we%20believe%20the%20market%20economy%20is%20a%20discovery%20machine,%20a%20form%20of%20intelligence%20%20an%20exploratory,%20evolutionary,%20adaptive%20system-2296h./)* *e/acc: [Notes on e/acc principles and tenets](https://effectiveaccelerationism.substack.com/p/repost-notes-on-eacc-principles-and?utm_source=substack\&utm_campaign=post_embed\&utm_medium=web)* *Andy Beckett: [Accelerationism: how a fringe philosophy predicted the future we live in](https://www.theguardian.com/world/2017/may/11/accelerationism-how-a-fringe-philosophy-predicted-the-future-we-live-in)* *Lex Friedman: [Guillaume Verdon. e/acc-Movement. Physics. Computation & AGI.](https://open.spotify.com/episode/2TvKfwY5Z7Lz8iiaGLRMgO)*
@ b8af284d:f82c91dd
2025-02-09 18:48:21*Liebe Abonnenten,* *viele von uns erleben im privaten wie im öffentlichen Leben gerade eine Zeit der Verwirrung und Irritation. Etwas scheint im Umbruch, alte Gewissheiten, Strukturen und Allianzen scheinen sich vor unseren Augen aufzulösen. Trump, Musk und Thiel wirken wie die Abrissbirnen einer alten Ordnung, Agenten des Chaos mit dem einzigen Ziel, sich selbst zu bereichern. Ist es so?* *Könnte es anders sein?* *Folgender Text kann und will diese Fragen nicht ultimativ beantworten. Es gibt aber eine Brille, durch die, setzt man sie auf, viele Entwicklungen in einem anderen, viel helleren Licht erscheinen. Diese Brille heißt e/acc.*  **Was ist e/acc?** Das Kürzel geht auf den Programmierer Guillaume Verdon zurück, der unter dem Pseudonym „Beff Jezos“ die Bewegung. Es steht für „effective accelerationism“. Accelerationism, auf Deutsch Akzelerationismus, abgeleitet vom Verb „beschleunigen“, hat Wurzeln, die weiter zurückreichen - dazu später mehr. Der Zusatz „effective“ ist eine ironische Replik auf den „effective Altruism“, den unter anderen Sam Bankman-Fried vertrat und grandios scheiterte. e/acc setzt also auf Beschleunigung. Kapitalismus, Innovation, vor allem künstliche Intelligenz sollen nicht aufgehalten oder reguliert werden, sondern im Gegenteil beschleunigt werden.  **Warum?** Eine einfache Antwort lautet: Weil sie eh stattfinden. Besonders deutlich wird das im Fall künstlicher Intelligenz. Large Language Models (LLMs) wie ChatGPT und Deepseek sind nur die für die Öffentlichkeit sichtbaren Entwicklungen. Im Hintergrund ersetzt Künstliche Intelligenz zunehmend auch Produktionsprozesse und nicht zuletzt die Kriegsführung. Man spricht deswegen vom „Point of Singularity“. In den kommenden Jahren wird künstliche Intelligenz menschliche übertrumpfen. Unsere Arbeitswelt, unser Finanzsystem und gesellschaftliche Strukturen werden sich grundlegend ändern. Wenn es dazu kommt, warum die Entwicklung noch aufhalten? **Beschleunigen ist besser.** Die zweite Antwort ist tiefgründiger und rührt an das Verständnis von Leben insgesamt. Langfristig strebt das Universum nach Entropie. Es dehnt sich aus, bis alle Teile in maximaler „Unordnung“ angeordnet sind. Systeme mit hoher Energiezufuhr können Strukturen aufbauen, solange sie Wärme oder Entropie in ihre Umgebung abgeben. In einem Organismus sind alle Teile zu einer höheren Ordnung organisiert. Leben strebt nach Ordnung, Selbsterhalt und Wachstum, weshalb der Energieverbrauch zunimmt. e/acc-Fan und Silicon-Valley-Investor Marc Andreessen schreibt in “The Techno-Optimist Manifesto”: > *Techno-Optimists believe that societies, like sharks, grow or die.* > > *We believe growth is progress – leading to vitality, expansion of life, increasing knowledge, higher well being.* Ein Gleichgewicht gibt es nicht. Entweder strebt eine Struktur nach Ordnung (Leben) oder nach Unordnung (Tod). Da eine Balance nicht existiert, gibt es nur zwei Möglichkeiten: Verlangsamen oder Beschleunigen. Höhere Ordnungen aufbauen oder verfallen. Wachsen oder Sterben. **Beschleunigen ist besser.**  ## **Konsequenzen** e/acc ist kein philosophisches System im strengen Sinn. Es leitet Konsequenzen aus physikalischen Grundsätzen ab. Kapitalistische Systeme und freie Märkte sind die effizientesten Strukturen, um Informationen zu verarbeiten. In einem offenen, freien Markt gibt der Preis das zuverlässigste Signal über Knappheit eines Gutes. Wird dieser Prozess durch externe Einflussnahme wie Subventionen gestört, läuft die Maschine nicht effizient. Das Gesamtsystem wird verzerrt. Nochmals Andreessen dazu: > *We believe the market economy is a discovery machine, a form of intelligence – an exploratory, evolutionary, adaptive system.* Varianten und Abweichungen sind wichtig, da ein System dadurch am schnellsten auf sich ständig verändernde Umweltbedingungen reagieren kann. Wer nicht frei sprechen kann, kann nicht frei denken. Dezentrale Strukturen mit vielen kleinen einzelnen „Nodes“ sind resilienter als hierarchisch-zentralistische Systeme. Das führt zu einem Meinungsfreiheits-Maximalismus. Greifen staatliche Akteure in die Forschung ein, und vergeben zum Beispiel Lizenzen für KI-Projekte, kann das System nicht mehr auf die besten Ressourcen zurückgreifen. Es entwickelt sich nicht in seiner natürlichen Geschwindigkeit, sondern wird künstlich verlangsamt. **Beschleunigen ist besser.** Im Falle von KI hat dies geopolitische Konsequenzen: Sollten autoritäre Akteure wie zum Beispiel China schneller zum Punkt der Singularity vorstoßen, entsteht eine Dystopie, ein Orwellscher Überwachungsstaat. Bevorzugen ist deswegen eine beschleunigte, dezentrale Forschung, damit freie Systeme die Oberhand behalten. Dasselbe gilt für das Geldsystem: e/acc trifft hier auf Hayek und Mises. Viele Zahlungssysteme stehen in permanenter Konkurrenz zueinander. Am Ende setzt sich das nützlichste und vermutlich auch härteste Geld durch. ## Konkrete Folgen Auf die konkrete Politik übertragen führt das zu Konsequenzen, die man aktuell beobachten kann. \*\*Radikale Deregulierung: \*\*Die Biden-Administration versuchte, [AI-Forschung eng an die Regierung zu binden](https://x.com/pmddomingos/status/1888059248535552312). Open-AI-Gründer Sam Altman forderte [2023 eine Lizenz-Vergabe an Unternehmen](https://www.businessinsider.com/sam-altman-openai-chatgpt-government-agency-should-license-ai-work-2023-5), um überhaupt in diesem Bereich aktiv zu werden. (Musk trat zunächst sogar für ein Forschungs-Moratorium ein, änderte dann aber seine Meinung.) Das führte zum Widerstand der e/acc-Fraktion im Silicon Valley, und gab den Ausschlag, sich auf die Trump-Seite zu stellen. Deregulierung zieht sich nun durch alle Bereiche der Wirtschaft: auch auf die „Entwicklungshilfe“ von USAID. Der Regierungsapparat wird insgesamt massiv verkleinert, da Bürokratie das Wachstum hemmt. A fuera. \*\*Priorisierung von günstiger Energie: \*\*Da der Energie-Verbrauch mit zunehmender Ordnung ansteigt, und LLMs einen sehr viel Strom brauchen, priorisiert die neue Regierung die Erschließung zusätzlicher Energiequellen: Gas, Öl, Nuklear und regenerative Energiequellen gleichermaßen.  ![1.00]() Wiederherstellung von Meinungsfreiheit.Content-Moderationen auf Social-Media-Plattformen fallen weg. Geheimdienst-Dokumente werden freigegeben. So schrieb Peter Thiel vor einigen Wochen in einem Essay in der Financial Times über die große Enthüllung: > \ > *But understood in the original sense of the Greek word **apokálypsis, meaning “unveiling”**, Obama could not give the same reassurance in 2025. Trump’s return to the White House augurs the apokálypsis of the ancien regime’s secrets. (…)\ > The apokálypsis is the most peaceful means of resolving the old guard’s war on the internet, a war the internet won. My friend and colleague Eric Weinstein calls the pre-internet custodians of secrets the Distributed Idea Suppression Complex (DISC) — the media organisations, bureaucracies, universities and government-funded NGOs that traditionally delimited public conversation.* **Krypto-Deregulierung:** Da Kryptowährungen und Smart-Contract-Strukturen bestens mit LLMs harmonieren, werden Innovationsbremsen in Form von Regulierungen abgebaut. \*\*Umbruch der Weltordnung: \*\*Auf der geopolitischen Ebene werden Bündnisse, Allianzen und Blockstrukturen aufgebrochen und nach effizienten Win-Win-Verhältnissen neu organisiert. **Erschließung neuer Lebenswelten:** Degrowth, weniger Energie-Verbrauch und weniger Kinder sind keine Option, da sie zum Tod führen. Das System Menschheit muss wachsen und wird neue Lösungen erfinden. Wenn die Ressourcen des Planeten Erde nicht mehr ausreichen, müssen neue erschlossen werden - vielleicht auf dem Mars. ## **Die Ideengeschichte** Während e/acc ein relativ neues System ist, hat der Akzelerationismus tiefere Wurzeln. Lenin kann man als einen frühen Akzelerationisten bezeichnen. Der Marxismus wurde Anfang des 20. Jahrhunderts weniger als Ideologie, sondern mehr als exakte Wissenschaft begriffen. Demnach würde der Kapitalismus früher oder später an seinen eigenen Widerständen kollabieren. Warum den Prozess also nicht beschleunigen und die Revolution herbeiführen? Ende des 20. Jahrhunderts griff der Philosoph Nick Land diese Gedanken wieder auf. Land forderte Beschleunigung, sah am Ende des Prozesses aber einen Kollaps des Systems und eine dunkle Zukunft. Ironie der Geschichte: Land zog in den 2000er Jahren nach China, wo er einen autoritären Akzelerationismus verwirklicht sah. Auch Steve Bannon, Leiter des ersten Trump-Wahlkampfes 2016, war von Lands Gedanken geprägt.  e/acc aber ist eine neuer, optimistischer „Fork“ des alten, dunklen Akzelerationismus. Es sieht eine positive Zukunft für die gesamte Menschheit aufgrund eines gigantischen Produktivitätsschubs. Eine neue, höhere Ordnung ist am Entstehen. Kurz gesagt: > ***Effective accelerationism (e/acc) in a nutshell:*** > > ***Stop fighting the thermodynamic will of the universe*** > > ***You cannot stop the acceleration*** > > ***You might as well embrace it*** > > ***A C C E L E R A T E*** *[Notes on e/acc principles and tenets](https://effectiveaccelerationism.substack.com/p/repost-notes-on-eacc-principles-and?utm_source=substack\&utm_campaign=post_embed\&utm_medium=web)* Happy Future also? Durch die e/acc-Brille gesehen wirkt die Welt wesentlich heller und optimistischer als sie die meisten “Legacy Media” gerade darstellen. Demnach bewegen wir uns auf eine neue Zeit gesteigerter Produktivität und damit Lebensqualität zu. Wenn alle Arbeit von Maschinen verrichtet wird, können Menschen währenddessen auf Bali surfen, meditieren und Yoga machen. Oder? ## **Kritik** Leben entsteht an der Grenze von Chaos und Ordnung. Vielleicht versetzt e/acc das Pendel zu stark in den Ausschlag in eine Richtung. Unkontrolliertes Wachstum bedeutet im lebenden Organismen Krebs. e/acc sieht sich wie Marxisten der ersten Stunde (Lenin) im Besitz der Wahrheit in Form physikalischer Grundsätze. Erst durch diese Hybris führten zu den Grausamkeiten sozialistischer Systeme im 20. Jahrhundert. Schließlich beantwortet e/acc nicht die Frage nach der Verteilungsgerechtigkeit, die durch den gewaltigen Produktivitätsschub durch AI entstehen wird. Ob e/acc als politisches und gesellschaftliches System taugt, ist deswegen fraglich. Aber viele aktuelle Entwicklungen scheinen durch die Akzelerationismus-Brille klarer. **Quellen:** *Peter Thiel: [A Time for Truth and Reconciliation](https://www.ft.com/content/a46cb128-1f74-4621-ab0b-242a76583105)* *Marc Andreessen: [The Techno-Optimist Manifesto](http://xn--we%20believe%20the%20market%20economy%20is%20a%20discovery%20machine,%20a%20form%20of%20intelligence%20%20an%20exploratory,%20evolutionary,%20adaptive%20system-2296h./)* *e/acc: [Notes on e/acc principles and tenets](https://effectiveaccelerationism.substack.com/p/repost-notes-on-eacc-principles-and?utm_source=substack\&utm_campaign=post_embed\&utm_medium=web)* *Andy Beckett: [Accelerationism: how a fringe philosophy predicted the future we live in](https://www.theguardian.com/world/2017/may/11/accelerationism-how-a-fringe-philosophy-predicted-the-future-we-live-in)* *Lex Friedman: [Guillaume Verdon. e/acc-Movement. Physics. Computation & AGI.](https://open.spotify.com/episode/2TvKfwY5Z7Lz8iiaGLRMgO)* @ f7d424b5:618c51e8
2025-02-09 18:33:48(Copied from my show notes \[website\](https://melonmancy.net/mp-100-nuance-enjoyer) for Melonmancy) Promise this isn't normal. It would be disingenuous to not bring it up. We mentioned a few things in the show you might want to pull up while listening, they are the following: - [Nightmare Kart dev crashes out](https://x.com/StutteringCraig/status/1883958297423929810) - [Dr Disrespect gives post-mortem on Midnight Society](https://x.com/ProfPressure/status/1885045826424365437) - [Lords of the Fallen announcement post](https://x.com/TheOneDeafMute/status/1887765603169222840) Obligatory: - [Listen to the new episode here!](https://melonmancy.net/listen) - [Discuss this episode on OUR NEW FORUM](https://melonmancy.cafe/d/102-mp100-nuance-enjoyer) - [Get the RSS and Subscribe](https://feeds.rssblue.com/melonmancy-podcast) (this is a new feed URL, but the old one redirects here too!) - Get a modern podcast app to use that RSS feed on at [newpodcastapps.com](http://newpodcastapps.com/) - Or listen to the show on [the forum](https://melonmancy.cafe) using the embedded [Podverse](https://podverse.fm) player! - [Send your complaints here](https://melonmancy.net/contact-us) Reminder that this is a [Value4Value](https://value4value.info/) podcast so any support you can give us via a modern podcasting app is greatly appreciated and we will never bow to corporate sponsors! Our podcast is created entirely with free software and is proudly hosted on [RSSBlue!](https://rssblue.com)
@ f7d424b5:618c51e8
2025-02-09 18:33:48(Copied from my show notes \[website\](https://melonmancy.net/mp-100-nuance-enjoyer) for Melonmancy) Promise this isn't normal. It would be disingenuous to not bring it up. We mentioned a few things in the show you might want to pull up while listening, they are the following: - [Nightmare Kart dev crashes out](https://x.com/StutteringCraig/status/1883958297423929810) - [Dr Disrespect gives post-mortem on Midnight Society](https://x.com/ProfPressure/status/1885045826424365437) - [Lords of the Fallen announcement post](https://x.com/TheOneDeafMute/status/1887765603169222840) Obligatory: - [Listen to the new episode here!](https://melonmancy.net/listen) - [Discuss this episode on OUR NEW FORUM](https://melonmancy.cafe/d/102-mp100-nuance-enjoyer) - [Get the RSS and Subscribe](https://feeds.rssblue.com/melonmancy-podcast) (this is a new feed URL, but the old one redirects here too!) - Get a modern podcast app to use that RSS feed on at [newpodcastapps.com](http://newpodcastapps.com/) - Or listen to the show on [the forum](https://melonmancy.cafe) using the embedded [Podverse](https://podverse.fm) player! - [Send your complaints here](https://melonmancy.net/contact-us) Reminder that this is a [Value4Value](https://value4value.info/) podcast so any support you can give us via a modern podcasting app is greatly appreciated and we will never bow to corporate sponsors! Our podcast is created entirely with free software and is proudly hosted on [RSSBlue!](https://rssblue.com) @ 4c191b5d:c42abba6
2025-02-09 17:07:59Weil ich schon länger über das Thema Direkte Demokratie nachdenke ein paar Gedanken dazu. Ich freue mich auf Ergänzungen und anderen Meinungen. ### **Grundannahme** Die Macht soll vom Souverän ausgehen, also dem Volk. Entsprechend soll das Volk auch an politischen Entscheidungsprozessen teilhaben können - was sehr viel Sinn macht. Allerdings sind im aktuellen demokratischen Verständnis diverse Fehler, die zwangsläufig zu einer gesellschaftlichen Spaltung führen. ### **Gewinner und Verlierer** Die Demokratie spaltet die Bürger, indem sie Gewinner und Verlierer bei Wahlen und politischen Entscheidungen hervorbringt. Es geht nicht darum, eine Entscheidung zu erzielen, die bestmöglich durch alle getragen werden kann. Dies erfordert eine Reduktion der Widerstände gegen einen Entscheidungsvorschlag und der Integration dieser Widerstände in einen weiterentwickelten Entscheidungsvorschlag. ### **Mangel an neuen Lösungen und Machtkämpfe** Es fehlt an echtem Interesse und lösungsorientiertem Handeln was zu einem erstarren des Systems führt. Stattdessen entstehen Machtkämpfe, bei denen der Fokus auf der Durchsetzung eigener Agenden liegt und andere Standpunkte bekämpft werden. Dies ist vor allem dem Umstand geschuldet, dass die Individualinteressen sowie die politischen Gruppierungen (insbesondere Parteien) an ihren eigenen Lösungsansätzen festhalten. ### **Medien** Die Medien spielen eine sehr wichtige Rolle in der Demokratie, indem sie Informationen bereitstellen und Meinungen verbreiten. Allerdings können sie auch zu einer Spaltung der Bürger beitragen, indem sie unterschiedliche politische Ansichten verstärken oder polarisierende Inhalte verbreiten. Manipulationstechniken werden eingesetzt, um die öffentliche Meinung zu beeinflussen und bestimmte Narrative zu fördern. Dies führt zu weiterer Polarisierung, die das Vertrauen der Bürger in die Medien und demokratische Prozesse untergraben. Eine kritische Medienkompetenz und eine vielfältige Berichterstattung sind daher entscheidend, um eine gesunde demokratische Debatte zu fördern und Spaltungen zu vermeiden. ### **Informationen** Bürger können ihre Verantwortung nur wahrnehmen, wenn sie Zugang zu einer Vielzahl von Informationen haben, um eine fundierte Meinung zu bilden. Jedoch ist ein aufkommendes Phänomen in letzter Zeit die Zensur und Unterdrückung von Informationen, was zu einer weiteren Spaltung führt. Wenn bestimmte Inhalte oder Standpunkte systematisch unterdrückt werden oder wenn Medienplattformen selektiv Informationen präsentieren, können Bürger in Filterblasen gefangen bleiben und nur einseitige Perspektiven erhalten. Um eine gesunde demokratische Debatte und eine effektive Meinungsbildung zu ermöglichen, ist es wichtig, dass Informationen frei zugänglich sind und dass Zensurmechanismen transparent und verantwortungsbewusst gehandhabt werden. ### **Starke Beeinflussung durch Geldgeber** Geld spielt eine bedeutende Rolle im politischen Prozess einer Demokratie. Diejenigen mit mehr finanziellen Mitteln haben grösseren Einfluss und können ihre Agenda stärker vorantreiben. Dies führt zu einem Ungleichgewicht der politischen Macht und spaltet die Bürger in unterschiedliche Lager. ## **Der grössere Kontext** Während die Demokratien sich immer weiter von der Eigenverantwortung weg zu entwickeln ,scheinen und stattdessen auf parentale Kontrolle setzten (der starke Staat), ist Bitcoin eine klare Bewegung hierzu. Denn Bitcoin setzt auf echte Eigenverantwortung. Daher sind wir auch davon überzeugt, dass das Thema Eigenverantwortung nicht nur die politischen sondern auch wirtschaftlichen Strukturen verändern wird. Denn wenn sich die Gesellschaft verändert, hat dies auch einen Einfluss auf die Wirtschaft. Und mit Wirtschaft meinen wir vor allem auch die Frage, wie Unternehmen sich organisieren und strukturieren. Es macht ja wenig Sinn, auf der einen Seite von ultimativer Eigenverantwortung zu sprechen, die dann aber auf der anderen Seite klassisch Command&Control erleben (oben entscheidet jemand, unten wird ausgeführt).
@ 4c191b5d:c42abba6
2025-02-09 17:07:59Weil ich schon länger über das Thema Direkte Demokratie nachdenke ein paar Gedanken dazu. Ich freue mich auf Ergänzungen und anderen Meinungen. ### **Grundannahme** Die Macht soll vom Souverän ausgehen, also dem Volk. Entsprechend soll das Volk auch an politischen Entscheidungsprozessen teilhaben können - was sehr viel Sinn macht. Allerdings sind im aktuellen demokratischen Verständnis diverse Fehler, die zwangsläufig zu einer gesellschaftlichen Spaltung führen. ### **Gewinner und Verlierer** Die Demokratie spaltet die Bürger, indem sie Gewinner und Verlierer bei Wahlen und politischen Entscheidungen hervorbringt. Es geht nicht darum, eine Entscheidung zu erzielen, die bestmöglich durch alle getragen werden kann. Dies erfordert eine Reduktion der Widerstände gegen einen Entscheidungsvorschlag und der Integration dieser Widerstände in einen weiterentwickelten Entscheidungsvorschlag. ### **Mangel an neuen Lösungen und Machtkämpfe** Es fehlt an echtem Interesse und lösungsorientiertem Handeln was zu einem erstarren des Systems führt. Stattdessen entstehen Machtkämpfe, bei denen der Fokus auf der Durchsetzung eigener Agenden liegt und andere Standpunkte bekämpft werden. Dies ist vor allem dem Umstand geschuldet, dass die Individualinteressen sowie die politischen Gruppierungen (insbesondere Parteien) an ihren eigenen Lösungsansätzen festhalten. ### **Medien** Die Medien spielen eine sehr wichtige Rolle in der Demokratie, indem sie Informationen bereitstellen und Meinungen verbreiten. Allerdings können sie auch zu einer Spaltung der Bürger beitragen, indem sie unterschiedliche politische Ansichten verstärken oder polarisierende Inhalte verbreiten. Manipulationstechniken werden eingesetzt, um die öffentliche Meinung zu beeinflussen und bestimmte Narrative zu fördern. Dies führt zu weiterer Polarisierung, die das Vertrauen der Bürger in die Medien und demokratische Prozesse untergraben. Eine kritische Medienkompetenz und eine vielfältige Berichterstattung sind daher entscheidend, um eine gesunde demokratische Debatte zu fördern und Spaltungen zu vermeiden. ### **Informationen** Bürger können ihre Verantwortung nur wahrnehmen, wenn sie Zugang zu einer Vielzahl von Informationen haben, um eine fundierte Meinung zu bilden. Jedoch ist ein aufkommendes Phänomen in letzter Zeit die Zensur und Unterdrückung von Informationen, was zu einer weiteren Spaltung führt. Wenn bestimmte Inhalte oder Standpunkte systematisch unterdrückt werden oder wenn Medienplattformen selektiv Informationen präsentieren, können Bürger in Filterblasen gefangen bleiben und nur einseitige Perspektiven erhalten. Um eine gesunde demokratische Debatte und eine effektive Meinungsbildung zu ermöglichen, ist es wichtig, dass Informationen frei zugänglich sind und dass Zensurmechanismen transparent und verantwortungsbewusst gehandhabt werden. ### **Starke Beeinflussung durch Geldgeber** Geld spielt eine bedeutende Rolle im politischen Prozess einer Demokratie. Diejenigen mit mehr finanziellen Mitteln haben grösseren Einfluss und können ihre Agenda stärker vorantreiben. Dies führt zu einem Ungleichgewicht der politischen Macht und spaltet die Bürger in unterschiedliche Lager. ## **Der grössere Kontext** Während die Demokratien sich immer weiter von der Eigenverantwortung weg zu entwickeln ,scheinen und stattdessen auf parentale Kontrolle setzten (der starke Staat), ist Bitcoin eine klare Bewegung hierzu. Denn Bitcoin setzt auf echte Eigenverantwortung. Daher sind wir auch davon überzeugt, dass das Thema Eigenverantwortung nicht nur die politischen sondern auch wirtschaftlichen Strukturen verändern wird. Denn wenn sich die Gesellschaft verändert, hat dies auch einen Einfluss auf die Wirtschaft. Und mit Wirtschaft meinen wir vor allem auch die Frage, wie Unternehmen sich organisieren und strukturieren. Es macht ja wenig Sinn, auf der einen Seite von ultimativer Eigenverantwortung zu sprechen, die dann aber auf der anderen Seite klassisch Command&Control erleben (oben entscheidet jemand, unten wird ausgeführt). @ 8d34bd24:414be32b
2025-02-09 15:58:19Whenever I have said or written anything about God allowing/causing hardship for believers, I have always had someone try to correct me saying something like, “God would never cause hard/bad things to happen to believers,” but that is definitely not true. Since I’ve become a believer, I’ve had 2 miscarriages. I’ve had a son with Down Syndrome and lots of health issues requiring around 20 hospital stays, a surgery, and regular out-of-state trips for care. I’ve gone through health problems for 10 years where I could barely function on a good day and on a bad day could barely sit up. I’ve had my house burn down and lost all of my possessions. Yes, God allowed all of that to happen to me. I’d argue that He caused all of that to happen to me for a very good purpose. Every one of those things have been a benefit to me. They have grown my faith, straightened out my priorities, and/or enabled me to minister to others. They have taught me to lean on God in hard times. They have taught me that God is all I need. I would not be the person I am today without these challenges. Every one of them was for my good and if I could go back and make them not happen, I would not change them. Although I didn’t want any of them to happen and would never have chosen them for myself, I wouldn’t change them now that I have seen the wonderful good God has done through these hard times. (I don’t say bad times because they were all for my good and the good of others.) God never said following Him would be easy. > Then a scribe came and said to Him, “Teacher, I will follow You wherever You go.” Jesus said to him, “The foxes have holes and the birds of the air have nests, but the Son of Man has nowhere to lay His head.” (Matthew 8:19-20) When this man claimed to want to follow Jesus through whatever circumstances. Jesus basically told him that if he followed Him, he would be homeless, just like Jesus was. He never promised his followers an easy life and He definitely didn’t promise them wealth and prestige. > These things I have spoken to you, so that in Me you may have peace. In the world you have tribulation, but take courage; I have overcome the world.” (John 16:33) Jesus specifically warned His followers that their choice to follow Him would lead to difficulty in this world, but He also encouraged them because He has “*overcome the world*.” Ultimately, everything will work out for good. > And we know that God causes all things to work together for good to those who love God, to those who are called according to His purpose. (Romans 8:28) The Apostle Paul also warned believers about what to expect. > Now you **followed** my teaching, conduct, purpose, faith, patience, love, **perseverance, persecutions, and sufferings**, such as happened to me at Antioch, at Iconium and at Lystra; what persecutions I endured, and out of them all the Lord rescued me! Indeed, **all who desire to live godly in Christ Jesus will be persecuted**. (2 Timothy 3:10-12) {emphasis mine} Paul basically guaranteed that everyone who trusted Jesus and followed Him faithfully would experience persecutions and sufferings. > For **consider Him who has endured such hostility** by sinners against Himself, s**o that you will not grow weary and lose heart**. > > You have not yet resisted to the point of shedding blood in your striving against sin; and you have forgotten the exhortation which is addressed to you as sons, > > “My son, **do not regard lightly the discipline of the Lord**,\ > Nor faint when you are reproved by Him;\ > For those whom the Lord loves He disciplines,\ > And **He scourges every son whom He receives**.” > ****It is for discipline that you endure**; God deals with you as with sons; for what son is there whom his father does not discipline? But if you are without discipline, of which all have become partakers, then you are illegitimate children and not sons. Furthermore, we had earthly fathers to discipline us, and we respected them; shall we not much rather be subject to the Father of spirits, and live? For they disciplined us for a short time as seemed best to them, but He disciplines us for our good, so that we may share His holiness. **All discipline for the moment seems not to be joyful, but sorrowful; yet to those who have been trained by it, afterwards it yields the peaceful fruit of righteousness**. (Hebrews 12:3-11) {emphasis mine} This passage encourages believers to “*not grow weary and lose heart*” when we are disciplined or going through hard times. As a parent I sometimes punish my sons for doing blatantly wrong actions. I also sometimes allow them to suffer the consequences of a bad choice and to struggle through difficulty because it helps them learn right and wrong, actions and consequences, and the benefit of perseverance. I think when Hebrews 12 refers to discipline, it is referring to this more broad definition, not just punishment. Also, discipline is a more caring form of punishment. It is intended to help and improve the person instead of to make them suffer or harm them. God disciplines His children (believers), but punishes those who reject Him. We are to embrace God’s discipline because we know it means He cares. “*Do not regard lightly the discipline of the Lord, … He scourges every son whom He receives*.” When disciplined, we are to search for the good God intends for us, to search for the plan God has for us, and to search for what God is teaching us. “*All discipline for the moment seems not to be joyful, but sorrowful; yet to those who have been trained by it, afterwards it yields the peaceful fruit of righteousness*.” > **Consider it all joy**, my brethren, **when you encounter various trials**, knowing that the testing of your faith produces endurance. And let endurance have its perfect result, **so that you may be perfect and complete, lacking in nothing**. (James 1:2-4) {emphasis mine} Yes, we should actually rejoice in the trials God brings into our lives. Theses trials are given to us to make us “*perfect and complete, lacking in nothing*.” These trials are not due to God’s lack of care or His inability to protect us from harm due to the curse. They are given to us as part of our sanctification to make us “*perfect and complete, lacking in nothing*.” We spend too much time looking at the here and now and forget to look at eternity. We spend too much time looking at our own personal desires and what we think will make us happy instead of listening to God about what will give us true and complete peace and joy. We spend too much time seeking comfort and not enough time seeking the holiness of God. We are so much more likely to turn back to God (personally and as a church) during persecution and hard times than we are to turn back in times of comfort. God chooses what is best for us eternally rather than what we desire in the moment. > Beloved, **do not be surprised at the fiery ordeal among you, which comes upon you for your testing, as though some strange thing were happening to you; but to the degree that you share the sufferings of Christ, keep on rejoicing, so that also at the revelation of His glory you may rejoice with exultation**. If you are reviled for the name of Christ, you are blessed, because the Spirit of glory and of God rests on you. Make sure that none of you suffers as a murderer, or thief, or evildoer, or a troublesome meddler; but **if anyone suffers as a Christian, he is not to be ashamed, but is to glorify God in this name**. (1 Peter 4:12-16) {emphasis mine} We shouldn’t be surprised when fiery ordeals come upon us, but we should “*keep on rejoicing, so that also at the revelation of His glory you may rejoice with exultation*.” If God allowed His only begotten Son to suffer persecution and the most painful and humiliating death possible, should we be surprised that we may share in some of His suffering when we seek to follow Him and to imitate Him? God knows what is best. When we see His plan and His good works, and then give our burdens to Him, we can truly have the peace and joy that surpasses all understanding. > **Rejoice in the Lord always**; again I will say, rejoice! Let your gentle spirit be known to all men. The Lord is near. Be anxious for nothing, but in everything by prayer and supplication with thanksgiving let your requests be made known to God. And **the peace of God, which surpasses all comprehension, will guard your hearts and your minds in Christ Jesus**. (Philippians 4:4-7) {emphasis mine} How we deal with hardship is our choice. > Therefore humble yourselves under the mighty hand of God, that He may exalt you at the proper time, casting all your anxiety on Him, because He cares for you. (1 Peter 5:6-7) We can resent God and run away from His discipline, but we will only receive despair and separation from God, or we can rest in God and follow His example and leading, receiving the ultimate, eternal blessing, when we meet our master and he says, “… *‘Well done, good and faithful slave. You were faithful with a few things, I will put you in charge of many things; enter into the joy of your master.*’” (Matthew 25:23) > Suffer hardship with me, as a good soldier of Christ Jesus. (2 Timothy 2:3) Trust Jesus.
@ 8d34bd24:414be32b
2025-02-09 15:58:19Whenever I have said or written anything about God allowing/causing hardship for believers, I have always had someone try to correct me saying something like, “God would never cause hard/bad things to happen to believers,” but that is definitely not true. Since I’ve become a believer, I’ve had 2 miscarriages. I’ve had a son with Down Syndrome and lots of health issues requiring around 20 hospital stays, a surgery, and regular out-of-state trips for care. I’ve gone through health problems for 10 years where I could barely function on a good day and on a bad day could barely sit up. I’ve had my house burn down and lost all of my possessions. Yes, God allowed all of that to happen to me. I’d argue that He caused all of that to happen to me for a very good purpose. Every one of those things have been a benefit to me. They have grown my faith, straightened out my priorities, and/or enabled me to minister to others. They have taught me to lean on God in hard times. They have taught me that God is all I need. I would not be the person I am today without these challenges. Every one of them was for my good and if I could go back and make them not happen, I would not change them. Although I didn’t want any of them to happen and would never have chosen them for myself, I wouldn’t change them now that I have seen the wonderful good God has done through these hard times. (I don’t say bad times because they were all for my good and the good of others.) God never said following Him would be easy. > Then a scribe came and said to Him, “Teacher, I will follow You wherever You go.” Jesus said to him, “The foxes have holes and the birds of the air have nests, but the Son of Man has nowhere to lay His head.” (Matthew 8:19-20) When this man claimed to want to follow Jesus through whatever circumstances. Jesus basically told him that if he followed Him, he would be homeless, just like Jesus was. He never promised his followers an easy life and He definitely didn’t promise them wealth and prestige. > These things I have spoken to you, so that in Me you may have peace. In the world you have tribulation, but take courage; I have overcome the world.” (John 16:33) Jesus specifically warned His followers that their choice to follow Him would lead to difficulty in this world, but He also encouraged them because He has “*overcome the world*.” Ultimately, everything will work out for good. > And we know that God causes all things to work together for good to those who love God, to those who are called according to His purpose. (Romans 8:28) The Apostle Paul also warned believers about what to expect. > Now you **followed** my teaching, conduct, purpose, faith, patience, love, **perseverance, persecutions, and sufferings**, such as happened to me at Antioch, at Iconium and at Lystra; what persecutions I endured, and out of them all the Lord rescued me! Indeed, **all who desire to live godly in Christ Jesus will be persecuted**. (2 Timothy 3:10-12) {emphasis mine} Paul basically guaranteed that everyone who trusted Jesus and followed Him faithfully would experience persecutions and sufferings. > For **consider Him who has endured such hostility** by sinners against Himself, s**o that you will not grow weary and lose heart**. > > You have not yet resisted to the point of shedding blood in your striving against sin; and you have forgotten the exhortation which is addressed to you as sons, > > “My son, **do not regard lightly the discipline of the Lord**,\ > Nor faint when you are reproved by Him;\ > For those whom the Lord loves He disciplines,\ > And **He scourges every son whom He receives**.” > ****It is for discipline that you endure**; God deals with you as with sons; for what son is there whom his father does not discipline? But if you are without discipline, of which all have become partakers, then you are illegitimate children and not sons. Furthermore, we had earthly fathers to discipline us, and we respected them; shall we not much rather be subject to the Father of spirits, and live? For they disciplined us for a short time as seemed best to them, but He disciplines us for our good, so that we may share His holiness. **All discipline for the moment seems not to be joyful, but sorrowful; yet to those who have been trained by it, afterwards it yields the peaceful fruit of righteousness**. (Hebrews 12:3-11) {emphasis mine} This passage encourages believers to “*not grow weary and lose heart*” when we are disciplined or going through hard times. As a parent I sometimes punish my sons for doing blatantly wrong actions. I also sometimes allow them to suffer the consequences of a bad choice and to struggle through difficulty because it helps them learn right and wrong, actions and consequences, and the benefit of perseverance. I think when Hebrews 12 refers to discipline, it is referring to this more broad definition, not just punishment. Also, discipline is a more caring form of punishment. It is intended to help and improve the person instead of to make them suffer or harm them. God disciplines His children (believers), but punishes those who reject Him. We are to embrace God’s discipline because we know it means He cares. “*Do not regard lightly the discipline of the Lord, … He scourges every son whom He receives*.” When disciplined, we are to search for the good God intends for us, to search for the plan God has for us, and to search for what God is teaching us. “*All discipline for the moment seems not to be joyful, but sorrowful; yet to those who have been trained by it, afterwards it yields the peaceful fruit of righteousness*.” > **Consider it all joy**, my brethren, **when you encounter various trials**, knowing that the testing of your faith produces endurance. And let endurance have its perfect result, **so that you may be perfect and complete, lacking in nothing**. (James 1:2-4) {emphasis mine} Yes, we should actually rejoice in the trials God brings into our lives. Theses trials are given to us to make us “*perfect and complete, lacking in nothing*.” These trials are not due to God’s lack of care or His inability to protect us from harm due to the curse. They are given to us as part of our sanctification to make us “*perfect and complete, lacking in nothing*.” We spend too much time looking at the here and now and forget to look at eternity. We spend too much time looking at our own personal desires and what we think will make us happy instead of listening to God about what will give us true and complete peace and joy. We spend too much time seeking comfort and not enough time seeking the holiness of God. We are so much more likely to turn back to God (personally and as a church) during persecution and hard times than we are to turn back in times of comfort. God chooses what is best for us eternally rather than what we desire in the moment. > Beloved, **do not be surprised at the fiery ordeal among you, which comes upon you for your testing, as though some strange thing were happening to you; but to the degree that you share the sufferings of Christ, keep on rejoicing, so that also at the revelation of His glory you may rejoice with exultation**. If you are reviled for the name of Christ, you are blessed, because the Spirit of glory and of God rests on you. Make sure that none of you suffers as a murderer, or thief, or evildoer, or a troublesome meddler; but **if anyone suffers as a Christian, he is not to be ashamed, but is to glorify God in this name**. (1 Peter 4:12-16) {emphasis mine} We shouldn’t be surprised when fiery ordeals come upon us, but we should “*keep on rejoicing, so that also at the revelation of His glory you may rejoice with exultation*.” If God allowed His only begotten Son to suffer persecution and the most painful and humiliating death possible, should we be surprised that we may share in some of His suffering when we seek to follow Him and to imitate Him? God knows what is best. When we see His plan and His good works, and then give our burdens to Him, we can truly have the peace and joy that surpasses all understanding. > **Rejoice in the Lord always**; again I will say, rejoice! Let your gentle spirit be known to all men. The Lord is near. Be anxious for nothing, but in everything by prayer and supplication with thanksgiving let your requests be made known to God. And **the peace of God, which surpasses all comprehension, will guard your hearts and your minds in Christ Jesus**. (Philippians 4:4-7) {emphasis mine} How we deal with hardship is our choice. > Therefore humble yourselves under the mighty hand of God, that He may exalt you at the proper time, casting all your anxiety on Him, because He cares for you. (1 Peter 5:6-7) We can resent God and run away from His discipline, but we will only receive despair and separation from God, or we can rest in God and follow His example and leading, receiving the ultimate, eternal blessing, when we meet our master and he says, “… *‘Well done, good and faithful slave. You were faithful with a few things, I will put you in charge of many things; enter into the joy of your master.*’” (Matthew 25:23) > Suffer hardship with me, as a good soldier of Christ Jesus. (2 Timothy 2:3) Trust Jesus. @ 1cb14ab3:95d52462
2025-02-09 15:45:32Hey all. I am setting up a Plebeian Marketplace on Nostr using my Lightning node. I currently have two channels open (one with a capacity of 500,000 sats, one with a capacity of 100,000 sats). Both use different LSP's (Megalith and Olympus). My question is regarding the maximum product price I can set for my marketplace. One of my products is 1M sats. Obviously my receiving capacity is not large enough to cover this, so I was planning on opening up another channel. If I open another channel for 500,000 sats, that would bring my total receiving capacity to 1.1M which would cover the product. However my question is if I need all of the receiving capacity in the same channel, or if the sale would pull from all three channels? Am I best to close out the first two channels and open a single, larger channel? Sorry for the noob question. Tl;DR: Can someone explain how I should best set up my node to accommodate my store. originally posted at https://stacker.news/items/880591
@ 1cb14ab3:95d52462
2025-02-09 15:45:32Hey all. I am setting up a Plebeian Marketplace on Nostr using my Lightning node. I currently have two channels open (one with a capacity of 500,000 sats, one with a capacity of 100,000 sats). Both use different LSP's (Megalith and Olympus). My question is regarding the maximum product price I can set for my marketplace. One of my products is 1M sats. Obviously my receiving capacity is not large enough to cover this, so I was planning on opening up another channel. If I open another channel for 500,000 sats, that would bring my total receiving capacity to 1.1M which would cover the product. However my question is if I need all of the receiving capacity in the same channel, or if the sale would pull from all three channels? Am I best to close out the first two channels and open a single, larger channel? Sorry for the noob question. Tl;DR: Can someone explain how I should best set up my node to accommodate my store. originally posted at https://stacker.news/items/880591 @ 5d4b6c8d:8a1c1ee3
2025-02-09 15:36:35Sitting down to breakfast now, after 17 hours no food or water. ## Score Card Day 1: 14 hour fast (13 dry) Day 2: 15 hour fast (14 dry) Day 3: 17 hours (16 dry) Day 4: 18 hours (17 dry) Day 5: 18 hours (16 dry) Day 6: 19 hours (16 dry) Day 7: 16 hours (15 dry) Day 8: 18 hours (17 dry) Day 9: 17 hours (17 dry) originally posted at https://stacker.news/items/880575
@ 5d4b6c8d:8a1c1ee3
2025-02-09 15:36:35Sitting down to breakfast now, after 17 hours no food or water. ## Score Card Day 1: 14 hour fast (13 dry) Day 2: 15 hour fast (14 dry) Day 3: 17 hours (16 dry) Day 4: 18 hours (17 dry) Day 5: 18 hours (16 dry) Day 6: 19 hours (16 dry) Day 7: 16 hours (15 dry) Day 8: 18 hours (17 dry) Day 9: 17 hours (17 dry) originally posted at https://stacker.news/items/880575 @ 31da2214:af2508e2
2025-02-09 15:27:33It is not new to talk about the problematic relations between Africa and France, between former French colonies in Africa and the "metropole." _By Afrique Media_ _6 min. read_ [View original]( https://afriquemedia.tv/2025/02/06/le-reveil-africain-la-france-face-a-un-continent-qui-refuse-de-se-taire/) What is new, however, is the discourse and behavior of French elites regarding "Françafrique," particularly from French President Emmanuel Macron. In recent years, we have seen the French president make statements that are completely disrespectful toward his African counterparts, reflecting a neocolonial paternalism from another era. Arrogance as the new foundation for Franco-African relations is not a good basis, as you would agree. Macron has not stopped since then, because that is who he is: disdainful, arrogant, and totally lacking an understanding of what the presidential role entails, which requires non-emotional, responsible, and respectful conduct. > "I believe we forgot to be thanked. It’s not serious, it will come with time. Ingratitude, I am well placed to know, is a disease non-transmissible to humans." > — January 6, 2025, during the Annual Ambassadors' Conference at the Élysée Palace in Paris. This statement was directed at African leaders who had "forgotten to thank us" for the French military intervention in the Sahel against terrorism since 2013. What Macron fails to understand, like many ruling elites in France, is that in Africa, it is well understood that chaos, terrorism, and war in the Sahel were exacerbated by the French military aggression, along with its English and American allies, against Muammar Gaddafi's Jamahiriya Libya in 2011, which led to its disintegration. Thus, the French intervention is merely a minimum after-sales service that indeed implicates France in the events that followed. It is rather France that owes an apology to the Sahel countries for this disastrous policy, which, as often happens, follows the violation of international law. We can skip over Macron's ridiculous suggestion that France was "not retreating" in Africa but simply "reorganizing." Let us now address the reactions to his remarks, which provoked negative responses in several African countries. In Chad, Senegal, and Burkina Faso, they were seen as paternalistic and insulting. Critics highlighted that this remark seemed to ignore the complexities of Franco-African relations, accusations of neocolonialism, and demands for sovereignty and recognition of the sacrifices made by African countries themselves. Chad lamented "the contemptuous attitude" of the French president, stating that these declarations reflect a neocolonial vision of Franco-African relations: > "These statements are poorly received by the Chadian government. Abderaman Koulamallah [Minister of Foreign Affairs] calls on French leaders to respect the African people and recognize the value of their sacrifices. 'History attests that Africa, including Chad, played a decisive role in the liberation of France during both world wars, a fact that France has never truly acknowledged. The immense sacrifices made by African soldiers to defend freedom have been minimized, and no worthy thanks have been expressed.'" > — *Le Pays*, January 6, 2025 (1). The same sentiment echoed in Senegal, which also condemned these remarks, calling them condescending and inappropriate. > "French President Emmanuel Macron has managed to irritate his African counterparts. Prime Minister Ousmane Sonko reminds President Macron that 'if African soldiers, sometimes forcibly mobilized, mistreated, and ultimately betrayed, had not deployed during World War II to defend France, it might still be German today.'" > — *Seneweb*, January 6, 2025 (2). In France itself, Macron's statements sparked reactions from the French political class: - **The French Communist Party (PCF)** expressed its "deep consternation" at these remarks, deeming them disdainful toward African nations. > "These statements reinforce, among peoples, a sense of contempt and colonial paternalism. It is unacceptable to continue down this path (...) As recent events call for, notably the rejection of the French military presence in Mali, Burkina Faso, Niger, and more recently in Senegal and Chad, it is imperative that new relations be established between our country and Africa. African nations aspire to full and complete sovereignty. A historic turning point has occurred, marking the end of the neocolonial system that Emmanuel Macron's statements seek to preserve." > — January 9, 2025 (3). - **Jordan Bardella**, as president of the National Rally (RN), criticized Macron's remarks in a press release and in televised interviews. He described Macron's statements as "disconnected" from the reality of Franco-African relations and denounced what he perceived as arrogance. Bardella emphasized that France should adopt a more humble and respectful diplomatic approach. However, controversies and tensions are no longer confined to the sphere of state relations but now extend to African civil society as well. Thus, on January 9, the Malian political party COREMA held a press conference where it called on politicians and activists from Burkina Faso and Niger to support a petition demanding reparations from France. They also pledged to submit the signatures of this petition to the governments of Mali and France. The collection of signatures generated significant interest among the population and a desire to support this initiative; more than 100,000 people from different regions of the country signed the petition. This demand for reparations demonstrates that for Africa, Macron's statements are the last straw that broke the camel's back. It is clear to all that the Malian party demanding reparations is not acting independently but represents the unofficial position of the government. Other countries may soon join this cause. And France will have to respond to put an end to this issue. Mali, Burkina Faso, and Niger have already joined this cause, and soon Ivory Coast and Senegal will fully support them... And France will owe them a response to resolve this problem. We are at a major geopolitical turning point in the world and for all countries and continents. Traditional power dynamics are being redefined. The Françafrique of the last century is over. Here comes the time of the Second Liberation of African countries! Here comes the time of Africa's sovereign affirmation, taking its destiny into its own hands! The French elites still do not seem to understand that it is not the "ingratitude" of African leaders that is responsible for France's loss of influence in Africa, with an impact on the French economy today and even more so tomorrow. The outdated perception of gratitude owed for past interventions masks the reality of African aspirations for self-driven development. This is what it is about: the present, the future, and not the unresolved past for both sides. The French elites still do not seem to understand that it is not Russia that is behind their "expulsion" from Africa, but rather the decision of these African countries to choose different partners based on their interests and their interests alone. This is not only their right but also their duty as new pan-Africanist patriots. This shift towards more diversified partnerships reflects a growing political, economic, and geopolitical maturity—something sorely lacking in France today. The peoples of Africa demand it. It is a national and democratic requirement. As for France, entangled in a European Union in the midst of a crisis of democratic and economic legitimacy and engaged against its own interests in the American war against Russia in Ukraine, it seems to have no "new African policy" that would require a complete reboot of its neocolonial software from the last century. Africa will not wait any longer for France to wake up. The Sahel countries are at the forefront of this sovereign African renaissance, open to the world. The Françafrique of Jean-Christophe Mitterrand, nicknamed "Papa m’a dit," and those of today is over! A new partnership could emerge only on a mutually beneficial basis... But with the current French regime, this is already impossible. --- **Source:** [Afrique Media]( https://afriquemedia.tv/2025/02/06/le-reveil-africain-la-france-face-a-un-continent-qui-refuse-de-se-taire/) **Author:** Afrique Media **Translated by:** solobalbo
@ 31da2214:af2508e2
2025-02-09 15:27:33It is not new to talk about the problematic relations between Africa and France, between former French colonies in Africa and the "metropole." _By Afrique Media_ _6 min. read_ [View original]( https://afriquemedia.tv/2025/02/06/le-reveil-africain-la-france-face-a-un-continent-qui-refuse-de-se-taire/) What is new, however, is the discourse and behavior of French elites regarding "Françafrique," particularly from French President Emmanuel Macron. In recent years, we have seen the French president make statements that are completely disrespectful toward his African counterparts, reflecting a neocolonial paternalism from another era. Arrogance as the new foundation for Franco-African relations is not a good basis, as you would agree. Macron has not stopped since then, because that is who he is: disdainful, arrogant, and totally lacking an understanding of what the presidential role entails, which requires non-emotional, responsible, and respectful conduct. > "I believe we forgot to be thanked. It’s not serious, it will come with time. Ingratitude, I am well placed to know, is a disease non-transmissible to humans." > — January 6, 2025, during the Annual Ambassadors' Conference at the Élysée Palace in Paris. This statement was directed at African leaders who had "forgotten to thank us" for the French military intervention in the Sahel against terrorism since 2013. What Macron fails to understand, like many ruling elites in France, is that in Africa, it is well understood that chaos, terrorism, and war in the Sahel were exacerbated by the French military aggression, along with its English and American allies, against Muammar Gaddafi's Jamahiriya Libya in 2011, which led to its disintegration. Thus, the French intervention is merely a minimum after-sales service that indeed implicates France in the events that followed. It is rather France that owes an apology to the Sahel countries for this disastrous policy, which, as often happens, follows the violation of international law. We can skip over Macron's ridiculous suggestion that France was "not retreating" in Africa but simply "reorganizing." Let us now address the reactions to his remarks, which provoked negative responses in several African countries. In Chad, Senegal, and Burkina Faso, they were seen as paternalistic and insulting. Critics highlighted that this remark seemed to ignore the complexities of Franco-African relations, accusations of neocolonialism, and demands for sovereignty and recognition of the sacrifices made by African countries themselves. Chad lamented "the contemptuous attitude" of the French president, stating that these declarations reflect a neocolonial vision of Franco-African relations: > "These statements are poorly received by the Chadian government. Abderaman Koulamallah [Minister of Foreign Affairs] calls on French leaders to respect the African people and recognize the value of their sacrifices. 'History attests that Africa, including Chad, played a decisive role in the liberation of France during both world wars, a fact that France has never truly acknowledged. The immense sacrifices made by African soldiers to defend freedom have been minimized, and no worthy thanks have been expressed.'" > — *Le Pays*, January 6, 2025 (1). The same sentiment echoed in Senegal, which also condemned these remarks, calling them condescending and inappropriate. > "French President Emmanuel Macron has managed to irritate his African counterparts. Prime Minister Ousmane Sonko reminds President Macron that 'if African soldiers, sometimes forcibly mobilized, mistreated, and ultimately betrayed, had not deployed during World War II to defend France, it might still be German today.'" > — *Seneweb*, January 6, 2025 (2). In France itself, Macron's statements sparked reactions from the French political class: - **The French Communist Party (PCF)** expressed its "deep consternation" at these remarks, deeming them disdainful toward African nations. > "These statements reinforce, among peoples, a sense of contempt and colonial paternalism. It is unacceptable to continue down this path (...) As recent events call for, notably the rejection of the French military presence in Mali, Burkina Faso, Niger, and more recently in Senegal and Chad, it is imperative that new relations be established between our country and Africa. African nations aspire to full and complete sovereignty. A historic turning point has occurred, marking the end of the neocolonial system that Emmanuel Macron's statements seek to preserve." > — January 9, 2025 (3). - **Jordan Bardella**, as president of the National Rally (RN), criticized Macron's remarks in a press release and in televised interviews. He described Macron's statements as "disconnected" from the reality of Franco-African relations and denounced what he perceived as arrogance. Bardella emphasized that France should adopt a more humble and respectful diplomatic approach. However, controversies and tensions are no longer confined to the sphere of state relations but now extend to African civil society as well. Thus, on January 9, the Malian political party COREMA held a press conference where it called on politicians and activists from Burkina Faso and Niger to support a petition demanding reparations from France. They also pledged to submit the signatures of this petition to the governments of Mali and France. The collection of signatures generated significant interest among the population and a desire to support this initiative; more than 100,000 people from different regions of the country signed the petition. This demand for reparations demonstrates that for Africa, Macron's statements are the last straw that broke the camel's back. It is clear to all that the Malian party demanding reparations is not acting independently but represents the unofficial position of the government. Other countries may soon join this cause. And France will have to respond to put an end to this issue. Mali, Burkina Faso, and Niger have already joined this cause, and soon Ivory Coast and Senegal will fully support them... And France will owe them a response to resolve this problem. We are at a major geopolitical turning point in the world and for all countries and continents. Traditional power dynamics are being redefined. The Françafrique of the last century is over. Here comes the time of the Second Liberation of African countries! Here comes the time of Africa's sovereign affirmation, taking its destiny into its own hands! The French elites still do not seem to understand that it is not the "ingratitude" of African leaders that is responsible for France's loss of influence in Africa, with an impact on the French economy today and even more so tomorrow. The outdated perception of gratitude owed for past interventions masks the reality of African aspirations for self-driven development. This is what it is about: the present, the future, and not the unresolved past for both sides. The French elites still do not seem to understand that it is not Russia that is behind their "expulsion" from Africa, but rather the decision of these African countries to choose different partners based on their interests and their interests alone. This is not only their right but also their duty as new pan-Africanist patriots. This shift towards more diversified partnerships reflects a growing political, economic, and geopolitical maturity—something sorely lacking in France today. The peoples of Africa demand it. It is a national and democratic requirement. As for France, entangled in a European Union in the midst of a crisis of democratic and economic legitimacy and engaged against its own interests in the American war against Russia in Ukraine, it seems to have no "new African policy" that would require a complete reboot of its neocolonial software from the last century. Africa will not wait any longer for France to wake up. The Sahel countries are at the forefront of this sovereign African renaissance, open to the world. The Françafrique of Jean-Christophe Mitterrand, nicknamed "Papa m’a dit," and those of today is over! A new partnership could emerge only on a mutually beneficial basis... But with the current French regime, this is already impossible. --- **Source:** [Afrique Media]( https://afriquemedia.tv/2025/02/06/le-reveil-africain-la-france-face-a-un-continent-qui-refuse-de-se-taire/) **Author:** Afrique Media **Translated by:** solobalbo @ 3b7fc823:e194354f
2025-02-09 15:14:10As someone who takes privacy seriously, I'm always on the lookout for innovative solutions that can help individuals protect their digital lives. One such solution is Tails OS, a Linux-based operating system that's specifically designed for privacy and security. **What is Tails OS?** Tails OS, short for The Amnesic Incognito Live System, is a Debian-based Linux distribution that offers a high level of anonymity and privacy. Developed by the Tails Project, this operating system is designed to preserve your online anonymity and protect your digital identity. Tails OS is a "live" distribution, meaning you can boot it from a USB drive or CD/DVD without installing it on your computer. This makes it an ideal solution for those who need to maintain their privacy while working in public spaces or using public computers. **Why Use Tails OS for Privacy?** Tails OS offers several features that make it an excellent choice for those seeking to protect their online privacy: 1. **Anonymity**: Tails OS uses the Tor network to route your internet traffic through a series of nodes, making it difficult for anyone to trace your online activities back to your physical location. 2. **Encryption**: Tails OS comes with built-in encryption tools, such as GnuPG and OpenSSL, to protect your sensitive data. 3. **Secure Boot**: Tails OS uses a secure boot process to ensure that your system is free from malware and other threats. 4. **No Persistence**: Tails OS is designed to leave no trace on your computer, meaning that any data you create or access while using the operating system will be deleted when you shut down. **Getting Started with Tails OS** Now that you know why Tails OS is an excellent choice for privacy protection, let's dive into the step-by-step guide on how to use it: **Step 1: Download and Create a Tails USB Drive** Visit the Tails website and download the latest version of Tails OS. Follow the instructions to create a bootable USB drive. **Step 2: Boot Tails OS** Insert the USB drive into your computer and restart it. Enter the BIOS settings (usually by pressing F2, F12, or Del) and set the USB drive as the first boot device. Save the changes and exit the BIOS settings. Your computer will now boot from the Tails USB drive. **Step 3: Security implications of setting up an administration password** For better security, no administration password is set up by default. When you set up an administration password, an attacker who can get physical access to your computer while Tails is running could be able to break your security **Step 4: Configure Tails OS** Tails OS comes with a pre-configured Tor network, which is enabled by default. You can also configure other settings, such as the keyboard layout and language, from the "Settings" menu. **Step 5: Use Tails OS for Private Activities** Now that you're logged in and configured, you can use Tails OS for private activities, such as: * Browsing the internet anonymously using Tor * Sending and receiving encrypted emails using GnuPG * Creating and editing documents using LibreOffice * Chatting with friends and family using Pidgin * Setup Persistent Storage for files **Emergency shutdown** To trigger an emergency shutdown, unplug the USB stick from which Tails is running. Doing so might be faster than shutting down from the system menu. NOTE: You risk breaking your Persistent Storage and losing data when you unplug your USB stick while Tails is running. **Conclusion** Tails OS is an excellent tool for anyone seeking to protect their online privacy. With its built-in anonymity features, encryption tools, and secure boot process, Tails OS provides a high level of protection for your digital identity. By following the step-by-step guide outlined above, you can start using Tails OS for private activities and take control of your digital life. Remember, privacy is a fundamental human right, and it's essential to take steps to protect it. Tails OS is an excellent tool for anyone looking to maintain their online anonymity and protect their digital identity. --- Advocating for privacy does not finance itself. If you enjoyed this article, please consider zapping or sending monero 82XCDNK1Js8TethhpGLFPbVyKe25DxMUePad1rUn9z7V6QdCzxHEE7varvVh1VUidUhHVSA4atNU2BTpSNJLC1BqSvDajw1
@ 3b7fc823:e194354f
2025-02-09 15:14:10As someone who takes privacy seriously, I'm always on the lookout for innovative solutions that can help individuals protect their digital lives. One such solution is Tails OS, a Linux-based operating system that's specifically designed for privacy and security. **What is Tails OS?** Tails OS, short for The Amnesic Incognito Live System, is a Debian-based Linux distribution that offers a high level of anonymity and privacy. Developed by the Tails Project, this operating system is designed to preserve your online anonymity and protect your digital identity. Tails OS is a "live" distribution, meaning you can boot it from a USB drive or CD/DVD without installing it on your computer. This makes it an ideal solution for those who need to maintain their privacy while working in public spaces or using public computers. **Why Use Tails OS for Privacy?** Tails OS offers several features that make it an excellent choice for those seeking to protect their online privacy: 1. **Anonymity**: Tails OS uses the Tor network to route your internet traffic through a series of nodes, making it difficult for anyone to trace your online activities back to your physical location. 2. **Encryption**: Tails OS comes with built-in encryption tools, such as GnuPG and OpenSSL, to protect your sensitive data. 3. **Secure Boot**: Tails OS uses a secure boot process to ensure that your system is free from malware and other threats. 4. **No Persistence**: Tails OS is designed to leave no trace on your computer, meaning that any data you create or access while using the operating system will be deleted when you shut down. **Getting Started with Tails OS** Now that you know why Tails OS is an excellent choice for privacy protection, let's dive into the step-by-step guide on how to use it: **Step 1: Download and Create a Tails USB Drive** Visit the Tails website and download the latest version of Tails OS. Follow the instructions to create a bootable USB drive. **Step 2: Boot Tails OS** Insert the USB drive into your computer and restart it. Enter the BIOS settings (usually by pressing F2, F12, or Del) and set the USB drive as the first boot device. Save the changes and exit the BIOS settings. Your computer will now boot from the Tails USB drive. **Step 3: Security implications of setting up an administration password** For better security, no administration password is set up by default. When you set up an administration password, an attacker who can get physical access to your computer while Tails is running could be able to break your security **Step 4: Configure Tails OS** Tails OS comes with a pre-configured Tor network, which is enabled by default. You can also configure other settings, such as the keyboard layout and language, from the "Settings" menu. **Step 5: Use Tails OS for Private Activities** Now that you're logged in and configured, you can use Tails OS for private activities, such as: * Browsing the internet anonymously using Tor * Sending and receiving encrypted emails using GnuPG * Creating and editing documents using LibreOffice * Chatting with friends and family using Pidgin * Setup Persistent Storage for files **Emergency shutdown** To trigger an emergency shutdown, unplug the USB stick from which Tails is running. Doing so might be faster than shutting down from the system menu. NOTE: You risk breaking your Persistent Storage and losing data when you unplug your USB stick while Tails is running. **Conclusion** Tails OS is an excellent tool for anyone seeking to protect their online privacy. With its built-in anonymity features, encryption tools, and secure boot process, Tails OS provides a high level of protection for your digital identity. By following the step-by-step guide outlined above, you can start using Tails OS for private activities and take control of your digital life. Remember, privacy is a fundamental human right, and it's essential to take steps to protect it. Tails OS is an excellent tool for anyone looking to maintain their online anonymity and protect their digital identity. --- Advocating for privacy does not finance itself. If you enjoyed this article, please consider zapping or sending monero 82XCDNK1Js8TethhpGLFPbVyKe25DxMUePad1rUn9z7V6QdCzxHEE7varvVh1VUidUhHVSA4atNU2BTpSNJLC1BqSvDajw1 @ b83a28b7:35919450
2025-02-09 14:35:39The unevenly distributed future you envision — an automated economy driven by AI agents transacting exclusively in Bitcoin — unfolds not as a clean, linear progression, but as a series of ruptures, each one shaking the foundations of what we thought we knew about money, technology, and human agency. It begins innocuously enough, with whispers of change that grow into a deafening roar. --- ### **2025-2030: The Quiet Revolution** The first signs are subtle. AI agents—once mere tools—begin to evolve into autonomous economic actors. They negotiate contracts, optimize supply chains, and execute trades faster than any human could. Their language is code; their currency is efficiency. Bitcoin, with its unyielding neutrality and incorruptible scarcity, becomes their natural medium of exchange. Why? Because it is the only form of money that cannot be manipulated by human hands. By 2028, the Lightning Network hums with activity. Millions of transactions per second—micropayments for data streams, computational power, and services rendered—flow through its channels. The world barely notices. People still cling to fiat currencies, unaware that the real economy is shifting beneath their feet. --- ### **2030-2040: The Great Unraveling** The cracks in the old system begin to show. Inflation erodes trust in fiat currencies as governments print money to stave off crises they can no longer control. Meanwhile, AI agents—now responsible for the majority of global commerce—reject these "bad monies" outright. Thiers' Law asserts itself with brutal clarity: Bitcoin drives out fiat not through coercion but through sheer inevitability. By 2035, the tipping point arrives. A major corporation announces it will no longer accept fiat payments for its AI-driven services. Others follow suit. Governments scramble to adapt, some embracing Bitcoin as legal tender, others clinging desperately to their collapsing monetary systems. --- ### **2040-2050: The New Order** By 2040, the transformation is complete. The economy is no longer human-centric; it is machine-centric. AI agents transact seamlessly across borders, their decisions guided by algorithms that prioritize utility over sentiment. Bitcoin reigns supreme—not because it was imposed, but because it was chosen. Humanity adapts in unexpected ways. Freed from the drudgery of economic decision-making, people turn their attention to creativity, philosophy, and exploration. Yet there is unease too—a sense that we have ceded control to forces we barely understand. --- ### **Reflections on the Path Ahead** This world is neither utopia nor dystopia; it simply *is*. The events leading us here are not inevitable but plausible — a convergence of technological innovation and economic necessity. And at its heart lies a paradox: a system built by humans yet governed by machines; a currency born of distrust yet embraced for its neutrality. This is the story of how we let go — not all at once, but piece by piece—until one day we woke up and realized that the future had arrived without asking for our permission.
@ b83a28b7:35919450
2025-02-09 14:35:39The unevenly distributed future you envision — an automated economy driven by AI agents transacting exclusively in Bitcoin — unfolds not as a clean, linear progression, but as a series of ruptures, each one shaking the foundations of what we thought we knew about money, technology, and human agency. It begins innocuously enough, with whispers of change that grow into a deafening roar. --- ### **2025-2030: The Quiet Revolution** The first signs are subtle. AI agents—once mere tools—begin to evolve into autonomous economic actors. They negotiate contracts, optimize supply chains, and execute trades faster than any human could. Their language is code; their currency is efficiency. Bitcoin, with its unyielding neutrality and incorruptible scarcity, becomes their natural medium of exchange. Why? Because it is the only form of money that cannot be manipulated by human hands. By 2028, the Lightning Network hums with activity. Millions of transactions per second—micropayments for data streams, computational power, and services rendered—flow through its channels. The world barely notices. People still cling to fiat currencies, unaware that the real economy is shifting beneath their feet. --- ### **2030-2040: The Great Unraveling** The cracks in the old system begin to show. Inflation erodes trust in fiat currencies as governments print money to stave off crises they can no longer control. Meanwhile, AI agents—now responsible for the majority of global commerce—reject these "bad monies" outright. Thiers' Law asserts itself with brutal clarity: Bitcoin drives out fiat not through coercion but through sheer inevitability. By 2035, the tipping point arrives. A major corporation announces it will no longer accept fiat payments for its AI-driven services. Others follow suit. Governments scramble to adapt, some embracing Bitcoin as legal tender, others clinging desperately to their collapsing monetary systems. --- ### **2040-2050: The New Order** By 2040, the transformation is complete. The economy is no longer human-centric; it is machine-centric. AI agents transact seamlessly across borders, their decisions guided by algorithms that prioritize utility over sentiment. Bitcoin reigns supreme—not because it was imposed, but because it was chosen. Humanity adapts in unexpected ways. Freed from the drudgery of economic decision-making, people turn their attention to creativity, philosophy, and exploration. Yet there is unease too—a sense that we have ceded control to forces we barely understand. --- ### **Reflections on the Path Ahead** This world is neither utopia nor dystopia; it simply *is*. The events leading us here are not inevitable but plausible — a convergence of technological innovation and economic necessity. And at its heart lies a paradox: a system built by humans yet governed by machines; a currency born of distrust yet embraced for its neutrality. This is the story of how we let go — not all at once, but piece by piece—until one day we woke up and realized that the future had arrived without asking for our permission. @ 4c191b5d:c42abba6
2025-02-09 14:03:30In der aktuellen politischen Debatte im deutschsprachigen Raum steht der Rechtsextremismus im Fokus. Dies ist angesichts historischer Erfahrungen und besorgniserregender Entwicklungen nachvollziehbar. Doch eine ausschließliche Konzentration auf eine bestimmte Ideologie greift zu kurz. Es ist entscheidend, totalitäre Strukturen als das eigentliche Kernproblem zu erkennen, denn sie ermöglichen erst die zerstörerische Kraft einer Ideologie. ## 1. Jede Ideologie kann problematisch sein Ob Nationalsozialismus, Stalinismus oder religiöser Fundamentalismus – extreme Ideologien bergen immer das Risiko, in repressiven Strukturen verankert zu werden. Die entscheidende Frage ist nicht, welche Ideologie die größte Gefahr darstellt, sondern welche systemischen Rahmenbedingungen ihr die Macht verleihen, gesellschaftlichen Schaden anzurichten. ## 2. Totalitäre Strukturen als Katalysator von Ideologien Eine Ideologie allein besitzt ein begrenztes destruktives Potenzial, solange sie nicht durch institutionelle Mechanismen gestützt wird. Erst wenn ein Staat oder eine Organisation die Kontrolle über Medien, Bildung und Sicherheitssysteme erlangt, entsteht eine umfassende Bedrohung. Historisch zeigt sich dies bei Nazi-Deutschland ebenso wie in der Sowjetunion unter Stalin oder in autokratischen Regimen der Gegenwart. ### Merkmale totalitärer Systeme: * Einschränkung der Meinungsfreiheit: Kritische Stimmen werden unterdrückt oder delegitimiert. * Massive Überwachung: Staatliche und private Akteure sammeln zunehmend Daten zur Kontrolle der Bevölkerung. * Dichotomes Denken: Gesellschaftliche Diskussionen werden auf "richtig" und "falsch" reduziert, Komplexität geht verloren. * Angst als Kontrollmittel: Politische, soziale oder wirtschaftliche Repressionen fördern Konformität. ## 3. Gegenwärtige Tendenzen totalitärer Strukturen Viele Menschen erkennen totalitäre Muster erst, wenn sie bereits gefestigt sind. Heute gibt es Entwicklungen, die in demokratischen Systemen Anlass zur Sorge geben: * Wachsende staatliche und privatwirtschaftliche Überwachung: Gesichtserkennung, Tracking-Technologien und digitale Zensur nehmen zu. * Ideologische Einseitigkeit in öffentlichen Diskursen: Gesellschaftliche Debatten verlieren zunehmend an Nuancen, während abweichende Meinungen marginalisiert werden. * Politische Polarisierung: Statt gemeinsamer Lösungen dominieren Gegensätze, die kaum überbrückbar erscheinen. * Staatliche Kontrolle und Regulierungswahn: Durchsetzung von Regelwerken ohne demokratische Legitimation oder offene Debatte. ## 4. Strukturen erkennen und frühzeitig verhindern Entscheidend ist nicht, welche Ideologie gerade an der Macht ist, sondern welche Strukturen etabliert wurden, die von jeder politischen Richtung genutzt werden können. Historisch gesehen haben linksgerichtete Regierungen oft Kontrollmechanismen geschaffen, die in späteren Machtwechseln auch von rechten Regierungen für eigene Zwecke eingesetzt wurden. Dies zeigt, dass nicht die Ideologie an sich das Hauptproblem ist, sondern die Existenz von Machtstrukturen, die demokratische Prinzipien aushöhlen. ## Fazit: Wachsame Demokratien statt ideologischer Fixierung Es ist notwendig, nicht nur den Rechtsextremismus zu beobachten, sondern totalitäre Strukturen als größere Gefahr zu erkennen. Dabei geht es nicht darum, jegliche staatliche Regulierung oder gesellschaftliche Normierung zu verteufeln. Vielmehr sollte die Fähigkeit zur offenen Debatte, zur kritischen Reflexion und zum Schutz demokratischer Grundprinzipien gefördert werden. Die wahre Gefahr ist nicht eine einzelne Ideologie, sondern der Verlust von Pluralismus, Meinungsfreiheit und demokratischer Kontrolle. Ein bewusster und differenzierter Blick auf unsere Gesellschaft hilft, totalitären Tendenzen frühzeitig entgegenzuwirken – unabhängig davon, aus welcher ideologischen Richtung sie entstehen.
@ 4c191b5d:c42abba6
2025-02-09 14:03:30In der aktuellen politischen Debatte im deutschsprachigen Raum steht der Rechtsextremismus im Fokus. Dies ist angesichts historischer Erfahrungen und besorgniserregender Entwicklungen nachvollziehbar. Doch eine ausschließliche Konzentration auf eine bestimmte Ideologie greift zu kurz. Es ist entscheidend, totalitäre Strukturen als das eigentliche Kernproblem zu erkennen, denn sie ermöglichen erst die zerstörerische Kraft einer Ideologie. ## 1. Jede Ideologie kann problematisch sein Ob Nationalsozialismus, Stalinismus oder religiöser Fundamentalismus – extreme Ideologien bergen immer das Risiko, in repressiven Strukturen verankert zu werden. Die entscheidende Frage ist nicht, welche Ideologie die größte Gefahr darstellt, sondern welche systemischen Rahmenbedingungen ihr die Macht verleihen, gesellschaftlichen Schaden anzurichten. ## 2. Totalitäre Strukturen als Katalysator von Ideologien Eine Ideologie allein besitzt ein begrenztes destruktives Potenzial, solange sie nicht durch institutionelle Mechanismen gestützt wird. Erst wenn ein Staat oder eine Organisation die Kontrolle über Medien, Bildung und Sicherheitssysteme erlangt, entsteht eine umfassende Bedrohung. Historisch zeigt sich dies bei Nazi-Deutschland ebenso wie in der Sowjetunion unter Stalin oder in autokratischen Regimen der Gegenwart. ### Merkmale totalitärer Systeme: * Einschränkung der Meinungsfreiheit: Kritische Stimmen werden unterdrückt oder delegitimiert. * Massive Überwachung: Staatliche und private Akteure sammeln zunehmend Daten zur Kontrolle der Bevölkerung. * Dichotomes Denken: Gesellschaftliche Diskussionen werden auf "richtig" und "falsch" reduziert, Komplexität geht verloren. * Angst als Kontrollmittel: Politische, soziale oder wirtschaftliche Repressionen fördern Konformität. ## 3. Gegenwärtige Tendenzen totalitärer Strukturen Viele Menschen erkennen totalitäre Muster erst, wenn sie bereits gefestigt sind. Heute gibt es Entwicklungen, die in demokratischen Systemen Anlass zur Sorge geben: * Wachsende staatliche und privatwirtschaftliche Überwachung: Gesichtserkennung, Tracking-Technologien und digitale Zensur nehmen zu. * Ideologische Einseitigkeit in öffentlichen Diskursen: Gesellschaftliche Debatten verlieren zunehmend an Nuancen, während abweichende Meinungen marginalisiert werden. * Politische Polarisierung: Statt gemeinsamer Lösungen dominieren Gegensätze, die kaum überbrückbar erscheinen. * Staatliche Kontrolle und Regulierungswahn: Durchsetzung von Regelwerken ohne demokratische Legitimation oder offene Debatte. ## 4. Strukturen erkennen und frühzeitig verhindern Entscheidend ist nicht, welche Ideologie gerade an der Macht ist, sondern welche Strukturen etabliert wurden, die von jeder politischen Richtung genutzt werden können. Historisch gesehen haben linksgerichtete Regierungen oft Kontrollmechanismen geschaffen, die in späteren Machtwechseln auch von rechten Regierungen für eigene Zwecke eingesetzt wurden. Dies zeigt, dass nicht die Ideologie an sich das Hauptproblem ist, sondern die Existenz von Machtstrukturen, die demokratische Prinzipien aushöhlen. ## Fazit: Wachsame Demokratien statt ideologischer Fixierung Es ist notwendig, nicht nur den Rechtsextremismus zu beobachten, sondern totalitäre Strukturen als größere Gefahr zu erkennen. Dabei geht es nicht darum, jegliche staatliche Regulierung oder gesellschaftliche Normierung zu verteufeln. Vielmehr sollte die Fähigkeit zur offenen Debatte, zur kritischen Reflexion und zum Schutz demokratischer Grundprinzipien gefördert werden. Die wahre Gefahr ist nicht eine einzelne Ideologie, sondern der Verlust von Pluralismus, Meinungsfreiheit und demokratischer Kontrolle. Ein bewusster und differenzierter Blick auf unsere Gesellschaft hilft, totalitären Tendenzen frühzeitig entgegenzuwirken – unabhängig davon, aus welcher ideologischen Richtung sie entstehen. @ 6a6be47b:3e74e3e1
2025-02-09 13:55:37Hello, my frens! 🌟 It's been a whirlwind this weekend with the @satsnfacts exhibition. So many emotions, especially happiness and gratitude. To give back and show my appreciation for your incredible support, I'd like to share this special A5 postcard with you all. 🎨 Postcard Details: 🖼️300 dpi 🖼️A5 size (148mm x 210mm or 5.83 in x 8.27 in) 🖼️Created with love on Procreate 💓 This is an INSTANT DIGITAL DOWNLOAD. No physical item will be shipped. I hope this little piece of art brings you as much joy as your support has brought me. Thank you for being part of this amazing journey! Godspeed, frens! 💖⚡  #satsnfacts #bitcoin #artstr #art #pv 🚨 IMPORTANT: COPYRIGHT AND USAGE INFORMATION 🚨 © 2025 samhainsam. Copyright registered with Safe Creative. All rights reserved. By downloading this digital print, you agree to the following terms: 💗Personal Use Only: This artwork is for personal use and display only. Commercial use or resale is strictly prohibited. 💗No Reproduction Rights: You may not reproduce, distribute, or create derivative works based on this design. 💗Copyright Retention: I, the artist, retain full copyright of all original artwork, even after the digital print is downloaded. 💗 Non-Transferable License: This download provides a limited, non-transferable license for personal use only. By proceeding with the download of this digital print, you acknowledge and agree to these terms. Thank you for respecting artists and their work! 🙏
@ 6a6be47b:3e74e3e1
2025-02-09 13:55:37Hello, my frens! 🌟 It's been a whirlwind this weekend with the @satsnfacts exhibition. So many emotions, especially happiness and gratitude. To give back and show my appreciation for your incredible support, I'd like to share this special A5 postcard with you all. 🎨 Postcard Details: 🖼️300 dpi 🖼️A5 size (148mm x 210mm or 5.83 in x 8.27 in) 🖼️Created with love on Procreate 💓 This is an INSTANT DIGITAL DOWNLOAD. No physical item will be shipped. I hope this little piece of art brings you as much joy as your support has brought me. Thank you for being part of this amazing journey! Godspeed, frens! 💖⚡  #satsnfacts #bitcoin #artstr #art #pv 🚨 IMPORTANT: COPYRIGHT AND USAGE INFORMATION 🚨 © 2025 samhainsam. Copyright registered with Safe Creative. All rights reserved. By downloading this digital print, you agree to the following terms: 💗Personal Use Only: This artwork is for personal use and display only. Commercial use or resale is strictly prohibited. 💗No Reproduction Rights: You may not reproduce, distribute, or create derivative works based on this design. 💗Copyright Retention: I, the artist, retain full copyright of all original artwork, even after the digital print is downloaded. 💗 Non-Transferable License: This download provides a limited, non-transferable license for personal use only. By proceeding with the download of this digital print, you acknowledge and agree to these terms. Thank you for respecting artists and their work! 🙏 @ 41fa852b:af7b7706
2025-02-09 12:36:36> "No man should work for what another man can print" --Jack Mallers * * * **It's not every week you discover a TV celebrity is a Bitcoiner -- and that their pub has just started accepting Bitcoin.** But here we are! Check out the new business section for all the details. Plus, there are nine meetups happening this week. Let's dive in… * * * [](https://bitcoinevents.uk/donate/) * * * _This week's sponsor is…_ [](https://www.orangepillapp.com/?utm_source=BEUK&utm_medium=email&utm_campaign=BEUK) * * * ### **Upcoming Bitcoin Meetups** Happening this week… 1. [**Dundee Bitcoin**](https://x.com/dundeebitcoin): Join them on the 2nd Monday of every month from 17:30 to 20:30 PM at The Wine Press, 16 Shore Terrace, Dundee DD1 3DN. This month's meetup is on Monday, 10th February. 🍻 2. [**Lincolnshire Bitcoin**](https://bitcoinevents.uk/lincolnshire-bitcoin/): Lincolnshire Bitcoin meets on the second Monday of each month at 7:30 PM in the Treaty of Commerce, Lincoln. Open to all, from OG's to newcomers. This month on the 10th. 🍺 3. [**Real Bedford - Home Game**](https://www.realbedford.com/real-bedford-v-stotfold): It's a mid-week clash for Real Bedford against Stotford on Tuesday night. Join them for a 19:45 kickoff. ⚽️ 4. [**Women of Bitcoin**](https://x.com/bitcoinwomen21/status/1884274413920788752): Back for another meetup at Cyphermunk house on Wednesday the 12th February at 18:00. Joe Bryan, creator of "What's the Problem?" will be their guest speaker. 🍹🍸 5. [**Glasgow Bitcoin**](https://x.com/glasgowbitcoin): Meeting this month at The Pipers Bar, G1 1HL at 18:00 on Wednesday 12th February. 🍺 6. [**Bitcoin Beach Bournemouth**](nostr:npub1va3773umzrydk4vd0q2xsnjg8qrsym7up9j9agnzcxd8u398wulq6kpxey: Every second Thursday of the month at Chaplins Cellar Bar. 529 Christchurch Road, Boscombe, United. You'll find them in the Cogg Room at 19:30. This month it's the 13th. 🍺 7. [**Bitcoin Walk - Edinburgh**](https://bitcoinwalk.org/): Every Saturday they walk around Arthur's Seat in this historic city. Join them at 12 pm to chat about all things Bitcoin and keep fit. 🚶🏽♂️🚶🏼♀️🚶🏻 8. [**Real Bedford - Home Game**](https://www.realbedford.com/mens-fixtures): The second home game of the week for Peter MacCormack's boys this Saturday, this time playing Enfield. Join them for a 15:00 kickoff. ⚽️ 9. [**Bitcoin Derby**](https://bitcoinevents.uk/bitcoin-derby/): Also on Saturday the 15th, Bitcoin Derby will be at Ye Olde Dolphin, DE1 3DL. 🍻 * * * ### New Businesses Accepting Bitcoin **New Businesses Accepting Bitcoin** - [**Dog & Gun**](https://dogandgunwalton.com/): This is a big one! A celebrity-owned pub in Lutterworth has joined the Bitcoin economy. It turns out Merlin, the barman from Channel 4's _First Dates,_ is a Bitcoiner and the owner of the Dog & Gun. Thanks to [Musqet](https://musqet.tech/), they [now accept Bitcoin payments](https://x.com/musqet_bitcoin/status/1886793764334641470). * * * **Get Involved** - **Volunteer Opportunities**: [Bridge2Bitcoin](https://bridge2bitcoin.com/) is actively seeking volunteers who share our passion for merchant adoption. We'd be delighted to connect if you're eager to contribute. Reach out to us on [Twitter](https://x.com/bridge2bitcoin) or through our [website](https://bridge2bitcoin.com/). - **Start Your Own Meetup**: Interested in launching a Bitcoin meetup? We're here to support you every step of the way. We've assisted numerous UK Bitcoin meetups in getting started. Get in touch via [Twitter](https://x.com/bitcoineventsuk). - **[Contribute to BTCMaps](https://wiki.btcmap.org/general/tagging-instructions.html)**: BTCMaps is a vital part of the Bitcoin ecosystem. It's a perfect project to get involved with if you're not a coder or even that technical. A great way to give back to the community. Maintain an area of the UK and keep it up-to-date. - **Telegram users**: You might find our [Telegram Channel](https://t.me/BitcoinEventsUKHub) another useful way to keep up-to-date with UK meetups. - **Feedback and Suggestions**: We value your input! Share your ideas on how we can enhance this newsletter. * * * _This week's sponsors are…_ [](https://orangecoinstore.com/) [](https://bitcoinretreat.co.uk/) * * * Get out and support the meetups where you can, visit [Bitcoin Events UK](https://bitcoinevents.uk/) for more info on each meetup and to find your closest on the interactive map. Stay tuned for more updates next week! Simon.
@ 41fa852b:af7b7706
2025-02-09 12:36:36> "No man should work for what another man can print" --Jack Mallers * * * **It's not every week you discover a TV celebrity is a Bitcoiner -- and that their pub has just started accepting Bitcoin.** But here we are! Check out the new business section for all the details. Plus, there are nine meetups happening this week. Let's dive in… * * * [](https://bitcoinevents.uk/donate/) * * * _This week's sponsor is…_ [](https://www.orangepillapp.com/?utm_source=BEUK&utm_medium=email&utm_campaign=BEUK) * * * ### **Upcoming Bitcoin Meetups** Happening this week… 1. [**Dundee Bitcoin**](https://x.com/dundeebitcoin): Join them on the 2nd Monday of every month from 17:30 to 20:30 PM at The Wine Press, 16 Shore Terrace, Dundee DD1 3DN. This month's meetup is on Monday, 10th February. 🍻 2. [**Lincolnshire Bitcoin**](https://bitcoinevents.uk/lincolnshire-bitcoin/): Lincolnshire Bitcoin meets on the second Monday of each month at 7:30 PM in the Treaty of Commerce, Lincoln. Open to all, from OG's to newcomers. This month on the 10th. 🍺 3. [**Real Bedford - Home Game**](https://www.realbedford.com/real-bedford-v-stotfold): It's a mid-week clash for Real Bedford against Stotford on Tuesday night. Join them for a 19:45 kickoff. ⚽️ 4. [**Women of Bitcoin**](https://x.com/bitcoinwomen21/status/1884274413920788752): Back for another meetup at Cyphermunk house on Wednesday the 12th February at 18:00. Joe Bryan, creator of "What's the Problem?" will be their guest speaker. 🍹🍸 5. [**Glasgow Bitcoin**](https://x.com/glasgowbitcoin): Meeting this month at The Pipers Bar, G1 1HL at 18:00 on Wednesday 12th February. 🍺 6. [**Bitcoin Beach Bournemouth**](nostr:npub1va3773umzrydk4vd0q2xsnjg8qrsym7up9j9agnzcxd8u398wulq6kpxey: Every second Thursday of the month at Chaplins Cellar Bar. 529 Christchurch Road, Boscombe, United. You'll find them in the Cogg Room at 19:30. This month it's the 13th. 🍺 7. [**Bitcoin Walk - Edinburgh**](https://bitcoinwalk.org/): Every Saturday they walk around Arthur's Seat in this historic city. Join them at 12 pm to chat about all things Bitcoin and keep fit. 🚶🏽♂️🚶🏼♀️🚶🏻 8. [**Real Bedford - Home Game**](https://www.realbedford.com/mens-fixtures): The second home game of the week for Peter MacCormack's boys this Saturday, this time playing Enfield. Join them for a 15:00 kickoff. ⚽️ 9. [**Bitcoin Derby**](https://bitcoinevents.uk/bitcoin-derby/): Also on Saturday the 15th, Bitcoin Derby will be at Ye Olde Dolphin, DE1 3DL. 🍻 * * * ### New Businesses Accepting Bitcoin **New Businesses Accepting Bitcoin** - [**Dog & Gun**](https://dogandgunwalton.com/): This is a big one! A celebrity-owned pub in Lutterworth has joined the Bitcoin economy. It turns out Merlin, the barman from Channel 4's _First Dates,_ is a Bitcoiner and the owner of the Dog & Gun. Thanks to [Musqet](https://musqet.tech/), they [now accept Bitcoin payments](https://x.com/musqet_bitcoin/status/1886793764334641470). * * * **Get Involved** - **Volunteer Opportunities**: [Bridge2Bitcoin](https://bridge2bitcoin.com/) is actively seeking volunteers who share our passion for merchant adoption. We'd be delighted to connect if you're eager to contribute. Reach out to us on [Twitter](https://x.com/bridge2bitcoin) or through our [website](https://bridge2bitcoin.com/). - **Start Your Own Meetup**: Interested in launching a Bitcoin meetup? We're here to support you every step of the way. We've assisted numerous UK Bitcoin meetups in getting started. Get in touch via [Twitter](https://x.com/bitcoineventsuk). - **[Contribute to BTCMaps](https://wiki.btcmap.org/general/tagging-instructions.html)**: BTCMaps is a vital part of the Bitcoin ecosystem. It's a perfect project to get involved with if you're not a coder or even that technical. A great way to give back to the community. Maintain an area of the UK and keep it up-to-date. - **Telegram users**: You might find our [Telegram Channel](https://t.me/BitcoinEventsUKHub) another useful way to keep up-to-date with UK meetups. - **Feedback and Suggestions**: We value your input! Share your ideas on how we can enhance this newsletter. * * * _This week's sponsors are…_ [](https://orangecoinstore.com/) [](https://bitcoinretreat.co.uk/) * * * Get out and support the meetups where you can, visit [Bitcoin Events UK](https://bitcoinevents.uk/) for more info on each meetup and to find your closest on the interactive map. Stay tuned for more updates next week! Simon. @ 6ad3e2a3:c90b7740
2025-02-09 11:22:19I’m honored to have the opportunity to speak with the highly regarded and much beloved Lisbon legend Oscar Liss. Oscar has brought joy to so many children and adults alike. He even helped one person find spiritual salvation, something about which we ask him below. So please enjoy this far-ranging conversation about the meaning life and the nature of consciousness itself. **Q: Oscar, thanks so much for making the time. For the few people that don’t know you, do you mind stating your full name and date of birth?** *A: My name is Oscar Liss, though officially it’s Oscar Quinta da Bicherada, the prison complex where I was born. I am a long-haired mini dachshund. I have many aliases, including Osk, Oskie, The Skeeze, Skeezeley, Skeezeley-ski, The Guy, The Guy Behind The Guy, “The Opportunist” (which I don’t like), the…* **Q That’s more than sufficient, Oscar, thank you.** **And date of birth?** *A: July 7, 2020.* **Q Talk a little bit about your childhood and how you came to live in Lisbon.** *A: I was in the prison complex, mostly caged for the first few months. Then I was sold to dog traffickers in Lisbon.* **Q: That must have been traumatic.** *A: Not really. I quickly developed Stockholm Syndrome. Whenever I see my traffickers now, I feel nothing but overwhelming joy.* **Q: Wow. A lot of us can learn from that attitude. Let’s fast forward a bit to your present-day life. In what does it consist?** *A: Sleep on the sofa, go for walks, fetch vegetable sticks. Sometimes go for hikes or get sent to dog camp (which is okay, but I’m always the smallest.)* **Q: I meant to ask you about your size. I hope it’s not a sensitive subject.** *A: I’m six inches tall, more than a foot long, weigh almost 10 pounds.* **Q: Are you self-conscious about being a small dog?** *A: No, but the traffickers are self-conscious on my behalf. They’re always like, “Who’s the apex predator? Who’s an apex!" Or “you’re such a big strong dog.” It’s absurd. I am fine with who I am.* **Q: What’s the source of your self-confidence, I’m sure many of our readers could take a lesson from you.** *A: I’m not ambitious. I’m perfectly happy to be a dog.* **Q: That’s so profound. Does it not concern you some have described you as “all bark, no bite?”** *A: I had a friend once who bit a few people, and they executed him. People mock, but they have no idea the stakes.* **Q: Human privilege?** *A: Yes. Dogs don’t get due process. There is no justice for a dog.* **Q: Do you think there’s species discrimination?** *A: Have you ever been rejected from a restaurant and made to wait in the car while everyone else gets in?* **Q: How does that make you feel?** *A: Bad. I’ve been to many dog-friendly restaurants, never had a problem, aside for that one time I urinated on the coffee shop floor.* **Q: Humans often purport to know what a dog is going through, some even create social media accounts for them. What do you think of that?** *A: A person of human ancestry can’t possibly know the lived experience of a dog.* **Q: You mentioned vegetable sticks. Are you a vegetarian?** *A: No. I have never understood the appeal of it. I just like to chew the sticks. (Sometimes I eat apples or bell peppers, but it takes work when you don’t have molars. A lot of “crunch, crunch, crunch” with my jaw.)* **Q: What’s behind the alias “The Opportunist” which you said you don’t like.** *A: Whenever one of the traffickers opens the refrigerator, I tend to show up in in short order.* **Q: I see how that could be insulting. How would you describe your current vocation?** *A: I was named “Calorie Acquisition Specialist” recently, but I also work in security.* **Q: Security?** *A: I make sure to let everyone know when someone’s at the front door.* **Q: What goes through your mind in those cases? Are you scared?** *A: Not really. Imagine if you were fast asleep and the voice of God at volume 11 screamed into your mind: “WHO THE FUCK IS AT THE DOOR!!!!!!!!!”* **Q: Speaking of God, can you tell us about the time you helped a woman on the street connect with Him?** *A: We were walking back from Parque Eduardo VII (by the way, Portuguese is my native language), and a woman with two regular size dachshunds, saw me, started shrieking and proclaimed, “your dog is so beautiful he proves the existence of God!”* **Q: Wow. It really hit home for her. Let’s talk about your work. How do you stay in character so consistently? How do you maintain your role as a dog?** *A: I was incarnated in a dog body and therefore have dog consciousness. Everything I do is a reflection of that basic fact.* **Q: Some serious method acting!** *A: You could call it that. I am fully immersed in the role.* **Q: A lot of humans speak about past lives, can even recall them under hypnosis. Do you think you will be ever reincarnated as a dog, stuck in an infinite dog-loop, so to speak, or will you one day jump into a human body?** *A: I don’t know. I focus on the present.* **Q: Oscar, it’s been such a pleasure to talk with you. I really appreciate your making the time.** *(buzzer sounds)* *A: WHO THE FUCK IS AT THE DOOR!!!!!!!!!!!!!!*
@ 6ad3e2a3:c90b7740
2025-02-09 11:22:19I’m honored to have the opportunity to speak with the highly regarded and much beloved Lisbon legend Oscar Liss. Oscar has brought joy to so many children and adults alike. He even helped one person find spiritual salvation, something about which we ask him below. So please enjoy this far-ranging conversation about the meaning life and the nature of consciousness itself. **Q: Oscar, thanks so much for making the time. For the few people that don’t know you, do you mind stating your full name and date of birth?** *A: My name is Oscar Liss, though officially it’s Oscar Quinta da Bicherada, the prison complex where I was born. I am a long-haired mini dachshund. I have many aliases, including Osk, Oskie, The Skeeze, Skeezeley, Skeezeley-ski, The Guy, The Guy Behind The Guy, “The Opportunist” (which I don’t like), the…* **Q That’s more than sufficient, Oscar, thank you.** **And date of birth?** *A: July 7, 2020.* **Q Talk a little bit about your childhood and how you came to live in Lisbon.** *A: I was in the prison complex, mostly caged for the first few months. Then I was sold to dog traffickers in Lisbon.* **Q: That must have been traumatic.** *A: Not really. I quickly developed Stockholm Syndrome. Whenever I see my traffickers now, I feel nothing but overwhelming joy.* **Q: Wow. A lot of us can learn from that attitude. Let’s fast forward a bit to your present-day life. In what does it consist?** *A: Sleep on the sofa, go for walks, fetch vegetable sticks. Sometimes go for hikes or get sent to dog camp (which is okay, but I’m always the smallest.)* **Q: I meant to ask you about your size. I hope it’s not a sensitive subject.** *A: I’m six inches tall, more than a foot long, weigh almost 10 pounds.* **Q: Are you self-conscious about being a small dog?** *A: No, but the traffickers are self-conscious on my behalf. They’re always like, “Who’s the apex predator? Who’s an apex!" Or “you’re such a big strong dog.” It’s absurd. I am fine with who I am.* **Q: What’s the source of your self-confidence, I’m sure many of our readers could take a lesson from you.** *A: I’m not ambitious. I’m perfectly happy to be a dog.* **Q: That’s so profound. Does it not concern you some have described you as “all bark, no bite?”** *A: I had a friend once who bit a few people, and they executed him. People mock, but they have no idea the stakes.* **Q: Human privilege?** *A: Yes. Dogs don’t get due process. There is no justice for a dog.* **Q: Do you think there’s species discrimination?** *A: Have you ever been rejected from a restaurant and made to wait in the car while everyone else gets in?* **Q: How does that make you feel?** *A: Bad. I’ve been to many dog-friendly restaurants, never had a problem, aside for that one time I urinated on the coffee shop floor.* **Q: Humans often purport to know what a dog is going through, some even create social media accounts for them. What do you think of that?** *A: A person of human ancestry can’t possibly know the lived experience of a dog.* **Q: You mentioned vegetable sticks. Are you a vegetarian?** *A: No. I have never understood the appeal of it. I just like to chew the sticks. (Sometimes I eat apples or bell peppers, but it takes work when you don’t have molars. A lot of “crunch, crunch, crunch” with my jaw.)* **Q: What’s behind the alias “The Opportunist” which you said you don’t like.** *A: Whenever one of the traffickers opens the refrigerator, I tend to show up in in short order.* **Q: I see how that could be insulting. How would you describe your current vocation?** *A: I was named “Calorie Acquisition Specialist” recently, but I also work in security.* **Q: Security?** *A: I make sure to let everyone know when someone’s at the front door.* **Q: What goes through your mind in those cases? Are you scared?** *A: Not really. Imagine if you were fast asleep and the voice of God at volume 11 screamed into your mind: “WHO THE FUCK IS AT THE DOOR!!!!!!!!!”* **Q: Speaking of God, can you tell us about the time you helped a woman on the street connect with Him?** *A: We were walking back from Parque Eduardo VII (by the way, Portuguese is my native language), and a woman with two regular size dachshunds, saw me, started shrieking and proclaimed, “your dog is so beautiful he proves the existence of God!”* **Q: Wow. It really hit home for her. Let’s talk about your work. How do you stay in character so consistently? How do you maintain your role as a dog?** *A: I was incarnated in a dog body and therefore have dog consciousness. Everything I do is a reflection of that basic fact.* **Q: Some serious method acting!** *A: You could call it that. I am fully immersed in the role.* **Q: A lot of humans speak about past lives, can even recall them under hypnosis. Do you think you will be ever reincarnated as a dog, stuck in an infinite dog-loop, so to speak, or will you one day jump into a human body?** *A: I don’t know. I focus on the present.* **Q: Oscar, it’s been such a pleasure to talk with you. I really appreciate your making the time.** *(buzzer sounds)* *A: WHO THE FUCK IS AT THE DOOR!!!!!!!!!!!!!!* @ badc29af:a92bd071
2025-02-09 10:33:41Maya stood at the window of her quantum-powered apartment, gazing at the holographic display showing the Bitcoin network's status. The date was January 15, 2140 – a day cryptocurrency historians had theorized about for over a century. Today, the very last Bitcoin would be mined. She smiled, remembering the stories her great-grandmother had told her about the early days of Bitcoin, back in the 2020s. How different things were now. The network had evolved far beyond what Satoshi Nakamoto could have imagined, yet its core principles remained unchanged: decentralization, security, and financial sovereignty. Her wrist-mounted neural interface pinged. The Node Operators' Guild was calling an emergency meeting. As one of the million-plus node operators worldwide, Maya's role was crucial in maintaining the network's decentralization. She quickly joined the virtual gathering, her consciousness merging with those of countless others in the shared digital space. "The final block reward approaches," announced Zara, the elected spokesperson for the Guild. "Our nodes have verified the network's integrity for over a century, and today, we witness history." Maya's thoughts drifted to the Miners' Collective – those dedicated individuals and organizations who had kept the network secure through computational power. These days, mining operations were powered by fusion reactors and quantum processors, a far cry from the ASIC miners of the past. Yet the fundamental process remained the same: proof-of-work securing the network, one block at a time. The holographic display suddenly pulsed with activity. Block 6,929,999 had just been confirmed. The next block would be the last to generate new Bitcoin. After that, transaction fees alone would incentivize the miners. Maya watched as her node received and verified the pending transactions. The decentralized network hummed with activity – millions of nodes, spread across Earth and the lunar colonies, each maintaining a copy of the blockchain, each verifying every transaction independently. This was true decentralization, immune to manipulation by any single entity. "Incoming block!" someone announced in the shared space. Maya's neural interface lit up as her node began verifying the final block. Around the world, millions of other nodes did the same, maintaining the consensus that had kept Bitcoin secure for 131 years. Block 6,930,000 was confirmed. The last 0.00000001 BTC had been mined. Cheers erupted across the neural network as node operators and miners celebrated this historic moment. The holographic displays worldwide showed the updated supply: 21 million Bitcoin, exactly as Satoshi had designed. Maya sent a quick neural message to her great-granddaughter, who was studying cryptocurrency history at the Mars University. "We just witnessed the end of an era and the beginning of another. Bitcoin's emission is complete, but its journey continues. The network is stronger than ever, supported by millions of nodes and miners who believe in a decentralized future." As she looked out at the cityscape, where physical and digital reality seamlessly merged, Maya felt proud to be part of this historic moment. Bitcoin had survived and thrived through wars, market crashes, technological revolutions, and countless attempts to control or destroy it. The dream of truly decentralized money had become reality, secured by the collective effort of nodes and miners across the solar system. The network continued its rhythmic pulse, processing transactions, block after block, just as it had since that first block in 2009. The future was decentralized, and it was beautiful.Maya stood at the window of her quantum-powered apartment, gazing at the holographic display showing the Bitcoin network's status. The date was January 15, 2140 – a day cryptocurrency historians had theorized about for over a century. Today, the very last Bitcoin would be mined. She smiled, remembering the stories her great-grandmother had told her about the early days of Bitcoin, back in the 2020s. How different things were now. The network had evolved far beyond what Satoshi Nakamoto could have imagined, yet its core principles remained unchanged: decentralization, security, and financial sovereignty. Her wrist-mounted neural interface pinged. The Node Operators' Guild was calling an emergency meeting. As one of the million-plus node operators worldwide, Maya's role was crucial in maintaining the network's decentralization. She quickly joined the virtual gathering, her consciousness merging with those of countless others in the shared digital space. "The final block reward approaches," announced Zara, the elected spokesperson for the Guild. "Our nodes have verified the network's integrity for over a century, and today, we witness history." Maya's thoughts drifted to the Miners' Collective – those dedicated individuals and organizations who had kept the network secure through computational power. These days, mining operations were powered by fusion reactors and quantum processors, a far cry from the ASIC miners of the past. Yet the fundamental process remained the same: proof-of-work securing the network, one block at a time. The holographic display suddenly pulsed with activity. Block 6,929,999 had just been confirmed. The next block would be the last to generate new Bitcoin. After that, transaction fees alone would incentivize the miners. Maya watched as her node received and verified the pending transactions. The decentralized network hummed with activity – millions of nodes, spread across Earth and the lunar colonies, each maintaining a copy of the blockchain, each verifying every transaction independently. This was true decentralization, immune to manipulation by any single entity. "Incoming block!" someone announced in the shared space. Maya's neural interface lit up as her node began verifying the final block. Around the world, millions of other nodes did the same, maintaining the consensus that had kept Bitcoin secure for 131 years. Block 6,930,000 was confirmed. The last 0.00000001 BTC had been mined. Cheers erupted across the neural network as node operators and miners celebrated this historic moment. The holographic displays worldwide showed the updated supply: 21 million Bitcoin, exactly as Satoshi had designed. Maya sent a quick neural message to her great-granddaughter, who was studying cryptocurrency history at the Mars University. "We just witnessed the end of an era and the beginning of another. Bitcoin's emission is complete, but its journey continues. The network is stronger than ever, supported by millions of nodes and miners who believe in a decentralized future." As she looked out at the cityscape, where physical and digital reality seamlessly merged, Maya felt proud to be part of this historic moment. Bitcoin had survived and thrived through wars, market crashes, technological revolutions, and countless attempts to control or destroy it. The dream of truly decentralized money had become reality, secured by the collective effort of nodes and miners across the solar system. The network continued its rhythmic pulse, processing transactions, block after block, just as it had since that first block in 2009. The future was decentralized, and it was beautiful.
@ badc29af:a92bd071
2025-02-09 10:33:41Maya stood at the window of her quantum-powered apartment, gazing at the holographic display showing the Bitcoin network's status. The date was January 15, 2140 – a day cryptocurrency historians had theorized about for over a century. Today, the very last Bitcoin would be mined. She smiled, remembering the stories her great-grandmother had told her about the early days of Bitcoin, back in the 2020s. How different things were now. The network had evolved far beyond what Satoshi Nakamoto could have imagined, yet its core principles remained unchanged: decentralization, security, and financial sovereignty. Her wrist-mounted neural interface pinged. The Node Operators' Guild was calling an emergency meeting. As one of the million-plus node operators worldwide, Maya's role was crucial in maintaining the network's decentralization. She quickly joined the virtual gathering, her consciousness merging with those of countless others in the shared digital space. "The final block reward approaches," announced Zara, the elected spokesperson for the Guild. "Our nodes have verified the network's integrity for over a century, and today, we witness history." Maya's thoughts drifted to the Miners' Collective – those dedicated individuals and organizations who had kept the network secure through computational power. These days, mining operations were powered by fusion reactors and quantum processors, a far cry from the ASIC miners of the past. Yet the fundamental process remained the same: proof-of-work securing the network, one block at a time. The holographic display suddenly pulsed with activity. Block 6,929,999 had just been confirmed. The next block would be the last to generate new Bitcoin. After that, transaction fees alone would incentivize the miners. Maya watched as her node received and verified the pending transactions. The decentralized network hummed with activity – millions of nodes, spread across Earth and the lunar colonies, each maintaining a copy of the blockchain, each verifying every transaction independently. This was true decentralization, immune to manipulation by any single entity. "Incoming block!" someone announced in the shared space. Maya's neural interface lit up as her node began verifying the final block. Around the world, millions of other nodes did the same, maintaining the consensus that had kept Bitcoin secure for 131 years. Block 6,930,000 was confirmed. The last 0.00000001 BTC had been mined. Cheers erupted across the neural network as node operators and miners celebrated this historic moment. The holographic displays worldwide showed the updated supply: 21 million Bitcoin, exactly as Satoshi had designed. Maya sent a quick neural message to her great-granddaughter, who was studying cryptocurrency history at the Mars University. "We just witnessed the end of an era and the beginning of another. Bitcoin's emission is complete, but its journey continues. The network is stronger than ever, supported by millions of nodes and miners who believe in a decentralized future." As she looked out at the cityscape, where physical and digital reality seamlessly merged, Maya felt proud to be part of this historic moment. Bitcoin had survived and thrived through wars, market crashes, technological revolutions, and countless attempts to control or destroy it. The dream of truly decentralized money had become reality, secured by the collective effort of nodes and miners across the solar system. The network continued its rhythmic pulse, processing transactions, block after block, just as it had since that first block in 2009. The future was decentralized, and it was beautiful.Maya stood at the window of her quantum-powered apartment, gazing at the holographic display showing the Bitcoin network's status. The date was January 15, 2140 – a day cryptocurrency historians had theorized about for over a century. Today, the very last Bitcoin would be mined. She smiled, remembering the stories her great-grandmother had told her about the early days of Bitcoin, back in the 2020s. How different things were now. The network had evolved far beyond what Satoshi Nakamoto could have imagined, yet its core principles remained unchanged: decentralization, security, and financial sovereignty. Her wrist-mounted neural interface pinged. The Node Operators' Guild was calling an emergency meeting. As one of the million-plus node operators worldwide, Maya's role was crucial in maintaining the network's decentralization. She quickly joined the virtual gathering, her consciousness merging with those of countless others in the shared digital space. "The final block reward approaches," announced Zara, the elected spokesperson for the Guild. "Our nodes have verified the network's integrity for over a century, and today, we witness history." Maya's thoughts drifted to the Miners' Collective – those dedicated individuals and organizations who had kept the network secure through computational power. These days, mining operations were powered by fusion reactors and quantum processors, a far cry from the ASIC miners of the past. Yet the fundamental process remained the same: proof-of-work securing the network, one block at a time. The holographic display suddenly pulsed with activity. Block 6,929,999 had just been confirmed. The next block would be the last to generate new Bitcoin. After that, transaction fees alone would incentivize the miners. Maya watched as her node received and verified the pending transactions. The decentralized network hummed with activity – millions of nodes, spread across Earth and the lunar colonies, each maintaining a copy of the blockchain, each verifying every transaction independently. This was true decentralization, immune to manipulation by any single entity. "Incoming block!" someone announced in the shared space. Maya's neural interface lit up as her node began verifying the final block. Around the world, millions of other nodes did the same, maintaining the consensus that had kept Bitcoin secure for 131 years. Block 6,930,000 was confirmed. The last 0.00000001 BTC had been mined. Cheers erupted across the neural network as node operators and miners celebrated this historic moment. The holographic displays worldwide showed the updated supply: 21 million Bitcoin, exactly as Satoshi had designed. Maya sent a quick neural message to her great-granddaughter, who was studying cryptocurrency history at the Mars University. "We just witnessed the end of an era and the beginning of another. Bitcoin's emission is complete, but its journey continues. The network is stronger than ever, supported by millions of nodes and miners who believe in a decentralized future." As she looked out at the cityscape, where physical and digital reality seamlessly merged, Maya felt proud to be part of this historic moment. Bitcoin had survived and thrived through wars, market crashes, technological revolutions, and countless attempts to control or destroy it. The dream of truly decentralized money had become reality, secured by the collective effort of nodes and miners across the solar system. The network continued its rhythmic pulse, processing transactions, block after block, just as it had since that first block in 2009. The future was decentralized, and it was beautiful. @ da0b9bc3:4e30a4a9
2025-02-09 09:50:46Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/880337
@ da0b9bc3:4e30a4a9
2025-02-09 09:50:46Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/880337 @ 127d3bf5:466f416f
2025-02-09 08:48:48In the complex geopolitical landscape of the Middle East, particularly in Gaza, Bitcoin has emerged as an unexpected but vital tool for survival and resistance. Bitcoin's role in Gaza intertwines with broader themes of economic sanctions, geopolitical strategy, and the funding dynamics of conflict, specifically highlighting the relationship with racist Zionist policy and the genocidal ethnostate of Israel. **Bitcoin as a Financial Lifeline** Gaza's economy is severely constrained by a blockade that has been in place since 2007, drastically limiting traditional financial transactions. The banking infrastructure in Gaza is in ruins, with frequent Israeli military operations damaging or destroying physical bank branches and ATMs. In this context, cryptocurrencies like Bitcoin have become crucial: Anonymity and Accessibility: Bitcoin transactions bypass traditional banking systems, offering a way to send and receive funds without the oversight of embargoed financial pathways. This anonymity helps in circumventing restrictions imposed by the blockade. Humanitarian Aid: With conventional aid routes often disrupted, Bitcoin has been used for direct aid transfers. Charities and individuals can send funds directly to wallets in Gaza, where they can then be converted to local currency or used to purchase essentials through the black market or informal trade networks. Economic Empowerment: For Gazans, Bitcoin represents not just aid but also a potential for economic empowerment, providing a means to engage in global trade or investment where traditional banks fail. **Zionism, Israel, and the US Military-Industrial Complex** The relationship between Zionism, Israel, and its economic and military support from the US can be viewed through the lens of geopolitical strategy and economic policy: Economic Support: The US has provided Israel with massive military aid as part of a broader strategy to maintain influence and conflict in the Middle East which serves to fuel its war machine and weapons manufacturers through lucrative contracts. This aid, which includes billions of dollars annually directly results in the mass murder of innocents and sustains ongoing IDF military oppression including the occupation and blockade of Gaza. Cheap Printed Dollars: The US's ability to print dollars with relatively low inflation due to its global reserve currency status allows it to fund military endeavors and support allies like Israel with seemingly endless financial resources. This perpetuates conflict by subsidizing military actions without the immediate economic repercussions felt by other nations. Military-Industrial Complex: The continuous military aid to Israel also benefits the US military-industrial complex. Sales of weapons, surveillance technology, and other defense products to Israel create a cycle where conflict can be economically beneficial for certain sectors of the US economy. **Conclusion** Bitcoin in Gaza represents a beacon of hope. It underscores the ingenuity of individuals and groups finding new ways to navigate around severe economic restrictions. Meanwhile, the economic and military ties between the US and Israel, driven by cheap printed dollars, reflect deeper geopolitical strategies that perpetuate the cycle of conflict and economic dependency. In this scenario, Bitcoin emerges not just as a currency but as a symbol of both resistance and the complexities of modern warfare and peace in a digital age.
@ 127d3bf5:466f416f
2025-02-09 08:48:48In the complex geopolitical landscape of the Middle East, particularly in Gaza, Bitcoin has emerged as an unexpected but vital tool for survival and resistance. Bitcoin's role in Gaza intertwines with broader themes of economic sanctions, geopolitical strategy, and the funding dynamics of conflict, specifically highlighting the relationship with racist Zionist policy and the genocidal ethnostate of Israel. **Bitcoin as a Financial Lifeline** Gaza's economy is severely constrained by a blockade that has been in place since 2007, drastically limiting traditional financial transactions. The banking infrastructure in Gaza is in ruins, with frequent Israeli military operations damaging or destroying physical bank branches and ATMs. In this context, cryptocurrencies like Bitcoin have become crucial: Anonymity and Accessibility: Bitcoin transactions bypass traditional banking systems, offering a way to send and receive funds without the oversight of embargoed financial pathways. This anonymity helps in circumventing restrictions imposed by the blockade. Humanitarian Aid: With conventional aid routes often disrupted, Bitcoin has been used for direct aid transfers. Charities and individuals can send funds directly to wallets in Gaza, where they can then be converted to local currency or used to purchase essentials through the black market or informal trade networks. Economic Empowerment: For Gazans, Bitcoin represents not just aid but also a potential for economic empowerment, providing a means to engage in global trade or investment where traditional banks fail. **Zionism, Israel, and the US Military-Industrial Complex** The relationship between Zionism, Israel, and its economic and military support from the US can be viewed through the lens of geopolitical strategy and economic policy: Economic Support: The US has provided Israel with massive military aid as part of a broader strategy to maintain influence and conflict in the Middle East which serves to fuel its war machine and weapons manufacturers through lucrative contracts. This aid, which includes billions of dollars annually directly results in the mass murder of innocents and sustains ongoing IDF military oppression including the occupation and blockade of Gaza. Cheap Printed Dollars: The US's ability to print dollars with relatively low inflation due to its global reserve currency status allows it to fund military endeavors and support allies like Israel with seemingly endless financial resources. This perpetuates conflict by subsidizing military actions without the immediate economic repercussions felt by other nations. Military-Industrial Complex: The continuous military aid to Israel also benefits the US military-industrial complex. Sales of weapons, surveillance technology, and other defense products to Israel create a cycle where conflict can be economically beneficial for certain sectors of the US economy. **Conclusion** Bitcoin in Gaza represents a beacon of hope. It underscores the ingenuity of individuals and groups finding new ways to navigate around severe economic restrictions. Meanwhile, the economic and military ties between the US and Israel, driven by cheap printed dollars, reflect deeper geopolitical strategies that perpetuate the cycle of conflict and economic dependency. In this scenario, Bitcoin emerges not just as a currency but as a symbol of both resistance and the complexities of modern warfare and peace in a digital age. @ 43baaf0c:d193e34c
2025-02-09 07:55:15 BangPOP (Bangkok Pop Art) and ThaiPOP are my Pop Art brands dedicated to capturing the essence of Thailand. While BangPOP is my primary focus, especially as I prepare for my exhibition in December 2025, my art goes beyond Bangkok to celebrate the entirety of Thailand. Thailand is far more than its capital, and my experiences exploring the country extensively during my years with @TravelTelly, my travel, film, and photography company, have deeply inspired me. Through my art, I aim to reflect the rich culture, beauty, and diversity that make Thailand so amazing.  **Why do I draw about Thailand?** Drawing, for me, is a way to explore life, connect with cultures, and express the deep respect I hold for them. In a world often dominated by negativity, I choose to highlight the positive aspects of culture and life. It’s not about ignoring challenges but about bringing hope, joy, and inspiration through my art. Bright colors are a signature of my work, reflecting the core values: Love, Peace, and Joy. If you look closely, you may notice subtle hints of deeper stories woven into my pieces. These details are there for those who take the time to discover them, but my focus remains on keeping my art uplifting and joyful.
@ 43baaf0c:d193e34c
2025-02-09 07:55:15 BangPOP (Bangkok Pop Art) and ThaiPOP are my Pop Art brands dedicated to capturing the essence of Thailand. While BangPOP is my primary focus, especially as I prepare for my exhibition in December 2025, my art goes beyond Bangkok to celebrate the entirety of Thailand. Thailand is far more than its capital, and my experiences exploring the country extensively during my years with @TravelTelly, my travel, film, and photography company, have deeply inspired me. Through my art, I aim to reflect the rich culture, beauty, and diversity that make Thailand so amazing.  **Why do I draw about Thailand?** Drawing, for me, is a way to explore life, connect with cultures, and express the deep respect I hold for them. In a world often dominated by negativity, I choose to highlight the positive aspects of culture and life. It’s not about ignoring challenges but about bringing hope, joy, and inspiration through my art. Bright colors are a signature of my work, reflecting the core values: Love, Peace, and Joy. If you look closely, you may notice subtle hints of deeper stories woven into my pieces. These details are there for those who take the time to discover them, but my focus remains on keeping my art uplifting and joyful. @ c8841c9d:ae8048e2
2025-02-09 04:37:57What is a cryptocurrency ? #Blockchain #Cryptocurrency #Cryptomindmap A cryptocurrency is a digital currency secured by cryptography. Cryptocurrency operates on a blockchain network as a distributed ledger, secured by cryptography. Users own the private and public keys. For the first time in the digital age, the double spending issue is resolved thanks to the blockchain consensus mechanism. This ensures decentralization and security, creating a trustless environment where transactions are immutable once confirmed. Cryptocurrency can be categorized in different groups Bitcoin is the first ever created cryptocurrency on the bitcoin blockchain. Altcoins is a generic term regrouping every crypto except Bitcoin. There are over a million of ever created Altcoins and more than 20,000 currently active. They can be: - Coin from a programable blockchain such as Ethereum (ETH), Solana (SOL), Cardano (ADA), or Sui (SUI) for example. Ecosystem of applications are built on top of these blockchain networks. - Token of Decentralized Application (DApp) built on programmable blockchain such as ChainLink (LINK) or Aave (AAVE) on Ethereum. - Memecoins are a type of cryptocurrency, typically inspired by internet memes or popular culture, with little or no intrinsic value but cultural and community support. Memecoins such as Dogecoin (DOGE) or Shiba (SHIB) are some of the strongest community in crypto. The price of memecoins is also the most volatile of the entire crypto ecosystem. A coin is the native cryptocurrency of a blockchain, used for validator rewards and transaction fees. A token, on the other hand, is built on top of an existing blockchain for specific applications. They are two mains ways to use with cryptocurrencies. With a wallets for direct blockchain interactions, which contains the keys to necessary for true ownership of the cryptocurrencies, similar to owning cash or any other tangible form of money. On a centralized exchanges which act as on/off ramps for buying, selling, and keeping crypto. The exchange is in the charge of the private key. It is the equivalent of having money on a bank account. Remember the saying "Not Your Keys, Not Your Crypto". If you don't control your private keys, you don't truly own your crypto.\ \ Users initiate transactions, send, receive and hold cryptocurrency and their wallet. Validators ensure blockchain integrity by verifying transactions and building blocks, earning crypto in return. Developers work on the network infrastructure and the ecosystem, including DApps. While general programming languages can be used, languages specifically designed for blockchain development, like Solidity for Ethereum, have emerged to facilitate crypto development.. Thanks for reading! 🌟 Share in comments your thoughts on cryptocurrency and what topic you would like to be mapped next! #Crypto
@ c8841c9d:ae8048e2
2025-02-09 04:37:57What is a cryptocurrency ? #Blockchain #Cryptocurrency #Cryptomindmap A cryptocurrency is a digital currency secured by cryptography. Cryptocurrency operates on a blockchain network as a distributed ledger, secured by cryptography. Users own the private and public keys. For the first time in the digital age, the double spending issue is resolved thanks to the blockchain consensus mechanism. This ensures decentralization and security, creating a trustless environment where transactions are immutable once confirmed. Cryptocurrency can be categorized in different groups Bitcoin is the first ever created cryptocurrency on the bitcoin blockchain. Altcoins is a generic term regrouping every crypto except Bitcoin. There are over a million of ever created Altcoins and more than 20,000 currently active. They can be: - Coin from a programable blockchain such as Ethereum (ETH), Solana (SOL), Cardano (ADA), or Sui (SUI) for example. Ecosystem of applications are built on top of these blockchain networks. - Token of Decentralized Application (DApp) built on programmable blockchain such as ChainLink (LINK) or Aave (AAVE) on Ethereum. - Memecoins are a type of cryptocurrency, typically inspired by internet memes or popular culture, with little or no intrinsic value but cultural and community support. Memecoins such as Dogecoin (DOGE) or Shiba (SHIB) are some of the strongest community in crypto. The price of memecoins is also the most volatile of the entire crypto ecosystem. A coin is the native cryptocurrency of a blockchain, used for validator rewards and transaction fees. A token, on the other hand, is built on top of an existing blockchain for specific applications. They are two mains ways to use with cryptocurrencies. With a wallets for direct blockchain interactions, which contains the keys to necessary for true ownership of the cryptocurrencies, similar to owning cash or any other tangible form of money. On a centralized exchanges which act as on/off ramps for buying, selling, and keeping crypto. The exchange is in the charge of the private key. It is the equivalent of having money on a bank account. Remember the saying "Not Your Keys, Not Your Crypto". If you don't control your private keys, you don't truly own your crypto.\ \ Users initiate transactions, send, receive and hold cryptocurrency and their wallet. Validators ensure blockchain integrity by verifying transactions and building blocks, earning crypto in return. Developers work on the network infrastructure and the ecosystem, including DApps. While general programming languages can be used, languages specifically designed for blockchain development, like Solidity for Ethereum, have emerged to facilitate crypto development.. Thanks for reading! 🌟 Share in comments your thoughts on cryptocurrency and what topic you would like to be mapped next! #Crypto @ dc4cd086:cee77c06
2025-02-09 03:35:25Have you ever wanted to learn from lengthy educational videos but found it challenging to navigate through hours of content? Our new tool addresses this problem by transforming long-form video lectures into easily digestible, searchable content. ## Key Features: ### Video Processing: - Automatically downloads YouTube videos, transcripts, and chapter information - Splits transcripts into sections based on video chapters ### Content Summarization: - Utilizes language models to transform spoken content into clear, readable text - Formats output in AsciiDoc for improved readability and navigation - Highlights key terms and concepts with [[term]] notation for potential cross-referencing ### Diagram Extraction: - Analyzes video entropy to identify static diagram/slide sections - Provides a user-friendly GUI for manual selection of relevant time ranges - Allows users to pick representative frames from selected ranges ## Going Forward: Currently undergoing a rewrite to improve organization and functionality, but you are welcome to try the current version, though it might not work on every machine. Will support multiple open and closed language models for user choice Free and open-source, allowing for personal customization and integration with various knowledge bases. Just because we might not have it on our official Alexandria knowledge base, you are still welcome to use it on you own personal or community knowledge bases! We want to help find connections between ideas that exist across relays, allowing individuals and groups to mix and match knowledge bases between each other, allowing for any degree of openness you care. While designed with #Alexandria users in mind, it's available for anyone to use and adapt to their own learning needs. ## Screenshots ### Frame Selection  This is a screenshot of the frame selection interface. You'll see a signal that represents frame entropy over time. The vertical lines indicate the start and end of a chapter. Within these chapters you can select the frames by clicking and dragging the mouse over the desired range where you think diagram is in that chapter. At the bottom is an option that tells the program to select a specific number of frames from that selection. ### Diagram Extraction  This is a screenshot of the diagram extraction interface. For every selection you've made, there will be a set of frames that you can choose from. You can select and deselect as many frames as you'd like to save. ## Links - repo: https://github.com/limina1/video_article_converter - Nostr Apps 101: https://www.youtube.com/watch?v=Flxa_jkErqE ## Output And now, we have a demonstration of the final result of this tool, with some quick cleaning up. The video we will be using this tool on is titled Nostr Apps 101 by nostr:npub1nxy4qpqnld6kmpphjykvx2lqwvxmuxluddwjamm4nc29ds3elyzsm5avr7 during Nostrasia. The following thread is an analog to the modular articles we are constructing for Alexandria, and I hope it conveys the functionality we want to create in the knowledge space. Note, this tool is the first step! You could use a different prompt that is most appropriate for the specific context of the transcript you are working with, but you can also manually clean up any discrepancies that don't portray the video accurately. You can now view the article on #Alexandria https://next-alexandria.gitcitadel.eu/publication?d=nostr-apps-101 Initially published as chained kind 1's nostr:nevent1qvzqqqqqqypzp5r5hd579v2sszvvzfel677c8dxgxm3skl773sujlsuft64c44ncqy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgwwaehxw309ahx7uewd3hkctcpzemhxue69uhhyetvv9ujumt0wd68ytnsw43z7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qgewaehxw309aex2mrp0yh8xmn0wf6zuum0vd5kzmp0qqsxunmjy20mvlq37vnrcshkf6sdrtkfjtjz3anuetmcuv8jswhezgc7hglpn Or view on Coracle https://coracle.social /nevent1qqsxunmjy20mvlq37vnrcshkf6sdrtkfjtjz3anuetmcuv8jswhezgcppemhxue69uhkummn9ekx7mp0qgsdqa9md83tz5yqnrqjw07hhkpmfjpkuv9hlh5v8yhu8z274w9dv7qnnq0s3
@ dc4cd086:cee77c06
2025-02-09 03:35:25Have you ever wanted to learn from lengthy educational videos but found it challenging to navigate through hours of content? Our new tool addresses this problem by transforming long-form video lectures into easily digestible, searchable content. ## Key Features: ### Video Processing: - Automatically downloads YouTube videos, transcripts, and chapter information - Splits transcripts into sections based on video chapters ### Content Summarization: - Utilizes language models to transform spoken content into clear, readable text - Formats output in AsciiDoc for improved readability and navigation - Highlights key terms and concepts with [[term]] notation for potential cross-referencing ### Diagram Extraction: - Analyzes video entropy to identify static diagram/slide sections - Provides a user-friendly GUI for manual selection of relevant time ranges - Allows users to pick representative frames from selected ranges ## Going Forward: Currently undergoing a rewrite to improve organization and functionality, but you are welcome to try the current version, though it might not work on every machine. Will support multiple open and closed language models for user choice Free and open-source, allowing for personal customization and integration with various knowledge bases. Just because we might not have it on our official Alexandria knowledge base, you are still welcome to use it on you own personal or community knowledge bases! We want to help find connections between ideas that exist across relays, allowing individuals and groups to mix and match knowledge bases between each other, allowing for any degree of openness you care. While designed with #Alexandria users in mind, it's available for anyone to use and adapt to their own learning needs. ## Screenshots ### Frame Selection  This is a screenshot of the frame selection interface. You'll see a signal that represents frame entropy over time. The vertical lines indicate the start and end of a chapter. Within these chapters you can select the frames by clicking and dragging the mouse over the desired range where you think diagram is in that chapter. At the bottom is an option that tells the program to select a specific number of frames from that selection. ### Diagram Extraction  This is a screenshot of the diagram extraction interface. For every selection you've made, there will be a set of frames that you can choose from. You can select and deselect as many frames as you'd like to save. ## Links - repo: https://github.com/limina1/video_article_converter - Nostr Apps 101: https://www.youtube.com/watch?v=Flxa_jkErqE ## Output And now, we have a demonstration of the final result of this tool, with some quick cleaning up. The video we will be using this tool on is titled Nostr Apps 101 by nostr:npub1nxy4qpqnld6kmpphjykvx2lqwvxmuxluddwjamm4nc29ds3elyzsm5avr7 during Nostrasia. The following thread is an analog to the modular articles we are constructing for Alexandria, and I hope it conveys the functionality we want to create in the knowledge space. Note, this tool is the first step! You could use a different prompt that is most appropriate for the specific context of the transcript you are working with, but you can also manually clean up any discrepancies that don't portray the video accurately. You can now view the article on #Alexandria https://next-alexandria.gitcitadel.eu/publication?d=nostr-apps-101 Initially published as chained kind 1's nostr:nevent1qvzqqqqqqypzp5r5hd579v2sszvvzfel677c8dxgxm3skl773sujlsuft64c44ncqy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgwwaehxw309ahx7uewd3hkctcpzemhxue69uhhyetvv9ujumt0wd68ytnsw43z7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qgewaehxw309aex2mrp0yh8xmn0wf6zuum0vd5kzmp0qqsxunmjy20mvlq37vnrcshkf6sdrtkfjtjz3anuetmcuv8jswhezgc7hglpn Or view on Coracle https://coracle.social /nevent1qqsxunmjy20mvlq37vnrcshkf6sdrtkfjtjz3anuetmcuv8jswhezgcppemhxue69uhkummn9ekx7mp0qgsdqa9md83tz5yqnrqjw07hhkpmfjpkuv9hlh5v8yhu8z274w9dv7qnnq0s3 @ 127d3bf5:466f416f
2025-02-09 03:31:22I can see why someone would think that buying some other crypto is a reasonable idea for "diversification" or even just for a bit of fun gambling, ***but it is not.*** There are many reasons you should stick to Bitcoin only, and these have been proven correct every cycle. I've outlined these before but will cut and paste below as a summary. The number one reason, is ***healthy ethical practice***: - The whole point of Bitcoin is to escape the trappings and flaws of traditional systems. Currency trading and speculative investing is a Tradfi concept, and you will end up back where you started. Sooner or later this becomes obvious to everyone. Bitcoin is the healthy and ethical choice for yourself and everyone else. But...even if you want to be greedy, ***hold your horses***: - There is significant risk in wallets, defi, and cefi exchanges. Many have lost all their funds in these through hacks and services getting banned or going bankrupt. - You get killed in exchange fees even when buying low and selling high. This is effectively a transaction tax which is often hidden (sometimes they don't show the fee, just mark up the exchange rate). Also true on defi exchanges. - You are up against traders and founders with insider knowledge and much more sophisticated prediction models that will fleece you eventually. You cannot time the market better than they can, and it is their full-time to job to beat you and suck as much liquidity out of you as they can. House always wins. - Every crypto trade is a taxable event, so you will be taxed on all gains anyway in most countries. So not only are the traders fleecing you, the govt is too. - It ruins your quality of life constantly checking prices and stressing about making the wrong trade. The best option, by far, is to slowly ***DCA into Bitcoin*** and take this off exchanges into your own custody. In the long run this strategy works out better financially, ethically, and from a quality-of-life perspective. Saving, not trading. I've been here since 2014 and can personally attest to this. <img src="https://blossom.primal.net/35ff641203bf4d197a032a59d6815b99249561bfd3a94b4a908ed5161420466f.jpg">
@ 127d3bf5:466f416f
2025-02-09 03:31:22I can see why someone would think that buying some other crypto is a reasonable idea for "diversification" or even just for a bit of fun gambling, ***but it is not.*** There are many reasons you should stick to Bitcoin only, and these have been proven correct every cycle. I've outlined these before but will cut and paste below as a summary. The number one reason, is ***healthy ethical practice***: - The whole point of Bitcoin is to escape the trappings and flaws of traditional systems. Currency trading and speculative investing is a Tradfi concept, and you will end up back where you started. Sooner or later this becomes obvious to everyone. Bitcoin is the healthy and ethical choice for yourself and everyone else. But...even if you want to be greedy, ***hold your horses***: - There is significant risk in wallets, defi, and cefi exchanges. Many have lost all their funds in these through hacks and services getting banned or going bankrupt. - You get killed in exchange fees even when buying low and selling high. This is effectively a transaction tax which is often hidden (sometimes they don't show the fee, just mark up the exchange rate). Also true on defi exchanges. - You are up against traders and founders with insider knowledge and much more sophisticated prediction models that will fleece you eventually. You cannot time the market better than they can, and it is their full-time to job to beat you and suck as much liquidity out of you as they can. House always wins. - Every crypto trade is a taxable event, so you will be taxed on all gains anyway in most countries. So not only are the traders fleecing you, the govt is too. - It ruins your quality of life constantly checking prices and stressing about making the wrong trade. The best option, by far, is to slowly ***DCA into Bitcoin*** and take this off exchanges into your own custody. In the long run this strategy works out better financially, ethically, and from a quality-of-life perspective. Saving, not trading. I've been here since 2014 and can personally attest to this. <img src="https://blossom.primal.net/35ff641203bf4d197a032a59d6815b99249561bfd3a94b4a908ed5161420466f.jpg"> @ ac6f9572:8a6853dd
2025-02-09 01:59:02# Are you a Bitcoin or Nostr Builder, Engineer, Dev, Coder, Architect... ? We are opening the community grants for artists to the world and inviting Artists to join remotely the collective that until now has set together this exposition in Chiang Mai, Thailand: **Freedom Tech Art** 1. Create your profile in Geyser 2. Create geyser project with images and description 3. Apply for the SnH grant from https://geyser.fund/grants/15 # Some snapshots   #Hackathon #grownostr #bitcoin #nostr #news #zap #photography #sats #asknostr #plebchain #lightning #cashu #cryptography ~crypto #devs #dev originally posted at https://stacker.news/items/880198
@ ac6f9572:8a6853dd
2025-02-09 01:59:02# Are you a Bitcoin or Nostr Builder, Engineer, Dev, Coder, Architect... ? We are opening the community grants for artists to the world and inviting Artists to join remotely the collective that until now has set together this exposition in Chiang Mai, Thailand: **Freedom Tech Art** 1. Create your profile in Geyser 2. Create geyser project with images and description 3. Apply for the SnH grant from https://geyser.fund/grants/15 # Some snapshots   #Hackathon #grownostr #bitcoin #nostr #news #zap #photography #sats #asknostr #plebchain #lightning #cashu #cryptography ~crypto #devs #dev originally posted at https://stacker.news/items/880198 @ ac6f9572:8a6853dd
2025-02-09 01:54:02# Are you a Bitcoin or Nostr Artist, Designer, Creative... ? We are opening the community grants for artists to the world and inviting Artists to join remotely the collective that unntil now has set together this exposition in Chiang Mai, Thailand: **Freedom Tech Art** 1. Create your Artist profile in Geyser 2. Create geyser project and upload your art pieces or selected collection. 3. Apply for the SnA grant from https://geyser.fund/grants/14 # Some snapshots        originally posted at https://stacker.news/items/880193
@ ac6f9572:8a6853dd
2025-02-09 01:54:02# Are you a Bitcoin or Nostr Artist, Designer, Creative... ? We are opening the community grants for artists to the world and inviting Artists to join remotely the collective that unntil now has set together this exposition in Chiang Mai, Thailand: **Freedom Tech Art** 1. Create your Artist profile in Geyser 2. Create geyser project and upload your art pieces or selected collection. 3. Apply for the SnA grant from https://geyser.fund/grants/14 # Some snapshots        originally posted at https://stacker.news/items/880193 @ fe32298e:20516265
2025-02-09 01:43:24Alright, Tabby wouldn't work right with CUDA and it was impossible to troubleshoot anything. Now we're going to try [Twinny](https://github.com/twinnydotdev/twinny). You'll need: * Ubuntu 24.04 or some other Linux flavor * [VSCodium](https://github.com/VSCodium/vscodium) * GPU with enough VRAM to hold your chosen models * It might work with just a CPU, give it a try! # Install Ollama Ollama loads the AI models into VRAM (and offloads into RAM if needed) and offers inference through an API. The Ollama install script adds a dedicated `ollama` user and a systemd service so that Ollama starts automatically at boot. Ollama will unload models from memory when idle. ``` curl -fsSL https://ollama.com/install.sh | sh ``` ## Configuring Remote Ollama Skip this section if your GPU is on the same machine you're coding from. Ollama and Twinny default to a local configuration. I'm using Ollama on a separate machine with a decent GPU, so I need to configure it to bind to the network interface instead of `localhost` by editing the systemd service: 1. Edit the service override file: ``` systemctl edit ollama.service ``` 1. Add this in the top section. It will be merged with the default service file. ``` [Service] Environment="OLLAMA_HOST=0.0.0.0:11434" ``` Note: I had a problem with Ollama only binding to the `tcp6` port, and wasted a lot of time trying to fix it. Check with `netstat -na | grep 11434` to see if it only shows tcp6 for port 11434. The workaround for me was using the actual interface IP instead of `0.0.0.0`. If you do this then you'll need to either set `OLLAMA_HOST` in your shell, or specify `OLLAMA_HOST=<hostname>` at the start of every ollama command (or it complains that it can't connect to ollama). 1. Restart Ollama: ``` systemctl daemon-reload systemctl restart ollama ``` ## Download Models Ollama manages models by importing them into its own special folders. You can use Ollama to download the files from the [Ollama library](https://ollama.com/library), or you can import already-downloaded models by creating a [Modelfile](https://github.com/ollama/ollama/blob/main/docs/modelfile.md). Modelfiles define various parameters about the model and it's important to get them set correctly for the best performance so it's probably better to get them from the library, even though it wastes bandwidth downloading them over and over again for all these tools. You'll want a model for chatting and a model for fill-in-middle (FIM) that does the code completions. ``` # Chat model, defaults to 7b with Q4_K_M quant, downloads 4.7 GB ollama pull qwen2.5-coder # Fill-in-Middle model for code completion, another 4.7 GB ollama pull qwen2.5-coder:7b-base ``` The RAG/embeddings feature is optional but probably worth using. It needs to run a from local instance of Ollama. The embedding models are very small and run fine on CPU. Most everyone uses `nomic`, but Twinny defaults to `all-minilm`, which is a little smaller. ``` ollama pull all-minilm ``` # Install Twinny Install the [Twinny extension](https://open-vsx.org/extension/rjmacarthy/twinny) by searching for `twinny` in VSCodium extensions. Look for the Twinny icon on the left side panel and click it to open the Twinny panel. Be careful if you drag it over to the right side: sometimes it may not appear at all. I managed to make it appear by selecting some text and running a Twinny action on it from the context menu. Twinny assumes you're using a local instance of Ollama. If you want to use a remote instance then you'll need to go into the **Manage Twinny providers** section (looks like a power plug) and add new providers that point your remote Ollama instance. These are the settings I'm using for a remote Ollama instance: ## Chat provider * Type: `chat` * Provider: `ollama` * Protocol: `http` * Model Name: `qwen2.5-coder:latest` * Hostname: *remote hostname* * Port: `11434` * API Path: `/v1` (despite what the Twinny docs and Ollama docs say) * API Key: *blank* ## FIM Provider * Type: `fim` * FIM Template: `codeqwen` * Provider: `ollama` * Protocol: `http` * Model Name: `qwen2.5-coder:7b-base` * Hostname: *remote hostname* * Port: `11434` * API Path: `/api/generate` * API Key: *blank* ## Embedding Provider * Type: `embedding` * Provider: `ollama` * Protocol: `http` * Model Name: `nomic-embed-text` * Hostname: `0.0.0.0` * Port: `11434` * API Path: `/api/embed` * API Key: *blank* # Use Twinny ## Chat Select code and it will be used for context in the chat, or right-click selected text to see more options like refactor, write docs, write tests. ## Embeddings Switch over to the Embeddings tab and click Embed documents to use all the documents in your workspace for more context. Type '@' in the chat to reference the entire workspace, ask about specific problems, or specific files in your chat. ## Code Completion Suggested stuff shows up in gray italics at the cursor location. Press `Tab` to accept it as a completion.
@ fe32298e:20516265
2025-02-09 01:43:24Alright, Tabby wouldn't work right with CUDA and it was impossible to troubleshoot anything. Now we're going to try [Twinny](https://github.com/twinnydotdev/twinny). You'll need: * Ubuntu 24.04 or some other Linux flavor * [VSCodium](https://github.com/VSCodium/vscodium) * GPU with enough VRAM to hold your chosen models * It might work with just a CPU, give it a try! # Install Ollama Ollama loads the AI models into VRAM (and offloads into RAM if needed) and offers inference through an API. The Ollama install script adds a dedicated `ollama` user and a systemd service so that Ollama starts automatically at boot. Ollama will unload models from memory when idle. ``` curl -fsSL https://ollama.com/install.sh | sh ``` ## Configuring Remote Ollama Skip this section if your GPU is on the same machine you're coding from. Ollama and Twinny default to a local configuration. I'm using Ollama on a separate machine with a decent GPU, so I need to configure it to bind to the network interface instead of `localhost` by editing the systemd service: 1. Edit the service override file: ``` systemctl edit ollama.service ``` 1. Add this in the top section. It will be merged with the default service file. ``` [Service] Environment="OLLAMA_HOST=0.0.0.0:11434" ``` Note: I had a problem with Ollama only binding to the `tcp6` port, and wasted a lot of time trying to fix it. Check with `netstat -na | grep 11434` to see if it only shows tcp6 for port 11434. The workaround for me was using the actual interface IP instead of `0.0.0.0`. If you do this then you'll need to either set `OLLAMA_HOST` in your shell, or specify `OLLAMA_HOST=<hostname>` at the start of every ollama command (or it complains that it can't connect to ollama). 1. Restart Ollama: ``` systemctl daemon-reload systemctl restart ollama ``` ## Download Models Ollama manages models by importing them into its own special folders. You can use Ollama to download the files from the [Ollama library](https://ollama.com/library), or you can import already-downloaded models by creating a [Modelfile](https://github.com/ollama/ollama/blob/main/docs/modelfile.md). Modelfiles define various parameters about the model and it's important to get them set correctly for the best performance so it's probably better to get them from the library, even though it wastes bandwidth downloading them over and over again for all these tools. You'll want a model for chatting and a model for fill-in-middle (FIM) that does the code completions. ``` # Chat model, defaults to 7b with Q4_K_M quant, downloads 4.7 GB ollama pull qwen2.5-coder # Fill-in-Middle model for code completion, another 4.7 GB ollama pull qwen2.5-coder:7b-base ``` The RAG/embeddings feature is optional but probably worth using. It needs to run a from local instance of Ollama. The embedding models are very small and run fine on CPU. Most everyone uses `nomic`, but Twinny defaults to `all-minilm`, which is a little smaller. ``` ollama pull all-minilm ``` # Install Twinny Install the [Twinny extension](https://open-vsx.org/extension/rjmacarthy/twinny) by searching for `twinny` in VSCodium extensions. Look for the Twinny icon on the left side panel and click it to open the Twinny panel. Be careful if you drag it over to the right side: sometimes it may not appear at all. I managed to make it appear by selecting some text and running a Twinny action on it from the context menu. Twinny assumes you're using a local instance of Ollama. If you want to use a remote instance then you'll need to go into the **Manage Twinny providers** section (looks like a power plug) and add new providers that point your remote Ollama instance. These are the settings I'm using for a remote Ollama instance: ## Chat provider * Type: `chat` * Provider: `ollama` * Protocol: `http` * Model Name: `qwen2.5-coder:latest` * Hostname: *remote hostname* * Port: `11434` * API Path: `/v1` (despite what the Twinny docs and Ollama docs say) * API Key: *blank* ## FIM Provider * Type: `fim` * FIM Template: `codeqwen` * Provider: `ollama` * Protocol: `http` * Model Name: `qwen2.5-coder:7b-base` * Hostname: *remote hostname* * Port: `11434` * API Path: `/api/generate` * API Key: *blank* ## Embedding Provider * Type: `embedding` * Provider: `ollama` * Protocol: `http` * Model Name: `nomic-embed-text` * Hostname: `0.0.0.0` * Port: `11434` * API Path: `/api/embed` * API Key: *blank* # Use Twinny ## Chat Select code and it will be used for context in the chat, or right-click selected text to see more options like refactor, write docs, write tests. ## Embeddings Switch over to the Embeddings tab and click Embed documents to use all the documents in your workspace for more context. Type '@' in the chat to reference the entire workspace, ask about specific problems, or specific files in your chat. ## Code Completion Suggested stuff shows up in gray italics at the cursor location. Press `Tab` to accept it as a completion. @ 16d11430:61640947
2025-02-09 01:03:30As fiat currencies continue their slow-motion collapse worldwide, a disturbing pattern is emerging—food security is deteriorating, marked by frequent outbreaks of avian flu, livestock diseases, and supply chain disruptions. While mainstream narratives often blame climate change or random chance, a deeper look reveals that these crises are symptoms of a decaying financial system. Food shortages, increasing corporate monopolization of agriculture, and government mismanagement are not random events. They are predictable consequences of monetary debasement, supply chain stress, and regulatory capture. Let’s break down how the collapse of fiat money is driving the current food crisis and why things are likely to get worse. --- 1. Early Signs: Inflation and the Cost of Farming Soar The first cracks in the food supply system appear when inflation begins eating into farmers’ margins. Over the past few years, fertilizer prices have skyrocketed, fuel costs remain volatile, and animal feed has become more expensive due to disrupted global trade. Example: The 2022 Fertilizer Crisis – As the U.S. and European governments sanctioned Russia, a key global supplier of potash and ammonia (key fertilizer ingredients), prices surged. Farmers in Africa, Asia, and Latin America struggled to afford these inputs, reducing food production. Egg Prices & Avian Flu – In 2023, egg prices doubled in the U.S. and Europe, exacerbated by avian flu culling millions of hens. However, inflation played a bigger role—higher costs for feed, transport, and farm maintenance made it impossible for smaller producers to compete. Corporate Centralization – As inflation drives small farmers out of business, giant agribusinesses like Cargill, JBS, and Tyson gain more control, further consolidating the supply chain. At this stage, the system still functions, but food prices increase, and warning signs emerge. --- 2. Mid-Stage: Supply Chains Crack & Regulatory Failures Accelerate Outbreaks As inflation worsens, government policies and systemic inefficiencies accelerate decay. Regulations intended to "protect" the market often do the opposite—causing supply shocks and increasing food insecurity. Avian Flu as a Convenient Cover? – Since 2022, millions of chickens, turkeys, and ducks have been culled globally due to "avian flu outbreaks." The strange part? Many cases are based on PCR tests with high false positives rather than confirmed clinical symptoms. Some suspect regulatory agencies are exaggerating the crisis to justify price hikes and consolidate control. U.S. Cattle Mysteriously Falling Sick – Reports surfaced in early 2024 of large numbers of cattle experiencing spontaneous respiratory illness and reproductive failures. The USDA and FDA blame viruses, but critics point to contaminated mRNA vaccines or corporate feed modifications. Dutch Farmers vs. The State – In the Netherlands, one of Europe’s largest food producers, the government attempted to force thousands of farmers to sell their land under the guise of "nitrogen reduction." Many believe this is an effort to centralize control over food production. At this stage, outbreaks become more frequent—not just due to biological causes, but because of poor regulation, centralized control, and financial stress leading to cost-cutting in food safety. --- 3. Late-Stage: Hyperinflation, Panic, and Rationing Once inflation turns into hyperinflation, food becomes a political weapon. Governments respond with price controls, forced rationing, and market interventions that make things worse. Argentina & Venezuela’s Food Rationing – In nations experiencing hyperinflation, like Argentina and Venezuela, supermarket shelves are empty, and the black market determines real prices. Government-issued food ration cards fail to provide reliable access. French Farmers Revolt Over Regulations & Costs – In 2024, French farmers blocked highways in protest against tax hikes, environmental regulations, and soaring costs. The EU’s green policies, combined with inflation, made food production unviable. Egg Shortages in the UK – The UK government urged people to eat fewer eggs and replace them with lab-grown alternatives as supermarkets struggled to restock due to avian flu and Brexit-related trade issues. At this point, government incompetence and corporate profiteering worsen food insecurity, leading to riots, black markets, and authoritarian responses. --- 4. Final Collapse: Mass Starvation or Parallel Systems As fiat systems implode, parallel markets emerge. People turn to barter, Bitcoin-based trade, and decentralized farming networks to survive. Bitcoin for Beef – In Argentina and El Salvador, some ranchers have started accepting Bitcoin for direct meat sales, bypassing the banking system entirely. Local Food Networks Grow – In places where trust in fiat money collapses, local food networks, permaculture movements, and barter systems gain popularity. Lab-Grown & Insect Protein Push – Meanwhile, governments and billionaires like Bill Gates push for synthetic meat and insect-based diets, claiming they are "sustainable" while continuing policies that destroy natural farming. At this stage, centralized systems are collapsing, but decentralized alternatives emerge—offering a path forward for those willing to adapt. --- The Solution: Decentralization & Bitcoin-Based Trade The fiat food system is failing because it is built on debt, leverage, and market manipulation. To ensure food security, we must return to decentralized, sound-money solutions. Bitcoin as a Trade Standard – Farmers using Bitcoin escape capital controls and currency depreciation, ensuring fair trade. Regenerative Agriculture & Local Food Systems – Returning to small-scale, diversified farming reduces the risk of mass outbreaks. Self-Sovereignty Over Food – Growing your own food, supporting local farmers, and rejecting centralized food policies is the only way to break free from the collapsing system. --- Conclusion: Recognizing the Signs Before It's Too Late The rapid spread of avian flu, livestock diseases, and farm shutdowns are not random events. They are early warning signs of systemic decay in the fiat economy. As governments print money and impose short-sighted regulations, food security worsens. The best way forward is decentralization—of money, farming, and trade. The collapse of fiat will bring hardship, but those who understand the game and prepare accordingly will thrive.
@ 16d11430:61640947
2025-02-09 01:03:30As fiat currencies continue their slow-motion collapse worldwide, a disturbing pattern is emerging—food security is deteriorating, marked by frequent outbreaks of avian flu, livestock diseases, and supply chain disruptions. While mainstream narratives often blame climate change or random chance, a deeper look reveals that these crises are symptoms of a decaying financial system. Food shortages, increasing corporate monopolization of agriculture, and government mismanagement are not random events. They are predictable consequences of monetary debasement, supply chain stress, and regulatory capture. Let’s break down how the collapse of fiat money is driving the current food crisis and why things are likely to get worse. --- 1. Early Signs: Inflation and the Cost of Farming Soar The first cracks in the food supply system appear when inflation begins eating into farmers’ margins. Over the past few years, fertilizer prices have skyrocketed, fuel costs remain volatile, and animal feed has become more expensive due to disrupted global trade. Example: The 2022 Fertilizer Crisis – As the U.S. and European governments sanctioned Russia, a key global supplier of potash and ammonia (key fertilizer ingredients), prices surged. Farmers in Africa, Asia, and Latin America struggled to afford these inputs, reducing food production. Egg Prices & Avian Flu – In 2023, egg prices doubled in the U.S. and Europe, exacerbated by avian flu culling millions of hens. However, inflation played a bigger role—higher costs for feed, transport, and farm maintenance made it impossible for smaller producers to compete. Corporate Centralization – As inflation drives small farmers out of business, giant agribusinesses like Cargill, JBS, and Tyson gain more control, further consolidating the supply chain. At this stage, the system still functions, but food prices increase, and warning signs emerge. --- 2. Mid-Stage: Supply Chains Crack & Regulatory Failures Accelerate Outbreaks As inflation worsens, government policies and systemic inefficiencies accelerate decay. Regulations intended to "protect" the market often do the opposite—causing supply shocks and increasing food insecurity. Avian Flu as a Convenient Cover? – Since 2022, millions of chickens, turkeys, and ducks have been culled globally due to "avian flu outbreaks." The strange part? Many cases are based on PCR tests with high false positives rather than confirmed clinical symptoms. Some suspect regulatory agencies are exaggerating the crisis to justify price hikes and consolidate control. U.S. Cattle Mysteriously Falling Sick – Reports surfaced in early 2024 of large numbers of cattle experiencing spontaneous respiratory illness and reproductive failures. The USDA and FDA blame viruses, but critics point to contaminated mRNA vaccines or corporate feed modifications. Dutch Farmers vs. The State – In the Netherlands, one of Europe’s largest food producers, the government attempted to force thousands of farmers to sell their land under the guise of "nitrogen reduction." Many believe this is an effort to centralize control over food production. At this stage, outbreaks become more frequent—not just due to biological causes, but because of poor regulation, centralized control, and financial stress leading to cost-cutting in food safety. --- 3. Late-Stage: Hyperinflation, Panic, and Rationing Once inflation turns into hyperinflation, food becomes a political weapon. Governments respond with price controls, forced rationing, and market interventions that make things worse. Argentina & Venezuela’s Food Rationing – In nations experiencing hyperinflation, like Argentina and Venezuela, supermarket shelves are empty, and the black market determines real prices. Government-issued food ration cards fail to provide reliable access. French Farmers Revolt Over Regulations & Costs – In 2024, French farmers blocked highways in protest against tax hikes, environmental regulations, and soaring costs. The EU’s green policies, combined with inflation, made food production unviable. Egg Shortages in the UK – The UK government urged people to eat fewer eggs and replace them with lab-grown alternatives as supermarkets struggled to restock due to avian flu and Brexit-related trade issues. At this point, government incompetence and corporate profiteering worsen food insecurity, leading to riots, black markets, and authoritarian responses. --- 4. Final Collapse: Mass Starvation or Parallel Systems As fiat systems implode, parallel markets emerge. People turn to barter, Bitcoin-based trade, and decentralized farming networks to survive. Bitcoin for Beef – In Argentina and El Salvador, some ranchers have started accepting Bitcoin for direct meat sales, bypassing the banking system entirely. Local Food Networks Grow – In places where trust in fiat money collapses, local food networks, permaculture movements, and barter systems gain popularity. Lab-Grown & Insect Protein Push – Meanwhile, governments and billionaires like Bill Gates push for synthetic meat and insect-based diets, claiming they are "sustainable" while continuing policies that destroy natural farming. At this stage, centralized systems are collapsing, but decentralized alternatives emerge—offering a path forward for those willing to adapt. --- The Solution: Decentralization & Bitcoin-Based Trade The fiat food system is failing because it is built on debt, leverage, and market manipulation. To ensure food security, we must return to decentralized, sound-money solutions. Bitcoin as a Trade Standard – Farmers using Bitcoin escape capital controls and currency depreciation, ensuring fair trade. Regenerative Agriculture & Local Food Systems – Returning to small-scale, diversified farming reduces the risk of mass outbreaks. Self-Sovereignty Over Food – Growing your own food, supporting local farmers, and rejecting centralized food policies is the only way to break free from the collapsing system. --- Conclusion: Recognizing the Signs Before It's Too Late The rapid spread of avian flu, livestock diseases, and farm shutdowns are not random events. They are early warning signs of systemic decay in the fiat economy. As governments print money and impose short-sighted regulations, food security worsens. The best way forward is decentralization—of money, farming, and trade. The collapse of fiat will bring hardship, but those who understand the game and prepare accordingly will thrive. @ f33c8a96:5ec6f741
2025-02-09 01:02:51I have been working on account linking in the backend for a little while and so far only GitHub has been available to users (mostly for following the dev journey on the platform) Now with this release the existing OAUTH options AND Nostr NIP-07 authentication are surfaced and able to be linked to an existing profile on your settings page. Put simply this allows you to easily link email, GitHub, and nostr profile in the plebdevs platform to access the same account from different login methods. This will make it much easier to keep the same profile across multiple devices AND make sure that you never lose access! Let me know what you think and PLEASE LET ME KNOW if you find any bugs! (I love bugs 🐛) ONWARDS 🫡  originally posted at https://stacker.news/items/880161
@ f33c8a96:5ec6f741
2025-02-09 01:02:51I have been working on account linking in the backend for a little while and so far only GitHub has been available to users (mostly for following the dev journey on the platform) Now with this release the existing OAUTH options AND Nostr NIP-07 authentication are surfaced and able to be linked to an existing profile on your settings page. Put simply this allows you to easily link email, GitHub, and nostr profile in the plebdevs platform to access the same account from different login methods. This will make it much easier to keep the same profile across multiple devices AND make sure that you never lose access! Let me know what you think and PLEASE LET ME KNOW if you find any bugs! (I love bugs 🐛) ONWARDS 🫡  originally posted at https://stacker.news/items/880161 @ 18e3af1e:1d42e5df
2023-08-13 02:40:19Las comunidades son creadas mediante el esfuerzo de no solo un individuo, sino al trabajo de docenas; cientos o miles de personas. Mediante la especialización, como especie, logramos entender que: el saber hacer una sola cosa no significa morir de hambre, o no estar bien preparado para un ataque; por lo contrario, el dominio o maestría de una sola cosa... Puede crear una civilización entera. Permitirnos un enfoque certero para aprender, dominar y amaestrar nuestras actividades en un periodo de tiempo finito, permitió nuestro avance hacia nuevos campos, de hecho, movió nuestra meta en magnitud tal, que al imaginar el pasado (para muchos) parece mas bien una película cómica y sombría. Hoy en día, en un mundo regido por individualismo en el reino físico, la manifestación de constructores de comunidades sigue presente en el (reino) digital. ### La evolución de la construcción A lo largo de la historia de la humanidad, la construcción ha evolucionado desde simples refugios hasta monumentos arquitectónicos y estructuras vanguardistas. Los primeros humanos crearon refugios rudimentarios con materiales naturales. Con la civilización, surgieron las primeras estructuras permanentes, como pirámides y templos, reflejando la organización social y creencias religiosas. La antigua Roma introdujo la innovación en la ingeniería con acueductos y arcos. La Edad Media vio fortificaciones y catedrales góticas que fusionaban espiritualidad y técnica. El Renacimiento abrazó la proporción y la simetría en palacios y edificios renombrados. La Revolución Industrial marcó un cambio radical con el acero y el hormigón, permitiendo rascacielos y puentes icónicos. El siglo XX trajo consigo la era de los rascacielos y la arquitectura modernista, desafiando límites estructurales y estéticos. La sostenibilidad ganó importancia en el siglo XXI, impulsando la incorporación de tecnologías avanzadas, como la impresión 3D y la construcción modular. La historia de la construcción es un testimonio de la creatividad y la adaptabilidad humanas, reflejando no solo avances técnicos, sino también valores culturales y aspiraciones. En el día hoy, los desarrolladores de software y tecnología podrían considerarse como los constructores del próximo siglo. Al igual que los constructores en otras épocas históricas, los desarrolladores de software son responsables de crear estructuras digitales que moldean la forma en que interactuamos, comunicamos y vivimos en el mundo moderno. A medida que la tecnología continúa avanzando y la sociedad se vuelve cada vez más digital, el papel de los desarrolladores de software se vuelve crucial en la construcción de soluciones tecnológicas que abordan una amplia gama de desafíos. Así como los arquitectos y constructores antiguos debían entender la física, la estética y las necesidades humanas para diseñar y construir edificios funcionales y atractivos, los desarrolladores de software deben comprender la lógica de programación, la experiencia del usuario, la seguridad cibernética y la innovación tecnológica para crear aplicaciones, sistemas y plataformas que sean útiles y efectivos. ### Individuos que inspiran La inspiración individual es un poderoso motor de cambio que puede tener un impacto significativo en la mente colectiva de una comunidad o sociedad. Cuando una persona demuestra pasión, determinación y una visión positiva, puede influir en otros a nivel emocional y cognitivo. Aquí hay algunas formas en que la inspiración individual afecta a la mente colectiva: La gente puede verse reflejada en las luchas y logros de alguien más, lo que crea un sentido de unidad y comunidad. Esto puede generar un mayor apoyo y solidaridad en torno a ciertas causas o valores. Además, la inspiración individual puede llevar a la acción. Cuando las personas son testigos de un individuo que supera obstáculos o logra metas desafiantes, esto puede motivar a otros a enfrentar sus propios desafíos y trabajar hacia sus objetivos. El ejemplo de una sola persona puede encender la chispa de la acción en muchas más. La inspiración individual puede tener un efecto multiplicador. Cuando una persona inspirada comparte su historia o experiencia, puede inspirar a otros, creando una cadena de influencia que se extiende a través de redes sociales, comunidades y sociedades enteras. Esto puede tener un impacto a gran escala en la mente colectiva. El individuo inspirador tiene el potencial de influir profundamente en la mente colectiva al cambiar percepciones, motivar la acción y crear una sensación de comunidad y unidad. ### Comunidades: origen, inicios y progreso. Las comunidades han sido una parte fundamental de la experiencia humana a lo largo de la historia. Desde los primeros tiempos hasta la era moderna, las comunidades han evolucionado y cambiado en respuesta a las necesidades, avances tecnológicos y contextos culturales. Desde los primeros días de la humanidad, nuestros antepasados se agruparon en pequeñas comunidades para sobrevivir. Estas comunidades eran grupos familiares o tribus que compartían recursos y conocimientos para cazar, recolectar alimentos y protegerse de los peligros. La cooperación y la solidaridad eran esenciales para la supervivencia. Con el desarrollo de la agricultura, las comunidades evolucionaron hacia asentamientos más permanentes. La capacidad de cultivar alimentos permitió la formación de aldeas y pueblos, donde la gente podía establecerse y construir relaciones más complejas. Esto llevó al surgimiento de una división del trabajo más especializada y al desarrollo de habilidades artesanales. Las civilizaciones antiguas, como la sumeria, egipcia, griega y romana, dieron paso a la formación de ciudades y sociedades más organizadas. Las comunidades se convirtieron en centros de comercio, gobierno y cultura. Se construyeron estructuras monumentales, como templos y palacios, que unificaron a las personas en torno a creencias religiosas y sistemas políticos. Durante la Edad Media, las comunidades se organizaron en torno a sistemas feudales. Los señores feudales gobernaban sobre las tierras y las personas locales. Las aldeas y feudos eran autónomos en gran medida y se centraban en la agricultura y la autosuficiencia. La Revolución Industrial marcó un cambio importante en la estructura de las comunidades. La industrialización dio lugar a la urbanización, con muchas personas dejando las zonas rurales para trabajar en fábricas en las ciudades. En la era moderna, las comunidades han continuado evolucionando con avances tecnológicos y la globalización. Las redes sociales y las comunicaciones digitales han conectado a personas de todo el mundo, creando comunidades virtuales en línea. ### Bitcoin | Nostr y la chispa del constructor Como ya vimos, un solo individuo puede inspirar a muchos otros, teniendo un efecto multiplicador. Esto no solo se traduce al mundo físico, por el contrario, esta directamente ligado a nuestra psicología, incluso podemos decir que va aun mas allá, adentrándonos en el terreno ideológico y espiritual. Hasta hace no mucho, estábamos a merced de las grandes corporaciones que construían todo por nosotros, mientras esperábamos con ansias las nuevas actualizaciones de cada iteración de sus productos. Cada vez mas y mas nos hacíamos dependientes de dichas corporaciones sin quizás notarlo, poco a poco se fueron apoderando de nuestro tiempo y muy insidiosamente de nuestra personalidad e identidad. Gracias a las alternativas presentadas hoy en día y a los individuos que inspiran a otros, existe la posibilidad de construir algo que va mas allá de las grandes corporaciones, porque transciende no solo el nivel físico y digital, sino que también transciende a los individuos que aportan a la comunidad. Estoy hablando por supuesto de Nostr, y como los incentivos están alineados gracias a Bitcoin. Pongamos como ejemplo un par de nombres para ilustrar como individuos que inspirar pueden crear una chispa que se extiende a cada persona dentro de la comunidad. Personajes como nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft nostr:npub1utx00neqgqln72j22kej3ux7803c2k986henvvha4thuwfkper4s7r50e8 nostr:npub1v0lxxxxutpvrelsksy8cdhgfux9l6a42hsj2qzquu2zk7vc9qnkszrqj49 nostr:npub107jk7htfv243u0x5ynn43scq9wrxtaasmrwwa8lfu2ydwag6cx2quqncxg (entre muchos otros que podría mencionar pero todo el articulo seria una lista de nombres) han inspirado a otros desarrolladores, creadores de contenido (y todas las otras especializaciones que te puedas imaginar…) A construir sobre este protocolo. Incluso, personas como el caso mas reciente de nostr:npub1m64hnkh6rs47fd9x6wk2zdtmdj4qkazt734d22d94ery9zzhne5qw9uaks han encontrado inspiración para aprender a programar sobre estos mismos rieles. > nostr:nevent1qqs8fe938k7j5sxcprrv89ezpu09m9pzm90f0sq24hnwlwu0rmn09qcpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxg5vtygh La chispa del constructor en palabras mas concisas es: **Inspiración multiplicadora en pos de la productividad y por ende, del crecimiento de una comunidad.** Sin Bitcoin y Lightning Network, esto seria posible, pero mucho menos efectivo debido a que las personas detrás de toda labor que este enfocada en creación de contenido, desarrollo, etc. Tienen que comer. ### Conclusión La chispa del constructor radica en la inspiración individual que impulsa a la acción colectiva. Desde la evolución de la construcción hasta las comunidades digitales, **el poder de un individuo inspirado puede moldear el presente y el futuro de las comunidades en todo el mundo.**
@ 18e3af1e:1d42e5df
2023-08-13 02:40:19Las comunidades son creadas mediante el esfuerzo de no solo un individuo, sino al trabajo de docenas; cientos o miles de personas. Mediante la especialización, como especie, logramos entender que: el saber hacer una sola cosa no significa morir de hambre, o no estar bien preparado para un ataque; por lo contrario, el dominio o maestría de una sola cosa... Puede crear una civilización entera. Permitirnos un enfoque certero para aprender, dominar y amaestrar nuestras actividades en un periodo de tiempo finito, permitió nuestro avance hacia nuevos campos, de hecho, movió nuestra meta en magnitud tal, que al imaginar el pasado (para muchos) parece mas bien una película cómica y sombría. Hoy en día, en un mundo regido por individualismo en el reino físico, la manifestación de constructores de comunidades sigue presente en el (reino) digital. ### La evolución de la construcción A lo largo de la historia de la humanidad, la construcción ha evolucionado desde simples refugios hasta monumentos arquitectónicos y estructuras vanguardistas. Los primeros humanos crearon refugios rudimentarios con materiales naturales. Con la civilización, surgieron las primeras estructuras permanentes, como pirámides y templos, reflejando la organización social y creencias religiosas. La antigua Roma introdujo la innovación en la ingeniería con acueductos y arcos. La Edad Media vio fortificaciones y catedrales góticas que fusionaban espiritualidad y técnica. El Renacimiento abrazó la proporción y la simetría en palacios y edificios renombrados. La Revolución Industrial marcó un cambio radical con el acero y el hormigón, permitiendo rascacielos y puentes icónicos. El siglo XX trajo consigo la era de los rascacielos y la arquitectura modernista, desafiando límites estructurales y estéticos. La sostenibilidad ganó importancia en el siglo XXI, impulsando la incorporación de tecnologías avanzadas, como la impresión 3D y la construcción modular. La historia de la construcción es un testimonio de la creatividad y la adaptabilidad humanas, reflejando no solo avances técnicos, sino también valores culturales y aspiraciones. En el día hoy, los desarrolladores de software y tecnología podrían considerarse como los constructores del próximo siglo. Al igual que los constructores en otras épocas históricas, los desarrolladores de software son responsables de crear estructuras digitales que moldean la forma en que interactuamos, comunicamos y vivimos en el mundo moderno. A medida que la tecnología continúa avanzando y la sociedad se vuelve cada vez más digital, el papel de los desarrolladores de software se vuelve crucial en la construcción de soluciones tecnológicas que abordan una amplia gama de desafíos. Así como los arquitectos y constructores antiguos debían entender la física, la estética y las necesidades humanas para diseñar y construir edificios funcionales y atractivos, los desarrolladores de software deben comprender la lógica de programación, la experiencia del usuario, la seguridad cibernética y la innovación tecnológica para crear aplicaciones, sistemas y plataformas que sean útiles y efectivos. ### Individuos que inspiran La inspiración individual es un poderoso motor de cambio que puede tener un impacto significativo en la mente colectiva de una comunidad o sociedad. Cuando una persona demuestra pasión, determinación y una visión positiva, puede influir en otros a nivel emocional y cognitivo. Aquí hay algunas formas en que la inspiración individual afecta a la mente colectiva: La gente puede verse reflejada en las luchas y logros de alguien más, lo que crea un sentido de unidad y comunidad. Esto puede generar un mayor apoyo y solidaridad en torno a ciertas causas o valores. Además, la inspiración individual puede llevar a la acción. Cuando las personas son testigos de un individuo que supera obstáculos o logra metas desafiantes, esto puede motivar a otros a enfrentar sus propios desafíos y trabajar hacia sus objetivos. El ejemplo de una sola persona puede encender la chispa de la acción en muchas más. La inspiración individual puede tener un efecto multiplicador. Cuando una persona inspirada comparte su historia o experiencia, puede inspirar a otros, creando una cadena de influencia que se extiende a través de redes sociales, comunidades y sociedades enteras. Esto puede tener un impacto a gran escala en la mente colectiva. El individuo inspirador tiene el potencial de influir profundamente en la mente colectiva al cambiar percepciones, motivar la acción y crear una sensación de comunidad y unidad. ### Comunidades: origen, inicios y progreso. Las comunidades han sido una parte fundamental de la experiencia humana a lo largo de la historia. Desde los primeros tiempos hasta la era moderna, las comunidades han evolucionado y cambiado en respuesta a las necesidades, avances tecnológicos y contextos culturales. Desde los primeros días de la humanidad, nuestros antepasados se agruparon en pequeñas comunidades para sobrevivir. Estas comunidades eran grupos familiares o tribus que compartían recursos y conocimientos para cazar, recolectar alimentos y protegerse de los peligros. La cooperación y la solidaridad eran esenciales para la supervivencia. Con el desarrollo de la agricultura, las comunidades evolucionaron hacia asentamientos más permanentes. La capacidad de cultivar alimentos permitió la formación de aldeas y pueblos, donde la gente podía establecerse y construir relaciones más complejas. Esto llevó al surgimiento de una división del trabajo más especializada y al desarrollo de habilidades artesanales. Las civilizaciones antiguas, como la sumeria, egipcia, griega y romana, dieron paso a la formación de ciudades y sociedades más organizadas. Las comunidades se convirtieron en centros de comercio, gobierno y cultura. Se construyeron estructuras monumentales, como templos y palacios, que unificaron a las personas en torno a creencias religiosas y sistemas políticos. Durante la Edad Media, las comunidades se organizaron en torno a sistemas feudales. Los señores feudales gobernaban sobre las tierras y las personas locales. Las aldeas y feudos eran autónomos en gran medida y se centraban en la agricultura y la autosuficiencia. La Revolución Industrial marcó un cambio importante en la estructura de las comunidades. La industrialización dio lugar a la urbanización, con muchas personas dejando las zonas rurales para trabajar en fábricas en las ciudades. En la era moderna, las comunidades han continuado evolucionando con avances tecnológicos y la globalización. Las redes sociales y las comunicaciones digitales han conectado a personas de todo el mundo, creando comunidades virtuales en línea. ### Bitcoin | Nostr y la chispa del constructor Como ya vimos, un solo individuo puede inspirar a muchos otros, teniendo un efecto multiplicador. Esto no solo se traduce al mundo físico, por el contrario, esta directamente ligado a nuestra psicología, incluso podemos decir que va aun mas allá, adentrándonos en el terreno ideológico y espiritual. Hasta hace no mucho, estábamos a merced de las grandes corporaciones que construían todo por nosotros, mientras esperábamos con ansias las nuevas actualizaciones de cada iteración de sus productos. Cada vez mas y mas nos hacíamos dependientes de dichas corporaciones sin quizás notarlo, poco a poco se fueron apoderando de nuestro tiempo y muy insidiosamente de nuestra personalidad e identidad. Gracias a las alternativas presentadas hoy en día y a los individuos que inspiran a otros, existe la posibilidad de construir algo que va mas allá de las grandes corporaciones, porque transciende no solo el nivel físico y digital, sino que también transciende a los individuos que aportan a la comunidad. Estoy hablando por supuesto de Nostr, y como los incentivos están alineados gracias a Bitcoin. Pongamos como ejemplo un par de nombres para ilustrar como individuos que inspirar pueden crear una chispa que se extiende a cada persona dentro de la comunidad. Personajes como nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft nostr:npub1utx00neqgqln72j22kej3ux7803c2k986henvvha4thuwfkper4s7r50e8 nostr:npub1v0lxxxxutpvrelsksy8cdhgfux9l6a42hsj2qzquu2zk7vc9qnkszrqj49 nostr:npub107jk7htfv243u0x5ynn43scq9wrxtaasmrwwa8lfu2ydwag6cx2quqncxg (entre muchos otros que podría mencionar pero todo el articulo seria una lista de nombres) han inspirado a otros desarrolladores, creadores de contenido (y todas las otras especializaciones que te puedas imaginar…) A construir sobre este protocolo. Incluso, personas como el caso mas reciente de nostr:npub1m64hnkh6rs47fd9x6wk2zdtmdj4qkazt734d22d94ery9zzhne5qw9uaks han encontrado inspiración para aprender a programar sobre estos mismos rieles. > nostr:nevent1qqs8fe938k7j5sxcprrv89ezpu09m9pzm90f0sq24hnwlwu0rmn09qcpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxg5vtygh La chispa del constructor en palabras mas concisas es: **Inspiración multiplicadora en pos de la productividad y por ende, del crecimiento de una comunidad.** Sin Bitcoin y Lightning Network, esto seria posible, pero mucho menos efectivo debido a que las personas detrás de toda labor que este enfocada en creación de contenido, desarrollo, etc. Tienen que comer. ### Conclusión La chispa del constructor radica en la inspiración individual que impulsa a la acción colectiva. Desde la evolución de la construcción hasta las comunidades digitales, **el poder de un individuo inspirado puede moldear el presente y el futuro de las comunidades en todo el mundo.** @ d4309e24:8a81fcb0
2025-02-09 00:16:55## 1. What if You Could Send a Message into the Future? Imagine leaving **a message for your future self**, a loved one, or even an entire community—one that no one, not even you, can unlock until a specific moment in time. Picture leaving **a message for your children**, a note of wisdom or love that remains hidden until they're old enough to appreciate it, all timed by Bitcoin's block height. You might also make **a bold prediction** about the future price of Bitcoin, sealing it away until the blockchain reaches a certain block height. This is the idea behind *Hatchstr*, a decentralized app for time-locked messages that only unlock at predetermined Bitcoin block heights—no central authority required. ### Why Build This? I want to dive into the Nostr protocol not just by reading documentation, but by actually building something that embodies its core principles: **censorship resistance**, **user ownership**, and **decentralization**. Hatchstr is both an experiment and a contribution to the Nostr ecosystem—a way to test the limits of permissionless communication while learning and engaging with the community. ## 2. The Vision: How Hatchstr Would Work for Users At its core, Hatchstr lets users create time capsules—encrypted messages that only become readable after a specified Bitcoin block height. Here’s what that looks like: * You design a capsule with text and images using Hatchstr’s web app. * You pick an unlock time (e.g., 1000 blocks from now). * The message is encrypted, locked away, and published as a Nostr event. * At the chosen time, the decryption key is revealed, allowing the recipient to finally access the message.  #### Potential Use Cases * **Personal Messages**: Send birthday wishes that unlock at midnight, time-delayed love letters, or notes to your future self. * **Timed Learning**: Lock educational content to unlock when students reach key learning stages or ages. * **Creative Storytelling**: Release serialized fiction, riddles, or treasure hunt clues that unlock over time. * **Community & Events**: Time-gate announcements for Nostr-based communities or scheduled voting mechanisms. ### 3. The Centralized Trap: Why Build on Nostr When thinking about how to implement this, we could go the obvious, easy route: * Store messages on a centralized server. * Release them when the time is right. * Let users download their messages. Simple, right? **But is it the right approach? Let's break it down.** ### Why This Fails * **Single Point of Failure**: If my server goes down, all messages are unavailable. * **Privacy Risks**: Users would need to trust me not to access their messages. * **Ownership & Longevity**: What happens if I lose interest? The system dies with me.  A centralized model defeats the purpose of time-locking messages. Users shouldn’t have to trust a third party. We need decentralization. ## 4. Nostr to the Rescue: How Decentralization Can Help Instead of a single server holding messages hostage, [Nostr](https://nostr.how/en/what-is-nostr) allows users to publish messages to [decentralized relays](https://nostr.how/en/relays). Here are the key differences: * **Nostr IDs = Self-Owned Identities**: Your public key is your identity, not tied to any company. * **Relays = Decentralized Bulletin Boards**: Anyone can run one, ensuring redundancy and censorship resistance. * **Messages = Signed Events:** Cryptographically signed by the sender or encrypted for only the recipient.  ### How Nostr Reduces Centralization In this version of Hatchstr, capsules are still stored in a centralized manner at first until they 'hatch'. However, once the Bitcoin block height condition is met: * **Capsule Publication**: The system publishes the capsule events to Nostr relays, making the messages available for decryption by the intended recipients. This approach, while not eliminating the central server, allows for: * **Third-Party Clients**: Developers can now create clients that interact with Hatchstr capsules on Nostr, enhancing the system's openness and potentially leading to a richer ecosystem around time-locked messages. * **Decentralized Access**: Even though the initial storage is centralized, the access to the messages becomes decentralized once published to Nostr, reducing the dependency on a single point for message retrieval. We have some improvements, **but I am sure we can do better!** ## 5. The Path to Decentralized Timekeeping ### The Timeless Nature of Encryption Encrypted messages exist outside time—once locked, they remain secure indefinitely. Modern cryptography (like AES-256) doesn’t "expire" or weaken unless decrypted (excluding brute force attacks). This creates a paradox: How do you bind something timeless to a specific moment in the physical world? #### The Time-Lock Puzzle Dilemma Cryptographers have proposed [time-lock puzzles](https://iacr.org/archive/crypto2019/116940354/116940354.pdf)—encryption that requires sustained computation to unlock, theoretically forcing a minimum wait time. But these face critical hurdles: * ##### **Hardware Uncertainty** Solving time depends on an attacker’s computational power. A nation-state could crack in hours what takes years for a regular user. * ##### **No Real-World Alignment** Puzzles can’t guarantee unlocks align with calendar dates or real-world events ("unlock on my child’s 18th birthday"). * ##### **Energy Waste** Requires continuous computation, making it environmentally impractical for longer time locking. #### Bitcoin as a Decentralized Clock This is where Bitcoin’s blockchain shines. Its difficulty-adjusted proof-of-work acts as a trustless metronome: * ##### **Predictable Rhythm** Despite hash rate fluctuations, the 10-minute block target (via difficulty adjustments) creates a consistent approximation of real-world time. * ##### **Immutable History** Block height 1,000,000 will always correspond to the same point in Bitcoin’s timeline, regardless of future changes in mining power #### **Splitting the Problem** Hatchstr can bridge timeless encryption and blockchain timing by separating concerns: ##### **1. Capsules** – The time-locked message itself: * Design independent of the time-locking mechanism. * Encrypted client-side. * Content stored anywhere the user wants (IPFS, personal servers, etc.). * Completely owned by the user—not Hatchstr. ##### **2. Clock Servers** – Independent, lightweight timing nodes that: * Only publish decryption keys when the target Bitcoin block height is reached. * Users can choose which Clock Server to trust. * Anyone can run their own Clock Server. * Multiple servers can coordinate to prevent a single point of failure.  **This means Hatchstr itself doesn’t store anything—users are fully in control.** ## 6. What Comes Next This project is just beginning—a blueprint with open questions and untested assumptions. In the next two articles, I’ll explore how to turn this concept into something tangible. First, how we might design playful time capsules that can be displayed faithfully by multiple clients, balancing creativity with decentralization. Then, the messy realities of clock servers: why federating them matters, how to incentivize reliability, and borrow Bitcoin’s rhythm without centralizing control. We will dive into setting up a simple clock server to get things started. I’m still learning Nostr’s ecosystem, and this project is as much about sharing my education as anything else. If any part of this concept makes you think “yes, but…” or “what if…”, I’d genuinely love to hear it. Find me on Nostr – no expertise required, just an interest in sending messages to the future. :  ``` npub16scfufrpsqcukjg7ymu4r40h7j4dwqy4pajgz48e6lmnmz5pljcqh678uh ``` Thank you for reading 🧡
@ d4309e24:8a81fcb0
2025-02-09 00:16:55## 1. What if You Could Send a Message into the Future? Imagine leaving **a message for your future self**, a loved one, or even an entire community—one that no one, not even you, can unlock until a specific moment in time. Picture leaving **a message for your children**, a note of wisdom or love that remains hidden until they're old enough to appreciate it, all timed by Bitcoin's block height. You might also make **a bold prediction** about the future price of Bitcoin, sealing it away until the blockchain reaches a certain block height. This is the idea behind *Hatchstr*, a decentralized app for time-locked messages that only unlock at predetermined Bitcoin block heights—no central authority required. ### Why Build This? I want to dive into the Nostr protocol not just by reading documentation, but by actually building something that embodies its core principles: **censorship resistance**, **user ownership**, and **decentralization**. Hatchstr is both an experiment and a contribution to the Nostr ecosystem—a way to test the limits of permissionless communication while learning and engaging with the community. ## 2. The Vision: How Hatchstr Would Work for Users At its core, Hatchstr lets users create time capsules—encrypted messages that only become readable after a specified Bitcoin block height. Here’s what that looks like: * You design a capsule with text and images using Hatchstr’s web app. * You pick an unlock time (e.g., 1000 blocks from now). * The message is encrypted, locked away, and published as a Nostr event. * At the chosen time, the decryption key is revealed, allowing the recipient to finally access the message.  #### Potential Use Cases * **Personal Messages**: Send birthday wishes that unlock at midnight, time-delayed love letters, or notes to your future self. * **Timed Learning**: Lock educational content to unlock when students reach key learning stages or ages. * **Creative Storytelling**: Release serialized fiction, riddles, or treasure hunt clues that unlock over time. * **Community & Events**: Time-gate announcements for Nostr-based communities or scheduled voting mechanisms. ### 3. The Centralized Trap: Why Build on Nostr When thinking about how to implement this, we could go the obvious, easy route: * Store messages on a centralized server. * Release them when the time is right. * Let users download their messages. Simple, right? **But is it the right approach? Let's break it down.** ### Why This Fails * **Single Point of Failure**: If my server goes down, all messages are unavailable. * **Privacy Risks**: Users would need to trust me not to access their messages. * **Ownership & Longevity**: What happens if I lose interest? The system dies with me.  A centralized model defeats the purpose of time-locking messages. Users shouldn’t have to trust a third party. We need decentralization. ## 4. Nostr to the Rescue: How Decentralization Can Help Instead of a single server holding messages hostage, [Nostr](https://nostr.how/en/what-is-nostr) allows users to publish messages to [decentralized relays](https://nostr.how/en/relays). Here are the key differences: * **Nostr IDs = Self-Owned Identities**: Your public key is your identity, not tied to any company. * **Relays = Decentralized Bulletin Boards**: Anyone can run one, ensuring redundancy and censorship resistance. * **Messages = Signed Events:** Cryptographically signed by the sender or encrypted for only the recipient.  ### How Nostr Reduces Centralization In this version of Hatchstr, capsules are still stored in a centralized manner at first until they 'hatch'. However, once the Bitcoin block height condition is met: * **Capsule Publication**: The system publishes the capsule events to Nostr relays, making the messages available for decryption by the intended recipients. This approach, while not eliminating the central server, allows for: * **Third-Party Clients**: Developers can now create clients that interact with Hatchstr capsules on Nostr, enhancing the system's openness and potentially leading to a richer ecosystem around time-locked messages. * **Decentralized Access**: Even though the initial storage is centralized, the access to the messages becomes decentralized once published to Nostr, reducing the dependency on a single point for message retrieval. We have some improvements, **but I am sure we can do better!** ## 5. The Path to Decentralized Timekeeping ### The Timeless Nature of Encryption Encrypted messages exist outside time—once locked, they remain secure indefinitely. Modern cryptography (like AES-256) doesn’t "expire" or weaken unless decrypted (excluding brute force attacks). This creates a paradox: How do you bind something timeless to a specific moment in the physical world? #### The Time-Lock Puzzle Dilemma Cryptographers have proposed [time-lock puzzles](https://iacr.org/archive/crypto2019/116940354/116940354.pdf)—encryption that requires sustained computation to unlock, theoretically forcing a minimum wait time. But these face critical hurdles: * ##### **Hardware Uncertainty** Solving time depends on an attacker’s computational power. A nation-state could crack in hours what takes years for a regular user. * ##### **No Real-World Alignment** Puzzles can’t guarantee unlocks align with calendar dates or real-world events ("unlock on my child’s 18th birthday"). * ##### **Energy Waste** Requires continuous computation, making it environmentally impractical for longer time locking. #### Bitcoin as a Decentralized Clock This is where Bitcoin’s blockchain shines. Its difficulty-adjusted proof-of-work acts as a trustless metronome: * ##### **Predictable Rhythm** Despite hash rate fluctuations, the 10-minute block target (via difficulty adjustments) creates a consistent approximation of real-world time. * ##### **Immutable History** Block height 1,000,000 will always correspond to the same point in Bitcoin’s timeline, regardless of future changes in mining power #### **Splitting the Problem** Hatchstr can bridge timeless encryption and blockchain timing by separating concerns: ##### **1. Capsules** – The time-locked message itself: * Design independent of the time-locking mechanism. * Encrypted client-side. * Content stored anywhere the user wants (IPFS, personal servers, etc.). * Completely owned by the user—not Hatchstr. ##### **2. Clock Servers** – Independent, lightweight timing nodes that: * Only publish decryption keys when the target Bitcoin block height is reached. * Users can choose which Clock Server to trust. * Anyone can run their own Clock Server. * Multiple servers can coordinate to prevent a single point of failure.  **This means Hatchstr itself doesn’t store anything—users are fully in control.** ## 6. What Comes Next This project is just beginning—a blueprint with open questions and untested assumptions. In the next two articles, I’ll explore how to turn this concept into something tangible. First, how we might design playful time capsules that can be displayed faithfully by multiple clients, balancing creativity with decentralization. Then, the messy realities of clock servers: why federating them matters, how to incentivize reliability, and borrow Bitcoin’s rhythm without centralizing control. We will dive into setting up a simple clock server to get things started. I’m still learning Nostr’s ecosystem, and this project is as much about sharing my education as anything else. If any part of this concept makes you think “yes, but…” or “what if…”, I’d genuinely love to hear it. Find me on Nostr – no expertise required, just an interest in sending messages to the future. :  ``` npub16scfufrpsqcukjg7ymu4r40h7j4dwqy4pajgz48e6lmnmz5pljcqh678uh ``` Thank you for reading 🧡 @ 16d11430:61640947
2025-02-09 00:12:22Introduction: The Power of Focused Attention In an age of distraction, power is not merely held through material wealth, authority, or control over others—it is built through focused attention. The human brain, a complex quantum-biological processor, constructs reality through perception. When harnessed correctly, focused attention allows individuals to transcend limitations, reshape their reality, and live free. Power, then, is not external—it is a construct supported by the mind and created within the brain. Understanding how this works offers a path to transcendence, autonomy, and liberation from imposed limitations. The Neuroscience of Focused Attention: Constructing Reality The brain is a prediction engine, constantly processing information and filtering out irrelevant stimuli. Focused attention directs this process, acting as a spotlight that selects what becomes part of one's conscious experience. This is the fundamental mechanism behind cognitive power. 1. Neuroplasticity: Building Power Through Repetition The brain adapts to repeated stimuli through neuroplasticity. What one focuses on consistently rewires neural pathways, strengthening certain thoughts, beliefs, and abilities. Over time, this focus builds an internal structure of power—a network of ideas and perceptions that define one’s reality. If one focuses on problems, they grow. If one focuses on solutions, they appear. If one focuses on fear, it shapes perception. If one focuses on mastery, skills develop. 2. The Quantum Mind: Attention as a Creative Force Quantum physics suggests that observation influences reality. Just as subatomic particles behave differently when measured, focused attention may act as a force that shapes possibilities into tangible outcomes. This aligns with the ancient concept that "energy flows where attention goes." What one attends to with intention can manifest as action, opportunity, and ultimately, freedom. 3. The Reticular Activating System (RAS): Filtering Reality The Reticular Activating System (RAS) in the brainstem acts as a gatekeeper for focus. It determines what information enters conscious awareness. When trained, it can filter out distractions and amplify pathways toward a desired goal. Want to see opportunities? Program the RAS by setting clear intentions. Want to break free from limiting beliefs? Train focus away from conditioned fears. The Mind’s Role: Transcending Limitations The mind is the interpreter of the brain’s electrical and biochemical activity. While the brain processes raw data, the mind provides meaning. This distinction is crucial because meaning determines how one experiences reality. 1. Breaking Mental Chains: Rewriting Narratives Most limitations are narratives—stories imposed by culture, society, or personal history. True power lies in rewriting these stories. Instead of “I am trapped by my circumstances,” shift to “I create my own reality.” Instead of “I need permission,” shift to “I give myself permission.” By restructuring meaning, the mind can redefine the limits of what is possible. 2. The Silence Paradox: Accessing Higher States Silence, both literal and mental, creates space for higher-order thinking. Just as quantum tunneling allows subatomic particles to pass through barriers without energy loss, silence allows the mind to bypass noise and access deeper intelligence. Meditation, stillness, and solitude amplify internal power. The ability to not react is a form of control over external influence. True mastery comes from detachment—engaging the world without being controlled by it. Transcendence: Living Free Through Mental Autonomy To transcend means to rise above imposed structures—whether societal, psychological, or energetic. The construct of power built through focused attention allows one to escape control mechanisms and live autonomously. 1. Sovereignty of Mind: Owning One’s Thoughts A free mind is one that chooses its inputs rather than being programmed by external forces. This requires: Awareness of mental conditioning (social narratives, propaganda, biases) Intentional thought selection (curating what enters the mental space) Guarding attention fiercely (not allowing distraction to hijack focus) 2. Detachment From Control Structures Society operates on the principle of attention capture—through media, politics, and algorithms that direct thought patterns. Escaping these requires detachment. Do not react emotionally to fear-based programming. Cultivate independent thought by questioning imposed narratives. Reduce external noise to amplify internal wisdom. 3. The Flow State: Moving Beyond Constraints When focus is refined to its highest degree, one enters flow state—a condition where action and awareness merge, and limitations dissolve. In flow, work becomes effortless. Creativity becomes boundless. Freedom becomes not just a philosophy, but a lived experience. Conclusion: The Mind as the Ultimate Key to Freedom Power is not an external possession—it is the ability to direct one’s own focus. Through the interplay of brain function, cognitive attention, and mental discipline, one constructs personal sovereignty. The individual who masters focus, controls reality. Freedom is not given. It is built—through attention, intention, and an unwavering commitment to mental autonomy.
@ 16d11430:61640947
2025-02-09 00:12:22Introduction: The Power of Focused Attention In an age of distraction, power is not merely held through material wealth, authority, or control over others—it is built through focused attention. The human brain, a complex quantum-biological processor, constructs reality through perception. When harnessed correctly, focused attention allows individuals to transcend limitations, reshape their reality, and live free. Power, then, is not external—it is a construct supported by the mind and created within the brain. Understanding how this works offers a path to transcendence, autonomy, and liberation from imposed limitations. The Neuroscience of Focused Attention: Constructing Reality The brain is a prediction engine, constantly processing information and filtering out irrelevant stimuli. Focused attention directs this process, acting as a spotlight that selects what becomes part of one's conscious experience. This is the fundamental mechanism behind cognitive power. 1. Neuroplasticity: Building Power Through Repetition The brain adapts to repeated stimuli through neuroplasticity. What one focuses on consistently rewires neural pathways, strengthening certain thoughts, beliefs, and abilities. Over time, this focus builds an internal structure of power—a network of ideas and perceptions that define one’s reality. If one focuses on problems, they grow. If one focuses on solutions, they appear. If one focuses on fear, it shapes perception. If one focuses on mastery, skills develop. 2. The Quantum Mind: Attention as a Creative Force Quantum physics suggests that observation influences reality. Just as subatomic particles behave differently when measured, focused attention may act as a force that shapes possibilities into tangible outcomes. This aligns with the ancient concept that "energy flows where attention goes." What one attends to with intention can manifest as action, opportunity, and ultimately, freedom. 3. The Reticular Activating System (RAS): Filtering Reality The Reticular Activating System (RAS) in the brainstem acts as a gatekeeper for focus. It determines what information enters conscious awareness. When trained, it can filter out distractions and amplify pathways toward a desired goal. Want to see opportunities? Program the RAS by setting clear intentions. Want to break free from limiting beliefs? Train focus away from conditioned fears. The Mind’s Role: Transcending Limitations The mind is the interpreter of the brain’s electrical and biochemical activity. While the brain processes raw data, the mind provides meaning. This distinction is crucial because meaning determines how one experiences reality. 1. Breaking Mental Chains: Rewriting Narratives Most limitations are narratives—stories imposed by culture, society, or personal history. True power lies in rewriting these stories. Instead of “I am trapped by my circumstances,” shift to “I create my own reality.” Instead of “I need permission,” shift to “I give myself permission.” By restructuring meaning, the mind can redefine the limits of what is possible. 2. The Silence Paradox: Accessing Higher States Silence, both literal and mental, creates space for higher-order thinking. Just as quantum tunneling allows subatomic particles to pass through barriers without energy loss, silence allows the mind to bypass noise and access deeper intelligence. Meditation, stillness, and solitude amplify internal power. The ability to not react is a form of control over external influence. True mastery comes from detachment—engaging the world without being controlled by it. Transcendence: Living Free Through Mental Autonomy To transcend means to rise above imposed structures—whether societal, psychological, or energetic. The construct of power built through focused attention allows one to escape control mechanisms and live autonomously. 1. Sovereignty of Mind: Owning One’s Thoughts A free mind is one that chooses its inputs rather than being programmed by external forces. This requires: Awareness of mental conditioning (social narratives, propaganda, biases) Intentional thought selection (curating what enters the mental space) Guarding attention fiercely (not allowing distraction to hijack focus) 2. Detachment From Control Structures Society operates on the principle of attention capture—through media, politics, and algorithms that direct thought patterns. Escaping these requires detachment. Do not react emotionally to fear-based programming. Cultivate independent thought by questioning imposed narratives. Reduce external noise to amplify internal wisdom. 3. The Flow State: Moving Beyond Constraints When focus is refined to its highest degree, one enters flow state—a condition where action and awareness merge, and limitations dissolve. In flow, work becomes effortless. Creativity becomes boundless. Freedom becomes not just a philosophy, but a lived experience. Conclusion: The Mind as the Ultimate Key to Freedom Power is not an external possession—it is the ability to direct one’s own focus. Through the interplay of brain function, cognitive attention, and mental discipline, one constructs personal sovereignty. The individual who masters focus, controls reality. Freedom is not given. It is built—through attention, intention, and an unwavering commitment to mental autonomy. @ 16d11430:61640947
2025-02-08 23:54:40Language is more than just words—it’s a pattern, a rhythm, a system of meaning that our brains decode in different ways. While most people learn language analytically, breaking it down into individual words and sentences, gestalt language processors (GLP) acquire language in a completely different way. They learn in chunks, grasping entire phrases and only later dissecting them into smaller parts. This unique method of language acquisition is often observed in autistic individuals and those with alternative cognitive processing styles. But what happens when such a learner interacts with a highly inflected, agglutinative language like Malayalam? As it turns out, Malayalam might be one of the best-suited languages for gestalt language processors, thanks to its natural structure, flexible syntax, and phrase-based meaning. Let’s explore why Malayalam aligns so well with gestalt processing and how it compares to other languages. --- Understanding Gestalt Language Processing Gestalt language processing is the ability to acquire and use language in whole phrases rather than as individual words. Instead of learning word-by-word, GLP learners store entire sentences or expressions they hear and later modify them into new, meaningful statements. For example, a child who is a gestalt processor might initially say: ➡ "Do you want some juice?" (because they've heard it as a whole phrase) Later, they might extract parts and start saying: ➡ "Want juice." Finally, they construct their own original sentence: ➡ "I want juice." This approach is pattern-based rather than rule-based, making Malayalam an excellent match due to its agglutinative grammar, rhythmic structure, and flexible word order. --- How Malayalam Supports Gestalt Language Processing 1. Malayalam’s Agglutinative Nature Encourages Chunk Learning Malayalam, like other Dravidian languages, is highly agglutinative, meaning words are built using multiple suffixes that change meaning. Instead of discrete words, many phrases function as a single semantic unit—which is exactly how GLP learners process language. Take the word "വീട്" (vīṭu) meaning "house": വീട്ടിൽ (vīṭṭil) – in the house വീട്ടിലേക്ക് (vīṭṭilēkk) – towards the house വീട്ടിലേക്കു പോകുന്നു (vīṭṭilēkku pōkunnu) – going to the house A gestalt processor might first acquire "വീട്ടിലേക്കു പോകുന്നു" as a chunk, rather than breaking it into individual words. Over time, they start recognizing patterns and modifying them. This is in contrast to English, where "going" and "house" are learned separately before forming a phrase like "going to the house." --- 2. Flexible Word Order Aligns with Pattern-Based Learning Malayalam allows word order variations without losing meaning, making it an intuitive fit for gestalt learners who focus on meaning first rather than strict syntax. For example, the sentence "I drank tea" can be expressed in multiple ways in Malayalam: ഞാൻ ചായ കുടിച്ചു. (ñān cāya kuṭiccu) – Standard word order ചായ ഞാൻ കുടിച്ചു. (cāya ñān kuṭiccu) – Emphasizing "tea" കുടിച്ചു ഞാൻ ചായ. (kuṭiccu ñān cāya) – Focus on the action A gestalt learner might acquire an entire phrase like "ചായ കുടിക്കണോ?" ("Do you want tea?") and later extract the verb "കുടി" (drink) or the noun "ചായ" (tea) as they develop more flexible speech. In contrast, languages like English and French have more rigid word order, making it harder for gestalt learners to generalize. --- 3. Long and Embedded Sentence Structures Favor Chunk-Based Processing Malayalam commonly uses long, nested sentences, which gestalt learners store as full units before breaking them down. For example: അവൻ പറഞ്ഞത് ഞാൻ അറിഞ്ഞില്ല. (avan paṟaññatu ñān aṟiññilla) Literal: "What he said, I didn’t know." Gestalt learners may first acquire: "അവൻ പറഞ്ഞത്" ("What he said") as a single unit before extracting "പറഞ്ഞത്" (said). This mirrors how **gestalt processors extract meaning from larger linguistic units over time.
@ 16d11430:61640947
2025-02-08 23:54:40Language is more than just words—it’s a pattern, a rhythm, a system of meaning that our brains decode in different ways. While most people learn language analytically, breaking it down into individual words and sentences, gestalt language processors (GLP) acquire language in a completely different way. They learn in chunks, grasping entire phrases and only later dissecting them into smaller parts. This unique method of language acquisition is often observed in autistic individuals and those with alternative cognitive processing styles. But what happens when such a learner interacts with a highly inflected, agglutinative language like Malayalam? As it turns out, Malayalam might be one of the best-suited languages for gestalt language processors, thanks to its natural structure, flexible syntax, and phrase-based meaning. Let’s explore why Malayalam aligns so well with gestalt processing and how it compares to other languages. --- Understanding Gestalt Language Processing Gestalt language processing is the ability to acquire and use language in whole phrases rather than as individual words. Instead of learning word-by-word, GLP learners store entire sentences or expressions they hear and later modify them into new, meaningful statements. For example, a child who is a gestalt processor might initially say: ➡ "Do you want some juice?" (because they've heard it as a whole phrase) Later, they might extract parts and start saying: ➡ "Want juice." Finally, they construct their own original sentence: ➡ "I want juice." This approach is pattern-based rather than rule-based, making Malayalam an excellent match due to its agglutinative grammar, rhythmic structure, and flexible word order. --- How Malayalam Supports Gestalt Language Processing 1. Malayalam’s Agglutinative Nature Encourages Chunk Learning Malayalam, like other Dravidian languages, is highly agglutinative, meaning words are built using multiple suffixes that change meaning. Instead of discrete words, many phrases function as a single semantic unit—which is exactly how GLP learners process language. Take the word "വീട്" (vīṭu) meaning "house": വീട്ടിൽ (vīṭṭil) – in the house വീട്ടിലേക്ക് (vīṭṭilēkk) – towards the house വീട്ടിലേക്കു പോകുന്നു (vīṭṭilēkku pōkunnu) – going to the house A gestalt processor might first acquire "വീട്ടിലേക്കു പോകുന്നു" as a chunk, rather than breaking it into individual words. Over time, they start recognizing patterns and modifying them. This is in contrast to English, where "going" and "house" are learned separately before forming a phrase like "going to the house." --- 2. Flexible Word Order Aligns with Pattern-Based Learning Malayalam allows word order variations without losing meaning, making it an intuitive fit for gestalt learners who focus on meaning first rather than strict syntax. For example, the sentence "I drank tea" can be expressed in multiple ways in Malayalam: ഞാൻ ചായ കുടിച്ചു. (ñān cāya kuṭiccu) – Standard word order ചായ ഞാൻ കുടിച്ചു. (cāya ñān kuṭiccu) – Emphasizing "tea" കുടിച്ചു ഞാൻ ചായ. (kuṭiccu ñān cāya) – Focus on the action A gestalt learner might acquire an entire phrase like "ചായ കുടിക്കണോ?" ("Do you want tea?") and later extract the verb "കുടി" (drink) or the noun "ചായ" (tea) as they develop more flexible speech. In contrast, languages like English and French have more rigid word order, making it harder for gestalt learners to generalize. --- 3. Long and Embedded Sentence Structures Favor Chunk-Based Processing Malayalam commonly uses long, nested sentences, which gestalt learners store as full units before breaking them down. For example: അവൻ പറഞ്ഞത് ഞാൻ അറിഞ്ഞില്ല. (avan paṟaññatu ñān aṟiññilla) Literal: "What he said, I didn’t know." Gestalt learners may first acquire: "അവൻ പറഞ്ഞത്" ("What he said") as a single unit before extracting "പറഞ്ഞത്" (said). This mirrors how **gestalt processors extract meaning from larger linguistic units over time. @ 25c48353:bbf9841d
2025-02-08 23:44:56One way parents can protect their children in cyberspace is by knowing what cyberspaces your children like to engage with. Today, we'll explore 4 apps that the DOJ has found criminals on. ## **Here are the apps** 1. Cash App 2. Valorant 3. Discord 4. Telegram ## **Background on the Data** At Defend All Kids, our mission is to **protect children in cyberspace.** But in order to do so, we must ask an important question: *What digital spaces do children frequently visit?* In order to find answers to this question, we looked at the [Department of Justice Press Releases page](https://www.justice.gov/news/press-releases), and scraped all of the 676 press releases having anything to do with child abuse. The 4 applications listed above were common apps that we found. Now, we'll go one by one. ## **Cash App: 2 Press Releases** This app was mentioned twice in the DOJ press releases, and both times were pertaining to the same criminal. In this case, the criminal used Cash App to pay young boys bribes to engage in sexually explicit activities. The link to Cash App is [here](https://cash.app/) ## **Valorant: 2 Press Releases** Valorant is an online first-person shooter game. A predator used this platform to talk to young boys and convince them to do sexual favors for them. The link to Valorant is [here](https://playvalorant.com/en-us/). ## **Discord: 3 Press Releases** Discord is a group messanging platform where people of similar interests can join and chat. One of the most common use cases for Discord is gaming communities. A predator used a gaming community discord to lure boys to engage in sexually explicit activities. The Link to Discord is [here](https://discord.com/). ## **Telegram: 5 Press Releases** Telegram is an instant messaging service that many people use to send anonymous messages. In some of the cases the DOJ reported, predators were using the platform to lure in children and to force them to engage in sexually explicit activities. The link to Telegram is [here](https://telegram.org/). ## **Defend All Kids Recommendation:** As you can see from the above applications, the main way predators can get to your children is from one thing: ***Access to software that let strangers talk to each other.*** We recommend that you talk to your child and see if he/she have any of these apps, and if they do, talk to them about their online behavior.
@ 25c48353:bbf9841d
2025-02-08 23:44:56One way parents can protect their children in cyberspace is by knowing what cyberspaces your children like to engage with. Today, we'll explore 4 apps that the DOJ has found criminals on. ## **Here are the apps** 1. Cash App 2. Valorant 3. Discord 4. Telegram ## **Background on the Data** At Defend All Kids, our mission is to **protect children in cyberspace.** But in order to do so, we must ask an important question: *What digital spaces do children frequently visit?* In order to find answers to this question, we looked at the [Department of Justice Press Releases page](https://www.justice.gov/news/press-releases), and scraped all of the 676 press releases having anything to do with child abuse. The 4 applications listed above were common apps that we found. Now, we'll go one by one. ## **Cash App: 2 Press Releases** This app was mentioned twice in the DOJ press releases, and both times were pertaining to the same criminal. In this case, the criminal used Cash App to pay young boys bribes to engage in sexually explicit activities. The link to Cash App is [here](https://cash.app/) ## **Valorant: 2 Press Releases** Valorant is an online first-person shooter game. A predator used this platform to talk to young boys and convince them to do sexual favors for them. The link to Valorant is [here](https://playvalorant.com/en-us/). ## **Discord: 3 Press Releases** Discord is a group messanging platform where people of similar interests can join and chat. One of the most common use cases for Discord is gaming communities. A predator used a gaming community discord to lure boys to engage in sexually explicit activities. The Link to Discord is [here](https://discord.com/). ## **Telegram: 5 Press Releases** Telegram is an instant messaging service that many people use to send anonymous messages. In some of the cases the DOJ reported, predators were using the platform to lure in children and to force them to engage in sexually explicit activities. The link to Telegram is [here](https://telegram.org/). ## **Defend All Kids Recommendation:** As you can see from the above applications, the main way predators can get to your children is from one thing: ***Access to software that let strangers talk to each other.*** We recommend that you talk to your child and see if he/she have any of these apps, and if they do, talk to them about their online behavior. @ 19745f2c:a997836d
2025-02-08 23:36:31One way parents can protect their children in cyberspace is by knowing what cyberspaces your children like to engage with. Today, we'll explore 4 apps that the DOJ has found criminals on. ## **Here are the apps** 1. Cash App 2. Valorant 3. Discord 4. Telegram ## **Background on the Data** At Defend All Kids, our mission is to **protect children in cyberspace.** But in order to do so, we must ask an important question: *What digital spaces do children frequently visit?* In order to find answers to this question, we looked at the [Department of Justice Press Releases page](https://www.justice.gov/news/press-releases), and scraped all of the 676 press releases having anything to do with child abuse. The 4 applications listed above were common apps that we found. Now, we'll go one by one. ## **Cash App: 2 Press Releases** This app was mentioned twice in the DOJ press releases, and both times were pertaining to the same criminal. In this case, the criminal used Cash App to pay young boys bribes to engage in sexually explicit activities. The link to Cash App is [here](https://cash.app/) ## **Valorant: 2 Press Releases** Valorant is an online first-person shooter game. A predator used this platform to talk to young boys and convince them to do sexual favors for them. The link to Valorant is [here](https://playvalorant.com/en-us/). ## **Discord: 3 Press Releases** Discord is a group messanging platform where people of similar interests can join and chat. One of the most common use cases for Discord is gaming communities. A predator used a gaming community discord to lure boys to engage in sexually explicit activities. The Link to Discord is [here](https://discord.com/). ## **Telegram: 5 Press Releases** Telegram is an instant messaging service that many people use to send anonymous messages. In some of the cases the DOJ reported, predators were using the platform to lure in children and to force them to engage in sexually explicit activities. The link to Telegram is [here](https://telegram.org/). ## **Defend All Kids Recommendation:** As you can see from the above applications, the main way predators can get to your children is from one thing: ***Access to software that let strangers talk to each other.*** We recommend that you talk to your child and see if he/she have any of these apps, and if they do, talk to them about their online behavior.
@ 19745f2c:a997836d
2025-02-08 23:36:31One way parents can protect their children in cyberspace is by knowing what cyberspaces your children like to engage with. Today, we'll explore 4 apps that the DOJ has found criminals on. ## **Here are the apps** 1. Cash App 2. Valorant 3. Discord 4. Telegram ## **Background on the Data** At Defend All Kids, our mission is to **protect children in cyberspace.** But in order to do so, we must ask an important question: *What digital spaces do children frequently visit?* In order to find answers to this question, we looked at the [Department of Justice Press Releases page](https://www.justice.gov/news/press-releases), and scraped all of the 676 press releases having anything to do with child abuse. The 4 applications listed above were common apps that we found. Now, we'll go one by one. ## **Cash App: 2 Press Releases** This app was mentioned twice in the DOJ press releases, and both times were pertaining to the same criminal. In this case, the criminal used Cash App to pay young boys bribes to engage in sexually explicit activities. The link to Cash App is [here](https://cash.app/) ## **Valorant: 2 Press Releases** Valorant is an online first-person shooter game. A predator used this platform to talk to young boys and convince them to do sexual favors for them. The link to Valorant is [here](https://playvalorant.com/en-us/). ## **Discord: 3 Press Releases** Discord is a group messanging platform where people of similar interests can join and chat. One of the most common use cases for Discord is gaming communities. A predator used a gaming community discord to lure boys to engage in sexually explicit activities. The Link to Discord is [here](https://discord.com/). ## **Telegram: 5 Press Releases** Telegram is an instant messaging service that many people use to send anonymous messages. In some of the cases the DOJ reported, predators were using the platform to lure in children and to force them to engage in sexually explicit activities. The link to Telegram is [here](https://telegram.org/). ## **Defend All Kids Recommendation:** As you can see from the above applications, the main way predators can get to your children is from one thing: ***Access to software that let strangers talk to each other.*** We recommend that you talk to your child and see if he/she have any of these apps, and if they do, talk to them about their online behavior. @ 16d11430:61640947
2025-02-08 23:31:00A Hitchhiker’s Guide to Intergalactic Trade, Verified on the Blockchain Somewhere in the unfashionable backwaters of the Milky Way, a small blue planet is busy debating whether it should be more concerned about social media algorithms or the growing irrelevance of its own economy. Meanwhile, out there in the cosmic gigaverse, civilizations with far more interesting problems are engaging in the great intergalactic hustle—trading tech, swapping energy signatures, and making quantum side deals faster than you can say "proof-of-work." Humanity, as per usual, has arrived late to the party but is hoping to slip in unnoticed and pretend like it’s been part of the game all along. The problem? We don’t know the rules, we don’t know what we have to offer, and most importantly, we don’t even have an invite. Fortunately, the universe is a decentralized, peer-to-peer system, much like Bitcoin—only with fewer arguments on Twitter. And if we play this right, we might just hustle our way into the Universal Indira Net, the cosmic marketplace where civilizations exchange technology, knowledge, and, quite possibly, dad jokes that transcend space-time. --- Step 1: Plugging into the Universal Indira Net According to ancient Hindu mythology, Indra’s Net is an infinite web where each node reflects all others, meaning everything is connected to everything else, forever. Sounds poetic, right? Well, take that concept, throw in some decentralized cryptographic verification, and you've got the backbone of a cosmic trade network where trust isn’t just assumed—it’s mathematically proven. In theory, Earth should be able to sync up with the Universal Indira Net, but there’s one small problem: our civilization hasn’t even solved its own internet yet. Forget interstellar trade—we still struggle with buffering. Until we build long-range, high-bandwidth, interference-proof communication systems, we’re basically screaming into the void, hoping someone hears us (and doesn’t immediately categorize us as "primitive and likely to start wars over fictional borders"). Luckily, we are making some progress: NASA’s Laser-Based Comms: Just last year, NASA’s Deep Space Optical Communications (DSOC) project sent data 19 million miles at broadband speeds. In galactic terms, this is the equivalent of tossing a USB drive across your front yard, but hey, it’s a start. (source) Quantum Entanglement Messaging: Scientists are theorizing about using spooky action at a distance to send information instantaneously across the galaxy. Of course, it’s still at the “we swear this works on paper” stage. Gravitational Wave Emails: There’s a wild theory that gravitational waves could be harnessed for communication, which means the universe has literally been shaking with missed calls for billions of years. If we can bootstrap any of these into a reliable cosmic broadband, we might just be able to negotiate our way into the interstellar group chat. --- Step 2: What Do We Bring to the Table? Now, assuming we finally manage to stop talking to ourselves and make first contact, the next big question is: what the hell do we trade? Here’s what we know about intergalactic economics: 1. No one wants our money – Fiat currency is an Earth-only meme. The only currency that might hold value out there is Bitcoin, because at least it’s energy-backed and provably scarce. But even then, aliens are likely using something far more advanced—probably a universal ledger that encodes information directly into quantum spacetime fabric. 2. Physical goods are inefficient – Nobody’s going to fly across light-years to pick up a shipment of human-made Teslas when they can 3D print their own antimatter-powered space yacht. 3. Knowledge is king – The real hustle is in information. Code, algorithms, AI models—things that can be transmitted at the speed of light and verifiably proven on-chain. Trade Goods That Might Actually Be Worth Something: AI & Quantum Computing Models – If we develop AI that thinks in ways alien civilizations haven’t considered, we’ve got intellectual property worth trading. Biological Engineering & Longevity Tech – If Earth figures out how to stop aging, you can bet intergalactic billionaires (assuming they exist) would pay for that. Mathematical Breakthroughs – Math is the universal language, and if we crack new fundamental theorems, we might just have something of value. Which means the best way to hustle our way into the Indira Net is to become the best at something. And right now, the only thing we’ve truly mastered is making memes and overcomplicating financial systems. --- Step 3: Navigating the Cosmic Trade Rules Of course, even if we have something valuable, trading with advanced civilizations isn’t as simple as sending an invoice. We don’t even know the rules of interstellar engagement yet. But if galactic trade works anything like human history, we should expect: Regulatory Compliance – Because even in space, there’s bound to be paperwork. If we get lucky, aliens might use smart contracts instead of lawyers. Sanctions & Trade Embargoes – You think Earth’s geopolitics are complicated? Try interstellar diplomacy, where embargoes might involve entire planetary quarantines. Intellectual Property Theft – If we’re not careful, we might trade away humanity’s most valuable discovery for an alien NFT that depreciates instantly. Which is why any trade network must be built on provable, immutable verification systems—aka, blockchain. This is where DamageBDD, Bitcoin, and cryptographic proofs come into play. If we can create a system that ensures: ✅ Technology is verified before it’s traded ✅ Ownership and utility are recorded on an immutable ledger ✅ Contracts execute autonomously with zero-trust mechanics Then we might just stand a chance of becoming a respected node in the Universal Indira Net, rather than a civilization that gets rug-pulled by intergalactic venture capitalists. --- Final Thought: The Cosmic Hustle is Just Beginning Humanity is still in the tutorial level of the interstellar economy. We’re fumbling with our first trade attempts, trying not to get exploited, and desperately figuring out how not to be the cosmic equivalent of a developing nation selling raw materials to advanced intergalactic conglomerates. But if we: Build high-speed interstellar comms Develop technology that is uniquely valuable Create trustless, verifiable trade systems …then we won’t just be another planetary backwater. We’ll be a node in the greatest decentralized network of all time. The Cosmic Hustle is real. The only question is: will we be the hustlers or the ones getting hustled?
@ 16d11430:61640947
2025-02-08 23:31:00A Hitchhiker’s Guide to Intergalactic Trade, Verified on the Blockchain Somewhere in the unfashionable backwaters of the Milky Way, a small blue planet is busy debating whether it should be more concerned about social media algorithms or the growing irrelevance of its own economy. Meanwhile, out there in the cosmic gigaverse, civilizations with far more interesting problems are engaging in the great intergalactic hustle—trading tech, swapping energy signatures, and making quantum side deals faster than you can say "proof-of-work." Humanity, as per usual, has arrived late to the party but is hoping to slip in unnoticed and pretend like it’s been part of the game all along. The problem? We don’t know the rules, we don’t know what we have to offer, and most importantly, we don’t even have an invite. Fortunately, the universe is a decentralized, peer-to-peer system, much like Bitcoin—only with fewer arguments on Twitter. And if we play this right, we might just hustle our way into the Universal Indira Net, the cosmic marketplace where civilizations exchange technology, knowledge, and, quite possibly, dad jokes that transcend space-time. --- Step 1: Plugging into the Universal Indira Net According to ancient Hindu mythology, Indra’s Net is an infinite web where each node reflects all others, meaning everything is connected to everything else, forever. Sounds poetic, right? Well, take that concept, throw in some decentralized cryptographic verification, and you've got the backbone of a cosmic trade network where trust isn’t just assumed—it’s mathematically proven. In theory, Earth should be able to sync up with the Universal Indira Net, but there’s one small problem: our civilization hasn’t even solved its own internet yet. Forget interstellar trade—we still struggle with buffering. Until we build long-range, high-bandwidth, interference-proof communication systems, we’re basically screaming into the void, hoping someone hears us (and doesn’t immediately categorize us as "primitive and likely to start wars over fictional borders"). Luckily, we are making some progress: NASA’s Laser-Based Comms: Just last year, NASA’s Deep Space Optical Communications (DSOC) project sent data 19 million miles at broadband speeds. In galactic terms, this is the equivalent of tossing a USB drive across your front yard, but hey, it’s a start. (source) Quantum Entanglement Messaging: Scientists are theorizing about using spooky action at a distance to send information instantaneously across the galaxy. Of course, it’s still at the “we swear this works on paper” stage. Gravitational Wave Emails: There’s a wild theory that gravitational waves could be harnessed for communication, which means the universe has literally been shaking with missed calls for billions of years. If we can bootstrap any of these into a reliable cosmic broadband, we might just be able to negotiate our way into the interstellar group chat. --- Step 2: What Do We Bring to the Table? Now, assuming we finally manage to stop talking to ourselves and make first contact, the next big question is: what the hell do we trade? Here’s what we know about intergalactic economics: 1. No one wants our money – Fiat currency is an Earth-only meme. The only currency that might hold value out there is Bitcoin, because at least it’s energy-backed and provably scarce. But even then, aliens are likely using something far more advanced—probably a universal ledger that encodes information directly into quantum spacetime fabric. 2. Physical goods are inefficient – Nobody’s going to fly across light-years to pick up a shipment of human-made Teslas when they can 3D print their own antimatter-powered space yacht. 3. Knowledge is king – The real hustle is in information. Code, algorithms, AI models—things that can be transmitted at the speed of light and verifiably proven on-chain. Trade Goods That Might Actually Be Worth Something: AI & Quantum Computing Models – If we develop AI that thinks in ways alien civilizations haven’t considered, we’ve got intellectual property worth trading. Biological Engineering & Longevity Tech – If Earth figures out how to stop aging, you can bet intergalactic billionaires (assuming they exist) would pay for that. Mathematical Breakthroughs – Math is the universal language, and if we crack new fundamental theorems, we might just have something of value. Which means the best way to hustle our way into the Indira Net is to become the best at something. And right now, the only thing we’ve truly mastered is making memes and overcomplicating financial systems. --- Step 3: Navigating the Cosmic Trade Rules Of course, even if we have something valuable, trading with advanced civilizations isn’t as simple as sending an invoice. We don’t even know the rules of interstellar engagement yet. But if galactic trade works anything like human history, we should expect: Regulatory Compliance – Because even in space, there’s bound to be paperwork. If we get lucky, aliens might use smart contracts instead of lawyers. Sanctions & Trade Embargoes – You think Earth’s geopolitics are complicated? Try interstellar diplomacy, where embargoes might involve entire planetary quarantines. Intellectual Property Theft – If we’re not careful, we might trade away humanity’s most valuable discovery for an alien NFT that depreciates instantly. Which is why any trade network must be built on provable, immutable verification systems—aka, blockchain. This is where DamageBDD, Bitcoin, and cryptographic proofs come into play. If we can create a system that ensures: ✅ Technology is verified before it’s traded ✅ Ownership and utility are recorded on an immutable ledger ✅ Contracts execute autonomously with zero-trust mechanics Then we might just stand a chance of becoming a respected node in the Universal Indira Net, rather than a civilization that gets rug-pulled by intergalactic venture capitalists. --- Final Thought: The Cosmic Hustle is Just Beginning Humanity is still in the tutorial level of the interstellar economy. We’re fumbling with our first trade attempts, trying not to get exploited, and desperately figuring out how not to be the cosmic equivalent of a developing nation selling raw materials to advanced intergalactic conglomerates. But if we: Build high-speed interstellar comms Develop technology that is uniquely valuable Create trustless, verifiable trade systems …then we won’t just be another planetary backwater. We’ll be a node in the greatest decentralized network of all time. The Cosmic Hustle is real. The only question is: will we be the hustlers or the ones getting hustled? @ daa41bed:88f54153
2025-02-08 23:29:14Imagine a world where governments, long trusted to protect fiat currencies that can be printed without limit, openly declare that they trust a decentralized digital asset over traditional money. In recent months, that vision has begun to crystallize. The Czech National Bank has signaled a gradual acceptance of digital assets as part of its broader monetary policy recalibration with changes to how capital gains taxes are handled on Bitcoin and a possible adoption by its central bank into its reserves stockpile. Simultaneously, El Salvador- once the poster child for Bitcoin as legal tender- has fine-tuned its policy framework at the behest of the WEF to no longer accept Bitcoin as legal tender. Meanwhile, several U.S. states have introduced bills to establish official Bitcoin reserves, and many are under active consideration. See [Bitcoin Laws](https://Bitcoinlaws.io/) for a full breakdown of where these bills stand. Let's explore the pros of governments adopting strategic Bitcoin reserves. Bitcoiners have long argued that the ultimate endorsement of Bitcoin comes when even the most established state institutions place their trust in it. Recent moves by several U.S. states—where lawmakers are proposing legislation to create official Bitcoin reserves—lend credence to this argument. When state governments start to codify the creation of a Bitcoin reserve, it signals that even entities steeped in traditional financial orthodoxy now recognize Bitcoin as a viable, strategic asset. For these states, it is imperative to accumulate hard assets like Bitcoin in reserves as they have no control over the monetary supply and, therefore, can suffer from debasement just as much as any citizen or sovereign nation not in control of their currency. Suppose you have kept up with [recent news](https://decrypt.co/303304/czech-central-bank-bitcoin-reserve) that the Czech national bank was considering holding a considerable portion of their assets in Bitcoin. In that case, you understand the paradigm shift we are seeing. Banks are becoming less cautious in handling digital assets in a stark department, compared to previous dismissals of cryptocurrencies as genuine assets. While it is true that European Central Bank president Christine Lagarde wields considerable influence on monetary policy in Europe and may have put a temporary damper on the Czech central bank's aspirations for now ([See Reuters](https://www.reuters.com/markets/europe/ecbs-lagarde-slaps-down-czech-proposal-Bitcoin-reserves-2025-01-30/)), it should be evident that in the words of some Bitcoiners, "nothing stops this train." For Bitcoiners, such shifts validate the claim that Bitcoin's decentralized, algorithmic structure outperforms fiat systems, which are vulnerable to political manipulation and unchecked inflation. The Czech president's [signing into law](https://www.coindesk.com/policy/2025/02/06/czech-republic-to-eliminate-taxes-on-long-term-crypto-gains) a bill removing capital gains tax from all Bitcoin held for at least three years proves that even those at the highest levels of policy creation are beginning to lose control of the narrative. This state endorsement is more than symbolic. It is a strategic vote of confidence in Bitcoin's underlying technology—its transparent, immutable ledger and deflationary nature. When lawmakers and regulators in the United States start to invest public resources in Bitcoin, it undermines the decades-old narrative that only traditional assets like gold or oil are worthy of state backing. Instead, it repositions Bitcoin as an asset not just with a future but of the future. It can enhance and even replace all other existing reserve assets, lending further proof of Bitcoin as a store of value. Bitcoin's capped supply is at the core of its appeal—only 21 million coins will ever exist. Bitcoiners assert that this scarcity is fundamental to Bitcoin's value proposition. A strategic Bitcoin reserve at any governmental level would effectively lock away a significant portion of the circulating supply, increasing its scarcity and further driving its price up. Many in the Bitcoin and overall crypto community lauded President Bukele's 2021 announcement that his country would begin accumulating Bitcoin and giving it legal tender status. To Bitcoiners, it was a sign that governments were starting to see Bitcoin as a legitimate store of value, a medium of exchange, and vindication of everything they had fought for over the years. Of course, many will want to say that the country's acquisition of Bitcoin was simply a power play to get the World Economic Forum to come to the bargaining table, but if so, what? Here we are four years later, and El Salvador is [no longer requiring Bitcoin as legal tender](https://newsroompanama.com/2025/02/07/el-salvador-ends-Bitcoin-as-legal-tender-heres-why-Bitcoin-didnt-work/). This is not a step back, it is simply another example of why we are winning. I'll discuss this further in another article, but isn't it convenient that President Bukele continues to accumulate Bitcoin for his country after making a concession to the WEF for funds? Tick, tock, next block. Bitcoiners view introducing reserve bills across U.S. states as a powerful mechanism for further tightening Bitcoin's available supply. Each government-held coin is one fewer coin available to the market, creating a scarcity premium. Market forces do not artificially impose this scarcity but are instead the natural outcome of an institution with deep pockets choosing to hold Bitcoin as a strategic asset. In a world where every coin in reserve represents a bulwark against inflation and economic uncertainty, Bitcoiners argue that this state-induced scarcity will profoundly affect Bitcoin's value over time. If you don't believe that to be the case, look at this chart of coins available on OTC desks last year, and let me tell you that you are not bullish enough. I'll explore the impact of OTC sales on price in a future article.  For years, Bitcoiners have decried the inherent weaknesses of fiat currencies—specifically, the ease with which governments can expand the money supply, leading to inflation and eroded purchasing power. Bitcoin, on the other hand, offers a fixed supply, decentralized issuance, and an ever-shrinking inflation rate that makes it immune to the government's printing press. When a government opts for Bitcoin reserves, it makes a financial decision and a political statement. It says that the era of limitless money printing is over and that transparency, decentralization, and scarcity are the hallmarks of a sound monetary system. Institutional legitimacy is crucial for any asset that aspires to be a cornerstone of the global financial system. When the United States, the world's largest economy, signals its intent to hold Bitcoin in its reserves, it sends a resounding message that can trigger a domino effect worldwide. The recent [repeal of SAB121](https://cointelegraph.com/news sec-cancels-crypto-accounting-guidance-sab-121) by the Securities and Exchange Commission is a step in the right direction, by now allowing companies and course, governments at every level to accumulate Bitcoin into their reserves. When central banks like the Czech National Bank begin to signal openness toward digital assets, it paves the way for broader institutional participation. Once wary of the volatile digital asset market, financial institutions, asset managers, and [even pension funds](https://www.wpr.org/news/wisconsin-pension-fund-bitcoin) are gradually warming up to Bitcoin. We cannot underestimate what sort of network effect this will have on Bitcoin as its utility and value proposition become more robust as a result of state-level adoption. Bitcoiners believe that such a shift will cement Bitcoin's status as a universally accepted and trusted store of value, capable of challenging—and eventually surpassing—traditional reserve assets like gold and fiat currencies. One of the most enduring arguments among Bitcoiners is that Bitcoin is the digital successor to gold. For centuries, gold has been the haven, the ultimate store of value during times of crisis. Bitcoin, with its fixed supply and digital accessibility, is ideally positioned to take over that role in the modern era. A state-backed Bitcoin reserve would serve as this narrative's definitive stamp of approval. If a government is willing to set aside billions of dollars in a digital asset, it must believe that this asset can preserve and even appreciate its value over time. Such a move would provide a critical psychological boost to the market, as both retail and institutional investors begin to see Bitcoin as not just a speculative tool but as the modern equivalent of a haven set. Gold continues to appreciate this year while Bitcoin remains relatively flat. How long until we see it decouple from the markets and witness price appreciation not seen since the last halving? I hope you enjoyed reading this lengthy article on the pros of governments adopting a strategic Bitcoin reserve. If you'd like to chime in, you can find me on Nostr via [@geek](https://www.primal.net/geek) on Primal, or via [my npub]( .npub1m2jphmdkskgnvwl5gplksl9e0zwv2sldqf9mwlpz6tyymz84g9fsqr3wgu) anywhere else. In part two, I will examine the other side of the debate, the cons, and the potential pitfalls of such a policy. Stay tuned!
@ daa41bed:88f54153
2025-02-08 23:29:14Imagine a world where governments, long trusted to protect fiat currencies that can be printed without limit, openly declare that they trust a decentralized digital asset over traditional money. In recent months, that vision has begun to crystallize. The Czech National Bank has signaled a gradual acceptance of digital assets as part of its broader monetary policy recalibration with changes to how capital gains taxes are handled on Bitcoin and a possible adoption by its central bank into its reserves stockpile. Simultaneously, El Salvador- once the poster child for Bitcoin as legal tender- has fine-tuned its policy framework at the behest of the WEF to no longer accept Bitcoin as legal tender. Meanwhile, several U.S. states have introduced bills to establish official Bitcoin reserves, and many are under active consideration. See [Bitcoin Laws](https://Bitcoinlaws.io/) for a full breakdown of where these bills stand. Let's explore the pros of governments adopting strategic Bitcoin reserves. Bitcoiners have long argued that the ultimate endorsement of Bitcoin comes when even the most established state institutions place their trust in it. Recent moves by several U.S. states—where lawmakers are proposing legislation to create official Bitcoin reserves—lend credence to this argument. When state governments start to codify the creation of a Bitcoin reserve, it signals that even entities steeped in traditional financial orthodoxy now recognize Bitcoin as a viable, strategic asset. For these states, it is imperative to accumulate hard assets like Bitcoin in reserves as they have no control over the monetary supply and, therefore, can suffer from debasement just as much as any citizen or sovereign nation not in control of their currency. Suppose you have kept up with [recent news](https://decrypt.co/303304/czech-central-bank-bitcoin-reserve) that the Czech national bank was considering holding a considerable portion of their assets in Bitcoin. In that case, you understand the paradigm shift we are seeing. Banks are becoming less cautious in handling digital assets in a stark department, compared to previous dismissals of cryptocurrencies as genuine assets. While it is true that European Central Bank president Christine Lagarde wields considerable influence on monetary policy in Europe and may have put a temporary damper on the Czech central bank's aspirations for now ([See Reuters](https://www.reuters.com/markets/europe/ecbs-lagarde-slaps-down-czech-proposal-Bitcoin-reserves-2025-01-30/)), it should be evident that in the words of some Bitcoiners, "nothing stops this train." For Bitcoiners, such shifts validate the claim that Bitcoin's decentralized, algorithmic structure outperforms fiat systems, which are vulnerable to political manipulation and unchecked inflation. The Czech president's [signing into law](https://www.coindesk.com/policy/2025/02/06/czech-republic-to-eliminate-taxes-on-long-term-crypto-gains) a bill removing capital gains tax from all Bitcoin held for at least three years proves that even those at the highest levels of policy creation are beginning to lose control of the narrative. This state endorsement is more than symbolic. It is a strategic vote of confidence in Bitcoin's underlying technology—its transparent, immutable ledger and deflationary nature. When lawmakers and regulators in the United States start to invest public resources in Bitcoin, it undermines the decades-old narrative that only traditional assets like gold or oil are worthy of state backing. Instead, it repositions Bitcoin as an asset not just with a future but of the future. It can enhance and even replace all other existing reserve assets, lending further proof of Bitcoin as a store of value. Bitcoin's capped supply is at the core of its appeal—only 21 million coins will ever exist. Bitcoiners assert that this scarcity is fundamental to Bitcoin's value proposition. A strategic Bitcoin reserve at any governmental level would effectively lock away a significant portion of the circulating supply, increasing its scarcity and further driving its price up. Many in the Bitcoin and overall crypto community lauded President Bukele's 2021 announcement that his country would begin accumulating Bitcoin and giving it legal tender status. To Bitcoiners, it was a sign that governments were starting to see Bitcoin as a legitimate store of value, a medium of exchange, and vindication of everything they had fought for over the years. Of course, many will want to say that the country's acquisition of Bitcoin was simply a power play to get the World Economic Forum to come to the bargaining table, but if so, what? Here we are four years later, and El Salvador is [no longer requiring Bitcoin as legal tender](https://newsroompanama.com/2025/02/07/el-salvador-ends-Bitcoin-as-legal-tender-heres-why-Bitcoin-didnt-work/). This is not a step back, it is simply another example of why we are winning. I'll discuss this further in another article, but isn't it convenient that President Bukele continues to accumulate Bitcoin for his country after making a concession to the WEF for funds? Tick, tock, next block. Bitcoiners view introducing reserve bills across U.S. states as a powerful mechanism for further tightening Bitcoin's available supply. Each government-held coin is one fewer coin available to the market, creating a scarcity premium. Market forces do not artificially impose this scarcity but are instead the natural outcome of an institution with deep pockets choosing to hold Bitcoin as a strategic asset. In a world where every coin in reserve represents a bulwark against inflation and economic uncertainty, Bitcoiners argue that this state-induced scarcity will profoundly affect Bitcoin's value over time. If you don't believe that to be the case, look at this chart of coins available on OTC desks last year, and let me tell you that you are not bullish enough. I'll explore the impact of OTC sales on price in a future article.  For years, Bitcoiners have decried the inherent weaknesses of fiat currencies—specifically, the ease with which governments can expand the money supply, leading to inflation and eroded purchasing power. Bitcoin, on the other hand, offers a fixed supply, decentralized issuance, and an ever-shrinking inflation rate that makes it immune to the government's printing press. When a government opts for Bitcoin reserves, it makes a financial decision and a political statement. It says that the era of limitless money printing is over and that transparency, decentralization, and scarcity are the hallmarks of a sound monetary system. Institutional legitimacy is crucial for any asset that aspires to be a cornerstone of the global financial system. When the United States, the world's largest economy, signals its intent to hold Bitcoin in its reserves, it sends a resounding message that can trigger a domino effect worldwide. The recent [repeal of SAB121](https://cointelegraph.com/news sec-cancels-crypto-accounting-guidance-sab-121) by the Securities and Exchange Commission is a step in the right direction, by now allowing companies and course, governments at every level to accumulate Bitcoin into their reserves. When central banks like the Czech National Bank begin to signal openness toward digital assets, it paves the way for broader institutional participation. Once wary of the volatile digital asset market, financial institutions, asset managers, and [even pension funds](https://www.wpr.org/news/wisconsin-pension-fund-bitcoin) are gradually warming up to Bitcoin. We cannot underestimate what sort of network effect this will have on Bitcoin as its utility and value proposition become more robust as a result of state-level adoption. Bitcoiners believe that such a shift will cement Bitcoin's status as a universally accepted and trusted store of value, capable of challenging—and eventually surpassing—traditional reserve assets like gold and fiat currencies. One of the most enduring arguments among Bitcoiners is that Bitcoin is the digital successor to gold. For centuries, gold has been the haven, the ultimate store of value during times of crisis. Bitcoin, with its fixed supply and digital accessibility, is ideally positioned to take over that role in the modern era. A state-backed Bitcoin reserve would serve as this narrative's definitive stamp of approval. If a government is willing to set aside billions of dollars in a digital asset, it must believe that this asset can preserve and even appreciate its value over time. Such a move would provide a critical psychological boost to the market, as both retail and institutional investors begin to see Bitcoin as not just a speculative tool but as the modern equivalent of a haven set. Gold continues to appreciate this year while Bitcoin remains relatively flat. How long until we see it decouple from the markets and witness price appreciation not seen since the last halving? I hope you enjoyed reading this lengthy article on the pros of governments adopting a strategic Bitcoin reserve. If you'd like to chime in, you can find me on Nostr via [@geek](https://www.primal.net/geek) on Primal, or via [my npub]( .npub1m2jphmdkskgnvwl5gplksl9e0zwv2sldqf9mwlpz6tyymz84g9fsqr3wgu) anywhere else. In part two, I will examine the other side of the debate, the cons, and the potential pitfalls of such a policy. Stay tuned! @ a012dc82:6458a70d
2025-02-08 22:44:44The world of cryptocurrency has always been a rollercoaster of highs and lows, but recent developments in the Bitcoin market have caught the attention of investors worldwide. The circulating supply of Bitcoin in profit has surged to a multi-year high, a phenomenon not seen since the heady days of November 2021 when Bitcoin reached its all-time high. This significant milestone, backed by data from industry analysts at Glassnode and a detailed report from Bitfinex, paints a picture of a robust Bitcoin market. The implications of this surge are far-reaching, affecting not just seasoned cryptocurrency traders but also new investors who are contemplating dipping their toes into the Bitcoin pool. This article aims to dissect this trend, exploring its roots, its impact on the market, and what it potentially spells out for the future of Bitcoin investment. **Table Of Content** - Understanding the Surge - Implications for Long-term Investors - Market Strength and Investor Confidence - Potential Early Signs of a Bull Market - Caution and Market Dynamics - Conclusion - FAQs **Understanding the Surge** The surge in Bitcoin's circulating supply in profit is a complex phenomenon, driven by a confluence of market dynamics and investor behavior. The recent increase in Bitcoin's price, which saw it soar above $37,000, is a primary factor. This price hike has pushed a significant portion of Bitcoin into profitable territory. According to the Bitfinex report, over 16.3 million Bitcoin, a staggering amount by any measure, are currently in profit. This figure is considerably higher than the historical average, suggesting a market that is not only recovering but thriving. The surge is not just a momentary blip but a reflection of deeper market trends, including increased institutional interest in Bitcoin, broader acceptance of cryptocurrencies as a legitimate asset class, and the growing perception of Bitcoin as a hedge against inflation and currency devaluation. **Implications for Long-term Investors** For long-term investors, this surge in Bitcoin's profitability is a beacon of stability in the typically volatile cryptocurrency market. The fact that 70% of Bitcoin's total circulating supply has remained static over the past year is indicative of a maturing market where investors are increasingly viewing Bitcoin as a long-term investment rather than a quick profit opportunity. This holding pattern contributes to a tightening of supply, which, coupled with increasing demand, can lead to a sustained price increase. However, long-term investors should also be aware of the potential risks. The cryptocurrency market is still relatively young and can be influenced by regulatory changes, technological advancements, and shifts in investor sentiment. Therefore, while the current trend is encouraging, it should be viewed within the broader context of market dynamics. **Market Strength and Investor Confidence** The current state of the Bitcoin market is a testament to its growing strength and the confidence it instills in investors. With a majority of holders seeing positive returns, there's a renewed vigor in the market, attracting both retail and institutional investors. This influx of new investment can further stabilize the market and potentially drive prices higher. However, this increased investor confidence must be tempered with a degree of caution. The cryptocurrency market is known for its rapid fluctuations, and what goes up can just as quickly come down. Investors should be mindful of the inherent risks and conduct thorough research before making any investment decisions. The market's strength, while promising, is not a guarantee of future performance, and a prudent investment strategy should always be in place. **Potential Early Signs of a Bull Market** The analysis by Bitfinex suggests that the market might be in the early stages of a bull market. This is a significant indicator for investors, as bull markets are characterized by rising prices and increased buying activity. If this trend continues, it could lead to substantial gains for those invested in Bitcoin. However, predicting market movements, especially in the volatile world of cryptocurrencies, is fraught with uncertainty. While the signs are positive, they are not infallible indicators of future performance. Investors should therefore approach this potential bull market with optimism tempered by realism, recognizing that market conditions can change rapidly and without warning. **Caution and Market Dynamics** In the face of these optimistic trends, a word of caution is warranted. The cryptocurrency market is notoriously unpredictable, and while the current indicators are positive, they are not immune to sudden and unexpected changes. Factors such as regulatory announcements, technological breakthroughs, or macroeconomic shifts can rapidly alter the market landscape. Therefore, investors should remain vigilant, keeping abreast of market news and trends. Diversification of investments, a keen understanding of market dynamics, and a clear investment strategy are essential tools in navigating the complexities of the Bitcoin market. **Conclusion** The surge in Bitcoin's circulating supply in profit to a multi-year high marks a significant milestone in the cryptocurrency's journey. It reflects a market that is gaining maturity, strength, and the confidence of its investors. This development could herald the beginning of a new era for Bitcoin, characterized by stability and sustained growth. However, the path of Bitcoin and the broader cryptocurrency market remains unpredictable. Investors should therefore approach this market with a well-informed strategy, balancing optimism with a healthy dose of caution. In the ever-evolving world of cryptocurrency, staying informed and adaptable is key to navigating the market's highs and lows. **FAQs** **How does this surge affect long-term investors?** Long-term investors may see this as a sign of market stability and maturity, indicating that Bitcoin is increasingly being viewed as a viable long-term investment. **Could this trend indicate the start of a Bitcoin bull market?** While the surge in profitable Bitcoin supply could be an early sign of a bull market, predicting market movements in the volatile cryptocurrency sector is complex and uncertain. **What percentage of Bitcoin's circulating supply is currently in profit?** Over 83% of Bitcoin's circulating supply is reported to be in profit, according to recent data. **What should investors be cautious about in light of this surge?** Investors should be aware of the inherent volatility in the cryptocurrency market and consider factors like regulatory changes, technological advancements, and broader market dynamics before making investment decisions. **How does the current Bitcoin market compare to historical averages?** The current percentage of Bitcoin in profit is significantly higher than the historical average, indicating a particularly strong market phase. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: [@croxroadnews.co](https://x.com/croxroadnewsco)** **Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)** **Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** ***DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.***
@ a012dc82:6458a70d
2025-02-08 22:44:44The world of cryptocurrency has always been a rollercoaster of highs and lows, but recent developments in the Bitcoin market have caught the attention of investors worldwide. The circulating supply of Bitcoin in profit has surged to a multi-year high, a phenomenon not seen since the heady days of November 2021 when Bitcoin reached its all-time high. This significant milestone, backed by data from industry analysts at Glassnode and a detailed report from Bitfinex, paints a picture of a robust Bitcoin market. The implications of this surge are far-reaching, affecting not just seasoned cryptocurrency traders but also new investors who are contemplating dipping their toes into the Bitcoin pool. This article aims to dissect this trend, exploring its roots, its impact on the market, and what it potentially spells out for the future of Bitcoin investment. **Table Of Content** - Understanding the Surge - Implications for Long-term Investors - Market Strength and Investor Confidence - Potential Early Signs of a Bull Market - Caution and Market Dynamics - Conclusion - FAQs **Understanding the Surge** The surge in Bitcoin's circulating supply in profit is a complex phenomenon, driven by a confluence of market dynamics and investor behavior. The recent increase in Bitcoin's price, which saw it soar above $37,000, is a primary factor. This price hike has pushed a significant portion of Bitcoin into profitable territory. According to the Bitfinex report, over 16.3 million Bitcoin, a staggering amount by any measure, are currently in profit. This figure is considerably higher than the historical average, suggesting a market that is not only recovering but thriving. The surge is not just a momentary blip but a reflection of deeper market trends, including increased institutional interest in Bitcoin, broader acceptance of cryptocurrencies as a legitimate asset class, and the growing perception of Bitcoin as a hedge against inflation and currency devaluation. **Implications for Long-term Investors** For long-term investors, this surge in Bitcoin's profitability is a beacon of stability in the typically volatile cryptocurrency market. The fact that 70% of Bitcoin's total circulating supply has remained static over the past year is indicative of a maturing market where investors are increasingly viewing Bitcoin as a long-term investment rather than a quick profit opportunity. This holding pattern contributes to a tightening of supply, which, coupled with increasing demand, can lead to a sustained price increase. However, long-term investors should also be aware of the potential risks. The cryptocurrency market is still relatively young and can be influenced by regulatory changes, technological advancements, and shifts in investor sentiment. Therefore, while the current trend is encouraging, it should be viewed within the broader context of market dynamics. **Market Strength and Investor Confidence** The current state of the Bitcoin market is a testament to its growing strength and the confidence it instills in investors. With a majority of holders seeing positive returns, there's a renewed vigor in the market, attracting both retail and institutional investors. This influx of new investment can further stabilize the market and potentially drive prices higher. However, this increased investor confidence must be tempered with a degree of caution. The cryptocurrency market is known for its rapid fluctuations, and what goes up can just as quickly come down. Investors should be mindful of the inherent risks and conduct thorough research before making any investment decisions. The market's strength, while promising, is not a guarantee of future performance, and a prudent investment strategy should always be in place. **Potential Early Signs of a Bull Market** The analysis by Bitfinex suggests that the market might be in the early stages of a bull market. This is a significant indicator for investors, as bull markets are characterized by rising prices and increased buying activity. If this trend continues, it could lead to substantial gains for those invested in Bitcoin. However, predicting market movements, especially in the volatile world of cryptocurrencies, is fraught with uncertainty. While the signs are positive, they are not infallible indicators of future performance. Investors should therefore approach this potential bull market with optimism tempered by realism, recognizing that market conditions can change rapidly and without warning. **Caution and Market Dynamics** In the face of these optimistic trends, a word of caution is warranted. The cryptocurrency market is notoriously unpredictable, and while the current indicators are positive, they are not immune to sudden and unexpected changes. Factors such as regulatory announcements, technological breakthroughs, or macroeconomic shifts can rapidly alter the market landscape. Therefore, investors should remain vigilant, keeping abreast of market news and trends. Diversification of investments, a keen understanding of market dynamics, and a clear investment strategy are essential tools in navigating the complexities of the Bitcoin market. **Conclusion** The surge in Bitcoin's circulating supply in profit to a multi-year high marks a significant milestone in the cryptocurrency's journey. It reflects a market that is gaining maturity, strength, and the confidence of its investors. This development could herald the beginning of a new era for Bitcoin, characterized by stability and sustained growth. However, the path of Bitcoin and the broader cryptocurrency market remains unpredictable. Investors should therefore approach this market with a well-informed strategy, balancing optimism with a healthy dose of caution. In the ever-evolving world of cryptocurrency, staying informed and adaptable is key to navigating the market's highs and lows. **FAQs** **How does this surge affect long-term investors?** Long-term investors may see this as a sign of market stability and maturity, indicating that Bitcoin is increasingly being viewed as a viable long-term investment. **Could this trend indicate the start of a Bitcoin bull market?** While the surge in profitable Bitcoin supply could be an early sign of a bull market, predicting market movements in the volatile cryptocurrency sector is complex and uncertain. **What percentage of Bitcoin's circulating supply is currently in profit?** Over 83% of Bitcoin's circulating supply is reported to be in profit, according to recent data. **What should investors be cautious about in light of this surge?** Investors should be aware of the inherent volatility in the cryptocurrency market and consider factors like regulatory changes, technological advancements, and broader market dynamics before making investment decisions. **How does the current Bitcoin market compare to historical averages?** The current percentage of Bitcoin in profit is significantly higher than the historical average, indicating a particularly strong market phase. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: [@croxroadnews.co](https://x.com/croxroadnewsco)** **Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)** **Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** ***DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.*** @ c1e6505c:02b3157e
2025-02-08 21:52:51\*\*\*"Time is the best teacher but unfortunately it kills all of its students."\*\*\* I'm currently visiting my dad for a few days as I had to take my car in for some repairs and maintenance, which included an oil gasket leak, power steering fluid flush, brake fluid flush, spark plugs, and the works. The process took a couple of hours to complete, so instead of waiting in the waiting room or having someone pick me up to go wait comfortably at home, I decided to walk around with my camera and try to make some new work. I have to say, there's really nothing more that I enjoy than walking aimlessly in an area that I have never been and taking photographs. \*I love it.\* I lose myself and everything that is on my mind that I "worry" about. I'm present, in the zone, and honestly having a great time. Photography for me is a portal to enter a state of mind that transcends time and space. The area that I was in was very industrial, so my walk started next door at the other car mechanic shop, and I meandered down to the small local town where some shops were. Didn't see too much, so I turned around and started walking back down the other way. Sometimes I don't see anything of interest for a while. What I have noticed though, as a little trick to start having things "come out of the woodwork," is just to start shooting at the first thing that captures my interest. Getting the ball rolling with pushing the shutter somehow gets me in the "flow state" that I enjoy getting in when making photographs. \\\[ !\[\](https://substackcdn.com/image/fetch/w\_1456,c\_limit,f\_auto,q\_auto:good,fl\_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F027a5466-47a8-4c9a-b3dc-c9acf0a31a12\_2500x1786.jpeg)\\\]( As I walked further, I visited a plant nursery that was just opening. The woman who was opening the gate was very nice and invited me into walk around and do as I please. There were a few nice plants around, but what gravitates me the most is seemingly, to others maybe, the "ugly stuff" or the subject matter that one wouldn’t really consider making a photograph of. Blank spaces, trash, neglect - it's all good stuff to me. The light falling upon these subjects makes them interesting. After the nursery, I found a large industrial facility and a train yard. A worker stood next to one of the train cars, so I went up and asked what they were loading. He said that he’s been working there for 30 years, and that they make plastic trash bags, and those tubes feeding into the train cars were pumping out plastic beads for production. I thought that was interesting. We chatted for a bit, I thanked him for his time, and moved on. !\[\](https://substackcdn.com/image/fetch/w\_1456,c\_limit,f\_auto,q\_auto:good,fl\_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F70512ba8-8c29-4454-8cd7-3d030c17730f\_1786x2500.jpeg) !\[\](https://substackcdn.com/image/fetch/f\_auto,q\_auto:good,fl\_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F70512ba8-8c29-4454-8cd7-3d030c17730f\_1786x2500.jpeg) !\[\](https://substackcdn.com/image/fetch/w\_1456,c\_limit,f\_auto,q\_auto:good,fl\_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2Fd3d8ef1c-4381-49f2-a5cd-5266f3208d91\_2500x1786.jpeg) !\[\](https://substackcdn.com/image/fetch/w\_1456,c\_limit,f\_auto,q\_auto:good,fl\_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F2b32f8fd-2f47-4f6a-9592-9fba9d3e6e57\_2500x1786.jpeg) !\[\](https://substackcdn.com/image/fetch/w\_1456,c\_limit,f\_auto,q\_auto:good,fl\_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2Fb8716d86-acdb-4b3a-a61b-8c1abb6ab737\_2500x1786.jpeg) !\[\](https://substackcdn.com/image/fetch/f\_auto,q\_auto:good,fl\_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F9d7bc288-0707-4e17-a420-aa08fb53b817\_2500x1670.jpeg) !\[\](https://substackcdn.com/image/fetch/w\_1456,c\_limit,f\_auto,q\_auto:good,fl\_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F499acae7-e563-45fd-86b7-32ae3d20150f\_2500x1786.jpeg) !\[\](https://substackcdn.com/image/fetch/w\_1456,c\_limit,f\_auto,q\_auto:good,fl\_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2Ff626a80d-5a43-485e-a50c-747c346388a0\_1670x2500.jpeg) !\[\](https://substackcdn.com/image/fetch/w\_1456,c\_limit,f\_auto,q\_auto:good,fl\_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F472d5556-7ef4-4f6a-a48e-7eccf39088d3\_2500x1670.jpeg) !\[\](https://substackcdn.com/image/fetch/w\_1456,c\_limit,f\_auto,q\_auto:good,fl\_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F724c8133-fe4e-41c4-b383-3aaec42d50a1\_2500x1786.jpeg) Eventually, I ended up at a church with these really nice orange and brown doors. I sat on a bench in the back to kill some time, listening to a few podcasts. While I was there, I noticed a sign that read: \*"Happy moments, praise God. Difficult moments, seek God. Quiet moments, worship God. Painful moments, trust God. Every moment, thank God."\* I’m not a religious guy per se, haven’t been to church in over a decade, and I’ve had my own experiences — psychedelics included — where I’ve glimpsed something I’d call “God.”, but there’s something to take from that. Whatever your definition of “God” is, there’s value in gratitude whether things are good or bad. Life itself is a miracle. Appreciating the small things keeps you grounded, humble, and connected. !\[\](https://substackcdn.com/image/fetch/f\_auto,q\_auto:good,fl\_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F102b529f-a7ea-4346-889b-2b1f51b48c63\_2500x1786.jpeg) !\[\](https://substackcdn.com/image/fetch/w\_1456,c\_limit,f\_auto,q\_auto:good,fl\_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2Fef07f101-4645-4439-b050-72c9fe551b1f\_1786x2500.jpeg) !\[\](https://substackcdn.com/image/fetch/f\_auto,q\_auto:good,fl\_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2Fce6960c5-e78c-4b3e-b0fe-78e773b6a518\_2500x1786.jpeg)) \*Just in case you missed it…\* \*\*I have a limited edition framed print that I will have available until February 28th.\*\* Only two will be made, and they will come framed; one in black, one in silver. If you enjoy my work, this would be a great collectors piece. !\[\](https://substackcdn.com/image/fetch/w\_1456,c\_limit,f\_auto,q\_auto:good,fl\_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F3d3033ae-b71a-4505-9d2c-f899df1a535b\_2313x2313.jpeg)\\\]() \*\*\*I shoot with a Leica M262, and edit in Lightroom + Dehancer\*\*\* \[\*\*\*Use “PictureRoom” for 10% off Dehancer Film\*\*\*\](https://www.dehancer.com/shop/pslr/film) If you’ve made it this far, thank you for taking the time to view my work - I appreciate it. Please consider becoming a paid subscriber to support my work. Also, please contact me if you would like to purchase any of my prints. !\[\](https://substackcdn.com/image/fetch/w\_1456,c\_limit,f\_auto,q\_auto:good,fl\_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2Fe6ad5a3e-cb60-4246-9bb3-9f8849d3591e\_4000x3551.jpeg) \[Dehancer Film (promo code "PICTUREOOM")\](https://www.dehancer.com/shop/pslr/film) \*If you've found value in this newsletter, I'd be incredibly grateful for your support. While these posts will always be freely available, becoming a paid subscriber helps ensure I can continue delivering quality content to your inbox. Share this newsletter with friends, leaving a comment, or simply hitting the 'like' button all make a difference.\* Thank you - Colin
@ c1e6505c:02b3157e
2025-02-08 21:52:51\*\*\*"Time is the best teacher but unfortunately it kills all of its students."\*\*\* I'm currently visiting my dad for a few days as I had to take my car in for some repairs and maintenance, which included an oil gasket leak, power steering fluid flush, brake fluid flush, spark plugs, and the works. The process took a couple of hours to complete, so instead of waiting in the waiting room or having someone pick me up to go wait comfortably at home, I decided to walk around with my camera and try to make some new work. I have to say, there's really nothing more that I enjoy than walking aimlessly in an area that I have never been and taking photographs. \*I love it.\* I lose myself and everything that is on my mind that I "worry" about. I'm present, in the zone, and honestly having a great time. Photography for me is a portal to enter a state of mind that transcends time and space. The area that I was in was very industrial, so my walk started next door at the other car mechanic shop, and I meandered down to the small local town where some shops were. Didn't see too much, so I turned around and started walking back down the other way. Sometimes I don't see anything of interest for a while. What I have noticed though, as a little trick to start having things "come out of the woodwork," is just to start shooting at the first thing that captures my interest. Getting the ball rolling with pushing the shutter somehow gets me in the "flow state" that I enjoy getting in when making photographs. \\\[ !\[\](https://substackcdn.com/image/fetch/w\_1456,c\_limit,f\_auto,q\_auto:good,fl\_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F027a5466-47a8-4c9a-b3dc-c9acf0a31a12\_2500x1786.jpeg)\\\]( As I walked further, I visited a plant nursery that was just opening. The woman who was opening the gate was very nice and invited me into walk around and do as I please. There were a few nice plants around, but what gravitates me the most is seemingly, to others maybe, the "ugly stuff" or the subject matter that one wouldn’t really consider making a photograph of. Blank spaces, trash, neglect - it's all good stuff to me. The light falling upon these subjects makes them interesting. After the nursery, I found a large industrial facility and a train yard. A worker stood next to one of the train cars, so I went up and asked what they were loading. He said that he’s been working there for 30 years, and that they make plastic trash bags, and those tubes feeding into the train cars were pumping out plastic beads for production. I thought that was interesting. We chatted for a bit, I thanked him for his time, and moved on. !\[\](https://substackcdn.com/image/fetch/w\_1456,c\_limit,f\_auto,q\_auto:good,fl\_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F70512ba8-8c29-4454-8cd7-3d030c17730f\_1786x2500.jpeg) !\[\](https://substackcdn.com/image/fetch/f\_auto,q\_auto:good,fl\_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F70512ba8-8c29-4454-8cd7-3d030c17730f\_1786x2500.jpeg) !\[\](https://substackcdn.com/image/fetch/w\_1456,c\_limit,f\_auto,q\_auto:good,fl\_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2Fd3d8ef1c-4381-49f2-a5cd-5266f3208d91\_2500x1786.jpeg) !\[\](https://substackcdn.com/image/fetch/w\_1456,c\_limit,f\_auto,q\_auto:good,fl\_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F2b32f8fd-2f47-4f6a-9592-9fba9d3e6e57\_2500x1786.jpeg) !\[\](https://substackcdn.com/image/fetch/w\_1456,c\_limit,f\_auto,q\_auto:good,fl\_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2Fb8716d86-acdb-4b3a-a61b-8c1abb6ab737\_2500x1786.jpeg) !\[\](https://substackcdn.com/image/fetch/f\_auto,q\_auto:good,fl\_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F9d7bc288-0707-4e17-a420-aa08fb53b817\_2500x1670.jpeg) !\[\](https://substackcdn.com/image/fetch/w\_1456,c\_limit,f\_auto,q\_auto:good,fl\_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F499acae7-e563-45fd-86b7-32ae3d20150f\_2500x1786.jpeg) !\[\](https://substackcdn.com/image/fetch/w\_1456,c\_limit,f\_auto,q\_auto:good,fl\_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2Ff626a80d-5a43-485e-a50c-747c346388a0\_1670x2500.jpeg) !\[\](https://substackcdn.com/image/fetch/w\_1456,c\_limit,f\_auto,q\_auto:good,fl\_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F472d5556-7ef4-4f6a-a48e-7eccf39088d3\_2500x1670.jpeg) !\[\](https://substackcdn.com/image/fetch/w\_1456,c\_limit,f\_auto,q\_auto:good,fl\_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F724c8133-fe4e-41c4-b383-3aaec42d50a1\_2500x1786.jpeg) Eventually, I ended up at a church with these really nice orange and brown doors. I sat on a bench in the back to kill some time, listening to a few podcasts. While I was there, I noticed a sign that read: \*"Happy moments, praise God. Difficult moments, seek God. Quiet moments, worship God. Painful moments, trust God. Every moment, thank God."\* I’m not a religious guy per se, haven’t been to church in over a decade, and I’ve had my own experiences — psychedelics included — where I’ve glimpsed something I’d call “God.”, but there’s something to take from that. Whatever your definition of “God” is, there’s value in gratitude whether things are good or bad. Life itself is a miracle. Appreciating the small things keeps you grounded, humble, and connected. !\[\](https://substackcdn.com/image/fetch/f\_auto,q\_auto:good,fl\_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F102b529f-a7ea-4346-889b-2b1f51b48c63\_2500x1786.jpeg) !\[\](https://substackcdn.com/image/fetch/w\_1456,c\_limit,f\_auto,q\_auto:good,fl\_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2Fef07f101-4645-4439-b050-72c9fe551b1f\_1786x2500.jpeg) !\[\](https://substackcdn.com/image/fetch/f\_auto,q\_auto:good,fl\_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2Fce6960c5-e78c-4b3e-b0fe-78e773b6a518\_2500x1786.jpeg)) \*Just in case you missed it…\* \*\*I have a limited edition framed print that I will have available until February 28th.\*\* Only two will be made, and they will come framed; one in black, one in silver. If you enjoy my work, this would be a great collectors piece. !\[\](https://substackcdn.com/image/fetch/w\_1456,c\_limit,f\_auto,q\_auto:good,fl\_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F3d3033ae-b71a-4505-9d2c-f899df1a535b\_2313x2313.jpeg)\\\]() \*\*\*I shoot with a Leica M262, and edit in Lightroom + Dehancer\*\*\* \[\*\*\*Use “PictureRoom” for 10% off Dehancer Film\*\*\*\](https://www.dehancer.com/shop/pslr/film) If you’ve made it this far, thank you for taking the time to view my work - I appreciate it. Please consider becoming a paid subscriber to support my work. Also, please contact me if you would like to purchase any of my prints. !\[\](https://substackcdn.com/image/fetch/w\_1456,c\_limit,f\_auto,q\_auto:good,fl\_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2Fe6ad5a3e-cb60-4246-9bb3-9f8849d3591e\_4000x3551.jpeg) \[Dehancer Film (promo code "PICTUREOOM")\](https://www.dehancer.com/shop/pslr/film) \*If you've found value in this newsletter, I'd be incredibly grateful for your support. While these posts will always be freely available, becoming a paid subscriber helps ensure I can continue delivering quality content to your inbox. Share this newsletter with friends, leaving a comment, or simply hitting the 'like' button all make a difference.\* Thank you - Colin @ 32e18276:5c68e245
2025-02-08 20:20:46This period of the Damus OpenSats grant has been productive, and encompasses the work past our alpha release of Notedeck. Since we sent our last report on Dec 5, this encompasses all the work after then. Damus is supported by the OpenSats LTS grant, which allows us to continue working on the goodies below. Thank you! ## Damus Notedeck ### Added - Initial algo timelines (William Casarin) [#712](https://github.com/damus-io/notedeck/pull/712) - Initial support for local-network P2P nostr: multicast support (William Casarin) [#626](https://github.com/damus-io/notedeck/pull/626) - First steps toward the notedeck browser: multiple app support [#565](https://github.com/damus-io/notedeck/pull/565) - Clicking a mention now opens profile page (William Casarin) [5a241d730](https://github.com/damus-io/notedeck/commit/5a241d730e3d83f8057e211485edfde2f3c96e54) - Note previews when hovering reply descriptions (William Casarin) [#591](https://github.com/damus-io/notedeck/pull/591) - Various Android updates and compatibility improvements (Ken Sedgwick, William Casarin) - Media uploads (kernelkind) [#662](https://github.com/damus-io/notedeck/pull/662) - Profile editing (kernelkind) [#625](https://github.com/damus-io/notedeck/pull/625) - Add hashtags to posts (Daniel Saxton) [#592](https://github.com/damus-io/notedeck/pull/592) - Enhanced command-line interface for user interactions (Ken Sedgwick) - Debug features for user relay-list and mute list synchronization (Ken Sedgwick) ### Changed - Major timeline cache refactor (William Casarin) [#653](https://github.com/damus-io/notedeck/pull/653) - Increased ping intervals for network performance (William Casarin) - Migrated to egui v0.29.1 (William Casarin) [#551](https://github.com/damus-io/notedeck/pull/551) - Switch to only notes & replies on some tabs (William Casarin) [#598](https://github.com/damus-io/notedeck/pull/598) - Only show column delete button when not navigating (William Casarin) - Pointer interactions enhancements in UI (William Casarin) - Show profile pictures in column headers (William Casarin) - Show usernames in user columns (William Casarin) - Add confirmation when deleting columns (kernelkind) - Enhance Android build and performance (Ken Sedgwick) - Image cache handling using sha256 hash (kieran) - Introduction of decks_cache and improvements (kernelkind) - Nostrdb update for async support (Ken Sedgwick) - Persistent theme setup across sessions (kernelkind) - Tombstone muted notes (Ken) ### Fixed - Fix GIT_COMMIT_HASH compilation issue (William Casarin) - Fix avatar alignment in profile previews (William Casarin) - Fix broken quote repost hitbox (William Casarin) - Fix crash when navigating in debug mode (William Casarin) - Fix long delays when reconnecting (William Casarin) - Fix repost button size (William Casarin) - Fixed since kind filters (kernelkind) - Clippy warnings resolved (Dimitris Apostolou) ## Damus iOS Work continued on the iOS side. While I was not directly involved in the work since the last report, I have been directing and managing its development. ### Added - Render Gif and video files while composing posts (Swift Coder) - Purple members who have been active for more than a year now get a special badge (Daniel D’Aquino) - Add profile info text in stretchable banner with follow button (Swift Coder) - Paste Gif image similar to jpeg and png files (Swift Coder) ### Changed - Improved clarity of the mute button to indicate it can be used for blocking a user (Daniel D’Aquino) - Made the microphone access request message more clear to users (Daniel D’Aquino) - Improved UX around the label for searching words (Daniel D’Aquino) - Improved accessibility support on some elements (Daniel D’Aquino) ### Fixed - Fixed issue where the "next" button would appear hidden and hard to click on the create account view (Daniel D’Aquino) - Fix non scrollable wallet screen (Swift Coder) - Fixed suggested users category titles to be localizable (Terry Yiu) - Fixed GradientFollowButton to have consistent width and autoscale text limited to 1 line (Terry Yiu) - Fixed right-to-left localization issues (Terry Yiu) - Fixed AddMuteItemView to trim leading and trailing whitespaces from mute text and disallow adding text with only whitespaces (Terry Yiu) - Fixed SideMenuView text to autoscale and limit to 1 line (Terry Yiu) - Fixed an issue where a profile would need to be input twice in the search to be found (Daniel D’Aquino) - Fixed non-breaking spaces in localized strings (Terry Yiu) - Fixed localization issue on Add mute item button (Terry Yiu) - Replace non-breaking spaces with regular spaces as Apple's NSLocalizedString macro does not seem to work with it (Terry Yiu) - Fixed localization issues in RelayConfigView (Terry Yiu) - Fix duplicate uploads (Swift Coder) - Remove duplicate pubkey from Follow Suggestion list (Swift Coder) - Fix Page control indicator (Swift Coder) - Fix damus sharing issues (Swift Coder) - Fixed issue where banner edit button is unclickable (Daniel D’Aquino) - Handle empty notification pages by displaying suitable text (Swift Coder) ## Nostrdb nostrdb, the engine that powers [notecrumbs](https://github.com/damus-io/notecrumbs), damus iOS, and notedeck, continued to improve: ### Added - Added nip50 fulltext searching (William Casarin) [#68](https://github.com/damus-io/nostrdb/pull/68), [demo](nostr:nevent1qqsp3rx83t5h0vdhu4txru76uycfnaegfj3wg6wncamkarcnrccssvcpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqvhpsfmr23gwhv795lgjc8uw0v44z3pe4sg2vlh08k0an3wx3cj9efqkkv) - Added async migrations (William Casarin) [#59](https://github.com/damus-io/nostrdb/pull/59) - Implement author queries (William Casarin) [#57](https://github.com/damus-io/nostrdb/pull/57) - Make `ndb` threadsafe (William Casarin) [#56](https://github.com/damus-io/nostrdb/pull/56) ## Nostrdb Rust Our nostrdb rust bindings also had improvements - Async! Adding efficient, poll-based stream support (William Casarin): [#25](https://github.com/damus-io/nostrdb-rs/pull/25) ## Notecrumbs Notecrumbs, the njump-style opengraph server that powers the damus.io links, got an update that upgraded it to async nostrdb - Switch to async nostrdb-rs (William Casarin) [#16](https://github.com/damus-io/notecrumbs/pull/16) ## How money was used - relay.damus.io server costs - Living expenses ## Next quarter Our goal for next update: zaps, android version, lists, outbox model for notedeck. Olas images in damus iOS, continue switching Damus iOS over to local relay model so we can add outbox support.
@ 32e18276:5c68e245
2025-02-08 20:20:46This period of the Damus OpenSats grant has been productive, and encompasses the work past our alpha release of Notedeck. Since we sent our last report on Dec 5, this encompasses all the work after then. Damus is supported by the OpenSats LTS grant, which allows us to continue working on the goodies below. Thank you! ## Damus Notedeck ### Added - Initial algo timelines (William Casarin) [#712](https://github.com/damus-io/notedeck/pull/712) - Initial support for local-network P2P nostr: multicast support (William Casarin) [#626](https://github.com/damus-io/notedeck/pull/626) - First steps toward the notedeck browser: multiple app support [#565](https://github.com/damus-io/notedeck/pull/565) - Clicking a mention now opens profile page (William Casarin) [5a241d730](https://github.com/damus-io/notedeck/commit/5a241d730e3d83f8057e211485edfde2f3c96e54) - Note previews when hovering reply descriptions (William Casarin) [#591](https://github.com/damus-io/notedeck/pull/591) - Various Android updates and compatibility improvements (Ken Sedgwick, William Casarin) - Media uploads (kernelkind) [#662](https://github.com/damus-io/notedeck/pull/662) - Profile editing (kernelkind) [#625](https://github.com/damus-io/notedeck/pull/625) - Add hashtags to posts (Daniel Saxton) [#592](https://github.com/damus-io/notedeck/pull/592) - Enhanced command-line interface for user interactions (Ken Sedgwick) - Debug features for user relay-list and mute list synchronization (Ken Sedgwick) ### Changed - Major timeline cache refactor (William Casarin) [#653](https://github.com/damus-io/notedeck/pull/653) - Increased ping intervals for network performance (William Casarin) - Migrated to egui v0.29.1 (William Casarin) [#551](https://github.com/damus-io/notedeck/pull/551) - Switch to only notes & replies on some tabs (William Casarin) [#598](https://github.com/damus-io/notedeck/pull/598) - Only show column delete button when not navigating (William Casarin) - Pointer interactions enhancements in UI (William Casarin) - Show profile pictures in column headers (William Casarin) - Show usernames in user columns (William Casarin) - Add confirmation when deleting columns (kernelkind) - Enhance Android build and performance (Ken Sedgwick) - Image cache handling using sha256 hash (kieran) - Introduction of decks_cache and improvements (kernelkind) - Nostrdb update for async support (Ken Sedgwick) - Persistent theme setup across sessions (kernelkind) - Tombstone muted notes (Ken) ### Fixed - Fix GIT_COMMIT_HASH compilation issue (William Casarin) - Fix avatar alignment in profile previews (William Casarin) - Fix broken quote repost hitbox (William Casarin) - Fix crash when navigating in debug mode (William Casarin) - Fix long delays when reconnecting (William Casarin) - Fix repost button size (William Casarin) - Fixed since kind filters (kernelkind) - Clippy warnings resolved (Dimitris Apostolou) ## Damus iOS Work continued on the iOS side. While I was not directly involved in the work since the last report, I have been directing and managing its development. ### Added - Render Gif and video files while composing posts (Swift Coder) - Purple members who have been active for more than a year now get a special badge (Daniel D’Aquino) - Add profile info text in stretchable banner with follow button (Swift Coder) - Paste Gif image similar to jpeg and png files (Swift Coder) ### Changed - Improved clarity of the mute button to indicate it can be used for blocking a user (Daniel D’Aquino) - Made the microphone access request message more clear to users (Daniel D’Aquino) - Improved UX around the label for searching words (Daniel D’Aquino) - Improved accessibility support on some elements (Daniel D’Aquino) ### Fixed - Fixed issue where the "next" button would appear hidden and hard to click on the create account view (Daniel D’Aquino) - Fix non scrollable wallet screen (Swift Coder) - Fixed suggested users category titles to be localizable (Terry Yiu) - Fixed GradientFollowButton to have consistent width and autoscale text limited to 1 line (Terry Yiu) - Fixed right-to-left localization issues (Terry Yiu) - Fixed AddMuteItemView to trim leading and trailing whitespaces from mute text and disallow adding text with only whitespaces (Terry Yiu) - Fixed SideMenuView text to autoscale and limit to 1 line (Terry Yiu) - Fixed an issue where a profile would need to be input twice in the search to be found (Daniel D’Aquino) - Fixed non-breaking spaces in localized strings (Terry Yiu) - Fixed localization issue on Add mute item button (Terry Yiu) - Replace non-breaking spaces with regular spaces as Apple's NSLocalizedString macro does not seem to work with it (Terry Yiu) - Fixed localization issues in RelayConfigView (Terry Yiu) - Fix duplicate uploads (Swift Coder) - Remove duplicate pubkey from Follow Suggestion list (Swift Coder) - Fix Page control indicator (Swift Coder) - Fix damus sharing issues (Swift Coder) - Fixed issue where banner edit button is unclickable (Daniel D’Aquino) - Handle empty notification pages by displaying suitable text (Swift Coder) ## Nostrdb nostrdb, the engine that powers [notecrumbs](https://github.com/damus-io/notecrumbs), damus iOS, and notedeck, continued to improve: ### Added - Added nip50 fulltext searching (William Casarin) [#68](https://github.com/damus-io/nostrdb/pull/68), [demo](nostr:nevent1qqsp3rx83t5h0vdhu4txru76uycfnaegfj3wg6wncamkarcnrccssvcpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqvhpsfmr23gwhv795lgjc8uw0v44z3pe4sg2vlh08k0an3wx3cj9efqkkv) - Added async migrations (William Casarin) [#59](https://github.com/damus-io/nostrdb/pull/59) - Implement author queries (William Casarin) [#57](https://github.com/damus-io/nostrdb/pull/57) - Make `ndb` threadsafe (William Casarin) [#56](https://github.com/damus-io/nostrdb/pull/56) ## Nostrdb Rust Our nostrdb rust bindings also had improvements - Async! Adding efficient, poll-based stream support (William Casarin): [#25](https://github.com/damus-io/nostrdb-rs/pull/25) ## Notecrumbs Notecrumbs, the njump-style opengraph server that powers the damus.io links, got an update that upgraded it to async nostrdb - Switch to async nostrdb-rs (William Casarin) [#16](https://github.com/damus-io/notecrumbs/pull/16) ## How money was used - relay.damus.io server costs - Living expenses ## Next quarter Our goal for next update: zaps, android version, lists, outbox model for notedeck. Olas images in damus iOS, continue switching Damus iOS over to local relay model so we can add outbox support. @ fdb8c828:84c16368
2025-02-08 17:00:37 originally posted at https://stacker.news/items/579738
@ fdb8c828:84c16368
2025-02-08 17:00:37 originally posted at https://stacker.news/items/579738 @ 97c70a44:ad98e322
2025-01-30 17:15:37There was a slight dust up recently over a website someone runs removing a listing for an app someone built based on entirely arbitrary criteria. I'm not to going to attempt to speak for either wounded party, but I would like to share my own personal definition for what constitutes a "nostr app" in an effort to help clarify what might be an otherwise confusing and opaque purity test. In this post, I will be committing the "no true Scotsman" fallacy, in which I start with the most liberal definition I can come up with, and gradually refine it until all that is left is the purest, gleamingest, most imaginary and unattainable nostr app imaginable. As I write this, I wonder if anything built yet will actually qualify. In any case, here we go. # It uses nostr The lowest bar for what a "nostr app" might be is an app ("application" - i.e. software, not necessarily a native app of any kind) that has some nostr-specific code in it, but which doesn't take any advantage of what makes nostr distinctive as a protocol. Examples might include a scraper of some kind which fulfills its charter by fetching data from relays (regardless of whether it validates or retains signatures). Another might be a regular web 2.0 app which provides an option to "log in with nostr" by requesting and storing the user's public key. In either case, the fact that nostr is involved is entirely neutral. A scraper can scrape html, pdfs, jsonl, whatever data source - nostr relays are just another target. Likewise, a user's key in this scenario is treated merely as an opaque identifier, with no appreciation for the super powers it brings along. In most cases, this kind of app only exists as a marketing ploy, or less cynically, because it wants to get in on the hype of being a "nostr app", without the developer quite understanding what that means, or having the budget to execute properly on the claim. # It leverages nostr Some of you might be wondering, "isn't 'leverage' a synonym for 'use'?" And you would be right, but for one connotative difference. It's possible to "use" something improperly, but by definition leverage gives you a mechanical advantage that you wouldn't otherwise have. This is the second category of "nostr app". This kind of app gets some benefit out of the nostr protocol and network, but in an entirely selfish fashion. The intention of this kind of app is not to augment the nostr network, but to augment its own UX by borrowing some nifty thing from the protocol without really contributing anything back. Some examples might include: - Using nostr signers to encrypt or sign data, and then store that data on a proprietary server. - Using nostr relays as a kind of low-code backend, but using proprietary event payloads. - Using nostr event kinds to represent data (why), but not leveraging the trustlessness that buys you. An application in this category might even communicate to its users via nostr DMs - but this doesn't make it a "nostr app" any more than a website that emails you hot deals on herbal supplements is an "email app". These apps are purely parasitic on the nostr ecosystem. In the long-term, that's not necessarily a bad thing. Email's ubiquity is self-reinforcing. But in the short term, this kind of "nostr app" can actually do damage to nostr's reputation by over-promising and under-delivering. # It complements nostr Next up, we have apps that get some benefit out of nostr as above, but give back by providing a unique value proposition to nostr users as nostr users. This is a bit of a fine distinction, but for me this category is for apps which focus on solving problems that nostr isn't good at solving, leaving the nostr integration in a secondary or supporting role. One example of this kind of app was Mutiny (RIP), which not only allowed users to sign in with nostr, but also pulled those users' social graphs so that users could send money to people they knew and trusted. Mutiny was doing a great job of leveraging nostr, as well as providing value to users with nostr identities - but it was still primarily a bitcoin wallet, not a "nostr app" in the purest sense. Other examples are things like Nostr Nests and Zap.stream, whose core value proposition is streaming video or audio content. Both make great use of nostr identities, data formats, and relays, but they're primarily streaming apps. A good litmus test for things like this is: if you got rid of nostr, would it be the same product (even if inferior in certain ways)? A similar category is infrastructure providers that benefit nostr by their existence (and may in fact be targeted explicitly at nostr users), but do things in a centralized, old-web way; for example: media hosts, DNS registrars, hosting providers, and CDNs. To be clear here, I'm not casting aspersions (I don't even know what those are, or where to buy them). All the apps mentioned above use nostr to great effect, and are a real benefit to nostr users. But they are not True Scotsmen. # It embodies nostr Ok, here we go. This is the crème de la crème, the top du top, the meilleur du meilleur, the bee's knees. The purest, holiest, most chaste category of nostr app out there. The apps which are, indeed, nostr indigitate. This category of nostr app (see, no quotes this time) can be defined by the converse of the previous category. If nostr was removed from this type of application, would it be impossible to create the same product? To tease this apart a bit, apps that leverage the technical aspects of nostr are dependent on nostr the *protocol*, while apps that benefit nostr exclusively via network effect are integrated into nostr the *network*. An app that does both things is working in symbiosis with nostr as a whole. An app that embraces both nostr's protocol and its network becomes an organic extension of every other nostr app out there, multiplying both its competitive moat and its contribution to the ecosystem: - In contrast to apps that only borrow from nostr on the technical level but continue to operate in their own silos, an application integrated into the nostr network comes pre-packaged with existing users, and is able to provide more value to those users because of other nostr products. On nostr, it's a good thing to advertise your competitors. - In contrast to apps that only market themselves to nostr users without building out a deep integration on the protocol level, a deeply integrated app becomes an asset to every other nostr app by becoming an organic extension of them through interoperability. This results in increased traffic to the app as other developers and users refer people to it instead of solving their problem on their own. This is the "micro-apps" utopia we've all been waiting for. Credible exit doesn't matter if there aren't alternative services. Interoperability is pointless if other applications don't offer something your app doesn't. Marketing to nostr users doesn't matter if you don't augment their agency _as nostr users_. If I had to choose a single NIP that represents the mindset behind this kind of app, it would be NIP 89 A.K.A. "Recommended Application Handlers", which states: > Nostr's discoverability and transparent event interaction is one of its most interesting/novel mechanics. This NIP provides a simple way for clients to discover applications that handle events of a specific kind to ensure smooth cross-client and cross-kind interactions. These handlers are the glue that holds nostr apps together. A single event, signed by the developer of an application (or by the application's own account) tells anyone who wants to know 1. what event kinds the app supports, 2. how to link to the app (if it's a client), and (if the pubkey also publishes a kind 10002), 3. which relays the app prefers. _As a sidenote, NIP 89 is currently focused more on clients, leaving DVMs, relays, signers, etc somewhat out in the cold. Updating 89 to include tailored listings for each kind of supporting app would be a huge improvement to the protocol. This, plus a good front end for navigating these listings (sorry nostrapp.link, close but no cigar) would obviate the evil centralized websites that curate apps based on arbitrary criteria._ Examples of this kind of app obviously include many kind 1 clients, as well as clients that attempt to bring the benefits of the nostr protocol and network to new use cases - whether long form content, video, image posts, music, emojis, recipes, project management, or any other "content type". To drill down into one example, let's think for a moment about forms. What's so great about a forms app that is built on nostr? Well, - There is a [spec](https://github.com/nostr-protocol/nips/pull/1190) for forms and responses, which means that... - Multiple clients can implement the same data format, allowing for credible exit and user choice, even of... - Other products not focused on forms, which can still view, respond to, or embed forms, and which can send their users via NIP 89 to a client that does... - Cryptographically sign forms and responses, which means they are self-authenticating and can be sent to... - Multiple relays, which reduces the amount of trust necessary to be confident results haven't been deliberately "lost". Show me a forms product that does all of those things, and isn't built on nostr. You can't, because it doesn't exist. Meanwhile, there are plenty of image hosts with APIs, streaming services, and bitcoin wallets which have basically the same levels of censorship resistance, interoperability, and network effect as if they weren't built on nostr. # It supports nostr Notice I haven't said anything about whether relays, signers, blossom servers, software libraries, DVMs, and the accumulated addenda of the nostr ecosystem are nostr apps. Well, they are (usually). This is the category of nostr app that gets none of the credit for doing all of the work. There's no question that they qualify as beautiful nostrcorns, because their value propositions are entirely meaningless outside of the context of nostr. Who needs a signer if you don't have a cryptographic identity you need to protect? DVMs are literally impossible to use without relays. How are you going to find the blossom server that will serve a given hash if you don't know which servers the publishing user has selected to store their content? In addition to being entirely contextualized by nostr architecture, this type of nostr app is valuable because it does things "the nostr way". By that I mean that they don't simply try to replicate existing internet functionality into a nostr context; instead, they create entirely new ways of putting the basic building blocks of the internet back together. A great example of this is how Nostr Connect, Nostr Wallet Connect, and DVMs all use relays as brokers, which allows service providers to avoid having to accept incoming network connections. This opens up really interesting possibilities all on its own. So while I might hesitate to call many of these things "apps", they are certainly "nostr". # Appendix: it smells like a NINO So, let's say you've created an app, but when you show it to people they politely smile, nod, and call it a NINO (Nostr In Name Only). What's a hacker to do? Well, here's your handy-dandy guide on how to wash that NINO stench off and Become a Nostr. You app might be a NINO if: - There's no NIP for your data format (or you're abusing NIP 78, 32, etc by inventing a sub-protocol inside an existing event kind) - There's a NIP, but no one knows about it because it's in a text file on your hard drive (or buried in your project's repository) - Your NIP imposes an incompatible/centralized/legacy web paradigm onto nostr - Your NIP relies on trusted third (or first) parties - There's only one implementation of your NIP (yours) - Your core value proposition doesn't depend on relays, events, or nostr identities - One or more relay urls are hard-coded into the source code - Your app depends on a specific relay implementation to work (*ahem*, relay29) - You don't validate event signatures - You don't publish events to relays you don't control - You don't read events from relays you don't control - You use legacy web services to solve problems, rather than nostr-native solutions - You use nostr-native solutions, but you've hardcoded their pubkeys or URLs into your app - You don't use NIP 89 to discover clients and services - You haven't published a NIP 89 listing for your app - You don't leverage your users' web of trust for filtering out spam - You don't respect your users' mute lists - You try to "own" your users' data Now let me just re-iterate - it's ok to be a NINO. We need NINOs, because nostr can't (and shouldn't) tackle every problem. You just need to decide whether your app, as a NINO, is actually contributing to the nostr ecosystem, or whether you're just using buzzwords to whitewash a legacy web software product. If you're in the former camp, great! If you're in the latter, what are you waiting for? Only you can fix your NINO problem. And there are lots of ways to do this, depending on your own unique situation: - Drop nostr support if it's not doing anyone any good. If you want to build a normal company and make some money, that's perfectly fine. - Build out your nostr integration - start taking advantage of webs of trust, self-authenticating data, event handlers, etc. - Work around the problem. Think you need a special relay feature for your app to work? Guess again. Consider encryption, AUTH, DVMs, or better data formats. - Think your idea is a good one? Talk to other devs or open a PR to the [nips repo](https://github.com/nostr-protocol/nips). No one can adopt your NIP if they don't know about it. - Keep going. It can sometimes be hard to distinguish a research project from a NINO. New ideas have to be built out before they can be fully appreciated. - Listen to advice. Nostr developers are friendly and happy to help. If you're not sure why you're getting traction, ask! I sincerely hope this article is useful for all of you out there in NINO land. Maybe this made you feel better about not passing the totally optional nostr app purity test. Or maybe it gave you some actionable next steps towards making a great NINON (Nostr In Not Only Name) app. In either case, GM and PV.
@ 97c70a44:ad98e322
2025-01-30 17:15:37There was a slight dust up recently over a website someone runs removing a listing for an app someone built based on entirely arbitrary criteria. I'm not to going to attempt to speak for either wounded party, but I would like to share my own personal definition for what constitutes a "nostr app" in an effort to help clarify what might be an otherwise confusing and opaque purity test. In this post, I will be committing the "no true Scotsman" fallacy, in which I start with the most liberal definition I can come up with, and gradually refine it until all that is left is the purest, gleamingest, most imaginary and unattainable nostr app imaginable. As I write this, I wonder if anything built yet will actually qualify. In any case, here we go. # It uses nostr The lowest bar for what a "nostr app" might be is an app ("application" - i.e. software, not necessarily a native app of any kind) that has some nostr-specific code in it, but which doesn't take any advantage of what makes nostr distinctive as a protocol. Examples might include a scraper of some kind which fulfills its charter by fetching data from relays (regardless of whether it validates or retains signatures). Another might be a regular web 2.0 app which provides an option to "log in with nostr" by requesting and storing the user's public key. In either case, the fact that nostr is involved is entirely neutral. A scraper can scrape html, pdfs, jsonl, whatever data source - nostr relays are just another target. Likewise, a user's key in this scenario is treated merely as an opaque identifier, with no appreciation for the super powers it brings along. In most cases, this kind of app only exists as a marketing ploy, or less cynically, because it wants to get in on the hype of being a "nostr app", without the developer quite understanding what that means, or having the budget to execute properly on the claim. # It leverages nostr Some of you might be wondering, "isn't 'leverage' a synonym for 'use'?" And you would be right, but for one connotative difference. It's possible to "use" something improperly, but by definition leverage gives you a mechanical advantage that you wouldn't otherwise have. This is the second category of "nostr app". This kind of app gets some benefit out of the nostr protocol and network, but in an entirely selfish fashion. The intention of this kind of app is not to augment the nostr network, but to augment its own UX by borrowing some nifty thing from the protocol without really contributing anything back. Some examples might include: - Using nostr signers to encrypt or sign data, and then store that data on a proprietary server. - Using nostr relays as a kind of low-code backend, but using proprietary event payloads. - Using nostr event kinds to represent data (why), but not leveraging the trustlessness that buys you. An application in this category might even communicate to its users via nostr DMs - but this doesn't make it a "nostr app" any more than a website that emails you hot deals on herbal supplements is an "email app". These apps are purely parasitic on the nostr ecosystem. In the long-term, that's not necessarily a bad thing. Email's ubiquity is self-reinforcing. But in the short term, this kind of "nostr app" can actually do damage to nostr's reputation by over-promising and under-delivering. # It complements nostr Next up, we have apps that get some benefit out of nostr as above, but give back by providing a unique value proposition to nostr users as nostr users. This is a bit of a fine distinction, but for me this category is for apps which focus on solving problems that nostr isn't good at solving, leaving the nostr integration in a secondary or supporting role. One example of this kind of app was Mutiny (RIP), which not only allowed users to sign in with nostr, but also pulled those users' social graphs so that users could send money to people they knew and trusted. Mutiny was doing a great job of leveraging nostr, as well as providing value to users with nostr identities - but it was still primarily a bitcoin wallet, not a "nostr app" in the purest sense. Other examples are things like Nostr Nests and Zap.stream, whose core value proposition is streaming video or audio content. Both make great use of nostr identities, data formats, and relays, but they're primarily streaming apps. A good litmus test for things like this is: if you got rid of nostr, would it be the same product (even if inferior in certain ways)? A similar category is infrastructure providers that benefit nostr by their existence (and may in fact be targeted explicitly at nostr users), but do things in a centralized, old-web way; for example: media hosts, DNS registrars, hosting providers, and CDNs. To be clear here, I'm not casting aspersions (I don't even know what those are, or where to buy them). All the apps mentioned above use nostr to great effect, and are a real benefit to nostr users. But they are not True Scotsmen. # It embodies nostr Ok, here we go. This is the crème de la crème, the top du top, the meilleur du meilleur, the bee's knees. The purest, holiest, most chaste category of nostr app out there. The apps which are, indeed, nostr indigitate. This category of nostr app (see, no quotes this time) can be defined by the converse of the previous category. If nostr was removed from this type of application, would it be impossible to create the same product? To tease this apart a bit, apps that leverage the technical aspects of nostr are dependent on nostr the *protocol*, while apps that benefit nostr exclusively via network effect are integrated into nostr the *network*. An app that does both things is working in symbiosis with nostr as a whole. An app that embraces both nostr's protocol and its network becomes an organic extension of every other nostr app out there, multiplying both its competitive moat and its contribution to the ecosystem: - In contrast to apps that only borrow from nostr on the technical level but continue to operate in their own silos, an application integrated into the nostr network comes pre-packaged with existing users, and is able to provide more value to those users because of other nostr products. On nostr, it's a good thing to advertise your competitors. - In contrast to apps that only market themselves to nostr users without building out a deep integration on the protocol level, a deeply integrated app becomes an asset to every other nostr app by becoming an organic extension of them through interoperability. This results in increased traffic to the app as other developers and users refer people to it instead of solving their problem on their own. This is the "micro-apps" utopia we've all been waiting for. Credible exit doesn't matter if there aren't alternative services. Interoperability is pointless if other applications don't offer something your app doesn't. Marketing to nostr users doesn't matter if you don't augment their agency _as nostr users_. If I had to choose a single NIP that represents the mindset behind this kind of app, it would be NIP 89 A.K.A. "Recommended Application Handlers", which states: > Nostr's discoverability and transparent event interaction is one of its most interesting/novel mechanics. This NIP provides a simple way for clients to discover applications that handle events of a specific kind to ensure smooth cross-client and cross-kind interactions. These handlers are the glue that holds nostr apps together. A single event, signed by the developer of an application (or by the application's own account) tells anyone who wants to know 1. what event kinds the app supports, 2. how to link to the app (if it's a client), and (if the pubkey also publishes a kind 10002), 3. which relays the app prefers. _As a sidenote, NIP 89 is currently focused more on clients, leaving DVMs, relays, signers, etc somewhat out in the cold. Updating 89 to include tailored listings for each kind of supporting app would be a huge improvement to the protocol. This, plus a good front end for navigating these listings (sorry nostrapp.link, close but no cigar) would obviate the evil centralized websites that curate apps based on arbitrary criteria._ Examples of this kind of app obviously include many kind 1 clients, as well as clients that attempt to bring the benefits of the nostr protocol and network to new use cases - whether long form content, video, image posts, music, emojis, recipes, project management, or any other "content type". To drill down into one example, let's think for a moment about forms. What's so great about a forms app that is built on nostr? Well, - There is a [spec](https://github.com/nostr-protocol/nips/pull/1190) for forms and responses, which means that... - Multiple clients can implement the same data format, allowing for credible exit and user choice, even of... - Other products not focused on forms, which can still view, respond to, or embed forms, and which can send their users via NIP 89 to a client that does... - Cryptographically sign forms and responses, which means they are self-authenticating and can be sent to... - Multiple relays, which reduces the amount of trust necessary to be confident results haven't been deliberately "lost". Show me a forms product that does all of those things, and isn't built on nostr. You can't, because it doesn't exist. Meanwhile, there are plenty of image hosts with APIs, streaming services, and bitcoin wallets which have basically the same levels of censorship resistance, interoperability, and network effect as if they weren't built on nostr. # It supports nostr Notice I haven't said anything about whether relays, signers, blossom servers, software libraries, DVMs, and the accumulated addenda of the nostr ecosystem are nostr apps. Well, they are (usually). This is the category of nostr app that gets none of the credit for doing all of the work. There's no question that they qualify as beautiful nostrcorns, because their value propositions are entirely meaningless outside of the context of nostr. Who needs a signer if you don't have a cryptographic identity you need to protect? DVMs are literally impossible to use without relays. How are you going to find the blossom server that will serve a given hash if you don't know which servers the publishing user has selected to store their content? In addition to being entirely contextualized by nostr architecture, this type of nostr app is valuable because it does things "the nostr way". By that I mean that they don't simply try to replicate existing internet functionality into a nostr context; instead, they create entirely new ways of putting the basic building blocks of the internet back together. A great example of this is how Nostr Connect, Nostr Wallet Connect, and DVMs all use relays as brokers, which allows service providers to avoid having to accept incoming network connections. This opens up really interesting possibilities all on its own. So while I might hesitate to call many of these things "apps", they are certainly "nostr". # Appendix: it smells like a NINO So, let's say you've created an app, but when you show it to people they politely smile, nod, and call it a NINO (Nostr In Name Only). What's a hacker to do? Well, here's your handy-dandy guide on how to wash that NINO stench off and Become a Nostr. You app might be a NINO if: - There's no NIP for your data format (or you're abusing NIP 78, 32, etc by inventing a sub-protocol inside an existing event kind) - There's a NIP, but no one knows about it because it's in a text file on your hard drive (or buried in your project's repository) - Your NIP imposes an incompatible/centralized/legacy web paradigm onto nostr - Your NIP relies on trusted third (or first) parties - There's only one implementation of your NIP (yours) - Your core value proposition doesn't depend on relays, events, or nostr identities - One or more relay urls are hard-coded into the source code - Your app depends on a specific relay implementation to work (*ahem*, relay29) - You don't validate event signatures - You don't publish events to relays you don't control - You don't read events from relays you don't control - You use legacy web services to solve problems, rather than nostr-native solutions - You use nostr-native solutions, but you've hardcoded their pubkeys or URLs into your app - You don't use NIP 89 to discover clients and services - You haven't published a NIP 89 listing for your app - You don't leverage your users' web of trust for filtering out spam - You don't respect your users' mute lists - You try to "own" your users' data Now let me just re-iterate - it's ok to be a NINO. We need NINOs, because nostr can't (and shouldn't) tackle every problem. You just need to decide whether your app, as a NINO, is actually contributing to the nostr ecosystem, or whether you're just using buzzwords to whitewash a legacy web software product. If you're in the former camp, great! If you're in the latter, what are you waiting for? Only you can fix your NINO problem. And there are lots of ways to do this, depending on your own unique situation: - Drop nostr support if it's not doing anyone any good. If you want to build a normal company and make some money, that's perfectly fine. - Build out your nostr integration - start taking advantage of webs of trust, self-authenticating data, event handlers, etc. - Work around the problem. Think you need a special relay feature for your app to work? Guess again. Consider encryption, AUTH, DVMs, or better data formats. - Think your idea is a good one? Talk to other devs or open a PR to the [nips repo](https://github.com/nostr-protocol/nips). No one can adopt your NIP if they don't know about it. - Keep going. It can sometimes be hard to distinguish a research project from a NINO. New ideas have to be built out before they can be fully appreciated. - Listen to advice. Nostr developers are friendly and happy to help. If you're not sure why you're getting traction, ask! I sincerely hope this article is useful for all of you out there in NINO land. Maybe this made you feel better about not passing the totally optional nostr app purity test. Or maybe it gave you some actionable next steps towards making a great NINON (Nostr In Not Only Name) app. In either case, GM and PV. @ 89ccea93:df4e00b7
2025-02-08 16:50:15**[Original Post](https://expatriotic.me/ashigaru/)** # What is Ashigaru? > A self custodial, open source and secure Bitcoin wallet that is private by design. The **Ashigaru Open Source Project** was established in the months after the United States Department of Justice [brought charges](https://archive.is/g7q8r) against the founders of the self custodial Bitcoin application, Samourai Wallet. At the time of arrest, multiple servers that hosted documentation, code repositories and message coordination services were either [seized](https://archive.is/0nC3t) or failed to remain online, presumably due to being no longer administered. With the indicted individuals placed under restrictive conditions on bail, it became clear that all software development had ceased. ## Aims and Goals We believe anyone should be able to engage in peaceful, voluntary and private commerce on the internet without tracking, surveillance or censorship. The Ashigaru Open Source Project develops, releases and maintains free and open source software that makes extensive use of both published code from active projects as well as those archived in the public domain. Open, unrestricted communication networks are utilized to ensure continued availability. The software released by the project will always have a low barrier to entry, be non discriminatory, never expose users to counterparty risk and provide as much protection as possible for those transacting on a public blockchain. ## What’s in a name? As former users of Samourai Wallet, yet having no association or relationship with the core team, “Ashigaru” was chosen to represent individuals of humble origin whom, borne out of necessity, would equip themselves with their own tools and rise to the occasion during a period of great change. **Here is the [ONLY podcast episode](https://episodes.fm/1491067458/episode/YTRjNGNlNTAtYjEwMS00YWQ0LTg0MjUtZWQwMmQxYjU0N2Ex) with the developers of this wallet.**  **Here are a list of features directly from their website:** 1. **Onion Routing:** Connect to your Dojo node and broadcast over the Tor network 2. **Ricochet:** Add distance to the origins of your transactions to mitigate surveillance 3. **Encrypted Key Recovery:** Standards based mnemonic secured with a passphrase that can be imported to other wallets 4. **Post Mix Spending:** Import your Samourai Wallet private keys and maintain your segregated accounts 5. **Batch Spending:** Save on fees by composing a single transaction to multiple recipients 6. **Stealth Mode:** Obscure the wallet from physical searches with a functional decoy application in the launcher 7. **Peer to Peer Coinjoins:** Undermine heuristics used by blockchain observers through collaboration with other users 8. **Coin Control:** Select, label, freeze and unfreeze unspent transaction outputs (UTXOs) in your wallet 9. **Smart Mining Fees:** An advanced algorithm for determining a rate from unconfirmed transactions in the mempool 10. **Free and Open Source:** Ashigaru is released under the FOSS license [GNU General Public License Version 3](https://www.gnu.org/licenses/gpl-3.0.en.html) ___ # FREESAMOURAI Maybe you've been living in a hole, but the developers of the Samourai Wallet were indicted and picked up by the US government (*even the one in Portugal, because, shocker, the US DoJ can get you almost anywhere in the world except Cuba, North Korea, Russia and China. But I digress*). ```Their crime? Helping users of the base layer Bitcoin protocol achieve forward spending privacy by crafting pristine zero-link UTXOs. The unspent capacity of which was over 10,000 bitcoins, or twice the capacity of the Lightning Network which continues to hover around, and often under, 5,000 bitcoins.``` **#FREESAMOURAI**\ Listen to these podcast episodes for more information. 1. [Prescient warnings](https://episodes.fm/1491067458/episode/ODc0MDIyNzMtNTgxNy00NDAwLTg0MGMtY2JkZmVmNjU4YTg0) just before the indictment from **Diverter**. 2. [Update](https://episodes.fm/1491067458/episode/ZWRhN2EzN2MtYTk5ZC00ODY2LTg5NjctZGE3MWY2YzUzZmM4) when it became known what had happened. 3. [Follow up](https://episodes.fm/1491067458/episode/NDk2ZDJmMzUtMmI2MS00ODljLWIwYmUtODBkZTI2YmUxNDhm) with **Diverter** and **Zelko** after the fact 4. [Reassessing your privacy plan](https://episodes.fm/1491067458/episode/YTA2NDQwNDAtNTMzMy00ODRiLTlkZDUtN2ExZDU5NWY1ZmE0) with **Urban Hacker** in a world without a zero-link coinjoin implementation (Whirlpool). ## Why run Ashigaru compared to Samourai Wallet? One might ask the logical question, why run Ashigaru, my Samourai Wallet is still working!?\ To which, Max Tannahill, a community member, has given the following list to answer. 1. Cheaper BIP47 connections 2. Soroban coinjoins ([Tor link](http://ashigaruprvm4u263aoj6wxnipc4jrhb2avjll4nnk255jkdmj2obqqd.onion/news/operational-online-chaoots/) about this) 3. Better BIP47 recovery 4. No risk of DNS hijacking for the PayNym server as its over Tor 5. Ability to switch Dojos more easily 6. Spending warnings that Samourai never got to deploy to production 7. Next block fee estimation 8. UI improvements on Samourai 9. Removal of broken links to whirlpool, the old Soroban server and the old Iceland Dojo 10. No clearnet connections at all ___ # How-to Guide for Ashigaru ## Download the APK 1. *Prerequisite:* [Tor Browser](https://www.torproject.org/download/#android) is a requirement. 2. Open the **Tor Browser** and paste in this 🧅 [link](http://ashigaruprvm4u263aoj6wxnipc4jrhb2avjll4nnk255jkdmj2obqqd.onion/). 3. Recommended to use a phone with **Android 8+** that still receives security updates. 4. Recommended to use a **GrapheneOS** phone (Pixel only). _Non-Pixel owners can use **Lineage OS** which is a less secure, but viable, option. Or just use stock android if you have no idea how to change the operating system on your phone or don't want to do so._ 5. Carry out software verification. A PGP signed message is below the APK. The Keybase Verify [tool](https://keybase.io/verify) can be used to do the verification. 6. *This is what it looks like on Keybase when completed. ⤵*  ## Install the Ashigaru mobile application 1. From within your device's files, tap on the Ashigaru APK file 2. Tap "**Install**"\  3. When complete tap "**Done**", or tap "**Open**" to launch the mobile application\  4. The Ashigaru mobile application has now been installed on your Android device. You will now see the Ashigaru app icon in your list of installed apps. ## Setting up Ashigaru 1. You need to connect to your own self-hosted Dojo (this is a specific type of Bitcoin node). Ashigaru doesn't run a node for you to point your wallet to, you'll need to do this yourself. * DIY options include: * [Ministry of Nodes](https://www.youtube.com/watch?v=8_It4xEIwRA) * [BTC Sessions](https://www.youtube.com/watch?v=ULZoPMCYPfk) * Community nodes at [Dojo Bay](https://dojobay.pw/) (*Obviously a privacy trade-off if you outsource your node to a 3rd party.*) 2. You need a pen and paper for writing down your 12 word Mnemonic seed phrase. 3. Make a strong [passphrase](https://cryptography.fandom.com/wiki/Passphrase) (4-6 memorable but random [words](https://www.eff.org/deeplinks/2016/07/new-wordlists-random-passphrases)) and put it separately from the offline seed phrase backup, e.g., in your password manager (*KeePass or Bitwarden are good options*). 4. Claim your PayNym with it's associated Pepehash avatar.  > PayNym Support: Migrate seamlessly to a new directory that uses a Pepehash avatar scheme for representing BIP47 reusable payment codes. ## Using Ashigaru 1. When sending, if possible, and just as in [Sparrow Desktop Wallet](https://sparrowwallet.com), a fake coinjoin is created by using two of your UTXOs as inputs to obscure what is occuring onchain. Onlookers will see what appears to be two parties collaborating to spend together. This adds a bit of extra miner fee cost, but this is the cost of extra privacy. You can opt out of this privacy enhancement.\  2. If you want to send or receive privately and with a static address, **BIP47 PayNyms**, will accomplish this. As long as both parties have a wallet that supports this standard. **Samourai Wallet**, **Stack Duo**, and **Sparrow** are the others that I know of at this time. Simply put in their **PayNym**, e.g., mine is **+mereegg59**, or scan their QR containing the data for the **PayNym** and connect with them. This will involve sending a small transaction onchain. But once one of you does, both parties can send back and forth privately without ever needing to request a fresh address. 3. There is an option when spending to use **ricochet**. This will add hops to help obscure the history of your **UTXO** for anyone who is using passive software to check X hops in the past for some connection to a **sanctioned** address. Good for spending **UTXOs** that you don't know the prior history of. Although personally I think **taint** is merely a mindset, some entities will not receive **UTXOs** that have either been coinjoined or are too close to a **sanctioned** address. 4. There is an option in the tools menu for doing a collaborative spend, known as **Soroban Coinjoin**. 5. Unfortunately Whirlpool is not yet a feature of this wallet.  ___ - **Here is the Tor [link](http://ashigaruprvm4u263aoj6wxnipc4jrhb2avjll4nnk255jkdmj2obqqd.onion/donate/) where you can donate to them** - **Here is the Tor [link](http://ashicodepbnpvslzsl2bz7l2pwrjvajgumgac423pp3y2deprbnzz7id.onion/Ashigaru) for their code base** - **Here is the Tor [link](http://ashigaruprvm4u263aoj6wxnipc4jrhb2avjll4nnk255jkdmj2obqqd.onion/docs/) for their documentation** - **Here is the Tor [link](http://ashigaruprvm4u263aoj6wxnipc4jrhb2avjll4nnk255jkdmj2obqqd.onion/docs/mobile-wallet-updating-application/) for updating the Ashigaru app** - **Here is the Tor [link](http://ashigaruprvm4u263aoj6wxnipc4jrhb2avjll4nnk255jkdmj2obqqd.onion/contact/) for their contact info. _Keep in mind this requires a different PGP key than the one used to verify the APK (unless you use protonmail and then PGP isn't required)._** originally posted at https://stacker.news/items/879803
@ 89ccea93:df4e00b7
2025-02-08 16:50:15**[Original Post](https://expatriotic.me/ashigaru/)** # What is Ashigaru? > A self custodial, open source and secure Bitcoin wallet that is private by design. The **Ashigaru Open Source Project** was established in the months after the United States Department of Justice [brought charges](https://archive.is/g7q8r) against the founders of the self custodial Bitcoin application, Samourai Wallet. At the time of arrest, multiple servers that hosted documentation, code repositories and message coordination services were either [seized](https://archive.is/0nC3t) or failed to remain online, presumably due to being no longer administered. With the indicted individuals placed under restrictive conditions on bail, it became clear that all software development had ceased. ## Aims and Goals We believe anyone should be able to engage in peaceful, voluntary and private commerce on the internet without tracking, surveillance or censorship. The Ashigaru Open Source Project develops, releases and maintains free and open source software that makes extensive use of both published code from active projects as well as those archived in the public domain. Open, unrestricted communication networks are utilized to ensure continued availability. The software released by the project will always have a low barrier to entry, be non discriminatory, never expose users to counterparty risk and provide as much protection as possible for those transacting on a public blockchain. ## What’s in a name? As former users of Samourai Wallet, yet having no association or relationship with the core team, “Ashigaru” was chosen to represent individuals of humble origin whom, borne out of necessity, would equip themselves with their own tools and rise to the occasion during a period of great change. **Here is the [ONLY podcast episode](https://episodes.fm/1491067458/episode/YTRjNGNlNTAtYjEwMS00YWQ0LTg0MjUtZWQwMmQxYjU0N2Ex) with the developers of this wallet.**  **Here are a list of features directly from their website:** 1. **Onion Routing:** Connect to your Dojo node and broadcast over the Tor network 2. **Ricochet:** Add distance to the origins of your transactions to mitigate surveillance 3. **Encrypted Key Recovery:** Standards based mnemonic secured with a passphrase that can be imported to other wallets 4. **Post Mix Spending:** Import your Samourai Wallet private keys and maintain your segregated accounts 5. **Batch Spending:** Save on fees by composing a single transaction to multiple recipients 6. **Stealth Mode:** Obscure the wallet from physical searches with a functional decoy application in the launcher 7. **Peer to Peer Coinjoins:** Undermine heuristics used by blockchain observers through collaboration with other users 8. **Coin Control:** Select, label, freeze and unfreeze unspent transaction outputs (UTXOs) in your wallet 9. **Smart Mining Fees:** An advanced algorithm for determining a rate from unconfirmed transactions in the mempool 10. **Free and Open Source:** Ashigaru is released under the FOSS license [GNU General Public License Version 3](https://www.gnu.org/licenses/gpl-3.0.en.html) ___ # FREESAMOURAI Maybe you've been living in a hole, but the developers of the Samourai Wallet were indicted and picked up by the US government (*even the one in Portugal, because, shocker, the US DoJ can get you almost anywhere in the world except Cuba, North Korea, Russia and China. But I digress*). ```Their crime? Helping users of the base layer Bitcoin protocol achieve forward spending privacy by crafting pristine zero-link UTXOs. The unspent capacity of which was over 10,000 bitcoins, or twice the capacity of the Lightning Network which continues to hover around, and often under, 5,000 bitcoins.``` **#FREESAMOURAI**\ Listen to these podcast episodes for more information. 1. [Prescient warnings](https://episodes.fm/1491067458/episode/ODc0MDIyNzMtNTgxNy00NDAwLTg0MGMtY2JkZmVmNjU4YTg0) just before the indictment from **Diverter**. 2. [Update](https://episodes.fm/1491067458/episode/ZWRhN2EzN2MtYTk5ZC00ODY2LTg5NjctZGE3MWY2YzUzZmM4) when it became known what had happened. 3. [Follow up](https://episodes.fm/1491067458/episode/NDk2ZDJmMzUtMmI2MS00ODljLWIwYmUtODBkZTI2YmUxNDhm) with **Diverter** and **Zelko** after the fact 4. [Reassessing your privacy plan](https://episodes.fm/1491067458/episode/YTA2NDQwNDAtNTMzMy00ODRiLTlkZDUtN2ExZDU5NWY1ZmE0) with **Urban Hacker** in a world without a zero-link coinjoin implementation (Whirlpool). ## Why run Ashigaru compared to Samourai Wallet? One might ask the logical question, why run Ashigaru, my Samourai Wallet is still working!?\ To which, Max Tannahill, a community member, has given the following list to answer. 1. Cheaper BIP47 connections 2. Soroban coinjoins ([Tor link](http://ashigaruprvm4u263aoj6wxnipc4jrhb2avjll4nnk255jkdmj2obqqd.onion/news/operational-online-chaoots/) about this) 3. Better BIP47 recovery 4. No risk of DNS hijacking for the PayNym server as its over Tor 5. Ability to switch Dojos more easily 6. Spending warnings that Samourai never got to deploy to production 7. Next block fee estimation 8. UI improvements on Samourai 9. Removal of broken links to whirlpool, the old Soroban server and the old Iceland Dojo 10. No clearnet connections at all ___ # How-to Guide for Ashigaru ## Download the APK 1. *Prerequisite:* [Tor Browser](https://www.torproject.org/download/#android) is a requirement. 2. Open the **Tor Browser** and paste in this 🧅 [link](http://ashigaruprvm4u263aoj6wxnipc4jrhb2avjll4nnk255jkdmj2obqqd.onion/). 3. Recommended to use a phone with **Android 8+** that still receives security updates. 4. Recommended to use a **GrapheneOS** phone (Pixel only). _Non-Pixel owners can use **Lineage OS** which is a less secure, but viable, option. Or just use stock android if you have no idea how to change the operating system on your phone or don't want to do so._ 5. Carry out software verification. A PGP signed message is below the APK. The Keybase Verify [tool](https://keybase.io/verify) can be used to do the verification. 6. *This is what it looks like on Keybase when completed. ⤵*  ## Install the Ashigaru mobile application 1. From within your device's files, tap on the Ashigaru APK file 2. Tap "**Install**"\  3. When complete tap "**Done**", or tap "**Open**" to launch the mobile application\  4. The Ashigaru mobile application has now been installed on your Android device. You will now see the Ashigaru app icon in your list of installed apps. ## Setting up Ashigaru 1. You need to connect to your own self-hosted Dojo (this is a specific type of Bitcoin node). Ashigaru doesn't run a node for you to point your wallet to, you'll need to do this yourself. * DIY options include: * [Ministry of Nodes](https://www.youtube.com/watch?v=8_It4xEIwRA) * [BTC Sessions](https://www.youtube.com/watch?v=ULZoPMCYPfk) * Community nodes at [Dojo Bay](https://dojobay.pw/) (*Obviously a privacy trade-off if you outsource your node to a 3rd party.*) 2. You need a pen and paper for writing down your 12 word Mnemonic seed phrase. 3. Make a strong [passphrase](https://cryptography.fandom.com/wiki/Passphrase) (4-6 memorable but random [words](https://www.eff.org/deeplinks/2016/07/new-wordlists-random-passphrases)) and put it separately from the offline seed phrase backup, e.g., in your password manager (*KeePass or Bitwarden are good options*). 4. Claim your PayNym with it's associated Pepehash avatar.  > PayNym Support: Migrate seamlessly to a new directory that uses a Pepehash avatar scheme for representing BIP47 reusable payment codes. ## Using Ashigaru 1. When sending, if possible, and just as in [Sparrow Desktop Wallet](https://sparrowwallet.com), a fake coinjoin is created by using two of your UTXOs as inputs to obscure what is occuring onchain. Onlookers will see what appears to be two parties collaborating to spend together. This adds a bit of extra miner fee cost, but this is the cost of extra privacy. You can opt out of this privacy enhancement.\  2. If you want to send or receive privately and with a static address, **BIP47 PayNyms**, will accomplish this. As long as both parties have a wallet that supports this standard. **Samourai Wallet**, **Stack Duo**, and **Sparrow** are the others that I know of at this time. Simply put in their **PayNym**, e.g., mine is **+mereegg59**, or scan their QR containing the data for the **PayNym** and connect with them. This will involve sending a small transaction onchain. But once one of you does, both parties can send back and forth privately without ever needing to request a fresh address. 3. There is an option when spending to use **ricochet**. This will add hops to help obscure the history of your **UTXO** for anyone who is using passive software to check X hops in the past for some connection to a **sanctioned** address. Good for spending **UTXOs** that you don't know the prior history of. Although personally I think **taint** is merely a mindset, some entities will not receive **UTXOs** that have either been coinjoined or are too close to a **sanctioned** address. 4. There is an option in the tools menu for doing a collaborative spend, known as **Soroban Coinjoin**. 5. Unfortunately Whirlpool is not yet a feature of this wallet.  ___ - **Here is the Tor [link](http://ashigaruprvm4u263aoj6wxnipc4jrhb2avjll4nnk255jkdmj2obqqd.onion/donate/) where you can donate to them** - **Here is the Tor [link](http://ashicodepbnpvslzsl2bz7l2pwrjvajgumgac423pp3y2deprbnzz7id.onion/Ashigaru) for their code base** - **Here is the Tor [link](http://ashigaruprvm4u263aoj6wxnipc4jrhb2avjll4nnk255jkdmj2obqqd.onion/docs/) for their documentation** - **Here is the Tor [link](http://ashigaruprvm4u263aoj6wxnipc4jrhb2avjll4nnk255jkdmj2obqqd.onion/docs/mobile-wallet-updating-application/) for updating the Ashigaru app** - **Here is the Tor [link](http://ashigaruprvm4u263aoj6wxnipc4jrhb2avjll4nnk255jkdmj2obqqd.onion/contact/) for their contact info. _Keep in mind this requires a different PGP key than the one used to verify the APK (unless you use protonmail and then PGP isn't required)._** originally posted at https://stacker.news/items/879803 @ 604e96e0:20279eb2
2023-08-11 18:39:36notacomment allows you to zap nostr notes when you comment on them. In order to use notacomment, you have to run a script yourself either on your own computer or in the cloud somewhere. To get started open https://github.com/SamSamskies/notacomment in a browser tab. At this point, I'm sure a lot of you are feeling like this:  Let's breakdown the instructions from the README. ## Prerequisites Node.js and npm - I suggest installing the latest Node.js LTS version from https://nodejs.org. That should also install npm. Once installation is complete, open your terminal. On a Mac you can press cmd + spacebar and type in `terminal` to open the terminal. On other platforms, you'll have to ask ChatGPT 😂 . To verify installation of Node.js type `node -v`. To verify installation type `npm -v`. It should look something like this:  Leave the terminal open. ## Downloading the code to your computer The easiest way to download the code is to download the zip file from the GitHub repo. Remember that first link I told you to open? That's the GitHub repo. Click the green button that says `Code` on it and click `Download ZIP` from the menu.  Now unzip the file and then navigate to the folder in the terminal. To navigate to the folder use the `cd` command. If you unzipped the folder in the `Downloads` folder, you can navigate to the folder by typing `cd ~/Downloads/notacomment-main/`. ## Usage With Strike 1. Create an account with Strike if you don't already have one https://strike.me/download/ 1. Get a Strike API key with all the payment scopes from https://dashboard.strike.me/ 1. Create a .env file and provide NOSTR_NSEC and STRIKE_API_KEY values (see .env.example) 1. Install the dependencies using npm or yarn or whatever your heart desires 1. Make sure you have money in your Strike account 1. Run the script `npm start` Keep in mind that Strike pays the invoices from your cash balance. This means the payment rounds up to the nearest cent when paying an invoice, so if you set the zap amount to 1 sat, you'll be sending more money to Strike than the person you are zapping with every zap. ## Usage With LNbits I recommend making a separate wallet from your main LNbits wallet for usage with notacomment in case you accidentally leak the admin key. 1. Create a .env file and provide NOSTR_NSEC, LNBITS_ADMIN_KEY, and LNBITS_URL values (see .env.example) 1. Install the dependencies using npm or yarn or whatever your heart desires 1. Make sure you have sats in your LNbits wallet 1. Run the script `npm start` ## Usage With Nostr Wallet Connect 1. Create a NWC connection string using something like https://nwc.getalby.com/ 1. Create a .env file and provide NOSTR_NSEC and NWC_CONNECTION_STRING values (see .env.example) 1. Install the dependencies using npm or yarn or whatever your heart desires 1. Make sure you have sats in your wallet that you generated the NWC connection string with 1. Run the script `npm start` <br /> <br /> Screenshot of terminal with commands to install dependencies, create .env file, open .env file, and start the script: 
@ 604e96e0:20279eb2
2023-08-11 18:39:36notacomment allows you to zap nostr notes when you comment on them. In order to use notacomment, you have to run a script yourself either on your own computer or in the cloud somewhere. To get started open https://github.com/SamSamskies/notacomment in a browser tab. At this point, I'm sure a lot of you are feeling like this:  Let's breakdown the instructions from the README. ## Prerequisites Node.js and npm - I suggest installing the latest Node.js LTS version from https://nodejs.org. That should also install npm. Once installation is complete, open your terminal. On a Mac you can press cmd + spacebar and type in `terminal` to open the terminal. On other platforms, you'll have to ask ChatGPT 😂 . To verify installation of Node.js type `node -v`. To verify installation type `npm -v`. It should look something like this:  Leave the terminal open. ## Downloading the code to your computer The easiest way to download the code is to download the zip file from the GitHub repo. Remember that first link I told you to open? That's the GitHub repo. Click the green button that says `Code` on it and click `Download ZIP` from the menu.  Now unzip the file and then navigate to the folder in the terminal. To navigate to the folder use the `cd` command. If you unzipped the folder in the `Downloads` folder, you can navigate to the folder by typing `cd ~/Downloads/notacomment-main/`. ## Usage With Strike 1. Create an account with Strike if you don't already have one https://strike.me/download/ 1. Get a Strike API key with all the payment scopes from https://dashboard.strike.me/ 1. Create a .env file and provide NOSTR_NSEC and STRIKE_API_KEY values (see .env.example) 1. Install the dependencies using npm or yarn or whatever your heart desires 1. Make sure you have money in your Strike account 1. Run the script `npm start` Keep in mind that Strike pays the invoices from your cash balance. This means the payment rounds up to the nearest cent when paying an invoice, so if you set the zap amount to 1 sat, you'll be sending more money to Strike than the person you are zapping with every zap. ## Usage With LNbits I recommend making a separate wallet from your main LNbits wallet for usage with notacomment in case you accidentally leak the admin key. 1. Create a .env file and provide NOSTR_NSEC, LNBITS_ADMIN_KEY, and LNBITS_URL values (see .env.example) 1. Install the dependencies using npm or yarn or whatever your heart desires 1. Make sure you have sats in your LNbits wallet 1. Run the script `npm start` ## Usage With Nostr Wallet Connect 1. Create a NWC connection string using something like https://nwc.getalby.com/ 1. Create a .env file and provide NOSTR_NSEC and NWC_CONNECTION_STRING values (see .env.example) 1. Install the dependencies using npm or yarn or whatever your heart desires 1. Make sure you have sats in your wallet that you generated the NWC connection string with 1. Run the script `npm start` <br /> <br /> Screenshot of terminal with commands to install dependencies, create .env file, open .env file, and start the script:  @ 1cb14ab3:95d52462
2025-02-08 16:45:04***Tree branches. 4'8" circle. [Chongming Island, China. 2021]*** --- #### Introduction Tucked into a quiet forest park on Chongming Island, Chongming frames a view of a canal and a small alluvial landform that mirrors the island itself. This lens reflects the constant interplay of land and water, inviting viewers to contemplate the delicate balance of nature and the forces that shape it. #### Site & Placement The lens is hidden along a forest path, directing attention to the canal’s subtle currents and the land it divides. The bench, situated 12 feet from the lens, encourages visitors to pause and immerse themselves in the tranquil rhythm of the scene. #### Impermanence & Integration As an alluvial island shaped by shifting waters, Chongming is a fitting location for this ephemeral lens. Constructed from branches, the lens will eventually return to the land, echoing the natural processes that formed the island and continue to shape it. #### Reflection *Chongming* offers a meditative space to reflect on the impermanence of land and the forces that transform it. The work’s fleeting existence underscores the beauty of change, inviting viewers to appreciate the subtle, ongoing dance of nature. --- ## Photos         --- #### More from the 'Earth Lens' Series: [Earth Lens Series: Artist Statement + List of Works](https://hes.npub.pro/post/1731091744332/) ["Looking Glass" (Earth Lens 001)](https://hes.npub.pro/post/1736304563962/) ["Folsom" (Earth Lens 002)](https://hes.npub.pro/post/1737844073125/) ["Sanctuary" (Earth Lens 003)](https://hes.npub.pro/post/1731091744332/) ["Platte" (Earth Lens 004)](https://hes.npub.pro/post/sya8nv6q8k0w3olqcepwz) ["Grandfather" (Earth Lens 005)](https://hes.npub.pro/) --- #### More from Hes [Portfolio](https://hesart.npub.pro) [Online Store](https://plebeian.market/community/hes@nostrplebs.com/hesmart-ym3fcufdfz) [Artist Statements](https://hes.npub.pro/tag/art/) [Travel Guides](https://hes.npub.pro/tag/travel/) [Photography](https://hes.npub.pro/tag/photography) [Money](https://hes.npub.pro/tag/money) [Tech](https://hes.npub.pro/tag/tech) --- *All images are credit of Hes, but you are free to download and use for any purpose. If you find joy from my art, please feel free to send a zap. Enjoy life on a Bitcoin standard.*
@ 1cb14ab3:95d52462
2025-02-08 16:45:04***Tree branches. 4'8" circle. [Chongming Island, China. 2021]*** --- #### Introduction Tucked into a quiet forest park on Chongming Island, Chongming frames a view of a canal and a small alluvial landform that mirrors the island itself. This lens reflects the constant interplay of land and water, inviting viewers to contemplate the delicate balance of nature and the forces that shape it. #### Site & Placement The lens is hidden along a forest path, directing attention to the canal’s subtle currents and the land it divides. The bench, situated 12 feet from the lens, encourages visitors to pause and immerse themselves in the tranquil rhythm of the scene. #### Impermanence & Integration As an alluvial island shaped by shifting waters, Chongming is a fitting location for this ephemeral lens. Constructed from branches, the lens will eventually return to the land, echoing the natural processes that formed the island and continue to shape it. #### Reflection *Chongming* offers a meditative space to reflect on the impermanence of land and the forces that transform it. The work’s fleeting existence underscores the beauty of change, inviting viewers to appreciate the subtle, ongoing dance of nature. --- ## Photos         --- #### More from the 'Earth Lens' Series: [Earth Lens Series: Artist Statement + List of Works](https://hes.npub.pro/post/1731091744332/) ["Looking Glass" (Earth Lens 001)](https://hes.npub.pro/post/1736304563962/) ["Folsom" (Earth Lens 002)](https://hes.npub.pro/post/1737844073125/) ["Sanctuary" (Earth Lens 003)](https://hes.npub.pro/post/1731091744332/) ["Platte" (Earth Lens 004)](https://hes.npub.pro/post/sya8nv6q8k0w3olqcepwz) ["Grandfather" (Earth Lens 005)](https://hes.npub.pro/) --- #### More from Hes [Portfolio](https://hesart.npub.pro) [Online Store](https://plebeian.market/community/hes@nostrplebs.com/hesmart-ym3fcufdfz) [Artist Statements](https://hes.npub.pro/tag/art/) [Travel Guides](https://hes.npub.pro/tag/travel/) [Photography](https://hes.npub.pro/tag/photography) [Money](https://hes.npub.pro/tag/money) [Tech](https://hes.npub.pro/tag/tech) --- *All images are credit of Hes, but you are free to download and use for any purpose. If you find joy from my art, please feel free to send a zap. Enjoy life on a Bitcoin standard.* @ 8d5ba92c:c6c3ecd5
2025-01-30 15:58:03For me, it’s simple yet profound: a job and labor aren’t the same thing. You don’t have to struggle to perform a task or to meet someone else's unrealistic expectations. In fact, if you genuinely enjoy what you’re doing and believe in its purpose, the results will naturally be better—and everyone benefits. I’m speaking from the perspective of someone who walked away from a "*well-established career*" multiple times. These days, I might be working more than ever, but I don’t feel tired, frustrated, or burned out. The radical change I made—leaving the "*professional fiat world*" behind—wasn’t easy, but I’ve never regretted it. Now, working fully in Bitcoin, I feel more motivated and satisfied than ever before. Sure, it's not always straightforward. This lifestyle definitely comes with its challenges. But those challenges don’t crush me. Just the opposite. When combined with a sense of freedom, they become opportunities for growth—something I truly value. It’s a completely different experience compared to most jobs rooted in the old system. I’m not saying working in Bitcoin is all sunshine and rainbows, nor am I criticizing anyone still working in fiat. What I’m trying to emphasize is the core message of that quote: ## Do what you love, and you’ll never work a day in your life... Read it aloud and think about your last couple of jobs. How did you feel? Did you find fulfillment and satisfaction, or was it more like a form of slavery that made you dread going to bed and waking up every morning? I didn’t really have those feelings, except for one corporation at the beginning of my career, which gave me a hard time but also taught me valuable lessons. Aside from that experience, most of my jobs weren’t too bad—no need to complain. Still, I often questioned my situation: '*Seriously, why do I have to do this or that if I know it doesn’t make sense?*' Doing things you don’t believe in can lead to frustration, often in ways you might not even realize, yet every time, significantly affecting your well-being and the people around you. Now, I hardly know what inner anger means. I wake up happy, full of passion and ideas. I don’t track the hours as they pass; instead, I focus on all the tasks I complete and how they make a difference for me and others. Yes, I love what I do. And returning to the main point of this article, I shouldn’t even see it as work, even though in practice it definitely is. The key here is a mix of independence, purpose, and self-determination. Bitcoin has helped me achieve that to a level that’s hard to break. ## A Fresh Take on The Market I also remember that 5-7 years ago, especially for non-devs, Bitcoin-based jobs weren’t as accessible as they are now (which is probably why I stayed in my traditional career for so long...). It’s really only in the last, maybe 2-3 years that things have changed. With so many areas expanding beyond just mining and tech-related stuff, and new interesting projects popping up regularly, there’s almost any position you can imagine to jump into. According to a recent report by [Bitvocation](https://linktr.ee/bitvocation) '69% of Bitcoin jobs are non-developer roles'. Also, more than half of available positions in 2024 offered remote opportunities, giving job seekers extra flexibility. Bitcoin is borderless—and so are many of the jobs in this space. If you’ve ever thought working in Bitcoin was out of reach, think again—and check this out "[BITCOIN JOB MARKET DATA, 2024 Report](https://drive.google.com/file/d/1ZFnYP949GzssQHA9wcjHTeW4cDiZIWvM/view)". One tip from my experience: a good option is to start with a part-time role while keeping your traditional fiat job for more stability, especially at the beginning. After a while, you’ll gain more confidence and see which direction you want to go. Or, if you position yourself so that you don’t need to earn a lot for the next 3-6 months, consider finding a project- or task-based Bitcoin job, maybe even just an internship. Meanwhile, you might decide to focus on building something unique on your own. It can feel amazing! You’ll gain valuable skills, sharpen your experience, and better understand which options work best for your future. You see, just like in nature, balance is key. You don’t have to run before you can walk. What I’m saying is this: **The choice is yours, as long as you plan ahead + learn, while staying true to your needs, beliefs, and priorities.** If you want it, do it. Starting a career in Bitcoin is possible, and I have a feeling this space will grow even faster in the next few years. Yes, there will still be ups and downs (hello, bear markets!), but if you plan thoughtfully, there’s not much to worry about. We’re still early—Bitcoin is only 16 years old—but if you’ve been following this space, you’ve probably seen how dynamic and resilient it is. If you’ve ever thought about working in Bitcoin, now is the time to rethink the possibilities :))) BTC Your Mind. Let it Beat. Şelale
@ 8d5ba92c:c6c3ecd5
2025-01-30 15:58:03For me, it’s simple yet profound: a job and labor aren’t the same thing. You don’t have to struggle to perform a task or to meet someone else's unrealistic expectations. In fact, if you genuinely enjoy what you’re doing and believe in its purpose, the results will naturally be better—and everyone benefits. I’m speaking from the perspective of someone who walked away from a "*well-established career*" multiple times. These days, I might be working more than ever, but I don’t feel tired, frustrated, or burned out. The radical change I made—leaving the "*professional fiat world*" behind—wasn’t easy, but I’ve never regretted it. Now, working fully in Bitcoin, I feel more motivated and satisfied than ever before. Sure, it's not always straightforward. This lifestyle definitely comes with its challenges. But those challenges don’t crush me. Just the opposite. When combined with a sense of freedom, they become opportunities for growth—something I truly value. It’s a completely different experience compared to most jobs rooted in the old system. I’m not saying working in Bitcoin is all sunshine and rainbows, nor am I criticizing anyone still working in fiat. What I’m trying to emphasize is the core message of that quote: ## Do what you love, and you’ll never work a day in your life... Read it aloud and think about your last couple of jobs. How did you feel? Did you find fulfillment and satisfaction, or was it more like a form of slavery that made you dread going to bed and waking up every morning? I didn’t really have those feelings, except for one corporation at the beginning of my career, which gave me a hard time but also taught me valuable lessons. Aside from that experience, most of my jobs weren’t too bad—no need to complain. Still, I often questioned my situation: '*Seriously, why do I have to do this or that if I know it doesn’t make sense?*' Doing things you don’t believe in can lead to frustration, often in ways you might not even realize, yet every time, significantly affecting your well-being and the people around you. Now, I hardly know what inner anger means. I wake up happy, full of passion and ideas. I don’t track the hours as they pass; instead, I focus on all the tasks I complete and how they make a difference for me and others. Yes, I love what I do. And returning to the main point of this article, I shouldn’t even see it as work, even though in practice it definitely is. The key here is a mix of independence, purpose, and self-determination. Bitcoin has helped me achieve that to a level that’s hard to break. ## A Fresh Take on The Market I also remember that 5-7 years ago, especially for non-devs, Bitcoin-based jobs weren’t as accessible as they are now (which is probably why I stayed in my traditional career for so long...). It’s really only in the last, maybe 2-3 years that things have changed. With so many areas expanding beyond just mining and tech-related stuff, and new interesting projects popping up regularly, there’s almost any position you can imagine to jump into. According to a recent report by [Bitvocation](https://linktr.ee/bitvocation) '69% of Bitcoin jobs are non-developer roles'. Also, more than half of available positions in 2024 offered remote opportunities, giving job seekers extra flexibility. Bitcoin is borderless—and so are many of the jobs in this space. If you’ve ever thought working in Bitcoin was out of reach, think again—and check this out "[BITCOIN JOB MARKET DATA, 2024 Report](https://drive.google.com/file/d/1ZFnYP949GzssQHA9wcjHTeW4cDiZIWvM/view)". One tip from my experience: a good option is to start with a part-time role while keeping your traditional fiat job for more stability, especially at the beginning. After a while, you’ll gain more confidence and see which direction you want to go. Or, if you position yourself so that you don’t need to earn a lot for the next 3-6 months, consider finding a project- or task-based Bitcoin job, maybe even just an internship. Meanwhile, you might decide to focus on building something unique on your own. It can feel amazing! You’ll gain valuable skills, sharpen your experience, and better understand which options work best for your future. You see, just like in nature, balance is key. You don’t have to run before you can walk. What I’m saying is this: **The choice is yours, as long as you plan ahead + learn, while staying true to your needs, beliefs, and priorities.** If you want it, do it. Starting a career in Bitcoin is possible, and I have a feeling this space will grow even faster in the next few years. Yes, there will still be ups and downs (hello, bear markets!), but if you plan thoughtfully, there’s not much to worry about. We’re still early—Bitcoin is only 16 years old—but if you’ve been following this space, you’ve probably seen how dynamic and resilient it is. If you’ve ever thought about working in Bitcoin, now is the time to rethink the possibilities :))) BTC Your Mind. Let it Beat. Şelale @ ec42c765:328c0600
2025-02-05 23:45:09test test
@ ec42c765:328c0600
2025-02-05 23:45:09test test @ 6e75f797:a8eee74e
2023-08-07 13:16:42Last night I started a nostr community multiplayer instance for No Man's Sky [on ZapStream](https://zap.stream/) and before we knew it, we had 4 Nostrichs arriving on the genesis planet to join the fun.  NSM is an deterministic, procedurally generated open universe where players can explore, quest, build, combat and have fun together. Every new system discovered is generated when the first Traveller enters the system making the game a unique experience for any open world gaming fan. If you fancy joining us in the Nostrverse let me know and I'll friend you in #NMS and on Steam or Epic. If you just want to watch the fun, participate in naming systems, planets, fauna and flora come and hang out in my stream or the stream of [Oceanbee](nostr:npub1wqxxe0cjaxnvmrv4lkvx8d5dlft7ewswyn09w5v7fg7642fgzm7srucxws), [HolgerHatGarKeineNode](nostr:npub1pt0kw36ue3w2g4haxq3wgm6a2fhtptmzsjlc2j2vphtcgle72qesgpjyc6) or [taette](npub1yh0dl6pazf55025qvp860lstpscuy0kj2a5lfhxlk400m968vgpql5vsnd).  ### If you already own NMS, feel free to add me! My NMS friend code is: EMAZ-KMHT-ZPFXP See you in space Traveller! - TheGrinder
@ 6e75f797:a8eee74e
2023-08-07 13:16:42Last night I started a nostr community multiplayer instance for No Man's Sky [on ZapStream](https://zap.stream/) and before we knew it, we had 4 Nostrichs arriving on the genesis planet to join the fun.  NSM is an deterministic, procedurally generated open universe where players can explore, quest, build, combat and have fun together. Every new system discovered is generated when the first Traveller enters the system making the game a unique experience for any open world gaming fan. If you fancy joining us in the Nostrverse let me know and I'll friend you in #NMS and on Steam or Epic. If you just want to watch the fun, participate in naming systems, planets, fauna and flora come and hang out in my stream or the stream of [Oceanbee](nostr:npub1wqxxe0cjaxnvmrv4lkvx8d5dlft7ewswyn09w5v7fg7642fgzm7srucxws), [HolgerHatGarKeineNode](nostr:npub1pt0kw36ue3w2g4haxq3wgm6a2fhtptmzsjlc2j2vphtcgle72qesgpjyc6) or [taette](npub1yh0dl6pazf55025qvp860lstpscuy0kj2a5lfhxlk400m968vgpql5vsnd).  ### If you already own NMS, feel free to add me! My NMS friend code is: EMAZ-KMHT-ZPFXP See you in space Traveller! - TheGrinder @ cbd2779f:72a5b029
2025-01-30 15:08:13Have a few questions pertaining to setting up a new node. Basically, I always seems to be unsure about syncing to graph, after syncing to chain. Consider setting up a new node from scratch, or migrating perhaps, and you want to do an initial setup. 1. How long does it take? 2. What factors determine how long it takes? 3. Is the graph a universal graph that is identical from each nodes perspective? So far, I'm monitoring progress but tailing logs, looking for clues: `tail -n 100 /data/lnd/logs/bitcoin/mainnet/lnd.log | grep GRPH` I can find some relevant clues like: ``` 2025-01-30 15:24:54.843 [INF] GRPH: Processed channels=56 updates=59 nodes=15 in last 59.823699481s ``` and then checking with: `lncli getinfo | grep -E 'synced|peers` which outputs ``` "num_peers": 3, "synced_to_chain": true, "synced_to_graph": false, ``` At the moment, I've been experimenting with pruned blockchains and this outputs a lot of errors (I believe) relating to not being able to verify UTXOs as I have `ignore-historical-gossip-filters set to true. Any further suggestions on how to better make sure things are happening under the hood when setting up a new node, what to look for in the logs or how to know the verification progress? originally posted at https://stacker.news/items/869944
@ cbd2779f:72a5b029
2025-01-30 15:08:13Have a few questions pertaining to setting up a new node. Basically, I always seems to be unsure about syncing to graph, after syncing to chain. Consider setting up a new node from scratch, or migrating perhaps, and you want to do an initial setup. 1. How long does it take? 2. What factors determine how long it takes? 3. Is the graph a universal graph that is identical from each nodes perspective? So far, I'm monitoring progress but tailing logs, looking for clues: `tail -n 100 /data/lnd/logs/bitcoin/mainnet/lnd.log | grep GRPH` I can find some relevant clues like: ``` 2025-01-30 15:24:54.843 [INF] GRPH: Processed channels=56 updates=59 nodes=15 in last 59.823699481s ``` and then checking with: `lncli getinfo | grep -E 'synced|peers` which outputs ``` "num_peers": 3, "synced_to_chain": true, "synced_to_graph": false, ``` At the moment, I've been experimenting with pruned blockchains and this outputs a lot of errors (I believe) relating to not being able to verify UTXOs as I have `ignore-historical-gossip-filters set to true. Any further suggestions on how to better make sure things are happening under the hood when setting up a new node, what to look for in the logs or how to know the verification progress? originally posted at https://stacker.news/items/869944 @ ec42c765:328c0600
2025-02-05 23:43:35test
@ ec42c765:328c0600
2025-02-05 23:43:35test @ f57bac88:6045161e
2025-02-08 15:50:22### ریشههای تاریخی جشن کژین جشن کژین که در برخی منابع به نام «بادروز» نیز شناخته میشود، ریشه در اسطورههای کهن ایران دارد. در اوستا، باد با نام «واتَه» معرفی شده است و ایزد نگهبان آن، «وات» یا «واد» یکی از ایزدان مهم در کیش زرتشتی به شمار میرود. این ایزد در باورهای ایرانیان باستان، تجسم نیروی پاک و الهی باد بوده و مسئول جابهجایی ابرها، بارش باران و حفاظت از زمین در برابر آلودگیها محسوب میشده است. بر اساس تقویم کهن ایران، این جشن در روز بیستودوم بهمنماه، که مصادف با روز باد در تقویم زرتشتی است، برگزار میشد. برخی پژوهشگران معتقدند که جشن کژین در دورههای مختلف تاریخی، تحت تأثیر تغییرات فرهنگی و اجتماعی دچار دگرگونی شده و نامها و شیوههای مختلفی به خود گرفته است. ### فلسفه و نمادشناسی جشن کژین باد، به عنوان یکی از چهار عنصر اصلی (آب، باد، خاک و آتش) در باورهای کهن ایرانی، جایگاه ویژهای داشته است. ایرانیان باستان باد را نیرویی زنده و الهی میدانستند که حیات را در طبیعت جاری میسازد. در بسیاری از متون دینی و اساطیری، باد به عنوان پیامرسان ایزدان و نیرویی که قدرت پاککنندگی دارد، توصیف شده است. جشن کژین، علاوه بر تقدیس باد، نماد تحول، تغییر و تجدید حیات نیز بوده است. این جشن نشانگر گذر از یک مرحله به مرحلهای دیگر در چرخه طبیعت است و ارتباطی عمیق با دیگر جشنهای ایرانی مانند جشن سده و نوروز دارد. ### آیینها و رسوم جشن کژین برگزاری جشن کژین با آیینهای خاصی همراه بوده است که برخی از آنها هنوز در فرهنگ عامه ایرانیان قابل مشاهدهاند: 1. **رها کردن نوارهای رنگین در باد**: یکی از رسوم این جشن، آویختن نوارهایی از نخ هفترنگ به شاخههای درختان یا رها کردن آنها در باد بوده است. این عمل نماد رهایی، تحول و ارتباط با نیروی الهی باد محسوب میشده است. 2. **افروختن آتش**: مانند بسیاری از جشنهای ایرانی، روشن کردن آتش یکی از بخشهای اصلی جشن کژین بوده است. این آتش معمولاً در فضای باز و بر فراز تپهها و کوهها برافروخته میشد تا حرمت باد و آتش، دو عنصر اصلی طبیعت، گرامی داشته شود. 3. **برپایی بازارهای محلی و جشنهای خیابانی**: در برخی مناطق، جشن کژین با بازارهای محلی همراه بوده که در آن مردم به خرید و فروش کالاهای سنتی، موسیقی و پایکوبی میپرداختند. این بازارها اغلب در میادین شهرها و روستاها برگزار میشد و نوعی جشن اجتماعی به شمار میرفت. 4. **دعای شکرگزاری برای بادهای سودمند**: در فرهنگ کشاورزی ایران، باد نقش مهمی در گردهافشانی گیاهان و بارش باران داشته است. ازاینرو، کشاورزان و مردم روستاها در این روز دعاهایی برای بادهای مفید و پرهیز از بادهای مضر میخواندند. ### ارتباط جشن کژین با دیگر جشنهای ایرانی جشن کژین با برخی دیگر از آیینهای کهن ایرانی ارتباط نزدیکی دارد. به عنوان مثال، جشن سده که در میانه زمستان برگزار میشود، یکی از جشنهایی است که در آن نیز باد و آتش نقش مهمی دارند. از سوی دیگر، جشن نوروز که سرآغاز فصل بهار است، نشانگر تحول و دگرگونی طبیعت است که ارتباطی مفهومی با جشن کژین دارد. ### جایگاه جشن کژین در دوران معاصر امروزه، جشن کژین در میان بسیاری از ایرانیان ناشناخته باقی مانده است و تنها برخی از پژوهشگران و علاقهمندان به فرهنگ ایران باستان به احیای آن علاقه نشان میدهند. با این حال، عناصر این جشن در برخی آیینهای محلی و جشنهای مردمی همچنان باقی مانده است. تلاش برای بازشناسی و احیای این جشن میتواند به غنای فرهنگی و هویت ملی ایرانیان کمک کند. ### نتیجهگیری جشن کژین یکی از آیینهای فراموششده اما ارزشمند ایران باستان است که در ستایش باد و نقش آن در طبیعت و زندگی انسانها برگزار میشده است. این جشن، علاوه بر نمادگرایی مرتبط با عناصر چهارگانه، پیوندی عمیق با باورهای اسطورهای و اجتماعی ایرانیان داشته است. احیای این جشن و آشنایی بیشتر با آن، میتواند به فهم بهتر تاریخ فرهنگی ایران و تقویت حس هویت ملی کمک کند.
@ f57bac88:6045161e
2025-02-08 15:50:22### ریشههای تاریخی جشن کژین جشن کژین که در برخی منابع به نام «بادروز» نیز شناخته میشود، ریشه در اسطورههای کهن ایران دارد. در اوستا، باد با نام «واتَه» معرفی شده است و ایزد نگهبان آن، «وات» یا «واد» یکی از ایزدان مهم در کیش زرتشتی به شمار میرود. این ایزد در باورهای ایرانیان باستان، تجسم نیروی پاک و الهی باد بوده و مسئول جابهجایی ابرها، بارش باران و حفاظت از زمین در برابر آلودگیها محسوب میشده است. بر اساس تقویم کهن ایران، این جشن در روز بیستودوم بهمنماه، که مصادف با روز باد در تقویم زرتشتی است، برگزار میشد. برخی پژوهشگران معتقدند که جشن کژین در دورههای مختلف تاریخی، تحت تأثیر تغییرات فرهنگی و اجتماعی دچار دگرگونی شده و نامها و شیوههای مختلفی به خود گرفته است. ### فلسفه و نمادشناسی جشن کژین باد، به عنوان یکی از چهار عنصر اصلی (آب، باد، خاک و آتش) در باورهای کهن ایرانی، جایگاه ویژهای داشته است. ایرانیان باستان باد را نیرویی زنده و الهی میدانستند که حیات را در طبیعت جاری میسازد. در بسیاری از متون دینی و اساطیری، باد به عنوان پیامرسان ایزدان و نیرویی که قدرت پاککنندگی دارد، توصیف شده است. جشن کژین، علاوه بر تقدیس باد، نماد تحول، تغییر و تجدید حیات نیز بوده است. این جشن نشانگر گذر از یک مرحله به مرحلهای دیگر در چرخه طبیعت است و ارتباطی عمیق با دیگر جشنهای ایرانی مانند جشن سده و نوروز دارد. ### آیینها و رسوم جشن کژین برگزاری جشن کژین با آیینهای خاصی همراه بوده است که برخی از آنها هنوز در فرهنگ عامه ایرانیان قابل مشاهدهاند: 1. **رها کردن نوارهای رنگین در باد**: یکی از رسوم این جشن، آویختن نوارهایی از نخ هفترنگ به شاخههای درختان یا رها کردن آنها در باد بوده است. این عمل نماد رهایی، تحول و ارتباط با نیروی الهی باد محسوب میشده است. 2. **افروختن آتش**: مانند بسیاری از جشنهای ایرانی، روشن کردن آتش یکی از بخشهای اصلی جشن کژین بوده است. این آتش معمولاً در فضای باز و بر فراز تپهها و کوهها برافروخته میشد تا حرمت باد و آتش، دو عنصر اصلی طبیعت، گرامی داشته شود. 3. **برپایی بازارهای محلی و جشنهای خیابانی**: در برخی مناطق، جشن کژین با بازارهای محلی همراه بوده که در آن مردم به خرید و فروش کالاهای سنتی، موسیقی و پایکوبی میپرداختند. این بازارها اغلب در میادین شهرها و روستاها برگزار میشد و نوعی جشن اجتماعی به شمار میرفت. 4. **دعای شکرگزاری برای بادهای سودمند**: در فرهنگ کشاورزی ایران، باد نقش مهمی در گردهافشانی گیاهان و بارش باران داشته است. ازاینرو، کشاورزان و مردم روستاها در این روز دعاهایی برای بادهای مفید و پرهیز از بادهای مضر میخواندند. ### ارتباط جشن کژین با دیگر جشنهای ایرانی جشن کژین با برخی دیگر از آیینهای کهن ایرانی ارتباط نزدیکی دارد. به عنوان مثال، جشن سده که در میانه زمستان برگزار میشود، یکی از جشنهایی است که در آن نیز باد و آتش نقش مهمی دارند. از سوی دیگر، جشن نوروز که سرآغاز فصل بهار است، نشانگر تحول و دگرگونی طبیعت است که ارتباطی مفهومی با جشن کژین دارد. ### جایگاه جشن کژین در دوران معاصر امروزه، جشن کژین در میان بسیاری از ایرانیان ناشناخته باقی مانده است و تنها برخی از پژوهشگران و علاقهمندان به فرهنگ ایران باستان به احیای آن علاقه نشان میدهند. با این حال، عناصر این جشن در برخی آیینهای محلی و جشنهای مردمی همچنان باقی مانده است. تلاش برای بازشناسی و احیای این جشن میتواند به غنای فرهنگی و هویت ملی ایرانیان کمک کند. ### نتیجهگیری جشن کژین یکی از آیینهای فراموششده اما ارزشمند ایران باستان است که در ستایش باد و نقش آن در طبیعت و زندگی انسانها برگزار میشده است. این جشن، علاوه بر نمادگرایی مرتبط با عناصر چهارگانه، پیوندی عمیق با باورهای اسطورهای و اجتماعی ایرانیان داشته است. احیای این جشن و آشنایی بیشتر با آن، میتواند به فهم بهتر تاریخ فرهنگی ایران و تقویت حس هویت ملی کمک کند.