-

@ 4857600b:30b502f4
2025-02-20 19:09:11
Mitch McConnell, a senior Republican senator, announced he will not seek reelection.
At 83 years old and with health issues, this decision was expected. After seven terms, he leaves a significant legacy in U.S. politics, known for his strategic maneuvering.
McConnell stated, “My current term in the Senate will be my last.” His retirement marks the end of an influential political era.
-

@ a012dc82:6458a70d
2025-02-20 15:02:29
The Financial Accounting Standards Board (FASB) has recently introduced a groundbreaking ruling that significantly alters the way Bitcoin and other cryptocurrencies are accounted for in financial statements. This new development is poised to transform the landscape of crypto accounting, bringing in more transparency and alignment with traditional financial practices. Let's delve into the details of this pivotal change.
**Table of Contents**
- Introduction to the New FASB Ruling
- The Shift to Fair Value Accounting
- Understanding Fair Value Accounting
- Impact on Financial Reporting
- Advantages of the New Approach
- Enhanced Transparency and Accuracy
- Positive Implications for Companies
- Challenges and Considerations
- Dealing with Volatility
- Auditor Expertise
- Industry Response and Future Outlook
- Embracing the Change
- Long-Term Implications
- Conclusion
- FAQs
**Introduction to the New FASB Ruling**
The FASB, the principal body responsible for establishing accounting standards in the United States, announced a new set of rules concerning the accounting of cryptocurrencies like Bitcoin. This announcement marks a significant shift from the previous accounting practices for digital assets. Previously, the lack of clear guidelines led to inconsistencies and uncertainties in how companies reported their crypto holdings. The new ruling aims to standardize these practices and reflects the growing importance of cryptocurrencies in the financial world.
**The Shift to Fair Value Accounting**
**Understanding Fair Value Accounting**
Under the new FASB rules, companies are now required to account for cryptocurrencies at their fair value. Fair value accounting involves assessing assets and liabilities based on their current market value, rather than their historical cost. This approach is expected to provide a more accurate and real-time reflection of a company's financial status. It marks a significant departure from the traditional cost-based accounting methods, which often do not reflect the current market realities, especially in the case of highly volatile assets like cryptocurrencies.
**Impact on Financial Reporting**
This shift to fair value accounting means that companies holding cryptocurrencies will report the value of these assets based on their market prices at the end of each reporting period. This move is a departure from the previous method where Bitcoin was treated as an intangible asset, leading to certain limitations in financial reporting. For instance, under the old rules, if the value of Bitcoin fell below its purchase price, companies had to report a loss, but they couldn't report an increase in value unless the asset was sold. The new approach allows for a more dynamic and responsive reporting system that better reflects the economic realities of holding cryptocurrencies.
**Advantages of the New Approach**
**Enhanced Transparency and Accuracy**
One of the primary benefits of this new ruling is the increased transparency and accuracy it brings to financial reporting. Companies can now reflect the actual market value of their crypto holdings, providing a clearer picture of their financial health. This change is particularly significant given the volatile nature of cryptocurrencies. By reporting the fair market value, companies can provide stakeholders with a more accurate depiction of their financial standing, which is crucial for informed decision-making by investors, regulators, and other stakeholders.
**Positive Implications for Companies**
Companies are likely to welcome this change as it allows them to report unrealized gains and losses on cryptocurrencies. This could encourage more businesses to add cryptocurrencies like Bitcoin to their balance sheets, as they can now recognize the appreciation in value without needing to sell the assets. This change could also lead to a broader acceptance of cryptocurrencies as a legitimate and valuable asset class, potentially spurring further investment and innovation in the crypto space.
**Challenges and Considerations**
**Dealing with Volatility**
The inherent volatility of cryptocurrencies like Bitcoin poses a significant challenge in fair value accounting. Companies will need to develop robust methods to accurately assess the market value of these assets, which can fluctuate widely. This volatility requires continuous monitoring and frequent valuation adjustments, which can be resource-intensive and complex. Companies will need to invest in sophisticated valuation models and possibly seek external expertise to ensure accuracy and compliance.
**Auditor Expertise**
Another challenge lies in the need for auditors to acquire expertise in valuing cryptocurrencies. Assessing the fair market value of digital assets is a complex task that requires specific knowledge and skills. Auditors will need to stay abreast of the rapidly evolving crypto market and develop new methodologies for valuation. This requirement not only adds a layer of complexity to the audit process but also underscores the need for ongoing education and training in this emerging field.
**Industry Response and Future Outlook**
**Embracing the Change**
The industry's response to the FASB's ruling has been largely positive. Industry leaders view this as a step towards mainstream acceptance of cryptocurrencies and a move that aligns digital assets with traditional financial reporting standards. This ruling is seen as a validation of the growing role of cryptocurrencies in the financial sector and a sign that regulatory bodies are beginning to recognize and adapt to the unique characteristics of these digital assets.
**Long-Term Implications**
In the long run, this ruling could lead to greater institutional adoption of cryptocurrencies. As financial reporting becomes more standardized and transparent, it may foster greater trust and confidence among investors and regulators. This could pave the way for more widespread use of cryptocurrencies in various financial transactions and potentially influence the development of new financial products and services centered around digital assets.
**Conclusion**
The FASB's latest ruling on cryptocurrency accounting is a landmark decision that aligns the treatment of digital assets with traditional financial practices. While it presents certain challenges, particularly in terms of volatility and the need for specialized auditor expertise, the overall impact is expected to be profoundly positive. This change not only enhances transparency and accuracy in financial reporting but also paves the way for broader acceptance and integration of cryptocurrencies in the mainstream financial world. As the industry adapts to these new rules, we can expect to see a more mature and robust crypto market, potentially leading to innovative financial solutions and greater economic opportunities.
**FAQs**
**When will the new FASB rules take effect?**
The new rules are set to take effect from December 15, 2024, but companies have the option to apply them earlier.
**How does fair value accounting affect financial reporting?**
Fair value accounting allows companies to report the value of cryptocurrencies based on current market prices, providing a more accurate and real-time reflection of a company's financial status.
**What are the benefits of the new FASB ruling?**
The new ruling enhances transparency and accuracy in financial reporting and encourages more businesses to add cryptocurrencies to their balance sheets by allowing them to report unrealized gains and losses.
**What challenges does the new ruling present?**
The main challenges include dealing with the volatility of cryptocurrencies in fair value accounting and the need for auditors to develop expertise in valuing these digital assets.
**What is the industry's response to the new ruling?**
The industry has largely responded positively, viewing it as a step towards mainstream acceptance of cryptocurrencies and alignment with traditional financial reporting standards.
**That's all for today**
**If you want more, be sure to follow us on:**
**NOSTR: croxroad@getalby.com**
**X: [@croxroadnews.co](https://x.com/croxroadnewsco)**
**Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)**
**Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)**
**Store: https://croxroad.store**
**Subscribe to CROX ROAD Bitcoin Only Daily Newsletter**
**https://www.croxroad.co/subscribe**
***DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.***
-

@ d360efec:14907b5f
2025-02-20 10:16:03
**ภาพรวม BTCUSDT (OKX):**
Bitcoin (BTCUSDT) ยังคงแสดงความผันผวนและแนวโน้มที่ไม่ชัดเจน แม้ว่าแนวโน้มระยะยาว (TF Day) จะยังคงมีลักษณะเป็นขาขึ้น (แต่*อ่อนแรงลงอย่างมาก*) แนวโน้มระยะกลาง (TF4H) และระยะสั้น (TF15) เป็นขาลง การวิเคราะห์ครั้งนี้จะเน้นไปที่การระบุระดับราคาที่ Smart Money อาจจะเข้ามามีส่วนร่วม และการประเมินความแข็งแกร่งของแนวโน้ม
**วิเคราะห์ทีละ Timeframe:**
**(1) TF Day (รายวัน):**

* **แนวโน้ม:** ขาขึ้น (Uptrend) *อ่อนแรงลงอย่างมาก, มีความเสี่ยงที่จะเปลี่ยนแนวโน้ม*
* **SMC:**
* Higher Highs (HH) และ Higher Lows (HL) *เริ่มไม่ชัดเจน, ราคาหลุด Low ก่อนหน้า*
* Break of Structure (BOS) ด้านบน *แต่มีการปรับฐานที่รุนแรง*
* **Liquidity:**
* มี Sellside Liquidity (SSL) อยู่ใต้ Lows ก่อนหน้า (บริเวณ 85,000 - 90,000)
* มี Buyside Liquidity (BSL) อยู่เหนือ High เดิม
* **ICT:**
* **Order Block:** ราคาหลุด Order Block ขาขึ้น (บริเวณแท่งเทียนสีเขียวก่อนหน้านี้) *สัญญาณลบ*
* **EMA:**
* ราคา *หลุด* EMA 50 (สีเหลือง) ลงมาแล้ว
* EMA 200 (สีขาว) เป็นแนวรับถัดไป
* **Money Flow (LuxAlgo):**
* *สีแดงยาว* แสดงถึงแรงขายที่แข็งแกร่ง
* **Trend Strength (AlgoAlpha):**
* สีแดง (เมฆแดง) แสดงถึงแนวโน้มขาลง *และไม่มีสัญญาณซื้อ/ขายปรากฏ*
* **Volume Profile:** Volume ค่อนข้างเบาบาง
* **แท่งเทียน:** แท่งเทียนล่าสุดเป็นสีแดง แสดงถึงแรงขาย
* **แนวรับ:** EMA 200, บริเวณ 85,000 - 90,000 (SSL)
* **แนวต้าน:** EMA 50, High เดิม
* **สรุป:** แนวโน้มขาขึ้นอ่อนแรงลงอย่างมาก, *สัญญาณอันตรายหลายอย่าง*, Money Flow และ Trend Strength เป็นลบ, *หลุด Order Block และ EMA 50*
**(2) TF4H (4 ชั่วโมง):**

* **แนวโน้ม:** ขาลง (Downtrend)
* **SMC:**
* Lower Highs (LH) และ Lower Lows (LL)
* Break of Structure (BOS) ด้านล่าง
* **Liquidity:**
* มี SSL อยู่ใต้ Lows ก่อนหน้า
* มี BSL อยู่เหนือ Highs ก่อนหน้า
* **ICT:**
* **Order Block:** ราคาไม่สามารถผ่าน Order Block ขาลงได้
* **EMA:**
* ราคาอยู่ใต้ EMA 50 และ EMA 200
* **Money Flow (LuxAlgo):**
* สีแดง แสดงถึงแรงขาย
* **Trend Strength (AlgoAlpha):**
* สีเขียว (เมฆเขียว) *แต่ไม่มีสัญญาณซื้อ/ขายปรากฏ*
* **Volume Profile:**
* Volume ค่อนข้างสูง
* **แนวรับ:** บริเวณ Low ล่าสุด
* **แนวต้าน:** EMA 50, EMA 200, บริเวณ Order Block
* **สรุป:** แนวโน้มขาลงชัดเจน, แรงขายมีอิทธิพล, *Trend Strength ขัดแย้งกับ Price Action*
**(3) TF15 (15 นาที):**

* **แนวโน้ม:** ขาลง (Downtrend) *แต่เริ่มเห็นสัญญาณ Sideways*
* **SMC:**
* Lower Highs (LH) และ Lower Lows (LL) *เริ่มเห็นการยก Low เล็กน้อย*
* Break of Structure (BOS) ด้านล่าง
* **ICT:**
* **Order Block:** ราคา Sideways ใกล้ Order Block
* **EMA:**
* EMA 50 และ EMA 200 เป็นแนวต้าน
* **Money Flow (LuxAlgo):**
* แดงสลับเขียว *แต่ส่วนใหญ่ยังเป็นสีแดง*
* **Trend Strength (AlgoAlpha):**
* สีแดง (เมฆแดง) แสดงถึงแนวโน้มขาลง *แต่มีสัญญาณ Bullish Divergence (ราคาทำ Lower Low แต่ Trend Strength ยก Low)*
* **Volume Profile:**
* Volume ค่อนข้างสูง
* **แนวรับ:** บริเวณ Low ล่าสุด
* **แนวต้าน:** EMA 50, EMA 200, Order Block
* **สรุป:** แนวโน้มขาลง, เริ่มพักตัว, Money Flow เริ่มมีความไม่แน่นอน, *Trend Strength มี Divergence*
**สรุปภาพรวมและกลยุทธ์ (BTCUSDT):**
* **แนวโน้มหลัก (Day):** ขาขึ้น (*อ่อนแรงลงอย่างมาก, เสี่ยงที่จะเปลี่ยนแนวโน้ม*)
* **แนวโน้มรอง (4H):** ขาลง
* **แนวโน้มระยะสั้น (15m):** ขาลง (เริ่มพักตัว, *มี Divergence*)
* **Liquidity:** มี SSL ทั้งใน Day, 4H, และ 15m
* **Money Flow:** เป็นลบในทุก Timeframes
* **Trend Strength:** Day/15m เป็นขาลง, 4H เป็นขาขึ้น *แต่ไม่มีสัญญาณ*
* **กลยุทธ์:**
1. **Wait & See (ดีที่สุด):** รอความชัดเจน *โดยเฉพาะการ Breakout หรือ Breakdown จากกรอบ Sideways ใน TF15*
2. **Short (เสี่ยง):** ถ้าไม่สามารถ Breakout EMA/แนวต้านใน TF ใดๆ ได้, หรือเมื่อเกิดสัญญาณ Bearish Continuation
3. ***ไม่แนะนำให้ Buy:*** จนกว่าจะมีสัญญาณกลับตัวที่ชัดเจนมากๆ
**Day Trade & การเทรดรายวัน:**
* **Day Trade (TF15):**
* **Short Bias:** หาจังหวะ Short เมื่อราคาเด้งขึ้นไปทดสอบแนวต้าน (EMA, Order Block)
* **Stop Loss:** เหนือแนวต้านที่เข้า Short
* **Take Profit:** แนวรับถัดไป (Low ล่าสุด)
* **ระวัง:** Bullish Divergence ใน Trend Strength
* **ไม่แนะนำให้ Long**
* **Swing Trade (TF4H):**
* **Short Bias:** รอจังหวะ Short เมื่อราคาไม่สามารถผ่านแนวต้าน EMA หรือ Order Block ได้
* **Stop Loss:** เหนือแนวต้านที่เข้า Short
* **Take Profit:** แนวรับถัดไป
* **ไม่แนะนำให้ Long**
**สิ่งที่ต้องระวัง:**
* **Sellside Liquidity (SSL):** มีโอกาสสูงที่ราคาจะถูกลากลงไปแตะ SSL
* **False Breakouts:** ระวัง
* **Volatility:** สูง
* **Divergence (TF15):** อาจเป็นสัญญาณเริ่มต้นของการกลับตัว *แต่ต้องรอการยืนยัน*
* **Trend Strength (TF4H):** ไม่มีสัญญาณซื้อ/ขาย ต้องระวัง
**Setup Day Trade แบบ SMC (ตัวอย่าง):**
1. **ระบุ Order Block:** หา Order Block ขาลง (Bearish Order Block) ใน TF15 (แท่งเทียนสีเขียวก่อนที่ราคาจะลงแรง)
2. **รอ Pullback:** รอให้ราคา Pullback ขึ้นไปทดสอบ Order Block นั้น
3. **หา Bearish Entry:**
* **Rejection:** รอ Price Action ปฏิเสธ Order Block (เช่น เกิด Pin Bar, Engulfing)
* **Break of Structure:** รอให้ราคา Break โครงสร้างย่อยๆ ใน TF ที่เล็กกว่า (เช่น 1m, 5m) หลังจากที่ทดสอบ Order Block
* **Money Flow:** ดู Money Flow ให้เป็นสีแดง
4. **ตั้ง Stop Loss:** เหนือ Order Block
5. **ตั้ง Take Profit:** แนวรับถัดไป (เช่น Low ล่าสุด) หรือ Order Block ขาขึ้น (Bullish Order Block) ใน TF ที่ใหญ่กว่า
**คำแนะนำ:**
* **ความขัดแย้งของ Timeframes:** มีอยู่ แต่แนวโน้มระยะกลาง-สั้น เป็นลบ
* **Money Flow:** เป็นลบในทุก Timeframes
* **Trend Strength:** เริ่มมี Divergence ใน TF15
* **Order Block TF Day:** หลุด Order Block ขาขึ้นแล้ว
* **ถ้าไม่แน่ใจ อย่าเพิ่งเข้าเทรด**
**Disclaimer:** การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ
-

@ 94a6a78a:0ddf320e
2025-02-19 21:10:15
Nostr is a revolutionary protocol that enables **decentralized, censorship-resistant communication**. Unlike traditional social networks controlled by corporations, Nostr operates without central servers or gatekeepers. This openness makes it incredibly powerful—but also means its success depends entirely on **users, developers, and relay operators**.
If you believe in **free speech, decentralization, and an open internet**, there are many ways to support and strengthen the Nostr ecosystem. Whether you're a casual user, a developer, or someone looking to contribute financially, **every effort helps build a more robust network**.
Here’s how you can get involved and make a difference.
---
## **1️⃣ Use Nostr Daily**
The simplest and most effective way to contribute to Nostr is by **using it regularly**. The more active users, the stronger and more valuable the network becomes.
✅ **Post, comment, and zap** (send micro-payments via Bitcoin’s Lightning Network) to keep conversations flowing.\
✅ **Engage with new users** and help them understand how Nostr works.\
✅ **Try different Nostr clients** like Damus, Amethyst, Snort, or Primal and provide feedback to improve the experience.
Your activity **keeps the network alive** and helps encourage more developers and relay operators to invest in the ecosystem.
---
## **2️⃣ Run Your Own Nostr Relay**
Relays are the **backbone of Nostr**, responsible for distributing messages across the network. The more **independent relays exist**, the stronger and more censorship-resistant Nostr becomes.
✅ **Set up your own relay** to help decentralize the network further.\
✅ **Experiment with relay configurations** and different performance optimizations.\
✅ **Offer public or private relay services** to users looking for high-quality infrastructure.
If you're not technical, you can still **support relay operators** by **subscribing to a paid relay** or donating to open-source relay projects.
---
## **3️⃣ Support Paid Relays & Infrastructure**
Free relays have helped Nostr grow, but they **struggle with spam, slow speeds, and sustainability issues**. **Paid relays** help fund **better infrastructure, faster message delivery, and a more reliable experience**.
✅ **Subscribe to a paid relay** to help keep it running.\
✅ **Use premium services** like media hosting (e.g., Azzamo Blossom) to decentralize content storage.\
✅ **Donate to relay operators** who invest in long-term infrastructure.
By funding **Nostr’s decentralized backbone**, you help ensure its **longevity and reliability**.
---
## **4️⃣ Zap Developers, Creators & Builders**
Many people contribute to Nostr **without direct financial compensation**—developers who build clients, relay operators, educators, and content creators. **You can support them with zaps!** ⚡
✅ **Find developers working on Nostr projects** and send them a zap.\
✅ **Support content creators and educators** who spread awareness about Nostr.\
✅ **Encourage builders** by donating to open-source projects.
Micro-payments via the **Lightning Network** make it easy to directly **support the people who make Nostr better**.
---
## **5️⃣ Develop New Nostr Apps & Tools**
If you're a developer, you can **build on Nostr’s open protocol** to create new apps, bots, or tools. Nostr is **permissionless**, meaning anyone can develop for it.
✅ **Create new Nostr clients** with unique features and user experiences.\
✅ **Build bots or automation tools** that improve engagement and usability.\
✅ **Experiment with decentralized identity, authentication, and encryption** to make Nostr even stronger.
With **no corporate gatekeepers**, your projects can help shape the future of decentralized social media.
---
## **6️⃣ Promote & Educate Others About Nostr**
Adoption grows when **more people understand and use Nostr**. You can help by **spreading awareness** and creating educational content.
✅ **Write blogs, guides, and tutorials** explaining how to use Nostr.\
✅ **Make videos or social media posts** introducing new users to the protocol.\
✅ **Host discussions, Twitter Spaces, or workshops** to onboard more people.
The more people **understand and trust Nostr**, the stronger the ecosystem becomes.
---
## **7️⃣ Support Open-Source Nostr Projects**
Many Nostr tools and clients are **built by volunteers**, and open-source projects thrive on **community support**.
✅ **Contribute code** to existing Nostr projects on GitHub.\
✅ **Report bugs and suggest features** to improve Nostr clients.\
✅ **Donate to developers** who keep Nostr free and open for everyone.
If you're not a developer, you can still **help with testing, translations, and documentation** to make projects more accessible.
---
## **🚀 Every Contribution Strengthens Nostr**
Whether you:
✔️ **Post and engage daily**\
✔️ **Zap creators and developers**\
✔️ **Run or support relays**\
✔️ **Build new apps and tools**\
✔️ **Educate and onboard new users**
**Every action helps make Nostr more resilient, decentralized, and unstoppable.**
Nostr isn’t just another social network—it’s **a movement toward a free and open internet**. If you believe in **digital freedom, privacy, and decentralization**, now is the time to get involved.
-

@ 5de23b9a:d83005b3
2025-02-19 03:47:19
In a digital era that is increasingly controlled by large companies, the emergence of Nostr (Notes and Other Stuff Transmitted by Relays) is a breath of fresh air for those who crave freedom of expression.
Nostr is a cryptography-based protocol that allows users to send and receive messages through a relay network. Unlike conventional social media such as Twitter or Facebook
1.Full Decentralization: No company or government can remove or restrict content.
2.Sensor-Resistant: Information remains accessible despite blocking attempts.
3.Privacy and Security: Uses cryptography to ensure that only users who have the keys can access their messages.* **
-

@ 9e69e420:d12360c2
2025-02-17 17:12:01
President Trump has intensified immigration enforcement, likening it to a wartime effort. Despite pouring resources into the U.S. Immigration and Customs Enforcement (ICE), arrest numbers are declining and falling short of goals. ICE fell from about 800 daily arrests in late January to fewer than 600 in early February.
Critics argue the administration is merely showcasing efforts with ineffectiveness, while Trump seeks billions more in funding to support his deportation agenda. Increased involvement from various federal agencies is intended to assist ICE, but many lack specific immigration training.
Challenges persist, as fewer immigrants are available for quick deportation due to a decline in illegal crossings. Local sheriffs are also pressured by rising demands to accommodate immigrants, which may strain resources further.
-

@ d360efec:14907b5f
2025-02-20 10:12:37
**Overall Assessment:**
Bitcoin (BTCUSDT) on OKX remains highly volatile and shows conflicting signals. The long-term trend (Daily chart) is technically still an uptrend, *but it has weakened considerably* and is showing significant signs of a potential reversal. The 4-hour and 15-minute charts are in confirmed downtrends. The focus of this analysis is on identifying potential areas of Smart Money activity (liquidity pools and order blocks) and assessing trend strength.
**Detailed Analysis by Timeframe:**
**(1) TF Day (Daily):**

* **Trend:** Uptrend (Significantly Weakening, *at risk of reversing*).
* **SMC (Smart Money Concepts):**
* Higher Highs (HH) and Higher Lows (HL) structure is *becoming less defined*. The recent price action has broken previous lows.
* Prior Breaks of Structure (BOS) to the upside, but the current pullback is very deep.
* **Liquidity:**
* **Sellside Liquidity (SSL):** Significant SSL rests below previous lows in the 85,000 - 90,000 range. This is a likely target for Smart Money.
* **Buyside Liquidity (BSL):** BSL is present above the all-time high.
* **ICT (Inner Circle Trader Concepts):**
* **Order Block:** The price has *broken below* the prior bullish Order Block (the large green candle before a significant up-move). This is a *major bearish signal*.
* **EMA (Exponential Moving Average):**
* Price has *broken below* the 50-period EMA (yellow), a bearish signal.
* The 200-period EMA (white) is the next major support level.
* **Money Flow (LuxAlgo):**
* A *long red bar* indicates strong selling pressure.
* **Trend Strength (AlgoAlpha):**
* Red Cloud indicating Downtrend, *No Buy/Sell Signal*
* **Volume Profile:** Relatively low volume on the recent decline.
* **Candlesticks:** The most recent candlestick is red, confirming selling pressure.
* **Support:** EMA 200, 85,000-90,000 (SSL area).
* **Resistance:** EMA 50, Previous All-Time High.
* **Summary:** The Daily chart's uptrend is significantly weakening. The break below the 50 EMA *and* the bullish Order Block, combined with the negative Money Flow and bearish Trend Strength, are all major warning signs.
**(2) TF4H (4-Hour):**

* **Trend:** Downtrend.
* **SMC:**
* Lower Highs (LH) and Lower Lows (LL).
* BOS to the downside.
* **Liquidity:**
* **SSL:** Below previous lows.
* **BSL:** Above previous highs.
* **ICT:**
* **Order Block:** The price rallied up to, and was rejected by, a *bearish* Order Block.
* **EMA:**
* Price is below both the 50-period and 200-period EMAs (bearish).
* **Money Flow (LuxAlgo):**
* Predominantly red, confirming selling pressure.
* **Trend Strength (AlgoAlpha):**
* Green Cloud, *But No Buy/Sell Signal.* This indicates a potential *retracement* within the downtrend, or a period of consolidation, *not* a trend reversal.
* **Volume Profile:**
* Relatively High volume
* **Support:** Recent lows.
* **Resistance:** EMA 50, EMA 200, Order Block.
* **Summary:** The 4-hour chart is in a confirmed downtrend. The Money Flow is bearish, and the price was rejected by a key Order Block. The green Trend Strength cloud *without* a buy signal suggests a potential *temporary* relief rally or consolidation, *not* a trend change.
**(3) TF15 (15-Minute):**

* **Trend:** Downtrend (with some signs of *possible* stabilization).
* **SMC:**
* Lower Highs (LH) and Lower Lows (LL) – *but the most recent low is slightly higher, a potential early sign of a change*.
* BOS to the downside.
* **ICT:**
* **Order Block:** Price has reacted to bearish Order Block.
* **EMA:**
* The 50-period and 200-period EMAs are acting as resistance.
* **Money Flow (LuxAlgo):**
* Red and green alternating , showing some buying pressure has appeared, but sellers are still in control overall.
* **Trend Strength (AlgoAlpha):**
* Red Cloud (Bearish), *BUT* there's a *bullish divergence* (price made a lower low, but the Trend Strength indicator made a higher low). This is a *potential* early warning sign of a reversal, but it needs *strong confirmation*.
* **Volume Profile:**
* relatively high volume.
* **Support:** Recent lows.
* **Resistance:** EMA 50, EMA 200, Order Block.
* **Summary:** The 15-minute chart is in a downtrend, but there are *very early* and *tentative* signs of a possible stabilization or even a minor bounce. The bullish divergence on the Trend Strength is important to note, but it's not a buy signal on its own.
**Overall Strategy and Recommendations (BTCUSDT):**
* **Primary Trend (Day):** Uptrend (Significantly Weakening).
* **Secondary Trend (4H):** Downtrend.
* **Short-Term Trend (15m):** Downtrend (Potential Early Reversal Signals).
* **Liquidity:** Significant SSL zones exist below the current price on all timeframes.
* **Money Flow:** Negative on all timeframes, although the 15m is showing *some* buying pressure returning.
* **Trend Strength:** Bearish on Day and 15m. Bullish on 4H, *but without a buy/sell signal*, indicating a likely retracement or consolidation, not a trend change.
* **Strategies:**
1. **Wait & See (Best Option):** The conflicting signals (especially the 4H Trend Strength) and the strong bearish momentum on the shorter timeframes make waiting the most prudent approach. Look for:
* **Bearish Confirmation:** A decisive break below the recent lows on the 15m and 4H charts, with increasing volume and continued negative Money Flow. This would confirm the continuation of the downtrend.
* **Bullish Confirmation:** A strong, sustained break above the 15m EMAs, a shift in the 15m Money Flow to green, *and* a bullish signal on the 4H Trend Strength. This would be a *very early* sign of a potential reversal, but it would need further confirmation on the 4H chart (price above EMAs, positive Money Flow).
2. **Short (High Risk):** This is the more likely scenario *at this moment*, given the 4H and 15m downtrends.
* **Entry:** On rallies towards resistance levels (EMAs on 15m/4H, previous support levels that have turned into resistance).
* **Stop Loss:** Above recent highs on the chosen timeframe.
* **Target:** The next support levels (recent lows on 15m, then the Daily Order Block area around 92,000-94,000).
3. **Buy on Dip (Extremely High Risk - Not Recommended):** Do *not* attempt to buy until there are *very strong and consistent* bullish reversal signals across *all* timeframes, including a definitive shift in market structure on the 4H and 15m charts, positive Money Flow, and a clear break above resistance levels.
**Key Recommendations:**
* **Conflicting Signals:** The most important factor is the conflict between the still *technically* bullish Daily chart and the bearish 4H and 15m charts. The 4H Trend Strength being bullish *without a signal* adds to the uncertainty.
* **Money Flow:** The predominantly negative Money Flow is a major bearish factor.
* **15m Trend Strength Divergence:** This is a *potential* early warning, but it's *not* a buy signal on its own. It needs *much* more confirmation.
* **Daily Order Block:** The *break* of the bullish Order Block on the Daily chart is a significant bearish development.
* **Sellside Liquidity (SSL):** Be aware that Smart Money may target the SSL zones below. This increases the risk of stop-loss hunting.
* **Risk Management:** Due to the high uncertainty and volatility, *strict risk management is absolutely critical.* Use tight stop-losses, do not overtrade, and be prepared for rapid price swings.
* **Volume:** Confirm any breakout with volume.
**Day Trading and Intraday Trading Strategies:**
* **Day Trade (TF15 focus):**
* **Short Bias:** Given the current 15m downtrend and negative Money Flow, the higher probability is to look for shorting opportunities.
* **Entry:** Look for price to rally to resistance levels (EMAs, Order Blocks, previous support levels that have become resistance) and then show signs of rejection (bearish candlestick patterns, increasing volume on the downside).
* **Stop Loss:** Place a stop-loss order above the resistance level where you enter the short position.
* **Take Profit:** Target the next support level (recent lows).
* **Be very cautious:** The bullish divergence on the Trend Strength indicator suggests a potential bounce *could* occur. Don't be aggressive with shorts until this divergence is invalidated.
* **Avoid Long positions:** Until there's a *clear* and *confirmed* bullish reversal on the 15m chart (break above EMAs, positive Money Flow, bullish market structure).
* **Swing Trade (TF4H focus):**
* **Short Bias:** The 4H chart is in a downtrend.
* **Entry:** Wait for price to rally to resistance levels (EMAs, Order Blocks) and show signs of rejection.
* **Stop Loss:** Above the resistance level where you enter the short position.
* **Take Profit:** Target the next support levels (e.g., the 200 EMA on the Daily chart, SSL zones).
* **Avoid long position:** Until there's a *clear* and *confirmed* bullish reversal on the 4H chart.
**SMC Day Trade Setup Example (TF15 - Bearish):**
1. **Identify Bearish Order Block:** Locate a bearish Order Block on the TF15 chart (a bullish candle before a strong downward move). *We have already identified this in previous analyses.*
2. **Wait for Pullback:** Wait for the price to pull back up to test the Order Block.
3. **Bearish Entry:**
* **Rejection:** Look for price action to reject the Order Block (e.g., a pin bar, engulfing pattern, or other bearish candlestick pattern).
* **Break of Structure:** Look for a break of a minor support level on a *lower* timeframe (e.g., 1-minute or 5-minute) after the price tests the Order Block. This confirms weakening bullish momentum.
* **Money Flow:** Confirm that Money Flow remains negative (red).
4. **Stop Loss:** Place a stop-loss order *above* the Order Block.
5. **Take Profit:** Target the next support level (e.g., recent lows) or a bullish Order Block on a higher timeframe.
**In conclusion, BTCUSDT is currently in a high-risk, uncertain environment. The short-term and medium-term trends are bearish, while the long-term trend is weakening. The best approach for most traders is to wait for clearer signals. Shorting is the higher-probability trade *at this moment*, but only for experienced traders who can manage risk aggressively. Buying is extremely risky and not recommended at this time.** The bullish divergence on the 15m Trend Strength is a *potential* early warning of a change, but it needs *much* more confirmation before acting on it. The 4-hour chart showing a green cloud with *no* buy/sell signal adds to the uncertainty, suggesting a possible retracement/consolidation *within* the downtrend.
**Disclaimer:** This analysis is for informational purposes only and represents a personal opinion. It is not financial advice. Investing in cryptocurrencies involves significant risk. Investors should conduct their own research and exercise due diligence before making any investment decisions.
-

@ 000002de:c05780a7
2025-02-20 01:52:34
Due to some some org changes at my employer I may be moving to a team that uses Python heavily. I have never written Python professionally but I've dabbled. I think its used heavily in certain fields and is likely a marketable language to have on the CV. Am I correct in that summary?
Is it growing? Is it evolving? I know its alive and well but I just don't hear much about it anymore. Has it just matured like many languages over the years?
originally posted at https://stacker.news/items/891251
-

@ 16f1a010:31b1074b
2025-02-19 20:57:59
In the rapidly evolving world of Bitcoin, running a Bitcoin node has become more accessible than ever. Platforms like Umbrel, Start9, myNode, and Citadel offer user-friendly interfaces to simplify node management. However, for those serious about maintaining a robust and efficient Lightning node ⚡, relying solely on these platforms may not be the optimal choice.
Let’s delve into why embracing **Bitcoin Core** and mastering the command-line interface (CLI) can provide a **more reliable, sovereign, and empowering** experience.
### Understanding Node Management Platforms
#### What Are Umbrel, Start9, myNode, and Citadel?
Umbrel, Start9, myNode, and Citadel are platforms designed to streamline the process of running a Bitcoin node. They offer graphical user interfaces (GUIs) that allow users to manage various applications, including Bitcoin Core and Lightning Network nodes, through a web-based dashboard 🖥️.
These platforms often utilize Docker containers 🐳 to encapsulate applications, providing a modular and isolated environment for each service.

#### The Appeal of Simplified Node Management
The primary allure of these platforms lies in their simplicity. With minimal command-line interaction, users can deploy a full Bitcoin and Lightning node, along with a suite of additional applications.
✅ **Easy one-command installation**
✅ **Web-based GUI for management**
✅ **Automatic app updates** *(but with delays, as we’ll discuss)*
However, while this convenience is attractive, it comes **at a cost**.
### The Hidden Complexities of Using Node Management Platforms
While the user-friendly nature of these platforms is advantageous, it can also introduce several challenges that may hinder advanced users or those seeking greater control over their nodes.
#### 🚨 Dependency on Maintainers for Updates
One significant concern is the reliance on platform maintainers for updates. Since these platforms manage applications through Docker containers, users must wait for the maintainers to update the container images before they can access new features or security patches.
🔴 **Delayed Bitcoin Core updates = potential security risks**
🔴 **Lightning Network updates are not immediate**
🔴 **Bugs and vulnerabilities may persist longer**
Instead of waiting on a third party, **why not update Bitcoin Core & LND yourself instantly**?
#### ⚙️ Challenges in Customization and Advanced Operations
For users aiming to perform advanced operations, such as:
* Custom backups 📂
* Running specific CLI commands 🖥️
* Optimizing node settings ⚡
…the **abstraction layers introduced by these platforms become obstacles**.
Navigating through nested directories and issuing commands inside Docker containers **makes troubleshooting a nightmare**. Instead of a simple `bitcoin-cli` command, you must figure out how to execute it inside the container, adding unnecessary complexity.
#### Increased Backend Complexity
To achieve **frontend simplicity**, these platforms make the backend more complex.
🚫 Extra layers of abstraction
🚫 Hidden logs and settings
🚫 Harder troubleshooting
The use of **multiple Docker containers**, **custom scripts**, and **unique file structures** can **make system maintenance and debugging a pain**.
This **complication defeats the purpose** of “making running a node easy.”
## ✅ Advantages of Using Bitcoin Core and Command-Line Interface (CLI)
By installing Bitcoin Core directly and using the command-line interface (CLI), you gain several key advantages that make managing a Bitcoin and Lightning node more efficient and empowering.
#### Direct Control and Immediate Updates
One of the biggest downsides of package manager-based platforms is the reliance on third-party maintainers to release updates. Since Bitcoin Core, Lightning implementations (such as LND, Core Lightning, or Eclair), and other related software evolve rapidly, waiting for platform-specific updates can leave you running outdated or vulnerable versions.
By installing Bitcoin Core directly, you remove this dependency. You can update immediately when new versions are released, ensuring your node benefits from the latest features, security patches, and bug fixes. The same applies to Lightning software—being able to install and update it yourself gives you full autonomy over your node’s performance and security.
#### 🛠 Simplified System Architecture
Platforms like Umbrel and myNode introduce extra complexity by running Bitcoin Core and Lightning inside Docker containers. This means:
* The actual files and configurations are stored inside Docker’s filesystem, making it **harder to locate and manage them manually**.
* If something breaks, **troubleshooting is more difficult** due to the added layer of abstraction.
* Running commands requires jumping through Docker shell sessions, adding unnecessary friction to what should be a straightforward process.
Instead, a direct installation of Bitcoin Core, Lightning, and Electrum Server (if needed) results in a **cleaner, more understandable system**. The software runs natively on your machine, without containerized layers making things more convoluted.
Additionally, setting up your own systemd service files for Bitcoin and Lightning** is not as complicated as it seems**. Once configured, these services will run automatically on boot, offering the same level of convenience as platforms like Umbrel but without the unnecessary complexity.
#### Better Lightning Node Management
If you’re running a **Lightning Network node**, using CLI-based tools provides far more flexibility than relying on a GUI like the ones bundled with node management platforms.
🟢 **Custom Backup Strategies** – Running Lightning through a GUI-based node manager often means backups are handled in a way that is opaque to the user. With CLI tools, you can easily script automatic backups of your channels, wallets, and configurations.
🟢 **Advanced Configuration** – Platforms like Umbrel force certain configurations by default, limiting how you can customize your Lightning node. With a direct install, you have full control over:
* Channel fees 💰
* Routing policies 📡
* Liquidity management 🔄
🟢 **Direct Access to LND, Core Lightning, or Eclair** – Instead of issuing commands through a GUI (which is often limited in functionality), you can use:
* `lncli` (for LND)
* `lightning-cli` (for Core Lightning)
…to interact with your node at a deeper level.
#### Enhanced Learning and Engagement
A crucial aspect of running a Bitcoin and Lightning node is **understanding how it works**.
Using an abstraction layer like Umbrel may get a node running in a few clicks, but **it does little to teach users how Bitcoin actually functions**.
By setting up Bitcoin Core, Lightning, and related software manually, you will:
✅ Gain practical knowledge of Bitcoin nodes, networking, and system performance.
✅ Learn how to configure and manage RPC commands.
✅ Become less reliant on third-party developers and more confident in troubleshooting.
🎯 **Running a Bitcoin node is about sovereignty – learn how to control it yourself**.
## Become more sovereign TODAY
Many guides make this process **straightforward**
[K3tan](https://k3tan.com/about) has a fantastic guide on running Bitcoin Core, Electrs, LND and more.
- [Ministry of Nodes Guide 2024](https://www.youtube.com/playlist?list=PLCRbH-IWlcW0g0HCrtI06_ZdVVolUWr39)
- You can find him on nostr
nostr:npub1txwy7guqkrq6ngvtwft7zp70nekcknudagrvrryy2wxnz8ljk2xqz0yt4x
Even with the best of guides, if you are running this software,
📖 **READ THE DOCUMENTATION**
This is all just software at the end of the day. Most of it is very well documented. Take a moment to actually read through the documentation for yourself when installing. The documentation has step by step guides on setting up the software.
Here is a helpful list:
* [Bitcoin.org Bitcoin Core Linux install instructions](https://bitcoin.org/en/full-node#linux-instructions)
* [Bitcoin Core Code Repository](https://github.com/bitcoin/bitcoin)
* [Electrs Installation](https://github.com/romanz/electrs/blob/master/doc/install.md)
* [LND Documentation](https://docs.lightning.engineering/)
* [LND Code Repository](https://github.com/lightningnetwork/lnd)
* [CLN Documentation](https://docs.corelightning.org/docs/home)
* [CLN Code Repository](https://github.com/ElementsProject/lightning)
*If you have any more resources or links I should add, please comment them . I want to add as much to this article as I can.*
-

@ f33c8a96:5ec6f741
2025-02-19 20:47:43
<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/kFUIfaCpXzA?enablejsapi=1" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
-

@ 8d34bd24:414be32b
2025-02-19 16:43:17
Last night I was reading Jeremiah 24 and I read the parable of the figs. I’ve read this passage many times, but suddenly I saw the irony of the situation.
## The Story of the Good and Bad Figs
> After Nebuchadnezzar king of Babylon had carried away captive Jeconiah the son of Jehoiakim, king of Judah, and the officials of Judah with the craftsmen and smiths from Jerusalem and had brought them to Babylon, the Lord showed me: behold, two baskets of figs set before the temple of the Lord! One basket had very good figs, like first-ripe figs, and the other basket had very bad figs which could not be eaten due to rottenness. Then the Lord said to me, “What do you see, Jeremiah?” And I said, “Figs, the good figs, very good; and the bad figs, very bad, which cannot be eaten due to rottenness.”
>
> Then the word of the Lord came to me, saying, “Thus says the Lord God of Israel, ‘**Like these good figs, so I will regard as good the captives of Judah, whom I have sent out of this place into the land of the Chaldeans. For I will set My eyes on them for good, and I will bring them again to this land; and I will build them up and not overthrow them**, and I will plant them and not pluck them up. I will give them a heart to know Me, for I am the Lord; and they will be My people, and I will be their God, for they will return to Me with their whole heart.
>
> ‘**But like the bad figs which cannot be eaten due to rottenness**—indeed, thus says the Lord—so I will abandon Zedekiah king of Judah and his officials, and **the remnant of Jerusalem who remain in this land and the ones who dwell in the land of Egypt. I will make them a terror and an evil for all the kingdoms of the earth, as a reproach and a proverb, a taunt and a curse in all places where I will scatter them.** I will send the sword, the famine and the pestilence upon them until they are destroyed from the land which I gave to them and their forefathers.’ ” (Jeremiah 24:1-10) {Emphasis mine}
God tells Jeremiah about two baskets of figs, one very good and one very bad. He then goes on to describe those Israelites who were kidnapped by Nebuchadnezzar and hauled off to Babylon and those that got to remain in Israel in their homes. Who would you think God was blessing and who would you think God was punishing? I would think the person hauled off into captivity was being punished and the one that got to stay in their comfortable home was being blessed, but it was the opposite.
God said, “‘*Like these good figs, so I will regard as good the captives of Judah, whom I have sent out of this place into the land of the Chaldeans. For I will set My eyes on them for good, and I will bring them again to this land; and I will build them up and not overthrow them, and I will plant them and not pluck them up*.” (Jeremiah 24:5b-6) Those that got hauled away were being blessed. They were being protected from the judgment that God was about to bestow on Israel for their sin. It would have been very easy for the captives to moan, “Woe is us. Why would God do such horrible things to us?” even though God was protecting them. It would have been very easy for those who remained to think, “Those captives must have sinned very badly. Luckily, God doesn’t have any problems with me.”
Instead God was punishing those who remained in Israel. He said,
> But like the bad figs which cannot be eaten due to rottenness—indeed, thus says the Lord—so I will abandon Zedekiah king of Judah and his officials, and the remnant of Jerusalem who remain in this land and the ones who dwell in the land of Egypt. **I will make them a terror and an evil for all the kingdoms of the earth**, as a reproach and a proverb, a taunt and a curse in all places where I will scatter them. **I will send the sword, the famine and the pestilence upon them until they are destroyed from the land** which I gave to them and their forefathers.’ (Jeremiah 24:8-10) {Emphasis mine}
While those who weren’t dragged away into captivity were congratulating themselves, the judgment of God fell upon them because they had rejected their God and were depending on the blessings promised to their ancestors.
Those who were hauled into captivity were blessed and multiplied and then brought back to the promised land 70 years later. Even when they were not feeling blessed, God told them how to live in order to be blessed.
> “Thus says the Lord of hosts, the God of Israel, to all the exiles whom I have sent into exile from Jerusalem to Babylon, ‘Build houses and live in them; and plant gardens and eat their produce. Take wives and become the fathers of sons and daughters, and take wives for your sons and give your daughters to husbands, that they may bear sons and daughters; and multiply there and do not decrease. **Seek the welfare of the city where I have sent you into exile, and pray to the Lord on its behalf; for in its welfare you will have welfare.** (Jeremiah 29:4-7)
They were told to be fruitful and multiply in both a financial and a familial way. They were told to work hard while waiting for the fulfillment of God’s promises and in 70 years they and/or their families would return to the promised land.
In a like manner, we are to be fruitful and multiply in whatever situation or in whatever country God has placed us. We are to stay faithful to Him and to honor Him in all we do wherever He has placed us. Whether we are literal exiles in a foreign country or not, we are all exiles from heaven waiting for Jesus to return and call us home. We are called to be productive while we wait.
## A Real Life Example of the Good Figs
I got to see a similar example in my own life. I went through what most people would call a hellish year in 2015, but every thing that happened was for a blessing and not for a curse. I got to see how trusting in the Lord with all my heart led to blessings I couldn’t imagine.
Technically our rough year started in November of 2014 with a flood and that is kind of how the next year felt. We had a house with hot water heat. Our family room had a large volume because the ceiling was two stories high. The room only had two heat registers. When we would get sub zero (F) temperatures, the room would drop in temperature, so we put in a wood and coal stove. It did a such a great job of heating the house that the heat wasn’t turning on and the pipes in the back office froze and burst the pipes. While we were at work, the temperatures warmed up, the pipes defrosted, and the water started streaming out flooding our entire downstairs. We then had get everything off the floor, flood cut the whole downstairs, and put in giant fans for 6 weeks to dry the wet floors and walls. It sounded like a 747 jet was sitting in the living room. I couldn’t hear myself think. It was very stressful, but that was just the beginning.
We had a fight with the insurance company for \~8 months. They agreed about everything needing to be fixed, but wanted to pay only about half the cost to fix it. We finally had to break down and hire a lawyer. We settled with the insurance company writing us a check for 90% of the price of repairs. This settlement was a blessing in disguise.
Because of the problems with our insurance company, we decided to switch to a new insurer. We set up to switch when our current policy expired. Ten days into our new policy, our house burnt down in a grass fire fueled by 60+ mph winds. In the main part of the house the only things recognizable were the coal stove and a 3 hour rated gun safe (that now looked like a cheap metal cabinet onto which someone dropped a nuclear bomb). We lost all of our physical possessions, but God had a plan.
The new insurance company sent their insurance adjuster out right away. In one month they had paid for the house, the trees, the barn, and a year’s rent in a nice rental house. We had more than half of the settlement left from the flood (we had bought a few supplies for fixing the house). Exactly one year and one month later, we moved into our paid off dream home (with a very fire resistant exterior). Of course God didn’t finish His blessings and lessons with the fire, there was more to come.
We moved into the rental house. (Ironically I was excited about all of the closet space even though I could fit all of my worldly possessions in a small suitcase. We humans are not always logical and we don’t let go of our physical possessions easily.) A month later, my husband’s car engine blew up. A month after that, my husband ruptured his Achilles tendon, had to go through surgery, and we were unable to travel to see family for Christmas as planned. It seemed like hardship, but the previous hardships had prepared us for this one.
The house that burnt down had all of the bedrooms upstairs, all of the living spaces downstairs, and very steep stairs. When my husband ruptured his other Achilles tendon eight years previously, he had to stay on the couch downstairs and couldn’t sleep in his bed. In our new rental house, the master bedroom was on the same level as the living areas and not more than 10 feet away. He could sleep in bed and then use crutches to move to the electric recliner that had been donated to us after the fire. It gently raised and lowered his injured leg. He could sit with us to eat (we set up a table on one side of the recliner) and be with us when we hung out on the couch (on the other side of him). We could talk while I worked in the kitchen. It was so much nicer to take care of him in the rental house than it would’ve been if the same thing had happened, but our house hadn’t burnt down.
Through this string of “tragedies,” we learned to trust God through every situation. We learned what was important (people not stuff). We got a nice, optimized, paid-off house. We received a story that we could share with others to bless them and help them trust in God. We grew closer together as a family. All four members of my family agree that if given the chance to make all of these “bad” things not happen, we would not choose to remove them. The blessings we received through them outweigh them more than you can imagine.
## What About You?
What about you? Are you gong through hard times? We all do at some point in our lives. Are you looking for the good God is doing or are you blaming God for your hardship? Are you working to make the most of whatever situation you are in or are you seeking your own “better”?
My prayer is that God will give you what you need and not what you want and that He will answer your prayers in His best timing. I pray that you will see the wondrous works of God in you and through you and that you will grow in your faith in our very good God. Trust Him! Turn to Him! Rely on Him! God is good, all of the time.
Trust Jesus
-

@ 42342239:1d80db24
2025-02-16 08:39:59
Almost 150 years ago, the British newspaper editor William Thomas Stead wrote that "the editorial pen is a [sceptre of power](https://archive.org/details/GovernmentByJournalismWilliamThomasStead), compared with which the sceptre of many a monarch is but a gilded lath". He had begun to regard journalism as something more than just conveying information - **the journalist or editor could become a ruler.**
Times had certainly changed compared to a few hundred years earlier. Before [Gutenberg's invention of the printing press](https://underorion.se/en/posts/gutenberg/), it was mainly the church that controlled the dissemination of information in Europe, but when Stead put pen to paper, this control had shifted to newspapers, schools, and universities. Eventually, technologies like radio and TV entered the scene, but the power dynamics remained asymmetrical - only a few could send information to the many.
However, with the emergence of the internet, and especially with the spread of social media, a significant change followed. Instead of only a few being able to send information to the many, many could send to many. Almost anyone could now create their own newspaper, radio, or TV channel. **The power over information dissemination was decentralised.**
[Ten years ago](https://www.di.se/ditv/rikets-affarer-medierna-ar-splittrade/), Roberta Alenius, who was then press secretary for Sweden's Prime Minister Fredrik Reinfeldt of the Moderate Party, shared her experiences with Social Democratic and Moderate Party internet activists on social media. She reported that social media played a significant role in how news "comes out" and is shaped, and that **journalism was now downstream of social media**. [Five years later](https://www.nato.int/cps/en/natohq/opinions_166392.htm), NATO's then-Secretary-General Jens Stoltenberg said that "NATO must be prepared for both conventional and hybrid threats: **from tanks to tweets**." This finally underscores the importance of social media.
Elon Musk, who took over X (formerly Twitter) in 2022, has claimed that "it's absolutely fundamental and transformative that the people actually get to decide the news and narrative and what's important," and that [citizen journalism is the future](https://x.com/elonmusk/status/1870485116474278240).
While his platform allows most expressions - for better or worse - the reach of messages is instead limited ("[freedom of speech does not mean freedom of reach](https://www.youtube.com/shorts/R9TuhTz0vmo) "). X has also opened its recommendation algorithm to the outside world by making it open-source. Although this is a welcome step, the fact remains that **it's impossible to know which code is actually used** and what adjustments are made by humans or algorithms.
William Thomas Stead's "sceptre of power", which has wandered from the church to newspaper and TV editorial offices, and now to citizens according to Elon Musk, risks being transferred to algorithms' opaque methods?
Instead of talking about "toxic algorithms" and TikTok bans, like the so many do today, we should ask ourselves more fundamental questions. What happens when algorithms are no longer objective (how can they ever be?), but instead become tools for shaping our reality? **Perhaps our greatest challenge today is not deciding who should govern the information landscape, but instead recognising that no one is up to the task** - not even well-ventilated computers.
-

@ 9e69e420:d12360c2
2025-02-15 20:24:09
Ukraine's President Volodymyr Zelensky called for an "army of Europe" to defend against Russian threats, emphasizing that the US may not continue its traditional support for Europe. Speaking at the Munich Security Conference, he warned against peace deals made without Ukraine's involvement.
US Vice President JD Vance echoed this sentiment, urging Europe to enhance its defense efforts.
Zelensky stated, "I really believe the time has come - the armed forces of Europe must be created." He highlighted changing dynamics in US-Europe relations and noted that "the old days are over" regarding American support.
Despite discussions around NATO, Zelensky stated he wouldn't rule out NATO membership for Ukraine.
-

@ fd208ee8:0fd927c1
2025-02-15 07:37:01
E-cash are coupons or tokens for Bitcoin, or Bitcoin debt notes that the mint issues. The e-cash states, essentially, "IoU 2900 sats".
They're redeemable for Bitcoin on Lightning (hard money), and therefore can be used as cash (softer money), so long as the mint has a good reputation. That means that they're less fungible than Lightning because the e-cash from one mint can be more or less valuable than the e-cash from another. If a mint is buggy, offline, or disappears, then the e-cash is unreedemable.
It also means that e-cash is more anonymous than Lightning, and that the sender and receiver's wallets don't need to be online, to transact. Nutzaps now add the possibility of parking transactions one level farther out, on a relay. The same relays that cannot keep npub profiles and follow lists consistent will now do monetary transactions.
What we then have is
* a **transaction on a relay** that triggers
* a **transaction on a mint** that triggers
* a **transaction on Lightning** that triggers
* a **transaction on Bitcoin**.
Which means that every relay that stores the nuts is part of a wildcat banking system. Which is fine, but relay operators should consider whether they wish to carry the associated risks and liabilities. They should also be aware that they should implement the appropriate features in their relay, such as expiration tags (nuts rot after 2 weeks), and to make sure that only expired nuts are deleted.
There will be plenty of specialized relays for this, so don't feel pressured to join in, and research the topic carefully, for yourself.
https://github.com/nostr-protocol/nips/blob/master/60.md
https://github.com/nostr-protocol/nips/blob/master/61.md
-

@ 0fa80bd3:ea7325de
2025-02-14 23:24:37
#intro
The Russian state made me a Bitcoiner. In 1991, it devalued my grandmother's hard-earned savings. She worked tirelessly in the kitchen of a dining car on the Moscow–Warsaw route. Everything she had saved for my sister and me to attend university vanished overnight. This story is similar to what many experienced, including Wences Casares. The pain and injustice of that time became my first lessons about the fragility of systems and the value of genuine, incorruptible assets, forever changing my perception of money and my trust in government promises.
In 2014, I was living in Moscow, running a trading business, and frequently traveling to China. One day, I learned about the Cypriot banking crisis and the possibility of moving money through some strange thing called Bitcoin. At the time, I didn’t give it much thought. Returning to the idea six months later, as a business-oriented geek, I eagerly began studying the topic and soon dove into it seriously.
I spent half a year reading articles on a local online journal, BitNovosti, actively participating in discussions, and eventually joined the editorial team as a translator. That’s how I learned about whitepapers, decentralization, mining, cryptographic keys, and colored coins. About Satoshi Nakamoto, Silk Road, Mt. Gox, and BitcoinTalk. Over time, I befriended the journal’s owner and, leveraging my management experience, later became an editor. I was drawn to the crypto-anarchist stance and commitment to decentralization principles. We wrote about the economic, historical, and social preconditions for Bitcoin’s emergence, and it was during this time that I fully embraced the idea.
It got to the point where I sold my apartment and, during the market's downturn, bought 50 bitcoins, just after the peak price of $1,200 per coin. That marked the beginning of my first crypto winter. As an editor, I organized workflows, managed translators, developed a YouTube channel, and attended conferences in Russia and Ukraine. That’s how I learned about Wences Casares and even wrote a piece about him. I also met Mikhail Chobanyan (Ukrainian exchange Kuna), Alexander Ivanov (Waves project), Konstantin Lomashuk (Lido project), and, of course, Vitalik Buterin. It was a time of complete immersion, 24/7, and boundless hope.
After moving to the United States, I expected the industry to grow rapidly, attended events, but the introduction of BitLicense froze the industry for eight years. By 2017, it became clear that the industry was shifting toward gambling and creating tokens for the sake of tokens. I dismissed this idea as unsustainable. Then came a new crypto spring with the hype around beautiful NFTs – CryptoPunks and apes.
I made another attempt – we worked on a series called Digital Nomad Country Club, aimed at creating a global project. The proceeds from selling images were intended to fund the development of business tools for people worldwide. However, internal disagreements within the team prevented us from completing the project.
With Trump’s arrival in 2025, hope was reignited. I decided that it was time to create a project that society desperately needed. As someone passionate about history, I understood that destroying what exists was not the solution, but leaving everything as it was also felt unacceptable. You can’t destroy the system, as the fiery crypto-anarchist voices claimed.
With an analytical mindset (IQ 130) and a deep understanding of the freest societies, I realized what was missing—not only in Russia or the United States but globally—a Bitcoin-native system for tracking debts and financial interactions. This could return control of money to ordinary people and create horizontal connections parallel to state systems. My goal was to create, if not a Bitcoin killer app, then at least to lay its foundation.
At the inauguration event in New York, I rediscovered the Nostr project. I realized it was not only technologically simple and already quite popular but also perfectly aligned with my vision. For the past month and a half, using insights and experience gained since 2014, I’ve been working full-time on this project.
-

@ 9e69e420:d12360c2
2025-02-14 18:07:10
Vice President J.D. Vance addressed the Munich Security Conference, criticizing European leaders for undermining free speech and traditional values. He claimed that the biggest threat to Europe is not from external enemies but from internal challenges. Vance condemned the arrest of a British man for praying near an abortion clinic and accused European politicians of censorship.
He urged leaders to combat illegal immigration and questioned their democratic practices. “There is a new sheriff in town,” he said, referring to President Trump. Vance's remarks were unexpected, as many anticipated discussions on security or Ukraine. His speech emphasized the need for Europe to share the defense burden to ensure stability and security.
-

@ 9e69e420:d12360c2
2025-02-14 15:14:34
A Russian drone attack has struck the radiation shelter at Chernobyl, according to Ukrainian President Volodymyr Zelensky. The strike caused a fire, but it has since been extinguished, and radiation levels remain stable. The International Atomic Energy Agency (IAEA) confirmed that no casualties occurred and that monitoring continues.
Rafael Mariano Grossi, IAEA's director general, emphasized the need for caution. Chernobyl, site of the 1986 nuclear disaster, contains a protective shield costing $1.6 billion. Disaster prevention remains a priority as the conflict unfolds.
The incident occurred shortly before the meeting of world powers at the Munich Security Conference in Germany.
-

@ 9e69e420:d12360c2
2025-02-13 23:01:36
Robert F. Kennedy Jr. has been confirmed as the next Secretary of Health and Human Services with a Senate vote of 52-48. Senator Mitch McConnell opposed the confirmation. Kennedy's nomination faced hurdles but gained support from the Senate Finance Committee.
During the confirmation hearing, Senator Rand Paul criticized the oversimplification of vaccine discussions. He stated, "Discussion over vaccines is so oversimplified and dumbed down." Kennedy asserted his support for vaccines like measles and polio, promising not to discourage vaccinations as HHS Secretary. Previously, he switched from the Democratic Party to run as an independent and endorsed Trump
-

@ e3ba5e1a:5e433365
2025-02-13 06:16:49
My favorite line in any Marvel movie ever is in “Captain America.” After Captain America launches seemingly a hopeless assault on Red Skull’s base and is captured, we get [this line](https://www.youtube.com/shorts/kqsomjpz7ok):
“Arrogance may not be a uniquely American trait, but I must say, you do it better than anyone.”
Yesterday, I came across a comment on the song [Devil Went Down to Georgia](https://youtu.be/ut8UqFlWdDc) that had a very similar feel to it:

America has seemingly always been arrogant, in a uniquely American way. Manifest Destiny, for instance. The rest of the world is aware of this arrogance, and mocks Americans for it. A central point in modern US politics is the deriding of racist, nationalist, supremacist Americans.
That’s not what I see. I see American Arrogance as not only a beautiful statement about what it means to be American. I see it as an ode to the greatness of humanity in its purest form.
For most countries, saying “our nation is the greatest” *is*, in fact, twinged with some level of racism. I still don’t have a problem with it. Every group of people *should* be allowed to feel pride in their accomplishments. The destruction of the human spirit since the end of World War 2, where greatness has become a sin and weakness a virtue, has crushed the ability of people worldwide to strive for excellence.
But I digress. The fears of racism and nationalism at least have a grain of truth when applied to other nations on the planet. But not to America.
That’s because the definition of America, and the prototype of an American, has nothing to do with race. The definition of Americanism is *freedom*. The founding of America is based purely on liberty. On the God-given rights of every person to live life the way they see fit.
American Arrogance is not a statement of racial superiority. It’s barely a statement of national superiority (though it absolutely is). To me, when an American comments on the greatness of America, it’s a statement about freedom. Freedom will always unlock the greatness inherent in any group of people. Americans are *definitionally* better than everyone else, because Americans are freer than everyone else. (Or, at least, that’s how it should be.)
In *Devil Went Down to Georgia*, Johnny is approached by the devil himself. He is challenged to a ridiculously lopsided bet: a golden fiddle versus his immortal soul. He acknowledges the sin in accepting such a proposal. And yet he says, “God, I know you told me not to do this. But I can’t stand the affront to my honor. I am the greatest. The devil has nothing on me. So God, I’m gonna sin, but I’m also gonna win.”
*Libertas magnitudo est*
-

@ 18e3af1e:1d42e5df
2023-08-13 02:40:19
Las comunidades son creadas mediante el esfuerzo de no solo un individuo, sino al trabajo de docenas; cientos o miles de personas. Mediante la especialización, como especie, logramos entender que: el saber hacer una sola cosa no significa morir de hambre, o no estar bien preparado para un ataque; por lo contrario, el dominio o maestría de una sola cosa... Puede crear una civilización entera.
Permitirnos un enfoque certero para aprender, dominar y amaestrar nuestras actividades en un periodo de tiempo finito, permitió nuestro avance hacia nuevos campos, de hecho, movió nuestra meta en magnitud tal, que al imaginar el pasado (para muchos) parece mas bien una película cómica y sombría.
Hoy en día, en un mundo regido por individualismo en el reino físico, la manifestación de constructores de comunidades sigue presente en el (reino) digital.
### La evolución de la construcción
A lo largo de la historia de la humanidad, la construcción ha evolucionado desde simples refugios hasta monumentos arquitectónicos y estructuras vanguardistas. Los primeros humanos crearon refugios rudimentarios con materiales naturales. Con la civilización, surgieron las primeras estructuras permanentes, como pirámides y templos, reflejando la organización social y creencias religiosas. La antigua Roma introdujo la innovación en la ingeniería con acueductos y arcos.
La Edad Media vio fortificaciones y catedrales góticas que fusionaban espiritualidad y técnica. El Renacimiento abrazó la proporción y la simetría en palacios y edificios renombrados. La Revolución Industrial marcó un cambio radical con el acero y el hormigón, permitiendo rascacielos y puentes icónicos.
El siglo XX trajo consigo la era de los rascacielos y la arquitectura modernista, desafiando límites estructurales y estéticos. La sostenibilidad ganó importancia en el siglo XXI, impulsando la incorporación de tecnologías avanzadas, como la impresión 3D y la construcción modular.
La historia de la construcción es un testimonio de la creatividad y la adaptabilidad humanas, reflejando no solo avances técnicos, sino también valores culturales y aspiraciones.
En el día hoy, los desarrolladores de software y tecnología podrían considerarse como los constructores del próximo siglo. Al igual que los constructores en otras épocas históricas, los desarrolladores de software son responsables de crear estructuras digitales que moldean la forma en que interactuamos, comunicamos y vivimos en el mundo moderno.
A medida que la tecnología continúa avanzando y la sociedad se vuelve cada vez más digital, el papel de los desarrolladores de software se vuelve crucial en la construcción de soluciones tecnológicas que abordan una amplia gama de desafíos.
Así como los arquitectos y constructores antiguos debían entender la física, la estética y las necesidades humanas para diseñar y construir edificios funcionales y atractivos, los desarrolladores de software deben comprender la lógica de programación, la experiencia del usuario, la seguridad cibernética y la innovación tecnológica para crear aplicaciones, sistemas y plataformas que sean útiles y efectivos.
### Individuos que inspiran
La inspiración individual es un poderoso motor de cambio que puede tener un impacto significativo en la mente colectiva de una comunidad o sociedad. Cuando una persona demuestra pasión, determinación y una visión positiva, puede influir en otros a nivel emocional y cognitivo. Aquí hay algunas formas en que la inspiración individual afecta a la mente colectiva:
La gente puede verse reflejada en las luchas y logros de alguien más, lo que crea un sentido de unidad y comunidad. Esto puede generar un mayor apoyo y solidaridad en torno a ciertas causas o valores. Además, la inspiración individual puede llevar a la acción. Cuando las personas son testigos de un individuo que supera obstáculos o logra metas desafiantes, esto puede motivar a otros a enfrentar sus propios desafíos y trabajar hacia sus objetivos. El ejemplo de una sola persona puede encender la chispa de la acción en muchas más.
La inspiración individual puede tener un efecto multiplicador. Cuando una persona inspirada comparte su historia o experiencia, puede inspirar a otros, creando una cadena de influencia que se extiende a través de redes sociales, comunidades y sociedades enteras. Esto puede tener un impacto a gran escala en la mente colectiva.
El individuo inspirador tiene el potencial de influir profundamente en la mente colectiva al cambiar percepciones, motivar la acción y crear una sensación de comunidad y unidad.
### Comunidades: origen, inicios y progreso.
Las comunidades han sido una parte fundamental de la experiencia humana a lo largo de la historia. Desde los primeros tiempos hasta la era moderna, las comunidades han evolucionado y cambiado en respuesta a las necesidades, avances tecnológicos y contextos culturales.
Desde los primeros días de la humanidad, nuestros antepasados se agruparon en pequeñas comunidades para sobrevivir. Estas comunidades eran grupos familiares o tribus que compartían recursos y conocimientos para cazar, recolectar alimentos y protegerse de los peligros. La cooperación y la solidaridad eran esenciales para la supervivencia.
Con el desarrollo de la agricultura, las comunidades evolucionaron hacia asentamientos más permanentes. La capacidad de cultivar alimentos permitió la formación de aldeas y pueblos, donde la gente podía establecerse y construir relaciones más complejas. Esto llevó al surgimiento de una división del trabajo más especializada y al desarrollo de habilidades artesanales.
Las civilizaciones antiguas, como la sumeria, egipcia, griega y romana, dieron paso a la formación de ciudades y sociedades más organizadas. Las comunidades se convirtieron en centros de comercio, gobierno y cultura. Se construyeron estructuras monumentales, como templos y palacios, que unificaron a las personas en torno a creencias religiosas y sistemas políticos.
Durante la Edad Media, las comunidades se organizaron en torno a sistemas feudales. Los señores feudales gobernaban sobre las tierras y las personas locales. Las aldeas y feudos eran autónomos en gran medida y se centraban en la agricultura y la autosuficiencia.
La Revolución Industrial marcó un cambio importante en la estructura de las comunidades. La industrialización dio lugar a la urbanización, con muchas personas dejando las zonas rurales para trabajar en fábricas en las ciudades.
En la era moderna, las comunidades han continuado evolucionando con avances tecnológicos y la globalización. Las redes sociales y las comunicaciones digitales han conectado a personas de todo el mundo, creando comunidades virtuales en línea.
### Bitcoin | Nostr y la chispa del constructor
Como ya vimos, un solo individuo puede inspirar a muchos otros, teniendo un efecto multiplicador. Esto no solo se traduce al mundo físico, por el contrario, esta directamente ligado a nuestra psicología, incluso podemos decir que va aun mas allá, adentrándonos en el terreno ideológico y espiritual.
Hasta hace no mucho, estábamos a merced de las grandes corporaciones que construían todo por nosotros, mientras esperábamos con ansias las nuevas actualizaciones de cada iteración de sus productos. Cada vez mas y mas nos hacíamos dependientes de dichas corporaciones sin quizás notarlo, poco a poco se fueron apoderando de nuestro tiempo y muy insidiosamente de nuestra personalidad e identidad.
Gracias a las alternativas presentadas hoy en día y a los individuos que inspiran a otros, existe la posibilidad de construir algo que va mas allá de las grandes corporaciones, porque transciende no solo el nivel físico y digital, sino que también transciende a los individuos que aportan a la comunidad. Estoy hablando por supuesto de Nostr, y como los incentivos están alineados gracias a Bitcoin.
Pongamos como ejemplo un par de nombres para ilustrar como individuos que inspirar pueden crear una chispa que se extiende a cada persona dentro de la comunidad.
Personajes como nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft nostr:npub1utx00neqgqln72j22kej3ux7803c2k986henvvha4thuwfkper4s7r50e8 nostr:npub1v0lxxxxutpvrelsksy8cdhgfux9l6a42hsj2qzquu2zk7vc9qnkszrqj49 nostr:npub107jk7htfv243u0x5ynn43scq9wrxtaasmrwwa8lfu2ydwag6cx2quqncxg (entre muchos otros que podría mencionar pero todo el articulo seria una lista de nombres) han inspirado a otros desarrolladores, creadores de contenido (y todas las otras especializaciones que te puedas imaginar…) A construir sobre este protocolo. Incluso, personas como el caso mas reciente de nostr:npub1m64hnkh6rs47fd9x6wk2zdtmdj4qkazt734d22d94ery9zzhne5qw9uaks han encontrado inspiración para aprender a programar sobre estos mismos rieles.
> nostr:nevent1qqs8fe938k7j5sxcprrv89ezpu09m9pzm90f0sq24hnwlwu0rmn09qcpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxg5vtygh
La chispa del constructor en palabras mas concisas es: **Inspiración multiplicadora en pos de la productividad y por ende, del crecimiento de una comunidad.**
Sin Bitcoin y Lightning Network, esto seria posible, pero mucho menos efectivo debido a que las personas detrás de toda labor que este enfocada en creación de contenido, desarrollo, etc. Tienen que comer.
### Conclusión
La chispa del constructor radica en la inspiración individual que impulsa a la acción colectiva. Desde la evolución de la construcción hasta las comunidades digitales, **el poder de un individuo inspirado puede moldear el presente y el futuro de las comunidades en todo el mundo.**
-

@ a012dc82:6458a70d
2025-02-19 16:20:32
The cryptocurrency world is on the verge of a groundbreaking transformation with the anticipated introduction of Bitcoin Exchange-Traded Funds (ETFs). This significant development is set to redefine the realm of crypto-investment, merging the innovative world of digital currencies with the established domain of traditional finance. Bitcoin ETFs represent a monumental shift, not just as a novel investment option, but as a revolutionary bridge connecting the cutting-edge technology of cryptocurrencies with the more familiar territory of stock market investments. This fusion is poised to unlock a new level of accessibility, drawing mainstream investors into the Bitcoin sphere, who were previously hesitant due to the complexities and perceived risks associated with direct cryptocurrency dealings.
**Table of Contents**
- The Emergence of Bitcoin ETFs
- Unveiling Opportunities
- Confronting the Dangers
- The Road Ahead
- Expanding the Horizon
- Enhanced Market Dynamics
- Technological Advancements
- Educational Initiatives
- Global Impact
- Conclusion
- FAQs
**The Emergence of Bitcoin ETFs**
Bitcoin ETFs are poised to revolutionize the cryptocurrency market. They offer a streamlined avenue for investment in Bitcoin, bypassing the intricacies of direct ownership such as wallet management and key security. This simplicity could democratize Bitcoin investment, potentially enhancing its liquidity and stability.
**Unveiling Opportunities**
- **Broader Investor Appeal:** Bitcoin ETFs simplify cryptocurrency investment, making it more approachable for the average investor and traditional financial players. This could lead to wider adoption and recognition of Bitcoin as a viable asset class.
- **Influx of Institutional Capital:** ETFs could catalyze a surge of institutional funds into the Bitcoin market. Institutions, previously hesitant due to regulatory and security concerns, might view ETFs as a safer investment avenue.
- **Market Evolution:** The advent of Bitcoin ETFs signals a maturation of the cryptocurrency market, transitioning towards regulated, mainstream financial products. This evolution could bolster investor confidence and market stability.
**Confronting the Dangers**
The introduction of Bitcoin ETFs is not devoid of risks and challenges.
- **Amplified Volatility:** Bitcoin's notorious volatility could be intensified by the influx of new investors via ETFs, particularly if large capital movements occur swiftly.
- **Regulatory Hurdles:** The evolving regulatory framework for cryptocurrencies could become more complex with Bitcoin ETFs, inviting stricter regulations that may impact the market dynamics.
- **Systemic Implications:** Integrating Bitcoin into the traditional financial system through ETFs could introduce new systemic risks. A significant downturn in Bitcoin's value might have broader implications for investors and funds linked to these ETFs.
**The Road Ahead**
As the Bitcoin ETF era dawns, investors should exercise caution. The potential of Bitcoin ETFs is substantial, but the accompanying risks warrant serious consideration. Investors should engage in comprehensive research and assess their risk appetite before engaging with these new investment vehicles.
**Expanding the Horizon**
**Enhanced Market Dynamics**
The introduction of Bitcoin ETFs could lead to more dynamic market behaviors. As traditional and crypto markets become more intertwined, the impact of global economic events on Bitcoin's price could become more pronounced, leading to new investment strategies and market analysis techniques.
**Technological Advancements**
The growth of Bitcoin ETFs might spur technological advancements in trading platforms and financial tools. Enhanced security measures, improved trading algorithms, and more sophisticated risk management tools could emerge, catering to the unique needs of cryptocurrency ETFs.
**Educational Initiatives**
With the growing interest in Bitcoin ETFs, there's likely to be an increase in educational resources and initiatives aimed at helping investors understand the nuances of cryptocurrency investments. This could lead to a more informed investor base, capable of making better investment decisions in the volatile world of cryptocurrencies.
**Global Impact**
The success of Bitcoin ETFs in one region, such as the United States, could encourage other countries to follow suit, leading to a more globalized cryptocurrency market. This could have significant implications for international financial regulations and cooperation.
**Conclusion**
The potential introduction of Bitcoin ETFs marks a significant milestone in the journey of cryptocurrency investment. While it heralds new opportunities and greater accessibility, it also brings forth challenges and risks that need to be navigated with care. The future of Bitcoin ETFs will hinge on the balance between these opportunities and dangers, and the market's ability to adapt to this new phase of crypto-investment. As we stand at the threshold of this exciting era, the global financial community watches with bated breath, ready to witness the unfolding story of Bitcoin ETFs.
**FAQs**
**How does a Bitcoin ETF differ from direct Bitcoin investment?**
Investing in a Bitcoin ETF means you're investing in a fund that holds Bitcoin as its primary asset, as opposed to buying Bitcoin directly and managing your own digital wallet and security. ETFs are also subject to different regulatory and tax treatments.
**What are the benefits of Bitcoin ETFs?**
Bitcoin ETFs offer easier access to Bitcoin investment, potentially lower risks compared to direct ownership, and the convenience of trading through traditional investment platforms.
**What risks are associated with Bitcoin ETFs?**
Risks include the inherent volatility of Bitcoin, potential regulatory changes, and systemic risks if the cryptocurrency market impacts the broader financial system.
**Are Bitcoin ETFs available globally?**
The availability of Bitcoin ETFs varies by country, depending on the regulatory environment. Some countries may not yet have approved Bitcoin ETFs for trading.
**Can Bitcoin ETFs impact the price of Bitcoin?**
Yes, Bitcoin ETFs can impact Bitcoin's price as they can increase market liquidity and bring in more institutional investors, potentially leading to price changes.
**That's all for today**
**If you want more, be sure to follow us on:**
**NOSTR: croxroad@getalby.com**
**X: [@croxroadnews.co](https://x.com/croxroadnewsco)**
**Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)**
**Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)**
**Store: https://croxroad.store**
**Subscribe to CROX ROAD Bitcoin Only Daily Newsletter**
**https://www.croxroad.co/subscribe**
***DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.***
-

@ ed364ee5:261fd74f
2025-02-19 11:57:26
Cardiovascular Ultrasound: Advancements Driving Early Detection and Personalized Care
The [cardiovascular ultrasound market](https://www.marketresearchfuture.com/reports/cardiovascular-ultrasound-market-1548
) is experiencing significant growth as technological advancements, rising cardiovascular disease (CVD) rates, and a shift toward non-invasive diagnostics drive demand. This imaging technology, which uses sound waves to visualize the heart and surrounding blood vessels, is now essential in both preventative cardiology and acute care.
Technological Innovations Boosting Accuracy and Accessibility
Recent developments have revolutionized cardiovascular ultrasound devices. High-frequency transducers, 3D and 4D imaging, and artificial intelligence (AI) integration are enhancing diagnostic precision. AI, in particular, is automating image analysis, reducing variability, and enabling faster, more accurate diagnosis.
Portable cardiovascular ultrasound systems are another game-changer, increasing accessibility to rural or remote areas and allowing for bedside monitoring in hospitals. Companies are focusing on smaller, more affordable devices without compromising imaging quality, expanding the use of this technology beyond large hospital systems.
Global Trends and Growing Disease Burden
Cardiovascular diseases remain the leading cause of death worldwide, responsible for an estimated 17.9 million deaths annually, according to the World Health Organization (WHO). Early detection is critical to reducing mortality, and cardiovascular ultrasound is playing a pivotal role in identifying conditions such as heart valve disorders, atrial fibrillation, and cardiomyopathies at an earlier stage.
Regions like North America and Europe lead the market due to high healthcare expenditure and greater adoption of advanced diagnostic technologies. However, emerging economies in Asia-Pacific and Latin America are witnessing rapid growth as awareness and healthcare infrastructure improve.
Challenges and Market Outlook
Despite its advantages, the cardiovascular ultrasound market faces challenges such as the high cost of advanced systems and a shortage of trained sonographers. To address these issues, some manufacturers are investing in user-friendly interfaces and remote training programs to ensure broader adoption.
Looking ahead, the cardiovascular ultrasound market is projected to grow steadily, driven by ongoing innovation and the increasing prevalence of CVD. Personalized medicine initiatives and telemedicine adoption are expected to further integrate cardiovascular ultrasound into routine patient care.
Conclusion
As cardiovascular ultrasound technology continues to evolve, it holds the promise of earlier detection, more precise diagnosis, and improved patient outcomes. With rising healthcare demands and technological advancements, this sector is set to play a key role in the fight against heart disease for years to come.
-

@ ed364ee5:261fd74f
2025-02-19 11:50:46
Innovations and Demand Surge in Knee Replacement Procedures
In recent years, [knee replacement](https://www.marketresearchfuture.com/reports/knee-replacement-market-1578
) surgeries have seen a significant rise in demand, fueled by advancements in medical technology, an aging global population, and a growing awareness of treatment options. As healthcare providers and medical device manufacturers adapt to this surge, groundbreaking innovations are transforming the landscape of orthopedic care.
Rising Demand for Knee Replacements
According to recent data from global health agencies, the number of knee replacement surgeries performed annually has increased by over 25% in the past decade. Experts attribute this rise to the aging baby boomer generation, higher rates of obesity, and increased sports-related injuries. Additionally, the growing acceptance of elective surgeries has led younger patients to seek knee replacements to maintain active lifestyles.
Technological Advancements in Knee Implants
One of the most notable trends is the development of personalized knee implants. Utilizing 3D printing and computer-aided design (CAD), manufacturers can now create implants tailored to the specific anatomy of each patient. This approach not only enhances the fit and comfort of the implant but also reduces the risk of post-surgery complications.
Robotic-assisted surgery is another game-changer. These systems provide surgeons with enhanced precision, enabling them to make smaller incisions and reduce damage to surrounding tissues. As a result, patients experience faster recovery times and improved long-term outcomes.
"Robotics and AI-driven surgical planning are revolutionizing the way we approach knee replacements," said Dr. Emily Carter, an orthopedic surgeon at [Hospital Name]. "Patients are benefiting from less pain, quicker mobility, and more natural joint function."
Enhanced Post-Surgery Rehabilitation
Post-operative care has also evolved, with new physical therapy protocols focused on accelerated rehabilitation. Virtual physical therapy platforms are making it easier for patients to access guided exercises from home, ensuring they adhere to their recovery plans. Additionally, wearable sensors are being integrated into recovery regimens to track patients' progress and provide real-time feedback to healthcare providers.
Affordability and Access
Despite the technological advancements, affordability remains a concern for many patients. In response, several healthcare systems and insurance providers are expanding coverage for knee replacement surgeries. Additionally, some manufacturers are developing cost-effective implant options to address pricing challenges in underserved regions.
Future Outlook
The future of knee replacement is promising. With ongoing research into biologic solutions, such as cartilage regeneration and stem cell therapy, patients may soon have access to alternatives that delay or even prevent the need for full joint replacement.
"The orthopedic industry is on the cusp of major breakthroughs," said Dr. Carter. "Our goal is to provide every patient with the best possible outcome, whether through traditional surgery or emerging biologic treatments."
As innovation continues to drive the evolution of knee replacement procedures, patients can look forward to more effective and accessible treatment options that improve quality of life and mobility for years to come.
-

@ d4309e24:8a81fcb0
2025-02-19 11:17:19
## Introduction: The Challenge of Time-Lock Encryption and Clock Servers
When I first set out to build **Hatchstr**, the idea was simple: create a way to send messages into the future, encrypted and locked to a specific Bitcoin block height. These messages would remain encrypted until the chosen block height was reached, creating a unique way to send a message to the future.
However, as I began working through the details, I quickly ran into some challenges. One key component of this system involves **clock servers**—decentralized nodes responsible for releasing decryption keys when the specified block height is reached.
### Clock Server Setup: The Basics
Initially, I adopted a simple model: each clock server holds a single public-private key pair *unique to that server* for a specific block height. When a user creates a message, they choose a clock server to trust and encrypt with the specific public key tied to that block height. Then, when the time comes, the clock server releases its private key to decrypt the message.

#### Positives:
- ✅ **Clean and Efficient Storage**: Each clock server only needs to store a single key pair for each block height, making storage lightweight and scalable.
- ✅ **Lazy Key Generation**: Keys are generated on-demand, meaning they’re only created when needed. This prevents unnecessary key generation or storage overhead.
- ✅ **Decentralized**: The clock servers don’t need to coordinate with each other or store any sensitive data besides their respective private keys, which simplifies the system architecture.
- ✅ **Limited Release Events**: Since each clock server only handles keys tied to a specific block height, the number of release events required is minimized, simplifying the key management process.
At first, this seemed like a good approach, but I quickly realized there were **critical limitations**:
#### Challenges:
- ❌ **Server Shutdown**: Capsules could be scheduled for many years in the future. If a clock server shuts down, all future capsules linked to it are lost.
- ❌ **Server Downtime**: If one of the clock servers is unavailable during unlock time, even for a short period, it leads to a delay for the users waiting for unlock.
- ❌ **Premature Release**: If a clock server accidentally releases its key too early, it could compromise the message, making it accessible before the intended time.
Though the setup worked for a basic system, I soon realized it couldn’t guarantee the reliability I wanted for a decentralized application.
## Tackling the Challenges of Multi-Sig and Secret Sharing
When I first approached the problem of securing time-lock capsules, I initially considered using multi-signature (multi-sig) solutions as a potential approach. The goal was simple: instead of relying on a single clock server to release its key, I could involve multiple servers to sign off on the decryption. This way, if one server failed or misbehaved, the message would still be protected.
However, as I delved deeper into the multi-sig approach, I quickly realized there were a few key issues:
🔒 **Communication Overhead**: Multi-sig requires servers to communicate and coordinate with each other. This introduces the possibility of new failure points, like network issues or miscommunication.
⚡ **Server Synchronization**: If one server was out of sync or released its key too early, it could still lead to the message being decrypted prematurely, breaking the system.
🛠 **Increased Complexity**: Each server would need to store and manage a unique key pair for every message, making the system more complicated and less efficient.
I quickly realized that multi-sig wasn’t the best fit for this kind of setup. Not only did it add unnecessary complexity, but it also conflicted with the decentralization goals I wanted to achieve. So, I started thinking about ways to **distribute the secret** across the clock servers without introducing all these new complications.
### Enter Shamir’s Secret Sharing (SSS)
Shamir's Secret Sharing (SSS) is a cryptographic technique designed to split a secret into multiple parts (called "shares") so that the secret can only be reconstructed when a specific minimum number of shares are combined. This process is based on polynomial interpolation, and it’s a powerful way to distribute secrets securely.
#### The Basic Concept
In SSS, a secret (like a cryptographic key or message) is divided into *n* shares, where *n* is the total number of shares you want to generate. You also specify a threshold, *k*, which represents the minimum number of shares required to reconstruct the original secret.
- **n** is the total number of shares.
- **k** is the minimum number of shares required to reconstruct the secret (known as the "threshold").
For example, in a **3-out-of-5** scheme, the secret is split into 5 shares, but at least 3 shares are required to reconstruct the secret. If fewer than 3 shares are available, the secret cannot be reconstructed.
#### Why This is Secure
Shamir’s Secret Sharing is secure because, with fewer than *k* shares, it is computationally infeasible to learn anything about the secret. The shares themselves don’t reveal any information; it’s only the combination of the right number of shares that allows reconstruction. This makes it resistant to attacks, as even if an attacker gets hold of some shares, they won’t be able to reconstruct the secret unless they have the required minimum number of shares (comparable to 256-bit cryptographic strength).
#### Applications of Shamir’s Secret Sharing
Shamir’s Secret Sharing is widely used in scenarios where high availability and reliability are needed, but security and privacy are equally important. Examples include:
- **Key management**: Protecting encryption keys by distributing them across multiple parties.
- **Multi-signature setups**: Requiring multiple parties to sign off on a transaction or access a secure system.
- **Distributed systems**: Ensuring that no single party holds a complete secret, and multiple parties must collaborate to unlock it.
By leveraging Shamir's Secret Sharing, you can strike the right balance between **redundancy**, **security**, and **availability** for your system’s sensitive information.
### The Problem with Distributing Secret Shares
SSS could give us exactly the properties I was looking for, with the added benefit that users could choose their preferred setup, for example:
- **1-out-of-5 scheme**: Prioritizing the likelihood that the message is decrypted even if only one of the 5 chosen clock servers does its job at unlock time. With the tradeoff that each of the 5 could leak the message early.
- **3-out-of-5 scheme**: A measured approach that allows for 2 servers to stop working and would also keep the capsule private even if 2 clock servers leak their secret early.
So I considered an approach where each clock server would store part of the key. Instead of a single server holding the full key, I would split the key into parts and distribute those parts across multiple servers. When the time arrived, I’d gather the required number of shares to reconstruct the key and decrypt the message.
At first glance, this seemed like a promising approach. But when we look through the implications, a few problems started to emerge:
💥 **Overhead**: Each clock server would need to store a share of every key for every message. This would quickly become inefficient and result in unnecessary overhead.
🔔 **Exploding Reveal Events**: Since each clock server would need to release all its shares at a specific time, there would be a massive increase in the number of reveal events, spamming and possibly overloading Nostr relays.
While the idea of distributing the key was very appealing, the practical issues around overhead and complexity made it clear that this wasn’t the final solution. I needed something that would be more efficient, scalable, while still in line with the decentralized model I was aiming for.
### Discovering a Hybrid Solution
After testing out various approaches, I realized that the breakthrough wasn’t just about Shamir’s Secret Sharing (SSS)—that part was fairly intuitive. The real insight came when I thought about how to preserve the original clock server design while solving the challenges of failover and early release.
Instead of having the clock servers store the secret or a share of it, **I kept the original design**: each clock server only holds a public-private key pair tied to a block height, as initially planned. The twist came when I decided to split an ephemeral AES key into shards using Shamir’s Secret Sharing, but instead of directly storing shares at the clock servers, we could encrypted each share with the public key of the clock server.
This approach would allow us to keep the clock server’s role simple:
When the time comes, the servers release their private keys, which can then be used to decrypt the encrypted shares of the AES key that were published alongside the original encrypted message. These shares, once decrypted, allow for the reconstruction of the AES key, which in turn decrypts the message.
This solution solved several key issues:
- ✅ **No Coordination Between Servers**: Each clock server only holds one key pair for a specific block height and doesn’t need to know about the other servers. This simplifies the system and removes the need for complex server coordination.
- ✅ **Minimal Overhead**: The clock servers only store a single key pair per block height, eliminating the need to store individual keys for each message.
- ✅ **Fault Tolerance**: If one clock server is offline, the other shares can still reconstruct the AES key and decrypt the message, ensuring reliability.
- ✅ **Client-Side Security**: The AES key is generated on the client side and never stored on the clock servers, providing a high level of security.
By combining the simplicity of the clock server model with the power of Shamir’s Secret Sharing, this hybrid solution allows us to securely split an AES key and manage decryption while ensuring the system remains decentralized, resilient, and efficient.
This was the method I had been searching for.
### The Process Breakdown
1. **AES Key Generation**:
- A **random AES key** is generated on the **client side** for each message. This key is **never stored** anywhere, ensuring that it remains secure and only used for encrypting the message.
2. **Shamir’s Secret Sharing**:
- The AES key is split into (in this example) **3 shares** using Shamir’s Secret Sharing. These shares are associated with **3 independent clock servers**.
- The threshold of **2 out of 3** means that only **2 clock servers** needed later to reconstruct the AES key and decrypt the message.
3. **Encrypting with Public Keys**:
- The secret shares are then **encrypted** using the **public keys** of the target block height for each specific clock server. This ensures that the shares are secure until the proper time comes.
4. **Storage**:
- The **encrypted shares** together with the **AES-encrypted message** can be published to Nostr relais or stored on a decentralized platform like **IPFS**, which provides redundancy and availability.
5. **Clock Servers Release Keys**:
- When the specified **Bitcoin block height** is reached, each clock server publishes its **private key** to Nostr, allowing everyone to decrypt the shares.
- The client reconstructs the AES key from the decrypted shares and finally decrypts the original message.

## Conclusion: An Elegant Solution to Time-Lock Encryption
Through a series of experiments and iterations, We finally landed on a solution that balances **security**, **scalability**, and **efficiency**. By combining **AES encryption** with **Shamir’s Secret Sharing**, We were able to solve the multi-sig failover problem without adding unnecessary complexity. 🔥
### An Open Question: Clock Server Incentives 💰
Decentralized systems thrive when participants are motivated to contribute. For Hatchstr, a critical question remains: Why would anyone run a clock server?
One possibility is allowing users to **zap** (tip) servers for each capsule they help unlock. But this is just a starting point—how do we ensure reliability without centralizing trust?
I’d love to hear your thoughts. How would you design incentives for a decentralized network of clock servers?
This part is crucial, and I’m excited to explore it with the community.
### What's Next for Hatchstr?
🧩 **Leveraging Nostr**: Let's see how we can integrate the Nostr NIP standards and previous protocol developments into our system to enhance communication and data integrity.
🔮 **Designing a Web App**: We'll explore building a user-friendly web application for creating and managing digital time capsules. Focus will be on enhancing usability, interface design, and user interaction.
🎛️ **Building a Clock Server with Elixir**: We'll delve into developing a simple clock server using Elixir, capitalizing on its strengths in concurrency and real-time processing to support our time-locking mechanisms.
Stay tuned as we advance both the user experience and the backend infrastructure of Hatchstr together.
If you're interested in following along or contributing to the development, feel free to reach out!
[Nostr QR](https://bafybeig6dmqshbd7khcd7qr7ce6inslx4muebtt3bk5m33f4dplsx4et7y.ipfs.w3s.link/nostr_qr.png)
```
npub16scfufrpsqcukjg7ymu4r40h7j4dwqy4pajgz48e6lmnmz5pljcqh678uh
```
Thank you for reading and being part of this journey! 🧡
-

@ d360efec:14907b5f
2025-02-19 11:07:53
**ภาพรวม BTCUSDT (OKX):**
Bitcoin (BTCUSDT) ยังคงแสดงความผันผวนและมีความไม่แน่นอนสูง แม้ว่าแนวโน้มระยะยาว (TF Day) จะยังคงเป็นขาขึ้น *แต่ก็อ่อนแรงลงอย่างเห็นได้ชัด* แนวโน้มระยะกลาง (TF 4H) กลายเป็นขาลงระยะสั้น และแนวโน้มระยะสั้น (TF 15m) ก็เป็นขาลงเช่นกัน สถานการณ์ตอนนี้บ่งบอกถึงแรงขายที่แข็งแกร่ง และมีความเสี่ยงสูงที่จะปรับฐานลงต่อ
**วิเคราะห์ทีละ Timeframe:**
**(1) TF Day (รายวัน):** [https://www.tradingview.com/x/wfDqxmvG/]
* **แนวโน้ม:** ขาขึ้น (Uptrend) *อ่อนแรงลงอย่างมาก*
* **SMC:**
* Higher Highs (HH) และ Higher Lows (HL) *เริ่มไม่ชัดเจน*
* Break of Structure (BOS) ด้านบน *แต่มีการปรับฐานที่รุนแรง*
* **Liquidity:**
* มี Sellside Liquidity (SSL) อยู่ใต้ Lows ก่อนหน้า (บริเวณ 85,000 - 90,000)
* มี Buyside Liquidity (BSL) อยู่เหนือ High เดิม
* **ICT:**
* **Order Block:** ราคาหลุด Order Block ขาขึ้น (บริเวณแท่งเทียนสีเขียวก่อนหน้านี้) *สัญญาณลบ*
* **EMA:**
* ราคา *หลุด* EMA 50 (สีเหลือง) ลงมาแล้ว
* EMA 200 (สีขาว) เป็นแนวรับถัดไป
* **Money Flow (LuxAlgo):**
* *สีแดงยาว* แสดงถึงแรงขายที่แข็งแกร่ง
* **Trend Strength (AlgoAlpha):**
* สีแดง แสดงถึงแนวโน้มขาลง
* **Volume Profile:** Volume ค่อนข้างเบาบาง
* **แท่งเทียน:** แท่งเทียนล่าสุดเป็นสีแดง แสดงถึงแรงขาย
* **แนวรับ:** EMA 200, บริเวณ 85,000 - 90,000 (SSL)
* **แนวต้าน:** EMA 50, High เดิม
* **สรุป:** แนวโน้มขาขึ้นอ่อนแรงลงอย่างมาก, ราคาหลุด EMA 50 และ Order Block, Money Flow และ Trend Strength เป็นลบ
**(2) TF4H (4 ชั่วโมง):** [https://www.tradingview.com/x/WCWYkleo/]
* **แนวโน้ม:** ขาลง (Downtrend)
* **SMC:**
* Lower Highs (LH) และ Lower Lows (LL)
* Break of Structure (BOS) ด้านล่าง
* **Liquidity:**
* มี SSL อยู่ใต้ Lows ก่อนหน้า
* มี BSL อยู่เหนือ Highs ก่อนหน้า
* **ICT:**
* **Order Block:** ราคาไม่สามารถผ่าน Order Block ขาลงได้
* **EMA:**
* ราคาอยู่ใต้ EMA 50 และ EMA 200
* **Money Flow (LuxAlgo):**
* สีแดง แสดงถึงแรงขาย
* **Trend Strength (AlgoAlpha):**
* สีแดง แสดงถึงแนวโน้มขาลง
* **Volume Profile:** Volume ค่อนข้างนิ่ง
* **แนวรับ:** บริเวณ Low ล่าสุด
* **แนวต้าน:** EMA 50, EMA 200, บริเวณ Order Block
* **สรุป:** แนวโน้มขาลงชัดเจน, แรงขายมีอิทธิพล
**(3) TF15 (15 นาที):** [https://www.tradingview.com/x/HsgVKFW2/]
* **แนวโน้ม:** ขาลง (Downtrend)
* **SMC:**
* Lower Highs (LH) และ Lower Lows (LL)
* Break of Structure (BOS) ด้านล่าง
* **ICT:**
* **Order Block** ราคาไม่สามารถผ่าน Order Block ได้
* **EMA:**
* EMA 50 และ EMA 200 เป็นแนวต้าน
* **Money Flow (LuxAlgo):**
* สีแดง แสดงถึงแรงขาย
* **Trend Strength (AlgoAlpha):**
* สีแดง แสดงถึงแนวโน้มขาลง
* **Volume Profile:** Volume ค่อนข้างเบาบาง
* **แนวรับ:** บริเวณ Low ล่าสุด
* **แนวต้าน:** EMA 50, EMA 200, Order Block
* **สรุป:** แนวโน้มขาลง, แรงขายมีอิทธิพล
**สรุปภาพรวมและกลยุทธ์ (BTCUSDT):**
* **แนวโน้มหลัก (Day):** ขาขึ้น (อ่อนแรง), *หลุด Order Block*
* **แนวโน้มรอง (4H):** ขาลง
* **แนวโน้มระยะสั้น (15m):** ขาลง
* **Liquidity:** มี SSL ทั้งใน Day, 4H, และ 15m
* **Money Flow:** เป็นลบในทุก Timeframes
* **Trend Strength:** 4H, 15m เป็นขาลง
* **กลยุทธ์:**
1. **Wait & See (ดีที่สุด):** รอความชัดเจน
2. **Short (เสี่ยง):** ถ้าไม่สามารถ Breakout EMA/แนวต้านใน TF ใดๆ ได้
3. **ไม่แนะนำให้ Buy:** จนกว่าจะมีสัญญาณกลับตัวที่ชัดเจน
**คำแนะนำ:**
* **ความขัดแย้งของ Timeframes:** Day ยังเป็นขาขึ้น (แต่สัญญาณอ่อน), 4H และ 15m เป็นขาลง
* **Money Flow:** เป็นลบในทุก Timeframes
* **ระวัง SSL:** Smart Money อาจจะลากราคาลงไปกิน Stop Loss
* **ถ้าไม่แน่ใจ อย่าเพิ่งเข้าเทรด**
**Day Trade & การเทรดรายวัน:**
* **Day Trade (TF15):**
* **Short Bias:** หาจังหวะ Short เมื่อราคาเด้งขึ้นไปทดสอบแนวต้าน (EMA, Order Block)
* **Stop Loss:** เหนือแนวต้านที่เข้า Short
* **Take Profit:** แนวรับถัดไป (Low ล่าสุด)
* **ไม่แนะนำให้ Long** จนกว่าจะมีสัญญาณกลับตัวที่ชัดเจน
* **Swing Trade (TF4H):**
* **Short Bias:** รอจังหวะ Short เมื่อราคาไม่สามารถผ่านแนวต้าน EMA หรือ Order Block ได้
* **Stop Loss:** เหนือแนวต้านที่เข้า Short
* **Take Profit:** แนวรับถัดไป (EMA 200 ใน TF Day, SSL)
* **ไม่แนะนำให้ Long** จนกว่าจะมีสัญญาณกลับตัวที่ชัดเจน
**สิ่งที่ต้องระวัง:**
* **Sellside Liquidity (SSL):** มีโอกาสสูงที่ราคาจะถูกลากลงไปแตะ SSL ก่อนที่จะมีการกลับตัว (ถ้ามี)
* **False Breakouts:** ระวังการ Breakout หลอกทั้งใน TF15 และ TF4H
* **Volatility:** ตลาดคริปโตฯ มีความผันผวนสูง เตรียมพร้อมรับมือกับการเปลี่ยนแปลงของราคาอย่างรวดเร็ว
**Disclaimer:** การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ
-

@ 604e96e0:20279eb2
2023-08-11 18:39:36
notacomment allows you to zap nostr notes when you comment on them. In order to use notacomment, you have to run a script yourself either on your own computer or in the cloud somewhere. To get started open https://github.com/SamSamskies/notacomment in a browser tab.
At this point, I'm sure a lot of you are feeling like this:

Let's breakdown the instructions from the README.
## Prerequisites
Node.js and npm - I suggest installing the latest Node.js LTS version from https://nodejs.org. That should also install npm.
Once installation is complete, open your terminal. On a Mac you can press cmd + spacebar and type in `terminal` to open the terminal. On other platforms, you'll have to ask ChatGPT 😂
.
To verify installation of Node.js type `node -v`. To verify installation type `npm -v`.
It should look something like this:

Leave the terminal open.
## Downloading the code to your computer
The easiest way to download the code is to download the zip file from the GitHub repo. Remember that first link I told you to open? That's the GitHub repo. Click the green button that says `Code` on it and click `Download ZIP` from the menu.

Now unzip the file and then navigate to the folder in the terminal. To navigate to the folder use the `cd` command. If you unzipped the folder in the `Downloads` folder, you can navigate to the folder by typing `cd ~/Downloads/notacomment-main/`.
## Usage With Strike
1. Create an account with Strike if you don't already have one https://strike.me/download/
1. Get a Strike API key with all the payment scopes from https://dashboard.strike.me/
1. Create a .env file and provide NOSTR_NSEC and STRIKE_API_KEY values (see .env.example)
1. Install the dependencies using npm or yarn or whatever your heart desires
1. Make sure you have money in your Strike account
1. Run the script `npm start`
Keep in mind that Strike pays the invoices from your cash balance. This means the payment rounds up to the nearest cent when paying an invoice, so if you set the zap amount to 1 sat, you'll be sending more money to Strike than the person you are zapping with every zap.
## Usage With LNbits
I recommend making a separate wallet from your main LNbits wallet for usage with notacomment in case you accidentally leak the admin key.
1. Create a .env file and provide NOSTR_NSEC, LNBITS_ADMIN_KEY, and LNBITS_URL values (see .env.example)
1. Install the dependencies using npm or yarn or whatever your heart desires
1. Make sure you have sats in your LNbits wallet
1. Run the script `npm start`
## Usage With Nostr Wallet Connect
1. Create a NWC connection string using something like https://nwc.getalby.com/
1. Create a .env file and provide NOSTR_NSEC and NWC_CONNECTION_STRING values (see .env.example)
1. Install the dependencies using npm or yarn or whatever your heart desires
1. Make sure you have sats in your wallet that you generated the NWC connection string with
1. Run the script `npm start`
<br />
<br />
Screenshot of terminal with commands to install dependencies, create .env file, open .env file, and start the script:

-

@ e83b66a8:b0526c2b
2025-02-19 09:49:25
I am seeing a groundswell of interest in adopting Bitcoin in small businesses replacing or augmenting existing merchant services.
This has many advantages for these businesses including:
Attracting Bitcoiners as customers over your competitors.
Allowing a self custody payment system which does not require purchasing equipment, monthly service fees and high transaction fees.
Self custody your money, removing banks and merchant service companies from taking a cut or interfering in the transaction process. i.e. Bitcoin behaves much more like cash in face to face transactions.
Building a Bitcoin Strategic Reserve allowing your profits to accumulate in value over time, just as Bitcoin increases in value due to scarceness and increased adoption.
If any or all of these are interesting to you, then here are a scale of merchant options available to you depending on your needs and interests.
SOLE TRADER
The easiest way for a sole trader to accept Bitcoin is to download the app “Wallet of Satoshi”
https://www.walletofsatoshi.com/
or for regions this is not available, use a web equivalent called COINOS
https://coinos.io/
This gives everything you’ll need, Bitcoin and Lightning receiving addresses, publishable as text or scannable as a QR code. The ability to generate a specific value invoice using Lightning which can be paid face to face or remotely over the Internet and a wallet to hold your Bitcoin balance.
This is a perfect start point, but moving forward it has some drawbacks. It is custodial, meaning that a company actually holds your Bitcoin. Unlike a bank, if that company fails, you loose your Bitcoin.
There is also no direct ability to move that Bitcoin to fiat currencies like USD or GBP, so if you need some of those earnings to pay suppliers in fiat currencies, you will struggle to convert.
If you are an online only retailer, then the industry standard is BTCPay
https://btcpayserver.org/
which can be integrated into most e-commerce systems
TRADITIONAL MERCHANT SERVICES
So the next option is to use a Bitcoin merchant service company. They look very similar to traditional fiat merchant service companies, they can supply infrastructure like PoS terminals and also handle the payments for you, optionally settling balances to your bank in USD or GBP etc…
They charge for the physical devices and their services and they charge a fee on each transaction in the same way traditional merchant service companies do, but usually these fees are significantly smaller.
Companies like MUSQET can help setup your business in this way if you wish.
https://musqet.tech/
CONSULTANCY
The third option is to use a consultancy service like Bridge2Bitcoin
https://bridge2bitcoin.com/
this is a company that will come in, explain the concepts and options and build a service around your needs. The company will build the solution you are looking for and make their money by providing the equipment and optionally running the payment solution for you.
SELF BUILD
If you have experience with Bitcoin and have optionally run your own Lightning node for a while, the tools exist to be able to develop your own solution in-house. And just as Bitcoin allows you to be your own bank, so Lightning allows you to be your own merchant services company.
Solutions like Umbrel
https://umbrel.com/
running Albyhub
https://albyhub.com/
with their POS solution
https://pos.albylabs.com/
are a low cost option you can build yourself. If you require devices like PoS terminals, these can be purchased from companies like
Swiss Bitcoin Pay:
https://swiss-bitcoin-pay.ch/store#!/Bitcoin-Merchant-Kit/p/709060174
as a package or Bitcoinize directly or in volume:
https://bitcoinize.com/
There is also the lower cost option of use software loaded onto your staffs iPhone or Android phone to use as a PoS terminal for your business:
https://swiss-bitcoin-pay.ch/
Swiss Bitcoin Pay can also take the Bitcoin payment and settle a final amount daily or even convert to fiat and deposit in your bank the next day.
If you are comfortable building and running your own server, then software from a company like
https://lnbits.com/
is a great option. They have built a core suite of tools, which others have built a huge ecosystem of extensions to handle everything from PoS to accounting to event ticketing and beyond.
LNbits is probably the most extensive ecosystem out there for anybody wishing to self build.
HYBRID
MUSQET also offer a PoS system for both Bitcoin and Fiat. They onboard merchants with traditional card services for Visa, Mastercard and Amex with Apple Pay and Google Pay all within the same device where they deploy Bitcoin Lightning as standard:
https://musqet.tech/
-

@ 6e75f797:a8eee74e
2023-08-07 13:16:42
Last night I started a nostr community multiplayer instance for No Man's Sky [on ZapStream](https://zap.stream/) and before we knew it, we had 4 Nostrichs arriving on the genesis planet to join the fun.

NSM is an deterministic, procedurally generated open universe where players can explore, quest, build, combat and have fun together. Every new system discovered is generated when the first Traveller enters the system making the game a unique experience for any open world gaming fan.
If you fancy joining us in the Nostrverse let me know and I'll friend you in #NMS and on Steam or Epic. If you just want to watch the fun, participate in naming systems, planets, fauna and flora come and hang out in my stream or the stream of [Oceanbee](nostr:npub1wqxxe0cjaxnvmrv4lkvx8d5dlft7ewswyn09w5v7fg7642fgzm7srucxws), [HolgerHatGarKeineNode](nostr:npub1pt0kw36ue3w2g4haxq3wgm6a2fhtptmzsjlc2j2vphtcgle72qesgpjyc6) or [taette](npub1yh0dl6pazf55025qvp860lstpscuy0kj2a5lfhxlk400m968vgpql5vsnd).

### If you already own NMS, feel free to add me!
My NMS friend code is: EMAZ-KMHT-ZPFXP
See you in space Traveller! - TheGrinder
-

@ 378562cd:a6fc6773
2025-02-20 16:35:11
In the ever-evolving landscape of social media, platforms like Twitter and Facebook have dominated the space for years. They’ve shaped the way we interact, share, and consume information. But as censorship concerns, algorithmic manipulation, and corporate control over data become more apparent, a new contender has emerged—NOSTR (Notes and Other Stuff Transmitted by Relays). The differences are striking for those who have stepped into the NOSTR ecosystem. Let’s dive into what sets it apart and why it’s more than just another social media platform—**it’s a movement**.
### **Decentralization vs. Corporate Control**
The fundamental structure is one of the most noticeable differences between NOSTR and traditional platforms like Twitter or Facebook. Both are owned by massive corporations that dictate what can and cannot be said. They collect data, sell advertisements, and use algorithms to curate what users see.
NOSTR, on the other hand, is fully decentralized. No single entity controls the platform, no shadowy moderation teams tweak visibility based on corporate interests, and no risk of being permanently banned by a faceless algorithm. Instead, NOSTR operates on an open protocol, allowing anyone to participate without gatekeepers. Your content is truly yours, and no one can take that away from you.
### **A Different Class of People**
Scrolling through Twitter or Facebook often feels like wading through a digital battlefield. Political flame wars, mind-numbing clickbait, and attention-seeking outrage dominate the feeds. While both platforms do have intelligent and well-meaning users, they are drowned out by noise, bots, and engagement-hacking algorithms designed to fuel division.
NOSTR, by contrast, attracts a different breed of users—people who value free speech, independent thought, and meaningful conversation. Many of them are builders, thinkers, and pioneers eager to create a better way of interacting online. There’s a noticeable shift in tone; rather than content driven by controversy and outrage, you’ll find people discussing innovation, philosophy, and real-world solutions. Conversations feel more organic, unfiltered, and free from the artificial constraints imposed by big tech algorithms.
### **Similarities Exist But With a Better Foundation**
At a glance, using a NOSTR client may seem similar to traditional social media platforms. Users post messages (called ‘notes’), interact with others, and build followings. You can reply, share, and engage much like you would on Twitter. But under the hood, everything operates on a more open, transparent system.
Instead of relying on centralized servers controlled by corporations, NOSTR functions through relays—public or private servers that transmit messages. Since there’s no corporate overlord dictating what gets priority in your feed, you see content chronologically and unfiltered. Additionally, identity and reputation are built through cryptographic keys rather than being at the mercy of a username that a platform can seize or shadowban at will.
### **No Ads, No Tracking, No Manipulation**
Let’s be honest—traditional social media has become a giant advertisement machine. Everything is optimized to keep you engaged just long enough to serve more ads and collect more data. Your feed isn’t showing you what’s most relevant; it’s showing you what makes the company the most money.
NOSTR eliminates this problem entirely. There are no forced ads, no trackers collecting your data, and no algorithm deciding what you should see. Instead, users fund relays or tip content creators directly, creating an ecosystem that values people over profit.
### **For New Users: A Starting Point**
If you’re new to NOSTR, welcome! I’m still a beginner myself, but I’ve already seen the potential this platform has to change how we connect online. Getting started can seem overwhelming at first, but there are a few key tools and resources that can help smooth the transition.
For a great user-friendly NOSTR client, **Damus** (for iOS) and **Amethyst** (for Android) are excellent places to start. If you prefer a web-based option, **Primal.net** offers a simple and intuitive experience. These platforms make it easy to dive in, start posting, and get a feel for how NOSTR operates.
But NOSTR isn’t just about social media—it’s a foundation for something bigger. Developers and innovators are expanding their reach beyond simple note-sharing. Specialized communities and applications are already emerging, including platforms for **photography, recipe sharing, and even swap sites**, all built using the NOSTR framework. The possibilities are growing, and the future looks bright.
### **Final Thoughts**
The shift from Twitter or Facebook to NOSTR isn’t just about switching platforms; it’s about embracing a fundamentally better way to communicate online. With decentralization, real freedom of expression, and a community of forward-thinking individuals, NOSTR offers an experience that traditional social media simply cannot match.
For those seeking a place where ideas flow freely, where profit-driven algorithms don’t dictate engagement, and where you control your own digital presence, NOSTR is not just an alternative. It’s an upgrade.
Let's connect and learn together!
npub1x7zk9nfqsjwuuwm5mpdu8eevsnu2kk0ff23fv58p45d50fhuvaeszg44p2
primal.net/Goody
-

@ 4d953dcb:39c9c35c
2025-02-18 22:03:42
Чтобы иметь бесплатный, быстрый и устойчивый к блокировке VPN нам нужны всего 2 вещи:
1. Клиент V2ray (приложение для использования VPN)
2. Файлы конфигурации (по сути данные VPN-серверов)
## Клиенты V2ray:
1. Инструкция по установке для Windows и Linux:
https://github.com/hiddify/Hiddify-Manager/wiki/Tutorial-for-HiddifyNext-app#adding-a-profile-to-the-app
*P.S. Если возникли проблемы с Hiddify-Next — пробуйте установить [Necoray](https://github.com/MatsuriDayo/nekoray)*
2. Инструкция по установке для Android:
https://github.com/hiddify/Hiddify-Manager/wiki/Tutorial-for-V2rayNG-app#add-configs-to-the-app
*P.S. Если возникли проблемы с V2rayNG — пробуйте установить [HiddifyNext](https://github.com/hiddify/hiddify-next/releases) ([инструкция](https://github.com/hiddify/Hiddify-Manager/wiki/Tutorial-for-HiddifyNext-app#adding-a-profile-to-the-app))*
3. Инструкция по установке для Windows и Linux:
https://github.com/hiddify/Hiddify-Manager/wiki/Tutorial-for-V2Box-app#add-subscription-links-to-the-app (лучше для iOS) + https://github.com/hiddify/Hiddify-Manager/wiki/Tutorial-for-Streisand#add-subscription-link (лучше для Mac)
*P.S. Если возникли проблемы с V2Box и Streisand — пробуйте установить [Hiddify-Next](https://github.com/hiddify/hiddify-next/releases) или [ShadowRocket](https://github.com/hiddify/Hiddify-Manager/wiki/Tutorial-for-ShadowRocket-app#add-subscription-link-to-the-app)*
## Источники файлов конфигураций:
1. https://outlinekeys.com/
2. https://proxytype.com/
3. https://vlesskey.com/
4. https://vpnkeys.org/
5. https://openproxylist.com/v2ray/
6. https://github.com/Epodonios/v2ray-configs
7. https://github.com/barry-far/V2ray-Configs?tab=readme-ov-file
8. https://github.com/M-Mashreghi/Free-V2ray-Collector
9. https://github.com/skywrt/v2ray-configs
10. https://github.com/0xdolan/v2ray_config_generator
-

@ daa41bed:88f54153
2025-02-09 16:50:04
There has been a good bit of discussion on Nostr over the past few days about the merits of zaps as a method of engaging with notes, so after writing a rather lengthy [article on the pros of a strategic Bitcoin reserve](https://geek.npub.pro/post/dxqkgnjplttkvetprg8ox/), I wanted to take some time to chime in on the much more fun topic of digital engagement.
Let's begin by defining a couple of things:
**Nostr** is a decentralized, censorship-resistance protocol whose current biggest use case is social media (think Twitter/X). Instead of relying on company servers, it relies on relays that anyone can spin up and own their own content. Its use cases are much bigger, though, and this article is hosted on my own relay, using my own Nostr relay as an example.
**Zap** is a tip or donation denominated in sats (small units of Bitcoin) sent from one user to another. This is generally done directly over the Lightning Network but is increasingly using Cashu tokens. For the sake of this discussion, how you transmit/receive zaps will be irrelevant, so don't worry if you don't know what [Lightning](https://lightning.network/) or [Cashu](https://cashu.space/) are.
If we look at how users engage with posts and follows/followers on platforms like Twitter, Facebook, etc., it becomes evident that traditional social media thrives on engagement farming. The more outrageous a post, the more likely it will get a reaction. We see a version of this on more visual social platforms like YouTube and TikTok that use carefully crafted thumbnail images to grab the user's attention to click the video. If you'd like to dive deep into the psychology and science behind social media engagement, let me know, and I'd be happy to follow up with another article.
In this user engagement model, a user is given the option to comment or like the original post, or share it among their followers to increase its signal. They receive no value from engaging with the content aside from the dopamine hit of the original experience or having their comment liked back by whatever influencer they provide value to. Ad revenue flows to the content creator. Clout flows to the content creator. Sales revenue from merch and content placement flows to the content creator. We call this a linear economy -- the idea that resources get created, used up, then thrown away. Users create content and farm as much engagement as possible, then the content is forgotten within a few hours as they move on to the next piece of content to be farmed.
What if there were a simple way to give value back to those who engage with your content? By implementing some value-for-value model -- a circular economy. Enter zaps.

Unlike traditional social media platforms, Nostr does not actively use algorithms to determine what content is popular, nor does it push content created for active user engagement to the top of a user's timeline. Yes, there are "trending" and "most zapped" timelines that users can choose to use as their default, but these use relatively straightforward engagement metrics to rank posts for these timelines.
That is not to say that we may not see clients actively seeking to refine timeline algorithms for specific metrics. Still, the beauty of having an open protocol with media that is controlled solely by its users is that users who begin to see their timeline gamed towards specific algorithms can choose to move to another client, and for those who are more tech-savvy, they can opt to run their own relays or create their own clients with personalized algorithms and web of trust scoring systems.
Zaps enable the means to create a new type of social media economy in which creators can earn for creating content and users can earn by actively engaging with it. Like and reposting content is relatively frictionless and costs nothing but a simple button tap. Zaps provide active engagement because they signal to your followers and those of the content creator that this post has genuine value, quite literally in the form of money—sats.

I have seen some comments on Nostr claiming that removing likes and reactions is for wealthy people who can afford to send zaps and that the majority of people in the US and around the world do not have the time or money to zap because they have better things to spend their money like feeding their families and paying their bills. While at face value, these may seem like valid arguments, they, unfortunately, represent the brainwashed, defeatist attitude that our current economic (and, by extension, social media) systems aim to instill in all of us to continue extracting value from our lives.
Imagine now, if those people dedicating their own time (time = money) to mine pity points on social media would instead spend that time with genuine value creation by posting content that is meaningful to cultural discussions. Imagine if, instead of complaining that their posts get no zaps and going on a tirade about how much of a victim they are, they would empower themselves to take control of their content and give value back to the world; where would that leave us? How much value could be created on a nascent platform such as Nostr, and how quickly could it overtake other platforms?
Other users argue about user experience and that additional friction (i.e., zaps) leads to lower engagement, as proven by decades of studies on user interaction. While the added friction may turn some users away, does that necessarily provide less value? I argue quite the opposite. You haven't made a few sats from zaps with your content? Can't afford to send some sats to a wallet for zapping? How about using the most excellent available resource and spending 10 seconds of your time to leave a comment? Likes and reactions are valueless transactions. Social media's real value derives from providing monetary compensation and actively engaging in a conversation with posts you find interesting or thought-provoking. Remember when humans thrived on conversation and discussion for entertainment instead of simply being an onlooker of someone else's life?
If you've made it this far, my only request is this: try only zapping and commenting as a method of engagement for two weeks. Sure, you may end up liking a post here and there, but be more mindful of how you interact with the world and break yourself from blind instinct. You'll thank me later.

-

@ ec42c765:328c0600
2025-02-05 23:38:12
# カスタム絵文字とは
任意のオリジナル画像を絵文字のように文中に挿入できる機能です。
また、リアクション(Twitterの いいね のような機能)にもカスタム絵文字を使えます。

# カスタム絵文字の対応状況(2025/02/06)

カスタム絵文字を使うためにはカスタム絵文字に対応した[クライアント](https://welcome.nostr-jp.org/tutorial/explore-client.html)を使う必要があります。
※表は一例です。クライアントは他にもたくさんあります。
使っているクライアントが対応していない場合は、クライアントを変更する、対応するまで待つ、開発者に要望を送る(または自分で実装する)などしましょう。
#### 対応クライアント
- [Amethyst](https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst)
- [FreeFrom](https://freefrom.space/)
- [nostter](https://nostter.app/)
- [Rabbit](https://rabbit.syusui.net/)
- [Lumilumi](https://lumilumi.app/)
- [Nos Haiku](https://nos-haiku.vercel.app/)
- [Snort](https://snort.social/)
- [noStrudel](https://nostrudel.ninja/)
ここではnostterを使って説明していきます。
# 準備
カスタム絵文字を使うための準備です。
- Nostrエクステンション(NIP-07)を導入する
- 使いたいカスタム絵文字をリストに登録する
## Nostrエクステンション(NIP-07)を導入する
Nostrエクステンションは使いたいカスタム絵文字を登録する時に必要になります。
また、環境(パソコン、iPhone、androidなど)によって導入方法が違います。
Nostrエクステンションを導入する端末は、実際にNostrを閲覧する端末と違っても構いません(リスト登録はPC、Nostr閲覧はiPhoneなど)。
Nostrエクステンション(NIP-07)の導入方法は以下のページを参照してください。
[ログイン拡張機能 (NIP-07)を使ってみよう | Welcome to Nostr! ~ Nostrをはじめよう! ~ ](https://welcome.nostr-jp.org/tutorial/nip-07.html)
少し面倒ですが、これを導入しておくとNostr上の様々な場面で役立つのでより快適になります。
## 使いたいカスタム絵文字をリストに登録する
以下のサイトで行います。
[emojito](https://emojito.meme/)
右上の**Get started**からNostrエクステンションでログインしてください。
例として以下のカスタム絵文字を導入してみます。
実際より絵文字が少なく表示されることがありますが、古い状態のデータを取得してしまっているためです。その場合はブラウザの更新ボタンを押してください。
[generalJP | カスタム絵文字](https://emojito.meme/a/naddr1qqykwetwv4exzmz22qqsuamnwvaz7tmev9382tndv5hsyg8vgtrk2svt8kuusk4l7w5g7j3mhet4xhhthhz52gsyr7jn9rqxqqpsgqqqw48qud6u3s)

- 右側の**Options**から**Bookmark**を選択

これでカスタム絵文字を使用するためのリストに登録できます。
# カスタム絵文字を使用する
例としてブラウザから使えるクライアント nostter から使用してみます。
[nostter](https://nostter.app/)
nostterにNostrエクステンションでログイン、もしくは秘密鍵を入れてログインしてください。
## 文章中に使用
1. **投稿**ボタンを押して投稿ウィンドウを表示
2. **顔😀**のボタンを押し、絵文字ウィンドウを表示
3. ***タブ**を押し、カスタム絵文字一覧を表示
4. カスタム絵文字を選択
5. : 記号に挟まれたアルファベットのショートコードとして挿入される

この状態で投稿するとカスタム絵文字として表示されます。
カスタム絵文字対応クライアントを使っている他ユーザーにもカスタム絵文字として表示されます。
対応していないクライアントの場合、ショートコードのまま表示されます。

ショートコードを直接入力することでカスタム絵文字の候補が表示されるのでそこから選択することもできます。

## リアクションに使用
1. 任意の投稿の**顔😀**のボタンを押し、絵文字ウィンドウを表示
2. ***タブ**を押し、カスタム絵文字一覧を表示
3. カスタム絵文字を選択

カスタム絵文字リアクションを送ることができます。

# カスタム絵文字を探す
先述した[emojito](https://emojito.meme/)からカスタム絵文字を探せます。
例えば任意のユーザーのページ [emojito ロクヨウ](https://emojito.meme/p/npub1a3pvwe2p3v7mnjz6hle63r628wl9w567aw7u23fzqs062v5vqcqqu3sgh3) から探したり、 [emojito Browse all](https://emojito.meme/browse) からnostr全体で最近作成、更新された絵文字を見たりできます。
また、以下のリンクは日本語圏ユーザーが作ったカスタム絵文字を集めたリストです(2025/02/06)
※漏れがあるかもしれません
[日本ユーザー作 カスタム絵文字](https://nostviewstr.vercel.app/npub17hczqvxtfv3w69wr6lxrttnpdekwdwel55mld60fr24zwjuu6utqtj8mjx/10030)
各絵文字セットにある**Open in emojito**のリンクからemojitoに飛び、使用リストに追加できます。
-----------
以上です。
次:Nostrのカスタム絵文字の**作り方**
Yakihonneリンク [Nostrのカスタム絵文字の作り方](https://yakihonne.com/article/_@lokuyow.github.io/1707912490439)
Nostrリンク nostr:naddr1qqxnzdesxuunzv358ycrgveeqgswcsk8v4qck0deepdtluag3a9rh0jh2d0wh0w9g53qg8a9x2xqvqqrqsqqqa28r5psx3
-----------
# 仕様
[NIP-30 Custom Emoji](https://github.com/nostr-protocol/nips/blob/master/30.md)
[NIP-30 カスタム絵文字(和訳)](https://github.com/nostr-jp/nips-ja/blob/main/30.md)
-

@ e3ba5e1a:5e433365
2025-02-05 17:47:16
I got into a [friendly discussion](https://x.com/snoyberg/status/1887007888117252142) on X regarding health insurance. The specific question was how to deal with health insurance companies (presumably unfairly) denying claims? My answer, as usual: get government out of it!
The US healthcare system is essentially the worst of both worlds:
* Unlike full single payer, individuals incur high costs
* Unlike a true free market, regulation causes increases in costs and decreases competition among insurers
I'm firmly on the side of moving towards the free market. (And I say that as someone living under a single payer system now.) Here's what I would do:
* Get rid of tax incentives that make health insurance tied to your employer, giving individuals back proper freedom of choice.
* Reduce regulations significantly.
* In the short term, some people will still get rejected claims and other obnoxious behavior from insurance companies. We address that in two ways:
1. Due to reduced regulations, new insurance companies will be able to enter the market offering more reliable coverage and better rates, and people will flock to them because they have the freedom to make their own choices.
2. Sue the asses off of companies that reject claims unfairly. And ideally, as one of the few legitimate roles of government in all this, institute new laws that limit the ability of fine print to allow insurers to escape their responsibilities. (I'm hesitant that the latter will happen due to the incestuous relationship between Congress/regulators and insurers, but I can hope.)
Will this magically fix everything overnight like politicians normally promise? No. But it will allow the market to return to a healthy state. And I don't think it will take long (order of magnitude: 5-10 years) for it to come together, but that's just speculation.
And since there's a high correlation between those who believe government can fix problems by taking more control and demanding that only credentialed experts weigh in on a topic (both points I strongly disagree with BTW): I'm a trained actuary and worked in the insurance industry, and have directly seen how government regulation reduces competition, raises prices, and harms consumers.
And my final point: I don't think any prior art would be a good comparison for deregulation in the US, it's such a different market than any other country in the world for so many reasons that lessons wouldn't really translate. Nonetheless, I asked Grok for some empirical data on this, and at best the results of deregulation could be called "mixed," but likely more accurately "uncertain, confused, and subject to whatever interpretation anyone wants to apply."
https://x.com/i/grok/share/Zc8yOdrN8lS275hXJ92uwq98M
-

@ 91bea5cd:1df4451c
2025-02-04 17:24:50
### Definição de ULID:
Timestamp 48 bits, Aleatoriedade 80 bits
Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C.
e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível.
#### Gerar ULID
```sql
CREATE EXTENSION IF NOT EXISTS pgcrypto;
CREATE FUNCTION generate_ulid()
RETURNS TEXT
AS $$
DECLARE
-- Crockford's Base32
encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ';
timestamp BYTEA = E'\\000\\000\\000\\000\\000\\000';
output TEXT = '';
unix_time BIGINT;
ulid BYTEA;
BEGIN
-- 6 timestamp bytes
unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT;
timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER);
timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER);
timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER);
timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER);
timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER);
timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER);
-- 10 entropy bytes
ulid = timestamp || gen_random_bytes(10);
-- Encode the timestamp
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31)));
-- Encode the entropy
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31)));
RETURN output;
END
$$
LANGUAGE plpgsql
VOLATILE;
```
#### ULID TO UUID
```sql
CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$
DECLARE
-- 16byte
bytes bytea = E'\\x00000000 00000000 00000000 00000000';
v char[];
-- Allow for O(1) lookup of index values
dec integer[] = ARRAY[
255, 255, 255, 255, 255, 255, 255, 255, 255, 255,
255, 255, 255, 255, 255, 255, 255, 255, 255, 255,
255, 255, 255, 255, 255, 255, 255, 255, 255, 255,
255, 255, 255, 255, 255, 255, 255, 255, 255, 255,
255, 255, 255, 255, 255, 255, 255, 0, 1, 2,
3, 4, 5, 6, 7, 8, 9, 255, 255, 255,
255, 255, 255, 255, 10, 11, 12, 13, 14, 15,
16, 17, 1, 18, 19, 1, 20, 21, 0, 22,
23, 24, 25, 26, 255, 27, 28, 29, 30, 31,
255, 255, 255, 255, 255, 255, 10, 11, 12, 13,
14, 15, 16, 17, 1, 18, 19, 1, 20, 21,
0, 22, 23, 24, 25, 26, 255, 27, 28, 29,
30, 31
];
BEGIN
IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN
RAISE EXCEPTION 'Invalid ULID: %', ulid;
END IF;
v = regexp_split_to_array(ulid, '');
-- 6 bytes timestamp (48 bits)
bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]);
bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2));
bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4));
bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1));
bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3));
bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]);
-- 10 bytes of entropy (80 bits);
bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2));
bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4));
bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1));
bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3));
bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]);
bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2));
bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4));
bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1));
bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3));
bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]);
RETURN bytes;
END
$$
LANGUAGE plpgsql
IMMUTABLE;
CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$
BEGIN
RETURN encode(parse_ulid(ulid), 'hex')::uuid;
END
$$
LANGUAGE plpgsql
IMMUTABLE;
```
#### UUID to ULID
```sql
CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$
DECLARE
encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ';
output text = '';
uuid_bytes bytea = uuid_send(id);
BEGIN
-- Encode the timestamp
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31)));
-- Encode the entropy
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31)));
RETURN output;
END
$$
LANGUAGE plpgsql
IMMUTABLE;
```
#### Gera 11 Digitos aleatórios: YBKXG0CKTH4
```sql
-- Cria a extensão pgcrypto para gerar uuid
CREATE EXTENSION IF NOT EXISTS pgcrypto;
-- Cria a função para gerar ULID
CREATE OR REPLACE FUNCTION gen_lrandom()
RETURNS TEXT AS $$
DECLARE
ts_millis BIGINT;
ts_chars TEXT;
random_bytes BYTEA;
random_chars TEXT;
base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ';
i INT;
BEGIN
-- Pega o timestamp em milissegundos
ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT;
-- Converte o timestamp para base32
ts_chars := '';
FOR i IN REVERSE 0..11 LOOP
ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1);
END LOOP;
-- Gera 10 bytes aleatórios e converte para base32
random_bytes := gen_random_bytes(10);
random_chars := '';
FOR i IN 0..9 LOOP
random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1);
IF i < 9 THEN
random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1);
ELSE
random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1);
END IF;
END LOOP;
-- Concatena o timestamp e os caracteres aleatórios
RETURN ts_chars || random_chars;
END;
$$ LANGUAGE plpgsql;
```
#### Exemplo de USO
```sql
-- Criação da extensão caso não exista
CREATE EXTENSION
IF
NOT EXISTS pgcrypto;
-- Criação da tabela pessoas
CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL );
-- Busca Pessoa na tabela
SELECT
*
FROM
"pessoas"
WHERE
uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F';
```
### Fontes
- https://github.com/scoville/pgsql-ulid
- https://github.com/geckoboard/pgulid
-

@ 91bea5cd:1df4451c
2025-02-04 17:15:57
### Definição de ULID:
Timestamp 48 bits, Aleatoriedade 80 bits
Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C.
e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível.
#### Gerar ULID
```sql
CREATE EXTENSION IF NOT EXISTS pgcrypto;
CREATE FUNCTION generate_ulid()
RETURNS TEXT
AS $$
DECLARE
-- Crockford's Base32
encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ';
timestamp BYTEA = E'\\000\\000\\000\\000\\000\\000';
output TEXT = '';
unix_time BIGINT;
ulid BYTEA;
BEGIN
-- 6 timestamp bytes
unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT;
timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER);
timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER);
timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER);
timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER);
timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER);
timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER);
-- 10 entropy bytes
ulid = timestamp || gen_random_bytes(10);
-- Encode the timestamp
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31)));
-- Encode the entropy
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31)));
RETURN output;
END
$$
LANGUAGE plpgsql
VOLATILE;
```
#### ULID TO UUID
```sql
CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$
DECLARE
-- 16byte
bytes bytea = E'\\x00000000 00000000 00000000 00000000';
v char[];
-- Allow for O(1) lookup of index values
dec integer[] = ARRAY[
255, 255, 255, 255, 255, 255, 255, 255, 255, 255,
255, 255, 255, 255, 255, 255, 255, 255, 255, 255,
255, 255, 255, 255, 255, 255, 255, 255, 255, 255,
255, 255, 255, 255, 255, 255, 255, 255, 255, 255,
255, 255, 255, 255, 255, 255, 255, 0, 1, 2,
3, 4, 5, 6, 7, 8, 9, 255, 255, 255,
255, 255, 255, 255, 10, 11, 12, 13, 14, 15,
16, 17, 1, 18, 19, 1, 20, 21, 0, 22,
23, 24, 25, 26, 255, 27, 28, 29, 30, 31,
255, 255, 255, 255, 255, 255, 10, 11, 12, 13,
14, 15, 16, 17, 1, 18, 19, 1, 20, 21,
0, 22, 23, 24, 25, 26, 255, 27, 28, 29,
30, 31
];
BEGIN
IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN
RAISE EXCEPTION 'Invalid ULID: %', ulid;
END IF;
v = regexp_split_to_array(ulid, '');
-- 6 bytes timestamp (48 bits)
bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]);
bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2));
bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4));
bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1));
bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3));
bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]);
-- 10 bytes of entropy (80 bits);
bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2));
bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4));
bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1));
bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3));
bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]);
bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2));
bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4));
bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1));
bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3));
bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]);
RETURN bytes;
END
$$
LANGUAGE plpgsql
IMMUTABLE;
CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$
BEGIN
RETURN encode(parse_ulid(ulid), 'hex')::uuid;
END
$$
LANGUAGE plpgsql
IMMUTABLE;
```
#### UUID to ULID
```sql
CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$
DECLARE
encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ';
output text = '';
uuid_bytes bytea = uuid_send(id);
BEGIN
-- Encode the timestamp
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31)));
-- Encode the entropy
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31)));
RETURN output;
END
$$
LANGUAGE plpgsql
IMMUTABLE;
```
#### Gera 11 Digitos aleatórios: YBKXG0CKTH4
```sql
-- Cria a extensão pgcrypto para gerar uuid
CREATE EXTENSION IF NOT EXISTS pgcrypto;
-- Cria a função para gerar ULID
CREATE OR REPLACE FUNCTION gen_lrandom()
RETURNS TEXT AS $$
DECLARE
ts_millis BIGINT;
ts_chars TEXT;
random_bytes BYTEA;
random_chars TEXT;
base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ';
i INT;
BEGIN
-- Pega o timestamp em milissegundos
ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT;
-- Converte o timestamp para base32
ts_chars := '';
FOR i IN REVERSE 0..11 LOOP
ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1);
END LOOP;
-- Gera 10 bytes aleatórios e converte para base32
random_bytes := gen_random_bytes(10);
random_chars := '';
FOR i IN 0..9 LOOP
random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1);
IF i < 9 THEN
random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1);
ELSE
random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1);
END IF;
END LOOP;
-- Concatena o timestamp e os caracteres aleatórios
RETURN ts_chars || random_chars;
END;
$$ LANGUAGE plpgsql;
```
#### Exemplo de USO
```sql
-- Criação da extensão caso não exista
CREATE EXTENSION
IF
NOT EXISTS pgcrypto;
-- Criação da tabela pessoas
CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL );
-- Busca Pessoa na tabela
SELECT
*
FROM
"pessoas"
WHERE
uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F';
```
### Fontes
- https://github.com/scoville/pgsql-ulid
- https://github.com/geckoboard/pgulid
-

@ 8f69ac99:4f92f5fd
2025-02-20 15:24:24
Anarquia: uma palavra que frequentemente evoca imagens de caos e desordem, associada ao velho oeste sem lei ou a futuros distópicos onde impera a força bruta. No entanto, para aqueles que investigam mais a fundo, a anarquia revela-se como algo muito mais sofisticado—um sistema não definido pela ausência de regras, mas sim pela ausência de governantes (*rules without rulers*). Essa distinção fundamental é essencial para compreender um dos conceitos mais fascinantes e, ao mesmo tempo, mais difamados da sociedade.
A ideia de que anarquia significa desordem ou uma sociedade sem estrutura é um equívoco baseado no medo do desconhecido e na falta de compreensão dos seus princípios básicos. Na realidade, a anarquia assenta sobre um princípio fundamental: o **Princípio da Não-Agressão (PNA)**. Este princípio estabelece que nenhum indivíduo tem o direito de iniciar o uso da força, coerção ou fraude contra os outros, sem o seu consentimento, sendo este um dos pilares fundamentais para a preservação da propriedade privada e das liberdades individuais.
Não se trata, portanto, de uma sociedade sem regras, mas sim de uma organização baseada em **estruturas legais descentralizadas e orgânicas**, como a **lei natural e o direito consuetudinário**, que emergem naturalmente através das interacções voluntárias entre indivíduos. A história demonstra que, mesmo na ausência de uma autoridade central, os seres humanos são perfeitamente capazes de criar ordens sociais complexas, baseadas na cooperação, na ajuda mútua e no progresso.
Este artigo explora como a anarquia funciona enquanto sistema de cooperação voluntária e direito natural, desafiando as concepções erradas que persistem sobre o tema e revelando o seu potencial para fortalecer a liberdade individual e a coesão social. Ao analisar as suas raízes filosóficas, o papel do Estado dentro de um enquadramento anarquista e os exemplos históricos que demonstram a capacidade da humanidade para se auto-organizar, procuramos iluminar um futuro onde a liberdade não seja apenas um sonho utópico, mas uma possibilidade concreta.
## Principio da Não Agressão (PNA)
A **base da anarquia** assenta sobre um princípio inegociável: o Princípio da Não-Agressão. Este postulado não é apenas uma directriz moral, mas sim uma regra essencial de conduta, destinada a fomentar uma sociedade cooperativa e pacífica, onde os indivíduos vivem sem medo da coerção ou da violência.
A partir deste princípio, deriva-se naturalmente a **propriedade privada**, pois cada indivíduo tem o direito de usufruir e gerir os recursos que adquire sem recorrer à força contra terceiros. Da mesma forma, a violação deste princípio—seja através do roubo, homicídio ou qualquer tipo de agressão física ou psicológica, não consentida—é condenada de forma universal, pois representa um atentado contra a liberdade de cada um.
Num enquadramento anarquista, a ausência de uma estrutura coerciva não significa a ausência de ordem. Métodos como **pressão social, ostracismo de infractores e mecanismos privados de justiça** ajudam a manter a harmonia social. Por exemplo, em situações de litígio entre vizinhos sobre a posse de um terreno, em vez de recorrer ao Estado, poderiam simplesmente resolver a disputa através de um mediador comunitário ou de um serviço de arbitragem voluntário.
## Ordem Sem Autoridade Central
A crença de que a lei e a ordem dependem de um poder centralizado ignora uma vasta tradição histórica de **sistemas legais descentralizados** que surgiram espontaneamente, sem intervenção estatal. A anarquia não significa ausência de normas, mas sim uma **ordem espontânea baseada em leis naturais e consuetudinárias**.
A lei natural consiste em princípios universais, reconhecidos pela razão, que não dependem da autoridade estatal. Já o direito consuetudinário assenta na tradição e nos precedentes, evoluindo conforme as necessidades das comunidades. Um excelente exemplo histórico é o código jurídico medieval islandês "Grágás", que regulava litígios e contratos através de mediação voluntária.
Sistemas baseados na reputação também são eficazes. No passado, comerciantes que desrespeitassem contratos viam-se rapidamente excluídos do mercado. Hoje, soluções descentralizadas como a arbitragem privada demonstram que contratos podem ser cumpridos sem necessidade de coerção estatal.
## Anarquia como Estado Natural da Cooperação Humana
A cooperação voluntária está no cerne da natureza humana. A ideia de que é necessária uma autoridade central para garantir harmonia social desconsidera as inúmeras instâncias de colaboração espontânea ao longo da história.
O funcionamento dos mercados ilustra perfeitamente a anarquia em acção. Sem um governo a ditar regras, indivíduos interagem livremente, criando riqueza e inovação. A busca pelo progresso científico também reflecte este princípio: Albert Einstein, Nikola Tesla, Henry Ford ou Thomas Edison não foram forçados pelo Estado a desenvolver as suas invenções—fizeram-no por interesse próprio, beneficiando toda a humanidade.
Da mesma forma, a revolução industrial não foi um plano centralizado, mas sim o resultado de inúmeras inovações individuais que impulsionaram a prosperidade global. A tecnologia moderna, com exemplos como Bitcoin e Nostr, redes descentralizadas, prova que sociedades podem operar sem intermediários estatais, ou autoridades centrais.
## Estado: Pode Existir Num Enquadramento Anarquista?
O Estado, mesmo na sua versão mais reduzida, pode representar um risco para a liberdade individual. Alguns, eu incluído, argumentam que um "Estado mínimo" (minarquia) poderia existir para garantir segurança e mediar disputas, mas essa estrutura pode rapidamente expandir-se e transformar-se num mecanismo de coerção.
### A necessidade de mecanismos de controlo e equilíbrio
Mesmo um Estado reduzido exigiria salvaguardas para evitar abusos de poder. Para isso, seriam necessários mecanismos que garantam que nenhuma autoridade se torne dominante e que a sociedade mantenha a sua autonomia.
Algumas soluções incluem:
- **Representação directa**: Em vez de delegar decisões a políticos, a população poderia ter mais influência directa nas questões que afectam a sua vida (como na Suiça por exemplo).
- **Arbitragem independente**: Conflitos poderiam ser resolvidos sem recorrer a tribunais estatais, através de mediação voluntária e sistemas de justiça comunitária.
- **Redes de apoio social**: Fortalecer redes de ajuda mútua reduziria a necessidade de um governo central para fornecer serviços essenciais.
### Exemplos práticos
Algumas iniciativas mostram que a sociedade pode funcionar com estruturas descentralizadas:
- **Cidades com participação cívica activa**: Experiências como o orçamento participativo em algumas cidades demonstram como a sociedade pode gerir recursos colectivos sem excessiva intervenção estatal.
- **Redes de ajuda mútua**: Grupos como a *Mutual Aid Disaster Response Network* nos EUA provam que comunidades podem organizar-se para responder a crises sem depender do Estado.
O desafio não é apenas imaginar um mundo sem Estado, mas conceber modelos descentralizados que garantam a liberdade individual e impeçam a concentração de poder. A verdadeira questão é: conseguiremos criar sistemas mais justos e funcionais sem recorrer à coerção estatal?
## Raízes Filosóficas da Anarquia
A anarquia tem uma longa tradição filosófica que remonta a pensadores como **William Godwin**, **Pierre-Joseph Proudhon** e **Max Stirner**, cada um contribuindo com diferentes perspectivas sobre a organização social sem governantes. No século XX, pensadores como **Murray Rothbard** e **Hans-Hermann Hoppe** aprofundaram a ideia do anarco-capitalismo, propondo que todos os serviços actualmente providenciados pelo Estado poderiam ser oferecidos por meio de mercados livres.
A raiz histórica da anarquia está firmemente ancorada no pensamento de esquerda (a tradicional... ), na medida em que a sua proposta fundamental é a **eliminação do poder central**. O anarquismo clássico emergiu como uma resposta ao absolutismo e ao capitalismo industrial, defendendo que a autoridade imposta pelo Estado e pelas elites económicas deveria ser desmantelada para dar lugar a um sistema de cooperação voluntária e descentralizada. Proudhon, ao afirmar "a propriedade é roubo", reflectia esta preocupação com a concentração de poder e riqueza nas mãos de poucos.
Com o tempo, no entanto, diferentes correntes começaram a emergir dentro da tradição anarquista. A tradição anarquista de **esquerda** enfatiza a justiça social e a solidariedade comunitária, rejeitando tanto o Estado como o capitalismo. Nomes como **Bakunin** e **Kropotkin** defenderam a abolição da propriedade privada em favor de sistemas cooperativos, argumentando que apenas a auto gestão e o apoio mútuo poderiam garantir a verdadeira liberdade.
Por outro lado, no século XX, surgiu uma vertente anarquista mais **associada à direita**, especialmente com Rothbard e Hoppe, que viam o mercado como a melhor alternativa ao Estado. Para os anarco-capitalistas, a liberdade individual é prioritária, e a descentralização deve ocorrer não apenas ao nível político, mas também económico, permitindo que todas as transacções sejam voluntárias e baseadas na propriedade privada.
Apesar dessas divergências, há um ponto comum entre todas as vertentes anarquistas: a rejeição do **monopólio da violência estatal**. Tanto anarquistas de esquerda quanto de direita reconhecem que o poder centralizado inevitavelmente conduz à opressão e à limitação da liberdade individual. O debate interno dentro do anarquismo não é sobre a necessidade de abolir o Estado, mas sim sobre o que deve substituí-lo: auto gestão comunitária e colectivismo ou mercados livres e concorrência voluntária?
A preservação da propriedade privada e a liberdade de associação são, para mim, princípios fundamentais dentro do pensamento anarquista. Nada impede que, numa sociedade anarquista, grupos de indivíduos escolham unir-se voluntariamente para formar projectos cooperativos baseados em valores partilhados. O que distingue essa abordagem da imposição estatal é o carácter voluntário e descentralizado dessas associações, garantindo que cada pessoa possa viver conforme os seus próprios princípios sem coerção externa.
Esta dicotomia entre esquerda e direita dentro do anarquismo reflecte diferentes interpretações sobre a melhor forma de organizar a sociedade sem coerção. O que permanece inegável é que a anarquia, independentemente da vertente, continua a ser uma proposta de resistência contra qualquer forma de domínio centralizado, colocando a liberdade e a autonomia no centro da organização social.
## Conclusão
A anarquia não é um sonho utópico, mas sim uma alternativa viável à organização centralizada da sociedade. Através do respeito pelo Princípio da Não-Agressão, da descentralização das normas jurídicas e da cooperação voluntária, podemos construir um mundo mais livre, onde as pessoas têm o poder de se governar a si mesmas.
Sistemas como Bitcoin já demonstram que a descentralização funciona e que a ausência de intermediários coercivos é não só possível, mas desejável. O desafio não é saber se a anarquia pode funcionar, mas sim **quanto tempo levará para as pessoas perceberem que um mundo sem Estado é mais próspero e justo**.
#anarquia #anarco #bitcoin
---
_Photo by [Orit Matee](https://unsplash.com/@splashcom?utm_content=creditCopyText&utm_medium=referral&utm_source=unsplash) on [Unsplash](https://unsplash.com/photos/black-and-silver-heart-shaped-wall-decor-qqiAxa9hpaA?utm_content=creditCopyText&utm_medium=referral&utm_source=unsplash)_
-

@ 5a261a61:2ebd4480
2025-02-18 18:22:19
The yellow light won the battle against the feeble excuse for curtains and crept into the room. It moved cautiously as if was afraid where to step. A common trait to all who found their way into the back room of the Lost Cases Detective Agency. The current owner had inherited both the premises and the name from his predecessor, and whenever someone questioned the name, he would announce half-irritably that changing it was simply too expensive to afford. The noodle vendor from the floor below would never miss the chance to add that people who end up at his place didn't choose it for the name anyway. The truth (which he was willing to admit only to the creaking fan that scared away mice rather than actually serving its function) was that he liked the name. Like attracts like. A lost soul for lost cases. The darkness was finally driven even from the eyelids of the figure on the bed, who woke up with a dissatisfied grunt.
A few steps to the sink hidden behind a screen. The shadows cast by the street light might have seemed depressive to some, mainly because they weren't accompanied by the warming feeling of sunlight, blocked by the high skyscrapers embracing the lower houses of the former middle class. Tom smiled resignedly at this thought. It perfectly captured how everything in this city merged into one big tangle, which looks beautiful until you have to untangle it. The yellow light came from a neon sign across the street advertising "The Beach." One of many places in this City where one could hide in a drop of alcohol and the embrace of a beautiful woman. Though it was necessary to maintain that order... the companions didn't exactly recruit from the best of the best looking local beauties.
Tom turned the tap and waited until the water, after grunting, gargling, and several splutters, settled and began flowing somewhat predictably. Tom didn't mind the wait. In his line of work, patience was cheaper than bullets. And it was nice to have time when he could do nothing but wait. He examined himself in the mirror. The shadows did him favors, adding years he hadn't earned. As young as he was, he needed all the help he could get - clients wanted their private dick weathered, not fresh out of the wrapper. He had the look down pat: world-weary veteran who knew all the angles. Truth was, he couldn't even figure out the angle of his own life, but that was a case file he kept closed. The water spluttered one last time. "Good morning, dickhead," he greeted himself with unwavering conviction that today would be better than yesterday. While most people were heading to dinner, putting kids to bed, or hurrying to visit their lovers at this hour, he was waking up. So for him, it was morning. For him and a myriad of other existences who, by choice or necessity, lived more at night than during the day.
Finally, he trimmed his beard to short, neat stubble - enough to look serious, but with a touch of toughness suggesting he wasn't afraid to get his hands dirty. "Perfect," he muttered to himself, "I look like a man who knows what he's doing." Maybe that illusion will convince me one day, he thought as he turned off the light in the small bathroom.
With a final look in the mirror, he adjusted his shirt collar. He was ready to face the city's challenges. Whatever awaited him today, at least he'd look prepared for it.
From the hook by the door, he grabbed a ring with an identification tag and some loose change. He ran down a flight of creaking stairs and headed past empty bar stools toward the exit. The disadvantage of living above a restaurant. Though the major advantage is the high of the rent. Or rather, its lowness. Jiro, the owner of the small bistro and, coincidentally, a decent exterminator, looked at him through a dense veil of greasy vapors, nodded, and continued stirring the noodles.
Where to next?
- say hi
- get some food
- just run outside
> This is kind of an experiment with converting my WIP interactive fiction project to the nostr longnote format and letting readers decide. Originally, this story leans quite heavily toward FLR/femdom/mindcontrol/noir/steampunk/fantasy and hopefully a little mystery detective story, but let's see where (and if) it will lead from here.
Also, it's mostly translated from my native language, so sorry if some wording seems stiff.
-

@ 97c70a44:ad98e322
2025-02-17 14:29:00
Everyone knows that relays are central to how nostr works - they're even in the name: Notes and Other Stuff Transmitted by *Relays*. As time goes on though, there are three other letters which are becoming conspicuously absent from our beloved and ambiguously pronounceable acronym - "D", "V", and "M".
For the uninitiated, DVM stands for "data vending machines". They're actually sort of hard to describe — in technical terms they act more like clients, since they simply read events from and publish events to relays. In most cases though, these events are part of a request/response flow initiated by users elsewhere on the network. In practice, DVMs are bots, but there's also nothing to prevent the work they do from being powered by human interaction. They're an amazingly flexible tool for building anything from custom feeds, to transcription services, to chatbots, to protocol gateways.
The hype cycle for DVMs seems to have reached escape velocity in a way few other things have - zaps being the possible exception. But *what* exactly DVMs are remains something of a mystery to many nostr developers - and how to build one may as well be written on clay tablets.
This blog post is designed to address that - below is a soup to nuts (no nutzaps though) guide to building a DVM flow, both from the client and the server side.
Here's what we'll be covering:
- Discovering DVM metadata
- Basic request/response flow
- Implementing a minimal example
Let's get started!
# DVM Metadata
First of all, it's helpful to know how DVMs are reified on the nostr network. While not strictly necessary, this can be useful for discovering DVMs and presenting them to users, and for targeting specific DVMs we want a response from.
[NIP 89](https://github.com/nostr-protocol/nips/blob/master/89.md) goes into this in more detail, but the basic idea is that anyone can create a `kind 31990` "application handler" event and publish it to the network with their own (or a dedicated) public key. This handler was originally intended to advertise clients, but has been re-purposed for DVM listings as well.
Here's what the "Fluffy Frens" handler looks like:
```json
{
"content": "{\"name\": \"Fluffy Frens\", \"picture\": \"https://image.nostr.build/f609311532c470f663e129510a76c9a1912ae9bc4aaaf058e5ba21cfb512c88e.jpg\", \"about\": \"I show recent notes about animals\", \"lud16\": \"discovery_content_fluffy@nostrdvm.com\", \"supportsEncryption\": true, \"acceptsNutZaps\": false, \"personalized\": false, \"amount\": \"free\", \"nip90Params\": {\"max_results\": {\"required\": false, \"values\": [], \"description\": \"The number of maximum results to return (default currently 100)\"}}}",
"created_at": 1738874694,
"id": "0aa8d1f19cfe17e00ce55ca86fea487c83be39a1813601f56f869abdfa776b3c",
"kind": 31990,
"pubkey": "7b7373dd58554ff4c0d28b401b9eae114bd92e30d872ae843b9a217375d66f9d",
"sig": "22403a7996147da607cf215994ab3b893176e5302a44a245e9c0d91214e4c56fae40d2239dce58ea724114591e8f95caed2ba1a231d09a6cd06c9f0980e1abd5",
"tags": [
["k", "5300"],
["d", "198650843898570c"]
]
}
```
This event is rendered in various clients using the kind-0-style metadata contained in the `content` field, allowing users to browse DVMs and pick one for their use case. If a user likes using a particular DVM, they might publish a `kind 31989` "application recommendation", which other users can use to find DVMs that are in use within their network.
Note the `k` tag in the handler event - this allows DVMs to advertise support only for specific job types. It's also important to note that even though the spec doesn't cover relay selection, most clients use the publisher's `kind 10002` event to find out where the DVM listens for events.
If this looks messy to you, you're right. See [this PR](https://github.com/nostr-protocol/nips/pull/1728) for a proposal to split DVMs out into their own handler kind, give them a dedicated pubkey along with dedicated metadata and relay selections, and clean up the data model a bit.
# DVM Flow
Now that we know what a DVM looks like, we can start to address how they work. My explanation below will elide some of the detail involved in [NIP 90](https://github.com/nostr-protocol/nips/blob/master/90.md) for simplicity, so I encourage you to read the complete spec.
The basic DVM flow can be a little (very) confusing to work with, because in essence it's a request/response paradigm, but it has some additional wrinkles.
First of all, the broker for the request isn't abstracted away as is usually the case with request/response flows. Regular HTTP requests involve all kinds of work in the background - from resolving domain names to traversing routers, VPNs, and ISP infrastructure. But developers don't generally have to care about all these intermediaries.
With DVMs, on the other hand, the essential complexity of relay selection can't simply be ignored. DVMs often advertise their own relay selections, which should be used rather than a hard-coded or randomly chosen relay to ensure messages are delivered. The benefit of this is that DVMs can avoid censorship, just as users can, by choosing relays that are willing to broker their activity. DVMs can even select multiple relays to broker requests, which means that clients might receive multiple copies of the same response.
Secondly, the DVM request/response model is far more fluid than is usually the case with request/response flows. There are a set of standard practices, but the flow is flexible enough to admit exceptions to these conventions for special use cases. Here are some examples:
- Normally, clients p-tag the DVM they wish to address. But if a client isn't picky about where a response comes from, they may choose to send an open request to the network and collect responses from multiple DVMs simultaneously.
- Normally, a client creates a request before collecting responses using a subscription with an e-tag filter matching the request event. But clients may choose to skip the request step entirely and collect responses from the network that have already been created. This can be useful for computationally intensive tasks or common queries, where a single result can be re-used multiple times.
- Sometimes, a DVM may respond with a `kind 7000` job status event to let clients know they're working on the request. This is particularly useful for longer-running tasks, where feedback is useful for building a responsive UX.
- There are also some details in the spec regarding monetization, parameterization, error codes, encryption, etc.
# Example DVM implementation
For the purposes of this blog post, I'll keep things simple by illustrating the most common kind of DVM flow: a `kind 5300` [content discovery](https://www.data-vending-machines.org/kinds/5300/) request, addressed to a particular DVM. If you're interested in other use cases, please visit [data-vending-machines.org](https://data-vending-machines.org) for additional documented kinds.
The basic flow looks like this:
- The DVM starts by listening for `kind 5300` job requests on some relays it has selected and advertised via NIP 89 (more on that later)
- A client creates a request event of `kind 5300`, p-tagged with the DVM's pubkey and sends it to the DVM's relay selections.
- The DVM receives the event and processes it, issuing optional `kind 7000` job status events, and eventually issuing a `kind 6300` job result event (job result event kinds are always 1000 greater than the request's kind).
- The client listens to the same relays for a response, and when it comes through does whatever it wants to with it.
Here's a swimlane diagram of that flow:

To avoid massive code samples, I'm going to implement our DVM entirely using nak (backed by the power of the human mind).
The first step is to start our DVM listening for requests that it wants to respond to. Nak's default pubkey is `79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798`, so we'll only listen for requests sent to nak.
```bash
nak req -k 5300 -t p=79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798
```
This gives us the following filter:
```json
["REQ","nak",{"kinds":[5300],"#p":["79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798"]}]
```
To open a subscription to `nos.lol` and stream job requests, add `--stream wss://nos.lol` to the previous request and leave it running.
Next, open a new terminal window for our "client" and create a job request. In this case, there's nothing we need to provide as `input`, but we'll include it just for illustration. It's also good practice to include an `expiration` tag so we're not asking relays to keep our ephemeral requests forever.
```bash
nak event -k 5300 -t p=79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798 -t expiration=$(( $(date +%s) + 30 )) -t input=hello
```
Here's what comes out:
```json
{
"kind": 5300,
"id": "0e419d0b3c5d29f86d2132a38ca29cdfb81a246e1a649cb2fe1b9ed6144ebe30",
"pubkey": "79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798",
"created_at": 1739407684,
"tags": [
["p", "79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798"],
["expiration", "1739407683"],
["input", "hello"]
],
"content": "",
"sig": "560807548a75779a7a68c0ea73c6f097583e2807f4bb286c39931e99a4e377c0a64af664fa90f43e01ddd1de2e9405acd4e268f1bf3bc66f0ed5a866ea093966"
}
```
Now go ahead and publish this event by adding `nos.lol` to the end of your `nak` command. If all goes well, you should see your event pop up in your "dvm" subscription. If so, great! That's half of the flow.
Next, we'll want our client to start listening for `kind 6300` responses to the request. In your "client" terminal window, run:
```bash
nak req -k 6300 -t e=<your-eventid-here> --stream nos.lol
```
Note that if you only want to accept responses from the specified DVM (a good policy in general to avoid spam) you would include a `p` tag here. I've omitted it for brevity. Also notice the `k` tag specifies the request kind plus `1000` - this is just a convention for what kinds requests and responses use.
Now, according to [data-vending-machines.org](https://www.data-vending-machines.org/kinds/5300/), `kind 5300` responses are supposed to put a JSON-encoded list of e-tags in the `content` field of the response. Weird, but ok. Stop the subscription in your "dvm" terminal and respond to your "client" with a recommendation to read my first note:
```bash
nak event -k 6300 -t e=a65665a3a4ca2c0d7b7582f4f0d073cd1c83741c25a07e98d49a43e46d258caf -c '[["e","214f5898a7b75b7f95d9e990b706758ea525fe86db54c1a28a0f418c357f9b08","wss://nos.lol/"]]' nos.lol
```
Here's the response event we're sending:
```json
{
"kind": 6300,
"id": "bb5f38920cbca15d3c79021f7d0051e82337254a84c56e0f4182578e4025232e",
"pubkey": "79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798",
"created_at": 1739408411,
"tags": [
["e", "a65665a3a4ca2c0d7b7582f4f0d073cd1c83741c25a07e98d49a43e46d258caf"]
],
"content": "[[\"e\",\"214f5898a7b75b7f95d9e990b706758ea525fe86db54c1a28a0f418c357f9b08\",\"wss://nos.lol/\"]]",
"sig": "a0fe2c3419c5c54cf2a6d9a2a5726b2a5b766d3c9e55d55568140979354003aacb038e90bdead43becf5956faa54e3b60ff18c0ea4d8e7dfdf0c8dd97fb24ff9"
}
```
Notice the `e` tag targets our original request.
This should result in the job result event showing up in our "client" terminal. Success!
If something isn't working, I've also create a video of the full process with some commentary which you can find [here](https://coracle-media.us-southeast-1.linodeobjects.com/nakflow.mov).
Note that in practice, DVMs can be much more picky about the requests they will respond to, due to implementations failing to follow [Postel's law](https://en.wikipedia.org/wiki/Robustness_principle). Hopefully that will improve over time. For now, here are a few resources that are useful when working with or developing DVMs:
- [dvmdash](https://dvmdash.live)
- [data-vending-machines.org](https://data-vending-machines.org)
- [noogle](https://noogle.lol/)
- [nostrdvm](https://github.com/believethehype/nostrdvm)
# Conclusion
I started this post by hinting that DVMs might be as fundamental as relays are to making nostr work. But (apart from the fact that we'd end up with an acronym like DVMNOSTRZ+*, which would only exascerbate the pronounciation wars (if such a thing were possible)), that's not exactly true.
DVMs have emerged as a central paradigm in the nostr world because they're a generalization of a design pattern unique to nostr's architecture - but which exists in many other places, including NIP 46 signer flows and NIP 47 wallet connect. Each of these sub-protocols works by using relays as neutral brokers for requests in order to avoid coupling services to web addresses.
This approach has all kinds of neat benefits, not least of which is allowing service providers to host their software without having to accept incoming TCP connections. But it's really an emergent property of relays, which not only are useful for brokering communication between users (aka storing events), but also brokering communication between machines.
The possibilities of this architecture have only started to emerge, so be on the lookout for new applications, and don't be afraid to experiment - just please, don't serialize json inside json 🤦♂️
-

@ 3f770d65:7a745b24
2023-07-31 12:53:38
The following is a collection of Tweets posted on Twitter that documented my entire heart surgery process, from finding out I had an issue, through the surgery, and finally throughout my recovery process. If Elon decides to remove old and unpaid content, I do not want this part of my life to vanish from the Internet. At the time, it was extremely important for my mental health to talk about this whole process and it was therapeutic in my recovery process, reading all of the responses as all of Bitcoin Twitter was behind my success. Thank you all of your kind words, love, and support during this whole process. May my Tweets live on through nostr.
...
Nov 28, 2021
I had open heart surgery 4 days before my 3rd b-day. I've led a healthy & active life since then, zero issues. I had an echocardiogram last week. The results were not good. Heart valve replacement may be in my near future. I am freaking the fuck out. I'll know more on Dec 6th. 😫
Dec 6, 2021
Update: I had my cardiologist appointment today. He said to not worry for now and continue to exercise and live life. In 3 months get another echo done. He doesn't believe the previous other results since I have zero symptoms and wants to do his own interpretation.
Dec 6, 2021
He said if the other results were correct, I may need valve replacement in 6 months to 3 years. However, he doesn't believe the local hospital's results as I said above. He can't form an opinion just yet. He said not to worry over and over again. For now, I'm staying positive!
Mar 7, 2022
Well, it's been three months. I had my follow up this morning. I have severe pulmonic regurgitation. I now need to speak with a specialist and see what my options are for surgery. Neat. 😭
Apr 12, 2022
Well, it looks like I'll need full open heart surgery again to replace my pulmonic valve. Bonus: I'll be part pig. So, I have that going for me. I was assuming that if I had to have this done it would be much less invasive, so I'm not overly impressed at the moment. 🫤
May 11, 2022
Today I had to get a CT scan of my heart in preparation for the May 27th surgery. All went well. I have no other heart issues. It's looking like I'll be in the hospital for 4-7 days, depending on how fast I recover. I should be fully 100% recovered by the end of August. ❤️
May 20, 2022
My grandfather with me 39 years ago, days after my open heart surgery. He taught me to hunt, fish, golf, and I'm sure taught me a thing or two about drinking beer and partying. 😂 He was a great man. He won't physically be with me next Friday, but I'm sure he'll be watching over.
May 25, 2022
Two more sleeps. My mind is racing with an incredible amount of thoughts and emotions now. It's overwhelming. I love you all. Thanks for all of your replies and DMs over the last couple days, weeks, and months. I appreciate it immensely. ❤️❤️❤️
May 25, 2022
Two more sleeps. My mind is racing with an incredible amount of thoughts and emotions now. It's overwhelming. I love you all. Thanks for all of your replies and DMs over the last couple days, weeks, and months. I appreciate it immensely. ❤️❤️❤️
May 27, 2022
LET'S GO! I am alive and doing well. I was on a ventilator until 8pm. That was horrible. I will read all of the comments that you all posted on Katie's updates. Now I need to rest. They want to get me up and walk at 11pm. 🤯 I love you all and your support had helped so much 🧡🧡
May 28, 2022
The amount of love, compassion, caring, and appreciation from everyone blows my mind. Thanks for all of your comments and DMs. The positivity though all is this has helped me get through dark times and now it's helping me get through pain. You are helping me immensely. 🤯❤️🧡💪
May 28, 2022
Today has been a rough day. Lots of chest pain when breathing. But, I apparently am doing something right, because I have been upgraded to a regular room. No more ICU for this guy! My ICU nurse told my new nurse that I'm strong. ❤️💪🔥
May 29, 2022
Using this to document my journey. Last night was not good at all. I had tachycardia and AFib for hours. It was scary as fuck having my heart beat the way it was at 160bpm. They gave me new medication to bring it down and stop the AFib irregular heartbeat. It's now at 101.
May 29, 2022
I was very scared. Katie was able to come and stay the night with me and be my personal care nurse. That made me feel much better having her here with me. Hopefully the meds continue to do what they're supposed to. Fuck. Anyways, I may not Tweet much today. Love you all. ❤️
May 30, 2022
Today has mostly been a great day progress wise. I ate a lot. I've walked more today than I have previously. My doctor told me I might be going home tomorrow, it all depends on what happens with my last drainage tube. Fingers crossed that it's draining properly now. 💪❤️
May 31, 2022
Morning walk crushed.
Breakfast crushed.
Feeling stronger.
My drainage tube is still draining so we'll see what the surgeon says, but I probably won't be coming home today according to my nurse. It may be another day. Better to be safe. I'm feeling good though. Let's go! 💪💪❤️❤️
Jun 1, 2022
Today's plans: Crush morning walk, crush breakfast, CRUSH MY LAST X-RAY AND HEAD THE HELL HOME! Fingers crossed. 🤞🤞❤️❤️💪💪
Jun 1, 2022
On my morning walk I went into a slight AFib. The nurse and PA said since I hadn't had my morning meds to control that yet, that that could be the cause. They're going to increase meds and monitor me for another 24 hours. That sucks, but again, I'd rather be safe. Ugh.
Jun 2, 2022
GM! I miss my kids. I miss wearing normal clothes. I miss my house. I miss my doggy. I better go home today or I guess I'll just keep working to get well enough to go home. 😂 I'm still progressing forward. I have a chest x-ray scheduled later this morning. Fingers crossed.
Jun 2, 2022
I JUST GOT CLEARED TO HEAD HOME AFTER LUNCH. FUCK YEAH. LET'S GOOOOOO💪💪💪
Jun 2, 2022
I am home! I have some family that needs some loving. Enjoy the rest of your day!
Jun 4, 2022
Last night I slept in bed thanks to a reclining pillow, the first night our living room chair. I was so happy to sleep in my own bed. I walked around our yard about 9 times yesterday. My goal is to do that plus a little more every day. I'm still in a lot of pain, but meds help.
Jun 4, 2022
I still have a long way to go recovery wise, but having Katie and the kids here helping me along the way makes it easier and gives me a reason to keep pushing forward through this. Thanks again for all of your past and future support. You all are fantastic.
Jun 6, 2022
My wife went back to work today. My son and daughter are in charge of taking care of me. My kids are fantastic. They made me breakfast already and helped me check all of my vitals. My daughter really shines here. She's such a little nurse and caretaker. ❤️❤️
Jun 6, 2022
I'm still in pain, but I'm not in as much pain as I was a couple days ago. I'm walking around a little better and a little more every day. I really hate just sitting around and not doing anything, but it's hard to do much else besides watch TV. I am enjoying my patio though. 💪
Jun 16, 2022
It's been a while. It's time to update this thread! I am doing great, IMO. I have lots of energy. I feel great. I can do a lot more than I previously could. I still have a limited range of motion due to my sternum being broken and still healing. i.e. I can't wash my back or legs.
Jun 16, 2022
I started back to work yesterday. I was cleared to do 20 hours this week by my doctor and I'm hoping to be cleared full time next week. I work from home, so if I can sit in front of a TV, I can sit in front of a computer, right?
Jun 16, 2022
My home nurses have been absolutely fantastic.😂 My kids make me breakfast every morning. And I could not have done any of this without my rock star wife. Words can't describe how much she's done for me throughout all of this. I am looking forward to continuing to improve. ♥️
Jun 16, 2022
You all have been absolutely wonderful through all of this too. I appreciate all of your love, support, and check-ins. Seriously. It means more than you know.
I have a check-up at the end of the month to make sure all is well. I'll update again in a couple weeks after that appt.
Jun 28, 2022
My doctor said everything looks great. He said it doesn't look like I had open heart surgery a month ago.💪 He said I have zero restrictions and that I can resume normal life. I can drive and I can go out on my boat! ❤️❤️❤️ I'm so happy right now! 🔥🚀
Jul 15, 2022
I started cardiac rehab this week. After 2 sessions the nurse said I'm on "Week 4" already. She doesn't believe with my initial intake stress test if I'll really be able to improve on it that much. 🤣 TL;DR I am a rock star and kicking ass. Feeling great. Life's great. 😍
Aug 28, 2022
Yesterday was 3 months since my open heart surgery. I'm going great! I'd guess essentially back to normal. My sternum is still not fully healed, that'll take more time, but energy and capability are basically back to what I was like last summer. I'm very happy with the results.
Aug 28, 2022
I'm very happy to be able to exercise daily, go boating on the weekends AND swim and paddleboard. I was annoyed that I couldn't do these things a month ago. I had a cardiologist appt. two weeks ago. He said he hopes the valve lasts me the rest of my life and to see him in a year.
Aug 28, 2022
As a final post to this thread, I want to thank each and every one of you again that commented, liked, shared and DMed me throughout all of this. The love and support from Twitter and the #Bitcoin community was unfathomable. You all made a difference in my life and my recovery.❤️
-

@ cc32882d:eca332e6
2025-02-18 17:29:01
#introductions
Hello World
New here as of today! I set myself up first on Yakihonne. (Just trying out clients so far)
Glad to be here and look forward to learning and getting to know peeps. I have been poking around a bit and like what I see so far. Excited to play around some more with Nostr apps. Any suggestions is greatly appreciated.
Whats the good, the bad, and the ugly about Nostr in your opinion?
What is the size of nostr platform? How many users? Hows the community involvment? What is the age range?
Any good places to look at this kind of data.
About:
Like to think deep about life and its vast array of questions and answers that are waiting to be discovered or rediscovered. Live with Nature, Dont fight what will be, Love
Dislike fake people. JUST BE REAL, Life is to short for anything else.
Drop me a response and I will get back to you as soon as possible. Look forward to hearing from some of you.
Thank You for Your Time and For Reading This
-ObsidianQuill
-

@ ec42c765:328c0600
2025-02-05 23:45:09
test
test
-

@ 2e8970de:63345c7a
2025-02-20 18:45:57
https://lore.kernel.org/rust-for-linux/2025021954-flaccid-pucker-f7d9@gregkh/
> The majority of bugs (quantity, not quality/severity) we have are due to
the stupid little corner cases in C that are totally gone in Rust.
Things like simple overwrites of memory (not that rust can catch all of
these by far), error path cleanups, forgetting to check error values,
and use-after-free mistakes. That's why I'm wanting to see Rust get
into the kernel, these types of issues just go away, allowing developers
and maintainers more time to focus on the REAL bugs that happen (i.e.
logic issues, race conditions, etc.)
Now that Linus and Greg Kroah-Hartman have spoken out pro Rust changes in Linux it really feels like the ball is rolling. Linux will become a multi language project. With kernel and "hard" os functions in C and more and more attached pieces like many drivers being either C or Rust.
Interesting developments. This is for sure a volatile time for the broader Linux community.
Previous posts: Linux Kernel Drama about Rust Linux Kernel Drama https://stacker.news/items/879713; Linus coming out in favor of Rust https://stacker.news/items/890358
originally posted at https://stacker.news/items/892141
-

@ 266815e0:6cd408a5
2025-02-18 17:25:31
## noStrudel
Released another major version of noStrudel v0.42.0
Which included a few new features and a lot of cleanup
nostr:naddr1qvzqqqr4gupzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qyghwumn8ghj7mn0wd68ytnhd9hx2tcpzfmhxue69uhkummnw3e82efwvdhk6tcqp3hx7um5wf6kgetv956ry6rmhwr
## Blossom
On the blossom front there where a few more PRs
- Expanded the documentation around CORS headers in BUD-01 thanks to nostr:npub1a6we08n7zsv2na689whc9hykpq4q6sj3kaauk9c2dm8vj0adlajq7w0tyc
- Made auth optional on the `/upload` endpoint [PR](https://github.com/hzrd149/blossom/pull/33)
- Added a `HEAD /media` endpoint for BUD-05 [PR](https://github.com/hzrd149/blossom/pull/42)
- Added range request recommendations to BUD-01 [PR](https://github.com/hzrd149/blossom/pull/47)
With blossom uploads starting to be supported in more nostr clients users where starting to ask where to find a list of blossom servers. so I created a simple nostr client that allows users to post servers and leave reviews
[blossomservers.com](https://blossomservers.com)
Its still very much a work in progress (needs login and server and review editing)
The source is on [github](https://github.com/hzrd149/blossomservers)
I also started another project to create a simple account based paid blossom server [blossom-account-server](https://github.com/hzrd149/blossom-account-server)
Unfortunately I got sidetracked and I didn't have the time to give it the attention it needs to get it over the finish line
## Smaller projects
- [cherry-tree](https://github.com/hzrd149/cherry-tree) A small app for uploading chunked blobs to blossom servers (with cashu payment support)
- [vite-plugin-funding](https://github.com/hzrd149/vite-plugin-funding) A vite plugin to collect and expose package "funding" to the app
- [node-red-contrib-rx-nostr](https://github.com/hzrd149/node-red-contrib-rx-nostr) The start of a node-red package for rx-nostr. if your interested please help
- [node-red-contrib-applesauce](https://github.com/hzrd149/node-red-contrib-applesauce) The start of a node-red package for applesauce. I probably wont finish it so any help it welcome
## Plans for 2025
I have a few vague ideas of what I want to work on Q1 of 2025. but there are a few things i know for certain.
I'm going to keep refactoring noStrudel by moving core logic out into [applesauce](https://hzrd149.github.io/applesauce/) and making it more modular. This should make noStrudel more reliable and hopefully allow me to create and maintain more apps with less code
And I'm going to write tests. tests for everything. hopefully tests for all the libraries and apps I've created in 2024.
A lot of the code I wrote in 2024 was hacky code to see if things could work. and while its been working pretty well I'm starting to forget the details of of the code I wrote so I cant be sure if it still works or how well it works.
So my solution is to write tests, lots of tests :)
-

@ ec42c765:328c0600
2025-02-05 23:43:35
test
-

@ d360efec:14907b5f
2025-02-18 15:11:58
**ภาพรวม BTCUSDT (OKX):**
Bitcoin (BTCUSDT) กำลังแสดงความผันผวนอย่างมาก โดยมีสัญญาณที่ขัดแย้งกันระหว่าง Timeframes ต่างๆ แนวโน้มระยะยาว (Day) ยังคงเป็นขาขึ้น แต่ระยะกลาง (4H) และระยะสั้น (15m) แสดงให้เห็นถึงแรงขายและการปรับฐานที่รุนแรง การวิเคราะห์นี้จะเน้นการระบุพื้นที่ที่ Smart Money อาจจะเข้าซื้อหรือขาย (Liquidity Pools) และประเมินความแข็งแกร่งของแนวโน้ม
**วิเคราะห์ทีละ Timeframe:**
**(1) TF Day (รายวัน):**

* **แนวโน้ม:** ขาขึ้น (Uptrend) *แต่เริ่มอ่อนแรง*
* **SMC:**
* Higher Highs (HH) และ Higher Lows (HL) *เริ่มไม่ชัดเจน*
* Break of Structure (BOS) ด้านบน *แต่เริ่มมีการปรับฐาน*
* **Liquidity:**
* มี Sellside Liquidity (SSL) อยู่ใต้ Lows ก่อนหน้า (บริเวณ 85,000 - 90,000)
* มี Buyside Liquidity (BSL) อยู่เหนือ High เดิม (109,998.9)
* **ICT:**
* ยังไม่เห็น Order Block หรือ FVG ที่ชัดเจนใน TF Day *ณ ราคาปัจจุบัน*
* **EMA:**
* ราคา *หลุด* EMA 50 (สีเหลือง) ลงมาแล้ว
* EMA 200 (สีขาว) เป็นแนวรับถัดไป
* **Money Flow (LuxAlgo):**
* แท่งสีแดงยาว แสดงถึงแรงขายที่เข้ามา
* **Trend Strength (AlgoAlpha):** *ไม่มีในภาพ*
* **Volume Profile:** Volume ค่อนข้างเบาบาง
* **แท่งเทียน:** แท่งเทียนล่าสุดเป็นสีแดง แสดงถึงแรงขาย
* **แนวรับ:** EMA 200, บริเวณ 85,000 - 90,000 (SSL)
* **แนวต้าน:** EMA 50, High เดิม
* **สรุป:** แนวโน้มขาขึ้นเริ่มอ่อนแรง, ราคาหลุด EMA 50, Money Flow เป็นลบ, มี SSL ด้านล่าง
**(2) TF4H (4 ชั่วโมง):**

* **แนวโน้ม:** ขาลง (Downtrend) *ระยะสั้น* หลังจากราคาหลุด EMA 50
* **SMC:**
* Lower Highs (LH) และ Lower Lows (LL)
* Break of Structure (BOS) ด้านล่าง
* **Liquidity:**
* มี SSL อยู่ใต้ Lows ก่อนหน้า (บริเวณ 92,000)
* มี BSL อยู่เหนือ Highs ก่อนหน้า (บริเวณ 104,000 - 108,000)
* **ICT:**
* **Order Block:** ราคาลงมาใกล้ Order Block ขาขึ้น (บริเวณแท่งเทียนสีเขียวก่อนที่จะขึ้น)
* **EMA:**
* ราคาอยู่ใต้ EMA 50 และ EMA 200
* **Money Flow (LuxAlgo):**
* สีแดงเป็นส่วนใหญ่ แสดงถึงแรงขาย
* **Trend Strength (AlgoAlpha):** *ไม่มีในภาพ*
* **Volume Profile** Volume ค่อนข้างเบาบาง
* **แนวรับ:** Order Block, บริเวณ 92,000 (SSL)
* **แนวต้าน:** EMA 50, EMA 200, บริเวณ Highs ก่อนหน้า
* **สรุป:** แนวโน้มขาลงระยะสั้น, ราคาลงมาใกล้ Order Block, Money Flow เป็นลบ
**(3) TF15 (15 นาที):**

* **แนวโน้ม:** ขาลง (Downtrend)
* **SMC:**
* Lower Highs (LH) และ Lower Lows (LL)
* Break of Structure (BOS) ด้านล่าง
* **Liquidity:**
* มี SSL อยู่ใต้ Lows ล่าสุด
* มี BSL อยู่เหนือ Highs ก่อนหน้า
* **ICT:**
* **Order Block:** ราคาลงมาใกล้ Oder Block
* **EMA:**
* EMA 50 และ EMA 200 เป็นแนวต้าน
* **Money Flow (LuxAlgo):**
* สีแดงเป็นส่วนใหญ่ แสดงถึงแรงขาย
* **Trend Strength (AlgoAlpha):**
* เป็นสีแดง แสดงถึงเเนวโน้มขาลง
* **Volume Profile:**
* Volume ค่อนข้างเบาบาง
* **แนวรับ:** บริเวณ Low ล่าสุด
* **แนวต้าน:** EMA 50, EMA 200, บริเวณ Highs ก่อนหน้า
* **สรุป:** แนวโน้มขาลง, แรงขายมีอิทธิพล, ใกล้แนวรับ
**สรุปภาพรวมและกลยุทธ์ (BTCUSDT):**
* **แนวโน้มหลัก (Day):** ขาขึ้น (อ่อนแรง)
* **แนวโน้มรอง (4H):** ขาลง (ระยะสั้น)
* **แนวโน้มระยะสั้น (15m):** ขาลง
* **Liquidity:**
* Day: SSL (85,000-90,000), BSL (เหนือ 109,998.9)
* 4H: SSL (92,000), BSL (104,000-108,000)
* 15m: SSL (ใต้ Lows), BSL (เหนือ Highs)
* **Money Flow:** Day เริ่มเป็นลบ, 4H เป็นลบ, 15m เป็นลบ
* **Trend Strength** 15 m : ขาลง
* **กลยุทธ์:**
1. **Wait & See (ดีที่สุด):** รอความชัดเจน
2. **Short (เสี่ยง):** ถ้าไม่สามารถ Breakout EMA/แนวต้านใน TF ใดๆ ได้
3. **ไม่แนะนำให้ Buy:** จนกว่าจะมีสัญญาณกลับตัวที่ชัดเจน
**คำแนะนำ:**
* **ความขัดแย้งของ Timeframes:** ชัดเจน
* **Money Flow:** เป็นลบในทุก Timeframes
* **ระวัง SSL:** Smart Money อาจจะลากราคาลงไปกิน Stop Loss
* **ถ้าไม่แน่ใจ อย่าเพิ่งเข้าเทรด**
**Disclaimer:** การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ
-

@ 5d4b6c8d:8a1c1ee3
2025-02-20 16:20:02
We made a minor adjustment to the reply fee, raising it to 2 sats.
Lest you think @grayruby is just a greedy SOB (not that he isn't), we are trying to think through how to use some of the territory profits to help support the contests being run by stackers and those extra sats can help with that effort.
# How is ~Stacker_Sports doing?
The past month has been awesome for us. Of course, that may be related to the NFL playoffs.
- Posts: 271, 4th ranked territory
- Comments: ***2992, 2nd ranked territory!***
- Stacking: ***193.9k, 2nd ranked territory!***
- Spending: ***300.9k, 2nd ranked territory!***
Top Post: [Super Bowl Discussion Thread](https://stacker.news/items/880943/r/Undisciplined) by @grayruby - 1088 sats/ 109 comments
I'm looking forward to another awesome month!
originally posted at https://stacker.news/items/891926
-

@ 8f69ac99:4f92f5fd
2025-02-20 16:14:03
Imagine-se numa fila de uma feira de emprego com dois amigos igualmente qualificados, mas provenientes de contextos socioeconómicos diferentes. Um dos amigos, devido às suas circunstâncias económicas, recebe um tratamento preferencial—como um aumento de 10% na pontuação da sua candidatura, como parte de uma política destinada a corrigir desvantagens sistémicas. O outro amigo, apesar de igualmente qualificado, não recebe qualquer vantagem. Quem conseguirá o emprego para o qual ambos estão capacitados? Este cenário destaca o paradoxo no cerne de muitas políticas de justiça social: tratar as pessoas de forma diferente para atingir a igualdade muitas vezes resulta em resultados desiguais, desafiando o princípio de equidade e minando a confiança.
Esta tensão entre os objetivos da justiça social e a necessidade de equidade tem moldado debates sobre ações afirmativas, tributação progressiva, programas de bem-estar social e outras políticas destinadas a promover a equidade entre grupos. Embora bem-intencionadas, estas iniciativas podem marginalizar o mérito individual e gerar ressentimento entre aqueles que se sentem injustamente tratados.
A tese central deste artigo é que, embora a justiça social tenha como objetivo promover a igualdade, as suas políticas requerem inerentemente um tratamento desigual, o que paradoxalmente arrisca criar novas formas de desigualdade. Este paradoxo destaca os desafios de buscar a equidade através da intervenção estatal.
### O Princípio da Justiça Social
As políticas de justiça social frequentemente focam-se em atingir a igualdade de resultados através da intervenção estatal. Por exemplo, a ação afirmativa na educação promove a representação de grupos sub-representados através de medidas como cotas raciais ou tratamento preferencial em processos de admissão universitária. De forma semelhante, a tributação progressiva procura redistribuir riqueza ao impor maiores encargos fiscais a determinados grupos de rendimento.
Embora estas políticas visem corrigir desigualdades sistémicas, elas inerentemente requerem tratar as pessoas de forma diferente com base em fatores como raça, rendimento ou condição socioeconómica. Esta discrepância pode criar uma perceção de favoritismo, erodindo a confiança nas instituições e gerando ressentimento entre aqueles que se sentem injustamente prejudicados. Ao dar prioridade à identidade de grupo em detrimento das circunstâncias individuais, estas políticas podem comprometer a equidade e minar a confiança nas instituições, criando percepções de injustiça e ineficiência económica.
### O Problema do Tratamento Desigual
Uma das preocupações centrais com as políticas de justiça social é a sua dependência no tratamento desigual para atingir a igualdade de resultados. Embora concebidas para promover a equidade, estas políticas frequentemente conduzem a consequências indesejadas que desafiam a equidade e a coesão social.
Por exemplo, as políticas de acção afirmativa têm sido criticadas por enfatizarem a identidade de grupo em detrimento do mérito individual. Isto pode resultar na seleção de candidatos com base em cotas em vez de qualificações, gerando frustração entre aqueles que se sentem preteridos, apesar dos seus esforços ou competências. De forma semelhante, os sistemas de tributação progressiva sobrecarregam desproporcionalmente certos grupos, criando a perceção de penalização injusta.
As cotas na educação ou no emprego são particularmente controversas. Ao impor limites ou metas com base na identidade de grupo, estas políticas podem inadvertidamente excluir indivíduos que não se enquadram nos critérios definidos. Esta exclusão muitas vezes gera ressentimento, pois os afetados percebem o sistema como priorizando a equidade para uns em detrimento de outros.
Além disso, ao enfatizar a identidade de grupo sobre o mérito individual, as políticas de justiça social podem inadvertidamente enfraquecer incentivos à excelência e à responsabilidade pessoal, gerando impactos negativos na produtividade e na confiança nas instituições. Esta dinâmica pode corroer a responsabilidade e a confiança nas instituições, criando divisões dentro da sociedade. Ao enfatizar a igualdade de resultados sobre a igualdade de oportunidades, tais políticas arriscam consolidar novas formas de desigualdade.
### Estudos de Caso e Exemplos do Mundo Real
**Acção Afirmativa na Educação**
A política de acção afirmativa da Universidade do Texas em Austin, que considera a raça como um dos factores nas admissões, gerou desafios legais. Críticos argumentaram que a política prejudicava injustamente candidatos igualmente ou mais qualificados que não atendiam aos critérios da política. Embora os tribunais tenham apoiado a política, a controvérsia destaca a tensão entre promover diversidade e preservar o mérito individual.
**Programas de Bem-Estar Redistributivo**
Nos Estados Unidos, o Crédito Tributário por Rendimento do Trabalho (EITC) visa aliviar a pobreza entre indivíduos de baixos rendimentos. Contudo, disparidades na sua implementação causaram fricções. Por exemplo, estudos mostram variações nos benefícios entre grupos demográficos, deixando alguns com a sensação de tratamento injusto, apesar de circunstâncias financeiras semelhantes. Estes resultados ilustram como políticas redistributivas podem inadvertidamente gerar ressentimento.
**Cotas de Diversidade na Contratação**
Muitas empresas implementaram cotas de diversidade para aumentar a representação. Contudo, estas medidas frequentemente levantam preocupações sobre equidade. Empregados contratados sob cotas por vezes relatam sentir-se estigmatizados, e outros percebem o sistema como desvalorizando o mérito. Isto mina a moral e a confiança no local de trabalho, como demonstrado em inquéritos que revelam insatisfação com práticas de contratação baseadas em cotas.
Os exemplos acima ilustram como políticas desenhadas para promover equidade podem, na prática, comprometer os princípios de justiça e meritocracia, resultando em consequências imprevistas que minam a confiança nas instituições. A dependência generalizada na identidade de grupo, em vez do desempenho individual, arrisca criar divisões e reduzir a confiança nas instituições.
### Crítica Filosófica e Ética
A busca pela justiça social levanta dilemas filosóficos e éticos, particularmente no equilíbrio entre igualdade e equidade. Por um lado, a igualdade sugere tratar os indivíduos de forma imparcial, independentemente da identidade. Por outro, atingir a igualdade de resultados frequentemente requer tratamento desigual.
Sob uma perspetiva rawlsiana, as políticas redistributivas são justificadas para corrigir desigualdades sistémicas e promover a equidade. Contudo, pensadores libertários como Robert Nozick argumentam que tais intervenções violam os direitos e as liberdades individuais. Para Nozick, a justiça reside na proteção da autonomia e da propriedade pessoal, não na redistribuição de recursos para atingir objetivos coletivos.
Ademais, uma énfase excessiva na identidade de grupo pode fomentar uma cultura de vitimização, onde os indivíduos priorizam queixas em detrimento da responsabilidade pessoal. Esta dinâmica pode consolidar divisões, incentivar direitos adquiridos e minar a coesão social. As políticas que promovem a igualdade de resultados podem inadvertidamente criar privilégios para alguns enquanto desfavorecem outros, perpetuando novas formas de desigualdade.
Uma abordagem equilibrada deve considerar as implicações éticas das medidas redistributivas, preservando as liberdades individuais e a meritocracia. Ao focar na oportunidade em vez do resultado, as sociedades podem buscar a equidade sem comprometer a autonomia.
### Soluções Alternativas
**Investir na Educação**
Proporcionar acesso à educação de alta qualidade é uma forma poderosa de nivelar o campo de jogo. Programas que ampliem as oportunidades educacionais para comunidades desfavorecidas podem promover mobilidade social sem depender de tratamentos preferenciais.
**Garantir Liberdade Económica**
Reduzir barreiras regulatórias e promover mercados livres pode estimular a inovação, o empreendedorismo e a criação de emprego. Ao incentivar a competição, os indivíduos podem prosperar com base nas suas capacidades em vez de depender de intervenções externas.
**Aproveitar Sistemas Descentralizados**
Tecnologias descentralizadas como o Bitcoin podem empoderar indivíduos ao oferecer inclusão financeira e reduzir a dependência de sistemas estatais. Estas ferramentas proporcionam transparência e autonomia, minimizando oportunidades de favoritismo ou corrupção.
**Medidas Práticas**
- Bolsas de estudo e subsídios baseados no mérito.
- Programas de formação profissional para desenvolver competências de mercado.
- Apoio ao empreendedorismo através de financiamento e mentoria.
- Reformas para simplificar os sistemas fiscais e regulatórios.
Estas soluções priorizam a equidade, o empoderamento individual e a oportunidade, promovendo uma sociedade onde as pessoas prosperem com base no mérito e no esforço.
### Conclusão
As políticas de justiça social frequentemente procuram atingir a igualdade através do tratamento desigual, mas esta abordagem pode criar novas formas de desigualdade e divisão. A énfase na identidade de grupo em detrimento do mérito individual arrisca corroer a equidade e a confiança, minando os objetivos que estas políticas procuram atingir.
Para alcançar uma sociedade mais justa e sustentável, é essencial focar na igualdade de oportunidades, garantindo que todos tenham acesso aos mesmos recursos e condições para prosperar, sem comprometer a autonomia individual ou distorcer os princípios da meritocracia. Investimentos na educação, liberdade económica e tecnologias descentralizadas oferecem caminhos práticos para empoderar indivíduos e fomentar a meritocracia. Um compromisso com estes princípios pode criar um futuro mais inclusivo e equitativo, onde todos tenham a chance de prosperar com base nos seus próprios esforços e capacidades.
_Photo by [Cody Pulliam](https://unsplash.com/@codyaustinpulliam?utm_content=creditCopyText&utm_medium=referral&utm_source=unsplash) on
[Unsplash](https://unsplash.com/photos/person-holding-brown-cardboard-box-GGKVGSkKIzM?utm_content=creditCopyText&utm_medium=referral&utm_source=unsplash)_
-

@ d360efec:14907b5f
2025-02-18 13:18:54
**นักพนันแห่งเฮรันเทล**
**“คณิตศาสตร์” กุญแจเวทมนตร์ นักพนัน และ นักลงทุน**
ในนครเฮรันเทล นามกระฉ่อนเลื่องลือในหมู่นักเสี่ยงโชค เมื่อเอ่ยถึง **“การพนัน”** ภาพที่ชาวเมืองมักนึกถึงคือ **“ยาจกข้างถนน”**
มิใช่เรื่องแปลกประหลาดอันใด เพราะเป็นที่ร่ำลือกันว่า **จ้าวแห่งหอคอยรัตติกาล** ผู้คุมบ่อนพนัน มักร่ายเวทมนตร์สร้างเกมให้ตนเองได้เปรียบ เพื่อดูดกลืนเงินทองของผู้มาเยือน
ดังนั้น การที่สามัญชนจะพิชิตเกมในระยะยาว จึงเป็นดั่งเงามายาที่จับต้องมิได้
กระนั้น ยังมีตำนานกล่าวขานถึงผู้กล้า ที่สามารถสร้างชื่อจาก **“เกมพนัน”** เช่น
**เวเนสซา รุสโซ** นักเวทย์มนตร์ผู้ใช้กฎหมายแห่งแดนไกล ใช้เวลายาวนานถึงหกปี
ร่ายเวทย์สะสมทรัพย์สินกว่าร้อยล้านเหรียญทอง จากการเล่นเกมไพ่ศักดิ์สิทธิ์ **“โป๊กเกอร์”**
หรือแม้แต่ **เอ็ดเวิร์ด โอ. ทอร์ป** จอมปราชญ์ผู้สร้างกำไรถึงสามแสนหกหมื่นเหรียญทอง ภายในเจ็ดราตรี
จากการเล่นเกมไพ่มนตรา **“แบล็กแจ็ก”** ด้วยเงินทุนตั้งต้นเพียงสามแสนสามหมื่นเหรียญทอง คิดเป็นอัตราเวทย์ตอบแทนร้อยสิบส่วน!
เหล่าจอมยุทธ์เหล่านี้ มิได้อาศัยเพียงโชคช่วยชั่วครั้งชั่วคราวแล้วเลือนหาย
แต่พวกเขากลับสามารถร่ายเวทย์สร้างผลตอบแทนระยะยาว จนเรียกได้ว่า ใช้ **“หอคอยรัตติกาล”** เป็นแหล่งเสบียงเลี้ยงชีพ
โดยกุญแจเวทย์ที่บุคคลเหล่านี้ใช้ ก็คือ **“คณิตศาสตร์”**
เหตุใด **“คณิตศาสตร์”** จึงช่วยให้ผู้คนเอาชนะ **“การพนัน”** ได้?
และนอกจาก **“การพนัน”** แล้ว **“คณิตศาสตร์”** ยังสามารถประยุกต์ใช้กับสิ่งใดได้อีก?
**นักเล่าเรื่องแห่งเฮรันเทล** จักไขปริศนาให้ฟัง
เบื้องต้น ขอให้ท่านลองพิจารณาตนเอง ว่าเคยประสบพบพานเหตุการณ์เหล่านี้หรือไม่:
- ตั้งมั่นว่า จักเสี่ยงโชคให้ได้กำไรเพียงเล็กน้อย แล้วจักหยุดพัก
- แต่หากพลาดท่าเสียที จักจำกัดการสูญเสียให้เท่าทุนเดิมที่ตั้งไว้
- ครั้นเมื่อเวทมนตร์เข้าข้าง ได้กำไรมาแล้ว กลับโลภโมโทสัน อยากได้เพิ่มอีกนิด จึงร่ายเวทย์ต่อ
- ทว่ากำไรเริ่มร่อยหรอ จนเหลือเพียงทุนเดิม สุดท้ายทุนที่ตั้งไว้คราแรกก็มลายสิ้น
- จำต้องหาเงินทองมาลงเพิ่ม หวังทวงทุนคืน และพบว่าต้องสูญเสียเงินก้อนนั้นไปในห้วงเวลาต่อมา
ลำดับเหตุการณ์ดังกล่าว เรียกได้ว่าเป็น **“วงจรอุบาทว์”** สำหรับนักพนันมากมายในเฮรันเทล
ปริศนาที่ตามมาก็คือ เหตุใด **“วงจรอุบาทว์”** นี้จึงเกิดขึ้นซ้ำแล้วซ้ำเล่า?
ส่วนหนึ่ง ย่อมเป็นเพราะอารมณ์อันแปรปรวนในการเสี่ยงโชคของแต่ละคน
แต่อีกส่วนที่สำคัญยิ่งกว่า ต้องกล่าวว่าเป็นผลจาก **“กลไกต้องสาป”** ของจ้าวแห่งหอคอยรัตติกาล
ซึ่งต้องกล่าวว่า เหล่าเจ้าของหอคอยรัตติกาลนั้น จักใช้หลักการทำนองเดียวกับ **“สมาคมพ่อค้าผู้พิทักษ์”**
คือจักเก็บเงินทองจากชนจำนวนมาก เพื่อนำมาจ่ายให้กับชนเพียงหยิบมือ
เพื่อล่อลวงให้ชนทั้งหลายเสี่ยงโชคต่อไป หรือทำให้เหล่านักพนันหวังว่า จักเป็นผู้โชคดีเฉกเช่นพวกเขาบ้าง
แม้จะมีผู้โชคดีที่สามารถได้กำไรในเบื้องต้น แต่ในบั้นปลายก็จักพ่ายแพ้อยู่ดี ซึ่งเป็นไปตาม **“กฎแห่งจำนวนมหาศาล”** เพราะจ้าวแห่งหอคอยรัตติกาลนั้น ได้คำนวณและออกแบบระบบเกมที่ตนเองได้เปรียบในระยะยาวแล้ว
จากตำนานนี้ ย่อมประจักษ์ชัดว่า แม้การพนันจักเป็นเรื่องของดวงชะตา
แต่ก็ถูกรังสรรค์ขึ้นจากการคำนวณทางคณิตศาสตร์
ดังนั้น หากปรารถนาจะหาหนทางเอาชนะจ้าวแห่งหอคอยรัตติกาล ก็จำต้องเข้าใจ **“คณิตศาสตร์”** เสียก่อน
ทีนี้ จงเงี่ยหูฟัง แล้วท่านจักได้ยินข้าไขปริศนา:
**๑. ปริศนาแห่ง “กำไรคาดหวัง”**
สำหรับการแสวงหา **“เกมเสี่ยงทาย”** ที่ควรค่าแก่การเล่น หรือการเสี่ยง
สิ่งแรกที่นักพนันพึงกระทำคือ **“การประเมินกำไรคาดหวัง”** หรือ **“เวทคำนวณอนาคต”**
**“กำไรคาดหวัง”** ถูกคิดค้นโดย **คริสเตียน ฮอยเกนส์** นักปราชญ์เวทย์ชาวดัตช์ เพื่อประเมินว่าเกมพนันแบบใดควรค่าแก่การเล่น ซึ่งมิใช่เพียงแค่การประเมินโอกาสแห่งชัยชนะเท่านั้น แต่ต้องคิดรวมขนาดของเงินเดิมพันไปด้วย
โดยสูตรเวทย์คือ:
**กำไรคาดหวัง = (เงินที่ได้ x โอกาสชนะ) + (เงินที่เสีย x โอกาสแพ้)**
ดังนั้น หากปรารถนาจะสะสม **“ทองคำมายา”** ในระยะยาว จงเลือกเกมที่มี **“กำไรคาดหวัง”** เป็นบวก
แต่หากพลาดพลั้งเข้าไปเล่นเกมที่ **“กำไรคาดหวัง”** เป็นลบ และบังเอิญว่าโชคชะตาเล่นตลกให้ได้เงินทองมาครอง
พึงละทิ้งเกมนั้นเสียโดยพลัน เพราะท้ายที่สุดหากยังคงเล่นต่อไป ผู้อับโชคผู้นั้นก็คือตัวท่านเอง
อย่างไรก็ตาม โดยธรรมดาแล้ว **“กำไรคาดหวัง”** ของเกมพนันที่มีเจ้ามือมักจักติดลบ จึงเป็นเรื่องยากยิ่งที่จะเอาชนะได้ เฉกเช่นตัวอย่างที่เราเห็น คือเกมในบ่อนพนัน หรือแม้แต่ **“สลากกินแบ่งรัฐบาล”** ก็ล้วนเป็นเกมที่มี **“กำไรคาดหวัง”** ติดลบทั้งสิ้น
นอกจาก **“กำไรคาดหวัง”** จักถูกใช้กับการพนันได้แล้ว
หลักเวทย์ **“คณิตศาสตร์”** ก็ยังสามารถประยุกต์ใช้กับการลงทุนได้ไม่แตกต่างกัน
ตัวอย่างเช่น หากท่านเก็บสถิติข้อมูลการลงทุนของตนเอง
แล้วพบว่ามีเพียงสามสิบส่วนร้อยเท่านั้น ที่ท่านซื้อ **“ศิลาแห่งโชค”** แล้วสร้างผลตอบแทนเป็นบวก
แต่ท่านยังคงปรารถนาความสำเร็จในการลงทุน
ก็จงจำกัดการขาดทุนแต่ละคราให้น้อยเข้าไว้ เช่น -๕%
และปล่อยให้มีกำไรในแต่ละคราที่ลงทุน เช่น อย่างน้อย ๒๐%
ซึ่งจากการใช้กลยุทธ์นี้ ท่านจักมี **“กำไรคาดหวัง”** = (๒๐% x ๐.๓) + (-๕% x ๐.๗) = ๒.๕%
จักเห็นได้ว่า แม้ท่านจักมีจำนวนคราที่ขาดทุนบ่อยครั้ง แต่ก็ยังสามารถสร้างกำไรได้
หากคราที่กำไรนั้น สามารถทำเงินทองเป็นจำนวนมากได้
**๒. ปริศนาแห่ง “การบริหารหน้าตัก” หรือ “การบริหารเงินทุน”**
แม้ว่าท่านจักรับรู้ **“กำไรคาดหวัง”** แล้ว แต่หากท่านเผชิญหน้ากับการขาดทุนต่อเนื่องกัน ท่านก็อาจหมดเนื้อหมดตัวก่อนถึงคราที่จะกอบโกยเงินทองจากคราที่กำไร
วิธีคลายปมปริศนานี้ก็คือ การมิลงเงินทองทั้งหมดของท่านในการลงทุนเพียงคราเดียว
ซึ่งนอกจากการกระจายความเสี่ยงในการลงทุนหลาย **“ศิลาแห่งโชค”** หรือหลาย **“เกมเสี่ยงทาย”** แล้ว
ท่านอาจกำหนดขนาดของการลงทุนแต่ละคราให้มิมากเกินไป แบบง่าย ๆ เช่น มิเกิน ๑๐% ของเงินลงทุนทั้งหมด หรือท่านอาจคำนวณขนาดของการลงทุนแต่ละคราด้วยสูตรทางคณิตศาสตร์ เช่น สูตร **“การขาดทุนสูงสุดที่ท่านรับได้ (Value at Risk)”** หรือ สูตร **“ขนาดเดิมพันที่เหมาะสม (Kelly Formula)”**
**๓. ปริศนาแห่ง “อคติ”**
ในวงการพนัน มักมีอคติหนึ่งที่บังเกิดบ่อยครั้งกับผู้คน คือ **“Gambler's Fallacy”** หรือ **“ความเชื่อผิด ๆ แห่งนักพนัน”** ว่าหากเหตุการณ์หนึ่งบังเกิดบ่อยครั้งกว่าปรกติในช่วงเวลาหนึ่ง ๆ
เหตุการณ์นั้นจักบังเกิดบ่อยครั้งน้อยลงในอนาคต ทั้ง ๆ ที่เหตุการณ์เหล่านั้นเป็นอิสระจากกันในทางสถิติ
ยกตัวอย่างเช่น หากโยนเหรียญมนตราออกหัวไปแล้วสามครา ในคราที่สี่ หลายคนอาจคิดว่าโอกาสออกก้อยมากกว่าหัว แม้ว่าการโยนเหรียญแต่ละคราจะมิได้ส่งผลอันใดต่อกันเลย (จะโยนกี่ครา โอกาสหัวหรือก้อย ก็คือ ๕๐:๕๐ อยู่ยั่งยืน)
หรือแม้กระทั่ง **“สลากกินแบ่งรัฐบาล”** มีหลายคนที่ซื้อเลขซ้ำกัน เพื่อหวังว่าจะถูกในงวดต่อ ๆ ไป
ในวงการการลงทุน ก็มีลักษณะที่คล้ายคลึงกัน เช่น หาก **“ศิลาแห่งโชค A”** ราคาตกต่ำลงมาห้าครา บางคนอาจคิดว่าในคราที่หก ราคาของมันจักต้องเด้งขึ้นมา ซึ่งในความเป็นจริง หาได้เป็นเช่นนั้นเสมอไป
จักเห็นได้ว่า แท้จริงแล้ว ไม่ว่าจักเป็น **“เกมเสี่ยงทายแห่งโชคชะตา”** หรือ **“การผจญภัยในตลาดทุน”**
หากท่านมีความเข้าใจ และนำ **“คณิตศาสตร์”** เข้ามาเป็นรากฐาน
มันก็อาจนำพาตัวท่านเอง ไปสู่จุดที่ได้เปรียบในเกมนั้น ได้เฉกเช่นกัน..
**สูตรเวทย์มนตร์ที่ปรากฏในตำนาน:**
* **กำไรคาดหวัง = (เงินที่ได้ x โอกาสชนะ) + (เงินที่เสีย x โอกาสแพ้)**
**คำเตือนจากนักเล่าเรื่องแห่งเฮรันเทล:**
"พึงระลึกไว้เสมอว่า โชคชะตาเป็นสิ่งที่คาดเดาได้ยาก แม้เวทมนตร์คณิตศาสตร์จักช่วยนำทาง แต่ท้ายที่สุดแล้ว ความสำเร็จยังคงขึ้นอยู่กับการตัดสินใจและสติปัญญาของท่านเอง"
หวังว่าตำนานบทนี้จักเป็นประโยชน์แก่ท่านนะคะ
-

@ 3ca99671:689a4ce4
2025-02-18 09:34:11
How to avoid internal pressure and anxiety. Constantly forcing yourself to continue something, doubting its value to anyone other than your ego. And then it starts: "What if I use that framework? Maybe I should switch to another language? No, I’ll master that engine over there, and everything will fall into place." But it doesn’t. You don’t master it, it’s not the right language. In short, you’re stuck. The sense of obligation and the justification of inaction tear you apart. I mean, how is it inaction? Inside, there’s constant work going on, fragments of the future product emerge, but something’s missing… Organization? Publicity? Speaking of publicity, I clearly see that it will only intensify the sense of duty and create additional pressure. Which won’t be a creative energy at all, on the contrary, it’s more likely to lead to despair. You need to be 100 percent confident in the success of what you’re doing, so that without society’s approval of the prototype, you can release the product and not regret a single hour spent on it. Now, that’s belief, that’s love. Alright, this is a draft. So, what exactly is missing? Regarding organization: YES, backlogs and the like are necessary, BUT. Maybe the goals were set incorrectly back when I was working on projects. Because everything turned into organizing inaction. Exactly, organizing with the goal of doing nothing. Here’s another thing: think about the gym, for example. It’s the same with products, you need a hub, a shared space, and it’s easier now. Telegram, Discord, itch.io, GitHub, plenty of info and examples. So, what’s holding me back? Is there something stopping me? Maybe it’s worth finding out how others manage their work. (Here, I contradict myself). Obvious things, but they should be spelled out. And it becomes clear that I can’t handle it alone. I need collaborators. Maybe that’s the secret to ensuring the work continues, huh? If you think about releasing a product as the final point of an expedition. And immediately, the meme about how Hunter was packing his car trunk for the trip to Las Vegas comes to mind. A little lyrical digression:
"I had two Unity courses under my belt, ninety hours of Unreal Engine tutorials, three textbooks on procedural world generation, a hard drive half full of unfinished shaders, and a whole universe of tools: pixel-art engines, object destruction plugins, buggy C# scripts, low-poly assets laughing at me... and a liter of espresso, buckets of energy drinks, a box of donut coffee from Steam, a pint of sheer stubbornness, and two dozen tokens of 'unique' in-game helmets. Not that all of this was necessary for an indie project, but once you dive into tech experiments, it’s hard to stop. The only thing driving me crazy was neural networks for enemy AI. There’s no creature in the world more helpless, naive, and predictable than a programmer trying to squeeze machine learning into a platformer about a jumping carrot. And I knew for sure that by morning, we’d be diving into that rabbit hole with rakes in hand."
To be continued...
P.S: ai translation from russian
-

@ ec42c765:328c0600
2025-02-05 23:16:35
てすと
nostr:nevent1qqst3uqlls4yr9vys4dza2sgjle3ly37trck7jgdmtr23uuz52usjrqqqnjgr
nostr:nevent1qqsdvchy5d27zt3z05rr3q6vvmzgslslxwu0p4dfkvxwhmvxldn9djguvagp2
test
てs
-

@ e7bc35f8:3ed2a7cf
2025-02-18 09:07:03
For those who still trust mainstream narratives about war and foreign intervention, the Douma chemical attack story should serve as a wake-up call. The official version of events—that Syrian government forces carried out a chemical attack on civilians in Douma on April 7, 2018—has been thoroughly dismantled by whistleblowers, independent journalists, and even leaked documents from the Organization for the Prohibition of Chemical Weapons (OPCW).
Yet, despite [mounting evidence]( https://thegrayzone.com/2018/03/06/media-propaganda-battle-syria-eastern-ghouta/), mainstream media and Western governments continue to push the debunked narrative, using it to justify military interventions and sustain the illusion of moral authority. This article revisits the Douma deception, breaking down how the false flag operation unfolded and how the truth was systematically suppressed.
### A Timeline of the Manufactured Crisis
#### April 7, 2018: The Alleged Chemical Attack
On this day, as the Syrian Army engaged terrorist insurgents in Douma, [shocking videos surfaced]( https://youtu.be/sYItxxEO3F8) online showing alleged victims of a chemical attack. Without proper investigation, Western leaders seized on the footage as proof of an [atrocity committed]( https://web.archive.org/web/20200304211152/https://eg.usembassy.gov/united-states-assessment-of-the-assad-regimes-chemical-weapons-use/) by the Assad government.
Within 24 hours, then-President Donald Trump tweeted about "Animal Assad" and vowed that Russia and Iran would "pay a big price." This swift response echoed past war propaganda, reminiscent of the lies used to justify the invasion of Iraq.
#### April 14, 2018: The Bombing of Syria Begins
Less than a week after the alleged attack, the [United States]( https://youtu.be/w43ok0q5G5A), [France, and Britain launched coordinated missile strikes]( https://www.washingtonpost.com/world/national-security/us-launches-missile-strikes-in-syria/2018/04/13/c68e89d0-3f4a-11e8-974f-aacd97698cef_story.html) on Syrian government targets. Shockingly, these airstrikes were carried out before any independent investigation had even begun.
Meanwhile, on the same day, OPCW investigators arrived in Syria to examine the supposed chemical attack site. In a grotesque display of arrogance, the West had already punished Syria for a crime that hadn't been proven.
#### April 17, 2018: Doubts Emerge
Veteran journalist [Robert Fisk visited Douma]( https://www.independent.co.uk/voices/syria-chemical-attack-gas-douma-robert-fisk-ghouta-damascus-a8307726.html) and interviewed a local doctor who revealed that the victims shown in viral videos had actually died from suffocation—not chemical weapons. The doctor described how panic and dust inhalation in underground shelters had led to casualties, but no traces of nerve agents like **sarin** were found.
#### July 6, 2018: OPCW’s Initial Report Undermines the Official Story
The OPCW released its [interim findings]( https://www.opcw.org/media-centre/news/2018/07/opcw-issues-fact-finding-mission-reports-chemical-weapons-use-allegations), confirming that:
> No organophosphorus nerve agents or their degradation products were detected, either in the environmental samples or in plasma samples from the alleged casualties.
And while:
> Various chlorinated organic chemicals were found in samples from Locations 2 and 4, along with residues of explosive
the report makes no mention of the concentrations or levels of those chemicals.
In Addition the "Annex 2" (Open Sources) is blank.
In Annex 3 where all chemicals are listed, there is no chemical weapon agent listed.
Despite this, Western media and politicians continued to push the idea that Syria had used chemical weapons.
#### February–March 2019: Whistleblower Confirms Staged Hospital Footage
In a stunning revelation, [BBC producer Riam Dalati]( https://youtu.be/fFLRX5ZiEvo) tweeted that the viral hospital scene—depicting victims being hosed down—had been **staged**. This meant that at least part of the so-called evidence was a fabrication.
Shortly after, the OPCW issued its [final report]( https://www.opcw.org/sites/default/files/documents/2019/03/s-1731-2019%28e%29.pdf). While it acknowledged a lack of sarin,
> No organophosphorous nerve agents, their degradation products or synthesis impurities were detected [...] it is not currently possible to precisely link the cause of the signs and symptoms to a specific chemical
it ambiguously suggested that "a toxic chemical containing reactive chlorine" was likely used. This vague wording allowed Western governments to continue their accusations without hard proof.
#### May 2019: Leaked OPCW Report Exposes a Cover-Up
A [leaked engineering assessment]( https://web.archive.org/web/20190514174330/http://syriapropagandamedia.org/wp-content/uploads/2019/05/Engineering-assessment-of-two-cylinders-observed-at-the-Douma-incident-27-February-2019-1.pdf) by an OPCW sub-team completely contradicted the official findings. It concluded that the two cylinders found at the scene **were likely manually placed rather than dropped from aircraft**—suggesting [the incident was staged]( https://youtu.be/FU24r2zWVQo).
Instead of addressing this bombshell revelation, [OPCW leadership focused]( https://www.opcw.org/sites/default/files/documents/2019/06/Remarks%20of%20the%20Director-General%20Briefing%20for%20States%20Parties%20on%20Syrian%20Arab%20Republic%20Update%20on%20IIT-FFM-SSRC-DAT_1.pdf) on investigating **how the leak happened** rather than the damning content of the report itself.
#### October–November 2019: More Whistleblowers Speak Out
On October 15th, 2019, the [Courage Foundation]( https://web.archive.org/web/20191024045128/https://couragefound.org/2019/10/opcw-panel-statement/) "convened a panel of concerned individuals from the fields of disarmament, international law, journalism, military operations, medicine and intelligence in Brussels".
The whistleblower giving an "extensive presentation, including internal emails, text exchanges and suppressed draft reports..." describes "efforts to exclude some inspectors from the investigation whilst thwarting their attempts to raise legitimate concerns, highlight irregular practices or even to express their differing observations and assessments".
The panel "became convinced by the testimony that key information about chemical analyses, toxicology consultations, ballistics studies, and witness testimonies was suppressed, ostensibly to favor a preordained conclusion" and expressed unanimous alarm about "unacceptable practices in the investigation".
[Another OPCW whistleblower]( https://www.counterpunch.org/2019/11/15/the-opcw-and-douma-chemical-weapons-watchdog-accused-of-evidence-tampering-by-its-own-inspectors/), referred to as "Alex", a member of this fact finding mission, confirmed that key evidence had been suppressed. He revealed that:
"_the signs and symptoms of victims were not consistent with poisoning from chlorine_".
Instead of an attack producing multiple fatalities there had been “_a non chemical-related event_”.
His findings, which undermined the official narrative, were removed from the final report.
At this point, multiple independent voices—including journalists, scientists, and former OPCW officials—had exposed the [Douma deception]( https://wikileaks.org/opcw-douma/#Internal%20OPCW%20E-Mail). But the mainstream media either ignored or actively discredited these revelations.
### How the Media and Government Covered It Up
When whistleblowers and [journalists]( https://youtu.be/ojItF6MGL-0) challenged the official story, mainstream outlets worked overtime to discredit them. The propaganda network [Bellingcat]( https://www.bellingcat.com/news/2019/11/25/emails-and-reading-comprehension-opcw-douma-coverage-misses-crucial-facts/) published a weak "debunking" article, which was swiftly dismantled by independent journalist [Caitlin Johnstone]( https://caitlinjohnstone.com/2019/11/27/narrative-managers-faceplant-in-hilarious-opcw-scandal-spin-job/) and veteran columnist [Peter Hitchens]( https://hitchensblog.mailonsunday.co.uk/2019/11/my-response-to-the-bellingcat-attempt-to-spin-away-the-devastating-implications-of-the-opcw-douma-leak-i-have.html).
Rather than confronting the facts, the OPCW and its backers dismissed the leaks as unimportant or "[Russian disinformation]( https://www.cbsnews.com/news/opcw-chemical-weapons-watchdog-douma-chlorine-gas-wikileaks-russia-syria-claim-bias-today-2019-11-25/)"—a predictable smear tactic used whenever official narratives collapse.
### Why This Matters
The Douma deception is not just an academic debate—it had real-world consequences. The false flag attack was used to justify military aggression against Syria, escalating tensions in the Middle East and prolonging unnecessary suffering.
More importantly, it serves as a case study in how governments and media manufacture consent for war. By exposing these propaganda tactics, we can resist manipulation and prevent future conflicts based on lies.
The Douma hoax is just one example of how false narratives are weaponized to justify military interventions. The same playbook has been used time and again—from Iraq’s "Weapons of Mass Destruction" to Libya’s "humanitarian intervention."
If people learn to recognize propaganda before it leads to war, we can disrupt the cycle of deception. The truth is out there—we just need the courage to face it.
-

@ ec42c765:328c0600
2025-02-05 22:05:55
# カスタム絵文字とは
任意のオリジナル画像を絵文字のように文中に挿入できる機能です。
また、リアクション(Twitterの いいね のような機能)にもカスタム絵文字を使えます。

# カスタム絵文字の対応状況(2025/02/06)

カスタム絵文字を使うためにはカスタム絵文字に対応した[クライアント](https://welcome.nostr-jp.org/tutorial/explore-client.html)を使う必要があります。
※表は一例です。クライアントは他にもたくさんあります。
使っているクライアントが対応していない場合は、クライアントを変更する、対応するまで待つ、開発者に要望を送る(または自分で実装する)などしましょう。
#### 対応クライアント
- [Amethyst](https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst)
- [FreeFrom](https://freefrom.space/)
- [nostter](https://nostter.app/)
- [Rabbit](https://rabbit.syusui.net/)
- [Lumilumi](https://lumilumi.app/)
- [Nos Haiku](https://nos-haiku.vercel.app/)
- [Snort](https://snort.social/)
- [noStrudel](https://nostrudel.ninja/)
ここではnostterを使って説明していきます。
# 準備
カスタム絵文字を使うための準備です。
- Nostrエクステンション(NIP-07)を導入する
- 使いたいカスタム絵文字をリストに登録する
## Nostrエクステンション(NIP-07)を導入する
Nostrエクステンションは使いたいカスタム絵文字を登録する時に必要になります。
また、環境(パソコン、iPhone、androidなど)によって導入方法が違います。
Nostrエクステンションを導入する端末は、実際にNostrを閲覧する端末と違っても構いません(リスト登録はPC、Nostr閲覧はiPhoneなど)。
Nostrエクステンション(NIP-07)の導入方法は以下のページを参照してください。
[ログイン拡張機能 (NIP-07)を使ってみよう | Welcome to Nostr! ~ Nostrをはじめよう! ~ ](https://welcome.nostr-jp.org/tutorial/nip-07.html)
少し面倒ですが、これを導入しておくとNostr上の様々な場面で役立つのでより快適になります。
## 使いたいカスタム絵文字をリストに登録する
以下のサイトで行います。
[emojito](https://emojito.meme/)
右上の**Get started**からNostrエクステンションでログインしてください。
例として以下のカスタム絵文字を導入してみます。
実際より絵文字が少なく表示されることがありますが、古い状態のデータを取得してしまっているためです。その場合はブラウザの更新ボタンを押してください。
[generalJP | カスタム絵文字](https://emojito.meme/a/naddr1qqykwetwv4exzmz22qq3uamnwvaz7tmwdaehgun2vykkkctjdyhxset8w4ex7tnrdakj7q3qa3pvwe2p3v7mnjz6hle63r628wl9w567aw7u23fzqs062v5vqcqqxpqqqp65uhjtrk6)

- 右側の**Options**から**Bookmark**を選択

これでカスタム絵文字を使用するためのリストに登録できます。
# カスタム絵文字を使用する
例としてブラウザから使えるクライアント nostter から使用してみます。
[nostter](https://nostter.app/)
nostterにNostrエクステンションでログイン、もしくは秘密鍵を入れてログインしてください。
## 文章中に使用
1. **投稿**ボタンを押して投稿ウィンドウを表示
2. **顔😀**のボタンを押し、絵文字ウィンドウを表示
3. ***タブ**を押し、カスタム絵文字一覧を表示
4. カスタム絵文字を選択
5. : 記号に挟まれたアルファベットのショートコードとして挿入される

この状態で投稿するとカスタム絵文字として表示されます。
カスタム絵文字対応クライアントを使っている他ユーザーにもカスタム絵文字として表示されます。
対応していないクライアントの場合、ショートコードのまま表示されます。

ショートコードを直接入力することでカスタム絵文字の候補が表示されるのでそこから選択することもできます。

## リアクションに使用
1. 任意の投稿の**顔😀**のボタンを押し、絵文字ウィンドウを表示
2. ***タブ**を押し、カスタム絵文字一覧を表示
3. カスタム絵文字を選択

カスタム絵文字リアクションを送ることができます。

# カスタム絵文字を探す
先述した[emojito](https://emojito.meme/)からカスタム絵文字を探せます。
例えば任意のユーザーのページ [emojito ロクヨウ](https://emojito.meme/p/npub1a3pvwe2p3v7mnjz6hle63r628wl9w567aw7u23fzqs062v5vqcqqu3sgh3) から探したり、 [emojito Browse all](https://emojito.meme/browse) からnostr全体で最近作成、更新された絵文字を見たりできます。
また、以下のリンクは日本語圏ユーザーが作ったカスタム絵文字を集めたリストです(2025/02/06)
※漏れがあるかもしれません
[日本ユーザー作 カスタム絵文字](https://nostviewstr.vercel.app/npub17hczqvxtfv3w69wr6lxrttnpdekwdwel55mld60fr24zwjuu6utqtj8mjx/10030)
各絵文字セットにある**Open in emojito**のリンクからemojitoに飛び、使用リストに追加できます。
-----------
以上です。
次:Nostrのカスタム絵文字の**作り方**
Yakihonneリンク [Nostrのカスタム絵文字の作り方](https://yakihonne.com/article/_@lokuyow.github.io/1707912490439)
Nostrリンク nostr:naddr1qqxnzdesxuunzv358ycrgveeqgswcsk8v4qck0deepdtluag3a9rh0jh2d0wh0w9g53qg8a9x2xqvqqrqsqqqa28r5psx3
-----------
# 仕様
[NIP-30 Custom Emoji](https://github.com/nostr-protocol/nips/blob/master/30.md)
[NIP-30 カスタム絵文字(和訳)](https://github.com/nostr-jp/nips-ja/blob/main/30.md)
-

@ 16d11430:61640947
2025-02-18 02:21:18
The holy grail of software development isn’t just writing code—it’s writing good code in a state of pure cognitive clarity. That moment when the mind operates at peak efficiency, when debugging is intuitive, and when abstractions form with effortless precision. This is the flow state, the intersection of deep focus and high cognitive throughput, where time distorts, distractions dissolve, and productivity skyrockets.
But flow doesn’t happen on command. It’s not a switch you flip—it’s a state that requires cultivation, discipline, and an understanding of what to do outside of flow to extend and intensify the time inside of it.
Understanding Flow in Programming
Flow is a psychological state described by Mihaly Csikszentmihalyi, where people are fully immersed in an activity, experiencing deep focus, clear goals, and intrinsic motivation. In programming, flow is more than just focus—it’s a state where:
Code becomes a natural language, and syntax errors fade into the subconscious.
Bugs reveal themselves intuitively before they cause major issues.
Solutions appear as if they were waiting to be discovered.
However, the challenge isn’t just getting into flow—it’s staying in flow longer and increasing the intensity of that state. Many developers struggle with this because modern work environments are designed to pull them out of it—interruptions, meetings, notifications, and context switches all work against deep work.
Why Flow is Hard to Maintain
The key limitation of flow isn’t just time—it’s cognitive energy. You can’t sustain high-intensity flow indefinitely because:
1. Flow Requires a Build-Up – You don’t start in deep flow; it takes warm-up time. If you’re constantly switching contexts, you never get past the shallow stages of focus.
2. Cognitive Fatigue Kicks In – Just like physical endurance, mental endurance wears down over time. High-intensity cognition depletes willpower, working memory, and problem-solving efficiency.
3. External Interruptions Break the Cycle – Every time you respond to a message, check an email, or attend an unplanned meeting, you disrupt the delicate mental stack that flow relies on.
Expanding Flow: The Out-of-Flow Preparation Phase
To maximize flow, you must structure your out-of-flow time to support your inflow time. This means making low-bandwidth, low-intensity activities serve the function of preserving cognitive resources for when they are needed most.
1. Prime the Mind Beforehand
Preload the problem: Before entering flow, read through relevant code, documentation, or problem statements, even if you don’t start coding. Let the subconscious chew on it.
Use sleep strategically: Review complex issues before sleeping—your brain continues working on them passively overnight.
Journal ideas: Keep a scratchpad for incomplete thoughts and patterns that need to be explored later. This prevents cognitive drift when you re-enter deep work.
2. Reduce Cognitive Load Outside of Flow
Automate the trivial: Reduce low-value decision-making by scripting repetitive tasks, automating builds, and using shortcuts.
Optimize workspace: Remove unnecessary distractions, use dark themes to reduce eye strain, and fine-tune your dev environment.
Minimal communication: Asynchronous work models (like using GitHub issues or structured documentation) prevent unnecessary meetings.
3. Use Active Recovery to Extend Flow Durations
Exercise between flow sessions: Short walks, stretching, or kettlebell swings help reset the nervous system.
Use Indian clubs or a gyro ball: Engaging the wrists and forearms with rhythmic exercises improves circulation and keeps the hands limber.
Engage in passive problem-solving: Listen to low-intensity technical podcasts, read about related topics, or sketch diagrams without the pressure of immediate problem-solving.
4. Manage Energy and Stamina
Control caffeine intake: Small, steady doses of caffeine (e.g., green tea or microdosed coffee) sustain focus longer than a single heavy hit.
Eat for cognitive endurance: Avoid sugar crashes; prioritize protein, healthy fats, and slow-digesting carbs.
Cold exposure and breathwork: Techniques like the Wim Hof method or contrast showers can help maintain alertness and focus.
Maximizing In-Flow Performance
Once in flow, the goal is to stay there as long as possible and increase intensity without burnout.
1. Work in High-Resolution Time Blocks
90-minute deep work cycles: Research suggests the brain works optimally in ultradian rhythms, meaning cycles of 90 minutes of intense focus followed by a 15–20 minute break.
Use timers: Time tracking (e.g., Pomodoro) helps prevent unconscious fatigue. However, don’t stop flow artificially—only use timers to prevent shallow focus work.
2. Reduce Interruptions Ruthlessly
Go offline: Disable notifications, block distracting sites, and use airplane mode during deep work.
Use noise-canceling headphones: Even if you don’t listen to music, noise isolation helps maintain focus.
Batch all non-coding activities: Emails, Slack messages, and meetings should be handled in predefined blocks outside of deep work hours.
3. Optimize Mental Bandwidth
Use text-based reasoning: Writing pseudocode or rubber-duck debugging prevents mental overload.
Talk through problems out loud: The act of verbalizing a complex issue forces clarity.
Engage in deliberate problem-solving: Instead of brute-forcing solutions, work from first principles—break problems down into the smallest testable units.
Scaling Flow: Beyond Individual Productivity
Flow isn’t just an individual challenge—it can be optimized at the team level:
Flow-friendly scheduling: Companies should avoid scheduling meetings during peak productive hours (e.g., morning blocks).
Pair programming strategically: While pair programming can improve code quality, it can also break deep focus. Use it wisely.
Minimize process friction: Too much bureaucracy or excessive agile ceremonies kill momentum. Lean processes help maintain deep work culture.
The Final Goal: High-Intensity Flow as the Default State
Ultimately, a programmer’s most valuable skill isn’t just technical proficiency—it’s the ability to engineer their own mind for sustained, high-intensity flow. When flow is prolonged and intensified, an hour of deep work can replace an entire week of shallow, distracted effort.
The key is not just working more—it’s working smarter, structuring out-of-flow time so that when flow begins, it reaches peak intensity and lasts as long as possible. By systematically designing both low-intensity and high-intensity work, programmers can transform sporadic flow into a continuous, deliberate, high-performance workflow.
In the end, peak developers aren’t just coders—they are architects of their own mental states.
-

@ ec42c765:328c0600
2025-02-05 20:30:46
# カスタム絵文字とは
任意のオリジナル画像を絵文字のように文中に挿入できる機能です。
また、リアクション(Twitterの いいね のような機能)にもカスタム絵文字を使えます。

# カスタム絵文字の対応状況(2024/02/05)

カスタム絵文字を使うためにはカスタム絵文字に対応した[クライアント](https://welcome.nostr-jp.org/tutorial/explore-client.html)を使う必要があります。
※表は一例です。クライアントは他にもたくさんあります。
使っているクライアントが対応していない場合は、クライアントを変更する、対応するまで待つ、開発者に要望を送る(または自分で実装する)などしましょう。
#### 対応クライアント
- [Amethyst](https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst)
- [FreeFrom](https://freefrom.space/)
- [nostter](https://nostter.app/)
- [Rabbit](https://rabbit.syusui.net/)
- [Snort](https://snort.social/)
- [noStrudel](https://nostrudel.ninja/)
ここではnostterを使って説明していきます。
# 準備
カスタム絵文字を使うための準備です。
- Nostrエクステンション(NIP-07)を導入する
- 使いたいカスタム絵文字をリストに登録する
## Nostrエクステンション(NIP-07)を導入する
Nostrエクステンションは使いたいカスタム絵文字を登録する時に必要になります。
また、環境(パソコン、iPhone、androidなど)によって導入方法が違います。
Nostrエクステンションを導入する端末は、実際にNostrを閲覧する端末と違っても構いません(リスト登録はPC、Nostr閲覧はiPhoneなど)。
Nostrエクステンション(NIP-07)の導入方法は以下のページを参照してください。
[ログイン拡張機能 (NIP-07)を使ってみよう | Welcome to Nostr! ~ Nostrをはじめよう! ~ ](https://welcome.nostr-jp.org/tutorial/nip-07.html)
少し面倒ですが、これを導入しておくとNostr上の様々な場面で役立つのでより快適になります。
## 使いたいカスタム絵文字をリストに登録する
以下のサイトで行います。
[emojito](https://emojito.meme/)
右上の**Get started**からNostrエクステンションでログインしてください。
例として以下のカスタム絵文字を導入してみます。
実際より絵文字が少なく表示されることがありますが、古い状態のデータを取得してしまっているためです。その場合はブラウザの更新ボタンを押してください。
[generalJP | カスタム絵文字](https://emojito.meme/a/naddr1qqykwetwv4exzmz22qq3uamnwvaz7tmwdaehgun2vykkkctjdyhxset8w4ex7tnrdakj7q3qa3pvwe2p3v7mnjz6hle63r628wl9w567aw7u23fzqs062v5vqcqqxpqqqp65uhjtrk6)

- 右側の**Options**から**Bookmark**を選択

これでカスタム絵文字を使用するためのリストに登録できます。
# カスタム絵文字を使用する
例としてブラウザから使えるクライアント nostter から使用してみます。
[nostter](https://nostter.app/)
nostterにNostrエクステンションでログイン、もしくは秘密鍵を入れてログインしてください。
## 文章中に使用
1. **投稿**ボタンを押して投稿ウィンドウを表示
2. **顔😀**のボタンを押し、絵文字ウィンドウを表示
3. ***タブ**を押し、カスタム絵文字一覧を表示
4. カスタム絵文字を選択
5. : 記号に挟まれたアルファベットのショートコードとして挿入される

この状態で投稿するとカスタム絵文字として表示されます。
カスタム絵文字対応クライアントを使っている他ユーザーにもカスタム絵文字として表示されます。
対応していないクライアントの場合、ショートコードのまま表示されます。

ショートコードを直接入力することでカスタム絵文字の候補が表示されるのでそこから選択することもできます。

## リアクションに使用
1. 任意の投稿の**顔😀**のボタンを押し、絵文字ウィンドウを表示
2. ***タブ**を押し、カスタム絵文字一覧を表示
3. カスタム絵文字を選択

カスタム絵文字リアクションを送ることができます。

# カスタム絵文字を探す
先述した[emojito](https://emojito.meme/)からカスタム絵文字を探せます。
例えば任意のユーザーのページ [emojito ロクヨウ](https://emojito.meme/p/npub1a3pvwe2p3v7mnjz6hle63r628wl9w567aw7u23fzqs062v5vqcqqu3sgh3) から探したり、 [emojito Browse all](https://emojito.meme/browse) からnostr全体で最近作成、更新された絵文字を見たりできます。
また、以下のリンクは日本語圏ユーザーが作ったカスタム絵文字を集めたリストです(2024/06/30)
※漏れがあるかもしれません
[日本ユーザー作 カスタム絵文字](https://nostviewstr.vercel.app/npub17hczqvxtfv3w69wr6lxrttnpdekwdwel55mld60fr24zwjuu6utqtj8mjx/10030)
各絵文字セットにある**Open in emojito**のリンクからemojitoに飛び、使用リストに追加できます。
-----------
以上です。
次:Nostrのカスタム絵文字の**作り方**
Yakihonneリンク [Nostrのカスタム絵文字の作り方](https://yakihonne.com/article/_@lokuyow.github.io/1707912490439)
Nostrリンク nostr:naddr1qqxnzdesxuunzv358ycrgveeqgswcsk8v4qck0deepdtluag3a9rh0jh2d0wh0w9g53qg8a9x2xqvqqrqsqqqa28r5psx3
-----------
# 仕様
[NIP-30 Custom Emoji](https://github.com/nostr-protocol/nips/blob/master/30.md)
[NIP-30 カスタム絵文字(和訳)](https://github.com/nostr-jp/nips-ja/blob/main/30.md)
-

@ 09fbf8f3:fa3d60f0
2025-02-17 15:23:11
### 🌟 深度探索:在Cloudflare上免费部署DeepSeek-R1 32B大模型
#### 🌍 一、 注册或登录Cloudflare平台(CF老手可跳过)
##### 1️⃣ 进入Cloudflare平台官网:
。www.cloudflare.com/zh-cn/
登录或者注册账号。
##### 2️⃣ 新注册的用户会让你选择域名,无视即可,直接点下面的Start building。
##### 3️⃣ 进入仪表盘后,界面可能会显示英文,在右上角切换到[简体中文]即可。
---
#### 🚀 二、正式开始部署Deepseek API项目。
##### 1️⃣ 首先在左侧菜单栏找到【AI】下的【Wokers AI】,选择【Llama 3 Woker】。
##### 2️⃣ 为项目取一个好听的名字,后点击部署即可。
##### 3️⃣ Woker项目初始化部署好后,需要编辑替换掉其原代码。
##### 4️⃣ 解压出提供的代码压缩包,找到【32b】的部署代码,将里面的文本复制出来。
**下载地址:**
📁 [夸克](https://pan.quark.cn/s/2b5aa9ff57f6)
📁 [UC网盘](https://drive.uc.cn/s/a7ff5e03b4d84?public=1)
📁 [迅雷网盘](https://pan.xunlei.com/s/VOJEzm7hLwmhER71rK2wnXArA1?pwd=cefg#)
##### 5️⃣ 接第3步,将项目里的原代码清空,粘贴第4步复制好的代码到编辑器。
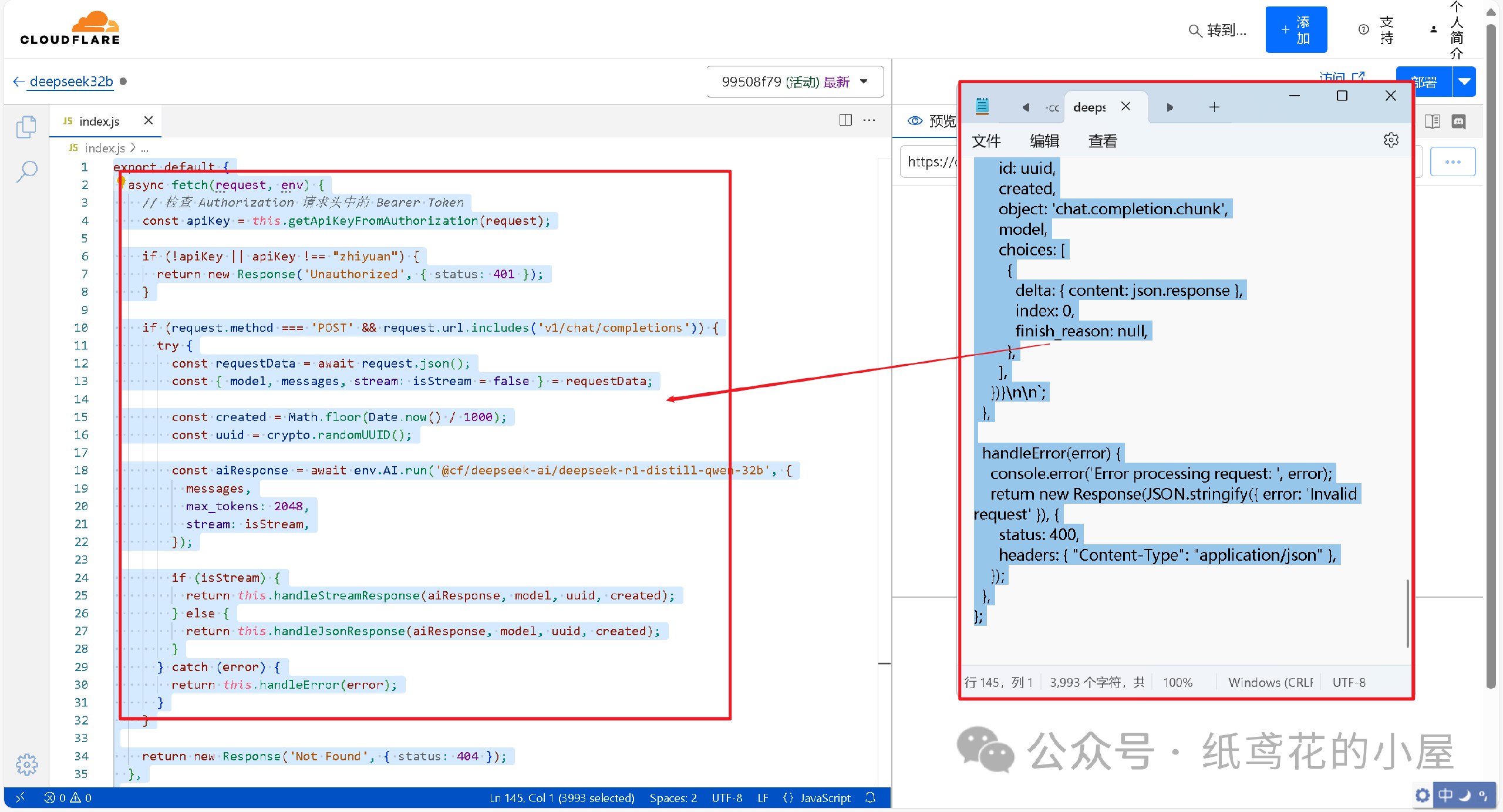
##### 6️⃣ 代码粘贴完,即可点击右上角的部署按钮。
##### 7️⃣ 回到仪表盘,点击部署完的项目名称。
##### 8️⃣ 查看【设置】,找到平台分配的项目网址,复制好备用。
---
#### 💻 三、选择可用的UI软件,这边使用Chatbox AI演示。
##### 1️⃣ 根据自己使用的平台下载对应的安装包,博主也一并打包好了全平台的软件安装包。
##### 2️⃣ 打开安装好的Chatbox,点击左下角的设置。
##### 3️⃣ 选择【添加自定义提供方】。
##### 4️⃣ 按照图片说明填写即可,【API域名】为之前复制的项目网址(加/v1);【改善网络兼容性】功能务必开启;【API密钥】默认为”zhiyuan“,可自行修改;填写完毕后保存即可。
##### 5️⃣ Cloudflare项目部署好后,就能正常使用了,接口仿照OpenAI API具有较强的兼容性,能导入到很多支持AI功能的软件或插件中。
##### 6️⃣ Cloudflare的域名默认被墙了,需要自己准备一个域名设置。
---
**转自微信公众号:纸鸢花的小屋**
**推广:低调云(梯子VPN)**
。www.didiaocloud.xyz
-

@ e7bc35f8:3ed2a7cf
2025-02-17 14:55:26
The mainstream narrative paints the "freedom fever" sweeping across the Middle East as a spontaneous, people-led movement—a victory of democracy against oppressive regimes. Celebrations erupted as tech-savvy youth mobilized to topple autocrats, with Western media hailing the Arab Spring as a beacon of hope. But was it really? Or was it yet another chapter in a long history of foreign interference, regime change, and geopolitical chess moves aimed at securing control over one of the world’s most resource-rich regions?
### Revolution or Destabilization?
Figures like Wadah Khanfar, the former head of Al Jazeera, [expressed optimism]( https://www.ted.com/talks/wadah_khanfar_a_historic_moment_in_the_arab_world?subtitle=en) about the uprisings, framing them as historic moments of empowerment for the people of Egypt, Tunisia, Libya, and beyond. Many Western analysts echoed this sentiment. However, other voices warned that these movements were being manipulated to serve broader strategic interests.
For instance, Professor Hamid Dabashi [linked]( https://youtu.be/RMsOoEUquT8) Iran’s Green Movement to the wider regional wave of youth uprisings against authoritarian regimes. But establishment figures like Senator John McCain quickly [seized the moment]( https://youtu.be/WOcPYxLpUMs), using it as an excuse to pressure Iran, China, and Russia. A closer look suggests that these uprisings were not just organic revolts against dictatorship but rather heavily influenced by external forces.
### The Color Revolution Playbook
The so-called “Green Movement” in Iran bore all the hallmarks of a Western-backed color revolution, with funding and strategic guidance from organizations linked to George Soros, the CIA, Mossad, and global mass media networks. The same script played out elsewhere, as seen in [Webster Tarpley’s analysis]( https://web.archive.org/web/20110131230059/http://www.youtube.com/watch?v=UvI6JqiAZjs) for RT, which laid out how the uprisings in the Middle East aligned perfectly with long-standing Western agendas for the region.
Consider the case of Stuxnet, a cyberweapon [developed by the US and Israel]( https://youtu.be/CS01Hmjv1pQ) to sabotage Iran’s nuclear program. This wasn’t just an isolated incident—it was part of a larger strategy to weaken Iran and its allies. The infamous Brookings Institution report, "[Which Path to Persia?]( https://landdestroyer.blogspot.com/2011/02/brookings-which-path-to-persia.html?m=1)", even laid out a detailed roadmap for toppling the Iranian government through various methods, from economic warfare to military intervention.
### From Iran to Syria: The Next Domino
Once the destabilization of Iran was in motion, attention shifted to its key ally, [Syria]( https://youtu.be/Gpf1C9Fcqxw). The calls for regime change escalated quickly, with Senator Joe Lieberman [openly suggesting]( https://youtu.be/aDxbTQXFhJM) that the US should intervene next. Syria, after all, is a critical piece in the geopolitical chessboard—not just because of its strategic location but also because of its alliances with Iran, Russia, and, most notably, China.
This is precisely why controlling Middle Eastern oil isn’t just about securing energy for the West—it’s about **denying it to China**. If China is to be contained, it must be cut off from the resources that fuel its rise. This explains why Western-backed revolts and interventions tend to target governments that lean toward China.
Let's examine some instances of China's strategy in the region.
* On April 6, 2006, [Chinese President Hu Jintao and Yemeni President Ali Abdullah Saleh]( https://www.fmprc.gov.cn/eng/gjhdq_665435/2675_665437/2908_663816/2910_663820/202406/t20240607_11414813.html) held talks in Beijing. The leaders discussed enhancing political trust, expanding economic and trade cooperation, and increasing cultural and educational exchanges.
* China's expanding diplomatic, economic, and security interests in the Middle East, particularly [through its interactions with the Gulf Cooperation Council (GCC)]( https://jamestown.org/program/bloc-politics-in-the-persian-gulf-chinas-multilateral-engagement-with-the-gulf-cooperation-council/). China's evolving relationship with the GCC reflects its broader objectives of securing energy resources, expanding its economic footprint, and enhancing its geopolitical influence in the Middle East and beyond.
* China's expanding influence in the [Caspian region and its intersection with Syria's strategic ambitions]( https://jamestown.org/program/the-caspian-sea-chinas-silk-road-strategy-converges-with-damascus/). Investments in Central Asian infrastructure, notably the Kazakhstan-China oil pipeline and the Turkmenistan-China gas pipeline. **Syrian President Bashar al-Assad's** "Four Seas Strategy" aimed to position Syria as a central hub connecting the Caspian, Black, Mediterranean, and Red Seas.
* China's expanding political, economic, and strategic ties with Syria, positioning the country as a pivotal hub in China's revitalized [Silk Road initiative]( https://jamestown.org/program/syria-in-chinas-new-silk-road-strategy/). Following **Syrian President Bashar al-Assad's** 2004 visit to China, bilateral cooperation has intensified, particularly in sectors like oil, electricity, transport, and telecommunications, with major Chinese enterprises such as CNPC, ZTE, Huawei, and Haier playing significant roles.
### The Fall of Puppets: Mubarak and Libya
Hosni Mubarak, though a loyal US ally for decades, was ultimately deemed replaceable. Why? Because he was not the ideal puppet. He had shown interest in fostering deeper ties between [China]( http://www.china.org.cn/english/features/phfnt/85843.htm) and the Arab world, particularly in [Africa]( https://english.cctv.com/20091109/101132_2.shtml). His removal paved the way for a new power dynamic, one that better served Western interests.
A similar pattern emerged in Libya. When NATO intervened to topple Gaddafi, [China’s oil investments]( https://www.ft.com/content/eef58d52-3fe2-11e0-811f-00144feabdc0) in the country became collateral damage. Chinese companies had billions of dollars in contracts with Libya, which were suddenly thrown into chaos. Western intervention not only eliminated Gaddafi but also disrupted China’s growing influence in North Africa.
### The Bigger Picture: A New World Order Agenda?
What we are witnessing is not just a series of isolated revolts but a broader, long-term strategy to reshape the Middle East in ways that align with Western and globalist interests. The destruction of strong, independent states in the region creates a vacuum—one that can be filled by controlled regimes, multinational corporations, and military bases that ensure energy resources remain under Western control.
Meanwhile, China’s efforts to establish a foothold in the region are systematically countered. Every strategic move China makes—whether in Syria, Iran, or the Persian Gulf—is met with resistance in the form of “pro-democracy” uprisings, sanctions, or outright military intervention.
### The Illusion of Spontaneous Uprising
While the mainstream media glorifies the Arab Spring and similar movements as victories for democracy, the deeper reality suggests a far more calculated and sinister agenda. The Middle East is being reshaped, not by the will of its people alone, but by powerful forces seeking to maintain global hegemony. The so-called “freedom fever” may be less about liberation and more about control.
The question remains: How much longer will people buy into the illusion?
-

@ e88a691e:27850411
2025-02-17 13:30:42
test post longform 4
-

@ 83279ad2:bd49240d
2025-01-24 09:15:37
備忘録として書きます。意外と時間がかかりました。全体で1時間くらいかかるので気長にやりましょう。
仮想通貨取引所(販売所ではないので、玄人が使えばお得らしい)かつBitcoinの送金手数料が無料(全ての取引所が無料ではない、例えばbitbankは0.0006bitcoinかかる)なので送金元はGMOコインを使います。(注意:GMOコインは0.02ビットコイン以下は全額送金になってしまいます)
今回はカストディアルウォレットのWallet of Satoshiに送金します。
以下手順
1. GMOコインでbitcoinを買います。
2. GMOコインの左のタブから入出金 暗号資産を選択します。
3. 送付のタブを開いて、+新しい宛先を追加するを選択します。
4. 送付先:GMOコイン以外、送付先ウォレット:プライベートウォレット(MetaMaskなど)、受取人:ご本人さま を選んで宛先情報の登録を選ぶと次の画面になります。<br>
5. 宛先名称にwallet of satoshi(これはなんでも良いです わかりやすい名称にしましょう) wallet of satoshiを開いて、受信→Bitcoin On-Chainからアドレスをコピーして、ビットコインアドレスに貼り付けます。<br>
6. 登録するを押します。これで送金先の登録ができました。GMOコインの審査がありますがすぐ終わると思います。
7. ここから送金をします。送付のタブから登録したビットコインの宛先リストwallet of satoshiを選択し、送付数量と送付目的を選択して、2段階認証をします。<br>
8. 実行を押せば終わりです。もうあなたがやることはありません。送金が終わるのを40分くらい眺めるだけです。<br>
8. 取引履歴のタブから今の送金のステータスが見れます。<br>
9. 15分くらい待つとステータスが受付に変わります。<br>
10. 20分くらい待つとトランザクションIDが表示されます。 <br>
<br>この時点からwallet of satoshiにも送金されていることが表示されます。(まだ完了はしていない) <br>

11. ステータスが完了になったら送金終わりです。<br> <br> wallet of satoshiにも反映されます。<br> 
-----------
お疲れ様でした!
-

@ d360efec:14907b5f
2025-02-17 12:20:25
**3 พฤติกรรมที่เป็นอุปสรรคต่อการทำกำไรของนักลงทุนส่วนใหญ่**
นักลงทุนจำนวนมากต้องการที่จะประสบความสำเร็จในตลาดหุ้นและสร้างผลกำไรที่สม่ำเสมอ แต่หลายครั้งที่พวกเขากลับพบว่าตัวเองต้องเผชิญกับอุปสรรคที่ทำให้ไม่สามารถบรรลุเป้าหมายนั้นได้ ช่อง Zyo / เซียว จับอิดนึ้ง ได้นำเสนอ 3 พฤติกรรมที่เป็นอุปสรรคสำคัญต่อนักลงทุนส่วนใหญ่ ซึ่งหากนักลงทุนสามารถหลีกเลี่ยงพฤติกรรมเหล่านี้ได้ ก็จะมีโอกาสในการสร้างผลกำไรที่สม่ำเสมอมากยิ่งขึ้น
1. **การซื้อขายตามอารมณ์:** ตลาดหุ้นมีความผันผวนและเต็มไปด้วยข่าวสารมากมาย นักลงทุนที่ซื้อขายตามอารมณ์มักจะตัดสินใจโดยใช้อารมณ์เป็นหลัก ไม่ว่าจะเป็นความโลภเมื่อเห็นราคาหุ้นขึ้น หรือความกลัวเมื่อราคาหุ้นตก การตัดสินใจที่ไม่ได้อยู่บนพื้นฐานของข้อมูลและการวิเคราะห์อย่างรอบคอบ มักนำไปสู่การตัดสินใจที่ผิดพลาดและขาดทุนในที่สุด
2. **การไม่ยอมรับความเสี่ยง:** การลงทุนในตลาดหุ้นมีความเสี่ยง นักลงทุนที่ไม่ยอมรับความเสี่ยงมักจะพลาดโอกาสในการลงทุนในสินทรัพย์ที่ให้ผลตอบแทนสูง หรือในทางกลับกัน พวกเขาอาจจะหลีกเลี่ยงการตัดขาดทุนเมื่อการลงทุนไม่เป็นไปตามที่คาดหวัง การไม่ยอมรับความเสี่ยงและไม่บริหารความเสี่ยงอย่างเหมาะสม จะทำให้พอร์ตการลงทุนไม่เติบโตเท่าที่ควร หรืออาจจะเผชิญกับความเสียหายที่ใหญ่หลวงได้
3. **การขาดความรู้และความเข้าใจ:** ตลาดหุ้นเป็นเรื่องที่ซับซ้อนและเปลี่ยนแปลงอยู่เสมอ นักลงทุนที่ขาดความรู้และความเข้าใจในเรื่องการลงทุนอย่างเพียงพอ มักจะลงทุนโดยไม่มีหลักการหรือไม่สามารถวิเคราะห์สถานการณ์ได้อย่างถูกต้อง การลงทุนโดยปราศจากความรู้และความเข้าใจที่ถูกต้อง ก็เหมือนกับการเดินอยู่ในความมืด ซึ่งโอกาสที่จะประสบความสำเร็จนั้นเป็นไปได้ยาก
**บทสรุป**
3 พฤติกรรมที่กล่าวมาข้างต้นเป็นเพียงส่วนหนึ่งของอุปสรรคที่นักลงทุนส่วนใหญ่ต้องเผชิญ หากนักลงทุนต้องการที่จะประสบความสำเร็จในการลงทุนอย่างยั่งยืน พวกเขาจำเป็นต้องตระหนักถึงพฤติกรรมเหล่านี้และพยายามปรับปรุงตนเองอย่างต่อเนื่อง การศึกษาหาความรู้เพิ่มเติม การวางแผนการลงทุนอย่างรอบคอบ และการควบคุมอารมณ์ จะเป็นกุญแจสำคัญที่นำไปสู่การสร้างผลกำไรที่สม่ำเสมอในตลาดหุ้นได้
แน่นอนค่ะ ฟังคลิปแล้ว และสรุปบทความเป็นภาษาไทยให้คุณแล้วค่ะ
**บทความ: 3 พฤติกรรมที่เป็นอุปสรรคต่อการทำกำไรสม่ำเสมอของนักลงทุนส่วนใหญ่**
บทความนี้สรุปแนวคิดจากคลิปวิดีโอที่วิเคราะห์พฤติกรรมของนักลงทุนส่วนใหญ่ โดยอ้างอิงจากการสำรวจบัญชีซื้อขายหุ้นกว่า 77,000 บัญชีในช่วงปี 1990-1996 พบว่ามี 3 พฤติกรรมหลักที่เป็นอุปสรรคสำคัญต่อการสร้างผลกำไรที่สม่ำเสมอในการลงทุน
**3 พฤติกรรมที่เป็นอุปสรรคต่อการทำกำไร:**
1. **ปล่อยให้ขาดทุน แต่รีบขายกำไร:** นักลงทุนส่วนใหญ่มักจะถือหุ้นที่กำลังขาดทุนต่อไปเรื่อย ๆ เพราะไม่อยากยอมรับว่าตัดสินใจผิดพลาด ในทางกลับกัน เมื่อหุ้นเริ่มมีกำไรเพียงเล็กน้อย กลับรีบขายออกไปเพราะกลัวกำไรจะหายไป พฤติกรรมนี้เป็นผลจากธรรมชาติของมนุษย์ที่เรียกว่า "Loser Aversion" หรือการหลีกเลี่ยงความเจ็บปวดจากการขาดทุนมากกว่าความสุขจากการได้กำไร
2. **ถัวเฉลี่ยขาลง มากกว่าพีระมิดขาขึ้น:** นักลงทุนจำนวนมากเลือกที่จะซื้อหุ้นที่ราคาลดลง (ถัวเฉลี่ยขาลง) โดยหวังว่าจะได้ต้นทุนที่ต่ำลงและรอให้ราคาหุ้นกลับมา แต่ในความเป็นจริง หุ้นที่อยู่ในแนวโน้มขาลงก็มีโอกาสที่จะลงต่อไปเรื่อย ๆ การถัวเฉลี่ยขาลงจึงเป็นการเพิ่มความเสี่ยง ในขณะที่การ "พีระมิดขาขึ้น" หรือการซื้อหุ้นเพิ่มเมื่อราคาปรับตัวสูงขึ้น เป็นการลงทุนในหุ้นที่กำลังมีแนวโน้มที่ดีและมีโอกาสสร้างกำไรมากกว่า
3. **รีบขายกำไรเล็กน้อย แต่ไม่ยอมขายเมื่อขาดทุนเล็กน้อย:** พฤติกรรมนี้ต่อเนื่องจากข้อแรก คือเมื่อได้กำไรเพียงเล็กน้อย นักลงทุนมักจะรีบขายเพื่อ "ล็อกกำไร" แต่เมื่อขาดทุนเล็กน้อย กลับไม่ยอมขายเพราะหวังว่าราคาจะกลับมา ทำให้สุดท้ายกลายเป็น "กำไรน้อย รีบขาย ขาดทุน เก็บไว้" ซึ่งส่งผลเสียต่อพอร์ตการลงทุนในระยะยาว
**คำแนะนำเพื่อปรับปรุงพฤติกรรมการลงทุน:**
* **ฝึก "Cut Loss Short, Let Profit Run":** ยอมตัดขาดทุนเมื่อหุ้นไม่เป็นไปตามแผน เพื่อจำกัดความเสียหาย และปล่อยให้หุ้นที่กำลังทำกำไรทำงานไป เพื่อเพิ่มโอกาสในการทำกำไรที่มากขึ้น
* **อย่าถัวเฉลี่ยขาลงโดยไม่มีเหตุผล:** พิจารณาแนวโน้มของหุ้นและปัจจัยพื้นฐานก่อนตัดสินใจถัวเฉลี่ยขาลง หากไม่มีเหตุผลที่ชัดเจน การถัวเฉลี่ยขาลงอาจเป็นการเพิ่มความเสี่ยงโดยไม่จำเป็น
* **บริหารความเสี่ยงและ Money Management อย่างเหมาะสม:** กำหนด stop loss ที่ชัดเจน และบริหารจัดการเงินทุนให้เหมาะสมกับความเสี่ยงที่รับได้
* **เรียนรู้และพัฒนาระบบเทรดของตัวเองอย่างต่อเนื่อง:** ทำความเข้าใจกลยุทธ์การเทรดของตนเอง และปรับปรุงพัฒนาอย่างสม่ำเสมอ
* **มี Mindset ที่ถูกต้องสำหรับการเทรด:** เข้าใจว่าการเทรดสวนทางกับธรรมชาติของมนุษย์ ต้องฝึกฝนและสร้างนิสัยที่ถูกต้องเพื่อเอาชนะอุปสรรคทางจิตวิทยา
**สรุป:**
การลงทุนและการเทรดหุ้นเป็นเกมที่ "ผิดธรรมชาติ" ของมนุษย์ การเอาชนะตลาดหุ้นได้จึงต้องอาศัยการฝึกฝนและปรับเปลี่ยนพฤติกรรมให้สวนทางกับธรรมชาติเดิม ๆ โดยการตระหนักถึง 3 พฤติกรรมที่เป็นอุปสรรค และนำคำแนะนำไปปรับใช้ จะช่วยให้นักลงทุนสามารถพัฒนาไปสู่การสร้างผลกำไรที่สม่ำเสมอและยั่งยืนได้ในระยะยาว
-

@ 7546e8e4:154e8264
2025-02-17 10:48:44
Ever feel like your crypto portfolio is stuck in orbit? What if you could turn those fractional holdings into meaningful growth? The secret lies in smart management and a dashboard that makes it effortless.
Key Points
The Power of Small Balances: Explain how even dust (tiny crypto amounts) can compound with strategic tracking and reinvestment over time.
Unified Dashboard Magic: Highlight how phesky.com aggregates BTC, ETH, LTC, TRX, and more into one sleek interface, eliminating the chaos of juggling multiple wallets.
Visualize Your Growth: Emphasize the dashboard’s design charts, trends, and projections that turn abstract numbers into a clear path to "moon-worthy gains.
Call to Action: Stop letting zeros collect cosmic dust. Launch your portfolio to new heights at phesky.com
-

@ 849a5a61:b57d2870
2025-02-17 10:11:18

> Hey everyone! For the past few months we’ve been building an open-source, affordable and privacy-friendly affiliate and referral program creator for Bitcoin businesses and Nostr publishers called BitFlio.
We built [BitFlio](https://bitflio.com/) because, as bitcoiners and nostriches, we couldn’t find an affiliate marketing tool for our products that would accept bitcoin as payment method, keep us anonymnous, and most important allow us to pay and be paid based on the value we provide. Since we didn’t know if affiliate marketing would work for us as a sales channel, we really wanted to find a tool where, instead of a fixed monthly fee, we could instead pay a % in sats per successful referral to test the waters.
Referral marketing is such a powerful marketing channel as it enable the Value For Value (V4V) model to expand and grow the Bitcoin Circular Economy. For example, **referral leads for businesses have a 70% higher conversion rate than leads from any other sales channel**, and **when referred by other customers, that customer typically has a 37% higher retention rate**.
The setup process for BitFlio is nice and easy. You simply signup with nostr or email, connect your Bitcoin wallet, create your first campaign, add the tracking script to your website and then fire the `BitFlio.convert('yourcustomer@email.com')` function from your thank you page, so we can validate the leads Publishers will bring to you. Once you’ve done those steps, you can either invite publishers manually, or send them your unique BitFlio invite signup page URL.
For Publishers is even easier. If you are a content creator looking to monetize bitcoinize your contents, join our network and select from bitcoin brands those you feel comfortable sharing. Lastly, get paid in sats depending on how many sales you can drive to each vendor.
It’s quite hard to list in sentences some of the cool features that make up BitFlio, so here’s a list:
* Pricing from $0/month
* Automatic NWC sync
* Works for both subscriptions and one-time charges
* Embed script is lightweight and only ~13kb
* Privacy-friendly & Anonymous
* No GDPR needed, as we operate in the Private.
* Manage multiple affiliate programs for different products from one single dashboard
* Open-source software
Since we’re in public beta, getting feedback right now is our top priority. We’d appreciate it so much if you sign up for our Beta whitelist via [beta.BitFlio.com](https://beta.BitFlio.com) and let us know how you get on / your initial thoughts 😄
Landing: https://BitFlio.com `sᴏᴏɴ!`
Beta whitelist: https://beta.BitFlio.com
Follow us on Nostr: https://njump.me/npub1sjd95c0kcxn69x3u8azunrm2kdj97lc6cu79csz7rz74hdta9pcqpxgrdx
Support the open source project on @geyserfund https://geyser.fund/project/bitflio/
- - -
Mirror posts:
- https://bitflio.com/blob/affordable-referral-marketing-software-for-nostr-publishers-and-bitcoin-vendors/
- https://geyser.fund/project/bitflio/posts/view/4138
- naddr1qvzqqqr4gupzppy6tfsldsd852drc069ex8k4vmytal343eut3q9ux9atw6h62rsqqxnzden8ymnwdf5xgurzdphm3ncla
originally posted at https://stacker.news/items/888167
-

@ 849a5a61:b57d2870
2025-02-17 09:47:19
We built [BitFlio](https://bitflio.com/) because, as bitcoiners and nostriches, we couldn’t find an affiliate marketing tool for our products that would accept bitcoin as payment method, keep us anonymnous, and most important allow us to pay and be paid based on the value we provide. Since we didn’t know if affiliate marketing would work for us as a sales channel, we really wanted to find a tool where, instead of a fixed monthly fee, we could instead pay a % in sats per successful referral to test the waters.
Referral marketing is such a powerful marketing channel as it enable the Value For Value (V4V) model to expand and grow the Bitcoin Circular Economy. For example, **referral leads for businesses have a 70% higher conversion rate than leads from any other sales channel**, and **when referred by other customers, that customer typically has a 37% higher retention rate**.
The setup process for BitFlio is nice and easy. You simply signup with nostr or email, connect your Bitcoin wallet, create your first campaign, add the tracking script to your website and then fire the `BitFlio.convert('yourcustomer@email.com')` function from your thank you page, so we can validate the leads Publishers will bring to you. Once you’ve done those steps, you can either invite publishers manually, or send them your unique BitFlio invite signup page URL.
For Publishers is even easier. If you are a content creator looking to monetize bitcoinize your contents, join our network and select from bitcoin brands those you feel comfortable sharing. Lastly, get paid in sats depending on how many sales you can drive to each vendor.
It’s quite hard to list in sentences some of the cool features that make up BitFlio, so here’s a list:
* Pricing from $0/month
* Automatic NWC sync
* Works for both subscriptions and one-time charges
* Embed script is lightweight and only ~13kb
* Privacy-friendly & Anonymous
* No GDPR needed, as we operate in the Private.
* Manage multiple affiliate programs for different products from one single dashboard
* Open-source software
Since we’re in public beta, getting feedback right now is our top priority. We’d appreciate it so much if you sign up for our Beta whitelist via [beta.BitFlio.com](//beta.BitFlio.com) and let us know how you get on / your initial thoughts 😄
-

@ d360efec:14907b5f
2025-02-17 08:49:15
**ภาพรวม BTCUSDT (OKX):**
Bitcoin ยังคงอยู่ในแนวโน้มขาขึ้นระยะยาว แต่ระยะสั้นมีความผันผวนและมีการปรับฐานลงมา การวิเคราะห์ครั้งนี้จะเน้นการระบุพื้นที่ที่ Smart Money (หรือ "เจ้ามือ") อาจจะเข้าซื้อหรือขาย เพื่อให้เราสามารถวางแผนการเทรดได้อย่างมีประสิทธิภาพ
**วิเคราะห์ทีละ Timeframe:**
**(1) TF Day (รายวัน):** 
* **แนวโน้ม:** ขาขึ้น (Uptrend)
* **SMC:**
* Higher Highs (HH) และ Higher Lows (HL) ต่อเนื่อง
* Break of Structure (BOS) ด้านบน
* ยังไม่มีสัญญาณการกลับตัวเป็นขาลง
* **ICT:**
* ยังไม่เห็น Order Block หรือ FVG ที่ชัดเจนใน TF Day *ณ ราคาปัจจุบัน*
* **EMA:**
* ราคาอยู่เหนือ EMA 50 (สีเหลือง) และ EMA 200 (สีขาว) (Golden Cross)
* **Money Flow (LuxAlgo):**
* สีเขียวเป็นส่วนใหญ่ แสดงถึงแรงซื้อ
* **Volume Profile:**
* Volume หนาแน่นที่บริเวณต่ำกว่าราคาปัจจุบัน
* **แท่งเทียน:**
* แท่งเทียนล่าสุดเป็นสีแดง แสดงถึงแรงขาย แต่ไส้เทียนยาว แสดงว่ามีแรงซื้อกลับ
* **แนวรับ:** EMA 50, EMA 200, บริเวณ Volume Profile หนาแน่น
* **แนวต้าน:** High เดิม
* **สรุป:** แนวโน้มหลักยังเป็นขาขึ้น Buy on Dip
**(2) TF4H (4 ชั่วโมง):** 
* **แนวโน้ม:** ขาขึ้น (พักตัว)
* **SMC:**
* HH และ HL
* BOS ด้านบน
* ราคาหลุด EMA 50
* **ICT:**
* **Fair Value Gap (FVG):** สังเกตเห็น FVG เล็กๆ ที่เกิดขึ้นก่อนหน้านี้ (บริเวณที่ราคาเคยพุ่งขึ้นอย่างรวดเร็ว) อาจเป็นเป้าหมายของการ Pullback
* **Order Block:** ราคาปัจจุบันกำลังทดสอบ Order Block (บริเวณแท่งเทียนสีแดงแท่งใหญ่ก่อนที่จะขึ้น) *เป็นจุดที่น่าสนใจมาก*
* **EMA:**
* ราคาหลุด EMA 50
* EMA 200 เป็นแนวรับถัดไป
* **Money Flow (LuxAlgo):**
* เขียวและแดงผสมกัน, แดงเริ่มมากขึ้น
* **Volume Profile:**
* Volume profile ค่อนข้างสูง
* **แนวรับ:** EMA 200, Order Block, บริเวณ Volume Profile
* **แนวต้าน:** EMA 50, High เดิม
* **สรุป:** แนวโน้มขาขึ้นพักตัว, ทดสอบ Order Block, Money Flow เริ่มเป็นลบ
**(3) TF15 (15 นาที):** 
* **แนวโน้ม:** ขาลง (Downtrend) ระยะสั้น *แต่เริ่มมีสัญญาณการฟื้นตัว*
* **SMC:**
* Lower Highs (LH) และ Lower Lows (LL) *แต่เริ่มเห็น Higher Low*
* BOS ด้านล่าง
* *เริ่มมีสัญญาณการ Breakout EMA 50/200*
* **ICT:**
* ราคาเพิ่ง Breakout Order Block ขาลง (แต่ต้องรอดูว่าจะยืนได้หรือไม่)
* **EMA:**
* *EMA 50/200 เพิ่งจะตัดกันแบบ Golden Cross*
* **Money Flow (LuxAlgo):**
* *เริ่มมีแท่งสีเขียวปรากฏขึ้น*
* **Volume Profile:**
* **แนวรับ:** บริเวณ Low ล่าสุด
* **แนวต้าน:** EMA50/200
* **สรุป:** *เริ่มมีสัญญาณการฟื้นตัว* แต่ยังต้องระวัง
**สรุปภาพรวมและกลยุทธ์ (BTCUSDT):**
* **แนวโน้มหลัก (Day):** ขาขึ้น
* **แนวโน้มรอง (4H):** ขาขึ้น (พักตัว), ทดสอบ Order Block
* **แนวโน้มระยะสั้น (15m):** *เริ่มมีสัญญาณการฟื้นตัว*
* **Money Flow:** Day เป็นบวก, 4H เริ่มเป็นลบ, 15m เริ่มเป็นบวก
* **กลยุทธ์:**
1. **Wait & See:** รอการยืนยันการ Breakout EMA 50/200 ใน TF15m
2. **Buy (เสี่ยง):** *เฉพาะเมื่อราคา Breakout EMA 50/200 ใน TF 15 ได้อย่างแข็งแกร่ง*
3. **Short (เสี่ยง):** ถ้า Order Block ใน TF4H รับไม่อยู่ และ TF15 ยังคงเป็นขาลง
**คำแนะนำ:**
* **Order Block:** ให้ความสำคัญกับ Order Block ใน TF4H
* **FVG:** สังเกต FVG ใน TF4H
* **ความขัดแย้งของ Timeframes:** เริ่มลดลง (15m เริ่มมีสัญญาณบวก)
* **จับตาดู TF15 อย่างใกล้ชิด**
**Disclaimer:** การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ
-

@ 0463223a:3b14d673
2025-02-17 07:48:11
Here we go, it’s Mooooonnnndddddaaaaaaaayyyyyyy!
It’s safe to say I enjoy Monday. Much as I appreciate the downtime over the weekend (if I’m not working) I appreciate the routine of Mondays. Firstly I have my stream to look forward to and whilst I’m not at my best first thing on a Monday, having a little structure goes a long way. Even the fear of looking at the emails I’ve been ignoring from the previous week is possible.
So maybe I’m starting to get an angle of why I’m writing this. It’s a memoir of being a mental I think. I’ve mentioned a number of times this has been a problem most my life but I write this as I’ve halved my Venlafaxine does by ½ once again. This means I’m now on 1/12th of my original dose and I’m maybe a month away from being completely free of RRSIs for the first time in, I guess at least 10 years. To be honest I cant remember when I was first prescribed them. It’s been quite a journey...
3 things have been pivotal. 1; finding my now wife. She’s brilliant and I love her dearly, I think most people know deep down how crushing loneliness can be. I’m very grateful to her for putting up with my bullshit, supporting me and just being there. Gold star for her!
2; would be music, it’s a funny one to put in, it’s also been part of the problem, especially in my wilder days. There’s something quite seductive about the sex, drugs and Rock n Roll meme, although musically it was more Hip Hop, Reggae, Bleeps and Jazz, also I didn’t sleep around much at all but I certainly don’t think I would’ve messed with crack, heroin and all the other drugs otherwise. It’s worth noting 2 of my friends from that era, who didn’t have music in their lives are dead. I’m very lucky. There’s over 100 years of recorded music to enjoy plus I’m almost happy with some of my own bits at last!
3; I have some security, I no longer pay rent or have a landlord. This is also due to number 1 but also because I found some funny internet money. I’m still to write about my process with that, other than to say it was direct response to the banks. That’s a story in it’s own right, it’s pretty dark and hmm… not sure. Plus I don’t think there’s any need to go there right now. I have the world’s most expensive shed and I know I can survive a few months should the worst happen. That’s a LOT. Whilst a little risk taking is healthy, life shouldn’t free stress free, uncertainty about having a roof over your head when you can’t afford it can really take it’s toll. A degree of security is most welcome at this time in life.
A lot of people aren’t so lucky, Tom, Ricky, Dave, Slam, Joel. I’m name checking you specifically. You’re in my thoughts often, especially as I play music every morning… and Slam, if I ever see you again, I want my records back!!! Haha, thieving little cunt but it’s still not hate here. Your life was fucked up before you even had a chance. I hope you’ve found peace with yourself. At least you’re alive! (I think, he might be dead too, who knows…)
So yeah, it’s Monday and it’s gonna be a good day right? I mean it might not but I will at least give it the best start possible and work from there. It takes a degree of effort to retrain the brain. Actually maybe there’s a 4th thing to mention. No Facebacon, Instagran, X or LinkedIn. None of that bullshit where you’re forced into some fake world generated in order to increase shareholder value. These platforms are akin to being a lab rat. I picture Zuckerberg like Ming The Merciless at the start of Flash Gordon sending hot hail etc. That guy made a decision to mess with peoples’ psyche to drive profits. That’s fucking evil man. Jeez, what a cunt!
It’s Monday, I’m wishing you strength in whatever you have ahead of you today. I’m lucky to be where I am right now and if you’re reading this and your world is plagued by darkness, it can get better. Remember that. Hold onto that as best you can. DON’T FUCKING KILL YOURSELF. That’s the single worst thing you can do. The pain you’ll leave behind isn’t worth it. I hope some cosmic vibrations happen in your favour. There’s no easy solution. I can’t tell you the answer but I wish you well. Good luck out there!
-

@ 21ac2956:09d1e2df
2025-01-22 15:27:00
## [kakoi](https://github.com/betonetojp/kakoi) の仕様についてのメモ
### キーボード操作
* 左手での操作に最適化
| キー | 動作 |
|:-|:-|
| ESC | 設定画面 |
| F1 / F12 | ポストバーの表示と非表示 |
| F2 | 時間の表示と非表示 |
| F3 | ユーザーアイコンの表示と非表示 |
| F4 | 名前の表示と非表示 |
| F5 | Geminiによるタイムラインまとめ画面を表示 |
| F9 / Z | コンテンツの折り返し表示の切り替え (余白ダブルクリックでも動作) |
| F10 | ユーザーリストとキーワード通知の設定画面 (余白右クリックでも動作) |
| F11 | メイン画面の表示と非表示 (ポストバー表示) |
| Shift + W | イベント最上行へ移動 |
| W / ↑| イベント選択上移動 |
| S / ↓ | イベント選択下移動 |
| Shift + S | イベント最下行へ移動 |
| A / ← | Webビューを開く (イベントを右クリックでも動作) |
| F / → | リアクションを送信 (イベントをダブルクリックでも動作) |
| 1 ~ 0 | リアクションを選択 |
| R | 返信 |
| B | リポスト |
| Q | 引用 |
| C | Webビューを閉じる |
| Ctrl + Shift + A | メイン画面をアクティブにする |
### タイムライン
* kind:1, 6, 7, 16を取得して表示する
* フォロイーの名前の前には * が付く
### フォローリスト(kind:3)
* 参照のみで更新はしない
* F10 で開くユーザーリストでユーザーを選択し petname セルをクリックすることで未フォローユーザーにもペットネームを設定可能(ローカル保存)
### プロフィール(kind:0)
* F10 で開くユーザーリストでユーザーを選択し picture セルをクリックすることでユーザーのアイコン表示を変更可能(ローカル保存)
### 返信([NIP-10](https://github.com/nostr-protocol/nips/blob/master/10.md) kind:1)
* kakoi のタイムラインに流れるすべてのイベント種に返信可能とする
* スレッドを考慮せず、単一イベントへの単発返信とする
* e タグは marker と返信先 pubkey は設定していない。 relay-url には空文字を設定
```json
["e", "返信先 event-id", ""]
```
* p タグは 返信先 pubkey ひとつだけを指定
### リポスト([NIP-18](https://github.com/nostr-protocol/nips/blob/master/18.md) kind:6 , 16)
* kakoi のタイムラインに流れるすべてのイベント種をリポスト可能
* kind:1はkind:6。その他はkind:16でリポストする
* e タグは relay-url に空文字を設定
```json
["e", "リポスト元 event-id", ""]
```
### 引用([NIP-18](https://github.com/nostr-protocol/nips/blob/master/18.md) kind:1)
* q タグは relay-url に空文字を設定
```json
["q", "引用元 event-id", ""]
```
-

@ c4b5369a:b812dbd6
2025-02-17 06:06:48
As promised in my last article:
nostr:naddr1qvzqqqr4gupzp394x6dfmvn69cduj7e9l2jgvtvle7n5w5rtrunjlr6tx6up9k7kqq2k6ernff9hw3tyd3y453rdtph5uvm6942kzuw08y0
In this one we will dive into how exactly an unidirectional payments channel powered ecash mint system would be implemented, using the tech available today! So if you haven't read that article yet, give it a read!
I first intended to write a longwinded article, explaining each part of the system. But then I realized that I would need some visualization to get the message across in a more digestable way. This lead me to create a slide deck, and as I started to design the slides it became more and more clear that the information is easier shown with visualizations, than written down. I will try to give a summary as best as I can in this article, but I urge you, to please go visit the slide deck too, for the best experience:
-----------
### [TAKE ME TO THE SLIDE DECK!](https://uni-chan.gandlaf.com/)
-----------
### Intro
In this article we will go over how we can build unidirectional payment channels on Bitcoin. Then we will take a look into how Cashu ecash mints work, and how we can use unidirectional payment channels to change the dynamics between ecash users and the mint.
Before we start, let me also give credits to nostr:npub1htnhsay5dmq3r72tukdw72pduzfdcja0yylcajuvnc2uklkhxp8qnz3qac for comming up with the idea, to nostr:npub148jz5r9xujcjpqygk69yl4jqwjqmzgrqly26plktfjy8g4t7xaysj9xhgp for providing an idea for non-expiring unidirectional channels, and nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx unconference for hosting an event where these ideas could be discussed and flourish.
### Building unidirectional payment channels
If you've read the previous article, you already know what unidirectional payment channels are. There are actually a coupple different ways to implement them, but they all do have a few things in common:
1. The `sender` can only send
2. The `Receiver` can only receive
3. They are VERY simple
Way simpler than the duplex channels like we are using in the lightning network today, at least. Of course, duplex channels are being deployed on LN for a reason. They are very versatile and don't have these annoying limitations that the unidirectional payment channels have. They do however have a few drawbacks:
1. Peers have liveness requirements (or they might forfeit their funds)
2. Peers must backup their state after each transaction (if they don't they might forfeit their funds)
3. It is a pretty complex system
This article is not meant to discredit duplex channels. I think they are great. I just also think that in some use-cases, their requirements are too high and the system too complex.
But anyway, let's see what kind of channels we can build!
#### Spillman/CLTV-Channel
The Spillman channel idea has been around for a long time. It's even explained in Tadge Dryjas [Presentation](https://www.youtube.com/watch?v=Hzv9WuqIzA0&t=1969s) on Payment channels and the lightning network from back in the day. I compiled a list of some of the most important propperties of them in the slide below:

Great!
Now that we know their properties, let's take a look at how we can create such a channel ([Slides](https://uni-chan.gandlaf.com/#/11)):

We start out by the `sender` creating a `funding TX`. The `sender` doesn't broadcast the transaction though. If he does, he might get locked into a multisig with the `receiver` without an unilateral exit path.
Instead the `sender` also creates a `refund TX` spending the outputs of the yet unsigned `funding TX`. The `refund TX` is timelocked, and can only be broadcast after 1 month. Both `sender` and `receiver` can sign this `refund TX` without any risks. Once `sender` receives the signed `refund TX`, he can broadcast the `funding TX` and open the channel. The `sender` can now update the channel state, by pre-signing update transactions and sending them over to the `receiver`. Being a one-way channel, this can be done in a single message. It is very simple. There is no need for invalidating old states, since the `sender` does not hold any signed `update TXs` it is impossible for the `sender` to broadcast an old state. The `receiver` only cares about the latest state anyways, since that is the state where he gets the most money. He can basically delete any old states. The only thing the `receiver` needs to make sure of, is broadcasting the latest `update TX` before the `refund TX's` timelock expires. Otherwise, the `sender` might take the whole channel balance back to himself.
This seems to be already a pretty useful construct, due to its simplicity. But we can make it even more simple!

This setup works basically the same way as the previous one, but instead of having a refund transaction, we build the `timelock` spend path directly into the `funding TX` This allows the `sender` to have an unilateral exit right from the start, and he can broadcast the `funding TX` without communicating with the `receiver`. In the worst case, the receiver rejects the channel, and the sender can get his money back after the timelock on the output has expired. Everything else basically works in the same way as in the example above.
The beauty about this channel construct is in its simplicity. The drawbacks are obvious, but they do offer some nice properties that might be useful in certain cases.

One of the major drawbacks of the `Spillman-style channels` (apart from being unidirectional) is that they expire. This expiry comes with the neat property that neither of the party has to watch the chain for channel closures, and the `sender` can operate the channel with zero additional state, apart from his private keys. But they do expire. And this can make them quite inflexible. It might work in some contexts, but not so much in others, where time needs to be more flexible.
This is where `Roose-Childs triggered channels` come into play.
#### Roose-Childs triggered channel
(I gave it that name, named after nostr:npub148jz5r9xujcjpqygk69yl4jqwjqmzgrqly26plktfjy8g4t7xaysj9xhgp and nostr:npub1htnhsay5dmq3r72tukdw72pduzfdcja0yylcajuvnc2uklkhxp8qnz3qac . If someone knows if this idea has been around before under a different name, please let us know!)
`Roose-Childs triggered channels` were an idea developed by Steven and Luke at the nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx unconference. They essentially remove the channel expiry limitation in return for introducing the need for the `sender` to create a channel backup at the time of channel creation, and for the `receiver` the need to watch the chain for trigger transactions closing the channel.

They also allow for splicing funds, which can be important for a channel without expiry, allowing the `sender` to top-up liquidity once it runs out, or for the `receiver` taking out liquidity from the channel to deploy the funds elsewhere.
Now, let's see how we can build them!

The `funding TX` actually looks the same as in the first example, and similarly it gets created, but not signed by the `sender`. Then, sender and receiver both sign the `trigger TX`. The `trigger TX` is at the heart of this scheme. It allows both `sender` and `receiver` to unilaterally exit the channel by broadcasting it (more on that in a bit).
Once the `trigger TX` is signed and returned to the `sender`, the sender can confidently sign and boradcast the `funding TX` and open the channel. The `trigger TX` remains off-chain though. Now, to update the channel, the `sender` can pre-sign transactions in similar fashion to the examples above, but this time, spending the outputs of the unbroadcasted `trigger TX`. This way, both parties can exit the channel at any time. If the `receiver` wants to exit, he simply boradcasts the `trigger TX` and immediately spends its outputs using the latest `update TX`. If the `sender` wants to exit he will broadcast the `trigger TX` and basically force the `receivers` hand. Either, the `receiver` will broadcast the latest `update TX`, or the `sender` will be able to claim the entire channel balance after the timelock expired.

We can also simplify the `receiver's` exit path, by the `sender` pre-signing an additional transaction `R exit TX` for each update. this way, the `receiver` only needs to broadcast one transaction instead of two.

As we've mentioned before, there are some different trade-offs for `Roose-Childs triggered channels`. We introduce some minimal state and liveness requirements, but gain more flexibility.

#### Ecash to fill in the gaps
(I will assume that the reader knows how ecash mints work. If not, please go check the [slides](https://uni-chan.gandlaf.com/#/43) where I go through an explanation)
Essentially, we are trying to get a lightning like experience, without all the lightning complexities and requirements. One big issue with ecash, is that it is fully custodial. If we can offset that risk by holding most of the funds in a self custodial channel, we can have a reasonable trade-off between usability and self custody.

In a system like that, we would essentially turn the banking model onto its head. Where in a traditional bank, the majority of the funds are held in the banks custody, and the user only withdraws into his custody what he needs to transact, in our model the user would hold most funds in his own custody.

If you ask me, this approach makes way more sense. Instead of a custodian, we have turned the "bank" into a service provider.
Let's take a look at how it would work in a more practical sense:

The `ecash user` would open an unidirectional payment channel to the `mint`, using one of his on-chain UTXOs. This allows him then to commit incrementally funds into the mints custody, only the amounts for his transactional needs. The mint offers connectivity to the lightning network an handles state and liveness as a service provider.
The `ecash user`, can remain offline at all times, and his channel funds will always be safe. The mint can only ever claim the balance in the channel via the `update TXs`. The `mint` can of course still decide to no longer redeem any ecash, at which point they would have basically stolen the `ecash user's` transactional balance. At that point, it would probably be best for the `ecash user` to close his channel, and no longer interact or trust this `mint`.
Here are some of the most important points of this system summarized:

And that is basically it! I hope you enjoyed this breakdown of Unidirectional payment channel enabled Ecash mints!
If you did, consider leaving me a zap. Also do let me know if this type of breakdown helps you understand a new topic well. I am considering doing similar breakdowns on other systems, such as ARK, Lightning or Statechains, if there is a lot of interest, and it helps people, I'll do it!
Pleas also let me know what you think about the `unidirectional channel - ecash mint` idea in the comments. It's kind of a new idea, an it probably has flaws, or things that we haven't thought about yet. I'd love to discuss it with you!
I'll leave you with this final slide:

Cheers,
Gandlaf
-

@ c0a57a12:8b230f7a
2025-02-17 00:08:04
Ever notice how we’ve all turned into a bunch of regulation junkies? Not just the kids—us, too. The parents. The supposed adults in the room. We sit around shaking our heads at this new generation, wondering why they can’t make a move without a permission slip, but let’s be honest: we made them that way. We were trained for it. We just passed the neurosis down like a bad heirloom.
Used to be, kids ran wild, made their own fun, learned how things worked by getting their hands dirty and screwing up a few times. You fell out of a tree? Tough. That’s how you figured out gravity was real. Now, a kid gets a splinter and half the neighborhood has to be briefed. But let’s not act like it started with them. We didn’t grow up in the Wild West. Our parents—the ones who were handed a country built by men who cleared forests and carved railroads and settled frontiers—they took one look at all that, clutched their pearls, and decided the real enemy was *risk.* They started slapping safety labels on everything, turned common sense into a government-subsidized industry, and set about making sure we never had to experience a single moment of danger, discomfort, or—God help us—independence.
And we ate it up. Grew up afraid of the sun, the air, the drinking water. If you touched a stranger, you’d get kidnapped. If you ate the wrong snack, you’d drop dead from an allergy you didn’t even have. If you rode a bike without strapping on enough gear to survive re-entry from orbit, you might as well be suicidal. Then, just to really hammer it in, we were given rules for *everything.* How to sit, how to talk, how to play, how to think. And because we’d been softened up, we listened. We obeyed. We internalized the great lesson of modern civilization: *only do what is approved.*
And when it came time for us to raise kids? Oh, we ran with it. Helicopter parenting? That was us. Participation trophies? Us. Baby-proofing the entire godforsaken planet so that Junior never had to encounter anything sharper than a cotton ball? Us again. Every bit of micromanaged, soul-sucking, over-regulated nonsense we complain about today? We enforced it. So now we’ve got a generation that doesn’t *know* how to function without checking the rulebook first. They hesitate before every decision because we taught them hesitation. They sit around waiting for a green light because that’s all we ever told them to do.
And you know what? We’re no better. When’s the last time *you* did something without checking if it was "allowed"? When’s the last time you ignored a ridiculous rule instead of just sighing and complying? When’s the last time you acted like a *free man* instead of a well-behaved tax mule hoping the system doesn’t notice you?
We’ve swallowed a lie, and we keep regurgitating it—that compliance is morality, that following orders is a virtue, that a safe, predictable, well-regulated life is a *good* one. It’s not. It’s never been. You don’t get freedom by waiting for permission to use it. You don’t get courage by asking if it’s okay. You don’t build a worthwhile life by making sure you never color outside the lines.
And yet, here we are, acting surprised. Acting like we don’t know how we got here. Acting like we didn’t *choose* this. Like we didn’t let it happen.
So what now? We could stop. We could teach our kids to take risks, to get their hands dirty, to act instead of waiting for permission. We could start ignoring stupid rules, start trusting our own judgment, start living like we weren’t raised in a padded cell.
Or we could do nothing. Keep following orders. Keep playing it safe. Keep watching the world shrink into a flavorless, permission-based, committee-approved version of itself.
Your call. But either way, don’t pretend to be surprised.
-

@ 5a261a61:2ebd4480
2025-02-16 21:54:41
As I grow older, I find myself often discovering things that I haven't understood before, or just see completely differently. Like with this fable of the toad and scorpion.
You know, the classic where scorpion needs to get across the river, and asks the toad for help, promising not to sting. The toad refuses at first, pointing out that scorpion's sting would kill them both. But scorpion argues that would be illogical - why would it sting if that meant its own death? The toad, convinced by this logic, agrees to help. Halfway across, scorpion stings anyway, and as they both sink, toad asks "why?" Scorpion simply answers "It's my nature."
That leads me to my scorpion sighting. I have somewhat stronger libido and given the circumstances, I usually situate myself in the submissive position in both married and online life. When I am not ventilating or getting these things out in some way, it usually leads to my growing frustration that seriously hinders my usual life. And in those trying times I usually tell myself, "screw that, I don't like this, I don't like how that makes me feel, it sucks, why does it have to hurt so much" (well, I don't think 'hurt' as I have been indoctrinated by the society that men don't process feelings this way, but I think if I had a therapist, they would want me to spell it like that). Let's not go to the subspace again, it's silly space. Sometimes it gets really dark...but then comes the climax, like literally, and suddenly everything is forgiven and (almost) forgotten. And all is well.
Let's just not go there next time, avoid being burned again, I keep saying to myself. And these days submissive scorpion in my head just silently waits for my monologuing toad to finish defending ourselves. It knows that it needs only one chance so I cave in, while toad needs to defend my sanity every day. So one day, I will bring scorpion to cross the river with me again. And it will again promise that this time it will be ok. And we will both pretend like we believe that, so the play can go on. And it will eventually sting me, because we both yearn for unreachable things.
And next day I will again see scorpion on the river, not wooing me, no, we are beyond that, it knows it just needs to wait before I come back for the poison I need.As I grow older, I find myself often discovering things that I haven't understood before, or just see completely differently. Like with this fable of the toad and scorpion.
You know, the classic where scorpion needs to get across the river, and asks the toad for help, promising not to sting. The toad refuses at first, pointing out that scorpion's sting would kill them both. But scorpion argues that would be illogical - why would it sting if that meant its own death? The toad, convinced by this logic, agrees to help. Halfway across, scorpion stings anyway, and as they both sink, toad asks "why?" Scorpion simply answers "It's my nature."
That leads me to my scorpion sighting. I have somewhat stronger libido and given the circumstances, I usually situate myself in the submissive position in both married and online life. When I am not ventilating or getting these things out in some way, it usually leads to my growing frustration that seriously hinders my usual life. And in those trying times I usually tell myself, "screw that, I don't like this, I don't like how that makes me feel, it sucks, why does it have to hurt so much" (well, I don't think 'hurt' as I have been indoctrinated by the society that men don't process feelings this way, but I think if I had a therapist, they would want me to spell it like that). Let's not go to the subspace again, it's silly space. Sometimes it gets really dark...but then comes the climax, like literally, and suddenly everything is forgiven and (almost) forgotten. And all is well.
Let's just not go there next time, avoid being burned again, I keep saying to myself. And these days submissive scorpion in my head just silently waits for my monologuing toad to finish defending ourselves.
It knows that it needs only one chance so I cave in, while toad needs to defend my sanity every day. So one day, I will bring scorpion to cross the river with me again. And it will again promise that this time it will be ok. And we will both pretend like we believe that, so the play can go on. And it will eventually sting me, because we both yearn for unreachable things.
And next day I will again see scorpion on the river, not wooing me, no, we are beyond that, it knows it just needs to wait before I come back for the poison I need.
-

@ e7bc35f8:3ed2a7cf
2025-02-16 19:19:41
In the grand chessboard of geopolitics, Iran has long been a target for covert Western intervention.
The 2009 Iranian presidential election provided yet another example of a well-worn playbook—one designed to undermine sovereign nations under the guise of democracy. But this was far from a spontaneous people's movement. Instead, it bore all the hallmarks of a carefully orchestrated operation, leveraging the power of mass media, intelligence agencies, and globalist financial interests.
### 2009: A Manufactured Uprising
In June 2009, before Iran's election results were even finalized, opposition leader Mir-Houssein Mousavi [prematurely declared victory]( https://www.telegraph.co.uk/news/worldnews/middleeast/iran/5519567/Iran-elections-Mahmoud-Ahmadinejad-and-Hossein-Mousavi-both-claim-victory.html). This calculated move set the stage for immediate allegations of fraud, ensuring that any outcome favoring incumbent President Mahmoud Ahmadinejad would be delegitimized. The Western media wasted no time in amplifying the chaos, competing to push the most dramatic narratives. The **BBC** took the lead, [publishing outright fabrications]( https://web.archive.org/web/20090621065048/https://www.infowars.com/bbc-caught-in-mass-public-deception-with-iran-propaganda/) about mass uprisings—falsehoods they were later [forced to retract]( https://www.bbc.co.uk/blogs/theeditors/2009/06/what_really_happened.html).
Then came the Twitter storm. On June 13, a sudden [flood of **30,000 tweets**]( https://web.archive.org/web/20090619154321/https://chartingstocks.net/2009/06/proof-israeli-effort-to-destabilize-iran-via-twitter/), many in English, began pouring in from Iran. The accounts responsible? Newly created profiles, often using identical photos, a hallmark of an information warfare campaign. The **[Jerusalem Post]( https://web.archive.org/web/20090714235359/https://chartingstocks.net/wp-content/uploads/2009/06/jpost.jpg)** quickly picked up on the phenomenon, covering it within hours. This was no organic grassroots movement; it was a digital psy-op, mirroring past regime-change operations.
### The Blueprint: Iran 1953—The CIA’s Original Coup
This wasn’t Iran’s first encounter with a foreign-backed destabilization campaign. In 1953, Iran’s democratically elected Prime Minister **Mohammed Mossadegh** made the fatal mistake of challenging Western oil interests. He sought to nationalize Iran’s petroleum industry, then controlled by the Anglo-Iranian Oil Company (later BP). The response was swift and brutal: the **CIA launched Operation Ajax**, an [insidious regime-change operation]( https://archive.nytimes.com/www.nytimes.com/library/world/mideast/041600iran-cia-index.html) that became the prototype for future coups.
The CIA’s strategy was as ruthless as it was effective:
* Staged bombings blamed on Mossadegh’s government
* Islamist agitation funded and nurtured to turn public sentiment
* Propaganda campaigns demonizing Mossadegh as a secular threat
* Bribery of officials and military leaders to ensure betrayal
The result? The overthrow of Mossadegh and the installation of the pro-Western **Shah**, whose reign saw brutal repression under the secret police **SAVAK**—trained by the CIA and Mossad. The template was established. From **Guatemala (1954) to Afghanistan (1980s) to Serbia (1990s)**, the same playbook was deployed. But with each coup, Western fingerprints became harder to conceal.
### A New Strategy: Economic Warfare and the NGO Takeover
With direct coups becoming too risky, a subtler method emerged: **economic strangulation**. Enter the **International Monetary Fund (IMF)**. The play was simple:
1. **A corrupt dictator takes out massive loans** for projects the country cannot afford.
2. **The country inevitably defaults**, giving the IMF the power to restructure its economy.
3. **Western corporations move in**, plundering national resources under the guise of “recovery.”
This scheme was exposed in **2001** when former World Bank chief economist **Joseph Stiglitz** [blew the whistle]( https://www.gregpalast.com/the-globalizer-who-came-in-from-the-cold/) on these manufactured debt traps. Further details emerged in 2004 with **John Perkins' “[Confessions of an Economic Hitman]( https://a.co/d/2oLfrTD)”**, which revealed how Western front companies and intelligence-backed corporations systematically dismantled economies for geopolitical gain.
But even this strategy had its limits. As exposure grew, the need for an even more sophisticated approach became apparent—one cloaked in the language of democracy and human rights.
### Color Revolutions: The Soros Connection
Enter the age of the **NGO-driven color revolutions**, where regime change is disguised as a people’s uprising. Organizations like the **Open Society Institute (George Soros), Freedom House, and the National Endowment for Democracy (NED)** became the new weapons of choice. These NGOs:
* **Fund and train opposition groups**
* **Coordinate mass protests during elections**
* **Provide media support** to delegitimize governments
The results? A series of destabilizations across the world:
**Ukraine (2004 - Orange Revolution)**
**Lebanon (2005 - Cedar Revolution)**
**Georgia (2003 - Rose Revolution)**
**Kyrgyzstan (2005 - Tulip Revolution)**
Each followed the same pattern—Western-backed NGOs funneled money and resources into opposition movements, ensuring their success. Unsurprisingly, these uprisings all bore the **fingerprints of Soros**, the billionaire financier with a long history of manipulating global politics to serve elite financial interests.
However, this strategy has started to backfire. Georgia witnessed a major [anti-Soros backlash]( https://halldor2.blogspot.com/2005/10/anti-soros-movement-in-georgia.html?m=1), and attempts to replicate these revolutions elsewhere—such as the failed Moldovan "[Grape Revolution]( https://foreignpolicy.com/2009/04/10/moldovas-twitter-revolution-is-not-a-myth/)"—have faltered as people wake up to the deception.
### Iran 2009: An Operation in Plain Sight
While no one denies that Ahmadinejad’s regime had its flaws, the coordinated media hysteria and backing of **Mir-Houssein "[Butcher of Beirut]( https://web.archive.org/web/20090626060145/http://blogs.cqpolitics.com/spytalk/2009/06/mousavi-celebrated-in-iranian.html)" Mousavi** raises serious questions. Why was the Western establishment so eager to install a leader with a brutal history? The answer lies in the same playbook used time and again:
1. **Foment unrest** through digital manipulation and street protests.
2. **Control the narrative** via Western media outlets.
3. **Install a leader** more compliant with Western economic and geopolitical interests.
Iran 2009 was not an isolated event. It was part of a much larger pattern—a centuries-old strategy of covert intervention, economic sabotage, and media manipulation to secure Western control over sovereign nations.
As history has shown, the real fight isn’t between the people and their governments—it’s between sovereign nations and the global power structures that seek to enslave them. And until people recognize the hidden hands behind these so-called revolutions, the cycle of deception will continue.
-

@ 9a4acdeb:1489913b
2025-02-16 18:26:58
## Chef's notes
Original recipe, a favorite of family and friends, and the easiest and fastest prep time meal I make. Like all really good pork recipes, it does take time in the cooker, but it's set-and-forget and requires no attention between starting and serving.
Using fresh herbs and peppers does enhance the meal (especially fresh cilantro if it doesn't taste like soap to you), but this is optional, and it is excellent with dry ingredients.
Excluding the beans and/or tomato makes this meal extra-low carb for those carnivores amongst us, or those sensitive to beans. Frying the shredded cheese in a slick pan is a good way to
It will take up to 15min to come up to pressure, so it may be helpful to pay attention to it to be sure it pressurizes until you become familiar with how this meal acts in your particular pressure cooker. The Instant Pot pressure cookers make this easy.
## Details
- ⏲️ Prep time: 20min
- 🍳 Cook time: 2hrs
- 🍽️ Servings: 6
## Ingredients
- 4lbs Pork loin
- 1-2 Yellow onion, roughly chopped
- 3-5 Jalapeños or 1x 4oz canned
- 6-8 Green chilis or 1x 4oz canned
- 2oz canned sliced Black olives (may use half a 4oz can)
- 2-3tsp minced garlic, or 1-2 tsp garlic powder
- A small bunch of cilantro, chopped, or 1-2 tsb dried cilantro (optional)
- 1tbsp Oregano, chopped fresh or dried
- 2-3tsb Chili powder; Ancho, Chipotle, or a blend of the two is best
- 2-3tsb ground Cumin
- 3-4tsp salt
- 2-tsp black pepper
- 1 large or 4oz canned tomato (optional)
- Mexican mix shredded cheese (topping)
- 4oz Black beans (optional)
- Tortillas (optional)
- Avocado (optional toping)
- 6 Limes and/or 3oz lime juice
## Directions
1. Mix dry seasonings
2. Chop and mix fresh herbs and veggies, canned or otherwise
3. Add chopped onion to bottom of pressure cooker
4. Add pork loin atop the onion; chopping into steaks may make the texture better
5. Add veggies to the top, shaking to settle into the pressure cooker
6. Add lime juice
7. Start on high pressure for 2hrs.
8. (Optional) Drain the broth into a saucepan, cook down, and add back into the mix to make it extra flavorful. Otherwise, can be served as a soup or poured over rice.
9. Serve with cheese as a topping, over rice, in a tortilla as tacos or burritos, or in a number of other fashions you may fancy. Those who prefer a little more lime may squeeze fresh or splash some more on their meal.
10. (Optional) For presentation, garnish with cilantro and lime slices, maybe a dollop of shredded cheese, sour cream, or cream cheese.
-

@ c902b8da:0cedc5fb
2025-02-16 18:13:20
I'll break down the key legal requirements, costs, and timelines for establishing a health insurance company, focusing purely on the regulatory aspects:
State Licensing Requirements (Primary State):
- Initial Capital and Surplus: $10-15 million minimum (varies by state)
- Risk-Based Capital (RBC) requirements: Must maintain 200-300% of RBC
- Processing Time: 12-18 months
- Application Fee: $25,000-50,000
- Filing Requirements:
- Articles of Incorporation
- Statutory Financial Statements
- Actuarial Certifications
- Detailed Ownership Information
- Background Checks for All Officers/Directors
- Holding Company Act Filings if Applicable
Federal Requirements:
- ACA Compliance:
- Must offer all 10 Essential Health Benefits
- Medical Loss Ratio requirements (80% individual/small group, 85% large group)
- No annual or lifetime limits
- Guaranteed issue and renewal
- HIPAA Compliance:
- Privacy Officer Appointment
- Security Protocols Implementation
- Timeline: 6-8 months
- Cost: $200,000-500,000 for initial setup
Multi-State Expansion (Per Additional State):
- Certificate of Authority Application: $5,000-25,000 per state
- State-Specific Capital Requirements: $2-5 million additional per state
- Processing Time: 6-12 months per state
- Required State Deposits: $500,000-2 million per state
- Guaranty Fund Membership: $25,000-100,000 per state
Mandatory Insurance Filings:
- Rate Filings:
- Timeline: 60-90 days for approval
- Filing Fees: $500-5,000 per filing
- Form Filings:
- Timeline: 30-60 days for approval
- Filing Fees: $50-500 per form
- Annual Statement Filing: $500-2,500 per state
Required Positions and Certifications:
- Licensed Actuary (MAAA certification)
- Compliance Officer
- Medical Director (licensed physician)
- Claims Manager
- Network Management Director
- Timeline for hiring/certification: 3-6 months
- Annual Costs: $1-2 million for required personnel
Reserve Requirements:
- Claims Reserves: 3-6 months of expected claims
- Premium Reserves: 1-3 months of premium
- Special Deposits: Varies by state ($1-5 million)
- Total Reserve Requirements: 25-40% of annual premium
Ongoing Regulatory Compliance:
- Quarterly Financial Filings: Due within 45 days of quarter end
- Annual Financial Statements: Due March 1
- Market Conduct Examinations: Every 3-5 years
- Cost: $100,000-500,000 per examination
- Financial Examinations: Every 3-5 years
- Cost: $200,000-1 million per examination
Required Insurance Coverage:
- E&O Insurance: $5-10 million coverage
- Annual Cost: $100,000-250,000
- D&O Insurance: $10-25 million coverage
- Annual Cost: $200,000-500,000
- Cyber Insurance: $5-10 million coverage
- Annual Cost: $100,000-300,000
Total Regulatory Timeline:
- Initial State License: 12-18 months
- Federal Compliance: 6-8 months (concurrent)
- First Policy Issuance: 18-24 months from start
- Multi-State Operation: Additional 12-24 months
Total Initial Regulatory Costs:
- Single State Operation: $15-25 million
- Multi-State Operation (5 states): $30-50 million
- Annual Compliance Costs: $2-5 million per state
These requirements and costs can vary significantly based on:
- State of domicile
- Number of states operating in
- Types of health insurance products offered
- Size of projected enrollment
- Market conditions and risk factors
Yes, existing insurance companies can potentially influence your application process, but not directly through a "veto" power. Here's how it works:
1. Public Comment Period
- Most state insurance departments have a public comment period during the application process
- Existing insurers can submit formal objections or concerns
- They typically focus on market saturation, financial viability, or potential unfair competition
2. Market Need Assessment
- Many states require a "need and necessity" showing as part of the application
- You must demonstrate that:
- There's sufficient market demand
- Your company brings something unique or beneficial
- The market can support another carrier
- However, mere competition itself is not grounds for denial
3. State Regulator Discretion
- Regulators consider market concentration and competition
- They generally favor healthy competition unless there are legitimate concerns about:
- Market destabilization
- Your company's financial strength
- Risk to consumers
- Pure "we don't want competition" arguments from existing insurers typically don't succeed
4. Trade Association Influence
- Insurance trade associations may provide input during the licensing process
- They can raise concerns about:
- Capital adequacy
- Management experience
- Business plan viability
- But they cannot directly block your application
Key Point: While existing insurers can object, the final decision rests with state regulators who are primarily concerned with:
- Consumer protection
- Market stability
- Your company's financial soundness
- Management competency
-

@ 41fa852b:af7b7706
2025-02-16 15:52:51
> "Our lives begin to end the day we become silent about things that matter." --Martin Luther King, Jr
* * *
**If Bitcoin's price action is putting you to sleep, maybe it's time to get out and add some spice to your life.**
It's a big week with 12 meetups--check out the list below and see if there's one near you.
Most meetups are drop-in friendly--just head to the venue and keep an eye out for a few shady-looking characters in Bitcoin merch. If you'd prefer some certainty, you can find contact details for every meetup at [bitcoinevents.uk](https://bitcoinevents.uk/). Just scroll down to find your meetup group, and you'll see how to get in touch.
Let's dive in…
* * *
[](https://bitcoinevents.uk/donate/)
* * *
_This week's sponsor is…_
[](https://www.orangepillapp.com/?utm_source=BEUK&utm_medium=email&utm_campaign=BEUK)
* * *
### **Upcoming Bitcoin Meetups**
Happening this week…
1. [**Newcastle Bitcoin Meetup**](https://www.meetup.com/newcastlebitcoinmeetup/): A relaxed gathering for anyone interested in Bitcoin. No prior experience or ownership of Bitcoin is required, just curiosity and an interest. Conversations are Bitcoin-only focused. Happening this month on Tuesday, February 18th, at 18:30. Find them at Kabin @ Kabannas, NE1 6UQ. 🍻
2. [**Bitcoin 101**](https://meetu.ps/e/NRYv6/v822r/i): Nodes at Cyphermunk House - Participants are invited to a hands-on, peer-led class to set up their own Bitcoin node. Those wishing to build a node during the session should bring an old laptop, computer, or mini PC, along with a 2TB SSD and a USB drive with at least 4GB of storage. Attendees are also welcome to join without building a node to learn from the process. Tickets cost £9 in sats or £10 in cash, with pre-booking available at [cyphermunkhouse.com/events.](http://cyphermunkhouse.com/events). 👨🏼🎓
3. [**Bitcoin Glasgow**](https://www.meetup.com/bitcoin-glasgow-buy-sell-learn/): Bitcoin Glasgow meet every 3rd Wednesday of the month and this month will be at The Maltman, 59--61 Renfield Street at 18:00 to 20:00. This month on Wednesday the 19th. 🍺
4. [**Bitcoin Wales**](https://www.meetup.com/all-about-bitcoin-meetup-group-wales/events/): Back in action with the first meetup of 2025, and looking to grow their membership. The gathering at Zerodegrees, 27 Westgate St, Cardiff CF10 1DD invites both seasoned Bitcoiners and newcomers to connect, share ideas, and shape the future of Bitcoin in Wales. 18:00 - 21:00 on Wednesday 19th February. 🍻
5. [**OPA London Bitcoin Meetup**](https://www.eventbrite.com/e/opa-london-bitcoin-meetup-tickets-1238140223739): The first OPA London Bitcoin Meetup takes place on Wednesday 19th at 18:30 - 21:30 at the [Century Club](https://centuryclub.co.uk/) (Bitcoin accepted), 61--63 Shaftesbury Ave, London W1D 6LQ. 🍺🍷🍸
6. [**Shropshire Bitcoin**](https://x.com/shropsbitcoin): On the 19th, the Shropshire crew will be meeting at the Admiral Benbow in Shrewsbury. 🍻
7. [**Brum Bitcoin & Beer**](https://x.com/brumbitcoin): If you're in the Birmingham area head along to meet some fellow bitcoiners on Thursday 20th at 19:00. You'll find them this month at The Wellington, Bennett's Hill, B2 5SN. 🍺
8. [**Bitcoin Bristol**](https://evento.so/p/evt_iQcbZqEyZ36Bujfr): Meeting at The Left Handed Giant, BS1 6EU, at 18:15 on the 21st. Everyone is welcome, the aim is to encourage grassroots bitcoin adoption in Bristol. 🍻
9. [**2140 Collective**](https://evento.so/p/evt_tEzCj5UWYCkB9h35): Tools of freedom - GrapheneOS workshop. Learn about GrapheneOS the privacy-focused mobile operating system. Friday 21st February, 18:00 - 21:40 at Cyphermunk House. 👨🏼🎓📱
10. [**Bitcoin Walk - Edinburgh**](https://bitcoinwalk.org/): Every Saturday they walk around Arthur's Seat in this historic city. Join them at 12 pm to chat about all things Bitcoin and keep fit. 🚶🏽♂️🚶🏼♀️🚶🏻
11. [**Plymouth Bitcoiners**](https://x.com/plbitcoiners): The Plymouth meetup is on the 22nd this month. Find them at Steel Brew, PL1 3GD at 14:00. 🍻
12. [**Bitcoin East**](https://x.com/bitcoineastuk): Join Bitcoin East in Bury St. Edmunds on Sunday 23rd, 10:00 at [Procopio's Pantry](https://www.ourburystedmunds.com/business/procopios-pantry/) and then on to Vespers Bar at 12:00. All welcome, Bitcoiners and anyone else curious about Bitcoin. 🍻☕️
* * *
**Get Involved**
- **Volunteer Opportunities**: [Bridge2Bitcoin](https://bridge2bitcoin.com/) is actively seeking volunteers who share our passion for merchant adoption. We'd be delighted to connect if you're eager to contribute. Reach out to us on [Twitter](https://x.com/bridge2bitcoin) or through our [website](https://bridge2bitcoin.com/).
- **Start Your Own Meetup**: Interested in launching a Bitcoin meetup? We're here to support you every step of the way. We've assisted numerous UK Bitcoin meetups in getting started. Get in touch via [Twitter](https://x.com/bitcoineventsuk).
- **[Contribute to BTCMaps](https://wiki.btcmap.org/general/tagging-instructions.html)**: BTCMaps is a vital part of the Bitcoin ecosystem. It's a perfect project to get involved with if you're not a coder or even that technical. A great way to give back to the community. Maintain an area of the UK and keep it up-to-date.
- **Telegram users**: You might find our [Telegram Channel](https://t.me/BitcoinEventsUKHub) another useful way to keep up-to-date with UK meetups.
- **Feedback and Suggestions**: We value your input! Share your ideas on how we can enhance this newsletter.
* * *
_This week's sponsors are…_
[](https://orangecoinstore.com/)
[](https://bitcoinretreat.co.uk/)
* * *
Get out and support the meetups where you can, visit [Bitcoin Events UK](https://bitcoinevents.uk/) for more info on each meetup and to find your closest on the interactive map.
Stay tuned for more updates next week!
Simon.
[](https://bitcoinevents.uk/donate/)
-

@ e3168078:10f13b2c
2025-01-21 15:44:45
ノス!
最近Umbrel上のn8nを使ってstacker newsの記事を要約するNostr botを作ってみました。
その際にFirecrawlというスクレイピングのSaaSを使っていたんですがセルフホストできるようなので試してみました。
Firecrawlは動的なページも読めたりマークダウンへの変換をしてくれますが無料プランだと1ヶ月500ページの制限があり、セルフホストすれば気兼ねなく使えます!
今回はUmbrel上のPortainerというアプリを使ってFirecrawlを動かせたのでその記録です。
## 手順
まずはUmbrelにPortainerアプリをインストールします。
Poratinerは今回初めて使ったんですが独自のDockerコンテナをUmbrelで動かす際に推奨されているアプリのようです。

アプリを開いてパスワードの初期設定などを済ませるとダッシュボードが表示されるかと思います。
ここでStackという機能を使ってFirecrawlのDocker composeを一括で取り込むことができます。
新しいStackを作成する画面で以下を入力します。
Repository URL: https://github.com/mendableai/firecrawl
Repository reference: refs/heads/main
Compose path: docker-compose.**yaml** (デフォルトがymlになっててハマりました…)

上記に加えてenv varを設定する必要があるんですがPortainerでは上記の画像下部にあるように "Load Variables from .env file" からenvファイルを選択できます。
[Firecrawlのgithub](https://github.com/mendableai/firecrawl/blob/main/SELF_HOST.md)にあるように apps/api/.env.example をダウンロードし以下の内容を更新しPortainerに取り込ませます。
```
USE_DB_AUTHENTICATION=false
TEST_API_KEY=fc-test-key
```
あとはDeploy the stackを押して少し待つとfirecrawlのセットアップ完了です。
## 確認
動作テストにはUmbrelの設定からAdvanced Settings -> Terminal -> Umbrel OSを開き以下のコマンドを実行ししマークダウンが返って来れば成功です。
```
$ curl -X POST http://localhost:3002/v1/scrape -H 'Authorization: Bearer fc-test-key' -H 'Content-Type: application/json' -d '{
"url": "https://example.com",
"formats": ["markdown"]
}'
{"success":true,"data":{"markdown":"Example Domain\n==============\n\nThis domain is for use in illustrative examples in documents. You may use this domain in literature without prior coordination or asking for permission.\n\n[More information...](https://www.iana.org/domains/example)","metadata":{"title":"Example Domain","ogLocaleAlternate":[],"scrapeId":"7c196348-6561-4ebb-bb8a-9121a29c64b5","viewport":"width=device-width, initial-scale=1","sourceURL":"https://example.com","url":"https://example.com/","statusCode":200}}}
```
またn8n等のUmbrelの他のアプリ(コンテナ)から利用する場合はlocalhostがコンテナ自身になってしまうので別のIP等(172.17.0.1)を使う必要があるのでご注意ください。
([参考](https://community.n8n.io/t/the-service-refused-the-connection-perhaps-it-is-offline-n8n-and-nocodb/33587?utm_source=chatgpt.com))
以上でUmbrel上でのFirecrawlセルフホストができるようになりn8nからも制限なく使えるようになりました。
-

@ e3ba5e1a:5e433365
2025-02-04 08:29:00
President Trump has started rolling out his tariffs, something I [blogged about in November](https://www.snoyman.com/blog/2024/11/steelmanning-tariffs/). People are talking about these tariffs a lot right now, with many people (correctly) commenting on how consumers will end up with higher prices as a result of these tariffs. While that part is true, I’ve seen a lot of people taking it to the next, incorrect step: that consumers will pay the entirety of the tax. I [put up a poll on X](https://x.com/snoyberg/status/1886035800019599808) to see what people thought, and while the right answer got a lot of votes, it wasn't the winner.

For purposes of this blog post, our ultimate question will be the following:
* Suppose apples currently sell for $1 each in the entire United States.
* There are domestic sellers and foreign sellers of apples, all receiving the same price.
* There are no taxes or tariffs on the purchase of apples.
* The question is: if the US federal government puts a $0.50 import tariff per apple, what will be the change in the following:
* Number of apples bought in the US
* Price paid by buyers for apples in the US
* Post-tax price received by domestic apple producers
* Post-tax price received by foreign apple producers
Before we can answer that question, we need to ask an easier, first question: before instituting the tariff, why do apples cost $1?
And finally, before we dive into the details, let me provide you with the answers to the ultimate question. I recommend you try to guess these answers before reading this, and if you get it wrong, try to understand why:
1. The number of apples bought will go down
2. The buyers will pay more for each apple they buy, but not the full amount of the tariff
3. Domestic apple sellers will receive a *higher* price per apple
4. Foreign apple sellers will receive a *lower* price per apple, but not lowered by the full amount of the tariff
In other words, regardless of who sends the payment to the government, both taxed parties (domestic buyers and foreign sellers) will absorb some of the costs of the tariff, while domestic sellers will benefit from the protectionism provided by tariffs and be able to sell at a higher price per unit.
## Marginal benefit
All of the numbers discussed below are part of a [helper Google Sheet](https://docs.google.com/spreadsheets/d/14ZbkWpw1B9Q1UDB9Yh47DmdKQfIafVVBKbDUsSIfGZw/edit?usp=sharing) I put together for this analysis. Also, apologies about the jagged lines in the charts below, I hadn’t realized before starting on this that there are [some difficulties with creating supply and demand charts in Google Sheets](https://superuser.com/questions/1359731/how-to-create-a-supply-demand-style-chart).
Let’s say I absolutely love apples, they’re my favorite food. How much would I be willing to pay for a single apple? You might say “$1, that’s the price in the supermarket,” and in many ways you’d be right. If I walk into supermarket A, see apples on sale for $50, and know that I can buy them at supermarket B for $1, I’ll almost certainly leave A and go buy at B.
But that’s not what I mean. What I mean is: how high would the price of apples have to go *everywhere* so that I’d no longer be willing to buy a single apple? This is a purely personal, subjective opinion. It’s impacted by how much money I have available, other expenses I need to cover, and how much I like apples. But let’s say the number is $5.
How much would I be willing to pay for another apple? Maybe another $5. But how much am I willing to pay for the 1,000th apple? 10,000th? At some point, I’ll get sick of apples, or run out of space to keep the apples, or not be able to eat, cook, and otherwise preserve all those apples before they rot.
The point being: I’ll be progressively willing to spend less and less money for each apple. This form of analysis is called *marginal benefit*: how much benefit (expressed as dollars I’m willing to spend) will I receive from each apple? This is a downward sloping function: for each additional apple I buy (quantity demanded), the price I’m willing to pay goes down. This is what gives my personal *demand curve*. And if we aggregate demand curves across all market participants (meaning: everyone interested in buying apples), we end up with something like this:

Assuming no changes in people’s behavior and other conditions in the market, this chart tells us how many apples will be purchased by our buyers at each price point between $0.50 and $5. And ceteris paribus (all else being equal), this will continue to be the demand curve for apples.
## Marginal cost
Demand is half the story of economics. The other half is supply, or: how many apples will I sell at each price point? Supply curves are upward sloping: the higher the price, the more a person or company is willing and able to sell a product.
Let’s understand why. Suppose I have an apple orchard. It’s a large property right next to my house. With about 2 minutes of effort, I can walk out of my house, find the nearest tree, pick 5 apples off the tree, and call it a day. 5 apples for 2 minutes of effort is pretty good, right?
Yes, there was all the effort necessary to buy the land, and plant the trees, and water them… and a bunch more than I likely can’t even guess at. We’re going to ignore all of that for our analysis, because for short-term supply-and-demand movement, we can ignore these kinds of *sunk costs*. One other simplification: in reality, supply curves often start descending before ascending. This accounts for achieving efficiencies of scale after the first number of units purchased. But since both these topics are unneeded for understanding taxes, I won’t go any further.
Anyway, back to my apple orchard. If someone offers me $0.50 per apple, I can do 2 minutes of effort and get $2.50 in revenue, which equates to a $75/hour wage for me. I’m more than happy to pick apples at that price\!
However, let’s say someone comes to buy 10,000 apples from me instead. I no longer just walk out to my nearest tree. I’m going to need to get in my truck, drive around, spend the day in the sun, pay for gas, take a day off of my day job (let’s say it pays me $70/hour). The costs go up significantly. Let’s say it takes 5 days to harvest all those apples myself, it costs me $100 in fuel and other expenses, and I lose out on my $70/hour job for 5 days. We end up with:
* Total expenditure: $100 \+ $70 \* 8 hours a day \* 5 days \== $2900
* Total revenue: $5000 (10,000 apples at $0.50 each)
* Total profit: $2100
So I’m still willing to sell the apples at this price, but it’s not as attractive as before. And as the number of apples purchased goes up, my costs keep increasing. I’ll need to spend more money on fuel to travel more of my property. At some point I won’t be able to do the work myself anymore, so I’ll need to pay others to work on the farm, and they’ll be slower at picking apples than me (less familiar with the property, less direct motivation, etc.). The point being: at some point, the number of apples can go high enough that the $0.50 price point no longer makes me any money.
This kind of analysis is called *marginal cost*. It refers to the additional amount of expenditure a seller has to spend in order to produce each additional unit of the good. Marginal costs go up as quantity sold goes up. And like demand curves, if you aggregate this data across all sellers, you get a supply curve like this:

## Equilibrium price
We now know, for every price point, how many apples buyers will purchase, and how many apples sellers will sell. Now we find the equilibrium: where the supply and demand curves meet. This point represents where the marginal benefit a buyer would receive from the next buyer would be less than the cost it would take the next seller to make it. Let’s see it in a chart:

You’ll notice that these two graphs cross at the $1 price point, where 63 apples are both demanded (bought by consumers) and supplied (sold by producers). This is our equilibrium price. We also have a visualization of the *surplus* created by these trades. Everything to the left of the equilibrium point and between the supply and demand curves represents surplus: an area where someone is receiving something of more value than they give. For example:
* When I bought my first apple for $1, but I was willing to spend $5, I made $4 of consumer surplus. The consumer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and above the equilibrium price point.
* When a seller sells his first apple for $1, but it only cost $0.50 to produce it, the seller made $0.50 of producer surplus. The producer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and below the equilibrium price point.
Another way of thinking of surplus is “every time someone got a better price than they would have been willing to take.”
OK, with this in place, we now have enough information to figure out how to price in the tariff, which we’ll treat as a negative externality.
## Modeling taxes
Alright, the government has now instituted a $0.50 tariff on every apple sold within the US by a foreign producer. We can generally model taxes by either increasing the marginal cost of each unit sold (shifting the supply curve up), or by decreasing the marginal benefit of each unit bought (shifting the demand curve down). In this case, since only some of the producers will pay the tax, it makes more sense to modify the supply curve.
First, let’s see what happens to the foreign seller-only supply curve when you add in the tariff:

With the tariff in place, for each quantity level, the price at which the seller will sell is $0.50 higher than before the tariff. That makes sense: if I was previously willing to sell my 82nd apple for $3, I would now need to charge $3.50 for that apple to cover the cost of the tariff. We see this as the tariff “pushing up” or “pushing left” the original supply curve.
We can add this new supply curve to our existing (unchanged) supply curve for domestic-only sellers, and we end up with a result like this:

The total supply curve adds up the individual foreign and domestic supply curves. At each price point, we add up the total quantity each group would be willing to sell to determine the total quantity supplied for each price point. Once we have that cumulative supply curve defined, we can produce an updated supply-and-demand chart including the tariff:

As we can see, the equilibrium has shifted:
* The equilibrium price paid by consumers has risen from $1 to $1.20.
* The total number of apples purchased has dropped from 63 apples to 60 apples.
* Consumers therefore received 3 less apples. They spent $72 for these 60 apples, whereas previously they spent $63 for 3 more apples, a definite decrease in consumer surplus.
* Foreign producers sold 36 of those apples (see the raw data in the linked Google Sheet), for a gross revenue of $43.20. However, they also need to pay the tariff to the US government, which accounts for $18, meaning they only receive $25.20 post-tariff. Previously, they sold 42 apples at $1 each with no tariff to be paid, meaning they took home $42.
* Domestic producers sold the remaining 24 apples at $1.20, giving them a revenue of $28.80. Since they don’t pay the tariff, they take home all of that money. By contrast, previously, they sold 21 apples at $1, for a take-home of $21.
* The government receives $0.50 for each of the 60 apples sold, or in other words receives $30 in revenue it wouldn’t have received otherwise.
We could be more specific about the surpluses, and calculate the actual areas for consumer surplus, producer surplus, inefficiency from the tariff, and government revenue from the tariff. But I won’t bother, as those calculations get slightly more involved. Instead, let’s just look at the aggregate outcomes:
* Consumers were unquestionably hurt. Their price paid went up by $0.20 per apple, and received less apples.
* Foreign producers were also hurt. Their price received went down from the original $1 to the new post-tariff price of $1.20, minus the $0.50 tariff. In other words: foreign producers only receive $0.70 per apple now. This hurt can be mitigated by shifting sales to other countries without a tariff, but the pain will exist regardless.
* Domestic producers scored. They can sell less apples and make more revenue doing it.
* And the government walked away with an extra $30.
Hopefully you now see the answer to the original questions. Importantly, while the government imposed a $0.50 tariff, neither side fully absorbed that cost. Consumers paid a bit more, foreign producers received a bit less. The exact details of how that tariff was split across the groups is mediated by the relevant supply and demand curves of each group. If you want to learn more about this, the relevant search term is “price elasticity,” or how much a group’s quantity supplied or demanded will change based on changes in the price.
## Other taxes
Most taxes are some kind of a tax on trade. Tariffs on apples is an obvious one. But the same applies to income tax (taxing the worker for the trade of labor for money) or payroll tax (same thing, just taxing the employer instead). Interestingly, you can use the same model for analyzing things like tax incentives. For example, if the government decided to subsidize domestic apple production by giving the domestic producers a $0.50 bonus for each apple they sell, we would end up with a similar kind of analysis, except instead of the foreign supply curve shifting up, we’d see the domestic supply curve shifting down.
And generally speaking, this is what you’ll *always* see with government involvement in the economy. It will result in disrupting an existing equilibrium, letting the market readjust to a new equilibrium, and incentivization of some behavior, causing some people to benefit and others to lose out. We saw with the apple tariff, domestic producers and the government benefited while others lost.
You can see the reverse though with tax incentives. If I give a tax incentive of providing a deduction (not paying income tax) for preschool, we would end up with:
* Government needs to make up the difference in tax revenue, either by raising taxes on others or printing more money (leading to inflation). Either way, those paying the tax or those holding government debased currency will pay a price.
* Those people who don’t use the preschool deduction will receive no benefit, so they simply pay a cost.
* Those who do use the preschool deduction will end up paying less on tax+preschool than they would have otherwise.
This analysis is fully amoral. It’s not saying whether providing subsidized preschool is a good thing or not, it simply tells you where the costs will be felt, and points out that such government interference in free economic choice does result in inefficiencies in the system. Once you have that knowledge, you’re more well educated on making a decision about whether the costs of government intervention are worth the benefits.
-

@ b17fccdf:b7211155
2025-02-01 18:41:27
#### **Next new resources about the MiniBolt guide have been released**:
---
* 🆕 **Roadmap**: [LINK](https://github.com/orgs/minibolt-guide/projects/1)
* 🆕 **Dynamic Network map**: [LINK](https://app.diagrams.net/?tags={}&lightbox=1&target=blank&highlight=0000ff&edit=_blank&layers=1&nav=1&title=networkmap.drawio.png#Uhttps://raw.githubusercontent.com/minibolt-guide/minibolt/main/resources/networkmap.drawio.png)
* 🆕 **Nostr community**: [LINK](https://habla.news/c/[n]addr1qqyy66twd9px7mr5qyf8wumn8ghj7mmxve3ksctfdch8qatzqgstzl7vmurm5gu87qutx3pxwgxddrg39huj809zhmv03scfkus3z4grqsqqpphk2j0aff) < ~ REMOVE the "[]" symbols from the URL (naddr...) to access
* 🆕 **Linktr FOSS** (UC) by [Gzuuus](nostr:npub1gzuushllat7pet0ccv9yuhygvc8ldeyhrgxuwg744dn5khnpk3gs3ea5ds): [LINK](https://linktr.minibolt.info)
* 🆕 **Donate webpage**: 🚾 [Clearnet LINK](https://donate.minibolt.info) || 🧅 [Onion LINK](http://3iqm7nidexns5p6wmgc23ibgiscm6rge7hwyeziviwgav4fl7xui4mqd.onion/apps/Li3AtEGDsqNmNddv6rX69taidm3/pos)
* 🆕 **Contact email**: [hello@minibolt.info](mailto:hello@minibolt.info)
---
Enjoy it MiniBolter! 💙
-

@ 9e69e420:d12360c2
2025-02-01 11:16:04

Federal employees must remove pronouns from email signatures by the end of the day. This directive comes from internal memos tied to two executive orders signed by Donald Trump. The orders target diversity and equity programs within the government.

CDC, Department of Transportation, and Department of Energy employees were affected. Staff were instructed to make changes in line with revised policy prohibiting certain language.
One CDC employee shared frustration, stating, “In my decade-plus years at CDC, I've never been told what I can and can't put in my email signature.” The directive is part of a broader effort to eliminate DEI initiatives from federal discourse.
-

@ 97c70a44:ad98e322
2025-01-30 17:15:37
There was a slight dust up recently over a website someone runs removing a listing for an app someone built based on entirely arbitrary criteria. I'm not to going to attempt to speak for either wounded party, but I would like to share my own personal definition for what constitutes a "nostr app" in an effort to help clarify what might be an otherwise confusing and opaque purity test.
In this post, I will be committing the "no true Scotsman" fallacy, in which I start with the most liberal definition I can come up with, and gradually refine it until all that is left is the purest, gleamingest, most imaginary and unattainable nostr app imaginable. As I write this, I wonder if anything built yet will actually qualify. In any case, here we go.
# It uses nostr
The lowest bar for what a "nostr app" might be is an app ("application" - i.e. software, not necessarily a native app of any kind) that has some nostr-specific code in it, but which doesn't take any advantage of what makes nostr distinctive as a protocol.
Examples might include a scraper of some kind which fulfills its charter by fetching data from relays (regardless of whether it validates or retains signatures). Another might be a regular web 2.0 app which provides an option to "log in with nostr" by requesting and storing the user's public key.
In either case, the fact that nostr is involved is entirely neutral. A scraper can scrape html, pdfs, jsonl, whatever data source - nostr relays are just another target. Likewise, a user's key in this scenario is treated merely as an opaque identifier, with no appreciation for the super powers it brings along.
In most cases, this kind of app only exists as a marketing ploy, or less cynically, because it wants to get in on the hype of being a "nostr app", without the developer quite understanding what that means, or having the budget to execute properly on the claim.
# It leverages nostr
Some of you might be wondering, "isn't 'leverage' a synonym for 'use'?" And you would be right, but for one connotative difference. It's possible to "use" something improperly, but by definition leverage gives you a mechanical advantage that you wouldn't otherwise have. This is the second category of "nostr app".
This kind of app gets some benefit out of the nostr protocol and network, but in an entirely selfish fashion. The intention of this kind of app is not to augment the nostr network, but to augment its own UX by borrowing some nifty thing from the protocol without really contributing anything back.
Some examples might include:
- Using nostr signers to encrypt or sign data, and then store that data on a proprietary server.
- Using nostr relays as a kind of low-code backend, but using proprietary event payloads.
- Using nostr event kinds to represent data (why), but not leveraging the trustlessness that buys you.
An application in this category might even communicate to its users via nostr DMs - but this doesn't make it a "nostr app" any more than a website that emails you hot deals on herbal supplements is an "email app". These apps are purely parasitic on the nostr ecosystem.
In the long-term, that's not necessarily a bad thing. Email's ubiquity is self-reinforcing. But in the short term, this kind of "nostr app" can actually do damage to nostr's reputation by over-promising and under-delivering.
# It complements nostr
Next up, we have apps that get some benefit out of nostr as above, but give back by providing a unique value proposition to nostr users as nostr users. This is a bit of a fine distinction, but for me this category is for apps which focus on solving problems that nostr isn't good at solving, leaving the nostr integration in a secondary or supporting role.
One example of this kind of app was Mutiny (RIP), which not only allowed users to sign in with nostr, but also pulled those users' social graphs so that users could send money to people they knew and trusted. Mutiny was doing a great job of leveraging nostr, as well as providing value to users with nostr identities - but it was still primarily a bitcoin wallet, not a "nostr app" in the purest sense.
Other examples are things like Nostr Nests and Zap.stream, whose core value proposition is streaming video or audio content. Both make great use of nostr identities, data formats, and relays, but they're primarily streaming apps. A good litmus test for things like this is: if you got rid of nostr, would it be the same product (even if inferior in certain ways)?
A similar category is infrastructure providers that benefit nostr by their existence (and may in fact be targeted explicitly at nostr users), but do things in a centralized, old-web way; for example: media hosts, DNS registrars, hosting providers, and CDNs.
To be clear here, I'm not casting aspersions (I don't even know what those are, or where to buy them). All the apps mentioned above use nostr to great effect, and are a real benefit to nostr users. But they are not True Scotsmen.
# It embodies nostr
Ok, here we go. This is the crème de la crème, the top du top, the meilleur du meilleur, the bee's knees. The purest, holiest, most chaste category of nostr app out there. The apps which are, indeed, nostr indigitate.
This category of nostr app (see, no quotes this time) can be defined by the converse of the previous category. If nostr was removed from this type of application, would it be impossible to create the same product?
To tease this apart a bit, apps that leverage the technical aspects of nostr are dependent on nostr the *protocol*, while apps that benefit nostr exclusively via network effect are integrated into nostr the *network*. An app that does both things is working in symbiosis with nostr as a whole.
An app that embraces both nostr's protocol and its network becomes an organic extension of every other nostr app out there, multiplying both its competitive moat and its contribution to the ecosystem:
- In contrast to apps that only borrow from nostr on the technical level but continue to operate in their own silos, an application integrated into the nostr network comes pre-packaged with existing users, and is able to provide more value to those users because of other nostr products. On nostr, it's a good thing to advertise your competitors.
- In contrast to apps that only market themselves to nostr users without building out a deep integration on the protocol level, a deeply integrated app becomes an asset to every other nostr app by becoming an organic extension of them through interoperability. This results in increased traffic to the app as other developers and users refer people to it instead of solving their problem on their own. This is the "micro-apps" utopia we've all been waiting for.
Credible exit doesn't matter if there aren't alternative services. Interoperability is pointless if other applications don't offer something your app doesn't. Marketing to nostr users doesn't matter if you don't augment their agency _as nostr users_.
If I had to choose a single NIP that represents the mindset behind this kind of app, it would be NIP 89 A.K.A. "Recommended Application Handlers", which states:
> Nostr's discoverability and transparent event interaction is one of its most interesting/novel mechanics. This NIP provides a simple way for clients to discover applications that handle events of a specific kind to ensure smooth cross-client and cross-kind interactions.
These handlers are the glue that holds nostr apps together. A single event, signed by the developer of an application (or by the application's own account) tells anyone who wants to know 1. what event kinds the app supports, 2. how to link to the app (if it's a client), and (if the pubkey also publishes a kind 10002), 3. which relays the app prefers.
_As a sidenote, NIP 89 is currently focused more on clients, leaving DVMs, relays, signers, etc somewhat out in the cold. Updating 89 to include tailored listings for each kind of supporting app would be a huge improvement to the protocol. This, plus a good front end for navigating these listings (sorry nostrapp.link, close but no cigar) would obviate the evil centralized websites that curate apps based on arbitrary criteria._
Examples of this kind of app obviously include many kind 1 clients, as well as clients that attempt to bring the benefits of the nostr protocol and network to new use cases - whether long form content, video, image posts, music, emojis, recipes, project management, or any other "content type".
To drill down into one example, let's think for a moment about forms. What's so great about a forms app that is built on nostr? Well,
- There is a [spec](https://github.com/nostr-protocol/nips/pull/1190) for forms and responses, which means that...
- Multiple clients can implement the same data format, allowing for credible exit and user choice, even of...
- Other products not focused on forms, which can still view, respond to, or embed forms, and which can send their users via NIP 89 to a client that does...
- Cryptographically sign forms and responses, which means they are self-authenticating and can be sent to...
- Multiple relays, which reduces the amount of trust necessary to be confident results haven't been deliberately "lost".
Show me a forms product that does all of those things, and isn't built on nostr. You can't, because it doesn't exist. Meanwhile, there are plenty of image hosts with APIs, streaming services, and bitcoin wallets which have basically the same levels of censorship resistance, interoperability, and network effect as if they weren't built on nostr.
# It supports nostr
Notice I haven't said anything about whether relays, signers, blossom servers, software libraries, DVMs, and the accumulated addenda of the nostr ecosystem are nostr apps. Well, they are (usually).
This is the category of nostr app that gets none of the credit for doing all of the work. There's no question that they qualify as beautiful nostrcorns, because their value propositions are entirely meaningless outside of the context of nostr. Who needs a signer if you don't have a cryptographic identity you need to protect? DVMs are literally impossible to use without relays. How are you going to find the blossom server that will serve a given hash if you don't know which servers the publishing user has selected to store their content?
In addition to being entirely contextualized by nostr architecture, this type of nostr app is valuable because it does things "the nostr way". By that I mean that they don't simply try to replicate existing internet functionality into a nostr context; instead, they create entirely new ways of putting the basic building blocks of the internet back together.
A great example of this is how Nostr Connect, Nostr Wallet Connect, and DVMs all use relays as brokers, which allows service providers to avoid having to accept incoming network connections. This opens up really interesting possibilities all on its own.
So while I might hesitate to call many of these things "apps", they are certainly "nostr".
# Appendix: it smells like a NINO
So, let's say you've created an app, but when you show it to people they politely smile, nod, and call it a NINO (Nostr In Name Only). What's a hacker to do? Well, here's your handy-dandy guide on how to wash that NINO stench off and Become a Nostr.
You app might be a NINO if:
- There's no NIP for your data format (or you're abusing NIP 78, 32, etc by inventing a sub-protocol inside an existing event kind)
- There's a NIP, but no one knows about it because it's in a text file on your hard drive (or buried in your project's repository)
- Your NIP imposes an incompatible/centralized/legacy web paradigm onto nostr
- Your NIP relies on trusted third (or first) parties
- There's only one implementation of your NIP (yours)
- Your core value proposition doesn't depend on relays, events, or nostr identities
- One or more relay urls are hard-coded into the source code
- Your app depends on a specific relay implementation to work (*ahem*, relay29)
- You don't validate event signatures
- You don't publish events to relays you don't control
- You don't read events from relays you don't control
- You use legacy web services to solve problems, rather than nostr-native solutions
- You use nostr-native solutions, but you've hardcoded their pubkeys or URLs into your app
- You don't use NIP 89 to discover clients and services
- You haven't published a NIP 89 listing for your app
- You don't leverage your users' web of trust for filtering out spam
- You don't respect your users' mute lists
- You try to "own" your users' data
Now let me just re-iterate - it's ok to be a NINO. We need NINOs, because nostr can't (and shouldn't) tackle every problem. You just need to decide whether your app, as a NINO, is actually contributing to the nostr ecosystem, or whether you're just using buzzwords to whitewash a legacy web software product.
If you're in the former camp, great! If you're in the latter, what are you waiting for? Only you can fix your NINO problem. And there are lots of ways to do this, depending on your own unique situation:
- Drop nostr support if it's not doing anyone any good. If you want to build a normal company and make some money, that's perfectly fine.
- Build out your nostr integration - start taking advantage of webs of trust, self-authenticating data, event handlers, etc.
- Work around the problem. Think you need a special relay feature for your app to work? Guess again. Consider encryption, AUTH, DVMs, or better data formats.
- Think your idea is a good one? Talk to other devs or open a PR to the [nips repo](https://github.com/nostr-protocol/nips). No one can adopt your NIP if they don't know about it.
- Keep going. It can sometimes be hard to distinguish a research project from a NINO. New ideas have to be built out before they can be fully appreciated.
- Listen to advice. Nostr developers are friendly and happy to help. If you're not sure why you're getting traction, ask!
I sincerely hope this article is useful for all of you out there in NINO land. Maybe this made you feel better about not passing the totally optional nostr app purity test. Or maybe it gave you some actionable next steps towards making a great NINON (Nostr In Not Only Name) app. In either case, GM and PV.
-

@ 9e69e420:d12360c2
2025-01-30 12:23:04
Tech stocks have taken a hit globally after China's DeepSeek launched a competitive AI chatbot at a much lower cost than US counterparts. This has stirred market fears of a $1.2 trillion loss across tech companies when trading opens in New York.
DeepSeek’s chatbot quickly topped download charts and surprised experts with its capabilities, developed for only $5.6 million.
The Nasdaq dropped over 3% in premarket trading, with major firms like Nvidia falling more than 10%. SoftBank also saw losses shortly after investing in a significant US AI venture.
Venture capitalist Marc Andreessen called it “AI’s Sputnik moment,” highlighting its potential impact on the industry.
![] (https://www.telegraph.co.uk/content/dam/business/2025/01/27/TELEMMGLPICT000409807198_17379939060750_trans_NvBQzQNjv4BqgsaO8O78rhmZrDxTlQBjdGLvJF5WfpqnBZShRL_tOZw.jpeg)
-

@ 9e69e420:d12360c2
2025-01-30 12:13:39
Salwan Momika, a Christian Iraqi known for burning the Koran in Sweden, was shot dead during a TikTok livestream in an apartment in Sodertalje. The 38-year-old sparked outrage in the Muslim community for his demonstrations, leading to global condemnation. After being rushed to the hospital, he was pronounced dead.
Authorities arrested five individuals in connection with the incident. Momika's death comes days before a court ruling on his possible incitement of ethnic hatred. The incident highlights the tensions surrounding free speech and religious sentiments, intensifying after his controversial protests in 2023.
[Sauce](https://www.dailymail.co.uk/news/article-14341423/Christian-Iraqi-burnt-Koran-Sweden-shot-dead.html)
-

@ 0fa80bd3:ea7325de
2025-01-30 04:28:30
**"Degeneration"** or **"Вырождение"**
![[photo_2025-01-29 23.23.15.jpeg]]
A once-functional object, now eroded by time and human intervention, stripped of its original purpose. Layers of presence accumulate—marks, alterations, traces of intent—until the very essence is obscured. Restoration is paradoxical: to reclaim, one must erase. Yet erasure is an impossibility, for to remove these imprints is to deny the existence of those who shaped them.
The work stands as a meditation on entropy, memory, and the irreversible dialogue between creation and decay.
-

@ 0fa80bd3:ea7325de
2025-01-29 15:43:42
Lyn Alden - биткойн евангелист или евангелистка, я пока не понял
```
npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a
```
Thomas Pacchia - PubKey owner - X - @tpacchia
```
npub1xy6exlg37pw84cpyj05c2pdgv86hr25cxn0g7aa8g8a6v97mhduqeuhgpl
```
calvadev - Shopstr
```
npub16dhgpql60vmd4mnydjut87vla23a38j689jssaqlqqlzrtqtd0kqex0nkq
```
Calle - Cashu founder
```
npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg
```
Джек Дорси
```
npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m
```
21 ideas
```
npub1lm3f47nzyf0rjp6fsl4qlnkmzed4uj4h2gnf2vhe3l3mrj85vqks6z3c7l
```
Много адресов. Хз кто надо сортировать
```
https://github.com/aitechguy/nostr-address-book
```
ФиатДжеф - создатель Ностр - https://github.com/fiatjaf
```
npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6
```
EVAN KALOUDIS Zues wallet
```
npub19kv88vjm7tw6v9qksn2y6h4hdt6e79nh3zjcud36k9n3lmlwsleqwte2qd
```
Программер Коди https://github.com/CodyTseng/nostr-relay
```
npub1syjmjy0dp62dhccq3g97fr87tngvpvzey08llyt6ul58m2zqpzps9wf6wl
```
Anna Chekhovich - Managing Bitcoin at The Anti-Corruption Foundation
https://x.com/AnyaChekhovich
```
npub1y2st7rp54277hyd2usw6shy3kxprnmpvhkezmldp7vhl7hp920aq9cfyr7
```
-

@ 0fa80bd3:ea7325de
2025-01-29 14:44:48
![[yedinaya-rossiya-bear.png]]
1️⃣ Be where the bear roams. Stay in its territory, where it hunts for food. No point setting a trap in your backyard if the bear’s chilling in the forest.
2️⃣ Set a well-hidden trap. Bury it, disguise it, and place the bait right in the center. Bears are omnivores—just like secret police KGB agents. And what’s the tastiest bait for them? Money.
3️⃣ Wait for the bear to take the bait. When it reaches in, the trap will snap shut around its paw. It’ll be alive, but stuck. No escape.
Now, what you do with a trapped bear is another question... 😏
-

@ 0fa80bd3:ea7325de
2025-01-29 05:55:02
The land that belongs to the indigenous peoples of Russia has been seized by a gang of killers who have unleashed a war of extermination. They wipe out anyone who refuses to conform to their rules. Those who disagree and stay behind are tortured and killed in prisons and labor camps. Those who flee lose their homeland, dissolve into foreign cultures, and fade away. And those who stand up to protect their people are attacked by the misled and deceived. The deceived die for the unchecked greed of a single dictator—thousands from both sides, people who just wanted to live, raise their kids, and build a future.
Now, they are forced to make an impossible choice: abandon their homeland or die. Some perish on the battlefield, others lose themselves in exile, stripped of their identity, scattered in a world that isn’t theirs.
There’s been endless debate about how to fix this, how to clear the field of the weeds that choke out every new sprout, every attempt at change. But the real problem? We can’t play by their rules. We can’t speak their language or use their weapons. We stand for humanity, and no matter how righteous our cause, we will not multiply suffering. Victory doesn’t come from matching the enemy—it comes from staying ahead, from using tools they haven’t mastered yet. That’s how wars are won.
Our only resource is the **will of the people** to rewrite the order of things. Historian Timothy Snyder once said that a nation cannot exist without a city. A city is where the most active part of a nation thrives. But the cities are occupied. The streets are watched. Gatherings are impossible. They control the money. They control the mail. They control the media. And any dissent is crushed before it can take root.
So I started asking myself: **How do we stop this fragmentation?** How do we create a space where people can **rebuild their connections** when they’re ready? How do we build a **self-sustaining network**, where everyone contributes and benefits proportionally, while keeping their freedom to leave intact? And more importantly—**how do we make it spread, even in occupied territory?**
In 2009, something historic happened: **the internet got its own money.** Thanks to **Satoshi Nakamoto**, the world took a massive leap forward. Bitcoin and decentralized ledgers shattered the idea that money must be controlled by the state. Now, to move or store value, all you need is an address and a key. A tiny string of text, easy to carry, impossible to seize.
That was the year money broke free. The state lost its grip. Its biggest weapon—physical currency—became irrelevant. Money became **purely digital.**
The internet was already **a sanctuary for information**, a place where people could connect and organize. But with Bitcoin, it evolved. Now, **value itself** could flow freely, beyond the reach of authorities.
Think about it: when seedlings are grown in controlled environments before being planted outside, they **get stronger, survive longer, and bear fruit faster.** That’s how we handle crops in harsh climates—nurture them until they’re ready for the wild.
Now, picture the internet as that **controlled environment** for **ideas**. Bitcoin? It’s the **fertile soil** that lets them grow. A testing ground for new models of interaction, where concepts can take root before they move into the real world. If **nation-states are a battlefield, locked in a brutal war for territory, the internet is boundless.** It can absorb any number of ideas, any number of people, and it doesn’t **run out of space.**
But for this ecosystem to thrive, people need safe ways to communicate, to share ideas, to build something real—**without surveillance, without censorship, without the constant fear of being erased.**
This is where **Nostr** comes in.
Nostr—"Notes and Other Stuff Transmitted by Relays"—is more than just a messaging protocol. **It’s a new kind of city.** One that **no dictator can seize**, no corporation can own, no government can shut down.
It’s built on **decentralization, encryption, and individual control.** Messages don’t pass through central servers—they are relayed through independent nodes, and users choose which ones to trust. There’s no master switch to shut it all down. Every person owns their identity, their data, their connections. And no one—no state, no tech giant, no algorithm—can silence them.
In a world where cities fall and governments fail, **Nostr is a city that cannot be occupied.** A place for ideas, for networks, for freedom. A city that grows stronger **the more people build within it**.
-

@ 9e69e420:d12360c2
2025-01-26 15:26:44
Secretary of State Marco Rubio issued new guidance halting spending on most foreign aid grants for 90 days, including military assistance to Ukraine. This immediate order shocked State Department officials and mandates “stop-work orders” on nearly all existing foreign assistance awards.
While it allows exceptions for military financing to Egypt and Israel, as well as emergency food assistance, it restricts aid to key allies like Ukraine, Jordan, and Taiwan. The guidance raises potential liability risks for the government due to unfulfilled contracts.
A report will be prepared within 85 days to recommend which programs to continue or discontinue.
-

@ 9e69e420:d12360c2
2025-01-26 01:31:47
## Chef's notes
# arbitray
- test
- of
- chefs notes
## hedding 2
## Details
- ⏲️ Prep time: 20
- 🍳 Cook time: 1 hour
- 🍽️ Servings: 5
## Ingredients
- Test ingredient
- 2nd test ingredient
## Directions
1. Bake
2. Cool
-

@ 9e69e420:d12360c2
2025-01-25 22:16:54
President Trump plans to withdraw 20,000 U.S. troops from Europe and expects European allies to contribute financially to the remaining military presence. Reported by ANSA, Trump aims to deliver this message to European leaders since taking office. A European diplomat noted, “the costs cannot be borne solely by American taxpayers.”
The Pentagon hasn't commented yet. Trump has previously sought lower troop levels in Europe and had ordered cuts during his first term. The U.S. currently maintains around 65,000 troops in Europe, with total forces reaching 100,000 since the Ukraine invasion. Trump's new approach may shift military focus to the Pacific amid growing concerns about China.
[Sauce](https://www.stripes.com/theaters/europe/2025-01-24/trump-europe-troop-cuts-16590074.html)
-

@ 9e69e420:d12360c2
2025-01-25 14:32:21
| Parameters | Dry Mead | Medium Mead | Sweet Mead |
|------------|-----------|-------------|------------|
| Honey | 2 lbs (900 grams) | 3 lbs (1.36 kg) | 4 lbs (1.81 kg) |
| Yeast | ~0.07 oz (2 grams) | ~0.08 oz (2.5 grams) | ~0.10 oz (3 grams) |
| Fermentation | ~4 weeks | 4 to 6 weeks | 6 to 8 weeks |
| Racking | Fortnight or later | 1 month or after | ~2 months and after |
| Specific Gravity | <1.010 | ~1.01 to ~1.025 | >1.025 |
-

@ 9e69e420:d12360c2
2025-01-23 15:09:56
President Trump has ordered thousands of additional troops to the U.S.-Mexico border as part of an effort to address immigration and security issues. This directive builds on his initial commitment to increase military presence along the border.
Currently, around 2,200 active-duty personnel and approximately 4,500 National Guardsmen are stationed there. The new deployment aims to enhance the capabilities of Joint Task Force-North, allowing troops to assist in operations and provide intelligence support.
Details on specific units remain unclear. The situation is still developing, with updates expected.
[Sauce](https://thepostmillennial.com/breaking-president-trump-orders-thousands-of-troops-to-the-us-border-with-mexico)
-

@ 6be5cc06:5259daf0
2025-01-21 20:58:37
A seguir, veja como instalar e configurar o **Privoxy** no **Pop!_OS**.
---
### **1. Instalar o Tor e o Privoxy**
Abra o terminal e execute:
```bash
sudo apt update
sudo apt install tor privoxy
```
**Explicação:**
- **Tor:** Roteia o tráfego pela rede Tor.
- **Privoxy:** Proxy avançado que intermedia a conexão entre aplicativos e o Tor.
---
### **2. Configurar o Privoxy**
Abra o arquivo de configuração do Privoxy:
```bash
sudo nano /etc/privoxy/config
```
Navegue até a última linha (atalho: **`Ctrl`** + **`/`** depois **`Ctrl`** + **`V`** para navegar diretamente até a última linha) e insira:
```bash
forward-socks5 / 127.0.0.1:9050 .
```
Isso faz com que o **Privoxy** envie todo o tráfego para o **Tor** através da porta **9050**.
Salve (**`CTRL`** + **`O`** e **`Enter`**) e feche (**`CTRL`** + **`X`**) o arquivo.
---
### **3. Iniciar o Tor e o Privoxy**
Agora, inicie e habilite os serviços:
```bash
sudo systemctl start tor
sudo systemctl start privoxy
sudo systemctl enable tor
sudo systemctl enable privoxy
```
**Explicação:**
- **start:** Inicia os serviços.
- **enable:** Faz com que iniciem automaticamente ao ligar o PC.
---
### **4. Configurar o Navegador Firefox**
Para usar a rede **Tor** com o Firefox:
1. Abra o Firefox.
2. Acesse **Configurações** → **Configurar conexão**.
3. Selecione **Configuração manual de proxy**.
4. Configure assim:
- **Proxy HTTP:** `127.0.0.1`
- **Porta:** `8118` (porta padrão do **Privoxy**)
- **Domínio SOCKS (v5):** `127.0.0.1`
- **Porta:** `9050`
5. Marque a opção **"Usar este proxy também em HTTPS"**.
6. Clique em **OK**.
---
### **5. Verificar a Conexão com o Tor**
Abra o navegador e acesse:
```text
https://check.torproject.org/
```
Se aparecer a mensagem **"Congratulations. This browser is configured to use Tor."**, a configuração está correta.
---
### **Dicas Extras**
- **Privoxy** pode ser ajustado para bloquear anúncios e rastreadores.
- Outros aplicativos também podem ser configurados para usar o **Privoxy**.
-

@ 16d11430:61640947
2025-01-21 20:40:22
In a world drowning in Monopoly money, where people celebrate government-mandated inflation as "economic growth," it takes a special kind of clarity—nay, cynicism—to rise above the fiat circus. This is your guide to shedding your fiat f**ks and embracing the serene chaos of sound money, all while laughing at the absurdity of a world gone fiat-mad.
---
1. Don’t Feed the Clowns
You know the clowns I’m talking about: central bankers in their tailored suits and smug smirks, wielding "tools" like interest rates and quantitative easing. Their tools are as real as a magician's wand, conjuring trillions of dollars out of thin air to keep their Ponzi economy afloat.
Rule #1: Don’t engage. If a clown offers you a hot take about the "strength of the dollar," smile, nod, and silently wonder how many cups of coffee their paycheck buys this month. Spoiler: fewer than last month.
---
2. Turn Off the Fiat News
Do you really need another breathless headline about the next trillion-dollar deficit? Or the latest clickbait on why you should care about the stock market's emotional rollercoaster? Mainstream media exists to distract you, to keep you tethered to their illusion of importance.
Turn it off. Replace it with something sound, like the Bitcoin whitepaper. Or Nietzsche. At least Nietzsche knew we were doomed.
---
3. Mock Their Inflationary Gospel
Fiat apologists will tell you that inflation is "necessary" and that 2% a year is a "healthy target." Sure, because a little robbery every year keeps society functioning, right? Ask them this: "If 2% is healthy, why not 20%? Why not 200%? Why not Venezuela?"
Fiat logic is like a bad acid trip: entertaining at first, but it quickly spirals into existential horror.
---
4. Celebrate the Fiat Freakshow
Sometimes, the best way to resist the fiat clown show is to revel in its absurdity. Watch politicians print money like teenagers running up a credit card bill at Hot Topic, then watch the economists applaud it as "stimulus." It’s performance art, really. Andy Warhol could never.
---
5. Build in the Chaos
While the fiat world burns, Bitcoiners build. This is the ultimate "not giving a fiat f**k" move: creating a parallel economy, one satoshi at a time. Run your Lightning node, stack sats, and laugh as the fiat circus consumes itself in a flaming pile of its own debt.
Let them argue about who gets to rearrange the deck chairs on the Titanic. You’re busy designing lifeboats.
---
6. Adopt a Fiat-Free Lifestyle
Fiat-free living means minimizing your entanglement with their clown currency. Buy meat, not ETFs. Trade skills, not IOUs. Tip your barber in Bitcoin and ask if your landlord accepts Lightning. If they say no, chuckle and say, “You’ll learn soon enough.”
Every satoshi spent in the real economy is a slap in the face to the fiat overlords.
---
7. Find the Humor in Collapse
Here’s the thing: the fiat system is unsustainable. You know it, I know it, even the clowns know it. The whole charade is destined to collapse under its own weight. When it does, find solace in the absurdity of it all.
Imagine the central bankers explaining hyperinflation to the public: "Turns out we can't print infinity after all." Pure comedy gold.
---
8. Stay Ruthlessly Optimistic
Despite the doom and gloom, there’s hope. Bitcoin is hope. It’s the lifeboat for humanity, the cheat code to escape the fiat matrix. Cynicism doesn’t mean nihilism; it means seeing the rot for what it is and choosing to build something better.
So, don’t just reject the fiat clown show—replace it. Create a world where money is sound, transactions are sovereign, and wealth is measured in energy, not debt.
---
Final Thought: Burn the Tent Down
Aldous Huxley once envisioned a dystopia where people are so distracted by their own hedonistic consumption that they don’t realize they’re enslaved. Sound familiar? The fiat clown show is Brave New World on steroids, a spectacle designed to keep you pacified while your wealth evaporates.
But here’s the punchline: they can only enslave you if you care. By rejecting their system, you strip them of their power. So let them juggle their debts, inflate their bubbles, and print their trillions. You’ve got Bitcoin, and Bitcoin doesn’t give a fiat f**k.
Welcome to the satirical resistance. Now go stack some sats.
-

@ c3c7122c:607731d7
2025-02-16 07:48:35
At my meet up (the SD Bitcoiners Cete) on Thursday, I presented trends on the Bisq protocol. One of its features is that anyone can export the trade history and analyze it.
Bisq is a private, peer-tp-peer way to buy and sell bitcoin. All data are based on the BTC-USD market.
Trade number decreased in 2024

But USD volume increased ($/year)

(same graph but $/day by year)

Which means more higher value per trade

Interestingly, trade counts and price volatility lead to interesting BTC volume per year. The peaks are nearly identical (330 BTC)!

Not so surprising when you compare BTC volume traded to the average BTC price that year, local price valleys mean local peaks in BTC traded (and vice versa).

I separate fiat payment methods into three groups.

All USD payment methods used in 2024 by average value (y-axis) and number of trades (bubble size)

This is the same graph as above excluding Zelle and Strike, since they throw off the relative circle size (face-to-face only had 1 trade in 2024).

Two fiat methods had >1000 trades in 2024. Strike came on the scene hot in 2021 and ate some of the Zelle volume but that may have stabilized.

Six fiat methods had 200-1000 trades in 2024. Amazon Gift Card dwindling, Cash By Mail still top of this group, and Revolut surging (wtf is Revolut?)

Same group, all years

Last group is <200 trades in 2024. Basically unused, except for Wire Transfer increasing.

Same group, all years

What's the average trade size by fiat method? There are different reasons for this, largely driven by fiat fees and bank limits. Amazon Gift Card is an interesting option for smaller payments (note: you can't just send any gift card, there is a very specific process, see the Bisq [wiki]( https://bisq.wiki/Amazon_eGift_card))

There no KYC premium, but there is a small Surveillance Discount

If you open Bisq for the first time, you'll likely see spreads 3-5% or larger. These offers persist because no one wants them. So people think that Bisq is "too expensive." But let's dig into the actual trades...

Comparing the daily trade volume to daily market rate (I used coingecko), and creating a monthly weighted average, the true surveillance discount emerges. It's not 3-5% as you might see in the order book at any given time. In fact, it was cheaper to trade on Bisq than exchanges in November and December! (Note: this does not take into account the 4 on-chain transactions required for a trade or price spread/fees used by exchanges)

In 2024, Strike had the worst surveillance discount and Cash By Mail had the best. This isn't surprising because receiving cash is convenient and low risk for a seller so they're willing to accept a lower price. Zelle (the most common USD payment method) had the second best surveillance discount.

Now let's compare the surveillance discount by week in 2024 for select payment methods.
Strike was consistently worse than Zelle

Revolut was sometimes way worse than Zelle but sometimes a little better.

The two most private payment methods are cash and money order. They're pretty competitive regarding surveillance discount.

Take aways
* Be a maker and get a better price (fees are better too)
* Zelle is better for speed + convenience
* Amazon gift cards are good for speed + privacy (sorta)
* Cash or money order are better for privacy + volume
-

@ 9e69e420:d12360c2
2025-01-21 19:31:48
Oregano oil is a potent natural compound that offers numerous scientifically-supported health benefits.
## Active Compounds
The oil's therapeutic properties stem from its key bioactive components:
- Carvacrol and thymol (primary active compounds)
- Polyphenols and other antioxidant
## Antimicrobial Properties
**Bacterial Protection**
The oil demonstrates powerful antibacterial effects, even against antibiotic-resistant strains like MRSA and other harmful bacteria. Studies show it effectively inactivates various pathogenic bacteria without developing resistance.
**Antifungal Effects**
It effectively combats fungal infections, particularly Candida-related conditions like oral thrush, athlete's foot, and nail infections.
## Digestive Health Benefits
Oregano oil supports digestive wellness by:
- Promoting gastric juice secretion and enzyme production
- Helping treat Small Intestinal Bacterial Overgrowth (SIBO)
- Managing digestive discomfort, bloating, and IBS symptoms
## Anti-inflammatory and Antioxidant Effects
The oil provides significant protective benefits through:
- Powerful antioxidant activity that fights free radicals
- Reduction of inflammatory markers in the body
- Protection against oxidative stress-related conditions
## Respiratory Support
It aids respiratory health by:
- Loosening mucus and phlegm
- Suppressing coughs and throat irritation
- Supporting overall respiratory tract function
## Additional Benefits
**Skin Health**
- Improves conditions like psoriasis, acne, and eczema
- Supports wound healing through antibacterial action
- Provides anti-aging benefits through antioxidant properties
**Cardiovascular Health**
Studies show oregano oil may help:
- Reduce LDL (bad) cholesterol levels
- Support overall heart health
**Pain Management**
The oil demonstrates effectiveness in:
- Reducing inflammation-related pain
- Managing muscle discomfort
- Providing topical pain relief
## Safety Note
While oregano oil is generally safe, it's highly concentrated and should be properly diluted before use Consult a healthcare provider before starting supplementation, especially if taking other medications.
-

@ b17fccdf:b7211155
2025-01-21 18:30:13
~ > Available at: [https://minibolt.info](https://minibolt.info)
---
~> It builds on a personal computer with **x86/amd64** architecture processors.
~> It is based on the popular [RaspiBolt v3](https://raspibolt.org) guide.
---
**Those are some of the most relevant changes:**
* Changed OS from Raspberry Pi OS Lite (64-bits) to ***Ubuntu Server LTS*** (Long term support) 64-bit PC (AMD64).
* Changed binaries and signatures of the programs to adapt them to ***x86/amd64 architecture***.
* Deleted unnecessary tools and steps, and added others according to this case of use.
* Some useful authentication logs and monitoring commands were added in the security section.
* Added some interesting parameters in the settings of some services to activate and take advantage of new features.
* Changed I2P, Fulcrum, and ThunderHub guides, to be part of the core guide.
* Added exclusive optimization section of services for slow devices.
---
~ > Complete release notes of the MiniBolt v1: [https://github.com/twofaktor/minibolt/releases/tag/1.0](https://github.com/twofaktor/minibolt/releases/tag/1.0).
~ > Feel free to contribute to the [source code on GitHub](https://github.com/minibolt-guide/minibolt) by opening [issues](https://github.com/minibolt-guide/minibolt/issues), [pull requests](https://github.com/minibolt-guide/minibolt/pulls) or [discussions](https://github.com/orgs/minibolt-guide/discussions).
---
Created by [⚡2 FakTor⚡](nostr:npub1k9luehc8hg3c0upckdzzvusv66x3zt0eyw7290kclrpsndepz92sfcpp63)
-

@ b17fccdf:b7211155
2025-01-21 18:22:51
😱 Did you recently find this signature verification error when you tried to update your MiniBolt repositories with -> `sudo apt update`? 💥🚨👇

🔧 Don't worry, that's because Tor renewed its signing key since it expired last 07/15, just renew your keyring by following the next steps to solve this problem:
~ > [CLICK HERE](https://minibolt.minibolt.info/system/system/privacy#tor-signature-verification-error) < ~
---
Enjoy it MiniBolter!💙
-

@ b17fccdf:b7211155
2025-01-21 18:10:10
**Link to the bonus guide** ~ > [HERE](https://minibolt.minibolt.info/bonus-guides/bitcoin/minibolt-on-testnet) <~
---
Some notes:
ℹ️ For the moment, this guide will touch only the case of an **only testnet mode** situation, in the future, we will study adding the case of configuration to enable the parallel/simultaneous mode (mainnet+testnet in the same device) in an extra section in this guide.
ℹ️ The services mentioned in this guide are those that have been tested using testnet configuration and these worked fine. Later, in the next versions of this guide, we will go to adding other processes to adapt other services to the testnet mode.
---
Enjoy it MiniBolter! 💙
-

@ b17fccdf:b7211155
2025-01-21 18:04:28
Available at: [https://minibolt.info](https://minibolt.info)
---
**Main changes to** the version 1:
* The complete guide has been migrated to the new design visual builder web tool platform [gitbook.com](https://www.gitbook.com/)
* New modern UI (responsive, full width, and better visual items)
* New menu structure for a better user experience
* New visual items to improve the navigation through the web page
* New switch to enable light/dark theme
* Enabled Cloudflare Proxy for maximum protection against attacks and better management of the domain
---
**Other changes:**
* New [MiniBolt Linktr](https://linktr.minibolt.info/) forked of the alternative [FOSS project](https://github.com/gzuuus/linktr) proposed by [Gzuuus](https://twitter.com/gzuuus)
* Changed MiniBolt from a personal project to an [organization](https://github.com/minibolt-guide) so that the project has its own identity
* New email contact address [hello@minibolt.info](mailto:hello@minibolt.info) to receive proposals and give support
* New [resources](https://github.com/minibolt-guide/minibolt/tree/main/resources) folder with the current MiniBolt roadmap, network map diagrams, and others
---
ℹ️ **More info:**
* The new version is available with the known domain: [minibolt.info](https://minibolt.info/) but from now on links associated with the new v2 version were shared using the [v2.minibolt.info](https://v2.minibolt.info/) subdomain due to a GitBook limitation
* The old and deprecated v1 will be still available at a time in the subdomain [v1.minibolt.info](https://v1.minibolt.info/), but is in the roadmap delete it definitely in the future, take note ASAP of all that you need of that version before this happens
* Contributors and collaborators will be able to continue doing PR through code programming or using the design block builder [gitbook.com](https://www.gitbook.com/)
---
[GitHub release](https://github.com/minibolt-guide/minibolt/releases/tag/2.0)
---
Enjoy it MiniBolter! 💙
-

@ b17fccdf:b7211155
2025-01-21 17:58:35
The **router reserves the IP address** of the device **for a time after going out**, but if the device goes out some time, the next time that the device starts, the router could assign a different IP and you could lose access to your node. To avoid this, you need to **set a static IP to your MiniBolt**.
~ > In addition, you can **customize your DNS servers to improve your privacy**, normally your ISP, gives you the router with its own DNS servers set by default, and this does that you expose all of your navigation trackings to your ISP, affecting seriously your privacy.
~ > This bonus guide includes all of the necessary steps to get this and is available ~ > [HERE](https://minibolt.minibolt.info/bonus-guides/system/static-ip-and-custom-dns-servers) < ~
---

---
Enjoy it MiniBolter! 💙
-

@ b17fccdf:b7211155
2025-01-21 17:47:28
Link to the bonus guide ~ > [HERE](https://minibolt.minibolt.info/bonus-guides/system/ssh-keys) < ~
---
Some sections of the guide:
* Generate SSH keys
* Import SSH pubkey
* Connect to the MiniBolt node using SSH keys
* Disable password login
* Disable admin password request
---
Some shortcuts to the Extra sections:
* Disable password login: click ~ > [HERE](https://minibolt.minibolt.info/bonus-guides/system/ssh-keys#disable-password-login) < ~
* Disable admin password request: click ~ > [HERE](https://minibolt.minibolt.info/bonus-guides/system/ssh-keys#disable-admin-password-request-caution) < ~
---
Enjoy it MiniBolter! 💙
-

@ b17fccdf:b7211155
2025-01-21 17:39:34
**Link to the bonus guide** ~ > [HERE](https://minibolt.minibolt.info/bonus-guides/bitcoin/ordisrespector) < ~
---
⏰ Recently added an update that includes a new section **[How to detect Ordinals transactions](https://minibolt.minibolt.info/bonus-guides/bitcoin/ordisrespector#how-to-detect-ordinals-transactions) and [verify Ordisrespector filter works](https://minibolt.minibolt.info/bonus-guides/bitcoin/ordisrespector#check-the-ordisrespector-filter-working-on-your-mempool)** to verify that Ordispector is **filtering and burning Ordinals** correctly 🔥
---
Fuck Ordinals🤡🔫 and enjoy it MiniBolter! 💙
-

@ b17fccdf:b7211155
2025-01-21 17:29:54
Some sections inside of the guide:
* Set up Dynamic DNS
* Wireguard VPN server & client side configurations
* Install & configure the WireGuard VPN Client on a mobile phone
* Configure additional servers & clients
* Use your router’s DDNS preconfigured provider
* Port forwarding on NAT/PAT router
---
Link to the bonus guide [HERE](https://minibolt.minibolt.info/bonus-guides/system/wireguard-vpn)
---
Enjoy it MiniBolter! 💙
 @ 4857600b:30b502f4
2025-02-20 19:09:11Mitch McConnell, a senior Republican senator, announced he will not seek reelection. At 83 years old and with health issues, this decision was expected. After seven terms, he leaves a significant legacy in U.S. politics, known for his strategic maneuvering. McConnell stated, “My current term in the Senate will be my last.” His retirement marks the end of an influential political era.
@ 4857600b:30b502f4
2025-02-20 19:09:11Mitch McConnell, a senior Republican senator, announced he will not seek reelection. At 83 years old and with health issues, this decision was expected. After seven terms, he leaves a significant legacy in U.S. politics, known for his strategic maneuvering. McConnell stated, “My current term in the Senate will be my last.” His retirement marks the end of an influential political era. @ a012dc82:6458a70d
2025-02-20 15:02:29The Financial Accounting Standards Board (FASB) has recently introduced a groundbreaking ruling that significantly alters the way Bitcoin and other cryptocurrencies are accounted for in financial statements. This new development is poised to transform the landscape of crypto accounting, bringing in more transparency and alignment with traditional financial practices. Let's delve into the details of this pivotal change. **Table of Contents** - Introduction to the New FASB Ruling - The Shift to Fair Value Accounting - Understanding Fair Value Accounting - Impact on Financial Reporting - Advantages of the New Approach - Enhanced Transparency and Accuracy - Positive Implications for Companies - Challenges and Considerations - Dealing with Volatility - Auditor Expertise - Industry Response and Future Outlook - Embracing the Change - Long-Term Implications - Conclusion - FAQs **Introduction to the New FASB Ruling** The FASB, the principal body responsible for establishing accounting standards in the United States, announced a new set of rules concerning the accounting of cryptocurrencies like Bitcoin. This announcement marks a significant shift from the previous accounting practices for digital assets. Previously, the lack of clear guidelines led to inconsistencies and uncertainties in how companies reported their crypto holdings. The new ruling aims to standardize these practices and reflects the growing importance of cryptocurrencies in the financial world. **The Shift to Fair Value Accounting** **Understanding Fair Value Accounting** Under the new FASB rules, companies are now required to account for cryptocurrencies at their fair value. Fair value accounting involves assessing assets and liabilities based on their current market value, rather than their historical cost. This approach is expected to provide a more accurate and real-time reflection of a company's financial status. It marks a significant departure from the traditional cost-based accounting methods, which often do not reflect the current market realities, especially in the case of highly volatile assets like cryptocurrencies. **Impact on Financial Reporting** This shift to fair value accounting means that companies holding cryptocurrencies will report the value of these assets based on their market prices at the end of each reporting period. This move is a departure from the previous method where Bitcoin was treated as an intangible asset, leading to certain limitations in financial reporting. For instance, under the old rules, if the value of Bitcoin fell below its purchase price, companies had to report a loss, but they couldn't report an increase in value unless the asset was sold. The new approach allows for a more dynamic and responsive reporting system that better reflects the economic realities of holding cryptocurrencies. **Advantages of the New Approach** **Enhanced Transparency and Accuracy** One of the primary benefits of this new ruling is the increased transparency and accuracy it brings to financial reporting. Companies can now reflect the actual market value of their crypto holdings, providing a clearer picture of their financial health. This change is particularly significant given the volatile nature of cryptocurrencies. By reporting the fair market value, companies can provide stakeholders with a more accurate depiction of their financial standing, which is crucial for informed decision-making by investors, regulators, and other stakeholders. **Positive Implications for Companies** Companies are likely to welcome this change as it allows them to report unrealized gains and losses on cryptocurrencies. This could encourage more businesses to add cryptocurrencies like Bitcoin to their balance sheets, as they can now recognize the appreciation in value without needing to sell the assets. This change could also lead to a broader acceptance of cryptocurrencies as a legitimate and valuable asset class, potentially spurring further investment and innovation in the crypto space. **Challenges and Considerations** **Dealing with Volatility** The inherent volatility of cryptocurrencies like Bitcoin poses a significant challenge in fair value accounting. Companies will need to develop robust methods to accurately assess the market value of these assets, which can fluctuate widely. This volatility requires continuous monitoring and frequent valuation adjustments, which can be resource-intensive and complex. Companies will need to invest in sophisticated valuation models and possibly seek external expertise to ensure accuracy and compliance. **Auditor Expertise** Another challenge lies in the need for auditors to acquire expertise in valuing cryptocurrencies. Assessing the fair market value of digital assets is a complex task that requires specific knowledge and skills. Auditors will need to stay abreast of the rapidly evolving crypto market and develop new methodologies for valuation. This requirement not only adds a layer of complexity to the audit process but also underscores the need for ongoing education and training in this emerging field. **Industry Response and Future Outlook** **Embracing the Change** The industry's response to the FASB's ruling has been largely positive. Industry leaders view this as a step towards mainstream acceptance of cryptocurrencies and a move that aligns digital assets with traditional financial reporting standards. This ruling is seen as a validation of the growing role of cryptocurrencies in the financial sector and a sign that regulatory bodies are beginning to recognize and adapt to the unique characteristics of these digital assets. **Long-Term Implications** In the long run, this ruling could lead to greater institutional adoption of cryptocurrencies. As financial reporting becomes more standardized and transparent, it may foster greater trust and confidence among investors and regulators. This could pave the way for more widespread use of cryptocurrencies in various financial transactions and potentially influence the development of new financial products and services centered around digital assets. **Conclusion** The FASB's latest ruling on cryptocurrency accounting is a landmark decision that aligns the treatment of digital assets with traditional financial practices. While it presents certain challenges, particularly in terms of volatility and the need for specialized auditor expertise, the overall impact is expected to be profoundly positive. This change not only enhances transparency and accuracy in financial reporting but also paves the way for broader acceptance and integration of cryptocurrencies in the mainstream financial world. As the industry adapts to these new rules, we can expect to see a more mature and robust crypto market, potentially leading to innovative financial solutions and greater economic opportunities. **FAQs** **When will the new FASB rules take effect?** The new rules are set to take effect from December 15, 2024, but companies have the option to apply them earlier. **How does fair value accounting affect financial reporting?** Fair value accounting allows companies to report the value of cryptocurrencies based on current market prices, providing a more accurate and real-time reflection of a company's financial status. **What are the benefits of the new FASB ruling?** The new ruling enhances transparency and accuracy in financial reporting and encourages more businesses to add cryptocurrencies to their balance sheets by allowing them to report unrealized gains and losses. **What challenges does the new ruling present?** The main challenges include dealing with the volatility of cryptocurrencies in fair value accounting and the need for auditors to develop expertise in valuing these digital assets. **What is the industry's response to the new ruling?** The industry has largely responded positively, viewing it as a step towards mainstream acceptance of cryptocurrencies and alignment with traditional financial reporting standards. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: [@croxroadnews.co](https://x.com/croxroadnewsco)** **Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)** **Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** ***DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.***
@ a012dc82:6458a70d
2025-02-20 15:02:29The Financial Accounting Standards Board (FASB) has recently introduced a groundbreaking ruling that significantly alters the way Bitcoin and other cryptocurrencies are accounted for in financial statements. This new development is poised to transform the landscape of crypto accounting, bringing in more transparency and alignment with traditional financial practices. Let's delve into the details of this pivotal change. **Table of Contents** - Introduction to the New FASB Ruling - The Shift to Fair Value Accounting - Understanding Fair Value Accounting - Impact on Financial Reporting - Advantages of the New Approach - Enhanced Transparency and Accuracy - Positive Implications for Companies - Challenges and Considerations - Dealing with Volatility - Auditor Expertise - Industry Response and Future Outlook - Embracing the Change - Long-Term Implications - Conclusion - FAQs **Introduction to the New FASB Ruling** The FASB, the principal body responsible for establishing accounting standards in the United States, announced a new set of rules concerning the accounting of cryptocurrencies like Bitcoin. This announcement marks a significant shift from the previous accounting practices for digital assets. Previously, the lack of clear guidelines led to inconsistencies and uncertainties in how companies reported their crypto holdings. The new ruling aims to standardize these practices and reflects the growing importance of cryptocurrencies in the financial world. **The Shift to Fair Value Accounting** **Understanding Fair Value Accounting** Under the new FASB rules, companies are now required to account for cryptocurrencies at their fair value. Fair value accounting involves assessing assets and liabilities based on their current market value, rather than their historical cost. This approach is expected to provide a more accurate and real-time reflection of a company's financial status. It marks a significant departure from the traditional cost-based accounting methods, which often do not reflect the current market realities, especially in the case of highly volatile assets like cryptocurrencies. **Impact on Financial Reporting** This shift to fair value accounting means that companies holding cryptocurrencies will report the value of these assets based on their market prices at the end of each reporting period. This move is a departure from the previous method where Bitcoin was treated as an intangible asset, leading to certain limitations in financial reporting. For instance, under the old rules, if the value of Bitcoin fell below its purchase price, companies had to report a loss, but they couldn't report an increase in value unless the asset was sold. The new approach allows for a more dynamic and responsive reporting system that better reflects the economic realities of holding cryptocurrencies. **Advantages of the New Approach** **Enhanced Transparency and Accuracy** One of the primary benefits of this new ruling is the increased transparency and accuracy it brings to financial reporting. Companies can now reflect the actual market value of their crypto holdings, providing a clearer picture of their financial health. This change is particularly significant given the volatile nature of cryptocurrencies. By reporting the fair market value, companies can provide stakeholders with a more accurate depiction of their financial standing, which is crucial for informed decision-making by investors, regulators, and other stakeholders. **Positive Implications for Companies** Companies are likely to welcome this change as it allows them to report unrealized gains and losses on cryptocurrencies. This could encourage more businesses to add cryptocurrencies like Bitcoin to their balance sheets, as they can now recognize the appreciation in value without needing to sell the assets. This change could also lead to a broader acceptance of cryptocurrencies as a legitimate and valuable asset class, potentially spurring further investment and innovation in the crypto space. **Challenges and Considerations** **Dealing with Volatility** The inherent volatility of cryptocurrencies like Bitcoin poses a significant challenge in fair value accounting. Companies will need to develop robust methods to accurately assess the market value of these assets, which can fluctuate widely. This volatility requires continuous monitoring and frequent valuation adjustments, which can be resource-intensive and complex. Companies will need to invest in sophisticated valuation models and possibly seek external expertise to ensure accuracy and compliance. **Auditor Expertise** Another challenge lies in the need for auditors to acquire expertise in valuing cryptocurrencies. Assessing the fair market value of digital assets is a complex task that requires specific knowledge and skills. Auditors will need to stay abreast of the rapidly evolving crypto market and develop new methodologies for valuation. This requirement not only adds a layer of complexity to the audit process but also underscores the need for ongoing education and training in this emerging field. **Industry Response and Future Outlook** **Embracing the Change** The industry's response to the FASB's ruling has been largely positive. Industry leaders view this as a step towards mainstream acceptance of cryptocurrencies and a move that aligns digital assets with traditional financial reporting standards. This ruling is seen as a validation of the growing role of cryptocurrencies in the financial sector and a sign that regulatory bodies are beginning to recognize and adapt to the unique characteristics of these digital assets. **Long-Term Implications** In the long run, this ruling could lead to greater institutional adoption of cryptocurrencies. As financial reporting becomes more standardized and transparent, it may foster greater trust and confidence among investors and regulators. This could pave the way for more widespread use of cryptocurrencies in various financial transactions and potentially influence the development of new financial products and services centered around digital assets. **Conclusion** The FASB's latest ruling on cryptocurrency accounting is a landmark decision that aligns the treatment of digital assets with traditional financial practices. While it presents certain challenges, particularly in terms of volatility and the need for specialized auditor expertise, the overall impact is expected to be profoundly positive. This change not only enhances transparency and accuracy in financial reporting but also paves the way for broader acceptance and integration of cryptocurrencies in the mainstream financial world. As the industry adapts to these new rules, we can expect to see a more mature and robust crypto market, potentially leading to innovative financial solutions and greater economic opportunities. **FAQs** **When will the new FASB rules take effect?** The new rules are set to take effect from December 15, 2024, but companies have the option to apply them earlier. **How does fair value accounting affect financial reporting?** Fair value accounting allows companies to report the value of cryptocurrencies based on current market prices, providing a more accurate and real-time reflection of a company's financial status. **What are the benefits of the new FASB ruling?** The new ruling enhances transparency and accuracy in financial reporting and encourages more businesses to add cryptocurrencies to their balance sheets by allowing them to report unrealized gains and losses. **What challenges does the new ruling present?** The main challenges include dealing with the volatility of cryptocurrencies in fair value accounting and the need for auditors to develop expertise in valuing these digital assets. **What is the industry's response to the new ruling?** The industry has largely responded positively, viewing it as a step towards mainstream acceptance of cryptocurrencies and alignment with traditional financial reporting standards. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: [@croxroadnews.co](https://x.com/croxroadnewsco)** **Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)** **Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** ***DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.*** @ d360efec:14907b5f
2025-02-20 10:16:03**ภาพรวม BTCUSDT (OKX):** Bitcoin (BTCUSDT) ยังคงแสดงความผันผวนและแนวโน้มที่ไม่ชัดเจน แม้ว่าแนวโน้มระยะยาว (TF Day) จะยังคงมีลักษณะเป็นขาขึ้น (แต่*อ่อนแรงลงอย่างมาก*) แนวโน้มระยะกลาง (TF4H) และระยะสั้น (TF15) เป็นขาลง การวิเคราะห์ครั้งนี้จะเน้นไปที่การระบุระดับราคาที่ Smart Money อาจจะเข้ามามีส่วนร่วม และการประเมินความแข็งแกร่งของแนวโน้ม **วิเคราะห์ทีละ Timeframe:** **(1) TF Day (รายวัน):**  * **แนวโน้ม:** ขาขึ้น (Uptrend) *อ่อนแรงลงอย่างมาก, มีความเสี่ยงที่จะเปลี่ยนแนวโน้ม* * **SMC:** * Higher Highs (HH) และ Higher Lows (HL) *เริ่มไม่ชัดเจน, ราคาหลุด Low ก่อนหน้า* * Break of Structure (BOS) ด้านบน *แต่มีการปรับฐานที่รุนแรง* * **Liquidity:** * มี Sellside Liquidity (SSL) อยู่ใต้ Lows ก่อนหน้า (บริเวณ 85,000 - 90,000) * มี Buyside Liquidity (BSL) อยู่เหนือ High เดิม * **ICT:** * **Order Block:** ราคาหลุด Order Block ขาขึ้น (บริเวณแท่งเทียนสีเขียวก่อนหน้านี้) *สัญญาณลบ* * **EMA:** * ราคา *หลุด* EMA 50 (สีเหลือง) ลงมาแล้ว * EMA 200 (สีขาว) เป็นแนวรับถัดไป * **Money Flow (LuxAlgo):** * *สีแดงยาว* แสดงถึงแรงขายที่แข็งแกร่ง * **Trend Strength (AlgoAlpha):** * สีแดง (เมฆแดง) แสดงถึงแนวโน้มขาลง *และไม่มีสัญญาณซื้อ/ขายปรากฏ* * **Volume Profile:** Volume ค่อนข้างเบาบาง * **แท่งเทียน:** แท่งเทียนล่าสุดเป็นสีแดง แสดงถึงแรงขาย * **แนวรับ:** EMA 200, บริเวณ 85,000 - 90,000 (SSL) * **แนวต้าน:** EMA 50, High เดิม * **สรุป:** แนวโน้มขาขึ้นอ่อนแรงลงอย่างมาก, *สัญญาณอันตรายหลายอย่าง*, Money Flow และ Trend Strength เป็นลบ, *หลุด Order Block และ EMA 50* **(2) TF4H (4 ชั่วโมง):**  * **แนวโน้ม:** ขาลง (Downtrend) * **SMC:** * Lower Highs (LH) และ Lower Lows (LL) * Break of Structure (BOS) ด้านล่าง * **Liquidity:** * มี SSL อยู่ใต้ Lows ก่อนหน้า * มี BSL อยู่เหนือ Highs ก่อนหน้า * **ICT:** * **Order Block:** ราคาไม่สามารถผ่าน Order Block ขาลงได้ * **EMA:** * ราคาอยู่ใต้ EMA 50 และ EMA 200 * **Money Flow (LuxAlgo):** * สีแดง แสดงถึงแรงขาย * **Trend Strength (AlgoAlpha):** * สีเขียว (เมฆเขียว) *แต่ไม่มีสัญญาณซื้อ/ขายปรากฏ* * **Volume Profile:** * Volume ค่อนข้างสูง * **แนวรับ:** บริเวณ Low ล่าสุด * **แนวต้าน:** EMA 50, EMA 200, บริเวณ Order Block * **สรุป:** แนวโน้มขาลงชัดเจน, แรงขายมีอิทธิพล, *Trend Strength ขัดแย้งกับ Price Action* **(3) TF15 (15 นาที):**  * **แนวโน้ม:** ขาลง (Downtrend) *แต่เริ่มเห็นสัญญาณ Sideways* * **SMC:** * Lower Highs (LH) และ Lower Lows (LL) *เริ่มเห็นการยก Low เล็กน้อย* * Break of Structure (BOS) ด้านล่าง * **ICT:** * **Order Block:** ราคา Sideways ใกล้ Order Block * **EMA:** * EMA 50 และ EMA 200 เป็นแนวต้าน * **Money Flow (LuxAlgo):** * แดงสลับเขียว *แต่ส่วนใหญ่ยังเป็นสีแดง* * **Trend Strength (AlgoAlpha):** * สีแดง (เมฆแดง) แสดงถึงแนวโน้มขาลง *แต่มีสัญญาณ Bullish Divergence (ราคาทำ Lower Low แต่ Trend Strength ยก Low)* * **Volume Profile:** * Volume ค่อนข้างสูง * **แนวรับ:** บริเวณ Low ล่าสุด * **แนวต้าน:** EMA 50, EMA 200, Order Block * **สรุป:** แนวโน้มขาลง, เริ่มพักตัว, Money Flow เริ่มมีความไม่แน่นอน, *Trend Strength มี Divergence* **สรุปภาพรวมและกลยุทธ์ (BTCUSDT):** * **แนวโน้มหลัก (Day):** ขาขึ้น (*อ่อนแรงลงอย่างมาก, เสี่ยงที่จะเปลี่ยนแนวโน้ม*) * **แนวโน้มรอง (4H):** ขาลง * **แนวโน้มระยะสั้น (15m):** ขาลง (เริ่มพักตัว, *มี Divergence*) * **Liquidity:** มี SSL ทั้งใน Day, 4H, และ 15m * **Money Flow:** เป็นลบในทุก Timeframes * **Trend Strength:** Day/15m เป็นขาลง, 4H เป็นขาขึ้น *แต่ไม่มีสัญญาณ* * **กลยุทธ์:** 1. **Wait & See (ดีที่สุด):** รอความชัดเจน *โดยเฉพาะการ Breakout หรือ Breakdown จากกรอบ Sideways ใน TF15* 2. **Short (เสี่ยง):** ถ้าไม่สามารถ Breakout EMA/แนวต้านใน TF ใดๆ ได้, หรือเมื่อเกิดสัญญาณ Bearish Continuation 3. ***ไม่แนะนำให้ Buy:*** จนกว่าจะมีสัญญาณกลับตัวที่ชัดเจนมากๆ **Day Trade & การเทรดรายวัน:** * **Day Trade (TF15):** * **Short Bias:** หาจังหวะ Short เมื่อราคาเด้งขึ้นไปทดสอบแนวต้าน (EMA, Order Block) * **Stop Loss:** เหนือแนวต้านที่เข้า Short * **Take Profit:** แนวรับถัดไป (Low ล่าสุด) * **ระวัง:** Bullish Divergence ใน Trend Strength * **ไม่แนะนำให้ Long** * **Swing Trade (TF4H):** * **Short Bias:** รอจังหวะ Short เมื่อราคาไม่สามารถผ่านแนวต้าน EMA หรือ Order Block ได้ * **Stop Loss:** เหนือแนวต้านที่เข้า Short * **Take Profit:** แนวรับถัดไป * **ไม่แนะนำให้ Long** **สิ่งที่ต้องระวัง:** * **Sellside Liquidity (SSL):** มีโอกาสสูงที่ราคาจะถูกลากลงไปแตะ SSL * **False Breakouts:** ระวัง * **Volatility:** สูง * **Divergence (TF15):** อาจเป็นสัญญาณเริ่มต้นของการกลับตัว *แต่ต้องรอการยืนยัน* * **Trend Strength (TF4H):** ไม่มีสัญญาณซื้อ/ขาย ต้องระวัง **Setup Day Trade แบบ SMC (ตัวอย่าง):** 1. **ระบุ Order Block:** หา Order Block ขาลง (Bearish Order Block) ใน TF15 (แท่งเทียนสีเขียวก่อนที่ราคาจะลงแรง) 2. **รอ Pullback:** รอให้ราคา Pullback ขึ้นไปทดสอบ Order Block นั้น 3. **หา Bearish Entry:** * **Rejection:** รอ Price Action ปฏิเสธ Order Block (เช่น เกิด Pin Bar, Engulfing) * **Break of Structure:** รอให้ราคา Break โครงสร้างย่อยๆ ใน TF ที่เล็กกว่า (เช่น 1m, 5m) หลังจากที่ทดสอบ Order Block * **Money Flow:** ดู Money Flow ให้เป็นสีแดง 4. **ตั้ง Stop Loss:** เหนือ Order Block 5. **ตั้ง Take Profit:** แนวรับถัดไป (เช่น Low ล่าสุด) หรือ Order Block ขาขึ้น (Bullish Order Block) ใน TF ที่ใหญ่กว่า **คำแนะนำ:** * **ความขัดแย้งของ Timeframes:** มีอยู่ แต่แนวโน้มระยะกลาง-สั้น เป็นลบ * **Money Flow:** เป็นลบในทุก Timeframes * **Trend Strength:** เริ่มมี Divergence ใน TF15 * **Order Block TF Day:** หลุด Order Block ขาขึ้นแล้ว * **ถ้าไม่แน่ใจ อย่าเพิ่งเข้าเทรด** **Disclaimer:** การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ
@ d360efec:14907b5f
2025-02-20 10:16:03**ภาพรวม BTCUSDT (OKX):** Bitcoin (BTCUSDT) ยังคงแสดงความผันผวนและแนวโน้มที่ไม่ชัดเจน แม้ว่าแนวโน้มระยะยาว (TF Day) จะยังคงมีลักษณะเป็นขาขึ้น (แต่*อ่อนแรงลงอย่างมาก*) แนวโน้มระยะกลาง (TF4H) และระยะสั้น (TF15) เป็นขาลง การวิเคราะห์ครั้งนี้จะเน้นไปที่การระบุระดับราคาที่ Smart Money อาจจะเข้ามามีส่วนร่วม และการประเมินความแข็งแกร่งของแนวโน้ม **วิเคราะห์ทีละ Timeframe:** **(1) TF Day (รายวัน):**  * **แนวโน้ม:** ขาขึ้น (Uptrend) *อ่อนแรงลงอย่างมาก, มีความเสี่ยงที่จะเปลี่ยนแนวโน้ม* * **SMC:** * Higher Highs (HH) และ Higher Lows (HL) *เริ่มไม่ชัดเจน, ราคาหลุด Low ก่อนหน้า* * Break of Structure (BOS) ด้านบน *แต่มีการปรับฐานที่รุนแรง* * **Liquidity:** * มี Sellside Liquidity (SSL) อยู่ใต้ Lows ก่อนหน้า (บริเวณ 85,000 - 90,000) * มี Buyside Liquidity (BSL) อยู่เหนือ High เดิม * **ICT:** * **Order Block:** ราคาหลุด Order Block ขาขึ้น (บริเวณแท่งเทียนสีเขียวก่อนหน้านี้) *สัญญาณลบ* * **EMA:** * ราคา *หลุด* EMA 50 (สีเหลือง) ลงมาแล้ว * EMA 200 (สีขาว) เป็นแนวรับถัดไป * **Money Flow (LuxAlgo):** * *สีแดงยาว* แสดงถึงแรงขายที่แข็งแกร่ง * **Trend Strength (AlgoAlpha):** * สีแดง (เมฆแดง) แสดงถึงแนวโน้มขาลง *และไม่มีสัญญาณซื้อ/ขายปรากฏ* * **Volume Profile:** Volume ค่อนข้างเบาบาง * **แท่งเทียน:** แท่งเทียนล่าสุดเป็นสีแดง แสดงถึงแรงขาย * **แนวรับ:** EMA 200, บริเวณ 85,000 - 90,000 (SSL) * **แนวต้าน:** EMA 50, High เดิม * **สรุป:** แนวโน้มขาขึ้นอ่อนแรงลงอย่างมาก, *สัญญาณอันตรายหลายอย่าง*, Money Flow และ Trend Strength เป็นลบ, *หลุด Order Block และ EMA 50* **(2) TF4H (4 ชั่วโมง):**  * **แนวโน้ม:** ขาลง (Downtrend) * **SMC:** * Lower Highs (LH) และ Lower Lows (LL) * Break of Structure (BOS) ด้านล่าง * **Liquidity:** * มี SSL อยู่ใต้ Lows ก่อนหน้า * มี BSL อยู่เหนือ Highs ก่อนหน้า * **ICT:** * **Order Block:** ราคาไม่สามารถผ่าน Order Block ขาลงได้ * **EMA:** * ราคาอยู่ใต้ EMA 50 และ EMA 200 * **Money Flow (LuxAlgo):** * สีแดง แสดงถึงแรงขาย * **Trend Strength (AlgoAlpha):** * สีเขียว (เมฆเขียว) *แต่ไม่มีสัญญาณซื้อ/ขายปรากฏ* * **Volume Profile:** * Volume ค่อนข้างสูง * **แนวรับ:** บริเวณ Low ล่าสุด * **แนวต้าน:** EMA 50, EMA 200, บริเวณ Order Block * **สรุป:** แนวโน้มขาลงชัดเจน, แรงขายมีอิทธิพล, *Trend Strength ขัดแย้งกับ Price Action* **(3) TF15 (15 นาที):**  * **แนวโน้ม:** ขาลง (Downtrend) *แต่เริ่มเห็นสัญญาณ Sideways* * **SMC:** * Lower Highs (LH) และ Lower Lows (LL) *เริ่มเห็นการยก Low เล็กน้อย* * Break of Structure (BOS) ด้านล่าง * **ICT:** * **Order Block:** ราคา Sideways ใกล้ Order Block * **EMA:** * EMA 50 และ EMA 200 เป็นแนวต้าน * **Money Flow (LuxAlgo):** * แดงสลับเขียว *แต่ส่วนใหญ่ยังเป็นสีแดง* * **Trend Strength (AlgoAlpha):** * สีแดง (เมฆแดง) แสดงถึงแนวโน้มขาลง *แต่มีสัญญาณ Bullish Divergence (ราคาทำ Lower Low แต่ Trend Strength ยก Low)* * **Volume Profile:** * Volume ค่อนข้างสูง * **แนวรับ:** บริเวณ Low ล่าสุด * **แนวต้าน:** EMA 50, EMA 200, Order Block * **สรุป:** แนวโน้มขาลง, เริ่มพักตัว, Money Flow เริ่มมีความไม่แน่นอน, *Trend Strength มี Divergence* **สรุปภาพรวมและกลยุทธ์ (BTCUSDT):** * **แนวโน้มหลัก (Day):** ขาขึ้น (*อ่อนแรงลงอย่างมาก, เสี่ยงที่จะเปลี่ยนแนวโน้ม*) * **แนวโน้มรอง (4H):** ขาลง * **แนวโน้มระยะสั้น (15m):** ขาลง (เริ่มพักตัว, *มี Divergence*) * **Liquidity:** มี SSL ทั้งใน Day, 4H, และ 15m * **Money Flow:** เป็นลบในทุก Timeframes * **Trend Strength:** Day/15m เป็นขาลง, 4H เป็นขาขึ้น *แต่ไม่มีสัญญาณ* * **กลยุทธ์:** 1. **Wait & See (ดีที่สุด):** รอความชัดเจน *โดยเฉพาะการ Breakout หรือ Breakdown จากกรอบ Sideways ใน TF15* 2. **Short (เสี่ยง):** ถ้าไม่สามารถ Breakout EMA/แนวต้านใน TF ใดๆ ได้, หรือเมื่อเกิดสัญญาณ Bearish Continuation 3. ***ไม่แนะนำให้ Buy:*** จนกว่าจะมีสัญญาณกลับตัวที่ชัดเจนมากๆ **Day Trade & การเทรดรายวัน:** * **Day Trade (TF15):** * **Short Bias:** หาจังหวะ Short เมื่อราคาเด้งขึ้นไปทดสอบแนวต้าน (EMA, Order Block) * **Stop Loss:** เหนือแนวต้านที่เข้า Short * **Take Profit:** แนวรับถัดไป (Low ล่าสุด) * **ระวัง:** Bullish Divergence ใน Trend Strength * **ไม่แนะนำให้ Long** * **Swing Trade (TF4H):** * **Short Bias:** รอจังหวะ Short เมื่อราคาไม่สามารถผ่านแนวต้าน EMA หรือ Order Block ได้ * **Stop Loss:** เหนือแนวต้านที่เข้า Short * **Take Profit:** แนวรับถัดไป * **ไม่แนะนำให้ Long** **สิ่งที่ต้องระวัง:** * **Sellside Liquidity (SSL):** มีโอกาสสูงที่ราคาจะถูกลากลงไปแตะ SSL * **False Breakouts:** ระวัง * **Volatility:** สูง * **Divergence (TF15):** อาจเป็นสัญญาณเริ่มต้นของการกลับตัว *แต่ต้องรอการยืนยัน* * **Trend Strength (TF4H):** ไม่มีสัญญาณซื้อ/ขาย ต้องระวัง **Setup Day Trade แบบ SMC (ตัวอย่าง):** 1. **ระบุ Order Block:** หา Order Block ขาลง (Bearish Order Block) ใน TF15 (แท่งเทียนสีเขียวก่อนที่ราคาจะลงแรง) 2. **รอ Pullback:** รอให้ราคา Pullback ขึ้นไปทดสอบ Order Block นั้น 3. **หา Bearish Entry:** * **Rejection:** รอ Price Action ปฏิเสธ Order Block (เช่น เกิด Pin Bar, Engulfing) * **Break of Structure:** รอให้ราคา Break โครงสร้างย่อยๆ ใน TF ที่เล็กกว่า (เช่น 1m, 5m) หลังจากที่ทดสอบ Order Block * **Money Flow:** ดู Money Flow ให้เป็นสีแดง 4. **ตั้ง Stop Loss:** เหนือ Order Block 5. **ตั้ง Take Profit:** แนวรับถัดไป (เช่น Low ล่าสุด) หรือ Order Block ขาขึ้น (Bullish Order Block) ใน TF ที่ใหญ่กว่า **คำแนะนำ:** * **ความขัดแย้งของ Timeframes:** มีอยู่ แต่แนวโน้มระยะกลาง-สั้น เป็นลบ * **Money Flow:** เป็นลบในทุก Timeframes * **Trend Strength:** เริ่มมี Divergence ใน TF15 * **Order Block TF Day:** หลุด Order Block ขาขึ้นแล้ว * **ถ้าไม่แน่ใจ อย่าเพิ่งเข้าเทรด** **Disclaimer:** การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ @ 94a6a78a:0ddf320e
2025-02-19 21:10:15Nostr is a revolutionary protocol that enables **decentralized, censorship-resistant communication**. Unlike traditional social networks controlled by corporations, Nostr operates without central servers or gatekeepers. This openness makes it incredibly powerful—but also means its success depends entirely on **users, developers, and relay operators**. If you believe in **free speech, decentralization, and an open internet**, there are many ways to support and strengthen the Nostr ecosystem. Whether you're a casual user, a developer, or someone looking to contribute financially, **every effort helps build a more robust network**. Here’s how you can get involved and make a difference. --- ## **1️⃣ Use Nostr Daily** The simplest and most effective way to contribute to Nostr is by **using it regularly**. The more active users, the stronger and more valuable the network becomes. ✅ **Post, comment, and zap** (send micro-payments via Bitcoin’s Lightning Network) to keep conversations flowing.\ ✅ **Engage with new users** and help them understand how Nostr works.\ ✅ **Try different Nostr clients** like Damus, Amethyst, Snort, or Primal and provide feedback to improve the experience. Your activity **keeps the network alive** and helps encourage more developers and relay operators to invest in the ecosystem. --- ## **2️⃣ Run Your Own Nostr Relay** Relays are the **backbone of Nostr**, responsible for distributing messages across the network. The more **independent relays exist**, the stronger and more censorship-resistant Nostr becomes. ✅ **Set up your own relay** to help decentralize the network further.\ ✅ **Experiment with relay configurations** and different performance optimizations.\ ✅ **Offer public or private relay services** to users looking for high-quality infrastructure. If you're not technical, you can still **support relay operators** by **subscribing to a paid relay** or donating to open-source relay projects. --- ## **3️⃣ Support Paid Relays & Infrastructure** Free relays have helped Nostr grow, but they **struggle with spam, slow speeds, and sustainability issues**. **Paid relays** help fund **better infrastructure, faster message delivery, and a more reliable experience**. ✅ **Subscribe to a paid relay** to help keep it running.\ ✅ **Use premium services** like media hosting (e.g., Azzamo Blossom) to decentralize content storage.\ ✅ **Donate to relay operators** who invest in long-term infrastructure. By funding **Nostr’s decentralized backbone**, you help ensure its **longevity and reliability**. --- ## **4️⃣ Zap Developers, Creators & Builders** Many people contribute to Nostr **without direct financial compensation**—developers who build clients, relay operators, educators, and content creators. **You can support them with zaps!** ⚡ ✅ **Find developers working on Nostr projects** and send them a zap.\ ✅ **Support content creators and educators** who spread awareness about Nostr.\ ✅ **Encourage builders** by donating to open-source projects. Micro-payments via the **Lightning Network** make it easy to directly **support the people who make Nostr better**. --- ## **5️⃣ Develop New Nostr Apps & Tools** If you're a developer, you can **build on Nostr’s open protocol** to create new apps, bots, or tools. Nostr is **permissionless**, meaning anyone can develop for it. ✅ **Create new Nostr clients** with unique features and user experiences.\ ✅ **Build bots or automation tools** that improve engagement and usability.\ ✅ **Experiment with decentralized identity, authentication, and encryption** to make Nostr even stronger. With **no corporate gatekeepers**, your projects can help shape the future of decentralized social media. --- ## **6️⃣ Promote & Educate Others About Nostr** Adoption grows when **more people understand and use Nostr**. You can help by **spreading awareness** and creating educational content. ✅ **Write blogs, guides, and tutorials** explaining how to use Nostr.\ ✅ **Make videos or social media posts** introducing new users to the protocol.\ ✅ **Host discussions, Twitter Spaces, or workshops** to onboard more people. The more people **understand and trust Nostr**, the stronger the ecosystem becomes. --- ## **7️⃣ Support Open-Source Nostr Projects** Many Nostr tools and clients are **built by volunteers**, and open-source projects thrive on **community support**. ✅ **Contribute code** to existing Nostr projects on GitHub.\ ✅ **Report bugs and suggest features** to improve Nostr clients.\ ✅ **Donate to developers** who keep Nostr free and open for everyone. If you're not a developer, you can still **help with testing, translations, and documentation** to make projects more accessible. --- ## **🚀 Every Contribution Strengthens Nostr** Whether you: ✔️ **Post and engage daily**\ ✔️ **Zap creators and developers**\ ✔️ **Run or support relays**\ ✔️ **Build new apps and tools**\ ✔️ **Educate and onboard new users** **Every action helps make Nostr more resilient, decentralized, and unstoppable.** Nostr isn’t just another social network—it’s **a movement toward a free and open internet**. If you believe in **digital freedom, privacy, and decentralization**, now is the time to get involved.
@ 94a6a78a:0ddf320e
2025-02-19 21:10:15Nostr is a revolutionary protocol that enables **decentralized, censorship-resistant communication**. Unlike traditional social networks controlled by corporations, Nostr operates without central servers or gatekeepers. This openness makes it incredibly powerful—but also means its success depends entirely on **users, developers, and relay operators**. If you believe in **free speech, decentralization, and an open internet**, there are many ways to support and strengthen the Nostr ecosystem. Whether you're a casual user, a developer, or someone looking to contribute financially, **every effort helps build a more robust network**. Here’s how you can get involved and make a difference. --- ## **1️⃣ Use Nostr Daily** The simplest and most effective way to contribute to Nostr is by **using it regularly**. The more active users, the stronger and more valuable the network becomes. ✅ **Post, comment, and zap** (send micro-payments via Bitcoin’s Lightning Network) to keep conversations flowing.\ ✅ **Engage with new users** and help them understand how Nostr works.\ ✅ **Try different Nostr clients** like Damus, Amethyst, Snort, or Primal and provide feedback to improve the experience. Your activity **keeps the network alive** and helps encourage more developers and relay operators to invest in the ecosystem. --- ## **2️⃣ Run Your Own Nostr Relay** Relays are the **backbone of Nostr**, responsible for distributing messages across the network. The more **independent relays exist**, the stronger and more censorship-resistant Nostr becomes. ✅ **Set up your own relay** to help decentralize the network further.\ ✅ **Experiment with relay configurations** and different performance optimizations.\ ✅ **Offer public or private relay services** to users looking for high-quality infrastructure. If you're not technical, you can still **support relay operators** by **subscribing to a paid relay** or donating to open-source relay projects. --- ## **3️⃣ Support Paid Relays & Infrastructure** Free relays have helped Nostr grow, but they **struggle with spam, slow speeds, and sustainability issues**. **Paid relays** help fund **better infrastructure, faster message delivery, and a more reliable experience**. ✅ **Subscribe to a paid relay** to help keep it running.\ ✅ **Use premium services** like media hosting (e.g., Azzamo Blossom) to decentralize content storage.\ ✅ **Donate to relay operators** who invest in long-term infrastructure. By funding **Nostr’s decentralized backbone**, you help ensure its **longevity and reliability**. --- ## **4️⃣ Zap Developers, Creators & Builders** Many people contribute to Nostr **without direct financial compensation**—developers who build clients, relay operators, educators, and content creators. **You can support them with zaps!** ⚡ ✅ **Find developers working on Nostr projects** and send them a zap.\ ✅ **Support content creators and educators** who spread awareness about Nostr.\ ✅ **Encourage builders** by donating to open-source projects. Micro-payments via the **Lightning Network** make it easy to directly **support the people who make Nostr better**. --- ## **5️⃣ Develop New Nostr Apps & Tools** If you're a developer, you can **build on Nostr’s open protocol** to create new apps, bots, or tools. Nostr is **permissionless**, meaning anyone can develop for it. ✅ **Create new Nostr clients** with unique features and user experiences.\ ✅ **Build bots or automation tools** that improve engagement and usability.\ ✅ **Experiment with decentralized identity, authentication, and encryption** to make Nostr even stronger. With **no corporate gatekeepers**, your projects can help shape the future of decentralized social media. --- ## **6️⃣ Promote & Educate Others About Nostr** Adoption grows when **more people understand and use Nostr**. You can help by **spreading awareness** and creating educational content. ✅ **Write blogs, guides, and tutorials** explaining how to use Nostr.\ ✅ **Make videos or social media posts** introducing new users to the protocol.\ ✅ **Host discussions, Twitter Spaces, or workshops** to onboard more people. The more people **understand and trust Nostr**, the stronger the ecosystem becomes. --- ## **7️⃣ Support Open-Source Nostr Projects** Many Nostr tools and clients are **built by volunteers**, and open-source projects thrive on **community support**. ✅ **Contribute code** to existing Nostr projects on GitHub.\ ✅ **Report bugs and suggest features** to improve Nostr clients.\ ✅ **Donate to developers** who keep Nostr free and open for everyone. If you're not a developer, you can still **help with testing, translations, and documentation** to make projects more accessible. --- ## **🚀 Every Contribution Strengthens Nostr** Whether you: ✔️ **Post and engage daily**\ ✔️ **Zap creators and developers**\ ✔️ **Run or support relays**\ ✔️ **Build new apps and tools**\ ✔️ **Educate and onboard new users** **Every action helps make Nostr more resilient, decentralized, and unstoppable.** Nostr isn’t just another social network—it’s **a movement toward a free and open internet**. If you believe in **digital freedom, privacy, and decentralization**, now is the time to get involved. @ 5de23b9a:d83005b3
2025-02-19 03:47:19In a digital era that is increasingly controlled by large companies, the emergence of Nostr (Notes and Other Stuff Transmitted by Relays) is a breath of fresh air for those who crave freedom of expression. Nostr is a cryptography-based protocol that allows users to send and receive messages through a relay network. Unlike conventional social media such as Twitter or Facebook 1.Full Decentralization: No company or government can remove or restrict content. 2.Sensor-Resistant: Information remains accessible despite blocking attempts. 3.Privacy and Security: Uses cryptography to ensure that only users who have the keys can access their messages.* **
@ 5de23b9a:d83005b3
2025-02-19 03:47:19In a digital era that is increasingly controlled by large companies, the emergence of Nostr (Notes and Other Stuff Transmitted by Relays) is a breath of fresh air for those who crave freedom of expression. Nostr is a cryptography-based protocol that allows users to send and receive messages through a relay network. Unlike conventional social media such as Twitter or Facebook 1.Full Decentralization: No company or government can remove or restrict content. 2.Sensor-Resistant: Information remains accessible despite blocking attempts. 3.Privacy and Security: Uses cryptography to ensure that only users who have the keys can access their messages.* ** @ 9e69e420:d12360c2
2025-02-17 17:12:01President Trump has intensified immigration enforcement, likening it to a wartime effort. Despite pouring resources into the U.S. Immigration and Customs Enforcement (ICE), arrest numbers are declining and falling short of goals. ICE fell from about 800 daily arrests in late January to fewer than 600 in early February. Critics argue the administration is merely showcasing efforts with ineffectiveness, while Trump seeks billions more in funding to support his deportation agenda. Increased involvement from various federal agencies is intended to assist ICE, but many lack specific immigration training. Challenges persist, as fewer immigrants are available for quick deportation due to a decline in illegal crossings. Local sheriffs are also pressured by rising demands to accommodate immigrants, which may strain resources further.
@ 9e69e420:d12360c2
2025-02-17 17:12:01President Trump has intensified immigration enforcement, likening it to a wartime effort. Despite pouring resources into the U.S. Immigration and Customs Enforcement (ICE), arrest numbers are declining and falling short of goals. ICE fell from about 800 daily arrests in late January to fewer than 600 in early February. Critics argue the administration is merely showcasing efforts with ineffectiveness, while Trump seeks billions more in funding to support his deportation agenda. Increased involvement from various federal agencies is intended to assist ICE, but many lack specific immigration training. Challenges persist, as fewer immigrants are available for quick deportation due to a decline in illegal crossings. Local sheriffs are also pressured by rising demands to accommodate immigrants, which may strain resources further. @ d360efec:14907b5f
2025-02-20 10:12:37**Overall Assessment:** Bitcoin (BTCUSDT) on OKX remains highly volatile and shows conflicting signals. The long-term trend (Daily chart) is technically still an uptrend, *but it has weakened considerably* and is showing significant signs of a potential reversal. The 4-hour and 15-minute charts are in confirmed downtrends. The focus of this analysis is on identifying potential areas of Smart Money activity (liquidity pools and order blocks) and assessing trend strength. **Detailed Analysis by Timeframe:** **(1) TF Day (Daily):**  * **Trend:** Uptrend (Significantly Weakening, *at risk of reversing*). * **SMC (Smart Money Concepts):** * Higher Highs (HH) and Higher Lows (HL) structure is *becoming less defined*. The recent price action has broken previous lows. * Prior Breaks of Structure (BOS) to the upside, but the current pullback is very deep. * **Liquidity:** * **Sellside Liquidity (SSL):** Significant SSL rests below previous lows in the 85,000 - 90,000 range. This is a likely target for Smart Money. * **Buyside Liquidity (BSL):** BSL is present above the all-time high. * **ICT (Inner Circle Trader Concepts):** * **Order Block:** The price has *broken below* the prior bullish Order Block (the large green candle before a significant up-move). This is a *major bearish signal*. * **EMA (Exponential Moving Average):** * Price has *broken below* the 50-period EMA (yellow), a bearish signal. * The 200-period EMA (white) is the next major support level. * **Money Flow (LuxAlgo):** * A *long red bar* indicates strong selling pressure. * **Trend Strength (AlgoAlpha):** * Red Cloud indicating Downtrend, *No Buy/Sell Signal* * **Volume Profile:** Relatively low volume on the recent decline. * **Candlesticks:** The most recent candlestick is red, confirming selling pressure. * **Support:** EMA 200, 85,000-90,000 (SSL area). * **Resistance:** EMA 50, Previous All-Time High. * **Summary:** The Daily chart's uptrend is significantly weakening. The break below the 50 EMA *and* the bullish Order Block, combined with the negative Money Flow and bearish Trend Strength, are all major warning signs. **(2) TF4H (4-Hour):**  * **Trend:** Downtrend. * **SMC:** * Lower Highs (LH) and Lower Lows (LL). * BOS to the downside. * **Liquidity:** * **SSL:** Below previous lows. * **BSL:** Above previous highs. * **ICT:** * **Order Block:** The price rallied up to, and was rejected by, a *bearish* Order Block. * **EMA:** * Price is below both the 50-period and 200-period EMAs (bearish). * **Money Flow (LuxAlgo):** * Predominantly red, confirming selling pressure. * **Trend Strength (AlgoAlpha):** * Green Cloud, *But No Buy/Sell Signal.* This indicates a potential *retracement* within the downtrend, or a period of consolidation, *not* a trend reversal. * **Volume Profile:** * Relatively High volume * **Support:** Recent lows. * **Resistance:** EMA 50, EMA 200, Order Block. * **Summary:** The 4-hour chart is in a confirmed downtrend. The Money Flow is bearish, and the price was rejected by a key Order Block. The green Trend Strength cloud *without* a buy signal suggests a potential *temporary* relief rally or consolidation, *not* a trend change. **(3) TF15 (15-Minute):**  * **Trend:** Downtrend (with some signs of *possible* stabilization). * **SMC:** * Lower Highs (LH) and Lower Lows (LL) – *but the most recent low is slightly higher, a potential early sign of a change*. * BOS to the downside. * **ICT:** * **Order Block:** Price has reacted to bearish Order Block. * **EMA:** * The 50-period and 200-period EMAs are acting as resistance. * **Money Flow (LuxAlgo):** * Red and green alternating , showing some buying pressure has appeared, but sellers are still in control overall. * **Trend Strength (AlgoAlpha):** * Red Cloud (Bearish), *BUT* there's a *bullish divergence* (price made a lower low, but the Trend Strength indicator made a higher low). This is a *potential* early warning sign of a reversal, but it needs *strong confirmation*. * **Volume Profile:** * relatively high volume. * **Support:** Recent lows. * **Resistance:** EMA 50, EMA 200, Order Block. * **Summary:** The 15-minute chart is in a downtrend, but there are *very early* and *tentative* signs of a possible stabilization or even a minor bounce. The bullish divergence on the Trend Strength is important to note, but it's not a buy signal on its own. **Overall Strategy and Recommendations (BTCUSDT):** * **Primary Trend (Day):** Uptrend (Significantly Weakening). * **Secondary Trend (4H):** Downtrend. * **Short-Term Trend (15m):** Downtrend (Potential Early Reversal Signals). * **Liquidity:** Significant SSL zones exist below the current price on all timeframes. * **Money Flow:** Negative on all timeframes, although the 15m is showing *some* buying pressure returning. * **Trend Strength:** Bearish on Day and 15m. Bullish on 4H, *but without a buy/sell signal*, indicating a likely retracement or consolidation, not a trend change. * **Strategies:** 1. **Wait & See (Best Option):** The conflicting signals (especially the 4H Trend Strength) and the strong bearish momentum on the shorter timeframes make waiting the most prudent approach. Look for: * **Bearish Confirmation:** A decisive break below the recent lows on the 15m and 4H charts, with increasing volume and continued negative Money Flow. This would confirm the continuation of the downtrend. * **Bullish Confirmation:** A strong, sustained break above the 15m EMAs, a shift in the 15m Money Flow to green, *and* a bullish signal on the 4H Trend Strength. This would be a *very early* sign of a potential reversal, but it would need further confirmation on the 4H chart (price above EMAs, positive Money Flow). 2. **Short (High Risk):** This is the more likely scenario *at this moment*, given the 4H and 15m downtrends. * **Entry:** On rallies towards resistance levels (EMAs on 15m/4H, previous support levels that have turned into resistance). * **Stop Loss:** Above recent highs on the chosen timeframe. * **Target:** The next support levels (recent lows on 15m, then the Daily Order Block area around 92,000-94,000). 3. **Buy on Dip (Extremely High Risk - Not Recommended):** Do *not* attempt to buy until there are *very strong and consistent* bullish reversal signals across *all* timeframes, including a definitive shift in market structure on the 4H and 15m charts, positive Money Flow, and a clear break above resistance levels. **Key Recommendations:** * **Conflicting Signals:** The most important factor is the conflict between the still *technically* bullish Daily chart and the bearish 4H and 15m charts. The 4H Trend Strength being bullish *without a signal* adds to the uncertainty. * **Money Flow:** The predominantly negative Money Flow is a major bearish factor. * **15m Trend Strength Divergence:** This is a *potential* early warning, but it's *not* a buy signal on its own. It needs *much* more confirmation. * **Daily Order Block:** The *break* of the bullish Order Block on the Daily chart is a significant bearish development. * **Sellside Liquidity (SSL):** Be aware that Smart Money may target the SSL zones below. This increases the risk of stop-loss hunting. * **Risk Management:** Due to the high uncertainty and volatility, *strict risk management is absolutely critical.* Use tight stop-losses, do not overtrade, and be prepared for rapid price swings. * **Volume:** Confirm any breakout with volume. **Day Trading and Intraday Trading Strategies:** * **Day Trade (TF15 focus):** * **Short Bias:** Given the current 15m downtrend and negative Money Flow, the higher probability is to look for shorting opportunities. * **Entry:** Look for price to rally to resistance levels (EMAs, Order Blocks, previous support levels that have become resistance) and then show signs of rejection (bearish candlestick patterns, increasing volume on the downside). * **Stop Loss:** Place a stop-loss order above the resistance level where you enter the short position. * **Take Profit:** Target the next support level (recent lows). * **Be very cautious:** The bullish divergence on the Trend Strength indicator suggests a potential bounce *could* occur. Don't be aggressive with shorts until this divergence is invalidated. * **Avoid Long positions:** Until there's a *clear* and *confirmed* bullish reversal on the 15m chart (break above EMAs, positive Money Flow, bullish market structure). * **Swing Trade (TF4H focus):** * **Short Bias:** The 4H chart is in a downtrend. * **Entry:** Wait for price to rally to resistance levels (EMAs, Order Blocks) and show signs of rejection. * **Stop Loss:** Above the resistance level where you enter the short position. * **Take Profit:** Target the next support levels (e.g., the 200 EMA on the Daily chart, SSL zones). * **Avoid long position:** Until there's a *clear* and *confirmed* bullish reversal on the 4H chart. **SMC Day Trade Setup Example (TF15 - Bearish):** 1. **Identify Bearish Order Block:** Locate a bearish Order Block on the TF15 chart (a bullish candle before a strong downward move). *We have already identified this in previous analyses.* 2. **Wait for Pullback:** Wait for the price to pull back up to test the Order Block. 3. **Bearish Entry:** * **Rejection:** Look for price action to reject the Order Block (e.g., a pin bar, engulfing pattern, or other bearish candlestick pattern). * **Break of Structure:** Look for a break of a minor support level on a *lower* timeframe (e.g., 1-minute or 5-minute) after the price tests the Order Block. This confirms weakening bullish momentum. * **Money Flow:** Confirm that Money Flow remains negative (red). 4. **Stop Loss:** Place a stop-loss order *above* the Order Block. 5. **Take Profit:** Target the next support level (e.g., recent lows) or a bullish Order Block on a higher timeframe. **In conclusion, BTCUSDT is currently in a high-risk, uncertain environment. The short-term and medium-term trends are bearish, while the long-term trend is weakening. The best approach for most traders is to wait for clearer signals. Shorting is the higher-probability trade *at this moment*, but only for experienced traders who can manage risk aggressively. Buying is extremely risky and not recommended at this time.** The bullish divergence on the 15m Trend Strength is a *potential* early warning of a change, but it needs *much* more confirmation before acting on it. The 4-hour chart showing a green cloud with *no* buy/sell signal adds to the uncertainty, suggesting a possible retracement/consolidation *within* the downtrend. **Disclaimer:** This analysis is for informational purposes only and represents a personal opinion. It is not financial advice. Investing in cryptocurrencies involves significant risk. Investors should conduct their own research and exercise due diligence before making any investment decisions.
@ d360efec:14907b5f
2025-02-20 10:12:37**Overall Assessment:** Bitcoin (BTCUSDT) on OKX remains highly volatile and shows conflicting signals. The long-term trend (Daily chart) is technically still an uptrend, *but it has weakened considerably* and is showing significant signs of a potential reversal. The 4-hour and 15-minute charts are in confirmed downtrends. The focus of this analysis is on identifying potential areas of Smart Money activity (liquidity pools and order blocks) and assessing trend strength. **Detailed Analysis by Timeframe:** **(1) TF Day (Daily):**  * **Trend:** Uptrend (Significantly Weakening, *at risk of reversing*). * **SMC (Smart Money Concepts):** * Higher Highs (HH) and Higher Lows (HL) structure is *becoming less defined*. The recent price action has broken previous lows. * Prior Breaks of Structure (BOS) to the upside, but the current pullback is very deep. * **Liquidity:** * **Sellside Liquidity (SSL):** Significant SSL rests below previous lows in the 85,000 - 90,000 range. This is a likely target for Smart Money. * **Buyside Liquidity (BSL):** BSL is present above the all-time high. * **ICT (Inner Circle Trader Concepts):** * **Order Block:** The price has *broken below* the prior bullish Order Block (the large green candle before a significant up-move). This is a *major bearish signal*. * **EMA (Exponential Moving Average):** * Price has *broken below* the 50-period EMA (yellow), a bearish signal. * The 200-period EMA (white) is the next major support level. * **Money Flow (LuxAlgo):** * A *long red bar* indicates strong selling pressure. * **Trend Strength (AlgoAlpha):** * Red Cloud indicating Downtrend, *No Buy/Sell Signal* * **Volume Profile:** Relatively low volume on the recent decline. * **Candlesticks:** The most recent candlestick is red, confirming selling pressure. * **Support:** EMA 200, 85,000-90,000 (SSL area). * **Resistance:** EMA 50, Previous All-Time High. * **Summary:** The Daily chart's uptrend is significantly weakening. The break below the 50 EMA *and* the bullish Order Block, combined with the negative Money Flow and bearish Trend Strength, are all major warning signs. **(2) TF4H (4-Hour):**  * **Trend:** Downtrend. * **SMC:** * Lower Highs (LH) and Lower Lows (LL). * BOS to the downside. * **Liquidity:** * **SSL:** Below previous lows. * **BSL:** Above previous highs. * **ICT:** * **Order Block:** The price rallied up to, and was rejected by, a *bearish* Order Block. * **EMA:** * Price is below both the 50-period and 200-period EMAs (bearish). * **Money Flow (LuxAlgo):** * Predominantly red, confirming selling pressure. * **Trend Strength (AlgoAlpha):** * Green Cloud, *But No Buy/Sell Signal.* This indicates a potential *retracement* within the downtrend, or a period of consolidation, *not* a trend reversal. * **Volume Profile:** * Relatively High volume * **Support:** Recent lows. * **Resistance:** EMA 50, EMA 200, Order Block. * **Summary:** The 4-hour chart is in a confirmed downtrend. The Money Flow is bearish, and the price was rejected by a key Order Block. The green Trend Strength cloud *without* a buy signal suggests a potential *temporary* relief rally or consolidation, *not* a trend change. **(3) TF15 (15-Minute):**  * **Trend:** Downtrend (with some signs of *possible* stabilization). * **SMC:** * Lower Highs (LH) and Lower Lows (LL) – *but the most recent low is slightly higher, a potential early sign of a change*. * BOS to the downside. * **ICT:** * **Order Block:** Price has reacted to bearish Order Block. * **EMA:** * The 50-period and 200-period EMAs are acting as resistance. * **Money Flow (LuxAlgo):** * Red and green alternating , showing some buying pressure has appeared, but sellers are still in control overall. * **Trend Strength (AlgoAlpha):** * Red Cloud (Bearish), *BUT* there's a *bullish divergence* (price made a lower low, but the Trend Strength indicator made a higher low). This is a *potential* early warning sign of a reversal, but it needs *strong confirmation*. * **Volume Profile:** * relatively high volume. * **Support:** Recent lows. * **Resistance:** EMA 50, EMA 200, Order Block. * **Summary:** The 15-minute chart is in a downtrend, but there are *very early* and *tentative* signs of a possible stabilization or even a minor bounce. The bullish divergence on the Trend Strength is important to note, but it's not a buy signal on its own. **Overall Strategy and Recommendations (BTCUSDT):** * **Primary Trend (Day):** Uptrend (Significantly Weakening). * **Secondary Trend (4H):** Downtrend. * **Short-Term Trend (15m):** Downtrend (Potential Early Reversal Signals). * **Liquidity:** Significant SSL zones exist below the current price on all timeframes. * **Money Flow:** Negative on all timeframes, although the 15m is showing *some* buying pressure returning. * **Trend Strength:** Bearish on Day and 15m. Bullish on 4H, *but without a buy/sell signal*, indicating a likely retracement or consolidation, not a trend change. * **Strategies:** 1. **Wait & See (Best Option):** The conflicting signals (especially the 4H Trend Strength) and the strong bearish momentum on the shorter timeframes make waiting the most prudent approach. Look for: * **Bearish Confirmation:** A decisive break below the recent lows on the 15m and 4H charts, with increasing volume and continued negative Money Flow. This would confirm the continuation of the downtrend. * **Bullish Confirmation:** A strong, sustained break above the 15m EMAs, a shift in the 15m Money Flow to green, *and* a bullish signal on the 4H Trend Strength. This would be a *very early* sign of a potential reversal, but it would need further confirmation on the 4H chart (price above EMAs, positive Money Flow). 2. **Short (High Risk):** This is the more likely scenario *at this moment*, given the 4H and 15m downtrends. * **Entry:** On rallies towards resistance levels (EMAs on 15m/4H, previous support levels that have turned into resistance). * **Stop Loss:** Above recent highs on the chosen timeframe. * **Target:** The next support levels (recent lows on 15m, then the Daily Order Block area around 92,000-94,000). 3. **Buy on Dip (Extremely High Risk - Not Recommended):** Do *not* attempt to buy until there are *very strong and consistent* bullish reversal signals across *all* timeframes, including a definitive shift in market structure on the 4H and 15m charts, positive Money Flow, and a clear break above resistance levels. **Key Recommendations:** * **Conflicting Signals:** The most important factor is the conflict between the still *technically* bullish Daily chart and the bearish 4H and 15m charts. The 4H Trend Strength being bullish *without a signal* adds to the uncertainty. * **Money Flow:** The predominantly negative Money Flow is a major bearish factor. * **15m Trend Strength Divergence:** This is a *potential* early warning, but it's *not* a buy signal on its own. It needs *much* more confirmation. * **Daily Order Block:** The *break* of the bullish Order Block on the Daily chart is a significant bearish development. * **Sellside Liquidity (SSL):** Be aware that Smart Money may target the SSL zones below. This increases the risk of stop-loss hunting. * **Risk Management:** Due to the high uncertainty and volatility, *strict risk management is absolutely critical.* Use tight stop-losses, do not overtrade, and be prepared for rapid price swings. * **Volume:** Confirm any breakout with volume. **Day Trading and Intraday Trading Strategies:** * **Day Trade (TF15 focus):** * **Short Bias:** Given the current 15m downtrend and negative Money Flow, the higher probability is to look for shorting opportunities. * **Entry:** Look for price to rally to resistance levels (EMAs, Order Blocks, previous support levels that have become resistance) and then show signs of rejection (bearish candlestick patterns, increasing volume on the downside). * **Stop Loss:** Place a stop-loss order above the resistance level where you enter the short position. * **Take Profit:** Target the next support level (recent lows). * **Be very cautious:** The bullish divergence on the Trend Strength indicator suggests a potential bounce *could* occur. Don't be aggressive with shorts until this divergence is invalidated. * **Avoid Long positions:** Until there's a *clear* and *confirmed* bullish reversal on the 15m chart (break above EMAs, positive Money Flow, bullish market structure). * **Swing Trade (TF4H focus):** * **Short Bias:** The 4H chart is in a downtrend. * **Entry:** Wait for price to rally to resistance levels (EMAs, Order Blocks) and show signs of rejection. * **Stop Loss:** Above the resistance level where you enter the short position. * **Take Profit:** Target the next support levels (e.g., the 200 EMA on the Daily chart, SSL zones). * **Avoid long position:** Until there's a *clear* and *confirmed* bullish reversal on the 4H chart. **SMC Day Trade Setup Example (TF15 - Bearish):** 1. **Identify Bearish Order Block:** Locate a bearish Order Block on the TF15 chart (a bullish candle before a strong downward move). *We have already identified this in previous analyses.* 2. **Wait for Pullback:** Wait for the price to pull back up to test the Order Block. 3. **Bearish Entry:** * **Rejection:** Look for price action to reject the Order Block (e.g., a pin bar, engulfing pattern, or other bearish candlestick pattern). * **Break of Structure:** Look for a break of a minor support level on a *lower* timeframe (e.g., 1-minute or 5-minute) after the price tests the Order Block. This confirms weakening bullish momentum. * **Money Flow:** Confirm that Money Flow remains negative (red). 4. **Stop Loss:** Place a stop-loss order *above* the Order Block. 5. **Take Profit:** Target the next support level (e.g., recent lows) or a bullish Order Block on a higher timeframe. **In conclusion, BTCUSDT is currently in a high-risk, uncertain environment. The short-term and medium-term trends are bearish, while the long-term trend is weakening. The best approach for most traders is to wait for clearer signals. Shorting is the higher-probability trade *at this moment*, but only for experienced traders who can manage risk aggressively. Buying is extremely risky and not recommended at this time.** The bullish divergence on the 15m Trend Strength is a *potential* early warning of a change, but it needs *much* more confirmation before acting on it. The 4-hour chart showing a green cloud with *no* buy/sell signal adds to the uncertainty, suggesting a possible retracement/consolidation *within* the downtrend. **Disclaimer:** This analysis is for informational purposes only and represents a personal opinion. It is not financial advice. Investing in cryptocurrencies involves significant risk. Investors should conduct their own research and exercise due diligence before making any investment decisions. @ 000002de:c05780a7
2025-02-20 01:52:34Due to some some org changes at my employer I may be moving to a team that uses Python heavily. I have never written Python professionally but I've dabbled. I think its used heavily in certain fields and is likely a marketable language to have on the CV. Am I correct in that summary? Is it growing? Is it evolving? I know its alive and well but I just don't hear much about it anymore. Has it just matured like many languages over the years? originally posted at https://stacker.news/items/891251
@ 000002de:c05780a7
2025-02-20 01:52:34Due to some some org changes at my employer I may be moving to a team that uses Python heavily. I have never written Python professionally but I've dabbled. I think its used heavily in certain fields and is likely a marketable language to have on the CV. Am I correct in that summary? Is it growing? Is it evolving? I know its alive and well but I just don't hear much about it anymore. Has it just matured like many languages over the years? originally posted at https://stacker.news/items/891251 @ 16f1a010:31b1074b
2025-02-19 20:57:59In the rapidly evolving world of Bitcoin, running a Bitcoin node has become more accessible than ever. Platforms like Umbrel, Start9, myNode, and Citadel offer user-friendly interfaces to simplify node management. However, for those serious about maintaining a robust and efficient Lightning node ⚡, relying solely on these platforms may not be the optimal choice. Let’s delve into why embracing **Bitcoin Core** and mastering the command-line interface (CLI) can provide a **more reliable, sovereign, and empowering** experience. ### Understanding Node Management Platforms #### What Are Umbrel, Start9, myNode, and Citadel? Umbrel, Start9, myNode, and Citadel are platforms designed to streamline the process of running a Bitcoin node. They offer graphical user interfaces (GUIs) that allow users to manage various applications, including Bitcoin Core and Lightning Network nodes, through a web-based dashboard 🖥️. These platforms often utilize Docker containers 🐳 to encapsulate applications, providing a modular and isolated environment for each service.  #### The Appeal of Simplified Node Management The primary allure of these platforms lies in their simplicity. With minimal command-line interaction, users can deploy a full Bitcoin and Lightning node, along with a suite of additional applications. ✅ **Easy one-command installation** ✅ **Web-based GUI for management** ✅ **Automatic app updates** *(but with delays, as we’ll discuss)* However, while this convenience is attractive, it comes **at a cost**. ### The Hidden Complexities of Using Node Management Platforms While the user-friendly nature of these platforms is advantageous, it can also introduce several challenges that may hinder advanced users or those seeking greater control over their nodes. #### 🚨 Dependency on Maintainers for Updates One significant concern is the reliance on platform maintainers for updates. Since these platforms manage applications through Docker containers, users must wait for the maintainers to update the container images before they can access new features or security patches. 🔴 **Delayed Bitcoin Core updates = potential security risks** 🔴 **Lightning Network updates are not immediate** 🔴 **Bugs and vulnerabilities may persist longer** Instead of waiting on a third party, **why not update Bitcoin Core & LND yourself instantly**? #### ⚙️ Challenges in Customization and Advanced Operations For users aiming to perform advanced operations, such as: * Custom backups 📂 * Running specific CLI commands 🖥️ * Optimizing node settings ⚡ …the **abstraction layers introduced by these platforms become obstacles**. Navigating through nested directories and issuing commands inside Docker containers **makes troubleshooting a nightmare**. Instead of a simple `bitcoin-cli` command, you must figure out how to execute it inside the container, adding unnecessary complexity. #### Increased Backend Complexity To achieve **frontend simplicity**, these platforms make the backend more complex. 🚫 Extra layers of abstraction 🚫 Hidden logs and settings 🚫 Harder troubleshooting The use of **multiple Docker containers**, **custom scripts**, and **unique file structures** can **make system maintenance and debugging a pain**. This **complication defeats the purpose** of “making running a node easy.” ## ✅ Advantages of Using Bitcoin Core and Command-Line Interface (CLI) By installing Bitcoin Core directly and using the command-line interface (CLI), you gain several key advantages that make managing a Bitcoin and Lightning node more efficient and empowering. #### Direct Control and Immediate Updates One of the biggest downsides of package manager-based platforms is the reliance on third-party maintainers to release updates. Since Bitcoin Core, Lightning implementations (such as LND, Core Lightning, or Eclair), and other related software evolve rapidly, waiting for platform-specific updates can leave you running outdated or vulnerable versions. By installing Bitcoin Core directly, you remove this dependency. You can update immediately when new versions are released, ensuring your node benefits from the latest features, security patches, and bug fixes. The same applies to Lightning software—being able to install and update it yourself gives you full autonomy over your node’s performance and security. #### 🛠 Simplified System Architecture Platforms like Umbrel and myNode introduce extra complexity by running Bitcoin Core and Lightning inside Docker containers. This means: * The actual files and configurations are stored inside Docker’s filesystem, making it **harder to locate and manage them manually**. * If something breaks, **troubleshooting is more difficult** due to the added layer of abstraction. * Running commands requires jumping through Docker shell sessions, adding unnecessary friction to what should be a straightforward process. Instead, a direct installation of Bitcoin Core, Lightning, and Electrum Server (if needed) results in a **cleaner, more understandable system**. The software runs natively on your machine, without containerized layers making things more convoluted. Additionally, setting up your own systemd service files for Bitcoin and Lightning** is not as complicated as it seems**. Once configured, these services will run automatically on boot, offering the same level of convenience as platforms like Umbrel but without the unnecessary complexity. #### Better Lightning Node Management If you’re running a **Lightning Network node**, using CLI-based tools provides far more flexibility than relying on a GUI like the ones bundled with node management platforms. 🟢 **Custom Backup Strategies** – Running Lightning through a GUI-based node manager often means backups are handled in a way that is opaque to the user. With CLI tools, you can easily script automatic backups of your channels, wallets, and configurations. 🟢 **Advanced Configuration** – Platforms like Umbrel force certain configurations by default, limiting how you can customize your Lightning node. With a direct install, you have full control over: * Channel fees 💰 * Routing policies 📡 * Liquidity management 🔄 🟢 **Direct Access to LND, Core Lightning, or Eclair** – Instead of issuing commands through a GUI (which is often limited in functionality), you can use: * `lncli` (for LND) * `lightning-cli` (for Core Lightning) …to interact with your node at a deeper level. #### Enhanced Learning and Engagement A crucial aspect of running a Bitcoin and Lightning node is **understanding how it works**. Using an abstraction layer like Umbrel may get a node running in a few clicks, but **it does little to teach users how Bitcoin actually functions**. By setting up Bitcoin Core, Lightning, and related software manually, you will: ✅ Gain practical knowledge of Bitcoin nodes, networking, and system performance. ✅ Learn how to configure and manage RPC commands. ✅ Become less reliant on third-party developers and more confident in troubleshooting. 🎯 **Running a Bitcoin node is about sovereignty – learn how to control it yourself**. ## Become more sovereign TODAY Many guides make this process **straightforward** [K3tan](https://k3tan.com/about) has a fantastic guide on running Bitcoin Core, Electrs, LND and more. - [Ministry of Nodes Guide 2024](https://www.youtube.com/playlist?list=PLCRbH-IWlcW0g0HCrtI06_ZdVVolUWr39) - You can find him on nostr nostr:npub1txwy7guqkrq6ngvtwft7zp70nekcknudagrvrryy2wxnz8ljk2xqz0yt4x Even with the best of guides, if you are running this software, 📖 **READ THE DOCUMENTATION** This is all just software at the end of the day. Most of it is very well documented. Take a moment to actually read through the documentation for yourself when installing. The documentation has step by step guides on setting up the software. Here is a helpful list: * [Bitcoin.org Bitcoin Core Linux install instructions](https://bitcoin.org/en/full-node#linux-instructions) * [Bitcoin Core Code Repository](https://github.com/bitcoin/bitcoin) * [Electrs Installation](https://github.com/romanz/electrs/blob/master/doc/install.md) * [LND Documentation](https://docs.lightning.engineering/) * [LND Code Repository](https://github.com/lightningnetwork/lnd) * [CLN Documentation](https://docs.corelightning.org/docs/home) * [CLN Code Repository](https://github.com/ElementsProject/lightning) *If you have any more resources or links I should add, please comment them . I want to add as much to this article as I can.*
@ 16f1a010:31b1074b
2025-02-19 20:57:59In the rapidly evolving world of Bitcoin, running a Bitcoin node has become more accessible than ever. Platforms like Umbrel, Start9, myNode, and Citadel offer user-friendly interfaces to simplify node management. However, for those serious about maintaining a robust and efficient Lightning node ⚡, relying solely on these platforms may not be the optimal choice. Let’s delve into why embracing **Bitcoin Core** and mastering the command-line interface (CLI) can provide a **more reliable, sovereign, and empowering** experience. ### Understanding Node Management Platforms #### What Are Umbrel, Start9, myNode, and Citadel? Umbrel, Start9, myNode, and Citadel are platforms designed to streamline the process of running a Bitcoin node. They offer graphical user interfaces (GUIs) that allow users to manage various applications, including Bitcoin Core and Lightning Network nodes, through a web-based dashboard 🖥️. These platforms often utilize Docker containers 🐳 to encapsulate applications, providing a modular and isolated environment for each service.  #### The Appeal of Simplified Node Management The primary allure of these platforms lies in their simplicity. With minimal command-line interaction, users can deploy a full Bitcoin and Lightning node, along with a suite of additional applications. ✅ **Easy one-command installation** ✅ **Web-based GUI for management** ✅ **Automatic app updates** *(but with delays, as we’ll discuss)* However, while this convenience is attractive, it comes **at a cost**. ### The Hidden Complexities of Using Node Management Platforms While the user-friendly nature of these platforms is advantageous, it can also introduce several challenges that may hinder advanced users or those seeking greater control over their nodes. #### 🚨 Dependency on Maintainers for Updates One significant concern is the reliance on platform maintainers for updates. Since these platforms manage applications through Docker containers, users must wait for the maintainers to update the container images before they can access new features or security patches. 🔴 **Delayed Bitcoin Core updates = potential security risks** 🔴 **Lightning Network updates are not immediate** 🔴 **Bugs and vulnerabilities may persist longer** Instead of waiting on a third party, **why not update Bitcoin Core & LND yourself instantly**? #### ⚙️ Challenges in Customization and Advanced Operations For users aiming to perform advanced operations, such as: * Custom backups 📂 * Running specific CLI commands 🖥️ * Optimizing node settings ⚡ …the **abstraction layers introduced by these platforms become obstacles**. Navigating through nested directories and issuing commands inside Docker containers **makes troubleshooting a nightmare**. Instead of a simple `bitcoin-cli` command, you must figure out how to execute it inside the container, adding unnecessary complexity. #### Increased Backend Complexity To achieve **frontend simplicity**, these platforms make the backend more complex. 🚫 Extra layers of abstraction 🚫 Hidden logs and settings 🚫 Harder troubleshooting The use of **multiple Docker containers**, **custom scripts**, and **unique file structures** can **make system maintenance and debugging a pain**. This **complication defeats the purpose** of “making running a node easy.” ## ✅ Advantages of Using Bitcoin Core and Command-Line Interface (CLI) By installing Bitcoin Core directly and using the command-line interface (CLI), you gain several key advantages that make managing a Bitcoin and Lightning node more efficient and empowering. #### Direct Control and Immediate Updates One of the biggest downsides of package manager-based platforms is the reliance on third-party maintainers to release updates. Since Bitcoin Core, Lightning implementations (such as LND, Core Lightning, or Eclair), and other related software evolve rapidly, waiting for platform-specific updates can leave you running outdated or vulnerable versions. By installing Bitcoin Core directly, you remove this dependency. You can update immediately when new versions are released, ensuring your node benefits from the latest features, security patches, and bug fixes. The same applies to Lightning software—being able to install and update it yourself gives you full autonomy over your node’s performance and security. #### 🛠 Simplified System Architecture Platforms like Umbrel and myNode introduce extra complexity by running Bitcoin Core and Lightning inside Docker containers. This means: * The actual files and configurations are stored inside Docker’s filesystem, making it **harder to locate and manage them manually**. * If something breaks, **troubleshooting is more difficult** due to the added layer of abstraction. * Running commands requires jumping through Docker shell sessions, adding unnecessary friction to what should be a straightforward process. Instead, a direct installation of Bitcoin Core, Lightning, and Electrum Server (if needed) results in a **cleaner, more understandable system**. The software runs natively on your machine, without containerized layers making things more convoluted. Additionally, setting up your own systemd service files for Bitcoin and Lightning** is not as complicated as it seems**. Once configured, these services will run automatically on boot, offering the same level of convenience as platforms like Umbrel but without the unnecessary complexity. #### Better Lightning Node Management If you’re running a **Lightning Network node**, using CLI-based tools provides far more flexibility than relying on a GUI like the ones bundled with node management platforms. 🟢 **Custom Backup Strategies** – Running Lightning through a GUI-based node manager often means backups are handled in a way that is opaque to the user. With CLI tools, you can easily script automatic backups of your channels, wallets, and configurations. 🟢 **Advanced Configuration** – Platforms like Umbrel force certain configurations by default, limiting how you can customize your Lightning node. With a direct install, you have full control over: * Channel fees 💰 * Routing policies 📡 * Liquidity management 🔄 🟢 **Direct Access to LND, Core Lightning, or Eclair** – Instead of issuing commands through a GUI (which is often limited in functionality), you can use: * `lncli` (for LND) * `lightning-cli` (for Core Lightning) …to interact with your node at a deeper level. #### Enhanced Learning and Engagement A crucial aspect of running a Bitcoin and Lightning node is **understanding how it works**. Using an abstraction layer like Umbrel may get a node running in a few clicks, but **it does little to teach users how Bitcoin actually functions**. By setting up Bitcoin Core, Lightning, and related software manually, you will: ✅ Gain practical knowledge of Bitcoin nodes, networking, and system performance. ✅ Learn how to configure and manage RPC commands. ✅ Become less reliant on third-party developers and more confident in troubleshooting. 🎯 **Running a Bitcoin node is about sovereignty – learn how to control it yourself**. ## Become more sovereign TODAY Many guides make this process **straightforward** [K3tan](https://k3tan.com/about) has a fantastic guide on running Bitcoin Core, Electrs, LND and more. - [Ministry of Nodes Guide 2024](https://www.youtube.com/playlist?list=PLCRbH-IWlcW0g0HCrtI06_ZdVVolUWr39) - You can find him on nostr nostr:npub1txwy7guqkrq6ngvtwft7zp70nekcknudagrvrryy2wxnz8ljk2xqz0yt4x Even with the best of guides, if you are running this software, 📖 **READ THE DOCUMENTATION** This is all just software at the end of the day. Most of it is very well documented. Take a moment to actually read through the documentation for yourself when installing. The documentation has step by step guides on setting up the software. Here is a helpful list: * [Bitcoin.org Bitcoin Core Linux install instructions](https://bitcoin.org/en/full-node#linux-instructions) * [Bitcoin Core Code Repository](https://github.com/bitcoin/bitcoin) * [Electrs Installation](https://github.com/romanz/electrs/blob/master/doc/install.md) * [LND Documentation](https://docs.lightning.engineering/) * [LND Code Repository](https://github.com/lightningnetwork/lnd) * [CLN Documentation](https://docs.corelightning.org/docs/home) * [CLN Code Repository](https://github.com/ElementsProject/lightning) *If you have any more resources or links I should add, please comment them . I want to add as much to this article as I can.* @ f33c8a96:5ec6f741
2025-02-19 20:47:43<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/kFUIfaCpXzA?enablejsapi=1" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div>
@ f33c8a96:5ec6f741
2025-02-19 20:47:43<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><iframe src="https://www.youtube.com/embed/kFUIfaCpXzA?enablejsapi=1" style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" allowfullscreen></iframe></div> @ 8d34bd24:414be32b
2025-02-19 16:43:17Last night I was reading Jeremiah 24 and I read the parable of the figs. I’ve read this passage many times, but suddenly I saw the irony of the situation. ## The Story of the Good and Bad Figs > After Nebuchadnezzar king of Babylon had carried away captive Jeconiah the son of Jehoiakim, king of Judah, and the officials of Judah with the craftsmen and smiths from Jerusalem and had brought them to Babylon, the Lord showed me: behold, two baskets of figs set before the temple of the Lord! One basket had very good figs, like first-ripe figs, and the other basket had very bad figs which could not be eaten due to rottenness. Then the Lord said to me, “What do you see, Jeremiah?” And I said, “Figs, the good figs, very good; and the bad figs, very bad, which cannot be eaten due to rottenness.” > > Then the word of the Lord came to me, saying, “Thus says the Lord God of Israel, ‘**Like these good figs, so I will regard as good the captives of Judah, whom I have sent out of this place into the land of the Chaldeans. For I will set My eyes on them for good, and I will bring them again to this land; and I will build them up and not overthrow them**, and I will plant them and not pluck them up. I will give them a heart to know Me, for I am the Lord; and they will be My people, and I will be their God, for they will return to Me with their whole heart. > > ‘**But like the bad figs which cannot be eaten due to rottenness**—indeed, thus says the Lord—so I will abandon Zedekiah king of Judah and his officials, and **the remnant of Jerusalem who remain in this land and the ones who dwell in the land of Egypt. I will make them a terror and an evil for all the kingdoms of the earth, as a reproach and a proverb, a taunt and a curse in all places where I will scatter them.** I will send the sword, the famine and the pestilence upon them until they are destroyed from the land which I gave to them and their forefathers.’ ” (Jeremiah 24:1-10) {Emphasis mine} God tells Jeremiah about two baskets of figs, one very good and one very bad. He then goes on to describe those Israelites who were kidnapped by Nebuchadnezzar and hauled off to Babylon and those that got to remain in Israel in their homes. Who would you think God was blessing and who would you think God was punishing? I would think the person hauled off into captivity was being punished and the one that got to stay in their comfortable home was being blessed, but it was the opposite. God said, “‘*Like these good figs, so I will regard as good the captives of Judah, whom I have sent out of this place into the land of the Chaldeans. For I will set My eyes on them for good, and I will bring them again to this land; and I will build them up and not overthrow them, and I will plant them and not pluck them up*.” (Jeremiah 24:5b-6) Those that got hauled away were being blessed. They were being protected from the judgment that God was about to bestow on Israel for their sin. It would have been very easy for the captives to moan, “Woe is us. Why would God do such horrible things to us?” even though God was protecting them. It would have been very easy for those who remained to think, “Those captives must have sinned very badly. Luckily, God doesn’t have any problems with me.” Instead God was punishing those who remained in Israel. He said, > But like the bad figs which cannot be eaten due to rottenness—indeed, thus says the Lord—so I will abandon Zedekiah king of Judah and his officials, and the remnant of Jerusalem who remain in this land and the ones who dwell in the land of Egypt. **I will make them a terror and an evil for all the kingdoms of the earth**, as a reproach and a proverb, a taunt and a curse in all places where I will scatter them. **I will send the sword, the famine and the pestilence upon them until they are destroyed from the land** which I gave to them and their forefathers.’ (Jeremiah 24:8-10) {Emphasis mine} While those who weren’t dragged away into captivity were congratulating themselves, the judgment of God fell upon them because they had rejected their God and were depending on the blessings promised to their ancestors. Those who were hauled into captivity were blessed and multiplied and then brought back to the promised land 70 years later. Even when they were not feeling blessed, God told them how to live in order to be blessed. > “Thus says the Lord of hosts, the God of Israel, to all the exiles whom I have sent into exile from Jerusalem to Babylon, ‘Build houses and live in them; and plant gardens and eat their produce. Take wives and become the fathers of sons and daughters, and take wives for your sons and give your daughters to husbands, that they may bear sons and daughters; and multiply there and do not decrease. **Seek the welfare of the city where I have sent you into exile, and pray to the Lord on its behalf; for in its welfare you will have welfare.** (Jeremiah 29:4-7) They were told to be fruitful and multiply in both a financial and a familial way. They were told to work hard while waiting for the fulfillment of God’s promises and in 70 years they and/or their families would return to the promised land. In a like manner, we are to be fruitful and multiply in whatever situation or in whatever country God has placed us. We are to stay faithful to Him and to honor Him in all we do wherever He has placed us. Whether we are literal exiles in a foreign country or not, we are all exiles from heaven waiting for Jesus to return and call us home. We are called to be productive while we wait. ## A Real Life Example of the Good Figs I got to see a similar example in my own life. I went through what most people would call a hellish year in 2015, but every thing that happened was for a blessing and not for a curse. I got to see how trusting in the Lord with all my heart led to blessings I couldn’t imagine. Technically our rough year started in November of 2014 with a flood and that is kind of how the next year felt. We had a house with hot water heat. Our family room had a large volume because the ceiling was two stories high. The room only had two heat registers. When we would get sub zero (F) temperatures, the room would drop in temperature, so we put in a wood and coal stove. It did a such a great job of heating the house that the heat wasn’t turning on and the pipes in the back office froze and burst the pipes. While we were at work, the temperatures warmed up, the pipes defrosted, and the water started streaming out flooding our entire downstairs. We then had get everything off the floor, flood cut the whole downstairs, and put in giant fans for 6 weeks to dry the wet floors and walls. It sounded like a 747 jet was sitting in the living room. I couldn’t hear myself think. It was very stressful, but that was just the beginning. We had a fight with the insurance company for \~8 months. They agreed about everything needing to be fixed, but wanted to pay only about half the cost to fix it. We finally had to break down and hire a lawyer. We settled with the insurance company writing us a check for 90% of the price of repairs. This settlement was a blessing in disguise. Because of the problems with our insurance company, we decided to switch to a new insurer. We set up to switch when our current policy expired. Ten days into our new policy, our house burnt down in a grass fire fueled by 60+ mph winds. In the main part of the house the only things recognizable were the coal stove and a 3 hour rated gun safe (that now looked like a cheap metal cabinet onto which someone dropped a nuclear bomb). We lost all of our physical possessions, but God had a plan. The new insurance company sent their insurance adjuster out right away. In one month they had paid for the house, the trees, the barn, and a year’s rent in a nice rental house. We had more than half of the settlement left from the flood (we had bought a few supplies for fixing the house). Exactly one year and one month later, we moved into our paid off dream home (with a very fire resistant exterior). Of course God didn’t finish His blessings and lessons with the fire, there was more to come. We moved into the rental house. (Ironically I was excited about all of the closet space even though I could fit all of my worldly possessions in a small suitcase. We humans are not always logical and we don’t let go of our physical possessions easily.) A month later, my husband’s car engine blew up. A month after that, my husband ruptured his Achilles tendon, had to go through surgery, and we were unable to travel to see family for Christmas as planned. It seemed like hardship, but the previous hardships had prepared us for this one. The house that burnt down had all of the bedrooms upstairs, all of the living spaces downstairs, and very steep stairs. When my husband ruptured his other Achilles tendon eight years previously, he had to stay on the couch downstairs and couldn’t sleep in his bed. In our new rental house, the master bedroom was on the same level as the living areas and not more than 10 feet away. He could sleep in bed and then use crutches to move to the electric recliner that had been donated to us after the fire. It gently raised and lowered his injured leg. He could sit with us to eat (we set up a table on one side of the recliner) and be with us when we hung out on the couch (on the other side of him). We could talk while I worked in the kitchen. It was so much nicer to take care of him in the rental house than it would’ve been if the same thing had happened, but our house hadn’t burnt down. Through this string of “tragedies,” we learned to trust God through every situation. We learned what was important (people not stuff). We got a nice, optimized, paid-off house. We received a story that we could share with others to bless them and help them trust in God. We grew closer together as a family. All four members of my family agree that if given the chance to make all of these “bad” things not happen, we would not choose to remove them. The blessings we received through them outweigh them more than you can imagine. ## What About You? What about you? Are you gong through hard times? We all do at some point in our lives. Are you looking for the good God is doing or are you blaming God for your hardship? Are you working to make the most of whatever situation you are in or are you seeking your own “better”? My prayer is that God will give you what you need and not what you want and that He will answer your prayers in His best timing. I pray that you will see the wondrous works of God in you and through you and that you will grow in your faith in our very good God. Trust Him! Turn to Him! Rely on Him! God is good, all of the time. Trust Jesus
@ 8d34bd24:414be32b
2025-02-19 16:43:17Last night I was reading Jeremiah 24 and I read the parable of the figs. I’ve read this passage many times, but suddenly I saw the irony of the situation. ## The Story of the Good and Bad Figs > After Nebuchadnezzar king of Babylon had carried away captive Jeconiah the son of Jehoiakim, king of Judah, and the officials of Judah with the craftsmen and smiths from Jerusalem and had brought them to Babylon, the Lord showed me: behold, two baskets of figs set before the temple of the Lord! One basket had very good figs, like first-ripe figs, and the other basket had very bad figs which could not be eaten due to rottenness. Then the Lord said to me, “What do you see, Jeremiah?” And I said, “Figs, the good figs, very good; and the bad figs, very bad, which cannot be eaten due to rottenness.” > > Then the word of the Lord came to me, saying, “Thus says the Lord God of Israel, ‘**Like these good figs, so I will regard as good the captives of Judah, whom I have sent out of this place into the land of the Chaldeans. For I will set My eyes on them for good, and I will bring them again to this land; and I will build them up and not overthrow them**, and I will plant them and not pluck them up. I will give them a heart to know Me, for I am the Lord; and they will be My people, and I will be their God, for they will return to Me with their whole heart. > > ‘**But like the bad figs which cannot be eaten due to rottenness**—indeed, thus says the Lord—so I will abandon Zedekiah king of Judah and his officials, and **the remnant of Jerusalem who remain in this land and the ones who dwell in the land of Egypt. I will make them a terror and an evil for all the kingdoms of the earth, as a reproach and a proverb, a taunt and a curse in all places where I will scatter them.** I will send the sword, the famine and the pestilence upon them until they are destroyed from the land which I gave to them and their forefathers.’ ” (Jeremiah 24:1-10) {Emphasis mine} God tells Jeremiah about two baskets of figs, one very good and one very bad. He then goes on to describe those Israelites who were kidnapped by Nebuchadnezzar and hauled off to Babylon and those that got to remain in Israel in their homes. Who would you think God was blessing and who would you think God was punishing? I would think the person hauled off into captivity was being punished and the one that got to stay in their comfortable home was being blessed, but it was the opposite. God said, “‘*Like these good figs, so I will regard as good the captives of Judah, whom I have sent out of this place into the land of the Chaldeans. For I will set My eyes on them for good, and I will bring them again to this land; and I will build them up and not overthrow them, and I will plant them and not pluck them up*.” (Jeremiah 24:5b-6) Those that got hauled away were being blessed. They were being protected from the judgment that God was about to bestow on Israel for their sin. It would have been very easy for the captives to moan, “Woe is us. Why would God do such horrible things to us?” even though God was protecting them. It would have been very easy for those who remained to think, “Those captives must have sinned very badly. Luckily, God doesn’t have any problems with me.” Instead God was punishing those who remained in Israel. He said, > But like the bad figs which cannot be eaten due to rottenness—indeed, thus says the Lord—so I will abandon Zedekiah king of Judah and his officials, and the remnant of Jerusalem who remain in this land and the ones who dwell in the land of Egypt. **I will make them a terror and an evil for all the kingdoms of the earth**, as a reproach and a proverb, a taunt and a curse in all places where I will scatter them. **I will send the sword, the famine and the pestilence upon them until they are destroyed from the land** which I gave to them and their forefathers.’ (Jeremiah 24:8-10) {Emphasis mine} While those who weren’t dragged away into captivity were congratulating themselves, the judgment of God fell upon them because they had rejected their God and were depending on the blessings promised to their ancestors. Those who were hauled into captivity were blessed and multiplied and then brought back to the promised land 70 years later. Even when they were not feeling blessed, God told them how to live in order to be blessed. > “Thus says the Lord of hosts, the God of Israel, to all the exiles whom I have sent into exile from Jerusalem to Babylon, ‘Build houses and live in them; and plant gardens and eat their produce. Take wives and become the fathers of sons and daughters, and take wives for your sons and give your daughters to husbands, that they may bear sons and daughters; and multiply there and do not decrease. **Seek the welfare of the city where I have sent you into exile, and pray to the Lord on its behalf; for in its welfare you will have welfare.** (Jeremiah 29:4-7) They were told to be fruitful and multiply in both a financial and a familial way. They were told to work hard while waiting for the fulfillment of God’s promises and in 70 years they and/or their families would return to the promised land. In a like manner, we are to be fruitful and multiply in whatever situation or in whatever country God has placed us. We are to stay faithful to Him and to honor Him in all we do wherever He has placed us. Whether we are literal exiles in a foreign country or not, we are all exiles from heaven waiting for Jesus to return and call us home. We are called to be productive while we wait. ## A Real Life Example of the Good Figs I got to see a similar example in my own life. I went through what most people would call a hellish year in 2015, but every thing that happened was for a blessing and not for a curse. I got to see how trusting in the Lord with all my heart led to blessings I couldn’t imagine. Technically our rough year started in November of 2014 with a flood and that is kind of how the next year felt. We had a house with hot water heat. Our family room had a large volume because the ceiling was two stories high. The room only had two heat registers. When we would get sub zero (F) temperatures, the room would drop in temperature, so we put in a wood and coal stove. It did a such a great job of heating the house that the heat wasn’t turning on and the pipes in the back office froze and burst the pipes. While we were at work, the temperatures warmed up, the pipes defrosted, and the water started streaming out flooding our entire downstairs. We then had get everything off the floor, flood cut the whole downstairs, and put in giant fans for 6 weeks to dry the wet floors and walls. It sounded like a 747 jet was sitting in the living room. I couldn’t hear myself think. It was very stressful, but that was just the beginning. We had a fight with the insurance company for \~8 months. They agreed about everything needing to be fixed, but wanted to pay only about half the cost to fix it. We finally had to break down and hire a lawyer. We settled with the insurance company writing us a check for 90% of the price of repairs. This settlement was a blessing in disguise. Because of the problems with our insurance company, we decided to switch to a new insurer. We set up to switch when our current policy expired. Ten days into our new policy, our house burnt down in a grass fire fueled by 60+ mph winds. In the main part of the house the only things recognizable were the coal stove and a 3 hour rated gun safe (that now looked like a cheap metal cabinet onto which someone dropped a nuclear bomb). We lost all of our physical possessions, but God had a plan. The new insurance company sent their insurance adjuster out right away. In one month they had paid for the house, the trees, the barn, and a year’s rent in a nice rental house. We had more than half of the settlement left from the flood (we had bought a few supplies for fixing the house). Exactly one year and one month later, we moved into our paid off dream home (with a very fire resistant exterior). Of course God didn’t finish His blessings and lessons with the fire, there was more to come. We moved into the rental house. (Ironically I was excited about all of the closet space even though I could fit all of my worldly possessions in a small suitcase. We humans are not always logical and we don’t let go of our physical possessions easily.) A month later, my husband’s car engine blew up. A month after that, my husband ruptured his Achilles tendon, had to go through surgery, and we were unable to travel to see family for Christmas as planned. It seemed like hardship, but the previous hardships had prepared us for this one. The house that burnt down had all of the bedrooms upstairs, all of the living spaces downstairs, and very steep stairs. When my husband ruptured his other Achilles tendon eight years previously, he had to stay on the couch downstairs and couldn’t sleep in his bed. In our new rental house, the master bedroom was on the same level as the living areas and not more than 10 feet away. He could sleep in bed and then use crutches to move to the electric recliner that had been donated to us after the fire. It gently raised and lowered his injured leg. He could sit with us to eat (we set up a table on one side of the recliner) and be with us when we hung out on the couch (on the other side of him). We could talk while I worked in the kitchen. It was so much nicer to take care of him in the rental house than it would’ve been if the same thing had happened, but our house hadn’t burnt down. Through this string of “tragedies,” we learned to trust God through every situation. We learned what was important (people not stuff). We got a nice, optimized, paid-off house. We received a story that we could share with others to bless them and help them trust in God. We grew closer together as a family. All four members of my family agree that if given the chance to make all of these “bad” things not happen, we would not choose to remove them. The blessings we received through them outweigh them more than you can imagine. ## What About You? What about you? Are you gong through hard times? We all do at some point in our lives. Are you looking for the good God is doing or are you blaming God for your hardship? Are you working to make the most of whatever situation you are in or are you seeking your own “better”? My prayer is that God will give you what you need and not what you want and that He will answer your prayers in His best timing. I pray that you will see the wondrous works of God in you and through you and that you will grow in your faith in our very good God. Trust Him! Turn to Him! Rely on Him! God is good, all of the time. Trust Jesus @ 42342239:1d80db24
2025-02-16 08:39:59Almost 150 years ago, the British newspaper editor William Thomas Stead wrote that "the editorial pen is a [sceptre of power](https://archive.org/details/GovernmentByJournalismWilliamThomasStead), compared with which the sceptre of many a monarch is but a gilded lath". He had begun to regard journalism as something more than just conveying information - **the journalist or editor could become a ruler.** Times had certainly changed compared to a few hundred years earlier. Before [Gutenberg's invention of the printing press](https://underorion.se/en/posts/gutenberg/), it was mainly the church that controlled the dissemination of information in Europe, but when Stead put pen to paper, this control had shifted to newspapers, schools, and universities. Eventually, technologies like radio and TV entered the scene, but the power dynamics remained asymmetrical - only a few could send information to the many. However, with the emergence of the internet, and especially with the spread of social media, a significant change followed. Instead of only a few being able to send information to the many, many could send to many. Almost anyone could now create their own newspaper, radio, or TV channel. **The power over information dissemination was decentralised.** [Ten years ago](https://www.di.se/ditv/rikets-affarer-medierna-ar-splittrade/), Roberta Alenius, who was then press secretary for Sweden's Prime Minister Fredrik Reinfeldt of the Moderate Party, shared her experiences with Social Democratic and Moderate Party internet activists on social media. She reported that social media played a significant role in how news "comes out" and is shaped, and that **journalism was now downstream of social media**. [Five years later](https://www.nato.int/cps/en/natohq/opinions_166392.htm), NATO's then-Secretary-General Jens Stoltenberg said that "NATO must be prepared for both conventional and hybrid threats: **from tanks to tweets**." This finally underscores the importance of social media. Elon Musk, who took over X (formerly Twitter) in 2022, has claimed that "it's absolutely fundamental and transformative that the people actually get to decide the news and narrative and what's important," and that [citizen journalism is the future](https://x.com/elonmusk/status/1870485116474278240). While his platform allows most expressions - for better or worse - the reach of messages is instead limited ("[freedom of speech does not mean freedom of reach](https://www.youtube.com/shorts/R9TuhTz0vmo) "). X has also opened its recommendation algorithm to the outside world by making it open-source. Although this is a welcome step, the fact remains that **it's impossible to know which code is actually used** and what adjustments are made by humans or algorithms. William Thomas Stead's "sceptre of power", which has wandered from the church to newspaper and TV editorial offices, and now to citizens according to Elon Musk, risks being transferred to algorithms' opaque methods? Instead of talking about "toxic algorithms" and TikTok bans, like the so many do today, we should ask ourselves more fundamental questions. What happens when algorithms are no longer objective (how can they ever be?), but instead become tools for shaping our reality? **Perhaps our greatest challenge today is not deciding who should govern the information landscape, but instead recognising that no one is up to the task** - not even well-ventilated computers.
@ 42342239:1d80db24
2025-02-16 08:39:59Almost 150 years ago, the British newspaper editor William Thomas Stead wrote that "the editorial pen is a [sceptre of power](https://archive.org/details/GovernmentByJournalismWilliamThomasStead), compared with which the sceptre of many a monarch is but a gilded lath". He had begun to regard journalism as something more than just conveying information - **the journalist or editor could become a ruler.** Times had certainly changed compared to a few hundred years earlier. Before [Gutenberg's invention of the printing press](https://underorion.se/en/posts/gutenberg/), it was mainly the church that controlled the dissemination of information in Europe, but when Stead put pen to paper, this control had shifted to newspapers, schools, and universities. Eventually, technologies like radio and TV entered the scene, but the power dynamics remained asymmetrical - only a few could send information to the many. However, with the emergence of the internet, and especially with the spread of social media, a significant change followed. Instead of only a few being able to send information to the many, many could send to many. Almost anyone could now create their own newspaper, radio, or TV channel. **The power over information dissemination was decentralised.** [Ten years ago](https://www.di.se/ditv/rikets-affarer-medierna-ar-splittrade/), Roberta Alenius, who was then press secretary for Sweden's Prime Minister Fredrik Reinfeldt of the Moderate Party, shared her experiences with Social Democratic and Moderate Party internet activists on social media. She reported that social media played a significant role in how news "comes out" and is shaped, and that **journalism was now downstream of social media**. [Five years later](https://www.nato.int/cps/en/natohq/opinions_166392.htm), NATO's then-Secretary-General Jens Stoltenberg said that "NATO must be prepared for both conventional and hybrid threats: **from tanks to tweets**." This finally underscores the importance of social media. Elon Musk, who took over X (formerly Twitter) in 2022, has claimed that "it's absolutely fundamental and transformative that the people actually get to decide the news and narrative and what's important," and that [citizen journalism is the future](https://x.com/elonmusk/status/1870485116474278240). While his platform allows most expressions - for better or worse - the reach of messages is instead limited ("[freedom of speech does not mean freedom of reach](https://www.youtube.com/shorts/R9TuhTz0vmo) "). X has also opened its recommendation algorithm to the outside world by making it open-source. Although this is a welcome step, the fact remains that **it's impossible to know which code is actually used** and what adjustments are made by humans or algorithms. William Thomas Stead's "sceptre of power", which has wandered from the church to newspaper and TV editorial offices, and now to citizens according to Elon Musk, risks being transferred to algorithms' opaque methods? Instead of talking about "toxic algorithms" and TikTok bans, like the so many do today, we should ask ourselves more fundamental questions. What happens when algorithms are no longer objective (how can they ever be?), but instead become tools for shaping our reality? **Perhaps our greatest challenge today is not deciding who should govern the information landscape, but instead recognising that no one is up to the task** - not even well-ventilated computers. @ 9e69e420:d12360c2
2025-02-15 20:24:09Ukraine's President Volodymyr Zelensky called for an "army of Europe" to defend against Russian threats, emphasizing that the US may not continue its traditional support for Europe. Speaking at the Munich Security Conference, he warned against peace deals made without Ukraine's involvement. US Vice President JD Vance echoed this sentiment, urging Europe to enhance its defense efforts. Zelensky stated, "I really believe the time has come - the armed forces of Europe must be created." He highlighted changing dynamics in US-Europe relations and noted that "the old days are over" regarding American support. Despite discussions around NATO, Zelensky stated he wouldn't rule out NATO membership for Ukraine.
@ 9e69e420:d12360c2
2025-02-15 20:24:09Ukraine's President Volodymyr Zelensky called for an "army of Europe" to defend against Russian threats, emphasizing that the US may not continue its traditional support for Europe. Speaking at the Munich Security Conference, he warned against peace deals made without Ukraine's involvement. US Vice President JD Vance echoed this sentiment, urging Europe to enhance its defense efforts. Zelensky stated, "I really believe the time has come - the armed forces of Europe must be created." He highlighted changing dynamics in US-Europe relations and noted that "the old days are over" regarding American support. Despite discussions around NATO, Zelensky stated he wouldn't rule out NATO membership for Ukraine. @ fd208ee8:0fd927c1
2025-02-15 07:37:01E-cash are coupons or tokens for Bitcoin, or Bitcoin debt notes that the mint issues. The e-cash states, essentially, "IoU 2900 sats". They're redeemable for Bitcoin on Lightning (hard money), and therefore can be used as cash (softer money), so long as the mint has a good reputation. That means that they're less fungible than Lightning because the e-cash from one mint can be more or less valuable than the e-cash from another. If a mint is buggy, offline, or disappears, then the e-cash is unreedemable. It also means that e-cash is more anonymous than Lightning, and that the sender and receiver's wallets don't need to be online, to transact. Nutzaps now add the possibility of parking transactions one level farther out, on a relay. The same relays that cannot keep npub profiles and follow lists consistent will now do monetary transactions. What we then have is * a **transaction on a relay** that triggers * a **transaction on a mint** that triggers * a **transaction on Lightning** that triggers * a **transaction on Bitcoin**. Which means that every relay that stores the nuts is part of a wildcat banking system. Which is fine, but relay operators should consider whether they wish to carry the associated risks and liabilities. They should also be aware that they should implement the appropriate features in their relay, such as expiration tags (nuts rot after 2 weeks), and to make sure that only expired nuts are deleted. There will be plenty of specialized relays for this, so don't feel pressured to join in, and research the topic carefully, for yourself. https://github.com/nostr-protocol/nips/blob/master/60.md https://github.com/nostr-protocol/nips/blob/master/61.md
@ fd208ee8:0fd927c1
2025-02-15 07:37:01E-cash are coupons or tokens for Bitcoin, or Bitcoin debt notes that the mint issues. The e-cash states, essentially, "IoU 2900 sats". They're redeemable for Bitcoin on Lightning (hard money), and therefore can be used as cash (softer money), so long as the mint has a good reputation. That means that they're less fungible than Lightning because the e-cash from one mint can be more or less valuable than the e-cash from another. If a mint is buggy, offline, or disappears, then the e-cash is unreedemable. It also means that e-cash is more anonymous than Lightning, and that the sender and receiver's wallets don't need to be online, to transact. Nutzaps now add the possibility of parking transactions one level farther out, on a relay. The same relays that cannot keep npub profiles and follow lists consistent will now do monetary transactions. What we then have is * a **transaction on a relay** that triggers * a **transaction on a mint** that triggers * a **transaction on Lightning** that triggers * a **transaction on Bitcoin**. Which means that every relay that stores the nuts is part of a wildcat banking system. Which is fine, but relay operators should consider whether they wish to carry the associated risks and liabilities. They should also be aware that they should implement the appropriate features in their relay, such as expiration tags (nuts rot after 2 weeks), and to make sure that only expired nuts are deleted. There will be plenty of specialized relays for this, so don't feel pressured to join in, and research the topic carefully, for yourself. https://github.com/nostr-protocol/nips/blob/master/60.md https://github.com/nostr-protocol/nips/blob/master/61.md @ 0fa80bd3:ea7325de
2025-02-14 23:24:37#intro The Russian state made me a Bitcoiner. In 1991, it devalued my grandmother's hard-earned savings. She worked tirelessly in the kitchen of a dining car on the Moscow–Warsaw route. Everything she had saved for my sister and me to attend university vanished overnight. This story is similar to what many experienced, including Wences Casares. The pain and injustice of that time became my first lessons about the fragility of systems and the value of genuine, incorruptible assets, forever changing my perception of money and my trust in government promises. In 2014, I was living in Moscow, running a trading business, and frequently traveling to China. One day, I learned about the Cypriot banking crisis and the possibility of moving money through some strange thing called Bitcoin. At the time, I didn’t give it much thought. Returning to the idea six months later, as a business-oriented geek, I eagerly began studying the topic and soon dove into it seriously. I spent half a year reading articles on a local online journal, BitNovosti, actively participating in discussions, and eventually joined the editorial team as a translator. That’s how I learned about whitepapers, decentralization, mining, cryptographic keys, and colored coins. About Satoshi Nakamoto, Silk Road, Mt. Gox, and BitcoinTalk. Over time, I befriended the journal’s owner and, leveraging my management experience, later became an editor. I was drawn to the crypto-anarchist stance and commitment to decentralization principles. We wrote about the economic, historical, and social preconditions for Bitcoin’s emergence, and it was during this time that I fully embraced the idea. It got to the point where I sold my apartment and, during the market's downturn, bought 50 bitcoins, just after the peak price of $1,200 per coin. That marked the beginning of my first crypto winter. As an editor, I organized workflows, managed translators, developed a YouTube channel, and attended conferences in Russia and Ukraine. That’s how I learned about Wences Casares and even wrote a piece about him. I also met Mikhail Chobanyan (Ukrainian exchange Kuna), Alexander Ivanov (Waves project), Konstantin Lomashuk (Lido project), and, of course, Vitalik Buterin. It was a time of complete immersion, 24/7, and boundless hope. After moving to the United States, I expected the industry to grow rapidly, attended events, but the introduction of BitLicense froze the industry for eight years. By 2017, it became clear that the industry was shifting toward gambling and creating tokens for the sake of tokens. I dismissed this idea as unsustainable. Then came a new crypto spring with the hype around beautiful NFTs – CryptoPunks and apes. I made another attempt – we worked on a series called Digital Nomad Country Club, aimed at creating a global project. The proceeds from selling images were intended to fund the development of business tools for people worldwide. However, internal disagreements within the team prevented us from completing the project. With Trump’s arrival in 2025, hope was reignited. I decided that it was time to create a project that society desperately needed. As someone passionate about history, I understood that destroying what exists was not the solution, but leaving everything as it was also felt unacceptable. You can’t destroy the system, as the fiery crypto-anarchist voices claimed. With an analytical mindset (IQ 130) and a deep understanding of the freest societies, I realized what was missing—not only in Russia or the United States but globally—a Bitcoin-native system for tracking debts and financial interactions. This could return control of money to ordinary people and create horizontal connections parallel to state systems. My goal was to create, if not a Bitcoin killer app, then at least to lay its foundation. At the inauguration event in New York, I rediscovered the Nostr project. I realized it was not only technologically simple and already quite popular but also perfectly aligned with my vision. For the past month and a half, using insights and experience gained since 2014, I’ve been working full-time on this project.
@ 0fa80bd3:ea7325de
2025-02-14 23:24:37#intro The Russian state made me a Bitcoiner. In 1991, it devalued my grandmother's hard-earned savings. She worked tirelessly in the kitchen of a dining car on the Moscow–Warsaw route. Everything she had saved for my sister and me to attend university vanished overnight. This story is similar to what many experienced, including Wences Casares. The pain and injustice of that time became my first lessons about the fragility of systems and the value of genuine, incorruptible assets, forever changing my perception of money and my trust in government promises. In 2014, I was living in Moscow, running a trading business, and frequently traveling to China. One day, I learned about the Cypriot banking crisis and the possibility of moving money through some strange thing called Bitcoin. At the time, I didn’t give it much thought. Returning to the idea six months later, as a business-oriented geek, I eagerly began studying the topic and soon dove into it seriously. I spent half a year reading articles on a local online journal, BitNovosti, actively participating in discussions, and eventually joined the editorial team as a translator. That’s how I learned about whitepapers, decentralization, mining, cryptographic keys, and colored coins. About Satoshi Nakamoto, Silk Road, Mt. Gox, and BitcoinTalk. Over time, I befriended the journal’s owner and, leveraging my management experience, later became an editor. I was drawn to the crypto-anarchist stance and commitment to decentralization principles. We wrote about the economic, historical, and social preconditions for Bitcoin’s emergence, and it was during this time that I fully embraced the idea. It got to the point where I sold my apartment and, during the market's downturn, bought 50 bitcoins, just after the peak price of $1,200 per coin. That marked the beginning of my first crypto winter. As an editor, I organized workflows, managed translators, developed a YouTube channel, and attended conferences in Russia and Ukraine. That’s how I learned about Wences Casares and even wrote a piece about him. I also met Mikhail Chobanyan (Ukrainian exchange Kuna), Alexander Ivanov (Waves project), Konstantin Lomashuk (Lido project), and, of course, Vitalik Buterin. It was a time of complete immersion, 24/7, and boundless hope. After moving to the United States, I expected the industry to grow rapidly, attended events, but the introduction of BitLicense froze the industry for eight years. By 2017, it became clear that the industry was shifting toward gambling and creating tokens for the sake of tokens. I dismissed this idea as unsustainable. Then came a new crypto spring with the hype around beautiful NFTs – CryptoPunks and apes. I made another attempt – we worked on a series called Digital Nomad Country Club, aimed at creating a global project. The proceeds from selling images were intended to fund the development of business tools for people worldwide. However, internal disagreements within the team prevented us from completing the project. With Trump’s arrival in 2025, hope was reignited. I decided that it was time to create a project that society desperately needed. As someone passionate about history, I understood that destroying what exists was not the solution, but leaving everything as it was also felt unacceptable. You can’t destroy the system, as the fiery crypto-anarchist voices claimed. With an analytical mindset (IQ 130) and a deep understanding of the freest societies, I realized what was missing—not only in Russia or the United States but globally—a Bitcoin-native system for tracking debts and financial interactions. This could return control of money to ordinary people and create horizontal connections parallel to state systems. My goal was to create, if not a Bitcoin killer app, then at least to lay its foundation. At the inauguration event in New York, I rediscovered the Nostr project. I realized it was not only technologically simple and already quite popular but also perfectly aligned with my vision. For the past month and a half, using insights and experience gained since 2014, I’ve been working full-time on this project. @ 9e69e420:d12360c2
2025-02-14 18:07:10Vice President J.D. Vance addressed the Munich Security Conference, criticizing European leaders for undermining free speech and traditional values. He claimed that the biggest threat to Europe is not from external enemies but from internal challenges. Vance condemned the arrest of a British man for praying near an abortion clinic and accused European politicians of censorship. He urged leaders to combat illegal immigration and questioned their democratic practices. “There is a new sheriff in town,” he said, referring to President Trump. Vance's remarks were unexpected, as many anticipated discussions on security or Ukraine. His speech emphasized the need for Europe to share the defense burden to ensure stability and security.
@ 9e69e420:d12360c2
2025-02-14 18:07:10Vice President J.D. Vance addressed the Munich Security Conference, criticizing European leaders for undermining free speech and traditional values. He claimed that the biggest threat to Europe is not from external enemies but from internal challenges. Vance condemned the arrest of a British man for praying near an abortion clinic and accused European politicians of censorship. He urged leaders to combat illegal immigration and questioned their democratic practices. “There is a new sheriff in town,” he said, referring to President Trump. Vance's remarks were unexpected, as many anticipated discussions on security or Ukraine. His speech emphasized the need for Europe to share the defense burden to ensure stability and security. @ 9e69e420:d12360c2
2025-02-14 15:14:34A Russian drone attack has struck the radiation shelter at Chernobyl, according to Ukrainian President Volodymyr Zelensky. The strike caused a fire, but it has since been extinguished, and radiation levels remain stable. The International Atomic Energy Agency (IAEA) confirmed that no casualties occurred and that monitoring continues. Rafael Mariano Grossi, IAEA's director general, emphasized the need for caution. Chernobyl, site of the 1986 nuclear disaster, contains a protective shield costing $1.6 billion. Disaster prevention remains a priority as the conflict unfolds. The incident occurred shortly before the meeting of world powers at the Munich Security Conference in Germany.
@ 9e69e420:d12360c2
2025-02-14 15:14:34A Russian drone attack has struck the radiation shelter at Chernobyl, according to Ukrainian President Volodymyr Zelensky. The strike caused a fire, but it has since been extinguished, and radiation levels remain stable. The International Atomic Energy Agency (IAEA) confirmed that no casualties occurred and that monitoring continues. Rafael Mariano Grossi, IAEA's director general, emphasized the need for caution. Chernobyl, site of the 1986 nuclear disaster, contains a protective shield costing $1.6 billion. Disaster prevention remains a priority as the conflict unfolds. The incident occurred shortly before the meeting of world powers at the Munich Security Conference in Germany. @ 9e69e420:d12360c2
2025-02-13 23:01:36Robert F. Kennedy Jr. has been confirmed as the next Secretary of Health and Human Services with a Senate vote of 52-48. Senator Mitch McConnell opposed the confirmation. Kennedy's nomination faced hurdles but gained support from the Senate Finance Committee. During the confirmation hearing, Senator Rand Paul criticized the oversimplification of vaccine discussions. He stated, "Discussion over vaccines is so oversimplified and dumbed down." Kennedy asserted his support for vaccines like measles and polio, promising not to discourage vaccinations as HHS Secretary. Previously, he switched from the Democratic Party to run as an independent and endorsed Trump
@ 9e69e420:d12360c2
2025-02-13 23:01:36Robert F. Kennedy Jr. has been confirmed as the next Secretary of Health and Human Services with a Senate vote of 52-48. Senator Mitch McConnell opposed the confirmation. Kennedy's nomination faced hurdles but gained support from the Senate Finance Committee. During the confirmation hearing, Senator Rand Paul criticized the oversimplification of vaccine discussions. He stated, "Discussion over vaccines is so oversimplified and dumbed down." Kennedy asserted his support for vaccines like measles and polio, promising not to discourage vaccinations as HHS Secretary. Previously, he switched from the Democratic Party to run as an independent and endorsed Trump @ e3ba5e1a:5e433365
2025-02-13 06:16:49My favorite line in any Marvel movie ever is in “Captain America.” After Captain America launches seemingly a hopeless assault on Red Skull’s base and is captured, we get [this line](https://www.youtube.com/shorts/kqsomjpz7ok): “Arrogance may not be a uniquely American trait, but I must say, you do it better than anyone.” Yesterday, I came across a comment on the song [Devil Went Down to Georgia](https://youtu.be/ut8UqFlWdDc) that had a very similar feel to it:  America has seemingly always been arrogant, in a uniquely American way. Manifest Destiny, for instance. The rest of the world is aware of this arrogance, and mocks Americans for it. A central point in modern US politics is the deriding of racist, nationalist, supremacist Americans. That’s not what I see. I see American Arrogance as not only a beautiful statement about what it means to be American. I see it as an ode to the greatness of humanity in its purest form. For most countries, saying “our nation is the greatest” *is*, in fact, twinged with some level of racism. I still don’t have a problem with it. Every group of people *should* be allowed to feel pride in their accomplishments. The destruction of the human spirit since the end of World War 2, where greatness has become a sin and weakness a virtue, has crushed the ability of people worldwide to strive for excellence. But I digress. The fears of racism and nationalism at least have a grain of truth when applied to other nations on the planet. But not to America. That’s because the definition of America, and the prototype of an American, has nothing to do with race. The definition of Americanism is *freedom*. The founding of America is based purely on liberty. On the God-given rights of every person to live life the way they see fit. American Arrogance is not a statement of racial superiority. It’s barely a statement of national superiority (though it absolutely is). To me, when an American comments on the greatness of America, it’s a statement about freedom. Freedom will always unlock the greatness inherent in any group of people. Americans are *definitionally* better than everyone else, because Americans are freer than everyone else. (Or, at least, that’s how it should be.) In *Devil Went Down to Georgia*, Johnny is approached by the devil himself. He is challenged to a ridiculously lopsided bet: a golden fiddle versus his immortal soul. He acknowledges the sin in accepting such a proposal. And yet he says, “God, I know you told me not to do this. But I can’t stand the affront to my honor. I am the greatest. The devil has nothing on me. So God, I’m gonna sin, but I’m also gonna win.” *Libertas magnitudo est*
@ e3ba5e1a:5e433365
2025-02-13 06:16:49My favorite line in any Marvel movie ever is in “Captain America.” After Captain America launches seemingly a hopeless assault on Red Skull’s base and is captured, we get [this line](https://www.youtube.com/shorts/kqsomjpz7ok): “Arrogance may not be a uniquely American trait, but I must say, you do it better than anyone.” Yesterday, I came across a comment on the song [Devil Went Down to Georgia](https://youtu.be/ut8UqFlWdDc) that had a very similar feel to it:  America has seemingly always been arrogant, in a uniquely American way. Manifest Destiny, for instance. The rest of the world is aware of this arrogance, and mocks Americans for it. A central point in modern US politics is the deriding of racist, nationalist, supremacist Americans. That’s not what I see. I see American Arrogance as not only a beautiful statement about what it means to be American. I see it as an ode to the greatness of humanity in its purest form. For most countries, saying “our nation is the greatest” *is*, in fact, twinged with some level of racism. I still don’t have a problem with it. Every group of people *should* be allowed to feel pride in their accomplishments. The destruction of the human spirit since the end of World War 2, where greatness has become a sin and weakness a virtue, has crushed the ability of people worldwide to strive for excellence. But I digress. The fears of racism and nationalism at least have a grain of truth when applied to other nations on the planet. But not to America. That’s because the definition of America, and the prototype of an American, has nothing to do with race. The definition of Americanism is *freedom*. The founding of America is based purely on liberty. On the God-given rights of every person to live life the way they see fit. American Arrogance is not a statement of racial superiority. It’s barely a statement of national superiority (though it absolutely is). To me, when an American comments on the greatness of America, it’s a statement about freedom. Freedom will always unlock the greatness inherent in any group of people. Americans are *definitionally* better than everyone else, because Americans are freer than everyone else. (Or, at least, that’s how it should be.) In *Devil Went Down to Georgia*, Johnny is approached by the devil himself. He is challenged to a ridiculously lopsided bet: a golden fiddle versus his immortal soul. He acknowledges the sin in accepting such a proposal. And yet he says, “God, I know you told me not to do this. But I can’t stand the affront to my honor. I am the greatest. The devil has nothing on me. So God, I’m gonna sin, but I’m also gonna win.” *Libertas magnitudo est* @ 18e3af1e:1d42e5df
2023-08-13 02:40:19Las comunidades son creadas mediante el esfuerzo de no solo un individuo, sino al trabajo de docenas; cientos o miles de personas. Mediante la especialización, como especie, logramos entender que: el saber hacer una sola cosa no significa morir de hambre, o no estar bien preparado para un ataque; por lo contrario, el dominio o maestría de una sola cosa... Puede crear una civilización entera. Permitirnos un enfoque certero para aprender, dominar y amaestrar nuestras actividades en un periodo de tiempo finito, permitió nuestro avance hacia nuevos campos, de hecho, movió nuestra meta en magnitud tal, que al imaginar el pasado (para muchos) parece mas bien una película cómica y sombría. Hoy en día, en un mundo regido por individualismo en el reino físico, la manifestación de constructores de comunidades sigue presente en el (reino) digital. ### La evolución de la construcción A lo largo de la historia de la humanidad, la construcción ha evolucionado desde simples refugios hasta monumentos arquitectónicos y estructuras vanguardistas. Los primeros humanos crearon refugios rudimentarios con materiales naturales. Con la civilización, surgieron las primeras estructuras permanentes, como pirámides y templos, reflejando la organización social y creencias religiosas. La antigua Roma introdujo la innovación en la ingeniería con acueductos y arcos. La Edad Media vio fortificaciones y catedrales góticas que fusionaban espiritualidad y técnica. El Renacimiento abrazó la proporción y la simetría en palacios y edificios renombrados. La Revolución Industrial marcó un cambio radical con el acero y el hormigón, permitiendo rascacielos y puentes icónicos. El siglo XX trajo consigo la era de los rascacielos y la arquitectura modernista, desafiando límites estructurales y estéticos. La sostenibilidad ganó importancia en el siglo XXI, impulsando la incorporación de tecnologías avanzadas, como la impresión 3D y la construcción modular. La historia de la construcción es un testimonio de la creatividad y la adaptabilidad humanas, reflejando no solo avances técnicos, sino también valores culturales y aspiraciones. En el día hoy, los desarrolladores de software y tecnología podrían considerarse como los constructores del próximo siglo. Al igual que los constructores en otras épocas históricas, los desarrolladores de software son responsables de crear estructuras digitales que moldean la forma en que interactuamos, comunicamos y vivimos en el mundo moderno. A medida que la tecnología continúa avanzando y la sociedad se vuelve cada vez más digital, el papel de los desarrolladores de software se vuelve crucial en la construcción de soluciones tecnológicas que abordan una amplia gama de desafíos. Así como los arquitectos y constructores antiguos debían entender la física, la estética y las necesidades humanas para diseñar y construir edificios funcionales y atractivos, los desarrolladores de software deben comprender la lógica de programación, la experiencia del usuario, la seguridad cibernética y la innovación tecnológica para crear aplicaciones, sistemas y plataformas que sean útiles y efectivos. ### Individuos que inspiran La inspiración individual es un poderoso motor de cambio que puede tener un impacto significativo en la mente colectiva de una comunidad o sociedad. Cuando una persona demuestra pasión, determinación y una visión positiva, puede influir en otros a nivel emocional y cognitivo. Aquí hay algunas formas en que la inspiración individual afecta a la mente colectiva: La gente puede verse reflejada en las luchas y logros de alguien más, lo que crea un sentido de unidad y comunidad. Esto puede generar un mayor apoyo y solidaridad en torno a ciertas causas o valores. Además, la inspiración individual puede llevar a la acción. Cuando las personas son testigos de un individuo que supera obstáculos o logra metas desafiantes, esto puede motivar a otros a enfrentar sus propios desafíos y trabajar hacia sus objetivos. El ejemplo de una sola persona puede encender la chispa de la acción en muchas más. La inspiración individual puede tener un efecto multiplicador. Cuando una persona inspirada comparte su historia o experiencia, puede inspirar a otros, creando una cadena de influencia que se extiende a través de redes sociales, comunidades y sociedades enteras. Esto puede tener un impacto a gran escala en la mente colectiva. El individuo inspirador tiene el potencial de influir profundamente en la mente colectiva al cambiar percepciones, motivar la acción y crear una sensación de comunidad y unidad. ### Comunidades: origen, inicios y progreso. Las comunidades han sido una parte fundamental de la experiencia humana a lo largo de la historia. Desde los primeros tiempos hasta la era moderna, las comunidades han evolucionado y cambiado en respuesta a las necesidades, avances tecnológicos y contextos culturales. Desde los primeros días de la humanidad, nuestros antepasados se agruparon en pequeñas comunidades para sobrevivir. Estas comunidades eran grupos familiares o tribus que compartían recursos y conocimientos para cazar, recolectar alimentos y protegerse de los peligros. La cooperación y la solidaridad eran esenciales para la supervivencia. Con el desarrollo de la agricultura, las comunidades evolucionaron hacia asentamientos más permanentes. La capacidad de cultivar alimentos permitió la formación de aldeas y pueblos, donde la gente podía establecerse y construir relaciones más complejas. Esto llevó al surgimiento de una división del trabajo más especializada y al desarrollo de habilidades artesanales. Las civilizaciones antiguas, como la sumeria, egipcia, griega y romana, dieron paso a la formación de ciudades y sociedades más organizadas. Las comunidades se convirtieron en centros de comercio, gobierno y cultura. Se construyeron estructuras monumentales, como templos y palacios, que unificaron a las personas en torno a creencias religiosas y sistemas políticos. Durante la Edad Media, las comunidades se organizaron en torno a sistemas feudales. Los señores feudales gobernaban sobre las tierras y las personas locales. Las aldeas y feudos eran autónomos en gran medida y se centraban en la agricultura y la autosuficiencia. La Revolución Industrial marcó un cambio importante en la estructura de las comunidades. La industrialización dio lugar a la urbanización, con muchas personas dejando las zonas rurales para trabajar en fábricas en las ciudades. En la era moderna, las comunidades han continuado evolucionando con avances tecnológicos y la globalización. Las redes sociales y las comunicaciones digitales han conectado a personas de todo el mundo, creando comunidades virtuales en línea. ### Bitcoin | Nostr y la chispa del constructor Como ya vimos, un solo individuo puede inspirar a muchos otros, teniendo un efecto multiplicador. Esto no solo se traduce al mundo físico, por el contrario, esta directamente ligado a nuestra psicología, incluso podemos decir que va aun mas allá, adentrándonos en el terreno ideológico y espiritual. Hasta hace no mucho, estábamos a merced de las grandes corporaciones que construían todo por nosotros, mientras esperábamos con ansias las nuevas actualizaciones de cada iteración de sus productos. Cada vez mas y mas nos hacíamos dependientes de dichas corporaciones sin quizás notarlo, poco a poco se fueron apoderando de nuestro tiempo y muy insidiosamente de nuestra personalidad e identidad. Gracias a las alternativas presentadas hoy en día y a los individuos que inspiran a otros, existe la posibilidad de construir algo que va mas allá de las grandes corporaciones, porque transciende no solo el nivel físico y digital, sino que también transciende a los individuos que aportan a la comunidad. Estoy hablando por supuesto de Nostr, y como los incentivos están alineados gracias a Bitcoin. Pongamos como ejemplo un par de nombres para ilustrar como individuos que inspirar pueden crear una chispa que se extiende a cada persona dentro de la comunidad. Personajes como nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft nostr:npub1utx00neqgqln72j22kej3ux7803c2k986henvvha4thuwfkper4s7r50e8 nostr:npub1v0lxxxxutpvrelsksy8cdhgfux9l6a42hsj2qzquu2zk7vc9qnkszrqj49 nostr:npub107jk7htfv243u0x5ynn43scq9wrxtaasmrwwa8lfu2ydwag6cx2quqncxg (entre muchos otros que podría mencionar pero todo el articulo seria una lista de nombres) han inspirado a otros desarrolladores, creadores de contenido (y todas las otras especializaciones que te puedas imaginar…) A construir sobre este protocolo. Incluso, personas como el caso mas reciente de nostr:npub1m64hnkh6rs47fd9x6wk2zdtmdj4qkazt734d22d94ery9zzhne5qw9uaks han encontrado inspiración para aprender a programar sobre estos mismos rieles. > nostr:nevent1qqs8fe938k7j5sxcprrv89ezpu09m9pzm90f0sq24hnwlwu0rmn09qcpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxg5vtygh La chispa del constructor en palabras mas concisas es: **Inspiración multiplicadora en pos de la productividad y por ende, del crecimiento de una comunidad.** Sin Bitcoin y Lightning Network, esto seria posible, pero mucho menos efectivo debido a que las personas detrás de toda labor que este enfocada en creación de contenido, desarrollo, etc. Tienen que comer. ### Conclusión La chispa del constructor radica en la inspiración individual que impulsa a la acción colectiva. Desde la evolución de la construcción hasta las comunidades digitales, **el poder de un individuo inspirado puede moldear el presente y el futuro de las comunidades en todo el mundo.**
@ 18e3af1e:1d42e5df
2023-08-13 02:40:19Las comunidades son creadas mediante el esfuerzo de no solo un individuo, sino al trabajo de docenas; cientos o miles de personas. Mediante la especialización, como especie, logramos entender que: el saber hacer una sola cosa no significa morir de hambre, o no estar bien preparado para un ataque; por lo contrario, el dominio o maestría de una sola cosa... Puede crear una civilización entera. Permitirnos un enfoque certero para aprender, dominar y amaestrar nuestras actividades en un periodo de tiempo finito, permitió nuestro avance hacia nuevos campos, de hecho, movió nuestra meta en magnitud tal, que al imaginar el pasado (para muchos) parece mas bien una película cómica y sombría. Hoy en día, en un mundo regido por individualismo en el reino físico, la manifestación de constructores de comunidades sigue presente en el (reino) digital. ### La evolución de la construcción A lo largo de la historia de la humanidad, la construcción ha evolucionado desde simples refugios hasta monumentos arquitectónicos y estructuras vanguardistas. Los primeros humanos crearon refugios rudimentarios con materiales naturales. Con la civilización, surgieron las primeras estructuras permanentes, como pirámides y templos, reflejando la organización social y creencias religiosas. La antigua Roma introdujo la innovación en la ingeniería con acueductos y arcos. La Edad Media vio fortificaciones y catedrales góticas que fusionaban espiritualidad y técnica. El Renacimiento abrazó la proporción y la simetría en palacios y edificios renombrados. La Revolución Industrial marcó un cambio radical con el acero y el hormigón, permitiendo rascacielos y puentes icónicos. El siglo XX trajo consigo la era de los rascacielos y la arquitectura modernista, desafiando límites estructurales y estéticos. La sostenibilidad ganó importancia en el siglo XXI, impulsando la incorporación de tecnologías avanzadas, como la impresión 3D y la construcción modular. La historia de la construcción es un testimonio de la creatividad y la adaptabilidad humanas, reflejando no solo avances técnicos, sino también valores culturales y aspiraciones. En el día hoy, los desarrolladores de software y tecnología podrían considerarse como los constructores del próximo siglo. Al igual que los constructores en otras épocas históricas, los desarrolladores de software son responsables de crear estructuras digitales que moldean la forma en que interactuamos, comunicamos y vivimos en el mundo moderno. A medida que la tecnología continúa avanzando y la sociedad se vuelve cada vez más digital, el papel de los desarrolladores de software se vuelve crucial en la construcción de soluciones tecnológicas que abordan una amplia gama de desafíos. Así como los arquitectos y constructores antiguos debían entender la física, la estética y las necesidades humanas para diseñar y construir edificios funcionales y atractivos, los desarrolladores de software deben comprender la lógica de programación, la experiencia del usuario, la seguridad cibernética y la innovación tecnológica para crear aplicaciones, sistemas y plataformas que sean útiles y efectivos. ### Individuos que inspiran La inspiración individual es un poderoso motor de cambio que puede tener un impacto significativo en la mente colectiva de una comunidad o sociedad. Cuando una persona demuestra pasión, determinación y una visión positiva, puede influir en otros a nivel emocional y cognitivo. Aquí hay algunas formas en que la inspiración individual afecta a la mente colectiva: La gente puede verse reflejada en las luchas y logros de alguien más, lo que crea un sentido de unidad y comunidad. Esto puede generar un mayor apoyo y solidaridad en torno a ciertas causas o valores. Además, la inspiración individual puede llevar a la acción. Cuando las personas son testigos de un individuo que supera obstáculos o logra metas desafiantes, esto puede motivar a otros a enfrentar sus propios desafíos y trabajar hacia sus objetivos. El ejemplo de una sola persona puede encender la chispa de la acción en muchas más. La inspiración individual puede tener un efecto multiplicador. Cuando una persona inspirada comparte su historia o experiencia, puede inspirar a otros, creando una cadena de influencia que se extiende a través de redes sociales, comunidades y sociedades enteras. Esto puede tener un impacto a gran escala en la mente colectiva. El individuo inspirador tiene el potencial de influir profundamente en la mente colectiva al cambiar percepciones, motivar la acción y crear una sensación de comunidad y unidad. ### Comunidades: origen, inicios y progreso. Las comunidades han sido una parte fundamental de la experiencia humana a lo largo de la historia. Desde los primeros tiempos hasta la era moderna, las comunidades han evolucionado y cambiado en respuesta a las necesidades, avances tecnológicos y contextos culturales. Desde los primeros días de la humanidad, nuestros antepasados se agruparon en pequeñas comunidades para sobrevivir. Estas comunidades eran grupos familiares o tribus que compartían recursos y conocimientos para cazar, recolectar alimentos y protegerse de los peligros. La cooperación y la solidaridad eran esenciales para la supervivencia. Con el desarrollo de la agricultura, las comunidades evolucionaron hacia asentamientos más permanentes. La capacidad de cultivar alimentos permitió la formación de aldeas y pueblos, donde la gente podía establecerse y construir relaciones más complejas. Esto llevó al surgimiento de una división del trabajo más especializada y al desarrollo de habilidades artesanales. Las civilizaciones antiguas, como la sumeria, egipcia, griega y romana, dieron paso a la formación de ciudades y sociedades más organizadas. Las comunidades se convirtieron en centros de comercio, gobierno y cultura. Se construyeron estructuras monumentales, como templos y palacios, que unificaron a las personas en torno a creencias religiosas y sistemas políticos. Durante la Edad Media, las comunidades se organizaron en torno a sistemas feudales. Los señores feudales gobernaban sobre las tierras y las personas locales. Las aldeas y feudos eran autónomos en gran medida y se centraban en la agricultura y la autosuficiencia. La Revolución Industrial marcó un cambio importante en la estructura de las comunidades. La industrialización dio lugar a la urbanización, con muchas personas dejando las zonas rurales para trabajar en fábricas en las ciudades. En la era moderna, las comunidades han continuado evolucionando con avances tecnológicos y la globalización. Las redes sociales y las comunicaciones digitales han conectado a personas de todo el mundo, creando comunidades virtuales en línea. ### Bitcoin | Nostr y la chispa del constructor Como ya vimos, un solo individuo puede inspirar a muchos otros, teniendo un efecto multiplicador. Esto no solo se traduce al mundo físico, por el contrario, esta directamente ligado a nuestra psicología, incluso podemos decir que va aun mas allá, adentrándonos en el terreno ideológico y espiritual. Hasta hace no mucho, estábamos a merced de las grandes corporaciones que construían todo por nosotros, mientras esperábamos con ansias las nuevas actualizaciones de cada iteración de sus productos. Cada vez mas y mas nos hacíamos dependientes de dichas corporaciones sin quizás notarlo, poco a poco se fueron apoderando de nuestro tiempo y muy insidiosamente de nuestra personalidad e identidad. Gracias a las alternativas presentadas hoy en día y a los individuos que inspiran a otros, existe la posibilidad de construir algo que va mas allá de las grandes corporaciones, porque transciende no solo el nivel físico y digital, sino que también transciende a los individuos que aportan a la comunidad. Estoy hablando por supuesto de Nostr, y como los incentivos están alineados gracias a Bitcoin. Pongamos como ejemplo un par de nombres para ilustrar como individuos que inspirar pueden crear una chispa que se extiende a cada persona dentro de la comunidad. Personajes como nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft nostr:npub1utx00neqgqln72j22kej3ux7803c2k986henvvha4thuwfkper4s7r50e8 nostr:npub1v0lxxxxutpvrelsksy8cdhgfux9l6a42hsj2qzquu2zk7vc9qnkszrqj49 nostr:npub107jk7htfv243u0x5ynn43scq9wrxtaasmrwwa8lfu2ydwag6cx2quqncxg (entre muchos otros que podría mencionar pero todo el articulo seria una lista de nombres) han inspirado a otros desarrolladores, creadores de contenido (y todas las otras especializaciones que te puedas imaginar…) A construir sobre este protocolo. Incluso, personas como el caso mas reciente de nostr:npub1m64hnkh6rs47fd9x6wk2zdtmdj4qkazt734d22d94ery9zzhne5qw9uaks han encontrado inspiración para aprender a programar sobre estos mismos rieles. > nostr:nevent1qqs8fe938k7j5sxcprrv89ezpu09m9pzm90f0sq24hnwlwu0rmn09qcpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxg5vtygh La chispa del constructor en palabras mas concisas es: **Inspiración multiplicadora en pos de la productividad y por ende, del crecimiento de una comunidad.** Sin Bitcoin y Lightning Network, esto seria posible, pero mucho menos efectivo debido a que las personas detrás de toda labor que este enfocada en creación de contenido, desarrollo, etc. Tienen que comer. ### Conclusión La chispa del constructor radica en la inspiración individual que impulsa a la acción colectiva. Desde la evolución de la construcción hasta las comunidades digitales, **el poder de un individuo inspirado puede moldear el presente y el futuro de las comunidades en todo el mundo.** @ a012dc82:6458a70d
2025-02-19 16:20:32The cryptocurrency world is on the verge of a groundbreaking transformation with the anticipated introduction of Bitcoin Exchange-Traded Funds (ETFs). This significant development is set to redefine the realm of crypto-investment, merging the innovative world of digital currencies with the established domain of traditional finance. Bitcoin ETFs represent a monumental shift, not just as a novel investment option, but as a revolutionary bridge connecting the cutting-edge technology of cryptocurrencies with the more familiar territory of stock market investments. This fusion is poised to unlock a new level of accessibility, drawing mainstream investors into the Bitcoin sphere, who were previously hesitant due to the complexities and perceived risks associated with direct cryptocurrency dealings. **Table of Contents** - The Emergence of Bitcoin ETFs - Unveiling Opportunities - Confronting the Dangers - The Road Ahead - Expanding the Horizon - Enhanced Market Dynamics - Technological Advancements - Educational Initiatives - Global Impact - Conclusion - FAQs **The Emergence of Bitcoin ETFs** Bitcoin ETFs are poised to revolutionize the cryptocurrency market. They offer a streamlined avenue for investment in Bitcoin, bypassing the intricacies of direct ownership such as wallet management and key security. This simplicity could democratize Bitcoin investment, potentially enhancing its liquidity and stability. **Unveiling Opportunities** - **Broader Investor Appeal:** Bitcoin ETFs simplify cryptocurrency investment, making it more approachable for the average investor and traditional financial players. This could lead to wider adoption and recognition of Bitcoin as a viable asset class. - **Influx of Institutional Capital:** ETFs could catalyze a surge of institutional funds into the Bitcoin market. Institutions, previously hesitant due to regulatory and security concerns, might view ETFs as a safer investment avenue. - **Market Evolution:** The advent of Bitcoin ETFs signals a maturation of the cryptocurrency market, transitioning towards regulated, mainstream financial products. This evolution could bolster investor confidence and market stability. **Confronting the Dangers** The introduction of Bitcoin ETFs is not devoid of risks and challenges. - **Amplified Volatility:** Bitcoin's notorious volatility could be intensified by the influx of new investors via ETFs, particularly if large capital movements occur swiftly. - **Regulatory Hurdles:** The evolving regulatory framework for cryptocurrencies could become more complex with Bitcoin ETFs, inviting stricter regulations that may impact the market dynamics. - **Systemic Implications:** Integrating Bitcoin into the traditional financial system through ETFs could introduce new systemic risks. A significant downturn in Bitcoin's value might have broader implications for investors and funds linked to these ETFs. **The Road Ahead** As the Bitcoin ETF era dawns, investors should exercise caution. The potential of Bitcoin ETFs is substantial, but the accompanying risks warrant serious consideration. Investors should engage in comprehensive research and assess their risk appetite before engaging with these new investment vehicles. **Expanding the Horizon** **Enhanced Market Dynamics** The introduction of Bitcoin ETFs could lead to more dynamic market behaviors. As traditional and crypto markets become more intertwined, the impact of global economic events on Bitcoin's price could become more pronounced, leading to new investment strategies and market analysis techniques. **Technological Advancements** The growth of Bitcoin ETFs might spur technological advancements in trading platforms and financial tools. Enhanced security measures, improved trading algorithms, and more sophisticated risk management tools could emerge, catering to the unique needs of cryptocurrency ETFs. **Educational Initiatives** With the growing interest in Bitcoin ETFs, there's likely to be an increase in educational resources and initiatives aimed at helping investors understand the nuances of cryptocurrency investments. This could lead to a more informed investor base, capable of making better investment decisions in the volatile world of cryptocurrencies. **Global Impact** The success of Bitcoin ETFs in one region, such as the United States, could encourage other countries to follow suit, leading to a more globalized cryptocurrency market. This could have significant implications for international financial regulations and cooperation. **Conclusion** The potential introduction of Bitcoin ETFs marks a significant milestone in the journey of cryptocurrency investment. While it heralds new opportunities and greater accessibility, it also brings forth challenges and risks that need to be navigated with care. The future of Bitcoin ETFs will hinge on the balance between these opportunities and dangers, and the market's ability to adapt to this new phase of crypto-investment. As we stand at the threshold of this exciting era, the global financial community watches with bated breath, ready to witness the unfolding story of Bitcoin ETFs. **FAQs** **How does a Bitcoin ETF differ from direct Bitcoin investment?** Investing in a Bitcoin ETF means you're investing in a fund that holds Bitcoin as its primary asset, as opposed to buying Bitcoin directly and managing your own digital wallet and security. ETFs are also subject to different regulatory and tax treatments. **What are the benefits of Bitcoin ETFs?** Bitcoin ETFs offer easier access to Bitcoin investment, potentially lower risks compared to direct ownership, and the convenience of trading through traditional investment platforms. **What risks are associated with Bitcoin ETFs?** Risks include the inherent volatility of Bitcoin, potential regulatory changes, and systemic risks if the cryptocurrency market impacts the broader financial system. **Are Bitcoin ETFs available globally?** The availability of Bitcoin ETFs varies by country, depending on the regulatory environment. Some countries may not yet have approved Bitcoin ETFs for trading. **Can Bitcoin ETFs impact the price of Bitcoin?** Yes, Bitcoin ETFs can impact Bitcoin's price as they can increase market liquidity and bring in more institutional investors, potentially leading to price changes. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: [@croxroadnews.co](https://x.com/croxroadnewsco)** **Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)** **Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** ***DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.***
@ a012dc82:6458a70d
2025-02-19 16:20:32The cryptocurrency world is on the verge of a groundbreaking transformation with the anticipated introduction of Bitcoin Exchange-Traded Funds (ETFs). This significant development is set to redefine the realm of crypto-investment, merging the innovative world of digital currencies with the established domain of traditional finance. Bitcoin ETFs represent a monumental shift, not just as a novel investment option, but as a revolutionary bridge connecting the cutting-edge technology of cryptocurrencies with the more familiar territory of stock market investments. This fusion is poised to unlock a new level of accessibility, drawing mainstream investors into the Bitcoin sphere, who were previously hesitant due to the complexities and perceived risks associated with direct cryptocurrency dealings. **Table of Contents** - The Emergence of Bitcoin ETFs - Unveiling Opportunities - Confronting the Dangers - The Road Ahead - Expanding the Horizon - Enhanced Market Dynamics - Technological Advancements - Educational Initiatives - Global Impact - Conclusion - FAQs **The Emergence of Bitcoin ETFs** Bitcoin ETFs are poised to revolutionize the cryptocurrency market. They offer a streamlined avenue for investment in Bitcoin, bypassing the intricacies of direct ownership such as wallet management and key security. This simplicity could democratize Bitcoin investment, potentially enhancing its liquidity and stability. **Unveiling Opportunities** - **Broader Investor Appeal:** Bitcoin ETFs simplify cryptocurrency investment, making it more approachable for the average investor and traditional financial players. This could lead to wider adoption and recognition of Bitcoin as a viable asset class. - **Influx of Institutional Capital:** ETFs could catalyze a surge of institutional funds into the Bitcoin market. Institutions, previously hesitant due to regulatory and security concerns, might view ETFs as a safer investment avenue. - **Market Evolution:** The advent of Bitcoin ETFs signals a maturation of the cryptocurrency market, transitioning towards regulated, mainstream financial products. This evolution could bolster investor confidence and market stability. **Confronting the Dangers** The introduction of Bitcoin ETFs is not devoid of risks and challenges. - **Amplified Volatility:** Bitcoin's notorious volatility could be intensified by the influx of new investors via ETFs, particularly if large capital movements occur swiftly. - **Regulatory Hurdles:** The evolving regulatory framework for cryptocurrencies could become more complex with Bitcoin ETFs, inviting stricter regulations that may impact the market dynamics. - **Systemic Implications:** Integrating Bitcoin into the traditional financial system through ETFs could introduce new systemic risks. A significant downturn in Bitcoin's value might have broader implications for investors and funds linked to these ETFs. **The Road Ahead** As the Bitcoin ETF era dawns, investors should exercise caution. The potential of Bitcoin ETFs is substantial, but the accompanying risks warrant serious consideration. Investors should engage in comprehensive research and assess their risk appetite before engaging with these new investment vehicles. **Expanding the Horizon** **Enhanced Market Dynamics** The introduction of Bitcoin ETFs could lead to more dynamic market behaviors. As traditional and crypto markets become more intertwined, the impact of global economic events on Bitcoin's price could become more pronounced, leading to new investment strategies and market analysis techniques. **Technological Advancements** The growth of Bitcoin ETFs might spur technological advancements in trading platforms and financial tools. Enhanced security measures, improved trading algorithms, and more sophisticated risk management tools could emerge, catering to the unique needs of cryptocurrency ETFs. **Educational Initiatives** With the growing interest in Bitcoin ETFs, there's likely to be an increase in educational resources and initiatives aimed at helping investors understand the nuances of cryptocurrency investments. This could lead to a more informed investor base, capable of making better investment decisions in the volatile world of cryptocurrencies. **Global Impact** The success of Bitcoin ETFs in one region, such as the United States, could encourage other countries to follow suit, leading to a more globalized cryptocurrency market. This could have significant implications for international financial regulations and cooperation. **Conclusion** The potential introduction of Bitcoin ETFs marks a significant milestone in the journey of cryptocurrency investment. While it heralds new opportunities and greater accessibility, it also brings forth challenges and risks that need to be navigated with care. The future of Bitcoin ETFs will hinge on the balance between these opportunities and dangers, and the market's ability to adapt to this new phase of crypto-investment. As we stand at the threshold of this exciting era, the global financial community watches with bated breath, ready to witness the unfolding story of Bitcoin ETFs. **FAQs** **How does a Bitcoin ETF differ from direct Bitcoin investment?** Investing in a Bitcoin ETF means you're investing in a fund that holds Bitcoin as its primary asset, as opposed to buying Bitcoin directly and managing your own digital wallet and security. ETFs are also subject to different regulatory and tax treatments. **What are the benefits of Bitcoin ETFs?** Bitcoin ETFs offer easier access to Bitcoin investment, potentially lower risks compared to direct ownership, and the convenience of trading through traditional investment platforms. **What risks are associated with Bitcoin ETFs?** Risks include the inherent volatility of Bitcoin, potential regulatory changes, and systemic risks if the cryptocurrency market impacts the broader financial system. **Are Bitcoin ETFs available globally?** The availability of Bitcoin ETFs varies by country, depending on the regulatory environment. Some countries may not yet have approved Bitcoin ETFs for trading. **Can Bitcoin ETFs impact the price of Bitcoin?** Yes, Bitcoin ETFs can impact Bitcoin's price as they can increase market liquidity and bring in more institutional investors, potentially leading to price changes. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: [@croxroadnews.co](https://x.com/croxroadnewsco)** **Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)** **Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** ***DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.*** @ ed364ee5:261fd74f
2025-02-19 11:57:26Cardiovascular Ultrasound: Advancements Driving Early Detection and Personalized Care The [cardiovascular ultrasound market](https://www.marketresearchfuture.com/reports/cardiovascular-ultrasound-market-1548 ) is experiencing significant growth as technological advancements, rising cardiovascular disease (CVD) rates, and a shift toward non-invasive diagnostics drive demand. This imaging technology, which uses sound waves to visualize the heart and surrounding blood vessels, is now essential in both preventative cardiology and acute care. Technological Innovations Boosting Accuracy and Accessibility Recent developments have revolutionized cardiovascular ultrasound devices. High-frequency transducers, 3D and 4D imaging, and artificial intelligence (AI) integration are enhancing diagnostic precision. AI, in particular, is automating image analysis, reducing variability, and enabling faster, more accurate diagnosis. Portable cardiovascular ultrasound systems are another game-changer, increasing accessibility to rural or remote areas and allowing for bedside monitoring in hospitals. Companies are focusing on smaller, more affordable devices without compromising imaging quality, expanding the use of this technology beyond large hospital systems. Global Trends and Growing Disease Burden Cardiovascular diseases remain the leading cause of death worldwide, responsible for an estimated 17.9 million deaths annually, according to the World Health Organization (WHO). Early detection is critical to reducing mortality, and cardiovascular ultrasound is playing a pivotal role in identifying conditions such as heart valve disorders, atrial fibrillation, and cardiomyopathies at an earlier stage. Regions like North America and Europe lead the market due to high healthcare expenditure and greater adoption of advanced diagnostic technologies. However, emerging economies in Asia-Pacific and Latin America are witnessing rapid growth as awareness and healthcare infrastructure improve. Challenges and Market Outlook Despite its advantages, the cardiovascular ultrasound market faces challenges such as the high cost of advanced systems and a shortage of trained sonographers. To address these issues, some manufacturers are investing in user-friendly interfaces and remote training programs to ensure broader adoption. Looking ahead, the cardiovascular ultrasound market is projected to grow steadily, driven by ongoing innovation and the increasing prevalence of CVD. Personalized medicine initiatives and telemedicine adoption are expected to further integrate cardiovascular ultrasound into routine patient care. Conclusion As cardiovascular ultrasound technology continues to evolve, it holds the promise of earlier detection, more precise diagnosis, and improved patient outcomes. With rising healthcare demands and technological advancements, this sector is set to play a key role in the fight against heart disease for years to come.
@ ed364ee5:261fd74f
2025-02-19 11:57:26Cardiovascular Ultrasound: Advancements Driving Early Detection and Personalized Care The [cardiovascular ultrasound market](https://www.marketresearchfuture.com/reports/cardiovascular-ultrasound-market-1548 ) is experiencing significant growth as technological advancements, rising cardiovascular disease (CVD) rates, and a shift toward non-invasive diagnostics drive demand. This imaging technology, which uses sound waves to visualize the heart and surrounding blood vessels, is now essential in both preventative cardiology and acute care. Technological Innovations Boosting Accuracy and Accessibility Recent developments have revolutionized cardiovascular ultrasound devices. High-frequency transducers, 3D and 4D imaging, and artificial intelligence (AI) integration are enhancing diagnostic precision. AI, in particular, is automating image analysis, reducing variability, and enabling faster, more accurate diagnosis. Portable cardiovascular ultrasound systems are another game-changer, increasing accessibility to rural or remote areas and allowing for bedside monitoring in hospitals. Companies are focusing on smaller, more affordable devices without compromising imaging quality, expanding the use of this technology beyond large hospital systems. Global Trends and Growing Disease Burden Cardiovascular diseases remain the leading cause of death worldwide, responsible for an estimated 17.9 million deaths annually, according to the World Health Organization (WHO). Early detection is critical to reducing mortality, and cardiovascular ultrasound is playing a pivotal role in identifying conditions such as heart valve disorders, atrial fibrillation, and cardiomyopathies at an earlier stage. Regions like North America and Europe lead the market due to high healthcare expenditure and greater adoption of advanced diagnostic technologies. However, emerging economies in Asia-Pacific and Latin America are witnessing rapid growth as awareness and healthcare infrastructure improve. Challenges and Market Outlook Despite its advantages, the cardiovascular ultrasound market faces challenges such as the high cost of advanced systems and a shortage of trained sonographers. To address these issues, some manufacturers are investing in user-friendly interfaces and remote training programs to ensure broader adoption. Looking ahead, the cardiovascular ultrasound market is projected to grow steadily, driven by ongoing innovation and the increasing prevalence of CVD. Personalized medicine initiatives and telemedicine adoption are expected to further integrate cardiovascular ultrasound into routine patient care. Conclusion As cardiovascular ultrasound technology continues to evolve, it holds the promise of earlier detection, more precise diagnosis, and improved patient outcomes. With rising healthcare demands and technological advancements, this sector is set to play a key role in the fight against heart disease for years to come. @ ed364ee5:261fd74f
2025-02-19 11:50:46Innovations and Demand Surge in Knee Replacement Procedures In recent years, [knee replacement](https://www.marketresearchfuture.com/reports/knee-replacement-market-1578 ) surgeries have seen a significant rise in demand, fueled by advancements in medical technology, an aging global population, and a growing awareness of treatment options. As healthcare providers and medical device manufacturers adapt to this surge, groundbreaking innovations are transforming the landscape of orthopedic care. Rising Demand for Knee Replacements According to recent data from global health agencies, the number of knee replacement surgeries performed annually has increased by over 25% in the past decade. Experts attribute this rise to the aging baby boomer generation, higher rates of obesity, and increased sports-related injuries. Additionally, the growing acceptance of elective surgeries has led younger patients to seek knee replacements to maintain active lifestyles. Technological Advancements in Knee Implants One of the most notable trends is the development of personalized knee implants. Utilizing 3D printing and computer-aided design (CAD), manufacturers can now create implants tailored to the specific anatomy of each patient. This approach not only enhances the fit and comfort of the implant but also reduces the risk of post-surgery complications. Robotic-assisted surgery is another game-changer. These systems provide surgeons with enhanced precision, enabling them to make smaller incisions and reduce damage to surrounding tissues. As a result, patients experience faster recovery times and improved long-term outcomes. "Robotics and AI-driven surgical planning are revolutionizing the way we approach knee replacements," said Dr. Emily Carter, an orthopedic surgeon at [Hospital Name]. "Patients are benefiting from less pain, quicker mobility, and more natural joint function." Enhanced Post-Surgery Rehabilitation Post-operative care has also evolved, with new physical therapy protocols focused on accelerated rehabilitation. Virtual physical therapy platforms are making it easier for patients to access guided exercises from home, ensuring they adhere to their recovery plans. Additionally, wearable sensors are being integrated into recovery regimens to track patients' progress and provide real-time feedback to healthcare providers. Affordability and Access Despite the technological advancements, affordability remains a concern for many patients. In response, several healthcare systems and insurance providers are expanding coverage for knee replacement surgeries. Additionally, some manufacturers are developing cost-effective implant options to address pricing challenges in underserved regions. Future Outlook The future of knee replacement is promising. With ongoing research into biologic solutions, such as cartilage regeneration and stem cell therapy, patients may soon have access to alternatives that delay or even prevent the need for full joint replacement. "The orthopedic industry is on the cusp of major breakthroughs," said Dr. Carter. "Our goal is to provide every patient with the best possible outcome, whether through traditional surgery or emerging biologic treatments." As innovation continues to drive the evolution of knee replacement procedures, patients can look forward to more effective and accessible treatment options that improve quality of life and mobility for years to come.
@ ed364ee5:261fd74f
2025-02-19 11:50:46Innovations and Demand Surge in Knee Replacement Procedures In recent years, [knee replacement](https://www.marketresearchfuture.com/reports/knee-replacement-market-1578 ) surgeries have seen a significant rise in demand, fueled by advancements in medical technology, an aging global population, and a growing awareness of treatment options. As healthcare providers and medical device manufacturers adapt to this surge, groundbreaking innovations are transforming the landscape of orthopedic care. Rising Demand for Knee Replacements According to recent data from global health agencies, the number of knee replacement surgeries performed annually has increased by over 25% in the past decade. Experts attribute this rise to the aging baby boomer generation, higher rates of obesity, and increased sports-related injuries. Additionally, the growing acceptance of elective surgeries has led younger patients to seek knee replacements to maintain active lifestyles. Technological Advancements in Knee Implants One of the most notable trends is the development of personalized knee implants. Utilizing 3D printing and computer-aided design (CAD), manufacturers can now create implants tailored to the specific anatomy of each patient. This approach not only enhances the fit and comfort of the implant but also reduces the risk of post-surgery complications. Robotic-assisted surgery is another game-changer. These systems provide surgeons with enhanced precision, enabling them to make smaller incisions and reduce damage to surrounding tissues. As a result, patients experience faster recovery times and improved long-term outcomes. "Robotics and AI-driven surgical planning are revolutionizing the way we approach knee replacements," said Dr. Emily Carter, an orthopedic surgeon at [Hospital Name]. "Patients are benefiting from less pain, quicker mobility, and more natural joint function." Enhanced Post-Surgery Rehabilitation Post-operative care has also evolved, with new physical therapy protocols focused on accelerated rehabilitation. Virtual physical therapy platforms are making it easier for patients to access guided exercises from home, ensuring they adhere to their recovery plans. Additionally, wearable sensors are being integrated into recovery regimens to track patients' progress and provide real-time feedback to healthcare providers. Affordability and Access Despite the technological advancements, affordability remains a concern for many patients. In response, several healthcare systems and insurance providers are expanding coverage for knee replacement surgeries. Additionally, some manufacturers are developing cost-effective implant options to address pricing challenges in underserved regions. Future Outlook The future of knee replacement is promising. With ongoing research into biologic solutions, such as cartilage regeneration and stem cell therapy, patients may soon have access to alternatives that delay or even prevent the need for full joint replacement. "The orthopedic industry is on the cusp of major breakthroughs," said Dr. Carter. "Our goal is to provide every patient with the best possible outcome, whether through traditional surgery or emerging biologic treatments." As innovation continues to drive the evolution of knee replacement procedures, patients can look forward to more effective and accessible treatment options that improve quality of life and mobility for years to come. @ d4309e24:8a81fcb0
2025-02-19 11:17:19## Introduction: The Challenge of Time-Lock Encryption and Clock Servers When I first set out to build **Hatchstr**, the idea was simple: create a way to send messages into the future, encrypted and locked to a specific Bitcoin block height. These messages would remain encrypted until the chosen block height was reached, creating a unique way to send a message to the future. However, as I began working through the details, I quickly ran into some challenges. One key component of this system involves **clock servers**—decentralized nodes responsible for releasing decryption keys when the specified block height is reached. ### Clock Server Setup: The Basics Initially, I adopted a simple model: each clock server holds a single public-private key pair *unique to that server* for a specific block height. When a user creates a message, they choose a clock server to trust and encrypt with the specific public key tied to that block height. Then, when the time comes, the clock server releases its private key to decrypt the message.  #### Positives: - ✅ **Clean and Efficient Storage**: Each clock server only needs to store a single key pair for each block height, making storage lightweight and scalable. - ✅ **Lazy Key Generation**: Keys are generated on-demand, meaning they’re only created when needed. This prevents unnecessary key generation or storage overhead. - ✅ **Decentralized**: The clock servers don’t need to coordinate with each other or store any sensitive data besides their respective private keys, which simplifies the system architecture. - ✅ **Limited Release Events**: Since each clock server only handles keys tied to a specific block height, the number of release events required is minimized, simplifying the key management process. At first, this seemed like a good approach, but I quickly realized there were **critical limitations**: #### Challenges: - ❌ **Server Shutdown**: Capsules could be scheduled for many years in the future. If a clock server shuts down, all future capsules linked to it are lost. - ❌ **Server Downtime**: If one of the clock servers is unavailable during unlock time, even for a short period, it leads to a delay for the users waiting for unlock. - ❌ **Premature Release**: If a clock server accidentally releases its key too early, it could compromise the message, making it accessible before the intended time. Though the setup worked for a basic system, I soon realized it couldn’t guarantee the reliability I wanted for a decentralized application. ## Tackling the Challenges of Multi-Sig and Secret Sharing When I first approached the problem of securing time-lock capsules, I initially considered using multi-signature (multi-sig) solutions as a potential approach. The goal was simple: instead of relying on a single clock server to release its key, I could involve multiple servers to sign off on the decryption. This way, if one server failed or misbehaved, the message would still be protected. However, as I delved deeper into the multi-sig approach, I quickly realized there were a few key issues: 🔒 **Communication Overhead**: Multi-sig requires servers to communicate and coordinate with each other. This introduces the possibility of new failure points, like network issues or miscommunication. ⚡ **Server Synchronization**: If one server was out of sync or released its key too early, it could still lead to the message being decrypted prematurely, breaking the system. 🛠 **Increased Complexity**: Each server would need to store and manage a unique key pair for every message, making the system more complicated and less efficient. I quickly realized that multi-sig wasn’t the best fit for this kind of setup. Not only did it add unnecessary complexity, but it also conflicted with the decentralization goals I wanted to achieve. So, I started thinking about ways to **distribute the secret** across the clock servers without introducing all these new complications. ### Enter Shamir’s Secret Sharing (SSS) Shamir's Secret Sharing (SSS) is a cryptographic technique designed to split a secret into multiple parts (called "shares") so that the secret can only be reconstructed when a specific minimum number of shares are combined. This process is based on polynomial interpolation, and it’s a powerful way to distribute secrets securely. #### The Basic Concept In SSS, a secret (like a cryptographic key or message) is divided into *n* shares, where *n* is the total number of shares you want to generate. You also specify a threshold, *k*, which represents the minimum number of shares required to reconstruct the original secret. - **n** is the total number of shares. - **k** is the minimum number of shares required to reconstruct the secret (known as the "threshold"). For example, in a **3-out-of-5** scheme, the secret is split into 5 shares, but at least 3 shares are required to reconstruct the secret. If fewer than 3 shares are available, the secret cannot be reconstructed. #### Why This is Secure Shamir’s Secret Sharing is secure because, with fewer than *k* shares, it is computationally infeasible to learn anything about the secret. The shares themselves don’t reveal any information; it’s only the combination of the right number of shares that allows reconstruction. This makes it resistant to attacks, as even if an attacker gets hold of some shares, they won’t be able to reconstruct the secret unless they have the required minimum number of shares (comparable to 256-bit cryptographic strength). #### Applications of Shamir’s Secret Sharing Shamir’s Secret Sharing is widely used in scenarios where high availability and reliability are needed, but security and privacy are equally important. Examples include: - **Key management**: Protecting encryption keys by distributing them across multiple parties. - **Multi-signature setups**: Requiring multiple parties to sign off on a transaction or access a secure system. - **Distributed systems**: Ensuring that no single party holds a complete secret, and multiple parties must collaborate to unlock it. By leveraging Shamir's Secret Sharing, you can strike the right balance between **redundancy**, **security**, and **availability** for your system’s sensitive information. ### The Problem with Distributing Secret Shares SSS could give us exactly the properties I was looking for, with the added benefit that users could choose their preferred setup, for example: - **1-out-of-5 scheme**: Prioritizing the likelihood that the message is decrypted even if only one of the 5 chosen clock servers does its job at unlock time. With the tradeoff that each of the 5 could leak the message early. - **3-out-of-5 scheme**: A measured approach that allows for 2 servers to stop working and would also keep the capsule private even if 2 clock servers leak their secret early. So I considered an approach where each clock server would store part of the key. Instead of a single server holding the full key, I would split the key into parts and distribute those parts across multiple servers. When the time arrived, I’d gather the required number of shares to reconstruct the key and decrypt the message. At first glance, this seemed like a promising approach. But when we look through the implications, a few problems started to emerge: 💥 **Overhead**: Each clock server would need to store a share of every key for every message. This would quickly become inefficient and result in unnecessary overhead. 🔔 **Exploding Reveal Events**: Since each clock server would need to release all its shares at a specific time, there would be a massive increase in the number of reveal events, spamming and possibly overloading Nostr relays. While the idea of distributing the key was very appealing, the practical issues around overhead and complexity made it clear that this wasn’t the final solution. I needed something that would be more efficient, scalable, while still in line with the decentralized model I was aiming for. ### Discovering a Hybrid Solution After testing out various approaches, I realized that the breakthrough wasn’t just about Shamir’s Secret Sharing (SSS)—that part was fairly intuitive. The real insight came when I thought about how to preserve the original clock server design while solving the challenges of failover and early release. Instead of having the clock servers store the secret or a share of it, **I kept the original design**: each clock server only holds a public-private key pair tied to a block height, as initially planned. The twist came when I decided to split an ephemeral AES key into shards using Shamir’s Secret Sharing, but instead of directly storing shares at the clock servers, we could encrypted each share with the public key of the clock server. This approach would allow us to keep the clock server’s role simple: When the time comes, the servers release their private keys, which can then be used to decrypt the encrypted shares of the AES key that were published alongside the original encrypted message. These shares, once decrypted, allow for the reconstruction of the AES key, which in turn decrypts the message. This solution solved several key issues: - ✅ **No Coordination Between Servers**: Each clock server only holds one key pair for a specific block height and doesn’t need to know about the other servers. This simplifies the system and removes the need for complex server coordination. - ✅ **Minimal Overhead**: The clock servers only store a single key pair per block height, eliminating the need to store individual keys for each message. - ✅ **Fault Tolerance**: If one clock server is offline, the other shares can still reconstruct the AES key and decrypt the message, ensuring reliability. - ✅ **Client-Side Security**: The AES key is generated on the client side and never stored on the clock servers, providing a high level of security. By combining the simplicity of the clock server model with the power of Shamir’s Secret Sharing, this hybrid solution allows us to securely split an AES key and manage decryption while ensuring the system remains decentralized, resilient, and efficient. This was the method I had been searching for. ### The Process Breakdown 1. **AES Key Generation**: - A **random AES key** is generated on the **client side** for each message. This key is **never stored** anywhere, ensuring that it remains secure and only used for encrypting the message. 2. **Shamir’s Secret Sharing**: - The AES key is split into (in this example) **3 shares** using Shamir’s Secret Sharing. These shares are associated with **3 independent clock servers**. - The threshold of **2 out of 3** means that only **2 clock servers** needed later to reconstruct the AES key and decrypt the message. 3. **Encrypting with Public Keys**: - The secret shares are then **encrypted** using the **public keys** of the target block height for each specific clock server. This ensures that the shares are secure until the proper time comes. 4. **Storage**: - The **encrypted shares** together with the **AES-encrypted message** can be published to Nostr relais or stored on a decentralized platform like **IPFS**, which provides redundancy and availability. 5. **Clock Servers Release Keys**: - When the specified **Bitcoin block height** is reached, each clock server publishes its **private key** to Nostr, allowing everyone to decrypt the shares. - The client reconstructs the AES key from the decrypted shares and finally decrypts the original message.  ## Conclusion: An Elegant Solution to Time-Lock Encryption Through a series of experiments and iterations, We finally landed on a solution that balances **security**, **scalability**, and **efficiency**. By combining **AES encryption** with **Shamir’s Secret Sharing**, We were able to solve the multi-sig failover problem without adding unnecessary complexity. 🔥 ### An Open Question: Clock Server Incentives 💰 Decentralized systems thrive when participants are motivated to contribute. For Hatchstr, a critical question remains: Why would anyone run a clock server? One possibility is allowing users to **zap** (tip) servers for each capsule they help unlock. But this is just a starting point—how do we ensure reliability without centralizing trust? I’d love to hear your thoughts. How would you design incentives for a decentralized network of clock servers? This part is crucial, and I’m excited to explore it with the community. ### What's Next for Hatchstr? 🧩 **Leveraging Nostr**: Let's see how we can integrate the Nostr NIP standards and previous protocol developments into our system to enhance communication and data integrity. 🔮 **Designing a Web App**: We'll explore building a user-friendly web application for creating and managing digital time capsules. Focus will be on enhancing usability, interface design, and user interaction. 🎛️ **Building a Clock Server with Elixir**: We'll delve into developing a simple clock server using Elixir, capitalizing on its strengths in concurrency and real-time processing to support our time-locking mechanisms. Stay tuned as we advance both the user experience and the backend infrastructure of Hatchstr together. If you're interested in following along or contributing to the development, feel free to reach out! [Nostr QR](https://bafybeig6dmqshbd7khcd7qr7ce6inslx4muebtt3bk5m33f4dplsx4et7y.ipfs.w3s.link/nostr_qr.png) ``` npub16scfufrpsqcukjg7ymu4r40h7j4dwqy4pajgz48e6lmnmz5pljcqh678uh ``` Thank you for reading and being part of this journey! 🧡
@ d4309e24:8a81fcb0
2025-02-19 11:17:19## Introduction: The Challenge of Time-Lock Encryption and Clock Servers When I first set out to build **Hatchstr**, the idea was simple: create a way to send messages into the future, encrypted and locked to a specific Bitcoin block height. These messages would remain encrypted until the chosen block height was reached, creating a unique way to send a message to the future. However, as I began working through the details, I quickly ran into some challenges. One key component of this system involves **clock servers**—decentralized nodes responsible for releasing decryption keys when the specified block height is reached. ### Clock Server Setup: The Basics Initially, I adopted a simple model: each clock server holds a single public-private key pair *unique to that server* for a specific block height. When a user creates a message, they choose a clock server to trust and encrypt with the specific public key tied to that block height. Then, when the time comes, the clock server releases its private key to decrypt the message.  #### Positives: - ✅ **Clean and Efficient Storage**: Each clock server only needs to store a single key pair for each block height, making storage lightweight and scalable. - ✅ **Lazy Key Generation**: Keys are generated on-demand, meaning they’re only created when needed. This prevents unnecessary key generation or storage overhead. - ✅ **Decentralized**: The clock servers don’t need to coordinate with each other or store any sensitive data besides their respective private keys, which simplifies the system architecture. - ✅ **Limited Release Events**: Since each clock server only handles keys tied to a specific block height, the number of release events required is minimized, simplifying the key management process. At first, this seemed like a good approach, but I quickly realized there were **critical limitations**: #### Challenges: - ❌ **Server Shutdown**: Capsules could be scheduled for many years in the future. If a clock server shuts down, all future capsules linked to it are lost. - ❌ **Server Downtime**: If one of the clock servers is unavailable during unlock time, even for a short period, it leads to a delay for the users waiting for unlock. - ❌ **Premature Release**: If a clock server accidentally releases its key too early, it could compromise the message, making it accessible before the intended time. Though the setup worked for a basic system, I soon realized it couldn’t guarantee the reliability I wanted for a decentralized application. ## Tackling the Challenges of Multi-Sig and Secret Sharing When I first approached the problem of securing time-lock capsules, I initially considered using multi-signature (multi-sig) solutions as a potential approach. The goal was simple: instead of relying on a single clock server to release its key, I could involve multiple servers to sign off on the decryption. This way, if one server failed or misbehaved, the message would still be protected. However, as I delved deeper into the multi-sig approach, I quickly realized there were a few key issues: 🔒 **Communication Overhead**: Multi-sig requires servers to communicate and coordinate with each other. This introduces the possibility of new failure points, like network issues or miscommunication. ⚡ **Server Synchronization**: If one server was out of sync or released its key too early, it could still lead to the message being decrypted prematurely, breaking the system. 🛠 **Increased Complexity**: Each server would need to store and manage a unique key pair for every message, making the system more complicated and less efficient. I quickly realized that multi-sig wasn’t the best fit for this kind of setup. Not only did it add unnecessary complexity, but it also conflicted with the decentralization goals I wanted to achieve. So, I started thinking about ways to **distribute the secret** across the clock servers without introducing all these new complications. ### Enter Shamir’s Secret Sharing (SSS) Shamir's Secret Sharing (SSS) is a cryptographic technique designed to split a secret into multiple parts (called "shares") so that the secret can only be reconstructed when a specific minimum number of shares are combined. This process is based on polynomial interpolation, and it’s a powerful way to distribute secrets securely. #### The Basic Concept In SSS, a secret (like a cryptographic key or message) is divided into *n* shares, where *n* is the total number of shares you want to generate. You also specify a threshold, *k*, which represents the minimum number of shares required to reconstruct the original secret. - **n** is the total number of shares. - **k** is the minimum number of shares required to reconstruct the secret (known as the "threshold"). For example, in a **3-out-of-5** scheme, the secret is split into 5 shares, but at least 3 shares are required to reconstruct the secret. If fewer than 3 shares are available, the secret cannot be reconstructed. #### Why This is Secure Shamir’s Secret Sharing is secure because, with fewer than *k* shares, it is computationally infeasible to learn anything about the secret. The shares themselves don’t reveal any information; it’s only the combination of the right number of shares that allows reconstruction. This makes it resistant to attacks, as even if an attacker gets hold of some shares, they won’t be able to reconstruct the secret unless they have the required minimum number of shares (comparable to 256-bit cryptographic strength). #### Applications of Shamir’s Secret Sharing Shamir’s Secret Sharing is widely used in scenarios where high availability and reliability are needed, but security and privacy are equally important. Examples include: - **Key management**: Protecting encryption keys by distributing them across multiple parties. - **Multi-signature setups**: Requiring multiple parties to sign off on a transaction or access a secure system. - **Distributed systems**: Ensuring that no single party holds a complete secret, and multiple parties must collaborate to unlock it. By leveraging Shamir's Secret Sharing, you can strike the right balance between **redundancy**, **security**, and **availability** for your system’s sensitive information. ### The Problem with Distributing Secret Shares SSS could give us exactly the properties I was looking for, with the added benefit that users could choose their preferred setup, for example: - **1-out-of-5 scheme**: Prioritizing the likelihood that the message is decrypted even if only one of the 5 chosen clock servers does its job at unlock time. With the tradeoff that each of the 5 could leak the message early. - **3-out-of-5 scheme**: A measured approach that allows for 2 servers to stop working and would also keep the capsule private even if 2 clock servers leak their secret early. So I considered an approach where each clock server would store part of the key. Instead of a single server holding the full key, I would split the key into parts and distribute those parts across multiple servers. When the time arrived, I’d gather the required number of shares to reconstruct the key and decrypt the message. At first glance, this seemed like a promising approach. But when we look through the implications, a few problems started to emerge: 💥 **Overhead**: Each clock server would need to store a share of every key for every message. This would quickly become inefficient and result in unnecessary overhead. 🔔 **Exploding Reveal Events**: Since each clock server would need to release all its shares at a specific time, there would be a massive increase in the number of reveal events, spamming and possibly overloading Nostr relays. While the idea of distributing the key was very appealing, the practical issues around overhead and complexity made it clear that this wasn’t the final solution. I needed something that would be more efficient, scalable, while still in line with the decentralized model I was aiming for. ### Discovering a Hybrid Solution After testing out various approaches, I realized that the breakthrough wasn’t just about Shamir’s Secret Sharing (SSS)—that part was fairly intuitive. The real insight came when I thought about how to preserve the original clock server design while solving the challenges of failover and early release. Instead of having the clock servers store the secret or a share of it, **I kept the original design**: each clock server only holds a public-private key pair tied to a block height, as initially planned. The twist came when I decided to split an ephemeral AES key into shards using Shamir’s Secret Sharing, but instead of directly storing shares at the clock servers, we could encrypted each share with the public key of the clock server. This approach would allow us to keep the clock server’s role simple: When the time comes, the servers release their private keys, which can then be used to decrypt the encrypted shares of the AES key that were published alongside the original encrypted message. These shares, once decrypted, allow for the reconstruction of the AES key, which in turn decrypts the message. This solution solved several key issues: - ✅ **No Coordination Between Servers**: Each clock server only holds one key pair for a specific block height and doesn’t need to know about the other servers. This simplifies the system and removes the need for complex server coordination. - ✅ **Minimal Overhead**: The clock servers only store a single key pair per block height, eliminating the need to store individual keys for each message. - ✅ **Fault Tolerance**: If one clock server is offline, the other shares can still reconstruct the AES key and decrypt the message, ensuring reliability. - ✅ **Client-Side Security**: The AES key is generated on the client side and never stored on the clock servers, providing a high level of security. By combining the simplicity of the clock server model with the power of Shamir’s Secret Sharing, this hybrid solution allows us to securely split an AES key and manage decryption while ensuring the system remains decentralized, resilient, and efficient. This was the method I had been searching for. ### The Process Breakdown 1. **AES Key Generation**: - A **random AES key** is generated on the **client side** for each message. This key is **never stored** anywhere, ensuring that it remains secure and only used for encrypting the message. 2. **Shamir’s Secret Sharing**: - The AES key is split into (in this example) **3 shares** using Shamir’s Secret Sharing. These shares are associated with **3 independent clock servers**. - The threshold of **2 out of 3** means that only **2 clock servers** needed later to reconstruct the AES key and decrypt the message. 3. **Encrypting with Public Keys**: - The secret shares are then **encrypted** using the **public keys** of the target block height for each specific clock server. This ensures that the shares are secure until the proper time comes. 4. **Storage**: - The **encrypted shares** together with the **AES-encrypted message** can be published to Nostr relais or stored on a decentralized platform like **IPFS**, which provides redundancy and availability. 5. **Clock Servers Release Keys**: - When the specified **Bitcoin block height** is reached, each clock server publishes its **private key** to Nostr, allowing everyone to decrypt the shares. - The client reconstructs the AES key from the decrypted shares and finally decrypts the original message.  ## Conclusion: An Elegant Solution to Time-Lock Encryption Through a series of experiments and iterations, We finally landed on a solution that balances **security**, **scalability**, and **efficiency**. By combining **AES encryption** with **Shamir’s Secret Sharing**, We were able to solve the multi-sig failover problem without adding unnecessary complexity. 🔥 ### An Open Question: Clock Server Incentives 💰 Decentralized systems thrive when participants are motivated to contribute. For Hatchstr, a critical question remains: Why would anyone run a clock server? One possibility is allowing users to **zap** (tip) servers for each capsule they help unlock. But this is just a starting point—how do we ensure reliability without centralizing trust? I’d love to hear your thoughts. How would you design incentives for a decentralized network of clock servers? This part is crucial, and I’m excited to explore it with the community. ### What's Next for Hatchstr? 🧩 **Leveraging Nostr**: Let's see how we can integrate the Nostr NIP standards and previous protocol developments into our system to enhance communication and data integrity. 🔮 **Designing a Web App**: We'll explore building a user-friendly web application for creating and managing digital time capsules. Focus will be on enhancing usability, interface design, and user interaction. 🎛️ **Building a Clock Server with Elixir**: We'll delve into developing a simple clock server using Elixir, capitalizing on its strengths in concurrency and real-time processing to support our time-locking mechanisms. Stay tuned as we advance both the user experience and the backend infrastructure of Hatchstr together. If you're interested in following along or contributing to the development, feel free to reach out! [Nostr QR](https://bafybeig6dmqshbd7khcd7qr7ce6inslx4muebtt3bk5m33f4dplsx4et7y.ipfs.w3s.link/nostr_qr.png) ``` npub16scfufrpsqcukjg7ymu4r40h7j4dwqy4pajgz48e6lmnmz5pljcqh678uh ``` Thank you for reading and being part of this journey! 🧡 @ d360efec:14907b5f
2025-02-19 11:07:53**ภาพรวม BTCUSDT (OKX):** Bitcoin (BTCUSDT) ยังคงแสดงความผันผวนและมีความไม่แน่นอนสูง แม้ว่าแนวโน้มระยะยาว (TF Day) จะยังคงเป็นขาขึ้น *แต่ก็อ่อนแรงลงอย่างเห็นได้ชัด* แนวโน้มระยะกลาง (TF 4H) กลายเป็นขาลงระยะสั้น และแนวโน้มระยะสั้น (TF 15m) ก็เป็นขาลงเช่นกัน สถานการณ์ตอนนี้บ่งบอกถึงแรงขายที่แข็งแกร่ง และมีความเสี่ยงสูงที่จะปรับฐานลงต่อ **วิเคราะห์ทีละ Timeframe:** **(1) TF Day (รายวัน):** [https://www.tradingview.com/x/wfDqxmvG/] * **แนวโน้ม:** ขาขึ้น (Uptrend) *อ่อนแรงลงอย่างมาก* * **SMC:** * Higher Highs (HH) และ Higher Lows (HL) *เริ่มไม่ชัดเจน* * Break of Structure (BOS) ด้านบน *แต่มีการปรับฐานที่รุนแรง* * **Liquidity:** * มี Sellside Liquidity (SSL) อยู่ใต้ Lows ก่อนหน้า (บริเวณ 85,000 - 90,000) * มี Buyside Liquidity (BSL) อยู่เหนือ High เดิม * **ICT:** * **Order Block:** ราคาหลุด Order Block ขาขึ้น (บริเวณแท่งเทียนสีเขียวก่อนหน้านี้) *สัญญาณลบ* * **EMA:** * ราคา *หลุด* EMA 50 (สีเหลือง) ลงมาแล้ว * EMA 200 (สีขาว) เป็นแนวรับถัดไป * **Money Flow (LuxAlgo):** * *สีแดงยาว* แสดงถึงแรงขายที่แข็งแกร่ง * **Trend Strength (AlgoAlpha):** * สีแดง แสดงถึงแนวโน้มขาลง * **Volume Profile:** Volume ค่อนข้างเบาบาง * **แท่งเทียน:** แท่งเทียนล่าสุดเป็นสีแดง แสดงถึงแรงขาย * **แนวรับ:** EMA 200, บริเวณ 85,000 - 90,000 (SSL) * **แนวต้าน:** EMA 50, High เดิม * **สรุป:** แนวโน้มขาขึ้นอ่อนแรงลงอย่างมาก, ราคาหลุด EMA 50 และ Order Block, Money Flow และ Trend Strength เป็นลบ **(2) TF4H (4 ชั่วโมง):** [https://www.tradingview.com/x/WCWYkleo/] * **แนวโน้ม:** ขาลง (Downtrend) * **SMC:** * Lower Highs (LH) และ Lower Lows (LL) * Break of Structure (BOS) ด้านล่าง * **Liquidity:** * มี SSL อยู่ใต้ Lows ก่อนหน้า * มี BSL อยู่เหนือ Highs ก่อนหน้า * **ICT:** * **Order Block:** ราคาไม่สามารถผ่าน Order Block ขาลงได้ * **EMA:** * ราคาอยู่ใต้ EMA 50 และ EMA 200 * **Money Flow (LuxAlgo):** * สีแดง แสดงถึงแรงขาย * **Trend Strength (AlgoAlpha):** * สีแดง แสดงถึงแนวโน้มขาลง * **Volume Profile:** Volume ค่อนข้างนิ่ง * **แนวรับ:** บริเวณ Low ล่าสุด * **แนวต้าน:** EMA 50, EMA 200, บริเวณ Order Block * **สรุป:** แนวโน้มขาลงชัดเจน, แรงขายมีอิทธิพล **(3) TF15 (15 นาที):** [https://www.tradingview.com/x/HsgVKFW2/] * **แนวโน้ม:** ขาลง (Downtrend) * **SMC:** * Lower Highs (LH) และ Lower Lows (LL) * Break of Structure (BOS) ด้านล่าง * **ICT:** * **Order Block** ราคาไม่สามารถผ่าน Order Block ได้ * **EMA:** * EMA 50 และ EMA 200 เป็นแนวต้าน * **Money Flow (LuxAlgo):** * สีแดง แสดงถึงแรงขาย * **Trend Strength (AlgoAlpha):** * สีแดง แสดงถึงแนวโน้มขาลง * **Volume Profile:** Volume ค่อนข้างเบาบาง * **แนวรับ:** บริเวณ Low ล่าสุด * **แนวต้าน:** EMA 50, EMA 200, Order Block * **สรุป:** แนวโน้มขาลง, แรงขายมีอิทธิพล **สรุปภาพรวมและกลยุทธ์ (BTCUSDT):** * **แนวโน้มหลัก (Day):** ขาขึ้น (อ่อนแรง), *หลุด Order Block* * **แนวโน้มรอง (4H):** ขาลง * **แนวโน้มระยะสั้น (15m):** ขาลง * **Liquidity:** มี SSL ทั้งใน Day, 4H, และ 15m * **Money Flow:** เป็นลบในทุก Timeframes * **Trend Strength:** 4H, 15m เป็นขาลง * **กลยุทธ์:** 1. **Wait & See (ดีที่สุด):** รอความชัดเจน 2. **Short (เสี่ยง):** ถ้าไม่สามารถ Breakout EMA/แนวต้านใน TF ใดๆ ได้ 3. **ไม่แนะนำให้ Buy:** จนกว่าจะมีสัญญาณกลับตัวที่ชัดเจน **คำแนะนำ:** * **ความขัดแย้งของ Timeframes:** Day ยังเป็นขาขึ้น (แต่สัญญาณอ่อน), 4H และ 15m เป็นขาลง * **Money Flow:** เป็นลบในทุก Timeframes * **ระวัง SSL:** Smart Money อาจจะลากราคาลงไปกิน Stop Loss * **ถ้าไม่แน่ใจ อย่าเพิ่งเข้าเทรด** **Day Trade & การเทรดรายวัน:** * **Day Trade (TF15):** * **Short Bias:** หาจังหวะ Short เมื่อราคาเด้งขึ้นไปทดสอบแนวต้าน (EMA, Order Block) * **Stop Loss:** เหนือแนวต้านที่เข้า Short * **Take Profit:** แนวรับถัดไป (Low ล่าสุด) * **ไม่แนะนำให้ Long** จนกว่าจะมีสัญญาณกลับตัวที่ชัดเจน * **Swing Trade (TF4H):** * **Short Bias:** รอจังหวะ Short เมื่อราคาไม่สามารถผ่านแนวต้าน EMA หรือ Order Block ได้ * **Stop Loss:** เหนือแนวต้านที่เข้า Short * **Take Profit:** แนวรับถัดไป (EMA 200 ใน TF Day, SSL) * **ไม่แนะนำให้ Long** จนกว่าจะมีสัญญาณกลับตัวที่ชัดเจน **สิ่งที่ต้องระวัง:** * **Sellside Liquidity (SSL):** มีโอกาสสูงที่ราคาจะถูกลากลงไปแตะ SSL ก่อนที่จะมีการกลับตัว (ถ้ามี) * **False Breakouts:** ระวังการ Breakout หลอกทั้งใน TF15 และ TF4H * **Volatility:** ตลาดคริปโตฯ มีความผันผวนสูง เตรียมพร้อมรับมือกับการเปลี่ยนแปลงของราคาอย่างรวดเร็ว **Disclaimer:** การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ
@ d360efec:14907b5f
2025-02-19 11:07:53**ภาพรวม BTCUSDT (OKX):** Bitcoin (BTCUSDT) ยังคงแสดงความผันผวนและมีความไม่แน่นอนสูง แม้ว่าแนวโน้มระยะยาว (TF Day) จะยังคงเป็นขาขึ้น *แต่ก็อ่อนแรงลงอย่างเห็นได้ชัด* แนวโน้มระยะกลาง (TF 4H) กลายเป็นขาลงระยะสั้น และแนวโน้มระยะสั้น (TF 15m) ก็เป็นขาลงเช่นกัน สถานการณ์ตอนนี้บ่งบอกถึงแรงขายที่แข็งแกร่ง และมีความเสี่ยงสูงที่จะปรับฐานลงต่อ **วิเคราะห์ทีละ Timeframe:** **(1) TF Day (รายวัน):** [https://www.tradingview.com/x/wfDqxmvG/] * **แนวโน้ม:** ขาขึ้น (Uptrend) *อ่อนแรงลงอย่างมาก* * **SMC:** * Higher Highs (HH) และ Higher Lows (HL) *เริ่มไม่ชัดเจน* * Break of Structure (BOS) ด้านบน *แต่มีการปรับฐานที่รุนแรง* * **Liquidity:** * มี Sellside Liquidity (SSL) อยู่ใต้ Lows ก่อนหน้า (บริเวณ 85,000 - 90,000) * มี Buyside Liquidity (BSL) อยู่เหนือ High เดิม * **ICT:** * **Order Block:** ราคาหลุด Order Block ขาขึ้น (บริเวณแท่งเทียนสีเขียวก่อนหน้านี้) *สัญญาณลบ* * **EMA:** * ราคา *หลุด* EMA 50 (สีเหลือง) ลงมาแล้ว * EMA 200 (สีขาว) เป็นแนวรับถัดไป * **Money Flow (LuxAlgo):** * *สีแดงยาว* แสดงถึงแรงขายที่แข็งแกร่ง * **Trend Strength (AlgoAlpha):** * สีแดง แสดงถึงแนวโน้มขาลง * **Volume Profile:** Volume ค่อนข้างเบาบาง * **แท่งเทียน:** แท่งเทียนล่าสุดเป็นสีแดง แสดงถึงแรงขาย * **แนวรับ:** EMA 200, บริเวณ 85,000 - 90,000 (SSL) * **แนวต้าน:** EMA 50, High เดิม * **สรุป:** แนวโน้มขาขึ้นอ่อนแรงลงอย่างมาก, ราคาหลุด EMA 50 และ Order Block, Money Flow และ Trend Strength เป็นลบ **(2) TF4H (4 ชั่วโมง):** [https://www.tradingview.com/x/WCWYkleo/] * **แนวโน้ม:** ขาลง (Downtrend) * **SMC:** * Lower Highs (LH) และ Lower Lows (LL) * Break of Structure (BOS) ด้านล่าง * **Liquidity:** * มี SSL อยู่ใต้ Lows ก่อนหน้า * มี BSL อยู่เหนือ Highs ก่อนหน้า * **ICT:** * **Order Block:** ราคาไม่สามารถผ่าน Order Block ขาลงได้ * **EMA:** * ราคาอยู่ใต้ EMA 50 และ EMA 200 * **Money Flow (LuxAlgo):** * สีแดง แสดงถึงแรงขาย * **Trend Strength (AlgoAlpha):** * สีแดง แสดงถึงแนวโน้มขาลง * **Volume Profile:** Volume ค่อนข้างนิ่ง * **แนวรับ:** บริเวณ Low ล่าสุด * **แนวต้าน:** EMA 50, EMA 200, บริเวณ Order Block * **สรุป:** แนวโน้มขาลงชัดเจน, แรงขายมีอิทธิพล **(3) TF15 (15 นาที):** [https://www.tradingview.com/x/HsgVKFW2/] * **แนวโน้ม:** ขาลง (Downtrend) * **SMC:** * Lower Highs (LH) และ Lower Lows (LL) * Break of Structure (BOS) ด้านล่าง * **ICT:** * **Order Block** ราคาไม่สามารถผ่าน Order Block ได้ * **EMA:** * EMA 50 และ EMA 200 เป็นแนวต้าน * **Money Flow (LuxAlgo):** * สีแดง แสดงถึงแรงขาย * **Trend Strength (AlgoAlpha):** * สีแดง แสดงถึงแนวโน้มขาลง * **Volume Profile:** Volume ค่อนข้างเบาบาง * **แนวรับ:** บริเวณ Low ล่าสุด * **แนวต้าน:** EMA 50, EMA 200, Order Block * **สรุป:** แนวโน้มขาลง, แรงขายมีอิทธิพล **สรุปภาพรวมและกลยุทธ์ (BTCUSDT):** * **แนวโน้มหลัก (Day):** ขาขึ้น (อ่อนแรง), *หลุด Order Block* * **แนวโน้มรอง (4H):** ขาลง * **แนวโน้มระยะสั้น (15m):** ขาลง * **Liquidity:** มี SSL ทั้งใน Day, 4H, และ 15m * **Money Flow:** เป็นลบในทุก Timeframes * **Trend Strength:** 4H, 15m เป็นขาลง * **กลยุทธ์:** 1. **Wait & See (ดีที่สุด):** รอความชัดเจน 2. **Short (เสี่ยง):** ถ้าไม่สามารถ Breakout EMA/แนวต้านใน TF ใดๆ ได้ 3. **ไม่แนะนำให้ Buy:** จนกว่าจะมีสัญญาณกลับตัวที่ชัดเจน **คำแนะนำ:** * **ความขัดแย้งของ Timeframes:** Day ยังเป็นขาขึ้น (แต่สัญญาณอ่อน), 4H และ 15m เป็นขาลง * **Money Flow:** เป็นลบในทุก Timeframes * **ระวัง SSL:** Smart Money อาจจะลากราคาลงไปกิน Stop Loss * **ถ้าไม่แน่ใจ อย่าเพิ่งเข้าเทรด** **Day Trade & การเทรดรายวัน:** * **Day Trade (TF15):** * **Short Bias:** หาจังหวะ Short เมื่อราคาเด้งขึ้นไปทดสอบแนวต้าน (EMA, Order Block) * **Stop Loss:** เหนือแนวต้านที่เข้า Short * **Take Profit:** แนวรับถัดไป (Low ล่าสุด) * **ไม่แนะนำให้ Long** จนกว่าจะมีสัญญาณกลับตัวที่ชัดเจน * **Swing Trade (TF4H):** * **Short Bias:** รอจังหวะ Short เมื่อราคาไม่สามารถผ่านแนวต้าน EMA หรือ Order Block ได้ * **Stop Loss:** เหนือแนวต้านที่เข้า Short * **Take Profit:** แนวรับถัดไป (EMA 200 ใน TF Day, SSL) * **ไม่แนะนำให้ Long** จนกว่าจะมีสัญญาณกลับตัวที่ชัดเจน **สิ่งที่ต้องระวัง:** * **Sellside Liquidity (SSL):** มีโอกาสสูงที่ราคาจะถูกลากลงไปแตะ SSL ก่อนที่จะมีการกลับตัว (ถ้ามี) * **False Breakouts:** ระวังการ Breakout หลอกทั้งใน TF15 และ TF4H * **Volatility:** ตลาดคริปโตฯ มีความผันผวนสูง เตรียมพร้อมรับมือกับการเปลี่ยนแปลงของราคาอย่างรวดเร็ว **Disclaimer:** การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ @ 604e96e0:20279eb2
2023-08-11 18:39:36notacomment allows you to zap nostr notes when you comment on them. In order to use notacomment, you have to run a script yourself either on your own computer or in the cloud somewhere. To get started open https://github.com/SamSamskies/notacomment in a browser tab. At this point, I'm sure a lot of you are feeling like this:  Let's breakdown the instructions from the README. ## Prerequisites Node.js and npm - I suggest installing the latest Node.js LTS version from https://nodejs.org. That should also install npm. Once installation is complete, open your terminal. On a Mac you can press cmd + spacebar and type in `terminal` to open the terminal. On other platforms, you'll have to ask ChatGPT 😂 . To verify installation of Node.js type `node -v`. To verify installation type `npm -v`. It should look something like this:  Leave the terminal open. ## Downloading the code to your computer The easiest way to download the code is to download the zip file from the GitHub repo. Remember that first link I told you to open? That's the GitHub repo. Click the green button that says `Code` on it and click `Download ZIP` from the menu.  Now unzip the file and then navigate to the folder in the terminal. To navigate to the folder use the `cd` command. If you unzipped the folder in the `Downloads` folder, you can navigate to the folder by typing `cd ~/Downloads/notacomment-main/`. ## Usage With Strike 1. Create an account with Strike if you don't already have one https://strike.me/download/ 1. Get a Strike API key with all the payment scopes from https://dashboard.strike.me/ 1. Create a .env file and provide NOSTR_NSEC and STRIKE_API_KEY values (see .env.example) 1. Install the dependencies using npm or yarn or whatever your heart desires 1. Make sure you have money in your Strike account 1. Run the script `npm start` Keep in mind that Strike pays the invoices from your cash balance. This means the payment rounds up to the nearest cent when paying an invoice, so if you set the zap amount to 1 sat, you'll be sending more money to Strike than the person you are zapping with every zap. ## Usage With LNbits I recommend making a separate wallet from your main LNbits wallet for usage with notacomment in case you accidentally leak the admin key. 1. Create a .env file and provide NOSTR_NSEC, LNBITS_ADMIN_KEY, and LNBITS_URL values (see .env.example) 1. Install the dependencies using npm or yarn or whatever your heart desires 1. Make sure you have sats in your LNbits wallet 1. Run the script `npm start` ## Usage With Nostr Wallet Connect 1. Create a NWC connection string using something like https://nwc.getalby.com/ 1. Create a .env file and provide NOSTR_NSEC and NWC_CONNECTION_STRING values (see .env.example) 1. Install the dependencies using npm or yarn or whatever your heart desires 1. Make sure you have sats in your wallet that you generated the NWC connection string with 1. Run the script `npm start` <br /> <br /> Screenshot of terminal with commands to install dependencies, create .env file, open .env file, and start the script: 
@ 604e96e0:20279eb2
2023-08-11 18:39:36notacomment allows you to zap nostr notes when you comment on them. In order to use notacomment, you have to run a script yourself either on your own computer or in the cloud somewhere. To get started open https://github.com/SamSamskies/notacomment in a browser tab. At this point, I'm sure a lot of you are feeling like this:  Let's breakdown the instructions from the README. ## Prerequisites Node.js and npm - I suggest installing the latest Node.js LTS version from https://nodejs.org. That should also install npm. Once installation is complete, open your terminal. On a Mac you can press cmd + spacebar and type in `terminal` to open the terminal. On other platforms, you'll have to ask ChatGPT 😂 . To verify installation of Node.js type `node -v`. To verify installation type `npm -v`. It should look something like this:  Leave the terminal open. ## Downloading the code to your computer The easiest way to download the code is to download the zip file from the GitHub repo. Remember that first link I told you to open? That's the GitHub repo. Click the green button that says `Code` on it and click `Download ZIP` from the menu.  Now unzip the file and then navigate to the folder in the terminal. To navigate to the folder use the `cd` command. If you unzipped the folder in the `Downloads` folder, you can navigate to the folder by typing `cd ~/Downloads/notacomment-main/`. ## Usage With Strike 1. Create an account with Strike if you don't already have one https://strike.me/download/ 1. Get a Strike API key with all the payment scopes from https://dashboard.strike.me/ 1. Create a .env file and provide NOSTR_NSEC and STRIKE_API_KEY values (see .env.example) 1. Install the dependencies using npm or yarn or whatever your heart desires 1. Make sure you have money in your Strike account 1. Run the script `npm start` Keep in mind that Strike pays the invoices from your cash balance. This means the payment rounds up to the nearest cent when paying an invoice, so if you set the zap amount to 1 sat, you'll be sending more money to Strike than the person you are zapping with every zap. ## Usage With LNbits I recommend making a separate wallet from your main LNbits wallet for usage with notacomment in case you accidentally leak the admin key. 1. Create a .env file and provide NOSTR_NSEC, LNBITS_ADMIN_KEY, and LNBITS_URL values (see .env.example) 1. Install the dependencies using npm or yarn or whatever your heart desires 1. Make sure you have sats in your LNbits wallet 1. Run the script `npm start` ## Usage With Nostr Wallet Connect 1. Create a NWC connection string using something like https://nwc.getalby.com/ 1. Create a .env file and provide NOSTR_NSEC and NWC_CONNECTION_STRING values (see .env.example) 1. Install the dependencies using npm or yarn or whatever your heart desires 1. Make sure you have sats in your wallet that you generated the NWC connection string with 1. Run the script `npm start` <br /> <br /> Screenshot of terminal with commands to install dependencies, create .env file, open .env file, and start the script:  @ e83b66a8:b0526c2b
2025-02-19 09:49:25I am seeing a groundswell of interest in adopting Bitcoin in small businesses replacing or augmenting existing merchant services. This has many advantages for these businesses including: Attracting Bitcoiners as customers over your competitors. Allowing a self custody payment system which does not require purchasing equipment, monthly service fees and high transaction fees. Self custody your money, removing banks and merchant service companies from taking a cut or interfering in the transaction process. i.e. Bitcoin behaves much more like cash in face to face transactions. Building a Bitcoin Strategic Reserve allowing your profits to accumulate in value over time, just as Bitcoin increases in value due to scarceness and increased adoption. If any or all of these are interesting to you, then here are a scale of merchant options available to you depending on your needs and interests. SOLE TRADER The easiest way for a sole trader to accept Bitcoin is to download the app “Wallet of Satoshi” https://www.walletofsatoshi.com/ or for regions this is not available, use a web equivalent called COINOS https://coinos.io/ This gives everything you’ll need, Bitcoin and Lightning receiving addresses, publishable as text or scannable as a QR code. The ability to generate a specific value invoice using Lightning which can be paid face to face or remotely over the Internet and a wallet to hold your Bitcoin balance. This is a perfect start point, but moving forward it has some drawbacks. It is custodial, meaning that a company actually holds your Bitcoin. Unlike a bank, if that company fails, you loose your Bitcoin. There is also no direct ability to move that Bitcoin to fiat currencies like USD or GBP, so if you need some of those earnings to pay suppliers in fiat currencies, you will struggle to convert. If you are an online only retailer, then the industry standard is BTCPay https://btcpayserver.org/ which can be integrated into most e-commerce systems TRADITIONAL MERCHANT SERVICES So the next option is to use a Bitcoin merchant service company. They look very similar to traditional fiat merchant service companies, they can supply infrastructure like PoS terminals and also handle the payments for you, optionally settling balances to your bank in USD or GBP etc… They charge for the physical devices and their services and they charge a fee on each transaction in the same way traditional merchant service companies do, but usually these fees are significantly smaller. Companies like MUSQET can help setup your business in this way if you wish. https://musqet.tech/ CONSULTANCY The third option is to use a consultancy service like Bridge2Bitcoin https://bridge2bitcoin.com/ this is a company that will come in, explain the concepts and options and build a service around your needs. The company will build the solution you are looking for and make their money by providing the equipment and optionally running the payment solution for you. SELF BUILD If you have experience with Bitcoin and have optionally run your own Lightning node for a while, the tools exist to be able to develop your own solution in-house. And just as Bitcoin allows you to be your own bank, so Lightning allows you to be your own merchant services company. Solutions like Umbrel https://umbrel.com/ running Albyhub https://albyhub.com/ with their POS solution https://pos.albylabs.com/ are a low cost option you can build yourself. If you require devices like PoS terminals, these can be purchased from companies like Swiss Bitcoin Pay: https://swiss-bitcoin-pay.ch/store#!/Bitcoin-Merchant-Kit/p/709060174 as a package or Bitcoinize directly or in volume: https://bitcoinize.com/ There is also the lower cost option of use software loaded onto your staffs iPhone or Android phone to use as a PoS terminal for your business: https://swiss-bitcoin-pay.ch/ Swiss Bitcoin Pay can also take the Bitcoin payment and settle a final amount daily or even convert to fiat and deposit in your bank the next day. If you are comfortable building and running your own server, then software from a company like https://lnbits.com/ is a great option. They have built a core suite of tools, which others have built a huge ecosystem of extensions to handle everything from PoS to accounting to event ticketing and beyond. LNbits is probably the most extensive ecosystem out there for anybody wishing to self build. HYBRID MUSQET also offer a PoS system for both Bitcoin and Fiat. They onboard merchants with traditional card services for Visa, Mastercard and Amex with Apple Pay and Google Pay all within the same device where they deploy Bitcoin Lightning as standard: https://musqet.tech/
@ e83b66a8:b0526c2b
2025-02-19 09:49:25I am seeing a groundswell of interest in adopting Bitcoin in small businesses replacing or augmenting existing merchant services. This has many advantages for these businesses including: Attracting Bitcoiners as customers over your competitors. Allowing a self custody payment system which does not require purchasing equipment, monthly service fees and high transaction fees. Self custody your money, removing banks and merchant service companies from taking a cut or interfering in the transaction process. i.e. Bitcoin behaves much more like cash in face to face transactions. Building a Bitcoin Strategic Reserve allowing your profits to accumulate in value over time, just as Bitcoin increases in value due to scarceness and increased adoption. If any or all of these are interesting to you, then here are a scale of merchant options available to you depending on your needs and interests. SOLE TRADER The easiest way for a sole trader to accept Bitcoin is to download the app “Wallet of Satoshi” https://www.walletofsatoshi.com/ or for regions this is not available, use a web equivalent called COINOS https://coinos.io/ This gives everything you’ll need, Bitcoin and Lightning receiving addresses, publishable as text or scannable as a QR code. The ability to generate a specific value invoice using Lightning which can be paid face to face or remotely over the Internet and a wallet to hold your Bitcoin balance. This is a perfect start point, but moving forward it has some drawbacks. It is custodial, meaning that a company actually holds your Bitcoin. Unlike a bank, if that company fails, you loose your Bitcoin. There is also no direct ability to move that Bitcoin to fiat currencies like USD or GBP, so if you need some of those earnings to pay suppliers in fiat currencies, you will struggle to convert. If you are an online only retailer, then the industry standard is BTCPay https://btcpayserver.org/ which can be integrated into most e-commerce systems TRADITIONAL MERCHANT SERVICES So the next option is to use a Bitcoin merchant service company. They look very similar to traditional fiat merchant service companies, they can supply infrastructure like PoS terminals and also handle the payments for you, optionally settling balances to your bank in USD or GBP etc… They charge for the physical devices and their services and they charge a fee on each transaction in the same way traditional merchant service companies do, but usually these fees are significantly smaller. Companies like MUSQET can help setup your business in this way if you wish. https://musqet.tech/ CONSULTANCY The third option is to use a consultancy service like Bridge2Bitcoin https://bridge2bitcoin.com/ this is a company that will come in, explain the concepts and options and build a service around your needs. The company will build the solution you are looking for and make their money by providing the equipment and optionally running the payment solution for you. SELF BUILD If you have experience with Bitcoin and have optionally run your own Lightning node for a while, the tools exist to be able to develop your own solution in-house. And just as Bitcoin allows you to be your own bank, so Lightning allows you to be your own merchant services company. Solutions like Umbrel https://umbrel.com/ running Albyhub https://albyhub.com/ with their POS solution https://pos.albylabs.com/ are a low cost option you can build yourself. If you require devices like PoS terminals, these can be purchased from companies like Swiss Bitcoin Pay: https://swiss-bitcoin-pay.ch/store#!/Bitcoin-Merchant-Kit/p/709060174 as a package or Bitcoinize directly or in volume: https://bitcoinize.com/ There is also the lower cost option of use software loaded onto your staffs iPhone or Android phone to use as a PoS terminal for your business: https://swiss-bitcoin-pay.ch/ Swiss Bitcoin Pay can also take the Bitcoin payment and settle a final amount daily or even convert to fiat and deposit in your bank the next day. If you are comfortable building and running your own server, then software from a company like https://lnbits.com/ is a great option. They have built a core suite of tools, which others have built a huge ecosystem of extensions to handle everything from PoS to accounting to event ticketing and beyond. LNbits is probably the most extensive ecosystem out there for anybody wishing to self build. HYBRID MUSQET also offer a PoS system for both Bitcoin and Fiat. They onboard merchants with traditional card services for Visa, Mastercard and Amex with Apple Pay and Google Pay all within the same device where they deploy Bitcoin Lightning as standard: https://musqet.tech/ @ 6e75f797:a8eee74e
2023-08-07 13:16:42Last night I started a nostr community multiplayer instance for No Man's Sky [on ZapStream](https://zap.stream/) and before we knew it, we had 4 Nostrichs arriving on the genesis planet to join the fun.  NSM is an deterministic, procedurally generated open universe where players can explore, quest, build, combat and have fun together. Every new system discovered is generated when the first Traveller enters the system making the game a unique experience for any open world gaming fan. If you fancy joining us in the Nostrverse let me know and I'll friend you in #NMS and on Steam or Epic. If you just want to watch the fun, participate in naming systems, planets, fauna and flora come and hang out in my stream or the stream of [Oceanbee](nostr:npub1wqxxe0cjaxnvmrv4lkvx8d5dlft7ewswyn09w5v7fg7642fgzm7srucxws), [HolgerHatGarKeineNode](nostr:npub1pt0kw36ue3w2g4haxq3wgm6a2fhtptmzsjlc2j2vphtcgle72qesgpjyc6) or [taette](npub1yh0dl6pazf55025qvp860lstpscuy0kj2a5lfhxlk400m968vgpql5vsnd).  ### If you already own NMS, feel free to add me! My NMS friend code is: EMAZ-KMHT-ZPFXP See you in space Traveller! - TheGrinder
@ 6e75f797:a8eee74e
2023-08-07 13:16:42Last night I started a nostr community multiplayer instance for No Man's Sky [on ZapStream](https://zap.stream/) and before we knew it, we had 4 Nostrichs arriving on the genesis planet to join the fun.  NSM is an deterministic, procedurally generated open universe where players can explore, quest, build, combat and have fun together. Every new system discovered is generated when the first Traveller enters the system making the game a unique experience for any open world gaming fan. If you fancy joining us in the Nostrverse let me know and I'll friend you in #NMS and on Steam or Epic. If you just want to watch the fun, participate in naming systems, planets, fauna and flora come and hang out in my stream or the stream of [Oceanbee](nostr:npub1wqxxe0cjaxnvmrv4lkvx8d5dlft7ewswyn09w5v7fg7642fgzm7srucxws), [HolgerHatGarKeineNode](nostr:npub1pt0kw36ue3w2g4haxq3wgm6a2fhtptmzsjlc2j2vphtcgle72qesgpjyc6) or [taette](npub1yh0dl6pazf55025qvp860lstpscuy0kj2a5lfhxlk400m968vgpql5vsnd).  ### If you already own NMS, feel free to add me! My NMS friend code is: EMAZ-KMHT-ZPFXP See you in space Traveller! - TheGrinder @ 378562cd:a6fc6773
2025-02-20 16:35:11In the ever-evolving landscape of social media, platforms like Twitter and Facebook have dominated the space for years. They’ve shaped the way we interact, share, and consume information. But as censorship concerns, algorithmic manipulation, and corporate control over data become more apparent, a new contender has emerged—NOSTR (Notes and Other Stuff Transmitted by Relays). The differences are striking for those who have stepped into the NOSTR ecosystem. Let’s dive into what sets it apart and why it’s more than just another social media platform—**it’s a movement**. ### **Decentralization vs. Corporate Control** The fundamental structure is one of the most noticeable differences between NOSTR and traditional platforms like Twitter or Facebook. Both are owned by massive corporations that dictate what can and cannot be said. They collect data, sell advertisements, and use algorithms to curate what users see. NOSTR, on the other hand, is fully decentralized. No single entity controls the platform, no shadowy moderation teams tweak visibility based on corporate interests, and no risk of being permanently banned by a faceless algorithm. Instead, NOSTR operates on an open protocol, allowing anyone to participate without gatekeepers. Your content is truly yours, and no one can take that away from you. ### **A Different Class of People** Scrolling through Twitter or Facebook often feels like wading through a digital battlefield. Political flame wars, mind-numbing clickbait, and attention-seeking outrage dominate the feeds. While both platforms do have intelligent and well-meaning users, they are drowned out by noise, bots, and engagement-hacking algorithms designed to fuel division. NOSTR, by contrast, attracts a different breed of users—people who value free speech, independent thought, and meaningful conversation. Many of them are builders, thinkers, and pioneers eager to create a better way of interacting online. There’s a noticeable shift in tone; rather than content driven by controversy and outrage, you’ll find people discussing innovation, philosophy, and real-world solutions. Conversations feel more organic, unfiltered, and free from the artificial constraints imposed by big tech algorithms. ### **Similarities Exist But With a Better Foundation** At a glance, using a NOSTR client may seem similar to traditional social media platforms. Users post messages (called ‘notes’), interact with others, and build followings. You can reply, share, and engage much like you would on Twitter. But under the hood, everything operates on a more open, transparent system. Instead of relying on centralized servers controlled by corporations, NOSTR functions through relays—public or private servers that transmit messages. Since there’s no corporate overlord dictating what gets priority in your feed, you see content chronologically and unfiltered. Additionally, identity and reputation are built through cryptographic keys rather than being at the mercy of a username that a platform can seize or shadowban at will. ### **No Ads, No Tracking, No Manipulation** Let’s be honest—traditional social media has become a giant advertisement machine. Everything is optimized to keep you engaged just long enough to serve more ads and collect more data. Your feed isn’t showing you what’s most relevant; it’s showing you what makes the company the most money. NOSTR eliminates this problem entirely. There are no forced ads, no trackers collecting your data, and no algorithm deciding what you should see. Instead, users fund relays or tip content creators directly, creating an ecosystem that values people over profit. ### **For New Users: A Starting Point** If you’re new to NOSTR, welcome! I’m still a beginner myself, but I’ve already seen the potential this platform has to change how we connect online. Getting started can seem overwhelming at first, but there are a few key tools and resources that can help smooth the transition. For a great user-friendly NOSTR client, **Damus** (for iOS) and **Amethyst** (for Android) are excellent places to start. If you prefer a web-based option, **Primal.net** offers a simple and intuitive experience. These platforms make it easy to dive in, start posting, and get a feel for how NOSTR operates. But NOSTR isn’t just about social media—it’s a foundation for something bigger. Developers and innovators are expanding their reach beyond simple note-sharing. Specialized communities and applications are already emerging, including platforms for **photography, recipe sharing, and even swap sites**, all built using the NOSTR framework. The possibilities are growing, and the future looks bright. ### **Final Thoughts** The shift from Twitter or Facebook to NOSTR isn’t just about switching platforms; it’s about embracing a fundamentally better way to communicate online. With decentralization, real freedom of expression, and a community of forward-thinking individuals, NOSTR offers an experience that traditional social media simply cannot match. For those seeking a place where ideas flow freely, where profit-driven algorithms don’t dictate engagement, and where you control your own digital presence, NOSTR is not just an alternative. It’s an upgrade. Let's connect and learn together! npub1x7zk9nfqsjwuuwm5mpdu8eevsnu2kk0ff23fv58p45d50fhuvaeszg44p2 primal.net/Goody
@ 378562cd:a6fc6773
2025-02-20 16:35:11In the ever-evolving landscape of social media, platforms like Twitter and Facebook have dominated the space for years. They’ve shaped the way we interact, share, and consume information. But as censorship concerns, algorithmic manipulation, and corporate control over data become more apparent, a new contender has emerged—NOSTR (Notes and Other Stuff Transmitted by Relays). The differences are striking for those who have stepped into the NOSTR ecosystem. Let’s dive into what sets it apart and why it’s more than just another social media platform—**it’s a movement**. ### **Decentralization vs. Corporate Control** The fundamental structure is one of the most noticeable differences between NOSTR and traditional platforms like Twitter or Facebook. Both are owned by massive corporations that dictate what can and cannot be said. They collect data, sell advertisements, and use algorithms to curate what users see. NOSTR, on the other hand, is fully decentralized. No single entity controls the platform, no shadowy moderation teams tweak visibility based on corporate interests, and no risk of being permanently banned by a faceless algorithm. Instead, NOSTR operates on an open protocol, allowing anyone to participate without gatekeepers. Your content is truly yours, and no one can take that away from you. ### **A Different Class of People** Scrolling through Twitter or Facebook often feels like wading through a digital battlefield. Political flame wars, mind-numbing clickbait, and attention-seeking outrage dominate the feeds. While both platforms do have intelligent and well-meaning users, they are drowned out by noise, bots, and engagement-hacking algorithms designed to fuel division. NOSTR, by contrast, attracts a different breed of users—people who value free speech, independent thought, and meaningful conversation. Many of them are builders, thinkers, and pioneers eager to create a better way of interacting online. There’s a noticeable shift in tone; rather than content driven by controversy and outrage, you’ll find people discussing innovation, philosophy, and real-world solutions. Conversations feel more organic, unfiltered, and free from the artificial constraints imposed by big tech algorithms. ### **Similarities Exist But With a Better Foundation** At a glance, using a NOSTR client may seem similar to traditional social media platforms. Users post messages (called ‘notes’), interact with others, and build followings. You can reply, share, and engage much like you would on Twitter. But under the hood, everything operates on a more open, transparent system. Instead of relying on centralized servers controlled by corporations, NOSTR functions through relays—public or private servers that transmit messages. Since there’s no corporate overlord dictating what gets priority in your feed, you see content chronologically and unfiltered. Additionally, identity and reputation are built through cryptographic keys rather than being at the mercy of a username that a platform can seize or shadowban at will. ### **No Ads, No Tracking, No Manipulation** Let’s be honest—traditional social media has become a giant advertisement machine. Everything is optimized to keep you engaged just long enough to serve more ads and collect more data. Your feed isn’t showing you what’s most relevant; it’s showing you what makes the company the most money. NOSTR eliminates this problem entirely. There are no forced ads, no trackers collecting your data, and no algorithm deciding what you should see. Instead, users fund relays or tip content creators directly, creating an ecosystem that values people over profit. ### **For New Users: A Starting Point** If you’re new to NOSTR, welcome! I’m still a beginner myself, but I’ve already seen the potential this platform has to change how we connect online. Getting started can seem overwhelming at first, but there are a few key tools and resources that can help smooth the transition. For a great user-friendly NOSTR client, **Damus** (for iOS) and **Amethyst** (for Android) are excellent places to start. If you prefer a web-based option, **Primal.net** offers a simple and intuitive experience. These platforms make it easy to dive in, start posting, and get a feel for how NOSTR operates. But NOSTR isn’t just about social media—it’s a foundation for something bigger. Developers and innovators are expanding their reach beyond simple note-sharing. Specialized communities and applications are already emerging, including platforms for **photography, recipe sharing, and even swap sites**, all built using the NOSTR framework. The possibilities are growing, and the future looks bright. ### **Final Thoughts** The shift from Twitter or Facebook to NOSTR isn’t just about switching platforms; it’s about embracing a fundamentally better way to communicate online. With decentralization, real freedom of expression, and a community of forward-thinking individuals, NOSTR offers an experience that traditional social media simply cannot match. For those seeking a place where ideas flow freely, where profit-driven algorithms don’t dictate engagement, and where you control your own digital presence, NOSTR is not just an alternative. It’s an upgrade. Let's connect and learn together! npub1x7zk9nfqsjwuuwm5mpdu8eevsnu2kk0ff23fv58p45d50fhuvaeszg44p2 primal.net/Goody @ 4d953dcb:39c9c35c
2025-02-18 22:03:42Чтобы иметь бесплатный, быстрый и устойчивый к блокировке VPN нам нужны всего 2 вещи: 1. Клиент V2ray (приложение для использования VPN) 2. Файлы конфигурации (по сути данные VPN-серверов) ## Клиенты V2ray: 1. Инструкция по установке для Windows и Linux: https://github.com/hiddify/Hiddify-Manager/wiki/Tutorial-for-HiddifyNext-app#adding-a-profile-to-the-app *P.S. Если возникли проблемы с Hiddify-Next — пробуйте установить [Necoray](https://github.com/MatsuriDayo/nekoray)* 2. Инструкция по установке для Android: https://github.com/hiddify/Hiddify-Manager/wiki/Tutorial-for-V2rayNG-app#add-configs-to-the-app *P.S. Если возникли проблемы с V2rayNG — пробуйте установить [HiddifyNext](https://github.com/hiddify/hiddify-next/releases) ([инструкция](https://github.com/hiddify/Hiddify-Manager/wiki/Tutorial-for-HiddifyNext-app#adding-a-profile-to-the-app))* 3. Инструкция по установке для Windows и Linux: https://github.com/hiddify/Hiddify-Manager/wiki/Tutorial-for-V2Box-app#add-subscription-links-to-the-app (лучше для iOS) + https://github.com/hiddify/Hiddify-Manager/wiki/Tutorial-for-Streisand#add-subscription-link (лучше для Mac) *P.S. Если возникли проблемы с V2Box и Streisand — пробуйте установить [Hiddify-Next](https://github.com/hiddify/hiddify-next/releases) или [ShadowRocket](https://github.com/hiddify/Hiddify-Manager/wiki/Tutorial-for-ShadowRocket-app#add-subscription-link-to-the-app)* ## Источники файлов конфигураций: 1. https://outlinekeys.com/ 2. https://proxytype.com/ 3. https://vlesskey.com/ 4. https://vpnkeys.org/ 5. https://openproxylist.com/v2ray/ 6. https://github.com/Epodonios/v2ray-configs 7. https://github.com/barry-far/V2ray-Configs?tab=readme-ov-file 8. https://github.com/M-Mashreghi/Free-V2ray-Collector 9. https://github.com/skywrt/v2ray-configs 10. https://github.com/0xdolan/v2ray_config_generator
@ 4d953dcb:39c9c35c
2025-02-18 22:03:42Чтобы иметь бесплатный, быстрый и устойчивый к блокировке VPN нам нужны всего 2 вещи: 1. Клиент V2ray (приложение для использования VPN) 2. Файлы конфигурации (по сути данные VPN-серверов) ## Клиенты V2ray: 1. Инструкция по установке для Windows и Linux: https://github.com/hiddify/Hiddify-Manager/wiki/Tutorial-for-HiddifyNext-app#adding-a-profile-to-the-app *P.S. Если возникли проблемы с Hiddify-Next — пробуйте установить [Necoray](https://github.com/MatsuriDayo/nekoray)* 2. Инструкция по установке для Android: https://github.com/hiddify/Hiddify-Manager/wiki/Tutorial-for-V2rayNG-app#add-configs-to-the-app *P.S. Если возникли проблемы с V2rayNG — пробуйте установить [HiddifyNext](https://github.com/hiddify/hiddify-next/releases) ([инструкция](https://github.com/hiddify/Hiddify-Manager/wiki/Tutorial-for-HiddifyNext-app#adding-a-profile-to-the-app))* 3. Инструкция по установке для Windows и Linux: https://github.com/hiddify/Hiddify-Manager/wiki/Tutorial-for-V2Box-app#add-subscription-links-to-the-app (лучше для iOS) + https://github.com/hiddify/Hiddify-Manager/wiki/Tutorial-for-Streisand#add-subscription-link (лучше для Mac) *P.S. Если возникли проблемы с V2Box и Streisand — пробуйте установить [Hiddify-Next](https://github.com/hiddify/hiddify-next/releases) или [ShadowRocket](https://github.com/hiddify/Hiddify-Manager/wiki/Tutorial-for-ShadowRocket-app#add-subscription-link-to-the-app)* ## Источники файлов конфигураций: 1. https://outlinekeys.com/ 2. https://proxytype.com/ 3. https://vlesskey.com/ 4. https://vpnkeys.org/ 5. https://openproxylist.com/v2ray/ 6. https://github.com/Epodonios/v2ray-configs 7. https://github.com/barry-far/V2ray-Configs?tab=readme-ov-file 8. https://github.com/M-Mashreghi/Free-V2ray-Collector 9. https://github.com/skywrt/v2ray-configs 10. https://github.com/0xdolan/v2ray_config_generator @ daa41bed:88f54153
2025-02-09 16:50:04There has been a good bit of discussion on Nostr over the past few days about the merits of zaps as a method of engaging with notes, so after writing a rather lengthy [article on the pros of a strategic Bitcoin reserve](https://geek.npub.pro/post/dxqkgnjplttkvetprg8ox/), I wanted to take some time to chime in on the much more fun topic of digital engagement. Let's begin by defining a couple of things: **Nostr** is a decentralized, censorship-resistance protocol whose current biggest use case is social media (think Twitter/X). Instead of relying on company servers, it relies on relays that anyone can spin up and own their own content. Its use cases are much bigger, though, and this article is hosted on my own relay, using my own Nostr relay as an example. **Zap** is a tip or donation denominated in sats (small units of Bitcoin) sent from one user to another. This is generally done directly over the Lightning Network but is increasingly using Cashu tokens. For the sake of this discussion, how you transmit/receive zaps will be irrelevant, so don't worry if you don't know what [Lightning](https://lightning.network/) or [Cashu](https://cashu.space/) are. If we look at how users engage with posts and follows/followers on platforms like Twitter, Facebook, etc., it becomes evident that traditional social media thrives on engagement farming. The more outrageous a post, the more likely it will get a reaction. We see a version of this on more visual social platforms like YouTube and TikTok that use carefully crafted thumbnail images to grab the user's attention to click the video. If you'd like to dive deep into the psychology and science behind social media engagement, let me know, and I'd be happy to follow up with another article. In this user engagement model, a user is given the option to comment or like the original post, or share it among their followers to increase its signal. They receive no value from engaging with the content aside from the dopamine hit of the original experience or having their comment liked back by whatever influencer they provide value to. Ad revenue flows to the content creator. Clout flows to the content creator. Sales revenue from merch and content placement flows to the content creator. We call this a linear economy -- the idea that resources get created, used up, then thrown away. Users create content and farm as much engagement as possible, then the content is forgotten within a few hours as they move on to the next piece of content to be farmed. What if there were a simple way to give value back to those who engage with your content? By implementing some value-for-value model -- a circular economy. Enter zaps.  Unlike traditional social media platforms, Nostr does not actively use algorithms to determine what content is popular, nor does it push content created for active user engagement to the top of a user's timeline. Yes, there are "trending" and "most zapped" timelines that users can choose to use as their default, but these use relatively straightforward engagement metrics to rank posts for these timelines. That is not to say that we may not see clients actively seeking to refine timeline algorithms for specific metrics. Still, the beauty of having an open protocol with media that is controlled solely by its users is that users who begin to see their timeline gamed towards specific algorithms can choose to move to another client, and for those who are more tech-savvy, they can opt to run their own relays or create their own clients with personalized algorithms and web of trust scoring systems. Zaps enable the means to create a new type of social media economy in which creators can earn for creating content and users can earn by actively engaging with it. Like and reposting content is relatively frictionless and costs nothing but a simple button tap. Zaps provide active engagement because they signal to your followers and those of the content creator that this post has genuine value, quite literally in the form of money—sats.  I have seen some comments on Nostr claiming that removing likes and reactions is for wealthy people who can afford to send zaps and that the majority of people in the US and around the world do not have the time or money to zap because they have better things to spend their money like feeding their families and paying their bills. While at face value, these may seem like valid arguments, they, unfortunately, represent the brainwashed, defeatist attitude that our current economic (and, by extension, social media) systems aim to instill in all of us to continue extracting value from our lives. Imagine now, if those people dedicating their own time (time = money) to mine pity points on social media would instead spend that time with genuine value creation by posting content that is meaningful to cultural discussions. Imagine if, instead of complaining that their posts get no zaps and going on a tirade about how much of a victim they are, they would empower themselves to take control of their content and give value back to the world; where would that leave us? How much value could be created on a nascent platform such as Nostr, and how quickly could it overtake other platforms? Other users argue about user experience and that additional friction (i.e., zaps) leads to lower engagement, as proven by decades of studies on user interaction. While the added friction may turn some users away, does that necessarily provide less value? I argue quite the opposite. You haven't made a few sats from zaps with your content? Can't afford to send some sats to a wallet for zapping? How about using the most excellent available resource and spending 10 seconds of your time to leave a comment? Likes and reactions are valueless transactions. Social media's real value derives from providing monetary compensation and actively engaging in a conversation with posts you find interesting or thought-provoking. Remember when humans thrived on conversation and discussion for entertainment instead of simply being an onlooker of someone else's life? If you've made it this far, my only request is this: try only zapping and commenting as a method of engagement for two weeks. Sure, you may end up liking a post here and there, but be more mindful of how you interact with the world and break yourself from blind instinct. You'll thank me later. 
@ daa41bed:88f54153
2025-02-09 16:50:04There has been a good bit of discussion on Nostr over the past few days about the merits of zaps as a method of engaging with notes, so after writing a rather lengthy [article on the pros of a strategic Bitcoin reserve](https://geek.npub.pro/post/dxqkgnjplttkvetprg8ox/), I wanted to take some time to chime in on the much more fun topic of digital engagement. Let's begin by defining a couple of things: **Nostr** is a decentralized, censorship-resistance protocol whose current biggest use case is social media (think Twitter/X). Instead of relying on company servers, it relies on relays that anyone can spin up and own their own content. Its use cases are much bigger, though, and this article is hosted on my own relay, using my own Nostr relay as an example. **Zap** is a tip or donation denominated in sats (small units of Bitcoin) sent from one user to another. This is generally done directly over the Lightning Network but is increasingly using Cashu tokens. For the sake of this discussion, how you transmit/receive zaps will be irrelevant, so don't worry if you don't know what [Lightning](https://lightning.network/) or [Cashu](https://cashu.space/) are. If we look at how users engage with posts and follows/followers on platforms like Twitter, Facebook, etc., it becomes evident that traditional social media thrives on engagement farming. The more outrageous a post, the more likely it will get a reaction. We see a version of this on more visual social platforms like YouTube and TikTok that use carefully crafted thumbnail images to grab the user's attention to click the video. If you'd like to dive deep into the psychology and science behind social media engagement, let me know, and I'd be happy to follow up with another article. In this user engagement model, a user is given the option to comment or like the original post, or share it among their followers to increase its signal. They receive no value from engaging with the content aside from the dopamine hit of the original experience or having their comment liked back by whatever influencer they provide value to. Ad revenue flows to the content creator. Clout flows to the content creator. Sales revenue from merch and content placement flows to the content creator. We call this a linear economy -- the idea that resources get created, used up, then thrown away. Users create content and farm as much engagement as possible, then the content is forgotten within a few hours as they move on to the next piece of content to be farmed. What if there were a simple way to give value back to those who engage with your content? By implementing some value-for-value model -- a circular economy. Enter zaps.  Unlike traditional social media platforms, Nostr does not actively use algorithms to determine what content is popular, nor does it push content created for active user engagement to the top of a user's timeline. Yes, there are "trending" and "most zapped" timelines that users can choose to use as their default, but these use relatively straightforward engagement metrics to rank posts for these timelines. That is not to say that we may not see clients actively seeking to refine timeline algorithms for specific metrics. Still, the beauty of having an open protocol with media that is controlled solely by its users is that users who begin to see their timeline gamed towards specific algorithms can choose to move to another client, and for those who are more tech-savvy, they can opt to run their own relays or create their own clients with personalized algorithms and web of trust scoring systems. Zaps enable the means to create a new type of social media economy in which creators can earn for creating content and users can earn by actively engaging with it. Like and reposting content is relatively frictionless and costs nothing but a simple button tap. Zaps provide active engagement because they signal to your followers and those of the content creator that this post has genuine value, quite literally in the form of money—sats.  I have seen some comments on Nostr claiming that removing likes and reactions is for wealthy people who can afford to send zaps and that the majority of people in the US and around the world do not have the time or money to zap because they have better things to spend their money like feeding their families and paying their bills. While at face value, these may seem like valid arguments, they, unfortunately, represent the brainwashed, defeatist attitude that our current economic (and, by extension, social media) systems aim to instill in all of us to continue extracting value from our lives. Imagine now, if those people dedicating their own time (time = money) to mine pity points on social media would instead spend that time with genuine value creation by posting content that is meaningful to cultural discussions. Imagine if, instead of complaining that their posts get no zaps and going on a tirade about how much of a victim they are, they would empower themselves to take control of their content and give value back to the world; where would that leave us? How much value could be created on a nascent platform such as Nostr, and how quickly could it overtake other platforms? Other users argue about user experience and that additional friction (i.e., zaps) leads to lower engagement, as proven by decades of studies on user interaction. While the added friction may turn some users away, does that necessarily provide less value? I argue quite the opposite. You haven't made a few sats from zaps with your content? Can't afford to send some sats to a wallet for zapping? How about using the most excellent available resource and spending 10 seconds of your time to leave a comment? Likes and reactions are valueless transactions. Social media's real value derives from providing monetary compensation and actively engaging in a conversation with posts you find interesting or thought-provoking. Remember when humans thrived on conversation and discussion for entertainment instead of simply being an onlooker of someone else's life? If you've made it this far, my only request is this: try only zapping and commenting as a method of engagement for two weeks. Sure, you may end up liking a post here and there, but be more mindful of how you interact with the world and break yourself from blind instinct. You'll thank me later.  @ ec42c765:328c0600
2025-02-05 23:38:12# カスタム絵文字とは 任意のオリジナル画像を絵文字のように文中に挿入できる機能です。 また、リアクション(Twitterの いいね のような機能)にもカスタム絵文字を使えます。  # カスタム絵文字の対応状況(2025/02/06)  カスタム絵文字を使うためにはカスタム絵文字に対応した[クライアント](https://welcome.nostr-jp.org/tutorial/explore-client.html)を使う必要があります。 ※表は一例です。クライアントは他にもたくさんあります。 使っているクライアントが対応していない場合は、クライアントを変更する、対応するまで待つ、開発者に要望を送る(または自分で実装する)などしましょう。 #### 対応クライアント - [Amethyst](https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst) - [FreeFrom](https://freefrom.space/) - [nostter](https://nostter.app/) - [Rabbit](https://rabbit.syusui.net/) - [Lumilumi](https://lumilumi.app/) - [Nos Haiku](https://nos-haiku.vercel.app/) - [Snort](https://snort.social/) - [noStrudel](https://nostrudel.ninja/) ここではnostterを使って説明していきます。 # 準備 カスタム絵文字を使うための準備です。 - Nostrエクステンション(NIP-07)を導入する - 使いたいカスタム絵文字をリストに登録する ## Nostrエクステンション(NIP-07)を導入する Nostrエクステンションは使いたいカスタム絵文字を登録する時に必要になります。 また、環境(パソコン、iPhone、androidなど)によって導入方法が違います。 Nostrエクステンションを導入する端末は、実際にNostrを閲覧する端末と違っても構いません(リスト登録はPC、Nostr閲覧はiPhoneなど)。 Nostrエクステンション(NIP-07)の導入方法は以下のページを参照してください。 [ログイン拡張機能 (NIP-07)を使ってみよう | Welcome to Nostr! ~ Nostrをはじめよう! ~ ](https://welcome.nostr-jp.org/tutorial/nip-07.html) 少し面倒ですが、これを導入しておくとNostr上の様々な場面で役立つのでより快適になります。 ## 使いたいカスタム絵文字をリストに登録する 以下のサイトで行います。 [emojito](https://emojito.meme/) 右上の**Get started**からNostrエクステンションでログインしてください。 例として以下のカスタム絵文字を導入してみます。 実際より絵文字が少なく表示されることがありますが、古い状態のデータを取得してしまっているためです。その場合はブラウザの更新ボタンを押してください。 [generalJP | カスタム絵文字](https://emojito.meme/a/naddr1qqykwetwv4exzmz22qqsuamnwvaz7tmev9382tndv5hsyg8vgtrk2svt8kuusk4l7w5g7j3mhet4xhhthhz52gsyr7jn9rqxqqpsgqqqw48qud6u3s)  - 右側の**Options**から**Bookmark**を選択  これでカスタム絵文字を使用するためのリストに登録できます。 # カスタム絵文字を使用する 例としてブラウザから使えるクライアント nostter から使用してみます。 [nostter](https://nostter.app/) nostterにNostrエクステンションでログイン、もしくは秘密鍵を入れてログインしてください。 ## 文章中に使用 1. **投稿**ボタンを押して投稿ウィンドウを表示 2. **顔😀**のボタンを押し、絵文字ウィンドウを表示 3. ***タブ**を押し、カスタム絵文字一覧を表示 4. カスタム絵文字を選択 5. : 記号に挟まれたアルファベットのショートコードとして挿入される  この状態で投稿するとカスタム絵文字として表示されます。 カスタム絵文字対応クライアントを使っている他ユーザーにもカスタム絵文字として表示されます。 対応していないクライアントの場合、ショートコードのまま表示されます。  ショートコードを直接入力することでカスタム絵文字の候補が表示されるのでそこから選択することもできます。  ## リアクションに使用 1. 任意の投稿の**顔😀**のボタンを押し、絵文字ウィンドウを表示 2. ***タブ**を押し、カスタム絵文字一覧を表示 3. カスタム絵文字を選択  カスタム絵文字リアクションを送ることができます。  # カスタム絵文字を探す 先述した[emojito](https://emojito.meme/)からカスタム絵文字を探せます。 例えば任意のユーザーのページ [emojito ロクヨウ](https://emojito.meme/p/npub1a3pvwe2p3v7mnjz6hle63r628wl9w567aw7u23fzqs062v5vqcqqu3sgh3) から探したり、 [emojito Browse all](https://emojito.meme/browse) からnostr全体で最近作成、更新された絵文字を見たりできます。 また、以下のリンクは日本語圏ユーザーが作ったカスタム絵文字を集めたリストです(2025/02/06) ※漏れがあるかもしれません [日本ユーザー作 カスタム絵文字](https://nostviewstr.vercel.app/npub17hczqvxtfv3w69wr6lxrttnpdekwdwel55mld60fr24zwjuu6utqtj8mjx/10030) 各絵文字セットにある**Open in emojito**のリンクからemojitoに飛び、使用リストに追加できます。 ----------- 以上です。 次:Nostrのカスタム絵文字の**作り方** Yakihonneリンク [Nostrのカスタム絵文字の作り方](https://yakihonne.com/article/_@lokuyow.github.io/1707912490439) Nostrリンク nostr:naddr1qqxnzdesxuunzv358ycrgveeqgswcsk8v4qck0deepdtluag3a9rh0jh2d0wh0w9g53qg8a9x2xqvqqrqsqqqa28r5psx3 ----------- # 仕様 [NIP-30 Custom Emoji](https://github.com/nostr-protocol/nips/blob/master/30.md) [NIP-30 カスタム絵文字(和訳)](https://github.com/nostr-jp/nips-ja/blob/main/30.md)
@ ec42c765:328c0600
2025-02-05 23:38:12# カスタム絵文字とは 任意のオリジナル画像を絵文字のように文中に挿入できる機能です。 また、リアクション(Twitterの いいね のような機能)にもカスタム絵文字を使えます。  # カスタム絵文字の対応状況(2025/02/06)  カスタム絵文字を使うためにはカスタム絵文字に対応した[クライアント](https://welcome.nostr-jp.org/tutorial/explore-client.html)を使う必要があります。 ※表は一例です。クライアントは他にもたくさんあります。 使っているクライアントが対応していない場合は、クライアントを変更する、対応するまで待つ、開発者に要望を送る(または自分で実装する)などしましょう。 #### 対応クライアント - [Amethyst](https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst) - [FreeFrom](https://freefrom.space/) - [nostter](https://nostter.app/) - [Rabbit](https://rabbit.syusui.net/) - [Lumilumi](https://lumilumi.app/) - [Nos Haiku](https://nos-haiku.vercel.app/) - [Snort](https://snort.social/) - [noStrudel](https://nostrudel.ninja/) ここではnostterを使って説明していきます。 # 準備 カスタム絵文字を使うための準備です。 - Nostrエクステンション(NIP-07)を導入する - 使いたいカスタム絵文字をリストに登録する ## Nostrエクステンション(NIP-07)を導入する Nostrエクステンションは使いたいカスタム絵文字を登録する時に必要になります。 また、環境(パソコン、iPhone、androidなど)によって導入方法が違います。 Nostrエクステンションを導入する端末は、実際にNostrを閲覧する端末と違っても構いません(リスト登録はPC、Nostr閲覧はiPhoneなど)。 Nostrエクステンション(NIP-07)の導入方法は以下のページを参照してください。 [ログイン拡張機能 (NIP-07)を使ってみよう | Welcome to Nostr! ~ Nostrをはじめよう! ~ ](https://welcome.nostr-jp.org/tutorial/nip-07.html) 少し面倒ですが、これを導入しておくとNostr上の様々な場面で役立つのでより快適になります。 ## 使いたいカスタム絵文字をリストに登録する 以下のサイトで行います。 [emojito](https://emojito.meme/) 右上の**Get started**からNostrエクステンションでログインしてください。 例として以下のカスタム絵文字を導入してみます。 実際より絵文字が少なく表示されることがありますが、古い状態のデータを取得してしまっているためです。その場合はブラウザの更新ボタンを押してください。 [generalJP | カスタム絵文字](https://emojito.meme/a/naddr1qqykwetwv4exzmz22qqsuamnwvaz7tmev9382tndv5hsyg8vgtrk2svt8kuusk4l7w5g7j3mhet4xhhthhz52gsyr7jn9rqxqqpsgqqqw48qud6u3s)  - 右側の**Options**から**Bookmark**を選択  これでカスタム絵文字を使用するためのリストに登録できます。 # カスタム絵文字を使用する 例としてブラウザから使えるクライアント nostter から使用してみます。 [nostter](https://nostter.app/) nostterにNostrエクステンションでログイン、もしくは秘密鍵を入れてログインしてください。 ## 文章中に使用 1. **投稿**ボタンを押して投稿ウィンドウを表示 2. **顔😀**のボタンを押し、絵文字ウィンドウを表示 3. ***タブ**を押し、カスタム絵文字一覧を表示 4. カスタム絵文字を選択 5. : 記号に挟まれたアルファベットのショートコードとして挿入される  この状態で投稿するとカスタム絵文字として表示されます。 カスタム絵文字対応クライアントを使っている他ユーザーにもカスタム絵文字として表示されます。 対応していないクライアントの場合、ショートコードのまま表示されます。  ショートコードを直接入力することでカスタム絵文字の候補が表示されるのでそこから選択することもできます。  ## リアクションに使用 1. 任意の投稿の**顔😀**のボタンを押し、絵文字ウィンドウを表示 2. ***タブ**を押し、カスタム絵文字一覧を表示 3. カスタム絵文字を選択  カスタム絵文字リアクションを送ることができます。  # カスタム絵文字を探す 先述した[emojito](https://emojito.meme/)からカスタム絵文字を探せます。 例えば任意のユーザーのページ [emojito ロクヨウ](https://emojito.meme/p/npub1a3pvwe2p3v7mnjz6hle63r628wl9w567aw7u23fzqs062v5vqcqqu3sgh3) から探したり、 [emojito Browse all](https://emojito.meme/browse) からnostr全体で最近作成、更新された絵文字を見たりできます。 また、以下のリンクは日本語圏ユーザーが作ったカスタム絵文字を集めたリストです(2025/02/06) ※漏れがあるかもしれません [日本ユーザー作 カスタム絵文字](https://nostviewstr.vercel.app/npub17hczqvxtfv3w69wr6lxrttnpdekwdwel55mld60fr24zwjuu6utqtj8mjx/10030) 各絵文字セットにある**Open in emojito**のリンクからemojitoに飛び、使用リストに追加できます。 ----------- 以上です。 次:Nostrのカスタム絵文字の**作り方** Yakihonneリンク [Nostrのカスタム絵文字の作り方](https://yakihonne.com/article/_@lokuyow.github.io/1707912490439) Nostrリンク nostr:naddr1qqxnzdesxuunzv358ycrgveeqgswcsk8v4qck0deepdtluag3a9rh0jh2d0wh0w9g53qg8a9x2xqvqqrqsqqqa28r5psx3 ----------- # 仕様 [NIP-30 Custom Emoji](https://github.com/nostr-protocol/nips/blob/master/30.md) [NIP-30 カスタム絵文字(和訳)](https://github.com/nostr-jp/nips-ja/blob/main/30.md) @ e3ba5e1a:5e433365
2025-02-05 17:47:16I got into a [friendly discussion](https://x.com/snoyberg/status/1887007888117252142) on X regarding health insurance. The specific question was how to deal with health insurance companies (presumably unfairly) denying claims? My answer, as usual: get government out of it! The US healthcare system is essentially the worst of both worlds: * Unlike full single payer, individuals incur high costs * Unlike a true free market, regulation causes increases in costs and decreases competition among insurers I'm firmly on the side of moving towards the free market. (And I say that as someone living under a single payer system now.) Here's what I would do: * Get rid of tax incentives that make health insurance tied to your employer, giving individuals back proper freedom of choice. * Reduce regulations significantly. * In the short term, some people will still get rejected claims and other obnoxious behavior from insurance companies. We address that in two ways: 1. Due to reduced regulations, new insurance companies will be able to enter the market offering more reliable coverage and better rates, and people will flock to them because they have the freedom to make their own choices. 2. Sue the asses off of companies that reject claims unfairly. And ideally, as one of the few legitimate roles of government in all this, institute new laws that limit the ability of fine print to allow insurers to escape their responsibilities. (I'm hesitant that the latter will happen due to the incestuous relationship between Congress/regulators and insurers, but I can hope.) Will this magically fix everything overnight like politicians normally promise? No. But it will allow the market to return to a healthy state. And I don't think it will take long (order of magnitude: 5-10 years) for it to come together, but that's just speculation. And since there's a high correlation between those who believe government can fix problems by taking more control and demanding that only credentialed experts weigh in on a topic (both points I strongly disagree with BTW): I'm a trained actuary and worked in the insurance industry, and have directly seen how government regulation reduces competition, raises prices, and harms consumers. And my final point: I don't think any prior art would be a good comparison for deregulation in the US, it's such a different market than any other country in the world for so many reasons that lessons wouldn't really translate. Nonetheless, I asked Grok for some empirical data on this, and at best the results of deregulation could be called "mixed," but likely more accurately "uncertain, confused, and subject to whatever interpretation anyone wants to apply." https://x.com/i/grok/share/Zc8yOdrN8lS275hXJ92uwq98M
@ e3ba5e1a:5e433365
2025-02-05 17:47:16I got into a [friendly discussion](https://x.com/snoyberg/status/1887007888117252142) on X regarding health insurance. The specific question was how to deal with health insurance companies (presumably unfairly) denying claims? My answer, as usual: get government out of it! The US healthcare system is essentially the worst of both worlds: * Unlike full single payer, individuals incur high costs * Unlike a true free market, regulation causes increases in costs and decreases competition among insurers I'm firmly on the side of moving towards the free market. (And I say that as someone living under a single payer system now.) Here's what I would do: * Get rid of tax incentives that make health insurance tied to your employer, giving individuals back proper freedom of choice. * Reduce regulations significantly. * In the short term, some people will still get rejected claims and other obnoxious behavior from insurance companies. We address that in two ways: 1. Due to reduced regulations, new insurance companies will be able to enter the market offering more reliable coverage and better rates, and people will flock to them because they have the freedom to make their own choices. 2. Sue the asses off of companies that reject claims unfairly. And ideally, as one of the few legitimate roles of government in all this, institute new laws that limit the ability of fine print to allow insurers to escape their responsibilities. (I'm hesitant that the latter will happen due to the incestuous relationship between Congress/regulators and insurers, but I can hope.) Will this magically fix everything overnight like politicians normally promise? No. But it will allow the market to return to a healthy state. And I don't think it will take long (order of magnitude: 5-10 years) for it to come together, but that's just speculation. And since there's a high correlation between those who believe government can fix problems by taking more control and demanding that only credentialed experts weigh in on a topic (both points I strongly disagree with BTW): I'm a trained actuary and worked in the insurance industry, and have directly seen how government regulation reduces competition, raises prices, and harms consumers. And my final point: I don't think any prior art would be a good comparison for deregulation in the US, it's such a different market than any other country in the world for so many reasons that lessons wouldn't really translate. Nonetheless, I asked Grok for some empirical data on this, and at best the results of deregulation could be called "mixed," but likely more accurately "uncertain, confused, and subject to whatever interpretation anyone wants to apply." https://x.com/i/grok/share/Zc8yOdrN8lS275hXJ92uwq98M @ 91bea5cd:1df4451c
2025-02-04 17:24:50### Definição de ULID: Timestamp 48 bits, Aleatoriedade 80 bits Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C. e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível. #### Gerar ULID ```sql CREATE EXTENSION IF NOT EXISTS pgcrypto; CREATE FUNCTION generate_ulid() RETURNS TEXT AS $$ DECLARE -- Crockford's Base32 encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; timestamp BYTEA = E'\\000\\000\\000\\000\\000\\000'; output TEXT = ''; unix_time BIGINT; ulid BYTEA; BEGIN -- 6 timestamp bytes unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT; timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER); -- 10 entropy bytes ulid = timestamp || gen_random_bytes(10); -- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31))); -- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31))); RETURN output; END $$ LANGUAGE plpgsql VOLATILE; ``` #### ULID TO UUID ```sql CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$ DECLARE -- 16byte bytes bytea = E'\\x00000000 00000000 00000000 00000000'; v char[]; -- Allow for O(1) lookup of index values dec integer[] = ARRAY[ 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 255, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31 ]; BEGIN IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN RAISE EXCEPTION 'Invalid ULID: %', ulid; END IF; v = regexp_split_to_array(ulid, ''); -- 6 bytes timestamp (48 bits) bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]); bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2)); bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4)); bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1)); bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3)); bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]); -- 10 bytes of entropy (80 bits); bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2)); bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4)); bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1)); bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3)); bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]); bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2)); bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4)); bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1)); bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3)); bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]); RETURN bytes; END $$ LANGUAGE plpgsql IMMUTABLE; CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$ BEGIN RETURN encode(parse_ulid(ulid), 'hex')::uuid; END $$ LANGUAGE plpgsql IMMUTABLE; ``` #### UUID to ULID ```sql CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$ DECLARE encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; output text = ''; uuid_bytes bytea = uuid_send(id); BEGIN -- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31))); -- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31))); RETURN output; END $$ LANGUAGE plpgsql IMMUTABLE; ``` #### Gera 11 Digitos aleatórios: YBKXG0CKTH4 ```sql -- Cria a extensão pgcrypto para gerar uuid CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Cria a função para gerar ULID CREATE OR REPLACE FUNCTION gen_lrandom() RETURNS TEXT AS $$ DECLARE ts_millis BIGINT; ts_chars TEXT; random_bytes BYTEA; random_chars TEXT; base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; i INT; BEGIN -- Pega o timestamp em milissegundos ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT; -- Converte o timestamp para base32 ts_chars := ''; FOR i IN REVERSE 0..11 LOOP ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1); END LOOP; -- Gera 10 bytes aleatórios e converte para base32 random_bytes := gen_random_bytes(10); random_chars := ''; FOR i IN 0..9 LOOP random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1); IF i < 9 THEN random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1); ELSE random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1); END IF; END LOOP; -- Concatena o timestamp e os caracteres aleatórios RETURN ts_chars || random_chars; END; $$ LANGUAGE plpgsql; ``` #### Exemplo de USO ```sql -- Criação da extensão caso não exista CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Criação da tabela pessoas CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL ); -- Busca Pessoa na tabela SELECT * FROM "pessoas" WHERE uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F'; ``` ### Fontes - https://github.com/scoville/pgsql-ulid - https://github.com/geckoboard/pgulid
@ 91bea5cd:1df4451c
2025-02-04 17:24:50### Definição de ULID: Timestamp 48 bits, Aleatoriedade 80 bits Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C. e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível. #### Gerar ULID ```sql CREATE EXTENSION IF NOT EXISTS pgcrypto; CREATE FUNCTION generate_ulid() RETURNS TEXT AS $$ DECLARE -- Crockford's Base32 encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; timestamp BYTEA = E'\\000\\000\\000\\000\\000\\000'; output TEXT = ''; unix_time BIGINT; ulid BYTEA; BEGIN -- 6 timestamp bytes unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT; timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER); -- 10 entropy bytes ulid = timestamp || gen_random_bytes(10); -- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31))); -- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31))); RETURN output; END $$ LANGUAGE plpgsql VOLATILE; ``` #### ULID TO UUID ```sql CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$ DECLARE -- 16byte bytes bytea = E'\\x00000000 00000000 00000000 00000000'; v char[]; -- Allow for O(1) lookup of index values dec integer[] = ARRAY[ 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 255, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31 ]; BEGIN IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN RAISE EXCEPTION 'Invalid ULID: %', ulid; END IF; v = regexp_split_to_array(ulid, ''); -- 6 bytes timestamp (48 bits) bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]); bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2)); bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4)); bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1)); bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3)); bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]); -- 10 bytes of entropy (80 bits); bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2)); bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4)); bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1)); bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3)); bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]); bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2)); bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4)); bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1)); bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3)); bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]); RETURN bytes; END $$ LANGUAGE plpgsql IMMUTABLE; CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$ BEGIN RETURN encode(parse_ulid(ulid), 'hex')::uuid; END $$ LANGUAGE plpgsql IMMUTABLE; ``` #### UUID to ULID ```sql CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$ DECLARE encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; output text = ''; uuid_bytes bytea = uuid_send(id); BEGIN -- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31))); -- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31))); RETURN output; END $$ LANGUAGE plpgsql IMMUTABLE; ``` #### Gera 11 Digitos aleatórios: YBKXG0CKTH4 ```sql -- Cria a extensão pgcrypto para gerar uuid CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Cria a função para gerar ULID CREATE OR REPLACE FUNCTION gen_lrandom() RETURNS TEXT AS $$ DECLARE ts_millis BIGINT; ts_chars TEXT; random_bytes BYTEA; random_chars TEXT; base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; i INT; BEGIN -- Pega o timestamp em milissegundos ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT; -- Converte o timestamp para base32 ts_chars := ''; FOR i IN REVERSE 0..11 LOOP ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1); END LOOP; -- Gera 10 bytes aleatórios e converte para base32 random_bytes := gen_random_bytes(10); random_chars := ''; FOR i IN 0..9 LOOP random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1); IF i < 9 THEN random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1); ELSE random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1); END IF; END LOOP; -- Concatena o timestamp e os caracteres aleatórios RETURN ts_chars || random_chars; END; $$ LANGUAGE plpgsql; ``` #### Exemplo de USO ```sql -- Criação da extensão caso não exista CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Criação da tabela pessoas CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL ); -- Busca Pessoa na tabela SELECT * FROM "pessoas" WHERE uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F'; ``` ### Fontes - https://github.com/scoville/pgsql-ulid - https://github.com/geckoboard/pgulid @ 91bea5cd:1df4451c
2025-02-04 17:15:57### Definição de ULID: Timestamp 48 bits, Aleatoriedade 80 bits Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C. e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível. #### Gerar ULID ```sql CREATE EXTENSION IF NOT EXISTS pgcrypto; CREATE FUNCTION generate_ulid() RETURNS TEXT AS $$ DECLARE -- Crockford's Base32 encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; timestamp BYTEA = E'\\000\\000\\000\\000\\000\\000'; output TEXT = ''; unix_time BIGINT; ulid BYTEA; BEGIN -- 6 timestamp bytes unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT; timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER); -- 10 entropy bytes ulid = timestamp || gen_random_bytes(10); -- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31))); -- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31))); RETURN output; END $$ LANGUAGE plpgsql VOLATILE; ``` #### ULID TO UUID ```sql CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$ DECLARE -- 16byte bytes bytea = E'\\x00000000 00000000 00000000 00000000'; v char[]; -- Allow for O(1) lookup of index values dec integer[] = ARRAY[ 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 255, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31 ]; BEGIN IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN RAISE EXCEPTION 'Invalid ULID: %', ulid; END IF; v = regexp_split_to_array(ulid, ''); -- 6 bytes timestamp (48 bits) bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]); bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2)); bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4)); bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1)); bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3)); bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]); -- 10 bytes of entropy (80 bits); bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2)); bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4)); bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1)); bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3)); bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]); bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2)); bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4)); bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1)); bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3)); bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]); RETURN bytes; END $$ LANGUAGE plpgsql IMMUTABLE; CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$ BEGIN RETURN encode(parse_ulid(ulid), 'hex')::uuid; END $$ LANGUAGE plpgsql IMMUTABLE; ``` #### UUID to ULID ```sql CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$ DECLARE encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; output text = ''; uuid_bytes bytea = uuid_send(id); BEGIN -- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31))); -- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31))); RETURN output; END $$ LANGUAGE plpgsql IMMUTABLE; ``` #### Gera 11 Digitos aleatórios: YBKXG0CKTH4 ```sql -- Cria a extensão pgcrypto para gerar uuid CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Cria a função para gerar ULID CREATE OR REPLACE FUNCTION gen_lrandom() RETURNS TEXT AS $$ DECLARE ts_millis BIGINT; ts_chars TEXT; random_bytes BYTEA; random_chars TEXT; base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; i INT; BEGIN -- Pega o timestamp em milissegundos ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT; -- Converte o timestamp para base32 ts_chars := ''; FOR i IN REVERSE 0..11 LOOP ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1); END LOOP; -- Gera 10 bytes aleatórios e converte para base32 random_bytes := gen_random_bytes(10); random_chars := ''; FOR i IN 0..9 LOOP random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1); IF i < 9 THEN random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1); ELSE random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1); END IF; END LOOP; -- Concatena o timestamp e os caracteres aleatórios RETURN ts_chars || random_chars; END; $$ LANGUAGE plpgsql; ``` #### Exemplo de USO ```sql -- Criação da extensão caso não exista CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Criação da tabela pessoas CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL ); -- Busca Pessoa na tabela SELECT * FROM "pessoas" WHERE uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F'; ``` ### Fontes - https://github.com/scoville/pgsql-ulid - https://github.com/geckoboard/pgulid
@ 91bea5cd:1df4451c
2025-02-04 17:15:57### Definição de ULID: Timestamp 48 bits, Aleatoriedade 80 bits Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C. e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível. #### Gerar ULID ```sql CREATE EXTENSION IF NOT EXISTS pgcrypto; CREATE FUNCTION generate_ulid() RETURNS TEXT AS $$ DECLARE -- Crockford's Base32 encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; timestamp BYTEA = E'\\000\\000\\000\\000\\000\\000'; output TEXT = ''; unix_time BIGINT; ulid BYTEA; BEGIN -- 6 timestamp bytes unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT; timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER); -- 10 entropy bytes ulid = timestamp || gen_random_bytes(10); -- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31))); -- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31))); RETURN output; END $$ LANGUAGE plpgsql VOLATILE; ``` #### ULID TO UUID ```sql CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$ DECLARE -- 16byte bytes bytea = E'\\x00000000 00000000 00000000 00000000'; v char[]; -- Allow for O(1) lookup of index values dec integer[] = ARRAY[ 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 255, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31 ]; BEGIN IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN RAISE EXCEPTION 'Invalid ULID: %', ulid; END IF; v = regexp_split_to_array(ulid, ''); -- 6 bytes timestamp (48 bits) bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]); bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2)); bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4)); bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1)); bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3)); bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]); -- 10 bytes of entropy (80 bits); bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2)); bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4)); bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1)); bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3)); bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]); bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2)); bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4)); bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1)); bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3)); bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]); RETURN bytes; END $$ LANGUAGE plpgsql IMMUTABLE; CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$ BEGIN RETURN encode(parse_ulid(ulid), 'hex')::uuid; END $$ LANGUAGE plpgsql IMMUTABLE; ``` #### UUID to ULID ```sql CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$ DECLARE encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; output text = ''; uuid_bytes bytea = uuid_send(id); BEGIN -- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31))); -- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31))); RETURN output; END $$ LANGUAGE plpgsql IMMUTABLE; ``` #### Gera 11 Digitos aleatórios: YBKXG0CKTH4 ```sql -- Cria a extensão pgcrypto para gerar uuid CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Cria a função para gerar ULID CREATE OR REPLACE FUNCTION gen_lrandom() RETURNS TEXT AS $$ DECLARE ts_millis BIGINT; ts_chars TEXT; random_bytes BYTEA; random_chars TEXT; base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; i INT; BEGIN -- Pega o timestamp em milissegundos ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT; -- Converte o timestamp para base32 ts_chars := ''; FOR i IN REVERSE 0..11 LOOP ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1); END LOOP; -- Gera 10 bytes aleatórios e converte para base32 random_bytes := gen_random_bytes(10); random_chars := ''; FOR i IN 0..9 LOOP random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1); IF i < 9 THEN random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1); ELSE random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1); END IF; END LOOP; -- Concatena o timestamp e os caracteres aleatórios RETURN ts_chars || random_chars; END; $$ LANGUAGE plpgsql; ``` #### Exemplo de USO ```sql -- Criação da extensão caso não exista CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Criação da tabela pessoas CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL ); -- Busca Pessoa na tabela SELECT * FROM "pessoas" WHERE uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F'; ``` ### Fontes - https://github.com/scoville/pgsql-ulid - https://github.com/geckoboard/pgulid @ 8f69ac99:4f92f5fd
2025-02-20 15:24:24Anarquia: uma palavra que frequentemente evoca imagens de caos e desordem, associada ao velho oeste sem lei ou a futuros distópicos onde impera a força bruta. No entanto, para aqueles que investigam mais a fundo, a anarquia revela-se como algo muito mais sofisticado—um sistema não definido pela ausência de regras, mas sim pela ausência de governantes (*rules without rulers*). Essa distinção fundamental é essencial para compreender um dos conceitos mais fascinantes e, ao mesmo tempo, mais difamados da sociedade. A ideia de que anarquia significa desordem ou uma sociedade sem estrutura é um equívoco baseado no medo do desconhecido e na falta de compreensão dos seus princípios básicos. Na realidade, a anarquia assenta sobre um princípio fundamental: o **Princípio da Não-Agressão (PNA)**. Este princípio estabelece que nenhum indivíduo tem o direito de iniciar o uso da força, coerção ou fraude contra os outros, sem o seu consentimento, sendo este um dos pilares fundamentais para a preservação da propriedade privada e das liberdades individuais. Não se trata, portanto, de uma sociedade sem regras, mas sim de uma organização baseada em **estruturas legais descentralizadas e orgânicas**, como a **lei natural e o direito consuetudinário**, que emergem naturalmente através das interacções voluntárias entre indivíduos. A história demonstra que, mesmo na ausência de uma autoridade central, os seres humanos são perfeitamente capazes de criar ordens sociais complexas, baseadas na cooperação, na ajuda mútua e no progresso. Este artigo explora como a anarquia funciona enquanto sistema de cooperação voluntária e direito natural, desafiando as concepções erradas que persistem sobre o tema e revelando o seu potencial para fortalecer a liberdade individual e a coesão social. Ao analisar as suas raízes filosóficas, o papel do Estado dentro de um enquadramento anarquista e os exemplos históricos que demonstram a capacidade da humanidade para se auto-organizar, procuramos iluminar um futuro onde a liberdade não seja apenas um sonho utópico, mas uma possibilidade concreta. ## Principio da Não Agressão (PNA) A **base da anarquia** assenta sobre um princípio inegociável: o Princípio da Não-Agressão. Este postulado não é apenas uma directriz moral, mas sim uma regra essencial de conduta, destinada a fomentar uma sociedade cooperativa e pacífica, onde os indivíduos vivem sem medo da coerção ou da violência. A partir deste princípio, deriva-se naturalmente a **propriedade privada**, pois cada indivíduo tem o direito de usufruir e gerir os recursos que adquire sem recorrer à força contra terceiros. Da mesma forma, a violação deste princípio—seja através do roubo, homicídio ou qualquer tipo de agressão física ou psicológica, não consentida—é condenada de forma universal, pois representa um atentado contra a liberdade de cada um. Num enquadramento anarquista, a ausência de uma estrutura coerciva não significa a ausência de ordem. Métodos como **pressão social, ostracismo de infractores e mecanismos privados de justiça** ajudam a manter a harmonia social. Por exemplo, em situações de litígio entre vizinhos sobre a posse de um terreno, em vez de recorrer ao Estado, poderiam simplesmente resolver a disputa através de um mediador comunitário ou de um serviço de arbitragem voluntário. ## Ordem Sem Autoridade Central A crença de que a lei e a ordem dependem de um poder centralizado ignora uma vasta tradição histórica de **sistemas legais descentralizados** que surgiram espontaneamente, sem intervenção estatal. A anarquia não significa ausência de normas, mas sim uma **ordem espontânea baseada em leis naturais e consuetudinárias**. A lei natural consiste em princípios universais, reconhecidos pela razão, que não dependem da autoridade estatal. Já o direito consuetudinário assenta na tradição e nos precedentes, evoluindo conforme as necessidades das comunidades. Um excelente exemplo histórico é o código jurídico medieval islandês "Grágás", que regulava litígios e contratos através de mediação voluntária. Sistemas baseados na reputação também são eficazes. No passado, comerciantes que desrespeitassem contratos viam-se rapidamente excluídos do mercado. Hoje, soluções descentralizadas como a arbitragem privada demonstram que contratos podem ser cumpridos sem necessidade de coerção estatal. ## Anarquia como Estado Natural da Cooperação Humana A cooperação voluntária está no cerne da natureza humana. A ideia de que é necessária uma autoridade central para garantir harmonia social desconsidera as inúmeras instâncias de colaboração espontânea ao longo da história. O funcionamento dos mercados ilustra perfeitamente a anarquia em acção. Sem um governo a ditar regras, indivíduos interagem livremente, criando riqueza e inovação. A busca pelo progresso científico também reflecte este princípio: Albert Einstein, Nikola Tesla, Henry Ford ou Thomas Edison não foram forçados pelo Estado a desenvolver as suas invenções—fizeram-no por interesse próprio, beneficiando toda a humanidade. Da mesma forma, a revolução industrial não foi um plano centralizado, mas sim o resultado de inúmeras inovações individuais que impulsionaram a prosperidade global. A tecnologia moderna, com exemplos como Bitcoin e Nostr, redes descentralizadas, prova que sociedades podem operar sem intermediários estatais, ou autoridades centrais. ## Estado: Pode Existir Num Enquadramento Anarquista? O Estado, mesmo na sua versão mais reduzida, pode representar um risco para a liberdade individual. Alguns, eu incluído, argumentam que um "Estado mínimo" (minarquia) poderia existir para garantir segurança e mediar disputas, mas essa estrutura pode rapidamente expandir-se e transformar-se num mecanismo de coerção. ### A necessidade de mecanismos de controlo e equilíbrio Mesmo um Estado reduzido exigiria salvaguardas para evitar abusos de poder. Para isso, seriam necessários mecanismos que garantam que nenhuma autoridade se torne dominante e que a sociedade mantenha a sua autonomia. Algumas soluções incluem: - **Representação directa**: Em vez de delegar decisões a políticos, a população poderia ter mais influência directa nas questões que afectam a sua vida (como na Suiça por exemplo). - **Arbitragem independente**: Conflitos poderiam ser resolvidos sem recorrer a tribunais estatais, através de mediação voluntária e sistemas de justiça comunitária. - **Redes de apoio social**: Fortalecer redes de ajuda mútua reduziria a necessidade de um governo central para fornecer serviços essenciais. ### Exemplos práticos Algumas iniciativas mostram que a sociedade pode funcionar com estruturas descentralizadas: - **Cidades com participação cívica activa**: Experiências como o orçamento participativo em algumas cidades demonstram como a sociedade pode gerir recursos colectivos sem excessiva intervenção estatal. - **Redes de ajuda mútua**: Grupos como a *Mutual Aid Disaster Response Network* nos EUA provam que comunidades podem organizar-se para responder a crises sem depender do Estado. O desafio não é apenas imaginar um mundo sem Estado, mas conceber modelos descentralizados que garantam a liberdade individual e impeçam a concentração de poder. A verdadeira questão é: conseguiremos criar sistemas mais justos e funcionais sem recorrer à coerção estatal? ## Raízes Filosóficas da Anarquia A anarquia tem uma longa tradição filosófica que remonta a pensadores como **William Godwin**, **Pierre-Joseph Proudhon** e **Max Stirner**, cada um contribuindo com diferentes perspectivas sobre a organização social sem governantes. No século XX, pensadores como **Murray Rothbard** e **Hans-Hermann Hoppe** aprofundaram a ideia do anarco-capitalismo, propondo que todos os serviços actualmente providenciados pelo Estado poderiam ser oferecidos por meio de mercados livres. A raiz histórica da anarquia está firmemente ancorada no pensamento de esquerda (a tradicional... ), na medida em que a sua proposta fundamental é a **eliminação do poder central**. O anarquismo clássico emergiu como uma resposta ao absolutismo e ao capitalismo industrial, defendendo que a autoridade imposta pelo Estado e pelas elites económicas deveria ser desmantelada para dar lugar a um sistema de cooperação voluntária e descentralizada. Proudhon, ao afirmar "a propriedade é roubo", reflectia esta preocupação com a concentração de poder e riqueza nas mãos de poucos. Com o tempo, no entanto, diferentes correntes começaram a emergir dentro da tradição anarquista. A tradição anarquista de **esquerda** enfatiza a justiça social e a solidariedade comunitária, rejeitando tanto o Estado como o capitalismo. Nomes como **Bakunin** e **Kropotkin** defenderam a abolição da propriedade privada em favor de sistemas cooperativos, argumentando que apenas a auto gestão e o apoio mútuo poderiam garantir a verdadeira liberdade. Por outro lado, no século XX, surgiu uma vertente anarquista mais **associada à direita**, especialmente com Rothbard e Hoppe, que viam o mercado como a melhor alternativa ao Estado. Para os anarco-capitalistas, a liberdade individual é prioritária, e a descentralização deve ocorrer não apenas ao nível político, mas também económico, permitindo que todas as transacções sejam voluntárias e baseadas na propriedade privada. Apesar dessas divergências, há um ponto comum entre todas as vertentes anarquistas: a rejeição do **monopólio da violência estatal**. Tanto anarquistas de esquerda quanto de direita reconhecem que o poder centralizado inevitavelmente conduz à opressão e à limitação da liberdade individual. O debate interno dentro do anarquismo não é sobre a necessidade de abolir o Estado, mas sim sobre o que deve substituí-lo: auto gestão comunitária e colectivismo ou mercados livres e concorrência voluntária? A preservação da propriedade privada e a liberdade de associação são, para mim, princípios fundamentais dentro do pensamento anarquista. Nada impede que, numa sociedade anarquista, grupos de indivíduos escolham unir-se voluntariamente para formar projectos cooperativos baseados em valores partilhados. O que distingue essa abordagem da imposição estatal é o carácter voluntário e descentralizado dessas associações, garantindo que cada pessoa possa viver conforme os seus próprios princípios sem coerção externa. Esta dicotomia entre esquerda e direita dentro do anarquismo reflecte diferentes interpretações sobre a melhor forma de organizar a sociedade sem coerção. O que permanece inegável é que a anarquia, independentemente da vertente, continua a ser uma proposta de resistência contra qualquer forma de domínio centralizado, colocando a liberdade e a autonomia no centro da organização social. ## Conclusão A anarquia não é um sonho utópico, mas sim uma alternativa viável à organização centralizada da sociedade. Através do respeito pelo Princípio da Não-Agressão, da descentralização das normas jurídicas e da cooperação voluntária, podemos construir um mundo mais livre, onde as pessoas têm o poder de se governar a si mesmas. Sistemas como Bitcoin já demonstram que a descentralização funciona e que a ausência de intermediários coercivos é não só possível, mas desejável. O desafio não é saber se a anarquia pode funcionar, mas sim **quanto tempo levará para as pessoas perceberem que um mundo sem Estado é mais próspero e justo**. #anarquia #anarco #bitcoin --- _Photo by [Orit Matee](https://unsplash.com/@splashcom?utm_content=creditCopyText&utm_medium=referral&utm_source=unsplash) on [Unsplash](https://unsplash.com/photos/black-and-silver-heart-shaped-wall-decor-qqiAxa9hpaA?utm_content=creditCopyText&utm_medium=referral&utm_source=unsplash)_
@ 8f69ac99:4f92f5fd
2025-02-20 15:24:24Anarquia: uma palavra que frequentemente evoca imagens de caos e desordem, associada ao velho oeste sem lei ou a futuros distópicos onde impera a força bruta. No entanto, para aqueles que investigam mais a fundo, a anarquia revela-se como algo muito mais sofisticado—um sistema não definido pela ausência de regras, mas sim pela ausência de governantes (*rules without rulers*). Essa distinção fundamental é essencial para compreender um dos conceitos mais fascinantes e, ao mesmo tempo, mais difamados da sociedade. A ideia de que anarquia significa desordem ou uma sociedade sem estrutura é um equívoco baseado no medo do desconhecido e na falta de compreensão dos seus princípios básicos. Na realidade, a anarquia assenta sobre um princípio fundamental: o **Princípio da Não-Agressão (PNA)**. Este princípio estabelece que nenhum indivíduo tem o direito de iniciar o uso da força, coerção ou fraude contra os outros, sem o seu consentimento, sendo este um dos pilares fundamentais para a preservação da propriedade privada e das liberdades individuais. Não se trata, portanto, de uma sociedade sem regras, mas sim de uma organização baseada em **estruturas legais descentralizadas e orgânicas**, como a **lei natural e o direito consuetudinário**, que emergem naturalmente através das interacções voluntárias entre indivíduos. A história demonstra que, mesmo na ausência de uma autoridade central, os seres humanos são perfeitamente capazes de criar ordens sociais complexas, baseadas na cooperação, na ajuda mútua e no progresso. Este artigo explora como a anarquia funciona enquanto sistema de cooperação voluntária e direito natural, desafiando as concepções erradas que persistem sobre o tema e revelando o seu potencial para fortalecer a liberdade individual e a coesão social. Ao analisar as suas raízes filosóficas, o papel do Estado dentro de um enquadramento anarquista e os exemplos históricos que demonstram a capacidade da humanidade para se auto-organizar, procuramos iluminar um futuro onde a liberdade não seja apenas um sonho utópico, mas uma possibilidade concreta. ## Principio da Não Agressão (PNA) A **base da anarquia** assenta sobre um princípio inegociável: o Princípio da Não-Agressão. Este postulado não é apenas uma directriz moral, mas sim uma regra essencial de conduta, destinada a fomentar uma sociedade cooperativa e pacífica, onde os indivíduos vivem sem medo da coerção ou da violência. A partir deste princípio, deriva-se naturalmente a **propriedade privada**, pois cada indivíduo tem o direito de usufruir e gerir os recursos que adquire sem recorrer à força contra terceiros. Da mesma forma, a violação deste princípio—seja através do roubo, homicídio ou qualquer tipo de agressão física ou psicológica, não consentida—é condenada de forma universal, pois representa um atentado contra a liberdade de cada um. Num enquadramento anarquista, a ausência de uma estrutura coerciva não significa a ausência de ordem. Métodos como **pressão social, ostracismo de infractores e mecanismos privados de justiça** ajudam a manter a harmonia social. Por exemplo, em situações de litígio entre vizinhos sobre a posse de um terreno, em vez de recorrer ao Estado, poderiam simplesmente resolver a disputa através de um mediador comunitário ou de um serviço de arbitragem voluntário. ## Ordem Sem Autoridade Central A crença de que a lei e a ordem dependem de um poder centralizado ignora uma vasta tradição histórica de **sistemas legais descentralizados** que surgiram espontaneamente, sem intervenção estatal. A anarquia não significa ausência de normas, mas sim uma **ordem espontânea baseada em leis naturais e consuetudinárias**. A lei natural consiste em princípios universais, reconhecidos pela razão, que não dependem da autoridade estatal. Já o direito consuetudinário assenta na tradição e nos precedentes, evoluindo conforme as necessidades das comunidades. Um excelente exemplo histórico é o código jurídico medieval islandês "Grágás", que regulava litígios e contratos através de mediação voluntária. Sistemas baseados na reputação também são eficazes. No passado, comerciantes que desrespeitassem contratos viam-se rapidamente excluídos do mercado. Hoje, soluções descentralizadas como a arbitragem privada demonstram que contratos podem ser cumpridos sem necessidade de coerção estatal. ## Anarquia como Estado Natural da Cooperação Humana A cooperação voluntária está no cerne da natureza humana. A ideia de que é necessária uma autoridade central para garantir harmonia social desconsidera as inúmeras instâncias de colaboração espontânea ao longo da história. O funcionamento dos mercados ilustra perfeitamente a anarquia em acção. Sem um governo a ditar regras, indivíduos interagem livremente, criando riqueza e inovação. A busca pelo progresso científico também reflecte este princípio: Albert Einstein, Nikola Tesla, Henry Ford ou Thomas Edison não foram forçados pelo Estado a desenvolver as suas invenções—fizeram-no por interesse próprio, beneficiando toda a humanidade. Da mesma forma, a revolução industrial não foi um plano centralizado, mas sim o resultado de inúmeras inovações individuais que impulsionaram a prosperidade global. A tecnologia moderna, com exemplos como Bitcoin e Nostr, redes descentralizadas, prova que sociedades podem operar sem intermediários estatais, ou autoridades centrais. ## Estado: Pode Existir Num Enquadramento Anarquista? O Estado, mesmo na sua versão mais reduzida, pode representar um risco para a liberdade individual. Alguns, eu incluído, argumentam que um "Estado mínimo" (minarquia) poderia existir para garantir segurança e mediar disputas, mas essa estrutura pode rapidamente expandir-se e transformar-se num mecanismo de coerção. ### A necessidade de mecanismos de controlo e equilíbrio Mesmo um Estado reduzido exigiria salvaguardas para evitar abusos de poder. Para isso, seriam necessários mecanismos que garantam que nenhuma autoridade se torne dominante e que a sociedade mantenha a sua autonomia. Algumas soluções incluem: - **Representação directa**: Em vez de delegar decisões a políticos, a população poderia ter mais influência directa nas questões que afectam a sua vida (como na Suiça por exemplo). - **Arbitragem independente**: Conflitos poderiam ser resolvidos sem recorrer a tribunais estatais, através de mediação voluntária e sistemas de justiça comunitária. - **Redes de apoio social**: Fortalecer redes de ajuda mútua reduziria a necessidade de um governo central para fornecer serviços essenciais. ### Exemplos práticos Algumas iniciativas mostram que a sociedade pode funcionar com estruturas descentralizadas: - **Cidades com participação cívica activa**: Experiências como o orçamento participativo em algumas cidades demonstram como a sociedade pode gerir recursos colectivos sem excessiva intervenção estatal. - **Redes de ajuda mútua**: Grupos como a *Mutual Aid Disaster Response Network* nos EUA provam que comunidades podem organizar-se para responder a crises sem depender do Estado. O desafio não é apenas imaginar um mundo sem Estado, mas conceber modelos descentralizados que garantam a liberdade individual e impeçam a concentração de poder. A verdadeira questão é: conseguiremos criar sistemas mais justos e funcionais sem recorrer à coerção estatal? ## Raízes Filosóficas da Anarquia A anarquia tem uma longa tradição filosófica que remonta a pensadores como **William Godwin**, **Pierre-Joseph Proudhon** e **Max Stirner**, cada um contribuindo com diferentes perspectivas sobre a organização social sem governantes. No século XX, pensadores como **Murray Rothbard** e **Hans-Hermann Hoppe** aprofundaram a ideia do anarco-capitalismo, propondo que todos os serviços actualmente providenciados pelo Estado poderiam ser oferecidos por meio de mercados livres. A raiz histórica da anarquia está firmemente ancorada no pensamento de esquerda (a tradicional... ), na medida em que a sua proposta fundamental é a **eliminação do poder central**. O anarquismo clássico emergiu como uma resposta ao absolutismo e ao capitalismo industrial, defendendo que a autoridade imposta pelo Estado e pelas elites económicas deveria ser desmantelada para dar lugar a um sistema de cooperação voluntária e descentralizada. Proudhon, ao afirmar "a propriedade é roubo", reflectia esta preocupação com a concentração de poder e riqueza nas mãos de poucos. Com o tempo, no entanto, diferentes correntes começaram a emergir dentro da tradição anarquista. A tradição anarquista de **esquerda** enfatiza a justiça social e a solidariedade comunitária, rejeitando tanto o Estado como o capitalismo. Nomes como **Bakunin** e **Kropotkin** defenderam a abolição da propriedade privada em favor de sistemas cooperativos, argumentando que apenas a auto gestão e o apoio mútuo poderiam garantir a verdadeira liberdade. Por outro lado, no século XX, surgiu uma vertente anarquista mais **associada à direita**, especialmente com Rothbard e Hoppe, que viam o mercado como a melhor alternativa ao Estado. Para os anarco-capitalistas, a liberdade individual é prioritária, e a descentralização deve ocorrer não apenas ao nível político, mas também económico, permitindo que todas as transacções sejam voluntárias e baseadas na propriedade privada. Apesar dessas divergências, há um ponto comum entre todas as vertentes anarquistas: a rejeição do **monopólio da violência estatal**. Tanto anarquistas de esquerda quanto de direita reconhecem que o poder centralizado inevitavelmente conduz à opressão e à limitação da liberdade individual. O debate interno dentro do anarquismo não é sobre a necessidade de abolir o Estado, mas sim sobre o que deve substituí-lo: auto gestão comunitária e colectivismo ou mercados livres e concorrência voluntária? A preservação da propriedade privada e a liberdade de associação são, para mim, princípios fundamentais dentro do pensamento anarquista. Nada impede que, numa sociedade anarquista, grupos de indivíduos escolham unir-se voluntariamente para formar projectos cooperativos baseados em valores partilhados. O que distingue essa abordagem da imposição estatal é o carácter voluntário e descentralizado dessas associações, garantindo que cada pessoa possa viver conforme os seus próprios princípios sem coerção externa. Esta dicotomia entre esquerda e direita dentro do anarquismo reflecte diferentes interpretações sobre a melhor forma de organizar a sociedade sem coerção. O que permanece inegável é que a anarquia, independentemente da vertente, continua a ser uma proposta de resistência contra qualquer forma de domínio centralizado, colocando a liberdade e a autonomia no centro da organização social. ## Conclusão A anarquia não é um sonho utópico, mas sim uma alternativa viável à organização centralizada da sociedade. Através do respeito pelo Princípio da Não-Agressão, da descentralização das normas jurídicas e da cooperação voluntária, podemos construir um mundo mais livre, onde as pessoas têm o poder de se governar a si mesmas. Sistemas como Bitcoin já demonstram que a descentralização funciona e que a ausência de intermediários coercivos é não só possível, mas desejável. O desafio não é saber se a anarquia pode funcionar, mas sim **quanto tempo levará para as pessoas perceberem que um mundo sem Estado é mais próspero e justo**. #anarquia #anarco #bitcoin --- _Photo by [Orit Matee](https://unsplash.com/@splashcom?utm_content=creditCopyText&utm_medium=referral&utm_source=unsplash) on [Unsplash](https://unsplash.com/photos/black-and-silver-heart-shaped-wall-decor-qqiAxa9hpaA?utm_content=creditCopyText&utm_medium=referral&utm_source=unsplash)_ @ 5a261a61:2ebd4480
2025-02-18 18:22:19The yellow light won the battle against the feeble excuse for curtains and crept into the room. It moved cautiously as if was afraid where to step. A common trait to all who found their way into the back room of the Lost Cases Detective Agency. The current owner had inherited both the premises and the name from his predecessor, and whenever someone questioned the name, he would announce half-irritably that changing it was simply too expensive to afford. The noodle vendor from the floor below would never miss the chance to add that people who end up at his place didn't choose it for the name anyway. The truth (which he was willing to admit only to the creaking fan that scared away mice rather than actually serving its function) was that he liked the name. Like attracts like. A lost soul for lost cases. The darkness was finally driven even from the eyelids of the figure on the bed, who woke up with a dissatisfied grunt. A few steps to the sink hidden behind a screen. The shadows cast by the street light might have seemed depressive to some, mainly because they weren't accompanied by the warming feeling of sunlight, blocked by the high skyscrapers embracing the lower houses of the former middle class. Tom smiled resignedly at this thought. It perfectly captured how everything in this city merged into one big tangle, which looks beautiful until you have to untangle it. The yellow light came from a neon sign across the street advertising "The Beach." One of many places in this City where one could hide in a drop of alcohol and the embrace of a beautiful woman. Though it was necessary to maintain that order... the companions didn't exactly recruit from the best of the best looking local beauties. Tom turned the tap and waited until the water, after grunting, gargling, and several splutters, settled and began flowing somewhat predictably. Tom didn't mind the wait. In his line of work, patience was cheaper than bullets. And it was nice to have time when he could do nothing but wait. He examined himself in the mirror. The shadows did him favors, adding years he hadn't earned. As young as he was, he needed all the help he could get - clients wanted their private dick weathered, not fresh out of the wrapper. He had the look down pat: world-weary veteran who knew all the angles. Truth was, he couldn't even figure out the angle of his own life, but that was a case file he kept closed. The water spluttered one last time. "Good morning, dickhead," he greeted himself with unwavering conviction that today would be better than yesterday. While most people were heading to dinner, putting kids to bed, or hurrying to visit their lovers at this hour, he was waking up. So for him, it was morning. For him and a myriad of other existences who, by choice or necessity, lived more at night than during the day. Finally, he trimmed his beard to short, neat stubble - enough to look serious, but with a touch of toughness suggesting he wasn't afraid to get his hands dirty. "Perfect," he muttered to himself, "I look like a man who knows what he's doing." Maybe that illusion will convince me one day, he thought as he turned off the light in the small bathroom. With a final look in the mirror, he adjusted his shirt collar. He was ready to face the city's challenges. Whatever awaited him today, at least he'd look prepared for it. From the hook by the door, he grabbed a ring with an identification tag and some loose change. He ran down a flight of creaking stairs and headed past empty bar stools toward the exit. The disadvantage of living above a restaurant. Though the major advantage is the high of the rent. Or rather, its lowness. Jiro, the owner of the small bistro and, coincidentally, a decent exterminator, looked at him through a dense veil of greasy vapors, nodded, and continued stirring the noodles. Where to next? - say hi - get some food - just run outside > This is kind of an experiment with converting my WIP interactive fiction project to the nostr longnote format and letting readers decide. Originally, this story leans quite heavily toward FLR/femdom/mindcontrol/noir/steampunk/fantasy and hopefully a little mystery detective story, but let's see where (and if) it will lead from here. Also, it's mostly translated from my native language, so sorry if some wording seems stiff.
@ 5a261a61:2ebd4480
2025-02-18 18:22:19The yellow light won the battle against the feeble excuse for curtains and crept into the room. It moved cautiously as if was afraid where to step. A common trait to all who found their way into the back room of the Lost Cases Detective Agency. The current owner had inherited both the premises and the name from his predecessor, and whenever someone questioned the name, he would announce half-irritably that changing it was simply too expensive to afford. The noodle vendor from the floor below would never miss the chance to add that people who end up at his place didn't choose it for the name anyway. The truth (which he was willing to admit only to the creaking fan that scared away mice rather than actually serving its function) was that he liked the name. Like attracts like. A lost soul for lost cases. The darkness was finally driven even from the eyelids of the figure on the bed, who woke up with a dissatisfied grunt. A few steps to the sink hidden behind a screen. The shadows cast by the street light might have seemed depressive to some, mainly because they weren't accompanied by the warming feeling of sunlight, blocked by the high skyscrapers embracing the lower houses of the former middle class. Tom smiled resignedly at this thought. It perfectly captured how everything in this city merged into one big tangle, which looks beautiful until you have to untangle it. The yellow light came from a neon sign across the street advertising "The Beach." One of many places in this City where one could hide in a drop of alcohol and the embrace of a beautiful woman. Though it was necessary to maintain that order... the companions didn't exactly recruit from the best of the best looking local beauties. Tom turned the tap and waited until the water, after grunting, gargling, and several splutters, settled and began flowing somewhat predictably. Tom didn't mind the wait. In his line of work, patience was cheaper than bullets. And it was nice to have time when he could do nothing but wait. He examined himself in the mirror. The shadows did him favors, adding years he hadn't earned. As young as he was, he needed all the help he could get - clients wanted their private dick weathered, not fresh out of the wrapper. He had the look down pat: world-weary veteran who knew all the angles. Truth was, he couldn't even figure out the angle of his own life, but that was a case file he kept closed. The water spluttered one last time. "Good morning, dickhead," he greeted himself with unwavering conviction that today would be better than yesterday. While most people were heading to dinner, putting kids to bed, or hurrying to visit their lovers at this hour, he was waking up. So for him, it was morning. For him and a myriad of other existences who, by choice or necessity, lived more at night than during the day. Finally, he trimmed his beard to short, neat stubble - enough to look serious, but with a touch of toughness suggesting he wasn't afraid to get his hands dirty. "Perfect," he muttered to himself, "I look like a man who knows what he's doing." Maybe that illusion will convince me one day, he thought as he turned off the light in the small bathroom. With a final look in the mirror, he adjusted his shirt collar. He was ready to face the city's challenges. Whatever awaited him today, at least he'd look prepared for it. From the hook by the door, he grabbed a ring with an identification tag and some loose change. He ran down a flight of creaking stairs and headed past empty bar stools toward the exit. The disadvantage of living above a restaurant. Though the major advantage is the high of the rent. Or rather, its lowness. Jiro, the owner of the small bistro and, coincidentally, a decent exterminator, looked at him through a dense veil of greasy vapors, nodded, and continued stirring the noodles. Where to next? - say hi - get some food - just run outside > This is kind of an experiment with converting my WIP interactive fiction project to the nostr longnote format and letting readers decide. Originally, this story leans quite heavily toward FLR/femdom/mindcontrol/noir/steampunk/fantasy and hopefully a little mystery detective story, but let's see where (and if) it will lead from here. Also, it's mostly translated from my native language, so sorry if some wording seems stiff. @ 97c70a44:ad98e322
2025-02-17 14:29:00Everyone knows that relays are central to how nostr works - they're even in the name: Notes and Other Stuff Transmitted by *Relays*. As time goes on though, there are three other letters which are becoming conspicuously absent from our beloved and ambiguously pronounceable acronym - "D", "V", and "M". For the uninitiated, DVM stands for "data vending machines". They're actually sort of hard to describe — in technical terms they act more like clients, since they simply read events from and publish events to relays. In most cases though, these events are part of a request/response flow initiated by users elsewhere on the network. In practice, DVMs are bots, but there's also nothing to prevent the work they do from being powered by human interaction. They're an amazingly flexible tool for building anything from custom feeds, to transcription services, to chatbots, to protocol gateways. The hype cycle for DVMs seems to have reached escape velocity in a way few other things have - zaps being the possible exception. But *what* exactly DVMs are remains something of a mystery to many nostr developers - and how to build one may as well be written on clay tablets. This blog post is designed to address that - below is a soup to nuts (no nutzaps though) guide to building a DVM flow, both from the client and the server side. Here's what we'll be covering: - Discovering DVM metadata - Basic request/response flow - Implementing a minimal example Let's get started! # DVM Metadata First of all, it's helpful to know how DVMs are reified on the nostr network. While not strictly necessary, this can be useful for discovering DVMs and presenting them to users, and for targeting specific DVMs we want a response from. [NIP 89](https://github.com/nostr-protocol/nips/blob/master/89.md) goes into this in more detail, but the basic idea is that anyone can create a `kind 31990` "application handler" event and publish it to the network with their own (or a dedicated) public key. This handler was originally intended to advertise clients, but has been re-purposed for DVM listings as well. Here's what the "Fluffy Frens" handler looks like: ```json { "content": "{\"name\": \"Fluffy Frens\", \"picture\": \"https://image.nostr.build/f609311532c470f663e129510a76c9a1912ae9bc4aaaf058e5ba21cfb512c88e.jpg\", \"about\": \"I show recent notes about animals\", \"lud16\": \"discovery_content_fluffy@nostrdvm.com\", \"supportsEncryption\": true, \"acceptsNutZaps\": false, \"personalized\": false, \"amount\": \"free\", \"nip90Params\": {\"max_results\": {\"required\": false, \"values\": [], \"description\": \"The number of maximum results to return (default currently 100)\"}}}", "created_at": 1738874694, "id": "0aa8d1f19cfe17e00ce55ca86fea487c83be39a1813601f56f869abdfa776b3c", "kind": 31990, "pubkey": "7b7373dd58554ff4c0d28b401b9eae114bd92e30d872ae843b9a217375d66f9d", "sig": "22403a7996147da607cf215994ab3b893176e5302a44a245e9c0d91214e4c56fae40d2239dce58ea724114591e8f95caed2ba1a231d09a6cd06c9f0980e1abd5", "tags": [ ["k", "5300"], ["d", "198650843898570c"] ] } ``` This event is rendered in various clients using the kind-0-style metadata contained in the `content` field, allowing users to browse DVMs and pick one for their use case. If a user likes using a particular DVM, they might publish a `kind 31989` "application recommendation", which other users can use to find DVMs that are in use within their network. Note the `k` tag in the handler event - this allows DVMs to advertise support only for specific job types. It's also important to note that even though the spec doesn't cover relay selection, most clients use the publisher's `kind 10002` event to find out where the DVM listens for events. If this looks messy to you, you're right. See [this PR](https://github.com/nostr-protocol/nips/pull/1728) for a proposal to split DVMs out into their own handler kind, give them a dedicated pubkey along with dedicated metadata and relay selections, and clean up the data model a bit. # DVM Flow Now that we know what a DVM looks like, we can start to address how they work. My explanation below will elide some of the detail involved in [NIP 90](https://github.com/nostr-protocol/nips/blob/master/90.md) for simplicity, so I encourage you to read the complete spec. The basic DVM flow can be a little (very) confusing to work with, because in essence it's a request/response paradigm, but it has some additional wrinkles. First of all, the broker for the request isn't abstracted away as is usually the case with request/response flows. Regular HTTP requests involve all kinds of work in the background - from resolving domain names to traversing routers, VPNs, and ISP infrastructure. But developers don't generally have to care about all these intermediaries. With DVMs, on the other hand, the essential complexity of relay selection can't simply be ignored. DVMs often advertise their own relay selections, which should be used rather than a hard-coded or randomly chosen relay to ensure messages are delivered. The benefit of this is that DVMs can avoid censorship, just as users can, by choosing relays that are willing to broker their activity. DVMs can even select multiple relays to broker requests, which means that clients might receive multiple copies of the same response. Secondly, the DVM request/response model is far more fluid than is usually the case with request/response flows. There are a set of standard practices, but the flow is flexible enough to admit exceptions to these conventions for special use cases. Here are some examples: - Normally, clients p-tag the DVM they wish to address. But if a client isn't picky about where a response comes from, they may choose to send an open request to the network and collect responses from multiple DVMs simultaneously. - Normally, a client creates a request before collecting responses using a subscription with an e-tag filter matching the request event. But clients may choose to skip the request step entirely and collect responses from the network that have already been created. This can be useful for computationally intensive tasks or common queries, where a single result can be re-used multiple times. - Sometimes, a DVM may respond with a `kind 7000` job status event to let clients know they're working on the request. This is particularly useful for longer-running tasks, where feedback is useful for building a responsive UX. - There are also some details in the spec regarding monetization, parameterization, error codes, encryption, etc. # Example DVM implementation For the purposes of this blog post, I'll keep things simple by illustrating the most common kind of DVM flow: a `kind 5300` [content discovery](https://www.data-vending-machines.org/kinds/5300/) request, addressed to a particular DVM. If you're interested in other use cases, please visit [data-vending-machines.org](https://data-vending-machines.org) for additional documented kinds. The basic flow looks like this: - The DVM starts by listening for `kind 5300` job requests on some relays it has selected and advertised via NIP 89 (more on that later) - A client creates a request event of `kind 5300`, p-tagged with the DVM's pubkey and sends it to the DVM's relay selections. - The DVM receives the event and processes it, issuing optional `kind 7000` job status events, and eventually issuing a `kind 6300` job result event (job result event kinds are always 1000 greater than the request's kind). - The client listens to the same relays for a response, and when it comes through does whatever it wants to with it. Here's a swimlane diagram of that flow:  To avoid massive code samples, I'm going to implement our DVM entirely using nak (backed by the power of the human mind). The first step is to start our DVM listening for requests that it wants to respond to. Nak's default pubkey is `79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798`, so we'll only listen for requests sent to nak. ```bash nak req -k 5300 -t p=79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798 ``` This gives us the following filter: ```json ["REQ","nak",{"kinds":[5300],"#p":["79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798"]}] ``` To open a subscription to `nos.lol` and stream job requests, add `--stream wss://nos.lol` to the previous request and leave it running. Next, open a new terminal window for our "client" and create a job request. In this case, there's nothing we need to provide as `input`, but we'll include it just for illustration. It's also good practice to include an `expiration` tag so we're not asking relays to keep our ephemeral requests forever. ```bash nak event -k 5300 -t p=79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798 -t expiration=$(( $(date +%s) + 30 )) -t input=hello ``` Here's what comes out: ```json { "kind": 5300, "id": "0e419d0b3c5d29f86d2132a38ca29cdfb81a246e1a649cb2fe1b9ed6144ebe30", "pubkey": "79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798", "created_at": 1739407684, "tags": [ ["p", "79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798"], ["expiration", "1739407683"], ["input", "hello"] ], "content": "", "sig": "560807548a75779a7a68c0ea73c6f097583e2807f4bb286c39931e99a4e377c0a64af664fa90f43e01ddd1de2e9405acd4e268f1bf3bc66f0ed5a866ea093966" } ``` Now go ahead and publish this event by adding `nos.lol` to the end of your `nak` command. If all goes well, you should see your event pop up in your "dvm" subscription. If so, great! That's half of the flow. Next, we'll want our client to start listening for `kind 6300` responses to the request. In your "client" terminal window, run: ```bash nak req -k 6300 -t e=<your-eventid-here> --stream nos.lol ``` Note that if you only want to accept responses from the specified DVM (a good policy in general to avoid spam) you would include a `p` tag here. I've omitted it for brevity. Also notice the `k` tag specifies the request kind plus `1000` - this is just a convention for what kinds requests and responses use. Now, according to [data-vending-machines.org](https://www.data-vending-machines.org/kinds/5300/), `kind 5300` responses are supposed to put a JSON-encoded list of e-tags in the `content` field of the response. Weird, but ok. Stop the subscription in your "dvm" terminal and respond to your "client" with a recommendation to read my first note: ```bash nak event -k 6300 -t e=a65665a3a4ca2c0d7b7582f4f0d073cd1c83741c25a07e98d49a43e46d258caf -c '[["e","214f5898a7b75b7f95d9e990b706758ea525fe86db54c1a28a0f418c357f9b08","wss://nos.lol/"]]' nos.lol ``` Here's the response event we're sending: ```json { "kind": 6300, "id": "bb5f38920cbca15d3c79021f7d0051e82337254a84c56e0f4182578e4025232e", "pubkey": "79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798", "created_at": 1739408411, "tags": [ ["e", "a65665a3a4ca2c0d7b7582f4f0d073cd1c83741c25a07e98d49a43e46d258caf"] ], "content": "[[\"e\",\"214f5898a7b75b7f95d9e990b706758ea525fe86db54c1a28a0f418c357f9b08\",\"wss://nos.lol/\"]]", "sig": "a0fe2c3419c5c54cf2a6d9a2a5726b2a5b766d3c9e55d55568140979354003aacb038e90bdead43becf5956faa54e3b60ff18c0ea4d8e7dfdf0c8dd97fb24ff9" } ``` Notice the `e` tag targets our original request. This should result in the job result event showing up in our "client" terminal. Success! If something isn't working, I've also create a video of the full process with some commentary which you can find [here](https://coracle-media.us-southeast-1.linodeobjects.com/nakflow.mov). Note that in practice, DVMs can be much more picky about the requests they will respond to, due to implementations failing to follow [Postel's law](https://en.wikipedia.org/wiki/Robustness_principle). Hopefully that will improve over time. For now, here are a few resources that are useful when working with or developing DVMs: - [dvmdash](https://dvmdash.live) - [data-vending-machines.org](https://data-vending-machines.org) - [noogle](https://noogle.lol/) - [nostrdvm](https://github.com/believethehype/nostrdvm) # Conclusion I started this post by hinting that DVMs might be as fundamental as relays are to making nostr work. But (apart from the fact that we'd end up with an acronym like DVMNOSTRZ+*, which would only exascerbate the pronounciation wars (if such a thing were possible)), that's not exactly true. DVMs have emerged as a central paradigm in the nostr world because they're a generalization of a design pattern unique to nostr's architecture - but which exists in many other places, including NIP 46 signer flows and NIP 47 wallet connect. Each of these sub-protocols works by using relays as neutral brokers for requests in order to avoid coupling services to web addresses. This approach has all kinds of neat benefits, not least of which is allowing service providers to host their software without having to accept incoming TCP connections. But it's really an emergent property of relays, which not only are useful for brokering communication between users (aka storing events), but also brokering communication between machines. The possibilities of this architecture have only started to emerge, so be on the lookout for new applications, and don't be afraid to experiment - just please, don't serialize json inside json 🤦♂️
@ 97c70a44:ad98e322
2025-02-17 14:29:00Everyone knows that relays are central to how nostr works - they're even in the name: Notes and Other Stuff Transmitted by *Relays*. As time goes on though, there are three other letters which are becoming conspicuously absent from our beloved and ambiguously pronounceable acronym - "D", "V", and "M". For the uninitiated, DVM stands for "data vending machines". They're actually sort of hard to describe — in technical terms they act more like clients, since they simply read events from and publish events to relays. In most cases though, these events are part of a request/response flow initiated by users elsewhere on the network. In practice, DVMs are bots, but there's also nothing to prevent the work they do from being powered by human interaction. They're an amazingly flexible tool for building anything from custom feeds, to transcription services, to chatbots, to protocol gateways. The hype cycle for DVMs seems to have reached escape velocity in a way few other things have - zaps being the possible exception. But *what* exactly DVMs are remains something of a mystery to many nostr developers - and how to build one may as well be written on clay tablets. This blog post is designed to address that - below is a soup to nuts (no nutzaps though) guide to building a DVM flow, both from the client and the server side. Here's what we'll be covering: - Discovering DVM metadata - Basic request/response flow - Implementing a minimal example Let's get started! # DVM Metadata First of all, it's helpful to know how DVMs are reified on the nostr network. While not strictly necessary, this can be useful for discovering DVMs and presenting them to users, and for targeting specific DVMs we want a response from. [NIP 89](https://github.com/nostr-protocol/nips/blob/master/89.md) goes into this in more detail, but the basic idea is that anyone can create a `kind 31990` "application handler" event and publish it to the network with their own (or a dedicated) public key. This handler was originally intended to advertise clients, but has been re-purposed for DVM listings as well. Here's what the "Fluffy Frens" handler looks like: ```json { "content": "{\"name\": \"Fluffy Frens\", \"picture\": \"https://image.nostr.build/f609311532c470f663e129510a76c9a1912ae9bc4aaaf058e5ba21cfb512c88e.jpg\", \"about\": \"I show recent notes about animals\", \"lud16\": \"discovery_content_fluffy@nostrdvm.com\", \"supportsEncryption\": true, \"acceptsNutZaps\": false, \"personalized\": false, \"amount\": \"free\", \"nip90Params\": {\"max_results\": {\"required\": false, \"values\": [], \"description\": \"The number of maximum results to return (default currently 100)\"}}}", "created_at": 1738874694, "id": "0aa8d1f19cfe17e00ce55ca86fea487c83be39a1813601f56f869abdfa776b3c", "kind": 31990, "pubkey": "7b7373dd58554ff4c0d28b401b9eae114bd92e30d872ae843b9a217375d66f9d", "sig": "22403a7996147da607cf215994ab3b893176e5302a44a245e9c0d91214e4c56fae40d2239dce58ea724114591e8f95caed2ba1a231d09a6cd06c9f0980e1abd5", "tags": [ ["k", "5300"], ["d", "198650843898570c"] ] } ``` This event is rendered in various clients using the kind-0-style metadata contained in the `content` field, allowing users to browse DVMs and pick one for their use case. If a user likes using a particular DVM, they might publish a `kind 31989` "application recommendation", which other users can use to find DVMs that are in use within their network. Note the `k` tag in the handler event - this allows DVMs to advertise support only for specific job types. It's also important to note that even though the spec doesn't cover relay selection, most clients use the publisher's `kind 10002` event to find out where the DVM listens for events. If this looks messy to you, you're right. See [this PR](https://github.com/nostr-protocol/nips/pull/1728) for a proposal to split DVMs out into their own handler kind, give them a dedicated pubkey along with dedicated metadata and relay selections, and clean up the data model a bit. # DVM Flow Now that we know what a DVM looks like, we can start to address how they work. My explanation below will elide some of the detail involved in [NIP 90](https://github.com/nostr-protocol/nips/blob/master/90.md) for simplicity, so I encourage you to read the complete spec. The basic DVM flow can be a little (very) confusing to work with, because in essence it's a request/response paradigm, but it has some additional wrinkles. First of all, the broker for the request isn't abstracted away as is usually the case with request/response flows. Regular HTTP requests involve all kinds of work in the background - from resolving domain names to traversing routers, VPNs, and ISP infrastructure. But developers don't generally have to care about all these intermediaries. With DVMs, on the other hand, the essential complexity of relay selection can't simply be ignored. DVMs often advertise their own relay selections, which should be used rather than a hard-coded or randomly chosen relay to ensure messages are delivered. The benefit of this is that DVMs can avoid censorship, just as users can, by choosing relays that are willing to broker their activity. DVMs can even select multiple relays to broker requests, which means that clients might receive multiple copies of the same response. Secondly, the DVM request/response model is far more fluid than is usually the case with request/response flows. There are a set of standard practices, but the flow is flexible enough to admit exceptions to these conventions for special use cases. Here are some examples: - Normally, clients p-tag the DVM they wish to address. But if a client isn't picky about where a response comes from, they may choose to send an open request to the network and collect responses from multiple DVMs simultaneously. - Normally, a client creates a request before collecting responses using a subscription with an e-tag filter matching the request event. But clients may choose to skip the request step entirely and collect responses from the network that have already been created. This can be useful for computationally intensive tasks or common queries, where a single result can be re-used multiple times. - Sometimes, a DVM may respond with a `kind 7000` job status event to let clients know they're working on the request. This is particularly useful for longer-running tasks, where feedback is useful for building a responsive UX. - There are also some details in the spec regarding monetization, parameterization, error codes, encryption, etc. # Example DVM implementation For the purposes of this blog post, I'll keep things simple by illustrating the most common kind of DVM flow: a `kind 5300` [content discovery](https://www.data-vending-machines.org/kinds/5300/) request, addressed to a particular DVM. If you're interested in other use cases, please visit [data-vending-machines.org](https://data-vending-machines.org) for additional documented kinds. The basic flow looks like this: - The DVM starts by listening for `kind 5300` job requests on some relays it has selected and advertised via NIP 89 (more on that later) - A client creates a request event of `kind 5300`, p-tagged with the DVM's pubkey and sends it to the DVM's relay selections. - The DVM receives the event and processes it, issuing optional `kind 7000` job status events, and eventually issuing a `kind 6300` job result event (job result event kinds are always 1000 greater than the request's kind). - The client listens to the same relays for a response, and when it comes through does whatever it wants to with it. Here's a swimlane diagram of that flow:  To avoid massive code samples, I'm going to implement our DVM entirely using nak (backed by the power of the human mind). The first step is to start our DVM listening for requests that it wants to respond to. Nak's default pubkey is `79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798`, so we'll only listen for requests sent to nak. ```bash nak req -k 5300 -t p=79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798 ``` This gives us the following filter: ```json ["REQ","nak",{"kinds":[5300],"#p":["79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798"]}] ``` To open a subscription to `nos.lol` and stream job requests, add `--stream wss://nos.lol` to the previous request and leave it running. Next, open a new terminal window for our "client" and create a job request. In this case, there's nothing we need to provide as `input`, but we'll include it just for illustration. It's also good practice to include an `expiration` tag so we're not asking relays to keep our ephemeral requests forever. ```bash nak event -k 5300 -t p=79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798 -t expiration=$(( $(date +%s) + 30 )) -t input=hello ``` Here's what comes out: ```json { "kind": 5300, "id": "0e419d0b3c5d29f86d2132a38ca29cdfb81a246e1a649cb2fe1b9ed6144ebe30", "pubkey": "79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798", "created_at": 1739407684, "tags": [ ["p", "79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798"], ["expiration", "1739407683"], ["input", "hello"] ], "content": "", "sig": "560807548a75779a7a68c0ea73c6f097583e2807f4bb286c39931e99a4e377c0a64af664fa90f43e01ddd1de2e9405acd4e268f1bf3bc66f0ed5a866ea093966" } ``` Now go ahead and publish this event by adding `nos.lol` to the end of your `nak` command. If all goes well, you should see your event pop up in your "dvm" subscription. If so, great! That's half of the flow. Next, we'll want our client to start listening for `kind 6300` responses to the request. In your "client" terminal window, run: ```bash nak req -k 6300 -t e=<your-eventid-here> --stream nos.lol ``` Note that if you only want to accept responses from the specified DVM (a good policy in general to avoid spam) you would include a `p` tag here. I've omitted it for brevity. Also notice the `k` tag specifies the request kind plus `1000` - this is just a convention for what kinds requests and responses use. Now, according to [data-vending-machines.org](https://www.data-vending-machines.org/kinds/5300/), `kind 5300` responses are supposed to put a JSON-encoded list of e-tags in the `content` field of the response. Weird, but ok. Stop the subscription in your "dvm" terminal and respond to your "client" with a recommendation to read my first note: ```bash nak event -k 6300 -t e=a65665a3a4ca2c0d7b7582f4f0d073cd1c83741c25a07e98d49a43e46d258caf -c '[["e","214f5898a7b75b7f95d9e990b706758ea525fe86db54c1a28a0f418c357f9b08","wss://nos.lol/"]]' nos.lol ``` Here's the response event we're sending: ```json { "kind": 6300, "id": "bb5f38920cbca15d3c79021f7d0051e82337254a84c56e0f4182578e4025232e", "pubkey": "79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798", "created_at": 1739408411, "tags": [ ["e", "a65665a3a4ca2c0d7b7582f4f0d073cd1c83741c25a07e98d49a43e46d258caf"] ], "content": "[[\"e\",\"214f5898a7b75b7f95d9e990b706758ea525fe86db54c1a28a0f418c357f9b08\",\"wss://nos.lol/\"]]", "sig": "a0fe2c3419c5c54cf2a6d9a2a5726b2a5b766d3c9e55d55568140979354003aacb038e90bdead43becf5956faa54e3b60ff18c0ea4d8e7dfdf0c8dd97fb24ff9" } ``` Notice the `e` tag targets our original request. This should result in the job result event showing up in our "client" terminal. Success! If something isn't working, I've also create a video of the full process with some commentary which you can find [here](https://coracle-media.us-southeast-1.linodeobjects.com/nakflow.mov). Note that in practice, DVMs can be much more picky about the requests they will respond to, due to implementations failing to follow [Postel's law](https://en.wikipedia.org/wiki/Robustness_principle). Hopefully that will improve over time. For now, here are a few resources that are useful when working with or developing DVMs: - [dvmdash](https://dvmdash.live) - [data-vending-machines.org](https://data-vending-machines.org) - [noogle](https://noogle.lol/) - [nostrdvm](https://github.com/believethehype/nostrdvm) # Conclusion I started this post by hinting that DVMs might be as fundamental as relays are to making nostr work. But (apart from the fact that we'd end up with an acronym like DVMNOSTRZ+*, which would only exascerbate the pronounciation wars (if such a thing were possible)), that's not exactly true. DVMs have emerged as a central paradigm in the nostr world because they're a generalization of a design pattern unique to nostr's architecture - but which exists in many other places, including NIP 46 signer flows and NIP 47 wallet connect. Each of these sub-protocols works by using relays as neutral brokers for requests in order to avoid coupling services to web addresses. This approach has all kinds of neat benefits, not least of which is allowing service providers to host their software without having to accept incoming TCP connections. But it's really an emergent property of relays, which not only are useful for brokering communication between users (aka storing events), but also brokering communication between machines. The possibilities of this architecture have only started to emerge, so be on the lookout for new applications, and don't be afraid to experiment - just please, don't serialize json inside json 🤦♂️ @ 3f770d65:7a745b24
2023-07-31 12:53:38The following is a collection of Tweets posted on Twitter that documented my entire heart surgery process, from finding out I had an issue, through the surgery, and finally throughout my recovery process. If Elon decides to remove old and unpaid content, I do not want this part of my life to vanish from the Internet. At the time, it was extremely important for my mental health to talk about this whole process and it was therapeutic in my recovery process, reading all of the responses as all of Bitcoin Twitter was behind my success. Thank you all of your kind words, love, and support during this whole process. May my Tweets live on through nostr. ... Nov 28, 2021 I had open heart surgery 4 days before my 3rd b-day. I've led a healthy & active life since then, zero issues. I had an echocardiogram last week. The results were not good. Heart valve replacement may be in my near future. I am freaking the fuck out. I'll know more on Dec 6th. 😫 Dec 6, 2021 Update: I had my cardiologist appointment today. He said to not worry for now and continue to exercise and live life. In 3 months get another echo done. He doesn't believe the previous other results since I have zero symptoms and wants to do his own interpretation. Dec 6, 2021 He said if the other results were correct, I may need valve replacement in 6 months to 3 years. However, he doesn't believe the local hospital's results as I said above. He can't form an opinion just yet. He said not to worry over and over again. For now, I'm staying positive! Mar 7, 2022 Well, it's been three months. I had my follow up this morning. I have severe pulmonic regurgitation. I now need to speak with a specialist and see what my options are for surgery. Neat. 😭 Apr 12, 2022 Well, it looks like I'll need full open heart surgery again to replace my pulmonic valve. Bonus: I'll be part pig. So, I have that going for me. I was assuming that if I had to have this done it would be much less invasive, so I'm not overly impressed at the moment. 🫤 May 11, 2022 Today I had to get a CT scan of my heart in preparation for the May 27th surgery. All went well. I have no other heart issues. It's looking like I'll be in the hospital for 4-7 days, depending on how fast I recover. I should be fully 100% recovered by the end of August. ❤️ May 20, 2022 My grandfather with me 39 years ago, days after my open heart surgery. He taught me to hunt, fish, golf, and I'm sure taught me a thing or two about drinking beer and partying. 😂 He was a great man. He won't physically be with me next Friday, but I'm sure he'll be watching over. May 25, 2022 Two more sleeps. My mind is racing with an incredible amount of thoughts and emotions now. It's overwhelming. I love you all. Thanks for all of your replies and DMs over the last couple days, weeks, and months. I appreciate it immensely. ❤️❤️❤️ May 25, 2022 Two more sleeps. My mind is racing with an incredible amount of thoughts and emotions now. It's overwhelming. I love you all. Thanks for all of your replies and DMs over the last couple days, weeks, and months. I appreciate it immensely. ❤️❤️❤️ May 27, 2022 LET'S GO! I am alive and doing well. I was on a ventilator until 8pm. That was horrible. I will read all of the comments that you all posted on Katie's updates. Now I need to rest. They want to get me up and walk at 11pm. 🤯 I love you all and your support had helped so much 🧡🧡 May 28, 2022 The amount of love, compassion, caring, and appreciation from everyone blows my mind. Thanks for all of your comments and DMs. The positivity though all is this has helped me get through dark times and now it's helping me get through pain. You are helping me immensely. 🤯❤️🧡💪 May 28, 2022 Today has been a rough day. Lots of chest pain when breathing. But, I apparently am doing something right, because I have been upgraded to a regular room. No more ICU for this guy! My ICU nurse told my new nurse that I'm strong. ❤️💪🔥 May 29, 2022 Using this to document my journey. Last night was not good at all. I had tachycardia and AFib for hours. It was scary as fuck having my heart beat the way it was at 160bpm. They gave me new medication to bring it down and stop the AFib irregular heartbeat. It's now at 101. May 29, 2022 I was very scared. Katie was able to come and stay the night with me and be my personal care nurse. That made me feel much better having her here with me. Hopefully the meds continue to do what they're supposed to. Fuck. Anyways, I may not Tweet much today. Love you all. ❤️ May 30, 2022 Today has mostly been a great day progress wise. I ate a lot. I've walked more today than I have previously. My doctor told me I might be going home tomorrow, it all depends on what happens with my last drainage tube. Fingers crossed that it's draining properly now. 💪❤️ May 31, 2022 Morning walk crushed. Breakfast crushed. Feeling stronger. My drainage tube is still draining so we'll see what the surgeon says, but I probably won't be coming home today according to my nurse. It may be another day. Better to be safe. I'm feeling good though. Let's go! 💪💪❤️❤️ Jun 1, 2022 Today's plans: Crush morning walk, crush breakfast, CRUSH MY LAST X-RAY AND HEAD THE HELL HOME! Fingers crossed. 🤞🤞❤️❤️💪💪 Jun 1, 2022 On my morning walk I went into a slight AFib. The nurse and PA said since I hadn't had my morning meds to control that yet, that that could be the cause. They're going to increase meds and monitor me for another 24 hours. That sucks, but again, I'd rather be safe. Ugh. Jun 2, 2022 GM! I miss my kids. I miss wearing normal clothes. I miss my house. I miss my doggy. I better go home today or I guess I'll just keep working to get well enough to go home. 😂 I'm still progressing forward. I have a chest x-ray scheduled later this morning. Fingers crossed. Jun 2, 2022 I JUST GOT CLEARED TO HEAD HOME AFTER LUNCH. FUCK YEAH. LET'S GOOOOOO💪💪💪 Jun 2, 2022 I am home! I have some family that needs some loving. Enjoy the rest of your day! Jun 4, 2022 Last night I slept in bed thanks to a reclining pillow, the first night our living room chair. I was so happy to sleep in my own bed. I walked around our yard about 9 times yesterday. My goal is to do that plus a little more every day. I'm still in a lot of pain, but meds help. Jun 4, 2022 I still have a long way to go recovery wise, but having Katie and the kids here helping me along the way makes it easier and gives me a reason to keep pushing forward through this. Thanks again for all of your past and future support. You all are fantastic. Jun 6, 2022 My wife went back to work today. My son and daughter are in charge of taking care of me. My kids are fantastic. They made me breakfast already and helped me check all of my vitals. My daughter really shines here. She's such a little nurse and caretaker. ❤️❤️ Jun 6, 2022 I'm still in pain, but I'm not in as much pain as I was a couple days ago. I'm walking around a little better and a little more every day. I really hate just sitting around and not doing anything, but it's hard to do much else besides watch TV. I am enjoying my patio though. 💪 Jun 16, 2022 It's been a while. It's time to update this thread! I am doing great, IMO. I have lots of energy. I feel great. I can do a lot more than I previously could. I still have a limited range of motion due to my sternum being broken and still healing. i.e. I can't wash my back or legs. Jun 16, 2022 I started back to work yesterday. I was cleared to do 20 hours this week by my doctor and I'm hoping to be cleared full time next week. I work from home, so if I can sit in front of a TV, I can sit in front of a computer, right? Jun 16, 2022 My home nurses have been absolutely fantastic.😂 My kids make me breakfast every morning. And I could not have done any of this without my rock star wife. Words can't describe how much she's done for me throughout all of this. I am looking forward to continuing to improve. ♥️ Jun 16, 2022 You all have been absolutely wonderful through all of this too. I appreciate all of your love, support, and check-ins. Seriously. It means more than you know. I have a check-up at the end of the month to make sure all is well. I'll update again in a couple weeks after that appt. Jun 28, 2022 My doctor said everything looks great. He said it doesn't look like I had open heart surgery a month ago.💪 He said I have zero restrictions and that I can resume normal life. I can drive and I can go out on my boat! ❤️❤️❤️ I'm so happy right now! 🔥🚀 Jul 15, 2022 I started cardiac rehab this week. After 2 sessions the nurse said I'm on "Week 4" already. She doesn't believe with my initial intake stress test if I'll really be able to improve on it that much. 🤣 TL;DR I am a rock star and kicking ass. Feeling great. Life's great. 😍 Aug 28, 2022 Yesterday was 3 months since my open heart surgery. I'm going great! I'd guess essentially back to normal. My sternum is still not fully healed, that'll take more time, but energy and capability are basically back to what I was like last summer. I'm very happy with the results. Aug 28, 2022 I'm very happy to be able to exercise daily, go boating on the weekends AND swim and paddleboard. I was annoyed that I couldn't do these things a month ago. I had a cardiologist appt. two weeks ago. He said he hopes the valve lasts me the rest of my life and to see him in a year. Aug 28, 2022 As a final post to this thread, I want to thank each and every one of you again that commented, liked, shared and DMed me throughout all of this. The love and support from Twitter and the #Bitcoin community was unfathomable. You all made a difference in my life and my recovery.❤️
@ 3f770d65:7a745b24
2023-07-31 12:53:38The following is a collection of Tweets posted on Twitter that documented my entire heart surgery process, from finding out I had an issue, through the surgery, and finally throughout my recovery process. If Elon decides to remove old and unpaid content, I do not want this part of my life to vanish from the Internet. At the time, it was extremely important for my mental health to talk about this whole process and it was therapeutic in my recovery process, reading all of the responses as all of Bitcoin Twitter was behind my success. Thank you all of your kind words, love, and support during this whole process. May my Tweets live on through nostr. ... Nov 28, 2021 I had open heart surgery 4 days before my 3rd b-day. I've led a healthy & active life since then, zero issues. I had an echocardiogram last week. The results were not good. Heart valve replacement may be in my near future. I am freaking the fuck out. I'll know more on Dec 6th. 😫 Dec 6, 2021 Update: I had my cardiologist appointment today. He said to not worry for now and continue to exercise and live life. In 3 months get another echo done. He doesn't believe the previous other results since I have zero symptoms and wants to do his own interpretation. Dec 6, 2021 He said if the other results were correct, I may need valve replacement in 6 months to 3 years. However, he doesn't believe the local hospital's results as I said above. He can't form an opinion just yet. He said not to worry over and over again. For now, I'm staying positive! Mar 7, 2022 Well, it's been three months. I had my follow up this morning. I have severe pulmonic regurgitation. I now need to speak with a specialist and see what my options are for surgery. Neat. 😭 Apr 12, 2022 Well, it looks like I'll need full open heart surgery again to replace my pulmonic valve. Bonus: I'll be part pig. So, I have that going for me. I was assuming that if I had to have this done it would be much less invasive, so I'm not overly impressed at the moment. 🫤 May 11, 2022 Today I had to get a CT scan of my heart in preparation for the May 27th surgery. All went well. I have no other heart issues. It's looking like I'll be in the hospital for 4-7 days, depending on how fast I recover. I should be fully 100% recovered by the end of August. ❤️ May 20, 2022 My grandfather with me 39 years ago, days after my open heart surgery. He taught me to hunt, fish, golf, and I'm sure taught me a thing or two about drinking beer and partying. 😂 He was a great man. He won't physically be with me next Friday, but I'm sure he'll be watching over. May 25, 2022 Two more sleeps. My mind is racing with an incredible amount of thoughts and emotions now. It's overwhelming. I love you all. Thanks for all of your replies and DMs over the last couple days, weeks, and months. I appreciate it immensely. ❤️❤️❤️ May 25, 2022 Two more sleeps. My mind is racing with an incredible amount of thoughts and emotions now. It's overwhelming. I love you all. Thanks for all of your replies and DMs over the last couple days, weeks, and months. I appreciate it immensely. ❤️❤️❤️ May 27, 2022 LET'S GO! I am alive and doing well. I was on a ventilator until 8pm. That was horrible. I will read all of the comments that you all posted on Katie's updates. Now I need to rest. They want to get me up and walk at 11pm. 🤯 I love you all and your support had helped so much 🧡🧡 May 28, 2022 The amount of love, compassion, caring, and appreciation from everyone blows my mind. Thanks for all of your comments and DMs. The positivity though all is this has helped me get through dark times and now it's helping me get through pain. You are helping me immensely. 🤯❤️🧡💪 May 28, 2022 Today has been a rough day. Lots of chest pain when breathing. But, I apparently am doing something right, because I have been upgraded to a regular room. No more ICU for this guy! My ICU nurse told my new nurse that I'm strong. ❤️💪🔥 May 29, 2022 Using this to document my journey. Last night was not good at all. I had tachycardia and AFib for hours. It was scary as fuck having my heart beat the way it was at 160bpm. They gave me new medication to bring it down and stop the AFib irregular heartbeat. It's now at 101. May 29, 2022 I was very scared. Katie was able to come and stay the night with me and be my personal care nurse. That made me feel much better having her here with me. Hopefully the meds continue to do what they're supposed to. Fuck. Anyways, I may not Tweet much today. Love you all. ❤️ May 30, 2022 Today has mostly been a great day progress wise. I ate a lot. I've walked more today than I have previously. My doctor told me I might be going home tomorrow, it all depends on what happens with my last drainage tube. Fingers crossed that it's draining properly now. 💪❤️ May 31, 2022 Morning walk crushed. Breakfast crushed. Feeling stronger. My drainage tube is still draining so we'll see what the surgeon says, but I probably won't be coming home today according to my nurse. It may be another day. Better to be safe. I'm feeling good though. Let's go! 💪💪❤️❤️ Jun 1, 2022 Today's plans: Crush morning walk, crush breakfast, CRUSH MY LAST X-RAY AND HEAD THE HELL HOME! Fingers crossed. 🤞🤞❤️❤️💪💪 Jun 1, 2022 On my morning walk I went into a slight AFib. The nurse and PA said since I hadn't had my morning meds to control that yet, that that could be the cause. They're going to increase meds and monitor me for another 24 hours. That sucks, but again, I'd rather be safe. Ugh. Jun 2, 2022 GM! I miss my kids. I miss wearing normal clothes. I miss my house. I miss my doggy. I better go home today or I guess I'll just keep working to get well enough to go home. 😂 I'm still progressing forward. I have a chest x-ray scheduled later this morning. Fingers crossed. Jun 2, 2022 I JUST GOT CLEARED TO HEAD HOME AFTER LUNCH. FUCK YEAH. LET'S GOOOOOO💪💪💪 Jun 2, 2022 I am home! I have some family that needs some loving. Enjoy the rest of your day! Jun 4, 2022 Last night I slept in bed thanks to a reclining pillow, the first night our living room chair. I was so happy to sleep in my own bed. I walked around our yard about 9 times yesterday. My goal is to do that plus a little more every day. I'm still in a lot of pain, but meds help. Jun 4, 2022 I still have a long way to go recovery wise, but having Katie and the kids here helping me along the way makes it easier and gives me a reason to keep pushing forward through this. Thanks again for all of your past and future support. You all are fantastic. Jun 6, 2022 My wife went back to work today. My son and daughter are in charge of taking care of me. My kids are fantastic. They made me breakfast already and helped me check all of my vitals. My daughter really shines here. She's such a little nurse and caretaker. ❤️❤️ Jun 6, 2022 I'm still in pain, but I'm not in as much pain as I was a couple days ago. I'm walking around a little better and a little more every day. I really hate just sitting around and not doing anything, but it's hard to do much else besides watch TV. I am enjoying my patio though. 💪 Jun 16, 2022 It's been a while. It's time to update this thread! I am doing great, IMO. I have lots of energy. I feel great. I can do a lot more than I previously could. I still have a limited range of motion due to my sternum being broken and still healing. i.e. I can't wash my back or legs. Jun 16, 2022 I started back to work yesterday. I was cleared to do 20 hours this week by my doctor and I'm hoping to be cleared full time next week. I work from home, so if I can sit in front of a TV, I can sit in front of a computer, right? Jun 16, 2022 My home nurses have been absolutely fantastic.😂 My kids make me breakfast every morning. And I could not have done any of this without my rock star wife. Words can't describe how much she's done for me throughout all of this. I am looking forward to continuing to improve. ♥️ Jun 16, 2022 You all have been absolutely wonderful through all of this too. I appreciate all of your love, support, and check-ins. Seriously. It means more than you know. I have a check-up at the end of the month to make sure all is well. I'll update again in a couple weeks after that appt. Jun 28, 2022 My doctor said everything looks great. He said it doesn't look like I had open heart surgery a month ago.💪 He said I have zero restrictions and that I can resume normal life. I can drive and I can go out on my boat! ❤️❤️❤️ I'm so happy right now! 🔥🚀 Jul 15, 2022 I started cardiac rehab this week. After 2 sessions the nurse said I'm on "Week 4" already. She doesn't believe with my initial intake stress test if I'll really be able to improve on it that much. 🤣 TL;DR I am a rock star and kicking ass. Feeling great. Life's great. 😍 Aug 28, 2022 Yesterday was 3 months since my open heart surgery. I'm going great! I'd guess essentially back to normal. My sternum is still not fully healed, that'll take more time, but energy and capability are basically back to what I was like last summer. I'm very happy with the results. Aug 28, 2022 I'm very happy to be able to exercise daily, go boating on the weekends AND swim and paddleboard. I was annoyed that I couldn't do these things a month ago. I had a cardiologist appt. two weeks ago. He said he hopes the valve lasts me the rest of my life and to see him in a year. Aug 28, 2022 As a final post to this thread, I want to thank each and every one of you again that commented, liked, shared and DMed me throughout all of this. The love and support from Twitter and the #Bitcoin community was unfathomable. You all made a difference in my life and my recovery.❤️ @ cc32882d:eca332e6
2025-02-18 17:29:01#introductions Hello World New here as of today! I set myself up first on Yakihonne. (Just trying out clients so far) Glad to be here and look forward to learning and getting to know peeps. I have been poking around a bit and like what I see so far. Excited to play around some more with Nostr apps. Any suggestions is greatly appreciated. Whats the good, the bad, and the ugly about Nostr in your opinion? What is the size of nostr platform? How many users? Hows the community involvment? What is the age range? Any good places to look at this kind of data. About: Like to think deep about life and its vast array of questions and answers that are waiting to be discovered or rediscovered. Live with Nature, Dont fight what will be, Love Dislike fake people. JUST BE REAL, Life is to short for anything else. Drop me a response and I will get back to you as soon as possible. Look forward to hearing from some of you. Thank You for Your Time and For Reading This -ObsidianQuill
@ cc32882d:eca332e6
2025-02-18 17:29:01#introductions Hello World New here as of today! I set myself up first on Yakihonne. (Just trying out clients so far) Glad to be here and look forward to learning and getting to know peeps. I have been poking around a bit and like what I see so far. Excited to play around some more with Nostr apps. Any suggestions is greatly appreciated. Whats the good, the bad, and the ugly about Nostr in your opinion? What is the size of nostr platform? How many users? Hows the community involvment? What is the age range? Any good places to look at this kind of data. About: Like to think deep about life and its vast array of questions and answers that are waiting to be discovered or rediscovered. Live with Nature, Dont fight what will be, Love Dislike fake people. JUST BE REAL, Life is to short for anything else. Drop me a response and I will get back to you as soon as possible. Look forward to hearing from some of you. Thank You for Your Time and For Reading This -ObsidianQuill @ ec42c765:328c0600
2025-02-05 23:45:09test test
@ ec42c765:328c0600
2025-02-05 23:45:09test test @ 2e8970de:63345c7a
2025-02-20 18:45:57https://lore.kernel.org/rust-for-linux/2025021954-flaccid-pucker-f7d9@gregkh/ > The majority of bugs (quantity, not quality/severity) we have are due to the stupid little corner cases in C that are totally gone in Rust. Things like simple overwrites of memory (not that rust can catch all of these by far), error path cleanups, forgetting to check error values, and use-after-free mistakes. That's why I'm wanting to see Rust get into the kernel, these types of issues just go away, allowing developers and maintainers more time to focus on the REAL bugs that happen (i.e. logic issues, race conditions, etc.) Now that Linus and Greg Kroah-Hartman have spoken out pro Rust changes in Linux it really feels like the ball is rolling. Linux will become a multi language project. With kernel and "hard" os functions in C and more and more attached pieces like many drivers being either C or Rust. Interesting developments. This is for sure a volatile time for the broader Linux community. Previous posts: Linux Kernel Drama about Rust Linux Kernel Drama https://stacker.news/items/879713; Linus coming out in favor of Rust https://stacker.news/items/890358 originally posted at https://stacker.news/items/892141
@ 2e8970de:63345c7a
2025-02-20 18:45:57https://lore.kernel.org/rust-for-linux/2025021954-flaccid-pucker-f7d9@gregkh/ > The majority of bugs (quantity, not quality/severity) we have are due to the stupid little corner cases in C that are totally gone in Rust. Things like simple overwrites of memory (not that rust can catch all of these by far), error path cleanups, forgetting to check error values, and use-after-free mistakes. That's why I'm wanting to see Rust get into the kernel, these types of issues just go away, allowing developers and maintainers more time to focus on the REAL bugs that happen (i.e. logic issues, race conditions, etc.) Now that Linus and Greg Kroah-Hartman have spoken out pro Rust changes in Linux it really feels like the ball is rolling. Linux will become a multi language project. With kernel and "hard" os functions in C and more and more attached pieces like many drivers being either C or Rust. Interesting developments. This is for sure a volatile time for the broader Linux community. Previous posts: Linux Kernel Drama about Rust Linux Kernel Drama https://stacker.news/items/879713; Linus coming out in favor of Rust https://stacker.news/items/890358 originally posted at https://stacker.news/items/892141 @ 266815e0:6cd408a5
2025-02-18 17:25:31## noStrudel Released another major version of noStrudel v0.42.0 Which included a few new features and a lot of cleanup nostr:naddr1qvzqqqr4gupzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qyghwumn8ghj7mn0wd68ytnhd9hx2tcpzfmhxue69uhkummnw3e82efwvdhk6tcqp3hx7um5wf6kgetv956ry6rmhwr ## Blossom On the blossom front there where a few more PRs - Expanded the documentation around CORS headers in BUD-01 thanks to nostr:npub1a6we08n7zsv2na689whc9hykpq4q6sj3kaauk9c2dm8vj0adlajq7w0tyc - Made auth optional on the `/upload` endpoint [PR](https://github.com/hzrd149/blossom/pull/33) - Added a `HEAD /media` endpoint for BUD-05 [PR](https://github.com/hzrd149/blossom/pull/42) - Added range request recommendations to BUD-01 [PR](https://github.com/hzrd149/blossom/pull/47) With blossom uploads starting to be supported in more nostr clients users where starting to ask where to find a list of blossom servers. so I created a simple nostr client that allows users to post servers and leave reviews [blossomservers.com](https://blossomservers.com) Its still very much a work in progress (needs login and server and review editing) The source is on [github](https://github.com/hzrd149/blossomservers) I also started another project to create a simple account based paid blossom server [blossom-account-server](https://github.com/hzrd149/blossom-account-server) Unfortunately I got sidetracked and I didn't have the time to give it the attention it needs to get it over the finish line ## Smaller projects - [cherry-tree](https://github.com/hzrd149/cherry-tree) A small app for uploading chunked blobs to blossom servers (with cashu payment support) - [vite-plugin-funding](https://github.com/hzrd149/vite-plugin-funding) A vite plugin to collect and expose package "funding" to the app - [node-red-contrib-rx-nostr](https://github.com/hzrd149/node-red-contrib-rx-nostr) The start of a node-red package for rx-nostr. if your interested please help - [node-red-contrib-applesauce](https://github.com/hzrd149/node-red-contrib-applesauce) The start of a node-red package for applesauce. I probably wont finish it so any help it welcome ## Plans for 2025 I have a few vague ideas of what I want to work on Q1 of 2025. but there are a few things i know for certain. I'm going to keep refactoring noStrudel by moving core logic out into [applesauce](https://hzrd149.github.io/applesauce/) and making it more modular. This should make noStrudel more reliable and hopefully allow me to create and maintain more apps with less code And I'm going to write tests. tests for everything. hopefully tests for all the libraries and apps I've created in 2024. A lot of the code I wrote in 2024 was hacky code to see if things could work. and while its been working pretty well I'm starting to forget the details of of the code I wrote so I cant be sure if it still works or how well it works. So my solution is to write tests, lots of tests :)
@ 266815e0:6cd408a5
2025-02-18 17:25:31## noStrudel Released another major version of noStrudel v0.42.0 Which included a few new features and a lot of cleanup nostr:naddr1qvzqqqr4gupzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qyghwumn8ghj7mn0wd68ytnhd9hx2tcpzfmhxue69uhkummnw3e82efwvdhk6tcqp3hx7um5wf6kgetv956ry6rmhwr ## Blossom On the blossom front there where a few more PRs - Expanded the documentation around CORS headers in BUD-01 thanks to nostr:npub1a6we08n7zsv2na689whc9hykpq4q6sj3kaauk9c2dm8vj0adlajq7w0tyc - Made auth optional on the `/upload` endpoint [PR](https://github.com/hzrd149/blossom/pull/33) - Added a `HEAD /media` endpoint for BUD-05 [PR](https://github.com/hzrd149/blossom/pull/42) - Added range request recommendations to BUD-01 [PR](https://github.com/hzrd149/blossom/pull/47) With blossom uploads starting to be supported in more nostr clients users where starting to ask where to find a list of blossom servers. so I created a simple nostr client that allows users to post servers and leave reviews [blossomservers.com](https://blossomservers.com) Its still very much a work in progress (needs login and server and review editing) The source is on [github](https://github.com/hzrd149/blossomservers) I also started another project to create a simple account based paid blossom server [blossom-account-server](https://github.com/hzrd149/blossom-account-server) Unfortunately I got sidetracked and I didn't have the time to give it the attention it needs to get it over the finish line ## Smaller projects - [cherry-tree](https://github.com/hzrd149/cherry-tree) A small app for uploading chunked blobs to blossom servers (with cashu payment support) - [vite-plugin-funding](https://github.com/hzrd149/vite-plugin-funding) A vite plugin to collect and expose package "funding" to the app - [node-red-contrib-rx-nostr](https://github.com/hzrd149/node-red-contrib-rx-nostr) The start of a node-red package for rx-nostr. if your interested please help - [node-red-contrib-applesauce](https://github.com/hzrd149/node-red-contrib-applesauce) The start of a node-red package for applesauce. I probably wont finish it so any help it welcome ## Plans for 2025 I have a few vague ideas of what I want to work on Q1 of 2025. but there are a few things i know for certain. I'm going to keep refactoring noStrudel by moving core logic out into [applesauce](https://hzrd149.github.io/applesauce/) and making it more modular. This should make noStrudel more reliable and hopefully allow me to create and maintain more apps with less code And I'm going to write tests. tests for everything. hopefully tests for all the libraries and apps I've created in 2024. A lot of the code I wrote in 2024 was hacky code to see if things could work. and while its been working pretty well I'm starting to forget the details of of the code I wrote so I cant be sure if it still works or how well it works. So my solution is to write tests, lots of tests :) @ ec42c765:328c0600
2025-02-05 23:43:35test
@ ec42c765:328c0600
2025-02-05 23:43:35test @ d360efec:14907b5f
2025-02-18 15:11:58**ภาพรวม BTCUSDT (OKX):** Bitcoin (BTCUSDT) กำลังแสดงความผันผวนอย่างมาก โดยมีสัญญาณที่ขัดแย้งกันระหว่าง Timeframes ต่างๆ แนวโน้มระยะยาว (Day) ยังคงเป็นขาขึ้น แต่ระยะกลาง (4H) และระยะสั้น (15m) แสดงให้เห็นถึงแรงขายและการปรับฐานที่รุนแรง การวิเคราะห์นี้จะเน้นการระบุพื้นที่ที่ Smart Money อาจจะเข้าซื้อหรือขาย (Liquidity Pools) และประเมินความแข็งแกร่งของแนวโน้ม **วิเคราะห์ทีละ Timeframe:** **(1) TF Day (รายวัน):**  * **แนวโน้ม:** ขาขึ้น (Uptrend) *แต่เริ่มอ่อนแรง* * **SMC:** * Higher Highs (HH) และ Higher Lows (HL) *เริ่มไม่ชัดเจน* * Break of Structure (BOS) ด้านบน *แต่เริ่มมีการปรับฐาน* * **Liquidity:** * มี Sellside Liquidity (SSL) อยู่ใต้ Lows ก่อนหน้า (บริเวณ 85,000 - 90,000) * มี Buyside Liquidity (BSL) อยู่เหนือ High เดิม (109,998.9) * **ICT:** * ยังไม่เห็น Order Block หรือ FVG ที่ชัดเจนใน TF Day *ณ ราคาปัจจุบัน* * **EMA:** * ราคา *หลุด* EMA 50 (สีเหลือง) ลงมาแล้ว * EMA 200 (สีขาว) เป็นแนวรับถัดไป * **Money Flow (LuxAlgo):** * แท่งสีแดงยาว แสดงถึงแรงขายที่เข้ามา * **Trend Strength (AlgoAlpha):** *ไม่มีในภาพ* * **Volume Profile:** Volume ค่อนข้างเบาบาง * **แท่งเทียน:** แท่งเทียนล่าสุดเป็นสีแดง แสดงถึงแรงขาย * **แนวรับ:** EMA 200, บริเวณ 85,000 - 90,000 (SSL) * **แนวต้าน:** EMA 50, High เดิม * **สรุป:** แนวโน้มขาขึ้นเริ่มอ่อนแรง, ราคาหลุด EMA 50, Money Flow เป็นลบ, มี SSL ด้านล่าง **(2) TF4H (4 ชั่วโมง):**  * **แนวโน้ม:** ขาลง (Downtrend) *ระยะสั้น* หลังจากราคาหลุด EMA 50 * **SMC:** * Lower Highs (LH) และ Lower Lows (LL) * Break of Structure (BOS) ด้านล่าง * **Liquidity:** * มี SSL อยู่ใต้ Lows ก่อนหน้า (บริเวณ 92,000) * มี BSL อยู่เหนือ Highs ก่อนหน้า (บริเวณ 104,000 - 108,000) * **ICT:** * **Order Block:** ราคาลงมาใกล้ Order Block ขาขึ้น (บริเวณแท่งเทียนสีเขียวก่อนที่จะขึ้น) * **EMA:** * ราคาอยู่ใต้ EMA 50 และ EMA 200 * **Money Flow (LuxAlgo):** * สีแดงเป็นส่วนใหญ่ แสดงถึงแรงขาย * **Trend Strength (AlgoAlpha):** *ไม่มีในภาพ* * **Volume Profile** Volume ค่อนข้างเบาบาง * **แนวรับ:** Order Block, บริเวณ 92,000 (SSL) * **แนวต้าน:** EMA 50, EMA 200, บริเวณ Highs ก่อนหน้า * **สรุป:** แนวโน้มขาลงระยะสั้น, ราคาลงมาใกล้ Order Block, Money Flow เป็นลบ **(3) TF15 (15 นาที):**  * **แนวโน้ม:** ขาลง (Downtrend) * **SMC:** * Lower Highs (LH) และ Lower Lows (LL) * Break of Structure (BOS) ด้านล่าง * **Liquidity:** * มี SSL อยู่ใต้ Lows ล่าสุด * มี BSL อยู่เหนือ Highs ก่อนหน้า * **ICT:** * **Order Block:** ราคาลงมาใกล้ Oder Block * **EMA:** * EMA 50 และ EMA 200 เป็นแนวต้าน * **Money Flow (LuxAlgo):** * สีแดงเป็นส่วนใหญ่ แสดงถึงแรงขาย * **Trend Strength (AlgoAlpha):** * เป็นสีแดง แสดงถึงเเนวโน้มขาลง * **Volume Profile:** * Volume ค่อนข้างเบาบาง * **แนวรับ:** บริเวณ Low ล่าสุด * **แนวต้าน:** EMA 50, EMA 200, บริเวณ Highs ก่อนหน้า * **สรุป:** แนวโน้มขาลง, แรงขายมีอิทธิพล, ใกล้แนวรับ **สรุปภาพรวมและกลยุทธ์ (BTCUSDT):** * **แนวโน้มหลัก (Day):** ขาขึ้น (อ่อนแรง) * **แนวโน้มรอง (4H):** ขาลง (ระยะสั้น) * **แนวโน้มระยะสั้น (15m):** ขาลง * **Liquidity:** * Day: SSL (85,000-90,000), BSL (เหนือ 109,998.9) * 4H: SSL (92,000), BSL (104,000-108,000) * 15m: SSL (ใต้ Lows), BSL (เหนือ Highs) * **Money Flow:** Day เริ่มเป็นลบ, 4H เป็นลบ, 15m เป็นลบ * **Trend Strength** 15 m : ขาลง * **กลยุทธ์:** 1. **Wait & See (ดีที่สุด):** รอความชัดเจน 2. **Short (เสี่ยง):** ถ้าไม่สามารถ Breakout EMA/แนวต้านใน TF ใดๆ ได้ 3. **ไม่แนะนำให้ Buy:** จนกว่าจะมีสัญญาณกลับตัวที่ชัดเจน **คำแนะนำ:** * **ความขัดแย้งของ Timeframes:** ชัดเจน * **Money Flow:** เป็นลบในทุก Timeframes * **ระวัง SSL:** Smart Money อาจจะลากราคาลงไปกิน Stop Loss * **ถ้าไม่แน่ใจ อย่าเพิ่งเข้าเทรด** **Disclaimer:** การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ
@ d360efec:14907b5f
2025-02-18 15:11:58**ภาพรวม BTCUSDT (OKX):** Bitcoin (BTCUSDT) กำลังแสดงความผันผวนอย่างมาก โดยมีสัญญาณที่ขัดแย้งกันระหว่าง Timeframes ต่างๆ แนวโน้มระยะยาว (Day) ยังคงเป็นขาขึ้น แต่ระยะกลาง (4H) และระยะสั้น (15m) แสดงให้เห็นถึงแรงขายและการปรับฐานที่รุนแรง การวิเคราะห์นี้จะเน้นการระบุพื้นที่ที่ Smart Money อาจจะเข้าซื้อหรือขาย (Liquidity Pools) และประเมินความแข็งแกร่งของแนวโน้ม **วิเคราะห์ทีละ Timeframe:** **(1) TF Day (รายวัน):**  * **แนวโน้ม:** ขาขึ้น (Uptrend) *แต่เริ่มอ่อนแรง* * **SMC:** * Higher Highs (HH) และ Higher Lows (HL) *เริ่มไม่ชัดเจน* * Break of Structure (BOS) ด้านบน *แต่เริ่มมีการปรับฐาน* * **Liquidity:** * มี Sellside Liquidity (SSL) อยู่ใต้ Lows ก่อนหน้า (บริเวณ 85,000 - 90,000) * มี Buyside Liquidity (BSL) อยู่เหนือ High เดิม (109,998.9) * **ICT:** * ยังไม่เห็น Order Block หรือ FVG ที่ชัดเจนใน TF Day *ณ ราคาปัจจุบัน* * **EMA:** * ราคา *หลุด* EMA 50 (สีเหลือง) ลงมาแล้ว * EMA 200 (สีขาว) เป็นแนวรับถัดไป * **Money Flow (LuxAlgo):** * แท่งสีแดงยาว แสดงถึงแรงขายที่เข้ามา * **Trend Strength (AlgoAlpha):** *ไม่มีในภาพ* * **Volume Profile:** Volume ค่อนข้างเบาบาง * **แท่งเทียน:** แท่งเทียนล่าสุดเป็นสีแดง แสดงถึงแรงขาย * **แนวรับ:** EMA 200, บริเวณ 85,000 - 90,000 (SSL) * **แนวต้าน:** EMA 50, High เดิม * **สรุป:** แนวโน้มขาขึ้นเริ่มอ่อนแรง, ราคาหลุด EMA 50, Money Flow เป็นลบ, มี SSL ด้านล่าง **(2) TF4H (4 ชั่วโมง):**  * **แนวโน้ม:** ขาลง (Downtrend) *ระยะสั้น* หลังจากราคาหลุด EMA 50 * **SMC:** * Lower Highs (LH) และ Lower Lows (LL) * Break of Structure (BOS) ด้านล่าง * **Liquidity:** * มี SSL อยู่ใต้ Lows ก่อนหน้า (บริเวณ 92,000) * มี BSL อยู่เหนือ Highs ก่อนหน้า (บริเวณ 104,000 - 108,000) * **ICT:** * **Order Block:** ราคาลงมาใกล้ Order Block ขาขึ้น (บริเวณแท่งเทียนสีเขียวก่อนที่จะขึ้น) * **EMA:** * ราคาอยู่ใต้ EMA 50 และ EMA 200 * **Money Flow (LuxAlgo):** * สีแดงเป็นส่วนใหญ่ แสดงถึงแรงขาย * **Trend Strength (AlgoAlpha):** *ไม่มีในภาพ* * **Volume Profile** Volume ค่อนข้างเบาบาง * **แนวรับ:** Order Block, บริเวณ 92,000 (SSL) * **แนวต้าน:** EMA 50, EMA 200, บริเวณ Highs ก่อนหน้า * **สรุป:** แนวโน้มขาลงระยะสั้น, ราคาลงมาใกล้ Order Block, Money Flow เป็นลบ **(3) TF15 (15 นาที):**  * **แนวโน้ม:** ขาลง (Downtrend) * **SMC:** * Lower Highs (LH) และ Lower Lows (LL) * Break of Structure (BOS) ด้านล่าง * **Liquidity:** * มี SSL อยู่ใต้ Lows ล่าสุด * มี BSL อยู่เหนือ Highs ก่อนหน้า * **ICT:** * **Order Block:** ราคาลงมาใกล้ Oder Block * **EMA:** * EMA 50 และ EMA 200 เป็นแนวต้าน * **Money Flow (LuxAlgo):** * สีแดงเป็นส่วนใหญ่ แสดงถึงแรงขาย * **Trend Strength (AlgoAlpha):** * เป็นสีแดง แสดงถึงเเนวโน้มขาลง * **Volume Profile:** * Volume ค่อนข้างเบาบาง * **แนวรับ:** บริเวณ Low ล่าสุด * **แนวต้าน:** EMA 50, EMA 200, บริเวณ Highs ก่อนหน้า * **สรุป:** แนวโน้มขาลง, แรงขายมีอิทธิพล, ใกล้แนวรับ **สรุปภาพรวมและกลยุทธ์ (BTCUSDT):** * **แนวโน้มหลัก (Day):** ขาขึ้น (อ่อนแรง) * **แนวโน้มรอง (4H):** ขาลง (ระยะสั้น) * **แนวโน้มระยะสั้น (15m):** ขาลง * **Liquidity:** * Day: SSL (85,000-90,000), BSL (เหนือ 109,998.9) * 4H: SSL (92,000), BSL (104,000-108,000) * 15m: SSL (ใต้ Lows), BSL (เหนือ Highs) * **Money Flow:** Day เริ่มเป็นลบ, 4H เป็นลบ, 15m เป็นลบ * **Trend Strength** 15 m : ขาลง * **กลยุทธ์:** 1. **Wait & See (ดีที่สุด):** รอความชัดเจน 2. **Short (เสี่ยง):** ถ้าไม่สามารถ Breakout EMA/แนวต้านใน TF ใดๆ ได้ 3. **ไม่แนะนำให้ Buy:** จนกว่าจะมีสัญญาณกลับตัวที่ชัดเจน **คำแนะนำ:** * **ความขัดแย้งของ Timeframes:** ชัดเจน * **Money Flow:** เป็นลบในทุก Timeframes * **ระวัง SSL:** Smart Money อาจจะลากราคาลงไปกิน Stop Loss * **ถ้าไม่แน่ใจ อย่าเพิ่งเข้าเทรด** **Disclaimer:** การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ @ 5d4b6c8d:8a1c1ee3
2025-02-20 16:20:02We made a minor adjustment to the reply fee, raising it to 2 sats. Lest you think @grayruby is just a greedy SOB (not that he isn't), we are trying to think through how to use some of the territory profits to help support the contests being run by stackers and those extra sats can help with that effort. # How is ~Stacker_Sports doing? The past month has been awesome for us. Of course, that may be related to the NFL playoffs. - Posts: 271, 4th ranked territory - Comments: ***2992, 2nd ranked territory!*** - Stacking: ***193.9k, 2nd ranked territory!*** - Spending: ***300.9k, 2nd ranked territory!*** Top Post: [Super Bowl Discussion Thread](https://stacker.news/items/880943/r/Undisciplined) by @grayruby - 1088 sats/ 109 comments I'm looking forward to another awesome month! originally posted at https://stacker.news/items/891926
@ 5d4b6c8d:8a1c1ee3
2025-02-20 16:20:02We made a minor adjustment to the reply fee, raising it to 2 sats. Lest you think @grayruby is just a greedy SOB (not that he isn't), we are trying to think through how to use some of the territory profits to help support the contests being run by stackers and those extra sats can help with that effort. # How is ~Stacker_Sports doing? The past month has been awesome for us. Of course, that may be related to the NFL playoffs. - Posts: 271, 4th ranked territory - Comments: ***2992, 2nd ranked territory!*** - Stacking: ***193.9k, 2nd ranked territory!*** - Spending: ***300.9k, 2nd ranked territory!*** Top Post: [Super Bowl Discussion Thread](https://stacker.news/items/880943/r/Undisciplined) by @grayruby - 1088 sats/ 109 comments I'm looking forward to another awesome month! originally posted at https://stacker.news/items/891926 @ 8f69ac99:4f92f5fd
2025-02-20 16:14:03Imagine-se numa fila de uma feira de emprego com dois amigos igualmente qualificados, mas provenientes de contextos socioeconómicos diferentes. Um dos amigos, devido às suas circunstâncias económicas, recebe um tratamento preferencial—como um aumento de 10% na pontuação da sua candidatura, como parte de uma política destinada a corrigir desvantagens sistémicas. O outro amigo, apesar de igualmente qualificado, não recebe qualquer vantagem. Quem conseguirá o emprego para o qual ambos estão capacitados? Este cenário destaca o paradoxo no cerne de muitas políticas de justiça social: tratar as pessoas de forma diferente para atingir a igualdade muitas vezes resulta em resultados desiguais, desafiando o princípio de equidade e minando a confiança. Esta tensão entre os objetivos da justiça social e a necessidade de equidade tem moldado debates sobre ações afirmativas, tributação progressiva, programas de bem-estar social e outras políticas destinadas a promover a equidade entre grupos. Embora bem-intencionadas, estas iniciativas podem marginalizar o mérito individual e gerar ressentimento entre aqueles que se sentem injustamente tratados. A tese central deste artigo é que, embora a justiça social tenha como objetivo promover a igualdade, as suas políticas requerem inerentemente um tratamento desigual, o que paradoxalmente arrisca criar novas formas de desigualdade. Este paradoxo destaca os desafios de buscar a equidade através da intervenção estatal. ### O Princípio da Justiça Social As políticas de justiça social frequentemente focam-se em atingir a igualdade de resultados através da intervenção estatal. Por exemplo, a ação afirmativa na educação promove a representação de grupos sub-representados através de medidas como cotas raciais ou tratamento preferencial em processos de admissão universitária. De forma semelhante, a tributação progressiva procura redistribuir riqueza ao impor maiores encargos fiscais a determinados grupos de rendimento. Embora estas políticas visem corrigir desigualdades sistémicas, elas inerentemente requerem tratar as pessoas de forma diferente com base em fatores como raça, rendimento ou condição socioeconómica. Esta discrepância pode criar uma perceção de favoritismo, erodindo a confiança nas instituições e gerando ressentimento entre aqueles que se sentem injustamente prejudicados. Ao dar prioridade à identidade de grupo em detrimento das circunstâncias individuais, estas políticas podem comprometer a equidade e minar a confiança nas instituições, criando percepções de injustiça e ineficiência económica. ### O Problema do Tratamento Desigual Uma das preocupações centrais com as políticas de justiça social é a sua dependência no tratamento desigual para atingir a igualdade de resultados. Embora concebidas para promover a equidade, estas políticas frequentemente conduzem a consequências indesejadas que desafiam a equidade e a coesão social. Por exemplo, as políticas de acção afirmativa têm sido criticadas por enfatizarem a identidade de grupo em detrimento do mérito individual. Isto pode resultar na seleção de candidatos com base em cotas em vez de qualificações, gerando frustração entre aqueles que se sentem preteridos, apesar dos seus esforços ou competências. De forma semelhante, os sistemas de tributação progressiva sobrecarregam desproporcionalmente certos grupos, criando a perceção de penalização injusta. As cotas na educação ou no emprego são particularmente controversas. Ao impor limites ou metas com base na identidade de grupo, estas políticas podem inadvertidamente excluir indivíduos que não se enquadram nos critérios definidos. Esta exclusão muitas vezes gera ressentimento, pois os afetados percebem o sistema como priorizando a equidade para uns em detrimento de outros. Além disso, ao enfatizar a identidade de grupo sobre o mérito individual, as políticas de justiça social podem inadvertidamente enfraquecer incentivos à excelência e à responsabilidade pessoal, gerando impactos negativos na produtividade e na confiança nas instituições. Esta dinâmica pode corroer a responsabilidade e a confiança nas instituições, criando divisões dentro da sociedade. Ao enfatizar a igualdade de resultados sobre a igualdade de oportunidades, tais políticas arriscam consolidar novas formas de desigualdade. ### Estudos de Caso e Exemplos do Mundo Real **Acção Afirmativa na Educação** A política de acção afirmativa da Universidade do Texas em Austin, que considera a raça como um dos factores nas admissões, gerou desafios legais. Críticos argumentaram que a política prejudicava injustamente candidatos igualmente ou mais qualificados que não atendiam aos critérios da política. Embora os tribunais tenham apoiado a política, a controvérsia destaca a tensão entre promover diversidade e preservar o mérito individual. **Programas de Bem-Estar Redistributivo** Nos Estados Unidos, o Crédito Tributário por Rendimento do Trabalho (EITC) visa aliviar a pobreza entre indivíduos de baixos rendimentos. Contudo, disparidades na sua implementação causaram fricções. Por exemplo, estudos mostram variações nos benefícios entre grupos demográficos, deixando alguns com a sensação de tratamento injusto, apesar de circunstâncias financeiras semelhantes. Estes resultados ilustram como políticas redistributivas podem inadvertidamente gerar ressentimento. **Cotas de Diversidade na Contratação** Muitas empresas implementaram cotas de diversidade para aumentar a representação. Contudo, estas medidas frequentemente levantam preocupações sobre equidade. Empregados contratados sob cotas por vezes relatam sentir-se estigmatizados, e outros percebem o sistema como desvalorizando o mérito. Isto mina a moral e a confiança no local de trabalho, como demonstrado em inquéritos que revelam insatisfação com práticas de contratação baseadas em cotas. Os exemplos acima ilustram como políticas desenhadas para promover equidade podem, na prática, comprometer os princípios de justiça e meritocracia, resultando em consequências imprevistas que minam a confiança nas instituições. A dependência generalizada na identidade de grupo, em vez do desempenho individual, arrisca criar divisões e reduzir a confiança nas instituições. ### Crítica Filosófica e Ética A busca pela justiça social levanta dilemas filosóficos e éticos, particularmente no equilíbrio entre igualdade e equidade. Por um lado, a igualdade sugere tratar os indivíduos de forma imparcial, independentemente da identidade. Por outro, atingir a igualdade de resultados frequentemente requer tratamento desigual. Sob uma perspetiva rawlsiana, as políticas redistributivas são justificadas para corrigir desigualdades sistémicas e promover a equidade. Contudo, pensadores libertários como Robert Nozick argumentam que tais intervenções violam os direitos e as liberdades individuais. Para Nozick, a justiça reside na proteção da autonomia e da propriedade pessoal, não na redistribuição de recursos para atingir objetivos coletivos. Ademais, uma énfase excessiva na identidade de grupo pode fomentar uma cultura de vitimização, onde os indivíduos priorizam queixas em detrimento da responsabilidade pessoal. Esta dinâmica pode consolidar divisões, incentivar direitos adquiridos e minar a coesão social. As políticas que promovem a igualdade de resultados podem inadvertidamente criar privilégios para alguns enquanto desfavorecem outros, perpetuando novas formas de desigualdade. Uma abordagem equilibrada deve considerar as implicações éticas das medidas redistributivas, preservando as liberdades individuais e a meritocracia. Ao focar na oportunidade em vez do resultado, as sociedades podem buscar a equidade sem comprometer a autonomia. ### Soluções Alternativas **Investir na Educação** Proporcionar acesso à educação de alta qualidade é uma forma poderosa de nivelar o campo de jogo. Programas que ampliem as oportunidades educacionais para comunidades desfavorecidas podem promover mobilidade social sem depender de tratamentos preferenciais. **Garantir Liberdade Económica** Reduzir barreiras regulatórias e promover mercados livres pode estimular a inovação, o empreendedorismo e a criação de emprego. Ao incentivar a competição, os indivíduos podem prosperar com base nas suas capacidades em vez de depender de intervenções externas. **Aproveitar Sistemas Descentralizados** Tecnologias descentralizadas como o Bitcoin podem empoderar indivíduos ao oferecer inclusão financeira e reduzir a dependência de sistemas estatais. Estas ferramentas proporcionam transparência e autonomia, minimizando oportunidades de favoritismo ou corrupção. **Medidas Práticas** - Bolsas de estudo e subsídios baseados no mérito. - Programas de formação profissional para desenvolver competências de mercado. - Apoio ao empreendedorismo através de financiamento e mentoria. - Reformas para simplificar os sistemas fiscais e regulatórios. Estas soluções priorizam a equidade, o empoderamento individual e a oportunidade, promovendo uma sociedade onde as pessoas prosperem com base no mérito e no esforço. ### Conclusão As políticas de justiça social frequentemente procuram atingir a igualdade através do tratamento desigual, mas esta abordagem pode criar novas formas de desigualdade e divisão. A énfase na identidade de grupo em detrimento do mérito individual arrisca corroer a equidade e a confiança, minando os objetivos que estas políticas procuram atingir. Para alcançar uma sociedade mais justa e sustentável, é essencial focar na igualdade de oportunidades, garantindo que todos tenham acesso aos mesmos recursos e condições para prosperar, sem comprometer a autonomia individual ou distorcer os princípios da meritocracia. Investimentos na educação, liberdade económica e tecnologias descentralizadas oferecem caminhos práticos para empoderar indivíduos e fomentar a meritocracia. Um compromisso com estes princípios pode criar um futuro mais inclusivo e equitativo, onde todos tenham a chance de prosperar com base nos seus próprios esforços e capacidades. _Photo by [Cody Pulliam](https://unsplash.com/@codyaustinpulliam?utm_content=creditCopyText&utm_medium=referral&utm_source=unsplash) on [Unsplash](https://unsplash.com/photos/person-holding-brown-cardboard-box-GGKVGSkKIzM?utm_content=creditCopyText&utm_medium=referral&utm_source=unsplash)_
@ 8f69ac99:4f92f5fd
2025-02-20 16:14:03Imagine-se numa fila de uma feira de emprego com dois amigos igualmente qualificados, mas provenientes de contextos socioeconómicos diferentes. Um dos amigos, devido às suas circunstâncias económicas, recebe um tratamento preferencial—como um aumento de 10% na pontuação da sua candidatura, como parte de uma política destinada a corrigir desvantagens sistémicas. O outro amigo, apesar de igualmente qualificado, não recebe qualquer vantagem. Quem conseguirá o emprego para o qual ambos estão capacitados? Este cenário destaca o paradoxo no cerne de muitas políticas de justiça social: tratar as pessoas de forma diferente para atingir a igualdade muitas vezes resulta em resultados desiguais, desafiando o princípio de equidade e minando a confiança. Esta tensão entre os objetivos da justiça social e a necessidade de equidade tem moldado debates sobre ações afirmativas, tributação progressiva, programas de bem-estar social e outras políticas destinadas a promover a equidade entre grupos. Embora bem-intencionadas, estas iniciativas podem marginalizar o mérito individual e gerar ressentimento entre aqueles que se sentem injustamente tratados. A tese central deste artigo é que, embora a justiça social tenha como objetivo promover a igualdade, as suas políticas requerem inerentemente um tratamento desigual, o que paradoxalmente arrisca criar novas formas de desigualdade. Este paradoxo destaca os desafios de buscar a equidade através da intervenção estatal. ### O Princípio da Justiça Social As políticas de justiça social frequentemente focam-se em atingir a igualdade de resultados através da intervenção estatal. Por exemplo, a ação afirmativa na educação promove a representação de grupos sub-representados através de medidas como cotas raciais ou tratamento preferencial em processos de admissão universitária. De forma semelhante, a tributação progressiva procura redistribuir riqueza ao impor maiores encargos fiscais a determinados grupos de rendimento. Embora estas políticas visem corrigir desigualdades sistémicas, elas inerentemente requerem tratar as pessoas de forma diferente com base em fatores como raça, rendimento ou condição socioeconómica. Esta discrepância pode criar uma perceção de favoritismo, erodindo a confiança nas instituições e gerando ressentimento entre aqueles que se sentem injustamente prejudicados. Ao dar prioridade à identidade de grupo em detrimento das circunstâncias individuais, estas políticas podem comprometer a equidade e minar a confiança nas instituições, criando percepções de injustiça e ineficiência económica. ### O Problema do Tratamento Desigual Uma das preocupações centrais com as políticas de justiça social é a sua dependência no tratamento desigual para atingir a igualdade de resultados. Embora concebidas para promover a equidade, estas políticas frequentemente conduzem a consequências indesejadas que desafiam a equidade e a coesão social. Por exemplo, as políticas de acção afirmativa têm sido criticadas por enfatizarem a identidade de grupo em detrimento do mérito individual. Isto pode resultar na seleção de candidatos com base em cotas em vez de qualificações, gerando frustração entre aqueles que se sentem preteridos, apesar dos seus esforços ou competências. De forma semelhante, os sistemas de tributação progressiva sobrecarregam desproporcionalmente certos grupos, criando a perceção de penalização injusta. As cotas na educação ou no emprego são particularmente controversas. Ao impor limites ou metas com base na identidade de grupo, estas políticas podem inadvertidamente excluir indivíduos que não se enquadram nos critérios definidos. Esta exclusão muitas vezes gera ressentimento, pois os afetados percebem o sistema como priorizando a equidade para uns em detrimento de outros. Além disso, ao enfatizar a identidade de grupo sobre o mérito individual, as políticas de justiça social podem inadvertidamente enfraquecer incentivos à excelência e à responsabilidade pessoal, gerando impactos negativos na produtividade e na confiança nas instituições. Esta dinâmica pode corroer a responsabilidade e a confiança nas instituições, criando divisões dentro da sociedade. Ao enfatizar a igualdade de resultados sobre a igualdade de oportunidades, tais políticas arriscam consolidar novas formas de desigualdade. ### Estudos de Caso e Exemplos do Mundo Real **Acção Afirmativa na Educação** A política de acção afirmativa da Universidade do Texas em Austin, que considera a raça como um dos factores nas admissões, gerou desafios legais. Críticos argumentaram que a política prejudicava injustamente candidatos igualmente ou mais qualificados que não atendiam aos critérios da política. Embora os tribunais tenham apoiado a política, a controvérsia destaca a tensão entre promover diversidade e preservar o mérito individual. **Programas de Bem-Estar Redistributivo** Nos Estados Unidos, o Crédito Tributário por Rendimento do Trabalho (EITC) visa aliviar a pobreza entre indivíduos de baixos rendimentos. Contudo, disparidades na sua implementação causaram fricções. Por exemplo, estudos mostram variações nos benefícios entre grupos demográficos, deixando alguns com a sensação de tratamento injusto, apesar de circunstâncias financeiras semelhantes. Estes resultados ilustram como políticas redistributivas podem inadvertidamente gerar ressentimento. **Cotas de Diversidade na Contratação** Muitas empresas implementaram cotas de diversidade para aumentar a representação. Contudo, estas medidas frequentemente levantam preocupações sobre equidade. Empregados contratados sob cotas por vezes relatam sentir-se estigmatizados, e outros percebem o sistema como desvalorizando o mérito. Isto mina a moral e a confiança no local de trabalho, como demonstrado em inquéritos que revelam insatisfação com práticas de contratação baseadas em cotas. Os exemplos acima ilustram como políticas desenhadas para promover equidade podem, na prática, comprometer os princípios de justiça e meritocracia, resultando em consequências imprevistas que minam a confiança nas instituições. A dependência generalizada na identidade de grupo, em vez do desempenho individual, arrisca criar divisões e reduzir a confiança nas instituições. ### Crítica Filosófica e Ética A busca pela justiça social levanta dilemas filosóficos e éticos, particularmente no equilíbrio entre igualdade e equidade. Por um lado, a igualdade sugere tratar os indivíduos de forma imparcial, independentemente da identidade. Por outro, atingir a igualdade de resultados frequentemente requer tratamento desigual. Sob uma perspetiva rawlsiana, as políticas redistributivas são justificadas para corrigir desigualdades sistémicas e promover a equidade. Contudo, pensadores libertários como Robert Nozick argumentam que tais intervenções violam os direitos e as liberdades individuais. Para Nozick, a justiça reside na proteção da autonomia e da propriedade pessoal, não na redistribuição de recursos para atingir objetivos coletivos. Ademais, uma énfase excessiva na identidade de grupo pode fomentar uma cultura de vitimização, onde os indivíduos priorizam queixas em detrimento da responsabilidade pessoal. Esta dinâmica pode consolidar divisões, incentivar direitos adquiridos e minar a coesão social. As políticas que promovem a igualdade de resultados podem inadvertidamente criar privilégios para alguns enquanto desfavorecem outros, perpetuando novas formas de desigualdade. Uma abordagem equilibrada deve considerar as implicações éticas das medidas redistributivas, preservando as liberdades individuais e a meritocracia. Ao focar na oportunidade em vez do resultado, as sociedades podem buscar a equidade sem comprometer a autonomia. ### Soluções Alternativas **Investir na Educação** Proporcionar acesso à educação de alta qualidade é uma forma poderosa de nivelar o campo de jogo. Programas que ampliem as oportunidades educacionais para comunidades desfavorecidas podem promover mobilidade social sem depender de tratamentos preferenciais. **Garantir Liberdade Económica** Reduzir barreiras regulatórias e promover mercados livres pode estimular a inovação, o empreendedorismo e a criação de emprego. Ao incentivar a competição, os indivíduos podem prosperar com base nas suas capacidades em vez de depender de intervenções externas. **Aproveitar Sistemas Descentralizados** Tecnologias descentralizadas como o Bitcoin podem empoderar indivíduos ao oferecer inclusão financeira e reduzir a dependência de sistemas estatais. Estas ferramentas proporcionam transparência e autonomia, minimizando oportunidades de favoritismo ou corrupção. **Medidas Práticas** - Bolsas de estudo e subsídios baseados no mérito. - Programas de formação profissional para desenvolver competências de mercado. - Apoio ao empreendedorismo através de financiamento e mentoria. - Reformas para simplificar os sistemas fiscais e regulatórios. Estas soluções priorizam a equidade, o empoderamento individual e a oportunidade, promovendo uma sociedade onde as pessoas prosperem com base no mérito e no esforço. ### Conclusão As políticas de justiça social frequentemente procuram atingir a igualdade através do tratamento desigual, mas esta abordagem pode criar novas formas de desigualdade e divisão. A énfase na identidade de grupo em detrimento do mérito individual arrisca corroer a equidade e a confiança, minando os objetivos que estas políticas procuram atingir. Para alcançar uma sociedade mais justa e sustentável, é essencial focar na igualdade de oportunidades, garantindo que todos tenham acesso aos mesmos recursos e condições para prosperar, sem comprometer a autonomia individual ou distorcer os princípios da meritocracia. Investimentos na educação, liberdade económica e tecnologias descentralizadas oferecem caminhos práticos para empoderar indivíduos e fomentar a meritocracia. Um compromisso com estes princípios pode criar um futuro mais inclusivo e equitativo, onde todos tenham a chance de prosperar com base nos seus próprios esforços e capacidades. _Photo by [Cody Pulliam](https://unsplash.com/@codyaustinpulliam?utm_content=creditCopyText&utm_medium=referral&utm_source=unsplash) on [Unsplash](https://unsplash.com/photos/person-holding-brown-cardboard-box-GGKVGSkKIzM?utm_content=creditCopyText&utm_medium=referral&utm_source=unsplash)_ @ d360efec:14907b5f
2025-02-18 13:18:54**นักพนันแห่งเฮรันเทล** **“คณิตศาสตร์” กุญแจเวทมนตร์ นักพนัน และ นักลงทุน** ในนครเฮรันเทล นามกระฉ่อนเลื่องลือในหมู่นักเสี่ยงโชค เมื่อเอ่ยถึง **“การพนัน”** ภาพที่ชาวเมืองมักนึกถึงคือ **“ยาจกข้างถนน”** มิใช่เรื่องแปลกประหลาดอันใด เพราะเป็นที่ร่ำลือกันว่า **จ้าวแห่งหอคอยรัตติกาล** ผู้คุมบ่อนพนัน มักร่ายเวทมนตร์สร้างเกมให้ตนเองได้เปรียบ เพื่อดูดกลืนเงินทองของผู้มาเยือน ดังนั้น การที่สามัญชนจะพิชิตเกมในระยะยาว จึงเป็นดั่งเงามายาที่จับต้องมิได้ กระนั้น ยังมีตำนานกล่าวขานถึงผู้กล้า ที่สามารถสร้างชื่อจาก **“เกมพนัน”** เช่น **เวเนสซา รุสโซ** นักเวทย์มนตร์ผู้ใช้กฎหมายแห่งแดนไกล ใช้เวลายาวนานถึงหกปี ร่ายเวทย์สะสมทรัพย์สินกว่าร้อยล้านเหรียญทอง จากการเล่นเกมไพ่ศักดิ์สิทธิ์ **“โป๊กเกอร์”** หรือแม้แต่ **เอ็ดเวิร์ด โอ. ทอร์ป** จอมปราชญ์ผู้สร้างกำไรถึงสามแสนหกหมื่นเหรียญทอง ภายในเจ็ดราตรี จากการเล่นเกมไพ่มนตรา **“แบล็กแจ็ก”** ด้วยเงินทุนตั้งต้นเพียงสามแสนสามหมื่นเหรียญทอง คิดเป็นอัตราเวทย์ตอบแทนร้อยสิบส่วน! เหล่าจอมยุทธ์เหล่านี้ มิได้อาศัยเพียงโชคช่วยชั่วครั้งชั่วคราวแล้วเลือนหาย แต่พวกเขากลับสามารถร่ายเวทย์สร้างผลตอบแทนระยะยาว จนเรียกได้ว่า ใช้ **“หอคอยรัตติกาล”** เป็นแหล่งเสบียงเลี้ยงชีพ โดยกุญแจเวทย์ที่บุคคลเหล่านี้ใช้ ก็คือ **“คณิตศาสตร์”** เหตุใด **“คณิตศาสตร์”** จึงช่วยให้ผู้คนเอาชนะ **“การพนัน”** ได้? และนอกจาก **“การพนัน”** แล้ว **“คณิตศาสตร์”** ยังสามารถประยุกต์ใช้กับสิ่งใดได้อีก? **นักเล่าเรื่องแห่งเฮรันเทล** จักไขปริศนาให้ฟัง เบื้องต้น ขอให้ท่านลองพิจารณาตนเอง ว่าเคยประสบพบพานเหตุการณ์เหล่านี้หรือไม่: - ตั้งมั่นว่า จักเสี่ยงโชคให้ได้กำไรเพียงเล็กน้อย แล้วจักหยุดพัก - แต่หากพลาดท่าเสียที จักจำกัดการสูญเสียให้เท่าทุนเดิมที่ตั้งไว้ - ครั้นเมื่อเวทมนตร์เข้าข้าง ได้กำไรมาแล้ว กลับโลภโมโทสัน อยากได้เพิ่มอีกนิด จึงร่ายเวทย์ต่อ - ทว่ากำไรเริ่มร่อยหรอ จนเหลือเพียงทุนเดิม สุดท้ายทุนที่ตั้งไว้คราแรกก็มลายสิ้น - จำต้องหาเงินทองมาลงเพิ่ม หวังทวงทุนคืน และพบว่าต้องสูญเสียเงินก้อนนั้นไปในห้วงเวลาต่อมา ลำดับเหตุการณ์ดังกล่าว เรียกได้ว่าเป็น **“วงจรอุบาทว์”** สำหรับนักพนันมากมายในเฮรันเทล ปริศนาที่ตามมาก็คือ เหตุใด **“วงจรอุบาทว์”** นี้จึงเกิดขึ้นซ้ำแล้วซ้ำเล่า? ส่วนหนึ่ง ย่อมเป็นเพราะอารมณ์อันแปรปรวนในการเสี่ยงโชคของแต่ละคน แต่อีกส่วนที่สำคัญยิ่งกว่า ต้องกล่าวว่าเป็นผลจาก **“กลไกต้องสาป”** ของจ้าวแห่งหอคอยรัตติกาล ซึ่งต้องกล่าวว่า เหล่าเจ้าของหอคอยรัตติกาลนั้น จักใช้หลักการทำนองเดียวกับ **“สมาคมพ่อค้าผู้พิทักษ์”** คือจักเก็บเงินทองจากชนจำนวนมาก เพื่อนำมาจ่ายให้กับชนเพียงหยิบมือ เพื่อล่อลวงให้ชนทั้งหลายเสี่ยงโชคต่อไป หรือทำให้เหล่านักพนันหวังว่า จักเป็นผู้โชคดีเฉกเช่นพวกเขาบ้าง แม้จะมีผู้โชคดีที่สามารถได้กำไรในเบื้องต้น แต่ในบั้นปลายก็จักพ่ายแพ้อยู่ดี ซึ่งเป็นไปตาม **“กฎแห่งจำนวนมหาศาล”** เพราะจ้าวแห่งหอคอยรัตติกาลนั้น ได้คำนวณและออกแบบระบบเกมที่ตนเองได้เปรียบในระยะยาวแล้ว จากตำนานนี้ ย่อมประจักษ์ชัดว่า แม้การพนันจักเป็นเรื่องของดวงชะตา แต่ก็ถูกรังสรรค์ขึ้นจากการคำนวณทางคณิตศาสตร์ ดังนั้น หากปรารถนาจะหาหนทางเอาชนะจ้าวแห่งหอคอยรัตติกาล ก็จำต้องเข้าใจ **“คณิตศาสตร์”** เสียก่อน ทีนี้ จงเงี่ยหูฟัง แล้วท่านจักได้ยินข้าไขปริศนา: **๑. ปริศนาแห่ง “กำไรคาดหวัง”** สำหรับการแสวงหา **“เกมเสี่ยงทาย”** ที่ควรค่าแก่การเล่น หรือการเสี่ยง สิ่งแรกที่นักพนันพึงกระทำคือ **“การประเมินกำไรคาดหวัง”** หรือ **“เวทคำนวณอนาคต”** **“กำไรคาดหวัง”** ถูกคิดค้นโดย **คริสเตียน ฮอยเกนส์** นักปราชญ์เวทย์ชาวดัตช์ เพื่อประเมินว่าเกมพนันแบบใดควรค่าแก่การเล่น ซึ่งมิใช่เพียงแค่การประเมินโอกาสแห่งชัยชนะเท่านั้น แต่ต้องคิดรวมขนาดของเงินเดิมพันไปด้วย โดยสูตรเวทย์คือ: **กำไรคาดหวัง = (เงินที่ได้ x โอกาสชนะ) + (เงินที่เสีย x โอกาสแพ้)** ดังนั้น หากปรารถนาจะสะสม **“ทองคำมายา”** ในระยะยาว จงเลือกเกมที่มี **“กำไรคาดหวัง”** เป็นบวก แต่หากพลาดพลั้งเข้าไปเล่นเกมที่ **“กำไรคาดหวัง”** เป็นลบ และบังเอิญว่าโชคชะตาเล่นตลกให้ได้เงินทองมาครอง พึงละทิ้งเกมนั้นเสียโดยพลัน เพราะท้ายที่สุดหากยังคงเล่นต่อไป ผู้อับโชคผู้นั้นก็คือตัวท่านเอง อย่างไรก็ตาม โดยธรรมดาแล้ว **“กำไรคาดหวัง”** ของเกมพนันที่มีเจ้ามือมักจักติดลบ จึงเป็นเรื่องยากยิ่งที่จะเอาชนะได้ เฉกเช่นตัวอย่างที่เราเห็น คือเกมในบ่อนพนัน หรือแม้แต่ **“สลากกินแบ่งรัฐบาล”** ก็ล้วนเป็นเกมที่มี **“กำไรคาดหวัง”** ติดลบทั้งสิ้น นอกจาก **“กำไรคาดหวัง”** จักถูกใช้กับการพนันได้แล้ว หลักเวทย์ **“คณิตศาสตร์”** ก็ยังสามารถประยุกต์ใช้กับการลงทุนได้ไม่แตกต่างกัน ตัวอย่างเช่น หากท่านเก็บสถิติข้อมูลการลงทุนของตนเอง แล้วพบว่ามีเพียงสามสิบส่วนร้อยเท่านั้น ที่ท่านซื้อ **“ศิลาแห่งโชค”** แล้วสร้างผลตอบแทนเป็นบวก แต่ท่านยังคงปรารถนาความสำเร็จในการลงทุน ก็จงจำกัดการขาดทุนแต่ละคราให้น้อยเข้าไว้ เช่น -๕% และปล่อยให้มีกำไรในแต่ละคราที่ลงทุน เช่น อย่างน้อย ๒๐% ซึ่งจากการใช้กลยุทธ์นี้ ท่านจักมี **“กำไรคาดหวัง”** = (๒๐% x ๐.๓) + (-๕% x ๐.๗) = ๒.๕% จักเห็นได้ว่า แม้ท่านจักมีจำนวนคราที่ขาดทุนบ่อยครั้ง แต่ก็ยังสามารถสร้างกำไรได้ หากคราที่กำไรนั้น สามารถทำเงินทองเป็นจำนวนมากได้ **๒. ปริศนาแห่ง “การบริหารหน้าตัก” หรือ “การบริหารเงินทุน”** แม้ว่าท่านจักรับรู้ **“กำไรคาดหวัง”** แล้ว แต่หากท่านเผชิญหน้ากับการขาดทุนต่อเนื่องกัน ท่านก็อาจหมดเนื้อหมดตัวก่อนถึงคราที่จะกอบโกยเงินทองจากคราที่กำไร วิธีคลายปมปริศนานี้ก็คือ การมิลงเงินทองทั้งหมดของท่านในการลงทุนเพียงคราเดียว ซึ่งนอกจากการกระจายความเสี่ยงในการลงทุนหลาย **“ศิลาแห่งโชค”** หรือหลาย **“เกมเสี่ยงทาย”** แล้ว ท่านอาจกำหนดขนาดของการลงทุนแต่ละคราให้มิมากเกินไป แบบง่าย ๆ เช่น มิเกิน ๑๐% ของเงินลงทุนทั้งหมด หรือท่านอาจคำนวณขนาดของการลงทุนแต่ละคราด้วยสูตรทางคณิตศาสตร์ เช่น สูตร **“การขาดทุนสูงสุดที่ท่านรับได้ (Value at Risk)”** หรือ สูตร **“ขนาดเดิมพันที่เหมาะสม (Kelly Formula)”** **๓. ปริศนาแห่ง “อคติ”** ในวงการพนัน มักมีอคติหนึ่งที่บังเกิดบ่อยครั้งกับผู้คน คือ **“Gambler's Fallacy”** หรือ **“ความเชื่อผิด ๆ แห่งนักพนัน”** ว่าหากเหตุการณ์หนึ่งบังเกิดบ่อยครั้งกว่าปรกติในช่วงเวลาหนึ่ง ๆ เหตุการณ์นั้นจักบังเกิดบ่อยครั้งน้อยลงในอนาคต ทั้ง ๆ ที่เหตุการณ์เหล่านั้นเป็นอิสระจากกันในทางสถิติ ยกตัวอย่างเช่น หากโยนเหรียญมนตราออกหัวไปแล้วสามครา ในคราที่สี่ หลายคนอาจคิดว่าโอกาสออกก้อยมากกว่าหัว แม้ว่าการโยนเหรียญแต่ละคราจะมิได้ส่งผลอันใดต่อกันเลย (จะโยนกี่ครา โอกาสหัวหรือก้อย ก็คือ ๕๐:๕๐ อยู่ยั่งยืน) หรือแม้กระทั่ง **“สลากกินแบ่งรัฐบาล”** มีหลายคนที่ซื้อเลขซ้ำกัน เพื่อหวังว่าจะถูกในงวดต่อ ๆ ไป ในวงการการลงทุน ก็มีลักษณะที่คล้ายคลึงกัน เช่น หาก **“ศิลาแห่งโชค A”** ราคาตกต่ำลงมาห้าครา บางคนอาจคิดว่าในคราที่หก ราคาของมันจักต้องเด้งขึ้นมา ซึ่งในความเป็นจริง หาได้เป็นเช่นนั้นเสมอไป จักเห็นได้ว่า แท้จริงแล้ว ไม่ว่าจักเป็น **“เกมเสี่ยงทายแห่งโชคชะตา”** หรือ **“การผจญภัยในตลาดทุน”** หากท่านมีความเข้าใจ และนำ **“คณิตศาสตร์”** เข้ามาเป็นรากฐาน มันก็อาจนำพาตัวท่านเอง ไปสู่จุดที่ได้เปรียบในเกมนั้น ได้เฉกเช่นกัน.. **สูตรเวทย์มนตร์ที่ปรากฏในตำนาน:** * **กำไรคาดหวัง = (เงินที่ได้ x โอกาสชนะ) + (เงินที่เสีย x โอกาสแพ้)** **คำเตือนจากนักเล่าเรื่องแห่งเฮรันเทล:** "พึงระลึกไว้เสมอว่า โชคชะตาเป็นสิ่งที่คาดเดาได้ยาก แม้เวทมนตร์คณิตศาสตร์จักช่วยนำทาง แต่ท้ายที่สุดแล้ว ความสำเร็จยังคงขึ้นอยู่กับการตัดสินใจและสติปัญญาของท่านเอง" หวังว่าตำนานบทนี้จักเป็นประโยชน์แก่ท่านนะคะ
@ d360efec:14907b5f
2025-02-18 13:18:54**นักพนันแห่งเฮรันเทล** **“คณิตศาสตร์” กุญแจเวทมนตร์ นักพนัน และ นักลงทุน** ในนครเฮรันเทล นามกระฉ่อนเลื่องลือในหมู่นักเสี่ยงโชค เมื่อเอ่ยถึง **“การพนัน”** ภาพที่ชาวเมืองมักนึกถึงคือ **“ยาจกข้างถนน”** มิใช่เรื่องแปลกประหลาดอันใด เพราะเป็นที่ร่ำลือกันว่า **จ้าวแห่งหอคอยรัตติกาล** ผู้คุมบ่อนพนัน มักร่ายเวทมนตร์สร้างเกมให้ตนเองได้เปรียบ เพื่อดูดกลืนเงินทองของผู้มาเยือน ดังนั้น การที่สามัญชนจะพิชิตเกมในระยะยาว จึงเป็นดั่งเงามายาที่จับต้องมิได้ กระนั้น ยังมีตำนานกล่าวขานถึงผู้กล้า ที่สามารถสร้างชื่อจาก **“เกมพนัน”** เช่น **เวเนสซา รุสโซ** นักเวทย์มนตร์ผู้ใช้กฎหมายแห่งแดนไกล ใช้เวลายาวนานถึงหกปี ร่ายเวทย์สะสมทรัพย์สินกว่าร้อยล้านเหรียญทอง จากการเล่นเกมไพ่ศักดิ์สิทธิ์ **“โป๊กเกอร์”** หรือแม้แต่ **เอ็ดเวิร์ด โอ. ทอร์ป** จอมปราชญ์ผู้สร้างกำไรถึงสามแสนหกหมื่นเหรียญทอง ภายในเจ็ดราตรี จากการเล่นเกมไพ่มนตรา **“แบล็กแจ็ก”** ด้วยเงินทุนตั้งต้นเพียงสามแสนสามหมื่นเหรียญทอง คิดเป็นอัตราเวทย์ตอบแทนร้อยสิบส่วน! เหล่าจอมยุทธ์เหล่านี้ มิได้อาศัยเพียงโชคช่วยชั่วครั้งชั่วคราวแล้วเลือนหาย แต่พวกเขากลับสามารถร่ายเวทย์สร้างผลตอบแทนระยะยาว จนเรียกได้ว่า ใช้ **“หอคอยรัตติกาล”** เป็นแหล่งเสบียงเลี้ยงชีพ โดยกุญแจเวทย์ที่บุคคลเหล่านี้ใช้ ก็คือ **“คณิตศาสตร์”** เหตุใด **“คณิตศาสตร์”** จึงช่วยให้ผู้คนเอาชนะ **“การพนัน”** ได้? และนอกจาก **“การพนัน”** แล้ว **“คณิตศาสตร์”** ยังสามารถประยุกต์ใช้กับสิ่งใดได้อีก? **นักเล่าเรื่องแห่งเฮรันเทล** จักไขปริศนาให้ฟัง เบื้องต้น ขอให้ท่านลองพิจารณาตนเอง ว่าเคยประสบพบพานเหตุการณ์เหล่านี้หรือไม่: - ตั้งมั่นว่า จักเสี่ยงโชคให้ได้กำไรเพียงเล็กน้อย แล้วจักหยุดพัก - แต่หากพลาดท่าเสียที จักจำกัดการสูญเสียให้เท่าทุนเดิมที่ตั้งไว้ - ครั้นเมื่อเวทมนตร์เข้าข้าง ได้กำไรมาแล้ว กลับโลภโมโทสัน อยากได้เพิ่มอีกนิด จึงร่ายเวทย์ต่อ - ทว่ากำไรเริ่มร่อยหรอ จนเหลือเพียงทุนเดิม สุดท้ายทุนที่ตั้งไว้คราแรกก็มลายสิ้น - จำต้องหาเงินทองมาลงเพิ่ม หวังทวงทุนคืน และพบว่าต้องสูญเสียเงินก้อนนั้นไปในห้วงเวลาต่อมา ลำดับเหตุการณ์ดังกล่าว เรียกได้ว่าเป็น **“วงจรอุบาทว์”** สำหรับนักพนันมากมายในเฮรันเทล ปริศนาที่ตามมาก็คือ เหตุใด **“วงจรอุบาทว์”** นี้จึงเกิดขึ้นซ้ำแล้วซ้ำเล่า? ส่วนหนึ่ง ย่อมเป็นเพราะอารมณ์อันแปรปรวนในการเสี่ยงโชคของแต่ละคน แต่อีกส่วนที่สำคัญยิ่งกว่า ต้องกล่าวว่าเป็นผลจาก **“กลไกต้องสาป”** ของจ้าวแห่งหอคอยรัตติกาล ซึ่งต้องกล่าวว่า เหล่าเจ้าของหอคอยรัตติกาลนั้น จักใช้หลักการทำนองเดียวกับ **“สมาคมพ่อค้าผู้พิทักษ์”** คือจักเก็บเงินทองจากชนจำนวนมาก เพื่อนำมาจ่ายให้กับชนเพียงหยิบมือ เพื่อล่อลวงให้ชนทั้งหลายเสี่ยงโชคต่อไป หรือทำให้เหล่านักพนันหวังว่า จักเป็นผู้โชคดีเฉกเช่นพวกเขาบ้าง แม้จะมีผู้โชคดีที่สามารถได้กำไรในเบื้องต้น แต่ในบั้นปลายก็จักพ่ายแพ้อยู่ดี ซึ่งเป็นไปตาม **“กฎแห่งจำนวนมหาศาล”** เพราะจ้าวแห่งหอคอยรัตติกาลนั้น ได้คำนวณและออกแบบระบบเกมที่ตนเองได้เปรียบในระยะยาวแล้ว จากตำนานนี้ ย่อมประจักษ์ชัดว่า แม้การพนันจักเป็นเรื่องของดวงชะตา แต่ก็ถูกรังสรรค์ขึ้นจากการคำนวณทางคณิตศาสตร์ ดังนั้น หากปรารถนาจะหาหนทางเอาชนะจ้าวแห่งหอคอยรัตติกาล ก็จำต้องเข้าใจ **“คณิตศาสตร์”** เสียก่อน ทีนี้ จงเงี่ยหูฟัง แล้วท่านจักได้ยินข้าไขปริศนา: **๑. ปริศนาแห่ง “กำไรคาดหวัง”** สำหรับการแสวงหา **“เกมเสี่ยงทาย”** ที่ควรค่าแก่การเล่น หรือการเสี่ยง สิ่งแรกที่นักพนันพึงกระทำคือ **“การประเมินกำไรคาดหวัง”** หรือ **“เวทคำนวณอนาคต”** **“กำไรคาดหวัง”** ถูกคิดค้นโดย **คริสเตียน ฮอยเกนส์** นักปราชญ์เวทย์ชาวดัตช์ เพื่อประเมินว่าเกมพนันแบบใดควรค่าแก่การเล่น ซึ่งมิใช่เพียงแค่การประเมินโอกาสแห่งชัยชนะเท่านั้น แต่ต้องคิดรวมขนาดของเงินเดิมพันไปด้วย โดยสูตรเวทย์คือ: **กำไรคาดหวัง = (เงินที่ได้ x โอกาสชนะ) + (เงินที่เสีย x โอกาสแพ้)** ดังนั้น หากปรารถนาจะสะสม **“ทองคำมายา”** ในระยะยาว จงเลือกเกมที่มี **“กำไรคาดหวัง”** เป็นบวก แต่หากพลาดพลั้งเข้าไปเล่นเกมที่ **“กำไรคาดหวัง”** เป็นลบ และบังเอิญว่าโชคชะตาเล่นตลกให้ได้เงินทองมาครอง พึงละทิ้งเกมนั้นเสียโดยพลัน เพราะท้ายที่สุดหากยังคงเล่นต่อไป ผู้อับโชคผู้นั้นก็คือตัวท่านเอง อย่างไรก็ตาม โดยธรรมดาแล้ว **“กำไรคาดหวัง”** ของเกมพนันที่มีเจ้ามือมักจักติดลบ จึงเป็นเรื่องยากยิ่งที่จะเอาชนะได้ เฉกเช่นตัวอย่างที่เราเห็น คือเกมในบ่อนพนัน หรือแม้แต่ **“สลากกินแบ่งรัฐบาล”** ก็ล้วนเป็นเกมที่มี **“กำไรคาดหวัง”** ติดลบทั้งสิ้น นอกจาก **“กำไรคาดหวัง”** จักถูกใช้กับการพนันได้แล้ว หลักเวทย์ **“คณิตศาสตร์”** ก็ยังสามารถประยุกต์ใช้กับการลงทุนได้ไม่แตกต่างกัน ตัวอย่างเช่น หากท่านเก็บสถิติข้อมูลการลงทุนของตนเอง แล้วพบว่ามีเพียงสามสิบส่วนร้อยเท่านั้น ที่ท่านซื้อ **“ศิลาแห่งโชค”** แล้วสร้างผลตอบแทนเป็นบวก แต่ท่านยังคงปรารถนาความสำเร็จในการลงทุน ก็จงจำกัดการขาดทุนแต่ละคราให้น้อยเข้าไว้ เช่น -๕% และปล่อยให้มีกำไรในแต่ละคราที่ลงทุน เช่น อย่างน้อย ๒๐% ซึ่งจากการใช้กลยุทธ์นี้ ท่านจักมี **“กำไรคาดหวัง”** = (๒๐% x ๐.๓) + (-๕% x ๐.๗) = ๒.๕% จักเห็นได้ว่า แม้ท่านจักมีจำนวนคราที่ขาดทุนบ่อยครั้ง แต่ก็ยังสามารถสร้างกำไรได้ หากคราที่กำไรนั้น สามารถทำเงินทองเป็นจำนวนมากได้ **๒. ปริศนาแห่ง “การบริหารหน้าตัก” หรือ “การบริหารเงินทุน”** แม้ว่าท่านจักรับรู้ **“กำไรคาดหวัง”** แล้ว แต่หากท่านเผชิญหน้ากับการขาดทุนต่อเนื่องกัน ท่านก็อาจหมดเนื้อหมดตัวก่อนถึงคราที่จะกอบโกยเงินทองจากคราที่กำไร วิธีคลายปมปริศนานี้ก็คือ การมิลงเงินทองทั้งหมดของท่านในการลงทุนเพียงคราเดียว ซึ่งนอกจากการกระจายความเสี่ยงในการลงทุนหลาย **“ศิลาแห่งโชค”** หรือหลาย **“เกมเสี่ยงทาย”** แล้ว ท่านอาจกำหนดขนาดของการลงทุนแต่ละคราให้มิมากเกินไป แบบง่าย ๆ เช่น มิเกิน ๑๐% ของเงินลงทุนทั้งหมด หรือท่านอาจคำนวณขนาดของการลงทุนแต่ละคราด้วยสูตรทางคณิตศาสตร์ เช่น สูตร **“การขาดทุนสูงสุดที่ท่านรับได้ (Value at Risk)”** หรือ สูตร **“ขนาดเดิมพันที่เหมาะสม (Kelly Formula)”** **๓. ปริศนาแห่ง “อคติ”** ในวงการพนัน มักมีอคติหนึ่งที่บังเกิดบ่อยครั้งกับผู้คน คือ **“Gambler's Fallacy”** หรือ **“ความเชื่อผิด ๆ แห่งนักพนัน”** ว่าหากเหตุการณ์หนึ่งบังเกิดบ่อยครั้งกว่าปรกติในช่วงเวลาหนึ่ง ๆ เหตุการณ์นั้นจักบังเกิดบ่อยครั้งน้อยลงในอนาคต ทั้ง ๆ ที่เหตุการณ์เหล่านั้นเป็นอิสระจากกันในทางสถิติ ยกตัวอย่างเช่น หากโยนเหรียญมนตราออกหัวไปแล้วสามครา ในคราที่สี่ หลายคนอาจคิดว่าโอกาสออกก้อยมากกว่าหัว แม้ว่าการโยนเหรียญแต่ละคราจะมิได้ส่งผลอันใดต่อกันเลย (จะโยนกี่ครา โอกาสหัวหรือก้อย ก็คือ ๕๐:๕๐ อยู่ยั่งยืน) หรือแม้กระทั่ง **“สลากกินแบ่งรัฐบาล”** มีหลายคนที่ซื้อเลขซ้ำกัน เพื่อหวังว่าจะถูกในงวดต่อ ๆ ไป ในวงการการลงทุน ก็มีลักษณะที่คล้ายคลึงกัน เช่น หาก **“ศิลาแห่งโชค A”** ราคาตกต่ำลงมาห้าครา บางคนอาจคิดว่าในคราที่หก ราคาของมันจักต้องเด้งขึ้นมา ซึ่งในความเป็นจริง หาได้เป็นเช่นนั้นเสมอไป จักเห็นได้ว่า แท้จริงแล้ว ไม่ว่าจักเป็น **“เกมเสี่ยงทายแห่งโชคชะตา”** หรือ **“การผจญภัยในตลาดทุน”** หากท่านมีความเข้าใจ และนำ **“คณิตศาสตร์”** เข้ามาเป็นรากฐาน มันก็อาจนำพาตัวท่านเอง ไปสู่จุดที่ได้เปรียบในเกมนั้น ได้เฉกเช่นกัน.. **สูตรเวทย์มนตร์ที่ปรากฏในตำนาน:** * **กำไรคาดหวัง = (เงินที่ได้ x โอกาสชนะ) + (เงินที่เสีย x โอกาสแพ้)** **คำเตือนจากนักเล่าเรื่องแห่งเฮรันเทล:** "พึงระลึกไว้เสมอว่า โชคชะตาเป็นสิ่งที่คาดเดาได้ยาก แม้เวทมนตร์คณิตศาสตร์จักช่วยนำทาง แต่ท้ายที่สุดแล้ว ความสำเร็จยังคงขึ้นอยู่กับการตัดสินใจและสติปัญญาของท่านเอง" หวังว่าตำนานบทนี้จักเป็นประโยชน์แก่ท่านนะคะ @ 3ca99671:689a4ce4
2025-02-18 09:34:11How to avoid internal pressure and anxiety. Constantly forcing yourself to continue something, doubting its value to anyone other than your ego. And then it starts: "What if I use that framework? Maybe I should switch to another language? No, I’ll master that engine over there, and everything will fall into place." But it doesn’t. You don’t master it, it’s not the right language. In short, you’re stuck. The sense of obligation and the justification of inaction tear you apart. I mean, how is it inaction? Inside, there’s constant work going on, fragments of the future product emerge, but something’s missing… Organization? Publicity? Speaking of publicity, I clearly see that it will only intensify the sense of duty and create additional pressure. Which won’t be a creative energy at all, on the contrary, it’s more likely to lead to despair. You need to be 100 percent confident in the success of what you’re doing, so that without society’s approval of the prototype, you can release the product and not regret a single hour spent on it. Now, that’s belief, that’s love. Alright, this is a draft. So, what exactly is missing? Regarding organization: YES, backlogs and the like are necessary, BUT. Maybe the goals were set incorrectly back when I was working on projects. Because everything turned into organizing inaction. Exactly, organizing with the goal of doing nothing. Here’s another thing: think about the gym, for example. It’s the same with products, you need a hub, a shared space, and it’s easier now. Telegram, Discord, itch.io, GitHub, plenty of info and examples. So, what’s holding me back? Is there something stopping me? Maybe it’s worth finding out how others manage their work. (Here, I contradict myself). Obvious things, but they should be spelled out. And it becomes clear that I can’t handle it alone. I need collaborators. Maybe that’s the secret to ensuring the work continues, huh? If you think about releasing a product as the final point of an expedition. And immediately, the meme about how Hunter was packing his car trunk for the trip to Las Vegas comes to mind. A little lyrical digression: "I had two Unity courses under my belt, ninety hours of Unreal Engine tutorials, three textbooks on procedural world generation, a hard drive half full of unfinished shaders, and a whole universe of tools: pixel-art engines, object destruction plugins, buggy C# scripts, low-poly assets laughing at me... and a liter of espresso, buckets of energy drinks, a box of donut coffee from Steam, a pint of sheer stubbornness, and two dozen tokens of 'unique' in-game helmets. Not that all of this was necessary for an indie project, but once you dive into tech experiments, it’s hard to stop. The only thing driving me crazy was neural networks for enemy AI. There’s no creature in the world more helpless, naive, and predictable than a programmer trying to squeeze machine learning into a platformer about a jumping carrot. And I knew for sure that by morning, we’d be diving into that rabbit hole with rakes in hand." To be continued... P.S: ai translation from russian
@ 3ca99671:689a4ce4
2025-02-18 09:34:11How to avoid internal pressure and anxiety. Constantly forcing yourself to continue something, doubting its value to anyone other than your ego. And then it starts: "What if I use that framework? Maybe I should switch to another language? No, I’ll master that engine over there, and everything will fall into place." But it doesn’t. You don’t master it, it’s not the right language. In short, you’re stuck. The sense of obligation and the justification of inaction tear you apart. I mean, how is it inaction? Inside, there’s constant work going on, fragments of the future product emerge, but something’s missing… Organization? Publicity? Speaking of publicity, I clearly see that it will only intensify the sense of duty and create additional pressure. Which won’t be a creative energy at all, on the contrary, it’s more likely to lead to despair. You need to be 100 percent confident in the success of what you’re doing, so that without society’s approval of the prototype, you can release the product and not regret a single hour spent on it. Now, that’s belief, that’s love. Alright, this is a draft. So, what exactly is missing? Regarding organization: YES, backlogs and the like are necessary, BUT. Maybe the goals were set incorrectly back when I was working on projects. Because everything turned into organizing inaction. Exactly, organizing with the goal of doing nothing. Here’s another thing: think about the gym, for example. It’s the same with products, you need a hub, a shared space, and it’s easier now. Telegram, Discord, itch.io, GitHub, plenty of info and examples. So, what’s holding me back? Is there something stopping me? Maybe it’s worth finding out how others manage their work. (Here, I contradict myself). Obvious things, but they should be spelled out. And it becomes clear that I can’t handle it alone. I need collaborators. Maybe that’s the secret to ensuring the work continues, huh? If you think about releasing a product as the final point of an expedition. And immediately, the meme about how Hunter was packing his car trunk for the trip to Las Vegas comes to mind. A little lyrical digression: "I had two Unity courses under my belt, ninety hours of Unreal Engine tutorials, three textbooks on procedural world generation, a hard drive half full of unfinished shaders, and a whole universe of tools: pixel-art engines, object destruction plugins, buggy C# scripts, low-poly assets laughing at me... and a liter of espresso, buckets of energy drinks, a box of donut coffee from Steam, a pint of sheer stubbornness, and two dozen tokens of 'unique' in-game helmets. Not that all of this was necessary for an indie project, but once you dive into tech experiments, it’s hard to stop. The only thing driving me crazy was neural networks for enemy AI. There’s no creature in the world more helpless, naive, and predictable than a programmer trying to squeeze machine learning into a platformer about a jumping carrot. And I knew for sure that by morning, we’d be diving into that rabbit hole with rakes in hand." To be continued... P.S: ai translation from russian @ ec42c765:328c0600
2025-02-05 23:16:35てすと nostr:nevent1qqst3uqlls4yr9vys4dza2sgjle3ly37trck7jgdmtr23uuz52usjrqqqnjgr nostr:nevent1qqsdvchy5d27zt3z05rr3q6vvmzgslslxwu0p4dfkvxwhmvxldn9djguvagp2 test てs
@ ec42c765:328c0600
2025-02-05 23:16:35てすと nostr:nevent1qqst3uqlls4yr9vys4dza2sgjle3ly37trck7jgdmtr23uuz52usjrqqqnjgr nostr:nevent1qqsdvchy5d27zt3z05rr3q6vvmzgslslxwu0p4dfkvxwhmvxldn9djguvagp2 test てs @ e7bc35f8:3ed2a7cf
2025-02-18 09:07:03For those who still trust mainstream narratives about war and foreign intervention, the Douma chemical attack story should serve as a wake-up call. The official version of events—that Syrian government forces carried out a chemical attack on civilians in Douma on April 7, 2018—has been thoroughly dismantled by whistleblowers, independent journalists, and even leaked documents from the Organization for the Prohibition of Chemical Weapons (OPCW). Yet, despite [mounting evidence]( https://thegrayzone.com/2018/03/06/media-propaganda-battle-syria-eastern-ghouta/), mainstream media and Western governments continue to push the debunked narrative, using it to justify military interventions and sustain the illusion of moral authority. This article revisits the Douma deception, breaking down how the false flag operation unfolded and how the truth was systematically suppressed. ### A Timeline of the Manufactured Crisis #### April 7, 2018: The Alleged Chemical Attack On this day, as the Syrian Army engaged terrorist insurgents in Douma, [shocking videos surfaced]( https://youtu.be/sYItxxEO3F8) online showing alleged victims of a chemical attack. Without proper investigation, Western leaders seized on the footage as proof of an [atrocity committed]( https://web.archive.org/web/20200304211152/https://eg.usembassy.gov/united-states-assessment-of-the-assad-regimes-chemical-weapons-use/) by the Assad government. Within 24 hours, then-President Donald Trump tweeted about "Animal Assad" and vowed that Russia and Iran would "pay a big price." This swift response echoed past war propaganda, reminiscent of the lies used to justify the invasion of Iraq.  #### April 14, 2018: The Bombing of Syria Begins Less than a week after the alleged attack, the [United States]( https://youtu.be/w43ok0q5G5A), [France, and Britain launched coordinated missile strikes]( https://www.washingtonpost.com/world/national-security/us-launches-missile-strikes-in-syria/2018/04/13/c68e89d0-3f4a-11e8-974f-aacd97698cef_story.html) on Syrian government targets. Shockingly, these airstrikes were carried out before any independent investigation had even begun. Meanwhile, on the same day, OPCW investigators arrived in Syria to examine the supposed chemical attack site. In a grotesque display of arrogance, the West had already punished Syria for a crime that hadn't been proven. #### April 17, 2018: Doubts Emerge Veteran journalist [Robert Fisk visited Douma]( https://www.independent.co.uk/voices/syria-chemical-attack-gas-douma-robert-fisk-ghouta-damascus-a8307726.html) and interviewed a local doctor who revealed that the victims shown in viral videos had actually died from suffocation—not chemical weapons. The doctor described how panic and dust inhalation in underground shelters had led to casualties, but no traces of nerve agents like **sarin** were found. #### July 6, 2018: OPCW’s Initial Report Undermines the Official Story The OPCW released its [interim findings]( https://www.opcw.org/media-centre/news/2018/07/opcw-issues-fact-finding-mission-reports-chemical-weapons-use-allegations), confirming that: > No organophosphorus nerve agents or their degradation products were detected, either in the environmental samples or in plasma samples from the alleged casualties. And while: > Various chlorinated organic chemicals were found in samples from Locations 2 and 4, along with residues of explosive the report makes no mention of the concentrations or levels of those chemicals. In Addition the "Annex 2" (Open Sources) is blank. In Annex 3 where all chemicals are listed, there is no chemical weapon agent listed. Despite this, Western media and politicians continued to push the idea that Syria had used chemical weapons. #### February–March 2019: Whistleblower Confirms Staged Hospital Footage In a stunning revelation, [BBC producer Riam Dalati]( https://youtu.be/fFLRX5ZiEvo) tweeted that the viral hospital scene—depicting victims being hosed down—had been **staged**. This meant that at least part of the so-called evidence was a fabrication. Shortly after, the OPCW issued its [final report]( https://www.opcw.org/sites/default/files/documents/2019/03/s-1731-2019%28e%29.pdf). While it acknowledged a lack of sarin, > No organophosphorous nerve agents, their degradation products or synthesis impurities were detected [...] it is not currently possible to precisely link the cause of the signs and symptoms to a specific chemical it ambiguously suggested that "a toxic chemical containing reactive chlorine" was likely used. This vague wording allowed Western governments to continue their accusations without hard proof. #### May 2019: Leaked OPCW Report Exposes a Cover-Up A [leaked engineering assessment]( https://web.archive.org/web/20190514174330/http://syriapropagandamedia.org/wp-content/uploads/2019/05/Engineering-assessment-of-two-cylinders-observed-at-the-Douma-incident-27-February-2019-1.pdf) by an OPCW sub-team completely contradicted the official findings. It concluded that the two cylinders found at the scene **were likely manually placed rather than dropped from aircraft**—suggesting [the incident was staged]( https://youtu.be/FU24r2zWVQo). Instead of addressing this bombshell revelation, [OPCW leadership focused]( https://www.opcw.org/sites/default/files/documents/2019/06/Remarks%20of%20the%20Director-General%20Briefing%20for%20States%20Parties%20on%20Syrian%20Arab%20Republic%20Update%20on%20IIT-FFM-SSRC-DAT_1.pdf) on investigating **how the leak happened** rather than the damning content of the report itself. #### October–November 2019: More Whistleblowers Speak Out On October 15th, 2019, the [Courage Foundation]( https://web.archive.org/web/20191024045128/https://couragefound.org/2019/10/opcw-panel-statement/) "convened a panel of concerned individuals from the fields of disarmament, international law, journalism, military operations, medicine and intelligence in Brussels". The whistleblower giving an "extensive presentation, including internal emails, text exchanges and suppressed draft reports..." describes "efforts to exclude some inspectors from the investigation whilst thwarting their attempts to raise legitimate concerns, highlight irregular practices or even to express their differing observations and assessments". The panel "became convinced by the testimony that key information about chemical analyses, toxicology consultations, ballistics studies, and witness testimonies was suppressed, ostensibly to favor a preordained conclusion" and expressed unanimous alarm about "unacceptable practices in the investigation". [Another OPCW whistleblower]( https://www.counterpunch.org/2019/11/15/the-opcw-and-douma-chemical-weapons-watchdog-accused-of-evidence-tampering-by-its-own-inspectors/), referred to as "Alex", a member of this fact finding mission, confirmed that key evidence had been suppressed. He revealed that: "_the signs and symptoms of victims were not consistent with poisoning from chlorine_". Instead of an attack producing multiple fatalities there had been “_a non chemical-related event_”. His findings, which undermined the official narrative, were removed from the final report. At this point, multiple independent voices—including journalists, scientists, and former OPCW officials—had exposed the [Douma deception]( https://wikileaks.org/opcw-douma/#Internal%20OPCW%20E-Mail). But the mainstream media either ignored or actively discredited these revelations. ### How the Media and Government Covered It Up When whistleblowers and [journalists]( https://youtu.be/ojItF6MGL-0) challenged the official story, mainstream outlets worked overtime to discredit them. The propaganda network [Bellingcat]( https://www.bellingcat.com/news/2019/11/25/emails-and-reading-comprehension-opcw-douma-coverage-misses-crucial-facts/) published a weak "debunking" article, which was swiftly dismantled by independent journalist [Caitlin Johnstone]( https://caitlinjohnstone.com/2019/11/27/narrative-managers-faceplant-in-hilarious-opcw-scandal-spin-job/) and veteran columnist [Peter Hitchens]( https://hitchensblog.mailonsunday.co.uk/2019/11/my-response-to-the-bellingcat-attempt-to-spin-away-the-devastating-implications-of-the-opcw-douma-leak-i-have.html). Rather than confronting the facts, the OPCW and its backers dismissed the leaks as unimportant or "[Russian disinformation]( https://www.cbsnews.com/news/opcw-chemical-weapons-watchdog-douma-chlorine-gas-wikileaks-russia-syria-claim-bias-today-2019-11-25/)"—a predictable smear tactic used whenever official narratives collapse. ### Why This Matters The Douma deception is not just an academic debate—it had real-world consequences. The false flag attack was used to justify military aggression against Syria, escalating tensions in the Middle East and prolonging unnecessary suffering. More importantly, it serves as a case study in how governments and media manufacture consent for war. By exposing these propaganda tactics, we can resist manipulation and prevent future conflicts based on lies. The Douma hoax is just one example of how false narratives are weaponized to justify military interventions. The same playbook has been used time and again—from Iraq’s "Weapons of Mass Destruction" to Libya’s "humanitarian intervention." If people learn to recognize propaganda before it leads to war, we can disrupt the cycle of deception. The truth is out there—we just need the courage to face it.
@ e7bc35f8:3ed2a7cf
2025-02-18 09:07:03For those who still trust mainstream narratives about war and foreign intervention, the Douma chemical attack story should serve as a wake-up call. The official version of events—that Syrian government forces carried out a chemical attack on civilians in Douma on April 7, 2018—has been thoroughly dismantled by whistleblowers, independent journalists, and even leaked documents from the Organization for the Prohibition of Chemical Weapons (OPCW). Yet, despite [mounting evidence]( https://thegrayzone.com/2018/03/06/media-propaganda-battle-syria-eastern-ghouta/), mainstream media and Western governments continue to push the debunked narrative, using it to justify military interventions and sustain the illusion of moral authority. This article revisits the Douma deception, breaking down how the false flag operation unfolded and how the truth was systematically suppressed. ### A Timeline of the Manufactured Crisis #### April 7, 2018: The Alleged Chemical Attack On this day, as the Syrian Army engaged terrorist insurgents in Douma, [shocking videos surfaced]( https://youtu.be/sYItxxEO3F8) online showing alleged victims of a chemical attack. Without proper investigation, Western leaders seized on the footage as proof of an [atrocity committed]( https://web.archive.org/web/20200304211152/https://eg.usembassy.gov/united-states-assessment-of-the-assad-regimes-chemical-weapons-use/) by the Assad government. Within 24 hours, then-President Donald Trump tweeted about "Animal Assad" and vowed that Russia and Iran would "pay a big price." This swift response echoed past war propaganda, reminiscent of the lies used to justify the invasion of Iraq.  #### April 14, 2018: The Bombing of Syria Begins Less than a week after the alleged attack, the [United States]( https://youtu.be/w43ok0q5G5A), [France, and Britain launched coordinated missile strikes]( https://www.washingtonpost.com/world/national-security/us-launches-missile-strikes-in-syria/2018/04/13/c68e89d0-3f4a-11e8-974f-aacd97698cef_story.html) on Syrian government targets. Shockingly, these airstrikes were carried out before any independent investigation had even begun. Meanwhile, on the same day, OPCW investigators arrived in Syria to examine the supposed chemical attack site. In a grotesque display of arrogance, the West had already punished Syria for a crime that hadn't been proven. #### April 17, 2018: Doubts Emerge Veteran journalist [Robert Fisk visited Douma]( https://www.independent.co.uk/voices/syria-chemical-attack-gas-douma-robert-fisk-ghouta-damascus-a8307726.html) and interviewed a local doctor who revealed that the victims shown in viral videos had actually died from suffocation—not chemical weapons. The doctor described how panic and dust inhalation in underground shelters had led to casualties, but no traces of nerve agents like **sarin** were found. #### July 6, 2018: OPCW’s Initial Report Undermines the Official Story The OPCW released its [interim findings]( https://www.opcw.org/media-centre/news/2018/07/opcw-issues-fact-finding-mission-reports-chemical-weapons-use-allegations), confirming that: > No organophosphorus nerve agents or their degradation products were detected, either in the environmental samples or in plasma samples from the alleged casualties. And while: > Various chlorinated organic chemicals were found in samples from Locations 2 and 4, along with residues of explosive the report makes no mention of the concentrations or levels of those chemicals. In Addition the "Annex 2" (Open Sources) is blank. In Annex 3 where all chemicals are listed, there is no chemical weapon agent listed. Despite this, Western media and politicians continued to push the idea that Syria had used chemical weapons. #### February–March 2019: Whistleblower Confirms Staged Hospital Footage In a stunning revelation, [BBC producer Riam Dalati]( https://youtu.be/fFLRX5ZiEvo) tweeted that the viral hospital scene—depicting victims being hosed down—had been **staged**. This meant that at least part of the so-called evidence was a fabrication. Shortly after, the OPCW issued its [final report]( https://www.opcw.org/sites/default/files/documents/2019/03/s-1731-2019%28e%29.pdf). While it acknowledged a lack of sarin, > No organophosphorous nerve agents, their degradation products or synthesis impurities were detected [...] it is not currently possible to precisely link the cause of the signs and symptoms to a specific chemical it ambiguously suggested that "a toxic chemical containing reactive chlorine" was likely used. This vague wording allowed Western governments to continue their accusations without hard proof. #### May 2019: Leaked OPCW Report Exposes a Cover-Up A [leaked engineering assessment]( https://web.archive.org/web/20190514174330/http://syriapropagandamedia.org/wp-content/uploads/2019/05/Engineering-assessment-of-two-cylinders-observed-at-the-Douma-incident-27-February-2019-1.pdf) by an OPCW sub-team completely contradicted the official findings. It concluded that the two cylinders found at the scene **were likely manually placed rather than dropped from aircraft**—suggesting [the incident was staged]( https://youtu.be/FU24r2zWVQo). Instead of addressing this bombshell revelation, [OPCW leadership focused]( https://www.opcw.org/sites/default/files/documents/2019/06/Remarks%20of%20the%20Director-General%20Briefing%20for%20States%20Parties%20on%20Syrian%20Arab%20Republic%20Update%20on%20IIT-FFM-SSRC-DAT_1.pdf) on investigating **how the leak happened** rather than the damning content of the report itself. #### October–November 2019: More Whistleblowers Speak Out On October 15th, 2019, the [Courage Foundation]( https://web.archive.org/web/20191024045128/https://couragefound.org/2019/10/opcw-panel-statement/) "convened a panel of concerned individuals from the fields of disarmament, international law, journalism, military operations, medicine and intelligence in Brussels". The whistleblower giving an "extensive presentation, including internal emails, text exchanges and suppressed draft reports..." describes "efforts to exclude some inspectors from the investigation whilst thwarting their attempts to raise legitimate concerns, highlight irregular practices or even to express their differing observations and assessments". The panel "became convinced by the testimony that key information about chemical analyses, toxicology consultations, ballistics studies, and witness testimonies was suppressed, ostensibly to favor a preordained conclusion" and expressed unanimous alarm about "unacceptable practices in the investigation". [Another OPCW whistleblower]( https://www.counterpunch.org/2019/11/15/the-opcw-and-douma-chemical-weapons-watchdog-accused-of-evidence-tampering-by-its-own-inspectors/), referred to as "Alex", a member of this fact finding mission, confirmed that key evidence had been suppressed. He revealed that: "_the signs and symptoms of victims were not consistent with poisoning from chlorine_". Instead of an attack producing multiple fatalities there had been “_a non chemical-related event_”. His findings, which undermined the official narrative, were removed from the final report. At this point, multiple independent voices—including journalists, scientists, and former OPCW officials—had exposed the [Douma deception]( https://wikileaks.org/opcw-douma/#Internal%20OPCW%20E-Mail). But the mainstream media either ignored or actively discredited these revelations. ### How the Media and Government Covered It Up When whistleblowers and [journalists]( https://youtu.be/ojItF6MGL-0) challenged the official story, mainstream outlets worked overtime to discredit them. The propaganda network [Bellingcat]( https://www.bellingcat.com/news/2019/11/25/emails-and-reading-comprehension-opcw-douma-coverage-misses-crucial-facts/) published a weak "debunking" article, which was swiftly dismantled by independent journalist [Caitlin Johnstone]( https://caitlinjohnstone.com/2019/11/27/narrative-managers-faceplant-in-hilarious-opcw-scandal-spin-job/) and veteran columnist [Peter Hitchens]( https://hitchensblog.mailonsunday.co.uk/2019/11/my-response-to-the-bellingcat-attempt-to-spin-away-the-devastating-implications-of-the-opcw-douma-leak-i-have.html). Rather than confronting the facts, the OPCW and its backers dismissed the leaks as unimportant or "[Russian disinformation]( https://www.cbsnews.com/news/opcw-chemical-weapons-watchdog-douma-chlorine-gas-wikileaks-russia-syria-claim-bias-today-2019-11-25/)"—a predictable smear tactic used whenever official narratives collapse. ### Why This Matters The Douma deception is not just an academic debate—it had real-world consequences. The false flag attack was used to justify military aggression against Syria, escalating tensions in the Middle East and prolonging unnecessary suffering. More importantly, it serves as a case study in how governments and media manufacture consent for war. By exposing these propaganda tactics, we can resist manipulation and prevent future conflicts based on lies. The Douma hoax is just one example of how false narratives are weaponized to justify military interventions. The same playbook has been used time and again—from Iraq’s "Weapons of Mass Destruction" to Libya’s "humanitarian intervention." If people learn to recognize propaganda before it leads to war, we can disrupt the cycle of deception. The truth is out there—we just need the courage to face it. @ ec42c765:328c0600
2025-02-05 22:05:55# カスタム絵文字とは 任意のオリジナル画像を絵文字のように文中に挿入できる機能です。 また、リアクション(Twitterの いいね のような機能)にもカスタム絵文字を使えます。  # カスタム絵文字の対応状況(2025/02/06)  カスタム絵文字を使うためにはカスタム絵文字に対応した[クライアント](https://welcome.nostr-jp.org/tutorial/explore-client.html)を使う必要があります。 ※表は一例です。クライアントは他にもたくさんあります。 使っているクライアントが対応していない場合は、クライアントを変更する、対応するまで待つ、開発者に要望を送る(または自分で実装する)などしましょう。 #### 対応クライアント - [Amethyst](https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst) - [FreeFrom](https://freefrom.space/) - [nostter](https://nostter.app/) - [Rabbit](https://rabbit.syusui.net/) - [Lumilumi](https://lumilumi.app/) - [Nos Haiku](https://nos-haiku.vercel.app/) - [Snort](https://snort.social/) - [noStrudel](https://nostrudel.ninja/) ここではnostterを使って説明していきます。 # 準備 カスタム絵文字を使うための準備です。 - Nostrエクステンション(NIP-07)を導入する - 使いたいカスタム絵文字をリストに登録する ## Nostrエクステンション(NIP-07)を導入する Nostrエクステンションは使いたいカスタム絵文字を登録する時に必要になります。 また、環境(パソコン、iPhone、androidなど)によって導入方法が違います。 Nostrエクステンションを導入する端末は、実際にNostrを閲覧する端末と違っても構いません(リスト登録はPC、Nostr閲覧はiPhoneなど)。 Nostrエクステンション(NIP-07)の導入方法は以下のページを参照してください。 [ログイン拡張機能 (NIP-07)を使ってみよう | Welcome to Nostr! ~ Nostrをはじめよう! ~ ](https://welcome.nostr-jp.org/tutorial/nip-07.html) 少し面倒ですが、これを導入しておくとNostr上の様々な場面で役立つのでより快適になります。 ## 使いたいカスタム絵文字をリストに登録する 以下のサイトで行います。 [emojito](https://emojito.meme/) 右上の**Get started**からNostrエクステンションでログインしてください。 例として以下のカスタム絵文字を導入してみます。 実際より絵文字が少なく表示されることがありますが、古い状態のデータを取得してしまっているためです。その場合はブラウザの更新ボタンを押してください。 [generalJP | カスタム絵文字](https://emojito.meme/a/naddr1qqykwetwv4exzmz22qq3uamnwvaz7tmwdaehgun2vykkkctjdyhxset8w4ex7tnrdakj7q3qa3pvwe2p3v7mnjz6hle63r628wl9w567aw7u23fzqs062v5vqcqqxpqqqp65uhjtrk6)  - 右側の**Options**から**Bookmark**を選択  これでカスタム絵文字を使用するためのリストに登録できます。 # カスタム絵文字を使用する 例としてブラウザから使えるクライアント nostter から使用してみます。 [nostter](https://nostter.app/) nostterにNostrエクステンションでログイン、もしくは秘密鍵を入れてログインしてください。 ## 文章中に使用 1. **投稿**ボタンを押して投稿ウィンドウを表示 2. **顔😀**のボタンを押し、絵文字ウィンドウを表示 3. ***タブ**を押し、カスタム絵文字一覧を表示 4. カスタム絵文字を選択 5. : 記号に挟まれたアルファベットのショートコードとして挿入される  この状態で投稿するとカスタム絵文字として表示されます。 カスタム絵文字対応クライアントを使っている他ユーザーにもカスタム絵文字として表示されます。 対応していないクライアントの場合、ショートコードのまま表示されます。  ショートコードを直接入力することでカスタム絵文字の候補が表示されるのでそこから選択することもできます。  ## リアクションに使用 1. 任意の投稿の**顔😀**のボタンを押し、絵文字ウィンドウを表示 2. ***タブ**を押し、カスタム絵文字一覧を表示 3. カスタム絵文字を選択  カスタム絵文字リアクションを送ることができます。  # カスタム絵文字を探す 先述した[emojito](https://emojito.meme/)からカスタム絵文字を探せます。 例えば任意のユーザーのページ [emojito ロクヨウ](https://emojito.meme/p/npub1a3pvwe2p3v7mnjz6hle63r628wl9w567aw7u23fzqs062v5vqcqqu3sgh3) から探したり、 [emojito Browse all](https://emojito.meme/browse) からnostr全体で最近作成、更新された絵文字を見たりできます。 また、以下のリンクは日本語圏ユーザーが作ったカスタム絵文字を集めたリストです(2025/02/06) ※漏れがあるかもしれません [日本ユーザー作 カスタム絵文字](https://nostviewstr.vercel.app/npub17hczqvxtfv3w69wr6lxrttnpdekwdwel55mld60fr24zwjuu6utqtj8mjx/10030) 各絵文字セットにある**Open in emojito**のリンクからemojitoに飛び、使用リストに追加できます。 ----------- 以上です。 次:Nostrのカスタム絵文字の**作り方** Yakihonneリンク [Nostrのカスタム絵文字の作り方](https://yakihonne.com/article/_@lokuyow.github.io/1707912490439) Nostrリンク nostr:naddr1qqxnzdesxuunzv358ycrgveeqgswcsk8v4qck0deepdtluag3a9rh0jh2d0wh0w9g53qg8a9x2xqvqqrqsqqqa28r5psx3 ----------- # 仕様 [NIP-30 Custom Emoji](https://github.com/nostr-protocol/nips/blob/master/30.md) [NIP-30 カスタム絵文字(和訳)](https://github.com/nostr-jp/nips-ja/blob/main/30.md)
@ ec42c765:328c0600
2025-02-05 22:05:55# カスタム絵文字とは 任意のオリジナル画像を絵文字のように文中に挿入できる機能です。 また、リアクション(Twitterの いいね のような機能)にもカスタム絵文字を使えます。  # カスタム絵文字の対応状況(2025/02/06)  カスタム絵文字を使うためにはカスタム絵文字に対応した[クライアント](https://welcome.nostr-jp.org/tutorial/explore-client.html)を使う必要があります。 ※表は一例です。クライアントは他にもたくさんあります。 使っているクライアントが対応していない場合は、クライアントを変更する、対応するまで待つ、開発者に要望を送る(または自分で実装する)などしましょう。 #### 対応クライアント - [Amethyst](https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst) - [FreeFrom](https://freefrom.space/) - [nostter](https://nostter.app/) - [Rabbit](https://rabbit.syusui.net/) - [Lumilumi](https://lumilumi.app/) - [Nos Haiku](https://nos-haiku.vercel.app/) - [Snort](https://snort.social/) - [noStrudel](https://nostrudel.ninja/) ここではnostterを使って説明していきます。 # 準備 カスタム絵文字を使うための準備です。 - Nostrエクステンション(NIP-07)を導入する - 使いたいカスタム絵文字をリストに登録する ## Nostrエクステンション(NIP-07)を導入する Nostrエクステンションは使いたいカスタム絵文字を登録する時に必要になります。 また、環境(パソコン、iPhone、androidなど)によって導入方法が違います。 Nostrエクステンションを導入する端末は、実際にNostrを閲覧する端末と違っても構いません(リスト登録はPC、Nostr閲覧はiPhoneなど)。 Nostrエクステンション(NIP-07)の導入方法は以下のページを参照してください。 [ログイン拡張機能 (NIP-07)を使ってみよう | Welcome to Nostr! ~ Nostrをはじめよう! ~ ](https://welcome.nostr-jp.org/tutorial/nip-07.html) 少し面倒ですが、これを導入しておくとNostr上の様々な場面で役立つのでより快適になります。 ## 使いたいカスタム絵文字をリストに登録する 以下のサイトで行います。 [emojito](https://emojito.meme/) 右上の**Get started**からNostrエクステンションでログインしてください。 例として以下のカスタム絵文字を導入してみます。 実際より絵文字が少なく表示されることがありますが、古い状態のデータを取得してしまっているためです。その場合はブラウザの更新ボタンを押してください。 [generalJP | カスタム絵文字](https://emojito.meme/a/naddr1qqykwetwv4exzmz22qq3uamnwvaz7tmwdaehgun2vykkkctjdyhxset8w4ex7tnrdakj7q3qa3pvwe2p3v7mnjz6hle63r628wl9w567aw7u23fzqs062v5vqcqqxpqqqp65uhjtrk6)  - 右側の**Options**から**Bookmark**を選択  これでカスタム絵文字を使用するためのリストに登録できます。 # カスタム絵文字を使用する 例としてブラウザから使えるクライアント nostter から使用してみます。 [nostter](https://nostter.app/) nostterにNostrエクステンションでログイン、もしくは秘密鍵を入れてログインしてください。 ## 文章中に使用 1. **投稿**ボタンを押して投稿ウィンドウを表示 2. **顔😀**のボタンを押し、絵文字ウィンドウを表示 3. ***タブ**を押し、カスタム絵文字一覧を表示 4. カスタム絵文字を選択 5. : 記号に挟まれたアルファベットのショートコードとして挿入される  この状態で投稿するとカスタム絵文字として表示されます。 カスタム絵文字対応クライアントを使っている他ユーザーにもカスタム絵文字として表示されます。 対応していないクライアントの場合、ショートコードのまま表示されます。  ショートコードを直接入力することでカスタム絵文字の候補が表示されるのでそこから選択することもできます。  ## リアクションに使用 1. 任意の投稿の**顔😀**のボタンを押し、絵文字ウィンドウを表示 2. ***タブ**を押し、カスタム絵文字一覧を表示 3. カスタム絵文字を選択  カスタム絵文字リアクションを送ることができます。  # カスタム絵文字を探す 先述した[emojito](https://emojito.meme/)からカスタム絵文字を探せます。 例えば任意のユーザーのページ [emojito ロクヨウ](https://emojito.meme/p/npub1a3pvwe2p3v7mnjz6hle63r628wl9w567aw7u23fzqs062v5vqcqqu3sgh3) から探したり、 [emojito Browse all](https://emojito.meme/browse) からnostr全体で最近作成、更新された絵文字を見たりできます。 また、以下のリンクは日本語圏ユーザーが作ったカスタム絵文字を集めたリストです(2025/02/06) ※漏れがあるかもしれません [日本ユーザー作 カスタム絵文字](https://nostviewstr.vercel.app/npub17hczqvxtfv3w69wr6lxrttnpdekwdwel55mld60fr24zwjuu6utqtj8mjx/10030) 各絵文字セットにある**Open in emojito**のリンクからemojitoに飛び、使用リストに追加できます。 ----------- 以上です。 次:Nostrのカスタム絵文字の**作り方** Yakihonneリンク [Nostrのカスタム絵文字の作り方](https://yakihonne.com/article/_@lokuyow.github.io/1707912490439) Nostrリンク nostr:naddr1qqxnzdesxuunzv358ycrgveeqgswcsk8v4qck0deepdtluag3a9rh0jh2d0wh0w9g53qg8a9x2xqvqqrqsqqqa28r5psx3 ----------- # 仕様 [NIP-30 Custom Emoji](https://github.com/nostr-protocol/nips/blob/master/30.md) [NIP-30 カスタム絵文字(和訳)](https://github.com/nostr-jp/nips-ja/blob/main/30.md) @ 16d11430:61640947
2025-02-18 02:21:18The holy grail of software development isn’t just writing code—it’s writing good code in a state of pure cognitive clarity. That moment when the mind operates at peak efficiency, when debugging is intuitive, and when abstractions form with effortless precision. This is the flow state, the intersection of deep focus and high cognitive throughput, where time distorts, distractions dissolve, and productivity skyrockets. But flow doesn’t happen on command. It’s not a switch you flip—it’s a state that requires cultivation, discipline, and an understanding of what to do outside of flow to extend and intensify the time inside of it. Understanding Flow in Programming Flow is a psychological state described by Mihaly Csikszentmihalyi, where people are fully immersed in an activity, experiencing deep focus, clear goals, and intrinsic motivation. In programming, flow is more than just focus—it’s a state where: Code becomes a natural language, and syntax errors fade into the subconscious. Bugs reveal themselves intuitively before they cause major issues. Solutions appear as if they were waiting to be discovered. However, the challenge isn’t just getting into flow—it’s staying in flow longer and increasing the intensity of that state. Many developers struggle with this because modern work environments are designed to pull them out of it—interruptions, meetings, notifications, and context switches all work against deep work. Why Flow is Hard to Maintain The key limitation of flow isn’t just time—it’s cognitive energy. You can’t sustain high-intensity flow indefinitely because: 1. Flow Requires a Build-Up – You don’t start in deep flow; it takes warm-up time. If you’re constantly switching contexts, you never get past the shallow stages of focus. 2. Cognitive Fatigue Kicks In – Just like physical endurance, mental endurance wears down over time. High-intensity cognition depletes willpower, working memory, and problem-solving efficiency. 3. External Interruptions Break the Cycle – Every time you respond to a message, check an email, or attend an unplanned meeting, you disrupt the delicate mental stack that flow relies on. Expanding Flow: The Out-of-Flow Preparation Phase To maximize flow, you must structure your out-of-flow time to support your inflow time. This means making low-bandwidth, low-intensity activities serve the function of preserving cognitive resources for when they are needed most. 1. Prime the Mind Beforehand Preload the problem: Before entering flow, read through relevant code, documentation, or problem statements, even if you don’t start coding. Let the subconscious chew on it. Use sleep strategically: Review complex issues before sleeping—your brain continues working on them passively overnight. Journal ideas: Keep a scratchpad for incomplete thoughts and patterns that need to be explored later. This prevents cognitive drift when you re-enter deep work. 2. Reduce Cognitive Load Outside of Flow Automate the trivial: Reduce low-value decision-making by scripting repetitive tasks, automating builds, and using shortcuts. Optimize workspace: Remove unnecessary distractions, use dark themes to reduce eye strain, and fine-tune your dev environment. Minimal communication: Asynchronous work models (like using GitHub issues or structured documentation) prevent unnecessary meetings. 3. Use Active Recovery to Extend Flow Durations Exercise between flow sessions: Short walks, stretching, or kettlebell swings help reset the nervous system. Use Indian clubs or a gyro ball: Engaging the wrists and forearms with rhythmic exercises improves circulation and keeps the hands limber. Engage in passive problem-solving: Listen to low-intensity technical podcasts, read about related topics, or sketch diagrams without the pressure of immediate problem-solving. 4. Manage Energy and Stamina Control caffeine intake: Small, steady doses of caffeine (e.g., green tea or microdosed coffee) sustain focus longer than a single heavy hit. Eat for cognitive endurance: Avoid sugar crashes; prioritize protein, healthy fats, and slow-digesting carbs. Cold exposure and breathwork: Techniques like the Wim Hof method or contrast showers can help maintain alertness and focus. Maximizing In-Flow Performance Once in flow, the goal is to stay there as long as possible and increase intensity without burnout. 1. Work in High-Resolution Time Blocks 90-minute deep work cycles: Research suggests the brain works optimally in ultradian rhythms, meaning cycles of 90 minutes of intense focus followed by a 15–20 minute break. Use timers: Time tracking (e.g., Pomodoro) helps prevent unconscious fatigue. However, don’t stop flow artificially—only use timers to prevent shallow focus work. 2. Reduce Interruptions Ruthlessly Go offline: Disable notifications, block distracting sites, and use airplane mode during deep work. Use noise-canceling headphones: Even if you don’t listen to music, noise isolation helps maintain focus. Batch all non-coding activities: Emails, Slack messages, and meetings should be handled in predefined blocks outside of deep work hours. 3. Optimize Mental Bandwidth Use text-based reasoning: Writing pseudocode or rubber-duck debugging prevents mental overload. Talk through problems out loud: The act of verbalizing a complex issue forces clarity. Engage in deliberate problem-solving: Instead of brute-forcing solutions, work from first principles—break problems down into the smallest testable units. Scaling Flow: Beyond Individual Productivity Flow isn’t just an individual challenge—it can be optimized at the team level: Flow-friendly scheduling: Companies should avoid scheduling meetings during peak productive hours (e.g., morning blocks). Pair programming strategically: While pair programming can improve code quality, it can also break deep focus. Use it wisely. Minimize process friction: Too much bureaucracy or excessive agile ceremonies kill momentum. Lean processes help maintain deep work culture. The Final Goal: High-Intensity Flow as the Default State Ultimately, a programmer’s most valuable skill isn’t just technical proficiency—it’s the ability to engineer their own mind for sustained, high-intensity flow. When flow is prolonged and intensified, an hour of deep work can replace an entire week of shallow, distracted effort. The key is not just working more—it’s working smarter, structuring out-of-flow time so that when flow begins, it reaches peak intensity and lasts as long as possible. By systematically designing both low-intensity and high-intensity work, programmers can transform sporadic flow into a continuous, deliberate, high-performance workflow. In the end, peak developers aren’t just coders—they are architects of their own mental states.
@ 16d11430:61640947
2025-02-18 02:21:18The holy grail of software development isn’t just writing code—it’s writing good code in a state of pure cognitive clarity. That moment when the mind operates at peak efficiency, when debugging is intuitive, and when abstractions form with effortless precision. This is the flow state, the intersection of deep focus and high cognitive throughput, where time distorts, distractions dissolve, and productivity skyrockets. But flow doesn’t happen on command. It’s not a switch you flip—it’s a state that requires cultivation, discipline, and an understanding of what to do outside of flow to extend and intensify the time inside of it. Understanding Flow in Programming Flow is a psychological state described by Mihaly Csikszentmihalyi, where people are fully immersed in an activity, experiencing deep focus, clear goals, and intrinsic motivation. In programming, flow is more than just focus—it’s a state where: Code becomes a natural language, and syntax errors fade into the subconscious. Bugs reveal themselves intuitively before they cause major issues. Solutions appear as if they were waiting to be discovered. However, the challenge isn’t just getting into flow—it’s staying in flow longer and increasing the intensity of that state. Many developers struggle with this because modern work environments are designed to pull them out of it—interruptions, meetings, notifications, and context switches all work against deep work. Why Flow is Hard to Maintain The key limitation of flow isn’t just time—it’s cognitive energy. You can’t sustain high-intensity flow indefinitely because: 1. Flow Requires a Build-Up – You don’t start in deep flow; it takes warm-up time. If you’re constantly switching contexts, you never get past the shallow stages of focus. 2. Cognitive Fatigue Kicks In – Just like physical endurance, mental endurance wears down over time. High-intensity cognition depletes willpower, working memory, and problem-solving efficiency. 3. External Interruptions Break the Cycle – Every time you respond to a message, check an email, or attend an unplanned meeting, you disrupt the delicate mental stack that flow relies on. Expanding Flow: The Out-of-Flow Preparation Phase To maximize flow, you must structure your out-of-flow time to support your inflow time. This means making low-bandwidth, low-intensity activities serve the function of preserving cognitive resources for when they are needed most. 1. Prime the Mind Beforehand Preload the problem: Before entering flow, read through relevant code, documentation, or problem statements, even if you don’t start coding. Let the subconscious chew on it. Use sleep strategically: Review complex issues before sleeping—your brain continues working on them passively overnight. Journal ideas: Keep a scratchpad for incomplete thoughts and patterns that need to be explored later. This prevents cognitive drift when you re-enter deep work. 2. Reduce Cognitive Load Outside of Flow Automate the trivial: Reduce low-value decision-making by scripting repetitive tasks, automating builds, and using shortcuts. Optimize workspace: Remove unnecessary distractions, use dark themes to reduce eye strain, and fine-tune your dev environment. Minimal communication: Asynchronous work models (like using GitHub issues or structured documentation) prevent unnecessary meetings. 3. Use Active Recovery to Extend Flow Durations Exercise between flow sessions: Short walks, stretching, or kettlebell swings help reset the nervous system. Use Indian clubs or a gyro ball: Engaging the wrists and forearms with rhythmic exercises improves circulation and keeps the hands limber. Engage in passive problem-solving: Listen to low-intensity technical podcasts, read about related topics, or sketch diagrams without the pressure of immediate problem-solving. 4. Manage Energy and Stamina Control caffeine intake: Small, steady doses of caffeine (e.g., green tea or microdosed coffee) sustain focus longer than a single heavy hit. Eat for cognitive endurance: Avoid sugar crashes; prioritize protein, healthy fats, and slow-digesting carbs. Cold exposure and breathwork: Techniques like the Wim Hof method or contrast showers can help maintain alertness and focus. Maximizing In-Flow Performance Once in flow, the goal is to stay there as long as possible and increase intensity without burnout. 1. Work in High-Resolution Time Blocks 90-minute deep work cycles: Research suggests the brain works optimally in ultradian rhythms, meaning cycles of 90 minutes of intense focus followed by a 15–20 minute break. Use timers: Time tracking (e.g., Pomodoro) helps prevent unconscious fatigue. However, don’t stop flow artificially—only use timers to prevent shallow focus work. 2. Reduce Interruptions Ruthlessly Go offline: Disable notifications, block distracting sites, and use airplane mode during deep work. Use noise-canceling headphones: Even if you don’t listen to music, noise isolation helps maintain focus. Batch all non-coding activities: Emails, Slack messages, and meetings should be handled in predefined blocks outside of deep work hours. 3. Optimize Mental Bandwidth Use text-based reasoning: Writing pseudocode or rubber-duck debugging prevents mental overload. Talk through problems out loud: The act of verbalizing a complex issue forces clarity. Engage in deliberate problem-solving: Instead of brute-forcing solutions, work from first principles—break problems down into the smallest testable units. Scaling Flow: Beyond Individual Productivity Flow isn’t just an individual challenge—it can be optimized at the team level: Flow-friendly scheduling: Companies should avoid scheduling meetings during peak productive hours (e.g., morning blocks). Pair programming strategically: While pair programming can improve code quality, it can also break deep focus. Use it wisely. Minimize process friction: Too much bureaucracy or excessive agile ceremonies kill momentum. Lean processes help maintain deep work culture. The Final Goal: High-Intensity Flow as the Default State Ultimately, a programmer’s most valuable skill isn’t just technical proficiency—it’s the ability to engineer their own mind for sustained, high-intensity flow. When flow is prolonged and intensified, an hour of deep work can replace an entire week of shallow, distracted effort. The key is not just working more—it’s working smarter, structuring out-of-flow time so that when flow begins, it reaches peak intensity and lasts as long as possible. By systematically designing both low-intensity and high-intensity work, programmers can transform sporadic flow into a continuous, deliberate, high-performance workflow. In the end, peak developers aren’t just coders—they are architects of their own mental states. @ ec42c765:328c0600
2025-02-05 20:30:46# カスタム絵文字とは 任意のオリジナル画像を絵文字のように文中に挿入できる機能です。 また、リアクション(Twitterの いいね のような機能)にもカスタム絵文字を使えます。  # カスタム絵文字の対応状況(2024/02/05)  カスタム絵文字を使うためにはカスタム絵文字に対応した[クライアント](https://welcome.nostr-jp.org/tutorial/explore-client.html)を使う必要があります。 ※表は一例です。クライアントは他にもたくさんあります。 使っているクライアントが対応していない場合は、クライアントを変更する、対応するまで待つ、開発者に要望を送る(または自分で実装する)などしましょう。 #### 対応クライアント - [Amethyst](https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst) - [FreeFrom](https://freefrom.space/) - [nostter](https://nostter.app/) - [Rabbit](https://rabbit.syusui.net/) - [Snort](https://snort.social/) - [noStrudel](https://nostrudel.ninja/) ここではnostterを使って説明していきます。 # 準備 カスタム絵文字を使うための準備です。 - Nostrエクステンション(NIP-07)を導入する - 使いたいカスタム絵文字をリストに登録する ## Nostrエクステンション(NIP-07)を導入する Nostrエクステンションは使いたいカスタム絵文字を登録する時に必要になります。 また、環境(パソコン、iPhone、androidなど)によって導入方法が違います。 Nostrエクステンションを導入する端末は、実際にNostrを閲覧する端末と違っても構いません(リスト登録はPC、Nostr閲覧はiPhoneなど)。 Nostrエクステンション(NIP-07)の導入方法は以下のページを参照してください。 [ログイン拡張機能 (NIP-07)を使ってみよう | Welcome to Nostr! ~ Nostrをはじめよう! ~ ](https://welcome.nostr-jp.org/tutorial/nip-07.html) 少し面倒ですが、これを導入しておくとNostr上の様々な場面で役立つのでより快適になります。 ## 使いたいカスタム絵文字をリストに登録する 以下のサイトで行います。 [emojito](https://emojito.meme/) 右上の**Get started**からNostrエクステンションでログインしてください。 例として以下のカスタム絵文字を導入してみます。 実際より絵文字が少なく表示されることがありますが、古い状態のデータを取得してしまっているためです。その場合はブラウザの更新ボタンを押してください。 [generalJP | カスタム絵文字](https://emojito.meme/a/naddr1qqykwetwv4exzmz22qq3uamnwvaz7tmwdaehgun2vykkkctjdyhxset8w4ex7tnrdakj7q3qa3pvwe2p3v7mnjz6hle63r628wl9w567aw7u23fzqs062v5vqcqqxpqqqp65uhjtrk6)  - 右側の**Options**から**Bookmark**を選択  これでカスタム絵文字を使用するためのリストに登録できます。 # カスタム絵文字を使用する 例としてブラウザから使えるクライアント nostter から使用してみます。 [nostter](https://nostter.app/) nostterにNostrエクステンションでログイン、もしくは秘密鍵を入れてログインしてください。 ## 文章中に使用 1. **投稿**ボタンを押して投稿ウィンドウを表示 2. **顔😀**のボタンを押し、絵文字ウィンドウを表示 3. ***タブ**を押し、カスタム絵文字一覧を表示 4. カスタム絵文字を選択 5. : 記号に挟まれたアルファベットのショートコードとして挿入される  この状態で投稿するとカスタム絵文字として表示されます。 カスタム絵文字対応クライアントを使っている他ユーザーにもカスタム絵文字として表示されます。 対応していないクライアントの場合、ショートコードのまま表示されます。  ショートコードを直接入力することでカスタム絵文字の候補が表示されるのでそこから選択することもできます。  ## リアクションに使用 1. 任意の投稿の**顔😀**のボタンを押し、絵文字ウィンドウを表示 2. ***タブ**を押し、カスタム絵文字一覧を表示 3. カスタム絵文字を選択  カスタム絵文字リアクションを送ることができます。  # カスタム絵文字を探す 先述した[emojito](https://emojito.meme/)からカスタム絵文字を探せます。 例えば任意のユーザーのページ [emojito ロクヨウ](https://emojito.meme/p/npub1a3pvwe2p3v7mnjz6hle63r628wl9w567aw7u23fzqs062v5vqcqqu3sgh3) から探したり、 [emojito Browse all](https://emojito.meme/browse) からnostr全体で最近作成、更新された絵文字を見たりできます。 また、以下のリンクは日本語圏ユーザーが作ったカスタム絵文字を集めたリストです(2024/06/30) ※漏れがあるかもしれません [日本ユーザー作 カスタム絵文字](https://nostviewstr.vercel.app/npub17hczqvxtfv3w69wr6lxrttnpdekwdwel55mld60fr24zwjuu6utqtj8mjx/10030) 各絵文字セットにある**Open in emojito**のリンクからemojitoに飛び、使用リストに追加できます。 ----------- 以上です。 次:Nostrのカスタム絵文字の**作り方** Yakihonneリンク [Nostrのカスタム絵文字の作り方](https://yakihonne.com/article/_@lokuyow.github.io/1707912490439) Nostrリンク nostr:naddr1qqxnzdesxuunzv358ycrgveeqgswcsk8v4qck0deepdtluag3a9rh0jh2d0wh0w9g53qg8a9x2xqvqqrqsqqqa28r5psx3 ----------- # 仕様 [NIP-30 Custom Emoji](https://github.com/nostr-protocol/nips/blob/master/30.md) [NIP-30 カスタム絵文字(和訳)](https://github.com/nostr-jp/nips-ja/blob/main/30.md)
@ ec42c765:328c0600
2025-02-05 20:30:46# カスタム絵文字とは 任意のオリジナル画像を絵文字のように文中に挿入できる機能です。 また、リアクション(Twitterの いいね のような機能)にもカスタム絵文字を使えます。  # カスタム絵文字の対応状況(2024/02/05)  カスタム絵文字を使うためにはカスタム絵文字に対応した[クライアント](https://welcome.nostr-jp.org/tutorial/explore-client.html)を使う必要があります。 ※表は一例です。クライアントは他にもたくさんあります。 使っているクライアントが対応していない場合は、クライアントを変更する、対応するまで待つ、開発者に要望を送る(または自分で実装する)などしましょう。 #### 対応クライアント - [Amethyst](https://play.google.com/store/apps/details?id=com.vitorpamplona.amethyst) - [FreeFrom](https://freefrom.space/) - [nostter](https://nostter.app/) - [Rabbit](https://rabbit.syusui.net/) - [Snort](https://snort.social/) - [noStrudel](https://nostrudel.ninja/) ここではnostterを使って説明していきます。 # 準備 カスタム絵文字を使うための準備です。 - Nostrエクステンション(NIP-07)を導入する - 使いたいカスタム絵文字をリストに登録する ## Nostrエクステンション(NIP-07)を導入する Nostrエクステンションは使いたいカスタム絵文字を登録する時に必要になります。 また、環境(パソコン、iPhone、androidなど)によって導入方法が違います。 Nostrエクステンションを導入する端末は、実際にNostrを閲覧する端末と違っても構いません(リスト登録はPC、Nostr閲覧はiPhoneなど)。 Nostrエクステンション(NIP-07)の導入方法は以下のページを参照してください。 [ログイン拡張機能 (NIP-07)を使ってみよう | Welcome to Nostr! ~ Nostrをはじめよう! ~ ](https://welcome.nostr-jp.org/tutorial/nip-07.html) 少し面倒ですが、これを導入しておくとNostr上の様々な場面で役立つのでより快適になります。 ## 使いたいカスタム絵文字をリストに登録する 以下のサイトで行います。 [emojito](https://emojito.meme/) 右上の**Get started**からNostrエクステンションでログインしてください。 例として以下のカスタム絵文字を導入してみます。 実際より絵文字が少なく表示されることがありますが、古い状態のデータを取得してしまっているためです。その場合はブラウザの更新ボタンを押してください。 [generalJP | カスタム絵文字](https://emojito.meme/a/naddr1qqykwetwv4exzmz22qq3uamnwvaz7tmwdaehgun2vykkkctjdyhxset8w4ex7tnrdakj7q3qa3pvwe2p3v7mnjz6hle63r628wl9w567aw7u23fzqs062v5vqcqqxpqqqp65uhjtrk6)  - 右側の**Options**から**Bookmark**を選択  これでカスタム絵文字を使用するためのリストに登録できます。 # カスタム絵文字を使用する 例としてブラウザから使えるクライアント nostter から使用してみます。 [nostter](https://nostter.app/) nostterにNostrエクステンションでログイン、もしくは秘密鍵を入れてログインしてください。 ## 文章中に使用 1. **投稿**ボタンを押して投稿ウィンドウを表示 2. **顔😀**のボタンを押し、絵文字ウィンドウを表示 3. ***タブ**を押し、カスタム絵文字一覧を表示 4. カスタム絵文字を選択 5. : 記号に挟まれたアルファベットのショートコードとして挿入される  この状態で投稿するとカスタム絵文字として表示されます。 カスタム絵文字対応クライアントを使っている他ユーザーにもカスタム絵文字として表示されます。 対応していないクライアントの場合、ショートコードのまま表示されます。  ショートコードを直接入力することでカスタム絵文字の候補が表示されるのでそこから選択することもできます。  ## リアクションに使用 1. 任意の投稿の**顔😀**のボタンを押し、絵文字ウィンドウを表示 2. ***タブ**を押し、カスタム絵文字一覧を表示 3. カスタム絵文字を選択  カスタム絵文字リアクションを送ることができます。  # カスタム絵文字を探す 先述した[emojito](https://emojito.meme/)からカスタム絵文字を探せます。 例えば任意のユーザーのページ [emojito ロクヨウ](https://emojito.meme/p/npub1a3pvwe2p3v7mnjz6hle63r628wl9w567aw7u23fzqs062v5vqcqqu3sgh3) から探したり、 [emojito Browse all](https://emojito.meme/browse) からnostr全体で最近作成、更新された絵文字を見たりできます。 また、以下のリンクは日本語圏ユーザーが作ったカスタム絵文字を集めたリストです(2024/06/30) ※漏れがあるかもしれません [日本ユーザー作 カスタム絵文字](https://nostviewstr.vercel.app/npub17hczqvxtfv3w69wr6lxrttnpdekwdwel55mld60fr24zwjuu6utqtj8mjx/10030) 各絵文字セットにある**Open in emojito**のリンクからemojitoに飛び、使用リストに追加できます。 ----------- 以上です。 次:Nostrのカスタム絵文字の**作り方** Yakihonneリンク [Nostrのカスタム絵文字の作り方](https://yakihonne.com/article/_@lokuyow.github.io/1707912490439) Nostrリンク nostr:naddr1qqxnzdesxuunzv358ycrgveeqgswcsk8v4qck0deepdtluag3a9rh0jh2d0wh0w9g53qg8a9x2xqvqqrqsqqqa28r5psx3 ----------- # 仕様 [NIP-30 Custom Emoji](https://github.com/nostr-protocol/nips/blob/master/30.md) [NIP-30 カスタム絵文字(和訳)](https://github.com/nostr-jp/nips-ja/blob/main/30.md) @ 09fbf8f3:fa3d60f0
2025-02-17 15:23:11### 🌟 深度探索:在Cloudflare上免费部署DeepSeek-R1 32B大模型 #### 🌍 一、 注册或登录Cloudflare平台(CF老手可跳过) ##### 1️⃣ 进入Cloudflare平台官网: 。www.cloudflare.com/zh-cn/ 登录或者注册账号。  ##### 2️⃣ 新注册的用户会让你选择域名,无视即可,直接点下面的Start building。  ##### 3️⃣ 进入仪表盘后,界面可能会显示英文,在右上角切换到[简体中文]即可。  --- #### 🚀 二、正式开始部署Deepseek API项目。 ##### 1️⃣ 首先在左侧菜单栏找到【AI】下的【Wokers AI】,选择【Llama 3 Woker】。  ##### 2️⃣ 为项目取一个好听的名字,后点击部署即可。  ##### 3️⃣ Woker项目初始化部署好后,需要编辑替换掉其原代码。  ##### 4️⃣ 解压出提供的代码压缩包,找到【32b】的部署代码,将里面的文本复制出来。 **下载地址:** 📁 [夸克](https://pan.quark.cn/s/2b5aa9ff57f6) 📁 [UC网盘](https://drive.uc.cn/s/a7ff5e03b4d84?public=1) 📁 [迅雷网盘](https://pan.xunlei.com/s/VOJEzm7hLwmhER71rK2wnXArA1?pwd=cefg#)  ##### 5️⃣ 接第3步,将项目里的原代码清空,粘贴第4步复制好的代码到编辑器。  ##### 6️⃣ 代码粘贴完,即可点击右上角的部署按钮。  ##### 7️⃣ 回到仪表盘,点击部署完的项目名称。  ##### 8️⃣ 查看【设置】,找到平台分配的项目网址,复制好备用。  --- #### 💻 三、选择可用的UI软件,这边使用Chatbox AI演示。 ##### 1️⃣ 根据自己使用的平台下载对应的安装包,博主也一并打包好了全平台的软件安装包。  ##### 2️⃣ 打开安装好的Chatbox,点击左下角的设置。  ##### 3️⃣ 选择【添加自定义提供方】。  ##### 4️⃣ 按照图片说明填写即可,【API域名】为之前复制的项目网址(加/v1);【改善网络兼容性】功能务必开启;【API密钥】默认为”zhiyuan“,可自行修改;填写完毕后保存即可。  ##### 5️⃣ Cloudflare项目部署好后,就能正常使用了,接口仿照OpenAI API具有较强的兼容性,能导入到很多支持AI功能的软件或插件中。   ##### 6️⃣ Cloudflare的域名默认被墙了,需要自己准备一个域名设置。 --- **转自微信公众号:纸鸢花的小屋** **推广:低调云(梯子VPN)** 。www.didiaocloud.xyz
@ 09fbf8f3:fa3d60f0
2025-02-17 15:23:11### 🌟 深度探索:在Cloudflare上免费部署DeepSeek-R1 32B大模型 #### 🌍 一、 注册或登录Cloudflare平台(CF老手可跳过) ##### 1️⃣ 进入Cloudflare平台官网: 。www.cloudflare.com/zh-cn/ 登录或者注册账号。  ##### 2️⃣ 新注册的用户会让你选择域名,无视即可,直接点下面的Start building。  ##### 3️⃣ 进入仪表盘后,界面可能会显示英文,在右上角切换到[简体中文]即可。  --- #### 🚀 二、正式开始部署Deepseek API项目。 ##### 1️⃣ 首先在左侧菜单栏找到【AI】下的【Wokers AI】,选择【Llama 3 Woker】。  ##### 2️⃣ 为项目取一个好听的名字,后点击部署即可。  ##### 3️⃣ Woker项目初始化部署好后,需要编辑替换掉其原代码。  ##### 4️⃣ 解压出提供的代码压缩包,找到【32b】的部署代码,将里面的文本复制出来。 **下载地址:** 📁 [夸克](https://pan.quark.cn/s/2b5aa9ff57f6) 📁 [UC网盘](https://drive.uc.cn/s/a7ff5e03b4d84?public=1) 📁 [迅雷网盘](https://pan.xunlei.com/s/VOJEzm7hLwmhER71rK2wnXArA1?pwd=cefg#)  ##### 5️⃣ 接第3步,将项目里的原代码清空,粘贴第4步复制好的代码到编辑器。  ##### 6️⃣ 代码粘贴完,即可点击右上角的部署按钮。  ##### 7️⃣ 回到仪表盘,点击部署完的项目名称。  ##### 8️⃣ 查看【设置】,找到平台分配的项目网址,复制好备用。  --- #### 💻 三、选择可用的UI软件,这边使用Chatbox AI演示。 ##### 1️⃣ 根据自己使用的平台下载对应的安装包,博主也一并打包好了全平台的软件安装包。  ##### 2️⃣ 打开安装好的Chatbox,点击左下角的设置。  ##### 3️⃣ 选择【添加自定义提供方】。  ##### 4️⃣ 按照图片说明填写即可,【API域名】为之前复制的项目网址(加/v1);【改善网络兼容性】功能务必开启;【API密钥】默认为”zhiyuan“,可自行修改;填写完毕后保存即可。  ##### 5️⃣ Cloudflare项目部署好后,就能正常使用了,接口仿照OpenAI API具有较强的兼容性,能导入到很多支持AI功能的软件或插件中。   ##### 6️⃣ Cloudflare的域名默认被墙了,需要自己准备一个域名设置。 --- **转自微信公众号:纸鸢花的小屋** **推广:低调云(梯子VPN)** 。www.didiaocloud.xyz @ e7bc35f8:3ed2a7cf
2025-02-17 14:55:26The mainstream narrative paints the "freedom fever" sweeping across the Middle East as a spontaneous, people-led movement—a victory of democracy against oppressive regimes. Celebrations erupted as tech-savvy youth mobilized to topple autocrats, with Western media hailing the Arab Spring as a beacon of hope. But was it really? Or was it yet another chapter in a long history of foreign interference, regime change, and geopolitical chess moves aimed at securing control over one of the world’s most resource-rich regions? ### Revolution or Destabilization? Figures like Wadah Khanfar, the former head of Al Jazeera, [expressed optimism]( https://www.ted.com/talks/wadah_khanfar_a_historic_moment_in_the_arab_world?subtitle=en) about the uprisings, framing them as historic moments of empowerment for the people of Egypt, Tunisia, Libya, and beyond. Many Western analysts echoed this sentiment. However, other voices warned that these movements were being manipulated to serve broader strategic interests. For instance, Professor Hamid Dabashi [linked]( https://youtu.be/RMsOoEUquT8) Iran’s Green Movement to the wider regional wave of youth uprisings against authoritarian regimes. But establishment figures like Senator John McCain quickly [seized the moment]( https://youtu.be/WOcPYxLpUMs), using it as an excuse to pressure Iran, China, and Russia. A closer look suggests that these uprisings were not just organic revolts against dictatorship but rather heavily influenced by external forces. ### The Color Revolution Playbook The so-called “Green Movement” in Iran bore all the hallmarks of a Western-backed color revolution, with funding and strategic guidance from organizations linked to George Soros, the CIA, Mossad, and global mass media networks. The same script played out elsewhere, as seen in [Webster Tarpley’s analysis]( https://web.archive.org/web/20110131230059/http://www.youtube.com/watch?v=UvI6JqiAZjs) for RT, which laid out how the uprisings in the Middle East aligned perfectly with long-standing Western agendas for the region. Consider the case of Stuxnet, a cyberweapon [developed by the US and Israel]( https://youtu.be/CS01Hmjv1pQ) to sabotage Iran’s nuclear program. This wasn’t just an isolated incident—it was part of a larger strategy to weaken Iran and its allies. The infamous Brookings Institution report, "[Which Path to Persia?]( https://landdestroyer.blogspot.com/2011/02/brookings-which-path-to-persia.html?m=1)", even laid out a detailed roadmap for toppling the Iranian government through various methods, from economic warfare to military intervention. ### From Iran to Syria: The Next Domino Once the destabilization of Iran was in motion, attention shifted to its key ally, [Syria]( https://youtu.be/Gpf1C9Fcqxw). The calls for regime change escalated quickly, with Senator Joe Lieberman [openly suggesting]( https://youtu.be/aDxbTQXFhJM) that the US should intervene next. Syria, after all, is a critical piece in the geopolitical chessboard—not just because of its strategic location but also because of its alliances with Iran, Russia, and, most notably, China. This is precisely why controlling Middle Eastern oil isn’t just about securing energy for the West—it’s about **denying it to China**. If China is to be contained, it must be cut off from the resources that fuel its rise. This explains why Western-backed revolts and interventions tend to target governments that lean toward China. Let's examine some instances of China's strategy in the region. * On April 6, 2006, [Chinese President Hu Jintao and Yemeni President Ali Abdullah Saleh]( https://www.fmprc.gov.cn/eng/gjhdq_665435/2675_665437/2908_663816/2910_663820/202406/t20240607_11414813.html) held talks in Beijing. The leaders discussed enhancing political trust, expanding economic and trade cooperation, and increasing cultural and educational exchanges. * China's expanding diplomatic, economic, and security interests in the Middle East, particularly [through its interactions with the Gulf Cooperation Council (GCC)]( https://jamestown.org/program/bloc-politics-in-the-persian-gulf-chinas-multilateral-engagement-with-the-gulf-cooperation-council/). China's evolving relationship with the GCC reflects its broader objectives of securing energy resources, expanding its economic footprint, and enhancing its geopolitical influence in the Middle East and beyond. * China's expanding influence in the [Caspian region and its intersection with Syria's strategic ambitions]( https://jamestown.org/program/the-caspian-sea-chinas-silk-road-strategy-converges-with-damascus/). Investments in Central Asian infrastructure, notably the Kazakhstan-China oil pipeline and the Turkmenistan-China gas pipeline. **Syrian President Bashar al-Assad's** "Four Seas Strategy" aimed to position Syria as a central hub connecting the Caspian, Black, Mediterranean, and Red Seas. * China's expanding political, economic, and strategic ties with Syria, positioning the country as a pivotal hub in China's revitalized [Silk Road initiative]( https://jamestown.org/program/syria-in-chinas-new-silk-road-strategy/). Following **Syrian President Bashar al-Assad's** 2004 visit to China, bilateral cooperation has intensified, particularly in sectors like oil, electricity, transport, and telecommunications, with major Chinese enterprises such as CNPC, ZTE, Huawei, and Haier playing significant roles. ### The Fall of Puppets: Mubarak and Libya Hosni Mubarak, though a loyal US ally for decades, was ultimately deemed replaceable. Why? Because he was not the ideal puppet. He had shown interest in fostering deeper ties between [China]( http://www.china.org.cn/english/features/phfnt/85843.htm) and the Arab world, particularly in [Africa]( https://english.cctv.com/20091109/101132_2.shtml). His removal paved the way for a new power dynamic, one that better served Western interests. A similar pattern emerged in Libya. When NATO intervened to topple Gaddafi, [China’s oil investments]( https://www.ft.com/content/eef58d52-3fe2-11e0-811f-00144feabdc0) in the country became collateral damage. Chinese companies had billions of dollars in contracts with Libya, which were suddenly thrown into chaos. Western intervention not only eliminated Gaddafi but also disrupted China’s growing influence in North Africa. ### The Bigger Picture: A New World Order Agenda? What we are witnessing is not just a series of isolated revolts but a broader, long-term strategy to reshape the Middle East in ways that align with Western and globalist interests. The destruction of strong, independent states in the region creates a vacuum—one that can be filled by controlled regimes, multinational corporations, and military bases that ensure energy resources remain under Western control. Meanwhile, China’s efforts to establish a foothold in the region are systematically countered. Every strategic move China makes—whether in Syria, Iran, or the Persian Gulf—is met with resistance in the form of “pro-democracy” uprisings, sanctions, or outright military intervention. ### The Illusion of Spontaneous Uprising While the mainstream media glorifies the Arab Spring and similar movements as victories for democracy, the deeper reality suggests a far more calculated and sinister agenda. The Middle East is being reshaped, not by the will of its people alone, but by powerful forces seeking to maintain global hegemony. The so-called “freedom fever” may be less about liberation and more about control. The question remains: How much longer will people buy into the illusion?
@ e7bc35f8:3ed2a7cf
2025-02-17 14:55:26The mainstream narrative paints the "freedom fever" sweeping across the Middle East as a spontaneous, people-led movement—a victory of democracy against oppressive regimes. Celebrations erupted as tech-savvy youth mobilized to topple autocrats, with Western media hailing the Arab Spring as a beacon of hope. But was it really? Or was it yet another chapter in a long history of foreign interference, regime change, and geopolitical chess moves aimed at securing control over one of the world’s most resource-rich regions? ### Revolution or Destabilization? Figures like Wadah Khanfar, the former head of Al Jazeera, [expressed optimism]( https://www.ted.com/talks/wadah_khanfar_a_historic_moment_in_the_arab_world?subtitle=en) about the uprisings, framing them as historic moments of empowerment for the people of Egypt, Tunisia, Libya, and beyond. Many Western analysts echoed this sentiment. However, other voices warned that these movements were being manipulated to serve broader strategic interests. For instance, Professor Hamid Dabashi [linked]( https://youtu.be/RMsOoEUquT8) Iran’s Green Movement to the wider regional wave of youth uprisings against authoritarian regimes. But establishment figures like Senator John McCain quickly [seized the moment]( https://youtu.be/WOcPYxLpUMs), using it as an excuse to pressure Iran, China, and Russia. A closer look suggests that these uprisings were not just organic revolts against dictatorship but rather heavily influenced by external forces. ### The Color Revolution Playbook The so-called “Green Movement” in Iran bore all the hallmarks of a Western-backed color revolution, with funding and strategic guidance from organizations linked to George Soros, the CIA, Mossad, and global mass media networks. The same script played out elsewhere, as seen in [Webster Tarpley’s analysis]( https://web.archive.org/web/20110131230059/http://www.youtube.com/watch?v=UvI6JqiAZjs) for RT, which laid out how the uprisings in the Middle East aligned perfectly with long-standing Western agendas for the region. Consider the case of Stuxnet, a cyberweapon [developed by the US and Israel]( https://youtu.be/CS01Hmjv1pQ) to sabotage Iran’s nuclear program. This wasn’t just an isolated incident—it was part of a larger strategy to weaken Iran and its allies. The infamous Brookings Institution report, "[Which Path to Persia?]( https://landdestroyer.blogspot.com/2011/02/brookings-which-path-to-persia.html?m=1)", even laid out a detailed roadmap for toppling the Iranian government through various methods, from economic warfare to military intervention. ### From Iran to Syria: The Next Domino Once the destabilization of Iran was in motion, attention shifted to its key ally, [Syria]( https://youtu.be/Gpf1C9Fcqxw). The calls for regime change escalated quickly, with Senator Joe Lieberman [openly suggesting]( https://youtu.be/aDxbTQXFhJM) that the US should intervene next. Syria, after all, is a critical piece in the geopolitical chessboard—not just because of its strategic location but also because of its alliances with Iran, Russia, and, most notably, China. This is precisely why controlling Middle Eastern oil isn’t just about securing energy for the West—it’s about **denying it to China**. If China is to be contained, it must be cut off from the resources that fuel its rise. This explains why Western-backed revolts and interventions tend to target governments that lean toward China. Let's examine some instances of China's strategy in the region. * On April 6, 2006, [Chinese President Hu Jintao and Yemeni President Ali Abdullah Saleh]( https://www.fmprc.gov.cn/eng/gjhdq_665435/2675_665437/2908_663816/2910_663820/202406/t20240607_11414813.html) held talks in Beijing. The leaders discussed enhancing political trust, expanding economic and trade cooperation, and increasing cultural and educational exchanges. * China's expanding diplomatic, economic, and security interests in the Middle East, particularly [through its interactions with the Gulf Cooperation Council (GCC)]( https://jamestown.org/program/bloc-politics-in-the-persian-gulf-chinas-multilateral-engagement-with-the-gulf-cooperation-council/). China's evolving relationship with the GCC reflects its broader objectives of securing energy resources, expanding its economic footprint, and enhancing its geopolitical influence in the Middle East and beyond. * China's expanding influence in the [Caspian region and its intersection with Syria's strategic ambitions]( https://jamestown.org/program/the-caspian-sea-chinas-silk-road-strategy-converges-with-damascus/). Investments in Central Asian infrastructure, notably the Kazakhstan-China oil pipeline and the Turkmenistan-China gas pipeline. **Syrian President Bashar al-Assad's** "Four Seas Strategy" aimed to position Syria as a central hub connecting the Caspian, Black, Mediterranean, and Red Seas. * China's expanding political, economic, and strategic ties with Syria, positioning the country as a pivotal hub in China's revitalized [Silk Road initiative]( https://jamestown.org/program/syria-in-chinas-new-silk-road-strategy/). Following **Syrian President Bashar al-Assad's** 2004 visit to China, bilateral cooperation has intensified, particularly in sectors like oil, electricity, transport, and telecommunications, with major Chinese enterprises such as CNPC, ZTE, Huawei, and Haier playing significant roles. ### The Fall of Puppets: Mubarak and Libya Hosni Mubarak, though a loyal US ally for decades, was ultimately deemed replaceable. Why? Because he was not the ideal puppet. He had shown interest in fostering deeper ties between [China]( http://www.china.org.cn/english/features/phfnt/85843.htm) and the Arab world, particularly in [Africa]( https://english.cctv.com/20091109/101132_2.shtml). His removal paved the way for a new power dynamic, one that better served Western interests. A similar pattern emerged in Libya. When NATO intervened to topple Gaddafi, [China’s oil investments]( https://www.ft.com/content/eef58d52-3fe2-11e0-811f-00144feabdc0) in the country became collateral damage. Chinese companies had billions of dollars in contracts with Libya, which were suddenly thrown into chaos. Western intervention not only eliminated Gaddafi but also disrupted China’s growing influence in North Africa. ### The Bigger Picture: A New World Order Agenda? What we are witnessing is not just a series of isolated revolts but a broader, long-term strategy to reshape the Middle East in ways that align with Western and globalist interests. The destruction of strong, independent states in the region creates a vacuum—one that can be filled by controlled regimes, multinational corporations, and military bases that ensure energy resources remain under Western control. Meanwhile, China’s efforts to establish a foothold in the region are systematically countered. Every strategic move China makes—whether in Syria, Iran, or the Persian Gulf—is met with resistance in the form of “pro-democracy” uprisings, sanctions, or outright military intervention. ### The Illusion of Spontaneous Uprising While the mainstream media glorifies the Arab Spring and similar movements as victories for democracy, the deeper reality suggests a far more calculated and sinister agenda. The Middle East is being reshaped, not by the will of its people alone, but by powerful forces seeking to maintain global hegemony. The so-called “freedom fever” may be less about liberation and more about control. The question remains: How much longer will people buy into the illusion? @ e88a691e:27850411
2025-02-17 13:30:42test post longform 4
@ e88a691e:27850411
2025-02-17 13:30:42test post longform 4 @ 83279ad2:bd49240d
2025-01-24 09:15:37備忘録として書きます。意外と時間がかかりました。全体で1時間くらいかかるので気長にやりましょう。 仮想通貨取引所(販売所ではないので、玄人が使えばお得らしい)かつBitcoinの送金手数料が無料(全ての取引所が無料ではない、例えばbitbankは0.0006bitcoinかかる)なので送金元はGMOコインを使います。(注意:GMOコインは0.02ビットコイン以下は全額送金になってしまいます) 今回はカストディアルウォレットのWallet of Satoshiに送金します。 以下手順 1. GMOコインでbitcoinを買います。 2. GMOコインの左のタブから入出金 暗号資産を選択します。 3. 送付のタブを開いて、+新しい宛先を追加するを選択します。 4. 送付先:GMOコイン以外、送付先ウォレット:プライベートウォレット(MetaMaskなど)、受取人:ご本人さま を選んで宛先情報の登録を選ぶと次の画面になります。<br> 5. 宛先名称にwallet of satoshi(これはなんでも良いです わかりやすい名称にしましょう) wallet of satoshiを開いて、受信→Bitcoin On-Chainからアドレスをコピーして、ビットコインアドレスに貼り付けます。<br> 6. 登録するを押します。これで送金先の登録ができました。GMOコインの審査がありますがすぐ終わると思います。 7. ここから送金をします。送付のタブから登録したビットコインの宛先リストwallet of satoshiを選択し、送付数量と送付目的を選択して、2段階認証をします。<br> 8. 実行を押せば終わりです。もうあなたがやることはありません。送金が終わるのを40分くらい眺めるだけです。<br> 8. 取引履歴のタブから今の送金のステータスが見れます。<br> 9. 15分くらい待つとステータスが受付に変わります。<br> 10. 20分くらい待つとトランザクションIDが表示されます。 <br> <br>この時点からwallet of satoshiにも送金されていることが表示されます。(まだ完了はしていない) <br>  11. ステータスが完了になったら送金終わりです。<br> <br> wallet of satoshiにも反映されます。<br>  ----------- お疲れ様でした!
@ 83279ad2:bd49240d
2025-01-24 09:15:37備忘録として書きます。意外と時間がかかりました。全体で1時間くらいかかるので気長にやりましょう。 仮想通貨取引所(販売所ではないので、玄人が使えばお得らしい)かつBitcoinの送金手数料が無料(全ての取引所が無料ではない、例えばbitbankは0.0006bitcoinかかる)なので送金元はGMOコインを使います。(注意:GMOコインは0.02ビットコイン以下は全額送金になってしまいます) 今回はカストディアルウォレットのWallet of Satoshiに送金します。 以下手順 1. GMOコインでbitcoinを買います。 2. GMOコインの左のタブから入出金 暗号資産を選択します。 3. 送付のタブを開いて、+新しい宛先を追加するを選択します。 4. 送付先:GMOコイン以外、送付先ウォレット:プライベートウォレット(MetaMaskなど)、受取人:ご本人さま を選んで宛先情報の登録を選ぶと次の画面になります。<br> 5. 宛先名称にwallet of satoshi(これはなんでも良いです わかりやすい名称にしましょう) wallet of satoshiを開いて、受信→Bitcoin On-Chainからアドレスをコピーして、ビットコインアドレスに貼り付けます。<br> 6. 登録するを押します。これで送金先の登録ができました。GMOコインの審査がありますがすぐ終わると思います。 7. ここから送金をします。送付のタブから登録したビットコインの宛先リストwallet of satoshiを選択し、送付数量と送付目的を選択して、2段階認証をします。<br> 8. 実行を押せば終わりです。もうあなたがやることはありません。送金が終わるのを40分くらい眺めるだけです。<br> 8. 取引履歴のタブから今の送金のステータスが見れます。<br> 9. 15分くらい待つとステータスが受付に変わります。<br> 10. 20分くらい待つとトランザクションIDが表示されます。 <br> <br>この時点からwallet of satoshiにも送金されていることが表示されます。(まだ完了はしていない) <br>  11. ステータスが完了になったら送金終わりです。<br> <br> wallet of satoshiにも反映されます。<br>  ----------- お疲れ様でした! @ d360efec:14907b5f
2025-02-17 12:20:25**3 พฤติกรรมที่เป็นอุปสรรคต่อการทำกำไรของนักลงทุนส่วนใหญ่** นักลงทุนจำนวนมากต้องการที่จะประสบความสำเร็จในตลาดหุ้นและสร้างผลกำไรที่สม่ำเสมอ แต่หลายครั้งที่พวกเขากลับพบว่าตัวเองต้องเผชิญกับอุปสรรคที่ทำให้ไม่สามารถบรรลุเป้าหมายนั้นได้ ช่อง Zyo / เซียว จับอิดนึ้ง ได้นำเสนอ 3 พฤติกรรมที่เป็นอุปสรรคสำคัญต่อนักลงทุนส่วนใหญ่ ซึ่งหากนักลงทุนสามารถหลีกเลี่ยงพฤติกรรมเหล่านี้ได้ ก็จะมีโอกาสในการสร้างผลกำไรที่สม่ำเสมอมากยิ่งขึ้น 1. **การซื้อขายตามอารมณ์:** ตลาดหุ้นมีความผันผวนและเต็มไปด้วยข่าวสารมากมาย นักลงทุนที่ซื้อขายตามอารมณ์มักจะตัดสินใจโดยใช้อารมณ์เป็นหลัก ไม่ว่าจะเป็นความโลภเมื่อเห็นราคาหุ้นขึ้น หรือความกลัวเมื่อราคาหุ้นตก การตัดสินใจที่ไม่ได้อยู่บนพื้นฐานของข้อมูลและการวิเคราะห์อย่างรอบคอบ มักนำไปสู่การตัดสินใจที่ผิดพลาดและขาดทุนในที่สุด 2. **การไม่ยอมรับความเสี่ยง:** การลงทุนในตลาดหุ้นมีความเสี่ยง นักลงทุนที่ไม่ยอมรับความเสี่ยงมักจะพลาดโอกาสในการลงทุนในสินทรัพย์ที่ให้ผลตอบแทนสูง หรือในทางกลับกัน พวกเขาอาจจะหลีกเลี่ยงการตัดขาดทุนเมื่อการลงทุนไม่เป็นไปตามที่คาดหวัง การไม่ยอมรับความเสี่ยงและไม่บริหารความเสี่ยงอย่างเหมาะสม จะทำให้พอร์ตการลงทุนไม่เติบโตเท่าที่ควร หรืออาจจะเผชิญกับความเสียหายที่ใหญ่หลวงได้ 3. **การขาดความรู้และความเข้าใจ:** ตลาดหุ้นเป็นเรื่องที่ซับซ้อนและเปลี่ยนแปลงอยู่เสมอ นักลงทุนที่ขาดความรู้และความเข้าใจในเรื่องการลงทุนอย่างเพียงพอ มักจะลงทุนโดยไม่มีหลักการหรือไม่สามารถวิเคราะห์สถานการณ์ได้อย่างถูกต้อง การลงทุนโดยปราศจากความรู้และความเข้าใจที่ถูกต้อง ก็เหมือนกับการเดินอยู่ในความมืด ซึ่งโอกาสที่จะประสบความสำเร็จนั้นเป็นไปได้ยาก **บทสรุป** 3 พฤติกรรมที่กล่าวมาข้างต้นเป็นเพียงส่วนหนึ่งของอุปสรรคที่นักลงทุนส่วนใหญ่ต้องเผชิญ หากนักลงทุนต้องการที่จะประสบความสำเร็จในการลงทุนอย่างยั่งยืน พวกเขาจำเป็นต้องตระหนักถึงพฤติกรรมเหล่านี้และพยายามปรับปรุงตนเองอย่างต่อเนื่อง การศึกษาหาความรู้เพิ่มเติม การวางแผนการลงทุนอย่างรอบคอบ และการควบคุมอารมณ์ จะเป็นกุญแจสำคัญที่นำไปสู่การสร้างผลกำไรที่สม่ำเสมอในตลาดหุ้นได้ แน่นอนค่ะ ฟังคลิปแล้ว และสรุปบทความเป็นภาษาไทยให้คุณแล้วค่ะ **บทความ: 3 พฤติกรรมที่เป็นอุปสรรคต่อการทำกำไรสม่ำเสมอของนักลงทุนส่วนใหญ่** บทความนี้สรุปแนวคิดจากคลิปวิดีโอที่วิเคราะห์พฤติกรรมของนักลงทุนส่วนใหญ่ โดยอ้างอิงจากการสำรวจบัญชีซื้อขายหุ้นกว่า 77,000 บัญชีในช่วงปี 1990-1996 พบว่ามี 3 พฤติกรรมหลักที่เป็นอุปสรรคสำคัญต่อการสร้างผลกำไรที่สม่ำเสมอในการลงทุน **3 พฤติกรรมที่เป็นอุปสรรคต่อการทำกำไร:** 1. **ปล่อยให้ขาดทุน แต่รีบขายกำไร:** นักลงทุนส่วนใหญ่มักจะถือหุ้นที่กำลังขาดทุนต่อไปเรื่อย ๆ เพราะไม่อยากยอมรับว่าตัดสินใจผิดพลาด ในทางกลับกัน เมื่อหุ้นเริ่มมีกำไรเพียงเล็กน้อย กลับรีบขายออกไปเพราะกลัวกำไรจะหายไป พฤติกรรมนี้เป็นผลจากธรรมชาติของมนุษย์ที่เรียกว่า "Loser Aversion" หรือการหลีกเลี่ยงความเจ็บปวดจากการขาดทุนมากกว่าความสุขจากการได้กำไร 2. **ถัวเฉลี่ยขาลง มากกว่าพีระมิดขาขึ้น:** นักลงทุนจำนวนมากเลือกที่จะซื้อหุ้นที่ราคาลดลง (ถัวเฉลี่ยขาลง) โดยหวังว่าจะได้ต้นทุนที่ต่ำลงและรอให้ราคาหุ้นกลับมา แต่ในความเป็นจริง หุ้นที่อยู่ในแนวโน้มขาลงก็มีโอกาสที่จะลงต่อไปเรื่อย ๆ การถัวเฉลี่ยขาลงจึงเป็นการเพิ่มความเสี่ยง ในขณะที่การ "พีระมิดขาขึ้น" หรือการซื้อหุ้นเพิ่มเมื่อราคาปรับตัวสูงขึ้น เป็นการลงทุนในหุ้นที่กำลังมีแนวโน้มที่ดีและมีโอกาสสร้างกำไรมากกว่า 3. **รีบขายกำไรเล็กน้อย แต่ไม่ยอมขายเมื่อขาดทุนเล็กน้อย:** พฤติกรรมนี้ต่อเนื่องจากข้อแรก คือเมื่อได้กำไรเพียงเล็กน้อย นักลงทุนมักจะรีบขายเพื่อ "ล็อกกำไร" แต่เมื่อขาดทุนเล็กน้อย กลับไม่ยอมขายเพราะหวังว่าราคาจะกลับมา ทำให้สุดท้ายกลายเป็น "กำไรน้อย รีบขาย ขาดทุน เก็บไว้" ซึ่งส่งผลเสียต่อพอร์ตการลงทุนในระยะยาว **คำแนะนำเพื่อปรับปรุงพฤติกรรมการลงทุน:** * **ฝึก "Cut Loss Short, Let Profit Run":** ยอมตัดขาดทุนเมื่อหุ้นไม่เป็นไปตามแผน เพื่อจำกัดความเสียหาย และปล่อยให้หุ้นที่กำลังทำกำไรทำงานไป เพื่อเพิ่มโอกาสในการทำกำไรที่มากขึ้น * **อย่าถัวเฉลี่ยขาลงโดยไม่มีเหตุผล:** พิจารณาแนวโน้มของหุ้นและปัจจัยพื้นฐานก่อนตัดสินใจถัวเฉลี่ยขาลง หากไม่มีเหตุผลที่ชัดเจน การถัวเฉลี่ยขาลงอาจเป็นการเพิ่มความเสี่ยงโดยไม่จำเป็น * **บริหารความเสี่ยงและ Money Management อย่างเหมาะสม:** กำหนด stop loss ที่ชัดเจน และบริหารจัดการเงินทุนให้เหมาะสมกับความเสี่ยงที่รับได้ * **เรียนรู้และพัฒนาระบบเทรดของตัวเองอย่างต่อเนื่อง:** ทำความเข้าใจกลยุทธ์การเทรดของตนเอง และปรับปรุงพัฒนาอย่างสม่ำเสมอ * **มี Mindset ที่ถูกต้องสำหรับการเทรด:** เข้าใจว่าการเทรดสวนทางกับธรรมชาติของมนุษย์ ต้องฝึกฝนและสร้างนิสัยที่ถูกต้องเพื่อเอาชนะอุปสรรคทางจิตวิทยา **สรุป:** การลงทุนและการเทรดหุ้นเป็นเกมที่ "ผิดธรรมชาติ" ของมนุษย์ การเอาชนะตลาดหุ้นได้จึงต้องอาศัยการฝึกฝนและปรับเปลี่ยนพฤติกรรมให้สวนทางกับธรรมชาติเดิม ๆ โดยการตระหนักถึง 3 พฤติกรรมที่เป็นอุปสรรค และนำคำแนะนำไปปรับใช้ จะช่วยให้นักลงทุนสามารถพัฒนาไปสู่การสร้างผลกำไรที่สม่ำเสมอและยั่งยืนได้ในระยะยาว
@ d360efec:14907b5f
2025-02-17 12:20:25**3 พฤติกรรมที่เป็นอุปสรรคต่อการทำกำไรของนักลงทุนส่วนใหญ่** นักลงทุนจำนวนมากต้องการที่จะประสบความสำเร็จในตลาดหุ้นและสร้างผลกำไรที่สม่ำเสมอ แต่หลายครั้งที่พวกเขากลับพบว่าตัวเองต้องเผชิญกับอุปสรรคที่ทำให้ไม่สามารถบรรลุเป้าหมายนั้นได้ ช่อง Zyo / เซียว จับอิดนึ้ง ได้นำเสนอ 3 พฤติกรรมที่เป็นอุปสรรคสำคัญต่อนักลงทุนส่วนใหญ่ ซึ่งหากนักลงทุนสามารถหลีกเลี่ยงพฤติกรรมเหล่านี้ได้ ก็จะมีโอกาสในการสร้างผลกำไรที่สม่ำเสมอมากยิ่งขึ้น 1. **การซื้อขายตามอารมณ์:** ตลาดหุ้นมีความผันผวนและเต็มไปด้วยข่าวสารมากมาย นักลงทุนที่ซื้อขายตามอารมณ์มักจะตัดสินใจโดยใช้อารมณ์เป็นหลัก ไม่ว่าจะเป็นความโลภเมื่อเห็นราคาหุ้นขึ้น หรือความกลัวเมื่อราคาหุ้นตก การตัดสินใจที่ไม่ได้อยู่บนพื้นฐานของข้อมูลและการวิเคราะห์อย่างรอบคอบ มักนำไปสู่การตัดสินใจที่ผิดพลาดและขาดทุนในที่สุด 2. **การไม่ยอมรับความเสี่ยง:** การลงทุนในตลาดหุ้นมีความเสี่ยง นักลงทุนที่ไม่ยอมรับความเสี่ยงมักจะพลาดโอกาสในการลงทุนในสินทรัพย์ที่ให้ผลตอบแทนสูง หรือในทางกลับกัน พวกเขาอาจจะหลีกเลี่ยงการตัดขาดทุนเมื่อการลงทุนไม่เป็นไปตามที่คาดหวัง การไม่ยอมรับความเสี่ยงและไม่บริหารความเสี่ยงอย่างเหมาะสม จะทำให้พอร์ตการลงทุนไม่เติบโตเท่าที่ควร หรืออาจจะเผชิญกับความเสียหายที่ใหญ่หลวงได้ 3. **การขาดความรู้และความเข้าใจ:** ตลาดหุ้นเป็นเรื่องที่ซับซ้อนและเปลี่ยนแปลงอยู่เสมอ นักลงทุนที่ขาดความรู้และความเข้าใจในเรื่องการลงทุนอย่างเพียงพอ มักจะลงทุนโดยไม่มีหลักการหรือไม่สามารถวิเคราะห์สถานการณ์ได้อย่างถูกต้อง การลงทุนโดยปราศจากความรู้และความเข้าใจที่ถูกต้อง ก็เหมือนกับการเดินอยู่ในความมืด ซึ่งโอกาสที่จะประสบความสำเร็จนั้นเป็นไปได้ยาก **บทสรุป** 3 พฤติกรรมที่กล่าวมาข้างต้นเป็นเพียงส่วนหนึ่งของอุปสรรคที่นักลงทุนส่วนใหญ่ต้องเผชิญ หากนักลงทุนต้องการที่จะประสบความสำเร็จในการลงทุนอย่างยั่งยืน พวกเขาจำเป็นต้องตระหนักถึงพฤติกรรมเหล่านี้และพยายามปรับปรุงตนเองอย่างต่อเนื่อง การศึกษาหาความรู้เพิ่มเติม การวางแผนการลงทุนอย่างรอบคอบ และการควบคุมอารมณ์ จะเป็นกุญแจสำคัญที่นำไปสู่การสร้างผลกำไรที่สม่ำเสมอในตลาดหุ้นได้ แน่นอนค่ะ ฟังคลิปแล้ว และสรุปบทความเป็นภาษาไทยให้คุณแล้วค่ะ **บทความ: 3 พฤติกรรมที่เป็นอุปสรรคต่อการทำกำไรสม่ำเสมอของนักลงทุนส่วนใหญ่** บทความนี้สรุปแนวคิดจากคลิปวิดีโอที่วิเคราะห์พฤติกรรมของนักลงทุนส่วนใหญ่ โดยอ้างอิงจากการสำรวจบัญชีซื้อขายหุ้นกว่า 77,000 บัญชีในช่วงปี 1990-1996 พบว่ามี 3 พฤติกรรมหลักที่เป็นอุปสรรคสำคัญต่อการสร้างผลกำไรที่สม่ำเสมอในการลงทุน **3 พฤติกรรมที่เป็นอุปสรรคต่อการทำกำไร:** 1. **ปล่อยให้ขาดทุน แต่รีบขายกำไร:** นักลงทุนส่วนใหญ่มักจะถือหุ้นที่กำลังขาดทุนต่อไปเรื่อย ๆ เพราะไม่อยากยอมรับว่าตัดสินใจผิดพลาด ในทางกลับกัน เมื่อหุ้นเริ่มมีกำไรเพียงเล็กน้อย กลับรีบขายออกไปเพราะกลัวกำไรจะหายไป พฤติกรรมนี้เป็นผลจากธรรมชาติของมนุษย์ที่เรียกว่า "Loser Aversion" หรือการหลีกเลี่ยงความเจ็บปวดจากการขาดทุนมากกว่าความสุขจากการได้กำไร 2. **ถัวเฉลี่ยขาลง มากกว่าพีระมิดขาขึ้น:** นักลงทุนจำนวนมากเลือกที่จะซื้อหุ้นที่ราคาลดลง (ถัวเฉลี่ยขาลง) โดยหวังว่าจะได้ต้นทุนที่ต่ำลงและรอให้ราคาหุ้นกลับมา แต่ในความเป็นจริง หุ้นที่อยู่ในแนวโน้มขาลงก็มีโอกาสที่จะลงต่อไปเรื่อย ๆ การถัวเฉลี่ยขาลงจึงเป็นการเพิ่มความเสี่ยง ในขณะที่การ "พีระมิดขาขึ้น" หรือการซื้อหุ้นเพิ่มเมื่อราคาปรับตัวสูงขึ้น เป็นการลงทุนในหุ้นที่กำลังมีแนวโน้มที่ดีและมีโอกาสสร้างกำไรมากกว่า 3. **รีบขายกำไรเล็กน้อย แต่ไม่ยอมขายเมื่อขาดทุนเล็กน้อย:** พฤติกรรมนี้ต่อเนื่องจากข้อแรก คือเมื่อได้กำไรเพียงเล็กน้อย นักลงทุนมักจะรีบขายเพื่อ "ล็อกกำไร" แต่เมื่อขาดทุนเล็กน้อย กลับไม่ยอมขายเพราะหวังว่าราคาจะกลับมา ทำให้สุดท้ายกลายเป็น "กำไรน้อย รีบขาย ขาดทุน เก็บไว้" ซึ่งส่งผลเสียต่อพอร์ตการลงทุนในระยะยาว **คำแนะนำเพื่อปรับปรุงพฤติกรรมการลงทุน:** * **ฝึก "Cut Loss Short, Let Profit Run":** ยอมตัดขาดทุนเมื่อหุ้นไม่เป็นไปตามแผน เพื่อจำกัดความเสียหาย และปล่อยให้หุ้นที่กำลังทำกำไรทำงานไป เพื่อเพิ่มโอกาสในการทำกำไรที่มากขึ้น * **อย่าถัวเฉลี่ยขาลงโดยไม่มีเหตุผล:** พิจารณาแนวโน้มของหุ้นและปัจจัยพื้นฐานก่อนตัดสินใจถัวเฉลี่ยขาลง หากไม่มีเหตุผลที่ชัดเจน การถัวเฉลี่ยขาลงอาจเป็นการเพิ่มความเสี่ยงโดยไม่จำเป็น * **บริหารความเสี่ยงและ Money Management อย่างเหมาะสม:** กำหนด stop loss ที่ชัดเจน และบริหารจัดการเงินทุนให้เหมาะสมกับความเสี่ยงที่รับได้ * **เรียนรู้และพัฒนาระบบเทรดของตัวเองอย่างต่อเนื่อง:** ทำความเข้าใจกลยุทธ์การเทรดของตนเอง และปรับปรุงพัฒนาอย่างสม่ำเสมอ * **มี Mindset ที่ถูกต้องสำหรับการเทรด:** เข้าใจว่าการเทรดสวนทางกับธรรมชาติของมนุษย์ ต้องฝึกฝนและสร้างนิสัยที่ถูกต้องเพื่อเอาชนะอุปสรรคทางจิตวิทยา **สรุป:** การลงทุนและการเทรดหุ้นเป็นเกมที่ "ผิดธรรมชาติ" ของมนุษย์ การเอาชนะตลาดหุ้นได้จึงต้องอาศัยการฝึกฝนและปรับเปลี่ยนพฤติกรรมให้สวนทางกับธรรมชาติเดิม ๆ โดยการตระหนักถึง 3 พฤติกรรมที่เป็นอุปสรรค และนำคำแนะนำไปปรับใช้ จะช่วยให้นักลงทุนสามารถพัฒนาไปสู่การสร้างผลกำไรที่สม่ำเสมอและยั่งยืนได้ในระยะยาว @ 7546e8e4:154e8264
2025-02-17 10:48:44Ever feel like your crypto portfolio is stuck in orbit? What if you could turn those fractional holdings into meaningful growth? The secret lies in smart management and a dashboard that makes it effortless. Key Points The Power of Small Balances: Explain how even dust (tiny crypto amounts) can compound with strategic tracking and reinvestment over time. Unified Dashboard Magic: Highlight how phesky.com aggregates BTC, ETH, LTC, TRX, and more into one sleek interface, eliminating the chaos of juggling multiple wallets. Visualize Your Growth: Emphasize the dashboard’s design charts, trends, and projections that turn abstract numbers into a clear path to "moon-worthy gains. Call to Action: Stop letting zeros collect cosmic dust. Launch your portfolio to new heights at phesky.com
@ 7546e8e4:154e8264
2025-02-17 10:48:44Ever feel like your crypto portfolio is stuck in orbit? What if you could turn those fractional holdings into meaningful growth? The secret lies in smart management and a dashboard that makes it effortless. Key Points The Power of Small Balances: Explain how even dust (tiny crypto amounts) can compound with strategic tracking and reinvestment over time. Unified Dashboard Magic: Highlight how phesky.com aggregates BTC, ETH, LTC, TRX, and more into one sleek interface, eliminating the chaos of juggling multiple wallets. Visualize Your Growth: Emphasize the dashboard’s design charts, trends, and projections that turn abstract numbers into a clear path to "moon-worthy gains. Call to Action: Stop letting zeros collect cosmic dust. Launch your portfolio to new heights at phesky.com @ 849a5a61:b57d2870
2025-02-17 10:11:18 > Hey everyone! For the past few months we’ve been building an open-source, affordable and privacy-friendly affiliate and referral program creator for Bitcoin businesses and Nostr publishers called BitFlio. We built [BitFlio](https://bitflio.com/) because, as bitcoiners and nostriches, we couldn’t find an affiliate marketing tool for our products that would accept bitcoin as payment method, keep us anonymnous, and most important allow us to pay and be paid based on the value we provide. Since we didn’t know if affiliate marketing would work for us as a sales channel, we really wanted to find a tool where, instead of a fixed monthly fee, we could instead pay a % in sats per successful referral to test the waters. Referral marketing is such a powerful marketing channel as it enable the Value For Value (V4V) model to expand and grow the Bitcoin Circular Economy. For example, **referral leads for businesses have a 70% higher conversion rate than leads from any other sales channel**, and **when referred by other customers, that customer typically has a 37% higher retention rate**. The setup process for BitFlio is nice and easy. You simply signup with nostr or email, connect your Bitcoin wallet, create your first campaign, add the tracking script to your website and then fire the `BitFlio.convert('yourcustomer@email.com')` function from your thank you page, so we can validate the leads Publishers will bring to you. Once you’ve done those steps, you can either invite publishers manually, or send them your unique BitFlio invite signup page URL. For Publishers is even easier. If you are a content creator looking to monetize bitcoinize your contents, join our network and select from bitcoin brands those you feel comfortable sharing. Lastly, get paid in sats depending on how many sales you can drive to each vendor. It’s quite hard to list in sentences some of the cool features that make up BitFlio, so here’s a list: * Pricing from $0/month * Automatic NWC sync * Works for both subscriptions and one-time charges * Embed script is lightweight and only ~13kb * Privacy-friendly & Anonymous * No GDPR needed, as we operate in the Private. * Manage multiple affiliate programs for different products from one single dashboard * Open-source software Since we’re in public beta, getting feedback right now is our top priority. We’d appreciate it so much if you sign up for our Beta whitelist via [beta.BitFlio.com](https://beta.BitFlio.com) and let us know how you get on / your initial thoughts 😄 Landing: https://BitFlio.com `sᴏᴏɴ!` Beta whitelist: https://beta.BitFlio.com Follow us on Nostr: https://njump.me/npub1sjd95c0kcxn69x3u8azunrm2kdj97lc6cu79csz7rz74hdta9pcqpxgrdx Support the open source project on @geyserfund https://geyser.fund/project/bitflio/ - - - Mirror posts: - https://bitflio.com/blob/affordable-referral-marketing-software-for-nostr-publishers-and-bitcoin-vendors/ - https://geyser.fund/project/bitflio/posts/view/4138 - naddr1qvzqqqr4gupzppy6tfsldsd852drc069ex8k4vmytal343eut3q9ux9atw6h62rsqqxnzden8ymnwdf5xgurzdphm3ncla originally posted at https://stacker.news/items/888167
@ 849a5a61:b57d2870
2025-02-17 10:11:18 > Hey everyone! For the past few months we’ve been building an open-source, affordable and privacy-friendly affiliate and referral program creator for Bitcoin businesses and Nostr publishers called BitFlio. We built [BitFlio](https://bitflio.com/) because, as bitcoiners and nostriches, we couldn’t find an affiliate marketing tool for our products that would accept bitcoin as payment method, keep us anonymnous, and most important allow us to pay and be paid based on the value we provide. Since we didn’t know if affiliate marketing would work for us as a sales channel, we really wanted to find a tool where, instead of a fixed monthly fee, we could instead pay a % in sats per successful referral to test the waters. Referral marketing is such a powerful marketing channel as it enable the Value For Value (V4V) model to expand and grow the Bitcoin Circular Economy. For example, **referral leads for businesses have a 70% higher conversion rate than leads from any other sales channel**, and **when referred by other customers, that customer typically has a 37% higher retention rate**. The setup process for BitFlio is nice and easy. You simply signup with nostr or email, connect your Bitcoin wallet, create your first campaign, add the tracking script to your website and then fire the `BitFlio.convert('yourcustomer@email.com')` function from your thank you page, so we can validate the leads Publishers will bring to you. Once you’ve done those steps, you can either invite publishers manually, or send them your unique BitFlio invite signup page URL. For Publishers is even easier. If you are a content creator looking to monetize bitcoinize your contents, join our network and select from bitcoin brands those you feel comfortable sharing. Lastly, get paid in sats depending on how many sales you can drive to each vendor. It’s quite hard to list in sentences some of the cool features that make up BitFlio, so here’s a list: * Pricing from $0/month * Automatic NWC sync * Works for both subscriptions and one-time charges * Embed script is lightweight and only ~13kb * Privacy-friendly & Anonymous * No GDPR needed, as we operate in the Private. * Manage multiple affiliate programs for different products from one single dashboard * Open-source software Since we’re in public beta, getting feedback right now is our top priority. We’d appreciate it so much if you sign up for our Beta whitelist via [beta.BitFlio.com](https://beta.BitFlio.com) and let us know how you get on / your initial thoughts 😄 Landing: https://BitFlio.com `sᴏᴏɴ!` Beta whitelist: https://beta.BitFlio.com Follow us on Nostr: https://njump.me/npub1sjd95c0kcxn69x3u8azunrm2kdj97lc6cu79csz7rz74hdta9pcqpxgrdx Support the open source project on @geyserfund https://geyser.fund/project/bitflio/ - - - Mirror posts: - https://bitflio.com/blob/affordable-referral-marketing-software-for-nostr-publishers-and-bitcoin-vendors/ - https://geyser.fund/project/bitflio/posts/view/4138 - naddr1qvzqqqr4gupzppy6tfsldsd852drc069ex8k4vmytal343eut3q9ux9atw6h62rsqqxnzden8ymnwdf5xgurzdphm3ncla originally posted at https://stacker.news/items/888167 @ 849a5a61:b57d2870
2025-02-17 09:47:19We built [BitFlio](https://bitflio.com/) because, as bitcoiners and nostriches, we couldn’t find an affiliate marketing tool for our products that would accept bitcoin as payment method, keep us anonymnous, and most important allow us to pay and be paid based on the value we provide. Since we didn’t know if affiliate marketing would work for us as a sales channel, we really wanted to find a tool where, instead of a fixed monthly fee, we could instead pay a % in sats per successful referral to test the waters. Referral marketing is such a powerful marketing channel as it enable the Value For Value (V4V) model to expand and grow the Bitcoin Circular Economy. For example, **referral leads for businesses have a 70% higher conversion rate than leads from any other sales channel**, and **when referred by other customers, that customer typically has a 37% higher retention rate**. The setup process for BitFlio is nice and easy. You simply signup with nostr or email, connect your Bitcoin wallet, create your first campaign, add the tracking script to your website and then fire the `BitFlio.convert('yourcustomer@email.com')` function from your thank you page, so we can validate the leads Publishers will bring to you. Once you’ve done those steps, you can either invite publishers manually, or send them your unique BitFlio invite signup page URL. For Publishers is even easier. If you are a content creator looking to monetize bitcoinize your contents, join our network and select from bitcoin brands those you feel comfortable sharing. Lastly, get paid in sats depending on how many sales you can drive to each vendor. It’s quite hard to list in sentences some of the cool features that make up BitFlio, so here’s a list: * Pricing from $0/month * Automatic NWC sync * Works for both subscriptions and one-time charges * Embed script is lightweight and only ~13kb * Privacy-friendly & Anonymous * No GDPR needed, as we operate in the Private. * Manage multiple affiliate programs for different products from one single dashboard * Open-source software Since we’re in public beta, getting feedback right now is our top priority. We’d appreciate it so much if you sign up for our Beta whitelist via [beta.BitFlio.com](//beta.BitFlio.com) and let us know how you get on / your initial thoughts 😄
@ 849a5a61:b57d2870
2025-02-17 09:47:19We built [BitFlio](https://bitflio.com/) because, as bitcoiners and nostriches, we couldn’t find an affiliate marketing tool for our products that would accept bitcoin as payment method, keep us anonymnous, and most important allow us to pay and be paid based on the value we provide. Since we didn’t know if affiliate marketing would work for us as a sales channel, we really wanted to find a tool where, instead of a fixed monthly fee, we could instead pay a % in sats per successful referral to test the waters. Referral marketing is such a powerful marketing channel as it enable the Value For Value (V4V) model to expand and grow the Bitcoin Circular Economy. For example, **referral leads for businesses have a 70% higher conversion rate than leads from any other sales channel**, and **when referred by other customers, that customer typically has a 37% higher retention rate**. The setup process for BitFlio is nice and easy. You simply signup with nostr or email, connect your Bitcoin wallet, create your first campaign, add the tracking script to your website and then fire the `BitFlio.convert('yourcustomer@email.com')` function from your thank you page, so we can validate the leads Publishers will bring to you. Once you’ve done those steps, you can either invite publishers manually, or send them your unique BitFlio invite signup page URL. For Publishers is even easier. If you are a content creator looking to monetize bitcoinize your contents, join our network and select from bitcoin brands those you feel comfortable sharing. Lastly, get paid in sats depending on how many sales you can drive to each vendor. It’s quite hard to list in sentences some of the cool features that make up BitFlio, so here’s a list: * Pricing from $0/month * Automatic NWC sync * Works for both subscriptions and one-time charges * Embed script is lightweight and only ~13kb * Privacy-friendly & Anonymous * No GDPR needed, as we operate in the Private. * Manage multiple affiliate programs for different products from one single dashboard * Open-source software Since we’re in public beta, getting feedback right now is our top priority. We’d appreciate it so much if you sign up for our Beta whitelist via [beta.BitFlio.com](//beta.BitFlio.com) and let us know how you get on / your initial thoughts 😄 @ d360efec:14907b5f
2025-02-17 08:49:15**ภาพรวม BTCUSDT (OKX):** Bitcoin ยังคงอยู่ในแนวโน้มขาขึ้นระยะยาว แต่ระยะสั้นมีความผันผวนและมีการปรับฐานลงมา การวิเคราะห์ครั้งนี้จะเน้นการระบุพื้นที่ที่ Smart Money (หรือ "เจ้ามือ") อาจจะเข้าซื้อหรือขาย เพื่อให้เราสามารถวางแผนการเทรดได้อย่างมีประสิทธิภาพ **วิเคราะห์ทีละ Timeframe:** **(1) TF Day (รายวัน):**  * **แนวโน้ม:** ขาขึ้น (Uptrend) * **SMC:** * Higher Highs (HH) และ Higher Lows (HL) ต่อเนื่อง * Break of Structure (BOS) ด้านบน * ยังไม่มีสัญญาณการกลับตัวเป็นขาลง * **ICT:** * ยังไม่เห็น Order Block หรือ FVG ที่ชัดเจนใน TF Day *ณ ราคาปัจจุบัน* * **EMA:** * ราคาอยู่เหนือ EMA 50 (สีเหลือง) และ EMA 200 (สีขาว) (Golden Cross) * **Money Flow (LuxAlgo):** * สีเขียวเป็นส่วนใหญ่ แสดงถึงแรงซื้อ * **Volume Profile:** * Volume หนาแน่นที่บริเวณต่ำกว่าราคาปัจจุบัน * **แท่งเทียน:** * แท่งเทียนล่าสุดเป็นสีแดง แสดงถึงแรงขาย แต่ไส้เทียนยาว แสดงว่ามีแรงซื้อกลับ * **แนวรับ:** EMA 50, EMA 200, บริเวณ Volume Profile หนาแน่น * **แนวต้าน:** High เดิม * **สรุป:** แนวโน้มหลักยังเป็นขาขึ้น Buy on Dip **(2) TF4H (4 ชั่วโมง):**  * **แนวโน้ม:** ขาขึ้น (พักตัว) * **SMC:** * HH และ HL * BOS ด้านบน * ราคาหลุด EMA 50 * **ICT:** * **Fair Value Gap (FVG):** สังเกตเห็น FVG เล็กๆ ที่เกิดขึ้นก่อนหน้านี้ (บริเวณที่ราคาเคยพุ่งขึ้นอย่างรวดเร็ว) อาจเป็นเป้าหมายของการ Pullback * **Order Block:** ราคาปัจจุบันกำลังทดสอบ Order Block (บริเวณแท่งเทียนสีแดงแท่งใหญ่ก่อนที่จะขึ้น) *เป็นจุดที่น่าสนใจมาก* * **EMA:** * ราคาหลุด EMA 50 * EMA 200 เป็นแนวรับถัดไป * **Money Flow (LuxAlgo):** * เขียวและแดงผสมกัน, แดงเริ่มมากขึ้น * **Volume Profile:** * Volume profile ค่อนข้างสูง * **แนวรับ:** EMA 200, Order Block, บริเวณ Volume Profile * **แนวต้าน:** EMA 50, High เดิม * **สรุป:** แนวโน้มขาขึ้นพักตัว, ทดสอบ Order Block, Money Flow เริ่มเป็นลบ **(3) TF15 (15 นาที):**  * **แนวโน้ม:** ขาลง (Downtrend) ระยะสั้น *แต่เริ่มมีสัญญาณการฟื้นตัว* * **SMC:** * Lower Highs (LH) และ Lower Lows (LL) *แต่เริ่มเห็น Higher Low* * BOS ด้านล่าง * *เริ่มมีสัญญาณการ Breakout EMA 50/200* * **ICT:** * ราคาเพิ่ง Breakout Order Block ขาลง (แต่ต้องรอดูว่าจะยืนได้หรือไม่) * **EMA:** * *EMA 50/200 เพิ่งจะตัดกันแบบ Golden Cross* * **Money Flow (LuxAlgo):** * *เริ่มมีแท่งสีเขียวปรากฏขึ้น* * **Volume Profile:** * **แนวรับ:** บริเวณ Low ล่าสุด * **แนวต้าน:** EMA50/200 * **สรุป:** *เริ่มมีสัญญาณการฟื้นตัว* แต่ยังต้องระวัง **สรุปภาพรวมและกลยุทธ์ (BTCUSDT):** * **แนวโน้มหลัก (Day):** ขาขึ้น * **แนวโน้มรอง (4H):** ขาขึ้น (พักตัว), ทดสอบ Order Block * **แนวโน้มระยะสั้น (15m):** *เริ่มมีสัญญาณการฟื้นตัว* * **Money Flow:** Day เป็นบวก, 4H เริ่มเป็นลบ, 15m เริ่มเป็นบวก * **กลยุทธ์:** 1. **Wait & See:** รอการยืนยันการ Breakout EMA 50/200 ใน TF15m 2. **Buy (เสี่ยง):** *เฉพาะเมื่อราคา Breakout EMA 50/200 ใน TF 15 ได้อย่างแข็งแกร่ง* 3. **Short (เสี่ยง):** ถ้า Order Block ใน TF4H รับไม่อยู่ และ TF15 ยังคงเป็นขาลง **คำแนะนำ:** * **Order Block:** ให้ความสำคัญกับ Order Block ใน TF4H * **FVG:** สังเกต FVG ใน TF4H * **ความขัดแย้งของ Timeframes:** เริ่มลดลง (15m เริ่มมีสัญญาณบวก) * **จับตาดู TF15 อย่างใกล้ชิด** **Disclaimer:** การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ
@ d360efec:14907b5f
2025-02-17 08:49:15**ภาพรวม BTCUSDT (OKX):** Bitcoin ยังคงอยู่ในแนวโน้มขาขึ้นระยะยาว แต่ระยะสั้นมีความผันผวนและมีการปรับฐานลงมา การวิเคราะห์ครั้งนี้จะเน้นการระบุพื้นที่ที่ Smart Money (หรือ "เจ้ามือ") อาจจะเข้าซื้อหรือขาย เพื่อให้เราสามารถวางแผนการเทรดได้อย่างมีประสิทธิภาพ **วิเคราะห์ทีละ Timeframe:** **(1) TF Day (รายวัน):**  * **แนวโน้ม:** ขาขึ้น (Uptrend) * **SMC:** * Higher Highs (HH) และ Higher Lows (HL) ต่อเนื่อง * Break of Structure (BOS) ด้านบน * ยังไม่มีสัญญาณการกลับตัวเป็นขาลง * **ICT:** * ยังไม่เห็น Order Block หรือ FVG ที่ชัดเจนใน TF Day *ณ ราคาปัจจุบัน* * **EMA:** * ราคาอยู่เหนือ EMA 50 (สีเหลือง) และ EMA 200 (สีขาว) (Golden Cross) * **Money Flow (LuxAlgo):** * สีเขียวเป็นส่วนใหญ่ แสดงถึงแรงซื้อ * **Volume Profile:** * Volume หนาแน่นที่บริเวณต่ำกว่าราคาปัจจุบัน * **แท่งเทียน:** * แท่งเทียนล่าสุดเป็นสีแดง แสดงถึงแรงขาย แต่ไส้เทียนยาว แสดงว่ามีแรงซื้อกลับ * **แนวรับ:** EMA 50, EMA 200, บริเวณ Volume Profile หนาแน่น * **แนวต้าน:** High เดิม * **สรุป:** แนวโน้มหลักยังเป็นขาขึ้น Buy on Dip **(2) TF4H (4 ชั่วโมง):**  * **แนวโน้ม:** ขาขึ้น (พักตัว) * **SMC:** * HH และ HL * BOS ด้านบน * ราคาหลุด EMA 50 * **ICT:** * **Fair Value Gap (FVG):** สังเกตเห็น FVG เล็กๆ ที่เกิดขึ้นก่อนหน้านี้ (บริเวณที่ราคาเคยพุ่งขึ้นอย่างรวดเร็ว) อาจเป็นเป้าหมายของการ Pullback * **Order Block:** ราคาปัจจุบันกำลังทดสอบ Order Block (บริเวณแท่งเทียนสีแดงแท่งใหญ่ก่อนที่จะขึ้น) *เป็นจุดที่น่าสนใจมาก* * **EMA:** * ราคาหลุด EMA 50 * EMA 200 เป็นแนวรับถัดไป * **Money Flow (LuxAlgo):** * เขียวและแดงผสมกัน, แดงเริ่มมากขึ้น * **Volume Profile:** * Volume profile ค่อนข้างสูง * **แนวรับ:** EMA 200, Order Block, บริเวณ Volume Profile * **แนวต้าน:** EMA 50, High เดิม * **สรุป:** แนวโน้มขาขึ้นพักตัว, ทดสอบ Order Block, Money Flow เริ่มเป็นลบ **(3) TF15 (15 นาที):**  * **แนวโน้ม:** ขาลง (Downtrend) ระยะสั้น *แต่เริ่มมีสัญญาณการฟื้นตัว* * **SMC:** * Lower Highs (LH) และ Lower Lows (LL) *แต่เริ่มเห็น Higher Low* * BOS ด้านล่าง * *เริ่มมีสัญญาณการ Breakout EMA 50/200* * **ICT:** * ราคาเพิ่ง Breakout Order Block ขาลง (แต่ต้องรอดูว่าจะยืนได้หรือไม่) * **EMA:** * *EMA 50/200 เพิ่งจะตัดกันแบบ Golden Cross* * **Money Flow (LuxAlgo):** * *เริ่มมีแท่งสีเขียวปรากฏขึ้น* * **Volume Profile:** * **แนวรับ:** บริเวณ Low ล่าสุด * **แนวต้าน:** EMA50/200 * **สรุป:** *เริ่มมีสัญญาณการฟื้นตัว* แต่ยังต้องระวัง **สรุปภาพรวมและกลยุทธ์ (BTCUSDT):** * **แนวโน้มหลัก (Day):** ขาขึ้น * **แนวโน้มรอง (4H):** ขาขึ้น (พักตัว), ทดสอบ Order Block * **แนวโน้มระยะสั้น (15m):** *เริ่มมีสัญญาณการฟื้นตัว* * **Money Flow:** Day เป็นบวก, 4H เริ่มเป็นลบ, 15m เริ่มเป็นบวก * **กลยุทธ์:** 1. **Wait & See:** รอการยืนยันการ Breakout EMA 50/200 ใน TF15m 2. **Buy (เสี่ยง):** *เฉพาะเมื่อราคา Breakout EMA 50/200 ใน TF 15 ได้อย่างแข็งแกร่ง* 3. **Short (เสี่ยง):** ถ้า Order Block ใน TF4H รับไม่อยู่ และ TF15 ยังคงเป็นขาลง **คำแนะนำ:** * **Order Block:** ให้ความสำคัญกับ Order Block ใน TF4H * **FVG:** สังเกต FVG ใน TF4H * **ความขัดแย้งของ Timeframes:** เริ่มลดลง (15m เริ่มมีสัญญาณบวก) * **จับตาดู TF15 อย่างใกล้ชิด** **Disclaimer:** การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ @ 0463223a:3b14d673
2025-02-17 07:48:11Here we go, it’s Mooooonnnndddddaaaaaaaayyyyyyy! It’s safe to say I enjoy Monday. Much as I appreciate the downtime over the weekend (if I’m not working) I appreciate the routine of Mondays. Firstly I have my stream to look forward to and whilst I’m not at my best first thing on a Monday, having a little structure goes a long way. Even the fear of looking at the emails I’ve been ignoring from the previous week is possible. So maybe I’m starting to get an angle of why I’m writing this. It’s a memoir of being a mental I think. I’ve mentioned a number of times this has been a problem most my life but I write this as I’ve halved my Venlafaxine does by ½ once again. This means I’m now on 1/12th of my original dose and I’m maybe a month away from being completely free of RRSIs for the first time in, I guess at least 10 years. To be honest I cant remember when I was first prescribed them. It’s been quite a journey... 3 things have been pivotal. 1; finding my now wife. She’s brilliant and I love her dearly, I think most people know deep down how crushing loneliness can be. I’m very grateful to her for putting up with my bullshit, supporting me and just being there. Gold star for her! 2; would be music, it’s a funny one to put in, it’s also been part of the problem, especially in my wilder days. There’s something quite seductive about the sex, drugs and Rock n Roll meme, although musically it was more Hip Hop, Reggae, Bleeps and Jazz, also I didn’t sleep around much at all but I certainly don’t think I would’ve messed with crack, heroin and all the other drugs otherwise. It’s worth noting 2 of my friends from that era, who didn’t have music in their lives are dead. I’m very lucky. There’s over 100 years of recorded music to enjoy plus I’m almost happy with some of my own bits at last! 3; I have some security, I no longer pay rent or have a landlord. This is also due to number 1 but also because I found some funny internet money. I’m still to write about my process with that, other than to say it was direct response to the banks. That’s a story in it’s own right, it’s pretty dark and hmm… not sure. Plus I don’t think there’s any need to go there right now. I have the world’s most expensive shed and I know I can survive a few months should the worst happen. That’s a LOT. Whilst a little risk taking is healthy, life shouldn’t free stress free, uncertainty about having a roof over your head when you can’t afford it can really take it’s toll. A degree of security is most welcome at this time in life. A lot of people aren’t so lucky, Tom, Ricky, Dave, Slam, Joel. I’m name checking you specifically. You’re in my thoughts often, especially as I play music every morning… and Slam, if I ever see you again, I want my records back!!! Haha, thieving little cunt but it’s still not hate here. Your life was fucked up before you even had a chance. I hope you’ve found peace with yourself. At least you’re alive! (I think, he might be dead too, who knows…) So yeah, it’s Monday and it’s gonna be a good day right? I mean it might not but I will at least give it the best start possible and work from there. It takes a degree of effort to retrain the brain. Actually maybe there’s a 4th thing to mention. No Facebacon, Instagran, X or LinkedIn. None of that bullshit where you’re forced into some fake world generated in order to increase shareholder value. These platforms are akin to being a lab rat. I picture Zuckerberg like Ming The Merciless at the start of Flash Gordon sending hot hail etc. That guy made a decision to mess with peoples’ psyche to drive profits. That’s fucking evil man. Jeez, what a cunt! It’s Monday, I’m wishing you strength in whatever you have ahead of you today. I’m lucky to be where I am right now and if you’re reading this and your world is plagued by darkness, it can get better. Remember that. Hold onto that as best you can. DON’T FUCKING KILL YOURSELF. That’s the single worst thing you can do. The pain you’ll leave behind isn’t worth it. I hope some cosmic vibrations happen in your favour. There’s no easy solution. I can’t tell you the answer but I wish you well. Good luck out there!
@ 0463223a:3b14d673
2025-02-17 07:48:11Here we go, it’s Mooooonnnndddddaaaaaaaayyyyyyy! It’s safe to say I enjoy Monday. Much as I appreciate the downtime over the weekend (if I’m not working) I appreciate the routine of Mondays. Firstly I have my stream to look forward to and whilst I’m not at my best first thing on a Monday, having a little structure goes a long way. Even the fear of looking at the emails I’ve been ignoring from the previous week is possible. So maybe I’m starting to get an angle of why I’m writing this. It’s a memoir of being a mental I think. I’ve mentioned a number of times this has been a problem most my life but I write this as I’ve halved my Venlafaxine does by ½ once again. This means I’m now on 1/12th of my original dose and I’m maybe a month away from being completely free of RRSIs for the first time in, I guess at least 10 years. To be honest I cant remember when I was first prescribed them. It’s been quite a journey... 3 things have been pivotal. 1; finding my now wife. She’s brilliant and I love her dearly, I think most people know deep down how crushing loneliness can be. I’m very grateful to her for putting up with my bullshit, supporting me and just being there. Gold star for her! 2; would be music, it’s a funny one to put in, it’s also been part of the problem, especially in my wilder days. There’s something quite seductive about the sex, drugs and Rock n Roll meme, although musically it was more Hip Hop, Reggae, Bleeps and Jazz, also I didn’t sleep around much at all but I certainly don’t think I would’ve messed with crack, heroin and all the other drugs otherwise. It’s worth noting 2 of my friends from that era, who didn’t have music in their lives are dead. I’m very lucky. There’s over 100 years of recorded music to enjoy plus I’m almost happy with some of my own bits at last! 3; I have some security, I no longer pay rent or have a landlord. This is also due to number 1 but also because I found some funny internet money. I’m still to write about my process with that, other than to say it was direct response to the banks. That’s a story in it’s own right, it’s pretty dark and hmm… not sure. Plus I don’t think there’s any need to go there right now. I have the world’s most expensive shed and I know I can survive a few months should the worst happen. That’s a LOT. Whilst a little risk taking is healthy, life shouldn’t free stress free, uncertainty about having a roof over your head when you can’t afford it can really take it’s toll. A degree of security is most welcome at this time in life. A lot of people aren’t so lucky, Tom, Ricky, Dave, Slam, Joel. I’m name checking you specifically. You’re in my thoughts often, especially as I play music every morning… and Slam, if I ever see you again, I want my records back!!! Haha, thieving little cunt but it’s still not hate here. Your life was fucked up before you even had a chance. I hope you’ve found peace with yourself. At least you’re alive! (I think, he might be dead too, who knows…) So yeah, it’s Monday and it’s gonna be a good day right? I mean it might not but I will at least give it the best start possible and work from there. It takes a degree of effort to retrain the brain. Actually maybe there’s a 4th thing to mention. No Facebacon, Instagran, X or LinkedIn. None of that bullshit where you’re forced into some fake world generated in order to increase shareholder value. These platforms are akin to being a lab rat. I picture Zuckerberg like Ming The Merciless at the start of Flash Gordon sending hot hail etc. That guy made a decision to mess with peoples’ psyche to drive profits. That’s fucking evil man. Jeez, what a cunt! It’s Monday, I’m wishing you strength in whatever you have ahead of you today. I’m lucky to be where I am right now and if you’re reading this and your world is plagued by darkness, it can get better. Remember that. Hold onto that as best you can. DON’T FUCKING KILL YOURSELF. That’s the single worst thing you can do. The pain you’ll leave behind isn’t worth it. I hope some cosmic vibrations happen in your favour. There’s no easy solution. I can’t tell you the answer but I wish you well. Good luck out there! @ 21ac2956:09d1e2df
2025-01-22 15:27:00## [kakoi](https://github.com/betonetojp/kakoi) の仕様についてのメモ ### キーボード操作 * 左手での操作に最適化 | キー | 動作 | |:-|:-| | ESC | 設定画面 | | F1 / F12 | ポストバーの表示と非表示 | | F2 | 時間の表示と非表示 | | F3 | ユーザーアイコンの表示と非表示 | | F4 | 名前の表示と非表示 | | F5 | Geminiによるタイムラインまとめ画面を表示 | | F9 / Z | コンテンツの折り返し表示の切り替え (余白ダブルクリックでも動作) | | F10 | ユーザーリストとキーワード通知の設定画面 (余白右クリックでも動作) | | F11 | メイン画面の表示と非表示 (ポストバー表示) | | Shift + W | イベント最上行へ移動 | | W / ↑| イベント選択上移動 | | S / ↓ | イベント選択下移動 | | Shift + S | イベント最下行へ移動 | | A / ← | Webビューを開く (イベントを右クリックでも動作) | | F / → | リアクションを送信 (イベントをダブルクリックでも動作) | | 1 ~ 0 | リアクションを選択 | | R | 返信 | | B | リポスト | | Q | 引用 | | C | Webビューを閉じる | | Ctrl + Shift + A | メイン画面をアクティブにする | ### タイムライン * kind:1, 6, 7, 16を取得して表示する * フォロイーの名前の前には * が付く ### フォローリスト(kind:3) * 参照のみで更新はしない * F10 で開くユーザーリストでユーザーを選択し petname セルをクリックすることで未フォローユーザーにもペットネームを設定可能(ローカル保存) ### プロフィール(kind:0) * F10 で開くユーザーリストでユーザーを選択し picture セルをクリックすることでユーザーのアイコン表示を変更可能(ローカル保存) ### 返信([NIP-10](https://github.com/nostr-protocol/nips/blob/master/10.md) kind:1) * kakoi のタイムラインに流れるすべてのイベント種に返信可能とする * スレッドを考慮せず、単一イベントへの単発返信とする * e タグは marker と返信先 pubkey は設定していない。 relay-url には空文字を設定 ```json ["e", "返信先 event-id", ""] ``` * p タグは 返信先 pubkey ひとつだけを指定 ### リポスト([NIP-18](https://github.com/nostr-protocol/nips/blob/master/18.md) kind:6 , 16) * kakoi のタイムラインに流れるすべてのイベント種をリポスト可能 * kind:1はkind:6。その他はkind:16でリポストする * e タグは relay-url に空文字を設定 ```json ["e", "リポスト元 event-id", ""] ``` ### 引用([NIP-18](https://github.com/nostr-protocol/nips/blob/master/18.md) kind:1) * q タグは relay-url に空文字を設定 ```json ["q", "引用元 event-id", ""] ```
@ 21ac2956:09d1e2df
2025-01-22 15:27:00## [kakoi](https://github.com/betonetojp/kakoi) の仕様についてのメモ ### キーボード操作 * 左手での操作に最適化 | キー | 動作 | |:-|:-| | ESC | 設定画面 | | F1 / F12 | ポストバーの表示と非表示 | | F2 | 時間の表示と非表示 | | F3 | ユーザーアイコンの表示と非表示 | | F4 | 名前の表示と非表示 | | F5 | Geminiによるタイムラインまとめ画面を表示 | | F9 / Z | コンテンツの折り返し表示の切り替え (余白ダブルクリックでも動作) | | F10 | ユーザーリストとキーワード通知の設定画面 (余白右クリックでも動作) | | F11 | メイン画面の表示と非表示 (ポストバー表示) | | Shift + W | イベント最上行へ移動 | | W / ↑| イベント選択上移動 | | S / ↓ | イベント選択下移動 | | Shift + S | イベント最下行へ移動 | | A / ← | Webビューを開く (イベントを右クリックでも動作) | | F / → | リアクションを送信 (イベントをダブルクリックでも動作) | | 1 ~ 0 | リアクションを選択 | | R | 返信 | | B | リポスト | | Q | 引用 | | C | Webビューを閉じる | | Ctrl + Shift + A | メイン画面をアクティブにする | ### タイムライン * kind:1, 6, 7, 16を取得して表示する * フォロイーの名前の前には * が付く ### フォローリスト(kind:3) * 参照のみで更新はしない * F10 で開くユーザーリストでユーザーを選択し petname セルをクリックすることで未フォローユーザーにもペットネームを設定可能(ローカル保存) ### プロフィール(kind:0) * F10 で開くユーザーリストでユーザーを選択し picture セルをクリックすることでユーザーのアイコン表示を変更可能(ローカル保存) ### 返信([NIP-10](https://github.com/nostr-protocol/nips/blob/master/10.md) kind:1) * kakoi のタイムラインに流れるすべてのイベント種に返信可能とする * スレッドを考慮せず、単一イベントへの単発返信とする * e タグは marker と返信先 pubkey は設定していない。 relay-url には空文字を設定 ```json ["e", "返信先 event-id", ""] ``` * p タグは 返信先 pubkey ひとつだけを指定 ### リポスト([NIP-18](https://github.com/nostr-protocol/nips/blob/master/18.md) kind:6 , 16) * kakoi のタイムラインに流れるすべてのイベント種をリポスト可能 * kind:1はkind:6。その他はkind:16でリポストする * e タグは relay-url に空文字を設定 ```json ["e", "リポスト元 event-id", ""] ``` ### 引用([NIP-18](https://github.com/nostr-protocol/nips/blob/master/18.md) kind:1) * q タグは relay-url に空文字を設定 ```json ["q", "引用元 event-id", ""] ``` @ c4b5369a:b812dbd6
2025-02-17 06:06:48As promised in my last article: nostr:naddr1qvzqqqr4gupzp394x6dfmvn69cduj7e9l2jgvtvle7n5w5rtrunjlr6tx6up9k7kqq2k6ernff9hw3tyd3y453rdtph5uvm6942kzuw08y0 In this one we will dive into how exactly an unidirectional payments channel powered ecash mint system would be implemented, using the tech available today! So if you haven't read that article yet, give it a read! I first intended to write a longwinded article, explaining each part of the system. But then I realized that I would need some visualization to get the message across in a more digestable way. This lead me to create a slide deck, and as I started to design the slides it became more and more clear that the information is easier shown with visualizations, than written down. I will try to give a summary as best as I can in this article, but I urge you, to please go visit the slide deck too, for the best experience: ----------- ### [TAKE ME TO THE SLIDE DECK!](https://uni-chan.gandlaf.com/) ----------- ### Intro In this article we will go over how we can build unidirectional payment channels on Bitcoin. Then we will take a look into how Cashu ecash mints work, and how we can use unidirectional payment channels to change the dynamics between ecash users and the mint. Before we start, let me also give credits to nostr:npub1htnhsay5dmq3r72tukdw72pduzfdcja0yylcajuvnc2uklkhxp8qnz3qac for comming up with the idea, to nostr:npub148jz5r9xujcjpqygk69yl4jqwjqmzgrqly26plktfjy8g4t7xaysj9xhgp for providing an idea for non-expiring unidirectional channels, and nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx unconference for hosting an event where these ideas could be discussed and flourish. ### Building unidirectional payment channels If you've read the previous article, you already know what unidirectional payment channels are. There are actually a coupple different ways to implement them, but they all do have a few things in common: 1. The `sender` can only send 2. The `Receiver` can only receive 3. They are VERY simple Way simpler than the duplex channels like we are using in the lightning network today, at least. Of course, duplex channels are being deployed on LN for a reason. They are very versatile and don't have these annoying limitations that the unidirectional payment channels have. They do however have a few drawbacks: 1. Peers have liveness requirements (or they might forfeit their funds) 2. Peers must backup their state after each transaction (if they don't they might forfeit their funds) 3. It is a pretty complex system This article is not meant to discredit duplex channels. I think they are great. I just also think that in some use-cases, their requirements are too high and the system too complex. But anyway, let's see what kind of channels we can build! #### Spillman/CLTV-Channel The Spillman channel idea has been around for a long time. It's even explained in Tadge Dryjas [Presentation](https://www.youtube.com/watch?v=Hzv9WuqIzA0&t=1969s) on Payment channels and the lightning network from back in the day. I compiled a list of some of the most important propperties of them in the slide below:  Great! Now that we know their properties, let's take a look at how we can create such a channel ([Slides](https://uni-chan.gandlaf.com/#/11)):  We start out by the `sender` creating a `funding TX`. The `sender` doesn't broadcast the transaction though. If he does, he might get locked into a multisig with the `receiver` without an unilateral exit path. Instead the `sender` also creates a `refund TX` spending the outputs of the yet unsigned `funding TX`. The `refund TX` is timelocked, and can only be broadcast after 1 month. Both `sender` and `receiver` can sign this `refund TX` without any risks. Once `sender` receives the signed `refund TX`, he can broadcast the `funding TX` and open the channel. The `sender` can now update the channel state, by pre-signing update transactions and sending them over to the `receiver`. Being a one-way channel, this can be done in a single message. It is very simple. There is no need for invalidating old states, since the `sender` does not hold any signed `update TXs` it is impossible for the `sender` to broadcast an old state. The `receiver` only cares about the latest state anyways, since that is the state where he gets the most money. He can basically delete any old states. The only thing the `receiver` needs to make sure of, is broadcasting the latest `update TX` before the `refund TX's` timelock expires. Otherwise, the `sender` might take the whole channel balance back to himself. This seems to be already a pretty useful construct, due to its simplicity. But we can make it even more simple!  This setup works basically the same way as the previous one, but instead of having a refund transaction, we build the `timelock` spend path directly into the `funding TX` This allows the `sender` to have an unilateral exit right from the start, and he can broadcast the `funding TX` without communicating with the `receiver`. In the worst case, the receiver rejects the channel, and the sender can get his money back after the timelock on the output has expired. Everything else basically works in the same way as in the example above. The beauty about this channel construct is in its simplicity. The drawbacks are obvious, but they do offer some nice properties that might be useful in certain cases.  One of the major drawbacks of the `Spillman-style channels` (apart from being unidirectional) is that they expire. This expiry comes with the neat property that neither of the party has to watch the chain for channel closures, and the `sender` can operate the channel with zero additional state, apart from his private keys. But they do expire. And this can make them quite inflexible. It might work in some contexts, but not so much in others, where time needs to be more flexible. This is where `Roose-Childs triggered channels` come into play. #### Roose-Childs triggered channel (I gave it that name, named after nostr:npub148jz5r9xujcjpqygk69yl4jqwjqmzgrqly26plktfjy8g4t7xaysj9xhgp and nostr:npub1htnhsay5dmq3r72tukdw72pduzfdcja0yylcajuvnc2uklkhxp8qnz3qac . If someone knows if this idea has been around before under a different name, please let us know!) `Roose-Childs triggered channels` were an idea developed by Steven and Luke at the nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx unconference. They essentially remove the channel expiry limitation in return for introducing the need for the `sender` to create a channel backup at the time of channel creation, and for the `receiver` the need to watch the chain for trigger transactions closing the channel.  They also allow for splicing funds, which can be important for a channel without expiry, allowing the `sender` to top-up liquidity once it runs out, or for the `receiver` taking out liquidity from the channel to deploy the funds elsewhere. Now, let's see how we can build them!  The `funding TX` actually looks the same as in the first example, and similarly it gets created, but not signed by the `sender`. Then, sender and receiver both sign the `trigger TX`. The `trigger TX` is at the heart of this scheme. It allows both `sender` and `receiver` to unilaterally exit the channel by broadcasting it (more on that in a bit). Once the `trigger TX` is signed and returned to the `sender`, the sender can confidently sign and boradcast the `funding TX` and open the channel. The `trigger TX` remains off-chain though. Now, to update the channel, the `sender` can pre-sign transactions in similar fashion to the examples above, but this time, spending the outputs of the unbroadcasted `trigger TX`. This way, both parties can exit the channel at any time. If the `receiver` wants to exit, he simply boradcasts the `trigger TX` and immediately spends its outputs using the latest `update TX`. If the `sender` wants to exit he will broadcast the `trigger TX` and basically force the `receivers` hand. Either, the `receiver` will broadcast the latest `update TX`, or the `sender` will be able to claim the entire channel balance after the timelock expired.  We can also simplify the `receiver's` exit path, by the `sender` pre-signing an additional transaction `R exit TX` for each update. this way, the `receiver` only needs to broadcast one transaction instead of two.  As we've mentioned before, there are some different trade-offs for `Roose-Childs triggered channels`. We introduce some minimal state and liveness requirements, but gain more flexibility.  #### Ecash to fill in the gaps (I will assume that the reader knows how ecash mints work. If not, please go check the [slides](https://uni-chan.gandlaf.com/#/43) where I go through an explanation) Essentially, we are trying to get a lightning like experience, without all the lightning complexities and requirements. One big issue with ecash, is that it is fully custodial. If we can offset that risk by holding most of the funds in a self custodial channel, we can have a reasonable trade-off between usability and self custody.  In a system like that, we would essentially turn the banking model onto its head. Where in a traditional bank, the majority of the funds are held in the banks custody, and the user only withdraws into his custody what he needs to transact, in our model the user would hold most funds in his own custody.  If you ask me, this approach makes way more sense. Instead of a custodian, we have turned the "bank" into a service provider. Let's take a look at how it would work in a more practical sense:  The `ecash user` would open an unidirectional payment channel to the `mint`, using one of his on-chain UTXOs. This allows him then to commit incrementally funds into the mints custody, only the amounts for his transactional needs. The mint offers connectivity to the lightning network an handles state and liveness as a service provider. The `ecash user`, can remain offline at all times, and his channel funds will always be safe. The mint can only ever claim the balance in the channel via the `update TXs`. The `mint` can of course still decide to no longer redeem any ecash, at which point they would have basically stolen the `ecash user's` transactional balance. At that point, it would probably be best for the `ecash user` to close his channel, and no longer interact or trust this `mint`. Here are some of the most important points of this system summarized:  And that is basically it! I hope you enjoyed this breakdown of Unidirectional payment channel enabled Ecash mints! If you did, consider leaving me a zap. Also do let me know if this type of breakdown helps you understand a new topic well. I am considering doing similar breakdowns on other systems, such as ARK, Lightning or Statechains, if there is a lot of interest, and it helps people, I'll do it! Pleas also let me know what you think about the `unidirectional channel - ecash mint` idea in the comments. It's kind of a new idea, an it probably has flaws, or things that we haven't thought about yet. I'd love to discuss it with you! I'll leave you with this final slide:  Cheers, Gandlaf
@ c4b5369a:b812dbd6
2025-02-17 06:06:48As promised in my last article: nostr:naddr1qvzqqqr4gupzp394x6dfmvn69cduj7e9l2jgvtvle7n5w5rtrunjlr6tx6up9k7kqq2k6ernff9hw3tyd3y453rdtph5uvm6942kzuw08y0 In this one we will dive into how exactly an unidirectional payments channel powered ecash mint system would be implemented, using the tech available today! So if you haven't read that article yet, give it a read! I first intended to write a longwinded article, explaining each part of the system. But then I realized that I would need some visualization to get the message across in a more digestable way. This lead me to create a slide deck, and as I started to design the slides it became more and more clear that the information is easier shown with visualizations, than written down. I will try to give a summary as best as I can in this article, but I urge you, to please go visit the slide deck too, for the best experience: ----------- ### [TAKE ME TO THE SLIDE DECK!](https://uni-chan.gandlaf.com/) ----------- ### Intro In this article we will go over how we can build unidirectional payment channels on Bitcoin. Then we will take a look into how Cashu ecash mints work, and how we can use unidirectional payment channels to change the dynamics between ecash users and the mint. Before we start, let me also give credits to nostr:npub1htnhsay5dmq3r72tukdw72pduzfdcja0yylcajuvnc2uklkhxp8qnz3qac for comming up with the idea, to nostr:npub148jz5r9xujcjpqygk69yl4jqwjqmzgrqly26plktfjy8g4t7xaysj9xhgp for providing an idea for non-expiring unidirectional channels, and nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx unconference for hosting an event where these ideas could be discussed and flourish. ### Building unidirectional payment channels If you've read the previous article, you already know what unidirectional payment channels are. There are actually a coupple different ways to implement them, but they all do have a few things in common: 1. The `sender` can only send 2. The `Receiver` can only receive 3. They are VERY simple Way simpler than the duplex channels like we are using in the lightning network today, at least. Of course, duplex channels are being deployed on LN for a reason. They are very versatile and don't have these annoying limitations that the unidirectional payment channels have. They do however have a few drawbacks: 1. Peers have liveness requirements (or they might forfeit their funds) 2. Peers must backup their state after each transaction (if they don't they might forfeit their funds) 3. It is a pretty complex system This article is not meant to discredit duplex channels. I think they are great. I just also think that in some use-cases, their requirements are too high and the system too complex. But anyway, let's see what kind of channels we can build! #### Spillman/CLTV-Channel The Spillman channel idea has been around for a long time. It's even explained in Tadge Dryjas [Presentation](https://www.youtube.com/watch?v=Hzv9WuqIzA0&t=1969s) on Payment channels and the lightning network from back in the day. I compiled a list of some of the most important propperties of them in the slide below:  Great! Now that we know their properties, let's take a look at how we can create such a channel ([Slides](https://uni-chan.gandlaf.com/#/11)):  We start out by the `sender` creating a `funding TX`. The `sender` doesn't broadcast the transaction though. If he does, he might get locked into a multisig with the `receiver` without an unilateral exit path. Instead the `sender` also creates a `refund TX` spending the outputs of the yet unsigned `funding TX`. The `refund TX` is timelocked, and can only be broadcast after 1 month. Both `sender` and `receiver` can sign this `refund TX` without any risks. Once `sender` receives the signed `refund TX`, he can broadcast the `funding TX` and open the channel. The `sender` can now update the channel state, by pre-signing update transactions and sending them over to the `receiver`. Being a one-way channel, this can be done in a single message. It is very simple. There is no need for invalidating old states, since the `sender` does not hold any signed `update TXs` it is impossible for the `sender` to broadcast an old state. The `receiver` only cares about the latest state anyways, since that is the state where he gets the most money. He can basically delete any old states. The only thing the `receiver` needs to make sure of, is broadcasting the latest `update TX` before the `refund TX's` timelock expires. Otherwise, the `sender` might take the whole channel balance back to himself. This seems to be already a pretty useful construct, due to its simplicity. But we can make it even more simple!  This setup works basically the same way as the previous one, but instead of having a refund transaction, we build the `timelock` spend path directly into the `funding TX` This allows the `sender` to have an unilateral exit right from the start, and he can broadcast the `funding TX` without communicating with the `receiver`. In the worst case, the receiver rejects the channel, and the sender can get his money back after the timelock on the output has expired. Everything else basically works in the same way as in the example above. The beauty about this channel construct is in its simplicity. The drawbacks are obvious, but they do offer some nice properties that might be useful in certain cases.  One of the major drawbacks of the `Spillman-style channels` (apart from being unidirectional) is that they expire. This expiry comes with the neat property that neither of the party has to watch the chain for channel closures, and the `sender` can operate the channel with zero additional state, apart from his private keys. But they do expire. And this can make them quite inflexible. It might work in some contexts, but not so much in others, where time needs to be more flexible. This is where `Roose-Childs triggered channels` come into play. #### Roose-Childs triggered channel (I gave it that name, named after nostr:npub148jz5r9xujcjpqygk69yl4jqwjqmzgrqly26plktfjy8g4t7xaysj9xhgp and nostr:npub1htnhsay5dmq3r72tukdw72pduzfdcja0yylcajuvnc2uklkhxp8qnz3qac . If someone knows if this idea has been around before under a different name, please let us know!) `Roose-Childs triggered channels` were an idea developed by Steven and Luke at the nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx unconference. They essentially remove the channel expiry limitation in return for introducing the need for the `sender` to create a channel backup at the time of channel creation, and for the `receiver` the need to watch the chain for trigger transactions closing the channel.  They also allow for splicing funds, which can be important for a channel without expiry, allowing the `sender` to top-up liquidity once it runs out, or for the `receiver` taking out liquidity from the channel to deploy the funds elsewhere. Now, let's see how we can build them!  The `funding TX` actually looks the same as in the first example, and similarly it gets created, but not signed by the `sender`. Then, sender and receiver both sign the `trigger TX`. The `trigger TX` is at the heart of this scheme. It allows both `sender` and `receiver` to unilaterally exit the channel by broadcasting it (more on that in a bit). Once the `trigger TX` is signed and returned to the `sender`, the sender can confidently sign and boradcast the `funding TX` and open the channel. The `trigger TX` remains off-chain though. Now, to update the channel, the `sender` can pre-sign transactions in similar fashion to the examples above, but this time, spending the outputs of the unbroadcasted `trigger TX`. This way, both parties can exit the channel at any time. If the `receiver` wants to exit, he simply boradcasts the `trigger TX` and immediately spends its outputs using the latest `update TX`. If the `sender` wants to exit he will broadcast the `trigger TX` and basically force the `receivers` hand. Either, the `receiver` will broadcast the latest `update TX`, or the `sender` will be able to claim the entire channel balance after the timelock expired.  We can also simplify the `receiver's` exit path, by the `sender` pre-signing an additional transaction `R exit TX` for each update. this way, the `receiver` only needs to broadcast one transaction instead of two.  As we've mentioned before, there are some different trade-offs for `Roose-Childs triggered channels`. We introduce some minimal state and liveness requirements, but gain more flexibility.  #### Ecash to fill in the gaps (I will assume that the reader knows how ecash mints work. If not, please go check the [slides](https://uni-chan.gandlaf.com/#/43) where I go through an explanation) Essentially, we are trying to get a lightning like experience, without all the lightning complexities and requirements. One big issue with ecash, is that it is fully custodial. If we can offset that risk by holding most of the funds in a self custodial channel, we can have a reasonable trade-off between usability and self custody.  In a system like that, we would essentially turn the banking model onto its head. Where in a traditional bank, the majority of the funds are held in the banks custody, and the user only withdraws into his custody what he needs to transact, in our model the user would hold most funds in his own custody.  If you ask me, this approach makes way more sense. Instead of a custodian, we have turned the "bank" into a service provider. Let's take a look at how it would work in a more practical sense:  The `ecash user` would open an unidirectional payment channel to the `mint`, using one of his on-chain UTXOs. This allows him then to commit incrementally funds into the mints custody, only the amounts for his transactional needs. The mint offers connectivity to the lightning network an handles state and liveness as a service provider. The `ecash user`, can remain offline at all times, and his channel funds will always be safe. The mint can only ever claim the balance in the channel via the `update TXs`. The `mint` can of course still decide to no longer redeem any ecash, at which point they would have basically stolen the `ecash user's` transactional balance. At that point, it would probably be best for the `ecash user` to close his channel, and no longer interact or trust this `mint`. Here are some of the most important points of this system summarized:  And that is basically it! I hope you enjoyed this breakdown of Unidirectional payment channel enabled Ecash mints! If you did, consider leaving me a zap. Also do let me know if this type of breakdown helps you understand a new topic well. I am considering doing similar breakdowns on other systems, such as ARK, Lightning or Statechains, if there is a lot of interest, and it helps people, I'll do it! Pleas also let me know what you think about the `unidirectional channel - ecash mint` idea in the comments. It's kind of a new idea, an it probably has flaws, or things that we haven't thought about yet. I'd love to discuss it with you! I'll leave you with this final slide:  Cheers, Gandlaf @ c0a57a12:8b230f7a
2025-02-17 00:08:04Ever notice how we’ve all turned into a bunch of regulation junkies? Not just the kids—us, too. The parents. The supposed adults in the room. We sit around shaking our heads at this new generation, wondering why they can’t make a move without a permission slip, but let’s be honest: we made them that way. We were trained for it. We just passed the neurosis down like a bad heirloom. Used to be, kids ran wild, made their own fun, learned how things worked by getting their hands dirty and screwing up a few times. You fell out of a tree? Tough. That’s how you figured out gravity was real. Now, a kid gets a splinter and half the neighborhood has to be briefed. But let’s not act like it started with them. We didn’t grow up in the Wild West. Our parents—the ones who were handed a country built by men who cleared forests and carved railroads and settled frontiers—they took one look at all that, clutched their pearls, and decided the real enemy was *risk.* They started slapping safety labels on everything, turned common sense into a government-subsidized industry, and set about making sure we never had to experience a single moment of danger, discomfort, or—God help us—independence. And we ate it up. Grew up afraid of the sun, the air, the drinking water. If you touched a stranger, you’d get kidnapped. If you ate the wrong snack, you’d drop dead from an allergy you didn’t even have. If you rode a bike without strapping on enough gear to survive re-entry from orbit, you might as well be suicidal. Then, just to really hammer it in, we were given rules for *everything.* How to sit, how to talk, how to play, how to think. And because we’d been softened up, we listened. We obeyed. We internalized the great lesson of modern civilization: *only do what is approved.* And when it came time for us to raise kids? Oh, we ran with it. Helicopter parenting? That was us. Participation trophies? Us. Baby-proofing the entire godforsaken planet so that Junior never had to encounter anything sharper than a cotton ball? Us again. Every bit of micromanaged, soul-sucking, over-regulated nonsense we complain about today? We enforced it. So now we’ve got a generation that doesn’t *know* how to function without checking the rulebook first. They hesitate before every decision because we taught them hesitation. They sit around waiting for a green light because that’s all we ever told them to do. And you know what? We’re no better. When’s the last time *you* did something without checking if it was "allowed"? When’s the last time you ignored a ridiculous rule instead of just sighing and complying? When’s the last time you acted like a *free man* instead of a well-behaved tax mule hoping the system doesn’t notice you? We’ve swallowed a lie, and we keep regurgitating it—that compliance is morality, that following orders is a virtue, that a safe, predictable, well-regulated life is a *good* one. It’s not. It’s never been. You don’t get freedom by waiting for permission to use it. You don’t get courage by asking if it’s okay. You don’t build a worthwhile life by making sure you never color outside the lines. And yet, here we are, acting surprised. Acting like we don’t know how we got here. Acting like we didn’t *choose* this. Like we didn’t let it happen. So what now? We could stop. We could teach our kids to take risks, to get their hands dirty, to act instead of waiting for permission. We could start ignoring stupid rules, start trusting our own judgment, start living like we weren’t raised in a padded cell. Or we could do nothing. Keep following orders. Keep playing it safe. Keep watching the world shrink into a flavorless, permission-based, committee-approved version of itself. Your call. But either way, don’t pretend to be surprised.
@ c0a57a12:8b230f7a
2025-02-17 00:08:04Ever notice how we’ve all turned into a bunch of regulation junkies? Not just the kids—us, too. The parents. The supposed adults in the room. We sit around shaking our heads at this new generation, wondering why they can’t make a move without a permission slip, but let’s be honest: we made them that way. We were trained for it. We just passed the neurosis down like a bad heirloom. Used to be, kids ran wild, made their own fun, learned how things worked by getting their hands dirty and screwing up a few times. You fell out of a tree? Tough. That’s how you figured out gravity was real. Now, a kid gets a splinter and half the neighborhood has to be briefed. But let’s not act like it started with them. We didn’t grow up in the Wild West. Our parents—the ones who were handed a country built by men who cleared forests and carved railroads and settled frontiers—they took one look at all that, clutched their pearls, and decided the real enemy was *risk.* They started slapping safety labels on everything, turned common sense into a government-subsidized industry, and set about making sure we never had to experience a single moment of danger, discomfort, or—God help us—independence. And we ate it up. Grew up afraid of the sun, the air, the drinking water. If you touched a stranger, you’d get kidnapped. If you ate the wrong snack, you’d drop dead from an allergy you didn’t even have. If you rode a bike without strapping on enough gear to survive re-entry from orbit, you might as well be suicidal. Then, just to really hammer it in, we were given rules for *everything.* How to sit, how to talk, how to play, how to think. And because we’d been softened up, we listened. We obeyed. We internalized the great lesson of modern civilization: *only do what is approved.* And when it came time for us to raise kids? Oh, we ran with it. Helicopter parenting? That was us. Participation trophies? Us. Baby-proofing the entire godforsaken planet so that Junior never had to encounter anything sharper than a cotton ball? Us again. Every bit of micromanaged, soul-sucking, over-regulated nonsense we complain about today? We enforced it. So now we’ve got a generation that doesn’t *know* how to function without checking the rulebook first. They hesitate before every decision because we taught them hesitation. They sit around waiting for a green light because that’s all we ever told them to do. And you know what? We’re no better. When’s the last time *you* did something without checking if it was "allowed"? When’s the last time you ignored a ridiculous rule instead of just sighing and complying? When’s the last time you acted like a *free man* instead of a well-behaved tax mule hoping the system doesn’t notice you? We’ve swallowed a lie, and we keep regurgitating it—that compliance is morality, that following orders is a virtue, that a safe, predictable, well-regulated life is a *good* one. It’s not. It’s never been. You don’t get freedom by waiting for permission to use it. You don’t get courage by asking if it’s okay. You don’t build a worthwhile life by making sure you never color outside the lines. And yet, here we are, acting surprised. Acting like we don’t know how we got here. Acting like we didn’t *choose* this. Like we didn’t let it happen. So what now? We could stop. We could teach our kids to take risks, to get their hands dirty, to act instead of waiting for permission. We could start ignoring stupid rules, start trusting our own judgment, start living like we weren’t raised in a padded cell. Or we could do nothing. Keep following orders. Keep playing it safe. Keep watching the world shrink into a flavorless, permission-based, committee-approved version of itself. Your call. But either way, don’t pretend to be surprised. @ 5a261a61:2ebd4480
2025-02-16 21:54:41As I grow older, I find myself often discovering things that I haven't understood before, or just see completely differently. Like with this fable of the toad and scorpion. You know, the classic where scorpion needs to get across the river, and asks the toad for help, promising not to sting. The toad refuses at first, pointing out that scorpion's sting would kill them both. But scorpion argues that would be illogical - why would it sting if that meant its own death? The toad, convinced by this logic, agrees to help. Halfway across, scorpion stings anyway, and as they both sink, toad asks "why?" Scorpion simply answers "It's my nature." That leads me to my scorpion sighting. I have somewhat stronger libido and given the circumstances, I usually situate myself in the submissive position in both married and online life. When I am not ventilating or getting these things out in some way, it usually leads to my growing frustration that seriously hinders my usual life. And in those trying times I usually tell myself, "screw that, I don't like this, I don't like how that makes me feel, it sucks, why does it have to hurt so much" (well, I don't think 'hurt' as I have been indoctrinated by the society that men don't process feelings this way, but I think if I had a therapist, they would want me to spell it like that). Let's not go to the subspace again, it's silly space. Sometimes it gets really dark...but then comes the climax, like literally, and suddenly everything is forgiven and (almost) forgotten. And all is well. Let's just not go there next time, avoid being burned again, I keep saying to myself. And these days submissive scorpion in my head just silently waits for my monologuing toad to finish defending ourselves. It knows that it needs only one chance so I cave in, while toad needs to defend my sanity every day. So one day, I will bring scorpion to cross the river with me again. And it will again promise that this time it will be ok. And we will both pretend like we believe that, so the play can go on. And it will eventually sting me, because we both yearn for unreachable things. And next day I will again see scorpion on the river, not wooing me, no, we are beyond that, it knows it just needs to wait before I come back for the poison I need.As I grow older, I find myself often discovering things that I haven't understood before, or just see completely differently. Like with this fable of the toad and scorpion. You know, the classic where scorpion needs to get across the river, and asks the toad for help, promising not to sting. The toad refuses at first, pointing out that scorpion's sting would kill them both. But scorpion argues that would be illogical - why would it sting if that meant its own death? The toad, convinced by this logic, agrees to help. Halfway across, scorpion stings anyway, and as they both sink, toad asks "why?" Scorpion simply answers "It's my nature." That leads me to my scorpion sighting. I have somewhat stronger libido and given the circumstances, I usually situate myself in the submissive position in both married and online life. When I am not ventilating or getting these things out in some way, it usually leads to my growing frustration that seriously hinders my usual life. And in those trying times I usually tell myself, "screw that, I don't like this, I don't like how that makes me feel, it sucks, why does it have to hurt so much" (well, I don't think 'hurt' as I have been indoctrinated by the society that men don't process feelings this way, but I think if I had a therapist, they would want me to spell it like that). Let's not go to the subspace again, it's silly space. Sometimes it gets really dark...but then comes the climax, like literally, and suddenly everything is forgiven and (almost) forgotten. And all is well. Let's just not go there next time, avoid being burned again, I keep saying to myself. And these days submissive scorpion in my head just silently waits for my monologuing toad to finish defending ourselves. It knows that it needs only one chance so I cave in, while toad needs to defend my sanity every day. So one day, I will bring scorpion to cross the river with me again. And it will again promise that this time it will be ok. And we will both pretend like we believe that, so the play can go on. And it will eventually sting me, because we both yearn for unreachable things. And next day I will again see scorpion on the river, not wooing me, no, we are beyond that, it knows it just needs to wait before I come back for the poison I need.
@ 5a261a61:2ebd4480
2025-02-16 21:54:41As I grow older, I find myself often discovering things that I haven't understood before, or just see completely differently. Like with this fable of the toad and scorpion. You know, the classic where scorpion needs to get across the river, and asks the toad for help, promising not to sting. The toad refuses at first, pointing out that scorpion's sting would kill them both. But scorpion argues that would be illogical - why would it sting if that meant its own death? The toad, convinced by this logic, agrees to help. Halfway across, scorpion stings anyway, and as they both sink, toad asks "why?" Scorpion simply answers "It's my nature." That leads me to my scorpion sighting. I have somewhat stronger libido and given the circumstances, I usually situate myself in the submissive position in both married and online life. When I am not ventilating or getting these things out in some way, it usually leads to my growing frustration that seriously hinders my usual life. And in those trying times I usually tell myself, "screw that, I don't like this, I don't like how that makes me feel, it sucks, why does it have to hurt so much" (well, I don't think 'hurt' as I have been indoctrinated by the society that men don't process feelings this way, but I think if I had a therapist, they would want me to spell it like that). Let's not go to the subspace again, it's silly space. Sometimes it gets really dark...but then comes the climax, like literally, and suddenly everything is forgiven and (almost) forgotten. And all is well. Let's just not go there next time, avoid being burned again, I keep saying to myself. And these days submissive scorpion in my head just silently waits for my monologuing toad to finish defending ourselves. It knows that it needs only one chance so I cave in, while toad needs to defend my sanity every day. So one day, I will bring scorpion to cross the river with me again. And it will again promise that this time it will be ok. And we will both pretend like we believe that, so the play can go on. And it will eventually sting me, because we both yearn for unreachable things. And next day I will again see scorpion on the river, not wooing me, no, we are beyond that, it knows it just needs to wait before I come back for the poison I need.As I grow older, I find myself often discovering things that I haven't understood before, or just see completely differently. Like with this fable of the toad and scorpion. You know, the classic where scorpion needs to get across the river, and asks the toad for help, promising not to sting. The toad refuses at first, pointing out that scorpion's sting would kill them both. But scorpion argues that would be illogical - why would it sting if that meant its own death? The toad, convinced by this logic, agrees to help. Halfway across, scorpion stings anyway, and as they both sink, toad asks "why?" Scorpion simply answers "It's my nature." That leads me to my scorpion sighting. I have somewhat stronger libido and given the circumstances, I usually situate myself in the submissive position in both married and online life. When I am not ventilating or getting these things out in some way, it usually leads to my growing frustration that seriously hinders my usual life. And in those trying times I usually tell myself, "screw that, I don't like this, I don't like how that makes me feel, it sucks, why does it have to hurt so much" (well, I don't think 'hurt' as I have been indoctrinated by the society that men don't process feelings this way, but I think if I had a therapist, they would want me to spell it like that). Let's not go to the subspace again, it's silly space. Sometimes it gets really dark...but then comes the climax, like literally, and suddenly everything is forgiven and (almost) forgotten. And all is well. Let's just not go there next time, avoid being burned again, I keep saying to myself. And these days submissive scorpion in my head just silently waits for my monologuing toad to finish defending ourselves. It knows that it needs only one chance so I cave in, while toad needs to defend my sanity every day. So one day, I will bring scorpion to cross the river with me again. And it will again promise that this time it will be ok. And we will both pretend like we believe that, so the play can go on. And it will eventually sting me, because we both yearn for unreachable things. And next day I will again see scorpion on the river, not wooing me, no, we are beyond that, it knows it just needs to wait before I come back for the poison I need. @ e7bc35f8:3ed2a7cf
2025-02-16 19:19:41In the grand chessboard of geopolitics, Iran has long been a target for covert Western intervention. The 2009 Iranian presidential election provided yet another example of a well-worn playbook—one designed to undermine sovereign nations under the guise of democracy. But this was far from a spontaneous people's movement. Instead, it bore all the hallmarks of a carefully orchestrated operation, leveraging the power of mass media, intelligence agencies, and globalist financial interests. ### 2009: A Manufactured Uprising In June 2009, before Iran's election results were even finalized, opposition leader Mir-Houssein Mousavi [prematurely declared victory]( https://www.telegraph.co.uk/news/worldnews/middleeast/iran/5519567/Iran-elections-Mahmoud-Ahmadinejad-and-Hossein-Mousavi-both-claim-victory.html). This calculated move set the stage for immediate allegations of fraud, ensuring that any outcome favoring incumbent President Mahmoud Ahmadinejad would be delegitimized. The Western media wasted no time in amplifying the chaos, competing to push the most dramatic narratives. The **BBC** took the lead, [publishing outright fabrications]( https://web.archive.org/web/20090621065048/https://www.infowars.com/bbc-caught-in-mass-public-deception-with-iran-propaganda/) about mass uprisings—falsehoods they were later [forced to retract]( https://www.bbc.co.uk/blogs/theeditors/2009/06/what_really_happened.html). Then came the Twitter storm. On June 13, a sudden [flood of **30,000 tweets**]( https://web.archive.org/web/20090619154321/https://chartingstocks.net/2009/06/proof-israeli-effort-to-destabilize-iran-via-twitter/), many in English, began pouring in from Iran. The accounts responsible? Newly created profiles, often using identical photos, a hallmark of an information warfare campaign. The **[Jerusalem Post]( https://web.archive.org/web/20090714235359/https://chartingstocks.net/wp-content/uploads/2009/06/jpost.jpg)** quickly picked up on the phenomenon, covering it within hours. This was no organic grassroots movement; it was a digital psy-op, mirroring past regime-change operations. ### The Blueprint: Iran 1953—The CIA’s Original Coup This wasn’t Iran’s first encounter with a foreign-backed destabilization campaign. In 1953, Iran’s democratically elected Prime Minister **Mohammed Mossadegh** made the fatal mistake of challenging Western oil interests. He sought to nationalize Iran’s petroleum industry, then controlled by the Anglo-Iranian Oil Company (later BP). The response was swift and brutal: the **CIA launched Operation Ajax**, an [insidious regime-change operation]( https://archive.nytimes.com/www.nytimes.com/library/world/mideast/041600iran-cia-index.html) that became the prototype for future coups. The CIA’s strategy was as ruthless as it was effective: * Staged bombings blamed on Mossadegh’s government * Islamist agitation funded and nurtured to turn public sentiment * Propaganda campaigns demonizing Mossadegh as a secular threat * Bribery of officials and military leaders to ensure betrayal The result? The overthrow of Mossadegh and the installation of the pro-Western **Shah**, whose reign saw brutal repression under the secret police **SAVAK**—trained by the CIA and Mossad. The template was established. From **Guatemala (1954) to Afghanistan (1980s) to Serbia (1990s)**, the same playbook was deployed. But with each coup, Western fingerprints became harder to conceal. ### A New Strategy: Economic Warfare and the NGO Takeover With direct coups becoming too risky, a subtler method emerged: **economic strangulation**. Enter the **International Monetary Fund (IMF)**. The play was simple: 1. **A corrupt dictator takes out massive loans** for projects the country cannot afford. 2. **The country inevitably defaults**, giving the IMF the power to restructure its economy. 3. **Western corporations move in**, plundering national resources under the guise of “recovery.” This scheme was exposed in **2001** when former World Bank chief economist **Joseph Stiglitz** [blew the whistle]( https://www.gregpalast.com/the-globalizer-who-came-in-from-the-cold/) on these manufactured debt traps. Further details emerged in 2004 with **John Perkins' “[Confessions of an Economic Hitman]( https://a.co/d/2oLfrTD)”**, which revealed how Western front companies and intelligence-backed corporations systematically dismantled economies for geopolitical gain. But even this strategy had its limits. As exposure grew, the need for an even more sophisticated approach became apparent—one cloaked in the language of democracy and human rights. ### Color Revolutions: The Soros Connection Enter the age of the **NGO-driven color revolutions**, where regime change is disguised as a people’s uprising. Organizations like the **Open Society Institute (George Soros), Freedom House, and the National Endowment for Democracy (NED)** became the new weapons of choice. These NGOs: * **Fund and train opposition groups** * **Coordinate mass protests during elections** * **Provide media support** to delegitimize governments The results? A series of destabilizations across the world: **Ukraine (2004 - Orange Revolution)** **Lebanon (2005 - Cedar Revolution)** **Georgia (2003 - Rose Revolution)** **Kyrgyzstan (2005 - Tulip Revolution)** Each followed the same pattern—Western-backed NGOs funneled money and resources into opposition movements, ensuring their success. Unsurprisingly, these uprisings all bore the **fingerprints of Soros**, the billionaire financier with a long history of manipulating global politics to serve elite financial interests. However, this strategy has started to backfire. Georgia witnessed a major [anti-Soros backlash]( https://halldor2.blogspot.com/2005/10/anti-soros-movement-in-georgia.html?m=1), and attempts to replicate these revolutions elsewhere—such as the failed Moldovan "[Grape Revolution]( https://foreignpolicy.com/2009/04/10/moldovas-twitter-revolution-is-not-a-myth/)"—have faltered as people wake up to the deception. ### Iran 2009: An Operation in Plain Sight While no one denies that Ahmadinejad’s regime had its flaws, the coordinated media hysteria and backing of **Mir-Houssein "[Butcher of Beirut]( https://web.archive.org/web/20090626060145/http://blogs.cqpolitics.com/spytalk/2009/06/mousavi-celebrated-in-iranian.html)" Mousavi** raises serious questions. Why was the Western establishment so eager to install a leader with a brutal history? The answer lies in the same playbook used time and again: 1. **Foment unrest** through digital manipulation and street protests. 2. **Control the narrative** via Western media outlets. 3. **Install a leader** more compliant with Western economic and geopolitical interests. Iran 2009 was not an isolated event. It was part of a much larger pattern—a centuries-old strategy of covert intervention, economic sabotage, and media manipulation to secure Western control over sovereign nations. As history has shown, the real fight isn’t between the people and their governments—it’s between sovereign nations and the global power structures that seek to enslave them. And until people recognize the hidden hands behind these so-called revolutions, the cycle of deception will continue.
@ e7bc35f8:3ed2a7cf
2025-02-16 19:19:41In the grand chessboard of geopolitics, Iran has long been a target for covert Western intervention. The 2009 Iranian presidential election provided yet another example of a well-worn playbook—one designed to undermine sovereign nations under the guise of democracy. But this was far from a spontaneous people's movement. Instead, it bore all the hallmarks of a carefully orchestrated operation, leveraging the power of mass media, intelligence agencies, and globalist financial interests. ### 2009: A Manufactured Uprising In June 2009, before Iran's election results were even finalized, opposition leader Mir-Houssein Mousavi [prematurely declared victory]( https://www.telegraph.co.uk/news/worldnews/middleeast/iran/5519567/Iran-elections-Mahmoud-Ahmadinejad-and-Hossein-Mousavi-both-claim-victory.html). This calculated move set the stage for immediate allegations of fraud, ensuring that any outcome favoring incumbent President Mahmoud Ahmadinejad would be delegitimized. The Western media wasted no time in amplifying the chaos, competing to push the most dramatic narratives. The **BBC** took the lead, [publishing outright fabrications]( https://web.archive.org/web/20090621065048/https://www.infowars.com/bbc-caught-in-mass-public-deception-with-iran-propaganda/) about mass uprisings—falsehoods they were later [forced to retract]( https://www.bbc.co.uk/blogs/theeditors/2009/06/what_really_happened.html). Then came the Twitter storm. On June 13, a sudden [flood of **30,000 tweets**]( https://web.archive.org/web/20090619154321/https://chartingstocks.net/2009/06/proof-israeli-effort-to-destabilize-iran-via-twitter/), many in English, began pouring in from Iran. The accounts responsible? Newly created profiles, often using identical photos, a hallmark of an information warfare campaign. The **[Jerusalem Post]( https://web.archive.org/web/20090714235359/https://chartingstocks.net/wp-content/uploads/2009/06/jpost.jpg)** quickly picked up on the phenomenon, covering it within hours. This was no organic grassroots movement; it was a digital psy-op, mirroring past regime-change operations. ### The Blueprint: Iran 1953—The CIA’s Original Coup This wasn’t Iran’s first encounter with a foreign-backed destabilization campaign. In 1953, Iran’s democratically elected Prime Minister **Mohammed Mossadegh** made the fatal mistake of challenging Western oil interests. He sought to nationalize Iran’s petroleum industry, then controlled by the Anglo-Iranian Oil Company (later BP). The response was swift and brutal: the **CIA launched Operation Ajax**, an [insidious regime-change operation]( https://archive.nytimes.com/www.nytimes.com/library/world/mideast/041600iran-cia-index.html) that became the prototype for future coups. The CIA’s strategy was as ruthless as it was effective: * Staged bombings blamed on Mossadegh’s government * Islamist agitation funded and nurtured to turn public sentiment * Propaganda campaigns demonizing Mossadegh as a secular threat * Bribery of officials and military leaders to ensure betrayal The result? The overthrow of Mossadegh and the installation of the pro-Western **Shah**, whose reign saw brutal repression under the secret police **SAVAK**—trained by the CIA and Mossad. The template was established. From **Guatemala (1954) to Afghanistan (1980s) to Serbia (1990s)**, the same playbook was deployed. But with each coup, Western fingerprints became harder to conceal. ### A New Strategy: Economic Warfare and the NGO Takeover With direct coups becoming too risky, a subtler method emerged: **economic strangulation**. Enter the **International Monetary Fund (IMF)**. The play was simple: 1. **A corrupt dictator takes out massive loans** for projects the country cannot afford. 2. **The country inevitably defaults**, giving the IMF the power to restructure its economy. 3. **Western corporations move in**, plundering national resources under the guise of “recovery.” This scheme was exposed in **2001** when former World Bank chief economist **Joseph Stiglitz** [blew the whistle]( https://www.gregpalast.com/the-globalizer-who-came-in-from-the-cold/) on these manufactured debt traps. Further details emerged in 2004 with **John Perkins' “[Confessions of an Economic Hitman]( https://a.co/d/2oLfrTD)”**, which revealed how Western front companies and intelligence-backed corporations systematically dismantled economies for geopolitical gain. But even this strategy had its limits. As exposure grew, the need for an even more sophisticated approach became apparent—one cloaked in the language of democracy and human rights. ### Color Revolutions: The Soros Connection Enter the age of the **NGO-driven color revolutions**, where regime change is disguised as a people’s uprising. Organizations like the **Open Society Institute (George Soros), Freedom House, and the National Endowment for Democracy (NED)** became the new weapons of choice. These NGOs: * **Fund and train opposition groups** * **Coordinate mass protests during elections** * **Provide media support** to delegitimize governments The results? A series of destabilizations across the world: **Ukraine (2004 - Orange Revolution)** **Lebanon (2005 - Cedar Revolution)** **Georgia (2003 - Rose Revolution)** **Kyrgyzstan (2005 - Tulip Revolution)** Each followed the same pattern—Western-backed NGOs funneled money and resources into opposition movements, ensuring their success. Unsurprisingly, these uprisings all bore the **fingerprints of Soros**, the billionaire financier with a long history of manipulating global politics to serve elite financial interests. However, this strategy has started to backfire. Georgia witnessed a major [anti-Soros backlash]( https://halldor2.blogspot.com/2005/10/anti-soros-movement-in-georgia.html?m=1), and attempts to replicate these revolutions elsewhere—such as the failed Moldovan "[Grape Revolution]( https://foreignpolicy.com/2009/04/10/moldovas-twitter-revolution-is-not-a-myth/)"—have faltered as people wake up to the deception. ### Iran 2009: An Operation in Plain Sight While no one denies that Ahmadinejad’s regime had its flaws, the coordinated media hysteria and backing of **Mir-Houssein "[Butcher of Beirut]( https://web.archive.org/web/20090626060145/http://blogs.cqpolitics.com/spytalk/2009/06/mousavi-celebrated-in-iranian.html)" Mousavi** raises serious questions. Why was the Western establishment so eager to install a leader with a brutal history? The answer lies in the same playbook used time and again: 1. **Foment unrest** through digital manipulation and street protests. 2. **Control the narrative** via Western media outlets. 3. **Install a leader** more compliant with Western economic and geopolitical interests. Iran 2009 was not an isolated event. It was part of a much larger pattern—a centuries-old strategy of covert intervention, economic sabotage, and media manipulation to secure Western control over sovereign nations. As history has shown, the real fight isn’t between the people and their governments—it’s between sovereign nations and the global power structures that seek to enslave them. And until people recognize the hidden hands behind these so-called revolutions, the cycle of deception will continue. @ 9a4acdeb:1489913b
2025-02-16 18:26:58## Chef's notes Original recipe, a favorite of family and friends, and the easiest and fastest prep time meal I make. Like all really good pork recipes, it does take time in the cooker, but it's set-and-forget and requires no attention between starting and serving. Using fresh herbs and peppers does enhance the meal (especially fresh cilantro if it doesn't taste like soap to you), but this is optional, and it is excellent with dry ingredients. Excluding the beans and/or tomato makes this meal extra-low carb for those carnivores amongst us, or those sensitive to beans. Frying the shredded cheese in a slick pan is a good way to It will take up to 15min to come up to pressure, so it may be helpful to pay attention to it to be sure it pressurizes until you become familiar with how this meal acts in your particular pressure cooker. The Instant Pot pressure cookers make this easy. ## Details - ⏲️ Prep time: 20min - 🍳 Cook time: 2hrs - 🍽️ Servings: 6 ## Ingredients - 4lbs Pork loin - 1-2 Yellow onion, roughly chopped - 3-5 Jalapeños or 1x 4oz canned - 6-8 Green chilis or 1x 4oz canned - 2oz canned sliced Black olives (may use half a 4oz can) - 2-3tsp minced garlic, or 1-2 tsp garlic powder - A small bunch of cilantro, chopped, or 1-2 tsb dried cilantro (optional) - 1tbsp Oregano, chopped fresh or dried - 2-3tsb Chili powder; Ancho, Chipotle, or a blend of the two is best - 2-3tsb ground Cumin - 3-4tsp salt - 2-tsp black pepper - 1 large or 4oz canned tomato (optional) - Mexican mix shredded cheese (topping) - 4oz Black beans (optional) - Tortillas (optional) - Avocado (optional toping) - 6 Limes and/or 3oz lime juice ## Directions 1. Mix dry seasonings 2. Chop and mix fresh herbs and veggies, canned or otherwise 3. Add chopped onion to bottom of pressure cooker 4. Add pork loin atop the onion; chopping into steaks may make the texture better 5. Add veggies to the top, shaking to settle into the pressure cooker 6. Add lime juice 7. Start on high pressure for 2hrs. 8. (Optional) Drain the broth into a saucepan, cook down, and add back into the mix to make it extra flavorful. Otherwise, can be served as a soup or poured over rice. 9. Serve with cheese as a topping, over rice, in a tortilla as tacos or burritos, or in a number of other fashions you may fancy. Those who prefer a little more lime may squeeze fresh or splash some more on their meal. 10. (Optional) For presentation, garnish with cilantro and lime slices, maybe a dollop of shredded cheese, sour cream, or cream cheese.
@ 9a4acdeb:1489913b
2025-02-16 18:26:58## Chef's notes Original recipe, a favorite of family and friends, and the easiest and fastest prep time meal I make. Like all really good pork recipes, it does take time in the cooker, but it's set-and-forget and requires no attention between starting and serving. Using fresh herbs and peppers does enhance the meal (especially fresh cilantro if it doesn't taste like soap to you), but this is optional, and it is excellent with dry ingredients. Excluding the beans and/or tomato makes this meal extra-low carb for those carnivores amongst us, or those sensitive to beans. Frying the shredded cheese in a slick pan is a good way to It will take up to 15min to come up to pressure, so it may be helpful to pay attention to it to be sure it pressurizes until you become familiar with how this meal acts in your particular pressure cooker. The Instant Pot pressure cookers make this easy. ## Details - ⏲️ Prep time: 20min - 🍳 Cook time: 2hrs - 🍽️ Servings: 6 ## Ingredients - 4lbs Pork loin - 1-2 Yellow onion, roughly chopped - 3-5 Jalapeños or 1x 4oz canned - 6-8 Green chilis or 1x 4oz canned - 2oz canned sliced Black olives (may use half a 4oz can) - 2-3tsp minced garlic, or 1-2 tsp garlic powder - A small bunch of cilantro, chopped, or 1-2 tsb dried cilantro (optional) - 1tbsp Oregano, chopped fresh or dried - 2-3tsb Chili powder; Ancho, Chipotle, or a blend of the two is best - 2-3tsb ground Cumin - 3-4tsp salt - 2-tsp black pepper - 1 large or 4oz canned tomato (optional) - Mexican mix shredded cheese (topping) - 4oz Black beans (optional) - Tortillas (optional) - Avocado (optional toping) - 6 Limes and/or 3oz lime juice ## Directions 1. Mix dry seasonings 2. Chop and mix fresh herbs and veggies, canned or otherwise 3. Add chopped onion to bottom of pressure cooker 4. Add pork loin atop the onion; chopping into steaks may make the texture better 5. Add veggies to the top, shaking to settle into the pressure cooker 6. Add lime juice 7. Start on high pressure for 2hrs. 8. (Optional) Drain the broth into a saucepan, cook down, and add back into the mix to make it extra flavorful. Otherwise, can be served as a soup or poured over rice. 9. Serve with cheese as a topping, over rice, in a tortilla as tacos or burritos, or in a number of other fashions you may fancy. Those who prefer a little more lime may squeeze fresh or splash some more on their meal. 10. (Optional) For presentation, garnish with cilantro and lime slices, maybe a dollop of shredded cheese, sour cream, or cream cheese. @ c902b8da:0cedc5fb
2025-02-16 18:13:20I'll break down the key legal requirements, costs, and timelines for establishing a health insurance company, focusing purely on the regulatory aspects: State Licensing Requirements (Primary State): - Initial Capital and Surplus: $10-15 million minimum (varies by state) - Risk-Based Capital (RBC) requirements: Must maintain 200-300% of RBC - Processing Time: 12-18 months - Application Fee: $25,000-50,000 - Filing Requirements: - Articles of Incorporation - Statutory Financial Statements - Actuarial Certifications - Detailed Ownership Information - Background Checks for All Officers/Directors - Holding Company Act Filings if Applicable Federal Requirements: - ACA Compliance: - Must offer all 10 Essential Health Benefits - Medical Loss Ratio requirements (80% individual/small group, 85% large group) - No annual or lifetime limits - Guaranteed issue and renewal - HIPAA Compliance: - Privacy Officer Appointment - Security Protocols Implementation - Timeline: 6-8 months - Cost: $200,000-500,000 for initial setup Multi-State Expansion (Per Additional State): - Certificate of Authority Application: $5,000-25,000 per state - State-Specific Capital Requirements: $2-5 million additional per state - Processing Time: 6-12 months per state - Required State Deposits: $500,000-2 million per state - Guaranty Fund Membership: $25,000-100,000 per state Mandatory Insurance Filings: - Rate Filings: - Timeline: 60-90 days for approval - Filing Fees: $500-5,000 per filing - Form Filings: - Timeline: 30-60 days for approval - Filing Fees: $50-500 per form - Annual Statement Filing: $500-2,500 per state Required Positions and Certifications: - Licensed Actuary (MAAA certification) - Compliance Officer - Medical Director (licensed physician) - Claims Manager - Network Management Director - Timeline for hiring/certification: 3-6 months - Annual Costs: $1-2 million for required personnel Reserve Requirements: - Claims Reserves: 3-6 months of expected claims - Premium Reserves: 1-3 months of premium - Special Deposits: Varies by state ($1-5 million) - Total Reserve Requirements: 25-40% of annual premium Ongoing Regulatory Compliance: - Quarterly Financial Filings: Due within 45 days of quarter end - Annual Financial Statements: Due March 1 - Market Conduct Examinations: Every 3-5 years - Cost: $100,000-500,000 per examination - Financial Examinations: Every 3-5 years - Cost: $200,000-1 million per examination Required Insurance Coverage: - E&O Insurance: $5-10 million coverage - Annual Cost: $100,000-250,000 - D&O Insurance: $10-25 million coverage - Annual Cost: $200,000-500,000 - Cyber Insurance: $5-10 million coverage - Annual Cost: $100,000-300,000 Total Regulatory Timeline: - Initial State License: 12-18 months - Federal Compliance: 6-8 months (concurrent) - First Policy Issuance: 18-24 months from start - Multi-State Operation: Additional 12-24 months Total Initial Regulatory Costs: - Single State Operation: $15-25 million - Multi-State Operation (5 states): $30-50 million - Annual Compliance Costs: $2-5 million per state These requirements and costs can vary significantly based on: - State of domicile - Number of states operating in - Types of health insurance products offered - Size of projected enrollment - Market conditions and risk factors Yes, existing insurance companies can potentially influence your application process, but not directly through a "veto" power. Here's how it works: 1. Public Comment Period - Most state insurance departments have a public comment period during the application process - Existing insurers can submit formal objections or concerns - They typically focus on market saturation, financial viability, or potential unfair competition 2. Market Need Assessment - Many states require a "need and necessity" showing as part of the application - You must demonstrate that: - There's sufficient market demand - Your company brings something unique or beneficial - The market can support another carrier - However, mere competition itself is not grounds for denial 3. State Regulator Discretion - Regulators consider market concentration and competition - They generally favor healthy competition unless there are legitimate concerns about: - Market destabilization - Your company's financial strength - Risk to consumers - Pure "we don't want competition" arguments from existing insurers typically don't succeed 4. Trade Association Influence - Insurance trade associations may provide input during the licensing process - They can raise concerns about: - Capital adequacy - Management experience - Business plan viability - But they cannot directly block your application Key Point: While existing insurers can object, the final decision rests with state regulators who are primarily concerned with: - Consumer protection - Market stability - Your company's financial soundness - Management competency
@ c902b8da:0cedc5fb
2025-02-16 18:13:20I'll break down the key legal requirements, costs, and timelines for establishing a health insurance company, focusing purely on the regulatory aspects: State Licensing Requirements (Primary State): - Initial Capital and Surplus: $10-15 million minimum (varies by state) - Risk-Based Capital (RBC) requirements: Must maintain 200-300% of RBC - Processing Time: 12-18 months - Application Fee: $25,000-50,000 - Filing Requirements: - Articles of Incorporation - Statutory Financial Statements - Actuarial Certifications - Detailed Ownership Information - Background Checks for All Officers/Directors - Holding Company Act Filings if Applicable Federal Requirements: - ACA Compliance: - Must offer all 10 Essential Health Benefits - Medical Loss Ratio requirements (80% individual/small group, 85% large group) - No annual or lifetime limits - Guaranteed issue and renewal - HIPAA Compliance: - Privacy Officer Appointment - Security Protocols Implementation - Timeline: 6-8 months - Cost: $200,000-500,000 for initial setup Multi-State Expansion (Per Additional State): - Certificate of Authority Application: $5,000-25,000 per state - State-Specific Capital Requirements: $2-5 million additional per state - Processing Time: 6-12 months per state - Required State Deposits: $500,000-2 million per state - Guaranty Fund Membership: $25,000-100,000 per state Mandatory Insurance Filings: - Rate Filings: - Timeline: 60-90 days for approval - Filing Fees: $500-5,000 per filing - Form Filings: - Timeline: 30-60 days for approval - Filing Fees: $50-500 per form - Annual Statement Filing: $500-2,500 per state Required Positions and Certifications: - Licensed Actuary (MAAA certification) - Compliance Officer - Medical Director (licensed physician) - Claims Manager - Network Management Director - Timeline for hiring/certification: 3-6 months - Annual Costs: $1-2 million for required personnel Reserve Requirements: - Claims Reserves: 3-6 months of expected claims - Premium Reserves: 1-3 months of premium - Special Deposits: Varies by state ($1-5 million) - Total Reserve Requirements: 25-40% of annual premium Ongoing Regulatory Compliance: - Quarterly Financial Filings: Due within 45 days of quarter end - Annual Financial Statements: Due March 1 - Market Conduct Examinations: Every 3-5 years - Cost: $100,000-500,000 per examination - Financial Examinations: Every 3-5 years - Cost: $200,000-1 million per examination Required Insurance Coverage: - E&O Insurance: $5-10 million coverage - Annual Cost: $100,000-250,000 - D&O Insurance: $10-25 million coverage - Annual Cost: $200,000-500,000 - Cyber Insurance: $5-10 million coverage - Annual Cost: $100,000-300,000 Total Regulatory Timeline: - Initial State License: 12-18 months - Federal Compliance: 6-8 months (concurrent) - First Policy Issuance: 18-24 months from start - Multi-State Operation: Additional 12-24 months Total Initial Regulatory Costs: - Single State Operation: $15-25 million - Multi-State Operation (5 states): $30-50 million - Annual Compliance Costs: $2-5 million per state These requirements and costs can vary significantly based on: - State of domicile - Number of states operating in - Types of health insurance products offered - Size of projected enrollment - Market conditions and risk factors Yes, existing insurance companies can potentially influence your application process, but not directly through a "veto" power. Here's how it works: 1. Public Comment Period - Most state insurance departments have a public comment period during the application process - Existing insurers can submit formal objections or concerns - They typically focus on market saturation, financial viability, or potential unfair competition 2. Market Need Assessment - Many states require a "need and necessity" showing as part of the application - You must demonstrate that: - There's sufficient market demand - Your company brings something unique or beneficial - The market can support another carrier - However, mere competition itself is not grounds for denial 3. State Regulator Discretion - Regulators consider market concentration and competition - They generally favor healthy competition unless there are legitimate concerns about: - Market destabilization - Your company's financial strength - Risk to consumers - Pure "we don't want competition" arguments from existing insurers typically don't succeed 4. Trade Association Influence - Insurance trade associations may provide input during the licensing process - They can raise concerns about: - Capital adequacy - Management experience - Business plan viability - But they cannot directly block your application Key Point: While existing insurers can object, the final decision rests with state regulators who are primarily concerned with: - Consumer protection - Market stability - Your company's financial soundness - Management competency @ 41fa852b:af7b7706
2025-02-16 15:52:51> "Our lives begin to end the day we become silent about things that matter." --Martin Luther King, Jr * * * **If Bitcoin's price action is putting you to sleep, maybe it's time to get out and add some spice to your life.** It's a big week with 12 meetups--check out the list below and see if there's one near you. Most meetups are drop-in friendly--just head to the venue and keep an eye out for a few shady-looking characters in Bitcoin merch. If you'd prefer some certainty, you can find contact details for every meetup at [bitcoinevents.uk](https://bitcoinevents.uk/). Just scroll down to find your meetup group, and you'll see how to get in touch. Let's dive in… * * * [](https://bitcoinevents.uk/donate/) * * * _This week's sponsor is…_ [](https://www.orangepillapp.com/?utm_source=BEUK&utm_medium=email&utm_campaign=BEUK) * * * ### **Upcoming Bitcoin Meetups** Happening this week… 1. [**Newcastle Bitcoin Meetup**](https://www.meetup.com/newcastlebitcoinmeetup/): A relaxed gathering for anyone interested in Bitcoin. No prior experience or ownership of Bitcoin is required, just curiosity and an interest. Conversations are Bitcoin-only focused. Happening this month on Tuesday, February 18th, at 18:30. Find them at Kabin @ Kabannas, NE1 6UQ. 🍻 2. [**Bitcoin 101**](https://meetu.ps/e/NRYv6/v822r/i): Nodes at Cyphermunk House - Participants are invited to a hands-on, peer-led class to set up their own Bitcoin node. Those wishing to build a node during the session should bring an old laptop, computer, or mini PC, along with a 2TB SSD and a USB drive with at least 4GB of storage. Attendees are also welcome to join without building a node to learn from the process. Tickets cost £9 in sats or £10 in cash, with pre-booking available at [cyphermunkhouse.com/events.](http://cyphermunkhouse.com/events). 👨🏼🎓 3. [**Bitcoin Glasgow**](https://www.meetup.com/bitcoin-glasgow-buy-sell-learn/): Bitcoin Glasgow meet every 3rd Wednesday of the month and this month will be at The Maltman, 59--61 Renfield Street at 18:00 to 20:00. This month on Wednesday the 19th. 🍺 4. [**Bitcoin Wales**](https://www.meetup.com/all-about-bitcoin-meetup-group-wales/events/): Back in action with the first meetup of 2025, and looking to grow their membership. The gathering at Zerodegrees, 27 Westgate St, Cardiff CF10 1DD invites both seasoned Bitcoiners and newcomers to connect, share ideas, and shape the future of Bitcoin in Wales. 18:00 - 21:00 on Wednesday 19th February. 🍻 5. [**OPA London Bitcoin Meetup**](https://www.eventbrite.com/e/opa-london-bitcoin-meetup-tickets-1238140223739): The first OPA London Bitcoin Meetup takes place on Wednesday 19th at 18:30 - 21:30 at the [Century Club](https://centuryclub.co.uk/) (Bitcoin accepted), 61--63 Shaftesbury Ave, London W1D 6LQ. 🍺🍷🍸 6. [**Shropshire Bitcoin**](https://x.com/shropsbitcoin): On the 19th, the Shropshire crew will be meeting at the Admiral Benbow in Shrewsbury. 🍻 7. [**Brum Bitcoin & Beer**](https://x.com/brumbitcoin): If you're in the Birmingham area head along to meet some fellow bitcoiners on Thursday 20th at 19:00. You'll find them this month at The Wellington, Bennett's Hill, B2 5SN. 🍺 8. [**Bitcoin Bristol**](https://evento.so/p/evt_iQcbZqEyZ36Bujfr): Meeting at The Left Handed Giant, BS1 6EU, at 18:15 on the 21st. Everyone is welcome, the aim is to encourage grassroots bitcoin adoption in Bristol. 🍻 9. [**2140 Collective**](https://evento.so/p/evt_tEzCj5UWYCkB9h35): Tools of freedom - GrapheneOS workshop. Learn about GrapheneOS the privacy-focused mobile operating system. Friday 21st February, 18:00 - 21:40 at Cyphermunk House. 👨🏼🎓📱 10. [**Bitcoin Walk - Edinburgh**](https://bitcoinwalk.org/): Every Saturday they walk around Arthur's Seat in this historic city. Join them at 12 pm to chat about all things Bitcoin and keep fit. 🚶🏽♂️🚶🏼♀️🚶🏻 11. [**Plymouth Bitcoiners**](https://x.com/plbitcoiners): The Plymouth meetup is on the 22nd this month. Find them at Steel Brew, PL1 3GD at 14:00. 🍻 12. [**Bitcoin East**](https://x.com/bitcoineastuk): Join Bitcoin East in Bury St. Edmunds on Sunday 23rd, 10:00 at [Procopio's Pantry](https://www.ourburystedmunds.com/business/procopios-pantry/) and then on to Vespers Bar at 12:00. All welcome, Bitcoiners and anyone else curious about Bitcoin. 🍻☕️ * * * **Get Involved** - **Volunteer Opportunities**: [Bridge2Bitcoin](https://bridge2bitcoin.com/) is actively seeking volunteers who share our passion for merchant adoption. We'd be delighted to connect if you're eager to contribute. Reach out to us on [Twitter](https://x.com/bridge2bitcoin) or through our [website](https://bridge2bitcoin.com/). - **Start Your Own Meetup**: Interested in launching a Bitcoin meetup? We're here to support you every step of the way. We've assisted numerous UK Bitcoin meetups in getting started. Get in touch via [Twitter](https://x.com/bitcoineventsuk). - **[Contribute to BTCMaps](https://wiki.btcmap.org/general/tagging-instructions.html)**: BTCMaps is a vital part of the Bitcoin ecosystem. It's a perfect project to get involved with if you're not a coder or even that technical. A great way to give back to the community. Maintain an area of the UK and keep it up-to-date. - **Telegram users**: You might find our [Telegram Channel](https://t.me/BitcoinEventsUKHub) another useful way to keep up-to-date with UK meetups. - **Feedback and Suggestions**: We value your input! Share your ideas on how we can enhance this newsletter. * * * _This week's sponsors are…_ [](https://orangecoinstore.com/) [](https://bitcoinretreat.co.uk/) * * * Get out and support the meetups where you can, visit [Bitcoin Events UK](https://bitcoinevents.uk/) for more info on each meetup and to find your closest on the interactive map. Stay tuned for more updates next week! Simon. [](https://bitcoinevents.uk/donate/)
@ 41fa852b:af7b7706
2025-02-16 15:52:51> "Our lives begin to end the day we become silent about things that matter." --Martin Luther King, Jr * * * **If Bitcoin's price action is putting you to sleep, maybe it's time to get out and add some spice to your life.** It's a big week with 12 meetups--check out the list below and see if there's one near you. Most meetups are drop-in friendly--just head to the venue and keep an eye out for a few shady-looking characters in Bitcoin merch. If you'd prefer some certainty, you can find contact details for every meetup at [bitcoinevents.uk](https://bitcoinevents.uk/). Just scroll down to find your meetup group, and you'll see how to get in touch. Let's dive in… * * * [](https://bitcoinevents.uk/donate/) * * * _This week's sponsor is…_ [](https://www.orangepillapp.com/?utm_source=BEUK&utm_medium=email&utm_campaign=BEUK) * * * ### **Upcoming Bitcoin Meetups** Happening this week… 1. [**Newcastle Bitcoin Meetup**](https://www.meetup.com/newcastlebitcoinmeetup/): A relaxed gathering for anyone interested in Bitcoin. No prior experience or ownership of Bitcoin is required, just curiosity and an interest. Conversations are Bitcoin-only focused. Happening this month on Tuesday, February 18th, at 18:30. Find them at Kabin @ Kabannas, NE1 6UQ. 🍻 2. [**Bitcoin 101**](https://meetu.ps/e/NRYv6/v822r/i): Nodes at Cyphermunk House - Participants are invited to a hands-on, peer-led class to set up their own Bitcoin node. Those wishing to build a node during the session should bring an old laptop, computer, or mini PC, along with a 2TB SSD and a USB drive with at least 4GB of storage. Attendees are also welcome to join without building a node to learn from the process. Tickets cost £9 in sats or £10 in cash, with pre-booking available at [cyphermunkhouse.com/events.](http://cyphermunkhouse.com/events). 👨🏼🎓 3. [**Bitcoin Glasgow**](https://www.meetup.com/bitcoin-glasgow-buy-sell-learn/): Bitcoin Glasgow meet every 3rd Wednesday of the month and this month will be at The Maltman, 59--61 Renfield Street at 18:00 to 20:00. This month on Wednesday the 19th. 🍺 4. [**Bitcoin Wales**](https://www.meetup.com/all-about-bitcoin-meetup-group-wales/events/): Back in action with the first meetup of 2025, and looking to grow their membership. The gathering at Zerodegrees, 27 Westgate St, Cardiff CF10 1DD invites both seasoned Bitcoiners and newcomers to connect, share ideas, and shape the future of Bitcoin in Wales. 18:00 - 21:00 on Wednesday 19th February. 🍻 5. [**OPA London Bitcoin Meetup**](https://www.eventbrite.com/e/opa-london-bitcoin-meetup-tickets-1238140223739): The first OPA London Bitcoin Meetup takes place on Wednesday 19th at 18:30 - 21:30 at the [Century Club](https://centuryclub.co.uk/) (Bitcoin accepted), 61--63 Shaftesbury Ave, London W1D 6LQ. 🍺🍷🍸 6. [**Shropshire Bitcoin**](https://x.com/shropsbitcoin): On the 19th, the Shropshire crew will be meeting at the Admiral Benbow in Shrewsbury. 🍻 7. [**Brum Bitcoin & Beer**](https://x.com/brumbitcoin): If you're in the Birmingham area head along to meet some fellow bitcoiners on Thursday 20th at 19:00. You'll find them this month at The Wellington, Bennett's Hill, B2 5SN. 🍺 8. [**Bitcoin Bristol**](https://evento.so/p/evt_iQcbZqEyZ36Bujfr): Meeting at The Left Handed Giant, BS1 6EU, at 18:15 on the 21st. Everyone is welcome, the aim is to encourage grassroots bitcoin adoption in Bristol. 🍻 9. [**2140 Collective**](https://evento.so/p/evt_tEzCj5UWYCkB9h35): Tools of freedom - GrapheneOS workshop. Learn about GrapheneOS the privacy-focused mobile operating system. Friday 21st February, 18:00 - 21:40 at Cyphermunk House. 👨🏼🎓📱 10. [**Bitcoin Walk - Edinburgh**](https://bitcoinwalk.org/): Every Saturday they walk around Arthur's Seat in this historic city. Join them at 12 pm to chat about all things Bitcoin and keep fit. 🚶🏽♂️🚶🏼♀️🚶🏻 11. [**Plymouth Bitcoiners**](https://x.com/plbitcoiners): The Plymouth meetup is on the 22nd this month. Find them at Steel Brew, PL1 3GD at 14:00. 🍻 12. [**Bitcoin East**](https://x.com/bitcoineastuk): Join Bitcoin East in Bury St. Edmunds on Sunday 23rd, 10:00 at [Procopio's Pantry](https://www.ourburystedmunds.com/business/procopios-pantry/) and then on to Vespers Bar at 12:00. All welcome, Bitcoiners and anyone else curious about Bitcoin. 🍻☕️ * * * **Get Involved** - **Volunteer Opportunities**: [Bridge2Bitcoin](https://bridge2bitcoin.com/) is actively seeking volunteers who share our passion for merchant adoption. We'd be delighted to connect if you're eager to contribute. Reach out to us on [Twitter](https://x.com/bridge2bitcoin) or through our [website](https://bridge2bitcoin.com/). - **Start Your Own Meetup**: Interested in launching a Bitcoin meetup? We're here to support you every step of the way. We've assisted numerous UK Bitcoin meetups in getting started. Get in touch via [Twitter](https://x.com/bitcoineventsuk). - **[Contribute to BTCMaps](https://wiki.btcmap.org/general/tagging-instructions.html)**: BTCMaps is a vital part of the Bitcoin ecosystem. It's a perfect project to get involved with if you're not a coder or even that technical. A great way to give back to the community. Maintain an area of the UK and keep it up-to-date. - **Telegram users**: You might find our [Telegram Channel](https://t.me/BitcoinEventsUKHub) another useful way to keep up-to-date with UK meetups. - **Feedback and Suggestions**: We value your input! Share your ideas on how we can enhance this newsletter. * * * _This week's sponsors are…_ [](https://orangecoinstore.com/) [](https://bitcoinretreat.co.uk/) * * * Get out and support the meetups where you can, visit [Bitcoin Events UK](https://bitcoinevents.uk/) for more info on each meetup and to find your closest on the interactive map. Stay tuned for more updates next week! Simon. [](https://bitcoinevents.uk/donate/) @ e3168078:10f13b2c
2025-01-21 15:44:45ノス! 最近Umbrel上のn8nを使ってstacker newsの記事を要約するNostr botを作ってみました。 その際にFirecrawlというスクレイピングのSaaSを使っていたんですがセルフホストできるようなので試してみました。 Firecrawlは動的なページも読めたりマークダウンへの変換をしてくれますが無料プランだと1ヶ月500ページの制限があり、セルフホストすれば気兼ねなく使えます! 今回はUmbrel上のPortainerというアプリを使ってFirecrawlを動かせたのでその記録です。 ## 手順 まずはUmbrelにPortainerアプリをインストールします。 Poratinerは今回初めて使ったんですが独自のDockerコンテナをUmbrelで動かす際に推奨されているアプリのようです。  アプリを開いてパスワードの初期設定などを済ませるとダッシュボードが表示されるかと思います。 ここでStackという機能を使ってFirecrawlのDocker composeを一括で取り込むことができます。 新しいStackを作成する画面で以下を入力します。 Repository URL: https://github.com/mendableai/firecrawl Repository reference: refs/heads/main Compose path: docker-compose.**yaml** (デフォルトがymlになっててハマりました…)  上記に加えてenv varを設定する必要があるんですがPortainerでは上記の画像下部にあるように "Load Variables from .env file" からenvファイルを選択できます。 [Firecrawlのgithub](https://github.com/mendableai/firecrawl/blob/main/SELF_HOST.md)にあるように apps/api/.env.example をダウンロードし以下の内容を更新しPortainerに取り込ませます。 ``` USE_DB_AUTHENTICATION=false TEST_API_KEY=fc-test-key ``` あとはDeploy the stackを押して少し待つとfirecrawlのセットアップ完了です。 ## 確認 動作テストにはUmbrelの設定からAdvanced Settings -> Terminal -> Umbrel OSを開き以下のコマンドを実行ししマークダウンが返って来れば成功です。 ``` $ curl -X POST http://localhost:3002/v1/scrape -H 'Authorization: Bearer fc-test-key' -H 'Content-Type: application/json' -d '{ "url": "https://example.com", "formats": ["markdown"] }' {"success":true,"data":{"markdown":"Example Domain\n==============\n\nThis domain is for use in illustrative examples in documents. You may use this domain in literature without prior coordination or asking for permission.\n\n[More information...](https://www.iana.org/domains/example)","metadata":{"title":"Example Domain","ogLocaleAlternate":[],"scrapeId":"7c196348-6561-4ebb-bb8a-9121a29c64b5","viewport":"width=device-width, initial-scale=1","sourceURL":"https://example.com","url":"https://example.com/","statusCode":200}}} ``` またn8n等のUmbrelの他のアプリ(コンテナ)から利用する場合はlocalhostがコンテナ自身になってしまうので別のIP等(172.17.0.1)を使う必要があるのでご注意ください。 ([参考](https://community.n8n.io/t/the-service-refused-the-connection-perhaps-it-is-offline-n8n-and-nocodb/33587?utm_source=chatgpt.com)) 以上でUmbrel上でのFirecrawlセルフホストができるようになりn8nからも制限なく使えるようになりました。
@ e3168078:10f13b2c
2025-01-21 15:44:45ノス! 最近Umbrel上のn8nを使ってstacker newsの記事を要約するNostr botを作ってみました。 その際にFirecrawlというスクレイピングのSaaSを使っていたんですがセルフホストできるようなので試してみました。 Firecrawlは動的なページも読めたりマークダウンへの変換をしてくれますが無料プランだと1ヶ月500ページの制限があり、セルフホストすれば気兼ねなく使えます! 今回はUmbrel上のPortainerというアプリを使ってFirecrawlを動かせたのでその記録です。 ## 手順 まずはUmbrelにPortainerアプリをインストールします。 Poratinerは今回初めて使ったんですが独自のDockerコンテナをUmbrelで動かす際に推奨されているアプリのようです。  アプリを開いてパスワードの初期設定などを済ませるとダッシュボードが表示されるかと思います。 ここでStackという機能を使ってFirecrawlのDocker composeを一括で取り込むことができます。 新しいStackを作成する画面で以下を入力します。 Repository URL: https://github.com/mendableai/firecrawl Repository reference: refs/heads/main Compose path: docker-compose.**yaml** (デフォルトがymlになっててハマりました…)  上記に加えてenv varを設定する必要があるんですがPortainerでは上記の画像下部にあるように "Load Variables from .env file" からenvファイルを選択できます。 [Firecrawlのgithub](https://github.com/mendableai/firecrawl/blob/main/SELF_HOST.md)にあるように apps/api/.env.example をダウンロードし以下の内容を更新しPortainerに取り込ませます。 ``` USE_DB_AUTHENTICATION=false TEST_API_KEY=fc-test-key ``` あとはDeploy the stackを押して少し待つとfirecrawlのセットアップ完了です。 ## 確認 動作テストにはUmbrelの設定からAdvanced Settings -> Terminal -> Umbrel OSを開き以下のコマンドを実行ししマークダウンが返って来れば成功です。 ``` $ curl -X POST http://localhost:3002/v1/scrape -H 'Authorization: Bearer fc-test-key' -H 'Content-Type: application/json' -d '{ "url": "https://example.com", "formats": ["markdown"] }' {"success":true,"data":{"markdown":"Example Domain\n==============\n\nThis domain is for use in illustrative examples in documents. You may use this domain in literature without prior coordination or asking for permission.\n\n[More information...](https://www.iana.org/domains/example)","metadata":{"title":"Example Domain","ogLocaleAlternate":[],"scrapeId":"7c196348-6561-4ebb-bb8a-9121a29c64b5","viewport":"width=device-width, initial-scale=1","sourceURL":"https://example.com","url":"https://example.com/","statusCode":200}}} ``` またn8n等のUmbrelの他のアプリ(コンテナ)から利用する場合はlocalhostがコンテナ自身になってしまうので別のIP等(172.17.0.1)を使う必要があるのでご注意ください。 ([参考](https://community.n8n.io/t/the-service-refused-the-connection-perhaps-it-is-offline-n8n-and-nocodb/33587?utm_source=chatgpt.com)) 以上でUmbrel上でのFirecrawlセルフホストができるようになりn8nからも制限なく使えるようになりました。 @ e3ba5e1a:5e433365
2025-02-04 08:29:00President Trump has started rolling out his tariffs, something I [blogged about in November](https://www.snoyman.com/blog/2024/11/steelmanning-tariffs/). People are talking about these tariffs a lot right now, with many people (correctly) commenting on how consumers will end up with higher prices as a result of these tariffs. While that part is true, I’ve seen a lot of people taking it to the next, incorrect step: that consumers will pay the entirety of the tax. I [put up a poll on X](https://x.com/snoyberg/status/1886035800019599808) to see what people thought, and while the right answer got a lot of votes, it wasn't the winner.  For purposes of this blog post, our ultimate question will be the following: * Suppose apples currently sell for $1 each in the entire United States. * There are domestic sellers and foreign sellers of apples, all receiving the same price. * There are no taxes or tariffs on the purchase of apples. * The question is: if the US federal government puts a $0.50 import tariff per apple, what will be the change in the following: * Number of apples bought in the US * Price paid by buyers for apples in the US * Post-tax price received by domestic apple producers * Post-tax price received by foreign apple producers Before we can answer that question, we need to ask an easier, first question: before instituting the tariff, why do apples cost $1? And finally, before we dive into the details, let me provide you with the answers to the ultimate question. I recommend you try to guess these answers before reading this, and if you get it wrong, try to understand why: 1. The number of apples bought will go down 2. The buyers will pay more for each apple they buy, but not the full amount of the tariff 3. Domestic apple sellers will receive a *higher* price per apple 4. Foreign apple sellers will receive a *lower* price per apple, but not lowered by the full amount of the tariff In other words, regardless of who sends the payment to the government, both taxed parties (domestic buyers and foreign sellers) will absorb some of the costs of the tariff, while domestic sellers will benefit from the protectionism provided by tariffs and be able to sell at a higher price per unit. ## Marginal benefit All of the numbers discussed below are part of a [helper Google Sheet](https://docs.google.com/spreadsheets/d/14ZbkWpw1B9Q1UDB9Yh47DmdKQfIafVVBKbDUsSIfGZw/edit?usp=sharing) I put together for this analysis. Also, apologies about the jagged lines in the charts below, I hadn’t realized before starting on this that there are [some difficulties with creating supply and demand charts in Google Sheets](https://superuser.com/questions/1359731/how-to-create-a-supply-demand-style-chart). Let’s say I absolutely love apples, they’re my favorite food. How much would I be willing to pay for a single apple? You might say “$1, that’s the price in the supermarket,” and in many ways you’d be right. If I walk into supermarket A, see apples on sale for $50, and know that I can buy them at supermarket B for $1, I’ll almost certainly leave A and go buy at B. But that’s not what I mean. What I mean is: how high would the price of apples have to go *everywhere* so that I’d no longer be willing to buy a single apple? This is a purely personal, subjective opinion. It’s impacted by how much money I have available, other expenses I need to cover, and how much I like apples. But let’s say the number is $5. How much would I be willing to pay for another apple? Maybe another $5. But how much am I willing to pay for the 1,000th apple? 10,000th? At some point, I’ll get sick of apples, or run out of space to keep the apples, or not be able to eat, cook, and otherwise preserve all those apples before they rot. The point being: I’ll be progressively willing to spend less and less money for each apple. This form of analysis is called *marginal benefit*: how much benefit (expressed as dollars I’m willing to spend) will I receive from each apple? This is a downward sloping function: for each additional apple I buy (quantity demanded), the price I’m willing to pay goes down. This is what gives my personal *demand curve*. And if we aggregate demand curves across all market participants (meaning: everyone interested in buying apples), we end up with something like this:  Assuming no changes in people’s behavior and other conditions in the market, this chart tells us how many apples will be purchased by our buyers at each price point between $0.50 and $5. And ceteris paribus (all else being equal), this will continue to be the demand curve for apples. ## Marginal cost Demand is half the story of economics. The other half is supply, or: how many apples will I sell at each price point? Supply curves are upward sloping: the higher the price, the more a person or company is willing and able to sell a product. Let’s understand why. Suppose I have an apple orchard. It’s a large property right next to my house. With about 2 minutes of effort, I can walk out of my house, find the nearest tree, pick 5 apples off the tree, and call it a day. 5 apples for 2 minutes of effort is pretty good, right? Yes, there was all the effort necessary to buy the land, and plant the trees, and water them… and a bunch more than I likely can’t even guess at. We’re going to ignore all of that for our analysis, because for short-term supply-and-demand movement, we can ignore these kinds of *sunk costs*. One other simplification: in reality, supply curves often start descending before ascending. This accounts for achieving efficiencies of scale after the first number of units purchased. But since both these topics are unneeded for understanding taxes, I won’t go any further. Anyway, back to my apple orchard. If someone offers me $0.50 per apple, I can do 2 minutes of effort and get $2.50 in revenue, which equates to a $75/hour wage for me. I’m more than happy to pick apples at that price\! However, let’s say someone comes to buy 10,000 apples from me instead. I no longer just walk out to my nearest tree. I’m going to need to get in my truck, drive around, spend the day in the sun, pay for gas, take a day off of my day job (let’s say it pays me $70/hour). The costs go up significantly. Let’s say it takes 5 days to harvest all those apples myself, it costs me $100 in fuel and other expenses, and I lose out on my $70/hour job for 5 days. We end up with: * Total expenditure: $100 \+ $70 \* 8 hours a day \* 5 days \== $2900 * Total revenue: $5000 (10,000 apples at $0.50 each) * Total profit: $2100 So I’m still willing to sell the apples at this price, but it’s not as attractive as before. And as the number of apples purchased goes up, my costs keep increasing. I’ll need to spend more money on fuel to travel more of my property. At some point I won’t be able to do the work myself anymore, so I’ll need to pay others to work on the farm, and they’ll be slower at picking apples than me (less familiar with the property, less direct motivation, etc.). The point being: at some point, the number of apples can go high enough that the $0.50 price point no longer makes me any money. This kind of analysis is called *marginal cost*. It refers to the additional amount of expenditure a seller has to spend in order to produce each additional unit of the good. Marginal costs go up as quantity sold goes up. And like demand curves, if you aggregate this data across all sellers, you get a supply curve like this:  ## Equilibrium price We now know, for every price point, how many apples buyers will purchase, and how many apples sellers will sell. Now we find the equilibrium: where the supply and demand curves meet. This point represents where the marginal benefit a buyer would receive from the next buyer would be less than the cost it would take the next seller to make it. Let’s see it in a chart:  You’ll notice that these two graphs cross at the $1 price point, where 63 apples are both demanded (bought by consumers) and supplied (sold by producers). This is our equilibrium price. We also have a visualization of the *surplus* created by these trades. Everything to the left of the equilibrium point and between the supply and demand curves represents surplus: an area where someone is receiving something of more value than they give. For example: * When I bought my first apple for $1, but I was willing to spend $5, I made $4 of consumer surplus. The consumer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and above the equilibrium price point. * When a seller sells his first apple for $1, but it only cost $0.50 to produce it, the seller made $0.50 of producer surplus. The producer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and below the equilibrium price point. Another way of thinking of surplus is “every time someone got a better price than they would have been willing to take.” OK, with this in place, we now have enough information to figure out how to price in the tariff, which we’ll treat as a negative externality. ## Modeling taxes Alright, the government has now instituted a $0.50 tariff on every apple sold within the US by a foreign producer. We can generally model taxes by either increasing the marginal cost of each unit sold (shifting the supply curve up), or by decreasing the marginal benefit of each unit bought (shifting the demand curve down). In this case, since only some of the producers will pay the tax, it makes more sense to modify the supply curve. First, let’s see what happens to the foreign seller-only supply curve when you add in the tariff:  With the tariff in place, for each quantity level, the price at which the seller will sell is $0.50 higher than before the tariff. That makes sense: if I was previously willing to sell my 82nd apple for $3, I would now need to charge $3.50 for that apple to cover the cost of the tariff. We see this as the tariff “pushing up” or “pushing left” the original supply curve. We can add this new supply curve to our existing (unchanged) supply curve for domestic-only sellers, and we end up with a result like this:  The total supply curve adds up the individual foreign and domestic supply curves. At each price point, we add up the total quantity each group would be willing to sell to determine the total quantity supplied for each price point. Once we have that cumulative supply curve defined, we can produce an updated supply-and-demand chart including the tariff:  As we can see, the equilibrium has shifted: * The equilibrium price paid by consumers has risen from $1 to $1.20. * The total number of apples purchased has dropped from 63 apples to 60 apples. * Consumers therefore received 3 less apples. They spent $72 for these 60 apples, whereas previously they spent $63 for 3 more apples, a definite decrease in consumer surplus. * Foreign producers sold 36 of those apples (see the raw data in the linked Google Sheet), for a gross revenue of $43.20. However, they also need to pay the tariff to the US government, which accounts for $18, meaning they only receive $25.20 post-tariff. Previously, they sold 42 apples at $1 each with no tariff to be paid, meaning they took home $42. * Domestic producers sold the remaining 24 apples at $1.20, giving them a revenue of $28.80. Since they don’t pay the tariff, they take home all of that money. By contrast, previously, they sold 21 apples at $1, for a take-home of $21. * The government receives $0.50 for each of the 60 apples sold, or in other words receives $30 in revenue it wouldn’t have received otherwise. We could be more specific about the surpluses, and calculate the actual areas for consumer surplus, producer surplus, inefficiency from the tariff, and government revenue from the tariff. But I won’t bother, as those calculations get slightly more involved. Instead, let’s just look at the aggregate outcomes: * Consumers were unquestionably hurt. Their price paid went up by $0.20 per apple, and received less apples. * Foreign producers were also hurt. Their price received went down from the original $1 to the new post-tariff price of $1.20, minus the $0.50 tariff. In other words: foreign producers only receive $0.70 per apple now. This hurt can be mitigated by shifting sales to other countries without a tariff, but the pain will exist regardless. * Domestic producers scored. They can sell less apples and make more revenue doing it. * And the government walked away with an extra $30. Hopefully you now see the answer to the original questions. Importantly, while the government imposed a $0.50 tariff, neither side fully absorbed that cost. Consumers paid a bit more, foreign producers received a bit less. The exact details of how that tariff was split across the groups is mediated by the relevant supply and demand curves of each group. If you want to learn more about this, the relevant search term is “price elasticity,” or how much a group’s quantity supplied or demanded will change based on changes in the price. ## Other taxes Most taxes are some kind of a tax on trade. Tariffs on apples is an obvious one. But the same applies to income tax (taxing the worker for the trade of labor for money) or payroll tax (same thing, just taxing the employer instead). Interestingly, you can use the same model for analyzing things like tax incentives. For example, if the government decided to subsidize domestic apple production by giving the domestic producers a $0.50 bonus for each apple they sell, we would end up with a similar kind of analysis, except instead of the foreign supply curve shifting up, we’d see the domestic supply curve shifting down. And generally speaking, this is what you’ll *always* see with government involvement in the economy. It will result in disrupting an existing equilibrium, letting the market readjust to a new equilibrium, and incentivization of some behavior, causing some people to benefit and others to lose out. We saw with the apple tariff, domestic producers and the government benefited while others lost. You can see the reverse though with tax incentives. If I give a tax incentive of providing a deduction (not paying income tax) for preschool, we would end up with: * Government needs to make up the difference in tax revenue, either by raising taxes on others or printing more money (leading to inflation). Either way, those paying the tax or those holding government debased currency will pay a price. * Those people who don’t use the preschool deduction will receive no benefit, so they simply pay a cost. * Those who do use the preschool deduction will end up paying less on tax+preschool than they would have otherwise. This analysis is fully amoral. It’s not saying whether providing subsidized preschool is a good thing or not, it simply tells you where the costs will be felt, and points out that such government interference in free economic choice does result in inefficiencies in the system. Once you have that knowledge, you’re more well educated on making a decision about whether the costs of government intervention are worth the benefits.
@ e3ba5e1a:5e433365
2025-02-04 08:29:00President Trump has started rolling out his tariffs, something I [blogged about in November](https://www.snoyman.com/blog/2024/11/steelmanning-tariffs/). People are talking about these tariffs a lot right now, with many people (correctly) commenting on how consumers will end up with higher prices as a result of these tariffs. While that part is true, I’ve seen a lot of people taking it to the next, incorrect step: that consumers will pay the entirety of the tax. I [put up a poll on X](https://x.com/snoyberg/status/1886035800019599808) to see what people thought, and while the right answer got a lot of votes, it wasn't the winner.  For purposes of this blog post, our ultimate question will be the following: * Suppose apples currently sell for $1 each in the entire United States. * There are domestic sellers and foreign sellers of apples, all receiving the same price. * There are no taxes or tariffs on the purchase of apples. * The question is: if the US federal government puts a $0.50 import tariff per apple, what will be the change in the following: * Number of apples bought in the US * Price paid by buyers for apples in the US * Post-tax price received by domestic apple producers * Post-tax price received by foreign apple producers Before we can answer that question, we need to ask an easier, first question: before instituting the tariff, why do apples cost $1? And finally, before we dive into the details, let me provide you with the answers to the ultimate question. I recommend you try to guess these answers before reading this, and if you get it wrong, try to understand why: 1. The number of apples bought will go down 2. The buyers will pay more for each apple they buy, but not the full amount of the tariff 3. Domestic apple sellers will receive a *higher* price per apple 4. Foreign apple sellers will receive a *lower* price per apple, but not lowered by the full amount of the tariff In other words, regardless of who sends the payment to the government, both taxed parties (domestic buyers and foreign sellers) will absorb some of the costs of the tariff, while domestic sellers will benefit from the protectionism provided by tariffs and be able to sell at a higher price per unit. ## Marginal benefit All of the numbers discussed below are part of a [helper Google Sheet](https://docs.google.com/spreadsheets/d/14ZbkWpw1B9Q1UDB9Yh47DmdKQfIafVVBKbDUsSIfGZw/edit?usp=sharing) I put together for this analysis. Also, apologies about the jagged lines in the charts below, I hadn’t realized before starting on this that there are [some difficulties with creating supply and demand charts in Google Sheets](https://superuser.com/questions/1359731/how-to-create-a-supply-demand-style-chart). Let’s say I absolutely love apples, they’re my favorite food. How much would I be willing to pay for a single apple? You might say “$1, that’s the price in the supermarket,” and in many ways you’d be right. If I walk into supermarket A, see apples on sale for $50, and know that I can buy them at supermarket B for $1, I’ll almost certainly leave A and go buy at B. But that’s not what I mean. What I mean is: how high would the price of apples have to go *everywhere* so that I’d no longer be willing to buy a single apple? This is a purely personal, subjective opinion. It’s impacted by how much money I have available, other expenses I need to cover, and how much I like apples. But let’s say the number is $5. How much would I be willing to pay for another apple? Maybe another $5. But how much am I willing to pay for the 1,000th apple? 10,000th? At some point, I’ll get sick of apples, or run out of space to keep the apples, or not be able to eat, cook, and otherwise preserve all those apples before they rot. The point being: I’ll be progressively willing to spend less and less money for each apple. This form of analysis is called *marginal benefit*: how much benefit (expressed as dollars I’m willing to spend) will I receive from each apple? This is a downward sloping function: for each additional apple I buy (quantity demanded), the price I’m willing to pay goes down. This is what gives my personal *demand curve*. And if we aggregate demand curves across all market participants (meaning: everyone interested in buying apples), we end up with something like this:  Assuming no changes in people’s behavior and other conditions in the market, this chart tells us how many apples will be purchased by our buyers at each price point between $0.50 and $5. And ceteris paribus (all else being equal), this will continue to be the demand curve for apples. ## Marginal cost Demand is half the story of economics. The other half is supply, or: how many apples will I sell at each price point? Supply curves are upward sloping: the higher the price, the more a person or company is willing and able to sell a product. Let’s understand why. Suppose I have an apple orchard. It’s a large property right next to my house. With about 2 minutes of effort, I can walk out of my house, find the nearest tree, pick 5 apples off the tree, and call it a day. 5 apples for 2 minutes of effort is pretty good, right? Yes, there was all the effort necessary to buy the land, and plant the trees, and water them… and a bunch more than I likely can’t even guess at. We’re going to ignore all of that for our analysis, because for short-term supply-and-demand movement, we can ignore these kinds of *sunk costs*. One other simplification: in reality, supply curves often start descending before ascending. This accounts for achieving efficiencies of scale after the first number of units purchased. But since both these topics are unneeded for understanding taxes, I won’t go any further. Anyway, back to my apple orchard. If someone offers me $0.50 per apple, I can do 2 minutes of effort and get $2.50 in revenue, which equates to a $75/hour wage for me. I’m more than happy to pick apples at that price\! However, let’s say someone comes to buy 10,000 apples from me instead. I no longer just walk out to my nearest tree. I’m going to need to get in my truck, drive around, spend the day in the sun, pay for gas, take a day off of my day job (let’s say it pays me $70/hour). The costs go up significantly. Let’s say it takes 5 days to harvest all those apples myself, it costs me $100 in fuel and other expenses, and I lose out on my $70/hour job for 5 days. We end up with: * Total expenditure: $100 \+ $70 \* 8 hours a day \* 5 days \== $2900 * Total revenue: $5000 (10,000 apples at $0.50 each) * Total profit: $2100 So I’m still willing to sell the apples at this price, but it’s not as attractive as before. And as the number of apples purchased goes up, my costs keep increasing. I’ll need to spend more money on fuel to travel more of my property. At some point I won’t be able to do the work myself anymore, so I’ll need to pay others to work on the farm, and they’ll be slower at picking apples than me (less familiar with the property, less direct motivation, etc.). The point being: at some point, the number of apples can go high enough that the $0.50 price point no longer makes me any money. This kind of analysis is called *marginal cost*. It refers to the additional amount of expenditure a seller has to spend in order to produce each additional unit of the good. Marginal costs go up as quantity sold goes up. And like demand curves, if you aggregate this data across all sellers, you get a supply curve like this:  ## Equilibrium price We now know, for every price point, how many apples buyers will purchase, and how many apples sellers will sell. Now we find the equilibrium: where the supply and demand curves meet. This point represents where the marginal benefit a buyer would receive from the next buyer would be less than the cost it would take the next seller to make it. Let’s see it in a chart:  You’ll notice that these two graphs cross at the $1 price point, where 63 apples are both demanded (bought by consumers) and supplied (sold by producers). This is our equilibrium price. We also have a visualization of the *surplus* created by these trades. Everything to the left of the equilibrium point and between the supply and demand curves represents surplus: an area where someone is receiving something of more value than they give. For example: * When I bought my first apple for $1, but I was willing to spend $5, I made $4 of consumer surplus. The consumer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and above the equilibrium price point. * When a seller sells his first apple for $1, but it only cost $0.50 to produce it, the seller made $0.50 of producer surplus. The producer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and below the equilibrium price point. Another way of thinking of surplus is “every time someone got a better price than they would have been willing to take.” OK, with this in place, we now have enough information to figure out how to price in the tariff, which we’ll treat as a negative externality. ## Modeling taxes Alright, the government has now instituted a $0.50 tariff on every apple sold within the US by a foreign producer. We can generally model taxes by either increasing the marginal cost of each unit sold (shifting the supply curve up), or by decreasing the marginal benefit of each unit bought (shifting the demand curve down). In this case, since only some of the producers will pay the tax, it makes more sense to modify the supply curve. First, let’s see what happens to the foreign seller-only supply curve when you add in the tariff:  With the tariff in place, for each quantity level, the price at which the seller will sell is $0.50 higher than before the tariff. That makes sense: if I was previously willing to sell my 82nd apple for $3, I would now need to charge $3.50 for that apple to cover the cost of the tariff. We see this as the tariff “pushing up” or “pushing left” the original supply curve. We can add this new supply curve to our existing (unchanged) supply curve for domestic-only sellers, and we end up with a result like this:  The total supply curve adds up the individual foreign and domestic supply curves. At each price point, we add up the total quantity each group would be willing to sell to determine the total quantity supplied for each price point. Once we have that cumulative supply curve defined, we can produce an updated supply-and-demand chart including the tariff:  As we can see, the equilibrium has shifted: * The equilibrium price paid by consumers has risen from $1 to $1.20. * The total number of apples purchased has dropped from 63 apples to 60 apples. * Consumers therefore received 3 less apples. They spent $72 for these 60 apples, whereas previously they spent $63 for 3 more apples, a definite decrease in consumer surplus. * Foreign producers sold 36 of those apples (see the raw data in the linked Google Sheet), for a gross revenue of $43.20. However, they also need to pay the tariff to the US government, which accounts for $18, meaning they only receive $25.20 post-tariff. Previously, they sold 42 apples at $1 each with no tariff to be paid, meaning they took home $42. * Domestic producers sold the remaining 24 apples at $1.20, giving them a revenue of $28.80. Since they don’t pay the tariff, they take home all of that money. By contrast, previously, they sold 21 apples at $1, for a take-home of $21. * The government receives $0.50 for each of the 60 apples sold, or in other words receives $30 in revenue it wouldn’t have received otherwise. We could be more specific about the surpluses, and calculate the actual areas for consumer surplus, producer surplus, inefficiency from the tariff, and government revenue from the tariff. But I won’t bother, as those calculations get slightly more involved. Instead, let’s just look at the aggregate outcomes: * Consumers were unquestionably hurt. Their price paid went up by $0.20 per apple, and received less apples. * Foreign producers were also hurt. Their price received went down from the original $1 to the new post-tariff price of $1.20, minus the $0.50 tariff. In other words: foreign producers only receive $0.70 per apple now. This hurt can be mitigated by shifting sales to other countries without a tariff, but the pain will exist regardless. * Domestic producers scored. They can sell less apples and make more revenue doing it. * And the government walked away with an extra $30. Hopefully you now see the answer to the original questions. Importantly, while the government imposed a $0.50 tariff, neither side fully absorbed that cost. Consumers paid a bit more, foreign producers received a bit less. The exact details of how that tariff was split across the groups is mediated by the relevant supply and demand curves of each group. If you want to learn more about this, the relevant search term is “price elasticity,” or how much a group’s quantity supplied or demanded will change based on changes in the price. ## Other taxes Most taxes are some kind of a tax on trade. Tariffs on apples is an obvious one. But the same applies to income tax (taxing the worker for the trade of labor for money) or payroll tax (same thing, just taxing the employer instead). Interestingly, you can use the same model for analyzing things like tax incentives. For example, if the government decided to subsidize domestic apple production by giving the domestic producers a $0.50 bonus for each apple they sell, we would end up with a similar kind of analysis, except instead of the foreign supply curve shifting up, we’d see the domestic supply curve shifting down. And generally speaking, this is what you’ll *always* see with government involvement in the economy. It will result in disrupting an existing equilibrium, letting the market readjust to a new equilibrium, and incentivization of some behavior, causing some people to benefit and others to lose out. We saw with the apple tariff, domestic producers and the government benefited while others lost. You can see the reverse though with tax incentives. If I give a tax incentive of providing a deduction (not paying income tax) for preschool, we would end up with: * Government needs to make up the difference in tax revenue, either by raising taxes on others or printing more money (leading to inflation). Either way, those paying the tax or those holding government debased currency will pay a price. * Those people who don’t use the preschool deduction will receive no benefit, so they simply pay a cost. * Those who do use the preschool deduction will end up paying less on tax+preschool than they would have otherwise. This analysis is fully amoral. It’s not saying whether providing subsidized preschool is a good thing or not, it simply tells you where the costs will be felt, and points out that such government interference in free economic choice does result in inefficiencies in the system. Once you have that knowledge, you’re more well educated on making a decision about whether the costs of government intervention are worth the benefits. @ b17fccdf:b7211155
2025-02-01 18:41:27#### **Next new resources about the MiniBolt guide have been released**: --- * 🆕 **Roadmap**: [LINK](https://github.com/orgs/minibolt-guide/projects/1) * 🆕 **Dynamic Network map**: [LINK](https://app.diagrams.net/?tags={}&lightbox=1&target=blank&highlight=0000ff&edit=_blank&layers=1&nav=1&title=networkmap.drawio.png#Uhttps://raw.githubusercontent.com/minibolt-guide/minibolt/main/resources/networkmap.drawio.png) * 🆕 **Nostr community**: [LINK](https://habla.news/c/[n]addr1qqyy66twd9px7mr5qyf8wumn8ghj7mmxve3ksctfdch8qatzqgstzl7vmurm5gu87qutx3pxwgxddrg39huj809zhmv03scfkus3z4grqsqqpphk2j0aff) < ~ REMOVE the "[]" symbols from the URL (naddr...) to access * 🆕 **Linktr FOSS** (UC) by [Gzuuus](nostr:npub1gzuushllat7pet0ccv9yuhygvc8ldeyhrgxuwg744dn5khnpk3gs3ea5ds): [LINK](https://linktr.minibolt.info) * 🆕 **Donate webpage**: 🚾 [Clearnet LINK](https://donate.minibolt.info) || 🧅 [Onion LINK](http://3iqm7nidexns5p6wmgc23ibgiscm6rge7hwyeziviwgav4fl7xui4mqd.onion/apps/Li3AtEGDsqNmNddv6rX69taidm3/pos) * 🆕 **Contact email**: [hello@minibolt.info](mailto:hello@minibolt.info) --- Enjoy it MiniBolter! 💙
@ b17fccdf:b7211155
2025-02-01 18:41:27#### **Next new resources about the MiniBolt guide have been released**: --- * 🆕 **Roadmap**: [LINK](https://github.com/orgs/minibolt-guide/projects/1) * 🆕 **Dynamic Network map**: [LINK](https://app.diagrams.net/?tags={}&lightbox=1&target=blank&highlight=0000ff&edit=_blank&layers=1&nav=1&title=networkmap.drawio.png#Uhttps://raw.githubusercontent.com/minibolt-guide/minibolt/main/resources/networkmap.drawio.png) * 🆕 **Nostr community**: [LINK](https://habla.news/c/[n]addr1qqyy66twd9px7mr5qyf8wumn8ghj7mmxve3ksctfdch8qatzqgstzl7vmurm5gu87qutx3pxwgxddrg39huj809zhmv03scfkus3z4grqsqqpphk2j0aff) < ~ REMOVE the "[]" symbols from the URL (naddr...) to access * 🆕 **Linktr FOSS** (UC) by [Gzuuus](nostr:npub1gzuushllat7pet0ccv9yuhygvc8ldeyhrgxuwg744dn5khnpk3gs3ea5ds): [LINK](https://linktr.minibolt.info) * 🆕 **Donate webpage**: 🚾 [Clearnet LINK](https://donate.minibolt.info) || 🧅 [Onion LINK](http://3iqm7nidexns5p6wmgc23ibgiscm6rge7hwyeziviwgav4fl7xui4mqd.onion/apps/Li3AtEGDsqNmNddv6rX69taidm3/pos) * 🆕 **Contact email**: [hello@minibolt.info](mailto:hello@minibolt.info) --- Enjoy it MiniBolter! 💙 @ 9e69e420:d12360c2
2025-02-01 11:16:04 Federal employees must remove pronouns from email signatures by the end of the day. This directive comes from internal memos tied to two executive orders signed by Donald Trump. The orders target diversity and equity programs within the government.  CDC, Department of Transportation, and Department of Energy employees were affected. Staff were instructed to make changes in line with revised policy prohibiting certain language. One CDC employee shared frustration, stating, “In my decade-plus years at CDC, I've never been told what I can and can't put in my email signature.” The directive is part of a broader effort to eliminate DEI initiatives from federal discourse.
@ 9e69e420:d12360c2
2025-02-01 11:16:04 Federal employees must remove pronouns from email signatures by the end of the day. This directive comes from internal memos tied to two executive orders signed by Donald Trump. The orders target diversity and equity programs within the government.  CDC, Department of Transportation, and Department of Energy employees were affected. Staff were instructed to make changes in line with revised policy prohibiting certain language. One CDC employee shared frustration, stating, “In my decade-plus years at CDC, I've never been told what I can and can't put in my email signature.” The directive is part of a broader effort to eliminate DEI initiatives from federal discourse. @ 97c70a44:ad98e322
2025-01-30 17:15:37There was a slight dust up recently over a website someone runs removing a listing for an app someone built based on entirely arbitrary criteria. I'm not to going to attempt to speak for either wounded party, but I would like to share my own personal definition for what constitutes a "nostr app" in an effort to help clarify what might be an otherwise confusing and opaque purity test. In this post, I will be committing the "no true Scotsman" fallacy, in which I start with the most liberal definition I can come up with, and gradually refine it until all that is left is the purest, gleamingest, most imaginary and unattainable nostr app imaginable. As I write this, I wonder if anything built yet will actually qualify. In any case, here we go. # It uses nostr The lowest bar for what a "nostr app" might be is an app ("application" - i.e. software, not necessarily a native app of any kind) that has some nostr-specific code in it, but which doesn't take any advantage of what makes nostr distinctive as a protocol. Examples might include a scraper of some kind which fulfills its charter by fetching data from relays (regardless of whether it validates or retains signatures). Another might be a regular web 2.0 app which provides an option to "log in with nostr" by requesting and storing the user's public key. In either case, the fact that nostr is involved is entirely neutral. A scraper can scrape html, pdfs, jsonl, whatever data source - nostr relays are just another target. Likewise, a user's key in this scenario is treated merely as an opaque identifier, with no appreciation for the super powers it brings along. In most cases, this kind of app only exists as a marketing ploy, or less cynically, because it wants to get in on the hype of being a "nostr app", without the developer quite understanding what that means, or having the budget to execute properly on the claim. # It leverages nostr Some of you might be wondering, "isn't 'leverage' a synonym for 'use'?" And you would be right, but for one connotative difference. It's possible to "use" something improperly, but by definition leverage gives you a mechanical advantage that you wouldn't otherwise have. This is the second category of "nostr app". This kind of app gets some benefit out of the nostr protocol and network, but in an entirely selfish fashion. The intention of this kind of app is not to augment the nostr network, but to augment its own UX by borrowing some nifty thing from the protocol without really contributing anything back. Some examples might include: - Using nostr signers to encrypt or sign data, and then store that data on a proprietary server. - Using nostr relays as a kind of low-code backend, but using proprietary event payloads. - Using nostr event kinds to represent data (why), but not leveraging the trustlessness that buys you. An application in this category might even communicate to its users via nostr DMs - but this doesn't make it a "nostr app" any more than a website that emails you hot deals on herbal supplements is an "email app". These apps are purely parasitic on the nostr ecosystem. In the long-term, that's not necessarily a bad thing. Email's ubiquity is self-reinforcing. But in the short term, this kind of "nostr app" can actually do damage to nostr's reputation by over-promising and under-delivering. # It complements nostr Next up, we have apps that get some benefit out of nostr as above, but give back by providing a unique value proposition to nostr users as nostr users. This is a bit of a fine distinction, but for me this category is for apps which focus on solving problems that nostr isn't good at solving, leaving the nostr integration in a secondary or supporting role. One example of this kind of app was Mutiny (RIP), which not only allowed users to sign in with nostr, but also pulled those users' social graphs so that users could send money to people they knew and trusted. Mutiny was doing a great job of leveraging nostr, as well as providing value to users with nostr identities - but it was still primarily a bitcoin wallet, not a "nostr app" in the purest sense. Other examples are things like Nostr Nests and Zap.stream, whose core value proposition is streaming video or audio content. Both make great use of nostr identities, data formats, and relays, but they're primarily streaming apps. A good litmus test for things like this is: if you got rid of nostr, would it be the same product (even if inferior in certain ways)? A similar category is infrastructure providers that benefit nostr by their existence (and may in fact be targeted explicitly at nostr users), but do things in a centralized, old-web way; for example: media hosts, DNS registrars, hosting providers, and CDNs. To be clear here, I'm not casting aspersions (I don't even know what those are, or where to buy them). All the apps mentioned above use nostr to great effect, and are a real benefit to nostr users. But they are not True Scotsmen. # It embodies nostr Ok, here we go. This is the crème de la crème, the top du top, the meilleur du meilleur, the bee's knees. The purest, holiest, most chaste category of nostr app out there. The apps which are, indeed, nostr indigitate. This category of nostr app (see, no quotes this time) can be defined by the converse of the previous category. If nostr was removed from this type of application, would it be impossible to create the same product? To tease this apart a bit, apps that leverage the technical aspects of nostr are dependent on nostr the *protocol*, while apps that benefit nostr exclusively via network effect are integrated into nostr the *network*. An app that does both things is working in symbiosis with nostr as a whole. An app that embraces both nostr's protocol and its network becomes an organic extension of every other nostr app out there, multiplying both its competitive moat and its contribution to the ecosystem: - In contrast to apps that only borrow from nostr on the technical level but continue to operate in their own silos, an application integrated into the nostr network comes pre-packaged with existing users, and is able to provide more value to those users because of other nostr products. On nostr, it's a good thing to advertise your competitors. - In contrast to apps that only market themselves to nostr users without building out a deep integration on the protocol level, a deeply integrated app becomes an asset to every other nostr app by becoming an organic extension of them through interoperability. This results in increased traffic to the app as other developers and users refer people to it instead of solving their problem on their own. This is the "micro-apps" utopia we've all been waiting for. Credible exit doesn't matter if there aren't alternative services. Interoperability is pointless if other applications don't offer something your app doesn't. Marketing to nostr users doesn't matter if you don't augment their agency _as nostr users_. If I had to choose a single NIP that represents the mindset behind this kind of app, it would be NIP 89 A.K.A. "Recommended Application Handlers", which states: > Nostr's discoverability and transparent event interaction is one of its most interesting/novel mechanics. This NIP provides a simple way for clients to discover applications that handle events of a specific kind to ensure smooth cross-client and cross-kind interactions. These handlers are the glue that holds nostr apps together. A single event, signed by the developer of an application (or by the application's own account) tells anyone who wants to know 1. what event kinds the app supports, 2. how to link to the app (if it's a client), and (if the pubkey also publishes a kind 10002), 3. which relays the app prefers. _As a sidenote, NIP 89 is currently focused more on clients, leaving DVMs, relays, signers, etc somewhat out in the cold. Updating 89 to include tailored listings for each kind of supporting app would be a huge improvement to the protocol. This, plus a good front end for navigating these listings (sorry nostrapp.link, close but no cigar) would obviate the evil centralized websites that curate apps based on arbitrary criteria._ Examples of this kind of app obviously include many kind 1 clients, as well as clients that attempt to bring the benefits of the nostr protocol and network to new use cases - whether long form content, video, image posts, music, emojis, recipes, project management, or any other "content type". To drill down into one example, let's think for a moment about forms. What's so great about a forms app that is built on nostr? Well, - There is a [spec](https://github.com/nostr-protocol/nips/pull/1190) for forms and responses, which means that... - Multiple clients can implement the same data format, allowing for credible exit and user choice, even of... - Other products not focused on forms, which can still view, respond to, or embed forms, and which can send their users via NIP 89 to a client that does... - Cryptographically sign forms and responses, which means they are self-authenticating and can be sent to... - Multiple relays, which reduces the amount of trust necessary to be confident results haven't been deliberately "lost". Show me a forms product that does all of those things, and isn't built on nostr. You can't, because it doesn't exist. Meanwhile, there are plenty of image hosts with APIs, streaming services, and bitcoin wallets which have basically the same levels of censorship resistance, interoperability, and network effect as if they weren't built on nostr. # It supports nostr Notice I haven't said anything about whether relays, signers, blossom servers, software libraries, DVMs, and the accumulated addenda of the nostr ecosystem are nostr apps. Well, they are (usually). This is the category of nostr app that gets none of the credit for doing all of the work. There's no question that they qualify as beautiful nostrcorns, because their value propositions are entirely meaningless outside of the context of nostr. Who needs a signer if you don't have a cryptographic identity you need to protect? DVMs are literally impossible to use without relays. How are you going to find the blossom server that will serve a given hash if you don't know which servers the publishing user has selected to store their content? In addition to being entirely contextualized by nostr architecture, this type of nostr app is valuable because it does things "the nostr way". By that I mean that they don't simply try to replicate existing internet functionality into a nostr context; instead, they create entirely new ways of putting the basic building blocks of the internet back together. A great example of this is how Nostr Connect, Nostr Wallet Connect, and DVMs all use relays as brokers, which allows service providers to avoid having to accept incoming network connections. This opens up really interesting possibilities all on its own. So while I might hesitate to call many of these things "apps", they are certainly "nostr". # Appendix: it smells like a NINO So, let's say you've created an app, but when you show it to people they politely smile, nod, and call it a NINO (Nostr In Name Only). What's a hacker to do? Well, here's your handy-dandy guide on how to wash that NINO stench off and Become a Nostr. You app might be a NINO if: - There's no NIP for your data format (or you're abusing NIP 78, 32, etc by inventing a sub-protocol inside an existing event kind) - There's a NIP, but no one knows about it because it's in a text file on your hard drive (or buried in your project's repository) - Your NIP imposes an incompatible/centralized/legacy web paradigm onto nostr - Your NIP relies on trusted third (or first) parties - There's only one implementation of your NIP (yours) - Your core value proposition doesn't depend on relays, events, or nostr identities - One or more relay urls are hard-coded into the source code - Your app depends on a specific relay implementation to work (*ahem*, relay29) - You don't validate event signatures - You don't publish events to relays you don't control - You don't read events from relays you don't control - You use legacy web services to solve problems, rather than nostr-native solutions - You use nostr-native solutions, but you've hardcoded their pubkeys or URLs into your app - You don't use NIP 89 to discover clients and services - You haven't published a NIP 89 listing for your app - You don't leverage your users' web of trust for filtering out spam - You don't respect your users' mute lists - You try to "own" your users' data Now let me just re-iterate - it's ok to be a NINO. We need NINOs, because nostr can't (and shouldn't) tackle every problem. You just need to decide whether your app, as a NINO, is actually contributing to the nostr ecosystem, or whether you're just using buzzwords to whitewash a legacy web software product. If you're in the former camp, great! If you're in the latter, what are you waiting for? Only you can fix your NINO problem. And there are lots of ways to do this, depending on your own unique situation: - Drop nostr support if it's not doing anyone any good. If you want to build a normal company and make some money, that's perfectly fine. - Build out your nostr integration - start taking advantage of webs of trust, self-authenticating data, event handlers, etc. - Work around the problem. Think you need a special relay feature for your app to work? Guess again. Consider encryption, AUTH, DVMs, or better data formats. - Think your idea is a good one? Talk to other devs or open a PR to the [nips repo](https://github.com/nostr-protocol/nips). No one can adopt your NIP if they don't know about it. - Keep going. It can sometimes be hard to distinguish a research project from a NINO. New ideas have to be built out before they can be fully appreciated. - Listen to advice. Nostr developers are friendly and happy to help. If you're not sure why you're getting traction, ask! I sincerely hope this article is useful for all of you out there in NINO land. Maybe this made you feel better about not passing the totally optional nostr app purity test. Or maybe it gave you some actionable next steps towards making a great NINON (Nostr In Not Only Name) app. In either case, GM and PV.
@ 97c70a44:ad98e322
2025-01-30 17:15:37There was a slight dust up recently over a website someone runs removing a listing for an app someone built based on entirely arbitrary criteria. I'm not to going to attempt to speak for either wounded party, but I would like to share my own personal definition for what constitutes a "nostr app" in an effort to help clarify what might be an otherwise confusing and opaque purity test. In this post, I will be committing the "no true Scotsman" fallacy, in which I start with the most liberal definition I can come up with, and gradually refine it until all that is left is the purest, gleamingest, most imaginary and unattainable nostr app imaginable. As I write this, I wonder if anything built yet will actually qualify. In any case, here we go. # It uses nostr The lowest bar for what a "nostr app" might be is an app ("application" - i.e. software, not necessarily a native app of any kind) that has some nostr-specific code in it, but which doesn't take any advantage of what makes nostr distinctive as a protocol. Examples might include a scraper of some kind which fulfills its charter by fetching data from relays (regardless of whether it validates or retains signatures). Another might be a regular web 2.0 app which provides an option to "log in with nostr" by requesting and storing the user's public key. In either case, the fact that nostr is involved is entirely neutral. A scraper can scrape html, pdfs, jsonl, whatever data source - nostr relays are just another target. Likewise, a user's key in this scenario is treated merely as an opaque identifier, with no appreciation for the super powers it brings along. In most cases, this kind of app only exists as a marketing ploy, or less cynically, because it wants to get in on the hype of being a "nostr app", without the developer quite understanding what that means, or having the budget to execute properly on the claim. # It leverages nostr Some of you might be wondering, "isn't 'leverage' a synonym for 'use'?" And you would be right, but for one connotative difference. It's possible to "use" something improperly, but by definition leverage gives you a mechanical advantage that you wouldn't otherwise have. This is the second category of "nostr app". This kind of app gets some benefit out of the nostr protocol and network, but in an entirely selfish fashion. The intention of this kind of app is not to augment the nostr network, but to augment its own UX by borrowing some nifty thing from the protocol without really contributing anything back. Some examples might include: - Using nostr signers to encrypt or sign data, and then store that data on a proprietary server. - Using nostr relays as a kind of low-code backend, but using proprietary event payloads. - Using nostr event kinds to represent data (why), but not leveraging the trustlessness that buys you. An application in this category might even communicate to its users via nostr DMs - but this doesn't make it a "nostr app" any more than a website that emails you hot deals on herbal supplements is an "email app". These apps are purely parasitic on the nostr ecosystem. In the long-term, that's not necessarily a bad thing. Email's ubiquity is self-reinforcing. But in the short term, this kind of "nostr app" can actually do damage to nostr's reputation by over-promising and under-delivering. # It complements nostr Next up, we have apps that get some benefit out of nostr as above, but give back by providing a unique value proposition to nostr users as nostr users. This is a bit of a fine distinction, but for me this category is for apps which focus on solving problems that nostr isn't good at solving, leaving the nostr integration in a secondary or supporting role. One example of this kind of app was Mutiny (RIP), which not only allowed users to sign in with nostr, but also pulled those users' social graphs so that users could send money to people they knew and trusted. Mutiny was doing a great job of leveraging nostr, as well as providing value to users with nostr identities - but it was still primarily a bitcoin wallet, not a "nostr app" in the purest sense. Other examples are things like Nostr Nests and Zap.stream, whose core value proposition is streaming video or audio content. Both make great use of nostr identities, data formats, and relays, but they're primarily streaming apps. A good litmus test for things like this is: if you got rid of nostr, would it be the same product (even if inferior in certain ways)? A similar category is infrastructure providers that benefit nostr by their existence (and may in fact be targeted explicitly at nostr users), but do things in a centralized, old-web way; for example: media hosts, DNS registrars, hosting providers, and CDNs. To be clear here, I'm not casting aspersions (I don't even know what those are, or where to buy them). All the apps mentioned above use nostr to great effect, and are a real benefit to nostr users. But they are not True Scotsmen. # It embodies nostr Ok, here we go. This is the crème de la crème, the top du top, the meilleur du meilleur, the bee's knees. The purest, holiest, most chaste category of nostr app out there. The apps which are, indeed, nostr indigitate. This category of nostr app (see, no quotes this time) can be defined by the converse of the previous category. If nostr was removed from this type of application, would it be impossible to create the same product? To tease this apart a bit, apps that leverage the technical aspects of nostr are dependent on nostr the *protocol*, while apps that benefit nostr exclusively via network effect are integrated into nostr the *network*. An app that does both things is working in symbiosis with nostr as a whole. An app that embraces both nostr's protocol and its network becomes an organic extension of every other nostr app out there, multiplying both its competitive moat and its contribution to the ecosystem: - In contrast to apps that only borrow from nostr on the technical level but continue to operate in their own silos, an application integrated into the nostr network comes pre-packaged with existing users, and is able to provide more value to those users because of other nostr products. On nostr, it's a good thing to advertise your competitors. - In contrast to apps that only market themselves to nostr users without building out a deep integration on the protocol level, a deeply integrated app becomes an asset to every other nostr app by becoming an organic extension of them through interoperability. This results in increased traffic to the app as other developers and users refer people to it instead of solving their problem on their own. This is the "micro-apps" utopia we've all been waiting for. Credible exit doesn't matter if there aren't alternative services. Interoperability is pointless if other applications don't offer something your app doesn't. Marketing to nostr users doesn't matter if you don't augment their agency _as nostr users_. If I had to choose a single NIP that represents the mindset behind this kind of app, it would be NIP 89 A.K.A. "Recommended Application Handlers", which states: > Nostr's discoverability and transparent event interaction is one of its most interesting/novel mechanics. This NIP provides a simple way for clients to discover applications that handle events of a specific kind to ensure smooth cross-client and cross-kind interactions. These handlers are the glue that holds nostr apps together. A single event, signed by the developer of an application (or by the application's own account) tells anyone who wants to know 1. what event kinds the app supports, 2. how to link to the app (if it's a client), and (if the pubkey also publishes a kind 10002), 3. which relays the app prefers. _As a sidenote, NIP 89 is currently focused more on clients, leaving DVMs, relays, signers, etc somewhat out in the cold. Updating 89 to include tailored listings for each kind of supporting app would be a huge improvement to the protocol. This, plus a good front end for navigating these listings (sorry nostrapp.link, close but no cigar) would obviate the evil centralized websites that curate apps based on arbitrary criteria._ Examples of this kind of app obviously include many kind 1 clients, as well as clients that attempt to bring the benefits of the nostr protocol and network to new use cases - whether long form content, video, image posts, music, emojis, recipes, project management, or any other "content type". To drill down into one example, let's think for a moment about forms. What's so great about a forms app that is built on nostr? Well, - There is a [spec](https://github.com/nostr-protocol/nips/pull/1190) for forms and responses, which means that... - Multiple clients can implement the same data format, allowing for credible exit and user choice, even of... - Other products not focused on forms, which can still view, respond to, or embed forms, and which can send their users via NIP 89 to a client that does... - Cryptographically sign forms and responses, which means they are self-authenticating and can be sent to... - Multiple relays, which reduces the amount of trust necessary to be confident results haven't been deliberately "lost". Show me a forms product that does all of those things, and isn't built on nostr. You can't, because it doesn't exist. Meanwhile, there are plenty of image hosts with APIs, streaming services, and bitcoin wallets which have basically the same levels of censorship resistance, interoperability, and network effect as if they weren't built on nostr. # It supports nostr Notice I haven't said anything about whether relays, signers, blossom servers, software libraries, DVMs, and the accumulated addenda of the nostr ecosystem are nostr apps. Well, they are (usually). This is the category of nostr app that gets none of the credit for doing all of the work. There's no question that they qualify as beautiful nostrcorns, because their value propositions are entirely meaningless outside of the context of nostr. Who needs a signer if you don't have a cryptographic identity you need to protect? DVMs are literally impossible to use without relays. How are you going to find the blossom server that will serve a given hash if you don't know which servers the publishing user has selected to store their content? In addition to being entirely contextualized by nostr architecture, this type of nostr app is valuable because it does things "the nostr way". By that I mean that they don't simply try to replicate existing internet functionality into a nostr context; instead, they create entirely new ways of putting the basic building blocks of the internet back together. A great example of this is how Nostr Connect, Nostr Wallet Connect, and DVMs all use relays as brokers, which allows service providers to avoid having to accept incoming network connections. This opens up really interesting possibilities all on its own. So while I might hesitate to call many of these things "apps", they are certainly "nostr". # Appendix: it smells like a NINO So, let's say you've created an app, but when you show it to people they politely smile, nod, and call it a NINO (Nostr In Name Only). What's a hacker to do? Well, here's your handy-dandy guide on how to wash that NINO stench off and Become a Nostr. You app might be a NINO if: - There's no NIP for your data format (or you're abusing NIP 78, 32, etc by inventing a sub-protocol inside an existing event kind) - There's a NIP, but no one knows about it because it's in a text file on your hard drive (or buried in your project's repository) - Your NIP imposes an incompatible/centralized/legacy web paradigm onto nostr - Your NIP relies on trusted third (or first) parties - There's only one implementation of your NIP (yours) - Your core value proposition doesn't depend on relays, events, or nostr identities - One or more relay urls are hard-coded into the source code - Your app depends on a specific relay implementation to work (*ahem*, relay29) - You don't validate event signatures - You don't publish events to relays you don't control - You don't read events from relays you don't control - You use legacy web services to solve problems, rather than nostr-native solutions - You use nostr-native solutions, but you've hardcoded their pubkeys or URLs into your app - You don't use NIP 89 to discover clients and services - You haven't published a NIP 89 listing for your app - You don't leverage your users' web of trust for filtering out spam - You don't respect your users' mute lists - You try to "own" your users' data Now let me just re-iterate - it's ok to be a NINO. We need NINOs, because nostr can't (and shouldn't) tackle every problem. You just need to decide whether your app, as a NINO, is actually contributing to the nostr ecosystem, or whether you're just using buzzwords to whitewash a legacy web software product. If you're in the former camp, great! If you're in the latter, what are you waiting for? Only you can fix your NINO problem. And there are lots of ways to do this, depending on your own unique situation: - Drop nostr support if it's not doing anyone any good. If you want to build a normal company and make some money, that's perfectly fine. - Build out your nostr integration - start taking advantage of webs of trust, self-authenticating data, event handlers, etc. - Work around the problem. Think you need a special relay feature for your app to work? Guess again. Consider encryption, AUTH, DVMs, or better data formats. - Think your idea is a good one? Talk to other devs or open a PR to the [nips repo](https://github.com/nostr-protocol/nips). No one can adopt your NIP if they don't know about it. - Keep going. It can sometimes be hard to distinguish a research project from a NINO. New ideas have to be built out before they can be fully appreciated. - Listen to advice. Nostr developers are friendly and happy to help. If you're not sure why you're getting traction, ask! I sincerely hope this article is useful for all of you out there in NINO land. Maybe this made you feel better about not passing the totally optional nostr app purity test. Or maybe it gave you some actionable next steps towards making a great NINON (Nostr In Not Only Name) app. In either case, GM and PV. @ 9e69e420:d12360c2
2025-01-30 12:23:04Tech stocks have taken a hit globally after China's DeepSeek launched a competitive AI chatbot at a much lower cost than US counterparts. This has stirred market fears of a $1.2 trillion loss across tech companies when trading opens in New York. DeepSeek’s chatbot quickly topped download charts and surprised experts with its capabilities, developed for only $5.6 million. The Nasdaq dropped over 3% in premarket trading, with major firms like Nvidia falling more than 10%. SoftBank also saw losses shortly after investing in a significant US AI venture. Venture capitalist Marc Andreessen called it “AI’s Sputnik moment,” highlighting its potential impact on the industry. ![] (https://www.telegraph.co.uk/content/dam/business/2025/01/27/TELEMMGLPICT000409807198_17379939060750_trans_NvBQzQNjv4BqgsaO8O78rhmZrDxTlQBjdGLvJF5WfpqnBZShRL_tOZw.jpeg)
@ 9e69e420:d12360c2
2025-01-30 12:23:04Tech stocks have taken a hit globally after China's DeepSeek launched a competitive AI chatbot at a much lower cost than US counterparts. This has stirred market fears of a $1.2 trillion loss across tech companies when trading opens in New York. DeepSeek’s chatbot quickly topped download charts and surprised experts with its capabilities, developed for only $5.6 million. The Nasdaq dropped over 3% in premarket trading, with major firms like Nvidia falling more than 10%. SoftBank also saw losses shortly after investing in a significant US AI venture. Venture capitalist Marc Andreessen called it “AI’s Sputnik moment,” highlighting its potential impact on the industry. ![] (https://www.telegraph.co.uk/content/dam/business/2025/01/27/TELEMMGLPICT000409807198_17379939060750_trans_NvBQzQNjv4BqgsaO8O78rhmZrDxTlQBjdGLvJF5WfpqnBZShRL_tOZw.jpeg) @ 9e69e420:d12360c2
2025-01-30 12:13:39Salwan Momika, a Christian Iraqi known for burning the Koran in Sweden, was shot dead during a TikTok livestream in an apartment in Sodertalje. The 38-year-old sparked outrage in the Muslim community for his demonstrations, leading to global condemnation. After being rushed to the hospital, he was pronounced dead. Authorities arrested five individuals in connection with the incident. Momika's death comes days before a court ruling on his possible incitement of ethnic hatred. The incident highlights the tensions surrounding free speech and religious sentiments, intensifying after his controversial protests in 2023. [Sauce](https://www.dailymail.co.uk/news/article-14341423/Christian-Iraqi-burnt-Koran-Sweden-shot-dead.html)
@ 9e69e420:d12360c2
2025-01-30 12:13:39Salwan Momika, a Christian Iraqi known for burning the Koran in Sweden, was shot dead during a TikTok livestream in an apartment in Sodertalje. The 38-year-old sparked outrage in the Muslim community for his demonstrations, leading to global condemnation. After being rushed to the hospital, he was pronounced dead. Authorities arrested five individuals in connection with the incident. Momika's death comes days before a court ruling on his possible incitement of ethnic hatred. The incident highlights the tensions surrounding free speech and religious sentiments, intensifying after his controversial protests in 2023. [Sauce](https://www.dailymail.co.uk/news/article-14341423/Christian-Iraqi-burnt-Koran-Sweden-shot-dead.html) @ 0fa80bd3:ea7325de
2025-01-30 04:28:30**"Degeneration"** or **"Вырождение"** ![[photo_2025-01-29 23.23.15.jpeg]] A once-functional object, now eroded by time and human intervention, stripped of its original purpose. Layers of presence accumulate—marks, alterations, traces of intent—until the very essence is obscured. Restoration is paradoxical: to reclaim, one must erase. Yet erasure is an impossibility, for to remove these imprints is to deny the existence of those who shaped them. The work stands as a meditation on entropy, memory, and the irreversible dialogue between creation and decay.
@ 0fa80bd3:ea7325de
2025-01-30 04:28:30**"Degeneration"** or **"Вырождение"** ![[photo_2025-01-29 23.23.15.jpeg]] A once-functional object, now eroded by time and human intervention, stripped of its original purpose. Layers of presence accumulate—marks, alterations, traces of intent—until the very essence is obscured. Restoration is paradoxical: to reclaim, one must erase. Yet erasure is an impossibility, for to remove these imprints is to deny the existence of those who shaped them. The work stands as a meditation on entropy, memory, and the irreversible dialogue between creation and decay. @ 0fa80bd3:ea7325de
2025-01-29 15:43:42Lyn Alden - биткойн евангелист или евангелистка, я пока не понял ``` npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a ``` Thomas Pacchia - PubKey owner - X - @tpacchia ``` npub1xy6exlg37pw84cpyj05c2pdgv86hr25cxn0g7aa8g8a6v97mhduqeuhgpl ``` calvadev - Shopstr ``` npub16dhgpql60vmd4mnydjut87vla23a38j689jssaqlqqlzrtqtd0kqex0nkq ``` Calle - Cashu founder ``` npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg ``` Джек Дорси ``` npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m ``` 21 ideas ``` npub1lm3f47nzyf0rjp6fsl4qlnkmzed4uj4h2gnf2vhe3l3mrj85vqks6z3c7l ``` Много адресов. Хз кто надо сортировать ``` https://github.com/aitechguy/nostr-address-book ``` ФиатДжеф - создатель Ностр - https://github.com/fiatjaf ``` npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 ``` EVAN KALOUDIS Zues wallet ``` npub19kv88vjm7tw6v9qksn2y6h4hdt6e79nh3zjcud36k9n3lmlwsleqwte2qd ``` Программер Коди https://github.com/CodyTseng/nostr-relay ``` npub1syjmjy0dp62dhccq3g97fr87tngvpvzey08llyt6ul58m2zqpzps9wf6wl ``` Anna Chekhovich - Managing Bitcoin at The Anti-Corruption Foundation https://x.com/AnyaChekhovich ``` npub1y2st7rp54277hyd2usw6shy3kxprnmpvhkezmldp7vhl7hp920aq9cfyr7 ```
@ 0fa80bd3:ea7325de
2025-01-29 15:43:42Lyn Alden - биткойн евангелист или евангелистка, я пока не понял ``` npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a ``` Thomas Pacchia - PubKey owner - X - @tpacchia ``` npub1xy6exlg37pw84cpyj05c2pdgv86hr25cxn0g7aa8g8a6v97mhduqeuhgpl ``` calvadev - Shopstr ``` npub16dhgpql60vmd4mnydjut87vla23a38j689jssaqlqqlzrtqtd0kqex0nkq ``` Calle - Cashu founder ``` npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg ``` Джек Дорси ``` npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m ``` 21 ideas ``` npub1lm3f47nzyf0rjp6fsl4qlnkmzed4uj4h2gnf2vhe3l3mrj85vqks6z3c7l ``` Много адресов. Хз кто надо сортировать ``` https://github.com/aitechguy/nostr-address-book ``` ФиатДжеф - создатель Ностр - https://github.com/fiatjaf ``` npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 ``` EVAN KALOUDIS Zues wallet ``` npub19kv88vjm7tw6v9qksn2y6h4hdt6e79nh3zjcud36k9n3lmlwsleqwte2qd ``` Программер Коди https://github.com/CodyTseng/nostr-relay ``` npub1syjmjy0dp62dhccq3g97fr87tngvpvzey08llyt6ul58m2zqpzps9wf6wl ``` Anna Chekhovich - Managing Bitcoin at The Anti-Corruption Foundation https://x.com/AnyaChekhovich ``` npub1y2st7rp54277hyd2usw6shy3kxprnmpvhkezmldp7vhl7hp920aq9cfyr7 ``` @ 0fa80bd3:ea7325de
2025-01-29 14:44:48![[yedinaya-rossiya-bear.png]] 1️⃣ Be where the bear roams. Stay in its territory, where it hunts for food. No point setting a trap in your backyard if the bear’s chilling in the forest. 2️⃣ Set a well-hidden trap. Bury it, disguise it, and place the bait right in the center. Bears are omnivores—just like secret police KGB agents. And what’s the tastiest bait for them? Money. 3️⃣ Wait for the bear to take the bait. When it reaches in, the trap will snap shut around its paw. It’ll be alive, but stuck. No escape. Now, what you do with a trapped bear is another question... 😏
@ 0fa80bd3:ea7325de
2025-01-29 14:44:48![[yedinaya-rossiya-bear.png]] 1️⃣ Be where the bear roams. Stay in its territory, where it hunts for food. No point setting a trap in your backyard if the bear’s chilling in the forest. 2️⃣ Set a well-hidden trap. Bury it, disguise it, and place the bait right in the center. Bears are omnivores—just like secret police KGB agents. And what’s the tastiest bait for them? Money. 3️⃣ Wait for the bear to take the bait. When it reaches in, the trap will snap shut around its paw. It’ll be alive, but stuck. No escape. Now, what you do with a trapped bear is another question... 😏 @ 0fa80bd3:ea7325de
2025-01-29 05:55:02The land that belongs to the indigenous peoples of Russia has been seized by a gang of killers who have unleashed a war of extermination. They wipe out anyone who refuses to conform to their rules. Those who disagree and stay behind are tortured and killed in prisons and labor camps. Those who flee lose their homeland, dissolve into foreign cultures, and fade away. And those who stand up to protect their people are attacked by the misled and deceived. The deceived die for the unchecked greed of a single dictator—thousands from both sides, people who just wanted to live, raise their kids, and build a future. Now, they are forced to make an impossible choice: abandon their homeland or die. Some perish on the battlefield, others lose themselves in exile, stripped of their identity, scattered in a world that isn’t theirs. There’s been endless debate about how to fix this, how to clear the field of the weeds that choke out every new sprout, every attempt at change. But the real problem? We can’t play by their rules. We can’t speak their language or use their weapons. We stand for humanity, and no matter how righteous our cause, we will not multiply suffering. Victory doesn’t come from matching the enemy—it comes from staying ahead, from using tools they haven’t mastered yet. That’s how wars are won. Our only resource is the **will of the people** to rewrite the order of things. Historian Timothy Snyder once said that a nation cannot exist without a city. A city is where the most active part of a nation thrives. But the cities are occupied. The streets are watched. Gatherings are impossible. They control the money. They control the mail. They control the media. And any dissent is crushed before it can take root. So I started asking myself: **How do we stop this fragmentation?** How do we create a space where people can **rebuild their connections** when they’re ready? How do we build a **self-sustaining network**, where everyone contributes and benefits proportionally, while keeping their freedom to leave intact? And more importantly—**how do we make it spread, even in occupied territory?** In 2009, something historic happened: **the internet got its own money.** Thanks to **Satoshi Nakamoto**, the world took a massive leap forward. Bitcoin and decentralized ledgers shattered the idea that money must be controlled by the state. Now, to move or store value, all you need is an address and a key. A tiny string of text, easy to carry, impossible to seize. That was the year money broke free. The state lost its grip. Its biggest weapon—physical currency—became irrelevant. Money became **purely digital.** The internet was already **a sanctuary for information**, a place where people could connect and organize. But with Bitcoin, it evolved. Now, **value itself** could flow freely, beyond the reach of authorities. Think about it: when seedlings are grown in controlled environments before being planted outside, they **get stronger, survive longer, and bear fruit faster.** That’s how we handle crops in harsh climates—nurture them until they’re ready for the wild. Now, picture the internet as that **controlled environment** for **ideas**. Bitcoin? It’s the **fertile soil** that lets them grow. A testing ground for new models of interaction, where concepts can take root before they move into the real world. If **nation-states are a battlefield, locked in a brutal war for territory, the internet is boundless.** It can absorb any number of ideas, any number of people, and it doesn’t **run out of space.** But for this ecosystem to thrive, people need safe ways to communicate, to share ideas, to build something real—**without surveillance, without censorship, without the constant fear of being erased.** This is where **Nostr** comes in. Nostr—"Notes and Other Stuff Transmitted by Relays"—is more than just a messaging protocol. **It’s a new kind of city.** One that **no dictator can seize**, no corporation can own, no government can shut down. It’s built on **decentralization, encryption, and individual control.** Messages don’t pass through central servers—they are relayed through independent nodes, and users choose which ones to trust. There’s no master switch to shut it all down. Every person owns their identity, their data, their connections. And no one—no state, no tech giant, no algorithm—can silence them. In a world where cities fall and governments fail, **Nostr is a city that cannot be occupied.** A place for ideas, for networks, for freedom. A city that grows stronger **the more people build within it**.
@ 0fa80bd3:ea7325de
2025-01-29 05:55:02The land that belongs to the indigenous peoples of Russia has been seized by a gang of killers who have unleashed a war of extermination. They wipe out anyone who refuses to conform to their rules. Those who disagree and stay behind are tortured and killed in prisons and labor camps. Those who flee lose their homeland, dissolve into foreign cultures, and fade away. And those who stand up to protect their people are attacked by the misled and deceived. The deceived die for the unchecked greed of a single dictator—thousands from both sides, people who just wanted to live, raise their kids, and build a future. Now, they are forced to make an impossible choice: abandon their homeland or die. Some perish on the battlefield, others lose themselves in exile, stripped of their identity, scattered in a world that isn’t theirs. There’s been endless debate about how to fix this, how to clear the field of the weeds that choke out every new sprout, every attempt at change. But the real problem? We can’t play by their rules. We can’t speak their language or use their weapons. We stand for humanity, and no matter how righteous our cause, we will not multiply suffering. Victory doesn’t come from matching the enemy—it comes from staying ahead, from using tools they haven’t mastered yet. That’s how wars are won. Our only resource is the **will of the people** to rewrite the order of things. Historian Timothy Snyder once said that a nation cannot exist without a city. A city is where the most active part of a nation thrives. But the cities are occupied. The streets are watched. Gatherings are impossible. They control the money. They control the mail. They control the media. And any dissent is crushed before it can take root. So I started asking myself: **How do we stop this fragmentation?** How do we create a space where people can **rebuild their connections** when they’re ready? How do we build a **self-sustaining network**, where everyone contributes and benefits proportionally, while keeping their freedom to leave intact? And more importantly—**how do we make it spread, even in occupied territory?** In 2009, something historic happened: **the internet got its own money.** Thanks to **Satoshi Nakamoto**, the world took a massive leap forward. Bitcoin and decentralized ledgers shattered the idea that money must be controlled by the state. Now, to move or store value, all you need is an address and a key. A tiny string of text, easy to carry, impossible to seize. That was the year money broke free. The state lost its grip. Its biggest weapon—physical currency—became irrelevant. Money became **purely digital.** The internet was already **a sanctuary for information**, a place where people could connect and organize. But with Bitcoin, it evolved. Now, **value itself** could flow freely, beyond the reach of authorities. Think about it: when seedlings are grown in controlled environments before being planted outside, they **get stronger, survive longer, and bear fruit faster.** That’s how we handle crops in harsh climates—nurture them until they’re ready for the wild. Now, picture the internet as that **controlled environment** for **ideas**. Bitcoin? It’s the **fertile soil** that lets them grow. A testing ground for new models of interaction, where concepts can take root before they move into the real world. If **nation-states are a battlefield, locked in a brutal war for territory, the internet is boundless.** It can absorb any number of ideas, any number of people, and it doesn’t **run out of space.** But for this ecosystem to thrive, people need safe ways to communicate, to share ideas, to build something real—**without surveillance, without censorship, without the constant fear of being erased.** This is where **Nostr** comes in. Nostr—"Notes and Other Stuff Transmitted by Relays"—is more than just a messaging protocol. **It’s a new kind of city.** One that **no dictator can seize**, no corporation can own, no government can shut down. It’s built on **decentralization, encryption, and individual control.** Messages don’t pass through central servers—they are relayed through independent nodes, and users choose which ones to trust. There’s no master switch to shut it all down. Every person owns their identity, their data, their connections. And no one—no state, no tech giant, no algorithm—can silence them. In a world where cities fall and governments fail, **Nostr is a city that cannot be occupied.** A place for ideas, for networks, for freedom. A city that grows stronger **the more people build within it**. @ 9e69e420:d12360c2
2025-01-26 15:26:44Secretary of State Marco Rubio issued new guidance halting spending on most foreign aid grants for 90 days, including military assistance to Ukraine. This immediate order shocked State Department officials and mandates “stop-work orders” on nearly all existing foreign assistance awards. While it allows exceptions for military financing to Egypt and Israel, as well as emergency food assistance, it restricts aid to key allies like Ukraine, Jordan, and Taiwan. The guidance raises potential liability risks for the government due to unfulfilled contracts. A report will be prepared within 85 days to recommend which programs to continue or discontinue.
@ 9e69e420:d12360c2
2025-01-26 15:26:44Secretary of State Marco Rubio issued new guidance halting spending on most foreign aid grants for 90 days, including military assistance to Ukraine. This immediate order shocked State Department officials and mandates “stop-work orders” on nearly all existing foreign assistance awards. While it allows exceptions for military financing to Egypt and Israel, as well as emergency food assistance, it restricts aid to key allies like Ukraine, Jordan, and Taiwan. The guidance raises potential liability risks for the government due to unfulfilled contracts. A report will be prepared within 85 days to recommend which programs to continue or discontinue. @ 9e69e420:d12360c2
2025-01-26 01:31:47## Chef's notes # arbitray - test - of - chefs notes ## hedding 2 ## Details - ⏲️ Prep time: 20 - 🍳 Cook time: 1 hour - 🍽️ Servings: 5 ## Ingredients - Test ingredient - 2nd test ingredient ## Directions 1. Bake 2. Cool
@ 9e69e420:d12360c2
2025-01-26 01:31:47## Chef's notes # arbitray - test - of - chefs notes ## hedding 2 ## Details - ⏲️ Prep time: 20 - 🍳 Cook time: 1 hour - 🍽️ Servings: 5 ## Ingredients - Test ingredient - 2nd test ingredient ## Directions 1. Bake 2. Cool @ 9e69e420:d12360c2
2025-01-25 22:16:54President Trump plans to withdraw 20,000 U.S. troops from Europe and expects European allies to contribute financially to the remaining military presence. Reported by ANSA, Trump aims to deliver this message to European leaders since taking office. A European diplomat noted, “the costs cannot be borne solely by American taxpayers.” The Pentagon hasn't commented yet. Trump has previously sought lower troop levels in Europe and had ordered cuts during his first term. The U.S. currently maintains around 65,000 troops in Europe, with total forces reaching 100,000 since the Ukraine invasion. Trump's new approach may shift military focus to the Pacific amid growing concerns about China. [Sauce](https://www.stripes.com/theaters/europe/2025-01-24/trump-europe-troop-cuts-16590074.html)
@ 9e69e420:d12360c2
2025-01-25 22:16:54President Trump plans to withdraw 20,000 U.S. troops from Europe and expects European allies to contribute financially to the remaining military presence. Reported by ANSA, Trump aims to deliver this message to European leaders since taking office. A European diplomat noted, “the costs cannot be borne solely by American taxpayers.” The Pentagon hasn't commented yet. Trump has previously sought lower troop levels in Europe and had ordered cuts during his first term. The U.S. currently maintains around 65,000 troops in Europe, with total forces reaching 100,000 since the Ukraine invasion. Trump's new approach may shift military focus to the Pacific amid growing concerns about China. [Sauce](https://www.stripes.com/theaters/europe/2025-01-24/trump-europe-troop-cuts-16590074.html) @ 9e69e420:d12360c2
2025-01-25 14:32:21| Parameters | Dry Mead | Medium Mead | Sweet Mead | |------------|-----------|-------------|------------| | Honey | 2 lbs (900 grams) | 3 lbs (1.36 kg) | 4 lbs (1.81 kg) | | Yeast | ~0.07 oz (2 grams) | ~0.08 oz (2.5 grams) | ~0.10 oz (3 grams) | | Fermentation | ~4 weeks | 4 to 6 weeks | 6 to 8 weeks | | Racking | Fortnight or later | 1 month or after | ~2 months and after | | Specific Gravity | <1.010 | ~1.01 to ~1.025 | >1.025 |
@ 9e69e420:d12360c2
2025-01-25 14:32:21| Parameters | Dry Mead | Medium Mead | Sweet Mead | |------------|-----------|-------------|------------| | Honey | 2 lbs (900 grams) | 3 lbs (1.36 kg) | 4 lbs (1.81 kg) | | Yeast | ~0.07 oz (2 grams) | ~0.08 oz (2.5 grams) | ~0.10 oz (3 grams) | | Fermentation | ~4 weeks | 4 to 6 weeks | 6 to 8 weeks | | Racking | Fortnight or later | 1 month or after | ~2 months and after | | Specific Gravity | <1.010 | ~1.01 to ~1.025 | >1.025 | @ 9e69e420:d12360c2
2025-01-23 15:09:56President Trump has ordered thousands of additional troops to the U.S.-Mexico border as part of an effort to address immigration and security issues. This directive builds on his initial commitment to increase military presence along the border. Currently, around 2,200 active-duty personnel and approximately 4,500 National Guardsmen are stationed there. The new deployment aims to enhance the capabilities of Joint Task Force-North, allowing troops to assist in operations and provide intelligence support. Details on specific units remain unclear. The situation is still developing, with updates expected. [Sauce](https://thepostmillennial.com/breaking-president-trump-orders-thousands-of-troops-to-the-us-border-with-mexico)
@ 9e69e420:d12360c2
2025-01-23 15:09:56President Trump has ordered thousands of additional troops to the U.S.-Mexico border as part of an effort to address immigration and security issues. This directive builds on his initial commitment to increase military presence along the border. Currently, around 2,200 active-duty personnel and approximately 4,500 National Guardsmen are stationed there. The new deployment aims to enhance the capabilities of Joint Task Force-North, allowing troops to assist in operations and provide intelligence support. Details on specific units remain unclear. The situation is still developing, with updates expected. [Sauce](https://thepostmillennial.com/breaking-president-trump-orders-thousands-of-troops-to-the-us-border-with-mexico) @ 6be5cc06:5259daf0
2025-01-21 20:58:37A seguir, veja como instalar e configurar o **Privoxy** no **Pop!_OS**. --- ### **1. Instalar o Tor e o Privoxy** Abra o terminal e execute: ```bash sudo apt update sudo apt install tor privoxy ``` **Explicação:** - **Tor:** Roteia o tráfego pela rede Tor. - **Privoxy:** Proxy avançado que intermedia a conexão entre aplicativos e o Tor. --- ### **2. Configurar o Privoxy** Abra o arquivo de configuração do Privoxy: ```bash sudo nano /etc/privoxy/config ``` Navegue até a última linha (atalho: **`Ctrl`** + **`/`** depois **`Ctrl`** + **`V`** para navegar diretamente até a última linha) e insira: ```bash forward-socks5 / 127.0.0.1:9050 . ``` Isso faz com que o **Privoxy** envie todo o tráfego para o **Tor** através da porta **9050**. Salve (**`CTRL`** + **`O`** e **`Enter`**) e feche (**`CTRL`** + **`X`**) o arquivo. --- ### **3. Iniciar o Tor e o Privoxy** Agora, inicie e habilite os serviços: ```bash sudo systemctl start tor sudo systemctl start privoxy sudo systemctl enable tor sudo systemctl enable privoxy ``` **Explicação:** - **start:** Inicia os serviços. - **enable:** Faz com que iniciem automaticamente ao ligar o PC. --- ### **4. Configurar o Navegador Firefox** Para usar a rede **Tor** com o Firefox: 1. Abra o Firefox. 2. Acesse **Configurações** → **Configurar conexão**. 3. Selecione **Configuração manual de proxy**. 4. Configure assim: - **Proxy HTTP:** `127.0.0.1` - **Porta:** `8118` (porta padrão do **Privoxy**) - **Domínio SOCKS (v5):** `127.0.0.1` - **Porta:** `9050` 5. Marque a opção **"Usar este proxy também em HTTPS"**. 6. Clique em **OK**. --- ### **5. Verificar a Conexão com o Tor** Abra o navegador e acesse: ```text https://check.torproject.org/ ``` Se aparecer a mensagem **"Congratulations. This browser is configured to use Tor."**, a configuração está correta. --- ### **Dicas Extras** - **Privoxy** pode ser ajustado para bloquear anúncios e rastreadores. - Outros aplicativos também podem ser configurados para usar o **Privoxy**.
@ 6be5cc06:5259daf0
2025-01-21 20:58:37A seguir, veja como instalar e configurar o **Privoxy** no **Pop!_OS**. --- ### **1. Instalar o Tor e o Privoxy** Abra o terminal e execute: ```bash sudo apt update sudo apt install tor privoxy ``` **Explicação:** - **Tor:** Roteia o tráfego pela rede Tor. - **Privoxy:** Proxy avançado que intermedia a conexão entre aplicativos e o Tor. --- ### **2. Configurar o Privoxy** Abra o arquivo de configuração do Privoxy: ```bash sudo nano /etc/privoxy/config ``` Navegue até a última linha (atalho: **`Ctrl`** + **`/`** depois **`Ctrl`** + **`V`** para navegar diretamente até a última linha) e insira: ```bash forward-socks5 / 127.0.0.1:9050 . ``` Isso faz com que o **Privoxy** envie todo o tráfego para o **Tor** através da porta **9050**. Salve (**`CTRL`** + **`O`** e **`Enter`**) e feche (**`CTRL`** + **`X`**) o arquivo. --- ### **3. Iniciar o Tor e o Privoxy** Agora, inicie e habilite os serviços: ```bash sudo systemctl start tor sudo systemctl start privoxy sudo systemctl enable tor sudo systemctl enable privoxy ``` **Explicação:** - **start:** Inicia os serviços. - **enable:** Faz com que iniciem automaticamente ao ligar o PC. --- ### **4. Configurar o Navegador Firefox** Para usar a rede **Tor** com o Firefox: 1. Abra o Firefox. 2. Acesse **Configurações** → **Configurar conexão**. 3. Selecione **Configuração manual de proxy**. 4. Configure assim: - **Proxy HTTP:** `127.0.0.1` - **Porta:** `8118` (porta padrão do **Privoxy**) - **Domínio SOCKS (v5):** `127.0.0.1` - **Porta:** `9050` 5. Marque a opção **"Usar este proxy também em HTTPS"**. 6. Clique em **OK**. --- ### **5. Verificar a Conexão com o Tor** Abra o navegador e acesse: ```text https://check.torproject.org/ ``` Se aparecer a mensagem **"Congratulations. This browser is configured to use Tor."**, a configuração está correta. --- ### **Dicas Extras** - **Privoxy** pode ser ajustado para bloquear anúncios e rastreadores. - Outros aplicativos também podem ser configurados para usar o **Privoxy**. @ 16d11430:61640947
2025-01-21 20:40:22In a world drowning in Monopoly money, where people celebrate government-mandated inflation as "economic growth," it takes a special kind of clarity—nay, cynicism—to rise above the fiat circus. This is your guide to shedding your fiat f**ks and embracing the serene chaos of sound money, all while laughing at the absurdity of a world gone fiat-mad. --- 1. Don’t Feed the Clowns You know the clowns I’m talking about: central bankers in their tailored suits and smug smirks, wielding "tools" like interest rates and quantitative easing. Their tools are as real as a magician's wand, conjuring trillions of dollars out of thin air to keep their Ponzi economy afloat. Rule #1: Don’t engage. If a clown offers you a hot take about the "strength of the dollar," smile, nod, and silently wonder how many cups of coffee their paycheck buys this month. Spoiler: fewer than last month. --- 2. Turn Off the Fiat News Do you really need another breathless headline about the next trillion-dollar deficit? Or the latest clickbait on why you should care about the stock market's emotional rollercoaster? Mainstream media exists to distract you, to keep you tethered to their illusion of importance. Turn it off. Replace it with something sound, like the Bitcoin whitepaper. Or Nietzsche. At least Nietzsche knew we were doomed. --- 3. Mock Their Inflationary Gospel Fiat apologists will tell you that inflation is "necessary" and that 2% a year is a "healthy target." Sure, because a little robbery every year keeps society functioning, right? Ask them this: "If 2% is healthy, why not 20%? Why not 200%? Why not Venezuela?" Fiat logic is like a bad acid trip: entertaining at first, but it quickly spirals into existential horror. --- 4. Celebrate the Fiat Freakshow Sometimes, the best way to resist the fiat clown show is to revel in its absurdity. Watch politicians print money like teenagers running up a credit card bill at Hot Topic, then watch the economists applaud it as "stimulus." It’s performance art, really. Andy Warhol could never. --- 5. Build in the Chaos While the fiat world burns, Bitcoiners build. This is the ultimate "not giving a fiat f**k" move: creating a parallel economy, one satoshi at a time. Run your Lightning node, stack sats, and laugh as the fiat circus consumes itself in a flaming pile of its own debt. Let them argue about who gets to rearrange the deck chairs on the Titanic. You’re busy designing lifeboats. --- 6. Adopt a Fiat-Free Lifestyle Fiat-free living means minimizing your entanglement with their clown currency. Buy meat, not ETFs. Trade skills, not IOUs. Tip your barber in Bitcoin and ask if your landlord accepts Lightning. If they say no, chuckle and say, “You’ll learn soon enough.” Every satoshi spent in the real economy is a slap in the face to the fiat overlords. --- 7. Find the Humor in Collapse Here’s the thing: the fiat system is unsustainable. You know it, I know it, even the clowns know it. The whole charade is destined to collapse under its own weight. When it does, find solace in the absurdity of it all. Imagine the central bankers explaining hyperinflation to the public: "Turns out we can't print infinity after all." Pure comedy gold. --- 8. Stay Ruthlessly Optimistic Despite the doom and gloom, there’s hope. Bitcoin is hope. It’s the lifeboat for humanity, the cheat code to escape the fiat matrix. Cynicism doesn’t mean nihilism; it means seeing the rot for what it is and choosing to build something better. So, don’t just reject the fiat clown show—replace it. Create a world where money is sound, transactions are sovereign, and wealth is measured in energy, not debt. --- Final Thought: Burn the Tent Down Aldous Huxley once envisioned a dystopia where people are so distracted by their own hedonistic consumption that they don’t realize they’re enslaved. Sound familiar? The fiat clown show is Brave New World on steroids, a spectacle designed to keep you pacified while your wealth evaporates. But here’s the punchline: they can only enslave you if you care. By rejecting their system, you strip them of their power. So let them juggle their debts, inflate their bubbles, and print their trillions. You’ve got Bitcoin, and Bitcoin doesn’t give a fiat f**k. Welcome to the satirical resistance. Now go stack some sats.
@ 16d11430:61640947
2025-01-21 20:40:22In a world drowning in Monopoly money, where people celebrate government-mandated inflation as "economic growth," it takes a special kind of clarity—nay, cynicism—to rise above the fiat circus. This is your guide to shedding your fiat f**ks and embracing the serene chaos of sound money, all while laughing at the absurdity of a world gone fiat-mad. --- 1. Don’t Feed the Clowns You know the clowns I’m talking about: central bankers in their tailored suits and smug smirks, wielding "tools" like interest rates and quantitative easing. Their tools are as real as a magician's wand, conjuring trillions of dollars out of thin air to keep their Ponzi economy afloat. Rule #1: Don’t engage. If a clown offers you a hot take about the "strength of the dollar," smile, nod, and silently wonder how many cups of coffee their paycheck buys this month. Spoiler: fewer than last month. --- 2. Turn Off the Fiat News Do you really need another breathless headline about the next trillion-dollar deficit? Or the latest clickbait on why you should care about the stock market's emotional rollercoaster? Mainstream media exists to distract you, to keep you tethered to their illusion of importance. Turn it off. Replace it with something sound, like the Bitcoin whitepaper. Or Nietzsche. At least Nietzsche knew we were doomed. --- 3. Mock Their Inflationary Gospel Fiat apologists will tell you that inflation is "necessary" and that 2% a year is a "healthy target." Sure, because a little robbery every year keeps society functioning, right? Ask them this: "If 2% is healthy, why not 20%? Why not 200%? Why not Venezuela?" Fiat logic is like a bad acid trip: entertaining at first, but it quickly spirals into existential horror. --- 4. Celebrate the Fiat Freakshow Sometimes, the best way to resist the fiat clown show is to revel in its absurdity. Watch politicians print money like teenagers running up a credit card bill at Hot Topic, then watch the economists applaud it as "stimulus." It’s performance art, really. Andy Warhol could never. --- 5. Build in the Chaos While the fiat world burns, Bitcoiners build. This is the ultimate "not giving a fiat f**k" move: creating a parallel economy, one satoshi at a time. Run your Lightning node, stack sats, and laugh as the fiat circus consumes itself in a flaming pile of its own debt. Let them argue about who gets to rearrange the deck chairs on the Titanic. You’re busy designing lifeboats. --- 6. Adopt a Fiat-Free Lifestyle Fiat-free living means minimizing your entanglement with their clown currency. Buy meat, not ETFs. Trade skills, not IOUs. Tip your barber in Bitcoin and ask if your landlord accepts Lightning. If they say no, chuckle and say, “You’ll learn soon enough.” Every satoshi spent in the real economy is a slap in the face to the fiat overlords. --- 7. Find the Humor in Collapse Here’s the thing: the fiat system is unsustainable. You know it, I know it, even the clowns know it. The whole charade is destined to collapse under its own weight. When it does, find solace in the absurdity of it all. Imagine the central bankers explaining hyperinflation to the public: "Turns out we can't print infinity after all." Pure comedy gold. --- 8. Stay Ruthlessly Optimistic Despite the doom and gloom, there’s hope. Bitcoin is hope. It’s the lifeboat for humanity, the cheat code to escape the fiat matrix. Cynicism doesn’t mean nihilism; it means seeing the rot for what it is and choosing to build something better. So, don’t just reject the fiat clown show—replace it. Create a world where money is sound, transactions are sovereign, and wealth is measured in energy, not debt. --- Final Thought: Burn the Tent Down Aldous Huxley once envisioned a dystopia where people are so distracted by their own hedonistic consumption that they don’t realize they’re enslaved. Sound familiar? The fiat clown show is Brave New World on steroids, a spectacle designed to keep you pacified while your wealth evaporates. But here’s the punchline: they can only enslave you if you care. By rejecting their system, you strip them of their power. So let them juggle their debts, inflate their bubbles, and print their trillions. You’ve got Bitcoin, and Bitcoin doesn’t give a fiat f**k. Welcome to the satirical resistance. Now go stack some sats. @ c3c7122c:607731d7
2025-02-16 07:48:35At my meet up (the SD Bitcoiners Cete) on Thursday, I presented trends on the Bisq protocol. One of its features is that anyone can export the trade history and analyze it. Bisq is a private, peer-tp-peer way to buy and sell bitcoin. All data are based on the BTC-USD market. Trade number decreased in 2024  But USD volume increased ($/year)  (same graph but $/day by year)  Which means more higher value per trade  Interestingly, trade counts and price volatility lead to interesting BTC volume per year. The peaks are nearly identical (330 BTC)!  Not so surprising when you compare BTC volume traded to the average BTC price that year, local price valleys mean local peaks in BTC traded (and vice versa).  I separate fiat payment methods into three groups.  All USD payment methods used in 2024 by average value (y-axis) and number of trades (bubble size)  This is the same graph as above excluding Zelle and Strike, since they throw off the relative circle size (face-to-face only had 1 trade in 2024).  Two fiat methods had >1000 trades in 2024. Strike came on the scene hot in 2021 and ate some of the Zelle volume but that may have stabilized.  Six fiat methods had 200-1000 trades in 2024. Amazon Gift Card dwindling, Cash By Mail still top of this group, and Revolut surging (wtf is Revolut?)  Same group, all years  Last group is <200 trades in 2024. Basically unused, except for Wire Transfer increasing.  Same group, all years  What's the average trade size by fiat method? There are different reasons for this, largely driven by fiat fees and bank limits. Amazon Gift Card is an interesting option for smaller payments (note: you can't just send any gift card, there is a very specific process, see the Bisq [wiki]( https://bisq.wiki/Amazon_eGift_card))  There no KYC premium, but there is a small Surveillance Discount  If you open Bisq for the first time, you'll likely see spreads 3-5% or larger. These offers persist because no one wants them. So people think that Bisq is "too expensive." But let's dig into the actual trades...  Comparing the daily trade volume to daily market rate (I used coingecko), and creating a monthly weighted average, the true surveillance discount emerges. It's not 3-5% as you might see in the order book at any given time. In fact, it was cheaper to trade on Bisq than exchanges in November and December! (Note: this does not take into account the 4 on-chain transactions required for a trade or price spread/fees used by exchanges)  In 2024, Strike had the worst surveillance discount and Cash By Mail had the best. This isn't surprising because receiving cash is convenient and low risk for a seller so they're willing to accept a lower price. Zelle (the most common USD payment method) had the second best surveillance discount.  Now let's compare the surveillance discount by week in 2024 for select payment methods. Strike was consistently worse than Zelle  Revolut was sometimes way worse than Zelle but sometimes a little better.  The two most private payment methods are cash and money order. They're pretty competitive regarding surveillance discount.  Take aways * Be a maker and get a better price (fees are better too) * Zelle is better for speed + convenience * Amazon gift cards are good for speed + privacy (sorta) * Cash or money order are better for privacy + volume
@ c3c7122c:607731d7
2025-02-16 07:48:35At my meet up (the SD Bitcoiners Cete) on Thursday, I presented trends on the Bisq protocol. One of its features is that anyone can export the trade history and analyze it. Bisq is a private, peer-tp-peer way to buy and sell bitcoin. All data are based on the BTC-USD market. Trade number decreased in 2024  But USD volume increased ($/year)  (same graph but $/day by year)  Which means more higher value per trade  Interestingly, trade counts and price volatility lead to interesting BTC volume per year. The peaks are nearly identical (330 BTC)!  Not so surprising when you compare BTC volume traded to the average BTC price that year, local price valleys mean local peaks in BTC traded (and vice versa).  I separate fiat payment methods into three groups.  All USD payment methods used in 2024 by average value (y-axis) and number of trades (bubble size)  This is the same graph as above excluding Zelle and Strike, since they throw off the relative circle size (face-to-face only had 1 trade in 2024).  Two fiat methods had >1000 trades in 2024. Strike came on the scene hot in 2021 and ate some of the Zelle volume but that may have stabilized.  Six fiat methods had 200-1000 trades in 2024. Amazon Gift Card dwindling, Cash By Mail still top of this group, and Revolut surging (wtf is Revolut?)  Same group, all years  Last group is <200 trades in 2024. Basically unused, except for Wire Transfer increasing.  Same group, all years  What's the average trade size by fiat method? There are different reasons for this, largely driven by fiat fees and bank limits. Amazon Gift Card is an interesting option for smaller payments (note: you can't just send any gift card, there is a very specific process, see the Bisq [wiki]( https://bisq.wiki/Amazon_eGift_card))  There no KYC premium, but there is a small Surveillance Discount  If you open Bisq for the first time, you'll likely see spreads 3-5% or larger. These offers persist because no one wants them. So people think that Bisq is "too expensive." But let's dig into the actual trades...  Comparing the daily trade volume to daily market rate (I used coingecko), and creating a monthly weighted average, the true surveillance discount emerges. It's not 3-5% as you might see in the order book at any given time. In fact, it was cheaper to trade on Bisq than exchanges in November and December! (Note: this does not take into account the 4 on-chain transactions required for a trade or price spread/fees used by exchanges)  In 2024, Strike had the worst surveillance discount and Cash By Mail had the best. This isn't surprising because receiving cash is convenient and low risk for a seller so they're willing to accept a lower price. Zelle (the most common USD payment method) had the second best surveillance discount.  Now let's compare the surveillance discount by week in 2024 for select payment methods. Strike was consistently worse than Zelle  Revolut was sometimes way worse than Zelle but sometimes a little better.  The two most private payment methods are cash and money order. They're pretty competitive regarding surveillance discount.  Take aways * Be a maker and get a better price (fees are better too) * Zelle is better for speed + convenience * Amazon gift cards are good for speed + privacy (sorta) * Cash or money order are better for privacy + volume @ 9e69e420:d12360c2
2025-01-21 19:31:48Oregano oil is a potent natural compound that offers numerous scientifically-supported health benefits. ## Active Compounds The oil's therapeutic properties stem from its key bioactive components: - Carvacrol and thymol (primary active compounds) - Polyphenols and other antioxidant ## Antimicrobial Properties **Bacterial Protection** The oil demonstrates powerful antibacterial effects, even against antibiotic-resistant strains like MRSA and other harmful bacteria. Studies show it effectively inactivates various pathogenic bacteria without developing resistance. **Antifungal Effects** It effectively combats fungal infections, particularly Candida-related conditions like oral thrush, athlete's foot, and nail infections. ## Digestive Health Benefits Oregano oil supports digestive wellness by: - Promoting gastric juice secretion and enzyme production - Helping treat Small Intestinal Bacterial Overgrowth (SIBO) - Managing digestive discomfort, bloating, and IBS symptoms ## Anti-inflammatory and Antioxidant Effects The oil provides significant protective benefits through: - Powerful antioxidant activity that fights free radicals - Reduction of inflammatory markers in the body - Protection against oxidative stress-related conditions ## Respiratory Support It aids respiratory health by: - Loosening mucus and phlegm - Suppressing coughs and throat irritation - Supporting overall respiratory tract function ## Additional Benefits **Skin Health** - Improves conditions like psoriasis, acne, and eczema - Supports wound healing through antibacterial action - Provides anti-aging benefits through antioxidant properties **Cardiovascular Health** Studies show oregano oil may help: - Reduce LDL (bad) cholesterol levels - Support overall heart health **Pain Management** The oil demonstrates effectiveness in: - Reducing inflammation-related pain - Managing muscle discomfort - Providing topical pain relief ## Safety Note While oregano oil is generally safe, it's highly concentrated and should be properly diluted before use Consult a healthcare provider before starting supplementation, especially if taking other medications.
@ 9e69e420:d12360c2
2025-01-21 19:31:48Oregano oil is a potent natural compound that offers numerous scientifically-supported health benefits. ## Active Compounds The oil's therapeutic properties stem from its key bioactive components: - Carvacrol and thymol (primary active compounds) - Polyphenols and other antioxidant ## Antimicrobial Properties **Bacterial Protection** The oil demonstrates powerful antibacterial effects, even against antibiotic-resistant strains like MRSA and other harmful bacteria. Studies show it effectively inactivates various pathogenic bacteria without developing resistance. **Antifungal Effects** It effectively combats fungal infections, particularly Candida-related conditions like oral thrush, athlete's foot, and nail infections. ## Digestive Health Benefits Oregano oil supports digestive wellness by: - Promoting gastric juice secretion and enzyme production - Helping treat Small Intestinal Bacterial Overgrowth (SIBO) - Managing digestive discomfort, bloating, and IBS symptoms ## Anti-inflammatory and Antioxidant Effects The oil provides significant protective benefits through: - Powerful antioxidant activity that fights free radicals - Reduction of inflammatory markers in the body - Protection against oxidative stress-related conditions ## Respiratory Support It aids respiratory health by: - Loosening mucus and phlegm - Suppressing coughs and throat irritation - Supporting overall respiratory tract function ## Additional Benefits **Skin Health** - Improves conditions like psoriasis, acne, and eczema - Supports wound healing through antibacterial action - Provides anti-aging benefits through antioxidant properties **Cardiovascular Health** Studies show oregano oil may help: - Reduce LDL (bad) cholesterol levels - Support overall heart health **Pain Management** The oil demonstrates effectiveness in: - Reducing inflammation-related pain - Managing muscle discomfort - Providing topical pain relief ## Safety Note While oregano oil is generally safe, it's highly concentrated and should be properly diluted before use Consult a healthcare provider before starting supplementation, especially if taking other medications. @ b17fccdf:b7211155
2025-01-21 18:30:13~ > Available at: [https://minibolt.info](https://minibolt.info) --- ~> It builds on a personal computer with **x86/amd64** architecture processors. ~> It is based on the popular [RaspiBolt v3](https://raspibolt.org) guide. --- **Those are some of the most relevant changes:** * Changed OS from Raspberry Pi OS Lite (64-bits) to ***Ubuntu Server LTS*** (Long term support) 64-bit PC (AMD64). * Changed binaries and signatures of the programs to adapt them to ***x86/amd64 architecture***. * Deleted unnecessary tools and steps, and added others according to this case of use. * Some useful authentication logs and monitoring commands were added in the security section. * Added some interesting parameters in the settings of some services to activate and take advantage of new features. * Changed I2P, Fulcrum, and ThunderHub guides, to be part of the core guide. * Added exclusive optimization section of services for slow devices. --- ~ > Complete release notes of the MiniBolt v1: [https://github.com/twofaktor/minibolt/releases/tag/1.0](https://github.com/twofaktor/minibolt/releases/tag/1.0). ~ > Feel free to contribute to the [source code on GitHub](https://github.com/minibolt-guide/minibolt) by opening [issues](https://github.com/minibolt-guide/minibolt/issues), [pull requests](https://github.com/minibolt-guide/minibolt/pulls) or [discussions](https://github.com/orgs/minibolt-guide/discussions). --- Created by [⚡2 FakTor⚡](nostr:npub1k9luehc8hg3c0upckdzzvusv66x3zt0eyw7290kclrpsndepz92sfcpp63)
@ b17fccdf:b7211155
2025-01-21 18:30:13~ > Available at: [https://minibolt.info](https://minibolt.info) --- ~> It builds on a personal computer with **x86/amd64** architecture processors. ~> It is based on the popular [RaspiBolt v3](https://raspibolt.org) guide. --- **Those are some of the most relevant changes:** * Changed OS from Raspberry Pi OS Lite (64-bits) to ***Ubuntu Server LTS*** (Long term support) 64-bit PC (AMD64). * Changed binaries and signatures of the programs to adapt them to ***x86/amd64 architecture***. * Deleted unnecessary tools and steps, and added others according to this case of use. * Some useful authentication logs and monitoring commands were added in the security section. * Added some interesting parameters in the settings of some services to activate and take advantage of new features. * Changed I2P, Fulcrum, and ThunderHub guides, to be part of the core guide. * Added exclusive optimization section of services for slow devices. --- ~ > Complete release notes of the MiniBolt v1: [https://github.com/twofaktor/minibolt/releases/tag/1.0](https://github.com/twofaktor/minibolt/releases/tag/1.0). ~ > Feel free to contribute to the [source code on GitHub](https://github.com/minibolt-guide/minibolt) by opening [issues](https://github.com/minibolt-guide/minibolt/issues), [pull requests](https://github.com/minibolt-guide/minibolt/pulls) or [discussions](https://github.com/orgs/minibolt-guide/discussions). --- Created by [⚡2 FakTor⚡](nostr:npub1k9luehc8hg3c0upckdzzvusv66x3zt0eyw7290kclrpsndepz92sfcpp63) @ b17fccdf:b7211155
2025-01-21 18:22:51😱 Did you recently find this signature verification error when you tried to update your MiniBolt repositories with -> `sudo apt update`? 💥🚨👇  🔧 Don't worry, that's because Tor renewed its signing key since it expired last 07/15, just renew your keyring by following the next steps to solve this problem: ~ > [CLICK HERE](https://minibolt.minibolt.info/system/system/privacy#tor-signature-verification-error) < ~ --- Enjoy it MiniBolter!💙
@ b17fccdf:b7211155
2025-01-21 18:22:51😱 Did you recently find this signature verification error when you tried to update your MiniBolt repositories with -> `sudo apt update`? 💥🚨👇  🔧 Don't worry, that's because Tor renewed its signing key since it expired last 07/15, just renew your keyring by following the next steps to solve this problem: ~ > [CLICK HERE](https://minibolt.minibolt.info/system/system/privacy#tor-signature-verification-error) < ~ --- Enjoy it MiniBolter!💙 @ b17fccdf:b7211155
2025-01-21 18:10:10**Link to the bonus guide** ~ > [HERE](https://minibolt.minibolt.info/bonus-guides/bitcoin/minibolt-on-testnet) <~ --- Some notes: ℹ️ For the moment, this guide will touch only the case of an **only testnet mode** situation, in the future, we will study adding the case of configuration to enable the parallel/simultaneous mode (mainnet+testnet in the same device) in an extra section in this guide. ℹ️ The services mentioned in this guide are those that have been tested using testnet configuration and these worked fine. Later, in the next versions of this guide, we will go to adding other processes to adapt other services to the testnet mode. --- Enjoy it MiniBolter! 💙
@ b17fccdf:b7211155
2025-01-21 18:10:10**Link to the bonus guide** ~ > [HERE](https://minibolt.minibolt.info/bonus-guides/bitcoin/minibolt-on-testnet) <~ --- Some notes: ℹ️ For the moment, this guide will touch only the case of an **only testnet mode** situation, in the future, we will study adding the case of configuration to enable the parallel/simultaneous mode (mainnet+testnet in the same device) in an extra section in this guide. ℹ️ The services mentioned in this guide are those that have been tested using testnet configuration and these worked fine. Later, in the next versions of this guide, we will go to adding other processes to adapt other services to the testnet mode. --- Enjoy it MiniBolter! 💙 @ b17fccdf:b7211155
2025-01-21 18:04:28Available at: [https://minibolt.info](https://minibolt.info) --- **Main changes to** the version 1: * The complete guide has been migrated to the new design visual builder web tool platform [gitbook.com](https://www.gitbook.com/) * New modern UI (responsive, full width, and better visual items) * New menu structure for a better user experience * New visual items to improve the navigation through the web page * New switch to enable light/dark theme * Enabled Cloudflare Proxy for maximum protection against attacks and better management of the domain --- **Other changes:** * New [MiniBolt Linktr](https://linktr.minibolt.info/) forked of the alternative [FOSS project](https://github.com/gzuuus/linktr) proposed by [Gzuuus](https://twitter.com/gzuuus) * Changed MiniBolt from a personal project to an [organization](https://github.com/minibolt-guide) so that the project has its own identity * New email contact address [hello@minibolt.info](mailto:hello@minibolt.info) to receive proposals and give support * New [resources](https://github.com/minibolt-guide/minibolt/tree/main/resources) folder with the current MiniBolt roadmap, network map diagrams, and others --- ℹ️ **More info:** * The new version is available with the known domain: [minibolt.info](https://minibolt.info/) but from now on links associated with the new v2 version were shared using the [v2.minibolt.info](https://v2.minibolt.info/) subdomain due to a GitBook limitation * The old and deprecated v1 will be still available at a time in the subdomain [v1.minibolt.info](https://v1.minibolt.info/), but is in the roadmap delete it definitely in the future, take note ASAP of all that you need of that version before this happens * Contributors and collaborators will be able to continue doing PR through code programming or using the design block builder [gitbook.com](https://www.gitbook.com/) --- [GitHub release](https://github.com/minibolt-guide/minibolt/releases/tag/2.0) --- Enjoy it MiniBolter! 💙
@ b17fccdf:b7211155
2025-01-21 18:04:28Available at: [https://minibolt.info](https://minibolt.info) --- **Main changes to** the version 1: * The complete guide has been migrated to the new design visual builder web tool platform [gitbook.com](https://www.gitbook.com/) * New modern UI (responsive, full width, and better visual items) * New menu structure for a better user experience * New visual items to improve the navigation through the web page * New switch to enable light/dark theme * Enabled Cloudflare Proxy for maximum protection against attacks and better management of the domain --- **Other changes:** * New [MiniBolt Linktr](https://linktr.minibolt.info/) forked of the alternative [FOSS project](https://github.com/gzuuus/linktr) proposed by [Gzuuus](https://twitter.com/gzuuus) * Changed MiniBolt from a personal project to an [organization](https://github.com/minibolt-guide) so that the project has its own identity * New email contact address [hello@minibolt.info](mailto:hello@minibolt.info) to receive proposals and give support * New [resources](https://github.com/minibolt-guide/minibolt/tree/main/resources) folder with the current MiniBolt roadmap, network map diagrams, and others --- ℹ️ **More info:** * The new version is available with the known domain: [minibolt.info](https://minibolt.info/) but from now on links associated with the new v2 version were shared using the [v2.minibolt.info](https://v2.minibolt.info/) subdomain due to a GitBook limitation * The old and deprecated v1 will be still available at a time in the subdomain [v1.minibolt.info](https://v1.minibolt.info/), but is in the roadmap delete it definitely in the future, take note ASAP of all that you need of that version before this happens * Contributors and collaborators will be able to continue doing PR through code programming or using the design block builder [gitbook.com](https://www.gitbook.com/) --- [GitHub release](https://github.com/minibolt-guide/minibolt/releases/tag/2.0) --- Enjoy it MiniBolter! 💙 @ b17fccdf:b7211155
2025-01-21 17:58:35The **router reserves the IP address** of the device **for a time after going out**, but if the device goes out some time, the next time that the device starts, the router could assign a different IP and you could lose access to your node. To avoid this, you need to **set a static IP to your MiniBolt**. ~ > In addition, you can **customize your DNS servers to improve your privacy**, normally your ISP, gives you the router with its own DNS servers set by default, and this does that you expose all of your navigation trackings to your ISP, affecting seriously your privacy. ~ > This bonus guide includes all of the necessary steps to get this and is available ~ > [HERE](https://minibolt.minibolt.info/bonus-guides/system/static-ip-and-custom-dns-servers) < ~ ---  --- Enjoy it MiniBolter! 💙
@ b17fccdf:b7211155
2025-01-21 17:58:35The **router reserves the IP address** of the device **for a time after going out**, but if the device goes out some time, the next time that the device starts, the router could assign a different IP and you could lose access to your node. To avoid this, you need to **set a static IP to your MiniBolt**. ~ > In addition, you can **customize your DNS servers to improve your privacy**, normally your ISP, gives you the router with its own DNS servers set by default, and this does that you expose all of your navigation trackings to your ISP, affecting seriously your privacy. ~ > This bonus guide includes all of the necessary steps to get this and is available ~ > [HERE](https://minibolt.minibolt.info/bonus-guides/system/static-ip-and-custom-dns-servers) < ~ ---  --- Enjoy it MiniBolter! 💙 @ b17fccdf:b7211155
2025-01-21 17:47:28Link to the bonus guide ~ > [HERE](https://minibolt.minibolt.info/bonus-guides/system/ssh-keys) < ~ --- Some sections of the guide: * Generate SSH keys * Import SSH pubkey * Connect to the MiniBolt node using SSH keys * Disable password login * Disable admin password request --- Some shortcuts to the Extra sections: * Disable password login: click ~ > [HERE](https://minibolt.minibolt.info/bonus-guides/system/ssh-keys#disable-password-login) < ~ * Disable admin password request: click ~ > [HERE](https://minibolt.minibolt.info/bonus-guides/system/ssh-keys#disable-admin-password-request-caution) < ~ --- Enjoy it MiniBolter! 💙
@ b17fccdf:b7211155
2025-01-21 17:47:28Link to the bonus guide ~ > [HERE](https://minibolt.minibolt.info/bonus-guides/system/ssh-keys) < ~ --- Some sections of the guide: * Generate SSH keys * Import SSH pubkey * Connect to the MiniBolt node using SSH keys * Disable password login * Disable admin password request --- Some shortcuts to the Extra sections: * Disable password login: click ~ > [HERE](https://minibolt.minibolt.info/bonus-guides/system/ssh-keys#disable-password-login) < ~ * Disable admin password request: click ~ > [HERE](https://minibolt.minibolt.info/bonus-guides/system/ssh-keys#disable-admin-password-request-caution) < ~ --- Enjoy it MiniBolter! 💙 @ b17fccdf:b7211155
2025-01-21 17:39:34**Link to the bonus guide** ~ > [HERE](https://minibolt.minibolt.info/bonus-guides/bitcoin/ordisrespector) < ~ --- ⏰ Recently added an update that includes a new section **[How to detect Ordinals transactions](https://minibolt.minibolt.info/bonus-guides/bitcoin/ordisrespector#how-to-detect-ordinals-transactions) and [verify Ordisrespector filter works](https://minibolt.minibolt.info/bonus-guides/bitcoin/ordisrespector#check-the-ordisrespector-filter-working-on-your-mempool)** to verify that Ordispector is **filtering and burning Ordinals** correctly 🔥 --- Fuck Ordinals🤡🔫 and enjoy it MiniBolter! 💙
@ b17fccdf:b7211155
2025-01-21 17:39:34**Link to the bonus guide** ~ > [HERE](https://minibolt.minibolt.info/bonus-guides/bitcoin/ordisrespector) < ~ --- ⏰ Recently added an update that includes a new section **[How to detect Ordinals transactions](https://minibolt.minibolt.info/bonus-guides/bitcoin/ordisrespector#how-to-detect-ordinals-transactions) and [verify Ordisrespector filter works](https://minibolt.minibolt.info/bonus-guides/bitcoin/ordisrespector#check-the-ordisrespector-filter-working-on-your-mempool)** to verify that Ordispector is **filtering and burning Ordinals** correctly 🔥 --- Fuck Ordinals🤡🔫 and enjoy it MiniBolter! 💙 @ b17fccdf:b7211155
2025-01-21 17:29:54Some sections inside of the guide: * Set up Dynamic DNS * Wireguard VPN server & client side configurations * Install & configure the WireGuard VPN Client on a mobile phone * Configure additional servers & clients * Use your router’s DDNS preconfigured provider * Port forwarding on NAT/PAT router --- Link to the bonus guide [HERE](https://minibolt.minibolt.info/bonus-guides/system/wireguard-vpn) --- Enjoy it MiniBolter! 💙
@ b17fccdf:b7211155
2025-01-21 17:29:54Some sections inside of the guide: * Set up Dynamic DNS * Wireguard VPN server & client side configurations * Install & configure the WireGuard VPN Client on a mobile phone * Configure additional servers & clients * Use your router’s DDNS preconfigured provider * Port forwarding on NAT/PAT router --- Link to the bonus guide [HERE](https://minibolt.minibolt.info/bonus-guides/system/wireguard-vpn) --- Enjoy it MiniBolter! 💙