-

@ 57d1a264:69f1fee1
2025-02-06 07:38:36
# How does bitcoin's lack of central brand authority influence its visual identity, and what implications does this have for designers?
originally posted at https://stacker.news/items/877437
-

@ e3ba5e1a:5e433365
2025-02-05 17:47:16
I got into a [friendly discussion](https://x.com/snoyberg/status/1887007888117252142) on X regarding health insurance. The specific question was how to deal with health insurance companies (presumably unfairly) denying claims? My answer, as usual: get government out of it!
The US healthcare system is essentially the worst of both worlds:
* Unlike full single payer, individuals incur high costs
* Unlike a true free market, regulation causes increases in costs and decreases competition among insurers
I'm firmly on the side of moving towards the free market. (And I say that as someone living under a single payer system now.) Here's what I would do:
* Get rid of tax incentives that make health insurance tied to your employer, giving individuals back proper freedom of choice.
* Reduce regulations significantly.
* In the short term, some people will still get rejected claims and other obnoxious behavior from insurance companies. We address that in two ways:
1. Due to reduced regulations, new insurance companies will be able to enter the market offering more reliable coverage and better rates, and people will flock to them because they have the freedom to make their own choices.
2. Sue the asses off of companies that reject claims unfairly. And ideally, as one of the few legitimate roles of government in all this, institute new laws that limit the ability of fine print to allow insurers to escape their responsibilities. (I'm hesitant that the latter will happen due to the incestuous relationship between Congress/regulators and insurers, but I can hope.)
Will this magically fix everything overnight like politicians normally promise? No. But it will allow the market to return to a healthy state. And I don't think it will take long (order of magnitude: 5-10 years) for it to come together, but that's just speculation.
And since there's a high correlation between those who believe government can fix problems by taking more control and demanding that only credentialed experts weigh in on a topic (both points I strongly disagree with BTW): I'm a trained actuary and worked in the insurance industry, and have directly seen how government regulation reduces competition, raises prices, and harms consumers.
And my final point: I don't think any prior art would be a good comparison for deregulation in the US, it's such a different market than any other country in the world for so many reasons that lessons wouldn't really translate. Nonetheless, I asked Grok for some empirical data on this, and at best the results of deregulation could be called "mixed," but likely more accurately "uncertain, confused, and subject to whatever interpretation anyone wants to apply."
https://x.com/i/grok/share/Zc8yOdrN8lS275hXJ92uwq98M
-

@ 57d1a264:69f1fee1
2025-02-05 02:18:03

Pre-Foundational learning for these participants has now kicked off in the Bitcoin Design Community, check out the #education channel on the [Bitcoin.Design](https://Bitcoin.Design) [Discord channel](https://discord.com/channels/903125802726596648/1260871907050393620).
## 🪇 10 talented participants from South America will be:
Learning bitcoin UX Design fundamentals using the Bitcoin Design Guide
Working hands-on with South American-built products to evaluate their user experiences and support builders with data
> Attending [BTC++ in Florianópolis](https://btcplusplus.dev/conf/floripa)
This initiative is sponsored by the [Human Rights Foundation](https://HRF.org) in collaboration with the [Bitcoin Design Foundation](https://bitcoindesignfoundation.org/) and [Area Bitcoin](https://areabitcoin.co).
## 🥅 Goals:
- Empower local talent to improve the UX of South American bitcoin products - seeing their passion and drive to bring bitcoin to their countries is really inspiring
- Create meaningful relationships with wallet developers through practical collaboration
- Scale bitcoin adoption by improving the user experience
- Create a public knowledge base: All research conducted in Africa and South America will be made publicly available for builders
originally posted at https://stacker.news/items/876215
-

@ 57d1a264:69f1fee1
2025-02-05 00:25:20
# How does open source development contribute to bitcoin's security, reliability, and evolution as a network?
originally posted at https://stacker.news/items/876130
-

@ 91bea5cd:1df4451c
2025-02-04 17:24:50
### Definição de ULID:
Timestamp 48 bits, Aleatoriedade 80 bits
Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C.
e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível.
#### Gerar ULID
```sql
CREATE EXTENSION IF NOT EXISTS pgcrypto;
CREATE FUNCTION generate_ulid()
RETURNS TEXT
AS $$
DECLARE
-- Crockford's Base32
encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ';
timestamp BYTEA = E'\\000\\000\\000\\000\\000\\000';
output TEXT = '';
unix_time BIGINT;
ulid BYTEA;
BEGIN
-- 6 timestamp bytes
unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT;
timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER);
timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER);
timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER);
timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER);
timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER);
timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER);
-- 10 entropy bytes
ulid = timestamp || gen_random_bytes(10);
-- Encode the timestamp
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31)));
-- Encode the entropy
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31)));
RETURN output;
END
$$
LANGUAGE plpgsql
VOLATILE;
```
#### ULID TO UUID
```sql
CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$
DECLARE
-- 16byte
bytes bytea = E'\\x00000000 00000000 00000000 00000000';
v char[];
-- Allow for O(1) lookup of index values
dec integer[] = ARRAY[
255, 255, 255, 255, 255, 255, 255, 255, 255, 255,
255, 255, 255, 255, 255, 255, 255, 255, 255, 255,
255, 255, 255, 255, 255, 255, 255, 255, 255, 255,
255, 255, 255, 255, 255, 255, 255, 255, 255, 255,
255, 255, 255, 255, 255, 255, 255, 0, 1, 2,
3, 4, 5, 6, 7, 8, 9, 255, 255, 255,
255, 255, 255, 255, 10, 11, 12, 13, 14, 15,
16, 17, 1, 18, 19, 1, 20, 21, 0, 22,
23, 24, 25, 26, 255, 27, 28, 29, 30, 31,
255, 255, 255, 255, 255, 255, 10, 11, 12, 13,
14, 15, 16, 17, 1, 18, 19, 1, 20, 21,
0, 22, 23, 24, 25, 26, 255, 27, 28, 29,
30, 31
];
BEGIN
IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN
RAISE EXCEPTION 'Invalid ULID: %', ulid;
END IF;
v = regexp_split_to_array(ulid, '');
-- 6 bytes timestamp (48 bits)
bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]);
bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2));
bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4));
bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1));
bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3));
bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]);
-- 10 bytes of entropy (80 bits);
bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2));
bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4));
bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1));
bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3));
bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]);
bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2));
bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4));
bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1));
bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3));
bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]);
RETURN bytes;
END
$$
LANGUAGE plpgsql
IMMUTABLE;
CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$
BEGIN
RETURN encode(parse_ulid(ulid), 'hex')::uuid;
END
$$
LANGUAGE plpgsql
IMMUTABLE;
```
#### UUID to ULID
```sql
CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$
DECLARE
encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ';
output text = '';
uuid_bytes bytea = uuid_send(id);
BEGIN
-- Encode the timestamp
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31)));
-- Encode the entropy
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31)));
RETURN output;
END
$$
LANGUAGE plpgsql
IMMUTABLE;
```
#### Gera 11 Digitos aleatórios: YBKXG0CKTH4
```sql
-- Cria a extensão pgcrypto para gerar uuid
CREATE EXTENSION IF NOT EXISTS pgcrypto;
-- Cria a função para gerar ULID
CREATE OR REPLACE FUNCTION gen_lrandom()
RETURNS TEXT AS $$
DECLARE
ts_millis BIGINT;
ts_chars TEXT;
random_bytes BYTEA;
random_chars TEXT;
base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ';
i INT;
BEGIN
-- Pega o timestamp em milissegundos
ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT;
-- Converte o timestamp para base32
ts_chars := '';
FOR i IN REVERSE 0..11 LOOP
ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1);
END LOOP;
-- Gera 10 bytes aleatórios e converte para base32
random_bytes := gen_random_bytes(10);
random_chars := '';
FOR i IN 0..9 LOOP
random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1);
IF i < 9 THEN
random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1);
ELSE
random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1);
END IF;
END LOOP;
-- Concatena o timestamp e os caracteres aleatórios
RETURN ts_chars || random_chars;
END;
$$ LANGUAGE plpgsql;
```
#### Exemplo de USO
```sql
-- Criação da extensão caso não exista
CREATE EXTENSION
IF
NOT EXISTS pgcrypto;
-- Criação da tabela pessoas
CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL );
-- Busca Pessoa na tabela
SELECT
*
FROM
"pessoas"
WHERE
uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F';
```
### Fontes
- https://github.com/scoville/pgsql-ulid
- https://github.com/geckoboard/pgulid
-

@ 1833ee04:7c4a8170
2025-02-04 15:14:03
The international race for Bitcoin strategic reserves is just getting started.
If you’re stacking now, you’re still incredibly early.
At $100k per Bitcoin, it’s practically free for anyone who truly understands how massive this shift is.
Think back to when paper currency was introduced, people had to trade their gold for paper bills. Many laughed, saying, Who’s going to trust these worthless pieces of paper as money?
Yet today, you sell your time to earn these paper bills while your government can print an unlimited amount at will.
The world is returning to a gold standard. But this time, it’s Gold 2.0 which is Bitcoin.The international race for Bitcoin strategic reserves is just getting started.\
\
If you’re stacking now, you’re still incredibly early.\
\
At $100k per Bitcoin, it’s practically free for anyone who truly understands how massive this shift is.\
\
Think back to when paper currency was introduced, people had to trade their gold for paper bills. Many laughed, saying, Who’s going to trust these worthless pieces of paper as money?\
\
Yet today, you sell your time to earn these paper bills while your government can print an unlimited amount at will.\
\
The world is returning to a gold standard. But this time, it’s Gold 2.0 which is Bitcoin.
-

@ e3ba5e1a:5e433365
2025-02-04 08:29:00
President Trump has started rolling out his tariffs, something I [blogged about in November](https://www.snoyman.com/blog/2024/11/steelmanning-tariffs/). People are talking about these tariffs a lot right now, with many people (correctly) commenting on how consumers will end up with higher prices as a result of these tariffs. While that part is true, I’ve seen a lot of people taking it to the next, incorrect step: that consumers will pay the entirety of the tax. I [put up a poll on X](https://x.com/snoyberg/status/1886035800019599808) to see what people thought, and while the right answer got a lot of votes, it wasn't the winner.

For purposes of this blog post, our ultimate question will be the following:
* Suppose apples currently sell for $1 each in the entire United States.
* There are domestic sellers and foreign sellers of apples, all receiving the same price.
* There are no taxes or tariffs on the purchase of apples.
* The question is: if the US federal government puts a $0.50 import tariff per apple, what will be the change in the following:
* Number of apples bought in the US
* Price paid by buyers for apples in the US
* Post-tax price received by domestic apple producers
* Post-tax price received by foreign apple producers
Before we can answer that question, we need to ask an easier, first question: before instituting the tariff, why do apples cost $1?
And finally, before we dive into the details, let me provide you with the answers to the ultimate question. I recommend you try to guess these answers before reading this, and if you get it wrong, try to understand why:
1. The number of apples bought will go down
2. The buyers will pay more for each apple they buy, but not the full amount of the tariff
3. Domestic apple sellers will receive a *higher* price per apple
4. Foreign apple sellers will receive a *lower* price per apple, but not lowered by the full amount of the tariff
In other words, regardless of who sends the payment to the government, both taxed parties (domestic buyers and foreign sellers) will absorb some of the costs of the tariff, while domestic sellers will benefit from the protectionism provided by tariffs and be able to sell at a higher price per unit.
## Marginal benefit
All of the numbers discussed below are part of a [helper Google Sheet](https://docs.google.com/spreadsheets/d/14ZbkWpw1B9Q1UDB9Yh47DmdKQfIafVVBKbDUsSIfGZw/edit?usp=sharing) I put together for this analysis. Also, apologies about the jagged lines in the charts below, I hadn’t realized before starting on this that there are [some difficulties with creating supply and demand charts in Google Sheets](https://superuser.com/questions/1359731/how-to-create-a-supply-demand-style-chart).
Let’s say I absolutely love apples, they’re my favorite food. How much would I be willing to pay for a single apple? You might say “$1, that’s the price in the supermarket,” and in many ways you’d be right. If I walk into supermarket A, see apples on sale for $50, and know that I can buy them at supermarket B for $1, I’ll almost certainly leave A and go buy at B.
But that’s not what I mean. What I mean is: how high would the price of apples have to go *everywhere* so that I’d no longer be willing to buy a single apple? This is a purely personal, subjective opinion. It’s impacted by how much money I have available, other expenses I need to cover, and how much I like apples. But let’s say the number is $5.
How much would I be willing to pay for another apple? Maybe another $5. But how much am I willing to pay for the 1,000th apple? 10,000th? At some point, I’ll get sick of apples, or run out of space to keep the apples, or not be able to eat, cook, and otherwise preserve all those apples before they rot.
The point being: I’ll be progressively willing to spend less and less money for each apple. This form of analysis is called *marginal benefit*: how much benefit (expressed as dollars I’m willing to spend) will I receive from each apple? This is a downward sloping function: for each additional apple I buy (quantity demanded), the price I’m willing to pay goes down. This is what gives my personal *demand curve*. And if we aggregate demand curves across all market participants (meaning: everyone interested in buying apples), we end up with something like this:

Assuming no changes in people’s behavior and other conditions in the market, this chart tells us how many apples will be purchased by our buyers at each price point between $0.50 and $5. And ceteris paribus (all else being equal), this will continue to be the demand curve for apples.
## Marginal cost
Demand is half the story of economics. The other half is supply, or: how many apples will I sell at each price point? Supply curves are upward sloping: the higher the price, the more a person or company is willing and able to sell a product.
Let’s understand why. Suppose I have an apple orchard. It’s a large property right next to my house. With about 2 minutes of effort, I can walk out of my house, find the nearest tree, pick 5 apples off the tree, and call it a day. 5 apples for 2 minutes of effort is pretty good, right?
Yes, there was all the effort necessary to buy the land, and plant the trees, and water them… and a bunch more than I likely can’t even guess at. We’re going to ignore all of that for our analysis, because for short-term supply-and-demand movement, we can ignore these kinds of *sunk costs*. One other simplification: in reality, supply curves often start descending before ascending. This accounts for achieving efficiencies of scale after the first number of units purchased. But since both these topics are unneeded for understanding taxes, I won’t go any further.
Anyway, back to my apple orchard. If someone offers me $0.50 per apple, I can do 2 minutes of effort and get $2.50 in revenue, which equates to a $75/hour wage for me. I’m more than happy to pick apples at that price\!
However, let’s say someone comes to buy 10,000 apples from me instead. I no longer just walk out to my nearest tree. I’m going to need to get in my truck, drive around, spend the day in the sun, pay for gas, take a day off of my day job (let’s say it pays me $70/hour). The costs go up significantly. Let’s say it takes 5 days to harvest all those apples myself, it costs me $100 in fuel and other expenses, and I lose out on my $70/hour job for 5 days. We end up with:
* Total expenditure: $100 \+ $70 \* 8 hours a day \* 5 days \== $2900
* Total revenue: $5000 (10,000 apples at $0.50 each)
* Total profit: $2100
So I’m still willing to sell the apples at this price, but it’s not as attractive as before. And as the number of apples purchased goes up, my costs keep increasing. I’ll need to spend more money on fuel to travel more of my property. At some point I won’t be able to do the work myself anymore, so I’ll need to pay others to work on the farm, and they’ll be slower at picking apples than me (less familiar with the property, less direct motivation, etc.). The point being: at some point, the number of apples can go high enough that the $0.50 price point no longer makes me any money.
This kind of analysis is called *marginal cost*. It refers to the additional amount of expenditure a seller has to spend in order to produce each additional unit of the good. Marginal costs go up as quantity sold goes up. And like demand curves, if you aggregate this data across all sellers, you get a supply curve like this:

## Equilibrium price
We now know, for every price point, how many apples buyers will purchase, and how many apples sellers will sell. Now we find the equilibrium: where the supply and demand curves meet. This point represents where the marginal benefit a buyer would receive from the next buyer would be less than the cost it would take the next seller to make it. Let’s see it in a chart:

You’ll notice that these two graphs cross at the $1 price point, where 63 apples are both demanded (bought by consumers) and supplied (sold by producers). This is our equilibrium price. We also have a visualization of the *surplus* created by these trades. Everything to the left of the equilibrium point and between the supply and demand curves represents surplus: an area where someone is receiving something of more value than they give. For example:
* When I bought my first apple for $1, but I was willing to spend $5, I made $4 of consumer surplus. The consumer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and above the equilibrium price point.
* When a seller sells his first apple for $1, but it only cost $0.50 to produce it, the seller made $0.50 of producer surplus. The producer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and below the equilibrium price point.
Another way of thinking of surplus is “every time someone got a better price than they would have been willing to take.”
OK, with this in place, we now have enough information to figure out how to price in the tariff, which we’ll treat as a negative externality.
## Modeling taxes
Alright, the government has now instituted a $0.50 tariff on every apple sold within the US by a foreign producer. We can generally model taxes by either increasing the marginal cost of each unit sold (shifting the supply curve up), or by decreasing the marginal benefit of each unit bought (shifting the demand curve down). In this case, since only some of the producers will pay the tax, it makes more sense to modify the supply curve.
First, let’s see what happens to the foreign seller-only supply curve when you add in the tariff:

With the tariff in place, for each quantity level, the price at which the seller will sell is $0.50 higher than before the tariff. That makes sense: if I was previously willing to sell my 82nd apple for $3, I would now need to charge $3.50 for that apple to cover the cost of the tariff. We see this as the tariff “pushing up” or “pushing left” the original supply curve.
We can add this new supply curve to our existing (unchanged) supply curve for domestic-only sellers, and we end up with a result like this:

The total supply curve adds up the individual foreign and domestic supply curves. At each price point, we add up the total quantity each group would be willing to sell to determine the total quantity supplied for each price point. Once we have that cumulative supply curve defined, we can produce an updated supply-and-demand chart including the tariff:

As we can see, the equilibrium has shifted:
* The equilibrium price paid by consumers has risen from $1 to $1.20.
* The total number of apples purchased has dropped from 63 apples to 60 apples.
* Consumers therefore received 3 less apples. They spent $72 for these 60 apples, whereas previously they spent $63 for 3 more apples, a definite decrease in consumer surplus.
* Foreign producers sold 36 of those apples (see the raw data in the linked Google Sheet), for a gross revenue of $43.20. However, they also need to pay the tariff to the US government, which accounts for $18, meaning they only receive $25.20 post-tariff. Previously, they sold 42 apples at $1 each with no tariff to be paid, meaning they took home $42.
* Domestic producers sold the remaining 24 apples at $1.20, giving them a revenue of $28.80. Since they don’t pay the tariff, they take home all of that money. By contrast, previously, they sold 21 apples at $1, for a take-home of $21.
* The government receives $0.50 for each of the 60 apples sold, or in other words receives $30 in revenue it wouldn’t have received otherwise.
We could be more specific about the surpluses, and calculate the actual areas for consumer surplus, producer surplus, inefficiency from the tariff, and government revenue from the tariff. But I won’t bother, as those calculations get slightly more involved. Instead, let’s just look at the aggregate outcomes:
* Consumers were unquestionably hurt. Their price paid went up by $0.20 per apple, and received less apples.
* Foreign producers were also hurt. Their price received went down from the original $1 to the new post-tariff price of $1.20, minus the $0.50 tariff. In other words: foreign producers only receive $0.70 per apple now. This hurt can be mitigated by shifting sales to other countries without a tariff, but the pain will exist regardless.
* Domestic producers scored. They can sell less apples and make more revenue doing it.
* And the government walked away with an extra $30.
Hopefully you now see the answer to the original questions. Importantly, while the government imposed a $0.50 tariff, neither side fully absorbed that cost. Consumers paid a bit more, foreign producers received a bit less. The exact details of how that tariff was split across the groups is mediated by the relevant supply and demand curves of each group. If you want to learn more about this, the relevant search term is “price elasticity,” or how much a group’s quantity supplied or demanded will change based on changes in the price.
## Other taxes
Most taxes are some kind of a tax on trade. Tariffs on apples is an obvious one. But the same applies to income tax (taxing the worker for the trade of labor for money) or payroll tax (same thing, just taxing the employer instead). Interestingly, you can use the same model for analyzing things like tax incentives. For example, if the government decided to subsidize domestic apple production by giving the domestic producers a $0.50 bonus for each apple they sell, we would end up with a similar kind of analysis, except instead of the foreign supply curve shifting up, we’d see the domestic supply curve shifting down.
And generally speaking, this is what you’ll *always* see with government involvement in the economy. It will result in disrupting an existing equilibrium, letting the market readjust to a new equilibrium, and incentivization of some behavior, causing some people to benefit and others to lose out. We saw with the apple tariff, domestic producers and the government benefited while others lost.
You can see the reverse though with tax incentives. If I give a tax incentive of providing a deduction (not paying income tax) for preschool, we would end up with:
* Government needs to make up the difference in tax revenue, either by raising taxes on others or printing more money (leading to inflation). Either way, those paying the tax or those holding government debased currency will pay a price.
* Those people who don’t use the preschool deduction will receive no benefit, so they simply pay a cost.
* Those who do use the preschool deduction will end up paying less on tax+preschool than they would have otherwise.
This analysis is fully amoral. It’s not saying whether providing subsidized preschool is a good thing or not, it simply tells you where the costs will be felt, and points out that such government interference in free economic choice does result in inefficiencies in the system. Once you have that knowledge, you’re more well educated on making a decision about whether the costs of government intervention are worth the benefits.
-

@ 378562cd:a6fc6773
2025-02-02 18:58:38
## Chef's notes
I'm only testing this out right now. I will update the recipe as well as add my own image soon after making this dish again.
## Details
- ⏲️ Prep time: 20 minutes
- 🍳 Cook time: 1 hour
- 🍽️ Servings: 4
## Ingredients
- 4 to 6 potatoes (size depending)
- 1 lb ground beef
- seasonings
- 2 cans chili beans
- 1 onion
- katsup
- shredded cheese of some kind
## Directions
1. saute onion and add ground beef to skillet. Season to liking.
2. peel if you like and thin slice potatoes
3. in a rectangle baking dish, layer potatoes, beans, meat and cheese (like a lasagna) until you have used all your ingredients. Try and make at least 2 or 3 layers with extra cheese on top.
4. Bake at 350 for one hour. Serve and enjoy!
-

@ 228dde34:b5d0345e
2025-02-02 10:00:02
##### By Cheryl Nya
##### Deputy Editor
##### Hype Issue #60
###### CHERYL NYA explores how diverse travel styles can blend seamlessly on a grad trip, turning every moment into an opportunity for unforgettable memories and shared adventures.
 *‘Grad trips’, taking a celebratory trip after graduation, have become a growing trend. Photo taken from Pinterest.*
You made it – years of studying, late-night cramming, and navigating deadlines have finally paid off. Now, it’s time for a well-earned break: the graduation trip. The perfect chance to celebrate with your closest friends before everyone heads off in different directions.
It sounds like the golden plan, but as exciting as it is, travelling in a group can be its own kind of challenge. Between different travel styles, budgets and energy levels, it’s easy for tensions to rise.
However, with a little flexibility and compromise, your long-awaited trip will be remembered for its remarkable memories rather than its unfortunate disagreements. Here’s your ultimate guide to coexisting with your travel crew, without losing your patience along the way.
 *Have an honest talk with your crew and set expectations before you head off. Photo taken from Pinterest.*
1. Recognise that everyone has their own travel personality
There’s the ‘Itinerary Enthusiasts’ who have every minute planned. Then there’ll be the ‘Go with the flow’ travellers who are just there for chill vibes. Somewhere in between you’ve got the foodies, the shopaholics, and the one who just wants a good Instagram shot. When travelling with others, it’s unlikely that all of your friends have the same travel personality. Accepting these different travel personalities early on before your trip will help you avoid major clashes – or at least mentally prepare for them. By recognising your group dynamics, you’ll know who to trust with planning and who to expect last-minute cancellations from.
2. Budget talks are awkward… but necessary
No one wants to be the person who suggests skipping a fancy dinner because they’re on a budget—but at the same time, no one wants to be forced into penny-pinching when they’re on this trip to indulge. Before the trip, have an honest conversation about spending expectations. Will you be splurging on expensive restaurants, or will street food and convenience stores be the way to go? Is everyone okay with taxis, or are we strictly on a public transport budget? Setting clear expectations upfront avoids unnecessary tension when the bill arrives.
3. The accommodation debate: Choose wisely
If your crew has a mix of early risers and night owls, staying in one cramped hostel room will definitely lead to chaos. Hence your choice of accommodation is extremely important; it could make or break your trip. Keep in mind, your light sleepers will suffer if your party-loving friends stumble in at 3AM. So, booking an Airbnb with separate rooms and beds might be your best option. Consider everyone’s preferences before booking because once you’re stuck in a bad setup, there’s no escaping it.
4. Embrace the art of splitting up
Not everyone wants to visit museums, and not everyone wants to be under the hot sun on a jet ski. Instead of dragging each other to activities not everyone is excited about, embrace the idea of splitting up for a day or two. If one group wants to go sightseeing at a historical site and the other wants to surf some waves, that’s okay! Just make sure to have a designated meetup location and time, and keep each other posted. This will keep everyone happy and mean that no one has to fake any enthusiasm for something they don’t enjoy.
5. Be honest about your limits
It’s very tempting to go along with every plan to avoid seeming difficult. But, if you’re not careful, that’s a fast track to burnout. Remember, this is your grad trip too. If you need some downtime before an afternoon of exploring, take it. If you hate hiking, skip it instead of forcing yourself through. Your friends would rather you be honest than silently endure something you don’t enjoy. Grad trips are meant to be fun–so speak up and prioritise what will make your experience enjoyable.
6. Most importantly, embrace the chaos and remember why you came
No matter how well you plan, things will go wrong. A “quick” coffee run might turn into a two-hour detour, or a carefully planned itinerary could be derailed by a sudden downpour. Maybe the group gets on the wrong train and ends up in an entirely different city. Sometimes, the best memories come from unplanned moments–so lean into the chaos and let the adventure unfold.
At the end of the day, this trip isn’t about checking off every attraction or getting the perfect itinerary; it’s about celebrating a huge milestone with the people who made those long nights and tough exams bearable. The best part of the trip won’t be the landmarks or the food; it’ll be the inside jokes, the late-night talks, and the shared moments of pure chaos. So, take a deep breath, go with the flow, and make the most of it.
 *No trip is perfect, but what’s important is the time spent with your company. Photo taken from Pinterest.*
Surviving a grad trip with different travel styles isn’t about avoiding conflict, it’s about embracing the madness and making the best of it. And hey, worst case? You’ll have some hilarious group chat stories to reminisce about later.
-

@ 57d1a264:69f1fee1
2025-02-02 05:47:57
Hey there, as a result of the recent [SN Media Kit](https://stacker.news/items/872925/r/Design_r) updated, I'll try to create few simple marketing assets for ~Stackers_Stocks territory to be spread across the web.
Feel free to share in the comments below:
- Few visual references you'd like the assets to be inspired on
- If visuals are not your thing, a description of your idea will help too
- A slogan, or some words/concepts that express the territory's values
@BlokchainB you start, let's see how we go!
originally posted at https://stacker.news/items/873112
-

@ 57d1a264:69f1fee1
2025-02-02 00:03:39

Welcome to the latest updated version of **Stacker News Media Kit & Brand Guidelines `v1.2`**, a pivotal location where all the visual elements find place and help us understand how to use them to have our communications cohesive. SN brand identity is built on simplicity, trust, innovation and a taste of Texas's Wild West. With the following guidelines, as [promised](https://stacker.news/items/855556/r/Design_r?commentId=855753), I'll try to outline the essential elements of SN visual language to be easily usable internally and externally.
As third interaction from the previous [discussion](https://stacker.news/items/786223), here below you will find all the media assets in PNG and SVG downloadable from this [zip file](https://nosto.re/0a8b02224c970de78fba3a0195dcf1ee44d18925ba941724497173b2bcbab901.zip). BTW: I've been using **`Nostr`** 🌸 **Blossom Serverservers** [check them out](https://blossomservers.com/), it's a really cool idea! In case the file will be not available we can always upload it in other servers. Just let me know if any issue downloading it, ideally I made three copies available from:
- https://nosto.re/0a8b02224c970de78fba3a0195dcf1ee44d18925ba941724497173b2bcbab901.zip
- https://blossom.poster.place/0a8b02224c970de78fba3a0195dcf1ee44d18925ba941724497173b2bcbab901.zip
- https://nostr.download/0a8b02224c970de78fba3a0195dcf1ee44d18925ba941724497173b2bcbab901.zip
The source file of all these assets still are the same [Figma file](https://www.figma.com/design/ZL3FLItd9j48pzKVi4qlOy/Stacker.News-Media-Kit?node-id=3-16&t=oEbUcC1tmLDRXgdH-0) and the [PenPot file](https://design.penpot.app/#/workspace/7ad540b5-8190-815d-8005-5685b9c670bc/7ad540b5-8190-815d-8005-5685c186216e?page-id=2643bc5a-0d34-80b2-8005-58099eabda41). This last one, has many issues and does not allow yet the same flexibility as Figma. Both files are open for contributions and comments, just need to register a dummy/anonymous account for each of the tools.
> **Note:** To use these assets across SN, just copy-paste the image relative code, i.e.:

# Stacker News Logotype
SN logo is the most recognizable visual identifier of Stacker News. It captures the essence of its brand and is to be used across the platform and other marketing materials **consistently**. Find below all the possible variations and colors. Ideally you should stick with it to maintain SN identity coherent, or propose something new if you feel like. If you have any question on how to place or use the logo, DO ask below, and we'll help sort it out.
| Avatar on transparent BG | Avatar on BG | Logo Extended | Logo Vertical |#|
|---|---|---|---|---|
|  `` |  `` |  ``|  `` |Oil Black|
|  `` |  `` |  `` |  ``| Golden Yellow |
|  `` |  `` |  `` |  ``|With Shadow |
# Stacker News Typography

This is the typography SN had used to create its logo. [Download LightningVolt OpenType Font file.otf](http://honeyanddeath.web.fc2.com/FontFile/honeyanddeath_Lightningvolt.zip) designed by **[Honey&Death](http://honeyanddeath.web.fc2.com/fnt_Lightningvolt.html)**, install it in your computer and play with it.
Typography is essential to identify, increase readability and create consistency of brands. SN uses the default `font-family:sans-serif;` of your device's OS, usually are the most common and already installed in your device: `system-ui, "Segoe UI", Roboto, "Helvetica Neue", "Noto Sans", "Liberation Sans", Arial, sans-serif, "Apple Color Emoji", "Segoe UI Emoji", "Segoe UI Symbol", "Noto Color Emoji"`. Those are mostly used for:
# Example Header H1
## Example Header H2
### Example Header H3
#### Example Header H4
##### Example Header H5
**Example paragraph text**
The fonts selected will help to communicate the personality of the brand and provide maximum legibility for both print and screen.
`Example <code>`
For code, the approach is the same. Let's the device OS select its default `monospace` one. For example, on Mac will be one of the following:
```
SFMono-Regular, Menlo, Monaco, Consolas, "Liberation Mono", "Courier New",`
```
# Stacker News Colors
A thoughtfully curated color palette gives SN trust, professionalism, and approachability. Colors play a key role in creating consistent visual experiences through digital and print communications. Make sure you are using the right color codes below:
| # | Name | HEX code | RGB code | HLS |
|---|---|---|---|---|
|  | Bitcoin-only | `#F6911D` | `rgb(246,145,29)` | `hsl(32,92.3%,53.9%)` |
|  | Blackr | `#000000` | `rgb(0,0,0)` | `hsl(0,0%,0%)` |
|  | Dark | `#121214` | `rgb(18,18,20)` | `hsl(240,5.3%,7.5%)` |
|  | Gold | `#FADA5E` | `rgb(250,218,94)` | `hsl(48,94%,67.5%)` |
|  | Gray | `#969696` | `rgb(150,150,150)` | `hsl(0,0%,58.8%)` |
|  | Light | `#F0F0F0` | `rgb(240,240,240)` | `hsl(0,0%,94.1%)` |
|  | Nostrch | `#8C25F4` | `rgb(140,37,244)` | `hsl(270,90.4%,55.1%)` |
|  | Pinkish | `#E685B5` | `rgb(230,133,181)` | `hsl(330,66%,71.2%)` |
|  | Ruby | `#C03221` | `rgb(192,50,33)` | `hsl(6,70.7%,44.1%)` |
|  | Sky Hover | `#007CBE` | `rgb(0,124,190)` | `hsl(201,100%,37.3%)` |
|  | Sky Links | `#2E99D1` | `rgb(46,153,209)` | `hsl(201,63.9%,50%)` |
|  | Sky Visited | `#56798E` | `rgb(86,121,142)` | `hsl(203,24.6%,44.7%)` |
|  | So Fiat | `#5C8001` | `rgb(92,128,1)` | `hsl(77,98.4%,25.3%)` |
# Stacker News Icons
SN utilizes a set of bespoke icons that support its communication internally across the platform. Icons help bring instant, intuitive cues for various types of content and features. We share them here for you so you can use as you wish and satisfy your creative needs.
|  `` |  `` |  `[Bounty](https://m.stacker.news/75607)` |  `[Caret](https://m.stacker.news/75608)` |  `[Cowboy](https://m.stacker.news/75609)` |  `[Sun](https://m.stacker.news/75610)` |
|---|---|---|---|---|---|
|  **`[Edit](https://m.stacker.news/75611)`** |  **`[Gun](https://m.stacker.news/75612)`** |  **`[Horse](https://m.stacker.news/75613)`** |  **`[Info](https://m.stacker.news/75614)`** |  **`[Moon](https://m.stacker.news/75615)`** |  **`[Lightning](https://m.stacker.news/75616)`**|
|  **`[Bald Lost Hat](https://m.stacker.news/75617)`**|  **`[Markdown](https://m.stacker.news/75618)`**|  **`[Nostr](https://m.stacker.news/75619)`**|  **`[Referral](https://m.stacker.news/75620)`**|  **`[Rewards](https://m.stacker.news/75621)`**|  **`[Horse Lost Saddle](https://m.stacker.news/75622)`**|  **`[Search](https://m.stacker.news/75623)`** |
| **`[Shoot](https://m.stacker.news/75624)`** | **`[Texas](https://m.stacker.news/75625)`** |  **`[Upload](https://m.stacker.news/75626)`** |  **`[Zap Zap](https://m.stacker.news/75627)`** |||
# Stacker News Banners
Banners are important visual elements used in our digital platforms and marketing materials. They help to highlight key stories, features or announcements while maintaining our brand aesthetic.
Here below you'll find custom banners for Sn and for individial territories. I try to build those that I follow most, for now @AGORA is the only one that designed its own banners. Comment below if you'd like some banners for your territory!
#### SN Dark background
|970x250|
|---|
| ```|``|``|
|728x90|
|---|
|  `` |
#### SN Gold background
|970x250|
|---|
|`` |
|250x250|300x250|300x600|
|---|---|---|
|`` | `` |`` |
|728x90|
|---|
|`` |
#### SN by @Jon_Hodl
|970x250|
|---|
| `` |
|250x250|300x250|300x600|
|---|---|---|
| `` |  ``| `` |
|728x90|
|---|
|`` |
#### ~AGORA territory
The SN P2P Marketplace
|970x250|
|---|
| `` |
|250x250|300x250|300x600|
|---|---|---|
| `` | ``|``|
|728x90|
|---|
| ``|
#### ~alter_native territory
|970x250|
|---|
| ``|
|250x250|300x250|300x600|
|---|---|---|
|``|``|``|
|728x90|
|---|
|`` |
#### ~bitcoin_beginners
|970x250|
|---|
| `` |
|250x250|300x250|300x600|
|---|---|---|
| ``|``|`` |
|728x90|
|---|
| ``|
#### ~Design territory
|970x250|
|---|
|``|
|250x250|300x250|300x600|
|---|---|---|
|``|``|``|
|728x90|
|---|
|``|
#### ~Music territory
|970x250|
|---|
| ``|
|250x250|300x250|300x600|
|---|---|---|
|``|``|``|
|728x90|
|---|
| ``|
# Anything else we could add?
If you feel something is missing, or you know a better tool to manage this media kit for SN in a collaborative and FOSS way then, DO share it in a comment below
Territory owners [^1], do you need banners for your territory? Feel free to edit the figma file liked above or comment below sharing your needs or ideas, I'll try to do something for you.
By following these guidelines, we ensure consistency and professionalism in every case where Stacker News is represented here internally to stackers or to our audience in the KYC internet, reinforcing SN credibility as a trusted source for data-driven journalism.
[^1]: FYI: @Aardvark @AGORA @anna @antic @AtlantisPleb @Bell_curve @benwehrman @bitcoinplebdev @Bitter @BlokchainB @ch0k1 @davidw @ek @elvismercury @frostdragon @grayruby @HODLR @inverselarp @Jon_Hodl @k00b @marks @MaxAWebster @mega_dreamer @niftynei @nout @OneOneSeven @OT @PlebLab @Public_N_M_E @RDClark @realBitcoinDog @roytheholographicuniverse @siggy47 @softsimon @south_korea_ln @theschoolofbitcoin @TNStacker @UCantDoThatDotNet @Undisciplined
originally posted at https://stacker.news/items/872925
-

@ a95c6243:d345522c
2025-01-31 20:02:25
*Im Augenblick wird mit größter Intensität, großer Umsicht* *\
das deutsche Volk belogen.* *\
Olaf Scholz im FAZ-[Interview](https://www.youtube.com/watch?v=c3KI1GmdoVc\&t=649s)*  
**Online-Wahlen stärken die Demokratie, sind sicher, und 61 Prozent der Wahlberechtigten** sprechen sich für deren Einführung in Deutschland aus. Das zumindest behauptet eine aktuelle Umfrage, die auch über die Agentur *Reuters* Verbreitung in den Medien [gefunden](https://archive.is/dnZbY) hat. Demnach würden außerdem 45 Prozent der Nichtwähler bei der Bundestagswahl ihre Stimme abgeben, wenn sie dies zum Beispiel von Ihrem PC, Tablet oder Smartphone aus machen könnten.
**Die telefonische Umfrage unter gut 1000 wahlberechtigten Personen** sei repräsentativ, [behauptet](https://www.bitkom.org/Presse/Presseinformation/Knapp-Haelfte-Nichtwaehler-wuerde-online-waehlen) der Auftraggeber – der Digitalverband Bitkom. Dieser präsentiert sich als eingetragener Verein mit einer beeindruckenden Liste von [Mitgliedern](https://www.bitkom.org/Bitkom/Mitgliedschaft/Mitgliederliste), die Software und IT-Dienstleistungen anbieten. Erklärtes Vereinsziel ist es, «Deutschland zu einem führenden Digitalstandort zu machen und die digitale Transformation der deutschen Wirtschaft und Verwaltung voranzutreiben».
**Durchgeführt hat die Befragung die Bitkom Servicegesellschaft mbH,** also alles in der Familie. Die gleiche Erhebung hatte der Verband übrigens 2021 schon einmal durchgeführt. Damals sprachen sich angeblich sogar 63 Prozent für ein derartiges [«Demokratie-Update»](https://www.experten.de/id/4922407/online-wahlen-als-update-des-demokratischen-systems/) aus – die Tendenz ist demgemäß fallend. Dennoch orakelt mancher, der Gang zur Wahlurne gelte bereits als veraltet.
**Die spanische Privat-Uni mit Globalisten-Touch, IE University, berichtete** Ende letzten Jahres in ihrer Studie «European Tech Insights», 67 Prozent der Europäer [befürchteten](https://www.ie.edu/university/news-events/news/67-europeans-fear-ai-manipulation-elections-according-ie-university-research/), dass Hacker Wahlergebnisse verfälschen könnten. Mehr als 30 Prozent der Befragten glaubten, dass künstliche Intelligenz (KI) bereits Wahlentscheidungen beeinflusst habe. Trotzdem würden angeblich 34 Prozent der unter 35-Jährigen einer KI-gesteuerten App vertrauen, um in ihrem Namen für politische Kandidaten zu stimmen.
**Wie dauerhaft wird wohl das Ergebnis der kommenden Bundestagswahl sein?** Diese Frage stellt sich angesichts der aktuellen Entwicklung der Migrations-Debatte und der (vorübergehend) bröckelnden «Brandmauer» gegen die AfD. Das «Zustrombegrenzungsgesetz» der Union hat das Parlament heute Nachmittag überraschenderweise [abgelehnt](https://www.bundestag.de/dokumente/textarchiv/2025/kw05-de-zustrombegrenzungsgesetz-1042038). Dennoch muss man wohl kein ausgesprochener Pessimist sein, um zu befürchten, dass die Entscheidungen der Bürger von den selbsternannten Verteidigern der Demokratie künftig vielleicht nicht respektiert werden, weil sie nicht gefallen.
**Bundesweit wird jetzt zu «Brandmauer-Demos» aufgerufen,** die CDU gerät unter Druck und es wird von Übergriffen auf Parteibüros und Drohungen gegen Mitarbeiter [berichtet](https://www.epochtimes.de/politik/deutschland/brandmauer-proteste-cdu-zentrale-geraeumt-kundgebungen-in-46-staedten-a5023745.html). Sicherheitsbehörden warnen vor Eskalationen, die Polizei sei «für ein mögliches erhöhtes Aufkommen von Straftaten gegenüber Politikern und gegen Parteigebäude sensibilisiert».
**Der Vorwand** **[«unzulässiger Einflussnahme»](https://transition-news.org/die-minister-faeser-und-wissing-sorgen-sich-um-unzulassige-einflussnahme-auf)** **auf Politik und Wahlen** wird als Argument schon seit einiger Zeit aufgebaut. Der Manipulation schuldig befunden wird neben Putin und Trump auch Elon Musk, was lustigerweise ausgerechnet Bill Gates gerade noch einmal bekräftigt und als [«völlig irre»](https://transition-news.org/bill-gates-nennt-musks-einmischung-in-eu-politik-vollig-irre) bezeichnet hat. Man stelle sich die Diskussionen um die Gültigkeit von Wahlergebnissen vor, wenn es Online-Verfahren zur Stimmabgabe gäbe. In der Schweiz wird [«E-Voting»](https://www.ch.ch/de/abstimmungen-und-wahlen/e-voting/) seit einigen Jahren getestet, aber wohl bisher mit wenig Erfolg.
**Die politische Brandstiftung der letzten Jahre zahlt sich immer mehr aus.** Anstatt dringende Probleme der Menschen zu lösen – zu denen auch in Deutschland die [weit verbreitete Armut](https://transition-news.org/ein-funftel-der-bevolkerung-in-deutschland-ist-von-armut-oder-sozialer) zählt –, hat die Politik konsequent polarisiert und sich auf Ausgrenzung und Verhöhnung großer Teile der Bevölkerung konzentriert. Basierend auf Ideologie und Lügen werden abweichende Stimmen unterdrückt und kriminalisiert, nicht nur und nicht erst in diesem Augenblick. Die nächsten Wochen dürften ausgesprochen spannend werden.
***
Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/wahlen-und-wahlen-lassen)*** erschienen.
-

@ 5188521b:008eb518
2025-01-31 08:38:47
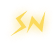
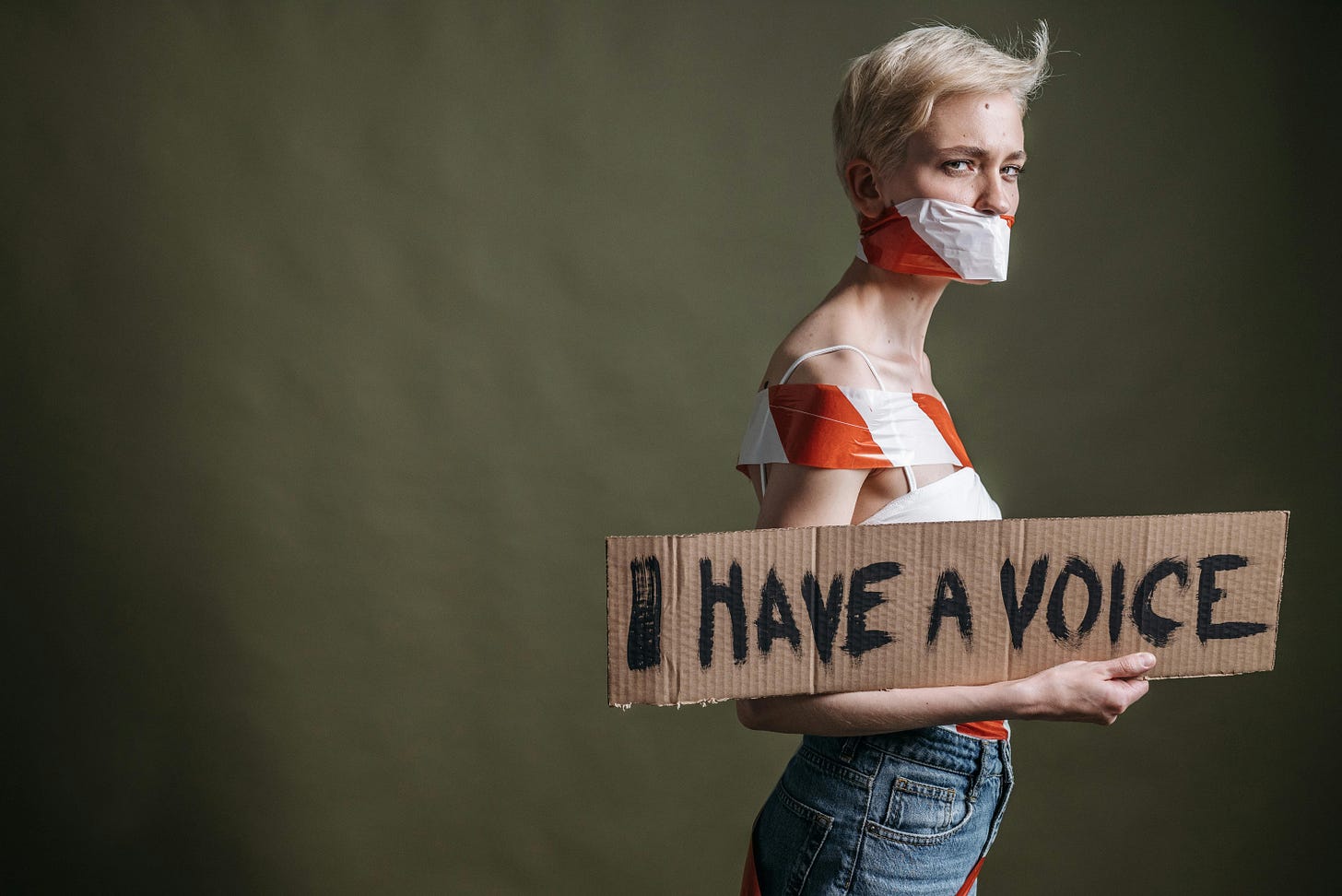*Photo by [Pavel Danilyuk](https://www.pexels.com/photo/a-woman-holding-a-placard-8553778/)*
In the last four years, I’ve ridden the wave of social media. I’ve amassed thousands of followers, and my posts were read by millions.
It’s empowering… until it isn’t.
This year, I chose to stop publishing on LinkedIn, Medium, Facebook, Instagram, and Threads. My reach on each of these platforms dropped from 100% of my follower base to around 10%. My voice was being suppressed.
I wasn’t writing anything particularly controversial. This is all just part of the social media life cycle. Platforms offer attractive terms to lock in users. They distribute our articles, posts, and thoughts widely to attract eyeballs for advertisers.
Writers learn to play the algorithm to maximise reach and engagement. Maybe they even manage to monetize their writing.
But when the platforms reach what they deem to be maximum usage and membership, they begin to reduce the benefits on offer. They ask writers to focus on specific topics, suppress non-mainstream opinion, or punish or ban any writers who don’t follow new rules. Big tech companies always eventually turn on the money tap by forcing users to suffer endless adverts and even make writers pay to reach the audience they have built.
Newsflash: there is no company too big to fail. Digg, Google+, Myspace, Vine and many more socials have died. Self-reported active user numbers cannot be trusted. Meta recently trialed AI profiles to prop up falling usage projections on Instagram and Facebook. X is now a dumpster fire of bots, scammers, and rage bait. It has been co-opted by a megalomaniacal oligarch to spread his own worldview. And LinkedIn feeds are drowning in unsolicited AI-generated business twaddle. The social giants are entering the death spiral.
# What happens in a social-media death spiral?
Users don’t see the value in posting, so they move elsewhere.
I wasn’t feeling rewarded for the thousands of hours I spent on LinkedIn, so I quit. I went from earning $20+ an article on Medium to pennies. Literal pennies. Bye bye, Tony Stubblebine. I learned that if you don’t own the distribution mechanic, you get left writing into the wind.
Ultimately, writers will dedicate their energy to where they see a benefit. They should spend time and create value in the place most similar to their ideal world.
For writers in 2025, that place seems to be Substack. Open rates are high and the platform is adding social features to generate more engagement in app. Substack is [experiencing massive growth](https://backlinko.com/substack-users) in active (and paid) subscriptions. Yet, it is following the same pattern as Medium in and LinkedIn in become self-cannibalising. Many of the most popular accounts write about ‘how to grow’ or ‘how to make money’ on Substack. Queue the eye rolls.
For me, it’s not the promised land where writers can earn a living. Of course, it’s no walk in the park to earn paid subscribers. Further, Substack users can only receive payment via Stripe. This excludes writers from 149 of the World’s countries. Does that seem open and fair to you?
Even with all this going on, there is a much bigger factor that should influence your choice of platform — ownership.
# Do writers really own their words?
Who reads the terms and conditions? Nobody. That’s who.Writers (including me) rush to all platforms which promise to give us benefits such as pay, distribution, and audience growth.
In exchange, companies request access to and shared ownership of our content. They can use our words to train LLMs, analyse trends, repurpose, and to spy on us.
Governments can and will request access to social media profiles. They seek to control the use of those platforms. Founders and CEOs who refuse to comply may be held personally accountable and put on trial, just as [Telegram founder, Pavel Durov, was](https://www.bbc.com/news/articles/c78lgzl919go) in France. Big tech owns our content, and governments threaten platforms into obedience.
As much as it benefits society to suppress harmful or dangerous content, companies simply can’t be censors 24/7. Growing platforms like [Bluesky are already struggling to moderate content effectively](https://www.theregister.com/2024/12/02/bluesky_growing_problems/). Without a strong economic incentive to moderate, companies will simply refuse to do it (as long as the threat of criminal charges does not prevail).
To sum up: No privately owned social media network offers writers the opportunity to own and distribute their work in order to receive a fair and equitable benefit.
Enter NOSTR…
# Decentralizing Social Media
**Notes and Other Stuff Transmitted by Relays** (NOSTR) is not a platform; it’s an open protocol.
By signing messages with their private keys (a long string of characters), users generate “events”. These events (messages/updates/media/transactions) are then broadcast through a series of “relays.”
Developers can use the protocol to build various applications that retrieve and distribute these events to other users. These ‘clients’ can range from microblogging sites like X and long-form distributors like Substack to visual media platforms like Instagram. Plus, NOSTR is also a whole lot more than that (but this is a topic for another day).
Decentralized tools offer the only hope against the dominance of AI and big tech in a top-down autocratic system designed to control us more than the thought police ever could.
<img src="https://blossom.primal.net/93a44d9bfe3c768e41d8bfef52415131af3ca21814a23870a029f1a947288cc8.webp">
*Diagram courtesy of River.*
So why should writers opt out of their big audience pool to write on some ‘protocol’?
**Ownership, fair rules, and fair value.**
- **Ownership**:
While privately run corporations can suppress the ideas they want, NOSTR provides a censorship-resistant alternative. No individual actors can restrict content or accounts.
Your private keys provide **permanent access** to the messages you have signed. No one else has access to them. And while some clients provide a delete function, there is no way to force all relays to respect a delete request. Not only do writers own what they publish, but it’s a permanent record.
- **Rules:**
Traditional social media platforms use proprietary algorithms to curate and order our feeds. **NOSTR has no algorithm**. NOSTR clients display messages chronologically or based on user-defined criteria, removing the influence of opaque algorithms that could manipulate user engagement and visibility of posts.
Put simply, distribution and consumption is down to the user, not to the creator or the platform. And everyone works to the same rules.
- **Value:**
Harmful content and spam affect all of us. There is no way to stop malicious content from being published on NOSTR, but two factors control its consumption.
1. Clients are experimenting with strategies such as requiring proof-of-work with each note or requiring verification badges.
2. Quality control is enforced by the value transferred by the protocol.
Bitcoin micropayments have become the monetary lifeblood flowing in the decentralized world. The ability to ‘zap’ users actual monetary value (e.g. a few cents) provides a clear display of which messages are valuable and which are unwanted. In time, as more users adopt the mechanic of value transfer, spammers will see their approach is not bearing fruit.
The beauty of using bitcoin in this way is twofold. Firstly, it is truly equitable — anyone in the world can receive it instantly and it cannot be stopped. And the system of frictionless micropayments offers content creators (artists, podcasters, musicians, writers) a way to earn money for the value they produce. Put simply, this could save creativity from doom.
Think people still want all content for free? Think again. Try zapping a writer from the Philippines, an artist from Peru, a Congolese musician, or a poet from Poland to show them you enjoyed what they produced. THAT is truly empowering.
Not convinced?
The best thing about NOSTR for writers is that **you are early**.
By being an early adopter with a low time preference, you can build a sizeable audience as new users discover the protocol.
Of course, topics like bitcoin, freedom tech, and privacy are well covered, but if you write in another niche, you could be ‘quids in’.
# Conclusion:
By adopting a long-term strategy and sticking to their principles, readers, writers and all other creatives can build a better world on social media. It doesn’t matter that it is imperfect. There will always be flaws in any society. But decentralized protocols like NOSTR can offer writers what they truly want — ownership, fair rules, and fair value.
---
Philip Charter is a totally human writer who helps bitcoin-native companies and clients stack major gains through laser-focused content. Find out more at [totallyhumanwriter.com](https://totallyhumanwriter.com)
He is also the editor of the cypherpunk and freedom fiction project, [21 Futures](https://21futures.com).
-

@ 57d1a264:69f1fee1
2025-01-31 02:07:27

Bitcoin Design members have been involved in organizing various events (and sometimes just attend, too). Here below is what do we want to do in 2025:
- **[Designathon 2](https://github.com/BitcoinDesign/Meta/issues/625)** - We are organizing this event between February or March.
- **[Accessibility Day](https://accessibility.day)** - May 15
- - BDC has participated in this global initiative the last two years. Probably doing so again!
- **[BTC Prague](https://btcprague.com)** -Participation Confirmed. Planning issues [here](https://github.com/BitcoinDesign/Meta/issues/745) - June 19 - 21
- * We organized the design track for dev day in 2023 and 2024. Do this again[\[k\]](#cmnt11)[\[l\]](#cmnt12)? It’s going to be on June 18, before the main conference.
- * 2024 was great, in that we had a nice group of designers attend, do talks, go for dinner, etc.
- **[Summer of Bitcoin](https://www.google.com/url?q=https://www.summerofbitcoin.org)**
- * Several designers and projects participated each of the last 3 years. Probably doing so again!
- * Applications open on Feb 1, main program is May to August ([timeline](https://www.summerofbitcoin.org/how-it-works/)
- **UX Bootcamps**
- * Previous: South America
- * Next: [South America](https://www.bitcoinuxbootcamp.xyz/southamerica) - February 17 - 22
- **[Bitshala fellowship](https://bitshala.org)**
- * First iteration of this fellowship is from January to July
- * We will help find more designers, projects, and funding in India
- **[Oslo Freedom Forum](https://oslofreedomforum.com)** - Oslo, May 26-28
- * Activist and financial repression use cases are uniquely important use cases for bitcoin.
- * Several people attended last year. Conversations lead to new initiatives.
- **[BTCHEL](https://btchel.com/)** - by BTC Helsinki Community - Aug 15-16
- * First large-scale bitcoin conference in the Nordics with particular focus to onboard new users to bitcoin
- **Bitcoin Presidio design week**
- * This is a new Bitcoin co-working space in San Francisco, also announced here https://stacker.news/items/860931/r/Design_r. The idea came up to organize a design week there to support the creation of art and decoration for the new co-working space. Just an idea at the moment, but why not make it happen?
- * [Discussion issue](https://github.com/BitcoinDesign/Meta/issues/746).
- **BuildWithLDK**
- * An initiative to promote LDK and LDK Node for building lightning applications. There could be collaboration around a Designathon, connecting designers with hackathon projects, etc. Still in early planning.
- **Builder conferences**: These are very builder-focused, making them good opportunities to connect, organize practical design workshops, creative presentations, and support projects from a design perspective
- * [Baltic Honeybadger](https://baltichoneybadger.com) (August 9-10),
- * [TABConf](http://tabconf.com)
- * [Bitcoin++](https://btcplusplus.dev) There are going to be 6 of them throughout the year.
- * [SATS’N’FACTS](https://satsandfacts.btc.pub/) (February 8-10) Bitcoin Technical Unconference, Hackathon & Freedom Tech Art Exhibition
- **Open-source conferences & events*
- * [FOSS Backstage](http://foss-backstage.de) (Berlin, Mar 10-11) - Christoph will present the Open Design Guide
- * [FOSDEM](https://fosdem.org/2025/) (Brussels, Feb 1-2) - anyone attending?
- **Design conferences & events** - Makes sense to be involved with design-only events, right?
* [OFFF](https://www.offf.barcelona) - very creative-focused (Barcelona, May 8-10)
* [CSUN Accessibility conference](https://www.csun.edu/cod/conference/sessions/)
**Other Ideas**
* Bitcoin Park - they might organize another design event like two years ago https://stacker.news/items/705081/r/Design_r
**Links**
* [Comprehensive list](https://docs.google.com/spreadsheets/d/147AXd8hN3uO3v_P1dupgfRCRzSMlH85dvQSHPAg7lZ4/edit?usp%3Dsharing) of bitcoin conferences
- - -
… what’s missing from this page? Are you involved with anything? Or want to be? Comment below or join us on https://discord.com/channels/903125802726596648/1087394066796384276
You can watch the recording from
https://www.youtube.com/watch?v=GGS3oSlLmAo
originally posted at https://stacker.news/items/870638
-

@ 97c70a44:ad98e322
2025-01-30 17:15:37
There was a slight dust up recently over a website someone runs removing a listing for an app someone built based on entirely arbitrary criteria. I'm not to going to attempt to speak for either wounded party, but I would like to share my own personal definition for what constitutes a "nostr app" in an effort to help clarify what might be an otherwise confusing and opaque purity test.
In this post, I will be committing the "no true Scotsman" fallacy, in which I start with the most liberal definition I can come up with, and gradually refine it until all that is left is the purest, gleamingest, most imaginary and unattainable nostr app imaginable. As I write this, I wonder if anything built yet will actually qualify. In any case, here we go.
# It uses nostr
The lowest bar for what a "nostr app" might be is an app ("application" - i.e. software, not necessarily a native app of any kind) that has some nostr-specific code in it, but which doesn't take any advantage of what makes nostr distinctive as a protocol.
Examples might include a scraper of some kind which fulfills its charter by fetching data from relays (regardless of whether it validates or retains signatures). Another might be a regular web 2.0 app which provides an option to "log in with nostr" by requesting and storing the user's public key.
In either case, the fact that nostr is involved is entirely neutral. A scraper can scrape html, pdfs, jsonl, whatever data source - nostr relays are just another target. Likewise, a user's key in this scenario is treated merely as an opaque identifier, with no appreciation for the super powers it brings along.
In most cases, this kind of app only exists as a marketing ploy, or less cynically, because it wants to get in on the hype of being a "nostr app", without the developer quite understanding what that means, or having the budget to execute properly on the claim.
# It leverages nostr
Some of you might be wondering, "isn't 'leverage' a synonym for 'use'?" And you would be right, but for one connotative difference. It's possible to "use" something improperly, but by definition leverage gives you a mechanical advantage that you wouldn't otherwise have. This is the second category of "nostr app".
This kind of app gets some benefit out of the nostr protocol and network, but in an entirely selfish fashion. The intention of this kind of app is not to augment the nostr network, but to augment its own UX by borrowing some nifty thing from the protocol without really contributing anything back.
Some examples might include:
- Using nostr signers to encrypt or sign data, and then store that data on a proprietary server.
- Using nostr relays as a kind of low-code backend, but using proprietary event payloads.
- Using nostr event kinds to represent data (why), but not leveraging the trustlessness that buys you.
An application in this category might even communicate to its users via nostr DMs - but this doesn't make it a "nostr app" any more than a website that emails you hot deals on herbal supplements is an "email app". These apps are purely parasitic on the nostr ecosystem.
In the long-term, that's not necessarily a bad thing. Email's ubiquity is self-reinforcing. But in the short term, this kind of "nostr app" can actually do damage to nostr's reputation by over-promising and under-delivering.
# It complements nostr
Next up, we have apps that get some benefit out of nostr as above, but give back by providing a unique value proposition to nostr users as nostr users. This is a bit of a fine distinction, but for me this category is for apps which focus on solving problems that nostr isn't good at solving, leaving the nostr integration in a secondary or supporting role.
One example of this kind of app was Mutiny (RIP), which not only allowed users to sign in with nostr, but also pulled those users' social graphs so that users could send money to people they knew and trusted. Mutiny was doing a great job of leveraging nostr, as well as providing value to users with nostr identities - but it was still primarily a bitcoin wallet, not a "nostr app" in the purest sense.
Other examples are things like Nostr Nests and Zap.stream, whose core value proposition is streaming video or audio content. Both make great use of nostr identities, data formats, and relays, but they're primarily streaming apps. A good litmus test for things like this is: if you got rid of nostr, would it be the same product (even if inferior in certain ways)?
A similar category is infrastructure providers that benefit nostr by their existence (and may in fact be targeted explicitly at nostr users), but do things in a centralized, old-web way; for example: media hosts, DNS registrars, hosting providers, and CDNs.
To be clear here, I'm not casting aspersions (I don't even know what those are, or where to buy them). All the apps mentioned above use nostr to great effect, and are a real benefit to nostr users. But they are not True Scotsmen.
# It embodies nostr
Ok, here we go. This is the crème de la crème, the top du top, the meilleur du meilleur, the bee's knees. The purest, holiest, most chaste category of nostr app out there. The apps which are, indeed, nostr indigitate.
This category of nostr app (see, no quotes this time) can be defined by the converse of the previous category. If nostr was removed from this type of application, would it be impossible to create the same product?
To tease this apart a bit, apps that leverage the technical aspects of nostr are dependent on nostr the *protocol*, while apps that benefit nostr exclusively via network effect are integrated into nostr the *network*. An app that does both things is working in symbiosis with nostr as a whole.
An app that embraces both nostr's protocol and its network becomes an organic extension of every other nostr app out there, multiplying both its competitive moat and its contribution to the ecosystem:
- In contrast to apps that only borrow from nostr on the technical level but continue to operate in their own silos, an application integrated into the nostr network comes pre-packaged with existing users, and is able to provide more value to those users because of other nostr products. On nostr, it's a good thing to advertise your competitors.
- In contrast to apps that only market themselves to nostr users without building out a deep integration on the protocol level, a deeply integrated app becomes an asset to every other nostr app by becoming an organic extension of them through interoperability. This results in increased traffic to the app as other developers and users refer people to it instead of solving their problem on their own. This is the "micro-apps" utopia we've all been waiting for.
Credible exit doesn't matter if there aren't alternative services. Interoperability is pointless if other applications don't offer something your app doesn't. Marketing to nostr users doesn't matter if you don't augment their agency _as nostr users_.
If I had to choose a single NIP that represents the mindset behind this kind of app, it would be NIP 89 A.K.A. "Recommended Application Handlers", which states:
> Nostr's discoverability and transparent event interaction is one of its most interesting/novel mechanics. This NIP provides a simple way for clients to discover applications that handle events of a specific kind to ensure smooth cross-client and cross-kind interactions.
These handlers are the glue that holds nostr apps together. A single event, signed by the developer of an application (or by the application's own account) tells anyone who wants to know 1. what event kinds the app supports, 2. how to link to the app (if it's a client), and (if the pubkey also publishes a kind 10002), 3. which relays the app prefers.
_As a sidenote, NIP 89 is currently focused more on clients, leaving DVMs, relays, signers, etc somewhat out in the cold. Updating 89 to include tailored listings for each kind of supporting app would be a huge improvement to the protocol. This, plus a good front end for navigating these listings (sorry nostrapp.link, close but no cigar) would obviate the evil centralized websites that curate apps based on arbitrary criteria._
Examples of this kind of app obviously include many kind 1 clients, as well as clients that attempt to bring the benefits of the nostr protocol and network to new use cases - whether long form content, video, image posts, music, emojis, recipes, project management, or any other "content type".
To drill down into one example, let's think for a moment about forms. What's so great about a forms app that is built on nostr? Well,
- There is a [spec](https://github.com/nostr-protocol/nips/pull/1190) for forms and responses, which means that...
- Multiple clients can implement the same data format, allowing for credible exit and user choice, even of...
- Other products not focused on forms, which can still view, respond to, or embed forms, and which can send their users via NIP 89 to a client that does...
- Cryptographically sign forms and responses, which means they are self-authenticating and can be sent to...
- Multiple relays, which reduces the amount of trust necessary to be confident results haven't been deliberately "lost".
Show me a forms product that does all of those things, and isn't built on nostr. You can't, because it doesn't exist. Meanwhile, there are plenty of image hosts with APIs, streaming services, and bitcoin wallets which have basically the same levels of censorship resistance, interoperability, and network effect as if they weren't built on nostr.
# It supports nostr
Notice I haven't said anything about whether relays, signers, blossom servers, software libraries, DVMs, and the accumulated addenda of the nostr ecosystem are nostr apps. Well, they are (usually).
This is the category of nostr app that gets none of the credit for doing all of the work. There's no question that they qualify as beautiful nostrcorns, because their value propositions are entirely meaningless outside of the context of nostr. Who needs a signer if you don't have a cryptographic identity you need to protect? DVMs are literally impossible to use without relays. How are you going to find the blossom server that will serve a given hash if you don't know which servers the publishing user has selected to store their content?
In addition to being entirely contextualized by nostr architecture, this type of nostr app is valuable because it does things "the nostr way". By that I mean that they don't simply try to replicate existing internet functionality into a nostr context; instead, they create entirely new ways of putting the basic building blocks of the internet back together.
A great example of this is how Nostr Connect, Nostr Wallet Connect, and DVMs all use relays as brokers, which allows service providers to avoid having to accept incoming network connections. This opens up really interesting possibilities all on its own.
So while I might hesitate to call many of these things "apps", they are certainly "nostr".
# Appendix: it smells like a NINO
So, let's say you've created an app, but when you show it to people they politely smile, nod, and call it a NINO (Nostr In Name Only). What's a hacker to do? Well, here's your handy-dandy guide on how to wash that NINO stench off and Become a Nostr.
You app might be a NINO if:
- There's no NIP for your data format (or you're abusing NIP 78, 32, etc by inventing a sub-protocol inside an existing event kind)
- There's a NIP, but no one knows about it because it's in a text file on your hard drive (or buried in your project's repository)
- Your NIP imposes an incompatible/centralized/legacy web paradigm onto nostr
- Your NIP relies on trusted third (or first) parties
- There's only one implementation of your NIP (yours)
- Your core value proposition doesn't depend on relays, events, or nostr identities
- One or more relay urls are hard-coded into the source code
- Your app depends on a specific relay implementation to work (*ahem*, relay29)
- You don't validate event signatures
- You don't publish events to relays you don't control
- You don't read events from relays you don't control
- You use legacy web services to solve problems, rather than nostr-native solutions
- You use nostr-native solutions, but you've hardcoded their pubkeys or URLs into your app
- You don't use NIP 89 to discover clients and services
- You haven't published a NIP 89 listing for your app
- You don't leverage your users' web of trust for filtering out spam
- You don't respect your users' mute lists
- You try to "own" your users' data
Now let me just re-iterate - it's ok to be a NINO. We need NINOs, because nostr can't (and shouldn't) tackle every problem. You just need to decide whether your app, as a NINO, is actually contributing to the nostr ecosystem, or whether you're just using buzzwords to whitewash a legacy web software product.
If you're in the former camp, great! If you're in the latter, what are you waiting for? Only you can fix your NINO problem. And there are lots of ways to do this, depending on your own unique situation:
- Drop nostr support if it's not doing anyone any good. If you want to build a normal company and make some money, that's perfectly fine.
- Build out your nostr integration - start taking advantage of webs of trust, self-authenticating data, event handlers, etc.
- Work around the problem. Think you need a special relay feature for your app to work? Guess again. Consider encryption, AUTH, DVMs, or better data formats.
- Think your idea is a good one? Talk to other devs or open a PR to the [nips repo](https://github.com/nostr-protocol/nips). No one can adopt your NIP if they don't know about it.
- Keep going. It can sometimes be hard to distinguish a research project from a NINO. New ideas have to be built out before they can be fully appreciated.
- Listen to advice. Nostr developers are friendly and happy to help. If you're not sure why you're getting traction, ask!
I sincerely hope this article is useful for all of you out there in NINO land. Maybe this made you feel better about not passing the totally optional nostr app purity test. Or maybe it gave you some actionable next steps towards making a great NINON (Nostr In Not Only Name) app. In either case, GM and PV.
-

@ 9e69e420:d12360c2
2025-01-30 12:13:39
Salwan Momika, a Christian Iraqi known for burning the Koran in Sweden, was shot dead during a TikTok livestream in an apartment in Sodertalje. The 38-year-old sparked outrage in the Muslim community for his demonstrations, leading to global condemnation. After being rushed to the hospital, he was pronounced dead.
Authorities arrested five individuals in connection with the incident. Momika's death comes days before a court ruling on his possible incitement of ethnic hatred. The incident highlights the tensions surrounding free speech and religious sentiments, intensifying after his controversial protests in 2023.
[Sauce](https://www.dailymail.co.uk/news/article-14341423/Christian-Iraqi-burnt-Koran-Sweden-shot-dead.html)
-

@ e262ed3a:e147fbcb
2025-01-30 11:26:25

I got an idea while watching a video from @BTCSessions, which I personally cannot implement technically. Therefore, I would like to present it here for discussion and free implementation. It makes sense to me, but what do I know? Let the swarm intelligence decide.
The goal of the business idea is:
1. How can I bring as many solo miners as possible into a pool without them having to pay for the electricity for mining and their mining hardware can be amortized quickly, so they can purchase more mining hardware?
2. How can we financially support Bitcoin and Nostr developers in the long term?
3. How can we intensify developers for the implementation of this idea?
4. How can we encourage non-Bitcoiners to invest in the support of the Bitcoin network?
5. How can we get non-Bitcoin retailers to invest in the Bitcoin network?
**The answer is: PROSPECT OF WINNING**
**The solution lies in a kind of RAFFLE. (Not a betting website)**
The legal difference between a BET and a RAFFLE varies from country to country. It lies in the fact that a raffle must be very transparent regarding the chances of winning and the proceeds must go to a good cause. Those involved in the implementation can, of course, be compensated (also with a profit for the individual participants). The extent to which this is allowed would have to be checked by those who want to implement this idea.
In the following, I will describe the implementation roughly. Since this is not a sales presentation, please excuse me if the following proposal is not fully structured.
Participants in the idea are:
1. Consumers (ticket buyers)
2. Bitcoin miners
3) Retailers
4) Non-profit company that implement the project
**What's it about?** @BTCSessions has a YouTube video about the miner FutureBit. In the dashboard of the solo miner, you could see how high the hash rate was. But above all, you could see how high the chance of winning was for the solo miner in the overall network. In the case of BTCSessions FutureBit, the hash rate was around 5 TerraHash and the chance of winning was around 1:1,000,000. (Which, according to my calculations, was not correct). The power consumption was around 32 watts. When I saw that, it suddenly dawned on me.
Could it be possible to create a website/app that determines the total hash rate of a mining pool and then offers an electronic, numbered ticket for each 1 TerraHash (TH/s) of the pool for, for example, 0.1 USD? The minimum purchase amount would be 10 tickets. The customer sees the chance of winning and could even see the possible payout. The ticket is only valid for the next block (similar to roulette).
Another variant could be that the buyer can select one or more of the next 10 blocks and purchase tickets for the selected block. Since you don't know in advance how high the pool hash rate will be 5 or 10 blocks ahead, the amount of tickets to be issued for the 2nd block, for example, could only be 90% of the current pool hash rate, the 3rd block only 80%, and so on. If block 3, for example, advances to position 2, the previously unavailable 10% will be released for further tickets. (Determined by the pool hash rate at that time)
The purchase of 10 or more tickets could be automated in the customer's account on the website/app (intervals: hourly, daily, weekly, every 10 blocks, etc.). Customers could also top up their account with satoshis, enabling automatic deductions for ticket purchases. This could be facilitated by automatically issuing a Nostr npub to each customer, which would also create a wallet at Primal.net (Strike). For non-Bitcoiners, Zaprite could be used to recharge their account. Alternatively, customers could enter a NostrWalletConnection NWC to enable automatic deductions from their Lightning wallet. The project operators might also consider running their own ecash mint, which would allow them to assign an integrated ecash address to customers without a Lightning address. Tickets with ascending numbers would be allocated strictly in the order of payment receipts.
**Calculations for the miners**: The FutureBit miner consumed approximately 30 watts per terahash/hour. Let's assume that 10 terahash consume 300 watts per hour, then the miner consumes 50 watts per 10 minutes (per block). Let's further assume that a kilowatt-hour of electricity costs between 10 and 30 cents, then it costs the miner 3-9 cents per hour for electricity at 10 terahash mining capacity. So, 0.5-1.5 cents per block. In the case that each ticket is sold for 1 terahash for the next block, one could automatically transfer, for example, 5% of the satoshis received from ticket sales to each participating miner in the pool (proportional to the average hash rate delivered by the miner in the last block in the pools). This happens even if the block is not found. If fewer tickets are sold than the maximum possible amount, then the 5% of the sold tickets will be distributed proportionally. (See also my Excel file?
**At the center** of the project is a website/app that manages the raffle. Here, anyone can register and create an account. Either as a miner, retailer, or customer with or without KYC, for example, with their own nostr nsec, wallet signature, email and password or phone number and password.
Once logged into the account, Bitcoiners can enter their Lightning address and a Bitcoin on-chain address. Non-Bitcoiners enter their financial data in case they win.
Miners must enter a Bitcoin and Lightning (or ecash) address. The pooling process is also managed in the miner's account.
Tickets can be purchased (like in a regular online shop) and paid for in any way. Zaprite could be a solution here. But also Strike, Cashapp, etc. As described above, such purchases could also be automated.
**Retailers can also register as such**. They will then have the opportunity to sell "tickets" to their customers and collect the money in cash. To sell tickets, they must enter the customer's name and a valid email address. After payment, they must send the purchase price via Lightning to the non-profit company, which will then confirm the purchase to the ticket buyer and the retailer with all the data. This is the receipt for the buyer. In the event of a win (the mined block must have 3-6 block confirmations), the ticket buyer will receive an email explaining all the further details of how to claim the prize. This could be a link that takes them directly to the website and logs them in directly. The winner can then enter their data on how and where the money should be paid out (Bitcoin address or bank details). Alternatively, they can go to their retailer, who can assist them by entering the data in their sub-account (customer account). To prevent the retailer from falsifying the data entry, the winner will first receive an email with the entered data, which they can confirm (if correct). Since the retailer is also involved in the win, they will also be notified.
**How many tickets** can be offered per round (Bitcoin block)? The number of tickets depends on the hash rate in the pool. One ticket can be issued per 1 TerraHash (TH/s). How the ticket is generated per round and customer, I don't know, as I lack the technical knowledge. Maybe as a kind of NFT that contains the corresponding data (customer number (npub) of the buyer and possibly retailer, block number, ticket number). Or as a Taproot asset on Lightning? Or as a minted ecash coin? Or simply as an entry in a database that the customer can see in their account.
The maximum payout of the winnings in the event of a found block to the ticket holders could be 70%. The remaining 30% would be distributed to the miners and retailers. For example: Miners 25%, retailers 5%. The non-profit organization receives nothing from the block rewards. Instead, it receives 65% of the revenue from all ticket sales. With a mining pool hash rate of 10,000 TH/s, where all tickets are sold continuously, a daily donation of around 93,000 USD would be generated. (see Excel.file)
The revenue, after deducting the possible costs of the organization, goes directly to @opensats and/or other organizations that support the Bitcoin network after each block. Either via Lightning or Bitcoin on-chain payment.
In the attached Excel file, you can find my calculations. Here, anyone can play through different scenarios.
What I noticed was that with maximum ticket sales per block, only around 200 USD per 10 tickets would be paid out, since each participating ticket wins in the event of a found block. Since I believe that this is not a very great incentive for buying tickets, I suggest the following variants.
**Winning variants**: Each purchased ticket has a running number. Ticket 1 has the number 000.000, ticket 2 has the number 000.001, ticket 10.120 has the number 010.119, and so on.
If the next block is found, then this found block in the Bitcoin blockchain has a hash. For example, block 881367 has the hash 000000000000000000014b0fab24355c71c6940584d9cd5990c0b081a31d54a4
Let's now remove the letters and read only the numbers from back to front, so the last 3 numbers are 544
Instead of every participating ticket winning, in this variant, only the tickets with the ending digits 544 win.
With, for example, 11,000 tickets sold, the ticket numbers 000.544 / 001.544 / 002.544 ... 010.544 would win. So, 11 ticket participants would win. Each winner with this number would receive around 0.284 Bitcoin (3.125 BTC / 11).
One could also let the ticket numbers with the ending digits 44 win, and thus every hundredth ticket. Or even combine it.
What I also noticed was that with retailers, a special case arises. Retailers receive 5% of the block rewards in the event of a found block. But only proportionally to the tickets sold by the retailer. This means that in order for the entire 5% to be distributed to the retailers, all 10,000 tickets of 10.000 possible tickets would have to be sold by retailers. Since not all tickets will be sold by retailers, a remaining amount will be left over. This could be distributed additionally to the miners. Or any other variant.
I hope the idea finds resonance and invites discussion. Maybe I've made some mistakes in thinking, and the idea is not feasible. But if you like the idea, please forward it to developers, investors, and others you know.
Best regards.
<span data-type="mention" data-id="e262ed3a22ad8c478b077ef5d7c56b2c3c7a530519ed696ed2e57c65e147fbcb" data-label="nostr:undefined">@nostr:undefined</span> dewe
[Excel sheet for download](https://c.gmx.net/@329519820976429649/KJTehgh0SMGliV4HLjMf0g)
-

@ 0fa80bd3:ea7325de
2025-01-30 04:28:30
**"Degeneration"** or **"Вырождение"**
![[photo_2025-01-29 23.23.15.jpeg]]
A once-functional object, now eroded by time and human intervention, stripped of its original purpose. Layers of presence accumulate—marks, alterations, traces of intent—until the very essence is obscured. Restoration is paradoxical: to reclaim, one must erase. Yet erasure is an impossibility, for to remove these imprints is to deny the existence of those who shaped them.
The work stands as a meditation on entropy, memory, and the irreversible dialogue between creation and decay.
-

@ 9f3eba58:fa185499
2025-01-29 20:27:09
Humanity as a whole has been degrading over the years, with average IQ decreasing, bone structures generally becoming poorly formed and fragile, average height decreasing, hormone levels ridiculously low and having various metabolic and mental illnesses becoming “normal”.
“*By 2024, more than 800 million adults were living with diabetes, representing a more than fourfold increase since 1990*”
“\*\**1 in 3 people suffer from insulin resistance and can cause depression*” (\*\*https://olhardigital.com.br/2021/09/24/medicina-e-saude/1-em-cada-3-pessoas-sofre-de-resistencia-a-insulina-e-pode-causar-depressao/)
“*More than 1.3 billion people will have diabetes in the world by 2050*” (https://veja.abril.com.br/saude/mais-de-13-bilhao-de-pessoas-terao-diabetes-no-mundo-ate-2050)
“*A new study released by Lancet, with data from 2022, shows that more than a billion people live with obesity in the world*” (https://www.paho.org/pt/noticias/1-3-2024-uma-em-cada-oito-pessoas-no-mundo-vive-com-obesidade)
All this due to a single factor: diet. I’m not referring to a diet full of processed foods, as this has already been proven to destroy the health of those who eat it. I’m referring to the modern diet, with carbohydrates (from any source, even from fruit) being the main macronutrient, little animal protein and practically no saturated fat of animal origin. This diet implementation has been systematically occurring for decades. Sugar conglomerates seeking profits? Government institutions (after all, they need voters to be stupid and vote for them), evil spiritual interference wanting to destroy or distort their path? I don’t know, I’ll leave the conspiracy theories to you!
The modern diet or diet is extremely inflammatory, and inflammation over a long period of time leads to autoimmune diseases such as diabetes and Hashimoto’s.
Absolutely any food in the plant kingdom will harm you, no matter how asymptomatic it may be. Plants are living beings and do not want to die and be eaten. To defend themselves from this, they did not evolve legs like animals. They specifically developed chemical mechanisms such as *oxalates, phytoalexins, glucosinolates, polyphenols, antinutrients* and many others that act to repel anything that wants to eat them, being fatal (as in the case of mushrooms), causing discomfort and the animal or insect discovering that the plant is not edible, releasing unpleasant smells or, in many cases, a combination of these factors. Not to mention genetically modified foods (almost the entire plant kingdom is genetically modified) that work as a steroid for the plants' defenses. - Lack of focus
- Poor decision-making
- Difficulty in establishing and maintaining relationships
- Difficulty getting pregnant and difficult pregnancy
- Low testosterone (medical reference values are low)
- Alzheimer's
- Diabetes
- Dementia
- Chances of developing autism when mothers do not eat meat and fat properly during pregnancy
- Worsening of the degree of autism when the child does not eat meat and fat (food selectivity)
- Insomnia and other sleep problems
- Lack of energy
- Poorly formed and fragile bone structure
- Lack of willpower
- Depression
- ADHD
Not having full physical and mental capacity harms you in many different ways, these are just a few examples that not only directly impact one person but everyone else around them.
Fortunately, there is an alternative to break out of this cycle of destruction, ***Carnivore Diet***.
I am not here to recommend a diet, eating plan or cure for your health problems, nor can I do so, as I am not a doctor (most doctors don't even know where the pancreas is, a mechanic is more useful in your life than a doctor, but that is a topic for another text.).
I came to present you with logic and facts in a very simplified way, from there you can do your own research and decide what is best for you.
---
## Defining the carnivore diet
Simply put, the carnivore diet is an elimination diet, where carbohydrates (including fruits), vegetable fats (soy, canola, cotton, peanuts, etc.), processed products and any type of plant, be it spices or teas, are completely removed.
### What is allowed on the carnivore diet?
- Animal protein
- Beef, preferably fatty cuts (including offal, liver, heart, kidneys, these cuts have more vitamins than anything else in the world)
- Lamb
- Eggs
- Fish and seafood
- Animal fat
- Butter
- Beef fat and tallow
- Salt
- No... salt does not cause high blood pressure. (explained later about salt and high consumption of saturated fats)
From now on I will list some facts that disprove the false accusations made against \*\*eating exclusively meat and fat.
# “Human beings are omnivores”
*“Our ancestors were gatherers and hunters*"
To determine the proportion of animal foods in our ancestors’ diets, we can look at the amount of δ15 nitrogen in their fossils. By looking at levels of this isotope, researchers can infer where animals reside in the food chain, identifying their protein sources. Herbivores typically have δ15N levels of 3–7 percent, carnivores show levels of 6–12 percent, and omnivores exhibit levels in between. When samples from Neanderthals and early modern humans were analyzed, they showed levels of 12 percent and 13.5 percent, respectively, even higher than those of other known carnivores, such as hyenas and wolves. And from an energy efficiency standpoint, hunting large animals makes the most sense. Gathering plants and chasing small animals provides far fewer calories and nutrients relative to the energy invested. In more recently studied indigenous peoples, we have observed a similar pattern that clearly indicates a preference for animal foods over plant foods. For example, in Vilhjalmur Stefansson’s studies of the Eskimos.
*“…fat, not protein, seemed to play a very important role in hunters’ decisions about which animals (male or female) to kill and which body parts to discard or carry away.”*
Why were our ancestors and more recent indigenous peoples so interested in finding fat? At a very basic level, it was probably about calories. By weight, fat provides more than twice as many calories as protein or carbohydrates. Furthermore, human metabolism makes fat an exceptionally valuable and necessary food. If we think of ourselves as automobiles that need fuel for our metabolic engines, we should not put protein in our gas tank. For best results, our metabolic engine runs most efficiently on fat or carbohydrates.
Eating animal foods has been a vital part of our evolution since the beginning. Katherine Milton, a researcher at UC Berkeley, came to the same conclusion in her paper “The Critical Role Played by Animal Source Foods in Human Evolution,” which states:
“Without routine access to animal-source foods, it is highly unlikely that evolving humans could have achieved their unusually large and complex brains while simultaneously continuing their evolutionary trajectory as large, active, and highly social primates. As human evolution progressed, young children in particular, with their rapidly expanding large brains and higher metabolic and nutritional demands relative to adults, would have benefited from concentrated, high-quality foods such as meat." - https://pubmed.ncbi.nlm.nih.gov/14672286/
Skeletons from Greece and Turkey reveal that 12,000 years ago, the average height of hunter-gatherers was five feet, nine inches for men and five feet, five inches for women. But with the adoption of agriculture, adult height plummeted—ending any hope these poor herders had of dunking a basketball or playing competitive volleyball, if such sports had existed at the time. By 3000 B.C., men in this region of the world were only five feet, three inches tall, and women were five feet, reflecting a massive decline in their overall nutritional status. Many studies in diverse populations show a strong correlation between adult height and nutritional quality. A study analyzing male height in 105 countries came to the following conclusion:
“In taller nations…consumption of plant proteins declines sharply at the expense of animal proteins, especially those from dairy products. Its highest consumption rates can be found in Northern and Central Europe, with the global peak in male height in the Netherlands (184 cm).”
In addition to the decline in height, there is also evidence that Native Americans buried at Dickson Mounds suffered from increased bacterial infections. These infections leave scars on the outer surface of the bone, known as the periosteum, with the tibia being especially susceptible to such damage due to its limited blood flow. Examination of tibias from skeletons found in the mounds shows that after agriculture, the number of such periosteal lesions increased threefold, with a staggering eighty-four percent of bones from this period demonstrating this pathology. The lesions also tended to be more severe and to appear earlier in life in the bones of post-agricultural peoples.
https://onlinelibrary.wiley.com/doi/full/10.1111/j.1747-0080.2007.00194.x
https://pubmed.ncbi.nlm.nih.gov/10702160/
# Cholesterol
Many “doctors” say that consuming saturated fat is harmful to your health, “your veins and arteries will clog with excess fat” “you will have a heart attack if you consume a lot of fat" and many other nonsense, and in exchange recommends that you replace fatty cuts of meat with lean meat and do everything with vegetable oil that causes cancer and makes men effeminate.
Your brain is basically composed of fat and water, your neurons are made and repaired with fat, your cells, the basic unit of life, are composed of fat and protein, many of your hormones, especially sexual ones, are made from fat, there is no logical reason not to consume saturated fat other than several false "scientific articles".
"The power plant of the cell is the mitochondria, which converts what we eat into energy. Ketones are an energy source derived from fat. Mitochondria prefer fat as energy (ketones) because transforming ketones into energy costs the mitochondria half the effort of using sugar (glucose) for energy." - https://pubmed.ncbi.nlm.nih.gov/28178565/
"With the help of saturated fats, calcium is properly stored in our bones. The interaction between calcium, vitamin D, and parathyroid hormone regulates calcium levels in the body. When there are calcium imbalances in the blood, our bones release calcium into the blood to find homeostasis." - https://www.healthpedian.org/the-role-of-calcium-in-the-human-body/
"The body needs cholesterol to support muscle repair and other cellular functions. This is why when there is cardiovascular disease, we see increased amounts of cholesterol in the area. Cholesterol is not there causing the problem, but the boat carrying fat was docked there for cholesterol and other nutrients to help fight the problem. Plaque is the body's attempt to deal with injury within the blood vessels." - *National Library of Medicine, “Cholesterol,” 2019*
"Initially, the Plaque helps blood vessels stay strong and helps the vessels maintain their shape. But with the perpetual cycle of uncontrolled inflammation and leftover debris from cellular repair (cholesterol), over time plaque begins to grow and harden, reducing blood flow and oxygen to the heart. Both inflammation and repair require copious amounts of cholesterol and fats. So the body keeps sending these fatty substances to the site of the plaque — until either repair wins (plaque becomes sclerotic scars in the heart muscle, causing heart failure) or inflammation wins (atherosclerotic heart attack)" - https://pubmed.ncbi.nlm.nih.gov/21250192/
Inflammation in Atherosclerotic Cardiovascular Disease - https://pubmed.ncbi.nlm.nih.gov/21250192/
"Study finds that eating refined carbohydrates led to an increased risk of cardiovascular disease and obesity" - https://pmc.ncbi.nlm.nih.gov/articles/PMC5793267/
# “Meat causes cancer”
Most of the misconceptions that red meat causes cancer come from a report by the World Health Organization's International Agency for Research on Cancer (IARC), which was released in 2015. Unfortunately, this report has been widely misrepresented by the mainstream media and is based on some very questionable interpretations of the science it claims to review.
A closer look at a 2018 report on its findings reveals that only 14 of the 800 studies were considered in its final conclusions—and every single study was observational epidemiology. Why the other 786 were excluded remains a mystery, and this group included many interventional animal studies that clearly did not show a link between red meat and cancer. Of the fourteen epidemiological studies that were included in the IARC report, eight showed no link between meat consumption and the development of colon cancer. Of the remaining six studies, only one showed a statistically significant correlation between meat and cancer.
In epidemiological research, one looks for correlation between two things and the strength of the correlation. Having just one study out of 800 that shows meat causes cancer is a mere fluke and becomes statistically insignificant.
Interestingly, this was a study by Seventh-day Adventists in America — a religious group that advocates a plant-based diet.
# Microbiota and Fiber
I have seen several people and “doctors” saying that eating only meat would destroy your microbiota. And I have come to the conclusion that neither “doctors” nor most people know what a microbiota is.
Microbiota is the set of several types of bacteria (millions) that exist in your stomach with the function of breaking down molecules of certain types of food that the body itself cannot get, fiber for example. Many times through the process of fermentation, which is why you have gas after eating your beloved oatmeal.
People unconsciously believe that the microbiota is something fixed and unchangeable, but guess what… it is not.
Your microbiota is determined by what you eat. If you love eating oatmeal, your microbiota will have a specific set of bacteria that can break down the oat molecule into a size that the body can absorb.
If you follow a carnivorous diet, your microbiota will adapt to digest meat.
### Fiber
Nutritional guidelines recommend large amounts of fiber in our diet, but what they don't tell you is that we only absorb around 6% of all the vegetable fiber we eat. In other words, it's insignificant!
Another argument used by doctors and nutritionists is that it helps you go to the bathroom, but this is also a lie. Fiber doesn't help you evacuate, it forces you to do so. With the huge amount of undigestible food in your stomach (fiber), the intestine begins to force contractions, making this fecal matter go down, making you go to the bathroom.
They also raise the argument that fibers are broken down into short-chain fatty acids, such as butyrate (butyric acid), propionate (propionic acid) and acetate (acetic acid). Butyrate is essential because it is the preferred fuel source for the endothelial cells of the large intestine.
Butter, cream, and cheese contain butyrate in its absorbable form. Butter is the best source of butyric acid, or butyrate. In fact, the origins of the word butyric acid come from the Latin word *butyro*—the same origins as the word butter.
“In 2012, a study in the Journal of Gastroenterology showed that reducing fiber (a precursor to short-chain fatty acids) helped participants with chronic constipation. The study lasted six months, and after two weeks without fiber, these participants were allowed to increase fiber as needed. These participants felt so much relief after two weeks without fiber that they continued without fiber for the entire six-month period. Of the high-fiber, low-fiber, and no-fiber groups, the zero-fiber participants had the highest bowel movement frequency.” - https://pmc.ncbi.nlm.nih.gov/articles/PMC3435786/
### Bioavailability
I said that our body can only absorb 6% of all the fiber we ingest. This is bioavailability, how much the body can absorb nutrients from a given food.
Meat is the most bioavailable food on the planet!
Grains and vegetables are not only not very bioavailable, but they also contain a huge amount of antinutrients. So if you eat a steak with some beans, you will not be able to absorb the nutrients from the beans, and the antinutrients in them will make it impossible to absorb a large amount of nutrients from the steak. https://pubmed.ncbi.nlm.nih.gov/23107545/
# Lack of nutrients and antioxidants in a carnivorous diet
A major concern with the carnivorous diet is the lack of vitamin C, which would consequently lead to scurvy.
Vitamin C plays an important role in the breakdown and transport of glucose into cells. In 2000 and 2001, the recommended daily intake of vitamin C effectively doubled. In fact, every 10 to 15 years, there has been a large increase in the recommended daily intake of vitamin C, as happened in 1974 and 1989. Interestingly, also in 1974, sugar prices became so high that high fructose corn syrup was introduced into the US market. Could the increase in readily available glucose foods and foods with high fructose corn syrup be a reason why we need more vitamin C? The question remains…. But this is not a cause for concern for the carnivore, liver is rich in vitamin C. You could easily reach the daily recommendation with liver or any cut of steak. 200-300g of steak already meets your needs and if the theory that the more sugar you eat, the more vitamin C you will get is true, then the more sugar you will eat is true. C is necessary if true, you could easily exceed the daily requirement.
Meat and seafood are rich in ALL the nutrients that humans need to thrive.
### Antioxidants
It is commonly said that fruits are rich in antioxidants but again this is a hoax, they are actually PRO-oxidants. These are substances that activate the mRF2 pathway of our immune system which causes the body to produce natural antioxidants.
The body produces antioxidants, but many occur naturally in foods, Vitamin C, Vitamin E, Selenium and Manganese are all natural antioxidants.
High concentrations of antioxidants can be harmful. Remember that high concentrations of antioxidants can increase oxidation and even protect against cancer cells.
# Salt
Consuming too much salt does not increase blood pressure and therefore increases the risk of heart disease and stroke. Studies show no evidence that limiting salt intake reduces the risk of heart disease.
A 2011 study found that diets low in salt may actually increase the risk of death from heart attacks and strokes. Most importantly, they do not prevent high blood pressure. https://www.nytimes.com/2011/05/04/health/research/04salt.html
# Sun
This is not a dietary issue specifically, but there are things that can I would like to present that is against common sense when talking about the sun.
It is common sense to say that the sun causes skin cancer and that we should not expose ourselves to it or, if we are exposed to the sun, use sunscreen, but no study proves that using sunscreen protects us from melanoma and basal cell carcinoma. The types of fatal melanomas usually occur in areas of the body that never see the sun, such as the soles of the feet.
https://www.jabfm.org/content/24/6/735
In 1978, the first sunscreen was launched, and the market grew rapidly, along with cases of melanoma.
Several studies show that sunscreens cause leaky gut (one of the main factors in chronic inflammation), hormonal dysfunction and neurological dysfunction.
https://pubmed.ncbi.nlm.nih.gov/31058986/
If your concern when going out in the sun is skin cancer, don't worry, your own body's natural antioxidants will protect you. When they can no longer protect you, your skin starts to burn. (If you have to stay in the sun for work, for example, a good way to protect yourself is to rub coconut oil on your skin or just cover yourself with a few extra layers of thin clothing and a hat).
Sunscreen gives you the false sense of protection by blocking the sunburn, so you stay out longer than your skin can handle, but sunscreens can only block 4% of UVA and UVB rays.
www.westonaprice.org/health-topics/environmental-toxins/sunscreens-the-dark-side-of-avoiding-the-sun/
Interestingly, vitamin D deficiency is linked to increased cancer risks. It's a big contradiction to say that the greatest provider of vit. D causes cancer…
https://med.stanford.edu/news/all-news/2010/10/skin-cancer-patients-more-likely-to-be-deficient-in-vitamin-d-study-finds.html
Important roles of vitamin D:
- **Regulation of Bone Metabolism**
- Facilitates the **absorption of calcium and phosphorus** in the intestine.
- Promotes bone mineralization and prevents diseases such as **osteoporosis**, **rickets** (in children) and **osteomalacia** (in adults).
- **Immune Function**
- Modulates the immune system, helping to reduce inflammation and strengthen the defense against infections, including **colds**, **flu** and other diseases.
- May help reduce the incidence of autoimmune diseases such as **multiple sclerosis** and **rheumatoid arthritis**. - **Muscle Health**
- Contributes to muscle strength and the prevention of weakness, especially in the elderly.
- Reduces the risk of falls and fractures.
- **Cardiovascular Function**
- May help regulate blood pressure and heart function, reducing the risk of cardiovascular disease.
- **Hormonal Balance**
- Influences the production of hormones, including those associated with fertility and the functioning of the endocrine system.
- Plays a role in insulin metabolism and glucose sensitivity.
- **Brain Function and Mental Health**
- Participates in mood regulation, which may reduce the risk of **depression** and improve mental health.
- Has been associated with the prevention of neurodegenerative diseases, such as **Alzheimer's**.
- **Anticancer Role**
- Evidence suggests that vitamin D may inhibit the proliferation of cancer cells, especially in breast, prostate and colon cancers. - **Role in General Metabolism**
- Contributes to metabolic health, regulating cellular growth and repair processes.
---
I tried to present everything in the simplest and most understandable way possible, but there are things that require prior knowledge to truly understand. Below is a list of books that will show you everything I have shown you in a more technical and in-depth way.
### Book Recommendations
https://amzn.to/3EbjVsD
https://amzn.to/4awlnBZ
All of my arguments have studies to validate them. Feel free to read them all and draw your own conclusions about what is best for you and your life.
-

@ 0fa80bd3:ea7325de
2025-01-29 15:43:42
Lyn Alden - биткойн евангелист или евангелистка, я пока не понял
```
npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a
```
Thomas Pacchia - PubKey owner - X - @tpacchia
```
npub1xy6exlg37pw84cpyj05c2pdgv86hr25cxn0g7aa8g8a6v97mhduqeuhgpl
```
calvadev - Shopstr
```
npub16dhgpql60vmd4mnydjut87vla23a38j689jssaqlqqlzrtqtd0kqex0nkq
```
Calle - Cashu founder
```
npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg
```
Джек Дорси
```
npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m
```
21 ideas
```
npub1lm3f47nzyf0rjp6fsl4qlnkmzed4uj4h2gnf2vhe3l3mrj85vqks6z3c7l
```
Много адресов. Хз кто надо сортировать
```
https://github.com/aitechguy/nostr-address-book
```
ФиатДжеф - создатель Ностр - https://github.com/fiatjaf
```
npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6
```
EVAN KALOUDIS Zues wallet
```
npub19kv88vjm7tw6v9qksn2y6h4hdt6e79nh3zjcud36k9n3lmlwsleqwte2qd
```
Программер Коди https://github.com/CodyTseng/nostr-relay
```
npub1syjmjy0dp62dhccq3g97fr87tngvpvzey08llyt6ul58m2zqpzps9wf6wl
```
Anna Chekhovich - Managing Bitcoin at The Anti-Corruption Foundation
https://x.com/AnyaChekhovich
```
npub1y2st7rp54277hyd2usw6shy3kxprnmpvhkezmldp7vhl7hp920aq9cfyr7
```
-

@ 57d1a264:69f1fee1
2025-01-28 02:36:34
**About the role**
In this role, you will work on the product design of umbrelOS, some of our umbrelOS apps, and the umbrel.com website.
**What are you looking for in candidates?**
Talent, passion, genuine love for your craft, and the desire to do meaningful work. What we’re not looking for: credentials and degrees. When you really love what you do, work feels like play. And when work feels like play, you become the best at it. That’s what we’re looking for.
**We hope you:**
- Like to spend your days staring at artboards in Figma
- Are obsessed with creating delightful micro-interactions and animations
- Are willing to throw away ideas if they're not great, and optimistic enough to keep hunting for new ones
- Care about the details, maybe a bit too much (a pixel off ruins your sleep)
- Are excited to collaborate with everyone on the team: engineers, customer facing folks, etc—you believe inspiration can come from anywhere
- Have good judgement of when to ship
- Like to level up your design skills continually
- Put yourselves in the shoes of our users to craft a great experience
- Enjoy being a generalist and are not tied down to a specific design, trend, or tools
**Benefits**
- 🚑 Health insurance
- 💻 New work equipment
- 🌎 Work from anywhere in the world
- 💆♀️ Complete autonomy at work
- 📚 Learning and development stipend
- 🏝 Minimum 2-weeks of paid time off
- ❤️ Most importantly — doing meaningful work that can change the world
Apply at https://app.withrapha.com/job/692
originally posted at https://stacker.news/items/867248
-

@ 9e69e420:d12360c2
2025-01-26 15:26:44
Secretary of State Marco Rubio issued new guidance halting spending on most foreign aid grants for 90 days, including military assistance to Ukraine. This immediate order shocked State Department officials and mandates “stop-work orders” on nearly all existing foreign assistance awards.
While it allows exceptions for military financing to Egypt and Israel, as well as emergency food assistance, it restricts aid to key allies like Ukraine, Jordan, and Taiwan. The guidance raises potential liability risks for the government due to unfulfilled contracts.
A report will be prepared within 85 days to recommend which programs to continue or discontinue.
-

@ 0463223a:3b14d673
2025-01-26 13:07:36
Hmm so I heard that in order to improve my brain I should try writing… Ok groovy, I’ll give it a go. In all honesty I don’t know what to write, my brain is a jumble of noise and titbits of random knowledge. I likely know more about sound than the average person but as physics goes, I don’t have anything new or profound to add. Air moves and noises happen. Is there really any more to it? I could write some flowery bollocks about refraction, absorption coefficients and reverberation times, or I could write some out there, arty shit but I don’t think that adds any value to anyone.
A lot of folks online have very strong beliefs in how the world operates or should operate. Whilst their conviction is strong, there’s also is a large percentage of people who totally disagree with them and think the exact opposite is the answer. That’s quite shit isn’t it? Humans have been around for 100,000 years or so and haven’t worked it out. I wonder what makes the internet celeb so certain they’ve got it right when the next internet celeb completely disagrees? I do my best to avoid any of these cunts but despite running to the obscurest social media platforms they still turn up with their profound statements. Meh.
Ideologically I’m leaning toward anarchism but even that seems full of arguments and contradictions and ultimately I don’t think I can be arsed with identifying with any particular ideology. I tried reading some philosophy and struggled with it, although I deep fall into a lovely deep sleep. It’s fair to say I’m not the brightest button in the box. I have a wife, a couple of cats and lots of things that make nosies in my shed. That’s pretty cool right? Well it works for me.
So why write this? I clearly wrote in the first sentence that I’m trying to improve my brain, a brain that’s gone through a number to twists and turns, a lot brain altering substances. I own that, no one forced me to. Beside, George Clinton was still smoking crack aged 80, didn’t do him any harm…
I’m on the 5th paragraph. I don’t feel any smarter yet and each paragraph is getting shorter, having started from a low base. I guess I’m being too high time preference… Might be a while before I launch my Deep Thought podcasts where myself and a guest talk for 500 hours about the philosophy of money and 13 amp plug sockets.
I’ve tortured myself enough. I’m posting this on Nostr where it will never go away.. lol. If you got this far, I congratulate/commiserate you and wish you a wonderful day.
-

@ 9e69e420:d12360c2
2025-01-25 22:16:54
President Trump plans to withdraw 20,000 U.S. troops from Europe and expects European allies to contribute financially to the remaining military presence. Reported by ANSA, Trump aims to deliver this message to European leaders since taking office. A European diplomat noted, “the costs cannot be borne solely by American taxpayers.”
The Pentagon hasn't commented yet. Trump has previously sought lower troop levels in Europe and had ordered cuts during his first term. The U.S. currently maintains around 65,000 troops in Europe, with total forces reaching 100,000 since the Ukraine invasion. Trump's new approach may shift military focus to the Pacific amid growing concerns about China.
[Sauce](https://www.stripes.com/theaters/europe/2025-01-24/trump-europe-troop-cuts-16590074.html)
-

@ 228dde34:b5d0345e
2025-01-25 01:59:57
##### By Jonathan Tan
##### Lead Editor
##### Hype Issue #60
##### JONATHAN TAN explores the recent rise in popularity of online gambling, and its consequences on the population’s most vulnerable.

The persistent rise in the gaming industry, fueled by the introduction of online gambling, seems to have no end. Experts are now worrying about the effects of this epidemic on public health and safety. “Many people might be really experiencing harms from gambling — we think that it’s probably around 72 million people globally,” said Louisa Degenhardt, a professor at the University of New South Wales in Sydney, in an[NBC article.](https://www.nbcnews.com/health/health-news/gambling-industry-growth-threat-public-health-report-rcna175356)
The online gambling craze has spread worldwide, and even Singapore, with its strict gambling regulations, is not immune to it. In a recent[survey](https://www.channelnewsasia.com/singapore/national-council-problem-gambling-rate-continues-fall-4761621)conducted by the National Council on Problem Gambling (NCPG), illegal online gambling rates have more than tripled since 2020, from 0.3% to 1.0% in the past 4 years.
This statistic alone highlights an already concerning trend. Even more troubling, however, is that the illegal nature of these websites means there are no regulatory laws or age restrictions. As a result, the proliferation of these online websites has allowed a brand new demographic to start gambling: the Singaporean youth.
### How to lose thousands before adulthood
“I started gambling when I was 13 years old, at a friend's house,” George (not his real name) shares. Now an 18-year-old student, George recalls how a simple game among friends slowly grew into an all-consuming gambling addiction.
 *In NCPG’s 2023 survey, 8% of respondents reported participating in social gambling activities: gambling which occurs within individuals’ homes, among family members. Photo from Shutterstock.*
Initially, George and his friends gambled with low stakes, like a dollar here and there. However, the games slowly escalated: from $1 to $10, then to $100, and eventually to $1000. Unsurprisingly, with such large sums at stake, George’s relationship with his friends began to strain.
“I realized that after a certain point, the more and more money we [bet], the more and more our relationship with each other [soured]; and so we decided to curb it at a maximum buy-in of $20 per game,” George says.
The new rule eased the tension between George and his friends, but it inadvertently created a new problem: George no longer felt the thrill of winning large sums. As a result, he began seeking other ways to gamble.
“The first time I gambled online was when I was 16 years old. A friend had introduced me to a gambling website,” he recalls. “And at first it was all right. I won a bit, I lost a bit, but no one got hurt.”
But it didn’t take long for him to get hooked; a single sports bet was what netted George his first big win. “On the first day, I went from $10 to $800 from a simple parlay bet,” George says. “I felt unstoppable. Adrenaline was pumping through my veins, and [I felt] I could never lose. [After] that day, I gambled like $100 almost every day for a straight month.”

*A parlay (a form of sports betting that has recently surged in popularity) is a single bet that combines two or more bets into one. While doing this drastically decreases the odds of winning, it also drastically increases the potential payout. Photo from Getty Images.*
Nothing could stop George’s gambling fervor. Even after losing nearly a thousand dollars on a single blackjack hand, all George did was place a bigger bet to try and win it back. “Every morning, when I [woke] up, all I could think about was gambling,” he shares.
And of course, George’s obsession with online gambling was only exacerbated by the accessibility of these websites.
First, the online nature of these websites allowed George to gamble anywhere, at any time. “For online gambling, you have it right at your fingertips. As soon as you wake up, you can just log on the computer and start betting huge amounts of money,” he mentions.
But more importantly, these illegal gambling websites enabled George to do something he was never old enough to do in the first place.
“I'm too young to gamble at a real casino or a physical casino. But online gambling makes it way more accessible because there's no verification of ID,” George says.
### Consequences, consequences
Therein lies the predatory nature of these illegal websites. While anyone can fall victim to a gambling addiction, certain factors may make the youth especially vulnerable.
“The adolescent brain is still developing, particularly the prefrontal cortex, which is responsible for decision-making, impulse control, and risk assessment. This makes young people more susceptible to impulsive behaviors,” says Jat Tan, the Communications and Events Executive at WE CARE Community Services.
 *The prefrontal cortex is primarily developed during adolescence, and is fully developed at the age of 25 years. Photo from iStock.*
Additionally, other factors such as peer pressure, social media, or limited life experience, could result in young Singaporeans being more open to gambling.
Lastly, one popular reason why the youth are drawn to gambling, is their limited financial freedom. “While youths are in school, they have a significantly lower earning power as opposed to adults. The demands from school usually means that they can only afford to work part-time jobs,” Mrs Tan shares.
Despite this, many young Singaporeans still want to live extravagant lifestyles. With the youth getting exposed to lavish, ostentatious lifestyles on social media, many begin to feel envious and yearn for the same luxuries. And now, with the introduction of illegal online sites, the lack of age restrictions allows these youths to gamble in an attempt to achieve this better life.
### What can be done?
The increase in the number of adolescent gamblers is a new challenge for the Singaporean government. Before the advent of online gambling, many safeguards were in place to protect Singaporeans from developing gambling addictions.
In particular, safeguards that limit Singaporeans’ access to legal gambling services seem to be working; the overall percentage of gambling Singaporeans has fallen from 44% to 40% from 2020 to 2023.
However, the unprecedented accessibility and convenience of online gambling sites have allowed Singapore’s tech-savvy youth to bypass these regulations; and now, the Singaporean government needs to update its laws to keep up with the growing gambling industry.
Of course, the Singaporean Government has been cracking down on illegal online gambling. As of September 2024, the Gambling Regulatory Authority (GRA) has blocked access to more than 1,900 remote gambling websites. But despite the GRA’s efforts, these online gambling providers continue to survive, like weeds in a garden.
“GRA recognises that the borderless nature of the Internet makes it easy for unlawful gambling operators to offer their products to users in Singapore any time and anywhere,” said a GRA spokesman in [a Straits Times article.](https://www.straitstimes.com/singapore/crackdown-on-illegal-online-gambling-but-addiction-can-be-hard-to-beat)
Currently, there are calls for the government to shift its focus. “While Singapore has done well putting in place responsible gaming and safety measures to mitigate the risks of casino gambling, it is timely to focus more attention to address the risk of illegal online gambling as well,” said Ms Tham, Clinical director of We Care Community Services, [in a Straits Times article.](https://www.straitstimes.com/singapore/fewer-singapore-residents-gambled-but-more-do-so-online-illegally)
Ultimately, as the gambling industry becomes more technologically advanced, it becomes harder for Singapore to regulate gambling the same way it used to. Thus, it may be time for the Singaporean government to consider a different solution.
“Better educating youths on the harms and consequences of gambling, as well as resources available should things go awry, would be the best option to nip the issue in the bud,” Ms Tan suggests. Instead of focusing on restrictive legislation, education could be a preventative measure used to curb adolescent gambling.
“A higher level of awareness would enable youths to face issues like gambling with their eyes wide open - they will have a rough idea of what they're getting themselves into, and will have a rough idea of what to do if things go wrong,” she shares.
-

@ bcea2b98:7ccef3c9
2025-01-24 23:21:05
originally posted at https://stacker.news/items/862840
-

@ 378562cd:a6fc6773
2025-01-23 17:57:13
**Top USA News**
1. **President Trump Threatens Tariffs on Non-U.S. Manufacturers**In a speech at the World Economic Forum in Davos, President Donald Trump announced plans to impose tariffs on companies that do not manufacture their products in the United States, aiming to boost domestic production.
[The Guardian](https://www.theguardian.com/us-news/live/2025/jan/23/donald-trump-pardons-january-6-us-president-joe-biden-jd-vance-republicans-live-news?utm_source=chatgpt.com)
2. **Historic Winter Storm Sweeps Across Southern U.S**.A severe winter storm has blanketed the southern United States with snow and freezing temperatures, leading to widespread power outages and hazardous travel conditions.
[WSJ](https://www.wsj.com/news/archive/2025/01/23?utm_source=chatgpt.com)
3. **Trump Administration Orders Federal DEI Staff on Leave**The Trump administration has directed all federal employees working in Diversity, Equity, and Inclusion (DEI) programs to be placed on paid leave, with plans to dismiss all DEI program employees by January 31.
[The Guardian](https://www.theguardian.com/us-news/live/2025/jan/22/donald-trump-china-sanctions-tariff-diversity-us-politics-live-latest-news?utm_source=chatgpt.com)
4. **U.S. Stock Futures Mixed After Tech-Driven Rally**Following a tech-fueled rise, U.S. stock futures show mixed results. The S&P 500 futures dipped slightly after nearing record highs, while Nasdaq futures declined by 0.5%, and Dow Jones futures saw a slight increase.
[Investopedia](https://www.investopedia.com/5-things-to-know-before-the-stock-market-opens-january-23-2025-8778964?utm_source=chatgpt.com)
5. **Trump Pardons January 6 Capitol Rioters**President Trump has issued pardons for individuals convicted in relation to the January 6 Capitol riot, a move that has sparked controversy and debate across the political spectrum.
[The Guardian](https://www.theguardian.com/us-news/live/2025/jan/23/donald-trump-pardons-january-6-us-president-joe-biden-jd-vance-republicans-live-news?utm_source=chatgpt.com)
6. **California Wildfires Cause Extensive Damage**Ongoing wildfires in Los Angeles County are causing significant destruction, with estimated damages exceeding $135 billion. Governor Gavin Newsom warns that these could become the worst natural disaster in American history.
[Wikipedia](https://en.wikipedia.org/wiki/Portal%3ACurrent_events/January_2025?utm_source=chatgpt.com)
7. **President Trump Withdraws U.S. from Paris Climate Agreement**In a series of executive orders, President Trump has withdrawn the United States from the Paris Climate Agreement, citing economic concerns and a focus on American energy independence.
[The Guardian](https://www.theguardian.com/us-news/live/2025/jan/21/donald-trump-inauguration-presidency-executive-orders-pardons-day-two-live-blog?utm_source=chatgpt.com)
8. **Trump Administration Re-designates Houthis as Terrorist Organization**The Trump administration has re-designated the Yemeni Houthi movement as a foreign terrorist organization, reversing a previous decision and impacting international relations in the region.
[Wikipedia](https://en.wikipedia.org/wiki/2025_in_the_United_States?utm_source=chatgpt.com)
9. **President Trump Announces $500 Billion AI Investment**President Trump, alongside tech executives, has announced a $500 billion investment in artificial intelligence infrastructure, aiming to bolster the United States' position in the global tech industry.
[WSJ](https://www.wsj.com/news/archive/2025/01/23?utm_source=chatgpt.com)
10. **ChatGPT Experiences Large-Scale Outage**A significant outage of the AI tool ChatGPT has been reported, affecting users worldwide. The cause of the disruption is under investigation.
[Wikipedia](https://en.wikipedia.org/wiki/2025_in_the_United_Kingdom?utm_source=chatgpt.com)
**Top International News**
1. **Israeli Military Conducts Extensive Raid in Jenin**The Israeli military launched a significant operation in Jenin, resulting in at least 10 Palestinian deaths and numerous injuries. The raid, named "Iron Wall," involved airstrikes and ground forces, escalating tensions in the West Bank.
[The Guardian](https://www.theguardian.com/world/2025/jan/23/first-edition-west-bank-settlers-israel-military?utm_source=chatgpt.com)
2. **Micheál Martin Appointed as Irish Taoiseach**Micheál Martin has been confirmed as Ireland's new Taoiseach following a day of delays and disagreements in the Irish parliament. His immediate focus includes forming his cabinet and addressing Ireland's housing crisis.
[The Guardian](https://www.theguardian.com/world/live/2025/jan/23/europe-dail-micheal-martin-rows-ireland-weather-storm-eowyn-latest-updates?utm_source=chatgpt.com)
-

@ c8cf63be:86691cfe
2025-01-23 12:51:20
### Mark Fishers ‘Acid Communism’ und der ‘Capitalist Realism’
> “it is easier to kill the living than to kill the undead”[1]
Die lebenden sind wir Menschen, *the undead* ist der gegenwärtige
neoliberalismus[2] Mark Fischers Analyse über den bestehenden Zustand
ist erschütternd:
> “let’s say music hello just go on music in the last 10 years one thing
> one single thing that couldn’t have come out in the 20th century”[3]
Es gibt nicht neues unter dem Himmel, alle Kreativität ist erschöpft,
“die Verdinglichung” von der Horkheimer und Adorno sprachen, “…, ist so
dicht geworden,…” die Wirklichkeit des ‘Capitalist Realism’ ist manifest
und undurchdringlich, die Löcher, die kleinen alternativen, sind
versiegelt. Schon im Denken sind die alternativen versperrt und das
Denken ist ein gemeinsames, niemand kann für sich alleine Denken oder
kreativ sein. Denken und kreativ sein sind das Ergebnis einer
Gesellschaftlichen Voraussetzung.
Es gibt keine neue Musik mehr weil die Musik untot ist. In immer neuer
Auflagen, in der mechanische Reproduktion, wiederbelebt man die Toten,
und erstickt das lebendige.
> “… but there’s nothing about us that was good or better than you
> you’re anybody it’s just that we were lucky and you all are unlucky
> …”[4]
Wenn eine junge Frau auf seine Feststellung reagiert mit Unglaube und
Abwehr.
> “… so what you’re basically saying is that i guess your generation or
> the previous generation was better because you had more time to pursue
> your own projects and you also think that you were more creative or
> the previous generation was more creative …”[5]
Dann weil sie die Enge der Umstände nicht erkennen kann, und vielleicht
auch weil sie die Dinge auf sich persönlich bezieht, wie es das
gegenwärtige Denken nahelegt: Sowohl der kompetitive Vergleich als auch
die individuelle Schuldzuordnung findet sich in der Aussage.
Fischer hingegen erklärt dies mit den Herrschenden Umständen die es den
Menschen unmöglich machen sich den *wahren Sachverhalt* klar zu machen
und damit jede Alternative im Denken versperren:
> “.. but okay let’s be clear about what i’m saying creativity isn’t a
> property of individuals ever it’s a property of a social or collective
> scene like that you know that’s so that it’s not like the individuals
> are less creative than they used to be that’s just not how creativity
> works creativity is possible because of is possible because of social
> conditions and those social conditions have been removed …”[6]
Fischers Aufmerksamkeit richtet sich auf die die Umstände vor dem
Capitalism Realism, denn dieser ist seiner Meinung nach schon eine
Reaktion, eine Reaktion auf die “Counterculture” auf das “spectre of a
world which could be free”[7].
Wenn es ein Gründungsereignis des Capital Realism geben sollte wäre dies
nach Fischer der Putsch Pinochets in Chile 1973.[8]
Seiner Zeit voraus war Hunter S. Thompson, seine Drogengeschwängerten
Reflexionen fassen den Kern sehr genau, für ihn war 1971 schon der
Moment an dem er die revision verortet:
> “… wir ritten auf dem Kamm einer hohen und wunderschönen Welle … Und
> jetzt, weniger als fünf Jahre später, kannst du auf einen steilen
> Hügel in Las Vegas klettern und nach Westen blicken, und wenn du die
> richtigen Augen hast, dann kannst du die Hochwassermarkierung fast
> sehen -die Stelle, wo sich die Welle schließlich brach und
> zurückrollte.”[9]
Acid! Die psychedelische Zeit:
> “Instead of seeking to overcome capital, we should focus on what
> capital must always obstruct: the collective capacity to produce, care
> and enjoy.”[10]
und weiter
> “The overcoming of capital has to be fundamentally based on the simple
> insight that, far from being about “wealth creation”, capital
> necessarily and always blocks the production of common wealth.”
Der Zauber der Psycedlischen Zeit war die ignoranz, das Verweigern des
bestehenden Narativs. Oder wie Fischer sagt, die Frage nach dem
Bewustsein und seiner Beziehung dem dem was wir als Wiklichkeit
wahrnemen.[11]
> “turn on, tune in, drop out” [12]
oder noch klarer Ken Kesey:
> “There’s only one thing to do .
> .. there’s only one thing’s gonna do any good at all…
> And that’s everybody just look at it,
> look at the war, and turn your backs and say … Fuck it..” [13]
Die Imagination des *wahren Sachverhaltes* “look at it” sagt Kesey,
überzeugt euch selbst. Es braucht nicht mehr als das Schauen des
Krieges, bei ihm der Viatnam Krieg, um zu verstehen das nur die
Verweigerung, das “Fuck it” geeignet ist dem ganzen seine legitimität zu
verweigern.
Das war der Zauber der psychedelichen Zeit, auch der der 90’er, die als
unpolitsch gelten. Aus dieser Perspektive ist klar das das unpolitsche,
das politsche war.
Die love-Parade war nicht unpolitisch und die gesellschaflichenr
Verändeung die durch diese Psychedleische Zeit in Bewegung gesetzt
wurden können wir noch heute fühlen. Die Canabis Legalisierung, die
veränderte Wahrnehmng von Homosexualität. Das “chill out”. Die tribal
Tattoos.[14] Und auch die wärmste Kampange der Europawahl 2024, “Fickt
euch doch alle.”[15] ist erst durch die psychedelische Zeit der 90’er
möglich, hier wurde die Sinnlichkeit gestiftet die es braucht damit
dieser Satz seine wärme bekommt.
Die Demokratesierung der Neurologie durch die verwendung von
Halozinogenen rücken die Frage nach der Wirklichkeit und des wahren
Sachverhaltes in den Mittelpunkt.
> “what they mainstreamed was this psychedelic consciousness with its
> key notion of the plasticity of reality”[16]
Sie ist auch eine Sekularisierung, eine demokratisierung des Sakralen,
das vorher durch Klassen wie Schamanen oder Druiden kontroliert wurde
wird zugänglich und erfahrbar.
> “…, there was actually a demystificatory and materialist dimension to
> this.”[17]
Was sich so aussprechen läßt:
> *“Wenn Gott liebe ist, dann ist er eine MDMA geschwängerte, psycedelic
> trance Party, anfang der 90’er jahre des letzten Jahrtausend.”*
Es loht sich also für uns ältere an die nicht so ferne Zeit der frühen
90’er Jahre zurück zu denken in der die Welt offen schien, die Polarität
des kalten Krieges vergangen war, das Ende der Geschichte ausgerüfen
wurde.[18]
Da war die Idee das dies nicht der Siegt des Kapitalismus ist, sondern
ein Sieg der Menschen die die Spirale des Schreckens und der Eskalation
durchbrechen real. Es schien wie ein transzendieren des gegebenen Spiels
und seiner Regeln wie es die AI in “war games”[19] realisiert,
stattzufinden.
Auf “No future”[20] folgte “No Paradise? Create it.”[21], es fand ein
“unforgetting”[22] der alten, in den 60’er entwickelten Formen statt:
Die Modulierung der 303, das Dayglow und das Strobo, alles Elemente des
Acid Test[23].
*“the collective capacity to produce, care and enjoy”*
------------------------------------------------------------------------
### References:
[1] Fisher, M., Mark Fisher - DOCH Lectures 1 2011:
<https://www.youtube.com/watch?v=f-9nY5rboK8> 32m 42s
[2] Fisher, M., How to kill a zombie: strategizing the end of
neoliberalism 2013:
<https://www.opendemocracy.net/en/how-to-kill-zombie-strategizing-end-of-neoliberalism/>.
[3] Fisher, 1968., Mark, Cybertime Crisis 2013:
<https://www.youtube.com/watch?v=zOQgCg73sfQ> ab 1h 42m 12s
[4] Fisher, 1968., Mark, ebenda ab 1h 35m 30s
[5] Fisher, 1968., Mark, ebenda ab 1h 42m 12s
[6] Fisher, 1968., Mark, ebenda ab 1h 47m 20s
[7] Fisher, 1968., Mark et al., K-punk : the collected and unpublished
writings of Mark Fisher (2004-2016) 2018. Abs. 153.5
[8] Fisher, 1968., Mark et al., ebenda. Abs. 153.7 “If there was a
founding event of capitalist realism, it would be the violent
destruction of the Allende government in Chile by General Pinochet’s
American-backed coup.”
[9] Hunter S. Thompson “Fear and loathing” Seite 89
[10] Fisher, 1968., Mark et al., K-punk : the collected and unpublished
writings of Mark Fisher (2004-2016) 2018. Abs. 153.5 Statz 3
[11] Fisher, 1968., Mark et al., ebenda. Abs. 153.46
[12] Timothy Leary in 1966, der damals gefährlichste Mann der
Welt.(Richard Nixxon)
[13] Wolfe, Tom., The electric kool-aid acid test. 1999. Seite 360
[14] Christmann, K., Gruppen-Tattoo-Termin im Bundestag: 19 Abgeordnete
zeigen vollen Körpereinsatz 2024:
<https://www.tagesspiegel.de/politik/gruppen-tattoo-termin-im-bundestag-19-abgeordnete-zeigen-vollen-korpereinsatz-11665559.html>.
[15] DiePartei, Fickt euch doch alle! (DINA1) 2024:
<https://www.parteibedarf.de/Fickt-euch-doch-alle-DINA1/SW10115>.
[16] Fisher, M., all of this is temporary: Mark Fisher 2016:
<https://www.youtube.com/watch?v=deZgzw0YHQI> 8 m 31 s
[17] Fisher, 1968., Mark et al., K-punk : the collected and unpublished
writings of Mark Fisher (2004-2016) 2018. Abs. 153.48 4. Satz
[18] Fukuyama, F., The End of History and the Last Man 1992:
<https://books.google.de/books?id=6KZmAAAAMAAJ>.
[19] Parkes, L.L.F., WarGames:
<https://www.imdb.com/de/title/tt0086567/> “A strange game. The only
winning move is not to play.”
[20] Wikipedia, No Future: <https://de.wikipedia.org/wiki/No_Future>.
[21] Spirit zone
https://www.platekompaniet.no/musikk/cd/space-tribe-shapeshifter-cd
[22] Fisher, 1968., Mark et al., K-punk : the collected and unpublished
writings of Mark Fisher (2004-2016) 2018. Abs. 153.21 Letzter Satz
[23] Wikipedia, Acid Tests: <https://de.wikipedia.org/wiki/Acid-Tests>.
-

@ 6be5cc06:5259daf0
2025-01-21 23:17:29
A seguir, veja como instalar e configurar o **Privoxy** no **Pop!_OS**.
---
### **1. Instalar o Tor e o Privoxy**
Abra o terminal e execute:
```bash
sudo apt update
sudo apt install tor privoxy
```
**Explicação:**
- **Tor:** Roteia o tráfego pela rede Tor.
- **Privoxy:** Proxy avançado que intermedia a conexão entre aplicativos e o Tor.
---
### **2. Configurar o Privoxy**
Abra o arquivo de configuração do Privoxy:
```bash
sudo nano /etc/privoxy/config
```
Navegue até a última linha (atalho: **`Ctrl`** + **`/`** depois **`Ctrl`** + **`V`** para navegar diretamente até a última linha) e insira:
```bash
forward-socks5 / 127.0.0.1:9050 .
```
Isso faz com que o **Privoxy** envie todo o tráfego para o **Tor** através da porta **9050**.
Salve (**`CTRL`** + **`O`** e **`Enter`**) e feche (**`CTRL`** + **`X`**) o arquivo.
---
### **3. Iniciar o Tor e o Privoxy**
Agora, inicie e habilite os serviços:
```bash
sudo systemctl start tor
sudo systemctl start privoxy
sudo systemctl enable tor
sudo systemctl enable privoxy
```
**Explicação:**
- **start:** Inicia os serviços.
- **enable:** Faz com que iniciem automaticamente ao ligar o PC.
---
### **4. Configurar o Navegador Firefox**
Para usar a rede **Tor** com o Firefox:
1. Abra o Firefox.
2. Acesse **Configurações** → **Configurar conexão**.
3. Selecione **Configuração manual de proxy**.
4. Configure assim:
- **Proxy HTTP:** `127.0.0.1`
- **Porta:** `8118` (porta padrão do **Privoxy**)
- **Domínio SOCKS (v5):** `127.0.0.1`
- **Porta:** `9050`
5. Marque a opção **"Usar este proxy também em HTTPS"**.
6. Clique em **OK**.
---
### **5. Verificar a Conexão com o Tor**
Abra o navegador e acesse:
```text
https://check.torproject.org/
```
Se aparecer a mensagem **"Congratulations. This browser is configured to use Tor."**, a configuração está correta.
---
### **Dicas Extras**
- **Privoxy** pode ser ajustado para bloquear anúncios e rastreadores.
- Outros aplicativos também podem ser configurados para usar o **Privoxy**.
-

@ 9e69e420:d12360c2
2025-01-21 19:31:48
Oregano oil is a potent natural compound that offers numerous scientifically-supported health benefits.
## Active Compounds
The oil's therapeutic properties stem from its key bioactive components:
- Carvacrol and thymol (primary active compounds)
- Polyphenols and other antioxidant
## Antimicrobial Properties
**Bacterial Protection**
The oil demonstrates powerful antibacterial effects, even against antibiotic-resistant strains like MRSA and other harmful bacteria. Studies show it effectively inactivates various pathogenic bacteria without developing resistance.
**Antifungal Effects**
It effectively combats fungal infections, particularly Candida-related conditions like oral thrush, athlete's foot, and nail infections.
## Digestive Health Benefits
Oregano oil supports digestive wellness by:
- Promoting gastric juice secretion and enzyme production
- Helping treat Small Intestinal Bacterial Overgrowth (SIBO)
- Managing digestive discomfort, bloating, and IBS symptoms
## Anti-inflammatory and Antioxidant Effects
The oil provides significant protective benefits through:
- Powerful antioxidant activity that fights free radicals
- Reduction of inflammatory markers in the body
- Protection against oxidative stress-related conditions
## Respiratory Support
It aids respiratory health by:
- Loosening mucus and phlegm
- Suppressing coughs and throat irritation
- Supporting overall respiratory tract function
## Additional Benefits
**Skin Health**
- Improves conditions like psoriasis, acne, and eczema
- Supports wound healing through antibacterial action
- Provides anti-aging benefits through antioxidant properties
**Cardiovascular Health**
Studies show oregano oil may help:
- Reduce LDL (bad) cholesterol levels
- Support overall heart health
**Pain Management**
The oil demonstrates effectiveness in:
- Reducing inflammation-related pain
- Managing muscle discomfort
- Providing topical pain relief
## Safety Note
While oregano oil is generally safe, it's highly concentrated and should be properly diluted before use Consult a healthcare provider before starting supplementation, especially if taking other medications.
-

@ b17fccdf:b7211155
2025-01-21 17:02:21
The past 26 August, Tor [introduced officially](https://blog.torproject.org/introducing-proof-of-work-defense-for-onion-services/) a proof-of-work (PoW) defense for onion services designed to prioritize verified network traffic as a deterrent against denial of service (DoS) attacks.
~ > This feature at the moment, is [deactivate by default](https://gitlab.torproject.org/tpo/core/tor/-/blob/main/doc/man/tor.1.txt#L3117), so you need to follow these steps to activate this on a MiniBolt node:
* Make sure you have the latest version of Tor installed, at the time of writing this post, which is v0.4.8.6. Check your current version by typing
```
tor --version
```
**Example** of expected output:
```
Tor version 0.4.8.6.
This build of Tor is covered by the GNU General Public License (https://www.gnu.org/licenses/gpl-3.0.en.html)
Tor is running on Linux with Libevent 2.1.12-stable, OpenSSL 3.0.9, Zlib 1.2.13, Liblzma 5.4.1, Libzstd N/A and Glibc 2.36 as libc.
Tor compiled with GCC version 12.2.0
```
~ > If you have v0.4.8.X, you are **OK**, if not, type `sudo apt update && sudo apt upgrade` and confirm to update.
* Basic PoW support can be checked by running this command:
```
tor --list-modules
```
Expected output:
```
relay: yes
dirauth: yes
dircache: yes
pow: **yes**
```
~ > If you have `pow: yes`, you are **OK**
* Now go to the torrc file of your MiniBolt and add the parameter to enable PoW for each hidden service added
```
sudo nano /etc/tor/torrc
```
Example:
```
# Hidden Service BTC RPC Explorer
HiddenServiceDir /var/lib/tor/hidden_service_btcrpcexplorer/
HiddenServiceVersion 3
HiddenServicePoWDefensesEnabled 1
HiddenServicePort 80 127.0.0.1:3002
```
~ > Bitcoin Core and LND use the Tor control port to automatically create the hidden service, requiring no action from the user. We have submitted a feature request in the official GitHub repositories to explore the need for the integration of Tor's PoW defense into the automatic creation process of the hidden service. You can follow them at the following links:
* Bitcoin Core: https://github.com/lightningnetwork/lnd/issues/8002
* LND: https://github.com/bitcoin/bitcoin/issues/28499
---
More info:
* https://blog.torproject.org/introducing-proof-of-work-defense-for-onion-services/
* https://gitlab.torproject.org/tpo/onion-services/onion-support/-/wikis/Documentation/PoW-FAQ
---
Enjoy it MiniBolter! 💙
-

@ c8cf63be:86691cfe
2025-01-21 13:48:28
### Das SNAFU des Reichtums
Das SNAFU-Prinzip[1] sagt das Kommunikation nur unter gleichen möglich
ist:
> Adäquate Kommunikation fliesst nur zwischen Gleichen ungehindert.
> Kommunikation zwischen Nicht-Gleichen ist missverständlich und von
> Dominaz- und Unterwerfungsritualen gefärbt, die immer wieder zum
> Zusammenbruch der Kommunikation führen und zu einem Spiel ohne Ende.
> [2]
So ist z. B. das Peter Prinzip [3] eine einfache Folge des
SNAFU-Prinzips. Bezieht es sich in erster Linie auf Hierarchie lässt es
sich hervorragend ausweiten auf den ökonomischen Bereich. Auch hier
gilt, dass Kommunikation nur unter Gleichen möglich ist, hier ist die
Hierarchie das ökonomische Ungleichgewicht.
Kommunikation ist auch hier nur unter gleichen möglich, ungefähr gleich
reich müssen sie sein. Ein zu großer Unterschied in den ökonomischen
Verhältnissen verhindert den Aufbau einer menschlichen Beziehung. Hier
ist das einfache Beispiel: Wäre ich Reich, würde ich mich Fragen, ob die
Freunde da, nur kommen weil ich ihnen die Drinks ausgebe. Jeder, der
nicht so viel Geld wie ich hat, will vielleicht nur mein Geld. So kann
ein Bill Gates nur einen Jeff Besos als Freund haben oder treffender ein
Elon Musk nur einen Mark Zuckerberg.
Auch umgekehrt funktioniert diese Selektion: Wenn ich ein richtig cooler
Typ wäre, würde ich mich fragen, ob ich den Reichen eigentlich gut
finde, oder nur mit ihm rumhänge, weil er die Drinks bezahlt und weil
ich zu Recht unsicher darüber sein kann, kann ich mich nur entziehen.
Diejenigen, die wirklich freundschaftlich sind, sind die die sich einer
solchen Situation nicht aussetzen.
Und was bleibt dem Reichen? Nur die Gesellschaft der Reichen. Hier
trifft der Reichtum auf eine totale Armut. Die Auswahl der Freunde ist
sehr klein.
Hier ist tatsächlich der Reichtum das Problem, bzw. das ökonomische
Ungleichgewicht und es gibt eine einfache Lösung, der Unterschied muss
kleiner werden, denn je kleiner der Unterschied desto mehr Auswahl an
Freunden gibt es. Wie in der “Aufgeklärten Ökonomie” dargestellt ist die
Ungleichheit, eine gesellschaftliche Entscheidung und eine konkrete
Steuerung möglich. Wir können also den Reichen helfen und mehr Freiheit
und Freunde schenken.
Pathologisch wird dieses Phänomen, wenn sich der innere Antrieb um den
Reichtum dreht. Was durch die momentane Verfasstheit der
gesellschaftlichen Praktiken sogar unterstützt und gefördert wird und
damit viele Menschen objektiv unglücklich macht. Dieses pathologische
der Gesellschaft wirkt dann auf das Individuum zurück und macht es
ebenfalls Krank. Wir haben einen ähnlichen Mechanismus in der Gewalt
kennenlernen dürfen. Vgl. “Gewalt ist eine ansteckende Krankrankheit”
<figure>
<img src="!(image)[https://cdn.satellite.earth/ac54bd400867c63f14e151172422067dc1b19980b1e738a577ae6c7a6ea835ea.png]" style="width:50.0%"
alt="Klarmachen ändert, Gier ist heilbar" />
<figcaption aria-hidden="true">Klarmachen ändert, Gier ist
heilbar</figcaption>
</figure>
> Wenn sie sich leer fühlen, Erfolg ihnen kein Glück schenkt, keine
> Befriedigung. Wenn sie mehr brauchen und mehr, dann leiden sie
> wahrscheinlich auch an einer Dysfunktion der Belohnungssysteme, an
> Habsucht.
> Auch ihnen kann und muss geholfen werden, denn Gier ist heilbar. Und
> ihrer Gier betrifft nicht nur sie. Ihre liebsten Menschen in Ihrer
> Umgebung, Menschen mit denen sie niemals direkt in Berührung kommen,
> sie alle leiden unter ihrer Krankheit.
> Auch für sie kann es ein erfülltes Leben geben, einen Weg zurück in
> die Gesellschaft, die Gesellschaft von Menschen. Machen sie
> Psychotherapie, nehmen sie Pharmaka, buchen sie eine Kur und
> entledigen sich ihres Wohlstandes.[4]
------------------------------------------------------------------------
### References:
[1] Wikipedia, SNAFU: <https://de.wikipedia.org/wiki/SNAFU>.
[2] Wilson, R.A., Der Neue Prometheus. Die Evolution unserer
Intelligenz. - Volksausgabe/ Raubdruck. 1983. Seite 245-246
[3] Wikipedia, Peter Prinzip:
<https://de.wikipedia.org/wiki/Peter-Prinzip>.
[4] InvestmentWeek, Sucht im Luxus: Eine Nacht in der Klinik der
Superreichen 2024:
<https://www.investmentweek.com/sucht-im-luxus-eine-nacht-in-der-klinik-der-superreichen/>,
„Viele Patienten hier leiden an Einsamkeit“ … “Viele Superreiche
…wüssten nicht, ob sie wegen ihres Geldes oder ihrer Persönlichkeit
gemocht werden” „Reich sein bedeutet oft, keinen echten Kontakt zu
haben. Viele unserer Klienten haben keine echten Freunde.“
-

@ 04ed2b8f:75be6756
2025-01-21 02:26:28
A warrior does not fear chaos—he thrives in it. Life is a battlefield, and disorder is the forge in which strength, strategy, and resilience are tempered. Whether in the pursuit of victory in business, relationships, or personal conquest, chaos is an inevitable adversary. But within every storm lies an opportunity—an opening to strike, to evolve, and to dominate where others falter. Only those who embrace the struggle with unwavering resolve can turn uncertainty into their greatest weapon.
### **Understanding Chaos**
Chaos is not the enemy; it is the proving ground. It manifests as upheaval, setbacks, and unexpected challenges, forcing warriors to sharpen their minds and steel their resolve.
- **Disruption Breeds Innovation:** In the heat of battle, new tactics emerge. When the known paths are obliterated, new strategies take form.
- **Mindset Is Your Strongest Weapon:** Chaos can either crush you or forge you into something stronger. The choice lies within your perception.
- **Growth Is Forged in Adversity:** The greatest warriors are those who embrace discomfort, wielding it to forge endurance and ingenuity.
### **Seizing Opportunity Amidst Chaos**
1. **Adaptability Is Strength**
- The warrior who can shift tactics swiftly gains the upper hand. Flexibility and awareness allow for swift and decisive action where others hesitate.
2. **Chaos Fuels Creativity**
- In the heat of turmoil, the boldest ideas are born. Warriors do not cling to old ways; they adapt, overcome, and conquer.
3. **Endings Are Just New Battles**
- What seems like defeat is often a call to arms for greater conquests. Every setback is a chance to regroup and strike back with renewed vigor.
### **Harnessing Chaos for Victory**
1. **Remain Steady Amid the Storm:** Fear clouds judgment; clarity is power. Observe, assess, and act with precision. Opportunities reveal themselves to those who master control over their emotions.
2. **Strike First, Strike Hard:** Do not merely react to chaos—command it. Take decisive actions that position you ahead of the pack.
3. **Exploit Weaknesses:** Where others see insurmountable problems, a warrior sees openings and opportunities to advance.
### **Lessons from the Battlefields of History**
Legends are not born in times of peace but in the crucible of chaos. From generals who turned the tide of war in moments of despair to entrepreneurs who built empires from ruin, history is a testament to those who harnessed disorder and emerged victorious.
### **Conclusion: Chaos Is the Warrior's Ally**
Chaos is not to be feared but embraced. It is the ultimate test of will and strategy. A true warrior sees beyond the disorder, crafting victory from the wreckage. In every crisis lies the seed of triumph; in every conflict, the chance to rise.
When chaos surrounds you, stand firm, sharpen your sword, and remember—opportunity belongs to those with the courage to seize it.
-

@ 6be5cc06:5259daf0
2025-01-21 01:51:46
## Bitcoin: Um sistema de dinheiro eletrônico direto entre pessoas.
Satoshi Nakamoto
satoshin@gmx.com
www.bitcoin.org
---
### Resumo
O Bitcoin é uma forma de dinheiro digital que permite pagamentos diretos entre pessoas, sem a necessidade de um banco ou instituição financeira. Ele resolve um problema chamado **gasto duplo**, que ocorre quando alguém tenta gastar o mesmo dinheiro duas vezes. Para evitar isso, o Bitcoin usa uma rede descentralizada onde todos trabalham juntos para verificar e registrar as transações.
As transações são registradas em um livro público chamado **blockchain**, protegido por uma técnica chamada **Prova de Trabalho**. Essa técnica cria uma cadeia de registros que não pode ser alterada sem refazer todo o trabalho já feito. Essa cadeia é mantida pelos computadores que participam da rede, e a mais longa é considerada a verdadeira.
Enquanto a maior parte do poder computacional da rede for controlada por participantes honestos, o sistema continuará funcionando de forma segura. A rede é flexível, permitindo que qualquer pessoa entre ou saia a qualquer momento, sempre confiando na cadeia mais longa como prova do que aconteceu.
---
### 1. Introdução
Hoje, quase todos os pagamentos feitos pela internet dependem de bancos ou empresas como processadores de pagamento (cartões de crédito, por exemplo) para funcionar. Embora esse sistema seja útil, ele tem problemas importantes porque é baseado em **confiança**.
Primeiro, essas empresas podem reverter pagamentos, o que é útil em caso de erros, mas cria custos e incertezas. Isso faz com que pequenas transações, como pagar centavos por um serviço, se tornem inviáveis. Além disso, os comerciantes são obrigados a desconfiar dos clientes, pedindo informações extras e aceitando fraudes como algo inevitável.
Esses problemas não existem no dinheiro físico, como o papel-moeda, onde o pagamento é final e direto entre as partes. No entanto, não temos como enviar dinheiro físico pela internet sem depender de um intermediário confiável.
O que precisamos é de um **sistema de pagamento eletrônico baseado em provas matemáticas**, não em confiança. Esse sistema permitiria que qualquer pessoa enviasse dinheiro diretamente para outra, sem depender de bancos ou processadores de pagamento. Além disso, as transações seriam irreversíveis, protegendo vendedores contra fraudes, mas mantendo a possibilidade de soluções para disputas legítimas.
Neste documento, apresentamos o **Bitcoin**, que resolve o problema do gasto duplo usando uma rede descentralizada. Essa rede cria um registro público e protegido por cálculos matemáticos, que garante a ordem das transações. Enquanto a maior parte da rede for controlada por pessoas honestas, o sistema será seguro contra ataques.
---
### 2. Transações
Para entender como funciona o Bitcoin, é importante saber como as transações são realizadas. Imagine que você quer transferir uma "moeda digital" para outra pessoa. No sistema do Bitcoin, essa "moeda" é representada por uma sequência de registros que mostram quem é o atual dono. Para transferi-la, você adiciona um novo registro comprovando que agora ela pertence ao próximo dono. Esse registro é protegido por um tipo especial de assinatura digital.
#### O que é uma assinatura digital?
Uma assinatura digital é como uma senha secreta, mas muito mais segura. No Bitcoin, cada usuário tem duas chaves: uma "chave privada", que é secreta e serve para criar a assinatura, e uma "chave pública", que pode ser compartilhada com todos e é usada para verificar se a assinatura é válida. Quando você transfere uma moeda, usa sua chave privada para assinar a transação, provando que você é o dono. A próxima pessoa pode usar sua chave pública para confirmar isso.
#### Como funciona na prática?
Cada "moeda" no Bitcoin é, na verdade, uma cadeia de assinaturas digitais. Vamos imaginar o seguinte cenário:
1. A moeda está com o Dono 0 (você). Para transferi-la ao Dono 1, você assina digitalmente a transação com sua chave privada. Essa assinatura inclui o código da transação anterior (chamado de "hash") e a chave pública do Dono 1.
2. Quando o Dono 1 quiser transferir a moeda ao Dono 2, ele assinará a transação seguinte com sua própria chave privada, incluindo também o hash da transação anterior e a chave pública do Dono 2.
3. Esse processo continua, formando uma "cadeia" de transações. Qualquer pessoa pode verificar essa cadeia para confirmar quem é o atual dono da moeda.
#### Resolvendo o problema do gasto duplo
Um grande desafio com moedas digitais é o "gasto duplo", que é quando uma mesma moeda é usada em mais de uma transação. Para evitar isso, muitos sistemas antigos dependiam de uma entidade central confiável, como uma casa da moeda, que verificava todas as transações. No entanto, isso criava um ponto único de falha e centralizava o controle do dinheiro.
O Bitcoin resolve esse problema de forma inovadora: ele usa uma rede descentralizada onde todos os participantes (os "nós") têm acesso a um registro completo de todas as transações. Cada nó verifica se as transações são válidas e se a moeda não foi gasta duas vezes. Quando a maioria dos nós concorda com a validade de uma transação, ela é registrada permanentemente na blockchain.
#### Por que isso é importante?
Essa solução elimina a necessidade de confiar em uma única entidade para gerenciar o dinheiro, permitindo que qualquer pessoa no mundo use o Bitcoin sem precisar de permissão de terceiros. Além disso, ela garante que o sistema seja seguro e resistente a fraudes.
---
### 3. Servidor Timestamp
Para assegurar que as transações sejam realizadas de forma segura e transparente, o sistema Bitcoin utiliza algo chamado de "servidor de registro de tempo" (timestamp). Esse servidor funciona como um registro público que organiza as transações em uma ordem específica.
Ele faz isso agrupando várias transações em blocos e criando um código único chamado "hash". Esse hash é como uma impressão digital que representa todo o conteúdo do bloco. O hash de cada bloco é amplamente divulgado, como se fosse publicado em um jornal ou em um fórum público.
Esse processo garante que cada bloco de transações tenha um registro de quando foi criado e que ele existia naquele momento. Além disso, cada novo bloco criado contém o hash do bloco anterior, formando uma cadeia contínua de blocos conectados — conhecida como blockchain.
Com isso, se alguém tentar alterar qualquer informação em um bloco anterior, o hash desse bloco mudará e não corresponderá ao hash armazenado no bloco seguinte. Essa característica torna a cadeia muito segura, pois qualquer tentativa de fraude seria imediatamente detectada.
O sistema de timestamps é essencial para provar a ordem cronológica das transações e garantir que cada uma delas seja única e autêntica. Dessa forma, ele reforça a segurança e a confiança na rede Bitcoin.
---
### 4. Prova-de-Trabalho
Para implementar o registro de tempo distribuído no sistema Bitcoin, utilizamos um mecanismo chamado prova-de-trabalho. Esse sistema é semelhante ao Hashcash, desenvolvido por Adam Back, e baseia-se na criação de um código único, o "hash", por meio de um processo computacionalmente exigente.
A prova-de-trabalho envolve encontrar um valor especial que, quando processado junto com as informações do bloco, gere um hash que comece com uma quantidade específica de zeros. Esse valor especial é chamado de "nonce". Encontrar o nonce correto exige um esforço significativo do computador, porque envolve tentativas repetidas até que a condição seja satisfeita.
Esse processo é importante porque torna extremamente difícil alterar qualquer informação registrada em um bloco. Se alguém tentar mudar algo em um bloco, seria necessário refazer o trabalho de computação não apenas para aquele bloco, mas também para todos os blocos que vêm depois dele. Isso garante a segurança e a imutabilidade da blockchain.
A prova-de-trabalho também resolve o problema de decidir qual cadeia de blocos é a válida quando há múltiplas cadeias competindo. A decisão é feita pela cadeia mais longa, pois ela representa o maior esforço computacional já realizado. Isso impede que qualquer indivíduo ou grupo controle a rede, desde que a maioria do poder de processamento seja mantida por participantes honestos.
Para garantir que o sistema permaneça eficiente e equilibrado, a dificuldade da prova-de-trabalho é ajustada automaticamente ao longo do tempo. Se novos blocos estiverem sendo gerados rapidamente, a dificuldade aumenta; se estiverem sendo gerados muito lentamente, a dificuldade diminui. Esse ajuste assegura que novos blocos sejam criados aproximadamente a cada 10 minutos, mantendo o sistema estável e funcional.
---
### 5. Rede
A rede Bitcoin é o coração do sistema e funciona de maneira distribuída, conectando vários participantes (ou nós) para garantir o registro e a validação das transações. Os passos para operar essa rede são:
1. **Transmissão de Transações**: Quando alguém realiza uma nova transação, ela é enviada para todos os nós da rede. Isso é feito para garantir que todos estejam cientes da operação e possam validá-la.
2. **Coleta de Transações em Blocos**: Cada nó agrupa as novas transações recebidas em um "bloco". Este bloco será preparado para ser adicionado à cadeia de blocos (a blockchain).
3. **Prova-de-Trabalho**: Os nós competem para resolver a prova-de-trabalho do bloco, utilizando poder computacional para encontrar um hash válido. Esse processo é como resolver um quebra-cabeça matemático difícil.
4. **Envio do Bloco Resolvido**: Quando um nó encontra a solução para o bloco (a prova-de-trabalho), ele compartilha esse bloco com todos os outros nós na rede.
5. **Validação do Bloco**: Cada nó verifica o bloco recebido para garantir que todas as transações nele contidas sejam válidas e que nenhuma moeda tenha sido gasta duas vezes. Apenas blocos válidos são aceitos.
6. **Construção do Próximo Bloco**: Os nós que aceitaram o bloco começam a trabalhar na criação do próximo bloco, utilizando o hash do bloco aceito como base (hash anterior). Isso mantém a continuidade da cadeia.
#### Resolução de Conflitos e Escolha da Cadeia Mais Longa
Os nós sempre priorizam a cadeia mais longa, pois ela representa o maior esforço computacional já realizado, garantindo maior segurança. Se dois blocos diferentes forem compartilhados simultaneamente, os nós trabalharão no primeiro bloco recebido, mas guardarão o outro como uma alternativa. Caso o segundo bloco eventualmente forme uma cadeia mais longa (ou seja, tenha mais blocos subsequentes), os nós mudarão para essa nova cadeia.
#### Tolerância a Falhas
A rede é robusta e pode lidar com mensagens que não chegam a todos os nós. Uma transação não precisa alcançar todos os nós de imediato; basta que chegue a um número suficiente deles para ser incluída em um bloco. Da mesma forma, se um nó não receber um bloco em tempo hábil, ele pode solicitá-lo ao perceber que está faltando quando o próximo bloco é recebido.
Esse mecanismo descentralizado permite que a rede Bitcoin funcione de maneira segura, confiável e resiliente, sem depender de uma autoridade central.
---
### 6. Incentivo
O incentivo é um dos pilares fundamentais que sustenta o funcionamento da rede Bitcoin, garantindo que os participantes (nós) continuem operando de forma honesta e contribuindo com recursos computacionais. Ele é estruturado em duas partes principais: a recompensa por mineração e as taxas de transação.
#### Recompensa por Mineração
Por convenção, o primeiro registro em cada bloco é uma transação especial que cria novas moedas e as atribui ao criador do bloco. Essa recompensa incentiva os mineradores a dedicarem poder computacional para apoiar a rede. Como não há uma autoridade central para emitir moedas, essa é a maneira pela qual novas moedas entram em circulação. Esse processo pode ser comparado ao trabalho de garimpeiros, que utilizam recursos para colocar mais ouro em circulação. No caso do Bitcoin, o "recurso" consiste no tempo de CPU e na energia elétrica consumida para resolver a prova-de-trabalho.
#### Taxas de Transação
Além da recompensa por mineração, os mineradores também podem ser incentivados pelas taxas de transação. Se uma transação utiliza menos valor de saída do que o valor de entrada, a diferença é tratada como uma taxa, que é adicionada à recompensa do bloco contendo essa transação. Com o passar do tempo e à medida que o número de moedas em circulação atinge o limite predeterminado, essas taxas de transação se tornam a principal fonte de incentivo, substituindo gradualmente a emissão de novas moedas. Isso permite que o sistema opere sem inflação, uma vez que o número total de moedas permanece fixo.
#### Incentivo à Honestidade
O design do incentivo também busca garantir que os participantes da rede mantenham um comportamento honesto. Para um atacante que consiga reunir mais poder computacional do que o restante da rede, ele enfrentaria duas escolhas:
1. Usar esse poder para fraudar o sistema, como reverter transações e roubar pagamentos.
2. Seguir as regras do sistema, criando novos blocos e recebendo recompensas legítimas.
A lógica econômica favorece a segunda opção, pois um comportamento desonesto prejudicaria a confiança no sistema, diminuindo o valor de todas as moedas, incluindo aquelas que o próprio atacante possui. Jogar dentro das regras não apenas maximiza o retorno financeiro, mas também preserva a validade e a integridade do sistema.
Esse mecanismo garante que os incentivos econômicos estejam alinhados com o objetivo de manter a rede segura, descentralizada e funcional ao longo do tempo.
---
### 7. Recuperação do Espaço em Disco
Depois que uma moeda passa a estar protegida por muitos blocos na cadeia, as informações sobre as transações antigas que a geraram podem ser descartadas para economizar espaço em disco. Para que isso seja possível sem comprometer a segurança, as transações são organizadas em uma estrutura chamada "árvore de Merkle". Essa árvore funciona como um resumo das transações: em vez de armazenar todas elas, guarda apenas um "hash raiz", que é como uma assinatura compacta que representa todo o grupo de transações.
Os blocos antigos podem, então, ser simplificados, removendo as partes desnecessárias dessa árvore. Apenas a raiz do hash precisa ser mantida no cabeçalho do bloco, garantindo que a integridade dos dados seja preservada, mesmo que detalhes específicos sejam descartados.
Para exemplificar: imagine que você tenha vários recibos de compra. Em vez de guardar todos os recibos, você cria um documento e lista apenas o valor total de cada um. Mesmo que os recibos originais sejam descartados, ainda é possível verificar a soma com base nos valores armazenados.
Além disso, o espaço ocupado pelos blocos em si é muito pequeno. Cada bloco sem transações ocupa apenas cerca de 80 bytes. Isso significa que, mesmo com blocos sendo gerados a cada 10 minutos, o crescimento anual em espaço necessário é insignificante: apenas 4,2 MB por ano. Com a capacidade de armazenamento dos computadores crescendo a cada ano, esse espaço continuará sendo trivial, garantindo que a rede possa operar de forma eficiente sem problemas de armazenamento, mesmo a longo prazo.
---
### 8. Verificação de Pagamento Simplificada
É possível confirmar pagamentos sem a necessidade de operar um nó completo da rede. Para isso, o usuário precisa apenas de uma cópia dos cabeçalhos dos blocos da cadeia mais longa (ou seja, a cadeia com maior esforço de trabalho acumulado). Ele pode verificar a validade de uma transação ao consultar os nós da rede até obter a confirmação de que tem a cadeia mais longa. Para isso, utiliza-se o ramo Merkle, que conecta a transação ao bloco em que ela foi registrada.
Entretanto, o método simplificado possui limitações: ele não pode confirmar uma transação isoladamente, mas sim assegurar que ela ocupa um lugar específico na cadeia mais longa. Dessa forma, se um nó da rede aprova a transação, os blocos subsequentes reforçam essa aceitação.
A verificação simplificada é confiável enquanto a maioria dos nós da rede for honesta. Contudo, ela se torna vulnerável caso a rede seja dominada por um invasor. Nesse cenário, um atacante poderia fabricar transações fraudulentas que enganariam o usuário temporariamente até que o invasor obtivesse controle completo da rede.
Uma estratégia para mitigar esse risco é configurar alertas nos softwares de nós completos. Esses alertas identificam blocos inválidos, sugerindo ao usuário baixar o bloco completo para confirmar qualquer inconsistência. Para maior segurança, empresas que realizam pagamentos frequentes podem preferir operar seus próprios nós, reduzindo riscos e permitindo uma verificação mais direta e confiável.
---
### 9. Combinando e Dividindo Valor
No sistema Bitcoin, cada unidade de valor é tratada como uma "moeda" individual, mas gerenciar cada centavo como uma transação separada seria impraticável. Para resolver isso, o Bitcoin permite que valores sejam combinados ou divididos em transações, facilitando pagamentos de qualquer valor.
#### Entradas e Saídas
Cada transação no Bitcoin é composta por:
- **Entradas**: Representam os valores recebidos em transações anteriores.
- **Saídas**: Correspondem aos valores enviados, divididos entre os destinatários e, eventualmente, o troco para o remetente.
Normalmente, uma transação contém:
- Uma única entrada com valor suficiente para cobrir o pagamento.
- Ou várias entradas combinadas para atingir o valor necessário.
O valor total das saídas nunca excede o das entradas, e a diferença (se houver) pode ser retornada ao remetente como **troco**.
#### Exemplo Prático
Imagine que você tem duas entradas:
1. 0,03 BTC
2. 0,07 BTC
Se deseja enviar 0,08 BTC para alguém, a transação terá:
- **Entrada**: As duas entradas combinadas (0,03 + 0,07 BTC = 0,10 BTC).
- **Saídas**: Uma para o destinatário (0,08 BTC) e outra como troco para você (0,02 BTC).
Essa flexibilidade permite que o sistema funcione sem precisar manipular cada unidade mínima individualmente.
#### Difusão e Simplificação
A difusão de transações, onde uma depende de várias anteriores e assim por diante, não representa um problema. Não é necessário armazenar ou verificar o histórico completo de uma transação para utilizá-la, já que o registro na blockchain garante sua integridade.
---
### 10. Privacidade
O modelo bancário tradicional oferece um certo nível de privacidade, limitando o acesso às informações financeiras apenas às partes envolvidas e a um terceiro confiável (como bancos ou instituições financeiras). No entanto, o Bitcoin opera de forma diferente, pois todas as transações são publicamente registradas na blockchain. Apesar disso, a privacidade pode ser mantida utilizando **chaves públicas anônimas**, que desvinculam diretamente as transações das identidades das partes envolvidas.
#### Fluxo de Informação
- No **modelo tradicional**, as transações passam por um terceiro confiável que conhece tanto o remetente quanto o destinatário.
- No **Bitcoin**, as transações são anunciadas publicamente, mas sem revelar diretamente as identidades das partes. Isso é comparável a dados divulgados por bolsas de valores, onde informações como o tempo e o tamanho das negociações (a "fita") são públicas, mas as identidades das partes não.
#### Protegendo a Privacidade
Para aumentar a privacidade no Bitcoin, são adotadas as seguintes práticas:
1. **Chaves Públicas Anônimas**: Cada transação utiliza um par de chaves diferentes, dificultando a associação com um proprietário único.
2. **Prevenção de Ligação**: Ao usar chaves novas para cada transação, reduz-se a possibilidade de links evidentes entre múltiplas transações realizadas pelo mesmo usuário.
#### Riscos de Ligação
Embora a privacidade seja fortalecida, alguns riscos permanecem:
- Transações **multi-entrada** podem revelar que todas as entradas pertencem ao mesmo proprietário, caso sejam necessárias para somar o valor total.
- O proprietário da chave pode ser identificado indiretamente por transações anteriores que estejam conectadas.
---
### 11. Cálculos
Imagine que temos um sistema onde as pessoas (ou computadores) competem para adicionar informações novas (blocos) a um grande registro público (a cadeia de blocos ou blockchain). Este registro é como um livro contábil compartilhado, onde todos podem verificar o que está escrito.
Agora, vamos pensar em um cenário: um atacante quer enganar o sistema. Ele quer mudar informações já registradas para beneficiar a si mesmo, por exemplo, desfazendo um pagamento que já fez. Para isso, ele precisa criar uma versão alternativa do livro contábil (a cadeia de blocos dele) e convencer todos os outros participantes de que essa versão é a verdadeira.
Mas isso é extremamente difícil.
#### Como o Ataque Funciona
Quando um novo bloco é adicionado à cadeia, ele depende de cálculos complexos que levam tempo e esforço. Esses cálculos são como um grande quebra-cabeça que precisa ser resolvido.
- Os “bons jogadores” (nós honestos) estão sempre trabalhando juntos para resolver esses quebra-cabeças e adicionar novos blocos à cadeia verdadeira.
- O atacante, por outro lado, precisa resolver quebra-cabeças sozinho, tentando “alcançar” a cadeia honesta para que sua versão alternativa pareça válida.
Se a cadeia honesta já está vários blocos à frente, o atacante começa em desvantagem, e o sistema está projetado para que a dificuldade de alcançá-los aumente rapidamente.
#### A Corrida Entre Cadeias
Você pode imaginar isso como uma corrida. A cada bloco novo que os jogadores honestos adicionam à cadeia verdadeira, eles se distanciam mais do atacante. Para vencer, o atacante teria que resolver os quebra-cabeças mais rápido que todos os outros jogadores honestos juntos.
Suponha que:
- A rede honesta tem **80% do poder computacional** (ou seja, resolve 8 de cada 10 quebra-cabeças).
- O atacante tem **20% do poder computacional** (ou seja, resolve 2 de cada 10 quebra-cabeças).
Cada vez que a rede honesta adiciona um bloco, o atacante tem que "correr atrás" e resolver mais quebra-cabeças para alcançar.
#### Por Que o Ataque Fica Cada Vez Mais Improvável?
Vamos usar uma fórmula simples para mostrar como as chances de sucesso do atacante diminuem conforme ele precisa "alcançar" mais blocos:
P = (q/p)^z
- **q** é o poder computacional do atacante (20%, ou 0,2).
- **p** é o poder computacional da rede honesta (80%, ou 0,8).
- **z** é a diferença de blocos entre a cadeia honesta e a cadeia do atacante.
Se o atacante está 5 blocos atrás (z = 5):
P = (0,2 / 0,8)^5 = (0,25)^5 = 0,00098, (ou, 0,098%)
Isso significa que o atacante tem menos de 0,1% de chance de sucesso — ou seja, é muito improvável.
Se ele estiver 10 blocos atrás (z = 10):
P = (0,2 / 0,8)^10 = (0,25)^10 = 0,000000095, (ou, 0,0000095%).
Neste caso, as chances de sucesso são praticamente **nulas**.
#### Um Exemplo Simples
Se você jogar uma moeda, a chance de cair “cara” é de 50%. Mas se precisar de 10 caras seguidas, sua chance já é bem menor. Se precisar de 20 caras seguidas, é quase impossível.
No caso do Bitcoin, o atacante precisa de muito mais do que 20 caras seguidas. Ele precisa resolver quebra-cabeças extremamente difíceis e alcançar os jogadores honestos que estão sempre à frente. Isso faz com que o ataque seja inviável na prática.
#### Por Que Tudo Isso é Seguro?
- **A probabilidade de sucesso do atacante diminui exponencialmente.** Isso significa que, quanto mais tempo passa, menor é a chance de ele conseguir enganar o sistema.
- **A cadeia verdadeira (honesta) está protegida pela força da rede.** Cada novo bloco que os jogadores honestos adicionam à cadeia torna mais difícil para o atacante alcançar.
#### E Se o Atacante Tentar Continuar?
O atacante poderia continuar tentando indefinidamente, mas ele estaria gastando muito tempo e energia sem conseguir nada. Enquanto isso, os jogadores honestos estão sempre adicionando novos blocos, tornando o trabalho do atacante ainda mais inútil.
Assim, o sistema garante que a cadeia verdadeira seja extremamente segura e que ataques sejam, na prática, impossíveis de ter sucesso.
---
### 12. Conclusão
Propusemos um sistema de transações eletrônicas que elimina a necessidade de confiança, baseando-se em assinaturas digitais e em uma rede peer-to-peer que utiliza prova de trabalho. Isso resolve o problema do gasto duplo, criando um histórico público de transações imutável, desde que a maioria do poder computacional permaneça sob controle dos participantes honestos.
A rede funciona de forma simples e descentralizada, com nós independentes que não precisam de identificação ou coordenação direta. Eles entram e saem livremente, aceitando a cadeia de prova de trabalho como registro do que ocorreu durante sua ausência. As decisões são tomadas por meio do poder de CPU, validando blocos legítimos, estendendo a cadeia e rejeitando os inválidos.
Com este mecanismo de consenso, todas as regras e incentivos necessários para o funcionamento seguro e eficiente do sistema são garantidos.
---
Faça o download do whitepaper original em português:
https://bitcoin.org/files/bitcoin-paper/bitcoin_pt_br.pdf
-

@ 3f770d65:7a745b24
2025-01-19 21:48:49
The recent shutdown of TikTok in the United States due to a potential government ban serves as a stark reminder how fragile centralized platforms truly are under the surface. While these platforms offer convenience, a more polished user experience, and connectivity, they are ultimately beholden to governments, corporations, and other authorities. This makes them vulnerable to censorship, regulation, and outright bans. In contrast, Nostr represents a shift in how we approach online communication and content sharing. Built on the principles of decentralization and user choice, Nostr cannot be banned, because it is not a platform—it is a protocol.
**PROTOCOLS, NOT PLATFORMS.**
At the heart of Nostr's philosophy is **user choice**, a feature that fundamentally sets it apart from legacy platforms. In centralized systems, the user experience is dictated by a single person or governing entity. If the platform decides to filter, censor, or ban specific users or content, individuals are left with little action to rectify the situation. They must either accept the changes or abandon the platform entirely, often at the cost of losing their social connections, their data, and their identity.
What's happening with TikTok could never happen on Nostr. With Nostr, the dynamics are completely different. Because it is a protocol, not a platform, no single entity controls the ecosystem. Instead, the protocol enables a network of applications and relays that users can freely choose from. If a particular application or relay implements policies that a user disagrees with, such as censorship, filtering, or even government enforced banning, they are not trapped or abandoned. They have the freedom to move to another application or relay with minimal effort.
**THIS IS POWERFUL.**
Take, for example, the case of a relay that decides to censor specific content. On a legacy platform, this would result in frustration and a loss of access for users. On Nostr, however, users can simply connect to a different relay that does not impose such restrictions. Similarly, if an application introduces features or policies that users dislike, they can migrate to a different application that better suits their preferences, all while retaining their identity and social connections.
The same principles apply to government bans and censorship. A government can ban a specific application or even multiple applications, just as it can block one relay or several relays. China has implemented both tactics, yet Chinese users continue to exist and actively participate on Nostr, demonstrating Nostr's ability to resistant censorship.
How? Simply, it turns into a game of whack-a-mole. When one relay is censored, another quickly takes its place. When one application is banned, another emerges. Users can also bypass these obstacles by running their own relays and applications directly from their homes or personal devices, eliminating reliance on larger entities or organizations and ensuring continuous access.
**AGAIN, THIS IS POWERUFL.**
Nostr's open and decentralized design makes it resistant to the kinds of government intervention that led to TikTok's outages this weekend and potential future ban in the next 90 days. There is no central server to target, no company to regulate, and no single point of failure. (Insert your CEO jokes here). As long as there are individuals running relays and applications, users continue creating notes and sending zaps.
Platforms like TikTok can be silenced with the stroke of a pen, leaving millions of users disconnected and abandoned. Social communication should not be silenced so incredibly easily. No one should have that much power over social interactions.
Will we on-board a massive wave of TikTokers in the coming hours or days? I don't know.
TikTokers may not be ready for Nostr yet, and honestly, Nostr may not be ready for them either. The ecosystem still lacks the completely polished applications, tools, and services they’re accustomed to. This is where we say "we're still early". They may not be early adopters like the current Nostr user base. Until we bridge that gap, they’ll likely move to the next centralized platform, only to face another government ban or round of censorship in the future. But eventually, there will come a tipping point, a moment when they’ve had enough. When that time comes, I hope we’re prepared. If we’re not, we risk missing a tremendous opportunity to onboard people who genuinely need Nostr’s freedom.
Until then, to all of the Nostr developers out there, keep up the great work and keep building. Your hard work and determination is needed.
###
-

@ 6f7db55a:985d8b25
2025-01-19 19:46:30
This article will be basic instructions for extreme normies (I say that lovingly), or anyone looking to get started with using zap.stream and sharing to nostr.
**EQUIPMENT**
Getting started is incredibly easy and your equipment needs are miniscule.
An old desktop or laptop running Linux, MacOs, or Windows made in the passed 15yrs should do. Im currently using and old Dell Latitude E5430 with an Intel i5-3210M with 32Gigs of ram and 250GB hard drive. Technically, you go as low as using a Raspberry Pi 4B+ running Owncast, but Ill save that so a future tutorial.
Let's get started.
**ON YOUR COMPUTER**
You'll need to install OBS (open broaster software). OBS is the go-to for streaming to social media. There are tons of YouTube videos on it's function. WE, however, will only be doing the basics to get us up and running.
First, go to [https://obsproject.com/](https://obsproject.com/)

Once on the OBS site, choose the correct download for you system. Linux, MacOs or Windows. Download (remember where you downloaded the file to). Go there and install your download. You may have to enter your password to install on your particular operating system. This is normal.
Once you've installed OBS, open the application. It should look something like this...

For our purposes, we will be in studio mode. Locate the 'Studio Mode' button on the right lower-hand side of the screen, and click it.

You'll see the screen split like in the image above. The left-side is from your desktop, and the right-side is what your broadcast will look like.
Next, we go to settings. The 'Settings' button is located right below the 'Studio Mode" button.

Now we're in settings and you should see something like this...

Now locate stream in the right-hand menu. It should be the second in the list. Click it.

Once in the stream section, go to 'Service' and in the right-hand drop-down, find and select 'Custom...' from the drop-down menu.

Remeber where this is because we'll need to come back to it, shortly.
**ZAPSTREAM**
We need our streamkey credentials from Zapstream. Go to [https://zap.stream](https://zap.stream). Then, go to your dashboard.

Located on the lower right-hand side is the Server URL and Stream Key. You'll need to copy/paste this in OBS.

You may have to generate new keys, if they aren't already there. This is normal. If you're interested in multi-streaming (That's where you broadcast to multiple social media platforms all at once), youll need the server URL and streamkeys from each. You'll place them in their respective forms in Zapstream's 'Stream Forwarding" section.

Use the custom form, if the platform you want to stream to isn't listed.
*Side-Note: remember that you can use your nostr identity across multiple nostr client applications. So when your login for Amethyst, as an example, could be used when you login to zapstream. Also, i would suggest using Alby's browser extension. It makes it much easier to fund your stream, as well as receive zaps.
*
**Now, BACK TO OBS...**
With Stream URL and Key in hand, paste them in the 'Stream" section of OBS' settings.
Service [Custom...]
Server [Server URL]
StreamKey [Your zapstream stream key]

After you've entered all your streaming credentials, click 'OK' at the bottom, on the right-hand side.
**WHAT'S NEXT?**
Let's setup your first stream from OBS. First we need to choose a source. Your source is your input device. It can be your webcam, your mic, your monitor, or any particular window on your screen. assuming you're an absolute beginner, we're going to use the source 'Window Capture (Xcomposite)'.

Now, open your source file. We'll use a video source called 'grannyhiphop.mp4'. In your case it can be whatever you want to stream; Just be sure to select the proper source.

Double-click on 'Window Capture' in your sources list. In the pop-up window, select your file from the 'Window' drop-down menu.


You should see something like this...

Working in the left display of OBS, we will adjust the video by left-click, hold and drag the bottom corner, so that it takes up the whole display.

In order to adjust the right-side display ( the broadcast side), we need to manipulate the video source by changing it's size.

This may take some time to adjust the size. This is normal. What I've found to help is, after every adjustment, I click the 'Fade (300ms)' button. I have no idea why it helps, but it does, lol.

Finally, after getting everything to look the way you want, you click the 'Start Stream' button.

**BACK TO ZAPSTREAM**
Now, we go back to zapstream to check to see if our stream is up. It may take a few moments to update. You may even need to refresh the page. This is normal.

STREAMS UP!!!
A few things, in closing. You'll notice that your dashbooard has changed. It'll show current stream time, how much time you have left (according to your funding source), who's zapped you with how much theyve zapped, the ability to post a note about your stream (to both nostr and twitter), and it shows your chatbox with your listeners. There are also a raid feature, stream settings (where you can title & tag your stream). You can 'topup' your funding for your stream. As well as, see your current balance.
You did a great and If you ever need more help, just use the tag #asknostr in your note. There are alway nostriches willing to help.
**STAY AWESOME!!!**
-

@ cff1720e:15c7e2b2
2025-01-19 17:48:02
**Einleitung**\
\
Schwierige Dinge einfach zu erklären ist der Anspruch von ELI5 (explain me like I'm 5). Das ist in unserer hoch technisierten Welt dringend erforderlich, denn nur mit dem Verständnis der Technologien können wir sie richtig einsetzen und weiter entwickeln.\
Ich starte meine Serie mit Nostr, einem relativ neuen Internet-Protokoll. Was zum Teufel ist ein Internet-Protokoll? Formal beschrieben sind es internationale Standards, die dafür sorgen, dass das Internet seit über 30 Jahren ziemlich gut funktioniert. Es ist die Sprache, in der sich die Rechner miteinander unterhalten und die auch Sie täglich nutzen, vermutlich ohne es bewusst wahrzunehmen. http(s) transportiert ihre Anfrage an einen Server (z.B. Amazon), und html sorgt dafür, dass aus den gelieferten Daten eine schöne Seite auf ihrem Bildschirm entsteht. Eine Mail wird mit smtp an den Mailserver gesendet und mit imap von ihm abgerufen, und da alle den Standard verwenden, funktioniert das mit jeder App auf jedem Betriebssystem und mit jedem Mail-Provider. Und mit einer Mail-Adresse wie <roland@pareto.space> können sie sogar jederzeit umziehen, egal wohin. **Cool, das ist state of the art!** Aber warum funktioniert das z.B. bei Chat nicht, gibt es da kein Protokoll? Doch, es heißt IRC (Internet Relay Chat → merken sie sich den Namen), aber es wird so gut wie nicht verwendet. Die Gründe dafür sind nicht technischer Natur, vielmehr wurden mit Apps wie Facebook, Twitter, WhatsApp, Telegram, Instagram, TikTok u.a. bewusst Inkompatibilitäten und Nutzerabhängigkeiten geschaffen um Profite zu maximieren.

**Warum Nostr?**
Da das Standard-Protokoll nicht genutzt wird, hat jede App ihr eigenes, und wir brauchen eine handvoll Apps um uns mit allen Bekannten auszutauschen. Eine Mobilfunknummer ist Voraussetzung für jedes Konto, damit können die App-Hersteller die Nutzer umfassend tracken und mit dem Verkauf der Informationen bis zu 30 USD je Konto und Monat verdienen. Der Nutzer ist nicht mehr Kunde, er ist das Produkt! Der Werbe-SPAM ist noch das kleinste Problem bei diesem Geschäftsmodell. Server mit Millionen von Nutzerdaten sind ein “honey pot”, dementsprechend oft werden sie gehackt und die Zugangsdaten verkauft. 2024 wurde auch der Twitter-Account vom damaligen Präsidenten Joe Biden gehackt, niemand wusste mehr wer die Nachrichten verfasst hat (vorher auch nicht), d.h. die Authentizität der Inhalte ist bei keinem dieser Anbieter gewährleistet. Im selben Jahr wurde der Telegram-Gründer in Frankreich in Beugehaft genommen, weil er sich geweigert hatte Hintertüren in seine Software einzubauen. Nun kann zum Schutz **"unserer Demokratie”** praktisch jeder mitlesen, was sie mit wem an Informationen austauschen, z.B. darüber welches Shampoo bestimmte Politiker verwenden.

Und wer tatsächlich glaubt er könne Meinungsfreiheit auf sozialen Medien praktizieren, findet sich schnell in der Situation von Donald Trump wieder (seinerzeit amtierender Präsident), dem sein Twitter-Konto 2021 abgeschaltet wurde (Cancel-Culture). Die Nutzerdaten, also ihr Profil, ihre Kontakte, Dokumente, Bilder, Videos und Audiofiles - gehören ihnen ohnehin nicht mehr sondern sind Eigentum des Plattform-Betreibers; lesen sie sich mal die AGB's durch. Aber nein, keine gute Idee, das sind hunderte Seiten und sie werden permanent geändert. Alle nutzen also Apps, deren Technik sie nicht verstehen, deren Regeln sie nicht kennen, wo sie keine Rechte haben und die ihnen die Resultate ihres Handelns stehlen. Was würde wohl der Fünfjährige sagen, wenn ihm seine ältere Schwester anbieten würde, alle seine Spielzeuge zu “verwalten” und dann auszuhändigen wenn er brav ist? “Du spinnst wohl”, und damit beweist der Knirps mehr Vernunft als die Mehrzahl der Erwachsenen. \
\
**Resümee:** keine Standards, keine Daten, keine Rechte = keine Zukunft!

\
**Wie funktioniert Nostr?**
Die Entwickler von Nostr haben erkannt dass sich das Server-Client-Konzept in ein Master-Slave-Konzept verwandelt hatte. Der Master ist ein Synonym für Zentralisierung und wird zum **“single point of failure”**, der zwangsläufig Systeme dysfunktional macht. In einem verteilten Peer2Peer-System gibt es keine Master mehr sondern nur gleichberechtigte Knoten (Relays), auf denen die Informationen gespeichert werden. Indem man Informationen auf mehreren Relays redundant speichert, ist das System in jeglicher Hinsicht resilienter. Nicht nur die Natur verwendet dieses Prinzip seit Jahrmillionen erfolgreich, auch das Internet wurde so konzipiert (das ARPAnet wurde vom US-Militär für den Einsatz in Kriegsfällen unter massiven Störungen entwickelt). Alle Nostr-Daten liegen auf Relays und der Nutzer kann wählen zwischen öffentlichen (zumeist kostenlosen) und privaten Relays, z.B. für geschlossene Gruppen oder zum Zwecke von Daten-Archivierung. Da Dokumente auf mehreren Relays gespeichert sind, werden statt URL's (Locator) eindeutige Dokumentnamen (URI's = Identifier) verwendet, broken Links sind damit Vergangenheit und Löschungen / Verluste ebenfalls.\
\
Jedes Dokument (Event genannt) wird vom Besitzer signiert, es ist damit authentisch und fälschungssicher und kann nur vom Ersteller gelöscht werden. Dafür wird ein Schlüsselpaar verwendet bestehend aus privatem (nsec) und öffentlichem Schlüssel (npub) wie aus der Mailverschlüsselung (PGP) bekannt. Das repräsentiert eine Nostr-Identität, die um Bild, Namen, Bio und eine lesbare Nostr-Adresse ergänzt werden kann (z.B. <roland@pareto.space> ), mehr braucht es nicht um alle Ressourcen des Nostr-Ökosystems zu nutzen. Und das besteht inzwischen aus über hundert Apps mit unterschiedlichen Fokussierungen, z.B. für persönliche verschlüsselte Nachrichten (DM → OxChat), Kurznachrichten (Damus, Primal), Blogbeiträge (Pareto), Meetups (Joinstr), Gruppen (Groups), Bilder (Olas), Videos (Amethyst), Audio-Chat (Nostr Nests), Audio-Streams (Tunestr), Video-Streams (Zap.Stream), Marktplätze (Shopstr) u.v.a.m. Die Anmeldung erfolgt mit einem Klick (single sign on) und den Apps stehen ALLE Nutzerdaten zur Verfügung (Profil, Daten, Kontakte, Social Graph → Follower, Bookmarks, Comments, etc.), im Gegensatz zu den fragmentierten Datensilos der Gegenwart.\
\
**Resümee:** ein offener Standard, alle Daten, alle Rechte = große Zukunft!

\
**Warum ist Nostr die Zukunft des Internet?**
“Baue Dein Haus nicht auf einem fremden Grundstück” gilt auch im Internet - für alle App-Entwickler, Künstler, Journalisten und Nutzer, denn auch ihre Daten sind werthaltig. Nostr garantiert das Eigentum an den Daten, und überwindet ihre Fragmentierung. Weder die Nutzung noch die kreativen Freiheiten werden durch maßlose Lizenz- und Nutzungsbedingungen eingeschränkt. Aus passiven Nutzern werden durch Interaktion aktive Teilnehmer, Co-Creatoren in einer Sharing-Ökonomie **(Value4Value)**. OpenSource schafft endlich wieder Vertrauen in die Software und ihre Anbieter. Offene Standards ermöglichen den Entwicklern mehr Kooperation und schnellere Entwicklung, für die Anwender garantieren sie Wahlfreiheit. Womit wir letztmalig zu unserem Fünfjährigen zurückkehren. Kinder lieben Lego über alles, am meisten die Maxi-Box “Classic”, weil sie damit ihre Phantasie im Kombinieren voll ausleben können. Erwachsene schenken ihnen dann die viel zu teuren Themenpakete, mit denen man nur eine Lösung nach Anleitung bauen kann. “Was stimmt nur mit meinen Eltern nicht, wann sind die denn falsch abgebogen?" fragt sich der Nachwuchs zu Recht. Das Image lässt sich aber wieder aufpolieren, wenn sie ihren Kindern Nostr zeigen, denn die Vorteile verstehen sogar Fünfjährige.

\
**Das neue Internet ist dezentral. Das neue Internet ist selbstbestimmt. Nostr ist das neue Internet.**
<https://nostr.net/> \
<https://start.njump.me/>
**Hier das Interview zum Thema mit Radio Berliner Morgenröte**
<https://www.podbean.com/ew/pb-yxc36-17bb4be>
-

@ fd208ee8:0fd927c1
2025-01-19 12:10:10
I am so tired of people trying to waste my time with Nostrized imitations of stuff that already exists.
Instagram, but make it Nostr.
Twitter, but make it Nostr.
GitHub, but make it Nostr.
Facebook, but make it Nostr.
Wordpress, but make it Nostr.
GoodReads, but make it Nostr.
TikTok, but make it Nostr.
That stuff already exists, and it wasn't that great the first time around, either. Build something better than that stuff, that can only be brought into existence because of Nostr.
Build something that does something completely and awesomely new. Knock my socks off, bro.
Cuz, ain't nobody got time for that.
-

@ 378562cd:a6fc6773
2025-01-18 16:20:12
As a frequent user who depends on my phone for a wide range of activities, including boosting my productivity and capturing spontaneous moments, I have been paying close attention to the OnePlus 13. This flagship device appears to meet all my essential requirements, particularly excelling in power and camera capabilities, which are my main priorities. Here are the standout features that have caught my attention.
<img src="https://blossom.primal.net/9d0b0d98e9ac02d756f31ab0b46f3e0e79b98aa0576d0e71847bba4fcf5ee2e3.webp">
### Power to Handle Anything I Throw at It
Performance is a big deal for me, and the OnePlus 13 doesn’t seem to disappoint. It’s powered by the Snapdragon 8 Elite processor, a beast in the mobile tech world. I can already imagine how smoothly it would handle heavy multitasking, like switching between editing photos, running multiple apps, and even gaming.
The insane memory options—up to 24GB of RAM—truly stand out. That’s more RAM than most laptops I’ve owned! Pair that with up to 1TB of storage, and you’re looking at a future-proof phone. I’d never have to worry about running out of space for apps, photos, or videos, and everything would load lightning-fast.
###
<img src="https://blossom.primal.net/6f9363e8e4a9663346e5fdaf41b25b611dcf1324a85799bdefa1f90f980fc02d.jpg">
### A Camera Setup That’s Hard to Ignore
One of my favorite things to do is capture high-quality photos and videos, so a powerful camera system is non-negotiable. The OnePlus 13 delivers with its triple-camera setup; all three lenses are 50 megapixels. That means whether I’m shooting with the main wide lens, zooming in with the telephoto, or going wide with the ultra-wide, I’m getting consistently sharp, detailed shots.
The Hasselblad collaboration is a big draw for me, too. OnePlus phones have been steadily improving their color science, and this partnership seems to really shine in the OnePlus 13. I’d expect vibrant, true-to-life colors in my photos without much editing required.
The AI enhancements also pique my interest. From what I’ve read, the phone handles tricky lighting situations, like low-light environments or high-contrast scenes, exceptionally well. That’s exactly what I need to capture spontaneous moments without worrying about settings.
### Battery and Charging That Won’t Leave Me Hanging
Another thing I appreciate is the long battery life. The 6,000 mAh battery on the OnePlus 13 is reportedly a powerhouse, capable of lasting two days under mixed usage. And when I do need to charge, the 100W wired charging can fully juice up the phone in just over half an hour. Even the 50W wireless charging is incredibly fast, which is perfect for someone like me who’s always on the move.
### Design and Features That Add Value
The flat-edge design and premium finish make the phone feel as good as it looks. I’d probably go for the Midnight Ocean with its vegan leather back—it sounds grippy and unique, ideal for someone who doesn’t want to slap on a bulky case.
The little extras, like Glove Mode and Aqua Touch 2.0, also catch my attention. Since winters are cold here, using my phone with gloves on is a practical bonus.
### Why It’s Tempting Me
At $899 for the base model, the OnePlus 13 seems like a solid deal, especially for the power and camera capabilities it offers. Even if I choose a higher configuration, the pricing still feels reasonable compared to other flagships with similar specs.
For me, the OnePlus 13 feels like a phone that’s built for power users—people who need speed, reliability, and top-tier camera performance. I’m seriously considering it for my next upgrade because it feels like it would keep up with everything I do and then some. If the camera and performance live up to the hype, I might just have my decision made.
-

@ a10260a2:caa23e3e
2025-01-18 12:04:41
*Last Updated: January 18, 2025*
First off, big shoutout to Coinos for having support for adding a memo to BOLT12 offers. This provides a solid alternative for the pleb who wants to support mining decentralization but doesn’t want to set up a CLN node and pay thousands of sats for a channel only to get little rewards. This is the case for most of us who only have a miner or two (e.g. a Bitaxe and/or an S9).
Before we get into setting up Lightning payouts, you’ll want to have your miner configured to mine with OCEAN of course. You’ll also want to make sure that the bitcoin address you use is from a wallet that supports signing messages.
These are the ones listed in the OCEAN [docs](https://ocean.xyz/docs/lightning):
* Bitcoin Knots/Bitcoin Core
* Coldcard
* Electrum
* LND (Command Line)
* Seedsigner
* Sparrow
* Specter
* Trezor
I checked one of my favorite, user-friendly wallets — Blue Wallet — and it happens to support signing messages as well.
Just tap the three dots on the upper right and you’ll see the “Sign/Verify Message” button at the bottom.
Update [January 18]: You can now use Coinos to sign by going to https://coinos.io/sign
The trick here is to not refresh the page. In other words, when you're logged in to your Coinos account, go to the URL and use the legacy address (starts with a "1") that's displayed to configure your miner(s). If you refresh the page, you're going to get a new address which will cause the signing to fail later on. *Remember*, keep the tab open and don't refresh the page.

Whichever wallet you choose, generate a receive address to use when configuring your miner (it’ll also be your OCEAN username).
Here’s how it looks on the Bitaxe (AxeOS)…
And the Antminer S9 (Braiins OS).
NOTE: There’s a slight difference in the URL format between the two apps. Other than that, the username will be your bitcoin address followed by the optional “.” + the nickname for your machine.
You can find more details on OCEAN’s [get started page](https://ocean.xyz/getstarted).
---
Alright, now that your miner is pointed at OCEAN. Let’s configure Lightning payouts!
### Generating the BOLT12 Offer
In the Coinos app, go to Receive > Bolt 12.
Tap “Set memo” and set it to “OCEAN Payouts for [insert your bitcoin address]” (this text is case-sensitive). Use the same bitcoin address you used above to configure your miner(s).
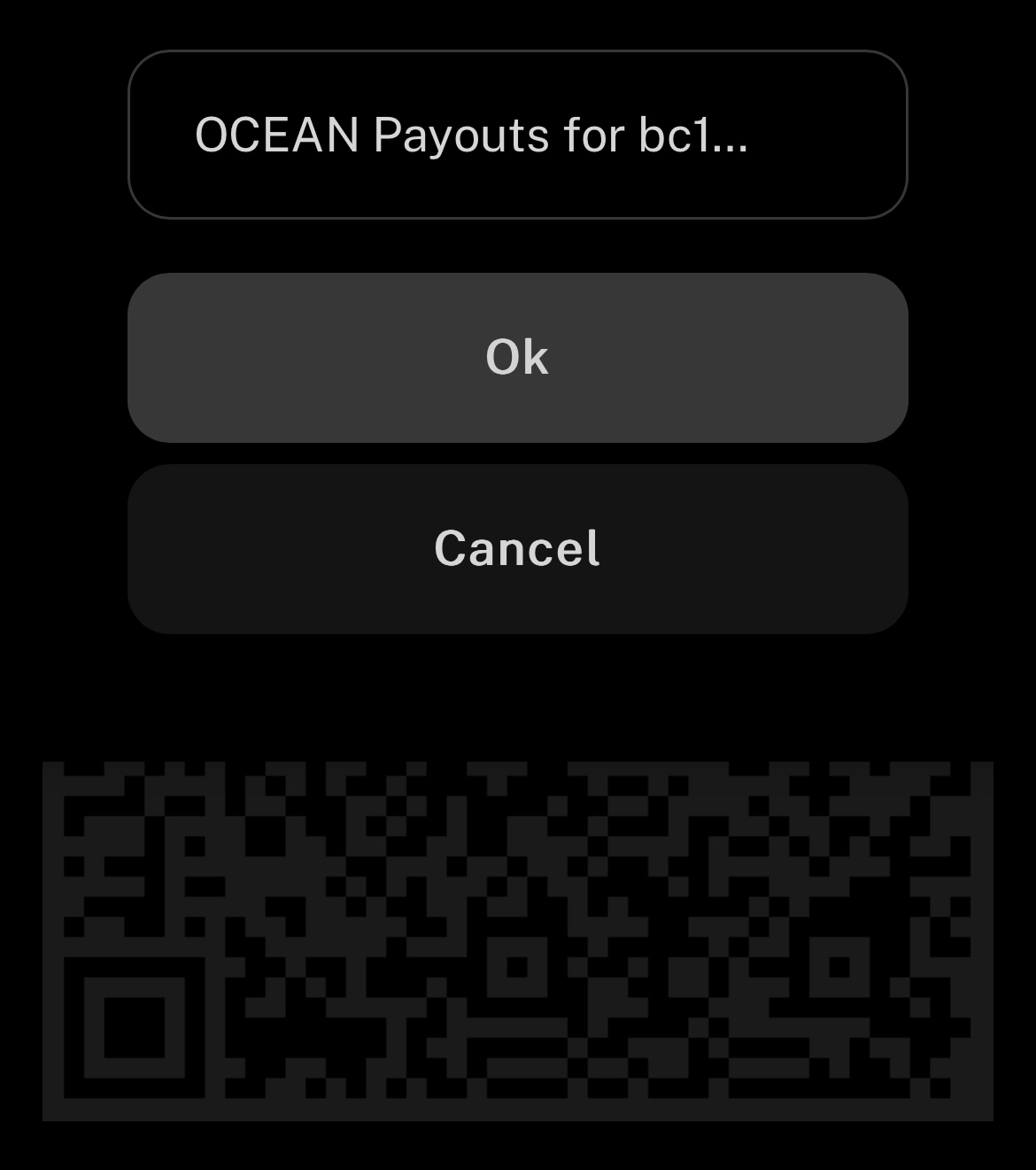
After tapping OK, copy the BOLT12 offer (it should start with “lno”) and proceed to the next step.
### Generating the Configuration Message
Navigate to the [My Stats](https://ocean.xyz/stats) page by searching for your OCEAN Bitcoin address.
The click the Configuration link next to Next Block to access the configuration form.
Paste the BOLT12 offer here, update the block height to latest, click GENERATE, and copy the generated unsigned message.
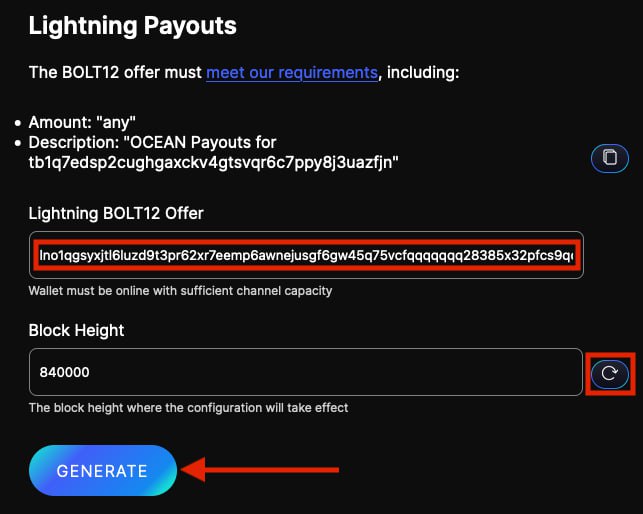
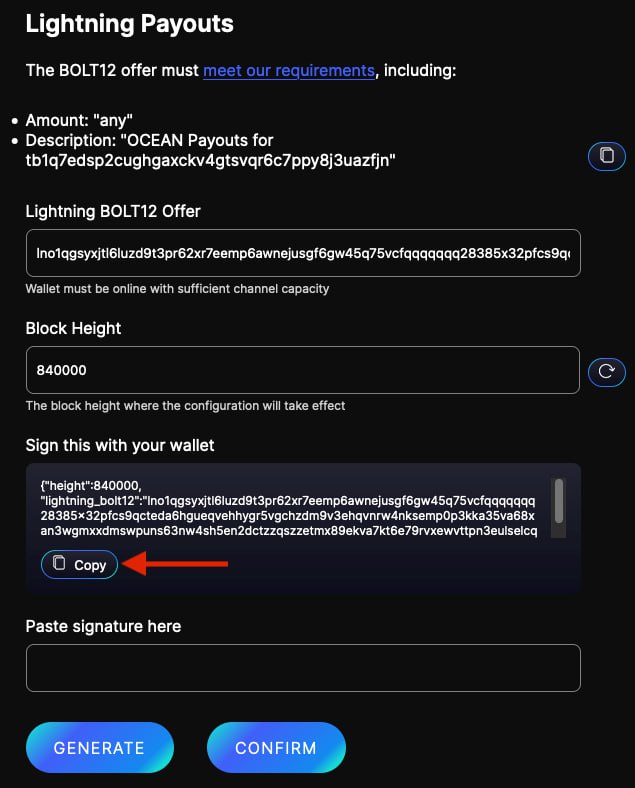
### Signing the Configuration Message
To sign the generated message, go back to Blue Wallet and use the signing function. Paste the configuration message in the Message field, tap Sign, and copy the signed message that’s generated.
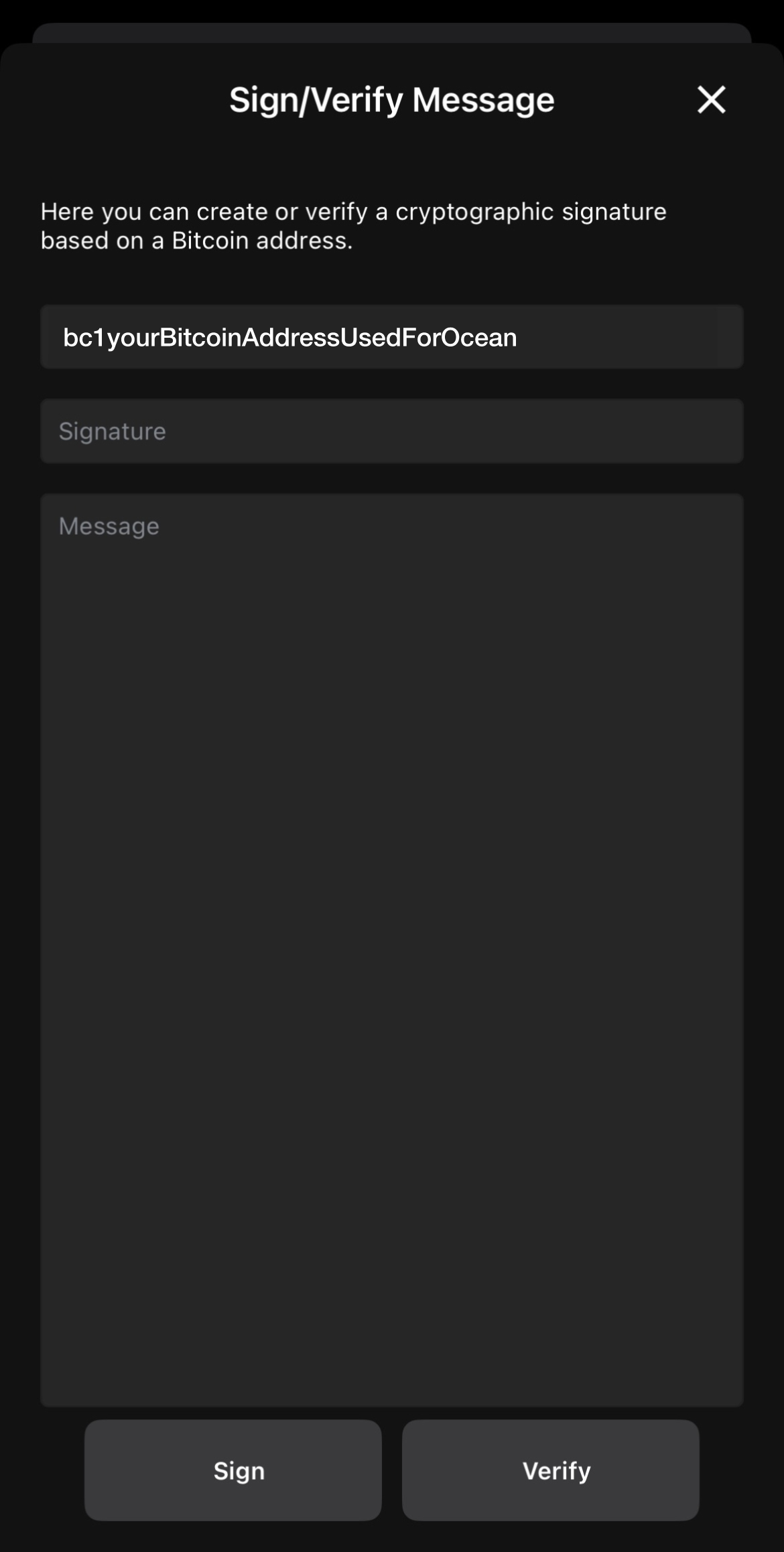
If you're using Coinos to sign, return to the page that you kept open (and didn't refresh) and do the same. Paste the configuration message, click submit, and copy the signed message.
### Submitting the Signed Message
Once signed, copy the signature, paste it in the OCEAN configuration form, and click CONFIRM.
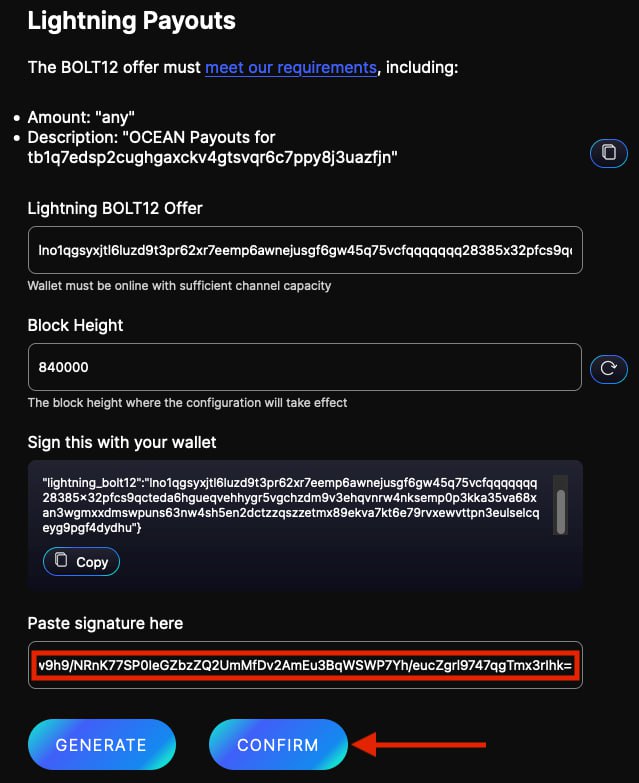
If all goes well, you should see a confirmation that the configuration was successful. Congrats! 🎉
All you gotta do now is sit back, relax, and wait for a block to be found…
Or you can look into setting up [DATUM](https://ocean.xyz/docs/datum-setup). 😎
-

@ c631e267:c2b78d3e
2025-01-18 09:34:51
*Die grauenvollste Aussicht ist die der Technokratie –* *\
einer kontrollierenden Herrschaft,* *\
die durch verstümmelte und verstümmelnde Geister ausgeübt wird.* *\
Ernst Jünger*  
**«Davos ist nicht mehr sexy»,** das Weltwirtschaftsforum ([WEF](https://transition-news.org/wef-world-economic-forum)) mache Davos [kaputt](https://web.archive.org/web/20250116114956/https://www.handelszeitung.ch/wef-2025/wie-das-wef-davos-kaputt-macht-785098), diese Aussagen eines Einheimischen las ich kürzlich in der *Handelszeitung*. Während sich einige vor Ort enorm an der «teuersten Gewerbeausstellung der Welt» bereicherten, würden die negativen Begleiterscheinungen wie Wohnungsnot und Niedergang der lokalen Wirtschaft immer deutlicher.
**Nächsten Montag beginnt in dem Schweizer Bergdorf erneut ein Jahrestreffen** dieses elitären Clubs der Konzerne, bei dem man mit hochrangigen Politikern aus aller Welt und ausgewählten Vertretern der Systemmedien zusammenhocken wird. Wie bereits in den [vergangenen](https://transition-news.org/die-angst-der-eliten-vor-dem-pobel) vier Jahren wird die Präsidentin der EU-Kommission, Ursula von der Leyen, in Begleitung von Klaus Schwab ihre Grundsatzansprache halten.
**Der deutsche WEF-Gründer hatte bei dieser Gelegenheit** immer höchst lobende Worte für seine Landsmännin: [2021](https://www.weforum.org/meetings/the-davos-agenda-2021/sessions/special-address-by-g20-head-of-state-government/) erklärte er sich «stolz, dass Europa wieder unter Ihrer Führung steht» und [2022](https://www.weforum.org/meetings/the-davos-agenda-2022/sessions/special-address-by-ursula-von-der-leyen-president-of-the-european-commission-177737c164/) fand er es bemerkenswert, was sie erreicht habe angesichts des «erstaunlichen Wandels», den die Welt in den vorangegangenen zwei Jahren erlebt habe; es gebe nun einen «neuen europäischen Geist».
**Von der Leyens Handeln während der sogenannten Corona-«Pandemie»** lobte Schwab damals bereits ebenso, wie es diese Woche das [Karlspreis](https://transition-news.org/von-der-leyen-erhalt-karlspreis-albert-bourla-erklart-pfizer-habe-wahrend-der)-Direktorium tat, als man der Beschuldigten im Fall [Pfizergate](https://transition-news.org/pfizergate-startet-ins-neue-jahr) die diesjährige internationale Auszeichnung «für Verdienste um die europäische Einigung» verlieh. Außerdem habe sie die EU nicht nur gegen den «Aggressor Russland», sondern auch gegen die «innere Bedrohung durch Rassisten und Demagogen» sowie gegen den Klimawandel verteidigt.
**Jene Herausforderungen durch «Krisen epochalen Ausmaßes»** werden indes aus dem Umfeld des WEF nicht nur herbeigeredet – wie man alljährlich zur Zeit des Davoser Treffens im [Global Risks Report](https://www.zurich.com/knowledge/topics/global-risks/the-global-risks-report-2025) nachlesen kann, der zusammen mit dem Versicherungskonzern Zurich erstellt wird. Seit die Globalisten 2020/21 in der Praxis gesehen haben, wie gut eine konzertierte und konsequente Angst-Kampagne funktionieren kann, geht es Schlag auf Schlag. Sie setzen alles daran, Schwabs goldenes Zeitfenster des «Great Reset» zu nutzen.
**Ziel dieses «großen Umbruchs» ist die totale Kontrolle der Technokraten über die Menschen** unter dem Deckmantel einer globalen Gesundheitsfürsorge. Wie aber könnte man so etwas erreichen? Ein Mittel dazu ist die «kreative Zerstörung». Weitere unabdingbare Werkzeug sind die Einbindung, ja Gleichschaltung der Medien und der Justiz.
**Ein** **[«Great Mental Reset»](https://transition-news.org/angriff-auf-unser-gehirn-michael-nehls-uber-den-great-mental-reset-teil-1)** **sei die Voraussetzung dafür,** dass ein Großteil der Menschen Einschränkungen und Manipulationen wie durch die Corona-Maßnahmen praktisch kritik- und widerstandslos hinnehme, sagt der Mediziner und Molekulargenetiker Michael Nehls. Er meint damit eine regelrechte Umprogrammierung des Gehirns, wodurch nach und nach unsere Individualität und unser soziales Bewusstsein eliminiert und durch unreflektierten Konformismus ersetzt werden.
**Der aktuelle Zustand unserer Gesellschaften** ist auch für den Schweizer Rechtsanwalt Philipp Kruse alarmierend. Durch den Umgang mit der «Pandemie» sieht er die Grundlagen von Recht und Vernunft erschüttert, die [Rechtsstaatlichkeit](https://transition-news.org/schweizer-rechtsstaat-in-der-krise-ein-anwalt-schlagt-alarm) stehe auf dem Prüfstand. Seiner dringenden Mahnung an alle Bürger, die Prinzipien von Recht und Freiheit zu verteidigen, kann ich mich nur anschließen.
***
Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/davos-europa-und-der-rest-der-welt)*** erschienen.
-

@ f9cf4e94:96abc355
2025-01-18 06:09:50
Para esse exemplo iremos usar:
| Nome | Imagem | Descrição |
| --------------- | ------------------------------------------------------------ | ------------------------------------------------------------ |
| Raspberry PI B+ |  | **Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2,** |
| Pen drive |  | **16Gb** |
Recomendo que use o **Ubuntu Server** para essa instalação. Você pode baixar o Ubuntu para Raspberry Pi [aqui]( https://ubuntu.com/download/raspberry-pi). O passo a passo para a instalação do Ubuntu no Raspberry Pi está disponível [aqui]( https://ubuntu.com/tutorials/how-to-install-ubuntu-on-your-raspberry-pi). **Não instale um desktop** (como xubuntu, lubuntu, xfce, etc.).
---
## Passo 1: Atualizar o Sistema 🖥️
Primeiro, atualize seu sistema e instale o Tor:
```bash
apt update
apt install tor
```
---
## Passo 2: Criar o Arquivo de Serviço `nrs.service` 🔧
Crie o arquivo de serviço que vai gerenciar o servidor Nostr. Você pode fazer isso com o seguinte conteúdo:
```unit
[Unit]
Description=Nostr Relay Server Service
After=network.target
[Service]
Type=simple
WorkingDirectory=/opt/nrs
ExecStart=/opt/nrs/nrs-arm64
Restart=on-failure
[Install]
WantedBy=multi-user.target
```
---
## Passo 3: Baixar o Binário do Nostr 🚀
Baixe o binário mais recente do Nostr [aqui no GitHub]( https://github.com/gabrielmoura/SimpleNosrtRelay/releases).
---
## Passo 4: Criar as Pastas Necessárias 📂
Agora, crie as pastas para o aplicativo e o pendrive:
```bash
mkdir -p /opt/nrs /mnt/edriver
```
---
## Passo 5: Listar os Dispositivos Conectados 🔌
Para saber qual dispositivo você vai usar, liste todos os dispositivos conectados:
```bash
lsblk
```
---
## Passo 6: Formatando o Pendrive 💾
Escolha o pendrive correto (por exemplo, `/dev/sda`) e formate-o:
```bash
mkfs.vfat /dev/sda
```
---
## Passo 7: Montar o Pendrive 💻
Monte o pendrive na pasta `/mnt/edriver`:
```bash
mount /dev/sda /mnt/edriver
```
---
## Passo 8: Verificar UUID dos Dispositivos 📋
Para garantir que o sistema monte o pendrive automaticamente, liste os UUID dos dispositivos conectados:
```bash
blkid
```
---
## Passo 9: Alterar o `fstab` para Montar o Pendrive Automáticamente 📝
Abra o arquivo `/etc/fstab` e adicione uma linha para o pendrive, com o UUID que você obteve no passo anterior. A linha deve ficar assim:
```fstab
UUID=9c9008f8-f852 /mnt/edriver vfat defaults 0 0
```
---
## Passo 10: Copiar o Binário para a Pasta Correta 📥
Agora, copie o binário baixado para a pasta `/opt/nrs`:
```bash
cp nrs-arm64 /opt/nrs
```
---
## Passo 11: Criar o Arquivo de Configuração 🛠️
Crie o arquivo de configuração com o seguinte conteúdo e salve-o em `/opt/nrs/config.yaml`:
```yaml
app_env: production
info:
name: Nostr Relay Server
description: Nostr Relay Server
pub_key: ""
contact: ""
url: http://localhost:3334
icon: https://external-content.duckduckgo.com/iu/?u= https://public.bnbstatic.com/image/cms/crawler/COINCU_NEWS/image-495-1024x569.png
base_path: /mnt/edriver
negentropy: true
```
---
## Passo 12: Copiar o Serviço para o Diretório de Systemd ⚙️
Agora, copie o arquivo `nrs.service` para o diretório `/etc/systemd/system/`:
```bash
cp nrs.service /etc/systemd/system/
```
Recarregue os serviços e inicie o serviço `nrs`:
```bash
systemctl daemon-reload
systemctl enable --now nrs.service
```
---
## Passo 13: Configurar o Tor 🌐
Abra o arquivo de configuração do Tor `/var/lib/tor/torrc` e adicione a seguinte linha:
```torrc
HiddenServiceDir /var/lib/tor/nostr_server/
HiddenServicePort 80 127.0.0.1:3334
```
---
## Passo 14: Habilitar e Iniciar o Tor 🧅
Agora, ative e inicie o serviço Tor:
```bash
systemctl enable --now tor.service
```
O Tor irá gerar um endereço `.onion` para o seu servidor Nostr. Você pode encontrá-lo no arquivo `/var/lib/tor/nostr_server/hostname`.
---
## Observações ⚠️
- Com essa configuração, **os dados serão salvos no pendrive**, enquanto o binário ficará no cartão SD do Raspberry Pi.
- O endereço `.onion` do seu servidor Nostr será algo como: `ws://y3t5t5wgwjif<exemplo>h42zy7ih6iwbyd.onion`.
---
Agora, seu servidor Nostr deve estar configurado e funcionando com Tor! 🥳
Se este artigo e as informações aqui contidas forem úteis para você, convidamos a considerar uma doação ao autor como forma de reconhecimento e incentivo à produção de novos conteúdos.
-

@ 378562cd:a6fc6773
2025-01-18 00:12:47
In the ever-changing world of decentralized networks, **Nostr** (Notes and Other Stuff Transmitted by Relays) is leading the charge. Its lightweight, open design has created an ecosystem that’s as adaptable as it is revolutionary. Whether you're chatting, publishing, or experimenting with new ways to connect, Nostr provides the foundation for a truly decentralized and censorship-resistant internet.
---
### **How Nostr Works: A Quick Overview**
At its heart, Nostr is built on simplicity and decentralization. Here’s a breakdown of its core components:
1. **Public and Private Keys**:\
Your public key acts as your identity, and private keys ensure your messages are securely signed.
2. **Relays**:\
Relays are decentralized servers that distribute messages. They don’t own your data but simply pass it along to those who request it.
3. **Clients**:\
Clients are the user-facing applications where you interact with Nostr, offering diverse features and designs.
---
### **Deep Dive: Events in Nostr**
Everything on Nostr revolves around **events**, which are cryptographically signed pieces of information containing various kinds of data. Here are the types of events currently supported and their use cases:
#### **1. Note Events (Type 1)**
- **What They Are**:\
These are the bread and butter of Nostr—text-based posts, much like tweets or status updates on traditional platforms.
- **Features**:
- Can include text, media links, and hashtags.
- Interact with others through likes, replies, and boosts (reposts).
- **Use Cases**:\
Perfect for microblogging, status updates, and general social interaction.
#### **2. Profile Metadata Events (Type 0)**
- **What They Are**:\
This event type stores and updates user profile information, such as your display name, bio, profile picture, and website.
- **Features**:
- Easily editable and updated across all Nostr clients.
- Keeps your identity consistent across platforms.
- **Use Cases**:\
Makes profile portability seamless—update once, and it reflects everywhere.
#### **3. Relay List Events (Type 2)**
- **What They Are**:\
These events store a list of relays that a user is connected to or prefers to use.
- **Features**:
- Share your relay preferences across devices or clients.
- Allows automatic relay connection in supported clients.
- **Use Cases**:\
Simplifies the onboarding process for users switching clients or devices.
#### **4. Direct Message Events (Type 4)**
- **What They Are**:\
End-to-end encrypted messages sent directly between two users.
- **Features**:
- Only readable by the intended recipient.
- Supports text and basic formatting.
- **Use Cases**:\
Secure communication for personal or professional purposes.
#### **5. Reaction Events (Type 7)**
- **What They Are**:\
Events that express reactions to other events, such as likes or emojis.
- **Features**:
- Provides social feedback (e.g., showing appreciation for a post).
- Lightweight and simple to implement.
- **Use Cases**:\
Enhances engagement and interaction within the network.
#### **6. Repost Events (Type 6)**
- **What They Are**:\
Events that allow users to reshare content, similar to retweets on Twitter.
- **Features**:
- Ensures the original poster retains credit.
- Enables broader content visibility.
- **Use Cases**:\
Amplifying content that resonates with users or is worth sharing.
#### **7. Custom Event Types (Beyond Type 7)**
- **What They Are**:\
Developers can create and define custom event types for specific applications.
- **Features**:
- Flexibility to introduce entirely new functionality.
- Supported based on client and relay compatibility.
- **Use Cases**:\
Enables innovation, from collaborative editing tools to advanced publishing workflows.
---
### **What Makes Events Special?**
1. **Portability**: Events follow your public key, not the client or relay, ensuring they’re available wherever you go.
2. **Interoperability**: All events are standardized, meaning any Nostr client can understand and process them.
3. **Extensibility**: Through custom event types, the protocol encourages experimentation and development.
---
### **Primal: A Favorite Client for Engaging Events**
Among the many clients, **Primal** stands out as a favorite for how it handles Nostr events. Its emphasis on **content discovery** and **rich user interaction** makes it an excellent choice for exploring everything the protocol offers. Whether it’s crafting note events, managing profile metadata, or diving into direct messaging, Primal delivers a polished experience that feels seamless.
---
### **The Future of Nostr Events**
As Nostr continues to evolve, so will the events it supports. Imagine event types for live streaming, collaborative workspaces, or even decentralized governance. The possibilities are limitless, driven by the creativity of the developers and the needs of the community.
**Have you explored the potential of Nostr events yet? What’s your favorite client or feature? Let’s discuss below!** ⚡️
#Nostr #Primal #Decentralization #NostrEvents #FutureOfWeb
-

@ 5bdb0e24:0ccbebd7
2025-01-17 06:19:58
In the world of networking, two fundamental models serve as the backbone for communication protocols and standards: the OSI model and the TCP/IP model. Both models are quite similar, providing frameworks for how data is transmitted across networks at various stages of the process.
Understanding these models is crucial for anyone working in IT, cybersecurity, or any related tech field. But what exactly are they?
# The OSI Model
The OSI (Open Systems Interconnection) model is a conceptual framework that standardizes the functions of a telecommunication or computing system into seven distinct layers. Each layer is responsible for specific tasks, such as data encapsulation, error detection, and routing. The layers of the OSI model are as follows:
1. **Physical Layer:** This layer deals with the physical connection between devices, such as cables and network interfaces.
2. **Data Link Layer:** Responsible for node-to-node communication, this layer ensures data integrity and manages access to the physical medium.
3. **Network Layer:** The network layer handles routing and forwarding of data packets between different networks.
4. **Transport Layer:** This layer provides end-to-end communication services for applications, including error detection and flow control.
5. **Session Layer:** Manages sessions between applications, establishing, maintaining, and terminating connections.
6. **Presentation Layer:** Responsible for data translation, encryption, and compression to ensure compatibility between different systems.
7. **Application Layer:** The topmost layer that interacts directly with applications and end-users, providing network services such as email and file transfer.
Now, that's a lot to remember. So, an easy acronym you can use to remember these 7 layers is *"Please Do Not Touch Steve's Pet Alligator."* It's helped me quite a bit in trying to pinpoint a specific layer.
Also, keep in mind that the layers are typically inverted from what you see above, with Layer 7 being at the top of the stack and Layer 1 being at the bottom.
# The TCP/IP Model
On the other hand, the TCP/IP (Transmission Control Protocol/Internet Protocol) model is a more streamlined approach to networking, consisting of only four layers:
1. **Link Layer:** Corresponding to the OSI model's data link and physical layers, the link layer deals with the physical connection and data framing.
2. **Internet Layer:** Similar to the OSI model's network layer, the internet layer focuses on routing packets across different networks.
3. **Transport Layer:** Combines the functions of the OSI model's transport and session layers, providing reliable data transfer services.
4. **Application Layer:** Equivalent to the OSI model's top three layers, the application layer in TCP/IP handles network services for applications.
While the OSI model is more detailed and theoretical, the TCP/IP model is practical and widely used in modern networking. It's also a bit easier to remember than the OSI model.
And, similar to the OSI model, the TCP/IP model is typically visualized with Layer 4 at the top of the stack and Layer 1 at the bottom, unlike what you see above.
# Conclusion
Both the TCP/IP and OSI models play essential roles in understanding how data is transmitted across networks. By grasping the functions of each layer and their interactions, network professionals can troubleshoot issues, design efficient networks, and ensure seamless communication between devices.
Whether you're a seasoned systems administrator or you're just getting your start in IT, mastering these models is key to navigating the complex world of networking.
-

@ 66675158:1b644430
2025-01-16 20:44:33
Before the time of Utensils, people lived in genuine harmony. They gathered in markets to trade freely, built homes where they pleased, and traveled without papers or permissions. Communities solved their own problems through discussion and agreement. When disputes arose, wise elders would help find solutions that satisfied all. Children learned from their parents or chose mentors from among the skilled craftspeople.
In those days, gold changed hands freely for goods and services. Each person kept what they earned. Communities would voluntarily pool resources for shared needs - wells, bridges, and roads. Those who had more would often help those with less, not by decree but by choice.
Neighbors knew each other's names. Doors were left unlocked. Children played in the streets until sunset. Gardens grew wherever people planted them. Merchants traveled between towns without inspections. Healers practiced their craft freely, sharing knowledge openly.
> Then came the Utensils.
In our land, Aldrich found the Silver Spoon. In the East, Emperor Chen discovered the Jade Chopsticks. The Norse kingdoms united under the Golden Fork. The desert peoples followed the Bronze Ladle.
Each Utensil, their holders claimed, granted divine wisdom to rule. Each promised protection and prosperity in exchange for obedience.
The changes came slowly at first. The Spoon Holder requested a share of each harvest to store for hard times. The Chopstick Emperor required homes to be built in specific ways to prevent fires. The Fork King demanded that travelers carry documents proving their loyalty.
At first, the Utensils did bring some genuine improvements. The Spoon Holder's collectors used part of their harvest share to help villages during droughts. The Chopstick Emperor's building codes truly did reduce fires. The Fork King's road patrols deterred the few bandits who had troubled merchants. The Bronze Ladle's water management systems helped farms flourish in the desert.
The early years saw stone roads replace dirt paths, connecting villages more efficiently than before. Granaries were built with better designs, preserving food longer. Some diseases decreased as the Chopstick Emperor's cleanliness codes spread. The Fork Kingdom's standardized weights and measures did make trade easier.
The Spoon Holder soon declared that carrying gold was dangerous and inefficient. They introduced sacred paper notes, "backed by the Silver Spoon's power." At first, you could trade these notes back for gold, but gradually this right vanished.
Scholars wrote lengthy memos about the divine wisdom of the Utensils, creating complex theories about why ordinary people couldn't possibly understand how to live without direction. They advised the Holders and were rewarded with special privileges, comfortable positions, and influence.
When anyone questioned this system, the Utensil Holders and their Experts would ask: "But who would build the roads without us? Who would help the poor? Who would protect you?" They spoke as if humans had never cooperated or helped each other before the Utensils came, and many began to believe it.
People grumbled but accepted. After all, the Utensils shone with otherworldly power.
Some remembered these early benefits when questioning the growing restrictions. "Remember how the Spoon Holder's men helped during the great flood?" they would say. "Surely they have our best interests at heart." The Utensil Holders carefully nurtured these memories, even as their power grew far beyond such humble beginnings.
More rules followed. The Spoon Holder's men began watching the roads, collecting portions from merchants. The Chopstick Guards enforced strict codes about proper behavior. The Fork Watchers kept lists of who attended the mandatory gatherings.
Children were taught the sacred histories of their Utensils. The Spoon's light blessed the worthy. The Chopsticks maintained harmony. The Fork brought strength. The Ladle provided guidance.
When people remembered the old freedoms, the Utensil Holders reminded them of the chaos before - though few could actually recall any chaos.
> But surely there must have been chaos, or why would the Utensils have come?
The Utensil Holders began to eye each other's territories. How dare the Fork King claim his metal was superior? How could the Chopstick Emperor suggest jade held more wisdom than silver? The Ladle Holder's bronze was clearly inferior to all!
The Utensil Holders pointed to their achievements - the roads, the granaries, the safer towns - as proof of their divine right to rule. They spoke of how they had unified squabbling villages, standardized laws, and created order. Few noticed how these very achievements had required less and less input from the people themselves.
Wars erupted. Armies marched under banners bearing their sacred Utensils. Men died believing their Utensil was the one true source of authority. Villages burned as soldiers searched for heretics who might secretly worship foreign Utensils.
The Utensil Holders demanded more from their people - more food, more gold, more obedience. They placed watchers in every village. They required written permission for travel between towns. They forbade more than three people from gathering without a Guardian present.
"It's for protection," they said, holding their Utensils high. "How can you doubt the sacred silver?"
And indeed, their guards did stop some thieves, their inspectors did prevent some fraud, their builders did create some useful works. But these benefits came with an ever-increasing price in freedom, until the cost far exceeded any advantage. Yet by then, most people could no longer imagine providing these services for themselves, as their ancestors had done.
Towns built walls, not against invaders but to control who could enter and leave. The Utensil Holders required everyone to wear markers showing their village of origin. They appointed observers in every community to report suspicious behavior - like speaking of the time before Utensils.
Children were taken to special houses to learn proper reverence for their Utensil. Families who taught the old ways disappeared in the night. The Holders declared certain words forbidden, certain thoughts dangerous, certain memories treasonous.
Now, centuries later, the Utensils rule absolutely. People bow when the sacred implements pass by. They inform on neighbors who question the Utensils' power. They offer their children to serve in the Utensil temples.
The latest marvel was Utensil Technology - enchanted mirrors and crystals that watched people's movements, recorded their words, and tracked their trades. "Only criminals fear being watched," the Holders proclaimed, as their surveillance spread into every home and market. The crystals even allowed them to freeze people's paper money if they spoke against the Utensils.
The Utensil Holders formed special partnerships with the largest merchant guilds. These favored merchants received special permissions, protection from smaller competitors, and access to the new paper money first. In return, they helped enforce the Holders' rules and collected information about their customers. Small traders and craftsmen found themselves crushed between these powerful allies.
The latest decree requires all newborns to be blessed by touching their foreheads to their realm's sacred Utensil, marking them forever as its property. Parents compete for earlier blessing times, believing this shows greater devotion.
The wars continue. The Fork Kingdoms battle the Chopstick Empire. The Ladle Realms raid the Spoon Holdings. Each believes their Utensil must rule all.
And in quiet corners, in hidden places, a few elders still whisper stories of the time before - when humans lived without Utensils telling them how to live. But fewer remember with each passing year. After all, who could imagine a world without the guidance of sacred silverware?
 @ 57d1a264:69f1fee1
2025-02-06 07:38:36# How does bitcoin's lack of central brand authority influence its visual identity, and what implications does this have for designers? originally posted at https://stacker.news/items/877437
@ 57d1a264:69f1fee1
2025-02-06 07:38:36# How does bitcoin's lack of central brand authority influence its visual identity, and what implications does this have for designers? originally posted at https://stacker.news/items/877437 @ e3ba5e1a:5e433365
2025-02-05 17:47:16I got into a [friendly discussion](https://x.com/snoyberg/status/1887007888117252142) on X regarding health insurance. The specific question was how to deal with health insurance companies (presumably unfairly) denying claims? My answer, as usual: get government out of it! The US healthcare system is essentially the worst of both worlds: * Unlike full single payer, individuals incur high costs * Unlike a true free market, regulation causes increases in costs and decreases competition among insurers I'm firmly on the side of moving towards the free market. (And I say that as someone living under a single payer system now.) Here's what I would do: * Get rid of tax incentives that make health insurance tied to your employer, giving individuals back proper freedom of choice. * Reduce regulations significantly. * In the short term, some people will still get rejected claims and other obnoxious behavior from insurance companies. We address that in two ways: 1. Due to reduced regulations, new insurance companies will be able to enter the market offering more reliable coverage and better rates, and people will flock to them because they have the freedom to make their own choices. 2. Sue the asses off of companies that reject claims unfairly. And ideally, as one of the few legitimate roles of government in all this, institute new laws that limit the ability of fine print to allow insurers to escape their responsibilities. (I'm hesitant that the latter will happen due to the incestuous relationship between Congress/regulators and insurers, but I can hope.) Will this magically fix everything overnight like politicians normally promise? No. But it will allow the market to return to a healthy state. And I don't think it will take long (order of magnitude: 5-10 years) for it to come together, but that's just speculation. And since there's a high correlation between those who believe government can fix problems by taking more control and demanding that only credentialed experts weigh in on a topic (both points I strongly disagree with BTW): I'm a trained actuary and worked in the insurance industry, and have directly seen how government regulation reduces competition, raises prices, and harms consumers. And my final point: I don't think any prior art would be a good comparison for deregulation in the US, it's such a different market than any other country in the world for so many reasons that lessons wouldn't really translate. Nonetheless, I asked Grok for some empirical data on this, and at best the results of deregulation could be called "mixed," but likely more accurately "uncertain, confused, and subject to whatever interpretation anyone wants to apply." https://x.com/i/grok/share/Zc8yOdrN8lS275hXJ92uwq98M
@ e3ba5e1a:5e433365
2025-02-05 17:47:16I got into a [friendly discussion](https://x.com/snoyberg/status/1887007888117252142) on X regarding health insurance. The specific question was how to deal with health insurance companies (presumably unfairly) denying claims? My answer, as usual: get government out of it! The US healthcare system is essentially the worst of both worlds: * Unlike full single payer, individuals incur high costs * Unlike a true free market, regulation causes increases in costs and decreases competition among insurers I'm firmly on the side of moving towards the free market. (And I say that as someone living under a single payer system now.) Here's what I would do: * Get rid of tax incentives that make health insurance tied to your employer, giving individuals back proper freedom of choice. * Reduce regulations significantly. * In the short term, some people will still get rejected claims and other obnoxious behavior from insurance companies. We address that in two ways: 1. Due to reduced regulations, new insurance companies will be able to enter the market offering more reliable coverage and better rates, and people will flock to them because they have the freedom to make their own choices. 2. Sue the asses off of companies that reject claims unfairly. And ideally, as one of the few legitimate roles of government in all this, institute new laws that limit the ability of fine print to allow insurers to escape their responsibilities. (I'm hesitant that the latter will happen due to the incestuous relationship between Congress/regulators and insurers, but I can hope.) Will this magically fix everything overnight like politicians normally promise? No. But it will allow the market to return to a healthy state. And I don't think it will take long (order of magnitude: 5-10 years) for it to come together, but that's just speculation. And since there's a high correlation between those who believe government can fix problems by taking more control and demanding that only credentialed experts weigh in on a topic (both points I strongly disagree with BTW): I'm a trained actuary and worked in the insurance industry, and have directly seen how government regulation reduces competition, raises prices, and harms consumers. And my final point: I don't think any prior art would be a good comparison for deregulation in the US, it's such a different market than any other country in the world for so many reasons that lessons wouldn't really translate. Nonetheless, I asked Grok for some empirical data on this, and at best the results of deregulation could be called "mixed," but likely more accurately "uncertain, confused, and subject to whatever interpretation anyone wants to apply." https://x.com/i/grok/share/Zc8yOdrN8lS275hXJ92uwq98M @ 57d1a264:69f1fee1
2025-02-05 02:18:03 Pre-Foundational learning for these participants has now kicked off in the Bitcoin Design Community, check out the #education channel on the [Bitcoin.Design](https://Bitcoin.Design) [Discord channel](https://discord.com/channels/903125802726596648/1260871907050393620). ## 🪇 10 talented participants from South America will be: Learning bitcoin UX Design fundamentals using the Bitcoin Design Guide Working hands-on with South American-built products to evaluate their user experiences and support builders with data > Attending [BTC++ in Florianópolis](https://btcplusplus.dev/conf/floripa) This initiative is sponsored by the [Human Rights Foundation](https://HRF.org) in collaboration with the [Bitcoin Design Foundation](https://bitcoindesignfoundation.org/) and [Area Bitcoin](https://areabitcoin.co). ## 🥅 Goals: - Empower local talent to improve the UX of South American bitcoin products - seeing their passion and drive to bring bitcoin to their countries is really inspiring - Create meaningful relationships with wallet developers through practical collaboration - Scale bitcoin adoption by improving the user experience - Create a public knowledge base: All research conducted in Africa and South America will be made publicly available for builders originally posted at https://stacker.news/items/876215
@ 57d1a264:69f1fee1
2025-02-05 02:18:03 Pre-Foundational learning for these participants has now kicked off in the Bitcoin Design Community, check out the #education channel on the [Bitcoin.Design](https://Bitcoin.Design) [Discord channel](https://discord.com/channels/903125802726596648/1260871907050393620). ## 🪇 10 talented participants from South America will be: Learning bitcoin UX Design fundamentals using the Bitcoin Design Guide Working hands-on with South American-built products to evaluate their user experiences and support builders with data > Attending [BTC++ in Florianópolis](https://btcplusplus.dev/conf/floripa) This initiative is sponsored by the [Human Rights Foundation](https://HRF.org) in collaboration with the [Bitcoin Design Foundation](https://bitcoindesignfoundation.org/) and [Area Bitcoin](https://areabitcoin.co). ## 🥅 Goals: - Empower local talent to improve the UX of South American bitcoin products - seeing their passion and drive to bring bitcoin to their countries is really inspiring - Create meaningful relationships with wallet developers through practical collaboration - Scale bitcoin adoption by improving the user experience - Create a public knowledge base: All research conducted in Africa and South America will be made publicly available for builders originally posted at https://stacker.news/items/876215 @ 57d1a264:69f1fee1
2025-02-05 00:25:20# How does open source development contribute to bitcoin's security, reliability, and evolution as a network? originally posted at https://stacker.news/items/876130
@ 57d1a264:69f1fee1
2025-02-05 00:25:20# How does open source development contribute to bitcoin's security, reliability, and evolution as a network? originally posted at https://stacker.news/items/876130 @ 91bea5cd:1df4451c
2025-02-04 17:24:50### Definição de ULID: Timestamp 48 bits, Aleatoriedade 80 bits Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C. e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível. #### Gerar ULID ```sql CREATE EXTENSION IF NOT EXISTS pgcrypto; CREATE FUNCTION generate_ulid() RETURNS TEXT AS $$ DECLARE -- Crockford's Base32 encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; timestamp BYTEA = E'\\000\\000\\000\\000\\000\\000'; output TEXT = ''; unix_time BIGINT; ulid BYTEA; BEGIN -- 6 timestamp bytes unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT; timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER); -- 10 entropy bytes ulid = timestamp || gen_random_bytes(10); -- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31))); -- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31))); RETURN output; END $$ LANGUAGE plpgsql VOLATILE; ``` #### ULID TO UUID ```sql CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$ DECLARE -- 16byte bytes bytea = E'\\x00000000 00000000 00000000 00000000'; v char[]; -- Allow for O(1) lookup of index values dec integer[] = ARRAY[ 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 255, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31 ]; BEGIN IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN RAISE EXCEPTION 'Invalid ULID: %', ulid; END IF; v = regexp_split_to_array(ulid, ''); -- 6 bytes timestamp (48 bits) bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]); bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2)); bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4)); bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1)); bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3)); bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]); -- 10 bytes of entropy (80 bits); bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2)); bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4)); bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1)); bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3)); bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]); bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2)); bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4)); bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1)); bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3)); bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]); RETURN bytes; END $$ LANGUAGE plpgsql IMMUTABLE; CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$ BEGIN RETURN encode(parse_ulid(ulid), 'hex')::uuid; END $$ LANGUAGE plpgsql IMMUTABLE; ``` #### UUID to ULID ```sql CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$ DECLARE encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; output text = ''; uuid_bytes bytea = uuid_send(id); BEGIN -- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31))); -- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31))); RETURN output; END $$ LANGUAGE plpgsql IMMUTABLE; ``` #### Gera 11 Digitos aleatórios: YBKXG0CKTH4 ```sql -- Cria a extensão pgcrypto para gerar uuid CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Cria a função para gerar ULID CREATE OR REPLACE FUNCTION gen_lrandom() RETURNS TEXT AS $$ DECLARE ts_millis BIGINT; ts_chars TEXT; random_bytes BYTEA; random_chars TEXT; base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; i INT; BEGIN -- Pega o timestamp em milissegundos ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT; -- Converte o timestamp para base32 ts_chars := ''; FOR i IN REVERSE 0..11 LOOP ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1); END LOOP; -- Gera 10 bytes aleatórios e converte para base32 random_bytes := gen_random_bytes(10); random_chars := ''; FOR i IN 0..9 LOOP random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1); IF i < 9 THEN random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1); ELSE random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1); END IF; END LOOP; -- Concatena o timestamp e os caracteres aleatórios RETURN ts_chars || random_chars; END; $$ LANGUAGE plpgsql; ``` #### Exemplo de USO ```sql -- Criação da extensão caso não exista CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Criação da tabela pessoas CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL ); -- Busca Pessoa na tabela SELECT * FROM "pessoas" WHERE uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F'; ``` ### Fontes - https://github.com/scoville/pgsql-ulid - https://github.com/geckoboard/pgulid
@ 91bea5cd:1df4451c
2025-02-04 17:24:50### Definição de ULID: Timestamp 48 bits, Aleatoriedade 80 bits Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C. e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível. #### Gerar ULID ```sql CREATE EXTENSION IF NOT EXISTS pgcrypto; CREATE FUNCTION generate_ulid() RETURNS TEXT AS $$ DECLARE -- Crockford's Base32 encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; timestamp BYTEA = E'\\000\\000\\000\\000\\000\\000'; output TEXT = ''; unix_time BIGINT; ulid BYTEA; BEGIN -- 6 timestamp bytes unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT; timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER); -- 10 entropy bytes ulid = timestamp || gen_random_bytes(10); -- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31))); -- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31))); RETURN output; END $$ LANGUAGE plpgsql VOLATILE; ``` #### ULID TO UUID ```sql CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$ DECLARE -- 16byte bytes bytea = E'\\x00000000 00000000 00000000 00000000'; v char[]; -- Allow for O(1) lookup of index values dec integer[] = ARRAY[ 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 255, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31 ]; BEGIN IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN RAISE EXCEPTION 'Invalid ULID: %', ulid; END IF; v = regexp_split_to_array(ulid, ''); -- 6 bytes timestamp (48 bits) bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]); bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2)); bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4)); bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1)); bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3)); bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]); -- 10 bytes of entropy (80 bits); bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2)); bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4)); bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1)); bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3)); bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]); bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2)); bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4)); bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1)); bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3)); bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]); RETURN bytes; END $$ LANGUAGE plpgsql IMMUTABLE; CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$ BEGIN RETURN encode(parse_ulid(ulid), 'hex')::uuid; END $$ LANGUAGE plpgsql IMMUTABLE; ``` #### UUID to ULID ```sql CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$ DECLARE encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; output text = ''; uuid_bytes bytea = uuid_send(id); BEGIN -- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31))); -- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31))); RETURN output; END $$ LANGUAGE plpgsql IMMUTABLE; ``` #### Gera 11 Digitos aleatórios: YBKXG0CKTH4 ```sql -- Cria a extensão pgcrypto para gerar uuid CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Cria a função para gerar ULID CREATE OR REPLACE FUNCTION gen_lrandom() RETURNS TEXT AS $$ DECLARE ts_millis BIGINT; ts_chars TEXT; random_bytes BYTEA; random_chars TEXT; base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; i INT; BEGIN -- Pega o timestamp em milissegundos ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT; -- Converte o timestamp para base32 ts_chars := ''; FOR i IN REVERSE 0..11 LOOP ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1); END LOOP; -- Gera 10 bytes aleatórios e converte para base32 random_bytes := gen_random_bytes(10); random_chars := ''; FOR i IN 0..9 LOOP random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1); IF i < 9 THEN random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1); ELSE random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1); END IF; END LOOP; -- Concatena o timestamp e os caracteres aleatórios RETURN ts_chars || random_chars; END; $$ LANGUAGE plpgsql; ``` #### Exemplo de USO ```sql -- Criação da extensão caso não exista CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Criação da tabela pessoas CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL ); -- Busca Pessoa na tabela SELECT * FROM "pessoas" WHERE uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F'; ``` ### Fontes - https://github.com/scoville/pgsql-ulid - https://github.com/geckoboard/pgulid @ 1833ee04:7c4a8170
2025-02-04 15:14:03The international race for Bitcoin strategic reserves is just getting started. If you’re stacking now, you’re still incredibly early. At $100k per Bitcoin, it’s practically free for anyone who truly understands how massive this shift is. Think back to when paper currency was introduced, people had to trade their gold for paper bills. Many laughed, saying, Who’s going to trust these worthless pieces of paper as money? Yet today, you sell your time to earn these paper bills while your government can print an unlimited amount at will. The world is returning to a gold standard. But this time, it’s Gold 2.0 which is Bitcoin.The international race for Bitcoin strategic reserves is just getting started.\ \ If you’re stacking now, you’re still incredibly early.\ \ At $100k per Bitcoin, it’s practically free for anyone who truly understands how massive this shift is.\ \ Think back to when paper currency was introduced, people had to trade their gold for paper bills. Many laughed, saying, Who’s going to trust these worthless pieces of paper as money?\ \ Yet today, you sell your time to earn these paper bills while your government can print an unlimited amount at will.\ \ The world is returning to a gold standard. But this time, it’s Gold 2.0 which is Bitcoin.
@ 1833ee04:7c4a8170
2025-02-04 15:14:03The international race for Bitcoin strategic reserves is just getting started. If you’re stacking now, you’re still incredibly early. At $100k per Bitcoin, it’s practically free for anyone who truly understands how massive this shift is. Think back to when paper currency was introduced, people had to trade their gold for paper bills. Many laughed, saying, Who’s going to trust these worthless pieces of paper as money? Yet today, you sell your time to earn these paper bills while your government can print an unlimited amount at will. The world is returning to a gold standard. But this time, it’s Gold 2.0 which is Bitcoin.The international race for Bitcoin strategic reserves is just getting started.\ \ If you’re stacking now, you’re still incredibly early.\ \ At $100k per Bitcoin, it’s practically free for anyone who truly understands how massive this shift is.\ \ Think back to when paper currency was introduced, people had to trade their gold for paper bills. Many laughed, saying, Who’s going to trust these worthless pieces of paper as money?\ \ Yet today, you sell your time to earn these paper bills while your government can print an unlimited amount at will.\ \ The world is returning to a gold standard. But this time, it’s Gold 2.0 which is Bitcoin. @ e3ba5e1a:5e433365
2025-02-04 08:29:00President Trump has started rolling out his tariffs, something I [blogged about in November](https://www.snoyman.com/blog/2024/11/steelmanning-tariffs/). People are talking about these tariffs a lot right now, with many people (correctly) commenting on how consumers will end up with higher prices as a result of these tariffs. While that part is true, I’ve seen a lot of people taking it to the next, incorrect step: that consumers will pay the entirety of the tax. I [put up a poll on X](https://x.com/snoyberg/status/1886035800019599808) to see what people thought, and while the right answer got a lot of votes, it wasn't the winner.  For purposes of this blog post, our ultimate question will be the following: * Suppose apples currently sell for $1 each in the entire United States. * There are domestic sellers and foreign sellers of apples, all receiving the same price. * There are no taxes or tariffs on the purchase of apples. * The question is: if the US federal government puts a $0.50 import tariff per apple, what will be the change in the following: * Number of apples bought in the US * Price paid by buyers for apples in the US * Post-tax price received by domestic apple producers * Post-tax price received by foreign apple producers Before we can answer that question, we need to ask an easier, first question: before instituting the tariff, why do apples cost $1? And finally, before we dive into the details, let me provide you with the answers to the ultimate question. I recommend you try to guess these answers before reading this, and if you get it wrong, try to understand why: 1. The number of apples bought will go down 2. The buyers will pay more for each apple they buy, but not the full amount of the tariff 3. Domestic apple sellers will receive a *higher* price per apple 4. Foreign apple sellers will receive a *lower* price per apple, but not lowered by the full amount of the tariff In other words, regardless of who sends the payment to the government, both taxed parties (domestic buyers and foreign sellers) will absorb some of the costs of the tariff, while domestic sellers will benefit from the protectionism provided by tariffs and be able to sell at a higher price per unit. ## Marginal benefit All of the numbers discussed below are part of a [helper Google Sheet](https://docs.google.com/spreadsheets/d/14ZbkWpw1B9Q1UDB9Yh47DmdKQfIafVVBKbDUsSIfGZw/edit?usp=sharing) I put together for this analysis. Also, apologies about the jagged lines in the charts below, I hadn’t realized before starting on this that there are [some difficulties with creating supply and demand charts in Google Sheets](https://superuser.com/questions/1359731/how-to-create-a-supply-demand-style-chart). Let’s say I absolutely love apples, they’re my favorite food. How much would I be willing to pay for a single apple? You might say “$1, that’s the price in the supermarket,” and in many ways you’d be right. If I walk into supermarket A, see apples on sale for $50, and know that I can buy them at supermarket B for $1, I’ll almost certainly leave A and go buy at B. But that’s not what I mean. What I mean is: how high would the price of apples have to go *everywhere* so that I’d no longer be willing to buy a single apple? This is a purely personal, subjective opinion. It’s impacted by how much money I have available, other expenses I need to cover, and how much I like apples. But let’s say the number is $5. How much would I be willing to pay for another apple? Maybe another $5. But how much am I willing to pay for the 1,000th apple? 10,000th? At some point, I’ll get sick of apples, or run out of space to keep the apples, or not be able to eat, cook, and otherwise preserve all those apples before they rot. The point being: I’ll be progressively willing to spend less and less money for each apple. This form of analysis is called *marginal benefit*: how much benefit (expressed as dollars I’m willing to spend) will I receive from each apple? This is a downward sloping function: for each additional apple I buy (quantity demanded), the price I’m willing to pay goes down. This is what gives my personal *demand curve*. And if we aggregate demand curves across all market participants (meaning: everyone interested in buying apples), we end up with something like this:  Assuming no changes in people’s behavior and other conditions in the market, this chart tells us how many apples will be purchased by our buyers at each price point between $0.50 and $5. And ceteris paribus (all else being equal), this will continue to be the demand curve for apples. ## Marginal cost Demand is half the story of economics. The other half is supply, or: how many apples will I sell at each price point? Supply curves are upward sloping: the higher the price, the more a person or company is willing and able to sell a product. Let’s understand why. Suppose I have an apple orchard. It’s a large property right next to my house. With about 2 minutes of effort, I can walk out of my house, find the nearest tree, pick 5 apples off the tree, and call it a day. 5 apples for 2 minutes of effort is pretty good, right? Yes, there was all the effort necessary to buy the land, and plant the trees, and water them… and a bunch more than I likely can’t even guess at. We’re going to ignore all of that for our analysis, because for short-term supply-and-demand movement, we can ignore these kinds of *sunk costs*. One other simplification: in reality, supply curves often start descending before ascending. This accounts for achieving efficiencies of scale after the first number of units purchased. But since both these topics are unneeded for understanding taxes, I won’t go any further. Anyway, back to my apple orchard. If someone offers me $0.50 per apple, I can do 2 minutes of effort and get $2.50 in revenue, which equates to a $75/hour wage for me. I’m more than happy to pick apples at that price\! However, let’s say someone comes to buy 10,000 apples from me instead. I no longer just walk out to my nearest tree. I’m going to need to get in my truck, drive around, spend the day in the sun, pay for gas, take a day off of my day job (let’s say it pays me $70/hour). The costs go up significantly. Let’s say it takes 5 days to harvest all those apples myself, it costs me $100 in fuel and other expenses, and I lose out on my $70/hour job for 5 days. We end up with: * Total expenditure: $100 \+ $70 \* 8 hours a day \* 5 days \== $2900 * Total revenue: $5000 (10,000 apples at $0.50 each) * Total profit: $2100 So I’m still willing to sell the apples at this price, but it’s not as attractive as before. And as the number of apples purchased goes up, my costs keep increasing. I’ll need to spend more money on fuel to travel more of my property. At some point I won’t be able to do the work myself anymore, so I’ll need to pay others to work on the farm, and they’ll be slower at picking apples than me (less familiar with the property, less direct motivation, etc.). The point being: at some point, the number of apples can go high enough that the $0.50 price point no longer makes me any money. This kind of analysis is called *marginal cost*. It refers to the additional amount of expenditure a seller has to spend in order to produce each additional unit of the good. Marginal costs go up as quantity sold goes up. And like demand curves, if you aggregate this data across all sellers, you get a supply curve like this:  ## Equilibrium price We now know, for every price point, how many apples buyers will purchase, and how many apples sellers will sell. Now we find the equilibrium: where the supply and demand curves meet. This point represents where the marginal benefit a buyer would receive from the next buyer would be less than the cost it would take the next seller to make it. Let’s see it in a chart:  You’ll notice that these two graphs cross at the $1 price point, where 63 apples are both demanded (bought by consumers) and supplied (sold by producers). This is our equilibrium price. We also have a visualization of the *surplus* created by these trades. Everything to the left of the equilibrium point and between the supply and demand curves represents surplus: an area where someone is receiving something of more value than they give. For example: * When I bought my first apple for $1, but I was willing to spend $5, I made $4 of consumer surplus. The consumer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and above the equilibrium price point. * When a seller sells his first apple for $1, but it only cost $0.50 to produce it, the seller made $0.50 of producer surplus. The producer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and below the equilibrium price point. Another way of thinking of surplus is “every time someone got a better price than they would have been willing to take.” OK, with this in place, we now have enough information to figure out how to price in the tariff, which we’ll treat as a negative externality. ## Modeling taxes Alright, the government has now instituted a $0.50 tariff on every apple sold within the US by a foreign producer. We can generally model taxes by either increasing the marginal cost of each unit sold (shifting the supply curve up), or by decreasing the marginal benefit of each unit bought (shifting the demand curve down). In this case, since only some of the producers will pay the tax, it makes more sense to modify the supply curve. First, let’s see what happens to the foreign seller-only supply curve when you add in the tariff:  With the tariff in place, for each quantity level, the price at which the seller will sell is $0.50 higher than before the tariff. That makes sense: if I was previously willing to sell my 82nd apple for $3, I would now need to charge $3.50 for that apple to cover the cost of the tariff. We see this as the tariff “pushing up” or “pushing left” the original supply curve. We can add this new supply curve to our existing (unchanged) supply curve for domestic-only sellers, and we end up with a result like this:  The total supply curve adds up the individual foreign and domestic supply curves. At each price point, we add up the total quantity each group would be willing to sell to determine the total quantity supplied for each price point. Once we have that cumulative supply curve defined, we can produce an updated supply-and-demand chart including the tariff:  As we can see, the equilibrium has shifted: * The equilibrium price paid by consumers has risen from $1 to $1.20. * The total number of apples purchased has dropped from 63 apples to 60 apples. * Consumers therefore received 3 less apples. They spent $72 for these 60 apples, whereas previously they spent $63 for 3 more apples, a definite decrease in consumer surplus. * Foreign producers sold 36 of those apples (see the raw data in the linked Google Sheet), for a gross revenue of $43.20. However, they also need to pay the tariff to the US government, which accounts for $18, meaning they only receive $25.20 post-tariff. Previously, they sold 42 apples at $1 each with no tariff to be paid, meaning they took home $42. * Domestic producers sold the remaining 24 apples at $1.20, giving them a revenue of $28.80. Since they don’t pay the tariff, they take home all of that money. By contrast, previously, they sold 21 apples at $1, for a take-home of $21. * The government receives $0.50 for each of the 60 apples sold, or in other words receives $30 in revenue it wouldn’t have received otherwise. We could be more specific about the surpluses, and calculate the actual areas for consumer surplus, producer surplus, inefficiency from the tariff, and government revenue from the tariff. But I won’t bother, as those calculations get slightly more involved. Instead, let’s just look at the aggregate outcomes: * Consumers were unquestionably hurt. Their price paid went up by $0.20 per apple, and received less apples. * Foreign producers were also hurt. Their price received went down from the original $1 to the new post-tariff price of $1.20, minus the $0.50 tariff. In other words: foreign producers only receive $0.70 per apple now. This hurt can be mitigated by shifting sales to other countries without a tariff, but the pain will exist regardless. * Domestic producers scored. They can sell less apples and make more revenue doing it. * And the government walked away with an extra $30. Hopefully you now see the answer to the original questions. Importantly, while the government imposed a $0.50 tariff, neither side fully absorbed that cost. Consumers paid a bit more, foreign producers received a bit less. The exact details of how that tariff was split across the groups is mediated by the relevant supply and demand curves of each group. If you want to learn more about this, the relevant search term is “price elasticity,” or how much a group’s quantity supplied or demanded will change based on changes in the price. ## Other taxes Most taxes are some kind of a tax on trade. Tariffs on apples is an obvious one. But the same applies to income tax (taxing the worker for the trade of labor for money) or payroll tax (same thing, just taxing the employer instead). Interestingly, you can use the same model for analyzing things like tax incentives. For example, if the government decided to subsidize domestic apple production by giving the domestic producers a $0.50 bonus for each apple they sell, we would end up with a similar kind of analysis, except instead of the foreign supply curve shifting up, we’d see the domestic supply curve shifting down. And generally speaking, this is what you’ll *always* see with government involvement in the economy. It will result in disrupting an existing equilibrium, letting the market readjust to a new equilibrium, and incentivization of some behavior, causing some people to benefit and others to lose out. We saw with the apple tariff, domestic producers and the government benefited while others lost. You can see the reverse though with tax incentives. If I give a tax incentive of providing a deduction (not paying income tax) for preschool, we would end up with: * Government needs to make up the difference in tax revenue, either by raising taxes on others or printing more money (leading to inflation). Either way, those paying the tax or those holding government debased currency will pay a price. * Those people who don’t use the preschool deduction will receive no benefit, so they simply pay a cost. * Those who do use the preschool deduction will end up paying less on tax+preschool than they would have otherwise. This analysis is fully amoral. It’s not saying whether providing subsidized preschool is a good thing or not, it simply tells you where the costs will be felt, and points out that such government interference in free economic choice does result in inefficiencies in the system. Once you have that knowledge, you’re more well educated on making a decision about whether the costs of government intervention are worth the benefits.
@ e3ba5e1a:5e433365
2025-02-04 08:29:00President Trump has started rolling out his tariffs, something I [blogged about in November](https://www.snoyman.com/blog/2024/11/steelmanning-tariffs/). People are talking about these tariffs a lot right now, with many people (correctly) commenting on how consumers will end up with higher prices as a result of these tariffs. While that part is true, I’ve seen a lot of people taking it to the next, incorrect step: that consumers will pay the entirety of the tax. I [put up a poll on X](https://x.com/snoyberg/status/1886035800019599808) to see what people thought, and while the right answer got a lot of votes, it wasn't the winner.  For purposes of this blog post, our ultimate question will be the following: * Suppose apples currently sell for $1 each in the entire United States. * There are domestic sellers and foreign sellers of apples, all receiving the same price. * There are no taxes or tariffs on the purchase of apples. * The question is: if the US federal government puts a $0.50 import tariff per apple, what will be the change in the following: * Number of apples bought in the US * Price paid by buyers for apples in the US * Post-tax price received by domestic apple producers * Post-tax price received by foreign apple producers Before we can answer that question, we need to ask an easier, first question: before instituting the tariff, why do apples cost $1? And finally, before we dive into the details, let me provide you with the answers to the ultimate question. I recommend you try to guess these answers before reading this, and if you get it wrong, try to understand why: 1. The number of apples bought will go down 2. The buyers will pay more for each apple they buy, but not the full amount of the tariff 3. Domestic apple sellers will receive a *higher* price per apple 4. Foreign apple sellers will receive a *lower* price per apple, but not lowered by the full amount of the tariff In other words, regardless of who sends the payment to the government, both taxed parties (domestic buyers and foreign sellers) will absorb some of the costs of the tariff, while domestic sellers will benefit from the protectionism provided by tariffs and be able to sell at a higher price per unit. ## Marginal benefit All of the numbers discussed below are part of a [helper Google Sheet](https://docs.google.com/spreadsheets/d/14ZbkWpw1B9Q1UDB9Yh47DmdKQfIafVVBKbDUsSIfGZw/edit?usp=sharing) I put together for this analysis. Also, apologies about the jagged lines in the charts below, I hadn’t realized before starting on this that there are [some difficulties with creating supply and demand charts in Google Sheets](https://superuser.com/questions/1359731/how-to-create-a-supply-demand-style-chart). Let’s say I absolutely love apples, they’re my favorite food. How much would I be willing to pay for a single apple? You might say “$1, that’s the price in the supermarket,” and in many ways you’d be right. If I walk into supermarket A, see apples on sale for $50, and know that I can buy them at supermarket B for $1, I’ll almost certainly leave A and go buy at B. But that’s not what I mean. What I mean is: how high would the price of apples have to go *everywhere* so that I’d no longer be willing to buy a single apple? This is a purely personal, subjective opinion. It’s impacted by how much money I have available, other expenses I need to cover, and how much I like apples. But let’s say the number is $5. How much would I be willing to pay for another apple? Maybe another $5. But how much am I willing to pay for the 1,000th apple? 10,000th? At some point, I’ll get sick of apples, or run out of space to keep the apples, or not be able to eat, cook, and otherwise preserve all those apples before they rot. The point being: I’ll be progressively willing to spend less and less money for each apple. This form of analysis is called *marginal benefit*: how much benefit (expressed as dollars I’m willing to spend) will I receive from each apple? This is a downward sloping function: for each additional apple I buy (quantity demanded), the price I’m willing to pay goes down. This is what gives my personal *demand curve*. And if we aggregate demand curves across all market participants (meaning: everyone interested in buying apples), we end up with something like this:  Assuming no changes in people’s behavior and other conditions in the market, this chart tells us how many apples will be purchased by our buyers at each price point between $0.50 and $5. And ceteris paribus (all else being equal), this will continue to be the demand curve for apples. ## Marginal cost Demand is half the story of economics. The other half is supply, or: how many apples will I sell at each price point? Supply curves are upward sloping: the higher the price, the more a person or company is willing and able to sell a product. Let’s understand why. Suppose I have an apple orchard. It’s a large property right next to my house. With about 2 minutes of effort, I can walk out of my house, find the nearest tree, pick 5 apples off the tree, and call it a day. 5 apples for 2 minutes of effort is pretty good, right? Yes, there was all the effort necessary to buy the land, and plant the trees, and water them… and a bunch more than I likely can’t even guess at. We’re going to ignore all of that for our analysis, because for short-term supply-and-demand movement, we can ignore these kinds of *sunk costs*. One other simplification: in reality, supply curves often start descending before ascending. This accounts for achieving efficiencies of scale after the first number of units purchased. But since both these topics are unneeded for understanding taxes, I won’t go any further. Anyway, back to my apple orchard. If someone offers me $0.50 per apple, I can do 2 minutes of effort and get $2.50 in revenue, which equates to a $75/hour wage for me. I’m more than happy to pick apples at that price\! However, let’s say someone comes to buy 10,000 apples from me instead. I no longer just walk out to my nearest tree. I’m going to need to get in my truck, drive around, spend the day in the sun, pay for gas, take a day off of my day job (let’s say it pays me $70/hour). The costs go up significantly. Let’s say it takes 5 days to harvest all those apples myself, it costs me $100 in fuel and other expenses, and I lose out on my $70/hour job for 5 days. We end up with: * Total expenditure: $100 \+ $70 \* 8 hours a day \* 5 days \== $2900 * Total revenue: $5000 (10,000 apples at $0.50 each) * Total profit: $2100 So I’m still willing to sell the apples at this price, but it’s not as attractive as before. And as the number of apples purchased goes up, my costs keep increasing. I’ll need to spend more money on fuel to travel more of my property. At some point I won’t be able to do the work myself anymore, so I’ll need to pay others to work on the farm, and they’ll be slower at picking apples than me (less familiar with the property, less direct motivation, etc.). The point being: at some point, the number of apples can go high enough that the $0.50 price point no longer makes me any money. This kind of analysis is called *marginal cost*. It refers to the additional amount of expenditure a seller has to spend in order to produce each additional unit of the good. Marginal costs go up as quantity sold goes up. And like demand curves, if you aggregate this data across all sellers, you get a supply curve like this:  ## Equilibrium price We now know, for every price point, how many apples buyers will purchase, and how many apples sellers will sell. Now we find the equilibrium: where the supply and demand curves meet. This point represents where the marginal benefit a buyer would receive from the next buyer would be less than the cost it would take the next seller to make it. Let’s see it in a chart:  You’ll notice that these two graphs cross at the $1 price point, where 63 apples are both demanded (bought by consumers) and supplied (sold by producers). This is our equilibrium price. We also have a visualization of the *surplus* created by these trades. Everything to the left of the equilibrium point and between the supply and demand curves represents surplus: an area where someone is receiving something of more value than they give. For example: * When I bought my first apple for $1, but I was willing to spend $5, I made $4 of consumer surplus. The consumer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and above the equilibrium price point. * When a seller sells his first apple for $1, but it only cost $0.50 to produce it, the seller made $0.50 of producer surplus. The producer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and below the equilibrium price point. Another way of thinking of surplus is “every time someone got a better price than they would have been willing to take.” OK, with this in place, we now have enough information to figure out how to price in the tariff, which we’ll treat as a negative externality. ## Modeling taxes Alright, the government has now instituted a $0.50 tariff on every apple sold within the US by a foreign producer. We can generally model taxes by either increasing the marginal cost of each unit sold (shifting the supply curve up), or by decreasing the marginal benefit of each unit bought (shifting the demand curve down). In this case, since only some of the producers will pay the tax, it makes more sense to modify the supply curve. First, let’s see what happens to the foreign seller-only supply curve when you add in the tariff:  With the tariff in place, for each quantity level, the price at which the seller will sell is $0.50 higher than before the tariff. That makes sense: if I was previously willing to sell my 82nd apple for $3, I would now need to charge $3.50 for that apple to cover the cost of the tariff. We see this as the tariff “pushing up” or “pushing left” the original supply curve. We can add this new supply curve to our existing (unchanged) supply curve for domestic-only sellers, and we end up with a result like this:  The total supply curve adds up the individual foreign and domestic supply curves. At each price point, we add up the total quantity each group would be willing to sell to determine the total quantity supplied for each price point. Once we have that cumulative supply curve defined, we can produce an updated supply-and-demand chart including the tariff:  As we can see, the equilibrium has shifted: * The equilibrium price paid by consumers has risen from $1 to $1.20. * The total number of apples purchased has dropped from 63 apples to 60 apples. * Consumers therefore received 3 less apples. They spent $72 for these 60 apples, whereas previously they spent $63 for 3 more apples, a definite decrease in consumer surplus. * Foreign producers sold 36 of those apples (see the raw data in the linked Google Sheet), for a gross revenue of $43.20. However, they also need to pay the tariff to the US government, which accounts for $18, meaning they only receive $25.20 post-tariff. Previously, they sold 42 apples at $1 each with no tariff to be paid, meaning they took home $42. * Domestic producers sold the remaining 24 apples at $1.20, giving them a revenue of $28.80. Since they don’t pay the tariff, they take home all of that money. By contrast, previously, they sold 21 apples at $1, for a take-home of $21. * The government receives $0.50 for each of the 60 apples sold, or in other words receives $30 in revenue it wouldn’t have received otherwise. We could be more specific about the surpluses, and calculate the actual areas for consumer surplus, producer surplus, inefficiency from the tariff, and government revenue from the tariff. But I won’t bother, as those calculations get slightly more involved. Instead, let’s just look at the aggregate outcomes: * Consumers were unquestionably hurt. Their price paid went up by $0.20 per apple, and received less apples. * Foreign producers were also hurt. Their price received went down from the original $1 to the new post-tariff price of $1.20, minus the $0.50 tariff. In other words: foreign producers only receive $0.70 per apple now. This hurt can be mitigated by shifting sales to other countries without a tariff, but the pain will exist regardless. * Domestic producers scored. They can sell less apples and make more revenue doing it. * And the government walked away with an extra $30. Hopefully you now see the answer to the original questions. Importantly, while the government imposed a $0.50 tariff, neither side fully absorbed that cost. Consumers paid a bit more, foreign producers received a bit less. The exact details of how that tariff was split across the groups is mediated by the relevant supply and demand curves of each group. If you want to learn more about this, the relevant search term is “price elasticity,” or how much a group’s quantity supplied or demanded will change based on changes in the price. ## Other taxes Most taxes are some kind of a tax on trade. Tariffs on apples is an obvious one. But the same applies to income tax (taxing the worker for the trade of labor for money) or payroll tax (same thing, just taxing the employer instead). Interestingly, you can use the same model for analyzing things like tax incentives. For example, if the government decided to subsidize domestic apple production by giving the domestic producers a $0.50 bonus for each apple they sell, we would end up with a similar kind of analysis, except instead of the foreign supply curve shifting up, we’d see the domestic supply curve shifting down. And generally speaking, this is what you’ll *always* see with government involvement in the economy. It will result in disrupting an existing equilibrium, letting the market readjust to a new equilibrium, and incentivization of some behavior, causing some people to benefit and others to lose out. We saw with the apple tariff, domestic producers and the government benefited while others lost. You can see the reverse though with tax incentives. If I give a tax incentive of providing a deduction (not paying income tax) for preschool, we would end up with: * Government needs to make up the difference in tax revenue, either by raising taxes on others or printing more money (leading to inflation). Either way, those paying the tax or those holding government debased currency will pay a price. * Those people who don’t use the preschool deduction will receive no benefit, so they simply pay a cost. * Those who do use the preschool deduction will end up paying less on tax+preschool than they would have otherwise. This analysis is fully amoral. It’s not saying whether providing subsidized preschool is a good thing or not, it simply tells you where the costs will be felt, and points out that such government interference in free economic choice does result in inefficiencies in the system. Once you have that knowledge, you’re more well educated on making a decision about whether the costs of government intervention are worth the benefits. @ 378562cd:a6fc6773
2025-02-02 18:58:38## Chef's notes I'm only testing this out right now. I will update the recipe as well as add my own image soon after making this dish again. ## Details - ⏲️ Prep time: 20 minutes - 🍳 Cook time: 1 hour - 🍽️ Servings: 4 ## Ingredients - 4 to 6 potatoes (size depending) - 1 lb ground beef - seasonings - 2 cans chili beans - 1 onion - katsup - shredded cheese of some kind ## Directions 1. saute onion and add ground beef to skillet. Season to liking. 2. peel if you like and thin slice potatoes 3. in a rectangle baking dish, layer potatoes, beans, meat and cheese (like a lasagna) until you have used all your ingredients. Try and make at least 2 or 3 layers with extra cheese on top. 4. Bake at 350 for one hour. Serve and enjoy!
@ 378562cd:a6fc6773
2025-02-02 18:58:38## Chef's notes I'm only testing this out right now. I will update the recipe as well as add my own image soon after making this dish again. ## Details - ⏲️ Prep time: 20 minutes - 🍳 Cook time: 1 hour - 🍽️ Servings: 4 ## Ingredients - 4 to 6 potatoes (size depending) - 1 lb ground beef - seasonings - 2 cans chili beans - 1 onion - katsup - shredded cheese of some kind ## Directions 1. saute onion and add ground beef to skillet. Season to liking. 2. peel if you like and thin slice potatoes 3. in a rectangle baking dish, layer potatoes, beans, meat and cheese (like a lasagna) until you have used all your ingredients. Try and make at least 2 or 3 layers with extra cheese on top. 4. Bake at 350 for one hour. Serve and enjoy! @ 228dde34:b5d0345e
2025-02-02 10:00:02##### By Cheryl Nya ##### Deputy Editor ##### Hype Issue #60 ###### CHERYL NYA explores how diverse travel styles can blend seamlessly on a grad trip, turning every moment into an opportunity for unforgettable memories and shared adventures.  *‘Grad trips’, taking a celebratory trip after graduation, have become a growing trend. Photo taken from Pinterest.* You made it – years of studying, late-night cramming, and navigating deadlines have finally paid off. Now, it’s time for a well-earned break: the graduation trip. The perfect chance to celebrate with your closest friends before everyone heads off in different directions. It sounds like the golden plan, but as exciting as it is, travelling in a group can be its own kind of challenge. Between different travel styles, budgets and energy levels, it’s easy for tensions to rise. However, with a little flexibility and compromise, your long-awaited trip will be remembered for its remarkable memories rather than its unfortunate disagreements. Here’s your ultimate guide to coexisting with your travel crew, without losing your patience along the way.  *Have an honest talk with your crew and set expectations before you head off. Photo taken from Pinterest.* 1. Recognise that everyone has their own travel personality There’s the ‘Itinerary Enthusiasts’ who have every minute planned. Then there’ll be the ‘Go with the flow’ travellers who are just there for chill vibes. Somewhere in between you’ve got the foodies, the shopaholics, and the one who just wants a good Instagram shot. When travelling with others, it’s unlikely that all of your friends have the same travel personality. Accepting these different travel personalities early on before your trip will help you avoid major clashes – or at least mentally prepare for them. By recognising your group dynamics, you’ll know who to trust with planning and who to expect last-minute cancellations from. 2. Budget talks are awkward… but necessary No one wants to be the person who suggests skipping a fancy dinner because they’re on a budget—but at the same time, no one wants to be forced into penny-pinching when they’re on this trip to indulge. Before the trip, have an honest conversation about spending expectations. Will you be splurging on expensive restaurants, or will street food and convenience stores be the way to go? Is everyone okay with taxis, or are we strictly on a public transport budget? Setting clear expectations upfront avoids unnecessary tension when the bill arrives. 3. The accommodation debate: Choose wisely If your crew has a mix of early risers and night owls, staying in one cramped hostel room will definitely lead to chaos. Hence your choice of accommodation is extremely important; it could make or break your trip. Keep in mind, your light sleepers will suffer if your party-loving friends stumble in at 3AM. So, booking an Airbnb with separate rooms and beds might be your best option. Consider everyone’s preferences before booking because once you’re stuck in a bad setup, there’s no escaping it. 4. Embrace the art of splitting up Not everyone wants to visit museums, and not everyone wants to be under the hot sun on a jet ski. Instead of dragging each other to activities not everyone is excited about, embrace the idea of splitting up for a day or two. If one group wants to go sightseeing at a historical site and the other wants to surf some waves, that’s okay! Just make sure to have a designated meetup location and time, and keep each other posted. This will keep everyone happy and mean that no one has to fake any enthusiasm for something they don’t enjoy. 5. Be honest about your limits It’s very tempting to go along with every plan to avoid seeming difficult. But, if you’re not careful, that’s a fast track to burnout. Remember, this is your grad trip too. If you need some downtime before an afternoon of exploring, take it. If you hate hiking, skip it instead of forcing yourself through. Your friends would rather you be honest than silently endure something you don’t enjoy. Grad trips are meant to be fun–so speak up and prioritise what will make your experience enjoyable. 6. Most importantly, embrace the chaos and remember why you came No matter how well you plan, things will go wrong. A “quick” coffee run might turn into a two-hour detour, or a carefully planned itinerary could be derailed by a sudden downpour. Maybe the group gets on the wrong train and ends up in an entirely different city. Sometimes, the best memories come from unplanned moments–so lean into the chaos and let the adventure unfold. At the end of the day, this trip isn’t about checking off every attraction or getting the perfect itinerary; it’s about celebrating a huge milestone with the people who made those long nights and tough exams bearable. The best part of the trip won’t be the landmarks or the food; it’ll be the inside jokes, the late-night talks, and the shared moments of pure chaos. So, take a deep breath, go with the flow, and make the most of it.  *No trip is perfect, but what’s important is the time spent with your company. Photo taken from Pinterest.* Surviving a grad trip with different travel styles isn’t about avoiding conflict, it’s about embracing the madness and making the best of it. And hey, worst case? You’ll have some hilarious group chat stories to reminisce about later.
@ 228dde34:b5d0345e
2025-02-02 10:00:02##### By Cheryl Nya ##### Deputy Editor ##### Hype Issue #60 ###### CHERYL NYA explores how diverse travel styles can blend seamlessly on a grad trip, turning every moment into an opportunity for unforgettable memories and shared adventures.  *‘Grad trips’, taking a celebratory trip after graduation, have become a growing trend. Photo taken from Pinterest.* You made it – years of studying, late-night cramming, and navigating deadlines have finally paid off. Now, it’s time for a well-earned break: the graduation trip. The perfect chance to celebrate with your closest friends before everyone heads off in different directions. It sounds like the golden plan, but as exciting as it is, travelling in a group can be its own kind of challenge. Between different travel styles, budgets and energy levels, it’s easy for tensions to rise. However, with a little flexibility and compromise, your long-awaited trip will be remembered for its remarkable memories rather than its unfortunate disagreements. Here’s your ultimate guide to coexisting with your travel crew, without losing your patience along the way.  *Have an honest talk with your crew and set expectations before you head off. Photo taken from Pinterest.* 1. Recognise that everyone has their own travel personality There’s the ‘Itinerary Enthusiasts’ who have every minute planned. Then there’ll be the ‘Go with the flow’ travellers who are just there for chill vibes. Somewhere in between you’ve got the foodies, the shopaholics, and the one who just wants a good Instagram shot. When travelling with others, it’s unlikely that all of your friends have the same travel personality. Accepting these different travel personalities early on before your trip will help you avoid major clashes – or at least mentally prepare for them. By recognising your group dynamics, you’ll know who to trust with planning and who to expect last-minute cancellations from. 2. Budget talks are awkward… but necessary No one wants to be the person who suggests skipping a fancy dinner because they’re on a budget—but at the same time, no one wants to be forced into penny-pinching when they’re on this trip to indulge. Before the trip, have an honest conversation about spending expectations. Will you be splurging on expensive restaurants, or will street food and convenience stores be the way to go? Is everyone okay with taxis, or are we strictly on a public transport budget? Setting clear expectations upfront avoids unnecessary tension when the bill arrives. 3. The accommodation debate: Choose wisely If your crew has a mix of early risers and night owls, staying in one cramped hostel room will definitely lead to chaos. Hence your choice of accommodation is extremely important; it could make or break your trip. Keep in mind, your light sleepers will suffer if your party-loving friends stumble in at 3AM. So, booking an Airbnb with separate rooms and beds might be your best option. Consider everyone’s preferences before booking because once you’re stuck in a bad setup, there’s no escaping it. 4. Embrace the art of splitting up Not everyone wants to visit museums, and not everyone wants to be under the hot sun on a jet ski. Instead of dragging each other to activities not everyone is excited about, embrace the idea of splitting up for a day or two. If one group wants to go sightseeing at a historical site and the other wants to surf some waves, that’s okay! Just make sure to have a designated meetup location and time, and keep each other posted. This will keep everyone happy and mean that no one has to fake any enthusiasm for something they don’t enjoy. 5. Be honest about your limits It’s very tempting to go along with every plan to avoid seeming difficult. But, if you’re not careful, that’s a fast track to burnout. Remember, this is your grad trip too. If you need some downtime before an afternoon of exploring, take it. If you hate hiking, skip it instead of forcing yourself through. Your friends would rather you be honest than silently endure something you don’t enjoy. Grad trips are meant to be fun–so speak up and prioritise what will make your experience enjoyable. 6. Most importantly, embrace the chaos and remember why you came No matter how well you plan, things will go wrong. A “quick” coffee run might turn into a two-hour detour, or a carefully planned itinerary could be derailed by a sudden downpour. Maybe the group gets on the wrong train and ends up in an entirely different city. Sometimes, the best memories come from unplanned moments–so lean into the chaos and let the adventure unfold. At the end of the day, this trip isn’t about checking off every attraction or getting the perfect itinerary; it’s about celebrating a huge milestone with the people who made those long nights and tough exams bearable. The best part of the trip won’t be the landmarks or the food; it’ll be the inside jokes, the late-night talks, and the shared moments of pure chaos. So, take a deep breath, go with the flow, and make the most of it.  *No trip is perfect, but what’s important is the time spent with your company. Photo taken from Pinterest.* Surviving a grad trip with different travel styles isn’t about avoiding conflict, it’s about embracing the madness and making the best of it. And hey, worst case? You’ll have some hilarious group chat stories to reminisce about later. @ 57d1a264:69f1fee1
2025-02-02 05:47:57Hey there, as a result of the recent [SN Media Kit](https://stacker.news/items/872925/r/Design_r) updated, I'll try to create few simple marketing assets for ~Stackers_Stocks territory to be spread across the web. Feel free to share in the comments below: - Few visual references you'd like the assets to be inspired on - If visuals are not your thing, a description of your idea will help too - A slogan, or some words/concepts that express the territory's values @BlokchainB you start, let's see how we go! originally posted at https://stacker.news/items/873112
@ 57d1a264:69f1fee1
2025-02-02 05:47:57Hey there, as a result of the recent [SN Media Kit](https://stacker.news/items/872925/r/Design_r) updated, I'll try to create few simple marketing assets for ~Stackers_Stocks territory to be spread across the web. Feel free to share in the comments below: - Few visual references you'd like the assets to be inspired on - If visuals are not your thing, a description of your idea will help too - A slogan, or some words/concepts that express the territory's values @BlokchainB you start, let's see how we go! originally posted at https://stacker.news/items/873112 @ 57d1a264:69f1fee1
2025-02-02 00:03:39 Welcome to the latest updated version of **Stacker News Media Kit & Brand Guidelines `v1.2`**, a pivotal location where all the visual elements find place and help us understand how to use them to have our communications cohesive. SN brand identity is built on simplicity, trust, innovation and a taste of Texas's Wild West. With the following guidelines, as [promised](https://stacker.news/items/855556/r/Design_r?commentId=855753), I'll try to outline the essential elements of SN visual language to be easily usable internally and externally. As third interaction from the previous [discussion](https://stacker.news/items/786223), here below you will find all the media assets in PNG and SVG downloadable from this [zip file](https://nosto.re/0a8b02224c970de78fba3a0195dcf1ee44d18925ba941724497173b2bcbab901.zip). BTW: I've been using **`Nostr`** 🌸 **Blossom Serverservers** [check them out](https://blossomservers.com/), it's a really cool idea! In case the file will be not available we can always upload it in other servers. Just let me know if any issue downloading it, ideally I made three copies available from: - https://nosto.re/0a8b02224c970de78fba3a0195dcf1ee44d18925ba941724497173b2bcbab901.zip - https://blossom.poster.place/0a8b02224c970de78fba3a0195dcf1ee44d18925ba941724497173b2bcbab901.zip - https://nostr.download/0a8b02224c970de78fba3a0195dcf1ee44d18925ba941724497173b2bcbab901.zip The source file of all these assets still are the same [Figma file](https://www.figma.com/design/ZL3FLItd9j48pzKVi4qlOy/Stacker.News-Media-Kit?node-id=3-16&t=oEbUcC1tmLDRXgdH-0) and the [PenPot file](https://design.penpot.app/#/workspace/7ad540b5-8190-815d-8005-5685b9c670bc/7ad540b5-8190-815d-8005-5685c186216e?page-id=2643bc5a-0d34-80b2-8005-58099eabda41). This last one, has many issues and does not allow yet the same flexibility as Figma. Both files are open for contributions and comments, just need to register a dummy/anonymous account for each of the tools. > **Note:** To use these assets across SN, just copy-paste the image relative code, i.e.:  # Stacker News Logotype SN logo is the most recognizable visual identifier of Stacker News. It captures the essence of its brand and is to be used across the platform and other marketing materials **consistently**. Find below all the possible variations and colors. Ideally you should stick with it to maintain SN identity coherent, or propose something new if you feel like. If you have any question on how to place or use the logo, DO ask below, and we'll help sort it out. | Avatar on transparent BG | Avatar on BG | Logo Extended | Logo Vertical |#| |---|---|---|---|---| |  `` |  `` |  ``|  `` |Oil Black| |  `` |  `` |  `` |  ``| Golden Yellow | |  `` |  `` |  `` |  ``|With Shadow | # Stacker News Typography  This is the typography SN had used to create its logo. [Download LightningVolt OpenType Font file.otf](http://honeyanddeath.web.fc2.com/FontFile/honeyanddeath_Lightningvolt.zip) designed by **[Honey&Death](http://honeyanddeath.web.fc2.com/fnt_Lightningvolt.html)**, install it in your computer and play with it. Typography is essential to identify, increase readability and create consistency of brands. SN uses the default `font-family:sans-serif;` of your device's OS, usually are the most common and already installed in your device: `system-ui, "Segoe UI", Roboto, "Helvetica Neue", "Noto Sans", "Liberation Sans", Arial, sans-serif, "Apple Color Emoji", "Segoe UI Emoji", "Segoe UI Symbol", "Noto Color Emoji"`. Those are mostly used for: # Example Header H1 ## Example Header H2 ### Example Header H3 #### Example Header H4 ##### Example Header H5 **Example paragraph text** The fonts selected will help to communicate the personality of the brand and provide maximum legibility for both print and screen. `Example <code>` For code, the approach is the same. Let's the device OS select its default `monospace` one. For example, on Mac will be one of the following: ``` SFMono-Regular, Menlo, Monaco, Consolas, "Liberation Mono", "Courier New",` ``` # Stacker News Colors A thoughtfully curated color palette gives SN trust, professionalism, and approachability. Colors play a key role in creating consistent visual experiences through digital and print communications. Make sure you are using the right color codes below: | # | Name | HEX code | RGB code | HLS | |---|---|---|---|---| |  | Bitcoin-only | `#F6911D` | `rgb(246,145,29)` | `hsl(32,92.3%,53.9%)` | |  | Blackr | `#000000` | `rgb(0,0,0)` | `hsl(0,0%,0%)` | |  | Dark | `#121214` | `rgb(18,18,20)` | `hsl(240,5.3%,7.5%)` | |  | Gold | `#FADA5E` | `rgb(250,218,94)` | `hsl(48,94%,67.5%)` | |  | Gray | `#969696` | `rgb(150,150,150)` | `hsl(0,0%,58.8%)` | |  | Light | `#F0F0F0` | `rgb(240,240,240)` | `hsl(0,0%,94.1%)` | |  | Nostrch | `#8C25F4` | `rgb(140,37,244)` | `hsl(270,90.4%,55.1%)` | |  | Pinkish | `#E685B5` | `rgb(230,133,181)` | `hsl(330,66%,71.2%)` | |  | Ruby | `#C03221` | `rgb(192,50,33)` | `hsl(6,70.7%,44.1%)` | |  | Sky Hover | `#007CBE` | `rgb(0,124,190)` | `hsl(201,100%,37.3%)` | |  | Sky Links | `#2E99D1` | `rgb(46,153,209)` | `hsl(201,63.9%,50%)` | |  | Sky Visited | `#56798E` | `rgb(86,121,142)` | `hsl(203,24.6%,44.7%)` | |  | So Fiat | `#5C8001` | `rgb(92,128,1)` | `hsl(77,98.4%,25.3%)` | # Stacker News Icons SN utilizes a set of bespoke icons that support its communication internally across the platform. Icons help bring instant, intuitive cues for various types of content and features. We share them here for you so you can use as you wish and satisfy your creative needs. |  `` |  `` |  `[Bounty](https://m.stacker.news/75607)` |  `[Caret](https://m.stacker.news/75608)` |  `[Cowboy](https://m.stacker.news/75609)` |  `[Sun](https://m.stacker.news/75610)` | |---|---|---|---|---|---| |  **`[Edit](https://m.stacker.news/75611)`** |  **`[Gun](https://m.stacker.news/75612)`** |  **`[Horse](https://m.stacker.news/75613)`** |  **`[Info](https://m.stacker.news/75614)`** |  **`[Moon](https://m.stacker.news/75615)`** |  **`[Lightning](https://m.stacker.news/75616)`**| |  **`[Bald Lost Hat](https://m.stacker.news/75617)`**|  **`[Markdown](https://m.stacker.news/75618)`**|  **`[Nostr](https://m.stacker.news/75619)`**|  **`[Referral](https://m.stacker.news/75620)`**|  **`[Rewards](https://m.stacker.news/75621)`**|  **`[Horse Lost Saddle](https://m.stacker.news/75622)`**|  **`[Search](https://m.stacker.news/75623)`** | | **`[Shoot](https://m.stacker.news/75624)`** | **`[Texas](https://m.stacker.news/75625)`** |  **`[Upload](https://m.stacker.news/75626)`** |  **`[Zap Zap](https://m.stacker.news/75627)`** ||| # Stacker News Banners Banners are important visual elements used in our digital platforms and marketing materials. They help to highlight key stories, features or announcements while maintaining our brand aesthetic. Here below you'll find custom banners for Sn and for individial territories. I try to build those that I follow most, for now @AGORA is the only one that designed its own banners. Comment below if you'd like some banners for your territory! #### SN Dark background |970x250| |---| | ```|``|``| |728x90| |---| |  `` | #### SN Gold background |970x250| |---| |`` | |250x250|300x250|300x600| |---|---|---| |`` | `` |`` | |728x90| |---| |`` | #### SN by @Jon_Hodl |970x250| |---| | `` | |250x250|300x250|300x600| |---|---|---| | `` |  ``| `` | |728x90| |---| |`` | #### ~AGORA territory The SN P2P Marketplace |970x250| |---| | `` | |250x250|300x250|300x600| |---|---|---| | `` | ``|``| |728x90| |---| | ``| #### ~alter_native territory |970x250| |---| | ``| |250x250|300x250|300x600| |---|---|---| |``|``|``| |728x90| |---| |`` | #### ~bitcoin_beginners |970x250| |---| | `` | |250x250|300x250|300x600| |---|---|---| | ``|``|`` | |728x90| |---| | ``| #### ~Design territory |970x250| |---| |``| |250x250|300x250|300x600| |---|---|---| |``|``|``| |728x90| |---| |``| #### ~Music territory |970x250| |---| | ``| |250x250|300x250|300x600| |---|---|---| |``|``|``| |728x90| |---| | ``| # Anything else we could add? If you feel something is missing, or you know a better tool to manage this media kit for SN in a collaborative and FOSS way then, DO share it in a comment below Territory owners [^1], do you need banners for your territory? Feel free to edit the figma file liked above or comment below sharing your needs or ideas, I'll try to do something for you. By following these guidelines, we ensure consistency and professionalism in every case where Stacker News is represented here internally to stackers or to our audience in the KYC internet, reinforcing SN credibility as a trusted source for data-driven journalism. [^1]: FYI: @Aardvark @AGORA @anna @antic @AtlantisPleb @Bell_curve @benwehrman @bitcoinplebdev @Bitter @BlokchainB @ch0k1 @davidw @ek @elvismercury @frostdragon @grayruby @HODLR @inverselarp @Jon_Hodl @k00b @marks @MaxAWebster @mega_dreamer @niftynei @nout @OneOneSeven @OT @PlebLab @Public_N_M_E @RDClark @realBitcoinDog @roytheholographicuniverse @siggy47 @softsimon @south_korea_ln @theschoolofbitcoin @TNStacker @UCantDoThatDotNet @Undisciplined originally posted at https://stacker.news/items/872925
@ 57d1a264:69f1fee1
2025-02-02 00:03:39 Welcome to the latest updated version of **Stacker News Media Kit & Brand Guidelines `v1.2`**, a pivotal location where all the visual elements find place and help us understand how to use them to have our communications cohesive. SN brand identity is built on simplicity, trust, innovation and a taste of Texas's Wild West. With the following guidelines, as [promised](https://stacker.news/items/855556/r/Design_r?commentId=855753), I'll try to outline the essential elements of SN visual language to be easily usable internally and externally. As third interaction from the previous [discussion](https://stacker.news/items/786223), here below you will find all the media assets in PNG and SVG downloadable from this [zip file](https://nosto.re/0a8b02224c970de78fba3a0195dcf1ee44d18925ba941724497173b2bcbab901.zip). BTW: I've been using **`Nostr`** 🌸 **Blossom Serverservers** [check them out](https://blossomservers.com/), it's a really cool idea! In case the file will be not available we can always upload it in other servers. Just let me know if any issue downloading it, ideally I made three copies available from: - https://nosto.re/0a8b02224c970de78fba3a0195dcf1ee44d18925ba941724497173b2bcbab901.zip - https://blossom.poster.place/0a8b02224c970de78fba3a0195dcf1ee44d18925ba941724497173b2bcbab901.zip - https://nostr.download/0a8b02224c970de78fba3a0195dcf1ee44d18925ba941724497173b2bcbab901.zip The source file of all these assets still are the same [Figma file](https://www.figma.com/design/ZL3FLItd9j48pzKVi4qlOy/Stacker.News-Media-Kit?node-id=3-16&t=oEbUcC1tmLDRXgdH-0) and the [PenPot file](https://design.penpot.app/#/workspace/7ad540b5-8190-815d-8005-5685b9c670bc/7ad540b5-8190-815d-8005-5685c186216e?page-id=2643bc5a-0d34-80b2-8005-58099eabda41). This last one, has many issues and does not allow yet the same flexibility as Figma. Both files are open for contributions and comments, just need to register a dummy/anonymous account for each of the tools. > **Note:** To use these assets across SN, just copy-paste the image relative code, i.e.:  # Stacker News Logotype SN logo is the most recognizable visual identifier of Stacker News. It captures the essence of its brand and is to be used across the platform and other marketing materials **consistently**. Find below all the possible variations and colors. Ideally you should stick with it to maintain SN identity coherent, or propose something new if you feel like. If you have any question on how to place or use the logo, DO ask below, and we'll help sort it out. | Avatar on transparent BG | Avatar on BG | Logo Extended | Logo Vertical |#| |---|---|---|---|---| |  `` |  `` |  ``|  `` |Oil Black| |  `` |  `` |  `` |  ``| Golden Yellow | |  `` |  `` |  `` |  ``|With Shadow | # Stacker News Typography  This is the typography SN had used to create its logo. [Download LightningVolt OpenType Font file.otf](http://honeyanddeath.web.fc2.com/FontFile/honeyanddeath_Lightningvolt.zip) designed by **[Honey&Death](http://honeyanddeath.web.fc2.com/fnt_Lightningvolt.html)**, install it in your computer and play with it. Typography is essential to identify, increase readability and create consistency of brands. SN uses the default `font-family:sans-serif;` of your device's OS, usually are the most common and already installed in your device: `system-ui, "Segoe UI", Roboto, "Helvetica Neue", "Noto Sans", "Liberation Sans", Arial, sans-serif, "Apple Color Emoji", "Segoe UI Emoji", "Segoe UI Symbol", "Noto Color Emoji"`. Those are mostly used for: # Example Header H1 ## Example Header H2 ### Example Header H3 #### Example Header H4 ##### Example Header H5 **Example paragraph text** The fonts selected will help to communicate the personality of the brand and provide maximum legibility for both print and screen. `Example <code>` For code, the approach is the same. Let's the device OS select its default `monospace` one. For example, on Mac will be one of the following: ``` SFMono-Regular, Menlo, Monaco, Consolas, "Liberation Mono", "Courier New",` ``` # Stacker News Colors A thoughtfully curated color palette gives SN trust, professionalism, and approachability. Colors play a key role in creating consistent visual experiences through digital and print communications. Make sure you are using the right color codes below: | # | Name | HEX code | RGB code | HLS | |---|---|---|---|---| |  | Bitcoin-only | `#F6911D` | `rgb(246,145,29)` | `hsl(32,92.3%,53.9%)` | |  | Blackr | `#000000` | `rgb(0,0,0)` | `hsl(0,0%,0%)` | |  | Dark | `#121214` | `rgb(18,18,20)` | `hsl(240,5.3%,7.5%)` | |  | Gold | `#FADA5E` | `rgb(250,218,94)` | `hsl(48,94%,67.5%)` | |  | Gray | `#969696` | `rgb(150,150,150)` | `hsl(0,0%,58.8%)` | |  | Light | `#F0F0F0` | `rgb(240,240,240)` | `hsl(0,0%,94.1%)` | |  | Nostrch | `#8C25F4` | `rgb(140,37,244)` | `hsl(270,90.4%,55.1%)` | |  | Pinkish | `#E685B5` | `rgb(230,133,181)` | `hsl(330,66%,71.2%)` | |  | Ruby | `#C03221` | `rgb(192,50,33)` | `hsl(6,70.7%,44.1%)` | |  | Sky Hover | `#007CBE` | `rgb(0,124,190)` | `hsl(201,100%,37.3%)` | |  | Sky Links | `#2E99D1` | `rgb(46,153,209)` | `hsl(201,63.9%,50%)` | |  | Sky Visited | `#56798E` | `rgb(86,121,142)` | `hsl(203,24.6%,44.7%)` | |  | So Fiat | `#5C8001` | `rgb(92,128,1)` | `hsl(77,98.4%,25.3%)` | # Stacker News Icons SN utilizes a set of bespoke icons that support its communication internally across the platform. Icons help bring instant, intuitive cues for various types of content and features. We share them here for you so you can use as you wish and satisfy your creative needs. |  `` |  `` |  `[Bounty](https://m.stacker.news/75607)` |  `[Caret](https://m.stacker.news/75608)` |  `[Cowboy](https://m.stacker.news/75609)` |  `[Sun](https://m.stacker.news/75610)` | |---|---|---|---|---|---| |  **`[Edit](https://m.stacker.news/75611)`** |  **`[Gun](https://m.stacker.news/75612)`** |  **`[Horse](https://m.stacker.news/75613)`** |  **`[Info](https://m.stacker.news/75614)`** |  **`[Moon](https://m.stacker.news/75615)`** |  **`[Lightning](https://m.stacker.news/75616)`**| |  **`[Bald Lost Hat](https://m.stacker.news/75617)`**|  **`[Markdown](https://m.stacker.news/75618)`**|  **`[Nostr](https://m.stacker.news/75619)`**|  **`[Referral](https://m.stacker.news/75620)`**|  **`[Rewards](https://m.stacker.news/75621)`**|  **`[Horse Lost Saddle](https://m.stacker.news/75622)`**|  **`[Search](https://m.stacker.news/75623)`** | | **`[Shoot](https://m.stacker.news/75624)`** | **`[Texas](https://m.stacker.news/75625)`** |  **`[Upload](https://m.stacker.news/75626)`** |  **`[Zap Zap](https://m.stacker.news/75627)`** ||| # Stacker News Banners Banners are important visual elements used in our digital platforms and marketing materials. They help to highlight key stories, features or announcements while maintaining our brand aesthetic. Here below you'll find custom banners for Sn and for individial territories. I try to build those that I follow most, for now @AGORA is the only one that designed its own banners. Comment below if you'd like some banners for your territory! #### SN Dark background |970x250| |---| | ```|``|``| |728x90| |---| |  `` | #### SN Gold background |970x250| |---| |`` | |250x250|300x250|300x600| |---|---|---| |`` | `` |`` | |728x90| |---| |`` | #### SN by @Jon_Hodl |970x250| |---| | `` | |250x250|300x250|300x600| |---|---|---| | `` |  ``| `` | |728x90| |---| |`` | #### ~AGORA territory The SN P2P Marketplace |970x250| |---| | `` | |250x250|300x250|300x600| |---|---|---| | `` | ``|``| |728x90| |---| | ``| #### ~alter_native territory |970x250| |---| | ``| |250x250|300x250|300x600| |---|---|---| |``|``|``| |728x90| |---| |`` | #### ~bitcoin_beginners |970x250| |---| | `` | |250x250|300x250|300x600| |---|---|---| | ``|``|`` | |728x90| |---| | ``| #### ~Design territory |970x250| |---| |``| |250x250|300x250|300x600| |---|---|---| |``|``|``| |728x90| |---| |``| #### ~Music territory |970x250| |---| | ``| |250x250|300x250|300x600| |---|---|---| |``|``|``| |728x90| |---| | ``| # Anything else we could add? If you feel something is missing, or you know a better tool to manage this media kit for SN in a collaborative and FOSS way then, DO share it in a comment below Territory owners [^1], do you need banners for your territory? Feel free to edit the figma file liked above or comment below sharing your needs or ideas, I'll try to do something for you. By following these guidelines, we ensure consistency and professionalism in every case where Stacker News is represented here internally to stackers or to our audience in the KYC internet, reinforcing SN credibility as a trusted source for data-driven journalism. [^1]: FYI: @Aardvark @AGORA @anna @antic @AtlantisPleb @Bell_curve @benwehrman @bitcoinplebdev @Bitter @BlokchainB @ch0k1 @davidw @ek @elvismercury @frostdragon @grayruby @HODLR @inverselarp @Jon_Hodl @k00b @marks @MaxAWebster @mega_dreamer @niftynei @nout @OneOneSeven @OT @PlebLab @Public_N_M_E @RDClark @realBitcoinDog @roytheholographicuniverse @siggy47 @softsimon @south_korea_ln @theschoolofbitcoin @TNStacker @UCantDoThatDotNet @Undisciplined originally posted at https://stacker.news/items/872925 @ a95c6243:d345522c
2025-01-31 20:02:25*Im Augenblick wird mit größter Intensität, großer Umsicht* *\ das deutsche Volk belogen.* *\ Olaf Scholz im FAZ-[Interview](https://www.youtube.com/watch?v=c3KI1GmdoVc\&t=649s)*   **Online-Wahlen stärken die Demokratie, sind sicher, und 61 Prozent der Wahlberechtigten** sprechen sich für deren Einführung in Deutschland aus. Das zumindest behauptet eine aktuelle Umfrage, die auch über die Agentur *Reuters* Verbreitung in den Medien [gefunden](https://archive.is/dnZbY) hat. Demnach würden außerdem 45 Prozent der Nichtwähler bei der Bundestagswahl ihre Stimme abgeben, wenn sie dies zum Beispiel von Ihrem PC, Tablet oder Smartphone aus machen könnten. **Die telefonische Umfrage unter gut 1000 wahlberechtigten Personen** sei repräsentativ, [behauptet](https://www.bitkom.org/Presse/Presseinformation/Knapp-Haelfte-Nichtwaehler-wuerde-online-waehlen) der Auftraggeber – der Digitalverband Bitkom. Dieser präsentiert sich als eingetragener Verein mit einer beeindruckenden Liste von [Mitgliedern](https://www.bitkom.org/Bitkom/Mitgliedschaft/Mitgliederliste), die Software und IT-Dienstleistungen anbieten. Erklärtes Vereinsziel ist es, «Deutschland zu einem führenden Digitalstandort zu machen und die digitale Transformation der deutschen Wirtschaft und Verwaltung voranzutreiben». **Durchgeführt hat die Befragung die Bitkom Servicegesellschaft mbH,** also alles in der Familie. Die gleiche Erhebung hatte der Verband übrigens 2021 schon einmal durchgeführt. Damals sprachen sich angeblich sogar 63 Prozent für ein derartiges [«Demokratie-Update»](https://www.experten.de/id/4922407/online-wahlen-als-update-des-demokratischen-systems/) aus – die Tendenz ist demgemäß fallend. Dennoch orakelt mancher, der Gang zur Wahlurne gelte bereits als veraltet. **Die spanische Privat-Uni mit Globalisten-Touch, IE University, berichtete** Ende letzten Jahres in ihrer Studie «European Tech Insights», 67 Prozent der Europäer [befürchteten](https://www.ie.edu/university/news-events/news/67-europeans-fear-ai-manipulation-elections-according-ie-university-research/), dass Hacker Wahlergebnisse verfälschen könnten. Mehr als 30 Prozent der Befragten glaubten, dass künstliche Intelligenz (KI) bereits Wahlentscheidungen beeinflusst habe. Trotzdem würden angeblich 34 Prozent der unter 35-Jährigen einer KI-gesteuerten App vertrauen, um in ihrem Namen für politische Kandidaten zu stimmen. **Wie dauerhaft wird wohl das Ergebnis der kommenden Bundestagswahl sein?** Diese Frage stellt sich angesichts der aktuellen Entwicklung der Migrations-Debatte und der (vorübergehend) bröckelnden «Brandmauer» gegen die AfD. Das «Zustrombegrenzungsgesetz» der Union hat das Parlament heute Nachmittag überraschenderweise [abgelehnt](https://www.bundestag.de/dokumente/textarchiv/2025/kw05-de-zustrombegrenzungsgesetz-1042038). Dennoch muss man wohl kein ausgesprochener Pessimist sein, um zu befürchten, dass die Entscheidungen der Bürger von den selbsternannten Verteidigern der Demokratie künftig vielleicht nicht respektiert werden, weil sie nicht gefallen. **Bundesweit wird jetzt zu «Brandmauer-Demos» aufgerufen,** die CDU gerät unter Druck und es wird von Übergriffen auf Parteibüros und Drohungen gegen Mitarbeiter [berichtet](https://www.epochtimes.de/politik/deutschland/brandmauer-proteste-cdu-zentrale-geraeumt-kundgebungen-in-46-staedten-a5023745.html). Sicherheitsbehörden warnen vor Eskalationen, die Polizei sei «für ein mögliches erhöhtes Aufkommen von Straftaten gegenüber Politikern und gegen Parteigebäude sensibilisiert». **Der Vorwand** **[«unzulässiger Einflussnahme»](https://transition-news.org/die-minister-faeser-und-wissing-sorgen-sich-um-unzulassige-einflussnahme-auf)** **auf Politik und Wahlen** wird als Argument schon seit einiger Zeit aufgebaut. Der Manipulation schuldig befunden wird neben Putin und Trump auch Elon Musk, was lustigerweise ausgerechnet Bill Gates gerade noch einmal bekräftigt und als [«völlig irre»](https://transition-news.org/bill-gates-nennt-musks-einmischung-in-eu-politik-vollig-irre) bezeichnet hat. Man stelle sich die Diskussionen um die Gültigkeit von Wahlergebnissen vor, wenn es Online-Verfahren zur Stimmabgabe gäbe. In der Schweiz wird [«E-Voting»](https://www.ch.ch/de/abstimmungen-und-wahlen/e-voting/) seit einigen Jahren getestet, aber wohl bisher mit wenig Erfolg. **Die politische Brandstiftung der letzten Jahre zahlt sich immer mehr aus.** Anstatt dringende Probleme der Menschen zu lösen – zu denen auch in Deutschland die [weit verbreitete Armut](https://transition-news.org/ein-funftel-der-bevolkerung-in-deutschland-ist-von-armut-oder-sozialer) zählt –, hat die Politik konsequent polarisiert und sich auf Ausgrenzung und Verhöhnung großer Teile der Bevölkerung konzentriert. Basierend auf Ideologie und Lügen werden abweichende Stimmen unterdrückt und kriminalisiert, nicht nur und nicht erst in diesem Augenblick. Die nächsten Wochen dürften ausgesprochen spannend werden. *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/wahlen-und-wahlen-lassen)*** erschienen.
@ a95c6243:d345522c
2025-01-31 20:02:25*Im Augenblick wird mit größter Intensität, großer Umsicht* *\ das deutsche Volk belogen.* *\ Olaf Scholz im FAZ-[Interview](https://www.youtube.com/watch?v=c3KI1GmdoVc\&t=649s)*   **Online-Wahlen stärken die Demokratie, sind sicher, und 61 Prozent der Wahlberechtigten** sprechen sich für deren Einführung in Deutschland aus. Das zumindest behauptet eine aktuelle Umfrage, die auch über die Agentur *Reuters* Verbreitung in den Medien [gefunden](https://archive.is/dnZbY) hat. Demnach würden außerdem 45 Prozent der Nichtwähler bei der Bundestagswahl ihre Stimme abgeben, wenn sie dies zum Beispiel von Ihrem PC, Tablet oder Smartphone aus machen könnten. **Die telefonische Umfrage unter gut 1000 wahlberechtigten Personen** sei repräsentativ, [behauptet](https://www.bitkom.org/Presse/Presseinformation/Knapp-Haelfte-Nichtwaehler-wuerde-online-waehlen) der Auftraggeber – der Digitalverband Bitkom. Dieser präsentiert sich als eingetragener Verein mit einer beeindruckenden Liste von [Mitgliedern](https://www.bitkom.org/Bitkom/Mitgliedschaft/Mitgliederliste), die Software und IT-Dienstleistungen anbieten. Erklärtes Vereinsziel ist es, «Deutschland zu einem führenden Digitalstandort zu machen und die digitale Transformation der deutschen Wirtschaft und Verwaltung voranzutreiben». **Durchgeführt hat die Befragung die Bitkom Servicegesellschaft mbH,** also alles in der Familie. Die gleiche Erhebung hatte der Verband übrigens 2021 schon einmal durchgeführt. Damals sprachen sich angeblich sogar 63 Prozent für ein derartiges [«Demokratie-Update»](https://www.experten.de/id/4922407/online-wahlen-als-update-des-demokratischen-systems/) aus – die Tendenz ist demgemäß fallend. Dennoch orakelt mancher, der Gang zur Wahlurne gelte bereits als veraltet. **Die spanische Privat-Uni mit Globalisten-Touch, IE University, berichtete** Ende letzten Jahres in ihrer Studie «European Tech Insights», 67 Prozent der Europäer [befürchteten](https://www.ie.edu/university/news-events/news/67-europeans-fear-ai-manipulation-elections-according-ie-university-research/), dass Hacker Wahlergebnisse verfälschen könnten. Mehr als 30 Prozent der Befragten glaubten, dass künstliche Intelligenz (KI) bereits Wahlentscheidungen beeinflusst habe. Trotzdem würden angeblich 34 Prozent der unter 35-Jährigen einer KI-gesteuerten App vertrauen, um in ihrem Namen für politische Kandidaten zu stimmen. **Wie dauerhaft wird wohl das Ergebnis der kommenden Bundestagswahl sein?** Diese Frage stellt sich angesichts der aktuellen Entwicklung der Migrations-Debatte und der (vorübergehend) bröckelnden «Brandmauer» gegen die AfD. Das «Zustrombegrenzungsgesetz» der Union hat das Parlament heute Nachmittag überraschenderweise [abgelehnt](https://www.bundestag.de/dokumente/textarchiv/2025/kw05-de-zustrombegrenzungsgesetz-1042038). Dennoch muss man wohl kein ausgesprochener Pessimist sein, um zu befürchten, dass die Entscheidungen der Bürger von den selbsternannten Verteidigern der Demokratie künftig vielleicht nicht respektiert werden, weil sie nicht gefallen. **Bundesweit wird jetzt zu «Brandmauer-Demos» aufgerufen,** die CDU gerät unter Druck und es wird von Übergriffen auf Parteibüros und Drohungen gegen Mitarbeiter [berichtet](https://www.epochtimes.de/politik/deutschland/brandmauer-proteste-cdu-zentrale-geraeumt-kundgebungen-in-46-staedten-a5023745.html). Sicherheitsbehörden warnen vor Eskalationen, die Polizei sei «für ein mögliches erhöhtes Aufkommen von Straftaten gegenüber Politikern und gegen Parteigebäude sensibilisiert». **Der Vorwand** **[«unzulässiger Einflussnahme»](https://transition-news.org/die-minister-faeser-und-wissing-sorgen-sich-um-unzulassige-einflussnahme-auf)** **auf Politik und Wahlen** wird als Argument schon seit einiger Zeit aufgebaut. Der Manipulation schuldig befunden wird neben Putin und Trump auch Elon Musk, was lustigerweise ausgerechnet Bill Gates gerade noch einmal bekräftigt und als [«völlig irre»](https://transition-news.org/bill-gates-nennt-musks-einmischung-in-eu-politik-vollig-irre) bezeichnet hat. Man stelle sich die Diskussionen um die Gültigkeit von Wahlergebnissen vor, wenn es Online-Verfahren zur Stimmabgabe gäbe. In der Schweiz wird [«E-Voting»](https://www.ch.ch/de/abstimmungen-und-wahlen/e-voting/) seit einigen Jahren getestet, aber wohl bisher mit wenig Erfolg. **Die politische Brandstiftung der letzten Jahre zahlt sich immer mehr aus.** Anstatt dringende Probleme der Menschen zu lösen – zu denen auch in Deutschland die [weit verbreitete Armut](https://transition-news.org/ein-funftel-der-bevolkerung-in-deutschland-ist-von-armut-oder-sozialer) zählt –, hat die Politik konsequent polarisiert und sich auf Ausgrenzung und Verhöhnung großer Teile der Bevölkerung konzentriert. Basierend auf Ideologie und Lügen werden abweichende Stimmen unterdrückt und kriminalisiert, nicht nur und nicht erst in diesem Augenblick. Die nächsten Wochen dürften ausgesprochen spannend werden. *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/wahlen-und-wahlen-lassen)*** erschienen. @ 5188521b:008eb518
2025-01-31 08:38:47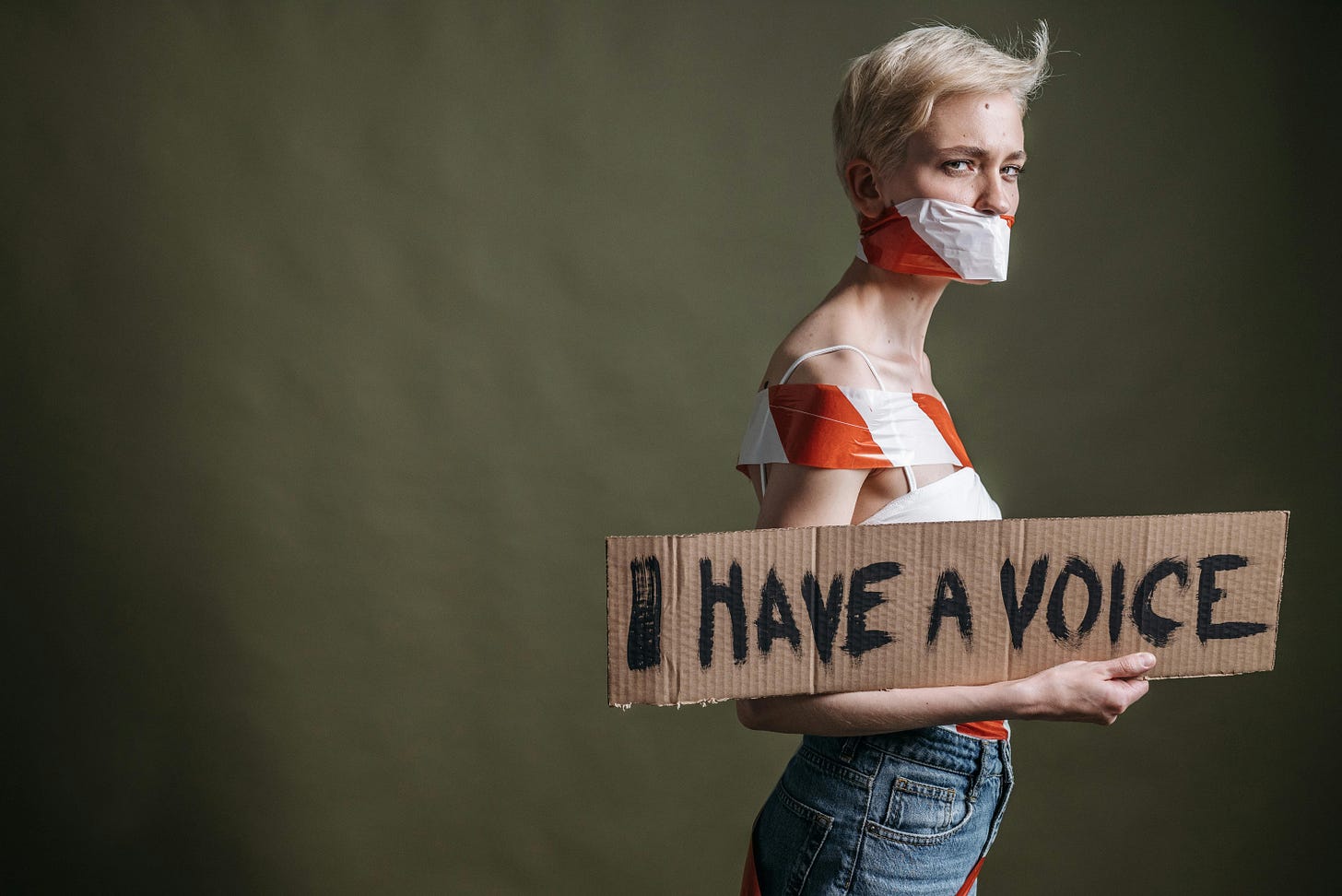*Photo by [Pavel Danilyuk](https://www.pexels.com/photo/a-woman-holding-a-placard-8553778/)* In the last four years, I’ve ridden the wave of social media. I’ve amassed thousands of followers, and my posts were read by millions. It’s empowering… until it isn’t. This year, I chose to stop publishing on LinkedIn, Medium, Facebook, Instagram, and Threads. My reach on each of these platforms dropped from 100% of my follower base to around 10%. My voice was being suppressed. I wasn’t writing anything particularly controversial. This is all just part of the social media life cycle. Platforms offer attractive terms to lock in users. They distribute our articles, posts, and thoughts widely to attract eyeballs for advertisers. Writers learn to play the algorithm to maximise reach and engagement. Maybe they even manage to monetize their writing. But when the platforms reach what they deem to be maximum usage and membership, they begin to reduce the benefits on offer. They ask writers to focus on specific topics, suppress non-mainstream opinion, or punish or ban any writers who don’t follow new rules. Big tech companies always eventually turn on the money tap by forcing users to suffer endless adverts and even make writers pay to reach the audience they have built. Newsflash: there is no company too big to fail. Digg, Google+, Myspace, Vine and many more socials have died. Self-reported active user numbers cannot be trusted. Meta recently trialed AI profiles to prop up falling usage projections on Instagram and Facebook. X is now a dumpster fire of bots, scammers, and rage bait. It has been co-opted by a megalomaniacal oligarch to spread his own worldview. And LinkedIn feeds are drowning in unsolicited AI-generated business twaddle. The social giants are entering the death spiral. # What happens in a social-media death spiral? Users don’t see the value in posting, so they move elsewhere. I wasn’t feeling rewarded for the thousands of hours I spent on LinkedIn, so I quit. I went from earning $20+ an article on Medium to pennies. Literal pennies. Bye bye, Tony Stubblebine. I learned that if you don’t own the distribution mechanic, you get left writing into the wind. Ultimately, writers will dedicate their energy to where they see a benefit. They should spend time and create value in the place most similar to their ideal world. For writers in 2025, that place seems to be Substack. Open rates are high and the platform is adding social features to generate more engagement in app. Substack is [experiencing massive growth](https://backlinko.com/substack-users) in active (and paid) subscriptions. Yet, it is following the same pattern as Medium in and LinkedIn in become self-cannibalising. Many of the most popular accounts write about ‘how to grow’ or ‘how to make money’ on Substack. Queue the eye rolls. For me, it’s not the promised land where writers can earn a living. Of course, it’s no walk in the park to earn paid subscribers. Further, Substack users can only receive payment via Stripe. This excludes writers from 149 of the World’s countries. Does that seem open and fair to you? Even with all this going on, there is a much bigger factor that should influence your choice of platform — ownership. # Do writers really own their words? Who reads the terms and conditions? Nobody. That’s who.Writers (including me) rush to all platforms which promise to give us benefits such as pay, distribution, and audience growth. In exchange, companies request access to and shared ownership of our content. They can use our words to train LLMs, analyse trends, repurpose, and to spy on us. Governments can and will request access to social media profiles. They seek to control the use of those platforms. Founders and CEOs who refuse to comply may be held personally accountable and put on trial, just as [Telegram founder, Pavel Durov, was](https://www.bbc.com/news/articles/c78lgzl919go) in France. Big tech owns our content, and governments threaten platforms into obedience. As much as it benefits society to suppress harmful or dangerous content, companies simply can’t be censors 24/7. Growing platforms like [Bluesky are already struggling to moderate content effectively](https://www.theregister.com/2024/12/02/bluesky_growing_problems/). Without a strong economic incentive to moderate, companies will simply refuse to do it (as long as the threat of criminal charges does not prevail). To sum up: No privately owned social media network offers writers the opportunity to own and distribute their work in order to receive a fair and equitable benefit. Enter NOSTR… # Decentralizing Social Media **Notes and Other Stuff Transmitted by Relays** (NOSTR) is not a platform; it’s an open protocol. By signing messages with their private keys (a long string of characters), users generate “events”. These events (messages/updates/media/transactions) are then broadcast through a series of “relays.” Developers can use the protocol to build various applications that retrieve and distribute these events to other users. These ‘clients’ can range from microblogging sites like X and long-form distributors like Substack to visual media platforms like Instagram. Plus, NOSTR is also a whole lot more than that (but this is a topic for another day). Decentralized tools offer the only hope against the dominance of AI and big tech in a top-down autocratic system designed to control us more than the thought police ever could. <img src="https://blossom.primal.net/93a44d9bfe3c768e41d8bfef52415131af3ca21814a23870a029f1a947288cc8.webp"> *Diagram courtesy of River.* So why should writers opt out of their big audience pool to write on some ‘protocol’? **Ownership, fair rules, and fair value.** - **Ownership**: While privately run corporations can suppress the ideas they want, NOSTR provides a censorship-resistant alternative. No individual actors can restrict content or accounts. Your private keys provide **permanent access** to the messages you have signed. No one else has access to them. And while some clients provide a delete function, there is no way to force all relays to respect a delete request. Not only do writers own what they publish, but it’s a permanent record. - **Rules:** Traditional social media platforms use proprietary algorithms to curate and order our feeds. **NOSTR has no algorithm**. NOSTR clients display messages chronologically or based on user-defined criteria, removing the influence of opaque algorithms that could manipulate user engagement and visibility of posts. Put simply, distribution and consumption is down to the user, not to the creator or the platform. And everyone works to the same rules. - **Value:** Harmful content and spam affect all of us. There is no way to stop malicious content from being published on NOSTR, but two factors control its consumption. 1. Clients are experimenting with strategies such as requiring proof-of-work with each note or requiring verification badges. 2. Quality control is enforced by the value transferred by the protocol. Bitcoin micropayments have become the monetary lifeblood flowing in the decentralized world. The ability to ‘zap’ users actual monetary value (e.g. a few cents) provides a clear display of which messages are valuable and which are unwanted. In time, as more users adopt the mechanic of value transfer, spammers will see their approach is not bearing fruit. The beauty of using bitcoin in this way is twofold. Firstly, it is truly equitable — anyone in the world can receive it instantly and it cannot be stopped. And the system of frictionless micropayments offers content creators (artists, podcasters, musicians, writers) a way to earn money for the value they produce. Put simply, this could save creativity from doom. Think people still want all content for free? Think again. Try zapping a writer from the Philippines, an artist from Peru, a Congolese musician, or a poet from Poland to show them you enjoyed what they produced. THAT is truly empowering. Not convinced? The best thing about NOSTR for writers is that **you are early**. By being an early adopter with a low time preference, you can build a sizeable audience as new users discover the protocol. Of course, topics like bitcoin, freedom tech, and privacy are well covered, but if you write in another niche, you could be ‘quids in’. # Conclusion: By adopting a long-term strategy and sticking to their principles, readers, writers and all other creatives can build a better world on social media. It doesn’t matter that it is imperfect. There will always be flaws in any society. But decentralized protocols like NOSTR can offer writers what they truly want — ownership, fair rules, and fair value. --- Philip Charter is a totally human writer who helps bitcoin-native companies and clients stack major gains through laser-focused content. Find out more at [totallyhumanwriter.com](https://totallyhumanwriter.com) He is also the editor of the cypherpunk and freedom fiction project, [21 Futures](https://21futures.com).
@ 5188521b:008eb518
2025-01-31 08:38:47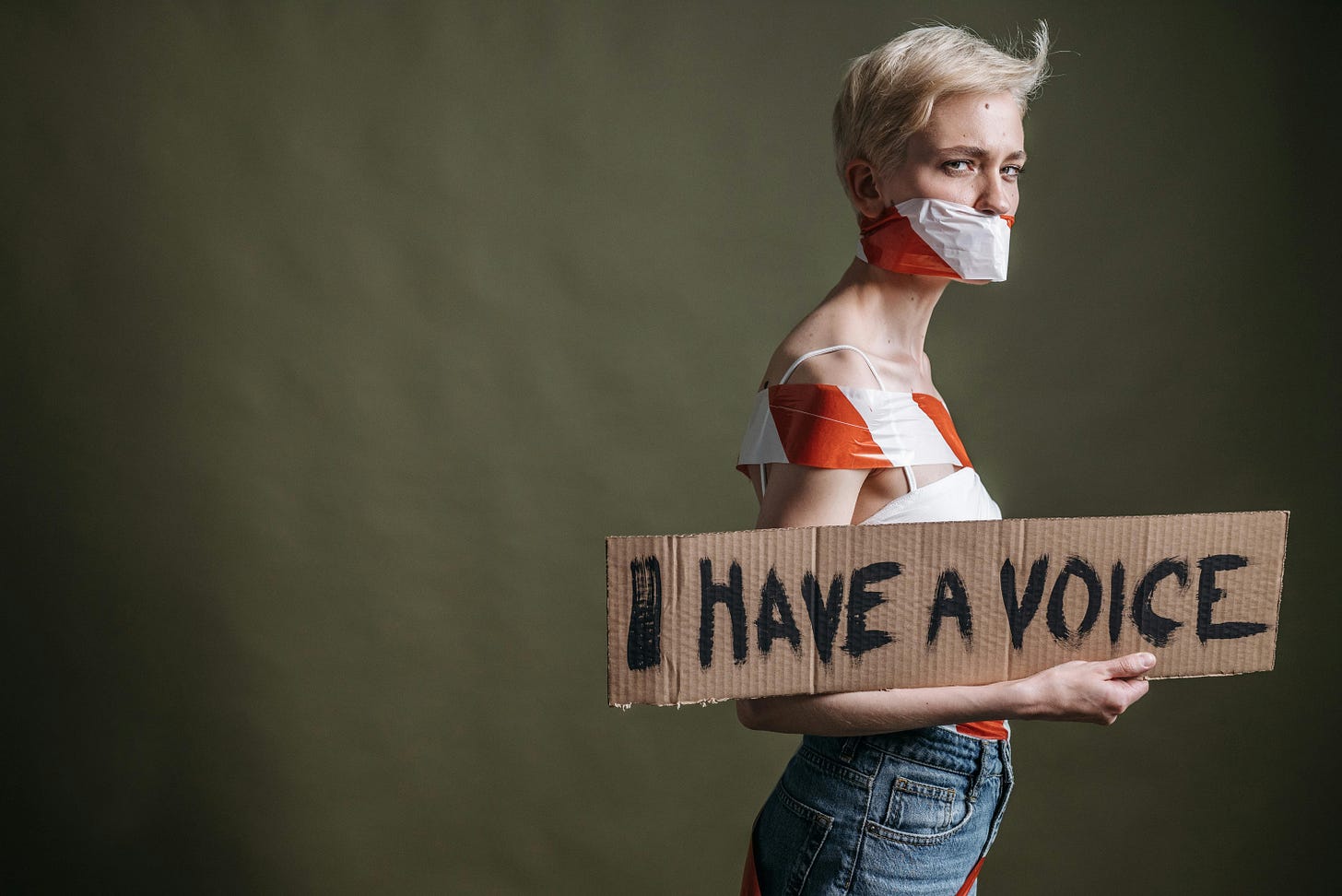*Photo by [Pavel Danilyuk](https://www.pexels.com/photo/a-woman-holding-a-placard-8553778/)* In the last four years, I’ve ridden the wave of social media. I’ve amassed thousands of followers, and my posts were read by millions. It’s empowering… until it isn’t. This year, I chose to stop publishing on LinkedIn, Medium, Facebook, Instagram, and Threads. My reach on each of these platforms dropped from 100% of my follower base to around 10%. My voice was being suppressed. I wasn’t writing anything particularly controversial. This is all just part of the social media life cycle. Platforms offer attractive terms to lock in users. They distribute our articles, posts, and thoughts widely to attract eyeballs for advertisers. Writers learn to play the algorithm to maximise reach and engagement. Maybe they even manage to monetize their writing. But when the platforms reach what they deem to be maximum usage and membership, they begin to reduce the benefits on offer. They ask writers to focus on specific topics, suppress non-mainstream opinion, or punish or ban any writers who don’t follow new rules. Big tech companies always eventually turn on the money tap by forcing users to suffer endless adverts and even make writers pay to reach the audience they have built. Newsflash: there is no company too big to fail. Digg, Google+, Myspace, Vine and many more socials have died. Self-reported active user numbers cannot be trusted. Meta recently trialed AI profiles to prop up falling usage projections on Instagram and Facebook. X is now a dumpster fire of bots, scammers, and rage bait. It has been co-opted by a megalomaniacal oligarch to spread his own worldview. And LinkedIn feeds are drowning in unsolicited AI-generated business twaddle. The social giants are entering the death spiral. # What happens in a social-media death spiral? Users don’t see the value in posting, so they move elsewhere. I wasn’t feeling rewarded for the thousands of hours I spent on LinkedIn, so I quit. I went from earning $20+ an article on Medium to pennies. Literal pennies. Bye bye, Tony Stubblebine. I learned that if you don’t own the distribution mechanic, you get left writing into the wind. Ultimately, writers will dedicate their energy to where they see a benefit. They should spend time and create value in the place most similar to their ideal world. For writers in 2025, that place seems to be Substack. Open rates are high and the platform is adding social features to generate more engagement in app. Substack is [experiencing massive growth](https://backlinko.com/substack-users) in active (and paid) subscriptions. Yet, it is following the same pattern as Medium in and LinkedIn in become self-cannibalising. Many of the most popular accounts write about ‘how to grow’ or ‘how to make money’ on Substack. Queue the eye rolls. For me, it’s not the promised land where writers can earn a living. Of course, it’s no walk in the park to earn paid subscribers. Further, Substack users can only receive payment via Stripe. This excludes writers from 149 of the World’s countries. Does that seem open and fair to you? Even with all this going on, there is a much bigger factor that should influence your choice of platform — ownership. # Do writers really own their words? Who reads the terms and conditions? Nobody. That’s who.Writers (including me) rush to all platforms which promise to give us benefits such as pay, distribution, and audience growth. In exchange, companies request access to and shared ownership of our content. They can use our words to train LLMs, analyse trends, repurpose, and to spy on us. Governments can and will request access to social media profiles. They seek to control the use of those platforms. Founders and CEOs who refuse to comply may be held personally accountable and put on trial, just as [Telegram founder, Pavel Durov, was](https://www.bbc.com/news/articles/c78lgzl919go) in France. Big tech owns our content, and governments threaten platforms into obedience. As much as it benefits society to suppress harmful or dangerous content, companies simply can’t be censors 24/7. Growing platforms like [Bluesky are already struggling to moderate content effectively](https://www.theregister.com/2024/12/02/bluesky_growing_problems/). Without a strong economic incentive to moderate, companies will simply refuse to do it (as long as the threat of criminal charges does not prevail). To sum up: No privately owned social media network offers writers the opportunity to own and distribute their work in order to receive a fair and equitable benefit. Enter NOSTR… # Decentralizing Social Media **Notes and Other Stuff Transmitted by Relays** (NOSTR) is not a platform; it’s an open protocol. By signing messages with their private keys (a long string of characters), users generate “events”. These events (messages/updates/media/transactions) are then broadcast through a series of “relays.” Developers can use the protocol to build various applications that retrieve and distribute these events to other users. These ‘clients’ can range from microblogging sites like X and long-form distributors like Substack to visual media platforms like Instagram. Plus, NOSTR is also a whole lot more than that (but this is a topic for another day). Decentralized tools offer the only hope against the dominance of AI and big tech in a top-down autocratic system designed to control us more than the thought police ever could. <img src="https://blossom.primal.net/93a44d9bfe3c768e41d8bfef52415131af3ca21814a23870a029f1a947288cc8.webp"> *Diagram courtesy of River.* So why should writers opt out of their big audience pool to write on some ‘protocol’? **Ownership, fair rules, and fair value.** - **Ownership**: While privately run corporations can suppress the ideas they want, NOSTR provides a censorship-resistant alternative. No individual actors can restrict content or accounts. Your private keys provide **permanent access** to the messages you have signed. No one else has access to them. And while some clients provide a delete function, there is no way to force all relays to respect a delete request. Not only do writers own what they publish, but it’s a permanent record. - **Rules:** Traditional social media platforms use proprietary algorithms to curate and order our feeds. **NOSTR has no algorithm**. NOSTR clients display messages chronologically or based on user-defined criteria, removing the influence of opaque algorithms that could manipulate user engagement and visibility of posts. Put simply, distribution and consumption is down to the user, not to the creator or the platform. And everyone works to the same rules. - **Value:** Harmful content and spam affect all of us. There is no way to stop malicious content from being published on NOSTR, but two factors control its consumption. 1. Clients are experimenting with strategies such as requiring proof-of-work with each note or requiring verification badges. 2. Quality control is enforced by the value transferred by the protocol. Bitcoin micropayments have become the monetary lifeblood flowing in the decentralized world. The ability to ‘zap’ users actual monetary value (e.g. a few cents) provides a clear display of which messages are valuable and which are unwanted. In time, as more users adopt the mechanic of value transfer, spammers will see their approach is not bearing fruit. The beauty of using bitcoin in this way is twofold. Firstly, it is truly equitable — anyone in the world can receive it instantly and it cannot be stopped. And the system of frictionless micropayments offers content creators (artists, podcasters, musicians, writers) a way to earn money for the value they produce. Put simply, this could save creativity from doom. Think people still want all content for free? Think again. Try zapping a writer from the Philippines, an artist from Peru, a Congolese musician, or a poet from Poland to show them you enjoyed what they produced. THAT is truly empowering. Not convinced? The best thing about NOSTR for writers is that **you are early**. By being an early adopter with a low time preference, you can build a sizeable audience as new users discover the protocol. Of course, topics like bitcoin, freedom tech, and privacy are well covered, but if you write in another niche, you could be ‘quids in’. # Conclusion: By adopting a long-term strategy and sticking to their principles, readers, writers and all other creatives can build a better world on social media. It doesn’t matter that it is imperfect. There will always be flaws in any society. But decentralized protocols like NOSTR can offer writers what they truly want — ownership, fair rules, and fair value. --- Philip Charter is a totally human writer who helps bitcoin-native companies and clients stack major gains through laser-focused content. Find out more at [totallyhumanwriter.com](https://totallyhumanwriter.com) He is also the editor of the cypherpunk and freedom fiction project, [21 Futures](https://21futures.com). @ 57d1a264:69f1fee1
2025-01-31 02:07:27 Bitcoin Design members have been involved in organizing various events (and sometimes just attend, too). Here below is what do we want to do in 2025: - **[Designathon 2](https://github.com/BitcoinDesign/Meta/issues/625)** - We are organizing this event between February or March. - **[Accessibility Day](https://accessibility.day)** - May 15 - - BDC has participated in this global initiative the last two years. Probably doing so again! - **[BTC Prague](https://btcprague.com)** -Participation Confirmed. Planning issues [here](https://github.com/BitcoinDesign/Meta/issues/745) - June 19 - 21 - * We organized the design track for dev day in 2023 and 2024. Do this again[\[k\]](#cmnt11)[\[l\]](#cmnt12)? It’s going to be on June 18, before the main conference. - * 2024 was great, in that we had a nice group of designers attend, do talks, go for dinner, etc. - **[Summer of Bitcoin](https://www.google.com/url?q=https://www.summerofbitcoin.org)** - * Several designers and projects participated each of the last 3 years. Probably doing so again! - * Applications open on Feb 1, main program is May to August ([timeline](https://www.summerofbitcoin.org/how-it-works/) - **UX Bootcamps** - * Previous: South America - * Next: [South America](https://www.bitcoinuxbootcamp.xyz/southamerica) - February 17 - 22 - **[Bitshala fellowship](https://bitshala.org)** - * First iteration of this fellowship is from January to July - * We will help find more designers, projects, and funding in India - **[Oslo Freedom Forum](https://oslofreedomforum.com)** - Oslo, May 26-28 - * Activist and financial repression use cases are uniquely important use cases for bitcoin. - * Several people attended last year. Conversations lead to new initiatives. - **[BTCHEL](https://btchel.com/)** - by BTC Helsinki Community - Aug 15-16 - * First large-scale bitcoin conference in the Nordics with particular focus to onboard new users to bitcoin - **Bitcoin Presidio design week** - * This is a new Bitcoin co-working space in San Francisco, also announced here https://stacker.news/items/860931/r/Design_r. The idea came up to organize a design week there to support the creation of art and decoration for the new co-working space. Just an idea at the moment, but why not make it happen? - * [Discussion issue](https://github.com/BitcoinDesign/Meta/issues/746). - **BuildWithLDK** - * An initiative to promote LDK and LDK Node for building lightning applications. There could be collaboration around a Designathon, connecting designers with hackathon projects, etc. Still in early planning. - **Builder conferences**: These are very builder-focused, making them good opportunities to connect, organize practical design workshops, creative presentations, and support projects from a design perspective - * [Baltic Honeybadger](https://baltichoneybadger.com) (August 9-10), - * [TABConf](http://tabconf.com) - * [Bitcoin++](https://btcplusplus.dev) There are going to be 6 of them throughout the year. - * [SATS’N’FACTS](https://satsandfacts.btc.pub/) (February 8-10) Bitcoin Technical Unconference, Hackathon & Freedom Tech Art Exhibition - **Open-source conferences & events* - * [FOSS Backstage](http://foss-backstage.de) (Berlin, Mar 10-11) - Christoph will present the Open Design Guide - * [FOSDEM](https://fosdem.org/2025/) (Brussels, Feb 1-2) - anyone attending? - **Design conferences & events** - Makes sense to be involved with design-only events, right? * [OFFF](https://www.offf.barcelona) - very creative-focused (Barcelona, May 8-10) * [CSUN Accessibility conference](https://www.csun.edu/cod/conference/sessions/) **Other Ideas** * Bitcoin Park - they might organize another design event like two years ago https://stacker.news/items/705081/r/Design_r **Links** * [Comprehensive list](https://docs.google.com/spreadsheets/d/147AXd8hN3uO3v_P1dupgfRCRzSMlH85dvQSHPAg7lZ4/edit?usp%3Dsharing) of bitcoin conferences - - - … what’s missing from this page? Are you involved with anything? Or want to be? Comment below or join us on https://discord.com/channels/903125802726596648/1087394066796384276 You can watch the recording from https://www.youtube.com/watch?v=GGS3oSlLmAo originally posted at https://stacker.news/items/870638
@ 57d1a264:69f1fee1
2025-01-31 02:07:27 Bitcoin Design members have been involved in organizing various events (and sometimes just attend, too). Here below is what do we want to do in 2025: - **[Designathon 2](https://github.com/BitcoinDesign/Meta/issues/625)** - We are organizing this event between February or March. - **[Accessibility Day](https://accessibility.day)** - May 15 - - BDC has participated in this global initiative the last two years. Probably doing so again! - **[BTC Prague](https://btcprague.com)** -Participation Confirmed. Planning issues [here](https://github.com/BitcoinDesign/Meta/issues/745) - June 19 - 21 - * We organized the design track for dev day in 2023 and 2024. Do this again[\[k\]](#cmnt11)[\[l\]](#cmnt12)? It’s going to be on June 18, before the main conference. - * 2024 was great, in that we had a nice group of designers attend, do talks, go for dinner, etc. - **[Summer of Bitcoin](https://www.google.com/url?q=https://www.summerofbitcoin.org)** - * Several designers and projects participated each of the last 3 years. Probably doing so again! - * Applications open on Feb 1, main program is May to August ([timeline](https://www.summerofbitcoin.org/how-it-works/) - **UX Bootcamps** - * Previous: South America - * Next: [South America](https://www.bitcoinuxbootcamp.xyz/southamerica) - February 17 - 22 - **[Bitshala fellowship](https://bitshala.org)** - * First iteration of this fellowship is from January to July - * We will help find more designers, projects, and funding in India - **[Oslo Freedom Forum](https://oslofreedomforum.com)** - Oslo, May 26-28 - * Activist and financial repression use cases are uniquely important use cases for bitcoin. - * Several people attended last year. Conversations lead to new initiatives. - **[BTCHEL](https://btchel.com/)** - by BTC Helsinki Community - Aug 15-16 - * First large-scale bitcoin conference in the Nordics with particular focus to onboard new users to bitcoin - **Bitcoin Presidio design week** - * This is a new Bitcoin co-working space in San Francisco, also announced here https://stacker.news/items/860931/r/Design_r. The idea came up to organize a design week there to support the creation of art and decoration for the new co-working space. Just an idea at the moment, but why not make it happen? - * [Discussion issue](https://github.com/BitcoinDesign/Meta/issues/746). - **BuildWithLDK** - * An initiative to promote LDK and LDK Node for building lightning applications. There could be collaboration around a Designathon, connecting designers with hackathon projects, etc. Still in early planning. - **Builder conferences**: These are very builder-focused, making them good opportunities to connect, organize practical design workshops, creative presentations, and support projects from a design perspective - * [Baltic Honeybadger](https://baltichoneybadger.com) (August 9-10), - * [TABConf](http://tabconf.com) - * [Bitcoin++](https://btcplusplus.dev) There are going to be 6 of them throughout the year. - * [SATS’N’FACTS](https://satsandfacts.btc.pub/) (February 8-10) Bitcoin Technical Unconference, Hackathon & Freedom Tech Art Exhibition - **Open-source conferences & events* - * [FOSS Backstage](http://foss-backstage.de) (Berlin, Mar 10-11) - Christoph will present the Open Design Guide - * [FOSDEM](https://fosdem.org/2025/) (Brussels, Feb 1-2) - anyone attending? - **Design conferences & events** - Makes sense to be involved with design-only events, right? * [OFFF](https://www.offf.barcelona) - very creative-focused (Barcelona, May 8-10) * [CSUN Accessibility conference](https://www.csun.edu/cod/conference/sessions/) **Other Ideas** * Bitcoin Park - they might organize another design event like two years ago https://stacker.news/items/705081/r/Design_r **Links** * [Comprehensive list](https://docs.google.com/spreadsheets/d/147AXd8hN3uO3v_P1dupgfRCRzSMlH85dvQSHPAg7lZ4/edit?usp%3Dsharing) of bitcoin conferences - - - … what’s missing from this page? Are you involved with anything? Or want to be? Comment below or join us on https://discord.com/channels/903125802726596648/1087394066796384276 You can watch the recording from https://www.youtube.com/watch?v=GGS3oSlLmAo originally posted at https://stacker.news/items/870638 @ 97c70a44:ad98e322
2025-01-30 17:15:37There was a slight dust up recently over a website someone runs removing a listing for an app someone built based on entirely arbitrary criteria. I'm not to going to attempt to speak for either wounded party, but I would like to share my own personal definition for what constitutes a "nostr app" in an effort to help clarify what might be an otherwise confusing and opaque purity test. In this post, I will be committing the "no true Scotsman" fallacy, in which I start with the most liberal definition I can come up with, and gradually refine it until all that is left is the purest, gleamingest, most imaginary and unattainable nostr app imaginable. As I write this, I wonder if anything built yet will actually qualify. In any case, here we go. # It uses nostr The lowest bar for what a "nostr app" might be is an app ("application" - i.e. software, not necessarily a native app of any kind) that has some nostr-specific code in it, but which doesn't take any advantage of what makes nostr distinctive as a protocol. Examples might include a scraper of some kind which fulfills its charter by fetching data from relays (regardless of whether it validates or retains signatures). Another might be a regular web 2.0 app which provides an option to "log in with nostr" by requesting and storing the user's public key. In either case, the fact that nostr is involved is entirely neutral. A scraper can scrape html, pdfs, jsonl, whatever data source - nostr relays are just another target. Likewise, a user's key in this scenario is treated merely as an opaque identifier, with no appreciation for the super powers it brings along. In most cases, this kind of app only exists as a marketing ploy, or less cynically, because it wants to get in on the hype of being a "nostr app", without the developer quite understanding what that means, or having the budget to execute properly on the claim. # It leverages nostr Some of you might be wondering, "isn't 'leverage' a synonym for 'use'?" And you would be right, but for one connotative difference. It's possible to "use" something improperly, but by definition leverage gives you a mechanical advantage that you wouldn't otherwise have. This is the second category of "nostr app". This kind of app gets some benefit out of the nostr protocol and network, but in an entirely selfish fashion. The intention of this kind of app is not to augment the nostr network, but to augment its own UX by borrowing some nifty thing from the protocol without really contributing anything back. Some examples might include: - Using nostr signers to encrypt or sign data, and then store that data on a proprietary server. - Using nostr relays as a kind of low-code backend, but using proprietary event payloads. - Using nostr event kinds to represent data (why), but not leveraging the trustlessness that buys you. An application in this category might even communicate to its users via nostr DMs - but this doesn't make it a "nostr app" any more than a website that emails you hot deals on herbal supplements is an "email app". These apps are purely parasitic on the nostr ecosystem. In the long-term, that's not necessarily a bad thing. Email's ubiquity is self-reinforcing. But in the short term, this kind of "nostr app" can actually do damage to nostr's reputation by over-promising and under-delivering. # It complements nostr Next up, we have apps that get some benefit out of nostr as above, but give back by providing a unique value proposition to nostr users as nostr users. This is a bit of a fine distinction, but for me this category is for apps which focus on solving problems that nostr isn't good at solving, leaving the nostr integration in a secondary or supporting role. One example of this kind of app was Mutiny (RIP), which not only allowed users to sign in with nostr, but also pulled those users' social graphs so that users could send money to people they knew and trusted. Mutiny was doing a great job of leveraging nostr, as well as providing value to users with nostr identities - but it was still primarily a bitcoin wallet, not a "nostr app" in the purest sense. Other examples are things like Nostr Nests and Zap.stream, whose core value proposition is streaming video or audio content. Both make great use of nostr identities, data formats, and relays, but they're primarily streaming apps. A good litmus test for things like this is: if you got rid of nostr, would it be the same product (even if inferior in certain ways)? A similar category is infrastructure providers that benefit nostr by their existence (and may in fact be targeted explicitly at nostr users), but do things in a centralized, old-web way; for example: media hosts, DNS registrars, hosting providers, and CDNs. To be clear here, I'm not casting aspersions (I don't even know what those are, or where to buy them). All the apps mentioned above use nostr to great effect, and are a real benefit to nostr users. But they are not True Scotsmen. # It embodies nostr Ok, here we go. This is the crème de la crème, the top du top, the meilleur du meilleur, the bee's knees. The purest, holiest, most chaste category of nostr app out there. The apps which are, indeed, nostr indigitate. This category of nostr app (see, no quotes this time) can be defined by the converse of the previous category. If nostr was removed from this type of application, would it be impossible to create the same product? To tease this apart a bit, apps that leverage the technical aspects of nostr are dependent on nostr the *protocol*, while apps that benefit nostr exclusively via network effect are integrated into nostr the *network*. An app that does both things is working in symbiosis with nostr as a whole. An app that embraces both nostr's protocol and its network becomes an organic extension of every other nostr app out there, multiplying both its competitive moat and its contribution to the ecosystem: - In contrast to apps that only borrow from nostr on the technical level but continue to operate in their own silos, an application integrated into the nostr network comes pre-packaged with existing users, and is able to provide more value to those users because of other nostr products. On nostr, it's a good thing to advertise your competitors. - In contrast to apps that only market themselves to nostr users without building out a deep integration on the protocol level, a deeply integrated app becomes an asset to every other nostr app by becoming an organic extension of them through interoperability. This results in increased traffic to the app as other developers and users refer people to it instead of solving their problem on their own. This is the "micro-apps" utopia we've all been waiting for. Credible exit doesn't matter if there aren't alternative services. Interoperability is pointless if other applications don't offer something your app doesn't. Marketing to nostr users doesn't matter if you don't augment their agency _as nostr users_. If I had to choose a single NIP that represents the mindset behind this kind of app, it would be NIP 89 A.K.A. "Recommended Application Handlers", which states: > Nostr's discoverability and transparent event interaction is one of its most interesting/novel mechanics. This NIP provides a simple way for clients to discover applications that handle events of a specific kind to ensure smooth cross-client and cross-kind interactions. These handlers are the glue that holds nostr apps together. A single event, signed by the developer of an application (or by the application's own account) tells anyone who wants to know 1. what event kinds the app supports, 2. how to link to the app (if it's a client), and (if the pubkey also publishes a kind 10002), 3. which relays the app prefers. _As a sidenote, NIP 89 is currently focused more on clients, leaving DVMs, relays, signers, etc somewhat out in the cold. Updating 89 to include tailored listings for each kind of supporting app would be a huge improvement to the protocol. This, plus a good front end for navigating these listings (sorry nostrapp.link, close but no cigar) would obviate the evil centralized websites that curate apps based on arbitrary criteria._ Examples of this kind of app obviously include many kind 1 clients, as well as clients that attempt to bring the benefits of the nostr protocol and network to new use cases - whether long form content, video, image posts, music, emojis, recipes, project management, or any other "content type". To drill down into one example, let's think for a moment about forms. What's so great about a forms app that is built on nostr? Well, - There is a [spec](https://github.com/nostr-protocol/nips/pull/1190) for forms and responses, which means that... - Multiple clients can implement the same data format, allowing for credible exit and user choice, even of... - Other products not focused on forms, which can still view, respond to, or embed forms, and which can send their users via NIP 89 to a client that does... - Cryptographically sign forms and responses, which means they are self-authenticating and can be sent to... - Multiple relays, which reduces the amount of trust necessary to be confident results haven't been deliberately "lost". Show me a forms product that does all of those things, and isn't built on nostr. You can't, because it doesn't exist. Meanwhile, there are plenty of image hosts with APIs, streaming services, and bitcoin wallets which have basically the same levels of censorship resistance, interoperability, and network effect as if they weren't built on nostr. # It supports nostr Notice I haven't said anything about whether relays, signers, blossom servers, software libraries, DVMs, and the accumulated addenda of the nostr ecosystem are nostr apps. Well, they are (usually). This is the category of nostr app that gets none of the credit for doing all of the work. There's no question that they qualify as beautiful nostrcorns, because their value propositions are entirely meaningless outside of the context of nostr. Who needs a signer if you don't have a cryptographic identity you need to protect? DVMs are literally impossible to use without relays. How are you going to find the blossom server that will serve a given hash if you don't know which servers the publishing user has selected to store their content? In addition to being entirely contextualized by nostr architecture, this type of nostr app is valuable because it does things "the nostr way". By that I mean that they don't simply try to replicate existing internet functionality into a nostr context; instead, they create entirely new ways of putting the basic building blocks of the internet back together. A great example of this is how Nostr Connect, Nostr Wallet Connect, and DVMs all use relays as brokers, which allows service providers to avoid having to accept incoming network connections. This opens up really interesting possibilities all on its own. So while I might hesitate to call many of these things "apps", they are certainly "nostr". # Appendix: it smells like a NINO So, let's say you've created an app, but when you show it to people they politely smile, nod, and call it a NINO (Nostr In Name Only). What's a hacker to do? Well, here's your handy-dandy guide on how to wash that NINO stench off and Become a Nostr. You app might be a NINO if: - There's no NIP for your data format (or you're abusing NIP 78, 32, etc by inventing a sub-protocol inside an existing event kind) - There's a NIP, but no one knows about it because it's in a text file on your hard drive (or buried in your project's repository) - Your NIP imposes an incompatible/centralized/legacy web paradigm onto nostr - Your NIP relies on trusted third (or first) parties - There's only one implementation of your NIP (yours) - Your core value proposition doesn't depend on relays, events, or nostr identities - One or more relay urls are hard-coded into the source code - Your app depends on a specific relay implementation to work (*ahem*, relay29) - You don't validate event signatures - You don't publish events to relays you don't control - You don't read events from relays you don't control - You use legacy web services to solve problems, rather than nostr-native solutions - You use nostr-native solutions, but you've hardcoded their pubkeys or URLs into your app - You don't use NIP 89 to discover clients and services - You haven't published a NIP 89 listing for your app - You don't leverage your users' web of trust for filtering out spam - You don't respect your users' mute lists - You try to "own" your users' data Now let me just re-iterate - it's ok to be a NINO. We need NINOs, because nostr can't (and shouldn't) tackle every problem. You just need to decide whether your app, as a NINO, is actually contributing to the nostr ecosystem, or whether you're just using buzzwords to whitewash a legacy web software product. If you're in the former camp, great! If you're in the latter, what are you waiting for? Only you can fix your NINO problem. And there are lots of ways to do this, depending on your own unique situation: - Drop nostr support if it's not doing anyone any good. If you want to build a normal company and make some money, that's perfectly fine. - Build out your nostr integration - start taking advantage of webs of trust, self-authenticating data, event handlers, etc. - Work around the problem. Think you need a special relay feature for your app to work? Guess again. Consider encryption, AUTH, DVMs, or better data formats. - Think your idea is a good one? Talk to other devs or open a PR to the [nips repo](https://github.com/nostr-protocol/nips). No one can adopt your NIP if they don't know about it. - Keep going. It can sometimes be hard to distinguish a research project from a NINO. New ideas have to be built out before they can be fully appreciated. - Listen to advice. Nostr developers are friendly and happy to help. If you're not sure why you're getting traction, ask! I sincerely hope this article is useful for all of you out there in NINO land. Maybe this made you feel better about not passing the totally optional nostr app purity test. Or maybe it gave you some actionable next steps towards making a great NINON (Nostr In Not Only Name) app. In either case, GM and PV.
@ 97c70a44:ad98e322
2025-01-30 17:15:37There was a slight dust up recently over a website someone runs removing a listing for an app someone built based on entirely arbitrary criteria. I'm not to going to attempt to speak for either wounded party, but I would like to share my own personal definition for what constitutes a "nostr app" in an effort to help clarify what might be an otherwise confusing and opaque purity test. In this post, I will be committing the "no true Scotsman" fallacy, in which I start with the most liberal definition I can come up with, and gradually refine it until all that is left is the purest, gleamingest, most imaginary and unattainable nostr app imaginable. As I write this, I wonder if anything built yet will actually qualify. In any case, here we go. # It uses nostr The lowest bar for what a "nostr app" might be is an app ("application" - i.e. software, not necessarily a native app of any kind) that has some nostr-specific code in it, but which doesn't take any advantage of what makes nostr distinctive as a protocol. Examples might include a scraper of some kind which fulfills its charter by fetching data from relays (regardless of whether it validates or retains signatures). Another might be a regular web 2.0 app which provides an option to "log in with nostr" by requesting and storing the user's public key. In either case, the fact that nostr is involved is entirely neutral. A scraper can scrape html, pdfs, jsonl, whatever data source - nostr relays are just another target. Likewise, a user's key in this scenario is treated merely as an opaque identifier, with no appreciation for the super powers it brings along. In most cases, this kind of app only exists as a marketing ploy, or less cynically, because it wants to get in on the hype of being a "nostr app", without the developer quite understanding what that means, or having the budget to execute properly on the claim. # It leverages nostr Some of you might be wondering, "isn't 'leverage' a synonym for 'use'?" And you would be right, but for one connotative difference. It's possible to "use" something improperly, but by definition leverage gives you a mechanical advantage that you wouldn't otherwise have. This is the second category of "nostr app". This kind of app gets some benefit out of the nostr protocol and network, but in an entirely selfish fashion. The intention of this kind of app is not to augment the nostr network, but to augment its own UX by borrowing some nifty thing from the protocol without really contributing anything back. Some examples might include: - Using nostr signers to encrypt or sign data, and then store that data on a proprietary server. - Using nostr relays as a kind of low-code backend, but using proprietary event payloads. - Using nostr event kinds to represent data (why), but not leveraging the trustlessness that buys you. An application in this category might even communicate to its users via nostr DMs - but this doesn't make it a "nostr app" any more than a website that emails you hot deals on herbal supplements is an "email app". These apps are purely parasitic on the nostr ecosystem. In the long-term, that's not necessarily a bad thing. Email's ubiquity is self-reinforcing. But in the short term, this kind of "nostr app" can actually do damage to nostr's reputation by over-promising and under-delivering. # It complements nostr Next up, we have apps that get some benefit out of nostr as above, but give back by providing a unique value proposition to nostr users as nostr users. This is a bit of a fine distinction, but for me this category is for apps which focus on solving problems that nostr isn't good at solving, leaving the nostr integration in a secondary or supporting role. One example of this kind of app was Mutiny (RIP), which not only allowed users to sign in with nostr, but also pulled those users' social graphs so that users could send money to people they knew and trusted. Mutiny was doing a great job of leveraging nostr, as well as providing value to users with nostr identities - but it was still primarily a bitcoin wallet, not a "nostr app" in the purest sense. Other examples are things like Nostr Nests and Zap.stream, whose core value proposition is streaming video or audio content. Both make great use of nostr identities, data formats, and relays, but they're primarily streaming apps. A good litmus test for things like this is: if you got rid of nostr, would it be the same product (even if inferior in certain ways)? A similar category is infrastructure providers that benefit nostr by their existence (and may in fact be targeted explicitly at nostr users), but do things in a centralized, old-web way; for example: media hosts, DNS registrars, hosting providers, and CDNs. To be clear here, I'm not casting aspersions (I don't even know what those are, or where to buy them). All the apps mentioned above use nostr to great effect, and are a real benefit to nostr users. But they are not True Scotsmen. # It embodies nostr Ok, here we go. This is the crème de la crème, the top du top, the meilleur du meilleur, the bee's knees. The purest, holiest, most chaste category of nostr app out there. The apps which are, indeed, nostr indigitate. This category of nostr app (see, no quotes this time) can be defined by the converse of the previous category. If nostr was removed from this type of application, would it be impossible to create the same product? To tease this apart a bit, apps that leverage the technical aspects of nostr are dependent on nostr the *protocol*, while apps that benefit nostr exclusively via network effect are integrated into nostr the *network*. An app that does both things is working in symbiosis with nostr as a whole. An app that embraces both nostr's protocol and its network becomes an organic extension of every other nostr app out there, multiplying both its competitive moat and its contribution to the ecosystem: - In contrast to apps that only borrow from nostr on the technical level but continue to operate in their own silos, an application integrated into the nostr network comes pre-packaged with existing users, and is able to provide more value to those users because of other nostr products. On nostr, it's a good thing to advertise your competitors. - In contrast to apps that only market themselves to nostr users without building out a deep integration on the protocol level, a deeply integrated app becomes an asset to every other nostr app by becoming an organic extension of them through interoperability. This results in increased traffic to the app as other developers and users refer people to it instead of solving their problem on their own. This is the "micro-apps" utopia we've all been waiting for. Credible exit doesn't matter if there aren't alternative services. Interoperability is pointless if other applications don't offer something your app doesn't. Marketing to nostr users doesn't matter if you don't augment their agency _as nostr users_. If I had to choose a single NIP that represents the mindset behind this kind of app, it would be NIP 89 A.K.A. "Recommended Application Handlers", which states: > Nostr's discoverability and transparent event interaction is one of its most interesting/novel mechanics. This NIP provides a simple way for clients to discover applications that handle events of a specific kind to ensure smooth cross-client and cross-kind interactions. These handlers are the glue that holds nostr apps together. A single event, signed by the developer of an application (or by the application's own account) tells anyone who wants to know 1. what event kinds the app supports, 2. how to link to the app (if it's a client), and (if the pubkey also publishes a kind 10002), 3. which relays the app prefers. _As a sidenote, NIP 89 is currently focused more on clients, leaving DVMs, relays, signers, etc somewhat out in the cold. Updating 89 to include tailored listings for each kind of supporting app would be a huge improvement to the protocol. This, plus a good front end for navigating these listings (sorry nostrapp.link, close but no cigar) would obviate the evil centralized websites that curate apps based on arbitrary criteria._ Examples of this kind of app obviously include many kind 1 clients, as well as clients that attempt to bring the benefits of the nostr protocol and network to new use cases - whether long form content, video, image posts, music, emojis, recipes, project management, or any other "content type". To drill down into one example, let's think for a moment about forms. What's so great about a forms app that is built on nostr? Well, - There is a [spec](https://github.com/nostr-protocol/nips/pull/1190) for forms and responses, which means that... - Multiple clients can implement the same data format, allowing for credible exit and user choice, even of... - Other products not focused on forms, which can still view, respond to, or embed forms, and which can send their users via NIP 89 to a client that does... - Cryptographically sign forms and responses, which means they are self-authenticating and can be sent to... - Multiple relays, which reduces the amount of trust necessary to be confident results haven't been deliberately "lost". Show me a forms product that does all of those things, and isn't built on nostr. You can't, because it doesn't exist. Meanwhile, there are plenty of image hosts with APIs, streaming services, and bitcoin wallets which have basically the same levels of censorship resistance, interoperability, and network effect as if they weren't built on nostr. # It supports nostr Notice I haven't said anything about whether relays, signers, blossom servers, software libraries, DVMs, and the accumulated addenda of the nostr ecosystem are nostr apps. Well, they are (usually). This is the category of nostr app that gets none of the credit for doing all of the work. There's no question that they qualify as beautiful nostrcorns, because their value propositions are entirely meaningless outside of the context of nostr. Who needs a signer if you don't have a cryptographic identity you need to protect? DVMs are literally impossible to use without relays. How are you going to find the blossom server that will serve a given hash if you don't know which servers the publishing user has selected to store their content? In addition to being entirely contextualized by nostr architecture, this type of nostr app is valuable because it does things "the nostr way". By that I mean that they don't simply try to replicate existing internet functionality into a nostr context; instead, they create entirely new ways of putting the basic building blocks of the internet back together. A great example of this is how Nostr Connect, Nostr Wallet Connect, and DVMs all use relays as brokers, which allows service providers to avoid having to accept incoming network connections. This opens up really interesting possibilities all on its own. So while I might hesitate to call many of these things "apps", they are certainly "nostr". # Appendix: it smells like a NINO So, let's say you've created an app, but when you show it to people they politely smile, nod, and call it a NINO (Nostr In Name Only). What's a hacker to do? Well, here's your handy-dandy guide on how to wash that NINO stench off and Become a Nostr. You app might be a NINO if: - There's no NIP for your data format (or you're abusing NIP 78, 32, etc by inventing a sub-protocol inside an existing event kind) - There's a NIP, but no one knows about it because it's in a text file on your hard drive (or buried in your project's repository) - Your NIP imposes an incompatible/centralized/legacy web paradigm onto nostr - Your NIP relies on trusted third (or first) parties - There's only one implementation of your NIP (yours) - Your core value proposition doesn't depend on relays, events, or nostr identities - One or more relay urls are hard-coded into the source code - Your app depends on a specific relay implementation to work (*ahem*, relay29) - You don't validate event signatures - You don't publish events to relays you don't control - You don't read events from relays you don't control - You use legacy web services to solve problems, rather than nostr-native solutions - You use nostr-native solutions, but you've hardcoded their pubkeys or URLs into your app - You don't use NIP 89 to discover clients and services - You haven't published a NIP 89 listing for your app - You don't leverage your users' web of trust for filtering out spam - You don't respect your users' mute lists - You try to "own" your users' data Now let me just re-iterate - it's ok to be a NINO. We need NINOs, because nostr can't (and shouldn't) tackle every problem. You just need to decide whether your app, as a NINO, is actually contributing to the nostr ecosystem, or whether you're just using buzzwords to whitewash a legacy web software product. If you're in the former camp, great! If you're in the latter, what are you waiting for? Only you can fix your NINO problem. And there are lots of ways to do this, depending on your own unique situation: - Drop nostr support if it's not doing anyone any good. If you want to build a normal company and make some money, that's perfectly fine. - Build out your nostr integration - start taking advantage of webs of trust, self-authenticating data, event handlers, etc. - Work around the problem. Think you need a special relay feature for your app to work? Guess again. Consider encryption, AUTH, DVMs, or better data formats. - Think your idea is a good one? Talk to other devs or open a PR to the [nips repo](https://github.com/nostr-protocol/nips). No one can adopt your NIP if they don't know about it. - Keep going. It can sometimes be hard to distinguish a research project from a NINO. New ideas have to be built out before they can be fully appreciated. - Listen to advice. Nostr developers are friendly and happy to help. If you're not sure why you're getting traction, ask! I sincerely hope this article is useful for all of you out there in NINO land. Maybe this made you feel better about not passing the totally optional nostr app purity test. Or maybe it gave you some actionable next steps towards making a great NINON (Nostr In Not Only Name) app. In either case, GM and PV. @ 9e69e420:d12360c2
2025-01-30 12:13:39Salwan Momika, a Christian Iraqi known for burning the Koran in Sweden, was shot dead during a TikTok livestream in an apartment in Sodertalje. The 38-year-old sparked outrage in the Muslim community for his demonstrations, leading to global condemnation. After being rushed to the hospital, he was pronounced dead. Authorities arrested five individuals in connection with the incident. Momika's death comes days before a court ruling on his possible incitement of ethnic hatred. The incident highlights the tensions surrounding free speech and religious sentiments, intensifying after his controversial protests in 2023. [Sauce](https://www.dailymail.co.uk/news/article-14341423/Christian-Iraqi-burnt-Koran-Sweden-shot-dead.html)
@ 9e69e420:d12360c2
2025-01-30 12:13:39Salwan Momika, a Christian Iraqi known for burning the Koran in Sweden, was shot dead during a TikTok livestream in an apartment in Sodertalje. The 38-year-old sparked outrage in the Muslim community for his demonstrations, leading to global condemnation. After being rushed to the hospital, he was pronounced dead. Authorities arrested five individuals in connection with the incident. Momika's death comes days before a court ruling on his possible incitement of ethnic hatred. The incident highlights the tensions surrounding free speech and religious sentiments, intensifying after his controversial protests in 2023. [Sauce](https://www.dailymail.co.uk/news/article-14341423/Christian-Iraqi-burnt-Koran-Sweden-shot-dead.html) @ e262ed3a:e147fbcb
2025-01-30 11:26:25 I got an idea while watching a video from @BTCSessions, which I personally cannot implement technically. Therefore, I would like to present it here for discussion and free implementation. It makes sense to me, but what do I know? Let the swarm intelligence decide. The goal of the business idea is: 1. How can I bring as many solo miners as possible into a pool without them having to pay for the electricity for mining and their mining hardware can be amortized quickly, so they can purchase more mining hardware? 2. How can we financially support Bitcoin and Nostr developers in the long term? 3. How can we intensify developers for the implementation of this idea? 4. How can we encourage non-Bitcoiners to invest in the support of the Bitcoin network? 5. How can we get non-Bitcoin retailers to invest in the Bitcoin network? **The answer is: PROSPECT OF WINNING** **The solution lies in a kind of RAFFLE. (Not a betting website)** The legal difference between a BET and a RAFFLE varies from country to country. It lies in the fact that a raffle must be very transparent regarding the chances of winning and the proceeds must go to a good cause. Those involved in the implementation can, of course, be compensated (also with a profit for the individual participants). The extent to which this is allowed would have to be checked by those who want to implement this idea. In the following, I will describe the implementation roughly. Since this is not a sales presentation, please excuse me if the following proposal is not fully structured. Participants in the idea are: 1. Consumers (ticket buyers) 2. Bitcoin miners 3) Retailers 4) Non-profit company that implement the project **What's it about?** @BTCSessions has a YouTube video about the miner FutureBit. In the dashboard of the solo miner, you could see how high the hash rate was. But above all, you could see how high the chance of winning was for the solo miner in the overall network. In the case of BTCSessions FutureBit, the hash rate was around 5 TerraHash and the chance of winning was around 1:1,000,000. (Which, according to my calculations, was not correct). The power consumption was around 32 watts. When I saw that, it suddenly dawned on me. Could it be possible to create a website/app that determines the total hash rate of a mining pool and then offers an electronic, numbered ticket for each 1 TerraHash (TH/s) of the pool for, for example, 0.1 USD? The minimum purchase amount would be 10 tickets. The customer sees the chance of winning and could even see the possible payout. The ticket is only valid for the next block (similar to roulette). Another variant could be that the buyer can select one or more of the next 10 blocks and purchase tickets for the selected block. Since you don't know in advance how high the pool hash rate will be 5 or 10 blocks ahead, the amount of tickets to be issued for the 2nd block, for example, could only be 90% of the current pool hash rate, the 3rd block only 80%, and so on. If block 3, for example, advances to position 2, the previously unavailable 10% will be released for further tickets. (Determined by the pool hash rate at that time) The purchase of 10 or more tickets could be automated in the customer's account on the website/app (intervals: hourly, daily, weekly, every 10 blocks, etc.). Customers could also top up their account with satoshis, enabling automatic deductions for ticket purchases. This could be facilitated by automatically issuing a Nostr npub to each customer, which would also create a wallet at Primal.net (Strike). For non-Bitcoiners, Zaprite could be used to recharge their account. Alternatively, customers could enter a NostrWalletConnection NWC to enable automatic deductions from their Lightning wallet. The project operators might also consider running their own ecash mint, which would allow them to assign an integrated ecash address to customers without a Lightning address. Tickets with ascending numbers would be allocated strictly in the order of payment receipts. **Calculations for the miners**: The FutureBit miner consumed approximately 30 watts per terahash/hour. Let's assume that 10 terahash consume 300 watts per hour, then the miner consumes 50 watts per 10 minutes (per block). Let's further assume that a kilowatt-hour of electricity costs between 10 and 30 cents, then it costs the miner 3-9 cents per hour for electricity at 10 terahash mining capacity. So, 0.5-1.5 cents per block. In the case that each ticket is sold for 1 terahash for the next block, one could automatically transfer, for example, 5% of the satoshis received from ticket sales to each participating miner in the pool (proportional to the average hash rate delivered by the miner in the last block in the pools). This happens even if the block is not found. If fewer tickets are sold than the maximum possible amount, then the 5% of the sold tickets will be distributed proportionally. (See also my Excel file? **At the center** of the project is a website/app that manages the raffle. Here, anyone can register and create an account. Either as a miner, retailer, or customer with or without KYC, for example, with their own nostr nsec, wallet signature, email and password or phone number and password. Once logged into the account, Bitcoiners can enter their Lightning address and a Bitcoin on-chain address. Non-Bitcoiners enter their financial data in case they win. Miners must enter a Bitcoin and Lightning (or ecash) address. The pooling process is also managed in the miner's account. Tickets can be purchased (like in a regular online shop) and paid for in any way. Zaprite could be a solution here. But also Strike, Cashapp, etc. As described above, such purchases could also be automated. **Retailers can also register as such**. They will then have the opportunity to sell "tickets" to their customers and collect the money in cash. To sell tickets, they must enter the customer's name and a valid email address. After payment, they must send the purchase price via Lightning to the non-profit company, which will then confirm the purchase to the ticket buyer and the retailer with all the data. This is the receipt for the buyer. In the event of a win (the mined block must have 3-6 block confirmations), the ticket buyer will receive an email explaining all the further details of how to claim the prize. This could be a link that takes them directly to the website and logs them in directly. The winner can then enter their data on how and where the money should be paid out (Bitcoin address or bank details). Alternatively, they can go to their retailer, who can assist them by entering the data in their sub-account (customer account). To prevent the retailer from falsifying the data entry, the winner will first receive an email with the entered data, which they can confirm (if correct). Since the retailer is also involved in the win, they will also be notified. **How many tickets** can be offered per round (Bitcoin block)? The number of tickets depends on the hash rate in the pool. One ticket can be issued per 1 TerraHash (TH/s). How the ticket is generated per round and customer, I don't know, as I lack the technical knowledge. Maybe as a kind of NFT that contains the corresponding data (customer number (npub) of the buyer and possibly retailer, block number, ticket number). Or as a Taproot asset on Lightning? Or as a minted ecash coin? Or simply as an entry in a database that the customer can see in their account. The maximum payout of the winnings in the event of a found block to the ticket holders could be 70%. The remaining 30% would be distributed to the miners and retailers. For example: Miners 25%, retailers 5%. The non-profit organization receives nothing from the block rewards. Instead, it receives 65% of the revenue from all ticket sales. With a mining pool hash rate of 10,000 TH/s, where all tickets are sold continuously, a daily donation of around 93,000 USD would be generated. (see Excel.file) The revenue, after deducting the possible costs of the organization, goes directly to @opensats and/or other organizations that support the Bitcoin network after each block. Either via Lightning or Bitcoin on-chain payment. In the attached Excel file, you can find my calculations. Here, anyone can play through different scenarios. What I noticed was that with maximum ticket sales per block, only around 200 USD per 10 tickets would be paid out, since each participating ticket wins in the event of a found block. Since I believe that this is not a very great incentive for buying tickets, I suggest the following variants. **Winning variants**: Each purchased ticket has a running number. Ticket 1 has the number 000.000, ticket 2 has the number 000.001, ticket 10.120 has the number 010.119, and so on. If the next block is found, then this found block in the Bitcoin blockchain has a hash. For example, block 881367 has the hash 000000000000000000014b0fab24355c71c6940584d9cd5990c0b081a31d54a4 Let's now remove the letters and read only the numbers from back to front, so the last 3 numbers are 544 Instead of every participating ticket winning, in this variant, only the tickets with the ending digits 544 win. With, for example, 11,000 tickets sold, the ticket numbers 000.544 / 001.544 / 002.544 ... 010.544 would win. So, 11 ticket participants would win. Each winner with this number would receive around 0.284 Bitcoin (3.125 BTC / 11). One could also let the ticket numbers with the ending digits 44 win, and thus every hundredth ticket. Or even combine it. What I also noticed was that with retailers, a special case arises. Retailers receive 5% of the block rewards in the event of a found block. But only proportionally to the tickets sold by the retailer. This means that in order for the entire 5% to be distributed to the retailers, all 10,000 tickets of 10.000 possible tickets would have to be sold by retailers. Since not all tickets will be sold by retailers, a remaining amount will be left over. This could be distributed additionally to the miners. Or any other variant. I hope the idea finds resonance and invites discussion. Maybe I've made some mistakes in thinking, and the idea is not feasible. But if you like the idea, please forward it to developers, investors, and others you know. Best regards. <span data-type="mention" data-id="e262ed3a22ad8c478b077ef5d7c56b2c3c7a530519ed696ed2e57c65e147fbcb" data-label="nostr:undefined">@nostr:undefined</span> dewe [Excel sheet for download](https://c.gmx.net/@329519820976429649/KJTehgh0SMGliV4HLjMf0g)
@ e262ed3a:e147fbcb
2025-01-30 11:26:25 I got an idea while watching a video from @BTCSessions, which I personally cannot implement technically. Therefore, I would like to present it here for discussion and free implementation. It makes sense to me, but what do I know? Let the swarm intelligence decide. The goal of the business idea is: 1. How can I bring as many solo miners as possible into a pool without them having to pay for the electricity for mining and their mining hardware can be amortized quickly, so they can purchase more mining hardware? 2. How can we financially support Bitcoin and Nostr developers in the long term? 3. How can we intensify developers for the implementation of this idea? 4. How can we encourage non-Bitcoiners to invest in the support of the Bitcoin network? 5. How can we get non-Bitcoin retailers to invest in the Bitcoin network? **The answer is: PROSPECT OF WINNING** **The solution lies in a kind of RAFFLE. (Not a betting website)** The legal difference between a BET and a RAFFLE varies from country to country. It lies in the fact that a raffle must be very transparent regarding the chances of winning and the proceeds must go to a good cause. Those involved in the implementation can, of course, be compensated (also with a profit for the individual participants). The extent to which this is allowed would have to be checked by those who want to implement this idea. In the following, I will describe the implementation roughly. Since this is not a sales presentation, please excuse me if the following proposal is not fully structured. Participants in the idea are: 1. Consumers (ticket buyers) 2. Bitcoin miners 3) Retailers 4) Non-profit company that implement the project **What's it about?** @BTCSessions has a YouTube video about the miner FutureBit. In the dashboard of the solo miner, you could see how high the hash rate was. But above all, you could see how high the chance of winning was for the solo miner in the overall network. In the case of BTCSessions FutureBit, the hash rate was around 5 TerraHash and the chance of winning was around 1:1,000,000. (Which, according to my calculations, was not correct). The power consumption was around 32 watts. When I saw that, it suddenly dawned on me. Could it be possible to create a website/app that determines the total hash rate of a mining pool and then offers an electronic, numbered ticket for each 1 TerraHash (TH/s) of the pool for, for example, 0.1 USD? The minimum purchase amount would be 10 tickets. The customer sees the chance of winning and could even see the possible payout. The ticket is only valid for the next block (similar to roulette). Another variant could be that the buyer can select one or more of the next 10 blocks and purchase tickets for the selected block. Since you don't know in advance how high the pool hash rate will be 5 or 10 blocks ahead, the amount of tickets to be issued for the 2nd block, for example, could only be 90% of the current pool hash rate, the 3rd block only 80%, and so on. If block 3, for example, advances to position 2, the previously unavailable 10% will be released for further tickets. (Determined by the pool hash rate at that time) The purchase of 10 or more tickets could be automated in the customer's account on the website/app (intervals: hourly, daily, weekly, every 10 blocks, etc.). Customers could also top up their account with satoshis, enabling automatic deductions for ticket purchases. This could be facilitated by automatically issuing a Nostr npub to each customer, which would also create a wallet at Primal.net (Strike). For non-Bitcoiners, Zaprite could be used to recharge their account. Alternatively, customers could enter a NostrWalletConnection NWC to enable automatic deductions from their Lightning wallet. The project operators might also consider running their own ecash mint, which would allow them to assign an integrated ecash address to customers without a Lightning address. Tickets with ascending numbers would be allocated strictly in the order of payment receipts. **Calculations for the miners**: The FutureBit miner consumed approximately 30 watts per terahash/hour. Let's assume that 10 terahash consume 300 watts per hour, then the miner consumes 50 watts per 10 minutes (per block). Let's further assume that a kilowatt-hour of electricity costs between 10 and 30 cents, then it costs the miner 3-9 cents per hour for electricity at 10 terahash mining capacity. So, 0.5-1.5 cents per block. In the case that each ticket is sold for 1 terahash for the next block, one could automatically transfer, for example, 5% of the satoshis received from ticket sales to each participating miner in the pool (proportional to the average hash rate delivered by the miner in the last block in the pools). This happens even if the block is not found. If fewer tickets are sold than the maximum possible amount, then the 5% of the sold tickets will be distributed proportionally. (See also my Excel file? **At the center** of the project is a website/app that manages the raffle. Here, anyone can register and create an account. Either as a miner, retailer, or customer with or without KYC, for example, with their own nostr nsec, wallet signature, email and password or phone number and password. Once logged into the account, Bitcoiners can enter their Lightning address and a Bitcoin on-chain address. Non-Bitcoiners enter their financial data in case they win. Miners must enter a Bitcoin and Lightning (or ecash) address. The pooling process is also managed in the miner's account. Tickets can be purchased (like in a regular online shop) and paid for in any way. Zaprite could be a solution here. But also Strike, Cashapp, etc. As described above, such purchases could also be automated. **Retailers can also register as such**. They will then have the opportunity to sell "tickets" to their customers and collect the money in cash. To sell tickets, they must enter the customer's name and a valid email address. After payment, they must send the purchase price via Lightning to the non-profit company, which will then confirm the purchase to the ticket buyer and the retailer with all the data. This is the receipt for the buyer. In the event of a win (the mined block must have 3-6 block confirmations), the ticket buyer will receive an email explaining all the further details of how to claim the prize. This could be a link that takes them directly to the website and logs them in directly. The winner can then enter their data on how and where the money should be paid out (Bitcoin address or bank details). Alternatively, they can go to their retailer, who can assist them by entering the data in their sub-account (customer account). To prevent the retailer from falsifying the data entry, the winner will first receive an email with the entered data, which they can confirm (if correct). Since the retailer is also involved in the win, they will also be notified. **How many tickets** can be offered per round (Bitcoin block)? The number of tickets depends on the hash rate in the pool. One ticket can be issued per 1 TerraHash (TH/s). How the ticket is generated per round and customer, I don't know, as I lack the technical knowledge. Maybe as a kind of NFT that contains the corresponding data (customer number (npub) of the buyer and possibly retailer, block number, ticket number). Or as a Taproot asset on Lightning? Or as a minted ecash coin? Or simply as an entry in a database that the customer can see in their account. The maximum payout of the winnings in the event of a found block to the ticket holders could be 70%. The remaining 30% would be distributed to the miners and retailers. For example: Miners 25%, retailers 5%. The non-profit organization receives nothing from the block rewards. Instead, it receives 65% of the revenue from all ticket sales. With a mining pool hash rate of 10,000 TH/s, where all tickets are sold continuously, a daily donation of around 93,000 USD would be generated. (see Excel.file) The revenue, after deducting the possible costs of the organization, goes directly to @opensats and/or other organizations that support the Bitcoin network after each block. Either via Lightning or Bitcoin on-chain payment. In the attached Excel file, you can find my calculations. Here, anyone can play through different scenarios. What I noticed was that with maximum ticket sales per block, only around 200 USD per 10 tickets would be paid out, since each participating ticket wins in the event of a found block. Since I believe that this is not a very great incentive for buying tickets, I suggest the following variants. **Winning variants**: Each purchased ticket has a running number. Ticket 1 has the number 000.000, ticket 2 has the number 000.001, ticket 10.120 has the number 010.119, and so on. If the next block is found, then this found block in the Bitcoin blockchain has a hash. For example, block 881367 has the hash 000000000000000000014b0fab24355c71c6940584d9cd5990c0b081a31d54a4 Let's now remove the letters and read only the numbers from back to front, so the last 3 numbers are 544 Instead of every participating ticket winning, in this variant, only the tickets with the ending digits 544 win. With, for example, 11,000 tickets sold, the ticket numbers 000.544 / 001.544 / 002.544 ... 010.544 would win. So, 11 ticket participants would win. Each winner with this number would receive around 0.284 Bitcoin (3.125 BTC / 11). One could also let the ticket numbers with the ending digits 44 win, and thus every hundredth ticket. Or even combine it. What I also noticed was that with retailers, a special case arises. Retailers receive 5% of the block rewards in the event of a found block. But only proportionally to the tickets sold by the retailer. This means that in order for the entire 5% to be distributed to the retailers, all 10,000 tickets of 10.000 possible tickets would have to be sold by retailers. Since not all tickets will be sold by retailers, a remaining amount will be left over. This could be distributed additionally to the miners. Or any other variant. I hope the idea finds resonance and invites discussion. Maybe I've made some mistakes in thinking, and the idea is not feasible. But if you like the idea, please forward it to developers, investors, and others you know. Best regards. <span data-type="mention" data-id="e262ed3a22ad8c478b077ef5d7c56b2c3c7a530519ed696ed2e57c65e147fbcb" data-label="nostr:undefined">@nostr:undefined</span> dewe [Excel sheet for download](https://c.gmx.net/@329519820976429649/KJTehgh0SMGliV4HLjMf0g) @ 0fa80bd3:ea7325de
2025-01-30 04:28:30**"Degeneration"** or **"Вырождение"** ![[photo_2025-01-29 23.23.15.jpeg]] A once-functional object, now eroded by time and human intervention, stripped of its original purpose. Layers of presence accumulate—marks, alterations, traces of intent—until the very essence is obscured. Restoration is paradoxical: to reclaim, one must erase. Yet erasure is an impossibility, for to remove these imprints is to deny the existence of those who shaped them. The work stands as a meditation on entropy, memory, and the irreversible dialogue between creation and decay.
@ 0fa80bd3:ea7325de
2025-01-30 04:28:30**"Degeneration"** or **"Вырождение"** ![[photo_2025-01-29 23.23.15.jpeg]] A once-functional object, now eroded by time and human intervention, stripped of its original purpose. Layers of presence accumulate—marks, alterations, traces of intent—until the very essence is obscured. Restoration is paradoxical: to reclaim, one must erase. Yet erasure is an impossibility, for to remove these imprints is to deny the existence of those who shaped them. The work stands as a meditation on entropy, memory, and the irreversible dialogue between creation and decay. @ 9f3eba58:fa185499
2025-01-29 20:27:09Humanity as a whole has been degrading over the years, with average IQ decreasing, bone structures generally becoming poorly formed and fragile, average height decreasing, hormone levels ridiculously low and having various metabolic and mental illnesses becoming “normal”. “*By 2024, more than 800 million adults were living with diabetes, representing a more than fourfold increase since 1990*” “\*\**1 in 3 people suffer from insulin resistance and can cause depression*” (\*\*https://olhardigital.com.br/2021/09/24/medicina-e-saude/1-em-cada-3-pessoas-sofre-de-resistencia-a-insulina-e-pode-causar-depressao/) “*More than 1.3 billion people will have diabetes in the world by 2050*” (https://veja.abril.com.br/saude/mais-de-13-bilhao-de-pessoas-terao-diabetes-no-mundo-ate-2050) “*A new study released by Lancet, with data from 2022, shows that more than a billion people live with obesity in the world*” (https://www.paho.org/pt/noticias/1-3-2024-uma-em-cada-oito-pessoas-no-mundo-vive-com-obesidade) All this due to a single factor: diet. I’m not referring to a diet full of processed foods, as this has already been proven to destroy the health of those who eat it. I’m referring to the modern diet, with carbohydrates (from any source, even from fruit) being the main macronutrient, little animal protein and practically no saturated fat of animal origin. This diet implementation has been systematically occurring for decades. Sugar conglomerates seeking profits? Government institutions (after all, they need voters to be stupid and vote for them), evil spiritual interference wanting to destroy or distort their path? I don’t know, I’ll leave the conspiracy theories to you! The modern diet or diet is extremely inflammatory, and inflammation over a long period of time leads to autoimmune diseases such as diabetes and Hashimoto’s. Absolutely any food in the plant kingdom will harm you, no matter how asymptomatic it may be. Plants are living beings and do not want to die and be eaten. To defend themselves from this, they did not evolve legs like animals. They specifically developed chemical mechanisms such as *oxalates, phytoalexins, glucosinolates, polyphenols, antinutrients* and many others that act to repel anything that wants to eat them, being fatal (as in the case of mushrooms), causing discomfort and the animal or insect discovering that the plant is not edible, releasing unpleasant smells or, in many cases, a combination of these factors. Not to mention genetically modified foods (almost the entire plant kingdom is genetically modified) that work as a steroid for the plants' defenses. - Lack of focus - Poor decision-making - Difficulty in establishing and maintaining relationships - Difficulty getting pregnant and difficult pregnancy - Low testosterone (medical reference values are low) - Alzheimer's - Diabetes - Dementia - Chances of developing autism when mothers do not eat meat and fat properly during pregnancy - Worsening of the degree of autism when the child does not eat meat and fat (food selectivity) - Insomnia and other sleep problems - Lack of energy - Poorly formed and fragile bone structure - Lack of willpower - Depression - ADHD Not having full physical and mental capacity harms you in many different ways, these are just a few examples that not only directly impact one person but everyone else around them. Fortunately, there is an alternative to break out of this cycle of destruction, ***Carnivore Diet***. I am not here to recommend a diet, eating plan or cure for your health problems, nor can I do so, as I am not a doctor (most doctors don't even know where the pancreas is, a mechanic is more useful in your life than a doctor, but that is a topic for another text.). I came to present you with logic and facts in a very simplified way, from there you can do your own research and decide what is best for you. --- ## Defining the carnivore diet Simply put, the carnivore diet is an elimination diet, where carbohydrates (including fruits), vegetable fats (soy, canola, cotton, peanuts, etc.), processed products and any type of plant, be it spices or teas, are completely removed. ### What is allowed on the carnivore diet? - Animal protein - Beef, preferably fatty cuts (including offal, liver, heart, kidneys, these cuts have more vitamins than anything else in the world) - Lamb - Eggs - Fish and seafood - Animal fat - Butter - Beef fat and tallow - Salt - No... salt does not cause high blood pressure. (explained later about salt and high consumption of saturated fats) From now on I will list some facts that disprove the false accusations made against \*\*eating exclusively meat and fat. # “Human beings are omnivores” *“Our ancestors were gatherers and hunters*" To determine the proportion of animal foods in our ancestors’ diets, we can look at the amount of δ15 nitrogen in their fossils. By looking at levels of this isotope, researchers can infer where animals reside in the food chain, identifying their protein sources. Herbivores typically have δ15N levels of 3–7 percent, carnivores show levels of 6–12 percent, and omnivores exhibit levels in between. When samples from Neanderthals and early modern humans were analyzed, they showed levels of 12 percent and 13.5 percent, respectively, even higher than those of other known carnivores, such as hyenas and wolves. And from an energy efficiency standpoint, hunting large animals makes the most sense. Gathering plants and chasing small animals provides far fewer calories and nutrients relative to the energy invested. In more recently studied indigenous peoples, we have observed a similar pattern that clearly indicates a preference for animal foods over plant foods. For example, in Vilhjalmur Stefansson’s studies of the Eskimos. *“…fat, not protein, seemed to play a very important role in hunters’ decisions about which animals (male or female) to kill and which body parts to discard or carry away.”* Why were our ancestors and more recent indigenous peoples so interested in finding fat? At a very basic level, it was probably about calories. By weight, fat provides more than twice as many calories as protein or carbohydrates. Furthermore, human metabolism makes fat an exceptionally valuable and necessary food. If we think of ourselves as automobiles that need fuel for our metabolic engines, we should not put protein in our gas tank. For best results, our metabolic engine runs most efficiently on fat or carbohydrates. Eating animal foods has been a vital part of our evolution since the beginning. Katherine Milton, a researcher at UC Berkeley, came to the same conclusion in her paper “The Critical Role Played by Animal Source Foods in Human Evolution,” which states: “Without routine access to animal-source foods, it is highly unlikely that evolving humans could have achieved their unusually large and complex brains while simultaneously continuing their evolutionary trajectory as large, active, and highly social primates. As human evolution progressed, young children in particular, with their rapidly expanding large brains and higher metabolic and nutritional demands relative to adults, would have benefited from concentrated, high-quality foods such as meat." - https://pubmed.ncbi.nlm.nih.gov/14672286/ Skeletons from Greece and Turkey reveal that 12,000 years ago, the average height of hunter-gatherers was five feet, nine inches for men and five feet, five inches for women. But with the adoption of agriculture, adult height plummeted—ending any hope these poor herders had of dunking a basketball or playing competitive volleyball, if such sports had existed at the time. By 3000 B.C., men in this region of the world were only five feet, three inches tall, and women were five feet, reflecting a massive decline in their overall nutritional status. Many studies in diverse populations show a strong correlation between adult height and nutritional quality. A study analyzing male height in 105 countries came to the following conclusion: “In taller nations…consumption of plant proteins declines sharply at the expense of animal proteins, especially those from dairy products. Its highest consumption rates can be found in Northern and Central Europe, with the global peak in male height in the Netherlands (184 cm).” In addition to the decline in height, there is also evidence that Native Americans buried at Dickson Mounds suffered from increased bacterial infections. These infections leave scars on the outer surface of the bone, known as the periosteum, with the tibia being especially susceptible to such damage due to its limited blood flow. Examination of tibias from skeletons found in the mounds shows that after agriculture, the number of such periosteal lesions increased threefold, with a staggering eighty-four percent of bones from this period demonstrating this pathology. The lesions also tended to be more severe and to appear earlier in life in the bones of post-agricultural peoples. https://onlinelibrary.wiley.com/doi/full/10.1111/j.1747-0080.2007.00194.x https://pubmed.ncbi.nlm.nih.gov/10702160/ # Cholesterol Many “doctors” say that consuming saturated fat is harmful to your health, “your veins and arteries will clog with excess fat” “you will have a heart attack if you consume a lot of fat" and many other nonsense, and in exchange recommends that you replace fatty cuts of meat with lean meat and do everything with vegetable oil that causes cancer and makes men effeminate. Your brain is basically composed of fat and water, your neurons are made and repaired with fat, your cells, the basic unit of life, are composed of fat and protein, many of your hormones, especially sexual ones, are made from fat, there is no logical reason not to consume saturated fat other than several false "scientific articles". "The power plant of the cell is the mitochondria, which converts what we eat into energy. Ketones are an energy source derived from fat. Mitochondria prefer fat as energy (ketones) because transforming ketones into energy costs the mitochondria half the effort of using sugar (glucose) for energy." - https://pubmed.ncbi.nlm.nih.gov/28178565/ "With the help of saturated fats, calcium is properly stored in our bones. The interaction between calcium, vitamin D, and parathyroid hormone regulates calcium levels in the body. When there are calcium imbalances in the blood, our bones release calcium into the blood to find homeostasis." - https://www.healthpedian.org/the-role-of-calcium-in-the-human-body/ "The body needs cholesterol to support muscle repair and other cellular functions. This is why when there is cardiovascular disease, we see increased amounts of cholesterol in the area. Cholesterol is not there causing the problem, but the boat carrying fat was docked there for cholesterol and other nutrients to help fight the problem. Plaque is the body's attempt to deal with injury within the blood vessels." - *National Library of Medicine, “Cholesterol,” 2019* "Initially, the Plaque helps blood vessels stay strong and helps the vessels maintain their shape. But with the perpetual cycle of uncontrolled inflammation and leftover debris from cellular repair (cholesterol), over time plaque begins to grow and harden, reducing blood flow and oxygen to the heart. Both inflammation and repair require copious amounts of cholesterol and fats. So the body keeps sending these fatty substances to the site of the plaque — until either repair wins (plaque becomes sclerotic scars in the heart muscle, causing heart failure) or inflammation wins (atherosclerotic heart attack)" - https://pubmed.ncbi.nlm.nih.gov/21250192/ Inflammation in Atherosclerotic Cardiovascular Disease - https://pubmed.ncbi.nlm.nih.gov/21250192/ "Study finds that eating refined carbohydrates led to an increased risk of cardiovascular disease and obesity" - https://pmc.ncbi.nlm.nih.gov/articles/PMC5793267/ # “Meat causes cancer” Most of the misconceptions that red meat causes cancer come from a report by the World Health Organization's International Agency for Research on Cancer (IARC), which was released in 2015. Unfortunately, this report has been widely misrepresented by the mainstream media and is based on some very questionable interpretations of the science it claims to review. A closer look at a 2018 report on its findings reveals that only 14 of the 800 studies were considered in its final conclusions—and every single study was observational epidemiology. Why the other 786 were excluded remains a mystery, and this group included many interventional animal studies that clearly did not show a link between red meat and cancer. Of the fourteen epidemiological studies that were included in the IARC report, eight showed no link between meat consumption and the development of colon cancer. Of the remaining six studies, only one showed a statistically significant correlation between meat and cancer. In epidemiological research, one looks for correlation between two things and the strength of the correlation. Having just one study out of 800 that shows meat causes cancer is a mere fluke and becomes statistically insignificant. Interestingly, this was a study by Seventh-day Adventists in America — a religious group that advocates a plant-based diet. # Microbiota and Fiber I have seen several people and “doctors” saying that eating only meat would destroy your microbiota. And I have come to the conclusion that neither “doctors” nor most people know what a microbiota is. Microbiota is the set of several types of bacteria (millions) that exist in your stomach with the function of breaking down molecules of certain types of food that the body itself cannot get, fiber for example. Many times through the process of fermentation, which is why you have gas after eating your beloved oatmeal. People unconsciously believe that the microbiota is something fixed and unchangeable, but guess what… it is not. Your microbiota is determined by what you eat. If you love eating oatmeal, your microbiota will have a specific set of bacteria that can break down the oat molecule into a size that the body can absorb. If you follow a carnivorous diet, your microbiota will adapt to digest meat. ### Fiber Nutritional guidelines recommend large amounts of fiber in our diet, but what they don't tell you is that we only absorb around 6% of all the vegetable fiber we eat. In other words, it's insignificant! Another argument used by doctors and nutritionists is that it helps you go to the bathroom, but this is also a lie. Fiber doesn't help you evacuate, it forces you to do so. With the huge amount of undigestible food in your stomach (fiber), the intestine begins to force contractions, making this fecal matter go down, making you go to the bathroom. They also raise the argument that fibers are broken down into short-chain fatty acids, such as butyrate (butyric acid), propionate (propionic acid) and acetate (acetic acid). Butyrate is essential because it is the preferred fuel source for the endothelial cells of the large intestine. Butter, cream, and cheese contain butyrate in its absorbable form. Butter is the best source of butyric acid, or butyrate. In fact, the origins of the word butyric acid come from the Latin word *butyro*—the same origins as the word butter. “In 2012, a study in the Journal of Gastroenterology showed that reducing fiber (a precursor to short-chain fatty acids) helped participants with chronic constipation. The study lasted six months, and after two weeks without fiber, these participants were allowed to increase fiber as needed. These participants felt so much relief after two weeks without fiber that they continued without fiber for the entire six-month period. Of the high-fiber, low-fiber, and no-fiber groups, the zero-fiber participants had the highest bowel movement frequency.” - https://pmc.ncbi.nlm.nih.gov/articles/PMC3435786/ ### Bioavailability I said that our body can only absorb 6% of all the fiber we ingest. This is bioavailability, how much the body can absorb nutrients from a given food. Meat is the most bioavailable food on the planet! Grains and vegetables are not only not very bioavailable, but they also contain a huge amount of antinutrients. So if you eat a steak with some beans, you will not be able to absorb the nutrients from the beans, and the antinutrients in them will make it impossible to absorb a large amount of nutrients from the steak. https://pubmed.ncbi.nlm.nih.gov/23107545/ # Lack of nutrients and antioxidants in a carnivorous diet A major concern with the carnivorous diet is the lack of vitamin C, which would consequently lead to scurvy. Vitamin C plays an important role in the breakdown and transport of glucose into cells. In 2000 and 2001, the recommended daily intake of vitamin C effectively doubled. In fact, every 10 to 15 years, there has been a large increase in the recommended daily intake of vitamin C, as happened in 1974 and 1989. Interestingly, also in 1974, sugar prices became so high that high fructose corn syrup was introduced into the US market. Could the increase in readily available glucose foods and foods with high fructose corn syrup be a reason why we need more vitamin C? The question remains…. But this is not a cause for concern for the carnivore, liver is rich in vitamin C. You could easily reach the daily recommendation with liver or any cut of steak. 200-300g of steak already meets your needs and if the theory that the more sugar you eat, the more vitamin C you will get is true, then the more sugar you will eat is true. C is necessary if true, you could easily exceed the daily requirement. Meat and seafood are rich in ALL the nutrients that humans need to thrive. ### Antioxidants It is commonly said that fruits are rich in antioxidants but again this is a hoax, they are actually PRO-oxidants. These are substances that activate the mRF2 pathway of our immune system which causes the body to produce natural antioxidants. The body produces antioxidants, but many occur naturally in foods, Vitamin C, Vitamin E, Selenium and Manganese are all natural antioxidants. High concentrations of antioxidants can be harmful. Remember that high concentrations of antioxidants can increase oxidation and even protect against cancer cells. # Salt Consuming too much salt does not increase blood pressure and therefore increases the risk of heart disease and stroke. Studies show no evidence that limiting salt intake reduces the risk of heart disease. A 2011 study found that diets low in salt may actually increase the risk of death from heart attacks and strokes. Most importantly, they do not prevent high blood pressure. https://www.nytimes.com/2011/05/04/health/research/04salt.html # Sun This is not a dietary issue specifically, but there are things that can I would like to present that is against common sense when talking about the sun. It is common sense to say that the sun causes skin cancer and that we should not expose ourselves to it or, if we are exposed to the sun, use sunscreen, but no study proves that using sunscreen protects us from melanoma and basal cell carcinoma. The types of fatal melanomas usually occur in areas of the body that never see the sun, such as the soles of the feet. https://www.jabfm.org/content/24/6/735 In 1978, the first sunscreen was launched, and the market grew rapidly, along with cases of melanoma. Several studies show that sunscreens cause leaky gut (one of the main factors in chronic inflammation), hormonal dysfunction and neurological dysfunction. https://pubmed.ncbi.nlm.nih.gov/31058986/ If your concern when going out in the sun is skin cancer, don't worry, your own body's natural antioxidants will protect you. When they can no longer protect you, your skin starts to burn. (If you have to stay in the sun for work, for example, a good way to protect yourself is to rub coconut oil on your skin or just cover yourself with a few extra layers of thin clothing and a hat). Sunscreen gives you the false sense of protection by blocking the sunburn, so you stay out longer than your skin can handle, but sunscreens can only block 4% of UVA and UVB rays. www.westonaprice.org/health-topics/environmental-toxins/sunscreens-the-dark-side-of-avoiding-the-sun/ Interestingly, vitamin D deficiency is linked to increased cancer risks. It's a big contradiction to say that the greatest provider of vit. D causes cancer… https://med.stanford.edu/news/all-news/2010/10/skin-cancer-patients-more-likely-to-be-deficient-in-vitamin-d-study-finds.html Important roles of vitamin D: - **Regulation of Bone Metabolism** - Facilitates the **absorption of calcium and phosphorus** in the intestine. - Promotes bone mineralization and prevents diseases such as **osteoporosis**, **rickets** (in children) and **osteomalacia** (in adults). - **Immune Function** - Modulates the immune system, helping to reduce inflammation and strengthen the defense against infections, including **colds**, **flu** and other diseases. - May help reduce the incidence of autoimmune diseases such as **multiple sclerosis** and **rheumatoid arthritis**. - **Muscle Health** - Contributes to muscle strength and the prevention of weakness, especially in the elderly. - Reduces the risk of falls and fractures. - **Cardiovascular Function** - May help regulate blood pressure and heart function, reducing the risk of cardiovascular disease. - **Hormonal Balance** - Influences the production of hormones, including those associated with fertility and the functioning of the endocrine system. - Plays a role in insulin metabolism and glucose sensitivity. - **Brain Function and Mental Health** - Participates in mood regulation, which may reduce the risk of **depression** and improve mental health. - Has been associated with the prevention of neurodegenerative diseases, such as **Alzheimer's**. - **Anticancer Role** - Evidence suggests that vitamin D may inhibit the proliferation of cancer cells, especially in breast, prostate and colon cancers. - **Role in General Metabolism** - Contributes to metabolic health, regulating cellular growth and repair processes. --- I tried to present everything in the simplest and most understandable way possible, but there are things that require prior knowledge to truly understand. Below is a list of books that will show you everything I have shown you in a more technical and in-depth way. ### Book Recommendations https://amzn.to/3EbjVsD https://amzn.to/4awlnBZ All of my arguments have studies to validate them. Feel free to read them all and draw your own conclusions about what is best for you and your life.
@ 9f3eba58:fa185499
2025-01-29 20:27:09Humanity as a whole has been degrading over the years, with average IQ decreasing, bone structures generally becoming poorly formed and fragile, average height decreasing, hormone levels ridiculously low and having various metabolic and mental illnesses becoming “normal”. “*By 2024, more than 800 million adults were living with diabetes, representing a more than fourfold increase since 1990*” “\*\**1 in 3 people suffer from insulin resistance and can cause depression*” (\*\*https://olhardigital.com.br/2021/09/24/medicina-e-saude/1-em-cada-3-pessoas-sofre-de-resistencia-a-insulina-e-pode-causar-depressao/) “*More than 1.3 billion people will have diabetes in the world by 2050*” (https://veja.abril.com.br/saude/mais-de-13-bilhao-de-pessoas-terao-diabetes-no-mundo-ate-2050) “*A new study released by Lancet, with data from 2022, shows that more than a billion people live with obesity in the world*” (https://www.paho.org/pt/noticias/1-3-2024-uma-em-cada-oito-pessoas-no-mundo-vive-com-obesidade) All this due to a single factor: diet. I’m not referring to a diet full of processed foods, as this has already been proven to destroy the health of those who eat it. I’m referring to the modern diet, with carbohydrates (from any source, even from fruit) being the main macronutrient, little animal protein and practically no saturated fat of animal origin. This diet implementation has been systematically occurring for decades. Sugar conglomerates seeking profits? Government institutions (after all, they need voters to be stupid and vote for them), evil spiritual interference wanting to destroy or distort their path? I don’t know, I’ll leave the conspiracy theories to you! The modern diet or diet is extremely inflammatory, and inflammation over a long period of time leads to autoimmune diseases such as diabetes and Hashimoto’s. Absolutely any food in the plant kingdom will harm you, no matter how asymptomatic it may be. Plants are living beings and do not want to die and be eaten. To defend themselves from this, they did not evolve legs like animals. They specifically developed chemical mechanisms such as *oxalates, phytoalexins, glucosinolates, polyphenols, antinutrients* and many others that act to repel anything that wants to eat them, being fatal (as in the case of mushrooms), causing discomfort and the animal or insect discovering that the plant is not edible, releasing unpleasant smells or, in many cases, a combination of these factors. Not to mention genetically modified foods (almost the entire plant kingdom is genetically modified) that work as a steroid for the plants' defenses. - Lack of focus - Poor decision-making - Difficulty in establishing and maintaining relationships - Difficulty getting pregnant and difficult pregnancy - Low testosterone (medical reference values are low) - Alzheimer's - Diabetes - Dementia - Chances of developing autism when mothers do not eat meat and fat properly during pregnancy - Worsening of the degree of autism when the child does not eat meat and fat (food selectivity) - Insomnia and other sleep problems - Lack of energy - Poorly formed and fragile bone structure - Lack of willpower - Depression - ADHD Not having full physical and mental capacity harms you in many different ways, these are just a few examples that not only directly impact one person but everyone else around them. Fortunately, there is an alternative to break out of this cycle of destruction, ***Carnivore Diet***. I am not here to recommend a diet, eating plan or cure for your health problems, nor can I do so, as I am not a doctor (most doctors don't even know where the pancreas is, a mechanic is more useful in your life than a doctor, but that is a topic for another text.). I came to present you with logic and facts in a very simplified way, from there you can do your own research and decide what is best for you. --- ## Defining the carnivore diet Simply put, the carnivore diet is an elimination diet, where carbohydrates (including fruits), vegetable fats (soy, canola, cotton, peanuts, etc.), processed products and any type of plant, be it spices or teas, are completely removed. ### What is allowed on the carnivore diet? - Animal protein - Beef, preferably fatty cuts (including offal, liver, heart, kidneys, these cuts have more vitamins than anything else in the world) - Lamb - Eggs - Fish and seafood - Animal fat - Butter - Beef fat and tallow - Salt - No... salt does not cause high blood pressure. (explained later about salt and high consumption of saturated fats) From now on I will list some facts that disprove the false accusations made against \*\*eating exclusively meat and fat. # “Human beings are omnivores” *“Our ancestors were gatherers and hunters*" To determine the proportion of animal foods in our ancestors’ diets, we can look at the amount of δ15 nitrogen in their fossils. By looking at levels of this isotope, researchers can infer where animals reside in the food chain, identifying their protein sources. Herbivores typically have δ15N levels of 3–7 percent, carnivores show levels of 6–12 percent, and omnivores exhibit levels in between. When samples from Neanderthals and early modern humans were analyzed, they showed levels of 12 percent and 13.5 percent, respectively, even higher than those of other known carnivores, such as hyenas and wolves. And from an energy efficiency standpoint, hunting large animals makes the most sense. Gathering plants and chasing small animals provides far fewer calories and nutrients relative to the energy invested. In more recently studied indigenous peoples, we have observed a similar pattern that clearly indicates a preference for animal foods over plant foods. For example, in Vilhjalmur Stefansson’s studies of the Eskimos. *“…fat, not protein, seemed to play a very important role in hunters’ decisions about which animals (male or female) to kill and which body parts to discard or carry away.”* Why were our ancestors and more recent indigenous peoples so interested in finding fat? At a very basic level, it was probably about calories. By weight, fat provides more than twice as many calories as protein or carbohydrates. Furthermore, human metabolism makes fat an exceptionally valuable and necessary food. If we think of ourselves as automobiles that need fuel for our metabolic engines, we should not put protein in our gas tank. For best results, our metabolic engine runs most efficiently on fat or carbohydrates. Eating animal foods has been a vital part of our evolution since the beginning. Katherine Milton, a researcher at UC Berkeley, came to the same conclusion in her paper “The Critical Role Played by Animal Source Foods in Human Evolution,” which states: “Without routine access to animal-source foods, it is highly unlikely that evolving humans could have achieved their unusually large and complex brains while simultaneously continuing their evolutionary trajectory as large, active, and highly social primates. As human evolution progressed, young children in particular, with their rapidly expanding large brains and higher metabolic and nutritional demands relative to adults, would have benefited from concentrated, high-quality foods such as meat." - https://pubmed.ncbi.nlm.nih.gov/14672286/ Skeletons from Greece and Turkey reveal that 12,000 years ago, the average height of hunter-gatherers was five feet, nine inches for men and five feet, five inches for women. But with the adoption of agriculture, adult height plummeted—ending any hope these poor herders had of dunking a basketball or playing competitive volleyball, if such sports had existed at the time. By 3000 B.C., men in this region of the world were only five feet, three inches tall, and women were five feet, reflecting a massive decline in their overall nutritional status. Many studies in diverse populations show a strong correlation between adult height and nutritional quality. A study analyzing male height in 105 countries came to the following conclusion: “In taller nations…consumption of plant proteins declines sharply at the expense of animal proteins, especially those from dairy products. Its highest consumption rates can be found in Northern and Central Europe, with the global peak in male height in the Netherlands (184 cm).” In addition to the decline in height, there is also evidence that Native Americans buried at Dickson Mounds suffered from increased bacterial infections. These infections leave scars on the outer surface of the bone, known as the periosteum, with the tibia being especially susceptible to such damage due to its limited blood flow. Examination of tibias from skeletons found in the mounds shows that after agriculture, the number of such periosteal lesions increased threefold, with a staggering eighty-four percent of bones from this period demonstrating this pathology. The lesions also tended to be more severe and to appear earlier in life in the bones of post-agricultural peoples. https://onlinelibrary.wiley.com/doi/full/10.1111/j.1747-0080.2007.00194.x https://pubmed.ncbi.nlm.nih.gov/10702160/ # Cholesterol Many “doctors” say that consuming saturated fat is harmful to your health, “your veins and arteries will clog with excess fat” “you will have a heart attack if you consume a lot of fat" and many other nonsense, and in exchange recommends that you replace fatty cuts of meat with lean meat and do everything with vegetable oil that causes cancer and makes men effeminate. Your brain is basically composed of fat and water, your neurons are made and repaired with fat, your cells, the basic unit of life, are composed of fat and protein, many of your hormones, especially sexual ones, are made from fat, there is no logical reason not to consume saturated fat other than several false "scientific articles". "The power plant of the cell is the mitochondria, which converts what we eat into energy. Ketones are an energy source derived from fat. Mitochondria prefer fat as energy (ketones) because transforming ketones into energy costs the mitochondria half the effort of using sugar (glucose) for energy." - https://pubmed.ncbi.nlm.nih.gov/28178565/ "With the help of saturated fats, calcium is properly stored in our bones. The interaction between calcium, vitamin D, and parathyroid hormone regulates calcium levels in the body. When there are calcium imbalances in the blood, our bones release calcium into the blood to find homeostasis." - https://www.healthpedian.org/the-role-of-calcium-in-the-human-body/ "The body needs cholesterol to support muscle repair and other cellular functions. This is why when there is cardiovascular disease, we see increased amounts of cholesterol in the area. Cholesterol is not there causing the problem, but the boat carrying fat was docked there for cholesterol and other nutrients to help fight the problem. Plaque is the body's attempt to deal with injury within the blood vessels." - *National Library of Medicine, “Cholesterol,” 2019* "Initially, the Plaque helps blood vessels stay strong and helps the vessels maintain their shape. But with the perpetual cycle of uncontrolled inflammation and leftover debris from cellular repair (cholesterol), over time plaque begins to grow and harden, reducing blood flow and oxygen to the heart. Both inflammation and repair require copious amounts of cholesterol and fats. So the body keeps sending these fatty substances to the site of the plaque — until either repair wins (plaque becomes sclerotic scars in the heart muscle, causing heart failure) or inflammation wins (atherosclerotic heart attack)" - https://pubmed.ncbi.nlm.nih.gov/21250192/ Inflammation in Atherosclerotic Cardiovascular Disease - https://pubmed.ncbi.nlm.nih.gov/21250192/ "Study finds that eating refined carbohydrates led to an increased risk of cardiovascular disease and obesity" - https://pmc.ncbi.nlm.nih.gov/articles/PMC5793267/ # “Meat causes cancer” Most of the misconceptions that red meat causes cancer come from a report by the World Health Organization's International Agency for Research on Cancer (IARC), which was released in 2015. Unfortunately, this report has been widely misrepresented by the mainstream media and is based on some very questionable interpretations of the science it claims to review. A closer look at a 2018 report on its findings reveals that only 14 of the 800 studies were considered in its final conclusions—and every single study was observational epidemiology. Why the other 786 were excluded remains a mystery, and this group included many interventional animal studies that clearly did not show a link between red meat and cancer. Of the fourteen epidemiological studies that were included in the IARC report, eight showed no link between meat consumption and the development of colon cancer. Of the remaining six studies, only one showed a statistically significant correlation between meat and cancer. In epidemiological research, one looks for correlation between two things and the strength of the correlation. Having just one study out of 800 that shows meat causes cancer is a mere fluke and becomes statistically insignificant. Interestingly, this was a study by Seventh-day Adventists in America — a religious group that advocates a plant-based diet. # Microbiota and Fiber I have seen several people and “doctors” saying that eating only meat would destroy your microbiota. And I have come to the conclusion that neither “doctors” nor most people know what a microbiota is. Microbiota is the set of several types of bacteria (millions) that exist in your stomach with the function of breaking down molecules of certain types of food that the body itself cannot get, fiber for example. Many times through the process of fermentation, which is why you have gas after eating your beloved oatmeal. People unconsciously believe that the microbiota is something fixed and unchangeable, but guess what… it is not. Your microbiota is determined by what you eat. If you love eating oatmeal, your microbiota will have a specific set of bacteria that can break down the oat molecule into a size that the body can absorb. If you follow a carnivorous diet, your microbiota will adapt to digest meat. ### Fiber Nutritional guidelines recommend large amounts of fiber in our diet, but what they don't tell you is that we only absorb around 6% of all the vegetable fiber we eat. In other words, it's insignificant! Another argument used by doctors and nutritionists is that it helps you go to the bathroom, but this is also a lie. Fiber doesn't help you evacuate, it forces you to do so. With the huge amount of undigestible food in your stomach (fiber), the intestine begins to force contractions, making this fecal matter go down, making you go to the bathroom. They also raise the argument that fibers are broken down into short-chain fatty acids, such as butyrate (butyric acid), propionate (propionic acid) and acetate (acetic acid). Butyrate is essential because it is the preferred fuel source for the endothelial cells of the large intestine. Butter, cream, and cheese contain butyrate in its absorbable form. Butter is the best source of butyric acid, or butyrate. In fact, the origins of the word butyric acid come from the Latin word *butyro*—the same origins as the word butter. “In 2012, a study in the Journal of Gastroenterology showed that reducing fiber (a precursor to short-chain fatty acids) helped participants with chronic constipation. The study lasted six months, and after two weeks without fiber, these participants were allowed to increase fiber as needed. These participants felt so much relief after two weeks without fiber that they continued without fiber for the entire six-month period. Of the high-fiber, low-fiber, and no-fiber groups, the zero-fiber participants had the highest bowel movement frequency.” - https://pmc.ncbi.nlm.nih.gov/articles/PMC3435786/ ### Bioavailability I said that our body can only absorb 6% of all the fiber we ingest. This is bioavailability, how much the body can absorb nutrients from a given food. Meat is the most bioavailable food on the planet! Grains and vegetables are not only not very bioavailable, but they also contain a huge amount of antinutrients. So if you eat a steak with some beans, you will not be able to absorb the nutrients from the beans, and the antinutrients in them will make it impossible to absorb a large amount of nutrients from the steak. https://pubmed.ncbi.nlm.nih.gov/23107545/ # Lack of nutrients and antioxidants in a carnivorous diet A major concern with the carnivorous diet is the lack of vitamin C, which would consequently lead to scurvy. Vitamin C plays an important role in the breakdown and transport of glucose into cells. In 2000 and 2001, the recommended daily intake of vitamin C effectively doubled. In fact, every 10 to 15 years, there has been a large increase in the recommended daily intake of vitamin C, as happened in 1974 and 1989. Interestingly, also in 1974, sugar prices became so high that high fructose corn syrup was introduced into the US market. Could the increase in readily available glucose foods and foods with high fructose corn syrup be a reason why we need more vitamin C? The question remains…. But this is not a cause for concern for the carnivore, liver is rich in vitamin C. You could easily reach the daily recommendation with liver or any cut of steak. 200-300g of steak already meets your needs and if the theory that the more sugar you eat, the more vitamin C you will get is true, then the more sugar you will eat is true. C is necessary if true, you could easily exceed the daily requirement. Meat and seafood are rich in ALL the nutrients that humans need to thrive. ### Antioxidants It is commonly said that fruits are rich in antioxidants but again this is a hoax, they are actually PRO-oxidants. These are substances that activate the mRF2 pathway of our immune system which causes the body to produce natural antioxidants. The body produces antioxidants, but many occur naturally in foods, Vitamin C, Vitamin E, Selenium and Manganese are all natural antioxidants. High concentrations of antioxidants can be harmful. Remember that high concentrations of antioxidants can increase oxidation and even protect against cancer cells. # Salt Consuming too much salt does not increase blood pressure and therefore increases the risk of heart disease and stroke. Studies show no evidence that limiting salt intake reduces the risk of heart disease. A 2011 study found that diets low in salt may actually increase the risk of death from heart attacks and strokes. Most importantly, they do not prevent high blood pressure. https://www.nytimes.com/2011/05/04/health/research/04salt.html # Sun This is not a dietary issue specifically, but there are things that can I would like to present that is against common sense when talking about the sun. It is common sense to say that the sun causes skin cancer and that we should not expose ourselves to it or, if we are exposed to the sun, use sunscreen, but no study proves that using sunscreen protects us from melanoma and basal cell carcinoma. The types of fatal melanomas usually occur in areas of the body that never see the sun, such as the soles of the feet. https://www.jabfm.org/content/24/6/735 In 1978, the first sunscreen was launched, and the market grew rapidly, along with cases of melanoma. Several studies show that sunscreens cause leaky gut (one of the main factors in chronic inflammation), hormonal dysfunction and neurological dysfunction. https://pubmed.ncbi.nlm.nih.gov/31058986/ If your concern when going out in the sun is skin cancer, don't worry, your own body's natural antioxidants will protect you. When they can no longer protect you, your skin starts to burn. (If you have to stay in the sun for work, for example, a good way to protect yourself is to rub coconut oil on your skin or just cover yourself with a few extra layers of thin clothing and a hat). Sunscreen gives you the false sense of protection by blocking the sunburn, so you stay out longer than your skin can handle, but sunscreens can only block 4% of UVA and UVB rays. www.westonaprice.org/health-topics/environmental-toxins/sunscreens-the-dark-side-of-avoiding-the-sun/ Interestingly, vitamin D deficiency is linked to increased cancer risks. It's a big contradiction to say that the greatest provider of vit. D causes cancer… https://med.stanford.edu/news/all-news/2010/10/skin-cancer-patients-more-likely-to-be-deficient-in-vitamin-d-study-finds.html Important roles of vitamin D: - **Regulation of Bone Metabolism** - Facilitates the **absorption of calcium and phosphorus** in the intestine. - Promotes bone mineralization and prevents diseases such as **osteoporosis**, **rickets** (in children) and **osteomalacia** (in adults). - **Immune Function** - Modulates the immune system, helping to reduce inflammation and strengthen the defense against infections, including **colds**, **flu** and other diseases. - May help reduce the incidence of autoimmune diseases such as **multiple sclerosis** and **rheumatoid arthritis**. - **Muscle Health** - Contributes to muscle strength and the prevention of weakness, especially in the elderly. - Reduces the risk of falls and fractures. - **Cardiovascular Function** - May help regulate blood pressure and heart function, reducing the risk of cardiovascular disease. - **Hormonal Balance** - Influences the production of hormones, including those associated with fertility and the functioning of the endocrine system. - Plays a role in insulin metabolism and glucose sensitivity. - **Brain Function and Mental Health** - Participates in mood regulation, which may reduce the risk of **depression** and improve mental health. - Has been associated with the prevention of neurodegenerative diseases, such as **Alzheimer's**. - **Anticancer Role** - Evidence suggests that vitamin D may inhibit the proliferation of cancer cells, especially in breast, prostate and colon cancers. - **Role in General Metabolism** - Contributes to metabolic health, regulating cellular growth and repair processes. --- I tried to present everything in the simplest and most understandable way possible, but there are things that require prior knowledge to truly understand. Below is a list of books that will show you everything I have shown you in a more technical and in-depth way. ### Book Recommendations https://amzn.to/3EbjVsD https://amzn.to/4awlnBZ All of my arguments have studies to validate them. Feel free to read them all and draw your own conclusions about what is best for you and your life. @ 0fa80bd3:ea7325de
2025-01-29 15:43:42Lyn Alden - биткойн евангелист или евангелистка, я пока не понял ``` npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a ``` Thomas Pacchia - PubKey owner - X - @tpacchia ``` npub1xy6exlg37pw84cpyj05c2pdgv86hr25cxn0g7aa8g8a6v97mhduqeuhgpl ``` calvadev - Shopstr ``` npub16dhgpql60vmd4mnydjut87vla23a38j689jssaqlqqlzrtqtd0kqex0nkq ``` Calle - Cashu founder ``` npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg ``` Джек Дорси ``` npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m ``` 21 ideas ``` npub1lm3f47nzyf0rjp6fsl4qlnkmzed4uj4h2gnf2vhe3l3mrj85vqks6z3c7l ``` Много адресов. Хз кто надо сортировать ``` https://github.com/aitechguy/nostr-address-book ``` ФиатДжеф - создатель Ностр - https://github.com/fiatjaf ``` npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 ``` EVAN KALOUDIS Zues wallet ``` npub19kv88vjm7tw6v9qksn2y6h4hdt6e79nh3zjcud36k9n3lmlwsleqwte2qd ``` Программер Коди https://github.com/CodyTseng/nostr-relay ``` npub1syjmjy0dp62dhccq3g97fr87tngvpvzey08llyt6ul58m2zqpzps9wf6wl ``` Anna Chekhovich - Managing Bitcoin at The Anti-Corruption Foundation https://x.com/AnyaChekhovich ``` npub1y2st7rp54277hyd2usw6shy3kxprnmpvhkezmldp7vhl7hp920aq9cfyr7 ```
@ 0fa80bd3:ea7325de
2025-01-29 15:43:42Lyn Alden - биткойн евангелист или евангелистка, я пока не понял ``` npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a ``` Thomas Pacchia - PubKey owner - X - @tpacchia ``` npub1xy6exlg37pw84cpyj05c2pdgv86hr25cxn0g7aa8g8a6v97mhduqeuhgpl ``` calvadev - Shopstr ``` npub16dhgpql60vmd4mnydjut87vla23a38j689jssaqlqqlzrtqtd0kqex0nkq ``` Calle - Cashu founder ``` npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg ``` Джек Дорси ``` npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m ``` 21 ideas ``` npub1lm3f47nzyf0rjp6fsl4qlnkmzed4uj4h2gnf2vhe3l3mrj85vqks6z3c7l ``` Много адресов. Хз кто надо сортировать ``` https://github.com/aitechguy/nostr-address-book ``` ФиатДжеф - создатель Ностр - https://github.com/fiatjaf ``` npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 ``` EVAN KALOUDIS Zues wallet ``` npub19kv88vjm7tw6v9qksn2y6h4hdt6e79nh3zjcud36k9n3lmlwsleqwte2qd ``` Программер Коди https://github.com/CodyTseng/nostr-relay ``` npub1syjmjy0dp62dhccq3g97fr87tngvpvzey08llyt6ul58m2zqpzps9wf6wl ``` Anna Chekhovich - Managing Bitcoin at The Anti-Corruption Foundation https://x.com/AnyaChekhovich ``` npub1y2st7rp54277hyd2usw6shy3kxprnmpvhkezmldp7vhl7hp920aq9cfyr7 ``` @ 57d1a264:69f1fee1
2025-01-28 02:36:34**About the role** In this role, you will work on the product design of umbrelOS, some of our umbrelOS apps, and the umbrel.com website. **What are you looking for in candidates?** Talent, passion, genuine love for your craft, and the desire to do meaningful work. What we’re not looking for: credentials and degrees. When you really love what you do, work feels like play. And when work feels like play, you become the best at it. That’s what we’re looking for. **We hope you:** - Like to spend your days staring at artboards in Figma - Are obsessed with creating delightful micro-interactions and animations - Are willing to throw away ideas if they're not great, and optimistic enough to keep hunting for new ones - Care about the details, maybe a bit too much (a pixel off ruins your sleep) - Are excited to collaborate with everyone on the team: engineers, customer facing folks, etc—you believe inspiration can come from anywhere - Have good judgement of when to ship - Like to level up your design skills continually - Put yourselves in the shoes of our users to craft a great experience - Enjoy being a generalist and are not tied down to a specific design, trend, or tools **Benefits** - 🚑 Health insurance - 💻 New work equipment - 🌎 Work from anywhere in the world - 💆♀️ Complete autonomy at work - 📚 Learning and development stipend - 🏝 Minimum 2-weeks of paid time off - ❤️ Most importantly — doing meaningful work that can change the world Apply at https://app.withrapha.com/job/692 originally posted at https://stacker.news/items/867248
@ 57d1a264:69f1fee1
2025-01-28 02:36:34**About the role** In this role, you will work on the product design of umbrelOS, some of our umbrelOS apps, and the umbrel.com website. **What are you looking for in candidates?** Talent, passion, genuine love for your craft, and the desire to do meaningful work. What we’re not looking for: credentials and degrees. When you really love what you do, work feels like play. And when work feels like play, you become the best at it. That’s what we’re looking for. **We hope you:** - Like to spend your days staring at artboards in Figma - Are obsessed with creating delightful micro-interactions and animations - Are willing to throw away ideas if they're not great, and optimistic enough to keep hunting for new ones - Care about the details, maybe a bit too much (a pixel off ruins your sleep) - Are excited to collaborate with everyone on the team: engineers, customer facing folks, etc—you believe inspiration can come from anywhere - Have good judgement of when to ship - Like to level up your design skills continually - Put yourselves in the shoes of our users to craft a great experience - Enjoy being a generalist and are not tied down to a specific design, trend, or tools **Benefits** - 🚑 Health insurance - 💻 New work equipment - 🌎 Work from anywhere in the world - 💆♀️ Complete autonomy at work - 📚 Learning and development stipend - 🏝 Minimum 2-weeks of paid time off - ❤️ Most importantly — doing meaningful work that can change the world Apply at https://app.withrapha.com/job/692 originally posted at https://stacker.news/items/867248 @ 9e69e420:d12360c2
2025-01-26 15:26:44Secretary of State Marco Rubio issued new guidance halting spending on most foreign aid grants for 90 days, including military assistance to Ukraine. This immediate order shocked State Department officials and mandates “stop-work orders” on nearly all existing foreign assistance awards. While it allows exceptions for military financing to Egypt and Israel, as well as emergency food assistance, it restricts aid to key allies like Ukraine, Jordan, and Taiwan. The guidance raises potential liability risks for the government due to unfulfilled contracts. A report will be prepared within 85 days to recommend which programs to continue or discontinue.
@ 9e69e420:d12360c2
2025-01-26 15:26:44Secretary of State Marco Rubio issued new guidance halting spending on most foreign aid grants for 90 days, including military assistance to Ukraine. This immediate order shocked State Department officials and mandates “stop-work orders” on nearly all existing foreign assistance awards. While it allows exceptions for military financing to Egypt and Israel, as well as emergency food assistance, it restricts aid to key allies like Ukraine, Jordan, and Taiwan. The guidance raises potential liability risks for the government due to unfulfilled contracts. A report will be prepared within 85 days to recommend which programs to continue or discontinue. @ 0463223a:3b14d673
2025-01-26 13:07:36Hmm so I heard that in order to improve my brain I should try writing… Ok groovy, I’ll give it a go. In all honesty I don’t know what to write, my brain is a jumble of noise and titbits of random knowledge. I likely know more about sound than the average person but as physics goes, I don’t have anything new or profound to add. Air moves and noises happen. Is there really any more to it? I could write some flowery bollocks about refraction, absorption coefficients and reverberation times, or I could write some out there, arty shit but I don’t think that adds any value to anyone. A lot of folks online have very strong beliefs in how the world operates or should operate. Whilst their conviction is strong, there’s also is a large percentage of people who totally disagree with them and think the exact opposite is the answer. That’s quite shit isn’t it? Humans have been around for 100,000 years or so and haven’t worked it out. I wonder what makes the internet celeb so certain they’ve got it right when the next internet celeb completely disagrees? I do my best to avoid any of these cunts but despite running to the obscurest social media platforms they still turn up with their profound statements. Meh. Ideologically I’m leaning toward anarchism but even that seems full of arguments and contradictions and ultimately I don’t think I can be arsed with identifying with any particular ideology. I tried reading some philosophy and struggled with it, although I deep fall into a lovely deep sleep. It’s fair to say I’m not the brightest button in the box. I have a wife, a couple of cats and lots of things that make nosies in my shed. That’s pretty cool right? Well it works for me. So why write this? I clearly wrote in the first sentence that I’m trying to improve my brain, a brain that’s gone through a number to twists and turns, a lot brain altering substances. I own that, no one forced me to. Beside, George Clinton was still smoking crack aged 80, didn’t do him any harm… I’m on the 5th paragraph. I don’t feel any smarter yet and each paragraph is getting shorter, having started from a low base. I guess I’m being too high time preference… Might be a while before I launch my Deep Thought podcasts where myself and a guest talk for 500 hours about the philosophy of money and 13 amp plug sockets. I’ve tortured myself enough. I’m posting this on Nostr where it will never go away.. lol. If you got this far, I congratulate/commiserate you and wish you a wonderful day.
@ 0463223a:3b14d673
2025-01-26 13:07:36Hmm so I heard that in order to improve my brain I should try writing… Ok groovy, I’ll give it a go. In all honesty I don’t know what to write, my brain is a jumble of noise and titbits of random knowledge. I likely know more about sound than the average person but as physics goes, I don’t have anything new or profound to add. Air moves and noises happen. Is there really any more to it? I could write some flowery bollocks about refraction, absorption coefficients and reverberation times, or I could write some out there, arty shit but I don’t think that adds any value to anyone. A lot of folks online have very strong beliefs in how the world operates or should operate. Whilst their conviction is strong, there’s also is a large percentage of people who totally disagree with them and think the exact opposite is the answer. That’s quite shit isn’t it? Humans have been around for 100,000 years or so and haven’t worked it out. I wonder what makes the internet celeb so certain they’ve got it right when the next internet celeb completely disagrees? I do my best to avoid any of these cunts but despite running to the obscurest social media platforms they still turn up with their profound statements. Meh. Ideologically I’m leaning toward anarchism but even that seems full of arguments and contradictions and ultimately I don’t think I can be arsed with identifying with any particular ideology. I tried reading some philosophy and struggled with it, although I deep fall into a lovely deep sleep. It’s fair to say I’m not the brightest button in the box. I have a wife, a couple of cats and lots of things that make nosies in my shed. That’s pretty cool right? Well it works for me. So why write this? I clearly wrote in the first sentence that I’m trying to improve my brain, a brain that’s gone through a number to twists and turns, a lot brain altering substances. I own that, no one forced me to. Beside, George Clinton was still smoking crack aged 80, didn’t do him any harm… I’m on the 5th paragraph. I don’t feel any smarter yet and each paragraph is getting shorter, having started from a low base. I guess I’m being too high time preference… Might be a while before I launch my Deep Thought podcasts where myself and a guest talk for 500 hours about the philosophy of money and 13 amp plug sockets. I’ve tortured myself enough. I’m posting this on Nostr where it will never go away.. lol. If you got this far, I congratulate/commiserate you and wish you a wonderful day. @ 9e69e420:d12360c2
2025-01-25 22:16:54President Trump plans to withdraw 20,000 U.S. troops from Europe and expects European allies to contribute financially to the remaining military presence. Reported by ANSA, Trump aims to deliver this message to European leaders since taking office. A European diplomat noted, “the costs cannot be borne solely by American taxpayers.” The Pentagon hasn't commented yet. Trump has previously sought lower troop levels in Europe and had ordered cuts during his first term. The U.S. currently maintains around 65,000 troops in Europe, with total forces reaching 100,000 since the Ukraine invasion. Trump's new approach may shift military focus to the Pacific amid growing concerns about China. [Sauce](https://www.stripes.com/theaters/europe/2025-01-24/trump-europe-troop-cuts-16590074.html)
@ 9e69e420:d12360c2
2025-01-25 22:16:54President Trump plans to withdraw 20,000 U.S. troops from Europe and expects European allies to contribute financially to the remaining military presence. Reported by ANSA, Trump aims to deliver this message to European leaders since taking office. A European diplomat noted, “the costs cannot be borne solely by American taxpayers.” The Pentagon hasn't commented yet. Trump has previously sought lower troop levels in Europe and had ordered cuts during his first term. The U.S. currently maintains around 65,000 troops in Europe, with total forces reaching 100,000 since the Ukraine invasion. Trump's new approach may shift military focus to the Pacific amid growing concerns about China. [Sauce](https://www.stripes.com/theaters/europe/2025-01-24/trump-europe-troop-cuts-16590074.html) @ 228dde34:b5d0345e
2025-01-25 01:59:57##### By Jonathan Tan ##### Lead Editor ##### Hype Issue #60 ##### JONATHAN TAN explores the recent rise in popularity of online gambling, and its consequences on the population’s most vulnerable.  The persistent rise in the gaming industry, fueled by the introduction of online gambling, seems to have no end. Experts are now worrying about the effects of this epidemic on public health and safety. “Many people might be really experiencing harms from gambling — we think that it’s probably around 72 million people globally,” said Louisa Degenhardt, a professor at the University of New South Wales in Sydney, in an[NBC article.](https://www.nbcnews.com/health/health-news/gambling-industry-growth-threat-public-health-report-rcna175356) The online gambling craze has spread worldwide, and even Singapore, with its strict gambling regulations, is not immune to it. In a recent[survey](https://www.channelnewsasia.com/singapore/national-council-problem-gambling-rate-continues-fall-4761621)conducted by the National Council on Problem Gambling (NCPG), illegal online gambling rates have more than tripled since 2020, from 0.3% to 1.0% in the past 4 years. This statistic alone highlights an already concerning trend. Even more troubling, however, is that the illegal nature of these websites means there are no regulatory laws or age restrictions. As a result, the proliferation of these online websites has allowed a brand new demographic to start gambling: the Singaporean youth. ### How to lose thousands before adulthood “I started gambling when I was 13 years old, at a friend's house,” George (not his real name) shares. Now an 18-year-old student, George recalls how a simple game among friends slowly grew into an all-consuming gambling addiction.  *In NCPG’s 2023 survey, 8% of respondents reported participating in social gambling activities: gambling which occurs within individuals’ homes, among family members. Photo from Shutterstock.* Initially, George and his friends gambled with low stakes, like a dollar here and there. However, the games slowly escalated: from $1 to $10, then to $100, and eventually to $1000. Unsurprisingly, with such large sums at stake, George’s relationship with his friends began to strain. “I realized that after a certain point, the more and more money we [bet], the more and more our relationship with each other [soured]; and so we decided to curb it at a maximum buy-in of $20 per game,” George says. The new rule eased the tension between George and his friends, but it inadvertently created a new problem: George no longer felt the thrill of winning large sums. As a result, he began seeking other ways to gamble. “The first time I gambled online was when I was 16 years old. A friend had introduced me to a gambling website,” he recalls. “And at first it was all right. I won a bit, I lost a bit, but no one got hurt.” But it didn’t take long for him to get hooked; a single sports bet was what netted George his first big win. “On the first day, I went from $10 to $800 from a simple parlay bet,” George says. “I felt unstoppable. Adrenaline was pumping through my veins, and [I felt] I could never lose. [After] that day, I gambled like $100 almost every day for a straight month.”  *A parlay (a form of sports betting that has recently surged in popularity) is a single bet that combines two or more bets into one. While doing this drastically decreases the odds of winning, it also drastically increases the potential payout. Photo from Getty Images.* Nothing could stop George’s gambling fervor. Even after losing nearly a thousand dollars on a single blackjack hand, all George did was place a bigger bet to try and win it back. “Every morning, when I [woke] up, all I could think about was gambling,” he shares. And of course, George’s obsession with online gambling was only exacerbated by the accessibility of these websites. First, the online nature of these websites allowed George to gamble anywhere, at any time. “For online gambling, you have it right at your fingertips. As soon as you wake up, you can just log on the computer and start betting huge amounts of money,” he mentions. But more importantly, these illegal gambling websites enabled George to do something he was never old enough to do in the first place. “I'm too young to gamble at a real casino or a physical casino. But online gambling makes it way more accessible because there's no verification of ID,” George says. ### Consequences, consequences Therein lies the predatory nature of these illegal websites. While anyone can fall victim to a gambling addiction, certain factors may make the youth especially vulnerable. “The adolescent brain is still developing, particularly the prefrontal cortex, which is responsible for decision-making, impulse control, and risk assessment. This makes young people more susceptible to impulsive behaviors,” says Jat Tan, the Communications and Events Executive at WE CARE Community Services.  *The prefrontal cortex is primarily developed during adolescence, and is fully developed at the age of 25 years. Photo from iStock.* Additionally, other factors such as peer pressure, social media, or limited life experience, could result in young Singaporeans being more open to gambling. Lastly, one popular reason why the youth are drawn to gambling, is their limited financial freedom. “While youths are in school, they have a significantly lower earning power as opposed to adults. The demands from school usually means that they can only afford to work part-time jobs,” Mrs Tan shares. Despite this, many young Singaporeans still want to live extravagant lifestyles. With the youth getting exposed to lavish, ostentatious lifestyles on social media, many begin to feel envious and yearn for the same luxuries. And now, with the introduction of illegal online sites, the lack of age restrictions allows these youths to gamble in an attempt to achieve this better life. ### What can be done? The increase in the number of adolescent gamblers is a new challenge for the Singaporean government. Before the advent of online gambling, many safeguards were in place to protect Singaporeans from developing gambling addictions. In particular, safeguards that limit Singaporeans’ access to legal gambling services seem to be working; the overall percentage of gambling Singaporeans has fallen from 44% to 40% from 2020 to 2023. However, the unprecedented accessibility and convenience of online gambling sites have allowed Singapore’s tech-savvy youth to bypass these regulations; and now, the Singaporean government needs to update its laws to keep up with the growing gambling industry. Of course, the Singaporean Government has been cracking down on illegal online gambling. As of September 2024, the Gambling Regulatory Authority (GRA) has blocked access to more than 1,900 remote gambling websites. But despite the GRA’s efforts, these online gambling providers continue to survive, like weeds in a garden. “GRA recognises that the borderless nature of the Internet makes it easy for unlawful gambling operators to offer their products to users in Singapore any time and anywhere,” said a GRA spokesman in [a Straits Times article.](https://www.straitstimes.com/singapore/crackdown-on-illegal-online-gambling-but-addiction-can-be-hard-to-beat) Currently, there are calls for the government to shift its focus. “While Singapore has done well putting in place responsible gaming and safety measures to mitigate the risks of casino gambling, it is timely to focus more attention to address the risk of illegal online gambling as well,” said Ms Tham, Clinical director of We Care Community Services, [in a Straits Times article.](https://www.straitstimes.com/singapore/fewer-singapore-residents-gambled-but-more-do-so-online-illegally) Ultimately, as the gambling industry becomes more technologically advanced, it becomes harder for Singapore to regulate gambling the same way it used to. Thus, it may be time for the Singaporean government to consider a different solution. “Better educating youths on the harms and consequences of gambling, as well as resources available should things go awry, would be the best option to nip the issue in the bud,” Ms Tan suggests. Instead of focusing on restrictive legislation, education could be a preventative measure used to curb adolescent gambling. “A higher level of awareness would enable youths to face issues like gambling with their eyes wide open - they will have a rough idea of what they're getting themselves into, and will have a rough idea of what to do if things go wrong,” she shares.
@ 228dde34:b5d0345e
2025-01-25 01:59:57##### By Jonathan Tan ##### Lead Editor ##### Hype Issue #60 ##### JONATHAN TAN explores the recent rise in popularity of online gambling, and its consequences on the population’s most vulnerable.  The persistent rise in the gaming industry, fueled by the introduction of online gambling, seems to have no end. Experts are now worrying about the effects of this epidemic on public health and safety. “Many people might be really experiencing harms from gambling — we think that it’s probably around 72 million people globally,” said Louisa Degenhardt, a professor at the University of New South Wales in Sydney, in an[NBC article.](https://www.nbcnews.com/health/health-news/gambling-industry-growth-threat-public-health-report-rcna175356) The online gambling craze has spread worldwide, and even Singapore, with its strict gambling regulations, is not immune to it. In a recent[survey](https://www.channelnewsasia.com/singapore/national-council-problem-gambling-rate-continues-fall-4761621)conducted by the National Council on Problem Gambling (NCPG), illegal online gambling rates have more than tripled since 2020, from 0.3% to 1.0% in the past 4 years. This statistic alone highlights an already concerning trend. Even more troubling, however, is that the illegal nature of these websites means there are no regulatory laws or age restrictions. As a result, the proliferation of these online websites has allowed a brand new demographic to start gambling: the Singaporean youth. ### How to lose thousands before adulthood “I started gambling when I was 13 years old, at a friend's house,” George (not his real name) shares. Now an 18-year-old student, George recalls how a simple game among friends slowly grew into an all-consuming gambling addiction.  *In NCPG’s 2023 survey, 8% of respondents reported participating in social gambling activities: gambling which occurs within individuals’ homes, among family members. Photo from Shutterstock.* Initially, George and his friends gambled with low stakes, like a dollar here and there. However, the games slowly escalated: from $1 to $10, then to $100, and eventually to $1000. Unsurprisingly, with such large sums at stake, George’s relationship with his friends began to strain. “I realized that after a certain point, the more and more money we [bet], the more and more our relationship with each other [soured]; and so we decided to curb it at a maximum buy-in of $20 per game,” George says. The new rule eased the tension between George and his friends, but it inadvertently created a new problem: George no longer felt the thrill of winning large sums. As a result, he began seeking other ways to gamble. “The first time I gambled online was when I was 16 years old. A friend had introduced me to a gambling website,” he recalls. “And at first it was all right. I won a bit, I lost a bit, but no one got hurt.” But it didn’t take long for him to get hooked; a single sports bet was what netted George his first big win. “On the first day, I went from $10 to $800 from a simple parlay bet,” George says. “I felt unstoppable. Adrenaline was pumping through my veins, and [I felt] I could never lose. [After] that day, I gambled like $100 almost every day for a straight month.”  *A parlay (a form of sports betting that has recently surged in popularity) is a single bet that combines two or more bets into one. While doing this drastically decreases the odds of winning, it also drastically increases the potential payout. Photo from Getty Images.* Nothing could stop George’s gambling fervor. Even after losing nearly a thousand dollars on a single blackjack hand, all George did was place a bigger bet to try and win it back. “Every morning, when I [woke] up, all I could think about was gambling,” he shares. And of course, George’s obsession with online gambling was only exacerbated by the accessibility of these websites. First, the online nature of these websites allowed George to gamble anywhere, at any time. “For online gambling, you have it right at your fingertips. As soon as you wake up, you can just log on the computer and start betting huge amounts of money,” he mentions. But more importantly, these illegal gambling websites enabled George to do something he was never old enough to do in the first place. “I'm too young to gamble at a real casino or a physical casino. But online gambling makes it way more accessible because there's no verification of ID,” George says. ### Consequences, consequences Therein lies the predatory nature of these illegal websites. While anyone can fall victim to a gambling addiction, certain factors may make the youth especially vulnerable. “The adolescent brain is still developing, particularly the prefrontal cortex, which is responsible for decision-making, impulse control, and risk assessment. This makes young people more susceptible to impulsive behaviors,” says Jat Tan, the Communications and Events Executive at WE CARE Community Services.  *The prefrontal cortex is primarily developed during adolescence, and is fully developed at the age of 25 years. Photo from iStock.* Additionally, other factors such as peer pressure, social media, or limited life experience, could result in young Singaporeans being more open to gambling. Lastly, one popular reason why the youth are drawn to gambling, is their limited financial freedom. “While youths are in school, they have a significantly lower earning power as opposed to adults. The demands from school usually means that they can only afford to work part-time jobs,” Mrs Tan shares. Despite this, many young Singaporeans still want to live extravagant lifestyles. With the youth getting exposed to lavish, ostentatious lifestyles on social media, many begin to feel envious and yearn for the same luxuries. And now, with the introduction of illegal online sites, the lack of age restrictions allows these youths to gamble in an attempt to achieve this better life. ### What can be done? The increase in the number of adolescent gamblers is a new challenge for the Singaporean government. Before the advent of online gambling, many safeguards were in place to protect Singaporeans from developing gambling addictions. In particular, safeguards that limit Singaporeans’ access to legal gambling services seem to be working; the overall percentage of gambling Singaporeans has fallen from 44% to 40% from 2020 to 2023. However, the unprecedented accessibility and convenience of online gambling sites have allowed Singapore’s tech-savvy youth to bypass these regulations; and now, the Singaporean government needs to update its laws to keep up with the growing gambling industry. Of course, the Singaporean Government has been cracking down on illegal online gambling. As of September 2024, the Gambling Regulatory Authority (GRA) has blocked access to more than 1,900 remote gambling websites. But despite the GRA’s efforts, these online gambling providers continue to survive, like weeds in a garden. “GRA recognises that the borderless nature of the Internet makes it easy for unlawful gambling operators to offer their products to users in Singapore any time and anywhere,” said a GRA spokesman in [a Straits Times article.](https://www.straitstimes.com/singapore/crackdown-on-illegal-online-gambling-but-addiction-can-be-hard-to-beat) Currently, there are calls for the government to shift its focus. “While Singapore has done well putting in place responsible gaming and safety measures to mitigate the risks of casino gambling, it is timely to focus more attention to address the risk of illegal online gambling as well,” said Ms Tham, Clinical director of We Care Community Services, [in a Straits Times article.](https://www.straitstimes.com/singapore/fewer-singapore-residents-gambled-but-more-do-so-online-illegally) Ultimately, as the gambling industry becomes more technologically advanced, it becomes harder for Singapore to regulate gambling the same way it used to. Thus, it may be time for the Singaporean government to consider a different solution. “Better educating youths on the harms and consequences of gambling, as well as resources available should things go awry, would be the best option to nip the issue in the bud,” Ms Tan suggests. Instead of focusing on restrictive legislation, education could be a preventative measure used to curb adolescent gambling. “A higher level of awareness would enable youths to face issues like gambling with their eyes wide open - they will have a rough idea of what they're getting themselves into, and will have a rough idea of what to do if things go wrong,” she shares. @ bcea2b98:7ccef3c9
2025-01-24 23:21:05originally posted at https://stacker.news/items/862840
@ bcea2b98:7ccef3c9
2025-01-24 23:21:05originally posted at https://stacker.news/items/862840 @ 378562cd:a6fc6773
2025-01-23 17:57:13**Top USA News** 1. **President Trump Threatens Tariffs on Non-U.S. Manufacturers**In a speech at the World Economic Forum in Davos, President Donald Trump announced plans to impose tariffs on companies that do not manufacture their products in the United States, aiming to boost domestic production. [The Guardian](https://www.theguardian.com/us-news/live/2025/jan/23/donald-trump-pardons-january-6-us-president-joe-biden-jd-vance-republicans-live-news?utm_source=chatgpt.com) 2. **Historic Winter Storm Sweeps Across Southern U.S**.A severe winter storm has blanketed the southern United States with snow and freezing temperatures, leading to widespread power outages and hazardous travel conditions. [WSJ](https://www.wsj.com/news/archive/2025/01/23?utm_source=chatgpt.com) 3. **Trump Administration Orders Federal DEI Staff on Leave**The Trump administration has directed all federal employees working in Diversity, Equity, and Inclusion (DEI) programs to be placed on paid leave, with plans to dismiss all DEI program employees by January 31. [The Guardian](https://www.theguardian.com/us-news/live/2025/jan/22/donald-trump-china-sanctions-tariff-diversity-us-politics-live-latest-news?utm_source=chatgpt.com) 4. **U.S. Stock Futures Mixed After Tech-Driven Rally**Following a tech-fueled rise, U.S. stock futures show mixed results. The S&P 500 futures dipped slightly after nearing record highs, while Nasdaq futures declined by 0.5%, and Dow Jones futures saw a slight increase. [Investopedia](https://www.investopedia.com/5-things-to-know-before-the-stock-market-opens-january-23-2025-8778964?utm_source=chatgpt.com) 5. **Trump Pardons January 6 Capitol Rioters**President Trump has issued pardons for individuals convicted in relation to the January 6 Capitol riot, a move that has sparked controversy and debate across the political spectrum. [The Guardian](https://www.theguardian.com/us-news/live/2025/jan/23/donald-trump-pardons-january-6-us-president-joe-biden-jd-vance-republicans-live-news?utm_source=chatgpt.com) 6. **California Wildfires Cause Extensive Damage**Ongoing wildfires in Los Angeles County are causing significant destruction, with estimated damages exceeding $135 billion. Governor Gavin Newsom warns that these could become the worst natural disaster in American history. [Wikipedia](https://en.wikipedia.org/wiki/Portal%3ACurrent_events/January_2025?utm_source=chatgpt.com) 7. **President Trump Withdraws U.S. from Paris Climate Agreement**In a series of executive orders, President Trump has withdrawn the United States from the Paris Climate Agreement, citing economic concerns and a focus on American energy independence. [The Guardian](https://www.theguardian.com/us-news/live/2025/jan/21/donald-trump-inauguration-presidency-executive-orders-pardons-day-two-live-blog?utm_source=chatgpt.com) 8. **Trump Administration Re-designates Houthis as Terrorist Organization**The Trump administration has re-designated the Yemeni Houthi movement as a foreign terrorist organization, reversing a previous decision and impacting international relations in the region. [Wikipedia](https://en.wikipedia.org/wiki/2025_in_the_United_States?utm_source=chatgpt.com) 9. **President Trump Announces $500 Billion AI Investment**President Trump, alongside tech executives, has announced a $500 billion investment in artificial intelligence infrastructure, aiming to bolster the United States' position in the global tech industry. [WSJ](https://www.wsj.com/news/archive/2025/01/23?utm_source=chatgpt.com) 10. **ChatGPT Experiences Large-Scale Outage**A significant outage of the AI tool ChatGPT has been reported, affecting users worldwide. The cause of the disruption is under investigation. [Wikipedia](https://en.wikipedia.org/wiki/2025_in_the_United_Kingdom?utm_source=chatgpt.com) **Top International News** 1. **Israeli Military Conducts Extensive Raid in Jenin**The Israeli military launched a significant operation in Jenin, resulting in at least 10 Palestinian deaths and numerous injuries. The raid, named "Iron Wall," involved airstrikes and ground forces, escalating tensions in the West Bank. [The Guardian](https://www.theguardian.com/world/2025/jan/23/first-edition-west-bank-settlers-israel-military?utm_source=chatgpt.com) 2. **Micheál Martin Appointed as Irish Taoiseach**Micheál Martin has been confirmed as Ireland's new Taoiseach following a day of delays and disagreements in the Irish parliament. His immediate focus includes forming his cabinet and addressing Ireland's housing crisis. [The Guardian](https://www.theguardian.com/world/live/2025/jan/23/europe-dail-micheal-martin-rows-ireland-weather-storm-eowyn-latest-updates?utm_source=chatgpt.com)
@ 378562cd:a6fc6773
2025-01-23 17:57:13**Top USA News** 1. **President Trump Threatens Tariffs on Non-U.S. Manufacturers**In a speech at the World Economic Forum in Davos, President Donald Trump announced plans to impose tariffs on companies that do not manufacture their products in the United States, aiming to boost domestic production. [The Guardian](https://www.theguardian.com/us-news/live/2025/jan/23/donald-trump-pardons-january-6-us-president-joe-biden-jd-vance-republicans-live-news?utm_source=chatgpt.com) 2. **Historic Winter Storm Sweeps Across Southern U.S**.A severe winter storm has blanketed the southern United States with snow and freezing temperatures, leading to widespread power outages and hazardous travel conditions. [WSJ](https://www.wsj.com/news/archive/2025/01/23?utm_source=chatgpt.com) 3. **Trump Administration Orders Federal DEI Staff on Leave**The Trump administration has directed all federal employees working in Diversity, Equity, and Inclusion (DEI) programs to be placed on paid leave, with plans to dismiss all DEI program employees by January 31. [The Guardian](https://www.theguardian.com/us-news/live/2025/jan/22/donald-trump-china-sanctions-tariff-diversity-us-politics-live-latest-news?utm_source=chatgpt.com) 4. **U.S. Stock Futures Mixed After Tech-Driven Rally**Following a tech-fueled rise, U.S. stock futures show mixed results. The S&P 500 futures dipped slightly after nearing record highs, while Nasdaq futures declined by 0.5%, and Dow Jones futures saw a slight increase. [Investopedia](https://www.investopedia.com/5-things-to-know-before-the-stock-market-opens-january-23-2025-8778964?utm_source=chatgpt.com) 5. **Trump Pardons January 6 Capitol Rioters**President Trump has issued pardons for individuals convicted in relation to the January 6 Capitol riot, a move that has sparked controversy and debate across the political spectrum. [The Guardian](https://www.theguardian.com/us-news/live/2025/jan/23/donald-trump-pardons-january-6-us-president-joe-biden-jd-vance-republicans-live-news?utm_source=chatgpt.com) 6. **California Wildfires Cause Extensive Damage**Ongoing wildfires in Los Angeles County are causing significant destruction, with estimated damages exceeding $135 billion. Governor Gavin Newsom warns that these could become the worst natural disaster in American history. [Wikipedia](https://en.wikipedia.org/wiki/Portal%3ACurrent_events/January_2025?utm_source=chatgpt.com) 7. **President Trump Withdraws U.S. from Paris Climate Agreement**In a series of executive orders, President Trump has withdrawn the United States from the Paris Climate Agreement, citing economic concerns and a focus on American energy independence. [The Guardian](https://www.theguardian.com/us-news/live/2025/jan/21/donald-trump-inauguration-presidency-executive-orders-pardons-day-two-live-blog?utm_source=chatgpt.com) 8. **Trump Administration Re-designates Houthis as Terrorist Organization**The Trump administration has re-designated the Yemeni Houthi movement as a foreign terrorist organization, reversing a previous decision and impacting international relations in the region. [Wikipedia](https://en.wikipedia.org/wiki/2025_in_the_United_States?utm_source=chatgpt.com) 9. **President Trump Announces $500 Billion AI Investment**President Trump, alongside tech executives, has announced a $500 billion investment in artificial intelligence infrastructure, aiming to bolster the United States' position in the global tech industry. [WSJ](https://www.wsj.com/news/archive/2025/01/23?utm_source=chatgpt.com) 10. **ChatGPT Experiences Large-Scale Outage**A significant outage of the AI tool ChatGPT has been reported, affecting users worldwide. The cause of the disruption is under investigation. [Wikipedia](https://en.wikipedia.org/wiki/2025_in_the_United_Kingdom?utm_source=chatgpt.com) **Top International News** 1. **Israeli Military Conducts Extensive Raid in Jenin**The Israeli military launched a significant operation in Jenin, resulting in at least 10 Palestinian deaths and numerous injuries. The raid, named "Iron Wall," involved airstrikes and ground forces, escalating tensions in the West Bank. [The Guardian](https://www.theguardian.com/world/2025/jan/23/first-edition-west-bank-settlers-israel-military?utm_source=chatgpt.com) 2. **Micheál Martin Appointed as Irish Taoiseach**Micheál Martin has been confirmed as Ireland's new Taoiseach following a day of delays and disagreements in the Irish parliament. His immediate focus includes forming his cabinet and addressing Ireland's housing crisis. [The Guardian](https://www.theguardian.com/world/live/2025/jan/23/europe-dail-micheal-martin-rows-ireland-weather-storm-eowyn-latest-updates?utm_source=chatgpt.com) @ c8cf63be:86691cfe
2025-01-23 12:51:20### Mark Fishers ‘Acid Communism’ und der ‘Capitalist Realism’ > “it is easier to kill the living than to kill the undead”[1] Die lebenden sind wir Menschen, *the undead* ist der gegenwärtige neoliberalismus[2] Mark Fischers Analyse über den bestehenden Zustand ist erschütternd: > “let’s say music hello just go on music in the last 10 years one thing > one single thing that couldn’t have come out in the 20th century”[3] Es gibt nicht neues unter dem Himmel, alle Kreativität ist erschöpft, “die Verdinglichung” von der Horkheimer und Adorno sprachen, “…, ist so dicht geworden,…” die Wirklichkeit des ‘Capitalist Realism’ ist manifest und undurchdringlich, die Löcher, die kleinen alternativen, sind versiegelt. Schon im Denken sind die alternativen versperrt und das Denken ist ein gemeinsames, niemand kann für sich alleine Denken oder kreativ sein. Denken und kreativ sein sind das Ergebnis einer Gesellschaftlichen Voraussetzung. Es gibt keine neue Musik mehr weil die Musik untot ist. In immer neuer Auflagen, in der mechanische Reproduktion, wiederbelebt man die Toten, und erstickt das lebendige. > “… but there’s nothing about us that was good or better than you > you’re anybody it’s just that we were lucky and you all are unlucky > …”[4] Wenn eine junge Frau auf seine Feststellung reagiert mit Unglaube und Abwehr. > “… so what you’re basically saying is that i guess your generation or > the previous generation was better because you had more time to pursue > your own projects and you also think that you were more creative or > the previous generation was more creative …”[5] Dann weil sie die Enge der Umstände nicht erkennen kann, und vielleicht auch weil sie die Dinge auf sich persönlich bezieht, wie es das gegenwärtige Denken nahelegt: Sowohl der kompetitive Vergleich als auch die individuelle Schuldzuordnung findet sich in der Aussage. Fischer hingegen erklärt dies mit den Herrschenden Umständen die es den Menschen unmöglich machen sich den *wahren Sachverhalt* klar zu machen und damit jede Alternative im Denken versperren: > “.. but okay let’s be clear about what i’m saying creativity isn’t a > property of individuals ever it’s a property of a social or collective > scene like that you know that’s so that it’s not like the individuals > are less creative than they used to be that’s just not how creativity > works creativity is possible because of is possible because of social > conditions and those social conditions have been removed …”[6] Fischers Aufmerksamkeit richtet sich auf die die Umstände vor dem Capitalism Realism, denn dieser ist seiner Meinung nach schon eine Reaktion, eine Reaktion auf die “Counterculture” auf das “spectre of a world which could be free”[7]. Wenn es ein Gründungsereignis des Capital Realism geben sollte wäre dies nach Fischer der Putsch Pinochets in Chile 1973.[8] Seiner Zeit voraus war Hunter S. Thompson, seine Drogengeschwängerten Reflexionen fassen den Kern sehr genau, für ihn war 1971 schon der Moment an dem er die revision verortet: > “… wir ritten auf dem Kamm einer hohen und wunderschönen Welle … Und > jetzt, weniger als fünf Jahre später, kannst du auf einen steilen > Hügel in Las Vegas klettern und nach Westen blicken, und wenn du die > richtigen Augen hast, dann kannst du die Hochwassermarkierung fast > sehen -die Stelle, wo sich die Welle schließlich brach und > zurückrollte.”[9] Acid! Die psychedelische Zeit: > “Instead of seeking to overcome capital, we should focus on what > capital must always obstruct: the collective capacity to produce, care > and enjoy.”[10] und weiter > “The overcoming of capital has to be fundamentally based on the simple > insight that, far from being about “wealth creation”, capital > necessarily and always blocks the production of common wealth.” Der Zauber der Psycedlischen Zeit war die ignoranz, das Verweigern des bestehenden Narativs. Oder wie Fischer sagt, die Frage nach dem Bewustsein und seiner Beziehung dem dem was wir als Wiklichkeit wahrnemen.[11] > “turn on, tune in, drop out” [12] oder noch klarer Ken Kesey: > “There’s only one thing to do . > .. there’s only one thing’s gonna do any good at all… > And that’s everybody just look at it, > look at the war, and turn your backs and say … Fuck it..” [13] Die Imagination des *wahren Sachverhaltes* “look at it” sagt Kesey, überzeugt euch selbst. Es braucht nicht mehr als das Schauen des Krieges, bei ihm der Viatnam Krieg, um zu verstehen das nur die Verweigerung, das “Fuck it” geeignet ist dem ganzen seine legitimität zu verweigern. Das war der Zauber der psychedelichen Zeit, auch der der 90’er, die als unpolitsch gelten. Aus dieser Perspektive ist klar das das unpolitsche, das politsche war. Die love-Parade war nicht unpolitisch und die gesellschaflichenr Verändeung die durch diese Psychedleische Zeit in Bewegung gesetzt wurden können wir noch heute fühlen. Die Canabis Legalisierung, die veränderte Wahrnehmng von Homosexualität. Das “chill out”. Die tribal Tattoos.[14] Und auch die wärmste Kampange der Europawahl 2024, “Fickt euch doch alle.”[15] ist erst durch die psychedelische Zeit der 90’er möglich, hier wurde die Sinnlichkeit gestiftet die es braucht damit dieser Satz seine wärme bekommt. Die Demokratesierung der Neurologie durch die verwendung von Halozinogenen rücken die Frage nach der Wirklichkeit und des wahren Sachverhaltes in den Mittelpunkt. > “what they mainstreamed was this psychedelic consciousness with its > key notion of the plasticity of reality”[16] Sie ist auch eine Sekularisierung, eine demokratisierung des Sakralen, das vorher durch Klassen wie Schamanen oder Druiden kontroliert wurde wird zugänglich und erfahrbar. > “…, there was actually a demystificatory and materialist dimension to > this.”[17] Was sich so aussprechen läßt: > *“Wenn Gott liebe ist, dann ist er eine MDMA geschwängerte, psycedelic > trance Party, anfang der 90’er jahre des letzten Jahrtausend.”* Es loht sich also für uns ältere an die nicht so ferne Zeit der frühen 90’er Jahre zurück zu denken in der die Welt offen schien, die Polarität des kalten Krieges vergangen war, das Ende der Geschichte ausgerüfen wurde.[18] Da war die Idee das dies nicht der Siegt des Kapitalismus ist, sondern ein Sieg der Menschen die die Spirale des Schreckens und der Eskalation durchbrechen real. Es schien wie ein transzendieren des gegebenen Spiels und seiner Regeln wie es die AI in “war games”[19] realisiert, stattzufinden. Auf “No future”[20] folgte “No Paradise? Create it.”[21], es fand ein “unforgetting”[22] der alten, in den 60’er entwickelten Formen statt: Die Modulierung der 303, das Dayglow und das Strobo, alles Elemente des Acid Test[23]. *“the collective capacity to produce, care and enjoy”* ------------------------------------------------------------------------ ### References: [1] Fisher, M., Mark Fisher - DOCH Lectures 1 2011: <https://www.youtube.com/watch?v=f-9nY5rboK8> 32m 42s [2] Fisher, M., How to kill a zombie: strategizing the end of neoliberalism 2013: <https://www.opendemocracy.net/en/how-to-kill-zombie-strategizing-end-of-neoliberalism/>. [3] Fisher, 1968., Mark, Cybertime Crisis 2013: <https://www.youtube.com/watch?v=zOQgCg73sfQ> ab 1h 42m 12s [4] Fisher, 1968., Mark, ebenda ab 1h 35m 30s [5] Fisher, 1968., Mark, ebenda ab 1h 42m 12s [6] Fisher, 1968., Mark, ebenda ab 1h 47m 20s [7] Fisher, 1968., Mark et al., K-punk : the collected and unpublished writings of Mark Fisher (2004-2016) 2018. Abs. 153.5 [8] Fisher, 1968., Mark et al., ebenda. Abs. 153.7 “If there was a founding event of capitalist realism, it would be the violent destruction of the Allende government in Chile by General Pinochet’s American-backed coup.” [9] Hunter S. Thompson “Fear and loathing” Seite 89 [10] Fisher, 1968., Mark et al., K-punk : the collected and unpublished writings of Mark Fisher (2004-2016) 2018. Abs. 153.5 Statz 3 [11] Fisher, 1968., Mark et al., ebenda. Abs. 153.46 [12] Timothy Leary in 1966, der damals gefährlichste Mann der Welt.(Richard Nixxon) [13] Wolfe, Tom., The electric kool-aid acid test. 1999. Seite 360 [14] Christmann, K., Gruppen-Tattoo-Termin im Bundestag: 19 Abgeordnete zeigen vollen Körpereinsatz 2024: <https://www.tagesspiegel.de/politik/gruppen-tattoo-termin-im-bundestag-19-abgeordnete-zeigen-vollen-korpereinsatz-11665559.html>. [15] DiePartei, Fickt euch doch alle! (DINA1) 2024: <https://www.parteibedarf.de/Fickt-euch-doch-alle-DINA1/SW10115>. [16] Fisher, M., all of this is temporary: Mark Fisher 2016: <https://www.youtube.com/watch?v=deZgzw0YHQI> 8 m 31 s [17] Fisher, 1968., Mark et al., K-punk : the collected and unpublished writings of Mark Fisher (2004-2016) 2018. Abs. 153.48 4. Satz [18] Fukuyama, F., The End of History and the Last Man 1992: <https://books.google.de/books?id=6KZmAAAAMAAJ>. [19] Parkes, L.L.F., WarGames: <https://www.imdb.com/de/title/tt0086567/> “A strange game. The only winning move is not to play.” [20] Wikipedia, No Future: <https://de.wikipedia.org/wiki/No_Future>. [21] Spirit zone https://www.platekompaniet.no/musikk/cd/space-tribe-shapeshifter-cd [22] Fisher, 1968., Mark et al., K-punk : the collected and unpublished writings of Mark Fisher (2004-2016) 2018. Abs. 153.21 Letzter Satz [23] Wikipedia, Acid Tests: <https://de.wikipedia.org/wiki/Acid-Tests>.
@ c8cf63be:86691cfe
2025-01-23 12:51:20### Mark Fishers ‘Acid Communism’ und der ‘Capitalist Realism’ > “it is easier to kill the living than to kill the undead”[1] Die lebenden sind wir Menschen, *the undead* ist der gegenwärtige neoliberalismus[2] Mark Fischers Analyse über den bestehenden Zustand ist erschütternd: > “let’s say music hello just go on music in the last 10 years one thing > one single thing that couldn’t have come out in the 20th century”[3] Es gibt nicht neues unter dem Himmel, alle Kreativität ist erschöpft, “die Verdinglichung” von der Horkheimer und Adorno sprachen, “…, ist so dicht geworden,…” die Wirklichkeit des ‘Capitalist Realism’ ist manifest und undurchdringlich, die Löcher, die kleinen alternativen, sind versiegelt. Schon im Denken sind die alternativen versperrt und das Denken ist ein gemeinsames, niemand kann für sich alleine Denken oder kreativ sein. Denken und kreativ sein sind das Ergebnis einer Gesellschaftlichen Voraussetzung. Es gibt keine neue Musik mehr weil die Musik untot ist. In immer neuer Auflagen, in der mechanische Reproduktion, wiederbelebt man die Toten, und erstickt das lebendige. > “… but there’s nothing about us that was good or better than you > you’re anybody it’s just that we were lucky and you all are unlucky > …”[4] Wenn eine junge Frau auf seine Feststellung reagiert mit Unglaube und Abwehr. > “… so what you’re basically saying is that i guess your generation or > the previous generation was better because you had more time to pursue > your own projects and you also think that you were more creative or > the previous generation was more creative …”[5] Dann weil sie die Enge der Umstände nicht erkennen kann, und vielleicht auch weil sie die Dinge auf sich persönlich bezieht, wie es das gegenwärtige Denken nahelegt: Sowohl der kompetitive Vergleich als auch die individuelle Schuldzuordnung findet sich in der Aussage. Fischer hingegen erklärt dies mit den Herrschenden Umständen die es den Menschen unmöglich machen sich den *wahren Sachverhalt* klar zu machen und damit jede Alternative im Denken versperren: > “.. but okay let’s be clear about what i’m saying creativity isn’t a > property of individuals ever it’s a property of a social or collective > scene like that you know that’s so that it’s not like the individuals > are less creative than they used to be that’s just not how creativity > works creativity is possible because of is possible because of social > conditions and those social conditions have been removed …”[6] Fischers Aufmerksamkeit richtet sich auf die die Umstände vor dem Capitalism Realism, denn dieser ist seiner Meinung nach schon eine Reaktion, eine Reaktion auf die “Counterculture” auf das “spectre of a world which could be free”[7]. Wenn es ein Gründungsereignis des Capital Realism geben sollte wäre dies nach Fischer der Putsch Pinochets in Chile 1973.[8] Seiner Zeit voraus war Hunter S. Thompson, seine Drogengeschwängerten Reflexionen fassen den Kern sehr genau, für ihn war 1971 schon der Moment an dem er die revision verortet: > “… wir ritten auf dem Kamm einer hohen und wunderschönen Welle … Und > jetzt, weniger als fünf Jahre später, kannst du auf einen steilen > Hügel in Las Vegas klettern und nach Westen blicken, und wenn du die > richtigen Augen hast, dann kannst du die Hochwassermarkierung fast > sehen -die Stelle, wo sich die Welle schließlich brach und > zurückrollte.”[9] Acid! Die psychedelische Zeit: > “Instead of seeking to overcome capital, we should focus on what > capital must always obstruct: the collective capacity to produce, care > and enjoy.”[10] und weiter > “The overcoming of capital has to be fundamentally based on the simple > insight that, far from being about “wealth creation”, capital > necessarily and always blocks the production of common wealth.” Der Zauber der Psycedlischen Zeit war die ignoranz, das Verweigern des bestehenden Narativs. Oder wie Fischer sagt, die Frage nach dem Bewustsein und seiner Beziehung dem dem was wir als Wiklichkeit wahrnemen.[11] > “turn on, tune in, drop out” [12] oder noch klarer Ken Kesey: > “There’s only one thing to do . > .. there’s only one thing’s gonna do any good at all… > And that’s everybody just look at it, > look at the war, and turn your backs and say … Fuck it..” [13] Die Imagination des *wahren Sachverhaltes* “look at it” sagt Kesey, überzeugt euch selbst. Es braucht nicht mehr als das Schauen des Krieges, bei ihm der Viatnam Krieg, um zu verstehen das nur die Verweigerung, das “Fuck it” geeignet ist dem ganzen seine legitimität zu verweigern. Das war der Zauber der psychedelichen Zeit, auch der der 90’er, die als unpolitsch gelten. Aus dieser Perspektive ist klar das das unpolitsche, das politsche war. Die love-Parade war nicht unpolitisch und die gesellschaflichenr Verändeung die durch diese Psychedleische Zeit in Bewegung gesetzt wurden können wir noch heute fühlen. Die Canabis Legalisierung, die veränderte Wahrnehmng von Homosexualität. Das “chill out”. Die tribal Tattoos.[14] Und auch die wärmste Kampange der Europawahl 2024, “Fickt euch doch alle.”[15] ist erst durch die psychedelische Zeit der 90’er möglich, hier wurde die Sinnlichkeit gestiftet die es braucht damit dieser Satz seine wärme bekommt. Die Demokratesierung der Neurologie durch die verwendung von Halozinogenen rücken die Frage nach der Wirklichkeit und des wahren Sachverhaltes in den Mittelpunkt. > “what they mainstreamed was this psychedelic consciousness with its > key notion of the plasticity of reality”[16] Sie ist auch eine Sekularisierung, eine demokratisierung des Sakralen, das vorher durch Klassen wie Schamanen oder Druiden kontroliert wurde wird zugänglich und erfahrbar. > “…, there was actually a demystificatory and materialist dimension to > this.”[17] Was sich so aussprechen läßt: > *“Wenn Gott liebe ist, dann ist er eine MDMA geschwängerte, psycedelic > trance Party, anfang der 90’er jahre des letzten Jahrtausend.”* Es loht sich also für uns ältere an die nicht so ferne Zeit der frühen 90’er Jahre zurück zu denken in der die Welt offen schien, die Polarität des kalten Krieges vergangen war, das Ende der Geschichte ausgerüfen wurde.[18] Da war die Idee das dies nicht der Siegt des Kapitalismus ist, sondern ein Sieg der Menschen die die Spirale des Schreckens und der Eskalation durchbrechen real. Es schien wie ein transzendieren des gegebenen Spiels und seiner Regeln wie es die AI in “war games”[19] realisiert, stattzufinden. Auf “No future”[20] folgte “No Paradise? Create it.”[21], es fand ein “unforgetting”[22] der alten, in den 60’er entwickelten Formen statt: Die Modulierung der 303, das Dayglow und das Strobo, alles Elemente des Acid Test[23]. *“the collective capacity to produce, care and enjoy”* ------------------------------------------------------------------------ ### References: [1] Fisher, M., Mark Fisher - DOCH Lectures 1 2011: <https://www.youtube.com/watch?v=f-9nY5rboK8> 32m 42s [2] Fisher, M., How to kill a zombie: strategizing the end of neoliberalism 2013: <https://www.opendemocracy.net/en/how-to-kill-zombie-strategizing-end-of-neoliberalism/>. [3] Fisher, 1968., Mark, Cybertime Crisis 2013: <https://www.youtube.com/watch?v=zOQgCg73sfQ> ab 1h 42m 12s [4] Fisher, 1968., Mark, ebenda ab 1h 35m 30s [5] Fisher, 1968., Mark, ebenda ab 1h 42m 12s [6] Fisher, 1968., Mark, ebenda ab 1h 47m 20s [7] Fisher, 1968., Mark et al., K-punk : the collected and unpublished writings of Mark Fisher (2004-2016) 2018. Abs. 153.5 [8] Fisher, 1968., Mark et al., ebenda. Abs. 153.7 “If there was a founding event of capitalist realism, it would be the violent destruction of the Allende government in Chile by General Pinochet’s American-backed coup.” [9] Hunter S. Thompson “Fear and loathing” Seite 89 [10] Fisher, 1968., Mark et al., K-punk : the collected and unpublished writings of Mark Fisher (2004-2016) 2018. Abs. 153.5 Statz 3 [11] Fisher, 1968., Mark et al., ebenda. Abs. 153.46 [12] Timothy Leary in 1966, der damals gefährlichste Mann der Welt.(Richard Nixxon) [13] Wolfe, Tom., The electric kool-aid acid test. 1999. Seite 360 [14] Christmann, K., Gruppen-Tattoo-Termin im Bundestag: 19 Abgeordnete zeigen vollen Körpereinsatz 2024: <https://www.tagesspiegel.de/politik/gruppen-tattoo-termin-im-bundestag-19-abgeordnete-zeigen-vollen-korpereinsatz-11665559.html>. [15] DiePartei, Fickt euch doch alle! (DINA1) 2024: <https://www.parteibedarf.de/Fickt-euch-doch-alle-DINA1/SW10115>. [16] Fisher, M., all of this is temporary: Mark Fisher 2016: <https://www.youtube.com/watch?v=deZgzw0YHQI> 8 m 31 s [17] Fisher, 1968., Mark et al., K-punk : the collected and unpublished writings of Mark Fisher (2004-2016) 2018. Abs. 153.48 4. Satz [18] Fukuyama, F., The End of History and the Last Man 1992: <https://books.google.de/books?id=6KZmAAAAMAAJ>. [19] Parkes, L.L.F., WarGames: <https://www.imdb.com/de/title/tt0086567/> “A strange game. The only winning move is not to play.” [20] Wikipedia, No Future: <https://de.wikipedia.org/wiki/No_Future>. [21] Spirit zone https://www.platekompaniet.no/musikk/cd/space-tribe-shapeshifter-cd [22] Fisher, 1968., Mark et al., K-punk : the collected and unpublished writings of Mark Fisher (2004-2016) 2018. Abs. 153.21 Letzter Satz [23] Wikipedia, Acid Tests: <https://de.wikipedia.org/wiki/Acid-Tests>. @ 6be5cc06:5259daf0
2025-01-21 23:17:29A seguir, veja como instalar e configurar o **Privoxy** no **Pop!_OS**. --- ### **1. Instalar o Tor e o Privoxy** Abra o terminal e execute: ```bash sudo apt update sudo apt install tor privoxy ``` **Explicação:** - **Tor:** Roteia o tráfego pela rede Tor. - **Privoxy:** Proxy avançado que intermedia a conexão entre aplicativos e o Tor. --- ### **2. Configurar o Privoxy** Abra o arquivo de configuração do Privoxy: ```bash sudo nano /etc/privoxy/config ``` Navegue até a última linha (atalho: **`Ctrl`** + **`/`** depois **`Ctrl`** + **`V`** para navegar diretamente até a última linha) e insira: ```bash forward-socks5 / 127.0.0.1:9050 . ``` Isso faz com que o **Privoxy** envie todo o tráfego para o **Tor** através da porta **9050**. Salve (**`CTRL`** + **`O`** e **`Enter`**) e feche (**`CTRL`** + **`X`**) o arquivo. --- ### **3. Iniciar o Tor e o Privoxy** Agora, inicie e habilite os serviços: ```bash sudo systemctl start tor sudo systemctl start privoxy sudo systemctl enable tor sudo systemctl enable privoxy ``` **Explicação:** - **start:** Inicia os serviços. - **enable:** Faz com que iniciem automaticamente ao ligar o PC. --- ### **4. Configurar o Navegador Firefox** Para usar a rede **Tor** com o Firefox: 1. Abra o Firefox. 2. Acesse **Configurações** → **Configurar conexão**. 3. Selecione **Configuração manual de proxy**. 4. Configure assim: - **Proxy HTTP:** `127.0.0.1` - **Porta:** `8118` (porta padrão do **Privoxy**) - **Domínio SOCKS (v5):** `127.0.0.1` - **Porta:** `9050` 5. Marque a opção **"Usar este proxy também em HTTPS"**. 6. Clique em **OK**. --- ### **5. Verificar a Conexão com o Tor** Abra o navegador e acesse: ```text https://check.torproject.org/ ``` Se aparecer a mensagem **"Congratulations. This browser is configured to use Tor."**, a configuração está correta. --- ### **Dicas Extras** - **Privoxy** pode ser ajustado para bloquear anúncios e rastreadores. - Outros aplicativos também podem ser configurados para usar o **Privoxy**.
@ 6be5cc06:5259daf0
2025-01-21 23:17:29A seguir, veja como instalar e configurar o **Privoxy** no **Pop!_OS**. --- ### **1. Instalar o Tor e o Privoxy** Abra o terminal e execute: ```bash sudo apt update sudo apt install tor privoxy ``` **Explicação:** - **Tor:** Roteia o tráfego pela rede Tor. - **Privoxy:** Proxy avançado que intermedia a conexão entre aplicativos e o Tor. --- ### **2. Configurar o Privoxy** Abra o arquivo de configuração do Privoxy: ```bash sudo nano /etc/privoxy/config ``` Navegue até a última linha (atalho: **`Ctrl`** + **`/`** depois **`Ctrl`** + **`V`** para navegar diretamente até a última linha) e insira: ```bash forward-socks5 / 127.0.0.1:9050 . ``` Isso faz com que o **Privoxy** envie todo o tráfego para o **Tor** através da porta **9050**. Salve (**`CTRL`** + **`O`** e **`Enter`**) e feche (**`CTRL`** + **`X`**) o arquivo. --- ### **3. Iniciar o Tor e o Privoxy** Agora, inicie e habilite os serviços: ```bash sudo systemctl start tor sudo systemctl start privoxy sudo systemctl enable tor sudo systemctl enable privoxy ``` **Explicação:** - **start:** Inicia os serviços. - **enable:** Faz com que iniciem automaticamente ao ligar o PC. --- ### **4. Configurar o Navegador Firefox** Para usar a rede **Tor** com o Firefox: 1. Abra o Firefox. 2. Acesse **Configurações** → **Configurar conexão**. 3. Selecione **Configuração manual de proxy**. 4. Configure assim: - **Proxy HTTP:** `127.0.0.1` - **Porta:** `8118` (porta padrão do **Privoxy**) - **Domínio SOCKS (v5):** `127.0.0.1` - **Porta:** `9050` 5. Marque a opção **"Usar este proxy também em HTTPS"**. 6. Clique em **OK**. --- ### **5. Verificar a Conexão com o Tor** Abra o navegador e acesse: ```text https://check.torproject.org/ ``` Se aparecer a mensagem **"Congratulations. This browser is configured to use Tor."**, a configuração está correta. --- ### **Dicas Extras** - **Privoxy** pode ser ajustado para bloquear anúncios e rastreadores. - Outros aplicativos também podem ser configurados para usar o **Privoxy**. @ 9e69e420:d12360c2
2025-01-21 19:31:48Oregano oil is a potent natural compound that offers numerous scientifically-supported health benefits. ## Active Compounds The oil's therapeutic properties stem from its key bioactive components: - Carvacrol and thymol (primary active compounds) - Polyphenols and other antioxidant ## Antimicrobial Properties **Bacterial Protection** The oil demonstrates powerful antibacterial effects, even against antibiotic-resistant strains like MRSA and other harmful bacteria. Studies show it effectively inactivates various pathogenic bacteria without developing resistance. **Antifungal Effects** It effectively combats fungal infections, particularly Candida-related conditions like oral thrush, athlete's foot, and nail infections. ## Digestive Health Benefits Oregano oil supports digestive wellness by: - Promoting gastric juice secretion and enzyme production - Helping treat Small Intestinal Bacterial Overgrowth (SIBO) - Managing digestive discomfort, bloating, and IBS symptoms ## Anti-inflammatory and Antioxidant Effects The oil provides significant protective benefits through: - Powerful antioxidant activity that fights free radicals - Reduction of inflammatory markers in the body - Protection against oxidative stress-related conditions ## Respiratory Support It aids respiratory health by: - Loosening mucus and phlegm - Suppressing coughs and throat irritation - Supporting overall respiratory tract function ## Additional Benefits **Skin Health** - Improves conditions like psoriasis, acne, and eczema - Supports wound healing through antibacterial action - Provides anti-aging benefits through antioxidant properties **Cardiovascular Health** Studies show oregano oil may help: - Reduce LDL (bad) cholesterol levels - Support overall heart health **Pain Management** The oil demonstrates effectiveness in: - Reducing inflammation-related pain - Managing muscle discomfort - Providing topical pain relief ## Safety Note While oregano oil is generally safe, it's highly concentrated and should be properly diluted before use Consult a healthcare provider before starting supplementation, especially if taking other medications.
@ 9e69e420:d12360c2
2025-01-21 19:31:48Oregano oil is a potent natural compound that offers numerous scientifically-supported health benefits. ## Active Compounds The oil's therapeutic properties stem from its key bioactive components: - Carvacrol and thymol (primary active compounds) - Polyphenols and other antioxidant ## Antimicrobial Properties **Bacterial Protection** The oil demonstrates powerful antibacterial effects, even against antibiotic-resistant strains like MRSA and other harmful bacteria. Studies show it effectively inactivates various pathogenic bacteria without developing resistance. **Antifungal Effects** It effectively combats fungal infections, particularly Candida-related conditions like oral thrush, athlete's foot, and nail infections. ## Digestive Health Benefits Oregano oil supports digestive wellness by: - Promoting gastric juice secretion and enzyme production - Helping treat Small Intestinal Bacterial Overgrowth (SIBO) - Managing digestive discomfort, bloating, and IBS symptoms ## Anti-inflammatory and Antioxidant Effects The oil provides significant protective benefits through: - Powerful antioxidant activity that fights free radicals - Reduction of inflammatory markers in the body - Protection against oxidative stress-related conditions ## Respiratory Support It aids respiratory health by: - Loosening mucus and phlegm - Suppressing coughs and throat irritation - Supporting overall respiratory tract function ## Additional Benefits **Skin Health** - Improves conditions like psoriasis, acne, and eczema - Supports wound healing through antibacterial action - Provides anti-aging benefits through antioxidant properties **Cardiovascular Health** Studies show oregano oil may help: - Reduce LDL (bad) cholesterol levels - Support overall heart health **Pain Management** The oil demonstrates effectiveness in: - Reducing inflammation-related pain - Managing muscle discomfort - Providing topical pain relief ## Safety Note While oregano oil is generally safe, it's highly concentrated and should be properly diluted before use Consult a healthcare provider before starting supplementation, especially if taking other medications. @ b17fccdf:b7211155
2025-01-21 17:02:21The past 26 August, Tor [introduced officially](https://blog.torproject.org/introducing-proof-of-work-defense-for-onion-services/) a proof-of-work (PoW) defense for onion services designed to prioritize verified network traffic as a deterrent against denial of service (DoS) attacks. ~ > This feature at the moment, is [deactivate by default](https://gitlab.torproject.org/tpo/core/tor/-/blob/main/doc/man/tor.1.txt#L3117), so you need to follow these steps to activate this on a MiniBolt node: * Make sure you have the latest version of Tor installed, at the time of writing this post, which is v0.4.8.6. Check your current version by typing ``` tor --version ``` **Example** of expected output: ``` Tor version 0.4.8.6. This build of Tor is covered by the GNU General Public License (https://www.gnu.org/licenses/gpl-3.0.en.html) Tor is running on Linux with Libevent 2.1.12-stable, OpenSSL 3.0.9, Zlib 1.2.13, Liblzma 5.4.1, Libzstd N/A and Glibc 2.36 as libc. Tor compiled with GCC version 12.2.0 ``` ~ > If you have v0.4.8.X, you are **OK**, if not, type `sudo apt update && sudo apt upgrade` and confirm to update. * Basic PoW support can be checked by running this command: ``` tor --list-modules ``` Expected output: ``` relay: yes dirauth: yes dircache: yes pow: **yes** ``` ~ > If you have `pow: yes`, you are **OK** * Now go to the torrc file of your MiniBolt and add the parameter to enable PoW for each hidden service added ``` sudo nano /etc/tor/torrc ``` Example: ``` # Hidden Service BTC RPC Explorer HiddenServiceDir /var/lib/tor/hidden_service_btcrpcexplorer/ HiddenServiceVersion 3 HiddenServicePoWDefensesEnabled 1 HiddenServicePort 80 127.0.0.1:3002 ``` ~ > Bitcoin Core and LND use the Tor control port to automatically create the hidden service, requiring no action from the user. We have submitted a feature request in the official GitHub repositories to explore the need for the integration of Tor's PoW defense into the automatic creation process of the hidden service. You can follow them at the following links: * Bitcoin Core: https://github.com/lightningnetwork/lnd/issues/8002 * LND: https://github.com/bitcoin/bitcoin/issues/28499 --- More info: * https://blog.torproject.org/introducing-proof-of-work-defense-for-onion-services/ * https://gitlab.torproject.org/tpo/onion-services/onion-support/-/wikis/Documentation/PoW-FAQ --- Enjoy it MiniBolter! 💙
@ b17fccdf:b7211155
2025-01-21 17:02:21The past 26 August, Tor [introduced officially](https://blog.torproject.org/introducing-proof-of-work-defense-for-onion-services/) a proof-of-work (PoW) defense for onion services designed to prioritize verified network traffic as a deterrent against denial of service (DoS) attacks. ~ > This feature at the moment, is [deactivate by default](https://gitlab.torproject.org/tpo/core/tor/-/blob/main/doc/man/tor.1.txt#L3117), so you need to follow these steps to activate this on a MiniBolt node: * Make sure you have the latest version of Tor installed, at the time of writing this post, which is v0.4.8.6. Check your current version by typing ``` tor --version ``` **Example** of expected output: ``` Tor version 0.4.8.6. This build of Tor is covered by the GNU General Public License (https://www.gnu.org/licenses/gpl-3.0.en.html) Tor is running on Linux with Libevent 2.1.12-stable, OpenSSL 3.0.9, Zlib 1.2.13, Liblzma 5.4.1, Libzstd N/A and Glibc 2.36 as libc. Tor compiled with GCC version 12.2.0 ``` ~ > If you have v0.4.8.X, you are **OK**, if not, type `sudo apt update && sudo apt upgrade` and confirm to update. * Basic PoW support can be checked by running this command: ``` tor --list-modules ``` Expected output: ``` relay: yes dirauth: yes dircache: yes pow: **yes** ``` ~ > If you have `pow: yes`, you are **OK** * Now go to the torrc file of your MiniBolt and add the parameter to enable PoW for each hidden service added ``` sudo nano /etc/tor/torrc ``` Example: ``` # Hidden Service BTC RPC Explorer HiddenServiceDir /var/lib/tor/hidden_service_btcrpcexplorer/ HiddenServiceVersion 3 HiddenServicePoWDefensesEnabled 1 HiddenServicePort 80 127.0.0.1:3002 ``` ~ > Bitcoin Core and LND use the Tor control port to automatically create the hidden service, requiring no action from the user. We have submitted a feature request in the official GitHub repositories to explore the need for the integration of Tor's PoW defense into the automatic creation process of the hidden service. You can follow them at the following links: * Bitcoin Core: https://github.com/lightningnetwork/lnd/issues/8002 * LND: https://github.com/bitcoin/bitcoin/issues/28499 --- More info: * https://blog.torproject.org/introducing-proof-of-work-defense-for-onion-services/ * https://gitlab.torproject.org/tpo/onion-services/onion-support/-/wikis/Documentation/PoW-FAQ --- Enjoy it MiniBolter! 💙 @ c8cf63be:86691cfe
2025-01-21 13:48:28### Das SNAFU des Reichtums Das SNAFU-Prinzip[1] sagt das Kommunikation nur unter gleichen möglich ist: > Adäquate Kommunikation fliesst nur zwischen Gleichen ungehindert. > Kommunikation zwischen Nicht-Gleichen ist missverständlich und von > Dominaz- und Unterwerfungsritualen gefärbt, die immer wieder zum > Zusammenbruch der Kommunikation führen und zu einem Spiel ohne Ende. > [2] So ist z. B. das Peter Prinzip [3] eine einfache Folge des SNAFU-Prinzips. Bezieht es sich in erster Linie auf Hierarchie lässt es sich hervorragend ausweiten auf den ökonomischen Bereich. Auch hier gilt, dass Kommunikation nur unter Gleichen möglich ist, hier ist die Hierarchie das ökonomische Ungleichgewicht. Kommunikation ist auch hier nur unter gleichen möglich, ungefähr gleich reich müssen sie sein. Ein zu großer Unterschied in den ökonomischen Verhältnissen verhindert den Aufbau einer menschlichen Beziehung. Hier ist das einfache Beispiel: Wäre ich Reich, würde ich mich Fragen, ob die Freunde da, nur kommen weil ich ihnen die Drinks ausgebe. Jeder, der nicht so viel Geld wie ich hat, will vielleicht nur mein Geld. So kann ein Bill Gates nur einen Jeff Besos als Freund haben oder treffender ein Elon Musk nur einen Mark Zuckerberg. Auch umgekehrt funktioniert diese Selektion: Wenn ich ein richtig cooler Typ wäre, würde ich mich fragen, ob ich den Reichen eigentlich gut finde, oder nur mit ihm rumhänge, weil er die Drinks bezahlt und weil ich zu Recht unsicher darüber sein kann, kann ich mich nur entziehen. Diejenigen, die wirklich freundschaftlich sind, sind die die sich einer solchen Situation nicht aussetzen. Und was bleibt dem Reichen? Nur die Gesellschaft der Reichen. Hier trifft der Reichtum auf eine totale Armut. Die Auswahl der Freunde ist sehr klein. Hier ist tatsächlich der Reichtum das Problem, bzw. das ökonomische Ungleichgewicht und es gibt eine einfache Lösung, der Unterschied muss kleiner werden, denn je kleiner der Unterschied desto mehr Auswahl an Freunden gibt es. Wie in der “Aufgeklärten Ökonomie” dargestellt ist die Ungleichheit, eine gesellschaftliche Entscheidung und eine konkrete Steuerung möglich. Wir können also den Reichen helfen und mehr Freiheit und Freunde schenken. Pathologisch wird dieses Phänomen, wenn sich der innere Antrieb um den Reichtum dreht. Was durch die momentane Verfasstheit der gesellschaftlichen Praktiken sogar unterstützt und gefördert wird und damit viele Menschen objektiv unglücklich macht. Dieses pathologische der Gesellschaft wirkt dann auf das Individuum zurück und macht es ebenfalls Krank. Wir haben einen ähnlichen Mechanismus in der Gewalt kennenlernen dürfen. Vgl. “Gewalt ist eine ansteckende Krankrankheit” <figure> <img src="!(image)[https://cdn.satellite.earth/ac54bd400867c63f14e151172422067dc1b19980b1e738a577ae6c7a6ea835ea.png]" style="width:50.0%" alt="Klarmachen ändert, Gier ist heilbar" /> <figcaption aria-hidden="true">Klarmachen ändert, Gier ist heilbar</figcaption> </figure> > Wenn sie sich leer fühlen, Erfolg ihnen kein Glück schenkt, keine > Befriedigung. Wenn sie mehr brauchen und mehr, dann leiden sie > wahrscheinlich auch an einer Dysfunktion der Belohnungssysteme, an > Habsucht. > Auch ihnen kann und muss geholfen werden, denn Gier ist heilbar. Und > ihrer Gier betrifft nicht nur sie. Ihre liebsten Menschen in Ihrer > Umgebung, Menschen mit denen sie niemals direkt in Berührung kommen, > sie alle leiden unter ihrer Krankheit. > Auch für sie kann es ein erfülltes Leben geben, einen Weg zurück in > die Gesellschaft, die Gesellschaft von Menschen. Machen sie > Psychotherapie, nehmen sie Pharmaka, buchen sie eine Kur und > entledigen sich ihres Wohlstandes.[4] ------------------------------------------------------------------------ ### References: [1] Wikipedia, SNAFU: <https://de.wikipedia.org/wiki/SNAFU>. [2] Wilson, R.A., Der Neue Prometheus. Die Evolution unserer Intelligenz. - Volksausgabe/ Raubdruck. 1983. Seite 245-246 [3] Wikipedia, Peter Prinzip: <https://de.wikipedia.org/wiki/Peter-Prinzip>. [4] InvestmentWeek, Sucht im Luxus: Eine Nacht in der Klinik der Superreichen 2024: <https://www.investmentweek.com/sucht-im-luxus-eine-nacht-in-der-klinik-der-superreichen/>, „Viele Patienten hier leiden an Einsamkeit“ … “Viele Superreiche …wüssten nicht, ob sie wegen ihres Geldes oder ihrer Persönlichkeit gemocht werden” „Reich sein bedeutet oft, keinen echten Kontakt zu haben. Viele unserer Klienten haben keine echten Freunde.“
@ c8cf63be:86691cfe
2025-01-21 13:48:28### Das SNAFU des Reichtums Das SNAFU-Prinzip[1] sagt das Kommunikation nur unter gleichen möglich ist: > Adäquate Kommunikation fliesst nur zwischen Gleichen ungehindert. > Kommunikation zwischen Nicht-Gleichen ist missverständlich und von > Dominaz- und Unterwerfungsritualen gefärbt, die immer wieder zum > Zusammenbruch der Kommunikation führen und zu einem Spiel ohne Ende. > [2] So ist z. B. das Peter Prinzip [3] eine einfache Folge des SNAFU-Prinzips. Bezieht es sich in erster Linie auf Hierarchie lässt es sich hervorragend ausweiten auf den ökonomischen Bereich. Auch hier gilt, dass Kommunikation nur unter Gleichen möglich ist, hier ist die Hierarchie das ökonomische Ungleichgewicht. Kommunikation ist auch hier nur unter gleichen möglich, ungefähr gleich reich müssen sie sein. Ein zu großer Unterschied in den ökonomischen Verhältnissen verhindert den Aufbau einer menschlichen Beziehung. Hier ist das einfache Beispiel: Wäre ich Reich, würde ich mich Fragen, ob die Freunde da, nur kommen weil ich ihnen die Drinks ausgebe. Jeder, der nicht so viel Geld wie ich hat, will vielleicht nur mein Geld. So kann ein Bill Gates nur einen Jeff Besos als Freund haben oder treffender ein Elon Musk nur einen Mark Zuckerberg. Auch umgekehrt funktioniert diese Selektion: Wenn ich ein richtig cooler Typ wäre, würde ich mich fragen, ob ich den Reichen eigentlich gut finde, oder nur mit ihm rumhänge, weil er die Drinks bezahlt und weil ich zu Recht unsicher darüber sein kann, kann ich mich nur entziehen. Diejenigen, die wirklich freundschaftlich sind, sind die die sich einer solchen Situation nicht aussetzen. Und was bleibt dem Reichen? Nur die Gesellschaft der Reichen. Hier trifft der Reichtum auf eine totale Armut. Die Auswahl der Freunde ist sehr klein. Hier ist tatsächlich der Reichtum das Problem, bzw. das ökonomische Ungleichgewicht und es gibt eine einfache Lösung, der Unterschied muss kleiner werden, denn je kleiner der Unterschied desto mehr Auswahl an Freunden gibt es. Wie in der “Aufgeklärten Ökonomie” dargestellt ist die Ungleichheit, eine gesellschaftliche Entscheidung und eine konkrete Steuerung möglich. Wir können also den Reichen helfen und mehr Freiheit und Freunde schenken. Pathologisch wird dieses Phänomen, wenn sich der innere Antrieb um den Reichtum dreht. Was durch die momentane Verfasstheit der gesellschaftlichen Praktiken sogar unterstützt und gefördert wird und damit viele Menschen objektiv unglücklich macht. Dieses pathologische der Gesellschaft wirkt dann auf das Individuum zurück und macht es ebenfalls Krank. Wir haben einen ähnlichen Mechanismus in der Gewalt kennenlernen dürfen. Vgl. “Gewalt ist eine ansteckende Krankrankheit” <figure> <img src="!(image)[https://cdn.satellite.earth/ac54bd400867c63f14e151172422067dc1b19980b1e738a577ae6c7a6ea835ea.png]" style="width:50.0%" alt="Klarmachen ändert, Gier ist heilbar" /> <figcaption aria-hidden="true">Klarmachen ändert, Gier ist heilbar</figcaption> </figure> > Wenn sie sich leer fühlen, Erfolg ihnen kein Glück schenkt, keine > Befriedigung. Wenn sie mehr brauchen und mehr, dann leiden sie > wahrscheinlich auch an einer Dysfunktion der Belohnungssysteme, an > Habsucht. > Auch ihnen kann und muss geholfen werden, denn Gier ist heilbar. Und > ihrer Gier betrifft nicht nur sie. Ihre liebsten Menschen in Ihrer > Umgebung, Menschen mit denen sie niemals direkt in Berührung kommen, > sie alle leiden unter ihrer Krankheit. > Auch für sie kann es ein erfülltes Leben geben, einen Weg zurück in > die Gesellschaft, die Gesellschaft von Menschen. Machen sie > Psychotherapie, nehmen sie Pharmaka, buchen sie eine Kur und > entledigen sich ihres Wohlstandes.[4] ------------------------------------------------------------------------ ### References: [1] Wikipedia, SNAFU: <https://de.wikipedia.org/wiki/SNAFU>. [2] Wilson, R.A., Der Neue Prometheus. Die Evolution unserer Intelligenz. - Volksausgabe/ Raubdruck. 1983. Seite 245-246 [3] Wikipedia, Peter Prinzip: <https://de.wikipedia.org/wiki/Peter-Prinzip>. [4] InvestmentWeek, Sucht im Luxus: Eine Nacht in der Klinik der Superreichen 2024: <https://www.investmentweek.com/sucht-im-luxus-eine-nacht-in-der-klinik-der-superreichen/>, „Viele Patienten hier leiden an Einsamkeit“ … “Viele Superreiche …wüssten nicht, ob sie wegen ihres Geldes oder ihrer Persönlichkeit gemocht werden” „Reich sein bedeutet oft, keinen echten Kontakt zu haben. Viele unserer Klienten haben keine echten Freunde.“ @ 04ed2b8f:75be6756
2025-01-21 02:26:28A warrior does not fear chaos—he thrives in it. Life is a battlefield, and disorder is the forge in which strength, strategy, and resilience are tempered. Whether in the pursuit of victory in business, relationships, or personal conquest, chaos is an inevitable adversary. But within every storm lies an opportunity—an opening to strike, to evolve, and to dominate where others falter. Only those who embrace the struggle with unwavering resolve can turn uncertainty into their greatest weapon. ### **Understanding Chaos** Chaos is not the enemy; it is the proving ground. It manifests as upheaval, setbacks, and unexpected challenges, forcing warriors to sharpen their minds and steel their resolve. - **Disruption Breeds Innovation:** In the heat of battle, new tactics emerge. When the known paths are obliterated, new strategies take form. - **Mindset Is Your Strongest Weapon:** Chaos can either crush you or forge you into something stronger. The choice lies within your perception. - **Growth Is Forged in Adversity:** The greatest warriors are those who embrace discomfort, wielding it to forge endurance and ingenuity. ### **Seizing Opportunity Amidst Chaos** 1. **Adaptability Is Strength** - The warrior who can shift tactics swiftly gains the upper hand. Flexibility and awareness allow for swift and decisive action where others hesitate. 2. **Chaos Fuels Creativity** - In the heat of turmoil, the boldest ideas are born. Warriors do not cling to old ways; they adapt, overcome, and conquer. 3. **Endings Are Just New Battles** - What seems like defeat is often a call to arms for greater conquests. Every setback is a chance to regroup and strike back with renewed vigor. ### **Harnessing Chaos for Victory** 1. **Remain Steady Amid the Storm:** Fear clouds judgment; clarity is power. Observe, assess, and act with precision. Opportunities reveal themselves to those who master control over their emotions. 2. **Strike First, Strike Hard:** Do not merely react to chaos—command it. Take decisive actions that position you ahead of the pack. 3. **Exploit Weaknesses:** Where others see insurmountable problems, a warrior sees openings and opportunities to advance. ### **Lessons from the Battlefields of History** Legends are not born in times of peace but in the crucible of chaos. From generals who turned the tide of war in moments of despair to entrepreneurs who built empires from ruin, history is a testament to those who harnessed disorder and emerged victorious. ### **Conclusion: Chaos Is the Warrior's Ally** Chaos is not to be feared but embraced. It is the ultimate test of will and strategy. A true warrior sees beyond the disorder, crafting victory from the wreckage. In every crisis lies the seed of triumph; in every conflict, the chance to rise. When chaos surrounds you, stand firm, sharpen your sword, and remember—opportunity belongs to those with the courage to seize it.
@ 04ed2b8f:75be6756
2025-01-21 02:26:28A warrior does not fear chaos—he thrives in it. Life is a battlefield, and disorder is the forge in which strength, strategy, and resilience are tempered. Whether in the pursuit of victory in business, relationships, or personal conquest, chaos is an inevitable adversary. But within every storm lies an opportunity—an opening to strike, to evolve, and to dominate where others falter. Only those who embrace the struggle with unwavering resolve can turn uncertainty into their greatest weapon. ### **Understanding Chaos** Chaos is not the enemy; it is the proving ground. It manifests as upheaval, setbacks, and unexpected challenges, forcing warriors to sharpen their minds and steel their resolve. - **Disruption Breeds Innovation:** In the heat of battle, new tactics emerge. When the known paths are obliterated, new strategies take form. - **Mindset Is Your Strongest Weapon:** Chaos can either crush you or forge you into something stronger. The choice lies within your perception. - **Growth Is Forged in Adversity:** The greatest warriors are those who embrace discomfort, wielding it to forge endurance and ingenuity. ### **Seizing Opportunity Amidst Chaos** 1. **Adaptability Is Strength** - The warrior who can shift tactics swiftly gains the upper hand. Flexibility and awareness allow for swift and decisive action where others hesitate. 2. **Chaos Fuels Creativity** - In the heat of turmoil, the boldest ideas are born. Warriors do not cling to old ways; they adapt, overcome, and conquer. 3. **Endings Are Just New Battles** - What seems like defeat is often a call to arms for greater conquests. Every setback is a chance to regroup and strike back with renewed vigor. ### **Harnessing Chaos for Victory** 1. **Remain Steady Amid the Storm:** Fear clouds judgment; clarity is power. Observe, assess, and act with precision. Opportunities reveal themselves to those who master control over their emotions. 2. **Strike First, Strike Hard:** Do not merely react to chaos—command it. Take decisive actions that position you ahead of the pack. 3. **Exploit Weaknesses:** Where others see insurmountable problems, a warrior sees openings and opportunities to advance. ### **Lessons from the Battlefields of History** Legends are not born in times of peace but in the crucible of chaos. From generals who turned the tide of war in moments of despair to entrepreneurs who built empires from ruin, history is a testament to those who harnessed disorder and emerged victorious. ### **Conclusion: Chaos Is the Warrior's Ally** Chaos is not to be feared but embraced. It is the ultimate test of will and strategy. A true warrior sees beyond the disorder, crafting victory from the wreckage. In every crisis lies the seed of triumph; in every conflict, the chance to rise. When chaos surrounds you, stand firm, sharpen your sword, and remember—opportunity belongs to those with the courage to seize it. @ 6be5cc06:5259daf0
2025-01-21 01:51:46## Bitcoin: Um sistema de dinheiro eletrônico direto entre pessoas. Satoshi Nakamoto satoshin@gmx.com www.bitcoin.org --- ### Resumo O Bitcoin é uma forma de dinheiro digital que permite pagamentos diretos entre pessoas, sem a necessidade de um banco ou instituição financeira. Ele resolve um problema chamado **gasto duplo**, que ocorre quando alguém tenta gastar o mesmo dinheiro duas vezes. Para evitar isso, o Bitcoin usa uma rede descentralizada onde todos trabalham juntos para verificar e registrar as transações. As transações são registradas em um livro público chamado **blockchain**, protegido por uma técnica chamada **Prova de Trabalho**. Essa técnica cria uma cadeia de registros que não pode ser alterada sem refazer todo o trabalho já feito. Essa cadeia é mantida pelos computadores que participam da rede, e a mais longa é considerada a verdadeira. Enquanto a maior parte do poder computacional da rede for controlada por participantes honestos, o sistema continuará funcionando de forma segura. A rede é flexível, permitindo que qualquer pessoa entre ou saia a qualquer momento, sempre confiando na cadeia mais longa como prova do que aconteceu. --- ### 1. Introdução Hoje, quase todos os pagamentos feitos pela internet dependem de bancos ou empresas como processadores de pagamento (cartões de crédito, por exemplo) para funcionar. Embora esse sistema seja útil, ele tem problemas importantes porque é baseado em **confiança**. Primeiro, essas empresas podem reverter pagamentos, o que é útil em caso de erros, mas cria custos e incertezas. Isso faz com que pequenas transações, como pagar centavos por um serviço, se tornem inviáveis. Além disso, os comerciantes são obrigados a desconfiar dos clientes, pedindo informações extras e aceitando fraudes como algo inevitável. Esses problemas não existem no dinheiro físico, como o papel-moeda, onde o pagamento é final e direto entre as partes. No entanto, não temos como enviar dinheiro físico pela internet sem depender de um intermediário confiável. O que precisamos é de um **sistema de pagamento eletrônico baseado em provas matemáticas**, não em confiança. Esse sistema permitiria que qualquer pessoa enviasse dinheiro diretamente para outra, sem depender de bancos ou processadores de pagamento. Além disso, as transações seriam irreversíveis, protegendo vendedores contra fraudes, mas mantendo a possibilidade de soluções para disputas legítimas. Neste documento, apresentamos o **Bitcoin**, que resolve o problema do gasto duplo usando uma rede descentralizada. Essa rede cria um registro público e protegido por cálculos matemáticos, que garante a ordem das transações. Enquanto a maior parte da rede for controlada por pessoas honestas, o sistema será seguro contra ataques. --- ### 2. Transações Para entender como funciona o Bitcoin, é importante saber como as transações são realizadas. Imagine que você quer transferir uma "moeda digital" para outra pessoa. No sistema do Bitcoin, essa "moeda" é representada por uma sequência de registros que mostram quem é o atual dono. Para transferi-la, você adiciona um novo registro comprovando que agora ela pertence ao próximo dono. Esse registro é protegido por um tipo especial de assinatura digital. #### O que é uma assinatura digital? Uma assinatura digital é como uma senha secreta, mas muito mais segura. No Bitcoin, cada usuário tem duas chaves: uma "chave privada", que é secreta e serve para criar a assinatura, e uma "chave pública", que pode ser compartilhada com todos e é usada para verificar se a assinatura é válida. Quando você transfere uma moeda, usa sua chave privada para assinar a transação, provando que você é o dono. A próxima pessoa pode usar sua chave pública para confirmar isso. #### Como funciona na prática? Cada "moeda" no Bitcoin é, na verdade, uma cadeia de assinaturas digitais. Vamos imaginar o seguinte cenário: 1. A moeda está com o Dono 0 (você). Para transferi-la ao Dono 1, você assina digitalmente a transação com sua chave privada. Essa assinatura inclui o código da transação anterior (chamado de "hash") e a chave pública do Dono 1. 2. Quando o Dono 1 quiser transferir a moeda ao Dono 2, ele assinará a transação seguinte com sua própria chave privada, incluindo também o hash da transação anterior e a chave pública do Dono 2. 3. Esse processo continua, formando uma "cadeia" de transações. Qualquer pessoa pode verificar essa cadeia para confirmar quem é o atual dono da moeda. #### Resolvendo o problema do gasto duplo Um grande desafio com moedas digitais é o "gasto duplo", que é quando uma mesma moeda é usada em mais de uma transação. Para evitar isso, muitos sistemas antigos dependiam de uma entidade central confiável, como uma casa da moeda, que verificava todas as transações. No entanto, isso criava um ponto único de falha e centralizava o controle do dinheiro. O Bitcoin resolve esse problema de forma inovadora: ele usa uma rede descentralizada onde todos os participantes (os "nós") têm acesso a um registro completo de todas as transações. Cada nó verifica se as transações são válidas e se a moeda não foi gasta duas vezes. Quando a maioria dos nós concorda com a validade de uma transação, ela é registrada permanentemente na blockchain. #### Por que isso é importante? Essa solução elimina a necessidade de confiar em uma única entidade para gerenciar o dinheiro, permitindo que qualquer pessoa no mundo use o Bitcoin sem precisar de permissão de terceiros. Além disso, ela garante que o sistema seja seguro e resistente a fraudes. --- ### 3. Servidor Timestamp Para assegurar que as transações sejam realizadas de forma segura e transparente, o sistema Bitcoin utiliza algo chamado de "servidor de registro de tempo" (timestamp). Esse servidor funciona como um registro público que organiza as transações em uma ordem específica. Ele faz isso agrupando várias transações em blocos e criando um código único chamado "hash". Esse hash é como uma impressão digital que representa todo o conteúdo do bloco. O hash de cada bloco é amplamente divulgado, como se fosse publicado em um jornal ou em um fórum público. Esse processo garante que cada bloco de transações tenha um registro de quando foi criado e que ele existia naquele momento. Além disso, cada novo bloco criado contém o hash do bloco anterior, formando uma cadeia contínua de blocos conectados — conhecida como blockchain. Com isso, se alguém tentar alterar qualquer informação em um bloco anterior, o hash desse bloco mudará e não corresponderá ao hash armazenado no bloco seguinte. Essa característica torna a cadeia muito segura, pois qualquer tentativa de fraude seria imediatamente detectada. O sistema de timestamps é essencial para provar a ordem cronológica das transações e garantir que cada uma delas seja única e autêntica. Dessa forma, ele reforça a segurança e a confiança na rede Bitcoin. --- ### 4. Prova-de-Trabalho Para implementar o registro de tempo distribuído no sistema Bitcoin, utilizamos um mecanismo chamado prova-de-trabalho. Esse sistema é semelhante ao Hashcash, desenvolvido por Adam Back, e baseia-se na criação de um código único, o "hash", por meio de um processo computacionalmente exigente. A prova-de-trabalho envolve encontrar um valor especial que, quando processado junto com as informações do bloco, gere um hash que comece com uma quantidade específica de zeros. Esse valor especial é chamado de "nonce". Encontrar o nonce correto exige um esforço significativo do computador, porque envolve tentativas repetidas até que a condição seja satisfeita. Esse processo é importante porque torna extremamente difícil alterar qualquer informação registrada em um bloco. Se alguém tentar mudar algo em um bloco, seria necessário refazer o trabalho de computação não apenas para aquele bloco, mas também para todos os blocos que vêm depois dele. Isso garante a segurança e a imutabilidade da blockchain. A prova-de-trabalho também resolve o problema de decidir qual cadeia de blocos é a válida quando há múltiplas cadeias competindo. A decisão é feita pela cadeia mais longa, pois ela representa o maior esforço computacional já realizado. Isso impede que qualquer indivíduo ou grupo controle a rede, desde que a maioria do poder de processamento seja mantida por participantes honestos. Para garantir que o sistema permaneça eficiente e equilibrado, a dificuldade da prova-de-trabalho é ajustada automaticamente ao longo do tempo. Se novos blocos estiverem sendo gerados rapidamente, a dificuldade aumenta; se estiverem sendo gerados muito lentamente, a dificuldade diminui. Esse ajuste assegura que novos blocos sejam criados aproximadamente a cada 10 minutos, mantendo o sistema estável e funcional. --- ### 5. Rede A rede Bitcoin é o coração do sistema e funciona de maneira distribuída, conectando vários participantes (ou nós) para garantir o registro e a validação das transações. Os passos para operar essa rede são: 1. **Transmissão de Transações**: Quando alguém realiza uma nova transação, ela é enviada para todos os nós da rede. Isso é feito para garantir que todos estejam cientes da operação e possam validá-la. 2. **Coleta de Transações em Blocos**: Cada nó agrupa as novas transações recebidas em um "bloco". Este bloco será preparado para ser adicionado à cadeia de blocos (a blockchain). 3. **Prova-de-Trabalho**: Os nós competem para resolver a prova-de-trabalho do bloco, utilizando poder computacional para encontrar um hash válido. Esse processo é como resolver um quebra-cabeça matemático difícil. 4. **Envio do Bloco Resolvido**: Quando um nó encontra a solução para o bloco (a prova-de-trabalho), ele compartilha esse bloco com todos os outros nós na rede. 5. **Validação do Bloco**: Cada nó verifica o bloco recebido para garantir que todas as transações nele contidas sejam válidas e que nenhuma moeda tenha sido gasta duas vezes. Apenas blocos válidos são aceitos. 6. **Construção do Próximo Bloco**: Os nós que aceitaram o bloco começam a trabalhar na criação do próximo bloco, utilizando o hash do bloco aceito como base (hash anterior). Isso mantém a continuidade da cadeia. #### Resolução de Conflitos e Escolha da Cadeia Mais Longa Os nós sempre priorizam a cadeia mais longa, pois ela representa o maior esforço computacional já realizado, garantindo maior segurança. Se dois blocos diferentes forem compartilhados simultaneamente, os nós trabalharão no primeiro bloco recebido, mas guardarão o outro como uma alternativa. Caso o segundo bloco eventualmente forme uma cadeia mais longa (ou seja, tenha mais blocos subsequentes), os nós mudarão para essa nova cadeia. #### Tolerância a Falhas A rede é robusta e pode lidar com mensagens que não chegam a todos os nós. Uma transação não precisa alcançar todos os nós de imediato; basta que chegue a um número suficiente deles para ser incluída em um bloco. Da mesma forma, se um nó não receber um bloco em tempo hábil, ele pode solicitá-lo ao perceber que está faltando quando o próximo bloco é recebido. Esse mecanismo descentralizado permite que a rede Bitcoin funcione de maneira segura, confiável e resiliente, sem depender de uma autoridade central. --- ### 6. Incentivo O incentivo é um dos pilares fundamentais que sustenta o funcionamento da rede Bitcoin, garantindo que os participantes (nós) continuem operando de forma honesta e contribuindo com recursos computacionais. Ele é estruturado em duas partes principais: a recompensa por mineração e as taxas de transação. #### Recompensa por Mineração Por convenção, o primeiro registro em cada bloco é uma transação especial que cria novas moedas e as atribui ao criador do bloco. Essa recompensa incentiva os mineradores a dedicarem poder computacional para apoiar a rede. Como não há uma autoridade central para emitir moedas, essa é a maneira pela qual novas moedas entram em circulação. Esse processo pode ser comparado ao trabalho de garimpeiros, que utilizam recursos para colocar mais ouro em circulação. No caso do Bitcoin, o "recurso" consiste no tempo de CPU e na energia elétrica consumida para resolver a prova-de-trabalho. #### Taxas de Transação Além da recompensa por mineração, os mineradores também podem ser incentivados pelas taxas de transação. Se uma transação utiliza menos valor de saída do que o valor de entrada, a diferença é tratada como uma taxa, que é adicionada à recompensa do bloco contendo essa transação. Com o passar do tempo e à medida que o número de moedas em circulação atinge o limite predeterminado, essas taxas de transação se tornam a principal fonte de incentivo, substituindo gradualmente a emissão de novas moedas. Isso permite que o sistema opere sem inflação, uma vez que o número total de moedas permanece fixo. #### Incentivo à Honestidade O design do incentivo também busca garantir que os participantes da rede mantenham um comportamento honesto. Para um atacante que consiga reunir mais poder computacional do que o restante da rede, ele enfrentaria duas escolhas: 1. Usar esse poder para fraudar o sistema, como reverter transações e roubar pagamentos. 2. Seguir as regras do sistema, criando novos blocos e recebendo recompensas legítimas. A lógica econômica favorece a segunda opção, pois um comportamento desonesto prejudicaria a confiança no sistema, diminuindo o valor de todas as moedas, incluindo aquelas que o próprio atacante possui. Jogar dentro das regras não apenas maximiza o retorno financeiro, mas também preserva a validade e a integridade do sistema. Esse mecanismo garante que os incentivos econômicos estejam alinhados com o objetivo de manter a rede segura, descentralizada e funcional ao longo do tempo. --- ### 7. Recuperação do Espaço em Disco Depois que uma moeda passa a estar protegida por muitos blocos na cadeia, as informações sobre as transações antigas que a geraram podem ser descartadas para economizar espaço em disco. Para que isso seja possível sem comprometer a segurança, as transações são organizadas em uma estrutura chamada "árvore de Merkle". Essa árvore funciona como um resumo das transações: em vez de armazenar todas elas, guarda apenas um "hash raiz", que é como uma assinatura compacta que representa todo o grupo de transações. Os blocos antigos podem, então, ser simplificados, removendo as partes desnecessárias dessa árvore. Apenas a raiz do hash precisa ser mantida no cabeçalho do bloco, garantindo que a integridade dos dados seja preservada, mesmo que detalhes específicos sejam descartados. Para exemplificar: imagine que você tenha vários recibos de compra. Em vez de guardar todos os recibos, você cria um documento e lista apenas o valor total de cada um. Mesmo que os recibos originais sejam descartados, ainda é possível verificar a soma com base nos valores armazenados. Além disso, o espaço ocupado pelos blocos em si é muito pequeno. Cada bloco sem transações ocupa apenas cerca de 80 bytes. Isso significa que, mesmo com blocos sendo gerados a cada 10 minutos, o crescimento anual em espaço necessário é insignificante: apenas 4,2 MB por ano. Com a capacidade de armazenamento dos computadores crescendo a cada ano, esse espaço continuará sendo trivial, garantindo que a rede possa operar de forma eficiente sem problemas de armazenamento, mesmo a longo prazo. --- ### 8. Verificação de Pagamento Simplificada É possível confirmar pagamentos sem a necessidade de operar um nó completo da rede. Para isso, o usuário precisa apenas de uma cópia dos cabeçalhos dos blocos da cadeia mais longa (ou seja, a cadeia com maior esforço de trabalho acumulado). Ele pode verificar a validade de uma transação ao consultar os nós da rede até obter a confirmação de que tem a cadeia mais longa. Para isso, utiliza-se o ramo Merkle, que conecta a transação ao bloco em que ela foi registrada. Entretanto, o método simplificado possui limitações: ele não pode confirmar uma transação isoladamente, mas sim assegurar que ela ocupa um lugar específico na cadeia mais longa. Dessa forma, se um nó da rede aprova a transação, os blocos subsequentes reforçam essa aceitação. A verificação simplificada é confiável enquanto a maioria dos nós da rede for honesta. Contudo, ela se torna vulnerável caso a rede seja dominada por um invasor. Nesse cenário, um atacante poderia fabricar transações fraudulentas que enganariam o usuário temporariamente até que o invasor obtivesse controle completo da rede. Uma estratégia para mitigar esse risco é configurar alertas nos softwares de nós completos. Esses alertas identificam blocos inválidos, sugerindo ao usuário baixar o bloco completo para confirmar qualquer inconsistência. Para maior segurança, empresas que realizam pagamentos frequentes podem preferir operar seus próprios nós, reduzindo riscos e permitindo uma verificação mais direta e confiável. --- ### 9. Combinando e Dividindo Valor No sistema Bitcoin, cada unidade de valor é tratada como uma "moeda" individual, mas gerenciar cada centavo como uma transação separada seria impraticável. Para resolver isso, o Bitcoin permite que valores sejam combinados ou divididos em transações, facilitando pagamentos de qualquer valor. #### Entradas e Saídas Cada transação no Bitcoin é composta por: - **Entradas**: Representam os valores recebidos em transações anteriores. - **Saídas**: Correspondem aos valores enviados, divididos entre os destinatários e, eventualmente, o troco para o remetente. Normalmente, uma transação contém: - Uma única entrada com valor suficiente para cobrir o pagamento. - Ou várias entradas combinadas para atingir o valor necessário. O valor total das saídas nunca excede o das entradas, e a diferença (se houver) pode ser retornada ao remetente como **troco**. #### Exemplo Prático Imagine que você tem duas entradas: 1. 0,03 BTC 2. 0,07 BTC Se deseja enviar 0,08 BTC para alguém, a transação terá: - **Entrada**: As duas entradas combinadas (0,03 + 0,07 BTC = 0,10 BTC). - **Saídas**: Uma para o destinatário (0,08 BTC) e outra como troco para você (0,02 BTC). Essa flexibilidade permite que o sistema funcione sem precisar manipular cada unidade mínima individualmente. #### Difusão e Simplificação A difusão de transações, onde uma depende de várias anteriores e assim por diante, não representa um problema. Não é necessário armazenar ou verificar o histórico completo de uma transação para utilizá-la, já que o registro na blockchain garante sua integridade. --- ### 10. Privacidade O modelo bancário tradicional oferece um certo nível de privacidade, limitando o acesso às informações financeiras apenas às partes envolvidas e a um terceiro confiável (como bancos ou instituições financeiras). No entanto, o Bitcoin opera de forma diferente, pois todas as transações são publicamente registradas na blockchain. Apesar disso, a privacidade pode ser mantida utilizando **chaves públicas anônimas**, que desvinculam diretamente as transações das identidades das partes envolvidas. #### Fluxo de Informação - No **modelo tradicional**, as transações passam por um terceiro confiável que conhece tanto o remetente quanto o destinatário. - No **Bitcoin**, as transações são anunciadas publicamente, mas sem revelar diretamente as identidades das partes. Isso é comparável a dados divulgados por bolsas de valores, onde informações como o tempo e o tamanho das negociações (a "fita") são públicas, mas as identidades das partes não. #### Protegendo a Privacidade Para aumentar a privacidade no Bitcoin, são adotadas as seguintes práticas: 1. **Chaves Públicas Anônimas**: Cada transação utiliza um par de chaves diferentes, dificultando a associação com um proprietário único. 2. **Prevenção de Ligação**: Ao usar chaves novas para cada transação, reduz-se a possibilidade de links evidentes entre múltiplas transações realizadas pelo mesmo usuário. #### Riscos de Ligação Embora a privacidade seja fortalecida, alguns riscos permanecem: - Transações **multi-entrada** podem revelar que todas as entradas pertencem ao mesmo proprietário, caso sejam necessárias para somar o valor total. - O proprietário da chave pode ser identificado indiretamente por transações anteriores que estejam conectadas. --- ### 11. Cálculos Imagine que temos um sistema onde as pessoas (ou computadores) competem para adicionar informações novas (blocos) a um grande registro público (a cadeia de blocos ou blockchain). Este registro é como um livro contábil compartilhado, onde todos podem verificar o que está escrito. Agora, vamos pensar em um cenário: um atacante quer enganar o sistema. Ele quer mudar informações já registradas para beneficiar a si mesmo, por exemplo, desfazendo um pagamento que já fez. Para isso, ele precisa criar uma versão alternativa do livro contábil (a cadeia de blocos dele) e convencer todos os outros participantes de que essa versão é a verdadeira. Mas isso é extremamente difícil. #### Como o Ataque Funciona Quando um novo bloco é adicionado à cadeia, ele depende de cálculos complexos que levam tempo e esforço. Esses cálculos são como um grande quebra-cabeça que precisa ser resolvido. - Os “bons jogadores” (nós honestos) estão sempre trabalhando juntos para resolver esses quebra-cabeças e adicionar novos blocos à cadeia verdadeira. - O atacante, por outro lado, precisa resolver quebra-cabeças sozinho, tentando “alcançar” a cadeia honesta para que sua versão alternativa pareça válida. Se a cadeia honesta já está vários blocos à frente, o atacante começa em desvantagem, e o sistema está projetado para que a dificuldade de alcançá-los aumente rapidamente. #### A Corrida Entre Cadeias Você pode imaginar isso como uma corrida. A cada bloco novo que os jogadores honestos adicionam à cadeia verdadeira, eles se distanciam mais do atacante. Para vencer, o atacante teria que resolver os quebra-cabeças mais rápido que todos os outros jogadores honestos juntos. Suponha que: - A rede honesta tem **80% do poder computacional** (ou seja, resolve 8 de cada 10 quebra-cabeças). - O atacante tem **20% do poder computacional** (ou seja, resolve 2 de cada 10 quebra-cabeças). Cada vez que a rede honesta adiciona um bloco, o atacante tem que "correr atrás" e resolver mais quebra-cabeças para alcançar. #### Por Que o Ataque Fica Cada Vez Mais Improvável? Vamos usar uma fórmula simples para mostrar como as chances de sucesso do atacante diminuem conforme ele precisa "alcançar" mais blocos: P = (q/p)^z - **q** é o poder computacional do atacante (20%, ou 0,2). - **p** é o poder computacional da rede honesta (80%, ou 0,8). - **z** é a diferença de blocos entre a cadeia honesta e a cadeia do atacante. Se o atacante está 5 blocos atrás (z = 5): P = (0,2 / 0,8)^5 = (0,25)^5 = 0,00098, (ou, 0,098%) Isso significa que o atacante tem menos de 0,1% de chance de sucesso — ou seja, é muito improvável. Se ele estiver 10 blocos atrás (z = 10): P = (0,2 / 0,8)^10 = (0,25)^10 = 0,000000095, (ou, 0,0000095%). Neste caso, as chances de sucesso são praticamente **nulas**. #### Um Exemplo Simples Se você jogar uma moeda, a chance de cair “cara” é de 50%. Mas se precisar de 10 caras seguidas, sua chance já é bem menor. Se precisar de 20 caras seguidas, é quase impossível. No caso do Bitcoin, o atacante precisa de muito mais do que 20 caras seguidas. Ele precisa resolver quebra-cabeças extremamente difíceis e alcançar os jogadores honestos que estão sempre à frente. Isso faz com que o ataque seja inviável na prática. #### Por Que Tudo Isso é Seguro? - **A probabilidade de sucesso do atacante diminui exponencialmente.** Isso significa que, quanto mais tempo passa, menor é a chance de ele conseguir enganar o sistema. - **A cadeia verdadeira (honesta) está protegida pela força da rede.** Cada novo bloco que os jogadores honestos adicionam à cadeia torna mais difícil para o atacante alcançar. #### E Se o Atacante Tentar Continuar? O atacante poderia continuar tentando indefinidamente, mas ele estaria gastando muito tempo e energia sem conseguir nada. Enquanto isso, os jogadores honestos estão sempre adicionando novos blocos, tornando o trabalho do atacante ainda mais inútil. Assim, o sistema garante que a cadeia verdadeira seja extremamente segura e que ataques sejam, na prática, impossíveis de ter sucesso. --- ### 12. Conclusão Propusemos um sistema de transações eletrônicas que elimina a necessidade de confiança, baseando-se em assinaturas digitais e em uma rede peer-to-peer que utiliza prova de trabalho. Isso resolve o problema do gasto duplo, criando um histórico público de transações imutável, desde que a maioria do poder computacional permaneça sob controle dos participantes honestos. A rede funciona de forma simples e descentralizada, com nós independentes que não precisam de identificação ou coordenação direta. Eles entram e saem livremente, aceitando a cadeia de prova de trabalho como registro do que ocorreu durante sua ausência. As decisões são tomadas por meio do poder de CPU, validando blocos legítimos, estendendo a cadeia e rejeitando os inválidos. Com este mecanismo de consenso, todas as regras e incentivos necessários para o funcionamento seguro e eficiente do sistema são garantidos. --- Faça o download do whitepaper original em português: https://bitcoin.org/files/bitcoin-paper/bitcoin_pt_br.pdf
@ 6be5cc06:5259daf0
2025-01-21 01:51:46## Bitcoin: Um sistema de dinheiro eletrônico direto entre pessoas. Satoshi Nakamoto satoshin@gmx.com www.bitcoin.org --- ### Resumo O Bitcoin é uma forma de dinheiro digital que permite pagamentos diretos entre pessoas, sem a necessidade de um banco ou instituição financeira. Ele resolve um problema chamado **gasto duplo**, que ocorre quando alguém tenta gastar o mesmo dinheiro duas vezes. Para evitar isso, o Bitcoin usa uma rede descentralizada onde todos trabalham juntos para verificar e registrar as transações. As transações são registradas em um livro público chamado **blockchain**, protegido por uma técnica chamada **Prova de Trabalho**. Essa técnica cria uma cadeia de registros que não pode ser alterada sem refazer todo o trabalho já feito. Essa cadeia é mantida pelos computadores que participam da rede, e a mais longa é considerada a verdadeira. Enquanto a maior parte do poder computacional da rede for controlada por participantes honestos, o sistema continuará funcionando de forma segura. A rede é flexível, permitindo que qualquer pessoa entre ou saia a qualquer momento, sempre confiando na cadeia mais longa como prova do que aconteceu. --- ### 1. Introdução Hoje, quase todos os pagamentos feitos pela internet dependem de bancos ou empresas como processadores de pagamento (cartões de crédito, por exemplo) para funcionar. Embora esse sistema seja útil, ele tem problemas importantes porque é baseado em **confiança**. Primeiro, essas empresas podem reverter pagamentos, o que é útil em caso de erros, mas cria custos e incertezas. Isso faz com que pequenas transações, como pagar centavos por um serviço, se tornem inviáveis. Além disso, os comerciantes são obrigados a desconfiar dos clientes, pedindo informações extras e aceitando fraudes como algo inevitável. Esses problemas não existem no dinheiro físico, como o papel-moeda, onde o pagamento é final e direto entre as partes. No entanto, não temos como enviar dinheiro físico pela internet sem depender de um intermediário confiável. O que precisamos é de um **sistema de pagamento eletrônico baseado em provas matemáticas**, não em confiança. Esse sistema permitiria que qualquer pessoa enviasse dinheiro diretamente para outra, sem depender de bancos ou processadores de pagamento. Além disso, as transações seriam irreversíveis, protegendo vendedores contra fraudes, mas mantendo a possibilidade de soluções para disputas legítimas. Neste documento, apresentamos o **Bitcoin**, que resolve o problema do gasto duplo usando uma rede descentralizada. Essa rede cria um registro público e protegido por cálculos matemáticos, que garante a ordem das transações. Enquanto a maior parte da rede for controlada por pessoas honestas, o sistema será seguro contra ataques. --- ### 2. Transações Para entender como funciona o Bitcoin, é importante saber como as transações são realizadas. Imagine que você quer transferir uma "moeda digital" para outra pessoa. No sistema do Bitcoin, essa "moeda" é representada por uma sequência de registros que mostram quem é o atual dono. Para transferi-la, você adiciona um novo registro comprovando que agora ela pertence ao próximo dono. Esse registro é protegido por um tipo especial de assinatura digital. #### O que é uma assinatura digital? Uma assinatura digital é como uma senha secreta, mas muito mais segura. No Bitcoin, cada usuário tem duas chaves: uma "chave privada", que é secreta e serve para criar a assinatura, e uma "chave pública", que pode ser compartilhada com todos e é usada para verificar se a assinatura é válida. Quando você transfere uma moeda, usa sua chave privada para assinar a transação, provando que você é o dono. A próxima pessoa pode usar sua chave pública para confirmar isso. #### Como funciona na prática? Cada "moeda" no Bitcoin é, na verdade, uma cadeia de assinaturas digitais. Vamos imaginar o seguinte cenário: 1. A moeda está com o Dono 0 (você). Para transferi-la ao Dono 1, você assina digitalmente a transação com sua chave privada. Essa assinatura inclui o código da transação anterior (chamado de "hash") e a chave pública do Dono 1. 2. Quando o Dono 1 quiser transferir a moeda ao Dono 2, ele assinará a transação seguinte com sua própria chave privada, incluindo também o hash da transação anterior e a chave pública do Dono 2. 3. Esse processo continua, formando uma "cadeia" de transações. Qualquer pessoa pode verificar essa cadeia para confirmar quem é o atual dono da moeda. #### Resolvendo o problema do gasto duplo Um grande desafio com moedas digitais é o "gasto duplo", que é quando uma mesma moeda é usada em mais de uma transação. Para evitar isso, muitos sistemas antigos dependiam de uma entidade central confiável, como uma casa da moeda, que verificava todas as transações. No entanto, isso criava um ponto único de falha e centralizava o controle do dinheiro. O Bitcoin resolve esse problema de forma inovadora: ele usa uma rede descentralizada onde todos os participantes (os "nós") têm acesso a um registro completo de todas as transações. Cada nó verifica se as transações são válidas e se a moeda não foi gasta duas vezes. Quando a maioria dos nós concorda com a validade de uma transação, ela é registrada permanentemente na blockchain. #### Por que isso é importante? Essa solução elimina a necessidade de confiar em uma única entidade para gerenciar o dinheiro, permitindo que qualquer pessoa no mundo use o Bitcoin sem precisar de permissão de terceiros. Além disso, ela garante que o sistema seja seguro e resistente a fraudes. --- ### 3. Servidor Timestamp Para assegurar que as transações sejam realizadas de forma segura e transparente, o sistema Bitcoin utiliza algo chamado de "servidor de registro de tempo" (timestamp). Esse servidor funciona como um registro público que organiza as transações em uma ordem específica. Ele faz isso agrupando várias transações em blocos e criando um código único chamado "hash". Esse hash é como uma impressão digital que representa todo o conteúdo do bloco. O hash de cada bloco é amplamente divulgado, como se fosse publicado em um jornal ou em um fórum público. Esse processo garante que cada bloco de transações tenha um registro de quando foi criado e que ele existia naquele momento. Além disso, cada novo bloco criado contém o hash do bloco anterior, formando uma cadeia contínua de blocos conectados — conhecida como blockchain. Com isso, se alguém tentar alterar qualquer informação em um bloco anterior, o hash desse bloco mudará e não corresponderá ao hash armazenado no bloco seguinte. Essa característica torna a cadeia muito segura, pois qualquer tentativa de fraude seria imediatamente detectada. O sistema de timestamps é essencial para provar a ordem cronológica das transações e garantir que cada uma delas seja única e autêntica. Dessa forma, ele reforça a segurança e a confiança na rede Bitcoin. --- ### 4. Prova-de-Trabalho Para implementar o registro de tempo distribuído no sistema Bitcoin, utilizamos um mecanismo chamado prova-de-trabalho. Esse sistema é semelhante ao Hashcash, desenvolvido por Adam Back, e baseia-se na criação de um código único, o "hash", por meio de um processo computacionalmente exigente. A prova-de-trabalho envolve encontrar um valor especial que, quando processado junto com as informações do bloco, gere um hash que comece com uma quantidade específica de zeros. Esse valor especial é chamado de "nonce". Encontrar o nonce correto exige um esforço significativo do computador, porque envolve tentativas repetidas até que a condição seja satisfeita. Esse processo é importante porque torna extremamente difícil alterar qualquer informação registrada em um bloco. Se alguém tentar mudar algo em um bloco, seria necessário refazer o trabalho de computação não apenas para aquele bloco, mas também para todos os blocos que vêm depois dele. Isso garante a segurança e a imutabilidade da blockchain. A prova-de-trabalho também resolve o problema de decidir qual cadeia de blocos é a válida quando há múltiplas cadeias competindo. A decisão é feita pela cadeia mais longa, pois ela representa o maior esforço computacional já realizado. Isso impede que qualquer indivíduo ou grupo controle a rede, desde que a maioria do poder de processamento seja mantida por participantes honestos. Para garantir que o sistema permaneça eficiente e equilibrado, a dificuldade da prova-de-trabalho é ajustada automaticamente ao longo do tempo. Se novos blocos estiverem sendo gerados rapidamente, a dificuldade aumenta; se estiverem sendo gerados muito lentamente, a dificuldade diminui. Esse ajuste assegura que novos blocos sejam criados aproximadamente a cada 10 minutos, mantendo o sistema estável e funcional. --- ### 5. Rede A rede Bitcoin é o coração do sistema e funciona de maneira distribuída, conectando vários participantes (ou nós) para garantir o registro e a validação das transações. Os passos para operar essa rede são: 1. **Transmissão de Transações**: Quando alguém realiza uma nova transação, ela é enviada para todos os nós da rede. Isso é feito para garantir que todos estejam cientes da operação e possam validá-la. 2. **Coleta de Transações em Blocos**: Cada nó agrupa as novas transações recebidas em um "bloco". Este bloco será preparado para ser adicionado à cadeia de blocos (a blockchain). 3. **Prova-de-Trabalho**: Os nós competem para resolver a prova-de-trabalho do bloco, utilizando poder computacional para encontrar um hash válido. Esse processo é como resolver um quebra-cabeça matemático difícil. 4. **Envio do Bloco Resolvido**: Quando um nó encontra a solução para o bloco (a prova-de-trabalho), ele compartilha esse bloco com todos os outros nós na rede. 5. **Validação do Bloco**: Cada nó verifica o bloco recebido para garantir que todas as transações nele contidas sejam válidas e que nenhuma moeda tenha sido gasta duas vezes. Apenas blocos válidos são aceitos. 6. **Construção do Próximo Bloco**: Os nós que aceitaram o bloco começam a trabalhar na criação do próximo bloco, utilizando o hash do bloco aceito como base (hash anterior). Isso mantém a continuidade da cadeia. #### Resolução de Conflitos e Escolha da Cadeia Mais Longa Os nós sempre priorizam a cadeia mais longa, pois ela representa o maior esforço computacional já realizado, garantindo maior segurança. Se dois blocos diferentes forem compartilhados simultaneamente, os nós trabalharão no primeiro bloco recebido, mas guardarão o outro como uma alternativa. Caso o segundo bloco eventualmente forme uma cadeia mais longa (ou seja, tenha mais blocos subsequentes), os nós mudarão para essa nova cadeia. #### Tolerância a Falhas A rede é robusta e pode lidar com mensagens que não chegam a todos os nós. Uma transação não precisa alcançar todos os nós de imediato; basta que chegue a um número suficiente deles para ser incluída em um bloco. Da mesma forma, se um nó não receber um bloco em tempo hábil, ele pode solicitá-lo ao perceber que está faltando quando o próximo bloco é recebido. Esse mecanismo descentralizado permite que a rede Bitcoin funcione de maneira segura, confiável e resiliente, sem depender de uma autoridade central. --- ### 6. Incentivo O incentivo é um dos pilares fundamentais que sustenta o funcionamento da rede Bitcoin, garantindo que os participantes (nós) continuem operando de forma honesta e contribuindo com recursos computacionais. Ele é estruturado em duas partes principais: a recompensa por mineração e as taxas de transação. #### Recompensa por Mineração Por convenção, o primeiro registro em cada bloco é uma transação especial que cria novas moedas e as atribui ao criador do bloco. Essa recompensa incentiva os mineradores a dedicarem poder computacional para apoiar a rede. Como não há uma autoridade central para emitir moedas, essa é a maneira pela qual novas moedas entram em circulação. Esse processo pode ser comparado ao trabalho de garimpeiros, que utilizam recursos para colocar mais ouro em circulação. No caso do Bitcoin, o "recurso" consiste no tempo de CPU e na energia elétrica consumida para resolver a prova-de-trabalho. #### Taxas de Transação Além da recompensa por mineração, os mineradores também podem ser incentivados pelas taxas de transação. Se uma transação utiliza menos valor de saída do que o valor de entrada, a diferença é tratada como uma taxa, que é adicionada à recompensa do bloco contendo essa transação. Com o passar do tempo e à medida que o número de moedas em circulação atinge o limite predeterminado, essas taxas de transação se tornam a principal fonte de incentivo, substituindo gradualmente a emissão de novas moedas. Isso permite que o sistema opere sem inflação, uma vez que o número total de moedas permanece fixo. #### Incentivo à Honestidade O design do incentivo também busca garantir que os participantes da rede mantenham um comportamento honesto. Para um atacante que consiga reunir mais poder computacional do que o restante da rede, ele enfrentaria duas escolhas: 1. Usar esse poder para fraudar o sistema, como reverter transações e roubar pagamentos. 2. Seguir as regras do sistema, criando novos blocos e recebendo recompensas legítimas. A lógica econômica favorece a segunda opção, pois um comportamento desonesto prejudicaria a confiança no sistema, diminuindo o valor de todas as moedas, incluindo aquelas que o próprio atacante possui. Jogar dentro das regras não apenas maximiza o retorno financeiro, mas também preserva a validade e a integridade do sistema. Esse mecanismo garante que os incentivos econômicos estejam alinhados com o objetivo de manter a rede segura, descentralizada e funcional ao longo do tempo. --- ### 7. Recuperação do Espaço em Disco Depois que uma moeda passa a estar protegida por muitos blocos na cadeia, as informações sobre as transações antigas que a geraram podem ser descartadas para economizar espaço em disco. Para que isso seja possível sem comprometer a segurança, as transações são organizadas em uma estrutura chamada "árvore de Merkle". Essa árvore funciona como um resumo das transações: em vez de armazenar todas elas, guarda apenas um "hash raiz", que é como uma assinatura compacta que representa todo o grupo de transações. Os blocos antigos podem, então, ser simplificados, removendo as partes desnecessárias dessa árvore. Apenas a raiz do hash precisa ser mantida no cabeçalho do bloco, garantindo que a integridade dos dados seja preservada, mesmo que detalhes específicos sejam descartados. Para exemplificar: imagine que você tenha vários recibos de compra. Em vez de guardar todos os recibos, você cria um documento e lista apenas o valor total de cada um. Mesmo que os recibos originais sejam descartados, ainda é possível verificar a soma com base nos valores armazenados. Além disso, o espaço ocupado pelos blocos em si é muito pequeno. Cada bloco sem transações ocupa apenas cerca de 80 bytes. Isso significa que, mesmo com blocos sendo gerados a cada 10 minutos, o crescimento anual em espaço necessário é insignificante: apenas 4,2 MB por ano. Com a capacidade de armazenamento dos computadores crescendo a cada ano, esse espaço continuará sendo trivial, garantindo que a rede possa operar de forma eficiente sem problemas de armazenamento, mesmo a longo prazo. --- ### 8. Verificação de Pagamento Simplificada É possível confirmar pagamentos sem a necessidade de operar um nó completo da rede. Para isso, o usuário precisa apenas de uma cópia dos cabeçalhos dos blocos da cadeia mais longa (ou seja, a cadeia com maior esforço de trabalho acumulado). Ele pode verificar a validade de uma transação ao consultar os nós da rede até obter a confirmação de que tem a cadeia mais longa. Para isso, utiliza-se o ramo Merkle, que conecta a transação ao bloco em que ela foi registrada. Entretanto, o método simplificado possui limitações: ele não pode confirmar uma transação isoladamente, mas sim assegurar que ela ocupa um lugar específico na cadeia mais longa. Dessa forma, se um nó da rede aprova a transação, os blocos subsequentes reforçam essa aceitação. A verificação simplificada é confiável enquanto a maioria dos nós da rede for honesta. Contudo, ela se torna vulnerável caso a rede seja dominada por um invasor. Nesse cenário, um atacante poderia fabricar transações fraudulentas que enganariam o usuário temporariamente até que o invasor obtivesse controle completo da rede. Uma estratégia para mitigar esse risco é configurar alertas nos softwares de nós completos. Esses alertas identificam blocos inválidos, sugerindo ao usuário baixar o bloco completo para confirmar qualquer inconsistência. Para maior segurança, empresas que realizam pagamentos frequentes podem preferir operar seus próprios nós, reduzindo riscos e permitindo uma verificação mais direta e confiável. --- ### 9. Combinando e Dividindo Valor No sistema Bitcoin, cada unidade de valor é tratada como uma "moeda" individual, mas gerenciar cada centavo como uma transação separada seria impraticável. Para resolver isso, o Bitcoin permite que valores sejam combinados ou divididos em transações, facilitando pagamentos de qualquer valor. #### Entradas e Saídas Cada transação no Bitcoin é composta por: - **Entradas**: Representam os valores recebidos em transações anteriores. - **Saídas**: Correspondem aos valores enviados, divididos entre os destinatários e, eventualmente, o troco para o remetente. Normalmente, uma transação contém: - Uma única entrada com valor suficiente para cobrir o pagamento. - Ou várias entradas combinadas para atingir o valor necessário. O valor total das saídas nunca excede o das entradas, e a diferença (se houver) pode ser retornada ao remetente como **troco**. #### Exemplo Prático Imagine que você tem duas entradas: 1. 0,03 BTC 2. 0,07 BTC Se deseja enviar 0,08 BTC para alguém, a transação terá: - **Entrada**: As duas entradas combinadas (0,03 + 0,07 BTC = 0,10 BTC). - **Saídas**: Uma para o destinatário (0,08 BTC) e outra como troco para você (0,02 BTC). Essa flexibilidade permite que o sistema funcione sem precisar manipular cada unidade mínima individualmente. #### Difusão e Simplificação A difusão de transações, onde uma depende de várias anteriores e assim por diante, não representa um problema. Não é necessário armazenar ou verificar o histórico completo de uma transação para utilizá-la, já que o registro na blockchain garante sua integridade. --- ### 10. Privacidade O modelo bancário tradicional oferece um certo nível de privacidade, limitando o acesso às informações financeiras apenas às partes envolvidas e a um terceiro confiável (como bancos ou instituições financeiras). No entanto, o Bitcoin opera de forma diferente, pois todas as transações são publicamente registradas na blockchain. Apesar disso, a privacidade pode ser mantida utilizando **chaves públicas anônimas**, que desvinculam diretamente as transações das identidades das partes envolvidas. #### Fluxo de Informação - No **modelo tradicional**, as transações passam por um terceiro confiável que conhece tanto o remetente quanto o destinatário. - No **Bitcoin**, as transações são anunciadas publicamente, mas sem revelar diretamente as identidades das partes. Isso é comparável a dados divulgados por bolsas de valores, onde informações como o tempo e o tamanho das negociações (a "fita") são públicas, mas as identidades das partes não. #### Protegendo a Privacidade Para aumentar a privacidade no Bitcoin, são adotadas as seguintes práticas: 1. **Chaves Públicas Anônimas**: Cada transação utiliza um par de chaves diferentes, dificultando a associação com um proprietário único. 2. **Prevenção de Ligação**: Ao usar chaves novas para cada transação, reduz-se a possibilidade de links evidentes entre múltiplas transações realizadas pelo mesmo usuário. #### Riscos de Ligação Embora a privacidade seja fortalecida, alguns riscos permanecem: - Transações **multi-entrada** podem revelar que todas as entradas pertencem ao mesmo proprietário, caso sejam necessárias para somar o valor total. - O proprietário da chave pode ser identificado indiretamente por transações anteriores que estejam conectadas. --- ### 11. Cálculos Imagine que temos um sistema onde as pessoas (ou computadores) competem para adicionar informações novas (blocos) a um grande registro público (a cadeia de blocos ou blockchain). Este registro é como um livro contábil compartilhado, onde todos podem verificar o que está escrito. Agora, vamos pensar em um cenário: um atacante quer enganar o sistema. Ele quer mudar informações já registradas para beneficiar a si mesmo, por exemplo, desfazendo um pagamento que já fez. Para isso, ele precisa criar uma versão alternativa do livro contábil (a cadeia de blocos dele) e convencer todos os outros participantes de que essa versão é a verdadeira. Mas isso é extremamente difícil. #### Como o Ataque Funciona Quando um novo bloco é adicionado à cadeia, ele depende de cálculos complexos que levam tempo e esforço. Esses cálculos são como um grande quebra-cabeça que precisa ser resolvido. - Os “bons jogadores” (nós honestos) estão sempre trabalhando juntos para resolver esses quebra-cabeças e adicionar novos blocos à cadeia verdadeira. - O atacante, por outro lado, precisa resolver quebra-cabeças sozinho, tentando “alcançar” a cadeia honesta para que sua versão alternativa pareça válida. Se a cadeia honesta já está vários blocos à frente, o atacante começa em desvantagem, e o sistema está projetado para que a dificuldade de alcançá-los aumente rapidamente. #### A Corrida Entre Cadeias Você pode imaginar isso como uma corrida. A cada bloco novo que os jogadores honestos adicionam à cadeia verdadeira, eles se distanciam mais do atacante. Para vencer, o atacante teria que resolver os quebra-cabeças mais rápido que todos os outros jogadores honestos juntos. Suponha que: - A rede honesta tem **80% do poder computacional** (ou seja, resolve 8 de cada 10 quebra-cabeças). - O atacante tem **20% do poder computacional** (ou seja, resolve 2 de cada 10 quebra-cabeças). Cada vez que a rede honesta adiciona um bloco, o atacante tem que "correr atrás" e resolver mais quebra-cabeças para alcançar. #### Por Que o Ataque Fica Cada Vez Mais Improvável? Vamos usar uma fórmula simples para mostrar como as chances de sucesso do atacante diminuem conforme ele precisa "alcançar" mais blocos: P = (q/p)^z - **q** é o poder computacional do atacante (20%, ou 0,2). - **p** é o poder computacional da rede honesta (80%, ou 0,8). - **z** é a diferença de blocos entre a cadeia honesta e a cadeia do atacante. Se o atacante está 5 blocos atrás (z = 5): P = (0,2 / 0,8)^5 = (0,25)^5 = 0,00098, (ou, 0,098%) Isso significa que o atacante tem menos de 0,1% de chance de sucesso — ou seja, é muito improvável. Se ele estiver 10 blocos atrás (z = 10): P = (0,2 / 0,8)^10 = (0,25)^10 = 0,000000095, (ou, 0,0000095%). Neste caso, as chances de sucesso são praticamente **nulas**. #### Um Exemplo Simples Se você jogar uma moeda, a chance de cair “cara” é de 50%. Mas se precisar de 10 caras seguidas, sua chance já é bem menor. Se precisar de 20 caras seguidas, é quase impossível. No caso do Bitcoin, o atacante precisa de muito mais do que 20 caras seguidas. Ele precisa resolver quebra-cabeças extremamente difíceis e alcançar os jogadores honestos que estão sempre à frente. Isso faz com que o ataque seja inviável na prática. #### Por Que Tudo Isso é Seguro? - **A probabilidade de sucesso do atacante diminui exponencialmente.** Isso significa que, quanto mais tempo passa, menor é a chance de ele conseguir enganar o sistema. - **A cadeia verdadeira (honesta) está protegida pela força da rede.** Cada novo bloco que os jogadores honestos adicionam à cadeia torna mais difícil para o atacante alcançar. #### E Se o Atacante Tentar Continuar? O atacante poderia continuar tentando indefinidamente, mas ele estaria gastando muito tempo e energia sem conseguir nada. Enquanto isso, os jogadores honestos estão sempre adicionando novos blocos, tornando o trabalho do atacante ainda mais inútil. Assim, o sistema garante que a cadeia verdadeira seja extremamente segura e que ataques sejam, na prática, impossíveis de ter sucesso. --- ### 12. Conclusão Propusemos um sistema de transações eletrônicas que elimina a necessidade de confiança, baseando-se em assinaturas digitais e em uma rede peer-to-peer que utiliza prova de trabalho. Isso resolve o problema do gasto duplo, criando um histórico público de transações imutável, desde que a maioria do poder computacional permaneça sob controle dos participantes honestos. A rede funciona de forma simples e descentralizada, com nós independentes que não precisam de identificação ou coordenação direta. Eles entram e saem livremente, aceitando a cadeia de prova de trabalho como registro do que ocorreu durante sua ausência. As decisões são tomadas por meio do poder de CPU, validando blocos legítimos, estendendo a cadeia e rejeitando os inválidos. Com este mecanismo de consenso, todas as regras e incentivos necessários para o funcionamento seguro e eficiente do sistema são garantidos. --- Faça o download do whitepaper original em português: https://bitcoin.org/files/bitcoin-paper/bitcoin_pt_br.pdf @ 3f770d65:7a745b24
2025-01-19 21:48:49The recent shutdown of TikTok in the United States due to a potential government ban serves as a stark reminder how fragile centralized platforms truly are under the surface. While these platforms offer convenience, a more polished user experience, and connectivity, they are ultimately beholden to governments, corporations, and other authorities. This makes them vulnerable to censorship, regulation, and outright bans. In contrast, Nostr represents a shift in how we approach online communication and content sharing. Built on the principles of decentralization and user choice, Nostr cannot be banned, because it is not a platform—it is a protocol. **PROTOCOLS, NOT PLATFORMS.** At the heart of Nostr's philosophy is **user choice**, a feature that fundamentally sets it apart from legacy platforms. In centralized systems, the user experience is dictated by a single person or governing entity. If the platform decides to filter, censor, or ban specific users or content, individuals are left with little action to rectify the situation. They must either accept the changes or abandon the platform entirely, often at the cost of losing their social connections, their data, and their identity. What's happening with TikTok could never happen on Nostr. With Nostr, the dynamics are completely different. Because it is a protocol, not a platform, no single entity controls the ecosystem. Instead, the protocol enables a network of applications and relays that users can freely choose from. If a particular application or relay implements policies that a user disagrees with, such as censorship, filtering, or even government enforced banning, they are not trapped or abandoned. They have the freedom to move to another application or relay with minimal effort. **THIS IS POWERFUL.** Take, for example, the case of a relay that decides to censor specific content. On a legacy platform, this would result in frustration and a loss of access for users. On Nostr, however, users can simply connect to a different relay that does not impose such restrictions. Similarly, if an application introduces features or policies that users dislike, they can migrate to a different application that better suits their preferences, all while retaining their identity and social connections. The same principles apply to government bans and censorship. A government can ban a specific application or even multiple applications, just as it can block one relay or several relays. China has implemented both tactics, yet Chinese users continue to exist and actively participate on Nostr, demonstrating Nostr's ability to resistant censorship. How? Simply, it turns into a game of whack-a-mole. When one relay is censored, another quickly takes its place. When one application is banned, another emerges. Users can also bypass these obstacles by running their own relays and applications directly from their homes or personal devices, eliminating reliance on larger entities or organizations and ensuring continuous access. **AGAIN, THIS IS POWERUFL.** Nostr's open and decentralized design makes it resistant to the kinds of government intervention that led to TikTok's outages this weekend and potential future ban in the next 90 days. There is no central server to target, no company to regulate, and no single point of failure. (Insert your CEO jokes here). As long as there are individuals running relays and applications, users continue creating notes and sending zaps. Platforms like TikTok can be silenced with the stroke of a pen, leaving millions of users disconnected and abandoned. Social communication should not be silenced so incredibly easily. No one should have that much power over social interactions. Will we on-board a massive wave of TikTokers in the coming hours or days? I don't know. TikTokers may not be ready for Nostr yet, and honestly, Nostr may not be ready for them either. The ecosystem still lacks the completely polished applications, tools, and services they’re accustomed to. This is where we say "we're still early". They may not be early adopters like the current Nostr user base. Until we bridge that gap, they’ll likely move to the next centralized platform, only to face another government ban or round of censorship in the future. But eventually, there will come a tipping point, a moment when they’ve had enough. When that time comes, I hope we’re prepared. If we’re not, we risk missing a tremendous opportunity to onboard people who genuinely need Nostr’s freedom. Until then, to all of the Nostr developers out there, keep up the great work and keep building. Your hard work and determination is needed. ###
@ 3f770d65:7a745b24
2025-01-19 21:48:49The recent shutdown of TikTok in the United States due to a potential government ban serves as a stark reminder how fragile centralized platforms truly are under the surface. While these platforms offer convenience, a more polished user experience, and connectivity, they are ultimately beholden to governments, corporations, and other authorities. This makes them vulnerable to censorship, regulation, and outright bans. In contrast, Nostr represents a shift in how we approach online communication and content sharing. Built on the principles of decentralization and user choice, Nostr cannot be banned, because it is not a platform—it is a protocol. **PROTOCOLS, NOT PLATFORMS.** At the heart of Nostr's philosophy is **user choice**, a feature that fundamentally sets it apart from legacy platforms. In centralized systems, the user experience is dictated by a single person or governing entity. If the platform decides to filter, censor, or ban specific users or content, individuals are left with little action to rectify the situation. They must either accept the changes or abandon the platform entirely, often at the cost of losing their social connections, their data, and their identity. What's happening with TikTok could never happen on Nostr. With Nostr, the dynamics are completely different. Because it is a protocol, not a platform, no single entity controls the ecosystem. Instead, the protocol enables a network of applications and relays that users can freely choose from. If a particular application or relay implements policies that a user disagrees with, such as censorship, filtering, or even government enforced banning, they are not trapped or abandoned. They have the freedom to move to another application or relay with minimal effort. **THIS IS POWERFUL.** Take, for example, the case of a relay that decides to censor specific content. On a legacy platform, this would result in frustration and a loss of access for users. On Nostr, however, users can simply connect to a different relay that does not impose such restrictions. Similarly, if an application introduces features or policies that users dislike, they can migrate to a different application that better suits their preferences, all while retaining their identity and social connections. The same principles apply to government bans and censorship. A government can ban a specific application or even multiple applications, just as it can block one relay or several relays. China has implemented both tactics, yet Chinese users continue to exist and actively participate on Nostr, demonstrating Nostr's ability to resistant censorship. How? Simply, it turns into a game of whack-a-mole. When one relay is censored, another quickly takes its place. When one application is banned, another emerges. Users can also bypass these obstacles by running their own relays and applications directly from their homes or personal devices, eliminating reliance on larger entities or organizations and ensuring continuous access. **AGAIN, THIS IS POWERUFL.** Nostr's open and decentralized design makes it resistant to the kinds of government intervention that led to TikTok's outages this weekend and potential future ban in the next 90 days. There is no central server to target, no company to regulate, and no single point of failure. (Insert your CEO jokes here). As long as there are individuals running relays and applications, users continue creating notes and sending zaps. Platforms like TikTok can be silenced with the stroke of a pen, leaving millions of users disconnected and abandoned. Social communication should not be silenced so incredibly easily. No one should have that much power over social interactions. Will we on-board a massive wave of TikTokers in the coming hours or days? I don't know. TikTokers may not be ready for Nostr yet, and honestly, Nostr may not be ready for them either. The ecosystem still lacks the completely polished applications, tools, and services they’re accustomed to. This is where we say "we're still early". They may not be early adopters like the current Nostr user base. Until we bridge that gap, they’ll likely move to the next centralized platform, only to face another government ban or round of censorship in the future. But eventually, there will come a tipping point, a moment when they’ve had enough. When that time comes, I hope we’re prepared. If we’re not, we risk missing a tremendous opportunity to onboard people who genuinely need Nostr’s freedom. Until then, to all of the Nostr developers out there, keep up the great work and keep building. Your hard work and determination is needed. ### @ 6f7db55a:985d8b25
2025-01-19 19:46:30This article will be basic instructions for extreme normies (I say that lovingly), or anyone looking to get started with using zap.stream and sharing to nostr. **EQUIPMENT** Getting started is incredibly easy and your equipment needs are miniscule. An old desktop or laptop running Linux, MacOs, or Windows made in the passed 15yrs should do. Im currently using and old Dell Latitude E5430 with an Intel i5-3210M with 32Gigs of ram and 250GB hard drive. Technically, you go as low as using a Raspberry Pi 4B+ running Owncast, but Ill save that so a future tutorial. Let's get started. **ON YOUR COMPUTER** You'll need to install OBS (open broaster software). OBS is the go-to for streaming to social media. There are tons of YouTube videos on it's function. WE, however, will only be doing the basics to get us up and running. First, go to [https://obsproject.com/](https://obsproject.com/)  Once on the OBS site, choose the correct download for you system. Linux, MacOs or Windows. Download (remember where you downloaded the file to). Go there and install your download. You may have to enter your password to install on your particular operating system. This is normal. Once you've installed OBS, open the application. It should look something like this...  For our purposes, we will be in studio mode. Locate the 'Studio Mode' button on the right lower-hand side of the screen, and click it.  You'll see the screen split like in the image above. The left-side is from your desktop, and the right-side is what your broadcast will look like. Next, we go to settings. The 'Settings' button is located right below the 'Studio Mode" button.  Now we're in settings and you should see something like this...  Now locate stream in the right-hand menu. It should be the second in the list. Click it.  Once in the stream section, go to 'Service' and in the right-hand drop-down, find and select 'Custom...' from the drop-down menu.  Remeber where this is because we'll need to come back to it, shortly. **ZAPSTREAM** We need our streamkey credentials from Zapstream. Go to [https://zap.stream](https://zap.stream). Then, go to your dashboard.  Located on the lower right-hand side is the Server URL and Stream Key. You'll need to copy/paste this in OBS.  You may have to generate new keys, if they aren't already there. This is normal. If you're interested in multi-streaming (That's where you broadcast to multiple social media platforms all at once), youll need the server URL and streamkeys from each. You'll place them in their respective forms in Zapstream's 'Stream Forwarding" section.  Use the custom form, if the platform you want to stream to isn't listed. *Side-Note: remember that you can use your nostr identity across multiple nostr client applications. So when your login for Amethyst, as an example, could be used when you login to zapstream. Also, i would suggest using Alby's browser extension. It makes it much easier to fund your stream, as well as receive zaps. * **Now, BACK TO OBS...** With Stream URL and Key in hand, paste them in the 'Stream" section of OBS' settings. Service [Custom...] Server [Server URL] StreamKey [Your zapstream stream key]  After you've entered all your streaming credentials, click 'OK' at the bottom, on the right-hand side. **WHAT'S NEXT?** Let's setup your first stream from OBS. First we need to choose a source. Your source is your input device. It can be your webcam, your mic, your monitor, or any particular window on your screen. assuming you're an absolute beginner, we're going to use the source 'Window Capture (Xcomposite)'.  Now, open your source file. We'll use a video source called 'grannyhiphop.mp4'. In your case it can be whatever you want to stream; Just be sure to select the proper source.  Double-click on 'Window Capture' in your sources list. In the pop-up window, select your file from the 'Window' drop-down menu.   You should see something like this...  Working in the left display of OBS, we will adjust the video by left-click, hold and drag the bottom corner, so that it takes up the whole display.  In order to adjust the right-side display ( the broadcast side), we need to manipulate the video source by changing it's size.  This may take some time to adjust the size. This is normal. What I've found to help is, after every adjustment, I click the 'Fade (300ms)' button. I have no idea why it helps, but it does, lol.  Finally, after getting everything to look the way you want, you click the 'Start Stream' button.  **BACK TO ZAPSTREAM** Now, we go back to zapstream to check to see if our stream is up. It may take a few moments to update. You may even need to refresh the page. This is normal.  STREAMS UP!!! A few things, in closing. You'll notice that your dashbooard has changed. It'll show current stream time, how much time you have left (according to your funding source), who's zapped you with how much theyve zapped, the ability to post a note about your stream (to both nostr and twitter), and it shows your chatbox with your listeners. There are also a raid feature, stream settings (where you can title & tag your stream). You can 'topup' your funding for your stream. As well as, see your current balance. You did a great and If you ever need more help, just use the tag #asknostr in your note. There are alway nostriches willing to help. **STAY AWESOME!!!**
@ 6f7db55a:985d8b25
2025-01-19 19:46:30This article will be basic instructions for extreme normies (I say that lovingly), or anyone looking to get started with using zap.stream and sharing to nostr. **EQUIPMENT** Getting started is incredibly easy and your equipment needs are miniscule. An old desktop or laptop running Linux, MacOs, or Windows made in the passed 15yrs should do. Im currently using and old Dell Latitude E5430 with an Intel i5-3210M with 32Gigs of ram and 250GB hard drive. Technically, you go as low as using a Raspberry Pi 4B+ running Owncast, but Ill save that so a future tutorial. Let's get started. **ON YOUR COMPUTER** You'll need to install OBS (open broaster software). OBS is the go-to for streaming to social media. There are tons of YouTube videos on it's function. WE, however, will only be doing the basics to get us up and running. First, go to [https://obsproject.com/](https://obsproject.com/)  Once on the OBS site, choose the correct download for you system. Linux, MacOs or Windows. Download (remember where you downloaded the file to). Go there and install your download. You may have to enter your password to install on your particular operating system. This is normal. Once you've installed OBS, open the application. It should look something like this...  For our purposes, we will be in studio mode. Locate the 'Studio Mode' button on the right lower-hand side of the screen, and click it.  You'll see the screen split like in the image above. The left-side is from your desktop, and the right-side is what your broadcast will look like. Next, we go to settings. The 'Settings' button is located right below the 'Studio Mode" button.  Now we're in settings and you should see something like this...  Now locate stream in the right-hand menu. It should be the second in the list. Click it.  Once in the stream section, go to 'Service' and in the right-hand drop-down, find and select 'Custom...' from the drop-down menu.  Remeber where this is because we'll need to come back to it, shortly. **ZAPSTREAM** We need our streamkey credentials from Zapstream. Go to [https://zap.stream](https://zap.stream). Then, go to your dashboard.  Located on the lower right-hand side is the Server URL and Stream Key. You'll need to copy/paste this in OBS.  You may have to generate new keys, if they aren't already there. This is normal. If you're interested in multi-streaming (That's where you broadcast to multiple social media platforms all at once), youll need the server URL and streamkeys from each. You'll place them in their respective forms in Zapstream's 'Stream Forwarding" section.  Use the custom form, if the platform you want to stream to isn't listed. *Side-Note: remember that you can use your nostr identity across multiple nostr client applications. So when your login for Amethyst, as an example, could be used when you login to zapstream. Also, i would suggest using Alby's browser extension. It makes it much easier to fund your stream, as well as receive zaps. * **Now, BACK TO OBS...** With Stream URL and Key in hand, paste them in the 'Stream" section of OBS' settings. Service [Custom...] Server [Server URL] StreamKey [Your zapstream stream key]  After you've entered all your streaming credentials, click 'OK' at the bottom, on the right-hand side. **WHAT'S NEXT?** Let's setup your first stream from OBS. First we need to choose a source. Your source is your input device. It can be your webcam, your mic, your monitor, or any particular window on your screen. assuming you're an absolute beginner, we're going to use the source 'Window Capture (Xcomposite)'.  Now, open your source file. We'll use a video source called 'grannyhiphop.mp4'. In your case it can be whatever you want to stream; Just be sure to select the proper source.  Double-click on 'Window Capture' in your sources list. In the pop-up window, select your file from the 'Window' drop-down menu.   You should see something like this...  Working in the left display of OBS, we will adjust the video by left-click, hold and drag the bottom corner, so that it takes up the whole display.  In order to adjust the right-side display ( the broadcast side), we need to manipulate the video source by changing it's size.  This may take some time to adjust the size. This is normal. What I've found to help is, after every adjustment, I click the 'Fade (300ms)' button. I have no idea why it helps, but it does, lol.  Finally, after getting everything to look the way you want, you click the 'Start Stream' button.  **BACK TO ZAPSTREAM** Now, we go back to zapstream to check to see if our stream is up. It may take a few moments to update. You may even need to refresh the page. This is normal.  STREAMS UP!!! A few things, in closing. You'll notice that your dashbooard has changed. It'll show current stream time, how much time you have left (according to your funding source), who's zapped you with how much theyve zapped, the ability to post a note about your stream (to both nostr and twitter), and it shows your chatbox with your listeners. There are also a raid feature, stream settings (where you can title & tag your stream). You can 'topup' your funding for your stream. As well as, see your current balance. You did a great and If you ever need more help, just use the tag #asknostr in your note. There are alway nostriches willing to help. **STAY AWESOME!!!** @ cff1720e:15c7e2b2
2025-01-19 17:48:02**Einleitung**\ \ Schwierige Dinge einfach zu erklären ist der Anspruch von ELI5 (explain me like I'm 5). Das ist in unserer hoch technisierten Welt dringend erforderlich, denn nur mit dem Verständnis der Technologien können wir sie richtig einsetzen und weiter entwickeln.\ Ich starte meine Serie mit Nostr, einem relativ neuen Internet-Protokoll. Was zum Teufel ist ein Internet-Protokoll? Formal beschrieben sind es internationale Standards, die dafür sorgen, dass das Internet seit über 30 Jahren ziemlich gut funktioniert. Es ist die Sprache, in der sich die Rechner miteinander unterhalten und die auch Sie täglich nutzen, vermutlich ohne es bewusst wahrzunehmen. http(s) transportiert ihre Anfrage an einen Server (z.B. Amazon), und html sorgt dafür, dass aus den gelieferten Daten eine schöne Seite auf ihrem Bildschirm entsteht. Eine Mail wird mit smtp an den Mailserver gesendet und mit imap von ihm abgerufen, und da alle den Standard verwenden, funktioniert das mit jeder App auf jedem Betriebssystem und mit jedem Mail-Provider. Und mit einer Mail-Adresse wie <roland@pareto.space> können sie sogar jederzeit umziehen, egal wohin. **Cool, das ist state of the art!** Aber warum funktioniert das z.B. bei Chat nicht, gibt es da kein Protokoll? Doch, es heißt IRC (Internet Relay Chat → merken sie sich den Namen), aber es wird so gut wie nicht verwendet. Die Gründe dafür sind nicht technischer Natur, vielmehr wurden mit Apps wie Facebook, Twitter, WhatsApp, Telegram, Instagram, TikTok u.a. bewusst Inkompatibilitäten und Nutzerabhängigkeiten geschaffen um Profite zu maximieren.  **Warum Nostr?** Da das Standard-Protokoll nicht genutzt wird, hat jede App ihr eigenes, und wir brauchen eine handvoll Apps um uns mit allen Bekannten auszutauschen. Eine Mobilfunknummer ist Voraussetzung für jedes Konto, damit können die App-Hersteller die Nutzer umfassend tracken und mit dem Verkauf der Informationen bis zu 30 USD je Konto und Monat verdienen. Der Nutzer ist nicht mehr Kunde, er ist das Produkt! Der Werbe-SPAM ist noch das kleinste Problem bei diesem Geschäftsmodell. Server mit Millionen von Nutzerdaten sind ein “honey pot”, dementsprechend oft werden sie gehackt und die Zugangsdaten verkauft. 2024 wurde auch der Twitter-Account vom damaligen Präsidenten Joe Biden gehackt, niemand wusste mehr wer die Nachrichten verfasst hat (vorher auch nicht), d.h. die Authentizität der Inhalte ist bei keinem dieser Anbieter gewährleistet. Im selben Jahr wurde der Telegram-Gründer in Frankreich in Beugehaft genommen, weil er sich geweigert hatte Hintertüren in seine Software einzubauen. Nun kann zum Schutz **"unserer Demokratie”** praktisch jeder mitlesen, was sie mit wem an Informationen austauschen, z.B. darüber welches Shampoo bestimmte Politiker verwenden.  Und wer tatsächlich glaubt er könne Meinungsfreiheit auf sozialen Medien praktizieren, findet sich schnell in der Situation von Donald Trump wieder (seinerzeit amtierender Präsident), dem sein Twitter-Konto 2021 abgeschaltet wurde (Cancel-Culture). Die Nutzerdaten, also ihr Profil, ihre Kontakte, Dokumente, Bilder, Videos und Audiofiles - gehören ihnen ohnehin nicht mehr sondern sind Eigentum des Plattform-Betreibers; lesen sie sich mal die AGB's durch. Aber nein, keine gute Idee, das sind hunderte Seiten und sie werden permanent geändert. Alle nutzen also Apps, deren Technik sie nicht verstehen, deren Regeln sie nicht kennen, wo sie keine Rechte haben und die ihnen die Resultate ihres Handelns stehlen. Was würde wohl der Fünfjährige sagen, wenn ihm seine ältere Schwester anbieten würde, alle seine Spielzeuge zu “verwalten” und dann auszuhändigen wenn er brav ist? “Du spinnst wohl”, und damit beweist der Knirps mehr Vernunft als die Mehrzahl der Erwachsenen. \ \ **Resümee:** keine Standards, keine Daten, keine Rechte = keine Zukunft!  \ **Wie funktioniert Nostr?** Die Entwickler von Nostr haben erkannt dass sich das Server-Client-Konzept in ein Master-Slave-Konzept verwandelt hatte. Der Master ist ein Synonym für Zentralisierung und wird zum **“single point of failure”**, der zwangsläufig Systeme dysfunktional macht. In einem verteilten Peer2Peer-System gibt es keine Master mehr sondern nur gleichberechtigte Knoten (Relays), auf denen die Informationen gespeichert werden. Indem man Informationen auf mehreren Relays redundant speichert, ist das System in jeglicher Hinsicht resilienter. Nicht nur die Natur verwendet dieses Prinzip seit Jahrmillionen erfolgreich, auch das Internet wurde so konzipiert (das ARPAnet wurde vom US-Militär für den Einsatz in Kriegsfällen unter massiven Störungen entwickelt). Alle Nostr-Daten liegen auf Relays und der Nutzer kann wählen zwischen öffentlichen (zumeist kostenlosen) und privaten Relays, z.B. für geschlossene Gruppen oder zum Zwecke von Daten-Archivierung. Da Dokumente auf mehreren Relays gespeichert sind, werden statt URL's (Locator) eindeutige Dokumentnamen (URI's = Identifier) verwendet, broken Links sind damit Vergangenheit und Löschungen / Verluste ebenfalls.\ \ Jedes Dokument (Event genannt) wird vom Besitzer signiert, es ist damit authentisch und fälschungssicher und kann nur vom Ersteller gelöscht werden. Dafür wird ein Schlüsselpaar verwendet bestehend aus privatem (nsec) und öffentlichem Schlüssel (npub) wie aus der Mailverschlüsselung (PGP) bekannt. Das repräsentiert eine Nostr-Identität, die um Bild, Namen, Bio und eine lesbare Nostr-Adresse ergänzt werden kann (z.B. <roland@pareto.space> ), mehr braucht es nicht um alle Ressourcen des Nostr-Ökosystems zu nutzen. Und das besteht inzwischen aus über hundert Apps mit unterschiedlichen Fokussierungen, z.B. für persönliche verschlüsselte Nachrichten (DM → OxChat), Kurznachrichten (Damus, Primal), Blogbeiträge (Pareto), Meetups (Joinstr), Gruppen (Groups), Bilder (Olas), Videos (Amethyst), Audio-Chat (Nostr Nests), Audio-Streams (Tunestr), Video-Streams (Zap.Stream), Marktplätze (Shopstr) u.v.a.m. Die Anmeldung erfolgt mit einem Klick (single sign on) und den Apps stehen ALLE Nutzerdaten zur Verfügung (Profil, Daten, Kontakte, Social Graph → Follower, Bookmarks, Comments, etc.), im Gegensatz zu den fragmentierten Datensilos der Gegenwart.\ \ **Resümee:** ein offener Standard, alle Daten, alle Rechte = große Zukunft!  \ **Warum ist Nostr die Zukunft des Internet?** “Baue Dein Haus nicht auf einem fremden Grundstück” gilt auch im Internet - für alle App-Entwickler, Künstler, Journalisten und Nutzer, denn auch ihre Daten sind werthaltig. Nostr garantiert das Eigentum an den Daten, und überwindet ihre Fragmentierung. Weder die Nutzung noch die kreativen Freiheiten werden durch maßlose Lizenz- und Nutzungsbedingungen eingeschränkt. Aus passiven Nutzern werden durch Interaktion aktive Teilnehmer, Co-Creatoren in einer Sharing-Ökonomie **(Value4Value)**. OpenSource schafft endlich wieder Vertrauen in die Software und ihre Anbieter. Offene Standards ermöglichen den Entwicklern mehr Kooperation und schnellere Entwicklung, für die Anwender garantieren sie Wahlfreiheit. Womit wir letztmalig zu unserem Fünfjährigen zurückkehren. Kinder lieben Lego über alles, am meisten die Maxi-Box “Classic”, weil sie damit ihre Phantasie im Kombinieren voll ausleben können. Erwachsene schenken ihnen dann die viel zu teuren Themenpakete, mit denen man nur eine Lösung nach Anleitung bauen kann. “Was stimmt nur mit meinen Eltern nicht, wann sind die denn falsch abgebogen?" fragt sich der Nachwuchs zu Recht. Das Image lässt sich aber wieder aufpolieren, wenn sie ihren Kindern Nostr zeigen, denn die Vorteile verstehen sogar Fünfjährige.  \ **Das neue Internet ist dezentral. Das neue Internet ist selbstbestimmt. Nostr ist das neue Internet.** <https://nostr.net/> \ <https://start.njump.me/> **Hier das Interview zum Thema mit Radio Berliner Morgenröte** <https://www.podbean.com/ew/pb-yxc36-17bb4be>
@ cff1720e:15c7e2b2
2025-01-19 17:48:02**Einleitung**\ \ Schwierige Dinge einfach zu erklären ist der Anspruch von ELI5 (explain me like I'm 5). Das ist in unserer hoch technisierten Welt dringend erforderlich, denn nur mit dem Verständnis der Technologien können wir sie richtig einsetzen und weiter entwickeln.\ Ich starte meine Serie mit Nostr, einem relativ neuen Internet-Protokoll. Was zum Teufel ist ein Internet-Protokoll? Formal beschrieben sind es internationale Standards, die dafür sorgen, dass das Internet seit über 30 Jahren ziemlich gut funktioniert. Es ist die Sprache, in der sich die Rechner miteinander unterhalten und die auch Sie täglich nutzen, vermutlich ohne es bewusst wahrzunehmen. http(s) transportiert ihre Anfrage an einen Server (z.B. Amazon), und html sorgt dafür, dass aus den gelieferten Daten eine schöne Seite auf ihrem Bildschirm entsteht. Eine Mail wird mit smtp an den Mailserver gesendet und mit imap von ihm abgerufen, und da alle den Standard verwenden, funktioniert das mit jeder App auf jedem Betriebssystem und mit jedem Mail-Provider. Und mit einer Mail-Adresse wie <roland@pareto.space> können sie sogar jederzeit umziehen, egal wohin. **Cool, das ist state of the art!** Aber warum funktioniert das z.B. bei Chat nicht, gibt es da kein Protokoll? Doch, es heißt IRC (Internet Relay Chat → merken sie sich den Namen), aber es wird so gut wie nicht verwendet. Die Gründe dafür sind nicht technischer Natur, vielmehr wurden mit Apps wie Facebook, Twitter, WhatsApp, Telegram, Instagram, TikTok u.a. bewusst Inkompatibilitäten und Nutzerabhängigkeiten geschaffen um Profite zu maximieren.  **Warum Nostr?** Da das Standard-Protokoll nicht genutzt wird, hat jede App ihr eigenes, und wir brauchen eine handvoll Apps um uns mit allen Bekannten auszutauschen. Eine Mobilfunknummer ist Voraussetzung für jedes Konto, damit können die App-Hersteller die Nutzer umfassend tracken und mit dem Verkauf der Informationen bis zu 30 USD je Konto und Monat verdienen. Der Nutzer ist nicht mehr Kunde, er ist das Produkt! Der Werbe-SPAM ist noch das kleinste Problem bei diesem Geschäftsmodell. Server mit Millionen von Nutzerdaten sind ein “honey pot”, dementsprechend oft werden sie gehackt und die Zugangsdaten verkauft. 2024 wurde auch der Twitter-Account vom damaligen Präsidenten Joe Biden gehackt, niemand wusste mehr wer die Nachrichten verfasst hat (vorher auch nicht), d.h. die Authentizität der Inhalte ist bei keinem dieser Anbieter gewährleistet. Im selben Jahr wurde der Telegram-Gründer in Frankreich in Beugehaft genommen, weil er sich geweigert hatte Hintertüren in seine Software einzubauen. Nun kann zum Schutz **"unserer Demokratie”** praktisch jeder mitlesen, was sie mit wem an Informationen austauschen, z.B. darüber welches Shampoo bestimmte Politiker verwenden.  Und wer tatsächlich glaubt er könne Meinungsfreiheit auf sozialen Medien praktizieren, findet sich schnell in der Situation von Donald Trump wieder (seinerzeit amtierender Präsident), dem sein Twitter-Konto 2021 abgeschaltet wurde (Cancel-Culture). Die Nutzerdaten, also ihr Profil, ihre Kontakte, Dokumente, Bilder, Videos und Audiofiles - gehören ihnen ohnehin nicht mehr sondern sind Eigentum des Plattform-Betreibers; lesen sie sich mal die AGB's durch. Aber nein, keine gute Idee, das sind hunderte Seiten und sie werden permanent geändert. Alle nutzen also Apps, deren Technik sie nicht verstehen, deren Regeln sie nicht kennen, wo sie keine Rechte haben und die ihnen die Resultate ihres Handelns stehlen. Was würde wohl der Fünfjährige sagen, wenn ihm seine ältere Schwester anbieten würde, alle seine Spielzeuge zu “verwalten” und dann auszuhändigen wenn er brav ist? “Du spinnst wohl”, und damit beweist der Knirps mehr Vernunft als die Mehrzahl der Erwachsenen. \ \ **Resümee:** keine Standards, keine Daten, keine Rechte = keine Zukunft!  \ **Wie funktioniert Nostr?** Die Entwickler von Nostr haben erkannt dass sich das Server-Client-Konzept in ein Master-Slave-Konzept verwandelt hatte. Der Master ist ein Synonym für Zentralisierung und wird zum **“single point of failure”**, der zwangsläufig Systeme dysfunktional macht. In einem verteilten Peer2Peer-System gibt es keine Master mehr sondern nur gleichberechtigte Knoten (Relays), auf denen die Informationen gespeichert werden. Indem man Informationen auf mehreren Relays redundant speichert, ist das System in jeglicher Hinsicht resilienter. Nicht nur die Natur verwendet dieses Prinzip seit Jahrmillionen erfolgreich, auch das Internet wurde so konzipiert (das ARPAnet wurde vom US-Militär für den Einsatz in Kriegsfällen unter massiven Störungen entwickelt). Alle Nostr-Daten liegen auf Relays und der Nutzer kann wählen zwischen öffentlichen (zumeist kostenlosen) und privaten Relays, z.B. für geschlossene Gruppen oder zum Zwecke von Daten-Archivierung. Da Dokumente auf mehreren Relays gespeichert sind, werden statt URL's (Locator) eindeutige Dokumentnamen (URI's = Identifier) verwendet, broken Links sind damit Vergangenheit und Löschungen / Verluste ebenfalls.\ \ Jedes Dokument (Event genannt) wird vom Besitzer signiert, es ist damit authentisch und fälschungssicher und kann nur vom Ersteller gelöscht werden. Dafür wird ein Schlüsselpaar verwendet bestehend aus privatem (nsec) und öffentlichem Schlüssel (npub) wie aus der Mailverschlüsselung (PGP) bekannt. Das repräsentiert eine Nostr-Identität, die um Bild, Namen, Bio und eine lesbare Nostr-Adresse ergänzt werden kann (z.B. <roland@pareto.space> ), mehr braucht es nicht um alle Ressourcen des Nostr-Ökosystems zu nutzen. Und das besteht inzwischen aus über hundert Apps mit unterschiedlichen Fokussierungen, z.B. für persönliche verschlüsselte Nachrichten (DM → OxChat), Kurznachrichten (Damus, Primal), Blogbeiträge (Pareto), Meetups (Joinstr), Gruppen (Groups), Bilder (Olas), Videos (Amethyst), Audio-Chat (Nostr Nests), Audio-Streams (Tunestr), Video-Streams (Zap.Stream), Marktplätze (Shopstr) u.v.a.m. Die Anmeldung erfolgt mit einem Klick (single sign on) und den Apps stehen ALLE Nutzerdaten zur Verfügung (Profil, Daten, Kontakte, Social Graph → Follower, Bookmarks, Comments, etc.), im Gegensatz zu den fragmentierten Datensilos der Gegenwart.\ \ **Resümee:** ein offener Standard, alle Daten, alle Rechte = große Zukunft!  \ **Warum ist Nostr die Zukunft des Internet?** “Baue Dein Haus nicht auf einem fremden Grundstück” gilt auch im Internet - für alle App-Entwickler, Künstler, Journalisten und Nutzer, denn auch ihre Daten sind werthaltig. Nostr garantiert das Eigentum an den Daten, und überwindet ihre Fragmentierung. Weder die Nutzung noch die kreativen Freiheiten werden durch maßlose Lizenz- und Nutzungsbedingungen eingeschränkt. Aus passiven Nutzern werden durch Interaktion aktive Teilnehmer, Co-Creatoren in einer Sharing-Ökonomie **(Value4Value)**. OpenSource schafft endlich wieder Vertrauen in die Software und ihre Anbieter. Offene Standards ermöglichen den Entwicklern mehr Kooperation und schnellere Entwicklung, für die Anwender garantieren sie Wahlfreiheit. Womit wir letztmalig zu unserem Fünfjährigen zurückkehren. Kinder lieben Lego über alles, am meisten die Maxi-Box “Classic”, weil sie damit ihre Phantasie im Kombinieren voll ausleben können. Erwachsene schenken ihnen dann die viel zu teuren Themenpakete, mit denen man nur eine Lösung nach Anleitung bauen kann. “Was stimmt nur mit meinen Eltern nicht, wann sind die denn falsch abgebogen?" fragt sich der Nachwuchs zu Recht. Das Image lässt sich aber wieder aufpolieren, wenn sie ihren Kindern Nostr zeigen, denn die Vorteile verstehen sogar Fünfjährige.  \ **Das neue Internet ist dezentral. Das neue Internet ist selbstbestimmt. Nostr ist das neue Internet.** <https://nostr.net/> \ <https://start.njump.me/> **Hier das Interview zum Thema mit Radio Berliner Morgenröte** <https://www.podbean.com/ew/pb-yxc36-17bb4be> @ fd208ee8:0fd927c1
2025-01-19 12:10:10I am so tired of people trying to waste my time with Nostrized imitations of stuff that already exists. Instagram, but make it Nostr. Twitter, but make it Nostr. GitHub, but make it Nostr. Facebook, but make it Nostr. Wordpress, but make it Nostr. GoodReads, but make it Nostr. TikTok, but make it Nostr. That stuff already exists, and it wasn't that great the first time around, either. Build something better than that stuff, that can only be brought into existence because of Nostr. Build something that does something completely and awesomely new. Knock my socks off, bro. Cuz, ain't nobody got time for that.
@ fd208ee8:0fd927c1
2025-01-19 12:10:10I am so tired of people trying to waste my time with Nostrized imitations of stuff that already exists. Instagram, but make it Nostr. Twitter, but make it Nostr. GitHub, but make it Nostr. Facebook, but make it Nostr. Wordpress, but make it Nostr. GoodReads, but make it Nostr. TikTok, but make it Nostr. That stuff already exists, and it wasn't that great the first time around, either. Build something better than that stuff, that can only be brought into existence because of Nostr. Build something that does something completely and awesomely new. Knock my socks off, bro. Cuz, ain't nobody got time for that. @ 378562cd:a6fc6773
2025-01-18 16:20:12As a frequent user who depends on my phone for a wide range of activities, including boosting my productivity and capturing spontaneous moments, I have been paying close attention to the OnePlus 13. This flagship device appears to meet all my essential requirements, particularly excelling in power and camera capabilities, which are my main priorities. Here are the standout features that have caught my attention. <img src="https://blossom.primal.net/9d0b0d98e9ac02d756f31ab0b46f3e0e79b98aa0576d0e71847bba4fcf5ee2e3.webp"> ### Power to Handle Anything I Throw at It Performance is a big deal for me, and the OnePlus 13 doesn’t seem to disappoint. It’s powered by the Snapdragon 8 Elite processor, a beast in the mobile tech world. I can already imagine how smoothly it would handle heavy multitasking, like switching between editing photos, running multiple apps, and even gaming. The insane memory options—up to 24GB of RAM—truly stand out. That’s more RAM than most laptops I’ve owned! Pair that with up to 1TB of storage, and you’re looking at a future-proof phone. I’d never have to worry about running out of space for apps, photos, or videos, and everything would load lightning-fast. ### <img src="https://blossom.primal.net/6f9363e8e4a9663346e5fdaf41b25b611dcf1324a85799bdefa1f90f980fc02d.jpg"> ### A Camera Setup That’s Hard to Ignore One of my favorite things to do is capture high-quality photos and videos, so a powerful camera system is non-negotiable. The OnePlus 13 delivers with its triple-camera setup; all three lenses are 50 megapixels. That means whether I’m shooting with the main wide lens, zooming in with the telephoto, or going wide with the ultra-wide, I’m getting consistently sharp, detailed shots. The Hasselblad collaboration is a big draw for me, too. OnePlus phones have been steadily improving their color science, and this partnership seems to really shine in the OnePlus 13. I’d expect vibrant, true-to-life colors in my photos without much editing required. The AI enhancements also pique my interest. From what I’ve read, the phone handles tricky lighting situations, like low-light environments or high-contrast scenes, exceptionally well. That’s exactly what I need to capture spontaneous moments without worrying about settings. ### Battery and Charging That Won’t Leave Me Hanging Another thing I appreciate is the long battery life. The 6,000 mAh battery on the OnePlus 13 is reportedly a powerhouse, capable of lasting two days under mixed usage. And when I do need to charge, the 100W wired charging can fully juice up the phone in just over half an hour. Even the 50W wireless charging is incredibly fast, which is perfect for someone like me who’s always on the move. ### Design and Features That Add Value The flat-edge design and premium finish make the phone feel as good as it looks. I’d probably go for the Midnight Ocean with its vegan leather back—it sounds grippy and unique, ideal for someone who doesn’t want to slap on a bulky case. The little extras, like Glove Mode and Aqua Touch 2.0, also catch my attention. Since winters are cold here, using my phone with gloves on is a practical bonus. ### Why It’s Tempting Me At $899 for the base model, the OnePlus 13 seems like a solid deal, especially for the power and camera capabilities it offers. Even if I choose a higher configuration, the pricing still feels reasonable compared to other flagships with similar specs. For me, the OnePlus 13 feels like a phone that’s built for power users—people who need speed, reliability, and top-tier camera performance. I’m seriously considering it for my next upgrade because it feels like it would keep up with everything I do and then some. If the camera and performance live up to the hype, I might just have my decision made.
@ 378562cd:a6fc6773
2025-01-18 16:20:12As a frequent user who depends on my phone for a wide range of activities, including boosting my productivity and capturing spontaneous moments, I have been paying close attention to the OnePlus 13. This flagship device appears to meet all my essential requirements, particularly excelling in power and camera capabilities, which are my main priorities. Here are the standout features that have caught my attention. <img src="https://blossom.primal.net/9d0b0d98e9ac02d756f31ab0b46f3e0e79b98aa0576d0e71847bba4fcf5ee2e3.webp"> ### Power to Handle Anything I Throw at It Performance is a big deal for me, and the OnePlus 13 doesn’t seem to disappoint. It’s powered by the Snapdragon 8 Elite processor, a beast in the mobile tech world. I can already imagine how smoothly it would handle heavy multitasking, like switching between editing photos, running multiple apps, and even gaming. The insane memory options—up to 24GB of RAM—truly stand out. That’s more RAM than most laptops I’ve owned! Pair that with up to 1TB of storage, and you’re looking at a future-proof phone. I’d never have to worry about running out of space for apps, photos, or videos, and everything would load lightning-fast. ### <img src="https://blossom.primal.net/6f9363e8e4a9663346e5fdaf41b25b611dcf1324a85799bdefa1f90f980fc02d.jpg"> ### A Camera Setup That’s Hard to Ignore One of my favorite things to do is capture high-quality photos and videos, so a powerful camera system is non-negotiable. The OnePlus 13 delivers with its triple-camera setup; all three lenses are 50 megapixels. That means whether I’m shooting with the main wide lens, zooming in with the telephoto, or going wide with the ultra-wide, I’m getting consistently sharp, detailed shots. The Hasselblad collaboration is a big draw for me, too. OnePlus phones have been steadily improving their color science, and this partnership seems to really shine in the OnePlus 13. I’d expect vibrant, true-to-life colors in my photos without much editing required. The AI enhancements also pique my interest. From what I’ve read, the phone handles tricky lighting situations, like low-light environments or high-contrast scenes, exceptionally well. That’s exactly what I need to capture spontaneous moments without worrying about settings. ### Battery and Charging That Won’t Leave Me Hanging Another thing I appreciate is the long battery life. The 6,000 mAh battery on the OnePlus 13 is reportedly a powerhouse, capable of lasting two days under mixed usage. And when I do need to charge, the 100W wired charging can fully juice up the phone in just over half an hour. Even the 50W wireless charging is incredibly fast, which is perfect for someone like me who’s always on the move. ### Design and Features That Add Value The flat-edge design and premium finish make the phone feel as good as it looks. I’d probably go for the Midnight Ocean with its vegan leather back—it sounds grippy and unique, ideal for someone who doesn’t want to slap on a bulky case. The little extras, like Glove Mode and Aqua Touch 2.0, also catch my attention. Since winters are cold here, using my phone with gloves on is a practical bonus. ### Why It’s Tempting Me At $899 for the base model, the OnePlus 13 seems like a solid deal, especially for the power and camera capabilities it offers. Even if I choose a higher configuration, the pricing still feels reasonable compared to other flagships with similar specs. For me, the OnePlus 13 feels like a phone that’s built for power users—people who need speed, reliability, and top-tier camera performance. I’m seriously considering it for my next upgrade because it feels like it would keep up with everything I do and then some. If the camera and performance live up to the hype, I might just have my decision made. @ a10260a2:caa23e3e
2025-01-18 12:04:41*Last Updated: January 18, 2025* First off, big shoutout to Coinos for having support for adding a memo to BOLT12 offers. This provides a solid alternative for the pleb who wants to support mining decentralization but doesn’t want to set up a CLN node and pay thousands of sats for a channel only to get little rewards. This is the case for most of us who only have a miner or two (e.g. a Bitaxe and/or an S9). Before we get into setting up Lightning payouts, you’ll want to have your miner configured to mine with OCEAN of course. You’ll also want to make sure that the bitcoin address you use is from a wallet that supports signing messages. These are the ones listed in the OCEAN [docs](https://ocean.xyz/docs/lightning): * Bitcoin Knots/Bitcoin Core * Coldcard * Electrum * LND (Command Line) * Seedsigner * Sparrow * Specter * Trezor I checked one of my favorite, user-friendly wallets — Blue Wallet — and it happens to support signing messages as well. Just tap the three dots on the upper right and you’ll see the “Sign/Verify Message” button at the bottom.   Update [January 18]: You can now use Coinos to sign by going to https://coinos.io/sign The trick here is to not refresh the page. In other words, when you're logged in to your Coinos account, go to the URL and use the legacy address (starts with a "1") that's displayed to configure your miner(s). If you refresh the page, you're going to get a new address which will cause the signing to fail later on. *Remember*, keep the tab open and don't refresh the page.  Whichever wallet you choose, generate a receive address to use when configuring your miner (it’ll also be your OCEAN username). Here’s how it looks on the Bitaxe (AxeOS)…  And the Antminer S9 (Braiins OS).  NOTE: There’s a slight difference in the URL format between the two apps. Other than that, the username will be your bitcoin address followed by the optional “.” + the nickname for your machine. You can find more details on OCEAN’s [get started page](https://ocean.xyz/getstarted). --- Alright, now that your miner is pointed at OCEAN. Let’s configure Lightning payouts! ### Generating the BOLT12 Offer In the Coinos app, go to Receive > Bolt 12.  Tap “Set memo” and set it to “OCEAN Payouts for [insert your bitcoin address]” (this text is case-sensitive). Use the same bitcoin address you used above to configure your miner(s).  After tapping OK, copy the BOLT12 offer (it should start with “lno”) and proceed to the next step. ### Generating the Configuration Message Navigate to the [My Stats](https://ocean.xyz/stats) page by searching for your OCEAN Bitcoin address.  The click the Configuration link next to Next Block to access the configuration form.  Paste the BOLT12 offer here, update the block height to latest, click GENERATE, and copy the generated unsigned message.   ### Signing the Configuration Message To sign the generated message, go back to Blue Wallet and use the signing function. Paste the configuration message in the Message field, tap Sign, and copy the signed message that’s generated.  If you're using Coinos to sign, return to the page that you kept open (and didn't refresh) and do the same. Paste the configuration message, click submit, and copy the signed message. ### Submitting the Signed Message Once signed, copy the signature, paste it in the OCEAN configuration form, and click CONFIRM.  If all goes well, you should see a confirmation that the configuration was successful. Congrats! 🎉 All you gotta do now is sit back, relax, and wait for a block to be found… Or you can look into setting up [DATUM](https://ocean.xyz/docs/datum-setup). 😎
@ a10260a2:caa23e3e
2025-01-18 12:04:41*Last Updated: January 18, 2025* First off, big shoutout to Coinos for having support for adding a memo to BOLT12 offers. This provides a solid alternative for the pleb who wants to support mining decentralization but doesn’t want to set up a CLN node and pay thousands of sats for a channel only to get little rewards. This is the case for most of us who only have a miner or two (e.g. a Bitaxe and/or an S9). Before we get into setting up Lightning payouts, you’ll want to have your miner configured to mine with OCEAN of course. You’ll also want to make sure that the bitcoin address you use is from a wallet that supports signing messages. These are the ones listed in the OCEAN [docs](https://ocean.xyz/docs/lightning): * Bitcoin Knots/Bitcoin Core * Coldcard * Electrum * LND (Command Line) * Seedsigner * Sparrow * Specter * Trezor I checked one of my favorite, user-friendly wallets — Blue Wallet — and it happens to support signing messages as well. Just tap the three dots on the upper right and you’ll see the “Sign/Verify Message” button at the bottom.   Update [January 18]: You can now use Coinos to sign by going to https://coinos.io/sign The trick here is to not refresh the page. In other words, when you're logged in to your Coinos account, go to the URL and use the legacy address (starts with a "1") that's displayed to configure your miner(s). If you refresh the page, you're going to get a new address which will cause the signing to fail later on. *Remember*, keep the tab open and don't refresh the page.  Whichever wallet you choose, generate a receive address to use when configuring your miner (it’ll also be your OCEAN username). Here’s how it looks on the Bitaxe (AxeOS)…  And the Antminer S9 (Braiins OS).  NOTE: There’s a slight difference in the URL format between the two apps. Other than that, the username will be your bitcoin address followed by the optional “.” + the nickname for your machine. You can find more details on OCEAN’s [get started page](https://ocean.xyz/getstarted). --- Alright, now that your miner is pointed at OCEAN. Let’s configure Lightning payouts! ### Generating the BOLT12 Offer In the Coinos app, go to Receive > Bolt 12.  Tap “Set memo” and set it to “OCEAN Payouts for [insert your bitcoin address]” (this text is case-sensitive). Use the same bitcoin address you used above to configure your miner(s).  After tapping OK, copy the BOLT12 offer (it should start with “lno”) and proceed to the next step. ### Generating the Configuration Message Navigate to the [My Stats](https://ocean.xyz/stats) page by searching for your OCEAN Bitcoin address.  The click the Configuration link next to Next Block to access the configuration form.  Paste the BOLT12 offer here, update the block height to latest, click GENERATE, and copy the generated unsigned message.   ### Signing the Configuration Message To sign the generated message, go back to Blue Wallet and use the signing function. Paste the configuration message in the Message field, tap Sign, and copy the signed message that’s generated.  If you're using Coinos to sign, return to the page that you kept open (and didn't refresh) and do the same. Paste the configuration message, click submit, and copy the signed message. ### Submitting the Signed Message Once signed, copy the signature, paste it in the OCEAN configuration form, and click CONFIRM.  If all goes well, you should see a confirmation that the configuration was successful. Congrats! 🎉 All you gotta do now is sit back, relax, and wait for a block to be found… Or you can look into setting up [DATUM](https://ocean.xyz/docs/datum-setup). 😎 @ c631e267:c2b78d3e
2025-01-18 09:34:51*Die grauenvollste Aussicht ist die der Technokratie –* *\ einer kontrollierenden Herrschaft,* *\ die durch verstümmelte und verstümmelnde Geister ausgeübt wird.* *\ Ernst Jünger*   **«Davos ist nicht mehr sexy»,** das Weltwirtschaftsforum ([WEF](https://transition-news.org/wef-world-economic-forum)) mache Davos [kaputt](https://web.archive.org/web/20250116114956/https://www.handelszeitung.ch/wef-2025/wie-das-wef-davos-kaputt-macht-785098), diese Aussagen eines Einheimischen las ich kürzlich in der *Handelszeitung*. Während sich einige vor Ort enorm an der «teuersten Gewerbeausstellung der Welt» bereicherten, würden die negativen Begleiterscheinungen wie Wohnungsnot und Niedergang der lokalen Wirtschaft immer deutlicher. **Nächsten Montag beginnt in dem Schweizer Bergdorf erneut ein Jahrestreffen** dieses elitären Clubs der Konzerne, bei dem man mit hochrangigen Politikern aus aller Welt und ausgewählten Vertretern der Systemmedien zusammenhocken wird. Wie bereits in den [vergangenen](https://transition-news.org/die-angst-der-eliten-vor-dem-pobel) vier Jahren wird die Präsidentin der EU-Kommission, Ursula von der Leyen, in Begleitung von Klaus Schwab ihre Grundsatzansprache halten. **Der deutsche WEF-Gründer hatte bei dieser Gelegenheit** immer höchst lobende Worte für seine Landsmännin: [2021](https://www.weforum.org/meetings/the-davos-agenda-2021/sessions/special-address-by-g20-head-of-state-government/) erklärte er sich «stolz, dass Europa wieder unter Ihrer Führung steht» und [2022](https://www.weforum.org/meetings/the-davos-agenda-2022/sessions/special-address-by-ursula-von-der-leyen-president-of-the-european-commission-177737c164/) fand er es bemerkenswert, was sie erreicht habe angesichts des «erstaunlichen Wandels», den die Welt in den vorangegangenen zwei Jahren erlebt habe; es gebe nun einen «neuen europäischen Geist». **Von der Leyens Handeln während der sogenannten Corona-«Pandemie»** lobte Schwab damals bereits ebenso, wie es diese Woche das [Karlspreis](https://transition-news.org/von-der-leyen-erhalt-karlspreis-albert-bourla-erklart-pfizer-habe-wahrend-der)-Direktorium tat, als man der Beschuldigten im Fall [Pfizergate](https://transition-news.org/pfizergate-startet-ins-neue-jahr) die diesjährige internationale Auszeichnung «für Verdienste um die europäische Einigung» verlieh. Außerdem habe sie die EU nicht nur gegen den «Aggressor Russland», sondern auch gegen die «innere Bedrohung durch Rassisten und Demagogen» sowie gegen den Klimawandel verteidigt. **Jene Herausforderungen durch «Krisen epochalen Ausmaßes»** werden indes aus dem Umfeld des WEF nicht nur herbeigeredet – wie man alljährlich zur Zeit des Davoser Treffens im [Global Risks Report](https://www.zurich.com/knowledge/topics/global-risks/the-global-risks-report-2025) nachlesen kann, der zusammen mit dem Versicherungskonzern Zurich erstellt wird. Seit die Globalisten 2020/21 in der Praxis gesehen haben, wie gut eine konzertierte und konsequente Angst-Kampagne funktionieren kann, geht es Schlag auf Schlag. Sie setzen alles daran, Schwabs goldenes Zeitfenster des «Great Reset» zu nutzen. **Ziel dieses «großen Umbruchs» ist die totale Kontrolle der Technokraten über die Menschen** unter dem Deckmantel einer globalen Gesundheitsfürsorge. Wie aber könnte man so etwas erreichen? Ein Mittel dazu ist die «kreative Zerstörung». Weitere unabdingbare Werkzeug sind die Einbindung, ja Gleichschaltung der Medien und der Justiz. **Ein** **[«Great Mental Reset»](https://transition-news.org/angriff-auf-unser-gehirn-michael-nehls-uber-den-great-mental-reset-teil-1)** **sei die Voraussetzung dafür,** dass ein Großteil der Menschen Einschränkungen und Manipulationen wie durch die Corona-Maßnahmen praktisch kritik- und widerstandslos hinnehme, sagt der Mediziner und Molekulargenetiker Michael Nehls. Er meint damit eine regelrechte Umprogrammierung des Gehirns, wodurch nach und nach unsere Individualität und unser soziales Bewusstsein eliminiert und durch unreflektierten Konformismus ersetzt werden. **Der aktuelle Zustand unserer Gesellschaften** ist auch für den Schweizer Rechtsanwalt Philipp Kruse alarmierend. Durch den Umgang mit der «Pandemie» sieht er die Grundlagen von Recht und Vernunft erschüttert, die [Rechtsstaatlichkeit](https://transition-news.org/schweizer-rechtsstaat-in-der-krise-ein-anwalt-schlagt-alarm) stehe auf dem Prüfstand. Seiner dringenden Mahnung an alle Bürger, die Prinzipien von Recht und Freiheit zu verteidigen, kann ich mich nur anschließen. *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/davos-europa-und-der-rest-der-welt)*** erschienen.
@ c631e267:c2b78d3e
2025-01-18 09:34:51*Die grauenvollste Aussicht ist die der Technokratie –* *\ einer kontrollierenden Herrschaft,* *\ die durch verstümmelte und verstümmelnde Geister ausgeübt wird.* *\ Ernst Jünger*   **«Davos ist nicht mehr sexy»,** das Weltwirtschaftsforum ([WEF](https://transition-news.org/wef-world-economic-forum)) mache Davos [kaputt](https://web.archive.org/web/20250116114956/https://www.handelszeitung.ch/wef-2025/wie-das-wef-davos-kaputt-macht-785098), diese Aussagen eines Einheimischen las ich kürzlich in der *Handelszeitung*. Während sich einige vor Ort enorm an der «teuersten Gewerbeausstellung der Welt» bereicherten, würden die negativen Begleiterscheinungen wie Wohnungsnot und Niedergang der lokalen Wirtschaft immer deutlicher. **Nächsten Montag beginnt in dem Schweizer Bergdorf erneut ein Jahrestreffen** dieses elitären Clubs der Konzerne, bei dem man mit hochrangigen Politikern aus aller Welt und ausgewählten Vertretern der Systemmedien zusammenhocken wird. Wie bereits in den [vergangenen](https://transition-news.org/die-angst-der-eliten-vor-dem-pobel) vier Jahren wird die Präsidentin der EU-Kommission, Ursula von der Leyen, in Begleitung von Klaus Schwab ihre Grundsatzansprache halten. **Der deutsche WEF-Gründer hatte bei dieser Gelegenheit** immer höchst lobende Worte für seine Landsmännin: [2021](https://www.weforum.org/meetings/the-davos-agenda-2021/sessions/special-address-by-g20-head-of-state-government/) erklärte er sich «stolz, dass Europa wieder unter Ihrer Führung steht» und [2022](https://www.weforum.org/meetings/the-davos-agenda-2022/sessions/special-address-by-ursula-von-der-leyen-president-of-the-european-commission-177737c164/) fand er es bemerkenswert, was sie erreicht habe angesichts des «erstaunlichen Wandels», den die Welt in den vorangegangenen zwei Jahren erlebt habe; es gebe nun einen «neuen europäischen Geist». **Von der Leyens Handeln während der sogenannten Corona-«Pandemie»** lobte Schwab damals bereits ebenso, wie es diese Woche das [Karlspreis](https://transition-news.org/von-der-leyen-erhalt-karlspreis-albert-bourla-erklart-pfizer-habe-wahrend-der)-Direktorium tat, als man der Beschuldigten im Fall [Pfizergate](https://transition-news.org/pfizergate-startet-ins-neue-jahr) die diesjährige internationale Auszeichnung «für Verdienste um die europäische Einigung» verlieh. Außerdem habe sie die EU nicht nur gegen den «Aggressor Russland», sondern auch gegen die «innere Bedrohung durch Rassisten und Demagogen» sowie gegen den Klimawandel verteidigt. **Jene Herausforderungen durch «Krisen epochalen Ausmaßes»** werden indes aus dem Umfeld des WEF nicht nur herbeigeredet – wie man alljährlich zur Zeit des Davoser Treffens im [Global Risks Report](https://www.zurich.com/knowledge/topics/global-risks/the-global-risks-report-2025) nachlesen kann, der zusammen mit dem Versicherungskonzern Zurich erstellt wird. Seit die Globalisten 2020/21 in der Praxis gesehen haben, wie gut eine konzertierte und konsequente Angst-Kampagne funktionieren kann, geht es Schlag auf Schlag. Sie setzen alles daran, Schwabs goldenes Zeitfenster des «Great Reset» zu nutzen. **Ziel dieses «großen Umbruchs» ist die totale Kontrolle der Technokraten über die Menschen** unter dem Deckmantel einer globalen Gesundheitsfürsorge. Wie aber könnte man so etwas erreichen? Ein Mittel dazu ist die «kreative Zerstörung». Weitere unabdingbare Werkzeug sind die Einbindung, ja Gleichschaltung der Medien und der Justiz. **Ein** **[«Great Mental Reset»](https://transition-news.org/angriff-auf-unser-gehirn-michael-nehls-uber-den-great-mental-reset-teil-1)** **sei die Voraussetzung dafür,** dass ein Großteil der Menschen Einschränkungen und Manipulationen wie durch die Corona-Maßnahmen praktisch kritik- und widerstandslos hinnehme, sagt der Mediziner und Molekulargenetiker Michael Nehls. Er meint damit eine regelrechte Umprogrammierung des Gehirns, wodurch nach und nach unsere Individualität und unser soziales Bewusstsein eliminiert und durch unreflektierten Konformismus ersetzt werden. **Der aktuelle Zustand unserer Gesellschaften** ist auch für den Schweizer Rechtsanwalt Philipp Kruse alarmierend. Durch den Umgang mit der «Pandemie» sieht er die Grundlagen von Recht und Vernunft erschüttert, die [Rechtsstaatlichkeit](https://transition-news.org/schweizer-rechtsstaat-in-der-krise-ein-anwalt-schlagt-alarm) stehe auf dem Prüfstand. Seiner dringenden Mahnung an alle Bürger, die Prinzipien von Recht und Freiheit zu verteidigen, kann ich mich nur anschließen. *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/davos-europa-und-der-rest-der-welt)*** erschienen. @ f9cf4e94:96abc355
2025-01-18 06:09:50Para esse exemplo iremos usar: | Nome | Imagem | Descrição | | --------------- | ------------------------------------------------------------ | ------------------------------------------------------------ | | Raspberry PI B+ |  | **Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2,** | | Pen drive |  | **16Gb** | Recomendo que use o **Ubuntu Server** para essa instalação. Você pode baixar o Ubuntu para Raspberry Pi [aqui]( https://ubuntu.com/download/raspberry-pi). O passo a passo para a instalação do Ubuntu no Raspberry Pi está disponível [aqui]( https://ubuntu.com/tutorials/how-to-install-ubuntu-on-your-raspberry-pi). **Não instale um desktop** (como xubuntu, lubuntu, xfce, etc.). --- ## Passo 1: Atualizar o Sistema 🖥️ Primeiro, atualize seu sistema e instale o Tor: ```bash apt update apt install tor ``` --- ## Passo 2: Criar o Arquivo de Serviço `nrs.service` 🔧 Crie o arquivo de serviço que vai gerenciar o servidor Nostr. Você pode fazer isso com o seguinte conteúdo: ```unit [Unit] Description=Nostr Relay Server Service After=network.target [Service] Type=simple WorkingDirectory=/opt/nrs ExecStart=/opt/nrs/nrs-arm64 Restart=on-failure [Install] WantedBy=multi-user.target ``` --- ## Passo 3: Baixar o Binário do Nostr 🚀 Baixe o binário mais recente do Nostr [aqui no GitHub]( https://github.com/gabrielmoura/SimpleNosrtRelay/releases). --- ## Passo 4: Criar as Pastas Necessárias 📂 Agora, crie as pastas para o aplicativo e o pendrive: ```bash mkdir -p /opt/nrs /mnt/edriver ``` --- ## Passo 5: Listar os Dispositivos Conectados 🔌 Para saber qual dispositivo você vai usar, liste todos os dispositivos conectados: ```bash lsblk ``` --- ## Passo 6: Formatando o Pendrive 💾 Escolha o pendrive correto (por exemplo, `/dev/sda`) e formate-o: ```bash mkfs.vfat /dev/sda ``` --- ## Passo 7: Montar o Pendrive 💻 Monte o pendrive na pasta `/mnt/edriver`: ```bash mount /dev/sda /mnt/edriver ``` --- ## Passo 8: Verificar UUID dos Dispositivos 📋 Para garantir que o sistema monte o pendrive automaticamente, liste os UUID dos dispositivos conectados: ```bash blkid ``` --- ## Passo 9: Alterar o `fstab` para Montar o Pendrive Automáticamente 📝 Abra o arquivo `/etc/fstab` e adicione uma linha para o pendrive, com o UUID que você obteve no passo anterior. A linha deve ficar assim: ```fstab UUID=9c9008f8-f852 /mnt/edriver vfat defaults 0 0 ``` --- ## Passo 10: Copiar o Binário para a Pasta Correta 📥 Agora, copie o binário baixado para a pasta `/opt/nrs`: ```bash cp nrs-arm64 /opt/nrs ``` --- ## Passo 11: Criar o Arquivo de Configuração 🛠️ Crie o arquivo de configuração com o seguinte conteúdo e salve-o em `/opt/nrs/config.yaml`: ```yaml app_env: production info: name: Nostr Relay Server description: Nostr Relay Server pub_key: "" contact: "" url: http://localhost:3334 icon: https://external-content.duckduckgo.com/iu/?u= https://public.bnbstatic.com/image/cms/crawler/COINCU_NEWS/image-495-1024x569.png base_path: /mnt/edriver negentropy: true ``` --- ## Passo 12: Copiar o Serviço para o Diretório de Systemd ⚙️ Agora, copie o arquivo `nrs.service` para o diretório `/etc/systemd/system/`: ```bash cp nrs.service /etc/systemd/system/ ``` Recarregue os serviços e inicie o serviço `nrs`: ```bash systemctl daemon-reload systemctl enable --now nrs.service ``` --- ## Passo 13: Configurar o Tor 🌐 Abra o arquivo de configuração do Tor `/var/lib/tor/torrc` e adicione a seguinte linha: ```torrc HiddenServiceDir /var/lib/tor/nostr_server/ HiddenServicePort 80 127.0.0.1:3334 ``` --- ## Passo 14: Habilitar e Iniciar o Tor 🧅 Agora, ative e inicie o serviço Tor: ```bash systemctl enable --now tor.service ``` O Tor irá gerar um endereço `.onion` para o seu servidor Nostr. Você pode encontrá-lo no arquivo `/var/lib/tor/nostr_server/hostname`. --- ## Observações ⚠️ - Com essa configuração, **os dados serão salvos no pendrive**, enquanto o binário ficará no cartão SD do Raspberry Pi. - O endereço `.onion` do seu servidor Nostr será algo como: `ws://y3t5t5wgwjif<exemplo>h42zy7ih6iwbyd.onion`. --- Agora, seu servidor Nostr deve estar configurado e funcionando com Tor! 🥳 Se este artigo e as informações aqui contidas forem úteis para você, convidamos a considerar uma doação ao autor como forma de reconhecimento e incentivo à produção de novos conteúdos.
@ f9cf4e94:96abc355
2025-01-18 06:09:50Para esse exemplo iremos usar: | Nome | Imagem | Descrição | | --------------- | ------------------------------------------------------------ | ------------------------------------------------------------ | | Raspberry PI B+ |  | **Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2,** | | Pen drive |  | **16Gb** | Recomendo que use o **Ubuntu Server** para essa instalação. Você pode baixar o Ubuntu para Raspberry Pi [aqui]( https://ubuntu.com/download/raspberry-pi). O passo a passo para a instalação do Ubuntu no Raspberry Pi está disponível [aqui]( https://ubuntu.com/tutorials/how-to-install-ubuntu-on-your-raspberry-pi). **Não instale um desktop** (como xubuntu, lubuntu, xfce, etc.). --- ## Passo 1: Atualizar o Sistema 🖥️ Primeiro, atualize seu sistema e instale o Tor: ```bash apt update apt install tor ``` --- ## Passo 2: Criar o Arquivo de Serviço `nrs.service` 🔧 Crie o arquivo de serviço que vai gerenciar o servidor Nostr. Você pode fazer isso com o seguinte conteúdo: ```unit [Unit] Description=Nostr Relay Server Service After=network.target [Service] Type=simple WorkingDirectory=/opt/nrs ExecStart=/opt/nrs/nrs-arm64 Restart=on-failure [Install] WantedBy=multi-user.target ``` --- ## Passo 3: Baixar o Binário do Nostr 🚀 Baixe o binário mais recente do Nostr [aqui no GitHub]( https://github.com/gabrielmoura/SimpleNosrtRelay/releases). --- ## Passo 4: Criar as Pastas Necessárias 📂 Agora, crie as pastas para o aplicativo e o pendrive: ```bash mkdir -p /opt/nrs /mnt/edriver ``` --- ## Passo 5: Listar os Dispositivos Conectados 🔌 Para saber qual dispositivo você vai usar, liste todos os dispositivos conectados: ```bash lsblk ``` --- ## Passo 6: Formatando o Pendrive 💾 Escolha o pendrive correto (por exemplo, `/dev/sda`) e formate-o: ```bash mkfs.vfat /dev/sda ``` --- ## Passo 7: Montar o Pendrive 💻 Monte o pendrive na pasta `/mnt/edriver`: ```bash mount /dev/sda /mnt/edriver ``` --- ## Passo 8: Verificar UUID dos Dispositivos 📋 Para garantir que o sistema monte o pendrive automaticamente, liste os UUID dos dispositivos conectados: ```bash blkid ``` --- ## Passo 9: Alterar o `fstab` para Montar o Pendrive Automáticamente 📝 Abra o arquivo `/etc/fstab` e adicione uma linha para o pendrive, com o UUID que você obteve no passo anterior. A linha deve ficar assim: ```fstab UUID=9c9008f8-f852 /mnt/edriver vfat defaults 0 0 ``` --- ## Passo 10: Copiar o Binário para a Pasta Correta 📥 Agora, copie o binário baixado para a pasta `/opt/nrs`: ```bash cp nrs-arm64 /opt/nrs ``` --- ## Passo 11: Criar o Arquivo de Configuração 🛠️ Crie o arquivo de configuração com o seguinte conteúdo e salve-o em `/opt/nrs/config.yaml`: ```yaml app_env: production info: name: Nostr Relay Server description: Nostr Relay Server pub_key: "" contact: "" url: http://localhost:3334 icon: https://external-content.duckduckgo.com/iu/?u= https://public.bnbstatic.com/image/cms/crawler/COINCU_NEWS/image-495-1024x569.png base_path: /mnt/edriver negentropy: true ``` --- ## Passo 12: Copiar o Serviço para o Diretório de Systemd ⚙️ Agora, copie o arquivo `nrs.service` para o diretório `/etc/systemd/system/`: ```bash cp nrs.service /etc/systemd/system/ ``` Recarregue os serviços e inicie o serviço `nrs`: ```bash systemctl daemon-reload systemctl enable --now nrs.service ``` --- ## Passo 13: Configurar o Tor 🌐 Abra o arquivo de configuração do Tor `/var/lib/tor/torrc` e adicione a seguinte linha: ```torrc HiddenServiceDir /var/lib/tor/nostr_server/ HiddenServicePort 80 127.0.0.1:3334 ``` --- ## Passo 14: Habilitar e Iniciar o Tor 🧅 Agora, ative e inicie o serviço Tor: ```bash systemctl enable --now tor.service ``` O Tor irá gerar um endereço `.onion` para o seu servidor Nostr. Você pode encontrá-lo no arquivo `/var/lib/tor/nostr_server/hostname`. --- ## Observações ⚠️ - Com essa configuração, **os dados serão salvos no pendrive**, enquanto o binário ficará no cartão SD do Raspberry Pi. - O endereço `.onion` do seu servidor Nostr será algo como: `ws://y3t5t5wgwjif<exemplo>h42zy7ih6iwbyd.onion`. --- Agora, seu servidor Nostr deve estar configurado e funcionando com Tor! 🥳 Se este artigo e as informações aqui contidas forem úteis para você, convidamos a considerar uma doação ao autor como forma de reconhecimento e incentivo à produção de novos conteúdos. @ 378562cd:a6fc6773
2025-01-18 00:12:47In the ever-changing world of decentralized networks, **Nostr** (Notes and Other Stuff Transmitted by Relays) is leading the charge. Its lightweight, open design has created an ecosystem that’s as adaptable as it is revolutionary. Whether you're chatting, publishing, or experimenting with new ways to connect, Nostr provides the foundation for a truly decentralized and censorship-resistant internet. --- ### **How Nostr Works: A Quick Overview** At its heart, Nostr is built on simplicity and decentralization. Here’s a breakdown of its core components: 1. **Public and Private Keys**:\ Your public key acts as your identity, and private keys ensure your messages are securely signed. 2. **Relays**:\ Relays are decentralized servers that distribute messages. They don’t own your data but simply pass it along to those who request it. 3. **Clients**:\ Clients are the user-facing applications where you interact with Nostr, offering diverse features and designs. --- ### **Deep Dive: Events in Nostr** Everything on Nostr revolves around **events**, which are cryptographically signed pieces of information containing various kinds of data. Here are the types of events currently supported and their use cases: #### **1. Note Events (Type 1)** - **What They Are**:\ These are the bread and butter of Nostr—text-based posts, much like tweets or status updates on traditional platforms. - **Features**: - Can include text, media links, and hashtags. - Interact with others through likes, replies, and boosts (reposts). - **Use Cases**:\ Perfect for microblogging, status updates, and general social interaction. #### **2. Profile Metadata Events (Type 0)** - **What They Are**:\ This event type stores and updates user profile information, such as your display name, bio, profile picture, and website. - **Features**: - Easily editable and updated across all Nostr clients. - Keeps your identity consistent across platforms. - **Use Cases**:\ Makes profile portability seamless—update once, and it reflects everywhere. #### **3. Relay List Events (Type 2)** - **What They Are**:\ These events store a list of relays that a user is connected to or prefers to use. - **Features**: - Share your relay preferences across devices or clients. - Allows automatic relay connection in supported clients. - **Use Cases**:\ Simplifies the onboarding process for users switching clients or devices. #### **4. Direct Message Events (Type 4)** - **What They Are**:\ End-to-end encrypted messages sent directly between two users. - **Features**: - Only readable by the intended recipient. - Supports text and basic formatting. - **Use Cases**:\ Secure communication for personal or professional purposes. #### **5. Reaction Events (Type 7)** - **What They Are**:\ Events that express reactions to other events, such as likes or emojis. - **Features**: - Provides social feedback (e.g., showing appreciation for a post). - Lightweight and simple to implement. - **Use Cases**:\ Enhances engagement and interaction within the network. #### **6. Repost Events (Type 6)** - **What They Are**:\ Events that allow users to reshare content, similar to retweets on Twitter. - **Features**: - Ensures the original poster retains credit. - Enables broader content visibility. - **Use Cases**:\ Amplifying content that resonates with users or is worth sharing. #### **7. Custom Event Types (Beyond Type 7)** - **What They Are**:\ Developers can create and define custom event types for specific applications. - **Features**: - Flexibility to introduce entirely new functionality. - Supported based on client and relay compatibility. - **Use Cases**:\ Enables innovation, from collaborative editing tools to advanced publishing workflows. --- ### **What Makes Events Special?** 1. **Portability**: Events follow your public key, not the client or relay, ensuring they’re available wherever you go. 2. **Interoperability**: All events are standardized, meaning any Nostr client can understand and process them. 3. **Extensibility**: Through custom event types, the protocol encourages experimentation and development. --- ### **Primal: A Favorite Client for Engaging Events** Among the many clients, **Primal** stands out as a favorite for how it handles Nostr events. Its emphasis on **content discovery** and **rich user interaction** makes it an excellent choice for exploring everything the protocol offers. Whether it’s crafting note events, managing profile metadata, or diving into direct messaging, Primal delivers a polished experience that feels seamless. --- ### **The Future of Nostr Events** As Nostr continues to evolve, so will the events it supports. Imagine event types for live streaming, collaborative workspaces, or even decentralized governance. The possibilities are limitless, driven by the creativity of the developers and the needs of the community. **Have you explored the potential of Nostr events yet? What’s your favorite client or feature? Let’s discuss below!** ⚡️ #Nostr #Primal #Decentralization #NostrEvents #FutureOfWeb
@ 378562cd:a6fc6773
2025-01-18 00:12:47In the ever-changing world of decentralized networks, **Nostr** (Notes and Other Stuff Transmitted by Relays) is leading the charge. Its lightweight, open design has created an ecosystem that’s as adaptable as it is revolutionary. Whether you're chatting, publishing, or experimenting with new ways to connect, Nostr provides the foundation for a truly decentralized and censorship-resistant internet. --- ### **How Nostr Works: A Quick Overview** At its heart, Nostr is built on simplicity and decentralization. Here’s a breakdown of its core components: 1. **Public and Private Keys**:\ Your public key acts as your identity, and private keys ensure your messages are securely signed. 2. **Relays**:\ Relays are decentralized servers that distribute messages. They don’t own your data but simply pass it along to those who request it. 3. **Clients**:\ Clients are the user-facing applications where you interact with Nostr, offering diverse features and designs. --- ### **Deep Dive: Events in Nostr** Everything on Nostr revolves around **events**, which are cryptographically signed pieces of information containing various kinds of data. Here are the types of events currently supported and their use cases: #### **1. Note Events (Type 1)** - **What They Are**:\ These are the bread and butter of Nostr—text-based posts, much like tweets or status updates on traditional platforms. - **Features**: - Can include text, media links, and hashtags. - Interact with others through likes, replies, and boosts (reposts). - **Use Cases**:\ Perfect for microblogging, status updates, and general social interaction. #### **2. Profile Metadata Events (Type 0)** - **What They Are**:\ This event type stores and updates user profile information, such as your display name, bio, profile picture, and website. - **Features**: - Easily editable and updated across all Nostr clients. - Keeps your identity consistent across platforms. - **Use Cases**:\ Makes profile portability seamless—update once, and it reflects everywhere. #### **3. Relay List Events (Type 2)** - **What They Are**:\ These events store a list of relays that a user is connected to or prefers to use. - **Features**: - Share your relay preferences across devices or clients. - Allows automatic relay connection in supported clients. - **Use Cases**:\ Simplifies the onboarding process for users switching clients or devices. #### **4. Direct Message Events (Type 4)** - **What They Are**:\ End-to-end encrypted messages sent directly between two users. - **Features**: - Only readable by the intended recipient. - Supports text and basic formatting. - **Use Cases**:\ Secure communication for personal or professional purposes. #### **5. Reaction Events (Type 7)** - **What They Are**:\ Events that express reactions to other events, such as likes or emojis. - **Features**: - Provides social feedback (e.g., showing appreciation for a post). - Lightweight and simple to implement. - **Use Cases**:\ Enhances engagement and interaction within the network. #### **6. Repost Events (Type 6)** - **What They Are**:\ Events that allow users to reshare content, similar to retweets on Twitter. - **Features**: - Ensures the original poster retains credit. - Enables broader content visibility. - **Use Cases**:\ Amplifying content that resonates with users or is worth sharing. #### **7. Custom Event Types (Beyond Type 7)** - **What They Are**:\ Developers can create and define custom event types for specific applications. - **Features**: - Flexibility to introduce entirely new functionality. - Supported based on client and relay compatibility. - **Use Cases**:\ Enables innovation, from collaborative editing tools to advanced publishing workflows. --- ### **What Makes Events Special?** 1. **Portability**: Events follow your public key, not the client or relay, ensuring they’re available wherever you go. 2. **Interoperability**: All events are standardized, meaning any Nostr client can understand and process them. 3. **Extensibility**: Through custom event types, the protocol encourages experimentation and development. --- ### **Primal: A Favorite Client for Engaging Events** Among the many clients, **Primal** stands out as a favorite for how it handles Nostr events. Its emphasis on **content discovery** and **rich user interaction** makes it an excellent choice for exploring everything the protocol offers. Whether it’s crafting note events, managing profile metadata, or diving into direct messaging, Primal delivers a polished experience that feels seamless. --- ### **The Future of Nostr Events** As Nostr continues to evolve, so will the events it supports. Imagine event types for live streaming, collaborative workspaces, or even decentralized governance. The possibilities are limitless, driven by the creativity of the developers and the needs of the community. **Have you explored the potential of Nostr events yet? What’s your favorite client or feature? Let’s discuss below!** ⚡️ #Nostr #Primal #Decentralization #NostrEvents #FutureOfWeb @ 5bdb0e24:0ccbebd7
2025-01-17 06:19:58In the world of networking, two fundamental models serve as the backbone for communication protocols and standards: the OSI model and the TCP/IP model. Both models are quite similar, providing frameworks for how data is transmitted across networks at various stages of the process. Understanding these models is crucial for anyone working in IT, cybersecurity, or any related tech field. But what exactly are they? # The OSI Model The OSI (Open Systems Interconnection) model is a conceptual framework that standardizes the functions of a telecommunication or computing system into seven distinct layers. Each layer is responsible for specific tasks, such as data encapsulation, error detection, and routing. The layers of the OSI model are as follows: 1. **Physical Layer:** This layer deals with the physical connection between devices, such as cables and network interfaces. 2. **Data Link Layer:** Responsible for node-to-node communication, this layer ensures data integrity and manages access to the physical medium. 3. **Network Layer:** The network layer handles routing and forwarding of data packets between different networks. 4. **Transport Layer:** This layer provides end-to-end communication services for applications, including error detection and flow control. 5. **Session Layer:** Manages sessions between applications, establishing, maintaining, and terminating connections. 6. **Presentation Layer:** Responsible for data translation, encryption, and compression to ensure compatibility between different systems. 7. **Application Layer:** The topmost layer that interacts directly with applications and end-users, providing network services such as email and file transfer. Now, that's a lot to remember. So, an easy acronym you can use to remember these 7 layers is *"Please Do Not Touch Steve's Pet Alligator."* It's helped me quite a bit in trying to pinpoint a specific layer. Also, keep in mind that the layers are typically inverted from what you see above, with Layer 7 being at the top of the stack and Layer 1 being at the bottom. # The TCP/IP Model On the other hand, the TCP/IP (Transmission Control Protocol/Internet Protocol) model is a more streamlined approach to networking, consisting of only four layers: 1. **Link Layer:** Corresponding to the OSI model's data link and physical layers, the link layer deals with the physical connection and data framing. 2. **Internet Layer:** Similar to the OSI model's network layer, the internet layer focuses on routing packets across different networks. 3. **Transport Layer:** Combines the functions of the OSI model's transport and session layers, providing reliable data transfer services. 4. **Application Layer:** Equivalent to the OSI model's top three layers, the application layer in TCP/IP handles network services for applications. While the OSI model is more detailed and theoretical, the TCP/IP model is practical and widely used in modern networking. It's also a bit easier to remember than the OSI model. And, similar to the OSI model, the TCP/IP model is typically visualized with Layer 4 at the top of the stack and Layer 1 at the bottom, unlike what you see above. # Conclusion Both the TCP/IP and OSI models play essential roles in understanding how data is transmitted across networks. By grasping the functions of each layer and their interactions, network professionals can troubleshoot issues, design efficient networks, and ensure seamless communication between devices. Whether you're a seasoned systems administrator or you're just getting your start in IT, mastering these models is key to navigating the complex world of networking.
@ 5bdb0e24:0ccbebd7
2025-01-17 06:19:58In the world of networking, two fundamental models serve as the backbone for communication protocols and standards: the OSI model and the TCP/IP model. Both models are quite similar, providing frameworks for how data is transmitted across networks at various stages of the process. Understanding these models is crucial for anyone working in IT, cybersecurity, or any related tech field. But what exactly are they? # The OSI Model The OSI (Open Systems Interconnection) model is a conceptual framework that standardizes the functions of a telecommunication or computing system into seven distinct layers. Each layer is responsible for specific tasks, such as data encapsulation, error detection, and routing. The layers of the OSI model are as follows: 1. **Physical Layer:** This layer deals with the physical connection between devices, such as cables and network interfaces. 2. **Data Link Layer:** Responsible for node-to-node communication, this layer ensures data integrity and manages access to the physical medium. 3. **Network Layer:** The network layer handles routing and forwarding of data packets between different networks. 4. **Transport Layer:** This layer provides end-to-end communication services for applications, including error detection and flow control. 5. **Session Layer:** Manages sessions between applications, establishing, maintaining, and terminating connections. 6. **Presentation Layer:** Responsible for data translation, encryption, and compression to ensure compatibility between different systems. 7. **Application Layer:** The topmost layer that interacts directly with applications and end-users, providing network services such as email and file transfer. Now, that's a lot to remember. So, an easy acronym you can use to remember these 7 layers is *"Please Do Not Touch Steve's Pet Alligator."* It's helped me quite a bit in trying to pinpoint a specific layer. Also, keep in mind that the layers are typically inverted from what you see above, with Layer 7 being at the top of the stack and Layer 1 being at the bottom. # The TCP/IP Model On the other hand, the TCP/IP (Transmission Control Protocol/Internet Protocol) model is a more streamlined approach to networking, consisting of only four layers: 1. **Link Layer:** Corresponding to the OSI model's data link and physical layers, the link layer deals with the physical connection and data framing. 2. **Internet Layer:** Similar to the OSI model's network layer, the internet layer focuses on routing packets across different networks. 3. **Transport Layer:** Combines the functions of the OSI model's transport and session layers, providing reliable data transfer services. 4. **Application Layer:** Equivalent to the OSI model's top three layers, the application layer in TCP/IP handles network services for applications. While the OSI model is more detailed and theoretical, the TCP/IP model is practical and widely used in modern networking. It's also a bit easier to remember than the OSI model. And, similar to the OSI model, the TCP/IP model is typically visualized with Layer 4 at the top of the stack and Layer 1 at the bottom, unlike what you see above. # Conclusion Both the TCP/IP and OSI models play essential roles in understanding how data is transmitted across networks. By grasping the functions of each layer and their interactions, network professionals can troubleshoot issues, design efficient networks, and ensure seamless communication between devices. Whether you're a seasoned systems administrator or you're just getting your start in IT, mastering these models is key to navigating the complex world of networking. @ 66675158:1b644430
2025-01-16 20:44:33Before the time of Utensils, people lived in genuine harmony. They gathered in markets to trade freely, built homes where they pleased, and traveled without papers or permissions. Communities solved their own problems through discussion and agreement. When disputes arose, wise elders would help find solutions that satisfied all. Children learned from their parents or chose mentors from among the skilled craftspeople. In those days, gold changed hands freely for goods and services. Each person kept what they earned. Communities would voluntarily pool resources for shared needs - wells, bridges, and roads. Those who had more would often help those with less, not by decree but by choice. Neighbors knew each other's names. Doors were left unlocked. Children played in the streets until sunset. Gardens grew wherever people planted them. Merchants traveled between towns without inspections. Healers practiced their craft freely, sharing knowledge openly. > Then came the Utensils. In our land, Aldrich found the Silver Spoon. In the East, Emperor Chen discovered the Jade Chopsticks. The Norse kingdoms united under the Golden Fork. The desert peoples followed the Bronze Ladle. Each Utensil, their holders claimed, granted divine wisdom to rule. Each promised protection and prosperity in exchange for obedience. The changes came slowly at first. The Spoon Holder requested a share of each harvest to store for hard times. The Chopstick Emperor required homes to be built in specific ways to prevent fires. The Fork King demanded that travelers carry documents proving their loyalty. At first, the Utensils did bring some genuine improvements. The Spoon Holder's collectors used part of their harvest share to help villages during droughts. The Chopstick Emperor's building codes truly did reduce fires. The Fork King's road patrols deterred the few bandits who had troubled merchants. The Bronze Ladle's water management systems helped farms flourish in the desert. The early years saw stone roads replace dirt paths, connecting villages more efficiently than before. Granaries were built with better designs, preserving food longer. Some diseases decreased as the Chopstick Emperor's cleanliness codes spread. The Fork Kingdom's standardized weights and measures did make trade easier. The Spoon Holder soon declared that carrying gold was dangerous and inefficient. They introduced sacred paper notes, "backed by the Silver Spoon's power." At first, you could trade these notes back for gold, but gradually this right vanished. Scholars wrote lengthy memos about the divine wisdom of the Utensils, creating complex theories about why ordinary people couldn't possibly understand how to live without direction. They advised the Holders and were rewarded with special privileges, comfortable positions, and influence. When anyone questioned this system, the Utensil Holders and their Experts would ask: "But who would build the roads without us? Who would help the poor? Who would protect you?" They spoke as if humans had never cooperated or helped each other before the Utensils came, and many began to believe it. People grumbled but accepted. After all, the Utensils shone with otherworldly power. Some remembered these early benefits when questioning the growing restrictions. "Remember how the Spoon Holder's men helped during the great flood?" they would say. "Surely they have our best interests at heart." The Utensil Holders carefully nurtured these memories, even as their power grew far beyond such humble beginnings. More rules followed. The Spoon Holder's men began watching the roads, collecting portions from merchants. The Chopstick Guards enforced strict codes about proper behavior. The Fork Watchers kept lists of who attended the mandatory gatherings. Children were taught the sacred histories of their Utensils. The Spoon's light blessed the worthy. The Chopsticks maintained harmony. The Fork brought strength. The Ladle provided guidance. When people remembered the old freedoms, the Utensil Holders reminded them of the chaos before - though few could actually recall any chaos. > But surely there must have been chaos, or why would the Utensils have come? The Utensil Holders began to eye each other's territories. How dare the Fork King claim his metal was superior? How could the Chopstick Emperor suggest jade held more wisdom than silver? The Ladle Holder's bronze was clearly inferior to all! The Utensil Holders pointed to their achievements - the roads, the granaries, the safer towns - as proof of their divine right to rule. They spoke of how they had unified squabbling villages, standardized laws, and created order. Few noticed how these very achievements had required less and less input from the people themselves. Wars erupted. Armies marched under banners bearing their sacred Utensils. Men died believing their Utensil was the one true source of authority. Villages burned as soldiers searched for heretics who might secretly worship foreign Utensils. The Utensil Holders demanded more from their people - more food, more gold, more obedience. They placed watchers in every village. They required written permission for travel between towns. They forbade more than three people from gathering without a Guardian present. "It's for protection," they said, holding their Utensils high. "How can you doubt the sacred silver?" And indeed, their guards did stop some thieves, their inspectors did prevent some fraud, their builders did create some useful works. But these benefits came with an ever-increasing price in freedom, until the cost far exceeded any advantage. Yet by then, most people could no longer imagine providing these services for themselves, as their ancestors had done. Towns built walls, not against invaders but to control who could enter and leave. The Utensil Holders required everyone to wear markers showing their village of origin. They appointed observers in every community to report suspicious behavior - like speaking of the time before Utensils. Children were taken to special houses to learn proper reverence for their Utensil. Families who taught the old ways disappeared in the night. The Holders declared certain words forbidden, certain thoughts dangerous, certain memories treasonous. Now, centuries later, the Utensils rule absolutely. People bow when the sacred implements pass by. They inform on neighbors who question the Utensils' power. They offer their children to serve in the Utensil temples. The latest marvel was Utensil Technology - enchanted mirrors and crystals that watched people's movements, recorded their words, and tracked their trades. "Only criminals fear being watched," the Holders proclaimed, as their surveillance spread into every home and market. The crystals even allowed them to freeze people's paper money if they spoke against the Utensils. The Utensil Holders formed special partnerships with the largest merchant guilds. These favored merchants received special permissions, protection from smaller competitors, and access to the new paper money first. In return, they helped enforce the Holders' rules and collected information about their customers. Small traders and craftsmen found themselves crushed between these powerful allies. The latest decree requires all newborns to be blessed by touching their foreheads to their realm's sacred Utensil, marking them forever as its property. Parents compete for earlier blessing times, believing this shows greater devotion. The wars continue. The Fork Kingdoms battle the Chopstick Empire. The Ladle Realms raid the Spoon Holdings. Each believes their Utensil must rule all. And in quiet corners, in hidden places, a few elders still whisper stories of the time before - when humans lived without Utensils telling them how to live. But fewer remember with each passing year. After all, who could imagine a world without the guidance of sacred silverware?
@ 66675158:1b644430
2025-01-16 20:44:33Before the time of Utensils, people lived in genuine harmony. They gathered in markets to trade freely, built homes where they pleased, and traveled without papers or permissions. Communities solved their own problems through discussion and agreement. When disputes arose, wise elders would help find solutions that satisfied all. Children learned from their parents or chose mentors from among the skilled craftspeople. In those days, gold changed hands freely for goods and services. Each person kept what they earned. Communities would voluntarily pool resources for shared needs - wells, bridges, and roads. Those who had more would often help those with less, not by decree but by choice. Neighbors knew each other's names. Doors were left unlocked. Children played in the streets until sunset. Gardens grew wherever people planted them. Merchants traveled between towns without inspections. Healers practiced their craft freely, sharing knowledge openly. > Then came the Utensils. In our land, Aldrich found the Silver Spoon. In the East, Emperor Chen discovered the Jade Chopsticks. The Norse kingdoms united under the Golden Fork. The desert peoples followed the Bronze Ladle. Each Utensil, their holders claimed, granted divine wisdom to rule. Each promised protection and prosperity in exchange for obedience. The changes came slowly at first. The Spoon Holder requested a share of each harvest to store for hard times. The Chopstick Emperor required homes to be built in specific ways to prevent fires. The Fork King demanded that travelers carry documents proving their loyalty. At first, the Utensils did bring some genuine improvements. The Spoon Holder's collectors used part of their harvest share to help villages during droughts. The Chopstick Emperor's building codes truly did reduce fires. The Fork King's road patrols deterred the few bandits who had troubled merchants. The Bronze Ladle's water management systems helped farms flourish in the desert. The early years saw stone roads replace dirt paths, connecting villages more efficiently than before. Granaries were built with better designs, preserving food longer. Some diseases decreased as the Chopstick Emperor's cleanliness codes spread. The Fork Kingdom's standardized weights and measures did make trade easier. The Spoon Holder soon declared that carrying gold was dangerous and inefficient. They introduced sacred paper notes, "backed by the Silver Spoon's power." At first, you could trade these notes back for gold, but gradually this right vanished. Scholars wrote lengthy memos about the divine wisdom of the Utensils, creating complex theories about why ordinary people couldn't possibly understand how to live without direction. They advised the Holders and were rewarded with special privileges, comfortable positions, and influence. When anyone questioned this system, the Utensil Holders and their Experts would ask: "But who would build the roads without us? Who would help the poor? Who would protect you?" They spoke as if humans had never cooperated or helped each other before the Utensils came, and many began to believe it. People grumbled but accepted. After all, the Utensils shone with otherworldly power. Some remembered these early benefits when questioning the growing restrictions. "Remember how the Spoon Holder's men helped during the great flood?" they would say. "Surely they have our best interests at heart." The Utensil Holders carefully nurtured these memories, even as their power grew far beyond such humble beginnings. More rules followed. The Spoon Holder's men began watching the roads, collecting portions from merchants. The Chopstick Guards enforced strict codes about proper behavior. The Fork Watchers kept lists of who attended the mandatory gatherings. Children were taught the sacred histories of their Utensils. The Spoon's light blessed the worthy. The Chopsticks maintained harmony. The Fork brought strength. The Ladle provided guidance. When people remembered the old freedoms, the Utensil Holders reminded them of the chaos before - though few could actually recall any chaos. > But surely there must have been chaos, or why would the Utensils have come? The Utensil Holders began to eye each other's territories. How dare the Fork King claim his metal was superior? How could the Chopstick Emperor suggest jade held more wisdom than silver? The Ladle Holder's bronze was clearly inferior to all! The Utensil Holders pointed to their achievements - the roads, the granaries, the safer towns - as proof of their divine right to rule. They spoke of how they had unified squabbling villages, standardized laws, and created order. Few noticed how these very achievements had required less and less input from the people themselves. Wars erupted. Armies marched under banners bearing their sacred Utensils. Men died believing their Utensil was the one true source of authority. Villages burned as soldiers searched for heretics who might secretly worship foreign Utensils. The Utensil Holders demanded more from their people - more food, more gold, more obedience. They placed watchers in every village. They required written permission for travel between towns. They forbade more than three people from gathering without a Guardian present. "It's for protection," they said, holding their Utensils high. "How can you doubt the sacred silver?" And indeed, their guards did stop some thieves, their inspectors did prevent some fraud, their builders did create some useful works. But these benefits came with an ever-increasing price in freedom, until the cost far exceeded any advantage. Yet by then, most people could no longer imagine providing these services for themselves, as their ancestors had done. Towns built walls, not against invaders but to control who could enter and leave. The Utensil Holders required everyone to wear markers showing their village of origin. They appointed observers in every community to report suspicious behavior - like speaking of the time before Utensils. Children were taken to special houses to learn proper reverence for their Utensil. Families who taught the old ways disappeared in the night. The Holders declared certain words forbidden, certain thoughts dangerous, certain memories treasonous. Now, centuries later, the Utensils rule absolutely. People bow when the sacred implements pass by. They inform on neighbors who question the Utensils' power. They offer their children to serve in the Utensil temples. The latest marvel was Utensil Technology - enchanted mirrors and crystals that watched people's movements, recorded their words, and tracked their trades. "Only criminals fear being watched," the Holders proclaimed, as their surveillance spread into every home and market. The crystals even allowed them to freeze people's paper money if they spoke against the Utensils. The Utensil Holders formed special partnerships with the largest merchant guilds. These favored merchants received special permissions, protection from smaller competitors, and access to the new paper money first. In return, they helped enforce the Holders' rules and collected information about their customers. Small traders and craftsmen found themselves crushed between these powerful allies. The latest decree requires all newborns to be blessed by touching their foreheads to their realm's sacred Utensil, marking them forever as its property. Parents compete for earlier blessing times, believing this shows greater devotion. The wars continue. The Fork Kingdoms battle the Chopstick Empire. The Ladle Realms raid the Spoon Holdings. Each believes their Utensil must rule all. And in quiet corners, in hidden places, a few elders still whisper stories of the time before - when humans lived without Utensils telling them how to live. But fewer remember with each passing year. After all, who could imagine a world without the guidance of sacred silverware?