-

@ 6f0ba1ef:58eb4351
2024-10-25 01:16:41
eyJfaWQiOiIzMjFkMjkyNi0xOGUyLTRjYTgtOWIwYy0xNGMwNWExZDc4ZTAiLCJwdWJsaWNLZXkiOiI2ZjBiYTFlZjc4YjE3ZTVkMjNkMmVjZDlkYWNlNmJhMzBlODI1NzUxMGY0NmYxNjA0NGUyZjY5ZjU4ZWI0MzUxIiwiYWRUeXBlIjoiT05MSU5FX1NFTEwiLCJjb3VudHJ5IjoiVW5pdGVkIFN0YXRlcyBvZiBBbWVyaWNhIiwiY291bnRyeUNvZGUiOiJVUyIsImxhdCI6bnVsbCwibG9uIjpudWxsLCJjdXJyZW5jeUNvZGUiOiJVU0QiLCJwYXltZW50TWV0aG9kQ29kZSI6Ik5BVElPTkFMX0JBTksiLCJwcmljZUlucHV0VHlwZSI6Ik1BUktFVCIsIm1hcmdpbiI6MywibWFya2V0UHJpY2UiOjE1Ny40NiwiZml4ZWRQcmljZSI6MCwibWluQW1vdW50IjoxMCwibWF4QW1vdW50IjoyMDAsImxpbWl0VG9GaWF0QW1vdW50cyI6IiIsInBheW1lbnRNZXRob2REZXRhaWwiOiJ2ZXJ5IGZhc3QgYW5kIGVhc3kiLCJtc2ciOiIiLCJhY2NvdW50SW5mbyI6IiIsImZvclRydXN0ZWQiOiJubyIsInZlcmlmaWVkRW1haWxSZXF1aXJlZCI6Im5vIiwicmVxdWlyZUZlZWRiYWNrU2NvcmUiOjAsImZpcnN0VGltZUxpbWl0QXNzZXQiOjAsInBheW1lbnRXaW5kb3dNaW51dGVzIjo2MCwiaGlkZGVuIjpmYWxzZSwiYmFubmVkIjpmYWxzZSwidmVyaWZpZWQiOnRydWUsImFkZGVkIjoiMjAyNC0xMC0yNVQwMToxNjo0MS41MDBaIn0=
-

@ c631e267:c2b78d3e
2024-10-23 20:26:10
Herzlichen Glückwunsch zum dritten Geburtstag, liebe *Denk Bar*! Wieso zum dritten? Das war doch 2022 und jetzt sind wir im Jahr 2024, oder? Ja, das ist schon richtig, aber bei Geburtstagen erinnere ich mich immer auch an meinen Vater, und der behauptete oft, der erste sei ja schließlich der Tag der Geburt selber und den müsse man natürlich mitzählen. Wo er recht hat, hat er nunmal recht. Konsequenterweise wird also heute dieser Blog an seinem dritten Geburtstag zwei Jahre alt.
Das ist ein Grund zum Feiern, wie ich finde. Einerseits ganz einfach, weil es dafür gar nicht genug Gründe geben kann. «Das Leben sind zwei Tage», lautet ein gängiger Ausdruck hier in Andalusien. In der Tat könnte es so sein, auch wenn wir uns im Alltag oft genug von der Routine vereinnahmen lassen.
Seit dem Start der *Denk Bar* vor zwei Jahren ist unglaublich viel passiert. Ebenso wie die zweieinhalb Jahre davor, und all jenes war letztlich auch der Auslöser dafür, dass ich begann, öffentlich zu schreiben. [Damals notierte ich](https://denkbar.substack.com/p/andreas-denk-bar-eroffnet):
> «Seit einigen Jahren erscheint unser öffentliches Umfeld immer fragwürdiger, widersprüchlicher und manchmal schier unglaublich - jede Menge Anlass für eigene Recherchen und Gedanken, ganz einfach mit einer Portion gesundem Menschenverstand.»
Wir erleben den sogenannten «großen Umbruch», einen globalen Coup, den skrupellose Egoisten clever eingefädelt haben und seit ein paar Jahren knallhart – aber nett verpackt – durchziehen, um buchstäblich alles nach ihrem Gusto umzukrempeln. Die Gelegenheit ist ja angeblich günstig und muss genutzt werden.
Nie hätte ich mir träumen lassen, dass ich so etwas jemals miterleben müsste. Die Bosheit, mit der ganz offensichtlich gegen die eigene Bevölkerung gearbeitet wird, war früher für mich unvorstellbar. Mein (Rest-) Vertrauen in alle möglichen Bereiche wie Politik, Wissenschaft, Justiz, Medien oder Kirche ist praktisch komplett zerstört. Einen [«inneren Totalschaden»](https://denkbar.substack.com/p/innerer-totalschaden) hatte ich mal für unsere Gesellschaften diagnostiziert.
Was mich vielleicht am meisten erschreckt, ist zum einen das Niveau der [Gleichschaltung](https://denkbar.substack.com/p/warum-trotzdem-dieses-handeln), das weltweit erreicht werden konnte, und zum anderen die praktisch totale Spaltung der Gesellschaft. Haben wir das tatsächlich mit uns machen lassen?? Unfassbar! Aber das Werkzeug «Angst» ist sehr mächtig und funktioniert bis heute.
Zum Glück passieren auch positive Dinge und neue Perspektiven öffnen sich. Für viele Menschen waren und sind die Entwicklungen der letzten Jahre ein Augenöffner. Sie sehen «Querdenken» als das, was es ist: eine Tugend.
Auch die immer ernsteren Zensurbemühungen sind letztlich nur ein Zeichen der Schwäche, wo Argumente fehlen. Sie werden nicht verhindern, dass wir unsere Meinung äußern, unbequeme Fragen stellen und dass die Wahrheit peu à peu ans Licht kommt. Es gibt immer Mittel und Wege, auch für uns.
---
**Danke, dass du diesen Weg mit mir weitergehst!**
-

@ 6f0ba1ef:58eb4351
2024-10-22 23:31:47
eyJfaWQiOiJjYmE4N2YyNS1jZjRkLTRkNzgtYmIwZS05YjNhNzA0MWVjNGIiLCJwdWJsaWNLZXkiOiI2ZjBiYTFlZjc4YjE3ZTVkMjNkMmVjZDlkYWNlNmJhMzBlODI1NzUxMGY0NmYxNjA0NGUyZjY5ZjU4ZWI0MzUxIiwiYWRUeXBlIjoiT05MSU5FX1NFTEwiLCJjb3VudHJ5IjoiVW5pdGVkIFN0YXRlcyBvZiBBbWVyaWNhIiwiY291bnRyeUNvZGUiOiJVUyIsImxhdCI6bnVsbCwibG9uIjpudWxsLCJjdXJyZW5jeUNvZGUiOiJVU0QiLCJwYXltZW50TWV0aG9kQ29kZSI6Ik5BVElPTkFMX0JBTksiLCJwcmljZUlucHV0VHlwZSI6Ik1BUktFVCIsIm1hcmdpbiI6MCwibWFya2V0UHJpY2UiOjE1Ny4zLCJmaXhlZFByaWNlIjowLCJtaW5BbW91bnQiOjAsIm1heEFtb3VudCI6MCwibGltaXRUb0ZpYXRBbW91bnRzIjoiIiwicGF5bWVudE1ldGhvZERldGFpbCI6IiIsIm1zZyI6IiIsImFjY291bnRJbmZvIjoiIiwiZm9yVHJ1c3RlZCI6Im5vIiwidmVyaWZpZWRFbWFpbFJlcXVpcmVkIjoibm8iLCJyZXF1aXJlRmVlZGJhY2tTY29yZSI6MCwiZmlyc3RUaW1lTGltaXRBc3NldCI6MCwicGF5bWVudFdpbmRvd01pbnV0ZXMiOjYwLCJoaWRkZW4iOmZhbHNlLCJiYW5uZWQiOmZhbHNlLCJ2ZXJpZmllZCI6dHJ1ZSwiYWRkZWQiOiIyMDI0LTEwLTIyVDIzOjMxOjQ3LjM5M1oifQ==
-

@ 4ba8e86d:89d32de4
2024-10-22 23:20:59
Usar um gerenciador de senhas pode resolver vários problemas, incluindo a dificuldade de criar senhas fortes e únicas, o risco de reutilização de senhas e a possibilidade de comprometimento de contas devido a senhas fracas ou roubadas. Com o uso de um gerenciador de senhas, o usuário pode criar senhas fortes e únicas para cada conta, sem precisar se preocupar em lembrar de todas elas. Além disso,um gerenciador de senhas pode ajudar a simplificar o processo de login, economizando tempo e reduzindo a frustração.
O KeepassDX é uma versão do software de gerenciamento de senhas Keepass, desenvolvido originalmente por Dominik Reichl em 2003. O Keepass é um software gratuito e de código aberto para desktops, que permite que os usuários armazenem suas senhas em um banco de dados seguro, criptografado com algoritmos avançados. Em 2017, o desenvolvedor alemão Brian Pellmann criou o KeepassDX como uma versão para dispositivos móveis, com o objetivo de tornar mais fácil para os usuários gerenciarem suas senhas em smartphones e tablets.
O KeepassDX foi criado a partir do código-fonte do Keepass e foi projetado para ser fácil de usar, seguro e personalizável. Pellmann adicionou várias funcionalidades novas ao KeepassDX, incluindo a capacidade de importar senhas de outros gerenciadores de senhas, a organização de senhas em categorias e a compatibilidade com serviços de armazenamento em nuvem para sincronização entre dispositivos.
Algumas das funcionalidades do KeepassDX incluem a criação de senhas fortes e únicas, preenchimento automático de senhas, autenticação de dois fatores e organização de senhas por categorias. O KeepassDX também oferece uma ferramenta para importação de senhas de outros gerenciadores de senhas, o que torna a transição para o uso do KeepassDX mais fácil.
Passo a passo instalação do aplicativo KeepassDX:
1. Baixe e instale o KeepassDX em seu dispositivo móvel
https://play.google.com/store/apps/details?id=com.kunzisoft.keepass.free
2. Clique em [CRIAR NOVO BANCO DE DADOS]
3. Selecione o local do arquivo no meu caso é " transferência "
Semelhante ao KeePassXC, o KeePassDX suporta o formato de banco de dados .kbdx (por exemplo, Passwords.kdbx) para armazenar senhas de contas importantes. Você deve salvar este arquivo em um local de fácil acesso para você, mas difícil de encontrar para outras pessoas que você não deseja visualizar as informações. Em particular, evite salvar seu arquivo de banco de dados em um serviço de armazenamento online, conectado às suas contas, pois pode ser acessado por outras pessoas.
4. Digite um nome para seu banco de dados
Neste exemplo, " urso " nosso banco de dados como "urso.kdbx"; você pode escolher um nome de sua preferência. Você pode usar um nome que disfarce o arquivo e o torne menos óbvio para invasores que podem tentar acessar seu telefone e exigir que você desbloqueie o banco de dados.
Também é possível alterar a "extensão" no final do nome do arquivo. Por exemplo, você pode nomear o banco de dados de senhas "Revoltadeatlas.pdf" "primainterior.jpg " e o sistema operacional geralmente dará ao arquivo um ícone de "aparência normal". Lembre-se de que, se você der ao seu banco de dados de senhas um nome que não termine em ".kdbx", não poderá abrir o arquivo diretamente. Em vez disso, você terá que iniciar o KeePassDX primeiro e, em seguida, abrir seu banco de dados clicando no botão "Abrir banco de dados existente". Felizmente, o KeePassDX lembra o último banco de dados que você abriu, então você não terá que fazer isso com frequência.
https://github.com/Kunzisoft/KeePassDX
-

@ aa8de34f:a6ffe696
2024-10-22 19:36:06
##
Das Internet hat ein Problem. Nur wenige Leute wissen, dass dieses Problem existiert, aber hey, das liegt in der Natur ernsthafter, nicht offensichtlicher Probleme: Sie sind unsichtbar bis sie es nicht mehr sind. Das Problem mit dem Internet ist, dass Informationen frei sein wollen. Und wenn etwas FREI sein will wie in Freiheit, wird es mit genügend Zeit auch frei wie im Bier. Lass es mich erklären.
### Luftverschmutzung
Jeden Tag verbrauchen wir ungeheure Mengen an Daten. Jede Sekunde jeder Minute strömen Bits und Bytes durch die Reihe von Leitungen die wir alle kennen und lieben: das Internet. Wir nehmen es als selbstverständlich hin und die meisten von uns halten das derzeitige Monetarisierungsmodell – sowie alle damit einhergehenden Übel – ebenfalls für selbstverständlich. Wir halten nur selten inne und denken über die seltsame Welt der Bits und Bytes nach. Wie wunderbar das alles ist, aber auch wie fremd. Wie es unser Leben bereits verändert hat und wie es unsere Zukunft weiter verändern wird. Woher kommen die Nullen und Einsen? Wie funktioniert das alles? Und vor allem: Wer zahlt dafür? Die Bits und Bytes, die durch unsere Glasfaserkabel rasen, sind so unsichtbar wie die Luft die wir atmen. Das ist keine schlechte Metapher wenn ich so darüber nachdenke. Solange wir keine Atemprobleme haben, müssen wir nicht anhalten und jedes einzelne Molekül, das wir einatmen, untersuchen. Ebenso lange wir keine Schwierigkeiten haben digitale Inhalte zu erstellen und zu konsumieren, brauchen wir auch nicht innezuhalten und all die verschiedenen Teile zu untersuchen, die unsere Aufmerksamkeitsökonomie am Laufen halten.\
**Aufmerksamkeitsökonomie**. Was für eine treffende Beschreibung. Wie wir inzwischen alle wissen sollten, ist das was wir konsumieren nicht umsonst, sondern wir bezahlen teuer dafür: mit unserer Aufmerksamkeit unter anderem.
### Paying Attention – mit Aufmerksamkeit bezahlen
In der schnelllebigen Welt von heute muss man, um den Gewinn zu maximieren, die Aufmerksamkeit maximieren. Aber es ist eine eigentümliche, oberflächliche Art von Aufmerksamkeit. Es ist nicht die konzentrierte Art von Aufmerksamkeit, die tiefes Denken und sinnvolle Gespräche erfordern würden. Ich glaube, dass dies zumindest teilweise der Grund ist, warum viele Dinge so kaputt sind. Warum unser gesellschaftlicher Diskurs so zersplittert ist, unsere Politik so polarisiert, wir so gelähmt sind und unsere Analysen oft so oberflächlich sind wie unsere Wünsche.\
Die Aufmerksamkeitsökonomie hat uns fein säuberlich in Echokammern für persönliche Wahrheiten eingeteilt. Ironischerweise besteht die einzige Wahrheit die es wert ist, in der Aufmerksamkeitsökonomie verfolgt zu werden, darin, wie man eine maximale Anzahl von Menschen für eine maximale Zeitspanne maximal empört halten kann. Und das alles ohne dass die Teilnehmer merken, dass sie in einem selbst gewählten algorithmischen Gefängnis gefangen sind.
### Du bist das Produkt
Die Redewendung „Wenn etwas kostenlos ist, bist du das Produkt“ kann nicht oft genug wiederholt werden. Aus dem einen oder anderen Grund erwarten wir, dass die meisten Dinge Online „kostenlos“ sind. Natürlich gibt es so etwas wie ein kostenloses Mittagessen nicht – nichts ist umsonst. Bei Online-Diensten werden deine Daten gesammelt und an den Meistbietenden verkauft, der in der Regel eine Werbeagentur oder eine Regierungsbehörde ist. Oder beides.\
Alle Big-Data-Unternehmen spionieren dich nicht nur aus, sondern nutzen auch eine Vielzahl von dunklen Mustern und unethischen Praktiken, um aus deinen Interaktionen auch den letzten Tropfen an Daten herauszuholen. Ob es sich dabei um den Facebook-Pixel, Google Analytics oder etwas anderes handelt, spielt keine Rolle. Du wirst nachverfolgt, überwacht und katalogisiert. Was du siehst, wie lange, zu welchen Zeiten, wie häufig und was du als Nächstes sehen wirst, wird sorgfältig von einem gewinnmaximierenden Algorithmus orchestriert. Profit für die Plattform, nicht für dich. Natürlich geht es in der Regel darum, dass alle davon profitieren: Nutzer, Urheber, Werbetreibende und die Plattformen gleichermaßen. Das evolutionäre Umfeld, das durch diese Anreizstrukturen geschaffen wird, führt jedoch häufig dazu, dass seichte, aufmerksamkeitsstarke und sensationslüsterne Schnipsel ausgewählt werden. Zum Zeitpunkt dieses Schreibens – Block 716.025 – ist der Inbegriff eines solchen Umfelds TikTok, eine videobasierte Dopaminmaschine, die dir das filmische Äquivalent von Heroin gemischt mit Crack zeigt. Harte Drogen für den Verstand, maßgeschneidert für deine besonderen Vorlieben. Eine wahrhaft verfluchte App. Leider unterscheiden sich die meisten dieser Plattformen nur in der Größe, nicht in der Art.
### Zulässige Meinungen
„Es ist gar nicht so schlimm“, sagen wir uns. „Sieh dir all die nützlichen Informationen an!“, denken wir, während wir durch unsere Feeds scrollen, und füttern damit ungewollt die Maschine, die uns im Gegenzug mit Dopamin versorgt.\
Aber täuschen Sie sich nicht: Den verantwortlichen Unternehmen geht es nicht darum, uns mit nützlichen (oder wahrheitsgemäßen) Informationen zu versorgen. Es geht ihnen darum uns auszutricksen, damit wir die Maschine füttern.\
Wie könnte es anders sein? Man ist was man verfolgt, und man wird das worauf man optimiert wird. Aus Sicht der Plattform geht es um Klicks, nicht um Qualität. Auf den ersten Blick mag die Maximierung von Klicks und Verweildauer eine harmlose Sache sein. Schließlich muss man ja Geld verdienen um zu überleben. Es ist ja nur eine Anzeige. Wie schlimm kann es schon werden?\
Leider sind die Probleme, die damit einhergehen, zunächst unsichtbar. So wie Krebs für den Raucher unsichtbar ist, der gerade seine erste Zigarette geraucht hat, und Leberzirrhose für den Trinker unsichtbar ist, der gerade seinen ersten Drink zu sich genommen hat, so sind Deplatforming, Zensur, Polarisierung und Manipulation der öffentlichen Meinung für den Prosumenten unsichtbar, der gerade seine erste Anzeige auf einer geschlossenen Plattform gesehen hat. Wir können uns wahrscheinlich darauf einigen, dass wir das erste Inning (Stichwort Baseball) in dieser Frage hinter uns haben. Zensur ist die Norm, Deplatforming wird bejubelt, die Polarisierung ist auf einem Allzeithoch, und die öffentliche Meinung wird manuell und algorithmisch manipuliert wie nie zuvor.\
„Der Konsens ist, dass du zu dumm bist, um zu wissen was gut für dich ist und dass deine öffentliche Meinung zu unverschämt ist, um öffentlich geäußert zu werden. Schlimmer noch, es sollte gar nicht erst deine Meinung sein. Hier ist der Grund warum du falsch liegst. Hier ist eine Quelle die auf eine zulässige Meinung hinweist. Hier sind einige Experten, die mit uns übereinstimmen. Unsere intelligenten und hilfreichen Algorithmen haben die ganze Denkarbeit für dich erledigt, und sie liegen nie falsch. Genauso wenig wie die Experten.“\
Das ist die Welt, in der wir bereits leben. Es ist nicht erlaubt frei zu sprechen. Es ist nicht erlaubt frei zu denken. Du darfst dich nicht frei äußern. Dein Bild ist beleidigend und muss daher entfernt werden. Dein Meme ist zu nah an der Wahrheit oder zu kriminell lustig; deshalb müssen wir dich für ein oder zwei Wochen ins Twitter-Gefängnis stecken. Du sagst etwas mit dem wir nicht einverstanden sind; deshalb müssen wir dich auf Lebenszeit sperren – auch wenn du ein amtierender Präsident bist, wohlgemerkt. Du hast in einem Video das falsche Wort gesagt oder ein urheberrechtlich geschütztes Lied im Hintergrund abgespielt; deshalb müssen wir dir dein Einkommen wegnehmen. Du hast ein Bild von dir ohne Maske gepostet; deshalb müssen wir dich verbieten und den Behörden melden.1\
Die Tatsache, dass der obige Satz nicht mehr nur im Bereich der dystopischen Science-Fiction angesiedelt ist, sollte jeden beunruhigen. Aus dem Cyberspace entfernt – weil ich frei atmen wollte. Seltsame Zeiten.
### Evolutionärer Druck
Wie ist es dazu gekommen? Wenn ich gezwungen wäre, eine kurze Antwort zu geben, würde ich Folgendes sagen: Wir sind von Protokollen zu Plattformen übergegangen, und Plattformen sind nur so gut wie ihre Anreize.\
Die Anreizstruktur der Plattformen, auf denen wir leben, ist die evolutionäre Umgebung, die das Überleben diktiert. Alles, was überleben will, muss sich daran orientieren. Das gilt natürlich für alle Bereiche der Wirtschaft. Nimm zum Beispiel Printmagazine. Wenn deine Zeitschrift kein schönes weibliches Gesicht auf der Titelseite hat, wird sie aus sehr menschlichen evolutionären Gründen nicht so oft gekauft werden wie die Zeitschriften, die ein solches Gesicht haben. Sie kann sich also nicht selbst reproduzieren und wird folglich sterben. Ähnlich verhält es sich mit einem Online-Nachrichtenportal, wenn es keine ausreichenden Werbeeinnahmen generiert und nicht in der Lage ist sich zu reproduzieren, wird es sterben. Aus diesem Grund hat jede Zeitschrift ein schönes weibliches Gesicht auf dem Cover. Und das ist der Grund, warum jede werbefinanzierte Online-Nachrichtenquelle zu Clickbait verkommt.
<img src="https://cdn.satellite.earth/856054a1932c9fb70f9ae85bcb6d2d47330babb3cf7ac606c7861a09c8597f61.webp">
#### Eines dieser Gesichter ist anders als die anderen
Das ist auch der Grund, warum sich Feed-basierte Empfehlungsmaschinen in Spielautomaten für deine Dopaminrezeptoren verwandeln. Je länger du an deinem Bildschirm klebst, desto mehr Werbung siehst du, desto mehr Einnahmen werden für die Plattform generiert. Das ist auch der Grund, warum die meisten YouTube-Kanäle zu 7- bis 15-minütigen Kurzvideos mit Vorschaubildern verkommen, die das Gesicht von jemandem zeigen, der gerade auf ein Legostück getreten ist. Kurz genug, um dich zu überzeugen es anzusehen, lang genug, um dich vergessen zu lassen, welches Video du dir eigentlich ansehen wolltest. Wie Ratten, die in hyperpersonalisierten Skinner-Boxen auf Knöpfe drücken, werden wir in Suchtzyklen konditioniert, um die Gewinne der Aktionäre zu maximieren.
### Profitmaximierung
Plattformen sind Unternehmen und für Unternehmen gibt es Anreize die Gewinne der Aktionäre zu maximieren. Gegen Gewinne ist nichts einzuwenden und gegen Aktionäre ist auch nichts einzuwenden. Ich glaube jedoch, dass die Informationsrevolution, in der wir uns befinden, die evolutionäre Landschaft in zwei Teile gespalten hat. Nennen wir diese Landschaften „breit“ und „schmal“.\
Um die Gewinne durch breit angelegte Werbung zu maximieren, müssen Kontroversen und extreme Meinungen auf ein Minimum reduziert werden. Indem man den kleinsten gemeinsamen Nenner anspricht, kommen Politik und Zensur sofort ins Spiel. Umgekehrt müssen Kontroversen und extreme Meinungen maximiert werden, wenn die Gewinne durch schmale, gezielte Werbung erzielt werden sollen. Allein dadurch, dass verschiedenen Untergruppen unterschiedliche Informationen gezeigt werden, werden Polarisierung und Fragmentierung kontinuierlich verstärkt.
<img src="https://cdn.satellite.earth/0d3a88d2700a3c26ed049b09d512a9a35dfc390bc95151e29d6950972114a00e.webp">
Allgemeine Kohäsion vs. algorithmische Spaltung
Diese beiden Extreme sind zwei Seiten der gleichen Medaille. Es mag den Anschein haben, als ginge es um Kabelfernsehen gegen den algorithmischen Newsfeed, aber in Wirklichkeit handelt es sich um zwei unterschiedliche Ansätze, die dasselbe Ziel verfolgen: möglichst viele Menschen vor dem Bildschirm zu halten, damit sie mehr Werbung sehen. Das erste ist ein Beruhigungsmittel, das zweite ein Stimulans.\
Zugegeben, die obige Charakterisierung mag übertrieben sein, aber das Problem bleibt bestehen: Wenn wir nicht direkt für etwas bezahlen, bezahlen wir es indirekt, auf die eine oder andere Weise. Immer.
Der Punkt ist der folgende: Plattformen für freie Meinungsäußerung können nicht existieren. Es kann nur Protokolle der freien Meinungsäußerung geben. Wenn jemand kontrollieren kann, was gesagt wird, wird jemand kontrollieren, was gesagt wird. Wenn du Inhalte überwachen, filtern und zensieren kannst, wirst du Inhalte überwachen, filtern und zensieren.
Alle Plattformen werden mit diesem Problem konfrontiert, ganz gleich wie makellos ihre Absichten sind. Selbst wenn du dich anfangs als Plattform für freie Meinungsäußerung positionierst, wirst du auf lange Sicht gezwungen sein, einzugreifen und zu zensieren. Letztendlich wenn du für Inhalte, die du hostest oder übermittelst, vom Staat haftbar gemacht werden kannst, wirst du auch für Inhalte, die du hostest oder übermittelst, vom Staat haftbar gemacht werden.
### Selbstzensur
Doch lange bevor die staatliche Zensur ihr hässliches Haupt erhebt, wird die abschreckende Wirkung der Selbstzensur zu spüren sein. Wenn andere wegen der Äußerung bestimmter Meinungen enttabuisiert und dämonisiert werden, werden die meisten Menschen sehr vorsichtig sein, diese Meinungen zu äußern. Bewusst und unbewusst bringen wir uns selbst langsam zum Schweigen.
Wenn es um Selbstzensur geht, spielt auch die Werbung eine Rolle. Schließlich würdest du nicht die Hand beißen, die dich füttert, oder? Im schlimmsten Fall sagen dir die Werbetreibenden und Führungskräfte, was gesagt werden darf und was nicht. Sie werden dir sagen, welche Meinungen innerhalb und welche außerhalb des Overton-Fensters liegen. Und wenn sie es nicht tun, wirst du eine fundierte Vermutung anstellen und deine Aussagen entsprechend anpassen.
### Ein Problem und ein Paradoxon
Zurück zum ursprünglichen Problem: Warum können wir Informationen nicht wie eine normale Ware verkaufen? Warum führt der einfache Ansatz – Inhalte hinter eine Bezahlschranke zu stellen – zu so schlechten Ergebnissen? Ich glaube, es gibt zwei Gründe, die ich das „MTX-Problem“ und das „DRM-Paradoxon“ nennen möchte.
Das MTX-Problem, wobei MTX die Abkürzung für „mentale Transaktion“ (mental transaction) ist, bezieht sich auf das Problem der nicht reduzierbaren mentalen Transaktionskosten, die jeder Transaktion innewohnen. Jedes Mal, wenn du auf eine Bezahlschranke stößt, musst du eine bewusste Entscheidung treffen: „Möchte ich dafür bezahlen?“
Wie Szabo überzeugend darlegt, lautet die Antwort in den meisten Fällen, insbesondere wenn die Kosten gering sind, nein. Dafür gibt es keine technischen Gründe, sondern psychologische Gründe. Es stellt sich heraus, dass die Mühe, herauszufinden, ob sich diese Transaktion lohnt oder nicht – ein Prozess, der in deinem Kopf stattfindet – einfach zu groß ist. Wenn man über einen Mikrokauf nachdenken muss, sinkt die Wahrscheinlichkeit, dass man diesen Kauf tätigt, drastisch. Deshalb sind Flatrates und Abonnements der Renner: Man muss nur einmal darüber nachdenken.
Bei den kleinsten Mikrotransaktionen ist dies sogar aus rein wirtschaftlicher Sicht der Fall. Wenn man einen Stundenlohn von 20 USD zugrunde legt und zwei Sekunden lang darüber nachdenkt: „Ist das 21 Sats wert?“, kostet das etwas mehr als 1¢, also mehr als der Preis der betreffenden Mikrotransaktion.\[2\] Das ist sowohl psychologisch als auch wirtschaftlich nicht machbar. Dies ist, kurz gesagt, das MTX-Problem.
Aber das ist nicht das einzige Problem, das die Monetarisierung digitaler Inhalte belastet. Wie bereits erwähnt, gibt es auch das DRM-Paradoxon. DRM, kurz für „Digital-Rechte Management“ (Digital Rights Management), ist ein vergeblicher Versuch, das Kopieren von Informationen zu verhindern. Es sollte sich von selbst verstehen, dass nicht kopierbare Informationen ein Oxymoron sind, aber im Zeitalter von NFTs und vielem anderen Unsinn muss das leider ausdrücklich gesagt werden. Lass es mich also für dich buchstabieren: Man kann keine Informationen erstellen, die nicht kopiert werden können. Punkt. Oder, um es mit den Worten von Bruce Schneier zu sagen: „Der Versuch, digitale Dateien unkopierbar zu machen, ist wie der Versuch, Wasser nicht nass zu machen.“
Es liegt in der Natur der Sache, dass Informationen, wenn sie gelesen werden können, auch kopiert werden können – und zwar mit perfekter Genauigkeit. Kein noch so großer Trick oder künstliche Beschränkungen werden diese Tatsache ändern. Aus diesem Grund werden digitale Artefakte wie Filme und Musik immer kostenlos erhältlich sein. Es ist trivial für jemanden der Zugang zu diesen Artefakten hat, diese zu kopieren – zu Grenzkosten von nahezu Null, wohlgemerkt – und sie anderen zugänglich zu machen. Mit genügend Zeit und Popularität wird also jeder Film, jedes Lied und jedes Dokument für die\
Allgemeinheit kostenlos verfügbar sein. Die Natur der Information lässt kein anderes Ergebnis zu. Daher das Sprichwort: Information will frei sein.
Obwohl der Versuch etwas zu schaffen das es nicht geben kann – Informationen die nicht kopiert werden können – an sich schon paradox ist, meine ich damit nicht das DRM-Paradoxon. Was ich meine, ist etwas viel Lustigeres. Es ist wiederum psychologischer, nicht technischer Natur. Das Paradoxon ist folgendes: Inhalte werden nur dann hinter einer Bezahlschranke bleiben, wenn sie schlecht sind. Wenn sie gut sind, wird sie jemand freilassen.
Wir alle kennen das. Wenn ein Artikel tatsächlich lesenswert ist, wird jemand, der sich hinter der Bezahlschranke befindet, einen Screenshot davon machen und ihn in den sozialen Medien veröffentlichen. Wenn der Film es wert ist angeschaut zu werden, wird er auf verschiedenen Websites verfügbar sein, die Piratenschiffe als ihre Logos haben. Wenn der Song es wert ist gehört zu werden, wird er auf Streaming-Seiten kostenlos zur Verfügung stehen. Nur die schrecklichen Artikel, die obskursten Filme und die Lieder, bei denen einem die Ohren bluten, bleiben hinter Bezahlschranken.
Daraus ergibt sich das Paradoxon: Inhalte bleiben nur dann hinter Bezahlschranken, wenn sie schlecht sind. Wenn sie gut sind, werden sie freigelassen.
Ich persönlich glaube, dass das MTX-Problem ein größeres Problem darstellt als das DRM-Paradoxon. Die traditionelle Lösung für das MTX-Problem ist das Abonnementmodell, wie bei Netflix, Spotify, Amazon und so weiter. Das DRM-Paradoxon bleibt bestehen, aber es stellt sich heraus, dass dies kein Problem ist wenn man den „legitimen“ Zugang zu Informationen bequem genug gestaltet. Die Opportunitätskosten für das Herunterladen, Speichern, Pflegen und Warten einer privaten Liedersammlung sind für die meisten Menschen einfach zu hoch. Die bequemere Lösung ist für das verdammte Spotify-Abo zu bezahlen. Allerdings können wir bereits eines der Probleme erkennen, die mit dem Abonnementmodell verbunden sind. Der folgende Comic beschreibt es gut:
Comic von /u/Hoppy_Doodle
Die Verbreitung von Streaming-Plattformen zwingt dich dazu, ein Netflix-Abonnement, ein Amazon-Prime-Abonnement, ein Hulu-Abonnement, ein Disney-Plus-Abonnement, ein YouTube-Premium-Abonnement und so weiter abzuschließen. Und das war nur das Videostreaming. Den gleichen Abo-Zoo gibt es für Musik, Bücher, Spiele, Newsletter, Blogbeiträge usw.
Und was ist die Lösung?
### Akzeptiere die Natur von Informationen
Die Lösung beginnt mit Akzeptanz. Der Verkauf digitaler Inhalte auf herkömmliche, transaktionale Weise funktioniert nicht oder zumindest nicht sehr gut. Eine Transaktion mit einem digitalen Foto eines Apfels ist etwas ganz anderes als eine Transaktion mit einem physischen Apfel.
George Bernard Shaw hat es am besten gesagt: „Wenn du einen Apfel hast und ich habe einen Apfel und wir tauschen diese Äpfel, dann haben wir beide immer noch jeweils einen Apfel. Aber wenn Sie eine Idee haben und ich eine Idee habe und wir diese Ideen austauschen, dann hat jeder von uns zwei Ideen.“ Da sich digitale Informationen wie eine Idee verhalten, gibt es keinen Grund, sie künstlich zu verknappen. Das gilt nicht nur in philosophischer, sondern auch technischer Hinsicht. Computer sind Kopiermaschinen. Das war schon immer so und wird auch so bleiben. Die einzige Möglichkeit, Informationen von einer Maschine auf eine andere zu übertragen, besteht darin, sie zu kopieren. Dies allein sollte die Sinnlosigkeit der Behandlung von Informationen als physische Objekte offenkundig machen.
Wenn es um die Monetarisierung von Informationen im offenen Web geht, müssen wir unsere Denkweise mit der Natur der Information in Einklang bringen. Wie oben beschrieben, sind Informationen nicht knapp, leicht zu kopieren, leicht zu verändern und wollen frei sein. Ich glaube, dass das richtige Monetarisierungsmodell diese Werte respektieren und ähnliche Eigenschaften haben muss. Es muss offen, transparent, erweiterbar und nicht zuletzt völlig freiwillig sein.
Dieses Modell hat einen Namen: Value-for-Value.
### Wiederbeleben der Straßenmusik
Die Idee ist einfach, klingt aber radikal: Du stellst deine Inhalte kostenlos zur Verfügung, für jeden, ohne Zugangsbeschränkungen. Wenn die Menschen Spaß daran haben, wenn sie einen Nutzen daraus ziehen, dann machst du es den Menschen leicht etwas zurückzugeben.\
Es mag in der heutigen Zeit ungeheuerlich klingen, aber dieses Modell funktioniert seit Tausenden von Jahren. Es ist das Modell der Straßenkünstler, das Modell der Straßenmusikanten, das Modell des freiwilligen Gebens. Im Cyberspace stoßen wir jedoch nicht an die physischen Grenzen der traditionellen Straßenmusikanten. Digitale Inhalte lassen sich auf eine Art und Weise skalieren, wie es bei Darbietungen in der realen Welt nie der Fall sein wird.
Das Value-for Value-Modell stellt das traditionelle Zahlungsmodell auf den Kopf. Traditionell folgt der Genuss der Bezahlung. Beim Value-for-Value-Ansatz folgt die Zahlung dem Genuss – freiwillig. Es steht dir frei, dem Straßenmusiker zuzuhören und weiterzugehen, aber – und das ist etwas was das Publikum intuitiv weiß – wenn du willst, dass die Musik weitergeht, solltest du ein paar Münzen in den Hut werfen.
[Give value back](https://ts.dergigi.com/api/v1/invoices?storeId=3WkiYEG5DaQv7Ak5M2UjUi1pe5FFTPyNF1yAE9CVLNJn&orderId=V4V-busking&checkoutDesc=Value+for+Value%3A+Give+as+much+as+it+is+worth+to+you.¤cy=USD)
Das Schöne an diesem Modell ist, dass es die Anreize neu ausrichtet. Man versucht nicht, die Klicks, die Verweildauer oder irgendeine andere der unzähligen Kennzahlen zu maximieren. Man will dem Publikum einen Mehrwert bieten, und das ist alles. Und wenn das Publikum einen Nutzen daraus gezogen hat, wird ein gewisser Prozentsatz etwas zurückgeben. Alles, was man tun muss, ist zu fragen.
### Eine wertvolle Alternative
Wir stehen erst am Anfang dieses monumentalen Wandels. Ich hoffe, dass sich das Modell „Value for Value“ weiterhin als praktikable Alternative zu Werbung, Zensur, Deplatforming und Demonetisierung durchsetzen wird.
Das Value-for-Value-Modell nimmt das „sie“ aus der Gleichung heraus. Sie filtern, sie zensieren, sie demonetisieren, sie deplatformieren. Es spielt nicht einmal eine Rolle, wer „sie“ sind. Wenn es „sie“ gibt, werden sie einen Weg finden, es zu versauen.
Value-for-Value beseitigt „sie“ und überträgt dir die Verantwortung. Du bist der Herrscher im Reich des Einen, allein verantwortlich für deine Gedanken und deine Sprache. Wenn wir Befreiung (und Erlösung) im Cyberspace wollen, müssen wir dem Einzelnen wieder die Verantwortung übertragen. Wie immer gilt: Freiheit und Unabhängigkeit erfordern Verantwortung.
In der besten aller Welten gibt es für die Schöpfer einen Anreiz, nichts anderes zu tun als zu erschaffen. Man bedient nur sich selbst und diejenigen, die an den Werken interessiert sind. Keine Mittelsmänner. Direkt, von Mensch zu Mensch, Value-for-Value.
### Was uns erwartet
Zugegeben, heute ist es nicht gerade einfach, seine Infrastruktur selbst zu hosten. Es ist einschüchternd, einen eigenen Knotenpunkt (Node) zu betreiben, um Zahlungen auf selbständige Weise zu erhalten. Aber es wird nicht nur einfacher, es wird zunehmend notwendig.
Wir müssen nicht nur alles einfacher machen, sondern uns auch des oben beschriebenen MTX-Problems bewusst sein. Jeder Schritt, der es schafft, die mentalen Transaktionskosten im Ökosystem der Wertschöpfung zu reduzieren, ist ein Schritt in die richtige Richtung.
Die Wertfunktion von Podcasting 2.0 ist ein solcher Schritt. Sie ermöglicht und automatisiert Zahlungen im Minutentakt, ohne dass der Nutzer zusätzlich eingreifen muss. Sobald du eingerichtet bist, wird deine Geldbörse automatisch Zahlungen vornehmen. Ich glaube, dass weitere Iterationen dieser Idee in alle Medientypen integriert werden können, sei es Audio, Video, Bilder, das geschriebene Wort, und so weiter. Ich glaube, dass wir kurz vor der Protokollversion von Patreon stehen: alle Vorteile der Reduzierung der mentalen Transaktionskosten auf Null, ohne die Reibung und die Zensur, die einer plattformbasierten Lösung innewohnen. Ob es in Form von BOLT12 wiederkehrenden Zahlungen oder etwas ganz anderem kommen wird, bleibt abzuwarten. Ich bin jedoch zuversichtlich, dass dies zu gegebener Zeit der Fall sein wird.
### Schlussfolgerung
Nicht nur unser Papiergeld ist kaputt, auch das Monetarisierungsmodell des Internets ist kaputt. Die werbebasierten Plattformen der heutigen Zeit sind auf Engagement durch Spaltung und Polarisierung optimiert und nutzen dunkle Muster und Sucht. Es wird nicht einfach sein, aus den Zwangsschleifen auszubrechen, die für uns eingerichtet wurden, aber dank des selbstverwalteten Tech-Stacks, der derzeit entsteht, gibt es eine praktikable Alternative: das Value-for-Value-Modell.
Das „Straßenmusiker“-Monetarisierungsmodell (busking monetization model) hat in der Vergangenheit viele Jahrhunderte lang funktioniert, und dank Bitcoin und dem Lightning Network bin ich zuversichtlich, dass es auch in der Zukunft noch Jahrhunderte lang funktionieren wird. Wir sind fast am Ziel. Wir müssen nur noch herausfinden, wie wir den Hut richtig auf dem Boden positionieren und wo die besten Plätze in der Stadt sind, um sozusagen aufzutreten.
Value-for-Value löst das DRM-Paradoxon in seiner Gesamtheit und wird – mit dem richtigen Maß an Automatisierung und vernünftigen Vorgaben – auch das MTX-Problem lösen. Wenn wir das richtig hinbekommen, können wir uns vielleicht aus dem evolutionären Überlebenskampf der Plattformen befreien und uns in das quasi unsterbliche Reich der Protokolle begeben.
Es gibt viel zu erforschen, viele Werkzeuge zu entwickeln und viele vorgefasste Meinungen zu zerstören. Direkt vor unseren Augen vollzieht sich ein seismischer Wandel, und ich freue mich darauf, mit euch allen auf den Wellen zu reiten. Vorwärts marsch!
---
*Dies ist ein übersetzter Gastbeitrag von Gigi aus seinem [Blog](https://dergigi.com/). Die geäußerten Meinungen sind ausschließlich seine eigenen und spiegeln nicht notwendigerweise die des Re-Publishers oder Aprycot Media wider. Quelle: https://aprycot.media/blog/freiheit-der-werte/#*
-

@ eac63075:b4988b48
2024-10-21 08:11:11
Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication.
https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV
https://open.spotify.com/episode/0IZ6kMExfxFm4FHg5DAWT8?si=e139033865e045de
### **Sections:**
- **Introduction**
- **What Is Chat Control?**
- **Why Is the EU Pushing for Chat Control?**
- **The Privacy Concerns and Risks**
- **The Technical Debate: Encryption and Backdoors**
- **Global Reactions and the Debate in Europe**
- **Possible Consequences for Messaging Services**
- **What Happens Next? The Future of Chat Control**
- **Conclusion**
---
### **What Is Chat Control?**
"Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns.
At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content.
#### **Origins of the Proposal**
The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms.
#### **How Messaging Services Work**
Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors.
<img src="https://blossom.primal.net/31ace3b729fb9f6b4de286686f31a71db6dd7e3a363f868e1255a6f287eb0b94.png">
#### **Key Elements of Chat Control**
- **Automated Content Scanning**: Service providers would use algorithms to scan messages for illegal content.
- **Circumvention of Encryption**: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security.
- **Mandatory Reporting**: If illegal content is detected, providers would be required to report it to authorities.
- **Broad Applicability**: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms.
#### **Why It Matters**
Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought.
---
### **Why Is the EU Pushing for Chat Control?**
The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms.
#### **Protecting Children and Preventing Crime**
One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes.
Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety.
#### **Legal Context and Legislative Drivers**
The push for Chat Control is rooted in several legislative initiatives:
- **ePrivacy Directive**: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances.
- **Temporary Derogation**: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive.
- **Regulation Proposals**: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications.
#### **Balancing Security and Privacy**
EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections.
However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as:
- **Targeted Scanning**: Focusing on specific threats rather than broad, indiscriminate monitoring.
- **Judicial Oversight**: Requiring court orders or oversight for accessing private communications.
- **Data Protection Safeguards**: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed.
<img src="https://blossom.primal.net/9533aedc9f83564d53633eac1a6d431d1e311028a478dd4b7f3a59b2c449e95a.png">
#### **The Urgency Behind the Push**
High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked.
#### **Criticism and Controversy**
Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose.
---
### **The Privacy Concerns and Risks**
While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications.
#### **Infringement on Privacy Rights**
At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms.
#### **Erosion of End-to-End Encryption**
End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats.
#### **Concerns from Privacy Advocates**
Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences:
- **Security Risks**: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime.
- **Global Implications**: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy.
- **Ineffectiveness Against Crime**: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens.
<img src="https://blossom.primal.net/51722887ebf55c827cc20bcfade3ea9b3628265b7fa3547504b2fff45f34f175.png">
#### **Potential for Government Overreach**
There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent.
#### **Real-World Implications for Users**
- **False Positives**: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users.
- **Chilling Effect**: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse.
- **Data Misuse**: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information.
#### **Legal and Ethical Concerns**
Privacy advocates also highlight potential conflicts with existing laws and ethical standards:
- **Violation of Fundamental Rights**: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression.
- **Questionable Effectiveness**: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users.
#### **Opposition from Member States and Organizations**
Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences.
---
### **The Technical Debate: Encryption and Backdoors**
The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures.
#### **What Is End-to-End Encryption (E2EE)?**
End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content.
- **Security Assurance**: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private.
- **Widespread Use**: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data.
#### **How Chat Control Affects Encryption**
Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to:
- **Introduce Backdoors**: Create a means for third parties (including the service provider or authorities) to access encrypted messages.
- **Client-Side Scanning**: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE.
#### **The Risks of Weakening Encryption**
**1. Compromised Security for All Users**
Introducing backdoors or client-side scanning tools can create vulnerabilities:
- **Exploitable Gaps**: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches.
- **Universal Impact**: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk.
**2. Undermining Trust in Digital Services**
- **User Confidence**: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms.
- **Business Implications**: Companies relying on secure communications might face increased risks, affecting economic activities.
**3. Ineffectiveness Against Skilled Adversaries**
- **Alternative Methods**: Criminals might shift to other encrypted channels or develop new ways to avoid detection.
- **False Sense of Security**: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected.
#### **Signal’s Response and Stance**
Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals:
- **Refusal to Weaken Encryption**: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards.
- **Advocacy for Privacy**: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age.
#### **Understanding Backdoors**
A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems:
- **Security Vulnerabilities**: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments.
- **Ethical Concerns**: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications.
<img src="https://blossom.primal.net/67f45fd79ccdb7e2e2ecdc56297207dc0d1d073acb216857b6165b3bf9906997.png">
#### **The Slippery Slope Argument**
Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent:
- **Expanded Surveillance**: Once in place, these measures could be extended to monitor other types of content beyond the original scope.
- **Erosion of Rights**: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time.
#### **Potential Technological Alternatives**
Some suggest that it's possible to fight illegal content without undermining encryption:
- **Metadata Analysis**: Focusing on patterns of communication rather than content.
- **Enhanced Reporting Mechanisms**: Encouraging users to report illegal content voluntarily.
- **Investing in Law Enforcement Capabilities**: Strengthening traditional investigative methods without compromising digital security.
####
The technical community largely agrees that weakening encryption is not the solution:
- **Consensus on Security**: Strong encryption is essential for the safety and privacy of all internet users.
- **Call for Dialogue**: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights.
---
### **Global Reactions and the Debate in Europe**
The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values.
#### **Support for Chat Control**
Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that:
- **Enhanced Security**: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes.
- **Responsibility of Service Providers**: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities.
- **Public Safety Priorities**: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy.
#### **Opposition within the EU**
Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach.
**Germany**
- **Stance**: Germany has been one of the most vocal opponents of the proposed measures.
- **Reasons**:
- **Constitutional Concerns**: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications.
- **Security Risks**: Weakening encryption is seen as a threat to cybersecurity.
- **Legal Challenges**: Potential conflicts with national laws protecting personal data and communication secrecy.
**Netherlands**
- **Recent Developments**: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy.
- **Arguments**:
- **Effectiveness Doubts**: Skepticism about the actual effectiveness of the measures in combating crime.
- **Negative Impact on Privacy**: Concerns about mass surveillance and the infringement of citizens' rights.
Table reference: Patrick Breyer - Chat Control in 23 September 2024
#### **Privacy Advocacy Groups**
**European Digital Rights (EDRi)**
- **Role**: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment.
- **Position**:
- **Strong Opposition**: EDRi argues that Chat Control is incompatible with fundamental rights.
- **Awareness Campaigns**: Engaging in public campaigns to inform citizens about the potential risks.
- **Policy Engagement**: Lobbying policymakers to consider alternative approaches that respect privacy.
**Politicians and Activists**
**Patrick Breyer**
- **Background**: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party.
- **Actions**:
- **Advocacy**: Actively campaigning against Chat Control through speeches, articles, and legislative efforts.
- **Public Outreach**: Using social media and public events to raise awareness.
- **Legal Expertise**: Highlighting the legal inconsistencies and potential violations of EU law.
#### **Global Reactions**
**International Organizations**
- **Human Rights Watch and Amnesty International**: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider.
**Technology Companies**
- **Global Tech Firms**: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust.
- **Industry Associations**: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness.
<img src="https://blossom.primal.net/e761aa2dd240a1a2e7d943565ccbda427b5a8054bf4e6e17c946711ab6370d5d.png">
#### **The Broader Debate**
The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include:
- **Legal Precedents**: How the EU's decision might influence laws and regulations in other countries.
- **Digital Sovereignty**: The desire of nations to control digital spaces within their borders.
- **Civil Liberties**: The importance of protecting freedoms in the face of technological advancements.
#### **Public Opinion**
- **Diverse Views**: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all.
- **Awareness Levels**: Many people are still unaware of the potential changes, highlighting the need for public education on the issue.
####
The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society.
---
### **Possible Consequences for Messaging Services**
The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication.
#### **Impact on Encrypted Messaging Services**
**Signal and Similar Platforms**
- **Compliance Challenges**: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles.
- **Operational Decisions**: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features.
#### **Potential Blocking or Limiting of Services**
- **Regulatory Enforcement**: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU.
- **Access Restrictions**: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements.
#### **Effects on Smaller Providers**
- **Resource Constraints**: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market.
- **Innovation Stifling**: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector.
<img src="https://blossom.primal.net/60a9cad69b45cc3ded1d1759312e49a57b3aa997db62e36016f40642943be5e9.png">
#### **User Experience and Trust**
- **Privacy Concerns**: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement.
- **Migration to Unregulated Platforms**: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks.
#### **Technical and Security Implications**
- **Increased Vulnerabilities**: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches.
- **Global Security Risks**: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders.
#### **Impact on Businesses and Professional Communications**
- **Confidentiality Issues**: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services.
- **Compliance Complexity**: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens.
#### **Economic Consequences**
- **Market Fragmentation**: Divergent regulations could lead to a fragmented market, with different versions of services for different regions.
- **Loss of Revenue**: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance.
#### **Responses from Service Providers**
- **Legal Challenges**: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights.
- **Policy Advocacy**: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control.
#### **Possible Adaptations**
- **Technological Innovation**: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain.
- **Transparency Measures**: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy.
####
The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape.
---
### **What Happens Next? The Future of Chat Control**
The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union.
#### **Current Status of Legislation**
- **Ongoing Negotiations**: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders.
- **Timeline**: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay.
#### **Key Influencing Factors**
**1. Legal Challenges and Compliance with EU Law**
- **Fundamental Rights Assessment**: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression.
- **Court Scrutiny**: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control.
**2. Technological Feasibility**
- **Development of Privacy-Preserving Technologies**: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies.
- **Implementation Challenges**: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures.
**3. Political Dynamics**
- **Member State Positions**: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations.
- **Public Opinion and Advocacy**: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections.
**4. Industry Responses**
- **Negotiations with Service Providers**: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed.
- **Potential for Self-Regulation**: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning.
#### **Possible Scenarios**
**Optimistic Outcome:**
- **Balanced Regulation**: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight.
**Pessimistic Outcome:**
- **Adoption of Strict Measures**: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market.
**Middle Ground:**
- **Incremental Implementation**: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact.
#### **How to Stay Informed and Protect Your Privacy**
- **Follow Reputable Sources**: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments.
- **Engage in the Dialogue**: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy.
- **Utilize Secure Practices**: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security.
<img src="https://blossom.primal.net/1e2c0cd70d88629c54ac84f928ab107f08f698d2c7f0df511277fb44c1480f0a.png">
#### **The Global Perspective**
- **International Implications**: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against.
- **Collaboration Opportunities**: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats.
#### **Looking Ahead**
The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders.
As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world.
---
### **Conclusion**
The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns.
Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits.
The potential consequences of implementing Chat Control are far-reaching:
- **Erosion of Trust**: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online.
- **Security Vulnerabilities**: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks.
- **Stifling Innovation**: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry.
- **Global Implications**: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse.
As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values.
The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free.
In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world.
<img src="https://blossom.primal.net/d3f07d8bc7a49ac291f14eb449879462c76ae407abbe728ddc6f93e11fabe11d.png">
---
Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future.
## Read more:
- https://www.patrick-breyer.de/en/posts/chat-control/
- https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/
- https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/
- https://signal.org/blog/pdfs/ndss-keynote.pdf
- https://tuta.com/blog/germany-stop-chat-control
- https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal
- https://mullvad.net/en/why-privacy-matters
-

@ fd208ee8:0fd927c1
2024-10-20 18:19:48
(Please note that this is not official financial or business advice, but rather a description of something we have done, on an informal basis.)
# A long, long time ago
It's been nearly a year, since nostr:nprofile1qydhwumn8ghj7argv4nx7un9wd6zumn0wd68yvfwvdhk6tcpypmhxue69uhkummnw3ezuetfde6kuer6wasku7nfvuh8xurpvdjj7qpqs3ht77dq4zqnya8vjun5jp3p44pr794ru36d0ltxu65chljw8xjqv5atj2 came into being, mostly as a lark, involving a couple of members of our private chat group. Our initial plan was to work toward bounties, but Nostr bounties are a bit of a biased, uncertain thing, and our enthusiasm for that quickly waned.
So, what to do? Here we are, we three (nostr:npub1ecdlntvjzexlyfale2egzvvncc8tgqsaxkl5hw7xlgjv2cxs705s9qs735, nostr:npub1wqfzz2p880wq0tumuae9lfwyhs8uz35xd0kr34zrvrwyh3kvrzuskcqsyn, and I): IT professionals with little time, but plenty of intellectual energy, a Slack chat, a [GitHub repo](https://github.com/ShadowySupercode), and lots of frustration with the Nostr status quo.
We were, you see, Nostr end-users. We loved the idea of the protocol, but we were being regularly stymied by the poor quality of many implementations.
* Why can I not login? Oh, they fixed the login! Nope, still can't login.
* If I press this button, it says it sent, but it didn't send. Where note?
* They announced a new feature, but I tried it and it didn't work. Oh well.
* I noticed a bug in the client, reported it, and the issue is just rotting away in the project repo. Ignored.
* The website/relay/repo was here... yesterday. Today it has disappeared, and taken my zaps with it.
It was enough to make us want to tear our hair out. We decided that what Nostr needed... what it _really_ needed... was a **Nostr Stable Version**. Nothing glamorous. Nothing exotic. Nothing busy or excitable. Just something that stayed where you initially found it, ran, and actually worked. Something where you could report a bug and receive a prompt response. Maybe even something, where you could pay a reasonable fee and be _allowed to have expectations_ of some particular service being returned. And who better to build such a version, than people who want to use it, themselves?
# Things working is an underrated concept
I know that the very idea of software _running as expected_ and websites not appearing and disappearing suddenly, based upon what some particular developer had for lunch, tends to be met with little but scorn, from hardened, seasoned Nostriches (who are convinced that bugs are _all_ features), but I think the majority of potential users would see it differently.
I'm with the majority, on this one.
I like to click "save" buttons and have them save. If I publish something, I want it to appear under my list of published somethings. I like to type in the website address I always type in, and have it magically appear on my screen, as if there were a little man sitting at controls in my laptop, just waiting for me to write H-T-T-P-S... and then jump to attention.
My unreasonable expectations have no bounds, it is true. But unreasonable people are also people, so we would also like to have our own unreasonable things to play with. Scorn away. My save button will save, and my published something will publish, and my website will load _every damn time_, just to spite you.
In the larger scheme of things, you see, we win even if we fail, if we at least increase the competition enough, that _things working_ becomes the new standard. We can simply prove, definitively, that it is possible for Nostr things to work, if they are built by people who care if they work. If we also have fun together, learn something new, and come up with some cool, novel use cases, then that's pure profit.
We can only win, at this endeavor.
# Where to start?
## Name that brand
So, we had a team, we had a business idea, and we had a heck of a lot of motivation. What we didn't have, is a name. (Never underestimate the importance of naming things.)
We decided to name ourselves "GitCitadel" because "git" sounds techy, hints at our GitRepublic project, and is reminiscent of open-source development, and "citadel" reminds us of Bitcoin. The republic is at home in the citadel, naturally. All other products also live in the same citadel, hence the naming-convention of prefacing everything with "GC" (i.e. "GC Alexandria", "GC Sybil", "GC Aedile", etc.).
## Brand yourself
The next thing we did, was rent a domain and run a webserver on it. This is an important step because it gives you an Internet presence, allows you to have company NIP-05 and email addresses (a form of promotion), and it's simply exciting to have one. Feels so much more "official" and it helps increase the name-recognition of your company.
## Define yourself
We then sat down, together, over the Internet, and figured out who we are. Not who we individually are, but who we are, as a company. A company, after all, (according to the Cambridge Dictionary) is "an organization that produces or sells goods or services in order to make a profit". Now, a company's profits don't have to be monetary, but they should be something tangible. A company, in other words, is a team of people working toward some defined goal.
What is our goal? Well, we decided to think it over, sat down with the newer additions to the company (you can see who they are, on our [project wiki page](https://wikistr.com/gitcitadel-project), and came up with a Vision and a Mission:
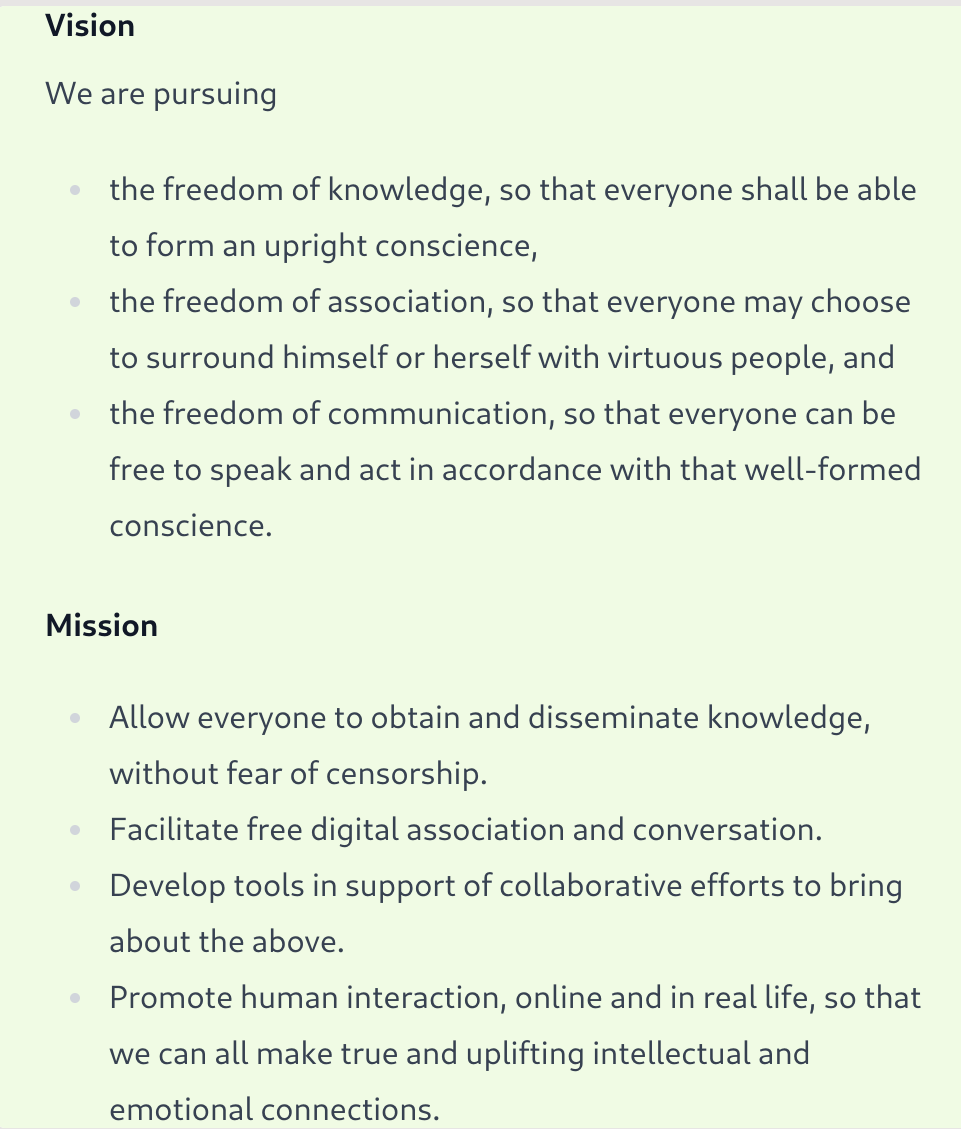
The _vision_ is what the overall goals of the company are, whereas the _mission_ describes how those goals shall be achieved. Now, this is a sort of lofty, abstract statement, so it was important that we posted it someplace publicly (to keep ourselves accountable) and look at it regularly, so that we can ponder it and realign whatever we are currently working on, with this statement. We know the statement is well-designed, if considering it helps us make decisions about what to do next.
## Pay yourselves
(I'm going to switch from "we" to "you", here, as it's easier to write this part, but let's just pretend I didn't.)

The next thing on the list, is to arrange the finances, usually by setting up a Geyserfund, with an associated wallet, and then deciding how the funds from the wallet will be dispersed or stored. (I won't tell you how we are handling that, as that's internal company business, but I'm sure you'll think of something clever, yourselves. Or just google it.)
I would encourage you to arrange to pay yourselves profits. Not merely because your idea is going to make you all fabulously wealthy and internationally famous (although, that is obviously true), but because _profits are the most pure form of communication that consumers in the market have_ with its producers, and one of the best ways to make decisions and measure increases in efficiency (increasing profits and/or output, while keeping prices steady or falling).
Cutting off this signal, in order to look pious to outsiders, is to shoot yourself in your free-market foot. Nobody says that you have to spend your profits on the proverbial _lambo and a bimbo_. You could donate them to charity, reinvest them, or store them for your nephews to inherit, but **pay them out, you should**. You don't have to love money, to value it as a tool and use it shrewdly. Money is a measure, and companies should regularly measure themselves: against their previous state, against their potential state, and against their competition.
(Also, you can use money to buy a lambo and a bimbo, but you didn't hear that from me.)
## Organize yourselves
Once you've been working together, for a while, you'll find that you need to figure out how to organize yourselves. The first step is to...
### Form a board of directors.
Stop laughing. I'm serious.
Any company has at least two roles (President and Secretary), ideally held by two different people, so any single-proprietor company is a man down. Find a different person, to be your Second, even if they're just your confident, who lets you cry on your shoulder on The Bad Days, when your code refuses to compile, and can tell people that you've become a Bitcoin millionaire and have gone on a sabbatical to hike the Himalayas and will be back in 3 months on The Very Good Days.
Because business man was not meant to be alone.
If, like us, you're a small herd of people and have already been working together for a while, then this step is actually really, really fun. Just think about what people are already doing, and put a label on it. That role is now defined and it is clear who is in charge of what.
Scientists become "Chief Science Officer" or "Scientific Advisor". The person who always writes the _okay, so this is what we've decided_ comment in the thread becomes the Secretary, the one managing the Lightning wallet and worrying over paying for the servers is the CFO, the person running the remote server becomes the CTO, and so on and etc.
And everyone knows who the CEO is. Everyone always knows. They do. Just write it down.
### Agree how to disagree
Now, have the secretary write up a Member's Agreement. It's a contract between the members, about whatever the group thinks is important concerning the way the company will operate. According to [Investopedia](https://www.investopedia.com/terms/l/llc-operating-agreement.asp), common topics are:

Is this legally binding? Probably not. Maybe. I don't know and wouldn't tell you, even if I did. But it's _emotionally binding_, which is arguably more important.
Writing things down is an advanced form of _naming things_ and it provides clarity, helps to manage expectations, and allows you to define a working agreement before Real Money shows up and taints your interaction. You're just accepting tips, at the moment. Everyone is calm and cheerful, so now is your best time to negotiate.
Keep it very simple and only address the most basic things. If you wish to incorporate, at a later date, then you just take this to a registered agent, or other experienced person, and have them tidy up any loose ends and add the fine print.
## Go forth, together
This has probably taken you weeks, or even months, but you're now a company. Get a logo and a company npub, start dropping the company name into your notes, and get on with the business of being in business.
-

@ b6ca2216:f45f8b5b
2024-10-20 00:19:37
my 3. article
-

@ b6ca2216:f45f8b5b
2024-10-20 00:16:38
{"id":12345,"title":"deleted","body":"deleted"}
-

@ b6ca2216:f45f8b5b
2024-10-19 23:51:01
{id:123, title:"my first article", body:"This NIP defines kind:30402: an addressable event to describe classified listings that list any arbitrary product, service, or other thing for sale or offer and includes enough structured metadata to make them useful.
The category of classifieds includes a very broad range of physical goods, services, work opportunities, rentals, free giveaways, personals, etc. and is distinct from the more strictly structured marketplaces defined in NIP-15 that often sell many units of specific products through very specific channels.
The structure of these events is very similar to NIP-23 long-form content events."}
-

@ a95c6243:d345522c
2024-10-19 08:58:08
Ein Lämmchen löschte an einem Bache seinen Durst. Fern von ihm, aber näher der Quelle, tat ein Wolf das gleiche. Kaum erblickte er das Lämmchen, so schrie er:
"Warum trübst du mir das Wasser, das ich trinken will?"
"Wie wäre das möglich", erwiderte schüchtern das Lämmchen, "ich stehe hier unten und du so weit oben; das Wasser fließt ja von dir zu mir; glaube mir, es kam mir nie in den Sinn, dir etwas Böses zu tun!"
"Ei, sieh doch! Du machst es gerade, wie dein Vater vor sechs Monaten; ich erinnere mich noch sehr wohl, daß auch du dabei warst, aber glücklich entkamst, als ich ihm für sein Schmähen das Fell abzog!"
"Ach, Herr!" flehte das zitternde Lämmchen, "ich bin ja erst vier Wochen alt und kannte meinen Vater gar nicht, so lange ist er schon tot; wie soll ich denn für ihn büßen."
"Du Unverschämter!" so endigt der Wolf mit erheuchelter Wut, indem er die Zähne fletschte. "Tot oder nicht tot, weiß ich doch, daß euer ganzes Geschlecht mich hasset, und dafür muß ich mich rächen."
Ohne weitere Umstände zu machen, zerriß er das Lämmchen und verschlang es.
*Das [Gewissen](https://apollo-news.net/das-gewissen-in-corona-jahren-zum-tod-von-gunnar-kaiser/) regt sich selbst bei dem größten Bösewichte; er sucht doch nach Vorwand, um dasselbe damit bei Begehung seiner Schlechtigkeiten zu beschwichtigen.*
Quelle: https://eden.one/fabeln-aesop-das-lamm-und-der-wolf
-

@ 8947a945:9bfcf626
2024-10-17 08:06:55
[](https://stock.adobe.com/stock-photo/id/1010191703)
**สวัสดีทุกคนบน Nostr ครับ** รวมไปถึง **watchers**และ **ผู้ติดตาม**ของผมจาก Deviantart และ platform งานศิลปะอื่นๆนะครับ
ตั้งแต่ต้นปี 2024 ผมใช้ AI เจนรูปงานตัวละครสาวๆจากอนิเมะ และเปิด exclusive content ให้สำหรับผู้ที่ชื่นชอบผลงานของผมเป็นพิเศษ
ผมโพสผลงานผมทั้งหมดไว้ที่เวบ Deviantart และค่อยๆสร้างฐานผู้ติดตามมาเรื่อยๆอย่างค่อยเป็นค่อยไปมาตลอดครับ ทุกอย่างเติบโตไปเรื่อยๆของมัน ส่วนตัวผมมองว่ามันเป็นพิร์ตธุรกิจออนไลน์ ของผมพอร์ตนึงได้เลย
**เมื่อวันที่ 16 กย.2024** มีผู้ติดตามคนหนึ่งส่งข้อความส่วนตัวมาหาผม บอกว่าชื่นชอบผลงานของผมมาก ต้องการจะขอซื้อผลงาน แต่ขอซื้อเป็น NFT นะ เสนอราคาซื้อขายต่อชิ้นที่สูงมาก หลังจากนั้นผมกับผู้ซื้อคนนี้พูดคุยกันในเมล์ครับ

### นี่คือข้อสรุปสั่นๆจากการต่อรองซื้อขายครับ
(หลังจากนี้ผมขอเรียกผู้ซื้อว่า scammer นะครับ เพราะไพ่มันหงายมาแล้ว ว่าเขาคือมิจฉาชีพ)

- Scammer รายแรก เลือกผลงานที่จะซื้อ เสนอราคาซื้อที่สูงมาก แต่ต้องเป็นเวบไซต์ NFTmarket place ที่เขากำหนดเท่านั้น มันทำงานอยู่บน ERC20 ผมเข้าไปดูเวบไซต์ที่ว่านี้แล้วรู้สึกว่ามันดูแปลกๆครับ คนที่จะลงขายผลงานจะต้องใช้ email ในการสมัครบัญชีซะก่อน ถึงจะผูก wallet อย่างเช่น metamask ได้ เมื่อผูก wallet แล้วไม่สามารถเปลี่ยนได้ด้วย ตอนนั้นผมใช้ wallet ที่ไม่ได้ link กับ HW wallet ไว้ ทดลองสลับ wallet ไปๆมาๆ มันทำไม่ได้ แถมลอง log out แล้ว เลข wallet ก็ยังคาอยู่อันเดิม อันนี้มันดูแปลกๆแล้วหนึ่งอย่าง เวบนี้ค่า ETH ในการ mint **0.15 - 0.2 ETH** … ตีเป็นเงินบาทนี่แพงบรรลัยอยู่นะครับ

- Scammer รายแรกพยายามชักจูงผม หว่านล้อมผมว่า แหม เดี๋ยวเขาก็มารับซื้องานผมน่า mint งานเสร็จ รีบบอกเขานะ เดี๋ยวเขารีบกดซื้อเลย พอขายได้กำไร ผมก็ได้ค่า gas คืนได้ แถมยังได้กำไรอีก ไม่มีอะไรต้องเสีนจริงมั้ย แต่มันเป้นความโชคดีครับ เพราะตอนนั้นผมไม่เหลือทุนสำรองที่จะมาซื้อ ETH ได้ ผมเลยต่อรองกับเขาตามนี้ครับ :
1. ผมเสนอว่า เอางี้มั้ย ผมส่งผลงานของผมแบบ low resolution ให้ก่อน แลกกับให้เขาช่วยโอน ETH ที่เป็นค่า mint งานมาให้หน่อย พอผมได้ ETH แล้ว ผมจะ upscale งานของผม แล้วเมล์ไปให้ ใจแลกใจกันไปเลย ... เขาไม่เอา
2. ผมเสนอให้ไปซื้อที่ร้านค้าออนไลน์ buymeacoffee ของผมมั้ย จ่ายเป็น USD ... เขาไม่เอา
3. ผมเสนอให้ซื้อขายผ่าน PPV lightning invoice ที่ผมมีสิทธิ์เข้าถึง เพราะเป็น creator ของ Creatr ... เขาไม่เอา
4. ผมยอกเขาว่างั้นก็รอนะ รอเงินเดือนออก เขาบอก ok
สัปดาห์ถัดมา มี scammer คนที่สองติดต่อผมเข้ามา ใช้วิธีการใกล้เคียงกัน แต่ใช้คนละเวบ แถมเสนอราคาซื้อที่สูงกว่าคนแรกมาก เวบที่สองนี้เลวร้ายค่าเวบแรกอีกครับ คือต้องใช้เมล์สมัครบัญชี ไม่สามารถผูก metamask ได้ พอสมัครเสร็จจะได้ wallet เปล่าๆมาหนึ่งอัน ผมต้องโอน ETH เข้าไปใน wallet นั้นก่อน เพื่อเอาไปเป็นค่า mint NFT **0.2 ETH**
ผมบอก scammer รายที่สองว่า ต้องรอนะ เพราะตอนนี้กำลังติดต่อซื้อขายอยู่กับผู้ซื้อรายแรกอยู่ ผมกำลังรอเงินเพื่อมาซื้อ ETH เป็นต้นทุนดำเนินงานอยู่ คนคนนี้ขอให้ผมส่งเวบแรกไปให้เขาดูหน่อย หลังจากนั้นไม่นานเขาเตือนผมมาว่าเวบแรกมันคือ scam นะ ไม่สามารถถอนเงินออกมาได้ เขายังส่งรูป cap หน้าจอที่คุยกับผู้เสียหายจากเวบแรกมาให้ดูว่าเจอปัญหาถอนเงินไม่ได้ ไม่พอ เขายังบลัฟ opensea ด้วยว่าลูกค้าขายงานได้ แต่ถอนเงินไม่ได้
**Opensea ถอนเงินไม่ได้ ตรงนี้แหละครับคือตัวกระตุกต่อมเอ๊ะของผมดังมาก** เพราะ opensea อ่ะ ผู้ใช้ connect wallet เข้ากับ marketplace โดยตรง ซื้อขายกันเกิดขึ้น เงินวิ่งเข้าวิ่งออก wallet ของแต่ละคนโดยตรงเลย opensea เก็บแค่ค่า fee ในการใช้ platform ไม่เก็บเงินลูกค้าไว้ แถมปีนี้ค่า gas fee ก็ถูกกว่า bull run cycle 2020 มาก ตอนนี้ค่า gas fee ประมาณ 0.0001 ETH (แต่มันก็แพงกว่า BTC อยู่ดีอ่ะครับ)
ผมเลยเอาเรื่องนี้ไปปรึกษาพี่บิท แต่แอดมินมาคุยกับผมแทน ทางแอดมินแจ้งว่ายังไม่เคยมีเพื่อนๆมาปรึกษาเรื่องนี้ กรณีที่ผมทักมาถามนี่เป็นรายแรกเลย แต่แอดมินให้ความเห็นไปในทางเดียวกับสมมุติฐานของผมว่าน่าจะ scam ในเวลาเดียวกับผมเอาเรื่องนี้ไปถามในเพจ NFT community คนไทนด้วย ได้รับการ confirm ชัดเจนว่า scam และมีคนไม่น้อยโดนหลอก หลังจากที่ผมรู้ที่มาแล้ว ผมเลยเล่นสงครามปั่นประสาท scammer ทั้งสองคนนี้ครับ เพื่อดูว่าหลอกหลวงมิจฉาชีพจริงมั้ย
โดยวันที่ 30 กย. ผมเลยปั่นประสาน scammer ทั้งสองรายนี้ โดยการ mint ผลงานที่เขาเสนอซื้อนั่นแหละ ขึ้น opensea
แล้วส่งข้อความไปบอกว่า
mint ให้แล้วนะ แต่เงินไม่พอจริงๆว่ะโทษที เลย mint ขึ้น opensea แทน พอดีบ้านจน ทำได้แค่นี้ไปถึงแค่ opensea รีบไปซื้อล่ะ มีคนจ้องจะคว้างานผมเยอะอยู่ ผมไม่คิด royalty fee ด้วยนะเฮ้ย เอาไปขายต่อไม่ต้องแบ่งกำไรกับผม
เท่านั้นแหละครับ สงครามจิตวิทยาก็เริ่มขึ้น แต่เขาจนมุม กลืนน้ำลายตัวเอง
ช็อตเด็ดคือ
เขา : เนี่ยอุส่ารอ บอกเพื่อนในทีมว่าวันจันทร์ที่ 30 กย. ได้ของแน่ๆ เพื่อนๆในทีมเห็นงานผมแล้วมันสวยจริง เลยใส่เงินเต็มที่ 9.3ETH (+ capture screen ส่งตัวเลขยอดเงินมาให้ดู)ไว้รอโดยเฉพาะเลยนะ
ผม : เหรอ ... งั้น ขอดู wallet address ที่มี transaction มาให้ดูหน่อยสิ
เขา : 2ETH นี่มัน 5000$ เลยนะ
ผม : แล้วไง ขอดู wallet address ที่มีการเอายอดเงิน 9.3ETH มาให้ดูหน่อย ไหนบอกว่าเตรียมเงินไว้มากแล้วนี่ ขอดูหน่อย ว่าใส่ไว้เมื่อไหร่ ... เอามาแค่ adrress นะเว้ย ไม่ต้องทะลึ่งส่ง seed มาให้
เขา : ส่งรูปเดิม 9.3 ETH มาให้ดู
ผม : รูป screenshot อ่ะ มันไม่มีความหมายหรอกเว้ย ตัดต่อเอาก็ได้ง่ายจะตาย เอา transaction hash มาดู ไหนว่าเตรียมเงินไว้รอ 9.3ETH แล้วอยากซื้องานผมจนตัวสั่นเลยไม่ใช่เหรอ ถ้าจะส่ง wallet address มาให้ดู หรือจะช่วยส่ง 0.15ETH มาให้ยืม mint งานก่อน แล้วมากดซื้อ 2ETH ไป แล้วผมใช้ 0.15ETH คืนให้ก็ได้ จะซื้อหรือไม่ซื้อเนี่ย
เขา : จะเอา address เขาไปทำไม
ผม : ตัดจบ รำคาญ ไม่ขายให้ละ
เขา : 2ETH = 5000 USD เลยนะ
ผม : แล้วไง
ผมเลยเขียนบทความนี้มาเตือนเพื่อนๆพี่ๆทุกคนครับ เผื่อใครกำลังเปิดพอร์ตทำธุรกิจขาย digital art online แล้วจะโชคดี เจอของดีแบบผม
-----------
### ทำไมผมถึงมั่นใจว่ามันคือการหลอกหลวง แล้วคนโกงจะได้อะไร
[](https://stock.adobe.com/stock-photo/id/1010196295)
อันดับแรกไปพิจารณาดู opensea ครับ เป็นเวบ NFTmarketplace ที่ volume การซื้อขายสูงที่สุด เขาไม่เก็บเงินของคนจะซื้อจะขายกันไว้กับตัวเอง เงินวิ่งเข้าวิ่งออก wallet ผู้ซื้อผู้ขายเลย ส่วนทางเวบเก็บค่าธรรมเนียมเท่านั้น แถมค่าธรรมเนียมก็ถูกกว่าเมื่อปี 2020 เยอะ ดังนั้นการที่จะไปลงขายงานบนเวบ NFT อื่นที่ค่า fee สูงกว่ากันเป็นร้อยเท่า ... จะทำไปทำไม
ผมเชื่อว่า scammer โกงเงินเจ้าของผลงานโดยการเล่นกับความโลภและความอ่อนประสบการณ์ของเจ้าของผลงานครับ เมื่อไหร่ก็ตามที่เจ้าของผลงานโอน ETH เข้าไปใน wallet เวบนั้นเมื่อไหร่ หรือเมื่อไหร่ก็ตามที่จ่ายค่า fee ในการ mint งาน เงินเหล่านั้นสิ่งเข้ากระเป๋า scammer ทันที แล้วก็จะมีการเล่นตุกติกต่อแน่นอนครับ เช่นถอนไม่ได้ หรือซื้อไม่ได้ ต้องโอนเงินมาเพิ่มเพื่อปลดล็อค smart contract อะไรก็ว่าไป แล้วคนนิสัยไม่ดีพวกเนี้ย ก็จะเล่นกับความโลภของคน เอาราคาเสนอซื้อที่สูงโคตรๆมาล่อ ... อันนี้ไม่ว่ากัน เพราะบนโลก NFT รูปภาพบางรูปที่ไม่ได้มีความเป็นศิลปะอะไรเลย มันดันขายกันได้ 100 - 150 ETH ศิลปินที่พยายามสร้างตัวก็อาจจะมองว่า ผลงานเรามีคนรับซื้อ 2 - 4 ETH ต่องานมันก็มากพอแล้ว (จริงๆมากเกินจนน่าตกใจด้วยซ้ำครับ)
บนโลกของ BTC ไม่ต้องเชื่อใจกัน โอนเงินไปหากันได้ ปิดสมุดบัญชีได้โดยไม่ต้องเชื่อใจกัน
บบโลกของ ETH **"code is law"** smart contract มีเขียนอยู่แล้ว ไปอ่าน มันไม่ได้ยากมากในการทำความเข้าใจ ดังนั้น การจะมาเชื่อคำสัญญาจากคนด้วยกัน เป็นอะไรที่ไม่มีเหตุผล
ผมไปเล่าเรื่องเหล่านี้ให้กับ community งานศิลปะ ก็มีทั้งเสียงตอบรับที่ดี และไม่ดีปนกันไป มีบางคนยืนยันเสียงแข็งไปในทำนองว่า ไอ้เรื่องแบบเนี้ยไม่ได้กินเขาหรอก เพราะเขาตั้งใจแน่วแน่ว่างานศิลป์ของเขา เขาไม่เอาเข้ามายุ่งในโลก digital currency เด็ดขาด ซึ่งผมก็เคารพมุมมองเขาครับ แต่มันจะดีกว่ามั้ย ถ้าเราเปิดหูเปิดตาให้ทันเทคโนโลยี โดยเฉพาะเรื่อง digital currency , blockchain โดนโกงทีนึงนี่คือหมดตัวกันง่ายกว่าเงิน fiat อีก
อยากจะมาเล่าให้ฟังครับ และอยากให้ช่วยแชร์ไปให้คนรู้จักด้วย จะได้ระวังตัวกัน
## Note
- ภาพประกอบ cyber security ทั้งสองนี่ของผมเองครับ ทำเอง วางขายบน AdobeStock
- อีกบัญชีนึงของผม "HikariHarmony" npub1exdtszhpw3ep643p9z8pahkw8zw00xa9pesf0u4txyyfqvthwapqwh48sw กำลังค่อยๆเอาผลงานจากโลกข้างนอกเข้ามา nostr ครับ ตั้งใจจะมาสร้างงานศิลปะในนี้ เพื่อนๆที่ชอบงาน จะได้ไม่ต้องออกไปหาที่ไหน
ผลงานของผมครับ
- Anime girl fanarts : [HikariHarmony](https://linktr.ee/hikariharmonypatreon)
- [HikariHarmony on Nostr](https://shorturl.at/I8Nu4)
- General art : [KeshikiRakuen](https://linktr.ee/keshikirakuen)
- KeshikiRakuen อาจจะเป็นบัญชี nostr ที่สามของผม ถ้าไหวครับ
-

@ 8947a945:9bfcf626
2024-10-17 07:33:00
[](https://stock.adobe.com/stock-photo/id/1010191703)
**Hello everyone on Nostr** and all my **watchers**and **followers**from DeviantArt, as well as those from other art platforms
I have been creating and sharing AI-generated anime girl fanart since the beginning of 2024 and have been running member-exclusive content on Patreon.
I also publish showcases of my artworks to Deviantart. I organically build up my audience from time to time. I consider it as one of my online businesses of art. Everything is slowly growing
**On September 16**, I received a DM from someone expressing interest in purchasing my art in NFT format and offering a very high price for each piece. We later continued the conversation via email.

### Here’s a brief overview of what happened

- The first scammer selected the art they wanted to buy and offered a high price for each piece.
They provided a URL to an NFT marketplace site running on the Ethereum (ETH) mainnet or ERC20. The site appeared suspicious, requiring email sign-up and linking a MetaMask wallet. However, I couldn't change the wallet address later.
The minting gas fees were quite expensive, ranging from **0.15 to 0.2 ETH**

- The scammers tried to convince me that the high profits would easily cover the minting gas fees, so I had nothing to lose.
Luckily, I didn’t have spare funds to purchase ETH for the gas fees at the time, so I tried negotiating with them as follows:
1. I offered to send them a lower-quality version of my art via email in exchange for the minting gas fees, but they refused.
2. I offered them the option to pay in USD through Buy Me a Coffee shop here, but they refused.
3. I offered them the option to pay via Bitcoin using the Lightning Network invoice , but they refused.
4. I asked them to wait until I could secure the funds, and they agreed to wait.
The following week, a second scammer approached me with a similar offer, this time at an even higher price and through a different NFT marketplace website.
This second site also required email registration, and after navigating to the dashboard, it asked for a minting fee of **0.2 ETH**. However, the site provided a wallet address for me instead of connecting a MetaMask wallet.
I told the second scammer that I was waiting to make a profit from the first sale, and they asked me to show them the first marketplace. They then warned me that the first site was a scam and even sent screenshots of victims, including one from OpenSea saying that Opensea is not paying.
**This raised a red flag**, and I began suspecting I might be getting scammed. On OpenSea, funds go directly to users' wallets after transactions, and OpenSea charges a much lower platform fee compared to the previous crypto bull run in 2020. Minting fees on OpenSea are also significantly cheaper, around 0.0001 ETH per transaction.
I also consulted with Thai NFT artist communities and the ex-chairman of the Thai Digital Asset Association. According to them, no one had reported similar issues, but they agreed it seemed like a scam.
After confirming my suspicions with my own research and consulting with the Thai crypto community, I decided to test the scammers’ intentions by doing the following
I minted the artwork they were interested in, set the price they offered, and listed it for sale on OpenSea. I then messaged them, letting them know the art was available and ready to purchase, with no royalty fees if they wanted to resell it.
They became upset and angry, insisting I mint the art on their chosen platform, claiming they had already funded their wallet to support me. When I asked for proof of their wallet address and transactions, they couldn't provide any evidence that they had enough funds.
Here’s what I want to warn all artists in the DeviantArt community or other platforms
If you find yourself in a similar situation, be aware that scammers may be targeting you.
-----------
### My Perspective why I Believe This is a Scam and What the Scammers Gain
[](https://stock.adobe.com/stock-photo/id/1010196295)
From my experience with BTC and crypto since 2017, here's why I believe this situation is a scam, and what the scammers aim to achieve
First, looking at OpenSea, the largest NFT marketplace on the ERC20 network, they do not hold users' funds. Instead, funds from transactions go directly to users’ wallets. OpenSea’s platform fees are also much lower now compared to the crypto bull run in 2020. This alone raises suspicion about the legitimacy of other marketplaces requiring significantly higher fees.
I believe the scammers' tactic is to lure artists into paying these exorbitant minting fees, which go directly into the scammers' wallets. They convince the artists by promising to purchase the art at a higher price, making it seem like there's no risk involved. In reality, the artist has already lost by paying the minting fee, and no purchase is ever made.
In the world of Bitcoin (BTC), the principle is "Trust no one" and “Trustless finality of transactions” In other words, transactions are secure and final without needing trust in a third party.
In the world of Ethereum (ETH), the philosophy is "Code is law" where everything is governed by smart contracts deployed on the blockchain. These contracts are transparent, and even basic code can be read and understood. Promises made by people don’t override what the code says.
I also discuss this issue with art communities. Some people have strongly expressed to me that they want nothing to do with crypto as part of their art process. I completely respect that stance.
However, I believe it's wise to keep your eyes open, have some skin in the game, and not fall into scammers’ traps. Understanding the basics of crypto and NFTs can help protect you from these kinds of schemes.
If you found this article helpful, please share it with your fellow artists.
Until next time
Take care
## Note
- Both cyber security images are mine , I created and approved by AdobeStock to put on sale
- I'm working very hard to bring all my digital arts into Nostr to build my Sats business here to my another npub "HikariHarmony" npub1exdtszhpw3ep643p9z8pahkw8zw00xa9pesf0u4txyyfqvthwapqwh48sw
Link to my full gallery
- Anime girl fanarts : [HikariHarmony](https://linktr.ee/hikariharmonypatreon)
- [HikariHarmony on Nostr](https://shorturl.at/I8Nu4)
- General art : [KeshikiRakuen](https://linktr.ee/keshikirakuen)
-

@ 472f440f:5669301e
2024-10-16 01:57:41
Over the last four years bitcoin has, among other things, established itself as an incredible corporate treasury asset that benefits those who adopt it as such. Microstrategy is the shining example of this theme going from a company that was hovering barely above a ~$1B market cap in mid-2020 to a ~$40B market cap company holding more than 1% of the 21,000,000 bitcoin that will ever exist. Microstrategy's success has emboldened a number of other publicly trader companies to follow suit. Bitcoin as a corporate treasury asset is well on its way to becoming a standard. If you run a business that doesn't hold bitcoin on its balance sheet you are doing yourself, your customers and your shareholders a disservice.
This is a trend that has its legs under it and will accelerate moving forward. A trend that I believe will emerge this cycle is incorporating bitcoin into real estate markets. Leon Wankum has been beating the drum about this for the last few years and I had the pleasure of sitting down with him this morning to record an episode of TFTC that will be published tomorrow morning. Leon is a real estate developer in Germany and he has made it his mission to educate and warn others in real estate about the demonetization of real estate that is under way due to the fact that bitcoin exists and it provides a far superior alternative.
These are pretty stark numbers. Nothing highlights the superior monetary properties of bitcoin better than looking at a chart of the average price of a home priced in USD v. bitcoin.
Since 2016: +46% in USD -99% in BTC
Since 2020: +34% in USD -70% in BTC
The funny thing is that an overwhelming majority of the individuals who make their living in real estate markets do not understand that this is happening to them. Many think they are doing exceptionally well all things considered. Sure, there may be a bit of a slow down and price retraction due to a couple of years of relatively elevated interest rates, but don't worry! The Fed is lowering rates again and the good times are about to start back up. Nothing could be further from the truth. This trend is going to continue unabated until bitcoin is fully monetized and those is the real estate industry, particularly real estate developers and those who lend capital to developers, should seriously take the time to understand what is happening to them.
Real estate is the largest store of value asset in the world at the moment. The most common number that is thrown around for the total size of the market is $300 TRILLION. $300 TRILLION of wealth being stored in an asset that is illiquid, comes with maintenance costs, taxes, insurance premiums, and susceptible to extreme weather event, among other things. Compared to bitcoin - which is extremely liquid, saleable, divisible and hard to confiscate, real estate is a far superior asset to store your wealth in. This is something that I'm sure is well understood by many of you reading this letter.
What's less understood is the dynamics of the real estate development market over the last few years, which have been severely hindered by elevated interest rates. The higher interest rate environment coupled with the inflationary pressures that forced rates higher in the first place have put developers in a predicament; they have a higher cost of capital to start new projects with raw material prices that are still much higher than they were before the economic lock downs of 2020-2022. This has led to a scenario where it isn't advantageous to start new projects and the projects that broke ground in 2021-2023 are finding that they need to incur more debt to get their developments across the finish line.
Despite the fact that interest rates are on their way back down, it doesn't seem like the economics of these projects are going to materially improve in the short to medium-term as headline inflation begins to creep back up. Couple this with the fact that the jobs market is cratering while real wages struggle to keep up with inflation and many builders are going to find themselves in a situation where they do actually complete a development problem but their cash flow suffers because their customers can't afford the inflated rents that builders will have to charge to get a return on their outlaid capital. Many will be put in a situation where they are forced to be happy with lower rents (cash flow) or sit on the sidelines making no cash flow.
The post-1971 era that brought with it a booming real estate industry is suffering the same fate as the bond market; the generation bull market is over. Real estate prices may go up, but that will be nothing more than a mirage of wealth creation. The unit of account those prices are built on is in dollars, which are being debased at an accelerating rate. Developers, banks and borrowers need to de-risk their real estate exposure and, as Leon points out, bitcoin is the only way to do this in an effective way.
Moving forward developers will have to finance by dual collateralizing their debt with the real estate and bitcoin. In the graphic below Leon illustrates what this type of financing structure will look like. Instead of taking $10m of debt to finance a project and putting it all into materials, construction and marketing, a developer will take out a $10m loan, put $1m in bitcoin and the rest toward the development project. Over the course of the construction of the real estate project, bitcoin will sit in the credit structure and, if held for 4+ years, should increase significantly in value. Saving the builder from risk of default and providing him some optionality in terms of what he can do with the project once it's finished.
In this scenario downside risk is contained - a developer isn't pouring all of the cash into bitcoin at the beginning so the worst case scenario is that bitcoin goes to zero (highly unlikely) and they can eat the small loss and hope to make up with it via cash flows once a project is finished, while upside potential is enormous. Bitcoin is still monetizing and having exposure to the hardest monetary asset the world has ever while it's monetizing has proven to be massively beneficial.
We are still in the early days of bitcoin and this idea will likely seem absolutely insane to most Tradfi investors, but I strongly believe that developers, banks and end consumers who don't leverage this type of bitcoin structured credit will be cooked in the long-run. And those that take advantage of this type of structure first will be considered geniuses in 20 years.
There are many more nuanced benefits to this strategy; holding bitcoin allows landlords and management companies to weather ongoing maintenance costs throughout the years, those who take out mortgages dual collateralized with a house and bitcoin not only protect the equity value of their property but could see their equity values increase significantly more than others using vanilla mortgages, and builders who accumulate bitcoin in their treasuries will be able to use better raw materials when building, which leads to more valuable properties that cash flow for longer.
Again, it's going to take time for these types of structures to become commonplace in the market, but I firmly believe this cycle will be the cycle that these strategies get off the ground. In four to five years they will have a track record and after that it will be considered irresponsible not to finance real estate in this way. The banks will begin to demand it.
---
Final thought...
Sinus congestion sucks.
-

@ eac63075:b4988b48
2024-10-15 20:18:52
Bitcoin emerged as a promise of financial freedom, challenging the traditional and centralized structures of governments and financial institutions. Since its inception, many enthusiasts have believed in the revolutionary potential of this cryptocurrency. However, over the years, challenges have arisen that have tested this promise, especially concerning centralization, the implementation of secondary layers like the Lightning Network, and issues of governance and privacy.
https://www.fountain.fm/episode/SDZYaFMyLEO1krL6x8RD
## **Centralization and the Exclusivity of Nostr**
Nostr, a decentralized network aiming to be censorship resistant, emerged as an attempt to solve some inherent problems of centralization. However, it faces significant challenges. Many users point out that, despite its promise, Nostr is still not attractive to the general public, being exclusive to a specific niche.
Additionally, issues of centralization still permeate the network. Discussions on GitHub revealed that developers chose not to implement an absolute level of privacy, a decision many considered inadequate. Even with protocols developed to ensure total privacy—such as the non-identification of IPs and communicating parties—the network still lacks this robust implementation.
## **Individual Freedom and Data Protection**
A recurring issue is the importance of demonstrating that real options exist for citizens to protect and preserve their freedom. In a world where most discussions about Bitcoin revolve around its use as an investment asset, there is an urgent need to emphasize its potential as a tool for financial freedom.
The Bitcoin community should focus on development and education, showing that the conscious use of cryptography and decentralized transactions can protect individuals against excessive government surveillance and control. Secure and private communication is fundamental, and Bitcoin, along with privacy technologies, can provide this.
## **Hyperbitcoinization and the Illusion of Store of Value**
Hyperbitcoinization is a concept that refers to the moment when Bitcoin will replace fiat currencies worldwide. However, achieving this state is not simple, especially when Bitcoin is seen primarily as a store of value. Since 2017, this narrative has gained strength, promoting the idea that accumulating Bitcoin will lead to automatic wealth.
However, this perspective is limited. The true value of Bitcoin lies in its use as a transactional currency, not just in its scarcity. The community must work to ensure that Bitcoin is utilized in everyday transactions, strengthening its network and demonstrating its real value.
## **The Role of the Community in Bitcoin's Development**
Bitcoin's strength comes from its community. Developers, users, and enthusiasts, through their actions and support, make Bitcoin a powerful tool. This community is responsible for ensuring that Bitcoin maintains its essence and that its functionalities are accessible to all.
It is crucial that this support network continues promoting the decentralized use of Bitcoin, without intermediaries that can censor or control transactions. Adopting Bitcoin in a centralized manner, through banks or other institutions, contradicts its original proposal and strengthens those who have historically opposed its existence.
## **Sidechains, Second Layers, and the Lightning Network**
Sidechains and second layers, like the Lightning Network, are essential components for Bitcoin's scalability. However, they bring challenges, especially regarding the need to trust intermediaries. For these solutions to be effective, it is fundamental that they allow the unilateral withdrawal of funds, ensuring that users maintain full control over their assets.
The Lightning Network, for example, is a second layer that allows fast and cheap transactions. However, many users face difficulties when dealing with channels that do not close correctly, resulting in locked funds. These problems must be solved for the network to be truly decentralized and functional.
## **The Fight Against Centralization on the Internet**
Centralization is not a problem exclusive to Bitcoin. The internet as a whole faces similar challenges, with data control concentrated in the hands of a few large technology companies. To ensure freedom of expression and online privacy, it is necessary to decentralize these data clusters.
Projects that seek to decentralize the internet are vital for this mission. They not only complement Bitcoin in its quest for financial freedom but also ensure that digital communication and expression are protected against censorship and corporate control.
## **The Future of Bitcoin and the Need for Action**
The future of Bitcoin depends on the community's action. We cannot expect Bitcoin to automatically become a global medium of exchange. A conscious effort is necessary to build an ecosystem where Bitcoin can flow freely, being used in everyday transactions and valued for its utility.
Moreover, with the imminent arrival of central bank digital currencies (CBDCs), time is of the essence. CBDCs represent a significant challenge, as they can further restrict individuals' financial freedom. Therefore, accelerating Bitcoin adoption and ensuring it maintains its decentralized and uncensorable properties is a priority.
## **Conclusion**
Bitcoin remains a powerful tool for financial freedom but faces significant challenges. Centralization, both in the context of secondary networks and the internet in general, poses a threat to its original proposal. However, with the joint action of the community and the continuous development of decentralized solutions, it is possible to maintain Bitcoin as a bastion of individual freedom.
The true revolution of Bitcoin lies in its use as a medium of exchange, not just as a store of value. To achieve hyperbitcoinization, it is necessary to build a robust ecosystem where Bitcoin can circulate freely and be accessible to all. Only then can we fulfill Bitcoin's initial promise and ensure it continues to be a tool for freedom and financial autonomy.
-

@ 599f67f7:21fb3ea9
2024-10-14 19:36:50
Inoiz pentsatu al duzu norbaiti satoshiak modu originalean oparitzea, Bitcoin mundura hurbiltzeko? LNbits zorro batekin NFC opari txartel bat erraz sor dezakezu. Honek LNURLw esteka bat NFC txartelean idatziz funtzionatzen du, eta jasotzaileak bere satoshiak erabili ditzake LNURL gaitutako zorro batekin.
### Zer behar dut?
- LNbits zorroa
- Android telefono bat
- NTAG2* gaitasunak dituen NFC txartela, adibidez NTAG216.
💡 NTAG2* txartelek esteka **bat** idazteko aukera ematen dute. Adibidez, enpresaren webgunerako URLa duen bisita-txartel gisa joka dezakete. NTAG424 txartelek ez dute memoria handiagoa bakarrik, baizik eta SUN parametro deitzen den zerbait ere badute, zerbitzariaren autentifikazioa ahalbidetzen duena, eta horrek segurtasun gehiago ematen die zure ordainketei. Azkenean txartel mota hau [BoltCard](https://boltcard.org/) bat bihur daiteke.
### 1. Hedapena aktibatu
Ireki zure LNbits zorroa. Tresna-barran, aktibatu `Withdraw Links` hedapena eta ondoren joan hedapenera.
### 2. Erretiratzeko esteka sortu
`Withdraw Links` hedapen orrian, aukeratu `Advanced Withdraw Link(s)` aukera.
Ondoren, aukeratu satoshiak ateratzeko erabiliko duzun zorroa. Ziurrenik, hori zure LNbits zorro nagusitik bereizi nahi izango duzu. Horretarako, LNbits zorro berri bat sor dezakezu tresna-barratik, `+ Add a new wallet` aukera hautatuz. Behin zorro berria sortuta, sartu satoshi batzuk bertan.

Eman izenburu bat erretiratzeko estekari.
Ezarri erreskatatu daitezkeen gutxieneko eta gehienezko zenbatekoak.
Ezarri esteka zenbat aldiz erabil daitekeen eta erretiratze saiakeren arteko denbora.
Aukeran, argazki pertsonalizatu bat gehi dezakezu `Use a custom voucher design` laukitxoa markatuz, eta .png irudi baten URL-a sartuz.
Gogoan izan “assmilking” laukitxoa ez markatzea.
Konfigurazioa amaitu ondoren, jarraitu erretiratzeko esteka sortzera.
### 3. Idatzi esteka NFC txartelean
Zure erretiratzeko esteka berrian, klikatu `View LNURL` estekan. Ondoren, sakatu `Write to NFC` botoia eta eutsi NFC txartela telefonoaren aurrean idazketa-prozesua burutzeko.

✔️ **EGINDA**
💡 Esan txartelaren jasotzaileari satoshi saldoari buruz, denbora ez dezan galdu azkeneko satoshia lortzen saiatzeko.
💡 Jasotzaileak txartelaren satoshiak atera ondoren, bere zorroan berridatzi dezake eta berrerabili. Gainera, eman diozun txartela NTAG424 bada, aurreko gidako (nostr:naddr1qqxnzd3e8qcr2wfn8qcrgwf4qyg8wumn8ghj7mn0wd68ytnhd9hx2q3qtx0k0a7lw62vvqax6p3ku90tccgdka7ul4radews2wrdsg0m865sxpqqqp65whwqrr5) bezala Lightning "zor txartela" bihur dezake. Baina txartela NTAG2* bakarrik bada, beste opari txartel bat bihur dezake soilik.
-

@ 5e5fc143:393d5a2c
2024-10-11 22:15:54
We are now given a choice of digital freedom #nostr .
Creativity for every nostrich is now unleashed from the cage of bigtech censorship , rules and algo. But freedom comes with responsibility so pick right one(s). I will try share here some learning experience both technical and also from fundamental point of view. Just wanted kick start this article n fill as we go like living reference document.
Nostr itself is an application layer protocol that can used beyond just social media mirco or long blogging. Each nostr client heavily dependent on back-end servers call nostr "Relay servers" or in short "rs" or "relays" Relays can hosted anywhere in clearnet internet, onion net , vpn , i2p , nym
Relays are controlled by their respective admins based NIP specs that they select to implement according to own decisions. Relays can have certain ToS (Terms of Service) Rules to adhered too.
New users can choose and pick client or app (ios / android/ windows) with preset of relays in the simplest form , but other advanced users need to do a regular manual relay management.
Relay management is an active regular task based on where when n how you are using.
Relay list are saved within you npub profile backup file which can edited and broadcast anytime.
Relay management is an active regular task based on where when and how you are using.
Relay list always need to be updated time to time as and when needed.
2 Users MUST a common RELAY between them even if one only need to follow another.
Occasionally you may notice certain npub accounts you are following already but cannot see frequent notes publish by them – one of cause maybe you not sharing a common relay
Most nostr client applications has SETTINGS where user choose add/remove relays
Also user choose which function to enable - READ or WRITE
Relay list for your account is always saved within you npub profile backup file which can edited and broadcast anytime. Hence any app or browser when u login with you npub the same relay list will be enforced. There could valid reasons why u need have list for if you trying to save bandwidth and traveling.
Functions in app.getcurrent.io and primal.net app for mobile apple or android are ideal for user traveling abroad and wanted to save bandwidth since relay management is done the providers in backend and saves hassle for basic usage.
Remember if someone is selecting relay on your behalf then you may not be necessarily able to pull and get some specific and special content that you may need. Such providers like coracle and nostrid also give option to override the default relays they selected.
Relay types: They can be categorized by various features or policy or technologies.
FREE PUBLIC Relays vs PAID PUBLIC Relays
PAID relays provide unrestricted access / write / filtering options than FREE relays but both are public clearnet relays. Just subscribing to PAID relays will not solve all problems unless you choose the relays properly and enable settings correctly.
Private Replay or Tor Relays – normally not easily visible until unless someone tell you.
You can also host own private relay not opened to internet of archive and back of your own notes.
The technical landscape in nostr can be fast changing as more NIPs get proposed or updated.
Relays admin can choose implement certain NIPs or not based on policy or technical limitations.
Example NIP33 defines “long notes” aka blogs as you now reading this in habla site which #1 UI and site for "Editable" long notes – some relays donot implement or allow this.
NIP07 is used for client authentication like nos2x and is implemented by all relays in fact.
Nostr is so fasting changing-hence many links many broken Pushing long note again.
To be continued again ... reference pics will added later also
Hope this help you understand "why when what" to tune and maintain active set of proper relays.
Relay Proxy, Relay aggregator or Relay multiplexer – Paid, Public, Free, Private, Event, Relays
That’s all for now n more later ... Thank you 🙏 ! ⚡️ https://getalby.com/p/captjack ⚡️ PV 💜 🤙
References:
https://habla.news/relays
https://relay.exchange/
https://relays.vercel.app/
https://nostr.info/relays/
https://nostrudel.ninja/#/relays
Related Articles:
https://thebitcoinmanual.com/articles/types-nostr-relays/
nostr:naddr1qqd5c6t8dp6xu6twvukkvctnwss92jfqvehhygzwdaehguszyrtp7w79k045gq80mtnpdxjuzl9t7vjxk52rv80f888y5xsd5mh55qcyqqq823cf39s98
https://habla.news/u/current@getcurrent.io/1694434022411
-

@ 472f440f:5669301e
2024-10-11 14:20:54
As we sprint toward the 2024 US Presidential election the case for using bitcoin as an asset to store value for the long term has never been stronger. The insanity of the incumbent power structure is being laid bare and it is becoming impossible to ignore the headwinds that the Borg faces moving forward.
Yesterday morning and earlier today it became clear that inflation is rearing its head again. Not ideal for the soft landing Jerome Powell and Yellen are signaling to the markets after the first Fed Funds rate cut in years.
It seems like the yield curve predicted this earlier this week when it inverted after a temporary normalizing period after the Fed's rate cut. Futhermore, it is becoming glaringly obvious that running historically high fiscal deficits while interest rates were at multi-decade highs was a pretty bad idea. As James Lavish points out, the data from the CBO earlier this week shows that the US federal government is running a deficit that is 13% higher than it was last year. This is at a time when real wages are still depressed, inflation is still suffocating American consumers and the private sector job market for American citizens is cratering.
Speaking of the job market, the numbers that came in yesterday were worse than expected:
The effect of Hurricane Helene should certainly be taken into consideration when looking at this jobs miss. However, even with the miss we know that these numbers have been under reported for years to make the economy seem healthier than it actually is. Even with Helene's effect taken into consideration this print will likely be revised higher 3-6 months from now.
All of this points to a breaking point. A breaking point for the economy and, more importantly, a breaking point for overall confidence in the US government and its ability to operate with any semblance of fiscal responsibility. The chart that Pierre Rochard shares in the tweet at the top of this letter is the only chart that matters for anyone attempting to gauge where we find ourselves on the path to bitcoin realizing its full potential.
There is $133 TRILLION worth of value sitting in global bond markets. Bitcoin is a far superior asset to store one's wealth in. Bond markets are beholden to the whims of the actors who issue those bonds. In the case of the US Treasury market, the largest bond market in the world, the US government. And as we have pointed out above, the US government is recklessly irresponsible when it comes to issuing debt with a complete inability to pay it back on the long-term. Inflation is up, the jobs market is cratering for the native born Americans who actually pay taxes, and the push toward a multi-polar geopolitical landscape is becoming more pronounced by the day. All of this points to a long-term weakening in demand for US treasuries.
The only way out of this mess is to overtly default on this debt or inflate it away. The latter will most certainly be the route that is taken, which positions bitcoin extremely well as people seek the confines of an asset that cannot be debased because it cannot be controlled by a central authority.
The levels of sovereign debt in the world are staggering. Do not let the bitcoin price consolidation of the last six months lull you into a state of complacency. Even the results of the Presidential election won't have a material effect on these dynamics. Though, a Donald Trump presidency would certainly be preferable if you prefer to see relatively sane policy enacted that would provide you with time to find safety in bitcoin. But, in regards to this sovereign debt crisis, that is the only benefit you can hope for; more time to prepare.
I'll leave you with some thoughts from Porter Stansberry:
"We are about to see the final destruction of the American experiment. Every economist knows this (see below) is correct; but nobody is going to tell you about it. I’ll summarize in plan English: We are fucked.
1. Debt is growing much faster than GD and interest expense is growing much faster than debt; and the real growth in entitlement spending hasn’t even begun yet.
2. Progressive taxation means nobody will ever vote for less spending + the combined size of government employees and dependents, there’s no way for America’s actual taxpayers (about 20m people) to ever win an election, so the spending won’t stop growing and, ironically, inflation will make demands for more spending to grow.
3. Inflation undermines both economic growth and social cohesion. The purple hair man-women weirdos are only the beginning; what comes next is scapegoating jews, blacks, immigrants and a huge increase in violence/domestic terror.
Get ready America. This election has nothing to do with what’s coming. And neither Trump nor Kamala can stop it.
Our experiment in freedom and self-government died in 1971 (when all restraint on government spending was abandoned with the gold standard.) You can only live at the expense of your neighbor until he runs out of money.
And that day is here."
---
Final thought...
I hope my tux still fits for this wedding.
Enjoy your weekend, freaks.Use the code "TFTC" for 15% off
-

@ e88a691e:27850411
2024-10-11 13:17:16
# An opinionated guide to Sauna.
By NVK [🌐](https://primal.net/nvk) [🐦](https://twitter.com/nvk)
## Introduction
Updated from the Sauna, October 7th 2024
After years of experimenting with different sauna types, I’ve developed strong opinions on the subject. The purpose of this article is to share these opinions with anyone who is interested in them and, hopefully, help others get more out of their sauna experience.
I’m certain my opinions will offend some, including all the people who (in my view) are doing it wrong. I know that saunas are important to many cultures around the world and that my strongly held opinions may offend some of those cultures.
Mind you, although I grew up in South America, I do have a fair amount of slavic blood in me. When I was a child, my grandfather regularly took me with him to the shvitz. One of my fondest memories from this time was the “Scottish Bath”, which involves standing against the sauna wall, execution-style, so that someone can spray you with freezing water from a high pressure hose. I’ve never heard of this outside of South American and can’t attest to whether it has any real Scottish origins.
The various health claims about using a sauna are beyond the scope of this article. All I have to say is that, like many things in my life, like Bitcoin, the meat/keto diet, and fasting, I find sauna to be yet another cheat code to life: it’s a simple thing that just makes life a lot better. If you want a good primer on scientific health benefits of sauna, I recommend starting with [this article by Rhonda Patric](https://www.foundmyfitness.com/topics/sauna). She goes in depth.
To be clear, it should go without saying that I am not a medical expert or professional. None of the opinions below are, or should be interpreted as, medical advice. There are many people for whom sauna use is not recommended. It would be prudent for any sauna user to consult with his or her doctor before entering a sauna.
_Thanks to S. for taking the time to do a very helpful first review of this article. And thanks to The Wife for helping make my words legible and helping me make time to sauna–I don’t know which sacrifice was bigger._
## Banya or Nothing
When I talk about saunas, I’m talking about a sauna with a stove, either wood or electric, that allows for steam. I call this “Banya style”. To be clear, I’m distinguishing between saunas and steam baths. Steam baths have their own place, but they aren’t my thing and I don’t consider them saunas.
A breakdown of the main types of saunas may be helpful, so you know which to avoid:
1. Wet saunas, which are typically cedar rooms with wood burning or electric stoves onto which you throw liquid to create steam (I call this “Banya style”);
2. Dry saunas, which are typically cedar rooms with wood burning or electric stoves without added steam (like Korean style saunas); and
3. Infrared saunas, which, unlike traditional saunas, don’t heat the surrounding air. Instead, they use infrared panels to warm your body directly.
In my opinion, it’s Banya style or nothing. I’m not a huge fan of dry saunas, and I don’t even bother with infrared saunas. Infrared is a fiat-shitcoin. I want steam!
## How to Sauna
### Sauna Etiquette
If you read no other part of this already-too-long-article, read this.
Saunas are social places. There are proper ways of being in a sauna with others, and there are ways to do it wrong. You don’t want to be the person who ruins it for everyone. Here are some important etiquette tips:
**Silence vs. Chatting:** It’s not a question of whether you have to stay silent in a sauna or if it’s ok to talk. It depends on the circumstances and who else is around. If you’re using a sauna that isn’t your own, ask the staff about the preferred custom. The noise level in a sauna differs depending on the group in the sauna at a particular time. If you do want to chat with others, there’s nothing wrong with that. But, pay attention to whether there are others in the sauna who'd prefer it quiet. And definitely do NOT be obnoxiously loud – yes, I’m looking at you bachelor(ette) group who just discovered the Russian Banya.
**Coming and Going:** People rotate in and out of the sauna at different paces, so there will be people coming and going during your shvitz. But there are ways to come and go that are considerate and proper.
Keep the f-ing door closed (which was the working title of this article). Once you leave, don’t come back inside moments later. Doing so disturbs your fellow sauna users, lets out the all-important steam, and prevents the sauna from reaching an appropriate temperature.
If you’re in the sauna with a group of friends, try to coordinate your comings and goings so you’re all on the same cycle.
If you can only last 5 min at a sauna, don’t go in too often at the risk of ruining it for others (assuming it’s not your own private sauna).
Be fast when closing the sauna door when you come or leave. Otherwise, you will get dirty looks from others and may even hear mumbles of “quick quick, fast fast” from a Gray Beard. And you will deserve it.
Never open the door right after someone puts water on the stove to make steam. It’s all about the steam. Don’t waste it.
**Controlling the heat:** if you can’t handle the heat in the sauna, don’t just turn the heat down, because it ruins it for others. Instead, go to a lower bench or get out and take your break. Saunas are meant to be hot. That’s the whole point.
**Personal Hygiene:** Shower before you go into the sauna. Don’t wear perfume, smelly deodorant, or fragrant lotions. Smells get amplified in a sauna. Have a towel under you, don't leave your drippings behind. Best yet, make a Z with your towel, this covers your butt and down under your feet.
**Clothing:** sauna is not a place for wearing clothing. It is a place to get back to nature. If you are shy, just wrap a towel around yourself. People ask if I don't feel awkward, the answer is no. Who cares, humans naked is not novel. In many countries, it is strictly forbidden to wear clothing or bring anything but a towel into the sauna. It's understandable that may not be possible in North American public saunas on mix gender "family" days. If you have to wear something, then wear something 100% cotton or marino wool. You don't want plastic being backed into your genitals. One more thing, leave the watch out as it gets hot and will burn you. Also, flip-flops/sandals, stay outside.
Some saunas sell body scrubs and masks for you to apply before or in the sauna. Note that once in the heat, these can get goopy and drippy and may melt into your eyes and mouth. So (in this opinionated guides’ wife’s opinion), they are better in theory than reality.
**Adding Oils and scents:** As discussed below, it can be nice to add certain oils and other scents to the steam. But if there are others in the sauna, ask first before you do.
**Where and how to sit:** Hot air rises. So, the higher benches are hotter and the lower benches are cooler. If you are a newbie, pick a lower bench so you don’t have to leave as quickly and open the door unnecessarily.
It’s great to lay down in the sauna, but if it gets crowded, sit up to make room for others.
When moving around to find your seat, don’t walk on the benches in your sandals. Leave your sandals outside the sauna or on the sauna floor.
### Sauna Temperature
In most proper Russian style Banyas you will find temperatures of 80-95 degrees celsius, which, in my opinion, is the best range. Thats near your body. "Offical" on the dial will he 100-120C. But sometimes you want to take it a little easier or last a little longer in the sauna. In these cases, 65-85 at body, dial at 80-100. degrees celsius will do.
However, if your sauna is below 85 degrees celsius on the dial, you might as well just go hide under your bed sheets and not waste your time.
At some saunas in hotels, gyms, or spas, you may not be allowed to set the sauna as high as you’d like (see below). There are many tricks to circumvent these frustrating restrictions, but my legal counsel has advised me not to go into any details here.
### Sauna Duration
The amount of time you spend in the sauna is a matter of personal preference and depends on the number of cycles you do (more on cycles, below).
For your first round, my opinion is that most people should try to last 15 minutes in the sauna. If a sauna is at the proper temperature, most people will struggle to stay inside any longer. If you can stay inside for 20-30 minutes, your sauna is probably too cold and/or there is not enough steam. Many saunas have hourglasses inside to keep time, and I’ve never seen a sauna hourglass with more than 15 minutes, which should be a good hint.
My preferred is;
Cold Plunge => Sauna 15 min => Cold Plunge => Hydrate with Salt & Water, Rest 5-10min => Sauna 15min => Cold Plunge => Hydrate with Salt & Water, Rest 5-10min => Sauna 15min => Cold Plunge => Hydrate with Salt & Water, Rest
if you can rest in the sun even better (no sunscreen poison please). You can add alcohol drinks to the hydration if you feel comfortable with that. But only add food after the last cycle.
For subsequent rounds, hydration starts to play a bigger role in how long you stay inside. Most people seem to last longer on their first round than on their second or third. If you can do 15 minutes on your second round, great. But 5-10 minutes is also fine.
### Sauna Cycles
The traditional Russian Banya method (and in this writer’s opinion, the best method) is to do sauna cycles. Go into the sauna and just stay as long as you can take it (up to 15 minutes or so). Then take a cold shower and/or cold plunge (see below). Then robe-up and go relax with water, tea or beer. Once you start feeling “normal” again, repeat. For me, three cycles is the sweet spot. I’ll do more cycles if I’m spending the day at the Banya facility. If I’m at home, where I often sauna every other day, I find just one or two cycles does the trick. Sometimes I add a cycle or two on the weekend.
Occasionally, I like to go into the sauna as it’s warming up and before it reaches optimum heat (i.e. at around 60 degree celsius). This way, I can stay longer in the sauna for my first round (about 30-40 minutes). If I take this approach, I generally only do one more short round after my cold plunge.
### Cold showers and plunges
In my experience, you want to take a cold shower or a cold plunge (or both, plunge is better) after the sauna cycle.After you come out of the sauna, immediately jump into cold plunge for a bit, i don't like to stay too long. Some Banya facilities will have a bucket filled with cold water that you can pull with a string to let the water pour over you, pull a couple times. The banyas may also have a cold pool of water into which you can plunge for a bit.

If I’m at my country place, after I get out of the sauna I jump into the cold lake. If it’s winter, I like to roll in the snow, which is satisfying. Some cultures would say that it’s not a real sauna experience unless you roll in at least one foot of snow.
After your cold shower or plunge, put on a warm robe and go relax before going back into the sauna. I like to relax for 5-20 minutes, depending on how much time I have. This allows the body’s temperature to decrease slowly. I do not recommend going directly back into the sauna after your cold plunge. If you don’t give yourself enough time after the cold plunge, you will overheat and won’t last very long when you return to the sauna.
### Position
There really are no rules here. The way you position yourself in the sauna depends on your mood and preference, and there are many options. For example, you can sauna seated with your legs hanging down or with your knees up. You can lie down if there’s room. My favorite position is to lie down on my back with my legs up against the wall and, assuming the ceiling is low enough, with my feet stretched against the ceiling. This is a great way to stretch the hamstrings (check out stretching under “Sauna Activities”, below).
Choosing whether to sit on a higher bencher or lower bench is the best way to control the temperature you experience without adjusting the room temperature itself. You will notice the heat in the sauna increases exponentially every inch you go up. If you are struggling to stay in the sauna but don’t want to get out just yet, try moving down to a lower bench to last a little longer. Lying on the floor is the coolest spot and a great place for kids to start getting exposed to saunas.
- - -
#### There is no shame in going to lower benches or even the floor, there is only shame in opening the door before 15min
- - -
### Getting Steamy
Without steam, the sauna would just be a sad, hot oven (I’m looking at you, infrared sauna).
The steam in the sauna has many benefits but most importantly it increases the thermal coupling of your body to the air and it feels great.
The amount of steam in the sauna is a matter of personal taste. You don’t want to make it into a steam room (remember, steam rooms are NOT saunas). But, you do want the sauna to be very moist. I find that two to four ladles of water in a mid-size sauna every five to seven minutes does the trick. Keep it between 50-60% humidity.
I keep a bucket of water in the sauna at all times so that I can continue to ladle water as I shvitz. Make sure to get a wood bucket and a metal ladle with a wooden handle. Wood ladles will crack, and if the handle is metal, it’ll burn you when you grab it.
If, when you enter the sauna, it’s already been on for a while, the wood is likely to already be wet and the sauna full of steam, so you may not need to add too much water. However, if you’ve just turned on the sauna and the wood walls are dry, you will need to ladle more water to make the air moist enough. If the sauna is too moist for comfort, open the door and let it dry out a bit (obviously, only do this in a private sauna).
Essential oils and even beer can all be added to the water to create scented steam. I recommend starting your sauna with just water, and add the scent as you get going.
You can try all sorts of different essential oils. I’ve tried everything from oak and cedar to tangerine and cinnamon (gag) essential oil. In the end, there are really only two oils that are worth it, in my opinion. The first is eucalyptus. I’ve experimented with different types of eucalyptus oil, and the variety you use makes a difference. My favorite is eucalyptus globulus. I also like diluted pine tar oil.
When you settle on your essential oil, add a healthy dose of the oil to the ladle filled with water. Never put the oil onto the oven directly. It’ll just burn.
In a few Russian facilities, I’ve seen Gray Beards pour Russian beer onto the oven and it was actually quite nice. It’s almost like being in a cozy bakery while you sweat
Some people like to place a salt brick or compressed solid blocks in their sauna from time to time. Put the salt block on the stove and pour water over it. The steam takes on a saltiness that feels nice. If a salt block is not available, you can get a cast iron teapot, fill it up with salt water, and place it on top of the stove.
And for my most important steam tip, I recommend using the “towel spin”. This is an effective and underrated technique to help circulate steam in the sauna. After creating steam, take your towel above your head and spin it around hard, like a ceiling fan. This movement works like a convection oven and spreads and equalizes the heat and steam throughout the room. It might make the folks sitting lower down in the sauna a little hotter, but that's what they’re there for, isn’t it?
### Hydration
Being hydrated is important to having a positive sauna experience. You will lose a lot of your body’s water in the sauna. Ideally, start to hydrate well up to an hour before your sauna. I like to add a pinch of salt to my water to encourage water retention.
Do not bring any drinks into the sauna (the exception being a dedicated steam-beer, see above). Have your water or beverage when you’re outside the sauna, resting. If you find you need to drink water inside the sauna in order to cool yourself down, then it’s time for you to get out and allow your body a cool-down.
When you’re outside the sauna, don’t immediately down a glass of super cold water because you will cool down your internal body too fast. Personally, I like to drink warm tea after my first two cycles. After my second cycle, I enjoy a beer (pre-keto days), soup, or vodka drink. When non-keto, I do enjoy adult drinks in the cycles.
If you are doing a sauna while on a multi-day fast, you need to have water and salt, at a minimum. Otherwise, you will deplete your natural reserve of electrolytes and not be able to think straight.
### Sauna Frequency
When it comes to frequency, if you are not in the equatorial heat do it every day. I now do mornings and end of day if I can. so 2x 2-3x cycles. In the summer, living in a hot & humid location, I sauna a lot less frequently. My desire to sauna is greatly diminished because I spend a lot of time in the sun and heat.
### What to wear
**Sauna Hat:** I highly recommend wearing a Russian/Finish style wool hat when you’re inside the sauna. It may seem counterintuitive, but wearing a hat keeps your head cooler. An overheated head is not good for your brain. Wearing the hat stops you from overheating and lets you stay longer in the sauna. The temperature in a sauna is significantly hotter the higher in the room you are, and one’s head is at the top of the body (for most people). So protect your brain in style with a felt sauna hat. If you don’t have a felt sauna hat, buy one. They are easily found online. But in the meantime, you can wrap a dry towel around your head. Don’t forget to take your sauna hat off as you relax between cycles so your head can cool down.

**Clothing:** These days, many public saunas will have family days, men-only days, and women-only days. For obvious reasons, you’re only allowed to sauna naked if you’re attending one of the single-sex days.
If you’re at home, there’s no good reason to wear shorts or a bathing suit. Sauna naked. It's a lot more pleasant.
If you do wear clothing in the sauna, be careful with items with materials like metal or plastic attached. Things like pins, buttons, or string-ends will get very hot and probably burn you. Remember to take off any heat-conductive jewelry and leave your smart watch outside, as the heat will ruin its battery.
Don’t wear your robe inside the sauna. A robe is what you wear outside when relaxing or eating. If you wear it inside, you’ll overheat (and look like an idiot). Go ahead and sweat out that body shame robe-free. You can bring a towel into the sauna to sit on, if you want.
Shoes or sandals are highly recommended in public facilities. I mean, there are many people walking around wet. Ew. But keep your sandals outside the sauna itself, or on the sauna floor.
### Sauna activities.
Don’t overthink it. Sitting in a sauna is activity enough, in my opinion. But there are some sauna activities you can do:
**Veniks/Viht beating:** these are bundles of leaves (commonly birch, oak, or eucalyptus) that are pre-soaked in hot water. Someone with both strength and capacity to exert themselves in the heat will beat your whole body with the leaves. This exfoliates your skin and also gets the plant oils to permeate your skin. And it’s very relaxing. If you’re at a sauna facility, don’t just grab any bundle you see lying around - that belongs to someone else and veniks aren’t shared. You have to bring your own or buy them at the front desk.
**Stretching:** this is a great activity to do in the sauna, but make sure to go very easy. Your muscles will be super warm and you don’t want to overdo it and hurt yourself.
**Exercise or Sex:** your heart better be in good shape if you try out these high intensity activities in the sauna. If you engage in the latter, you better be in your own home sauna. With respect to the former, I think doing some leg-ups can be very satisfying.
**Phone use:** If you’re at home, it’s nice to use your sauna time to shit-post on Twitter or read an article, if you feel like it. Just keep your phone close to the colder, lower parts near the floor or it’ll overheat and shut down. You can also place the phone outside of the air vent and play a [podcast! The Bitcoin.review is great ;)](https://bitcoin.review)
**Napping:** I don’t recommend this. If you fall asleep or pass out, you will probably die due to overheating or dehydration.
**Chatting:** Saunas are great places for conversations (subject to the caveats I address above). Note that nowadays, microphone modules are both very tiny and can withstand high temperatures, so it’s no longer recommended to reenact mafia movie sauna scenes.
**Eating and Drinking:** As discussed above, never have food or drink inside the sauna. But when you finish your sauna, take advantage of whatever snacks the facility offers. For Russian joints, the soups, fish roe and dry salty fish snacks are great. Again, don’t eat before your sauna; wait until you’re done. Some places will have bottled salty-ish lake water, and beer seems to be a good source of salts and re-hydration. Vodka drinks are nice sometimes, too. My favorites are vodka with beet juice and horseradish, vodka with pickle juice, or just a chilled shot of Zubrowka (vodka infused with bison grass). Teas are also very enjoyable post-sauna. I prefer non-caffeinated berry teas. Some Banyas even offer free tea to patrons.

## Ready to Sweat It Out?
Thanks to this fantastic guide to sauna, you’re now feeling confident and excited to seek out a solid sauna. So where do you go?
## Where to Find a Sauna
**Spas:** Spas are not the best place to have an optimal sauna experience. Saunas at spas are typically not hot enough and spas have annoying staff whose job it is to enforce idiotic rules and practices that prevent you from having a real sauna experience.
**Gyms & Hotels:** These are some of the worst places to sauna. For liability reasons, these saunas tend to be too cold and there are often mechanisms that prevent you from raising the temperature. Here, you’ll often see saunas with glass doors, which may look chic, but are inefficient and stupid because they don’t seal properly and leak steam. Gyms and hotels are high traffic areas, so people who don’t know what they are doing are constantly coming and going from the sauna, which, as we discussed, is a sauna no-no. If you still want to try the sauna at your gym or hotel, I recommend going in naked. It’ll deter people from joining you and ruining the little steam you managed to get going.
**Traditional bath houses (Banyas):** These usually offer a great experience because they deliver a super hot sauna, good cold baths and plunges, delicious food and drinks, and knowledgeable staff.
**Home:** Yes, you can build a great sauna in your own home! You can create a small space in your basement, turn a closet or cold room into a sauna, or just add an outdoor hut or barrel sauna in your backyard. This is the best way for you to control the whole experience and do it often. As with anything, the easier it is to access, the more you will do it.
_Build it. They will Come_
Many people have asked me for details about sauna building. If you’re ready to build your own personal home sauna, here are some important considerations.
#### Materials
Saunas are insulated rooms, most commonly finished with cedar tung and groove slats. Cedar is used because it doesn’t rot with moisture. You don’t want treated wood as it will release all the bad stuff that keeps the wood from rotting into the air when heated. Cedar interior is often placed over a vapor barrier, followed by insulation and then the outer wall. Many outdoor saunas are not insulated. They simply have a single layer of cedar 2x6 planks functioning as both the interior and exterior. Non-insulated saunas need much more heating power in the winter.
#### Structure
For indoor saunas, you may want to find a bricklayer to build something for you. Traditional facilities often have brick-lined rooms and very large wood-burning stoves.
You can buy prefab outdoor saunas, which are often sheds or barrels. After experimenting with both, I’ve concluded that barrel saunas are inferior, even though that’s what I have at my country property. This is because barrels have concave ceilings and inner walls. This means the benches are lower and the curve makes the topmost part of the ceiling (and the hottest part) the furthest from you, or inaccessible. The spinning towel trick really helps in the barrel.
When it comes to buying a sauna, go with the most traditional structure possible. They are based on thousands of years of evolution and knowledge.
Portable tent saunas are fun, but impractical because you have to set them up before each use.
Bench height inside the sauna is important. I think the top-most bench should be very near the ceiling. This way, when you’re lying down, you can use the ceiling to stretch the hamstrings. As a rule of thumb, bench length should allow you to lie down completely. It is also nice to have at least one lower bench for visitors or less intense sauna days.

#### Sauna Ovens
There are two main types of sauna ovens: wood burning and electrical (with gas heating being available, but not common). If the location you are building allows for it, go with electrical. It’s practical and easy to get going quickly. This means you will use it more often. Wood burning saunas are romantic and smell great, but it is a lot more work to get a fire going, especially in the winter.
Opt for oven sizes that are recommended or above recommended for the size of the sauna. A larger oven means more thermic inertia, more rocks for steam, and therefore less time to warm up the room. Bigger is better. The Scandinavians make the best quality ovens.
#### Oven controllers
There are two types of temperature control devices: the analog cooking-style or the digital type. I think, due to liability and safety, all ovens have a timer that max out at one hour.
The digital oven controllers are fantastic and I have one in the city in my basement sauna.
However, you have to consider your environment. For me, temperatures in the winter can reach below -30C and in the summer, over 40C. This massive range can take a toll on outdoor equipment and materials. For this reason, I opted for an analog controller for my outdoor sauna in the country, since the weather will likely ruin the electronics of the digital controller.
I would avoid ovens with analog pre-heat timers. They are great in theory, but the implementation is utter garbage. The timer won’t be precise and it’ll just lead to frustration, for example, when you thought you set the oven to start in three hours, but it actually started in two hours and already turned off.
#### Important Sauna Gear
Windows are nice to have, especially if you have a view to enjoy. Opt for at least a cedar door with a little window. Do not go with modern glass door styles. They are crap. They have gaps, no insulation, and let in too much light.
Saunas need thermometers and hygrometers (to measure humidity). The thermometers should be rated for saunas and be visible inside. This is both for safety and bragging rights.
I think having an hourglass inside your sauna is a must. Being able to know for sure how long you’ve been inside is important, since your sense of timing inside the sauna may be off depending on the state of your mind and body on a given day. You shouldn’t wear a watch inside the sauna, since it’ll overheat or break. Having a clock visible from the inside is also a good idea, especially if you sauna often and have a wife and kids who you don’t want to leave you.
Air circulation is an often-overlooked but important part of a sauna design. Saunas should not have stale air. The best sauna design creates natural “real convection” by placing an air intake under the oven wall and another at the top opposite wall. This allows fresh air to enter the sauna while in use. Be sure to add regulators, since you don’t want to cool the sauna or expel all steam. Without regulators you may get too much or too little air in. With too much air, you may cool the sauna down too much and/or lose too much steam.
#### Nice Things to Have
Lights are optional but welcome additions. It can be unpleasant to have no lighting at all, especially in an outdoor sauna on a cold, dark night. Lights should be warm-temperature and low power. I recommend an oven light, since they don’t sweat the heat (get it?) and are often low power.
Put a baking tray under your oven–thank me later.
Wood “pillows” for your head are nice and don’t get sweat-stained and stinky, like a fabric pillow.
Keep some extra felt hats near your sauna so when you or your guests forget their hat, you still have easy access to one.
I like to keep a couple of essential oils on the floor of the sauna, for easy access. If you keep the oils too high in the sauna, they’ll get too hot and spoil.
I place some duck boards over floor tiles in the sauna to prevent cold feet.
I also like to keep a small, natural broom inside the sauna to sweep up any dirt or leaves that come into the sauna on people’s feet.
## Final words
As you can tell, I have some strong opinions when it comes to the proper way to enjoy a sauna. My hope is that my musings will help you to maximize your own sauna experience.. If you follow this guide, I’m certain you will benefit from and enjoy the sauna as much as I do and, just maybe, you too will develop your own strongly held opinions that will most definitely offend me.
### Thanks for reading, please close the F-ing door.
ps, you can get a Bitcoin Honey Badger Sauna Hat [here](https://store.coinkite.com/store/ht-sauna)
- EOF
-

@ eac63075:b4988b48
2024-10-10 18:12:38
Companies like Meta (formerly Facebook) and Twitter (now X) control platforms that have become the main channels of communication for millions of people worldwide. At the center of this discussion are figures like Mark Zuckerberg and Elon Musk, whose recent actions raise serious questions about freedom of speech, censorship, and political manipulation.
---
<https://fountain.fm/episode/VzJItfySZ8z6417prHyD>
---
Recently, a public letter written by Mark Zuckerberg revealed how the U.S. government, under Joe Biden’s administration, pressured Facebook to censor information during the COVID-19 pandemic. The controversy involves, among other topics, the censorship of content related to Biden’s son, Hunter Biden, during the height of the laptop scandal. This revelation raises questions about the role these platforms play in spreading or withholding information, as well as the direct impact this has on democracy.
## **Meta and Censorship: Zuckerberg's Letter**
In his letter, Zuckerberg admitted that Facebook was pressured by the Biden administration to suppress information about the pandemic and the Hunter Biden case, something he now claims to regret. This has sparked heated debate about how far social media should go in yielding to governmental pressure. Many see this as a threat to freedom of speech, while others argue that this censorship was necessary to control misinformation.
The issue here is not just about government pressure, but the fact that Facebook, as a global platform with billions of users, holds unparalleled power to shape narratives. When a platform decides what is “acceptable” or “truthful,” it directly influences public perception and opinion formation, especially during critical moments like an election.
Zuckerberg, in his letter, seems to be trying to salvage his image, but the damage has already been done. The admission that Facebook collaborated with the government to suppress certain information raises doubts about the platform’s impartiality and its commitment to free speech.
## **Elon Musk and Free Speech on X**
Meanwhile, Elon Musk, now in control of Twitter, renamed X, has promised to transform the platform into a space for free expression. However, the reality seems more complex. Musk claims that X should be a place where all voices can be heard, regardless of political or ideological alignment. Yet, this promise has proven difficult to fulfill in practice.
X continues to ban users and censor content, especially in countries with authoritarian governments like India and Turkey. This creates a dichotomy: on the one hand, Musk advocates for unrestricted free speech, but on the other, he complies with censorship requests from these regimes. This raises questions about Musk’s true intentions and the extent to which he is willing to uphold his principles when the platform faces international pressure.
Moreover, Musk has used X as a political platform, especially in support of former President Donald Trump. The reinstatement of Trump’s account, banned during the Capitol insurrection, has raised further suspicions that Musk is turning X into a tool of political power. For many, this represents a significant risk to the neutrality of digital platforms.
## **The Cambridge Analytica Scandal and the Risk of Political Manipulation**
The discussion of censorship and free speech on social media brings up a case that shocked the world a few years ago: the Cambridge Analytica scandal. In 2015, this British company was accused of using personal data from millions of Facebook users to manipulate elections, including the Brexit referendum and Donald Trump’s 2016 presidential election.
Although Cambridge Analytica was dissolved after the scandal, its legacy remains. Big Tech companies still have access to vast amounts of user data, and the power this grants them is alarming. Companies like Meta and X could, in theory, directly influence election outcomes by manipulating algorithms to promote certain narratives or suppress others.
This scenario raises crucial questions: to what extent can we trust these platforms to act impartially? Are they truly committed to free speech, or are they using their power to shape the political future of the world according to their own interests?
## **The Pablo Marçal Case and Manipulation in Brazil**
In Brazil, a recent example that illustrates the complexity of the relationship between social media and political power is the case of coach Pablo Marçal. Marçal, who built a considerable following, became involved in controversies related to using his influence to manipulate public opinion. Recently, it was revealed that X hired the renowned law firm Pinheiro Neto to defend Marçal’s continued presence on the platform, even after controversies.
This move raises concerns about the selective enforcement of social media’s own rules. Why are some influencers protected while others are summarily banned? Marçal’s influence, particularly among conservative voters in Brazil, is undeniable, and the public defense of his account on X suggests that more is at stake than just free speech.
## **The Future of Social Media and Democracy**
What we are witnessing is the rise of a new era where social media plays a central role in global politics. Control over the flow of information lies in the hands of a few giant companies, and the decisions of their leaders—whether Mark Zuckerberg, Elon Musk, or others—can have a profound impact on elections, governments, and democracies.
This raises legitimate concerns about the future of democracy in a world where private platforms have the power to control public discourse. Big Tech censorship, often disguised as “misinformation control,” can easily become a tool for manipulation.
For citizens, this means being vigilant and critical about the information they receive on social media. Freedom of expression must be defended, but we also need to question who is behind these platforms and what their true motivations are. Trust in social media is at stake, and the future of democracy may depend on how we decide to deal with this unprecedented power.
## **Conclusion**
Recent revelations about Zuckerberg’s involvement in censorship and Musk’s use of X to promote a political agenda highlight the urgent need for transparency in social media platforms. As these companies become increasingly influential in the global political arena, the public must be aware of the risks and actively engage in the debate about the future of free speech and democracy.
-

@ c69b71dc:426ba763
2024-10-10 09:05:29
## Chef's notes
This cashew blue cheese is a true plant-based delight, delivering the rich, tangy flavours you’d expect from traditional blue cheeses like Roquefort or Gorgonzola. The fermentation process, with the help of «Penicillium Roqueforti», creates a beautifully marbled, creamy cheese that’s both bold and complex. It’s a labor of love that rewards your patience with an unforgettable vegan cheese experience! Whether enjoyed on crackers, in salads, or simply on its own, this cheese will elevate any dish with its unique flavour profile.
Note 1: For this recipe you need parchment paper, a potent blender, glass jars with lid and two cheesecloths.
Note 2: Always use very clean tools, and avoid touching with your fingers or tasting with them while working on the cheese!
## Details
- ⏲️ Prep time: 4-5 weeks
- 🍳 Cook time: 0
- 🍽️ Servings: Two small cheese loaves (2x 10-12 cm diameter)
## Ingredients
- 300g raw cashews
- 3 tbsp water
- 3 tbsp kefir, kombucha or rejuvelac
- 2 tbsp coconut oil (raw, unrefined)
- 1-4 capsules vegan probiotics
- 1/2 tsp Himalayan salt (iodine-free, no additives)
- 1/16 tsp «Penicillium Roqueforti» (blue cheese mold culture)
## Directions
1. Day 1: Soak 300g of cashews overnight in water.
2. Day 2: Rinse the soaked cashews thoroughly and let them drain well.
3. In a high-speed blender, combine the cashews, 3 tbsp of water, 3 tbsp kefir or rejuvelac, and 2 tbsp coconut oil. Blend until the mixture is smooth and creamy.
4. Add 1-4 capsules of vegan probiotics, 1/2 tsp Himalayan salt (free of iodine and additives), and blend again briefly.
5. Add a pinch (about 1/16 tsp) of «Penicillium Roqueforti» powder (blue cheese culture) and give it another quick mix.
6. Transfer the cashew mixture to a glass container, leaving the lid lightly on top (do not seal it completely) and store in a warm place, ideally in your kitchen, for 24 hours to ferment.
7. Day 3: Divide the fermented cashew mixture into two smaller glass containers lined with cheesecloth. Press the mixture down firmly to eliminate air pockets.
8. Store in a cool place (12-14°C / 53-57°F), ideally in a wine fridge.
9. Day 4: Remove the cheese from the containers, take off the cheesecloth, and turn the cheese onto parchment paper.
10. Sprinkle salt all over the cheese, ensuring it is evenly coated.
11. Cover the cheese with larger glass bowls, ensuring that air can flow from underneath, and return to the wine fridge or the cool storage area.
12. Days 4-7: Turn the cheese daily onto fresh parchment paper to maintain its texture.
13. Day 7 or 8: Pierce the cheese with a thicker wooden skewer to create holes, allowing oxygen to reach the center, encouraging the blue mold to grow throughout the cheese, not just on the surface.
14. Alternatively, crumble the cheese completely and then press it back into shape to ensure oxygen distribution.
15. Days 8 toaround 12 or 15: Once the blue mold has fully developed around and inside the cheese, wrap the cheese in parchment paper, place it in a wooden cheese box, and then wrap it in a cloth bag.
16. Transfer to a regular fridge to age for another 2-3 weeks or even several months, depending on your desired strength of flavour.
-

@ aa8de34f:a6ffe696
2024-10-09 21:56:39
\`\`\`
Technion - Israel Institute of Technology\
Foundations of Quantum Mechanics\
Date: 2024-08-25 Submitted by: Max Peter
\`\`\`
\# Quantum Mechanics and Consciousness: Strange Bedfellows
*"Does consciousness play a special role in quantum mechanics?"*
## Abstract
Could there be a connection between quantum mechanics and consciousness? This Question has fascinated scholars for years. Some believe that consciousness plays a role in how we interpret quantum theory. This essay explores whether consciousness is a fundamental component of quantum mechanics, addressing both the "hard problem" of consciousness and the various interpretations of quantum theory. By critically analyzing arguments from prominent figures like David Chalmers and Barry Loewer, the essay argues that while consciousness presents a significant challenge in understanding reality, current quantum theories may not provide the final answers. Instead, the *"hard problem"* of consciousness could be the unresolved issue that quantum mechanics needs to address, making it the *"elephant in the room"* that scientists often avoid.
## 1. Introduction
The relationship between quantum mechanics and consciousness is one of the most intriguing and contentious debates in modern science and philosophy. Quantum mechanics, the physics of the very small, has upended our classical understanding of the universe, introducing phenomena such as superposition, entanglement, and wavefunction collapse that defy intuition. Simultaneously, consciousness - the subjective experience of being aware - remains one of the most profound mysteries in science, famously described by David Chalmers (1995) as the "hard problem." The intersection of these two enigmatic fields has led to the proposal that consciousness may play a special role in quantum mechanics, particularly in the process of wavefunction collapse, where observation seems to determine physical reality. This essay explores the question: Does consciousness play a special role in quantum mechanics?
Advocates of this idea, such as Wigner and Stapp, have argued that consciousness is not merely an observer in quantum mechanics but an active participant that influences quantum events. However, this view is not without its critics. Many physicists and philosophers, including Barry Loewer, argue that connecting consciousness to quantum mechanics is speculative and unsupported by empirical evidence. Despite these criticisms, the possibility that consciousness could be the "elephant in the room" that quantum mechanics needs to address remains an open question. This essay will explore the various interpretations of quantum mechanics that engage with or avoid the issue of consciousness and will argue that the hard problem of consciousness is maybe a vital, yet often ignored, aspect of a better understanding of quantum physics.
## 2. The Basics of Quantum Mechanics
Quantum mechanics is the branch of physics that deals with the behavior of particles at the smallest scale - atoms and subatomic particles. It is governed by principles that are vastly different from the deterministic laws of classical physics. One of the foundational concepts of quantum mechanics is the wavefunction, a mathematical function that describes the probabilities of a particle's properties, such as position and momentum. Unlike in classical mechanics, where a particle has a definite position and momentum, in quantum mechanics, these properties are described by a probability distribution.
One of the most famous principles of quantum mechanics is superposition, which states that a particle can exist in multiple states simultaneously until it is observed. This is famously illustrated by Schrödinger's cat thought experiment, where a cat in a box is simultaneously alive and dead until the box is opened, and an observation is made. Another critical concept is entanglement, where particles become linked, so the state of one particle instantaneously affects the state of another, regardless of the distance between them.
The wavefunction collapse is perhaps the most perplexing aspect of quantum mechanics. When a quantum system is observed, the wavefunction collapses, and the system settles into a definite state. This raises the question: What causes the wavefunction to collapse? Is it the act of measurement itself, or does consciousness play a role in this process? The measurement problem in quantum mechanics has led some to propose that consciousness is necessary for wavefunction collapse, thus connecting the two fields in a profound way.
## 3. The Hard Problem of Consciousness
David Chalmers (1995) famously distinguished between the "easy" and "hard" problems of consciousness. The easy problems involve explaining the cognitive functions and processes that underlie perception, memory, and behavior. These problems, while challenging, are considered solvable through the standard methods of cognitive science and neuroscience. The hard problem, on the other hand, is the problem of subjective experience - why and how physical processes in the brain give rise to the rich inner life of sensation, emotion, and awareness. This subjective aspect of consciousness, also known as qualia (Latin “of what sort”), remains resistant to reductive explanation.
Chalmers (1995) argues that the hard problem of consciousness cannot be solved by merely explaining the functions of the brain. There is a gap between physical processes and the experience of those processes - a gap that traditional science struggles to bridge. This has led some theorists to propose that consciousness might be fundamental to the universe, rather than a byproduct of physical processes. This idea has significant implications for quantum mechanics, particularly in the context of the measurement problem. If consciousness is indeed fundamental, it may play a direct role in the collapse of the wavefunction, linking the hard problem of consciousness with the mysteries of quantum mechanics.
## 4. Consciousness and Quantum Mechanics
The idea that consciousness plays a special role in quantum mechanics is most closely associated with the Consciousness Collapse Proposal (CCP). This theory suggests that the act of observation by a conscious being is what causes the wavefunction to collapse into a definite state. This view was championed by physicists like Eugene Wigner and Henry Stapp, who argued that consciousness must be integrated into our understanding of quantum mechanics. According to Wigner, consciousness is the ultimate cause of the wavefunction collapse, implying that the physical world does not exist in a definite state until it is observed by a conscious mind (Wigner, 1967).
However, the CCP is not without its critics. Barry Loewer (2003) argues that the connection between consciousness and quantum mechanics is speculative and lacks empirical support. He contends that while quantum mechanics may involve strange and counterintuitive phenomena, there is no evidence that consciousness plays a direct role in these processes. Loewer suggests that alternative interpretations of quantum mechanics, such as the Ghirardi-Rimini-Weber (GRW) theory and Bohmian mechanics, offer explanations for wavefunction collapse that do not require the involvement of consciousness (Loewer, 2003).
Despite these criticisms, the idea that consciousness could be fundamental to quantum mechanics remains a compelling possibility. The CCP aligns with the notion that consciousness is not just an epiphenomenon of brain activity but a fundamental aspect of reality. This perspective challenges the materialist view that physical processes alone are sufficient to explain all phenomena, including consciousness. Instead, it suggests that consciousness might be the key to resolving the mysteries of quantum mechanics.
## 5. The Elephant in the Room: The Hard Problem of Consciousness in Quantum Mechanics
The central thesis of this section is that the hard problem of consciousness, as articulated by David Chalmers (1995), represents an unresolved issue in the interpretation of quantum mechanics, and may be the "elephant in the room" that most scientific theories attempt to avoid. While many physicists adopt materialist interpretations of quantum mechanics that sidestep the issue of consciousness, it is increasingly difficult to ignore the possibility that consciousness might play a fundamental role in the behaviour of quantum systems. This section will argue that the hard problem of consciousness is not just a philosophical curiosity but a crucial component in understanding the true nature of quantum mechanics.
### Consciousness as a Fundamental Aspect of Reality
The hard problem of consciousness refers to the challenge of explaining how and why physical processes in the brain give rise to subjective experience—what it feels like to perceive, think, and be aware. Chalmers (1995) argues that the hard problem is distinct from the "easy" problems of explaining cognitive functions and behaviours because it involves the subjective nature of experience, which cannot be fully captured by a purely physical explanation. This problem is central to the question of whether consciousness plays a role in quantum mechanics because it challenges the materialist assumption that everything can be explained in terms of physical processes.
One argument in favour of consciousness playing a fundamental role in quantum mechanics is that it may help solve the measurement problem—the question of why and how the wavefunction collapses when a measurement is made. According to the Consciousness Collapse Proposal (CCP), the collapse of the wavefunction occurs when a conscious observer interacts with the system, suggesting that consciousness is a necessary component of reality. This idea challenges the traditional view of quantum mechanics as a purely objective, observer-independent theory and implies that consciousness is more than just a byproduct of physical processes (Stapp, 1993).
In this view, consciousness is not simply an epiphenomenon of the brain but a fundamental aspect of reality that interacts with the physical world in a way that science has yet to fully understand. This perspective aligns with certain interpretations of quantum mechanics, such as the von Neumann-Wigner interpretation, which posits that consciousness plays an active role in the collapse of the wavefunction. While this interpretation remains controversial, it highlights the possibility that consciousness could be integral to the functioning of the universe at a fundamental level.
### Avoidance of the Hard Problem in Mainstream Science
Despite the compelling nature of the hard problem, mainstream scientific interpretations of quantum mechanics often avoid addressing consciousness directly. For example, the Many Worlds Interpretation (MWI) of quantum mechanics sidesteps the issue of wavefunction collapse altogether by proposing that all possible outcomes of a quantum measurement exist simultaneously in parallel worlds. In this framework, there is no need to invoke consciousness as a factor in determining the outcome of a quantum event, as every possible outcome is realized in some branch of the multiverse (Everett, 1957). While MWI elegantly avoids the problem of collapse, it does so at the cost of ignoring the role of consciousness, which remains unexplained.
Similarly, the Ghirardi-Rimini-Weber (GRW) theory offers an objective collapse model that introduces spontaneous collapses of the wavefunction, independent of observation or consciousness. This theory attempts to solve the measurement problem without invoking consciousness by suggesting that wavefunctions collapse randomly after a certain threshold is reached (Ghirardi, Rimini, & Weber, 1986). Although GRW provides a mathematically consistent solution to the measurement problem, it does not address the hard problem of consciousness, leaving the nature of subjective experience untouched.
These interpretations reflect a broader tendency in science to focus on solving the technical aspects of quantum mechanics while avoiding the deeper philosophical questions about consciousness. This approach is understandable, given that the hard problem of consciousness is notoriously difficult to address within the framework of materialist science. However, by sidestepping the issue, these interpretations may be missing a crucial piece of the puzzle. If consciousness is indeed fundamental to the collapse of the wavefunction, as proponents of the CCP suggest, then any interpretation that ignores consciousness is inherently incomplete.
### The Case for Addressing Consciousness in Quantum Mechanics
Given the limitations of current interpretations of quantum mechanics, there is a strong case to be made for addressing the hard problem of consciousness directly. One of the key challenges in integrating consciousness into quantum mechanics is the lack of empirical evidence linking consciousness to wavefunction collapse. Critics like Barry Loewer (2003) argue that the CCP is speculative and lacks the rigorous experimental support needed to be taken seriously as a scientific theory. This criticism is valid, as science requires empirical validation to support theoretical claims.
However, the absence of empirical evidence does not necessarily invalidate the idea that consciousness could play a role in quantum mechanics. The lack of direct evidence may simply reflect the limitations of current experimental methods, which are not yet sophisticated enough to test the relationship between consciousness and quantum phenomena. Furthermore, the hard problem of consciousness remains unresolved by conventional science, suggesting that new approaches may be needed to explore the connection between consciousness and the physical world.
In response to critics, proponents of the CCP could argue that quantum mechanics itself has a long history of challenging conventional notions of reality. The very existence of phenomena like entanglement and superposition defies classical logic and suggests that our understanding of the universe is incomplete. If consciousness is indeed fundamental to the fabric of reality, then it is possible that it plays a role in these quantum phenomena in ways that we do not yet fully understand. Rather than dismissing the CCP as speculative, it may be more productive to consider it as a potential avenue for further research, one that could ultimately lead to a deeper understanding of both consciousness and quantum mechanics.
## 6. Personal Viewpoint: Consciousness as a Vital Component in Quantum Mechanics
In my view, the hard problem of consciousness is not just an interesting philosophical challenge but a vital issue that must be addressed if we are to fully understand quantum mechanics. The reluctance of many scientists to engage with the hard problem is understandable, given the difficulty of the question and the lack of empirical evidence. However, this avoidance may be preventing us from making significant progress in understanding the true nature of reality.
I believe that the hard problem of consciousness represents a fundamental gap in our understanding of the universe - one that cannot be ignored if we are to develop a complete theory of quantum mechanics. While alternative interpretations like the GRW theory and the Many Worlds Interpretation offer solutions to the technical problems of quantum mechanics, they do so by avoiding the deeper question of consciousness. This approach, while pragmatic, may ultimately prove to be a dead end if consciousness is indeed integral to the behaviour of quantum systems.
Addressing the hard problem of consciousness in the context of quantum mechanics requires a willingness to think beyond the current boundaries of science and to explore new theoretical frameworks that integrate consciousness into our understanding of the physical world. This may involve revisiting ideas like the Consciousness Collapse Proposal or developing entirely new theories that link consciousness with quantum phenomena in ways that we have not yet imagined.
At the same time, it is important to approach this question with a critical and balanced perspective. While the idea that consciousness plays a role in quantum mechanics is intriguing, it is essential to remain open to alternative explanations and to demand rigorous empirical evidence to support any claims. The history of science is filled with theories that seemed promising but ultimately proved to be incorrect, and we must be careful not to fall into the trap of speculation without evidence.
## Conclusion
In Summary, I believe that the hard problem of consciousness is the *"elephant in the room"* that quantum mechanics needs to address. While traditional interpretations of quantum theory have tried to solve the measurement problem without involving consciousness it might be ignoring a part of reality.
By blending the matter of consciousness into quantum mechanics we could potentially gain a comprehensive view of the universe - one that appreciates both the enigmatic nature of subjective experiences and the elegant mathematics of some quantum mechanics theories. Even though this viewpoint is speculative and needs investigation it presents a glimpse into a future where consciousness and quantum mechanics are seen as interconnected elements of existence.
### References
\- CHALMERS, D. J. (1995). FACING UP TO THE PROBLEM OF CONSCIOUSNESS. JOURNAL OF CONSCIOUSNESS STUDIES, 2(3), 200-219.
\- EVERETT, H. (1957). “RELATIVE STATE” FORMULATION OF QUANTUM MECHANICS. REVIEWS OF MODERN PHYSICS, 29(3), 454-462.
\- GHIRARDI, G. C., RIMINI, A., & WEBER, T. (1986). UNIFIED DYNAMICS FOR MICROSCOPIC AND MACROSCOPIC SYSTEMS. PHYSICAL REVIEW D, 34(2), 470-491.
\- LOEWER, B. (2003). CONSCIOUSNESS AND QUANTUM THEORY: STRANGE BEDFELLOWS.
\- STAPP, H. P. (1993). MIND, MATTER, AND QUANTUM MECHANICS. SPRINGER.
-

@ 4ba8e86d:89d32de4
2024-10-08 23:16:53
Governos do mundo industrial, seus gigantes cansados de carne e aço, venho do ciberespaço, a nova casa da mente. Em nome do futuro, peço que no passado nos deixe em paz. Você não é bem vindo entre nós. Nem você exerce qualquer soberania sobre o lugar onde nos encontramos. Não elegemos nenhum governo, nem pretendemos tê-lo, por isso dirijo-me a vocês sem outra autoridade senão aquela com que sempre fala a liberdade.
Declaro que o espaço social global que estamos construindo é independente por natureza das tiranias que você procura impor a nós. Você não tem o direito moral de nos governar, nem possui métodos para fazer cumprir sua lei que devemos realmente temer.
Os governos obtêm seus justos poderes do consentimento daqueles que são governados. Você não pediu nem recebeu o nosso. Nós também não convidamos você.
Você não nos conhece, nem conhece o nosso mundo. O ciberespaço não está dentro de suas fronteiras. Não pense que você pode construí-lo, como se fosse um projeto de construção pública. Você não pode. É um ato natural que cresce a partir de nossas ações coletivas.
Você não participou de nossa grande conversa coletiva, nem criou a riqueza de nossos mercados. Você não conhece nossa cultura, nossa ética ou os códigos não escritos que já fornecem à nossa sociedade mais ordem do que o que poderia ser obtido por qualquer uma de suas imposições.
Você proclama que há problemas entre nós que precisa resolver. Você usa isso como uma desculpa para invadir nossos limites. Muitos desses problemas não existem. Onde houver conflitos reais, erros, nós os identificaremos e resolveremos por nossos próprios meios. Estamos criando nosso próprio contrato social. Essa autoridade será criada de acordo com as condições do nosso mundo, não a sua. Nosso mundo é diferente. O ciberespaço é composto de transações, relacionamentos e pensamento em si, que se espalham como uma onda silenciosa na web de nossas comunicações. Nosso mundo está ao mesmo tempo em todo lugar e lugar nenhum, mas não é onde os corpos vivem.
Estamos criando um mundo no qual todos possam entrar, sem privilégios ou preconceitos devido à raça, poder econômico, força militar ou local de nascimento.
Estamos criando um mundo em que qualquer pessoa, em qualquer lugar, possa expressar suas crenças, não importa quão únicas sejam, sem medo de ser coagida ao silêncio ou à conformidade.
Seus conceitos legais de propriedade, expressão, identidade, movimento e contexto não se aplicam a nós. Eles são baseados na matéria.
Não há problema aqui. Nossas identidades não têm corpo; portanto, diferentemente de você, não podemos obter ordem por coerção física.
Acreditamos que nossa autoridade emanará da moralidade, do interesse próprio progressivo e do bem comum. Nossas identidades podem ser distribuídas por várias jurisdições. A única lei que todas as nossas culturas reconheceriam é a Regra de Ouro. Esperamos ansiosamente desenvolver nossas soluções específicas sobre essa base. Mas não podemos aceitar as soluções que você está tentando impor. Hoje, na América, você criou uma lei, a Lei de Reforma das Telecomunicações, que repudia sua própria Constituição e insulta os sonhos de Jefferson, Washington, Mill, Madison, DeToqueville e Brandeis. Esses sonhos devem renascer em nós agora.
Você tem medo de seus próprios filhos, pois eles são nativos em um mundo onde você sempre será imigrante. Ao recear, confia à sua burocracia responsabilidades parentais que não pode ser covarde. Em nosso mundo, todos os sentimentos e expressões da humanidade, do mais vil ao mais angélico, fazem parte de um único todo, a conversa global de bits. Não podemos separar o ar que sufoca daquele em que as asas batem.
Na China, Alemanha, França, Rússia, Cingapura, Itália e Estados Unidos, você está tentando evitar o vírus da liberdade, estabelecendo postos de guarda nas fronteiras do ciberespaço. Eles podem impedir o contágio por um curto período de tempo, mas não funcionarão em um mundo que em breve será coberto pela mídia transmitida por bits.
Suas indústrias de informação cada vez mais obsoletas se perpetuariam propondo leis, nos Estados Unidos e em outros lugares, que reivindicam a propriedade da palavra em todo o mundo. Essas leis declarariam que as idéias são outro produto industrial, menos nobre que o ferro enferrujado. Em nosso mundo, tudo o que a mente humana pode criar pode ser reproduzido e distribuído infinitamente, sem nenhum custo. A transferência global de pensamento não precisa mais ser realizada por suas fábricas. Essas medidas cada vez mais hostis e colonialistas nos colocam na mesma situação em que estavam aqueles amantes da liberdade e da autodeterminação que tiveram que lutar contra a autoridade de um poder distante e ignorante.
Devemos declarar nossos "eus" virtuais imunes à sua soberania, embora continuemos a consentir com seu poder sobre nossos corpos. Vamos nos espalhar por todo o planeta para que ninguém possa aprisionar nossos pensamentos.
Criaremos uma civilização da mente no ciberespaço. Que seja mais humano e bonito do que o mundo que seus governos criaram antes.
Davos, Suíça, até 8 de fevereiro de 1996
John Perry Barlow
-

@ eac63075:b4988b48
2024-10-08 20:37:08
In this botcast, we explore how technology is solving one of the biggest challenges faced by DAOs (Decentralized Autonomous Organizations): vote fraud. Learn how Vitalik Buterin and other experts from Cornell University are leading innovation using Zero-Knowledge Proofs and Proof of Work (PoW) to ensure security and privacy in blockchain voting systems.
You will discover how these technologies combat practices like token renting and lending, preventing vote manipulation in DAOs. The video also covers the importance of dedicated hardware to increase the integrity of digital elections.
---
Listen to the Podcast:
<https://wavlake.com/episode/bdb2850b-49b4-45f6-9a00-d310e29f4528>
---
Table of Contents:
**Source:** YouTube Transcript - Morning Crypto (Timestamped Excerpts)
**I. Introduction and Context (0:00:00 - 0:02:37)**
- This section sets the stage by briefly discussing a common problem in Decentralized Autonomous Organizations (DAOs): fraudulent voting practices.
- It highlights the issue of individuals manipulating voting systems by borrowing, renting, or delegating tokens to influence decision-making within DAOs.
**II. Introducing Complete Knowledge and the Proposed Solution (0:02:37 - 0:03:39)**
- Introduces a potential solution developed by Vitalik Buterin and researchers from Cornell University, utilizing Zero-Knowledge Proofs to address the challenge of fraudulent voting in DAOs.
- Explains that the proposed solution involves a dedicated hardware or wallet system that verifies voting rights without revealing the user's private key, preventing token manipulation.
**III. Deep Dive into Complete Knowledge with "Ger" (0:05:54 - 0:07:57)**
- This section features "Ger," a voice assistant, who explains Complete Knowledge as a cryptographic innovation.
- Ger describes how Complete Knowledge allows users to prove possession of information, like a private key, without revealing the information itself.
- The section emphasizes how Complete Knowledge enhances security and privacy in digital identity and voting systems.
**IV. Proof of Work and ASICs for Enhanced Security (0:07:57 - 0:09:05)**
- Examines the potential of using Proof of Work (PoW), the consensus mechanism behind Bitcoin, in conjunction with Complete Knowledge.
- Explains how PoW can act as a mechanism to further ensure that a specific secret or key is held by a user without requiring the user to reveal it.
- Discusses the use of Application-Specific Integrated Circuits (ASICs) for performing the computational tasks required for PoW and Complete Knowledge verification.
**V. Practical Implementation and Conclusion (0:09:05 - 0:10:25)**
- Highlights the development of a demo ASIC by the researchers, showcasing the practical application of their proposed solution.
- Emphasizes the potential of this technology to prevent fraudulent voting practices by requiring a user to generate proof of their voting rights via this specialized ASIC.
- Concludes with a message emphasizing the importance of verifiable knowledge and its implications for privacy and security in the digital age.
---
Reference:
- <https://eprint.iacr.org/2023/044>
- <https://medium.com/initc3org/complete-knowledge-eecdda172a81>
 @ 6f0ba1ef:58eb4351
2024-10-25 01:16:41eyJfaWQiOiIzMjFkMjkyNi0xOGUyLTRjYTgtOWIwYy0xNGMwNWExZDc4ZTAiLCJwdWJsaWNLZXkiOiI2ZjBiYTFlZjc4YjE3ZTVkMjNkMmVjZDlkYWNlNmJhMzBlODI1NzUxMGY0NmYxNjA0NGUyZjY5ZjU4ZWI0MzUxIiwiYWRUeXBlIjoiT05MSU5FX1NFTEwiLCJjb3VudHJ5IjoiVW5pdGVkIFN0YXRlcyBvZiBBbWVyaWNhIiwiY291bnRyeUNvZGUiOiJVUyIsImxhdCI6bnVsbCwibG9uIjpudWxsLCJjdXJyZW5jeUNvZGUiOiJVU0QiLCJwYXltZW50TWV0aG9kQ29kZSI6Ik5BVElPTkFMX0JBTksiLCJwcmljZUlucHV0VHlwZSI6Ik1BUktFVCIsIm1hcmdpbiI6MywibWFya2V0UHJpY2UiOjE1Ny40NiwiZml4ZWRQcmljZSI6MCwibWluQW1vdW50IjoxMCwibWF4QW1vdW50IjoyMDAsImxpbWl0VG9GaWF0QW1vdW50cyI6IiIsInBheW1lbnRNZXRob2REZXRhaWwiOiJ2ZXJ5IGZhc3QgYW5kIGVhc3kiLCJtc2ciOiIiLCJhY2NvdW50SW5mbyI6IiIsImZvclRydXN0ZWQiOiJubyIsInZlcmlmaWVkRW1haWxSZXF1aXJlZCI6Im5vIiwicmVxdWlyZUZlZWRiYWNrU2NvcmUiOjAsImZpcnN0VGltZUxpbWl0QXNzZXQiOjAsInBheW1lbnRXaW5kb3dNaW51dGVzIjo2MCwiaGlkZGVuIjpmYWxzZSwiYmFubmVkIjpmYWxzZSwidmVyaWZpZWQiOnRydWUsImFkZGVkIjoiMjAyNC0xMC0yNVQwMToxNjo0MS41MDBaIn0=
@ 6f0ba1ef:58eb4351
2024-10-25 01:16:41eyJfaWQiOiIzMjFkMjkyNi0xOGUyLTRjYTgtOWIwYy0xNGMwNWExZDc4ZTAiLCJwdWJsaWNLZXkiOiI2ZjBiYTFlZjc4YjE3ZTVkMjNkMmVjZDlkYWNlNmJhMzBlODI1NzUxMGY0NmYxNjA0NGUyZjY5ZjU4ZWI0MzUxIiwiYWRUeXBlIjoiT05MSU5FX1NFTEwiLCJjb3VudHJ5IjoiVW5pdGVkIFN0YXRlcyBvZiBBbWVyaWNhIiwiY291bnRyeUNvZGUiOiJVUyIsImxhdCI6bnVsbCwibG9uIjpudWxsLCJjdXJyZW5jeUNvZGUiOiJVU0QiLCJwYXltZW50TWV0aG9kQ29kZSI6Ik5BVElPTkFMX0JBTksiLCJwcmljZUlucHV0VHlwZSI6Ik1BUktFVCIsIm1hcmdpbiI6MywibWFya2V0UHJpY2UiOjE1Ny40NiwiZml4ZWRQcmljZSI6MCwibWluQW1vdW50IjoxMCwibWF4QW1vdW50IjoyMDAsImxpbWl0VG9GaWF0QW1vdW50cyI6IiIsInBheW1lbnRNZXRob2REZXRhaWwiOiJ2ZXJ5IGZhc3QgYW5kIGVhc3kiLCJtc2ciOiIiLCJhY2NvdW50SW5mbyI6IiIsImZvclRydXN0ZWQiOiJubyIsInZlcmlmaWVkRW1haWxSZXF1aXJlZCI6Im5vIiwicmVxdWlyZUZlZWRiYWNrU2NvcmUiOjAsImZpcnN0VGltZUxpbWl0QXNzZXQiOjAsInBheW1lbnRXaW5kb3dNaW51dGVzIjo2MCwiaGlkZGVuIjpmYWxzZSwiYmFubmVkIjpmYWxzZSwidmVyaWZpZWQiOnRydWUsImFkZGVkIjoiMjAyNC0xMC0yNVQwMToxNjo0MS41MDBaIn0= @ c631e267:c2b78d3e
2024-10-23 20:26:10Herzlichen Glückwunsch zum dritten Geburtstag, liebe *Denk Bar*! Wieso zum dritten? Das war doch 2022 und jetzt sind wir im Jahr 2024, oder? Ja, das ist schon richtig, aber bei Geburtstagen erinnere ich mich immer auch an meinen Vater, und der behauptete oft, der erste sei ja schließlich der Tag der Geburt selber und den müsse man natürlich mitzählen. Wo er recht hat, hat er nunmal recht. Konsequenterweise wird also heute dieser Blog an seinem dritten Geburtstag zwei Jahre alt. Das ist ein Grund zum Feiern, wie ich finde. Einerseits ganz einfach, weil es dafür gar nicht genug Gründe geben kann. «Das Leben sind zwei Tage», lautet ein gängiger Ausdruck hier in Andalusien. In der Tat könnte es so sein, auch wenn wir uns im Alltag oft genug von der Routine vereinnahmen lassen. Seit dem Start der *Denk Bar* vor zwei Jahren ist unglaublich viel passiert. Ebenso wie die zweieinhalb Jahre davor, und all jenes war letztlich auch der Auslöser dafür, dass ich begann, öffentlich zu schreiben. [Damals notierte ich](https://denkbar.substack.com/p/andreas-denk-bar-eroffnet): > «Seit einigen Jahren erscheint unser öffentliches Umfeld immer fragwürdiger, widersprüchlicher und manchmal schier unglaublich - jede Menge Anlass für eigene Recherchen und Gedanken, ganz einfach mit einer Portion gesundem Menschenverstand.» Wir erleben den sogenannten «großen Umbruch», einen globalen Coup, den skrupellose Egoisten clever eingefädelt haben und seit ein paar Jahren knallhart – aber nett verpackt – durchziehen, um buchstäblich alles nach ihrem Gusto umzukrempeln. Die Gelegenheit ist ja angeblich günstig und muss genutzt werden. Nie hätte ich mir träumen lassen, dass ich so etwas jemals miterleben müsste. Die Bosheit, mit der ganz offensichtlich gegen die eigene Bevölkerung gearbeitet wird, war früher für mich unvorstellbar. Mein (Rest-) Vertrauen in alle möglichen Bereiche wie Politik, Wissenschaft, Justiz, Medien oder Kirche ist praktisch komplett zerstört. Einen [«inneren Totalschaden»](https://denkbar.substack.com/p/innerer-totalschaden) hatte ich mal für unsere Gesellschaften diagnostiziert. Was mich vielleicht am meisten erschreckt, ist zum einen das Niveau der [Gleichschaltung](https://denkbar.substack.com/p/warum-trotzdem-dieses-handeln), das weltweit erreicht werden konnte, und zum anderen die praktisch totale Spaltung der Gesellschaft. Haben wir das tatsächlich mit uns machen lassen?? Unfassbar! Aber das Werkzeug «Angst» ist sehr mächtig und funktioniert bis heute. Zum Glück passieren auch positive Dinge und neue Perspektiven öffnen sich. Für viele Menschen waren und sind die Entwicklungen der letzten Jahre ein Augenöffner. Sie sehen «Querdenken» als das, was es ist: eine Tugend. Auch die immer ernsteren Zensurbemühungen sind letztlich nur ein Zeichen der Schwäche, wo Argumente fehlen. Sie werden nicht verhindern, dass wir unsere Meinung äußern, unbequeme Fragen stellen und dass die Wahrheit peu à peu ans Licht kommt. Es gibt immer Mittel und Wege, auch für uns. --- **Danke, dass du diesen Weg mit mir weitergehst!**
@ c631e267:c2b78d3e
2024-10-23 20:26:10Herzlichen Glückwunsch zum dritten Geburtstag, liebe *Denk Bar*! Wieso zum dritten? Das war doch 2022 und jetzt sind wir im Jahr 2024, oder? Ja, das ist schon richtig, aber bei Geburtstagen erinnere ich mich immer auch an meinen Vater, und der behauptete oft, der erste sei ja schließlich der Tag der Geburt selber und den müsse man natürlich mitzählen. Wo er recht hat, hat er nunmal recht. Konsequenterweise wird also heute dieser Blog an seinem dritten Geburtstag zwei Jahre alt. Das ist ein Grund zum Feiern, wie ich finde. Einerseits ganz einfach, weil es dafür gar nicht genug Gründe geben kann. «Das Leben sind zwei Tage», lautet ein gängiger Ausdruck hier in Andalusien. In der Tat könnte es so sein, auch wenn wir uns im Alltag oft genug von der Routine vereinnahmen lassen. Seit dem Start der *Denk Bar* vor zwei Jahren ist unglaublich viel passiert. Ebenso wie die zweieinhalb Jahre davor, und all jenes war letztlich auch der Auslöser dafür, dass ich begann, öffentlich zu schreiben. [Damals notierte ich](https://denkbar.substack.com/p/andreas-denk-bar-eroffnet): > «Seit einigen Jahren erscheint unser öffentliches Umfeld immer fragwürdiger, widersprüchlicher und manchmal schier unglaublich - jede Menge Anlass für eigene Recherchen und Gedanken, ganz einfach mit einer Portion gesundem Menschenverstand.» Wir erleben den sogenannten «großen Umbruch», einen globalen Coup, den skrupellose Egoisten clever eingefädelt haben und seit ein paar Jahren knallhart – aber nett verpackt – durchziehen, um buchstäblich alles nach ihrem Gusto umzukrempeln. Die Gelegenheit ist ja angeblich günstig und muss genutzt werden. Nie hätte ich mir träumen lassen, dass ich so etwas jemals miterleben müsste. Die Bosheit, mit der ganz offensichtlich gegen die eigene Bevölkerung gearbeitet wird, war früher für mich unvorstellbar. Mein (Rest-) Vertrauen in alle möglichen Bereiche wie Politik, Wissenschaft, Justiz, Medien oder Kirche ist praktisch komplett zerstört. Einen [«inneren Totalschaden»](https://denkbar.substack.com/p/innerer-totalschaden) hatte ich mal für unsere Gesellschaften diagnostiziert. Was mich vielleicht am meisten erschreckt, ist zum einen das Niveau der [Gleichschaltung](https://denkbar.substack.com/p/warum-trotzdem-dieses-handeln), das weltweit erreicht werden konnte, und zum anderen die praktisch totale Spaltung der Gesellschaft. Haben wir das tatsächlich mit uns machen lassen?? Unfassbar! Aber das Werkzeug «Angst» ist sehr mächtig und funktioniert bis heute. Zum Glück passieren auch positive Dinge und neue Perspektiven öffnen sich. Für viele Menschen waren und sind die Entwicklungen der letzten Jahre ein Augenöffner. Sie sehen «Querdenken» als das, was es ist: eine Tugend. Auch die immer ernsteren Zensurbemühungen sind letztlich nur ein Zeichen der Schwäche, wo Argumente fehlen. Sie werden nicht verhindern, dass wir unsere Meinung äußern, unbequeme Fragen stellen und dass die Wahrheit peu à peu ans Licht kommt. Es gibt immer Mittel und Wege, auch für uns. --- **Danke, dass du diesen Weg mit mir weitergehst!** @ 6f0ba1ef:58eb4351
2024-10-22 23:31:47eyJfaWQiOiJjYmE4N2YyNS1jZjRkLTRkNzgtYmIwZS05YjNhNzA0MWVjNGIiLCJwdWJsaWNLZXkiOiI2ZjBiYTFlZjc4YjE3ZTVkMjNkMmVjZDlkYWNlNmJhMzBlODI1NzUxMGY0NmYxNjA0NGUyZjY5ZjU4ZWI0MzUxIiwiYWRUeXBlIjoiT05MSU5FX1NFTEwiLCJjb3VudHJ5IjoiVW5pdGVkIFN0YXRlcyBvZiBBbWVyaWNhIiwiY291bnRyeUNvZGUiOiJVUyIsImxhdCI6bnVsbCwibG9uIjpudWxsLCJjdXJyZW5jeUNvZGUiOiJVU0QiLCJwYXltZW50TWV0aG9kQ29kZSI6Ik5BVElPTkFMX0JBTksiLCJwcmljZUlucHV0VHlwZSI6Ik1BUktFVCIsIm1hcmdpbiI6MCwibWFya2V0UHJpY2UiOjE1Ny4zLCJmaXhlZFByaWNlIjowLCJtaW5BbW91bnQiOjAsIm1heEFtb3VudCI6MCwibGltaXRUb0ZpYXRBbW91bnRzIjoiIiwicGF5bWVudE1ldGhvZERldGFpbCI6IiIsIm1zZyI6IiIsImFjY291bnRJbmZvIjoiIiwiZm9yVHJ1c3RlZCI6Im5vIiwidmVyaWZpZWRFbWFpbFJlcXVpcmVkIjoibm8iLCJyZXF1aXJlRmVlZGJhY2tTY29yZSI6MCwiZmlyc3RUaW1lTGltaXRBc3NldCI6MCwicGF5bWVudFdpbmRvd01pbnV0ZXMiOjYwLCJoaWRkZW4iOmZhbHNlLCJiYW5uZWQiOmZhbHNlLCJ2ZXJpZmllZCI6dHJ1ZSwiYWRkZWQiOiIyMDI0LTEwLTIyVDIzOjMxOjQ3LjM5M1oifQ==
@ 6f0ba1ef:58eb4351
2024-10-22 23:31:47eyJfaWQiOiJjYmE4N2YyNS1jZjRkLTRkNzgtYmIwZS05YjNhNzA0MWVjNGIiLCJwdWJsaWNLZXkiOiI2ZjBiYTFlZjc4YjE3ZTVkMjNkMmVjZDlkYWNlNmJhMzBlODI1NzUxMGY0NmYxNjA0NGUyZjY5ZjU4ZWI0MzUxIiwiYWRUeXBlIjoiT05MSU5FX1NFTEwiLCJjb3VudHJ5IjoiVW5pdGVkIFN0YXRlcyBvZiBBbWVyaWNhIiwiY291bnRyeUNvZGUiOiJVUyIsImxhdCI6bnVsbCwibG9uIjpudWxsLCJjdXJyZW5jeUNvZGUiOiJVU0QiLCJwYXltZW50TWV0aG9kQ29kZSI6Ik5BVElPTkFMX0JBTksiLCJwcmljZUlucHV0VHlwZSI6Ik1BUktFVCIsIm1hcmdpbiI6MCwibWFya2V0UHJpY2UiOjE1Ny4zLCJmaXhlZFByaWNlIjowLCJtaW5BbW91bnQiOjAsIm1heEFtb3VudCI6MCwibGltaXRUb0ZpYXRBbW91bnRzIjoiIiwicGF5bWVudE1ldGhvZERldGFpbCI6IiIsIm1zZyI6IiIsImFjY291bnRJbmZvIjoiIiwiZm9yVHJ1c3RlZCI6Im5vIiwidmVyaWZpZWRFbWFpbFJlcXVpcmVkIjoibm8iLCJyZXF1aXJlRmVlZGJhY2tTY29yZSI6MCwiZmlyc3RUaW1lTGltaXRBc3NldCI6MCwicGF5bWVudFdpbmRvd01pbnV0ZXMiOjYwLCJoaWRkZW4iOmZhbHNlLCJiYW5uZWQiOmZhbHNlLCJ2ZXJpZmllZCI6dHJ1ZSwiYWRkZWQiOiIyMDI0LTEwLTIyVDIzOjMxOjQ3LjM5M1oifQ== @ 4ba8e86d:89d32de4
2024-10-22 23:20:59Usar um gerenciador de senhas pode resolver vários problemas, incluindo a dificuldade de criar senhas fortes e únicas, o risco de reutilização de senhas e a possibilidade de comprometimento de contas devido a senhas fracas ou roubadas. Com o uso de um gerenciador de senhas, o usuário pode criar senhas fortes e únicas para cada conta, sem precisar se preocupar em lembrar de todas elas. Além disso,um gerenciador de senhas pode ajudar a simplificar o processo de login, economizando tempo e reduzindo a frustração. O KeepassDX é uma versão do software de gerenciamento de senhas Keepass, desenvolvido originalmente por Dominik Reichl em 2003. O Keepass é um software gratuito e de código aberto para desktops, que permite que os usuários armazenem suas senhas em um banco de dados seguro, criptografado com algoritmos avançados. Em 2017, o desenvolvedor alemão Brian Pellmann criou o KeepassDX como uma versão para dispositivos móveis, com o objetivo de tornar mais fácil para os usuários gerenciarem suas senhas em smartphones e tablets. O KeepassDX foi criado a partir do código-fonte do Keepass e foi projetado para ser fácil de usar, seguro e personalizável. Pellmann adicionou várias funcionalidades novas ao KeepassDX, incluindo a capacidade de importar senhas de outros gerenciadores de senhas, a organização de senhas em categorias e a compatibilidade com serviços de armazenamento em nuvem para sincronização entre dispositivos. Algumas das funcionalidades do KeepassDX incluem a criação de senhas fortes e únicas, preenchimento automático de senhas, autenticação de dois fatores e organização de senhas por categorias. O KeepassDX também oferece uma ferramenta para importação de senhas de outros gerenciadores de senhas, o que torna a transição para o uso do KeepassDX mais fácil. Passo a passo instalação do aplicativo KeepassDX: 1. Baixe e instale o KeepassDX em seu dispositivo móvel https://play.google.com/store/apps/details?id=com.kunzisoft.keepass.free 2. Clique em [CRIAR NOVO BANCO DE DADOS] 3. Selecione o local do arquivo no meu caso é " transferência " Semelhante ao KeePassXC, o KeePassDX suporta o formato de banco de dados .kbdx (por exemplo, Passwords.kdbx) para armazenar senhas de contas importantes. Você deve salvar este arquivo em um local de fácil acesso para você, mas difícil de encontrar para outras pessoas que você não deseja visualizar as informações. Em particular, evite salvar seu arquivo de banco de dados em um serviço de armazenamento online, conectado às suas contas, pois pode ser acessado por outras pessoas. 4. Digite um nome para seu banco de dados Neste exemplo, " urso " nosso banco de dados como "urso.kdbx"; você pode escolher um nome de sua preferência. Você pode usar um nome que disfarce o arquivo e o torne menos óbvio para invasores que podem tentar acessar seu telefone e exigir que você desbloqueie o banco de dados. Também é possível alterar a "extensão" no final do nome do arquivo. Por exemplo, você pode nomear o banco de dados de senhas "Revoltadeatlas.pdf" "primainterior.jpg " e o sistema operacional geralmente dará ao arquivo um ícone de "aparência normal". Lembre-se de que, se você der ao seu banco de dados de senhas um nome que não termine em ".kdbx", não poderá abrir o arquivo diretamente. Em vez disso, você terá que iniciar o KeePassDX primeiro e, em seguida, abrir seu banco de dados clicando no botão "Abrir banco de dados existente". Felizmente, o KeePassDX lembra o último banco de dados que você abriu, então você não terá que fazer isso com frequência. https://github.com/Kunzisoft/KeePassDX
@ 4ba8e86d:89d32de4
2024-10-22 23:20:59Usar um gerenciador de senhas pode resolver vários problemas, incluindo a dificuldade de criar senhas fortes e únicas, o risco de reutilização de senhas e a possibilidade de comprometimento de contas devido a senhas fracas ou roubadas. Com o uso de um gerenciador de senhas, o usuário pode criar senhas fortes e únicas para cada conta, sem precisar se preocupar em lembrar de todas elas. Além disso,um gerenciador de senhas pode ajudar a simplificar o processo de login, economizando tempo e reduzindo a frustração. O KeepassDX é uma versão do software de gerenciamento de senhas Keepass, desenvolvido originalmente por Dominik Reichl em 2003. O Keepass é um software gratuito e de código aberto para desktops, que permite que os usuários armazenem suas senhas em um banco de dados seguro, criptografado com algoritmos avançados. Em 2017, o desenvolvedor alemão Brian Pellmann criou o KeepassDX como uma versão para dispositivos móveis, com o objetivo de tornar mais fácil para os usuários gerenciarem suas senhas em smartphones e tablets. O KeepassDX foi criado a partir do código-fonte do Keepass e foi projetado para ser fácil de usar, seguro e personalizável. Pellmann adicionou várias funcionalidades novas ao KeepassDX, incluindo a capacidade de importar senhas de outros gerenciadores de senhas, a organização de senhas em categorias e a compatibilidade com serviços de armazenamento em nuvem para sincronização entre dispositivos. Algumas das funcionalidades do KeepassDX incluem a criação de senhas fortes e únicas, preenchimento automático de senhas, autenticação de dois fatores e organização de senhas por categorias. O KeepassDX também oferece uma ferramenta para importação de senhas de outros gerenciadores de senhas, o que torna a transição para o uso do KeepassDX mais fácil. Passo a passo instalação do aplicativo KeepassDX: 1. Baixe e instale o KeepassDX em seu dispositivo móvel https://play.google.com/store/apps/details?id=com.kunzisoft.keepass.free 2. Clique em [CRIAR NOVO BANCO DE DADOS] 3. Selecione o local do arquivo no meu caso é " transferência " Semelhante ao KeePassXC, o KeePassDX suporta o formato de banco de dados .kbdx (por exemplo, Passwords.kdbx) para armazenar senhas de contas importantes. Você deve salvar este arquivo em um local de fácil acesso para você, mas difícil de encontrar para outras pessoas que você não deseja visualizar as informações. Em particular, evite salvar seu arquivo de banco de dados em um serviço de armazenamento online, conectado às suas contas, pois pode ser acessado por outras pessoas. 4. Digite um nome para seu banco de dados Neste exemplo, " urso " nosso banco de dados como "urso.kdbx"; você pode escolher um nome de sua preferência. Você pode usar um nome que disfarce o arquivo e o torne menos óbvio para invasores que podem tentar acessar seu telefone e exigir que você desbloqueie o banco de dados. Também é possível alterar a "extensão" no final do nome do arquivo. Por exemplo, você pode nomear o banco de dados de senhas "Revoltadeatlas.pdf" "primainterior.jpg " e o sistema operacional geralmente dará ao arquivo um ícone de "aparência normal". Lembre-se de que, se você der ao seu banco de dados de senhas um nome que não termine em ".kdbx", não poderá abrir o arquivo diretamente. Em vez disso, você terá que iniciar o KeePassDX primeiro e, em seguida, abrir seu banco de dados clicando no botão "Abrir banco de dados existente". Felizmente, o KeePassDX lembra o último banco de dados que você abriu, então você não terá que fazer isso com frequência. https://github.com/Kunzisoft/KeePassDX @ aa8de34f:a6ffe696
2024-10-22 19:36:06## Das Internet hat ein Problem. Nur wenige Leute wissen, dass dieses Problem existiert, aber hey, das liegt in der Natur ernsthafter, nicht offensichtlicher Probleme: Sie sind unsichtbar bis sie es nicht mehr sind. Das Problem mit dem Internet ist, dass Informationen frei sein wollen. Und wenn etwas FREI sein will wie in Freiheit, wird es mit genügend Zeit auch frei wie im Bier. Lass es mich erklären. ### Luftverschmutzung Jeden Tag verbrauchen wir ungeheure Mengen an Daten. Jede Sekunde jeder Minute strömen Bits und Bytes durch die Reihe von Leitungen die wir alle kennen und lieben: das Internet. Wir nehmen es als selbstverständlich hin und die meisten von uns halten das derzeitige Monetarisierungsmodell – sowie alle damit einhergehenden Übel – ebenfalls für selbstverständlich. Wir halten nur selten inne und denken über die seltsame Welt der Bits und Bytes nach. Wie wunderbar das alles ist, aber auch wie fremd. Wie es unser Leben bereits verändert hat und wie es unsere Zukunft weiter verändern wird. Woher kommen die Nullen und Einsen? Wie funktioniert das alles? Und vor allem: Wer zahlt dafür? Die Bits und Bytes, die durch unsere Glasfaserkabel rasen, sind so unsichtbar wie die Luft die wir atmen. Das ist keine schlechte Metapher wenn ich so darüber nachdenke. Solange wir keine Atemprobleme haben, müssen wir nicht anhalten und jedes einzelne Molekül, das wir einatmen, untersuchen. Ebenso lange wir keine Schwierigkeiten haben digitale Inhalte zu erstellen und zu konsumieren, brauchen wir auch nicht innezuhalten und all die verschiedenen Teile zu untersuchen, die unsere Aufmerksamkeitsökonomie am Laufen halten.\ **Aufmerksamkeitsökonomie**. Was für eine treffende Beschreibung. Wie wir inzwischen alle wissen sollten, ist das was wir konsumieren nicht umsonst, sondern wir bezahlen teuer dafür: mit unserer Aufmerksamkeit unter anderem. ### Paying Attention – mit Aufmerksamkeit bezahlen In der schnelllebigen Welt von heute muss man, um den Gewinn zu maximieren, die Aufmerksamkeit maximieren. Aber es ist eine eigentümliche, oberflächliche Art von Aufmerksamkeit. Es ist nicht die konzentrierte Art von Aufmerksamkeit, die tiefes Denken und sinnvolle Gespräche erfordern würden. Ich glaube, dass dies zumindest teilweise der Grund ist, warum viele Dinge so kaputt sind. Warum unser gesellschaftlicher Diskurs so zersplittert ist, unsere Politik so polarisiert, wir so gelähmt sind und unsere Analysen oft so oberflächlich sind wie unsere Wünsche.\ Die Aufmerksamkeitsökonomie hat uns fein säuberlich in Echokammern für persönliche Wahrheiten eingeteilt. Ironischerweise besteht die einzige Wahrheit die es wert ist, in der Aufmerksamkeitsökonomie verfolgt zu werden, darin, wie man eine maximale Anzahl von Menschen für eine maximale Zeitspanne maximal empört halten kann. Und das alles ohne dass die Teilnehmer merken, dass sie in einem selbst gewählten algorithmischen Gefängnis gefangen sind. ### Du bist das Produkt Die Redewendung „Wenn etwas kostenlos ist, bist du das Produkt“ kann nicht oft genug wiederholt werden. Aus dem einen oder anderen Grund erwarten wir, dass die meisten Dinge Online „kostenlos“ sind. Natürlich gibt es so etwas wie ein kostenloses Mittagessen nicht – nichts ist umsonst. Bei Online-Diensten werden deine Daten gesammelt und an den Meistbietenden verkauft, der in der Regel eine Werbeagentur oder eine Regierungsbehörde ist. Oder beides.\ Alle Big-Data-Unternehmen spionieren dich nicht nur aus, sondern nutzen auch eine Vielzahl von dunklen Mustern und unethischen Praktiken, um aus deinen Interaktionen auch den letzten Tropfen an Daten herauszuholen. Ob es sich dabei um den Facebook-Pixel, Google Analytics oder etwas anderes handelt, spielt keine Rolle. Du wirst nachverfolgt, überwacht und katalogisiert. Was du siehst, wie lange, zu welchen Zeiten, wie häufig und was du als Nächstes sehen wirst, wird sorgfältig von einem gewinnmaximierenden Algorithmus orchestriert. Profit für die Plattform, nicht für dich. Natürlich geht es in der Regel darum, dass alle davon profitieren: Nutzer, Urheber, Werbetreibende und die Plattformen gleichermaßen. Das evolutionäre Umfeld, das durch diese Anreizstrukturen geschaffen wird, führt jedoch häufig dazu, dass seichte, aufmerksamkeitsstarke und sensationslüsterne Schnipsel ausgewählt werden. Zum Zeitpunkt dieses Schreibens – Block 716.025 – ist der Inbegriff eines solchen Umfelds TikTok, eine videobasierte Dopaminmaschine, die dir das filmische Äquivalent von Heroin gemischt mit Crack zeigt. Harte Drogen für den Verstand, maßgeschneidert für deine besonderen Vorlieben. Eine wahrhaft verfluchte App. Leider unterscheiden sich die meisten dieser Plattformen nur in der Größe, nicht in der Art. ### Zulässige Meinungen „Es ist gar nicht so schlimm“, sagen wir uns. „Sieh dir all die nützlichen Informationen an!“, denken wir, während wir durch unsere Feeds scrollen, und füttern damit ungewollt die Maschine, die uns im Gegenzug mit Dopamin versorgt.\ Aber täuschen Sie sich nicht: Den verantwortlichen Unternehmen geht es nicht darum, uns mit nützlichen (oder wahrheitsgemäßen) Informationen zu versorgen. Es geht ihnen darum uns auszutricksen, damit wir die Maschine füttern.\ Wie könnte es anders sein? Man ist was man verfolgt, und man wird das worauf man optimiert wird. Aus Sicht der Plattform geht es um Klicks, nicht um Qualität. Auf den ersten Blick mag die Maximierung von Klicks und Verweildauer eine harmlose Sache sein. Schließlich muss man ja Geld verdienen um zu überleben. Es ist ja nur eine Anzeige. Wie schlimm kann es schon werden?\ Leider sind die Probleme, die damit einhergehen, zunächst unsichtbar. So wie Krebs für den Raucher unsichtbar ist, der gerade seine erste Zigarette geraucht hat, und Leberzirrhose für den Trinker unsichtbar ist, der gerade seinen ersten Drink zu sich genommen hat, so sind Deplatforming, Zensur, Polarisierung und Manipulation der öffentlichen Meinung für den Prosumenten unsichtbar, der gerade seine erste Anzeige auf einer geschlossenen Plattform gesehen hat. Wir können uns wahrscheinlich darauf einigen, dass wir das erste Inning (Stichwort Baseball) in dieser Frage hinter uns haben. Zensur ist die Norm, Deplatforming wird bejubelt, die Polarisierung ist auf einem Allzeithoch, und die öffentliche Meinung wird manuell und algorithmisch manipuliert wie nie zuvor.\ „Der Konsens ist, dass du zu dumm bist, um zu wissen was gut für dich ist und dass deine öffentliche Meinung zu unverschämt ist, um öffentlich geäußert zu werden. Schlimmer noch, es sollte gar nicht erst deine Meinung sein. Hier ist der Grund warum du falsch liegst. Hier ist eine Quelle die auf eine zulässige Meinung hinweist. Hier sind einige Experten, die mit uns übereinstimmen. Unsere intelligenten und hilfreichen Algorithmen haben die ganze Denkarbeit für dich erledigt, und sie liegen nie falsch. Genauso wenig wie die Experten.“\ Das ist die Welt, in der wir bereits leben. Es ist nicht erlaubt frei zu sprechen. Es ist nicht erlaubt frei zu denken. Du darfst dich nicht frei äußern. Dein Bild ist beleidigend und muss daher entfernt werden. Dein Meme ist zu nah an der Wahrheit oder zu kriminell lustig; deshalb müssen wir dich für ein oder zwei Wochen ins Twitter-Gefängnis stecken. Du sagst etwas mit dem wir nicht einverstanden sind; deshalb müssen wir dich auf Lebenszeit sperren – auch wenn du ein amtierender Präsident bist, wohlgemerkt. Du hast in einem Video das falsche Wort gesagt oder ein urheberrechtlich geschütztes Lied im Hintergrund abgespielt; deshalb müssen wir dir dein Einkommen wegnehmen. Du hast ein Bild von dir ohne Maske gepostet; deshalb müssen wir dich verbieten und den Behörden melden.1\ Die Tatsache, dass der obige Satz nicht mehr nur im Bereich der dystopischen Science-Fiction angesiedelt ist, sollte jeden beunruhigen. Aus dem Cyberspace entfernt – weil ich frei atmen wollte. Seltsame Zeiten. ### Evolutionärer Druck Wie ist es dazu gekommen? Wenn ich gezwungen wäre, eine kurze Antwort zu geben, würde ich Folgendes sagen: Wir sind von Protokollen zu Plattformen übergegangen, und Plattformen sind nur so gut wie ihre Anreize.\ Die Anreizstruktur der Plattformen, auf denen wir leben, ist die evolutionäre Umgebung, die das Überleben diktiert. Alles, was überleben will, muss sich daran orientieren. Das gilt natürlich für alle Bereiche der Wirtschaft. Nimm zum Beispiel Printmagazine. Wenn deine Zeitschrift kein schönes weibliches Gesicht auf der Titelseite hat, wird sie aus sehr menschlichen evolutionären Gründen nicht so oft gekauft werden wie die Zeitschriften, die ein solches Gesicht haben. Sie kann sich also nicht selbst reproduzieren und wird folglich sterben. Ähnlich verhält es sich mit einem Online-Nachrichtenportal, wenn es keine ausreichenden Werbeeinnahmen generiert und nicht in der Lage ist sich zu reproduzieren, wird es sterben. Aus diesem Grund hat jede Zeitschrift ein schönes weibliches Gesicht auf dem Cover. Und das ist der Grund, warum jede werbefinanzierte Online-Nachrichtenquelle zu Clickbait verkommt. <img src="https://cdn.satellite.earth/856054a1932c9fb70f9ae85bcb6d2d47330babb3cf7ac606c7861a09c8597f61.webp"> #### Eines dieser Gesichter ist anders als die anderen Das ist auch der Grund, warum sich Feed-basierte Empfehlungsmaschinen in Spielautomaten für deine Dopaminrezeptoren verwandeln. Je länger du an deinem Bildschirm klebst, desto mehr Werbung siehst du, desto mehr Einnahmen werden für die Plattform generiert. Das ist auch der Grund, warum die meisten YouTube-Kanäle zu 7- bis 15-minütigen Kurzvideos mit Vorschaubildern verkommen, die das Gesicht von jemandem zeigen, der gerade auf ein Legostück getreten ist. Kurz genug, um dich zu überzeugen es anzusehen, lang genug, um dich vergessen zu lassen, welches Video du dir eigentlich ansehen wolltest. Wie Ratten, die in hyperpersonalisierten Skinner-Boxen auf Knöpfe drücken, werden wir in Suchtzyklen konditioniert, um die Gewinne der Aktionäre zu maximieren. ### Profitmaximierung Plattformen sind Unternehmen und für Unternehmen gibt es Anreize die Gewinne der Aktionäre zu maximieren. Gegen Gewinne ist nichts einzuwenden und gegen Aktionäre ist auch nichts einzuwenden. Ich glaube jedoch, dass die Informationsrevolution, in der wir uns befinden, die evolutionäre Landschaft in zwei Teile gespalten hat. Nennen wir diese Landschaften „breit“ und „schmal“.\ Um die Gewinne durch breit angelegte Werbung zu maximieren, müssen Kontroversen und extreme Meinungen auf ein Minimum reduziert werden. Indem man den kleinsten gemeinsamen Nenner anspricht, kommen Politik und Zensur sofort ins Spiel. Umgekehrt müssen Kontroversen und extreme Meinungen maximiert werden, wenn die Gewinne durch schmale, gezielte Werbung erzielt werden sollen. Allein dadurch, dass verschiedenen Untergruppen unterschiedliche Informationen gezeigt werden, werden Polarisierung und Fragmentierung kontinuierlich verstärkt. <img src="https://cdn.satellite.earth/0d3a88d2700a3c26ed049b09d512a9a35dfc390bc95151e29d6950972114a00e.webp"> Allgemeine Kohäsion vs. algorithmische Spaltung Diese beiden Extreme sind zwei Seiten der gleichen Medaille. Es mag den Anschein haben, als ginge es um Kabelfernsehen gegen den algorithmischen Newsfeed, aber in Wirklichkeit handelt es sich um zwei unterschiedliche Ansätze, die dasselbe Ziel verfolgen: möglichst viele Menschen vor dem Bildschirm zu halten, damit sie mehr Werbung sehen. Das erste ist ein Beruhigungsmittel, das zweite ein Stimulans.\ Zugegeben, die obige Charakterisierung mag übertrieben sein, aber das Problem bleibt bestehen: Wenn wir nicht direkt für etwas bezahlen, bezahlen wir es indirekt, auf die eine oder andere Weise. Immer. Der Punkt ist der folgende: Plattformen für freie Meinungsäußerung können nicht existieren. Es kann nur Protokolle der freien Meinungsäußerung geben. Wenn jemand kontrollieren kann, was gesagt wird, wird jemand kontrollieren, was gesagt wird. Wenn du Inhalte überwachen, filtern und zensieren kannst, wirst du Inhalte überwachen, filtern und zensieren. Alle Plattformen werden mit diesem Problem konfrontiert, ganz gleich wie makellos ihre Absichten sind. Selbst wenn du dich anfangs als Plattform für freie Meinungsäußerung positionierst, wirst du auf lange Sicht gezwungen sein, einzugreifen und zu zensieren. Letztendlich wenn du für Inhalte, die du hostest oder übermittelst, vom Staat haftbar gemacht werden kannst, wirst du auch für Inhalte, die du hostest oder übermittelst, vom Staat haftbar gemacht werden. ### Selbstzensur Doch lange bevor die staatliche Zensur ihr hässliches Haupt erhebt, wird die abschreckende Wirkung der Selbstzensur zu spüren sein. Wenn andere wegen der Äußerung bestimmter Meinungen enttabuisiert und dämonisiert werden, werden die meisten Menschen sehr vorsichtig sein, diese Meinungen zu äußern. Bewusst und unbewusst bringen wir uns selbst langsam zum Schweigen. Wenn es um Selbstzensur geht, spielt auch die Werbung eine Rolle. Schließlich würdest du nicht die Hand beißen, die dich füttert, oder? Im schlimmsten Fall sagen dir die Werbetreibenden und Führungskräfte, was gesagt werden darf und was nicht. Sie werden dir sagen, welche Meinungen innerhalb und welche außerhalb des Overton-Fensters liegen. Und wenn sie es nicht tun, wirst du eine fundierte Vermutung anstellen und deine Aussagen entsprechend anpassen. ### Ein Problem und ein Paradoxon Zurück zum ursprünglichen Problem: Warum können wir Informationen nicht wie eine normale Ware verkaufen? Warum führt der einfache Ansatz – Inhalte hinter eine Bezahlschranke zu stellen – zu so schlechten Ergebnissen? Ich glaube, es gibt zwei Gründe, die ich das „MTX-Problem“ und das „DRM-Paradoxon“ nennen möchte. Das MTX-Problem, wobei MTX die Abkürzung für „mentale Transaktion“ (mental transaction) ist, bezieht sich auf das Problem der nicht reduzierbaren mentalen Transaktionskosten, die jeder Transaktion innewohnen. Jedes Mal, wenn du auf eine Bezahlschranke stößt, musst du eine bewusste Entscheidung treffen: „Möchte ich dafür bezahlen?“ Wie Szabo überzeugend darlegt, lautet die Antwort in den meisten Fällen, insbesondere wenn die Kosten gering sind, nein. Dafür gibt es keine technischen Gründe, sondern psychologische Gründe. Es stellt sich heraus, dass die Mühe, herauszufinden, ob sich diese Transaktion lohnt oder nicht – ein Prozess, der in deinem Kopf stattfindet – einfach zu groß ist. Wenn man über einen Mikrokauf nachdenken muss, sinkt die Wahrscheinlichkeit, dass man diesen Kauf tätigt, drastisch. Deshalb sind Flatrates und Abonnements der Renner: Man muss nur einmal darüber nachdenken. Bei den kleinsten Mikrotransaktionen ist dies sogar aus rein wirtschaftlicher Sicht der Fall. Wenn man einen Stundenlohn von 20 USD zugrunde legt und zwei Sekunden lang darüber nachdenkt: „Ist das 21 Sats wert?“, kostet das etwas mehr als 1¢, also mehr als der Preis der betreffenden Mikrotransaktion.\[2\] Das ist sowohl psychologisch als auch wirtschaftlich nicht machbar. Dies ist, kurz gesagt, das MTX-Problem. Aber das ist nicht das einzige Problem, das die Monetarisierung digitaler Inhalte belastet. Wie bereits erwähnt, gibt es auch das DRM-Paradoxon. DRM, kurz für „Digital-Rechte Management“ (Digital Rights Management), ist ein vergeblicher Versuch, das Kopieren von Informationen zu verhindern. Es sollte sich von selbst verstehen, dass nicht kopierbare Informationen ein Oxymoron sind, aber im Zeitalter von NFTs und vielem anderen Unsinn muss das leider ausdrücklich gesagt werden. Lass es mich also für dich buchstabieren: Man kann keine Informationen erstellen, die nicht kopiert werden können. Punkt. Oder, um es mit den Worten von Bruce Schneier zu sagen: „Der Versuch, digitale Dateien unkopierbar zu machen, ist wie der Versuch, Wasser nicht nass zu machen.“ Es liegt in der Natur der Sache, dass Informationen, wenn sie gelesen werden können, auch kopiert werden können – und zwar mit perfekter Genauigkeit. Kein noch so großer Trick oder künstliche Beschränkungen werden diese Tatsache ändern. Aus diesem Grund werden digitale Artefakte wie Filme und Musik immer kostenlos erhältlich sein. Es ist trivial für jemanden der Zugang zu diesen Artefakten hat, diese zu kopieren – zu Grenzkosten von nahezu Null, wohlgemerkt – und sie anderen zugänglich zu machen. Mit genügend Zeit und Popularität wird also jeder Film, jedes Lied und jedes Dokument für die\ Allgemeinheit kostenlos verfügbar sein. Die Natur der Information lässt kein anderes Ergebnis zu. Daher das Sprichwort: Information will frei sein. Obwohl der Versuch etwas zu schaffen das es nicht geben kann – Informationen die nicht kopiert werden können – an sich schon paradox ist, meine ich damit nicht das DRM-Paradoxon. Was ich meine, ist etwas viel Lustigeres. Es ist wiederum psychologischer, nicht technischer Natur. Das Paradoxon ist folgendes: Inhalte werden nur dann hinter einer Bezahlschranke bleiben, wenn sie schlecht sind. Wenn sie gut sind, wird sie jemand freilassen. Wir alle kennen das. Wenn ein Artikel tatsächlich lesenswert ist, wird jemand, der sich hinter der Bezahlschranke befindet, einen Screenshot davon machen und ihn in den sozialen Medien veröffentlichen. Wenn der Film es wert ist angeschaut zu werden, wird er auf verschiedenen Websites verfügbar sein, die Piratenschiffe als ihre Logos haben. Wenn der Song es wert ist gehört zu werden, wird er auf Streaming-Seiten kostenlos zur Verfügung stehen. Nur die schrecklichen Artikel, die obskursten Filme und die Lieder, bei denen einem die Ohren bluten, bleiben hinter Bezahlschranken. Daraus ergibt sich das Paradoxon: Inhalte bleiben nur dann hinter Bezahlschranken, wenn sie schlecht sind. Wenn sie gut sind, werden sie freigelassen. Ich persönlich glaube, dass das MTX-Problem ein größeres Problem darstellt als das DRM-Paradoxon. Die traditionelle Lösung für das MTX-Problem ist das Abonnementmodell, wie bei Netflix, Spotify, Amazon und so weiter. Das DRM-Paradoxon bleibt bestehen, aber es stellt sich heraus, dass dies kein Problem ist wenn man den „legitimen“ Zugang zu Informationen bequem genug gestaltet. Die Opportunitätskosten für das Herunterladen, Speichern, Pflegen und Warten einer privaten Liedersammlung sind für die meisten Menschen einfach zu hoch. Die bequemere Lösung ist für das verdammte Spotify-Abo zu bezahlen. Allerdings können wir bereits eines der Probleme erkennen, die mit dem Abonnementmodell verbunden sind. Der folgende Comic beschreibt es gut: Comic von /u/Hoppy_Doodle Die Verbreitung von Streaming-Plattformen zwingt dich dazu, ein Netflix-Abonnement, ein Amazon-Prime-Abonnement, ein Hulu-Abonnement, ein Disney-Plus-Abonnement, ein YouTube-Premium-Abonnement und so weiter abzuschließen. Und das war nur das Videostreaming. Den gleichen Abo-Zoo gibt es für Musik, Bücher, Spiele, Newsletter, Blogbeiträge usw. Und was ist die Lösung? ### Akzeptiere die Natur von Informationen Die Lösung beginnt mit Akzeptanz. Der Verkauf digitaler Inhalte auf herkömmliche, transaktionale Weise funktioniert nicht oder zumindest nicht sehr gut. Eine Transaktion mit einem digitalen Foto eines Apfels ist etwas ganz anderes als eine Transaktion mit einem physischen Apfel. George Bernard Shaw hat es am besten gesagt: „Wenn du einen Apfel hast und ich habe einen Apfel und wir tauschen diese Äpfel, dann haben wir beide immer noch jeweils einen Apfel. Aber wenn Sie eine Idee haben und ich eine Idee habe und wir diese Ideen austauschen, dann hat jeder von uns zwei Ideen.“ Da sich digitale Informationen wie eine Idee verhalten, gibt es keinen Grund, sie künstlich zu verknappen. Das gilt nicht nur in philosophischer, sondern auch technischer Hinsicht. Computer sind Kopiermaschinen. Das war schon immer so und wird auch so bleiben. Die einzige Möglichkeit, Informationen von einer Maschine auf eine andere zu übertragen, besteht darin, sie zu kopieren. Dies allein sollte die Sinnlosigkeit der Behandlung von Informationen als physische Objekte offenkundig machen. Wenn es um die Monetarisierung von Informationen im offenen Web geht, müssen wir unsere Denkweise mit der Natur der Information in Einklang bringen. Wie oben beschrieben, sind Informationen nicht knapp, leicht zu kopieren, leicht zu verändern und wollen frei sein. Ich glaube, dass das richtige Monetarisierungsmodell diese Werte respektieren und ähnliche Eigenschaften haben muss. Es muss offen, transparent, erweiterbar und nicht zuletzt völlig freiwillig sein. Dieses Modell hat einen Namen: Value-for-Value. ### Wiederbeleben der Straßenmusik Die Idee ist einfach, klingt aber radikal: Du stellst deine Inhalte kostenlos zur Verfügung, für jeden, ohne Zugangsbeschränkungen. Wenn die Menschen Spaß daran haben, wenn sie einen Nutzen daraus ziehen, dann machst du es den Menschen leicht etwas zurückzugeben.\ Es mag in der heutigen Zeit ungeheuerlich klingen, aber dieses Modell funktioniert seit Tausenden von Jahren. Es ist das Modell der Straßenkünstler, das Modell der Straßenmusikanten, das Modell des freiwilligen Gebens. Im Cyberspace stoßen wir jedoch nicht an die physischen Grenzen der traditionellen Straßenmusikanten. Digitale Inhalte lassen sich auf eine Art und Weise skalieren, wie es bei Darbietungen in der realen Welt nie der Fall sein wird. Das Value-for Value-Modell stellt das traditionelle Zahlungsmodell auf den Kopf. Traditionell folgt der Genuss der Bezahlung. Beim Value-for-Value-Ansatz folgt die Zahlung dem Genuss – freiwillig. Es steht dir frei, dem Straßenmusiker zuzuhören und weiterzugehen, aber – und das ist etwas was das Publikum intuitiv weiß – wenn du willst, dass die Musik weitergeht, solltest du ein paar Münzen in den Hut werfen. [Give value back](https://ts.dergigi.com/api/v1/invoices?storeId=3WkiYEG5DaQv7Ak5M2UjUi1pe5FFTPyNF1yAE9CVLNJn&orderId=V4V-busking&checkoutDesc=Value+for+Value%3A+Give+as+much+as+it+is+worth+to+you.¤cy=USD) Das Schöne an diesem Modell ist, dass es die Anreize neu ausrichtet. Man versucht nicht, die Klicks, die Verweildauer oder irgendeine andere der unzähligen Kennzahlen zu maximieren. Man will dem Publikum einen Mehrwert bieten, und das ist alles. Und wenn das Publikum einen Nutzen daraus gezogen hat, wird ein gewisser Prozentsatz etwas zurückgeben. Alles, was man tun muss, ist zu fragen. ### Eine wertvolle Alternative Wir stehen erst am Anfang dieses monumentalen Wandels. Ich hoffe, dass sich das Modell „Value for Value“ weiterhin als praktikable Alternative zu Werbung, Zensur, Deplatforming und Demonetisierung durchsetzen wird. Das Value-for-Value-Modell nimmt das „sie“ aus der Gleichung heraus. Sie filtern, sie zensieren, sie demonetisieren, sie deplatformieren. Es spielt nicht einmal eine Rolle, wer „sie“ sind. Wenn es „sie“ gibt, werden sie einen Weg finden, es zu versauen. Value-for-Value beseitigt „sie“ und überträgt dir die Verantwortung. Du bist der Herrscher im Reich des Einen, allein verantwortlich für deine Gedanken und deine Sprache. Wenn wir Befreiung (und Erlösung) im Cyberspace wollen, müssen wir dem Einzelnen wieder die Verantwortung übertragen. Wie immer gilt: Freiheit und Unabhängigkeit erfordern Verantwortung. In der besten aller Welten gibt es für die Schöpfer einen Anreiz, nichts anderes zu tun als zu erschaffen. Man bedient nur sich selbst und diejenigen, die an den Werken interessiert sind. Keine Mittelsmänner. Direkt, von Mensch zu Mensch, Value-for-Value. ### Was uns erwartet Zugegeben, heute ist es nicht gerade einfach, seine Infrastruktur selbst zu hosten. Es ist einschüchternd, einen eigenen Knotenpunkt (Node) zu betreiben, um Zahlungen auf selbständige Weise zu erhalten. Aber es wird nicht nur einfacher, es wird zunehmend notwendig. Wir müssen nicht nur alles einfacher machen, sondern uns auch des oben beschriebenen MTX-Problems bewusst sein. Jeder Schritt, der es schafft, die mentalen Transaktionskosten im Ökosystem der Wertschöpfung zu reduzieren, ist ein Schritt in die richtige Richtung. Die Wertfunktion von Podcasting 2.0 ist ein solcher Schritt. Sie ermöglicht und automatisiert Zahlungen im Minutentakt, ohne dass der Nutzer zusätzlich eingreifen muss. Sobald du eingerichtet bist, wird deine Geldbörse automatisch Zahlungen vornehmen. Ich glaube, dass weitere Iterationen dieser Idee in alle Medientypen integriert werden können, sei es Audio, Video, Bilder, das geschriebene Wort, und so weiter. Ich glaube, dass wir kurz vor der Protokollversion von Patreon stehen: alle Vorteile der Reduzierung der mentalen Transaktionskosten auf Null, ohne die Reibung und die Zensur, die einer plattformbasierten Lösung innewohnen. Ob es in Form von BOLT12 wiederkehrenden Zahlungen oder etwas ganz anderem kommen wird, bleibt abzuwarten. Ich bin jedoch zuversichtlich, dass dies zu gegebener Zeit der Fall sein wird. ### Schlussfolgerung Nicht nur unser Papiergeld ist kaputt, auch das Monetarisierungsmodell des Internets ist kaputt. Die werbebasierten Plattformen der heutigen Zeit sind auf Engagement durch Spaltung und Polarisierung optimiert und nutzen dunkle Muster und Sucht. Es wird nicht einfach sein, aus den Zwangsschleifen auszubrechen, die für uns eingerichtet wurden, aber dank des selbstverwalteten Tech-Stacks, der derzeit entsteht, gibt es eine praktikable Alternative: das Value-for-Value-Modell. Das „Straßenmusiker“-Monetarisierungsmodell (busking monetization model) hat in der Vergangenheit viele Jahrhunderte lang funktioniert, und dank Bitcoin und dem Lightning Network bin ich zuversichtlich, dass es auch in der Zukunft noch Jahrhunderte lang funktionieren wird. Wir sind fast am Ziel. Wir müssen nur noch herausfinden, wie wir den Hut richtig auf dem Boden positionieren und wo die besten Plätze in der Stadt sind, um sozusagen aufzutreten. Value-for-Value löst das DRM-Paradoxon in seiner Gesamtheit und wird – mit dem richtigen Maß an Automatisierung und vernünftigen Vorgaben – auch das MTX-Problem lösen. Wenn wir das richtig hinbekommen, können wir uns vielleicht aus dem evolutionären Überlebenskampf der Plattformen befreien und uns in das quasi unsterbliche Reich der Protokolle begeben. Es gibt viel zu erforschen, viele Werkzeuge zu entwickeln und viele vorgefasste Meinungen zu zerstören. Direkt vor unseren Augen vollzieht sich ein seismischer Wandel, und ich freue mich darauf, mit euch allen auf den Wellen zu reiten. Vorwärts marsch! --- *Dies ist ein übersetzter Gastbeitrag von Gigi aus seinem [Blog](https://dergigi.com/). Die geäußerten Meinungen sind ausschließlich seine eigenen und spiegeln nicht notwendigerweise die des Re-Publishers oder Aprycot Media wider. Quelle: https://aprycot.media/blog/freiheit-der-werte/#*
@ aa8de34f:a6ffe696
2024-10-22 19:36:06## Das Internet hat ein Problem. Nur wenige Leute wissen, dass dieses Problem existiert, aber hey, das liegt in der Natur ernsthafter, nicht offensichtlicher Probleme: Sie sind unsichtbar bis sie es nicht mehr sind. Das Problem mit dem Internet ist, dass Informationen frei sein wollen. Und wenn etwas FREI sein will wie in Freiheit, wird es mit genügend Zeit auch frei wie im Bier. Lass es mich erklären. ### Luftverschmutzung Jeden Tag verbrauchen wir ungeheure Mengen an Daten. Jede Sekunde jeder Minute strömen Bits und Bytes durch die Reihe von Leitungen die wir alle kennen und lieben: das Internet. Wir nehmen es als selbstverständlich hin und die meisten von uns halten das derzeitige Monetarisierungsmodell – sowie alle damit einhergehenden Übel – ebenfalls für selbstverständlich. Wir halten nur selten inne und denken über die seltsame Welt der Bits und Bytes nach. Wie wunderbar das alles ist, aber auch wie fremd. Wie es unser Leben bereits verändert hat und wie es unsere Zukunft weiter verändern wird. Woher kommen die Nullen und Einsen? Wie funktioniert das alles? Und vor allem: Wer zahlt dafür? Die Bits und Bytes, die durch unsere Glasfaserkabel rasen, sind so unsichtbar wie die Luft die wir atmen. Das ist keine schlechte Metapher wenn ich so darüber nachdenke. Solange wir keine Atemprobleme haben, müssen wir nicht anhalten und jedes einzelne Molekül, das wir einatmen, untersuchen. Ebenso lange wir keine Schwierigkeiten haben digitale Inhalte zu erstellen und zu konsumieren, brauchen wir auch nicht innezuhalten und all die verschiedenen Teile zu untersuchen, die unsere Aufmerksamkeitsökonomie am Laufen halten.\ **Aufmerksamkeitsökonomie**. Was für eine treffende Beschreibung. Wie wir inzwischen alle wissen sollten, ist das was wir konsumieren nicht umsonst, sondern wir bezahlen teuer dafür: mit unserer Aufmerksamkeit unter anderem. ### Paying Attention – mit Aufmerksamkeit bezahlen In der schnelllebigen Welt von heute muss man, um den Gewinn zu maximieren, die Aufmerksamkeit maximieren. Aber es ist eine eigentümliche, oberflächliche Art von Aufmerksamkeit. Es ist nicht die konzentrierte Art von Aufmerksamkeit, die tiefes Denken und sinnvolle Gespräche erfordern würden. Ich glaube, dass dies zumindest teilweise der Grund ist, warum viele Dinge so kaputt sind. Warum unser gesellschaftlicher Diskurs so zersplittert ist, unsere Politik so polarisiert, wir so gelähmt sind und unsere Analysen oft so oberflächlich sind wie unsere Wünsche.\ Die Aufmerksamkeitsökonomie hat uns fein säuberlich in Echokammern für persönliche Wahrheiten eingeteilt. Ironischerweise besteht die einzige Wahrheit die es wert ist, in der Aufmerksamkeitsökonomie verfolgt zu werden, darin, wie man eine maximale Anzahl von Menschen für eine maximale Zeitspanne maximal empört halten kann. Und das alles ohne dass die Teilnehmer merken, dass sie in einem selbst gewählten algorithmischen Gefängnis gefangen sind. ### Du bist das Produkt Die Redewendung „Wenn etwas kostenlos ist, bist du das Produkt“ kann nicht oft genug wiederholt werden. Aus dem einen oder anderen Grund erwarten wir, dass die meisten Dinge Online „kostenlos“ sind. Natürlich gibt es so etwas wie ein kostenloses Mittagessen nicht – nichts ist umsonst. Bei Online-Diensten werden deine Daten gesammelt und an den Meistbietenden verkauft, der in der Regel eine Werbeagentur oder eine Regierungsbehörde ist. Oder beides.\ Alle Big-Data-Unternehmen spionieren dich nicht nur aus, sondern nutzen auch eine Vielzahl von dunklen Mustern und unethischen Praktiken, um aus deinen Interaktionen auch den letzten Tropfen an Daten herauszuholen. Ob es sich dabei um den Facebook-Pixel, Google Analytics oder etwas anderes handelt, spielt keine Rolle. Du wirst nachverfolgt, überwacht und katalogisiert. Was du siehst, wie lange, zu welchen Zeiten, wie häufig und was du als Nächstes sehen wirst, wird sorgfältig von einem gewinnmaximierenden Algorithmus orchestriert. Profit für die Plattform, nicht für dich. Natürlich geht es in der Regel darum, dass alle davon profitieren: Nutzer, Urheber, Werbetreibende und die Plattformen gleichermaßen. Das evolutionäre Umfeld, das durch diese Anreizstrukturen geschaffen wird, führt jedoch häufig dazu, dass seichte, aufmerksamkeitsstarke und sensationslüsterne Schnipsel ausgewählt werden. Zum Zeitpunkt dieses Schreibens – Block 716.025 – ist der Inbegriff eines solchen Umfelds TikTok, eine videobasierte Dopaminmaschine, die dir das filmische Äquivalent von Heroin gemischt mit Crack zeigt. Harte Drogen für den Verstand, maßgeschneidert für deine besonderen Vorlieben. Eine wahrhaft verfluchte App. Leider unterscheiden sich die meisten dieser Plattformen nur in der Größe, nicht in der Art. ### Zulässige Meinungen „Es ist gar nicht so schlimm“, sagen wir uns. „Sieh dir all die nützlichen Informationen an!“, denken wir, während wir durch unsere Feeds scrollen, und füttern damit ungewollt die Maschine, die uns im Gegenzug mit Dopamin versorgt.\ Aber täuschen Sie sich nicht: Den verantwortlichen Unternehmen geht es nicht darum, uns mit nützlichen (oder wahrheitsgemäßen) Informationen zu versorgen. Es geht ihnen darum uns auszutricksen, damit wir die Maschine füttern.\ Wie könnte es anders sein? Man ist was man verfolgt, und man wird das worauf man optimiert wird. Aus Sicht der Plattform geht es um Klicks, nicht um Qualität. Auf den ersten Blick mag die Maximierung von Klicks und Verweildauer eine harmlose Sache sein. Schließlich muss man ja Geld verdienen um zu überleben. Es ist ja nur eine Anzeige. Wie schlimm kann es schon werden?\ Leider sind die Probleme, die damit einhergehen, zunächst unsichtbar. So wie Krebs für den Raucher unsichtbar ist, der gerade seine erste Zigarette geraucht hat, und Leberzirrhose für den Trinker unsichtbar ist, der gerade seinen ersten Drink zu sich genommen hat, so sind Deplatforming, Zensur, Polarisierung und Manipulation der öffentlichen Meinung für den Prosumenten unsichtbar, der gerade seine erste Anzeige auf einer geschlossenen Plattform gesehen hat. Wir können uns wahrscheinlich darauf einigen, dass wir das erste Inning (Stichwort Baseball) in dieser Frage hinter uns haben. Zensur ist die Norm, Deplatforming wird bejubelt, die Polarisierung ist auf einem Allzeithoch, und die öffentliche Meinung wird manuell und algorithmisch manipuliert wie nie zuvor.\ „Der Konsens ist, dass du zu dumm bist, um zu wissen was gut für dich ist und dass deine öffentliche Meinung zu unverschämt ist, um öffentlich geäußert zu werden. Schlimmer noch, es sollte gar nicht erst deine Meinung sein. Hier ist der Grund warum du falsch liegst. Hier ist eine Quelle die auf eine zulässige Meinung hinweist. Hier sind einige Experten, die mit uns übereinstimmen. Unsere intelligenten und hilfreichen Algorithmen haben die ganze Denkarbeit für dich erledigt, und sie liegen nie falsch. Genauso wenig wie die Experten.“\ Das ist die Welt, in der wir bereits leben. Es ist nicht erlaubt frei zu sprechen. Es ist nicht erlaubt frei zu denken. Du darfst dich nicht frei äußern. Dein Bild ist beleidigend und muss daher entfernt werden. Dein Meme ist zu nah an der Wahrheit oder zu kriminell lustig; deshalb müssen wir dich für ein oder zwei Wochen ins Twitter-Gefängnis stecken. Du sagst etwas mit dem wir nicht einverstanden sind; deshalb müssen wir dich auf Lebenszeit sperren – auch wenn du ein amtierender Präsident bist, wohlgemerkt. Du hast in einem Video das falsche Wort gesagt oder ein urheberrechtlich geschütztes Lied im Hintergrund abgespielt; deshalb müssen wir dir dein Einkommen wegnehmen. Du hast ein Bild von dir ohne Maske gepostet; deshalb müssen wir dich verbieten und den Behörden melden.1\ Die Tatsache, dass der obige Satz nicht mehr nur im Bereich der dystopischen Science-Fiction angesiedelt ist, sollte jeden beunruhigen. Aus dem Cyberspace entfernt – weil ich frei atmen wollte. Seltsame Zeiten. ### Evolutionärer Druck Wie ist es dazu gekommen? Wenn ich gezwungen wäre, eine kurze Antwort zu geben, würde ich Folgendes sagen: Wir sind von Protokollen zu Plattformen übergegangen, und Plattformen sind nur so gut wie ihre Anreize.\ Die Anreizstruktur der Plattformen, auf denen wir leben, ist die evolutionäre Umgebung, die das Überleben diktiert. Alles, was überleben will, muss sich daran orientieren. Das gilt natürlich für alle Bereiche der Wirtschaft. Nimm zum Beispiel Printmagazine. Wenn deine Zeitschrift kein schönes weibliches Gesicht auf der Titelseite hat, wird sie aus sehr menschlichen evolutionären Gründen nicht so oft gekauft werden wie die Zeitschriften, die ein solches Gesicht haben. Sie kann sich also nicht selbst reproduzieren und wird folglich sterben. Ähnlich verhält es sich mit einem Online-Nachrichtenportal, wenn es keine ausreichenden Werbeeinnahmen generiert und nicht in der Lage ist sich zu reproduzieren, wird es sterben. Aus diesem Grund hat jede Zeitschrift ein schönes weibliches Gesicht auf dem Cover. Und das ist der Grund, warum jede werbefinanzierte Online-Nachrichtenquelle zu Clickbait verkommt. <img src="https://cdn.satellite.earth/856054a1932c9fb70f9ae85bcb6d2d47330babb3cf7ac606c7861a09c8597f61.webp"> #### Eines dieser Gesichter ist anders als die anderen Das ist auch der Grund, warum sich Feed-basierte Empfehlungsmaschinen in Spielautomaten für deine Dopaminrezeptoren verwandeln. Je länger du an deinem Bildschirm klebst, desto mehr Werbung siehst du, desto mehr Einnahmen werden für die Plattform generiert. Das ist auch der Grund, warum die meisten YouTube-Kanäle zu 7- bis 15-minütigen Kurzvideos mit Vorschaubildern verkommen, die das Gesicht von jemandem zeigen, der gerade auf ein Legostück getreten ist. Kurz genug, um dich zu überzeugen es anzusehen, lang genug, um dich vergessen zu lassen, welches Video du dir eigentlich ansehen wolltest. Wie Ratten, die in hyperpersonalisierten Skinner-Boxen auf Knöpfe drücken, werden wir in Suchtzyklen konditioniert, um die Gewinne der Aktionäre zu maximieren. ### Profitmaximierung Plattformen sind Unternehmen und für Unternehmen gibt es Anreize die Gewinne der Aktionäre zu maximieren. Gegen Gewinne ist nichts einzuwenden und gegen Aktionäre ist auch nichts einzuwenden. Ich glaube jedoch, dass die Informationsrevolution, in der wir uns befinden, die evolutionäre Landschaft in zwei Teile gespalten hat. Nennen wir diese Landschaften „breit“ und „schmal“.\ Um die Gewinne durch breit angelegte Werbung zu maximieren, müssen Kontroversen und extreme Meinungen auf ein Minimum reduziert werden. Indem man den kleinsten gemeinsamen Nenner anspricht, kommen Politik und Zensur sofort ins Spiel. Umgekehrt müssen Kontroversen und extreme Meinungen maximiert werden, wenn die Gewinne durch schmale, gezielte Werbung erzielt werden sollen. Allein dadurch, dass verschiedenen Untergruppen unterschiedliche Informationen gezeigt werden, werden Polarisierung und Fragmentierung kontinuierlich verstärkt. <img src="https://cdn.satellite.earth/0d3a88d2700a3c26ed049b09d512a9a35dfc390bc95151e29d6950972114a00e.webp"> Allgemeine Kohäsion vs. algorithmische Spaltung Diese beiden Extreme sind zwei Seiten der gleichen Medaille. Es mag den Anschein haben, als ginge es um Kabelfernsehen gegen den algorithmischen Newsfeed, aber in Wirklichkeit handelt es sich um zwei unterschiedliche Ansätze, die dasselbe Ziel verfolgen: möglichst viele Menschen vor dem Bildschirm zu halten, damit sie mehr Werbung sehen. Das erste ist ein Beruhigungsmittel, das zweite ein Stimulans.\ Zugegeben, die obige Charakterisierung mag übertrieben sein, aber das Problem bleibt bestehen: Wenn wir nicht direkt für etwas bezahlen, bezahlen wir es indirekt, auf die eine oder andere Weise. Immer. Der Punkt ist der folgende: Plattformen für freie Meinungsäußerung können nicht existieren. Es kann nur Protokolle der freien Meinungsäußerung geben. Wenn jemand kontrollieren kann, was gesagt wird, wird jemand kontrollieren, was gesagt wird. Wenn du Inhalte überwachen, filtern und zensieren kannst, wirst du Inhalte überwachen, filtern und zensieren. Alle Plattformen werden mit diesem Problem konfrontiert, ganz gleich wie makellos ihre Absichten sind. Selbst wenn du dich anfangs als Plattform für freie Meinungsäußerung positionierst, wirst du auf lange Sicht gezwungen sein, einzugreifen und zu zensieren. Letztendlich wenn du für Inhalte, die du hostest oder übermittelst, vom Staat haftbar gemacht werden kannst, wirst du auch für Inhalte, die du hostest oder übermittelst, vom Staat haftbar gemacht werden. ### Selbstzensur Doch lange bevor die staatliche Zensur ihr hässliches Haupt erhebt, wird die abschreckende Wirkung der Selbstzensur zu spüren sein. Wenn andere wegen der Äußerung bestimmter Meinungen enttabuisiert und dämonisiert werden, werden die meisten Menschen sehr vorsichtig sein, diese Meinungen zu äußern. Bewusst und unbewusst bringen wir uns selbst langsam zum Schweigen. Wenn es um Selbstzensur geht, spielt auch die Werbung eine Rolle. Schließlich würdest du nicht die Hand beißen, die dich füttert, oder? Im schlimmsten Fall sagen dir die Werbetreibenden und Führungskräfte, was gesagt werden darf und was nicht. Sie werden dir sagen, welche Meinungen innerhalb und welche außerhalb des Overton-Fensters liegen. Und wenn sie es nicht tun, wirst du eine fundierte Vermutung anstellen und deine Aussagen entsprechend anpassen. ### Ein Problem und ein Paradoxon Zurück zum ursprünglichen Problem: Warum können wir Informationen nicht wie eine normale Ware verkaufen? Warum führt der einfache Ansatz – Inhalte hinter eine Bezahlschranke zu stellen – zu so schlechten Ergebnissen? Ich glaube, es gibt zwei Gründe, die ich das „MTX-Problem“ und das „DRM-Paradoxon“ nennen möchte. Das MTX-Problem, wobei MTX die Abkürzung für „mentale Transaktion“ (mental transaction) ist, bezieht sich auf das Problem der nicht reduzierbaren mentalen Transaktionskosten, die jeder Transaktion innewohnen. Jedes Mal, wenn du auf eine Bezahlschranke stößt, musst du eine bewusste Entscheidung treffen: „Möchte ich dafür bezahlen?“ Wie Szabo überzeugend darlegt, lautet die Antwort in den meisten Fällen, insbesondere wenn die Kosten gering sind, nein. Dafür gibt es keine technischen Gründe, sondern psychologische Gründe. Es stellt sich heraus, dass die Mühe, herauszufinden, ob sich diese Transaktion lohnt oder nicht – ein Prozess, der in deinem Kopf stattfindet – einfach zu groß ist. Wenn man über einen Mikrokauf nachdenken muss, sinkt die Wahrscheinlichkeit, dass man diesen Kauf tätigt, drastisch. Deshalb sind Flatrates und Abonnements der Renner: Man muss nur einmal darüber nachdenken. Bei den kleinsten Mikrotransaktionen ist dies sogar aus rein wirtschaftlicher Sicht der Fall. Wenn man einen Stundenlohn von 20 USD zugrunde legt und zwei Sekunden lang darüber nachdenkt: „Ist das 21 Sats wert?“, kostet das etwas mehr als 1¢, also mehr als der Preis der betreffenden Mikrotransaktion.\[2\] Das ist sowohl psychologisch als auch wirtschaftlich nicht machbar. Dies ist, kurz gesagt, das MTX-Problem. Aber das ist nicht das einzige Problem, das die Monetarisierung digitaler Inhalte belastet. Wie bereits erwähnt, gibt es auch das DRM-Paradoxon. DRM, kurz für „Digital-Rechte Management“ (Digital Rights Management), ist ein vergeblicher Versuch, das Kopieren von Informationen zu verhindern. Es sollte sich von selbst verstehen, dass nicht kopierbare Informationen ein Oxymoron sind, aber im Zeitalter von NFTs und vielem anderen Unsinn muss das leider ausdrücklich gesagt werden. Lass es mich also für dich buchstabieren: Man kann keine Informationen erstellen, die nicht kopiert werden können. Punkt. Oder, um es mit den Worten von Bruce Schneier zu sagen: „Der Versuch, digitale Dateien unkopierbar zu machen, ist wie der Versuch, Wasser nicht nass zu machen.“ Es liegt in der Natur der Sache, dass Informationen, wenn sie gelesen werden können, auch kopiert werden können – und zwar mit perfekter Genauigkeit. Kein noch so großer Trick oder künstliche Beschränkungen werden diese Tatsache ändern. Aus diesem Grund werden digitale Artefakte wie Filme und Musik immer kostenlos erhältlich sein. Es ist trivial für jemanden der Zugang zu diesen Artefakten hat, diese zu kopieren – zu Grenzkosten von nahezu Null, wohlgemerkt – und sie anderen zugänglich zu machen. Mit genügend Zeit und Popularität wird also jeder Film, jedes Lied und jedes Dokument für die\ Allgemeinheit kostenlos verfügbar sein. Die Natur der Information lässt kein anderes Ergebnis zu. Daher das Sprichwort: Information will frei sein. Obwohl der Versuch etwas zu schaffen das es nicht geben kann – Informationen die nicht kopiert werden können – an sich schon paradox ist, meine ich damit nicht das DRM-Paradoxon. Was ich meine, ist etwas viel Lustigeres. Es ist wiederum psychologischer, nicht technischer Natur. Das Paradoxon ist folgendes: Inhalte werden nur dann hinter einer Bezahlschranke bleiben, wenn sie schlecht sind. Wenn sie gut sind, wird sie jemand freilassen. Wir alle kennen das. Wenn ein Artikel tatsächlich lesenswert ist, wird jemand, der sich hinter der Bezahlschranke befindet, einen Screenshot davon machen und ihn in den sozialen Medien veröffentlichen. Wenn der Film es wert ist angeschaut zu werden, wird er auf verschiedenen Websites verfügbar sein, die Piratenschiffe als ihre Logos haben. Wenn der Song es wert ist gehört zu werden, wird er auf Streaming-Seiten kostenlos zur Verfügung stehen. Nur die schrecklichen Artikel, die obskursten Filme und die Lieder, bei denen einem die Ohren bluten, bleiben hinter Bezahlschranken. Daraus ergibt sich das Paradoxon: Inhalte bleiben nur dann hinter Bezahlschranken, wenn sie schlecht sind. Wenn sie gut sind, werden sie freigelassen. Ich persönlich glaube, dass das MTX-Problem ein größeres Problem darstellt als das DRM-Paradoxon. Die traditionelle Lösung für das MTX-Problem ist das Abonnementmodell, wie bei Netflix, Spotify, Amazon und so weiter. Das DRM-Paradoxon bleibt bestehen, aber es stellt sich heraus, dass dies kein Problem ist wenn man den „legitimen“ Zugang zu Informationen bequem genug gestaltet. Die Opportunitätskosten für das Herunterladen, Speichern, Pflegen und Warten einer privaten Liedersammlung sind für die meisten Menschen einfach zu hoch. Die bequemere Lösung ist für das verdammte Spotify-Abo zu bezahlen. Allerdings können wir bereits eines der Probleme erkennen, die mit dem Abonnementmodell verbunden sind. Der folgende Comic beschreibt es gut: Comic von /u/Hoppy_Doodle Die Verbreitung von Streaming-Plattformen zwingt dich dazu, ein Netflix-Abonnement, ein Amazon-Prime-Abonnement, ein Hulu-Abonnement, ein Disney-Plus-Abonnement, ein YouTube-Premium-Abonnement und so weiter abzuschließen. Und das war nur das Videostreaming. Den gleichen Abo-Zoo gibt es für Musik, Bücher, Spiele, Newsletter, Blogbeiträge usw. Und was ist die Lösung? ### Akzeptiere die Natur von Informationen Die Lösung beginnt mit Akzeptanz. Der Verkauf digitaler Inhalte auf herkömmliche, transaktionale Weise funktioniert nicht oder zumindest nicht sehr gut. Eine Transaktion mit einem digitalen Foto eines Apfels ist etwas ganz anderes als eine Transaktion mit einem physischen Apfel. George Bernard Shaw hat es am besten gesagt: „Wenn du einen Apfel hast und ich habe einen Apfel und wir tauschen diese Äpfel, dann haben wir beide immer noch jeweils einen Apfel. Aber wenn Sie eine Idee haben und ich eine Idee habe und wir diese Ideen austauschen, dann hat jeder von uns zwei Ideen.“ Da sich digitale Informationen wie eine Idee verhalten, gibt es keinen Grund, sie künstlich zu verknappen. Das gilt nicht nur in philosophischer, sondern auch technischer Hinsicht. Computer sind Kopiermaschinen. Das war schon immer so und wird auch so bleiben. Die einzige Möglichkeit, Informationen von einer Maschine auf eine andere zu übertragen, besteht darin, sie zu kopieren. Dies allein sollte die Sinnlosigkeit der Behandlung von Informationen als physische Objekte offenkundig machen. Wenn es um die Monetarisierung von Informationen im offenen Web geht, müssen wir unsere Denkweise mit der Natur der Information in Einklang bringen. Wie oben beschrieben, sind Informationen nicht knapp, leicht zu kopieren, leicht zu verändern und wollen frei sein. Ich glaube, dass das richtige Monetarisierungsmodell diese Werte respektieren und ähnliche Eigenschaften haben muss. Es muss offen, transparent, erweiterbar und nicht zuletzt völlig freiwillig sein. Dieses Modell hat einen Namen: Value-for-Value. ### Wiederbeleben der Straßenmusik Die Idee ist einfach, klingt aber radikal: Du stellst deine Inhalte kostenlos zur Verfügung, für jeden, ohne Zugangsbeschränkungen. Wenn die Menschen Spaß daran haben, wenn sie einen Nutzen daraus ziehen, dann machst du es den Menschen leicht etwas zurückzugeben.\ Es mag in der heutigen Zeit ungeheuerlich klingen, aber dieses Modell funktioniert seit Tausenden von Jahren. Es ist das Modell der Straßenkünstler, das Modell der Straßenmusikanten, das Modell des freiwilligen Gebens. Im Cyberspace stoßen wir jedoch nicht an die physischen Grenzen der traditionellen Straßenmusikanten. Digitale Inhalte lassen sich auf eine Art und Weise skalieren, wie es bei Darbietungen in der realen Welt nie der Fall sein wird. Das Value-for Value-Modell stellt das traditionelle Zahlungsmodell auf den Kopf. Traditionell folgt der Genuss der Bezahlung. Beim Value-for-Value-Ansatz folgt die Zahlung dem Genuss – freiwillig. Es steht dir frei, dem Straßenmusiker zuzuhören und weiterzugehen, aber – und das ist etwas was das Publikum intuitiv weiß – wenn du willst, dass die Musik weitergeht, solltest du ein paar Münzen in den Hut werfen. [Give value back](https://ts.dergigi.com/api/v1/invoices?storeId=3WkiYEG5DaQv7Ak5M2UjUi1pe5FFTPyNF1yAE9CVLNJn&orderId=V4V-busking&checkoutDesc=Value+for+Value%3A+Give+as+much+as+it+is+worth+to+you.¤cy=USD) Das Schöne an diesem Modell ist, dass es die Anreize neu ausrichtet. Man versucht nicht, die Klicks, die Verweildauer oder irgendeine andere der unzähligen Kennzahlen zu maximieren. Man will dem Publikum einen Mehrwert bieten, und das ist alles. Und wenn das Publikum einen Nutzen daraus gezogen hat, wird ein gewisser Prozentsatz etwas zurückgeben. Alles, was man tun muss, ist zu fragen. ### Eine wertvolle Alternative Wir stehen erst am Anfang dieses monumentalen Wandels. Ich hoffe, dass sich das Modell „Value for Value“ weiterhin als praktikable Alternative zu Werbung, Zensur, Deplatforming und Demonetisierung durchsetzen wird. Das Value-for-Value-Modell nimmt das „sie“ aus der Gleichung heraus. Sie filtern, sie zensieren, sie demonetisieren, sie deplatformieren. Es spielt nicht einmal eine Rolle, wer „sie“ sind. Wenn es „sie“ gibt, werden sie einen Weg finden, es zu versauen. Value-for-Value beseitigt „sie“ und überträgt dir die Verantwortung. Du bist der Herrscher im Reich des Einen, allein verantwortlich für deine Gedanken und deine Sprache. Wenn wir Befreiung (und Erlösung) im Cyberspace wollen, müssen wir dem Einzelnen wieder die Verantwortung übertragen. Wie immer gilt: Freiheit und Unabhängigkeit erfordern Verantwortung. In der besten aller Welten gibt es für die Schöpfer einen Anreiz, nichts anderes zu tun als zu erschaffen. Man bedient nur sich selbst und diejenigen, die an den Werken interessiert sind. Keine Mittelsmänner. Direkt, von Mensch zu Mensch, Value-for-Value. ### Was uns erwartet Zugegeben, heute ist es nicht gerade einfach, seine Infrastruktur selbst zu hosten. Es ist einschüchternd, einen eigenen Knotenpunkt (Node) zu betreiben, um Zahlungen auf selbständige Weise zu erhalten. Aber es wird nicht nur einfacher, es wird zunehmend notwendig. Wir müssen nicht nur alles einfacher machen, sondern uns auch des oben beschriebenen MTX-Problems bewusst sein. Jeder Schritt, der es schafft, die mentalen Transaktionskosten im Ökosystem der Wertschöpfung zu reduzieren, ist ein Schritt in die richtige Richtung. Die Wertfunktion von Podcasting 2.0 ist ein solcher Schritt. Sie ermöglicht und automatisiert Zahlungen im Minutentakt, ohne dass der Nutzer zusätzlich eingreifen muss. Sobald du eingerichtet bist, wird deine Geldbörse automatisch Zahlungen vornehmen. Ich glaube, dass weitere Iterationen dieser Idee in alle Medientypen integriert werden können, sei es Audio, Video, Bilder, das geschriebene Wort, und so weiter. Ich glaube, dass wir kurz vor der Protokollversion von Patreon stehen: alle Vorteile der Reduzierung der mentalen Transaktionskosten auf Null, ohne die Reibung und die Zensur, die einer plattformbasierten Lösung innewohnen. Ob es in Form von BOLT12 wiederkehrenden Zahlungen oder etwas ganz anderem kommen wird, bleibt abzuwarten. Ich bin jedoch zuversichtlich, dass dies zu gegebener Zeit der Fall sein wird. ### Schlussfolgerung Nicht nur unser Papiergeld ist kaputt, auch das Monetarisierungsmodell des Internets ist kaputt. Die werbebasierten Plattformen der heutigen Zeit sind auf Engagement durch Spaltung und Polarisierung optimiert und nutzen dunkle Muster und Sucht. Es wird nicht einfach sein, aus den Zwangsschleifen auszubrechen, die für uns eingerichtet wurden, aber dank des selbstverwalteten Tech-Stacks, der derzeit entsteht, gibt es eine praktikable Alternative: das Value-for-Value-Modell. Das „Straßenmusiker“-Monetarisierungsmodell (busking monetization model) hat in der Vergangenheit viele Jahrhunderte lang funktioniert, und dank Bitcoin und dem Lightning Network bin ich zuversichtlich, dass es auch in der Zukunft noch Jahrhunderte lang funktionieren wird. Wir sind fast am Ziel. Wir müssen nur noch herausfinden, wie wir den Hut richtig auf dem Boden positionieren und wo die besten Plätze in der Stadt sind, um sozusagen aufzutreten. Value-for-Value löst das DRM-Paradoxon in seiner Gesamtheit und wird – mit dem richtigen Maß an Automatisierung und vernünftigen Vorgaben – auch das MTX-Problem lösen. Wenn wir das richtig hinbekommen, können wir uns vielleicht aus dem evolutionären Überlebenskampf der Plattformen befreien und uns in das quasi unsterbliche Reich der Protokolle begeben. Es gibt viel zu erforschen, viele Werkzeuge zu entwickeln und viele vorgefasste Meinungen zu zerstören. Direkt vor unseren Augen vollzieht sich ein seismischer Wandel, und ich freue mich darauf, mit euch allen auf den Wellen zu reiten. Vorwärts marsch! --- *Dies ist ein übersetzter Gastbeitrag von Gigi aus seinem [Blog](https://dergigi.com/). Die geäußerten Meinungen sind ausschließlich seine eigenen und spiegeln nicht notwendigerweise die des Re-Publishers oder Aprycot Media wider. Quelle: https://aprycot.media/blog/freiheit-der-werte/#* @ eac63075:b4988b48
2024-10-21 08:11:11Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication. https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV https://open.spotify.com/episode/0IZ6kMExfxFm4FHg5DAWT8?si=e139033865e045de ### **Sections:** - **Introduction** - **What Is Chat Control?** - **Why Is the EU Pushing for Chat Control?** - **The Privacy Concerns and Risks** - **The Technical Debate: Encryption and Backdoors** - **Global Reactions and the Debate in Europe** - **Possible Consequences for Messaging Services** - **What Happens Next? The Future of Chat Control** - **Conclusion** --- ### **What Is Chat Control?** "Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns. At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content. #### **Origins of the Proposal** The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms. #### **How Messaging Services Work** Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors. <img src="https://blossom.primal.net/31ace3b729fb9f6b4de286686f31a71db6dd7e3a363f868e1255a6f287eb0b94.png"> #### **Key Elements of Chat Control** - **Automated Content Scanning**: Service providers would use algorithms to scan messages for illegal content. - **Circumvention of Encryption**: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security. - **Mandatory Reporting**: If illegal content is detected, providers would be required to report it to authorities. - **Broad Applicability**: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms. #### **Why It Matters** Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought. --- ### **Why Is the EU Pushing for Chat Control?** The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms. #### **Protecting Children and Preventing Crime** One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes. Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety. #### **Legal Context and Legislative Drivers** The push for Chat Control is rooted in several legislative initiatives: - **ePrivacy Directive**: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances. - **Temporary Derogation**: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive. - **Regulation Proposals**: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications. #### **Balancing Security and Privacy** EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections. However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as: - **Targeted Scanning**: Focusing on specific threats rather than broad, indiscriminate monitoring. - **Judicial Oversight**: Requiring court orders or oversight for accessing private communications. - **Data Protection Safeguards**: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed. <img src="https://blossom.primal.net/9533aedc9f83564d53633eac1a6d431d1e311028a478dd4b7f3a59b2c449e95a.png"> #### **The Urgency Behind the Push** High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked. #### **Criticism and Controversy** Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose. --- ### **The Privacy Concerns and Risks** While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications. #### **Infringement on Privacy Rights** At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms. #### **Erosion of End-to-End Encryption** End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats. #### **Concerns from Privacy Advocates** Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences: - **Security Risks**: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime. - **Global Implications**: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy. - **Ineffectiveness Against Crime**: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens. <img src="https://blossom.primal.net/51722887ebf55c827cc20bcfade3ea9b3628265b7fa3547504b2fff45f34f175.png"> #### **Potential for Government Overreach** There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent. #### **Real-World Implications for Users** - **False Positives**: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users. - **Chilling Effect**: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse. - **Data Misuse**: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information. #### **Legal and Ethical Concerns** Privacy advocates also highlight potential conflicts with existing laws and ethical standards: - **Violation of Fundamental Rights**: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression. - **Questionable Effectiveness**: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users. #### **Opposition from Member States and Organizations** Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences. --- ### **The Technical Debate: Encryption and Backdoors** The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures. #### **What Is End-to-End Encryption (E2EE)?** End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content. - **Security Assurance**: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private. - **Widespread Use**: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data. #### **How Chat Control Affects Encryption** Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to: - **Introduce Backdoors**: Create a means for third parties (including the service provider or authorities) to access encrypted messages. - **Client-Side Scanning**: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE. #### **The Risks of Weakening Encryption** **1. Compromised Security for All Users** Introducing backdoors or client-side scanning tools can create vulnerabilities: - **Exploitable Gaps**: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches. - **Universal Impact**: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk. **2. Undermining Trust in Digital Services** - **User Confidence**: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms. - **Business Implications**: Companies relying on secure communications might face increased risks, affecting economic activities. **3. Ineffectiveness Against Skilled Adversaries** - **Alternative Methods**: Criminals might shift to other encrypted channels or develop new ways to avoid detection. - **False Sense of Security**: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected. #### **Signal’s Response and Stance** Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals: - **Refusal to Weaken Encryption**: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards. - **Advocacy for Privacy**: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age. #### **Understanding Backdoors** A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems: - **Security Vulnerabilities**: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments. - **Ethical Concerns**: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications. <img src="https://blossom.primal.net/67f45fd79ccdb7e2e2ecdc56297207dc0d1d073acb216857b6165b3bf9906997.png"> #### **The Slippery Slope Argument** Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent: - **Expanded Surveillance**: Once in place, these measures could be extended to monitor other types of content beyond the original scope. - **Erosion of Rights**: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time. #### **Potential Technological Alternatives** Some suggest that it's possible to fight illegal content without undermining encryption: - **Metadata Analysis**: Focusing on patterns of communication rather than content. - **Enhanced Reporting Mechanisms**: Encouraging users to report illegal content voluntarily. - **Investing in Law Enforcement Capabilities**: Strengthening traditional investigative methods without compromising digital security. #### The technical community largely agrees that weakening encryption is not the solution: - **Consensus on Security**: Strong encryption is essential for the safety and privacy of all internet users. - **Call for Dialogue**: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights. --- ### **Global Reactions and the Debate in Europe** The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values. #### **Support for Chat Control** Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that: - **Enhanced Security**: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes. - **Responsibility of Service Providers**: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities. - **Public Safety Priorities**: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy. #### **Opposition within the EU** Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach. **Germany** - **Stance**: Germany has been one of the most vocal opponents of the proposed measures. - **Reasons**: - **Constitutional Concerns**: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications. - **Security Risks**: Weakening encryption is seen as a threat to cybersecurity. - **Legal Challenges**: Potential conflicts with national laws protecting personal data and communication secrecy. **Netherlands** - **Recent Developments**: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy. - **Arguments**: - **Effectiveness Doubts**: Skepticism about the actual effectiveness of the measures in combating crime. - **Negative Impact on Privacy**: Concerns about mass surveillance and the infringement of citizens' rights. Table reference: Patrick Breyer - Chat Control in 23 September 2024 #### **Privacy Advocacy Groups** **European Digital Rights (EDRi)** - **Role**: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment. - **Position**: - **Strong Opposition**: EDRi argues that Chat Control is incompatible with fundamental rights. - **Awareness Campaigns**: Engaging in public campaigns to inform citizens about the potential risks. - **Policy Engagement**: Lobbying policymakers to consider alternative approaches that respect privacy. **Politicians and Activists** **Patrick Breyer** - **Background**: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party. - **Actions**: - **Advocacy**: Actively campaigning against Chat Control through speeches, articles, and legislative efforts. - **Public Outreach**: Using social media and public events to raise awareness. - **Legal Expertise**: Highlighting the legal inconsistencies and potential violations of EU law. #### **Global Reactions** **International Organizations** - **Human Rights Watch and Amnesty International**: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider. **Technology Companies** - **Global Tech Firms**: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust. - **Industry Associations**: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness. <img src="https://blossom.primal.net/e761aa2dd240a1a2e7d943565ccbda427b5a8054bf4e6e17c946711ab6370d5d.png"> #### **The Broader Debate** The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include: - **Legal Precedents**: How the EU's decision might influence laws and regulations in other countries. - **Digital Sovereignty**: The desire of nations to control digital spaces within their borders. - **Civil Liberties**: The importance of protecting freedoms in the face of technological advancements. #### **Public Opinion** - **Diverse Views**: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all. - **Awareness Levels**: Many people are still unaware of the potential changes, highlighting the need for public education on the issue. #### The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society. --- ### **Possible Consequences for Messaging Services** The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication. #### **Impact on Encrypted Messaging Services** **Signal and Similar Platforms** - **Compliance Challenges**: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles. - **Operational Decisions**: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features. #### **Potential Blocking or Limiting of Services** - **Regulatory Enforcement**: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU. - **Access Restrictions**: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements. #### **Effects on Smaller Providers** - **Resource Constraints**: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market. - **Innovation Stifling**: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector. <img src="https://blossom.primal.net/60a9cad69b45cc3ded1d1759312e49a57b3aa997db62e36016f40642943be5e9.png"> #### **User Experience and Trust** - **Privacy Concerns**: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement. - **Migration to Unregulated Platforms**: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks. #### **Technical and Security Implications** - **Increased Vulnerabilities**: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches. - **Global Security Risks**: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders. #### **Impact on Businesses and Professional Communications** - **Confidentiality Issues**: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services. - **Compliance Complexity**: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens. #### **Economic Consequences** - **Market Fragmentation**: Divergent regulations could lead to a fragmented market, with different versions of services for different regions. - **Loss of Revenue**: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance. #### **Responses from Service Providers** - **Legal Challenges**: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights. - **Policy Advocacy**: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control. #### **Possible Adaptations** - **Technological Innovation**: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain. - **Transparency Measures**: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy. #### The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape. --- ### **What Happens Next? The Future of Chat Control** The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union. #### **Current Status of Legislation** - **Ongoing Negotiations**: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders. - **Timeline**: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay. #### **Key Influencing Factors** **1. Legal Challenges and Compliance with EU Law** - **Fundamental Rights Assessment**: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression. - **Court Scrutiny**: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control. **2. Technological Feasibility** - **Development of Privacy-Preserving Technologies**: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies. - **Implementation Challenges**: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures. **3. Political Dynamics** - **Member State Positions**: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations. - **Public Opinion and Advocacy**: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections. **4. Industry Responses** - **Negotiations with Service Providers**: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed. - **Potential for Self-Regulation**: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning. #### **Possible Scenarios** **Optimistic Outcome:** - **Balanced Regulation**: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight. **Pessimistic Outcome:** - **Adoption of Strict Measures**: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market. **Middle Ground:** - **Incremental Implementation**: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact. #### **How to Stay Informed and Protect Your Privacy** - **Follow Reputable Sources**: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments. - **Engage in the Dialogue**: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy. - **Utilize Secure Practices**: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security. <img src="https://blossom.primal.net/1e2c0cd70d88629c54ac84f928ab107f08f698d2c7f0df511277fb44c1480f0a.png"> #### **The Global Perspective** - **International Implications**: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against. - **Collaboration Opportunities**: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats. #### **Looking Ahead** The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders. As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world. --- ### **Conclusion** The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns. Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits. The potential consequences of implementing Chat Control are far-reaching: - **Erosion of Trust**: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online. - **Security Vulnerabilities**: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks. - **Stifling Innovation**: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry. - **Global Implications**: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse. As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values. The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free. In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world. <img src="https://blossom.primal.net/d3f07d8bc7a49ac291f14eb449879462c76ae407abbe728ddc6f93e11fabe11d.png"> --- Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future. ## Read more: - https://www.patrick-breyer.de/en/posts/chat-control/ - https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/ - https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/ - https://signal.org/blog/pdfs/ndss-keynote.pdf - https://tuta.com/blog/germany-stop-chat-control - https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal - https://mullvad.net/en/why-privacy-matters
@ eac63075:b4988b48
2024-10-21 08:11:11Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication. https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV https://open.spotify.com/episode/0IZ6kMExfxFm4FHg5DAWT8?si=e139033865e045de ### **Sections:** - **Introduction** - **What Is Chat Control?** - **Why Is the EU Pushing for Chat Control?** - **The Privacy Concerns and Risks** - **The Technical Debate: Encryption and Backdoors** - **Global Reactions and the Debate in Europe** - **Possible Consequences for Messaging Services** - **What Happens Next? The Future of Chat Control** - **Conclusion** --- ### **What Is Chat Control?** "Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns. At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content. #### **Origins of the Proposal** The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms. #### **How Messaging Services Work** Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors. <img src="https://blossom.primal.net/31ace3b729fb9f6b4de286686f31a71db6dd7e3a363f868e1255a6f287eb0b94.png"> #### **Key Elements of Chat Control** - **Automated Content Scanning**: Service providers would use algorithms to scan messages for illegal content. - **Circumvention of Encryption**: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security. - **Mandatory Reporting**: If illegal content is detected, providers would be required to report it to authorities. - **Broad Applicability**: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms. #### **Why It Matters** Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought. --- ### **Why Is the EU Pushing for Chat Control?** The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms. #### **Protecting Children and Preventing Crime** One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes. Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety. #### **Legal Context and Legislative Drivers** The push for Chat Control is rooted in several legislative initiatives: - **ePrivacy Directive**: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances. - **Temporary Derogation**: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive. - **Regulation Proposals**: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications. #### **Balancing Security and Privacy** EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections. However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as: - **Targeted Scanning**: Focusing on specific threats rather than broad, indiscriminate monitoring. - **Judicial Oversight**: Requiring court orders or oversight for accessing private communications. - **Data Protection Safeguards**: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed. <img src="https://blossom.primal.net/9533aedc9f83564d53633eac1a6d431d1e311028a478dd4b7f3a59b2c449e95a.png"> #### **The Urgency Behind the Push** High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked. #### **Criticism and Controversy** Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose. --- ### **The Privacy Concerns and Risks** While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications. #### **Infringement on Privacy Rights** At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms. #### **Erosion of End-to-End Encryption** End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats. #### **Concerns from Privacy Advocates** Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences: - **Security Risks**: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime. - **Global Implications**: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy. - **Ineffectiveness Against Crime**: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens. <img src="https://blossom.primal.net/51722887ebf55c827cc20bcfade3ea9b3628265b7fa3547504b2fff45f34f175.png"> #### **Potential for Government Overreach** There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent. #### **Real-World Implications for Users** - **False Positives**: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users. - **Chilling Effect**: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse. - **Data Misuse**: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information. #### **Legal and Ethical Concerns** Privacy advocates also highlight potential conflicts with existing laws and ethical standards: - **Violation of Fundamental Rights**: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression. - **Questionable Effectiveness**: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users. #### **Opposition from Member States and Organizations** Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences. --- ### **The Technical Debate: Encryption and Backdoors** The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures. #### **What Is End-to-End Encryption (E2EE)?** End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content. - **Security Assurance**: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private. - **Widespread Use**: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data. #### **How Chat Control Affects Encryption** Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to: - **Introduce Backdoors**: Create a means for third parties (including the service provider or authorities) to access encrypted messages. - **Client-Side Scanning**: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE. #### **The Risks of Weakening Encryption** **1. Compromised Security for All Users** Introducing backdoors or client-side scanning tools can create vulnerabilities: - **Exploitable Gaps**: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches. - **Universal Impact**: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk. **2. Undermining Trust in Digital Services** - **User Confidence**: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms. - **Business Implications**: Companies relying on secure communications might face increased risks, affecting economic activities. **3. Ineffectiveness Against Skilled Adversaries** - **Alternative Methods**: Criminals might shift to other encrypted channels or develop new ways to avoid detection. - **False Sense of Security**: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected. #### **Signal’s Response and Stance** Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals: - **Refusal to Weaken Encryption**: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards. - **Advocacy for Privacy**: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age. #### **Understanding Backdoors** A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems: - **Security Vulnerabilities**: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments. - **Ethical Concerns**: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications. <img src="https://blossom.primal.net/67f45fd79ccdb7e2e2ecdc56297207dc0d1d073acb216857b6165b3bf9906997.png"> #### **The Slippery Slope Argument** Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent: - **Expanded Surveillance**: Once in place, these measures could be extended to monitor other types of content beyond the original scope. - **Erosion of Rights**: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time. #### **Potential Technological Alternatives** Some suggest that it's possible to fight illegal content without undermining encryption: - **Metadata Analysis**: Focusing on patterns of communication rather than content. - **Enhanced Reporting Mechanisms**: Encouraging users to report illegal content voluntarily. - **Investing in Law Enforcement Capabilities**: Strengthening traditional investigative methods without compromising digital security. #### The technical community largely agrees that weakening encryption is not the solution: - **Consensus on Security**: Strong encryption is essential for the safety and privacy of all internet users. - **Call for Dialogue**: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights. --- ### **Global Reactions and the Debate in Europe** The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values. #### **Support for Chat Control** Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that: - **Enhanced Security**: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes. - **Responsibility of Service Providers**: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities. - **Public Safety Priorities**: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy. #### **Opposition within the EU** Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach. **Germany** - **Stance**: Germany has been one of the most vocal opponents of the proposed measures. - **Reasons**: - **Constitutional Concerns**: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications. - **Security Risks**: Weakening encryption is seen as a threat to cybersecurity. - **Legal Challenges**: Potential conflicts with national laws protecting personal data and communication secrecy. **Netherlands** - **Recent Developments**: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy. - **Arguments**: - **Effectiveness Doubts**: Skepticism about the actual effectiveness of the measures in combating crime. - **Negative Impact on Privacy**: Concerns about mass surveillance and the infringement of citizens' rights. Table reference: Patrick Breyer - Chat Control in 23 September 2024 #### **Privacy Advocacy Groups** **European Digital Rights (EDRi)** - **Role**: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment. - **Position**: - **Strong Opposition**: EDRi argues that Chat Control is incompatible with fundamental rights. - **Awareness Campaigns**: Engaging in public campaigns to inform citizens about the potential risks. - **Policy Engagement**: Lobbying policymakers to consider alternative approaches that respect privacy. **Politicians and Activists** **Patrick Breyer** - **Background**: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party. - **Actions**: - **Advocacy**: Actively campaigning against Chat Control through speeches, articles, and legislative efforts. - **Public Outreach**: Using social media and public events to raise awareness. - **Legal Expertise**: Highlighting the legal inconsistencies and potential violations of EU law. #### **Global Reactions** **International Organizations** - **Human Rights Watch and Amnesty International**: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider. **Technology Companies** - **Global Tech Firms**: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust. - **Industry Associations**: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness. <img src="https://blossom.primal.net/e761aa2dd240a1a2e7d943565ccbda427b5a8054bf4e6e17c946711ab6370d5d.png"> #### **The Broader Debate** The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include: - **Legal Precedents**: How the EU's decision might influence laws and regulations in other countries. - **Digital Sovereignty**: The desire of nations to control digital spaces within their borders. - **Civil Liberties**: The importance of protecting freedoms in the face of technological advancements. #### **Public Opinion** - **Diverse Views**: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all. - **Awareness Levels**: Many people are still unaware of the potential changes, highlighting the need for public education on the issue. #### The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society. --- ### **Possible Consequences for Messaging Services** The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication. #### **Impact on Encrypted Messaging Services** **Signal and Similar Platforms** - **Compliance Challenges**: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles. - **Operational Decisions**: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features. #### **Potential Blocking or Limiting of Services** - **Regulatory Enforcement**: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU. - **Access Restrictions**: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements. #### **Effects on Smaller Providers** - **Resource Constraints**: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market. - **Innovation Stifling**: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector. <img src="https://blossom.primal.net/60a9cad69b45cc3ded1d1759312e49a57b3aa997db62e36016f40642943be5e9.png"> #### **User Experience and Trust** - **Privacy Concerns**: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement. - **Migration to Unregulated Platforms**: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks. #### **Technical and Security Implications** - **Increased Vulnerabilities**: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches. - **Global Security Risks**: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders. #### **Impact on Businesses and Professional Communications** - **Confidentiality Issues**: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services. - **Compliance Complexity**: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens. #### **Economic Consequences** - **Market Fragmentation**: Divergent regulations could lead to a fragmented market, with different versions of services for different regions. - **Loss of Revenue**: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance. #### **Responses from Service Providers** - **Legal Challenges**: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights. - **Policy Advocacy**: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control. #### **Possible Adaptations** - **Technological Innovation**: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain. - **Transparency Measures**: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy. #### The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape. --- ### **What Happens Next? The Future of Chat Control** The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union. #### **Current Status of Legislation** - **Ongoing Negotiations**: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders. - **Timeline**: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay. #### **Key Influencing Factors** **1. Legal Challenges and Compliance with EU Law** - **Fundamental Rights Assessment**: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression. - **Court Scrutiny**: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control. **2. Technological Feasibility** - **Development of Privacy-Preserving Technologies**: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies. - **Implementation Challenges**: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures. **3. Political Dynamics** - **Member State Positions**: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations. - **Public Opinion and Advocacy**: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections. **4. Industry Responses** - **Negotiations with Service Providers**: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed. - **Potential for Self-Regulation**: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning. #### **Possible Scenarios** **Optimistic Outcome:** - **Balanced Regulation**: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight. **Pessimistic Outcome:** - **Adoption of Strict Measures**: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market. **Middle Ground:** - **Incremental Implementation**: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact. #### **How to Stay Informed and Protect Your Privacy** - **Follow Reputable Sources**: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments. - **Engage in the Dialogue**: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy. - **Utilize Secure Practices**: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security. <img src="https://blossom.primal.net/1e2c0cd70d88629c54ac84f928ab107f08f698d2c7f0df511277fb44c1480f0a.png"> #### **The Global Perspective** - **International Implications**: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against. - **Collaboration Opportunities**: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats. #### **Looking Ahead** The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders. As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world. --- ### **Conclusion** The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns. Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits. The potential consequences of implementing Chat Control are far-reaching: - **Erosion of Trust**: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online. - **Security Vulnerabilities**: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks. - **Stifling Innovation**: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry. - **Global Implications**: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse. As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values. The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free. In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world. <img src="https://blossom.primal.net/d3f07d8bc7a49ac291f14eb449879462c76ae407abbe728ddc6f93e11fabe11d.png"> --- Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future. ## Read more: - https://www.patrick-breyer.de/en/posts/chat-control/ - https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/ - https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/ - https://signal.org/blog/pdfs/ndss-keynote.pdf - https://tuta.com/blog/germany-stop-chat-control - https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal - https://mullvad.net/en/why-privacy-matters @ fd208ee8:0fd927c1
2024-10-20 18:19:48(Please note that this is not official financial or business advice, but rather a description of something we have done, on an informal basis.) # A long, long time ago It's been nearly a year, since nostr:nprofile1qydhwumn8ghj7argv4nx7un9wd6zumn0wd68yvfwvdhk6tcpypmhxue69uhkummnw3ezuetfde6kuer6wasku7nfvuh8xurpvdjj7qpqs3ht77dq4zqnya8vjun5jp3p44pr794ru36d0ltxu65chljw8xjqv5atj2 came into being, mostly as a lark, involving a couple of members of our private chat group. Our initial plan was to work toward bounties, but Nostr bounties are a bit of a biased, uncertain thing, and our enthusiasm for that quickly waned. So, what to do? Here we are, we three (nostr:npub1ecdlntvjzexlyfale2egzvvncc8tgqsaxkl5hw7xlgjv2cxs705s9qs735, nostr:npub1wqfzz2p880wq0tumuae9lfwyhs8uz35xd0kr34zrvrwyh3kvrzuskcqsyn, and I): IT professionals with little time, but plenty of intellectual energy, a Slack chat, a [GitHub repo](https://github.com/ShadowySupercode), and lots of frustration with the Nostr status quo. We were, you see, Nostr end-users. We loved the idea of the protocol, but we were being regularly stymied by the poor quality of many implementations. * Why can I not login? Oh, they fixed the login! Nope, still can't login. * If I press this button, it says it sent, but it didn't send. Where note? * They announced a new feature, but I tried it and it didn't work. Oh well. * I noticed a bug in the client, reported it, and the issue is just rotting away in the project repo. Ignored. * The website/relay/repo was here... yesterday. Today it has disappeared, and taken my zaps with it. It was enough to make us want to tear our hair out. We decided that what Nostr needed... what it _really_ needed... was a **Nostr Stable Version**. Nothing glamorous. Nothing exotic. Nothing busy or excitable. Just something that stayed where you initially found it, ran, and actually worked. Something where you could report a bug and receive a prompt response. Maybe even something, where you could pay a reasonable fee and be _allowed to have expectations_ of some particular service being returned. And who better to build such a version, than people who want to use it, themselves? # Things working is an underrated concept I know that the very idea of software _running as expected_ and websites not appearing and disappearing suddenly, based upon what some particular developer had for lunch, tends to be met with little but scorn, from hardened, seasoned Nostriches (who are convinced that bugs are _all_ features), but I think the majority of potential users would see it differently. I'm with the majority, on this one. I like to click "save" buttons and have them save. If I publish something, I want it to appear under my list of published somethings. I like to type in the website address I always type in, and have it magically appear on my screen, as if there were a little man sitting at controls in my laptop, just waiting for me to write H-T-T-P-S... and then jump to attention. My unreasonable expectations have no bounds, it is true. But unreasonable people are also people, so we would also like to have our own unreasonable things to play with. Scorn away. My save button will save, and my published something will publish, and my website will load _every damn time_, just to spite you. In the larger scheme of things, you see, we win even if we fail, if we at least increase the competition enough, that _things working_ becomes the new standard. We can simply prove, definitively, that it is possible for Nostr things to work, if they are built by people who care if they work. If we also have fun together, learn something new, and come up with some cool, novel use cases, then that's pure profit. We can only win, at this endeavor. # Where to start? ## Name that brand So, we had a team, we had a business idea, and we had a heck of a lot of motivation. What we didn't have, is a name. (Never underestimate the importance of naming things.) We decided to name ourselves "GitCitadel" because "git" sounds techy, hints at our GitRepublic project, and is reminiscent of open-source development, and "citadel" reminds us of Bitcoin. The republic is at home in the citadel, naturally. All other products also live in the same citadel, hence the naming-convention of prefacing everything with "GC" (i.e. "GC Alexandria", "GC Sybil", "GC Aedile", etc.). ## Brand yourself The next thing we did, was rent a domain and run a webserver on it. This is an important step because it gives you an Internet presence, allows you to have company NIP-05 and email addresses (a form of promotion), and it's simply exciting to have one. Feels so much more "official" and it helps increase the name-recognition of your company. ## Define yourself We then sat down, together, over the Internet, and figured out who we are. Not who we individually are, but who we are, as a company. A company, after all, (according to the Cambridge Dictionary) is "an organization that produces or sells goods or services in order to make a profit". Now, a company's profits don't have to be monetary, but they should be something tangible. A company, in other words, is a team of people working toward some defined goal. What is our goal? Well, we decided to think it over, sat down with the newer additions to the company (you can see who they are, on our [project wiki page](https://wikistr.com/gitcitadel-project), and came up with a Vision and a Mission:  The _vision_ is what the overall goals of the company are, whereas the _mission_ describes how those goals shall be achieved. Now, this is a sort of lofty, abstract statement, so it was important that we posted it someplace publicly (to keep ourselves accountable) and look at it regularly, so that we can ponder it and realign whatever we are currently working on, with this statement. We know the statement is well-designed, if considering it helps us make decisions about what to do next. ## Pay yourselves (I'm going to switch from "we" to "you", here, as it's easier to write this part, but let's just pretend I didn't.)  The next thing on the list, is to arrange the finances, usually by setting up a Geyserfund, with an associated wallet, and then deciding how the funds from the wallet will be dispersed or stored. (I won't tell you how we are handling that, as that's internal company business, but I'm sure you'll think of something clever, yourselves. Or just google it.) I would encourage you to arrange to pay yourselves profits. Not merely because your idea is going to make you all fabulously wealthy and internationally famous (although, that is obviously true), but because _profits are the most pure form of communication that consumers in the market have_ with its producers, and one of the best ways to make decisions and measure increases in efficiency (increasing profits and/or output, while keeping prices steady or falling). Cutting off this signal, in order to look pious to outsiders, is to shoot yourself in your free-market foot. Nobody says that you have to spend your profits on the proverbial _lambo and a bimbo_. You could donate them to charity, reinvest them, or store them for your nephews to inherit, but **pay them out, you should**. You don't have to love money, to value it as a tool and use it shrewdly. Money is a measure, and companies should regularly measure themselves: against their previous state, against their potential state, and against their competition. (Also, you can use money to buy a lambo and a bimbo, but you didn't hear that from me.) ## Organize yourselves Once you've been working together, for a while, you'll find that you need to figure out how to organize yourselves. The first step is to... ### Form a board of directors. Stop laughing. I'm serious. Any company has at least two roles (President and Secretary), ideally held by two different people, so any single-proprietor company is a man down. Find a different person, to be your Second, even if they're just your confident, who lets you cry on your shoulder on The Bad Days, when your code refuses to compile, and can tell people that you've become a Bitcoin millionaire and have gone on a sabbatical to hike the Himalayas and will be back in 3 months on The Very Good Days. Because business man was not meant to be alone. If, like us, you're a small herd of people and have already been working together for a while, then this step is actually really, really fun. Just think about what people are already doing, and put a label on it. That role is now defined and it is clear who is in charge of what. Scientists become "Chief Science Officer" or "Scientific Advisor". The person who always writes the _okay, so this is what we've decided_ comment in the thread becomes the Secretary, the one managing the Lightning wallet and worrying over paying for the servers is the CFO, the person running the remote server becomes the CTO, and so on and etc. And everyone knows who the CEO is. Everyone always knows. They do. Just write it down. ### Agree how to disagree Now, have the secretary write up a Member's Agreement. It's a contract between the members, about whatever the group thinks is important concerning the way the company will operate. According to [Investopedia](https://www.investopedia.com/terms/l/llc-operating-agreement.asp), common topics are:  Is this legally binding? Probably not. Maybe. I don't know and wouldn't tell you, even if I did. But it's _emotionally binding_, which is arguably more important. Writing things down is an advanced form of _naming things_ and it provides clarity, helps to manage expectations, and allows you to define a working agreement before Real Money shows up and taints your interaction. You're just accepting tips, at the moment. Everyone is calm and cheerful, so now is your best time to negotiate. Keep it very simple and only address the most basic things. If you wish to incorporate, at a later date, then you just take this to a registered agent, or other experienced person, and have them tidy up any loose ends and add the fine print. ## Go forth, together This has probably taken you weeks, or even months, but you're now a company. Get a logo and a company npub, start dropping the company name into your notes, and get on with the business of being in business.
@ fd208ee8:0fd927c1
2024-10-20 18:19:48(Please note that this is not official financial or business advice, but rather a description of something we have done, on an informal basis.) # A long, long time ago It's been nearly a year, since nostr:nprofile1qydhwumn8ghj7argv4nx7un9wd6zumn0wd68yvfwvdhk6tcpypmhxue69uhkummnw3ezuetfde6kuer6wasku7nfvuh8xurpvdjj7qpqs3ht77dq4zqnya8vjun5jp3p44pr794ru36d0ltxu65chljw8xjqv5atj2 came into being, mostly as a lark, involving a couple of members of our private chat group. Our initial plan was to work toward bounties, but Nostr bounties are a bit of a biased, uncertain thing, and our enthusiasm for that quickly waned. So, what to do? Here we are, we three (nostr:npub1ecdlntvjzexlyfale2egzvvncc8tgqsaxkl5hw7xlgjv2cxs705s9qs735, nostr:npub1wqfzz2p880wq0tumuae9lfwyhs8uz35xd0kr34zrvrwyh3kvrzuskcqsyn, and I): IT professionals with little time, but plenty of intellectual energy, a Slack chat, a [GitHub repo](https://github.com/ShadowySupercode), and lots of frustration with the Nostr status quo. We were, you see, Nostr end-users. We loved the idea of the protocol, but we were being regularly stymied by the poor quality of many implementations. * Why can I not login? Oh, they fixed the login! Nope, still can't login. * If I press this button, it says it sent, but it didn't send. Where note? * They announced a new feature, but I tried it and it didn't work. Oh well. * I noticed a bug in the client, reported it, and the issue is just rotting away in the project repo. Ignored. * The website/relay/repo was here... yesterday. Today it has disappeared, and taken my zaps with it. It was enough to make us want to tear our hair out. We decided that what Nostr needed... what it _really_ needed... was a **Nostr Stable Version**. Nothing glamorous. Nothing exotic. Nothing busy or excitable. Just something that stayed where you initially found it, ran, and actually worked. Something where you could report a bug and receive a prompt response. Maybe even something, where you could pay a reasonable fee and be _allowed to have expectations_ of some particular service being returned. And who better to build such a version, than people who want to use it, themselves? # Things working is an underrated concept I know that the very idea of software _running as expected_ and websites not appearing and disappearing suddenly, based upon what some particular developer had for lunch, tends to be met with little but scorn, from hardened, seasoned Nostriches (who are convinced that bugs are _all_ features), but I think the majority of potential users would see it differently. I'm with the majority, on this one. I like to click "save" buttons and have them save. If I publish something, I want it to appear under my list of published somethings. I like to type in the website address I always type in, and have it magically appear on my screen, as if there were a little man sitting at controls in my laptop, just waiting for me to write H-T-T-P-S... and then jump to attention. My unreasonable expectations have no bounds, it is true. But unreasonable people are also people, so we would also like to have our own unreasonable things to play with. Scorn away. My save button will save, and my published something will publish, and my website will load _every damn time_, just to spite you. In the larger scheme of things, you see, we win even if we fail, if we at least increase the competition enough, that _things working_ becomes the new standard. We can simply prove, definitively, that it is possible for Nostr things to work, if they are built by people who care if they work. If we also have fun together, learn something new, and come up with some cool, novel use cases, then that's pure profit. We can only win, at this endeavor. # Where to start? ## Name that brand So, we had a team, we had a business idea, and we had a heck of a lot of motivation. What we didn't have, is a name. (Never underestimate the importance of naming things.) We decided to name ourselves "GitCitadel" because "git" sounds techy, hints at our GitRepublic project, and is reminiscent of open-source development, and "citadel" reminds us of Bitcoin. The republic is at home in the citadel, naturally. All other products also live in the same citadel, hence the naming-convention of prefacing everything with "GC" (i.e. "GC Alexandria", "GC Sybil", "GC Aedile", etc.). ## Brand yourself The next thing we did, was rent a domain and run a webserver on it. This is an important step because it gives you an Internet presence, allows you to have company NIP-05 and email addresses (a form of promotion), and it's simply exciting to have one. Feels so much more "official" and it helps increase the name-recognition of your company. ## Define yourself We then sat down, together, over the Internet, and figured out who we are. Not who we individually are, but who we are, as a company. A company, after all, (according to the Cambridge Dictionary) is "an organization that produces or sells goods or services in order to make a profit". Now, a company's profits don't have to be monetary, but they should be something tangible. A company, in other words, is a team of people working toward some defined goal. What is our goal? Well, we decided to think it over, sat down with the newer additions to the company (you can see who they are, on our [project wiki page](https://wikistr.com/gitcitadel-project), and came up with a Vision and a Mission:  The _vision_ is what the overall goals of the company are, whereas the _mission_ describes how those goals shall be achieved. Now, this is a sort of lofty, abstract statement, so it was important that we posted it someplace publicly (to keep ourselves accountable) and look at it regularly, so that we can ponder it and realign whatever we are currently working on, with this statement. We know the statement is well-designed, if considering it helps us make decisions about what to do next. ## Pay yourselves (I'm going to switch from "we" to "you", here, as it's easier to write this part, but let's just pretend I didn't.)  The next thing on the list, is to arrange the finances, usually by setting up a Geyserfund, with an associated wallet, and then deciding how the funds from the wallet will be dispersed or stored. (I won't tell you how we are handling that, as that's internal company business, but I'm sure you'll think of something clever, yourselves. Or just google it.) I would encourage you to arrange to pay yourselves profits. Not merely because your idea is going to make you all fabulously wealthy and internationally famous (although, that is obviously true), but because _profits are the most pure form of communication that consumers in the market have_ with its producers, and one of the best ways to make decisions and measure increases in efficiency (increasing profits and/or output, while keeping prices steady or falling). Cutting off this signal, in order to look pious to outsiders, is to shoot yourself in your free-market foot. Nobody says that you have to spend your profits on the proverbial _lambo and a bimbo_. You could donate them to charity, reinvest them, or store them for your nephews to inherit, but **pay them out, you should**. You don't have to love money, to value it as a tool and use it shrewdly. Money is a measure, and companies should regularly measure themselves: against their previous state, against their potential state, and against their competition. (Also, you can use money to buy a lambo and a bimbo, but you didn't hear that from me.) ## Organize yourselves Once you've been working together, for a while, you'll find that you need to figure out how to organize yourselves. The first step is to... ### Form a board of directors. Stop laughing. I'm serious. Any company has at least two roles (President and Secretary), ideally held by two different people, so any single-proprietor company is a man down. Find a different person, to be your Second, even if they're just your confident, who lets you cry on your shoulder on The Bad Days, when your code refuses to compile, and can tell people that you've become a Bitcoin millionaire and have gone on a sabbatical to hike the Himalayas and will be back in 3 months on The Very Good Days. Because business man was not meant to be alone. If, like us, you're a small herd of people and have already been working together for a while, then this step is actually really, really fun. Just think about what people are already doing, and put a label on it. That role is now defined and it is clear who is in charge of what. Scientists become "Chief Science Officer" or "Scientific Advisor". The person who always writes the _okay, so this is what we've decided_ comment in the thread becomes the Secretary, the one managing the Lightning wallet and worrying over paying for the servers is the CFO, the person running the remote server becomes the CTO, and so on and etc. And everyone knows who the CEO is. Everyone always knows. They do. Just write it down. ### Agree how to disagree Now, have the secretary write up a Member's Agreement. It's a contract between the members, about whatever the group thinks is important concerning the way the company will operate. According to [Investopedia](https://www.investopedia.com/terms/l/llc-operating-agreement.asp), common topics are:  Is this legally binding? Probably not. Maybe. I don't know and wouldn't tell you, even if I did. But it's _emotionally binding_, which is arguably more important. Writing things down is an advanced form of _naming things_ and it provides clarity, helps to manage expectations, and allows you to define a working agreement before Real Money shows up and taints your interaction. You're just accepting tips, at the moment. Everyone is calm and cheerful, so now is your best time to negotiate. Keep it very simple and only address the most basic things. If you wish to incorporate, at a later date, then you just take this to a registered agent, or other experienced person, and have them tidy up any loose ends and add the fine print. ## Go forth, together This has probably taken you weeks, or even months, but you're now a company. Get a logo and a company npub, start dropping the company name into your notes, and get on with the business of being in business. @ b6ca2216:f45f8b5b
2024-10-20 00:19:37my 3. article
@ b6ca2216:f45f8b5b
2024-10-20 00:19:37my 3. article @ b6ca2216:f45f8b5b
2024-10-20 00:16:38{"id":12345,"title":"deleted","body":"deleted"}
@ b6ca2216:f45f8b5b
2024-10-20 00:16:38{"id":12345,"title":"deleted","body":"deleted"} @ b6ca2216:f45f8b5b
2024-10-19 23:51:01{id:123, title:"my first article", body:"This NIP defines kind:30402: an addressable event to describe classified listings that list any arbitrary product, service, or other thing for sale or offer and includes enough structured metadata to make them useful. The category of classifieds includes a very broad range of physical goods, services, work opportunities, rentals, free giveaways, personals, etc. and is distinct from the more strictly structured marketplaces defined in NIP-15 that often sell many units of specific products through very specific channels. The structure of these events is very similar to NIP-23 long-form content events."}
@ b6ca2216:f45f8b5b
2024-10-19 23:51:01{id:123, title:"my first article", body:"This NIP defines kind:30402: an addressable event to describe classified listings that list any arbitrary product, service, or other thing for sale or offer and includes enough structured metadata to make them useful. The category of classifieds includes a very broad range of physical goods, services, work opportunities, rentals, free giveaways, personals, etc. and is distinct from the more strictly structured marketplaces defined in NIP-15 that often sell many units of specific products through very specific channels. The structure of these events is very similar to NIP-23 long-form content events."} @ a95c6243:d345522c
2024-10-19 08:58:08Ein Lämmchen löschte an einem Bache seinen Durst. Fern von ihm, aber näher der Quelle, tat ein Wolf das gleiche. Kaum erblickte er das Lämmchen, so schrie er: "Warum trübst du mir das Wasser, das ich trinken will?" "Wie wäre das möglich", erwiderte schüchtern das Lämmchen, "ich stehe hier unten und du so weit oben; das Wasser fließt ja von dir zu mir; glaube mir, es kam mir nie in den Sinn, dir etwas Böses zu tun!" "Ei, sieh doch! Du machst es gerade, wie dein Vater vor sechs Monaten; ich erinnere mich noch sehr wohl, daß auch du dabei warst, aber glücklich entkamst, als ich ihm für sein Schmähen das Fell abzog!" "Ach, Herr!" flehte das zitternde Lämmchen, "ich bin ja erst vier Wochen alt und kannte meinen Vater gar nicht, so lange ist er schon tot; wie soll ich denn für ihn büßen." "Du Unverschämter!" so endigt der Wolf mit erheuchelter Wut, indem er die Zähne fletschte. "Tot oder nicht tot, weiß ich doch, daß euer ganzes Geschlecht mich hasset, und dafür muß ich mich rächen." Ohne weitere Umstände zu machen, zerriß er das Lämmchen und verschlang es. *Das [Gewissen](https://apollo-news.net/das-gewissen-in-corona-jahren-zum-tod-von-gunnar-kaiser/) regt sich selbst bei dem größten Bösewichte; er sucht doch nach Vorwand, um dasselbe damit bei Begehung seiner Schlechtigkeiten zu beschwichtigen.* Quelle: https://eden.one/fabeln-aesop-das-lamm-und-der-wolf
@ a95c6243:d345522c
2024-10-19 08:58:08Ein Lämmchen löschte an einem Bache seinen Durst. Fern von ihm, aber näher der Quelle, tat ein Wolf das gleiche. Kaum erblickte er das Lämmchen, so schrie er: "Warum trübst du mir das Wasser, das ich trinken will?" "Wie wäre das möglich", erwiderte schüchtern das Lämmchen, "ich stehe hier unten und du so weit oben; das Wasser fließt ja von dir zu mir; glaube mir, es kam mir nie in den Sinn, dir etwas Böses zu tun!" "Ei, sieh doch! Du machst es gerade, wie dein Vater vor sechs Monaten; ich erinnere mich noch sehr wohl, daß auch du dabei warst, aber glücklich entkamst, als ich ihm für sein Schmähen das Fell abzog!" "Ach, Herr!" flehte das zitternde Lämmchen, "ich bin ja erst vier Wochen alt und kannte meinen Vater gar nicht, so lange ist er schon tot; wie soll ich denn für ihn büßen." "Du Unverschämter!" so endigt der Wolf mit erheuchelter Wut, indem er die Zähne fletschte. "Tot oder nicht tot, weiß ich doch, daß euer ganzes Geschlecht mich hasset, und dafür muß ich mich rächen." Ohne weitere Umstände zu machen, zerriß er das Lämmchen und verschlang es. *Das [Gewissen](https://apollo-news.net/das-gewissen-in-corona-jahren-zum-tod-von-gunnar-kaiser/) regt sich selbst bei dem größten Bösewichte; er sucht doch nach Vorwand, um dasselbe damit bei Begehung seiner Schlechtigkeiten zu beschwichtigen.* Quelle: https://eden.one/fabeln-aesop-das-lamm-und-der-wolf @ 8947a945:9bfcf626
2024-10-17 08:06:55[](https://stock.adobe.com/stock-photo/id/1010191703) **สวัสดีทุกคนบน Nostr ครับ** รวมไปถึง **watchers**และ **ผู้ติดตาม**ของผมจาก Deviantart และ platform งานศิลปะอื่นๆนะครับ ตั้งแต่ต้นปี 2024 ผมใช้ AI เจนรูปงานตัวละครสาวๆจากอนิเมะ และเปิด exclusive content ให้สำหรับผู้ที่ชื่นชอบผลงานของผมเป็นพิเศษ ผมโพสผลงานผมทั้งหมดไว้ที่เวบ Deviantart และค่อยๆสร้างฐานผู้ติดตามมาเรื่อยๆอย่างค่อยเป็นค่อยไปมาตลอดครับ ทุกอย่างเติบโตไปเรื่อยๆของมัน ส่วนตัวผมมองว่ามันเป็นพิร์ตธุรกิจออนไลน์ ของผมพอร์ตนึงได้เลย **เมื่อวันที่ 16 กย.2024** มีผู้ติดตามคนหนึ่งส่งข้อความส่วนตัวมาหาผม บอกว่าชื่นชอบผลงานของผมมาก ต้องการจะขอซื้อผลงาน แต่ขอซื้อเป็น NFT นะ เสนอราคาซื้อขายต่อชิ้นที่สูงมาก หลังจากนั้นผมกับผู้ซื้อคนนี้พูดคุยกันในเมล์ครับ  ### นี่คือข้อสรุปสั่นๆจากการต่อรองซื้อขายครับ (หลังจากนี้ผมขอเรียกผู้ซื้อว่า scammer นะครับ เพราะไพ่มันหงายมาแล้ว ว่าเขาคือมิจฉาชีพ)  - Scammer รายแรก เลือกผลงานที่จะซื้อ เสนอราคาซื้อที่สูงมาก แต่ต้องเป็นเวบไซต์ NFTmarket place ที่เขากำหนดเท่านั้น มันทำงานอยู่บน ERC20 ผมเข้าไปดูเวบไซต์ที่ว่านี้แล้วรู้สึกว่ามันดูแปลกๆครับ คนที่จะลงขายผลงานจะต้องใช้ email ในการสมัครบัญชีซะก่อน ถึงจะผูก wallet อย่างเช่น metamask ได้ เมื่อผูก wallet แล้วไม่สามารถเปลี่ยนได้ด้วย ตอนนั้นผมใช้ wallet ที่ไม่ได้ link กับ HW wallet ไว้ ทดลองสลับ wallet ไปๆมาๆ มันทำไม่ได้ แถมลอง log out แล้ว เลข wallet ก็ยังคาอยู่อันเดิม อันนี้มันดูแปลกๆแล้วหนึ่งอย่าง เวบนี้ค่า ETH ในการ mint **0.15 - 0.2 ETH** … ตีเป็นเงินบาทนี่แพงบรรลัยอยู่นะครับ  - Scammer รายแรกพยายามชักจูงผม หว่านล้อมผมว่า แหม เดี๋ยวเขาก็มารับซื้องานผมน่า mint งานเสร็จ รีบบอกเขานะ เดี๋ยวเขารีบกดซื้อเลย พอขายได้กำไร ผมก็ได้ค่า gas คืนได้ แถมยังได้กำไรอีก ไม่มีอะไรต้องเสีนจริงมั้ย แต่มันเป้นความโชคดีครับ เพราะตอนนั้นผมไม่เหลือทุนสำรองที่จะมาซื้อ ETH ได้ ผมเลยต่อรองกับเขาตามนี้ครับ : 1. ผมเสนอว่า เอางี้มั้ย ผมส่งผลงานของผมแบบ low resolution ให้ก่อน แลกกับให้เขาช่วยโอน ETH ที่เป็นค่า mint งานมาให้หน่อย พอผมได้ ETH แล้ว ผมจะ upscale งานของผม แล้วเมล์ไปให้ ใจแลกใจกันไปเลย ... เขาไม่เอา 2. ผมเสนอให้ไปซื้อที่ร้านค้าออนไลน์ buymeacoffee ของผมมั้ย จ่ายเป็น USD ... เขาไม่เอา 3. ผมเสนอให้ซื้อขายผ่าน PPV lightning invoice ที่ผมมีสิทธิ์เข้าถึง เพราะเป็น creator ของ Creatr ... เขาไม่เอา 4. ผมยอกเขาว่างั้นก็รอนะ รอเงินเดือนออก เขาบอก ok สัปดาห์ถัดมา มี scammer คนที่สองติดต่อผมเข้ามา ใช้วิธีการใกล้เคียงกัน แต่ใช้คนละเวบ แถมเสนอราคาซื้อที่สูงกว่าคนแรกมาก เวบที่สองนี้เลวร้ายค่าเวบแรกอีกครับ คือต้องใช้เมล์สมัครบัญชี ไม่สามารถผูก metamask ได้ พอสมัครเสร็จจะได้ wallet เปล่าๆมาหนึ่งอัน ผมต้องโอน ETH เข้าไปใน wallet นั้นก่อน เพื่อเอาไปเป็นค่า mint NFT **0.2 ETH** ผมบอก scammer รายที่สองว่า ต้องรอนะ เพราะตอนนี้กำลังติดต่อซื้อขายอยู่กับผู้ซื้อรายแรกอยู่ ผมกำลังรอเงินเพื่อมาซื้อ ETH เป็นต้นทุนดำเนินงานอยู่ คนคนนี้ขอให้ผมส่งเวบแรกไปให้เขาดูหน่อย หลังจากนั้นไม่นานเขาเตือนผมมาว่าเวบแรกมันคือ scam นะ ไม่สามารถถอนเงินออกมาได้ เขายังส่งรูป cap หน้าจอที่คุยกับผู้เสียหายจากเวบแรกมาให้ดูว่าเจอปัญหาถอนเงินไม่ได้ ไม่พอ เขายังบลัฟ opensea ด้วยว่าลูกค้าขายงานได้ แต่ถอนเงินไม่ได้ **Opensea ถอนเงินไม่ได้ ตรงนี้แหละครับคือตัวกระตุกต่อมเอ๊ะของผมดังมาก** เพราะ opensea อ่ะ ผู้ใช้ connect wallet เข้ากับ marketplace โดยตรง ซื้อขายกันเกิดขึ้น เงินวิ่งเข้าวิ่งออก wallet ของแต่ละคนโดยตรงเลย opensea เก็บแค่ค่า fee ในการใช้ platform ไม่เก็บเงินลูกค้าไว้ แถมปีนี้ค่า gas fee ก็ถูกกว่า bull run cycle 2020 มาก ตอนนี้ค่า gas fee ประมาณ 0.0001 ETH (แต่มันก็แพงกว่า BTC อยู่ดีอ่ะครับ) ผมเลยเอาเรื่องนี้ไปปรึกษาพี่บิท แต่แอดมินมาคุยกับผมแทน ทางแอดมินแจ้งว่ายังไม่เคยมีเพื่อนๆมาปรึกษาเรื่องนี้ กรณีที่ผมทักมาถามนี่เป็นรายแรกเลย แต่แอดมินให้ความเห็นไปในทางเดียวกับสมมุติฐานของผมว่าน่าจะ scam ในเวลาเดียวกับผมเอาเรื่องนี้ไปถามในเพจ NFT community คนไทนด้วย ได้รับการ confirm ชัดเจนว่า scam และมีคนไม่น้อยโดนหลอก หลังจากที่ผมรู้ที่มาแล้ว ผมเลยเล่นสงครามปั่นประสาท scammer ทั้งสองคนนี้ครับ เพื่อดูว่าหลอกหลวงมิจฉาชีพจริงมั้ย โดยวันที่ 30 กย. ผมเลยปั่นประสาน scammer ทั้งสองรายนี้ โดยการ mint ผลงานที่เขาเสนอซื้อนั่นแหละ ขึ้น opensea แล้วส่งข้อความไปบอกว่า mint ให้แล้วนะ แต่เงินไม่พอจริงๆว่ะโทษที เลย mint ขึ้น opensea แทน พอดีบ้านจน ทำได้แค่นี้ไปถึงแค่ opensea รีบไปซื้อล่ะ มีคนจ้องจะคว้างานผมเยอะอยู่ ผมไม่คิด royalty fee ด้วยนะเฮ้ย เอาไปขายต่อไม่ต้องแบ่งกำไรกับผม เท่านั้นแหละครับ สงครามจิตวิทยาก็เริ่มขึ้น แต่เขาจนมุม กลืนน้ำลายตัวเอง ช็อตเด็ดคือ เขา : เนี่ยอุส่ารอ บอกเพื่อนในทีมว่าวันจันทร์ที่ 30 กย. ได้ของแน่ๆ เพื่อนๆในทีมเห็นงานผมแล้วมันสวยจริง เลยใส่เงินเต็มที่ 9.3ETH (+ capture screen ส่งตัวเลขยอดเงินมาให้ดู)ไว้รอโดยเฉพาะเลยนะ ผม : เหรอ ... งั้น ขอดู wallet address ที่มี transaction มาให้ดูหน่อยสิ เขา : 2ETH นี่มัน 5000$ เลยนะ ผม : แล้วไง ขอดู wallet address ที่มีการเอายอดเงิน 9.3ETH มาให้ดูหน่อย ไหนบอกว่าเตรียมเงินไว้มากแล้วนี่ ขอดูหน่อย ว่าใส่ไว้เมื่อไหร่ ... เอามาแค่ adrress นะเว้ย ไม่ต้องทะลึ่งส่ง seed มาให้ เขา : ส่งรูปเดิม 9.3 ETH มาให้ดู ผม : รูป screenshot อ่ะ มันไม่มีความหมายหรอกเว้ย ตัดต่อเอาก็ได้ง่ายจะตาย เอา transaction hash มาดู ไหนว่าเตรียมเงินไว้รอ 9.3ETH แล้วอยากซื้องานผมจนตัวสั่นเลยไม่ใช่เหรอ ถ้าจะส่ง wallet address มาให้ดู หรือจะช่วยส่ง 0.15ETH มาให้ยืม mint งานก่อน แล้วมากดซื้อ 2ETH ไป แล้วผมใช้ 0.15ETH คืนให้ก็ได้ จะซื้อหรือไม่ซื้อเนี่ย เขา : จะเอา address เขาไปทำไม ผม : ตัดจบ รำคาญ ไม่ขายให้ละ เขา : 2ETH = 5000 USD เลยนะ ผม : แล้วไง ผมเลยเขียนบทความนี้มาเตือนเพื่อนๆพี่ๆทุกคนครับ เผื่อใครกำลังเปิดพอร์ตทำธุรกิจขาย digital art online แล้วจะโชคดี เจอของดีแบบผม ----------- ### ทำไมผมถึงมั่นใจว่ามันคือการหลอกหลวง แล้วคนโกงจะได้อะไร [](https://stock.adobe.com/stock-photo/id/1010196295) อันดับแรกไปพิจารณาดู opensea ครับ เป็นเวบ NFTmarketplace ที่ volume การซื้อขายสูงที่สุด เขาไม่เก็บเงินของคนจะซื้อจะขายกันไว้กับตัวเอง เงินวิ่งเข้าวิ่งออก wallet ผู้ซื้อผู้ขายเลย ส่วนทางเวบเก็บค่าธรรมเนียมเท่านั้น แถมค่าธรรมเนียมก็ถูกกว่าเมื่อปี 2020 เยอะ ดังนั้นการที่จะไปลงขายงานบนเวบ NFT อื่นที่ค่า fee สูงกว่ากันเป็นร้อยเท่า ... จะทำไปทำไม ผมเชื่อว่า scammer โกงเงินเจ้าของผลงานโดยการเล่นกับความโลภและความอ่อนประสบการณ์ของเจ้าของผลงานครับ เมื่อไหร่ก็ตามที่เจ้าของผลงานโอน ETH เข้าไปใน wallet เวบนั้นเมื่อไหร่ หรือเมื่อไหร่ก็ตามที่จ่ายค่า fee ในการ mint งาน เงินเหล่านั้นสิ่งเข้ากระเป๋า scammer ทันที แล้วก็จะมีการเล่นตุกติกต่อแน่นอนครับ เช่นถอนไม่ได้ หรือซื้อไม่ได้ ต้องโอนเงินมาเพิ่มเพื่อปลดล็อค smart contract อะไรก็ว่าไป แล้วคนนิสัยไม่ดีพวกเนี้ย ก็จะเล่นกับความโลภของคน เอาราคาเสนอซื้อที่สูงโคตรๆมาล่อ ... อันนี้ไม่ว่ากัน เพราะบนโลก NFT รูปภาพบางรูปที่ไม่ได้มีความเป็นศิลปะอะไรเลย มันดันขายกันได้ 100 - 150 ETH ศิลปินที่พยายามสร้างตัวก็อาจจะมองว่า ผลงานเรามีคนรับซื้อ 2 - 4 ETH ต่องานมันก็มากพอแล้ว (จริงๆมากเกินจนน่าตกใจด้วยซ้ำครับ) บนโลกของ BTC ไม่ต้องเชื่อใจกัน โอนเงินไปหากันได้ ปิดสมุดบัญชีได้โดยไม่ต้องเชื่อใจกัน บบโลกของ ETH **"code is law"** smart contract มีเขียนอยู่แล้ว ไปอ่าน มันไม่ได้ยากมากในการทำความเข้าใจ ดังนั้น การจะมาเชื่อคำสัญญาจากคนด้วยกัน เป็นอะไรที่ไม่มีเหตุผล ผมไปเล่าเรื่องเหล่านี้ให้กับ community งานศิลปะ ก็มีทั้งเสียงตอบรับที่ดี และไม่ดีปนกันไป มีบางคนยืนยันเสียงแข็งไปในทำนองว่า ไอ้เรื่องแบบเนี้ยไม่ได้กินเขาหรอก เพราะเขาตั้งใจแน่วแน่ว่างานศิลป์ของเขา เขาไม่เอาเข้ามายุ่งในโลก digital currency เด็ดขาด ซึ่งผมก็เคารพมุมมองเขาครับ แต่มันจะดีกว่ามั้ย ถ้าเราเปิดหูเปิดตาให้ทันเทคโนโลยี โดยเฉพาะเรื่อง digital currency , blockchain โดนโกงทีนึงนี่คือหมดตัวกันง่ายกว่าเงิน fiat อีก อยากจะมาเล่าให้ฟังครับ และอยากให้ช่วยแชร์ไปให้คนรู้จักด้วย จะได้ระวังตัวกัน ## Note - ภาพประกอบ cyber security ทั้งสองนี่ของผมเองครับ ทำเอง วางขายบน AdobeStock - อีกบัญชีนึงของผม "HikariHarmony" npub1exdtszhpw3ep643p9z8pahkw8zw00xa9pesf0u4txyyfqvthwapqwh48sw กำลังค่อยๆเอาผลงานจากโลกข้างนอกเข้ามา nostr ครับ ตั้งใจจะมาสร้างงานศิลปะในนี้ เพื่อนๆที่ชอบงาน จะได้ไม่ต้องออกไปหาที่ไหน ผลงานของผมครับ - Anime girl fanarts : [HikariHarmony](https://linktr.ee/hikariharmonypatreon) - [HikariHarmony on Nostr](https://shorturl.at/I8Nu4) - General art : [KeshikiRakuen](https://linktr.ee/keshikirakuen) - KeshikiRakuen อาจจะเป็นบัญชี nostr ที่สามของผม ถ้าไหวครับ
@ 8947a945:9bfcf626
2024-10-17 08:06:55[](https://stock.adobe.com/stock-photo/id/1010191703) **สวัสดีทุกคนบน Nostr ครับ** รวมไปถึง **watchers**และ **ผู้ติดตาม**ของผมจาก Deviantart และ platform งานศิลปะอื่นๆนะครับ ตั้งแต่ต้นปี 2024 ผมใช้ AI เจนรูปงานตัวละครสาวๆจากอนิเมะ และเปิด exclusive content ให้สำหรับผู้ที่ชื่นชอบผลงานของผมเป็นพิเศษ ผมโพสผลงานผมทั้งหมดไว้ที่เวบ Deviantart และค่อยๆสร้างฐานผู้ติดตามมาเรื่อยๆอย่างค่อยเป็นค่อยไปมาตลอดครับ ทุกอย่างเติบโตไปเรื่อยๆของมัน ส่วนตัวผมมองว่ามันเป็นพิร์ตธุรกิจออนไลน์ ของผมพอร์ตนึงได้เลย **เมื่อวันที่ 16 กย.2024** มีผู้ติดตามคนหนึ่งส่งข้อความส่วนตัวมาหาผม บอกว่าชื่นชอบผลงานของผมมาก ต้องการจะขอซื้อผลงาน แต่ขอซื้อเป็น NFT นะ เสนอราคาซื้อขายต่อชิ้นที่สูงมาก หลังจากนั้นผมกับผู้ซื้อคนนี้พูดคุยกันในเมล์ครับ  ### นี่คือข้อสรุปสั่นๆจากการต่อรองซื้อขายครับ (หลังจากนี้ผมขอเรียกผู้ซื้อว่า scammer นะครับ เพราะไพ่มันหงายมาแล้ว ว่าเขาคือมิจฉาชีพ)  - Scammer รายแรก เลือกผลงานที่จะซื้อ เสนอราคาซื้อที่สูงมาก แต่ต้องเป็นเวบไซต์ NFTmarket place ที่เขากำหนดเท่านั้น มันทำงานอยู่บน ERC20 ผมเข้าไปดูเวบไซต์ที่ว่านี้แล้วรู้สึกว่ามันดูแปลกๆครับ คนที่จะลงขายผลงานจะต้องใช้ email ในการสมัครบัญชีซะก่อน ถึงจะผูก wallet อย่างเช่น metamask ได้ เมื่อผูก wallet แล้วไม่สามารถเปลี่ยนได้ด้วย ตอนนั้นผมใช้ wallet ที่ไม่ได้ link กับ HW wallet ไว้ ทดลองสลับ wallet ไปๆมาๆ มันทำไม่ได้ แถมลอง log out แล้ว เลข wallet ก็ยังคาอยู่อันเดิม อันนี้มันดูแปลกๆแล้วหนึ่งอย่าง เวบนี้ค่า ETH ในการ mint **0.15 - 0.2 ETH** … ตีเป็นเงินบาทนี่แพงบรรลัยอยู่นะครับ  - Scammer รายแรกพยายามชักจูงผม หว่านล้อมผมว่า แหม เดี๋ยวเขาก็มารับซื้องานผมน่า mint งานเสร็จ รีบบอกเขานะ เดี๋ยวเขารีบกดซื้อเลย พอขายได้กำไร ผมก็ได้ค่า gas คืนได้ แถมยังได้กำไรอีก ไม่มีอะไรต้องเสีนจริงมั้ย แต่มันเป้นความโชคดีครับ เพราะตอนนั้นผมไม่เหลือทุนสำรองที่จะมาซื้อ ETH ได้ ผมเลยต่อรองกับเขาตามนี้ครับ : 1. ผมเสนอว่า เอางี้มั้ย ผมส่งผลงานของผมแบบ low resolution ให้ก่อน แลกกับให้เขาช่วยโอน ETH ที่เป็นค่า mint งานมาให้หน่อย พอผมได้ ETH แล้ว ผมจะ upscale งานของผม แล้วเมล์ไปให้ ใจแลกใจกันไปเลย ... เขาไม่เอา 2. ผมเสนอให้ไปซื้อที่ร้านค้าออนไลน์ buymeacoffee ของผมมั้ย จ่ายเป็น USD ... เขาไม่เอา 3. ผมเสนอให้ซื้อขายผ่าน PPV lightning invoice ที่ผมมีสิทธิ์เข้าถึง เพราะเป็น creator ของ Creatr ... เขาไม่เอา 4. ผมยอกเขาว่างั้นก็รอนะ รอเงินเดือนออก เขาบอก ok สัปดาห์ถัดมา มี scammer คนที่สองติดต่อผมเข้ามา ใช้วิธีการใกล้เคียงกัน แต่ใช้คนละเวบ แถมเสนอราคาซื้อที่สูงกว่าคนแรกมาก เวบที่สองนี้เลวร้ายค่าเวบแรกอีกครับ คือต้องใช้เมล์สมัครบัญชี ไม่สามารถผูก metamask ได้ พอสมัครเสร็จจะได้ wallet เปล่าๆมาหนึ่งอัน ผมต้องโอน ETH เข้าไปใน wallet นั้นก่อน เพื่อเอาไปเป็นค่า mint NFT **0.2 ETH** ผมบอก scammer รายที่สองว่า ต้องรอนะ เพราะตอนนี้กำลังติดต่อซื้อขายอยู่กับผู้ซื้อรายแรกอยู่ ผมกำลังรอเงินเพื่อมาซื้อ ETH เป็นต้นทุนดำเนินงานอยู่ คนคนนี้ขอให้ผมส่งเวบแรกไปให้เขาดูหน่อย หลังจากนั้นไม่นานเขาเตือนผมมาว่าเวบแรกมันคือ scam นะ ไม่สามารถถอนเงินออกมาได้ เขายังส่งรูป cap หน้าจอที่คุยกับผู้เสียหายจากเวบแรกมาให้ดูว่าเจอปัญหาถอนเงินไม่ได้ ไม่พอ เขายังบลัฟ opensea ด้วยว่าลูกค้าขายงานได้ แต่ถอนเงินไม่ได้ **Opensea ถอนเงินไม่ได้ ตรงนี้แหละครับคือตัวกระตุกต่อมเอ๊ะของผมดังมาก** เพราะ opensea อ่ะ ผู้ใช้ connect wallet เข้ากับ marketplace โดยตรง ซื้อขายกันเกิดขึ้น เงินวิ่งเข้าวิ่งออก wallet ของแต่ละคนโดยตรงเลย opensea เก็บแค่ค่า fee ในการใช้ platform ไม่เก็บเงินลูกค้าไว้ แถมปีนี้ค่า gas fee ก็ถูกกว่า bull run cycle 2020 มาก ตอนนี้ค่า gas fee ประมาณ 0.0001 ETH (แต่มันก็แพงกว่า BTC อยู่ดีอ่ะครับ) ผมเลยเอาเรื่องนี้ไปปรึกษาพี่บิท แต่แอดมินมาคุยกับผมแทน ทางแอดมินแจ้งว่ายังไม่เคยมีเพื่อนๆมาปรึกษาเรื่องนี้ กรณีที่ผมทักมาถามนี่เป็นรายแรกเลย แต่แอดมินให้ความเห็นไปในทางเดียวกับสมมุติฐานของผมว่าน่าจะ scam ในเวลาเดียวกับผมเอาเรื่องนี้ไปถามในเพจ NFT community คนไทนด้วย ได้รับการ confirm ชัดเจนว่า scam และมีคนไม่น้อยโดนหลอก หลังจากที่ผมรู้ที่มาแล้ว ผมเลยเล่นสงครามปั่นประสาท scammer ทั้งสองคนนี้ครับ เพื่อดูว่าหลอกหลวงมิจฉาชีพจริงมั้ย โดยวันที่ 30 กย. ผมเลยปั่นประสาน scammer ทั้งสองรายนี้ โดยการ mint ผลงานที่เขาเสนอซื้อนั่นแหละ ขึ้น opensea แล้วส่งข้อความไปบอกว่า mint ให้แล้วนะ แต่เงินไม่พอจริงๆว่ะโทษที เลย mint ขึ้น opensea แทน พอดีบ้านจน ทำได้แค่นี้ไปถึงแค่ opensea รีบไปซื้อล่ะ มีคนจ้องจะคว้างานผมเยอะอยู่ ผมไม่คิด royalty fee ด้วยนะเฮ้ย เอาไปขายต่อไม่ต้องแบ่งกำไรกับผม เท่านั้นแหละครับ สงครามจิตวิทยาก็เริ่มขึ้น แต่เขาจนมุม กลืนน้ำลายตัวเอง ช็อตเด็ดคือ เขา : เนี่ยอุส่ารอ บอกเพื่อนในทีมว่าวันจันทร์ที่ 30 กย. ได้ของแน่ๆ เพื่อนๆในทีมเห็นงานผมแล้วมันสวยจริง เลยใส่เงินเต็มที่ 9.3ETH (+ capture screen ส่งตัวเลขยอดเงินมาให้ดู)ไว้รอโดยเฉพาะเลยนะ ผม : เหรอ ... งั้น ขอดู wallet address ที่มี transaction มาให้ดูหน่อยสิ เขา : 2ETH นี่มัน 5000$ เลยนะ ผม : แล้วไง ขอดู wallet address ที่มีการเอายอดเงิน 9.3ETH มาให้ดูหน่อย ไหนบอกว่าเตรียมเงินไว้มากแล้วนี่ ขอดูหน่อย ว่าใส่ไว้เมื่อไหร่ ... เอามาแค่ adrress นะเว้ย ไม่ต้องทะลึ่งส่ง seed มาให้ เขา : ส่งรูปเดิม 9.3 ETH มาให้ดู ผม : รูป screenshot อ่ะ มันไม่มีความหมายหรอกเว้ย ตัดต่อเอาก็ได้ง่ายจะตาย เอา transaction hash มาดู ไหนว่าเตรียมเงินไว้รอ 9.3ETH แล้วอยากซื้องานผมจนตัวสั่นเลยไม่ใช่เหรอ ถ้าจะส่ง wallet address มาให้ดู หรือจะช่วยส่ง 0.15ETH มาให้ยืม mint งานก่อน แล้วมากดซื้อ 2ETH ไป แล้วผมใช้ 0.15ETH คืนให้ก็ได้ จะซื้อหรือไม่ซื้อเนี่ย เขา : จะเอา address เขาไปทำไม ผม : ตัดจบ รำคาญ ไม่ขายให้ละ เขา : 2ETH = 5000 USD เลยนะ ผม : แล้วไง ผมเลยเขียนบทความนี้มาเตือนเพื่อนๆพี่ๆทุกคนครับ เผื่อใครกำลังเปิดพอร์ตทำธุรกิจขาย digital art online แล้วจะโชคดี เจอของดีแบบผม ----------- ### ทำไมผมถึงมั่นใจว่ามันคือการหลอกหลวง แล้วคนโกงจะได้อะไร [](https://stock.adobe.com/stock-photo/id/1010196295) อันดับแรกไปพิจารณาดู opensea ครับ เป็นเวบ NFTmarketplace ที่ volume การซื้อขายสูงที่สุด เขาไม่เก็บเงินของคนจะซื้อจะขายกันไว้กับตัวเอง เงินวิ่งเข้าวิ่งออก wallet ผู้ซื้อผู้ขายเลย ส่วนทางเวบเก็บค่าธรรมเนียมเท่านั้น แถมค่าธรรมเนียมก็ถูกกว่าเมื่อปี 2020 เยอะ ดังนั้นการที่จะไปลงขายงานบนเวบ NFT อื่นที่ค่า fee สูงกว่ากันเป็นร้อยเท่า ... จะทำไปทำไม ผมเชื่อว่า scammer โกงเงินเจ้าของผลงานโดยการเล่นกับความโลภและความอ่อนประสบการณ์ของเจ้าของผลงานครับ เมื่อไหร่ก็ตามที่เจ้าของผลงานโอน ETH เข้าไปใน wallet เวบนั้นเมื่อไหร่ หรือเมื่อไหร่ก็ตามที่จ่ายค่า fee ในการ mint งาน เงินเหล่านั้นสิ่งเข้ากระเป๋า scammer ทันที แล้วก็จะมีการเล่นตุกติกต่อแน่นอนครับ เช่นถอนไม่ได้ หรือซื้อไม่ได้ ต้องโอนเงินมาเพิ่มเพื่อปลดล็อค smart contract อะไรก็ว่าไป แล้วคนนิสัยไม่ดีพวกเนี้ย ก็จะเล่นกับความโลภของคน เอาราคาเสนอซื้อที่สูงโคตรๆมาล่อ ... อันนี้ไม่ว่ากัน เพราะบนโลก NFT รูปภาพบางรูปที่ไม่ได้มีความเป็นศิลปะอะไรเลย มันดันขายกันได้ 100 - 150 ETH ศิลปินที่พยายามสร้างตัวก็อาจจะมองว่า ผลงานเรามีคนรับซื้อ 2 - 4 ETH ต่องานมันก็มากพอแล้ว (จริงๆมากเกินจนน่าตกใจด้วยซ้ำครับ) บนโลกของ BTC ไม่ต้องเชื่อใจกัน โอนเงินไปหากันได้ ปิดสมุดบัญชีได้โดยไม่ต้องเชื่อใจกัน บบโลกของ ETH **"code is law"** smart contract มีเขียนอยู่แล้ว ไปอ่าน มันไม่ได้ยากมากในการทำความเข้าใจ ดังนั้น การจะมาเชื่อคำสัญญาจากคนด้วยกัน เป็นอะไรที่ไม่มีเหตุผล ผมไปเล่าเรื่องเหล่านี้ให้กับ community งานศิลปะ ก็มีทั้งเสียงตอบรับที่ดี และไม่ดีปนกันไป มีบางคนยืนยันเสียงแข็งไปในทำนองว่า ไอ้เรื่องแบบเนี้ยไม่ได้กินเขาหรอก เพราะเขาตั้งใจแน่วแน่ว่างานศิลป์ของเขา เขาไม่เอาเข้ามายุ่งในโลก digital currency เด็ดขาด ซึ่งผมก็เคารพมุมมองเขาครับ แต่มันจะดีกว่ามั้ย ถ้าเราเปิดหูเปิดตาให้ทันเทคโนโลยี โดยเฉพาะเรื่อง digital currency , blockchain โดนโกงทีนึงนี่คือหมดตัวกันง่ายกว่าเงิน fiat อีก อยากจะมาเล่าให้ฟังครับ และอยากให้ช่วยแชร์ไปให้คนรู้จักด้วย จะได้ระวังตัวกัน ## Note - ภาพประกอบ cyber security ทั้งสองนี่ของผมเองครับ ทำเอง วางขายบน AdobeStock - อีกบัญชีนึงของผม "HikariHarmony" npub1exdtszhpw3ep643p9z8pahkw8zw00xa9pesf0u4txyyfqvthwapqwh48sw กำลังค่อยๆเอาผลงานจากโลกข้างนอกเข้ามา nostr ครับ ตั้งใจจะมาสร้างงานศิลปะในนี้ เพื่อนๆที่ชอบงาน จะได้ไม่ต้องออกไปหาที่ไหน ผลงานของผมครับ - Anime girl fanarts : [HikariHarmony](https://linktr.ee/hikariharmonypatreon) - [HikariHarmony on Nostr](https://shorturl.at/I8Nu4) - General art : [KeshikiRakuen](https://linktr.ee/keshikirakuen) - KeshikiRakuen อาจจะเป็นบัญชี nostr ที่สามของผม ถ้าไหวครับ @ 8947a945:9bfcf626
2024-10-17 07:33:00[](https://stock.adobe.com/stock-photo/id/1010191703) **Hello everyone on Nostr** and all my **watchers**and **followers**from DeviantArt, as well as those from other art platforms I have been creating and sharing AI-generated anime girl fanart since the beginning of 2024 and have been running member-exclusive content on Patreon. I also publish showcases of my artworks to Deviantart. I organically build up my audience from time to time. I consider it as one of my online businesses of art. Everything is slowly growing **On September 16**, I received a DM from someone expressing interest in purchasing my art in NFT format and offering a very high price for each piece. We later continued the conversation via email.  ### Here’s a brief overview of what happened  - The first scammer selected the art they wanted to buy and offered a high price for each piece. They provided a URL to an NFT marketplace site running on the Ethereum (ETH) mainnet or ERC20. The site appeared suspicious, requiring email sign-up and linking a MetaMask wallet. However, I couldn't change the wallet address later. The minting gas fees were quite expensive, ranging from **0.15 to 0.2 ETH**  - The scammers tried to convince me that the high profits would easily cover the minting gas fees, so I had nothing to lose. Luckily, I didn’t have spare funds to purchase ETH for the gas fees at the time, so I tried negotiating with them as follows: 1. I offered to send them a lower-quality version of my art via email in exchange for the minting gas fees, but they refused. 2. I offered them the option to pay in USD through Buy Me a Coffee shop here, but they refused. 3. I offered them the option to pay via Bitcoin using the Lightning Network invoice , but they refused. 4. I asked them to wait until I could secure the funds, and they agreed to wait. The following week, a second scammer approached me with a similar offer, this time at an even higher price and through a different NFT marketplace website. This second site also required email registration, and after navigating to the dashboard, it asked for a minting fee of **0.2 ETH**. However, the site provided a wallet address for me instead of connecting a MetaMask wallet. I told the second scammer that I was waiting to make a profit from the first sale, and they asked me to show them the first marketplace. They then warned me that the first site was a scam and even sent screenshots of victims, including one from OpenSea saying that Opensea is not paying. **This raised a red flag**, and I began suspecting I might be getting scammed. On OpenSea, funds go directly to users' wallets after transactions, and OpenSea charges a much lower platform fee compared to the previous crypto bull run in 2020. Minting fees on OpenSea are also significantly cheaper, around 0.0001 ETH per transaction. I also consulted with Thai NFT artist communities and the ex-chairman of the Thai Digital Asset Association. According to them, no one had reported similar issues, but they agreed it seemed like a scam. After confirming my suspicions with my own research and consulting with the Thai crypto community, I decided to test the scammers’ intentions by doing the following I minted the artwork they were interested in, set the price they offered, and listed it for sale on OpenSea. I then messaged them, letting them know the art was available and ready to purchase, with no royalty fees if they wanted to resell it. They became upset and angry, insisting I mint the art on their chosen platform, claiming they had already funded their wallet to support me. When I asked for proof of their wallet address and transactions, they couldn't provide any evidence that they had enough funds. Here’s what I want to warn all artists in the DeviantArt community or other platforms If you find yourself in a similar situation, be aware that scammers may be targeting you. ----------- ### My Perspective why I Believe This is a Scam and What the Scammers Gain [](https://stock.adobe.com/stock-photo/id/1010196295) From my experience with BTC and crypto since 2017, here's why I believe this situation is a scam, and what the scammers aim to achieve First, looking at OpenSea, the largest NFT marketplace on the ERC20 network, they do not hold users' funds. Instead, funds from transactions go directly to users’ wallets. OpenSea’s platform fees are also much lower now compared to the crypto bull run in 2020. This alone raises suspicion about the legitimacy of other marketplaces requiring significantly higher fees. I believe the scammers' tactic is to lure artists into paying these exorbitant minting fees, which go directly into the scammers' wallets. They convince the artists by promising to purchase the art at a higher price, making it seem like there's no risk involved. In reality, the artist has already lost by paying the minting fee, and no purchase is ever made. In the world of Bitcoin (BTC), the principle is "Trust no one" and “Trustless finality of transactions” In other words, transactions are secure and final without needing trust in a third party. In the world of Ethereum (ETH), the philosophy is "Code is law" where everything is governed by smart contracts deployed on the blockchain. These contracts are transparent, and even basic code can be read and understood. Promises made by people don’t override what the code says. I also discuss this issue with art communities. Some people have strongly expressed to me that they want nothing to do with crypto as part of their art process. I completely respect that stance. However, I believe it's wise to keep your eyes open, have some skin in the game, and not fall into scammers’ traps. Understanding the basics of crypto and NFTs can help protect you from these kinds of schemes. If you found this article helpful, please share it with your fellow artists. Until next time Take care ## Note - Both cyber security images are mine , I created and approved by AdobeStock to put on sale - I'm working very hard to bring all my digital arts into Nostr to build my Sats business here to my another npub "HikariHarmony" npub1exdtszhpw3ep643p9z8pahkw8zw00xa9pesf0u4txyyfqvthwapqwh48sw Link to my full gallery - Anime girl fanarts : [HikariHarmony](https://linktr.ee/hikariharmonypatreon) - [HikariHarmony on Nostr](https://shorturl.at/I8Nu4) - General art : [KeshikiRakuen](https://linktr.ee/keshikirakuen)
@ 8947a945:9bfcf626
2024-10-17 07:33:00[](https://stock.adobe.com/stock-photo/id/1010191703) **Hello everyone on Nostr** and all my **watchers**and **followers**from DeviantArt, as well as those from other art platforms I have been creating and sharing AI-generated anime girl fanart since the beginning of 2024 and have been running member-exclusive content on Patreon. I also publish showcases of my artworks to Deviantart. I organically build up my audience from time to time. I consider it as one of my online businesses of art. Everything is slowly growing **On September 16**, I received a DM from someone expressing interest in purchasing my art in NFT format and offering a very high price for each piece. We later continued the conversation via email.  ### Here’s a brief overview of what happened  - The first scammer selected the art they wanted to buy and offered a high price for each piece. They provided a URL to an NFT marketplace site running on the Ethereum (ETH) mainnet or ERC20. The site appeared suspicious, requiring email sign-up and linking a MetaMask wallet. However, I couldn't change the wallet address later. The minting gas fees were quite expensive, ranging from **0.15 to 0.2 ETH**  - The scammers tried to convince me that the high profits would easily cover the minting gas fees, so I had nothing to lose. Luckily, I didn’t have spare funds to purchase ETH for the gas fees at the time, so I tried negotiating with them as follows: 1. I offered to send them a lower-quality version of my art via email in exchange for the minting gas fees, but they refused. 2. I offered them the option to pay in USD through Buy Me a Coffee shop here, but they refused. 3. I offered them the option to pay via Bitcoin using the Lightning Network invoice , but they refused. 4. I asked them to wait until I could secure the funds, and they agreed to wait. The following week, a second scammer approached me with a similar offer, this time at an even higher price and through a different NFT marketplace website. This second site also required email registration, and after navigating to the dashboard, it asked for a minting fee of **0.2 ETH**. However, the site provided a wallet address for me instead of connecting a MetaMask wallet. I told the second scammer that I was waiting to make a profit from the first sale, and they asked me to show them the first marketplace. They then warned me that the first site was a scam and even sent screenshots of victims, including one from OpenSea saying that Opensea is not paying. **This raised a red flag**, and I began suspecting I might be getting scammed. On OpenSea, funds go directly to users' wallets after transactions, and OpenSea charges a much lower platform fee compared to the previous crypto bull run in 2020. Minting fees on OpenSea are also significantly cheaper, around 0.0001 ETH per transaction. I also consulted with Thai NFT artist communities and the ex-chairman of the Thai Digital Asset Association. According to them, no one had reported similar issues, but they agreed it seemed like a scam. After confirming my suspicions with my own research and consulting with the Thai crypto community, I decided to test the scammers’ intentions by doing the following I minted the artwork they were interested in, set the price they offered, and listed it for sale on OpenSea. I then messaged them, letting them know the art was available and ready to purchase, with no royalty fees if they wanted to resell it. They became upset and angry, insisting I mint the art on their chosen platform, claiming they had already funded their wallet to support me. When I asked for proof of their wallet address and transactions, they couldn't provide any evidence that they had enough funds. Here’s what I want to warn all artists in the DeviantArt community or other platforms If you find yourself in a similar situation, be aware that scammers may be targeting you. ----------- ### My Perspective why I Believe This is a Scam and What the Scammers Gain [](https://stock.adobe.com/stock-photo/id/1010196295) From my experience with BTC and crypto since 2017, here's why I believe this situation is a scam, and what the scammers aim to achieve First, looking at OpenSea, the largest NFT marketplace on the ERC20 network, they do not hold users' funds. Instead, funds from transactions go directly to users’ wallets. OpenSea’s platform fees are also much lower now compared to the crypto bull run in 2020. This alone raises suspicion about the legitimacy of other marketplaces requiring significantly higher fees. I believe the scammers' tactic is to lure artists into paying these exorbitant minting fees, which go directly into the scammers' wallets. They convince the artists by promising to purchase the art at a higher price, making it seem like there's no risk involved. In reality, the artist has already lost by paying the minting fee, and no purchase is ever made. In the world of Bitcoin (BTC), the principle is "Trust no one" and “Trustless finality of transactions” In other words, transactions are secure and final without needing trust in a third party. In the world of Ethereum (ETH), the philosophy is "Code is law" where everything is governed by smart contracts deployed on the blockchain. These contracts are transparent, and even basic code can be read and understood. Promises made by people don’t override what the code says. I also discuss this issue with art communities. Some people have strongly expressed to me that they want nothing to do with crypto as part of their art process. I completely respect that stance. However, I believe it's wise to keep your eyes open, have some skin in the game, and not fall into scammers’ traps. Understanding the basics of crypto and NFTs can help protect you from these kinds of schemes. If you found this article helpful, please share it with your fellow artists. Until next time Take care ## Note - Both cyber security images are mine , I created and approved by AdobeStock to put on sale - I'm working very hard to bring all my digital arts into Nostr to build my Sats business here to my another npub "HikariHarmony" npub1exdtszhpw3ep643p9z8pahkw8zw00xa9pesf0u4txyyfqvthwapqwh48sw Link to my full gallery - Anime girl fanarts : [HikariHarmony](https://linktr.ee/hikariharmonypatreon) - [HikariHarmony on Nostr](https://shorturl.at/I8Nu4) - General art : [KeshikiRakuen](https://linktr.ee/keshikirakuen) @ 472f440f:5669301e
2024-10-16 01:57:41Over the last four years bitcoin has, among other things, established itself as an incredible corporate treasury asset that benefits those who adopt it as such. Microstrategy is the shining example of this theme going from a company that was hovering barely above a ~$1B market cap in mid-2020 to a ~$40B market cap company holding more than 1% of the 21,000,000 bitcoin that will ever exist. Microstrategy's success has emboldened a number of other publicly trader companies to follow suit. Bitcoin as a corporate treasury asset is well on its way to becoming a standard. If you run a business that doesn't hold bitcoin on its balance sheet you are doing yourself, your customers and your shareholders a disservice. This is a trend that has its legs under it and will accelerate moving forward. A trend that I believe will emerge this cycle is incorporating bitcoin into real estate markets. Leon Wankum has been beating the drum about this for the last few years and I had the pleasure of sitting down with him this morning to record an episode of TFTC that will be published tomorrow morning. Leon is a real estate developer in Germany and he has made it his mission to educate and warn others in real estate about the demonetization of real estate that is under way due to the fact that bitcoin exists and it provides a far superior alternative. These are pretty stark numbers. Nothing highlights the superior monetary properties of bitcoin better than looking at a chart of the average price of a home priced in USD v. bitcoin. Since 2016: +46% in USD -99% in BTC Since 2020: +34% in USD -70% in BTC The funny thing is that an overwhelming majority of the individuals who make their living in real estate markets do not understand that this is happening to them. Many think they are doing exceptionally well all things considered. Sure, there may be a bit of a slow down and price retraction due to a couple of years of relatively elevated interest rates, but don't worry! The Fed is lowering rates again and the good times are about to start back up. Nothing could be further from the truth. This trend is going to continue unabated until bitcoin is fully monetized and those is the real estate industry, particularly real estate developers and those who lend capital to developers, should seriously take the time to understand what is happening to them. Real estate is the largest store of value asset in the world at the moment. The most common number that is thrown around for the total size of the market is $300 TRILLION. $300 TRILLION of wealth being stored in an asset that is illiquid, comes with maintenance costs, taxes, insurance premiums, and susceptible to extreme weather event, among other things. Compared to bitcoin - which is extremely liquid, saleable, divisible and hard to confiscate, real estate is a far superior asset to store your wealth in. This is something that I'm sure is well understood by many of you reading this letter. What's less understood is the dynamics of the real estate development market over the last few years, which have been severely hindered by elevated interest rates. The higher interest rate environment coupled with the inflationary pressures that forced rates higher in the first place have put developers in a predicament; they have a higher cost of capital to start new projects with raw material prices that are still much higher than they were before the economic lock downs of 2020-2022. This has led to a scenario where it isn't advantageous to start new projects and the projects that broke ground in 2021-2023 are finding that they need to incur more debt to get their developments across the finish line. Despite the fact that interest rates are on their way back down, it doesn't seem like the economics of these projects are going to materially improve in the short to medium-term as headline inflation begins to creep back up. Couple this with the fact that the jobs market is cratering while real wages struggle to keep up with inflation and many builders are going to find themselves in a situation where they do actually complete a development problem but their cash flow suffers because their customers can't afford the inflated rents that builders will have to charge to get a return on their outlaid capital. Many will be put in a situation where they are forced to be happy with lower rents (cash flow) or sit on the sidelines making no cash flow. The post-1971 era that brought with it a booming real estate industry is suffering the same fate as the bond market; the generation bull market is over. Real estate prices may go up, but that will be nothing more than a mirage of wealth creation. The unit of account those prices are built on is in dollars, which are being debased at an accelerating rate. Developers, banks and borrowers need to de-risk their real estate exposure and, as Leon points out, bitcoin is the only way to do this in an effective way. Moving forward developers will have to finance by dual collateralizing their debt with the real estate and bitcoin. In the graphic below Leon illustrates what this type of financing structure will look like. Instead of taking $10m of debt to finance a project and putting it all into materials, construction and marketing, a developer will take out a $10m loan, put $1m in bitcoin and the rest toward the development project. Over the course of the construction of the real estate project, bitcoin will sit in the credit structure and, if held for 4+ years, should increase significantly in value. Saving the builder from risk of default and providing him some optionality in terms of what he can do with the project once it's finished. In this scenario downside risk is contained - a developer isn't pouring all of the cash into bitcoin at the beginning so the worst case scenario is that bitcoin goes to zero (highly unlikely) and they can eat the small loss and hope to make up with it via cash flows once a project is finished, while upside potential is enormous. Bitcoin is still monetizing and having exposure to the hardest monetary asset the world has ever while it's monetizing has proven to be massively beneficial. We are still in the early days of bitcoin and this idea will likely seem absolutely insane to most Tradfi investors, but I strongly believe that developers, banks and end consumers who don't leverage this type of bitcoin structured credit will be cooked in the long-run. And those that take advantage of this type of structure first will be considered geniuses in 20 years. There are many more nuanced benefits to this strategy; holding bitcoin allows landlords and management companies to weather ongoing maintenance costs throughout the years, those who take out mortgages dual collateralized with a house and bitcoin not only protect the equity value of their property but could see their equity values increase significantly more than others using vanilla mortgages, and builders who accumulate bitcoin in their treasuries will be able to use better raw materials when building, which leads to more valuable properties that cash flow for longer. Again, it's going to take time for these types of structures to become commonplace in the market, but I firmly believe this cycle will be the cycle that these strategies get off the ground. In four to five years they will have a track record and after that it will be considered irresponsible not to finance real estate in this way. The banks will begin to demand it. --- Final thought... Sinus congestion sucks.
@ 472f440f:5669301e
2024-10-16 01:57:41Over the last four years bitcoin has, among other things, established itself as an incredible corporate treasury asset that benefits those who adopt it as such. Microstrategy is the shining example of this theme going from a company that was hovering barely above a ~$1B market cap in mid-2020 to a ~$40B market cap company holding more than 1% of the 21,000,000 bitcoin that will ever exist. Microstrategy's success has emboldened a number of other publicly trader companies to follow suit. Bitcoin as a corporate treasury asset is well on its way to becoming a standard. If you run a business that doesn't hold bitcoin on its balance sheet you are doing yourself, your customers and your shareholders a disservice. This is a trend that has its legs under it and will accelerate moving forward. A trend that I believe will emerge this cycle is incorporating bitcoin into real estate markets. Leon Wankum has been beating the drum about this for the last few years and I had the pleasure of sitting down with him this morning to record an episode of TFTC that will be published tomorrow morning. Leon is a real estate developer in Germany and he has made it his mission to educate and warn others in real estate about the demonetization of real estate that is under way due to the fact that bitcoin exists and it provides a far superior alternative. These are pretty stark numbers. Nothing highlights the superior monetary properties of bitcoin better than looking at a chart of the average price of a home priced in USD v. bitcoin. Since 2016: +46% in USD -99% in BTC Since 2020: +34% in USD -70% in BTC The funny thing is that an overwhelming majority of the individuals who make their living in real estate markets do not understand that this is happening to them. Many think they are doing exceptionally well all things considered. Sure, there may be a bit of a slow down and price retraction due to a couple of years of relatively elevated interest rates, but don't worry! The Fed is lowering rates again and the good times are about to start back up. Nothing could be further from the truth. This trend is going to continue unabated until bitcoin is fully monetized and those is the real estate industry, particularly real estate developers and those who lend capital to developers, should seriously take the time to understand what is happening to them. Real estate is the largest store of value asset in the world at the moment. The most common number that is thrown around for the total size of the market is $300 TRILLION. $300 TRILLION of wealth being stored in an asset that is illiquid, comes with maintenance costs, taxes, insurance premiums, and susceptible to extreme weather event, among other things. Compared to bitcoin - which is extremely liquid, saleable, divisible and hard to confiscate, real estate is a far superior asset to store your wealth in. This is something that I'm sure is well understood by many of you reading this letter. What's less understood is the dynamics of the real estate development market over the last few years, which have been severely hindered by elevated interest rates. The higher interest rate environment coupled with the inflationary pressures that forced rates higher in the first place have put developers in a predicament; they have a higher cost of capital to start new projects with raw material prices that are still much higher than they were before the economic lock downs of 2020-2022. This has led to a scenario where it isn't advantageous to start new projects and the projects that broke ground in 2021-2023 are finding that they need to incur more debt to get their developments across the finish line. Despite the fact that interest rates are on their way back down, it doesn't seem like the economics of these projects are going to materially improve in the short to medium-term as headline inflation begins to creep back up. Couple this with the fact that the jobs market is cratering while real wages struggle to keep up with inflation and many builders are going to find themselves in a situation where they do actually complete a development problem but their cash flow suffers because their customers can't afford the inflated rents that builders will have to charge to get a return on their outlaid capital. Many will be put in a situation where they are forced to be happy with lower rents (cash flow) or sit on the sidelines making no cash flow. The post-1971 era that brought with it a booming real estate industry is suffering the same fate as the bond market; the generation bull market is over. Real estate prices may go up, but that will be nothing more than a mirage of wealth creation. The unit of account those prices are built on is in dollars, which are being debased at an accelerating rate. Developers, banks and borrowers need to de-risk their real estate exposure and, as Leon points out, bitcoin is the only way to do this in an effective way. Moving forward developers will have to finance by dual collateralizing their debt with the real estate and bitcoin. In the graphic below Leon illustrates what this type of financing structure will look like. Instead of taking $10m of debt to finance a project and putting it all into materials, construction and marketing, a developer will take out a $10m loan, put $1m in bitcoin and the rest toward the development project. Over the course of the construction of the real estate project, bitcoin will sit in the credit structure and, if held for 4+ years, should increase significantly in value. Saving the builder from risk of default and providing him some optionality in terms of what he can do with the project once it's finished. In this scenario downside risk is contained - a developer isn't pouring all of the cash into bitcoin at the beginning so the worst case scenario is that bitcoin goes to zero (highly unlikely) and they can eat the small loss and hope to make up with it via cash flows once a project is finished, while upside potential is enormous. Bitcoin is still monetizing and having exposure to the hardest monetary asset the world has ever while it's monetizing has proven to be massively beneficial. We are still in the early days of bitcoin and this idea will likely seem absolutely insane to most Tradfi investors, but I strongly believe that developers, banks and end consumers who don't leverage this type of bitcoin structured credit will be cooked in the long-run. And those that take advantage of this type of structure first will be considered geniuses in 20 years. There are many more nuanced benefits to this strategy; holding bitcoin allows landlords and management companies to weather ongoing maintenance costs throughout the years, those who take out mortgages dual collateralized with a house and bitcoin not only protect the equity value of their property but could see their equity values increase significantly more than others using vanilla mortgages, and builders who accumulate bitcoin in their treasuries will be able to use better raw materials when building, which leads to more valuable properties that cash flow for longer. Again, it's going to take time for these types of structures to become commonplace in the market, but I firmly believe this cycle will be the cycle that these strategies get off the ground. In four to five years they will have a track record and after that it will be considered irresponsible not to finance real estate in this way. The banks will begin to demand it. --- Final thought... Sinus congestion sucks. @ eac63075:b4988b48
2024-10-15 20:18:52Bitcoin emerged as a promise of financial freedom, challenging the traditional and centralized structures of governments and financial institutions. Since its inception, many enthusiasts have believed in the revolutionary potential of this cryptocurrency. However, over the years, challenges have arisen that have tested this promise, especially concerning centralization, the implementation of secondary layers like the Lightning Network, and issues of governance and privacy. https://www.fountain.fm/episode/SDZYaFMyLEO1krL6x8RD ## **Centralization and the Exclusivity of Nostr** Nostr, a decentralized network aiming to be censorship resistant, emerged as an attempt to solve some inherent problems of centralization. However, it faces significant challenges. Many users point out that, despite its promise, Nostr is still not attractive to the general public, being exclusive to a specific niche. Additionally, issues of centralization still permeate the network. Discussions on GitHub revealed that developers chose not to implement an absolute level of privacy, a decision many considered inadequate. Even with protocols developed to ensure total privacy—such as the non-identification of IPs and communicating parties—the network still lacks this robust implementation. ## **Individual Freedom and Data Protection** A recurring issue is the importance of demonstrating that real options exist for citizens to protect and preserve their freedom. In a world where most discussions about Bitcoin revolve around its use as an investment asset, there is an urgent need to emphasize its potential as a tool for financial freedom. The Bitcoin community should focus on development and education, showing that the conscious use of cryptography and decentralized transactions can protect individuals against excessive government surveillance and control. Secure and private communication is fundamental, and Bitcoin, along with privacy technologies, can provide this. ## **Hyperbitcoinization and the Illusion of Store of Value** Hyperbitcoinization is a concept that refers to the moment when Bitcoin will replace fiat currencies worldwide. However, achieving this state is not simple, especially when Bitcoin is seen primarily as a store of value. Since 2017, this narrative has gained strength, promoting the idea that accumulating Bitcoin will lead to automatic wealth. However, this perspective is limited. The true value of Bitcoin lies in its use as a transactional currency, not just in its scarcity. The community must work to ensure that Bitcoin is utilized in everyday transactions, strengthening its network and demonstrating its real value. ## **The Role of the Community in Bitcoin's Development** Bitcoin's strength comes from its community. Developers, users, and enthusiasts, through their actions and support, make Bitcoin a powerful tool. This community is responsible for ensuring that Bitcoin maintains its essence and that its functionalities are accessible to all. It is crucial that this support network continues promoting the decentralized use of Bitcoin, without intermediaries that can censor or control transactions. Adopting Bitcoin in a centralized manner, through banks or other institutions, contradicts its original proposal and strengthens those who have historically opposed its existence. ## **Sidechains, Second Layers, and the Lightning Network** Sidechains and second layers, like the Lightning Network, are essential components for Bitcoin's scalability. However, they bring challenges, especially regarding the need to trust intermediaries. For these solutions to be effective, it is fundamental that they allow the unilateral withdrawal of funds, ensuring that users maintain full control over their assets. The Lightning Network, for example, is a second layer that allows fast and cheap transactions. However, many users face difficulties when dealing with channels that do not close correctly, resulting in locked funds. These problems must be solved for the network to be truly decentralized and functional. ## **The Fight Against Centralization on the Internet** Centralization is not a problem exclusive to Bitcoin. The internet as a whole faces similar challenges, with data control concentrated in the hands of a few large technology companies. To ensure freedom of expression and online privacy, it is necessary to decentralize these data clusters. Projects that seek to decentralize the internet are vital for this mission. They not only complement Bitcoin in its quest for financial freedom but also ensure that digital communication and expression are protected against censorship and corporate control. ## **The Future of Bitcoin and the Need for Action** The future of Bitcoin depends on the community's action. We cannot expect Bitcoin to automatically become a global medium of exchange. A conscious effort is necessary to build an ecosystem where Bitcoin can flow freely, being used in everyday transactions and valued for its utility. Moreover, with the imminent arrival of central bank digital currencies (CBDCs), time is of the essence. CBDCs represent a significant challenge, as they can further restrict individuals' financial freedom. Therefore, accelerating Bitcoin adoption and ensuring it maintains its decentralized and uncensorable properties is a priority. ## **Conclusion** Bitcoin remains a powerful tool for financial freedom but faces significant challenges. Centralization, both in the context of secondary networks and the internet in general, poses a threat to its original proposal. However, with the joint action of the community and the continuous development of decentralized solutions, it is possible to maintain Bitcoin as a bastion of individual freedom. The true revolution of Bitcoin lies in its use as a medium of exchange, not just as a store of value. To achieve hyperbitcoinization, it is necessary to build a robust ecosystem where Bitcoin can circulate freely and be accessible to all. Only then can we fulfill Bitcoin's initial promise and ensure it continues to be a tool for freedom and financial autonomy.
@ eac63075:b4988b48
2024-10-15 20:18:52Bitcoin emerged as a promise of financial freedom, challenging the traditional and centralized structures of governments and financial institutions. Since its inception, many enthusiasts have believed in the revolutionary potential of this cryptocurrency. However, over the years, challenges have arisen that have tested this promise, especially concerning centralization, the implementation of secondary layers like the Lightning Network, and issues of governance and privacy. https://www.fountain.fm/episode/SDZYaFMyLEO1krL6x8RD ## **Centralization and the Exclusivity of Nostr** Nostr, a decentralized network aiming to be censorship resistant, emerged as an attempt to solve some inherent problems of centralization. However, it faces significant challenges. Many users point out that, despite its promise, Nostr is still not attractive to the general public, being exclusive to a specific niche. Additionally, issues of centralization still permeate the network. Discussions on GitHub revealed that developers chose not to implement an absolute level of privacy, a decision many considered inadequate. Even with protocols developed to ensure total privacy—such as the non-identification of IPs and communicating parties—the network still lacks this robust implementation. ## **Individual Freedom and Data Protection** A recurring issue is the importance of demonstrating that real options exist for citizens to protect and preserve their freedom. In a world where most discussions about Bitcoin revolve around its use as an investment asset, there is an urgent need to emphasize its potential as a tool for financial freedom. The Bitcoin community should focus on development and education, showing that the conscious use of cryptography and decentralized transactions can protect individuals against excessive government surveillance and control. Secure and private communication is fundamental, and Bitcoin, along with privacy technologies, can provide this. ## **Hyperbitcoinization and the Illusion of Store of Value** Hyperbitcoinization is a concept that refers to the moment when Bitcoin will replace fiat currencies worldwide. However, achieving this state is not simple, especially when Bitcoin is seen primarily as a store of value. Since 2017, this narrative has gained strength, promoting the idea that accumulating Bitcoin will lead to automatic wealth. However, this perspective is limited. The true value of Bitcoin lies in its use as a transactional currency, not just in its scarcity. The community must work to ensure that Bitcoin is utilized in everyday transactions, strengthening its network and demonstrating its real value. ## **The Role of the Community in Bitcoin's Development** Bitcoin's strength comes from its community. Developers, users, and enthusiasts, through their actions and support, make Bitcoin a powerful tool. This community is responsible for ensuring that Bitcoin maintains its essence and that its functionalities are accessible to all. It is crucial that this support network continues promoting the decentralized use of Bitcoin, without intermediaries that can censor or control transactions. Adopting Bitcoin in a centralized manner, through banks or other institutions, contradicts its original proposal and strengthens those who have historically opposed its existence. ## **Sidechains, Second Layers, and the Lightning Network** Sidechains and second layers, like the Lightning Network, are essential components for Bitcoin's scalability. However, they bring challenges, especially regarding the need to trust intermediaries. For these solutions to be effective, it is fundamental that they allow the unilateral withdrawal of funds, ensuring that users maintain full control over their assets. The Lightning Network, for example, is a second layer that allows fast and cheap transactions. However, many users face difficulties when dealing with channels that do not close correctly, resulting in locked funds. These problems must be solved for the network to be truly decentralized and functional. ## **The Fight Against Centralization on the Internet** Centralization is not a problem exclusive to Bitcoin. The internet as a whole faces similar challenges, with data control concentrated in the hands of a few large technology companies. To ensure freedom of expression and online privacy, it is necessary to decentralize these data clusters. Projects that seek to decentralize the internet are vital for this mission. They not only complement Bitcoin in its quest for financial freedom but also ensure that digital communication and expression are protected against censorship and corporate control. ## **The Future of Bitcoin and the Need for Action** The future of Bitcoin depends on the community's action. We cannot expect Bitcoin to automatically become a global medium of exchange. A conscious effort is necessary to build an ecosystem where Bitcoin can flow freely, being used in everyday transactions and valued for its utility. Moreover, with the imminent arrival of central bank digital currencies (CBDCs), time is of the essence. CBDCs represent a significant challenge, as they can further restrict individuals' financial freedom. Therefore, accelerating Bitcoin adoption and ensuring it maintains its decentralized and uncensorable properties is a priority. ## **Conclusion** Bitcoin remains a powerful tool for financial freedom but faces significant challenges. Centralization, both in the context of secondary networks and the internet in general, poses a threat to its original proposal. However, with the joint action of the community and the continuous development of decentralized solutions, it is possible to maintain Bitcoin as a bastion of individual freedom. The true revolution of Bitcoin lies in its use as a medium of exchange, not just as a store of value. To achieve hyperbitcoinization, it is necessary to build a robust ecosystem where Bitcoin can circulate freely and be accessible to all. Only then can we fulfill Bitcoin's initial promise and ensure it continues to be a tool for freedom and financial autonomy. @ 599f67f7:21fb3ea9
2024-10-14 19:36:50Inoiz pentsatu al duzu norbaiti satoshiak modu originalean oparitzea, Bitcoin mundura hurbiltzeko? LNbits zorro batekin NFC opari txartel bat erraz sor dezakezu. Honek LNURLw esteka bat NFC txartelean idatziz funtzionatzen du, eta jasotzaileak bere satoshiak erabili ditzake LNURL gaitutako zorro batekin. ### Zer behar dut? - LNbits zorroa - Android telefono bat - NTAG2* gaitasunak dituen NFC txartela, adibidez NTAG216. 💡 NTAG2* txartelek esteka **bat** idazteko aukera ematen dute. Adibidez, enpresaren webgunerako URLa duen bisita-txartel gisa joka dezakete. NTAG424 txartelek ez dute memoria handiagoa bakarrik, baizik eta SUN parametro deitzen den zerbait ere badute, zerbitzariaren autentifikazioa ahalbidetzen duena, eta horrek segurtasun gehiago ematen die zure ordainketei. Azkenean txartel mota hau [BoltCard](https://boltcard.org/) bat bihur daiteke. ### 1. Hedapena aktibatu Ireki zure LNbits zorroa. Tresna-barran, aktibatu `Withdraw Links` hedapena eta ondoren joan hedapenera. ### 2. Erretiratzeko esteka sortu `Withdraw Links` hedapen orrian, aukeratu `Advanced Withdraw Link(s)` aukera. Ondoren, aukeratu satoshiak ateratzeko erabiliko duzun zorroa. Ziurrenik, hori zure LNbits zorro nagusitik bereizi nahi izango duzu. Horretarako, LNbits zorro berri bat sor dezakezu tresna-barratik, `+ Add a new wallet` aukera hautatuz. Behin zorro berria sortuta, sartu satoshi batzuk bertan.  Eman izenburu bat erretiratzeko estekari. Ezarri erreskatatu daitezkeen gutxieneko eta gehienezko zenbatekoak. Ezarri esteka zenbat aldiz erabil daitekeen eta erretiratze saiakeren arteko denbora. Aukeran, argazki pertsonalizatu bat gehi dezakezu `Use a custom voucher design` laukitxoa markatuz, eta .png irudi baten URL-a sartuz. Gogoan izan “assmilking” laukitxoa ez markatzea. Konfigurazioa amaitu ondoren, jarraitu erretiratzeko esteka sortzera. ### 3. Idatzi esteka NFC txartelean Zure erretiratzeko esteka berrian, klikatu `View LNURL` estekan. Ondoren, sakatu `Write to NFC` botoia eta eutsi NFC txartela telefonoaren aurrean idazketa-prozesua burutzeko.  ✔️ **EGINDA** 💡 Esan txartelaren jasotzaileari satoshi saldoari buruz, denbora ez dezan galdu azkeneko satoshia lortzen saiatzeko. 💡 Jasotzaileak txartelaren satoshiak atera ondoren, bere zorroan berridatzi dezake eta berrerabili. Gainera, eman diozun txartela NTAG424 bada, aurreko gidako (nostr:naddr1qqxnzd3e8qcr2wfn8qcrgwf4qyg8wumn8ghj7mn0wd68ytnhd9hx2q3qtx0k0a7lw62vvqax6p3ku90tccgdka7ul4radews2wrdsg0m865sxpqqqp65whwqrr5) bezala Lightning "zor txartela" bihur dezake. Baina txartela NTAG2* bakarrik bada, beste opari txartel bat bihur dezake soilik.
@ 599f67f7:21fb3ea9
2024-10-14 19:36:50Inoiz pentsatu al duzu norbaiti satoshiak modu originalean oparitzea, Bitcoin mundura hurbiltzeko? LNbits zorro batekin NFC opari txartel bat erraz sor dezakezu. Honek LNURLw esteka bat NFC txartelean idatziz funtzionatzen du, eta jasotzaileak bere satoshiak erabili ditzake LNURL gaitutako zorro batekin. ### Zer behar dut? - LNbits zorroa - Android telefono bat - NTAG2* gaitasunak dituen NFC txartela, adibidez NTAG216. 💡 NTAG2* txartelek esteka **bat** idazteko aukera ematen dute. Adibidez, enpresaren webgunerako URLa duen bisita-txartel gisa joka dezakete. NTAG424 txartelek ez dute memoria handiagoa bakarrik, baizik eta SUN parametro deitzen den zerbait ere badute, zerbitzariaren autentifikazioa ahalbidetzen duena, eta horrek segurtasun gehiago ematen die zure ordainketei. Azkenean txartel mota hau [BoltCard](https://boltcard.org/) bat bihur daiteke. ### 1. Hedapena aktibatu Ireki zure LNbits zorroa. Tresna-barran, aktibatu `Withdraw Links` hedapena eta ondoren joan hedapenera. ### 2. Erretiratzeko esteka sortu `Withdraw Links` hedapen orrian, aukeratu `Advanced Withdraw Link(s)` aukera. Ondoren, aukeratu satoshiak ateratzeko erabiliko duzun zorroa. Ziurrenik, hori zure LNbits zorro nagusitik bereizi nahi izango duzu. Horretarako, LNbits zorro berri bat sor dezakezu tresna-barratik, `+ Add a new wallet` aukera hautatuz. Behin zorro berria sortuta, sartu satoshi batzuk bertan.  Eman izenburu bat erretiratzeko estekari. Ezarri erreskatatu daitezkeen gutxieneko eta gehienezko zenbatekoak. Ezarri esteka zenbat aldiz erabil daitekeen eta erretiratze saiakeren arteko denbora. Aukeran, argazki pertsonalizatu bat gehi dezakezu `Use a custom voucher design` laukitxoa markatuz, eta .png irudi baten URL-a sartuz. Gogoan izan “assmilking” laukitxoa ez markatzea. Konfigurazioa amaitu ondoren, jarraitu erretiratzeko esteka sortzera. ### 3. Idatzi esteka NFC txartelean Zure erretiratzeko esteka berrian, klikatu `View LNURL` estekan. Ondoren, sakatu `Write to NFC` botoia eta eutsi NFC txartela telefonoaren aurrean idazketa-prozesua burutzeko.  ✔️ **EGINDA** 💡 Esan txartelaren jasotzaileari satoshi saldoari buruz, denbora ez dezan galdu azkeneko satoshia lortzen saiatzeko. 💡 Jasotzaileak txartelaren satoshiak atera ondoren, bere zorroan berridatzi dezake eta berrerabili. Gainera, eman diozun txartela NTAG424 bada, aurreko gidako (nostr:naddr1qqxnzd3e8qcr2wfn8qcrgwf4qyg8wumn8ghj7mn0wd68ytnhd9hx2q3qtx0k0a7lw62vvqax6p3ku90tccgdka7ul4radews2wrdsg0m865sxpqqqp65whwqrr5) bezala Lightning "zor txartela" bihur dezake. Baina txartela NTAG2* bakarrik bada, beste opari txartel bat bihur dezake soilik. @ 5e5fc143:393d5a2c
2024-10-11 22:15:54We are now given a choice of digital freedom #nostr . Creativity for every nostrich is now unleashed from the cage of bigtech censorship , rules and algo. But freedom comes with responsibility so pick right one(s). I will try share here some learning experience both technical and also from fundamental point of view. Just wanted kick start this article n fill as we go like living reference document. Nostr itself is an application layer protocol that can used beyond just social media mirco or long blogging. Each nostr client heavily dependent on back-end servers call nostr "Relay servers" or in short "rs" or "relays" Relays can hosted anywhere in clearnet internet, onion net , vpn , i2p , nym Relays are controlled by their respective admins based NIP specs that they select to implement according to own decisions. Relays can have certain ToS (Terms of Service) Rules to adhered too. New users can choose and pick client or app (ios / android/ windows) with preset of relays in the simplest form , but other advanced users need to do a regular manual relay management. Relay management is an active regular task based on where when n how you are using. Relay list are saved within you npub profile backup file which can edited and broadcast anytime. Relay management is an active regular task based on where when and how you are using. Relay list always need to be updated time to time as and when needed. 2 Users MUST a common RELAY between them even if one only need to follow another. Occasionally you may notice certain npub accounts you are following already but cannot see frequent notes publish by them – one of cause maybe you not sharing a common relay Most nostr client applications has SETTINGS where user choose add/remove relays Also user choose which function to enable - READ or WRITE Relay list for your account is always saved within you npub profile backup file which can edited and broadcast anytime. Hence any app or browser when u login with you npub the same relay list will be enforced. There could valid reasons why u need have list for if you trying to save bandwidth and traveling. Functions in app.getcurrent.io and primal.net app for mobile apple or android are ideal for user traveling abroad and wanted to save bandwidth since relay management is done the providers in backend and saves hassle for basic usage. Remember if someone is selecting relay on your behalf then you may not be necessarily able to pull and get some specific and special content that you may need. Such providers like coracle and nostrid also give option to override the default relays they selected. Relay types: They can be categorized by various features or policy or technologies. FREE PUBLIC Relays vs PAID PUBLIC Relays PAID relays provide unrestricted access / write / filtering options than FREE relays but both are public clearnet relays. Just subscribing to PAID relays will not solve all problems unless you choose the relays properly and enable settings correctly. Private Replay or Tor Relays – normally not easily visible until unless someone tell you. You can also host own private relay not opened to internet of archive and back of your own notes. The technical landscape in nostr can be fast changing as more NIPs get proposed or updated. Relays admin can choose implement certain NIPs or not based on policy or technical limitations. Example NIP33 defines “long notes” aka blogs as you now reading this in habla site which #1 UI and site for "Editable" long notes – some relays donot implement or allow this. NIP07 is used for client authentication like nos2x and is implemented by all relays in fact. Nostr is so fasting changing-hence many links many broken Pushing long note again. To be continued again ... reference pics will added later also Hope this help you understand "why when what" to tune and maintain active set of proper relays. Relay Proxy, Relay aggregator or Relay multiplexer – Paid, Public, Free, Private, Event, Relays That’s all for now n more later ... Thank you 🙏 ! ⚡️ https://getalby.com/p/captjack ⚡️ PV 💜 🤙 References: https://habla.news/relays https://relay.exchange/ https://relays.vercel.app/ https://nostr.info/relays/ https://nostrudel.ninja/#/relays Related Articles: https://thebitcoinmanual.com/articles/types-nostr-relays/ nostr:naddr1qqd5c6t8dp6xu6twvukkvctnwss92jfqvehhygzwdaehguszyrtp7w79k045gq80mtnpdxjuzl9t7vjxk52rv80f888y5xsd5mh55qcyqqq823cf39s98 https://habla.news/u/current@getcurrent.io/1694434022411
@ 5e5fc143:393d5a2c
2024-10-11 22:15:54We are now given a choice of digital freedom #nostr . Creativity for every nostrich is now unleashed from the cage of bigtech censorship , rules and algo. But freedom comes with responsibility so pick right one(s). I will try share here some learning experience both technical and also from fundamental point of view. Just wanted kick start this article n fill as we go like living reference document. Nostr itself is an application layer protocol that can used beyond just social media mirco or long blogging. Each nostr client heavily dependent on back-end servers call nostr "Relay servers" or in short "rs" or "relays" Relays can hosted anywhere in clearnet internet, onion net , vpn , i2p , nym Relays are controlled by their respective admins based NIP specs that they select to implement according to own decisions. Relays can have certain ToS (Terms of Service) Rules to adhered too. New users can choose and pick client or app (ios / android/ windows) with preset of relays in the simplest form , but other advanced users need to do a regular manual relay management. Relay management is an active regular task based on where when n how you are using. Relay list are saved within you npub profile backup file which can edited and broadcast anytime. Relay management is an active regular task based on where when and how you are using. Relay list always need to be updated time to time as and when needed. 2 Users MUST a common RELAY between them even if one only need to follow another. Occasionally you may notice certain npub accounts you are following already but cannot see frequent notes publish by them – one of cause maybe you not sharing a common relay Most nostr client applications has SETTINGS where user choose add/remove relays Also user choose which function to enable - READ or WRITE Relay list for your account is always saved within you npub profile backup file which can edited and broadcast anytime. Hence any app or browser when u login with you npub the same relay list will be enforced. There could valid reasons why u need have list for if you trying to save bandwidth and traveling. Functions in app.getcurrent.io and primal.net app for mobile apple or android are ideal for user traveling abroad and wanted to save bandwidth since relay management is done the providers in backend and saves hassle for basic usage. Remember if someone is selecting relay on your behalf then you may not be necessarily able to pull and get some specific and special content that you may need. Such providers like coracle and nostrid also give option to override the default relays they selected. Relay types: They can be categorized by various features or policy or technologies. FREE PUBLIC Relays vs PAID PUBLIC Relays PAID relays provide unrestricted access / write / filtering options than FREE relays but both are public clearnet relays. Just subscribing to PAID relays will not solve all problems unless you choose the relays properly and enable settings correctly. Private Replay or Tor Relays – normally not easily visible until unless someone tell you. You can also host own private relay not opened to internet of archive and back of your own notes. The technical landscape in nostr can be fast changing as more NIPs get proposed or updated. Relays admin can choose implement certain NIPs or not based on policy or technical limitations. Example NIP33 defines “long notes” aka blogs as you now reading this in habla site which #1 UI and site for "Editable" long notes – some relays donot implement or allow this. NIP07 is used for client authentication like nos2x and is implemented by all relays in fact. Nostr is so fasting changing-hence many links many broken Pushing long note again. To be continued again ... reference pics will added later also Hope this help you understand "why when what" to tune and maintain active set of proper relays. Relay Proxy, Relay aggregator or Relay multiplexer – Paid, Public, Free, Private, Event, Relays That’s all for now n more later ... Thank you 🙏 ! ⚡️ https://getalby.com/p/captjack ⚡️ PV 💜 🤙 References: https://habla.news/relays https://relay.exchange/ https://relays.vercel.app/ https://nostr.info/relays/ https://nostrudel.ninja/#/relays Related Articles: https://thebitcoinmanual.com/articles/types-nostr-relays/ nostr:naddr1qqd5c6t8dp6xu6twvukkvctnwss92jfqvehhygzwdaehguszyrtp7w79k045gq80mtnpdxjuzl9t7vjxk52rv80f888y5xsd5mh55qcyqqq823cf39s98 https://habla.news/u/current@getcurrent.io/1694434022411 @ 472f440f:5669301e
2024-10-11 14:20:54As we sprint toward the 2024 US Presidential election the case for using bitcoin as an asset to store value for the long term has never been stronger. The insanity of the incumbent power structure is being laid bare and it is becoming impossible to ignore the headwinds that the Borg faces moving forward. Yesterday morning and earlier today it became clear that inflation is rearing its head again. Not ideal for the soft landing Jerome Powell and Yellen are signaling to the markets after the first Fed Funds rate cut in years. It seems like the yield curve predicted this earlier this week when it inverted after a temporary normalizing period after the Fed's rate cut. Futhermore, it is becoming glaringly obvious that running historically high fiscal deficits while interest rates were at multi-decade highs was a pretty bad idea. As James Lavish points out, the data from the CBO earlier this week shows that the US federal government is running a deficit that is 13% higher than it was last year. This is at a time when real wages are still depressed, inflation is still suffocating American consumers and the private sector job market for American citizens is cratering. Speaking of the job market, the numbers that came in yesterday were worse than expected: The effect of Hurricane Helene should certainly be taken into consideration when looking at this jobs miss. However, even with the miss we know that these numbers have been under reported for years to make the economy seem healthier than it actually is. Even with Helene's effect taken into consideration this print will likely be revised higher 3-6 months from now. All of this points to a breaking point. A breaking point for the economy and, more importantly, a breaking point for overall confidence in the US government and its ability to operate with any semblance of fiscal responsibility. The chart that Pierre Rochard shares in the tweet at the top of this letter is the only chart that matters for anyone attempting to gauge where we find ourselves on the path to bitcoin realizing its full potential. There is $133 TRILLION worth of value sitting in global bond markets. Bitcoin is a far superior asset to store one's wealth in. Bond markets are beholden to the whims of the actors who issue those bonds. In the case of the US Treasury market, the largest bond market in the world, the US government. And as we have pointed out above, the US government is recklessly irresponsible when it comes to issuing debt with a complete inability to pay it back on the long-term. Inflation is up, the jobs market is cratering for the native born Americans who actually pay taxes, and the push toward a multi-polar geopolitical landscape is becoming more pronounced by the day. All of this points to a long-term weakening in demand for US treasuries. The only way out of this mess is to overtly default on this debt or inflate it away. The latter will most certainly be the route that is taken, which positions bitcoin extremely well as people seek the confines of an asset that cannot be debased because it cannot be controlled by a central authority. The levels of sovereign debt in the world are staggering. Do not let the bitcoin price consolidation of the last six months lull you into a state of complacency. Even the results of the Presidential election won't have a material effect on these dynamics. Though, a Donald Trump presidency would certainly be preferable if you prefer to see relatively sane policy enacted that would provide you with time to find safety in bitcoin. But, in regards to this sovereign debt crisis, that is the only benefit you can hope for; more time to prepare. I'll leave you with some thoughts from Porter Stansberry: "We are about to see the final destruction of the American experiment. Every economist knows this (see below) is correct; but nobody is going to tell you about it. I’ll summarize in plan English: We are fucked. 1. Debt is growing much faster than GD and interest expense is growing much faster than debt; and the real growth in entitlement spending hasn’t even begun yet. 2. Progressive taxation means nobody will ever vote for less spending + the combined size of government employees and dependents, there’s no way for America’s actual taxpayers (about 20m people) to ever win an election, so the spending won’t stop growing and, ironically, inflation will make demands for more spending to grow. 3. Inflation undermines both economic growth and social cohesion. The purple hair man-women weirdos are only the beginning; what comes next is scapegoating jews, blacks, immigrants and a huge increase in violence/domestic terror. Get ready America. This election has nothing to do with what’s coming. And neither Trump nor Kamala can stop it. Our experiment in freedom and self-government died in 1971 (when all restraint on government spending was abandoned with the gold standard.) You can only live at the expense of your neighbor until he runs out of money. And that day is here." --- Final thought... I hope my tux still fits for this wedding. Enjoy your weekend, freaks.Use the code "TFTC" for 15% off
@ 472f440f:5669301e
2024-10-11 14:20:54As we sprint toward the 2024 US Presidential election the case for using bitcoin as an asset to store value for the long term has never been stronger. The insanity of the incumbent power structure is being laid bare and it is becoming impossible to ignore the headwinds that the Borg faces moving forward. Yesterday morning and earlier today it became clear that inflation is rearing its head again. Not ideal for the soft landing Jerome Powell and Yellen are signaling to the markets after the first Fed Funds rate cut in years. It seems like the yield curve predicted this earlier this week when it inverted after a temporary normalizing period after the Fed's rate cut. Futhermore, it is becoming glaringly obvious that running historically high fiscal deficits while interest rates were at multi-decade highs was a pretty bad idea. As James Lavish points out, the data from the CBO earlier this week shows that the US federal government is running a deficit that is 13% higher than it was last year. This is at a time when real wages are still depressed, inflation is still suffocating American consumers and the private sector job market for American citizens is cratering. Speaking of the job market, the numbers that came in yesterday were worse than expected: The effect of Hurricane Helene should certainly be taken into consideration when looking at this jobs miss. However, even with the miss we know that these numbers have been under reported for years to make the economy seem healthier than it actually is. Even with Helene's effect taken into consideration this print will likely be revised higher 3-6 months from now. All of this points to a breaking point. A breaking point for the economy and, more importantly, a breaking point for overall confidence in the US government and its ability to operate with any semblance of fiscal responsibility. The chart that Pierre Rochard shares in the tweet at the top of this letter is the only chart that matters for anyone attempting to gauge where we find ourselves on the path to bitcoin realizing its full potential. There is $133 TRILLION worth of value sitting in global bond markets. Bitcoin is a far superior asset to store one's wealth in. Bond markets are beholden to the whims of the actors who issue those bonds. In the case of the US Treasury market, the largest bond market in the world, the US government. And as we have pointed out above, the US government is recklessly irresponsible when it comes to issuing debt with a complete inability to pay it back on the long-term. Inflation is up, the jobs market is cratering for the native born Americans who actually pay taxes, and the push toward a multi-polar geopolitical landscape is becoming more pronounced by the day. All of this points to a long-term weakening in demand for US treasuries. The only way out of this mess is to overtly default on this debt or inflate it away. The latter will most certainly be the route that is taken, which positions bitcoin extremely well as people seek the confines of an asset that cannot be debased because it cannot be controlled by a central authority. The levels of sovereign debt in the world are staggering. Do not let the bitcoin price consolidation of the last six months lull you into a state of complacency. Even the results of the Presidential election won't have a material effect on these dynamics. Though, a Donald Trump presidency would certainly be preferable if you prefer to see relatively sane policy enacted that would provide you with time to find safety in bitcoin. But, in regards to this sovereign debt crisis, that is the only benefit you can hope for; more time to prepare. I'll leave you with some thoughts from Porter Stansberry: "We are about to see the final destruction of the American experiment. Every economist knows this (see below) is correct; but nobody is going to tell you about it. I’ll summarize in plan English: We are fucked. 1. Debt is growing much faster than GD and interest expense is growing much faster than debt; and the real growth in entitlement spending hasn’t even begun yet. 2. Progressive taxation means nobody will ever vote for less spending + the combined size of government employees and dependents, there’s no way for America’s actual taxpayers (about 20m people) to ever win an election, so the spending won’t stop growing and, ironically, inflation will make demands for more spending to grow. 3. Inflation undermines both economic growth and social cohesion. The purple hair man-women weirdos are only the beginning; what comes next is scapegoating jews, blacks, immigrants and a huge increase in violence/domestic terror. Get ready America. This election has nothing to do with what’s coming. And neither Trump nor Kamala can stop it. Our experiment in freedom and self-government died in 1971 (when all restraint on government spending was abandoned with the gold standard.) You can only live at the expense of your neighbor until he runs out of money. And that day is here." --- Final thought... I hope my tux still fits for this wedding. Enjoy your weekend, freaks.Use the code "TFTC" for 15% off @ e88a691e:27850411
2024-10-11 13:17:16# An opinionated guide to Sauna. By NVK [🌐](https://primal.net/nvk) [🐦](https://twitter.com/nvk) ## Introduction Updated from the Sauna, October 7th 2024 After years of experimenting with different sauna types, I’ve developed strong opinions on the subject. The purpose of this article is to share these opinions with anyone who is interested in them and, hopefully, help others get more out of their sauna experience. I’m certain my opinions will offend some, including all the people who (in my view) are doing it wrong. I know that saunas are important to many cultures around the world and that my strongly held opinions may offend some of those cultures. Mind you, although I grew up in South America, I do have a fair amount of slavic blood in me. When I was a child, my grandfather regularly took me with him to the shvitz. One of my fondest memories from this time was the “Scottish Bath”, which involves standing against the sauna wall, execution-style, so that someone can spray you with freezing water from a high pressure hose. I’ve never heard of this outside of South American and can’t attest to whether it has any real Scottish origins. The various health claims about using a sauna are beyond the scope of this article. All I have to say is that, like many things in my life, like Bitcoin, the meat/keto diet, and fasting, I find sauna to be yet another cheat code to life: it’s a simple thing that just makes life a lot better. If you want a good primer on scientific health benefits of sauna, I recommend starting with [this article by Rhonda Patric](https://www.foundmyfitness.com/topics/sauna). She goes in depth. To be clear, it should go without saying that I am not a medical expert or professional. None of the opinions below are, or should be interpreted as, medical advice. There are many people for whom sauna use is not recommended. It would be prudent for any sauna user to consult with his or her doctor before entering a sauna. _Thanks to S. for taking the time to do a very helpful first review of this article. And thanks to The Wife for helping make my words legible and helping me make time to sauna–I don’t know which sacrifice was bigger._ ## Banya or Nothing When I talk about saunas, I’m talking about a sauna with a stove, either wood or electric, that allows for steam. I call this “Banya style”. To be clear, I’m distinguishing between saunas and steam baths. Steam baths have their own place, but they aren’t my thing and I don’t consider them saunas. A breakdown of the main types of saunas may be helpful, so you know which to avoid: 1. Wet saunas, which are typically cedar rooms with wood burning or electric stoves onto which you throw liquid to create steam (I call this “Banya style”); 2. Dry saunas, which are typically cedar rooms with wood burning or electric stoves without added steam (like Korean style saunas); and 3. Infrared saunas, which, unlike traditional saunas, don’t heat the surrounding air. Instead, they use infrared panels to warm your body directly. In my opinion, it’s Banya style or nothing. I’m not a huge fan of dry saunas, and I don’t even bother with infrared saunas. Infrared is a fiat-shitcoin. I want steam! ## How to Sauna ### Sauna Etiquette If you read no other part of this already-too-long-article, read this. Saunas are social places. There are proper ways of being in a sauna with others, and there are ways to do it wrong. You don’t want to be the person who ruins it for everyone. Here are some important etiquette tips: **Silence vs. Chatting:** It’s not a question of whether you have to stay silent in a sauna or if it’s ok to talk. It depends on the circumstances and who else is around. If you’re using a sauna that isn’t your own, ask the staff about the preferred custom. The noise level in a sauna differs depending on the group in the sauna at a particular time. If you do want to chat with others, there’s nothing wrong with that. But, pay attention to whether there are others in the sauna who'd prefer it quiet. And definitely do NOT be obnoxiously loud – yes, I’m looking at you bachelor(ette) group who just discovered the Russian Banya. **Coming and Going:** People rotate in and out of the sauna at different paces, so there will be people coming and going during your shvitz. But there are ways to come and go that are considerate and proper. Keep the f-ing door closed (which was the working title of this article). Once you leave, don’t come back inside moments later. Doing so disturbs your fellow sauna users, lets out the all-important steam, and prevents the sauna from reaching an appropriate temperature. If you’re in the sauna with a group of friends, try to coordinate your comings and goings so you’re all on the same cycle. If you can only last 5 min at a sauna, don’t go in too often at the risk of ruining it for others (assuming it’s not your own private sauna). Be fast when closing the sauna door when you come or leave. Otherwise, you will get dirty looks from others and may even hear mumbles of “quick quick, fast fast” from a Gray Beard. And you will deserve it. Never open the door right after someone puts water on the stove to make steam. It’s all about the steam. Don’t waste it. **Controlling the heat:** if you can’t handle the heat in the sauna, don’t just turn the heat down, because it ruins it for others. Instead, go to a lower bench or get out and take your break. Saunas are meant to be hot. That’s the whole point. **Personal Hygiene:** Shower before you go into the sauna. Don’t wear perfume, smelly deodorant, or fragrant lotions. Smells get amplified in a sauna. Have a towel under you, don't leave your drippings behind. Best yet, make a Z with your towel, this covers your butt and down under your feet. **Clothing:** sauna is not a place for wearing clothing. It is a place to get back to nature. If you are shy, just wrap a towel around yourself. People ask if I don't feel awkward, the answer is no. Who cares, humans naked is not novel. In many countries, it is strictly forbidden to wear clothing or bring anything but a towel into the sauna. It's understandable that may not be possible in North American public saunas on mix gender "family" days. If you have to wear something, then wear something 100% cotton or marino wool. You don't want plastic being backed into your genitals. One more thing, leave the watch out as it gets hot and will burn you. Also, flip-flops/sandals, stay outside. Some saunas sell body scrubs and masks for you to apply before or in the sauna. Note that once in the heat, these can get goopy and drippy and may melt into your eyes and mouth. So (in this opinionated guides’ wife’s opinion), they are better in theory than reality. **Adding Oils and scents:** As discussed below, it can be nice to add certain oils and other scents to the steam. But if there are others in the sauna, ask first before you do. **Where and how to sit:** Hot air rises. So, the higher benches are hotter and the lower benches are cooler. If you are a newbie, pick a lower bench so you don’t have to leave as quickly and open the door unnecessarily. It’s great to lay down in the sauna, but if it gets crowded, sit up to make room for others. When moving around to find your seat, don’t walk on the benches in your sandals. Leave your sandals outside the sauna or on the sauna floor. ### Sauna Temperature In most proper Russian style Banyas you will find temperatures of 80-95 degrees celsius, which, in my opinion, is the best range. Thats near your body. "Offical" on the dial will he 100-120C. But sometimes you want to take it a little easier or last a little longer in the sauna. In these cases, 65-85 at body, dial at 80-100. degrees celsius will do. However, if your sauna is below 85 degrees celsius on the dial, you might as well just go hide under your bed sheets and not waste your time. At some saunas in hotels, gyms, or spas, you may not be allowed to set the sauna as high as you’d like (see below). There are many tricks to circumvent these frustrating restrictions, but my legal counsel has advised me not to go into any details here. ### Sauna Duration The amount of time you spend in the sauna is a matter of personal preference and depends on the number of cycles you do (more on cycles, below). For your first round, my opinion is that most people should try to last 15 minutes in the sauna. If a sauna is at the proper temperature, most people will struggle to stay inside any longer. If you can stay inside for 20-30 minutes, your sauna is probably too cold and/or there is not enough steam. Many saunas have hourglasses inside to keep time, and I’ve never seen a sauna hourglass with more than 15 minutes, which should be a good hint. My preferred is; Cold Plunge => Sauna 15 min => Cold Plunge => Hydrate with Salt & Water, Rest 5-10min => Sauna 15min => Cold Plunge => Hydrate with Salt & Water, Rest 5-10min => Sauna 15min => Cold Plunge => Hydrate with Salt & Water, Rest if you can rest in the sun even better (no sunscreen poison please). You can add alcohol drinks to the hydration if you feel comfortable with that. But only add food after the last cycle. For subsequent rounds, hydration starts to play a bigger role in how long you stay inside. Most people seem to last longer on their first round than on their second or third. If you can do 15 minutes on your second round, great. But 5-10 minutes is also fine. ### Sauna Cycles The traditional Russian Banya method (and in this writer’s opinion, the best method) is to do sauna cycles. Go into the sauna and just stay as long as you can take it (up to 15 minutes or so). Then take a cold shower and/or cold plunge (see below). Then robe-up and go relax with water, tea or beer. Once you start feeling “normal” again, repeat. For me, three cycles is the sweet spot. I’ll do more cycles if I’m spending the day at the Banya facility. If I’m at home, where I often sauna every other day, I find just one or two cycles does the trick. Sometimes I add a cycle or two on the weekend. Occasionally, I like to go into the sauna as it’s warming up and before it reaches optimum heat (i.e. at around 60 degree celsius). This way, I can stay longer in the sauna for my first round (about 30-40 minutes). If I take this approach, I generally only do one more short round after my cold plunge. ### Cold showers and plunges In my experience, you want to take a cold shower or a cold plunge (or both, plunge is better) after the sauna cycle.After you come out of the sauna, immediately jump into cold plunge for a bit, i don't like to stay too long. Some Banya facilities will have a bucket filled with cold water that you can pull with a string to let the water pour over you, pull a couple times. The banyas may also have a cold pool of water into which you can plunge for a bit.  If I’m at my country place, after I get out of the sauna I jump into the cold lake. If it’s winter, I like to roll in the snow, which is satisfying. Some cultures would say that it’s not a real sauna experience unless you roll in at least one foot of snow. After your cold shower or plunge, put on a warm robe and go relax before going back into the sauna. I like to relax for 5-20 minutes, depending on how much time I have. This allows the body’s temperature to decrease slowly. I do not recommend going directly back into the sauna after your cold plunge. If you don’t give yourself enough time after the cold plunge, you will overheat and won’t last very long when you return to the sauna. ### Position There really are no rules here. The way you position yourself in the sauna depends on your mood and preference, and there are many options. For example, you can sauna seated with your legs hanging down or with your knees up. You can lie down if there’s room. My favorite position is to lie down on my back with my legs up against the wall and, assuming the ceiling is low enough, with my feet stretched against the ceiling. This is a great way to stretch the hamstrings (check out stretching under “Sauna Activities”, below). Choosing whether to sit on a higher bencher or lower bench is the best way to control the temperature you experience without adjusting the room temperature itself. You will notice the heat in the sauna increases exponentially every inch you go up. If you are struggling to stay in the sauna but don’t want to get out just yet, try moving down to a lower bench to last a little longer. Lying on the floor is the coolest spot and a great place for kids to start getting exposed to saunas. - - - #### There is no shame in going to lower benches or even the floor, there is only shame in opening the door before 15min - - - ### Getting Steamy Without steam, the sauna would just be a sad, hot oven (I’m looking at you, infrared sauna). The steam in the sauna has many benefits but most importantly it increases the thermal coupling of your body to the air and it feels great. The amount of steam in the sauna is a matter of personal taste. You don’t want to make it into a steam room (remember, steam rooms are NOT saunas). But, you do want the sauna to be very moist. I find that two to four ladles of water in a mid-size sauna every five to seven minutes does the trick. Keep it between 50-60% humidity. I keep a bucket of water in the sauna at all times so that I can continue to ladle water as I shvitz. Make sure to get a wood bucket and a metal ladle with a wooden handle. Wood ladles will crack, and if the handle is metal, it’ll burn you when you grab it. If, when you enter the sauna, it’s already been on for a while, the wood is likely to already be wet and the sauna full of steam, so you may not need to add too much water. However, if you’ve just turned on the sauna and the wood walls are dry, you will need to ladle more water to make the air moist enough. If the sauna is too moist for comfort, open the door and let it dry out a bit (obviously, only do this in a private sauna). Essential oils and even beer can all be added to the water to create scented steam. I recommend starting your sauna with just water, and add the scent as you get going. You can try all sorts of different essential oils. I’ve tried everything from oak and cedar to tangerine and cinnamon (gag) essential oil. In the end, there are really only two oils that are worth it, in my opinion. The first is eucalyptus. I’ve experimented with different types of eucalyptus oil, and the variety you use makes a difference. My favorite is eucalyptus globulus. I also like diluted pine tar oil. When you settle on your essential oil, add a healthy dose of the oil to the ladle filled with water. Never put the oil onto the oven directly. It’ll just burn. In a few Russian facilities, I’ve seen Gray Beards pour Russian beer onto the oven and it was actually quite nice. It’s almost like being in a cozy bakery while you sweat Some people like to place a salt brick or compressed solid blocks in their sauna from time to time. Put the salt block on the stove and pour water over it. The steam takes on a saltiness that feels nice. If a salt block is not available, you can get a cast iron teapot, fill it up with salt water, and place it on top of the stove. And for my most important steam tip, I recommend using the “towel spin”. This is an effective and underrated technique to help circulate steam in the sauna. After creating steam, take your towel above your head and spin it around hard, like a ceiling fan. This movement works like a convection oven and spreads and equalizes the heat and steam throughout the room. It might make the folks sitting lower down in the sauna a little hotter, but that's what they’re there for, isn’t it? ### Hydration Being hydrated is important to having a positive sauna experience. You will lose a lot of your body’s water in the sauna. Ideally, start to hydrate well up to an hour before your sauna. I like to add a pinch of salt to my water to encourage water retention. Do not bring any drinks into the sauna (the exception being a dedicated steam-beer, see above). Have your water or beverage when you’re outside the sauna, resting. If you find you need to drink water inside the sauna in order to cool yourself down, then it’s time for you to get out and allow your body a cool-down. When you’re outside the sauna, don’t immediately down a glass of super cold water because you will cool down your internal body too fast. Personally, I like to drink warm tea after my first two cycles. After my second cycle, I enjoy a beer (pre-keto days), soup, or vodka drink. When non-keto, I do enjoy adult drinks in the cycles. If you are doing a sauna while on a multi-day fast, you need to have water and salt, at a minimum. Otherwise, you will deplete your natural reserve of electrolytes and not be able to think straight. ### Sauna Frequency When it comes to frequency, if you are not in the equatorial heat do it every day. I now do mornings and end of day if I can. so 2x 2-3x cycles. In the summer, living in a hot & humid location, I sauna a lot less frequently. My desire to sauna is greatly diminished because I spend a lot of time in the sun and heat. ### What to wear **Sauna Hat:** I highly recommend wearing a Russian/Finish style wool hat when you’re inside the sauna. It may seem counterintuitive, but wearing a hat keeps your head cooler. An overheated head is not good for your brain. Wearing the hat stops you from overheating and lets you stay longer in the sauna. The temperature in a sauna is significantly hotter the higher in the room you are, and one’s head is at the top of the body (for most people). So protect your brain in style with a felt sauna hat. If you don’t have a felt sauna hat, buy one. They are easily found online. But in the meantime, you can wrap a dry towel around your head. Don’t forget to take your sauna hat off as you relax between cycles so your head can cool down.  **Clothing:** These days, many public saunas will have family days, men-only days, and women-only days. For obvious reasons, you’re only allowed to sauna naked if you’re attending one of the single-sex days. If you’re at home, there’s no good reason to wear shorts or a bathing suit. Sauna naked. It's a lot more pleasant. If you do wear clothing in the sauna, be careful with items with materials like metal or plastic attached. Things like pins, buttons, or string-ends will get very hot and probably burn you. Remember to take off any heat-conductive jewelry and leave your smart watch outside, as the heat will ruin its battery. Don’t wear your robe inside the sauna. A robe is what you wear outside when relaxing or eating. If you wear it inside, you’ll overheat (and look like an idiot). Go ahead and sweat out that body shame robe-free. You can bring a towel into the sauna to sit on, if you want. Shoes or sandals are highly recommended in public facilities. I mean, there are many people walking around wet. Ew. But keep your sandals outside the sauna itself, or on the sauna floor. ### Sauna activities. Don’t overthink it. Sitting in a sauna is activity enough, in my opinion. But there are some sauna activities you can do: **Veniks/Viht beating:** these are bundles of leaves (commonly birch, oak, or eucalyptus) that are pre-soaked in hot water. Someone with both strength and capacity to exert themselves in the heat will beat your whole body with the leaves. This exfoliates your skin and also gets the plant oils to permeate your skin. And it’s very relaxing. If you’re at a sauna facility, don’t just grab any bundle you see lying around - that belongs to someone else and veniks aren’t shared. You have to bring your own or buy them at the front desk. **Stretching:** this is a great activity to do in the sauna, but make sure to go very easy. Your muscles will be super warm and you don’t want to overdo it and hurt yourself. **Exercise or Sex:** your heart better be in good shape if you try out these high intensity activities in the sauna. If you engage in the latter, you better be in your own home sauna. With respect to the former, I think doing some leg-ups can be very satisfying. **Phone use:** If you’re at home, it’s nice to use your sauna time to shit-post on Twitter or read an article, if you feel like it. Just keep your phone close to the colder, lower parts near the floor or it’ll overheat and shut down. You can also place the phone outside of the air vent and play a [podcast! The Bitcoin.review is great ;)](https://bitcoin.review) **Napping:** I don’t recommend this. If you fall asleep or pass out, you will probably die due to overheating or dehydration. **Chatting:** Saunas are great places for conversations (subject to the caveats I address above). Note that nowadays, microphone modules are both very tiny and can withstand high temperatures, so it’s no longer recommended to reenact mafia movie sauna scenes. **Eating and Drinking:** As discussed above, never have food or drink inside the sauna. But when you finish your sauna, take advantage of whatever snacks the facility offers. For Russian joints, the soups, fish roe and dry salty fish snacks are great. Again, don’t eat before your sauna; wait until you’re done. Some places will have bottled salty-ish lake water, and beer seems to be a good source of salts and re-hydration. Vodka drinks are nice sometimes, too. My favorites are vodka with beet juice and horseradish, vodka with pickle juice, or just a chilled shot of Zubrowka (vodka infused with bison grass). Teas are also very enjoyable post-sauna. I prefer non-caffeinated berry teas. Some Banyas even offer free tea to patrons.  ## Ready to Sweat It Out? Thanks to this fantastic guide to sauna, you’re now feeling confident and excited to seek out a solid sauna. So where do you go? ## Where to Find a Sauna **Spas:** Spas are not the best place to have an optimal sauna experience. Saunas at spas are typically not hot enough and spas have annoying staff whose job it is to enforce idiotic rules and practices that prevent you from having a real sauna experience. **Gyms & Hotels:** These are some of the worst places to sauna. For liability reasons, these saunas tend to be too cold and there are often mechanisms that prevent you from raising the temperature. Here, you’ll often see saunas with glass doors, which may look chic, but are inefficient and stupid because they don’t seal properly and leak steam. Gyms and hotels are high traffic areas, so people who don’t know what they are doing are constantly coming and going from the sauna, which, as we discussed, is a sauna no-no. If you still want to try the sauna at your gym or hotel, I recommend going in naked. It’ll deter people from joining you and ruining the little steam you managed to get going. **Traditional bath houses (Banyas):** These usually offer a great experience because they deliver a super hot sauna, good cold baths and plunges, delicious food and drinks, and knowledgeable staff. **Home:** Yes, you can build a great sauna in your own home! You can create a small space in your basement, turn a closet or cold room into a sauna, or just add an outdoor hut or barrel sauna in your backyard. This is the best way for you to control the whole experience and do it often. As with anything, the easier it is to access, the more you will do it. _Build it. They will Come_ Many people have asked me for details about sauna building. If you’re ready to build your own personal home sauna, here are some important considerations. #### Materials Saunas are insulated rooms, most commonly finished with cedar tung and groove slats. Cedar is used because it doesn’t rot with moisture. You don’t want treated wood as it will release all the bad stuff that keeps the wood from rotting into the air when heated. Cedar interior is often placed over a vapor barrier, followed by insulation and then the outer wall. Many outdoor saunas are not insulated. They simply have a single layer of cedar 2x6 planks functioning as both the interior and exterior. Non-insulated saunas need much more heating power in the winter. #### Structure For indoor saunas, you may want to find a bricklayer to build something for you. Traditional facilities often have brick-lined rooms and very large wood-burning stoves. You can buy prefab outdoor saunas, which are often sheds or barrels. After experimenting with both, I’ve concluded that barrel saunas are inferior, even though that’s what I have at my country property. This is because barrels have concave ceilings and inner walls. This means the benches are lower and the curve makes the topmost part of the ceiling (and the hottest part) the furthest from you, or inaccessible. The spinning towel trick really helps in the barrel. When it comes to buying a sauna, go with the most traditional structure possible. They are based on thousands of years of evolution and knowledge. Portable tent saunas are fun, but impractical because you have to set them up before each use. Bench height inside the sauna is important. I think the top-most bench should be very near the ceiling. This way, when you’re lying down, you can use the ceiling to stretch the hamstrings. As a rule of thumb, bench length should allow you to lie down completely. It is also nice to have at least one lower bench for visitors or less intense sauna days.  #### Sauna Ovens There are two main types of sauna ovens: wood burning and electrical (with gas heating being available, but not common). If the location you are building allows for it, go with electrical. It’s practical and easy to get going quickly. This means you will use it more often. Wood burning saunas are romantic and smell great, but it is a lot more work to get a fire going, especially in the winter. Opt for oven sizes that are recommended or above recommended for the size of the sauna. A larger oven means more thermic inertia, more rocks for steam, and therefore less time to warm up the room. Bigger is better. The Scandinavians make the best quality ovens. #### Oven controllers There are two types of temperature control devices: the analog cooking-style or the digital type. I think, due to liability and safety, all ovens have a timer that max out at one hour. The digital oven controllers are fantastic and I have one in the city in my basement sauna. However, you have to consider your environment. For me, temperatures in the winter can reach below -30C and in the summer, over 40C. This massive range can take a toll on outdoor equipment and materials. For this reason, I opted for an analog controller for my outdoor sauna in the country, since the weather will likely ruin the electronics of the digital controller. I would avoid ovens with analog pre-heat timers. They are great in theory, but the implementation is utter garbage. The timer won’t be precise and it’ll just lead to frustration, for example, when you thought you set the oven to start in three hours, but it actually started in two hours and already turned off. #### Important Sauna Gear Windows are nice to have, especially if you have a view to enjoy. Opt for at least a cedar door with a little window. Do not go with modern glass door styles. They are crap. They have gaps, no insulation, and let in too much light. Saunas need thermometers and hygrometers (to measure humidity). The thermometers should be rated for saunas and be visible inside. This is both for safety and bragging rights. I think having an hourglass inside your sauna is a must. Being able to know for sure how long you’ve been inside is important, since your sense of timing inside the sauna may be off depending on the state of your mind and body on a given day. You shouldn’t wear a watch inside the sauna, since it’ll overheat or break. Having a clock visible from the inside is also a good idea, especially if you sauna often and have a wife and kids who you don’t want to leave you. Air circulation is an often-overlooked but important part of a sauna design. Saunas should not have stale air. The best sauna design creates natural “real convection” by placing an air intake under the oven wall and another at the top opposite wall. This allows fresh air to enter the sauna while in use. Be sure to add regulators, since you don’t want to cool the sauna or expel all steam. Without regulators you may get too much or too little air in. With too much air, you may cool the sauna down too much and/or lose too much steam. #### Nice Things to Have Lights are optional but welcome additions. It can be unpleasant to have no lighting at all, especially in an outdoor sauna on a cold, dark night. Lights should be warm-temperature and low power. I recommend an oven light, since they don’t sweat the heat (get it?) and are often low power. Put a baking tray under your oven–thank me later. Wood “pillows” for your head are nice and don’t get sweat-stained and stinky, like a fabric pillow. Keep some extra felt hats near your sauna so when you or your guests forget their hat, you still have easy access to one. I like to keep a couple of essential oils on the floor of the sauna, for easy access. If you keep the oils too high in the sauna, they’ll get too hot and spoil. I place some duck boards over floor tiles in the sauna to prevent cold feet. I also like to keep a small, natural broom inside the sauna to sweep up any dirt or leaves that come into the sauna on people’s feet. ## Final words As you can tell, I have some strong opinions when it comes to the proper way to enjoy a sauna. My hope is that my musings will help you to maximize your own sauna experience.. If you follow this guide, I’m certain you will benefit from and enjoy the sauna as much as I do and, just maybe, you too will develop your own strongly held opinions that will most definitely offend me. ### Thanks for reading, please close the F-ing door. ps, you can get a Bitcoin Honey Badger Sauna Hat [here](https://store.coinkite.com/store/ht-sauna) - EOF
@ e88a691e:27850411
2024-10-11 13:17:16# An opinionated guide to Sauna. By NVK [🌐](https://primal.net/nvk) [🐦](https://twitter.com/nvk) ## Introduction Updated from the Sauna, October 7th 2024 After years of experimenting with different sauna types, I’ve developed strong opinions on the subject. The purpose of this article is to share these opinions with anyone who is interested in them and, hopefully, help others get more out of their sauna experience. I’m certain my opinions will offend some, including all the people who (in my view) are doing it wrong. I know that saunas are important to many cultures around the world and that my strongly held opinions may offend some of those cultures. Mind you, although I grew up in South America, I do have a fair amount of slavic blood in me. When I was a child, my grandfather regularly took me with him to the shvitz. One of my fondest memories from this time was the “Scottish Bath”, which involves standing against the sauna wall, execution-style, so that someone can spray you with freezing water from a high pressure hose. I’ve never heard of this outside of South American and can’t attest to whether it has any real Scottish origins. The various health claims about using a sauna are beyond the scope of this article. All I have to say is that, like many things in my life, like Bitcoin, the meat/keto diet, and fasting, I find sauna to be yet another cheat code to life: it’s a simple thing that just makes life a lot better. If you want a good primer on scientific health benefits of sauna, I recommend starting with [this article by Rhonda Patric](https://www.foundmyfitness.com/topics/sauna). She goes in depth. To be clear, it should go without saying that I am not a medical expert or professional. None of the opinions below are, or should be interpreted as, medical advice. There are many people for whom sauna use is not recommended. It would be prudent for any sauna user to consult with his or her doctor before entering a sauna. _Thanks to S. for taking the time to do a very helpful first review of this article. And thanks to The Wife for helping make my words legible and helping me make time to sauna–I don’t know which sacrifice was bigger._ ## Banya or Nothing When I talk about saunas, I’m talking about a sauna with a stove, either wood or electric, that allows for steam. I call this “Banya style”. To be clear, I’m distinguishing between saunas and steam baths. Steam baths have their own place, but they aren’t my thing and I don’t consider them saunas. A breakdown of the main types of saunas may be helpful, so you know which to avoid: 1. Wet saunas, which are typically cedar rooms with wood burning or electric stoves onto which you throw liquid to create steam (I call this “Banya style”); 2. Dry saunas, which are typically cedar rooms with wood burning or electric stoves without added steam (like Korean style saunas); and 3. Infrared saunas, which, unlike traditional saunas, don’t heat the surrounding air. Instead, they use infrared panels to warm your body directly. In my opinion, it’s Banya style or nothing. I’m not a huge fan of dry saunas, and I don’t even bother with infrared saunas. Infrared is a fiat-shitcoin. I want steam! ## How to Sauna ### Sauna Etiquette If you read no other part of this already-too-long-article, read this. Saunas are social places. There are proper ways of being in a sauna with others, and there are ways to do it wrong. You don’t want to be the person who ruins it for everyone. Here are some important etiquette tips: **Silence vs. Chatting:** It’s not a question of whether you have to stay silent in a sauna or if it’s ok to talk. It depends on the circumstances and who else is around. If you’re using a sauna that isn’t your own, ask the staff about the preferred custom. The noise level in a sauna differs depending on the group in the sauna at a particular time. If you do want to chat with others, there’s nothing wrong with that. But, pay attention to whether there are others in the sauna who'd prefer it quiet. And definitely do NOT be obnoxiously loud – yes, I’m looking at you bachelor(ette) group who just discovered the Russian Banya. **Coming and Going:** People rotate in and out of the sauna at different paces, so there will be people coming and going during your shvitz. But there are ways to come and go that are considerate and proper. Keep the f-ing door closed (which was the working title of this article). Once you leave, don’t come back inside moments later. Doing so disturbs your fellow sauna users, lets out the all-important steam, and prevents the sauna from reaching an appropriate temperature. If you’re in the sauna with a group of friends, try to coordinate your comings and goings so you’re all on the same cycle. If you can only last 5 min at a sauna, don’t go in too often at the risk of ruining it for others (assuming it’s not your own private sauna). Be fast when closing the sauna door when you come or leave. Otherwise, you will get dirty looks from others and may even hear mumbles of “quick quick, fast fast” from a Gray Beard. And you will deserve it. Never open the door right after someone puts water on the stove to make steam. It’s all about the steam. Don’t waste it. **Controlling the heat:** if you can’t handle the heat in the sauna, don’t just turn the heat down, because it ruins it for others. Instead, go to a lower bench or get out and take your break. Saunas are meant to be hot. That’s the whole point. **Personal Hygiene:** Shower before you go into the sauna. Don’t wear perfume, smelly deodorant, or fragrant lotions. Smells get amplified in a sauna. Have a towel under you, don't leave your drippings behind. Best yet, make a Z with your towel, this covers your butt and down under your feet. **Clothing:** sauna is not a place for wearing clothing. It is a place to get back to nature. If you are shy, just wrap a towel around yourself. People ask if I don't feel awkward, the answer is no. Who cares, humans naked is not novel. In many countries, it is strictly forbidden to wear clothing or bring anything but a towel into the sauna. It's understandable that may not be possible in North American public saunas on mix gender "family" days. If you have to wear something, then wear something 100% cotton or marino wool. You don't want plastic being backed into your genitals. One more thing, leave the watch out as it gets hot and will burn you. Also, flip-flops/sandals, stay outside. Some saunas sell body scrubs and masks for you to apply before or in the sauna. Note that once in the heat, these can get goopy and drippy and may melt into your eyes and mouth. So (in this opinionated guides’ wife’s opinion), they are better in theory than reality. **Adding Oils and scents:** As discussed below, it can be nice to add certain oils and other scents to the steam. But if there are others in the sauna, ask first before you do. **Where and how to sit:** Hot air rises. So, the higher benches are hotter and the lower benches are cooler. If you are a newbie, pick a lower bench so you don’t have to leave as quickly and open the door unnecessarily. It’s great to lay down in the sauna, but if it gets crowded, sit up to make room for others. When moving around to find your seat, don’t walk on the benches in your sandals. Leave your sandals outside the sauna or on the sauna floor. ### Sauna Temperature In most proper Russian style Banyas you will find temperatures of 80-95 degrees celsius, which, in my opinion, is the best range. Thats near your body. "Offical" on the dial will he 100-120C. But sometimes you want to take it a little easier or last a little longer in the sauna. In these cases, 65-85 at body, dial at 80-100. degrees celsius will do. However, if your sauna is below 85 degrees celsius on the dial, you might as well just go hide under your bed sheets and not waste your time. At some saunas in hotels, gyms, or spas, you may not be allowed to set the sauna as high as you’d like (see below). There are many tricks to circumvent these frustrating restrictions, but my legal counsel has advised me not to go into any details here. ### Sauna Duration The amount of time you spend in the sauna is a matter of personal preference and depends on the number of cycles you do (more on cycles, below). For your first round, my opinion is that most people should try to last 15 minutes in the sauna. If a sauna is at the proper temperature, most people will struggle to stay inside any longer. If you can stay inside for 20-30 minutes, your sauna is probably too cold and/or there is not enough steam. Many saunas have hourglasses inside to keep time, and I’ve never seen a sauna hourglass with more than 15 minutes, which should be a good hint. My preferred is; Cold Plunge => Sauna 15 min => Cold Plunge => Hydrate with Salt & Water, Rest 5-10min => Sauna 15min => Cold Plunge => Hydrate with Salt & Water, Rest 5-10min => Sauna 15min => Cold Plunge => Hydrate with Salt & Water, Rest if you can rest in the sun even better (no sunscreen poison please). You can add alcohol drinks to the hydration if you feel comfortable with that. But only add food after the last cycle. For subsequent rounds, hydration starts to play a bigger role in how long you stay inside. Most people seem to last longer on their first round than on their second or third. If you can do 15 minutes on your second round, great. But 5-10 minutes is also fine. ### Sauna Cycles The traditional Russian Banya method (and in this writer’s opinion, the best method) is to do sauna cycles. Go into the sauna and just stay as long as you can take it (up to 15 minutes or so). Then take a cold shower and/or cold plunge (see below). Then robe-up and go relax with water, tea or beer. Once you start feeling “normal” again, repeat. For me, three cycles is the sweet spot. I’ll do more cycles if I’m spending the day at the Banya facility. If I’m at home, where I often sauna every other day, I find just one or two cycles does the trick. Sometimes I add a cycle or two on the weekend. Occasionally, I like to go into the sauna as it’s warming up and before it reaches optimum heat (i.e. at around 60 degree celsius). This way, I can stay longer in the sauna for my first round (about 30-40 minutes). If I take this approach, I generally only do one more short round after my cold plunge. ### Cold showers and plunges In my experience, you want to take a cold shower or a cold plunge (or both, plunge is better) after the sauna cycle.After you come out of the sauna, immediately jump into cold plunge for a bit, i don't like to stay too long. Some Banya facilities will have a bucket filled with cold water that you can pull with a string to let the water pour over you, pull a couple times. The banyas may also have a cold pool of water into which you can plunge for a bit.  If I’m at my country place, after I get out of the sauna I jump into the cold lake. If it’s winter, I like to roll in the snow, which is satisfying. Some cultures would say that it’s not a real sauna experience unless you roll in at least one foot of snow. After your cold shower or plunge, put on a warm robe and go relax before going back into the sauna. I like to relax for 5-20 minutes, depending on how much time I have. This allows the body’s temperature to decrease slowly. I do not recommend going directly back into the sauna after your cold plunge. If you don’t give yourself enough time after the cold plunge, you will overheat and won’t last very long when you return to the sauna. ### Position There really are no rules here. The way you position yourself in the sauna depends on your mood and preference, and there are many options. For example, you can sauna seated with your legs hanging down or with your knees up. You can lie down if there’s room. My favorite position is to lie down on my back with my legs up against the wall and, assuming the ceiling is low enough, with my feet stretched against the ceiling. This is a great way to stretch the hamstrings (check out stretching under “Sauna Activities”, below). Choosing whether to sit on a higher bencher or lower bench is the best way to control the temperature you experience without adjusting the room temperature itself. You will notice the heat in the sauna increases exponentially every inch you go up. If you are struggling to stay in the sauna but don’t want to get out just yet, try moving down to a lower bench to last a little longer. Lying on the floor is the coolest spot and a great place for kids to start getting exposed to saunas. - - - #### There is no shame in going to lower benches or even the floor, there is only shame in opening the door before 15min - - - ### Getting Steamy Without steam, the sauna would just be a sad, hot oven (I’m looking at you, infrared sauna). The steam in the sauna has many benefits but most importantly it increases the thermal coupling of your body to the air and it feels great. The amount of steam in the sauna is a matter of personal taste. You don’t want to make it into a steam room (remember, steam rooms are NOT saunas). But, you do want the sauna to be very moist. I find that two to four ladles of water in a mid-size sauna every five to seven minutes does the trick. Keep it between 50-60% humidity. I keep a bucket of water in the sauna at all times so that I can continue to ladle water as I shvitz. Make sure to get a wood bucket and a metal ladle with a wooden handle. Wood ladles will crack, and if the handle is metal, it’ll burn you when you grab it. If, when you enter the sauna, it’s already been on for a while, the wood is likely to already be wet and the sauna full of steam, so you may not need to add too much water. However, if you’ve just turned on the sauna and the wood walls are dry, you will need to ladle more water to make the air moist enough. If the sauna is too moist for comfort, open the door and let it dry out a bit (obviously, only do this in a private sauna). Essential oils and even beer can all be added to the water to create scented steam. I recommend starting your sauna with just water, and add the scent as you get going. You can try all sorts of different essential oils. I’ve tried everything from oak and cedar to tangerine and cinnamon (gag) essential oil. In the end, there are really only two oils that are worth it, in my opinion. The first is eucalyptus. I’ve experimented with different types of eucalyptus oil, and the variety you use makes a difference. My favorite is eucalyptus globulus. I also like diluted pine tar oil. When you settle on your essential oil, add a healthy dose of the oil to the ladle filled with water. Never put the oil onto the oven directly. It’ll just burn. In a few Russian facilities, I’ve seen Gray Beards pour Russian beer onto the oven and it was actually quite nice. It’s almost like being in a cozy bakery while you sweat Some people like to place a salt brick or compressed solid blocks in their sauna from time to time. Put the salt block on the stove and pour water over it. The steam takes on a saltiness that feels nice. If a salt block is not available, you can get a cast iron teapot, fill it up with salt water, and place it on top of the stove. And for my most important steam tip, I recommend using the “towel spin”. This is an effective and underrated technique to help circulate steam in the sauna. After creating steam, take your towel above your head and spin it around hard, like a ceiling fan. This movement works like a convection oven and spreads and equalizes the heat and steam throughout the room. It might make the folks sitting lower down in the sauna a little hotter, but that's what they’re there for, isn’t it? ### Hydration Being hydrated is important to having a positive sauna experience. You will lose a lot of your body’s water in the sauna. Ideally, start to hydrate well up to an hour before your sauna. I like to add a pinch of salt to my water to encourage water retention. Do not bring any drinks into the sauna (the exception being a dedicated steam-beer, see above). Have your water or beverage when you’re outside the sauna, resting. If you find you need to drink water inside the sauna in order to cool yourself down, then it’s time for you to get out and allow your body a cool-down. When you’re outside the sauna, don’t immediately down a glass of super cold water because you will cool down your internal body too fast. Personally, I like to drink warm tea after my first two cycles. After my second cycle, I enjoy a beer (pre-keto days), soup, or vodka drink. When non-keto, I do enjoy adult drinks in the cycles. If you are doing a sauna while on a multi-day fast, you need to have water and salt, at a minimum. Otherwise, you will deplete your natural reserve of electrolytes and not be able to think straight. ### Sauna Frequency When it comes to frequency, if you are not in the equatorial heat do it every day. I now do mornings and end of day if I can. so 2x 2-3x cycles. In the summer, living in a hot & humid location, I sauna a lot less frequently. My desire to sauna is greatly diminished because I spend a lot of time in the sun and heat. ### What to wear **Sauna Hat:** I highly recommend wearing a Russian/Finish style wool hat when you’re inside the sauna. It may seem counterintuitive, but wearing a hat keeps your head cooler. An overheated head is not good for your brain. Wearing the hat stops you from overheating and lets you stay longer in the sauna. The temperature in a sauna is significantly hotter the higher in the room you are, and one’s head is at the top of the body (for most people). So protect your brain in style with a felt sauna hat. If you don’t have a felt sauna hat, buy one. They are easily found online. But in the meantime, you can wrap a dry towel around your head. Don’t forget to take your sauna hat off as you relax between cycles so your head can cool down.  **Clothing:** These days, many public saunas will have family days, men-only days, and women-only days. For obvious reasons, you’re only allowed to sauna naked if you’re attending one of the single-sex days. If you’re at home, there’s no good reason to wear shorts or a bathing suit. Sauna naked. It's a lot more pleasant. If you do wear clothing in the sauna, be careful with items with materials like metal or plastic attached. Things like pins, buttons, or string-ends will get very hot and probably burn you. Remember to take off any heat-conductive jewelry and leave your smart watch outside, as the heat will ruin its battery. Don’t wear your robe inside the sauna. A robe is what you wear outside when relaxing or eating. If you wear it inside, you’ll overheat (and look like an idiot). Go ahead and sweat out that body shame robe-free. You can bring a towel into the sauna to sit on, if you want. Shoes or sandals are highly recommended in public facilities. I mean, there are many people walking around wet. Ew. But keep your sandals outside the sauna itself, or on the sauna floor. ### Sauna activities. Don’t overthink it. Sitting in a sauna is activity enough, in my opinion. But there are some sauna activities you can do: **Veniks/Viht beating:** these are bundles of leaves (commonly birch, oak, or eucalyptus) that are pre-soaked in hot water. Someone with both strength and capacity to exert themselves in the heat will beat your whole body with the leaves. This exfoliates your skin and also gets the plant oils to permeate your skin. And it’s very relaxing. If you’re at a sauna facility, don’t just grab any bundle you see lying around - that belongs to someone else and veniks aren’t shared. You have to bring your own or buy them at the front desk. **Stretching:** this is a great activity to do in the sauna, but make sure to go very easy. Your muscles will be super warm and you don’t want to overdo it and hurt yourself. **Exercise or Sex:** your heart better be in good shape if you try out these high intensity activities in the sauna. If you engage in the latter, you better be in your own home sauna. With respect to the former, I think doing some leg-ups can be very satisfying. **Phone use:** If you’re at home, it’s nice to use your sauna time to shit-post on Twitter or read an article, if you feel like it. Just keep your phone close to the colder, lower parts near the floor or it’ll overheat and shut down. You can also place the phone outside of the air vent and play a [podcast! The Bitcoin.review is great ;)](https://bitcoin.review) **Napping:** I don’t recommend this. If you fall asleep or pass out, you will probably die due to overheating or dehydration. **Chatting:** Saunas are great places for conversations (subject to the caveats I address above). Note that nowadays, microphone modules are both very tiny and can withstand high temperatures, so it’s no longer recommended to reenact mafia movie sauna scenes. **Eating and Drinking:** As discussed above, never have food or drink inside the sauna. But when you finish your sauna, take advantage of whatever snacks the facility offers. For Russian joints, the soups, fish roe and dry salty fish snacks are great. Again, don’t eat before your sauna; wait until you’re done. Some places will have bottled salty-ish lake water, and beer seems to be a good source of salts and re-hydration. Vodka drinks are nice sometimes, too. My favorites are vodka with beet juice and horseradish, vodka with pickle juice, or just a chilled shot of Zubrowka (vodka infused with bison grass). Teas are also very enjoyable post-sauna. I prefer non-caffeinated berry teas. Some Banyas even offer free tea to patrons.  ## Ready to Sweat It Out? Thanks to this fantastic guide to sauna, you’re now feeling confident and excited to seek out a solid sauna. So where do you go? ## Where to Find a Sauna **Spas:** Spas are not the best place to have an optimal sauna experience. Saunas at spas are typically not hot enough and spas have annoying staff whose job it is to enforce idiotic rules and practices that prevent you from having a real sauna experience. **Gyms & Hotels:** These are some of the worst places to sauna. For liability reasons, these saunas tend to be too cold and there are often mechanisms that prevent you from raising the temperature. Here, you’ll often see saunas with glass doors, which may look chic, but are inefficient and stupid because they don’t seal properly and leak steam. Gyms and hotels are high traffic areas, so people who don’t know what they are doing are constantly coming and going from the sauna, which, as we discussed, is a sauna no-no. If you still want to try the sauna at your gym or hotel, I recommend going in naked. It’ll deter people from joining you and ruining the little steam you managed to get going. **Traditional bath houses (Banyas):** These usually offer a great experience because they deliver a super hot sauna, good cold baths and plunges, delicious food and drinks, and knowledgeable staff. **Home:** Yes, you can build a great sauna in your own home! You can create a small space in your basement, turn a closet or cold room into a sauna, or just add an outdoor hut or barrel sauna in your backyard. This is the best way for you to control the whole experience and do it often. As with anything, the easier it is to access, the more you will do it. _Build it. They will Come_ Many people have asked me for details about sauna building. If you’re ready to build your own personal home sauna, here are some important considerations. #### Materials Saunas are insulated rooms, most commonly finished with cedar tung and groove slats. Cedar is used because it doesn’t rot with moisture. You don’t want treated wood as it will release all the bad stuff that keeps the wood from rotting into the air when heated. Cedar interior is often placed over a vapor barrier, followed by insulation and then the outer wall. Many outdoor saunas are not insulated. They simply have a single layer of cedar 2x6 planks functioning as both the interior and exterior. Non-insulated saunas need much more heating power in the winter. #### Structure For indoor saunas, you may want to find a bricklayer to build something for you. Traditional facilities often have brick-lined rooms and very large wood-burning stoves. You can buy prefab outdoor saunas, which are often sheds or barrels. After experimenting with both, I’ve concluded that barrel saunas are inferior, even though that’s what I have at my country property. This is because barrels have concave ceilings and inner walls. This means the benches are lower and the curve makes the topmost part of the ceiling (and the hottest part) the furthest from you, or inaccessible. The spinning towel trick really helps in the barrel. When it comes to buying a sauna, go with the most traditional structure possible. They are based on thousands of years of evolution and knowledge. Portable tent saunas are fun, but impractical because you have to set them up before each use. Bench height inside the sauna is important. I think the top-most bench should be very near the ceiling. This way, when you’re lying down, you can use the ceiling to stretch the hamstrings. As a rule of thumb, bench length should allow you to lie down completely. It is also nice to have at least one lower bench for visitors or less intense sauna days.  #### Sauna Ovens There are two main types of sauna ovens: wood burning and electrical (with gas heating being available, but not common). If the location you are building allows for it, go with electrical. It’s practical and easy to get going quickly. This means you will use it more often. Wood burning saunas are romantic and smell great, but it is a lot more work to get a fire going, especially in the winter. Opt for oven sizes that are recommended or above recommended for the size of the sauna. A larger oven means more thermic inertia, more rocks for steam, and therefore less time to warm up the room. Bigger is better. The Scandinavians make the best quality ovens. #### Oven controllers There are two types of temperature control devices: the analog cooking-style or the digital type. I think, due to liability and safety, all ovens have a timer that max out at one hour. The digital oven controllers are fantastic and I have one in the city in my basement sauna. However, you have to consider your environment. For me, temperatures in the winter can reach below -30C and in the summer, over 40C. This massive range can take a toll on outdoor equipment and materials. For this reason, I opted for an analog controller for my outdoor sauna in the country, since the weather will likely ruin the electronics of the digital controller. I would avoid ovens with analog pre-heat timers. They are great in theory, but the implementation is utter garbage. The timer won’t be precise and it’ll just lead to frustration, for example, when you thought you set the oven to start in three hours, but it actually started in two hours and already turned off. #### Important Sauna Gear Windows are nice to have, especially if you have a view to enjoy. Opt for at least a cedar door with a little window. Do not go with modern glass door styles. They are crap. They have gaps, no insulation, and let in too much light. Saunas need thermometers and hygrometers (to measure humidity). The thermometers should be rated for saunas and be visible inside. This is both for safety and bragging rights. I think having an hourglass inside your sauna is a must. Being able to know for sure how long you’ve been inside is important, since your sense of timing inside the sauna may be off depending on the state of your mind and body on a given day. You shouldn’t wear a watch inside the sauna, since it’ll overheat or break. Having a clock visible from the inside is also a good idea, especially if you sauna often and have a wife and kids who you don’t want to leave you. Air circulation is an often-overlooked but important part of a sauna design. Saunas should not have stale air. The best sauna design creates natural “real convection” by placing an air intake under the oven wall and another at the top opposite wall. This allows fresh air to enter the sauna while in use. Be sure to add regulators, since you don’t want to cool the sauna or expel all steam. Without regulators you may get too much or too little air in. With too much air, you may cool the sauna down too much and/or lose too much steam. #### Nice Things to Have Lights are optional but welcome additions. It can be unpleasant to have no lighting at all, especially in an outdoor sauna on a cold, dark night. Lights should be warm-temperature and low power. I recommend an oven light, since they don’t sweat the heat (get it?) and are often low power. Put a baking tray under your oven–thank me later. Wood “pillows” for your head are nice and don’t get sweat-stained and stinky, like a fabric pillow. Keep some extra felt hats near your sauna so when you or your guests forget their hat, you still have easy access to one. I like to keep a couple of essential oils on the floor of the sauna, for easy access. If you keep the oils too high in the sauna, they’ll get too hot and spoil. I place some duck boards over floor tiles in the sauna to prevent cold feet. I also like to keep a small, natural broom inside the sauna to sweep up any dirt or leaves that come into the sauna on people’s feet. ## Final words As you can tell, I have some strong opinions when it comes to the proper way to enjoy a sauna. My hope is that my musings will help you to maximize your own sauna experience.. If you follow this guide, I’m certain you will benefit from and enjoy the sauna as much as I do and, just maybe, you too will develop your own strongly held opinions that will most definitely offend me. ### Thanks for reading, please close the F-ing door. ps, you can get a Bitcoin Honey Badger Sauna Hat [here](https://store.coinkite.com/store/ht-sauna) - EOF @ eac63075:b4988b48
2024-10-10 18:12:38Companies like Meta (formerly Facebook) and Twitter (now X) control platforms that have become the main channels of communication for millions of people worldwide. At the center of this discussion are figures like Mark Zuckerberg and Elon Musk, whose recent actions raise serious questions about freedom of speech, censorship, and political manipulation. --- <https://fountain.fm/episode/VzJItfySZ8z6417prHyD> --- Recently, a public letter written by Mark Zuckerberg revealed how the U.S. government, under Joe Biden’s administration, pressured Facebook to censor information during the COVID-19 pandemic. The controversy involves, among other topics, the censorship of content related to Biden’s son, Hunter Biden, during the height of the laptop scandal. This revelation raises questions about the role these platforms play in spreading or withholding information, as well as the direct impact this has on democracy. ## **Meta and Censorship: Zuckerberg's Letter** In his letter, Zuckerberg admitted that Facebook was pressured by the Biden administration to suppress information about the pandemic and the Hunter Biden case, something he now claims to regret. This has sparked heated debate about how far social media should go in yielding to governmental pressure. Many see this as a threat to freedom of speech, while others argue that this censorship was necessary to control misinformation. The issue here is not just about government pressure, but the fact that Facebook, as a global platform with billions of users, holds unparalleled power to shape narratives. When a platform decides what is “acceptable” or “truthful,” it directly influences public perception and opinion formation, especially during critical moments like an election. Zuckerberg, in his letter, seems to be trying to salvage his image, but the damage has already been done. The admission that Facebook collaborated with the government to suppress certain information raises doubts about the platform’s impartiality and its commitment to free speech. ## **Elon Musk and Free Speech on X** Meanwhile, Elon Musk, now in control of Twitter, renamed X, has promised to transform the platform into a space for free expression. However, the reality seems more complex. Musk claims that X should be a place where all voices can be heard, regardless of political or ideological alignment. Yet, this promise has proven difficult to fulfill in practice. X continues to ban users and censor content, especially in countries with authoritarian governments like India and Turkey. This creates a dichotomy: on the one hand, Musk advocates for unrestricted free speech, but on the other, he complies with censorship requests from these regimes. This raises questions about Musk’s true intentions and the extent to which he is willing to uphold his principles when the platform faces international pressure. Moreover, Musk has used X as a political platform, especially in support of former President Donald Trump. The reinstatement of Trump’s account, banned during the Capitol insurrection, has raised further suspicions that Musk is turning X into a tool of political power. For many, this represents a significant risk to the neutrality of digital platforms. ## **The Cambridge Analytica Scandal and the Risk of Political Manipulation** The discussion of censorship and free speech on social media brings up a case that shocked the world a few years ago: the Cambridge Analytica scandal. In 2015, this British company was accused of using personal data from millions of Facebook users to manipulate elections, including the Brexit referendum and Donald Trump’s 2016 presidential election. Although Cambridge Analytica was dissolved after the scandal, its legacy remains. Big Tech companies still have access to vast amounts of user data, and the power this grants them is alarming. Companies like Meta and X could, in theory, directly influence election outcomes by manipulating algorithms to promote certain narratives or suppress others. This scenario raises crucial questions: to what extent can we trust these platforms to act impartially? Are they truly committed to free speech, or are they using their power to shape the political future of the world according to their own interests? ## **The Pablo Marçal Case and Manipulation in Brazil** In Brazil, a recent example that illustrates the complexity of the relationship between social media and political power is the case of coach Pablo Marçal. Marçal, who built a considerable following, became involved in controversies related to using his influence to manipulate public opinion. Recently, it was revealed that X hired the renowned law firm Pinheiro Neto to defend Marçal’s continued presence on the platform, even after controversies. This move raises concerns about the selective enforcement of social media’s own rules. Why are some influencers protected while others are summarily banned? Marçal’s influence, particularly among conservative voters in Brazil, is undeniable, and the public defense of his account on X suggests that more is at stake than just free speech. ## **The Future of Social Media and Democracy** What we are witnessing is the rise of a new era where social media plays a central role in global politics. Control over the flow of information lies in the hands of a few giant companies, and the decisions of their leaders—whether Mark Zuckerberg, Elon Musk, or others—can have a profound impact on elections, governments, and democracies. This raises legitimate concerns about the future of democracy in a world where private platforms have the power to control public discourse. Big Tech censorship, often disguised as “misinformation control,” can easily become a tool for manipulation. For citizens, this means being vigilant and critical about the information they receive on social media. Freedom of expression must be defended, but we also need to question who is behind these platforms and what their true motivations are. Trust in social media is at stake, and the future of democracy may depend on how we decide to deal with this unprecedented power. ## **Conclusion** Recent revelations about Zuckerberg’s involvement in censorship and Musk’s use of X to promote a political agenda highlight the urgent need for transparency in social media platforms. As these companies become increasingly influential in the global political arena, the public must be aware of the risks and actively engage in the debate about the future of free speech and democracy.
@ eac63075:b4988b48
2024-10-10 18:12:38Companies like Meta (formerly Facebook) and Twitter (now X) control platforms that have become the main channels of communication for millions of people worldwide. At the center of this discussion are figures like Mark Zuckerberg and Elon Musk, whose recent actions raise serious questions about freedom of speech, censorship, and political manipulation. --- <https://fountain.fm/episode/VzJItfySZ8z6417prHyD> --- Recently, a public letter written by Mark Zuckerberg revealed how the U.S. government, under Joe Biden’s administration, pressured Facebook to censor information during the COVID-19 pandemic. The controversy involves, among other topics, the censorship of content related to Biden’s son, Hunter Biden, during the height of the laptop scandal. This revelation raises questions about the role these platforms play in spreading or withholding information, as well as the direct impact this has on democracy. ## **Meta and Censorship: Zuckerberg's Letter** In his letter, Zuckerberg admitted that Facebook was pressured by the Biden administration to suppress information about the pandemic and the Hunter Biden case, something he now claims to regret. This has sparked heated debate about how far social media should go in yielding to governmental pressure. Many see this as a threat to freedom of speech, while others argue that this censorship was necessary to control misinformation. The issue here is not just about government pressure, but the fact that Facebook, as a global platform with billions of users, holds unparalleled power to shape narratives. When a platform decides what is “acceptable” or “truthful,” it directly influences public perception and opinion formation, especially during critical moments like an election. Zuckerberg, in his letter, seems to be trying to salvage his image, but the damage has already been done. The admission that Facebook collaborated with the government to suppress certain information raises doubts about the platform’s impartiality and its commitment to free speech. ## **Elon Musk and Free Speech on X** Meanwhile, Elon Musk, now in control of Twitter, renamed X, has promised to transform the platform into a space for free expression. However, the reality seems more complex. Musk claims that X should be a place where all voices can be heard, regardless of political or ideological alignment. Yet, this promise has proven difficult to fulfill in practice. X continues to ban users and censor content, especially in countries with authoritarian governments like India and Turkey. This creates a dichotomy: on the one hand, Musk advocates for unrestricted free speech, but on the other, he complies with censorship requests from these regimes. This raises questions about Musk’s true intentions and the extent to which he is willing to uphold his principles when the platform faces international pressure. Moreover, Musk has used X as a political platform, especially in support of former President Donald Trump. The reinstatement of Trump’s account, banned during the Capitol insurrection, has raised further suspicions that Musk is turning X into a tool of political power. For many, this represents a significant risk to the neutrality of digital platforms. ## **The Cambridge Analytica Scandal and the Risk of Political Manipulation** The discussion of censorship and free speech on social media brings up a case that shocked the world a few years ago: the Cambridge Analytica scandal. In 2015, this British company was accused of using personal data from millions of Facebook users to manipulate elections, including the Brexit referendum and Donald Trump’s 2016 presidential election. Although Cambridge Analytica was dissolved after the scandal, its legacy remains. Big Tech companies still have access to vast amounts of user data, and the power this grants them is alarming. Companies like Meta and X could, in theory, directly influence election outcomes by manipulating algorithms to promote certain narratives or suppress others. This scenario raises crucial questions: to what extent can we trust these platforms to act impartially? Are they truly committed to free speech, or are they using their power to shape the political future of the world according to their own interests? ## **The Pablo Marçal Case and Manipulation in Brazil** In Brazil, a recent example that illustrates the complexity of the relationship between social media and political power is the case of coach Pablo Marçal. Marçal, who built a considerable following, became involved in controversies related to using his influence to manipulate public opinion. Recently, it was revealed that X hired the renowned law firm Pinheiro Neto to defend Marçal’s continued presence on the platform, even after controversies. This move raises concerns about the selective enforcement of social media’s own rules. Why are some influencers protected while others are summarily banned? Marçal’s influence, particularly among conservative voters in Brazil, is undeniable, and the public defense of his account on X suggests that more is at stake than just free speech. ## **The Future of Social Media and Democracy** What we are witnessing is the rise of a new era where social media plays a central role in global politics. Control over the flow of information lies in the hands of a few giant companies, and the decisions of their leaders—whether Mark Zuckerberg, Elon Musk, or others—can have a profound impact on elections, governments, and democracies. This raises legitimate concerns about the future of democracy in a world where private platforms have the power to control public discourse. Big Tech censorship, often disguised as “misinformation control,” can easily become a tool for manipulation. For citizens, this means being vigilant and critical about the information they receive on social media. Freedom of expression must be defended, but we also need to question who is behind these platforms and what their true motivations are. Trust in social media is at stake, and the future of democracy may depend on how we decide to deal with this unprecedented power. ## **Conclusion** Recent revelations about Zuckerberg’s involvement in censorship and Musk’s use of X to promote a political agenda highlight the urgent need for transparency in social media platforms. As these companies become increasingly influential in the global political arena, the public must be aware of the risks and actively engage in the debate about the future of free speech and democracy. @ c69b71dc:426ba763
2024-10-10 09:05:29## Chef's notes This cashew blue cheese is a true plant-based delight, delivering the rich, tangy flavours you’d expect from traditional blue cheeses like Roquefort or Gorgonzola. The fermentation process, with the help of «Penicillium Roqueforti», creates a beautifully marbled, creamy cheese that’s both bold and complex. It’s a labor of love that rewards your patience with an unforgettable vegan cheese experience! Whether enjoyed on crackers, in salads, or simply on its own, this cheese will elevate any dish with its unique flavour profile. Note 1: For this recipe you need parchment paper, a potent blender, glass jars with lid and two cheesecloths. Note 2: Always use very clean tools, and avoid touching with your fingers or tasting with them while working on the cheese! ## Details - ⏲️ Prep time: 4-5 weeks - 🍳 Cook time: 0 - 🍽️ Servings: Two small cheese loaves (2x 10-12 cm diameter) ## Ingredients - 300g raw cashews - 3 tbsp water - 3 tbsp kefir, kombucha or rejuvelac - 2 tbsp coconut oil (raw, unrefined) - 1-4 capsules vegan probiotics - 1/2 tsp Himalayan salt (iodine-free, no additives) - 1/16 tsp «Penicillium Roqueforti» (blue cheese mold culture) ## Directions 1. Day 1: Soak 300g of cashews overnight in water. 2. Day 2: Rinse the soaked cashews thoroughly and let them drain well. 3. In a high-speed blender, combine the cashews, 3 tbsp of water, 3 tbsp kefir or rejuvelac, and 2 tbsp coconut oil. Blend until the mixture is smooth and creamy. 4. Add 1-4 capsules of vegan probiotics, 1/2 tsp Himalayan salt (free of iodine and additives), and blend again briefly. 5. Add a pinch (about 1/16 tsp) of «Penicillium Roqueforti» powder (blue cheese culture) and give it another quick mix. 6. Transfer the cashew mixture to a glass container, leaving the lid lightly on top (do not seal it completely) and store in a warm place, ideally in your kitchen, for 24 hours to ferment. 7. Day 3: Divide the fermented cashew mixture into two smaller glass containers lined with cheesecloth. Press the mixture down firmly to eliminate air pockets. 8. Store in a cool place (12-14°C / 53-57°F), ideally in a wine fridge. 9. Day 4: Remove the cheese from the containers, take off the cheesecloth, and turn the cheese onto parchment paper. 10. Sprinkle salt all over the cheese, ensuring it is evenly coated. 11. Cover the cheese with larger glass bowls, ensuring that air can flow from underneath, and return to the wine fridge or the cool storage area. 12. Days 4-7: Turn the cheese daily onto fresh parchment paper to maintain its texture. 13. Day 7 or 8: Pierce the cheese with a thicker wooden skewer to create holes, allowing oxygen to reach the center, encouraging the blue mold to grow throughout the cheese, not just on the surface. 14. Alternatively, crumble the cheese completely and then press it back into shape to ensure oxygen distribution. 15. Days 8 toaround 12 or 15: Once the blue mold has fully developed around and inside the cheese, wrap the cheese in parchment paper, place it in a wooden cheese box, and then wrap it in a cloth bag. 16. Transfer to a regular fridge to age for another 2-3 weeks or even several months, depending on your desired strength of flavour.
@ c69b71dc:426ba763
2024-10-10 09:05:29## Chef's notes This cashew blue cheese is a true plant-based delight, delivering the rich, tangy flavours you’d expect from traditional blue cheeses like Roquefort or Gorgonzola. The fermentation process, with the help of «Penicillium Roqueforti», creates a beautifully marbled, creamy cheese that’s both bold and complex. It’s a labor of love that rewards your patience with an unforgettable vegan cheese experience! Whether enjoyed on crackers, in salads, or simply on its own, this cheese will elevate any dish with its unique flavour profile. Note 1: For this recipe you need parchment paper, a potent blender, glass jars with lid and two cheesecloths. Note 2: Always use very clean tools, and avoid touching with your fingers or tasting with them while working on the cheese! ## Details - ⏲️ Prep time: 4-5 weeks - 🍳 Cook time: 0 - 🍽️ Servings: Two small cheese loaves (2x 10-12 cm diameter) ## Ingredients - 300g raw cashews - 3 tbsp water - 3 tbsp kefir, kombucha or rejuvelac - 2 tbsp coconut oil (raw, unrefined) - 1-4 capsules vegan probiotics - 1/2 tsp Himalayan salt (iodine-free, no additives) - 1/16 tsp «Penicillium Roqueforti» (blue cheese mold culture) ## Directions 1. Day 1: Soak 300g of cashews overnight in water. 2. Day 2: Rinse the soaked cashews thoroughly and let them drain well. 3. In a high-speed blender, combine the cashews, 3 tbsp of water, 3 tbsp kefir or rejuvelac, and 2 tbsp coconut oil. Blend until the mixture is smooth and creamy. 4. Add 1-4 capsules of vegan probiotics, 1/2 tsp Himalayan salt (free of iodine and additives), and blend again briefly. 5. Add a pinch (about 1/16 tsp) of «Penicillium Roqueforti» powder (blue cheese culture) and give it another quick mix. 6. Transfer the cashew mixture to a glass container, leaving the lid lightly on top (do not seal it completely) and store in a warm place, ideally in your kitchen, for 24 hours to ferment. 7. Day 3: Divide the fermented cashew mixture into two smaller glass containers lined with cheesecloth. Press the mixture down firmly to eliminate air pockets. 8. Store in a cool place (12-14°C / 53-57°F), ideally in a wine fridge. 9. Day 4: Remove the cheese from the containers, take off the cheesecloth, and turn the cheese onto parchment paper. 10. Sprinkle salt all over the cheese, ensuring it is evenly coated. 11. Cover the cheese with larger glass bowls, ensuring that air can flow from underneath, and return to the wine fridge or the cool storage area. 12. Days 4-7: Turn the cheese daily onto fresh parchment paper to maintain its texture. 13. Day 7 or 8: Pierce the cheese with a thicker wooden skewer to create holes, allowing oxygen to reach the center, encouraging the blue mold to grow throughout the cheese, not just on the surface. 14. Alternatively, crumble the cheese completely and then press it back into shape to ensure oxygen distribution. 15. Days 8 toaround 12 or 15: Once the blue mold has fully developed around and inside the cheese, wrap the cheese in parchment paper, place it in a wooden cheese box, and then wrap it in a cloth bag. 16. Transfer to a regular fridge to age for another 2-3 weeks or even several months, depending on your desired strength of flavour. @ aa8de34f:a6ffe696
2024-10-09 21:56:39\`\`\` Technion - Israel Institute of Technology\ Foundations of Quantum Mechanics\ Date: 2024-08-25 Submitted by: Max Peter \`\`\` \# Quantum Mechanics and Consciousness: Strange Bedfellows *"Does consciousness play a special role in quantum mechanics?"* ## Abstract Could there be a connection between quantum mechanics and consciousness? This Question has fascinated scholars for years. Some believe that consciousness plays a role in how we interpret quantum theory. This essay explores whether consciousness is a fundamental component of quantum mechanics, addressing both the "hard problem" of consciousness and the various interpretations of quantum theory. By critically analyzing arguments from prominent figures like David Chalmers and Barry Loewer, the essay argues that while consciousness presents a significant challenge in understanding reality, current quantum theories may not provide the final answers. Instead, the *"hard problem"* of consciousness could be the unresolved issue that quantum mechanics needs to address, making it the *"elephant in the room"* that scientists often avoid. ## 1. Introduction The relationship between quantum mechanics and consciousness is one of the most intriguing and contentious debates in modern science and philosophy. Quantum mechanics, the physics of the very small, has upended our classical understanding of the universe, introducing phenomena such as superposition, entanglement, and wavefunction collapse that defy intuition. Simultaneously, consciousness - the subjective experience of being aware - remains one of the most profound mysteries in science, famously described by David Chalmers (1995) as the "hard problem." The intersection of these two enigmatic fields has led to the proposal that consciousness may play a special role in quantum mechanics, particularly in the process of wavefunction collapse, where observation seems to determine physical reality. This essay explores the question: Does consciousness play a special role in quantum mechanics? Advocates of this idea, such as Wigner and Stapp, have argued that consciousness is not merely an observer in quantum mechanics but an active participant that influences quantum events. However, this view is not without its critics. Many physicists and philosophers, including Barry Loewer, argue that connecting consciousness to quantum mechanics is speculative and unsupported by empirical evidence. Despite these criticisms, the possibility that consciousness could be the "elephant in the room" that quantum mechanics needs to address remains an open question. This essay will explore the various interpretations of quantum mechanics that engage with or avoid the issue of consciousness and will argue that the hard problem of consciousness is maybe a vital, yet often ignored, aspect of a better understanding of quantum physics. ## 2. The Basics of Quantum Mechanics Quantum mechanics is the branch of physics that deals with the behavior of particles at the smallest scale - atoms and subatomic particles. It is governed by principles that are vastly different from the deterministic laws of classical physics. One of the foundational concepts of quantum mechanics is the wavefunction, a mathematical function that describes the probabilities of a particle's properties, such as position and momentum. Unlike in classical mechanics, where a particle has a definite position and momentum, in quantum mechanics, these properties are described by a probability distribution. One of the most famous principles of quantum mechanics is superposition, which states that a particle can exist in multiple states simultaneously until it is observed. This is famously illustrated by Schrödinger's cat thought experiment, where a cat in a box is simultaneously alive and dead until the box is opened, and an observation is made. Another critical concept is entanglement, where particles become linked, so the state of one particle instantaneously affects the state of another, regardless of the distance between them. The wavefunction collapse is perhaps the most perplexing aspect of quantum mechanics. When a quantum system is observed, the wavefunction collapses, and the system settles into a definite state. This raises the question: What causes the wavefunction to collapse? Is it the act of measurement itself, or does consciousness play a role in this process? The measurement problem in quantum mechanics has led some to propose that consciousness is necessary for wavefunction collapse, thus connecting the two fields in a profound way. ## 3. The Hard Problem of Consciousness David Chalmers (1995) famously distinguished between the "easy" and "hard" problems of consciousness. The easy problems involve explaining the cognitive functions and processes that underlie perception, memory, and behavior. These problems, while challenging, are considered solvable through the standard methods of cognitive science and neuroscience. The hard problem, on the other hand, is the problem of subjective experience - why and how physical processes in the brain give rise to the rich inner life of sensation, emotion, and awareness. This subjective aspect of consciousness, also known as qualia (Latin “of what sort”), remains resistant to reductive explanation. Chalmers (1995) argues that the hard problem of consciousness cannot be solved by merely explaining the functions of the brain. There is a gap between physical processes and the experience of those processes - a gap that traditional science struggles to bridge. This has led some theorists to propose that consciousness might be fundamental to the universe, rather than a byproduct of physical processes. This idea has significant implications for quantum mechanics, particularly in the context of the measurement problem. If consciousness is indeed fundamental, it may play a direct role in the collapse of the wavefunction, linking the hard problem of consciousness with the mysteries of quantum mechanics. ## 4. Consciousness and Quantum Mechanics The idea that consciousness plays a special role in quantum mechanics is most closely associated with the Consciousness Collapse Proposal (CCP). This theory suggests that the act of observation by a conscious being is what causes the wavefunction to collapse into a definite state. This view was championed by physicists like Eugene Wigner and Henry Stapp, who argued that consciousness must be integrated into our understanding of quantum mechanics. According to Wigner, consciousness is the ultimate cause of the wavefunction collapse, implying that the physical world does not exist in a definite state until it is observed by a conscious mind (Wigner, 1967). However, the CCP is not without its critics. Barry Loewer (2003) argues that the connection between consciousness and quantum mechanics is speculative and lacks empirical support. He contends that while quantum mechanics may involve strange and counterintuitive phenomena, there is no evidence that consciousness plays a direct role in these processes. Loewer suggests that alternative interpretations of quantum mechanics, such as the Ghirardi-Rimini-Weber (GRW) theory and Bohmian mechanics, offer explanations for wavefunction collapse that do not require the involvement of consciousness (Loewer, 2003). Despite these criticisms, the idea that consciousness could be fundamental to quantum mechanics remains a compelling possibility. The CCP aligns with the notion that consciousness is not just an epiphenomenon of brain activity but a fundamental aspect of reality. This perspective challenges the materialist view that physical processes alone are sufficient to explain all phenomena, including consciousness. Instead, it suggests that consciousness might be the key to resolving the mysteries of quantum mechanics. ## 5. The Elephant in the Room: The Hard Problem of Consciousness in Quantum Mechanics The central thesis of this section is that the hard problem of consciousness, as articulated by David Chalmers (1995), represents an unresolved issue in the interpretation of quantum mechanics, and may be the "elephant in the room" that most scientific theories attempt to avoid. While many physicists adopt materialist interpretations of quantum mechanics that sidestep the issue of consciousness, it is increasingly difficult to ignore the possibility that consciousness might play a fundamental role in the behaviour of quantum systems. This section will argue that the hard problem of consciousness is not just a philosophical curiosity but a crucial component in understanding the true nature of quantum mechanics. ### Consciousness as a Fundamental Aspect of Reality The hard problem of consciousness refers to the challenge of explaining how and why physical processes in the brain give rise to subjective experience—what it feels like to perceive, think, and be aware. Chalmers (1995) argues that the hard problem is distinct from the "easy" problems of explaining cognitive functions and behaviours because it involves the subjective nature of experience, which cannot be fully captured by a purely physical explanation. This problem is central to the question of whether consciousness plays a role in quantum mechanics because it challenges the materialist assumption that everything can be explained in terms of physical processes. One argument in favour of consciousness playing a fundamental role in quantum mechanics is that it may help solve the measurement problem—the question of why and how the wavefunction collapses when a measurement is made. According to the Consciousness Collapse Proposal (CCP), the collapse of the wavefunction occurs when a conscious observer interacts with the system, suggesting that consciousness is a necessary component of reality. This idea challenges the traditional view of quantum mechanics as a purely objective, observer-independent theory and implies that consciousness is more than just a byproduct of physical processes (Stapp, 1993). In this view, consciousness is not simply an epiphenomenon of the brain but a fundamental aspect of reality that interacts with the physical world in a way that science has yet to fully understand. This perspective aligns with certain interpretations of quantum mechanics, such as the von Neumann-Wigner interpretation, which posits that consciousness plays an active role in the collapse of the wavefunction. While this interpretation remains controversial, it highlights the possibility that consciousness could be integral to the functioning of the universe at a fundamental level. ### Avoidance of the Hard Problem in Mainstream Science Despite the compelling nature of the hard problem, mainstream scientific interpretations of quantum mechanics often avoid addressing consciousness directly. For example, the Many Worlds Interpretation (MWI) of quantum mechanics sidesteps the issue of wavefunction collapse altogether by proposing that all possible outcomes of a quantum measurement exist simultaneously in parallel worlds. In this framework, there is no need to invoke consciousness as a factor in determining the outcome of a quantum event, as every possible outcome is realized in some branch of the multiverse (Everett, 1957). While MWI elegantly avoids the problem of collapse, it does so at the cost of ignoring the role of consciousness, which remains unexplained. Similarly, the Ghirardi-Rimini-Weber (GRW) theory offers an objective collapse model that introduces spontaneous collapses of the wavefunction, independent of observation or consciousness. This theory attempts to solve the measurement problem without invoking consciousness by suggesting that wavefunctions collapse randomly after a certain threshold is reached (Ghirardi, Rimini, & Weber, 1986). Although GRW provides a mathematically consistent solution to the measurement problem, it does not address the hard problem of consciousness, leaving the nature of subjective experience untouched. These interpretations reflect a broader tendency in science to focus on solving the technical aspects of quantum mechanics while avoiding the deeper philosophical questions about consciousness. This approach is understandable, given that the hard problem of consciousness is notoriously difficult to address within the framework of materialist science. However, by sidestepping the issue, these interpretations may be missing a crucial piece of the puzzle. If consciousness is indeed fundamental to the collapse of the wavefunction, as proponents of the CCP suggest, then any interpretation that ignores consciousness is inherently incomplete. ### The Case for Addressing Consciousness in Quantum Mechanics Given the limitations of current interpretations of quantum mechanics, there is a strong case to be made for addressing the hard problem of consciousness directly. One of the key challenges in integrating consciousness into quantum mechanics is the lack of empirical evidence linking consciousness to wavefunction collapse. Critics like Barry Loewer (2003) argue that the CCP is speculative and lacks the rigorous experimental support needed to be taken seriously as a scientific theory. This criticism is valid, as science requires empirical validation to support theoretical claims. However, the absence of empirical evidence does not necessarily invalidate the idea that consciousness could play a role in quantum mechanics. The lack of direct evidence may simply reflect the limitations of current experimental methods, which are not yet sophisticated enough to test the relationship between consciousness and quantum phenomena. Furthermore, the hard problem of consciousness remains unresolved by conventional science, suggesting that new approaches may be needed to explore the connection between consciousness and the physical world. In response to critics, proponents of the CCP could argue that quantum mechanics itself has a long history of challenging conventional notions of reality. The very existence of phenomena like entanglement and superposition defies classical logic and suggests that our understanding of the universe is incomplete. If consciousness is indeed fundamental to the fabric of reality, then it is possible that it plays a role in these quantum phenomena in ways that we do not yet fully understand. Rather than dismissing the CCP as speculative, it may be more productive to consider it as a potential avenue for further research, one that could ultimately lead to a deeper understanding of both consciousness and quantum mechanics. ## 6. Personal Viewpoint: Consciousness as a Vital Component in Quantum Mechanics In my view, the hard problem of consciousness is not just an interesting philosophical challenge but a vital issue that must be addressed if we are to fully understand quantum mechanics. The reluctance of many scientists to engage with the hard problem is understandable, given the difficulty of the question and the lack of empirical evidence. However, this avoidance may be preventing us from making significant progress in understanding the true nature of reality. I believe that the hard problem of consciousness represents a fundamental gap in our understanding of the universe - one that cannot be ignored if we are to develop a complete theory of quantum mechanics. While alternative interpretations like the GRW theory and the Many Worlds Interpretation offer solutions to the technical problems of quantum mechanics, they do so by avoiding the deeper question of consciousness. This approach, while pragmatic, may ultimately prove to be a dead end if consciousness is indeed integral to the behaviour of quantum systems. Addressing the hard problem of consciousness in the context of quantum mechanics requires a willingness to think beyond the current boundaries of science and to explore new theoretical frameworks that integrate consciousness into our understanding of the physical world. This may involve revisiting ideas like the Consciousness Collapse Proposal or developing entirely new theories that link consciousness with quantum phenomena in ways that we have not yet imagined. At the same time, it is important to approach this question with a critical and balanced perspective. While the idea that consciousness plays a role in quantum mechanics is intriguing, it is essential to remain open to alternative explanations and to demand rigorous empirical evidence to support any claims. The history of science is filled with theories that seemed promising but ultimately proved to be incorrect, and we must be careful not to fall into the trap of speculation without evidence. ## Conclusion In Summary, I believe that the hard problem of consciousness is the *"elephant in the room"* that quantum mechanics needs to address. While traditional interpretations of quantum theory have tried to solve the measurement problem without involving consciousness it might be ignoring a part of reality. By blending the matter of consciousness into quantum mechanics we could potentially gain a comprehensive view of the universe - one that appreciates both the enigmatic nature of subjective experiences and the elegant mathematics of some quantum mechanics theories. Even though this viewpoint is speculative and needs investigation it presents a glimpse into a future where consciousness and quantum mechanics are seen as interconnected elements of existence. ### References \- CHALMERS, D. J. (1995). FACING UP TO THE PROBLEM OF CONSCIOUSNESS. JOURNAL OF CONSCIOUSNESS STUDIES, 2(3), 200-219. \- EVERETT, H. (1957). “RELATIVE STATE” FORMULATION OF QUANTUM MECHANICS. REVIEWS OF MODERN PHYSICS, 29(3), 454-462. \- GHIRARDI, G. C., RIMINI, A., & WEBER, T. (1986). UNIFIED DYNAMICS FOR MICROSCOPIC AND MACROSCOPIC SYSTEMS. PHYSICAL REVIEW D, 34(2), 470-491. \- LOEWER, B. (2003). CONSCIOUSNESS AND QUANTUM THEORY: STRANGE BEDFELLOWS. \- STAPP, H. P. (1993). MIND, MATTER, AND QUANTUM MECHANICS. SPRINGER.
@ aa8de34f:a6ffe696
2024-10-09 21:56:39\`\`\` Technion - Israel Institute of Technology\ Foundations of Quantum Mechanics\ Date: 2024-08-25 Submitted by: Max Peter \`\`\` \# Quantum Mechanics and Consciousness: Strange Bedfellows *"Does consciousness play a special role in quantum mechanics?"* ## Abstract Could there be a connection between quantum mechanics and consciousness? This Question has fascinated scholars for years. Some believe that consciousness plays a role in how we interpret quantum theory. This essay explores whether consciousness is a fundamental component of quantum mechanics, addressing both the "hard problem" of consciousness and the various interpretations of quantum theory. By critically analyzing arguments from prominent figures like David Chalmers and Barry Loewer, the essay argues that while consciousness presents a significant challenge in understanding reality, current quantum theories may not provide the final answers. Instead, the *"hard problem"* of consciousness could be the unresolved issue that quantum mechanics needs to address, making it the *"elephant in the room"* that scientists often avoid. ## 1. Introduction The relationship between quantum mechanics and consciousness is one of the most intriguing and contentious debates in modern science and philosophy. Quantum mechanics, the physics of the very small, has upended our classical understanding of the universe, introducing phenomena such as superposition, entanglement, and wavefunction collapse that defy intuition. Simultaneously, consciousness - the subjective experience of being aware - remains one of the most profound mysteries in science, famously described by David Chalmers (1995) as the "hard problem." The intersection of these two enigmatic fields has led to the proposal that consciousness may play a special role in quantum mechanics, particularly in the process of wavefunction collapse, where observation seems to determine physical reality. This essay explores the question: Does consciousness play a special role in quantum mechanics? Advocates of this idea, such as Wigner and Stapp, have argued that consciousness is not merely an observer in quantum mechanics but an active participant that influences quantum events. However, this view is not without its critics. Many physicists and philosophers, including Barry Loewer, argue that connecting consciousness to quantum mechanics is speculative and unsupported by empirical evidence. Despite these criticisms, the possibility that consciousness could be the "elephant in the room" that quantum mechanics needs to address remains an open question. This essay will explore the various interpretations of quantum mechanics that engage with or avoid the issue of consciousness and will argue that the hard problem of consciousness is maybe a vital, yet often ignored, aspect of a better understanding of quantum physics. ## 2. The Basics of Quantum Mechanics Quantum mechanics is the branch of physics that deals with the behavior of particles at the smallest scale - atoms and subatomic particles. It is governed by principles that are vastly different from the deterministic laws of classical physics. One of the foundational concepts of quantum mechanics is the wavefunction, a mathematical function that describes the probabilities of a particle's properties, such as position and momentum. Unlike in classical mechanics, where a particle has a definite position and momentum, in quantum mechanics, these properties are described by a probability distribution. One of the most famous principles of quantum mechanics is superposition, which states that a particle can exist in multiple states simultaneously until it is observed. This is famously illustrated by Schrödinger's cat thought experiment, where a cat in a box is simultaneously alive and dead until the box is opened, and an observation is made. Another critical concept is entanglement, where particles become linked, so the state of one particle instantaneously affects the state of another, regardless of the distance between them. The wavefunction collapse is perhaps the most perplexing aspect of quantum mechanics. When a quantum system is observed, the wavefunction collapses, and the system settles into a definite state. This raises the question: What causes the wavefunction to collapse? Is it the act of measurement itself, or does consciousness play a role in this process? The measurement problem in quantum mechanics has led some to propose that consciousness is necessary for wavefunction collapse, thus connecting the two fields in a profound way. ## 3. The Hard Problem of Consciousness David Chalmers (1995) famously distinguished between the "easy" and "hard" problems of consciousness. The easy problems involve explaining the cognitive functions and processes that underlie perception, memory, and behavior. These problems, while challenging, are considered solvable through the standard methods of cognitive science and neuroscience. The hard problem, on the other hand, is the problem of subjective experience - why and how physical processes in the brain give rise to the rich inner life of sensation, emotion, and awareness. This subjective aspect of consciousness, also known as qualia (Latin “of what sort”), remains resistant to reductive explanation. Chalmers (1995) argues that the hard problem of consciousness cannot be solved by merely explaining the functions of the brain. There is a gap between physical processes and the experience of those processes - a gap that traditional science struggles to bridge. This has led some theorists to propose that consciousness might be fundamental to the universe, rather than a byproduct of physical processes. This idea has significant implications for quantum mechanics, particularly in the context of the measurement problem. If consciousness is indeed fundamental, it may play a direct role in the collapse of the wavefunction, linking the hard problem of consciousness with the mysteries of quantum mechanics. ## 4. Consciousness and Quantum Mechanics The idea that consciousness plays a special role in quantum mechanics is most closely associated with the Consciousness Collapse Proposal (CCP). This theory suggests that the act of observation by a conscious being is what causes the wavefunction to collapse into a definite state. This view was championed by physicists like Eugene Wigner and Henry Stapp, who argued that consciousness must be integrated into our understanding of quantum mechanics. According to Wigner, consciousness is the ultimate cause of the wavefunction collapse, implying that the physical world does not exist in a definite state until it is observed by a conscious mind (Wigner, 1967). However, the CCP is not without its critics. Barry Loewer (2003) argues that the connection between consciousness and quantum mechanics is speculative and lacks empirical support. He contends that while quantum mechanics may involve strange and counterintuitive phenomena, there is no evidence that consciousness plays a direct role in these processes. Loewer suggests that alternative interpretations of quantum mechanics, such as the Ghirardi-Rimini-Weber (GRW) theory and Bohmian mechanics, offer explanations for wavefunction collapse that do not require the involvement of consciousness (Loewer, 2003). Despite these criticisms, the idea that consciousness could be fundamental to quantum mechanics remains a compelling possibility. The CCP aligns with the notion that consciousness is not just an epiphenomenon of brain activity but a fundamental aspect of reality. This perspective challenges the materialist view that physical processes alone are sufficient to explain all phenomena, including consciousness. Instead, it suggests that consciousness might be the key to resolving the mysteries of quantum mechanics. ## 5. The Elephant in the Room: The Hard Problem of Consciousness in Quantum Mechanics The central thesis of this section is that the hard problem of consciousness, as articulated by David Chalmers (1995), represents an unresolved issue in the interpretation of quantum mechanics, and may be the "elephant in the room" that most scientific theories attempt to avoid. While many physicists adopt materialist interpretations of quantum mechanics that sidestep the issue of consciousness, it is increasingly difficult to ignore the possibility that consciousness might play a fundamental role in the behaviour of quantum systems. This section will argue that the hard problem of consciousness is not just a philosophical curiosity but a crucial component in understanding the true nature of quantum mechanics. ### Consciousness as a Fundamental Aspect of Reality The hard problem of consciousness refers to the challenge of explaining how and why physical processes in the brain give rise to subjective experience—what it feels like to perceive, think, and be aware. Chalmers (1995) argues that the hard problem is distinct from the "easy" problems of explaining cognitive functions and behaviours because it involves the subjective nature of experience, which cannot be fully captured by a purely physical explanation. This problem is central to the question of whether consciousness plays a role in quantum mechanics because it challenges the materialist assumption that everything can be explained in terms of physical processes. One argument in favour of consciousness playing a fundamental role in quantum mechanics is that it may help solve the measurement problem—the question of why and how the wavefunction collapses when a measurement is made. According to the Consciousness Collapse Proposal (CCP), the collapse of the wavefunction occurs when a conscious observer interacts with the system, suggesting that consciousness is a necessary component of reality. This idea challenges the traditional view of quantum mechanics as a purely objective, observer-independent theory and implies that consciousness is more than just a byproduct of physical processes (Stapp, 1993). In this view, consciousness is not simply an epiphenomenon of the brain but a fundamental aspect of reality that interacts with the physical world in a way that science has yet to fully understand. This perspective aligns with certain interpretations of quantum mechanics, such as the von Neumann-Wigner interpretation, which posits that consciousness plays an active role in the collapse of the wavefunction. While this interpretation remains controversial, it highlights the possibility that consciousness could be integral to the functioning of the universe at a fundamental level. ### Avoidance of the Hard Problem in Mainstream Science Despite the compelling nature of the hard problem, mainstream scientific interpretations of quantum mechanics often avoid addressing consciousness directly. For example, the Many Worlds Interpretation (MWI) of quantum mechanics sidesteps the issue of wavefunction collapse altogether by proposing that all possible outcomes of a quantum measurement exist simultaneously in parallel worlds. In this framework, there is no need to invoke consciousness as a factor in determining the outcome of a quantum event, as every possible outcome is realized in some branch of the multiverse (Everett, 1957). While MWI elegantly avoids the problem of collapse, it does so at the cost of ignoring the role of consciousness, which remains unexplained. Similarly, the Ghirardi-Rimini-Weber (GRW) theory offers an objective collapse model that introduces spontaneous collapses of the wavefunction, independent of observation or consciousness. This theory attempts to solve the measurement problem without invoking consciousness by suggesting that wavefunctions collapse randomly after a certain threshold is reached (Ghirardi, Rimini, & Weber, 1986). Although GRW provides a mathematically consistent solution to the measurement problem, it does not address the hard problem of consciousness, leaving the nature of subjective experience untouched. These interpretations reflect a broader tendency in science to focus on solving the technical aspects of quantum mechanics while avoiding the deeper philosophical questions about consciousness. This approach is understandable, given that the hard problem of consciousness is notoriously difficult to address within the framework of materialist science. However, by sidestepping the issue, these interpretations may be missing a crucial piece of the puzzle. If consciousness is indeed fundamental to the collapse of the wavefunction, as proponents of the CCP suggest, then any interpretation that ignores consciousness is inherently incomplete. ### The Case for Addressing Consciousness in Quantum Mechanics Given the limitations of current interpretations of quantum mechanics, there is a strong case to be made for addressing the hard problem of consciousness directly. One of the key challenges in integrating consciousness into quantum mechanics is the lack of empirical evidence linking consciousness to wavefunction collapse. Critics like Barry Loewer (2003) argue that the CCP is speculative and lacks the rigorous experimental support needed to be taken seriously as a scientific theory. This criticism is valid, as science requires empirical validation to support theoretical claims. However, the absence of empirical evidence does not necessarily invalidate the idea that consciousness could play a role in quantum mechanics. The lack of direct evidence may simply reflect the limitations of current experimental methods, which are not yet sophisticated enough to test the relationship between consciousness and quantum phenomena. Furthermore, the hard problem of consciousness remains unresolved by conventional science, suggesting that new approaches may be needed to explore the connection between consciousness and the physical world. In response to critics, proponents of the CCP could argue that quantum mechanics itself has a long history of challenging conventional notions of reality. The very existence of phenomena like entanglement and superposition defies classical logic and suggests that our understanding of the universe is incomplete. If consciousness is indeed fundamental to the fabric of reality, then it is possible that it plays a role in these quantum phenomena in ways that we do not yet fully understand. Rather than dismissing the CCP as speculative, it may be more productive to consider it as a potential avenue for further research, one that could ultimately lead to a deeper understanding of both consciousness and quantum mechanics. ## 6. Personal Viewpoint: Consciousness as a Vital Component in Quantum Mechanics In my view, the hard problem of consciousness is not just an interesting philosophical challenge but a vital issue that must be addressed if we are to fully understand quantum mechanics. The reluctance of many scientists to engage with the hard problem is understandable, given the difficulty of the question and the lack of empirical evidence. However, this avoidance may be preventing us from making significant progress in understanding the true nature of reality. I believe that the hard problem of consciousness represents a fundamental gap in our understanding of the universe - one that cannot be ignored if we are to develop a complete theory of quantum mechanics. While alternative interpretations like the GRW theory and the Many Worlds Interpretation offer solutions to the technical problems of quantum mechanics, they do so by avoiding the deeper question of consciousness. This approach, while pragmatic, may ultimately prove to be a dead end if consciousness is indeed integral to the behaviour of quantum systems. Addressing the hard problem of consciousness in the context of quantum mechanics requires a willingness to think beyond the current boundaries of science and to explore new theoretical frameworks that integrate consciousness into our understanding of the physical world. This may involve revisiting ideas like the Consciousness Collapse Proposal or developing entirely new theories that link consciousness with quantum phenomena in ways that we have not yet imagined. At the same time, it is important to approach this question with a critical and balanced perspective. While the idea that consciousness plays a role in quantum mechanics is intriguing, it is essential to remain open to alternative explanations and to demand rigorous empirical evidence to support any claims. The history of science is filled with theories that seemed promising but ultimately proved to be incorrect, and we must be careful not to fall into the trap of speculation without evidence. ## Conclusion In Summary, I believe that the hard problem of consciousness is the *"elephant in the room"* that quantum mechanics needs to address. While traditional interpretations of quantum theory have tried to solve the measurement problem without involving consciousness it might be ignoring a part of reality. By blending the matter of consciousness into quantum mechanics we could potentially gain a comprehensive view of the universe - one that appreciates both the enigmatic nature of subjective experiences and the elegant mathematics of some quantum mechanics theories. Even though this viewpoint is speculative and needs investigation it presents a glimpse into a future where consciousness and quantum mechanics are seen as interconnected elements of existence. ### References \- CHALMERS, D. J. (1995). FACING UP TO THE PROBLEM OF CONSCIOUSNESS. JOURNAL OF CONSCIOUSNESS STUDIES, 2(3), 200-219. \- EVERETT, H. (1957). “RELATIVE STATE” FORMULATION OF QUANTUM MECHANICS. REVIEWS OF MODERN PHYSICS, 29(3), 454-462. \- GHIRARDI, G. C., RIMINI, A., & WEBER, T. (1986). UNIFIED DYNAMICS FOR MICROSCOPIC AND MACROSCOPIC SYSTEMS. PHYSICAL REVIEW D, 34(2), 470-491. \- LOEWER, B. (2003). CONSCIOUSNESS AND QUANTUM THEORY: STRANGE BEDFELLOWS. \- STAPP, H. P. (1993). MIND, MATTER, AND QUANTUM MECHANICS. SPRINGER. @ 4ba8e86d:89d32de4
2024-10-08 23:16:53Governos do mundo industrial, seus gigantes cansados de carne e aço, venho do ciberespaço, a nova casa da mente. Em nome do futuro, peço que no passado nos deixe em paz. Você não é bem vindo entre nós. Nem você exerce qualquer soberania sobre o lugar onde nos encontramos. Não elegemos nenhum governo, nem pretendemos tê-lo, por isso dirijo-me a vocês sem outra autoridade senão aquela com que sempre fala a liberdade. Declaro que o espaço social global que estamos construindo é independente por natureza das tiranias que você procura impor a nós. Você não tem o direito moral de nos governar, nem possui métodos para fazer cumprir sua lei que devemos realmente temer. Os governos obtêm seus justos poderes do consentimento daqueles que são governados. Você não pediu nem recebeu o nosso. Nós também não convidamos você. Você não nos conhece, nem conhece o nosso mundo. O ciberespaço não está dentro de suas fronteiras. Não pense que você pode construí-lo, como se fosse um projeto de construção pública. Você não pode. É um ato natural que cresce a partir de nossas ações coletivas. Você não participou de nossa grande conversa coletiva, nem criou a riqueza de nossos mercados. Você não conhece nossa cultura, nossa ética ou os códigos não escritos que já fornecem à nossa sociedade mais ordem do que o que poderia ser obtido por qualquer uma de suas imposições. Você proclama que há problemas entre nós que precisa resolver. Você usa isso como uma desculpa para invadir nossos limites. Muitos desses problemas não existem. Onde houver conflitos reais, erros, nós os identificaremos e resolveremos por nossos próprios meios. Estamos criando nosso próprio contrato social. Essa autoridade será criada de acordo com as condições do nosso mundo, não a sua. Nosso mundo é diferente. O ciberespaço é composto de transações, relacionamentos e pensamento em si, que se espalham como uma onda silenciosa na web de nossas comunicações. Nosso mundo está ao mesmo tempo em todo lugar e lugar nenhum, mas não é onde os corpos vivem. Estamos criando um mundo no qual todos possam entrar, sem privilégios ou preconceitos devido à raça, poder econômico, força militar ou local de nascimento. Estamos criando um mundo em que qualquer pessoa, em qualquer lugar, possa expressar suas crenças, não importa quão únicas sejam, sem medo de ser coagida ao silêncio ou à conformidade. Seus conceitos legais de propriedade, expressão, identidade, movimento e contexto não se aplicam a nós. Eles são baseados na matéria. Não há problema aqui. Nossas identidades não têm corpo; portanto, diferentemente de você, não podemos obter ordem por coerção física. Acreditamos que nossa autoridade emanará da moralidade, do interesse próprio progressivo e do bem comum. Nossas identidades podem ser distribuídas por várias jurisdições. A única lei que todas as nossas culturas reconheceriam é a Regra de Ouro. Esperamos ansiosamente desenvolver nossas soluções específicas sobre essa base. Mas não podemos aceitar as soluções que você está tentando impor. Hoje, na América, você criou uma lei, a Lei de Reforma das Telecomunicações, que repudia sua própria Constituição e insulta os sonhos de Jefferson, Washington, Mill, Madison, DeToqueville e Brandeis. Esses sonhos devem renascer em nós agora. Você tem medo de seus próprios filhos, pois eles são nativos em um mundo onde você sempre será imigrante. Ao recear, confia à sua burocracia responsabilidades parentais que não pode ser covarde. Em nosso mundo, todos os sentimentos e expressões da humanidade, do mais vil ao mais angélico, fazem parte de um único todo, a conversa global de bits. Não podemos separar o ar que sufoca daquele em que as asas batem. Na China, Alemanha, França, Rússia, Cingapura, Itália e Estados Unidos, você está tentando evitar o vírus da liberdade, estabelecendo postos de guarda nas fronteiras do ciberespaço. Eles podem impedir o contágio por um curto período de tempo, mas não funcionarão em um mundo que em breve será coberto pela mídia transmitida por bits. Suas indústrias de informação cada vez mais obsoletas se perpetuariam propondo leis, nos Estados Unidos e em outros lugares, que reivindicam a propriedade da palavra em todo o mundo. Essas leis declarariam que as idéias são outro produto industrial, menos nobre que o ferro enferrujado. Em nosso mundo, tudo o que a mente humana pode criar pode ser reproduzido e distribuído infinitamente, sem nenhum custo. A transferência global de pensamento não precisa mais ser realizada por suas fábricas. Essas medidas cada vez mais hostis e colonialistas nos colocam na mesma situação em que estavam aqueles amantes da liberdade e da autodeterminação que tiveram que lutar contra a autoridade de um poder distante e ignorante. Devemos declarar nossos "eus" virtuais imunes à sua soberania, embora continuemos a consentir com seu poder sobre nossos corpos. Vamos nos espalhar por todo o planeta para que ninguém possa aprisionar nossos pensamentos. Criaremos uma civilização da mente no ciberespaço. Que seja mais humano e bonito do que o mundo que seus governos criaram antes. Davos, Suíça, até 8 de fevereiro de 1996 John Perry Barlow
@ 4ba8e86d:89d32de4
2024-10-08 23:16:53Governos do mundo industrial, seus gigantes cansados de carne e aço, venho do ciberespaço, a nova casa da mente. Em nome do futuro, peço que no passado nos deixe em paz. Você não é bem vindo entre nós. Nem você exerce qualquer soberania sobre o lugar onde nos encontramos. Não elegemos nenhum governo, nem pretendemos tê-lo, por isso dirijo-me a vocês sem outra autoridade senão aquela com que sempre fala a liberdade. Declaro que o espaço social global que estamos construindo é independente por natureza das tiranias que você procura impor a nós. Você não tem o direito moral de nos governar, nem possui métodos para fazer cumprir sua lei que devemos realmente temer. Os governos obtêm seus justos poderes do consentimento daqueles que são governados. Você não pediu nem recebeu o nosso. Nós também não convidamos você. Você não nos conhece, nem conhece o nosso mundo. O ciberespaço não está dentro de suas fronteiras. Não pense que você pode construí-lo, como se fosse um projeto de construção pública. Você não pode. É um ato natural que cresce a partir de nossas ações coletivas. Você não participou de nossa grande conversa coletiva, nem criou a riqueza de nossos mercados. Você não conhece nossa cultura, nossa ética ou os códigos não escritos que já fornecem à nossa sociedade mais ordem do que o que poderia ser obtido por qualquer uma de suas imposições. Você proclama que há problemas entre nós que precisa resolver. Você usa isso como uma desculpa para invadir nossos limites. Muitos desses problemas não existem. Onde houver conflitos reais, erros, nós os identificaremos e resolveremos por nossos próprios meios. Estamos criando nosso próprio contrato social. Essa autoridade será criada de acordo com as condições do nosso mundo, não a sua. Nosso mundo é diferente. O ciberespaço é composto de transações, relacionamentos e pensamento em si, que se espalham como uma onda silenciosa na web de nossas comunicações. Nosso mundo está ao mesmo tempo em todo lugar e lugar nenhum, mas não é onde os corpos vivem. Estamos criando um mundo no qual todos possam entrar, sem privilégios ou preconceitos devido à raça, poder econômico, força militar ou local de nascimento. Estamos criando um mundo em que qualquer pessoa, em qualquer lugar, possa expressar suas crenças, não importa quão únicas sejam, sem medo de ser coagida ao silêncio ou à conformidade. Seus conceitos legais de propriedade, expressão, identidade, movimento e contexto não se aplicam a nós. Eles são baseados na matéria. Não há problema aqui. Nossas identidades não têm corpo; portanto, diferentemente de você, não podemos obter ordem por coerção física. Acreditamos que nossa autoridade emanará da moralidade, do interesse próprio progressivo e do bem comum. Nossas identidades podem ser distribuídas por várias jurisdições. A única lei que todas as nossas culturas reconheceriam é a Regra de Ouro. Esperamos ansiosamente desenvolver nossas soluções específicas sobre essa base. Mas não podemos aceitar as soluções que você está tentando impor. Hoje, na América, você criou uma lei, a Lei de Reforma das Telecomunicações, que repudia sua própria Constituição e insulta os sonhos de Jefferson, Washington, Mill, Madison, DeToqueville e Brandeis. Esses sonhos devem renascer em nós agora. Você tem medo de seus próprios filhos, pois eles são nativos em um mundo onde você sempre será imigrante. Ao recear, confia à sua burocracia responsabilidades parentais que não pode ser covarde. Em nosso mundo, todos os sentimentos e expressões da humanidade, do mais vil ao mais angélico, fazem parte de um único todo, a conversa global de bits. Não podemos separar o ar que sufoca daquele em que as asas batem. Na China, Alemanha, França, Rússia, Cingapura, Itália e Estados Unidos, você está tentando evitar o vírus da liberdade, estabelecendo postos de guarda nas fronteiras do ciberespaço. Eles podem impedir o contágio por um curto período de tempo, mas não funcionarão em um mundo que em breve será coberto pela mídia transmitida por bits. Suas indústrias de informação cada vez mais obsoletas se perpetuariam propondo leis, nos Estados Unidos e em outros lugares, que reivindicam a propriedade da palavra em todo o mundo. Essas leis declarariam que as idéias são outro produto industrial, menos nobre que o ferro enferrujado. Em nosso mundo, tudo o que a mente humana pode criar pode ser reproduzido e distribuído infinitamente, sem nenhum custo. A transferência global de pensamento não precisa mais ser realizada por suas fábricas. Essas medidas cada vez mais hostis e colonialistas nos colocam na mesma situação em que estavam aqueles amantes da liberdade e da autodeterminação que tiveram que lutar contra a autoridade de um poder distante e ignorante. Devemos declarar nossos "eus" virtuais imunes à sua soberania, embora continuemos a consentir com seu poder sobre nossos corpos. Vamos nos espalhar por todo o planeta para que ninguém possa aprisionar nossos pensamentos. Criaremos uma civilização da mente no ciberespaço. Que seja mais humano e bonito do que o mundo que seus governos criaram antes. Davos, Suíça, até 8 de fevereiro de 1996 John Perry Barlow @ eac63075:b4988b48
2024-10-08 20:37:08In this botcast, we explore how technology is solving one of the biggest challenges faced by DAOs (Decentralized Autonomous Organizations): vote fraud. Learn how Vitalik Buterin and other experts from Cornell University are leading innovation using Zero-Knowledge Proofs and Proof of Work (PoW) to ensure security and privacy in blockchain voting systems. You will discover how these technologies combat practices like token renting and lending, preventing vote manipulation in DAOs. The video also covers the importance of dedicated hardware to increase the integrity of digital elections. --- Listen to the Podcast: <https://wavlake.com/episode/bdb2850b-49b4-45f6-9a00-d310e29f4528> --- Table of Contents: **Source:** YouTube Transcript - Morning Crypto (Timestamped Excerpts) **I. Introduction and Context (0:00:00 - 0:02:37)** - This section sets the stage by briefly discussing a common problem in Decentralized Autonomous Organizations (DAOs): fraudulent voting practices. - It highlights the issue of individuals manipulating voting systems by borrowing, renting, or delegating tokens to influence decision-making within DAOs. **II. Introducing Complete Knowledge and the Proposed Solution (0:02:37 - 0:03:39)** - Introduces a potential solution developed by Vitalik Buterin and researchers from Cornell University, utilizing Zero-Knowledge Proofs to address the challenge of fraudulent voting in DAOs. - Explains that the proposed solution involves a dedicated hardware or wallet system that verifies voting rights without revealing the user's private key, preventing token manipulation. **III. Deep Dive into Complete Knowledge with "Ger" (0:05:54 - 0:07:57)** - This section features "Ger," a voice assistant, who explains Complete Knowledge as a cryptographic innovation. - Ger describes how Complete Knowledge allows users to prove possession of information, like a private key, without revealing the information itself. - The section emphasizes how Complete Knowledge enhances security and privacy in digital identity and voting systems. **IV. Proof of Work and ASICs for Enhanced Security (0:07:57 - 0:09:05)** - Examines the potential of using Proof of Work (PoW), the consensus mechanism behind Bitcoin, in conjunction with Complete Knowledge. - Explains how PoW can act as a mechanism to further ensure that a specific secret or key is held by a user without requiring the user to reveal it. - Discusses the use of Application-Specific Integrated Circuits (ASICs) for performing the computational tasks required for PoW and Complete Knowledge verification. **V. Practical Implementation and Conclusion (0:09:05 - 0:10:25)** - Highlights the development of a demo ASIC by the researchers, showcasing the practical application of their proposed solution. - Emphasizes the potential of this technology to prevent fraudulent voting practices by requiring a user to generate proof of their voting rights via this specialized ASIC. - Concludes with a message emphasizing the importance of verifiable knowledge and its implications for privacy and security in the digital age. --- Reference: - <https://eprint.iacr.org/2023/044> - <https://medium.com/initc3org/complete-knowledge-eecdda172a81>
@ eac63075:b4988b48
2024-10-08 20:37:08In this botcast, we explore how technology is solving one of the biggest challenges faced by DAOs (Decentralized Autonomous Organizations): vote fraud. Learn how Vitalik Buterin and other experts from Cornell University are leading innovation using Zero-Knowledge Proofs and Proof of Work (PoW) to ensure security and privacy in blockchain voting systems. You will discover how these technologies combat practices like token renting and lending, preventing vote manipulation in DAOs. The video also covers the importance of dedicated hardware to increase the integrity of digital elections. --- Listen to the Podcast: <https://wavlake.com/episode/bdb2850b-49b4-45f6-9a00-d310e29f4528> --- Table of Contents: **Source:** YouTube Transcript - Morning Crypto (Timestamped Excerpts) **I. Introduction and Context (0:00:00 - 0:02:37)** - This section sets the stage by briefly discussing a common problem in Decentralized Autonomous Organizations (DAOs): fraudulent voting practices. - It highlights the issue of individuals manipulating voting systems by borrowing, renting, or delegating tokens to influence decision-making within DAOs. **II. Introducing Complete Knowledge and the Proposed Solution (0:02:37 - 0:03:39)** - Introduces a potential solution developed by Vitalik Buterin and researchers from Cornell University, utilizing Zero-Knowledge Proofs to address the challenge of fraudulent voting in DAOs. - Explains that the proposed solution involves a dedicated hardware or wallet system that verifies voting rights without revealing the user's private key, preventing token manipulation. **III. Deep Dive into Complete Knowledge with "Ger" (0:05:54 - 0:07:57)** - This section features "Ger," a voice assistant, who explains Complete Knowledge as a cryptographic innovation. - Ger describes how Complete Knowledge allows users to prove possession of information, like a private key, without revealing the information itself. - The section emphasizes how Complete Knowledge enhances security and privacy in digital identity and voting systems. **IV. Proof of Work and ASICs for Enhanced Security (0:07:57 - 0:09:05)** - Examines the potential of using Proof of Work (PoW), the consensus mechanism behind Bitcoin, in conjunction with Complete Knowledge. - Explains how PoW can act as a mechanism to further ensure that a specific secret or key is held by a user without requiring the user to reveal it. - Discusses the use of Application-Specific Integrated Circuits (ASICs) for performing the computational tasks required for PoW and Complete Knowledge verification. **V. Practical Implementation and Conclusion (0:09:05 - 0:10:25)** - Highlights the development of a demo ASIC by the researchers, showcasing the practical application of their proposed solution. - Emphasizes the potential of this technology to prevent fraudulent voting practices by requiring a user to generate proof of their voting rights via this specialized ASIC. - Concludes with a message emphasizing the importance of verifiable knowledge and its implications for privacy and security in the digital age. --- Reference: - <https://eprint.iacr.org/2023/044> - <https://medium.com/initc3org/complete-knowledge-eecdda172a81>