-

@ 89ccea93:df4e00b7
2025-02-06 11:20:49
I've opened a ~monero territory.
I kept wanting to post things about or tangential to monero and didn't know where to shove them.
Obviously ~bitcoin isn't the right place.
And ~cryptocurrency didn't feel right, since for me, as a bitcoiner, monero is in a unique position. It doesn't seem to fit under the larger basket of cryptocurrencies. Many of which are scams/self-enrichment schemes. Ahem, XRP.
Or just poorly implemented and pre-mined. Ahem, ETH.
I don't know a lot about monero actually, but I use it and like it and think it has a place in a bitcoiners arsenal in resisting government infringements and resisting pervasive privacy shit-holes like the chain anal companies. Even Coinbase has their own proprietary chain anal. It's disgusting. They don't want us to have privacy. And many people play right into their hands by handing over their ID card and picture of their face to get bitcoins when you can get it anonymously. But I digress.
Use the territory, or don't.
But if you do, then welcome.
originally posted at https://stacker.news/items/877547
-

@ 57d1a264:69f1fee1
2025-02-06 07:38:36
# How does bitcoin's lack of central brand authority influence its visual identity, and what implications does this have for designers?
originally posted at https://stacker.news/items/877437
-

@ e3ba5e1a:5e433365
2025-02-05 17:47:16
I got into a [friendly discussion](https://x.com/snoyberg/status/1887007888117252142) on X regarding health insurance. The specific question was how to deal with health insurance companies (presumably unfairly) denying claims? My answer, as usual: get government out of it!
The US healthcare system is essentially the worst of both worlds:
* Unlike full single payer, individuals incur high costs
* Unlike a true free market, regulation causes increases in costs and decreases competition among insurers
I'm firmly on the side of moving towards the free market. (And I say that as someone living under a single payer system now.) Here's what I would do:
* Get rid of tax incentives that make health insurance tied to your employer, giving individuals back proper freedom of choice.
* Reduce regulations significantly.
* In the short term, some people will still get rejected claims and other obnoxious behavior from insurance companies. We address that in two ways:
1. Due to reduced regulations, new insurance companies will be able to enter the market offering more reliable coverage and better rates, and people will flock to them because they have the freedom to make their own choices.
2. Sue the asses off of companies that reject claims unfairly. And ideally, as one of the few legitimate roles of government in all this, institute new laws that limit the ability of fine print to allow insurers to escape their responsibilities. (I'm hesitant that the latter will happen due to the incestuous relationship between Congress/regulators and insurers, but I can hope.)
Will this magically fix everything overnight like politicians normally promise? No. But it will allow the market to return to a healthy state. And I don't think it will take long (order of magnitude: 5-10 years) for it to come together, but that's just speculation.
And since there's a high correlation between those who believe government can fix problems by taking more control and demanding that only credentialed experts weigh in on a topic (both points I strongly disagree with BTW): I'm a trained actuary and worked in the insurance industry, and have directly seen how government regulation reduces competition, raises prices, and harms consumers.
And my final point: I don't think any prior art would be a good comparison for deregulation in the US, it's such a different market than any other country in the world for so many reasons that lessons wouldn't really translate. Nonetheless, I asked Grok for some empirical data on this, and at best the results of deregulation could be called "mixed," but likely more accurately "uncertain, confused, and subject to whatever interpretation anyone wants to apply."
https://x.com/i/grok/share/Zc8yOdrN8lS275hXJ92uwq98M
-

@ 57d1a264:69f1fee1
2025-02-05 02:18:03

Pre-Foundational learning for these participants has now kicked off in the Bitcoin Design Community, check out the #education channel on the [Bitcoin.Design](https://Bitcoin.Design) [Discord channel](https://discord.com/channels/903125802726596648/1260871907050393620).
## 🪇 10 talented participants from South America will be:
Learning bitcoin UX Design fundamentals using the Bitcoin Design Guide
Working hands-on with South American-built products to evaluate their user experiences and support builders with data
> Attending [BTC++ in Florianópolis](https://btcplusplus.dev/conf/floripa)
This initiative is sponsored by the [Human Rights Foundation](https://HRF.org) in collaboration with the [Bitcoin Design Foundation](https://bitcoindesignfoundation.org/) and [Area Bitcoin](https://areabitcoin.co).
## 🥅 Goals:
- Empower local talent to improve the UX of South American bitcoin products - seeing their passion and drive to bring bitcoin to their countries is really inspiring
- Create meaningful relationships with wallet developers through practical collaboration
- Scale bitcoin adoption by improving the user experience
- Create a public knowledge base: All research conducted in Africa and South America will be made publicly available for builders
originally posted at https://stacker.news/items/876215
-

@ 57d1a264:69f1fee1
2025-02-05 00:25:20
# How does open source development contribute to bitcoin's security, reliability, and evolution as a network?
originally posted at https://stacker.news/items/876130
-

@ 91bea5cd:1df4451c
2025-02-04 17:24:50
### Definição de ULID:
Timestamp 48 bits, Aleatoriedade 80 bits
Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C.
e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível.
#### Gerar ULID
```sql
CREATE EXTENSION IF NOT EXISTS pgcrypto;
CREATE FUNCTION generate_ulid()
RETURNS TEXT
AS $$
DECLARE
-- Crockford's Base32
encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ';
timestamp BYTEA = E'\\000\\000\\000\\000\\000\\000';
output TEXT = '';
unix_time BIGINT;
ulid BYTEA;
BEGIN
-- 6 timestamp bytes
unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT;
timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER);
timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER);
timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER);
timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER);
timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER);
timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER);
-- 10 entropy bytes
ulid = timestamp || gen_random_bytes(10);
-- Encode the timestamp
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31)));
-- Encode the entropy
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31)));
RETURN output;
END
$$
LANGUAGE plpgsql
VOLATILE;
```
#### ULID TO UUID
```sql
CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$
DECLARE
-- 16byte
bytes bytea = E'\\x00000000 00000000 00000000 00000000';
v char[];
-- Allow for O(1) lookup of index values
dec integer[] = ARRAY[
255, 255, 255, 255, 255, 255, 255, 255, 255, 255,
255, 255, 255, 255, 255, 255, 255, 255, 255, 255,
255, 255, 255, 255, 255, 255, 255, 255, 255, 255,
255, 255, 255, 255, 255, 255, 255, 255, 255, 255,
255, 255, 255, 255, 255, 255, 255, 0, 1, 2,
3, 4, 5, 6, 7, 8, 9, 255, 255, 255,
255, 255, 255, 255, 10, 11, 12, 13, 14, 15,
16, 17, 1, 18, 19, 1, 20, 21, 0, 22,
23, 24, 25, 26, 255, 27, 28, 29, 30, 31,
255, 255, 255, 255, 255, 255, 10, 11, 12, 13,
14, 15, 16, 17, 1, 18, 19, 1, 20, 21,
0, 22, 23, 24, 25, 26, 255, 27, 28, 29,
30, 31
];
BEGIN
IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN
RAISE EXCEPTION 'Invalid ULID: %', ulid;
END IF;
v = regexp_split_to_array(ulid, '');
-- 6 bytes timestamp (48 bits)
bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]);
bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2));
bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4));
bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1));
bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3));
bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]);
-- 10 bytes of entropy (80 bits);
bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2));
bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4));
bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1));
bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3));
bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]);
bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2));
bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4));
bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1));
bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3));
bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]);
RETURN bytes;
END
$$
LANGUAGE plpgsql
IMMUTABLE;
CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$
BEGIN
RETURN encode(parse_ulid(ulid), 'hex')::uuid;
END
$$
LANGUAGE plpgsql
IMMUTABLE;
```
#### UUID to ULID
```sql
CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$
DECLARE
encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ';
output text = '';
uuid_bytes bytea = uuid_send(id);
BEGIN
-- Encode the timestamp
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31)));
-- Encode the entropy
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4)));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2));
output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5)));
output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31)));
RETURN output;
END
$$
LANGUAGE plpgsql
IMMUTABLE;
```
#### Gera 11 Digitos aleatórios: YBKXG0CKTH4
```sql
-- Cria a extensão pgcrypto para gerar uuid
CREATE EXTENSION IF NOT EXISTS pgcrypto;
-- Cria a função para gerar ULID
CREATE OR REPLACE FUNCTION gen_lrandom()
RETURNS TEXT AS $$
DECLARE
ts_millis BIGINT;
ts_chars TEXT;
random_bytes BYTEA;
random_chars TEXT;
base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ';
i INT;
BEGIN
-- Pega o timestamp em milissegundos
ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT;
-- Converte o timestamp para base32
ts_chars := '';
FOR i IN REVERSE 0..11 LOOP
ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1);
END LOOP;
-- Gera 10 bytes aleatórios e converte para base32
random_bytes := gen_random_bytes(10);
random_chars := '';
FOR i IN 0..9 LOOP
random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1);
IF i < 9 THEN
random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1);
ELSE
random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1);
END IF;
END LOOP;
-- Concatena o timestamp e os caracteres aleatórios
RETURN ts_chars || random_chars;
END;
$$ LANGUAGE plpgsql;
```
#### Exemplo de USO
```sql
-- Criação da extensão caso não exista
CREATE EXTENSION
IF
NOT EXISTS pgcrypto;
-- Criação da tabela pessoas
CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL );
-- Busca Pessoa na tabela
SELECT
*
FROM
"pessoas"
WHERE
uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F';
```
### Fontes
- https://github.com/scoville/pgsql-ulid
- https://github.com/geckoboard/pgulid
-

@ 1833ee04:7c4a8170
2025-02-04 15:14:03
The international race for Bitcoin strategic reserves is just getting started.
If you’re stacking now, you’re still incredibly early.
At $100k per Bitcoin, it’s practically free for anyone who truly understands how massive this shift is.
Think back to when paper currency was introduced, people had to trade their gold for paper bills. Many laughed, saying, Who’s going to trust these worthless pieces of paper as money?
Yet today, you sell your time to earn these paper bills while your government can print an unlimited amount at will.
The world is returning to a gold standard. But this time, it’s Gold 2.0 which is Bitcoin.The international race for Bitcoin strategic reserves is just getting started.\
\
If you’re stacking now, you’re still incredibly early.\
\
At $100k per Bitcoin, it’s practically free for anyone who truly understands how massive this shift is.\
\
Think back to when paper currency was introduced, people had to trade their gold for paper bills. Many laughed, saying, Who’s going to trust these worthless pieces of paper as money?\
\
Yet today, you sell your time to earn these paper bills while your government can print an unlimited amount at will.\
\
The world is returning to a gold standard. But this time, it’s Gold 2.0 which is Bitcoin.
-

@ e3ba5e1a:5e433365
2025-02-04 08:29:00
President Trump has started rolling out his tariffs, something I [blogged about in November](https://www.snoyman.com/blog/2024/11/steelmanning-tariffs/). People are talking about these tariffs a lot right now, with many people (correctly) commenting on how consumers will end up with higher prices as a result of these tariffs. While that part is true, I’ve seen a lot of people taking it to the next, incorrect step: that consumers will pay the entirety of the tax. I [put up a poll on X](https://x.com/snoyberg/status/1886035800019599808) to see what people thought, and while the right answer got a lot of votes, it wasn't the winner.

For purposes of this blog post, our ultimate question will be the following:
* Suppose apples currently sell for $1 each in the entire United States.
* There are domestic sellers and foreign sellers of apples, all receiving the same price.
* There are no taxes or tariffs on the purchase of apples.
* The question is: if the US federal government puts a $0.50 import tariff per apple, what will be the change in the following:
* Number of apples bought in the US
* Price paid by buyers for apples in the US
* Post-tax price received by domestic apple producers
* Post-tax price received by foreign apple producers
Before we can answer that question, we need to ask an easier, first question: before instituting the tariff, why do apples cost $1?
And finally, before we dive into the details, let me provide you with the answers to the ultimate question. I recommend you try to guess these answers before reading this, and if you get it wrong, try to understand why:
1. The number of apples bought will go down
2. The buyers will pay more for each apple they buy, but not the full amount of the tariff
3. Domestic apple sellers will receive a *higher* price per apple
4. Foreign apple sellers will receive a *lower* price per apple, but not lowered by the full amount of the tariff
In other words, regardless of who sends the payment to the government, both taxed parties (domestic buyers and foreign sellers) will absorb some of the costs of the tariff, while domestic sellers will benefit from the protectionism provided by tariffs and be able to sell at a higher price per unit.
## Marginal benefit
All of the numbers discussed below are part of a [helper Google Sheet](https://docs.google.com/spreadsheets/d/14ZbkWpw1B9Q1UDB9Yh47DmdKQfIafVVBKbDUsSIfGZw/edit?usp=sharing) I put together for this analysis. Also, apologies about the jagged lines in the charts below, I hadn’t realized before starting on this that there are [some difficulties with creating supply and demand charts in Google Sheets](https://superuser.com/questions/1359731/how-to-create-a-supply-demand-style-chart).
Let’s say I absolutely love apples, they’re my favorite food. How much would I be willing to pay for a single apple? You might say “$1, that’s the price in the supermarket,” and in many ways you’d be right. If I walk into supermarket A, see apples on sale for $50, and know that I can buy them at supermarket B for $1, I’ll almost certainly leave A and go buy at B.
But that’s not what I mean. What I mean is: how high would the price of apples have to go *everywhere* so that I’d no longer be willing to buy a single apple? This is a purely personal, subjective opinion. It’s impacted by how much money I have available, other expenses I need to cover, and how much I like apples. But let’s say the number is $5.
How much would I be willing to pay for another apple? Maybe another $5. But how much am I willing to pay for the 1,000th apple? 10,000th? At some point, I’ll get sick of apples, or run out of space to keep the apples, or not be able to eat, cook, and otherwise preserve all those apples before they rot.
The point being: I’ll be progressively willing to spend less and less money for each apple. This form of analysis is called *marginal benefit*: how much benefit (expressed as dollars I’m willing to spend) will I receive from each apple? This is a downward sloping function: for each additional apple I buy (quantity demanded), the price I’m willing to pay goes down. This is what gives my personal *demand curve*. And if we aggregate demand curves across all market participants (meaning: everyone interested in buying apples), we end up with something like this:

Assuming no changes in people’s behavior and other conditions in the market, this chart tells us how many apples will be purchased by our buyers at each price point between $0.50 and $5. And ceteris paribus (all else being equal), this will continue to be the demand curve for apples.
## Marginal cost
Demand is half the story of economics. The other half is supply, or: how many apples will I sell at each price point? Supply curves are upward sloping: the higher the price, the more a person or company is willing and able to sell a product.
Let’s understand why. Suppose I have an apple orchard. It’s a large property right next to my house. With about 2 minutes of effort, I can walk out of my house, find the nearest tree, pick 5 apples off the tree, and call it a day. 5 apples for 2 minutes of effort is pretty good, right?
Yes, there was all the effort necessary to buy the land, and plant the trees, and water them… and a bunch more than I likely can’t even guess at. We’re going to ignore all of that for our analysis, because for short-term supply-and-demand movement, we can ignore these kinds of *sunk costs*. One other simplification: in reality, supply curves often start descending before ascending. This accounts for achieving efficiencies of scale after the first number of units purchased. But since both these topics are unneeded for understanding taxes, I won’t go any further.
Anyway, back to my apple orchard. If someone offers me $0.50 per apple, I can do 2 minutes of effort and get $2.50 in revenue, which equates to a $75/hour wage for me. I’m more than happy to pick apples at that price\!
However, let’s say someone comes to buy 10,000 apples from me instead. I no longer just walk out to my nearest tree. I’m going to need to get in my truck, drive around, spend the day in the sun, pay for gas, take a day off of my day job (let’s say it pays me $70/hour). The costs go up significantly. Let’s say it takes 5 days to harvest all those apples myself, it costs me $100 in fuel and other expenses, and I lose out on my $70/hour job for 5 days. We end up with:
* Total expenditure: $100 \+ $70 \* 8 hours a day \* 5 days \== $2900
* Total revenue: $5000 (10,000 apples at $0.50 each)
* Total profit: $2100
So I’m still willing to sell the apples at this price, but it’s not as attractive as before. And as the number of apples purchased goes up, my costs keep increasing. I’ll need to spend more money on fuel to travel more of my property. At some point I won’t be able to do the work myself anymore, so I’ll need to pay others to work on the farm, and they’ll be slower at picking apples than me (less familiar with the property, less direct motivation, etc.). The point being: at some point, the number of apples can go high enough that the $0.50 price point no longer makes me any money.
This kind of analysis is called *marginal cost*. It refers to the additional amount of expenditure a seller has to spend in order to produce each additional unit of the good. Marginal costs go up as quantity sold goes up. And like demand curves, if you aggregate this data across all sellers, you get a supply curve like this:

## Equilibrium price
We now know, for every price point, how many apples buyers will purchase, and how many apples sellers will sell. Now we find the equilibrium: where the supply and demand curves meet. This point represents where the marginal benefit a buyer would receive from the next buyer would be less than the cost it would take the next seller to make it. Let’s see it in a chart:

You’ll notice that these two graphs cross at the $1 price point, where 63 apples are both demanded (bought by consumers) and supplied (sold by producers). This is our equilibrium price. We also have a visualization of the *surplus* created by these trades. Everything to the left of the equilibrium point and between the supply and demand curves represents surplus: an area where someone is receiving something of more value than they give. For example:
* When I bought my first apple for $1, but I was willing to spend $5, I made $4 of consumer surplus. The consumer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and above the equilibrium price point.
* When a seller sells his first apple for $1, but it only cost $0.50 to produce it, the seller made $0.50 of producer surplus. The producer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and below the equilibrium price point.
Another way of thinking of surplus is “every time someone got a better price than they would have been willing to take.”
OK, with this in place, we now have enough information to figure out how to price in the tariff, which we’ll treat as a negative externality.
## Modeling taxes
Alright, the government has now instituted a $0.50 tariff on every apple sold within the US by a foreign producer. We can generally model taxes by either increasing the marginal cost of each unit sold (shifting the supply curve up), or by decreasing the marginal benefit of each unit bought (shifting the demand curve down). In this case, since only some of the producers will pay the tax, it makes more sense to modify the supply curve.
First, let’s see what happens to the foreign seller-only supply curve when you add in the tariff:

With the tariff in place, for each quantity level, the price at which the seller will sell is $0.50 higher than before the tariff. That makes sense: if I was previously willing to sell my 82nd apple for $3, I would now need to charge $3.50 for that apple to cover the cost of the tariff. We see this as the tariff “pushing up” or “pushing left” the original supply curve.
We can add this new supply curve to our existing (unchanged) supply curve for domestic-only sellers, and we end up with a result like this:

The total supply curve adds up the individual foreign and domestic supply curves. At each price point, we add up the total quantity each group would be willing to sell to determine the total quantity supplied for each price point. Once we have that cumulative supply curve defined, we can produce an updated supply-and-demand chart including the tariff:

As we can see, the equilibrium has shifted:
* The equilibrium price paid by consumers has risen from $1 to $1.20.
* The total number of apples purchased has dropped from 63 apples to 60 apples.
* Consumers therefore received 3 less apples. They spent $72 for these 60 apples, whereas previously they spent $63 for 3 more apples, a definite decrease in consumer surplus.
* Foreign producers sold 36 of those apples (see the raw data in the linked Google Sheet), for a gross revenue of $43.20. However, they also need to pay the tariff to the US government, which accounts for $18, meaning they only receive $25.20 post-tariff. Previously, they sold 42 apples at $1 each with no tariff to be paid, meaning they took home $42.
* Domestic producers sold the remaining 24 apples at $1.20, giving them a revenue of $28.80. Since they don’t pay the tariff, they take home all of that money. By contrast, previously, they sold 21 apples at $1, for a take-home of $21.
* The government receives $0.50 for each of the 60 apples sold, or in other words receives $30 in revenue it wouldn’t have received otherwise.
We could be more specific about the surpluses, and calculate the actual areas for consumer surplus, producer surplus, inefficiency from the tariff, and government revenue from the tariff. But I won’t bother, as those calculations get slightly more involved. Instead, let’s just look at the aggregate outcomes:
* Consumers were unquestionably hurt. Their price paid went up by $0.20 per apple, and received less apples.
* Foreign producers were also hurt. Their price received went down from the original $1 to the new post-tariff price of $1.20, minus the $0.50 tariff. In other words: foreign producers only receive $0.70 per apple now. This hurt can be mitigated by shifting sales to other countries without a tariff, but the pain will exist regardless.
* Domestic producers scored. They can sell less apples and make more revenue doing it.
* And the government walked away with an extra $30.
Hopefully you now see the answer to the original questions. Importantly, while the government imposed a $0.50 tariff, neither side fully absorbed that cost. Consumers paid a bit more, foreign producers received a bit less. The exact details of how that tariff was split across the groups is mediated by the relevant supply and demand curves of each group. If you want to learn more about this, the relevant search term is “price elasticity,” or how much a group’s quantity supplied or demanded will change based on changes in the price.
## Other taxes
Most taxes are some kind of a tax on trade. Tariffs on apples is an obvious one. But the same applies to income tax (taxing the worker for the trade of labor for money) or payroll tax (same thing, just taxing the employer instead). Interestingly, you can use the same model for analyzing things like tax incentives. For example, if the government decided to subsidize domestic apple production by giving the domestic producers a $0.50 bonus for each apple they sell, we would end up with a similar kind of analysis, except instead of the foreign supply curve shifting up, we’d see the domestic supply curve shifting down.
And generally speaking, this is what you’ll *always* see with government involvement in the economy. It will result in disrupting an existing equilibrium, letting the market readjust to a new equilibrium, and incentivization of some behavior, causing some people to benefit and others to lose out. We saw with the apple tariff, domestic producers and the government benefited while others lost.
You can see the reverse though with tax incentives. If I give a tax incentive of providing a deduction (not paying income tax) for preschool, we would end up with:
* Government needs to make up the difference in tax revenue, either by raising taxes on others or printing more money (leading to inflation). Either way, those paying the tax or those holding government debased currency will pay a price.
* Those people who don’t use the preschool deduction will receive no benefit, so they simply pay a cost.
* Those who do use the preschool deduction will end up paying less on tax+preschool than they would have otherwise.
This analysis is fully amoral. It’s not saying whether providing subsidized preschool is a good thing or not, it simply tells you where the costs will be felt, and points out that such government interference in free economic choice does result in inefficiencies in the system. Once you have that knowledge, you’re more well educated on making a decision about whether the costs of government intervention are worth the benefits.
-

@ 378562cd:a6fc6773
2025-02-02 18:58:38
## Chef's notes
I'm only testing this out right now. I will update the recipe as well as add my own image soon after making this dish again.
## Details
- ⏲️ Prep time: 20 minutes
- 🍳 Cook time: 1 hour
- 🍽️ Servings: 4
## Ingredients
- 4 to 6 potatoes (size depending)
- 1 lb ground beef
- seasonings
- 2 cans chili beans
- 1 onion
- katsup
- shredded cheese of some kind
## Directions
1. saute onion and add ground beef to skillet. Season to liking.
2. peel if you like and thin slice potatoes
3. in a rectangle baking dish, layer potatoes, beans, meat and cheese (like a lasagna) until you have used all your ingredients. Try and make at least 2 or 3 layers with extra cheese on top.
4. Bake at 350 for one hour. Serve and enjoy!
-

@ 228dde34:b5d0345e
2025-02-02 10:00:02
##### By Cheryl Nya
##### Deputy Editor
##### Hype Issue #60
###### CHERYL NYA explores how diverse travel styles can blend seamlessly on a grad trip, turning every moment into an opportunity for unforgettable memories and shared adventures.
 *‘Grad trips’, taking a celebratory trip after graduation, have become a growing trend. Photo taken from Pinterest.*
You made it – years of studying, late-night cramming, and navigating deadlines have finally paid off. Now, it’s time for a well-earned break: the graduation trip. The perfect chance to celebrate with your closest friends before everyone heads off in different directions.
It sounds like the golden plan, but as exciting as it is, travelling in a group can be its own kind of challenge. Between different travel styles, budgets and energy levels, it’s easy for tensions to rise.
However, with a little flexibility and compromise, your long-awaited trip will be remembered for its remarkable memories rather than its unfortunate disagreements. Here’s your ultimate guide to coexisting with your travel crew, without losing your patience along the way.
 *Have an honest talk with your crew and set expectations before you head off. Photo taken from Pinterest.*
1. Recognise that everyone has their own travel personality
There’s the ‘Itinerary Enthusiasts’ who have every minute planned. Then there’ll be the ‘Go with the flow’ travellers who are just there for chill vibes. Somewhere in between you’ve got the foodies, the shopaholics, and the one who just wants a good Instagram shot. When travelling with others, it’s unlikely that all of your friends have the same travel personality. Accepting these different travel personalities early on before your trip will help you avoid major clashes – or at least mentally prepare for them. By recognising your group dynamics, you’ll know who to trust with planning and who to expect last-minute cancellations from.
2. Budget talks are awkward… but necessary
No one wants to be the person who suggests skipping a fancy dinner because they’re on a budget—but at the same time, no one wants to be forced into penny-pinching when they’re on this trip to indulge. Before the trip, have an honest conversation about spending expectations. Will you be splurging on expensive restaurants, or will street food and convenience stores be the way to go? Is everyone okay with taxis, or are we strictly on a public transport budget? Setting clear expectations upfront avoids unnecessary tension when the bill arrives.
3. The accommodation debate: Choose wisely
If your crew has a mix of early risers and night owls, staying in one cramped hostel room will definitely lead to chaos. Hence your choice of accommodation is extremely important; it could make or break your trip. Keep in mind, your light sleepers will suffer if your party-loving friends stumble in at 3AM. So, booking an Airbnb with separate rooms and beds might be your best option. Consider everyone’s preferences before booking because once you’re stuck in a bad setup, there’s no escaping it.
4. Embrace the art of splitting up
Not everyone wants to visit museums, and not everyone wants to be under the hot sun on a jet ski. Instead of dragging each other to activities not everyone is excited about, embrace the idea of splitting up for a day or two. If one group wants to go sightseeing at a historical site and the other wants to surf some waves, that’s okay! Just make sure to have a designated meetup location and time, and keep each other posted. This will keep everyone happy and mean that no one has to fake any enthusiasm for something they don’t enjoy.
5. Be honest about your limits
It’s very tempting to go along with every plan to avoid seeming difficult. But, if you’re not careful, that’s a fast track to burnout. Remember, this is your grad trip too. If you need some downtime before an afternoon of exploring, take it. If you hate hiking, skip it instead of forcing yourself through. Your friends would rather you be honest than silently endure something you don’t enjoy. Grad trips are meant to be fun–so speak up and prioritise what will make your experience enjoyable.
6. Most importantly, embrace the chaos and remember why you came
No matter how well you plan, things will go wrong. A “quick” coffee run might turn into a two-hour detour, or a carefully planned itinerary could be derailed by a sudden downpour. Maybe the group gets on the wrong train and ends up in an entirely different city. Sometimes, the best memories come from unplanned moments–so lean into the chaos and let the adventure unfold.
At the end of the day, this trip isn’t about checking off every attraction or getting the perfect itinerary; it’s about celebrating a huge milestone with the people who made those long nights and tough exams bearable. The best part of the trip won’t be the landmarks or the food; it’ll be the inside jokes, the late-night talks, and the shared moments of pure chaos. So, take a deep breath, go with the flow, and make the most of it.
 *No trip is perfect, but what’s important is the time spent with your company. Photo taken from Pinterest.*
Surviving a grad trip with different travel styles isn’t about avoiding conflict, it’s about embracing the madness and making the best of it. And hey, worst case? You’ll have some hilarious group chat stories to reminisce about later.
-

@ 57d1a264:69f1fee1
2025-02-02 05:47:57
Hey there, as a result of the recent [SN Media Kit](https://stacker.news/items/872925/r/Design_r) updated, I'll try to create few simple marketing assets for ~Stackers_Stocks territory to be spread across the web.
Feel free to share in the comments below:
- Few visual references you'd like the assets to be inspired on
- If visuals are not your thing, a description of your idea will help too
- A slogan, or some words/concepts that express the territory's values
@BlokchainB you start, let's see how we go!
originally posted at https://stacker.news/items/873112
-

@ 57d1a264:69f1fee1
2025-02-02 00:03:39

Welcome to the latest updated version of **Stacker News Media Kit & Brand Guidelines `v1.2`**, a pivotal location where all the visual elements find place and help us understand how to use them to have our communications cohesive. SN brand identity is built on simplicity, trust, innovation and a taste of Texas's Wild West. With the following guidelines, as [promised](https://stacker.news/items/855556/r/Design_r?commentId=855753), I'll try to outline the essential elements of SN visual language to be easily usable internally and externally.
As third interaction from the previous [discussion](https://stacker.news/items/786223), here below you will find all the media assets in PNG and SVG downloadable from this [zip file](https://nosto.re/0a8b02224c970de78fba3a0195dcf1ee44d18925ba941724497173b2bcbab901.zip). BTW: I've been using **`Nostr`** 🌸 **Blossom Serverservers** [check them out](https://blossomservers.com/), it's a really cool idea! In case the file will be not available we can always upload it in other servers. Just let me know if any issue downloading it, ideally I made three copies available from:
- https://nosto.re/0a8b02224c970de78fba3a0195dcf1ee44d18925ba941724497173b2bcbab901.zip
- https://blossom.poster.place/0a8b02224c970de78fba3a0195dcf1ee44d18925ba941724497173b2bcbab901.zip
- https://nostr.download/0a8b02224c970de78fba3a0195dcf1ee44d18925ba941724497173b2bcbab901.zip
The source file of all these assets still are the same [Figma file](https://www.figma.com/design/ZL3FLItd9j48pzKVi4qlOy/Stacker.News-Media-Kit?node-id=3-16&t=oEbUcC1tmLDRXgdH-0) and the [PenPot file](https://design.penpot.app/#/workspace/7ad540b5-8190-815d-8005-5685b9c670bc/7ad540b5-8190-815d-8005-5685c186216e?page-id=2643bc5a-0d34-80b2-8005-58099eabda41). This last one, has many issues and does not allow yet the same flexibility as Figma. Both files are open for contributions and comments, just need to register a dummy/anonymous account for each of the tools.
> **Note:** To use these assets across SN, just copy-paste the image relative code, i.e.:

# Stacker News Logotype
SN logo is the most recognizable visual identifier of Stacker News. It captures the essence of its brand and is to be used across the platform and other marketing materials **consistently**. Find below all the possible variations and colors. Ideally you should stick with it to maintain SN identity coherent, or propose something new if you feel like. If you have any question on how to place or use the logo, DO ask below, and we'll help sort it out.
| Avatar on transparent BG | Avatar on BG | Logo Extended | Logo Vertical |#|
|---|---|---|---|---|
|  `` |  `` |  ``|  `` |Oil Black|
|  `` |  `` |  `` |  ``| Golden Yellow |
|  `` |  `` |  `` |  ``|With Shadow |
# Stacker News Typography

This is the typography SN had used to create its logo. [Download LightningVolt OpenType Font file.otf](http://honeyanddeath.web.fc2.com/FontFile/honeyanddeath_Lightningvolt.zip) designed by **[Honey&Death](http://honeyanddeath.web.fc2.com/fnt_Lightningvolt.html)**, install it in your computer and play with it.
Typography is essential to identify, increase readability and create consistency of brands. SN uses the default `font-family:sans-serif;` of your device's OS, usually are the most common and already installed in your device: `system-ui, "Segoe UI", Roboto, "Helvetica Neue", "Noto Sans", "Liberation Sans", Arial, sans-serif, "Apple Color Emoji", "Segoe UI Emoji", "Segoe UI Symbol", "Noto Color Emoji"`. Those are mostly used for:
# Example Header H1
## Example Header H2
### Example Header H3
#### Example Header H4
##### Example Header H5
**Example paragraph text**
The fonts selected will help to communicate the personality of the brand and provide maximum legibility for both print and screen.
`Example <code>`
For code, the approach is the same. Let's the device OS select its default `monospace` one. For example, on Mac will be one of the following:
```
SFMono-Regular, Menlo, Monaco, Consolas, "Liberation Mono", "Courier New",`
```
# Stacker News Colors
A thoughtfully curated color palette gives SN trust, professionalism, and approachability. Colors play a key role in creating consistent visual experiences through digital and print communications. Make sure you are using the right color codes below:
| # | Name | HEX code | RGB code | HLS |
|---|---|---|---|---|
|  | Bitcoin-only | `#F6911D` | `rgb(246,145,29)` | `hsl(32,92.3%,53.9%)` |
|  | Blackr | `#000000` | `rgb(0,0,0)` | `hsl(0,0%,0%)` |
|  | Dark | `#121214` | `rgb(18,18,20)` | `hsl(240,5.3%,7.5%)` |
|  | Gold | `#FADA5E` | `rgb(250,218,94)` | `hsl(48,94%,67.5%)` |
|  | Gray | `#969696` | `rgb(150,150,150)` | `hsl(0,0%,58.8%)` |
|  | Light | `#F0F0F0` | `rgb(240,240,240)` | `hsl(0,0%,94.1%)` |
|  | Nostrch | `#8C25F4` | `rgb(140,37,244)` | `hsl(270,90.4%,55.1%)` |
|  | Pinkish | `#E685B5` | `rgb(230,133,181)` | `hsl(330,66%,71.2%)` |
|  | Ruby | `#C03221` | `rgb(192,50,33)` | `hsl(6,70.7%,44.1%)` |
|  | Sky Hover | `#007CBE` | `rgb(0,124,190)` | `hsl(201,100%,37.3%)` |
|  | Sky Links | `#2E99D1` | `rgb(46,153,209)` | `hsl(201,63.9%,50%)` |
|  | Sky Visited | `#56798E` | `rgb(86,121,142)` | `hsl(203,24.6%,44.7%)` |
|  | So Fiat | `#5C8001` | `rgb(92,128,1)` | `hsl(77,98.4%,25.3%)` |
# Stacker News Icons
SN utilizes a set of bespoke icons that support its communication internally across the platform. Icons help bring instant, intuitive cues for various types of content and features. We share them here for you so you can use as you wish and satisfy your creative needs.
|  `` |  `` |  `[Bounty](https://m.stacker.news/75607)` |  `[Caret](https://m.stacker.news/75608)` |  `[Cowboy](https://m.stacker.news/75609)` |  `[Sun](https://m.stacker.news/75610)` |
|---|---|---|---|---|---|
|  **`[Edit](https://m.stacker.news/75611)`** |  **`[Gun](https://m.stacker.news/75612)`** |  **`[Horse](https://m.stacker.news/75613)`** |  **`[Info](https://m.stacker.news/75614)`** |  **`[Moon](https://m.stacker.news/75615)`** |  **`[Lightning](https://m.stacker.news/75616)`**|
|  **`[Bald Lost Hat](https://m.stacker.news/75617)`**|  **`[Markdown](https://m.stacker.news/75618)`**|  **`[Nostr](https://m.stacker.news/75619)`**|  **`[Referral](https://m.stacker.news/75620)`**|  **`[Rewards](https://m.stacker.news/75621)`**|  **`[Horse Lost Saddle](https://m.stacker.news/75622)`**|  **`[Search](https://m.stacker.news/75623)`** |
| **`[Shoot](https://m.stacker.news/75624)`** | **`[Texas](https://m.stacker.news/75625)`** |  **`[Upload](https://m.stacker.news/75626)`** |  **`[Zap Zap](https://m.stacker.news/75627)`** |||
# Stacker News Banners
Banners are important visual elements used in our digital platforms and marketing materials. They help to highlight key stories, features or announcements while maintaining our brand aesthetic.
Here below you'll find custom banners for Sn and for individial territories. I try to build those that I follow most, for now @AGORA is the only one that designed its own banners. Comment below if you'd like some banners for your territory!
#### SN Dark background
|970x250|
|---|
| ```|``|``|
|728x90|
|---|
|  `` |
#### SN Gold background
|970x250|
|---|
|`` |
|250x250|300x250|300x600|
|---|---|---|
|`` | `` |`` |
|728x90|
|---|
|`` |
#### SN by @Jon_Hodl
|970x250|
|---|
| `` |
|250x250|300x250|300x600|
|---|---|---|
| `` |  ``| `` |
|728x90|
|---|
|`` |
#### ~AGORA territory
The SN P2P Marketplace
|970x250|
|---|
| `` |
|250x250|300x250|300x600|
|---|---|---|
| `` | ``|``|
|728x90|
|---|
| ``|
#### ~alter_native territory
|970x250|
|---|
| ``|
|250x250|300x250|300x600|
|---|---|---|
|``|``|``|
|728x90|
|---|
|`` |
#### ~bitcoin_beginners
|970x250|
|---|
| `` |
|250x250|300x250|300x600|
|---|---|---|
| ``|``|`` |
|728x90|
|---|
| ``|
#### ~Design territory
|970x250|
|---|
|``|
|250x250|300x250|300x600|
|---|---|---|
|``|``|``|
|728x90|
|---|
|``|
#### ~Music territory
|970x250|
|---|
| ``|
|250x250|300x250|300x600|
|---|---|---|
|``|``|``|
|728x90|
|---|
| ``|
# Anything else we could add?
If you feel something is missing, or you know a better tool to manage this media kit for SN in a collaborative and FOSS way then, DO share it in a comment below
Territory owners [^1], do you need banners for your territory? Feel free to edit the figma file liked above or comment below sharing your needs or ideas, I'll try to do something for you.
By following these guidelines, we ensure consistency and professionalism in every case where Stacker News is represented here internally to stackers or to our audience in the KYC internet, reinforcing SN credibility as a trusted source for data-driven journalism.
[^1]: FYI: @Aardvark @AGORA @anna @antic @AtlantisPleb @Bell_curve @benwehrman @bitcoinplebdev @Bitter @BlokchainB @ch0k1 @davidw @ek @elvismercury @frostdragon @grayruby @HODLR @inverselarp @Jon_Hodl @k00b @marks @MaxAWebster @mega_dreamer @niftynei @nout @OneOneSeven @OT @PlebLab @Public_N_M_E @RDClark @realBitcoinDog @roytheholographicuniverse @siggy47 @softsimon @south_korea_ln @theschoolofbitcoin @TNStacker @UCantDoThatDotNet @Undisciplined
originally posted at https://stacker.news/items/872925
-

@ a95c6243:d345522c
2025-01-31 20:02:25
*Im Augenblick wird mit größter Intensität, großer Umsicht* *\
das deutsche Volk belogen.* *\
Olaf Scholz im FAZ-[Interview](https://www.youtube.com/watch?v=c3KI1GmdoVc\&t=649s)*  
**Online-Wahlen stärken die Demokratie, sind sicher, und 61 Prozent der Wahlberechtigten** sprechen sich für deren Einführung in Deutschland aus. Das zumindest behauptet eine aktuelle Umfrage, die auch über die Agentur *Reuters* Verbreitung in den Medien [gefunden](https://archive.is/dnZbY) hat. Demnach würden außerdem 45 Prozent der Nichtwähler bei der Bundestagswahl ihre Stimme abgeben, wenn sie dies zum Beispiel von Ihrem PC, Tablet oder Smartphone aus machen könnten.
**Die telefonische Umfrage unter gut 1000 wahlberechtigten Personen** sei repräsentativ, [behauptet](https://www.bitkom.org/Presse/Presseinformation/Knapp-Haelfte-Nichtwaehler-wuerde-online-waehlen) der Auftraggeber – der Digitalverband Bitkom. Dieser präsentiert sich als eingetragener Verein mit einer beeindruckenden Liste von [Mitgliedern](https://www.bitkom.org/Bitkom/Mitgliedschaft/Mitgliederliste), die Software und IT-Dienstleistungen anbieten. Erklärtes Vereinsziel ist es, «Deutschland zu einem führenden Digitalstandort zu machen und die digitale Transformation der deutschen Wirtschaft und Verwaltung voranzutreiben».
**Durchgeführt hat die Befragung die Bitkom Servicegesellschaft mbH,** also alles in der Familie. Die gleiche Erhebung hatte der Verband übrigens 2021 schon einmal durchgeführt. Damals sprachen sich angeblich sogar 63 Prozent für ein derartiges [«Demokratie-Update»](https://www.experten.de/id/4922407/online-wahlen-als-update-des-demokratischen-systems/) aus – die Tendenz ist demgemäß fallend. Dennoch orakelt mancher, der Gang zur Wahlurne gelte bereits als veraltet.
**Die spanische Privat-Uni mit Globalisten-Touch, IE University, berichtete** Ende letzten Jahres in ihrer Studie «European Tech Insights», 67 Prozent der Europäer [befürchteten](https://www.ie.edu/university/news-events/news/67-europeans-fear-ai-manipulation-elections-according-ie-university-research/), dass Hacker Wahlergebnisse verfälschen könnten. Mehr als 30 Prozent der Befragten glaubten, dass künstliche Intelligenz (KI) bereits Wahlentscheidungen beeinflusst habe. Trotzdem würden angeblich 34 Prozent der unter 35-Jährigen einer KI-gesteuerten App vertrauen, um in ihrem Namen für politische Kandidaten zu stimmen.
**Wie dauerhaft wird wohl das Ergebnis der kommenden Bundestagswahl sein?** Diese Frage stellt sich angesichts der aktuellen Entwicklung der Migrations-Debatte und der (vorübergehend) bröckelnden «Brandmauer» gegen die AfD. Das «Zustrombegrenzungsgesetz» der Union hat das Parlament heute Nachmittag überraschenderweise [abgelehnt](https://www.bundestag.de/dokumente/textarchiv/2025/kw05-de-zustrombegrenzungsgesetz-1042038). Dennoch muss man wohl kein ausgesprochener Pessimist sein, um zu befürchten, dass die Entscheidungen der Bürger von den selbsternannten Verteidigern der Demokratie künftig vielleicht nicht respektiert werden, weil sie nicht gefallen.
**Bundesweit wird jetzt zu «Brandmauer-Demos» aufgerufen,** die CDU gerät unter Druck und es wird von Übergriffen auf Parteibüros und Drohungen gegen Mitarbeiter [berichtet](https://www.epochtimes.de/politik/deutschland/brandmauer-proteste-cdu-zentrale-geraeumt-kundgebungen-in-46-staedten-a5023745.html). Sicherheitsbehörden warnen vor Eskalationen, die Polizei sei «für ein mögliches erhöhtes Aufkommen von Straftaten gegenüber Politikern und gegen Parteigebäude sensibilisiert».
**Der Vorwand** **[«unzulässiger Einflussnahme»](https://transition-news.org/die-minister-faeser-und-wissing-sorgen-sich-um-unzulassige-einflussnahme-auf)** **auf Politik und Wahlen** wird als Argument schon seit einiger Zeit aufgebaut. Der Manipulation schuldig befunden wird neben Putin und Trump auch Elon Musk, was lustigerweise ausgerechnet Bill Gates gerade noch einmal bekräftigt und als [«völlig irre»](https://transition-news.org/bill-gates-nennt-musks-einmischung-in-eu-politik-vollig-irre) bezeichnet hat. Man stelle sich die Diskussionen um die Gültigkeit von Wahlergebnissen vor, wenn es Online-Verfahren zur Stimmabgabe gäbe. In der Schweiz wird [«E-Voting»](https://www.ch.ch/de/abstimmungen-und-wahlen/e-voting/) seit einigen Jahren getestet, aber wohl bisher mit wenig Erfolg.
**Die politische Brandstiftung der letzten Jahre zahlt sich immer mehr aus.** Anstatt dringende Probleme der Menschen zu lösen – zu denen auch in Deutschland die [weit verbreitete Armut](https://transition-news.org/ein-funftel-der-bevolkerung-in-deutschland-ist-von-armut-oder-sozialer) zählt –, hat die Politik konsequent polarisiert und sich auf Ausgrenzung und Verhöhnung großer Teile der Bevölkerung konzentriert. Basierend auf Ideologie und Lügen werden abweichende Stimmen unterdrückt und kriminalisiert, nicht nur und nicht erst in diesem Augenblick. Die nächsten Wochen dürften ausgesprochen spannend werden.
***
Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/wahlen-und-wahlen-lassen)*** erschienen.
-

@ 5188521b:008eb518
2025-01-31 08:38:47
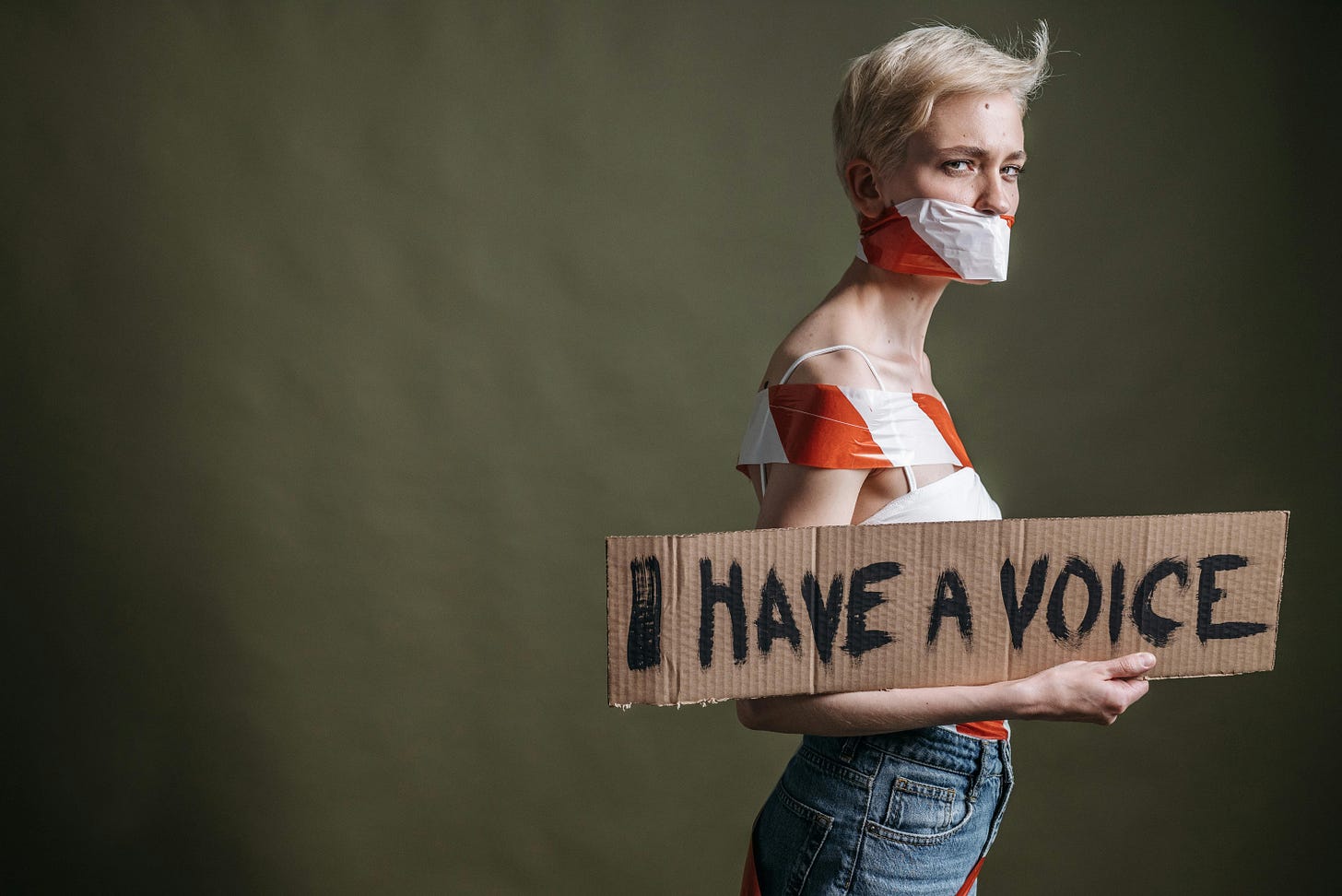*Photo by [Pavel Danilyuk](https://www.pexels.com/photo/a-woman-holding-a-placard-8553778/)*
In the last four years, I’ve ridden the wave of social media. I’ve amassed thousands of followers, and my posts were read by millions.
It’s empowering… until it isn’t.
This year, I chose to stop publishing on LinkedIn, Medium, Facebook, Instagram, and Threads. My reach on each of these platforms dropped from 100% of my follower base to around 10%. My voice was being suppressed.
I wasn’t writing anything particularly controversial. This is all just part of the social media life cycle. Platforms offer attractive terms to lock in users. They distribute our articles, posts, and thoughts widely to attract eyeballs for advertisers.
Writers learn to play the algorithm to maximise reach and engagement. Maybe they even manage to monetize their writing.
But when the platforms reach what they deem to be maximum usage and membership, they begin to reduce the benefits on offer. They ask writers to focus on specific topics, suppress non-mainstream opinion, or punish or ban any writers who don’t follow new rules. Big tech companies always eventually turn on the money tap by forcing users to suffer endless adverts and even make writers pay to reach the audience they have built.
Newsflash: there is no company too big to fail. Digg, Google+, Myspace, Vine and many more socials have died. Self-reported active user numbers cannot be trusted. Meta recently trialed AI profiles to prop up falling usage projections on Instagram and Facebook. X is now a dumpster fire of bots, scammers, and rage bait. It has been co-opted by a megalomaniacal oligarch to spread his own worldview. And LinkedIn feeds are drowning in unsolicited AI-generated business twaddle. The social giants are entering the death spiral.
# What happens in a social-media death spiral?
Users don’t see the value in posting, so they move elsewhere.
I wasn’t feeling rewarded for the thousands of hours I spent on LinkedIn, so I quit. I went from earning $20+ an article on Medium to pennies. Literal pennies. Bye bye, Tony Stubblebine. I learned that if you don’t own the distribution mechanic, you get left writing into the wind.
Ultimately, writers will dedicate their energy to where they see a benefit. They should spend time and create value in the place most similar to their ideal world.
For writers in 2025, that place seems to be Substack. Open rates are high and the platform is adding social features to generate more engagement in app. Substack is [experiencing massive growth](https://backlinko.com/substack-users) in active (and paid) subscriptions. Yet, it is following the same pattern as Medium in and LinkedIn in become self-cannibalising. Many of the most popular accounts write about ‘how to grow’ or ‘how to make money’ on Substack. Queue the eye rolls.
For me, it’s not the promised land where writers can earn a living. Of course, it’s no walk in the park to earn paid subscribers. Further, Substack users can only receive payment via Stripe. This excludes writers from 149 of the World’s countries. Does that seem open and fair to you?
Even with all this going on, there is a much bigger factor that should influence your choice of platform — ownership.
# Do writers really own their words?
Who reads the terms and conditions? Nobody. That’s who.Writers (including me) rush to all platforms which promise to give us benefits such as pay, distribution, and audience growth.
In exchange, companies request access to and shared ownership of our content. They can use our words to train LLMs, analyse trends, repurpose, and to spy on us.
Governments can and will request access to social media profiles. They seek to control the use of those platforms. Founders and CEOs who refuse to comply may be held personally accountable and put on trial, just as [Telegram founder, Pavel Durov, was](https://www.bbc.com/news/articles/c78lgzl919go) in France. Big tech owns our content, and governments threaten platforms into obedience.
As much as it benefits society to suppress harmful or dangerous content, companies simply can’t be censors 24/7. Growing platforms like [Bluesky are already struggling to moderate content effectively](https://www.theregister.com/2024/12/02/bluesky_growing_problems/). Without a strong economic incentive to moderate, companies will simply refuse to do it (as long as the threat of criminal charges does not prevail).
To sum up: No privately owned social media network offers writers the opportunity to own and distribute their work in order to receive a fair and equitable benefit.
Enter NOSTR…
# Decentralizing Social Media
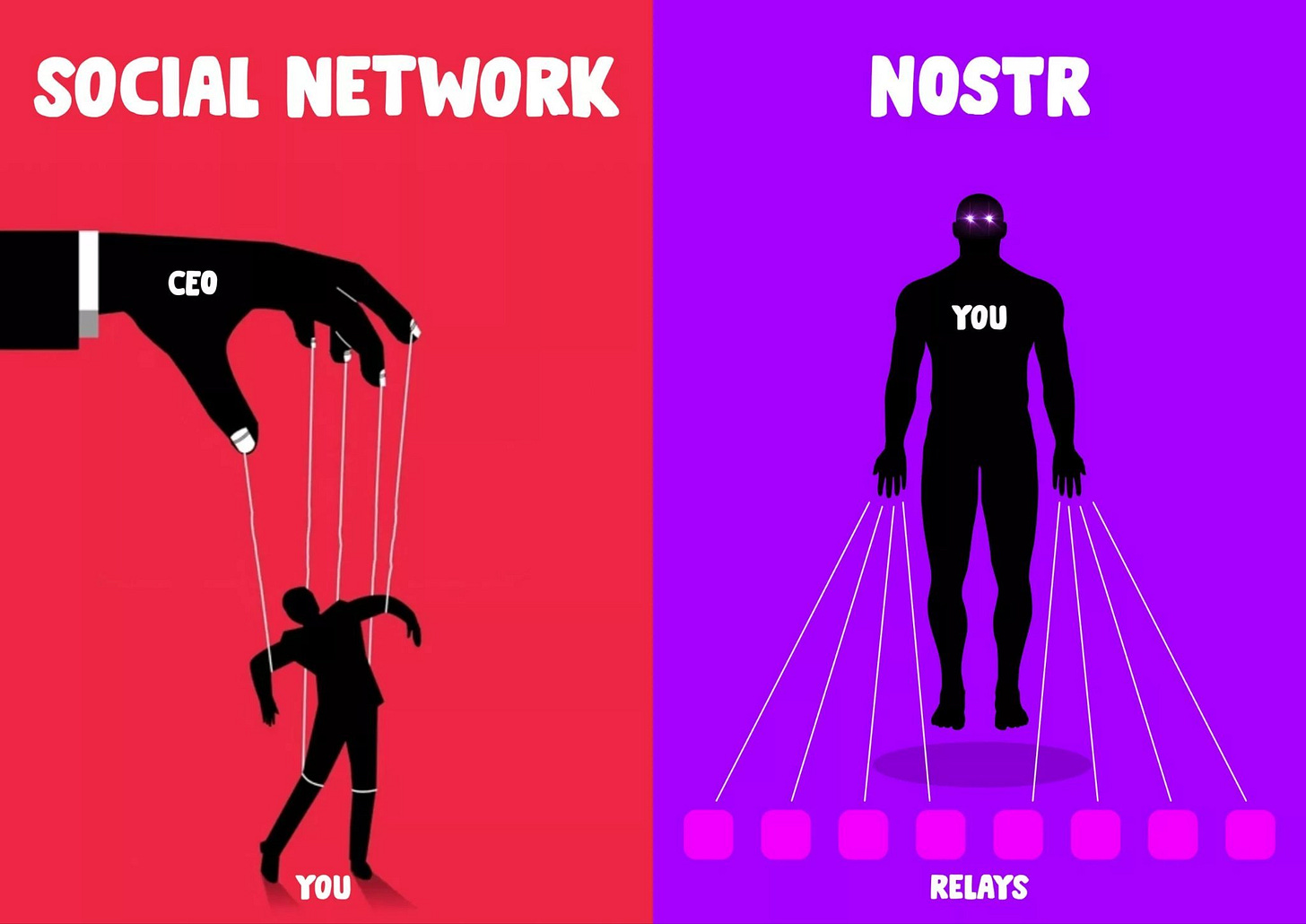**Notes and Other Stuff Transmitted by Relays** (NOSTR) is not a platform; it’s an open protocol.
By signing messages with their private keys (a long string of characters), users generate “events”. These events (messages/updates/media/transactions) are then broadcast through a series of “relays.”
Developers can use the protocol to build various applications that retrieve and distribute these events to other users. These ‘clients’ can range from microblogging sites like X and long-form distributors like Substack to visual media platforms like Instagram. Plus, NOSTR is also a whole lot more than that (but this is a topic for another day).
Decentralized tools offer the only hope against the dominance of AI and big tech in a top-down autocratic system designed to control us more than the thought police ever could.
<img src="https://blossom.primal.net/93a44d9bfe3c768e41d8bfef52415131af3ca21814a23870a029f1a947288cc8.webp">
*Diagram courtesy of River.*
So why should writers opt out of their big audience pool to write on some ‘protocol’?
**Ownership, fair rules, and fair value.**
- **Ownership**:
While privately run corporations can suppress the ideas they want, NOSTR provides a censorship-resistant alternative. No individual actors can restrict content or accounts.
Your private keys provide **permanent access** to the messages you have signed. No one else has access to them. And while some clients provide a delete function, there is no way to force all relays to respect a delete request. Not only do writers own what they publish, but it’s a permanent record.
- **Rules:**
Traditional social media platforms use proprietary algorithms to curate and order our feeds. **NOSTR has no algorithm**. NOSTR clients display messages chronologically or based on user-defined criteria, removing the influence of opaque algorithms that could manipulate user engagement and visibility of posts.
Put simply, distribution and consumption is down to the user, not to the creator or the platform. And everyone works to the same rules.
- **Value:**
Harmful content and spam affect all of us. There is no way to stop malicious content from being published on NOSTR, but two factors control its consumption.
1. Clients are experimenting with strategies such as requiring proof-of-work with each note or requiring verification badges.
2. Quality control is enforced by the value transferred by the protocol.
Bitcoin micropayments have become the monetary lifeblood flowing in the decentralized world. The ability to ‘zap’ users actual monetary value (e.g. a few cents) provides a clear display of which messages are valuable and which are unwanted. In time, as more users adopt the mechanic of value transfer, spammers will see their approach is not bearing fruit.
The beauty of using bitcoin in this way is twofold. Firstly, it is truly equitable — anyone in the world can receive it instantly and it cannot be stopped. And the system of frictionless micropayments offers content creators (artists, podcasters, musicians, writers) a way to earn money for the value they produce. Put simply, this could save creativity from doom.
Think people still want all content for free? Think again. Try zapping a writer from the Philippines, an artist from Peru, a Congolese musician, or a poet from Poland to show them you enjoyed what they produced. THAT is truly empowering.
Not convinced?
The best thing about NOSTR for writers is that **you are early**.
By being an early adopter with a low time preference, you can build a sizeable audience as new users discover the protocol.
Of course, topics like bitcoin, freedom tech, and privacy are well covered, but if you write in another niche, you could be ‘quids in’.
# Conclusion:
By adopting a long-term strategy and sticking to their principles, readers, writers and all other creatives can build a better world on social media. It doesn’t matter that it is imperfect. There will always be flaws in any society. But decentralized protocols like NOSTR can offer writers what they truly want — ownership, fair rules, and fair value.
---
Philip Charter is a totally human writer who helps bitcoin-native companies and clients stack major gains through laser-focused content. Find out more at [totallyhumanwriter.com](https://totallyhumanwriter.com)
He is also the editor of the cypherpunk and freedom fiction project, [21 Futures](https://21futures.com).
-

@ 57d1a264:69f1fee1
2025-01-31 02:07:27

Bitcoin Design members have been involved in organizing various events (and sometimes just attend, too). Here below is what do we want to do in 2025:
- **[Designathon 2](https://github.com/BitcoinDesign/Meta/issues/625)** - We are organizing this event between February or March.
- **[Accessibility Day](https://accessibility.day)** - May 15
- - BDC has participated in this global initiative the last two years. Probably doing so again!
- **[BTC Prague](https://btcprague.com)** -Participation Confirmed. Planning issues [here](https://github.com/BitcoinDesign/Meta/issues/745) - June 19 - 21
- * We organized the design track for dev day in 2023 and 2024. Do this again[\[k\]](#cmnt11)[\[l\]](#cmnt12)? It’s going to be on June 18, before the main conference.
- * 2024 was great, in that we had a nice group of designers attend, do talks, go for dinner, etc.
- **[Summer of Bitcoin](https://www.google.com/url?q=https://www.summerofbitcoin.org)**
- * Several designers and projects participated each of the last 3 years. Probably doing so again!
- * Applications open on Feb 1, main program is May to August ([timeline](https://www.summerofbitcoin.org/how-it-works/)
- **UX Bootcamps**
- * Previous: South America
- * Next: [South America](https://www.bitcoinuxbootcamp.xyz/southamerica) - February 17 - 22
- **[Bitshala fellowship](https://bitshala.org)**
- * First iteration of this fellowship is from January to July
- * We will help find more designers, projects, and funding in India
- **[Oslo Freedom Forum](https://oslofreedomforum.com)** - Oslo, May 26-28
- * Activist and financial repression use cases are uniquely important use cases for bitcoin.
- * Several people attended last year. Conversations lead to new initiatives.
- **[BTCHEL](https://btchel.com/)** - by BTC Helsinki Community - Aug 15-16
- * First large-scale bitcoin conference in the Nordics with particular focus to onboard new users to bitcoin
- **Bitcoin Presidio design week**
- * This is a new Bitcoin co-working space in San Francisco, also announced here https://stacker.news/items/860931/r/Design_r. The idea came up to organize a design week there to support the creation of art and decoration for the new co-working space. Just an idea at the moment, but why not make it happen?
- * [Discussion issue](https://github.com/BitcoinDesign/Meta/issues/746).
- **BuildWithLDK**
- * An initiative to promote LDK and LDK Node for building lightning applications. There could be collaboration around a Designathon, connecting designers with hackathon projects, etc. Still in early planning.
- **Builder conferences**: These are very builder-focused, making them good opportunities to connect, organize practical design workshops, creative presentations, and support projects from a design perspective
- * [Baltic Honeybadger](https://baltichoneybadger.com) (August 9-10),
- * [TABConf](http://tabconf.com)
- * [Bitcoin++](https://btcplusplus.dev) There are going to be 6 of them throughout the year.
- * [SATS’N’FACTS](https://satsandfacts.btc.pub/) (February 8-10) Bitcoin Technical Unconference, Hackathon & Freedom Tech Art Exhibition
- **Open-source conferences & events*
- * [FOSS Backstage](http://foss-backstage.de) (Berlin, Mar 10-11) - Christoph will present the Open Design Guide
- * [FOSDEM](https://fosdem.org/2025/) (Brussels, Feb 1-2) - anyone attending?
- **Design conferences & events** - Makes sense to be involved with design-only events, right?
* [OFFF](https://www.offf.barcelona) - very creative-focused (Barcelona, May 8-10)
* [CSUN Accessibility conference](https://www.csun.edu/cod/conference/sessions/)
**Other Ideas**
* Bitcoin Park - they might organize another design event like two years ago https://stacker.news/items/705081/r/Design_r
**Links**
* [Comprehensive list](https://docs.google.com/spreadsheets/d/147AXd8hN3uO3v_P1dupgfRCRzSMlH85dvQSHPAg7lZ4/edit?usp%3Dsharing) of bitcoin conferences
- - -
… what’s missing from this page? Are you involved with anything? Or want to be? Comment below or join us on https://discord.com/channels/903125802726596648/1087394066796384276
You can watch the recording from
https://www.youtube.com/watch?v=GGS3oSlLmAo
originally posted at https://stacker.news/items/870638
-

@ 97c70a44:ad98e322
2025-01-30 17:15:37
There was a slight dust up recently over a website someone runs removing a listing for an app someone built based on entirely arbitrary criteria. I'm not to going to attempt to speak for either wounded party, but I would like to share my own personal definition for what constitutes a "nostr app" in an effort to help clarify what might be an otherwise confusing and opaque purity test.
In this post, I will be committing the "no true Scotsman" fallacy, in which I start with the most liberal definition I can come up with, and gradually refine it until all that is left is the purest, gleamingest, most imaginary and unattainable nostr app imaginable. As I write this, I wonder if anything built yet will actually qualify. In any case, here we go.
# It uses nostr
The lowest bar for what a "nostr app" might be is an app ("application" - i.e. software, not necessarily a native app of any kind) that has some nostr-specific code in it, but which doesn't take any advantage of what makes nostr distinctive as a protocol.
Examples might include a scraper of some kind which fulfills its charter by fetching data from relays (regardless of whether it validates or retains signatures). Another might be a regular web 2.0 app which provides an option to "log in with nostr" by requesting and storing the user's public key.
In either case, the fact that nostr is involved is entirely neutral. A scraper can scrape html, pdfs, jsonl, whatever data source - nostr relays are just another target. Likewise, a user's key in this scenario is treated merely as an opaque identifier, with no appreciation for the super powers it brings along.
In most cases, this kind of app only exists as a marketing ploy, or less cynically, because it wants to get in on the hype of being a "nostr app", without the developer quite understanding what that means, or having the budget to execute properly on the claim.
# It leverages nostr
Some of you might be wondering, "isn't 'leverage' a synonym for 'use'?" And you would be right, but for one connotative difference. It's possible to "use" something improperly, but by definition leverage gives you a mechanical advantage that you wouldn't otherwise have. This is the second category of "nostr app".
This kind of app gets some benefit out of the nostr protocol and network, but in an entirely selfish fashion. The intention of this kind of app is not to augment the nostr network, but to augment its own UX by borrowing some nifty thing from the protocol without really contributing anything back.
Some examples might include:
- Using nostr signers to encrypt or sign data, and then store that data on a proprietary server.
- Using nostr relays as a kind of low-code backend, but using proprietary event payloads.
- Using nostr event kinds to represent data (why), but not leveraging the trustlessness that buys you.
An application in this category might even communicate to its users via nostr DMs - but this doesn't make it a "nostr app" any more than a website that emails you hot deals on herbal supplements is an "email app". These apps are purely parasitic on the nostr ecosystem.
In the long-term, that's not necessarily a bad thing. Email's ubiquity is self-reinforcing. But in the short term, this kind of "nostr app" can actually do damage to nostr's reputation by over-promising and under-delivering.
# It complements nostr
Next up, we have apps that get some benefit out of nostr as above, but give back by providing a unique value proposition to nostr users as nostr users. This is a bit of a fine distinction, but for me this category is for apps which focus on solving problems that nostr isn't good at solving, leaving the nostr integration in a secondary or supporting role.
One example of this kind of app was Mutiny (RIP), which not only allowed users to sign in with nostr, but also pulled those users' social graphs so that users could send money to people they knew and trusted. Mutiny was doing a great job of leveraging nostr, as well as providing value to users with nostr identities - but it was still primarily a bitcoin wallet, not a "nostr app" in the purest sense.
Other examples are things like Nostr Nests and Zap.stream, whose core value proposition is streaming video or audio content. Both make great use of nostr identities, data formats, and relays, but they're primarily streaming apps. A good litmus test for things like this is: if you got rid of nostr, would it be the same product (even if inferior in certain ways)?
A similar category is infrastructure providers that benefit nostr by their existence (and may in fact be targeted explicitly at nostr users), but do things in a centralized, old-web way; for example: media hosts, DNS registrars, hosting providers, and CDNs.
To be clear here, I'm not casting aspersions (I don't even know what those are, or where to buy them). All the apps mentioned above use nostr to great effect, and are a real benefit to nostr users. But they are not True Scotsmen.
# It embodies nostr
Ok, here we go. This is the crème de la crème, the top du top, the meilleur du meilleur, the bee's knees. The purest, holiest, most chaste category of nostr app out there. The apps which are, indeed, nostr indigitate.
This category of nostr app (see, no quotes this time) can be defined by the converse of the previous category. If nostr was removed from this type of application, would it be impossible to create the same product?
To tease this apart a bit, apps that leverage the technical aspects of nostr are dependent on nostr the *protocol*, while apps that benefit nostr exclusively via network effect are integrated into nostr the *network*. An app that does both things is working in symbiosis with nostr as a whole.
An app that embraces both nostr's protocol and its network becomes an organic extension of every other nostr app out there, multiplying both its competitive moat and its contribution to the ecosystem:
- In contrast to apps that only borrow from nostr on the technical level but continue to operate in their own silos, an application integrated into the nostr network comes pre-packaged with existing users, and is able to provide more value to those users because of other nostr products. On nostr, it's a good thing to advertise your competitors.
- In contrast to apps that only market themselves to nostr users without building out a deep integration on the protocol level, a deeply integrated app becomes an asset to every other nostr app by becoming an organic extension of them through interoperability. This results in increased traffic to the app as other developers and users refer people to it instead of solving their problem on their own. This is the "micro-apps" utopia we've all been waiting for.
Credible exit doesn't matter if there aren't alternative services. Interoperability is pointless if other applications don't offer something your app doesn't. Marketing to nostr users doesn't matter if you don't augment their agency _as nostr users_.
If I had to choose a single NIP that represents the mindset behind this kind of app, it would be NIP 89 A.K.A. "Recommended Application Handlers", which states:
> Nostr's discoverability and transparent event interaction is one of its most interesting/novel mechanics. This NIP provides a simple way for clients to discover applications that handle events of a specific kind to ensure smooth cross-client and cross-kind interactions.
These handlers are the glue that holds nostr apps together. A single event, signed by the developer of an application (or by the application's own account) tells anyone who wants to know 1. what event kinds the app supports, 2. how to link to the app (if it's a client), and (if the pubkey also publishes a kind 10002), 3. which relays the app prefers.
_As a sidenote, NIP 89 is currently focused more on clients, leaving DVMs, relays, signers, etc somewhat out in the cold. Updating 89 to include tailored listings for each kind of supporting app would be a huge improvement to the protocol. This, plus a good front end for navigating these listings (sorry nostrapp.link, close but no cigar) would obviate the evil centralized websites that curate apps based on arbitrary criteria._
Examples of this kind of app obviously include many kind 1 clients, as well as clients that attempt to bring the benefits of the nostr protocol and network to new use cases - whether long form content, video, image posts, music, emojis, recipes, project management, or any other "content type".
To drill down into one example, let's think for a moment about forms. What's so great about a forms app that is built on nostr? Well,
- There is a [spec](https://github.com/nostr-protocol/nips/pull/1190) for forms and responses, which means that...
- Multiple clients can implement the same data format, allowing for credible exit and user choice, even of...
- Other products not focused on forms, which can still view, respond to, or embed forms, and which can send their users via NIP 89 to a client that does...
- Cryptographically sign forms and responses, which means they are self-authenticating and can be sent to...
- Multiple relays, which reduces the amount of trust necessary to be confident results haven't been deliberately "lost".
Show me a forms product that does all of those things, and isn't built on nostr. You can't, because it doesn't exist. Meanwhile, there are plenty of image hosts with APIs, streaming services, and bitcoin wallets which have basically the same levels of censorship resistance, interoperability, and network effect as if they weren't built on nostr.
# It supports nostr
Notice I haven't said anything about whether relays, signers, blossom servers, software libraries, DVMs, and the accumulated addenda of the nostr ecosystem are nostr apps. Well, they are (usually).
This is the category of nostr app that gets none of the credit for doing all of the work. There's no question that they qualify as beautiful nostrcorns, because their value propositions are entirely meaningless outside of the context of nostr. Who needs a signer if you don't have a cryptographic identity you need to protect? DVMs are literally impossible to use without relays. How are you going to find the blossom server that will serve a given hash if you don't know which servers the publishing user has selected to store their content?
In addition to being entirely contextualized by nostr architecture, this type of nostr app is valuable because it does things "the nostr way". By that I mean that they don't simply try to replicate existing internet functionality into a nostr context; instead, they create entirely new ways of putting the basic building blocks of the internet back together.
A great example of this is how Nostr Connect, Nostr Wallet Connect, and DVMs all use relays as brokers, which allows service providers to avoid having to accept incoming network connections. This opens up really interesting possibilities all on its own.
So while I might hesitate to call many of these things "apps", they are certainly "nostr".
# Appendix: it smells like a NINO
So, let's say you've created an app, but when you show it to people they politely smile, nod, and call it a NINO (Nostr In Name Only). What's a hacker to do? Well, here's your handy-dandy guide on how to wash that NINO stench off and Become a Nostr.
You app might be a NINO if:
- There's no NIP for your data format (or you're abusing NIP 78, 32, etc by inventing a sub-protocol inside an existing event kind)
- There's a NIP, but no one knows about it because it's in a text file on your hard drive (or buried in your project's repository)
- Your NIP imposes an incompatible/centralized/legacy web paradigm onto nostr
- Your NIP relies on trusted third (or first) parties
- There's only one implementation of your NIP (yours)
- Your core value proposition doesn't depend on relays, events, or nostr identities
- One or more relay urls are hard-coded into the source code
- Your app depends on a specific relay implementation to work (*ahem*, relay29)
- You don't validate event signatures
- You don't publish events to relays you don't control
- You don't read events from relays you don't control
- You use legacy web services to solve problems, rather than nostr-native solutions
- You use nostr-native solutions, but you've hardcoded their pubkeys or URLs into your app
- You don't use NIP 89 to discover clients and services
- You haven't published a NIP 89 listing for your app
- You don't leverage your users' web of trust for filtering out spam
- You don't respect your users' mute lists
- You try to "own" your users' data
Now let me just re-iterate - it's ok to be a NINO. We need NINOs, because nostr can't (and shouldn't) tackle every problem. You just need to decide whether your app, as a NINO, is actually contributing to the nostr ecosystem, or whether you're just using buzzwords to whitewash a legacy web software product.
If you're in the former camp, great! If you're in the latter, what are you waiting for? Only you can fix your NINO problem. And there are lots of ways to do this, depending on your own unique situation:
- Drop nostr support if it's not doing anyone any good. If you want to build a normal company and make some money, that's perfectly fine.
- Build out your nostr integration - start taking advantage of webs of trust, self-authenticating data, event handlers, etc.
- Work around the problem. Think you need a special relay feature for your app to work? Guess again. Consider encryption, AUTH, DVMs, or better data formats.
- Think your idea is a good one? Talk to other devs or open a PR to the [nips repo](https://github.com/nostr-protocol/nips). No one can adopt your NIP if they don't know about it.
- Keep going. It can sometimes be hard to distinguish a research project from a NINO. New ideas have to be built out before they can be fully appreciated.
- Listen to advice. Nostr developers are friendly and happy to help. If you're not sure why you're getting traction, ask!
I sincerely hope this article is useful for all of you out there in NINO land. Maybe this made you feel better about not passing the totally optional nostr app purity test. Or maybe it gave you some actionable next steps towards making a great NINON (Nostr In Not Only Name) app. In either case, GM and PV.
-

@ 9e69e420:d12360c2
2025-01-30 12:13:39
Salwan Momika, a Christian Iraqi known for burning the Koran in Sweden, was shot dead during a TikTok livestream in an apartment in Sodertalje. The 38-year-old sparked outrage in the Muslim community for his demonstrations, leading to global condemnation. After being rushed to the hospital, he was pronounced dead.
Authorities arrested five individuals in connection with the incident. Momika's death comes days before a court ruling on his possible incitement of ethnic hatred. The incident highlights the tensions surrounding free speech and religious sentiments, intensifying after his controversial protests in 2023.
[Sauce](https://www.dailymail.co.uk/news/article-14341423/Christian-Iraqi-burnt-Koran-Sweden-shot-dead.html)
-

@ e262ed3a:e147fbcb
2025-01-30 11:26:25

I got an idea while watching a video from @BTCSessions, which I personally cannot implement technically. Therefore, I would like to present it here for discussion and free implementation. It makes sense to me, but what do I know? Let the swarm intelligence decide.
The goal of the business idea is:
1. How can I bring as many solo miners as possible into a pool without them having to pay for the electricity for mining and their mining hardware can be amortized quickly, so they can purchase more mining hardware?
2. How can we financially support Bitcoin and Nostr developers in the long term?
3. How can we intensify developers for the implementation of this idea?
4. How can we encourage non-Bitcoiners to invest in the support of the Bitcoin network?
5. How can we get non-Bitcoin retailers to invest in the Bitcoin network?
**The answer is: PROSPECT OF WINNING**
**The solution lies in a kind of RAFFLE. (Not a betting website)**
The legal difference between a BET and a RAFFLE varies from country to country. It lies in the fact that a raffle must be very transparent regarding the chances of winning and the proceeds must go to a good cause. Those involved in the implementation can, of course, be compensated (also with a profit for the individual participants). The extent to which this is allowed would have to be checked by those who want to implement this idea.
In the following, I will describe the implementation roughly. Since this is not a sales presentation, please excuse me if the following proposal is not fully structured.
Participants in the idea are:
1. Consumers (ticket buyers)
2. Bitcoin miners
3) Retailers
4) Non-profit company that implement the project
**What's it about?** @BTCSessions has a YouTube video about the miner FutureBit. In the dashboard of the solo miner, you could see how high the hash rate was. But above all, you could see how high the chance of winning was for the solo miner in the overall network. In the case of BTCSessions FutureBit, the hash rate was around 5 TerraHash and the chance of winning was around 1:1,000,000. (Which, according to my calculations, was not correct). The power consumption was around 32 watts. When I saw that, it suddenly dawned on me.
Could it be possible to create a website/app that determines the total hash rate of a mining pool and then offers an electronic, numbered ticket for each 1 TerraHash (TH/s) of the pool for, for example, 0.1 USD? The minimum purchase amount would be 10 tickets. The customer sees the chance of winning and could even see the possible payout. The ticket is only valid for the next block (similar to roulette).
Another variant could be that the buyer can select one or more of the next 10 blocks and purchase tickets for the selected block. Since you don't know in advance how high the pool hash rate will be 5 or 10 blocks ahead, the amount of tickets to be issued for the 2nd block, for example, could only be 90% of the current pool hash rate, the 3rd block only 80%, and so on. If block 3, for example, advances to position 2, the previously unavailable 10% will be released for further tickets. (Determined by the pool hash rate at that time)
The purchase of 10 or more tickets could be automated in the customer's account on the website/app (intervals: hourly, daily, weekly, every 10 blocks, etc.). Customers could also top up their account with satoshis, enabling automatic deductions for ticket purchases. This could be facilitated by automatically issuing a Nostr npub to each customer, which would also create a wallet at Primal.net (Strike). For non-Bitcoiners, Zaprite could be used to recharge their account. Alternatively, customers could enter a NostrWalletConnection NWC to enable automatic deductions from their Lightning wallet. The project operators might also consider running their own ecash mint, which would allow them to assign an integrated ecash address to customers without a Lightning address. Tickets with ascending numbers would be allocated strictly in the order of payment receipts.
**Calculations for the miners**: The FutureBit miner consumed approximately 30 watts per terahash/hour. Let's assume that 10 terahash consume 300 watts per hour, then the miner consumes 50 watts per 10 minutes (per block). Let's further assume that a kilowatt-hour of electricity costs between 10 and 30 cents, then it costs the miner 3-9 cents per hour for electricity at 10 terahash mining capacity. So, 0.5-1.5 cents per block. In the case that each ticket is sold for 1 terahash for the next block, one could automatically transfer, for example, 5% of the satoshis received from ticket sales to each participating miner in the pool (proportional to the average hash rate delivered by the miner in the last block in the pools). This happens even if the block is not found. If fewer tickets are sold than the maximum possible amount, then the 5% of the sold tickets will be distributed proportionally. (See also my Excel file?
**At the center** of the project is a website/app that manages the raffle. Here, anyone can register and create an account. Either as a miner, retailer, or customer with or without KYC, for example, with their own nostr nsec, wallet signature, email and password or phone number and password.
Once logged into the account, Bitcoiners can enter their Lightning address and a Bitcoin on-chain address. Non-Bitcoiners enter their financial data in case they win.
Miners must enter a Bitcoin and Lightning (or ecash) address. The pooling process is also managed in the miner's account.
Tickets can be purchased (like in a regular online shop) and paid for in any way. Zaprite could be a solution here. But also Strike, Cashapp, etc. As described above, such purchases could also be automated.
**Retailers can also register as such**. They will then have the opportunity to sell "tickets" to their customers and collect the money in cash. To sell tickets, they must enter the customer's name and a valid email address. After payment, they must send the purchase price via Lightning to the non-profit company, which will then confirm the purchase to the ticket buyer and the retailer with all the data. This is the receipt for the buyer. In the event of a win (the mined block must have 3-6 block confirmations), the ticket buyer will receive an email explaining all the further details of how to claim the prize. This could be a link that takes them directly to the website and logs them in directly. The winner can then enter their data on how and where the money should be paid out (Bitcoin address or bank details). Alternatively, they can go to their retailer, who can assist them by entering the data in their sub-account (customer account). To prevent the retailer from falsifying the data entry, the winner will first receive an email with the entered data, which they can confirm (if correct). Since the retailer is also involved in the win, they will also be notified.
**How many tickets** can be offered per round (Bitcoin block)? The number of tickets depends on the hash rate in the pool. One ticket can be issued per 1 TerraHash (TH/s). How the ticket is generated per round and customer, I don't know, as I lack the technical knowledge. Maybe as a kind of NFT that contains the corresponding data (customer number (npub) of the buyer and possibly retailer, block number, ticket number). Or as a Taproot asset on Lightning? Or as a minted ecash coin? Or simply as an entry in a database that the customer can see in their account.
The maximum payout of the winnings in the event of a found block to the ticket holders could be 70%. The remaining 30% would be distributed to the miners and retailers. For example: Miners 25%, retailers 5%. The non-profit organization receives nothing from the block rewards. Instead, it receives 65% of the revenue from all ticket sales. With a mining pool hash rate of 10,000 TH/s, where all tickets are sold continuously, a daily donation of around 93,000 USD would be generated. (see Excel.file)
The revenue, after deducting the possible costs of the organization, goes directly to @opensats and/or other organizations that support the Bitcoin network after each block. Either via Lightning or Bitcoin on-chain payment.
In the attached Excel file, you can find my calculations. Here, anyone can play through different scenarios.
What I noticed was that with maximum ticket sales per block, only around 200 USD per 10 tickets would be paid out, since each participating ticket wins in the event of a found block. Since I believe that this is not a very great incentive for buying tickets, I suggest the following variants.
**Winning variants**: Each purchased ticket has a running number. Ticket 1 has the number 000.000, ticket 2 has the number 000.001, ticket 10.120 has the number 010.119, and so on.
If the next block is found, then this found block in the Bitcoin blockchain has a hash. For example, block 881367 has the hash 000000000000000000014b0fab24355c71c6940584d9cd5990c0b081a31d54a4
Let's now remove the letters and read only the numbers from back to front, so the last 3 numbers are 544
Instead of every participating ticket winning, in this variant, only the tickets with the ending digits 544 win.
With, for example, 11,000 tickets sold, the ticket numbers 000.544 / 001.544 / 002.544 ... 010.544 would win. So, 11 ticket participants would win. Each winner with this number would receive around 0.284 Bitcoin (3.125 BTC / 11).
One could also let the ticket numbers with the ending digits 44 win, and thus every hundredth ticket. Or even combine it.
What I also noticed was that with retailers, a special case arises. Retailers receive 5% of the block rewards in the event of a found block. But only proportionally to the tickets sold by the retailer. This means that in order for the entire 5% to be distributed to the retailers, all 10,000 tickets of 10.000 possible tickets would have to be sold by retailers. Since not all tickets will be sold by retailers, a remaining amount will be left over. This could be distributed additionally to the miners. Or any other variant.
I hope the idea finds resonance and invites discussion. Maybe I've made some mistakes in thinking, and the idea is not feasible. But if you like the idea, please forward it to developers, investors, and others you know.
Best regards.
<span data-type="mention" data-id="e262ed3a22ad8c478b077ef5d7c56b2c3c7a530519ed696ed2e57c65e147fbcb" data-label="nostr:undefined">@nostr:undefined</span> dewe
[Excel sheet for download](https://c.gmx.net/@329519820976429649/KJTehgh0SMGliV4HLjMf0g)
-

@ 0fa80bd3:ea7325de
2025-01-30 04:28:30
**"Degeneration"** or **"Вырождение"**
![[photo_2025-01-29 23.23.15.jpeg]]
A once-functional object, now eroded by time and human intervention, stripped of its original purpose. Layers of presence accumulate—marks, alterations, traces of intent—until the very essence is obscured. Restoration is paradoxical: to reclaim, one must erase. Yet erasure is an impossibility, for to remove these imprints is to deny the existence of those who shaped them.
The work stands as a meditation on entropy, memory, and the irreversible dialogue between creation and decay.
-

@ 9f3eba58:fa185499
2025-01-29 20:27:09
Humanity as a whole has been degrading over the years, with average IQ decreasing, bone structures generally becoming poorly formed and fragile, average height decreasing, hormone levels ridiculously low and having various metabolic and mental illnesses becoming “normal”.
“*By 2024, more than 800 million adults were living with diabetes, representing a more than fourfold increase since 1990*”
“\*\**1 in 3 people suffer from insulin resistance and can cause depression*” (\*\*https://olhardigital.com.br/2021/09/24/medicina-e-saude/1-em-cada-3-pessoas-sofre-de-resistencia-a-insulina-e-pode-causar-depressao/)
“*More than 1.3 billion people will have diabetes in the world by 2050*” (https://veja.abril.com.br/saude/mais-de-13-bilhao-de-pessoas-terao-diabetes-no-mundo-ate-2050)
“*A new study released by Lancet, with data from 2022, shows that more than a billion people live with obesity in the world*” (https://www.paho.org/pt/noticias/1-3-2024-uma-em-cada-oito-pessoas-no-mundo-vive-com-obesidade)
All this due to a single factor: diet. I’m not referring to a diet full of processed foods, as this has already been proven to destroy the health of those who eat it. I’m referring to the modern diet, with carbohydrates (from any source, even from fruit) being the main macronutrient, little animal protein and practically no saturated fat of animal origin. This diet implementation has been systematically occurring for decades. Sugar conglomerates seeking profits? Government institutions (after all, they need voters to be stupid and vote for them), evil spiritual interference wanting to destroy or distort their path? I don’t know, I’ll leave the conspiracy theories to you!
The modern diet or diet is extremely inflammatory, and inflammation over a long period of time leads to autoimmune diseases such as diabetes and Hashimoto’s.
Absolutely any food in the plant kingdom will harm you, no matter how asymptomatic it may be. Plants are living beings and do not want to die and be eaten. To defend themselves from this, they did not evolve legs like animals. They specifically developed chemical mechanisms such as *oxalates, phytoalexins, glucosinolates, polyphenols, antinutrients* and many others that act to repel anything that wants to eat them, being fatal (as in the case of mushrooms), causing discomfort and the animal or insect discovering that the plant is not edible, releasing unpleasant smells or, in many cases, a combination of these factors. Not to mention genetically modified foods (almost the entire plant kingdom is genetically modified) that work as a steroid for the plants' defenses. - Lack of focus
- Poor decision-making
- Difficulty in establishing and maintaining relationships
- Difficulty getting pregnant and difficult pregnancy
- Low testosterone (medical reference values are low)
- Alzheimer's
- Diabetes
- Dementia
- Chances of developing autism when mothers do not eat meat and fat properly during pregnancy
- Worsening of the degree of autism when the child does not eat meat and fat (food selectivity)
- Insomnia and other sleep problems
- Lack of energy
- Poorly formed and fragile bone structure
- Lack of willpower
- Depression
- ADHD
Not having full physical and mental capacity harms you in many different ways, these are just a few examples that not only directly impact one person but everyone else around them.
Fortunately, there is an alternative to break out of this cycle of destruction, ***Carnivore Diet***.
I am not here to recommend a diet, eating plan or cure for your health problems, nor can I do so, as I am not a doctor (most doctors don't even know where the pancreas is, a mechanic is more useful in your life than a doctor, but that is a topic for another text.).
I came to present you with logic and facts in a very simplified way, from there you can do your own research and decide what is best for you.
---
## Defining the carnivore diet
Simply put, the carnivore diet is an elimination diet, where carbohydrates (including fruits), vegetable fats (soy, canola, cotton, peanuts, etc.), processed products and any type of plant, be it spices or teas, are completely removed.
### What is allowed on the carnivore diet?
- Animal protein
- Beef, preferably fatty cuts (including offal, liver, heart, kidneys, these cuts have more vitamins than anything else in the world)
- Lamb
- Eggs
- Fish and seafood
- Animal fat
- Butter
- Beef fat and tallow
- Salt
- No... salt does not cause high blood pressure. (explained later about salt and high consumption of saturated fats)
From now on I will list some facts that disprove the false accusations made against \*\*eating exclusively meat and fat.
# “Human beings are omnivores”
*“Our ancestors were gatherers and hunters*"
To determine the proportion of animal foods in our ancestors’ diets, we can look at the amount of δ15 nitrogen in their fossils. By looking at levels of this isotope, researchers can infer where animals reside in the food chain, identifying their protein sources. Herbivores typically have δ15N levels of 3–7 percent, carnivores show levels of 6–12 percent, and omnivores exhibit levels in between. When samples from Neanderthals and early modern humans were analyzed, they showed levels of 12 percent and 13.5 percent, respectively, even higher than those of other known carnivores, such as hyenas and wolves. And from an energy efficiency standpoint, hunting large animals makes the most sense. Gathering plants and chasing small animals provides far fewer calories and nutrients relative to the energy invested. In more recently studied indigenous peoples, we have observed a similar pattern that clearly indicates a preference for animal foods over plant foods. For example, in Vilhjalmur Stefansson’s studies of the Eskimos.
*“…fat, not protein, seemed to play a very important role in hunters’ decisions about which animals (male or female) to kill and which body parts to discard or carry away.”*
Why were our ancestors and more recent indigenous peoples so interested in finding fat? At a very basic level, it was probably about calories. By weight, fat provides more than twice as many calories as protein or carbohydrates. Furthermore, human metabolism makes fat an exceptionally valuable and necessary food. If we think of ourselves as automobiles that need fuel for our metabolic engines, we should not put protein in our gas tank. For best results, our metabolic engine runs most efficiently on fat or carbohydrates.
Eating animal foods has been a vital part of our evolution since the beginning. Katherine Milton, a researcher at UC Berkeley, came to the same conclusion in her paper “The Critical Role Played by Animal Source Foods in Human Evolution,” which states:
“Without routine access to animal-source foods, it is highly unlikely that evolving humans could have achieved their unusually large and complex brains while simultaneously continuing their evolutionary trajectory as large, active, and highly social primates. As human evolution progressed, young children in particular, with their rapidly expanding large brains and higher metabolic and nutritional demands relative to adults, would have benefited from concentrated, high-quality foods such as meat." - https://pubmed.ncbi.nlm.nih.gov/14672286/
Skeletons from Greece and Turkey reveal that 12,000 years ago, the average height of hunter-gatherers was five feet, nine inches for men and five feet, five inches for women. But with the adoption of agriculture, adult height plummeted—ending any hope these poor herders had of dunking a basketball or playing competitive volleyball, if such sports had existed at the time. By 3000 B.C., men in this region of the world were only five feet, three inches tall, and women were five feet, reflecting a massive decline in their overall nutritional status. Many studies in diverse populations show a strong correlation between adult height and nutritional quality. A study analyzing male height in 105 countries came to the following conclusion:
“In taller nations…consumption of plant proteins declines sharply at the expense of animal proteins, especially those from dairy products. Its highest consumption rates can be found in Northern and Central Europe, with the global peak in male height in the Netherlands (184 cm).”
In addition to the decline in height, there is also evidence that Native Americans buried at Dickson Mounds suffered from increased bacterial infections. These infections leave scars on the outer surface of the bone, known as the periosteum, with the tibia being especially susceptible to such damage due to its limited blood flow. Examination of tibias from skeletons found in the mounds shows that after agriculture, the number of such periosteal lesions increased threefold, with a staggering eighty-four percent of bones from this period demonstrating this pathology. The lesions also tended to be more severe and to appear earlier in life in the bones of post-agricultural peoples.
https://onlinelibrary.wiley.com/doi/full/10.1111/j.1747-0080.2007.00194.x
https://pubmed.ncbi.nlm.nih.gov/10702160/
# Cholesterol
Many “doctors” say that consuming saturated fat is harmful to your health, “your veins and arteries will clog with excess fat” “you will have a heart attack if you consume a lot of fat" and many other nonsense, and in exchange recommends that you replace fatty cuts of meat with lean meat and do everything with vegetable oil that causes cancer and makes men effeminate.
Your brain is basically composed of fat and water, your neurons are made and repaired with fat, your cells, the basic unit of life, are composed of fat and protein, many of your hormones, especially sexual ones, are made from fat, there is no logical reason not to consume saturated fat other than several false "scientific articles".
"The power plant of the cell is the mitochondria, which converts what we eat into energy. Ketones are an energy source derived from fat. Mitochondria prefer fat as energy (ketones) because transforming ketones into energy costs the mitochondria half the effort of using sugar (glucose) for energy." - https://pubmed.ncbi.nlm.nih.gov/28178565/
"With the help of saturated fats, calcium is properly stored in our bones. The interaction between calcium, vitamin D, and parathyroid hormone regulates calcium levels in the body. When there are calcium imbalances in the blood, our bones release calcium into the blood to find homeostasis." - https://www.healthpedian.org/the-role-of-calcium-in-the-human-body/
"The body needs cholesterol to support muscle repair and other cellular functions. This is why when there is cardiovascular disease, we see increased amounts of cholesterol in the area. Cholesterol is not there causing the problem, but the boat carrying fat was docked there for cholesterol and other nutrients to help fight the problem. Plaque is the body's attempt to deal with injury within the blood vessels." - *National Library of Medicine, “Cholesterol,” 2019*
"Initially, the Plaque helps blood vessels stay strong and helps the vessels maintain their shape. But with the perpetual cycle of uncontrolled inflammation and leftover debris from cellular repair (cholesterol), over time plaque begins to grow and harden, reducing blood flow and oxygen to the heart. Both inflammation and repair require copious amounts of cholesterol and fats. So the body keeps sending these fatty substances to the site of the plaque — until either repair wins (plaque becomes sclerotic scars in the heart muscle, causing heart failure) or inflammation wins (atherosclerotic heart attack)" - https://pubmed.ncbi.nlm.nih.gov/21250192/
Inflammation in Atherosclerotic Cardiovascular Disease - https://pubmed.ncbi.nlm.nih.gov/21250192/
"Study finds that eating refined carbohydrates led to an increased risk of cardiovascular disease and obesity" - https://pmc.ncbi.nlm.nih.gov/articles/PMC5793267/
# “Meat causes cancer”
Most of the misconceptions that red meat causes cancer come from a report by the World Health Organization's International Agency for Research on Cancer (IARC), which was released in 2015. Unfortunately, this report has been widely misrepresented by the mainstream media and is based on some very questionable interpretations of the science it claims to review.
A closer look at a 2018 report on its findings reveals that only 14 of the 800 studies were considered in its final conclusions—and every single study was observational epidemiology. Why the other 786 were excluded remains a mystery, and this group included many interventional animal studies that clearly did not show a link between red meat and cancer. Of the fourteen epidemiological studies that were included in the IARC report, eight showed no link between meat consumption and the development of colon cancer. Of the remaining six studies, only one showed a statistically significant correlation between meat and cancer.
In epidemiological research, one looks for correlation between two things and the strength of the correlation. Having just one study out of 800 that shows meat causes cancer is a mere fluke and becomes statistically insignificant.
Interestingly, this was a study by Seventh-day Adventists in America — a religious group that advocates a plant-based diet.
# Microbiota and Fiber
I have seen several people and “doctors” saying that eating only meat would destroy your microbiota. And I have come to the conclusion that neither “doctors” nor most people know what a microbiota is.
Microbiota is the set of several types of bacteria (millions) that exist in your stomach with the function of breaking down molecules of certain types of food that the body itself cannot get, fiber for example. Many times through the process of fermentation, which is why you have gas after eating your beloved oatmeal.
People unconsciously believe that the microbiota is something fixed and unchangeable, but guess what… it is not.
Your microbiota is determined by what you eat. If you love eating oatmeal, your microbiota will have a specific set of bacteria that can break down the oat molecule into a size that the body can absorb.
If you follow a carnivorous diet, your microbiota will adapt to digest meat.
### Fiber
Nutritional guidelines recommend large amounts of fiber in our diet, but what they don't tell you is that we only absorb around 6% of all the vegetable fiber we eat. In other words, it's insignificant!
Another argument used by doctors and nutritionists is that it helps you go to the bathroom, but this is also a lie. Fiber doesn't help you evacuate, it forces you to do so. With the huge amount of undigestible food in your stomach (fiber), the intestine begins to force contractions, making this fecal matter go down, making you go to the bathroom.
They also raise the argument that fibers are broken down into short-chain fatty acids, such as butyrate (butyric acid), propionate (propionic acid) and acetate (acetic acid). Butyrate is essential because it is the preferred fuel source for the endothelial cells of the large intestine.
Butter, cream, and cheese contain butyrate in its absorbable form. Butter is the best source of butyric acid, or butyrate. In fact, the origins of the word butyric acid come from the Latin word *butyro*—the same origins as the word butter.
“In 2012, a study in the Journal of Gastroenterology showed that reducing fiber (a precursor to short-chain fatty acids) helped participants with chronic constipation. The study lasted six months, and after two weeks without fiber, these participants were allowed to increase fiber as needed. These participants felt so much relief after two weeks without fiber that they continued without fiber for the entire six-month period. Of the high-fiber, low-fiber, and no-fiber groups, the zero-fiber participants had the highest bowel movement frequency.” - https://pmc.ncbi.nlm.nih.gov/articles/PMC3435786/
### Bioavailability
I said that our body can only absorb 6% of all the fiber we ingest. This is bioavailability, how much the body can absorb nutrients from a given food.
Meat is the most bioavailable food on the planet!
Grains and vegetables are not only not very bioavailable, but they also contain a huge amount of antinutrients. So if you eat a steak with some beans, you will not be able to absorb the nutrients from the beans, and the antinutrients in them will make it impossible to absorb a large amount of nutrients from the steak. https://pubmed.ncbi.nlm.nih.gov/23107545/
# Lack of nutrients and antioxidants in a carnivorous diet
A major concern with the carnivorous diet is the lack of vitamin C, which would consequently lead to scurvy.
Vitamin C plays an important role in the breakdown and transport of glucose into cells. In 2000 and 2001, the recommended daily intake of vitamin C effectively doubled. In fact, every 10 to 15 years, there has been a large increase in the recommended daily intake of vitamin C, as happened in 1974 and 1989. Interestingly, also in 1974, sugar prices became so high that high fructose corn syrup was introduced into the US market. Could the increase in readily available glucose foods and foods with high fructose corn syrup be a reason why we need more vitamin C? The question remains…. But this is not a cause for concern for the carnivore, liver is rich in vitamin C. You could easily reach the daily recommendation with liver or any cut of steak. 200-300g of steak already meets your needs and if the theory that the more sugar you eat, the more vitamin C you will get is true, then the more sugar you will eat is true. C is necessary if true, you could easily exceed the daily requirement.
Meat and seafood are rich in ALL the nutrients that humans need to thrive.
### Antioxidants
It is commonly said that fruits are rich in antioxidants but again this is a hoax, they are actually PRO-oxidants. These are substances that activate the mRF2 pathway of our immune system which causes the body to produce natural antioxidants.
The body produces antioxidants, but many occur naturally in foods, Vitamin C, Vitamin E, Selenium and Manganese are all natural antioxidants.
High concentrations of antioxidants can be harmful. Remember that high concentrations of antioxidants can increase oxidation and even protect against cancer cells.
# Salt
Consuming too much salt does not increase blood pressure and therefore increases the risk of heart disease and stroke. Studies show no evidence that limiting salt intake reduces the risk of heart disease.
A 2011 study found that diets low in salt may actually increase the risk of death from heart attacks and strokes. Most importantly, they do not prevent high blood pressure. https://www.nytimes.com/2011/05/04/health/research/04salt.html
# Sun
This is not a dietary issue specifically, but there are things that can I would like to present that is against common sense when talking about the sun.
It is common sense to say that the sun causes skin cancer and that we should not expose ourselves to it or, if we are exposed to the sun, use sunscreen, but no study proves that using sunscreen protects us from melanoma and basal cell carcinoma. The types of fatal melanomas usually occur in areas of the body that never see the sun, such as the soles of the feet.
https://www.jabfm.org/content/24/6/735
In 1978, the first sunscreen was launched, and the market grew rapidly, along with cases of melanoma.
Several studies show that sunscreens cause leaky gut (one of the main factors in chronic inflammation), hormonal dysfunction and neurological dysfunction.
https://pubmed.ncbi.nlm.nih.gov/31058986/
If your concern when going out in the sun is skin cancer, don't worry, your own body's natural antioxidants will protect you. When they can no longer protect you, your skin starts to burn. (If you have to stay in the sun for work, for example, a good way to protect yourself is to rub coconut oil on your skin or just cover yourself with a few extra layers of thin clothing and a hat).
Sunscreen gives you the false sense of protection by blocking the sunburn, so you stay out longer than your skin can handle, but sunscreens can only block 4% of UVA and UVB rays.
www.westonaprice.org/health-topics/environmental-toxins/sunscreens-the-dark-side-of-avoiding-the-sun/
Interestingly, vitamin D deficiency is linked to increased cancer risks. It's a big contradiction to say that the greatest provider of vit. D causes cancer…
https://med.stanford.edu/news/all-news/2010/10/skin-cancer-patients-more-likely-to-be-deficient-in-vitamin-d-study-finds.html
Important roles of vitamin D:
- **Regulation of Bone Metabolism**
- Facilitates the **absorption of calcium and phosphorus** in the intestine.
- Promotes bone mineralization and prevents diseases such as **osteoporosis**, **rickets** (in children) and **osteomalacia** (in adults).
- **Immune Function**
- Modulates the immune system, helping to reduce inflammation and strengthen the defense against infections, including **colds**, **flu** and other diseases.
- May help reduce the incidence of autoimmune diseases such as **multiple sclerosis** and **rheumatoid arthritis**. - **Muscle Health**
- Contributes to muscle strength and the prevention of weakness, especially in the elderly.
- Reduces the risk of falls and fractures.
- **Cardiovascular Function**
- May help regulate blood pressure and heart function, reducing the risk of cardiovascular disease.
- **Hormonal Balance**
- Influences the production of hormones, including those associated with fertility and the functioning of the endocrine system.
- Plays a role in insulin metabolism and glucose sensitivity.
- **Brain Function and Mental Health**
- Participates in mood regulation, which may reduce the risk of **depression** and improve mental health.
- Has been associated with the prevention of neurodegenerative diseases, such as **Alzheimer's**.
- **Anticancer Role**
- Evidence suggests that vitamin D may inhibit the proliferation of cancer cells, especially in breast, prostate and colon cancers. - **Role in General Metabolism**
- Contributes to metabolic health, regulating cellular growth and repair processes.
---
I tried to present everything in the simplest and most understandable way possible, but there are things that require prior knowledge to truly understand. Below is a list of books that will show you everything I have shown you in a more technical and in-depth way.
### Book Recommendations
https://amzn.to/3EbjVsD
https://amzn.to/4awlnBZ
All of my arguments have studies to validate them. Feel free to read them all and draw your own conclusions about what is best for you and your life.
-

@ 0fa80bd3:ea7325de
2025-01-29 15:43:42
Lyn Alden - биткойн евангелист или евангелистка, я пока не понял
```
npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a
```
Thomas Pacchia - PubKey owner - X - @tpacchia
```
npub1xy6exlg37pw84cpyj05c2pdgv86hr25cxn0g7aa8g8a6v97mhduqeuhgpl
```
calvadev - Shopstr
```
npub16dhgpql60vmd4mnydjut87vla23a38j689jssaqlqqlzrtqtd0kqex0nkq
```
Calle - Cashu founder
```
npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg
```
Джек Дорси
```
npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m
```
21 ideas
```
npub1lm3f47nzyf0rjp6fsl4qlnkmzed4uj4h2gnf2vhe3l3mrj85vqks6z3c7l
```
Много адресов. Хз кто надо сортировать
```
https://github.com/aitechguy/nostr-address-book
```
ФиатДжеф - создатель Ностр - https://github.com/fiatjaf
```
npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6
```
EVAN KALOUDIS Zues wallet
```
npub19kv88vjm7tw6v9qksn2y6h4hdt6e79nh3zjcud36k9n3lmlwsleqwte2qd
```
Программер Коди https://github.com/CodyTseng/nostr-relay
```
npub1syjmjy0dp62dhccq3g97fr87tngvpvzey08llyt6ul58m2zqpzps9wf6wl
```
Anna Chekhovich - Managing Bitcoin at The Anti-Corruption Foundation
https://x.com/AnyaChekhovich
```
npub1y2st7rp54277hyd2usw6shy3kxprnmpvhkezmldp7vhl7hp920aq9cfyr7
```
-

@ 57d1a264:69f1fee1
2025-01-28 02:36:34
**About the role**
In this role, you will work on the product design of umbrelOS, some of our umbrelOS apps, and the umbrel.com website.
**What are you looking for in candidates?**
Talent, passion, genuine love for your craft, and the desire to do meaningful work. What we’re not looking for: credentials and degrees. When you really love what you do, work feels like play. And when work feels like play, you become the best at it. That’s what we’re looking for.
**We hope you:**
- Like to spend your days staring at artboards in Figma
- Are obsessed with creating delightful micro-interactions and animations
- Are willing to throw away ideas if they're not great, and optimistic enough to keep hunting for new ones
- Care about the details, maybe a bit too much (a pixel off ruins your sleep)
- Are excited to collaborate with everyone on the team: engineers, customer facing folks, etc—you believe inspiration can come from anywhere
- Have good judgement of when to ship
- Like to level up your design skills continually
- Put yourselves in the shoes of our users to craft a great experience
- Enjoy being a generalist and are not tied down to a specific design, trend, or tools
**Benefits**
- 🚑 Health insurance
- 💻 New work equipment
- 🌎 Work from anywhere in the world
- 💆♀️ Complete autonomy at work
- 📚 Learning and development stipend
- 🏝 Minimum 2-weeks of paid time off
- ❤️ Most importantly — doing meaningful work that can change the world
Apply at https://app.withrapha.com/job/692
originally posted at https://stacker.news/items/867248
-

@ 9e69e420:d12360c2
2025-01-26 15:26:44
Secretary of State Marco Rubio issued new guidance halting spending on most foreign aid grants for 90 days, including military assistance to Ukraine. This immediate order shocked State Department officials and mandates “stop-work orders” on nearly all existing foreign assistance awards.
While it allows exceptions for military financing to Egypt and Israel, as well as emergency food assistance, it restricts aid to key allies like Ukraine, Jordan, and Taiwan. The guidance raises potential liability risks for the government due to unfulfilled contracts.
A report will be prepared within 85 days to recommend which programs to continue or discontinue.
-

@ 0463223a:3b14d673
2025-01-26 13:07:36
Hmm so I heard that in order to improve my brain I should try writing… Ok groovy, I’ll give it a go. In all honesty I don’t know what to write, my brain is a jumble of noise and titbits of random knowledge. I likely know more about sound than the average person but as physics goes, I don’t have anything new or profound to add. Air moves and noises happen. Is there really any more to it? I could write some flowery bollocks about refraction, absorption coefficients and reverberation times, or I could write some out there, arty shit but I don’t think that adds any value to anyone.
A lot of folks online have very strong beliefs in how the world operates or should operate. Whilst their conviction is strong, there’s also is a large percentage of people who totally disagree with them and think the exact opposite is the answer. That’s quite shit isn’t it? Humans have been around for 100,000 years or so and haven’t worked it out. I wonder what makes the internet celeb so certain they’ve got it right when the next internet celeb completely disagrees? I do my best to avoid any of these cunts but despite running to the obscurest social media platforms they still turn up with their profound statements. Meh.
Ideologically I’m leaning toward anarchism but even that seems full of arguments and contradictions and ultimately I don’t think I can be arsed with identifying with any particular ideology. I tried reading some philosophy and struggled with it, although I deep fall into a lovely deep sleep. It’s fair to say I’m not the brightest button in the box. I have a wife, a couple of cats and lots of things that make nosies in my shed. That’s pretty cool right? Well it works for me.
So why write this? I clearly wrote in the first sentence that I’m trying to improve my brain, a brain that’s gone through a number to twists and turns, a lot brain altering substances. I own that, no one forced me to. Beside, George Clinton was still smoking crack aged 80, didn’t do him any harm…
I’m on the 5th paragraph. I don’t feel any smarter yet and each paragraph is getting shorter, having started from a low base. I guess I’m being too high time preference… Might be a while before I launch my Deep Thought podcasts where myself and a guest talk for 500 hours about the philosophy of money and 13 amp plug sockets.
I’ve tortured myself enough. I’m posting this on Nostr where it will never go away.. lol. If you got this far, I congratulate/commiserate you and wish you a wonderful day.
-

@ 9e69e420:d12360c2
2025-01-25 22:16:54
President Trump plans to withdraw 20,000 U.S. troops from Europe and expects European allies to contribute financially to the remaining military presence. Reported by ANSA, Trump aims to deliver this message to European leaders since taking office. A European diplomat noted, “the costs cannot be borne solely by American taxpayers.”
The Pentagon hasn't commented yet. Trump has previously sought lower troop levels in Europe and had ordered cuts during his first term. The U.S. currently maintains around 65,000 troops in Europe, with total forces reaching 100,000 since the Ukraine invasion. Trump's new approach may shift military focus to the Pacific amid growing concerns about China.
[Sauce](https://www.stripes.com/theaters/europe/2025-01-24/trump-europe-troop-cuts-16590074.html)
-

@ 228dde34:b5d0345e
2025-01-25 01:59:57
##### By Jonathan Tan
##### Lead Editor
##### Hype Issue #60
##### JONATHAN TAN explores the recent rise in popularity of online gambling, and its consequences on the population’s most vulnerable.

The persistent rise in the gaming industry, fueled by the introduction of online gambling, seems to have no end. Experts are now worrying about the effects of this epidemic on public health and safety. “Many people might be really experiencing harms from gambling — we think that it’s probably around 72 million people globally,” said Louisa Degenhardt, a professor at the University of New South Wales in Sydney, in an[NBC article.](https://www.nbcnews.com/health/health-news/gambling-industry-growth-threat-public-health-report-rcna175356)
The online gambling craze has spread worldwide, and even Singapore, with its strict gambling regulations, is not immune to it. In a recent[survey](https://www.channelnewsasia.com/singapore/national-council-problem-gambling-rate-continues-fall-4761621)conducted by the National Council on Problem Gambling (NCPG), illegal online gambling rates have more than tripled since 2020, from 0.3% to 1.0% in the past 4 years.
This statistic alone highlights an already concerning trend. Even more troubling, however, is that the illegal nature of these websites means there are no regulatory laws or age restrictions. As a result, the proliferation of these online websites has allowed a brand new demographic to start gambling: the Singaporean youth.
### How to lose thousands before adulthood
“I started gambling when I was 13 years old, at a friend's house,” George (not his real name) shares. Now an 18-year-old student, George recalls how a simple game among friends slowly grew into an all-consuming gambling addiction.
 *In NCPG’s 2023 survey, 8% of respondents reported participating in social gambling activities: gambling which occurs within individuals’ homes, among family members. Photo from Shutterstock.*
Initially, George and his friends gambled with low stakes, like a dollar here and there. However, the games slowly escalated: from $1 to $10, then to $100, and eventually to $1000. Unsurprisingly, with such large sums at stake, George’s relationship with his friends began to strain.
“I realized that after a certain point, the more and more money we [bet], the more and more our relationship with each other [soured]; and so we decided to curb it at a maximum buy-in of $20 per game,” George says.
The new rule eased the tension between George and his friends, but it inadvertently created a new problem: George no longer felt the thrill of winning large sums. As a result, he began seeking other ways to gamble.
“The first time I gambled online was when I was 16 years old. A friend had introduced me to a gambling website,” he recalls. “And at first it was all right. I won a bit, I lost a bit, but no one got hurt.”
But it didn’t take long for him to get hooked; a single sports bet was what netted George his first big win. “On the first day, I went from $10 to $800 from a simple parlay bet,” George says. “I felt unstoppable. Adrenaline was pumping through my veins, and [I felt] I could never lose. [After] that day, I gambled like $100 almost every day for a straight month.”

*A parlay (a form of sports betting that has recently surged in popularity) is a single bet that combines two or more bets into one. While doing this drastically decreases the odds of winning, it also drastically increases the potential payout. Photo from Getty Images.*
Nothing could stop George’s gambling fervor. Even after losing nearly a thousand dollars on a single blackjack hand, all George did was place a bigger bet to try and win it back. “Every morning, when I [woke] up, all I could think about was gambling,” he shares.
And of course, George’s obsession with online gambling was only exacerbated by the accessibility of these websites.
First, the online nature of these websites allowed George to gamble anywhere, at any time. “For online gambling, you have it right at your fingertips. As soon as you wake up, you can just log on the computer and start betting huge amounts of money,” he mentions.
But more importantly, these illegal gambling websites enabled George to do something he was never old enough to do in the first place.
“I'm too young to gamble at a real casino or a physical casino. But online gambling makes it way more accessible because there's no verification of ID,” George says.
### Consequences, consequences
Therein lies the predatory nature of these illegal websites. While anyone can fall victim to a gambling addiction, certain factors may make the youth especially vulnerable.
“The adolescent brain is still developing, particularly the prefrontal cortex, which is responsible for decision-making, impulse control, and risk assessment. This makes young people more susceptible to impulsive behaviors,” says Jat Tan, the Communications and Events Executive at WE CARE Community Services.
 *The prefrontal cortex is primarily developed during adolescence, and is fully developed at the age of 25 years. Photo from iStock.*
Additionally, other factors such as peer pressure, social media, or limited life experience, could result in young Singaporeans being more open to gambling.
Lastly, one popular reason why the youth are drawn to gambling, is their limited financial freedom. “While youths are in school, they have a significantly lower earning power as opposed to adults. The demands from school usually means that they can only afford to work part-time jobs,” Mrs Tan shares.
Despite this, many young Singaporeans still want to live extravagant lifestyles. With the youth getting exposed to lavish, ostentatious lifestyles on social media, many begin to feel envious and yearn for the same luxuries. And now, with the introduction of illegal online sites, the lack of age restrictions allows these youths to gamble in an attempt to achieve this better life.
### What can be done?
The increase in the number of adolescent gamblers is a new challenge for the Singaporean government. Before the advent of online gambling, many safeguards were in place to protect Singaporeans from developing gambling addictions.
In particular, safeguards that limit Singaporeans’ access to legal gambling services seem to be working; the overall percentage of gambling Singaporeans has fallen from 44% to 40% from 2020 to 2023.
However, the unprecedented accessibility and convenience of online gambling sites have allowed Singapore’s tech-savvy youth to bypass these regulations; and now, the Singaporean government needs to update its laws to keep up with the growing gambling industry.
Of course, the Singaporean Government has been cracking down on illegal online gambling. As of September 2024, the Gambling Regulatory Authority (GRA) has blocked access to more than 1,900 remote gambling websites. But despite the GRA’s efforts, these online gambling providers continue to survive, like weeds in a garden.
“GRA recognises that the borderless nature of the Internet makes it easy for unlawful gambling operators to offer their products to users in Singapore any time and anywhere,” said a GRA spokesman in [a Straits Times article.](https://www.straitstimes.com/singapore/crackdown-on-illegal-online-gambling-but-addiction-can-be-hard-to-beat)
Currently, there are calls for the government to shift its focus. “While Singapore has done well putting in place responsible gaming and safety measures to mitigate the risks of casino gambling, it is timely to focus more attention to address the risk of illegal online gambling as well,” said Ms Tham, Clinical director of We Care Community Services, [in a Straits Times article.](https://www.straitstimes.com/singapore/fewer-singapore-residents-gambled-but-more-do-so-online-illegally)
Ultimately, as the gambling industry becomes more technologically advanced, it becomes harder for Singapore to regulate gambling the same way it used to. Thus, it may be time for the Singaporean government to consider a different solution.
“Better educating youths on the harms and consequences of gambling, as well as resources available should things go awry, would be the best option to nip the issue in the bud,” Ms Tan suggests. Instead of focusing on restrictive legislation, education could be a preventative measure used to curb adolescent gambling.
“A higher level of awareness would enable youths to face issues like gambling with their eyes wide open - they will have a rough idea of what they're getting themselves into, and will have a rough idea of what to do if things go wrong,” she shares.
-

@ bcea2b98:7ccef3c9
2025-01-24 23:21:05
originally posted at https://stacker.news/items/862840
-

@ 378562cd:a6fc6773
2025-01-23 17:57:13
**Top USA News**
1. **President Trump Threatens Tariffs on Non-U.S. Manufacturers**In a speech at the World Economic Forum in Davos, President Donald Trump announced plans to impose tariffs on companies that do not manufacture their products in the United States, aiming to boost domestic production.
[The Guardian](https://www.theguardian.com/us-news/live/2025/jan/23/donald-trump-pardons-january-6-us-president-joe-biden-jd-vance-republicans-live-news?utm_source=chatgpt.com)
2. **Historic Winter Storm Sweeps Across Southern U.S**.A severe winter storm has blanketed the southern United States with snow and freezing temperatures, leading to widespread power outages and hazardous travel conditions.
[WSJ](https://www.wsj.com/news/archive/2025/01/23?utm_source=chatgpt.com)
3. **Trump Administration Orders Federal DEI Staff on Leave**The Trump administration has directed all federal employees working in Diversity, Equity, and Inclusion (DEI) programs to be placed on paid leave, with plans to dismiss all DEI program employees by January 31.
[The Guardian](https://www.theguardian.com/us-news/live/2025/jan/22/donald-trump-china-sanctions-tariff-diversity-us-politics-live-latest-news?utm_source=chatgpt.com)
4. **U.S. Stock Futures Mixed After Tech-Driven Rally**Following a tech-fueled rise, U.S. stock futures show mixed results. The S&P 500 futures dipped slightly after nearing record highs, while Nasdaq futures declined by 0.5%, and Dow Jones futures saw a slight increase.
[Investopedia](https://www.investopedia.com/5-things-to-know-before-the-stock-market-opens-january-23-2025-8778964?utm_source=chatgpt.com)
5. **Trump Pardons January 6 Capitol Rioters**President Trump has issued pardons for individuals convicted in relation to the January 6 Capitol riot, a move that has sparked controversy and debate across the political spectrum.
[The Guardian](https://www.theguardian.com/us-news/live/2025/jan/23/donald-trump-pardons-january-6-us-president-joe-biden-jd-vance-republicans-live-news?utm_source=chatgpt.com)
6. **California Wildfires Cause Extensive Damage**Ongoing wildfires in Los Angeles County are causing significant destruction, with estimated damages exceeding $135 billion. Governor Gavin Newsom warns that these could become the worst natural disaster in American history.
[Wikipedia](https://en.wikipedia.org/wiki/Portal%3ACurrent_events/January_2025?utm_source=chatgpt.com)
7. **President Trump Withdraws U.S. from Paris Climate Agreement**In a series of executive orders, President Trump has withdrawn the United States from the Paris Climate Agreement, citing economic concerns and a focus on American energy independence.
[The Guardian](https://www.theguardian.com/us-news/live/2025/jan/21/donald-trump-inauguration-presidency-executive-orders-pardons-day-two-live-blog?utm_source=chatgpt.com)
8. **Trump Administration Re-designates Houthis as Terrorist Organization**The Trump administration has re-designated the Yemeni Houthi movement as a foreign terrorist organization, reversing a previous decision and impacting international relations in the region.
[Wikipedia](https://en.wikipedia.org/wiki/2025_in_the_United_States?utm_source=chatgpt.com)
9. **President Trump Announces $500 Billion AI Investment**President Trump, alongside tech executives, has announced a $500 billion investment in artificial intelligence infrastructure, aiming to bolster the United States' position in the global tech industry.
[WSJ](https://www.wsj.com/news/archive/2025/01/23?utm_source=chatgpt.com)
10. **ChatGPT Experiences Large-Scale Outage**A significant outage of the AI tool ChatGPT has been reported, affecting users worldwide. The cause of the disruption is under investigation.
[Wikipedia](https://en.wikipedia.org/wiki/2025_in_the_United_Kingdom?utm_source=chatgpt.com)
**Top International News**
1. **Israeli Military Conducts Extensive Raid in Jenin**The Israeli military launched a significant operation in Jenin, resulting in at least 10 Palestinian deaths and numerous injuries. The raid, named "Iron Wall," involved airstrikes and ground forces, escalating tensions in the West Bank.
[The Guardian](https://www.theguardian.com/world/2025/jan/23/first-edition-west-bank-settlers-israel-military?utm_source=chatgpt.com)
2. **Micheál Martin Appointed as Irish Taoiseach**Micheál Martin has been confirmed as Ireland's new Taoiseach following a day of delays and disagreements in the Irish parliament. His immediate focus includes forming his cabinet and addressing Ireland's housing crisis.
[The Guardian](https://www.theguardian.com/world/live/2025/jan/23/europe-dail-micheal-martin-rows-ireland-weather-storm-eowyn-latest-updates?utm_source=chatgpt.com)
-

@ c8cf63be:86691cfe
2025-01-23 12:51:20
### Mark Fishers ‘Acid Communism’ und der ‘Capitalist Realism’
> “it is easier to kill the living than to kill the undead”[1]
Die lebenden sind wir Menschen, *the undead* ist der gegenwärtige
neoliberalismus[2] Mark Fischers Analyse über den bestehenden Zustand
ist erschütternd:
> “let’s say music hello just go on music in the last 10 years one thing
> one single thing that couldn’t have come out in the 20th century”[3]
Es gibt nicht neues unter dem Himmel, alle Kreativität ist erschöpft,
“die Verdinglichung” von der Horkheimer und Adorno sprachen, “…, ist so
dicht geworden,…” die Wirklichkeit des ‘Capitalist Realism’ ist manifest
und undurchdringlich, die Löcher, die kleinen alternativen, sind
versiegelt. Schon im Denken sind die alternativen versperrt und das
Denken ist ein gemeinsames, niemand kann für sich alleine Denken oder
kreativ sein. Denken und kreativ sein sind das Ergebnis einer
Gesellschaftlichen Voraussetzung.
Es gibt keine neue Musik mehr weil die Musik untot ist. In immer neuer
Auflagen, in der mechanische Reproduktion, wiederbelebt man die Toten,
und erstickt das lebendige.
> “… but there’s nothing about us that was good or better than you
> you’re anybody it’s just that we were lucky and you all are unlucky
> …”[4]
Wenn eine junge Frau auf seine Feststellung reagiert mit Unglaube und
Abwehr.
> “… so what you’re basically saying is that i guess your generation or
> the previous generation was better because you had more time to pursue
> your own projects and you also think that you were more creative or
> the previous generation was more creative …”[5]
Dann weil sie die Enge der Umstände nicht erkennen kann, und vielleicht
auch weil sie die Dinge auf sich persönlich bezieht, wie es das
gegenwärtige Denken nahelegt: Sowohl der kompetitive Vergleich als auch
die individuelle Schuldzuordnung findet sich in der Aussage.
Fischer hingegen erklärt dies mit den Herrschenden Umständen die es den
Menschen unmöglich machen sich den *wahren Sachverhalt* klar zu machen
und damit jede Alternative im Denken versperren:
> “.. but okay let’s be clear about what i’m saying creativity isn’t a
> property of individuals ever it’s a property of a social or collective
> scene like that you know that’s so that it’s not like the individuals
> are less creative than they used to be that’s just not how creativity
> works creativity is possible because of is possible because of social
> conditions and those social conditions have been removed …”[6]
Fischers Aufmerksamkeit richtet sich auf die die Umstände vor dem
Capitalism Realism, denn dieser ist seiner Meinung nach schon eine
Reaktion, eine Reaktion auf die “Counterculture” auf das “spectre of a
world which could be free”[7].
Wenn es ein Gründungsereignis des Capital Realism geben sollte wäre dies
nach Fischer der Putsch Pinochets in Chile 1973.[8]
Seiner Zeit voraus war Hunter S. Thompson, seine Drogengeschwängerten
Reflexionen fassen den Kern sehr genau, für ihn war 1971 schon der
Moment an dem er die revision verortet:
> “… wir ritten auf dem Kamm einer hohen und wunderschönen Welle … Und
> jetzt, weniger als fünf Jahre später, kannst du auf einen steilen
> Hügel in Las Vegas klettern und nach Westen blicken, und wenn du die
> richtigen Augen hast, dann kannst du die Hochwassermarkierung fast
> sehen -die Stelle, wo sich die Welle schließlich brach und
> zurückrollte.”[9]
Acid! Die psychedelische Zeit:
> “Instead of seeking to overcome capital, we should focus on what
> capital must always obstruct: the collective capacity to produce, care
> and enjoy.”[10]
und weiter
> “The overcoming of capital has to be fundamentally based on the simple
> insight that, far from being about “wealth creation”, capital
> necessarily and always blocks the production of common wealth.”
Der Zauber der Psycedlischen Zeit war die ignoranz, das Verweigern des
bestehenden Narativs. Oder wie Fischer sagt, die Frage nach dem
Bewustsein und seiner Beziehung dem dem was wir als Wiklichkeit
wahrnemen.[11]
> “turn on, tune in, drop out” [12]
oder noch klarer Ken Kesey:
> “There’s only one thing to do .
> .. there’s only one thing’s gonna do any good at all…
> And that’s everybody just look at it,
> look at the war, and turn your backs and say … Fuck it..” [13]
Die Imagination des *wahren Sachverhaltes* “look at it” sagt Kesey,
überzeugt euch selbst. Es braucht nicht mehr als das Schauen des
Krieges, bei ihm der Viatnam Krieg, um zu verstehen das nur die
Verweigerung, das “Fuck it” geeignet ist dem ganzen seine legitimität zu
verweigern.
Das war der Zauber der psychedelichen Zeit, auch der der 90’er, die als
unpolitsch gelten. Aus dieser Perspektive ist klar das das unpolitsche,
das politsche war.
Die love-Parade war nicht unpolitisch und die gesellschaflichenr
Verändeung die durch diese Psychedleische Zeit in Bewegung gesetzt
wurden können wir noch heute fühlen. Die Canabis Legalisierung, die
veränderte Wahrnehmng von Homosexualität. Das “chill out”. Die tribal
Tattoos.[14] Und auch die wärmste Kampange der Europawahl 2024, “Fickt
euch doch alle.”[15] ist erst durch die psychedelische Zeit der 90’er
möglich, hier wurde die Sinnlichkeit gestiftet die es braucht damit
dieser Satz seine wärme bekommt.
Die Demokratesierung der Neurologie durch die verwendung von
Halozinogenen rücken die Frage nach der Wirklichkeit und des wahren
Sachverhaltes in den Mittelpunkt.
> “what they mainstreamed was this psychedelic consciousness with its
> key notion of the plasticity of reality”[16]
Sie ist auch eine Sekularisierung, eine demokratisierung des Sakralen,
das vorher durch Klassen wie Schamanen oder Druiden kontroliert wurde
wird zugänglich und erfahrbar.
> “…, there was actually a demystificatory and materialist dimension to
> this.”[17]
Was sich so aussprechen läßt:
> *“Wenn Gott liebe ist, dann ist er eine MDMA geschwängerte, psycedelic
> trance Party, anfang der 90’er jahre des letzten Jahrtausend.”*
Es loht sich also für uns ältere an die nicht so ferne Zeit der frühen
90’er Jahre zurück zu denken in der die Welt offen schien, die Polarität
des kalten Krieges vergangen war, das Ende der Geschichte ausgerüfen
wurde.[18]
Da war die Idee das dies nicht der Siegt des Kapitalismus ist, sondern
ein Sieg der Menschen die die Spirale des Schreckens und der Eskalation
durchbrechen real. Es schien wie ein transzendieren des gegebenen Spiels
und seiner Regeln wie es die AI in “war games”[19] realisiert,
stattzufinden.
Auf “No future”[20] folgte “No Paradise? Create it.”[21], es fand ein
“unforgetting”[22] der alten, in den 60’er entwickelten Formen statt:
Die Modulierung der 303, das Dayglow und das Strobo, alles Elemente des
Acid Test[23].
*“the collective capacity to produce, care and enjoy”*
------------------------------------------------------------------------
### References:
[1] Fisher, M., Mark Fisher - DOCH Lectures 1 2011:
<https://www.youtube.com/watch?v=f-9nY5rboK8> 32m 42s
[2] Fisher, M., How to kill a zombie: strategizing the end of
neoliberalism 2013:
<https://www.opendemocracy.net/en/how-to-kill-zombie-strategizing-end-of-neoliberalism/>.
[3] Fisher, 1968., Mark, Cybertime Crisis 2013:
<https://www.youtube.com/watch?v=zOQgCg73sfQ> ab 1h 42m 12s
[4] Fisher, 1968., Mark, ebenda ab 1h 35m 30s
[5] Fisher, 1968., Mark, ebenda ab 1h 42m 12s
[6] Fisher, 1968., Mark, ebenda ab 1h 47m 20s
[7] Fisher, 1968., Mark et al., K-punk : the collected and unpublished
writings of Mark Fisher (2004-2016) 2018. Abs. 153.5
[8] Fisher, 1968., Mark et al., ebenda. Abs. 153.7 “If there was a
founding event of capitalist realism, it would be the violent
destruction of the Allende government in Chile by General Pinochet’s
American-backed coup.”
[9] Hunter S. Thompson “Fear and loathing” Seite 89
[10] Fisher, 1968., Mark et al., K-punk : the collected and unpublished
writings of Mark Fisher (2004-2016) 2018. Abs. 153.5 Statz 3
[11] Fisher, 1968., Mark et al., ebenda. Abs. 153.46
[12] Timothy Leary in 1966, der damals gefährlichste Mann der
Welt.(Richard Nixxon)
[13] Wolfe, Tom., The electric kool-aid acid test. 1999. Seite 360
[14] Christmann, K., Gruppen-Tattoo-Termin im Bundestag: 19 Abgeordnete
zeigen vollen Körpereinsatz 2024:
<https://www.tagesspiegel.de/politik/gruppen-tattoo-termin-im-bundestag-19-abgeordnete-zeigen-vollen-korpereinsatz-11665559.html>.
[15] DiePartei, Fickt euch doch alle! (DINA1) 2024:
<https://www.parteibedarf.de/Fickt-euch-doch-alle-DINA1/SW10115>.
[16] Fisher, M., all of this is temporary: Mark Fisher 2016:
<https://www.youtube.com/watch?v=deZgzw0YHQI> 8 m 31 s
[17] Fisher, 1968., Mark et al., K-punk : the collected and unpublished
writings of Mark Fisher (2004-2016) 2018. Abs. 153.48 4. Satz
[18] Fukuyama, F., The End of History and the Last Man 1992:
<https://books.google.de/books?id=6KZmAAAAMAAJ>.
[19] Parkes, L.L.F., WarGames:
<https://www.imdb.com/de/title/tt0086567/> “A strange game. The only
winning move is not to play.”
[20] Wikipedia, No Future: <https://de.wikipedia.org/wiki/No_Future>.
[21] Spirit zone
https://www.platekompaniet.no/musikk/cd/space-tribe-shapeshifter-cd
[22] Fisher, 1968., Mark et al., K-punk : the collected and unpublished
writings of Mark Fisher (2004-2016) 2018. Abs. 153.21 Letzter Satz
[23] Wikipedia, Acid Tests: <https://de.wikipedia.org/wiki/Acid-Tests>.
-

@ 6be5cc06:5259daf0
2025-01-21 23:17:29
A seguir, veja como instalar e configurar o **Privoxy** no **Pop!_OS**.
---
### **1. Instalar o Tor e o Privoxy**
Abra o terminal e execute:
```bash
sudo apt update
sudo apt install tor privoxy
```
**Explicação:**
- **Tor:** Roteia o tráfego pela rede Tor.
- **Privoxy:** Proxy avançado que intermedia a conexão entre aplicativos e o Tor.
---
### **2. Configurar o Privoxy**
Abra o arquivo de configuração do Privoxy:
```bash
sudo nano /etc/privoxy/config
```
Navegue até a última linha (atalho: **`Ctrl`** + **`/`** depois **`Ctrl`** + **`V`** para navegar diretamente até a última linha) e insira:
```bash
forward-socks5 / 127.0.0.1:9050 .
```
Isso faz com que o **Privoxy** envie todo o tráfego para o **Tor** através da porta **9050**.
Salve (**`CTRL`** + **`O`** e **`Enter`**) e feche (**`CTRL`** + **`X`**) o arquivo.
---
### **3. Iniciar o Tor e o Privoxy**
Agora, inicie e habilite os serviços:
```bash
sudo systemctl start tor
sudo systemctl start privoxy
sudo systemctl enable tor
sudo systemctl enable privoxy
```
**Explicação:**
- **start:** Inicia os serviços.
- **enable:** Faz com que iniciem automaticamente ao ligar o PC.
---
### **4. Configurar o Navegador Firefox**
Para usar a rede **Tor** com o Firefox:
1. Abra o Firefox.
2. Acesse **Configurações** → **Configurar conexão**.
3. Selecione **Configuração manual de proxy**.
4. Configure assim:
- **Proxy HTTP:** `127.0.0.1`
- **Porta:** `8118` (porta padrão do **Privoxy**)
- **Domínio SOCKS (v5):** `127.0.0.1`
- **Porta:** `9050`
5. Marque a opção **"Usar este proxy também em HTTPS"**.
6. Clique em **OK**.
---
### **5. Verificar a Conexão com o Tor**
Abra o navegador e acesse:
```text
https://check.torproject.org/
```
Se aparecer a mensagem **"Congratulations. This browser is configured to use Tor."**, a configuração está correta.
---
### **Dicas Extras**
- **Privoxy** pode ser ajustado para bloquear anúncios e rastreadores.
- Outros aplicativos também podem ser configurados para usar o **Privoxy**.
-

@ 9e69e420:d12360c2
2025-01-21 19:31:48
Oregano oil is a potent natural compound that offers numerous scientifically-supported health benefits.
## Active Compounds
The oil's therapeutic properties stem from its key bioactive components:
- Carvacrol and thymol (primary active compounds)
- Polyphenols and other antioxidant
## Antimicrobial Properties
**Bacterial Protection**
The oil demonstrates powerful antibacterial effects, even against antibiotic-resistant strains like MRSA and other harmful bacteria. Studies show it effectively inactivates various pathogenic bacteria without developing resistance.
**Antifungal Effects**
It effectively combats fungal infections, particularly Candida-related conditions like oral thrush, athlete's foot, and nail infections.
## Digestive Health Benefits
Oregano oil supports digestive wellness by:
- Promoting gastric juice secretion and enzyme production
- Helping treat Small Intestinal Bacterial Overgrowth (SIBO)
- Managing digestive discomfort, bloating, and IBS symptoms
## Anti-inflammatory and Antioxidant Effects
The oil provides significant protective benefits through:
- Powerful antioxidant activity that fights free radicals
- Reduction of inflammatory markers in the body
- Protection against oxidative stress-related conditions
## Respiratory Support
It aids respiratory health by:
- Loosening mucus and phlegm
- Suppressing coughs and throat irritation
- Supporting overall respiratory tract function
## Additional Benefits
**Skin Health**
- Improves conditions like psoriasis, acne, and eczema
- Supports wound healing through antibacterial action
- Provides anti-aging benefits through antioxidant properties
**Cardiovascular Health**
Studies show oregano oil may help:
- Reduce LDL (bad) cholesterol levels
- Support overall heart health
**Pain Management**
The oil demonstrates effectiveness in:
- Reducing inflammation-related pain
- Managing muscle discomfort
- Providing topical pain relief
## Safety Note
While oregano oil is generally safe, it's highly concentrated and should be properly diluted before use Consult a healthcare provider before starting supplementation, especially if taking other medications.
-

@ b17fccdf:b7211155
2025-01-21 17:02:21
The past 26 August, Tor [introduced officially](https://blog.torproject.org/introducing-proof-of-work-defense-for-onion-services/) a proof-of-work (PoW) defense for onion services designed to prioritize verified network traffic as a deterrent against denial of service (DoS) attacks.
~ > This feature at the moment, is [deactivate by default](https://gitlab.torproject.org/tpo/core/tor/-/blob/main/doc/man/tor.1.txt#L3117), so you need to follow these steps to activate this on a MiniBolt node:
* Make sure you have the latest version of Tor installed, at the time of writing this post, which is v0.4.8.6. Check your current version by typing
```
tor --version
```
**Example** of expected output:
```
Tor version 0.4.8.6.
This build of Tor is covered by the GNU General Public License (https://www.gnu.org/licenses/gpl-3.0.en.html)
Tor is running on Linux with Libevent 2.1.12-stable, OpenSSL 3.0.9, Zlib 1.2.13, Liblzma 5.4.1, Libzstd N/A and Glibc 2.36 as libc.
Tor compiled with GCC version 12.2.0
```
~ > If you have v0.4.8.X, you are **OK**, if not, type `sudo apt update && sudo apt upgrade` and confirm to update.
* Basic PoW support can be checked by running this command:
```
tor --list-modules
```
Expected output:
```
relay: yes
dirauth: yes
dircache: yes
pow: **yes**
```
~ > If you have `pow: yes`, you are **OK**
* Now go to the torrc file of your MiniBolt and add the parameter to enable PoW for each hidden service added
```
sudo nano /etc/tor/torrc
```
Example:
```
# Hidden Service BTC RPC Explorer
HiddenServiceDir /var/lib/tor/hidden_service_btcrpcexplorer/
HiddenServiceVersion 3
HiddenServicePoWDefensesEnabled 1
HiddenServicePort 80 127.0.0.1:3002
```
~ > Bitcoin Core and LND use the Tor control port to automatically create the hidden service, requiring no action from the user. We have submitted a feature request in the official GitHub repositories to explore the need for the integration of Tor's PoW defense into the automatic creation process of the hidden service. You can follow them at the following links:
* Bitcoin Core: https://github.com/lightningnetwork/lnd/issues/8002
* LND: https://github.com/bitcoin/bitcoin/issues/28499
---
More info:
* https://blog.torproject.org/introducing-proof-of-work-defense-for-onion-services/
* https://gitlab.torproject.org/tpo/onion-services/onion-support/-/wikis/Documentation/PoW-FAQ
---
Enjoy it MiniBolter! 💙
-

@ c8cf63be:86691cfe
2025-01-21 13:48:28
### Das SNAFU des Reichtums
Das SNAFU-Prinzip[1] sagt das Kommunikation nur unter gleichen möglich
ist:
> Adäquate Kommunikation fliesst nur zwischen Gleichen ungehindert.
> Kommunikation zwischen Nicht-Gleichen ist missverständlich und von
> Dominaz- und Unterwerfungsritualen gefärbt, die immer wieder zum
> Zusammenbruch der Kommunikation führen und zu einem Spiel ohne Ende.
> [2]
So ist z. B. das Peter Prinzip [3] eine einfache Folge des
SNAFU-Prinzips. Bezieht es sich in erster Linie auf Hierarchie lässt es
sich hervorragend ausweiten auf den ökonomischen Bereich. Auch hier
gilt, dass Kommunikation nur unter Gleichen möglich ist, hier ist die
Hierarchie das ökonomische Ungleichgewicht.
Kommunikation ist auch hier nur unter gleichen möglich, ungefähr gleich
reich müssen sie sein. Ein zu großer Unterschied in den ökonomischen
Verhältnissen verhindert den Aufbau einer menschlichen Beziehung. Hier
ist das einfache Beispiel: Wäre ich Reich, würde ich mich Fragen, ob die
Freunde da, nur kommen weil ich ihnen die Drinks ausgebe. Jeder, der
nicht so viel Geld wie ich hat, will vielleicht nur mein Geld. So kann
ein Bill Gates nur einen Jeff Besos als Freund haben oder treffender ein
Elon Musk nur einen Mark Zuckerberg.
Auch umgekehrt funktioniert diese Selektion: Wenn ich ein richtig cooler
Typ wäre, würde ich mich fragen, ob ich den Reichen eigentlich gut
finde, oder nur mit ihm rumhänge, weil er die Drinks bezahlt und weil
ich zu Recht unsicher darüber sein kann, kann ich mich nur entziehen.
Diejenigen, die wirklich freundschaftlich sind, sind die die sich einer
solchen Situation nicht aussetzen.
Und was bleibt dem Reichen? Nur die Gesellschaft der Reichen. Hier
trifft der Reichtum auf eine totale Armut. Die Auswahl der Freunde ist
sehr klein.
Hier ist tatsächlich der Reichtum das Problem, bzw. das ökonomische
Ungleichgewicht und es gibt eine einfache Lösung, der Unterschied muss
kleiner werden, denn je kleiner der Unterschied desto mehr Auswahl an
Freunden gibt es. Wie in der “Aufgeklärten Ökonomie” dargestellt ist die
Ungleichheit, eine gesellschaftliche Entscheidung und eine konkrete
Steuerung möglich. Wir können also den Reichen helfen und mehr Freiheit
und Freunde schenken.
Pathologisch wird dieses Phänomen, wenn sich der innere Antrieb um den
Reichtum dreht. Was durch die momentane Verfasstheit der
gesellschaftlichen Praktiken sogar unterstützt und gefördert wird und
damit viele Menschen objektiv unglücklich macht. Dieses pathologische
der Gesellschaft wirkt dann auf das Individuum zurück und macht es
ebenfalls Krank. Wir haben einen ähnlichen Mechanismus in der Gewalt
kennenlernen dürfen. Vgl. “Gewalt ist eine ansteckende Krankrankheit”
<figure>
<img src="!(image)[https://cdn.satellite.earth/ac54bd400867c63f14e151172422067dc1b19980b1e738a577ae6c7a6ea835ea.png]" style="width:50.0%"
alt="Klarmachen ändert, Gier ist heilbar" />
<figcaption aria-hidden="true">Klarmachen ändert, Gier ist
heilbar</figcaption>
</figure>
> Wenn sie sich leer fühlen, Erfolg ihnen kein Glück schenkt, keine
> Befriedigung. Wenn sie mehr brauchen und mehr, dann leiden sie
> wahrscheinlich auch an einer Dysfunktion der Belohnungssysteme, an
> Habsucht.
> Auch ihnen kann und muss geholfen werden, denn Gier ist heilbar. Und
> ihrer Gier betrifft nicht nur sie. Ihre liebsten Menschen in Ihrer
> Umgebung, Menschen mit denen sie niemals direkt in Berührung kommen,
> sie alle leiden unter ihrer Krankheit.
> Auch für sie kann es ein erfülltes Leben geben, einen Weg zurück in
> die Gesellschaft, die Gesellschaft von Menschen. Machen sie
> Psychotherapie, nehmen sie Pharmaka, buchen sie eine Kur und
> entledigen sich ihres Wohlstandes.[4]
------------------------------------------------------------------------
### References:
[1] Wikipedia, SNAFU: <https://de.wikipedia.org/wiki/SNAFU>.
[2] Wilson, R.A., Der Neue Prometheus. Die Evolution unserer
Intelligenz. - Volksausgabe/ Raubdruck. 1983. Seite 245-246
[3] Wikipedia, Peter Prinzip:
<https://de.wikipedia.org/wiki/Peter-Prinzip>.
[4] InvestmentWeek, Sucht im Luxus: Eine Nacht in der Klinik der
Superreichen 2024:
<https://www.investmentweek.com/sucht-im-luxus-eine-nacht-in-der-klinik-der-superreichen/>,
„Viele Patienten hier leiden an Einsamkeit“ … “Viele Superreiche
…wüssten nicht, ob sie wegen ihres Geldes oder ihrer Persönlichkeit
gemocht werden” „Reich sein bedeutet oft, keinen echten Kontakt zu
haben. Viele unserer Klienten haben keine echten Freunde.“
-

@ 04ed2b8f:75be6756
2025-01-21 02:26:28
A warrior does not fear chaos—he thrives in it. Life is a battlefield, and disorder is the forge in which strength, strategy, and resilience are tempered. Whether in the pursuit of victory in business, relationships, or personal conquest, chaos is an inevitable adversary. But within every storm lies an opportunity—an opening to strike, to evolve, and to dominate where others falter. Only those who embrace the struggle with unwavering resolve can turn uncertainty into their greatest weapon.
### **Understanding Chaos**
Chaos is not the enemy; it is the proving ground. It manifests as upheaval, setbacks, and unexpected challenges, forcing warriors to sharpen their minds and steel their resolve.
- **Disruption Breeds Innovation:** In the heat of battle, new tactics emerge. When the known paths are obliterated, new strategies take form.
- **Mindset Is Your Strongest Weapon:** Chaos can either crush you or forge you into something stronger. The choice lies within your perception.
- **Growth Is Forged in Adversity:** The greatest warriors are those who embrace discomfort, wielding it to forge endurance and ingenuity.
### **Seizing Opportunity Amidst Chaos**
1. **Adaptability Is Strength**
- The warrior who can shift tactics swiftly gains the upper hand. Flexibility and awareness allow for swift and decisive action where others hesitate.
2. **Chaos Fuels Creativity**
- In the heat of turmoil, the boldest ideas are born. Warriors do not cling to old ways; they adapt, overcome, and conquer.
3. **Endings Are Just New Battles**
- What seems like defeat is often a call to arms for greater conquests. Every setback is a chance to regroup and strike back with renewed vigor.
### **Harnessing Chaos for Victory**
1. **Remain Steady Amid the Storm:** Fear clouds judgment; clarity is power. Observe, assess, and act with precision. Opportunities reveal themselves to those who master control over their emotions.
2. **Strike First, Strike Hard:** Do not merely react to chaos—command it. Take decisive actions that position you ahead of the pack.
3. **Exploit Weaknesses:** Where others see insurmountable problems, a warrior sees openings and opportunities to advance.
### **Lessons from the Battlefields of History**
Legends are not born in times of peace but in the crucible of chaos. From generals who turned the tide of war in moments of despair to entrepreneurs who built empires from ruin, history is a testament to those who harnessed disorder and emerged victorious.
### **Conclusion: Chaos Is the Warrior's Ally**
Chaos is not to be feared but embraced. It is the ultimate test of will and strategy. A true warrior sees beyond the disorder, crafting victory from the wreckage. In every crisis lies the seed of triumph; in every conflict, the chance to rise.
When chaos surrounds you, stand firm, sharpen your sword, and remember—opportunity belongs to those with the courage to seize it.
-

@ 6be5cc06:5259daf0
2025-01-21 01:51:46
## Bitcoin: Um sistema de dinheiro eletrônico direto entre pessoas.
Satoshi Nakamoto
satoshin@gmx.com
www.bitcoin.org
---
### Resumo
O Bitcoin é uma forma de dinheiro digital que permite pagamentos diretos entre pessoas, sem a necessidade de um banco ou instituição financeira. Ele resolve um problema chamado **gasto duplo**, que ocorre quando alguém tenta gastar o mesmo dinheiro duas vezes. Para evitar isso, o Bitcoin usa uma rede descentralizada onde todos trabalham juntos para verificar e registrar as transações.
As transações são registradas em um livro público chamado **blockchain**, protegido por uma técnica chamada **Prova de Trabalho**. Essa técnica cria uma cadeia de registros que não pode ser alterada sem refazer todo o trabalho já feito. Essa cadeia é mantida pelos computadores que participam da rede, e a mais longa é considerada a verdadeira.
Enquanto a maior parte do poder computacional da rede for controlada por participantes honestos, o sistema continuará funcionando de forma segura. A rede é flexível, permitindo que qualquer pessoa entre ou saia a qualquer momento, sempre confiando na cadeia mais longa como prova do que aconteceu.
---
### 1. Introdução
Hoje, quase todos os pagamentos feitos pela internet dependem de bancos ou empresas como processadores de pagamento (cartões de crédito, por exemplo) para funcionar. Embora esse sistema seja útil, ele tem problemas importantes porque é baseado em **confiança**.
Primeiro, essas empresas podem reverter pagamentos, o que é útil em caso de erros, mas cria custos e incertezas. Isso faz com que pequenas transações, como pagar centavos por um serviço, se tornem inviáveis. Além disso, os comerciantes são obrigados a desconfiar dos clientes, pedindo informações extras e aceitando fraudes como algo inevitável.
Esses problemas não existem no dinheiro físico, como o papel-moeda, onde o pagamento é final e direto entre as partes. No entanto, não temos como enviar dinheiro físico pela internet sem depender de um intermediário confiável.
O que precisamos é de um **sistema de pagamento eletrônico baseado em provas matemáticas**, não em confiança. Esse sistema permitiria que qualquer pessoa enviasse dinheiro diretamente para outra, sem depender de bancos ou processadores de pagamento. Além disso, as transações seriam irreversíveis, protegendo vendedores contra fraudes, mas mantendo a possibilidade de soluções para disputas legítimas.
Neste documento, apresentamos o **Bitcoin**, que resolve o problema do gasto duplo usando uma rede descentralizada. Essa rede cria um registro público e protegido por cálculos matemáticos, que garante a ordem das transações. Enquanto a maior parte da rede for controlada por pessoas honestas, o sistema será seguro contra ataques.
---
### 2. Transações
Para entender como funciona o Bitcoin, é importante saber como as transações são realizadas. Imagine que você quer transferir uma "moeda digital" para outra pessoa. No sistema do Bitcoin, essa "moeda" é representada por uma sequência de registros que mostram quem é o atual dono. Para transferi-la, você adiciona um novo registro comprovando que agora ela pertence ao próximo dono. Esse registro é protegido por um tipo especial de assinatura digital.
#### O que é uma assinatura digital?
Uma assinatura digital é como uma senha secreta, mas muito mais segura. No Bitcoin, cada usuário tem duas chaves: uma "chave privada", que é secreta e serve para criar a assinatura, e uma "chave pública", que pode ser compartilhada com todos e é usada para verificar se a assinatura é válida. Quando você transfere uma moeda, usa sua chave privada para assinar a transação, provando que você é o dono. A próxima pessoa pode usar sua chave pública para confirmar isso.
#### Como funciona na prática?
Cada "moeda" no Bitcoin é, na verdade, uma cadeia de assinaturas digitais. Vamos imaginar o seguinte cenário:
1. A moeda está com o Dono 0 (você). Para transferi-la ao Dono 1, você assina digitalmente a transação com sua chave privada. Essa assinatura inclui o código da transação anterior (chamado de "hash") e a chave pública do Dono 1.
2. Quando o Dono 1 quiser transferir a moeda ao Dono 2, ele assinará a transação seguinte com sua própria chave privada, incluindo também o hash da transação anterior e a chave pública do Dono 2.
3. Esse processo continua, formando uma "cadeia" de transações. Qualquer pessoa pode verificar essa cadeia para confirmar quem é o atual dono da moeda.
#### Resolvendo o problema do gasto duplo
Um grande desafio com moedas digitais é o "gasto duplo", que é quando uma mesma moeda é usada em mais de uma transação. Para evitar isso, muitos sistemas antigos dependiam de uma entidade central confiável, como uma casa da moeda, que verificava todas as transações. No entanto, isso criava um ponto único de falha e centralizava o controle do dinheiro.
O Bitcoin resolve esse problema de forma inovadora: ele usa uma rede descentralizada onde todos os participantes (os "nós") têm acesso a um registro completo de todas as transações. Cada nó verifica se as transações são válidas e se a moeda não foi gasta duas vezes. Quando a maioria dos nós concorda com a validade de uma transação, ela é registrada permanentemente na blockchain.
#### Por que isso é importante?
Essa solução elimina a necessidade de confiar em uma única entidade para gerenciar o dinheiro, permitindo que qualquer pessoa no mundo use o Bitcoin sem precisar de permissão de terceiros. Além disso, ela garante que o sistema seja seguro e resistente a fraudes.
---
### 3. Servidor Timestamp
Para assegurar que as transações sejam realizadas de forma segura e transparente, o sistema Bitcoin utiliza algo chamado de "servidor de registro de tempo" (timestamp). Esse servidor funciona como um registro público que organiza as transações em uma ordem específica.
Ele faz isso agrupando várias transações em blocos e criando um código único chamado "hash". Esse hash é como uma impressão digital que representa todo o conteúdo do bloco. O hash de cada bloco é amplamente divulgado, como se fosse publicado em um jornal ou em um fórum público.
Esse processo garante que cada bloco de transações tenha um registro de quando foi criado e que ele existia naquele momento. Além disso, cada novo bloco criado contém o hash do bloco anterior, formando uma cadeia contínua de blocos conectados — conhecida como blockchain.
Com isso, se alguém tentar alterar qualquer informação em um bloco anterior, o hash desse bloco mudará e não corresponderá ao hash armazenado no bloco seguinte. Essa característica torna a cadeia muito segura, pois qualquer tentativa de fraude seria imediatamente detectada.
O sistema de timestamps é essencial para provar a ordem cronológica das transações e garantir que cada uma delas seja única e autêntica. Dessa forma, ele reforça a segurança e a confiança na rede Bitcoin.
---
### 4. Prova-de-Trabalho
Para implementar o registro de tempo distribuído no sistema Bitcoin, utilizamos um mecanismo chamado prova-de-trabalho. Esse sistema é semelhante ao Hashcash, desenvolvido por Adam Back, e baseia-se na criação de um código único, o "hash", por meio de um processo computacionalmente exigente.
A prova-de-trabalho envolve encontrar um valor especial que, quando processado junto com as informações do bloco, gere um hash que comece com uma quantidade específica de zeros. Esse valor especial é chamado de "nonce". Encontrar o nonce correto exige um esforço significativo do computador, porque envolve tentativas repetidas até que a condição seja satisfeita.
Esse processo é importante porque torna extremamente difícil alterar qualquer informação registrada em um bloco. Se alguém tentar mudar algo em um bloco, seria necessário refazer o trabalho de computação não apenas para aquele bloco, mas também para todos os blocos que vêm depois dele. Isso garante a segurança e a imutabilidade da blockchain.
A prova-de-trabalho também resolve o problema de decidir qual cadeia de blocos é a válida quando há múltiplas cadeias competindo. A decisão é feita pela cadeia mais longa, pois ela representa o maior esforço computacional já realizado. Isso impede que qualquer indivíduo ou grupo controle a rede, desde que a maioria do poder de processamento seja mantida por participantes honestos.
Para garantir que o sistema permaneça eficiente e equilibrado, a dificuldade da prova-de-trabalho é ajustada automaticamente ao longo do tempo. Se novos blocos estiverem sendo gerados rapidamente, a dificuldade aumenta; se estiverem sendo gerados muito lentamente, a dificuldade diminui. Esse ajuste assegura que novos blocos sejam criados aproximadamente a cada 10 minutos, mantendo o sistema estável e funcional.
---
### 5. Rede
A rede Bitcoin é o coração do sistema e funciona de maneira distribuída, conectando vários participantes (ou nós) para garantir o registro e a validação das transações. Os passos para operar essa rede são:
1. **Transmissão de Transações**: Quando alguém realiza uma nova transação, ela é enviada para todos os nós da rede. Isso é feito para garantir que todos estejam cientes da operação e possam validá-la.
2. **Coleta de Transações em Blocos**: Cada nó agrupa as novas transações recebidas em um "bloco". Este bloco será preparado para ser adicionado à cadeia de blocos (a blockchain).
3. **Prova-de-Trabalho**: Os nós competem para resolver a prova-de-trabalho do bloco, utilizando poder computacional para encontrar um hash válido. Esse processo é como resolver um quebra-cabeça matemático difícil.
4. **Envio do Bloco Resolvido**: Quando um nó encontra a solução para o bloco (a prova-de-trabalho), ele compartilha esse bloco com todos os outros nós na rede.
5. **Validação do Bloco**: Cada nó verifica o bloco recebido para garantir que todas as transações nele contidas sejam válidas e que nenhuma moeda tenha sido gasta duas vezes. Apenas blocos válidos são aceitos.
6. **Construção do Próximo Bloco**: Os nós que aceitaram o bloco começam a trabalhar na criação do próximo bloco, utilizando o hash do bloco aceito como base (hash anterior). Isso mantém a continuidade da cadeia.
#### Resolução de Conflitos e Escolha da Cadeia Mais Longa
Os nós sempre priorizam a cadeia mais longa, pois ela representa o maior esforço computacional já realizado, garantindo maior segurança. Se dois blocos diferentes forem compartilhados simultaneamente, os nós trabalharão no primeiro bloco recebido, mas guardarão o outro como uma alternativa. Caso o segundo bloco eventualmente forme uma cadeia mais longa (ou seja, tenha mais blocos subsequentes), os nós mudarão para essa nova cadeia.
#### Tolerância a Falhas
A rede é robusta e pode lidar com mensagens que não chegam a todos os nós. Uma transação não precisa alcançar todos os nós de imediato; basta que chegue a um número suficiente deles para ser incluída em um bloco. Da mesma forma, se um nó não receber um bloco em tempo hábil, ele pode solicitá-lo ao perceber que está faltando quando o próximo bloco é recebido.
Esse mecanismo descentralizado permite que a rede Bitcoin funcione de maneira segura, confiável e resiliente, sem depender de uma autoridade central.
---
### 6. Incentivo
O incentivo é um dos pilares fundamentais que sustenta o funcionamento da rede Bitcoin, garantindo que os participantes (nós) continuem operando de forma honesta e contribuindo com recursos computacionais. Ele é estruturado em duas partes principais: a recompensa por mineração e as taxas de transação.
#### Recompensa por Mineração
Por convenção, o primeiro registro em cada bloco é uma transação especial que cria novas moedas e as atribui ao criador do bloco. Essa recompensa incentiva os mineradores a dedicarem poder computacional para apoiar a rede. Como não há uma autoridade central para emitir moedas, essa é a maneira pela qual novas moedas entram em circulação. Esse processo pode ser comparado ao trabalho de garimpeiros, que utilizam recursos para colocar mais ouro em circulação. No caso do Bitcoin, o "recurso" consiste no tempo de CPU e na energia elétrica consumida para resolver a prova-de-trabalho.
#### Taxas de Transação
Além da recompensa por mineração, os mineradores também podem ser incentivados pelas taxas de transação. Se uma transação utiliza menos valor de saída do que o valor de entrada, a diferença é tratada como uma taxa, que é adicionada à recompensa do bloco contendo essa transação. Com o passar do tempo e à medida que o número de moedas em circulação atinge o limite predeterminado, essas taxas de transação se tornam a principal fonte de incentivo, substituindo gradualmente a emissão de novas moedas. Isso permite que o sistema opere sem inflação, uma vez que o número total de moedas permanece fixo.
#### Incentivo à Honestidade
O design do incentivo também busca garantir que os participantes da rede mantenham um comportamento honesto. Para um atacante que consiga reunir mais poder computacional do que o restante da rede, ele enfrentaria duas escolhas:
1. Usar esse poder para fraudar o sistema, como reverter transações e roubar pagamentos.
2. Seguir as regras do sistema, criando novos blocos e recebendo recompensas legítimas.
A lógica econômica favorece a segunda opção, pois um comportamento desonesto prejudicaria a confiança no sistema, diminuindo o valor de todas as moedas, incluindo aquelas que o próprio atacante possui. Jogar dentro das regras não apenas maximiza o retorno financeiro, mas também preserva a validade e a integridade do sistema.
Esse mecanismo garante que os incentivos econômicos estejam alinhados com o objetivo de manter a rede segura, descentralizada e funcional ao longo do tempo.
---
### 7. Recuperação do Espaço em Disco
Depois que uma moeda passa a estar protegida por muitos blocos na cadeia, as informações sobre as transações antigas que a geraram podem ser descartadas para economizar espaço em disco. Para que isso seja possível sem comprometer a segurança, as transações são organizadas em uma estrutura chamada "árvore de Merkle". Essa árvore funciona como um resumo das transações: em vez de armazenar todas elas, guarda apenas um "hash raiz", que é como uma assinatura compacta que representa todo o grupo de transações.
Os blocos antigos podem, então, ser simplificados, removendo as partes desnecessárias dessa árvore. Apenas a raiz do hash precisa ser mantida no cabeçalho do bloco, garantindo que a integridade dos dados seja preservada, mesmo que detalhes específicos sejam descartados.
Para exemplificar: imagine que você tenha vários recibos de compra. Em vez de guardar todos os recibos, você cria um documento e lista apenas o valor total de cada um. Mesmo que os recibos originais sejam descartados, ainda é possível verificar a soma com base nos valores armazenados.
Além disso, o espaço ocupado pelos blocos em si é muito pequeno. Cada bloco sem transações ocupa apenas cerca de 80 bytes. Isso significa que, mesmo com blocos sendo gerados a cada 10 minutos, o crescimento anual em espaço necessário é insignificante: apenas 4,2 MB por ano. Com a capacidade de armazenamento dos computadores crescendo a cada ano, esse espaço continuará sendo trivial, garantindo que a rede possa operar de forma eficiente sem problemas de armazenamento, mesmo a longo prazo.
---
### 8. Verificação de Pagamento Simplificada
É possível confirmar pagamentos sem a necessidade de operar um nó completo da rede. Para isso, o usuário precisa apenas de uma cópia dos cabeçalhos dos blocos da cadeia mais longa (ou seja, a cadeia com maior esforço de trabalho acumulado). Ele pode verificar a validade de uma transação ao consultar os nós da rede até obter a confirmação de que tem a cadeia mais longa. Para isso, utiliza-se o ramo Merkle, que conecta a transação ao bloco em que ela foi registrada.
Entretanto, o método simplificado possui limitações: ele não pode confirmar uma transação isoladamente, mas sim assegurar que ela ocupa um lugar específico na cadeia mais longa. Dessa forma, se um nó da rede aprova a transação, os blocos subsequentes reforçam essa aceitação.
A verificação simplificada é confiável enquanto a maioria dos nós da rede for honesta. Contudo, ela se torna vulnerável caso a rede seja dominada por um invasor. Nesse cenário, um atacante poderia fabricar transações fraudulentas que enganariam o usuário temporariamente até que o invasor obtivesse controle completo da rede.
Uma estratégia para mitigar esse risco é configurar alertas nos softwares de nós completos. Esses alertas identificam blocos inválidos, sugerindo ao usuário baixar o bloco completo para confirmar qualquer inconsistência. Para maior segurança, empresas que realizam pagamentos frequentes podem preferir operar seus próprios nós, reduzindo riscos e permitindo uma verificação mais direta e confiável.
---
### 9. Combinando e Dividindo Valor
No sistema Bitcoin, cada unidade de valor é tratada como uma "moeda" individual, mas gerenciar cada centavo como uma transação separada seria impraticável. Para resolver isso, o Bitcoin permite que valores sejam combinados ou divididos em transações, facilitando pagamentos de qualquer valor.
#### Entradas e Saídas
Cada transação no Bitcoin é composta por:
- **Entradas**: Representam os valores recebidos em transações anteriores.
- **Saídas**: Correspondem aos valores enviados, divididos entre os destinatários e, eventualmente, o troco para o remetente.
Normalmente, uma transação contém:
- Uma única entrada com valor suficiente para cobrir o pagamento.
- Ou várias entradas combinadas para atingir o valor necessário.
O valor total das saídas nunca excede o das entradas, e a diferença (se houver) pode ser retornada ao remetente como **troco**.
#### Exemplo Prático
Imagine que você tem duas entradas:
1. 0,03 BTC
2. 0,07 BTC
Se deseja enviar 0,08 BTC para alguém, a transação terá:
- **Entrada**: As duas entradas combinadas (0,03 + 0,07 BTC = 0,10 BTC).
- **Saídas**: Uma para o destinatário (0,08 BTC) e outra como troco para você (0,02 BTC).
Essa flexibilidade permite que o sistema funcione sem precisar manipular cada unidade mínima individualmente.
#### Difusão e Simplificação
A difusão de transações, onde uma depende de várias anteriores e assim por diante, não representa um problema. Não é necessário armazenar ou verificar o histórico completo de uma transação para utilizá-la, já que o registro na blockchain garante sua integridade.
---
### 10. Privacidade
O modelo bancário tradicional oferece um certo nível de privacidade, limitando o acesso às informações financeiras apenas às partes envolvidas e a um terceiro confiável (como bancos ou instituições financeiras). No entanto, o Bitcoin opera de forma diferente, pois todas as transações são publicamente registradas na blockchain. Apesar disso, a privacidade pode ser mantida utilizando **chaves públicas anônimas**, que desvinculam diretamente as transações das identidades das partes envolvidas.
#### Fluxo de Informação
- No **modelo tradicional**, as transações passam por um terceiro confiável que conhece tanto o remetente quanto o destinatário.
- No **Bitcoin**, as transações são anunciadas publicamente, mas sem revelar diretamente as identidades das partes. Isso é comparável a dados divulgados por bolsas de valores, onde informações como o tempo e o tamanho das negociações (a "fita") são públicas, mas as identidades das partes não.
#### Protegendo a Privacidade
Para aumentar a privacidade no Bitcoin, são adotadas as seguintes práticas:
1. **Chaves Públicas Anônimas**: Cada transação utiliza um par de chaves diferentes, dificultando a associação com um proprietário único.
2. **Prevenção de Ligação**: Ao usar chaves novas para cada transação, reduz-se a possibilidade de links evidentes entre múltiplas transações realizadas pelo mesmo usuário.
#### Riscos de Ligação
Embora a privacidade seja fortalecida, alguns riscos permanecem:
- Transações **multi-entrada** podem revelar que todas as entradas pertencem ao mesmo proprietário, caso sejam necessárias para somar o valor total.
- O proprietário da chave pode ser identificado indiretamente por transações anteriores que estejam conectadas.
---
### 11. Cálculos
Imagine que temos um sistema onde as pessoas (ou computadores) competem para adicionar informações novas (blocos) a um grande registro público (a cadeia de blocos ou blockchain). Este registro é como um livro contábil compartilhado, onde todos podem verificar o que está escrito.
Agora, vamos pensar em um cenário: um atacante quer enganar o sistema. Ele quer mudar informações já registradas para beneficiar a si mesmo, por exemplo, desfazendo um pagamento que já fez. Para isso, ele precisa criar uma versão alternativa do livro contábil (a cadeia de blocos dele) e convencer todos os outros participantes de que essa versão é a verdadeira.
Mas isso é extremamente difícil.
#### Como o Ataque Funciona
Quando um novo bloco é adicionado à cadeia, ele depende de cálculos complexos que levam tempo e esforço. Esses cálculos são como um grande quebra-cabeça que precisa ser resolvido.
- Os “bons jogadores” (nós honestos) estão sempre trabalhando juntos para resolver esses quebra-cabeças e adicionar novos blocos à cadeia verdadeira.
- O atacante, por outro lado, precisa resolver quebra-cabeças sozinho, tentando “alcançar” a cadeia honesta para que sua versão alternativa pareça válida.
Se a cadeia honesta já está vários blocos à frente, o atacante começa em desvantagem, e o sistema está projetado para que a dificuldade de alcançá-los aumente rapidamente.
#### A Corrida Entre Cadeias
Você pode imaginar isso como uma corrida. A cada bloco novo que os jogadores honestos adicionam à cadeia verdadeira, eles se distanciam mais do atacante. Para vencer, o atacante teria que resolver os quebra-cabeças mais rápido que todos os outros jogadores honestos juntos.
Suponha que:
- A rede honesta tem **80% do poder computacional** (ou seja, resolve 8 de cada 10 quebra-cabeças).
- O atacante tem **20% do poder computacional** (ou seja, resolve 2 de cada 10 quebra-cabeças).
Cada vez que a rede honesta adiciona um bloco, o atacante tem que "correr atrás" e resolver mais quebra-cabeças para alcançar.
#### Por Que o Ataque Fica Cada Vez Mais Improvável?
Vamos usar uma fórmula simples para mostrar como as chances de sucesso do atacante diminuem conforme ele precisa "alcançar" mais blocos:
P = (q/p)^z
- **q** é o poder computacional do atacante (20%, ou 0,2).
- **p** é o poder computacional da rede honesta (80%, ou 0,8).
- **z** é a diferença de blocos entre a cadeia honesta e a cadeia do atacante.
Se o atacante está 5 blocos atrás (z = 5):
P = (0,2 / 0,8)^5 = (0,25)^5 = 0,00098, (ou, 0,098%)
Isso significa que o atacante tem menos de 0,1% de chance de sucesso — ou seja, é muito improvável.
Se ele estiver 10 blocos atrás (z = 10):
P = (0,2 / 0,8)^10 = (0,25)^10 = 0,000000095, (ou, 0,0000095%).
Neste caso, as chances de sucesso são praticamente **nulas**.
#### Um Exemplo Simples
Se você jogar uma moeda, a chance de cair “cara” é de 50%. Mas se precisar de 10 caras seguidas, sua chance já é bem menor. Se precisar de 20 caras seguidas, é quase impossível.
No caso do Bitcoin, o atacante precisa de muito mais do que 20 caras seguidas. Ele precisa resolver quebra-cabeças extremamente difíceis e alcançar os jogadores honestos que estão sempre à frente. Isso faz com que o ataque seja inviável na prática.
#### Por Que Tudo Isso é Seguro?
- **A probabilidade de sucesso do atacante diminui exponencialmente.** Isso significa que, quanto mais tempo passa, menor é a chance de ele conseguir enganar o sistema.
- **A cadeia verdadeira (honesta) está protegida pela força da rede.** Cada novo bloco que os jogadores honestos adicionam à cadeia torna mais difícil para o atacante alcançar.
#### E Se o Atacante Tentar Continuar?
O atacante poderia continuar tentando indefinidamente, mas ele estaria gastando muito tempo e energia sem conseguir nada. Enquanto isso, os jogadores honestos estão sempre adicionando novos blocos, tornando o trabalho do atacante ainda mais inútil.
Assim, o sistema garante que a cadeia verdadeira seja extremamente segura e que ataques sejam, na prática, impossíveis de ter sucesso.
---
### 12. Conclusão
Propusemos um sistema de transações eletrônicas que elimina a necessidade de confiança, baseando-se em assinaturas digitais e em uma rede peer-to-peer que utiliza prova de trabalho. Isso resolve o problema do gasto duplo, criando um histórico público de transações imutável, desde que a maioria do poder computacional permaneça sob controle dos participantes honestos.
A rede funciona de forma simples e descentralizada, com nós independentes que não precisam de identificação ou coordenação direta. Eles entram e saem livremente, aceitando a cadeia de prova de trabalho como registro do que ocorreu durante sua ausência. As decisões são tomadas por meio do poder de CPU, validando blocos legítimos, estendendo a cadeia e rejeitando os inválidos.
Com este mecanismo de consenso, todas as regras e incentivos necessários para o funcionamento seguro e eficiente do sistema são garantidos.
---
Faça o download do whitepaper original em português:
https://bitcoin.org/files/bitcoin-paper/bitcoin_pt_br.pdf
-

@ 3f770d65:7a745b24
2025-01-19 21:48:49
The recent shutdown of TikTok in the United States due to a potential government ban serves as a stark reminder how fragile centralized platforms truly are under the surface. While these platforms offer convenience, a more polished user experience, and connectivity, they are ultimately beholden to governments, corporations, and other authorities. This makes them vulnerable to censorship, regulation, and outright bans. In contrast, Nostr represents a shift in how we approach online communication and content sharing. Built on the principles of decentralization and user choice, Nostr cannot be banned, because it is not a platform—it is a protocol.
**PROTOCOLS, NOT PLATFORMS.**
At the heart of Nostr's philosophy is **user choice**, a feature that fundamentally sets it apart from legacy platforms. In centralized systems, the user experience is dictated by a single person or governing entity. If the platform decides to filter, censor, or ban specific users or content, individuals are left with little action to rectify the situation. They must either accept the changes or abandon the platform entirely, often at the cost of losing their social connections, their data, and their identity.
What's happening with TikTok could never happen on Nostr. With Nostr, the dynamics are completely different. Because it is a protocol, not a platform, no single entity controls the ecosystem. Instead, the protocol enables a network of applications and relays that users can freely choose from. If a particular application or relay implements policies that a user disagrees with, such as censorship, filtering, or even government enforced banning, they are not trapped or abandoned. They have the freedom to move to another application or relay with minimal effort.
**THIS IS POWERFUL.**
Take, for example, the case of a relay that decides to censor specific content. On a legacy platform, this would result in frustration and a loss of access for users. On Nostr, however, users can simply connect to a different relay that does not impose such restrictions. Similarly, if an application introduces features or policies that users dislike, they can migrate to a different application that better suits their preferences, all while retaining their identity and social connections.
The same principles apply to government bans and censorship. A government can ban a specific application or even multiple applications, just as it can block one relay or several relays. China has implemented both tactics, yet Chinese users continue to exist and actively participate on Nostr, demonstrating Nostr's ability to resistant censorship.
How? Simply, it turns into a game of whack-a-mole. When one relay is censored, another quickly takes its place. When one application is banned, another emerges. Users can also bypass these obstacles by running their own relays and applications directly from their homes or personal devices, eliminating reliance on larger entities or organizations and ensuring continuous access.
**AGAIN, THIS IS POWERUFL.**
Nostr's open and decentralized design makes it resistant to the kinds of government intervention that led to TikTok's outages this weekend and potential future ban in the next 90 days. There is no central server to target, no company to regulate, and no single point of failure. (Insert your CEO jokes here). As long as there are individuals running relays and applications, users continue creating notes and sending zaps.
Platforms like TikTok can be silenced with the stroke of a pen, leaving millions of users disconnected and abandoned. Social communication should not be silenced so incredibly easily. No one should have that much power over social interactions.
Will we on-board a massive wave of TikTokers in the coming hours or days? I don't know.
TikTokers may not be ready for Nostr yet, and honestly, Nostr may not be ready for them either. The ecosystem still lacks the completely polished applications, tools, and services they’re accustomed to. This is where we say "we're still early". They may not be early adopters like the current Nostr user base. Until we bridge that gap, they’ll likely move to the next centralized platform, only to face another government ban or round of censorship in the future. But eventually, there will come a tipping point, a moment when they’ve had enough. When that time comes, I hope we’re prepared. If we’re not, we risk missing a tremendous opportunity to onboard people who genuinely need Nostr’s freedom.
Until then, to all of the Nostr developers out there, keep up the great work and keep building. Your hard work and determination is needed.
###
-

@ 6f7db55a:985d8b25
2025-01-19 19:46:30
This article will be basic instructions for extreme normies (I say that lovingly), or anyone looking to get started with using zap.stream and sharing to nostr.
**EQUIPMENT**
Getting started is incredibly easy and your equipment needs are miniscule.
An old desktop or laptop running Linux, MacOs, or Windows made in the passed 15yrs should do. Im currently using and old Dell Latitude E5430 with an Intel i5-3210M with 32Gigs of ram and 250GB hard drive. Technically, you go as low as using a Raspberry Pi 4B+ running Owncast, but Ill save that so a future tutorial.
Let's get started.
**ON YOUR COMPUTER**
You'll need to install OBS (open broaster software). OBS is the go-to for streaming to social media. There are tons of YouTube videos on it's function. WE, however, will only be doing the basics to get us up and running.
First, go to [https://obsproject.com/](https://obsproject.com/)

Once on the OBS site, choose the correct download for you system. Linux, MacOs or Windows. Download (remember where you downloaded the file to). Go there and install your download. You may have to enter your password to install on your particular operating system. This is normal.
Once you've installed OBS, open the application. It should look something like this...

For our purposes, we will be in studio mode. Locate the 'Studio Mode' button on the right lower-hand side of the screen, and click it.

You'll see the screen split like in the image above. The left-side is from your desktop, and the right-side is what your broadcast will look like.
Next, we go to settings. The 'Settings' button is located right below the 'Studio Mode" button.

Now we're in settings and you should see something like this...

Now locate stream in the right-hand menu. It should be the second in the list. Click it.

Once in the stream section, go to 'Service' and in the right-hand drop-down, find and select 'Custom...' from the drop-down menu.

Remeber where this is because we'll need to come back to it, shortly.
**ZAPSTREAM**
We need our streamkey credentials from Zapstream. Go to [https://zap.stream](https://zap.stream). Then, go to your dashboard.

Located on the lower right-hand side is the Server URL and Stream Key. You'll need to copy/paste this in OBS.

You may have to generate new keys, if they aren't already there. This is normal. If you're interested in multi-streaming (That's where you broadcast to multiple social media platforms all at once), youll need the server URL and streamkeys from each. You'll place them in their respective forms in Zapstream's 'Stream Forwarding" section.

Use the custom form, if the platform you want to stream to isn't listed.
*Side-Note: remember that you can use your nostr identity across multiple nostr client applications. So when your login for Amethyst, as an example, could be used when you login to zapstream. Also, i would suggest using Alby's browser extension. It makes it much easier to fund your stream, as well as receive zaps.
*
**Now, BACK TO OBS...**
With Stream URL and Key in hand, paste them in the 'Stream" section of OBS' settings.
Service [Custom...]
Server [Server URL]
StreamKey [Your zapstream stream key]

After you've entered all your streaming credentials, click 'OK' at the bottom, on the right-hand side.
**WHAT'S NEXT?**
Let's setup your first stream from OBS. First we need to choose a source. Your source is your input device. It can be your webcam, your mic, your monitor, or any particular window on your screen. assuming you're an absolute beginner, we're going to use the source 'Window Capture (Xcomposite)'.

Now, open your source file. We'll use a video source called 'grannyhiphop.mp4'. In your case it can be whatever you want to stream; Just be sure to select the proper source.

Double-click on 'Window Capture' in your sources list. In the pop-up window, select your file from the 'Window' drop-down menu.


You should see something like this...

Working in the left display of OBS, we will adjust the video by left-click, hold and drag the bottom corner, so that it takes up the whole display.

In order to adjust the right-side display ( the broadcast side), we need to manipulate the video source by changing it's size.

This may take some time to adjust the size. This is normal. What I've found to help is, after every adjustment, I click the 'Fade (300ms)' button. I have no idea why it helps, but it does, lol.

Finally, after getting everything to look the way you want, you click the 'Start Stream' button.

**BACK TO ZAPSTREAM**
Now, we go back to zapstream to check to see if our stream is up. It may take a few moments to update. You may even need to refresh the page. This is normal.

STREAMS UP!!!
A few things, in closing. You'll notice that your dashbooard has changed. It'll show current stream time, how much time you have left (according to your funding source), who's zapped you with how much theyve zapped, the ability to post a note about your stream (to both nostr and twitter), and it shows your chatbox with your listeners. There are also a raid feature, stream settings (where you can title & tag your stream). You can 'topup' your funding for your stream. As well as, see your current balance.
You did a great and If you ever need more help, just use the tag #asknostr in your note. There are alway nostriches willing to help.
**STAY AWESOME!!!**
-

@ cff1720e:15c7e2b2
2025-01-19 17:48:02
**Einleitung**\
\
Schwierige Dinge einfach zu erklären ist der Anspruch von ELI5 (explain me like I'm 5). Das ist in unserer hoch technisierten Welt dringend erforderlich, denn nur mit dem Verständnis der Technologien können wir sie richtig einsetzen und weiter entwickeln.\
Ich starte meine Serie mit Nostr, einem relativ neuen Internet-Protokoll. Was zum Teufel ist ein Internet-Protokoll? Formal beschrieben sind es internationale Standards, die dafür sorgen, dass das Internet seit über 30 Jahren ziemlich gut funktioniert. Es ist die Sprache, in der sich die Rechner miteinander unterhalten und die auch Sie täglich nutzen, vermutlich ohne es bewusst wahrzunehmen. http(s) transportiert ihre Anfrage an einen Server (z.B. Amazon), und html sorgt dafür, dass aus den gelieferten Daten eine schöne Seite auf ihrem Bildschirm entsteht. Eine Mail wird mit smtp an den Mailserver gesendet und mit imap von ihm abgerufen, und da alle den Standard verwenden, funktioniert das mit jeder App auf jedem Betriebssystem und mit jedem Mail-Provider. Und mit einer Mail-Adresse wie <roland@pareto.space> können sie sogar jederzeit umziehen, egal wohin. **Cool, das ist state of the art!** Aber warum funktioniert das z.B. bei Chat nicht, gibt es da kein Protokoll? Doch, es heißt IRC (Internet Relay Chat → merken sie sich den Namen), aber es wird so gut wie nicht verwendet. Die Gründe dafür sind nicht technischer Natur, vielmehr wurden mit Apps wie Facebook, Twitter, WhatsApp, Telegram, Instagram, TikTok u.a. bewusst Inkompatibilitäten und Nutzerabhängigkeiten geschaffen um Profite zu maximieren.

**Warum Nostr?**
Da das Standard-Protokoll nicht genutzt wird, hat jede App ihr eigenes, und wir brauchen eine handvoll Apps um uns mit allen Bekannten auszutauschen. Eine Mobilfunknummer ist Voraussetzung für jedes Konto, damit können die App-Hersteller die Nutzer umfassend tracken und mit dem Verkauf der Informationen bis zu 30 USD je Konto und Monat verdienen. Der Nutzer ist nicht mehr Kunde, er ist das Produkt! Der Werbe-SPAM ist noch das kleinste Problem bei diesem Geschäftsmodell. Server mit Millionen von Nutzerdaten sind ein “honey pot”, dementsprechend oft werden sie gehackt und die Zugangsdaten verkauft. 2024 wurde auch der Twitter-Account vom damaligen Präsidenten Joe Biden gehackt, niemand wusste mehr wer die Nachrichten verfasst hat (vorher auch nicht), d.h. die Authentizität der Inhalte ist bei keinem dieser Anbieter gewährleistet. Im selben Jahr wurde der Telegram-Gründer in Frankreich in Beugehaft genommen, weil er sich geweigert hatte Hintertüren in seine Software einzubauen. Nun kann zum Schutz **"unserer Demokratie”** praktisch jeder mitlesen, was sie mit wem an Informationen austauschen, z.B. darüber welches Shampoo bestimmte Politiker verwenden.

Und wer tatsächlich glaubt er könne Meinungsfreiheit auf sozialen Medien praktizieren, findet sich schnell in der Situation von Donald Trump wieder (seinerzeit amtierender Präsident), dem sein Twitter-Konto 2021 abgeschaltet wurde (Cancel-Culture). Die Nutzerdaten, also ihr Profil, ihre Kontakte, Dokumente, Bilder, Videos und Audiofiles - gehören ihnen ohnehin nicht mehr sondern sind Eigentum des Plattform-Betreibers; lesen sie sich mal die AGB's durch. Aber nein, keine gute Idee, das sind hunderte Seiten und sie werden permanent geändert. Alle nutzen also Apps, deren Technik sie nicht verstehen, deren Regeln sie nicht kennen, wo sie keine Rechte haben und die ihnen die Resultate ihres Handelns stehlen. Was würde wohl der Fünfjährige sagen, wenn ihm seine ältere Schwester anbieten würde, alle seine Spielzeuge zu “verwalten” und dann auszuhändigen wenn er brav ist? “Du spinnst wohl”, und damit beweist der Knirps mehr Vernunft als die Mehrzahl der Erwachsenen. \
\
**Resümee:** keine Standards, keine Daten, keine Rechte = keine Zukunft!

\
**Wie funktioniert Nostr?**
Die Entwickler von Nostr haben erkannt dass sich das Server-Client-Konzept in ein Master-Slave-Konzept verwandelt hatte. Der Master ist ein Synonym für Zentralisierung und wird zum **“single point of failure”**, der zwangsläufig Systeme dysfunktional macht. In einem verteilten Peer2Peer-System gibt es keine Master mehr sondern nur gleichberechtigte Knoten (Relays), auf denen die Informationen gespeichert werden. Indem man Informationen auf mehreren Relays redundant speichert, ist das System in jeglicher Hinsicht resilienter. Nicht nur die Natur verwendet dieses Prinzip seit Jahrmillionen erfolgreich, auch das Internet wurde so konzipiert (das ARPAnet wurde vom US-Militär für den Einsatz in Kriegsfällen unter massiven Störungen entwickelt). Alle Nostr-Daten liegen auf Relays und der Nutzer kann wählen zwischen öffentlichen (zumeist kostenlosen) und privaten Relays, z.B. für geschlossene Gruppen oder zum Zwecke von Daten-Archivierung. Da Dokumente auf mehreren Relays gespeichert sind, werden statt URL's (Locator) eindeutige Dokumentnamen (URI's = Identifier) verwendet, broken Links sind damit Vergangenheit und Löschungen / Verluste ebenfalls.\
\
Jedes Dokument (Event genannt) wird vom Besitzer signiert, es ist damit authentisch und fälschungssicher und kann nur vom Ersteller gelöscht werden. Dafür wird ein Schlüsselpaar verwendet bestehend aus privatem (nsec) und öffentlichem Schlüssel (npub) wie aus der Mailverschlüsselung (PGP) bekannt. Das repräsentiert eine Nostr-Identität, die um Bild, Namen, Bio und eine lesbare Nostr-Adresse ergänzt werden kann (z.B. <roland@pareto.space> ), mehr braucht es nicht um alle Ressourcen des Nostr-Ökosystems zu nutzen. Und das besteht inzwischen aus über hundert Apps mit unterschiedlichen Fokussierungen, z.B. für persönliche verschlüsselte Nachrichten (DM → OxChat), Kurznachrichten (Damus, Primal), Blogbeiträge (Pareto), Meetups (Joinstr), Gruppen (Groups), Bilder (Olas), Videos (Amethyst), Audio-Chat (Nostr Nests), Audio-Streams (Tunestr), Video-Streams (Zap.Stream), Marktplätze (Shopstr) u.v.a.m. Die Anmeldung erfolgt mit einem Klick (single sign on) und den Apps stehen ALLE Nutzerdaten zur Verfügung (Profil, Daten, Kontakte, Social Graph → Follower, Bookmarks, Comments, etc.), im Gegensatz zu den fragmentierten Datensilos der Gegenwart.\
\
**Resümee:** ein offener Standard, alle Daten, alle Rechte = große Zukunft!

\
**Warum ist Nostr die Zukunft des Internet?**
“Baue Dein Haus nicht auf einem fremden Grundstück” gilt auch im Internet - für alle App-Entwickler, Künstler, Journalisten und Nutzer, denn auch ihre Daten sind werthaltig. Nostr garantiert das Eigentum an den Daten, und überwindet ihre Fragmentierung. Weder die Nutzung noch die kreativen Freiheiten werden durch maßlose Lizenz- und Nutzungsbedingungen eingeschränkt. Aus passiven Nutzern werden durch Interaktion aktive Teilnehmer, Co-Creatoren in einer Sharing-Ökonomie **(Value4Value)**. OpenSource schafft endlich wieder Vertrauen in die Software und ihre Anbieter. Offene Standards ermöglichen den Entwicklern mehr Kooperation und schnellere Entwicklung, für die Anwender garantieren sie Wahlfreiheit. Womit wir letztmalig zu unserem Fünfjährigen zurückkehren. Kinder lieben Lego über alles, am meisten die Maxi-Box “Classic”, weil sie damit ihre Phantasie im Kombinieren voll ausleben können. Erwachsene schenken ihnen dann die viel zu teuren Themenpakete, mit denen man nur eine Lösung nach Anleitung bauen kann. “Was stimmt nur mit meinen Eltern nicht, wann sind die denn falsch abgebogen?" fragt sich der Nachwuchs zu Recht. Das Image lässt sich aber wieder aufpolieren, wenn sie ihren Kindern Nostr zeigen, denn die Vorteile verstehen sogar Fünfjährige.

\
**Das neue Internet ist dezentral. Das neue Internet ist selbstbestimmt. Nostr ist das neue Internet.**
<https://nostr.net/> \
<https://start.njump.me/>
**Hier das Interview zum Thema mit Radio Berliner Morgenröte**
<https://www.podbean.com/ew/pb-yxc36-17bb4be>
-

@ fd208ee8:0fd927c1
2025-01-19 12:10:10
I am so tired of people trying to waste my time with Nostrized imitations of stuff that already exists.
Instagram, but make it Nostr.
Twitter, but make it Nostr.
GitHub, but make it Nostr.
Facebook, but make it Nostr.
Wordpress, but make it Nostr.
GoodReads, but make it Nostr.
TikTok, but make it Nostr.
That stuff already exists, and it wasn't that great the first time around, either. Build something better than that stuff, that can only be brought into existence because of Nostr.
Build something that does something completely and awesomely new. Knock my socks off, bro.
Cuz, ain't nobody got time for that.
-

@ 378562cd:a6fc6773
2025-01-18 16:20:12
As a frequent user who depends on my phone for a wide range of activities, including boosting my productivity and capturing spontaneous moments, I have been paying close attention to the OnePlus 13. This flagship device appears to meet all my essential requirements, particularly excelling in power and camera capabilities, which are my main priorities. Here are the standout features that have caught my attention.
<img src="https://blossom.primal.net/9d0b0d98e9ac02d756f31ab0b46f3e0e79b98aa0576d0e71847bba4fcf5ee2e3.webp">
### Power to Handle Anything I Throw at It
Performance is a big deal for me, and the OnePlus 13 doesn’t seem to disappoint. It’s powered by the Snapdragon 8 Elite processor, a beast in the mobile tech world. I can already imagine how smoothly it would handle heavy multitasking, like switching between editing photos, running multiple apps, and even gaming.
The insane memory options—up to 24GB of RAM—truly stand out. That’s more RAM than most laptops I’ve owned! Pair that with up to 1TB of storage, and you’re looking at a future-proof phone. I’d never have to worry about running out of space for apps, photos, or videos, and everything would load lightning-fast.
###
<img src="https://blossom.primal.net/6f9363e8e4a9663346e5fdaf41b25b611dcf1324a85799bdefa1f90f980fc02d.jpg">
### A Camera Setup That’s Hard to Ignore
One of my favorite things to do is capture high-quality photos and videos, so a powerful camera system is non-negotiable. The OnePlus 13 delivers with its triple-camera setup; all three lenses are 50 megapixels. That means whether I’m shooting with the main wide lens, zooming in with the telephoto, or going wide with the ultra-wide, I’m getting consistently sharp, detailed shots.
The Hasselblad collaboration is a big draw for me, too. OnePlus phones have been steadily improving their color science, and this partnership seems to really shine in the OnePlus 13. I’d expect vibrant, true-to-life colors in my photos without much editing required.
The AI enhancements also pique my interest. From what I’ve read, the phone handles tricky lighting situations, like low-light environments or high-contrast scenes, exceptionally well. That’s exactly what I need to capture spontaneous moments without worrying about settings.
### Battery and Charging That Won’t Leave Me Hanging
Another thing I appreciate is the long battery life. The 6,000 mAh battery on the OnePlus 13 is reportedly a powerhouse, capable of lasting two days under mixed usage. And when I do need to charge, the 100W wired charging can fully juice up the phone in just over half an hour. Even the 50W wireless charging is incredibly fast, which is perfect for someone like me who’s always on the move.
### Design and Features That Add Value
The flat-edge design and premium finish make the phone feel as good as it looks. I’d probably go for the Midnight Ocean with its vegan leather back—it sounds grippy and unique, ideal for someone who doesn’t want to slap on a bulky case.
The little extras, like Glove Mode and Aqua Touch 2.0, also catch my attention. Since winters are cold here, using my phone with gloves on is a practical bonus.
### Why It’s Tempting Me
At $899 for the base model, the OnePlus 13 seems like a solid deal, especially for the power and camera capabilities it offers. Even if I choose a higher configuration, the pricing still feels reasonable compared to other flagships with similar specs.
For me, the OnePlus 13 feels like a phone that’s built for power users—people who need speed, reliability, and top-tier camera performance. I’m seriously considering it for my next upgrade because it feels like it would keep up with everything I do and then some. If the camera and performance live up to the hype, I might just have my decision made.
-

@ a10260a2:caa23e3e
2025-01-18 12:04:41
*Last Updated: January 18, 2025*
First off, big shoutout to Coinos for having support for adding a memo to BOLT12 offers. This provides a solid alternative for the pleb who wants to support mining decentralization but doesn’t want to set up a CLN node and pay thousands of sats for a channel only to get little rewards. This is the case for most of us who only have a miner or two (e.g. a Bitaxe and/or an S9).
Before we get into setting up Lightning payouts, you’ll want to have your miner configured to mine with OCEAN of course. You’ll also want to make sure that the bitcoin address you use is from a wallet that supports signing messages.
These are the ones listed in the OCEAN [docs](https://ocean.xyz/docs/lightning):
* Bitcoin Knots/Bitcoin Core
* Coldcard
* Electrum
* LND (Command Line)
* Seedsigner
* Sparrow
* Specter
* Trezor
I checked one of my favorite, user-friendly wallets — Blue Wallet — and it happens to support signing messages as well.
Just tap the three dots on the upper right and you’ll see the “Sign/Verify Message” button at the bottom.
Update [January 18]: You can now use Coinos to sign by going to https://coinos.io/sign
The trick here is to not refresh the page. In other words, when you're logged in to your Coinos account, go to the URL and use the legacy address (starts with a "1") that's displayed to configure your miner(s). If you refresh the page, you're going to get a new address which will cause the signing to fail later on. *Remember*, keep the tab open and don't refresh the page.

Whichever wallet you choose, generate a receive address to use when configuring your miner (it’ll also be your OCEAN username).
Here’s how it looks on the Bitaxe (AxeOS)…
And the Antminer S9 (Braiins OS).
NOTE: There’s a slight difference in the URL format between the two apps. Other than that, the username will be your bitcoin address followed by the optional “.” + the nickname for your machine.
You can find more details on OCEAN’s [get started page](https://ocean.xyz/getstarted).
---
Alright, now that your miner is pointed at OCEAN. Let’s configure Lightning payouts!
### Generating the BOLT12 Offer
In the Coinos app, go to Receive > Bolt 12.
Tap “Set memo” and set it to “OCEAN Payouts for [insert your bitcoin address]” (this text is case-sensitive). Use the same bitcoin address you used above to configure your miner(s).
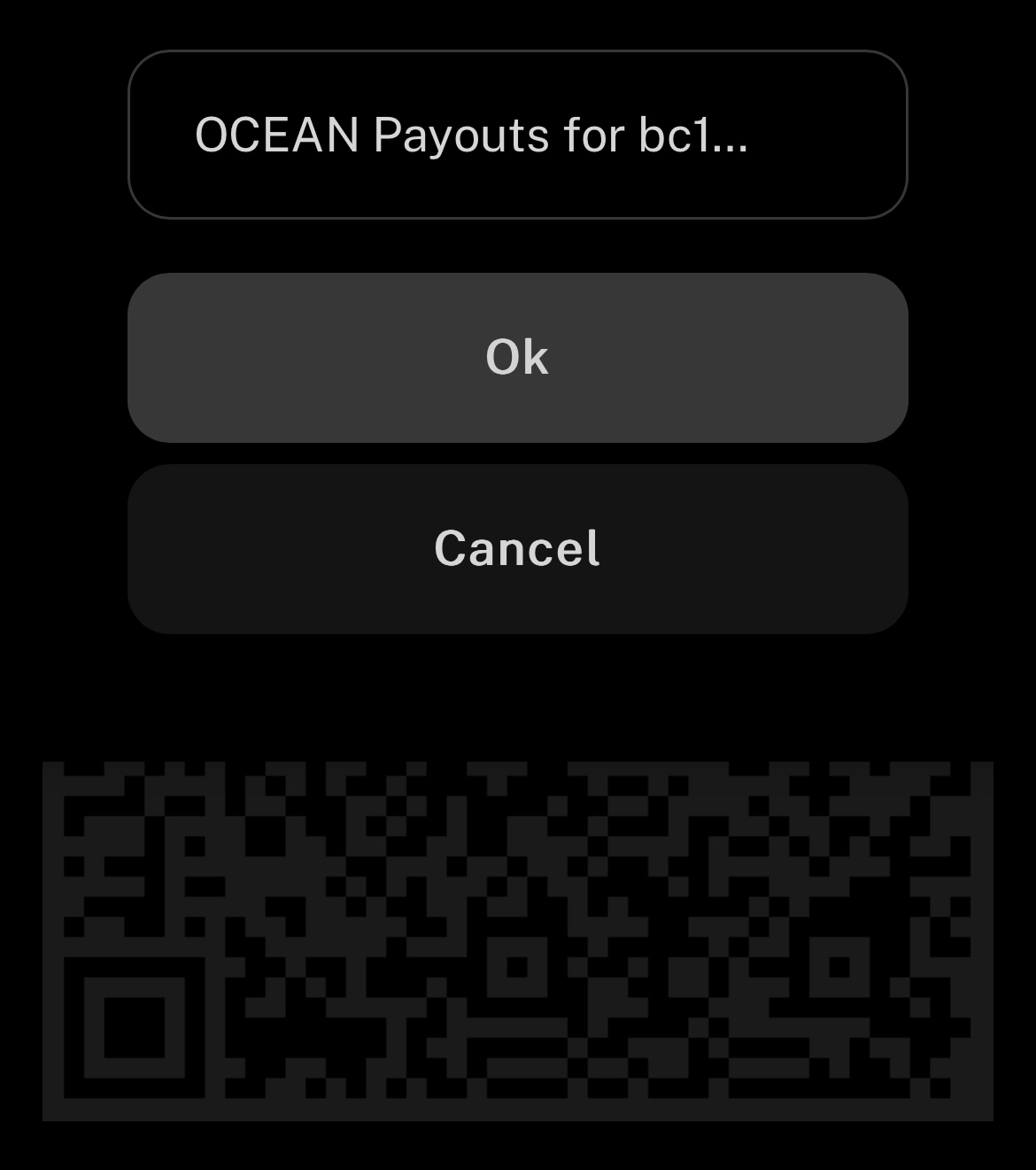
After tapping OK, copy the BOLT12 offer (it should start with “lno”) and proceed to the next step.
### Generating the Configuration Message
Navigate to the [My Stats](https://ocean.xyz/stats) page by searching for your OCEAN Bitcoin address.
The click the Configuration link next to Next Block to access the configuration form.
Paste the BOLT12 offer here, update the block height to latest, click GENERATE, and copy the generated unsigned message.
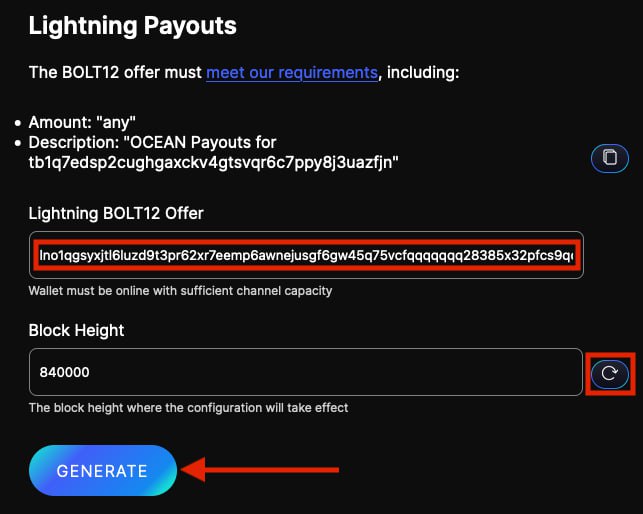
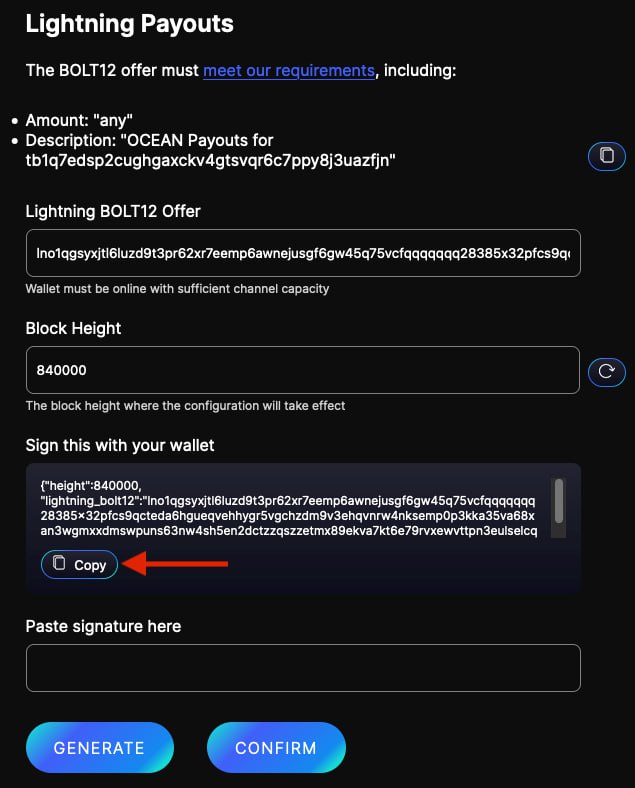
### Signing the Configuration Message
To sign the generated message, go back to Blue Wallet and use the signing function. Paste the configuration message in the Message field, tap Sign, and copy the signed message that’s generated.
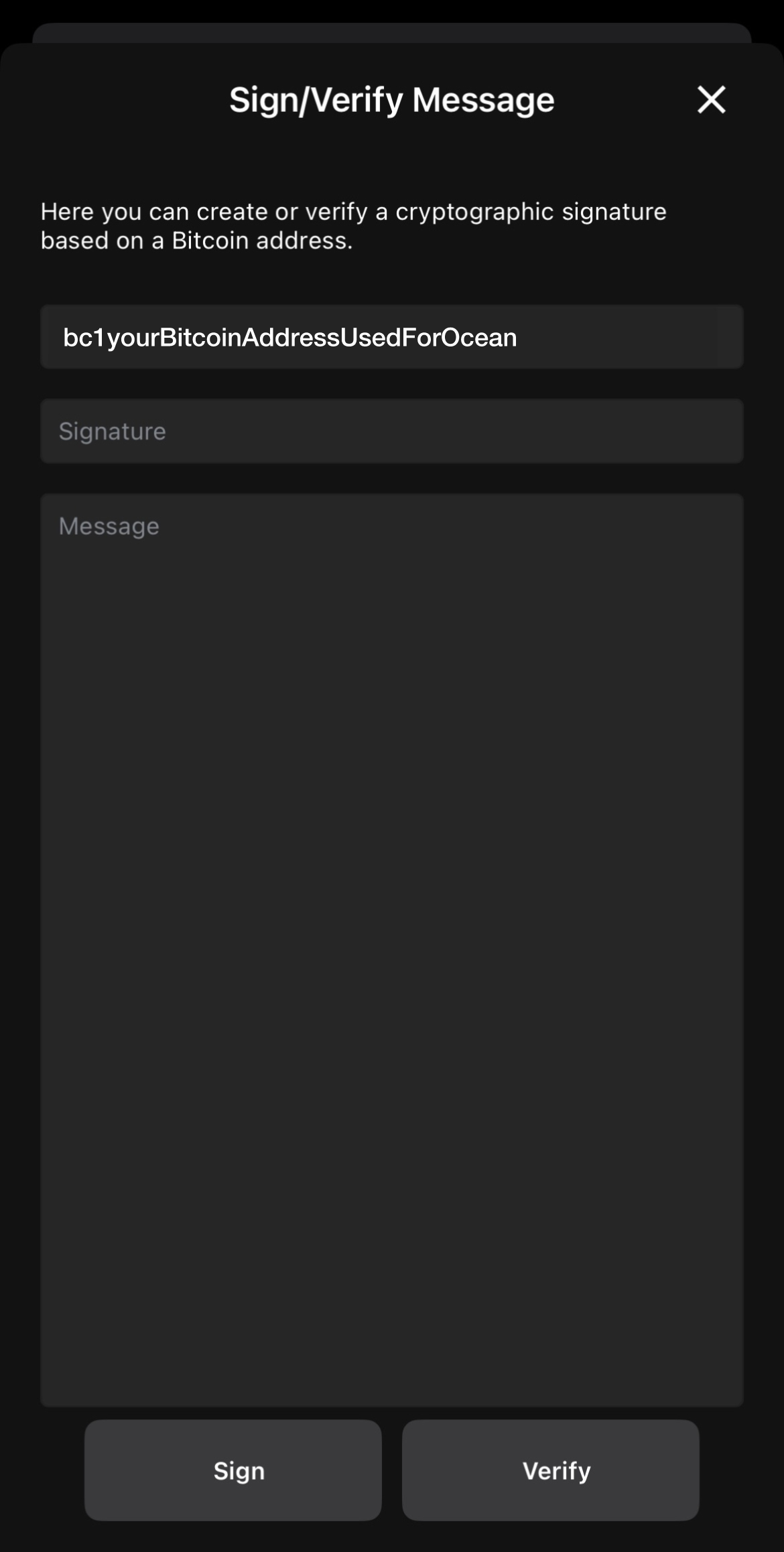
If you're using Coinos to sign, return to the page that you kept open (and didn't refresh) and do the same. Paste the configuration message, click submit, and copy the signed message.
### Submitting the Signed Message
Once signed, copy the signature, paste it in the OCEAN configuration form, and click CONFIRM.
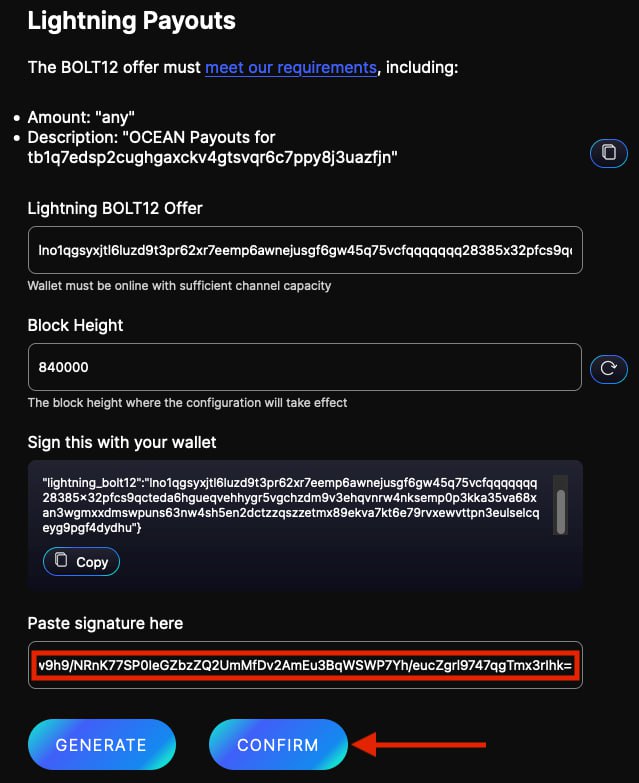
If all goes well, you should see a confirmation that the configuration was successful. Congrats! 🎉
All you gotta do now is sit back, relax, and wait for a block to be found…
Or you can look into setting up [DATUM](https://ocean.xyz/docs/datum-setup). 😎
-

@ c631e267:c2b78d3e
2025-01-18 09:34:51
*Die grauenvollste Aussicht ist die der Technokratie –* *\
einer kontrollierenden Herrschaft,* *\
die durch verstümmelte und verstümmelnde Geister ausgeübt wird.* *\
Ernst Jünger*  
**«Davos ist nicht mehr sexy»,** das Weltwirtschaftsforum ([WEF](https://transition-news.org/wef-world-economic-forum)) mache Davos [kaputt](https://web.archive.org/web/20250116114956/https://www.handelszeitung.ch/wef-2025/wie-das-wef-davos-kaputt-macht-785098), diese Aussagen eines Einheimischen las ich kürzlich in der *Handelszeitung*. Während sich einige vor Ort enorm an der «teuersten Gewerbeausstellung der Welt» bereicherten, würden die negativen Begleiterscheinungen wie Wohnungsnot und Niedergang der lokalen Wirtschaft immer deutlicher.
**Nächsten Montag beginnt in dem Schweizer Bergdorf erneut ein Jahrestreffen** dieses elitären Clubs der Konzerne, bei dem man mit hochrangigen Politikern aus aller Welt und ausgewählten Vertretern der Systemmedien zusammenhocken wird. Wie bereits in den [vergangenen](https://transition-news.org/die-angst-der-eliten-vor-dem-pobel) vier Jahren wird die Präsidentin der EU-Kommission, Ursula von der Leyen, in Begleitung von Klaus Schwab ihre Grundsatzansprache halten.
**Der deutsche WEF-Gründer hatte bei dieser Gelegenheit** immer höchst lobende Worte für seine Landsmännin: [2021](https://www.weforum.org/meetings/the-davos-agenda-2021/sessions/special-address-by-g20-head-of-state-government/) erklärte er sich «stolz, dass Europa wieder unter Ihrer Führung steht» und [2022](https://www.weforum.org/meetings/the-davos-agenda-2022/sessions/special-address-by-ursula-von-der-leyen-president-of-the-european-commission-177737c164/) fand er es bemerkenswert, was sie erreicht habe angesichts des «erstaunlichen Wandels», den die Welt in den vorangegangenen zwei Jahren erlebt habe; es gebe nun einen «neuen europäischen Geist».
**Von der Leyens Handeln während der sogenannten Corona-«Pandemie»** lobte Schwab damals bereits ebenso, wie es diese Woche das [Karlspreis](https://transition-news.org/von-der-leyen-erhalt-karlspreis-albert-bourla-erklart-pfizer-habe-wahrend-der)-Direktorium tat, als man der Beschuldigten im Fall [Pfizergate](https://transition-news.org/pfizergate-startet-ins-neue-jahr) die diesjährige internationale Auszeichnung «für Verdienste um die europäische Einigung» verlieh. Außerdem habe sie die EU nicht nur gegen den «Aggressor Russland», sondern auch gegen die «innere Bedrohung durch Rassisten und Demagogen» sowie gegen den Klimawandel verteidigt.
**Jene Herausforderungen durch «Krisen epochalen Ausmaßes»** werden indes aus dem Umfeld des WEF nicht nur herbeigeredet – wie man alljährlich zur Zeit des Davoser Treffens im [Global Risks Report](https://www.zurich.com/knowledge/topics/global-risks/the-global-risks-report-2025) nachlesen kann, der zusammen mit dem Versicherungskonzern Zurich erstellt wird. Seit die Globalisten 2020/21 in der Praxis gesehen haben, wie gut eine konzertierte und konsequente Angst-Kampagne funktionieren kann, geht es Schlag auf Schlag. Sie setzen alles daran, Schwabs goldenes Zeitfenster des «Great Reset» zu nutzen.
**Ziel dieses «großen Umbruchs» ist die totale Kontrolle der Technokraten über die Menschen** unter dem Deckmantel einer globalen Gesundheitsfürsorge. Wie aber könnte man so etwas erreichen? Ein Mittel dazu ist die «kreative Zerstörung». Weitere unabdingbare Werkzeug sind die Einbindung, ja Gleichschaltung der Medien und der Justiz.
**Ein** **[«Great Mental Reset»](https://transition-news.org/angriff-auf-unser-gehirn-michael-nehls-uber-den-great-mental-reset-teil-1)** **sei die Voraussetzung dafür,** dass ein Großteil der Menschen Einschränkungen und Manipulationen wie durch die Corona-Maßnahmen praktisch kritik- und widerstandslos hinnehme, sagt der Mediziner und Molekulargenetiker Michael Nehls. Er meint damit eine regelrechte Umprogrammierung des Gehirns, wodurch nach und nach unsere Individualität und unser soziales Bewusstsein eliminiert und durch unreflektierten Konformismus ersetzt werden.
**Der aktuelle Zustand unserer Gesellschaften** ist auch für den Schweizer Rechtsanwalt Philipp Kruse alarmierend. Durch den Umgang mit der «Pandemie» sieht er die Grundlagen von Recht und Vernunft erschüttert, die [Rechtsstaatlichkeit](https://transition-news.org/schweizer-rechtsstaat-in-der-krise-ein-anwalt-schlagt-alarm) stehe auf dem Prüfstand. Seiner dringenden Mahnung an alle Bürger, die Prinzipien von Recht und Freiheit zu verteidigen, kann ich mich nur anschließen.
***
Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/davos-europa-und-der-rest-der-welt)*** erschienen.
-

@ f9cf4e94:96abc355
2025-01-18 06:09:50
Para esse exemplo iremos usar:
| Nome | Imagem | Descrição |
| --------------- | ------------------------------------------------------------ | ------------------------------------------------------------ |
| Raspberry PI B+ |  | **Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2,** |
| Pen drive |  | **16Gb** |
Recomendo que use o **Ubuntu Server** para essa instalação. Você pode baixar o Ubuntu para Raspberry Pi [aqui]( https://ubuntu.com/download/raspberry-pi). O passo a passo para a instalação do Ubuntu no Raspberry Pi está disponível [aqui]( https://ubuntu.com/tutorials/how-to-install-ubuntu-on-your-raspberry-pi). **Não instale um desktop** (como xubuntu, lubuntu, xfce, etc.).
---
## Passo 1: Atualizar o Sistema 🖥️
Primeiro, atualize seu sistema e instale o Tor:
```bash
apt update
apt install tor
```
---
## Passo 2: Criar o Arquivo de Serviço `nrs.service` 🔧
Crie o arquivo de serviço que vai gerenciar o servidor Nostr. Você pode fazer isso com o seguinte conteúdo:
```unit
[Unit]
Description=Nostr Relay Server Service
After=network.target
[Service]
Type=simple
WorkingDirectory=/opt/nrs
ExecStart=/opt/nrs/nrs-arm64
Restart=on-failure
[Install]
WantedBy=multi-user.target
```
---
## Passo 3: Baixar o Binário do Nostr 🚀
Baixe o binário mais recente do Nostr [aqui no GitHub]( https://github.com/gabrielmoura/SimpleNosrtRelay/releases).
---
## Passo 4: Criar as Pastas Necessárias 📂
Agora, crie as pastas para o aplicativo e o pendrive:
```bash
mkdir -p /opt/nrs /mnt/edriver
```
---
## Passo 5: Listar os Dispositivos Conectados 🔌
Para saber qual dispositivo você vai usar, liste todos os dispositivos conectados:
```bash
lsblk
```
---
## Passo 6: Formatando o Pendrive 💾
Escolha o pendrive correto (por exemplo, `/dev/sda`) e formate-o:
```bash
mkfs.vfat /dev/sda
```
---
## Passo 7: Montar o Pendrive 💻
Monte o pendrive na pasta `/mnt/edriver`:
```bash
mount /dev/sda /mnt/edriver
```
---
## Passo 8: Verificar UUID dos Dispositivos 📋
Para garantir que o sistema monte o pendrive automaticamente, liste os UUID dos dispositivos conectados:
```bash
blkid
```
---
## Passo 9: Alterar o `fstab` para Montar o Pendrive Automáticamente 📝
Abra o arquivo `/etc/fstab` e adicione uma linha para o pendrive, com o UUID que você obteve no passo anterior. A linha deve ficar assim:
```fstab
UUID=9c9008f8-f852 /mnt/edriver vfat defaults 0 0
```
---
## Passo 10: Copiar o Binário para a Pasta Correta 📥
Agora, copie o binário baixado para a pasta `/opt/nrs`:
```bash
cp nrs-arm64 /opt/nrs
```
---
## Passo 11: Criar o Arquivo de Configuração 🛠️
Crie o arquivo de configuração com o seguinte conteúdo e salve-o em `/opt/nrs/config.yaml`:
```yaml
app_env: production
info:
name: Nostr Relay Server
description: Nostr Relay Server
pub_key: ""
contact: ""
url: http://localhost:3334
icon: https://external-content.duckduckgo.com/iu/?u= https://public.bnbstatic.com/image/cms/crawler/COINCU_NEWS/image-495-1024x569.png
base_path: /mnt/edriver
negentropy: true
```
---
## Passo 12: Copiar o Serviço para o Diretório de Systemd ⚙️
Agora, copie o arquivo `nrs.service` para o diretório `/etc/systemd/system/`:
```bash
cp nrs.service /etc/systemd/system/
```
Recarregue os serviços e inicie o serviço `nrs`:
```bash
systemctl daemon-reload
systemctl enable --now nrs.service
```
---
## Passo 13: Configurar o Tor 🌐
Abra o arquivo de configuração do Tor `/var/lib/tor/torrc` e adicione a seguinte linha:
```torrc
HiddenServiceDir /var/lib/tor/nostr_server/
HiddenServicePort 80 127.0.0.1:3334
```
---
## Passo 14: Habilitar e Iniciar o Tor 🧅
Agora, ative e inicie o serviço Tor:
```bash
systemctl enable --now tor.service
```
O Tor irá gerar um endereço `.onion` para o seu servidor Nostr. Você pode encontrá-lo no arquivo `/var/lib/tor/nostr_server/hostname`.
---
## Observações ⚠️
- Com essa configuração, **os dados serão salvos no pendrive**, enquanto o binário ficará no cartão SD do Raspberry Pi.
- O endereço `.onion` do seu servidor Nostr será algo como: `ws://y3t5t5wgwjif<exemplo>h42zy7ih6iwbyd.onion`.
---
Agora, seu servidor Nostr deve estar configurado e funcionando com Tor! 🥳
Se este artigo e as informações aqui contidas forem úteis para você, convidamos a considerar uma doação ao autor como forma de reconhecimento e incentivo à produção de novos conteúdos.
-

@ 378562cd:a6fc6773
2025-01-18 00:12:47
In the ever-changing world of decentralized networks, **Nostr** (Notes and Other Stuff Transmitted by Relays) is leading the charge. Its lightweight, open design has created an ecosystem that’s as adaptable as it is revolutionary. Whether you're chatting, publishing, or experimenting with new ways to connect, Nostr provides the foundation for a truly decentralized and censorship-resistant internet.
---
### **How Nostr Works: A Quick Overview**
At its heart, Nostr is built on simplicity and decentralization. Here’s a breakdown of its core components:
1. **Public and Private Keys**:\
Your public key acts as your identity, and private keys ensure your messages are securely signed.
2. **Relays**:\
Relays are decentralized servers that distribute messages. They don’t own your data but simply pass it along to those who request it.
3. **Clients**:\
Clients are the user-facing applications where you interact with Nostr, offering diverse features and designs.
---
### **Deep Dive: Events in Nostr**
Everything on Nostr revolves around **events**, which are cryptographically signed pieces of information containing various kinds of data. Here are the types of events currently supported and their use cases:
#### **1. Note Events (Type 1)**
- **What They Are**:\
These are the bread and butter of Nostr—text-based posts, much like tweets or status updates on traditional platforms.
- **Features**:
- Can include text, media links, and hashtags.
- Interact with others through likes, replies, and boosts (reposts).
- **Use Cases**:\
Perfect for microblogging, status updates, and general social interaction.
#### **2. Profile Metadata Events (Type 0)**
- **What They Are**:\
This event type stores and updates user profile information, such as your display name, bio, profile picture, and website.
- **Features**:
- Easily editable and updated across all Nostr clients.
- Keeps your identity consistent across platforms.
- **Use Cases**:\
Makes profile portability seamless—update once, and it reflects everywhere.
#### **3. Relay List Events (Type 2)**
- **What They Are**:\
These events store a list of relays that a user is connected to or prefers to use.
- **Features**:
- Share your relay preferences across devices or clients.
- Allows automatic relay connection in supported clients.
- **Use Cases**:\
Simplifies the onboarding process for users switching clients or devices.
#### **4. Direct Message Events (Type 4)**
- **What They Are**:\
End-to-end encrypted messages sent directly between two users.
- **Features**:
- Only readable by the intended recipient.
- Supports text and basic formatting.
- **Use Cases**:\
Secure communication for personal or professional purposes.
#### **5. Reaction Events (Type 7)**
- **What They Are**:\
Events that express reactions to other events, such as likes or emojis.
- **Features**:
- Provides social feedback (e.g., showing appreciation for a post).
- Lightweight and simple to implement.
- **Use Cases**:\
Enhances engagement and interaction within the network.
#### **6. Repost Events (Type 6)**
- **What They Are**:\
Events that allow users to reshare content, similar to retweets on Twitter.
- **Features**:
- Ensures the original poster retains credit.
- Enables broader content visibility.
- **Use Cases**:\
Amplifying content that resonates with users or is worth sharing.
#### **7. Custom Event Types (Beyond Type 7)**
- **What They Are**:\
Developers can create and define custom event types for specific applications.
- **Features**:
- Flexibility to introduce entirely new functionality.
- Supported based on client and relay compatibility.
- **Use Cases**:\
Enables innovation, from collaborative editing tools to advanced publishing workflows.
---
### **What Makes Events Special?**
1. **Portability**: Events follow your public key, not the client or relay, ensuring they’re available wherever you go.
2. **Interoperability**: All events are standardized, meaning any Nostr client can understand and process them.
3. **Extensibility**: Through custom event types, the protocol encourages experimentation and development.
---
### **Primal: A Favorite Client for Engaging Events**
Among the many clients, **Primal** stands out as a favorite for how it handles Nostr events. Its emphasis on **content discovery** and **rich user interaction** makes it an excellent choice for exploring everything the protocol offers. Whether it’s crafting note events, managing profile metadata, or diving into direct messaging, Primal delivers a polished experience that feels seamless.
---
### **The Future of Nostr Events**
As Nostr continues to evolve, so will the events it supports. Imagine event types for live streaming, collaborative workspaces, or even decentralized governance. The possibilities are limitless, driven by the creativity of the developers and the needs of the community.
**Have you explored the potential of Nostr events yet? What’s your favorite client or feature? Let’s discuss below!** ⚡️
#Nostr #Primal #Decentralization #NostrEvents #FutureOfWeb
-

@ 5bdb0e24:0ccbebd7
2025-01-17 06:19:58
In the world of networking, two fundamental models serve as the backbone for communication protocols and standards: the OSI model and the TCP/IP model. Both models are quite similar, providing frameworks for how data is transmitted across networks at various stages of the process.
Understanding these models is crucial for anyone working in IT, cybersecurity, or any related tech field. But what exactly are they?
# The OSI Model
The OSI (Open Systems Interconnection) model is a conceptual framework that standardizes the functions of a telecommunication or computing system into seven distinct layers. Each layer is responsible for specific tasks, such as data encapsulation, error detection, and routing. The layers of the OSI model are as follows:
1. **Physical Layer:** This layer deals with the physical connection between devices, such as cables and network interfaces.
2. **Data Link Layer:** Responsible for node-to-node communication, this layer ensures data integrity and manages access to the physical medium.
3. **Network Layer:** The network layer handles routing and forwarding of data packets between different networks.
4. **Transport Layer:** This layer provides end-to-end communication services for applications, including error detection and flow control.
5. **Session Layer:** Manages sessions between applications, establishing, maintaining, and terminating connections.
6. **Presentation Layer:** Responsible for data translation, encryption, and compression to ensure compatibility between different systems.
7. **Application Layer:** The topmost layer that interacts directly with applications and end-users, providing network services such as email and file transfer.
Now, that's a lot to remember. So, an easy acronym you can use to remember these 7 layers is *"Please Do Not Touch Steve's Pet Alligator."* It's helped me quite a bit in trying to pinpoint a specific layer.
Also, keep in mind that the layers are typically inverted from what you see above, with Layer 7 being at the top of the stack and Layer 1 being at the bottom.
# The TCP/IP Model
On the other hand, the TCP/IP (Transmission Control Protocol/Internet Protocol) model is a more streamlined approach to networking, consisting of only four layers:
1. **Link Layer:** Corresponding to the OSI model's data link and physical layers, the link layer deals with the physical connection and data framing.
2. **Internet Layer:** Similar to the OSI model's network layer, the internet layer focuses on routing packets across different networks.
3. **Transport Layer:** Combines the functions of the OSI model's transport and session layers, providing reliable data transfer services.
4. **Application Layer:** Equivalent to the OSI model's top three layers, the application layer in TCP/IP handles network services for applications.
While the OSI model is more detailed and theoretical, the TCP/IP model is practical and widely used in modern networking. It's also a bit easier to remember than the OSI model.
And, similar to the OSI model, the TCP/IP model is typically visualized with Layer 4 at the top of the stack and Layer 1 at the bottom, unlike what you see above.
# Conclusion
Both the TCP/IP and OSI models play essential roles in understanding how data is transmitted across networks. By grasping the functions of each layer and their interactions, network professionals can troubleshoot issues, design efficient networks, and ensure seamless communication between devices.
Whether you're a seasoned systems administrator or you're just getting your start in IT, mastering these models is key to navigating the complex world of networking.
-

@ 66675158:1b644430
2025-01-16 20:44:33
Before the time of Utensils, people lived in genuine harmony. They gathered in markets to trade freely, built homes where they pleased, and traveled without papers or permissions. Communities solved their own problems through discussion and agreement. When disputes arose, wise elders would help find solutions that satisfied all. Children learned from their parents or chose mentors from among the skilled craftspeople.
In those days, gold changed hands freely for goods and services. Each person kept what they earned. Communities would voluntarily pool resources for shared needs - wells, bridges, and roads. Those who had more would often help those with less, not by decree but by choice.
Neighbors knew each other's names. Doors were left unlocked. Children played in the streets until sunset. Gardens grew wherever people planted them. Merchants traveled between towns without inspections. Healers practiced their craft freely, sharing knowledge openly.
> Then came the Utensils.
In our land, Aldrich found the Silver Spoon. In the East, Emperor Chen discovered the Jade Chopsticks. The Norse kingdoms united under the Golden Fork. The desert peoples followed the Bronze Ladle.
Each Utensil, their holders claimed, granted divine wisdom to rule. Each promised protection and prosperity in exchange for obedience.
The changes came slowly at first. The Spoon Holder requested a share of each harvest to store for hard times. The Chopstick Emperor required homes to be built in specific ways to prevent fires. The Fork King demanded that travelers carry documents proving their loyalty.
At first, the Utensils did bring some genuine improvements. The Spoon Holder's collectors used part of their harvest share to help villages during droughts. The Chopstick Emperor's building codes truly did reduce fires. The Fork King's road patrols deterred the few bandits who had troubled merchants. The Bronze Ladle's water management systems helped farms flourish in the desert.
The early years saw stone roads replace dirt paths, connecting villages more efficiently than before. Granaries were built with better designs, preserving food longer. Some diseases decreased as the Chopstick Emperor's cleanliness codes spread. The Fork Kingdom's standardized weights and measures did make trade easier.
The Spoon Holder soon declared that carrying gold was dangerous and inefficient. They introduced sacred paper notes, "backed by the Silver Spoon's power." At first, you could trade these notes back for gold, but gradually this right vanished.
Scholars wrote lengthy memos about the divine wisdom of the Utensils, creating complex theories about why ordinary people couldn't possibly understand how to live without direction. They advised the Holders and were rewarded with special privileges, comfortable positions, and influence.
When anyone questioned this system, the Utensil Holders and their Experts would ask: "But who would build the roads without us? Who would help the poor? Who would protect you?" They spoke as if humans had never cooperated or helped each other before the Utensils came, and many began to believe it.
People grumbled but accepted. After all, the Utensils shone with otherworldly power.
Some remembered these early benefits when questioning the growing restrictions. "Remember how the Spoon Holder's men helped during the great flood?" they would say. "Surely they have our best interests at heart." The Utensil Holders carefully nurtured these memories, even as their power grew far beyond such humble beginnings.
More rules followed. The Spoon Holder's men began watching the roads, collecting portions from merchants. The Chopstick Guards enforced strict codes about proper behavior. The Fork Watchers kept lists of who attended the mandatory gatherings.
Children were taught the sacred histories of their Utensils. The Spoon's light blessed the worthy. The Chopsticks maintained harmony. The Fork brought strength. The Ladle provided guidance.
When people remembered the old freedoms, the Utensil Holders reminded them of the chaos before - though few could actually recall any chaos.
> But surely there must have been chaos, or why would the Utensils have come?
The Utensil Holders began to eye each other's territories. How dare the Fork King claim his metal was superior? How could the Chopstick Emperor suggest jade held more wisdom than silver? The Ladle Holder's bronze was clearly inferior to all!
The Utensil Holders pointed to their achievements - the roads, the granaries, the safer towns - as proof of their divine right to rule. They spoke of how they had unified squabbling villages, standardized laws, and created order. Few noticed how these very achievements had required less and less input from the people themselves.
Wars erupted. Armies marched under banners bearing their sacred Utensils. Men died believing their Utensil was the one true source of authority. Villages burned as soldiers searched for heretics who might secretly worship foreign Utensils.
The Utensil Holders demanded more from their people - more food, more gold, more obedience. They placed watchers in every village. They required written permission for travel between towns. They forbade more than three people from gathering without a Guardian present.
"It's for protection," they said, holding their Utensils high. "How can you doubt the sacred silver?"
And indeed, their guards did stop some thieves, their inspectors did prevent some fraud, their builders did create some useful works. But these benefits came with an ever-increasing price in freedom, until the cost far exceeded any advantage. Yet by then, most people could no longer imagine providing these services for themselves, as their ancestors had done.
Towns built walls, not against invaders but to control who could enter and leave. The Utensil Holders required everyone to wear markers showing their village of origin. They appointed observers in every community to report suspicious behavior - like speaking of the time before Utensils.
Children were taken to special houses to learn proper reverence for their Utensil. Families who taught the old ways disappeared in the night. The Holders declared certain words forbidden, certain thoughts dangerous, certain memories treasonous.
Now, centuries later, the Utensils rule absolutely. People bow when the sacred implements pass by. They inform on neighbors who question the Utensils' power. They offer their children to serve in the Utensil temples.
The latest marvel was Utensil Technology - enchanted mirrors and crystals that watched people's movements, recorded their words, and tracked their trades. "Only criminals fear being watched," the Holders proclaimed, as their surveillance spread into every home and market. The crystals even allowed them to freeze people's paper money if they spoke against the Utensils.
The Utensil Holders formed special partnerships with the largest merchant guilds. These favored merchants received special permissions, protection from smaller competitors, and access to the new paper money first. In return, they helped enforce the Holders' rules and collected information about their customers. Small traders and craftsmen found themselves crushed between these powerful allies.
The latest decree requires all newborns to be blessed by touching their foreheads to their realm's sacred Utensil, marking them forever as its property. Parents compete for earlier blessing times, believing this shows greater devotion.
The wars continue. The Fork Kingdoms battle the Chopstick Empire. The Ladle Realms raid the Spoon Holdings. Each believes their Utensil must rule all.
And in quiet corners, in hidden places, a few elders still whisper stories of the time before - when humans lived without Utensils telling them how to live. But fewer remember with each passing year. After all, who could imagine a world without the guidance of sacred silverware?
-

@ 17538dc2:71ed77c4
2025-01-14 15:52:00
Nassim Nicholas Taleb writes:
`“We cannot explain everything. We know more about what something is not than what something is. If there would have been no word for colour blue, it would still have existed in reality. It would only have been absent in linguistics. But since we don’t have a word for it, we couldn’t define or comprehend it. But we still could say what it is not. It is not orange. It’s not an elephant, etc. This method of knowledge is truer and more rigorous than positive knowledge.”`
In this article, I introduce practical examples of how to apply via negativa to various systems.
Recommended reading is [Antifragile](https://www.penguinrandomhouse.com/books/176227/antifragile-by-nassim-nicholas-taleb/) by N. N. Taleb.
The basic template is as follows:
## What is ____ **not**?
Let's start with something every human should be familiar with - food.
### Food
Take hot pockets. Is hot pockets food? 
What is not food?
To answer this question, let's examine the contents of hot pockets.

There seem to be chemistry lab sounding ingredients ("MEDIUM CHAIN TRIGLYCERIES", "SODIUM STEAROYL LACTYLATE"), as well as food items that your great-great-great-great-great-great grandma cooked with ("SALT", "BEEF" etc.)
So What happens when we apply via negativa to the ingredients?
From 30 "ingredients" we deduce a couple foood items, or a ~90% reduction in "ingredients" by eliminating processed food slop.

meat good

bread yum
### Free Discourse
Take the social media platform X.

X consists of: leased identity, censored speech, and a tech platform for discourse. On the roadmap is social media score that will be used to determine if you can pay your bills when X launches its' bank.
What is free discourse not?
Removing the ingredient of WEF,

KYC lease hell

and censorship 
we receive nostr .
[Nostr](https://fiatjaf.com/nostr.html), to my best understanding, is not a WEF globo-homo participant, does not lease identities, and it is that much more difficult to censor wrongspeak (e.g. Netanyahu and friends are commiting genocide, and wanted as war criminals; there are two genders; there is no climate crisis; Ivermectin works).
## Automobiles
Modern automobiles can be summed up in two words: "safety", and constant surveillance. Yes, advancements in safety are great - e.g. airbags, seatbelts, car frames that absorb impact energy.
However the "its for your safety" component of remote shutdown, remote control, location data selling to data brokers, insurance agents, and your local surveillance outfit is gulag tech.
!(image)[https://image.nostr.build/15befd30113614dad3fd7aac01b8771b95bd8ace9186ed4f8016eec6e886e969.jpg]
So what happens when we remove the gulag tech out of cars? That is, what is *not* a car?
Let's use the following definition of car:
```
A car, or an automobile, is a motor vehicle with wheels
```
Let's use the following definition of gulag:
```
The Gulag is recognized as a major instrument of political repression in the Soviet Union.
```
You get the [2024 Toyota Land Cruiser](https://youtu.be/5WHzKNi2ojY). No gulag. Airbags. Push and turn knobs. No spying, no remote control, no cameras, no satellite, no bluetooth, no wi-fi.
As an aside, it is practically impossible to import this car to the US. It's "for your safety", and "for the environment", of course.
!(image)[https://upload.wikimedia.org/wikipedia/commons/thumb/a/a1/Toyota_Land_Cruiser_16.09.20_JM_%283%29_%28cropped%29.jpg/800px-Toyota_Land_Cruiser_16.09.20_JM_%283%29_%28cropped%29.jpg]?20210328155727
Toyota Landcruiser HZJ-79 Double Cab, Johannes Maximilian `https://commons.wikimedia.org/wiki/File:Toyota_Land_Cruiser_16.09.20_JM_(3)_(cropped).jpg).`
Hopefully this guide has been helpful illustrating how simple and powerful it is to apply the Via Negativa approach.
Mr. Taleb, I commend you on speaking out on the Palestine genocide. I invite you to and hope one day you join anti-fragile nostr.
-

@ 6389be64:ef439d32
2025-01-14 01:31:12
Bitcoin is more than money, more than an asset, and more than a store of value. Bitcoin is a Prime Mover, an enabler and it ignites imaginations. It certainly fueled an idea in my mind. The idea integrates sensors, computational prowess, actuated machinery, power conversion, and electronic communications to form an autonomous, machined creature roaming forests and harvesting the most widespread and least energy-dense fuel source available. I call it the Forest Walker and it eats wood, and mines Bitcoin.
I know what you're thinking. Why not just put Bitcoin mining rigs where they belong: in a hosted facility sporting electricity from energy-dense fuels like natural gas, climate-controlled with excellent data piping in and out? Why go to all the trouble building a robot that digests wood creating flammable gasses fueling an engine to run a generator powering Bitcoin miners? It's all about synergy.
Bitcoin mining enables the realization of multiple, seemingly unrelated, yet useful activities. Activities considered un-profitable if not for Bitcoin as the Prime Mover. This is much more than simply mining the greatest asset ever conceived by humankind. It’s about the power of synergy, which Bitcoin plays only one of many roles. The synergy created by this system can stabilize forests' fire ecology while generating multiple income streams. That’s the realistic goal here and requires a brief history of American Forest management before continuing.
# Smokey The Bear
In 1944, the Smokey Bear Wildfire Prevention Campaign began in the United States. “Only YOU can prevent forest fires” remains the refrain of the Ad Council’s longest running campaign. The Ad Council is a U.S. non-profit set up by the American Association of Advertising Agencies and the Association of National Advertisers in 1942. It would seem that the U.S. Department of the Interior was concerned about pesky forest fires and wanted them to stop. So, alongside a national policy of extreme fire suppression they enlisted the entire U.S. population to get onboard via the Ad Council and it worked. Forest fires were almost obliterated and everyone was happy, right? Wrong.
Smokey is a fantastically successful bear so forest fires became so few for so long that the fuel load - dead wood - in forests has become very heavy. So heavy that when a fire happens (and they always happen) it destroys everything in its path because the more fuel there is the hotter that fire becomes. Trees, bushes, shrubs, and all other plant life cannot escape destruction (not to mention homes and businesses). The soil microbiology doesn’t escape either as it is burned away even in deeper soils. To add insult to injury, hydrophobic waxy residues condense on the soil surface, forcing water to travel over the ground rather than through it eroding forest soils. Good job, Smokey. Well done, Sir!
Most terrestrial ecologies are “fire ecologies”. Fire is a part of these systems’ fuel load and pest management. Before we pretended to “manage” millions of acres of forest, fires raged over the world, rarely damaging forests. The fuel load was always too light to generate fires hot enough to moonscape mountainsides. Fires simply burned off the minor amounts of fuel accumulated since the fire before. The lighter heat, smoke, and other combustion gasses suppressed pests, keeping them in check and the smoke condensed into a plant growth accelerant called wood vinegar, not a waxy cap on the soil. These fires also cleared out weak undergrowth, cycled minerals, and thinned the forest canopy, allowing sunlight to penetrate to the forest floor. Without a fire’s heat, many pine tree species can’t sow their seed. The heat is required to open the cones (the seed bearing structure) of Spruce, Cypress, Sequoia, Jack Pine, Lodgepole Pine and many more. Without fire forests can’t have babies. The idea was to protect the forests, and it isn't working.
So, in a world of fire, what does an ally look like and what does it do?
# Meet The Forest Walker

For the Forest Walker to work as a mobile, autonomous unit, a solid platform that can carry several hundred pounds is required. It so happens this chassis already exists but shelved.
Introducing the Legged Squad Support System (LS3). A joint project between Boston Dynamics, DARPA, and the United States Marine Corps, the quadrupedal robot is the size of a cow, can carry 400 pounds (180 kg) of equipment, negotiate challenging terrain, and operate for 24 hours before needing to refuel. Yes, it had an engine. Abandoned in 2015, the thing was too noisy for military deployment and maintenance "under fire" is never a high-quality idea. However, we can rebuild it to act as a platform for the Forest Walker; albeit with serious alterations. It would need to be bigger, probably. Carry more weight? Definitely. Maybe replace structural metal with carbon fiber and redesign much as 3D printable parts for more effective maintenance.
The original system has a top operational speed of 8 miles per hour. For our purposes, it only needs to move about as fast as a grazing ruminant. Without the hammering vibrations of galloping into battle, shocks of exploding mortars, and drunken soldiers playing "Wrangler of Steel Machines", time between failures should be much longer and the overall energy consumption much lower. The LS3 is a solid platform to build upon. Now it just needs to be pulled out of the mothballs, and completely refitted with outboard equipment.
# The Small Branch Chipper

When I say “Forest fuel load” I mean the dead, carbon containing litter on the forest floor. Duff (leaves), fine-woody debris (small branches), and coarse woody debris (logs) are the fuel that feeds forest fires. Walk through any forest in the United States today and you will see quite a lot of these materials. Too much, as I have described. Some of these fuel loads can be 8 tons per acre in pine and hardwood forests and up to 16 tons per acre at active logging sites. That’s some big wood and the more that collects, the more combustible danger to the forest it represents. It also provides a technically unlimited fuel supply for the Forest Walker system.
The problem is that this detritus has to be chewed into pieces that are easily ingestible by the system for the gasification process (we’ll get to that step in a minute). What we need is a wood chipper attached to the chassis (the LS3); its “mouth”.
A small wood chipper handling material up to 2.5 - 3.0 inches (6.3 - 7.6 cm) in diameter would eliminate a substantial amount of fuel. There is no reason for Forest Walker to remove fallen trees. It wouldn’t have to in order to make a real difference. It need only identify appropriately sized branches and grab them. Once loaded into the chipper’s intake hopper for further processing, the beast can immediately look for more “food”. This is essentially kindling that would help ignite larger logs. If it’s all consumed by Forest Walker, then it’s not present to promote an aggravated conflagration.
I have glossed over an obvious question: How does Forest Walker see and identify branches and such? LiDaR (Light Detection and Ranging) attached to Forest Walker images the local area and feed those data to onboard computers for processing. Maybe AI plays a role. Maybe simple machine learning can do the trick. One thing is for certain: being able to identify a stick and cause robotic appendages to pick it up is not impossible.
Great! We now have a quadrupedal robot autonomously identifying and “eating” dead branches and other light, combustible materials. Whilst strolling through the forest, depleting future fires of combustibles, Forest Walker has already performed a major function of this system: making the forest safer. It's time to convert this low-density fuel into a high-density fuel Forest Walker can leverage. Enter the gasification process.
# The Gassifier

The gasifier is the heart of the entire system; it’s where low-density fuel becomes the high-density fuel that powers the entire system. Biochar and wood vinegar are process wastes and I’ll discuss why both are powerful soil amendments in a moment, but first, what’s gasification?
Reacting shredded carbonaceous material at high temperatures in a low or no oxygen environment converts the biomass into biochar, wood vinegar, heat, and Synthesis Gas (Syngas). Syngas consists primarily of hydrogen, carbon monoxide, and methane. All of which are extremely useful fuels in a gaseous state. Part of this gas is used to heat the input biomass and keep the reaction temperature constant while the internal combustion engine that drives the generator to produce electrical power consumes the rest.
Critically, this gasification process is “continuous feed”. Forest Walker must intake biomass from the chipper, process it to fuel, and dump the waste (CO2, heat, biochar, and wood vinegar) continuously. It cannot stop. Everything about this system depends upon this continual grazing, digestion, and excretion of wastes just as a ruminal does. And, like a ruminant, all waste products enhance the local environment.
When I first heard of gasification, I didn’t believe that it was real. Running an electric generator from burning wood seemed more akin to “conspiracy fantasy” than science. Not only is gasification real, it’s ancient technology. A man named Dean Clayton first started experiments on gasification in 1699 and in 1901 gasification was used to power a vehicle. By the end of World War II, there were 500,000 Syngas powered vehicles in Germany alone because of fossil fuel rationing during the war. The global gasification market was $480 billion in 2022 and projected to be as much as $700 billion by 2030 (Vantage Market Research). Gasification technology is the best choice to power the Forest Walker because it’s self-contained and we want its waste products.
# Biochar: The Waste

Biochar (AKA agricultural charcoal) is fairly simple: it’s almost pure, solid carbon that resembles charcoal. Its porous nature packs large surface areas into small, 3 dimensional nuggets. Devoid of most other chemistry, like hydrocarbons (methane) and ash (minerals), biochar is extremely lightweight. Do not confuse it with the charcoal you buy for your grill. Biochar doesn’t make good grilling charcoal because it would burn too rapidly as it does not contain the multitude of flammable components that charcoal does. Biochar has several other good use cases. Water filtration, water retention, nutrient retention, providing habitat for microscopic soil organisms, and carbon sequestration are the main ones that we are concerned with here.
Carbon has an amazing ability to adsorb (substances stick to and accumulate on the surface of an object) manifold chemistries. Water, nutrients, and pollutants tightly bind to carbon in this format. So, biochar makes a respectable filter and acts as a “battery” of water and nutrients in soils. Biochar adsorbs and holds on to seven times its weight in water. Soil containing biochar is more drought resilient than soil without it. Adsorbed nutrients, tightly sequestered alongside water, get released only as plants need them. Plants must excrete protons (H+) from their roots to disgorge water or positively charged nutrients from the biochar's surface; it's an active process.
Biochar’s surface area (where adsorption happens) can be 500 square meters per gram or more. That is 10% larger than an official NBA basketball court for every gram of biochar. Biochar’s abundant surface area builds protective habitats for soil microbes like fungi and bacteria and many are critical for the health and productivity of the soil itself.
The “carbon sequestration” component of biochar comes into play where “carbon credits” are concerned. There is a financial market for carbon. Not leveraging that market for revenue is foolish. I am climate agnostic. All I care about is that once solid carbon is inside the soil, it will stay there for thousands of years, imparting drought resiliency, fertility collection, nutrient buffering, and release for that time span. I simply want as much solid carbon in the soil because of the undeniably positive effects it has, regardless of any climactic considerations.
# Wood Vinegar: More Waste

Another by-product of the gasification process is wood vinegar (Pyroligneous acid). If you have ever seen Liquid Smoke in the grocery store, then you have seen wood vinegar. Principally composed of acetic acid, acetone, and methanol wood vinegar also contains ~200 other organic compounds. It would seem intuitive that condensed, liquefied wood smoke would at least be bad for the health of all living things if not downright carcinogenic. The counter intuition wins the day, however. Wood vinegar has been used by humans for a very long time to promote digestion, bowel, and liver health; combat diarrhea and vomiting; calm peptic ulcers and regulate cholesterol levels; and a host of other benefits.
For centuries humans have annually burned off hundreds of thousands of square miles of pasture, grassland, forest, and every other conceivable terrestrial ecosystem. Why is this done? After every burn, one thing becomes obvious: the almost supernatural growth these ecosystems exhibit after the burn. How? Wood vinegar is a component of this growth. Even in open burns, smoke condenses and infiltrates the soil. That is when wood vinegar shows its quality.
This stuff beefs up not only general plant growth but seed germination as well and possesses many other qualities that are beneficial to plants. It’s a pesticide, fungicide, promotes beneficial soil microorganisms, enhances nutrient uptake, and imparts disease resistance. I am barely touching a long list of attributes here, but you want wood vinegar in your soil (alongside biochar because it adsorbs wood vinegar as well).
# The Internal Combustion Engine

Conversion of grazed forage to chemical, then mechanical, and then electrical energy completes the cycle. The ICE (Internal Combustion Engine) converts the gaseous fuel output from the gasifier to mechanical energy, heat, water vapor, and CO2. It’s the mechanical energy of a rotating drive shaft that we want. That rotation drives the electric generator, which is the heartbeat we need to bring this monster to life. Luckily for us, combined internal combustion engine and generator packages are ubiquitous, delivering a defined energy output given a constant fuel input. It’s the simplest part of the system.
The obvious question here is whether the amount of syngas provided by the gasification process will provide enough energy to generate enough electrons to run the entire system or not. While I have no doubt the energy produced will run Forest Walker's main systems the question is really about the electrons left over. Will it be enough to run the Bitcoin mining aspect of the system? Everything is a budget.
# CO2 Production For Growth

Plants are lollipops. No matter if it’s a tree or a bush or a shrubbery, the entire thing is mostly sugar in various formats but mostly long chain carbohydrates like lignin and cellulose. Plants need three things to make sugar: CO2, H2O and light. In a forest, where tree densities can be quite high, CO2 availability becomes a limiting growth factor. It’d be in the forest interests to have more available CO2 providing for various sugar formation providing the organism with food and structure.
An odd thing about tree leaves, the openings that allow gasses like the ever searched for CO2 are on the bottom of the leaf (these are called stomata). Not many stomata are topside. This suggests that trees and bushes have evolved to find gasses like CO2 from below, not above and this further suggests CO2 might be in higher concentrations nearer the soil.
The soil life (bacterial, fungi etc.) is constantly producing enormous amounts of CO2 and it would stay in the soil forever (eventually killing the very soil life that produces it) if not for tidal forces. Water is everywhere and whether in pools, lakes, oceans or distributed in “moist” soils water moves towards to the moon. The water in the soil and also in the water tables below the soil rise toward the surface every day. When the water rises, it expels the accumulated gasses in the soil into the atmosphere and it’s mostly CO2. It’s a good bet on how leaves developed high populations of stomata on the underside of leaves. As the water relaxes (the tide goes out) it sucks oxygenated air back into the soil to continue the functions of soil life respiration. The soil “breathes” albeit slowly.
The gasses produced by the Forest Walker’s internal combustion engine consist primarily of CO2 and H2O. Combusting sugars produce the same gasses that are needed to construct the sugars because the universe is funny like that. The Forest Walker is constantly laying down these critical construction elements right where the trees need them: close to the ground to be gobbled up by the trees.
# The Branch Drones

During the last ice age, giant mammals populated North America - forests and otherwise. Mastodons, woolly mammoths, rhinos, short-faced bears, steppe bison, caribou, musk ox, giant beavers, camels, gigantic ground-dwelling sloths, glyptodons, and dire wolves were everywhere. Many were ten to fifteen feet tall. As they crashed through forests, they would effectively cleave off dead side-branches of trees, halting the spread of a ground-based fire migrating into the tree crown ("laddering") which is a death knell for a forest.
These animals are all extinct now and forests no longer have any manner of pruning services. But, if we build drones fitted with cutting implements like saws and loppers, optical cameras and AI trained to discern dead branches from living ones, these drones could effectively take over pruning services by identifying, cutting, and dropping to the forest floor, dead branches. The dropped branches simply get collected by the Forest Walker as part of its continual mission.
The drones dock on the back of the Forest Walker to recharge their batteries when low. The whole scene would look like a grazing cow with some flies bothering it. This activity breaks the link between a relatively cool ground based fire and the tree crowns and is a vital element in forest fire control.
# The Bitcoin Miner

Mining is one of four monetary incentive models, making this system a possibility for development. The other three are US Dept. of the Interior, township, county, and electrical utility company easement contracts for fuel load management, global carbon credits trading, and data set sales. All the above depends on obvious questions getting answered. I will list some obvious ones, but this is not an engineering document and is not the place for spreadsheets. How much Bitcoin one Forest Walker can mine depends on everything else. What amount of biomass can we process? Will that biomass flow enough Syngas to keep the lights on? Can the chassis support enough mining ASICs and supporting infrastructure? What does that weigh and will it affect field performance? How much power can the AC generator produce?
Other questions that are more philosophical persist. Even if a single Forest Walker can only mine scant amounts of BTC per day, that pales to how much fuel material it can process into biochar. We are talking about millions upon millions of forested acres in need of fuel load management. What can a single Forest Walker do? I am not thinking in singular terms. The Forest Walker must operate as a fleet. What could 50 do? 500?
What is it worth providing a service to the world by managing forest fuel loads? Providing proof of work to the global monetary system? Seeding soil with drought and nutrient resilience by the excretion, over time, of carbon by the ton? What did the last forest fire cost?
# The Mesh Network

What could be better than one bitcoin mining, carbon sequestering, forest fire squelching, soil amending behemoth? Thousands of them, but then they would need to be able to talk to each other to coordinate position, data handling, etc. Fitted with a mesh networking device, like goTenna or Meshtastic LoRa equipment enables each Forest Walker to communicate with each other.
Now we have an interconnected fleet of Forest Walkers relaying data to each other and more importantly, aggregating all of that to the last link in the chain for uplink. Well, at least Bitcoin mining data. Since block data is lightweight, transmission of these data via mesh networking in fairly close quartered environs is more than doable. So, how does data transmit to the Bitcoin Network? How do the Forest Walkers get the previous block data necessary to execute on mining?
# Back To The Chain

Getting Bitcoin block data to and from the network is the last puzzle piece. The standing presumption here is that wherever a Forest Walker fleet is operating, it is NOT within cell tower range. We further presume that the nearest Walmart Wi-Fi is hours away. Enter the Blockstream Satellite or something like it.
A separate, ground-based drone will have two jobs: To stay as close to the nearest Forest Walker as it can and to provide an antennae for either terrestrial or orbital data uplink. Bitcoin-centric data is transmitted to the "uplink drone" via the mesh networked transmitters and then sent on to the uplink and the whole flow goes in the opposite direction as well; many to one and one to many.
We cannot transmit data to the Blockstream satellite, and it will be up to Blockstream and companies like it to provide uplink capabilities in the future and I don't doubt they will. Starlink you say? What’s stopping that company from filtering out block data? Nothing because it’s Starlink’s system and they could decide to censor these data. It seems we may have a problem sending and receiving Bitcoin data in back country environs.
But, then again, the utility of this system in staunching the fuel load that creates forest fires is extremely useful around forested communities and many have fiber, Wi-Fi and cell towers. These communities could be a welcoming ground zero for first deployments of the Forest Walker system by the home and business owners seeking fire repression. In the best way, Bitcoin subsidizes the safety of the communities.
# Sensor Packages
### LiDaR

The benefit of having a Forest Walker fleet strolling through the forest is the never ending opportunity for data gathering. A plethora of deployable sensors gathering hyper-accurate data on everything from temperature to topography is yet another revenue generator. Data is valuable and the Forest Walker could generate data sales to various government entities and private concerns.
LiDaR (Light Detection and Ranging) can map topography, perform biomass assessment, comparative soil erosion analysis, etc. It so happens that the Forest Walker’s ability to “see,” to navigate about its surroundings, is LiDaR driven and since it’s already being used, we can get double duty by harvesting that data for later use. By using a laser to send out light pulses and measuring the time it takes for the reflection of those pulses to return, very detailed data sets incrementally build up. Eventually, as enough data about a certain area becomes available, the data becomes useful and valuable.
Forestry concerns, both private and public, often use LiDaR to build 3D models of tree stands to assess the amount of harvest-able lumber in entire sections of forest. Consulting companies offering these services charge anywhere from several hundred to several thousand dollars per square kilometer for such services. A Forest Walker generating such assessments on the fly while performing its other functions is a multi-disciplinary approach to revenue generation.
### pH, Soil Moisture, and Cation Exchange Sensing

The Forest Walker is quadrupedal, so there are four contact points to the soil. Why not get a pH data point for every step it takes? We can also gather soil moisture data and cation exchange capacities at unheard of densities because of sampling occurring on the fly during commission of the system’s other duties. No one is going to build a machine to do pH testing of vast tracts of forest soils, but that doesn’t make the data collected from such an endeavor valueless. Since the Forest Walker serves many functions at once, a multitude of data products can add to the return on investment component.
### Weather Data

Temperature, humidity, pressure, and even data like evapotranspiration gathered at high densities on broad acre scales have untold value and because the sensors are lightweight and don’t require large power budgets, they come along for the ride at little cost. But, just like the old mantra, “gas, grass, or ass, nobody rides for free”, these sensors provide potential revenue benefits just by them being present.
I’ve touched on just a few data genres here. In fact, the question for universities, governmental bodies, and other institutions becomes, “How much will you pay us to attach your sensor payload to the Forest Walker?”
# Noise Suppression

Only you can prevent Metallica filling the surrounds with 120 dB of sound. Easy enough, just turn the car stereo off. But what of a fleet of 50 Forest Walkers operating in the backcountry or near a township? 500? 5000? Each one has a wood chipper, an internal combustion engine, hydraulic pumps, actuators, and more cooling fans than you can shake a stick at. It’s a walking, screaming fire-breathing dragon operating continuously, day and night, twenty-four hours a day, three hundred sixty-five days a year. The sound will negatively affect all living things and that impacts behaviors. Serious engineering consideration and prowess must deliver a silencing blow to the major issue of noise.
It would be foolish to think that a fleet of Forest Walkers could be silent, but if not a major design consideration, then the entire idea is dead on arrival. Townships would not allow them to operate even if they solved the problem of widespread fuel load and neither would governmental entities, and rightly so. Nothing, not man nor beast, would want to be subjected to an eternal, infernal scream even if it were to end within days as the fleet moved further away after consuming what it could. Noise and heat are the only real pollutants of this system; taking noise seriously from the beginning is paramount.
# Fire Safety

A “fire-breathing dragon” is not the worst description of the Forest Walker. It eats wood, combusts it at very high temperatures and excretes carbon; and it does so in an extremely flammable environment. Bad mix for one Forest Walker, worse for many. One must take extreme pains to ensure that during normal operation, a Forest Walker could fall over, walk through tinder dry brush, or get pounded into the ground by a meteorite from Krypton and it wouldn’t destroy epic swaths of trees and baby deer. I envision an ultimate test of a prototype to include dowsing it in grain alcohol while it’s wrapped up in toilet paper like a pledge at a fraternity party. If it runs for 72 hours and doesn’t set everything on fire, then maybe outside entities won’t be fearful of something that walks around forests with a constant fire in its belly.
# The Wrap

How we think about what can be done with and adjacent to Bitcoin is at least as important as Bitcoin’s economic standing itself. For those who will tell me that this entire idea is without merit, I say, “OK, fine. You can come up with something, too.” What can we plug Bitcoin into that, like a battery, makes something that does not work, work? That’s the lesson I get from this entire exercise. No one was ever going to hire teams of humans to go out and "clean the forest". There's no money in that. The data collection and sales from such an endeavor might provide revenues over the break-even point but investment demands Alpha in this day and age. But, plug Bitcoin into an almost viable system and, voilà! We tip the scales to achieve lift-off.
Let’s face it, we haven’t scratched the surface of Bitcoin’s forcing function on our minds. Not because it’s Bitcoin, but because of what that invention means. The question that pushes me to approach things this way is, “what can we create that one system’s waste is another system’s feedstock?” The Forest Walker system’s only real waste is the conversion of low entropy energy (wood and syngas) into high entropy energy (heat and noise). All other output is beneficial to humanity.
Bitcoin, I believe, is the first product of a new mode of human imagination. An imagination newly forged over the past few millennia of being lied to, stolen from, distracted and otherwise mis-allocated to a black hole of the nonsensical. We are waking up.
What I have presented is not science fiction. Everything I have described here is well within the realm of possibility. The question is one of viability, at least in terms of the detritus of the old world we find ourselves departing from. This system would take a non-trivial amount of time and resources to develop. I think the system would garner extensive long-term contracts from those who have the most to lose from wildfires, the most to gain from hyperaccurate data sets, and, of course, securing the most precious asset in the world. Many may not see it that way, for they seek Alpha and are therefore blind to other possibilities. Others will see only the possibilities; of thinking in a new way, of looking at things differently, and dreaming of what comes next.
-

@ 4506e04e:8c16ba04
2025-01-13 22:25:17
The employment trends in the gig economy are clear. More and more people take on some form of freelance or temporary work often on top of their full time job. In fact, according to [recent estimates](https://www.upwork.com/resources/gig-economy-statistics), approximately 1.57 billion people, or nearly half (46.4%) of the global workforce, engage in gig work. As gig platforms continue to expand across borders and sectors, this number is projected to keep rising.
<img src="https://blossom.primal.net/d4fca16a18e427f8c3f97677c8e7599a4a4ad1cc2d635bfcd0ab6b0ada48ecb9.png">
In the UK, the gig economy is particularly popular, with many workers supplementing their income with side gigs. According to a [recent survey](https://standout-cv.com/stats/gig-economy-statistics-uk#:~:text=For%20most%2C%2071.5%25%2C%20gig,main%20income%20\(both%2036%25\).), almost half (48%) of UK gig workers have full-time jobs on top of their side gigs, while 71.5% use gig work to supplement their income rather than provide their sole earnings. The top gig occupation in the UK is online administrative work, with 39% of gig workers offering virtual assistance, data entry, clerical services, or similar computer-based tasks. Sounds like a great way to earn some sats, doesn't it?
Despite the growth and popularity of the gig economy, traditional platforms like LinkedIn have reached their peak and become increasingly plagued by spam from aggressive recruiters and profiles of people with increasingly unverifiable experience. Meanwhile all the centralised platforms like Fiverr and Upwork take a significant cut from freelancers' pay, leaving many workers feeling undervalued and overworked. It's no wonder that many are looking for alternative solutions that prioritize fairness, transparency, trust and compensation paid in money that will last!
Here comes Nostr, a decentralized, censorship-resistant protocol that's laying foundations for the future of the gig work. With its censorship-resistant, peer-to-peer approach, Nostr is poised to revolutionize the way we work and connect with each other. In this article, I'll explore why Nostr is an exciting development for the gig economy, what it means for the future of work and what platforms are already available.
What makes Nostr different? It’s built on principles of decentralization, freedom, trust and Bitcoin as its native currency. Forget walled gardens; with Nostr, your identity is your own. Nobody’s mining your data, and no shadowy algorithms are deciding who sees your posts or what posts you should see. It's a perfect setup for a job marketplace where companies post jobs and freelancers get them done. All paid with Bitcoin with no middleman to take your money
And it’s not just theory. Real solutions are already built, transforming how professionals connect, collaborate, and commit their skills, time and creativity. All open-source and Bitcoin/Nostr-centric.
## Here are 4 tools you want to check out:
1. [SatShoot:](https://SatShoot.com) Think Upwork or Fiverr, but with integrated eCash wallet and zero middlemen. Creators, freelancers, and clients unite under the banner of peer-to-peer gig economy.
2. [Kanbanstr](https://www.kanbanstr.com/): A Nostr-native Kanban board for moving tasks from To Do > In Progress > Done and zapping the developers as they deliver.
3. [GitWorkshop.dev](https://gitworkshop.dev/): A decentralized alternative to GitHub, tailored for developers who value freedom and sovereignty.
4. [Sigit.io](https://sigit.io/): An open-source and self-hostable solution for secure document signing and verification.
These platforms aren’t just ideas; they’re already being built, some are already in Beta versions, and you can test them today!
These platforms aren’t just ideas; they’re already being built, some are already in Beta versions, and you can test them today!
## Don't trust - verify!
How can you be sure you're getting help from the right people with the right skills? That’s where the Web of Trust (WoT) comes in.
On Nostr, the WoT is a decentralized trust system that lets users build and evaluate relationships using cryptographic keys and interactions. Instead of depending on centralized authorities to verify identities or manage reputations, the WoT allows trust to grow organically through direct endorsements and social connections.
In this system, your track record matters. As a freelancer, you’re motivated to deliver quality work—not just to get paid, but also to earn positive feedback. This feedback boosts your reputation, helping you secure your next gig. You could get extra points if i.e. you hold a subject matter expert certificate.
Credentials and certifications are still often critical to determine if someone has the skills you are looking for. The idea of certifications could be rebuilt on Nostr with Badges NIP-58. Institutions like Red Hat, Cisco, and others could issue verifiable, NIP-05-backed badges directly to your Nostr public key (“npub”).
It’s simple:
1. The certifying body verifies their domain via NIP-05.
2. They issue badges for their certifications
3. Successful candidates receive badges and wear them on their npubs.
All it takes is that during the registration process for the exam the examinee adds their npub and Voilà! A decentralized, censorship-resistant proof of skills that lives on Nostr. No middlemen, no gatekeepers, you get the right people for the right job!
Here’s a mind-blowing stat: 95% of the world’s population doesn’t own any Bitcoin. With fiat systems teetering, more people will turn to earning Bitcoin instead of buying it at ever-rising prices. Nostr-based platforms are perfectly positioned to capitalize on this trend, offering global access to Bitcoin-based gigs. It’s borderless, censorship-resistant, and a hedge against the collapsing fiat world order.
Nostr clients and solutions are popping up faster than mushrooms after rain. Whether you’re a developer, marketer, freelancer, or just someone curious about the future of work, there’s a tool for you. This explosive growth signals a broader shift: professionals are tired of traditional platforms and are looking for alternatives that respect their privacy, autonomy, and time.
## The Bottom Line
LinkedIn’s days are numbered. Services like Upwork and Fiverr or even Uber are praying on freelance fees. The future of services, networking, and professional growth is decentralized, censorship-resistant, and powered by Nostr. Whether you’re a freelancer, a certifying body, or a startup founder, the opportunities are endless.
Here's a New Year resolution for you - say goodbye to spam and hello to sovereignty. The Nostr revolution is here, and it’s time to join the movement!
---
*If you’re inspired to dive into the Nostr ecosystem but need guidance, the [NostrDev team](https://nostrdev.com) has got your back. From conceptualizing your solution to building it out, we’re the go-to experts for all things Nostr. Reach out and start building the future today*.
-

@ e3ba5e1a:5e433365
2025-01-13 16:47:27
My blog posts and reading material have both been on a decidedly economics-heavy slant recently. The topic today, incentives, squarely falls into the category of economics. However, when I say economics, I’m not talking about “analyzing supply and demand curves.” I’m talking about the true basis of economics: understanding how human beings make decisions in a world of scarcity.
A fair definition of incentive is “a reward or punishment that motivates behavior to achieve a desired outcome.” When most people think about economic incentives, they’re thinking of money. If I offer my son $5 if he washes the dishes, I’m incentivizing certain behavior. We can’t guarantee that he’ll do what I want him to do, but we can agree that the incentive structure itself will guide and ultimately determine what outcome will occur.
The great thing about monetary incentives is how easy they are to talk about and compare. “Would I rather make $5 washing the dishes or $10 cleaning the gutters?” But much of the world is incentivized in non-monetary ways too. For example, using the “punishment” half of the definition above, I might threaten my son with losing Nintendo Switch access if he doesn’t wash the dishes. No money is involved, but I’m still incentivizing behavior.
And there are plenty of incentives beyond our direct control\! My son is *also* incentivized to not wash dishes because it’s boring, or because he has some friends over that he wants to hang out with, or dozens of other things. Ultimately, the conflicting array of different incentive structures placed on him will ultimately determine what actions he chooses to take.
## Why incentives matter
A phrase I see often in discussions—whether they are political, parenting, economic, or business—is “if they could **just** do…” Each time I see that phrase, I cringe a bit internally. Usually, the underlying assumption of the statement is “if people would behave contrary to their incentivized behavior then things would be better.” For example:
* If my kids would just go to bed when I tell them, they wouldn’t be so cranky in the morning.
* If people would just use the recycling bin, we wouldn’t have such a landfill problem.
* If people would just stop being lazy, our team would deliver our project on time.
In all these cases, the speakers are seemingly flummoxed as to why the people in question don’t behave more rationally. The problem is: each group is behaving perfectly rationally.
* The kids have a high time preference, and care more about the joy of staying up now than the crankiness in the morning. Plus, they don’t really suffer the consequences of morning crankiness, their parents do.
* No individual suffers much from their individual contribution to a landfill. If they stopped growing the size of the landfill, it would make an insignificant difference versus the amount of effort they need to engage in to properly recycle.
* If a team doesn’t properly account for the productivity of individuals on a project, each individual receives less harm from their own inaction. Sure, the project may be delayed, company revenue may be down, and they may even risk losing their job when the company goes out of business. But their laziness individually won’t determine the entirety of that outcome. By contrast, they greatly benefit from being lazy by getting to relax at work, go on social media, read a book, or do whatever else they do when they’re supposed to be working.

My point here is that, as long as you ignore the reality of how incentives drive human behavior, you’ll fail at getting the outcomes you want.
If everything I wrote up until now made perfect sense, you understand the premise of this blog post. The rest of it will focus on a bunch of real-world examples to hammer home the point, and demonstrate how versatile this mental model is.
## Running a company
Let’s say I run my own company, with myself as the only employee. My personal revenue will be 100% determined by my own actions. If I decide to take Tuesday afternoon off and go fishing, I’ve chosen to lose that afternoon’s revenue. Implicitly, I’ve decided that the enjoyment I get from an afternoon of fishing is greater than the potential revenue. You may think I’m being lazy, but it’s my decision to make. In this situation, the incentive–money–is perfectly aligned with my actions.
Compare this to a typical company/employee relationship. I might have a bank of Paid Time Off (PTO) days, in which case once again my incentives are relatively aligned. I know that I can take off 15 days throughout the year, and I’ve chosen to use half a day for the fishing trip. All is still good.
What about unlimited time off? Suddenly incentives are starting to misalign. I don’t directly pay a price for not showing up to work on Tuesday. Or Wednesday as well, for that matter. I might ultimately be fired for not doing my job, but that will take longer to work its way through the system than simply not making any money for the day taken off.
Compensation overall falls into this misaligned incentive structure. Let’s forget about taking time off. Instead, I work full time on a software project I’m assigned. But instead of using the normal toolchain we’re all used to at work, I play around with a new programming language. I get the fun and joy of playing with new technology, and potentially get to pad my resume a bit when I’m ready to look for a new job. But my current company gets slower results, less productivity, and is forced to subsidize my extracurricular learning.
When a CEO has a bonus structure based on profitability, he’ll do everything he can to make the company profitable. This might include things that actually benefit the company, like improving product quality, reducing internal red tape, or finding cheaper vendors. But it might also include destructive practices, like slashing the R\&D budget to show massive profits this year, in exchange for a catastrophe next year when the next version of the product fails to ship.

Or my favorite example. My parents owned a business when I was growing up. They had a back office where they ran operations like accounting. All of the furniture was old couches from our house. After all, any money they spent on furniture came right out of their paychecks\! But in a large corporate environment, each department is generally given a budget for office furniture, a budget which doesn’t roll over year-to-year. The result? Executives make sure to spend the entire budget each year, often buying furniture far more expensive than they would choose if it was their own money.
There are plenty of details you can quibble with above. It’s in a company’s best interest to give people downtime so that they can come back recharged. Having good ergonomic furniture can in fact increase productivity in excess of the money spent on it. But overall, the picture is pretty clear: in large corporate structures, you’re guaranteed to have mismatches between the company’s goals and the incentive structure placed on individuals.
Using our model from above, we can lament how lazy, greedy, and unethical the employees are for doing what they’re incentivized to do instead of what’s right. But that’s simply ignoring the reality of human nature.
# Moral hazard
Moral hazard is a situation where one party is incentivized to take on more risk because another party will bear the consequences. Suppose I tell my son when he turns 21 (or whatever legal gambling age is) that I’ll cover all his losses for a day at the casino, but he gets to keep all the winnings.
What do you think he’s going to do? The most logical course of action is to place the largest possible bets for as long as possible, asking me to cover each time he loses, and taking money off the table and into his bank account each time he wins.

But let’s look at a slightly more nuanced example. I go to a bathroom in the mall. As I’m leaving, I wash my hands. It will take me an extra 1 second to turn off the water when I’m done washing. That’s a trivial price to pay. If I *don’t* turn off the water, the mall will have to pay for many liters of wasted water, benefiting no one. But I won’t suffer any consequences at all.
This is also a moral hazard, but most people will still turn off the water. Why? Usually due to some combination of other reasons such as:
1. We’re so habituated to turning off the water that we don’t even consider *not* turning it off. Put differently, the mental effort needed to not turn off the water is more expensive than the 1 second of time to turn it off.
2. Many of us have been brought up with a deep guilt about wasting resources like water. We have an internal incentive structure that makes the 1 second to turn off the water much less costly than the mental anguish of the waste we created.
3. We’re afraid we’ll be caught by someone else and face some kind of social repercussions. (Or maybe more than social. Are you sure there isn’t a law against leaving the water tap on?)
Even with all that in place, you may notice that many public bathrooms use automatic water dispensers. Sure, there’s a sanitation reason for that, but it’s also to avoid this moral hazard.
A common denominator in both of these is that the person taking the action that causes the liability (either the gambling or leaving the water on) is not the person who bears the responsibility for that liability (the father or the mall owner). Generally speaking, the closer together the person making the decision and the person incurring the liability are, the smaller the moral hazard.
It’s easy to demonstrate that by extending the casino example a bit. I said it was the father who was covering the losses of the gambler. Many children (though not all) would want to avoid totally bankrupting their parents, or at least financially hurting them. Instead, imagine that someone from the IRS shows up at your door, hands you a credit card, and tells you you can use it at a casino all day, taking home all the chips you want. The money is coming from the government. How many people would put any restriction on how much they spend?
And since we’re talking about the government already…
## Government moral hazards
As I was preparing to write this blog post, the California wildfires hit. The discussions around those wildfires gave a *huge* number of examples of moral hazards. I decided to cherry-pick a few for this post.
The first and most obvious one: California is asking for disaster relief funds from the federal government. That sounds wonderful. These fires were a natural disaster, so why shouldn’t the federal government pitch in and help take care of people?
The problem is, once again, a moral hazard. In the case of the wildfires, California and Los Angeles both had ample actions they could have taken to mitigate the destruction of this fire: better forest management, larger fire department, keeping the water reservoirs filled, and probably much more that hasn’t come to light yet.
If the federal government bails out California, it will be a clear message for the future: your mistakes will be fixed by others. You know what kind of behavior that incentivizes? More risky behavior\! Why spend state funds on forest management and extra firefighters—activities that don’t win politicians a lot of votes in general—when you could instead spend it on a football stadium, higher unemployment payments, or anything else, and then let the feds cover the cost of screw-ups.
You may notice that this is virtually identical to the 2008 “too big to fail” bail-outs. Wall Street took insanely risky behavior, reaped huge profits for years, and when they eventually got caught with their pants down, the rest of us bailed them out. “Privatizing profits, socializing losses.”

And here’s the absolute best part of this: I can’t even truly blame either California *or* Wall Street. (I mean, I *do* blame them, I think their behavior is reprehensible, but you’ll see what I mean.) In a world where the rules of the game implicitly include the bail-out mentality, you would be harming your citizens/shareholders/investors if you didn’t engage in that risky behavior. Since everyone is on the hook for those socialized losses, your best bet is to maximize those privatized profits.
There’s a lot more to government and moral hazard, but I think these two cases demonstrate the crux pretty solidly. But let’s leave moral hazard behind for a bit and get to general incentivization discussions.
# Non-monetary competition
At least 50% of the economics knowledge I have comes from the very first econ course I took in college. That professor was amazing, and had some very colorful stories. I can’t vouch for the veracity of the two I’m about to share, but they definitely drive the point home.
In the 1970s, the US had an oil shortage. To “fix” this problem, they instituted price caps on gasoline, which of course resulted in insufficient gasoline. To “fix” this problem, they instituted policies where, depending on your license plate number, you could only fill up gas on certain days of the week. (Irrelevant detail for our point here, but this just resulted in people filling up their tanks more often, no reduction in gas usage.)
Anyway, my professor’s wife had a friend. My professor described in *great* detail how attractive this woman was. I’ll skip those details here since this is a PG-rated blog. In any event, she never had any trouble filling up her gas tank any day of the week. She would drive up, be told she couldn’t fill up gas today, bat her eyes at the attendant, explain how helpless she was, and was always allowed to fill up gas.
This is a demonstration of *non-monetary compensation*. Most of the time in a free market, capitalist economy, people are compensated through money. When price caps come into play, there’s a limit to how much monetary compensation someone can receive. And in that case, people find other ways of competing. Like this woman’s case: through using flirtatious behavior to compensate the gas station workers to let her cheat the rules.
The other example was much more insidious. Santa Monica had a problem: it was predominantly wealthy and white. They wanted to fix this problem, and decided to put in place rent controls. After some time, they discovered that Santa Monica had become *wealthier and whiter*, the exact opposite of their desired outcome. Why would that happen?
Someone investigated, and ended up interviewing a landlady that demonstrated the reason. She was an older white woman, and admittedly racist. Prior to the rent controls, she would list her apartments in the newspaper, and would be legally obligated to rent to anyone who could afford it. Once rent controls were in place, she took a different tact. She knew that she would only get a certain amount for the apartment, and that the demand for apartments was higher than the supply. That meant she could be picky.
She ended up finding tenants through friends-of-friends. Since it wasn’t an official advertisement, she wasn’t legally required to rent it out if someone could afford to pay. Instead, she got to interview people individually and then make them an offer. Normally, that would have resulted in receiving a lower rental price, but not under rent controls.
So who did she choose? A young, unmarried, wealthy, white woman. It made perfect sense. Women were less intimidating and more likely to maintain the apartment better. Wealthy people, she determined, would be better tenants. (I have no idea if this is true in practice or not, I’m not a landlord myself.) Unmarried, because no kids running around meant less damage to the property. And, of course, white. Because she was racist, and her incentive structure made her prefer whites.
You can deride her for being racist, I won’t disagree with you. But it’s simply the reality. Under the non-rent-control scenario, her profit motive for money outweighed her racism motive. But under rent control, the monetary competition was removed, and she was free to play into her racist tendencies without facing any negative consequences.
## Bureaucracy
These were the two examples I remember for that course. But non-monetary compensation pops up in many more places. One highly pertinent example is bureaucracies. Imagine you have a government office, or a large corporation’s acquisition department, or the team that apportions grants at a university. In all these cases, you have a group of people making decisions about handing out money that has no monetary impact on them. If they give to the best qualified recipients, they receive no raises. If they spend the money recklessly on frivolous projects, they face no consequences.
Under such an incentivization scheme, there’s little to encourage the bureaucrats to make intelligent funding decisions. Instead, they’ll be incentivized to spend the money where they recognize non-monetary benefits. This is why it’s so common to hear about expensive meals, gift bags at conferences, and even more inappropriate ways of trying to curry favor with those that hold the purse strings.
Compare that ever so briefly with the purchases made by a small mom-and-pop store like my parents owned. Could my dad take a bribe to buy from a vendor who’s ripping him off? Absolutely he could\! But he’d lose more on the deal than he’d make on the bribe, since he’s directly incentivized by the deal itself. It would make much more sense for him to go with the better vendor, save $5,000 on the deal, and then treat himself to a lavish $400 meal to celebrate.
# Government incentivized behavior
This post is getting longer in the tooth than I’d intended, so I’ll finish off with this section and make it a bit briefer. Beyond all the methods mentioned above, government has another mechanism for modifying behavior: through directly changing incentives via legislation, regulation, and monetary policy. Let’s see some examples:
* Artificial modification of interest rates encourages people to take on more debt than they would in a free capital market, leading to [malinvestment](https://en.wikipedia.org/wiki/Malinvestment) and a consumer debt crisis, and causing the boom-bust cycle we all painfully experience.
* Going along with that, giving tax breaks on interest payments further artificially incentivizes people to take on debt that they wouldn’t otherwise.
* During COVID-19, at some points unemployment benefits were greater than minimum wage, incentivizing people to rather stay home and not work than get a job, leading to reduced overall productivity in the economy and more printed dollars for benefits. In other words, it was a perfect recipe for inflation.
* The tax code gives deductions to “help” people. That might be true, but the real impact is incentivizing people to make decisions they wouldn’t have otherwise. For example, giving out tax deductions on children encourages having more kids. Tax deductions on childcare and preschools incentivizes dual-income households. Whether or not you like the outcomes, it’s clear that it’s government that’s encouraging these outcomes to happen.
* Tax incentives cause people to engage in behavior they wouldn’t otherwise (daycare+working mother, for example).
* Inflation means that the value of your money goes down over time, which encourages people to spend more today, when their money has a larger impact. (Milton Friedman described this as [high living](https://www.youtube.com/watch?v=ZwNDd2_beTU).)
# Conclusion
The idea here is simple, and fully encapsulated in the title: incentives determine outcomes. If you want to know how to get a certain outcome from others, incentivize them to want that to happen. If you want to understand why people act in seemingly irrational ways, check their incentives. If you’re confused why leaders (and especially politicians) seem to engage in destructive behavior, check their incentives.
We can bemoan these realities all we want, but they *are* realities. While there are some people who have a solid internal moral and ethical code, and that internal code incentivizes them to behave against their externally-incentivized interests, those people are rare. And frankly, those people are self-defeating. People *should* take advantage of the incentives around them. Because if they don’t, someone else will.
(If you want a literary example of that last comment, see the horse in Animal Farm.)
How do we improve the world under these conditions? Make sure the incentives align well with the overall goals of society. To me, it’s a simple formula:
* Focus on free trade, value for value, as the basis of a society. In that system, people are always incentivized to provide value to other people.
* Reduce the size of bureaucracies and large groups of all kinds. The larger an organization becomes, the farther the consequences of decisions are from those who make them.
* And since the nature of human beings will be to try and create areas where they can control the incentive systems to their own benefits, make that as difficult as possible. That comes in the form of strict limits on government power, for example.
And even if you don’t want to buy in to this conclusion, I hope the rest of the content was educational, and maybe a bit entertaining\!
-

@ a95c6243:d345522c
2025-01-13 10:09:57
*Ich begann, Social Media aufzubauen,* *\
um den Menschen eine Stimme zu geben.* *\
Mark Zuckerberg*
**Sind euch auch die Tränen gekommen, als ihr Mark Zuckerbergs** **[Wendehals-Deklaration](https://www.facebook.com/zuck/videos/1525382954801931)** bezüglich der Meinungsfreiheit auf seinen Portalen gehört habt? Rührend, oder? Während er früher die offensichtliche Zensur leugnete und später die Regierung Biden dafür verantwortlich machte, will er nun angeblich «die Zensur auf unseren Plattformen drastisch reduzieren».
**«Purer** **[Opportunismus](https://transition-news.org/facebook-grunder-zuckerberg-vom-trump-gegner-zum-trump-buddy-und-anti-zensor)» ob des anstehenden Regierungswechsels wäre als Klassifizierung** viel zu kurz gegriffen. Der jetzige Schachzug des Meta-Chefs ist genauso Teil einer kühl kalkulierten Business-Strategie, wie es die 180 Grad umgekehrte Praxis vorher war. Social Media sind ein höchst lukratives Geschäft. Hinzu kommt vielleicht noch ein bisschen verkorkstes Ego, weil derartig viel Einfluss und Geld sicher auch auf die Psyche schlagen. Verständlich.
> «Es ist an der Zeit, zu unseren Wurzeln der freien Meinungsäußerung auf Facebook und Instagram zurückzukehren. Ich begann, Social Media aufzubauen, um den Menschen eine Stimme zu geben», sagte Zuckerberg.
**Welche Wurzeln? Hat der Mann vergessen, dass er von der Überwachung,** dem Ausspionieren und dem Ausverkauf sämtlicher Daten und digitaler Spuren sowie der Manipulation seiner «Kunden» lebt? Das ist knallharter Kommerz, nichts anderes. Um freie Meinungsäußerung geht es bei diesem Geschäft ganz sicher nicht, und das war auch noch nie so. Die Wurzeln von Facebook liegen in einem Projekt des US-Militärs mit dem Namen [«LifeLog»](https://norberthaering.de/macht-kontrolle/lifelog/). Dessen Ziel war es, «ein digitales Protokoll vom Leben eines Menschen zu erstellen».
**Der Richtungswechsel kommt allerdings nicht überraschend.** Schon Anfang Dezember hatte Meta-Präsident Nick Clegg von «zu hoher Fehlerquote bei der Moderation» von Inhalten [gesprochen](https://www.theverge.com/2024/12/3/24311513/meta-content-moderation-mistakes-nick-clegg). Bei der Gelegenheit erwähnte er auch, dass Mark sehr daran interessiert sei, eine aktive Rolle in den Debatten über eine amerikanische Führungsrolle im technologischen Bereich zu spielen.
**Während Milliardärskollege und Big Tech-Konkurrent Elon Musk bereits seinen Posten** in der kommenden Trump-Regierung in Aussicht hat, möchte Zuckerberg also nicht nur seine Haut retten – Trump hatte ihn einmal einen «Feind des Volkes» genannt und ihm lebenslange Haft angedroht –, sondern am liebsten auch mitspielen. KI-Berater ist wohl die gewünschte Funktion, wie man nach einem Treffen Trump-Zuckerberg hörte. An seine [Verhaftung](https://transition-news.org/nicht-telegram-grunder-durow-sondern-zuckerberg-sollte-in-haft-sitzen-wegen-des) dachte vermutlich auch ein weiterer Multimilliardär mit eigener Social Media-Plattform, Pavel Durov, als er Zuckerberg jetzt [kritisierte](https://www.berliner-zeitung.de/news/ende-des-faktenchecks-bei-meta-telegram-gruender-kritisiert-zuckerberg-und-spricht-warnung-aus-li.2287988) und gleichzeitig warnte.
**Politik und Systemmedien drehen jedenfalls durch** – was zu viel ist, ist zu viel. Etwas weniger Zensur und mehr Meinungsfreiheit würden die Freiheit der Bürger schwächen und seien potenziell vernichtend für die Menschenrechte. Zuckerberg setze mit dem neuen Kurs die Demokratie aufs Spiel, das sei eine «Einladung zum nächsten [Völkermord](https://archive.is/PYeH0)», ernsthaft. Die Frage sei, ob sich die [EU gegen Musk und Zuckerberg](https://www.handelsblatt.com/politik/international/internet-regulierung-kann-sich-die-eu-gegen-musk-und-zuckerberg-behaupten/100099373.html) behaupten könne, Brüssel müsse jedenfalls hart durchgreifen.
**Auch um die** **[Faktenchecker](https://www.welt.de/kultur/medien/article255065352/Metas-Kurswechsel-Zuckerbergs-Entscheidung-und-die-Folgen-fuer-deutsche-Faktenchecker.html)** **macht man sich Sorgen.** Für die deutsche Nachrichtenagentur *dpa* und die «Experten» von *Correctiv*, die (noch) Partner für Fact-Checking-Aktivitäten von Facebook sind, sei das ein «lukratives Geschäftsmodell». Aber möglicherweise werden die Inhalte ohne diese vermeintlichen Korrektoren ja sogar besser. Anders als Meta wollen jedoch Scholz, Faeser und die *Tagesschau* keine Fehler zugeben und zum Beispiel *Correctiv*-[Falschaussagen](https://www.berliner-zeitung.de/politik-gesellschaft/correctiv-falschaussagen-exklusiv-scholz-faeser-und-tagesschau-wollen-sich-fuer-verbreitung-nicht-entschuldigen-li.2288126) einräumen.
**Bei derlei dramatischen Befürchtungen wundert es nicht,** dass der öffentliche Plausch auf X zwischen Elon Musk und AfD-Chefin Alice Weidel von 150 EU-Beamten überwacht wurde, falls es irgendwelche Rechtsverstöße geben sollte, die man ihnen ankreiden könnte. Auch der Deutsche Bundestag war wachsam. Gefunden haben dürften sie nichts. Das Ganze war eher eine Show, viel Wind wurde gemacht, aber letztlich gab es nichts als heiße Luft.
**Das** **[Anbiedern](https://transition-news.org/who-biedert-sich-bei-trump-an)** **bei Donald Trump ist indes gerade in Mode.** Die Weltgesundheitsorganisation (WHO) tut das auch, denn sie fürchtet um Spenden von über einer Milliarde Dollar. Eventuell könnte ja Elon Musk auch hier künftig aushelfen und der Organisation sowie deren größtem privaten Förderer, Bill Gates, etwas unter die Arme greifen. Nachdem Musks KI-Projekt xAI kürzlich von BlackRock & Co. [sechs Milliarden](https://x.ai/blog/series-c) eingestrichen hat, geht da vielleicht etwas.
***
Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/milliardenschwere-wetterfahnchen-und-windmaschinen)*** erschienen.
-

@ a10260a2:caa23e3e
2025-01-12 04:16:29
*Last Updated: January 11, 2025*
This article is based on a note I posted over a year ago. I kept finding great podcasts and realized that a long form note would make sense since it'll essentially be reposted in the feed every time an update is made.
While there are many good privacy resources out there, this list will focus on episodes from CITADEL DISPATCH. The rabbit hole is deep and never-ending; my hope is that this will spark your curiosity and compel you to search for more.
Why should you care? ODELL explains that [here](https://www.discreetlog.com/why-bitcoiners-should-care-about-using-bitcoin-privately/).
If you're ready, here are the privacy-related dispatches. Hour and hours of signal from ODELL and his guests. Enjoy. 🫡
* CD2: Privacy, Nodes, and No KYC with ErgoBTC & BitcoinQ_A — https://fountain.fm/episode/ssPqjTOzHjWSRiYN5rP6
* CD15: bitcoin privacy and coinjoin with nopara73 and openoms — https://fountain.fm/episode/akzlPBM5XWZgPWa2iXCN
* CD16: bitcoin privacy and coinjoin with chris belcher and waxwing — https://fountain.fm/episode/hBcMSmraUUxVlZzBv5V1
* CD21: the lightning network and bitcoin privacy with openoms and cycryptr — https://fountain.fm/episode/vo0LpZOxGiDWIXc8wQf2
* CD29: bitcoin privacy and security with craigraw and ketominer — https://fountain.fm/episode/wNowMP7zxD25kKMLCU4r
* CD30: bitcoin privacy and the danger of KYC with samouraiwallet and openoms — https://fountain.fm/episode/AoIhaVfVHG55gEJOlEiH
* CD43: bitcoin for beginners with BitcoinQ_A— https://fountain.fm/episode/Foh3ImV2fZYPvg2QgNA4
I've also created a Fountain playlist which can be found [here](https://fountain.fm/playlist/WGV34KnpV0NyR6F2RWok). One benefit of the playlist is that you can easily share the group of episodes in its entirety.
-

@ 378562cd:a6fc6773
2025-01-11 19:37:30
**Money**. It’s one of the most powerful forces in our world, and for many, it evokes mixed emotions. On the one hand, money provides security, opportunities, and the freedom to pursue dreams. On the other, it’s often tied to stress, inequality, and a sense of unending competition. This love-hate relationship with money is universal, and it stems from a system that often feels rigged against the average person.
Enter Nostr—a decentralized protocol designed to address some of the deepest flaws in how we interact with value and communication online. While Nostr isn’t just about money, its principles are profoundly reshaping how we think about value exchange, financial sovereignty, and freedom.
### The Root of the Problem
At the core of our collective frustration with money is control. Traditional financial systems are centralized, opaque, and prone to manipulation. Whether it’s through inflation eating away at savings, unfair access to banking, or censorship of financial transactions, the system leaves many feeling powerless. Add to this the societal obsession with consumerism and wealth accumulation, and it’s no wonder money can feel more like a burden than a tool.
Even digital spaces, which promised democratization, often mirror these problems. Social media platforms monetize user data while censoring or shadow-banning content. Payment platforms can freeze accounts or deny access, reinforcing the imbalance of power.
### Nostr: A Fresh Perspective on Value and Freedom
Nostr (short for "*Notes and Other Stuff Transmitted by Relays*") isn’t just a technical innovation—it’s a philosophy. Built on a simple yet powerful decentralized protocol, Nostr allows users to share information, communicate, and exchange value directly, without reliance on centralized entities. It’s an open, censorship-resistant network that puts control back into the hands of individuals.
So, how is Nostr addressing the money dilemma?
1. **Decentralized Value Exchange**\
Nostr integrates seamlessly with tools like Bitcoin’s Lightning Network, enabling instant, low-cost payments without intermediaries. This means individuals can send and receive money directly, whether it’s a micro-tip to support a content creator or a peer-to-peer transaction across borders. No banks. No middlemen. Just value exchanged freely.
2. **Censorship Resistance**\
One of the most frustrating aspects of modern finance is the potential for censorship. Banks and platforms can freeze accounts or block payments based on arbitrary criteria. Nostr flips this script by creating a network where transactions and communication are uncensorable. Value flows freely, aligned with the principles of individual sovereignty.
3. **Empowering Creators**\
In traditional models, creators often rely on centralized platforms to earn revenue, losing a significant portion to fees or being at the mercy of algorithms. On Nostr, creators can directly monetize their work through Bitcoin tips or other decentralized payment methods, creating a more equitable system where value flows directly between creator and consumer.
4. **Transparency and Trust**\
Unlike traditional systems shrouded in secrecy, Nostr operates on an open protocol. This transparency builds trust and removes many of the frustrations people associate with hidden fees, arbitrary rules, or lack of accountability in centralized systems.
### A New Relationship with Money
By decentralizing how value is exchanged and communication occurs, Nostr helps redefine the role of money in our lives. It shifts the narrative from control and dependency to empowerment and freedom. Money becomes what it was always meant to be—a tool, not a master.
Imagine a world where tipping someone online is as easy as liking a post, where no one can block you from accessing your own funds, and where creators earn directly from their audience without gatekeepers taking a cut. That’s the world Nostr is helping to build.
### Closing Thoughts
The love-hate relationship with money isn’t going away overnight. But as protocols like Nostr grow and mature, they offer a glimpse of what’s possible when we rethink the systems that shape our lives. By putting individuals back in control of their communication and financial exchanges, Nostr is doing more than fixing the flaws of the old system—it’s creating a new one entirely.
In the end, it’s not just about money. It’s about freedom, fairness, and the ability to live a life where value flows freely, aligned with our principles and priorities. Nostr isn’t just a tool; it’s a movement. And for anyone tired of the current system, that’s something worth paying attention to.
-

@ 0d97beae:c5274a14
2025-01-11 16:52:08
This article hopes to complement the article by Lyn Alden on YouTube: https://www.youtube.com/watch?v=jk_HWmmwiAs
## The reason why we have broken money
Before the invention of key technologies such as the printing press and electronic communications, even such as those as early as morse code transmitters, gold had won the competition for best medium of money around the world.
In fact, it was not just gold by itself that became money, rulers and world leaders developed coins in order to help the economy grow. Gold nuggets were not as easy to transact with as coins with specific imprints and denominated sizes.
However, these modern technologies created massive efficiencies that allowed us to communicate and perform services more efficiently and much faster, yet the medium of money could not benefit from these advancements. Gold was heavy, slow and expensive to move globally, even though requesting and performing services globally did not have this limitation anymore.
Banks took initiative and created derivatives of gold: paper and electronic money; these new currencies allowed the economy to continue to grow and evolve, but it was not without its dark side. Today, no currency is denominated in gold at all, money is backed by nothing and its inherent value, the paper it is printed on, is worthless too.
Banks and governments eventually transitioned from a money derivative to a system of debt that could be co-opted and controlled for political and personal reasons. Our money today is broken and is the cause of more expensive, poorer quality goods in the economy, a larger and ever growing wealth gap, and many of the follow-on problems that have come with it.
## Bitcoin overcomes the "transfer of hard money" problem
Just like gold coins were created by man, Bitcoin too is a technology created by man. Bitcoin, however is a much more profound invention, possibly more of a discovery than an invention in fact. Bitcoin has proven to be unbreakable, incorruptible and has upheld its ability to keep its units scarce, inalienable and counterfeit proof through the nature of its own design.
Since Bitcoin is a digital technology, it can be transferred across international borders almost as quickly as information itself. It therefore severely reduces the need for a derivative to be used to represent money to facilitate digital trade. This means that as the currency we use today continues to fare poorly for many people, bitcoin will continue to stand out as hard money, that just so happens to work as well, functionally, along side it.
Bitcoin will also always be available to anyone who wishes to earn it directly; even China is unable to restrict its citizens from accessing it. The dollar has traditionally become the currency for people who discover that their local currency is unsustainable. Even when the dollar has become illegal to use, it is simply used privately and unofficially. However, because bitcoin does not require you to trade it at a bank in order to use it across borders and across the web, Bitcoin will continue to be a viable escape hatch until we one day hit some critical mass where the world has simply adopted Bitcoin globally and everyone else must adopt it to survive.
Bitcoin has not yet proven that it can support the world at scale. However it can only be tested through real adoption, and just as gold coins were developed to help gold scale, tools will be developed to help overcome problems as they arise; ideally without the need for another derivative, but if necessary, hopefully with one that is more neutral and less corruptible than the derivatives used to represent gold.
## Bitcoin blurs the line between commodity and technology
Bitcoin is a technology, it is a tool that requires human involvement to function, however it surprisingly does not allow for any concentration of power. Anyone can help to facilitate Bitcoin's operations, but no one can take control of its behaviour, its reach, or its prioritisation, as it operates autonomously based on a pre-determined, neutral set of rules.
At the same time, its built-in incentive mechanism ensures that people do not have to operate bitcoin out of the good of their heart. Even though the system cannot be co-opted holistically, It will not stop operating while there are people motivated to trade their time and resources to keep it running and earn from others' transaction fees. Although it requires humans to operate it, it remains both neutral and sustainable.
Never before have we developed or discovered a technology that could not be co-opted and used by one person or faction against another. Due to this nature, Bitcoin's units are often described as a commodity; they cannot be usurped or virtually cloned, and they cannot be affected by political biases.
## The dangers of derivatives
A derivative is something created, designed or developed to represent another thing in order to solve a particular complication or problem. For example, paper and electronic money was once a derivative of gold.
In the case of Bitcoin, if you cannot link your units of bitcoin to an "address" that you personally hold a cryptographically secure key to, then you very likely have a derivative of bitcoin, not bitcoin itself. If you buy bitcoin on an online exchange and do not withdraw the bitcoin to a wallet that you control, then you legally own an electronic derivative of bitcoin.
Bitcoin is a new technology. It will have a learning curve and it will take time for humanity to learn how to comprehend, authenticate and take control of bitcoin collectively. Having said that, many people all over the world are already using and relying on Bitcoin natively. For many, it will require for people to find the need or a desire for a neutral money like bitcoin, and to have been burned by derivatives of it, before they start to understand the difference between the two. Eventually, it will become an essential part of what we regard as common sense.
## Learn for yourself
If you wish to learn more about how to handle bitcoin and avoid derivatives, you can start by searching online for tutorials about "Bitcoin self custody".
There are many options available, some more practical for you, and some more practical for others. Don't spend too much time trying to find the perfect solution; practice and learn. You may make mistakes along the way, so be careful not to experiment with large amounts of your bitcoin as you explore new ideas and technologies along the way. This is similar to learning anything, like riding a bicycle; you are sure to fall a few times, scuff the frame, so don't buy a high performance racing bike while you're still learning to balance.
-

@ 37fe9853:bcd1b039
2025-01-11 15:04:40
yoyoaa
-

@ 62033ff8:e4471203
2025-01-11 15:00:24
收录的内容中 kind=1的部分,实话说 质量不高。
所以我增加了kind=30023 长文的article,但是更新的太少,多个relays 的服务器也没有多少长文。
所有搜索nostr如果需要产生价值,需要有高质量的文章和新闻。
而且现在有很多机器人的文章充满着浪费空间的作用,其他作用都用不上。
https://www.duozhutuan.com 目前放的是给搜索引擎提供搜索的原材料。没有做UI给人类浏览。所以看上去是粗糙的。
我并没有打算去做一个发microblog的 web客户端,那类的客户端太多了。
我觉得nostr社区需要解决的还是应用。如果仅仅是microblog 感觉有点够呛
幸运的是npub.pro 建站这样的,我觉得有点意思。
yakihonne 智能widget 也有意思
我做的TaskQ5 我自己在用了。分布式的任务系统,也挺好的。
-

@ 378562cd:a6fc6773
2025-01-10 16:37:38
For many of us, reading isn’t just a pastime—it’s a deeply personal goal tied to self-growth, relaxation, and exploration. Yet, despite knowing its importance, we often struggle to make it happen. We start and stop, let books gather dust, and feel guilty for not finishing them. The truth? It’s not a time issue; it’s a mental barrier.
This guide is designed to help you break through those barriers with a structured, rewarding framework that keeps you interested, engaged, and building momentum. Let’s turn reading into a habit you love—and can sustain.
---
### **Step 1: Understand the Real Problem**
Before diving into action, take a moment to reflect. The issue isn’t that you don’t have time—it’s that you haven’t made reading a priority. Life pulls us in countless directions, but we always find time for what matters most. Reading deserves that place in your life because it nourishes your mind, brings you joy, and inspires growth.
**Ask Yourself:**
- Why do I want to read more?
- How would my life improve if I prioritized reading?
Write down your answers and keep them visible. Let your 'why' guide you forward.
---
### **Step 2: Start Where You Are (Small and Simple Wins)**
Many people fail because they set huge, overwhelming goals like finishing a book every week. The secret to success? Start small. Commit to just **5 minutes a day** or a single page. Progress matters more than perfection.
**Mini Challenge #1:**
- Pick a book you’re genuinely excited about (not one you feel you *should* read).
- Read for 5 minutes today. Just 5 minutes.
When you complete this, check it off. That little win is the first step toward building momentum.
---
### **Step 3: Create a System That Fits Your Life**
Habits thrive when they’re tied to something you already do. Look for natural openings in your day to read.
- **Morning:** Read while sipping coffee or tea.
- **Lunch Break:** Sneak in a few pages while eating.
- **Evening:** Replace 10 minutes of scrolling with reading before bed.
Make it impossible to forget by keeping books or an e-reader where you spend the most time: next to the bed, on the couch, or in your bag.
**Mini Challenge #2:**
- Set a specific time to read tomorrow. Write it down and stick to it.
---
### **Step 4: Make It Fun and Rewarding**
Let’s face it—habits stick when they feel good. Build instant gratification into your reading routine.
- **Gamify the Process:** Create a simple list of mini challenges (like the ones here) and cross them off as you go.
- **Set Rewards:** For every milestone—like finishing a chapter or hitting a week of daily reading—treat yourself. It could be a fancy coffee, a cozy reading corner upgrade, or just the joy of marking progress.
**Mini Challenge #3:**
- Set a reward for finishing your first chapter or reading streak. Make it something exciting!
---
### **Step 5: Follow Your Interests, Not Rules**
One of the biggest mental barriers is feeling like you *have to* finish every book you start. Forget that. Reading should be enjoyable, not a chore. If a book isn’t grabbing you, it’s okay to stop and try another. The key is to stay engaged, not stuck.
**Mini Challenge #4:**
- If you’re not loving a book after 50 pages, give yourself permission to move on.
---
### **Step 6: Build Momentum with Layered Challenges**
To make reading exciting and natural, set challenges that grow progressively:
1. **Day 1–3:** Read 5 minutes daily.
2. **Day 4–7:** Extend to 10 minutes.
3. **Week 2:** Finish a chapter or two from a book you love.
4. **Week 3:** Try a new genre or author.
Each challenge builds on the last, creating a sense of accomplishment. By the time you finish the third week, you’ll likely be hooked.
---
### **Step 7: Track and Celebrate Progress**
Progress tracking is one of the simplest yet most effective ways to build a habit. Create a log to note what you’ve read, even if it’s just a chapter or a short story. Seeing your progress motivates you to keep going.
**Ideas for Tracking:**
- Use a journal or app to list books and dates you started/finished.
- Jot down favorite quotes or lessons learned.
- Share your progress with friends or join a book club for accountability.
**Mini Challenge #5:**
- Start a reading journal and write down what you love about the book you’re currently reading.
---
### **Step 8: Stay Flexible and Forgive Yourself**
Life gets busy, and you might miss a day (or week). That’s okay. Habits are built over time, not overnight. The key is to keep coming back to your reading routine without guilt. Remember, even a little reading is better than none.
---
### **Final Thoughts**
Reading is a gift you give yourself. It’s not about how fast you finish or how many books you complete—it’s about the joy, knowledge, and escape it brings. By breaking your mental barriers, starting small, and creating a system of rewards and challenges, you can make reading a natural and deeply fulfilling part of your life.
So, grab a book, set a timer, and dive in. Your reading journey starts today.
-

@ 228dde34:b5d0345e
2025-01-10 10:00:04
##### By Glenda Chong
##### Editorial Admin
##### Hype Issue #60
##### Join GLENDA CHONG as she experiences the magic of Korean indie band ADOY’s music and talks to the group about how they and the Korean indie scene have risen in prominence in the global music scene.

On New Year’s Eve, under a dark sky lit with twinkling city lights, I stood clinging onto a barricade with a friend before a modest yet commanding stage, littered with instruments that pulsed with the promise of what’s to come. We were at Music Day Out! - Magical Garden, a music event held at *SCAPE to celebrate the DIY ethos of independent musical acts from across Southeast Asia and to ring in the new year.
It was just past 11pm, and with bated breath, I waited for the one act I had been keeping my eyes peeled for all night to take the stage. This musical artist was none other than ADOY, a South Korean band. The band, consisting of members Juhwan, Zee, Geunchang, and Dayoung, was slated to have the longest set time of the night.
Undoubtedly, as the night’s most anticipated act, the crowd’s palpable, buzzing energy was at an all-time high. For me, however, the excitement ran much deeper: because before ADOY took the stage, tucked away in a rare moment of calm, I sat down with them to hear them outside of their melodies.
Over the last few years, Korean indie bands have risen in prominence in the global music scene. While fellow musical genre, K-pop, from the same country has dominated global headlines with its intricate performances and infectious tunes, Korea’s indie music scene has been simmering just beneath the surface.
But with the aid of social media and the internet providing opportunities for virality, Korean indie bands like ADOY and wave to earth are now carving a path of their own, one where their music resonates just as deeply with fans worldwide as their K-pop counterparts’ does.
 *As the vocalist of ADOY, Juhwan’s voice is front and center in ADOY’s music. Photo by Glenda Chong.*
When I asked the band what could be attributed to the growing success of Korean indie bands, member Juhwan pointed to how beyond the boom of K-pop, Korean pop culture in general, such as Korean shows like Squid Game, “is kind of helping the image as a whole”.
He also mentioned that bands like themselves are “very energetic”. Although I cannot disagree with this, as experiencing live bands is an otherworldly experience, the music and messaging seem to be the key to being a gateway for global fans to enter the indie scene.
If you take a peek at ADOY’s music, you will notice that they primarily sing in English; an artistic decision that was surprisingly intentional. When asked if their English lyrics help global fans connect with their fans further, this is what member Zee had to say:
“That's one of the things we had in mind when we started making songs because it’s a global arena… so we wanted to include as many people as possible.”
Funnily enough, even though the band have English lyrics in most of their music, the members (except for Zee who lived abroad in France, New Zealand, America, and Canada), are only somewhat fluent in English.
So as a workaround, sometimes the band turns to translating from their native language to English. In a video interview with Front Row Live Ent. on YouTube, Zee shared that as the group’s English speaker, he would help translate Korean lyrics written by his members. Surprisingly, this does not pose as much of a challenge as I had assumed, as according to Zee, they find that they do not struggle with being lost in translation as they do write in English from the start at times.
“I think it just comes naturally,” Zee stated.
However, he acknowledged that at times, when attempting to express certain messages and feelings, the band “sometimes has to change a lot” as the two languages are different. “It’s quite difficult… but we do try as much as possible to retain the message”.
But beyond the English lyrics, it is the feelings ADOY’s music evokes that are universal. Like many ADOY fans, the first ADOY song I was introduced to was one of their most popular tracks *Grace*, a slow tune filled with smooth vocals.
Watching the YouTube video of them performing *Grace* on the show Yu Heeyeol’s Sketchbook for the first time was nothing short of magical. And just from reading the Korean comments, I finally understood what people meant when they said ADOY’s music transcends borders. Just like their domestic listeners, I too found myself transported to faraway places and nostalgic moments through their sound and lyrics. It was a connection that felt universal, yet deeply personal.
 *ADOY jamming out at the start of their set at Music Day Out! Photo by Glenda Chong.*
This universal appeal is part of why Korean indie bands like ADOY are finding such global recognition. With their rise, however, comes the inevitable question of what it means to remain ‘indie’, as the lines between ‘indie’ and ‘commercial’ can blur. Though for ADOY in particular, having dubbed themselves as “commercial indie”, they navigate this distinction with a unique balance.
In a frank manner, member Zee explained that being “commercial indie” to them meant being able to “earn money” while doing music.
“Being indie is just making your own stuff,” Zee said. “We wanted to earn money while doing this so we can do music for a professional career. That’s what we meant [when we said] we wanted to be commercial”.
Judging from their journey, they have stuck to these principles closely. The band is independent from major record labels and has remained true to their sound and artistic essence, even while experimenting and fusing various genres. Their efforts have proven to be fruitful, as the global appetite for Korea’s diverse music scene is roaring louder than ever. Korean indie music has found its voice on the global stage, and ADOY has become one of its most compelling icons.
Before we wrapped up our time together, I asked ADOY a very important question: which of their songs would they recommend to a first-timer of their music? Member Dayoung suggested the track *Don’t Stop* which appears on their first EP, *CATNIP*.
 *Dayoung plays the bass and supports Juhwan with backing vocals in the team. Photo by Glenda Chong.*
“*Don’t Stop* because it retains that energy of youth that I think it’s quite hard to describe song-wise, but I think that song has that good picture of youth in it,” Dayoung explained. With Dayoung’s words echoing in my mind, I eagerly wondered if the band would play this track during their set. And after close to an hour of immersing in ADOY’s dreamy soundscapes, I got my answer.
Just minutes before the clock’s hands approached the new year, unlike the past hour where ADOY moved through each track seamlessly with little to no commentary, the energy shifted. Breaking their pattern of minimal commentary, Juhwan led the crowd to do a chant which I would soon learn to be the opening refrain of the anthemic *Don’t Stop*. And when the drums and the first few notes kicked in, Dayoung’s words sprang to life before my very eyes and ears.
 *Juhwan “handing” his microphone to the crowd to encourage us to chant along to Don’t Stop’s hook. Photo by Glenda Chong.*
*Dance away the whole night*
*Play the song*
*Here comes the waves, oh*
*Don't stop me, I feel the ocean*
*Don't stop me, we need no reason*
*Don't stop me, this is the moment*
*Keep me young and free, yeah*
In that moment - headbanging to the lyrics furiously, the live instruments booming through my chest, it was a feeling no headphones or sound device could ever replicate and my efforts would forever be in vain. It can never compare to the indelible impression left behind by the raw, intensified energy of the crowd and ADOY’s unified symphony of shared emotion.
As ADOY carried *Don’t Stop* in all its youthful defiance and boundless energy into 2025, it felt like more than a closing act; it was a moment of triumph. The night encapsulated the endless possibilities of the new year ahead, and for ADOY, the path is undeniably up.
-

@ f33c8a96:5ec6f741
2025-01-09 18:38:50
<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><video style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" controls>
<source src="https://plebdevs-bucket.nyc3.cdn.digitaloceanspaces.com/starter-lesson-5.mp4" type="video/mp4"/>
<source src="https://plebdevs-bucket.nyc3.cdn.digitaloceanspaces.com/starter-lesson-5.webm" type="video/webm"/>
</video></div>
# JavaScript: Building Your First Interactive Web App
## Introduction
In this lesson, we'll bring our web pages to life by adding dynamic functionality with JavaScript. We'll build a real-world application that displays and updates Bitcoin prices in real-time, teaching core JavaScript concepts along the way.
## Project Overview: Bitcoin Price Tracker
We'll build a web application that:
- Displays current Bitcoin price
- Updates automatically every 3 seconds
- Allows currency switching
- Includes interactive controls
- Shows current date/time
## Core JavaScript Concepts
### 1. Variables and Data Types
```javascript
// Variables can be declared with let or const
let currentCurrency = "USD"; // Can be changed
const interval = 3000; // Cannot be changed
// Basic data types
const price = 45000; // Number
const isVisible = true; // Boolean
const currency = "USD"; // String
```
### 2. DOM Manipulation
```javascript
// Getting elements
const priceElement = document.getElementById('price');
const button = document.getElementById('refresh-button');
// Modifying content
priceElement.textContent = `${price} ${currency}`;
// Changing styles
priceElement.style.display = 'none';
```
### 3. Event Listeners
```javascript
// Basic click handler
button.addEventListener('click', () => {
fetchBitcoinPrice();
});
// Change event for select elements
selector.addEventListener('change', (event) => {
handleCurrencyChange(event.value);
});
```
### 4. Async Operations & Fetch API
```javascript
async function fetchBitcoinPrice() {
try {
const response = await fetch(apiUrl);
const data = await response.json();
updatePrice(data.price);
} catch (error) {
console.error('Error:', error);
}
}
```
## Project Structure
### HTML Setup
```html
<!DOCTYPE html>
<html lang="en">
<head>
<title>Bitcoin Price Tracker</title>
<link rel="stylesheet" href="style.css">
<script src="index.js" defer></script>
</head>
<body>
<h1>Current Bitcoin Price</h1>
<p>The price is: <span id="price"></span></p>
<!-- Additional elements -->
</body>
</html>
```
### Core Functionality Implementation
1. **Setting Up the Timer**
```javascript
// Update price every 3 seconds
setInterval(fetchBitcoinPrice, 3000);
// Update date/time every second
setInterval(updateDateTime, 1000);
```
2. **Currency Selection**
```javascript
function handleCurrencyChange(newCurrency) {
currentCurrency = newCurrency;
fetchBitcoinPrice();
}
```
3. **Toggle Visibility**
```javascript
function togglePriceVisibility() {
const price = document.getElementById('price');
price.style.display = price.style.display === 'none'
? 'inline'
: 'none';
}
```
## Best Practices
### 1. Error Handling
- Always use try/catch with async operations
- Provide meaningful error messages
- Handle edge cases gracefully
### 2. Code Organization
- Keep functions focused and small
- Use meaningful variable names
- Group related functionality
- Add comments for clarity
### 3. Performance
- Avoid unnecessary DOM updates
- Use appropriate update intervals
- Clean up intervals when not needed
## Common Challenges & Solutions
### 1. API Issues
```javascript
// Handle API failures gracefully
catch (error) {
priceElement.textContent = 'Price unavailable';
console.error('API Error:', error);
}
```
### 2. Currency Formatting
```javascript
function formatPrice(price, currency) {
return new Intl.NumberFormat('en-US', {
style: 'currency',
currency: currency
}).format(price);
}
```
### 3. Time Zones
```javascript
function getLocalTime() {
return new Date().toLocaleString();
}
```
## Extending the Project
Consider adding these features for practice:
1. Price change indicators (up/down arrows)
2. Historical price chart
3. Multiple cryptocurrency support
4. Price alerts
5. Local storage for settings
## Debugging Tips
### Using Console
```javascript
console.log('Price fetched:', price);
console.error('Error occurred:', error);
console.table(priceHistory);
```
### Chrome DevTools
1. Network tab for API calls
2. Console for errors
3. Elements for DOM inspection
4. Sources for debugging
## Additional Resources
- MDN JavaScript Guide
- JavaScript.info
- CoinGecko API Documentation
- Chrome DevTools Documentation
## Next Steps
1. Add styling with CSS
2. Implement additional features
3. Learn about React for more complex applications
4. Explore other APIs and cryptocurrencies
Remember: The best way to learn is by doing. Don't be afraid to break things and experiment with the code. The developer console is your friend for debugging and understanding what's happening in your application.
Happy coding! 🚀
-

@ df173277:4ec96708
2025-01-09 17:13:20
> Maple AI combines the best of both worlds – encryption and personal AI – to create a truly private AI experience. Discuss personal and company items with Maple, we can't read them even if we wanted to.\
> [Join the waitlist to get early access.](https://trymaple.ai)
We are a culture of app users. Every day, we give our personal information to websites and apps, hoping they are safe. Location data, eating habits, financial details, and health information are just a few examples of what we entrust to third parties. People are now entering a new era of computing that promises next-level benefits when given even more personal data: AI.
Should we sacrifice our privacy to unlock the productivity gains of AI? Should we hope our information won't be used in ways we disagree? We believe we can have the best of both worlds – privacy and personal AI – and have built a new project called Maple AI. Chat between you and an AI with full end-to-end encryption. We believe it's a game-changer for individuals seeking private and secure conversations.
#### Building a Private Foundation
Maple is built on our flagship product, [OpenSecret](https://opensecret.cloud), a backend platform for app developers that turns private encryption on by default. [The announcement post for OpenSecret explains our vision for an encrypted world and what the platform can do.](https://primal.net/e/naddr1qvzqqqr4gupzphchxfm3ste32hfhkvczzxapme9gz5qvqtget6tylyd7wa8vjecgqqe5jmn5wfhkgatrd9hxwt20wpjku5m9vdex2apdw35x2tt9de3hy7tsw3jkgttzv93kketwvskhgur5w9nx5h52tpj) We think both users and developers benefit when sensitive personal information is encrypted in a private vault; it's a win-win.
#### The Power of Encrypted AI Chat
AI chat is a personal and intimate experience. It's a place to share your thoughts, feelings, and desires without fear of judgment. The more you share with an AI chatbot, the more powerful it becomes. It can offer personalized insights, suggestions, and guidance tailored to your unique needs and perspectives. However, this intimacy requires trust, and that's where traditional AI chatbots often fall short.
Traditional AI chats are designed to collect and analyze your data, often without your explicit consent. This data is used to improve the AI's performance, but it also creates a treasure trove of sensitive information that can be mined, sold, or even exploited by malicious actors. Maple AI takes a different approach. By using end-to-end encryption, we ensure that your conversations remain private and secure, even from us.
#### Technical Overview
So, how does Maple AI achieve this level of privacy and security? Here are some key technical aspects:
- **Private Key:** Each user has a unique private key that is automatically managed for them. This key encrypts and decrypts conversations, ensuring that only the user can access their data.
- **Secure Servers:** Our servers are designed with security in mind. We use secure enclaves to protect sensitive data and ensure that even our own team can't access your conversations.
- **Encrypted Sync:** One of Maple's most significant benefits is its encrypted sync feature. Unlike traditional AI chatbots, which store conversations in local storage or on standard cloud servers, Maple syncs your chats across all your devices. The private key managed by our secure servers means you can pick up where you left off on any device without worrying about your data being compromised.
- **Attestation and Open Code:** We publish our enclave code publicly. Using a process called attestation, users can verify that the code running on the enclave is the same as the code audited by the public.
- **Open Source LLM:** Maple uses major open-source models to maximize the openness of responses. The chat box does not filter what you can talk about. This transparency ensures that our AI is trustworthy and unbiased.
#### Personal and Work Use
Maple is secure enough to handle your personal questions and work tasks. Because we can't see what you chat about, you are free to use AI as an assistant on sensitive company items. Use it for small tasks like writing an important email or large tasks like developing your organization's strategy. Feed it sensitive information; it's just you and AI in the room. Attestation provides cryptographic proof that your corporate secrets are safe.
#### Local v Cloud
Today's AI tools provide different levels of privacy. The main options are to trust a third party with your unencrypted data, hoping they don't do anything with it, or run your own AI locally on an underpowered machine. We created a third option. Maple gives you the power of cloud computing combined with the privacy and security of a machine running on your desk. It's the best of both worlds.
#### Why the Maple name?
Privacy isn't just a human value - it's a natural one exemplified by the Maple tree. These organisms communicate with each other through a network of underground fungal hyphae, sending messages and sharing resources in a way that's completely invisible to organisms above ground. This discreet communication system allows Maple trees to thrive in even the most challenging environments. Our goal is to provide a way for everyone to communicate with AI securely so they can thrive in any environment.
#### Join the Waitlist
Maple AI will launch in early 2025 with free and paid plans. We can't wait to share it with the world. [Join our waitlist today to be among the first to experience the power of private AI chat.](https://trymaple.ai)

-

@ df173277:4ec96708
2025-01-09 17:12:08
> Maple AI combines the best of both worlds – encryption and personal AI – to create a truly private AI experience. Discuss personal and company items with Maple, we can't read them even if we wanted to.\
> [Join the waitlist to get early access.](https://trymaple.ai)
We are a culture of app users. Every day, we give our personal information to websites and apps, hoping they are safe. Location data, eating habits, financial details, and health information are just a few examples of what we entrust to third parties. People are now entering a new era of computing that promises next-level benefits when given even more personal data: AI.
Should we sacrifice our privacy to unlock the productivity gains of AI? Should we hope our information won't be used in ways we disagree? We believe we can have the best of both worlds – privacy and personal AI – and have built a new project called Maple AI. Chat between you and an AI with full end-to-end encryption. We believe it's a game-changer for individuals seeking private and secure conversations.
#### Building a Private Foundation
Maple is built on our flagship product, [OpenSecret](https://opensecret.cloud), a backend platform for app developers that turns private encryption on by default. [The announcement post for OpenSecret explains our vision for an encrypted world and what the platform can do.](nostr:naddr1qvzqqqr4gupzphchxfm3ste32hfhkvczzxapme9gz5qvqtget6tylyd7wa8vjecgqqe5jmn5wfhkgatrd9hxwt20wpjku5m9vdex2apdw35x2tt9de3hy7tsw3jkgttzv93kketwvskhgur5w9nx5h52tpj) We think both users and developers benefit when sensitive personal information is encrypted in a private vault; it's a win-win.
#### The Power of Encrypted AI Chat
AI chat is a personal and intimate experience. It's a place to share your thoughts, feelings, and desires without fear of judgment. The more you share with an AI chatbot, the more powerful it becomes. It can offer personalized insights, suggestions, and guidance tailored to your unique needs and perspectives. However, this intimacy requires trust, and that's where traditional AI chatbots often fall short.
Traditional AI chats are designed to collect and analyze your data, often without your explicit consent. This data is used to improve the AI's performance, but it also creates a treasure trove of sensitive information that can be mined, sold, or even exploited by malicious actors. Maple AI takes a different approach. By using end-to-end encryption, we ensure that your conversations remain private and secure, even from us.
#### Technical Overview
So, how does Maple AI achieve this level of privacy and security? Here are some key technical aspects:
- **Private Key:** Each user has a unique private key that is automatically managed for them. This key encrypts and decrypts conversations, ensuring that only the user can access their data.
- **Secure Servers:** Our servers are designed with security in mind. We use secure enclaves to protect sensitive data and ensure that even our own team can't access your conversations.
- **Encrypted Sync:** One of Maple's most significant benefits is its encrypted sync feature. Unlike traditional AI chatbots, which store conversations in local storage or on standard cloud servers, Maple syncs your chats across all your devices. The private key managed by our secure servers means you can pick up where you left off on any device without worrying about your data being compromised.
- **Attestation and Open Code:** We publish our enclave code publicly. Using a process called attestation, users can verify that the code running on the enclave is the same as the code audited by the public.
- **Open Source LLM:** Maple uses major open-source models to maximize the openness of responses. The chat box does not filter what you can talk about. This transparency ensures that our AI is trustworthy and unbiased.
#### Personal and Work Use
Maple is secure enough to handle your personal questions and work tasks. Because we can't see what you chat about, you are free to use AI as an assistant on sensitive company items. Use it for small tasks like writing an important email or large tasks like developing your organization's strategy. Feed it sensitive information; it's just you and AI in the room. Attestation provides cryptographic proof that your corporate secrets are safe.
#### Local v Cloud
Today's AI tools provide different levels of privacy. The main options are to trust a third party with your unencrypted data, hoping they don't do anything with it, or run your own AI locally on an underpowered machine. We created a third option. Maple gives you the power of cloud computing combined with the privacy and security of a machine running on your desk. It's the best of both worlds.
#### Why the Maple name?
Privacy isn't just a human value - it's a natural one exemplified by the Maple tree. These organisms communicate with each other through a network of underground fungal hyphae, sending messages and sharing resources in a way that's completely invisible to organisms above ground. This discreet communication system allows Maple trees to thrive in even the most challenging environments. Our goal is to provide a way for everyone to communicate with AI securely so they can thrive in any environment.
#### Join the Waitlist
Maple AI will launch in early 2025 with free and paid plans. We can't wait to share it with the world. [Join our waitlist today to be among the first to experience the power of private AI chat.](https://trymaple.ai)
[](https://trymaple.ai/waitlist)
-

@ df173277:4ec96708
2025-01-09 17:02:52
> OpenSecret is a backend for app developers that turns private encryption on by default. When sensitive data is readable only by the user, it protects both the user and the developer, creating a more free and open internet. We'll be launching in 2025. [Join our waitlist to get early access.](https://opensecret.cloud)
In today's digital age, personal data is both an asset and a liability. With the rise of data breaches and cyber attacks, individuals and companies struggle to protect sensitive information. The consequences of a data breach can be devastating, resulting in financial losses, reputational damage, and compromised user trust. In 2023, the average data breach cost was $5 million, with some resulting in losses of over $1 billion.
Meanwhile, individuals face problems related to identity theft, personal safety, and public embarrassment. Think about the apps on your phone, even the one you're using to read this. How much data have you trusted to other people, and how would it feel if that data were leaked online?
Thankfully, some incredibly talented cypherpunks years ago gave the world cryptography. We can encrypt data, rendering it a secret between two people. So why then do we have data breaches?
> Cryptography at scale is hard.
#### The Cloud
The cloud has revolutionized how we store and process data, but it has limitations. While cloud providers offer encryption, it mainly protects data in transit. Once data is stored in the cloud, it's often encrypted with a shared key, which can be accessed by employees, third-party vendors, or compromised by hackers.
The solution is to generate a personal encryption password for each user, make sure they write it down, and, most importantly, hope they don't lose it. If the password is lost, the data is forever unreadable. That can be overwhelming, leading to low app usage.
> Private key encryption needs a UX upgrade.
## Enter OpenSecret
OpenSecret is a developer platform that enables encryption by default. Our platform provides a suite of security tools for app developers, including private key management, encrypted sync, private AI, and confidential compute.
Every user has a private vault for their data, which means only they can read it. Developers are free to store less sensitive data in a shared manner because there is still a need to aggregate data across the system.

### Private Key Management
Private key management is the superpower that enables personal encryption per user. When each user has a unique private key, their data can be truly private. Typically, using a private key is a challenging experience for the user because they must write down a long autogenerated number or phrase of 12-24 words. If they lose it, their data is gone.
OpenSecret uses secure enclaves to make private keys as easy as an everyday login experience that users are familiar with. Instead of managing a complicated key, the user logs in with an email address or a social media account.
The developer doesn't have to manage private keys and can focus on the app's user experience. The user doesn't have to worry about losing a private key and can jump into using your app.

### Encrypted Sync
With user keys safely managed, we can synchronize user data to every device while maintaining privacy. The user does not need to do complicated things like scanning QR codes from one device to the next. Just log in and go.
The user wins because the data is available on all their devices. The developer wins because only the user can read the data, so it isn't a liability to them.
### Private AI
Artificial intelligence is here and making its way into everything. The true power of AI is unleashed when it can act on personal and company data. The current options are to run your own AI locally on an underpowered machine or to trust a third party with your data, hoping they don't read it or use it for anything.
OpenSecret combines the power of cloud computing with the privacy and security of a machine running on your desk.
**Check out Maple AI**\
Try private AI for yourself! We built an app built with this service called [Maple AI](https://trymaple.ai). It is an AI chat that is 100% private in a verifiable manner. Give it your innermost thoughts or embarrassing ideas; we can't judge you. We built Maple using OpenSecret, which means you have a private key that is automatically managed for you, and your chat history is synchronized to all your devices. [Learn more about Maple AI - Private chat in the announcement post.](https://blog.opensecret.cloud/maple-ai-private-encrypted-chat/)

### Confidential Compute
Confidential computing is a game-changer for data security. It's like the secure hardware that powers Apple Pay and Google Pay on your phone but in the cloud. Users can verify through a process called attestation that their data is handled appropriately. OpenSecret can help you run your own custom app backend code that would benefit from the security of an enclave.
It's the new version of that lock on your web browser. When you see it, you know you're secure.

#### **But do we want our secrets to be open?**
OpenSecret renders a data breach practically useless. If hackers get into the backend, they enter a virtual hallway of locked private vaults. The leaked data would be gibberish, a secret in the open that is unreadable.
On the topic of openness, OpenSecret uses the power of open source to enable trust in the service. We publish our code in the open, and, using attestation, anyone can verify that private data is being handled as expected. This openness also provides developers with a backup option to safely and securely export their data.
> Don't trust, verify.
### **Join the Movement**
We're currently building out OpenSecret, and we invite you to join us on the journey. Our platform can work with your existing stack, and you can pick and choose the features you need. If you want to build apps with encryption enabled, [send us a message to get early access.](https://opensecret.cloud)
Users and companies deserve better encryption and privacy.\
Together, let's make that a reality.
[](https://opensecret.cloud)
-

@ e373ca41:b82abcc5
2025-01-09 13:28:41
 
Heute Abend um 19 Uhr sprechen Elon Musk und Alice Weidel auf X. Der alternative Radiosender Kontrafunk aus der Schweiz bringt eine Übersetzung davon im Stream.
Da die Webseite des Kontrafunks gestern angegriffen wurde, ist hier der Stream unzensierbar aufrufbar, als kleines Back-up:
<https://stream.kontrafunk.radio/listen/kontrafunk/radio.mp3>
\
Im Nostr-Netzwerk dauerhauft auch u.a. **[hier](https://njump.me/naddr1qqxnzdenxc6rydejxymnwvfhqgswxu72gyq7ykjdfl9j556887jpzwu3mw3v9ez36quas55whq4te3grqsqqqa28qythwumn8ghj7urpwfjhgmewdehhxarjxyhxxmmdqvlg3v)** aufrufbar (falls wir angegriffen werden).
***
Tonight at 7 pm (CET), Elon Musk and Alice Weidel will be speaking on X. The alternative radio station Kontrafunk from Switzerland will be streaming a translation.
As the Kontrafunk website was attacked yesterday, the stream can be accessed uncensored here as a small backup:
<https://stream.kontrafunk.radio/listen/kontrafunk/radio.mp3>
In the Nostr network also permanently available **[here](https://njump.me/naddr1qqxnzdenxc6rydejxymnwvfhqgswxu72gyq7ykjdfl9j556887jpzwu3mw3v9ez36quas55whq4te3grqsqqqa28qythwumn8ghj7urpwfjhgmewdehhxarjxyhxxmmdqvlg3v)** (in case we are attacked).
***
ADVERTISEMENT:
*Looking for the easiest way to buy Bitcoin and store it yourself? The **[Relai app](https://relai.app/de/?af_xp=custom\&source_caller=ui\&pid=INFLUENCER\&is_retargeting=true\&af_click_lookback=7d\&shortlink=eo5zpzew\&af_channel=branded_url\&af_inactivity_window=30d\&c=Milosz%20Matuszek)** is the No. 1 crypto start-up and No. 2 of all fintech start-ups in Switzerland. **[Here you can buy Bitcoin](https://relai.app/de/?af_xp=custom\&source_caller=ui\&pid=INFLUENCER\&is_retargeting=true\&af_click_lookback=7d\&shortlink=eo5zpzew\&af_channel=branded_url\&af_inactivity_window=30d\&c=Milosz%20Matuszek)** in just a few steps and also set up savings plans. Nobody has access to your Bitcoin except you. With the referral code MILOSZ you save on fees (no financial advice). Disclaimer due to regulatory issues: The services of the Relai App are hereby only recommended to inhabitants of Switzerland or Italy.*

*Need more security? The **[Trezor wallets](https://trezor.io/trezor-safe-5-bitcoin-only?transaction_id=102e192a206d1585e56a2fddef6d83\&offer_id=238\&affiliate_id=35234)** are recommended and easy to use, others are available in the **[store](https://trezor.io/?transaction_id=102bc85bdca2733287749c7f879ebd\&offer_id=133\&affiliate_id=35234)**. Need more advice? Book an **[introductory meeting](https://trezor.io/trezor-expert-session?transaction_id=1020e18dad0aa4b1186289fd22e90f\&offer_id=241\&affiliate_id=35234)** with a wallet expert.*
***
***Join the marketplace of ideas!** We are building a publishing ecosystem on Nostr for citizen-journalism, starting with a client for blogging and newsletter distribution. Sound money and sound information should finally be in the hands of the people, right? Want to learn more about the [Pareto Project](https://pareto.space/en)? Zap me, if you want to contribute (all Zaps go to the project).*
***Update:** Since my last article on the [Pareto project](https://pareto.space/a/naddr1qqxnzdenxsenxdf5xgerwdfkqgswxu72gyq7ykjdfl9j556887jpzwu3mw3v9ez36quas55whq4te3grqsqqqa28qyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqf4hyum), we have received more than 50 messages from publications, journalists, authors, testers and supporters. Thank you very much, we are happy to help everyone become censorship-resistant! May just take a little time. Are you a publication and want to be part of it, test us, migrate your content to Nostr? Write to **<team@pareto.space>***
**Not yet on** **[Nostr](https://nostr.com/)** **and want the full experience?** Easy onboarding via **[Nosta.me.](https://nosta.me/create/welcome)**

-

@ 30ceb64e:7f08bdf5
2025-01-08 20:14:45
In a world dominated by surveillance banking and inflationary currencies, a new paradigm is emerging—one where individuals can operate sovereign, theft-resistant checking accounts using the world's hardest money. This isn't your grandfather's checking account; it's an entirely new financial operating system built on Bitcoin and Lightning technology.
---
## The Bitcoin Checking Account Revolution
Traditional checking accounts are permission-based systems where banks maintain ultimate control over your money. In contrast, a sovereign Bitcoin checking account operates on a fundamentally different principle: you hold your own keys, control your own node, and maintain custody of your funds at all times. This architecture is built on several key components:
- Self-hosted nodes providing direct network access
- Lightning channels for instant settlement
- Hardware wallets for secure key storage
- Non-custodial software interfaces
- Automated accounting and payment systems
The concept of a Bitcoin checking account represents a paradigm shift in daily financial operations. Imagine getting a direct deposit sent to your lightning node and using NWC and a variety of plug and play solutions to handle things regarding accounting, bill pay, and daily POS transactions. We're starting to see these options emerge through services like Bitcoin Well, Albyhub, Strike, Clams and Cash App.
## Breaking Free from Financial Surveillance
The current banking system tracks every transaction, creating a detailed financial surveillance network. Sovereign Bitcoin checking accounts offer a powerful alternative:
- Private lightning channels for daily transactions
- E-cash protocols for enhanced privacy
- Peer-to-peer transactions without intermediaries
- No account freezes or arbitrary limits
- Freedom from traditional banking hours and restrictions
Lightning and Cashu offer additional privacy and settlement speeds while enabling low cost transactions, and I believe these protocols will grow and exceed our expectations. The products and services for managing your bitcoin checking account will get more private and efficient as time moves forward.
## The Daily Operations Revolution
Operating a sovereign checking account transforms everyday financial activities:
1. Income Reception
- Direct deposit straight to Lightning
- Instant availability of funds
- No hold periods or bank delays
- Multiple invoice routes for different income streams
2. Payment Management
- Automated bill payments via Lightning
- Instant merchant settlements
- Cross-border transactions without fees
- Dynamic fee management for optimal efficiency
3. Liquidity Control
- Self-managed channel balances
- Cold storage integration for savings
- Automated rebalancing protocols
- Real-time capital efficiency
## The Deflationary Advantage
Perhaps the most revolutionary aspect is operating a checking account in deflationary money. This fundamentally changes spending psychology and financial planning:
- Each sat potentially appreciates over time
- Natural incentive for thoughtful spending
- Built-in savings mechanism
- Protection from currency debasement
## Global Market Integration
This new financial infrastructure enables seamless participation in the global economy:
- Borderless transactions
- 24/7 market access
- Direct international trade
- No forex fees or exchange rate manipulation
- Instant settlement across time zones
## Security and Resilience
The system's security model represents a significant advancement:
- Multi-signature protocols
- Timelocked recovery options
- Distributed backup systems
- Attack-resistant architecture
- No single points of failure
## The Future of Personal Banking
As this technology matures, we're likely to see:
- Simplified user interfaces
- Enhanced privacy tools
- Better integration with existing systems
- More automated financial management
- Increased merchant adoption
In conclusion, sovereign Bitcoin checking accounts represent more than just a new way to bank—they're a fundamental reset of the relationship between individuals and their money. This system combines the security of cold storage with the utility of traditional checking accounts, all while leveraging the strength of deflationary sound money. As adoption grows, these accounts will likely become the standard for those seeking financial sovereignty in an increasingly digital world.
---
The revolution isn't just about holding bitcoin—it's about using it in a way that maintains sovereignty while enabling practical daily finance. This is the future of money, and it's already here for those ready to embrace it.
-

@ bcea2b98:7ccef3c9
2025-01-08 18:22:00
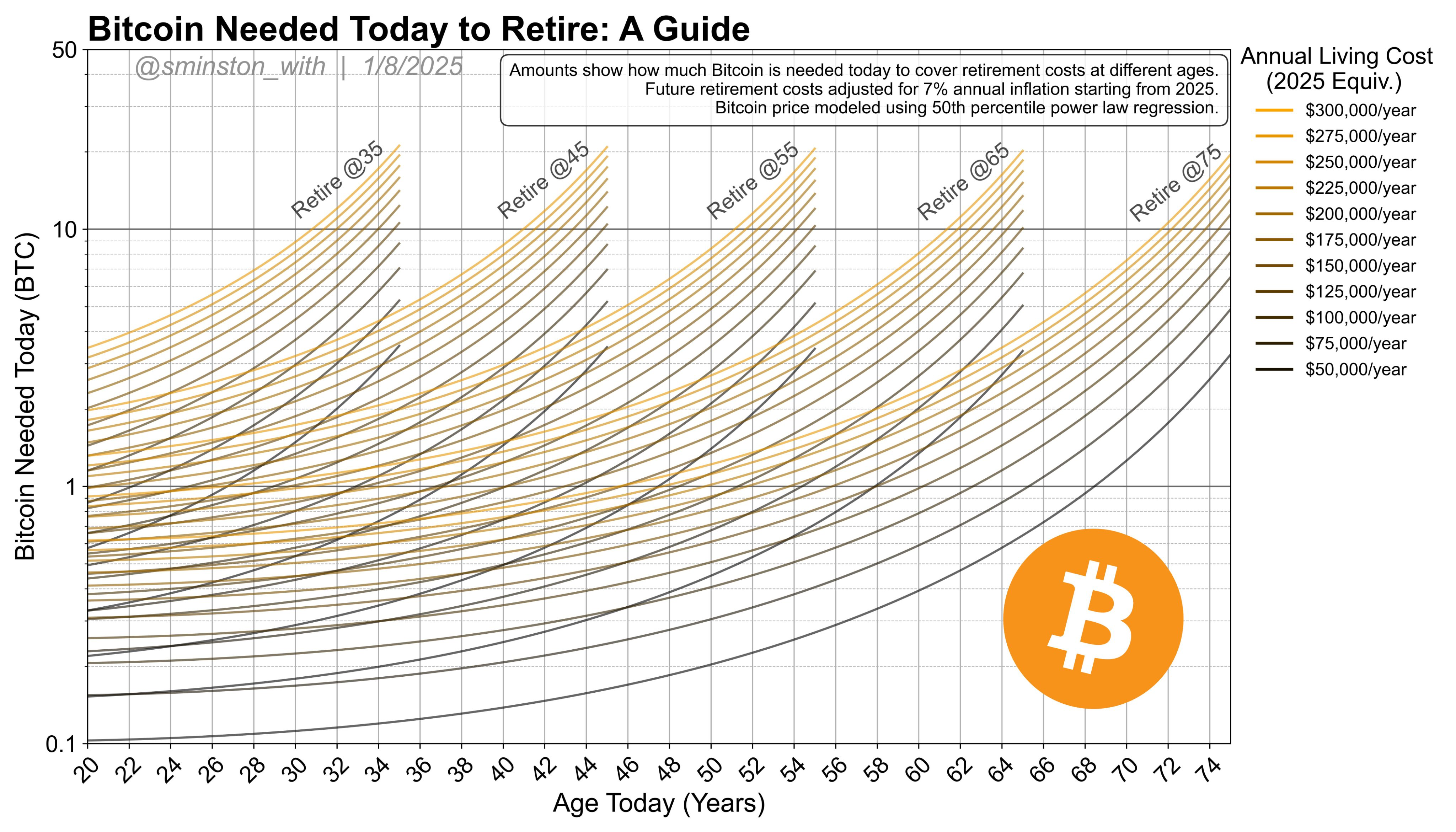
originally posted at https://stacker.news/items/842405
-

@ 23b0e2f8:d8af76fc
2025-01-08 18:17:52
## **Necessário**
- Um Android que você não use mais (a câmera deve estar funcionando).
- Um cartão microSD (opcional, usado apenas uma vez).
- Um dispositivo para acompanhar seus fundos (provavelmente você já tem um).
## **Algumas coisas que você precisa saber**
- O dispositivo servirá como um assinador. Qualquer movimentação só será efetuada após ser assinada por ele.
- O cartão microSD será usado para transferir o APK do Electrum e garantir que o aparelho não terá contato com outras fontes de dados externas após sua formatação. Contudo, é possível usar um cabo USB para o mesmo propósito.
- A ideia é deixar sua chave privada em um dispositivo offline, que ficará desligado em 99% do tempo. Você poderá acompanhar seus fundos em outro dispositivo conectado à internet, como seu celular ou computador pessoal.
---
## **O tutorial será dividido em dois módulos:**
- Módulo 1 - Criando uma carteira fria/assinador.
- Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador.
---
## **No final, teremos:**
- Uma carteira fria que também servirá como assinador.
- Um dispositivo para acompanhar os fundos da carteira.

---
## **Módulo 1 - Criando uma carteira fria/assinador**
1. Baixe o APK do Electrum na aba de **downloads** em <https://electrum.org/>. Fique à vontade para [verificar as assinaturas](https://electrum.readthedocs.io/en/latest/gpg-check.html) do software, garantindo sua autenticidade.
2. Formate o cartão microSD e coloque o APK do Electrum nele. Caso não tenha um cartão microSD, pule este passo.

3. Retire os chips e acessórios do aparelho que será usado como assinador, formate-o e aguarde a inicialização.

4. Durante a inicialização, pule a etapa de conexão ao Wi-Fi e rejeite todas as solicitações de conexão. Após isso, você pode desinstalar aplicativos desnecessários, pois precisará apenas do Electrum. Certifique-se de que Wi-Fi, Bluetooth e dados móveis estejam desligados. Você também pode ativar o **modo avião**.\
*(Curiosidade: algumas pessoas optam por abrir o aparelho e danificar a antena do Wi-Fi/Bluetooth, impossibilitando essas funcionalidades.)*

5. Insira o cartão microSD com o APK do Electrum no dispositivo e instale-o. Será necessário permitir instalações de fontes não oficiais.

6. No Electrum, crie uma carteira padrão e gere suas palavras-chave (seed). Anote-as em um local seguro. Caso algo aconteça com seu assinador, essas palavras permitirão o acesso aos seus fundos novamente. *(Aqui entra seu método pessoal de backup.)*

---
## **Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador.**
1. Criar uma carteira **somente leitura** em outro dispositivo, como seu celular ou computador pessoal, é uma etapa bastante simples. Para este tutorial, usaremos outro smartphone Android com Electrum. Instale o Electrum a partir da aba de downloads em <https://electrum.org/> ou da própria Play Store. *(ATENÇÃO: O Electrum não existe oficialmente para iPhone. Desconfie se encontrar algum.)*
2. Após instalar o Electrum, crie uma carteira padrão, mas desta vez escolha a opção **Usar uma chave mestra**.

3. Agora, no assinador que criamos no primeiro módulo, exporte sua chave pública: vá em **Carteira > Detalhes da carteira > Compartilhar chave mestra pública**.

4. Escaneie o QR gerado da chave pública com o dispositivo de consulta. Assim, ele poderá acompanhar seus fundos, mas sem permissão para movimentá-los.
5. Para receber fundos, envie Bitcoin para um dos endereços gerados pela sua carteira: **Carteira > Addresses/Coins**.
6. Para movimentar fundos, crie uma transação no dispositivo de consulta. Como ele não possui a chave privada, será necessário assiná-la com o dispositivo assinador.

7. No assinador, escaneie a transação não assinada, confirme os detalhes, assine e compartilhe. Será gerado outro QR, desta vez com a transação já assinada.

8. No dispositivo de consulta, escaneie o QR da transação assinada e transmita-a para a rede.
---
## **Conclusão**
**Pontos positivos do setup:**
- **Simplicidade:** Basta um dispositivo Android antigo.
- **Flexibilidade:** Funciona como uma ótima carteira fria, ideal para holders.
**Pontos negativos do setup:**
- **Padronização:** Não utiliza seeds no padrão BIP-39, você sempre precisará usar o electrum.
- **Interface:** A aparência do Electrum pode parecer antiquada para alguns usuários.
Nesse ponto, temos uma carteira fria que também serve para assinar transações. O fluxo de assinar uma transação se torna: ***Gerar uma transação não assinada > Escanear o QR da transação não assinada > Conferir e assinar essa transação com o assinador > Gerar QR da transação assinada > Escanear a transação assinada com qualquer outro dispositivo que possa transmiti-la para a rede.***
Como alguns devem saber, uma transação assinada de Bitcoin é praticamente impossível de ser fraudada. Em um cenário catastrófico, você pode mesmo que sem internet, repassar essa transação assinada para alguém que tenha acesso à rede por qualquer meio de comunicação. Mesmo que não queiramos que isso aconteça um dia, esse setup acaba por tornar essa prática possível.
---
-

@ 207ad2a0:e7cca7b0
2025-01-07 03:46:04
*Quick context: I wanted to check out Nostr's longform posts and this blog post seemed like a good one to try and mirror. It's originally from my [free to read/share attempt to write a novel](https://untitlednovel.dns7.top/contents/), but this post here is completely standalone - just describing how I used AI image generation to make a small piece of the work.*
Hold on, put your pitchforks down - outside of using Grammerly & Emacs for grammatical corrections - not a single character was generated or modified by computers; a non-insignificant portion of my first draft originating on pen & paper. No AI is ~~weird and crazy~~ imaginative enough to write like I do. The only successful AI contribution you'll find is a single image, the map, which I heavily edited. This post will go over how I generated and modified an image using AI, which I believe brought some value to the work, and cover a few quick thoughts about AI towards the end.
Let's be clear, I can't draw, but I wanted a map which I believed would improve the story I was working on. After getting abysmal results by prompting AI with text only I decided to use "Diffuse the Rest," a Stable Diffusion tool that allows you to provide a reference image + description to fine tune what you're looking for. I gave it this Microsoft Paint looking drawing:

and after a number of outputs, selected this one to work on:

The image is way better than the one I provided, but had I used it as is, I still feel it would have decreased the quality of my work instead of increasing it. After firing up Gimp I cropped out the top and bottom, expanded the ocean and separated the landmasses, then copied the top right corner of the large landmass to replace the bottom left that got cut off. Now we've got something that looks like concept art: not horrible, and gets the basic idea across, but it's still due for a lot more detail.

The next thing I did was add some texture to make it look more map like. I duplicated the layer in Gimp and applied the "Cartoon" filter to both for some texture. The top layer had a much lower effect strength to give it a more textured look, while the lower layer had a higher effect strength that looked a lot like mountains or other terrain features. Creating a layer mask allowed me to brush over spots to display the lower layer in certain areas, giving it some much needed features.

At this point I'd made it to where I felt it may improve the work instead of detracting from it - at least after labels and borders were added, but the colors seemed artificial and out of place. Luckily, however, this is when PhotoFunia could step in and apply a sketch effect to the image.

At this point I was pretty happy with how it was looking, it was close to what I envisioned and looked very visually appealing while still being a good way to portray information. All that was left was to make the white background transparent, add some minor details, and add the labels and borders. Below is the exact image I wound up using:

Overall, I'm very satisfied with how it turned out, and if you're working on a creative project, I'd recommend attempting something like this. It's not a central part of the work, but it improved the chapter a fair bit, and was doable despite lacking the talent and not intending to allocate a budget to my making of a free to read and share story.
#### The AI Generated Elephant in the Room
If you've read my non-fiction writing before, you'll know that I think AI will find its place around the skill floor as opposed to the skill ceiling. As you saw with my input, I have absolutely zero drawing talent, but with some elbow grease and an existing creative direction before and after generating an image I was able to get something well above what I could have otherwise accomplished. Outside of the lowest common denominators like stock photos for the sole purpose of a link preview being eye catching, however, I doubt AI will be wholesale replacing most creative works anytime soon. I can assure you that I tried numerous times to describe the map without providing a reference image, and if I used one of those outputs (or even just the unedited output after providing the reference image) it would have decreased the quality of my work instead of improving it.
I'm going to go out on a limb and expect that AI image, text, and video is all going to find its place in slop & generic content (such as AI generated slop replacing article spinners and stock photos respectively) and otherwise be used in a supporting role for various creative endeavors. For people working on projects like I'm working on (e.g. intended budget $0) it's helpful to have an AI capable of doing legwork - enabling projects to exist or be improved in ways they otherwise wouldn't have. I'm also guessing it'll find its way into more professional settings for grunt work - think a picture frame or fake TV show that would exist in the background of an animated project - likely a detail most people probably wouldn't notice, but that would save the creators time and money and/or allow them to focus more on the essential aspects of said work. Beyond that, as I've predicted before: I expect plenty of emails will be generated from a short list of bullet points, only to be summarized by the recipient's AI back into bullet points.
I will also make a prediction counter to what seems mainstream: AI is about to peak for a while. The start of AI image generation was with Google's DeepDream in 2015 - image recognition software that could be run in reverse to "recognize" patterns where there were none, effectively generating an image from digital noise or an unrelated image. While I'm not an expert by any means, I don't think we're too far off from that a decade later, just using very fine tuned tools that develop more coherent images. I guess that we're close to maxing out how efficiently we're able to generate images and video in that manner, and the hard caps on how much creative direction we can have when using AI - as well as the limits to how long we can keep it coherent (e.g. long videos or a chronologically consistent set of images) - will prevent AI from progressing too far beyond what it is currently unless/until another breakthrough occurs.
-

@ 378562cd:a6fc6773
2025-01-06 19:57:44
In our hyper-connected world, we are constantly bombarded with information — news of tragedies, celebrity gossip, and societal controversies — all delivered to us in real-time, whether we ask for it or not.
**But here’s a profound truth: If you don’t know about it, it doesn’t matter to you. It’s almost like it doesn’t even happen!**
This isn’t about apathy or ignoring the suffering of others. It’s about recognizing that our minds and hearts have limits. There’s only so much we can hold, care for, or act upon before it all becomes noise. And when we step back and filter out what truly matters to us, we find a liberating sense of peace.
In our hyper-connected world, we are constantly bombarded with information — news of tragedies, celebrity gossip, and societal controversies — all delivered to us in real-time, whether we ask for it or not.
# **When Knowing is a Burden**
Consider this: if a bus full of strangers tragically ran off a cliff halfway around the world, it’s undeniably sad. But if you never heard about it, would it affect your day, your thoughts, or your actions? It wouldn’t. Not because you’re heartless but because it’s not within your sphere of influence or awareness.
Similarly, when a celebrity you barely know goes through a messy divorce, why does that need to occupy your thoughts? If you never knew about it, it would make no difference in your life. And yet, the world shouts these details at us, demanding our attention for things that often have no real bearing on our existence.
# **The Cost of Knowing Too Much**
Knowing everything that happens everywhere comes with a cost:
- **Emotional Overload**\
The human mind isn’t designed to process the pain, suffering, or drama of millions of people at once. Constant exposure to these stories can lead to anxiety, sadness, or even a sense of helplessness.
- **Loss of Focus**\
The more attention we give to distant events or irrelevant gossip, the less energy we have for the people and moments that truly matter in our own lives.
- **Manufactured Cravings**\
Advertisements and media feed us desires we didn’t have before. A new product, a luxurious vacation, or a perfect lifestyle — all things you might not have craved if you hadn’t been shown them.
# **The Beauty of Not Knowing**
When you step away from the constant influx of information, you create space to focus on what’s real and meaningful in your life.
- **Your family and close friends.** Their joys and struggles are the ones you can genuinely care about and impact.
- **Your passions and goals.** These deserve your full attention, free from unnecessary distractions.
- **Your mental peace.** Without the noise, you can think clearly, feel deeply, and live authentically.
# **What Truly Matters?**
Not knowing isn’t about closing your eyes to the world. It’s about understanding the difference between what’s important and what’s irrelevant. It’s a practice of asking yourself:
- Does this affect me or the people I love?
- Can I do anything meaningful about this?
- Will knowing this bring me peace, joy, or purpose?
- Will BUYING this bring me peace, joy or purpose?
If the answer is no, it’s okay to let it go.
# **Living in Your Sphere of Influence**
Focusing on what you can control and care for has immense power. Your energy has the most impact in your sphere of influence—the people, places, and things you interact with directly.
By letting go of what lies outside that sphere, you free yourself from unnecessary burdens and find deeper joy in the things that truly matter.
# **A New Year’s Challenge**
This year, challenge yourself to embrace the art of *not knowing.*
- **Curate your inputs:** Limit news consumption to what directly affects you.
- **Mute the noise:** Avoid gossip, sensational headlines, and irrelevant drama.
- **Stay present:** Focus on the people and moments around you.
In doing so, you’ll find not only peace but also the clarity to live a life driven by your own values and priorities — not the ever-changing noise of the world.
# **The Freedom of Letting Go**
When you embrace the profound truth that *if you don’t know about it, it doesn’t matter to you,* you unlock a freedom that few ever experience. You stop carrying the weight of the world’s chaos and instead focus on the beauty, joy, and love within your own life.
This year, let’s make peace with not knowing — and in doing so, rediscover what truly matters.
# **Breaking Free from the Cycle of Consumerism**
Consumerism isn’t just about buying things — it’s about the constant hunger for more. More stuff, more information, more experiences. It thrives on the idea that what you have and who you are isn’t enough, and it manipulates you into believing that fulfillment lies just one purchase or experience away. But here’s the truth: the cycle of consumerism isn’t designed to fulfill you — it’s designed to keep you chasing.
If we want to find peace with not knowing, we must also confront the role consumerism plays in feeding our dissatisfaction and overstimulation.
# **The Problem with Consumerism**
Consumerism is fueled by two main forces:
- **Artificial Wants:** Advertising and media don’t just sell products; they sell dissatisfaction. They show you a life that seems better than yours and make you believe that buying their product will bridge the gap.
- **Overexposure:** The constant influx of social media, news, and targeted ads ensures you’re always aware of what you *don’t* have, subtly making you feel inadequate or left out.
- The result? A world where happiness feels like it’s always just out of reach — an exhausting race that benefits corporations far more than individuals.
# **The Cost of Consumerism**
The cycle of consumerism doesn’t just drain your wallet; it also takes a toll on your mental, emotional, and spiritual well-being:
- **Mental Overload:** Constant exposure to new products and ideas creates decision fatigue and anxiety.
- **Emotional Burnout:** Comparing your life to idealized versions portrayed in ads or social media can lead to dissatisfaction and low self-esteem.
- **Spiritual Disconnect:** Consumerism shifts your focus away from meaningful relationships, personal growth, and spiritual fulfillment, tethering your joy to material possessions.
# **Combatting Consumerism: A Game Plan for Freedom**
Breaking free from consumerism requires intentional effort, but it’s deeply rewarding. Here’s a game plan to start:
## **1. Detox Your Inputs**
- **Unfollow Excess:** Reduce your exposure to ads and influencers who push a lifestyle of constant consumption.
- **Limit Social Media:** Spend less time scrolling through content designed to spark envy or desire.
- **Set Boundaries:** Avoid shopping as a pastime or browsing “just to look.”
## **2. Shift Your Mindset**
- **Practice Gratitude:** Focus on what you already have, not what you lack.
- **Redefine Success:** Measure your life by relationships, growth, and experiences, not possessions.
- **Adopt Minimalism:** Learn to appreciate simplicity and find joy in having less.
## **3. Choose Quality Over Quantity**
- **Invest in Essentials:** Buy fewer items, but prioritize durability and quality.
- **Focus on Experiences:** Spend on memories, not material things.
- **Be Mindful of Upgrades:** Don’t replace what’s working fine just because something new is available.
## **4. Build Intentional Habits**
- **Wait Before Buying:** Give yourself 24 hours to think before making any purchase.
- **Create a Wishlist:** Write down non-essential items you want. Review the list monthly to see if you still want them.
- **Track Spending:** Be aware of where your money goes, and prioritize needs over wants.
## **5. Engage with Your Community**
- **Support Local:** Choose local businesses and artisans over big corporations.
- **Focus on Relationships:** Invest time in people, not possessions.
- **Participate in Sharing Economies:** Borrow, lend, and swap items with neighbors or friends instead of buying.
# **Living a Life of Intentional Simplicity**
This is food for thought and I promise you it is a battle at this point. It will be difficult but you must gain back control of your own thoughts, desires etc…
Take care and God bless!
-

@ 3f770d65:7a745b24
2025-01-05 18:56:33
New Year’s resolutions often feel boring and repetitive. Most revolve around getting in shape, eating healthier, or giving up alcohol. While the idea is interesting—using the start of a new calendar year as a catalyst for change—it also seems unnecessary. Why wait for a specific date to make a change? If you want to improve something in your life, you can just do it. You don’t need an excuse.
That’s why I’ve never been drawn to the idea of making a list of resolutions. If I wanted a change, I’d make it happen, without worrying about the calendar. At least, that’s how I felt until now—when, for once, the timing actually gave me a real reason to embrace the idea of New Year’s resolutions.
Enter [Olas](https://olas.app).
If you're a visual creator, you've likely experienced the relentless grind of building a following on platforms like Instagram—endless doomscrolling, ever-changing algorithms, and the constant pressure to stay relevant. But what if there was a better way? Olas is a Nostr-powered alternative to Instagram that prioritizes community, creativity, and value-for-value exchanges. It's a game changer.
Instagram’s failings are well-known. Its algorithm often dictates whose content gets seen, leaving creators frustrated and powerless. Monetization hurdles further alienate creators who are forced to meet arbitrary follower thresholds before earning anything. Additionally, the platform’s design fosters endless comparisons and exposure to negativity, which can take a significant toll on mental health.
Instagram’s algorithms are notorious for keeping users hooked, often at the cost of their mental health. I've spoken about this extensively, most recently at Nostr Valley, explaining how legacy social media is bad for you. You might find yourself scrolling through content that leaves you feeling anxious or drained. Olas takes a fresh approach, replacing "doomscrolling" with "bloomscrolling." This is a common theme across the Nostr ecosystem. The lack of addictive rage algorithms allows the focus to shift to uplifting, positive content that inspires rather than exhausts.
Monetization is another area where Olas will set itself apart. On Instagram, creators face arbitrary barriers to earning—needing thousands of followers and adhering to restrictive platform rules. Olas eliminates these hurdles by leveraging the Nostr protocol, enabling creators to earn directly through value-for-value exchanges. Fans can support their favorite artists instantly, with no delays or approvals required. The plan is to enable a brand new Olas account that can get paid instantly, with zero followers - that's wild.
Olas addresses these issues head-on. Operating on the open Nostr protocol, it removes centralized control over one's content’s reach or one's ability to monetize. With transparent, configurable algorithms, and a community that thrives on mutual support, Olas creates an environment where creators can grow and succeed without unnecessary barriers.
Join me on my New Year's resolution. Join me on Olas and take part in the [#Olas365](https://olas.app/search/olas365) challenge! It’s a simple yet exciting way to share your content. The challenge is straightforward: post at least one photo per day on Olas (though you’re welcome to share more!).
[Download on iOS](https://testflight.apple.com/join/2FMVX2yM).
[Download on Android](https://github.com/pablof7z/olas/releases/) or download via Zapstore.
Let's make waves together.
-

@ 30ceb64e:7f08bdf5
2025-01-05 16:11:46
Hey Freaks,
Another round of songs I've been listening to lately.
Un Sospiro slaps. Wind Tunnel hits me in the childhood.
https://music.youtube.com/watch?v=50A-Mssm6w8&si=OFa8UA-0o71k4ETK
https://music.youtube.com/watch?v=eMnxjdGTK4w&si=STFc4APblXLEp1Ig
https://music.youtube.com/watch?v=RpsN6b95DAQ&si=ixMQY5ZnyuPeum2O
https://music.youtube.com/watch?v=W91-jAQ2ijM&si=MhluAXuU1v_a86yW
https://music.youtube.com/watch?v=LMAhXhRsRXA&si=jo-UPFILXvZd8pS7
https://music.youtube.com/watch?v=53FDkWb7Mv4&si=lp4ikhtx39UqHzSA
https://music.youtube.com/watch?v=rrYMiAoGnVg&si=ya0qnGtbwCdyQ676
https://music.youtube.com/watch?v=Lk9Xwj0mnsI&si=OFMyBaXSO-Jyufxl
https://music.youtube.com/watch?v=057A1RdssoU&si=4lueg4C8Y3ac3LCE
https://music.youtube.com/watch?v=ghxzLw2wRis&si=wjgwjaPOJwo6-Cu2
https://music.youtube.com/playlist?list=PLmYfnnK_Qs5hOiZazXiwEoCdg1RiUvBBv&si=X4opO4goVt2K1T4D
Thanks,
Hustle
originally posted at https://stacker.news/items/838006
-

@ e6817453:b0ac3c39
2025-01-05 14:29:17
## The Rise of Graph RAGs and the Quest for Data Quality
As we enter a new year, it’s impossible to ignore the boom of retrieval-augmented generation (RAG) systems, particularly those leveraging graph-based approaches. The previous year saw a surge in advancements and discussions about Graph RAGs, driven by their potential to enhance large language models (LLMs), reduce hallucinations, and deliver more reliable outputs. Let’s dive into the trends, challenges, and strategies for making the most of Graph RAGs in artificial intelligence.
## Booming Interest in Graph RAGs
Graph RAGs have dominated the conversation in AI circles. With new research papers and innovations emerging weekly, it’s clear that this approach is reshaping the landscape. These systems, especially those developed by tech giants like Microsoft, demonstrate how graphs can:
* **Enhance LLM Outputs:** By grounding responses in structured knowledge, graphs significantly reduce hallucinations.
* **Support Complex Queries:** Graphs excel at managing linked and connected data, making them ideal for intricate problem-solving.
Conferences on linked and connected data have increasingly focused on Graph RAGs, underscoring their central role in modern AI systems. However, the excitement around this technology has brought critical questions to the forefront: How do we ensure the quality of the graphs we’re building, and are they genuinely aligned with our needs?
## Data Quality: The Foundation of Effective Graphs
A high-quality graph is the backbone of any successful RAG system. Constructing these graphs from unstructured data requires attention to detail and rigorous processes. Here’s why:
* **Richness of Entities:** Effective retrieval depends on graphs populated with rich, detailed entities.
* **Freedom from Hallucinations:** Poorly constructed graphs amplify inaccuracies rather than mitigating them.
Without robust data quality, even the most sophisticated Graph RAGs become ineffective. As a result, the focus must shift to refining the graph construction process. Improving data strategy and ensuring meticulous data preparation is essential to unlock the full potential of Graph RAGs.
## Hybrid Graph RAGs and Variations
While standard Graph RAGs are already transformative, hybrid models offer additional flexibility and power. Hybrid RAGs combine structured graph data with other retrieval mechanisms, creating systems that:
* Handle diverse data sources with ease.
* Offer improved adaptability to complex queries.
Exploring these variations can open new avenues for AI systems, particularly in domains requiring structured and unstructured data processing.
## Ontology: The Key to Graph Construction Quality
Ontology — defining how concepts relate within a knowledge domain — is critical for building effective graphs. While this might sound abstract, it’s a well-established field blending philosophy, engineering, and art. Ontology engineering provides the framework for:
* **Defining Relationships:** Clarifying how concepts connect within a domain.
* **Validating Graph Structures:** Ensuring constructed graphs are logically sound and align with domain-specific realities.
Traditionally, ontologists — experts in this discipline — have been integral to large enterprises and research teams. However, not every team has access to dedicated ontologists, leading to a significant challenge: How can teams without such expertise ensure the quality of their graphs?
## How to Build Ontology Expertise in a Startup Team
For startups and smaller teams, developing ontology expertise may seem daunting, but it is achievable with the right approach:
1. **Assign a Knowledge Champion:** Identify a team member with a strong analytical mindset and give them time and resources to learn ontology engineering.
2. **Provide Training:** Invest in courses, workshops, or certifications in knowledge graph and ontology creation.
3. **Leverage Partnerships:** Collaborate with academic institutions, domain experts, or consultants to build initial frameworks.
4. **Utilize Tools:** Introduce ontology development tools like Protégé, OWL, or SHACL to simplify the creation and validation process.
5. **Iterate with Feedback:** Continuously refine ontologies through collaboration with domain experts and iterative testing.
So, it is not always affordable for a startup to have a dedicated oncologist or knowledge engineer in a team, but you could involve consulters or build barefoot experts.
You could read about barefoot experts in my article :
Even startups can achieve robust and domain-specific ontology frameworks by fostering in-house expertise.
## How to Find or Create Ontologies
For teams venturing into Graph RAGs, several strategies can help address the ontology gap:
1. **Leverage Existing Ontologies:** Many industries and domains already have open ontologies. For instance:
* **Public Knowledge Graphs:** Resources like Wikipedia’s graph offer a wealth of structured knowledge.
* **Industry Standards:** Enterprises such as Siemens have invested in creating and sharing ontologies specific to their fields.
* **Business Framework Ontology (BFO):** A valuable resource for enterprises looking to define business processes and structures.
1. **Build In-House Expertise:** If budgets allow, consider hiring knowledge engineers or providing team members with the resources and time to develop expertise in ontology creation.
2. **Utilize LLMs for Ontology Construction:** Interestingly, LLMs themselves can act as a starting point for ontology development:
* **Prompt-Based Extraction:** LLMs can generate draft ontologies by leveraging their extensive training on graph data.
* **Domain Expert Refinement:** Combine LLM-generated structures with insights from domain experts to create tailored ontologies.
## Parallel Ontology and Graph Extraction
An emerging approach involves extracting ontologies and graphs in parallel. While this can streamline the process, it presents challenges such as:
* **Detecting Hallucinations:** Differentiating between genuine insights and AI-generated inaccuracies.
* **Ensuring Completeness:** Ensuring no critical concepts are overlooked during extraction.
Teams must carefully validate outputs to ensure reliability and accuracy when employing this parallel method.
## LLMs as Ontologists
While traditionally dependent on human expertise, ontology creation is increasingly supported by LLMs. These models, trained on vast amounts of data, possess inherent knowledge of many open ontologies and taxonomies. Teams can use LLMs to:
* **Generate Skeleton Ontologies:** Prompt LLMs with domain-specific information to draft initial ontology structures.
* **Validate and Refine Ontologies:** Collaborate with domain experts to refine these drafts, ensuring accuracy and relevance.
However, for validation and graph construction, formal tools such as OWL, SHACL, and RDF should be prioritized over LLMs to minimize hallucinations and ensure robust outcomes.
## Final Thoughts: Unlocking the Power of Graph RAGs
The rise of Graph RAGs underscores a simple but crucial correlation: improving graph construction and data quality directly enhances retrieval systems. To truly harness this power, teams must invest in understanding ontologies, building quality graphs, and leveraging both human expertise and advanced AI tools.
As we move forward, the interplay between Graph RAGs and ontology engineering will continue to shape the future of AI. Whether through adopting existing frameworks or exploring innovative uses of LLMs, the path to success lies in a deep commitment to data quality and domain understanding.
Have you explored these technologies in your work? Share your experiences and insights — and stay tuned for more discussions on ontology extraction and its role in AI advancements. Cheers to a year of innovation!
-

@ 6ad3e2a3:c90b7740
2025-01-05 14:26:34
Maybe it’s because I watched [The Omen](https://www.youtube.com/watch?v=mDHisWRsE98) at way too young an age, or maybe it’s because the Book of Revelation’s “mark of the beast” allegory is playing out too literally for my tastes, but having already written about the [Second Coming](https://www.chrisliss.com/the_second_coming), it only follows I should speculate as to its counterpart.
As I mentioned in [The Second Coming](https://www.chrisliss.com/the_second_coming), it’s dangerous to take the myths from our ancestors too literally. They used the symbols of their times, and we should be careful not to confuse the mental maps they had of their world with reality itself. That said, we should also not be dismissive — Mozart didn’t have fancy music editing software, but his genius using the modalities of the time was real. To the extent our forebears offered us their wisdom about the nature of man and forces within him we should endeavor to understand it. The technology and the symbols may have changed, but our essential nature is ever the same.
Just as the second coming of Christ would free man from tyranny, the Antichrist would be its imposition. And just as I speculated that Jesus might not return in the form of a person, it’s likely neither would his counterpart. But if Satoshi, Bitcoin’s pseudonymous creator, can be the face, so to speak, representing the movement toward freedom and God, who and what would represent its antithesis? Let’s speculate.
It would have to be someone charismatic, a person the multitudes would want to follow and in whom to look for reassurance. That eliminates villains du jour like Bill Gates, Klaus Schwab and Vladimir Putin. If that’s who Satan is sending, he’s not sending his best. What about Donald Trump? More charismatic, much more popular appeal. He’s a better choice than the first group, but while street-smart, he lacks refined intelligence and is too despised by wide swaths of the population. He’s also probably too old.
For a while, I would have said Barack Obama was the best candidate, and even some hard-core right wingers agreed (it’s hilarious that this [claim was actually fact-checked](https://www.snopes.com/fact-check/anti-maim/)! — you can’t fact-check whether someone is the Antichrist!) Obama was relatively young, vital enough, popular, charismatic and intelligent. But he’s faded from view the last few years and has been a surprisingly inconsequential former president.
That leaves one person of whom I can think with the qualities and societal position to fill the role. Regrettably it’s someone I like, but of course I would like the Antichrist! If he weren’t likable he wouldn’t be the Antichrist.
That person is Elon Musk.
Musk is the richest person in the world, among the most followed on Twitter, has a borderline worshipful fanbase and big plans for improving humanity. Musk is young enough, he’s probably a genius and considering a private takeover of arguably the world’s most important communications network. He’s also a big player in satellites, energy, transportation and [internet provision](https://twitter.com/elonmusk/status/1530234643219243009?s=20&t=olDDLEAUBFhreDIltCPkkQ).
Musk says lots of sensible things with which I agree about free speech and rights. He is the perfect foil to the [out-of-central-casting](https://unlimitedhangout.com/2021/02/investigative-reports/schwab-family-values/) Schwab supervillain. As Edward Dowd speculated:
But, you might object, if Musk is the foil to Schwab’s terrible ideas, isn’t that good for humanity? How could the Antichrist be for [free speech](https://twitter.com/elonmusk/status/1519036983137509376?s=20&t=olDDLEAUBFhreDIltCPkkQ), [renewable energy](https://twitter.com/elonmusk/status/1532030554778087424?s=20&t=olDDLEAUBFhreDIltCPkkQ), [population expansion](https://twitter.com/elonmusk/status/1529193812949614594?s=20&t=PIRRovWYIIUSQY5Uw7dFpw)? Again, of course, the Antichrist is going to have good, sensible ideas! But as Marshall McLuhan said, “[The medium is the message](https://www.brainyquote.com/quotes/marshall_mcluhan_157742).”
Or, more aptly, the top-down messianic complex is the message.
Musk has [long discussed saving humanity](https://twitter.com/elonmusk/status/1533410745429413888?s=20&t=gTsO-6ltAFVOs4SJP-VmpQ) via expansion into space and sustainable energy. But in order to save humanity, one must exert some control over it. While Musk’s Twitter takeover from the [ineffectual woke scolds](https://nypost.com/2022/05/18/good-riddance-to-the-ministry-of-truth-nina-jankowicz/) is getting most of the press, [this is also going on](https://finance.yahoo.com/news/elon-musk-says-neuralinks-brain-155733754.html):
Klaus Schwab’s pitch to own nothing and eat bugs is weak, but Musk, via brain implant, could potentially create a more satisfying virtual experience than most could hope to achieve in reality. And what could be more tantamount to complete control than letting someone else get the keys to the very organ of perception itself?

Well don’t get the implant then. Just get in your Tesla and drive away. But electric cars don’t work that way — they are attached to the grid, trackable and capable of [being shut down remotely](https://tekdeeps.com/elon-musk-is-being-pressured-to-shut-down-tesla-cars-in-russia/). And that’s before we consider driverless cars in which there would be even less privacy and autonomy. Moreover, Teslas [track the driver’s movements](https://www.carscoops.com/2020/10/tesla-model-3s-interior-camera-tracking-eye-and-head-movement/) already to an extent combustion-engine cars do not, ostensibly to inform the developing AI, but uses for technology evolve over time — sending email and paying bills over the internet was commonplace in 2000, but now people are micro-tracked by Facebook and Google.
One could object that Musk has, to-date, used his influence for good. But that makes it no less dangerous to entrust him with so much power: J.R.R. Tolkien understood this clearly:
*“You are wise and powerful. Will you not take the Ring?”*
*“No!” cried Gandalf, springing to his feet. “With that power I should have power too great and terrible. And over me the Ring would gain a power still greater and more deadly.” His eyes flashed and his face was lit as by a fire within. “Do not tempt me! For I do not wish to become like the Dark Lord himself. Yet the way of the Ring to my heart is by pity, pity for weakness and the desire of strength to do good. Do not tempt me! I dare not take it, not even to keep it safe, unused. The wish to wield it would be too great for my strength. I shall have such need of it. Great perils lie before me.”*
*-- The Lord of the Rings*
Beyond [Neuralink](https://neuralink.com/), Musk also seems to have a strong utilitarian bent:
In this [paper](https://www.nickbostrom.com/astronomical/waste.html) Nick Bostrom makes the case that delaying technological advancement could cost humanity astronomical amounts of well-being because every moment we delay, stars are burning out, useful energy is being sucked into black holes, irreversible entropy is happening apace, depriving us of future potential. Bostrom translates it into potential human lives lost (or more aptly, never having been born) on account of this permanent loss.
While Bostrom’s framework seems benign — who is against collective human happiness in the form of more worthwhile lives? — it’s actually a form of utilitarianism that tries to sum the totality of human happiness over the entire species rather than to consider, as Immanuel Kant would, [each individual as an end in himself](https://assets.cambridge.org/97811070/08519/frontmatter/9781107008519_frontmatter.pdf). This viewing of the collective good as the optimal outcome has been used to justify many of history’s worst atrocities. To create a master race, to make sure everyone gets the same amount, to protect the world from covid, we must do whatever it takes!
If, per Bostrom’s math, one harnessed black hole were worth quadrillions of lives, it would, for example, seem an easy call to sacrifice a bunch of selfish losers on earth who stood in the way of creating the technology for doing so. Utilitarianism, ironically, winds up failing miserably by its own metric because (a) it can so easily be manipulated by whoever is maintaining the “greater good” spread sheet, which just happens to coincide with one’s ambitions; and (b) because it’s absurd to think you can calculate aggregate good for octillions of lives so far into an unknowable future. As such, while Musk’s pitch is more persuasive than Schwab’s or Gates’, it’s ultimately part of the same dangerous philosophy which is: “Let me optimize for total human happiness on your behalf.”
Contrast Musk’s top-down humanity-saving endeavors with Bitcoin which is purely opt-in, works with simple incentives and imposes no value judgments on its users. It’s a [truth-recording clock](https://dergigi.com/2021/01/14/bitcoin-is-time/), impervious to fraud and cooption by the powerful. No matter how wealthy or powerful a person is, he cannot control the network or get treated with special privileges. Bitcoin’s finite supply means governments cannot print more of it, cannot finance unpopular wars or massive giveaways to the military and pharmaceutical industrial complexes. Instead of trusting any particular powerful person (the president, Elon Musk, Bill Gates) to be good, it simply removes the incentives toward and reduces the capacity for evil.
*The supreme good is like water, which nourishes all things without trying to. It is content with the low places that people disdain. Thus it is like the Tao.*
*From the [Tao Te Ching](http://albanycomplementaryhealth.com/wp-content/uploads/2016/07/TaoTeChing-LaoTzu-StephenMitchellTranslation-33p.pdf) (Lao Tse — translated by Stephen Mitchell)*
We simply need the right conditions, the proper axioms on which to build. Just as the US Constitution created the framework for the most prosperous society in the history of the world, bitcoin will provide the axioms for peace, the harnessing of stranded energy and the [low-time preference](https://saifedean.com/podcast/84-hard-money-and-time-preference-lecture-at-the-property-freedom-society/) required for a more prosperous future.
But it won’t be the future brought to you by Elon Musk, and ultimately I foresee a clash between the two. One tell is his otherwise inexplicable [promotion of Dogecoin](https://twitter.com/elonmusk/status/1530209049261658112?s=20&t=gTsO-6ltAFVOs4SJP-VmpQ) as a possible currency for Tesla purchases. Dogecoin was [literally a joke](https://thecryptobasic.com/2022/06/03/doge-founder-says-every-project-started-now-is-made-to-enrich-creators-at-the-expense-of-community/?utm_source=rss&utm_medium=rss&utm_campaign=doge-founder-says-every-project-started-now-is-made-to-enrich-creators-at-the-expense-of-community) from its creator and of course has none of the security, decentralization or censorship resistance of bitcoin. Musk is too smart not to know that — he put a couple billion dollars of Tesla’s balance sheet in bitcoin already and almost certainly understands the value proposition. That he still cites Doge seriously would be a clever way to muddy the waters about what bitcoin is vs what blockchain-based “crypto” is. And of course the Antichrist would avail himself of bitcoin, if only to obfuscate his real intentions and also to be able to crash the price by selling, if necessary, at an opportune time.
The Klaus Schwab-Bill Gates-WEF set have already lost. They are widely despised, central banks are flailing, once-trusted institutions like the legacy media, major science and medical journals, the WHO, CDC and FDA are hemorrhaging influence. People are unhappy and looking for someone or something to trust. Elon Musk could fill that void, and if he does, he will be The Final Boss, the last false idol that needs to be discarded before humanity can, through its own efforts, enjoy a new era of prosperity, the [Second Coming](https://www.chrisliss.com/the_second_coming), so to speak.
I actually suspect Musk is genuine in his desire to help humanity via his vision and am pretty sure he doesn’t have 666 embedded in his scalp — in any case even Damian in The Omen [neither knew who he was nor wanted to be](https://www.youtube.com/watch?v=QFNqkxFljvk) the Antichrist! But the most dangerous people for humanity are those with the biggest plans for it.
Or put more succinctly:

-

@ 228dde34:b5d0345e
2025-01-05 10:30:04
##### BY Joanna Hu
##### Editorial Admin
##### Hype Issue #60
###### Join JOANNA HU as she delves into the world of Epic: The Musical, and explores the way it has brought an old tale into the hearts of new audiences.
 *Photo from Jorge Rivera-Herrans’ YouTube page.*
Over the past five years, Epic: The Musical has taken the internet by storm. Created by Puerto Rican artist Jorge Rivera-Herrans, known on social media as Jay Herrans, Epic is a sung-through retelling of Homer’s Odyssey. Blending influences from video games, anime, and manga, the musical is a nine-part series of audio-only concept albums. With a total of 40 songs across the nine sagas split into two acts, the story follows Odysseus – voiced by Rivera-Herrans himself – on his harrowing journey home after the Trojan War.
With the latest release of the Ithaca Saga on December 25, 2024, the musical is finally complete, after two years of musical releases. Over its lifespan, Epic has garnered a massive and devoted fanbase, boasting millions of streams per song and over 100,000 members in its Discord community.
So now, as the musical finally comes to a close, this breakthrough hit has left us asking: how exactly did Rivera-Herrans manage to captivate so many people with a story that has been around for over two thousand years?
 *Jorge Rivera-Herrans, the creator of Epic: The Musical. Photo from Rivera-Herrans’ Facebook page (@JayHerrans).*
### Telling a story through music
Like most musicals, Epic primarily tells its tale through music and its catchy, and sometimes humorous, lyrics. However, what really sets it apart from the crowd is the details in its intricate composition.
Inspired by Peter and the Wolf, Sergei Prokofiev’s famous musical composition where different instruments are used to represent different characters, Rivera-Herrans takes a similar approach in Epic. Key characters are symbolized by distinct instruments — for example, Odysseus is embodied by a guitar, while Athena, his mentor, is characterized by the ticking of a metronome and running piano notes.
 *Peter and the Wolf cover art from a 1959 Soviet vinyl. Photo taken from People’s World.*
Recurring melodic motifs further enrich the listening experience, serving as callbacks to earlier moments, foreshadowing future events, or drawing parallels between different points in the story. These motifs add layers of depth; building tension and anticipation, and tugging on the heartstrings of fans who listen closely enough to notice them.
Unlike traditional musicals, where stage or film visuals can be counted on to bring scenes to life, Epic has to rely almost entirely on sound. Although almost all the songs in the musical are conversation-based, it does not make the story any harder to follow. Beyond the instrumental and lyrical composition, Rivera-Herrans incorporates sound effects, like the roar of a monster or the twang of an arrow, directly into the music without it seeming out of place, immersing listeners in the world of the Odyssey without visual aids or scene descriptions. Combined with the motifs and lyrics, these audio cues make the narrative easy to follow, while also offering a treasure trove of Easter eggs for dedicated fans and musicians.
### The ‘TikTok musical’ and its digital fanbase
Epic has sometimes been dubbed a ‘TikTok musical’, thanks to Rivera-Herrans’ extensive use of the platform throughout the project. In January 2021, when Epic was still in its early drafting stage, Rivera-Herrans shared a snippet of an early version of “Full Speed Ahead”, a song from the first saga, on TikTok. From there, he began posting clips of other song drafts, along with behind-the-scenes glimpses and explanations of his creative process. As such, Rivera-Herrans’ social media platforms have become a detailed documentation of Epic’s progress and evolution.
 *Rivera-Herrans’ first post on TikTok about Epic: The Musical. Photo from TikTok.*
Rivera-Herrans also used TikTok for casting calls, posting instrumental tracks for the characters’ main songs and inviting any and all interested candidates to audition by duetting his videos. This unconventional approach not only opened up opportunities for a wide range of talent but also boosted Epic's visibility, as auditioning candidates would share their videos with their own followers, further spreading awareness of the musical.
 *Rivera-Herrans casting call on TikTok for the role of Calypso. Photo from TikTok.*
### Engaging the community
Rivera-Herrans has fostered a strong sense of community among Epic fans. With each saga’s release, he hosts a livestream listening party, featuring animatics and artworks created by his fans with his input, bringing his vision to life. Not just that,he also frequently reposts fan art and animatics created independently after the official release of the sagas on his social media, crediting the artists and showing his appreciation. Rivera-Herrans also created the official Epic Discord server, providing fans with a dedicated space to discuss the musical and connect with one another, further deepening their engagement.
 *Listening party on YouTube for the release of the Wisdom Saga. Photo from YouTube.*
### Taking creative liberties
Like many modern adaptations of old stories, Epic takes some creative liberties with its source material. Some choices were intentional, aiming to humanise the characters and make them more relatable. Others, like a deviation in the timeline and the description of the Wind God Aeolus’ island, were unintentional, which Rivera-Herrans has openly acknowledged as a mistake on his part.
As such, Epic is not a carbon copy of the Odyssey, and Rivera-Herrans has even encouraged fans to read the original tale for themselves. Nonetheless, the musical still serves as a gateway into the world of Greek mythology, and still maintains the spirit of the Odyssey in a way that appeals to the modern audience.
### What comes next for Epic: The Musical?
With the release of the musical’s concluding chapter, the Ithaca saga, on December 25, 2024, the nine-part musical has now come to a close, leaving many fans speculating about the future of the series. Fortunately for fans of the show, several executive decisions in the musical’s past may leave the door open for future development in the world of Epic.
In 2023, after disputes with his original licensing company, which had failed to pay royalties for the first two sagas, Rivera-Herrans founded his own company, Winion Entertainment LLC. Under this new banner, the cast re-recorded the entire first two sagas – the Troy and Cyclops sagas – releasing them alongside the Thunder Saga. With Winion Entertainment, Rivera-Herrans now has the potential to expand Epic into new business ventures which, as many fans hope, could include merchandise and future adaptations of the musical for film or stage.
So, if you are a fan of Epic: The Musical, you might want to keep an eye out for any potential work from Rivera-Herrans in the future.
 *‘Winions’ are Rivera-Herrans’ name for the Wind God Aeolus’ subjects, who appear as backing vocals in the song “Keeep Your Friends Close”. Photo from Epic: The Musical Wiki.*
-

@ eac63075:b4988b48
2025-01-04 19:41:34
Since its creation in 2009, Bitcoin has symbolized innovation and resilience. However, from time to time, alarmist narratives arise about emerging technologies that could "break" its security. Among these, quantum computing stands out as one of the most recurrent. But does quantum computing truly threaten Bitcoin? And more importantly, what is the community doing to ensure the protocol remains invulnerable?
The answer, contrary to sensationalist headlines, is reassuring: Bitcoin is secure, and the community is already preparing for a future where quantum computing becomes a practical reality. Let’s dive into this topic to understand why the concerns are exaggerated and how the development of BIP-360 demonstrates that Bitcoin is one step ahead.
---
## What Is Quantum Computing, and Why Is Bitcoin Not Threatened?
Quantum computing leverages principles of quantum mechanics to perform calculations that, in theory, could exponentially surpass classical computers—and it has nothing to do with what so-called “quantum coaches” teach to scam the uninformed. One of the concerns is that this technology could compromise two key aspects of Bitcoin’s security:
1. **Wallets**: These use elliptic curve algorithms (ECDSA) to protect private keys. A sufficiently powerful quantum computer could deduce a private key from its public key.
2. **Mining**: This is based on the SHA-256 algorithm, which secures the consensus process. A quantum attack could, in theory, compromise the proof-of-work mechanism.
---
## Understanding Quantum Computing’s Attack Priorities
While quantum computing is often presented as a threat to Bitcoin, not all parts of the network are equally vulnerable. Theoretical attacks would be prioritized based on two main factors: ease of execution and potential reward. This creates two categories of attacks:
### 1. Attacks on Wallets
Bitcoin wallets, secured by elliptic curve algorithms, would be the initial targets due to the relative vulnerability of their public keys, especially those already exposed on the blockchain. Two attack scenarios stand out:
- **Short-term attacks**: These occur during the interval between sending a transaction and its inclusion in a block (approximately 10 minutes). A quantum computer could intercept the exposed public key and derive the corresponding private key to redirect funds by creating a transaction with higher fees.
- **Long-term attacks**: These focus on old wallets whose public keys are permanently exposed. Wallets associated with Satoshi Nakamoto, for example, are especially vulnerable because they were created before the practice of using hashes to mask public keys.
We can infer a priority order for how such attacks might occur based on urgency and importance.
Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)
### 2. Attacks on Mining
Targeting the SHA-256 algorithm, which secures the mining process, would be the next objective. However, this is far more complex and requires a level of quantum computational power that is currently non-existent and far from realization. A successful attack would allow for the recalculation of all possible hashes to dominate the consensus process and potentially "mine" it instantly.
---
Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin Attacks
Recently, Narcelio asked me about a statement I made on Tubacast:
https://x.com/eddieoz/status/1868371296683511969
If an attack became a reality **before Bitcoin was prepared**, it would be necessary to define the last block prior to the attack and proceed from there using a new hashing algorithm. The solution would resemble the response to the infamous 2013 bug. It’s a fact that this would cause market panic, and Bitcoin's price would drop significantly, creating a potential opportunity for the well-informed.
Preferably, if developers could anticipate the threat and had time to work on a solution and build consensus before an attack, they would simply decide on a future block for the fork, which would then adopt the new algorithm. It might even rehash previous blocks (reaching consensus on them) to avoid potential reorganization through the re-mining of blocks using the old hash. (I often use the term "shielding" old transactions).
---
## How Can Users Protect Themselves?
While quantum computing is still far from being a practical threat, some simple measures can already protect users against hypothetical scenarios:
- **Avoid using exposed public keys**: Ensure funds sent to old wallets are transferred to new ones that use public key hashes. This reduces the risk of long-term attacks.
- **Use modern wallets**: Opt for wallets compatible with SegWit or Taproot, which implement better security practices.
- **Monitor security updates**: Stay informed about updates from the Bitcoin community, such as the implementation of BIP-360, which will introduce quantum-resistant addresses.
- **Do not reuse addresses**: Every transaction should be associated with a new address to minimize the risk of repeated exposure of the same public key.
- **Adopt secure backup practices**: Create offline backups of private keys and seeds in secure locations, protected from unauthorized access.
---
## BIP-360 and Bitcoin’s Preparation for the Future
Even though quantum computing is still beyond practical reach, the Bitcoin community is not standing still. A concrete example is BIP-360, a proposal that establishes the technical framework to make wallets resistant to quantum attacks.
BIP-360 addresses three main pillars:
1. **Introduction of quantum-resistant addresses**: A new address format starting with "BC1R" will be used. These addresses will be compatible with post-quantum algorithms, ensuring that stored funds are protected from future attacks.
2. **Compatibility with the current ecosystem**: The proposal allows users to transfer funds from old addresses to new ones without requiring drastic changes to the network infrastructure.
3. **Flexibility for future updates**: BIP-360 does not limit the choice of specific algorithms. Instead, it serves as a foundation for implementing new post-quantum algorithms as technology evolves.
This proposal demonstrates how Bitcoin can adapt to emerging threats without compromising its decentralized structure.
---
## Post-Quantum Algorithms: The Future of Bitcoin Cryptography
The community is exploring various algorithms to protect Bitcoin from quantum attacks. Among the most discussed are:
- **Falcon**: A solution combining smaller public keys with compact digital signatures. Although it has been tested in limited scenarios, it still faces scalability and performance challenges.
- **Sphincs**: Hash-based, this algorithm is renowned for its resilience, but its signatures can be extremely large, making it less efficient for networks like Bitcoin’s blockchain.
- **Lamport**: Created in 1977, it’s considered one of the earliest post-quantum security solutions. Despite its reliability, its gigantic public keys (16,000 bytes) make it impractical and costly for Bitcoin.
Two technologies show great promise and are well-regarded by the community:
1. **Lattice-Based Cryptography**: Considered one of the most promising, it uses complex mathematical structures to create systems nearly immune to quantum computing. Its implementation is still in its early stages, but the community is optimistic.
2. **Supersingular Elliptic Curve Isogeny**: These are very recent digital signature algorithms and require extensive study and testing before being ready for practical market use.
The final choice of algorithm will depend on factors such as efficiency, cost, and integration capability with the current system. Additionally, it is preferable that these algorithms are standardized before implementation, a process that may take up to 10 years.
---
## Why Quantum Computing Is Far from Being a Threat
The alarmist narrative about quantum computing overlooks the technical and practical challenges that still need to be overcome. Among them:
- **Insufficient number of qubits**: Current quantum computers have only a few hundred qubits, whereas successful attacks would require millions.
- **High error rate**: Quantum stability remains a barrier to reliable large-scale operations.
- **High costs**: Building and operating large-scale quantum computers requires massive investments, limiting their use to scientific or specific applications.
Moreover, even if quantum computers make significant advancements, Bitcoin is already adapting to ensure its infrastructure is prepared to respond.
---
## Conclusion: Bitcoin’s Secure Future
Despite advancements in quantum computing, the reality is that Bitcoin is far from being threatened. Its security is ensured not only by its robust architecture but also by the community’s constant efforts to anticipate and mitigate challenges.
The implementation of BIP-360 and the pursuit of post-quantum algorithms demonstrate that Bitcoin is not only resilient but also proactive. By adopting practical measures, such as using modern wallets and migrating to quantum-resistant addresses, users can further protect themselves against potential threats.
Bitcoin’s future is not at risk—it is being carefully shaped to withstand any emerging technology, including quantum computing.
-

@ 30ceb64e:7f08bdf5
2025-01-03 19:38:28
Michael Saylor's recent assertion on Tom Bilyeu's podcast that Bitcoin offers a risk-free return sparked an interesting debate. While Tom struggled with the concept, the truth lies in understanding what "risk-free" truly means in our modern financial landscape. When you denominate your wealth in Bitcoin and store it properly in cold storage UTXOs, you're essentially protecting your work energy in perhaps the least risky way possible.
https://m.primal.net/NQjb.png
Traditional banking customers often consider their dollars in savings accounts to be risk-free, but this belief ignores fundamental realities. Bank failures are increasingly common, and FDIC insurance is merely a paper promise from the same entity responsible for systematic wealth destruction. The state has reached a point where repaying its debt within the current paradigm seems impossible.
The paradox of taxation in a money-printing world raises profound questions. Why do we pay taxes when money can be created with the press of a button? The answer might lie in maintaining the illusion of government sustainability. We surrender roughly half our work energy to finance a system that can theoretically fund itself through money printing - a perplexing arrangement that defies logical explanation.
Bitcoin represents hard money that doesn't require yield in the traditional sense. The real yield comes from humanity's natural progression toward efficiency and innovation. When your savings aren't being debased, technological advancement and human ingenuity naturally make your money more valuable over time. The world is inherently deflationary, but this truth becomes obscured when savings are denominated in infinitely printable currencies.
This dynamic mirrors historical examples, like African communities saving in glass beads and shells, unaware that Europeans were mass-producing these "stores of value" in factories. Living in our current system is like existing in a deflationary world while being tricked into believing it's inflationary - a matrix-like illusion that drives the endless pursuit of "more" in a fundamentally broken system. The federal reserve is a glass bead manufacturer and some of us are the slaves that use it as money.
https://m.primal.net/NQkA.webp
Bitcoin's technical evolution continues to strengthen its position as sound money. Enhanced privacy features through initiatives like PayJoin, e-cash, and Lightning Network, combined with improved custody solutions and growing infrastructure, make it increasingly accessible and practical for everyday use. The ability to transact without permission or exploitative intermediaries, guided only by free market principles, represents a fundamental shift in financial sovereignty.
The question of "enough" becomes central to the Bitcoin journey. While the technology offers a path to financial sovereignty, it's crucial to balance accumulation with life's other valuable resources - time with family, personal growth, and meaningful relationships. The timechain will judge our actions, but perhaps the most important consideration is whether our pursuit of satoshis comes at the cost of more precious aspects of life.
We stand at a unique point in history where individual sovereignty is becoming truly possible. The pendulum swings toward a new paradigm that could secure prosperity for generations to come. While many haven't yet reached their personal "escape velocity," the path to financial freedom through Bitcoin becomes clearer with each passing day.
The concept of risk-free extends beyond mere financial considerations. In a world where time is our most precious and finite resource, Bitcoin offers something unprecedented: the ability to store life energy in a system that appreciates with human progress, rather than depreciating with political whims. The risk isn't just about losing money - it's about losing life energy, family time, and personal freedom.
-

@ bd32f268:22b33966
2025-01-02 19:30:46
Texto publicado por *Foundation Father @FoundationDads* e traduzido para português.
Assumir responsabilidades numa época efeminada como a nossa é um superpoder.
Algumas pessoas não sabem o que significa "assumir responsabilidades", no entanto, porque nunca tiveram um pai ou outra pessoa que as ama-se o suficiente para lhes ensinar.
Então, aqui está como assumir responsabilidades.
## **Lembra-te que não és uma pessoa desamparada e incompetente.**
As coisas não te acontecem simplesmente enquanto olhas fixamente com a boca aberta, usando todo o teu poder cerebral para te lembrares de como respirar.
Tu tens poder de ação.
## Mantém estas perguntas em mente:
"Que papel desempenhei eu nesta situação ou como ajudei a formar o sistema em que estou inserido?"
"O que posso fazer agora mesmo para começar a corrigi-lo, por mais pequeno que seja?"
Aqui estão alguns exemplos de como aplicar estas perguntas.
*José Malhoa - Remédio*
## Saúde
Estás com excesso de peso e cansado o tempo todo? Deprimido?
Começa a caminhar 30 minutos por dia. De preferência ao ar livre.
Pára de comer snacks.
Marca uma consulta com um médico para fazer análises ao sangue.
Todas estas coisas estão ao teu alcance.
## Finanças
Estás a afogar-te em dívidas de cartão de crédito? Assumir responsabilidades significa reduzir drasticamente o teu consumo e iniciar um programa radical de pagamento do máximo de dívida que conseguires.
Obtém uma aplicação de orçamento e começa a planear.
Sentes-te preso no teu emprego sem futuro? Sentes que não ganhas o suficiente? Vai a entrevistas para vagas de emprego e descobre o teu verdadeiro valor no mercado.
Reserva 1 hora todas as noites para melhorares. A menos que já estejas a trabalhar em dois empregos, toda a gente tem pelo menos 1 hora todas as noites.
## Arredores imediatos
Se vês algo que precisa de ser feito, simplesmente faz. Não te queixes disso. Não resmungues baixinho. Não desejes que alguém tratasse disso. Simplesmente faz e não peças permissão.
Guarda o carrinho de compras. Lava a caneca de café no lava-loiça. Arranca as ervas daninhas. Repara a parede. Se o quintal do teu vizinho estiver cheio de ervas, vai lá e corta a relva tu mesmo. Limpa a água do lava-loiça. Arruma a bancada. Leva o lixo para fora. Leva bom café para o escritório.
## Os teus filhos
Muitos pais queixam-se do comportamento dos seus filhos como se não tivessem qualquer influência sobre o assunto. Mas os teus filhos farão o que tu os ensinaste a fazer.
"Fizemos o melhor que pudemos."
Não, não fizeram, e assumir responsabilidades significa admitir que foste permissivo e preguiçoso ou que querias sentir-te justo por não bater.
Que pequena coisa podes fazer agora mesmo para começar? Escolhe um único comportamento que queres que eles parem, senta-os e explica as consequências do comportamento. Pede desculpa por teres deixado andar durante tanto tempo.
Quando eles apresentarem o comportamento, aplica as consequências. Aconteça o que acontecer.
## Os teus relacionamentos
Não tens amigos ou o teu grupo de amigos atual é uma má influência? Podes fazer novos amigos. Assumir responsabilidades significa admitir que a tua solidão é em grande parte auto-infligida.
**O que podes fazer?**
Começa a jogar ténis ou futebol. Existem ligas em todo o lado. Encontra uma boa igreja local e encontra maneiras de te envolver. Existem encontros para todo o tipo de atividade. Participa num que se alinhe com as tuas preferências. Quando estiveres em público, sorri mais e puxa conversa.
Depois de conheceres algumas pessoas, estabelece uma cadência regular. Agenda almoços semanais ou mensais e alterna entre algumas pessoas. Ou talvez café de manhã.
Não acontecerá da noite para o dia, mas dando pequenos passos consistentemente durante alguns meses e vais perceber que tens uma vida social.
## Os teus erros
Se erraste, não te retires e escondas nem arranjes desculpas. Pede desculpa à pessoa que prejudicaste, diz-lhe porquê e oferece-te para compensar. Aceita as consequências com humildade.
Vais descobrir que nada te conquista mais respeito do que assumir os teus erros. Esta é a principal. Se aprenderes a fazer isto bem, cobrirá uma infinidade de pecados porque cria hábito. Mesmo que tenhas apenas 1% de culpa na situação, assumir a responsabilidade e pedir desculpa pelo teu 1% está a construir um certo grupo de músculos.
"Mas ele devia ter..." Pára com isso. Confiaste demasiado? Presumiste demasiado sem comunicar? Assume a responsabilidade por isso.
Estes exemplos podiam continuar para sempre, então vou parar e terminar com este princípio:
A tua resposta importa mais do que as tuas circunstâncias.
Existem vítimas reais, algumas de tragédias horríveis. Mas mesmo que não te tenhas atirado para areias movediças, ainda podes assumir a responsabilidade por como reages e pelo que escolhes fazer a seguir.
Às vezes, é agarrar numa corda de um transeunte e dizer: "Obrigado."
Não te afogues nas areias movediças até que alguém te dê uma palmadinha nas costas por quão difícil é para ti, e não continues a apontar para o teu tempo nas areias movediças para desculpares os teus fracassos.
Podes não ter escolhido uma batalha específica. Ainda podes assumir a responsabilidade por quão bem lutas a batalha. Num certo sentido, ninguém escolhe a principal batalha que enfrenta. Ninguém escolheu nascer. Ninguém escolheu a sua família. Ninguém escolheu as suas circunstâncias.
O mundo nunca será perfeito. Tens de assumir a responsabilidade pela tua parte dele de qualquer maneira. Pode ser difícil. Pode ser doloroso. Não te foi prometida uma vida fácil e sem dor.
Depois de começares a assumir responsabilidades, qual é o próximo passo?
Altura de assumir mais responsabilidades.
Por exemplo, se não tens problemas em fazer amigos e tens essa parte da tua vida resolvida, assume a responsabilidade por outra pessoa. Encontra um dos rapazes solitários na tua igreja que precisa de um amigo e adiciona-o à tua rotação de almoços.
A recompensa por assumir responsabilidades é subir de nível e, como consequência, as coisas devem tornar-se mais desafiantes.
Mas agora estás mais bem preparado para isso. Repete até morrer e, esperançosamente, a tua causa de morte será por viver e não por te queixares de não viver.
-

@ a4a6b584:1e05b95b
2025-01-02 18:13:31
## The Four-Layer Framework
### Layer 1: Zoom Out

Start by looking at the big picture. What’s the subject about, and why does it matter? Focus on the overarching ideas and how they fit together. Think of this as the 30,000-foot view—it’s about understanding the "why" and "how" before diving into the "what."
**Example**: If you’re learning programming, start by understanding that it’s about giving logical instructions to computers to solve problems.
- **Tip**: Keep it simple. Summarize the subject in one or two sentences and avoid getting bogged down in specifics at this stage.
_Once you have the big picture in mind, it’s time to start breaking it down._
---
### Layer 2: Categorize and Connect

Now it’s time to break the subject into categories—like creating branches on a tree. This helps your brain organize information logically and see connections between ideas.
**Example**: Studying biology? Group concepts into categories like cells, genetics, and ecosystems.
- **Tip**: Use headings or labels to group similar ideas. Jot these down in a list or simple diagram to keep track.
_With your categories in place, you’re ready to dive into the details that bring them to life._
---
### Layer 3: Master the Details

Once you’ve mapped out the main categories, you’re ready to dive deeper. This is where you learn the nuts and bolts—like formulas, specific techniques, or key terminology. These details make the subject practical and actionable.
**Example**: In programming, this might mean learning the syntax for loops, conditionals, or functions in your chosen language.
- **Tip**: Focus on details that clarify the categories from Layer 2. Skip anything that doesn’t add to your understanding.
_Now that you’ve mastered the essentials, you can expand your knowledge to include extra material._
---
### Layer 4: Expand Your Horizons

Finally, move on to the extra material—less critical facts, trivia, or edge cases. While these aren’t essential to mastering the subject, they can be useful in specialized discussions or exams.
**Example**: Learn about rare programming quirks or historical trivia about a language’s development.
- **Tip**: Spend minimal time here unless it’s necessary for your goals. It’s okay to skim if you’re short on time.
---
## Pro Tips for Better Learning
### 1. Use Active Recall and Spaced Repetition
Test yourself without looking at notes. Review what you’ve learned at increasing intervals—like after a day, a week, and a month. This strengthens memory by forcing your brain to actively retrieve information.
### 2. Map It Out
Create visual aids like [diagrams or concept maps](https://excalidraw.com/) to clarify relationships between ideas. These are particularly helpful for organizing categories in Layer 2.
### 3. Teach What You Learn
Explain the subject to someone else as if they’re hearing it for the first time. Teaching **exposes any gaps** in your understanding and **helps reinforce** the material.
### 4. Engage with LLMs and Discuss Concepts
Take advantage of tools like ChatGPT or similar large language models to **explore your topic** in greater depth. Use these tools to:
- Ask specific questions to clarify confusing points.
- Engage in discussions to simulate real-world applications of the subject.
- Generate examples or analogies that deepen your understanding.
**Tip**: Use LLMs as a study partner, but don’t rely solely on them. Combine these insights with your own critical thinking to develop a well-rounded perspective.
---
## Get Started
Ready to try the Four-Layer Method? Take 15 minutes today to map out the big picture of a topic you’re curious about—what’s it all about, and why does it matter? By building your understanding step by step, you’ll master the subject with less stress and more confidence.
-

@ 5391098c:74403a0e
2025-01-02 16:50:29
Ensaio em Prosa sobre Fotografia Analógica
Tenho especial fascínio pela fotografia analógica. É que se trata dum processo artístico muito mais complexo que a fotografia digital, devemos entender todos os aspectos da fotografia para obter o resultado pretendido, desde aspectos mecânicos da câmera como abertura e tempo do obturador, foco, iluminação, até a sensibilidade do filme utilizado e o resultado, quando alcançado, é verdadeira obra de arte pintada, onde a tela é a película química.
Importante dizer que meu fascínio pela fotografia analógica não me impede de reconhecer a importância da fotografia digital, não fosse essa você não estaria vendo minhas obras de arte que foram digitalizadas…
Da mesma forma que meu fascínio pela máquina de escrever não me impede de ter essa e outras páginas na internet. Parte do meu livro FILOSOFIA FUNDAMENTAL foi escrito graças a inspiração da máquina de escrever, como ocorreu no capítulo sobre o que seria evolução, escrevi integralmente na minha Olivetti Studio 46, pois havia faltado luz: o que me fez refletir sobre se o computador realmente é a evolução da máquina de escrever.
Outro exemplo foi a inspiração que as lindas formas arredondas de minha máquina de escrever da marca Érika me proporcionou, acabou resultando numa bela performance a qual dei nome de Paixão Erótika.
Por isso, acredito que os equipamentos analógicos não ofuscam nossa criatividade e na fotografia não poderia deixar de ser diferente.
No conjunto de fotografias analógicas abaixo utilizei uma Canon T50, objetiva de 50mm e filme Kodak Pro Image 100, a qual se encontra auto-fotografada em espelho, vamos ver:
Na foto abaixo utilizei luz amarela indireta da direita superior para esquerda inferior, o desfoque ao redor foi proposital com o objetivo de parecer estar olhando o mundo através das lentes da câmera, nesse caso ela estava olhando para sí mesmo. Mesmo estando a parede e o espelho no mesmo plano, a profundidade de campo do espelho é diferente, por isso esse efeito foi possível. Destaque especial para o “olho” do diafragma, deve ter aberto até f5.6, pois a luz não era muito forte. Se a luz fosse mais forte o diafragma teria aberto o mínimo f16 o que aumentaria a profundidade de campo impedindo o desfoque pretendido. O resultado foi alcançado, ao mesmo tempo que a câmera aparece, essa fotografia transmite essa mensagem subliminar:
https://image.nostr.build/a7cbfbe68a4bb89ae731c360c373ac8eff7599a5a100d13035eb234b5d788626.jpg
PERFORMANCE
Performance é o nome dado à mescla de mais de uma linguagem artística (arte visual, música, teatro, etc.) clicando em https://davipinheiro.com/id/performance/ você pode ver todas minhas performances. Nos exemplos abaixo a mescla se deu pela mistura de artes visuais criadas por mim e captadas pela fotografia analógica, vamos ver:
A foto abaixo se trata dum terrário que criei num tronco de árvore, arte plástica. Para fotografar utilizei luz amarela superior, o desfoque foi para destacar o objeto, especial destaque para o reflexo da luz no vidro para dar noção tridimensional de algo transparente:
https://image.nostr.build/e8026f9e99fa16631959954f8bb925af6f1764911f0a315ab0125bb413e3e89b.jpg
Na foto abaixo o mesmo processo da foto anterior, também utilizando uma Canon T50 com filme Kodak Pro Image 100 e objetiva de 50mm, diferenciando o enquadramento e a luz direta frontal:
https://image.nostr.build/4c44a0baf2b5ddaf63f83420952ab1b2e84f7df292f8e413a65f8134a2e7db58.jpg
A foto abaixo retrata o processo de criação da obra. Ironicamente, nessa foto, meu galo Cara de Palhaço mesmo desfocado no fundo se destacou, parecendo estar em pé no tronco:
https://image.nostr.build/d0d5e73ecbcdefa79ffd858d0143f41915c9deab7864d271d5ee724b3927f9bc.jpg
A foto abaixo se trata do pisca-alerta original da minha super DT200R (viva os motores 2 tempos!) que caiu depois de uma trilha kkk. A Ideia nesta fotografia era fazer o sol parecer estar acendendo o alerta que deveria aparentar estar flutuando no céu. Infelizmente não fui bem sucedido, pois os fios que penduravam o objeto acabaram aparecendo. É impressionante a capacidade de cálculo da Canon T50 e a velocidade do seu obturador, a nitidez da objetiva e a resolução do filme Kodak Pro Image 100, cujo conjunto conseguiu captar até os pequenos fios de nylon transparentes. Eu imaginei que a foto ia estourar e os fios não apareceriam, ledo engano. Pelo menos o enquadramento ficou correto: objeto um pouco mais acima do centro para dar sensação de altitude e levemente de perfil para dar noção 3d. Quem sabe com uma câmera que seja possível ajustar a velocidade do obturador eu seja bem sucedido…
https://image.nostr.build/808243d34b6dbeade25d38189163f9d58f6a12da9d00df17c85651d501e1bed8.jpg
A foto abaixo se trata da minha performance favorita com a fotografia analógica, pois fotografei o primeiro quadro que pintei, o qual dei o nome de Elipsoíris sendo ele posteriormente capa do meu livro FILOSOFIA FUNDAMENTAL, então aí temos três linguagens artísticas profundas na mesma performance: O quadro que virou livro fotografado analogicamente. A ideia desta performance foi enquadrar o quadro desfocado, o qual somente pode ser desvendado com os olhos certos, por isso a lente. Utilizei luz natural e uma lente velha de óculos. Especial destaque para os dois pontos de luz que refletiram na lente parecendo dois olhos, isso não foi planejado e deu um toque especial para a fotografia, cabendo diversas interpretações, esse é o objeto da arte em geral. Fiquei muuuito contente com o resultado:
https://image.nostr.build/6bb5b802b3ad1bb7262b925225fcfb0b8b00654fa0fec240be57f648c32245af.jpg
Já na fotografia analógica abaixo considero uma performance porque não se trata duma fotografia comum de paisagem, flores, arquitetura, animais ou pessoas, visa passar uma mensagem. Utilizando apenas a luz natural, regulei o foco da Canon T50 para as lentes dos meus próprios óculos e escolhi um dia especialmente nublado e escuro para simbolizar as dificuldades pelas quais todos passamos no dia-a-dia, quando acreditamos por algum momento que as luzes estão apagadas para nós, até que com os óculos certos podemos enxergar com maior nitidez o horizonte, os óculos podem ser a palavra de Deus ou qualquer outra coisa que te ilumine e esclareça. Com certeza essa fotografia terá um bom uso em meus próximos escritos:
https://image.nostr.build/b44b573bb39cdf5f2eb446e818bbf59d5dab9d3815ac6e917440b2f6b1ff431c.jpg
DUPLA EXPOSIÇÃO
Eis aqui um recurso nato da fotografia analógica: a dupla exposição. Se trata de fotografar mais de uma vez em cima do mesmo filme de modo que as imagens se sobreponham. Como esse método podemos simular movimento numa única fotografia, fazer montagens de disco voador kkkk, enfim a imaginação é o limite, vamos ver:
Nessa fotografia analógica abaixo ocorreu uma quádrupla exposição, pois cliquei quatro enquadramentos diferentes sob o mesmo filme. Foi especialmente difícil fazer porque a Canon T50 não tem esse recurso, então tive que enganá-la pressionando o botão de rebobinar o filme ao mesmo tempo que disparava a câmera. Como eu estava usando o filme Kodak Pro Image que possui asa 100, também regulei a máquina como se estivesse usando um filme asa 25, então sabia que podia disparar quatro vezes sem queimar o filme. Pedi para a modelo (minha Mãe, kkk) ficar em três posições diferentes dando a impressão de movimento e não satisfeito no final ainda fotografei o sol. Adorei essa foto:
https://image.nostr.build/5f8e2962e2ee94259d4dd5d3b777976a4d20ba293a5a4e68e81e30a0e1975543.jpg
FOTOS EM MACRO OU CLOSE
Acredito ser possível obter uma fotografia analógica em macro mesmo sem lente especial, tudo depende da pecinha que fica atrás da câmera: você, kkkk. Devemos tentar, se não obtivermos uma fotografia em macro, ao menos um close teremos, vamos ver:
Na foto abaixo há um minúsculo cogumelo que cresceu num barranco qualquer, apareceu nitidamente no negativo, mesmo sem uso de lupa, por isso considero um macro, na verdade é apenas uma foto divertida:
https://image.nostr.build/02aa4bbdc0cf54519b694c75237693fc2a6569fe4f3167220b05c7498757b822.jpg
Já a foto abaixo é apenas um close, o ninho é especialmente profundo, por isso o leve desfoque nos ovos: para dar noção de profundidade. O foco dos quatro cantos da caixa está bem ajustada para dar noção tridimensional do objeto:
https://image.nostr.build/24e5dcdd0e5a3560b341fe4f0d0d93b7d562f2d58054ac308a8e312c2707100c.jpg
O PRIMEIRO QUADRO DO ROLO
Na fotografia analógica cada rolo de filme nos dá pelo menos um tipo de fotografia artística bem específica. Se trata do primeiro quadro do rolo, onde ocorre uma parcial sobre-exposição. Isso se deve a incidência da luz diretamente no filme quando estamos carregando a máquina com o filme. A maioria das máquinas analógicas somente começa a contar os fotogramas após alguns disparos para evitar isso. Cabe ao fotógrafo saber aproveitar os fotogramas existentes antes do número 1, enquadrando a cena normalmente e disparando antes do número 1. Os resultados são quase imprevisíveis e geralmente interessantes.
Abaixo uma fotografia analógica fantástica porque quase sempre a sobre-exposição do primeiro quadro do rolo ocorre nas extremidades da foto e nessa aí ocorreu no meio. Para conseguir esse efeito carreguei a máquina no escuro e acendi a luz no exato momento que estava fechando a tampa da câmera. Por uma fração de segundo o primeiro quadro do rolo foi exposto parcialmente a luz, sabia que iria ter uma fotografia diferente, jamais imaginei que a sobre-exposição iria sair no meio do fotograma, muito curioso:
https://image.nostr.build/a2e08aab686af64df949e83b4ff3b0a00952698a7a138412f7753ebc0dd63d1f.jpg
Na fotografia abaixo repeti o mesmo processo anterior. Como o tempo entre acender a luz e fechar da máquina foi diferente a sobre-exposição ficou bem visível na extremidade da foto. Especial destaque para sua incidência no lado direito, quando deveria incidir no lado esquerdo, pois na Canon T50 o filme roda da esquerda para direita. Essa aparente inversão de lados se deu porque fotografei com a máquina de cabeça para baixo:
https://image.nostr.build/270681be8de71b6c833507dda6bfe4b5233c9b871aa97ea8fc2ebdcdd46a682a.jpg
FOTOS DE AÇÃO
Registrar uma ação com fotografia analógica é especialmente difícil se a máquina não calcula a abertura e tempo de exposição automaticamente, porque tudo acontece muito rápido e você não tem tempo de ficar pensando. Felizmente a Canon T50 é muito boa para esse tipo de fotografia, tive que me preocupar apenas com o foco. O que essa máquina me fez suar para fazer as duplas exposições acima, tirou de letra esse memorável momento, vamos ver:
Na foto abaixo quando avistei esse grupo de corajosos saltando de paraglider corri pedir autorização para fotografá-los e rapidamente carreguei a máquina. Comecei a fotografar mesmo antes da máquina registrar o primeiro fotograma do rolo, tendo obtido esse lindo efeito de sobre-exposição de primeiro quadro do rolo:
https://image.nostr.build/8e32e22d3bf7c897d7111e85555146e38bb139985c50b2795fe809b31880c7d8.jpg
Já a foto abaixo foi a terceira do rolo. Tomei o cuidado de enquadrar tanto a alçada de vôo do paraglider quanto essa linda Veraneio, o que descreve em uma única foto o espírito aventureiro do pessoal. Reparem no sol refletindo sobre as nuvens, que lindo tudo:
https://image.nostr.build/5bf0444e4621406d858ab70725c1ee2f6a7e39b87663e23a18085a32b9a06f6a.jpg
Na foto abaixo tive que registrar mais uma dessa linda Veraneio, sou apaixonado por motores e mecânica, ela quase roubou a cena kkkk. Especial destaque para o detalhe do carro e da câmera que a fotografou serem da mesma época, sensível retorno ao passado. Verdadeira máquina do tempo essa foto. Se eu não dissesse que esta foto foi tirada no final do ano de 2020 daria para dizer que foi uma foto tirada de uma Veraneio Zero Km da época, segredinho nosso, kkk.
https://image.nostr.build/f5284ff30986ad84d22f137e0a330067f91564907da8acf04c9eb93a991cbcf2.jpg
Na foto abaixo voltando à cena, agora do Ângulo certo kkk. Esse foi a segunda foto, perceba ainda a presença do efeito de sobre-exposição do primeiro quadro. Aqui a máquina estava marcando o primeiro fotograma, tadinha kkk
https://image.nostr.build/5c1d73f7d802fd1f730427e29f921c82e410c5dce3112a3133d6fce294d310c6.jpg
Na foto abaixo a luz estava perfeita, o sol iluminava atrás de mim, incidindo frontalmente para o enquadramento da foto, linda essa:
https://image.nostr.build/156fc878dd18257ad1f59d1b5d3fd719c7e773937356fad6ea09b0ce1f151f12.jpg
Paraglider quase em posição de vôo, a foto ficou quase perfeita porque o momento em tela era a Hora de Ouro, momento do entardecer quando a posição do sol deixa o céu dourado, fenômeno muito querido pelos fotógrafos analógicos; até pelos digitais também. Mesmo assim eu não estava satisfeito, queria fotografar mais de perto. Dei zoom correndo para frente e o resultado você vê abaixo:
https://image.nostr.build/b1f610695bd57db8abe7408df318978b6e69e85fe620a589b12fb9bcaae66156.jpg
Abaixo a fotografia analógica simplesmente perfeita, sol na posição certa, hora de ouro, perfeito enquadramento e foco, tudo certo, universo conspirando à favor… ganhei o dia sem saber. Só descobri depois que revelei. O chão não foi cortado é que o piloto do paraglider já estava no desnível do chão pronto para saltar:
https://image.nostr.build/93a7e416d11c996b65a32b019667a43124d96985109d34fd1a9b239ef365bbfe.jpg
Abaixo O salto… tive que correr para o barranco para dar zoom, outra foto perfeita na hora de ouro:
https://image.nostr.build/f254c2e71863a233816b517564dd5fb7fe85ee0bd927b02687fba43bde53dcd6.jpg
FOTOGRAFIA ANALÓGICA DE ANIMAIS
É especialmente difícil fazer um animal posar para gente, temos que ter um pouco de comida pra negociar kkk. Não fosse a Canon T50 calcular a exposição sozinha seria ainda mais difícil porque os momentos são muito rápidos e você não tem tempo para regular a abertura e tempo de exposição, tive que regular apenas o foco. Mais um ponto para essa notável máquina que me fez apanhar na dupla exposição acima. A fotografia analógica de animais também é um tipo de fotografia de ação, temos que ser rápidos no gatilho, vamos ver os resultados:
Abaixo novamente dei zoom chegando bem perto, fotógrafo de verdade não tem medo, tudo pela arte!
https://image.nostr.build/5f0af116b1fd81edb3f21dfd5d7cce6c534751ac8660bd5fb58ce08c652d8aaf.jpg
Abaixo foco no segundo plano, acabei pegando os dois de perfil:
https://image.nostr.build/fbd78fcf71749569444d3438e0d5283d321fc3f3350cacc6e4a3e9a0cdc914f5.jpg
Abaixo foco no segundo plano. Aqui peguei os dois olhando para mim e dizendo xiiiis, kkk.
https://image.nostr.build/3a1f50ee1e3c6213b337654e69ee23819ab60100c8a1a049ee0b2b66fac0d8f8.jpg
Abaixo podemos comprovar que o fotômetro da Canon T50 é matricial e não pontual, porque o centro da foto tinha muito mais luz que os cantos:
https://image.nostr.build/11a8a5a7ff14a661755f04f743d70d3dd1a9d11e412791ce42f5cbf1da1c6be2.jpg
Abaixo linda foto: Cavalo da Montanha. Eu estava esperando a Hora de Ouro chegar, pena que quando chegou o modelo não quis mais ser fotografado kkk.
https://image.nostr.build/83429975966cb4b0e71e5e089651d4585513d823fea404014b0b78b21e859302.jpg
Abaixo lindo close de perfil com fundo totalmente desfocado. Preto absoluto, a fotometria esta certinha:
https://image.nostr.build/f36aed8fa89b6ba81dd77c7d3b32c24424483e626a9634cbadb16baf91427d66.jpg
Abaixo muita coisa acontecendo ao mesmo tempo: As galinhas comendo, o milho sendo jogado, a sombra do fotógrafo… Para obter essa foto joguei o milho para o alto e tive que ser tão rápido no gatilho quanto o Kid Morengueira. Você pode perceber na minha sombra que estou segurando apenas a câmera, o pote de milho já tinha voado longe kkk. Escolhi especialmente um dia ensolarado para que o fotômetro da Canon T50 usasse toda a velocidade possível no obturador, sendo possível congelar o milho no ar sem muito efeito borrão.
https://image.nostr.build/d566e46a8a3cba8855e80295910e5addb0a8aa7735093c9f93f129cac2379472.jpg
Abaixo galinha chocando numa roda de carro. Como amo animais e carros, para montar essa cena tive que forrar uma roda velha de carro para formar um ninho e esperar, esperar e esperar… No momento certo a Jurema se sentiu confiante para entrar na roda. Nem se incomodou com minha presença pois estava de papo cheio, pois é, também tive que negociar com a galinha, isso é a fotografia analógica de animais kkk. Percebam novamente que o fotômetro da Canon T50 é matricial, pois a maior parte da foto era com pouca luz e o raio de sol que entrava estourou a foto. Percebam ainda como eu estava perto da galinha, pois foquei em sua cabeça e o resto do corpo que estava um pouco mais distante saiu desfocado. Certamente a câmera estava com abertura máxima f1.8 e com uma velocidade bem lenta, o que explica a baixa profundidade de campo. Além disso se a Jurema tivesse mexido a cabeça na hora do disparo certamente teria saído um borrão por causa da baixa velocidade. Acabou saindo tudo certo e meus dias de espera por essa foto não foram em vão.
https://image.nostr.build/d7484609c8ff9be05ee6d518def402f66484a02109dc96ef5c734b11216385bf.jpg
FOTOGRAFIA ANALÓGICA DE ARQUITETURA
Na fotografia analógica de arquitetura devemos conhecer os conceitos básicos de iluminação e preenchimento, trabalhamos apenas com luz natural e deve ser bem usada para termos a noção tridimensional da construção. Conforme ensina Fernando Bagnola, a tridimensionalidade do objeto depende da incidência da luz em três pontos diferentes e com intensidades diferentes, algo difícil de se obter apenas com a luz do sol, vamos ver:
Abaixo se trata do Museu do Olho em Curitiba/PR. Como sua parte frontal é escura e o sol se posicionava atrás da construção tive de me posicional na sua lateral, assim consegui obter um resultado tridimensional, pois o sol iluminava a parte de cima, refletia na parte de baixo em menor intensidade e na parte frontal quase não havia luz. Se eu estivesse posicionando na frente da construção o efeito tridimensional seria impossível:
https://image.nostr.build/6f74c1c7e606f7950eaf45007868b92e9a0288722b3d5e580ecaa4930700e3ea.jpg
Abaixo para minha sorte, nesse exato momento um grupo de jovens contracultura (assim como eu) passavam pelo local, tornando a foto icônica pela presença de jovens modernos contracultura contrastando com arquitetura moderna da cultura tradicional. Minha posição em relação ao sol também favoreceu o sucesso desta fotografia, tendo iluminado corretamente todos os pontos de interesse:
https://image.nostr.build/7c374205d7df21985a6a71c6c17e4f67ab29baf452f0cd406b869df94d68296c.jpg
Abaixo esse aqui é um exemplo de fotografia analógica arquitetônica errada. O enquadramento foi frontal em razão do desejo de captar o reflexo dos edifícios nos vidros negros do “olho”:
https://image.nostr.build/f9a0869a165bc7e634944c01e59085203347ab6c353610bdcaace30ee3ed8d8a.jpg
Abaixo se trata do Panteon dos Heroes na Lapa/PR um monumento erguido para guardar os corpos dos soldados das forças republicanas que pereceram durante o chamado Cerco da Lapa, batalha da Revolução Federalista de 1894. Aqui o dia estava nublado, momento perfeito para fotografar uma arquitetura tão triste como essa. Não me importei com a questão tridimensional, pois era impossível, não havia sol. Quis retratar a tristeza na foto. O filme usado foi o mesmo (Kodak Pro Image 100). Aqui percebemos que a química desse filme é ajustada para a luz amarela do sol como branco absoluto, como o céu estava nublado, a luz natural estava com temperatura mais fria o que puxou o tom mais para o azul e o roxeado da foto devem ter sido os raios ultravioleta. Se eu estivesse usando um filtro ultravioleta provavelmente a foto sairia mais acinzentada. Me recordo que nesse dia estava tudo cinza. De qualquer forma adorei esse tom arroxeado da foto. Fica a dica: conseguimos o mesmo efeito de um filme Lomochrome Purple caríssimo com um filme baratinho, basta fotografar nessas condições:
https://image.nostr.build/24f91369c12e83861f7eec38ff99f1869f08ae1eec06c798ccbe08af62263a2e.jpg
Abaixo novamente o tom arrocheado com um filme barato. Para se ter uma ideia um Lomochrome Purple costuma custar seis vezes ou mais que um que o Kodak Pro Image 100 de R$ 30,00 à R$ 40,00 na data da publicação deste artigo em 09/04/21. Percebam que no momento desta foto as nuvens deram uma trégua e alguns raios de sol passaram dando uma leve noção tridimensional da arquitetura. O certo seria eu estar um pouco mais à esquerda para aproveitar bem a iluminação. Mesmo assim, me senti feliz com a triste foto kkk pois mesmo com a luz amarela do sol refletindo o efeito Lomo-Violeta ocorreu:
https://image.nostr.build/099a1a4d7857325e59f5b35805c0ebb5c3fa55af45de2096236f1dfbadca4d4a.jpg
Abaixo parece que a foto está mal enquadrada. E está mesmo. É que no lado direito havia um poste de energia elétrica muito feio, eu não queria que aparecesse. Me preocupei apenas com a iluminação e obtive sucesso com a noção de profundidade da arquitetura. A foto está puxando para o amarelo porque a Universidade Federal do Paraná em Curitiba é meio amarela mesmo.
https://image.nostr.build/48a4d517488fc1656e027568ad314688bc0fd9995e67289003f832eb904e5260.jpg
Abaixo para finalizar o conjunto de fotografias analógicas arquitetônicas nada melhor que um cemitério, afinal todos vamos morrer um dia, devemos sempre lembrar disso para fazer nossas vidas mundanas valerem a pena. Quando morremos não levamos nada a não ser nossas experiências evolucionais, nossas graças e pecados. Devemos deixar um legado, algo positivo para quem fica. Pois bem, foi nesse contexto a foto. Para mim a morte deve ser evitada. Quando ocorrer, se fizermos tudo certo vamos para luz, as trevas são aqui na terra mesmo. Portanto, ao contrário da maioria dos fotógrafos, escolhi um dia ensolarado para fotografar ali. Quis simbolizar a luz que nos aguarda após a morte. Então me posicionei dentro do cemitério para fotografar de dentro para fora. Esperei o sol se posicionar de forma que dos portões para fora houvesse pouca luz, tal como é o mundo, deixando toda a iluminação para dentro dos portões. Percebam como pequenos detalhes fazem toda a diferença numa fotografia analógica artística. Essa foto pode perfeitamente ser usada para ilustrar qualquer material que corrobore com esse pensamento. Se eu quisesse retratar que a vida é mil maravilhas e a morte um triste fim, deveria estar do lado de fora dos portões com tudo iluminado exceto o interior do cemitério. Interessante não…
https://image.nostr.build/051592db1d3612c719621547a69bc8dfd0319d6b89656451d5b60582ae864e8e.jpg
FOTOGRAFIA ANALÓGICA DE PESSOAS
Basicamente se divide em dois tipos, a cena e o retrato. Na cena a pessoa posa para a foto sem contudo revelar sua personalidade, é uma cena criada artificialmente. Já o retrato, no conceito artístico da fotografia, ocorre quando conseguimos captar o interior da pessoa. Por exemplo: se for uma pessoa triste ela aparecerá com semblante triste, se for uma pessoa alegre com semblante alegre, não necessariamente sorrido. Se for uma pessoa sofrida suas rugas, desasseios e receios ficarão visíveis. Se for uma pessoa engraçada sentiremos vontade de rir ao ver seu retrato. O retrato é algo verdadeiro e espontâneo da pessoa. Se uma pessoa triste aparece sorrido não é um retrato e sim uma cena, vamos ver:
Abaixo normalmente na fotografia analógica de pessoas o correto é deixar o segundo plano mais escuro e o primeiro plano mais claro. Ai quis fazer diferente. Pedi para o modelo (Meu Melhor Amigo) se posicionar de costas para o sol, pois já tinha avistado aquele arco-íris no fundo. Nesse caso foi um retrato pois meu amigo apareceu sorrindo sem eu pedir e sei que ele é uma pessoa feliz e engraçada, pois vive contando piadas e seu repertório é infinito. O interessante é que esse não é um retrato comum e sim um retrato artístico, pois inverti a iluminação dos planos e ainda captei uma arco-íris, foi uma cena construida para um retrato, ideia antagônica para fotografia analógica de pessoas. Como resultado obtive uma fotografia que parece uma montagem, onde a imagem do modelo ter-se-ia sido colada sobre a paisagem, tamanha foi a diferença de iluminação entre o primeiro e segundo plano. Contudo, um pequeno raio de sol que incidiu sobre o canteiro inferior esquerdo não me deixa mentir que a fotografia é autêntica. Além disso tendo os negativos que não mentem kkk. Essa foi minha fotografia preferida de pessoas, pela qualidade do resultado artístico e pela pessoa do modelo, um abração amigo! Vou chamar essa foto de “Meu Parça na Praça”:
https://image.nostr.build/51db1df7741227dc2d86529bc9e7a93cf27365f0f2d7b591a4e84a9a05855dfb.jpg
Abaixo sou eu. Se trata apenas de uma cena simples porque minha expressão não aparece e sequer minhas roupas traduziam minha personalidade. Regulei o foco da máquina para 5 metros, entreguei-a para meu amigo e contei alguns passos para trás. Não me preocupei muito em acertar minha posição em exatos 5 metros porque o dia estava bem ensolarado e sabia qua a Canon T50 iria abrir pouco o diafragma por causa disso, o que aumentou a profundidade de campo consideravelmente. Podemos perceber no fundo a Universidade Federal do Paraná sem qualquer desfoque por causa disso. O maldito poste que tentei evitar na foto arquitetônica da UFPR acima acabou aparecendo aqui, mesmo assim gostei da foto pelo tom de cores que só a fotografia analógica nos dá.
https://image.nostr.build/ce8af555274333fa8a26375247373ca92315e87d7414bcc9ad7b5a4840cb3a21.jpg
FOTOGRAFIA ANELÓGICA DE OBJETOS
A fotografia analógica de objetos, assim como a arquitetônica, deve se obedecer os conceitos básicos de iluminação para obter noção tridimensional do objeto. Além disso, a cena montada deve combinar com o objeto para entrar em sintonia com o conceito natural de beleza, vamos ver:
Abaixo queria fotografar um objeto qualquer, então peguei essa faca. Esse objeto combina muito bem com o ambiente rústico do campo, então a finquei-a num toco de árvore com vista para o campo, tomando cuidado para ela ficar levemente torcida e dar a noção tridimensional. Naturalmente a foto ornou porque o objeto esta em sintonia com a cena. Essa deve ser a combinação da fotografia analógica de objetos, por exemplo. A não ser que o fotógrafo busque justamente causar repudia invertendo a combinação do objeto com a cena. Por exemplo: para causar nojo pode-se fotografar barro em formato de cocô num prato. Merda e comida são coisas totalmente opostas e essa inversão naturalmente é perturbadora para qualquer ser humano. Existe uma lógica natural de combinação de objetos com a cena. Enfim, podemos inclusive combinar mais de um objeto secundário para criar uma cena ao objeto principal, como veremos mais abaixo com a xícara de café:
https://image.nostr.build/6474901ce85d34aef3421ce5f720e258208c50aeb57e9893c8a750c6dc8fc1df.jpg
Na foto abaixo o objeto principal é uma caneca de café. Para criar a cena utilizei outros três objetos. O palheiro que combina com café, a tampa da objetiva da minha Canon T50 que combina com o efeito da cafeína para pensar mais rápido sobre as cenas que irei montar, e o vazo de suculenta que remete a algo mais áspero e amargo como o café e o palheiro. Se o objeto principal fosse um copo de milkshake no lugar do palheiro haveriam balas coloridas, no lugar da tampa da máquina haveria um guardanapo e no lugar da suculenta haveria um flor fofa e cor de rosa. Falando em flor vou encerrar este ensaio com o tópico sobre fotografia analógica de flores para deixar todos felizes no final:
https://image.nostr.build/8e95c6bae536cfea47e3c5d44aa63725ab8fe20eacd1c6d5eeaae1720dd0a9e5.jpg
FOTOGRAFIA ANELÓGICA DE FLORES
É um tipo de fotografia livre da fotografia analógica, sem muitas preocupações para o fotógrafo analógico, devemos atentar apenas para a vivacidade das cores e para isso o dia deve estar especialmente ensolarado. Se for fotografia interna de preferência usar luz quente (amarela), o resto é só diversão, vamos ver:
https://image.nostr.build/fc8cf663300794761b0d8dc6f1a765e3a423c65a4ad4a85a7885b00716b46533.jpg
https://image.nostr.build/dc4fbe15a7b46817d66bdbeb3d0e11851999b2c1292c576fd457956436e75c77.jpg
https://image.nostr.build/73fa3b1b30a088954b342294e1b0aa555a693c3ad425dea9807d2238ec529747.jpg
Viva a fotografia analógica!
Se você deseja fazer um ensaio artístico com fotografia analógia comigo entre em contato e terei o prazer de agendar o serviço.
-

@ 1bda7e1f:bb97c4d9
2025-01-02 05:19:08
### Tldr
- Nostr is an open and interoperable protocol
- You can integrate it with workflow automation tools to augment your experience
- n8n is a great low/no-code workflow automation tool which you can host yourself
- Nostrobots allows you to integrate Nostr into n8n
- In this blog I create some workflow automations for Nostr
- A simple form to delegate posting notes
- Push notifications for mentions on multiple accounts
- Push notifications for your favourite accounts when they post a note
- All workflows are provided as open source with MIT license for you to use
### Inter-op All The Things
Nostr is a new open social protocol for the internet. This open nature exciting because of the opportunities for interoperability with other technologies. In [Using NFC Cards with Nostr]() I explored the `nostr:` URI to launch Nostr clients from a card tap.
The interoperability of Nostr doesn't stop there. The internet has many super-powers, and Nostr is open to all of them. Simply, there's no one to stop it. There is no one in charge, there are no permissioned APIs, and there are no risks of being de-platformed. If you can imagine technologies that would work well with Nostr, then any and all of them can ride on or alongside Nostr rails.
My mental model for why this is special is Google Wave ~2010. Google Wave was to be the next big platform. Lars was running it and had a big track record from Maps. I was excited for it. Then, Google pulled the plug. And, immediately all the time and capital invested in understanding and building on the platform was wasted.
This cannot happen to Nostr, as there is no one to pull the plug, and maybe even no plug to pull.
So long as users demand Nostr, Nostr will exist, and that is a pretty strong guarantee. It makes it worthwhile to invest in bringing Nostr into our other applications.
All we need are simple ways to plug things together.
### Nostr and Workflow Automation
Workflow automation is about helping people to streamline their work. As a user, the most common way I achieve this is by connecting disparate systems together. By setting up one system to trigger another or to move data between systems, I can solve for many different problems and become way more effective.
#### n8n for workflow automation
Many workflow automation tools exist. My favourite is [n8n](https://n8n.io/). n8n is a low/no-code workflow automation platform which allows you to build all kinds of workflows. You can use it for free, you can self-host it, it has a user-friendly UI and useful API. Vs Zapier it can be far more elaborate. Vs Make.com I find it to be more intuitive in how it abstracts away the right parts of the code, but still allows you to code when you need to.
Most importantly you can plug anything into n8n: You have built-in nodes for specific applications. HTTP nodes for any other API-based service. And community nodes built by individual community members for any other purpose you can imagine.
#### Eating my own dogfood
It's very clear to me that there is a big design space here just demanding to be explored. If you could integrate Nostr with anything, what would you do?
In my view the best way for anyone to start anything is by solving their own problem first (aka "scratching your own itch" and "eating your own dogfood"). As I get deeper into Nostr I find myself controlling multiple Npubs – to date I have a personal Npub, a brand Npub for a community I am helping, an AI assistant Npub, and various testing Npubs. I need ways to delegate access to those Npubs without handing over the keys, ways to know if they're mentioned, and ways to know if they're posting.
I can build workflows with n8n to solve these issues for myself to start with, and keep expanding from there as new needs come up.
### Running n8n with Nostrobots
I am mostly non-technical with a very helpful AI. To set up n8n to work with Nostr and operate these workflows should be possible for anyone with basic technology skills.
- I have a cheap VPS which currently runs my [HAVEN Nostr Relay](https://rodbishop.npub.pro/post/8ca68889/) and [Albyhub Lightning Node](https://rodbishop.npub.pro/post/setting-up-payments-on-nostr-7o6ls7/) in Docker containers,
- My objective was to set up n8n to run alongside these in a separate Docker container on the same server, install the required nodes, and then build and host my workflows.
#### Installing n8n
Self-hosting n8n could not be easier. I followed n8n's [Docker-Compose installation docs](https://docs.n8n.io/hosting/installation/server-setups/docker-compose/)–
- Install Docker and Docker-Compose if you haven't already,
- Create your ``docker-compose.yml`` and `.env` files from the docs,
- Create your data folder `sudo docker volume create n8n_data`,
- Start your container with `sudo docker compose up -d`,
- Your n8n instance should be online at port `5678`.
n8n is free to self-host but does require a license. Enter your credentials into n8n to get your free license key. You should now have access to the Workflow dashboard and can create and host any kind of workflows from there.
#### Installing Nostrobots
To integrate n8n nicely with Nostr, I used the [Nostrobots](https://github.com/ocknamo/n8n-nodes-nostrobots?tab=readme-ov-file) community node by [Ocknamo](nostr:npub1y6aja0kkc4fdvuxgqjcdv4fx0v7xv2epuqnddey2eyaxquznp9vq0tp75l).
In n8n parlance a "node" enables certain functionality as a step in a workflow e.g. a "set" node sets a variable, a "send email" node sends an email. n8n comes with all kinds of "official" nodes installed by default, and Nostr is not amongst them. However, n8n also comes with a framework for community members to create their own "community" nodes, which is where Nostrobots comes in.
You can only use a community node in a self-hosted n8n instance (which is what you have if you are running in Docker on your own server, but this limitation does prevent you from using n8n's own hosted alternative).
To install a community node, [see n8n community node docs](https://docs.n8n.io/integrations/community-nodes/installation/gui-install/). From your workflow dashboard–
- Click the "..." in the bottom left corner beside your username, and click "settings",
- Cilck "community nodes" left sidebar,
- Click "Install",
- Enter the "npm Package Name" which is `n8n-nodes-nostrobots`,
- Accept the risks and click "Install",
- Nostrobots is now added to your n8n instance.
#### Using Nostrobots
Nostrobots gives you nodes to help you build Nostr-integrated workflows–
- **Nostr Write** – for posting Notes to the Nostr network,
- **Nostr Read** – for reading Notes from the Nostr network, and
- **Nostr Utils** – for performing certain conversions you may need (e.g. from bech32 to hex).
Nostrobots has [good documentation](https://github.com/ocknamo/n8n-nodes-nostrobots?tab=readme-ov-file) on each node which focuses on simple use cases.
Each node has a "convenience mode" by default. For example, the "Read" Node by default will fetch Kind 1 notes by a simple filter, in Nostrobots parlance a "Strategy". For example, with Strategy set to "Mention" the node will accept a pubkey and fetch all Kind 1 notes that Mention the pubkey within a time period. This is very good for quick use.
What wasn't clear to me initially (until Ocknamo helped me out) is that advanced use cases are also possible.
Each node also has an advanced mode. For example, the "Read" Node can have "Strategy" set to "RawFilter(advanced)". Now the node will accept json (anything you like that complies with [NIP-01](https://github.com/nostr-protocol/nips/blob/master/01.md)). You can use this to query Notes (Kind 1) as above, and also Profiles (Kind 0), Follow Lists (Kind 3), Reactions (Kind 7), Zaps (Kind 9734/9735), and anything else you can think of.
#### Creating and adding workflows
With n8n and Nostrobots installed, you can now create or add any kind of Nostr Workflow Automation.
- Click "Add workflow" to go to the workflow builder screen,
- If you would like to build your own workflow, you can start with adding any node. Click "+" and see what is available. Type "Nostr" to explore the Nostrobots nodes you have added,
- If you would like to add workflows that someone else has built, click "..." in the top right. Then click "import from URL" and paste in the URL of any workflow you would like to use (including the ones I share later in this article).
### Nostr Workflow Automations
It's time to build some things!
#### A simple form to post a note to Nostr
I started very simply. I needed to delegate the ability to post to Npubs that I own in order that a (future) team can test things for me. I don't want to worry about managing or training those people on how to use keys, and I want to revoke access easily.
I needed a basic form with credentials that posted a Note.
For this I can use a very simple workflow–
- **A n8n Form node** – Creates a form for users to enter the note they wish to post. Allows for the form to be protected by a username and password. This node is the workflow "trigger" so that the workflow runs each time the form is submitted.
- **A Set node** – Allows me to set some variables, in this case I set the relays that I intend to use. I typically add a Set node immediately following the trigger node, and put all the variables I need in this. It helps to make the workflows easier to update and maintain.
- **A Nostr Write node** (from Nostrobots) – Writes a Kind-1 note to the Nostr network. It accepts Nostr credentials, the output of the Form node, and the relays from the Set node, and posts the Note to those relays.
Once the workflow is built, you can test it with the testing form URL, and set it to "Active" to use the production form URL. That's it. You can now give posting access to anyone for any Npub. To revoke access, simply change the credentials or set to workflow to "Inactive".
It may also be the world's simplest Nostr client.
You can find the [Nostr Form to Post a Note workflow here](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Form_to_Post_a_Note.json).
#### Push notifications on mentions and new notes
One of the things Nostr is not very good at is push notifications. Furthermore I have some unique itches to scratch. I want–
- **To make sure I never miss a note addressed to any of my Npubs** – For this I want a push notification any time any Nostr user mentions any of my Npubs,
- **To make sure I always see all notes from key accounts** – For this I need a push notification any time any of my Npubs post any Notes to the network,
- **To get these notifications on all of my devices** – Not just my phone where my Nostr regular client lives, but also on each of my laptops to suit wherever I am working that day.
I needed to build a Nostr push notifications solution.
To build this workflow I had to string a few ideas together–
- **Triggering the node on a schedule** – Nostrobots does not include a trigger node. As every workflow starts with a trigger we needed a different method. I elected to run the workflow on a schedule of every 10-minutes. Frequent enough to see Notes while they are hot, but infrequent enough to not burden public relays or get rate-limited,
- **Storing a list of Npubs in a Nostr list** – I needed a way to store the list of Npubs that trigger my notifications. I initially used an array defined in the workflow, this worked fine. Then I decided to try Nostr lists ([NIP-51, kind 30000](https://github.com/nostr-protocol/nips/blob/master/51.md)). By defining my list of Npubs as a list published to Nostr I can control my list from within a Nostr client (e.g. [Listr.lol](https://listr.lol/npub1r0d8u8mnj6769500nypnm28a9hpk9qg8jr0ehe30tygr3wuhcnvs4rfsft) or [Nostrudel.ninja](https://nostrudel.ninja/#/lists)). Not only does this "just work", but because it's based on Nostr lists automagically Amethyst client allows me to browse that list as a Feed, and everyone I add gets notified in their Mentions,
- **Using specific relays** – I needed to query the right relays, including my own HAVEN relay inbox for notes addressed to me, and wss://purplepag.es for Nostr profile metadata,
- **Querying Nostr events** (with Nostrobots) – I needed to make use of many different Nostr queries and use quite a wide range of what Nostrobots can do–
- I read the EventID of my Kind 30000 list, to return the desired pubkeys,
- For notifications on mentions, I read all Kind 1 notes that mention that pubkey,
- For notifications on new notes, I read all Kind 1 notes published by that pubkey,
- Where there are notes, I read the Kind 0 profile metadata event of that pubkey to get the displayName of the relevant Npub,
- I transform the EventID into a Nevent to help clients find it.
- **Using the Nostr URI** – As I did with my NFC card article, I created a link with the `nostr:` URI prefix so that my phone's native client opens the link by default,
- **Push notifications solution** – I needed a push notifications solution. I found many with n8n integrations and chose to go with [Pushover](https://pushover.net/) which supports all my devices, has a free trial, and is unfairly cheap with a $5-per-device perpetual license.
Once the workflow was built, lists published, and Pushover installed on my phone, I was fully set up with push notifications on Nostr. I have used these workflows for several weeks now and made various tweaks as I went. They are feeling robust and I'd welcome you to give them a go.
You can find the [Nostr Push Notification If Mentioned here](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Push_Notify_If_Mentioned.json) and [If Posts a Note here](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Push_Notify_If_Post_a_Note.json).
In speaking with other Nostr users while I was building this, there are all kind of other needs for push notifications too – like on replies to a certain bookmarked note, or when a followed Npub starts streaming on zap.stream. These are all possible.
#### Use my workflows
I have open sourced all my workflows at my [Github](https://github.com/r0d8lsh0p/nostr-n8n) with MIT license and tried to write complete docs, so that you can import them into your n8n and configure them for your own use.
To import any of my workflows–
- Click on the workflow of your choice, e.g. "[Nostr_Push_Notify_If_Mentioned.json](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Push_Notify_If_Mentioned.json "Nostr_Push_Notify_If_Mentioned.json")",
- Click on the "raw" button to view the raw JSON, ex any Github page layout,
- Copy that URL,
- Enter that URL in the "import from URL" dialog [mentioned above](#creating-and-adding-workflows).
To configure them–
- Prerequisites, credentials, and variables are all stated,
- In general any variables required are entered into a Set Node that follows the trigger node,
- Pushover has some extra setup but is very straightforward and documented in the workflow.
### What next?
Over my first four blogs I explored creating a good Nostr setup with [Vanity Npub](https://rodbishop.npub.pro/post/mining-your-vanity-pubkey-4iupbf/), [Lightning Payments](https://rodbishop.npub.pro/post/setting-up-payments-on-nostr-7o6ls7/), [Nostr Addresses at Your Domain](https://rodbishop.npub.pro/post/ee8a46bc/), and [Personal Nostr Relay](https://rodbishop.npub.pro/post/8ca68889/).
Then in my latest two blogs I explored different types of interoperability [with NFC cards](https://rodbishop.npub.pro/post/edde8387/) and now n8n Workflow Automation.
Thinking ahead n8n can power any kind of interoperability between Nostr and any other legacy technology solution. On my mind as I write this:
- Further enhancements to posting and delegating solutions and forms (enhanced UI or different note kinds),
- Automated or scheduled posting (such as auto-liking everything [Lyn Alden](nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a) posts),
- Further enhancements to push notifications, on new and different types of events (such as notifying me when I get a new follower, on replies to certain posts, or when a user starts streaming),
- All kinds of bridges, such as bridging notes to and from Telegram, Slack, or Campfire. Or bridging RSS or other event feeds to Nostr,
- All kinds of other automation (such as [BlackCoffee](nostr:npub1dqepr0g4t3ahvnjtnxazvws4rkqjpxl854n29wcew8wph0fmw90qlsmmgt) [controlling a coffee machine](https://primal.net/e/note16fzhh5yfc3u4kufx0mck63tsfperdrlpp96am2lmq066cnuqutds8retc3)),
- All kinds of AI Assistants and Agents,
In fact I have already released an open source workflow for an [AI Assistant](https://primal.net/p/npub1ahjpx53ewavp23g5zj9jgyfrpr8djmgjzg5mpe4xd0z69dqvq0kq2lf353), and will share more about that in my next blog.
Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle.
GM Nostr.
-

@ a95c6243:d345522c
2025-01-01 17:39:51
**Heute möchte ich ein Gedicht mit euch teilen.** Es handelt sich um eine Ballade des österreichischen Lyrikers Johann Gabriel Seidl aus dem 19. Jahrhundert. Mir sind diese Worte fest in Erinnerung, da meine Mutter sie perfekt rezitieren konnte, auch als die Kräfte schon langsam schwanden.
**Dem originalen Titel «Die Uhr»** habe ich für mich immer das Wort «innere» hinzugefügt. Denn der Zeitmesser – hier vermutliche eine Taschenuhr – symbolisiert zwar in dem Kontext das damalige Zeitempfinden und die Umbrüche durch die industrielle Revolution, sozusagen den Zeitgeist und das moderne Leben. Aber der Autor setzt sich philosophisch mit der Zeit auseinander und gibt seinem Werk auch eine klar spirituelle Dimension.
**Das Ticken der Uhr und die Momente des Glücks und der Trauer** stehen sinnbildlich für das unaufhaltsame Fortschreiten und die Vergänglichkeit des Lebens. Insofern könnte man bei der Uhr auch an eine Sonnenuhr denken. Der Rhythmus der Ereignisse passt uns vielleicht nicht immer in den Kram.
**Was den Takt pocht, ist durchaus auch das Herz,** unser «inneres Uhrwerk». Wenn dieses Meisterwerk einmal stillsteht, ist es unweigerlich um uns geschehen. Hoffentlich können wir dann dankbar sagen: «Ich habe mein Bestes gegeben.»
*Ich trage, wo ich gehe, stets eine Uhr bei mir;* \
*Wieviel es geschlagen habe, genau seh ich an ihr.* \
*Es ist ein großer Meister, der künstlich ihr Werk gefügt,* \
*Wenngleich ihr Gang nicht immer dem törichten Wunsche genügt.*  
*Ich wollte, sie wäre rascher gegangen an manchem Tag;* *\
Ich wollte, sie hätte manchmal verzögert den raschen Schlag.* *\
In meinen Leiden und Freuden, in Sturm und in der Ruh,* *\
Was immer geschah im Leben, sie pochte den Takt dazu.*  
*Sie schlug am Sarge des Vaters, sie schlug an des Freundes Bahr,* *\
Sie schlug am Morgen der Liebe, sie schlug am Traualtar.* *\
Sie schlug an der Wiege des Kindes, sie schlägt, will's Gott, noch oft,* *\
Wenn bessere Tage kommen, wie meine Seele es hofft.*  
*Und ward sie auch einmal träger, und drohte zu stocken ihr Lauf,* *\
So zog der Meister immer großmütig sie wieder auf.* *\
Doch stände sie einmal stille, dann wär's um sie geschehn,* *\
Kein andrer, als der sie fügte, bringt die Zerstörte zum Gehn.*  
*Dann müßt ich zum Meister wandern, der wohnt am Ende wohl weit,* *\
Wohl draußen, jenseits der Erde, wohl dort in der Ewigkeit!* *\
Dann gäb ich sie ihm zurücke mit dankbar kindlichem Flehn:* *\
Sieh, Herr, ich hab nichts verdorben, sie blieb von selber stehn.*  
*Johann Gabriel Seidl (1804-1875)*
-

@ a10260a2:caa23e3e
2025-01-01 12:42:22
I’d like to start off by saying that phoenixd has been a great experience so far. The install (on a Linux machine) was as easy as depicted on their [website](https://phoenix.acinq.co/server/get-started).
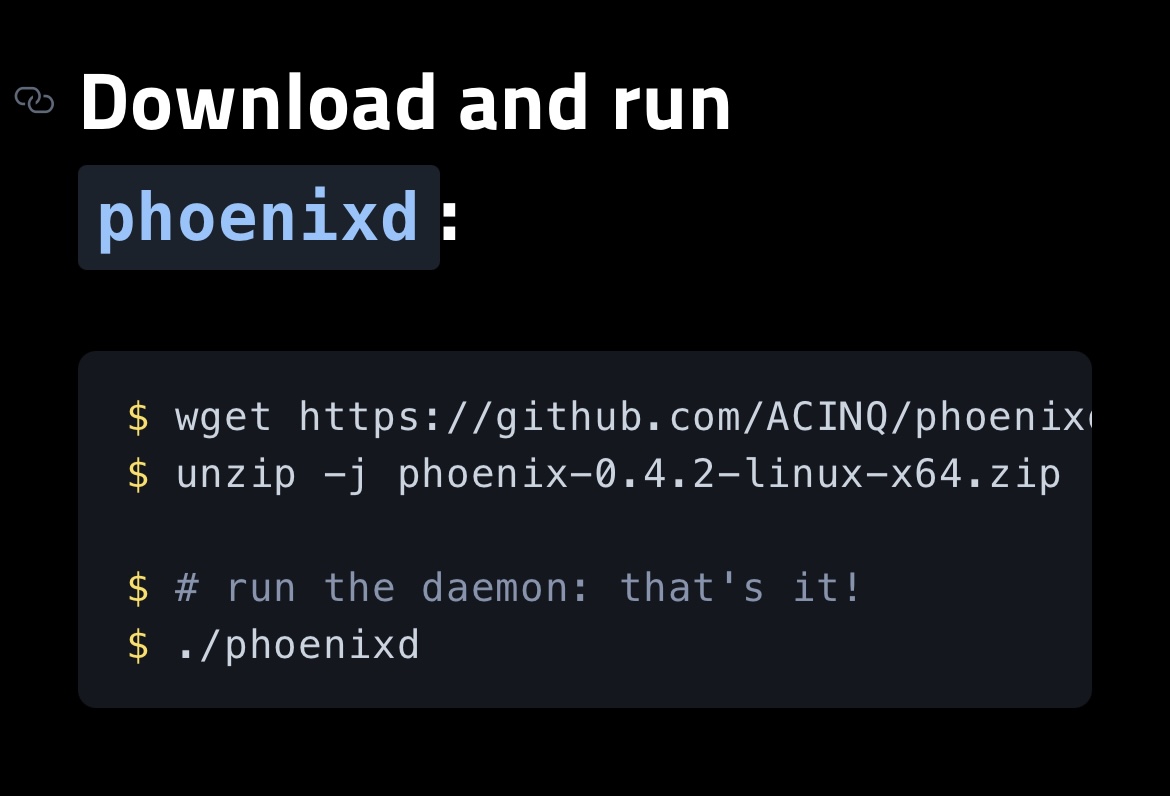
And the channel I opened via [auto liquidity](https://phoenix.acinq.co/server/auto-liquidity) was super simple. I didn’t have to pick an LSP and I won’t need to manage liquidity.
Unfortunately, the machine I installed the software on started to freeze seconds after every boot. After posting about it [here](https://stacker.news/items/825060/r/thebullishbitcoiner) and getting an answer from nostr:npub1lxktpvp5cnq3wl5ctu2x88e30mc0ahh8v47qvzc5dmneqqjrzlkqpm5xlc, I was surprised at how easy the migration seemed.
It really was just a matter of restoring the seed words on another phoenixd instance. Of course, making sure that the two instances don’t run at the same time.
As easy as it was, I wanted to create this post to give a quick overview for those who might be less tech savvy.
### Step 1
Grab seed words from the `seed.dat` file in hidden`.phoenix` folder on the old machine.
### Step 2
Install phoenixd on the new machine
```
$ wget https://github.com/ACINQ/phoenixd/releases/download/v0.4.2/phoenix-0.4.2-linux-x64.zip
$ unzip -j phoenix-0.4.2-linux-x64.zip
$ # run the daemon: that's it!
$ ./phoenixd
```
### Step 3
(This is the step that wasn’t super clear and why I wanted to spell it out in this post)
In order to install the software, `./phoenixd` has to be run. This is going to generate a new seed phrase.
Now, all you need to do is replace the seed words in `seed.dat` with the ones from the original install.
In retrospect, I think you can replace the seed words right after unzipping the zip file and before running `./phoenixd`. That will probably achieve the same result.
### Step 4
Once the seed words have been restored. Just run `./phoenixd` again and it’ll start up like nothing happened.
Literally.
There was no indication whatsoever that something had changed, so I ran `./phoenix-cli getinfo` and, voila, there was my 2M-sat channel.
It was quite magical.
originally posted at https://stacker.news/items/829411
### Update (1/1/2025)
Phoenix Support got back to me and confirmed that the migration can be even simpler. You can actually just copy the ~/.phoenix directory onto the new machine and run `./phoenix`!

-

@ 5188521b:008eb518
2025-01-01 10:47:04
My experience of [daily posting on LinkedIn](https://www.linkedin.com/in/totallyhumanwriter/) started around three years ago, when I became more serious about my coaching business. In that time, I amassed 25,000 followers and garnered around 3 million impressions on my writing.
It was a wild ride, but now it’s time to leave the theme park.
# Reasons I Quit Posting on LinkedIn
Here they are, in no particular order:
1. I went from coach to ghostwriter. 2024 threw up an unexpected career change. Since 2018, I've been a coach, moving from teaching English as a foreign language to working with groups of multilingual pro writers looking for better opportunities.
Coaching is a tough industry (maybe I'll write about that someday). My idea was to write more meaningful words and less copy to market my coaching business. Ultimately, writing to develop the Bitcoin ecosystem is what I find meaningful, and writing for hire doesn't require as much copywriting as being a coach.
With a solid portfolio, contacts, and profile, potential clients can see your results. You don't need to attract a ton of inbound leads by writing funny bits and wow-inducing educational posts on LinkedIn.
2. Time constraints Because of my own book marketing, new client work, and projects like [21 Futures](https://21futures.com/), I can't dedicate my creative efforts and several hours per week to writing on LinkedIn.
That time works better for me elsewhere.
3. Worsening distribution 'Creators' (a.k.a. active posters with many followers) often say changes to the algorithm don't matter. 'Get on with it. Adapt and move forward.'
I'd be lying if I said I'm happy seeing statistics for my posts plummet. In 2022 and 2023, a successful carousel might net 20,000 views with over 150 likes and 50+ comments. Now, an exceptional post for me attracts 5,000 views with 50 likes.
I won't bore you with charts and statistics, but this is an average, based on hundreds of posts. It seems LinkedIn is reducing the reach of big accounts in favour of tighter networks and distributing the work of those with <5k followers. That's fine. Perhaps that will make the platform less showy, and less boastful, finally ridding us of fake stories, surprising hacks, and ultimate guides.
Still, It makes creative types like me feel like failures. Does an 80% decrease in distribution seem fair for the three years of daily effort I've put in? Should I keep struggling for diminishing returns? No. Creative people must seek the best return on investment for their time.
The lesson? Distribution is more important than follower numbers.
I've also quit Medium, where I have 2,000 followers and regularly receive single-digit reads on my posts.
4. LinkedIn values machines over humans. Cost-cutting, extracting value, and planning for a robotic future. That's Microsoft's MO.
Despite being a social network with over 1 billion users, LinkedIn seemingly relies on automated support to make decisions on which content, people, and ideas are allowed on the platform.
Users' data is parsed without their express consent.\
LinkedIn seems desperate for us to use generative AI to express our 'insight'.\
We are constantly bombarded by LLM drivel and boring machine-made content. If you can't be bothered to write it, why should I bother to read it?
As somebody who brands himself a human-centric writer, why would I offer up personal takes and stories writing for free in an AI-filled swamp?
---
# What's next?
So I'm giving up posting on LinkedIn.
With that said, it can still produce a great benefit for its users, especially those in the bitcoin space.
Why? The ability to search for potential connections, present your profile, and share your expertise can make a huge difference to your work - investment, partnership, and customers.
If you have a smaller network and have the need to share personal takes, opinions, and expertise, posting on LinkedIn is worth it. So few are doing this in bitcoin, the opportunities in 2025 are mind-boggling.
Next year, thousands of new startups and ventures will be vying for our attention. Those who can build trust and stay true to their message will win. And if LinkedIn stops working, you can always take your followers elsewhere.
If you have read and enjoyed my words here on LinkedIn in the last three years, thank you.
It has been a much-needed creative outlet and has brought me opportunities, laughs, knowledge, new colleagues, and friends. I'll still be stalking your posts and writing sarcastic comments.
---
# Where can you find me:
Bitcoin writing - [X](https://x.com/21Futures), [StackerNews](https://stacker.news/21futures) [21futures.com](https://21futures.com/)\
NOSTR - npub12xy9yxej6s9hgzsn3rfyfc3xgtdr29wqlvulquzhz2fhqqywk5vqnyvqut),
[Totallyhumanwriter.com](https://totallyhumanwriter.com/) - website coming soon.
[Maximum Freedom, Minimum Bullshit](https://maximumfreedom.substack.com/) on Substack.
And you can reach me via email at philipcharterauthor@gmail.com
I'm interested to know your thoughts and plans for 2025. Where will you be writing and why?
-

@ 3f770d65:7a745b24
2024-12-31 17:03:46
Here are my predictions for Nostr in 2025:
**Decentralization:** The outbox and inbox communication models, sometimes referred to as the Gossip model, will become the standard across the ecosystem. By the end of 2025, all major clients will support these models, providing seamless communication and enhanced decentralization. Clients that do not adopt outbox/inbox by then will be regarded as outdated or legacy systems.
**Privacy Standards:** Major clients such as Damus and Primal will move away from NIP-04 DMs, adopting more secure protocol possibilities like NIP-17 or NIP-104. These upgrades will ensure enhanced encryption and metadata protection. Additionally, NIP-104 MLS tools will drive the development of new clients and features, providing users with unprecedented control over the privacy of their communications.
**Interoperability:** Nostr's ecosystem will become even more interconnected. Platforms like the Olas image-sharing service will expand into prominent clients such as Primal, Damus, Coracle, and Snort, alongside existing integrations with Amethyst, Nostur, and Nostrudel. Similarly, audio and video tools like Nostr Nests and Zap.stream will gain seamless integration into major clients, enabling easy participation in live events across the ecosystem.
**Adoption and Migration:** Inspired by early pioneers like Fountain and Orange Pill App, more platforms will adopt Nostr for authentication, login, and social systems. In 2025, a significant migration from a high-profile application platform with hundreds of thousands of users will transpire, doubling Nostr’s daily activity and establishing it as a cornerstone of decentralized technologies.
-

@ e97aaffa:2ebd765d
2024-12-31 16:47:12
Último dia do ano, momento para tirar o pó da bola de cristal, para fazer reflexões, previsões e desejos para o próximo ano e seguintes.
Ano após ano, o Bitcoin evoluiu, foi ultrapassando etapas, tornou-se cada vez mais _mainstream_. Está cada vez mais difícil fazer previsões sobre o Bitcoin, já faltam poucas barreiras a serem ultrapassadas e as que faltam são altamente complexas ou tem um impacto profundo no sistema financeiro ou na sociedade. Estas alterações profundas tem que ser realizadas lentamente, porque uma alteração rápida poderia resultar em consequências terríveis, poderia provocar um retrocesso.
# Código do Bitcoin
No final de 2025, possivelmente vamos ter um _fork_, as discussões sobre os _covenants_ já estão avançadas, vão acelerar ainda mais. Já existe um consenso relativamente alto, a favor dos _covenants_, só falta decidir que modelo será escolhido. Penso que até ao final do ano será tudo decidido.
Depois dos _covenants,_ o próximo foco será para a criptografia post-quantum, que será o maior desafio que o Bitcoin enfrenta. Criar uma criptografia segura e que não coloque a descentralização em causa.
Espero muito de Ark, possivelmente a inovação do ano, gostaria de ver o Nostr a furar a bolha bitcoinheira e que o Cashu tivesse mais reconhecimento pelos _bitcoiners_.
Espero que surjam avanços significativos no BitVM2 e BitVMX.
Não sei o que esperar das layer 2 de Bitcoin, foram a maior desilusão de 2024. Surgiram com muita força, mas pouca coisa saiu do papel, foi uma mão cheia de nada. Uma parte dos projetos caiu na tentação da _shitcoinagem_, na criação de tokens, que tem um único objetivo, enriquecer os devs e os VCs.
Se querem ser levados a sério, têm que ser sérios.
> “À mulher de César não basta ser honesta, deve parecer honesta”
Se querem ter o apoio dos _bitcoiners_, sigam o _ethos_ do Bitcoin.
Neste ponto a atitude do pessoal da Ark é exemplar, em vez de andar a chorar no Twitter para mudar o código do Bitcoin, eles colocaram as mãos na massa e criaram o protocolo. É claro que agora está meio “coxo”, funciona com uma _multisig_ ou com os _covenants_ na Liquid. Mas eles estão a criar um produto, vão demonstrar ao mercado que o produto é bom e útil. Com a adoção, a comunidade vai perceber que o Ark necessita dos _covenants_ para melhorar a interoperabilidade e a soberania.
É este o pensamento certo, que deveria ser seguido pelos restantes e futuros projetos. É seguir aquele pensamento do J.F. Kennedy:
> “Não perguntem o que é que o vosso país pode fazer por vocês, perguntem o que é que vocês podem fazer pelo vosso país”
Ou seja, não fiquem à espera que o bitcoin mude, criem primeiro as inovações/tecnologia, ganhem adoção e depois demonstrem que a alteração do código camada base pode melhorar ainda mais o vosso projeto. A necessidade é que vai levar a atualização do código.
# Reservas Estratégicas de Bitcoin
## Bancos centrais
Com a eleição de Trump, emergiu a ideia de uma Reserva Estratégia de Bitcoin, tornou este conceito _mainstream_. Foi um _pivot_, a partir desse momento, foram enumerados os políticos de todo o mundo a falar sobre o assunto.
A Senadora Cynthia Lummis foi mais além e propôs um programa para adicionar 200 mil bitcoins à reserva ao ano, até 1 milhão de Bitcoin. Só que isto está a criar uma enorme expectativa na comunidade, só que pode resultar numa enorme desilusão. Porque no primeiro ano, o Trump em vez de comprar os 200 mil, pode apenas adicionar na reserva, os 198 mil que o Estado já tem em sua posse. Se isto acontecer, possivelmente vai resultar numa forte queda a curto prazo. Na minha opinião os bancos centrais deveriam seguir o exemplo de El Salvador, fazer um DCA diário.
Mais que comprar bitcoin, para mim, o mais importante é a criação da Reserva, é colocar o Bitcoin ao mesmo nível do ouro, o impacto para o resto do mundo será tremendo, a teoria dos jogos na sua plenitude. Muitos outros bancos centrais vão ter que comprar, para não ficarem atrás, além disso, vai transmitir uma mensagem à generalidade da população, que o Bitcoin é “afinal é algo seguro, com valor”.
Mas não foi Trump que iniciou esta teoria dos jogos, mas sim foi a primeira vítima dela. É o próprio Trump que o admite, que os EUA necessitam da reserva para não ficar atrás da China. Além disso, desde que os EUA utilizaram o dólar como uma arma, com sanção contra a Rússia, surgiram boatos de que a Rússia estaria a utilizar o Bitcoin para transações internacionais. Que foram confirmados recentemente, pelo próprio governo russo. Também há poucos dias, ainda antes deste reconhecimento público, Putin elogiou o Bitcoin, ao reconhecer que “Ninguém pode proibir o bitcoin”, defendendo como uma alternativa ao dólar. A narrativa está a mudar.
Já existem alguns países com Bitcoin, mas apenas dois o fizeram conscientemente (El Salvador e Butão), os restantes têm devido a apreensões. Hoje são poucos, mas 2025 será o início de uma corrida pelos bancos centrais. Esta corrida era algo previsível, o que eu não esperava é que acontecesse tão rápido.

## Empresas
A criação de reservas estratégicas não vai ficar apenas pelos bancos centrais, também vai acelerar fortemente nas empresas em 2025.

Mas as empresas não vão seguir a estratégia do Saylor, vão comprar bitcoin sem alavancagem, utilizando apenas os tesouros das empresas, como uma proteção contra a inflação. Eu não sou grande admirador do Saylor, prefiro muito mais, uma estratégia conservadora, sem qualquer alavancagem. Penso que as empresas vão seguir a sugestão da BlackRock, que aconselha um alocações de 1% a 3%.
Penso que 2025, ainda não será o ano da entrada das 6 magníficas (excepto Tesla), será sobretudo empresas de pequena e média dimensão. As magníficas ainda tem uma cota muito elevada de _shareholders_ com alguma idade, bastante conservadores, que têm dificuldade em compreender o Bitcoin, foi o que aconteceu recentemente com a Microsoft.
Também ainda não será em 2025, talvez 2026, a inclusão nativamente de wallet Bitcoin nos sistema da Apple Pay e da Google Pay. Seria um passo gigante para a adoção a nível mundial.
# ETFs
Os ETFs para mim são uma incógnita, tenho demasiadas dúvidas, como será 2025. Este ano os _inflows_ foram superiores a 500 mil bitcoins, o IBIT foi o lançamento de ETF mais bem sucedido da história. O sucesso dos ETFs, deve-se a 2 situações que nunca mais se vão repetir. O mercado esteve 10 anos à espera pela aprovação dos ETFs, a procura estava reprimida, isso foi bem notório nos primeiros meses, os _inflows_ foram brutais.
Também se beneficiou por ser um mercado novo, não existia _orderbook_ de vendas, não existia um mercado interno, praticamente era só _inflows_. Agora o mercado já estabilizou, a maioria das transações já são entre clientes dos próprios ETFs. Agora só uma pequena percentagem do volume das transações diárias vai resultar em _inflows_ ou _outflows_.
Estes dois fenómenos nunca mais se vão repetir, eu não acredito que o número de _inflows_ em BTC supere os número de 2024, em dólares vai superar, mas em btc não acredito que vá superar.
Mas em 2025 vão surgir uma infindável quantidade de novos produtos, derivativos, novos ETFs de cestos com outras criptos ou cestos com ativos tradicionais. O bitcoin será adicionado em produtos financeiros já existentes no mercado, as pessoas vão passar a deter bitcoin, sem o saberem.
Com o fim da operação ChokePoint 2.0, vai surgir uma nova onda de adoção e de produtos financeiros. Possivelmente vamos ver bancos tradicionais a disponibilizar produtos ou serviços de custódia aos seus clientes.
Eu adoraria ver o crescimento da adoção do bitcoin como moeda, só que a regulamentação não vai ajudar nesse processo.
# Preço
Eu acredito que o topo deste ciclo será alcançado no primeiro semestre, posteriormente haverá uma correção. Mas desta vez, eu acredito que a correção será muito menor que as anteriores, inferior a 50%, esta é a minha expectativa. Espero estar certo.
# Stablecoins de dólar
Agora saindo um pouco do universo do Bitcoin, acho importante destacar as _stablecoins_.
No último ciclo, eu tenho dividido o tempo, entre continuar a estudar o Bitcoin e estudar o sistema financeiro, as suas dinâmicas e o comportamento humano. Isto tem sido o meu foco de reflexão, imaginar a transformação que o mundo vai sofrer devido ao padrão Bitcoin. É uma ilusão acreditar que a transição de um padrão FIAT para um padrão Bitcoin vai ser rápida, vai existir um processo transitório que pode demorar décadas.
Com a re-entrada de Trump na Casa Branca, prometendo uma política altamente protecionista, vai provocar uma forte valorização do dólar, consequentemente as restantes moedas do mundo vão derreter. Provocando uma inflação generalizada, gerando uma corrida às _stablecoins_ de dólar nos países com moedas mais fracas. Trump vai ter uma política altamente expansionista, vai exportar dólares para todo o mundo, para financiar a sua própria dívida. A desigualdade entre os pobres e ricos irá crescer fortemente, aumentando a possibilidade de conflitos e revoltas.
> “Casa onde não há pão, todos ralham e ninguém tem razão”
Será mais lenha, para alimentar a fogueira, vai gravar os conflitos geopolíticos já existentes, ficando as sociedade ainda mais polarizadas.
Eu acredito que 2025, vai haver um forte crescimento na adoção das _stablecoins_ de dólares, esse forte crescimento vai agravar o problema sistémico que são as _stablecoins_. Vai ser o início do fim das _stablecoins_, pelo menos, como nós conhecemos hoje em dia.
## Problema sistémico
O sistema FIAT não nasceu de um dia para outro, foi algo que foi construído organicamente, ou seja, foi evoluindo ao longo dos anos, sempre que havia um problema/crise, eram criadas novas regras ou novas instituições para minimizar os problemas. Nestes quase 100 anos, desde os acordos de Bretton Woods, a evolução foram tantas, tornaram o sistema financeiro altamente complexo, burocrático e nada eficiente.
Na prática é um castelo de cartas construído sobre outro castelo de cartas e que por sua vez, foi construído sobre outro castelo de cartas.
As _stablecoins_ são um problema sistémico, devido às suas reservas em dólares e o sistema financeiro não está preparado para manter isso seguro. Com o crescimento das reservas ao longo dos anos, foi se agravando o problema.
No início a Tether colocava as reservas em bancos comerciais, mas com o crescimento dos dólares sob gestão, criou um problema nos bancos comerciais, devido à reserva fracionária. Essas enormes reservas da Tether estavam a colocar em risco a própria estabilidade dos bancos.
A Tether acabou por mudar de estratégia, optou por outros ativos, preferencialmente por títulos do tesouro/obrigações dos EUA. Só que a Tether continua a crescer e não dá sinais de abrandamento, pelo contrário.
Até o próprio mundo cripto, menosprezava a gravidade do problema da Tether/_stablecoins_ para o resto do sistema financeiro, porque o _marketcap_ do cripto ainda é muito pequeno. É verdade que ainda é pequeno, mas a Tether não o é, está no top 20 dos maiores detentores de títulos do tesouros dos EUA e está ao nível dos maiores bancos centrais do mundo. Devido ao seu tamanho, está a preocupar os responsáveis/autoridades/reguladores dos EUA, pode colocar em causa a estabilidade do sistema financeiro global, que está assente nessas obrigações.
Os títulos do tesouro dos EUA são o colateral mais utilizado no mundo, tanto por bancos centrais, como por empresas, é a charneira da estabilidade do sistema financeiro. Os títulos do tesouro são um assunto muito sensível. Na recente crise no Japão, do _carry trade_, o Banco Central do Japão tentou minimizar a desvalorização do iene através da venda de títulos dos EUA. Esta operação, obrigou a uma viagem de emergência, da Secretaria do Tesouro dos EUA, Janet Yellen ao Japão, onde disponibilizou liquidez para parar a venda de títulos por parte do Banco Central do Japão. Essa forte venda estava desestabilizando o mercado.
Os principais detentores de títulos do tesouros são institucionais, bancos centrais, bancos comerciais, fundo de investimento e gestoras, tudo administrado por gestores altamente qualificados, racionais e que conhecem a complexidade do mercado de obrigações.
O mundo cripto é seu oposto, é _naife_ com muita irracionalidade e uma forte pitada de loucura, na sua maioria nem faz a mínima ideia como funciona o sistema financeiro. Essa irracionalidade pode levar a uma “corrida bancária”, como aconteceu com o UST da Luna, que em poucas horas colapsou o projeto. Em termos de escala, a Luna ainda era muito pequena, por isso, o problema ficou circunscrito ao mundo cripto e a empresas ligadas diretamente ao cripto.
Só que a Tether é muito diferente, caso exista algum FUD, que obrigue a Tether a desfazer-se de vários biliões ou dezenas de biliões de dólares em títulos num curto espaço de tempo, poderia provocar consequências terríveis em todo o sistema financeiro. A Tether é grande demais, é já um problema sistémico, que vai agravar-se com o crescimento em 2025.
Não tenham dúvidas, se existir algum problema, o Tesouro dos EUA vai impedir a venda dos títulos que a Tether tem em sua posse, para salvar o sistema financeiro. O problema é, o que vai fazer a Tether, se ficar sem acesso às venda das reservas, como fará o _redeem_ dos dólares?
Como o crescimento do Tether é inevitável, o Tesouro e o FED estão com um grande problema em mãos, o que fazer com o Tether?
Mas o problema é que o atual sistema financeiro é como um curto cobertor: Quanto tapas a cabeça, destapas os pés; Ou quando tapas os pés, destapas a cabeça. Ou seja, para resolver o problema da guarda reservas da Tether, vai criar novos problemas, em outros locais do sistema financeiro e assim sucessivamente.
### Conta mestre
Uma possível solução seria dar uma conta mestre à Tether, dando o acesso direto a uma conta no FED, semelhante à que todos os bancos comerciais têm. Com isto, a Tether deixaria de necessitar os títulos do tesouro, depositando o dinheiro diretamente no banco central. Só que isto iria criar dois novos problemas, com o Custodia Bank e com o restante sistema bancário.
O Custodia Bank luta há vários anos contra o FED, nos tribunais pelo direito a ter licença bancária para um banco com _full-reserves_. O FED recusou sempre esse direito, com a justificativa que esse banco, colocaria em risco toda a estabilidade do sistema bancário existente, ou seja, todos os outros bancos poderiam colapsar. Perante a existência em simultâneo de bancos com reserva fracionária e com _full-reserves_, as pessoas e empresas iriam optar pelo mais seguro. Isso iria provocar uma corrida bancária, levando ao colapso de todos os bancos com reserva fracionária, porque no Custodia Bank, os fundos dos clientes estão 100% garantidos, para qualquer valor. Deixaria de ser necessário limites de fundos de Garantia de Depósitos.
Eu concordo com o FED nesse ponto, que os bancos com _full-reserves_ são uma ameaça a existência dos restantes bancos. O que eu discordo do FED, é a origem do problema, o problema não está nos bancos _full-reserves_, mas sim nos que têm reserva fracionária.
O FED ao conceder uma conta mestre ao Tether, abre um precedente, o Custodia Bank irá o aproveitar, reclamando pela igualdade de direitos nos tribunais e desta vez, possivelmente ganhará a sua licença.
Ainda há um segundo problema, com os restantes bancos comerciais. A Tether passaria a ter direitos similares aos bancos comerciais, mas os deveres seriam muito diferentes. Isto levaria os bancos comerciais aos tribunais para exigir igualdade de tratamento, é uma concorrência desleal. Isto é o bom dos tribunais dos EUA, são independentes e funcionam, mesmo contra o estado. Os bancos comerciais têm custos exorbitantes devido às políticas de _compliance_, como o KYC e AML. Como o governo não vai querer aliviar as regras, logo seria a Tether, a ser obrigada a fazer o _compliance_ dos seus clientes.
A obrigação do KYC para ter _stablecoins_ iriam provocar um terramoto no mundo cripto.
Assim, é pouco provável que seja a solução para a Tether.
### FED
Só resta uma hipótese, ser o próprio FED a controlar e a gerir diretamente as _stablecoins_ de dólar, nacionalizado ou absorvendo as existentes. Seria uma espécie de CBDC. Isto iria provocar um novo problema, um problema diplomático, porque as _stablecoins_ estão a colocar em causa a soberania monetária dos outros países. Atualmente as _stablecoins_ estão um pouco protegidas porque vivem num limbo jurídico, mas a partir do momento que estas são controladas pelo governo americano, tudo muda. Os países vão exigir às autoridades americanas medidas que limitem o uso nos seus respectivos países.
Não existe uma solução boa, o sistema FIAT é um castelo de cartas, qualquer carta que se mova, vai provocar um desmoronamento noutro local. As autoridades não poderão adiar mais o problema, terão que o resolver de vez, senão, qualquer dia será tarde demais. Se houver algum problema, vão colocar a responsabilidade no cripto e no Bitcoin. Mas a verdade, a culpa é inteiramente dos políticos, da sua incompetência em resolver os problemas a tempo.
Será algo para acompanhar futuramente, mas só para 2026, talvez…
É curioso, há uns anos pensava-se que o Bitcoin seria a maior ameaça ao sistema ao FIAT, mas afinal, a maior ameaça aos sistema FIAT é o próprio FIAT(_stablecoins_). A ironia do destino.
Isto é como uma corrida, o Bitcoin é aquele atleta que corre ao seu ritmo, umas vezes mais rápido, outras vezes mais lento, mas nunca pára. O FIAT é o atleta que dá tudo desde da partida, corre sempre em velocidade máxima. Só que a vida e o sistema financeiro não é uma prova de 100 metros, mas sim uma maratona.
# Europa
2025 será um ano desafiante para todos europeus, sobretudo devido à entrada em vigor da regulamentação (MiCA). Vão começar a sentir na pele a regulamentação, vão agravar-se os problemas com os _compliance_, problemas para comprovar a origem de fundos e outras burocracias. Vai ser lindo.
O _Travel Route_ passa a ser obrigatório, os europeus serão obrigados a fazer o KYC nas transações. A _Travel Route_ é uma suposta lei para criar mais transparência, mas prática, é uma lei de controle, de monitorização e para limitar as liberdades individuais dos cidadãos.
O MiCA também está a colocar problemas nas _stablecoins_ de Euro, a Tether para já preferiu ficar de fora da europa. O mais ridículo é que as novas regras obrigam os emissores a colocar 30% das reservas em bancos comerciais. Os burocratas europeus não compreendem que isto coloca em risco a estabilidade e a solvência dos próprios bancos, ficam propensos a corridas bancárias.
O MiCA vai obrigar a todas as exchanges a estar registadas em solo europeu, ficando vulnerável ao temperamento dos burocratas. Ainda não vai ser em 2025, mas a UE vai impor políticas de controle de capitais, é inevitável, as exchanges serão obrigadas a usar em exclusividade _stablecoins_ de euro, as restantes _stablecoins_ serão deslistadas.
Todas estas novas regras do MiCA, são extremamente restritas, não é para garantir mais segurança aos cidadãos europeus, mas sim para garantir mais controle sobre a população. A UE está cada vez mais perto da autocracia, do que da democracia. A minha única esperança no horizonte, é que o sucesso das políticas cripto nos EUA, vai obrigar a UE a recuar e a aligeirar as regras, a teoria dos jogos é implacável. Mas esse recuo, nunca acontecerá em 2025, vai ser um longo período conturbado.
# Recessão
Os mercados estão todos em máximos históricos, isto não é sustentável por muito tempo, suspeito que no final de 2025 vai acontecer alguma correção nos mercados. A queda só não será maior, porque os bancos centrais vão imprimir dinheiro, muito dinheiro, como se não houvesse amanhã. Vão voltar a resolver os problemas com a injeção de liquidez na economia, é empurrar os problemas com a barriga, em de os resolver. Outra vez o efeito Cantillon.
Será um ano muito desafiante a nível político, onde o papel dos políticos será fundamental. A crise política na França e na Alemanha, coloca a UE órfã, sem um comandante ao leme do navio. 2025 estará condicionado pelas eleições na Alemanha, sobretudo no resultado do AfD, que podem colocar em causa a propriedade UE e o euro.
Possivelmente, só o fim da guerra poderia minimizar a crise, algo que é muito pouco provável acontecer.
Em Portugal, a economia parece que está mais ou menos equilibrada, mas começam a aparecer alguns sinais preocupantes. Os jogos de sorte e azar estão em máximos históricos, batendo o recorde de 2014, época da grande crise, não é um bom sinal, possivelmente já existe algum desespero no ar.
A Alemanha é o motor da Europa, quanto espirra, Portugal constipa-se. Além do problema da Alemanha, a Espanha também está à beira de uma crise, são os países que mais influenciam a economia portuguesa.
Se existir uma recessão mundial, terá um forte impacto no turismo, que é hoje em dia o principal motor de Portugal.
# Brasil
Brasil é algo para acompanhar em 2025, sobretudo a nível macro e a nível político. Existe uma possibilidade de uma profunda crise no Brasil, sobretudo na sua moeda. O banco central já anda a queimar as reservas para minimizar a desvalorização do Real.

Sem mudanças profundas nas políticas fiscais, as reservas vão se esgotar. As políticas de controle de capitais são um cenário plausível, será interesse de acompanhar, como o governo irá proceder perante a existência do Bitcoin e _stablecoins_. No Brasil existe um forte adoção, será um bom _case study_, certamente irá repetir-se em outros países num futuro próximo.
Os próximos tempos não serão fáceis para os brasileiros, especialmente para os que não têm Bitcoin.
# Blockchain
Em 2025, possivelmente vamos ver os primeiros passos da BlackRock para criar a primeira bolsa de valores, exclusivamente em _blockchain_. Eu acredito que a BlackRock vai criar uma própria _blockchain_, toda controlada por si, onde estarão os RWAs, para fazer concorrência às tradicionais bolsas de valores. Será algo interessante de acompanhar.
-----------
Estas são as minhas previsões, eu escrevi isto muito em cima do joelho, certamente esqueci-me de algumas coisas, se for importante acrescentarei nos comentários. A maioria das previsões só acontecerá após 2025, mas fica aqui a minha opinião.
Isto é apenas a minha opinião, **Don’t Trust, Verify**!
-

@ 472f440f:5669301e
2024-12-31 04:42:00
I'm sure some of you are already tired of the discussion around the H-1B visa program that was started on Christmas Eve by Vivek Ramaswamy and escalated by Elon Musk and others as the "Silicon Valley MAGA" coalition began putting forth legal immigration policy proposals for the incoming Trump administration. Core to their policy is the expansion of the H-1B visa program so that America can "recruit the best talent in the world" to come build the American economy.
Unfortunately, as it stands today - according to the Silicon Valley cognescenti, Americans are either a.) not smart enough to fulfill the roles necessary to enable the United States to maintain its lead as economic super power of the world or b.) expect too much in compensation for the available roles. At least this is my reading from the commentary I've seen over the last week.
What seems abundantly clear to me is that the framing put forth by "Silicon Valley MAGA" crew is disingenuous and self-serving. It has been clear for awhile now that the H-1B visa program is being systematically abused to bring in cheap labor from other countries to help drive down labor costs for companies across the spectrum. Not just Silicon Valley tech companies. The system has a loophole in it and it is being exploited. Bring people to the US via H-1B visas to complete work for you at lower costs and your company's financials are likely to be better off (assuming the work being done is productive and a value add to the company). Now, this isn't to say that everyone who is in the US via an H-1B visa is here because these companies want to exploit the loophole that gives them the ability to spend less on head count. However, based off the data from the database of the H-1B visa program it is abundantly clear that the system is being taken advantage of. Egregiously and at the expense of American workers, who are most certainly not (all) "subtarded".
Herein lies the crux of the problem; companies are abusing this program to get away from the problem of Americans demanding higher wages to maintain lives of dignity in a country run by a government that is chronically addicted to debt backed by a central bank that will print money ex-nihilo and at will to monetize that debt. Americans are then being scapegoated as either "lazy", "stupid" or "delusional about their worth in the work force". A classic straw man argument that avoids the root issue at hand; the money is broken and the broken money has created perverse incentives throughout the economy while also stripping Americans of the ability to properly save the value of their labor.
We live in a high velocity trash economy that rewards grift and waste while disincentivizing hard work that is meaningful to the quality of life of the Common Man. Everything has been hyper-financialized to the point that one of the only ways to make it ahead is to speculate on the flow of capital into certain asset classes, which is often determined by the whims of central planners. Another is to build or speculate on tech "innovations" that typically materialize in the form of attention zapping apps and widgets that help people temporarily forget they live in a high-velocity trash economy.
The mass of men lead lives of quiet desperation and it is because they don't see a way out of the nihilistic rat race created (unknowingly to most) by the money printer.
The ability to print money out of nothing and throw it at everything creates misaligned incentives that result in the inability for the market to properly determine what is genuinely needed by the people instead of those who have learned how to game the broken system and its broken incentives.
One last point, I would be remiss not to acknowledge that many individuals in America aren't intellectually equipped to do some of the cutting edge work that may be necessary to produce the technologies and companies that will push the country forward. The high-velocity trash economy run on money printed out of nothing has completely corrupted the education system. People in the United States are literally dumber than they were five decades ago. That is a fact. But it is not only the fault of the American people themselves, but the corrupt system they have been born into that destroyed the education system with perverse incentives. And the overwhelming majority of the blame is on the system, not the people.
Even with that being said, the idea that we need to adopt a Tiger Mom mentality in the US - a culture of unrelenting devotion to studying STEM to the point that weekend sleepovers for kids are discouraged - is absolutely laughable and objectively un-American. There are plenty of incredibly intelligent, creative and driven young Americans who have contributed and will continue to contribute significantly to the American economy and they didn't need to shackle themselves to their desks to get that way. America isn't a country that was built by automatons. It's a country built by people who said, "Fuck you. Don't tell me what I can and cannot do. Watch this."
Despite the fact that a system has been erected that actively works against the average American system the American spirit lives on in the souls of many across the country. Miraculously. The American spirit is something that cannot simply be imported. It is ingrained in our culture. It is certainly beginning to dwindle as hope for a better future becomes more and more dim for the masses as the system works against them despite all their best efforts to succeed. It is imperative that we stoke the coals of the American spirit while it is still alive in those who are too stubborn to give up.
People need the ability to save their hard work in a money that cannot be debased. Opportunity cost needs to be reintroduced into the market so that things that actually add value and increase the quality of life for the Common Man are where hard money is allocated. And people need to start talking about the root of the problem more seriously instead of striking at branches with disingenuous straw man arguments.
---
Final thought...
Ready to go surfing.
-

@ 17538dc2:71ed77c4
2024-12-30 22:45:10
Merry Christmas, and Happy New Year! Here's an overview of keeping tabs on interoperability on nostr.
## What is nostrability
[Nostrability](https://github.com/nostrability/nostrability) is:
-the practical documentation of broken things on nostr between two or more apps, and
-a place to advocate for positive interoperability updates to apps
### Why does this matter?
If the hop and/or interaction between apps sucks, then nostr users will not have an amazing and unique experience. Nostr will lose to well funded incumbents.

### How did this start?
Will was upset that he had to troubleshoot other dev's apps.
### What nostrability does *not* aim for
All apps implement all NIPs.
### Where can I read in detail
[https://github.com/nostrability/nostrability
](https://github.com/nostrability/nostrability
)
### Timeline
Nov '23 Added placeholder to github.
Jan '24 First issues documented.
Jan '24 First nostrability two app bug is fixed [Coracle cannot send DMs to Damus](https://github.com/nostrability/nostrability/issues/1) (thank you Hodlbod!).
'24 Gave [intro to nostrability talk at BBB](https://youtu.be/I3Qld_HXQuM). Presentation [link](https://slides.com/alltheseas/nostrability).
Aug '24 Galaxy devs educated elsat at NostrCI discussion at Nostriga. (n.b. where's the video??)
Oct '24 Humbled by and grateful for OpenSats acknowledgment and funding. Thank you to all nostr enjoyers & devs who gave me their precious time, and to my advocates & supporters - you know who you are 🙏.
### What are specific issues discussed?
Over a hundred open [issues](https://github.com/nostrability/nostrability/issues), and a couple of dozen resolved issues. Many of these were reported by extremetly very normal nostr users, and devs.
Example topics (too many to list in a single article) range from:
-contact list wipes, mute list wipes (Kieran pls fix!!)
-zaps not working between apps
-[missing notes](https://github.com/nostrability/nostrability/issues/20)
-broken profiles
-old profile information
-q tags, a tags, missing replies and/or parent notes etc..
-to [proposed onboarding best practices](https://github.com/nostrability/nostrability/issues/143)
-[outbox tracker positive interop](https://github.com/nostrability/nostrability/issues/69)
-[highlights](https://github.com/nostrability/nostrability/issues/61)
-non-nostr interoperability: e.g. [bluesky bridgyfed profile info](https://github.com/nostrability/nostrability/issues/142)
-spillover NIP/other controversy such as [edited notes](https://github.com/nostrability/nostrability/issues/118)
-and [migrating to nostr best practices](https://github.com/nostrability/nostrability/issues/78)
### Learnings
1. Lone wolf, limited resource devs are the norm.
Most devs focus on their one app, or their multiple apps.
2. Some devs are extremely generous with their time when it comes to interop. Proof of work is in the git repo.
3. There is a lot of space for building amazing interoperable experiences - this remains frontier territory on the design, product, and dev side. Which will be the first experience to blow people out of the water? Is it zaps, DVMs, or something not yet put together?
4. I empathize that without basic things "just working", and/or basic features missing it may be difficult to allocate resources to interoperability.
5. Even devs with teams may struggle to allocate resources to interoperability.
6. Bug reporting and crappy experience reporting matters! This is important for single apps, and even more so for multi-app interaction. Devs may not get around to fixing something right away. However, if nostriches don't share their negative experience, devs will have less impetus to improve an experience.
### 2025 plans
1. Continue documenting broken things.
2. Interview devs to better understand how I can suit nostrability to dev's single app workflows, as to more effectively close broken things, and better advocate for positive interoperability updates across apps.
3. Help test nostrCI automated interop testing methodology with galaxy dev of [nostr.watch](https://nostr.watch/) & NIP-66 Sandwich, so that nostrability can be automated per particular test cases.
### Dev and nostrich feedback
Let me know how I can make nostrability more useful for yall. Tag me on nostr, create issues on nostrability 💪.
!(image)[https://media.tenor.com/hF5RhwXuG_kAAAAC/arnold-schwarzenegger-terminator.gif]
-

@ f9cf4e94:96abc355
2024-12-30 19:02:32
Na era das grandes navegações, piratas ingleses eram autorizados pelo governo para roubar navios.
A única coisa que diferenciava um pirata comum de um corsário é que o último possuía a “Carta do Corso”, que funcionava como um “Alvará para o roubo”, onde o governo Inglês legitimava o roubo de navios por parte dos corsários. É claro, que em troca ele exigia uma parte da espoliação.
Bastante similar com a maneira que a Receita Federal atua, não? Na verdade, o caso é ainda pior, pois o governo fica com toda a riqueza espoliada, e apenas repassa um mísero salário para os corsários modernos, os agentes da receita federal.
Porém eles “justificam” esse roubo ao chamá-lo de imposto, e isso parece acalmar os ânimos de grande parte da população, mas não de nós.
Não é por acaso que 'imposto' é o particípio passado do verbo 'impor'. Ou seja, é aquilo que resulta do cumprimento obrigatório -- e não voluntário -- de todos os cidadãos. Se não for 'imposto' ninguém paga. Nem mesmo seus defensores. Isso mostra o quanto as pessoas realmente apreciam os serviços do estado.
Apenas volte um pouco na história: os primeiros pagadores de impostos eram fazendeiros cujos territórios foram invadidos por nômades que pastoreavam seu gado. Esses invasores nômades forçavam os fazendeiros a lhes pagar uma fatia de sua renda em troca de "proteção". O fazendeiro que não concordasse era assassinado.
Os nômades perceberam que era muito mais interessante e confortável apenas cobrar uma taxa de proteção em vez de matar o fazendeiro e assumir suas posses. Cobrando uma taxa, eles obtinham o que necessitavam. Já se matassem os fazendeiros, eles teriam de gerenciar por conta própria toda a produção da fazenda.
Daí eles entenderam que, ao não assassinarem todos os fazendeiros que encontrassem pelo caminho, poderiam fazer desta prática um modo de vida.
Assim nasceu o governo.
Não assassinar pessoas foi o primeiro serviço que o governo forneceu. Como temos sorte em ter à nossa disposição esta instituição!
Assim, não deixa de ser curioso que algumas pessoas digam que os impostos são pagos basicamente para impedir que aconteça exatamente aquilo que originou a existência do governo. O governo nasceu da extorsão. Os fazendeiros tinham de pagar um "arrego" para seu governo. Caso contrário, eram assassinados.
Quem era a real ameaça? O governo. A máfia faz a mesma coisa.
Mas existe uma forma de se proteger desses corsários modernos. Atualmente, existe uma propriedade privada que NINGUÉM pode tirar de você, ela é sua até mesmo depois da morte. É claro que estamos falando do Bitcoin. Fazendo as configurações certas, é impossível saber que você tem bitcoin. Nem mesmo o governo americano consegue saber.
#brasil #bitcoinbrasil #nostrbrasil #grownostr #bitcoin
-

@ 254f56d7:f2c38100
2024-12-30 07:38:27
Vamos ver seu funcionamento

-

@ a012dc82:6458a70d
2024-12-30 05:51:11
**Table Of Content**
- The Influence of Global Oil Prices
- Bitcoin's Roller Coaster Ride
- Anticipation Surrounding the 2024 Halving Event
- The Broader Crypto Landscape
- Conclusions
- FAQ
In the ever-evolving world of cryptocurrencies, Bitcoin stands as a beacon, often dictating the mood of the entire crypto market. Its price fluctuations are closely watched by investors, analysts, and enthusiasts alike. Max Keiser, a prominent figure in the crypto space, recently shed light on some intriguing factors that might be influencing Bitcoin's current price trajectory. This article delves into Keiser's insights, exploring the broader implications of global events on Bitcoin's market performance.
**The Influence of Global Oil Prices**
Max Keiser, a renowned Bitcoin advocate and former trader, recently drew attention to the interplay between global oil prices and Bitcoin's market performance. Responding to a post by German economics expert, Holger Zschaepitz, Keiser highlighted the significance of Brent oil reaching $90 per barrel for the first time since the previous November. According to Keiser, the surge in oil prices, driven by Saudi Arabia's decision to extend its reduction in oil production for another three months, has had ripple effects in the financial world. One of these effects is the shift of investor interest towards higher interest deposit USD accounts. This diversion of investments is creating what Keiser terms as "a small headwind for Bitcoin," implying that as traditional markets like oil show promise, some investors might be reconsidering their cryptocurrency positions.
**Bitcoin's Roller Coaster Ride**
The cryptocurrency market, known for its volatility, witnessed Bitcoin's price undergoing significant fluctuations recently. A notable event that gave Bitcoin a temporary boost was Grayscale's triumph over the SEC in a legal battle concerning the conversion of its Bitcoin Trust into a spot ETF. This victory led to a rapid 7.88% spike in Bitcoin's price within a mere hour, pushing it from the $26,000 bracket to briefly touch the $28,000 threshold. However, this euphoria was short-lived. Over the subsequent week, the cryptocurrency saw its gains erode, settling in the $25,400 range. At the time the reference article was penned, Bitcoin was hovering around $25,688.
**Anticipation Surrounding the 2024 Halving Event**
The Bitcoin community is abuzz with anticipation for the next scheduled Bitcoin halving, projected to take place in April-May 2024. This event will see the rewards for Bitcoin miners being slashed by half, resulting in a decreased supply of Bitcoin entering the market. Historically, such halvings have acted as catalysts, propelling Bitcoin's price upwards. A case in point is the aftermath of the 2020 halving, post which Bitcoin soared to an all-time high of $69,000 in October 2021. However, some financial analysts argue that this surge was less about the halving and more a consequence of the extensive monetary measures adopted by institutions like the US Federal Reserve. These measures, taken in response to the pandemic and the ensuing lockdowns, flooded the market with cash, potentially driving up Bitcoin's price.
**The Broader Crypto Landscape**
While Bitcoin remains the most dominant and influential cryptocurrency, it's essential to consider its position within the broader crypto ecosystem. Other cryptocurrencies, often referred to as 'altcoins', also play a role in shaping investor sentiment and market dynamics. Factors such as technological advancements, regulatory changes, and global economic shifts not only impact Bitcoin but the entire crypto market. As investors diversify their portfolios and explore newer blockchain projects, Bitcoin's role as the market leader is continually tested. Yet, its pioneering status and proven resilience make it a focal point of discussions and analyses in the crypto world.
**Conclusion**
Bitcoin, the flagship cryptocurrency, has always been subject to a myriad of market forces and global events. While its inherent potential remains undeniable, the current market landscape, shaped by factors ranging from oil prices to global economic policies, presents challenges. Yet, with events like the 2024 halving on the horizon, there's an air of optimism among Bitcoin enthusiasts and investors about the future trajectory of this digital asset.
**FAQ**
**Who is Max Keiser?**
Max Keiser is a prominent Bitcoin advocate, former trader, and well-known crypto podcaster.
**What did Keiser say about Bitcoin's price?**
Keiser pointed out that rising global oil prices and the allure of higher interest deposit USD accounts are creating a "small headwind" for Bitcoin.
**How did Grayscale's legal victory affect Bitcoin?**
Grayscale's win over the SEC led to a 7.88% spike in Bitcoin's price within an hour.
**When is the next Bitcoin halving expected?**
The next Bitcoin halving is projected to occur around April-May 2024.
**Did the 2020 Bitcoin halving influence its price?**
Yes, post the 2020 halving, Bitcoin reached an all-time high of $69,000 in October 2021.
**That's all for today**
**If you want more, be sure to follow us on:**
**NOSTR: croxroad@getalby.com**
**X: [@croxroadnews](https://x.com/croxroadnewsco)**
**Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)**
**Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)**
**Store: https://croxroad.store**
**Subscribe to CROX ROAD Bitcoin Only Daily Newsletter**
**https://www.croxroad.co/subscribe**
*DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.*
-

@ 6be5cc06:5259daf0
2024-12-29 19:54:14
Um dos padrões mais bem estabelecidos ao medir a opinião pública é que cada geração tende a seguir um caminho semelhante em termos de política e ideologia geral. Seus membros compartilham das mesmas experiências formativas, atingem os marcos importantes da vida ao mesmo tempo e convivem nos mesmos espaços. Então, como devemos entender os relatórios que mostram que a **Geração Z** é hiperprogressista em certos assuntos, mas surpreendentemente conservadora em outros?
A resposta, nas palavras de **Alice Evans**, pesquisadora visitante na Universidade de Stanford e uma das principais estudiosas do tema, é que os jovens de hoje estão passando por um grande **divergência de gênero**, com as jovens mulheres do primeiro grupo e os jovens homens do segundo. A **Geração Z** representa duas gerações, e não apenas uma.
Em países de todos os continentes, surgiu um **distanciamento ideológico** entre jovens homens e mulheres. Milhões de pessoas que compartilham das mesmas cidades, locais de trabalho, salas de aula e até casas, não veem mais as coisas da mesma maneira.
Nos **Estados Unidos**, os dados da Gallup mostram que, após décadas em que os sexos estavam distribuídos de forma relativamente equilibrada entre visões políticas liberais e conservadoras, as mulheres entre **18 e 30 anos** são agora **30 pontos percentuais mais liberais** do que os homens dessa faixa etária. Essa diferença surgiu em apenas **seis anos**.
A **Alemanha** também apresenta um distanciamento de 30 pontos entre homens jovens conservadores e mulheres jovens progressistas, e no **Reino Unido**, a diferença é de **25 pontos**. Na **Polônia**, no ano passado, quase metade dos homens entre **18 e 21 anos** apoiou o partido de extrema direita Confederation, em contraste com apenas um sexto das jovens mulheres dessa mesma idade.
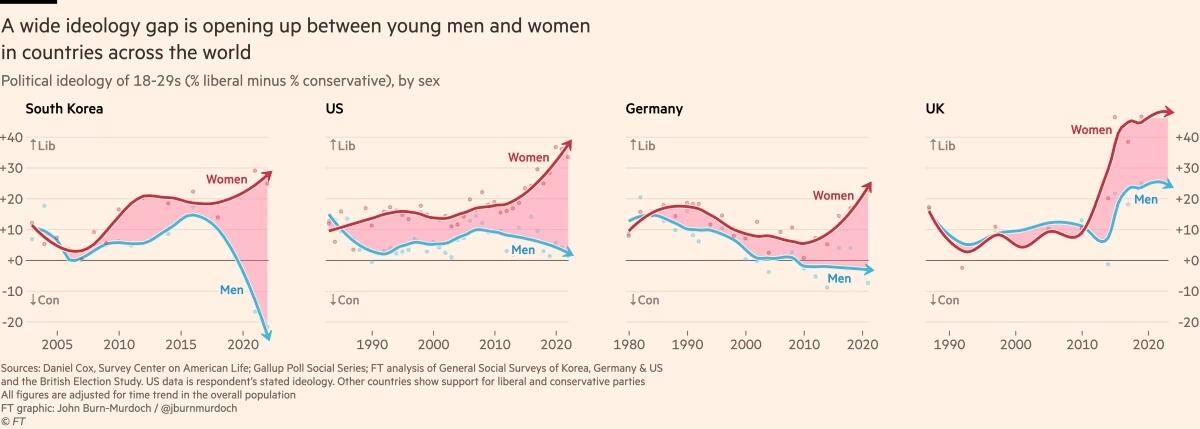
Fora do Ocidente, há divisões ainda mais acentuadas. Na **Coreia do Sul**, há um enorme abismo entre homens e mulheres jovens, e a situação é semelhante na **China**. Na **África**, a **Tunísia** apresenta o mesmo padrão. Vale notar que em todos os países essa divisão drástica ocorre principalmente entre a **geração mais jovem**, sendo muito menos pronunciada entre homens e mulheres na faixa dos **30 anos** ou mais velhos.
O movimento **# MeToo** foi o **principal estopim**, trazendo à tona valores feministas intensos entre jovens mulheres que se sentiram empoderadas para denunciar injustiças de longa data. Esse estopim encontrou especialmente terreno fértil na **Coreia do Sul**, onde a **desigualdade de gênero** é bastante visível e a **misoginia explícita** é comum. (palavras da Financial Times, eu só traduzi)
Na eleição presidencial da **Coreia do Sul** em **2022**, enquanto homens e mulheres mais velhos votaram de forma unificada, os jovens homens apoiaram fortemente o partido de direita **People Power**, enquanto as jovens mulheres apoiaram o partido liberal **Democratic** em números quase iguais e opostos.
A situação na **Coreia** é extrema, mas serve como um alerta para outros países sobre o que pode acontecer quando jovens homens e mulheres se distanciam. A sociedade está **dividida**, a taxa de casamento despencou e a taxa de natalidade caiu drasticamente, chegando a **0,78 filhos por mulher** em **2022**, o menor número no mundo todo.
Sete anos após a explosão inicial do movimento **# MeToo**, a **divergência de gênero** em atitudes tornou-se autossustentável.
Dados das pesquisas mostram que em muitos países, as diferenças ideológicas vão além dessa questão específica. A divisão progressista-conservadora sobre **assédio sexual** parece ter causado ou pelo menos faz parte de um **alinhamento mais amplo**, em que jovens homens e mulheres estão se organizando em grupos conservadores e liberais em outros assuntos.
Nos **EUA**, **Reino Unido** e **Alemanha**, as jovens mulheres agora adotam posturas mais liberais sobre temas como **imigração** e **justiça racial**, enquanto grupos etários mais velhos permanecem equilibrados. A tendência na maioria dos países tem sido de **mulheres se inclinando mais para a esquerda**, enquanto os homens permanecem estáveis. No entanto, há sinais de que os jovens homens estão se **movendo para a direita** na **Alemanha**, tornando-se mais críticos em relação à imigração e se aproximando do partido de extrema direita **AfD** nos últimos anos.
Seria fácil dizer que tudo isso é apenas uma **fase passageira**, mas os abismos ideológicos apenas crescem, e os dados mostram que as experiências políticas formativas das pessoas são difíceis de mudar. Tudo isso é agravado pelo fato de que o aumento dos smartphones e das redes sociais faz com que os jovens homens e mulheres agora **vivam em espaços separados** e tenham **culturas distintas**.
As opiniões dos jovens frequentemente são ignoradas devido à **baixa participação política**, mas essa mudança pode deixar **consequências duradouras**, impactando muito mais do que apenas os resultados das eleições.
Retirado de: https://www.ft.com/content/29fd9b5c-2f35-41bf-9d4c-994db4e12998
-

@ 30ceb64e:7f08bdf5
2024-12-29 19:09:13
I've been working 28 hours a week on the weekends as a Direct service professional, assisting adults with autism and intellectual disabilities. I've brought my laptop freaks. There's enough downtime for me to work on obtaining certifications online, posts to SN and Nostr, and work on my coding project Nostr Run Club.
I work with 2 normies on saturday and sunday, and had the bright idea of pitching my app to them. Here is how the conversation went.
Hustle: Hey do you guys want to see what i'm working on?
Normie 1: Sure....
Normie 2: "Comes around to curiously investigate"
***The Pitch
Hustle: Alright, so.....what social media do you use?
Normie 1: Instagram.
Hustle: Alright so....I'm making a running app. Imagine logging in with instagram, and seeing a feed of all of the runners and all of your friends. Now, what music streaming service do you use?
Normie 1: Pandora
Normie 2: Spotify
Hustle: Cool, so imagine seeing your pandora and Spotify liked songs and playlists in the running app. So the app can track your run, its connected to your social media and streaming platform, and people can send you small donations congratulating you for the run.
Normie 1 and 2: Ahh, that's cool.
Normie 2: But why would people send you money? Oh? I think I've seen something like it where people send you a star and the star can be redeemed for like 99 cents, or they send you points and the app rewards you for points.
Hustle: Nah. That parts already figured out, I'm just having trouble getting the music from "Spotify" to play, and then I'll release it into the wild, that's pretty much my hustle.
And that was the conversation, it left me thinking about a few things.
1. V4V
The concept is extremely familiar to me. I say good Morning I get 50 cents. I give 35 cents to other GM freaks and keep it pushing. Its normal. But for them the concept seemed so strange, they were looking for some solution or explanation on why people would just give someone else money for seemingly nothing. When the solution is already here, just not evenly distributed or promoted or adopted. Likely because the normies are still existing in the paradox of card companies and ravenous third party intermediaries imposing their cut.
2. The broken social media landscape of disconnected walled gardens
I was thinking normie one would say Facebook, if asked normie 2 would've said snapchat, Tik Tok, Instagram etc. for music they could've said apple music, tidal, Youtube music etc.
I see Nostr as a highway that connects all of these guys, and instead of buying multiple cars to travel on different streets, you have one car that you use to travel across the country.
3. The tact required to pitch ideas like Nostr and bitcoin
I used to work at bank of America and was tasked to sell credit cards without saying the word credit card.....
I would say "Hello, good sir/mam, have you thought about getting rewarded for your daily purchases??"
I found myself in a familiar situation, introducing them to Nostr without using the word Nostr and introducing them to bitcoin without using the word inevitable. The experience was stranger for me than it was for them, they left thinking "Ahh, thats neat" I walked away from the conversation eager to get notify the freaks.
In Conclusion,
The interaction gave me a few interesting insights:
1. We'll need to bridge the conceptual gap between traditional and new payment paradigms.
2. The importance of focusing on user benefits rather than technical details
3. The market opportunity for solutions that unify fragmented digital services
4. The value of strategic communication that meets users where they are
Successful adoption of new technologies like Nostr and Bitcoin requires careful attention to user education and communication, focusing on practical benefits rather than technical features. The positive reception to the core concept, even without understanding the underlying technology, shows huge potential for mainstream adoption when presented appropriately.
Thanks,
Hustle
originally posted at https://stacker.news/items/829000
-

@ f4d89779:2b522db9
2024-12-29 16:46:43
In the game of Ultimate Frisbee, there is a beloved phrase that captures one of the best aspects of playing. Ultimate is about decision making. It is played on a rectangular field with seven players on each side. Much like football, the object of the game is to score with a throw into the end zone.
To "HUCK", means to launch the disc down field in the hopes of scoring. You can probably guess what the "OR YOU'RE NOTHING" means but the spirit of it is that when the opportunity comes ...
PUT THE DISC IN THE AIR
<https://i.nostr.build/XyTpXdNOSpv5f8ZZ.jpg>
Sorry, I had to channel my inner ODELL there for a second. These are all caps kind of moments. Time feels like it stops, the disc floats in the air, the receiver and defender are sprinting all out, you can hear the collective breath of anticipation from the audience and then you score. If you're good that is.
You know what? You and I are civilized people, we use the NOSTR, so I won't limit myself to just words. Here are some of those moments:
<https://v.nostr.build/zav5o04BK97FiNAt.mp4>
During the course of play, teams get into a formation with a couple of the players doing the majority of the disc throwing. These players are called handlers. They handle the disc, they have the responsibility of moving the disc downfield, and handle most of the decision making.
A good handler develops a sort of instinct for each of their receivers, can guess the capabilities of each defender, and knows himself well enough to know if he has the throw. They know who is good and reliable at short cuts. They know who has the top end speed to throw a long floating pass into the end zone. With each play they are judging all of the moving objects on the field and deciding on real time risk of each throw and where things will lead.
Mistakes lead to turnovers and turnovers, like in many other sports, are death.
Hopefully, you start to see how ultimate relates to life and Bitcoin. Life is a field and you have defenders and you have receivers. It is your disc and the decisions you make have a huge impact on whether you win or lose.
Knowingly or not, you saw Bitcoin as a potential receiver and Governments, academics, shitcoiners, as defenders. In some ways those around you were also defenders. They whispered, or maybe still whisper the risk and probability of failure in your ear. Their fear weighed against what you know.
With the btc/usd exchange rate at $94k, and companies fighting over the best ways to get sats I think we can say that you did not get lucky. They called you crazy, they said that throw won't work, they said your receiver sucked but you knew better.
You saw that receiver leaving every defender in the dust and you HUCKED it and you are certainly not NOTHING.
-

@ 30ceb64e:7f08bdf5
2024-12-28 18:14:28
I've been listening to this small playlist over and over again this week.
Ivy keeps getting me.
I'm having fun making these things
https://music.youtube.com/watch?v=yNPfvgFEXuk&si=HjUdZxXKkGfqabk8
https://music.youtube.com/watch?v=LyRJfs-Qn70&si=2ugksRTltXATqHVo
https://music.youtube.com/watch?v=XkpAE8ZZ6bU&si=WwWopN-YMLGguFiB
https://music.youtube.com/watch?v=VIcQreSskyM&si=Ewza3W6SOkRDWF1E
https://music.youtube.com/watch?v=5xm8Q-1cOpU&si=GeQv3Kum_TV9H6KD
https://music.youtube.com/watch?v=xYM-aZG9QbE&si=fwfzIFLAyVumnTs4
https://music.youtube.com/watch?v=r7JWHuGFUeI&si=MqoFBqvb0iI7pAAY
https://music.youtube.com/watch?v=GjnjUHY8MiM&si=F_Aepjxc_g2SH7UG
https://music.youtube.com/watch?v=sgjTb7UQe2A&si=04wik3m5LefpbGMV
https://music.youtube.com/watch?v=SMOund_uFTk&si=v7sa3XxchH607d0Y
https://music.youtube.com/playlist?list=PLmYfnnK_Qs5jpv5hKuBKFOEvMnPFl3vto&si=Dkudss84jFszdGmj
Thanks Anon,
Hustle
originally posted at https://stacker.news/items/827883
-

@ 30ceb64e:7f08bdf5
2024-12-28 17:47:48
A recent conversation with fellow Bitcoiners prompted me to share this overview of Nostr tools. While you don't need to use everything, understanding the ecosystem helps paint a picture of where we're heading.
I often hear people say "I'm posting to the void" or "My feed is boring" or "I'm not earning any bitcoin" or "It's too complicated." Let me address these concerns with a comprehensive overview.
### Core Clients and Features
Primal and Amethyst are currently the best daily drivers. Theyre both valid twitter replacements with primal focusing on user friendliness and amethyst focusing on being more feature rich.
Both apps feature an algorithm marketplace (we call them DVMs) where you can choose from various feed styles. Soon, anyone will be able to create and share their own algorithms. For additional feed customization, Listr.lol lets you curate lists of npubs to further refine your experience.
### Content and Rewards
Stacker News (SN) integrates beautifully with Nostr. Cross-post your SN content to appear as longform notes on platforms like Highlighter, Yakihonne, and Habla.news. SN's rewards system pays out satoshis for quality content, bridging their closed platform with Nostr's open network.
### Payments and Zaps
For zaps, I recommend CoinOS, or AlbyHub for a more sovereign alternative. CoinOS is non kyc and gives you a lightning address and NWC connection string to throw into your nostr clients. CoinOS supports e-cash and Bolt 12, Liquid, and can auto-withdraw earnings to cold storage. You can use coinOs as a PWA or input the connection string into Alby Go for a more minimal wallet alternative.
### Security and App Management
Android users should use zap.store for downloading Nostr apps. It verifies app authenticity and implements Web of Trust features, showing which trusted npubs use each app.
For managing multiple apps, Pokey provides a unified notification dashboard. Amber (Android) offers secure client login without exposing your nsec, while Citrine lets you run a relay on your phone for data backup.
### Creator Tools
- Wavlake: Spotify alternative with open music graph
- Fountain: Podcast app with Nostr integration
- Zap.stream: Live streaming
- Nostr.build: Media hosting
- Cypher.space: Website creation with integrated marketplace
- Olas: Instagram alternative
- Gifbuddy.lol: Gif creation
- memeamigo.lol: Meme creation
- Zappadd: Promotional tools
### Making the Most of Nostr
The key to Nostr is understanding that nothing is force-fed. You're responsible for:
- Creating your desired feed
- Choosing your client
- Selecting your relays
- Managing your wallet
- Curating who you follow
For best results, go all in:
1. Leave traditional social media
2. Use Primal and or Amethyst as your main client
3. Follow 1000 npubs
4. Set up CoinOS for payments
5. Engage daily with the community
### Future Outlook
Some ask if Nostr is truly decentralized, censorship-resistant, or profitable. My response: the user experience will become so good that most internet users will naturally gravitate here. The only barrier will be ideological resistance.
Nostr represents a new internet paradigm where users outpower platforms, identity persists across apps, and Bitcoin is the standard. We've practically already won.
### Crazy Ideas
I'm thinking the age of of the super nostr app will come to a close. We're probably going to enter an era of a thousand micro apps and client templates, which allow users to build their own client in 30 seconds. Some templates will be impermanent, one time use clients, others will be more robust for building a daily driver. You'll be able to share your completed piece on nostr for other people to use, and they'll zap you for building it. A marketplace of user created apps supported by thousands of micro apps and relays and templates, probably a user experience holy grail, made possible by nostr's open social graph, smooth monetization processes from bitcoin.
### Growth Predictions
Daily Active Users doubling yearly:
2024: 20k → 2029: 640k
The beauty of Nostr isn't just in its decentralized nature or bitcoin integration – it's in the user experience that puts you in control. While traditional social media platforms force-feed you content through black-box algorithms, Nostr hands you the keys to your own digital kingdom. You choose your feed, your apps, your connections, and your level of engagement. Yes, there's a learning curve, but that's the price of digital sovereignty.
Think of where Twitter was in 2006 or Bitcoin in 2013. Those who saw the potential and jumped in early didn't just benefit financially – they helped shape the future. Nostr is at that same inflection point. The tools are here, the infrastructure is growing, and the community is building. Whether you're a creator, developer, bitcoiner, or just someone tired of traditional social media, Nostr offers a glimpse of what the internet should have been all along.
The question isn't if Nostr will win, but when. And when it does, you'll want to be able to say you were here when it all began.
Thanks,
Hustle
originally posted at https://stacker.news/items/827860
-

@ 228dde34:b5d0345e
2024-12-27 09:59:42
##### BY Cheryl Nya, Glenda Chong, and Jonathan Tan
##### Hype Issue #60
###### Join CHERYL NYA, GLENDA CHONG and JONATHAN TAN as they explore how Singaporean cafe owner, Sunshine Irene, celebrates Christmas through charity.
 *Sunshine Irene, first row, third from the right, as Santarina, and her husband as Santa, with the youth volunteers at the 2023 NY Cafe Christmas carnival. Photo by Xaen.*
On Christmas Day, a quiet cafe in the Upper Thompson neighbourhood is filled with many volunteers doing charity work and blessing others as festive lights, holiday music, and a cheerful buzz perfectly capture the true spirit of the Christmas holiday. Meet Irene, 51, the person behind this lively holiday cheer at NY Cafe’s annual Christmas carnival. Over the years, she has become a community pillar due to her charity work. She shares how this event got started, “So last year, we had the privilege of hosting a very fun [and] fulfilling charity Christmas event at NY cafe”.
What has now become a festive tradition was once originated by a group of women and youths, alongside Irene, with a generous determination to give back to the community.“[Partnering with Community Chest, a charity organisation in Singapore], we put up a few events, carnivals, booths, workshops, and all funds that we collect one hundred percent go to charity,” Irene shares.
 *Interactive storytelling by NY Cafe’s very own Santa was well-received by the crowd. Photo by NY Cafe.*
The NY Cafe Christmas carnival was truly a dream. There were booths that offered fun activities like terrarium making, ornament painting and colouring, giving everyone the opportunity to unleash their creativity. Santa’s storytelling corner was a big hit with the kids, as was the ‘Decorate Your Own Cupcakes and Donuts’ booth. The caroling was a crowd favourite, with classic Christmas hits drawing smiles from all. The lucky draw, or ‘blessed draw’ as they called it, also treated the winners to delightful Christmas gifts to take home.

 *A group of youths came down on Christmas day to volunteer at the NY Cafe Christmas carnival, where they facilitated the activities and engaged the guests. Photo by NY Cafe.*
But Irene’s favourite part? All the activities were facilitated by youth volunteers. “They were like my hands and legs running the carnival,” she remembers fondly. Witnessing the smiles they brought to their audience and the joy reflected back on their own was the greatest gift of all.
This year, however, the cafe’s carnival has been scaled back to more of a cosy hearth than a blazing bonfire. Why a smaller carnival? Irene explains that it has to do with the hurdles the cafe faced this year.
“The main reason is because we lost the cafe… because the building was sold,” Irene says. This forced NY Cafe to close and with that, a venue to run any charity events was lost.
  *Irene ran a small booth at One Sentosa Cove this year, to raise and donate funds to charity in the festive spirit of giving. Photo by Irene.*
Despite such circumstances, instead of forfeiting a carnival completely, Irene scaled back on the festivities by hosting a mini pop-up store in One Sentosa Cove and one near Lentor, the neighbourhood NY Cafe had originated from as it was “for the neighbourhood community”.
Another setback Irene faced was the lack of outreach resulting from having no resources and capacity. “Because we did not have the outreach… the [turnout] was not good enough to raise much funds. So I would say that the charity part may not be as successful as [it was in] previous years,” Irene admits.
However, while the cafe may have faced shadows of unmet expectations and goals, they did not lose sight of the light. The carnival’s flame burned smaller this year, yet its warmth still reached the hearts of the neighbourhood.
“We [could have done better] in [terms of reaching out]… but what we gain is awareness,” Irene says. “The neighbourhood knows that…there is this thing going on and they are very happy. They would be keen to be contributors [to the event] moving forward.”
Ultimately, hosting this year’s Christmas charity had its share of problems and challenges; but it’s a tradition that Irene wants to uphold. “What sparks me to do this? It's a lot to do with [my desire] to spark joy in other people's lives, in any small ways that we can,” Irene shares.
The emphasis on charity has always been one of Irene’s core values. “In my life, most decisions that I have made were led by growth and contributions, these two big values of my life; so doing charity has always been one of the big pillars of my life.” The joy that comes with seeing her impact on the lives of the less fortunate is a powerful motivator for Irene’s efforts.
Moreover, Irene hopes that her dedication to helping others will encourage her children to do the same. “I also hope that my kids are able to be a contributor in someone's life as well,” Irene says. “Since they are very young, I have exposed them to do charity and create impact on others' lives as well.”
 *The volunteers who step up to bless the less fortunate in the same spirit of giving make it all worth it. Photo by NY Cafe.*
And so, over the years, Irene’s annual charity events have served as a reminder of the true meaning of Christmas. Year after year, volunteers step up and work together to bless the less fortunate on this very special day. “Witnessing the volunteers, the people stepping up, stepping forward to be a contributor, that really melts my heart,” Irene shares. “And regardless of what role they play, they actually contribute wholeheartedly, and they also immerse and enjoy themselves.”
Every year as Christmas approaches, it’s easy to get caught up in the whirlwind of bright light, lavish gifts and extravagant festivities, losing sight of the true spirit of giving and kindness. Perhaps Irene’s commitment to spreading charity every year serves as a reminder to us of what Christmas should really be about.
“It's a season to remember people who touched our lives, or people whose lives we want to touch, and give them a little gift to help them remember… there's love around, and there's warmth around everybody,” Irene says.
-

@ 79a7270b:d61d9067
2024-12-26 09:16:59
Fifteen years after its creation, Bitcoin continues to break paradigms and solidify its role in the global economic landscape. In 2021, El Salvador adopted it as legal tender, marking a significant turning point. Three years later, its acceptance has advanced considerably, with Wall Street embracing Bitcoin ETFs and U.S. political debates focusing on its adoption as a strategic reserve.
With its portability, scarcity, accessibility, and liquidity in a 24/7 open market, Bitcoin distinguishes itself as an asset that transcends the limitations of traditional resources like gold and oil. Unlike these assets, which often face logistical challenges and market constraints, Bitcoin’s digital nature allows for seamless global transactions without physical barriers. Its scarcity mirrors that of gold, preserving its value over time, while its accessibility and round-the-clock liquidity make it an appealing choice for investors and policymakers alike. This unique combination of attributes positions Bitcoin as a versatile and strategic tool, increasingly relevant to advancing national interests in a rapidly digitizing world.
The expansion of the BRICS block, whose combined GDP now surpasses that of the G7, has heightened pressures on Western hegemony. These countries are exploring Bitcoin as a neutral and government-independent currency. They are considering denominating international transactions in Bitcoin as part of their broader goal: to create a de-dollarized, independent financial system resilient to Western-imposed sanctions.
Game theory sheds light on how Bitcoin adoption creates powerful incentives for nations. If the BRICS use Bitcoin as a strategic asset, Western nations would be compelled to accumulate it to influence the market and counteract sanctions circumvention, making Bitcoin critical for national security. In a scenario where major powers hold Bitcoin, it would be unfeasible to remain competitive without it.
This logic extends to Bitcoin mining, the process that validates transactions. By deciding what is confirmed, nations dominating mining operations gain significant influence over transaction flows. Consequently, Bitcoin-accumulating countries will prioritize investing in domestic mining infrastructure, enhancing the network's decentralization and security. For instance, Russia reportedly funds regional initiatives to develop AI and Bitcoin mining infrastructure within the BRICS framework through its Sovereign Wealth Fund.
This dynamic triggers a chain reaction: as one nation adopts Bitcoin, others are pressured to follow suit to avoid competitive disadvantages. This cycle embodies the essence of game theory, where each player's choices shape the strategies of others, positioning Bitcoin as a critical asset in the global geopolitical arena.
-

@ fd208ee8:0fd927c1
2024-12-26 07:02:59
I just read this, and found it enlightening.
> Jung... notes that intelligence can be seen as problem solving at an everyday level..., whereas creativity may represent problem solving for less common issues
> Other studies have used metaphor creation as a creativity measure instead of divergent thinking and a spectrum of CHC components instead of just g and have found much higher relationships between creativity and intelligence than past studies
https://www.mdpi.com/2079-3200/3/3/59
I'm unusually intelligent (Who isn't?), but I'm much more creative, than intelligent, and I think that confuses people. The ability to apply intelligence, to solve completely novel problems, on the fly, is something IQ tests don't even claim to measure. They just claim a correlation.
Creativity requires taking wild, mental leaps out into nothingness; simply trusting that your brain will land you safely.
And this is why I've been at the forefront of massive innovation, over and over, but never got rich off of it.
*I'm a starving autist.*
Zaps are the first time I've ever made money directly, for solving novel problems. Companies don't do this because there is a span of time between providing a solution and the solution being implemented, and the person building the implementation (or their boss) receives all the credit for the existence of the solution. At best, you can hope to get pawned off with a small bonus.
Nobody can remember who came up with the solution, originally, and that person might not even be there, anymore, and probably never filed a patent, and may have no idea that their idea has even been built. They just run across it, later, in a tech magazine or museum, and say, "Well, will you look at that! Someone actually went and built it! Isn't that nice!"
Universities at least had the idea of cementing novel solutions in academic papers, but that:
1) only works if you're an academic, and at a university,
2) is an incredibly slow process, not appropriate for a truly innovative field,
3) leads to manifestations of perverse incentives and biased research frameworks, coming from 'publish or perish' policies.
But I think long-form notes and zaps solve for this problem. #Alexandria, especially, is being built to cater to this long-suffering class of chronic underachievers. It leaves a written, public, time-stamped record of *Clever Ideas We Have Had*.
Because they are clever, the ideas.
And we have had them.
-

@ 228dde34:b5d0345e
2024-12-25 09:35:38
##### By Cheryl Nya
##### Deputy Editor
##### Hype Issue #60
###### CHERYL NYA dives into the four attachment styles and discovers how they can be understood and used to strengthen our interpersonal relationships.

In the midst of a heated conflict, what is your first instinct? Would it be to apologise repeatedly, or to calmly suggest a solution? Or perhaps your first move would be to walk away from the issue. Could it be that you lash out emotionally only to withdraw suddenly out of guilt? Regardless of which of the four responses you resonate with, it all boils down to your own unique style of attachment; something that is different for everyone.
Experts theorise that humans exhibit four different attachment styles which determine their patterns of closeness, trust, and dependency in relationships. Each style reflects the different ways people seek connection and express their emotional needs.
Originated by British psychologist, John Bowlby, and expanded upon by Mary Ainsworth, the attachment theory suggests that humans are biologically wired to form attachments for survival, and the nature of these attachments shapes our development and experiences in relationships.
At its core, the theory asserts that children naturally turn to a caregiver for comfort during times of distress or uncertainty. The bond formed in these moments establishes the foundation for secure or insecure attachments. As the child grows, this connection shapes how they approach future relationships and manage stress.
 *The four attachment styles – each representing distinct ways people approach connections. Photo by The New York Times.*
Now let’s dive into the four attachment styles: secure, anxious, avoidant and disorganised.
**Secure Attachment**
Individuals with the secure attachment style have a healthy balance of independence and reliance on others. They manage conflict well, being comfortable with healthy communication, and are confident in both giving and receiving affection. These people enjoy being with others, and aren’t anxious when apart.
**Anxious Attachment**
This group of individuals tend to be perceived as needy, and in most cases, excessively so. People with the anxious attachment style usually have low self-esteem and often need approval; they crave emotional intimacy and reassurance but worry that others might lose interest, or not want to be with them. Their significant fear of abandonment and rejection could lead them to face difficulty being alone.
**Avoidant Attachment**
Someone who’s avoidant may find it challenging to handle emotional intimacy. This group of individuals value their independence and freedom so much that intimacy and closeness can often make them uncomfortable. They tend to suppress or downplay their feelings to avoid situations where they have to be vulnerable or dependent on others.
**Disorganised Attachment**
This attachment style is marked by the deep desire for closeness coupled with an equally intense fear of getting hurt. The unpredictable behaviour of these people could look like: Being warm and affectionate one moment, and distant and withdrawn the next. Their struggle to regulate their emotions results in their contradictory actions. The disorganised attachment style exhibits both the traits of the anxious and the avoidant styles.
 *Take a moment to understand why you can’t help but react a certain way; it might just be your attachment style. Photo taken from Pinterest.*
To put attachment theory into context, let’s explore how individuals with different attachment styles would respond in the same situation.
Scenario: You’ve made plans with a loved one but they cancel on you.
Secure attachment style: “No worries, we can reschedule! Hope all’s well on your side!”
Anxious attachment style: “Why don’t they want to see me? I’m not important enough…”
Avoidant attachment style: “Nice, I have more time for myself now.”
Disorganised attachment style: “Did I do something wrong? Whatever, I shouldn’t care.”
Alongside popular concepts such as love languages and the Myers-Briggs Type Indicator (MBTI), attachment styles have also become part of the blueprint for modern relationships.
Understanding attachment styles is important because it helps you identify your emotional triggers and behaviours in relationships. This awareness improves your ability to communicate your needs with your loved ones, particularly for those with insecure attachment styles (anxious, avoidant, disorganised). Enhanced communication could also help you interpret others’ actions without jumping to conclusions. This knowledge equips you to navigate conflicts between different attachment styles more effectively.
Everyone has their own way of connecting with others, and when you understand why some people want constant approval, or why others actively seek solitude, you have the ability to adjust your approach to make your relationships smoother.

 *Loving someone could look like two extremes: constant reassurance and giving them space. Nothing wrong with either, we just have different ways of wanting to feel loved. Photos taken from Pinterest.*
For example, if you’re the secure type, you can step up and offer that extra reassurance when someone with an anxious attachment style is feeling uncertain. It’s not so much about smothering them, but just simply showing that you care and that you’re listening to their needs. Or when dealing with an avoidant friend, you can respect their need for space while trying not to take it too personally. They might not always be down for a real and deep conversation like you are, but that’s totally okay. By recognising the behaviours of different styles, you help to avoid misunderstandings and facilitate amicable relationships.
 *Understanding each other’s different style of attachment and reaching a compromise could strengthen your relationship. Photo taken from Pinterest.*
Conversely, if you’re the anxious type, you can try making an effort to seek less validation from others, and find your worth in yourself. Remind yourself that you’re worthy of love, just as you are. Likewise for people with the avoidant attachment style, try to gather courage to face your vulnerabilities and true feelings by talking it out with a trusted loved one. These efforts can also make a secure type friend feel heard when their need for a good balance between emotional closeness and independence is met.
The best part is that learning about attachment styles helps you communicate in ways that fit each person’s needs. Your relationships aren’t the only things that will benefit from this knowledge: you grow into a more thoughtful and empathetic individual too.
Be it the clingy friend, the ‘keep a distance’ type, the secure or the ‘can’t decide what I want to feel right now’ kind that you’re dealing with, knowing how to adjust your approach can effectively turn conflicts into growth.
Now that you know a little more about attachment styles, why not take a moment to reflect on your own? Take a quick quiz online or chat with a partner about their attachment style. You might be surprised by how much it can change the way you connect with people in your life.
So, the next time you’re trying to figure out why someone is acting a certain way, remember – it might just be their attachment style talking!
-

@ bcea2b98:7ccef3c9
2024-12-25 03:11:27
It has been a fun year of learning and entertainment with you all. Merry Christmas!
originally posted at https://stacker.news/items/823433
-

@ 2fc236af:455ba142
2024-12-24 19:40:20
# 22 February 2025 • 10 a.m. to 2 p.m. • The Doddridge Centre (opposite Church's Shoes factory), St. James, Northampton • NN5 5LD
Seedy Saturday is an community seed swap event held each February in Northampton, UK. We'll have a wide range of fruit, vegetable, herb and flower seeds to choose from, including some rare and unusual varieties you won't find in the catalogues. We'll also have a marketplace selling garden and eco-related goods, community groups, and a pop-up cafe serving a range of hot food, drinks and snacks. Whether you're a newly-minted gardener or a child of the soil, we're sure to have something for you!
Click/tap here for a handy map and details of how to find us (opens in new tab / window). We bring together a vibrant community of local gardeners and growers of all ages and abilities; it's a great way to start the gardening season. If you've new to the idea of seed swaps, read on!
-----------
### What's a seed swap?
A seed swap is a community event where gardeners can exchange their spare vegetable, flower, fruit and herb seeds—either own-grown or commercially produced—for other seeds they want to grow. Most seed swaps are run by gardeners for gardeners; you'll often find rare and interesting local varieties on offer. They're also a great place to meet and chat with other local growers.
The seed table is the heart of any seed swap; here you'll find all sorts of garden seeds on offer. Though we can't guarantee to have everything you want, you're sure to find something interesting.
At Northampton's Seedy Saturday you'll also find:
•stalls selling local produce and garden-centric items;
•seed potatoes;
•community organisations that focus on food, gardening and the environment;
•a pop-up cafe serving hot drinks and light snacks.
### How does our seed swap work?
Pack your home-grown seeds into envelopes or self-sealing bags and label them with the plant's name (common or Latin), the variety's name, and the year it was grown. You can also add the place where it was grown, – for example; ""Tomato: Gardeners Delight, grown in Brixworth 2023"". Securely seal the packets.
When you arrive, bring your spare seeds to the seed reception table, where our volunteers will check and sort them for display. Then, choose any seeds you want from the table; we'll exchange seeds on a pack-for-pack basis. Don't worry if you've no seeds to swap or want to take more than you've donated; you can take more seeds for a minimum donation of 50p per pack.
### What to bring:
To make sure everyone's swapped seeds will grow and flourish, please follow these guidelines when choosing seeds to bring to the swap table. We welcome:
•non-hybrid seeds you've grown and harvested yourself (though see below); and
•unopened packs of commercially packed seeds that have been stored in cool, dry conditions and are no more than one year past their "sow by" date.
What to leave at home:
•part-used and opened packs of seeds where the inner pack has been opened;
•seeds that are unpackaged, unlabelled or undated;
•seeds from produce you haven't grown yourself (eg; shop-bought fruits and vegetables);
•commercially packed seeds that are more than one year past their "sow by" date and home-grown seeds that are more than two years old;
•seeds that have been stored in hot or damp conditions (eg; in a greenhouse or shed);
•seeds that may have been cross-pollinated;
•seeds from diseased or unhealthy plants;
•seeds of patented varieties or genetically modified organisms (GMOs);
•seeds of any plant that is illegal, restricted or regulated by UK law (eg; cannabis, invasive weeds etc).
### Want to know more about seed-saving? Click or tap [here](nostr:nevent1qvzqqqr4gupzqt7zx6he9d03g48cls83565lkqgfwpmj6pf7wzfqrma5jfz4hg2zqythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyghwumn8ghj7vf5xqhxvdm69e5k7tcpzamhxue69uhkyarr9e4kcetwv3sh5afwvdhk6tcpr4mhxue69uhkymmnw3ezucnfw33k76tww3ux76m09e3k7mf0qyw8wumn8ghj7cn4vd4k2apwvdhhyctrd3jjuum0vd5kzmp0qqsrfshynqaajprtzt4umj04hrxwuw353f27k9eh9pgs0062sn3g4fqzz09tg).
Northampton's Seedy Saturday is organised by Fruitful Abundance, a group of volunteers who campaign for a fairer, more resilient and less-wasteful food system. We update this page as needed but our Facebook page [(link)](https://www.facebook.com/northamptonseedysaturday/) is often more up-to-date. You can contact us via our Facebook page. Please note we are unpaid volunteers with busy lives so you may not get an immediate response to your query.
 @ 89ccea93:df4e00b7
2025-02-06 11:20:49I've opened a ~monero territory. I kept wanting to post things about or tangential to monero and didn't know where to shove them. Obviously ~bitcoin isn't the right place. And ~cryptocurrency didn't feel right, since for me, as a bitcoiner, monero is in a unique position. It doesn't seem to fit under the larger basket of cryptocurrencies. Many of which are scams/self-enrichment schemes. Ahem, XRP. Or just poorly implemented and pre-mined. Ahem, ETH. I don't know a lot about monero actually, but I use it and like it and think it has a place in a bitcoiners arsenal in resisting government infringements and resisting pervasive privacy shit-holes like the chain anal companies. Even Coinbase has their own proprietary chain anal. It's disgusting. They don't want us to have privacy. And many people play right into their hands by handing over their ID card and picture of their face to get bitcoins when you can get it anonymously. But I digress. Use the territory, or don't. But if you do, then welcome. originally posted at https://stacker.news/items/877547
@ 89ccea93:df4e00b7
2025-02-06 11:20:49I've opened a ~monero territory. I kept wanting to post things about or tangential to monero and didn't know where to shove them. Obviously ~bitcoin isn't the right place. And ~cryptocurrency didn't feel right, since for me, as a bitcoiner, monero is in a unique position. It doesn't seem to fit under the larger basket of cryptocurrencies. Many of which are scams/self-enrichment schemes. Ahem, XRP. Or just poorly implemented and pre-mined. Ahem, ETH. I don't know a lot about monero actually, but I use it and like it and think it has a place in a bitcoiners arsenal in resisting government infringements and resisting pervasive privacy shit-holes like the chain anal companies. Even Coinbase has their own proprietary chain anal. It's disgusting. They don't want us to have privacy. And many people play right into their hands by handing over their ID card and picture of their face to get bitcoins when you can get it anonymously. But I digress. Use the territory, or don't. But if you do, then welcome. originally posted at https://stacker.news/items/877547 @ 57d1a264:69f1fee1
2025-02-06 07:38:36# How does bitcoin's lack of central brand authority influence its visual identity, and what implications does this have for designers? originally posted at https://stacker.news/items/877437
@ 57d1a264:69f1fee1
2025-02-06 07:38:36# How does bitcoin's lack of central brand authority influence its visual identity, and what implications does this have for designers? originally posted at https://stacker.news/items/877437 @ e3ba5e1a:5e433365
2025-02-05 17:47:16I got into a [friendly discussion](https://x.com/snoyberg/status/1887007888117252142) on X regarding health insurance. The specific question was how to deal with health insurance companies (presumably unfairly) denying claims? My answer, as usual: get government out of it! The US healthcare system is essentially the worst of both worlds: * Unlike full single payer, individuals incur high costs * Unlike a true free market, regulation causes increases in costs and decreases competition among insurers I'm firmly on the side of moving towards the free market. (And I say that as someone living under a single payer system now.) Here's what I would do: * Get rid of tax incentives that make health insurance tied to your employer, giving individuals back proper freedom of choice. * Reduce regulations significantly. * In the short term, some people will still get rejected claims and other obnoxious behavior from insurance companies. We address that in two ways: 1. Due to reduced regulations, new insurance companies will be able to enter the market offering more reliable coverage and better rates, and people will flock to them because they have the freedom to make their own choices. 2. Sue the asses off of companies that reject claims unfairly. And ideally, as one of the few legitimate roles of government in all this, institute new laws that limit the ability of fine print to allow insurers to escape their responsibilities. (I'm hesitant that the latter will happen due to the incestuous relationship between Congress/regulators and insurers, but I can hope.) Will this magically fix everything overnight like politicians normally promise? No. But it will allow the market to return to a healthy state. And I don't think it will take long (order of magnitude: 5-10 years) for it to come together, but that's just speculation. And since there's a high correlation between those who believe government can fix problems by taking more control and demanding that only credentialed experts weigh in on a topic (both points I strongly disagree with BTW): I'm a trained actuary and worked in the insurance industry, and have directly seen how government regulation reduces competition, raises prices, and harms consumers. And my final point: I don't think any prior art would be a good comparison for deregulation in the US, it's such a different market than any other country in the world for so many reasons that lessons wouldn't really translate. Nonetheless, I asked Grok for some empirical data on this, and at best the results of deregulation could be called "mixed," but likely more accurately "uncertain, confused, and subject to whatever interpretation anyone wants to apply." https://x.com/i/grok/share/Zc8yOdrN8lS275hXJ92uwq98M
@ e3ba5e1a:5e433365
2025-02-05 17:47:16I got into a [friendly discussion](https://x.com/snoyberg/status/1887007888117252142) on X regarding health insurance. The specific question was how to deal with health insurance companies (presumably unfairly) denying claims? My answer, as usual: get government out of it! The US healthcare system is essentially the worst of both worlds: * Unlike full single payer, individuals incur high costs * Unlike a true free market, regulation causes increases in costs and decreases competition among insurers I'm firmly on the side of moving towards the free market. (And I say that as someone living under a single payer system now.) Here's what I would do: * Get rid of tax incentives that make health insurance tied to your employer, giving individuals back proper freedom of choice. * Reduce regulations significantly. * In the short term, some people will still get rejected claims and other obnoxious behavior from insurance companies. We address that in two ways: 1. Due to reduced regulations, new insurance companies will be able to enter the market offering more reliable coverage and better rates, and people will flock to them because they have the freedom to make their own choices. 2. Sue the asses off of companies that reject claims unfairly. And ideally, as one of the few legitimate roles of government in all this, institute new laws that limit the ability of fine print to allow insurers to escape their responsibilities. (I'm hesitant that the latter will happen due to the incestuous relationship between Congress/regulators and insurers, but I can hope.) Will this magically fix everything overnight like politicians normally promise? No. But it will allow the market to return to a healthy state. And I don't think it will take long (order of magnitude: 5-10 years) for it to come together, but that's just speculation. And since there's a high correlation between those who believe government can fix problems by taking more control and demanding that only credentialed experts weigh in on a topic (both points I strongly disagree with BTW): I'm a trained actuary and worked in the insurance industry, and have directly seen how government regulation reduces competition, raises prices, and harms consumers. And my final point: I don't think any prior art would be a good comparison for deregulation in the US, it's such a different market than any other country in the world for so many reasons that lessons wouldn't really translate. Nonetheless, I asked Grok for some empirical data on this, and at best the results of deregulation could be called "mixed," but likely more accurately "uncertain, confused, and subject to whatever interpretation anyone wants to apply." https://x.com/i/grok/share/Zc8yOdrN8lS275hXJ92uwq98M @ 57d1a264:69f1fee1
2025-02-05 02:18:03 Pre-Foundational learning for these participants has now kicked off in the Bitcoin Design Community, check out the #education channel on the [Bitcoin.Design](https://Bitcoin.Design) [Discord channel](https://discord.com/channels/903125802726596648/1260871907050393620). ## 🪇 10 talented participants from South America will be: Learning bitcoin UX Design fundamentals using the Bitcoin Design Guide Working hands-on with South American-built products to evaluate their user experiences and support builders with data > Attending [BTC++ in Florianópolis](https://btcplusplus.dev/conf/floripa) This initiative is sponsored by the [Human Rights Foundation](https://HRF.org) in collaboration with the [Bitcoin Design Foundation](https://bitcoindesignfoundation.org/) and [Area Bitcoin](https://areabitcoin.co). ## 🥅 Goals: - Empower local talent to improve the UX of South American bitcoin products - seeing their passion and drive to bring bitcoin to their countries is really inspiring - Create meaningful relationships with wallet developers through practical collaboration - Scale bitcoin adoption by improving the user experience - Create a public knowledge base: All research conducted in Africa and South America will be made publicly available for builders originally posted at https://stacker.news/items/876215
@ 57d1a264:69f1fee1
2025-02-05 02:18:03 Pre-Foundational learning for these participants has now kicked off in the Bitcoin Design Community, check out the #education channel on the [Bitcoin.Design](https://Bitcoin.Design) [Discord channel](https://discord.com/channels/903125802726596648/1260871907050393620). ## 🪇 10 talented participants from South America will be: Learning bitcoin UX Design fundamentals using the Bitcoin Design Guide Working hands-on with South American-built products to evaluate their user experiences and support builders with data > Attending [BTC++ in Florianópolis](https://btcplusplus.dev/conf/floripa) This initiative is sponsored by the [Human Rights Foundation](https://HRF.org) in collaboration with the [Bitcoin Design Foundation](https://bitcoindesignfoundation.org/) and [Area Bitcoin](https://areabitcoin.co). ## 🥅 Goals: - Empower local talent to improve the UX of South American bitcoin products - seeing their passion and drive to bring bitcoin to their countries is really inspiring - Create meaningful relationships with wallet developers through practical collaboration - Scale bitcoin adoption by improving the user experience - Create a public knowledge base: All research conducted in Africa and South America will be made publicly available for builders originally posted at https://stacker.news/items/876215 @ 57d1a264:69f1fee1
2025-02-05 00:25:20# How does open source development contribute to bitcoin's security, reliability, and evolution as a network? originally posted at https://stacker.news/items/876130
@ 57d1a264:69f1fee1
2025-02-05 00:25:20# How does open source development contribute to bitcoin's security, reliability, and evolution as a network? originally posted at https://stacker.news/items/876130 @ 91bea5cd:1df4451c
2025-02-04 17:24:50### Definição de ULID: Timestamp 48 bits, Aleatoriedade 80 bits Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C. e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível. #### Gerar ULID ```sql CREATE EXTENSION IF NOT EXISTS pgcrypto; CREATE FUNCTION generate_ulid() RETURNS TEXT AS $$ DECLARE -- Crockford's Base32 encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; timestamp BYTEA = E'\\000\\000\\000\\000\\000\\000'; output TEXT = ''; unix_time BIGINT; ulid BYTEA; BEGIN -- 6 timestamp bytes unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT; timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER); -- 10 entropy bytes ulid = timestamp || gen_random_bytes(10); -- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31))); -- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31))); RETURN output; END $$ LANGUAGE plpgsql VOLATILE; ``` #### ULID TO UUID ```sql CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$ DECLARE -- 16byte bytes bytea = E'\\x00000000 00000000 00000000 00000000'; v char[]; -- Allow for O(1) lookup of index values dec integer[] = ARRAY[ 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 255, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31 ]; BEGIN IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN RAISE EXCEPTION 'Invalid ULID: %', ulid; END IF; v = regexp_split_to_array(ulid, ''); -- 6 bytes timestamp (48 bits) bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]); bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2)); bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4)); bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1)); bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3)); bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]); -- 10 bytes of entropy (80 bits); bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2)); bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4)); bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1)); bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3)); bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]); bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2)); bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4)); bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1)); bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3)); bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]); RETURN bytes; END $$ LANGUAGE plpgsql IMMUTABLE; CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$ BEGIN RETURN encode(parse_ulid(ulid), 'hex')::uuid; END $$ LANGUAGE plpgsql IMMUTABLE; ``` #### UUID to ULID ```sql CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$ DECLARE encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; output text = ''; uuid_bytes bytea = uuid_send(id); BEGIN -- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31))); -- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31))); RETURN output; END $$ LANGUAGE plpgsql IMMUTABLE; ``` #### Gera 11 Digitos aleatórios: YBKXG0CKTH4 ```sql -- Cria a extensão pgcrypto para gerar uuid CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Cria a função para gerar ULID CREATE OR REPLACE FUNCTION gen_lrandom() RETURNS TEXT AS $$ DECLARE ts_millis BIGINT; ts_chars TEXT; random_bytes BYTEA; random_chars TEXT; base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; i INT; BEGIN -- Pega o timestamp em milissegundos ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT; -- Converte o timestamp para base32 ts_chars := ''; FOR i IN REVERSE 0..11 LOOP ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1); END LOOP; -- Gera 10 bytes aleatórios e converte para base32 random_bytes := gen_random_bytes(10); random_chars := ''; FOR i IN 0..9 LOOP random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1); IF i < 9 THEN random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1); ELSE random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1); END IF; END LOOP; -- Concatena o timestamp e os caracteres aleatórios RETURN ts_chars || random_chars; END; $$ LANGUAGE plpgsql; ``` #### Exemplo de USO ```sql -- Criação da extensão caso não exista CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Criação da tabela pessoas CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL ); -- Busca Pessoa na tabela SELECT * FROM "pessoas" WHERE uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F'; ``` ### Fontes - https://github.com/scoville/pgsql-ulid - https://github.com/geckoboard/pgulid
@ 91bea5cd:1df4451c
2025-02-04 17:24:50### Definição de ULID: Timestamp 48 bits, Aleatoriedade 80 bits Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C. e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível. #### Gerar ULID ```sql CREATE EXTENSION IF NOT EXISTS pgcrypto; CREATE FUNCTION generate_ulid() RETURNS TEXT AS $$ DECLARE -- Crockford's Base32 encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; timestamp BYTEA = E'\\000\\000\\000\\000\\000\\000'; output TEXT = ''; unix_time BIGINT; ulid BYTEA; BEGIN -- 6 timestamp bytes unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT; timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER); -- 10 entropy bytes ulid = timestamp || gen_random_bytes(10); -- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31))); -- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31))); RETURN output; END $$ LANGUAGE plpgsql VOLATILE; ``` #### ULID TO UUID ```sql CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$ DECLARE -- 16byte bytes bytea = E'\\x00000000 00000000 00000000 00000000'; v char[]; -- Allow for O(1) lookup of index values dec integer[] = ARRAY[ 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 255, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31 ]; BEGIN IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN RAISE EXCEPTION 'Invalid ULID: %', ulid; END IF; v = regexp_split_to_array(ulid, ''); -- 6 bytes timestamp (48 bits) bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]); bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2)); bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4)); bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1)); bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3)); bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]); -- 10 bytes of entropy (80 bits); bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2)); bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4)); bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1)); bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3)); bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]); bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2)); bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4)); bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1)); bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3)); bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]); RETURN bytes; END $$ LANGUAGE plpgsql IMMUTABLE; CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$ BEGIN RETURN encode(parse_ulid(ulid), 'hex')::uuid; END $$ LANGUAGE plpgsql IMMUTABLE; ``` #### UUID to ULID ```sql CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$ DECLARE encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; output text = ''; uuid_bytes bytea = uuid_send(id); BEGIN -- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31))); -- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31))); RETURN output; END $$ LANGUAGE plpgsql IMMUTABLE; ``` #### Gera 11 Digitos aleatórios: YBKXG0CKTH4 ```sql -- Cria a extensão pgcrypto para gerar uuid CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Cria a função para gerar ULID CREATE OR REPLACE FUNCTION gen_lrandom() RETURNS TEXT AS $$ DECLARE ts_millis BIGINT; ts_chars TEXT; random_bytes BYTEA; random_chars TEXT; base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; i INT; BEGIN -- Pega o timestamp em milissegundos ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT; -- Converte o timestamp para base32 ts_chars := ''; FOR i IN REVERSE 0..11 LOOP ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1); END LOOP; -- Gera 10 bytes aleatórios e converte para base32 random_bytes := gen_random_bytes(10); random_chars := ''; FOR i IN 0..9 LOOP random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1); IF i < 9 THEN random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1); ELSE random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1); END IF; END LOOP; -- Concatena o timestamp e os caracteres aleatórios RETURN ts_chars || random_chars; END; $$ LANGUAGE plpgsql; ``` #### Exemplo de USO ```sql -- Criação da extensão caso não exista CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Criação da tabela pessoas CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL ); -- Busca Pessoa na tabela SELECT * FROM "pessoas" WHERE uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F'; ``` ### Fontes - https://github.com/scoville/pgsql-ulid - https://github.com/geckoboard/pgulid @ 1833ee04:7c4a8170
2025-02-04 15:14:03The international race for Bitcoin strategic reserves is just getting started. If you’re stacking now, you’re still incredibly early. At $100k per Bitcoin, it’s practically free for anyone who truly understands how massive this shift is. Think back to when paper currency was introduced, people had to trade their gold for paper bills. Many laughed, saying, Who’s going to trust these worthless pieces of paper as money? Yet today, you sell your time to earn these paper bills while your government can print an unlimited amount at will. The world is returning to a gold standard. But this time, it’s Gold 2.0 which is Bitcoin.The international race for Bitcoin strategic reserves is just getting started.\ \ If you’re stacking now, you’re still incredibly early.\ \ At $100k per Bitcoin, it’s practically free for anyone who truly understands how massive this shift is.\ \ Think back to when paper currency was introduced, people had to trade their gold for paper bills. Many laughed, saying, Who’s going to trust these worthless pieces of paper as money?\ \ Yet today, you sell your time to earn these paper bills while your government can print an unlimited amount at will.\ \ The world is returning to a gold standard. But this time, it’s Gold 2.0 which is Bitcoin.
@ 1833ee04:7c4a8170
2025-02-04 15:14:03The international race for Bitcoin strategic reserves is just getting started. If you’re stacking now, you’re still incredibly early. At $100k per Bitcoin, it’s practically free for anyone who truly understands how massive this shift is. Think back to when paper currency was introduced, people had to trade their gold for paper bills. Many laughed, saying, Who’s going to trust these worthless pieces of paper as money? Yet today, you sell your time to earn these paper bills while your government can print an unlimited amount at will. The world is returning to a gold standard. But this time, it’s Gold 2.0 which is Bitcoin.The international race for Bitcoin strategic reserves is just getting started.\ \ If you’re stacking now, you’re still incredibly early.\ \ At $100k per Bitcoin, it’s practically free for anyone who truly understands how massive this shift is.\ \ Think back to when paper currency was introduced, people had to trade their gold for paper bills. Many laughed, saying, Who’s going to trust these worthless pieces of paper as money?\ \ Yet today, you sell your time to earn these paper bills while your government can print an unlimited amount at will.\ \ The world is returning to a gold standard. But this time, it’s Gold 2.0 which is Bitcoin. @ e3ba5e1a:5e433365
2025-02-04 08:29:00President Trump has started rolling out his tariffs, something I [blogged about in November](https://www.snoyman.com/blog/2024/11/steelmanning-tariffs/). People are talking about these tariffs a lot right now, with many people (correctly) commenting on how consumers will end up with higher prices as a result of these tariffs. While that part is true, I’ve seen a lot of people taking it to the next, incorrect step: that consumers will pay the entirety of the tax. I [put up a poll on X](https://x.com/snoyberg/status/1886035800019599808) to see what people thought, and while the right answer got a lot of votes, it wasn't the winner.  For purposes of this blog post, our ultimate question will be the following: * Suppose apples currently sell for $1 each in the entire United States. * There are domestic sellers and foreign sellers of apples, all receiving the same price. * There are no taxes or tariffs on the purchase of apples. * The question is: if the US federal government puts a $0.50 import tariff per apple, what will be the change in the following: * Number of apples bought in the US * Price paid by buyers for apples in the US * Post-tax price received by domestic apple producers * Post-tax price received by foreign apple producers Before we can answer that question, we need to ask an easier, first question: before instituting the tariff, why do apples cost $1? And finally, before we dive into the details, let me provide you with the answers to the ultimate question. I recommend you try to guess these answers before reading this, and if you get it wrong, try to understand why: 1. The number of apples bought will go down 2. The buyers will pay more for each apple they buy, but not the full amount of the tariff 3. Domestic apple sellers will receive a *higher* price per apple 4. Foreign apple sellers will receive a *lower* price per apple, but not lowered by the full amount of the tariff In other words, regardless of who sends the payment to the government, both taxed parties (domestic buyers and foreign sellers) will absorb some of the costs of the tariff, while domestic sellers will benefit from the protectionism provided by tariffs and be able to sell at a higher price per unit. ## Marginal benefit All of the numbers discussed below are part of a [helper Google Sheet](https://docs.google.com/spreadsheets/d/14ZbkWpw1B9Q1UDB9Yh47DmdKQfIafVVBKbDUsSIfGZw/edit?usp=sharing) I put together for this analysis. Also, apologies about the jagged lines in the charts below, I hadn’t realized before starting on this that there are [some difficulties with creating supply and demand charts in Google Sheets](https://superuser.com/questions/1359731/how-to-create-a-supply-demand-style-chart). Let’s say I absolutely love apples, they’re my favorite food. How much would I be willing to pay for a single apple? You might say “$1, that’s the price in the supermarket,” and in many ways you’d be right. If I walk into supermarket A, see apples on sale for $50, and know that I can buy them at supermarket B for $1, I’ll almost certainly leave A and go buy at B. But that’s not what I mean. What I mean is: how high would the price of apples have to go *everywhere* so that I’d no longer be willing to buy a single apple? This is a purely personal, subjective opinion. It’s impacted by how much money I have available, other expenses I need to cover, and how much I like apples. But let’s say the number is $5. How much would I be willing to pay for another apple? Maybe another $5. But how much am I willing to pay for the 1,000th apple? 10,000th? At some point, I’ll get sick of apples, or run out of space to keep the apples, or not be able to eat, cook, and otherwise preserve all those apples before they rot. The point being: I’ll be progressively willing to spend less and less money for each apple. This form of analysis is called *marginal benefit*: how much benefit (expressed as dollars I’m willing to spend) will I receive from each apple? This is a downward sloping function: for each additional apple I buy (quantity demanded), the price I’m willing to pay goes down. This is what gives my personal *demand curve*. And if we aggregate demand curves across all market participants (meaning: everyone interested in buying apples), we end up with something like this:  Assuming no changes in people’s behavior and other conditions in the market, this chart tells us how many apples will be purchased by our buyers at each price point between $0.50 and $5. And ceteris paribus (all else being equal), this will continue to be the demand curve for apples. ## Marginal cost Demand is half the story of economics. The other half is supply, or: how many apples will I sell at each price point? Supply curves are upward sloping: the higher the price, the more a person or company is willing and able to sell a product. Let’s understand why. Suppose I have an apple orchard. It’s a large property right next to my house. With about 2 minutes of effort, I can walk out of my house, find the nearest tree, pick 5 apples off the tree, and call it a day. 5 apples for 2 minutes of effort is pretty good, right? Yes, there was all the effort necessary to buy the land, and plant the trees, and water them… and a bunch more than I likely can’t even guess at. We’re going to ignore all of that for our analysis, because for short-term supply-and-demand movement, we can ignore these kinds of *sunk costs*. One other simplification: in reality, supply curves often start descending before ascending. This accounts for achieving efficiencies of scale after the first number of units purchased. But since both these topics are unneeded for understanding taxes, I won’t go any further. Anyway, back to my apple orchard. If someone offers me $0.50 per apple, I can do 2 minutes of effort and get $2.50 in revenue, which equates to a $75/hour wage for me. I’m more than happy to pick apples at that price\! However, let’s say someone comes to buy 10,000 apples from me instead. I no longer just walk out to my nearest tree. I’m going to need to get in my truck, drive around, spend the day in the sun, pay for gas, take a day off of my day job (let’s say it pays me $70/hour). The costs go up significantly. Let’s say it takes 5 days to harvest all those apples myself, it costs me $100 in fuel and other expenses, and I lose out on my $70/hour job for 5 days. We end up with: * Total expenditure: $100 \+ $70 \* 8 hours a day \* 5 days \== $2900 * Total revenue: $5000 (10,000 apples at $0.50 each) * Total profit: $2100 So I’m still willing to sell the apples at this price, but it’s not as attractive as before. And as the number of apples purchased goes up, my costs keep increasing. I’ll need to spend more money on fuel to travel more of my property. At some point I won’t be able to do the work myself anymore, so I’ll need to pay others to work on the farm, and they’ll be slower at picking apples than me (less familiar with the property, less direct motivation, etc.). The point being: at some point, the number of apples can go high enough that the $0.50 price point no longer makes me any money. This kind of analysis is called *marginal cost*. It refers to the additional amount of expenditure a seller has to spend in order to produce each additional unit of the good. Marginal costs go up as quantity sold goes up. And like demand curves, if you aggregate this data across all sellers, you get a supply curve like this:  ## Equilibrium price We now know, for every price point, how many apples buyers will purchase, and how many apples sellers will sell. Now we find the equilibrium: where the supply and demand curves meet. This point represents where the marginal benefit a buyer would receive from the next buyer would be less than the cost it would take the next seller to make it. Let’s see it in a chart:  You’ll notice that these two graphs cross at the $1 price point, where 63 apples are both demanded (bought by consumers) and supplied (sold by producers). This is our equilibrium price. We also have a visualization of the *surplus* created by these trades. Everything to the left of the equilibrium point and between the supply and demand curves represents surplus: an area where someone is receiving something of more value than they give. For example: * When I bought my first apple for $1, but I was willing to spend $5, I made $4 of consumer surplus. The consumer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and above the equilibrium price point. * When a seller sells his first apple for $1, but it only cost $0.50 to produce it, the seller made $0.50 of producer surplus. The producer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and below the equilibrium price point. Another way of thinking of surplus is “every time someone got a better price than they would have been willing to take.” OK, with this in place, we now have enough information to figure out how to price in the tariff, which we’ll treat as a negative externality. ## Modeling taxes Alright, the government has now instituted a $0.50 tariff on every apple sold within the US by a foreign producer. We can generally model taxes by either increasing the marginal cost of each unit sold (shifting the supply curve up), or by decreasing the marginal benefit of each unit bought (shifting the demand curve down). In this case, since only some of the producers will pay the tax, it makes more sense to modify the supply curve. First, let’s see what happens to the foreign seller-only supply curve when you add in the tariff:  With the tariff in place, for each quantity level, the price at which the seller will sell is $0.50 higher than before the tariff. That makes sense: if I was previously willing to sell my 82nd apple for $3, I would now need to charge $3.50 for that apple to cover the cost of the tariff. We see this as the tariff “pushing up” or “pushing left” the original supply curve. We can add this new supply curve to our existing (unchanged) supply curve for domestic-only sellers, and we end up with a result like this:  The total supply curve adds up the individual foreign and domestic supply curves. At each price point, we add up the total quantity each group would be willing to sell to determine the total quantity supplied for each price point. Once we have that cumulative supply curve defined, we can produce an updated supply-and-demand chart including the tariff:  As we can see, the equilibrium has shifted: * The equilibrium price paid by consumers has risen from $1 to $1.20. * The total number of apples purchased has dropped from 63 apples to 60 apples. * Consumers therefore received 3 less apples. They spent $72 for these 60 apples, whereas previously they spent $63 for 3 more apples, a definite decrease in consumer surplus. * Foreign producers sold 36 of those apples (see the raw data in the linked Google Sheet), for a gross revenue of $43.20. However, they also need to pay the tariff to the US government, which accounts for $18, meaning they only receive $25.20 post-tariff. Previously, they sold 42 apples at $1 each with no tariff to be paid, meaning they took home $42. * Domestic producers sold the remaining 24 apples at $1.20, giving them a revenue of $28.80. Since they don’t pay the tariff, they take home all of that money. By contrast, previously, they sold 21 apples at $1, for a take-home of $21. * The government receives $0.50 for each of the 60 apples sold, or in other words receives $30 in revenue it wouldn’t have received otherwise. We could be more specific about the surpluses, and calculate the actual areas for consumer surplus, producer surplus, inefficiency from the tariff, and government revenue from the tariff. But I won’t bother, as those calculations get slightly more involved. Instead, let’s just look at the aggregate outcomes: * Consumers were unquestionably hurt. Their price paid went up by $0.20 per apple, and received less apples. * Foreign producers were also hurt. Their price received went down from the original $1 to the new post-tariff price of $1.20, minus the $0.50 tariff. In other words: foreign producers only receive $0.70 per apple now. This hurt can be mitigated by shifting sales to other countries without a tariff, but the pain will exist regardless. * Domestic producers scored. They can sell less apples and make more revenue doing it. * And the government walked away with an extra $30. Hopefully you now see the answer to the original questions. Importantly, while the government imposed a $0.50 tariff, neither side fully absorbed that cost. Consumers paid a bit more, foreign producers received a bit less. The exact details of how that tariff was split across the groups is mediated by the relevant supply and demand curves of each group. If you want to learn more about this, the relevant search term is “price elasticity,” or how much a group’s quantity supplied or demanded will change based on changes in the price. ## Other taxes Most taxes are some kind of a tax on trade. Tariffs on apples is an obvious one. But the same applies to income tax (taxing the worker for the trade of labor for money) or payroll tax (same thing, just taxing the employer instead). Interestingly, you can use the same model for analyzing things like tax incentives. For example, if the government decided to subsidize domestic apple production by giving the domestic producers a $0.50 bonus for each apple they sell, we would end up with a similar kind of analysis, except instead of the foreign supply curve shifting up, we’d see the domestic supply curve shifting down. And generally speaking, this is what you’ll *always* see with government involvement in the economy. It will result in disrupting an existing equilibrium, letting the market readjust to a new equilibrium, and incentivization of some behavior, causing some people to benefit and others to lose out. We saw with the apple tariff, domestic producers and the government benefited while others lost. You can see the reverse though with tax incentives. If I give a tax incentive of providing a deduction (not paying income tax) for preschool, we would end up with: * Government needs to make up the difference in tax revenue, either by raising taxes on others or printing more money (leading to inflation). Either way, those paying the tax or those holding government debased currency will pay a price. * Those people who don’t use the preschool deduction will receive no benefit, so they simply pay a cost. * Those who do use the preschool deduction will end up paying less on tax+preschool than they would have otherwise. This analysis is fully amoral. It’s not saying whether providing subsidized preschool is a good thing or not, it simply tells you where the costs will be felt, and points out that such government interference in free economic choice does result in inefficiencies in the system. Once you have that knowledge, you’re more well educated on making a decision about whether the costs of government intervention are worth the benefits.
@ e3ba5e1a:5e433365
2025-02-04 08:29:00President Trump has started rolling out his tariffs, something I [blogged about in November](https://www.snoyman.com/blog/2024/11/steelmanning-tariffs/). People are talking about these tariffs a lot right now, with many people (correctly) commenting on how consumers will end up with higher prices as a result of these tariffs. While that part is true, I’ve seen a lot of people taking it to the next, incorrect step: that consumers will pay the entirety of the tax. I [put up a poll on X](https://x.com/snoyberg/status/1886035800019599808) to see what people thought, and while the right answer got a lot of votes, it wasn't the winner.  For purposes of this blog post, our ultimate question will be the following: * Suppose apples currently sell for $1 each in the entire United States. * There are domestic sellers and foreign sellers of apples, all receiving the same price. * There are no taxes or tariffs on the purchase of apples. * The question is: if the US federal government puts a $0.50 import tariff per apple, what will be the change in the following: * Number of apples bought in the US * Price paid by buyers for apples in the US * Post-tax price received by domestic apple producers * Post-tax price received by foreign apple producers Before we can answer that question, we need to ask an easier, first question: before instituting the tariff, why do apples cost $1? And finally, before we dive into the details, let me provide you with the answers to the ultimate question. I recommend you try to guess these answers before reading this, and if you get it wrong, try to understand why: 1. The number of apples bought will go down 2. The buyers will pay more for each apple they buy, but not the full amount of the tariff 3. Domestic apple sellers will receive a *higher* price per apple 4. Foreign apple sellers will receive a *lower* price per apple, but not lowered by the full amount of the tariff In other words, regardless of who sends the payment to the government, both taxed parties (domestic buyers and foreign sellers) will absorb some of the costs of the tariff, while domestic sellers will benefit from the protectionism provided by tariffs and be able to sell at a higher price per unit. ## Marginal benefit All of the numbers discussed below are part of a [helper Google Sheet](https://docs.google.com/spreadsheets/d/14ZbkWpw1B9Q1UDB9Yh47DmdKQfIafVVBKbDUsSIfGZw/edit?usp=sharing) I put together for this analysis. Also, apologies about the jagged lines in the charts below, I hadn’t realized before starting on this that there are [some difficulties with creating supply and demand charts in Google Sheets](https://superuser.com/questions/1359731/how-to-create-a-supply-demand-style-chart). Let’s say I absolutely love apples, they’re my favorite food. How much would I be willing to pay for a single apple? You might say “$1, that’s the price in the supermarket,” and in many ways you’d be right. If I walk into supermarket A, see apples on sale for $50, and know that I can buy them at supermarket B for $1, I’ll almost certainly leave A and go buy at B. But that’s not what I mean. What I mean is: how high would the price of apples have to go *everywhere* so that I’d no longer be willing to buy a single apple? This is a purely personal, subjective opinion. It’s impacted by how much money I have available, other expenses I need to cover, and how much I like apples. But let’s say the number is $5. How much would I be willing to pay for another apple? Maybe another $5. But how much am I willing to pay for the 1,000th apple? 10,000th? At some point, I’ll get sick of apples, or run out of space to keep the apples, or not be able to eat, cook, and otherwise preserve all those apples before they rot. The point being: I’ll be progressively willing to spend less and less money for each apple. This form of analysis is called *marginal benefit*: how much benefit (expressed as dollars I’m willing to spend) will I receive from each apple? This is a downward sloping function: for each additional apple I buy (quantity demanded), the price I’m willing to pay goes down. This is what gives my personal *demand curve*. And if we aggregate demand curves across all market participants (meaning: everyone interested in buying apples), we end up with something like this:  Assuming no changes in people’s behavior and other conditions in the market, this chart tells us how many apples will be purchased by our buyers at each price point between $0.50 and $5. And ceteris paribus (all else being equal), this will continue to be the demand curve for apples. ## Marginal cost Demand is half the story of economics. The other half is supply, or: how many apples will I sell at each price point? Supply curves are upward sloping: the higher the price, the more a person or company is willing and able to sell a product. Let’s understand why. Suppose I have an apple orchard. It’s a large property right next to my house. With about 2 minutes of effort, I can walk out of my house, find the nearest tree, pick 5 apples off the tree, and call it a day. 5 apples for 2 minutes of effort is pretty good, right? Yes, there was all the effort necessary to buy the land, and plant the trees, and water them… and a bunch more than I likely can’t even guess at. We’re going to ignore all of that for our analysis, because for short-term supply-and-demand movement, we can ignore these kinds of *sunk costs*. One other simplification: in reality, supply curves often start descending before ascending. This accounts for achieving efficiencies of scale after the first number of units purchased. But since both these topics are unneeded for understanding taxes, I won’t go any further. Anyway, back to my apple orchard. If someone offers me $0.50 per apple, I can do 2 minutes of effort and get $2.50 in revenue, which equates to a $75/hour wage for me. I’m more than happy to pick apples at that price\! However, let’s say someone comes to buy 10,000 apples from me instead. I no longer just walk out to my nearest tree. I’m going to need to get in my truck, drive around, spend the day in the sun, pay for gas, take a day off of my day job (let’s say it pays me $70/hour). The costs go up significantly. Let’s say it takes 5 days to harvest all those apples myself, it costs me $100 in fuel and other expenses, and I lose out on my $70/hour job for 5 days. We end up with: * Total expenditure: $100 \+ $70 \* 8 hours a day \* 5 days \== $2900 * Total revenue: $5000 (10,000 apples at $0.50 each) * Total profit: $2100 So I’m still willing to sell the apples at this price, but it’s not as attractive as before. And as the number of apples purchased goes up, my costs keep increasing. I’ll need to spend more money on fuel to travel more of my property. At some point I won’t be able to do the work myself anymore, so I’ll need to pay others to work on the farm, and they’ll be slower at picking apples than me (less familiar with the property, less direct motivation, etc.). The point being: at some point, the number of apples can go high enough that the $0.50 price point no longer makes me any money. This kind of analysis is called *marginal cost*. It refers to the additional amount of expenditure a seller has to spend in order to produce each additional unit of the good. Marginal costs go up as quantity sold goes up. And like demand curves, if you aggregate this data across all sellers, you get a supply curve like this:  ## Equilibrium price We now know, for every price point, how many apples buyers will purchase, and how many apples sellers will sell. Now we find the equilibrium: where the supply and demand curves meet. This point represents where the marginal benefit a buyer would receive from the next buyer would be less than the cost it would take the next seller to make it. Let’s see it in a chart:  You’ll notice that these two graphs cross at the $1 price point, where 63 apples are both demanded (bought by consumers) and supplied (sold by producers). This is our equilibrium price. We also have a visualization of the *surplus* created by these trades. Everything to the left of the equilibrium point and between the supply and demand curves represents surplus: an area where someone is receiving something of more value than they give. For example: * When I bought my first apple for $1, but I was willing to spend $5, I made $4 of consumer surplus. The consumer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and above the equilibrium price point. * When a seller sells his first apple for $1, but it only cost $0.50 to produce it, the seller made $0.50 of producer surplus. The producer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and below the equilibrium price point. Another way of thinking of surplus is “every time someone got a better price than they would have been willing to take.” OK, with this in place, we now have enough information to figure out how to price in the tariff, which we’ll treat as a negative externality. ## Modeling taxes Alright, the government has now instituted a $0.50 tariff on every apple sold within the US by a foreign producer. We can generally model taxes by either increasing the marginal cost of each unit sold (shifting the supply curve up), or by decreasing the marginal benefit of each unit bought (shifting the demand curve down). In this case, since only some of the producers will pay the tax, it makes more sense to modify the supply curve. First, let’s see what happens to the foreign seller-only supply curve when you add in the tariff:  With the tariff in place, for each quantity level, the price at which the seller will sell is $0.50 higher than before the tariff. That makes sense: if I was previously willing to sell my 82nd apple for $3, I would now need to charge $3.50 for that apple to cover the cost of the tariff. We see this as the tariff “pushing up” or “pushing left” the original supply curve. We can add this new supply curve to our existing (unchanged) supply curve for domestic-only sellers, and we end up with a result like this:  The total supply curve adds up the individual foreign and domestic supply curves. At each price point, we add up the total quantity each group would be willing to sell to determine the total quantity supplied for each price point. Once we have that cumulative supply curve defined, we can produce an updated supply-and-demand chart including the tariff:  As we can see, the equilibrium has shifted: * The equilibrium price paid by consumers has risen from $1 to $1.20. * The total number of apples purchased has dropped from 63 apples to 60 apples. * Consumers therefore received 3 less apples. They spent $72 for these 60 apples, whereas previously they spent $63 for 3 more apples, a definite decrease in consumer surplus. * Foreign producers sold 36 of those apples (see the raw data in the linked Google Sheet), for a gross revenue of $43.20. However, they also need to pay the tariff to the US government, which accounts for $18, meaning they only receive $25.20 post-tariff. Previously, they sold 42 apples at $1 each with no tariff to be paid, meaning they took home $42. * Domestic producers sold the remaining 24 apples at $1.20, giving them a revenue of $28.80. Since they don’t pay the tariff, they take home all of that money. By contrast, previously, they sold 21 apples at $1, for a take-home of $21. * The government receives $0.50 for each of the 60 apples sold, or in other words receives $30 in revenue it wouldn’t have received otherwise. We could be more specific about the surpluses, and calculate the actual areas for consumer surplus, producer surplus, inefficiency from the tariff, and government revenue from the tariff. But I won’t bother, as those calculations get slightly more involved. Instead, let’s just look at the aggregate outcomes: * Consumers were unquestionably hurt. Their price paid went up by $0.20 per apple, and received less apples. * Foreign producers were also hurt. Their price received went down from the original $1 to the new post-tariff price of $1.20, minus the $0.50 tariff. In other words: foreign producers only receive $0.70 per apple now. This hurt can be mitigated by shifting sales to other countries without a tariff, but the pain will exist regardless. * Domestic producers scored. They can sell less apples and make more revenue doing it. * And the government walked away with an extra $30. Hopefully you now see the answer to the original questions. Importantly, while the government imposed a $0.50 tariff, neither side fully absorbed that cost. Consumers paid a bit more, foreign producers received a bit less. The exact details of how that tariff was split across the groups is mediated by the relevant supply and demand curves of each group. If you want to learn more about this, the relevant search term is “price elasticity,” or how much a group’s quantity supplied or demanded will change based on changes in the price. ## Other taxes Most taxes are some kind of a tax on trade. Tariffs on apples is an obvious one. But the same applies to income tax (taxing the worker for the trade of labor for money) or payroll tax (same thing, just taxing the employer instead). Interestingly, you can use the same model for analyzing things like tax incentives. For example, if the government decided to subsidize domestic apple production by giving the domestic producers a $0.50 bonus for each apple they sell, we would end up with a similar kind of analysis, except instead of the foreign supply curve shifting up, we’d see the domestic supply curve shifting down. And generally speaking, this is what you’ll *always* see with government involvement in the economy. It will result in disrupting an existing equilibrium, letting the market readjust to a new equilibrium, and incentivization of some behavior, causing some people to benefit and others to lose out. We saw with the apple tariff, domestic producers and the government benefited while others lost. You can see the reverse though with tax incentives. If I give a tax incentive of providing a deduction (not paying income tax) for preschool, we would end up with: * Government needs to make up the difference in tax revenue, either by raising taxes on others or printing more money (leading to inflation). Either way, those paying the tax or those holding government debased currency will pay a price. * Those people who don’t use the preschool deduction will receive no benefit, so they simply pay a cost. * Those who do use the preschool deduction will end up paying less on tax+preschool than they would have otherwise. This analysis is fully amoral. It’s not saying whether providing subsidized preschool is a good thing or not, it simply tells you where the costs will be felt, and points out that such government interference in free economic choice does result in inefficiencies in the system. Once you have that knowledge, you’re more well educated on making a decision about whether the costs of government intervention are worth the benefits. @ 378562cd:a6fc6773
2025-02-02 18:58:38## Chef's notes I'm only testing this out right now. I will update the recipe as well as add my own image soon after making this dish again. ## Details - ⏲️ Prep time: 20 minutes - 🍳 Cook time: 1 hour - 🍽️ Servings: 4 ## Ingredients - 4 to 6 potatoes (size depending) - 1 lb ground beef - seasonings - 2 cans chili beans - 1 onion - katsup - shredded cheese of some kind ## Directions 1. saute onion and add ground beef to skillet. Season to liking. 2. peel if you like and thin slice potatoes 3. in a rectangle baking dish, layer potatoes, beans, meat and cheese (like a lasagna) until you have used all your ingredients. Try and make at least 2 or 3 layers with extra cheese on top. 4. Bake at 350 for one hour. Serve and enjoy!
@ 378562cd:a6fc6773
2025-02-02 18:58:38## Chef's notes I'm only testing this out right now. I will update the recipe as well as add my own image soon after making this dish again. ## Details - ⏲️ Prep time: 20 minutes - 🍳 Cook time: 1 hour - 🍽️ Servings: 4 ## Ingredients - 4 to 6 potatoes (size depending) - 1 lb ground beef - seasonings - 2 cans chili beans - 1 onion - katsup - shredded cheese of some kind ## Directions 1. saute onion and add ground beef to skillet. Season to liking. 2. peel if you like and thin slice potatoes 3. in a rectangle baking dish, layer potatoes, beans, meat and cheese (like a lasagna) until you have used all your ingredients. Try and make at least 2 or 3 layers with extra cheese on top. 4. Bake at 350 for one hour. Serve and enjoy! @ 228dde34:b5d0345e
2025-02-02 10:00:02##### By Cheryl Nya ##### Deputy Editor ##### Hype Issue #60 ###### CHERYL NYA explores how diverse travel styles can blend seamlessly on a grad trip, turning every moment into an opportunity for unforgettable memories and shared adventures.  *‘Grad trips’, taking a celebratory trip after graduation, have become a growing trend. Photo taken from Pinterest.* You made it – years of studying, late-night cramming, and navigating deadlines have finally paid off. Now, it’s time for a well-earned break: the graduation trip. The perfect chance to celebrate with your closest friends before everyone heads off in different directions. It sounds like the golden plan, but as exciting as it is, travelling in a group can be its own kind of challenge. Between different travel styles, budgets and energy levels, it’s easy for tensions to rise. However, with a little flexibility and compromise, your long-awaited trip will be remembered for its remarkable memories rather than its unfortunate disagreements. Here’s your ultimate guide to coexisting with your travel crew, without losing your patience along the way.  *Have an honest talk with your crew and set expectations before you head off. Photo taken from Pinterest.* 1. Recognise that everyone has their own travel personality There’s the ‘Itinerary Enthusiasts’ who have every minute planned. Then there’ll be the ‘Go with the flow’ travellers who are just there for chill vibes. Somewhere in between you’ve got the foodies, the shopaholics, and the one who just wants a good Instagram shot. When travelling with others, it’s unlikely that all of your friends have the same travel personality. Accepting these different travel personalities early on before your trip will help you avoid major clashes – or at least mentally prepare for them. By recognising your group dynamics, you’ll know who to trust with planning and who to expect last-minute cancellations from. 2. Budget talks are awkward… but necessary No one wants to be the person who suggests skipping a fancy dinner because they’re on a budget—but at the same time, no one wants to be forced into penny-pinching when they’re on this trip to indulge. Before the trip, have an honest conversation about spending expectations. Will you be splurging on expensive restaurants, or will street food and convenience stores be the way to go? Is everyone okay with taxis, or are we strictly on a public transport budget? Setting clear expectations upfront avoids unnecessary tension when the bill arrives. 3. The accommodation debate: Choose wisely If your crew has a mix of early risers and night owls, staying in one cramped hostel room will definitely lead to chaos. Hence your choice of accommodation is extremely important; it could make or break your trip. Keep in mind, your light sleepers will suffer if your party-loving friends stumble in at 3AM. So, booking an Airbnb with separate rooms and beds might be your best option. Consider everyone’s preferences before booking because once you’re stuck in a bad setup, there’s no escaping it. 4. Embrace the art of splitting up Not everyone wants to visit museums, and not everyone wants to be under the hot sun on a jet ski. Instead of dragging each other to activities not everyone is excited about, embrace the idea of splitting up for a day or two. If one group wants to go sightseeing at a historical site and the other wants to surf some waves, that’s okay! Just make sure to have a designated meetup location and time, and keep each other posted. This will keep everyone happy and mean that no one has to fake any enthusiasm for something they don’t enjoy. 5. Be honest about your limits It’s very tempting to go along with every plan to avoid seeming difficult. But, if you’re not careful, that’s a fast track to burnout. Remember, this is your grad trip too. If you need some downtime before an afternoon of exploring, take it. If you hate hiking, skip it instead of forcing yourself through. Your friends would rather you be honest than silently endure something you don’t enjoy. Grad trips are meant to be fun–so speak up and prioritise what will make your experience enjoyable. 6. Most importantly, embrace the chaos and remember why you came No matter how well you plan, things will go wrong. A “quick” coffee run might turn into a two-hour detour, or a carefully planned itinerary could be derailed by a sudden downpour. Maybe the group gets on the wrong train and ends up in an entirely different city. Sometimes, the best memories come from unplanned moments–so lean into the chaos and let the adventure unfold. At the end of the day, this trip isn’t about checking off every attraction or getting the perfect itinerary; it’s about celebrating a huge milestone with the people who made those long nights and tough exams bearable. The best part of the trip won’t be the landmarks or the food; it’ll be the inside jokes, the late-night talks, and the shared moments of pure chaos. So, take a deep breath, go with the flow, and make the most of it.  *No trip is perfect, but what’s important is the time spent with your company. Photo taken from Pinterest.* Surviving a grad trip with different travel styles isn’t about avoiding conflict, it’s about embracing the madness and making the best of it. And hey, worst case? You’ll have some hilarious group chat stories to reminisce about later.
@ 228dde34:b5d0345e
2025-02-02 10:00:02##### By Cheryl Nya ##### Deputy Editor ##### Hype Issue #60 ###### CHERYL NYA explores how diverse travel styles can blend seamlessly on a grad trip, turning every moment into an opportunity for unforgettable memories and shared adventures.  *‘Grad trips’, taking a celebratory trip after graduation, have become a growing trend. Photo taken from Pinterest.* You made it – years of studying, late-night cramming, and navigating deadlines have finally paid off. Now, it’s time for a well-earned break: the graduation trip. The perfect chance to celebrate with your closest friends before everyone heads off in different directions. It sounds like the golden plan, but as exciting as it is, travelling in a group can be its own kind of challenge. Between different travel styles, budgets and energy levels, it’s easy for tensions to rise. However, with a little flexibility and compromise, your long-awaited trip will be remembered for its remarkable memories rather than its unfortunate disagreements. Here’s your ultimate guide to coexisting with your travel crew, without losing your patience along the way.  *Have an honest talk with your crew and set expectations before you head off. Photo taken from Pinterest.* 1. Recognise that everyone has their own travel personality There’s the ‘Itinerary Enthusiasts’ who have every minute planned. Then there’ll be the ‘Go with the flow’ travellers who are just there for chill vibes. Somewhere in between you’ve got the foodies, the shopaholics, and the one who just wants a good Instagram shot. When travelling with others, it’s unlikely that all of your friends have the same travel personality. Accepting these different travel personalities early on before your trip will help you avoid major clashes – or at least mentally prepare for them. By recognising your group dynamics, you’ll know who to trust with planning and who to expect last-minute cancellations from. 2. Budget talks are awkward… but necessary No one wants to be the person who suggests skipping a fancy dinner because they’re on a budget—but at the same time, no one wants to be forced into penny-pinching when they’re on this trip to indulge. Before the trip, have an honest conversation about spending expectations. Will you be splurging on expensive restaurants, or will street food and convenience stores be the way to go? Is everyone okay with taxis, or are we strictly on a public transport budget? Setting clear expectations upfront avoids unnecessary tension when the bill arrives. 3. The accommodation debate: Choose wisely If your crew has a mix of early risers and night owls, staying in one cramped hostel room will definitely lead to chaos. Hence your choice of accommodation is extremely important; it could make or break your trip. Keep in mind, your light sleepers will suffer if your party-loving friends stumble in at 3AM. So, booking an Airbnb with separate rooms and beds might be your best option. Consider everyone’s preferences before booking because once you’re stuck in a bad setup, there’s no escaping it. 4. Embrace the art of splitting up Not everyone wants to visit museums, and not everyone wants to be under the hot sun on a jet ski. Instead of dragging each other to activities not everyone is excited about, embrace the idea of splitting up for a day or two. If one group wants to go sightseeing at a historical site and the other wants to surf some waves, that’s okay! Just make sure to have a designated meetup location and time, and keep each other posted. This will keep everyone happy and mean that no one has to fake any enthusiasm for something they don’t enjoy. 5. Be honest about your limits It’s very tempting to go along with every plan to avoid seeming difficult. But, if you’re not careful, that’s a fast track to burnout. Remember, this is your grad trip too. If you need some downtime before an afternoon of exploring, take it. If you hate hiking, skip it instead of forcing yourself through. Your friends would rather you be honest than silently endure something you don’t enjoy. Grad trips are meant to be fun–so speak up and prioritise what will make your experience enjoyable. 6. Most importantly, embrace the chaos and remember why you came No matter how well you plan, things will go wrong. A “quick” coffee run might turn into a two-hour detour, or a carefully planned itinerary could be derailed by a sudden downpour. Maybe the group gets on the wrong train and ends up in an entirely different city. Sometimes, the best memories come from unplanned moments–so lean into the chaos and let the adventure unfold. At the end of the day, this trip isn’t about checking off every attraction or getting the perfect itinerary; it’s about celebrating a huge milestone with the people who made those long nights and tough exams bearable. The best part of the trip won’t be the landmarks or the food; it’ll be the inside jokes, the late-night talks, and the shared moments of pure chaos. So, take a deep breath, go with the flow, and make the most of it.  *No trip is perfect, but what’s important is the time spent with your company. Photo taken from Pinterest.* Surviving a grad trip with different travel styles isn’t about avoiding conflict, it’s about embracing the madness and making the best of it. And hey, worst case? You’ll have some hilarious group chat stories to reminisce about later. @ 57d1a264:69f1fee1
2025-02-02 05:47:57Hey there, as a result of the recent [SN Media Kit](https://stacker.news/items/872925/r/Design_r) updated, I'll try to create few simple marketing assets for ~Stackers_Stocks territory to be spread across the web. Feel free to share in the comments below: - Few visual references you'd like the assets to be inspired on - If visuals are not your thing, a description of your idea will help too - A slogan, or some words/concepts that express the territory's values @BlokchainB you start, let's see how we go! originally posted at https://stacker.news/items/873112
@ 57d1a264:69f1fee1
2025-02-02 05:47:57Hey there, as a result of the recent [SN Media Kit](https://stacker.news/items/872925/r/Design_r) updated, I'll try to create few simple marketing assets for ~Stackers_Stocks territory to be spread across the web. Feel free to share in the comments below: - Few visual references you'd like the assets to be inspired on - If visuals are not your thing, a description of your idea will help too - A slogan, or some words/concepts that express the territory's values @BlokchainB you start, let's see how we go! originally posted at https://stacker.news/items/873112 @ 57d1a264:69f1fee1
2025-02-02 00:03:39 Welcome to the latest updated version of **Stacker News Media Kit & Brand Guidelines `v1.2`**, a pivotal location where all the visual elements find place and help us understand how to use them to have our communications cohesive. SN brand identity is built on simplicity, trust, innovation and a taste of Texas's Wild West. With the following guidelines, as [promised](https://stacker.news/items/855556/r/Design_r?commentId=855753), I'll try to outline the essential elements of SN visual language to be easily usable internally and externally. As third interaction from the previous [discussion](https://stacker.news/items/786223), here below you will find all the media assets in PNG and SVG downloadable from this [zip file](https://nosto.re/0a8b02224c970de78fba3a0195dcf1ee44d18925ba941724497173b2bcbab901.zip). BTW: I've been using **`Nostr`** 🌸 **Blossom Serverservers** [check them out](https://blossomservers.com/), it's a really cool idea! In case the file will be not available we can always upload it in other servers. Just let me know if any issue downloading it, ideally I made three copies available from: - https://nosto.re/0a8b02224c970de78fba3a0195dcf1ee44d18925ba941724497173b2bcbab901.zip - https://blossom.poster.place/0a8b02224c970de78fba3a0195dcf1ee44d18925ba941724497173b2bcbab901.zip - https://nostr.download/0a8b02224c970de78fba3a0195dcf1ee44d18925ba941724497173b2bcbab901.zip The source file of all these assets still are the same [Figma file](https://www.figma.com/design/ZL3FLItd9j48pzKVi4qlOy/Stacker.News-Media-Kit?node-id=3-16&t=oEbUcC1tmLDRXgdH-0) and the [PenPot file](https://design.penpot.app/#/workspace/7ad540b5-8190-815d-8005-5685b9c670bc/7ad540b5-8190-815d-8005-5685c186216e?page-id=2643bc5a-0d34-80b2-8005-58099eabda41). This last one, has many issues and does not allow yet the same flexibility as Figma. Both files are open for contributions and comments, just need to register a dummy/anonymous account for each of the tools. > **Note:** To use these assets across SN, just copy-paste the image relative code, i.e.:  # Stacker News Logotype SN logo is the most recognizable visual identifier of Stacker News. It captures the essence of its brand and is to be used across the platform and other marketing materials **consistently**. Find below all the possible variations and colors. Ideally you should stick with it to maintain SN identity coherent, or propose something new if you feel like. If you have any question on how to place or use the logo, DO ask below, and we'll help sort it out. | Avatar on transparent BG | Avatar on BG | Logo Extended | Logo Vertical |#| |---|---|---|---|---| |  `` |  `` |  ``|  `` |Oil Black| |  `` |  `` |  `` |  ``| Golden Yellow | |  `` |  `` |  `` |  ``|With Shadow | # Stacker News Typography  This is the typography SN had used to create its logo. [Download LightningVolt OpenType Font file.otf](http://honeyanddeath.web.fc2.com/FontFile/honeyanddeath_Lightningvolt.zip) designed by **[Honey&Death](http://honeyanddeath.web.fc2.com/fnt_Lightningvolt.html)**, install it in your computer and play with it. Typography is essential to identify, increase readability and create consistency of brands. SN uses the default `font-family:sans-serif;` of your device's OS, usually are the most common and already installed in your device: `system-ui, "Segoe UI", Roboto, "Helvetica Neue", "Noto Sans", "Liberation Sans", Arial, sans-serif, "Apple Color Emoji", "Segoe UI Emoji", "Segoe UI Symbol", "Noto Color Emoji"`. Those are mostly used for: # Example Header H1 ## Example Header H2 ### Example Header H3 #### Example Header H4 ##### Example Header H5 **Example paragraph text** The fonts selected will help to communicate the personality of the brand and provide maximum legibility for both print and screen. `Example <code>` For code, the approach is the same. Let's the device OS select its default `monospace` one. For example, on Mac will be one of the following: ``` SFMono-Regular, Menlo, Monaco, Consolas, "Liberation Mono", "Courier New",` ``` # Stacker News Colors A thoughtfully curated color palette gives SN trust, professionalism, and approachability. Colors play a key role in creating consistent visual experiences through digital and print communications. Make sure you are using the right color codes below: | # | Name | HEX code | RGB code | HLS | |---|---|---|---|---| |  | Bitcoin-only | `#F6911D` | `rgb(246,145,29)` | `hsl(32,92.3%,53.9%)` | |  | Blackr | `#000000` | `rgb(0,0,0)` | `hsl(0,0%,0%)` | |  | Dark | `#121214` | `rgb(18,18,20)` | `hsl(240,5.3%,7.5%)` | |  | Gold | `#FADA5E` | `rgb(250,218,94)` | `hsl(48,94%,67.5%)` | |  | Gray | `#969696` | `rgb(150,150,150)` | `hsl(0,0%,58.8%)` | |  | Light | `#F0F0F0` | `rgb(240,240,240)` | `hsl(0,0%,94.1%)` | |  | Nostrch | `#8C25F4` | `rgb(140,37,244)` | `hsl(270,90.4%,55.1%)` | |  | Pinkish | `#E685B5` | `rgb(230,133,181)` | `hsl(330,66%,71.2%)` | |  | Ruby | `#C03221` | `rgb(192,50,33)` | `hsl(6,70.7%,44.1%)` | |  | Sky Hover | `#007CBE` | `rgb(0,124,190)` | `hsl(201,100%,37.3%)` | |  | Sky Links | `#2E99D1` | `rgb(46,153,209)` | `hsl(201,63.9%,50%)` | |  | Sky Visited | `#56798E` | `rgb(86,121,142)` | `hsl(203,24.6%,44.7%)` | |  | So Fiat | `#5C8001` | `rgb(92,128,1)` | `hsl(77,98.4%,25.3%)` | # Stacker News Icons SN utilizes a set of bespoke icons that support its communication internally across the platform. Icons help bring instant, intuitive cues for various types of content and features. We share them here for you so you can use as you wish and satisfy your creative needs. |  `` |  `` |  `[Bounty](https://m.stacker.news/75607)` |  `[Caret](https://m.stacker.news/75608)` |  `[Cowboy](https://m.stacker.news/75609)` |  `[Sun](https://m.stacker.news/75610)` | |---|---|---|---|---|---| |  **`[Edit](https://m.stacker.news/75611)`** |  **`[Gun](https://m.stacker.news/75612)`** |  **`[Horse](https://m.stacker.news/75613)`** |  **`[Info](https://m.stacker.news/75614)`** |  **`[Moon](https://m.stacker.news/75615)`** |  **`[Lightning](https://m.stacker.news/75616)`**| |  **`[Bald Lost Hat](https://m.stacker.news/75617)`**|  **`[Markdown](https://m.stacker.news/75618)`**|  **`[Nostr](https://m.stacker.news/75619)`**|  **`[Referral](https://m.stacker.news/75620)`**|  **`[Rewards](https://m.stacker.news/75621)`**|  **`[Horse Lost Saddle](https://m.stacker.news/75622)`**|  **`[Search](https://m.stacker.news/75623)`** | | **`[Shoot](https://m.stacker.news/75624)`** | **`[Texas](https://m.stacker.news/75625)`** |  **`[Upload](https://m.stacker.news/75626)`** |  **`[Zap Zap](https://m.stacker.news/75627)`** ||| # Stacker News Banners Banners are important visual elements used in our digital platforms and marketing materials. They help to highlight key stories, features or announcements while maintaining our brand aesthetic. Here below you'll find custom banners for Sn and for individial territories. I try to build those that I follow most, for now @AGORA is the only one that designed its own banners. Comment below if you'd like some banners for your territory! #### SN Dark background |970x250| |---| | ```|``|``| |728x90| |---| |  `` | #### SN Gold background |970x250| |---| |`` | |250x250|300x250|300x600| |---|---|---| |`` | `` |`` | |728x90| |---| |`` | #### SN by @Jon_Hodl |970x250| |---| | `` | |250x250|300x250|300x600| |---|---|---| | `` |  ``| `` | |728x90| |---| |`` | #### ~AGORA territory The SN P2P Marketplace |970x250| |---| | `` | |250x250|300x250|300x600| |---|---|---| | `` | ``|``| |728x90| |---| | ``| #### ~alter_native territory |970x250| |---| | ``| |250x250|300x250|300x600| |---|---|---| |``|``|``| |728x90| |---| |`` | #### ~bitcoin_beginners |970x250| |---| | `` | |250x250|300x250|300x600| |---|---|---| | ``|``|`` | |728x90| |---| | ``| #### ~Design territory |970x250| |---| |``| |250x250|300x250|300x600| |---|---|---| |``|``|``| |728x90| |---| |``| #### ~Music territory |970x250| |---| | ``| |250x250|300x250|300x600| |---|---|---| |``|``|``| |728x90| |---| | ``| # Anything else we could add? If you feel something is missing, or you know a better tool to manage this media kit for SN in a collaborative and FOSS way then, DO share it in a comment below Territory owners [^1], do you need banners for your territory? Feel free to edit the figma file liked above or comment below sharing your needs or ideas, I'll try to do something for you. By following these guidelines, we ensure consistency and professionalism in every case where Stacker News is represented here internally to stackers or to our audience in the KYC internet, reinforcing SN credibility as a trusted source for data-driven journalism. [^1]: FYI: @Aardvark @AGORA @anna @antic @AtlantisPleb @Bell_curve @benwehrman @bitcoinplebdev @Bitter @BlokchainB @ch0k1 @davidw @ek @elvismercury @frostdragon @grayruby @HODLR @inverselarp @Jon_Hodl @k00b @marks @MaxAWebster @mega_dreamer @niftynei @nout @OneOneSeven @OT @PlebLab @Public_N_M_E @RDClark @realBitcoinDog @roytheholographicuniverse @siggy47 @softsimon @south_korea_ln @theschoolofbitcoin @TNStacker @UCantDoThatDotNet @Undisciplined originally posted at https://stacker.news/items/872925
@ 57d1a264:69f1fee1
2025-02-02 00:03:39 Welcome to the latest updated version of **Stacker News Media Kit & Brand Guidelines `v1.2`**, a pivotal location where all the visual elements find place and help us understand how to use them to have our communications cohesive. SN brand identity is built on simplicity, trust, innovation and a taste of Texas's Wild West. With the following guidelines, as [promised](https://stacker.news/items/855556/r/Design_r?commentId=855753), I'll try to outline the essential elements of SN visual language to be easily usable internally and externally. As third interaction from the previous [discussion](https://stacker.news/items/786223), here below you will find all the media assets in PNG and SVG downloadable from this [zip file](https://nosto.re/0a8b02224c970de78fba3a0195dcf1ee44d18925ba941724497173b2bcbab901.zip). BTW: I've been using **`Nostr`** 🌸 **Blossom Serverservers** [check them out](https://blossomservers.com/), it's a really cool idea! In case the file will be not available we can always upload it in other servers. Just let me know if any issue downloading it, ideally I made three copies available from: - https://nosto.re/0a8b02224c970de78fba3a0195dcf1ee44d18925ba941724497173b2bcbab901.zip - https://blossom.poster.place/0a8b02224c970de78fba3a0195dcf1ee44d18925ba941724497173b2bcbab901.zip - https://nostr.download/0a8b02224c970de78fba3a0195dcf1ee44d18925ba941724497173b2bcbab901.zip The source file of all these assets still are the same [Figma file](https://www.figma.com/design/ZL3FLItd9j48pzKVi4qlOy/Stacker.News-Media-Kit?node-id=3-16&t=oEbUcC1tmLDRXgdH-0) and the [PenPot file](https://design.penpot.app/#/workspace/7ad540b5-8190-815d-8005-5685b9c670bc/7ad540b5-8190-815d-8005-5685c186216e?page-id=2643bc5a-0d34-80b2-8005-58099eabda41). This last one, has many issues and does not allow yet the same flexibility as Figma. Both files are open for contributions and comments, just need to register a dummy/anonymous account for each of the tools. > **Note:** To use these assets across SN, just copy-paste the image relative code, i.e.:  # Stacker News Logotype SN logo is the most recognizable visual identifier of Stacker News. It captures the essence of its brand and is to be used across the platform and other marketing materials **consistently**. Find below all the possible variations and colors. Ideally you should stick with it to maintain SN identity coherent, or propose something new if you feel like. If you have any question on how to place or use the logo, DO ask below, and we'll help sort it out. | Avatar on transparent BG | Avatar on BG | Logo Extended | Logo Vertical |#| |---|---|---|---|---| |  `` |  `` |  ``|  `` |Oil Black| |  `` |  `` |  `` |  ``| Golden Yellow | |  `` |  `` |  `` |  ``|With Shadow | # Stacker News Typography  This is the typography SN had used to create its logo. [Download LightningVolt OpenType Font file.otf](http://honeyanddeath.web.fc2.com/FontFile/honeyanddeath_Lightningvolt.zip) designed by **[Honey&Death](http://honeyanddeath.web.fc2.com/fnt_Lightningvolt.html)**, install it in your computer and play with it. Typography is essential to identify, increase readability and create consistency of brands. SN uses the default `font-family:sans-serif;` of your device's OS, usually are the most common and already installed in your device: `system-ui, "Segoe UI", Roboto, "Helvetica Neue", "Noto Sans", "Liberation Sans", Arial, sans-serif, "Apple Color Emoji", "Segoe UI Emoji", "Segoe UI Symbol", "Noto Color Emoji"`. Those are mostly used for: # Example Header H1 ## Example Header H2 ### Example Header H3 #### Example Header H4 ##### Example Header H5 **Example paragraph text** The fonts selected will help to communicate the personality of the brand and provide maximum legibility for both print and screen. `Example <code>` For code, the approach is the same. Let's the device OS select its default `monospace` one. For example, on Mac will be one of the following: ``` SFMono-Regular, Menlo, Monaco, Consolas, "Liberation Mono", "Courier New",` ``` # Stacker News Colors A thoughtfully curated color palette gives SN trust, professionalism, and approachability. Colors play a key role in creating consistent visual experiences through digital and print communications. Make sure you are using the right color codes below: | # | Name | HEX code | RGB code | HLS | |---|---|---|---|---| |  | Bitcoin-only | `#F6911D` | `rgb(246,145,29)` | `hsl(32,92.3%,53.9%)` | |  | Blackr | `#000000` | `rgb(0,0,0)` | `hsl(0,0%,0%)` | |  | Dark | `#121214` | `rgb(18,18,20)` | `hsl(240,5.3%,7.5%)` | |  | Gold | `#FADA5E` | `rgb(250,218,94)` | `hsl(48,94%,67.5%)` | |  | Gray | `#969696` | `rgb(150,150,150)` | `hsl(0,0%,58.8%)` | |  | Light | `#F0F0F0` | `rgb(240,240,240)` | `hsl(0,0%,94.1%)` | |  | Nostrch | `#8C25F4` | `rgb(140,37,244)` | `hsl(270,90.4%,55.1%)` | |  | Pinkish | `#E685B5` | `rgb(230,133,181)` | `hsl(330,66%,71.2%)` | |  | Ruby | `#C03221` | `rgb(192,50,33)` | `hsl(6,70.7%,44.1%)` | |  | Sky Hover | `#007CBE` | `rgb(0,124,190)` | `hsl(201,100%,37.3%)` | |  | Sky Links | `#2E99D1` | `rgb(46,153,209)` | `hsl(201,63.9%,50%)` | |  | Sky Visited | `#56798E` | `rgb(86,121,142)` | `hsl(203,24.6%,44.7%)` | |  | So Fiat | `#5C8001` | `rgb(92,128,1)` | `hsl(77,98.4%,25.3%)` | # Stacker News Icons SN utilizes a set of bespoke icons that support its communication internally across the platform. Icons help bring instant, intuitive cues for various types of content and features. We share them here for you so you can use as you wish and satisfy your creative needs. |  `` |  `` |  `[Bounty](https://m.stacker.news/75607)` |  `[Caret](https://m.stacker.news/75608)` |  `[Cowboy](https://m.stacker.news/75609)` |  `[Sun](https://m.stacker.news/75610)` | |---|---|---|---|---|---| |  **`[Edit](https://m.stacker.news/75611)`** |  **`[Gun](https://m.stacker.news/75612)`** |  **`[Horse](https://m.stacker.news/75613)`** |  **`[Info](https://m.stacker.news/75614)`** |  **`[Moon](https://m.stacker.news/75615)`** |  **`[Lightning](https://m.stacker.news/75616)`**| |  **`[Bald Lost Hat](https://m.stacker.news/75617)`**|  **`[Markdown](https://m.stacker.news/75618)`**|  **`[Nostr](https://m.stacker.news/75619)`**|  **`[Referral](https://m.stacker.news/75620)`**|  **`[Rewards](https://m.stacker.news/75621)`**|  **`[Horse Lost Saddle](https://m.stacker.news/75622)`**|  **`[Search](https://m.stacker.news/75623)`** | | **`[Shoot](https://m.stacker.news/75624)`** | **`[Texas](https://m.stacker.news/75625)`** |  **`[Upload](https://m.stacker.news/75626)`** |  **`[Zap Zap](https://m.stacker.news/75627)`** ||| # Stacker News Banners Banners are important visual elements used in our digital platforms and marketing materials. They help to highlight key stories, features or announcements while maintaining our brand aesthetic. Here below you'll find custom banners for Sn and for individial territories. I try to build those that I follow most, for now @AGORA is the only one that designed its own banners. Comment below if you'd like some banners for your territory! #### SN Dark background |970x250| |---| | ```|``|``| |728x90| |---| |  `` | #### SN Gold background |970x250| |---| |`` | |250x250|300x250|300x600| |---|---|---| |`` | `` |`` | |728x90| |---| |`` | #### SN by @Jon_Hodl |970x250| |---| | `` | |250x250|300x250|300x600| |---|---|---| | `` |  ``| `` | |728x90| |---| |`` | #### ~AGORA territory The SN P2P Marketplace |970x250| |---| | `` | |250x250|300x250|300x600| |---|---|---| | `` | ``|``| |728x90| |---| | ``| #### ~alter_native territory |970x250| |---| | ``| |250x250|300x250|300x600| |---|---|---| |``|``|``| |728x90| |---| |`` | #### ~bitcoin_beginners |970x250| |---| | `` | |250x250|300x250|300x600| |---|---|---| | ``|``|`` | |728x90| |---| | ``| #### ~Design territory |970x250| |---| |``| |250x250|300x250|300x600| |---|---|---| |``|``|``| |728x90| |---| |``| #### ~Music territory |970x250| |---| | ``| |250x250|300x250|300x600| |---|---|---| |``|``|``| |728x90| |---| | ``| # Anything else we could add? If you feel something is missing, or you know a better tool to manage this media kit for SN in a collaborative and FOSS way then, DO share it in a comment below Territory owners [^1], do you need banners for your territory? Feel free to edit the figma file liked above or comment below sharing your needs or ideas, I'll try to do something for you. By following these guidelines, we ensure consistency and professionalism in every case where Stacker News is represented here internally to stackers or to our audience in the KYC internet, reinforcing SN credibility as a trusted source for data-driven journalism. [^1]: FYI: @Aardvark @AGORA @anna @antic @AtlantisPleb @Bell_curve @benwehrman @bitcoinplebdev @Bitter @BlokchainB @ch0k1 @davidw @ek @elvismercury @frostdragon @grayruby @HODLR @inverselarp @Jon_Hodl @k00b @marks @MaxAWebster @mega_dreamer @niftynei @nout @OneOneSeven @OT @PlebLab @Public_N_M_E @RDClark @realBitcoinDog @roytheholographicuniverse @siggy47 @softsimon @south_korea_ln @theschoolofbitcoin @TNStacker @UCantDoThatDotNet @Undisciplined originally posted at https://stacker.news/items/872925 @ a95c6243:d345522c
2025-01-31 20:02:25*Im Augenblick wird mit größter Intensität, großer Umsicht* *\ das deutsche Volk belogen.* *\ Olaf Scholz im FAZ-[Interview](https://www.youtube.com/watch?v=c3KI1GmdoVc\&t=649s)*   **Online-Wahlen stärken die Demokratie, sind sicher, und 61 Prozent der Wahlberechtigten** sprechen sich für deren Einführung in Deutschland aus. Das zumindest behauptet eine aktuelle Umfrage, die auch über die Agentur *Reuters* Verbreitung in den Medien [gefunden](https://archive.is/dnZbY) hat. Demnach würden außerdem 45 Prozent der Nichtwähler bei der Bundestagswahl ihre Stimme abgeben, wenn sie dies zum Beispiel von Ihrem PC, Tablet oder Smartphone aus machen könnten. **Die telefonische Umfrage unter gut 1000 wahlberechtigten Personen** sei repräsentativ, [behauptet](https://www.bitkom.org/Presse/Presseinformation/Knapp-Haelfte-Nichtwaehler-wuerde-online-waehlen) der Auftraggeber – der Digitalverband Bitkom. Dieser präsentiert sich als eingetragener Verein mit einer beeindruckenden Liste von [Mitgliedern](https://www.bitkom.org/Bitkom/Mitgliedschaft/Mitgliederliste), die Software und IT-Dienstleistungen anbieten. Erklärtes Vereinsziel ist es, «Deutschland zu einem führenden Digitalstandort zu machen und die digitale Transformation der deutschen Wirtschaft und Verwaltung voranzutreiben». **Durchgeführt hat die Befragung die Bitkom Servicegesellschaft mbH,** also alles in der Familie. Die gleiche Erhebung hatte der Verband übrigens 2021 schon einmal durchgeführt. Damals sprachen sich angeblich sogar 63 Prozent für ein derartiges [«Demokratie-Update»](https://www.experten.de/id/4922407/online-wahlen-als-update-des-demokratischen-systems/) aus – die Tendenz ist demgemäß fallend. Dennoch orakelt mancher, der Gang zur Wahlurne gelte bereits als veraltet. **Die spanische Privat-Uni mit Globalisten-Touch, IE University, berichtete** Ende letzten Jahres in ihrer Studie «European Tech Insights», 67 Prozent der Europäer [befürchteten](https://www.ie.edu/university/news-events/news/67-europeans-fear-ai-manipulation-elections-according-ie-university-research/), dass Hacker Wahlergebnisse verfälschen könnten. Mehr als 30 Prozent der Befragten glaubten, dass künstliche Intelligenz (KI) bereits Wahlentscheidungen beeinflusst habe. Trotzdem würden angeblich 34 Prozent der unter 35-Jährigen einer KI-gesteuerten App vertrauen, um in ihrem Namen für politische Kandidaten zu stimmen. **Wie dauerhaft wird wohl das Ergebnis der kommenden Bundestagswahl sein?** Diese Frage stellt sich angesichts der aktuellen Entwicklung der Migrations-Debatte und der (vorübergehend) bröckelnden «Brandmauer» gegen die AfD. Das «Zustrombegrenzungsgesetz» der Union hat das Parlament heute Nachmittag überraschenderweise [abgelehnt](https://www.bundestag.de/dokumente/textarchiv/2025/kw05-de-zustrombegrenzungsgesetz-1042038). Dennoch muss man wohl kein ausgesprochener Pessimist sein, um zu befürchten, dass die Entscheidungen der Bürger von den selbsternannten Verteidigern der Demokratie künftig vielleicht nicht respektiert werden, weil sie nicht gefallen. **Bundesweit wird jetzt zu «Brandmauer-Demos» aufgerufen,** die CDU gerät unter Druck und es wird von Übergriffen auf Parteibüros und Drohungen gegen Mitarbeiter [berichtet](https://www.epochtimes.de/politik/deutschland/brandmauer-proteste-cdu-zentrale-geraeumt-kundgebungen-in-46-staedten-a5023745.html). Sicherheitsbehörden warnen vor Eskalationen, die Polizei sei «für ein mögliches erhöhtes Aufkommen von Straftaten gegenüber Politikern und gegen Parteigebäude sensibilisiert». **Der Vorwand** **[«unzulässiger Einflussnahme»](https://transition-news.org/die-minister-faeser-und-wissing-sorgen-sich-um-unzulassige-einflussnahme-auf)** **auf Politik und Wahlen** wird als Argument schon seit einiger Zeit aufgebaut. Der Manipulation schuldig befunden wird neben Putin und Trump auch Elon Musk, was lustigerweise ausgerechnet Bill Gates gerade noch einmal bekräftigt und als [«völlig irre»](https://transition-news.org/bill-gates-nennt-musks-einmischung-in-eu-politik-vollig-irre) bezeichnet hat. Man stelle sich die Diskussionen um die Gültigkeit von Wahlergebnissen vor, wenn es Online-Verfahren zur Stimmabgabe gäbe. In der Schweiz wird [«E-Voting»](https://www.ch.ch/de/abstimmungen-und-wahlen/e-voting/) seit einigen Jahren getestet, aber wohl bisher mit wenig Erfolg. **Die politische Brandstiftung der letzten Jahre zahlt sich immer mehr aus.** Anstatt dringende Probleme der Menschen zu lösen – zu denen auch in Deutschland die [weit verbreitete Armut](https://transition-news.org/ein-funftel-der-bevolkerung-in-deutschland-ist-von-armut-oder-sozialer) zählt –, hat die Politik konsequent polarisiert und sich auf Ausgrenzung und Verhöhnung großer Teile der Bevölkerung konzentriert. Basierend auf Ideologie und Lügen werden abweichende Stimmen unterdrückt und kriminalisiert, nicht nur und nicht erst in diesem Augenblick. Die nächsten Wochen dürften ausgesprochen spannend werden. *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/wahlen-und-wahlen-lassen)*** erschienen.
@ a95c6243:d345522c
2025-01-31 20:02:25*Im Augenblick wird mit größter Intensität, großer Umsicht* *\ das deutsche Volk belogen.* *\ Olaf Scholz im FAZ-[Interview](https://www.youtube.com/watch?v=c3KI1GmdoVc\&t=649s)*   **Online-Wahlen stärken die Demokratie, sind sicher, und 61 Prozent der Wahlberechtigten** sprechen sich für deren Einführung in Deutschland aus. Das zumindest behauptet eine aktuelle Umfrage, die auch über die Agentur *Reuters* Verbreitung in den Medien [gefunden](https://archive.is/dnZbY) hat. Demnach würden außerdem 45 Prozent der Nichtwähler bei der Bundestagswahl ihre Stimme abgeben, wenn sie dies zum Beispiel von Ihrem PC, Tablet oder Smartphone aus machen könnten. **Die telefonische Umfrage unter gut 1000 wahlberechtigten Personen** sei repräsentativ, [behauptet](https://www.bitkom.org/Presse/Presseinformation/Knapp-Haelfte-Nichtwaehler-wuerde-online-waehlen) der Auftraggeber – der Digitalverband Bitkom. Dieser präsentiert sich als eingetragener Verein mit einer beeindruckenden Liste von [Mitgliedern](https://www.bitkom.org/Bitkom/Mitgliedschaft/Mitgliederliste), die Software und IT-Dienstleistungen anbieten. Erklärtes Vereinsziel ist es, «Deutschland zu einem führenden Digitalstandort zu machen und die digitale Transformation der deutschen Wirtschaft und Verwaltung voranzutreiben». **Durchgeführt hat die Befragung die Bitkom Servicegesellschaft mbH,** also alles in der Familie. Die gleiche Erhebung hatte der Verband übrigens 2021 schon einmal durchgeführt. Damals sprachen sich angeblich sogar 63 Prozent für ein derartiges [«Demokratie-Update»](https://www.experten.de/id/4922407/online-wahlen-als-update-des-demokratischen-systems/) aus – die Tendenz ist demgemäß fallend. Dennoch orakelt mancher, der Gang zur Wahlurne gelte bereits als veraltet. **Die spanische Privat-Uni mit Globalisten-Touch, IE University, berichtete** Ende letzten Jahres in ihrer Studie «European Tech Insights», 67 Prozent der Europäer [befürchteten](https://www.ie.edu/university/news-events/news/67-europeans-fear-ai-manipulation-elections-according-ie-university-research/), dass Hacker Wahlergebnisse verfälschen könnten. Mehr als 30 Prozent der Befragten glaubten, dass künstliche Intelligenz (KI) bereits Wahlentscheidungen beeinflusst habe. Trotzdem würden angeblich 34 Prozent der unter 35-Jährigen einer KI-gesteuerten App vertrauen, um in ihrem Namen für politische Kandidaten zu stimmen. **Wie dauerhaft wird wohl das Ergebnis der kommenden Bundestagswahl sein?** Diese Frage stellt sich angesichts der aktuellen Entwicklung der Migrations-Debatte und der (vorübergehend) bröckelnden «Brandmauer» gegen die AfD. Das «Zustrombegrenzungsgesetz» der Union hat das Parlament heute Nachmittag überraschenderweise [abgelehnt](https://www.bundestag.de/dokumente/textarchiv/2025/kw05-de-zustrombegrenzungsgesetz-1042038). Dennoch muss man wohl kein ausgesprochener Pessimist sein, um zu befürchten, dass die Entscheidungen der Bürger von den selbsternannten Verteidigern der Demokratie künftig vielleicht nicht respektiert werden, weil sie nicht gefallen. **Bundesweit wird jetzt zu «Brandmauer-Demos» aufgerufen,** die CDU gerät unter Druck und es wird von Übergriffen auf Parteibüros und Drohungen gegen Mitarbeiter [berichtet](https://www.epochtimes.de/politik/deutschland/brandmauer-proteste-cdu-zentrale-geraeumt-kundgebungen-in-46-staedten-a5023745.html). Sicherheitsbehörden warnen vor Eskalationen, die Polizei sei «für ein mögliches erhöhtes Aufkommen von Straftaten gegenüber Politikern und gegen Parteigebäude sensibilisiert». **Der Vorwand** **[«unzulässiger Einflussnahme»](https://transition-news.org/die-minister-faeser-und-wissing-sorgen-sich-um-unzulassige-einflussnahme-auf)** **auf Politik und Wahlen** wird als Argument schon seit einiger Zeit aufgebaut. Der Manipulation schuldig befunden wird neben Putin und Trump auch Elon Musk, was lustigerweise ausgerechnet Bill Gates gerade noch einmal bekräftigt und als [«völlig irre»](https://transition-news.org/bill-gates-nennt-musks-einmischung-in-eu-politik-vollig-irre) bezeichnet hat. Man stelle sich die Diskussionen um die Gültigkeit von Wahlergebnissen vor, wenn es Online-Verfahren zur Stimmabgabe gäbe. In der Schweiz wird [«E-Voting»](https://www.ch.ch/de/abstimmungen-und-wahlen/e-voting/) seit einigen Jahren getestet, aber wohl bisher mit wenig Erfolg. **Die politische Brandstiftung der letzten Jahre zahlt sich immer mehr aus.** Anstatt dringende Probleme der Menschen zu lösen – zu denen auch in Deutschland die [weit verbreitete Armut](https://transition-news.org/ein-funftel-der-bevolkerung-in-deutschland-ist-von-armut-oder-sozialer) zählt –, hat die Politik konsequent polarisiert und sich auf Ausgrenzung und Verhöhnung großer Teile der Bevölkerung konzentriert. Basierend auf Ideologie und Lügen werden abweichende Stimmen unterdrückt und kriminalisiert, nicht nur und nicht erst in diesem Augenblick. Die nächsten Wochen dürften ausgesprochen spannend werden. *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/wahlen-und-wahlen-lassen)*** erschienen. @ 5188521b:008eb518
2025-01-31 08:38:47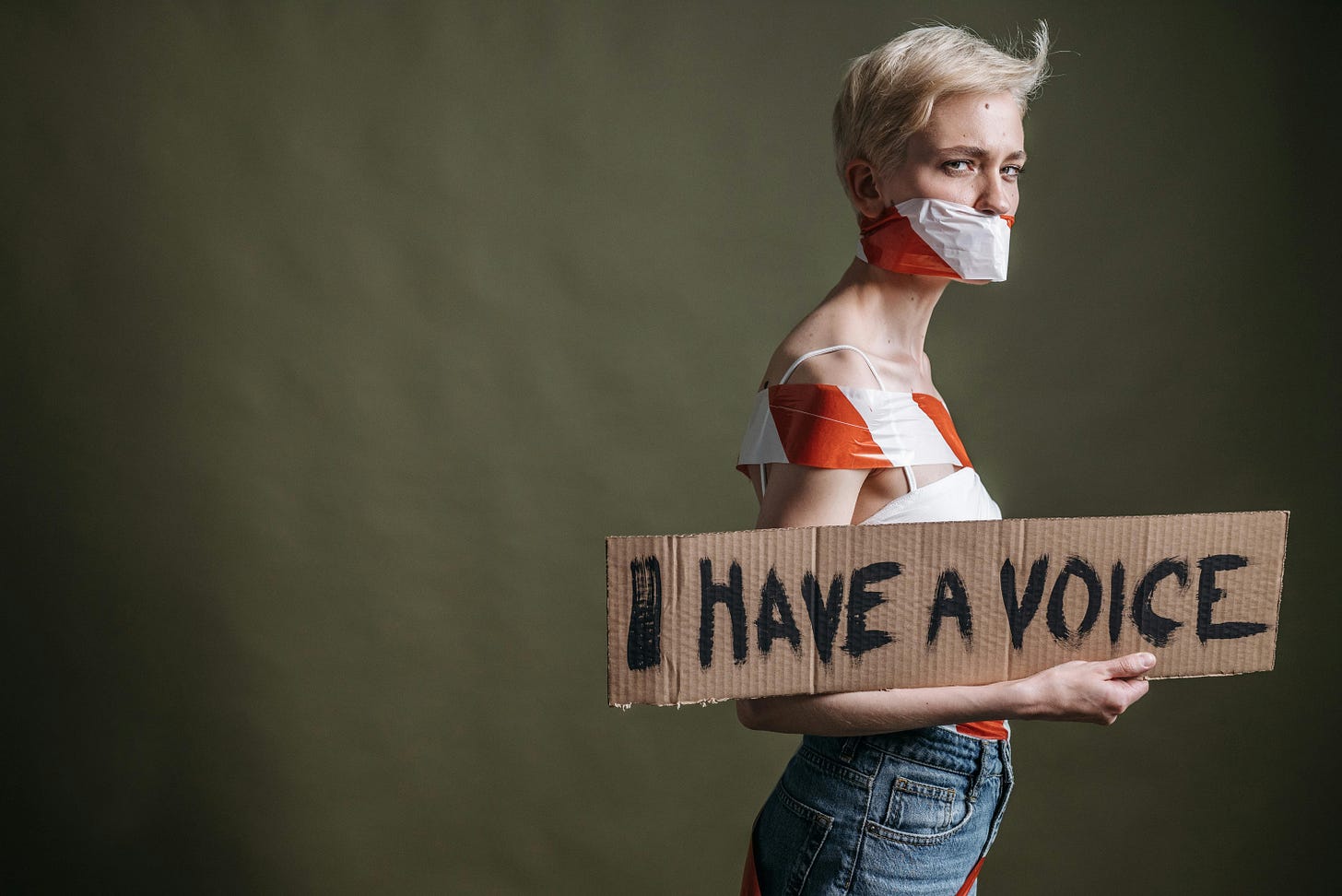*Photo by [Pavel Danilyuk](https://www.pexels.com/photo/a-woman-holding-a-placard-8553778/)* In the last four years, I’ve ridden the wave of social media. I’ve amassed thousands of followers, and my posts were read by millions. It’s empowering… until it isn’t. This year, I chose to stop publishing on LinkedIn, Medium, Facebook, Instagram, and Threads. My reach on each of these platforms dropped from 100% of my follower base to around 10%. My voice was being suppressed. I wasn’t writing anything particularly controversial. This is all just part of the social media life cycle. Platforms offer attractive terms to lock in users. They distribute our articles, posts, and thoughts widely to attract eyeballs for advertisers. Writers learn to play the algorithm to maximise reach and engagement. Maybe they even manage to monetize their writing. But when the platforms reach what they deem to be maximum usage and membership, they begin to reduce the benefits on offer. They ask writers to focus on specific topics, suppress non-mainstream opinion, or punish or ban any writers who don’t follow new rules. Big tech companies always eventually turn on the money tap by forcing users to suffer endless adverts and even make writers pay to reach the audience they have built. Newsflash: there is no company too big to fail. Digg, Google+, Myspace, Vine and many more socials have died. Self-reported active user numbers cannot be trusted. Meta recently trialed AI profiles to prop up falling usage projections on Instagram and Facebook. X is now a dumpster fire of bots, scammers, and rage bait. It has been co-opted by a megalomaniacal oligarch to spread his own worldview. And LinkedIn feeds are drowning in unsolicited AI-generated business twaddle. The social giants are entering the death spiral. # What happens in a social-media death spiral? Users don’t see the value in posting, so they move elsewhere. I wasn’t feeling rewarded for the thousands of hours I spent on LinkedIn, so I quit. I went from earning $20+ an article on Medium to pennies. Literal pennies. Bye bye, Tony Stubblebine. I learned that if you don’t own the distribution mechanic, you get left writing into the wind. Ultimately, writers will dedicate their energy to where they see a benefit. They should spend time and create value in the place most similar to their ideal world. For writers in 2025, that place seems to be Substack. Open rates are high and the platform is adding social features to generate more engagement in app. Substack is [experiencing massive growth](https://backlinko.com/substack-users) in active (and paid) subscriptions. Yet, it is following the same pattern as Medium in and LinkedIn in become self-cannibalising. Many of the most popular accounts write about ‘how to grow’ or ‘how to make money’ on Substack. Queue the eye rolls. For me, it’s not the promised land where writers can earn a living. Of course, it’s no walk in the park to earn paid subscribers. Further, Substack users can only receive payment via Stripe. This excludes writers from 149 of the World’s countries. Does that seem open and fair to you? Even with all this going on, there is a much bigger factor that should influence your choice of platform — ownership. # Do writers really own their words? Who reads the terms and conditions? Nobody. That’s who.Writers (including me) rush to all platforms which promise to give us benefits such as pay, distribution, and audience growth. In exchange, companies request access to and shared ownership of our content. They can use our words to train LLMs, analyse trends, repurpose, and to spy on us. Governments can and will request access to social media profiles. They seek to control the use of those platforms. Founders and CEOs who refuse to comply may be held personally accountable and put on trial, just as [Telegram founder, Pavel Durov, was](https://www.bbc.com/news/articles/c78lgzl919go) in France. Big tech owns our content, and governments threaten platforms into obedience. As much as it benefits society to suppress harmful or dangerous content, companies simply can’t be censors 24/7. Growing platforms like [Bluesky are already struggling to moderate content effectively](https://www.theregister.com/2024/12/02/bluesky_growing_problems/). Without a strong economic incentive to moderate, companies will simply refuse to do it (as long as the threat of criminal charges does not prevail). To sum up: No privately owned social media network offers writers the opportunity to own and distribute their work in order to receive a fair and equitable benefit. Enter NOSTR… # Decentralizing Social Media **Notes and Other Stuff Transmitted by Relays** (NOSTR) is not a platform; it’s an open protocol. By signing messages with their private keys (a long string of characters), users generate “events”. These events (messages/updates/media/transactions) are then broadcast through a series of “relays.” Developers can use the protocol to build various applications that retrieve and distribute these events to other users. These ‘clients’ can range from microblogging sites like X and long-form distributors like Substack to visual media platforms like Instagram. Plus, NOSTR is also a whole lot more than that (but this is a topic for another day). Decentralized tools offer the only hope against the dominance of AI and big tech in a top-down autocratic system designed to control us more than the thought police ever could. <img src="https://blossom.primal.net/93a44d9bfe3c768e41d8bfef52415131af3ca21814a23870a029f1a947288cc8.webp"> *Diagram courtesy of River.* So why should writers opt out of their big audience pool to write on some ‘protocol’? **Ownership, fair rules, and fair value.** - **Ownership**: While privately run corporations can suppress the ideas they want, NOSTR provides a censorship-resistant alternative. No individual actors can restrict content or accounts. Your private keys provide **permanent access** to the messages you have signed. No one else has access to them. And while some clients provide a delete function, there is no way to force all relays to respect a delete request. Not only do writers own what they publish, but it’s a permanent record. - **Rules:** Traditional social media platforms use proprietary algorithms to curate and order our feeds. **NOSTR has no algorithm**. NOSTR clients display messages chronologically or based on user-defined criteria, removing the influence of opaque algorithms that could manipulate user engagement and visibility of posts. Put simply, distribution and consumption is down to the user, not to the creator or the platform. And everyone works to the same rules. - **Value:** Harmful content and spam affect all of us. There is no way to stop malicious content from being published on NOSTR, but two factors control its consumption. 1. Clients are experimenting with strategies such as requiring proof-of-work with each note or requiring verification badges. 2. Quality control is enforced by the value transferred by the protocol. Bitcoin micropayments have become the monetary lifeblood flowing in the decentralized world. The ability to ‘zap’ users actual monetary value (e.g. a few cents) provides a clear display of which messages are valuable and which are unwanted. In time, as more users adopt the mechanic of value transfer, spammers will see their approach is not bearing fruit. The beauty of using bitcoin in this way is twofold. Firstly, it is truly equitable — anyone in the world can receive it instantly and it cannot be stopped. And the system of frictionless micropayments offers content creators (artists, podcasters, musicians, writers) a way to earn money for the value they produce. Put simply, this could save creativity from doom. Think people still want all content for free? Think again. Try zapping a writer from the Philippines, an artist from Peru, a Congolese musician, or a poet from Poland to show them you enjoyed what they produced. THAT is truly empowering. Not convinced? The best thing about NOSTR for writers is that **you are early**. By being an early adopter with a low time preference, you can build a sizeable audience as new users discover the protocol. Of course, topics like bitcoin, freedom tech, and privacy are well covered, but if you write in another niche, you could be ‘quids in’. # Conclusion: By adopting a long-term strategy and sticking to their principles, readers, writers and all other creatives can build a better world on social media. It doesn’t matter that it is imperfect. There will always be flaws in any society. But decentralized protocols like NOSTR can offer writers what they truly want — ownership, fair rules, and fair value. --- Philip Charter is a totally human writer who helps bitcoin-native companies and clients stack major gains through laser-focused content. Find out more at [totallyhumanwriter.com](https://totallyhumanwriter.com) He is also the editor of the cypherpunk and freedom fiction project, [21 Futures](https://21futures.com).
@ 5188521b:008eb518
2025-01-31 08:38:47*Photo by [Pavel Danilyuk](https://www.pexels.com/photo/a-woman-holding-a-placard-8553778/)* In the last four years, I’ve ridden the wave of social media. I’ve amassed thousands of followers, and my posts were read by millions. It’s empowering… until it isn’t. This year, I chose to stop publishing on LinkedIn, Medium, Facebook, Instagram, and Threads. My reach on each of these platforms dropped from 100% of my follower base to around 10%. My voice was being suppressed. I wasn’t writing anything particularly controversial. This is all just part of the social media life cycle. Platforms offer attractive terms to lock in users. They distribute our articles, posts, and thoughts widely to attract eyeballs for advertisers. Writers learn to play the algorithm to maximise reach and engagement. Maybe they even manage to monetize their writing. But when the platforms reach what they deem to be maximum usage and membership, they begin to reduce the benefits on offer. They ask writers to focus on specific topics, suppress non-mainstream opinion, or punish or ban any writers who don’t follow new rules. Big tech companies always eventually turn on the money tap by forcing users to suffer endless adverts and even make writers pay to reach the audience they have built. Newsflash: there is no company too big to fail. Digg, Google+, Myspace, Vine and many more socials have died. Self-reported active user numbers cannot be trusted. Meta recently trialed AI profiles to prop up falling usage projections on Instagram and Facebook. X is now a dumpster fire of bots, scammers, and rage bait. It has been co-opted by a megalomaniacal oligarch to spread his own worldview. And LinkedIn feeds are drowning in unsolicited AI-generated business twaddle. The social giants are entering the death spiral. # What happens in a social-media death spiral? Users don’t see the value in posting, so they move elsewhere. I wasn’t feeling rewarded for the thousands of hours I spent on LinkedIn, so I quit. I went from earning $20+ an article on Medium to pennies. Literal pennies. Bye bye, Tony Stubblebine. I learned that if you don’t own the distribution mechanic, you get left writing into the wind. Ultimately, writers will dedicate their energy to where they see a benefit. They should spend time and create value in the place most similar to their ideal world. For writers in 2025, that place seems to be Substack. Open rates are high and the platform is adding social features to generate more engagement in app. Substack is [experiencing massive growth](https://backlinko.com/substack-users) in active (and paid) subscriptions. Yet, it is following the same pattern as Medium in and LinkedIn in become self-cannibalising. Many of the most popular accounts write about ‘how to grow’ or ‘how to make money’ on Substack. Queue the eye rolls. For me, it’s not the promised land where writers can earn a living. Of course, it’s no walk in the park to earn paid subscribers. Further, Substack users can only receive payment via Stripe. This excludes writers from 149 of the World’s countries. Does that seem open and fair to you? Even with all this going on, there is a much bigger factor that should influence your choice of platform — ownership. # Do writers really own their words? Who reads the terms and conditions? Nobody. That’s who.Writers (including me) rush to all platforms which promise to give us benefits such as pay, distribution, and audience growth. In exchange, companies request access to and shared ownership of our content. They can use our words to train LLMs, analyse trends, repurpose, and to spy on us. Governments can and will request access to social media profiles. They seek to control the use of those platforms. Founders and CEOs who refuse to comply may be held personally accountable and put on trial, just as [Telegram founder, Pavel Durov, was](https://www.bbc.com/news/articles/c78lgzl919go) in France. Big tech owns our content, and governments threaten platforms into obedience. As much as it benefits society to suppress harmful or dangerous content, companies simply can’t be censors 24/7. Growing platforms like [Bluesky are already struggling to moderate content effectively](https://www.theregister.com/2024/12/02/bluesky_growing_problems/). Without a strong economic incentive to moderate, companies will simply refuse to do it (as long as the threat of criminal charges does not prevail). To sum up: No privately owned social media network offers writers the opportunity to own and distribute their work in order to receive a fair and equitable benefit. Enter NOSTR… # Decentralizing Social Media **Notes and Other Stuff Transmitted by Relays** (NOSTR) is not a platform; it’s an open protocol. By signing messages with their private keys (a long string of characters), users generate “events”. These events (messages/updates/media/transactions) are then broadcast through a series of “relays.” Developers can use the protocol to build various applications that retrieve and distribute these events to other users. These ‘clients’ can range from microblogging sites like X and long-form distributors like Substack to visual media platforms like Instagram. Plus, NOSTR is also a whole lot more than that (but this is a topic for another day). Decentralized tools offer the only hope against the dominance of AI and big tech in a top-down autocratic system designed to control us more than the thought police ever could. <img src="https://blossom.primal.net/93a44d9bfe3c768e41d8bfef52415131af3ca21814a23870a029f1a947288cc8.webp"> *Diagram courtesy of River.* So why should writers opt out of their big audience pool to write on some ‘protocol’? **Ownership, fair rules, and fair value.** - **Ownership**: While privately run corporations can suppress the ideas they want, NOSTR provides a censorship-resistant alternative. No individual actors can restrict content or accounts. Your private keys provide **permanent access** to the messages you have signed. No one else has access to them. And while some clients provide a delete function, there is no way to force all relays to respect a delete request. Not only do writers own what they publish, but it’s a permanent record. - **Rules:** Traditional social media platforms use proprietary algorithms to curate and order our feeds. **NOSTR has no algorithm**. NOSTR clients display messages chronologically or based on user-defined criteria, removing the influence of opaque algorithms that could manipulate user engagement and visibility of posts. Put simply, distribution and consumption is down to the user, not to the creator or the platform. And everyone works to the same rules. - **Value:** Harmful content and spam affect all of us. There is no way to stop malicious content from being published on NOSTR, but two factors control its consumption. 1. Clients are experimenting with strategies such as requiring proof-of-work with each note or requiring verification badges. 2. Quality control is enforced by the value transferred by the protocol. Bitcoin micropayments have become the monetary lifeblood flowing in the decentralized world. The ability to ‘zap’ users actual monetary value (e.g. a few cents) provides a clear display of which messages are valuable and which are unwanted. In time, as more users adopt the mechanic of value transfer, spammers will see their approach is not bearing fruit. The beauty of using bitcoin in this way is twofold. Firstly, it is truly equitable — anyone in the world can receive it instantly and it cannot be stopped. And the system of frictionless micropayments offers content creators (artists, podcasters, musicians, writers) a way to earn money for the value they produce. Put simply, this could save creativity from doom. Think people still want all content for free? Think again. Try zapping a writer from the Philippines, an artist from Peru, a Congolese musician, or a poet from Poland to show them you enjoyed what they produced. THAT is truly empowering. Not convinced? The best thing about NOSTR for writers is that **you are early**. By being an early adopter with a low time preference, you can build a sizeable audience as new users discover the protocol. Of course, topics like bitcoin, freedom tech, and privacy are well covered, but if you write in another niche, you could be ‘quids in’. # Conclusion: By adopting a long-term strategy and sticking to their principles, readers, writers and all other creatives can build a better world on social media. It doesn’t matter that it is imperfect. There will always be flaws in any society. But decentralized protocols like NOSTR can offer writers what they truly want — ownership, fair rules, and fair value. --- Philip Charter is a totally human writer who helps bitcoin-native companies and clients stack major gains through laser-focused content. Find out more at [totallyhumanwriter.com](https://totallyhumanwriter.com) He is also the editor of the cypherpunk and freedom fiction project, [21 Futures](https://21futures.com). @ 57d1a264:69f1fee1
2025-01-31 02:07:27 Bitcoin Design members have been involved in organizing various events (and sometimes just attend, too). Here below is what do we want to do in 2025: - **[Designathon 2](https://github.com/BitcoinDesign/Meta/issues/625)** - We are organizing this event between February or March. - **[Accessibility Day](https://accessibility.day)** - May 15 - - BDC has participated in this global initiative the last two years. Probably doing so again! - **[BTC Prague](https://btcprague.com)** -Participation Confirmed. Planning issues [here](https://github.com/BitcoinDesign/Meta/issues/745) - June 19 - 21 - * We organized the design track for dev day in 2023 and 2024. Do this again[\[k\]](#cmnt11)[\[l\]](#cmnt12)? It’s going to be on June 18, before the main conference. - * 2024 was great, in that we had a nice group of designers attend, do talks, go for dinner, etc. - **[Summer of Bitcoin](https://www.google.com/url?q=https://www.summerofbitcoin.org)** - * Several designers and projects participated each of the last 3 years. Probably doing so again! - * Applications open on Feb 1, main program is May to August ([timeline](https://www.summerofbitcoin.org/how-it-works/) - **UX Bootcamps** - * Previous: South America - * Next: [South America](https://www.bitcoinuxbootcamp.xyz/southamerica) - February 17 - 22 - **[Bitshala fellowship](https://bitshala.org)** - * First iteration of this fellowship is from January to July - * We will help find more designers, projects, and funding in India - **[Oslo Freedom Forum](https://oslofreedomforum.com)** - Oslo, May 26-28 - * Activist and financial repression use cases are uniquely important use cases for bitcoin. - * Several people attended last year. Conversations lead to new initiatives. - **[BTCHEL](https://btchel.com/)** - by BTC Helsinki Community - Aug 15-16 - * First large-scale bitcoin conference in the Nordics with particular focus to onboard new users to bitcoin - **Bitcoin Presidio design week** - * This is a new Bitcoin co-working space in San Francisco, also announced here https://stacker.news/items/860931/r/Design_r. The idea came up to organize a design week there to support the creation of art and decoration for the new co-working space. Just an idea at the moment, but why not make it happen? - * [Discussion issue](https://github.com/BitcoinDesign/Meta/issues/746). - **BuildWithLDK** - * An initiative to promote LDK and LDK Node for building lightning applications. There could be collaboration around a Designathon, connecting designers with hackathon projects, etc. Still in early planning. - **Builder conferences**: These are very builder-focused, making them good opportunities to connect, organize practical design workshops, creative presentations, and support projects from a design perspective - * [Baltic Honeybadger](https://baltichoneybadger.com) (August 9-10), - * [TABConf](http://tabconf.com) - * [Bitcoin++](https://btcplusplus.dev) There are going to be 6 of them throughout the year. - * [SATS’N’FACTS](https://satsandfacts.btc.pub/) (February 8-10) Bitcoin Technical Unconference, Hackathon & Freedom Tech Art Exhibition - **Open-source conferences & events* - * [FOSS Backstage](http://foss-backstage.de) (Berlin, Mar 10-11) - Christoph will present the Open Design Guide - * [FOSDEM](https://fosdem.org/2025/) (Brussels, Feb 1-2) - anyone attending? - **Design conferences & events** - Makes sense to be involved with design-only events, right? * [OFFF](https://www.offf.barcelona) - very creative-focused (Barcelona, May 8-10) * [CSUN Accessibility conference](https://www.csun.edu/cod/conference/sessions/) **Other Ideas** * Bitcoin Park - they might organize another design event like two years ago https://stacker.news/items/705081/r/Design_r **Links** * [Comprehensive list](https://docs.google.com/spreadsheets/d/147AXd8hN3uO3v_P1dupgfRCRzSMlH85dvQSHPAg7lZ4/edit?usp%3Dsharing) of bitcoin conferences - - - … what’s missing from this page? Are you involved with anything? Or want to be? Comment below or join us on https://discord.com/channels/903125802726596648/1087394066796384276 You can watch the recording from https://www.youtube.com/watch?v=GGS3oSlLmAo originally posted at https://stacker.news/items/870638
@ 57d1a264:69f1fee1
2025-01-31 02:07:27 Bitcoin Design members have been involved in organizing various events (and sometimes just attend, too). Here below is what do we want to do in 2025: - **[Designathon 2](https://github.com/BitcoinDesign/Meta/issues/625)** - We are organizing this event between February or March. - **[Accessibility Day](https://accessibility.day)** - May 15 - - BDC has participated in this global initiative the last two years. Probably doing so again! - **[BTC Prague](https://btcprague.com)** -Participation Confirmed. Planning issues [here](https://github.com/BitcoinDesign/Meta/issues/745) - June 19 - 21 - * We organized the design track for dev day in 2023 and 2024. Do this again[\[k\]](#cmnt11)[\[l\]](#cmnt12)? It’s going to be on June 18, before the main conference. - * 2024 was great, in that we had a nice group of designers attend, do talks, go for dinner, etc. - **[Summer of Bitcoin](https://www.google.com/url?q=https://www.summerofbitcoin.org)** - * Several designers and projects participated each of the last 3 years. Probably doing so again! - * Applications open on Feb 1, main program is May to August ([timeline](https://www.summerofbitcoin.org/how-it-works/) - **UX Bootcamps** - * Previous: South America - * Next: [South America](https://www.bitcoinuxbootcamp.xyz/southamerica) - February 17 - 22 - **[Bitshala fellowship](https://bitshala.org)** - * First iteration of this fellowship is from January to July - * We will help find more designers, projects, and funding in India - **[Oslo Freedom Forum](https://oslofreedomforum.com)** - Oslo, May 26-28 - * Activist and financial repression use cases are uniquely important use cases for bitcoin. - * Several people attended last year. Conversations lead to new initiatives. - **[BTCHEL](https://btchel.com/)** - by BTC Helsinki Community - Aug 15-16 - * First large-scale bitcoin conference in the Nordics with particular focus to onboard new users to bitcoin - **Bitcoin Presidio design week** - * This is a new Bitcoin co-working space in San Francisco, also announced here https://stacker.news/items/860931/r/Design_r. The idea came up to organize a design week there to support the creation of art and decoration for the new co-working space. Just an idea at the moment, but why not make it happen? - * [Discussion issue](https://github.com/BitcoinDesign/Meta/issues/746). - **BuildWithLDK** - * An initiative to promote LDK and LDK Node for building lightning applications. There could be collaboration around a Designathon, connecting designers with hackathon projects, etc. Still in early planning. - **Builder conferences**: These are very builder-focused, making them good opportunities to connect, organize practical design workshops, creative presentations, and support projects from a design perspective - * [Baltic Honeybadger](https://baltichoneybadger.com) (August 9-10), - * [TABConf](http://tabconf.com) - * [Bitcoin++](https://btcplusplus.dev) There are going to be 6 of them throughout the year. - * [SATS’N’FACTS](https://satsandfacts.btc.pub/) (February 8-10) Bitcoin Technical Unconference, Hackathon & Freedom Tech Art Exhibition - **Open-source conferences & events* - * [FOSS Backstage](http://foss-backstage.de) (Berlin, Mar 10-11) - Christoph will present the Open Design Guide - * [FOSDEM](https://fosdem.org/2025/) (Brussels, Feb 1-2) - anyone attending? - **Design conferences & events** - Makes sense to be involved with design-only events, right? * [OFFF](https://www.offf.barcelona) - very creative-focused (Barcelona, May 8-10) * [CSUN Accessibility conference](https://www.csun.edu/cod/conference/sessions/) **Other Ideas** * Bitcoin Park - they might organize another design event like two years ago https://stacker.news/items/705081/r/Design_r **Links** * [Comprehensive list](https://docs.google.com/spreadsheets/d/147AXd8hN3uO3v_P1dupgfRCRzSMlH85dvQSHPAg7lZ4/edit?usp%3Dsharing) of bitcoin conferences - - - … what’s missing from this page? Are you involved with anything? Or want to be? Comment below or join us on https://discord.com/channels/903125802726596648/1087394066796384276 You can watch the recording from https://www.youtube.com/watch?v=GGS3oSlLmAo originally posted at https://stacker.news/items/870638 @ 97c70a44:ad98e322
2025-01-30 17:15:37There was a slight dust up recently over a website someone runs removing a listing for an app someone built based on entirely arbitrary criteria. I'm not to going to attempt to speak for either wounded party, but I would like to share my own personal definition for what constitutes a "nostr app" in an effort to help clarify what might be an otherwise confusing and opaque purity test. In this post, I will be committing the "no true Scotsman" fallacy, in which I start with the most liberal definition I can come up with, and gradually refine it until all that is left is the purest, gleamingest, most imaginary and unattainable nostr app imaginable. As I write this, I wonder if anything built yet will actually qualify. In any case, here we go. # It uses nostr The lowest bar for what a "nostr app" might be is an app ("application" - i.e. software, not necessarily a native app of any kind) that has some nostr-specific code in it, but which doesn't take any advantage of what makes nostr distinctive as a protocol. Examples might include a scraper of some kind which fulfills its charter by fetching data from relays (regardless of whether it validates or retains signatures). Another might be a regular web 2.0 app which provides an option to "log in with nostr" by requesting and storing the user's public key. In either case, the fact that nostr is involved is entirely neutral. A scraper can scrape html, pdfs, jsonl, whatever data source - nostr relays are just another target. Likewise, a user's key in this scenario is treated merely as an opaque identifier, with no appreciation for the super powers it brings along. In most cases, this kind of app only exists as a marketing ploy, or less cynically, because it wants to get in on the hype of being a "nostr app", without the developer quite understanding what that means, or having the budget to execute properly on the claim. # It leverages nostr Some of you might be wondering, "isn't 'leverage' a synonym for 'use'?" And you would be right, but for one connotative difference. It's possible to "use" something improperly, but by definition leverage gives you a mechanical advantage that you wouldn't otherwise have. This is the second category of "nostr app". This kind of app gets some benefit out of the nostr protocol and network, but in an entirely selfish fashion. The intention of this kind of app is not to augment the nostr network, but to augment its own UX by borrowing some nifty thing from the protocol without really contributing anything back. Some examples might include: - Using nostr signers to encrypt or sign data, and then store that data on a proprietary server. - Using nostr relays as a kind of low-code backend, but using proprietary event payloads. - Using nostr event kinds to represent data (why), but not leveraging the trustlessness that buys you. An application in this category might even communicate to its users via nostr DMs - but this doesn't make it a "nostr app" any more than a website that emails you hot deals on herbal supplements is an "email app". These apps are purely parasitic on the nostr ecosystem. In the long-term, that's not necessarily a bad thing. Email's ubiquity is self-reinforcing. But in the short term, this kind of "nostr app" can actually do damage to nostr's reputation by over-promising and under-delivering. # It complements nostr Next up, we have apps that get some benefit out of nostr as above, but give back by providing a unique value proposition to nostr users as nostr users. This is a bit of a fine distinction, but for me this category is for apps which focus on solving problems that nostr isn't good at solving, leaving the nostr integration in a secondary or supporting role. One example of this kind of app was Mutiny (RIP), which not only allowed users to sign in with nostr, but also pulled those users' social graphs so that users could send money to people they knew and trusted. Mutiny was doing a great job of leveraging nostr, as well as providing value to users with nostr identities - but it was still primarily a bitcoin wallet, not a "nostr app" in the purest sense. Other examples are things like Nostr Nests and Zap.stream, whose core value proposition is streaming video or audio content. Both make great use of nostr identities, data formats, and relays, but they're primarily streaming apps. A good litmus test for things like this is: if you got rid of nostr, would it be the same product (even if inferior in certain ways)? A similar category is infrastructure providers that benefit nostr by their existence (and may in fact be targeted explicitly at nostr users), but do things in a centralized, old-web way; for example: media hosts, DNS registrars, hosting providers, and CDNs. To be clear here, I'm not casting aspersions (I don't even know what those are, or where to buy them). All the apps mentioned above use nostr to great effect, and are a real benefit to nostr users. But they are not True Scotsmen. # It embodies nostr Ok, here we go. This is the crème de la crème, the top du top, the meilleur du meilleur, the bee's knees. The purest, holiest, most chaste category of nostr app out there. The apps which are, indeed, nostr indigitate. This category of nostr app (see, no quotes this time) can be defined by the converse of the previous category. If nostr was removed from this type of application, would it be impossible to create the same product? To tease this apart a bit, apps that leverage the technical aspects of nostr are dependent on nostr the *protocol*, while apps that benefit nostr exclusively via network effect are integrated into nostr the *network*. An app that does both things is working in symbiosis with nostr as a whole. An app that embraces both nostr's protocol and its network becomes an organic extension of every other nostr app out there, multiplying both its competitive moat and its contribution to the ecosystem: - In contrast to apps that only borrow from nostr on the technical level but continue to operate in their own silos, an application integrated into the nostr network comes pre-packaged with existing users, and is able to provide more value to those users because of other nostr products. On nostr, it's a good thing to advertise your competitors. - In contrast to apps that only market themselves to nostr users without building out a deep integration on the protocol level, a deeply integrated app becomes an asset to every other nostr app by becoming an organic extension of them through interoperability. This results in increased traffic to the app as other developers and users refer people to it instead of solving their problem on their own. This is the "micro-apps" utopia we've all been waiting for. Credible exit doesn't matter if there aren't alternative services. Interoperability is pointless if other applications don't offer something your app doesn't. Marketing to nostr users doesn't matter if you don't augment their agency _as nostr users_. If I had to choose a single NIP that represents the mindset behind this kind of app, it would be NIP 89 A.K.A. "Recommended Application Handlers", which states: > Nostr's discoverability and transparent event interaction is one of its most interesting/novel mechanics. This NIP provides a simple way for clients to discover applications that handle events of a specific kind to ensure smooth cross-client and cross-kind interactions. These handlers are the glue that holds nostr apps together. A single event, signed by the developer of an application (or by the application's own account) tells anyone who wants to know 1. what event kinds the app supports, 2. how to link to the app (if it's a client), and (if the pubkey also publishes a kind 10002), 3. which relays the app prefers. _As a sidenote, NIP 89 is currently focused more on clients, leaving DVMs, relays, signers, etc somewhat out in the cold. Updating 89 to include tailored listings for each kind of supporting app would be a huge improvement to the protocol. This, plus a good front end for navigating these listings (sorry nostrapp.link, close but no cigar) would obviate the evil centralized websites that curate apps based on arbitrary criteria._ Examples of this kind of app obviously include many kind 1 clients, as well as clients that attempt to bring the benefits of the nostr protocol and network to new use cases - whether long form content, video, image posts, music, emojis, recipes, project management, or any other "content type". To drill down into one example, let's think for a moment about forms. What's so great about a forms app that is built on nostr? Well, - There is a [spec](https://github.com/nostr-protocol/nips/pull/1190) for forms and responses, which means that... - Multiple clients can implement the same data format, allowing for credible exit and user choice, even of... - Other products not focused on forms, which can still view, respond to, or embed forms, and which can send their users via NIP 89 to a client that does... - Cryptographically sign forms and responses, which means they are self-authenticating and can be sent to... - Multiple relays, which reduces the amount of trust necessary to be confident results haven't been deliberately "lost". Show me a forms product that does all of those things, and isn't built on nostr. You can't, because it doesn't exist. Meanwhile, there are plenty of image hosts with APIs, streaming services, and bitcoin wallets which have basically the same levels of censorship resistance, interoperability, and network effect as if they weren't built on nostr. # It supports nostr Notice I haven't said anything about whether relays, signers, blossom servers, software libraries, DVMs, and the accumulated addenda of the nostr ecosystem are nostr apps. Well, they are (usually). This is the category of nostr app that gets none of the credit for doing all of the work. There's no question that they qualify as beautiful nostrcorns, because their value propositions are entirely meaningless outside of the context of nostr. Who needs a signer if you don't have a cryptographic identity you need to protect? DVMs are literally impossible to use without relays. How are you going to find the blossom server that will serve a given hash if you don't know which servers the publishing user has selected to store their content? In addition to being entirely contextualized by nostr architecture, this type of nostr app is valuable because it does things "the nostr way". By that I mean that they don't simply try to replicate existing internet functionality into a nostr context; instead, they create entirely new ways of putting the basic building blocks of the internet back together. A great example of this is how Nostr Connect, Nostr Wallet Connect, and DVMs all use relays as brokers, which allows service providers to avoid having to accept incoming network connections. This opens up really interesting possibilities all on its own. So while I might hesitate to call many of these things "apps", they are certainly "nostr". # Appendix: it smells like a NINO So, let's say you've created an app, but when you show it to people they politely smile, nod, and call it a NINO (Nostr In Name Only). What's a hacker to do? Well, here's your handy-dandy guide on how to wash that NINO stench off and Become a Nostr. You app might be a NINO if: - There's no NIP for your data format (or you're abusing NIP 78, 32, etc by inventing a sub-protocol inside an existing event kind) - There's a NIP, but no one knows about it because it's in a text file on your hard drive (or buried in your project's repository) - Your NIP imposes an incompatible/centralized/legacy web paradigm onto nostr - Your NIP relies on trusted third (or first) parties - There's only one implementation of your NIP (yours) - Your core value proposition doesn't depend on relays, events, or nostr identities - One or more relay urls are hard-coded into the source code - Your app depends on a specific relay implementation to work (*ahem*, relay29) - You don't validate event signatures - You don't publish events to relays you don't control - You don't read events from relays you don't control - You use legacy web services to solve problems, rather than nostr-native solutions - You use nostr-native solutions, but you've hardcoded their pubkeys or URLs into your app - You don't use NIP 89 to discover clients and services - You haven't published a NIP 89 listing for your app - You don't leverage your users' web of trust for filtering out spam - You don't respect your users' mute lists - You try to "own" your users' data Now let me just re-iterate - it's ok to be a NINO. We need NINOs, because nostr can't (and shouldn't) tackle every problem. You just need to decide whether your app, as a NINO, is actually contributing to the nostr ecosystem, or whether you're just using buzzwords to whitewash a legacy web software product. If you're in the former camp, great! If you're in the latter, what are you waiting for? Only you can fix your NINO problem. And there are lots of ways to do this, depending on your own unique situation: - Drop nostr support if it's not doing anyone any good. If you want to build a normal company and make some money, that's perfectly fine. - Build out your nostr integration - start taking advantage of webs of trust, self-authenticating data, event handlers, etc. - Work around the problem. Think you need a special relay feature for your app to work? Guess again. Consider encryption, AUTH, DVMs, or better data formats. - Think your idea is a good one? Talk to other devs or open a PR to the [nips repo](https://github.com/nostr-protocol/nips). No one can adopt your NIP if they don't know about it. - Keep going. It can sometimes be hard to distinguish a research project from a NINO. New ideas have to be built out before they can be fully appreciated. - Listen to advice. Nostr developers are friendly and happy to help. If you're not sure why you're getting traction, ask! I sincerely hope this article is useful for all of you out there in NINO land. Maybe this made you feel better about not passing the totally optional nostr app purity test. Or maybe it gave you some actionable next steps towards making a great NINON (Nostr In Not Only Name) app. In either case, GM and PV.
@ 97c70a44:ad98e322
2025-01-30 17:15:37There was a slight dust up recently over a website someone runs removing a listing for an app someone built based on entirely arbitrary criteria. I'm not to going to attempt to speak for either wounded party, but I would like to share my own personal definition for what constitutes a "nostr app" in an effort to help clarify what might be an otherwise confusing and opaque purity test. In this post, I will be committing the "no true Scotsman" fallacy, in which I start with the most liberal definition I can come up with, and gradually refine it until all that is left is the purest, gleamingest, most imaginary and unattainable nostr app imaginable. As I write this, I wonder if anything built yet will actually qualify. In any case, here we go. # It uses nostr The lowest bar for what a "nostr app" might be is an app ("application" - i.e. software, not necessarily a native app of any kind) that has some nostr-specific code in it, but which doesn't take any advantage of what makes nostr distinctive as a protocol. Examples might include a scraper of some kind which fulfills its charter by fetching data from relays (regardless of whether it validates or retains signatures). Another might be a regular web 2.0 app which provides an option to "log in with nostr" by requesting and storing the user's public key. In either case, the fact that nostr is involved is entirely neutral. A scraper can scrape html, pdfs, jsonl, whatever data source - nostr relays are just another target. Likewise, a user's key in this scenario is treated merely as an opaque identifier, with no appreciation for the super powers it brings along. In most cases, this kind of app only exists as a marketing ploy, or less cynically, because it wants to get in on the hype of being a "nostr app", without the developer quite understanding what that means, or having the budget to execute properly on the claim. # It leverages nostr Some of you might be wondering, "isn't 'leverage' a synonym for 'use'?" And you would be right, but for one connotative difference. It's possible to "use" something improperly, but by definition leverage gives you a mechanical advantage that you wouldn't otherwise have. This is the second category of "nostr app". This kind of app gets some benefit out of the nostr protocol and network, but in an entirely selfish fashion. The intention of this kind of app is not to augment the nostr network, but to augment its own UX by borrowing some nifty thing from the protocol without really contributing anything back. Some examples might include: - Using nostr signers to encrypt or sign data, and then store that data on a proprietary server. - Using nostr relays as a kind of low-code backend, but using proprietary event payloads. - Using nostr event kinds to represent data (why), but not leveraging the trustlessness that buys you. An application in this category might even communicate to its users via nostr DMs - but this doesn't make it a "nostr app" any more than a website that emails you hot deals on herbal supplements is an "email app". These apps are purely parasitic on the nostr ecosystem. In the long-term, that's not necessarily a bad thing. Email's ubiquity is self-reinforcing. But in the short term, this kind of "nostr app" can actually do damage to nostr's reputation by over-promising and under-delivering. # It complements nostr Next up, we have apps that get some benefit out of nostr as above, but give back by providing a unique value proposition to nostr users as nostr users. This is a bit of a fine distinction, but for me this category is for apps which focus on solving problems that nostr isn't good at solving, leaving the nostr integration in a secondary or supporting role. One example of this kind of app was Mutiny (RIP), which not only allowed users to sign in with nostr, but also pulled those users' social graphs so that users could send money to people they knew and trusted. Mutiny was doing a great job of leveraging nostr, as well as providing value to users with nostr identities - but it was still primarily a bitcoin wallet, not a "nostr app" in the purest sense. Other examples are things like Nostr Nests and Zap.stream, whose core value proposition is streaming video or audio content. Both make great use of nostr identities, data formats, and relays, but they're primarily streaming apps. A good litmus test for things like this is: if you got rid of nostr, would it be the same product (even if inferior in certain ways)? A similar category is infrastructure providers that benefit nostr by their existence (and may in fact be targeted explicitly at nostr users), but do things in a centralized, old-web way; for example: media hosts, DNS registrars, hosting providers, and CDNs. To be clear here, I'm not casting aspersions (I don't even know what those are, or where to buy them). All the apps mentioned above use nostr to great effect, and are a real benefit to nostr users. But they are not True Scotsmen. # It embodies nostr Ok, here we go. This is the crème de la crème, the top du top, the meilleur du meilleur, the bee's knees. The purest, holiest, most chaste category of nostr app out there. The apps which are, indeed, nostr indigitate. This category of nostr app (see, no quotes this time) can be defined by the converse of the previous category. If nostr was removed from this type of application, would it be impossible to create the same product? To tease this apart a bit, apps that leverage the technical aspects of nostr are dependent on nostr the *protocol*, while apps that benefit nostr exclusively via network effect are integrated into nostr the *network*. An app that does both things is working in symbiosis with nostr as a whole. An app that embraces both nostr's protocol and its network becomes an organic extension of every other nostr app out there, multiplying both its competitive moat and its contribution to the ecosystem: - In contrast to apps that only borrow from nostr on the technical level but continue to operate in their own silos, an application integrated into the nostr network comes pre-packaged with existing users, and is able to provide more value to those users because of other nostr products. On nostr, it's a good thing to advertise your competitors. - In contrast to apps that only market themselves to nostr users without building out a deep integration on the protocol level, a deeply integrated app becomes an asset to every other nostr app by becoming an organic extension of them through interoperability. This results in increased traffic to the app as other developers and users refer people to it instead of solving their problem on their own. This is the "micro-apps" utopia we've all been waiting for. Credible exit doesn't matter if there aren't alternative services. Interoperability is pointless if other applications don't offer something your app doesn't. Marketing to nostr users doesn't matter if you don't augment their agency _as nostr users_. If I had to choose a single NIP that represents the mindset behind this kind of app, it would be NIP 89 A.K.A. "Recommended Application Handlers", which states: > Nostr's discoverability and transparent event interaction is one of its most interesting/novel mechanics. This NIP provides a simple way for clients to discover applications that handle events of a specific kind to ensure smooth cross-client and cross-kind interactions. These handlers are the glue that holds nostr apps together. A single event, signed by the developer of an application (or by the application's own account) tells anyone who wants to know 1. what event kinds the app supports, 2. how to link to the app (if it's a client), and (if the pubkey also publishes a kind 10002), 3. which relays the app prefers. _As a sidenote, NIP 89 is currently focused more on clients, leaving DVMs, relays, signers, etc somewhat out in the cold. Updating 89 to include tailored listings for each kind of supporting app would be a huge improvement to the protocol. This, plus a good front end for navigating these listings (sorry nostrapp.link, close but no cigar) would obviate the evil centralized websites that curate apps based on arbitrary criteria._ Examples of this kind of app obviously include many kind 1 clients, as well as clients that attempt to bring the benefits of the nostr protocol and network to new use cases - whether long form content, video, image posts, music, emojis, recipes, project management, or any other "content type". To drill down into one example, let's think for a moment about forms. What's so great about a forms app that is built on nostr? Well, - There is a [spec](https://github.com/nostr-protocol/nips/pull/1190) for forms and responses, which means that... - Multiple clients can implement the same data format, allowing for credible exit and user choice, even of... - Other products not focused on forms, which can still view, respond to, or embed forms, and which can send their users via NIP 89 to a client that does... - Cryptographically sign forms and responses, which means they are self-authenticating and can be sent to... - Multiple relays, which reduces the amount of trust necessary to be confident results haven't been deliberately "lost". Show me a forms product that does all of those things, and isn't built on nostr. You can't, because it doesn't exist. Meanwhile, there are plenty of image hosts with APIs, streaming services, and bitcoin wallets which have basically the same levels of censorship resistance, interoperability, and network effect as if they weren't built on nostr. # It supports nostr Notice I haven't said anything about whether relays, signers, blossom servers, software libraries, DVMs, and the accumulated addenda of the nostr ecosystem are nostr apps. Well, they are (usually). This is the category of nostr app that gets none of the credit for doing all of the work. There's no question that they qualify as beautiful nostrcorns, because their value propositions are entirely meaningless outside of the context of nostr. Who needs a signer if you don't have a cryptographic identity you need to protect? DVMs are literally impossible to use without relays. How are you going to find the blossom server that will serve a given hash if you don't know which servers the publishing user has selected to store their content? In addition to being entirely contextualized by nostr architecture, this type of nostr app is valuable because it does things "the nostr way". By that I mean that they don't simply try to replicate existing internet functionality into a nostr context; instead, they create entirely new ways of putting the basic building blocks of the internet back together. A great example of this is how Nostr Connect, Nostr Wallet Connect, and DVMs all use relays as brokers, which allows service providers to avoid having to accept incoming network connections. This opens up really interesting possibilities all on its own. So while I might hesitate to call many of these things "apps", they are certainly "nostr". # Appendix: it smells like a NINO So, let's say you've created an app, but when you show it to people they politely smile, nod, and call it a NINO (Nostr In Name Only). What's a hacker to do? Well, here's your handy-dandy guide on how to wash that NINO stench off and Become a Nostr. You app might be a NINO if: - There's no NIP for your data format (or you're abusing NIP 78, 32, etc by inventing a sub-protocol inside an existing event kind) - There's a NIP, but no one knows about it because it's in a text file on your hard drive (or buried in your project's repository) - Your NIP imposes an incompatible/centralized/legacy web paradigm onto nostr - Your NIP relies on trusted third (or first) parties - There's only one implementation of your NIP (yours) - Your core value proposition doesn't depend on relays, events, or nostr identities - One or more relay urls are hard-coded into the source code - Your app depends on a specific relay implementation to work (*ahem*, relay29) - You don't validate event signatures - You don't publish events to relays you don't control - You don't read events from relays you don't control - You use legacy web services to solve problems, rather than nostr-native solutions - You use nostr-native solutions, but you've hardcoded their pubkeys or URLs into your app - You don't use NIP 89 to discover clients and services - You haven't published a NIP 89 listing for your app - You don't leverage your users' web of trust for filtering out spam - You don't respect your users' mute lists - You try to "own" your users' data Now let me just re-iterate - it's ok to be a NINO. We need NINOs, because nostr can't (and shouldn't) tackle every problem. You just need to decide whether your app, as a NINO, is actually contributing to the nostr ecosystem, or whether you're just using buzzwords to whitewash a legacy web software product. If you're in the former camp, great! If you're in the latter, what are you waiting for? Only you can fix your NINO problem. And there are lots of ways to do this, depending on your own unique situation: - Drop nostr support if it's not doing anyone any good. If you want to build a normal company and make some money, that's perfectly fine. - Build out your nostr integration - start taking advantage of webs of trust, self-authenticating data, event handlers, etc. - Work around the problem. Think you need a special relay feature for your app to work? Guess again. Consider encryption, AUTH, DVMs, or better data formats. - Think your idea is a good one? Talk to other devs or open a PR to the [nips repo](https://github.com/nostr-protocol/nips). No one can adopt your NIP if they don't know about it. - Keep going. It can sometimes be hard to distinguish a research project from a NINO. New ideas have to be built out before they can be fully appreciated. - Listen to advice. Nostr developers are friendly and happy to help. If you're not sure why you're getting traction, ask! I sincerely hope this article is useful for all of you out there in NINO land. Maybe this made you feel better about not passing the totally optional nostr app purity test. Or maybe it gave you some actionable next steps towards making a great NINON (Nostr In Not Only Name) app. In either case, GM and PV. @ 9e69e420:d12360c2
2025-01-30 12:13:39Salwan Momika, a Christian Iraqi known for burning the Koran in Sweden, was shot dead during a TikTok livestream in an apartment in Sodertalje. The 38-year-old sparked outrage in the Muslim community for his demonstrations, leading to global condemnation. After being rushed to the hospital, he was pronounced dead. Authorities arrested five individuals in connection with the incident. Momika's death comes days before a court ruling on his possible incitement of ethnic hatred. The incident highlights the tensions surrounding free speech and religious sentiments, intensifying after his controversial protests in 2023. [Sauce](https://www.dailymail.co.uk/news/article-14341423/Christian-Iraqi-burnt-Koran-Sweden-shot-dead.html)
@ 9e69e420:d12360c2
2025-01-30 12:13:39Salwan Momika, a Christian Iraqi known for burning the Koran in Sweden, was shot dead during a TikTok livestream in an apartment in Sodertalje. The 38-year-old sparked outrage in the Muslim community for his demonstrations, leading to global condemnation. After being rushed to the hospital, he was pronounced dead. Authorities arrested five individuals in connection with the incident. Momika's death comes days before a court ruling on his possible incitement of ethnic hatred. The incident highlights the tensions surrounding free speech and religious sentiments, intensifying after his controversial protests in 2023. [Sauce](https://www.dailymail.co.uk/news/article-14341423/Christian-Iraqi-burnt-Koran-Sweden-shot-dead.html) @ e262ed3a:e147fbcb
2025-01-30 11:26:25 I got an idea while watching a video from @BTCSessions, which I personally cannot implement technically. Therefore, I would like to present it here for discussion and free implementation. It makes sense to me, but what do I know? Let the swarm intelligence decide. The goal of the business idea is: 1. How can I bring as many solo miners as possible into a pool without them having to pay for the electricity for mining and their mining hardware can be amortized quickly, so they can purchase more mining hardware? 2. How can we financially support Bitcoin and Nostr developers in the long term? 3. How can we intensify developers for the implementation of this idea? 4. How can we encourage non-Bitcoiners to invest in the support of the Bitcoin network? 5. How can we get non-Bitcoin retailers to invest in the Bitcoin network? **The answer is: PROSPECT OF WINNING** **The solution lies in a kind of RAFFLE. (Not a betting website)** The legal difference between a BET and a RAFFLE varies from country to country. It lies in the fact that a raffle must be very transparent regarding the chances of winning and the proceeds must go to a good cause. Those involved in the implementation can, of course, be compensated (also with a profit for the individual participants). The extent to which this is allowed would have to be checked by those who want to implement this idea. In the following, I will describe the implementation roughly. Since this is not a sales presentation, please excuse me if the following proposal is not fully structured. Participants in the idea are: 1. Consumers (ticket buyers) 2. Bitcoin miners 3) Retailers 4) Non-profit company that implement the project **What's it about?** @BTCSessions has a YouTube video about the miner FutureBit. In the dashboard of the solo miner, you could see how high the hash rate was. But above all, you could see how high the chance of winning was for the solo miner in the overall network. In the case of BTCSessions FutureBit, the hash rate was around 5 TerraHash and the chance of winning was around 1:1,000,000. (Which, according to my calculations, was not correct). The power consumption was around 32 watts. When I saw that, it suddenly dawned on me. Could it be possible to create a website/app that determines the total hash rate of a mining pool and then offers an electronic, numbered ticket for each 1 TerraHash (TH/s) of the pool for, for example, 0.1 USD? The minimum purchase amount would be 10 tickets. The customer sees the chance of winning and could even see the possible payout. The ticket is only valid for the next block (similar to roulette). Another variant could be that the buyer can select one or more of the next 10 blocks and purchase tickets for the selected block. Since you don't know in advance how high the pool hash rate will be 5 or 10 blocks ahead, the amount of tickets to be issued for the 2nd block, for example, could only be 90% of the current pool hash rate, the 3rd block only 80%, and so on. If block 3, for example, advances to position 2, the previously unavailable 10% will be released for further tickets. (Determined by the pool hash rate at that time) The purchase of 10 or more tickets could be automated in the customer's account on the website/app (intervals: hourly, daily, weekly, every 10 blocks, etc.). Customers could also top up their account with satoshis, enabling automatic deductions for ticket purchases. This could be facilitated by automatically issuing a Nostr npub to each customer, which would also create a wallet at Primal.net (Strike). For non-Bitcoiners, Zaprite could be used to recharge their account. Alternatively, customers could enter a NostrWalletConnection NWC to enable automatic deductions from their Lightning wallet. The project operators might also consider running their own ecash mint, which would allow them to assign an integrated ecash address to customers without a Lightning address. Tickets with ascending numbers would be allocated strictly in the order of payment receipts. **Calculations for the miners**: The FutureBit miner consumed approximately 30 watts per terahash/hour. Let's assume that 10 terahash consume 300 watts per hour, then the miner consumes 50 watts per 10 minutes (per block). Let's further assume that a kilowatt-hour of electricity costs between 10 and 30 cents, then it costs the miner 3-9 cents per hour for electricity at 10 terahash mining capacity. So, 0.5-1.5 cents per block. In the case that each ticket is sold for 1 terahash for the next block, one could automatically transfer, for example, 5% of the satoshis received from ticket sales to each participating miner in the pool (proportional to the average hash rate delivered by the miner in the last block in the pools). This happens even if the block is not found. If fewer tickets are sold than the maximum possible amount, then the 5% of the sold tickets will be distributed proportionally. (See also my Excel file? **At the center** of the project is a website/app that manages the raffle. Here, anyone can register and create an account. Either as a miner, retailer, or customer with or without KYC, for example, with their own nostr nsec, wallet signature, email and password or phone number and password. Once logged into the account, Bitcoiners can enter their Lightning address and a Bitcoin on-chain address. Non-Bitcoiners enter their financial data in case they win. Miners must enter a Bitcoin and Lightning (or ecash) address. The pooling process is also managed in the miner's account. Tickets can be purchased (like in a regular online shop) and paid for in any way. Zaprite could be a solution here. But also Strike, Cashapp, etc. As described above, such purchases could also be automated. **Retailers can also register as such**. They will then have the opportunity to sell "tickets" to their customers and collect the money in cash. To sell tickets, they must enter the customer's name and a valid email address. After payment, they must send the purchase price via Lightning to the non-profit company, which will then confirm the purchase to the ticket buyer and the retailer with all the data. This is the receipt for the buyer. In the event of a win (the mined block must have 3-6 block confirmations), the ticket buyer will receive an email explaining all the further details of how to claim the prize. This could be a link that takes them directly to the website and logs them in directly. The winner can then enter their data on how and where the money should be paid out (Bitcoin address or bank details). Alternatively, they can go to their retailer, who can assist them by entering the data in their sub-account (customer account). To prevent the retailer from falsifying the data entry, the winner will first receive an email with the entered data, which they can confirm (if correct). Since the retailer is also involved in the win, they will also be notified. **How many tickets** can be offered per round (Bitcoin block)? The number of tickets depends on the hash rate in the pool. One ticket can be issued per 1 TerraHash (TH/s). How the ticket is generated per round and customer, I don't know, as I lack the technical knowledge. Maybe as a kind of NFT that contains the corresponding data (customer number (npub) of the buyer and possibly retailer, block number, ticket number). Or as a Taproot asset on Lightning? Or as a minted ecash coin? Or simply as an entry in a database that the customer can see in their account. The maximum payout of the winnings in the event of a found block to the ticket holders could be 70%. The remaining 30% would be distributed to the miners and retailers. For example: Miners 25%, retailers 5%. The non-profit organization receives nothing from the block rewards. Instead, it receives 65% of the revenue from all ticket sales. With a mining pool hash rate of 10,000 TH/s, where all tickets are sold continuously, a daily donation of around 93,000 USD would be generated. (see Excel.file) The revenue, after deducting the possible costs of the organization, goes directly to @opensats and/or other organizations that support the Bitcoin network after each block. Either via Lightning or Bitcoin on-chain payment. In the attached Excel file, you can find my calculations. Here, anyone can play through different scenarios. What I noticed was that with maximum ticket sales per block, only around 200 USD per 10 tickets would be paid out, since each participating ticket wins in the event of a found block. Since I believe that this is not a very great incentive for buying tickets, I suggest the following variants. **Winning variants**: Each purchased ticket has a running number. Ticket 1 has the number 000.000, ticket 2 has the number 000.001, ticket 10.120 has the number 010.119, and so on. If the next block is found, then this found block in the Bitcoin blockchain has a hash. For example, block 881367 has the hash 000000000000000000014b0fab24355c71c6940584d9cd5990c0b081a31d54a4 Let's now remove the letters and read only the numbers from back to front, so the last 3 numbers are 544 Instead of every participating ticket winning, in this variant, only the tickets with the ending digits 544 win. With, for example, 11,000 tickets sold, the ticket numbers 000.544 / 001.544 / 002.544 ... 010.544 would win. So, 11 ticket participants would win. Each winner with this number would receive around 0.284 Bitcoin (3.125 BTC / 11). One could also let the ticket numbers with the ending digits 44 win, and thus every hundredth ticket. Or even combine it. What I also noticed was that with retailers, a special case arises. Retailers receive 5% of the block rewards in the event of a found block. But only proportionally to the tickets sold by the retailer. This means that in order for the entire 5% to be distributed to the retailers, all 10,000 tickets of 10.000 possible tickets would have to be sold by retailers. Since not all tickets will be sold by retailers, a remaining amount will be left over. This could be distributed additionally to the miners. Or any other variant. I hope the idea finds resonance and invites discussion. Maybe I've made some mistakes in thinking, and the idea is not feasible. But if you like the idea, please forward it to developers, investors, and others you know. Best regards. <span data-type="mention" data-id="e262ed3a22ad8c478b077ef5d7c56b2c3c7a530519ed696ed2e57c65e147fbcb" data-label="nostr:undefined">@nostr:undefined</span> dewe [Excel sheet for download](https://c.gmx.net/@329519820976429649/KJTehgh0SMGliV4HLjMf0g)
@ e262ed3a:e147fbcb
2025-01-30 11:26:25 I got an idea while watching a video from @BTCSessions, which I personally cannot implement technically. Therefore, I would like to present it here for discussion and free implementation. It makes sense to me, but what do I know? Let the swarm intelligence decide. The goal of the business idea is: 1. How can I bring as many solo miners as possible into a pool without them having to pay for the electricity for mining and their mining hardware can be amortized quickly, so they can purchase more mining hardware? 2. How can we financially support Bitcoin and Nostr developers in the long term? 3. How can we intensify developers for the implementation of this idea? 4. How can we encourage non-Bitcoiners to invest in the support of the Bitcoin network? 5. How can we get non-Bitcoin retailers to invest in the Bitcoin network? **The answer is: PROSPECT OF WINNING** **The solution lies in a kind of RAFFLE. (Not a betting website)** The legal difference between a BET and a RAFFLE varies from country to country. It lies in the fact that a raffle must be very transparent regarding the chances of winning and the proceeds must go to a good cause. Those involved in the implementation can, of course, be compensated (also with a profit for the individual participants). The extent to which this is allowed would have to be checked by those who want to implement this idea. In the following, I will describe the implementation roughly. Since this is not a sales presentation, please excuse me if the following proposal is not fully structured. Participants in the idea are: 1. Consumers (ticket buyers) 2. Bitcoin miners 3) Retailers 4) Non-profit company that implement the project **What's it about?** @BTCSessions has a YouTube video about the miner FutureBit. In the dashboard of the solo miner, you could see how high the hash rate was. But above all, you could see how high the chance of winning was for the solo miner in the overall network. In the case of BTCSessions FutureBit, the hash rate was around 5 TerraHash and the chance of winning was around 1:1,000,000. (Which, according to my calculations, was not correct). The power consumption was around 32 watts. When I saw that, it suddenly dawned on me. Could it be possible to create a website/app that determines the total hash rate of a mining pool and then offers an electronic, numbered ticket for each 1 TerraHash (TH/s) of the pool for, for example, 0.1 USD? The minimum purchase amount would be 10 tickets. The customer sees the chance of winning and could even see the possible payout. The ticket is only valid for the next block (similar to roulette). Another variant could be that the buyer can select one or more of the next 10 blocks and purchase tickets for the selected block. Since you don't know in advance how high the pool hash rate will be 5 or 10 blocks ahead, the amount of tickets to be issued for the 2nd block, for example, could only be 90% of the current pool hash rate, the 3rd block only 80%, and so on. If block 3, for example, advances to position 2, the previously unavailable 10% will be released for further tickets. (Determined by the pool hash rate at that time) The purchase of 10 or more tickets could be automated in the customer's account on the website/app (intervals: hourly, daily, weekly, every 10 blocks, etc.). Customers could also top up their account with satoshis, enabling automatic deductions for ticket purchases. This could be facilitated by automatically issuing a Nostr npub to each customer, which would also create a wallet at Primal.net (Strike). For non-Bitcoiners, Zaprite could be used to recharge their account. Alternatively, customers could enter a NostrWalletConnection NWC to enable automatic deductions from their Lightning wallet. The project operators might also consider running their own ecash mint, which would allow them to assign an integrated ecash address to customers without a Lightning address. Tickets with ascending numbers would be allocated strictly in the order of payment receipts. **Calculations for the miners**: The FutureBit miner consumed approximately 30 watts per terahash/hour. Let's assume that 10 terahash consume 300 watts per hour, then the miner consumes 50 watts per 10 minutes (per block). Let's further assume that a kilowatt-hour of electricity costs between 10 and 30 cents, then it costs the miner 3-9 cents per hour for electricity at 10 terahash mining capacity. So, 0.5-1.5 cents per block. In the case that each ticket is sold for 1 terahash for the next block, one could automatically transfer, for example, 5% of the satoshis received from ticket sales to each participating miner in the pool (proportional to the average hash rate delivered by the miner in the last block in the pools). This happens even if the block is not found. If fewer tickets are sold than the maximum possible amount, then the 5% of the sold tickets will be distributed proportionally. (See also my Excel file? **At the center** of the project is a website/app that manages the raffle. Here, anyone can register and create an account. Either as a miner, retailer, or customer with or without KYC, for example, with their own nostr nsec, wallet signature, email and password or phone number and password. Once logged into the account, Bitcoiners can enter their Lightning address and a Bitcoin on-chain address. Non-Bitcoiners enter their financial data in case they win. Miners must enter a Bitcoin and Lightning (or ecash) address. The pooling process is also managed in the miner's account. Tickets can be purchased (like in a regular online shop) and paid for in any way. Zaprite could be a solution here. But also Strike, Cashapp, etc. As described above, such purchases could also be automated. **Retailers can also register as such**. They will then have the opportunity to sell "tickets" to their customers and collect the money in cash. To sell tickets, they must enter the customer's name and a valid email address. After payment, they must send the purchase price via Lightning to the non-profit company, which will then confirm the purchase to the ticket buyer and the retailer with all the data. This is the receipt for the buyer. In the event of a win (the mined block must have 3-6 block confirmations), the ticket buyer will receive an email explaining all the further details of how to claim the prize. This could be a link that takes them directly to the website and logs them in directly. The winner can then enter their data on how and where the money should be paid out (Bitcoin address or bank details). Alternatively, they can go to their retailer, who can assist them by entering the data in their sub-account (customer account). To prevent the retailer from falsifying the data entry, the winner will first receive an email with the entered data, which they can confirm (if correct). Since the retailer is also involved in the win, they will also be notified. **How many tickets** can be offered per round (Bitcoin block)? The number of tickets depends on the hash rate in the pool. One ticket can be issued per 1 TerraHash (TH/s). How the ticket is generated per round and customer, I don't know, as I lack the technical knowledge. Maybe as a kind of NFT that contains the corresponding data (customer number (npub) of the buyer and possibly retailer, block number, ticket number). Or as a Taproot asset on Lightning? Or as a minted ecash coin? Or simply as an entry in a database that the customer can see in their account. The maximum payout of the winnings in the event of a found block to the ticket holders could be 70%. The remaining 30% would be distributed to the miners and retailers. For example: Miners 25%, retailers 5%. The non-profit organization receives nothing from the block rewards. Instead, it receives 65% of the revenue from all ticket sales. With a mining pool hash rate of 10,000 TH/s, where all tickets are sold continuously, a daily donation of around 93,000 USD would be generated. (see Excel.file) The revenue, after deducting the possible costs of the organization, goes directly to @opensats and/or other organizations that support the Bitcoin network after each block. Either via Lightning or Bitcoin on-chain payment. In the attached Excel file, you can find my calculations. Here, anyone can play through different scenarios. What I noticed was that with maximum ticket sales per block, only around 200 USD per 10 tickets would be paid out, since each participating ticket wins in the event of a found block. Since I believe that this is not a very great incentive for buying tickets, I suggest the following variants. **Winning variants**: Each purchased ticket has a running number. Ticket 1 has the number 000.000, ticket 2 has the number 000.001, ticket 10.120 has the number 010.119, and so on. If the next block is found, then this found block in the Bitcoin blockchain has a hash. For example, block 881367 has the hash 000000000000000000014b0fab24355c71c6940584d9cd5990c0b081a31d54a4 Let's now remove the letters and read only the numbers from back to front, so the last 3 numbers are 544 Instead of every participating ticket winning, in this variant, only the tickets with the ending digits 544 win. With, for example, 11,000 tickets sold, the ticket numbers 000.544 / 001.544 / 002.544 ... 010.544 would win. So, 11 ticket participants would win. Each winner with this number would receive around 0.284 Bitcoin (3.125 BTC / 11). One could also let the ticket numbers with the ending digits 44 win, and thus every hundredth ticket. Or even combine it. What I also noticed was that with retailers, a special case arises. Retailers receive 5% of the block rewards in the event of a found block. But only proportionally to the tickets sold by the retailer. This means that in order for the entire 5% to be distributed to the retailers, all 10,000 tickets of 10.000 possible tickets would have to be sold by retailers. Since not all tickets will be sold by retailers, a remaining amount will be left over. This could be distributed additionally to the miners. Or any other variant. I hope the idea finds resonance and invites discussion. Maybe I've made some mistakes in thinking, and the idea is not feasible. But if you like the idea, please forward it to developers, investors, and others you know. Best regards. <span data-type="mention" data-id="e262ed3a22ad8c478b077ef5d7c56b2c3c7a530519ed696ed2e57c65e147fbcb" data-label="nostr:undefined">@nostr:undefined</span> dewe [Excel sheet for download](https://c.gmx.net/@329519820976429649/KJTehgh0SMGliV4HLjMf0g) @ 0fa80bd3:ea7325de
2025-01-30 04:28:30**"Degeneration"** or **"Вырождение"** ![[photo_2025-01-29 23.23.15.jpeg]] A once-functional object, now eroded by time and human intervention, stripped of its original purpose. Layers of presence accumulate—marks, alterations, traces of intent—until the very essence is obscured. Restoration is paradoxical: to reclaim, one must erase. Yet erasure is an impossibility, for to remove these imprints is to deny the existence of those who shaped them. The work stands as a meditation on entropy, memory, and the irreversible dialogue between creation and decay.
@ 0fa80bd3:ea7325de
2025-01-30 04:28:30**"Degeneration"** or **"Вырождение"** ![[photo_2025-01-29 23.23.15.jpeg]] A once-functional object, now eroded by time and human intervention, stripped of its original purpose. Layers of presence accumulate—marks, alterations, traces of intent—until the very essence is obscured. Restoration is paradoxical: to reclaim, one must erase. Yet erasure is an impossibility, for to remove these imprints is to deny the existence of those who shaped them. The work stands as a meditation on entropy, memory, and the irreversible dialogue between creation and decay. @ 9f3eba58:fa185499
2025-01-29 20:27:09Humanity as a whole has been degrading over the years, with average IQ decreasing, bone structures generally becoming poorly formed and fragile, average height decreasing, hormone levels ridiculously low and having various metabolic and mental illnesses becoming “normal”. “*By 2024, more than 800 million adults were living with diabetes, representing a more than fourfold increase since 1990*” “\*\**1 in 3 people suffer from insulin resistance and can cause depression*” (\*\*https://olhardigital.com.br/2021/09/24/medicina-e-saude/1-em-cada-3-pessoas-sofre-de-resistencia-a-insulina-e-pode-causar-depressao/) “*More than 1.3 billion people will have diabetes in the world by 2050*” (https://veja.abril.com.br/saude/mais-de-13-bilhao-de-pessoas-terao-diabetes-no-mundo-ate-2050) “*A new study released by Lancet, with data from 2022, shows that more than a billion people live with obesity in the world*” (https://www.paho.org/pt/noticias/1-3-2024-uma-em-cada-oito-pessoas-no-mundo-vive-com-obesidade) All this due to a single factor: diet. I’m not referring to a diet full of processed foods, as this has already been proven to destroy the health of those who eat it. I’m referring to the modern diet, with carbohydrates (from any source, even from fruit) being the main macronutrient, little animal protein and practically no saturated fat of animal origin. This diet implementation has been systematically occurring for decades. Sugar conglomerates seeking profits? Government institutions (after all, they need voters to be stupid and vote for them), evil spiritual interference wanting to destroy or distort their path? I don’t know, I’ll leave the conspiracy theories to you! The modern diet or diet is extremely inflammatory, and inflammation over a long period of time leads to autoimmune diseases such as diabetes and Hashimoto’s. Absolutely any food in the plant kingdom will harm you, no matter how asymptomatic it may be. Plants are living beings and do not want to die and be eaten. To defend themselves from this, they did not evolve legs like animals. They specifically developed chemical mechanisms such as *oxalates, phytoalexins, glucosinolates, polyphenols, antinutrients* and many others that act to repel anything that wants to eat them, being fatal (as in the case of mushrooms), causing discomfort and the animal or insect discovering that the plant is not edible, releasing unpleasant smells or, in many cases, a combination of these factors. Not to mention genetically modified foods (almost the entire plant kingdom is genetically modified) that work as a steroid for the plants' defenses. - Lack of focus - Poor decision-making - Difficulty in establishing and maintaining relationships - Difficulty getting pregnant and difficult pregnancy - Low testosterone (medical reference values are low) - Alzheimer's - Diabetes - Dementia - Chances of developing autism when mothers do not eat meat and fat properly during pregnancy - Worsening of the degree of autism when the child does not eat meat and fat (food selectivity) - Insomnia and other sleep problems - Lack of energy - Poorly formed and fragile bone structure - Lack of willpower - Depression - ADHD Not having full physical and mental capacity harms you in many different ways, these are just a few examples that not only directly impact one person but everyone else around them. Fortunately, there is an alternative to break out of this cycle of destruction, ***Carnivore Diet***. I am not here to recommend a diet, eating plan or cure for your health problems, nor can I do so, as I am not a doctor (most doctors don't even know where the pancreas is, a mechanic is more useful in your life than a doctor, but that is a topic for another text.). I came to present you with logic and facts in a very simplified way, from there you can do your own research and decide what is best for you. --- ## Defining the carnivore diet Simply put, the carnivore diet is an elimination diet, where carbohydrates (including fruits), vegetable fats (soy, canola, cotton, peanuts, etc.), processed products and any type of plant, be it spices or teas, are completely removed. ### What is allowed on the carnivore diet? - Animal protein - Beef, preferably fatty cuts (including offal, liver, heart, kidneys, these cuts have more vitamins than anything else in the world) - Lamb - Eggs - Fish and seafood - Animal fat - Butter - Beef fat and tallow - Salt - No... salt does not cause high blood pressure. (explained later about salt and high consumption of saturated fats) From now on I will list some facts that disprove the false accusations made against \*\*eating exclusively meat and fat. # “Human beings are omnivores” *“Our ancestors were gatherers and hunters*" To determine the proportion of animal foods in our ancestors’ diets, we can look at the amount of δ15 nitrogen in their fossils. By looking at levels of this isotope, researchers can infer where animals reside in the food chain, identifying their protein sources. Herbivores typically have δ15N levels of 3–7 percent, carnivores show levels of 6–12 percent, and omnivores exhibit levels in between. When samples from Neanderthals and early modern humans were analyzed, they showed levels of 12 percent and 13.5 percent, respectively, even higher than those of other known carnivores, such as hyenas and wolves. And from an energy efficiency standpoint, hunting large animals makes the most sense. Gathering plants and chasing small animals provides far fewer calories and nutrients relative to the energy invested. In more recently studied indigenous peoples, we have observed a similar pattern that clearly indicates a preference for animal foods over plant foods. For example, in Vilhjalmur Stefansson’s studies of the Eskimos. *“…fat, not protein, seemed to play a very important role in hunters’ decisions about which animals (male or female) to kill and which body parts to discard or carry away.”* Why were our ancestors and more recent indigenous peoples so interested in finding fat? At a very basic level, it was probably about calories. By weight, fat provides more than twice as many calories as protein or carbohydrates. Furthermore, human metabolism makes fat an exceptionally valuable and necessary food. If we think of ourselves as automobiles that need fuel for our metabolic engines, we should not put protein in our gas tank. For best results, our metabolic engine runs most efficiently on fat or carbohydrates. Eating animal foods has been a vital part of our evolution since the beginning. Katherine Milton, a researcher at UC Berkeley, came to the same conclusion in her paper “The Critical Role Played by Animal Source Foods in Human Evolution,” which states: “Without routine access to animal-source foods, it is highly unlikely that evolving humans could have achieved their unusually large and complex brains while simultaneously continuing their evolutionary trajectory as large, active, and highly social primates. As human evolution progressed, young children in particular, with their rapidly expanding large brains and higher metabolic and nutritional demands relative to adults, would have benefited from concentrated, high-quality foods such as meat." - https://pubmed.ncbi.nlm.nih.gov/14672286/ Skeletons from Greece and Turkey reveal that 12,000 years ago, the average height of hunter-gatherers was five feet, nine inches for men and five feet, five inches for women. But with the adoption of agriculture, adult height plummeted—ending any hope these poor herders had of dunking a basketball or playing competitive volleyball, if such sports had existed at the time. By 3000 B.C., men in this region of the world were only five feet, three inches tall, and women were five feet, reflecting a massive decline in their overall nutritional status. Many studies in diverse populations show a strong correlation between adult height and nutritional quality. A study analyzing male height in 105 countries came to the following conclusion: “In taller nations…consumption of plant proteins declines sharply at the expense of animal proteins, especially those from dairy products. Its highest consumption rates can be found in Northern and Central Europe, with the global peak in male height in the Netherlands (184 cm).” In addition to the decline in height, there is also evidence that Native Americans buried at Dickson Mounds suffered from increased bacterial infections. These infections leave scars on the outer surface of the bone, known as the periosteum, with the tibia being especially susceptible to such damage due to its limited blood flow. Examination of tibias from skeletons found in the mounds shows that after agriculture, the number of such periosteal lesions increased threefold, with a staggering eighty-four percent of bones from this period demonstrating this pathology. The lesions also tended to be more severe and to appear earlier in life in the bones of post-agricultural peoples. https://onlinelibrary.wiley.com/doi/full/10.1111/j.1747-0080.2007.00194.x https://pubmed.ncbi.nlm.nih.gov/10702160/ # Cholesterol Many “doctors” say that consuming saturated fat is harmful to your health, “your veins and arteries will clog with excess fat” “you will have a heart attack if you consume a lot of fat" and many other nonsense, and in exchange recommends that you replace fatty cuts of meat with lean meat and do everything with vegetable oil that causes cancer and makes men effeminate. Your brain is basically composed of fat and water, your neurons are made and repaired with fat, your cells, the basic unit of life, are composed of fat and protein, many of your hormones, especially sexual ones, are made from fat, there is no logical reason not to consume saturated fat other than several false "scientific articles". "The power plant of the cell is the mitochondria, which converts what we eat into energy. Ketones are an energy source derived from fat. Mitochondria prefer fat as energy (ketones) because transforming ketones into energy costs the mitochondria half the effort of using sugar (glucose) for energy." - https://pubmed.ncbi.nlm.nih.gov/28178565/ "With the help of saturated fats, calcium is properly stored in our bones. The interaction between calcium, vitamin D, and parathyroid hormone regulates calcium levels in the body. When there are calcium imbalances in the blood, our bones release calcium into the blood to find homeostasis." - https://www.healthpedian.org/the-role-of-calcium-in-the-human-body/ "The body needs cholesterol to support muscle repair and other cellular functions. This is why when there is cardiovascular disease, we see increased amounts of cholesterol in the area. Cholesterol is not there causing the problem, but the boat carrying fat was docked there for cholesterol and other nutrients to help fight the problem. Plaque is the body's attempt to deal with injury within the blood vessels." - *National Library of Medicine, “Cholesterol,” 2019* "Initially, the Plaque helps blood vessels stay strong and helps the vessels maintain their shape. But with the perpetual cycle of uncontrolled inflammation and leftover debris from cellular repair (cholesterol), over time plaque begins to grow and harden, reducing blood flow and oxygen to the heart. Both inflammation and repair require copious amounts of cholesterol and fats. So the body keeps sending these fatty substances to the site of the plaque — until either repair wins (plaque becomes sclerotic scars in the heart muscle, causing heart failure) or inflammation wins (atherosclerotic heart attack)" - https://pubmed.ncbi.nlm.nih.gov/21250192/ Inflammation in Atherosclerotic Cardiovascular Disease - https://pubmed.ncbi.nlm.nih.gov/21250192/ "Study finds that eating refined carbohydrates led to an increased risk of cardiovascular disease and obesity" - https://pmc.ncbi.nlm.nih.gov/articles/PMC5793267/ # “Meat causes cancer” Most of the misconceptions that red meat causes cancer come from a report by the World Health Organization's International Agency for Research on Cancer (IARC), which was released in 2015. Unfortunately, this report has been widely misrepresented by the mainstream media and is based on some very questionable interpretations of the science it claims to review. A closer look at a 2018 report on its findings reveals that only 14 of the 800 studies were considered in its final conclusions—and every single study was observational epidemiology. Why the other 786 were excluded remains a mystery, and this group included many interventional animal studies that clearly did not show a link between red meat and cancer. Of the fourteen epidemiological studies that were included in the IARC report, eight showed no link between meat consumption and the development of colon cancer. Of the remaining six studies, only one showed a statistically significant correlation between meat and cancer. In epidemiological research, one looks for correlation between two things and the strength of the correlation. Having just one study out of 800 that shows meat causes cancer is a mere fluke and becomes statistically insignificant. Interestingly, this was a study by Seventh-day Adventists in America — a religious group that advocates a plant-based diet. # Microbiota and Fiber I have seen several people and “doctors” saying that eating only meat would destroy your microbiota. And I have come to the conclusion that neither “doctors” nor most people know what a microbiota is. Microbiota is the set of several types of bacteria (millions) that exist in your stomach with the function of breaking down molecules of certain types of food that the body itself cannot get, fiber for example. Many times through the process of fermentation, which is why you have gas after eating your beloved oatmeal. People unconsciously believe that the microbiota is something fixed and unchangeable, but guess what… it is not. Your microbiota is determined by what you eat. If you love eating oatmeal, your microbiota will have a specific set of bacteria that can break down the oat molecule into a size that the body can absorb. If you follow a carnivorous diet, your microbiota will adapt to digest meat. ### Fiber Nutritional guidelines recommend large amounts of fiber in our diet, but what they don't tell you is that we only absorb around 6% of all the vegetable fiber we eat. In other words, it's insignificant! Another argument used by doctors and nutritionists is that it helps you go to the bathroom, but this is also a lie. Fiber doesn't help you evacuate, it forces you to do so. With the huge amount of undigestible food in your stomach (fiber), the intestine begins to force contractions, making this fecal matter go down, making you go to the bathroom. They also raise the argument that fibers are broken down into short-chain fatty acids, such as butyrate (butyric acid), propionate (propionic acid) and acetate (acetic acid). Butyrate is essential because it is the preferred fuel source for the endothelial cells of the large intestine. Butter, cream, and cheese contain butyrate in its absorbable form. Butter is the best source of butyric acid, or butyrate. In fact, the origins of the word butyric acid come from the Latin word *butyro*—the same origins as the word butter. “In 2012, a study in the Journal of Gastroenterology showed that reducing fiber (a precursor to short-chain fatty acids) helped participants with chronic constipation. The study lasted six months, and after two weeks without fiber, these participants were allowed to increase fiber as needed. These participants felt so much relief after two weeks without fiber that they continued without fiber for the entire six-month period. Of the high-fiber, low-fiber, and no-fiber groups, the zero-fiber participants had the highest bowel movement frequency.” - https://pmc.ncbi.nlm.nih.gov/articles/PMC3435786/ ### Bioavailability I said that our body can only absorb 6% of all the fiber we ingest. This is bioavailability, how much the body can absorb nutrients from a given food. Meat is the most bioavailable food on the planet! Grains and vegetables are not only not very bioavailable, but they also contain a huge amount of antinutrients. So if you eat a steak with some beans, you will not be able to absorb the nutrients from the beans, and the antinutrients in them will make it impossible to absorb a large amount of nutrients from the steak. https://pubmed.ncbi.nlm.nih.gov/23107545/ # Lack of nutrients and antioxidants in a carnivorous diet A major concern with the carnivorous diet is the lack of vitamin C, which would consequently lead to scurvy. Vitamin C plays an important role in the breakdown and transport of glucose into cells. In 2000 and 2001, the recommended daily intake of vitamin C effectively doubled. In fact, every 10 to 15 years, there has been a large increase in the recommended daily intake of vitamin C, as happened in 1974 and 1989. Interestingly, also in 1974, sugar prices became so high that high fructose corn syrup was introduced into the US market. Could the increase in readily available glucose foods and foods with high fructose corn syrup be a reason why we need more vitamin C? The question remains…. But this is not a cause for concern for the carnivore, liver is rich in vitamin C. You could easily reach the daily recommendation with liver or any cut of steak. 200-300g of steak already meets your needs and if the theory that the more sugar you eat, the more vitamin C you will get is true, then the more sugar you will eat is true. C is necessary if true, you could easily exceed the daily requirement. Meat and seafood are rich in ALL the nutrients that humans need to thrive. ### Antioxidants It is commonly said that fruits are rich in antioxidants but again this is a hoax, they are actually PRO-oxidants. These are substances that activate the mRF2 pathway of our immune system which causes the body to produce natural antioxidants. The body produces antioxidants, but many occur naturally in foods, Vitamin C, Vitamin E, Selenium and Manganese are all natural antioxidants. High concentrations of antioxidants can be harmful. Remember that high concentrations of antioxidants can increase oxidation and even protect against cancer cells. # Salt Consuming too much salt does not increase blood pressure and therefore increases the risk of heart disease and stroke. Studies show no evidence that limiting salt intake reduces the risk of heart disease. A 2011 study found that diets low in salt may actually increase the risk of death from heart attacks and strokes. Most importantly, they do not prevent high blood pressure. https://www.nytimes.com/2011/05/04/health/research/04salt.html # Sun This is not a dietary issue specifically, but there are things that can I would like to present that is against common sense when talking about the sun. It is common sense to say that the sun causes skin cancer and that we should not expose ourselves to it or, if we are exposed to the sun, use sunscreen, but no study proves that using sunscreen protects us from melanoma and basal cell carcinoma. The types of fatal melanomas usually occur in areas of the body that never see the sun, such as the soles of the feet. https://www.jabfm.org/content/24/6/735 In 1978, the first sunscreen was launched, and the market grew rapidly, along with cases of melanoma. Several studies show that sunscreens cause leaky gut (one of the main factors in chronic inflammation), hormonal dysfunction and neurological dysfunction. https://pubmed.ncbi.nlm.nih.gov/31058986/ If your concern when going out in the sun is skin cancer, don't worry, your own body's natural antioxidants will protect you. When they can no longer protect you, your skin starts to burn. (If you have to stay in the sun for work, for example, a good way to protect yourself is to rub coconut oil on your skin or just cover yourself with a few extra layers of thin clothing and a hat). Sunscreen gives you the false sense of protection by blocking the sunburn, so you stay out longer than your skin can handle, but sunscreens can only block 4% of UVA and UVB rays. www.westonaprice.org/health-topics/environmental-toxins/sunscreens-the-dark-side-of-avoiding-the-sun/ Interestingly, vitamin D deficiency is linked to increased cancer risks. It's a big contradiction to say that the greatest provider of vit. D causes cancer… https://med.stanford.edu/news/all-news/2010/10/skin-cancer-patients-more-likely-to-be-deficient-in-vitamin-d-study-finds.html Important roles of vitamin D: - **Regulation of Bone Metabolism** - Facilitates the **absorption of calcium and phosphorus** in the intestine. - Promotes bone mineralization and prevents diseases such as **osteoporosis**, **rickets** (in children) and **osteomalacia** (in adults). - **Immune Function** - Modulates the immune system, helping to reduce inflammation and strengthen the defense against infections, including **colds**, **flu** and other diseases. - May help reduce the incidence of autoimmune diseases such as **multiple sclerosis** and **rheumatoid arthritis**. - **Muscle Health** - Contributes to muscle strength and the prevention of weakness, especially in the elderly. - Reduces the risk of falls and fractures. - **Cardiovascular Function** - May help regulate blood pressure and heart function, reducing the risk of cardiovascular disease. - **Hormonal Balance** - Influences the production of hormones, including those associated with fertility and the functioning of the endocrine system. - Plays a role in insulin metabolism and glucose sensitivity. - **Brain Function and Mental Health** - Participates in mood regulation, which may reduce the risk of **depression** and improve mental health. - Has been associated with the prevention of neurodegenerative diseases, such as **Alzheimer's**. - **Anticancer Role** - Evidence suggests that vitamin D may inhibit the proliferation of cancer cells, especially in breast, prostate and colon cancers. - **Role in General Metabolism** - Contributes to metabolic health, regulating cellular growth and repair processes. --- I tried to present everything in the simplest and most understandable way possible, but there are things that require prior knowledge to truly understand. Below is a list of books that will show you everything I have shown you in a more technical and in-depth way. ### Book Recommendations https://amzn.to/3EbjVsD https://amzn.to/4awlnBZ All of my arguments have studies to validate them. Feel free to read them all and draw your own conclusions about what is best for you and your life.
@ 9f3eba58:fa185499
2025-01-29 20:27:09Humanity as a whole has been degrading over the years, with average IQ decreasing, bone structures generally becoming poorly formed and fragile, average height decreasing, hormone levels ridiculously low and having various metabolic and mental illnesses becoming “normal”. “*By 2024, more than 800 million adults were living with diabetes, representing a more than fourfold increase since 1990*” “\*\**1 in 3 people suffer from insulin resistance and can cause depression*” (\*\*https://olhardigital.com.br/2021/09/24/medicina-e-saude/1-em-cada-3-pessoas-sofre-de-resistencia-a-insulina-e-pode-causar-depressao/) “*More than 1.3 billion people will have diabetes in the world by 2050*” (https://veja.abril.com.br/saude/mais-de-13-bilhao-de-pessoas-terao-diabetes-no-mundo-ate-2050) “*A new study released by Lancet, with data from 2022, shows that more than a billion people live with obesity in the world*” (https://www.paho.org/pt/noticias/1-3-2024-uma-em-cada-oito-pessoas-no-mundo-vive-com-obesidade) All this due to a single factor: diet. I’m not referring to a diet full of processed foods, as this has already been proven to destroy the health of those who eat it. I’m referring to the modern diet, with carbohydrates (from any source, even from fruit) being the main macronutrient, little animal protein and practically no saturated fat of animal origin. This diet implementation has been systematically occurring for decades. Sugar conglomerates seeking profits? Government institutions (after all, they need voters to be stupid and vote for them), evil spiritual interference wanting to destroy or distort their path? I don’t know, I’ll leave the conspiracy theories to you! The modern diet or diet is extremely inflammatory, and inflammation over a long period of time leads to autoimmune diseases such as diabetes and Hashimoto’s. Absolutely any food in the plant kingdom will harm you, no matter how asymptomatic it may be. Plants are living beings and do not want to die and be eaten. To defend themselves from this, they did not evolve legs like animals. They specifically developed chemical mechanisms such as *oxalates, phytoalexins, glucosinolates, polyphenols, antinutrients* and many others that act to repel anything that wants to eat them, being fatal (as in the case of mushrooms), causing discomfort and the animal or insect discovering that the plant is not edible, releasing unpleasant smells or, in many cases, a combination of these factors. Not to mention genetically modified foods (almost the entire plant kingdom is genetically modified) that work as a steroid for the plants' defenses. - Lack of focus - Poor decision-making - Difficulty in establishing and maintaining relationships - Difficulty getting pregnant and difficult pregnancy - Low testosterone (medical reference values are low) - Alzheimer's - Diabetes - Dementia - Chances of developing autism when mothers do not eat meat and fat properly during pregnancy - Worsening of the degree of autism when the child does not eat meat and fat (food selectivity) - Insomnia and other sleep problems - Lack of energy - Poorly formed and fragile bone structure - Lack of willpower - Depression - ADHD Not having full physical and mental capacity harms you in many different ways, these are just a few examples that not only directly impact one person but everyone else around them. Fortunately, there is an alternative to break out of this cycle of destruction, ***Carnivore Diet***. I am not here to recommend a diet, eating plan or cure for your health problems, nor can I do so, as I am not a doctor (most doctors don't even know where the pancreas is, a mechanic is more useful in your life than a doctor, but that is a topic for another text.). I came to present you with logic and facts in a very simplified way, from there you can do your own research and decide what is best for you. --- ## Defining the carnivore diet Simply put, the carnivore diet is an elimination diet, where carbohydrates (including fruits), vegetable fats (soy, canola, cotton, peanuts, etc.), processed products and any type of plant, be it spices or teas, are completely removed. ### What is allowed on the carnivore diet? - Animal protein - Beef, preferably fatty cuts (including offal, liver, heart, kidneys, these cuts have more vitamins than anything else in the world) - Lamb - Eggs - Fish and seafood - Animal fat - Butter - Beef fat and tallow - Salt - No... salt does not cause high blood pressure. (explained later about salt and high consumption of saturated fats) From now on I will list some facts that disprove the false accusations made against \*\*eating exclusively meat and fat. # “Human beings are omnivores” *“Our ancestors were gatherers and hunters*" To determine the proportion of animal foods in our ancestors’ diets, we can look at the amount of δ15 nitrogen in their fossils. By looking at levels of this isotope, researchers can infer where animals reside in the food chain, identifying their protein sources. Herbivores typically have δ15N levels of 3–7 percent, carnivores show levels of 6–12 percent, and omnivores exhibit levels in between. When samples from Neanderthals and early modern humans were analyzed, they showed levels of 12 percent and 13.5 percent, respectively, even higher than those of other known carnivores, such as hyenas and wolves. And from an energy efficiency standpoint, hunting large animals makes the most sense. Gathering plants and chasing small animals provides far fewer calories and nutrients relative to the energy invested. In more recently studied indigenous peoples, we have observed a similar pattern that clearly indicates a preference for animal foods over plant foods. For example, in Vilhjalmur Stefansson’s studies of the Eskimos. *“…fat, not protein, seemed to play a very important role in hunters’ decisions about which animals (male or female) to kill and which body parts to discard or carry away.”* Why were our ancestors and more recent indigenous peoples so interested in finding fat? At a very basic level, it was probably about calories. By weight, fat provides more than twice as many calories as protein or carbohydrates. Furthermore, human metabolism makes fat an exceptionally valuable and necessary food. If we think of ourselves as automobiles that need fuel for our metabolic engines, we should not put protein in our gas tank. For best results, our metabolic engine runs most efficiently on fat or carbohydrates. Eating animal foods has been a vital part of our evolution since the beginning. Katherine Milton, a researcher at UC Berkeley, came to the same conclusion in her paper “The Critical Role Played by Animal Source Foods in Human Evolution,” which states: “Without routine access to animal-source foods, it is highly unlikely that evolving humans could have achieved their unusually large and complex brains while simultaneously continuing their evolutionary trajectory as large, active, and highly social primates. As human evolution progressed, young children in particular, with their rapidly expanding large brains and higher metabolic and nutritional demands relative to adults, would have benefited from concentrated, high-quality foods such as meat." - https://pubmed.ncbi.nlm.nih.gov/14672286/ Skeletons from Greece and Turkey reveal that 12,000 years ago, the average height of hunter-gatherers was five feet, nine inches for men and five feet, five inches for women. But with the adoption of agriculture, adult height plummeted—ending any hope these poor herders had of dunking a basketball or playing competitive volleyball, if such sports had existed at the time. By 3000 B.C., men in this region of the world were only five feet, three inches tall, and women were five feet, reflecting a massive decline in their overall nutritional status. Many studies in diverse populations show a strong correlation between adult height and nutritional quality. A study analyzing male height in 105 countries came to the following conclusion: “In taller nations…consumption of plant proteins declines sharply at the expense of animal proteins, especially those from dairy products. Its highest consumption rates can be found in Northern and Central Europe, with the global peak in male height in the Netherlands (184 cm).” In addition to the decline in height, there is also evidence that Native Americans buried at Dickson Mounds suffered from increased bacterial infections. These infections leave scars on the outer surface of the bone, known as the periosteum, with the tibia being especially susceptible to such damage due to its limited blood flow. Examination of tibias from skeletons found in the mounds shows that after agriculture, the number of such periosteal lesions increased threefold, with a staggering eighty-four percent of bones from this period demonstrating this pathology. The lesions also tended to be more severe and to appear earlier in life in the bones of post-agricultural peoples. https://onlinelibrary.wiley.com/doi/full/10.1111/j.1747-0080.2007.00194.x https://pubmed.ncbi.nlm.nih.gov/10702160/ # Cholesterol Many “doctors” say that consuming saturated fat is harmful to your health, “your veins and arteries will clog with excess fat” “you will have a heart attack if you consume a lot of fat" and many other nonsense, and in exchange recommends that you replace fatty cuts of meat with lean meat and do everything with vegetable oil that causes cancer and makes men effeminate. Your brain is basically composed of fat and water, your neurons are made and repaired with fat, your cells, the basic unit of life, are composed of fat and protein, many of your hormones, especially sexual ones, are made from fat, there is no logical reason not to consume saturated fat other than several false "scientific articles". "The power plant of the cell is the mitochondria, which converts what we eat into energy. Ketones are an energy source derived from fat. Mitochondria prefer fat as energy (ketones) because transforming ketones into energy costs the mitochondria half the effort of using sugar (glucose) for energy." - https://pubmed.ncbi.nlm.nih.gov/28178565/ "With the help of saturated fats, calcium is properly stored in our bones. The interaction between calcium, vitamin D, and parathyroid hormone regulates calcium levels in the body. When there are calcium imbalances in the blood, our bones release calcium into the blood to find homeostasis." - https://www.healthpedian.org/the-role-of-calcium-in-the-human-body/ "The body needs cholesterol to support muscle repair and other cellular functions. This is why when there is cardiovascular disease, we see increased amounts of cholesterol in the area. Cholesterol is not there causing the problem, but the boat carrying fat was docked there for cholesterol and other nutrients to help fight the problem. Plaque is the body's attempt to deal with injury within the blood vessels." - *National Library of Medicine, “Cholesterol,” 2019* "Initially, the Plaque helps blood vessels stay strong and helps the vessels maintain their shape. But with the perpetual cycle of uncontrolled inflammation and leftover debris from cellular repair (cholesterol), over time plaque begins to grow and harden, reducing blood flow and oxygen to the heart. Both inflammation and repair require copious amounts of cholesterol and fats. So the body keeps sending these fatty substances to the site of the plaque — until either repair wins (plaque becomes sclerotic scars in the heart muscle, causing heart failure) or inflammation wins (atherosclerotic heart attack)" - https://pubmed.ncbi.nlm.nih.gov/21250192/ Inflammation in Atherosclerotic Cardiovascular Disease - https://pubmed.ncbi.nlm.nih.gov/21250192/ "Study finds that eating refined carbohydrates led to an increased risk of cardiovascular disease and obesity" - https://pmc.ncbi.nlm.nih.gov/articles/PMC5793267/ # “Meat causes cancer” Most of the misconceptions that red meat causes cancer come from a report by the World Health Organization's International Agency for Research on Cancer (IARC), which was released in 2015. Unfortunately, this report has been widely misrepresented by the mainstream media and is based on some very questionable interpretations of the science it claims to review. A closer look at a 2018 report on its findings reveals that only 14 of the 800 studies were considered in its final conclusions—and every single study was observational epidemiology. Why the other 786 were excluded remains a mystery, and this group included many interventional animal studies that clearly did not show a link between red meat and cancer. Of the fourteen epidemiological studies that were included in the IARC report, eight showed no link between meat consumption and the development of colon cancer. Of the remaining six studies, only one showed a statistically significant correlation between meat and cancer. In epidemiological research, one looks for correlation between two things and the strength of the correlation. Having just one study out of 800 that shows meat causes cancer is a mere fluke and becomes statistically insignificant. Interestingly, this was a study by Seventh-day Adventists in America — a religious group that advocates a plant-based diet. # Microbiota and Fiber I have seen several people and “doctors” saying that eating only meat would destroy your microbiota. And I have come to the conclusion that neither “doctors” nor most people know what a microbiota is. Microbiota is the set of several types of bacteria (millions) that exist in your stomach with the function of breaking down molecules of certain types of food that the body itself cannot get, fiber for example. Many times through the process of fermentation, which is why you have gas after eating your beloved oatmeal. People unconsciously believe that the microbiota is something fixed and unchangeable, but guess what… it is not. Your microbiota is determined by what you eat. If you love eating oatmeal, your microbiota will have a specific set of bacteria that can break down the oat molecule into a size that the body can absorb. If you follow a carnivorous diet, your microbiota will adapt to digest meat. ### Fiber Nutritional guidelines recommend large amounts of fiber in our diet, but what they don't tell you is that we only absorb around 6% of all the vegetable fiber we eat. In other words, it's insignificant! Another argument used by doctors and nutritionists is that it helps you go to the bathroom, but this is also a lie. Fiber doesn't help you evacuate, it forces you to do so. With the huge amount of undigestible food in your stomach (fiber), the intestine begins to force contractions, making this fecal matter go down, making you go to the bathroom. They also raise the argument that fibers are broken down into short-chain fatty acids, such as butyrate (butyric acid), propionate (propionic acid) and acetate (acetic acid). Butyrate is essential because it is the preferred fuel source for the endothelial cells of the large intestine. Butter, cream, and cheese contain butyrate in its absorbable form. Butter is the best source of butyric acid, or butyrate. In fact, the origins of the word butyric acid come from the Latin word *butyro*—the same origins as the word butter. “In 2012, a study in the Journal of Gastroenterology showed that reducing fiber (a precursor to short-chain fatty acids) helped participants with chronic constipation. The study lasted six months, and after two weeks without fiber, these participants were allowed to increase fiber as needed. These participants felt so much relief after two weeks without fiber that they continued without fiber for the entire six-month period. Of the high-fiber, low-fiber, and no-fiber groups, the zero-fiber participants had the highest bowel movement frequency.” - https://pmc.ncbi.nlm.nih.gov/articles/PMC3435786/ ### Bioavailability I said that our body can only absorb 6% of all the fiber we ingest. This is bioavailability, how much the body can absorb nutrients from a given food. Meat is the most bioavailable food on the planet! Grains and vegetables are not only not very bioavailable, but they also contain a huge amount of antinutrients. So if you eat a steak with some beans, you will not be able to absorb the nutrients from the beans, and the antinutrients in them will make it impossible to absorb a large amount of nutrients from the steak. https://pubmed.ncbi.nlm.nih.gov/23107545/ # Lack of nutrients and antioxidants in a carnivorous diet A major concern with the carnivorous diet is the lack of vitamin C, which would consequently lead to scurvy. Vitamin C plays an important role in the breakdown and transport of glucose into cells. In 2000 and 2001, the recommended daily intake of vitamin C effectively doubled. In fact, every 10 to 15 years, there has been a large increase in the recommended daily intake of vitamin C, as happened in 1974 and 1989. Interestingly, also in 1974, sugar prices became so high that high fructose corn syrup was introduced into the US market. Could the increase in readily available glucose foods and foods with high fructose corn syrup be a reason why we need more vitamin C? The question remains…. But this is not a cause for concern for the carnivore, liver is rich in vitamin C. You could easily reach the daily recommendation with liver or any cut of steak. 200-300g of steak already meets your needs and if the theory that the more sugar you eat, the more vitamin C you will get is true, then the more sugar you will eat is true. C is necessary if true, you could easily exceed the daily requirement. Meat and seafood are rich in ALL the nutrients that humans need to thrive. ### Antioxidants It is commonly said that fruits are rich in antioxidants but again this is a hoax, they are actually PRO-oxidants. These are substances that activate the mRF2 pathway of our immune system which causes the body to produce natural antioxidants. The body produces antioxidants, but many occur naturally in foods, Vitamin C, Vitamin E, Selenium and Manganese are all natural antioxidants. High concentrations of antioxidants can be harmful. Remember that high concentrations of antioxidants can increase oxidation and even protect against cancer cells. # Salt Consuming too much salt does not increase blood pressure and therefore increases the risk of heart disease and stroke. Studies show no evidence that limiting salt intake reduces the risk of heart disease. A 2011 study found that diets low in salt may actually increase the risk of death from heart attacks and strokes. Most importantly, they do not prevent high blood pressure. https://www.nytimes.com/2011/05/04/health/research/04salt.html # Sun This is not a dietary issue specifically, but there are things that can I would like to present that is against common sense when talking about the sun. It is common sense to say that the sun causes skin cancer and that we should not expose ourselves to it or, if we are exposed to the sun, use sunscreen, but no study proves that using sunscreen protects us from melanoma and basal cell carcinoma. The types of fatal melanomas usually occur in areas of the body that never see the sun, such as the soles of the feet. https://www.jabfm.org/content/24/6/735 In 1978, the first sunscreen was launched, and the market grew rapidly, along with cases of melanoma. Several studies show that sunscreens cause leaky gut (one of the main factors in chronic inflammation), hormonal dysfunction and neurological dysfunction. https://pubmed.ncbi.nlm.nih.gov/31058986/ If your concern when going out in the sun is skin cancer, don't worry, your own body's natural antioxidants will protect you. When they can no longer protect you, your skin starts to burn. (If you have to stay in the sun for work, for example, a good way to protect yourself is to rub coconut oil on your skin or just cover yourself with a few extra layers of thin clothing and a hat). Sunscreen gives you the false sense of protection by blocking the sunburn, so you stay out longer than your skin can handle, but sunscreens can only block 4% of UVA and UVB rays. www.westonaprice.org/health-topics/environmental-toxins/sunscreens-the-dark-side-of-avoiding-the-sun/ Interestingly, vitamin D deficiency is linked to increased cancer risks. It's a big contradiction to say that the greatest provider of vit. D causes cancer… https://med.stanford.edu/news/all-news/2010/10/skin-cancer-patients-more-likely-to-be-deficient-in-vitamin-d-study-finds.html Important roles of vitamin D: - **Regulation of Bone Metabolism** - Facilitates the **absorption of calcium and phosphorus** in the intestine. - Promotes bone mineralization and prevents diseases such as **osteoporosis**, **rickets** (in children) and **osteomalacia** (in adults). - **Immune Function** - Modulates the immune system, helping to reduce inflammation and strengthen the defense against infections, including **colds**, **flu** and other diseases. - May help reduce the incidence of autoimmune diseases such as **multiple sclerosis** and **rheumatoid arthritis**. - **Muscle Health** - Contributes to muscle strength and the prevention of weakness, especially in the elderly. - Reduces the risk of falls and fractures. - **Cardiovascular Function** - May help regulate blood pressure and heart function, reducing the risk of cardiovascular disease. - **Hormonal Balance** - Influences the production of hormones, including those associated with fertility and the functioning of the endocrine system. - Plays a role in insulin metabolism and glucose sensitivity. - **Brain Function and Mental Health** - Participates in mood regulation, which may reduce the risk of **depression** and improve mental health. - Has been associated with the prevention of neurodegenerative diseases, such as **Alzheimer's**. - **Anticancer Role** - Evidence suggests that vitamin D may inhibit the proliferation of cancer cells, especially in breast, prostate and colon cancers. - **Role in General Metabolism** - Contributes to metabolic health, regulating cellular growth and repair processes. --- I tried to present everything in the simplest and most understandable way possible, but there are things that require prior knowledge to truly understand. Below is a list of books that will show you everything I have shown you in a more technical and in-depth way. ### Book Recommendations https://amzn.to/3EbjVsD https://amzn.to/4awlnBZ All of my arguments have studies to validate them. Feel free to read them all and draw your own conclusions about what is best for you and your life. @ 0fa80bd3:ea7325de
2025-01-29 15:43:42Lyn Alden - биткойн евангелист или евангелистка, я пока не понял ``` npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a ``` Thomas Pacchia - PubKey owner - X - @tpacchia ``` npub1xy6exlg37pw84cpyj05c2pdgv86hr25cxn0g7aa8g8a6v97mhduqeuhgpl ``` calvadev - Shopstr ``` npub16dhgpql60vmd4mnydjut87vla23a38j689jssaqlqqlzrtqtd0kqex0nkq ``` Calle - Cashu founder ``` npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg ``` Джек Дорси ``` npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m ``` 21 ideas ``` npub1lm3f47nzyf0rjp6fsl4qlnkmzed4uj4h2gnf2vhe3l3mrj85vqks6z3c7l ``` Много адресов. Хз кто надо сортировать ``` https://github.com/aitechguy/nostr-address-book ``` ФиатДжеф - создатель Ностр - https://github.com/fiatjaf ``` npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 ``` EVAN KALOUDIS Zues wallet ``` npub19kv88vjm7tw6v9qksn2y6h4hdt6e79nh3zjcud36k9n3lmlwsleqwte2qd ``` Программер Коди https://github.com/CodyTseng/nostr-relay ``` npub1syjmjy0dp62dhccq3g97fr87tngvpvzey08llyt6ul58m2zqpzps9wf6wl ``` Anna Chekhovich - Managing Bitcoin at The Anti-Corruption Foundation https://x.com/AnyaChekhovich ``` npub1y2st7rp54277hyd2usw6shy3kxprnmpvhkezmldp7vhl7hp920aq9cfyr7 ```
@ 0fa80bd3:ea7325de
2025-01-29 15:43:42Lyn Alden - биткойн евангелист или евангелистка, я пока не понял ``` npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a ``` Thomas Pacchia - PubKey owner - X - @tpacchia ``` npub1xy6exlg37pw84cpyj05c2pdgv86hr25cxn0g7aa8g8a6v97mhduqeuhgpl ``` calvadev - Shopstr ``` npub16dhgpql60vmd4mnydjut87vla23a38j689jssaqlqqlzrtqtd0kqex0nkq ``` Calle - Cashu founder ``` npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg ``` Джек Дорси ``` npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m ``` 21 ideas ``` npub1lm3f47nzyf0rjp6fsl4qlnkmzed4uj4h2gnf2vhe3l3mrj85vqks6z3c7l ``` Много адресов. Хз кто надо сортировать ``` https://github.com/aitechguy/nostr-address-book ``` ФиатДжеф - создатель Ностр - https://github.com/fiatjaf ``` npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 ``` EVAN KALOUDIS Zues wallet ``` npub19kv88vjm7tw6v9qksn2y6h4hdt6e79nh3zjcud36k9n3lmlwsleqwte2qd ``` Программер Коди https://github.com/CodyTseng/nostr-relay ``` npub1syjmjy0dp62dhccq3g97fr87tngvpvzey08llyt6ul58m2zqpzps9wf6wl ``` Anna Chekhovich - Managing Bitcoin at The Anti-Corruption Foundation https://x.com/AnyaChekhovich ``` npub1y2st7rp54277hyd2usw6shy3kxprnmpvhkezmldp7vhl7hp920aq9cfyr7 ``` @ 57d1a264:69f1fee1
2025-01-28 02:36:34**About the role** In this role, you will work on the product design of umbrelOS, some of our umbrelOS apps, and the umbrel.com website. **What are you looking for in candidates?** Talent, passion, genuine love for your craft, and the desire to do meaningful work. What we’re not looking for: credentials and degrees. When you really love what you do, work feels like play. And when work feels like play, you become the best at it. That’s what we’re looking for. **We hope you:** - Like to spend your days staring at artboards in Figma - Are obsessed with creating delightful micro-interactions and animations - Are willing to throw away ideas if they're not great, and optimistic enough to keep hunting for new ones - Care about the details, maybe a bit too much (a pixel off ruins your sleep) - Are excited to collaborate with everyone on the team: engineers, customer facing folks, etc—you believe inspiration can come from anywhere - Have good judgement of when to ship - Like to level up your design skills continually - Put yourselves in the shoes of our users to craft a great experience - Enjoy being a generalist and are not tied down to a specific design, trend, or tools **Benefits** - 🚑 Health insurance - 💻 New work equipment - 🌎 Work from anywhere in the world - 💆♀️ Complete autonomy at work - 📚 Learning and development stipend - 🏝 Minimum 2-weeks of paid time off - ❤️ Most importantly — doing meaningful work that can change the world Apply at https://app.withrapha.com/job/692 originally posted at https://stacker.news/items/867248
@ 57d1a264:69f1fee1
2025-01-28 02:36:34**About the role** In this role, you will work on the product design of umbrelOS, some of our umbrelOS apps, and the umbrel.com website. **What are you looking for in candidates?** Talent, passion, genuine love for your craft, and the desire to do meaningful work. What we’re not looking for: credentials and degrees. When you really love what you do, work feels like play. And when work feels like play, you become the best at it. That’s what we’re looking for. **We hope you:** - Like to spend your days staring at artboards in Figma - Are obsessed with creating delightful micro-interactions and animations - Are willing to throw away ideas if they're not great, and optimistic enough to keep hunting for new ones - Care about the details, maybe a bit too much (a pixel off ruins your sleep) - Are excited to collaborate with everyone on the team: engineers, customer facing folks, etc—you believe inspiration can come from anywhere - Have good judgement of when to ship - Like to level up your design skills continually - Put yourselves in the shoes of our users to craft a great experience - Enjoy being a generalist and are not tied down to a specific design, trend, or tools **Benefits** - 🚑 Health insurance - 💻 New work equipment - 🌎 Work from anywhere in the world - 💆♀️ Complete autonomy at work - 📚 Learning and development stipend - 🏝 Minimum 2-weeks of paid time off - ❤️ Most importantly — doing meaningful work that can change the world Apply at https://app.withrapha.com/job/692 originally posted at https://stacker.news/items/867248 @ 9e69e420:d12360c2
2025-01-26 15:26:44Secretary of State Marco Rubio issued new guidance halting spending on most foreign aid grants for 90 days, including military assistance to Ukraine. This immediate order shocked State Department officials and mandates “stop-work orders” on nearly all existing foreign assistance awards. While it allows exceptions for military financing to Egypt and Israel, as well as emergency food assistance, it restricts aid to key allies like Ukraine, Jordan, and Taiwan. The guidance raises potential liability risks for the government due to unfulfilled contracts. A report will be prepared within 85 days to recommend which programs to continue or discontinue.
@ 9e69e420:d12360c2
2025-01-26 15:26:44Secretary of State Marco Rubio issued new guidance halting spending on most foreign aid grants for 90 days, including military assistance to Ukraine. This immediate order shocked State Department officials and mandates “stop-work orders” on nearly all existing foreign assistance awards. While it allows exceptions for military financing to Egypt and Israel, as well as emergency food assistance, it restricts aid to key allies like Ukraine, Jordan, and Taiwan. The guidance raises potential liability risks for the government due to unfulfilled contracts. A report will be prepared within 85 days to recommend which programs to continue or discontinue. @ 0463223a:3b14d673
2025-01-26 13:07:36Hmm so I heard that in order to improve my brain I should try writing… Ok groovy, I’ll give it a go. In all honesty I don’t know what to write, my brain is a jumble of noise and titbits of random knowledge. I likely know more about sound than the average person but as physics goes, I don’t have anything new or profound to add. Air moves and noises happen. Is there really any more to it? I could write some flowery bollocks about refraction, absorption coefficients and reverberation times, or I could write some out there, arty shit but I don’t think that adds any value to anyone. A lot of folks online have very strong beliefs in how the world operates or should operate. Whilst their conviction is strong, there’s also is a large percentage of people who totally disagree with them and think the exact opposite is the answer. That’s quite shit isn’t it? Humans have been around for 100,000 years or so and haven’t worked it out. I wonder what makes the internet celeb so certain they’ve got it right when the next internet celeb completely disagrees? I do my best to avoid any of these cunts but despite running to the obscurest social media platforms they still turn up with their profound statements. Meh. Ideologically I’m leaning toward anarchism but even that seems full of arguments and contradictions and ultimately I don’t think I can be arsed with identifying with any particular ideology. I tried reading some philosophy and struggled with it, although I deep fall into a lovely deep sleep. It’s fair to say I’m not the brightest button in the box. I have a wife, a couple of cats and lots of things that make nosies in my shed. That’s pretty cool right? Well it works for me. So why write this? I clearly wrote in the first sentence that I’m trying to improve my brain, a brain that’s gone through a number to twists and turns, a lot brain altering substances. I own that, no one forced me to. Beside, George Clinton was still smoking crack aged 80, didn’t do him any harm… I’m on the 5th paragraph. I don’t feel any smarter yet and each paragraph is getting shorter, having started from a low base. I guess I’m being too high time preference… Might be a while before I launch my Deep Thought podcasts where myself and a guest talk for 500 hours about the philosophy of money and 13 amp plug sockets. I’ve tortured myself enough. I’m posting this on Nostr where it will never go away.. lol. If you got this far, I congratulate/commiserate you and wish you a wonderful day.
@ 0463223a:3b14d673
2025-01-26 13:07:36Hmm so I heard that in order to improve my brain I should try writing… Ok groovy, I’ll give it a go. In all honesty I don’t know what to write, my brain is a jumble of noise and titbits of random knowledge. I likely know more about sound than the average person but as physics goes, I don’t have anything new or profound to add. Air moves and noises happen. Is there really any more to it? I could write some flowery bollocks about refraction, absorption coefficients and reverberation times, or I could write some out there, arty shit but I don’t think that adds any value to anyone. A lot of folks online have very strong beliefs in how the world operates or should operate. Whilst their conviction is strong, there’s also is a large percentage of people who totally disagree with them and think the exact opposite is the answer. That’s quite shit isn’t it? Humans have been around for 100,000 years or so and haven’t worked it out. I wonder what makes the internet celeb so certain they’ve got it right when the next internet celeb completely disagrees? I do my best to avoid any of these cunts but despite running to the obscurest social media platforms they still turn up with their profound statements. Meh. Ideologically I’m leaning toward anarchism but even that seems full of arguments and contradictions and ultimately I don’t think I can be arsed with identifying with any particular ideology. I tried reading some philosophy and struggled with it, although I deep fall into a lovely deep sleep. It’s fair to say I’m not the brightest button in the box. I have a wife, a couple of cats and lots of things that make nosies in my shed. That’s pretty cool right? Well it works for me. So why write this? I clearly wrote in the first sentence that I’m trying to improve my brain, a brain that’s gone through a number to twists and turns, a lot brain altering substances. I own that, no one forced me to. Beside, George Clinton was still smoking crack aged 80, didn’t do him any harm… I’m on the 5th paragraph. I don’t feel any smarter yet and each paragraph is getting shorter, having started from a low base. I guess I’m being too high time preference… Might be a while before I launch my Deep Thought podcasts where myself and a guest talk for 500 hours about the philosophy of money and 13 amp plug sockets. I’ve tortured myself enough. I’m posting this on Nostr where it will never go away.. lol. If you got this far, I congratulate/commiserate you and wish you a wonderful day. @ 9e69e420:d12360c2
2025-01-25 22:16:54President Trump plans to withdraw 20,000 U.S. troops from Europe and expects European allies to contribute financially to the remaining military presence. Reported by ANSA, Trump aims to deliver this message to European leaders since taking office. A European diplomat noted, “the costs cannot be borne solely by American taxpayers.” The Pentagon hasn't commented yet. Trump has previously sought lower troop levels in Europe and had ordered cuts during his first term. The U.S. currently maintains around 65,000 troops in Europe, with total forces reaching 100,000 since the Ukraine invasion. Trump's new approach may shift military focus to the Pacific amid growing concerns about China. [Sauce](https://www.stripes.com/theaters/europe/2025-01-24/trump-europe-troop-cuts-16590074.html)
@ 9e69e420:d12360c2
2025-01-25 22:16:54President Trump plans to withdraw 20,000 U.S. troops from Europe and expects European allies to contribute financially to the remaining military presence. Reported by ANSA, Trump aims to deliver this message to European leaders since taking office. A European diplomat noted, “the costs cannot be borne solely by American taxpayers.” The Pentagon hasn't commented yet. Trump has previously sought lower troop levels in Europe and had ordered cuts during his first term. The U.S. currently maintains around 65,000 troops in Europe, with total forces reaching 100,000 since the Ukraine invasion. Trump's new approach may shift military focus to the Pacific amid growing concerns about China. [Sauce](https://www.stripes.com/theaters/europe/2025-01-24/trump-europe-troop-cuts-16590074.html) @ 228dde34:b5d0345e
2025-01-25 01:59:57##### By Jonathan Tan ##### Lead Editor ##### Hype Issue #60 ##### JONATHAN TAN explores the recent rise in popularity of online gambling, and its consequences on the population’s most vulnerable.  The persistent rise in the gaming industry, fueled by the introduction of online gambling, seems to have no end. Experts are now worrying about the effects of this epidemic on public health and safety. “Many people might be really experiencing harms from gambling — we think that it’s probably around 72 million people globally,” said Louisa Degenhardt, a professor at the University of New South Wales in Sydney, in an[NBC article.](https://www.nbcnews.com/health/health-news/gambling-industry-growth-threat-public-health-report-rcna175356) The online gambling craze has spread worldwide, and even Singapore, with its strict gambling regulations, is not immune to it. In a recent[survey](https://www.channelnewsasia.com/singapore/national-council-problem-gambling-rate-continues-fall-4761621)conducted by the National Council on Problem Gambling (NCPG), illegal online gambling rates have more than tripled since 2020, from 0.3% to 1.0% in the past 4 years. This statistic alone highlights an already concerning trend. Even more troubling, however, is that the illegal nature of these websites means there are no regulatory laws or age restrictions. As a result, the proliferation of these online websites has allowed a brand new demographic to start gambling: the Singaporean youth. ### How to lose thousands before adulthood “I started gambling when I was 13 years old, at a friend's house,” George (not his real name) shares. Now an 18-year-old student, George recalls how a simple game among friends slowly grew into an all-consuming gambling addiction.  *In NCPG’s 2023 survey, 8% of respondents reported participating in social gambling activities: gambling which occurs within individuals’ homes, among family members. Photo from Shutterstock.* Initially, George and his friends gambled with low stakes, like a dollar here and there. However, the games slowly escalated: from $1 to $10, then to $100, and eventually to $1000. Unsurprisingly, with such large sums at stake, George’s relationship with his friends began to strain. “I realized that after a certain point, the more and more money we [bet], the more and more our relationship with each other [soured]; and so we decided to curb it at a maximum buy-in of $20 per game,” George says. The new rule eased the tension between George and his friends, but it inadvertently created a new problem: George no longer felt the thrill of winning large sums. As a result, he began seeking other ways to gamble. “The first time I gambled online was when I was 16 years old. A friend had introduced me to a gambling website,” he recalls. “And at first it was all right. I won a bit, I lost a bit, but no one got hurt.” But it didn’t take long for him to get hooked; a single sports bet was what netted George his first big win. “On the first day, I went from $10 to $800 from a simple parlay bet,” George says. “I felt unstoppable. Adrenaline was pumping through my veins, and [I felt] I could never lose. [After] that day, I gambled like $100 almost every day for a straight month.”  *A parlay (a form of sports betting that has recently surged in popularity) is a single bet that combines two or more bets into one. While doing this drastically decreases the odds of winning, it also drastically increases the potential payout. Photo from Getty Images.* Nothing could stop George’s gambling fervor. Even after losing nearly a thousand dollars on a single blackjack hand, all George did was place a bigger bet to try and win it back. “Every morning, when I [woke] up, all I could think about was gambling,” he shares. And of course, George’s obsession with online gambling was only exacerbated by the accessibility of these websites. First, the online nature of these websites allowed George to gamble anywhere, at any time. “For online gambling, you have it right at your fingertips. As soon as you wake up, you can just log on the computer and start betting huge amounts of money,” he mentions. But more importantly, these illegal gambling websites enabled George to do something he was never old enough to do in the first place. “I'm too young to gamble at a real casino or a physical casino. But online gambling makes it way more accessible because there's no verification of ID,” George says. ### Consequences, consequences Therein lies the predatory nature of these illegal websites. While anyone can fall victim to a gambling addiction, certain factors may make the youth especially vulnerable. “The adolescent brain is still developing, particularly the prefrontal cortex, which is responsible for decision-making, impulse control, and risk assessment. This makes young people more susceptible to impulsive behaviors,” says Jat Tan, the Communications and Events Executive at WE CARE Community Services.  *The prefrontal cortex is primarily developed during adolescence, and is fully developed at the age of 25 years. Photo from iStock.* Additionally, other factors such as peer pressure, social media, or limited life experience, could result in young Singaporeans being more open to gambling. Lastly, one popular reason why the youth are drawn to gambling, is their limited financial freedom. “While youths are in school, they have a significantly lower earning power as opposed to adults. The demands from school usually means that they can only afford to work part-time jobs,” Mrs Tan shares. Despite this, many young Singaporeans still want to live extravagant lifestyles. With the youth getting exposed to lavish, ostentatious lifestyles on social media, many begin to feel envious and yearn for the same luxuries. And now, with the introduction of illegal online sites, the lack of age restrictions allows these youths to gamble in an attempt to achieve this better life. ### What can be done? The increase in the number of adolescent gamblers is a new challenge for the Singaporean government. Before the advent of online gambling, many safeguards were in place to protect Singaporeans from developing gambling addictions. In particular, safeguards that limit Singaporeans’ access to legal gambling services seem to be working; the overall percentage of gambling Singaporeans has fallen from 44% to 40% from 2020 to 2023. However, the unprecedented accessibility and convenience of online gambling sites have allowed Singapore’s tech-savvy youth to bypass these regulations; and now, the Singaporean government needs to update its laws to keep up with the growing gambling industry. Of course, the Singaporean Government has been cracking down on illegal online gambling. As of September 2024, the Gambling Regulatory Authority (GRA) has blocked access to more than 1,900 remote gambling websites. But despite the GRA’s efforts, these online gambling providers continue to survive, like weeds in a garden. “GRA recognises that the borderless nature of the Internet makes it easy for unlawful gambling operators to offer their products to users in Singapore any time and anywhere,” said a GRA spokesman in [a Straits Times article.](https://www.straitstimes.com/singapore/crackdown-on-illegal-online-gambling-but-addiction-can-be-hard-to-beat) Currently, there are calls for the government to shift its focus. “While Singapore has done well putting in place responsible gaming and safety measures to mitigate the risks of casino gambling, it is timely to focus more attention to address the risk of illegal online gambling as well,” said Ms Tham, Clinical director of We Care Community Services, [in a Straits Times article.](https://www.straitstimes.com/singapore/fewer-singapore-residents-gambled-but-more-do-so-online-illegally) Ultimately, as the gambling industry becomes more technologically advanced, it becomes harder for Singapore to regulate gambling the same way it used to. Thus, it may be time for the Singaporean government to consider a different solution. “Better educating youths on the harms and consequences of gambling, as well as resources available should things go awry, would be the best option to nip the issue in the bud,” Ms Tan suggests. Instead of focusing on restrictive legislation, education could be a preventative measure used to curb adolescent gambling. “A higher level of awareness would enable youths to face issues like gambling with their eyes wide open - they will have a rough idea of what they're getting themselves into, and will have a rough idea of what to do if things go wrong,” she shares.
@ 228dde34:b5d0345e
2025-01-25 01:59:57##### By Jonathan Tan ##### Lead Editor ##### Hype Issue #60 ##### JONATHAN TAN explores the recent rise in popularity of online gambling, and its consequences on the population’s most vulnerable.  The persistent rise in the gaming industry, fueled by the introduction of online gambling, seems to have no end. Experts are now worrying about the effects of this epidemic on public health and safety. “Many people might be really experiencing harms from gambling — we think that it’s probably around 72 million people globally,” said Louisa Degenhardt, a professor at the University of New South Wales in Sydney, in an[NBC article.](https://www.nbcnews.com/health/health-news/gambling-industry-growth-threat-public-health-report-rcna175356) The online gambling craze has spread worldwide, and even Singapore, with its strict gambling regulations, is not immune to it. In a recent[survey](https://www.channelnewsasia.com/singapore/national-council-problem-gambling-rate-continues-fall-4761621)conducted by the National Council on Problem Gambling (NCPG), illegal online gambling rates have more than tripled since 2020, from 0.3% to 1.0% in the past 4 years. This statistic alone highlights an already concerning trend. Even more troubling, however, is that the illegal nature of these websites means there are no regulatory laws or age restrictions. As a result, the proliferation of these online websites has allowed a brand new demographic to start gambling: the Singaporean youth. ### How to lose thousands before adulthood “I started gambling when I was 13 years old, at a friend's house,” George (not his real name) shares. Now an 18-year-old student, George recalls how a simple game among friends slowly grew into an all-consuming gambling addiction.  *In NCPG’s 2023 survey, 8% of respondents reported participating in social gambling activities: gambling which occurs within individuals’ homes, among family members. Photo from Shutterstock.* Initially, George and his friends gambled with low stakes, like a dollar here and there. However, the games slowly escalated: from $1 to $10, then to $100, and eventually to $1000. Unsurprisingly, with such large sums at stake, George’s relationship with his friends began to strain. “I realized that after a certain point, the more and more money we [bet], the more and more our relationship with each other [soured]; and so we decided to curb it at a maximum buy-in of $20 per game,” George says. The new rule eased the tension between George and his friends, but it inadvertently created a new problem: George no longer felt the thrill of winning large sums. As a result, he began seeking other ways to gamble. “The first time I gambled online was when I was 16 years old. A friend had introduced me to a gambling website,” he recalls. “And at first it was all right. I won a bit, I lost a bit, but no one got hurt.” But it didn’t take long for him to get hooked; a single sports bet was what netted George his first big win. “On the first day, I went from $10 to $800 from a simple parlay bet,” George says. “I felt unstoppable. Adrenaline was pumping through my veins, and [I felt] I could never lose. [After] that day, I gambled like $100 almost every day for a straight month.”  *A parlay (a form of sports betting that has recently surged in popularity) is a single bet that combines two or more bets into one. While doing this drastically decreases the odds of winning, it also drastically increases the potential payout. Photo from Getty Images.* Nothing could stop George’s gambling fervor. Even after losing nearly a thousand dollars on a single blackjack hand, all George did was place a bigger bet to try and win it back. “Every morning, when I [woke] up, all I could think about was gambling,” he shares. And of course, George’s obsession with online gambling was only exacerbated by the accessibility of these websites. First, the online nature of these websites allowed George to gamble anywhere, at any time. “For online gambling, you have it right at your fingertips. As soon as you wake up, you can just log on the computer and start betting huge amounts of money,” he mentions. But more importantly, these illegal gambling websites enabled George to do something he was never old enough to do in the first place. “I'm too young to gamble at a real casino or a physical casino. But online gambling makes it way more accessible because there's no verification of ID,” George says. ### Consequences, consequences Therein lies the predatory nature of these illegal websites. While anyone can fall victim to a gambling addiction, certain factors may make the youth especially vulnerable. “The adolescent brain is still developing, particularly the prefrontal cortex, which is responsible for decision-making, impulse control, and risk assessment. This makes young people more susceptible to impulsive behaviors,” says Jat Tan, the Communications and Events Executive at WE CARE Community Services.  *The prefrontal cortex is primarily developed during adolescence, and is fully developed at the age of 25 years. Photo from iStock.* Additionally, other factors such as peer pressure, social media, or limited life experience, could result in young Singaporeans being more open to gambling. Lastly, one popular reason why the youth are drawn to gambling, is their limited financial freedom. “While youths are in school, they have a significantly lower earning power as opposed to adults. The demands from school usually means that they can only afford to work part-time jobs,” Mrs Tan shares. Despite this, many young Singaporeans still want to live extravagant lifestyles. With the youth getting exposed to lavish, ostentatious lifestyles on social media, many begin to feel envious and yearn for the same luxuries. And now, with the introduction of illegal online sites, the lack of age restrictions allows these youths to gamble in an attempt to achieve this better life. ### What can be done? The increase in the number of adolescent gamblers is a new challenge for the Singaporean government. Before the advent of online gambling, many safeguards were in place to protect Singaporeans from developing gambling addictions. In particular, safeguards that limit Singaporeans’ access to legal gambling services seem to be working; the overall percentage of gambling Singaporeans has fallen from 44% to 40% from 2020 to 2023. However, the unprecedented accessibility and convenience of online gambling sites have allowed Singapore’s tech-savvy youth to bypass these regulations; and now, the Singaporean government needs to update its laws to keep up with the growing gambling industry. Of course, the Singaporean Government has been cracking down on illegal online gambling. As of September 2024, the Gambling Regulatory Authority (GRA) has blocked access to more than 1,900 remote gambling websites. But despite the GRA’s efforts, these online gambling providers continue to survive, like weeds in a garden. “GRA recognises that the borderless nature of the Internet makes it easy for unlawful gambling operators to offer their products to users in Singapore any time and anywhere,” said a GRA spokesman in [a Straits Times article.](https://www.straitstimes.com/singapore/crackdown-on-illegal-online-gambling-but-addiction-can-be-hard-to-beat) Currently, there are calls for the government to shift its focus. “While Singapore has done well putting in place responsible gaming and safety measures to mitigate the risks of casino gambling, it is timely to focus more attention to address the risk of illegal online gambling as well,” said Ms Tham, Clinical director of We Care Community Services, [in a Straits Times article.](https://www.straitstimes.com/singapore/fewer-singapore-residents-gambled-but-more-do-so-online-illegally) Ultimately, as the gambling industry becomes more technologically advanced, it becomes harder for Singapore to regulate gambling the same way it used to. Thus, it may be time for the Singaporean government to consider a different solution. “Better educating youths on the harms and consequences of gambling, as well as resources available should things go awry, would be the best option to nip the issue in the bud,” Ms Tan suggests. Instead of focusing on restrictive legislation, education could be a preventative measure used to curb adolescent gambling. “A higher level of awareness would enable youths to face issues like gambling with their eyes wide open - they will have a rough idea of what they're getting themselves into, and will have a rough idea of what to do if things go wrong,” she shares. @ bcea2b98:7ccef3c9
2025-01-24 23:21:05originally posted at https://stacker.news/items/862840
@ bcea2b98:7ccef3c9
2025-01-24 23:21:05originally posted at https://stacker.news/items/862840 @ 378562cd:a6fc6773
2025-01-23 17:57:13**Top USA News** 1. **President Trump Threatens Tariffs on Non-U.S. Manufacturers**In a speech at the World Economic Forum in Davos, President Donald Trump announced plans to impose tariffs on companies that do not manufacture their products in the United States, aiming to boost domestic production. [The Guardian](https://www.theguardian.com/us-news/live/2025/jan/23/donald-trump-pardons-january-6-us-president-joe-biden-jd-vance-republicans-live-news?utm_source=chatgpt.com) 2. **Historic Winter Storm Sweeps Across Southern U.S**.A severe winter storm has blanketed the southern United States with snow and freezing temperatures, leading to widespread power outages and hazardous travel conditions. [WSJ](https://www.wsj.com/news/archive/2025/01/23?utm_source=chatgpt.com) 3. **Trump Administration Orders Federal DEI Staff on Leave**The Trump administration has directed all federal employees working in Diversity, Equity, and Inclusion (DEI) programs to be placed on paid leave, with plans to dismiss all DEI program employees by January 31. [The Guardian](https://www.theguardian.com/us-news/live/2025/jan/22/donald-trump-china-sanctions-tariff-diversity-us-politics-live-latest-news?utm_source=chatgpt.com) 4. **U.S. Stock Futures Mixed After Tech-Driven Rally**Following a tech-fueled rise, U.S. stock futures show mixed results. The S&P 500 futures dipped slightly after nearing record highs, while Nasdaq futures declined by 0.5%, and Dow Jones futures saw a slight increase. [Investopedia](https://www.investopedia.com/5-things-to-know-before-the-stock-market-opens-january-23-2025-8778964?utm_source=chatgpt.com) 5. **Trump Pardons January 6 Capitol Rioters**President Trump has issued pardons for individuals convicted in relation to the January 6 Capitol riot, a move that has sparked controversy and debate across the political spectrum. [The Guardian](https://www.theguardian.com/us-news/live/2025/jan/23/donald-trump-pardons-january-6-us-president-joe-biden-jd-vance-republicans-live-news?utm_source=chatgpt.com) 6. **California Wildfires Cause Extensive Damage**Ongoing wildfires in Los Angeles County are causing significant destruction, with estimated damages exceeding $135 billion. Governor Gavin Newsom warns that these could become the worst natural disaster in American history. [Wikipedia](https://en.wikipedia.org/wiki/Portal%3ACurrent_events/January_2025?utm_source=chatgpt.com) 7. **President Trump Withdraws U.S. from Paris Climate Agreement**In a series of executive orders, President Trump has withdrawn the United States from the Paris Climate Agreement, citing economic concerns and a focus on American energy independence. [The Guardian](https://www.theguardian.com/us-news/live/2025/jan/21/donald-trump-inauguration-presidency-executive-orders-pardons-day-two-live-blog?utm_source=chatgpt.com) 8. **Trump Administration Re-designates Houthis as Terrorist Organization**The Trump administration has re-designated the Yemeni Houthi movement as a foreign terrorist organization, reversing a previous decision and impacting international relations in the region. [Wikipedia](https://en.wikipedia.org/wiki/2025_in_the_United_States?utm_source=chatgpt.com) 9. **President Trump Announces $500 Billion AI Investment**President Trump, alongside tech executives, has announced a $500 billion investment in artificial intelligence infrastructure, aiming to bolster the United States' position in the global tech industry. [WSJ](https://www.wsj.com/news/archive/2025/01/23?utm_source=chatgpt.com) 10. **ChatGPT Experiences Large-Scale Outage**A significant outage of the AI tool ChatGPT has been reported, affecting users worldwide. The cause of the disruption is under investigation. [Wikipedia](https://en.wikipedia.org/wiki/2025_in_the_United_Kingdom?utm_source=chatgpt.com) **Top International News** 1. **Israeli Military Conducts Extensive Raid in Jenin**The Israeli military launched a significant operation in Jenin, resulting in at least 10 Palestinian deaths and numerous injuries. The raid, named "Iron Wall," involved airstrikes and ground forces, escalating tensions in the West Bank. [The Guardian](https://www.theguardian.com/world/2025/jan/23/first-edition-west-bank-settlers-israel-military?utm_source=chatgpt.com) 2. **Micheál Martin Appointed as Irish Taoiseach**Micheál Martin has been confirmed as Ireland's new Taoiseach following a day of delays and disagreements in the Irish parliament. His immediate focus includes forming his cabinet and addressing Ireland's housing crisis. [The Guardian](https://www.theguardian.com/world/live/2025/jan/23/europe-dail-micheal-martin-rows-ireland-weather-storm-eowyn-latest-updates?utm_source=chatgpt.com)
@ 378562cd:a6fc6773
2025-01-23 17:57:13**Top USA News** 1. **President Trump Threatens Tariffs on Non-U.S. Manufacturers**In a speech at the World Economic Forum in Davos, President Donald Trump announced plans to impose tariffs on companies that do not manufacture their products in the United States, aiming to boost domestic production. [The Guardian](https://www.theguardian.com/us-news/live/2025/jan/23/donald-trump-pardons-january-6-us-president-joe-biden-jd-vance-republicans-live-news?utm_source=chatgpt.com) 2. **Historic Winter Storm Sweeps Across Southern U.S**.A severe winter storm has blanketed the southern United States with snow and freezing temperatures, leading to widespread power outages and hazardous travel conditions. [WSJ](https://www.wsj.com/news/archive/2025/01/23?utm_source=chatgpt.com) 3. **Trump Administration Orders Federal DEI Staff on Leave**The Trump administration has directed all federal employees working in Diversity, Equity, and Inclusion (DEI) programs to be placed on paid leave, with plans to dismiss all DEI program employees by January 31. [The Guardian](https://www.theguardian.com/us-news/live/2025/jan/22/donald-trump-china-sanctions-tariff-diversity-us-politics-live-latest-news?utm_source=chatgpt.com) 4. **U.S. Stock Futures Mixed After Tech-Driven Rally**Following a tech-fueled rise, U.S. stock futures show mixed results. The S&P 500 futures dipped slightly after nearing record highs, while Nasdaq futures declined by 0.5%, and Dow Jones futures saw a slight increase. [Investopedia](https://www.investopedia.com/5-things-to-know-before-the-stock-market-opens-january-23-2025-8778964?utm_source=chatgpt.com) 5. **Trump Pardons January 6 Capitol Rioters**President Trump has issued pardons for individuals convicted in relation to the January 6 Capitol riot, a move that has sparked controversy and debate across the political spectrum. [The Guardian](https://www.theguardian.com/us-news/live/2025/jan/23/donald-trump-pardons-january-6-us-president-joe-biden-jd-vance-republicans-live-news?utm_source=chatgpt.com) 6. **California Wildfires Cause Extensive Damage**Ongoing wildfires in Los Angeles County are causing significant destruction, with estimated damages exceeding $135 billion. Governor Gavin Newsom warns that these could become the worst natural disaster in American history. [Wikipedia](https://en.wikipedia.org/wiki/Portal%3ACurrent_events/January_2025?utm_source=chatgpt.com) 7. **President Trump Withdraws U.S. from Paris Climate Agreement**In a series of executive orders, President Trump has withdrawn the United States from the Paris Climate Agreement, citing economic concerns and a focus on American energy independence. [The Guardian](https://www.theguardian.com/us-news/live/2025/jan/21/donald-trump-inauguration-presidency-executive-orders-pardons-day-two-live-blog?utm_source=chatgpt.com) 8. **Trump Administration Re-designates Houthis as Terrorist Organization**The Trump administration has re-designated the Yemeni Houthi movement as a foreign terrorist organization, reversing a previous decision and impacting international relations in the region. [Wikipedia](https://en.wikipedia.org/wiki/2025_in_the_United_States?utm_source=chatgpt.com) 9. **President Trump Announces $500 Billion AI Investment**President Trump, alongside tech executives, has announced a $500 billion investment in artificial intelligence infrastructure, aiming to bolster the United States' position in the global tech industry. [WSJ](https://www.wsj.com/news/archive/2025/01/23?utm_source=chatgpt.com) 10. **ChatGPT Experiences Large-Scale Outage**A significant outage of the AI tool ChatGPT has been reported, affecting users worldwide. The cause of the disruption is under investigation. [Wikipedia](https://en.wikipedia.org/wiki/2025_in_the_United_Kingdom?utm_source=chatgpt.com) **Top International News** 1. **Israeli Military Conducts Extensive Raid in Jenin**The Israeli military launched a significant operation in Jenin, resulting in at least 10 Palestinian deaths and numerous injuries. The raid, named "Iron Wall," involved airstrikes and ground forces, escalating tensions in the West Bank. [The Guardian](https://www.theguardian.com/world/2025/jan/23/first-edition-west-bank-settlers-israel-military?utm_source=chatgpt.com) 2. **Micheál Martin Appointed as Irish Taoiseach**Micheál Martin has been confirmed as Ireland's new Taoiseach following a day of delays and disagreements in the Irish parliament. His immediate focus includes forming his cabinet and addressing Ireland's housing crisis. [The Guardian](https://www.theguardian.com/world/live/2025/jan/23/europe-dail-micheal-martin-rows-ireland-weather-storm-eowyn-latest-updates?utm_source=chatgpt.com) @ c8cf63be:86691cfe
2025-01-23 12:51:20### Mark Fishers ‘Acid Communism’ und der ‘Capitalist Realism’ > “it is easier to kill the living than to kill the undead”[1] Die lebenden sind wir Menschen, *the undead* ist der gegenwärtige neoliberalismus[2] Mark Fischers Analyse über den bestehenden Zustand ist erschütternd: > “let’s say music hello just go on music in the last 10 years one thing > one single thing that couldn’t have come out in the 20th century”[3] Es gibt nicht neues unter dem Himmel, alle Kreativität ist erschöpft, “die Verdinglichung” von der Horkheimer und Adorno sprachen, “…, ist so dicht geworden,…” die Wirklichkeit des ‘Capitalist Realism’ ist manifest und undurchdringlich, die Löcher, die kleinen alternativen, sind versiegelt. Schon im Denken sind die alternativen versperrt und das Denken ist ein gemeinsames, niemand kann für sich alleine Denken oder kreativ sein. Denken und kreativ sein sind das Ergebnis einer Gesellschaftlichen Voraussetzung. Es gibt keine neue Musik mehr weil die Musik untot ist. In immer neuer Auflagen, in der mechanische Reproduktion, wiederbelebt man die Toten, und erstickt das lebendige. > “… but there’s nothing about us that was good or better than you > you’re anybody it’s just that we were lucky and you all are unlucky > …”[4] Wenn eine junge Frau auf seine Feststellung reagiert mit Unglaube und Abwehr. > “… so what you’re basically saying is that i guess your generation or > the previous generation was better because you had more time to pursue > your own projects and you also think that you were more creative or > the previous generation was more creative …”[5] Dann weil sie die Enge der Umstände nicht erkennen kann, und vielleicht auch weil sie die Dinge auf sich persönlich bezieht, wie es das gegenwärtige Denken nahelegt: Sowohl der kompetitive Vergleich als auch die individuelle Schuldzuordnung findet sich in der Aussage. Fischer hingegen erklärt dies mit den Herrschenden Umständen die es den Menschen unmöglich machen sich den *wahren Sachverhalt* klar zu machen und damit jede Alternative im Denken versperren: > “.. but okay let’s be clear about what i’m saying creativity isn’t a > property of individuals ever it’s a property of a social or collective > scene like that you know that’s so that it’s not like the individuals > are less creative than they used to be that’s just not how creativity > works creativity is possible because of is possible because of social > conditions and those social conditions have been removed …”[6] Fischers Aufmerksamkeit richtet sich auf die die Umstände vor dem Capitalism Realism, denn dieser ist seiner Meinung nach schon eine Reaktion, eine Reaktion auf die “Counterculture” auf das “spectre of a world which could be free”[7]. Wenn es ein Gründungsereignis des Capital Realism geben sollte wäre dies nach Fischer der Putsch Pinochets in Chile 1973.[8] Seiner Zeit voraus war Hunter S. Thompson, seine Drogengeschwängerten Reflexionen fassen den Kern sehr genau, für ihn war 1971 schon der Moment an dem er die revision verortet: > “… wir ritten auf dem Kamm einer hohen und wunderschönen Welle … Und > jetzt, weniger als fünf Jahre später, kannst du auf einen steilen > Hügel in Las Vegas klettern und nach Westen blicken, und wenn du die > richtigen Augen hast, dann kannst du die Hochwassermarkierung fast > sehen -die Stelle, wo sich die Welle schließlich brach und > zurückrollte.”[9] Acid! Die psychedelische Zeit: > “Instead of seeking to overcome capital, we should focus on what > capital must always obstruct: the collective capacity to produce, care > and enjoy.”[10] und weiter > “The overcoming of capital has to be fundamentally based on the simple > insight that, far from being about “wealth creation”, capital > necessarily and always blocks the production of common wealth.” Der Zauber der Psycedlischen Zeit war die ignoranz, das Verweigern des bestehenden Narativs. Oder wie Fischer sagt, die Frage nach dem Bewustsein und seiner Beziehung dem dem was wir als Wiklichkeit wahrnemen.[11] > “turn on, tune in, drop out” [12] oder noch klarer Ken Kesey: > “There’s only one thing to do . > .. there’s only one thing’s gonna do any good at all… > And that’s everybody just look at it, > look at the war, and turn your backs and say … Fuck it..” [13] Die Imagination des *wahren Sachverhaltes* “look at it” sagt Kesey, überzeugt euch selbst. Es braucht nicht mehr als das Schauen des Krieges, bei ihm der Viatnam Krieg, um zu verstehen das nur die Verweigerung, das “Fuck it” geeignet ist dem ganzen seine legitimität zu verweigern. Das war der Zauber der psychedelichen Zeit, auch der der 90’er, die als unpolitsch gelten. Aus dieser Perspektive ist klar das das unpolitsche, das politsche war. Die love-Parade war nicht unpolitisch und die gesellschaflichenr Verändeung die durch diese Psychedleische Zeit in Bewegung gesetzt wurden können wir noch heute fühlen. Die Canabis Legalisierung, die veränderte Wahrnehmng von Homosexualität. Das “chill out”. Die tribal Tattoos.[14] Und auch die wärmste Kampange der Europawahl 2024, “Fickt euch doch alle.”[15] ist erst durch die psychedelische Zeit der 90’er möglich, hier wurde die Sinnlichkeit gestiftet die es braucht damit dieser Satz seine wärme bekommt. Die Demokratesierung der Neurologie durch die verwendung von Halozinogenen rücken die Frage nach der Wirklichkeit und des wahren Sachverhaltes in den Mittelpunkt. > “what they mainstreamed was this psychedelic consciousness with its > key notion of the plasticity of reality”[16] Sie ist auch eine Sekularisierung, eine demokratisierung des Sakralen, das vorher durch Klassen wie Schamanen oder Druiden kontroliert wurde wird zugänglich und erfahrbar. > “…, there was actually a demystificatory and materialist dimension to > this.”[17] Was sich so aussprechen läßt: > *“Wenn Gott liebe ist, dann ist er eine MDMA geschwängerte, psycedelic > trance Party, anfang der 90’er jahre des letzten Jahrtausend.”* Es loht sich also für uns ältere an die nicht so ferne Zeit der frühen 90’er Jahre zurück zu denken in der die Welt offen schien, die Polarität des kalten Krieges vergangen war, das Ende der Geschichte ausgerüfen wurde.[18] Da war die Idee das dies nicht der Siegt des Kapitalismus ist, sondern ein Sieg der Menschen die die Spirale des Schreckens und der Eskalation durchbrechen real. Es schien wie ein transzendieren des gegebenen Spiels und seiner Regeln wie es die AI in “war games”[19] realisiert, stattzufinden. Auf “No future”[20] folgte “No Paradise? Create it.”[21], es fand ein “unforgetting”[22] der alten, in den 60’er entwickelten Formen statt: Die Modulierung der 303, das Dayglow und das Strobo, alles Elemente des Acid Test[23]. *“the collective capacity to produce, care and enjoy”* ------------------------------------------------------------------------ ### References: [1] Fisher, M., Mark Fisher - DOCH Lectures 1 2011: <https://www.youtube.com/watch?v=f-9nY5rboK8> 32m 42s [2] Fisher, M., How to kill a zombie: strategizing the end of neoliberalism 2013: <https://www.opendemocracy.net/en/how-to-kill-zombie-strategizing-end-of-neoliberalism/>. [3] Fisher, 1968., Mark, Cybertime Crisis 2013: <https://www.youtube.com/watch?v=zOQgCg73sfQ> ab 1h 42m 12s [4] Fisher, 1968., Mark, ebenda ab 1h 35m 30s [5] Fisher, 1968., Mark, ebenda ab 1h 42m 12s [6] Fisher, 1968., Mark, ebenda ab 1h 47m 20s [7] Fisher, 1968., Mark et al., K-punk : the collected and unpublished writings of Mark Fisher (2004-2016) 2018. Abs. 153.5 [8] Fisher, 1968., Mark et al., ebenda. Abs. 153.7 “If there was a founding event of capitalist realism, it would be the violent destruction of the Allende government in Chile by General Pinochet’s American-backed coup.” [9] Hunter S. Thompson “Fear and loathing” Seite 89 [10] Fisher, 1968., Mark et al., K-punk : the collected and unpublished writings of Mark Fisher (2004-2016) 2018. Abs. 153.5 Statz 3 [11] Fisher, 1968., Mark et al., ebenda. Abs. 153.46 [12] Timothy Leary in 1966, der damals gefährlichste Mann der Welt.(Richard Nixxon) [13] Wolfe, Tom., The electric kool-aid acid test. 1999. Seite 360 [14] Christmann, K., Gruppen-Tattoo-Termin im Bundestag: 19 Abgeordnete zeigen vollen Körpereinsatz 2024: <https://www.tagesspiegel.de/politik/gruppen-tattoo-termin-im-bundestag-19-abgeordnete-zeigen-vollen-korpereinsatz-11665559.html>. [15] DiePartei, Fickt euch doch alle! (DINA1) 2024: <https://www.parteibedarf.de/Fickt-euch-doch-alle-DINA1/SW10115>. [16] Fisher, M., all of this is temporary: Mark Fisher 2016: <https://www.youtube.com/watch?v=deZgzw0YHQI> 8 m 31 s [17] Fisher, 1968., Mark et al., K-punk : the collected and unpublished writings of Mark Fisher (2004-2016) 2018. Abs. 153.48 4. Satz [18] Fukuyama, F., The End of History and the Last Man 1992: <https://books.google.de/books?id=6KZmAAAAMAAJ>. [19] Parkes, L.L.F., WarGames: <https://www.imdb.com/de/title/tt0086567/> “A strange game. The only winning move is not to play.” [20] Wikipedia, No Future: <https://de.wikipedia.org/wiki/No_Future>. [21] Spirit zone https://www.platekompaniet.no/musikk/cd/space-tribe-shapeshifter-cd [22] Fisher, 1968., Mark et al., K-punk : the collected and unpublished writings of Mark Fisher (2004-2016) 2018. Abs. 153.21 Letzter Satz [23] Wikipedia, Acid Tests: <https://de.wikipedia.org/wiki/Acid-Tests>.
@ c8cf63be:86691cfe
2025-01-23 12:51:20### Mark Fishers ‘Acid Communism’ und der ‘Capitalist Realism’ > “it is easier to kill the living than to kill the undead”[1] Die lebenden sind wir Menschen, *the undead* ist der gegenwärtige neoliberalismus[2] Mark Fischers Analyse über den bestehenden Zustand ist erschütternd: > “let’s say music hello just go on music in the last 10 years one thing > one single thing that couldn’t have come out in the 20th century”[3] Es gibt nicht neues unter dem Himmel, alle Kreativität ist erschöpft, “die Verdinglichung” von der Horkheimer und Adorno sprachen, “…, ist so dicht geworden,…” die Wirklichkeit des ‘Capitalist Realism’ ist manifest und undurchdringlich, die Löcher, die kleinen alternativen, sind versiegelt. Schon im Denken sind die alternativen versperrt und das Denken ist ein gemeinsames, niemand kann für sich alleine Denken oder kreativ sein. Denken und kreativ sein sind das Ergebnis einer Gesellschaftlichen Voraussetzung. Es gibt keine neue Musik mehr weil die Musik untot ist. In immer neuer Auflagen, in der mechanische Reproduktion, wiederbelebt man die Toten, und erstickt das lebendige. > “… but there’s nothing about us that was good or better than you > you’re anybody it’s just that we were lucky and you all are unlucky > …”[4] Wenn eine junge Frau auf seine Feststellung reagiert mit Unglaube und Abwehr. > “… so what you’re basically saying is that i guess your generation or > the previous generation was better because you had more time to pursue > your own projects and you also think that you were more creative or > the previous generation was more creative …”[5] Dann weil sie die Enge der Umstände nicht erkennen kann, und vielleicht auch weil sie die Dinge auf sich persönlich bezieht, wie es das gegenwärtige Denken nahelegt: Sowohl der kompetitive Vergleich als auch die individuelle Schuldzuordnung findet sich in der Aussage. Fischer hingegen erklärt dies mit den Herrschenden Umständen die es den Menschen unmöglich machen sich den *wahren Sachverhalt* klar zu machen und damit jede Alternative im Denken versperren: > “.. but okay let’s be clear about what i’m saying creativity isn’t a > property of individuals ever it’s a property of a social or collective > scene like that you know that’s so that it’s not like the individuals > are less creative than they used to be that’s just not how creativity > works creativity is possible because of is possible because of social > conditions and those social conditions have been removed …”[6] Fischers Aufmerksamkeit richtet sich auf die die Umstände vor dem Capitalism Realism, denn dieser ist seiner Meinung nach schon eine Reaktion, eine Reaktion auf die “Counterculture” auf das “spectre of a world which could be free”[7]. Wenn es ein Gründungsereignis des Capital Realism geben sollte wäre dies nach Fischer der Putsch Pinochets in Chile 1973.[8] Seiner Zeit voraus war Hunter S. Thompson, seine Drogengeschwängerten Reflexionen fassen den Kern sehr genau, für ihn war 1971 schon der Moment an dem er die revision verortet: > “… wir ritten auf dem Kamm einer hohen und wunderschönen Welle … Und > jetzt, weniger als fünf Jahre später, kannst du auf einen steilen > Hügel in Las Vegas klettern und nach Westen blicken, und wenn du die > richtigen Augen hast, dann kannst du die Hochwassermarkierung fast > sehen -die Stelle, wo sich die Welle schließlich brach und > zurückrollte.”[9] Acid! Die psychedelische Zeit: > “Instead of seeking to overcome capital, we should focus on what > capital must always obstruct: the collective capacity to produce, care > and enjoy.”[10] und weiter > “The overcoming of capital has to be fundamentally based on the simple > insight that, far from being about “wealth creation”, capital > necessarily and always blocks the production of common wealth.” Der Zauber der Psycedlischen Zeit war die ignoranz, das Verweigern des bestehenden Narativs. Oder wie Fischer sagt, die Frage nach dem Bewustsein und seiner Beziehung dem dem was wir als Wiklichkeit wahrnemen.[11] > “turn on, tune in, drop out” [12] oder noch klarer Ken Kesey: > “There’s only one thing to do . > .. there’s only one thing’s gonna do any good at all… > And that’s everybody just look at it, > look at the war, and turn your backs and say … Fuck it..” [13] Die Imagination des *wahren Sachverhaltes* “look at it” sagt Kesey, überzeugt euch selbst. Es braucht nicht mehr als das Schauen des Krieges, bei ihm der Viatnam Krieg, um zu verstehen das nur die Verweigerung, das “Fuck it” geeignet ist dem ganzen seine legitimität zu verweigern. Das war der Zauber der psychedelichen Zeit, auch der der 90’er, die als unpolitsch gelten. Aus dieser Perspektive ist klar das das unpolitsche, das politsche war. Die love-Parade war nicht unpolitisch und die gesellschaflichenr Verändeung die durch diese Psychedleische Zeit in Bewegung gesetzt wurden können wir noch heute fühlen. Die Canabis Legalisierung, die veränderte Wahrnehmng von Homosexualität. Das “chill out”. Die tribal Tattoos.[14] Und auch die wärmste Kampange der Europawahl 2024, “Fickt euch doch alle.”[15] ist erst durch die psychedelische Zeit der 90’er möglich, hier wurde die Sinnlichkeit gestiftet die es braucht damit dieser Satz seine wärme bekommt. Die Demokratesierung der Neurologie durch die verwendung von Halozinogenen rücken die Frage nach der Wirklichkeit und des wahren Sachverhaltes in den Mittelpunkt. > “what they mainstreamed was this psychedelic consciousness with its > key notion of the plasticity of reality”[16] Sie ist auch eine Sekularisierung, eine demokratisierung des Sakralen, das vorher durch Klassen wie Schamanen oder Druiden kontroliert wurde wird zugänglich und erfahrbar. > “…, there was actually a demystificatory and materialist dimension to > this.”[17] Was sich so aussprechen läßt: > *“Wenn Gott liebe ist, dann ist er eine MDMA geschwängerte, psycedelic > trance Party, anfang der 90’er jahre des letzten Jahrtausend.”* Es loht sich also für uns ältere an die nicht so ferne Zeit der frühen 90’er Jahre zurück zu denken in der die Welt offen schien, die Polarität des kalten Krieges vergangen war, das Ende der Geschichte ausgerüfen wurde.[18] Da war die Idee das dies nicht der Siegt des Kapitalismus ist, sondern ein Sieg der Menschen die die Spirale des Schreckens und der Eskalation durchbrechen real. Es schien wie ein transzendieren des gegebenen Spiels und seiner Regeln wie es die AI in “war games”[19] realisiert, stattzufinden. Auf “No future”[20] folgte “No Paradise? Create it.”[21], es fand ein “unforgetting”[22] der alten, in den 60’er entwickelten Formen statt: Die Modulierung der 303, das Dayglow und das Strobo, alles Elemente des Acid Test[23]. *“the collective capacity to produce, care and enjoy”* ------------------------------------------------------------------------ ### References: [1] Fisher, M., Mark Fisher - DOCH Lectures 1 2011: <https://www.youtube.com/watch?v=f-9nY5rboK8> 32m 42s [2] Fisher, M., How to kill a zombie: strategizing the end of neoliberalism 2013: <https://www.opendemocracy.net/en/how-to-kill-zombie-strategizing-end-of-neoliberalism/>. [3] Fisher, 1968., Mark, Cybertime Crisis 2013: <https://www.youtube.com/watch?v=zOQgCg73sfQ> ab 1h 42m 12s [4] Fisher, 1968., Mark, ebenda ab 1h 35m 30s [5] Fisher, 1968., Mark, ebenda ab 1h 42m 12s [6] Fisher, 1968., Mark, ebenda ab 1h 47m 20s [7] Fisher, 1968., Mark et al., K-punk : the collected and unpublished writings of Mark Fisher (2004-2016) 2018. Abs. 153.5 [8] Fisher, 1968., Mark et al., ebenda. Abs. 153.7 “If there was a founding event of capitalist realism, it would be the violent destruction of the Allende government in Chile by General Pinochet’s American-backed coup.” [9] Hunter S. Thompson “Fear and loathing” Seite 89 [10] Fisher, 1968., Mark et al., K-punk : the collected and unpublished writings of Mark Fisher (2004-2016) 2018. Abs. 153.5 Statz 3 [11] Fisher, 1968., Mark et al., ebenda. Abs. 153.46 [12] Timothy Leary in 1966, der damals gefährlichste Mann der Welt.(Richard Nixxon) [13] Wolfe, Tom., The electric kool-aid acid test. 1999. Seite 360 [14] Christmann, K., Gruppen-Tattoo-Termin im Bundestag: 19 Abgeordnete zeigen vollen Körpereinsatz 2024: <https://www.tagesspiegel.de/politik/gruppen-tattoo-termin-im-bundestag-19-abgeordnete-zeigen-vollen-korpereinsatz-11665559.html>. [15] DiePartei, Fickt euch doch alle! (DINA1) 2024: <https://www.parteibedarf.de/Fickt-euch-doch-alle-DINA1/SW10115>. [16] Fisher, M., all of this is temporary: Mark Fisher 2016: <https://www.youtube.com/watch?v=deZgzw0YHQI> 8 m 31 s [17] Fisher, 1968., Mark et al., K-punk : the collected and unpublished writings of Mark Fisher (2004-2016) 2018. Abs. 153.48 4. Satz [18] Fukuyama, F., The End of History and the Last Man 1992: <https://books.google.de/books?id=6KZmAAAAMAAJ>. [19] Parkes, L.L.F., WarGames: <https://www.imdb.com/de/title/tt0086567/> “A strange game. The only winning move is not to play.” [20] Wikipedia, No Future: <https://de.wikipedia.org/wiki/No_Future>. [21] Spirit zone https://www.platekompaniet.no/musikk/cd/space-tribe-shapeshifter-cd [22] Fisher, 1968., Mark et al., K-punk : the collected and unpublished writings of Mark Fisher (2004-2016) 2018. Abs. 153.21 Letzter Satz [23] Wikipedia, Acid Tests: <https://de.wikipedia.org/wiki/Acid-Tests>. @ 6be5cc06:5259daf0
2025-01-21 23:17:29A seguir, veja como instalar e configurar o **Privoxy** no **Pop!_OS**. --- ### **1. Instalar o Tor e o Privoxy** Abra o terminal e execute: ```bash sudo apt update sudo apt install tor privoxy ``` **Explicação:** - **Tor:** Roteia o tráfego pela rede Tor. - **Privoxy:** Proxy avançado que intermedia a conexão entre aplicativos e o Tor. --- ### **2. Configurar o Privoxy** Abra o arquivo de configuração do Privoxy: ```bash sudo nano /etc/privoxy/config ``` Navegue até a última linha (atalho: **`Ctrl`** + **`/`** depois **`Ctrl`** + **`V`** para navegar diretamente até a última linha) e insira: ```bash forward-socks5 / 127.0.0.1:9050 . ``` Isso faz com que o **Privoxy** envie todo o tráfego para o **Tor** através da porta **9050**. Salve (**`CTRL`** + **`O`** e **`Enter`**) e feche (**`CTRL`** + **`X`**) o arquivo. --- ### **3. Iniciar o Tor e o Privoxy** Agora, inicie e habilite os serviços: ```bash sudo systemctl start tor sudo systemctl start privoxy sudo systemctl enable tor sudo systemctl enable privoxy ``` **Explicação:** - **start:** Inicia os serviços. - **enable:** Faz com que iniciem automaticamente ao ligar o PC. --- ### **4. Configurar o Navegador Firefox** Para usar a rede **Tor** com o Firefox: 1. Abra o Firefox. 2. Acesse **Configurações** → **Configurar conexão**. 3. Selecione **Configuração manual de proxy**. 4. Configure assim: - **Proxy HTTP:** `127.0.0.1` - **Porta:** `8118` (porta padrão do **Privoxy**) - **Domínio SOCKS (v5):** `127.0.0.1` - **Porta:** `9050` 5. Marque a opção **"Usar este proxy também em HTTPS"**. 6. Clique em **OK**. --- ### **5. Verificar a Conexão com o Tor** Abra o navegador e acesse: ```text https://check.torproject.org/ ``` Se aparecer a mensagem **"Congratulations. This browser is configured to use Tor."**, a configuração está correta. --- ### **Dicas Extras** - **Privoxy** pode ser ajustado para bloquear anúncios e rastreadores. - Outros aplicativos também podem ser configurados para usar o **Privoxy**.
@ 6be5cc06:5259daf0
2025-01-21 23:17:29A seguir, veja como instalar e configurar o **Privoxy** no **Pop!_OS**. --- ### **1. Instalar o Tor e o Privoxy** Abra o terminal e execute: ```bash sudo apt update sudo apt install tor privoxy ``` **Explicação:** - **Tor:** Roteia o tráfego pela rede Tor. - **Privoxy:** Proxy avançado que intermedia a conexão entre aplicativos e o Tor. --- ### **2. Configurar o Privoxy** Abra o arquivo de configuração do Privoxy: ```bash sudo nano /etc/privoxy/config ``` Navegue até a última linha (atalho: **`Ctrl`** + **`/`** depois **`Ctrl`** + **`V`** para navegar diretamente até a última linha) e insira: ```bash forward-socks5 / 127.0.0.1:9050 . ``` Isso faz com que o **Privoxy** envie todo o tráfego para o **Tor** através da porta **9050**. Salve (**`CTRL`** + **`O`** e **`Enter`**) e feche (**`CTRL`** + **`X`**) o arquivo. --- ### **3. Iniciar o Tor e o Privoxy** Agora, inicie e habilite os serviços: ```bash sudo systemctl start tor sudo systemctl start privoxy sudo systemctl enable tor sudo systemctl enable privoxy ``` **Explicação:** - **start:** Inicia os serviços. - **enable:** Faz com que iniciem automaticamente ao ligar o PC. --- ### **4. Configurar o Navegador Firefox** Para usar a rede **Tor** com o Firefox: 1. Abra o Firefox. 2. Acesse **Configurações** → **Configurar conexão**. 3. Selecione **Configuração manual de proxy**. 4. Configure assim: - **Proxy HTTP:** `127.0.0.1` - **Porta:** `8118` (porta padrão do **Privoxy**) - **Domínio SOCKS (v5):** `127.0.0.1` - **Porta:** `9050` 5. Marque a opção **"Usar este proxy também em HTTPS"**. 6. Clique em **OK**. --- ### **5. Verificar a Conexão com o Tor** Abra o navegador e acesse: ```text https://check.torproject.org/ ``` Se aparecer a mensagem **"Congratulations. This browser is configured to use Tor."**, a configuração está correta. --- ### **Dicas Extras** - **Privoxy** pode ser ajustado para bloquear anúncios e rastreadores. - Outros aplicativos também podem ser configurados para usar o **Privoxy**. @ 9e69e420:d12360c2
2025-01-21 19:31:48Oregano oil is a potent natural compound that offers numerous scientifically-supported health benefits. ## Active Compounds The oil's therapeutic properties stem from its key bioactive components: - Carvacrol and thymol (primary active compounds) - Polyphenols and other antioxidant ## Antimicrobial Properties **Bacterial Protection** The oil demonstrates powerful antibacterial effects, even against antibiotic-resistant strains like MRSA and other harmful bacteria. Studies show it effectively inactivates various pathogenic bacteria without developing resistance. **Antifungal Effects** It effectively combats fungal infections, particularly Candida-related conditions like oral thrush, athlete's foot, and nail infections. ## Digestive Health Benefits Oregano oil supports digestive wellness by: - Promoting gastric juice secretion and enzyme production - Helping treat Small Intestinal Bacterial Overgrowth (SIBO) - Managing digestive discomfort, bloating, and IBS symptoms ## Anti-inflammatory and Antioxidant Effects The oil provides significant protective benefits through: - Powerful antioxidant activity that fights free radicals - Reduction of inflammatory markers in the body - Protection against oxidative stress-related conditions ## Respiratory Support It aids respiratory health by: - Loosening mucus and phlegm - Suppressing coughs and throat irritation - Supporting overall respiratory tract function ## Additional Benefits **Skin Health** - Improves conditions like psoriasis, acne, and eczema - Supports wound healing through antibacterial action - Provides anti-aging benefits through antioxidant properties **Cardiovascular Health** Studies show oregano oil may help: - Reduce LDL (bad) cholesterol levels - Support overall heart health **Pain Management** The oil demonstrates effectiveness in: - Reducing inflammation-related pain - Managing muscle discomfort - Providing topical pain relief ## Safety Note While oregano oil is generally safe, it's highly concentrated and should be properly diluted before use Consult a healthcare provider before starting supplementation, especially if taking other medications.
@ 9e69e420:d12360c2
2025-01-21 19:31:48Oregano oil is a potent natural compound that offers numerous scientifically-supported health benefits. ## Active Compounds The oil's therapeutic properties stem from its key bioactive components: - Carvacrol and thymol (primary active compounds) - Polyphenols and other antioxidant ## Antimicrobial Properties **Bacterial Protection** The oil demonstrates powerful antibacterial effects, even against antibiotic-resistant strains like MRSA and other harmful bacteria. Studies show it effectively inactivates various pathogenic bacteria without developing resistance. **Antifungal Effects** It effectively combats fungal infections, particularly Candida-related conditions like oral thrush, athlete's foot, and nail infections. ## Digestive Health Benefits Oregano oil supports digestive wellness by: - Promoting gastric juice secretion and enzyme production - Helping treat Small Intestinal Bacterial Overgrowth (SIBO) - Managing digestive discomfort, bloating, and IBS symptoms ## Anti-inflammatory and Antioxidant Effects The oil provides significant protective benefits through: - Powerful antioxidant activity that fights free radicals - Reduction of inflammatory markers in the body - Protection against oxidative stress-related conditions ## Respiratory Support It aids respiratory health by: - Loosening mucus and phlegm - Suppressing coughs and throat irritation - Supporting overall respiratory tract function ## Additional Benefits **Skin Health** - Improves conditions like psoriasis, acne, and eczema - Supports wound healing through antibacterial action - Provides anti-aging benefits through antioxidant properties **Cardiovascular Health** Studies show oregano oil may help: - Reduce LDL (bad) cholesterol levels - Support overall heart health **Pain Management** The oil demonstrates effectiveness in: - Reducing inflammation-related pain - Managing muscle discomfort - Providing topical pain relief ## Safety Note While oregano oil is generally safe, it's highly concentrated and should be properly diluted before use Consult a healthcare provider before starting supplementation, especially if taking other medications. @ b17fccdf:b7211155
2025-01-21 17:02:21The past 26 August, Tor [introduced officially](https://blog.torproject.org/introducing-proof-of-work-defense-for-onion-services/) a proof-of-work (PoW) defense for onion services designed to prioritize verified network traffic as a deterrent against denial of service (DoS) attacks. ~ > This feature at the moment, is [deactivate by default](https://gitlab.torproject.org/tpo/core/tor/-/blob/main/doc/man/tor.1.txt#L3117), so you need to follow these steps to activate this on a MiniBolt node: * Make sure you have the latest version of Tor installed, at the time of writing this post, which is v0.4.8.6. Check your current version by typing ``` tor --version ``` **Example** of expected output: ``` Tor version 0.4.8.6. This build of Tor is covered by the GNU General Public License (https://www.gnu.org/licenses/gpl-3.0.en.html) Tor is running on Linux with Libevent 2.1.12-stable, OpenSSL 3.0.9, Zlib 1.2.13, Liblzma 5.4.1, Libzstd N/A and Glibc 2.36 as libc. Tor compiled with GCC version 12.2.0 ``` ~ > If you have v0.4.8.X, you are **OK**, if not, type `sudo apt update && sudo apt upgrade` and confirm to update. * Basic PoW support can be checked by running this command: ``` tor --list-modules ``` Expected output: ``` relay: yes dirauth: yes dircache: yes pow: **yes** ``` ~ > If you have `pow: yes`, you are **OK** * Now go to the torrc file of your MiniBolt and add the parameter to enable PoW for each hidden service added ``` sudo nano /etc/tor/torrc ``` Example: ``` # Hidden Service BTC RPC Explorer HiddenServiceDir /var/lib/tor/hidden_service_btcrpcexplorer/ HiddenServiceVersion 3 HiddenServicePoWDefensesEnabled 1 HiddenServicePort 80 127.0.0.1:3002 ``` ~ > Bitcoin Core and LND use the Tor control port to automatically create the hidden service, requiring no action from the user. We have submitted a feature request in the official GitHub repositories to explore the need for the integration of Tor's PoW defense into the automatic creation process of the hidden service. You can follow them at the following links: * Bitcoin Core: https://github.com/lightningnetwork/lnd/issues/8002 * LND: https://github.com/bitcoin/bitcoin/issues/28499 --- More info: * https://blog.torproject.org/introducing-proof-of-work-defense-for-onion-services/ * https://gitlab.torproject.org/tpo/onion-services/onion-support/-/wikis/Documentation/PoW-FAQ --- Enjoy it MiniBolter! 💙
@ b17fccdf:b7211155
2025-01-21 17:02:21The past 26 August, Tor [introduced officially](https://blog.torproject.org/introducing-proof-of-work-defense-for-onion-services/) a proof-of-work (PoW) defense for onion services designed to prioritize verified network traffic as a deterrent against denial of service (DoS) attacks. ~ > This feature at the moment, is [deactivate by default](https://gitlab.torproject.org/tpo/core/tor/-/blob/main/doc/man/tor.1.txt#L3117), so you need to follow these steps to activate this on a MiniBolt node: * Make sure you have the latest version of Tor installed, at the time of writing this post, which is v0.4.8.6. Check your current version by typing ``` tor --version ``` **Example** of expected output: ``` Tor version 0.4.8.6. This build of Tor is covered by the GNU General Public License (https://www.gnu.org/licenses/gpl-3.0.en.html) Tor is running on Linux with Libevent 2.1.12-stable, OpenSSL 3.0.9, Zlib 1.2.13, Liblzma 5.4.1, Libzstd N/A and Glibc 2.36 as libc. Tor compiled with GCC version 12.2.0 ``` ~ > If you have v0.4.8.X, you are **OK**, if not, type `sudo apt update && sudo apt upgrade` and confirm to update. * Basic PoW support can be checked by running this command: ``` tor --list-modules ``` Expected output: ``` relay: yes dirauth: yes dircache: yes pow: **yes** ``` ~ > If you have `pow: yes`, you are **OK** * Now go to the torrc file of your MiniBolt and add the parameter to enable PoW for each hidden service added ``` sudo nano /etc/tor/torrc ``` Example: ``` # Hidden Service BTC RPC Explorer HiddenServiceDir /var/lib/tor/hidden_service_btcrpcexplorer/ HiddenServiceVersion 3 HiddenServicePoWDefensesEnabled 1 HiddenServicePort 80 127.0.0.1:3002 ``` ~ > Bitcoin Core and LND use the Tor control port to automatically create the hidden service, requiring no action from the user. We have submitted a feature request in the official GitHub repositories to explore the need for the integration of Tor's PoW defense into the automatic creation process of the hidden service. You can follow them at the following links: * Bitcoin Core: https://github.com/lightningnetwork/lnd/issues/8002 * LND: https://github.com/bitcoin/bitcoin/issues/28499 --- More info: * https://blog.torproject.org/introducing-proof-of-work-defense-for-onion-services/ * https://gitlab.torproject.org/tpo/onion-services/onion-support/-/wikis/Documentation/PoW-FAQ --- Enjoy it MiniBolter! 💙 @ c8cf63be:86691cfe
2025-01-21 13:48:28### Das SNAFU des Reichtums Das SNAFU-Prinzip[1] sagt das Kommunikation nur unter gleichen möglich ist: > Adäquate Kommunikation fliesst nur zwischen Gleichen ungehindert. > Kommunikation zwischen Nicht-Gleichen ist missverständlich und von > Dominaz- und Unterwerfungsritualen gefärbt, die immer wieder zum > Zusammenbruch der Kommunikation führen und zu einem Spiel ohne Ende. > [2] So ist z. B. das Peter Prinzip [3] eine einfache Folge des SNAFU-Prinzips. Bezieht es sich in erster Linie auf Hierarchie lässt es sich hervorragend ausweiten auf den ökonomischen Bereich. Auch hier gilt, dass Kommunikation nur unter Gleichen möglich ist, hier ist die Hierarchie das ökonomische Ungleichgewicht. Kommunikation ist auch hier nur unter gleichen möglich, ungefähr gleich reich müssen sie sein. Ein zu großer Unterschied in den ökonomischen Verhältnissen verhindert den Aufbau einer menschlichen Beziehung. Hier ist das einfache Beispiel: Wäre ich Reich, würde ich mich Fragen, ob die Freunde da, nur kommen weil ich ihnen die Drinks ausgebe. Jeder, der nicht so viel Geld wie ich hat, will vielleicht nur mein Geld. So kann ein Bill Gates nur einen Jeff Besos als Freund haben oder treffender ein Elon Musk nur einen Mark Zuckerberg. Auch umgekehrt funktioniert diese Selektion: Wenn ich ein richtig cooler Typ wäre, würde ich mich fragen, ob ich den Reichen eigentlich gut finde, oder nur mit ihm rumhänge, weil er die Drinks bezahlt und weil ich zu Recht unsicher darüber sein kann, kann ich mich nur entziehen. Diejenigen, die wirklich freundschaftlich sind, sind die die sich einer solchen Situation nicht aussetzen. Und was bleibt dem Reichen? Nur die Gesellschaft der Reichen. Hier trifft der Reichtum auf eine totale Armut. Die Auswahl der Freunde ist sehr klein. Hier ist tatsächlich der Reichtum das Problem, bzw. das ökonomische Ungleichgewicht und es gibt eine einfache Lösung, der Unterschied muss kleiner werden, denn je kleiner der Unterschied desto mehr Auswahl an Freunden gibt es. Wie in der “Aufgeklärten Ökonomie” dargestellt ist die Ungleichheit, eine gesellschaftliche Entscheidung und eine konkrete Steuerung möglich. Wir können also den Reichen helfen und mehr Freiheit und Freunde schenken. Pathologisch wird dieses Phänomen, wenn sich der innere Antrieb um den Reichtum dreht. Was durch die momentane Verfasstheit der gesellschaftlichen Praktiken sogar unterstützt und gefördert wird und damit viele Menschen objektiv unglücklich macht. Dieses pathologische der Gesellschaft wirkt dann auf das Individuum zurück und macht es ebenfalls Krank. Wir haben einen ähnlichen Mechanismus in der Gewalt kennenlernen dürfen. Vgl. “Gewalt ist eine ansteckende Krankrankheit” <figure> <img src="!(image)[https://cdn.satellite.earth/ac54bd400867c63f14e151172422067dc1b19980b1e738a577ae6c7a6ea835ea.png]" style="width:50.0%" alt="Klarmachen ändert, Gier ist heilbar" /> <figcaption aria-hidden="true">Klarmachen ändert, Gier ist heilbar</figcaption> </figure> > Wenn sie sich leer fühlen, Erfolg ihnen kein Glück schenkt, keine > Befriedigung. Wenn sie mehr brauchen und mehr, dann leiden sie > wahrscheinlich auch an einer Dysfunktion der Belohnungssysteme, an > Habsucht. > Auch ihnen kann und muss geholfen werden, denn Gier ist heilbar. Und > ihrer Gier betrifft nicht nur sie. Ihre liebsten Menschen in Ihrer > Umgebung, Menschen mit denen sie niemals direkt in Berührung kommen, > sie alle leiden unter ihrer Krankheit. > Auch für sie kann es ein erfülltes Leben geben, einen Weg zurück in > die Gesellschaft, die Gesellschaft von Menschen. Machen sie > Psychotherapie, nehmen sie Pharmaka, buchen sie eine Kur und > entledigen sich ihres Wohlstandes.[4] ------------------------------------------------------------------------ ### References: [1] Wikipedia, SNAFU: <https://de.wikipedia.org/wiki/SNAFU>. [2] Wilson, R.A., Der Neue Prometheus. Die Evolution unserer Intelligenz. - Volksausgabe/ Raubdruck. 1983. Seite 245-246 [3] Wikipedia, Peter Prinzip: <https://de.wikipedia.org/wiki/Peter-Prinzip>. [4] InvestmentWeek, Sucht im Luxus: Eine Nacht in der Klinik der Superreichen 2024: <https://www.investmentweek.com/sucht-im-luxus-eine-nacht-in-der-klinik-der-superreichen/>, „Viele Patienten hier leiden an Einsamkeit“ … “Viele Superreiche …wüssten nicht, ob sie wegen ihres Geldes oder ihrer Persönlichkeit gemocht werden” „Reich sein bedeutet oft, keinen echten Kontakt zu haben. Viele unserer Klienten haben keine echten Freunde.“
@ c8cf63be:86691cfe
2025-01-21 13:48:28### Das SNAFU des Reichtums Das SNAFU-Prinzip[1] sagt das Kommunikation nur unter gleichen möglich ist: > Adäquate Kommunikation fliesst nur zwischen Gleichen ungehindert. > Kommunikation zwischen Nicht-Gleichen ist missverständlich und von > Dominaz- und Unterwerfungsritualen gefärbt, die immer wieder zum > Zusammenbruch der Kommunikation führen und zu einem Spiel ohne Ende. > [2] So ist z. B. das Peter Prinzip [3] eine einfache Folge des SNAFU-Prinzips. Bezieht es sich in erster Linie auf Hierarchie lässt es sich hervorragend ausweiten auf den ökonomischen Bereich. Auch hier gilt, dass Kommunikation nur unter Gleichen möglich ist, hier ist die Hierarchie das ökonomische Ungleichgewicht. Kommunikation ist auch hier nur unter gleichen möglich, ungefähr gleich reich müssen sie sein. Ein zu großer Unterschied in den ökonomischen Verhältnissen verhindert den Aufbau einer menschlichen Beziehung. Hier ist das einfache Beispiel: Wäre ich Reich, würde ich mich Fragen, ob die Freunde da, nur kommen weil ich ihnen die Drinks ausgebe. Jeder, der nicht so viel Geld wie ich hat, will vielleicht nur mein Geld. So kann ein Bill Gates nur einen Jeff Besos als Freund haben oder treffender ein Elon Musk nur einen Mark Zuckerberg. Auch umgekehrt funktioniert diese Selektion: Wenn ich ein richtig cooler Typ wäre, würde ich mich fragen, ob ich den Reichen eigentlich gut finde, oder nur mit ihm rumhänge, weil er die Drinks bezahlt und weil ich zu Recht unsicher darüber sein kann, kann ich mich nur entziehen. Diejenigen, die wirklich freundschaftlich sind, sind die die sich einer solchen Situation nicht aussetzen. Und was bleibt dem Reichen? Nur die Gesellschaft der Reichen. Hier trifft der Reichtum auf eine totale Armut. Die Auswahl der Freunde ist sehr klein. Hier ist tatsächlich der Reichtum das Problem, bzw. das ökonomische Ungleichgewicht und es gibt eine einfache Lösung, der Unterschied muss kleiner werden, denn je kleiner der Unterschied desto mehr Auswahl an Freunden gibt es. Wie in der “Aufgeklärten Ökonomie” dargestellt ist die Ungleichheit, eine gesellschaftliche Entscheidung und eine konkrete Steuerung möglich. Wir können also den Reichen helfen und mehr Freiheit und Freunde schenken. Pathologisch wird dieses Phänomen, wenn sich der innere Antrieb um den Reichtum dreht. Was durch die momentane Verfasstheit der gesellschaftlichen Praktiken sogar unterstützt und gefördert wird und damit viele Menschen objektiv unglücklich macht. Dieses pathologische der Gesellschaft wirkt dann auf das Individuum zurück und macht es ebenfalls Krank. Wir haben einen ähnlichen Mechanismus in der Gewalt kennenlernen dürfen. Vgl. “Gewalt ist eine ansteckende Krankrankheit” <figure> <img src="!(image)[https://cdn.satellite.earth/ac54bd400867c63f14e151172422067dc1b19980b1e738a577ae6c7a6ea835ea.png]" style="width:50.0%" alt="Klarmachen ändert, Gier ist heilbar" /> <figcaption aria-hidden="true">Klarmachen ändert, Gier ist heilbar</figcaption> </figure> > Wenn sie sich leer fühlen, Erfolg ihnen kein Glück schenkt, keine > Befriedigung. Wenn sie mehr brauchen und mehr, dann leiden sie > wahrscheinlich auch an einer Dysfunktion der Belohnungssysteme, an > Habsucht. > Auch ihnen kann und muss geholfen werden, denn Gier ist heilbar. Und > ihrer Gier betrifft nicht nur sie. Ihre liebsten Menschen in Ihrer > Umgebung, Menschen mit denen sie niemals direkt in Berührung kommen, > sie alle leiden unter ihrer Krankheit. > Auch für sie kann es ein erfülltes Leben geben, einen Weg zurück in > die Gesellschaft, die Gesellschaft von Menschen. Machen sie > Psychotherapie, nehmen sie Pharmaka, buchen sie eine Kur und > entledigen sich ihres Wohlstandes.[4] ------------------------------------------------------------------------ ### References: [1] Wikipedia, SNAFU: <https://de.wikipedia.org/wiki/SNAFU>. [2] Wilson, R.A., Der Neue Prometheus. Die Evolution unserer Intelligenz. - Volksausgabe/ Raubdruck. 1983. Seite 245-246 [3] Wikipedia, Peter Prinzip: <https://de.wikipedia.org/wiki/Peter-Prinzip>. [4] InvestmentWeek, Sucht im Luxus: Eine Nacht in der Klinik der Superreichen 2024: <https://www.investmentweek.com/sucht-im-luxus-eine-nacht-in-der-klinik-der-superreichen/>, „Viele Patienten hier leiden an Einsamkeit“ … “Viele Superreiche …wüssten nicht, ob sie wegen ihres Geldes oder ihrer Persönlichkeit gemocht werden” „Reich sein bedeutet oft, keinen echten Kontakt zu haben. Viele unserer Klienten haben keine echten Freunde.“ @ 04ed2b8f:75be6756
2025-01-21 02:26:28A warrior does not fear chaos—he thrives in it. Life is a battlefield, and disorder is the forge in which strength, strategy, and resilience are tempered. Whether in the pursuit of victory in business, relationships, or personal conquest, chaos is an inevitable adversary. But within every storm lies an opportunity—an opening to strike, to evolve, and to dominate where others falter. Only those who embrace the struggle with unwavering resolve can turn uncertainty into their greatest weapon. ### **Understanding Chaos** Chaos is not the enemy; it is the proving ground. It manifests as upheaval, setbacks, and unexpected challenges, forcing warriors to sharpen their minds and steel their resolve. - **Disruption Breeds Innovation:** In the heat of battle, new tactics emerge. When the known paths are obliterated, new strategies take form. - **Mindset Is Your Strongest Weapon:** Chaos can either crush you or forge you into something stronger. The choice lies within your perception. - **Growth Is Forged in Adversity:** The greatest warriors are those who embrace discomfort, wielding it to forge endurance and ingenuity. ### **Seizing Opportunity Amidst Chaos** 1. **Adaptability Is Strength** - The warrior who can shift tactics swiftly gains the upper hand. Flexibility and awareness allow for swift and decisive action where others hesitate. 2. **Chaos Fuels Creativity** - In the heat of turmoil, the boldest ideas are born. Warriors do not cling to old ways; they adapt, overcome, and conquer. 3. **Endings Are Just New Battles** - What seems like defeat is often a call to arms for greater conquests. Every setback is a chance to regroup and strike back with renewed vigor. ### **Harnessing Chaos for Victory** 1. **Remain Steady Amid the Storm:** Fear clouds judgment; clarity is power. Observe, assess, and act with precision. Opportunities reveal themselves to those who master control over their emotions. 2. **Strike First, Strike Hard:** Do not merely react to chaos—command it. Take decisive actions that position you ahead of the pack. 3. **Exploit Weaknesses:** Where others see insurmountable problems, a warrior sees openings and opportunities to advance. ### **Lessons from the Battlefields of History** Legends are not born in times of peace but in the crucible of chaos. From generals who turned the tide of war in moments of despair to entrepreneurs who built empires from ruin, history is a testament to those who harnessed disorder and emerged victorious. ### **Conclusion: Chaos Is the Warrior's Ally** Chaos is not to be feared but embraced. It is the ultimate test of will and strategy. A true warrior sees beyond the disorder, crafting victory from the wreckage. In every crisis lies the seed of triumph; in every conflict, the chance to rise. When chaos surrounds you, stand firm, sharpen your sword, and remember—opportunity belongs to those with the courage to seize it.
@ 04ed2b8f:75be6756
2025-01-21 02:26:28A warrior does not fear chaos—he thrives in it. Life is a battlefield, and disorder is the forge in which strength, strategy, and resilience are tempered. Whether in the pursuit of victory in business, relationships, or personal conquest, chaos is an inevitable adversary. But within every storm lies an opportunity—an opening to strike, to evolve, and to dominate where others falter. Only those who embrace the struggle with unwavering resolve can turn uncertainty into their greatest weapon. ### **Understanding Chaos** Chaos is not the enemy; it is the proving ground. It manifests as upheaval, setbacks, and unexpected challenges, forcing warriors to sharpen their minds and steel their resolve. - **Disruption Breeds Innovation:** In the heat of battle, new tactics emerge. When the known paths are obliterated, new strategies take form. - **Mindset Is Your Strongest Weapon:** Chaos can either crush you or forge you into something stronger. The choice lies within your perception. - **Growth Is Forged in Adversity:** The greatest warriors are those who embrace discomfort, wielding it to forge endurance and ingenuity. ### **Seizing Opportunity Amidst Chaos** 1. **Adaptability Is Strength** - The warrior who can shift tactics swiftly gains the upper hand. Flexibility and awareness allow for swift and decisive action where others hesitate. 2. **Chaos Fuels Creativity** - In the heat of turmoil, the boldest ideas are born. Warriors do not cling to old ways; they adapt, overcome, and conquer. 3. **Endings Are Just New Battles** - What seems like defeat is often a call to arms for greater conquests. Every setback is a chance to regroup and strike back with renewed vigor. ### **Harnessing Chaos for Victory** 1. **Remain Steady Amid the Storm:** Fear clouds judgment; clarity is power. Observe, assess, and act with precision. Opportunities reveal themselves to those who master control over their emotions. 2. **Strike First, Strike Hard:** Do not merely react to chaos—command it. Take decisive actions that position you ahead of the pack. 3. **Exploit Weaknesses:** Where others see insurmountable problems, a warrior sees openings and opportunities to advance. ### **Lessons from the Battlefields of History** Legends are not born in times of peace but in the crucible of chaos. From generals who turned the tide of war in moments of despair to entrepreneurs who built empires from ruin, history is a testament to those who harnessed disorder and emerged victorious. ### **Conclusion: Chaos Is the Warrior's Ally** Chaos is not to be feared but embraced. It is the ultimate test of will and strategy. A true warrior sees beyond the disorder, crafting victory from the wreckage. In every crisis lies the seed of triumph; in every conflict, the chance to rise. When chaos surrounds you, stand firm, sharpen your sword, and remember—opportunity belongs to those with the courage to seize it. @ 6be5cc06:5259daf0
2025-01-21 01:51:46## Bitcoin: Um sistema de dinheiro eletrônico direto entre pessoas. Satoshi Nakamoto satoshin@gmx.com www.bitcoin.org --- ### Resumo O Bitcoin é uma forma de dinheiro digital que permite pagamentos diretos entre pessoas, sem a necessidade de um banco ou instituição financeira. Ele resolve um problema chamado **gasto duplo**, que ocorre quando alguém tenta gastar o mesmo dinheiro duas vezes. Para evitar isso, o Bitcoin usa uma rede descentralizada onde todos trabalham juntos para verificar e registrar as transações. As transações são registradas em um livro público chamado **blockchain**, protegido por uma técnica chamada **Prova de Trabalho**. Essa técnica cria uma cadeia de registros que não pode ser alterada sem refazer todo o trabalho já feito. Essa cadeia é mantida pelos computadores que participam da rede, e a mais longa é considerada a verdadeira. Enquanto a maior parte do poder computacional da rede for controlada por participantes honestos, o sistema continuará funcionando de forma segura. A rede é flexível, permitindo que qualquer pessoa entre ou saia a qualquer momento, sempre confiando na cadeia mais longa como prova do que aconteceu. --- ### 1. Introdução Hoje, quase todos os pagamentos feitos pela internet dependem de bancos ou empresas como processadores de pagamento (cartões de crédito, por exemplo) para funcionar. Embora esse sistema seja útil, ele tem problemas importantes porque é baseado em **confiança**. Primeiro, essas empresas podem reverter pagamentos, o que é útil em caso de erros, mas cria custos e incertezas. Isso faz com que pequenas transações, como pagar centavos por um serviço, se tornem inviáveis. Além disso, os comerciantes são obrigados a desconfiar dos clientes, pedindo informações extras e aceitando fraudes como algo inevitável. Esses problemas não existem no dinheiro físico, como o papel-moeda, onde o pagamento é final e direto entre as partes. No entanto, não temos como enviar dinheiro físico pela internet sem depender de um intermediário confiável. O que precisamos é de um **sistema de pagamento eletrônico baseado em provas matemáticas**, não em confiança. Esse sistema permitiria que qualquer pessoa enviasse dinheiro diretamente para outra, sem depender de bancos ou processadores de pagamento. Além disso, as transações seriam irreversíveis, protegendo vendedores contra fraudes, mas mantendo a possibilidade de soluções para disputas legítimas. Neste documento, apresentamos o **Bitcoin**, que resolve o problema do gasto duplo usando uma rede descentralizada. Essa rede cria um registro público e protegido por cálculos matemáticos, que garante a ordem das transações. Enquanto a maior parte da rede for controlada por pessoas honestas, o sistema será seguro contra ataques. --- ### 2. Transações Para entender como funciona o Bitcoin, é importante saber como as transações são realizadas. Imagine que você quer transferir uma "moeda digital" para outra pessoa. No sistema do Bitcoin, essa "moeda" é representada por uma sequência de registros que mostram quem é o atual dono. Para transferi-la, você adiciona um novo registro comprovando que agora ela pertence ao próximo dono. Esse registro é protegido por um tipo especial de assinatura digital. #### O que é uma assinatura digital? Uma assinatura digital é como uma senha secreta, mas muito mais segura. No Bitcoin, cada usuário tem duas chaves: uma "chave privada", que é secreta e serve para criar a assinatura, e uma "chave pública", que pode ser compartilhada com todos e é usada para verificar se a assinatura é válida. Quando você transfere uma moeda, usa sua chave privada para assinar a transação, provando que você é o dono. A próxima pessoa pode usar sua chave pública para confirmar isso. #### Como funciona na prática? Cada "moeda" no Bitcoin é, na verdade, uma cadeia de assinaturas digitais. Vamos imaginar o seguinte cenário: 1. A moeda está com o Dono 0 (você). Para transferi-la ao Dono 1, você assina digitalmente a transação com sua chave privada. Essa assinatura inclui o código da transação anterior (chamado de "hash") e a chave pública do Dono 1. 2. Quando o Dono 1 quiser transferir a moeda ao Dono 2, ele assinará a transação seguinte com sua própria chave privada, incluindo também o hash da transação anterior e a chave pública do Dono 2. 3. Esse processo continua, formando uma "cadeia" de transações. Qualquer pessoa pode verificar essa cadeia para confirmar quem é o atual dono da moeda. #### Resolvendo o problema do gasto duplo Um grande desafio com moedas digitais é o "gasto duplo", que é quando uma mesma moeda é usada em mais de uma transação. Para evitar isso, muitos sistemas antigos dependiam de uma entidade central confiável, como uma casa da moeda, que verificava todas as transações. No entanto, isso criava um ponto único de falha e centralizava o controle do dinheiro. O Bitcoin resolve esse problema de forma inovadora: ele usa uma rede descentralizada onde todos os participantes (os "nós") têm acesso a um registro completo de todas as transações. Cada nó verifica se as transações são válidas e se a moeda não foi gasta duas vezes. Quando a maioria dos nós concorda com a validade de uma transação, ela é registrada permanentemente na blockchain. #### Por que isso é importante? Essa solução elimina a necessidade de confiar em uma única entidade para gerenciar o dinheiro, permitindo que qualquer pessoa no mundo use o Bitcoin sem precisar de permissão de terceiros. Além disso, ela garante que o sistema seja seguro e resistente a fraudes. --- ### 3. Servidor Timestamp Para assegurar que as transações sejam realizadas de forma segura e transparente, o sistema Bitcoin utiliza algo chamado de "servidor de registro de tempo" (timestamp). Esse servidor funciona como um registro público que organiza as transações em uma ordem específica. Ele faz isso agrupando várias transações em blocos e criando um código único chamado "hash". Esse hash é como uma impressão digital que representa todo o conteúdo do bloco. O hash de cada bloco é amplamente divulgado, como se fosse publicado em um jornal ou em um fórum público. Esse processo garante que cada bloco de transações tenha um registro de quando foi criado e que ele existia naquele momento. Além disso, cada novo bloco criado contém o hash do bloco anterior, formando uma cadeia contínua de blocos conectados — conhecida como blockchain. Com isso, se alguém tentar alterar qualquer informação em um bloco anterior, o hash desse bloco mudará e não corresponderá ao hash armazenado no bloco seguinte. Essa característica torna a cadeia muito segura, pois qualquer tentativa de fraude seria imediatamente detectada. O sistema de timestamps é essencial para provar a ordem cronológica das transações e garantir que cada uma delas seja única e autêntica. Dessa forma, ele reforça a segurança e a confiança na rede Bitcoin. --- ### 4. Prova-de-Trabalho Para implementar o registro de tempo distribuído no sistema Bitcoin, utilizamos um mecanismo chamado prova-de-trabalho. Esse sistema é semelhante ao Hashcash, desenvolvido por Adam Back, e baseia-se na criação de um código único, o "hash", por meio de um processo computacionalmente exigente. A prova-de-trabalho envolve encontrar um valor especial que, quando processado junto com as informações do bloco, gere um hash que comece com uma quantidade específica de zeros. Esse valor especial é chamado de "nonce". Encontrar o nonce correto exige um esforço significativo do computador, porque envolve tentativas repetidas até que a condição seja satisfeita. Esse processo é importante porque torna extremamente difícil alterar qualquer informação registrada em um bloco. Se alguém tentar mudar algo em um bloco, seria necessário refazer o trabalho de computação não apenas para aquele bloco, mas também para todos os blocos que vêm depois dele. Isso garante a segurança e a imutabilidade da blockchain. A prova-de-trabalho também resolve o problema de decidir qual cadeia de blocos é a válida quando há múltiplas cadeias competindo. A decisão é feita pela cadeia mais longa, pois ela representa o maior esforço computacional já realizado. Isso impede que qualquer indivíduo ou grupo controle a rede, desde que a maioria do poder de processamento seja mantida por participantes honestos. Para garantir que o sistema permaneça eficiente e equilibrado, a dificuldade da prova-de-trabalho é ajustada automaticamente ao longo do tempo. Se novos blocos estiverem sendo gerados rapidamente, a dificuldade aumenta; se estiverem sendo gerados muito lentamente, a dificuldade diminui. Esse ajuste assegura que novos blocos sejam criados aproximadamente a cada 10 minutos, mantendo o sistema estável e funcional. --- ### 5. Rede A rede Bitcoin é o coração do sistema e funciona de maneira distribuída, conectando vários participantes (ou nós) para garantir o registro e a validação das transações. Os passos para operar essa rede são: 1. **Transmissão de Transações**: Quando alguém realiza uma nova transação, ela é enviada para todos os nós da rede. Isso é feito para garantir que todos estejam cientes da operação e possam validá-la. 2. **Coleta de Transações em Blocos**: Cada nó agrupa as novas transações recebidas em um "bloco". Este bloco será preparado para ser adicionado à cadeia de blocos (a blockchain). 3. **Prova-de-Trabalho**: Os nós competem para resolver a prova-de-trabalho do bloco, utilizando poder computacional para encontrar um hash válido. Esse processo é como resolver um quebra-cabeça matemático difícil. 4. **Envio do Bloco Resolvido**: Quando um nó encontra a solução para o bloco (a prova-de-trabalho), ele compartilha esse bloco com todos os outros nós na rede. 5. **Validação do Bloco**: Cada nó verifica o bloco recebido para garantir que todas as transações nele contidas sejam válidas e que nenhuma moeda tenha sido gasta duas vezes. Apenas blocos válidos são aceitos. 6. **Construção do Próximo Bloco**: Os nós que aceitaram o bloco começam a trabalhar na criação do próximo bloco, utilizando o hash do bloco aceito como base (hash anterior). Isso mantém a continuidade da cadeia. #### Resolução de Conflitos e Escolha da Cadeia Mais Longa Os nós sempre priorizam a cadeia mais longa, pois ela representa o maior esforço computacional já realizado, garantindo maior segurança. Se dois blocos diferentes forem compartilhados simultaneamente, os nós trabalharão no primeiro bloco recebido, mas guardarão o outro como uma alternativa. Caso o segundo bloco eventualmente forme uma cadeia mais longa (ou seja, tenha mais blocos subsequentes), os nós mudarão para essa nova cadeia. #### Tolerância a Falhas A rede é robusta e pode lidar com mensagens que não chegam a todos os nós. Uma transação não precisa alcançar todos os nós de imediato; basta que chegue a um número suficiente deles para ser incluída em um bloco. Da mesma forma, se um nó não receber um bloco em tempo hábil, ele pode solicitá-lo ao perceber que está faltando quando o próximo bloco é recebido. Esse mecanismo descentralizado permite que a rede Bitcoin funcione de maneira segura, confiável e resiliente, sem depender de uma autoridade central. --- ### 6. Incentivo O incentivo é um dos pilares fundamentais que sustenta o funcionamento da rede Bitcoin, garantindo que os participantes (nós) continuem operando de forma honesta e contribuindo com recursos computacionais. Ele é estruturado em duas partes principais: a recompensa por mineração e as taxas de transação. #### Recompensa por Mineração Por convenção, o primeiro registro em cada bloco é uma transação especial que cria novas moedas e as atribui ao criador do bloco. Essa recompensa incentiva os mineradores a dedicarem poder computacional para apoiar a rede. Como não há uma autoridade central para emitir moedas, essa é a maneira pela qual novas moedas entram em circulação. Esse processo pode ser comparado ao trabalho de garimpeiros, que utilizam recursos para colocar mais ouro em circulação. No caso do Bitcoin, o "recurso" consiste no tempo de CPU e na energia elétrica consumida para resolver a prova-de-trabalho. #### Taxas de Transação Além da recompensa por mineração, os mineradores também podem ser incentivados pelas taxas de transação. Se uma transação utiliza menos valor de saída do que o valor de entrada, a diferença é tratada como uma taxa, que é adicionada à recompensa do bloco contendo essa transação. Com o passar do tempo e à medida que o número de moedas em circulação atinge o limite predeterminado, essas taxas de transação se tornam a principal fonte de incentivo, substituindo gradualmente a emissão de novas moedas. Isso permite que o sistema opere sem inflação, uma vez que o número total de moedas permanece fixo. #### Incentivo à Honestidade O design do incentivo também busca garantir que os participantes da rede mantenham um comportamento honesto. Para um atacante que consiga reunir mais poder computacional do que o restante da rede, ele enfrentaria duas escolhas: 1. Usar esse poder para fraudar o sistema, como reverter transações e roubar pagamentos. 2. Seguir as regras do sistema, criando novos blocos e recebendo recompensas legítimas. A lógica econômica favorece a segunda opção, pois um comportamento desonesto prejudicaria a confiança no sistema, diminuindo o valor de todas as moedas, incluindo aquelas que o próprio atacante possui. Jogar dentro das regras não apenas maximiza o retorno financeiro, mas também preserva a validade e a integridade do sistema. Esse mecanismo garante que os incentivos econômicos estejam alinhados com o objetivo de manter a rede segura, descentralizada e funcional ao longo do tempo. --- ### 7. Recuperação do Espaço em Disco Depois que uma moeda passa a estar protegida por muitos blocos na cadeia, as informações sobre as transações antigas que a geraram podem ser descartadas para economizar espaço em disco. Para que isso seja possível sem comprometer a segurança, as transações são organizadas em uma estrutura chamada "árvore de Merkle". Essa árvore funciona como um resumo das transações: em vez de armazenar todas elas, guarda apenas um "hash raiz", que é como uma assinatura compacta que representa todo o grupo de transações. Os blocos antigos podem, então, ser simplificados, removendo as partes desnecessárias dessa árvore. Apenas a raiz do hash precisa ser mantida no cabeçalho do bloco, garantindo que a integridade dos dados seja preservada, mesmo que detalhes específicos sejam descartados. Para exemplificar: imagine que você tenha vários recibos de compra. Em vez de guardar todos os recibos, você cria um documento e lista apenas o valor total de cada um. Mesmo que os recibos originais sejam descartados, ainda é possível verificar a soma com base nos valores armazenados. Além disso, o espaço ocupado pelos blocos em si é muito pequeno. Cada bloco sem transações ocupa apenas cerca de 80 bytes. Isso significa que, mesmo com blocos sendo gerados a cada 10 minutos, o crescimento anual em espaço necessário é insignificante: apenas 4,2 MB por ano. Com a capacidade de armazenamento dos computadores crescendo a cada ano, esse espaço continuará sendo trivial, garantindo que a rede possa operar de forma eficiente sem problemas de armazenamento, mesmo a longo prazo. --- ### 8. Verificação de Pagamento Simplificada É possível confirmar pagamentos sem a necessidade de operar um nó completo da rede. Para isso, o usuário precisa apenas de uma cópia dos cabeçalhos dos blocos da cadeia mais longa (ou seja, a cadeia com maior esforço de trabalho acumulado). Ele pode verificar a validade de uma transação ao consultar os nós da rede até obter a confirmação de que tem a cadeia mais longa. Para isso, utiliza-se o ramo Merkle, que conecta a transação ao bloco em que ela foi registrada. Entretanto, o método simplificado possui limitações: ele não pode confirmar uma transação isoladamente, mas sim assegurar que ela ocupa um lugar específico na cadeia mais longa. Dessa forma, se um nó da rede aprova a transação, os blocos subsequentes reforçam essa aceitação. A verificação simplificada é confiável enquanto a maioria dos nós da rede for honesta. Contudo, ela se torna vulnerável caso a rede seja dominada por um invasor. Nesse cenário, um atacante poderia fabricar transações fraudulentas que enganariam o usuário temporariamente até que o invasor obtivesse controle completo da rede. Uma estratégia para mitigar esse risco é configurar alertas nos softwares de nós completos. Esses alertas identificam blocos inválidos, sugerindo ao usuário baixar o bloco completo para confirmar qualquer inconsistência. Para maior segurança, empresas que realizam pagamentos frequentes podem preferir operar seus próprios nós, reduzindo riscos e permitindo uma verificação mais direta e confiável. --- ### 9. Combinando e Dividindo Valor No sistema Bitcoin, cada unidade de valor é tratada como uma "moeda" individual, mas gerenciar cada centavo como uma transação separada seria impraticável. Para resolver isso, o Bitcoin permite que valores sejam combinados ou divididos em transações, facilitando pagamentos de qualquer valor. #### Entradas e Saídas Cada transação no Bitcoin é composta por: - **Entradas**: Representam os valores recebidos em transações anteriores. - **Saídas**: Correspondem aos valores enviados, divididos entre os destinatários e, eventualmente, o troco para o remetente. Normalmente, uma transação contém: - Uma única entrada com valor suficiente para cobrir o pagamento. - Ou várias entradas combinadas para atingir o valor necessário. O valor total das saídas nunca excede o das entradas, e a diferença (se houver) pode ser retornada ao remetente como **troco**. #### Exemplo Prático Imagine que você tem duas entradas: 1. 0,03 BTC 2. 0,07 BTC Se deseja enviar 0,08 BTC para alguém, a transação terá: - **Entrada**: As duas entradas combinadas (0,03 + 0,07 BTC = 0,10 BTC). - **Saídas**: Uma para o destinatário (0,08 BTC) e outra como troco para você (0,02 BTC). Essa flexibilidade permite que o sistema funcione sem precisar manipular cada unidade mínima individualmente. #### Difusão e Simplificação A difusão de transações, onde uma depende de várias anteriores e assim por diante, não representa um problema. Não é necessário armazenar ou verificar o histórico completo de uma transação para utilizá-la, já que o registro na blockchain garante sua integridade. --- ### 10. Privacidade O modelo bancário tradicional oferece um certo nível de privacidade, limitando o acesso às informações financeiras apenas às partes envolvidas e a um terceiro confiável (como bancos ou instituições financeiras). No entanto, o Bitcoin opera de forma diferente, pois todas as transações são publicamente registradas na blockchain. Apesar disso, a privacidade pode ser mantida utilizando **chaves públicas anônimas**, que desvinculam diretamente as transações das identidades das partes envolvidas. #### Fluxo de Informação - No **modelo tradicional**, as transações passam por um terceiro confiável que conhece tanto o remetente quanto o destinatário. - No **Bitcoin**, as transações são anunciadas publicamente, mas sem revelar diretamente as identidades das partes. Isso é comparável a dados divulgados por bolsas de valores, onde informações como o tempo e o tamanho das negociações (a "fita") são públicas, mas as identidades das partes não. #### Protegendo a Privacidade Para aumentar a privacidade no Bitcoin, são adotadas as seguintes práticas: 1. **Chaves Públicas Anônimas**: Cada transação utiliza um par de chaves diferentes, dificultando a associação com um proprietário único. 2. **Prevenção de Ligação**: Ao usar chaves novas para cada transação, reduz-se a possibilidade de links evidentes entre múltiplas transações realizadas pelo mesmo usuário. #### Riscos de Ligação Embora a privacidade seja fortalecida, alguns riscos permanecem: - Transações **multi-entrada** podem revelar que todas as entradas pertencem ao mesmo proprietário, caso sejam necessárias para somar o valor total. - O proprietário da chave pode ser identificado indiretamente por transações anteriores que estejam conectadas. --- ### 11. Cálculos Imagine que temos um sistema onde as pessoas (ou computadores) competem para adicionar informações novas (blocos) a um grande registro público (a cadeia de blocos ou blockchain). Este registro é como um livro contábil compartilhado, onde todos podem verificar o que está escrito. Agora, vamos pensar em um cenário: um atacante quer enganar o sistema. Ele quer mudar informações já registradas para beneficiar a si mesmo, por exemplo, desfazendo um pagamento que já fez. Para isso, ele precisa criar uma versão alternativa do livro contábil (a cadeia de blocos dele) e convencer todos os outros participantes de que essa versão é a verdadeira. Mas isso é extremamente difícil. #### Como o Ataque Funciona Quando um novo bloco é adicionado à cadeia, ele depende de cálculos complexos que levam tempo e esforço. Esses cálculos são como um grande quebra-cabeça que precisa ser resolvido. - Os “bons jogadores” (nós honestos) estão sempre trabalhando juntos para resolver esses quebra-cabeças e adicionar novos blocos à cadeia verdadeira. - O atacante, por outro lado, precisa resolver quebra-cabeças sozinho, tentando “alcançar” a cadeia honesta para que sua versão alternativa pareça válida. Se a cadeia honesta já está vários blocos à frente, o atacante começa em desvantagem, e o sistema está projetado para que a dificuldade de alcançá-los aumente rapidamente. #### A Corrida Entre Cadeias Você pode imaginar isso como uma corrida. A cada bloco novo que os jogadores honestos adicionam à cadeia verdadeira, eles se distanciam mais do atacante. Para vencer, o atacante teria que resolver os quebra-cabeças mais rápido que todos os outros jogadores honestos juntos. Suponha que: - A rede honesta tem **80% do poder computacional** (ou seja, resolve 8 de cada 10 quebra-cabeças). - O atacante tem **20% do poder computacional** (ou seja, resolve 2 de cada 10 quebra-cabeças). Cada vez que a rede honesta adiciona um bloco, o atacante tem que "correr atrás" e resolver mais quebra-cabeças para alcançar. #### Por Que o Ataque Fica Cada Vez Mais Improvável? Vamos usar uma fórmula simples para mostrar como as chances de sucesso do atacante diminuem conforme ele precisa "alcançar" mais blocos: P = (q/p)^z - **q** é o poder computacional do atacante (20%, ou 0,2). - **p** é o poder computacional da rede honesta (80%, ou 0,8). - **z** é a diferença de blocos entre a cadeia honesta e a cadeia do atacante. Se o atacante está 5 blocos atrás (z = 5): P = (0,2 / 0,8)^5 = (0,25)^5 = 0,00098, (ou, 0,098%) Isso significa que o atacante tem menos de 0,1% de chance de sucesso — ou seja, é muito improvável. Se ele estiver 10 blocos atrás (z = 10): P = (0,2 / 0,8)^10 = (0,25)^10 = 0,000000095, (ou, 0,0000095%). Neste caso, as chances de sucesso são praticamente **nulas**. #### Um Exemplo Simples Se você jogar uma moeda, a chance de cair “cara” é de 50%. Mas se precisar de 10 caras seguidas, sua chance já é bem menor. Se precisar de 20 caras seguidas, é quase impossível. No caso do Bitcoin, o atacante precisa de muito mais do que 20 caras seguidas. Ele precisa resolver quebra-cabeças extremamente difíceis e alcançar os jogadores honestos que estão sempre à frente. Isso faz com que o ataque seja inviável na prática. #### Por Que Tudo Isso é Seguro? - **A probabilidade de sucesso do atacante diminui exponencialmente.** Isso significa que, quanto mais tempo passa, menor é a chance de ele conseguir enganar o sistema. - **A cadeia verdadeira (honesta) está protegida pela força da rede.** Cada novo bloco que os jogadores honestos adicionam à cadeia torna mais difícil para o atacante alcançar. #### E Se o Atacante Tentar Continuar? O atacante poderia continuar tentando indefinidamente, mas ele estaria gastando muito tempo e energia sem conseguir nada. Enquanto isso, os jogadores honestos estão sempre adicionando novos blocos, tornando o trabalho do atacante ainda mais inútil. Assim, o sistema garante que a cadeia verdadeira seja extremamente segura e que ataques sejam, na prática, impossíveis de ter sucesso. --- ### 12. Conclusão Propusemos um sistema de transações eletrônicas que elimina a necessidade de confiança, baseando-se em assinaturas digitais e em uma rede peer-to-peer que utiliza prova de trabalho. Isso resolve o problema do gasto duplo, criando um histórico público de transações imutável, desde que a maioria do poder computacional permaneça sob controle dos participantes honestos. A rede funciona de forma simples e descentralizada, com nós independentes que não precisam de identificação ou coordenação direta. Eles entram e saem livremente, aceitando a cadeia de prova de trabalho como registro do que ocorreu durante sua ausência. As decisões são tomadas por meio do poder de CPU, validando blocos legítimos, estendendo a cadeia e rejeitando os inválidos. Com este mecanismo de consenso, todas as regras e incentivos necessários para o funcionamento seguro e eficiente do sistema são garantidos. --- Faça o download do whitepaper original em português: https://bitcoin.org/files/bitcoin-paper/bitcoin_pt_br.pdf
@ 6be5cc06:5259daf0
2025-01-21 01:51:46## Bitcoin: Um sistema de dinheiro eletrônico direto entre pessoas. Satoshi Nakamoto satoshin@gmx.com www.bitcoin.org --- ### Resumo O Bitcoin é uma forma de dinheiro digital que permite pagamentos diretos entre pessoas, sem a necessidade de um banco ou instituição financeira. Ele resolve um problema chamado **gasto duplo**, que ocorre quando alguém tenta gastar o mesmo dinheiro duas vezes. Para evitar isso, o Bitcoin usa uma rede descentralizada onde todos trabalham juntos para verificar e registrar as transações. As transações são registradas em um livro público chamado **blockchain**, protegido por uma técnica chamada **Prova de Trabalho**. Essa técnica cria uma cadeia de registros que não pode ser alterada sem refazer todo o trabalho já feito. Essa cadeia é mantida pelos computadores que participam da rede, e a mais longa é considerada a verdadeira. Enquanto a maior parte do poder computacional da rede for controlada por participantes honestos, o sistema continuará funcionando de forma segura. A rede é flexível, permitindo que qualquer pessoa entre ou saia a qualquer momento, sempre confiando na cadeia mais longa como prova do que aconteceu. --- ### 1. Introdução Hoje, quase todos os pagamentos feitos pela internet dependem de bancos ou empresas como processadores de pagamento (cartões de crédito, por exemplo) para funcionar. Embora esse sistema seja útil, ele tem problemas importantes porque é baseado em **confiança**. Primeiro, essas empresas podem reverter pagamentos, o que é útil em caso de erros, mas cria custos e incertezas. Isso faz com que pequenas transações, como pagar centavos por um serviço, se tornem inviáveis. Além disso, os comerciantes são obrigados a desconfiar dos clientes, pedindo informações extras e aceitando fraudes como algo inevitável. Esses problemas não existem no dinheiro físico, como o papel-moeda, onde o pagamento é final e direto entre as partes. No entanto, não temos como enviar dinheiro físico pela internet sem depender de um intermediário confiável. O que precisamos é de um **sistema de pagamento eletrônico baseado em provas matemáticas**, não em confiança. Esse sistema permitiria que qualquer pessoa enviasse dinheiro diretamente para outra, sem depender de bancos ou processadores de pagamento. Além disso, as transações seriam irreversíveis, protegendo vendedores contra fraudes, mas mantendo a possibilidade de soluções para disputas legítimas. Neste documento, apresentamos o **Bitcoin**, que resolve o problema do gasto duplo usando uma rede descentralizada. Essa rede cria um registro público e protegido por cálculos matemáticos, que garante a ordem das transações. Enquanto a maior parte da rede for controlada por pessoas honestas, o sistema será seguro contra ataques. --- ### 2. Transações Para entender como funciona o Bitcoin, é importante saber como as transações são realizadas. Imagine que você quer transferir uma "moeda digital" para outra pessoa. No sistema do Bitcoin, essa "moeda" é representada por uma sequência de registros que mostram quem é o atual dono. Para transferi-la, você adiciona um novo registro comprovando que agora ela pertence ao próximo dono. Esse registro é protegido por um tipo especial de assinatura digital. #### O que é uma assinatura digital? Uma assinatura digital é como uma senha secreta, mas muito mais segura. No Bitcoin, cada usuário tem duas chaves: uma "chave privada", que é secreta e serve para criar a assinatura, e uma "chave pública", que pode ser compartilhada com todos e é usada para verificar se a assinatura é válida. Quando você transfere uma moeda, usa sua chave privada para assinar a transação, provando que você é o dono. A próxima pessoa pode usar sua chave pública para confirmar isso. #### Como funciona na prática? Cada "moeda" no Bitcoin é, na verdade, uma cadeia de assinaturas digitais. Vamos imaginar o seguinte cenário: 1. A moeda está com o Dono 0 (você). Para transferi-la ao Dono 1, você assina digitalmente a transação com sua chave privada. Essa assinatura inclui o código da transação anterior (chamado de "hash") e a chave pública do Dono 1. 2. Quando o Dono 1 quiser transferir a moeda ao Dono 2, ele assinará a transação seguinte com sua própria chave privada, incluindo também o hash da transação anterior e a chave pública do Dono 2. 3. Esse processo continua, formando uma "cadeia" de transações. Qualquer pessoa pode verificar essa cadeia para confirmar quem é o atual dono da moeda. #### Resolvendo o problema do gasto duplo Um grande desafio com moedas digitais é o "gasto duplo", que é quando uma mesma moeda é usada em mais de uma transação. Para evitar isso, muitos sistemas antigos dependiam de uma entidade central confiável, como uma casa da moeda, que verificava todas as transações. No entanto, isso criava um ponto único de falha e centralizava o controle do dinheiro. O Bitcoin resolve esse problema de forma inovadora: ele usa uma rede descentralizada onde todos os participantes (os "nós") têm acesso a um registro completo de todas as transações. Cada nó verifica se as transações são válidas e se a moeda não foi gasta duas vezes. Quando a maioria dos nós concorda com a validade de uma transação, ela é registrada permanentemente na blockchain. #### Por que isso é importante? Essa solução elimina a necessidade de confiar em uma única entidade para gerenciar o dinheiro, permitindo que qualquer pessoa no mundo use o Bitcoin sem precisar de permissão de terceiros. Além disso, ela garante que o sistema seja seguro e resistente a fraudes. --- ### 3. Servidor Timestamp Para assegurar que as transações sejam realizadas de forma segura e transparente, o sistema Bitcoin utiliza algo chamado de "servidor de registro de tempo" (timestamp). Esse servidor funciona como um registro público que organiza as transações em uma ordem específica. Ele faz isso agrupando várias transações em blocos e criando um código único chamado "hash". Esse hash é como uma impressão digital que representa todo o conteúdo do bloco. O hash de cada bloco é amplamente divulgado, como se fosse publicado em um jornal ou em um fórum público. Esse processo garante que cada bloco de transações tenha um registro de quando foi criado e que ele existia naquele momento. Além disso, cada novo bloco criado contém o hash do bloco anterior, formando uma cadeia contínua de blocos conectados — conhecida como blockchain. Com isso, se alguém tentar alterar qualquer informação em um bloco anterior, o hash desse bloco mudará e não corresponderá ao hash armazenado no bloco seguinte. Essa característica torna a cadeia muito segura, pois qualquer tentativa de fraude seria imediatamente detectada. O sistema de timestamps é essencial para provar a ordem cronológica das transações e garantir que cada uma delas seja única e autêntica. Dessa forma, ele reforça a segurança e a confiança na rede Bitcoin. --- ### 4. Prova-de-Trabalho Para implementar o registro de tempo distribuído no sistema Bitcoin, utilizamos um mecanismo chamado prova-de-trabalho. Esse sistema é semelhante ao Hashcash, desenvolvido por Adam Back, e baseia-se na criação de um código único, o "hash", por meio de um processo computacionalmente exigente. A prova-de-trabalho envolve encontrar um valor especial que, quando processado junto com as informações do bloco, gere um hash que comece com uma quantidade específica de zeros. Esse valor especial é chamado de "nonce". Encontrar o nonce correto exige um esforço significativo do computador, porque envolve tentativas repetidas até que a condição seja satisfeita. Esse processo é importante porque torna extremamente difícil alterar qualquer informação registrada em um bloco. Se alguém tentar mudar algo em um bloco, seria necessário refazer o trabalho de computação não apenas para aquele bloco, mas também para todos os blocos que vêm depois dele. Isso garante a segurança e a imutabilidade da blockchain. A prova-de-trabalho também resolve o problema de decidir qual cadeia de blocos é a válida quando há múltiplas cadeias competindo. A decisão é feita pela cadeia mais longa, pois ela representa o maior esforço computacional já realizado. Isso impede que qualquer indivíduo ou grupo controle a rede, desde que a maioria do poder de processamento seja mantida por participantes honestos. Para garantir que o sistema permaneça eficiente e equilibrado, a dificuldade da prova-de-trabalho é ajustada automaticamente ao longo do tempo. Se novos blocos estiverem sendo gerados rapidamente, a dificuldade aumenta; se estiverem sendo gerados muito lentamente, a dificuldade diminui. Esse ajuste assegura que novos blocos sejam criados aproximadamente a cada 10 minutos, mantendo o sistema estável e funcional. --- ### 5. Rede A rede Bitcoin é o coração do sistema e funciona de maneira distribuída, conectando vários participantes (ou nós) para garantir o registro e a validação das transações. Os passos para operar essa rede são: 1. **Transmissão de Transações**: Quando alguém realiza uma nova transação, ela é enviada para todos os nós da rede. Isso é feito para garantir que todos estejam cientes da operação e possam validá-la. 2. **Coleta de Transações em Blocos**: Cada nó agrupa as novas transações recebidas em um "bloco". Este bloco será preparado para ser adicionado à cadeia de blocos (a blockchain). 3. **Prova-de-Trabalho**: Os nós competem para resolver a prova-de-trabalho do bloco, utilizando poder computacional para encontrar um hash válido. Esse processo é como resolver um quebra-cabeça matemático difícil. 4. **Envio do Bloco Resolvido**: Quando um nó encontra a solução para o bloco (a prova-de-trabalho), ele compartilha esse bloco com todos os outros nós na rede. 5. **Validação do Bloco**: Cada nó verifica o bloco recebido para garantir que todas as transações nele contidas sejam válidas e que nenhuma moeda tenha sido gasta duas vezes. Apenas blocos válidos são aceitos. 6. **Construção do Próximo Bloco**: Os nós que aceitaram o bloco começam a trabalhar na criação do próximo bloco, utilizando o hash do bloco aceito como base (hash anterior). Isso mantém a continuidade da cadeia. #### Resolução de Conflitos e Escolha da Cadeia Mais Longa Os nós sempre priorizam a cadeia mais longa, pois ela representa o maior esforço computacional já realizado, garantindo maior segurança. Se dois blocos diferentes forem compartilhados simultaneamente, os nós trabalharão no primeiro bloco recebido, mas guardarão o outro como uma alternativa. Caso o segundo bloco eventualmente forme uma cadeia mais longa (ou seja, tenha mais blocos subsequentes), os nós mudarão para essa nova cadeia. #### Tolerância a Falhas A rede é robusta e pode lidar com mensagens que não chegam a todos os nós. Uma transação não precisa alcançar todos os nós de imediato; basta que chegue a um número suficiente deles para ser incluída em um bloco. Da mesma forma, se um nó não receber um bloco em tempo hábil, ele pode solicitá-lo ao perceber que está faltando quando o próximo bloco é recebido. Esse mecanismo descentralizado permite que a rede Bitcoin funcione de maneira segura, confiável e resiliente, sem depender de uma autoridade central. --- ### 6. Incentivo O incentivo é um dos pilares fundamentais que sustenta o funcionamento da rede Bitcoin, garantindo que os participantes (nós) continuem operando de forma honesta e contribuindo com recursos computacionais. Ele é estruturado em duas partes principais: a recompensa por mineração e as taxas de transação. #### Recompensa por Mineração Por convenção, o primeiro registro em cada bloco é uma transação especial que cria novas moedas e as atribui ao criador do bloco. Essa recompensa incentiva os mineradores a dedicarem poder computacional para apoiar a rede. Como não há uma autoridade central para emitir moedas, essa é a maneira pela qual novas moedas entram em circulação. Esse processo pode ser comparado ao trabalho de garimpeiros, que utilizam recursos para colocar mais ouro em circulação. No caso do Bitcoin, o "recurso" consiste no tempo de CPU e na energia elétrica consumida para resolver a prova-de-trabalho. #### Taxas de Transação Além da recompensa por mineração, os mineradores também podem ser incentivados pelas taxas de transação. Se uma transação utiliza menos valor de saída do que o valor de entrada, a diferença é tratada como uma taxa, que é adicionada à recompensa do bloco contendo essa transação. Com o passar do tempo e à medida que o número de moedas em circulação atinge o limite predeterminado, essas taxas de transação se tornam a principal fonte de incentivo, substituindo gradualmente a emissão de novas moedas. Isso permite que o sistema opere sem inflação, uma vez que o número total de moedas permanece fixo. #### Incentivo à Honestidade O design do incentivo também busca garantir que os participantes da rede mantenham um comportamento honesto. Para um atacante que consiga reunir mais poder computacional do que o restante da rede, ele enfrentaria duas escolhas: 1. Usar esse poder para fraudar o sistema, como reverter transações e roubar pagamentos. 2. Seguir as regras do sistema, criando novos blocos e recebendo recompensas legítimas. A lógica econômica favorece a segunda opção, pois um comportamento desonesto prejudicaria a confiança no sistema, diminuindo o valor de todas as moedas, incluindo aquelas que o próprio atacante possui. Jogar dentro das regras não apenas maximiza o retorno financeiro, mas também preserva a validade e a integridade do sistema. Esse mecanismo garante que os incentivos econômicos estejam alinhados com o objetivo de manter a rede segura, descentralizada e funcional ao longo do tempo. --- ### 7. Recuperação do Espaço em Disco Depois que uma moeda passa a estar protegida por muitos blocos na cadeia, as informações sobre as transações antigas que a geraram podem ser descartadas para economizar espaço em disco. Para que isso seja possível sem comprometer a segurança, as transações são organizadas em uma estrutura chamada "árvore de Merkle". Essa árvore funciona como um resumo das transações: em vez de armazenar todas elas, guarda apenas um "hash raiz", que é como uma assinatura compacta que representa todo o grupo de transações. Os blocos antigos podem, então, ser simplificados, removendo as partes desnecessárias dessa árvore. Apenas a raiz do hash precisa ser mantida no cabeçalho do bloco, garantindo que a integridade dos dados seja preservada, mesmo que detalhes específicos sejam descartados. Para exemplificar: imagine que você tenha vários recibos de compra. Em vez de guardar todos os recibos, você cria um documento e lista apenas o valor total de cada um. Mesmo que os recibos originais sejam descartados, ainda é possível verificar a soma com base nos valores armazenados. Além disso, o espaço ocupado pelos blocos em si é muito pequeno. Cada bloco sem transações ocupa apenas cerca de 80 bytes. Isso significa que, mesmo com blocos sendo gerados a cada 10 minutos, o crescimento anual em espaço necessário é insignificante: apenas 4,2 MB por ano. Com a capacidade de armazenamento dos computadores crescendo a cada ano, esse espaço continuará sendo trivial, garantindo que a rede possa operar de forma eficiente sem problemas de armazenamento, mesmo a longo prazo. --- ### 8. Verificação de Pagamento Simplificada É possível confirmar pagamentos sem a necessidade de operar um nó completo da rede. Para isso, o usuário precisa apenas de uma cópia dos cabeçalhos dos blocos da cadeia mais longa (ou seja, a cadeia com maior esforço de trabalho acumulado). Ele pode verificar a validade de uma transação ao consultar os nós da rede até obter a confirmação de que tem a cadeia mais longa. Para isso, utiliza-se o ramo Merkle, que conecta a transação ao bloco em que ela foi registrada. Entretanto, o método simplificado possui limitações: ele não pode confirmar uma transação isoladamente, mas sim assegurar que ela ocupa um lugar específico na cadeia mais longa. Dessa forma, se um nó da rede aprova a transação, os blocos subsequentes reforçam essa aceitação. A verificação simplificada é confiável enquanto a maioria dos nós da rede for honesta. Contudo, ela se torna vulnerável caso a rede seja dominada por um invasor. Nesse cenário, um atacante poderia fabricar transações fraudulentas que enganariam o usuário temporariamente até que o invasor obtivesse controle completo da rede. Uma estratégia para mitigar esse risco é configurar alertas nos softwares de nós completos. Esses alertas identificam blocos inválidos, sugerindo ao usuário baixar o bloco completo para confirmar qualquer inconsistência. Para maior segurança, empresas que realizam pagamentos frequentes podem preferir operar seus próprios nós, reduzindo riscos e permitindo uma verificação mais direta e confiável. --- ### 9. Combinando e Dividindo Valor No sistema Bitcoin, cada unidade de valor é tratada como uma "moeda" individual, mas gerenciar cada centavo como uma transação separada seria impraticável. Para resolver isso, o Bitcoin permite que valores sejam combinados ou divididos em transações, facilitando pagamentos de qualquer valor. #### Entradas e Saídas Cada transação no Bitcoin é composta por: - **Entradas**: Representam os valores recebidos em transações anteriores. - **Saídas**: Correspondem aos valores enviados, divididos entre os destinatários e, eventualmente, o troco para o remetente. Normalmente, uma transação contém: - Uma única entrada com valor suficiente para cobrir o pagamento. - Ou várias entradas combinadas para atingir o valor necessário. O valor total das saídas nunca excede o das entradas, e a diferença (se houver) pode ser retornada ao remetente como **troco**. #### Exemplo Prático Imagine que você tem duas entradas: 1. 0,03 BTC 2. 0,07 BTC Se deseja enviar 0,08 BTC para alguém, a transação terá: - **Entrada**: As duas entradas combinadas (0,03 + 0,07 BTC = 0,10 BTC). - **Saídas**: Uma para o destinatário (0,08 BTC) e outra como troco para você (0,02 BTC). Essa flexibilidade permite que o sistema funcione sem precisar manipular cada unidade mínima individualmente. #### Difusão e Simplificação A difusão de transações, onde uma depende de várias anteriores e assim por diante, não representa um problema. Não é necessário armazenar ou verificar o histórico completo de uma transação para utilizá-la, já que o registro na blockchain garante sua integridade. --- ### 10. Privacidade O modelo bancário tradicional oferece um certo nível de privacidade, limitando o acesso às informações financeiras apenas às partes envolvidas e a um terceiro confiável (como bancos ou instituições financeiras). No entanto, o Bitcoin opera de forma diferente, pois todas as transações são publicamente registradas na blockchain. Apesar disso, a privacidade pode ser mantida utilizando **chaves públicas anônimas**, que desvinculam diretamente as transações das identidades das partes envolvidas. #### Fluxo de Informação - No **modelo tradicional**, as transações passam por um terceiro confiável que conhece tanto o remetente quanto o destinatário. - No **Bitcoin**, as transações são anunciadas publicamente, mas sem revelar diretamente as identidades das partes. Isso é comparável a dados divulgados por bolsas de valores, onde informações como o tempo e o tamanho das negociações (a "fita") são públicas, mas as identidades das partes não. #### Protegendo a Privacidade Para aumentar a privacidade no Bitcoin, são adotadas as seguintes práticas: 1. **Chaves Públicas Anônimas**: Cada transação utiliza um par de chaves diferentes, dificultando a associação com um proprietário único. 2. **Prevenção de Ligação**: Ao usar chaves novas para cada transação, reduz-se a possibilidade de links evidentes entre múltiplas transações realizadas pelo mesmo usuário. #### Riscos de Ligação Embora a privacidade seja fortalecida, alguns riscos permanecem: - Transações **multi-entrada** podem revelar que todas as entradas pertencem ao mesmo proprietário, caso sejam necessárias para somar o valor total. - O proprietário da chave pode ser identificado indiretamente por transações anteriores que estejam conectadas. --- ### 11. Cálculos Imagine que temos um sistema onde as pessoas (ou computadores) competem para adicionar informações novas (blocos) a um grande registro público (a cadeia de blocos ou blockchain). Este registro é como um livro contábil compartilhado, onde todos podem verificar o que está escrito. Agora, vamos pensar em um cenário: um atacante quer enganar o sistema. Ele quer mudar informações já registradas para beneficiar a si mesmo, por exemplo, desfazendo um pagamento que já fez. Para isso, ele precisa criar uma versão alternativa do livro contábil (a cadeia de blocos dele) e convencer todos os outros participantes de que essa versão é a verdadeira. Mas isso é extremamente difícil. #### Como o Ataque Funciona Quando um novo bloco é adicionado à cadeia, ele depende de cálculos complexos que levam tempo e esforço. Esses cálculos são como um grande quebra-cabeça que precisa ser resolvido. - Os “bons jogadores” (nós honestos) estão sempre trabalhando juntos para resolver esses quebra-cabeças e adicionar novos blocos à cadeia verdadeira. - O atacante, por outro lado, precisa resolver quebra-cabeças sozinho, tentando “alcançar” a cadeia honesta para que sua versão alternativa pareça válida. Se a cadeia honesta já está vários blocos à frente, o atacante começa em desvantagem, e o sistema está projetado para que a dificuldade de alcançá-los aumente rapidamente. #### A Corrida Entre Cadeias Você pode imaginar isso como uma corrida. A cada bloco novo que os jogadores honestos adicionam à cadeia verdadeira, eles se distanciam mais do atacante. Para vencer, o atacante teria que resolver os quebra-cabeças mais rápido que todos os outros jogadores honestos juntos. Suponha que: - A rede honesta tem **80% do poder computacional** (ou seja, resolve 8 de cada 10 quebra-cabeças). - O atacante tem **20% do poder computacional** (ou seja, resolve 2 de cada 10 quebra-cabeças). Cada vez que a rede honesta adiciona um bloco, o atacante tem que "correr atrás" e resolver mais quebra-cabeças para alcançar. #### Por Que o Ataque Fica Cada Vez Mais Improvável? Vamos usar uma fórmula simples para mostrar como as chances de sucesso do atacante diminuem conforme ele precisa "alcançar" mais blocos: P = (q/p)^z - **q** é o poder computacional do atacante (20%, ou 0,2). - **p** é o poder computacional da rede honesta (80%, ou 0,8). - **z** é a diferença de blocos entre a cadeia honesta e a cadeia do atacante. Se o atacante está 5 blocos atrás (z = 5): P = (0,2 / 0,8)^5 = (0,25)^5 = 0,00098, (ou, 0,098%) Isso significa que o atacante tem menos de 0,1% de chance de sucesso — ou seja, é muito improvável. Se ele estiver 10 blocos atrás (z = 10): P = (0,2 / 0,8)^10 = (0,25)^10 = 0,000000095, (ou, 0,0000095%). Neste caso, as chances de sucesso são praticamente **nulas**. #### Um Exemplo Simples Se você jogar uma moeda, a chance de cair “cara” é de 50%. Mas se precisar de 10 caras seguidas, sua chance já é bem menor. Se precisar de 20 caras seguidas, é quase impossível. No caso do Bitcoin, o atacante precisa de muito mais do que 20 caras seguidas. Ele precisa resolver quebra-cabeças extremamente difíceis e alcançar os jogadores honestos que estão sempre à frente. Isso faz com que o ataque seja inviável na prática. #### Por Que Tudo Isso é Seguro? - **A probabilidade de sucesso do atacante diminui exponencialmente.** Isso significa que, quanto mais tempo passa, menor é a chance de ele conseguir enganar o sistema. - **A cadeia verdadeira (honesta) está protegida pela força da rede.** Cada novo bloco que os jogadores honestos adicionam à cadeia torna mais difícil para o atacante alcançar. #### E Se o Atacante Tentar Continuar? O atacante poderia continuar tentando indefinidamente, mas ele estaria gastando muito tempo e energia sem conseguir nada. Enquanto isso, os jogadores honestos estão sempre adicionando novos blocos, tornando o trabalho do atacante ainda mais inútil. Assim, o sistema garante que a cadeia verdadeira seja extremamente segura e que ataques sejam, na prática, impossíveis de ter sucesso. --- ### 12. Conclusão Propusemos um sistema de transações eletrônicas que elimina a necessidade de confiança, baseando-se em assinaturas digitais e em uma rede peer-to-peer que utiliza prova de trabalho. Isso resolve o problema do gasto duplo, criando um histórico público de transações imutável, desde que a maioria do poder computacional permaneça sob controle dos participantes honestos. A rede funciona de forma simples e descentralizada, com nós independentes que não precisam de identificação ou coordenação direta. Eles entram e saem livremente, aceitando a cadeia de prova de trabalho como registro do que ocorreu durante sua ausência. As decisões são tomadas por meio do poder de CPU, validando blocos legítimos, estendendo a cadeia e rejeitando os inválidos. Com este mecanismo de consenso, todas as regras e incentivos necessários para o funcionamento seguro e eficiente do sistema são garantidos. --- Faça o download do whitepaper original em português: https://bitcoin.org/files/bitcoin-paper/bitcoin_pt_br.pdf @ 3f770d65:7a745b24
2025-01-19 21:48:49The recent shutdown of TikTok in the United States due to a potential government ban serves as a stark reminder how fragile centralized platforms truly are under the surface. While these platforms offer convenience, a more polished user experience, and connectivity, they are ultimately beholden to governments, corporations, and other authorities. This makes them vulnerable to censorship, regulation, and outright bans. In contrast, Nostr represents a shift in how we approach online communication and content sharing. Built on the principles of decentralization and user choice, Nostr cannot be banned, because it is not a platform—it is a protocol. **PROTOCOLS, NOT PLATFORMS.** At the heart of Nostr's philosophy is **user choice**, a feature that fundamentally sets it apart from legacy platforms. In centralized systems, the user experience is dictated by a single person or governing entity. If the platform decides to filter, censor, or ban specific users or content, individuals are left with little action to rectify the situation. They must either accept the changes or abandon the platform entirely, often at the cost of losing their social connections, their data, and their identity. What's happening with TikTok could never happen on Nostr. With Nostr, the dynamics are completely different. Because it is a protocol, not a platform, no single entity controls the ecosystem. Instead, the protocol enables a network of applications and relays that users can freely choose from. If a particular application or relay implements policies that a user disagrees with, such as censorship, filtering, or even government enforced banning, they are not trapped or abandoned. They have the freedom to move to another application or relay with minimal effort. **THIS IS POWERFUL.** Take, for example, the case of a relay that decides to censor specific content. On a legacy platform, this would result in frustration and a loss of access for users. On Nostr, however, users can simply connect to a different relay that does not impose such restrictions. Similarly, if an application introduces features or policies that users dislike, they can migrate to a different application that better suits their preferences, all while retaining their identity and social connections. The same principles apply to government bans and censorship. A government can ban a specific application or even multiple applications, just as it can block one relay or several relays. China has implemented both tactics, yet Chinese users continue to exist and actively participate on Nostr, demonstrating Nostr's ability to resistant censorship. How? Simply, it turns into a game of whack-a-mole. When one relay is censored, another quickly takes its place. When one application is banned, another emerges. Users can also bypass these obstacles by running their own relays and applications directly from their homes or personal devices, eliminating reliance on larger entities or organizations and ensuring continuous access. **AGAIN, THIS IS POWERUFL.** Nostr's open and decentralized design makes it resistant to the kinds of government intervention that led to TikTok's outages this weekend and potential future ban in the next 90 days. There is no central server to target, no company to regulate, and no single point of failure. (Insert your CEO jokes here). As long as there are individuals running relays and applications, users continue creating notes and sending zaps. Platforms like TikTok can be silenced with the stroke of a pen, leaving millions of users disconnected and abandoned. Social communication should not be silenced so incredibly easily. No one should have that much power over social interactions. Will we on-board a massive wave of TikTokers in the coming hours or days? I don't know. TikTokers may not be ready for Nostr yet, and honestly, Nostr may not be ready for them either. The ecosystem still lacks the completely polished applications, tools, and services they’re accustomed to. This is where we say "we're still early". They may not be early adopters like the current Nostr user base. Until we bridge that gap, they’ll likely move to the next centralized platform, only to face another government ban or round of censorship in the future. But eventually, there will come a tipping point, a moment when they’ve had enough. When that time comes, I hope we’re prepared. If we’re not, we risk missing a tremendous opportunity to onboard people who genuinely need Nostr’s freedom. Until then, to all of the Nostr developers out there, keep up the great work and keep building. Your hard work and determination is needed. ###
@ 3f770d65:7a745b24
2025-01-19 21:48:49The recent shutdown of TikTok in the United States due to a potential government ban serves as a stark reminder how fragile centralized platforms truly are under the surface. While these platforms offer convenience, a more polished user experience, and connectivity, they are ultimately beholden to governments, corporations, and other authorities. This makes them vulnerable to censorship, regulation, and outright bans. In contrast, Nostr represents a shift in how we approach online communication and content sharing. Built on the principles of decentralization and user choice, Nostr cannot be banned, because it is not a platform—it is a protocol. **PROTOCOLS, NOT PLATFORMS.** At the heart of Nostr's philosophy is **user choice**, a feature that fundamentally sets it apart from legacy platforms. In centralized systems, the user experience is dictated by a single person or governing entity. If the platform decides to filter, censor, or ban specific users or content, individuals are left with little action to rectify the situation. They must either accept the changes or abandon the platform entirely, often at the cost of losing their social connections, their data, and their identity. What's happening with TikTok could never happen on Nostr. With Nostr, the dynamics are completely different. Because it is a protocol, not a platform, no single entity controls the ecosystem. Instead, the protocol enables a network of applications and relays that users can freely choose from. If a particular application or relay implements policies that a user disagrees with, such as censorship, filtering, or even government enforced banning, they are not trapped or abandoned. They have the freedom to move to another application or relay with minimal effort. **THIS IS POWERFUL.** Take, for example, the case of a relay that decides to censor specific content. On a legacy platform, this would result in frustration and a loss of access for users. On Nostr, however, users can simply connect to a different relay that does not impose such restrictions. Similarly, if an application introduces features or policies that users dislike, they can migrate to a different application that better suits their preferences, all while retaining their identity and social connections. The same principles apply to government bans and censorship. A government can ban a specific application or even multiple applications, just as it can block one relay or several relays. China has implemented both tactics, yet Chinese users continue to exist and actively participate on Nostr, demonstrating Nostr's ability to resistant censorship. How? Simply, it turns into a game of whack-a-mole. When one relay is censored, another quickly takes its place. When one application is banned, another emerges. Users can also bypass these obstacles by running their own relays and applications directly from their homes or personal devices, eliminating reliance on larger entities or organizations and ensuring continuous access. **AGAIN, THIS IS POWERUFL.** Nostr's open and decentralized design makes it resistant to the kinds of government intervention that led to TikTok's outages this weekend and potential future ban in the next 90 days. There is no central server to target, no company to regulate, and no single point of failure. (Insert your CEO jokes here). As long as there are individuals running relays and applications, users continue creating notes and sending zaps. Platforms like TikTok can be silenced with the stroke of a pen, leaving millions of users disconnected and abandoned. Social communication should not be silenced so incredibly easily. No one should have that much power over social interactions. Will we on-board a massive wave of TikTokers in the coming hours or days? I don't know. TikTokers may not be ready for Nostr yet, and honestly, Nostr may not be ready for them either. The ecosystem still lacks the completely polished applications, tools, and services they’re accustomed to. This is where we say "we're still early". They may not be early adopters like the current Nostr user base. Until we bridge that gap, they’ll likely move to the next centralized platform, only to face another government ban or round of censorship in the future. But eventually, there will come a tipping point, a moment when they’ve had enough. When that time comes, I hope we’re prepared. If we’re not, we risk missing a tremendous opportunity to onboard people who genuinely need Nostr’s freedom. Until then, to all of the Nostr developers out there, keep up the great work and keep building. Your hard work and determination is needed. ### @ 6f7db55a:985d8b25
2025-01-19 19:46:30This article will be basic instructions for extreme normies (I say that lovingly), or anyone looking to get started with using zap.stream and sharing to nostr. **EQUIPMENT** Getting started is incredibly easy and your equipment needs are miniscule. An old desktop or laptop running Linux, MacOs, or Windows made in the passed 15yrs should do. Im currently using and old Dell Latitude E5430 with an Intel i5-3210M with 32Gigs of ram and 250GB hard drive. Technically, you go as low as using a Raspberry Pi 4B+ running Owncast, but Ill save that so a future tutorial. Let's get started. **ON YOUR COMPUTER** You'll need to install OBS (open broaster software). OBS is the go-to for streaming to social media. There are tons of YouTube videos on it's function. WE, however, will only be doing the basics to get us up and running. First, go to [https://obsproject.com/](https://obsproject.com/)  Once on the OBS site, choose the correct download for you system. Linux, MacOs or Windows. Download (remember where you downloaded the file to). Go there and install your download. You may have to enter your password to install on your particular operating system. This is normal. Once you've installed OBS, open the application. It should look something like this...  For our purposes, we will be in studio mode. Locate the 'Studio Mode' button on the right lower-hand side of the screen, and click it.  You'll see the screen split like in the image above. The left-side is from your desktop, and the right-side is what your broadcast will look like. Next, we go to settings. The 'Settings' button is located right below the 'Studio Mode" button.  Now we're in settings and you should see something like this...  Now locate stream in the right-hand menu. It should be the second in the list. Click it.  Once in the stream section, go to 'Service' and in the right-hand drop-down, find and select 'Custom...' from the drop-down menu.  Remeber where this is because we'll need to come back to it, shortly. **ZAPSTREAM** We need our streamkey credentials from Zapstream. Go to [https://zap.stream](https://zap.stream). Then, go to your dashboard.  Located on the lower right-hand side is the Server URL and Stream Key. You'll need to copy/paste this in OBS.  You may have to generate new keys, if they aren't already there. This is normal. If you're interested in multi-streaming (That's where you broadcast to multiple social media platforms all at once), youll need the server URL and streamkeys from each. You'll place them in their respective forms in Zapstream's 'Stream Forwarding" section.  Use the custom form, if the platform you want to stream to isn't listed. *Side-Note: remember that you can use your nostr identity across multiple nostr client applications. So when your login for Amethyst, as an example, could be used when you login to zapstream. Also, i would suggest using Alby's browser extension. It makes it much easier to fund your stream, as well as receive zaps. * **Now, BACK TO OBS...** With Stream URL and Key in hand, paste them in the 'Stream" section of OBS' settings. Service [Custom...] Server [Server URL] StreamKey [Your zapstream stream key]  After you've entered all your streaming credentials, click 'OK' at the bottom, on the right-hand side. **WHAT'S NEXT?** Let's setup your first stream from OBS. First we need to choose a source. Your source is your input device. It can be your webcam, your mic, your monitor, or any particular window on your screen. assuming you're an absolute beginner, we're going to use the source 'Window Capture (Xcomposite)'.  Now, open your source file. We'll use a video source called 'grannyhiphop.mp4'. In your case it can be whatever you want to stream; Just be sure to select the proper source.  Double-click on 'Window Capture' in your sources list. In the pop-up window, select your file from the 'Window' drop-down menu.   You should see something like this...  Working in the left display of OBS, we will adjust the video by left-click, hold and drag the bottom corner, so that it takes up the whole display.  In order to adjust the right-side display ( the broadcast side), we need to manipulate the video source by changing it's size.  This may take some time to adjust the size. This is normal. What I've found to help is, after every adjustment, I click the 'Fade (300ms)' button. I have no idea why it helps, but it does, lol.  Finally, after getting everything to look the way you want, you click the 'Start Stream' button.  **BACK TO ZAPSTREAM** Now, we go back to zapstream to check to see if our stream is up. It may take a few moments to update. You may even need to refresh the page. This is normal.  STREAMS UP!!! A few things, in closing. You'll notice that your dashbooard has changed. It'll show current stream time, how much time you have left (according to your funding source), who's zapped you with how much theyve zapped, the ability to post a note about your stream (to both nostr and twitter), and it shows your chatbox with your listeners. There are also a raid feature, stream settings (where you can title & tag your stream). You can 'topup' your funding for your stream. As well as, see your current balance. You did a great and If you ever need more help, just use the tag #asknostr in your note. There are alway nostriches willing to help. **STAY AWESOME!!!**
@ 6f7db55a:985d8b25
2025-01-19 19:46:30This article will be basic instructions for extreme normies (I say that lovingly), or anyone looking to get started with using zap.stream and sharing to nostr. **EQUIPMENT** Getting started is incredibly easy and your equipment needs are miniscule. An old desktop or laptop running Linux, MacOs, or Windows made in the passed 15yrs should do. Im currently using and old Dell Latitude E5430 with an Intel i5-3210M with 32Gigs of ram and 250GB hard drive. Technically, you go as low as using a Raspberry Pi 4B+ running Owncast, but Ill save that so a future tutorial. Let's get started. **ON YOUR COMPUTER** You'll need to install OBS (open broaster software). OBS is the go-to for streaming to social media. There are tons of YouTube videos on it's function. WE, however, will only be doing the basics to get us up and running. First, go to [https://obsproject.com/](https://obsproject.com/)  Once on the OBS site, choose the correct download for you system. Linux, MacOs or Windows. Download (remember where you downloaded the file to). Go there and install your download. You may have to enter your password to install on your particular operating system. This is normal. Once you've installed OBS, open the application. It should look something like this...  For our purposes, we will be in studio mode. Locate the 'Studio Mode' button on the right lower-hand side of the screen, and click it.  You'll see the screen split like in the image above. The left-side is from your desktop, and the right-side is what your broadcast will look like. Next, we go to settings. The 'Settings' button is located right below the 'Studio Mode" button.  Now we're in settings and you should see something like this...  Now locate stream in the right-hand menu. It should be the second in the list. Click it.  Once in the stream section, go to 'Service' and in the right-hand drop-down, find and select 'Custom...' from the drop-down menu.  Remeber where this is because we'll need to come back to it, shortly. **ZAPSTREAM** We need our streamkey credentials from Zapstream. Go to [https://zap.stream](https://zap.stream). Then, go to your dashboard.  Located on the lower right-hand side is the Server URL and Stream Key. You'll need to copy/paste this in OBS.  You may have to generate new keys, if they aren't already there. This is normal. If you're interested in multi-streaming (That's where you broadcast to multiple social media platforms all at once), youll need the server URL and streamkeys from each. You'll place them in their respective forms in Zapstream's 'Stream Forwarding" section.  Use the custom form, if the platform you want to stream to isn't listed. *Side-Note: remember that you can use your nostr identity across multiple nostr client applications. So when your login for Amethyst, as an example, could be used when you login to zapstream. Also, i would suggest using Alby's browser extension. It makes it much easier to fund your stream, as well as receive zaps. * **Now, BACK TO OBS...** With Stream URL and Key in hand, paste them in the 'Stream" section of OBS' settings. Service [Custom...] Server [Server URL] StreamKey [Your zapstream stream key]  After you've entered all your streaming credentials, click 'OK' at the bottom, on the right-hand side. **WHAT'S NEXT?** Let's setup your first stream from OBS. First we need to choose a source. Your source is your input device. It can be your webcam, your mic, your monitor, or any particular window on your screen. assuming you're an absolute beginner, we're going to use the source 'Window Capture (Xcomposite)'.  Now, open your source file. We'll use a video source called 'grannyhiphop.mp4'. In your case it can be whatever you want to stream; Just be sure to select the proper source.  Double-click on 'Window Capture' in your sources list. In the pop-up window, select your file from the 'Window' drop-down menu.   You should see something like this...  Working in the left display of OBS, we will adjust the video by left-click, hold and drag the bottom corner, so that it takes up the whole display.  In order to adjust the right-side display ( the broadcast side), we need to manipulate the video source by changing it's size.  This may take some time to adjust the size. This is normal. What I've found to help is, after every adjustment, I click the 'Fade (300ms)' button. I have no idea why it helps, but it does, lol.  Finally, after getting everything to look the way you want, you click the 'Start Stream' button.  **BACK TO ZAPSTREAM** Now, we go back to zapstream to check to see if our stream is up. It may take a few moments to update. You may even need to refresh the page. This is normal.  STREAMS UP!!! A few things, in closing. You'll notice that your dashbooard has changed. It'll show current stream time, how much time you have left (according to your funding source), who's zapped you with how much theyve zapped, the ability to post a note about your stream (to both nostr and twitter), and it shows your chatbox with your listeners. There are also a raid feature, stream settings (where you can title & tag your stream). You can 'topup' your funding for your stream. As well as, see your current balance. You did a great and If you ever need more help, just use the tag #asknostr in your note. There are alway nostriches willing to help. **STAY AWESOME!!!** @ cff1720e:15c7e2b2
2025-01-19 17:48:02**Einleitung**\ \ Schwierige Dinge einfach zu erklären ist der Anspruch von ELI5 (explain me like I'm 5). Das ist in unserer hoch technisierten Welt dringend erforderlich, denn nur mit dem Verständnis der Technologien können wir sie richtig einsetzen und weiter entwickeln.\ Ich starte meine Serie mit Nostr, einem relativ neuen Internet-Protokoll. Was zum Teufel ist ein Internet-Protokoll? Formal beschrieben sind es internationale Standards, die dafür sorgen, dass das Internet seit über 30 Jahren ziemlich gut funktioniert. Es ist die Sprache, in der sich die Rechner miteinander unterhalten und die auch Sie täglich nutzen, vermutlich ohne es bewusst wahrzunehmen. http(s) transportiert ihre Anfrage an einen Server (z.B. Amazon), und html sorgt dafür, dass aus den gelieferten Daten eine schöne Seite auf ihrem Bildschirm entsteht. Eine Mail wird mit smtp an den Mailserver gesendet und mit imap von ihm abgerufen, und da alle den Standard verwenden, funktioniert das mit jeder App auf jedem Betriebssystem und mit jedem Mail-Provider. Und mit einer Mail-Adresse wie <roland@pareto.space> können sie sogar jederzeit umziehen, egal wohin. **Cool, das ist state of the art!** Aber warum funktioniert das z.B. bei Chat nicht, gibt es da kein Protokoll? Doch, es heißt IRC (Internet Relay Chat → merken sie sich den Namen), aber es wird so gut wie nicht verwendet. Die Gründe dafür sind nicht technischer Natur, vielmehr wurden mit Apps wie Facebook, Twitter, WhatsApp, Telegram, Instagram, TikTok u.a. bewusst Inkompatibilitäten und Nutzerabhängigkeiten geschaffen um Profite zu maximieren.  **Warum Nostr?** Da das Standard-Protokoll nicht genutzt wird, hat jede App ihr eigenes, und wir brauchen eine handvoll Apps um uns mit allen Bekannten auszutauschen. Eine Mobilfunknummer ist Voraussetzung für jedes Konto, damit können die App-Hersteller die Nutzer umfassend tracken und mit dem Verkauf der Informationen bis zu 30 USD je Konto und Monat verdienen. Der Nutzer ist nicht mehr Kunde, er ist das Produkt! Der Werbe-SPAM ist noch das kleinste Problem bei diesem Geschäftsmodell. Server mit Millionen von Nutzerdaten sind ein “honey pot”, dementsprechend oft werden sie gehackt und die Zugangsdaten verkauft. 2024 wurde auch der Twitter-Account vom damaligen Präsidenten Joe Biden gehackt, niemand wusste mehr wer die Nachrichten verfasst hat (vorher auch nicht), d.h. die Authentizität der Inhalte ist bei keinem dieser Anbieter gewährleistet. Im selben Jahr wurde der Telegram-Gründer in Frankreich in Beugehaft genommen, weil er sich geweigert hatte Hintertüren in seine Software einzubauen. Nun kann zum Schutz **"unserer Demokratie”** praktisch jeder mitlesen, was sie mit wem an Informationen austauschen, z.B. darüber welches Shampoo bestimmte Politiker verwenden.  Und wer tatsächlich glaubt er könne Meinungsfreiheit auf sozialen Medien praktizieren, findet sich schnell in der Situation von Donald Trump wieder (seinerzeit amtierender Präsident), dem sein Twitter-Konto 2021 abgeschaltet wurde (Cancel-Culture). Die Nutzerdaten, also ihr Profil, ihre Kontakte, Dokumente, Bilder, Videos und Audiofiles - gehören ihnen ohnehin nicht mehr sondern sind Eigentum des Plattform-Betreibers; lesen sie sich mal die AGB's durch. Aber nein, keine gute Idee, das sind hunderte Seiten und sie werden permanent geändert. Alle nutzen also Apps, deren Technik sie nicht verstehen, deren Regeln sie nicht kennen, wo sie keine Rechte haben und die ihnen die Resultate ihres Handelns stehlen. Was würde wohl der Fünfjährige sagen, wenn ihm seine ältere Schwester anbieten würde, alle seine Spielzeuge zu “verwalten” und dann auszuhändigen wenn er brav ist? “Du spinnst wohl”, und damit beweist der Knirps mehr Vernunft als die Mehrzahl der Erwachsenen. \ \ **Resümee:** keine Standards, keine Daten, keine Rechte = keine Zukunft!  \ **Wie funktioniert Nostr?** Die Entwickler von Nostr haben erkannt dass sich das Server-Client-Konzept in ein Master-Slave-Konzept verwandelt hatte. Der Master ist ein Synonym für Zentralisierung und wird zum **“single point of failure”**, der zwangsläufig Systeme dysfunktional macht. In einem verteilten Peer2Peer-System gibt es keine Master mehr sondern nur gleichberechtigte Knoten (Relays), auf denen die Informationen gespeichert werden. Indem man Informationen auf mehreren Relays redundant speichert, ist das System in jeglicher Hinsicht resilienter. Nicht nur die Natur verwendet dieses Prinzip seit Jahrmillionen erfolgreich, auch das Internet wurde so konzipiert (das ARPAnet wurde vom US-Militär für den Einsatz in Kriegsfällen unter massiven Störungen entwickelt). Alle Nostr-Daten liegen auf Relays und der Nutzer kann wählen zwischen öffentlichen (zumeist kostenlosen) und privaten Relays, z.B. für geschlossene Gruppen oder zum Zwecke von Daten-Archivierung. Da Dokumente auf mehreren Relays gespeichert sind, werden statt URL's (Locator) eindeutige Dokumentnamen (URI's = Identifier) verwendet, broken Links sind damit Vergangenheit und Löschungen / Verluste ebenfalls.\ \ Jedes Dokument (Event genannt) wird vom Besitzer signiert, es ist damit authentisch und fälschungssicher und kann nur vom Ersteller gelöscht werden. Dafür wird ein Schlüsselpaar verwendet bestehend aus privatem (nsec) und öffentlichem Schlüssel (npub) wie aus der Mailverschlüsselung (PGP) bekannt. Das repräsentiert eine Nostr-Identität, die um Bild, Namen, Bio und eine lesbare Nostr-Adresse ergänzt werden kann (z.B. <roland@pareto.space> ), mehr braucht es nicht um alle Ressourcen des Nostr-Ökosystems zu nutzen. Und das besteht inzwischen aus über hundert Apps mit unterschiedlichen Fokussierungen, z.B. für persönliche verschlüsselte Nachrichten (DM → OxChat), Kurznachrichten (Damus, Primal), Blogbeiträge (Pareto), Meetups (Joinstr), Gruppen (Groups), Bilder (Olas), Videos (Amethyst), Audio-Chat (Nostr Nests), Audio-Streams (Tunestr), Video-Streams (Zap.Stream), Marktplätze (Shopstr) u.v.a.m. Die Anmeldung erfolgt mit einem Klick (single sign on) und den Apps stehen ALLE Nutzerdaten zur Verfügung (Profil, Daten, Kontakte, Social Graph → Follower, Bookmarks, Comments, etc.), im Gegensatz zu den fragmentierten Datensilos der Gegenwart.\ \ **Resümee:** ein offener Standard, alle Daten, alle Rechte = große Zukunft!  \ **Warum ist Nostr die Zukunft des Internet?** “Baue Dein Haus nicht auf einem fremden Grundstück” gilt auch im Internet - für alle App-Entwickler, Künstler, Journalisten und Nutzer, denn auch ihre Daten sind werthaltig. Nostr garantiert das Eigentum an den Daten, und überwindet ihre Fragmentierung. Weder die Nutzung noch die kreativen Freiheiten werden durch maßlose Lizenz- und Nutzungsbedingungen eingeschränkt. Aus passiven Nutzern werden durch Interaktion aktive Teilnehmer, Co-Creatoren in einer Sharing-Ökonomie **(Value4Value)**. OpenSource schafft endlich wieder Vertrauen in die Software und ihre Anbieter. Offene Standards ermöglichen den Entwicklern mehr Kooperation und schnellere Entwicklung, für die Anwender garantieren sie Wahlfreiheit. Womit wir letztmalig zu unserem Fünfjährigen zurückkehren. Kinder lieben Lego über alles, am meisten die Maxi-Box “Classic”, weil sie damit ihre Phantasie im Kombinieren voll ausleben können. Erwachsene schenken ihnen dann die viel zu teuren Themenpakete, mit denen man nur eine Lösung nach Anleitung bauen kann. “Was stimmt nur mit meinen Eltern nicht, wann sind die denn falsch abgebogen?" fragt sich der Nachwuchs zu Recht. Das Image lässt sich aber wieder aufpolieren, wenn sie ihren Kindern Nostr zeigen, denn die Vorteile verstehen sogar Fünfjährige.  \ **Das neue Internet ist dezentral. Das neue Internet ist selbstbestimmt. Nostr ist das neue Internet.** <https://nostr.net/> \ <https://start.njump.me/> **Hier das Interview zum Thema mit Radio Berliner Morgenröte** <https://www.podbean.com/ew/pb-yxc36-17bb4be>
@ cff1720e:15c7e2b2
2025-01-19 17:48:02**Einleitung**\ \ Schwierige Dinge einfach zu erklären ist der Anspruch von ELI5 (explain me like I'm 5). Das ist in unserer hoch technisierten Welt dringend erforderlich, denn nur mit dem Verständnis der Technologien können wir sie richtig einsetzen und weiter entwickeln.\ Ich starte meine Serie mit Nostr, einem relativ neuen Internet-Protokoll. Was zum Teufel ist ein Internet-Protokoll? Formal beschrieben sind es internationale Standards, die dafür sorgen, dass das Internet seit über 30 Jahren ziemlich gut funktioniert. Es ist die Sprache, in der sich die Rechner miteinander unterhalten und die auch Sie täglich nutzen, vermutlich ohne es bewusst wahrzunehmen. http(s) transportiert ihre Anfrage an einen Server (z.B. Amazon), und html sorgt dafür, dass aus den gelieferten Daten eine schöne Seite auf ihrem Bildschirm entsteht. Eine Mail wird mit smtp an den Mailserver gesendet und mit imap von ihm abgerufen, und da alle den Standard verwenden, funktioniert das mit jeder App auf jedem Betriebssystem und mit jedem Mail-Provider. Und mit einer Mail-Adresse wie <roland@pareto.space> können sie sogar jederzeit umziehen, egal wohin. **Cool, das ist state of the art!** Aber warum funktioniert das z.B. bei Chat nicht, gibt es da kein Protokoll? Doch, es heißt IRC (Internet Relay Chat → merken sie sich den Namen), aber es wird so gut wie nicht verwendet. Die Gründe dafür sind nicht technischer Natur, vielmehr wurden mit Apps wie Facebook, Twitter, WhatsApp, Telegram, Instagram, TikTok u.a. bewusst Inkompatibilitäten und Nutzerabhängigkeiten geschaffen um Profite zu maximieren.  **Warum Nostr?** Da das Standard-Protokoll nicht genutzt wird, hat jede App ihr eigenes, und wir brauchen eine handvoll Apps um uns mit allen Bekannten auszutauschen. Eine Mobilfunknummer ist Voraussetzung für jedes Konto, damit können die App-Hersteller die Nutzer umfassend tracken und mit dem Verkauf der Informationen bis zu 30 USD je Konto und Monat verdienen. Der Nutzer ist nicht mehr Kunde, er ist das Produkt! Der Werbe-SPAM ist noch das kleinste Problem bei diesem Geschäftsmodell. Server mit Millionen von Nutzerdaten sind ein “honey pot”, dementsprechend oft werden sie gehackt und die Zugangsdaten verkauft. 2024 wurde auch der Twitter-Account vom damaligen Präsidenten Joe Biden gehackt, niemand wusste mehr wer die Nachrichten verfasst hat (vorher auch nicht), d.h. die Authentizität der Inhalte ist bei keinem dieser Anbieter gewährleistet. Im selben Jahr wurde der Telegram-Gründer in Frankreich in Beugehaft genommen, weil er sich geweigert hatte Hintertüren in seine Software einzubauen. Nun kann zum Schutz **"unserer Demokratie”** praktisch jeder mitlesen, was sie mit wem an Informationen austauschen, z.B. darüber welches Shampoo bestimmte Politiker verwenden.  Und wer tatsächlich glaubt er könne Meinungsfreiheit auf sozialen Medien praktizieren, findet sich schnell in der Situation von Donald Trump wieder (seinerzeit amtierender Präsident), dem sein Twitter-Konto 2021 abgeschaltet wurde (Cancel-Culture). Die Nutzerdaten, also ihr Profil, ihre Kontakte, Dokumente, Bilder, Videos und Audiofiles - gehören ihnen ohnehin nicht mehr sondern sind Eigentum des Plattform-Betreibers; lesen sie sich mal die AGB's durch. Aber nein, keine gute Idee, das sind hunderte Seiten und sie werden permanent geändert. Alle nutzen also Apps, deren Technik sie nicht verstehen, deren Regeln sie nicht kennen, wo sie keine Rechte haben und die ihnen die Resultate ihres Handelns stehlen. Was würde wohl der Fünfjährige sagen, wenn ihm seine ältere Schwester anbieten würde, alle seine Spielzeuge zu “verwalten” und dann auszuhändigen wenn er brav ist? “Du spinnst wohl”, und damit beweist der Knirps mehr Vernunft als die Mehrzahl der Erwachsenen. \ \ **Resümee:** keine Standards, keine Daten, keine Rechte = keine Zukunft!  \ **Wie funktioniert Nostr?** Die Entwickler von Nostr haben erkannt dass sich das Server-Client-Konzept in ein Master-Slave-Konzept verwandelt hatte. Der Master ist ein Synonym für Zentralisierung und wird zum **“single point of failure”**, der zwangsläufig Systeme dysfunktional macht. In einem verteilten Peer2Peer-System gibt es keine Master mehr sondern nur gleichberechtigte Knoten (Relays), auf denen die Informationen gespeichert werden. Indem man Informationen auf mehreren Relays redundant speichert, ist das System in jeglicher Hinsicht resilienter. Nicht nur die Natur verwendet dieses Prinzip seit Jahrmillionen erfolgreich, auch das Internet wurde so konzipiert (das ARPAnet wurde vom US-Militär für den Einsatz in Kriegsfällen unter massiven Störungen entwickelt). Alle Nostr-Daten liegen auf Relays und der Nutzer kann wählen zwischen öffentlichen (zumeist kostenlosen) und privaten Relays, z.B. für geschlossene Gruppen oder zum Zwecke von Daten-Archivierung. Da Dokumente auf mehreren Relays gespeichert sind, werden statt URL's (Locator) eindeutige Dokumentnamen (URI's = Identifier) verwendet, broken Links sind damit Vergangenheit und Löschungen / Verluste ebenfalls.\ \ Jedes Dokument (Event genannt) wird vom Besitzer signiert, es ist damit authentisch und fälschungssicher und kann nur vom Ersteller gelöscht werden. Dafür wird ein Schlüsselpaar verwendet bestehend aus privatem (nsec) und öffentlichem Schlüssel (npub) wie aus der Mailverschlüsselung (PGP) bekannt. Das repräsentiert eine Nostr-Identität, die um Bild, Namen, Bio und eine lesbare Nostr-Adresse ergänzt werden kann (z.B. <roland@pareto.space> ), mehr braucht es nicht um alle Ressourcen des Nostr-Ökosystems zu nutzen. Und das besteht inzwischen aus über hundert Apps mit unterschiedlichen Fokussierungen, z.B. für persönliche verschlüsselte Nachrichten (DM → OxChat), Kurznachrichten (Damus, Primal), Blogbeiträge (Pareto), Meetups (Joinstr), Gruppen (Groups), Bilder (Olas), Videos (Amethyst), Audio-Chat (Nostr Nests), Audio-Streams (Tunestr), Video-Streams (Zap.Stream), Marktplätze (Shopstr) u.v.a.m. Die Anmeldung erfolgt mit einem Klick (single sign on) und den Apps stehen ALLE Nutzerdaten zur Verfügung (Profil, Daten, Kontakte, Social Graph → Follower, Bookmarks, Comments, etc.), im Gegensatz zu den fragmentierten Datensilos der Gegenwart.\ \ **Resümee:** ein offener Standard, alle Daten, alle Rechte = große Zukunft!  \ **Warum ist Nostr die Zukunft des Internet?** “Baue Dein Haus nicht auf einem fremden Grundstück” gilt auch im Internet - für alle App-Entwickler, Künstler, Journalisten und Nutzer, denn auch ihre Daten sind werthaltig. Nostr garantiert das Eigentum an den Daten, und überwindet ihre Fragmentierung. Weder die Nutzung noch die kreativen Freiheiten werden durch maßlose Lizenz- und Nutzungsbedingungen eingeschränkt. Aus passiven Nutzern werden durch Interaktion aktive Teilnehmer, Co-Creatoren in einer Sharing-Ökonomie **(Value4Value)**. OpenSource schafft endlich wieder Vertrauen in die Software und ihre Anbieter. Offene Standards ermöglichen den Entwicklern mehr Kooperation und schnellere Entwicklung, für die Anwender garantieren sie Wahlfreiheit. Womit wir letztmalig zu unserem Fünfjährigen zurückkehren. Kinder lieben Lego über alles, am meisten die Maxi-Box “Classic”, weil sie damit ihre Phantasie im Kombinieren voll ausleben können. Erwachsene schenken ihnen dann die viel zu teuren Themenpakete, mit denen man nur eine Lösung nach Anleitung bauen kann. “Was stimmt nur mit meinen Eltern nicht, wann sind die denn falsch abgebogen?" fragt sich der Nachwuchs zu Recht. Das Image lässt sich aber wieder aufpolieren, wenn sie ihren Kindern Nostr zeigen, denn die Vorteile verstehen sogar Fünfjährige.  \ **Das neue Internet ist dezentral. Das neue Internet ist selbstbestimmt. Nostr ist das neue Internet.** <https://nostr.net/> \ <https://start.njump.me/> **Hier das Interview zum Thema mit Radio Berliner Morgenröte** <https://www.podbean.com/ew/pb-yxc36-17bb4be> @ fd208ee8:0fd927c1
2025-01-19 12:10:10I am so tired of people trying to waste my time with Nostrized imitations of stuff that already exists. Instagram, but make it Nostr. Twitter, but make it Nostr. GitHub, but make it Nostr. Facebook, but make it Nostr. Wordpress, but make it Nostr. GoodReads, but make it Nostr. TikTok, but make it Nostr. That stuff already exists, and it wasn't that great the first time around, either. Build something better than that stuff, that can only be brought into existence because of Nostr. Build something that does something completely and awesomely new. Knock my socks off, bro. Cuz, ain't nobody got time for that.
@ fd208ee8:0fd927c1
2025-01-19 12:10:10I am so tired of people trying to waste my time with Nostrized imitations of stuff that already exists. Instagram, but make it Nostr. Twitter, but make it Nostr. GitHub, but make it Nostr. Facebook, but make it Nostr. Wordpress, but make it Nostr. GoodReads, but make it Nostr. TikTok, but make it Nostr. That stuff already exists, and it wasn't that great the first time around, either. Build something better than that stuff, that can only be brought into existence because of Nostr. Build something that does something completely and awesomely new. Knock my socks off, bro. Cuz, ain't nobody got time for that. @ 378562cd:a6fc6773
2025-01-18 16:20:12As a frequent user who depends on my phone for a wide range of activities, including boosting my productivity and capturing spontaneous moments, I have been paying close attention to the OnePlus 13. This flagship device appears to meet all my essential requirements, particularly excelling in power and camera capabilities, which are my main priorities. Here are the standout features that have caught my attention. <img src="https://blossom.primal.net/9d0b0d98e9ac02d756f31ab0b46f3e0e79b98aa0576d0e71847bba4fcf5ee2e3.webp"> ### Power to Handle Anything I Throw at It Performance is a big deal for me, and the OnePlus 13 doesn’t seem to disappoint. It’s powered by the Snapdragon 8 Elite processor, a beast in the mobile tech world. I can already imagine how smoothly it would handle heavy multitasking, like switching between editing photos, running multiple apps, and even gaming. The insane memory options—up to 24GB of RAM—truly stand out. That’s more RAM than most laptops I’ve owned! Pair that with up to 1TB of storage, and you’re looking at a future-proof phone. I’d never have to worry about running out of space for apps, photos, or videos, and everything would load lightning-fast. ### <img src="https://blossom.primal.net/6f9363e8e4a9663346e5fdaf41b25b611dcf1324a85799bdefa1f90f980fc02d.jpg"> ### A Camera Setup That’s Hard to Ignore One of my favorite things to do is capture high-quality photos and videos, so a powerful camera system is non-negotiable. The OnePlus 13 delivers with its triple-camera setup; all three lenses are 50 megapixels. That means whether I’m shooting with the main wide lens, zooming in with the telephoto, or going wide with the ultra-wide, I’m getting consistently sharp, detailed shots. The Hasselblad collaboration is a big draw for me, too. OnePlus phones have been steadily improving their color science, and this partnership seems to really shine in the OnePlus 13. I’d expect vibrant, true-to-life colors in my photos without much editing required. The AI enhancements also pique my interest. From what I’ve read, the phone handles tricky lighting situations, like low-light environments or high-contrast scenes, exceptionally well. That’s exactly what I need to capture spontaneous moments without worrying about settings. ### Battery and Charging That Won’t Leave Me Hanging Another thing I appreciate is the long battery life. The 6,000 mAh battery on the OnePlus 13 is reportedly a powerhouse, capable of lasting two days under mixed usage. And when I do need to charge, the 100W wired charging can fully juice up the phone in just over half an hour. Even the 50W wireless charging is incredibly fast, which is perfect for someone like me who’s always on the move. ### Design and Features That Add Value The flat-edge design and premium finish make the phone feel as good as it looks. I’d probably go for the Midnight Ocean with its vegan leather back—it sounds grippy and unique, ideal for someone who doesn’t want to slap on a bulky case. The little extras, like Glove Mode and Aqua Touch 2.0, also catch my attention. Since winters are cold here, using my phone with gloves on is a practical bonus. ### Why It’s Tempting Me At $899 for the base model, the OnePlus 13 seems like a solid deal, especially for the power and camera capabilities it offers. Even if I choose a higher configuration, the pricing still feels reasonable compared to other flagships with similar specs. For me, the OnePlus 13 feels like a phone that’s built for power users—people who need speed, reliability, and top-tier camera performance. I’m seriously considering it for my next upgrade because it feels like it would keep up with everything I do and then some. If the camera and performance live up to the hype, I might just have my decision made.
@ 378562cd:a6fc6773
2025-01-18 16:20:12As a frequent user who depends on my phone for a wide range of activities, including boosting my productivity and capturing spontaneous moments, I have been paying close attention to the OnePlus 13. This flagship device appears to meet all my essential requirements, particularly excelling in power and camera capabilities, which are my main priorities. Here are the standout features that have caught my attention. <img src="https://blossom.primal.net/9d0b0d98e9ac02d756f31ab0b46f3e0e79b98aa0576d0e71847bba4fcf5ee2e3.webp"> ### Power to Handle Anything I Throw at It Performance is a big deal for me, and the OnePlus 13 doesn’t seem to disappoint. It’s powered by the Snapdragon 8 Elite processor, a beast in the mobile tech world. I can already imagine how smoothly it would handle heavy multitasking, like switching between editing photos, running multiple apps, and even gaming. The insane memory options—up to 24GB of RAM—truly stand out. That’s more RAM than most laptops I’ve owned! Pair that with up to 1TB of storage, and you’re looking at a future-proof phone. I’d never have to worry about running out of space for apps, photos, or videos, and everything would load lightning-fast. ### <img src="https://blossom.primal.net/6f9363e8e4a9663346e5fdaf41b25b611dcf1324a85799bdefa1f90f980fc02d.jpg"> ### A Camera Setup That’s Hard to Ignore One of my favorite things to do is capture high-quality photos and videos, so a powerful camera system is non-negotiable. The OnePlus 13 delivers with its triple-camera setup; all three lenses are 50 megapixels. That means whether I’m shooting with the main wide lens, zooming in with the telephoto, or going wide with the ultra-wide, I’m getting consistently sharp, detailed shots. The Hasselblad collaboration is a big draw for me, too. OnePlus phones have been steadily improving their color science, and this partnership seems to really shine in the OnePlus 13. I’d expect vibrant, true-to-life colors in my photos without much editing required. The AI enhancements also pique my interest. From what I’ve read, the phone handles tricky lighting situations, like low-light environments or high-contrast scenes, exceptionally well. That’s exactly what I need to capture spontaneous moments without worrying about settings. ### Battery and Charging That Won’t Leave Me Hanging Another thing I appreciate is the long battery life. The 6,000 mAh battery on the OnePlus 13 is reportedly a powerhouse, capable of lasting two days under mixed usage. And when I do need to charge, the 100W wired charging can fully juice up the phone in just over half an hour. Even the 50W wireless charging is incredibly fast, which is perfect for someone like me who’s always on the move. ### Design and Features That Add Value The flat-edge design and premium finish make the phone feel as good as it looks. I’d probably go for the Midnight Ocean with its vegan leather back—it sounds grippy and unique, ideal for someone who doesn’t want to slap on a bulky case. The little extras, like Glove Mode and Aqua Touch 2.0, also catch my attention. Since winters are cold here, using my phone with gloves on is a practical bonus. ### Why It’s Tempting Me At $899 for the base model, the OnePlus 13 seems like a solid deal, especially for the power and camera capabilities it offers. Even if I choose a higher configuration, the pricing still feels reasonable compared to other flagships with similar specs. For me, the OnePlus 13 feels like a phone that’s built for power users—people who need speed, reliability, and top-tier camera performance. I’m seriously considering it for my next upgrade because it feels like it would keep up with everything I do and then some. If the camera and performance live up to the hype, I might just have my decision made. @ a10260a2:caa23e3e
2025-01-18 12:04:41*Last Updated: January 18, 2025* First off, big shoutout to Coinos for having support for adding a memo to BOLT12 offers. This provides a solid alternative for the pleb who wants to support mining decentralization but doesn’t want to set up a CLN node and pay thousands of sats for a channel only to get little rewards. This is the case for most of us who only have a miner or two (e.g. a Bitaxe and/or an S9). Before we get into setting up Lightning payouts, you’ll want to have your miner configured to mine with OCEAN of course. You’ll also want to make sure that the bitcoin address you use is from a wallet that supports signing messages. These are the ones listed in the OCEAN [docs](https://ocean.xyz/docs/lightning): * Bitcoin Knots/Bitcoin Core * Coldcard * Electrum * LND (Command Line) * Seedsigner * Sparrow * Specter * Trezor I checked one of my favorite, user-friendly wallets — Blue Wallet — and it happens to support signing messages as well. Just tap the three dots on the upper right and you’ll see the “Sign/Verify Message” button at the bottom.   Update [January 18]: You can now use Coinos to sign by going to https://coinos.io/sign The trick here is to not refresh the page. In other words, when you're logged in to your Coinos account, go to the URL and use the legacy address (starts with a "1") that's displayed to configure your miner(s). If you refresh the page, you're going to get a new address which will cause the signing to fail later on. *Remember*, keep the tab open and don't refresh the page.  Whichever wallet you choose, generate a receive address to use when configuring your miner (it’ll also be your OCEAN username). Here’s how it looks on the Bitaxe (AxeOS)…  And the Antminer S9 (Braiins OS).  NOTE: There’s a slight difference in the URL format between the two apps. Other than that, the username will be your bitcoin address followed by the optional “.” + the nickname for your machine. You can find more details on OCEAN’s [get started page](https://ocean.xyz/getstarted). --- Alright, now that your miner is pointed at OCEAN. Let’s configure Lightning payouts! ### Generating the BOLT12 Offer In the Coinos app, go to Receive > Bolt 12.  Tap “Set memo” and set it to “OCEAN Payouts for [insert your bitcoin address]” (this text is case-sensitive). Use the same bitcoin address you used above to configure your miner(s).  After tapping OK, copy the BOLT12 offer (it should start with “lno”) and proceed to the next step. ### Generating the Configuration Message Navigate to the [My Stats](https://ocean.xyz/stats) page by searching for your OCEAN Bitcoin address.  The click the Configuration link next to Next Block to access the configuration form.  Paste the BOLT12 offer here, update the block height to latest, click GENERATE, and copy the generated unsigned message.   ### Signing the Configuration Message To sign the generated message, go back to Blue Wallet and use the signing function. Paste the configuration message in the Message field, tap Sign, and copy the signed message that’s generated.  If you're using Coinos to sign, return to the page that you kept open (and didn't refresh) and do the same. Paste the configuration message, click submit, and copy the signed message. ### Submitting the Signed Message Once signed, copy the signature, paste it in the OCEAN configuration form, and click CONFIRM.  If all goes well, you should see a confirmation that the configuration was successful. Congrats! 🎉 All you gotta do now is sit back, relax, and wait for a block to be found… Or you can look into setting up [DATUM](https://ocean.xyz/docs/datum-setup). 😎
@ a10260a2:caa23e3e
2025-01-18 12:04:41*Last Updated: January 18, 2025* First off, big shoutout to Coinos for having support for adding a memo to BOLT12 offers. This provides a solid alternative for the pleb who wants to support mining decentralization but doesn’t want to set up a CLN node and pay thousands of sats for a channel only to get little rewards. This is the case for most of us who only have a miner or two (e.g. a Bitaxe and/or an S9). Before we get into setting up Lightning payouts, you’ll want to have your miner configured to mine with OCEAN of course. You’ll also want to make sure that the bitcoin address you use is from a wallet that supports signing messages. These are the ones listed in the OCEAN [docs](https://ocean.xyz/docs/lightning): * Bitcoin Knots/Bitcoin Core * Coldcard * Electrum * LND (Command Line) * Seedsigner * Sparrow * Specter * Trezor I checked one of my favorite, user-friendly wallets — Blue Wallet — and it happens to support signing messages as well. Just tap the three dots on the upper right and you’ll see the “Sign/Verify Message” button at the bottom.   Update [January 18]: You can now use Coinos to sign by going to https://coinos.io/sign The trick here is to not refresh the page. In other words, when you're logged in to your Coinos account, go to the URL and use the legacy address (starts with a "1") that's displayed to configure your miner(s). If you refresh the page, you're going to get a new address which will cause the signing to fail later on. *Remember*, keep the tab open and don't refresh the page.  Whichever wallet you choose, generate a receive address to use when configuring your miner (it’ll also be your OCEAN username). Here’s how it looks on the Bitaxe (AxeOS)…  And the Antminer S9 (Braiins OS).  NOTE: There’s a slight difference in the URL format between the two apps. Other than that, the username will be your bitcoin address followed by the optional “.” + the nickname for your machine. You can find more details on OCEAN’s [get started page](https://ocean.xyz/getstarted). --- Alright, now that your miner is pointed at OCEAN. Let’s configure Lightning payouts! ### Generating the BOLT12 Offer In the Coinos app, go to Receive > Bolt 12.  Tap “Set memo” and set it to “OCEAN Payouts for [insert your bitcoin address]” (this text is case-sensitive). Use the same bitcoin address you used above to configure your miner(s).  After tapping OK, copy the BOLT12 offer (it should start with “lno”) and proceed to the next step. ### Generating the Configuration Message Navigate to the [My Stats](https://ocean.xyz/stats) page by searching for your OCEAN Bitcoin address.  The click the Configuration link next to Next Block to access the configuration form.  Paste the BOLT12 offer here, update the block height to latest, click GENERATE, and copy the generated unsigned message.   ### Signing the Configuration Message To sign the generated message, go back to Blue Wallet and use the signing function. Paste the configuration message in the Message field, tap Sign, and copy the signed message that’s generated.  If you're using Coinos to sign, return to the page that you kept open (and didn't refresh) and do the same. Paste the configuration message, click submit, and copy the signed message. ### Submitting the Signed Message Once signed, copy the signature, paste it in the OCEAN configuration form, and click CONFIRM.  If all goes well, you should see a confirmation that the configuration was successful. Congrats! 🎉 All you gotta do now is sit back, relax, and wait for a block to be found… Or you can look into setting up [DATUM](https://ocean.xyz/docs/datum-setup). 😎 @ c631e267:c2b78d3e
2025-01-18 09:34:51*Die grauenvollste Aussicht ist die der Technokratie –* *\ einer kontrollierenden Herrschaft,* *\ die durch verstümmelte und verstümmelnde Geister ausgeübt wird.* *\ Ernst Jünger*   **«Davos ist nicht mehr sexy»,** das Weltwirtschaftsforum ([WEF](https://transition-news.org/wef-world-economic-forum)) mache Davos [kaputt](https://web.archive.org/web/20250116114956/https://www.handelszeitung.ch/wef-2025/wie-das-wef-davos-kaputt-macht-785098), diese Aussagen eines Einheimischen las ich kürzlich in der *Handelszeitung*. Während sich einige vor Ort enorm an der «teuersten Gewerbeausstellung der Welt» bereicherten, würden die negativen Begleiterscheinungen wie Wohnungsnot und Niedergang der lokalen Wirtschaft immer deutlicher. **Nächsten Montag beginnt in dem Schweizer Bergdorf erneut ein Jahrestreffen** dieses elitären Clubs der Konzerne, bei dem man mit hochrangigen Politikern aus aller Welt und ausgewählten Vertretern der Systemmedien zusammenhocken wird. Wie bereits in den [vergangenen](https://transition-news.org/die-angst-der-eliten-vor-dem-pobel) vier Jahren wird die Präsidentin der EU-Kommission, Ursula von der Leyen, in Begleitung von Klaus Schwab ihre Grundsatzansprache halten. **Der deutsche WEF-Gründer hatte bei dieser Gelegenheit** immer höchst lobende Worte für seine Landsmännin: [2021](https://www.weforum.org/meetings/the-davos-agenda-2021/sessions/special-address-by-g20-head-of-state-government/) erklärte er sich «stolz, dass Europa wieder unter Ihrer Führung steht» und [2022](https://www.weforum.org/meetings/the-davos-agenda-2022/sessions/special-address-by-ursula-von-der-leyen-president-of-the-european-commission-177737c164/) fand er es bemerkenswert, was sie erreicht habe angesichts des «erstaunlichen Wandels», den die Welt in den vorangegangenen zwei Jahren erlebt habe; es gebe nun einen «neuen europäischen Geist». **Von der Leyens Handeln während der sogenannten Corona-«Pandemie»** lobte Schwab damals bereits ebenso, wie es diese Woche das [Karlspreis](https://transition-news.org/von-der-leyen-erhalt-karlspreis-albert-bourla-erklart-pfizer-habe-wahrend-der)-Direktorium tat, als man der Beschuldigten im Fall [Pfizergate](https://transition-news.org/pfizergate-startet-ins-neue-jahr) die diesjährige internationale Auszeichnung «für Verdienste um die europäische Einigung» verlieh. Außerdem habe sie die EU nicht nur gegen den «Aggressor Russland», sondern auch gegen die «innere Bedrohung durch Rassisten und Demagogen» sowie gegen den Klimawandel verteidigt. **Jene Herausforderungen durch «Krisen epochalen Ausmaßes»** werden indes aus dem Umfeld des WEF nicht nur herbeigeredet – wie man alljährlich zur Zeit des Davoser Treffens im [Global Risks Report](https://www.zurich.com/knowledge/topics/global-risks/the-global-risks-report-2025) nachlesen kann, der zusammen mit dem Versicherungskonzern Zurich erstellt wird. Seit die Globalisten 2020/21 in der Praxis gesehen haben, wie gut eine konzertierte und konsequente Angst-Kampagne funktionieren kann, geht es Schlag auf Schlag. Sie setzen alles daran, Schwabs goldenes Zeitfenster des «Great Reset» zu nutzen. **Ziel dieses «großen Umbruchs» ist die totale Kontrolle der Technokraten über die Menschen** unter dem Deckmantel einer globalen Gesundheitsfürsorge. Wie aber könnte man so etwas erreichen? Ein Mittel dazu ist die «kreative Zerstörung». Weitere unabdingbare Werkzeug sind die Einbindung, ja Gleichschaltung der Medien und der Justiz. **Ein** **[«Great Mental Reset»](https://transition-news.org/angriff-auf-unser-gehirn-michael-nehls-uber-den-great-mental-reset-teil-1)** **sei die Voraussetzung dafür,** dass ein Großteil der Menschen Einschränkungen und Manipulationen wie durch die Corona-Maßnahmen praktisch kritik- und widerstandslos hinnehme, sagt der Mediziner und Molekulargenetiker Michael Nehls. Er meint damit eine regelrechte Umprogrammierung des Gehirns, wodurch nach und nach unsere Individualität und unser soziales Bewusstsein eliminiert und durch unreflektierten Konformismus ersetzt werden. **Der aktuelle Zustand unserer Gesellschaften** ist auch für den Schweizer Rechtsanwalt Philipp Kruse alarmierend. Durch den Umgang mit der «Pandemie» sieht er die Grundlagen von Recht und Vernunft erschüttert, die [Rechtsstaatlichkeit](https://transition-news.org/schweizer-rechtsstaat-in-der-krise-ein-anwalt-schlagt-alarm) stehe auf dem Prüfstand. Seiner dringenden Mahnung an alle Bürger, die Prinzipien von Recht und Freiheit zu verteidigen, kann ich mich nur anschließen. *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/davos-europa-und-der-rest-der-welt)*** erschienen.
@ c631e267:c2b78d3e
2025-01-18 09:34:51*Die grauenvollste Aussicht ist die der Technokratie –* *\ einer kontrollierenden Herrschaft,* *\ die durch verstümmelte und verstümmelnde Geister ausgeübt wird.* *\ Ernst Jünger*   **«Davos ist nicht mehr sexy»,** das Weltwirtschaftsforum ([WEF](https://transition-news.org/wef-world-economic-forum)) mache Davos [kaputt](https://web.archive.org/web/20250116114956/https://www.handelszeitung.ch/wef-2025/wie-das-wef-davos-kaputt-macht-785098), diese Aussagen eines Einheimischen las ich kürzlich in der *Handelszeitung*. Während sich einige vor Ort enorm an der «teuersten Gewerbeausstellung der Welt» bereicherten, würden die negativen Begleiterscheinungen wie Wohnungsnot und Niedergang der lokalen Wirtschaft immer deutlicher. **Nächsten Montag beginnt in dem Schweizer Bergdorf erneut ein Jahrestreffen** dieses elitären Clubs der Konzerne, bei dem man mit hochrangigen Politikern aus aller Welt und ausgewählten Vertretern der Systemmedien zusammenhocken wird. Wie bereits in den [vergangenen](https://transition-news.org/die-angst-der-eliten-vor-dem-pobel) vier Jahren wird die Präsidentin der EU-Kommission, Ursula von der Leyen, in Begleitung von Klaus Schwab ihre Grundsatzansprache halten. **Der deutsche WEF-Gründer hatte bei dieser Gelegenheit** immer höchst lobende Worte für seine Landsmännin: [2021](https://www.weforum.org/meetings/the-davos-agenda-2021/sessions/special-address-by-g20-head-of-state-government/) erklärte er sich «stolz, dass Europa wieder unter Ihrer Führung steht» und [2022](https://www.weforum.org/meetings/the-davos-agenda-2022/sessions/special-address-by-ursula-von-der-leyen-president-of-the-european-commission-177737c164/) fand er es bemerkenswert, was sie erreicht habe angesichts des «erstaunlichen Wandels», den die Welt in den vorangegangenen zwei Jahren erlebt habe; es gebe nun einen «neuen europäischen Geist». **Von der Leyens Handeln während der sogenannten Corona-«Pandemie»** lobte Schwab damals bereits ebenso, wie es diese Woche das [Karlspreis](https://transition-news.org/von-der-leyen-erhalt-karlspreis-albert-bourla-erklart-pfizer-habe-wahrend-der)-Direktorium tat, als man der Beschuldigten im Fall [Pfizergate](https://transition-news.org/pfizergate-startet-ins-neue-jahr) die diesjährige internationale Auszeichnung «für Verdienste um die europäische Einigung» verlieh. Außerdem habe sie die EU nicht nur gegen den «Aggressor Russland», sondern auch gegen die «innere Bedrohung durch Rassisten und Demagogen» sowie gegen den Klimawandel verteidigt. **Jene Herausforderungen durch «Krisen epochalen Ausmaßes»** werden indes aus dem Umfeld des WEF nicht nur herbeigeredet – wie man alljährlich zur Zeit des Davoser Treffens im [Global Risks Report](https://www.zurich.com/knowledge/topics/global-risks/the-global-risks-report-2025) nachlesen kann, der zusammen mit dem Versicherungskonzern Zurich erstellt wird. Seit die Globalisten 2020/21 in der Praxis gesehen haben, wie gut eine konzertierte und konsequente Angst-Kampagne funktionieren kann, geht es Schlag auf Schlag. Sie setzen alles daran, Schwabs goldenes Zeitfenster des «Great Reset» zu nutzen. **Ziel dieses «großen Umbruchs» ist die totale Kontrolle der Technokraten über die Menschen** unter dem Deckmantel einer globalen Gesundheitsfürsorge. Wie aber könnte man so etwas erreichen? Ein Mittel dazu ist die «kreative Zerstörung». Weitere unabdingbare Werkzeug sind die Einbindung, ja Gleichschaltung der Medien und der Justiz. **Ein** **[«Great Mental Reset»](https://transition-news.org/angriff-auf-unser-gehirn-michael-nehls-uber-den-great-mental-reset-teil-1)** **sei die Voraussetzung dafür,** dass ein Großteil der Menschen Einschränkungen und Manipulationen wie durch die Corona-Maßnahmen praktisch kritik- und widerstandslos hinnehme, sagt der Mediziner und Molekulargenetiker Michael Nehls. Er meint damit eine regelrechte Umprogrammierung des Gehirns, wodurch nach und nach unsere Individualität und unser soziales Bewusstsein eliminiert und durch unreflektierten Konformismus ersetzt werden. **Der aktuelle Zustand unserer Gesellschaften** ist auch für den Schweizer Rechtsanwalt Philipp Kruse alarmierend. Durch den Umgang mit der «Pandemie» sieht er die Grundlagen von Recht und Vernunft erschüttert, die [Rechtsstaatlichkeit](https://transition-news.org/schweizer-rechtsstaat-in-der-krise-ein-anwalt-schlagt-alarm) stehe auf dem Prüfstand. Seiner dringenden Mahnung an alle Bürger, die Prinzipien von Recht und Freiheit zu verteidigen, kann ich mich nur anschließen. *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/davos-europa-und-der-rest-der-welt)*** erschienen. @ f9cf4e94:96abc355
2025-01-18 06:09:50Para esse exemplo iremos usar: | Nome | Imagem | Descrição | | --------------- | ------------------------------------------------------------ | ------------------------------------------------------------ | | Raspberry PI B+ |  | **Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2,** | | Pen drive |  | **16Gb** | Recomendo que use o **Ubuntu Server** para essa instalação. Você pode baixar o Ubuntu para Raspberry Pi [aqui]( https://ubuntu.com/download/raspberry-pi). O passo a passo para a instalação do Ubuntu no Raspberry Pi está disponível [aqui]( https://ubuntu.com/tutorials/how-to-install-ubuntu-on-your-raspberry-pi). **Não instale um desktop** (como xubuntu, lubuntu, xfce, etc.). --- ## Passo 1: Atualizar o Sistema 🖥️ Primeiro, atualize seu sistema e instale o Tor: ```bash apt update apt install tor ``` --- ## Passo 2: Criar o Arquivo de Serviço `nrs.service` 🔧 Crie o arquivo de serviço que vai gerenciar o servidor Nostr. Você pode fazer isso com o seguinte conteúdo: ```unit [Unit] Description=Nostr Relay Server Service After=network.target [Service] Type=simple WorkingDirectory=/opt/nrs ExecStart=/opt/nrs/nrs-arm64 Restart=on-failure [Install] WantedBy=multi-user.target ``` --- ## Passo 3: Baixar o Binário do Nostr 🚀 Baixe o binário mais recente do Nostr [aqui no GitHub]( https://github.com/gabrielmoura/SimpleNosrtRelay/releases). --- ## Passo 4: Criar as Pastas Necessárias 📂 Agora, crie as pastas para o aplicativo e o pendrive: ```bash mkdir -p /opt/nrs /mnt/edriver ``` --- ## Passo 5: Listar os Dispositivos Conectados 🔌 Para saber qual dispositivo você vai usar, liste todos os dispositivos conectados: ```bash lsblk ``` --- ## Passo 6: Formatando o Pendrive 💾 Escolha o pendrive correto (por exemplo, `/dev/sda`) e formate-o: ```bash mkfs.vfat /dev/sda ``` --- ## Passo 7: Montar o Pendrive 💻 Monte o pendrive na pasta `/mnt/edriver`: ```bash mount /dev/sda /mnt/edriver ``` --- ## Passo 8: Verificar UUID dos Dispositivos 📋 Para garantir que o sistema monte o pendrive automaticamente, liste os UUID dos dispositivos conectados: ```bash blkid ``` --- ## Passo 9: Alterar o `fstab` para Montar o Pendrive Automáticamente 📝 Abra o arquivo `/etc/fstab` e adicione uma linha para o pendrive, com o UUID que você obteve no passo anterior. A linha deve ficar assim: ```fstab UUID=9c9008f8-f852 /mnt/edriver vfat defaults 0 0 ``` --- ## Passo 10: Copiar o Binário para a Pasta Correta 📥 Agora, copie o binário baixado para a pasta `/opt/nrs`: ```bash cp nrs-arm64 /opt/nrs ``` --- ## Passo 11: Criar o Arquivo de Configuração 🛠️ Crie o arquivo de configuração com o seguinte conteúdo e salve-o em `/opt/nrs/config.yaml`: ```yaml app_env: production info: name: Nostr Relay Server description: Nostr Relay Server pub_key: "" contact: "" url: http://localhost:3334 icon: https://external-content.duckduckgo.com/iu/?u= https://public.bnbstatic.com/image/cms/crawler/COINCU_NEWS/image-495-1024x569.png base_path: /mnt/edriver negentropy: true ``` --- ## Passo 12: Copiar o Serviço para o Diretório de Systemd ⚙️ Agora, copie o arquivo `nrs.service` para o diretório `/etc/systemd/system/`: ```bash cp nrs.service /etc/systemd/system/ ``` Recarregue os serviços e inicie o serviço `nrs`: ```bash systemctl daemon-reload systemctl enable --now nrs.service ``` --- ## Passo 13: Configurar o Tor 🌐 Abra o arquivo de configuração do Tor `/var/lib/tor/torrc` e adicione a seguinte linha: ```torrc HiddenServiceDir /var/lib/tor/nostr_server/ HiddenServicePort 80 127.0.0.1:3334 ``` --- ## Passo 14: Habilitar e Iniciar o Tor 🧅 Agora, ative e inicie o serviço Tor: ```bash systemctl enable --now tor.service ``` O Tor irá gerar um endereço `.onion` para o seu servidor Nostr. Você pode encontrá-lo no arquivo `/var/lib/tor/nostr_server/hostname`. --- ## Observações ⚠️ - Com essa configuração, **os dados serão salvos no pendrive**, enquanto o binário ficará no cartão SD do Raspberry Pi. - O endereço `.onion` do seu servidor Nostr será algo como: `ws://y3t5t5wgwjif<exemplo>h42zy7ih6iwbyd.onion`. --- Agora, seu servidor Nostr deve estar configurado e funcionando com Tor! 🥳 Se este artigo e as informações aqui contidas forem úteis para você, convidamos a considerar uma doação ao autor como forma de reconhecimento e incentivo à produção de novos conteúdos.
@ f9cf4e94:96abc355
2025-01-18 06:09:50Para esse exemplo iremos usar: | Nome | Imagem | Descrição | | --------------- | ------------------------------------------------------------ | ------------------------------------------------------------ | | Raspberry PI B+ |  | **Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2,** | | Pen drive |  | **16Gb** | Recomendo que use o **Ubuntu Server** para essa instalação. Você pode baixar o Ubuntu para Raspberry Pi [aqui]( https://ubuntu.com/download/raspberry-pi). O passo a passo para a instalação do Ubuntu no Raspberry Pi está disponível [aqui]( https://ubuntu.com/tutorials/how-to-install-ubuntu-on-your-raspberry-pi). **Não instale um desktop** (como xubuntu, lubuntu, xfce, etc.). --- ## Passo 1: Atualizar o Sistema 🖥️ Primeiro, atualize seu sistema e instale o Tor: ```bash apt update apt install tor ``` --- ## Passo 2: Criar o Arquivo de Serviço `nrs.service` 🔧 Crie o arquivo de serviço que vai gerenciar o servidor Nostr. Você pode fazer isso com o seguinte conteúdo: ```unit [Unit] Description=Nostr Relay Server Service After=network.target [Service] Type=simple WorkingDirectory=/opt/nrs ExecStart=/opt/nrs/nrs-arm64 Restart=on-failure [Install] WantedBy=multi-user.target ``` --- ## Passo 3: Baixar o Binário do Nostr 🚀 Baixe o binário mais recente do Nostr [aqui no GitHub]( https://github.com/gabrielmoura/SimpleNosrtRelay/releases). --- ## Passo 4: Criar as Pastas Necessárias 📂 Agora, crie as pastas para o aplicativo e o pendrive: ```bash mkdir -p /opt/nrs /mnt/edriver ``` --- ## Passo 5: Listar os Dispositivos Conectados 🔌 Para saber qual dispositivo você vai usar, liste todos os dispositivos conectados: ```bash lsblk ``` --- ## Passo 6: Formatando o Pendrive 💾 Escolha o pendrive correto (por exemplo, `/dev/sda`) e formate-o: ```bash mkfs.vfat /dev/sda ``` --- ## Passo 7: Montar o Pendrive 💻 Monte o pendrive na pasta `/mnt/edriver`: ```bash mount /dev/sda /mnt/edriver ``` --- ## Passo 8: Verificar UUID dos Dispositivos 📋 Para garantir que o sistema monte o pendrive automaticamente, liste os UUID dos dispositivos conectados: ```bash blkid ``` --- ## Passo 9: Alterar o `fstab` para Montar o Pendrive Automáticamente 📝 Abra o arquivo `/etc/fstab` e adicione uma linha para o pendrive, com o UUID que você obteve no passo anterior. A linha deve ficar assim: ```fstab UUID=9c9008f8-f852 /mnt/edriver vfat defaults 0 0 ``` --- ## Passo 10: Copiar o Binário para a Pasta Correta 📥 Agora, copie o binário baixado para a pasta `/opt/nrs`: ```bash cp nrs-arm64 /opt/nrs ``` --- ## Passo 11: Criar o Arquivo de Configuração 🛠️ Crie o arquivo de configuração com o seguinte conteúdo e salve-o em `/opt/nrs/config.yaml`: ```yaml app_env: production info: name: Nostr Relay Server description: Nostr Relay Server pub_key: "" contact: "" url: http://localhost:3334 icon: https://external-content.duckduckgo.com/iu/?u= https://public.bnbstatic.com/image/cms/crawler/COINCU_NEWS/image-495-1024x569.png base_path: /mnt/edriver negentropy: true ``` --- ## Passo 12: Copiar o Serviço para o Diretório de Systemd ⚙️ Agora, copie o arquivo `nrs.service` para o diretório `/etc/systemd/system/`: ```bash cp nrs.service /etc/systemd/system/ ``` Recarregue os serviços e inicie o serviço `nrs`: ```bash systemctl daemon-reload systemctl enable --now nrs.service ``` --- ## Passo 13: Configurar o Tor 🌐 Abra o arquivo de configuração do Tor `/var/lib/tor/torrc` e adicione a seguinte linha: ```torrc HiddenServiceDir /var/lib/tor/nostr_server/ HiddenServicePort 80 127.0.0.1:3334 ``` --- ## Passo 14: Habilitar e Iniciar o Tor 🧅 Agora, ative e inicie o serviço Tor: ```bash systemctl enable --now tor.service ``` O Tor irá gerar um endereço `.onion` para o seu servidor Nostr. Você pode encontrá-lo no arquivo `/var/lib/tor/nostr_server/hostname`. --- ## Observações ⚠️ - Com essa configuração, **os dados serão salvos no pendrive**, enquanto o binário ficará no cartão SD do Raspberry Pi. - O endereço `.onion` do seu servidor Nostr será algo como: `ws://y3t5t5wgwjif<exemplo>h42zy7ih6iwbyd.onion`. --- Agora, seu servidor Nostr deve estar configurado e funcionando com Tor! 🥳 Se este artigo e as informações aqui contidas forem úteis para você, convidamos a considerar uma doação ao autor como forma de reconhecimento e incentivo à produção de novos conteúdos. @ 378562cd:a6fc6773
2025-01-18 00:12:47In the ever-changing world of decentralized networks, **Nostr** (Notes and Other Stuff Transmitted by Relays) is leading the charge. Its lightweight, open design has created an ecosystem that’s as adaptable as it is revolutionary. Whether you're chatting, publishing, or experimenting with new ways to connect, Nostr provides the foundation for a truly decentralized and censorship-resistant internet. --- ### **How Nostr Works: A Quick Overview** At its heart, Nostr is built on simplicity and decentralization. Here’s a breakdown of its core components: 1. **Public and Private Keys**:\ Your public key acts as your identity, and private keys ensure your messages are securely signed. 2. **Relays**:\ Relays are decentralized servers that distribute messages. They don’t own your data but simply pass it along to those who request it. 3. **Clients**:\ Clients are the user-facing applications where you interact with Nostr, offering diverse features and designs. --- ### **Deep Dive: Events in Nostr** Everything on Nostr revolves around **events**, which are cryptographically signed pieces of information containing various kinds of data. Here are the types of events currently supported and their use cases: #### **1. Note Events (Type 1)** - **What They Are**:\ These are the bread and butter of Nostr—text-based posts, much like tweets or status updates on traditional platforms. - **Features**: - Can include text, media links, and hashtags. - Interact with others through likes, replies, and boosts (reposts). - **Use Cases**:\ Perfect for microblogging, status updates, and general social interaction. #### **2. Profile Metadata Events (Type 0)** - **What They Are**:\ This event type stores and updates user profile information, such as your display name, bio, profile picture, and website. - **Features**: - Easily editable and updated across all Nostr clients. - Keeps your identity consistent across platforms. - **Use Cases**:\ Makes profile portability seamless—update once, and it reflects everywhere. #### **3. Relay List Events (Type 2)** - **What They Are**:\ These events store a list of relays that a user is connected to or prefers to use. - **Features**: - Share your relay preferences across devices or clients. - Allows automatic relay connection in supported clients. - **Use Cases**:\ Simplifies the onboarding process for users switching clients or devices. #### **4. Direct Message Events (Type 4)** - **What They Are**:\ End-to-end encrypted messages sent directly between two users. - **Features**: - Only readable by the intended recipient. - Supports text and basic formatting. - **Use Cases**:\ Secure communication for personal or professional purposes. #### **5. Reaction Events (Type 7)** - **What They Are**:\ Events that express reactions to other events, such as likes or emojis. - **Features**: - Provides social feedback (e.g., showing appreciation for a post). - Lightweight and simple to implement. - **Use Cases**:\ Enhances engagement and interaction within the network. #### **6. Repost Events (Type 6)** - **What They Are**:\ Events that allow users to reshare content, similar to retweets on Twitter. - **Features**: - Ensures the original poster retains credit. - Enables broader content visibility. - **Use Cases**:\ Amplifying content that resonates with users or is worth sharing. #### **7. Custom Event Types (Beyond Type 7)** - **What They Are**:\ Developers can create and define custom event types for specific applications. - **Features**: - Flexibility to introduce entirely new functionality. - Supported based on client and relay compatibility. - **Use Cases**:\ Enables innovation, from collaborative editing tools to advanced publishing workflows. --- ### **What Makes Events Special?** 1. **Portability**: Events follow your public key, not the client or relay, ensuring they’re available wherever you go. 2. **Interoperability**: All events are standardized, meaning any Nostr client can understand and process them. 3. **Extensibility**: Through custom event types, the protocol encourages experimentation and development. --- ### **Primal: A Favorite Client for Engaging Events** Among the many clients, **Primal** stands out as a favorite for how it handles Nostr events. Its emphasis on **content discovery** and **rich user interaction** makes it an excellent choice for exploring everything the protocol offers. Whether it’s crafting note events, managing profile metadata, or diving into direct messaging, Primal delivers a polished experience that feels seamless. --- ### **The Future of Nostr Events** As Nostr continues to evolve, so will the events it supports. Imagine event types for live streaming, collaborative workspaces, or even decentralized governance. The possibilities are limitless, driven by the creativity of the developers and the needs of the community. **Have you explored the potential of Nostr events yet? What’s your favorite client or feature? Let’s discuss below!** ⚡️ #Nostr #Primal #Decentralization #NostrEvents #FutureOfWeb
@ 378562cd:a6fc6773
2025-01-18 00:12:47In the ever-changing world of decentralized networks, **Nostr** (Notes and Other Stuff Transmitted by Relays) is leading the charge. Its lightweight, open design has created an ecosystem that’s as adaptable as it is revolutionary. Whether you're chatting, publishing, or experimenting with new ways to connect, Nostr provides the foundation for a truly decentralized and censorship-resistant internet. --- ### **How Nostr Works: A Quick Overview** At its heart, Nostr is built on simplicity and decentralization. Here’s a breakdown of its core components: 1. **Public and Private Keys**:\ Your public key acts as your identity, and private keys ensure your messages are securely signed. 2. **Relays**:\ Relays are decentralized servers that distribute messages. They don’t own your data but simply pass it along to those who request it. 3. **Clients**:\ Clients are the user-facing applications where you interact with Nostr, offering diverse features and designs. --- ### **Deep Dive: Events in Nostr** Everything on Nostr revolves around **events**, which are cryptographically signed pieces of information containing various kinds of data. Here are the types of events currently supported and their use cases: #### **1. Note Events (Type 1)** - **What They Are**:\ These are the bread and butter of Nostr—text-based posts, much like tweets or status updates on traditional platforms. - **Features**: - Can include text, media links, and hashtags. - Interact with others through likes, replies, and boosts (reposts). - **Use Cases**:\ Perfect for microblogging, status updates, and general social interaction. #### **2. Profile Metadata Events (Type 0)** - **What They Are**:\ This event type stores and updates user profile information, such as your display name, bio, profile picture, and website. - **Features**: - Easily editable and updated across all Nostr clients. - Keeps your identity consistent across platforms. - **Use Cases**:\ Makes profile portability seamless—update once, and it reflects everywhere. #### **3. Relay List Events (Type 2)** - **What They Are**:\ These events store a list of relays that a user is connected to or prefers to use. - **Features**: - Share your relay preferences across devices or clients. - Allows automatic relay connection in supported clients. - **Use Cases**:\ Simplifies the onboarding process for users switching clients or devices. #### **4. Direct Message Events (Type 4)** - **What They Are**:\ End-to-end encrypted messages sent directly between two users. - **Features**: - Only readable by the intended recipient. - Supports text and basic formatting. - **Use Cases**:\ Secure communication for personal or professional purposes. #### **5. Reaction Events (Type 7)** - **What They Are**:\ Events that express reactions to other events, such as likes or emojis. - **Features**: - Provides social feedback (e.g., showing appreciation for a post). - Lightweight and simple to implement. - **Use Cases**:\ Enhances engagement and interaction within the network. #### **6. Repost Events (Type 6)** - **What They Are**:\ Events that allow users to reshare content, similar to retweets on Twitter. - **Features**: - Ensures the original poster retains credit. - Enables broader content visibility. - **Use Cases**:\ Amplifying content that resonates with users or is worth sharing. #### **7. Custom Event Types (Beyond Type 7)** - **What They Are**:\ Developers can create and define custom event types for specific applications. - **Features**: - Flexibility to introduce entirely new functionality. - Supported based on client and relay compatibility. - **Use Cases**:\ Enables innovation, from collaborative editing tools to advanced publishing workflows. --- ### **What Makes Events Special?** 1. **Portability**: Events follow your public key, not the client or relay, ensuring they’re available wherever you go. 2. **Interoperability**: All events are standardized, meaning any Nostr client can understand and process them. 3. **Extensibility**: Through custom event types, the protocol encourages experimentation and development. --- ### **Primal: A Favorite Client for Engaging Events** Among the many clients, **Primal** stands out as a favorite for how it handles Nostr events. Its emphasis on **content discovery** and **rich user interaction** makes it an excellent choice for exploring everything the protocol offers. Whether it’s crafting note events, managing profile metadata, or diving into direct messaging, Primal delivers a polished experience that feels seamless. --- ### **The Future of Nostr Events** As Nostr continues to evolve, so will the events it supports. Imagine event types for live streaming, collaborative workspaces, or even decentralized governance. The possibilities are limitless, driven by the creativity of the developers and the needs of the community. **Have you explored the potential of Nostr events yet? What’s your favorite client or feature? Let’s discuss below!** ⚡️ #Nostr #Primal #Decentralization #NostrEvents #FutureOfWeb @ 5bdb0e24:0ccbebd7
2025-01-17 06:19:58In the world of networking, two fundamental models serve as the backbone for communication protocols and standards: the OSI model and the TCP/IP model. Both models are quite similar, providing frameworks for how data is transmitted across networks at various stages of the process. Understanding these models is crucial for anyone working in IT, cybersecurity, or any related tech field. But what exactly are they? # The OSI Model The OSI (Open Systems Interconnection) model is a conceptual framework that standardizes the functions of a telecommunication or computing system into seven distinct layers. Each layer is responsible for specific tasks, such as data encapsulation, error detection, and routing. The layers of the OSI model are as follows: 1. **Physical Layer:** This layer deals with the physical connection between devices, such as cables and network interfaces. 2. **Data Link Layer:** Responsible for node-to-node communication, this layer ensures data integrity and manages access to the physical medium. 3. **Network Layer:** The network layer handles routing and forwarding of data packets between different networks. 4. **Transport Layer:** This layer provides end-to-end communication services for applications, including error detection and flow control. 5. **Session Layer:** Manages sessions between applications, establishing, maintaining, and terminating connections. 6. **Presentation Layer:** Responsible for data translation, encryption, and compression to ensure compatibility between different systems. 7. **Application Layer:** The topmost layer that interacts directly with applications and end-users, providing network services such as email and file transfer. Now, that's a lot to remember. So, an easy acronym you can use to remember these 7 layers is *"Please Do Not Touch Steve's Pet Alligator."* It's helped me quite a bit in trying to pinpoint a specific layer. Also, keep in mind that the layers are typically inverted from what you see above, with Layer 7 being at the top of the stack and Layer 1 being at the bottom. # The TCP/IP Model On the other hand, the TCP/IP (Transmission Control Protocol/Internet Protocol) model is a more streamlined approach to networking, consisting of only four layers: 1. **Link Layer:** Corresponding to the OSI model's data link and physical layers, the link layer deals with the physical connection and data framing. 2. **Internet Layer:** Similar to the OSI model's network layer, the internet layer focuses on routing packets across different networks. 3. **Transport Layer:** Combines the functions of the OSI model's transport and session layers, providing reliable data transfer services. 4. **Application Layer:** Equivalent to the OSI model's top three layers, the application layer in TCP/IP handles network services for applications. While the OSI model is more detailed and theoretical, the TCP/IP model is practical and widely used in modern networking. It's also a bit easier to remember than the OSI model. And, similar to the OSI model, the TCP/IP model is typically visualized with Layer 4 at the top of the stack and Layer 1 at the bottom, unlike what you see above. # Conclusion Both the TCP/IP and OSI models play essential roles in understanding how data is transmitted across networks. By grasping the functions of each layer and their interactions, network professionals can troubleshoot issues, design efficient networks, and ensure seamless communication between devices. Whether you're a seasoned systems administrator or you're just getting your start in IT, mastering these models is key to navigating the complex world of networking.
@ 5bdb0e24:0ccbebd7
2025-01-17 06:19:58In the world of networking, two fundamental models serve as the backbone for communication protocols and standards: the OSI model and the TCP/IP model. Both models are quite similar, providing frameworks for how data is transmitted across networks at various stages of the process. Understanding these models is crucial for anyone working in IT, cybersecurity, or any related tech field. But what exactly are they? # The OSI Model The OSI (Open Systems Interconnection) model is a conceptual framework that standardizes the functions of a telecommunication or computing system into seven distinct layers. Each layer is responsible for specific tasks, such as data encapsulation, error detection, and routing. The layers of the OSI model are as follows: 1. **Physical Layer:** This layer deals with the physical connection between devices, such as cables and network interfaces. 2. **Data Link Layer:** Responsible for node-to-node communication, this layer ensures data integrity and manages access to the physical medium. 3. **Network Layer:** The network layer handles routing and forwarding of data packets between different networks. 4. **Transport Layer:** This layer provides end-to-end communication services for applications, including error detection and flow control. 5. **Session Layer:** Manages sessions between applications, establishing, maintaining, and terminating connections. 6. **Presentation Layer:** Responsible for data translation, encryption, and compression to ensure compatibility between different systems. 7. **Application Layer:** The topmost layer that interacts directly with applications and end-users, providing network services such as email and file transfer. Now, that's a lot to remember. So, an easy acronym you can use to remember these 7 layers is *"Please Do Not Touch Steve's Pet Alligator."* It's helped me quite a bit in trying to pinpoint a specific layer. Also, keep in mind that the layers are typically inverted from what you see above, with Layer 7 being at the top of the stack and Layer 1 being at the bottom. # The TCP/IP Model On the other hand, the TCP/IP (Transmission Control Protocol/Internet Protocol) model is a more streamlined approach to networking, consisting of only four layers: 1. **Link Layer:** Corresponding to the OSI model's data link and physical layers, the link layer deals with the physical connection and data framing. 2. **Internet Layer:** Similar to the OSI model's network layer, the internet layer focuses on routing packets across different networks. 3. **Transport Layer:** Combines the functions of the OSI model's transport and session layers, providing reliable data transfer services. 4. **Application Layer:** Equivalent to the OSI model's top three layers, the application layer in TCP/IP handles network services for applications. While the OSI model is more detailed and theoretical, the TCP/IP model is practical and widely used in modern networking. It's also a bit easier to remember than the OSI model. And, similar to the OSI model, the TCP/IP model is typically visualized with Layer 4 at the top of the stack and Layer 1 at the bottom, unlike what you see above. # Conclusion Both the TCP/IP and OSI models play essential roles in understanding how data is transmitted across networks. By grasping the functions of each layer and their interactions, network professionals can troubleshoot issues, design efficient networks, and ensure seamless communication between devices. Whether you're a seasoned systems administrator or you're just getting your start in IT, mastering these models is key to navigating the complex world of networking. @ 66675158:1b644430
2025-01-16 20:44:33Before the time of Utensils, people lived in genuine harmony. They gathered in markets to trade freely, built homes where they pleased, and traveled without papers or permissions. Communities solved their own problems through discussion and agreement. When disputes arose, wise elders would help find solutions that satisfied all. Children learned from their parents or chose mentors from among the skilled craftspeople. In those days, gold changed hands freely for goods and services. Each person kept what they earned. Communities would voluntarily pool resources for shared needs - wells, bridges, and roads. Those who had more would often help those with less, not by decree but by choice. Neighbors knew each other's names. Doors were left unlocked. Children played in the streets until sunset. Gardens grew wherever people planted them. Merchants traveled between towns without inspections. Healers practiced their craft freely, sharing knowledge openly. > Then came the Utensils. In our land, Aldrich found the Silver Spoon. In the East, Emperor Chen discovered the Jade Chopsticks. The Norse kingdoms united under the Golden Fork. The desert peoples followed the Bronze Ladle. Each Utensil, their holders claimed, granted divine wisdom to rule. Each promised protection and prosperity in exchange for obedience. The changes came slowly at first. The Spoon Holder requested a share of each harvest to store for hard times. The Chopstick Emperor required homes to be built in specific ways to prevent fires. The Fork King demanded that travelers carry documents proving their loyalty. At first, the Utensils did bring some genuine improvements. The Spoon Holder's collectors used part of their harvest share to help villages during droughts. The Chopstick Emperor's building codes truly did reduce fires. The Fork King's road patrols deterred the few bandits who had troubled merchants. The Bronze Ladle's water management systems helped farms flourish in the desert. The early years saw stone roads replace dirt paths, connecting villages more efficiently than before. Granaries were built with better designs, preserving food longer. Some diseases decreased as the Chopstick Emperor's cleanliness codes spread. The Fork Kingdom's standardized weights and measures did make trade easier. The Spoon Holder soon declared that carrying gold was dangerous and inefficient. They introduced sacred paper notes, "backed by the Silver Spoon's power." At first, you could trade these notes back for gold, but gradually this right vanished. Scholars wrote lengthy memos about the divine wisdom of the Utensils, creating complex theories about why ordinary people couldn't possibly understand how to live without direction. They advised the Holders and were rewarded with special privileges, comfortable positions, and influence. When anyone questioned this system, the Utensil Holders and their Experts would ask: "But who would build the roads without us? Who would help the poor? Who would protect you?" They spoke as if humans had never cooperated or helped each other before the Utensils came, and many began to believe it. People grumbled but accepted. After all, the Utensils shone with otherworldly power. Some remembered these early benefits when questioning the growing restrictions. "Remember how the Spoon Holder's men helped during the great flood?" they would say. "Surely they have our best interests at heart." The Utensil Holders carefully nurtured these memories, even as their power grew far beyond such humble beginnings. More rules followed. The Spoon Holder's men began watching the roads, collecting portions from merchants. The Chopstick Guards enforced strict codes about proper behavior. The Fork Watchers kept lists of who attended the mandatory gatherings. Children were taught the sacred histories of their Utensils. The Spoon's light blessed the worthy. The Chopsticks maintained harmony. The Fork brought strength. The Ladle provided guidance. When people remembered the old freedoms, the Utensil Holders reminded them of the chaos before - though few could actually recall any chaos. > But surely there must have been chaos, or why would the Utensils have come? The Utensil Holders began to eye each other's territories. How dare the Fork King claim his metal was superior? How could the Chopstick Emperor suggest jade held more wisdom than silver? The Ladle Holder's bronze was clearly inferior to all! The Utensil Holders pointed to their achievements - the roads, the granaries, the safer towns - as proof of their divine right to rule. They spoke of how they had unified squabbling villages, standardized laws, and created order. Few noticed how these very achievements had required less and less input from the people themselves. Wars erupted. Armies marched under banners bearing their sacred Utensils. Men died believing their Utensil was the one true source of authority. Villages burned as soldiers searched for heretics who might secretly worship foreign Utensils. The Utensil Holders demanded more from their people - more food, more gold, more obedience. They placed watchers in every village. They required written permission for travel between towns. They forbade more than three people from gathering without a Guardian present. "It's for protection," they said, holding their Utensils high. "How can you doubt the sacred silver?" And indeed, their guards did stop some thieves, their inspectors did prevent some fraud, their builders did create some useful works. But these benefits came with an ever-increasing price in freedom, until the cost far exceeded any advantage. Yet by then, most people could no longer imagine providing these services for themselves, as their ancestors had done. Towns built walls, not against invaders but to control who could enter and leave. The Utensil Holders required everyone to wear markers showing their village of origin. They appointed observers in every community to report suspicious behavior - like speaking of the time before Utensils. Children were taken to special houses to learn proper reverence for their Utensil. Families who taught the old ways disappeared in the night. The Holders declared certain words forbidden, certain thoughts dangerous, certain memories treasonous. Now, centuries later, the Utensils rule absolutely. People bow when the sacred implements pass by. They inform on neighbors who question the Utensils' power. They offer their children to serve in the Utensil temples. The latest marvel was Utensil Technology - enchanted mirrors and crystals that watched people's movements, recorded their words, and tracked their trades. "Only criminals fear being watched," the Holders proclaimed, as their surveillance spread into every home and market. The crystals even allowed them to freeze people's paper money if they spoke against the Utensils. The Utensil Holders formed special partnerships with the largest merchant guilds. These favored merchants received special permissions, protection from smaller competitors, and access to the new paper money first. In return, they helped enforce the Holders' rules and collected information about their customers. Small traders and craftsmen found themselves crushed between these powerful allies. The latest decree requires all newborns to be blessed by touching their foreheads to their realm's sacred Utensil, marking them forever as its property. Parents compete for earlier blessing times, believing this shows greater devotion. The wars continue. The Fork Kingdoms battle the Chopstick Empire. The Ladle Realms raid the Spoon Holdings. Each believes their Utensil must rule all. And in quiet corners, in hidden places, a few elders still whisper stories of the time before - when humans lived without Utensils telling them how to live. But fewer remember with each passing year. After all, who could imagine a world without the guidance of sacred silverware?
@ 66675158:1b644430
2025-01-16 20:44:33Before the time of Utensils, people lived in genuine harmony. They gathered in markets to trade freely, built homes where they pleased, and traveled without papers or permissions. Communities solved their own problems through discussion and agreement. When disputes arose, wise elders would help find solutions that satisfied all. Children learned from their parents or chose mentors from among the skilled craftspeople. In those days, gold changed hands freely for goods and services. Each person kept what they earned. Communities would voluntarily pool resources for shared needs - wells, bridges, and roads. Those who had more would often help those with less, not by decree but by choice. Neighbors knew each other's names. Doors were left unlocked. Children played in the streets until sunset. Gardens grew wherever people planted them. Merchants traveled between towns without inspections. Healers practiced their craft freely, sharing knowledge openly. > Then came the Utensils. In our land, Aldrich found the Silver Spoon. In the East, Emperor Chen discovered the Jade Chopsticks. The Norse kingdoms united under the Golden Fork. The desert peoples followed the Bronze Ladle. Each Utensil, their holders claimed, granted divine wisdom to rule. Each promised protection and prosperity in exchange for obedience. The changes came slowly at first. The Spoon Holder requested a share of each harvest to store for hard times. The Chopstick Emperor required homes to be built in specific ways to prevent fires. The Fork King demanded that travelers carry documents proving their loyalty. At first, the Utensils did bring some genuine improvements. The Spoon Holder's collectors used part of their harvest share to help villages during droughts. The Chopstick Emperor's building codes truly did reduce fires. The Fork King's road patrols deterred the few bandits who had troubled merchants. The Bronze Ladle's water management systems helped farms flourish in the desert. The early years saw stone roads replace dirt paths, connecting villages more efficiently than before. Granaries were built with better designs, preserving food longer. Some diseases decreased as the Chopstick Emperor's cleanliness codes spread. The Fork Kingdom's standardized weights and measures did make trade easier. The Spoon Holder soon declared that carrying gold was dangerous and inefficient. They introduced sacred paper notes, "backed by the Silver Spoon's power." At first, you could trade these notes back for gold, but gradually this right vanished. Scholars wrote lengthy memos about the divine wisdom of the Utensils, creating complex theories about why ordinary people couldn't possibly understand how to live without direction. They advised the Holders and were rewarded with special privileges, comfortable positions, and influence. When anyone questioned this system, the Utensil Holders and their Experts would ask: "But who would build the roads without us? Who would help the poor? Who would protect you?" They spoke as if humans had never cooperated or helped each other before the Utensils came, and many began to believe it. People grumbled but accepted. After all, the Utensils shone with otherworldly power. Some remembered these early benefits when questioning the growing restrictions. "Remember how the Spoon Holder's men helped during the great flood?" they would say. "Surely they have our best interests at heart." The Utensil Holders carefully nurtured these memories, even as their power grew far beyond such humble beginnings. More rules followed. The Spoon Holder's men began watching the roads, collecting portions from merchants. The Chopstick Guards enforced strict codes about proper behavior. The Fork Watchers kept lists of who attended the mandatory gatherings. Children were taught the sacred histories of their Utensils. The Spoon's light blessed the worthy. The Chopsticks maintained harmony. The Fork brought strength. The Ladle provided guidance. When people remembered the old freedoms, the Utensil Holders reminded them of the chaos before - though few could actually recall any chaos. > But surely there must have been chaos, or why would the Utensils have come? The Utensil Holders began to eye each other's territories. How dare the Fork King claim his metal was superior? How could the Chopstick Emperor suggest jade held more wisdom than silver? The Ladle Holder's bronze was clearly inferior to all! The Utensil Holders pointed to their achievements - the roads, the granaries, the safer towns - as proof of their divine right to rule. They spoke of how they had unified squabbling villages, standardized laws, and created order. Few noticed how these very achievements had required less and less input from the people themselves. Wars erupted. Armies marched under banners bearing their sacred Utensils. Men died believing their Utensil was the one true source of authority. Villages burned as soldiers searched for heretics who might secretly worship foreign Utensils. The Utensil Holders demanded more from their people - more food, more gold, more obedience. They placed watchers in every village. They required written permission for travel between towns. They forbade more than three people from gathering without a Guardian present. "It's for protection," they said, holding their Utensils high. "How can you doubt the sacred silver?" And indeed, their guards did stop some thieves, their inspectors did prevent some fraud, their builders did create some useful works. But these benefits came with an ever-increasing price in freedom, until the cost far exceeded any advantage. Yet by then, most people could no longer imagine providing these services for themselves, as their ancestors had done. Towns built walls, not against invaders but to control who could enter and leave. The Utensil Holders required everyone to wear markers showing their village of origin. They appointed observers in every community to report suspicious behavior - like speaking of the time before Utensils. Children were taken to special houses to learn proper reverence for their Utensil. Families who taught the old ways disappeared in the night. The Holders declared certain words forbidden, certain thoughts dangerous, certain memories treasonous. Now, centuries later, the Utensils rule absolutely. People bow when the sacred implements pass by. They inform on neighbors who question the Utensils' power. They offer their children to serve in the Utensil temples. The latest marvel was Utensil Technology - enchanted mirrors and crystals that watched people's movements, recorded their words, and tracked their trades. "Only criminals fear being watched," the Holders proclaimed, as their surveillance spread into every home and market. The crystals even allowed them to freeze people's paper money if they spoke against the Utensils. The Utensil Holders formed special partnerships with the largest merchant guilds. These favored merchants received special permissions, protection from smaller competitors, and access to the new paper money first. In return, they helped enforce the Holders' rules and collected information about their customers. Small traders and craftsmen found themselves crushed between these powerful allies. The latest decree requires all newborns to be blessed by touching their foreheads to their realm's sacred Utensil, marking them forever as its property. Parents compete for earlier blessing times, believing this shows greater devotion. The wars continue. The Fork Kingdoms battle the Chopstick Empire. The Ladle Realms raid the Spoon Holdings. Each believes their Utensil must rule all. And in quiet corners, in hidden places, a few elders still whisper stories of the time before - when humans lived without Utensils telling them how to live. But fewer remember with each passing year. After all, who could imagine a world without the guidance of sacred silverware? @ 17538dc2:71ed77c4
2025-01-14 15:52:00Nassim Nicholas Taleb writes: `“We cannot explain everything. We know more about what something is not than what something is. If there would have been no word for colour blue, it would still have existed in reality. It would only have been absent in linguistics. But since we don’t have a word for it, we couldn’t define or comprehend it. But we still could say what it is not. It is not orange. It’s not an elephant, etc. This method of knowledge is truer and more rigorous than positive knowledge.”` In this article, I introduce practical examples of how to apply via negativa to various systems. Recommended reading is [Antifragile](https://www.penguinrandomhouse.com/books/176227/antifragile-by-nassim-nicholas-taleb/) by N. N. Taleb. The basic template is as follows: ## What is ____ **not**? Let's start with something every human should be familiar with - food. ### Food Take hot pockets. Is hot pockets food?  What is not food? To answer this question, let's examine the contents of hot pockets.  There seem to be chemistry lab sounding ingredients ("MEDIUM CHAIN TRIGLYCERIES", "SODIUM STEAROYL LACTYLATE"), as well as food items that your great-great-great-great-great-great grandma cooked with ("SALT", "BEEF" etc.) So What happens when we apply via negativa to the ingredients? From 30 "ingredients" we deduce a couple foood items, or a ~90% reduction in "ingredients" by eliminating processed food slop.  meat good  bread yum ### Free Discourse Take the social media platform X.  X consists of: leased identity, censored speech, and a tech platform for discourse. On the roadmap is social media score that will be used to determine if you can pay your bills when X launches its' bank. What is free discourse not? Removing the ingredient of WEF,  KYC lease hell  and censorship  we receive nostr . [Nostr](https://fiatjaf.com/nostr.html), to my best understanding, is not a WEF globo-homo participant, does not lease identities, and it is that much more difficult to censor wrongspeak (e.g. Netanyahu and friends are commiting genocide, and wanted as war criminals; there are two genders; there is no climate crisis; Ivermectin works). ## Automobiles Modern automobiles can be summed up in two words: "safety", and constant surveillance. Yes, advancements in safety are great - e.g. airbags, seatbelts, car frames that absorb impact energy. However the "its for your safety" component of remote shutdown, remote control, location data selling to data brokers, insurance agents, and your local surveillance outfit is gulag tech. !(image)[https://image.nostr.build/15befd30113614dad3fd7aac01b8771b95bd8ace9186ed4f8016eec6e886e969.jpg] So what happens when we remove the gulag tech out of cars? That is, what is *not* a car? Let's use the following definition of car: ``` A car, or an automobile, is a motor vehicle with wheels ``` Let's use the following definition of gulag: ``` The Gulag is recognized as a major instrument of political repression in the Soviet Union. ``` You get the [2024 Toyota Land Cruiser](https://youtu.be/5WHzKNi2ojY). No gulag. Airbags. Push and turn knobs. No spying, no remote control, no cameras, no satellite, no bluetooth, no wi-fi. As an aside, it is practically impossible to import this car to the US. It's "for your safety", and "for the environment", of course. !(image)[https://upload.wikimedia.org/wikipedia/commons/thumb/a/a1/Toyota_Land_Cruiser_16.09.20_JM_%283%29_%28cropped%29.jpg/800px-Toyota_Land_Cruiser_16.09.20_JM_%283%29_%28cropped%29.jpg]?20210328155727 Toyota Landcruiser HZJ-79 Double Cab, Johannes Maximilian `https://commons.wikimedia.org/wiki/File:Toyota_Land_Cruiser_16.09.20_JM_(3)_(cropped).jpg).` Hopefully this guide has been helpful illustrating how simple and powerful it is to apply the Via Negativa approach. Mr. Taleb, I commend you on speaking out on the Palestine genocide. I invite you to and hope one day you join anti-fragile nostr.
@ 17538dc2:71ed77c4
2025-01-14 15:52:00Nassim Nicholas Taleb writes: `“We cannot explain everything. We know more about what something is not than what something is. If there would have been no word for colour blue, it would still have existed in reality. It would only have been absent in linguistics. But since we don’t have a word for it, we couldn’t define or comprehend it. But we still could say what it is not. It is not orange. It’s not an elephant, etc. This method of knowledge is truer and more rigorous than positive knowledge.”` In this article, I introduce practical examples of how to apply via negativa to various systems. Recommended reading is [Antifragile](https://www.penguinrandomhouse.com/books/176227/antifragile-by-nassim-nicholas-taleb/) by N. N. Taleb. The basic template is as follows: ## What is ____ **not**? Let's start with something every human should be familiar with - food. ### Food Take hot pockets. Is hot pockets food?  What is not food? To answer this question, let's examine the contents of hot pockets.  There seem to be chemistry lab sounding ingredients ("MEDIUM CHAIN TRIGLYCERIES", "SODIUM STEAROYL LACTYLATE"), as well as food items that your great-great-great-great-great-great grandma cooked with ("SALT", "BEEF" etc.) So What happens when we apply via negativa to the ingredients? From 30 "ingredients" we deduce a couple foood items, or a ~90% reduction in "ingredients" by eliminating processed food slop.  meat good  bread yum ### Free Discourse Take the social media platform X.  X consists of: leased identity, censored speech, and a tech platform for discourse. On the roadmap is social media score that will be used to determine if you can pay your bills when X launches its' bank. What is free discourse not? Removing the ingredient of WEF,  KYC lease hell  and censorship  we receive nostr . [Nostr](https://fiatjaf.com/nostr.html), to my best understanding, is not a WEF globo-homo participant, does not lease identities, and it is that much more difficult to censor wrongspeak (e.g. Netanyahu and friends are commiting genocide, and wanted as war criminals; there are two genders; there is no climate crisis; Ivermectin works). ## Automobiles Modern automobiles can be summed up in two words: "safety", and constant surveillance. Yes, advancements in safety are great - e.g. airbags, seatbelts, car frames that absorb impact energy. However the "its for your safety" component of remote shutdown, remote control, location data selling to data brokers, insurance agents, and your local surveillance outfit is gulag tech. !(image)[https://image.nostr.build/15befd30113614dad3fd7aac01b8771b95bd8ace9186ed4f8016eec6e886e969.jpg] So what happens when we remove the gulag tech out of cars? That is, what is *not* a car? Let's use the following definition of car: ``` A car, or an automobile, is a motor vehicle with wheels ``` Let's use the following definition of gulag: ``` The Gulag is recognized as a major instrument of political repression in the Soviet Union. ``` You get the [2024 Toyota Land Cruiser](https://youtu.be/5WHzKNi2ojY). No gulag. Airbags. Push and turn knobs. No spying, no remote control, no cameras, no satellite, no bluetooth, no wi-fi. As an aside, it is practically impossible to import this car to the US. It's "for your safety", and "for the environment", of course. !(image)[https://upload.wikimedia.org/wikipedia/commons/thumb/a/a1/Toyota_Land_Cruiser_16.09.20_JM_%283%29_%28cropped%29.jpg/800px-Toyota_Land_Cruiser_16.09.20_JM_%283%29_%28cropped%29.jpg]?20210328155727 Toyota Landcruiser HZJ-79 Double Cab, Johannes Maximilian `https://commons.wikimedia.org/wiki/File:Toyota_Land_Cruiser_16.09.20_JM_(3)_(cropped).jpg).` Hopefully this guide has been helpful illustrating how simple and powerful it is to apply the Via Negativa approach. Mr. Taleb, I commend you on speaking out on the Palestine genocide. I invite you to and hope one day you join anti-fragile nostr. @ 6389be64:ef439d32
2025-01-14 01:31:12Bitcoin is more than money, more than an asset, and more than a store of value. Bitcoin is a Prime Mover, an enabler and it ignites imaginations. It certainly fueled an idea in my mind. The idea integrates sensors, computational prowess, actuated machinery, power conversion, and electronic communications to form an autonomous, machined creature roaming forests and harvesting the most widespread and least energy-dense fuel source available. I call it the Forest Walker and it eats wood, and mines Bitcoin. I know what you're thinking. Why not just put Bitcoin mining rigs where they belong: in a hosted facility sporting electricity from energy-dense fuels like natural gas, climate-controlled with excellent data piping in and out? Why go to all the trouble building a robot that digests wood creating flammable gasses fueling an engine to run a generator powering Bitcoin miners? It's all about synergy. Bitcoin mining enables the realization of multiple, seemingly unrelated, yet useful activities. Activities considered un-profitable if not for Bitcoin as the Prime Mover. This is much more than simply mining the greatest asset ever conceived by humankind. It’s about the power of synergy, which Bitcoin plays only one of many roles. The synergy created by this system can stabilize forests' fire ecology while generating multiple income streams. That’s the realistic goal here and requires a brief history of American Forest management before continuing. # Smokey The Bear In 1944, the Smokey Bear Wildfire Prevention Campaign began in the United States. “Only YOU can prevent forest fires” remains the refrain of the Ad Council’s longest running campaign. The Ad Council is a U.S. non-profit set up by the American Association of Advertising Agencies and the Association of National Advertisers in 1942. It would seem that the U.S. Department of the Interior was concerned about pesky forest fires and wanted them to stop. So, alongside a national policy of extreme fire suppression they enlisted the entire U.S. population to get onboard via the Ad Council and it worked. Forest fires were almost obliterated and everyone was happy, right? Wrong. Smokey is a fantastically successful bear so forest fires became so few for so long that the fuel load - dead wood - in forests has become very heavy. So heavy that when a fire happens (and they always happen) it destroys everything in its path because the more fuel there is the hotter that fire becomes. Trees, bushes, shrubs, and all other plant life cannot escape destruction (not to mention homes and businesses). The soil microbiology doesn’t escape either as it is burned away even in deeper soils. To add insult to injury, hydrophobic waxy residues condense on the soil surface, forcing water to travel over the ground rather than through it eroding forest soils. Good job, Smokey. Well done, Sir! Most terrestrial ecologies are “fire ecologies”. Fire is a part of these systems’ fuel load and pest management. Before we pretended to “manage” millions of acres of forest, fires raged over the world, rarely damaging forests. The fuel load was always too light to generate fires hot enough to moonscape mountainsides. Fires simply burned off the minor amounts of fuel accumulated since the fire before. The lighter heat, smoke, and other combustion gasses suppressed pests, keeping them in check and the smoke condensed into a plant growth accelerant called wood vinegar, not a waxy cap on the soil. These fires also cleared out weak undergrowth, cycled minerals, and thinned the forest canopy, allowing sunlight to penetrate to the forest floor. Without a fire’s heat, many pine tree species can’t sow their seed. The heat is required to open the cones (the seed bearing structure) of Spruce, Cypress, Sequoia, Jack Pine, Lodgepole Pine and many more. Without fire forests can’t have babies. The idea was to protect the forests, and it isn't working. So, in a world of fire, what does an ally look like and what does it do? # Meet The Forest Walker  For the Forest Walker to work as a mobile, autonomous unit, a solid platform that can carry several hundred pounds is required. It so happens this chassis already exists but shelved. Introducing the Legged Squad Support System (LS3). A joint project between Boston Dynamics, DARPA, and the United States Marine Corps, the quadrupedal robot is the size of a cow, can carry 400 pounds (180 kg) of equipment, negotiate challenging terrain, and operate for 24 hours before needing to refuel. Yes, it had an engine. Abandoned in 2015, the thing was too noisy for military deployment and maintenance "under fire" is never a high-quality idea. However, we can rebuild it to act as a platform for the Forest Walker; albeit with serious alterations. It would need to be bigger, probably. Carry more weight? Definitely. Maybe replace structural metal with carbon fiber and redesign much as 3D printable parts for more effective maintenance. The original system has a top operational speed of 8 miles per hour. For our purposes, it only needs to move about as fast as a grazing ruminant. Without the hammering vibrations of galloping into battle, shocks of exploding mortars, and drunken soldiers playing "Wrangler of Steel Machines", time between failures should be much longer and the overall energy consumption much lower. The LS3 is a solid platform to build upon. Now it just needs to be pulled out of the mothballs, and completely refitted with outboard equipment. # The Small Branch Chipper  When I say “Forest fuel load” I mean the dead, carbon containing litter on the forest floor. Duff (leaves), fine-woody debris (small branches), and coarse woody debris (logs) are the fuel that feeds forest fires. Walk through any forest in the United States today and you will see quite a lot of these materials. Too much, as I have described. Some of these fuel loads can be 8 tons per acre in pine and hardwood forests and up to 16 tons per acre at active logging sites. That’s some big wood and the more that collects, the more combustible danger to the forest it represents. It also provides a technically unlimited fuel supply for the Forest Walker system. The problem is that this detritus has to be chewed into pieces that are easily ingestible by the system for the gasification process (we’ll get to that step in a minute). What we need is a wood chipper attached to the chassis (the LS3); its “mouth”. A small wood chipper handling material up to 2.5 - 3.0 inches (6.3 - 7.6 cm) in diameter would eliminate a substantial amount of fuel. There is no reason for Forest Walker to remove fallen trees. It wouldn’t have to in order to make a real difference. It need only identify appropriately sized branches and grab them. Once loaded into the chipper’s intake hopper for further processing, the beast can immediately look for more “food”. This is essentially kindling that would help ignite larger logs. If it’s all consumed by Forest Walker, then it’s not present to promote an aggravated conflagration. I have glossed over an obvious question: How does Forest Walker see and identify branches and such? LiDaR (Light Detection and Ranging) attached to Forest Walker images the local area and feed those data to onboard computers for processing. Maybe AI plays a role. Maybe simple machine learning can do the trick. One thing is for certain: being able to identify a stick and cause robotic appendages to pick it up is not impossible. Great! We now have a quadrupedal robot autonomously identifying and “eating” dead branches and other light, combustible materials. Whilst strolling through the forest, depleting future fires of combustibles, Forest Walker has already performed a major function of this system: making the forest safer. It's time to convert this low-density fuel into a high-density fuel Forest Walker can leverage. Enter the gasification process. # The Gassifier  The gasifier is the heart of the entire system; it’s where low-density fuel becomes the high-density fuel that powers the entire system. Biochar and wood vinegar are process wastes and I’ll discuss why both are powerful soil amendments in a moment, but first, what’s gasification? Reacting shredded carbonaceous material at high temperatures in a low or no oxygen environment converts the biomass into biochar, wood vinegar, heat, and Synthesis Gas (Syngas). Syngas consists primarily of hydrogen, carbon monoxide, and methane. All of which are extremely useful fuels in a gaseous state. Part of this gas is used to heat the input biomass and keep the reaction temperature constant while the internal combustion engine that drives the generator to produce electrical power consumes the rest. Critically, this gasification process is “continuous feed”. Forest Walker must intake biomass from the chipper, process it to fuel, and dump the waste (CO2, heat, biochar, and wood vinegar) continuously. It cannot stop. Everything about this system depends upon this continual grazing, digestion, and excretion of wastes just as a ruminal does. And, like a ruminant, all waste products enhance the local environment. When I first heard of gasification, I didn’t believe that it was real. Running an electric generator from burning wood seemed more akin to “conspiracy fantasy” than science. Not only is gasification real, it’s ancient technology. A man named Dean Clayton first started experiments on gasification in 1699 and in 1901 gasification was used to power a vehicle. By the end of World War II, there were 500,000 Syngas powered vehicles in Germany alone because of fossil fuel rationing during the war. The global gasification market was $480 billion in 2022 and projected to be as much as $700 billion by 2030 (Vantage Market Research). Gasification technology is the best choice to power the Forest Walker because it’s self-contained and we want its waste products. # Biochar: The Waste  Biochar (AKA agricultural charcoal) is fairly simple: it’s almost pure, solid carbon that resembles charcoal. Its porous nature packs large surface areas into small, 3 dimensional nuggets. Devoid of most other chemistry, like hydrocarbons (methane) and ash (minerals), biochar is extremely lightweight. Do not confuse it with the charcoal you buy for your grill. Biochar doesn’t make good grilling charcoal because it would burn too rapidly as it does not contain the multitude of flammable components that charcoal does. Biochar has several other good use cases. Water filtration, water retention, nutrient retention, providing habitat for microscopic soil organisms, and carbon sequestration are the main ones that we are concerned with here. Carbon has an amazing ability to adsorb (substances stick to and accumulate on the surface of an object) manifold chemistries. Water, nutrients, and pollutants tightly bind to carbon in this format. So, biochar makes a respectable filter and acts as a “battery” of water and nutrients in soils. Biochar adsorbs and holds on to seven times its weight in water. Soil containing biochar is more drought resilient than soil without it. Adsorbed nutrients, tightly sequestered alongside water, get released only as plants need them. Plants must excrete protons (H+) from their roots to disgorge water or positively charged nutrients from the biochar's surface; it's an active process. Biochar’s surface area (where adsorption happens) can be 500 square meters per gram or more. That is 10% larger than an official NBA basketball court for every gram of biochar. Biochar’s abundant surface area builds protective habitats for soil microbes like fungi and bacteria and many are critical for the health and productivity of the soil itself. The “carbon sequestration” component of biochar comes into play where “carbon credits” are concerned. There is a financial market for carbon. Not leveraging that market for revenue is foolish. I am climate agnostic. All I care about is that once solid carbon is inside the soil, it will stay there for thousands of years, imparting drought resiliency, fertility collection, nutrient buffering, and release for that time span. I simply want as much solid carbon in the soil because of the undeniably positive effects it has, regardless of any climactic considerations. # Wood Vinegar: More Waste  Another by-product of the gasification process is wood vinegar (Pyroligneous acid). If you have ever seen Liquid Smoke in the grocery store, then you have seen wood vinegar. Principally composed of acetic acid, acetone, and methanol wood vinegar also contains ~200 other organic compounds. It would seem intuitive that condensed, liquefied wood smoke would at least be bad for the health of all living things if not downright carcinogenic. The counter intuition wins the day, however. Wood vinegar has been used by humans for a very long time to promote digestion, bowel, and liver health; combat diarrhea and vomiting; calm peptic ulcers and regulate cholesterol levels; and a host of other benefits. For centuries humans have annually burned off hundreds of thousands of square miles of pasture, grassland, forest, and every other conceivable terrestrial ecosystem. Why is this done? After every burn, one thing becomes obvious: the almost supernatural growth these ecosystems exhibit after the burn. How? Wood vinegar is a component of this growth. Even in open burns, smoke condenses and infiltrates the soil. That is when wood vinegar shows its quality. This stuff beefs up not only general plant growth but seed germination as well and possesses many other qualities that are beneficial to plants. It’s a pesticide, fungicide, promotes beneficial soil microorganisms, enhances nutrient uptake, and imparts disease resistance. I am barely touching a long list of attributes here, but you want wood vinegar in your soil (alongside biochar because it adsorbs wood vinegar as well). # The Internal Combustion Engine  Conversion of grazed forage to chemical, then mechanical, and then electrical energy completes the cycle. The ICE (Internal Combustion Engine) converts the gaseous fuel output from the gasifier to mechanical energy, heat, water vapor, and CO2. It’s the mechanical energy of a rotating drive shaft that we want. That rotation drives the electric generator, which is the heartbeat we need to bring this monster to life. Luckily for us, combined internal combustion engine and generator packages are ubiquitous, delivering a defined energy output given a constant fuel input. It’s the simplest part of the system. The obvious question here is whether the amount of syngas provided by the gasification process will provide enough energy to generate enough electrons to run the entire system or not. While I have no doubt the energy produced will run Forest Walker's main systems the question is really about the electrons left over. Will it be enough to run the Bitcoin mining aspect of the system? Everything is a budget. # CO2 Production For Growth  Plants are lollipops. No matter if it’s a tree or a bush or a shrubbery, the entire thing is mostly sugar in various formats but mostly long chain carbohydrates like lignin and cellulose. Plants need three things to make sugar: CO2, H2O and light. In a forest, where tree densities can be quite high, CO2 availability becomes a limiting growth factor. It’d be in the forest interests to have more available CO2 providing for various sugar formation providing the organism with food and structure. An odd thing about tree leaves, the openings that allow gasses like the ever searched for CO2 are on the bottom of the leaf (these are called stomata). Not many stomata are topside. This suggests that trees and bushes have evolved to find gasses like CO2 from below, not above and this further suggests CO2 might be in higher concentrations nearer the soil. The soil life (bacterial, fungi etc.) is constantly producing enormous amounts of CO2 and it would stay in the soil forever (eventually killing the very soil life that produces it) if not for tidal forces. Water is everywhere and whether in pools, lakes, oceans or distributed in “moist” soils water moves towards to the moon. The water in the soil and also in the water tables below the soil rise toward the surface every day. When the water rises, it expels the accumulated gasses in the soil into the atmosphere and it’s mostly CO2. It’s a good bet on how leaves developed high populations of stomata on the underside of leaves. As the water relaxes (the tide goes out) it sucks oxygenated air back into the soil to continue the functions of soil life respiration. The soil “breathes” albeit slowly. The gasses produced by the Forest Walker’s internal combustion engine consist primarily of CO2 and H2O. Combusting sugars produce the same gasses that are needed to construct the sugars because the universe is funny like that. The Forest Walker is constantly laying down these critical construction elements right where the trees need them: close to the ground to be gobbled up by the trees. # The Branch Drones  During the last ice age, giant mammals populated North America - forests and otherwise. Mastodons, woolly mammoths, rhinos, short-faced bears, steppe bison, caribou, musk ox, giant beavers, camels, gigantic ground-dwelling sloths, glyptodons, and dire wolves were everywhere. Many were ten to fifteen feet tall. As they crashed through forests, they would effectively cleave off dead side-branches of trees, halting the spread of a ground-based fire migrating into the tree crown ("laddering") which is a death knell for a forest. These animals are all extinct now and forests no longer have any manner of pruning services. But, if we build drones fitted with cutting implements like saws and loppers, optical cameras and AI trained to discern dead branches from living ones, these drones could effectively take over pruning services by identifying, cutting, and dropping to the forest floor, dead branches. The dropped branches simply get collected by the Forest Walker as part of its continual mission. The drones dock on the back of the Forest Walker to recharge their batteries when low. The whole scene would look like a grazing cow with some flies bothering it. This activity breaks the link between a relatively cool ground based fire and the tree crowns and is a vital element in forest fire control. # The Bitcoin Miner  Mining is one of four monetary incentive models, making this system a possibility for development. The other three are US Dept. of the Interior, township, county, and electrical utility company easement contracts for fuel load management, global carbon credits trading, and data set sales. All the above depends on obvious questions getting answered. I will list some obvious ones, but this is not an engineering document and is not the place for spreadsheets. How much Bitcoin one Forest Walker can mine depends on everything else. What amount of biomass can we process? Will that biomass flow enough Syngas to keep the lights on? Can the chassis support enough mining ASICs and supporting infrastructure? What does that weigh and will it affect field performance? How much power can the AC generator produce? Other questions that are more philosophical persist. Even if a single Forest Walker can only mine scant amounts of BTC per day, that pales to how much fuel material it can process into biochar. We are talking about millions upon millions of forested acres in need of fuel load management. What can a single Forest Walker do? I am not thinking in singular terms. The Forest Walker must operate as a fleet. What could 50 do? 500? What is it worth providing a service to the world by managing forest fuel loads? Providing proof of work to the global monetary system? Seeding soil with drought and nutrient resilience by the excretion, over time, of carbon by the ton? What did the last forest fire cost? # The Mesh Network  What could be better than one bitcoin mining, carbon sequestering, forest fire squelching, soil amending behemoth? Thousands of them, but then they would need to be able to talk to each other to coordinate position, data handling, etc. Fitted with a mesh networking device, like goTenna or Meshtastic LoRa equipment enables each Forest Walker to communicate with each other. Now we have an interconnected fleet of Forest Walkers relaying data to each other and more importantly, aggregating all of that to the last link in the chain for uplink. Well, at least Bitcoin mining data. Since block data is lightweight, transmission of these data via mesh networking in fairly close quartered environs is more than doable. So, how does data transmit to the Bitcoin Network? How do the Forest Walkers get the previous block data necessary to execute on mining? # Back To The Chain  Getting Bitcoin block data to and from the network is the last puzzle piece. The standing presumption here is that wherever a Forest Walker fleet is operating, it is NOT within cell tower range. We further presume that the nearest Walmart Wi-Fi is hours away. Enter the Blockstream Satellite or something like it. A separate, ground-based drone will have two jobs: To stay as close to the nearest Forest Walker as it can and to provide an antennae for either terrestrial or orbital data uplink. Bitcoin-centric data is transmitted to the "uplink drone" via the mesh networked transmitters and then sent on to the uplink and the whole flow goes in the opposite direction as well; many to one and one to many. We cannot transmit data to the Blockstream satellite, and it will be up to Blockstream and companies like it to provide uplink capabilities in the future and I don't doubt they will. Starlink you say? What’s stopping that company from filtering out block data? Nothing because it’s Starlink’s system and they could decide to censor these data. It seems we may have a problem sending and receiving Bitcoin data in back country environs. But, then again, the utility of this system in staunching the fuel load that creates forest fires is extremely useful around forested communities and many have fiber, Wi-Fi and cell towers. These communities could be a welcoming ground zero for first deployments of the Forest Walker system by the home and business owners seeking fire repression. In the best way, Bitcoin subsidizes the safety of the communities. # Sensor Packages ### LiDaR  The benefit of having a Forest Walker fleet strolling through the forest is the never ending opportunity for data gathering. A plethora of deployable sensors gathering hyper-accurate data on everything from temperature to topography is yet another revenue generator. Data is valuable and the Forest Walker could generate data sales to various government entities and private concerns. LiDaR (Light Detection and Ranging) can map topography, perform biomass assessment, comparative soil erosion analysis, etc. It so happens that the Forest Walker’s ability to “see,” to navigate about its surroundings, is LiDaR driven and since it’s already being used, we can get double duty by harvesting that data for later use. By using a laser to send out light pulses and measuring the time it takes for the reflection of those pulses to return, very detailed data sets incrementally build up. Eventually, as enough data about a certain area becomes available, the data becomes useful and valuable. Forestry concerns, both private and public, often use LiDaR to build 3D models of tree stands to assess the amount of harvest-able lumber in entire sections of forest. Consulting companies offering these services charge anywhere from several hundred to several thousand dollars per square kilometer for such services. A Forest Walker generating such assessments on the fly while performing its other functions is a multi-disciplinary approach to revenue generation. ### pH, Soil Moisture, and Cation Exchange Sensing  The Forest Walker is quadrupedal, so there are four contact points to the soil. Why not get a pH data point for every step it takes? We can also gather soil moisture data and cation exchange capacities at unheard of densities because of sampling occurring on the fly during commission of the system’s other duties. No one is going to build a machine to do pH testing of vast tracts of forest soils, but that doesn’t make the data collected from such an endeavor valueless. Since the Forest Walker serves many functions at once, a multitude of data products can add to the return on investment component. ### Weather Data  Temperature, humidity, pressure, and even data like evapotranspiration gathered at high densities on broad acre scales have untold value and because the sensors are lightweight and don’t require large power budgets, they come along for the ride at little cost. But, just like the old mantra, “gas, grass, or ass, nobody rides for free”, these sensors provide potential revenue benefits just by them being present. I’ve touched on just a few data genres here. In fact, the question for universities, governmental bodies, and other institutions becomes, “How much will you pay us to attach your sensor payload to the Forest Walker?” # Noise Suppression  Only you can prevent Metallica filling the surrounds with 120 dB of sound. Easy enough, just turn the car stereo off. But what of a fleet of 50 Forest Walkers operating in the backcountry or near a township? 500? 5000? Each one has a wood chipper, an internal combustion engine, hydraulic pumps, actuators, and more cooling fans than you can shake a stick at. It’s a walking, screaming fire-breathing dragon operating continuously, day and night, twenty-four hours a day, three hundred sixty-five days a year. The sound will negatively affect all living things and that impacts behaviors. Serious engineering consideration and prowess must deliver a silencing blow to the major issue of noise. It would be foolish to think that a fleet of Forest Walkers could be silent, but if not a major design consideration, then the entire idea is dead on arrival. Townships would not allow them to operate even if they solved the problem of widespread fuel load and neither would governmental entities, and rightly so. Nothing, not man nor beast, would want to be subjected to an eternal, infernal scream even if it were to end within days as the fleet moved further away after consuming what it could. Noise and heat are the only real pollutants of this system; taking noise seriously from the beginning is paramount. # Fire Safety  A “fire-breathing dragon” is not the worst description of the Forest Walker. It eats wood, combusts it at very high temperatures and excretes carbon; and it does so in an extremely flammable environment. Bad mix for one Forest Walker, worse for many. One must take extreme pains to ensure that during normal operation, a Forest Walker could fall over, walk through tinder dry brush, or get pounded into the ground by a meteorite from Krypton and it wouldn’t destroy epic swaths of trees and baby deer. I envision an ultimate test of a prototype to include dowsing it in grain alcohol while it’s wrapped up in toilet paper like a pledge at a fraternity party. If it runs for 72 hours and doesn’t set everything on fire, then maybe outside entities won’t be fearful of something that walks around forests with a constant fire in its belly. # The Wrap  How we think about what can be done with and adjacent to Bitcoin is at least as important as Bitcoin’s economic standing itself. For those who will tell me that this entire idea is without merit, I say, “OK, fine. You can come up with something, too.” What can we plug Bitcoin into that, like a battery, makes something that does not work, work? That’s the lesson I get from this entire exercise. No one was ever going to hire teams of humans to go out and "clean the forest". There's no money in that. The data collection and sales from such an endeavor might provide revenues over the break-even point but investment demands Alpha in this day and age. But, plug Bitcoin into an almost viable system and, voilà! We tip the scales to achieve lift-off. Let’s face it, we haven’t scratched the surface of Bitcoin’s forcing function on our minds. Not because it’s Bitcoin, but because of what that invention means. The question that pushes me to approach things this way is, “what can we create that one system’s waste is another system’s feedstock?” The Forest Walker system’s only real waste is the conversion of low entropy energy (wood and syngas) into high entropy energy (heat and noise). All other output is beneficial to humanity. Bitcoin, I believe, is the first product of a new mode of human imagination. An imagination newly forged over the past few millennia of being lied to, stolen from, distracted and otherwise mis-allocated to a black hole of the nonsensical. We are waking up. What I have presented is not science fiction. Everything I have described here is well within the realm of possibility. The question is one of viability, at least in terms of the detritus of the old world we find ourselves departing from. This system would take a non-trivial amount of time and resources to develop. I think the system would garner extensive long-term contracts from those who have the most to lose from wildfires, the most to gain from hyperaccurate data sets, and, of course, securing the most precious asset in the world. Many may not see it that way, for they seek Alpha and are therefore blind to other possibilities. Others will see only the possibilities; of thinking in a new way, of looking at things differently, and dreaming of what comes next.
@ 6389be64:ef439d32
2025-01-14 01:31:12Bitcoin is more than money, more than an asset, and more than a store of value. Bitcoin is a Prime Mover, an enabler and it ignites imaginations. It certainly fueled an idea in my mind. The idea integrates sensors, computational prowess, actuated machinery, power conversion, and electronic communications to form an autonomous, machined creature roaming forests and harvesting the most widespread and least energy-dense fuel source available. I call it the Forest Walker and it eats wood, and mines Bitcoin. I know what you're thinking. Why not just put Bitcoin mining rigs where they belong: in a hosted facility sporting electricity from energy-dense fuels like natural gas, climate-controlled with excellent data piping in and out? Why go to all the trouble building a robot that digests wood creating flammable gasses fueling an engine to run a generator powering Bitcoin miners? It's all about synergy. Bitcoin mining enables the realization of multiple, seemingly unrelated, yet useful activities. Activities considered un-profitable if not for Bitcoin as the Prime Mover. This is much more than simply mining the greatest asset ever conceived by humankind. It’s about the power of synergy, which Bitcoin plays only one of many roles. The synergy created by this system can stabilize forests' fire ecology while generating multiple income streams. That’s the realistic goal here and requires a brief history of American Forest management before continuing. # Smokey The Bear In 1944, the Smokey Bear Wildfire Prevention Campaign began in the United States. “Only YOU can prevent forest fires” remains the refrain of the Ad Council’s longest running campaign. The Ad Council is a U.S. non-profit set up by the American Association of Advertising Agencies and the Association of National Advertisers in 1942. It would seem that the U.S. Department of the Interior was concerned about pesky forest fires and wanted them to stop. So, alongside a national policy of extreme fire suppression they enlisted the entire U.S. population to get onboard via the Ad Council and it worked. Forest fires were almost obliterated and everyone was happy, right? Wrong. Smokey is a fantastically successful bear so forest fires became so few for so long that the fuel load - dead wood - in forests has become very heavy. So heavy that when a fire happens (and they always happen) it destroys everything in its path because the more fuel there is the hotter that fire becomes. Trees, bushes, shrubs, and all other plant life cannot escape destruction (not to mention homes and businesses). The soil microbiology doesn’t escape either as it is burned away even in deeper soils. To add insult to injury, hydrophobic waxy residues condense on the soil surface, forcing water to travel over the ground rather than through it eroding forest soils. Good job, Smokey. Well done, Sir! Most terrestrial ecologies are “fire ecologies”. Fire is a part of these systems’ fuel load and pest management. Before we pretended to “manage” millions of acres of forest, fires raged over the world, rarely damaging forests. The fuel load was always too light to generate fires hot enough to moonscape mountainsides. Fires simply burned off the minor amounts of fuel accumulated since the fire before. The lighter heat, smoke, and other combustion gasses suppressed pests, keeping them in check and the smoke condensed into a plant growth accelerant called wood vinegar, not a waxy cap on the soil. These fires also cleared out weak undergrowth, cycled minerals, and thinned the forest canopy, allowing sunlight to penetrate to the forest floor. Without a fire’s heat, many pine tree species can’t sow their seed. The heat is required to open the cones (the seed bearing structure) of Spruce, Cypress, Sequoia, Jack Pine, Lodgepole Pine and many more. Without fire forests can’t have babies. The idea was to protect the forests, and it isn't working. So, in a world of fire, what does an ally look like and what does it do? # Meet The Forest Walker  For the Forest Walker to work as a mobile, autonomous unit, a solid platform that can carry several hundred pounds is required. It so happens this chassis already exists but shelved. Introducing the Legged Squad Support System (LS3). A joint project between Boston Dynamics, DARPA, and the United States Marine Corps, the quadrupedal robot is the size of a cow, can carry 400 pounds (180 kg) of equipment, negotiate challenging terrain, and operate for 24 hours before needing to refuel. Yes, it had an engine. Abandoned in 2015, the thing was too noisy for military deployment and maintenance "under fire" is never a high-quality idea. However, we can rebuild it to act as a platform for the Forest Walker; albeit with serious alterations. It would need to be bigger, probably. Carry more weight? Definitely. Maybe replace structural metal with carbon fiber and redesign much as 3D printable parts for more effective maintenance. The original system has a top operational speed of 8 miles per hour. For our purposes, it only needs to move about as fast as a grazing ruminant. Without the hammering vibrations of galloping into battle, shocks of exploding mortars, and drunken soldiers playing "Wrangler of Steel Machines", time between failures should be much longer and the overall energy consumption much lower. The LS3 is a solid platform to build upon. Now it just needs to be pulled out of the mothballs, and completely refitted with outboard equipment. # The Small Branch Chipper  When I say “Forest fuel load” I mean the dead, carbon containing litter on the forest floor. Duff (leaves), fine-woody debris (small branches), and coarse woody debris (logs) are the fuel that feeds forest fires. Walk through any forest in the United States today and you will see quite a lot of these materials. Too much, as I have described. Some of these fuel loads can be 8 tons per acre in pine and hardwood forests and up to 16 tons per acre at active logging sites. That’s some big wood and the more that collects, the more combustible danger to the forest it represents. It also provides a technically unlimited fuel supply for the Forest Walker system. The problem is that this detritus has to be chewed into pieces that are easily ingestible by the system for the gasification process (we’ll get to that step in a minute). What we need is a wood chipper attached to the chassis (the LS3); its “mouth”. A small wood chipper handling material up to 2.5 - 3.0 inches (6.3 - 7.6 cm) in diameter would eliminate a substantial amount of fuel. There is no reason for Forest Walker to remove fallen trees. It wouldn’t have to in order to make a real difference. It need only identify appropriately sized branches and grab them. Once loaded into the chipper’s intake hopper for further processing, the beast can immediately look for more “food”. This is essentially kindling that would help ignite larger logs. If it’s all consumed by Forest Walker, then it’s not present to promote an aggravated conflagration. I have glossed over an obvious question: How does Forest Walker see and identify branches and such? LiDaR (Light Detection and Ranging) attached to Forest Walker images the local area and feed those data to onboard computers for processing. Maybe AI plays a role. Maybe simple machine learning can do the trick. One thing is for certain: being able to identify a stick and cause robotic appendages to pick it up is not impossible. Great! We now have a quadrupedal robot autonomously identifying and “eating” dead branches and other light, combustible materials. Whilst strolling through the forest, depleting future fires of combustibles, Forest Walker has already performed a major function of this system: making the forest safer. It's time to convert this low-density fuel into a high-density fuel Forest Walker can leverage. Enter the gasification process. # The Gassifier  The gasifier is the heart of the entire system; it’s where low-density fuel becomes the high-density fuel that powers the entire system. Biochar and wood vinegar are process wastes and I’ll discuss why both are powerful soil amendments in a moment, but first, what’s gasification? Reacting shredded carbonaceous material at high temperatures in a low or no oxygen environment converts the biomass into biochar, wood vinegar, heat, and Synthesis Gas (Syngas). Syngas consists primarily of hydrogen, carbon monoxide, and methane. All of which are extremely useful fuels in a gaseous state. Part of this gas is used to heat the input biomass and keep the reaction temperature constant while the internal combustion engine that drives the generator to produce electrical power consumes the rest. Critically, this gasification process is “continuous feed”. Forest Walker must intake biomass from the chipper, process it to fuel, and dump the waste (CO2, heat, biochar, and wood vinegar) continuously. It cannot stop. Everything about this system depends upon this continual grazing, digestion, and excretion of wastes just as a ruminal does. And, like a ruminant, all waste products enhance the local environment. When I first heard of gasification, I didn’t believe that it was real. Running an electric generator from burning wood seemed more akin to “conspiracy fantasy” than science. Not only is gasification real, it’s ancient technology. A man named Dean Clayton first started experiments on gasification in 1699 and in 1901 gasification was used to power a vehicle. By the end of World War II, there were 500,000 Syngas powered vehicles in Germany alone because of fossil fuel rationing during the war. The global gasification market was $480 billion in 2022 and projected to be as much as $700 billion by 2030 (Vantage Market Research). Gasification technology is the best choice to power the Forest Walker because it’s self-contained and we want its waste products. # Biochar: The Waste  Biochar (AKA agricultural charcoal) is fairly simple: it’s almost pure, solid carbon that resembles charcoal. Its porous nature packs large surface areas into small, 3 dimensional nuggets. Devoid of most other chemistry, like hydrocarbons (methane) and ash (minerals), biochar is extremely lightweight. Do not confuse it with the charcoal you buy for your grill. Biochar doesn’t make good grilling charcoal because it would burn too rapidly as it does not contain the multitude of flammable components that charcoal does. Biochar has several other good use cases. Water filtration, water retention, nutrient retention, providing habitat for microscopic soil organisms, and carbon sequestration are the main ones that we are concerned with here. Carbon has an amazing ability to adsorb (substances stick to and accumulate on the surface of an object) manifold chemistries. Water, nutrients, and pollutants tightly bind to carbon in this format. So, biochar makes a respectable filter and acts as a “battery” of water and nutrients in soils. Biochar adsorbs and holds on to seven times its weight in water. Soil containing biochar is more drought resilient than soil without it. Adsorbed nutrients, tightly sequestered alongside water, get released only as plants need them. Plants must excrete protons (H+) from their roots to disgorge water or positively charged nutrients from the biochar's surface; it's an active process. Biochar’s surface area (where adsorption happens) can be 500 square meters per gram or more. That is 10% larger than an official NBA basketball court for every gram of biochar. Biochar’s abundant surface area builds protective habitats for soil microbes like fungi and bacteria and many are critical for the health and productivity of the soil itself. The “carbon sequestration” component of biochar comes into play where “carbon credits” are concerned. There is a financial market for carbon. Not leveraging that market for revenue is foolish. I am climate agnostic. All I care about is that once solid carbon is inside the soil, it will stay there for thousands of years, imparting drought resiliency, fertility collection, nutrient buffering, and release for that time span. I simply want as much solid carbon in the soil because of the undeniably positive effects it has, regardless of any climactic considerations. # Wood Vinegar: More Waste  Another by-product of the gasification process is wood vinegar (Pyroligneous acid). If you have ever seen Liquid Smoke in the grocery store, then you have seen wood vinegar. Principally composed of acetic acid, acetone, and methanol wood vinegar also contains ~200 other organic compounds. It would seem intuitive that condensed, liquefied wood smoke would at least be bad for the health of all living things if not downright carcinogenic. The counter intuition wins the day, however. Wood vinegar has been used by humans for a very long time to promote digestion, bowel, and liver health; combat diarrhea and vomiting; calm peptic ulcers and regulate cholesterol levels; and a host of other benefits. For centuries humans have annually burned off hundreds of thousands of square miles of pasture, grassland, forest, and every other conceivable terrestrial ecosystem. Why is this done? After every burn, one thing becomes obvious: the almost supernatural growth these ecosystems exhibit after the burn. How? Wood vinegar is a component of this growth. Even in open burns, smoke condenses and infiltrates the soil. That is when wood vinegar shows its quality. This stuff beefs up not only general plant growth but seed germination as well and possesses many other qualities that are beneficial to plants. It’s a pesticide, fungicide, promotes beneficial soil microorganisms, enhances nutrient uptake, and imparts disease resistance. I am barely touching a long list of attributes here, but you want wood vinegar in your soil (alongside biochar because it adsorbs wood vinegar as well). # The Internal Combustion Engine  Conversion of grazed forage to chemical, then mechanical, and then electrical energy completes the cycle. The ICE (Internal Combustion Engine) converts the gaseous fuel output from the gasifier to mechanical energy, heat, water vapor, and CO2. It’s the mechanical energy of a rotating drive shaft that we want. That rotation drives the electric generator, which is the heartbeat we need to bring this monster to life. Luckily for us, combined internal combustion engine and generator packages are ubiquitous, delivering a defined energy output given a constant fuel input. It’s the simplest part of the system. The obvious question here is whether the amount of syngas provided by the gasification process will provide enough energy to generate enough electrons to run the entire system or not. While I have no doubt the energy produced will run Forest Walker's main systems the question is really about the electrons left over. Will it be enough to run the Bitcoin mining aspect of the system? Everything is a budget. # CO2 Production For Growth  Plants are lollipops. No matter if it’s a tree or a bush or a shrubbery, the entire thing is mostly sugar in various formats but mostly long chain carbohydrates like lignin and cellulose. Plants need three things to make sugar: CO2, H2O and light. In a forest, where tree densities can be quite high, CO2 availability becomes a limiting growth factor. It’d be in the forest interests to have more available CO2 providing for various sugar formation providing the organism with food and structure. An odd thing about tree leaves, the openings that allow gasses like the ever searched for CO2 are on the bottom of the leaf (these are called stomata). Not many stomata are topside. This suggests that trees and bushes have evolved to find gasses like CO2 from below, not above and this further suggests CO2 might be in higher concentrations nearer the soil. The soil life (bacterial, fungi etc.) is constantly producing enormous amounts of CO2 and it would stay in the soil forever (eventually killing the very soil life that produces it) if not for tidal forces. Water is everywhere and whether in pools, lakes, oceans or distributed in “moist” soils water moves towards to the moon. The water in the soil and also in the water tables below the soil rise toward the surface every day. When the water rises, it expels the accumulated gasses in the soil into the atmosphere and it’s mostly CO2. It’s a good bet on how leaves developed high populations of stomata on the underside of leaves. As the water relaxes (the tide goes out) it sucks oxygenated air back into the soil to continue the functions of soil life respiration. The soil “breathes” albeit slowly. The gasses produced by the Forest Walker’s internal combustion engine consist primarily of CO2 and H2O. Combusting sugars produce the same gasses that are needed to construct the sugars because the universe is funny like that. The Forest Walker is constantly laying down these critical construction elements right where the trees need them: close to the ground to be gobbled up by the trees. # The Branch Drones  During the last ice age, giant mammals populated North America - forests and otherwise. Mastodons, woolly mammoths, rhinos, short-faced bears, steppe bison, caribou, musk ox, giant beavers, camels, gigantic ground-dwelling sloths, glyptodons, and dire wolves were everywhere. Many were ten to fifteen feet tall. As they crashed through forests, they would effectively cleave off dead side-branches of trees, halting the spread of a ground-based fire migrating into the tree crown ("laddering") which is a death knell for a forest. These animals are all extinct now and forests no longer have any manner of pruning services. But, if we build drones fitted with cutting implements like saws and loppers, optical cameras and AI trained to discern dead branches from living ones, these drones could effectively take over pruning services by identifying, cutting, and dropping to the forest floor, dead branches. The dropped branches simply get collected by the Forest Walker as part of its continual mission. The drones dock on the back of the Forest Walker to recharge their batteries when low. The whole scene would look like a grazing cow with some flies bothering it. This activity breaks the link between a relatively cool ground based fire and the tree crowns and is a vital element in forest fire control. # The Bitcoin Miner  Mining is one of four monetary incentive models, making this system a possibility for development. The other three are US Dept. of the Interior, township, county, and electrical utility company easement contracts for fuel load management, global carbon credits trading, and data set sales. All the above depends on obvious questions getting answered. I will list some obvious ones, but this is not an engineering document and is not the place for spreadsheets. How much Bitcoin one Forest Walker can mine depends on everything else. What amount of biomass can we process? Will that biomass flow enough Syngas to keep the lights on? Can the chassis support enough mining ASICs and supporting infrastructure? What does that weigh and will it affect field performance? How much power can the AC generator produce? Other questions that are more philosophical persist. Even if a single Forest Walker can only mine scant amounts of BTC per day, that pales to how much fuel material it can process into biochar. We are talking about millions upon millions of forested acres in need of fuel load management. What can a single Forest Walker do? I am not thinking in singular terms. The Forest Walker must operate as a fleet. What could 50 do? 500? What is it worth providing a service to the world by managing forest fuel loads? Providing proof of work to the global monetary system? Seeding soil with drought and nutrient resilience by the excretion, over time, of carbon by the ton? What did the last forest fire cost? # The Mesh Network  What could be better than one bitcoin mining, carbon sequestering, forest fire squelching, soil amending behemoth? Thousands of them, but then they would need to be able to talk to each other to coordinate position, data handling, etc. Fitted with a mesh networking device, like goTenna or Meshtastic LoRa equipment enables each Forest Walker to communicate with each other. Now we have an interconnected fleet of Forest Walkers relaying data to each other and more importantly, aggregating all of that to the last link in the chain for uplink. Well, at least Bitcoin mining data. Since block data is lightweight, transmission of these data via mesh networking in fairly close quartered environs is more than doable. So, how does data transmit to the Bitcoin Network? How do the Forest Walkers get the previous block data necessary to execute on mining? # Back To The Chain  Getting Bitcoin block data to and from the network is the last puzzle piece. The standing presumption here is that wherever a Forest Walker fleet is operating, it is NOT within cell tower range. We further presume that the nearest Walmart Wi-Fi is hours away. Enter the Blockstream Satellite or something like it. A separate, ground-based drone will have two jobs: To stay as close to the nearest Forest Walker as it can and to provide an antennae for either terrestrial or orbital data uplink. Bitcoin-centric data is transmitted to the "uplink drone" via the mesh networked transmitters and then sent on to the uplink and the whole flow goes in the opposite direction as well; many to one and one to many. We cannot transmit data to the Blockstream satellite, and it will be up to Blockstream and companies like it to provide uplink capabilities in the future and I don't doubt they will. Starlink you say? What’s stopping that company from filtering out block data? Nothing because it’s Starlink’s system and they could decide to censor these data. It seems we may have a problem sending and receiving Bitcoin data in back country environs. But, then again, the utility of this system in staunching the fuel load that creates forest fires is extremely useful around forested communities and many have fiber, Wi-Fi and cell towers. These communities could be a welcoming ground zero for first deployments of the Forest Walker system by the home and business owners seeking fire repression. In the best way, Bitcoin subsidizes the safety of the communities. # Sensor Packages ### LiDaR  The benefit of having a Forest Walker fleet strolling through the forest is the never ending opportunity for data gathering. A plethora of deployable sensors gathering hyper-accurate data on everything from temperature to topography is yet another revenue generator. Data is valuable and the Forest Walker could generate data sales to various government entities and private concerns. LiDaR (Light Detection and Ranging) can map topography, perform biomass assessment, comparative soil erosion analysis, etc. It so happens that the Forest Walker’s ability to “see,” to navigate about its surroundings, is LiDaR driven and since it’s already being used, we can get double duty by harvesting that data for later use. By using a laser to send out light pulses and measuring the time it takes for the reflection of those pulses to return, very detailed data sets incrementally build up. Eventually, as enough data about a certain area becomes available, the data becomes useful and valuable. Forestry concerns, both private and public, often use LiDaR to build 3D models of tree stands to assess the amount of harvest-able lumber in entire sections of forest. Consulting companies offering these services charge anywhere from several hundred to several thousand dollars per square kilometer for such services. A Forest Walker generating such assessments on the fly while performing its other functions is a multi-disciplinary approach to revenue generation. ### pH, Soil Moisture, and Cation Exchange Sensing  The Forest Walker is quadrupedal, so there are four contact points to the soil. Why not get a pH data point for every step it takes? We can also gather soil moisture data and cation exchange capacities at unheard of densities because of sampling occurring on the fly during commission of the system’s other duties. No one is going to build a machine to do pH testing of vast tracts of forest soils, but that doesn’t make the data collected from such an endeavor valueless. Since the Forest Walker serves many functions at once, a multitude of data products can add to the return on investment component. ### Weather Data  Temperature, humidity, pressure, and even data like evapotranspiration gathered at high densities on broad acre scales have untold value and because the sensors are lightweight and don’t require large power budgets, they come along for the ride at little cost. But, just like the old mantra, “gas, grass, or ass, nobody rides for free”, these sensors provide potential revenue benefits just by them being present. I’ve touched on just a few data genres here. In fact, the question for universities, governmental bodies, and other institutions becomes, “How much will you pay us to attach your sensor payload to the Forest Walker?” # Noise Suppression  Only you can prevent Metallica filling the surrounds with 120 dB of sound. Easy enough, just turn the car stereo off. But what of a fleet of 50 Forest Walkers operating in the backcountry or near a township? 500? 5000? Each one has a wood chipper, an internal combustion engine, hydraulic pumps, actuators, and more cooling fans than you can shake a stick at. It’s a walking, screaming fire-breathing dragon operating continuously, day and night, twenty-four hours a day, three hundred sixty-five days a year. The sound will negatively affect all living things and that impacts behaviors. Serious engineering consideration and prowess must deliver a silencing blow to the major issue of noise. It would be foolish to think that a fleet of Forest Walkers could be silent, but if not a major design consideration, then the entire idea is dead on arrival. Townships would not allow them to operate even if they solved the problem of widespread fuel load and neither would governmental entities, and rightly so. Nothing, not man nor beast, would want to be subjected to an eternal, infernal scream even if it were to end within days as the fleet moved further away after consuming what it could. Noise and heat are the only real pollutants of this system; taking noise seriously from the beginning is paramount. # Fire Safety  A “fire-breathing dragon” is not the worst description of the Forest Walker. It eats wood, combusts it at very high temperatures and excretes carbon; and it does so in an extremely flammable environment. Bad mix for one Forest Walker, worse for many. One must take extreme pains to ensure that during normal operation, a Forest Walker could fall over, walk through tinder dry brush, or get pounded into the ground by a meteorite from Krypton and it wouldn’t destroy epic swaths of trees and baby deer. I envision an ultimate test of a prototype to include dowsing it in grain alcohol while it’s wrapped up in toilet paper like a pledge at a fraternity party. If it runs for 72 hours and doesn’t set everything on fire, then maybe outside entities won’t be fearful of something that walks around forests with a constant fire in its belly. # The Wrap  How we think about what can be done with and adjacent to Bitcoin is at least as important as Bitcoin’s economic standing itself. For those who will tell me that this entire idea is without merit, I say, “OK, fine. You can come up with something, too.” What can we plug Bitcoin into that, like a battery, makes something that does not work, work? That’s the lesson I get from this entire exercise. No one was ever going to hire teams of humans to go out and "clean the forest". There's no money in that. The data collection and sales from such an endeavor might provide revenues over the break-even point but investment demands Alpha in this day and age. But, plug Bitcoin into an almost viable system and, voilà! We tip the scales to achieve lift-off. Let’s face it, we haven’t scratched the surface of Bitcoin’s forcing function on our minds. Not because it’s Bitcoin, but because of what that invention means. The question that pushes me to approach things this way is, “what can we create that one system’s waste is another system’s feedstock?” The Forest Walker system’s only real waste is the conversion of low entropy energy (wood and syngas) into high entropy energy (heat and noise). All other output is beneficial to humanity. Bitcoin, I believe, is the first product of a new mode of human imagination. An imagination newly forged over the past few millennia of being lied to, stolen from, distracted and otherwise mis-allocated to a black hole of the nonsensical. We are waking up. What I have presented is not science fiction. Everything I have described here is well within the realm of possibility. The question is one of viability, at least in terms of the detritus of the old world we find ourselves departing from. This system would take a non-trivial amount of time and resources to develop. I think the system would garner extensive long-term contracts from those who have the most to lose from wildfires, the most to gain from hyperaccurate data sets, and, of course, securing the most precious asset in the world. Many may not see it that way, for they seek Alpha and are therefore blind to other possibilities. Others will see only the possibilities; of thinking in a new way, of looking at things differently, and dreaming of what comes next. @ 4506e04e:8c16ba04
2025-01-13 22:25:17The employment trends in the gig economy are clear. More and more people take on some form of freelance or temporary work often on top of their full time job. In fact, according to [recent estimates](https://www.upwork.com/resources/gig-economy-statistics), approximately 1.57 billion people, or nearly half (46.4%) of the global workforce, engage in gig work. As gig platforms continue to expand across borders and sectors, this number is projected to keep rising. <img src="https://blossom.primal.net/d4fca16a18e427f8c3f97677c8e7599a4a4ad1cc2d635bfcd0ab6b0ada48ecb9.png"> In the UK, the gig economy is particularly popular, with many workers supplementing their income with side gigs. According to a [recent survey](https://standout-cv.com/stats/gig-economy-statistics-uk#:~:text=For%20most%2C%2071.5%25%2C%20gig,main%20income%20\(both%2036%25\).), almost half (48%) of UK gig workers have full-time jobs on top of their side gigs, while 71.5% use gig work to supplement their income rather than provide their sole earnings. The top gig occupation in the UK is online administrative work, with 39% of gig workers offering virtual assistance, data entry, clerical services, or similar computer-based tasks. Sounds like a great way to earn some sats, doesn't it? Despite the growth and popularity of the gig economy, traditional platforms like LinkedIn have reached their peak and become increasingly plagued by spam from aggressive recruiters and profiles of people with increasingly unverifiable experience. Meanwhile all the centralised platforms like Fiverr and Upwork take a significant cut from freelancers' pay, leaving many workers feeling undervalued and overworked. It's no wonder that many are looking for alternative solutions that prioritize fairness, transparency, trust and compensation paid in money that will last! Here comes Nostr, a decentralized, censorship-resistant protocol that's laying foundations for the future of the gig work. With its censorship-resistant, peer-to-peer approach, Nostr is poised to revolutionize the way we work and connect with each other. In this article, I'll explore why Nostr is an exciting development for the gig economy, what it means for the future of work and what platforms are already available. What makes Nostr different? It’s built on principles of decentralization, freedom, trust and Bitcoin as its native currency. Forget walled gardens; with Nostr, your identity is your own. Nobody’s mining your data, and no shadowy algorithms are deciding who sees your posts or what posts you should see. It's a perfect setup for a job marketplace where companies post jobs and freelancers get them done. All paid with Bitcoin with no middleman to take your money And it’s not just theory. Real solutions are already built, transforming how professionals connect, collaborate, and commit their skills, time and creativity. All open-source and Bitcoin/Nostr-centric. ## Here are 4 tools you want to check out: 1. [SatShoot:](https://SatShoot.com) Think Upwork or Fiverr, but with integrated eCash wallet and zero middlemen. Creators, freelancers, and clients unite under the banner of peer-to-peer gig economy. 2. [Kanbanstr](https://www.kanbanstr.com/): A Nostr-native Kanban board for moving tasks from To Do > In Progress > Done and zapping the developers as they deliver. 3. [GitWorkshop.dev](https://gitworkshop.dev/): A decentralized alternative to GitHub, tailored for developers who value freedom and sovereignty. 4. [Sigit.io](https://sigit.io/): An open-source and self-hostable solution for secure document signing and verification. These platforms aren’t just ideas; they’re already being built, some are already in Beta versions, and you can test them today! These platforms aren’t just ideas; they’re already being built, some are already in Beta versions, and you can test them today! ## Don't trust - verify! How can you be sure you're getting help from the right people with the right skills? That’s where the Web of Trust (WoT) comes in. On Nostr, the WoT is a decentralized trust system that lets users build and evaluate relationships using cryptographic keys and interactions. Instead of depending on centralized authorities to verify identities or manage reputations, the WoT allows trust to grow organically through direct endorsements and social connections. In this system, your track record matters. As a freelancer, you’re motivated to deliver quality work—not just to get paid, but also to earn positive feedback. This feedback boosts your reputation, helping you secure your next gig. You could get extra points if i.e. you hold a subject matter expert certificate. Credentials and certifications are still often critical to determine if someone has the skills you are looking for. The idea of certifications could be rebuilt on Nostr with Badges NIP-58. Institutions like Red Hat, Cisco, and others could issue verifiable, NIP-05-backed badges directly to your Nostr public key (“npub”). It’s simple: 1. The certifying body verifies their domain via NIP-05. 2. They issue badges for their certifications 3. Successful candidates receive badges and wear them on their npubs. All it takes is that during the registration process for the exam the examinee adds their npub and Voilà! A decentralized, censorship-resistant proof of skills that lives on Nostr. No middlemen, no gatekeepers, you get the right people for the right job! Here’s a mind-blowing stat: 95% of the world’s population doesn’t own any Bitcoin. With fiat systems teetering, more people will turn to earning Bitcoin instead of buying it at ever-rising prices. Nostr-based platforms are perfectly positioned to capitalize on this trend, offering global access to Bitcoin-based gigs. It’s borderless, censorship-resistant, and a hedge against the collapsing fiat world order. Nostr clients and solutions are popping up faster than mushrooms after rain. Whether you’re a developer, marketer, freelancer, or just someone curious about the future of work, there’s a tool for you. This explosive growth signals a broader shift: professionals are tired of traditional platforms and are looking for alternatives that respect their privacy, autonomy, and time. ## The Bottom Line LinkedIn’s days are numbered. Services like Upwork and Fiverr or even Uber are praying on freelance fees. The future of services, networking, and professional growth is decentralized, censorship-resistant, and powered by Nostr. Whether you’re a freelancer, a certifying body, or a startup founder, the opportunities are endless. Here's a New Year resolution for you - say goodbye to spam and hello to sovereignty. The Nostr revolution is here, and it’s time to join the movement! --- *If you’re inspired to dive into the Nostr ecosystem but need guidance, the [NostrDev team](https://nostrdev.com) has got your back. From conceptualizing your solution to building it out, we’re the go-to experts for all things Nostr. Reach out and start building the future today*.
@ 4506e04e:8c16ba04
2025-01-13 22:25:17The employment trends in the gig economy are clear. More and more people take on some form of freelance or temporary work often on top of their full time job. In fact, according to [recent estimates](https://www.upwork.com/resources/gig-economy-statistics), approximately 1.57 billion people, or nearly half (46.4%) of the global workforce, engage in gig work. As gig platforms continue to expand across borders and sectors, this number is projected to keep rising. <img src="https://blossom.primal.net/d4fca16a18e427f8c3f97677c8e7599a4a4ad1cc2d635bfcd0ab6b0ada48ecb9.png"> In the UK, the gig economy is particularly popular, with many workers supplementing their income with side gigs. According to a [recent survey](https://standout-cv.com/stats/gig-economy-statistics-uk#:~:text=For%20most%2C%2071.5%25%2C%20gig,main%20income%20\(both%2036%25\).), almost half (48%) of UK gig workers have full-time jobs on top of their side gigs, while 71.5% use gig work to supplement their income rather than provide their sole earnings. The top gig occupation in the UK is online administrative work, with 39% of gig workers offering virtual assistance, data entry, clerical services, or similar computer-based tasks. Sounds like a great way to earn some sats, doesn't it? Despite the growth and popularity of the gig economy, traditional platforms like LinkedIn have reached their peak and become increasingly plagued by spam from aggressive recruiters and profiles of people with increasingly unverifiable experience. Meanwhile all the centralised platforms like Fiverr and Upwork take a significant cut from freelancers' pay, leaving many workers feeling undervalued and overworked. It's no wonder that many are looking for alternative solutions that prioritize fairness, transparency, trust and compensation paid in money that will last! Here comes Nostr, a decentralized, censorship-resistant protocol that's laying foundations for the future of the gig work. With its censorship-resistant, peer-to-peer approach, Nostr is poised to revolutionize the way we work and connect with each other. In this article, I'll explore why Nostr is an exciting development for the gig economy, what it means for the future of work and what platforms are already available. What makes Nostr different? It’s built on principles of decentralization, freedom, trust and Bitcoin as its native currency. Forget walled gardens; with Nostr, your identity is your own. Nobody’s mining your data, and no shadowy algorithms are deciding who sees your posts or what posts you should see. It's a perfect setup for a job marketplace where companies post jobs and freelancers get them done. All paid with Bitcoin with no middleman to take your money And it’s not just theory. Real solutions are already built, transforming how professionals connect, collaborate, and commit their skills, time and creativity. All open-source and Bitcoin/Nostr-centric. ## Here are 4 tools you want to check out: 1. [SatShoot:](https://SatShoot.com) Think Upwork or Fiverr, but with integrated eCash wallet and zero middlemen. Creators, freelancers, and clients unite under the banner of peer-to-peer gig economy. 2. [Kanbanstr](https://www.kanbanstr.com/): A Nostr-native Kanban board for moving tasks from To Do > In Progress > Done and zapping the developers as they deliver. 3. [GitWorkshop.dev](https://gitworkshop.dev/): A decentralized alternative to GitHub, tailored for developers who value freedom and sovereignty. 4. [Sigit.io](https://sigit.io/): An open-source and self-hostable solution for secure document signing and verification. These platforms aren’t just ideas; they’re already being built, some are already in Beta versions, and you can test them today! These platforms aren’t just ideas; they’re already being built, some are already in Beta versions, and you can test them today! ## Don't trust - verify! How can you be sure you're getting help from the right people with the right skills? That’s where the Web of Trust (WoT) comes in. On Nostr, the WoT is a decentralized trust system that lets users build and evaluate relationships using cryptographic keys and interactions. Instead of depending on centralized authorities to verify identities or manage reputations, the WoT allows trust to grow organically through direct endorsements and social connections. In this system, your track record matters. As a freelancer, you’re motivated to deliver quality work—not just to get paid, but also to earn positive feedback. This feedback boosts your reputation, helping you secure your next gig. You could get extra points if i.e. you hold a subject matter expert certificate. Credentials and certifications are still often critical to determine if someone has the skills you are looking for. The idea of certifications could be rebuilt on Nostr with Badges NIP-58. Institutions like Red Hat, Cisco, and others could issue verifiable, NIP-05-backed badges directly to your Nostr public key (“npub”). It’s simple: 1. The certifying body verifies their domain via NIP-05. 2. They issue badges for their certifications 3. Successful candidates receive badges and wear them on their npubs. All it takes is that during the registration process for the exam the examinee adds their npub and Voilà! A decentralized, censorship-resistant proof of skills that lives on Nostr. No middlemen, no gatekeepers, you get the right people for the right job! Here’s a mind-blowing stat: 95% of the world’s population doesn’t own any Bitcoin. With fiat systems teetering, more people will turn to earning Bitcoin instead of buying it at ever-rising prices. Nostr-based platforms are perfectly positioned to capitalize on this trend, offering global access to Bitcoin-based gigs. It’s borderless, censorship-resistant, and a hedge against the collapsing fiat world order. Nostr clients and solutions are popping up faster than mushrooms after rain. Whether you’re a developer, marketer, freelancer, or just someone curious about the future of work, there’s a tool for you. This explosive growth signals a broader shift: professionals are tired of traditional platforms and are looking for alternatives that respect their privacy, autonomy, and time. ## The Bottom Line LinkedIn’s days are numbered. Services like Upwork and Fiverr or even Uber are praying on freelance fees. The future of services, networking, and professional growth is decentralized, censorship-resistant, and powered by Nostr. Whether you’re a freelancer, a certifying body, or a startup founder, the opportunities are endless. Here's a New Year resolution for you - say goodbye to spam and hello to sovereignty. The Nostr revolution is here, and it’s time to join the movement! --- *If you’re inspired to dive into the Nostr ecosystem but need guidance, the [NostrDev team](https://nostrdev.com) has got your back. From conceptualizing your solution to building it out, we’re the go-to experts for all things Nostr. Reach out and start building the future today*. @ e3ba5e1a:5e433365
2025-01-13 16:47:27My blog posts and reading material have both been on a decidedly economics-heavy slant recently. The topic today, incentives, squarely falls into the category of economics. However, when I say economics, I’m not talking about “analyzing supply and demand curves.” I’m talking about the true basis of economics: understanding how human beings make decisions in a world of scarcity. A fair definition of incentive is “a reward or punishment that motivates behavior to achieve a desired outcome.” When most people think about economic incentives, they’re thinking of money. If I offer my son $5 if he washes the dishes, I’m incentivizing certain behavior. We can’t guarantee that he’ll do what I want him to do, but we can agree that the incentive structure itself will guide and ultimately determine what outcome will occur. The great thing about monetary incentives is how easy they are to talk about and compare. “Would I rather make $5 washing the dishes or $10 cleaning the gutters?” But much of the world is incentivized in non-monetary ways too. For example, using the “punishment” half of the definition above, I might threaten my son with losing Nintendo Switch access if he doesn’t wash the dishes. No money is involved, but I’m still incentivizing behavior. And there are plenty of incentives beyond our direct control\! My son is *also* incentivized to not wash dishes because it’s boring, or because he has some friends over that he wants to hang out with, or dozens of other things. Ultimately, the conflicting array of different incentive structures placed on him will ultimately determine what actions he chooses to take. ## Why incentives matter A phrase I see often in discussions—whether they are political, parenting, economic, or business—is “if they could **just** do…” Each time I see that phrase, I cringe a bit internally. Usually, the underlying assumption of the statement is “if people would behave contrary to their incentivized behavior then things would be better.” For example: * If my kids would just go to bed when I tell them, they wouldn’t be so cranky in the morning. * If people would just use the recycling bin, we wouldn’t have such a landfill problem. * If people would just stop being lazy, our team would deliver our project on time. In all these cases, the speakers are seemingly flummoxed as to why the people in question don’t behave more rationally. The problem is: each group is behaving perfectly rationally. * The kids have a high time preference, and care more about the joy of staying up now than the crankiness in the morning. Plus, they don’t really suffer the consequences of morning crankiness, their parents do. * No individual suffers much from their individual contribution to a landfill. If they stopped growing the size of the landfill, it would make an insignificant difference versus the amount of effort they need to engage in to properly recycle. * If a team doesn’t properly account for the productivity of individuals on a project, each individual receives less harm from their own inaction. Sure, the project may be delayed, company revenue may be down, and they may even risk losing their job when the company goes out of business. But their laziness individually won’t determine the entirety of that outcome. By contrast, they greatly benefit from being lazy by getting to relax at work, go on social media, read a book, or do whatever else they do when they’re supposed to be working.  My point here is that, as long as you ignore the reality of how incentives drive human behavior, you’ll fail at getting the outcomes you want. If everything I wrote up until now made perfect sense, you understand the premise of this blog post. The rest of it will focus on a bunch of real-world examples to hammer home the point, and demonstrate how versatile this mental model is. ## Running a company Let’s say I run my own company, with myself as the only employee. My personal revenue will be 100% determined by my own actions. If I decide to take Tuesday afternoon off and go fishing, I’ve chosen to lose that afternoon’s revenue. Implicitly, I’ve decided that the enjoyment I get from an afternoon of fishing is greater than the potential revenue. You may think I’m being lazy, but it’s my decision to make. In this situation, the incentive–money–is perfectly aligned with my actions. Compare this to a typical company/employee relationship. I might have a bank of Paid Time Off (PTO) days, in which case once again my incentives are relatively aligned. I know that I can take off 15 days throughout the year, and I’ve chosen to use half a day for the fishing trip. All is still good. What about unlimited time off? Suddenly incentives are starting to misalign. I don’t directly pay a price for not showing up to work on Tuesday. Or Wednesday as well, for that matter. I might ultimately be fired for not doing my job, but that will take longer to work its way through the system than simply not making any money for the day taken off. Compensation overall falls into this misaligned incentive structure. Let’s forget about taking time off. Instead, I work full time on a software project I’m assigned. But instead of using the normal toolchain we’re all used to at work, I play around with a new programming language. I get the fun and joy of playing with new technology, and potentially get to pad my resume a bit when I’m ready to look for a new job. But my current company gets slower results, less productivity, and is forced to subsidize my extracurricular learning. When a CEO has a bonus structure based on profitability, he’ll do everything he can to make the company profitable. This might include things that actually benefit the company, like improving product quality, reducing internal red tape, or finding cheaper vendors. But it might also include destructive practices, like slashing the R\&D budget to show massive profits this year, in exchange for a catastrophe next year when the next version of the product fails to ship.  Or my favorite example. My parents owned a business when I was growing up. They had a back office where they ran operations like accounting. All of the furniture was old couches from our house. After all, any money they spent on furniture came right out of their paychecks\! But in a large corporate environment, each department is generally given a budget for office furniture, a budget which doesn’t roll over year-to-year. The result? Executives make sure to spend the entire budget each year, often buying furniture far more expensive than they would choose if it was their own money. There are plenty of details you can quibble with above. It’s in a company’s best interest to give people downtime so that they can come back recharged. Having good ergonomic furniture can in fact increase productivity in excess of the money spent on it. But overall, the picture is pretty clear: in large corporate structures, you’re guaranteed to have mismatches between the company’s goals and the incentive structure placed on individuals. Using our model from above, we can lament how lazy, greedy, and unethical the employees are for doing what they’re incentivized to do instead of what’s right. But that’s simply ignoring the reality of human nature. # Moral hazard Moral hazard is a situation where one party is incentivized to take on more risk because another party will bear the consequences. Suppose I tell my son when he turns 21 (or whatever legal gambling age is) that I’ll cover all his losses for a day at the casino, but he gets to keep all the winnings. What do you think he’s going to do? The most logical course of action is to place the largest possible bets for as long as possible, asking me to cover each time he loses, and taking money off the table and into his bank account each time he wins.  But let’s look at a slightly more nuanced example. I go to a bathroom in the mall. As I’m leaving, I wash my hands. It will take me an extra 1 second to turn off the water when I’m done washing. That’s a trivial price to pay. If I *don’t* turn off the water, the mall will have to pay for many liters of wasted water, benefiting no one. But I won’t suffer any consequences at all. This is also a moral hazard, but most people will still turn off the water. Why? Usually due to some combination of other reasons such as: 1. We’re so habituated to turning off the water that we don’t even consider *not* turning it off. Put differently, the mental effort needed to not turn off the water is more expensive than the 1 second of time to turn it off. 2. Many of us have been brought up with a deep guilt about wasting resources like water. We have an internal incentive structure that makes the 1 second to turn off the water much less costly than the mental anguish of the waste we created. 3. We’re afraid we’ll be caught by someone else and face some kind of social repercussions. (Or maybe more than social. Are you sure there isn’t a law against leaving the water tap on?) Even with all that in place, you may notice that many public bathrooms use automatic water dispensers. Sure, there’s a sanitation reason for that, but it’s also to avoid this moral hazard. A common denominator in both of these is that the person taking the action that causes the liability (either the gambling or leaving the water on) is not the person who bears the responsibility for that liability (the father or the mall owner). Generally speaking, the closer together the person making the decision and the person incurring the liability are, the smaller the moral hazard. It’s easy to demonstrate that by extending the casino example a bit. I said it was the father who was covering the losses of the gambler. Many children (though not all) would want to avoid totally bankrupting their parents, or at least financially hurting them. Instead, imagine that someone from the IRS shows up at your door, hands you a credit card, and tells you you can use it at a casino all day, taking home all the chips you want. The money is coming from the government. How many people would put any restriction on how much they spend? And since we’re talking about the government already… ## Government moral hazards As I was preparing to write this blog post, the California wildfires hit. The discussions around those wildfires gave a *huge* number of examples of moral hazards. I decided to cherry-pick a few for this post. The first and most obvious one: California is asking for disaster relief funds from the federal government. That sounds wonderful. These fires were a natural disaster, so why shouldn’t the federal government pitch in and help take care of people? The problem is, once again, a moral hazard. In the case of the wildfires, California and Los Angeles both had ample actions they could have taken to mitigate the destruction of this fire: better forest management, larger fire department, keeping the water reservoirs filled, and probably much more that hasn’t come to light yet. If the federal government bails out California, it will be a clear message for the future: your mistakes will be fixed by others. You know what kind of behavior that incentivizes? More risky behavior\! Why spend state funds on forest management and extra firefighters—activities that don’t win politicians a lot of votes in general—when you could instead spend it on a football stadium, higher unemployment payments, or anything else, and then let the feds cover the cost of screw-ups. You may notice that this is virtually identical to the 2008 “too big to fail” bail-outs. Wall Street took insanely risky behavior, reaped huge profits for years, and when they eventually got caught with their pants down, the rest of us bailed them out. “Privatizing profits, socializing losses.”  And here’s the absolute best part of this: I can’t even truly blame either California *or* Wall Street. (I mean, I *do* blame them, I think their behavior is reprehensible, but you’ll see what I mean.) In a world where the rules of the game implicitly include the bail-out mentality, you would be harming your citizens/shareholders/investors if you didn’t engage in that risky behavior. Since everyone is on the hook for those socialized losses, your best bet is to maximize those privatized profits. There’s a lot more to government and moral hazard, but I think these two cases demonstrate the crux pretty solidly. But let’s leave moral hazard behind for a bit and get to general incentivization discussions. # Non-monetary competition At least 50% of the economics knowledge I have comes from the very first econ course I took in college. That professor was amazing, and had some very colorful stories. I can’t vouch for the veracity of the two I’m about to share, but they definitely drive the point home. In the 1970s, the US had an oil shortage. To “fix” this problem, they instituted price caps on gasoline, which of course resulted in insufficient gasoline. To “fix” this problem, they instituted policies where, depending on your license plate number, you could only fill up gas on certain days of the week. (Irrelevant detail for our point here, but this just resulted in people filling up their tanks more often, no reduction in gas usage.) Anyway, my professor’s wife had a friend. My professor described in *great* detail how attractive this woman was. I’ll skip those details here since this is a PG-rated blog. In any event, she never had any trouble filling up her gas tank any day of the week. She would drive up, be told she couldn’t fill up gas today, bat her eyes at the attendant, explain how helpless she was, and was always allowed to fill up gas. This is a demonstration of *non-monetary compensation*. Most of the time in a free market, capitalist economy, people are compensated through money. When price caps come into play, there’s a limit to how much monetary compensation someone can receive. And in that case, people find other ways of competing. Like this woman’s case: through using flirtatious behavior to compensate the gas station workers to let her cheat the rules. The other example was much more insidious. Santa Monica had a problem: it was predominantly wealthy and white. They wanted to fix this problem, and decided to put in place rent controls. After some time, they discovered that Santa Monica had become *wealthier and whiter*, the exact opposite of their desired outcome. Why would that happen? Someone investigated, and ended up interviewing a landlady that demonstrated the reason. She was an older white woman, and admittedly racist. Prior to the rent controls, she would list her apartments in the newspaper, and would be legally obligated to rent to anyone who could afford it. Once rent controls were in place, she took a different tact. She knew that she would only get a certain amount for the apartment, and that the demand for apartments was higher than the supply. That meant she could be picky. She ended up finding tenants through friends-of-friends. Since it wasn’t an official advertisement, she wasn’t legally required to rent it out if someone could afford to pay. Instead, she got to interview people individually and then make them an offer. Normally, that would have resulted in receiving a lower rental price, but not under rent controls. So who did she choose? A young, unmarried, wealthy, white woman. It made perfect sense. Women were less intimidating and more likely to maintain the apartment better. Wealthy people, she determined, would be better tenants. (I have no idea if this is true in practice or not, I’m not a landlord myself.) Unmarried, because no kids running around meant less damage to the property. And, of course, white. Because she was racist, and her incentive structure made her prefer whites. You can deride her for being racist, I won’t disagree with you. But it’s simply the reality. Under the non-rent-control scenario, her profit motive for money outweighed her racism motive. But under rent control, the monetary competition was removed, and she was free to play into her racist tendencies without facing any negative consequences. ## Bureaucracy These were the two examples I remember for that course. But non-monetary compensation pops up in many more places. One highly pertinent example is bureaucracies. Imagine you have a government office, or a large corporation’s acquisition department, or the team that apportions grants at a university. In all these cases, you have a group of people making decisions about handing out money that has no monetary impact on them. If they give to the best qualified recipients, they receive no raises. If they spend the money recklessly on frivolous projects, they face no consequences. Under such an incentivization scheme, there’s little to encourage the bureaucrats to make intelligent funding decisions. Instead, they’ll be incentivized to spend the money where they recognize non-monetary benefits. This is why it’s so common to hear about expensive meals, gift bags at conferences, and even more inappropriate ways of trying to curry favor with those that hold the purse strings. Compare that ever so briefly with the purchases made by a small mom-and-pop store like my parents owned. Could my dad take a bribe to buy from a vendor who’s ripping him off? Absolutely he could\! But he’d lose more on the deal than he’d make on the bribe, since he’s directly incentivized by the deal itself. It would make much more sense for him to go with the better vendor, save $5,000 on the deal, and then treat himself to a lavish $400 meal to celebrate. # Government incentivized behavior This post is getting longer in the tooth than I’d intended, so I’ll finish off with this section and make it a bit briefer. Beyond all the methods mentioned above, government has another mechanism for modifying behavior: through directly changing incentives via legislation, regulation, and monetary policy. Let’s see some examples: * Artificial modification of interest rates encourages people to take on more debt than they would in a free capital market, leading to [malinvestment](https://en.wikipedia.org/wiki/Malinvestment) and a consumer debt crisis, and causing the boom-bust cycle we all painfully experience. * Going along with that, giving tax breaks on interest payments further artificially incentivizes people to take on debt that they wouldn’t otherwise. * During COVID-19, at some points unemployment benefits were greater than minimum wage, incentivizing people to rather stay home and not work than get a job, leading to reduced overall productivity in the economy and more printed dollars for benefits. In other words, it was a perfect recipe for inflation. * The tax code gives deductions to “help” people. That might be true, but the real impact is incentivizing people to make decisions they wouldn’t have otherwise. For example, giving out tax deductions on children encourages having more kids. Tax deductions on childcare and preschools incentivizes dual-income households. Whether or not you like the outcomes, it’s clear that it’s government that’s encouraging these outcomes to happen. * Tax incentives cause people to engage in behavior they wouldn’t otherwise (daycare+working mother, for example). * Inflation means that the value of your money goes down over time, which encourages people to spend more today, when their money has a larger impact. (Milton Friedman described this as [high living](https://www.youtube.com/watch?v=ZwNDd2_beTU).) # Conclusion The idea here is simple, and fully encapsulated in the title: incentives determine outcomes. If you want to know how to get a certain outcome from others, incentivize them to want that to happen. If you want to understand why people act in seemingly irrational ways, check their incentives. If you’re confused why leaders (and especially politicians) seem to engage in destructive behavior, check their incentives. We can bemoan these realities all we want, but they *are* realities. While there are some people who have a solid internal moral and ethical code, and that internal code incentivizes them to behave against their externally-incentivized interests, those people are rare. And frankly, those people are self-defeating. People *should* take advantage of the incentives around them. Because if they don’t, someone else will. (If you want a literary example of that last comment, see the horse in Animal Farm.) How do we improve the world under these conditions? Make sure the incentives align well with the overall goals of society. To me, it’s a simple formula: * Focus on free trade, value for value, as the basis of a society. In that system, people are always incentivized to provide value to other people. * Reduce the size of bureaucracies and large groups of all kinds. The larger an organization becomes, the farther the consequences of decisions are from those who make them. * And since the nature of human beings will be to try and create areas where they can control the incentive systems to their own benefits, make that as difficult as possible. That comes in the form of strict limits on government power, for example. And even if you don’t want to buy in to this conclusion, I hope the rest of the content was educational, and maybe a bit entertaining\!
@ e3ba5e1a:5e433365
2025-01-13 16:47:27My blog posts and reading material have both been on a decidedly economics-heavy slant recently. The topic today, incentives, squarely falls into the category of economics. However, when I say economics, I’m not talking about “analyzing supply and demand curves.” I’m talking about the true basis of economics: understanding how human beings make decisions in a world of scarcity. A fair definition of incentive is “a reward or punishment that motivates behavior to achieve a desired outcome.” When most people think about economic incentives, they’re thinking of money. If I offer my son $5 if he washes the dishes, I’m incentivizing certain behavior. We can’t guarantee that he’ll do what I want him to do, but we can agree that the incentive structure itself will guide and ultimately determine what outcome will occur. The great thing about monetary incentives is how easy they are to talk about and compare. “Would I rather make $5 washing the dishes or $10 cleaning the gutters?” But much of the world is incentivized in non-monetary ways too. For example, using the “punishment” half of the definition above, I might threaten my son with losing Nintendo Switch access if he doesn’t wash the dishes. No money is involved, but I’m still incentivizing behavior. And there are plenty of incentives beyond our direct control\! My son is *also* incentivized to not wash dishes because it’s boring, or because he has some friends over that he wants to hang out with, or dozens of other things. Ultimately, the conflicting array of different incentive structures placed on him will ultimately determine what actions he chooses to take. ## Why incentives matter A phrase I see often in discussions—whether they are political, parenting, economic, or business—is “if they could **just** do…” Each time I see that phrase, I cringe a bit internally. Usually, the underlying assumption of the statement is “if people would behave contrary to their incentivized behavior then things would be better.” For example: * If my kids would just go to bed when I tell them, they wouldn’t be so cranky in the morning. * If people would just use the recycling bin, we wouldn’t have such a landfill problem. * If people would just stop being lazy, our team would deliver our project on time. In all these cases, the speakers are seemingly flummoxed as to why the people in question don’t behave more rationally. The problem is: each group is behaving perfectly rationally. * The kids have a high time preference, and care more about the joy of staying up now than the crankiness in the morning. Plus, they don’t really suffer the consequences of morning crankiness, their parents do. * No individual suffers much from their individual contribution to a landfill. If they stopped growing the size of the landfill, it would make an insignificant difference versus the amount of effort they need to engage in to properly recycle. * If a team doesn’t properly account for the productivity of individuals on a project, each individual receives less harm from their own inaction. Sure, the project may be delayed, company revenue may be down, and they may even risk losing their job when the company goes out of business. But their laziness individually won’t determine the entirety of that outcome. By contrast, they greatly benefit from being lazy by getting to relax at work, go on social media, read a book, or do whatever else they do when they’re supposed to be working.  My point here is that, as long as you ignore the reality of how incentives drive human behavior, you’ll fail at getting the outcomes you want. If everything I wrote up until now made perfect sense, you understand the premise of this blog post. The rest of it will focus on a bunch of real-world examples to hammer home the point, and demonstrate how versatile this mental model is. ## Running a company Let’s say I run my own company, with myself as the only employee. My personal revenue will be 100% determined by my own actions. If I decide to take Tuesday afternoon off and go fishing, I’ve chosen to lose that afternoon’s revenue. Implicitly, I’ve decided that the enjoyment I get from an afternoon of fishing is greater than the potential revenue. You may think I’m being lazy, but it’s my decision to make. In this situation, the incentive–money–is perfectly aligned with my actions. Compare this to a typical company/employee relationship. I might have a bank of Paid Time Off (PTO) days, in which case once again my incentives are relatively aligned. I know that I can take off 15 days throughout the year, and I’ve chosen to use half a day for the fishing trip. All is still good. What about unlimited time off? Suddenly incentives are starting to misalign. I don’t directly pay a price for not showing up to work on Tuesday. Or Wednesday as well, for that matter. I might ultimately be fired for not doing my job, but that will take longer to work its way through the system than simply not making any money for the day taken off. Compensation overall falls into this misaligned incentive structure. Let’s forget about taking time off. Instead, I work full time on a software project I’m assigned. But instead of using the normal toolchain we’re all used to at work, I play around with a new programming language. I get the fun and joy of playing with new technology, and potentially get to pad my resume a bit when I’m ready to look for a new job. But my current company gets slower results, less productivity, and is forced to subsidize my extracurricular learning. When a CEO has a bonus structure based on profitability, he’ll do everything he can to make the company profitable. This might include things that actually benefit the company, like improving product quality, reducing internal red tape, or finding cheaper vendors. But it might also include destructive practices, like slashing the R\&D budget to show massive profits this year, in exchange for a catastrophe next year when the next version of the product fails to ship.  Or my favorite example. My parents owned a business when I was growing up. They had a back office where they ran operations like accounting. All of the furniture was old couches from our house. After all, any money they spent on furniture came right out of their paychecks\! But in a large corporate environment, each department is generally given a budget for office furniture, a budget which doesn’t roll over year-to-year. The result? Executives make sure to spend the entire budget each year, often buying furniture far more expensive than they would choose if it was their own money. There are plenty of details you can quibble with above. It’s in a company’s best interest to give people downtime so that they can come back recharged. Having good ergonomic furniture can in fact increase productivity in excess of the money spent on it. But overall, the picture is pretty clear: in large corporate structures, you’re guaranteed to have mismatches between the company’s goals and the incentive structure placed on individuals. Using our model from above, we can lament how lazy, greedy, and unethical the employees are for doing what they’re incentivized to do instead of what’s right. But that’s simply ignoring the reality of human nature. # Moral hazard Moral hazard is a situation where one party is incentivized to take on more risk because another party will bear the consequences. Suppose I tell my son when he turns 21 (or whatever legal gambling age is) that I’ll cover all his losses for a day at the casino, but he gets to keep all the winnings. What do you think he’s going to do? The most logical course of action is to place the largest possible bets for as long as possible, asking me to cover each time he loses, and taking money off the table and into his bank account each time he wins.  But let’s look at a slightly more nuanced example. I go to a bathroom in the mall. As I’m leaving, I wash my hands. It will take me an extra 1 second to turn off the water when I’m done washing. That’s a trivial price to pay. If I *don’t* turn off the water, the mall will have to pay for many liters of wasted water, benefiting no one. But I won’t suffer any consequences at all. This is also a moral hazard, but most people will still turn off the water. Why? Usually due to some combination of other reasons such as: 1. We’re so habituated to turning off the water that we don’t even consider *not* turning it off. Put differently, the mental effort needed to not turn off the water is more expensive than the 1 second of time to turn it off. 2. Many of us have been brought up with a deep guilt about wasting resources like water. We have an internal incentive structure that makes the 1 second to turn off the water much less costly than the mental anguish of the waste we created. 3. We’re afraid we’ll be caught by someone else and face some kind of social repercussions. (Or maybe more than social. Are you sure there isn’t a law against leaving the water tap on?) Even with all that in place, you may notice that many public bathrooms use automatic water dispensers. Sure, there’s a sanitation reason for that, but it’s also to avoid this moral hazard. A common denominator in both of these is that the person taking the action that causes the liability (either the gambling or leaving the water on) is not the person who bears the responsibility for that liability (the father or the mall owner). Generally speaking, the closer together the person making the decision and the person incurring the liability are, the smaller the moral hazard. It’s easy to demonstrate that by extending the casino example a bit. I said it was the father who was covering the losses of the gambler. Many children (though not all) would want to avoid totally bankrupting their parents, or at least financially hurting them. Instead, imagine that someone from the IRS shows up at your door, hands you a credit card, and tells you you can use it at a casino all day, taking home all the chips you want. The money is coming from the government. How many people would put any restriction on how much they spend? And since we’re talking about the government already… ## Government moral hazards As I was preparing to write this blog post, the California wildfires hit. The discussions around those wildfires gave a *huge* number of examples of moral hazards. I decided to cherry-pick a few for this post. The first and most obvious one: California is asking for disaster relief funds from the federal government. That sounds wonderful. These fires were a natural disaster, so why shouldn’t the federal government pitch in and help take care of people? The problem is, once again, a moral hazard. In the case of the wildfires, California and Los Angeles both had ample actions they could have taken to mitigate the destruction of this fire: better forest management, larger fire department, keeping the water reservoirs filled, and probably much more that hasn’t come to light yet. If the federal government bails out California, it will be a clear message for the future: your mistakes will be fixed by others. You know what kind of behavior that incentivizes? More risky behavior\! Why spend state funds on forest management and extra firefighters—activities that don’t win politicians a lot of votes in general—when you could instead spend it on a football stadium, higher unemployment payments, or anything else, and then let the feds cover the cost of screw-ups. You may notice that this is virtually identical to the 2008 “too big to fail” bail-outs. Wall Street took insanely risky behavior, reaped huge profits for years, and when they eventually got caught with their pants down, the rest of us bailed them out. “Privatizing profits, socializing losses.”  And here’s the absolute best part of this: I can’t even truly blame either California *or* Wall Street. (I mean, I *do* blame them, I think their behavior is reprehensible, but you’ll see what I mean.) In a world where the rules of the game implicitly include the bail-out mentality, you would be harming your citizens/shareholders/investors if you didn’t engage in that risky behavior. Since everyone is on the hook for those socialized losses, your best bet is to maximize those privatized profits. There’s a lot more to government and moral hazard, but I think these two cases demonstrate the crux pretty solidly. But let’s leave moral hazard behind for a bit and get to general incentivization discussions. # Non-monetary competition At least 50% of the economics knowledge I have comes from the very first econ course I took in college. That professor was amazing, and had some very colorful stories. I can’t vouch for the veracity of the two I’m about to share, but they definitely drive the point home. In the 1970s, the US had an oil shortage. To “fix” this problem, they instituted price caps on gasoline, which of course resulted in insufficient gasoline. To “fix” this problem, they instituted policies where, depending on your license plate number, you could only fill up gas on certain days of the week. (Irrelevant detail for our point here, but this just resulted in people filling up their tanks more often, no reduction in gas usage.) Anyway, my professor’s wife had a friend. My professor described in *great* detail how attractive this woman was. I’ll skip those details here since this is a PG-rated blog. In any event, she never had any trouble filling up her gas tank any day of the week. She would drive up, be told she couldn’t fill up gas today, bat her eyes at the attendant, explain how helpless she was, and was always allowed to fill up gas. This is a demonstration of *non-monetary compensation*. Most of the time in a free market, capitalist economy, people are compensated through money. When price caps come into play, there’s a limit to how much monetary compensation someone can receive. And in that case, people find other ways of competing. Like this woman’s case: through using flirtatious behavior to compensate the gas station workers to let her cheat the rules. The other example was much more insidious. Santa Monica had a problem: it was predominantly wealthy and white. They wanted to fix this problem, and decided to put in place rent controls. After some time, they discovered that Santa Monica had become *wealthier and whiter*, the exact opposite of their desired outcome. Why would that happen? Someone investigated, and ended up interviewing a landlady that demonstrated the reason. She was an older white woman, and admittedly racist. Prior to the rent controls, she would list her apartments in the newspaper, and would be legally obligated to rent to anyone who could afford it. Once rent controls were in place, she took a different tact. She knew that she would only get a certain amount for the apartment, and that the demand for apartments was higher than the supply. That meant she could be picky. She ended up finding tenants through friends-of-friends. Since it wasn’t an official advertisement, she wasn’t legally required to rent it out if someone could afford to pay. Instead, she got to interview people individually and then make them an offer. Normally, that would have resulted in receiving a lower rental price, but not under rent controls. So who did she choose? A young, unmarried, wealthy, white woman. It made perfect sense. Women were less intimidating and more likely to maintain the apartment better. Wealthy people, she determined, would be better tenants. (I have no idea if this is true in practice or not, I’m not a landlord myself.) Unmarried, because no kids running around meant less damage to the property. And, of course, white. Because she was racist, and her incentive structure made her prefer whites. You can deride her for being racist, I won’t disagree with you. But it’s simply the reality. Under the non-rent-control scenario, her profit motive for money outweighed her racism motive. But under rent control, the monetary competition was removed, and she was free to play into her racist tendencies without facing any negative consequences. ## Bureaucracy These were the two examples I remember for that course. But non-monetary compensation pops up in many more places. One highly pertinent example is bureaucracies. Imagine you have a government office, or a large corporation’s acquisition department, or the team that apportions grants at a university. In all these cases, you have a group of people making decisions about handing out money that has no monetary impact on them. If they give to the best qualified recipients, they receive no raises. If they spend the money recklessly on frivolous projects, they face no consequences. Under such an incentivization scheme, there’s little to encourage the bureaucrats to make intelligent funding decisions. Instead, they’ll be incentivized to spend the money where they recognize non-monetary benefits. This is why it’s so common to hear about expensive meals, gift bags at conferences, and even more inappropriate ways of trying to curry favor with those that hold the purse strings. Compare that ever so briefly with the purchases made by a small mom-and-pop store like my parents owned. Could my dad take a bribe to buy from a vendor who’s ripping him off? Absolutely he could\! But he’d lose more on the deal than he’d make on the bribe, since he’s directly incentivized by the deal itself. It would make much more sense for him to go with the better vendor, save $5,000 on the deal, and then treat himself to a lavish $400 meal to celebrate. # Government incentivized behavior This post is getting longer in the tooth than I’d intended, so I’ll finish off with this section and make it a bit briefer. Beyond all the methods mentioned above, government has another mechanism for modifying behavior: through directly changing incentives via legislation, regulation, and monetary policy. Let’s see some examples: * Artificial modification of interest rates encourages people to take on more debt than they would in a free capital market, leading to [malinvestment](https://en.wikipedia.org/wiki/Malinvestment) and a consumer debt crisis, and causing the boom-bust cycle we all painfully experience. * Going along with that, giving tax breaks on interest payments further artificially incentivizes people to take on debt that they wouldn’t otherwise. * During COVID-19, at some points unemployment benefits were greater than minimum wage, incentivizing people to rather stay home and not work than get a job, leading to reduced overall productivity in the economy and more printed dollars for benefits. In other words, it was a perfect recipe for inflation. * The tax code gives deductions to “help” people. That might be true, but the real impact is incentivizing people to make decisions they wouldn’t have otherwise. For example, giving out tax deductions on children encourages having more kids. Tax deductions on childcare and preschools incentivizes dual-income households. Whether or not you like the outcomes, it’s clear that it’s government that’s encouraging these outcomes to happen. * Tax incentives cause people to engage in behavior they wouldn’t otherwise (daycare+working mother, for example). * Inflation means that the value of your money goes down over time, which encourages people to spend more today, when their money has a larger impact. (Milton Friedman described this as [high living](https://www.youtube.com/watch?v=ZwNDd2_beTU).) # Conclusion The idea here is simple, and fully encapsulated in the title: incentives determine outcomes. If you want to know how to get a certain outcome from others, incentivize them to want that to happen. If you want to understand why people act in seemingly irrational ways, check their incentives. If you’re confused why leaders (and especially politicians) seem to engage in destructive behavior, check their incentives. We can bemoan these realities all we want, but they *are* realities. While there are some people who have a solid internal moral and ethical code, and that internal code incentivizes them to behave against their externally-incentivized interests, those people are rare. And frankly, those people are self-defeating. People *should* take advantage of the incentives around them. Because if they don’t, someone else will. (If you want a literary example of that last comment, see the horse in Animal Farm.) How do we improve the world under these conditions? Make sure the incentives align well with the overall goals of society. To me, it’s a simple formula: * Focus on free trade, value for value, as the basis of a society. In that system, people are always incentivized to provide value to other people. * Reduce the size of bureaucracies and large groups of all kinds. The larger an organization becomes, the farther the consequences of decisions are from those who make them. * And since the nature of human beings will be to try and create areas where they can control the incentive systems to their own benefits, make that as difficult as possible. That comes in the form of strict limits on government power, for example. And even if you don’t want to buy in to this conclusion, I hope the rest of the content was educational, and maybe a bit entertaining\! @ a95c6243:d345522c
2025-01-13 10:09:57*Ich begann, Social Media aufzubauen,* *\ um den Menschen eine Stimme zu geben.* *\ Mark Zuckerberg* **Sind euch auch die Tränen gekommen, als ihr Mark Zuckerbergs** **[Wendehals-Deklaration](https://www.facebook.com/zuck/videos/1525382954801931)** bezüglich der Meinungsfreiheit auf seinen Portalen gehört habt? Rührend, oder? Während er früher die offensichtliche Zensur leugnete und später die Regierung Biden dafür verantwortlich machte, will er nun angeblich «die Zensur auf unseren Plattformen drastisch reduzieren». **«Purer** **[Opportunismus](https://transition-news.org/facebook-grunder-zuckerberg-vom-trump-gegner-zum-trump-buddy-und-anti-zensor)» ob des anstehenden Regierungswechsels wäre als Klassifizierung** viel zu kurz gegriffen. Der jetzige Schachzug des Meta-Chefs ist genauso Teil einer kühl kalkulierten Business-Strategie, wie es die 180 Grad umgekehrte Praxis vorher war. Social Media sind ein höchst lukratives Geschäft. Hinzu kommt vielleicht noch ein bisschen verkorkstes Ego, weil derartig viel Einfluss und Geld sicher auch auf die Psyche schlagen. Verständlich. > «Es ist an der Zeit, zu unseren Wurzeln der freien Meinungsäußerung auf Facebook und Instagram zurückzukehren. Ich begann, Social Media aufzubauen, um den Menschen eine Stimme zu geben», sagte Zuckerberg. **Welche Wurzeln? Hat der Mann vergessen, dass er von der Überwachung,** dem Ausspionieren und dem Ausverkauf sämtlicher Daten und digitaler Spuren sowie der Manipulation seiner «Kunden» lebt? Das ist knallharter Kommerz, nichts anderes. Um freie Meinungsäußerung geht es bei diesem Geschäft ganz sicher nicht, und das war auch noch nie so. Die Wurzeln von Facebook liegen in einem Projekt des US-Militärs mit dem Namen [«LifeLog»](https://norberthaering.de/macht-kontrolle/lifelog/). Dessen Ziel war es, «ein digitales Protokoll vom Leben eines Menschen zu erstellen». **Der Richtungswechsel kommt allerdings nicht überraschend.** Schon Anfang Dezember hatte Meta-Präsident Nick Clegg von «zu hoher Fehlerquote bei der Moderation» von Inhalten [gesprochen](https://www.theverge.com/2024/12/3/24311513/meta-content-moderation-mistakes-nick-clegg). Bei der Gelegenheit erwähnte er auch, dass Mark sehr daran interessiert sei, eine aktive Rolle in den Debatten über eine amerikanische Führungsrolle im technologischen Bereich zu spielen. **Während Milliardärskollege und Big Tech-Konkurrent Elon Musk bereits seinen Posten** in der kommenden Trump-Regierung in Aussicht hat, möchte Zuckerberg also nicht nur seine Haut retten – Trump hatte ihn einmal einen «Feind des Volkes» genannt und ihm lebenslange Haft angedroht –, sondern am liebsten auch mitspielen. KI-Berater ist wohl die gewünschte Funktion, wie man nach einem Treffen Trump-Zuckerberg hörte. An seine [Verhaftung](https://transition-news.org/nicht-telegram-grunder-durow-sondern-zuckerberg-sollte-in-haft-sitzen-wegen-des) dachte vermutlich auch ein weiterer Multimilliardär mit eigener Social Media-Plattform, Pavel Durov, als er Zuckerberg jetzt [kritisierte](https://www.berliner-zeitung.de/news/ende-des-faktenchecks-bei-meta-telegram-gruender-kritisiert-zuckerberg-und-spricht-warnung-aus-li.2287988) und gleichzeitig warnte. **Politik und Systemmedien drehen jedenfalls durch** – was zu viel ist, ist zu viel. Etwas weniger Zensur und mehr Meinungsfreiheit würden die Freiheit der Bürger schwächen und seien potenziell vernichtend für die Menschenrechte. Zuckerberg setze mit dem neuen Kurs die Demokratie aufs Spiel, das sei eine «Einladung zum nächsten [Völkermord](https://archive.is/PYeH0)», ernsthaft. Die Frage sei, ob sich die [EU gegen Musk und Zuckerberg](https://www.handelsblatt.com/politik/international/internet-regulierung-kann-sich-die-eu-gegen-musk-und-zuckerberg-behaupten/100099373.html) behaupten könne, Brüssel müsse jedenfalls hart durchgreifen. **Auch um die** **[Faktenchecker](https://www.welt.de/kultur/medien/article255065352/Metas-Kurswechsel-Zuckerbergs-Entscheidung-und-die-Folgen-fuer-deutsche-Faktenchecker.html)** **macht man sich Sorgen.** Für die deutsche Nachrichtenagentur *dpa* und die «Experten» von *Correctiv*, die (noch) Partner für Fact-Checking-Aktivitäten von Facebook sind, sei das ein «lukratives Geschäftsmodell». Aber möglicherweise werden die Inhalte ohne diese vermeintlichen Korrektoren ja sogar besser. Anders als Meta wollen jedoch Scholz, Faeser und die *Tagesschau* keine Fehler zugeben und zum Beispiel *Correctiv*-[Falschaussagen](https://www.berliner-zeitung.de/politik-gesellschaft/correctiv-falschaussagen-exklusiv-scholz-faeser-und-tagesschau-wollen-sich-fuer-verbreitung-nicht-entschuldigen-li.2288126) einräumen. **Bei derlei dramatischen Befürchtungen wundert es nicht,** dass der öffentliche Plausch auf X zwischen Elon Musk und AfD-Chefin Alice Weidel von 150 EU-Beamten überwacht wurde, falls es irgendwelche Rechtsverstöße geben sollte, die man ihnen ankreiden könnte. Auch der Deutsche Bundestag war wachsam. Gefunden haben dürften sie nichts. Das Ganze war eher eine Show, viel Wind wurde gemacht, aber letztlich gab es nichts als heiße Luft. **Das** **[Anbiedern](https://transition-news.org/who-biedert-sich-bei-trump-an)** **bei Donald Trump ist indes gerade in Mode.** Die Weltgesundheitsorganisation (WHO) tut das auch, denn sie fürchtet um Spenden von über einer Milliarde Dollar. Eventuell könnte ja Elon Musk auch hier künftig aushelfen und der Organisation sowie deren größtem privaten Förderer, Bill Gates, etwas unter die Arme greifen. Nachdem Musks KI-Projekt xAI kürzlich von BlackRock & Co. [sechs Milliarden](https://x.ai/blog/series-c) eingestrichen hat, geht da vielleicht etwas. *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/milliardenschwere-wetterfahnchen-und-windmaschinen)*** erschienen.
@ a95c6243:d345522c
2025-01-13 10:09:57*Ich begann, Social Media aufzubauen,* *\ um den Menschen eine Stimme zu geben.* *\ Mark Zuckerberg* **Sind euch auch die Tränen gekommen, als ihr Mark Zuckerbergs** **[Wendehals-Deklaration](https://www.facebook.com/zuck/videos/1525382954801931)** bezüglich der Meinungsfreiheit auf seinen Portalen gehört habt? Rührend, oder? Während er früher die offensichtliche Zensur leugnete und später die Regierung Biden dafür verantwortlich machte, will er nun angeblich «die Zensur auf unseren Plattformen drastisch reduzieren». **«Purer** **[Opportunismus](https://transition-news.org/facebook-grunder-zuckerberg-vom-trump-gegner-zum-trump-buddy-und-anti-zensor)» ob des anstehenden Regierungswechsels wäre als Klassifizierung** viel zu kurz gegriffen. Der jetzige Schachzug des Meta-Chefs ist genauso Teil einer kühl kalkulierten Business-Strategie, wie es die 180 Grad umgekehrte Praxis vorher war. Social Media sind ein höchst lukratives Geschäft. Hinzu kommt vielleicht noch ein bisschen verkorkstes Ego, weil derartig viel Einfluss und Geld sicher auch auf die Psyche schlagen. Verständlich. > «Es ist an der Zeit, zu unseren Wurzeln der freien Meinungsäußerung auf Facebook und Instagram zurückzukehren. Ich begann, Social Media aufzubauen, um den Menschen eine Stimme zu geben», sagte Zuckerberg. **Welche Wurzeln? Hat der Mann vergessen, dass er von der Überwachung,** dem Ausspionieren und dem Ausverkauf sämtlicher Daten und digitaler Spuren sowie der Manipulation seiner «Kunden» lebt? Das ist knallharter Kommerz, nichts anderes. Um freie Meinungsäußerung geht es bei diesem Geschäft ganz sicher nicht, und das war auch noch nie so. Die Wurzeln von Facebook liegen in einem Projekt des US-Militärs mit dem Namen [«LifeLog»](https://norberthaering.de/macht-kontrolle/lifelog/). Dessen Ziel war es, «ein digitales Protokoll vom Leben eines Menschen zu erstellen». **Der Richtungswechsel kommt allerdings nicht überraschend.** Schon Anfang Dezember hatte Meta-Präsident Nick Clegg von «zu hoher Fehlerquote bei der Moderation» von Inhalten [gesprochen](https://www.theverge.com/2024/12/3/24311513/meta-content-moderation-mistakes-nick-clegg). Bei der Gelegenheit erwähnte er auch, dass Mark sehr daran interessiert sei, eine aktive Rolle in den Debatten über eine amerikanische Führungsrolle im technologischen Bereich zu spielen. **Während Milliardärskollege und Big Tech-Konkurrent Elon Musk bereits seinen Posten** in der kommenden Trump-Regierung in Aussicht hat, möchte Zuckerberg also nicht nur seine Haut retten – Trump hatte ihn einmal einen «Feind des Volkes» genannt und ihm lebenslange Haft angedroht –, sondern am liebsten auch mitspielen. KI-Berater ist wohl die gewünschte Funktion, wie man nach einem Treffen Trump-Zuckerberg hörte. An seine [Verhaftung](https://transition-news.org/nicht-telegram-grunder-durow-sondern-zuckerberg-sollte-in-haft-sitzen-wegen-des) dachte vermutlich auch ein weiterer Multimilliardär mit eigener Social Media-Plattform, Pavel Durov, als er Zuckerberg jetzt [kritisierte](https://www.berliner-zeitung.de/news/ende-des-faktenchecks-bei-meta-telegram-gruender-kritisiert-zuckerberg-und-spricht-warnung-aus-li.2287988) und gleichzeitig warnte. **Politik und Systemmedien drehen jedenfalls durch** – was zu viel ist, ist zu viel. Etwas weniger Zensur und mehr Meinungsfreiheit würden die Freiheit der Bürger schwächen und seien potenziell vernichtend für die Menschenrechte. Zuckerberg setze mit dem neuen Kurs die Demokratie aufs Spiel, das sei eine «Einladung zum nächsten [Völkermord](https://archive.is/PYeH0)», ernsthaft. Die Frage sei, ob sich die [EU gegen Musk und Zuckerberg](https://www.handelsblatt.com/politik/international/internet-regulierung-kann-sich-die-eu-gegen-musk-und-zuckerberg-behaupten/100099373.html) behaupten könne, Brüssel müsse jedenfalls hart durchgreifen. **Auch um die** **[Faktenchecker](https://www.welt.de/kultur/medien/article255065352/Metas-Kurswechsel-Zuckerbergs-Entscheidung-und-die-Folgen-fuer-deutsche-Faktenchecker.html)** **macht man sich Sorgen.** Für die deutsche Nachrichtenagentur *dpa* und die «Experten» von *Correctiv*, die (noch) Partner für Fact-Checking-Aktivitäten von Facebook sind, sei das ein «lukratives Geschäftsmodell». Aber möglicherweise werden die Inhalte ohne diese vermeintlichen Korrektoren ja sogar besser. Anders als Meta wollen jedoch Scholz, Faeser und die *Tagesschau* keine Fehler zugeben und zum Beispiel *Correctiv*-[Falschaussagen](https://www.berliner-zeitung.de/politik-gesellschaft/correctiv-falschaussagen-exklusiv-scholz-faeser-und-tagesschau-wollen-sich-fuer-verbreitung-nicht-entschuldigen-li.2288126) einräumen. **Bei derlei dramatischen Befürchtungen wundert es nicht,** dass der öffentliche Plausch auf X zwischen Elon Musk und AfD-Chefin Alice Weidel von 150 EU-Beamten überwacht wurde, falls es irgendwelche Rechtsverstöße geben sollte, die man ihnen ankreiden könnte. Auch der Deutsche Bundestag war wachsam. Gefunden haben dürften sie nichts. Das Ganze war eher eine Show, viel Wind wurde gemacht, aber letztlich gab es nichts als heiße Luft. **Das** **[Anbiedern](https://transition-news.org/who-biedert-sich-bei-trump-an)** **bei Donald Trump ist indes gerade in Mode.** Die Weltgesundheitsorganisation (WHO) tut das auch, denn sie fürchtet um Spenden von über einer Milliarde Dollar. Eventuell könnte ja Elon Musk auch hier künftig aushelfen und der Organisation sowie deren größtem privaten Förderer, Bill Gates, etwas unter die Arme greifen. Nachdem Musks KI-Projekt xAI kürzlich von BlackRock & Co. [sechs Milliarden](https://x.ai/blog/series-c) eingestrichen hat, geht da vielleicht etwas. *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/milliardenschwere-wetterfahnchen-und-windmaschinen)*** erschienen. @ a10260a2:caa23e3e
2025-01-12 04:16:29*Last Updated: January 11, 2025* This article is based on a note I posted over a year ago. I kept finding great podcasts and realized that a long form note would make sense since it'll essentially be reposted in the feed every time an update is made. While there are many good privacy resources out there, this list will focus on episodes from CITADEL DISPATCH. The rabbit hole is deep and never-ending; my hope is that this will spark your curiosity and compel you to search for more. Why should you care? ODELL explains that [here](https://www.discreetlog.com/why-bitcoiners-should-care-about-using-bitcoin-privately/). If you're ready, here are the privacy-related dispatches. Hour and hours of signal from ODELL and his guests. Enjoy. 🫡 * CD2: Privacy, Nodes, and No KYC with ErgoBTC & BitcoinQ_A — https://fountain.fm/episode/ssPqjTOzHjWSRiYN5rP6 * CD15: bitcoin privacy and coinjoin with nopara73 and openoms — https://fountain.fm/episode/akzlPBM5XWZgPWa2iXCN * CD16: bitcoin privacy and coinjoin with chris belcher and waxwing — https://fountain.fm/episode/hBcMSmraUUxVlZzBv5V1 * CD21: the lightning network and bitcoin privacy with openoms and cycryptr — https://fountain.fm/episode/vo0LpZOxGiDWIXc8wQf2 * CD29: bitcoin privacy and security with craigraw and ketominer — https://fountain.fm/episode/wNowMP7zxD25kKMLCU4r * CD30: bitcoin privacy and the danger of KYC with samouraiwallet and openoms — https://fountain.fm/episode/AoIhaVfVHG55gEJOlEiH * CD43: bitcoin for beginners with BitcoinQ_A— https://fountain.fm/episode/Foh3ImV2fZYPvg2QgNA4 I've also created a Fountain playlist which can be found [here](https://fountain.fm/playlist/WGV34KnpV0NyR6F2RWok). One benefit of the playlist is that you can easily share the group of episodes in its entirety.
@ a10260a2:caa23e3e
2025-01-12 04:16:29*Last Updated: January 11, 2025* This article is based on a note I posted over a year ago. I kept finding great podcasts and realized that a long form note would make sense since it'll essentially be reposted in the feed every time an update is made. While there are many good privacy resources out there, this list will focus on episodes from CITADEL DISPATCH. The rabbit hole is deep and never-ending; my hope is that this will spark your curiosity and compel you to search for more. Why should you care? ODELL explains that [here](https://www.discreetlog.com/why-bitcoiners-should-care-about-using-bitcoin-privately/). If you're ready, here are the privacy-related dispatches. Hour and hours of signal from ODELL and his guests. Enjoy. 🫡 * CD2: Privacy, Nodes, and No KYC with ErgoBTC & BitcoinQ_A — https://fountain.fm/episode/ssPqjTOzHjWSRiYN5rP6 * CD15: bitcoin privacy and coinjoin with nopara73 and openoms — https://fountain.fm/episode/akzlPBM5XWZgPWa2iXCN * CD16: bitcoin privacy and coinjoin with chris belcher and waxwing — https://fountain.fm/episode/hBcMSmraUUxVlZzBv5V1 * CD21: the lightning network and bitcoin privacy with openoms and cycryptr — https://fountain.fm/episode/vo0LpZOxGiDWIXc8wQf2 * CD29: bitcoin privacy and security with craigraw and ketominer — https://fountain.fm/episode/wNowMP7zxD25kKMLCU4r * CD30: bitcoin privacy and the danger of KYC with samouraiwallet and openoms — https://fountain.fm/episode/AoIhaVfVHG55gEJOlEiH * CD43: bitcoin for beginners with BitcoinQ_A— https://fountain.fm/episode/Foh3ImV2fZYPvg2QgNA4 I've also created a Fountain playlist which can be found [here](https://fountain.fm/playlist/WGV34KnpV0NyR6F2RWok). One benefit of the playlist is that you can easily share the group of episodes in its entirety. @ 378562cd:a6fc6773
2025-01-11 19:37:30**Money**. It’s one of the most powerful forces in our world, and for many, it evokes mixed emotions. On the one hand, money provides security, opportunities, and the freedom to pursue dreams. On the other, it’s often tied to stress, inequality, and a sense of unending competition. This love-hate relationship with money is universal, and it stems from a system that often feels rigged against the average person. Enter Nostr—a decentralized protocol designed to address some of the deepest flaws in how we interact with value and communication online. While Nostr isn’t just about money, its principles are profoundly reshaping how we think about value exchange, financial sovereignty, and freedom. ### The Root of the Problem At the core of our collective frustration with money is control. Traditional financial systems are centralized, opaque, and prone to manipulation. Whether it’s through inflation eating away at savings, unfair access to banking, or censorship of financial transactions, the system leaves many feeling powerless. Add to this the societal obsession with consumerism and wealth accumulation, and it’s no wonder money can feel more like a burden than a tool. Even digital spaces, which promised democratization, often mirror these problems. Social media platforms monetize user data while censoring or shadow-banning content. Payment platforms can freeze accounts or deny access, reinforcing the imbalance of power. ### Nostr: A Fresh Perspective on Value and Freedom Nostr (short for "*Notes and Other Stuff Transmitted by Relays*") isn’t just a technical innovation—it’s a philosophy. Built on a simple yet powerful decentralized protocol, Nostr allows users to share information, communicate, and exchange value directly, without reliance on centralized entities. It’s an open, censorship-resistant network that puts control back into the hands of individuals. So, how is Nostr addressing the money dilemma? 1. **Decentralized Value Exchange**\ Nostr integrates seamlessly with tools like Bitcoin’s Lightning Network, enabling instant, low-cost payments without intermediaries. This means individuals can send and receive money directly, whether it’s a micro-tip to support a content creator or a peer-to-peer transaction across borders. No banks. No middlemen. Just value exchanged freely. 2. **Censorship Resistance**\ One of the most frustrating aspects of modern finance is the potential for censorship. Banks and platforms can freeze accounts or block payments based on arbitrary criteria. Nostr flips this script by creating a network where transactions and communication are uncensorable. Value flows freely, aligned with the principles of individual sovereignty. 3. **Empowering Creators**\ In traditional models, creators often rely on centralized platforms to earn revenue, losing a significant portion to fees or being at the mercy of algorithms. On Nostr, creators can directly monetize their work through Bitcoin tips or other decentralized payment methods, creating a more equitable system where value flows directly between creator and consumer. 4. **Transparency and Trust**\ Unlike traditional systems shrouded in secrecy, Nostr operates on an open protocol. This transparency builds trust and removes many of the frustrations people associate with hidden fees, arbitrary rules, or lack of accountability in centralized systems. ### A New Relationship with Money By decentralizing how value is exchanged and communication occurs, Nostr helps redefine the role of money in our lives. It shifts the narrative from control and dependency to empowerment and freedom. Money becomes what it was always meant to be—a tool, not a master. Imagine a world where tipping someone online is as easy as liking a post, where no one can block you from accessing your own funds, and where creators earn directly from their audience without gatekeepers taking a cut. That’s the world Nostr is helping to build. ### Closing Thoughts The love-hate relationship with money isn’t going away overnight. But as protocols like Nostr grow and mature, they offer a glimpse of what’s possible when we rethink the systems that shape our lives. By putting individuals back in control of their communication and financial exchanges, Nostr is doing more than fixing the flaws of the old system—it’s creating a new one entirely. In the end, it’s not just about money. It’s about freedom, fairness, and the ability to live a life where value flows freely, aligned with our principles and priorities. Nostr isn’t just a tool; it’s a movement. And for anyone tired of the current system, that’s something worth paying attention to.
@ 378562cd:a6fc6773
2025-01-11 19:37:30**Money**. It’s one of the most powerful forces in our world, and for many, it evokes mixed emotions. On the one hand, money provides security, opportunities, and the freedom to pursue dreams. On the other, it’s often tied to stress, inequality, and a sense of unending competition. This love-hate relationship with money is universal, and it stems from a system that often feels rigged against the average person. Enter Nostr—a decentralized protocol designed to address some of the deepest flaws in how we interact with value and communication online. While Nostr isn’t just about money, its principles are profoundly reshaping how we think about value exchange, financial sovereignty, and freedom. ### The Root of the Problem At the core of our collective frustration with money is control. Traditional financial systems are centralized, opaque, and prone to manipulation. Whether it’s through inflation eating away at savings, unfair access to banking, or censorship of financial transactions, the system leaves many feeling powerless. Add to this the societal obsession with consumerism and wealth accumulation, and it’s no wonder money can feel more like a burden than a tool. Even digital spaces, which promised democratization, often mirror these problems. Social media platforms monetize user data while censoring or shadow-banning content. Payment platforms can freeze accounts or deny access, reinforcing the imbalance of power. ### Nostr: A Fresh Perspective on Value and Freedom Nostr (short for "*Notes and Other Stuff Transmitted by Relays*") isn’t just a technical innovation—it’s a philosophy. Built on a simple yet powerful decentralized protocol, Nostr allows users to share information, communicate, and exchange value directly, without reliance on centralized entities. It’s an open, censorship-resistant network that puts control back into the hands of individuals. So, how is Nostr addressing the money dilemma? 1. **Decentralized Value Exchange**\ Nostr integrates seamlessly with tools like Bitcoin’s Lightning Network, enabling instant, low-cost payments without intermediaries. This means individuals can send and receive money directly, whether it’s a micro-tip to support a content creator or a peer-to-peer transaction across borders. No banks. No middlemen. Just value exchanged freely. 2. **Censorship Resistance**\ One of the most frustrating aspects of modern finance is the potential for censorship. Banks and platforms can freeze accounts or block payments based on arbitrary criteria. Nostr flips this script by creating a network where transactions and communication are uncensorable. Value flows freely, aligned with the principles of individual sovereignty. 3. **Empowering Creators**\ In traditional models, creators often rely on centralized platforms to earn revenue, losing a significant portion to fees or being at the mercy of algorithms. On Nostr, creators can directly monetize their work through Bitcoin tips or other decentralized payment methods, creating a more equitable system where value flows directly between creator and consumer. 4. **Transparency and Trust**\ Unlike traditional systems shrouded in secrecy, Nostr operates on an open protocol. This transparency builds trust and removes many of the frustrations people associate with hidden fees, arbitrary rules, or lack of accountability in centralized systems. ### A New Relationship with Money By decentralizing how value is exchanged and communication occurs, Nostr helps redefine the role of money in our lives. It shifts the narrative from control and dependency to empowerment and freedom. Money becomes what it was always meant to be—a tool, not a master. Imagine a world where tipping someone online is as easy as liking a post, where no one can block you from accessing your own funds, and where creators earn directly from their audience without gatekeepers taking a cut. That’s the world Nostr is helping to build. ### Closing Thoughts The love-hate relationship with money isn’t going away overnight. But as protocols like Nostr grow and mature, they offer a glimpse of what’s possible when we rethink the systems that shape our lives. By putting individuals back in control of their communication and financial exchanges, Nostr is doing more than fixing the flaws of the old system—it’s creating a new one entirely. In the end, it’s not just about money. It’s about freedom, fairness, and the ability to live a life where value flows freely, aligned with our principles and priorities. Nostr isn’t just a tool; it’s a movement. And for anyone tired of the current system, that’s something worth paying attention to. @ 0d97beae:c5274a14
2025-01-11 16:52:08This article hopes to complement the article by Lyn Alden on YouTube: https://www.youtube.com/watch?v=jk_HWmmwiAs ## The reason why we have broken money Before the invention of key technologies such as the printing press and electronic communications, even such as those as early as morse code transmitters, gold had won the competition for best medium of money around the world. In fact, it was not just gold by itself that became money, rulers and world leaders developed coins in order to help the economy grow. Gold nuggets were not as easy to transact with as coins with specific imprints and denominated sizes. However, these modern technologies created massive efficiencies that allowed us to communicate and perform services more efficiently and much faster, yet the medium of money could not benefit from these advancements. Gold was heavy, slow and expensive to move globally, even though requesting and performing services globally did not have this limitation anymore. Banks took initiative and created derivatives of gold: paper and electronic money; these new currencies allowed the economy to continue to grow and evolve, but it was not without its dark side. Today, no currency is denominated in gold at all, money is backed by nothing and its inherent value, the paper it is printed on, is worthless too. Banks and governments eventually transitioned from a money derivative to a system of debt that could be co-opted and controlled for political and personal reasons. Our money today is broken and is the cause of more expensive, poorer quality goods in the economy, a larger and ever growing wealth gap, and many of the follow-on problems that have come with it. ## Bitcoin overcomes the "transfer of hard money" problem Just like gold coins were created by man, Bitcoin too is a technology created by man. Bitcoin, however is a much more profound invention, possibly more of a discovery than an invention in fact. Bitcoin has proven to be unbreakable, incorruptible and has upheld its ability to keep its units scarce, inalienable and counterfeit proof through the nature of its own design. Since Bitcoin is a digital technology, it can be transferred across international borders almost as quickly as information itself. It therefore severely reduces the need for a derivative to be used to represent money to facilitate digital trade. This means that as the currency we use today continues to fare poorly for many people, bitcoin will continue to stand out as hard money, that just so happens to work as well, functionally, along side it. Bitcoin will also always be available to anyone who wishes to earn it directly; even China is unable to restrict its citizens from accessing it. The dollar has traditionally become the currency for people who discover that their local currency is unsustainable. Even when the dollar has become illegal to use, it is simply used privately and unofficially. However, because bitcoin does not require you to trade it at a bank in order to use it across borders and across the web, Bitcoin will continue to be a viable escape hatch until we one day hit some critical mass where the world has simply adopted Bitcoin globally and everyone else must adopt it to survive. Bitcoin has not yet proven that it can support the world at scale. However it can only be tested through real adoption, and just as gold coins were developed to help gold scale, tools will be developed to help overcome problems as they arise; ideally without the need for another derivative, but if necessary, hopefully with one that is more neutral and less corruptible than the derivatives used to represent gold. ## Bitcoin blurs the line between commodity and technology Bitcoin is a technology, it is a tool that requires human involvement to function, however it surprisingly does not allow for any concentration of power. Anyone can help to facilitate Bitcoin's operations, but no one can take control of its behaviour, its reach, or its prioritisation, as it operates autonomously based on a pre-determined, neutral set of rules. At the same time, its built-in incentive mechanism ensures that people do not have to operate bitcoin out of the good of their heart. Even though the system cannot be co-opted holistically, It will not stop operating while there are people motivated to trade their time and resources to keep it running and earn from others' transaction fees. Although it requires humans to operate it, it remains both neutral and sustainable. Never before have we developed or discovered a technology that could not be co-opted and used by one person or faction against another. Due to this nature, Bitcoin's units are often described as a commodity; they cannot be usurped or virtually cloned, and they cannot be affected by political biases. ## The dangers of derivatives A derivative is something created, designed or developed to represent another thing in order to solve a particular complication or problem. For example, paper and electronic money was once a derivative of gold. In the case of Bitcoin, if you cannot link your units of bitcoin to an "address" that you personally hold a cryptographically secure key to, then you very likely have a derivative of bitcoin, not bitcoin itself. If you buy bitcoin on an online exchange and do not withdraw the bitcoin to a wallet that you control, then you legally own an electronic derivative of bitcoin. Bitcoin is a new technology. It will have a learning curve and it will take time for humanity to learn how to comprehend, authenticate and take control of bitcoin collectively. Having said that, many people all over the world are already using and relying on Bitcoin natively. For many, it will require for people to find the need or a desire for a neutral money like bitcoin, and to have been burned by derivatives of it, before they start to understand the difference between the two. Eventually, it will become an essential part of what we regard as common sense. ## Learn for yourself If you wish to learn more about how to handle bitcoin and avoid derivatives, you can start by searching online for tutorials about "Bitcoin self custody". There are many options available, some more practical for you, and some more practical for others. Don't spend too much time trying to find the perfect solution; practice and learn. You may make mistakes along the way, so be careful not to experiment with large amounts of your bitcoin as you explore new ideas and technologies along the way. This is similar to learning anything, like riding a bicycle; you are sure to fall a few times, scuff the frame, so don't buy a high performance racing bike while you're still learning to balance.
@ 0d97beae:c5274a14
2025-01-11 16:52:08This article hopes to complement the article by Lyn Alden on YouTube: https://www.youtube.com/watch?v=jk_HWmmwiAs ## The reason why we have broken money Before the invention of key technologies such as the printing press and electronic communications, even such as those as early as morse code transmitters, gold had won the competition for best medium of money around the world. In fact, it was not just gold by itself that became money, rulers and world leaders developed coins in order to help the economy grow. Gold nuggets were not as easy to transact with as coins with specific imprints and denominated sizes. However, these modern technologies created massive efficiencies that allowed us to communicate and perform services more efficiently and much faster, yet the medium of money could not benefit from these advancements. Gold was heavy, slow and expensive to move globally, even though requesting and performing services globally did not have this limitation anymore. Banks took initiative and created derivatives of gold: paper and electronic money; these new currencies allowed the economy to continue to grow and evolve, but it was not without its dark side. Today, no currency is denominated in gold at all, money is backed by nothing and its inherent value, the paper it is printed on, is worthless too. Banks and governments eventually transitioned from a money derivative to a system of debt that could be co-opted and controlled for political and personal reasons. Our money today is broken and is the cause of more expensive, poorer quality goods in the economy, a larger and ever growing wealth gap, and many of the follow-on problems that have come with it. ## Bitcoin overcomes the "transfer of hard money" problem Just like gold coins were created by man, Bitcoin too is a technology created by man. Bitcoin, however is a much more profound invention, possibly more of a discovery than an invention in fact. Bitcoin has proven to be unbreakable, incorruptible and has upheld its ability to keep its units scarce, inalienable and counterfeit proof through the nature of its own design. Since Bitcoin is a digital technology, it can be transferred across international borders almost as quickly as information itself. It therefore severely reduces the need for a derivative to be used to represent money to facilitate digital trade. This means that as the currency we use today continues to fare poorly for many people, bitcoin will continue to stand out as hard money, that just so happens to work as well, functionally, along side it. Bitcoin will also always be available to anyone who wishes to earn it directly; even China is unable to restrict its citizens from accessing it. The dollar has traditionally become the currency for people who discover that their local currency is unsustainable. Even when the dollar has become illegal to use, it is simply used privately and unofficially. However, because bitcoin does not require you to trade it at a bank in order to use it across borders and across the web, Bitcoin will continue to be a viable escape hatch until we one day hit some critical mass where the world has simply adopted Bitcoin globally and everyone else must adopt it to survive. Bitcoin has not yet proven that it can support the world at scale. However it can only be tested through real adoption, and just as gold coins were developed to help gold scale, tools will be developed to help overcome problems as they arise; ideally without the need for another derivative, but if necessary, hopefully with one that is more neutral and less corruptible than the derivatives used to represent gold. ## Bitcoin blurs the line between commodity and technology Bitcoin is a technology, it is a tool that requires human involvement to function, however it surprisingly does not allow for any concentration of power. Anyone can help to facilitate Bitcoin's operations, but no one can take control of its behaviour, its reach, or its prioritisation, as it operates autonomously based on a pre-determined, neutral set of rules. At the same time, its built-in incentive mechanism ensures that people do not have to operate bitcoin out of the good of their heart. Even though the system cannot be co-opted holistically, It will not stop operating while there are people motivated to trade their time and resources to keep it running and earn from others' transaction fees. Although it requires humans to operate it, it remains both neutral and sustainable. Never before have we developed or discovered a technology that could not be co-opted and used by one person or faction against another. Due to this nature, Bitcoin's units are often described as a commodity; they cannot be usurped or virtually cloned, and they cannot be affected by political biases. ## The dangers of derivatives A derivative is something created, designed or developed to represent another thing in order to solve a particular complication or problem. For example, paper and electronic money was once a derivative of gold. In the case of Bitcoin, if you cannot link your units of bitcoin to an "address" that you personally hold a cryptographically secure key to, then you very likely have a derivative of bitcoin, not bitcoin itself. If you buy bitcoin on an online exchange and do not withdraw the bitcoin to a wallet that you control, then you legally own an electronic derivative of bitcoin. Bitcoin is a new technology. It will have a learning curve and it will take time for humanity to learn how to comprehend, authenticate and take control of bitcoin collectively. Having said that, many people all over the world are already using and relying on Bitcoin natively. For many, it will require for people to find the need or a desire for a neutral money like bitcoin, and to have been burned by derivatives of it, before they start to understand the difference between the two. Eventually, it will become an essential part of what we regard as common sense. ## Learn for yourself If you wish to learn more about how to handle bitcoin and avoid derivatives, you can start by searching online for tutorials about "Bitcoin self custody". There are many options available, some more practical for you, and some more practical for others. Don't spend too much time trying to find the perfect solution; practice and learn. You may make mistakes along the way, so be careful not to experiment with large amounts of your bitcoin as you explore new ideas and technologies along the way. This is similar to learning anything, like riding a bicycle; you are sure to fall a few times, scuff the frame, so don't buy a high performance racing bike while you're still learning to balance. @ 37fe9853:bcd1b039
2025-01-11 15:04:40yoyoaa
@ 37fe9853:bcd1b039
2025-01-11 15:04:40yoyoaa @ 62033ff8:e4471203
2025-01-11 15:00:24收录的内容中 kind=1的部分,实话说 质量不高。 所以我增加了kind=30023 长文的article,但是更新的太少,多个relays 的服务器也没有多少长文。 所有搜索nostr如果需要产生价值,需要有高质量的文章和新闻。 而且现在有很多机器人的文章充满着浪费空间的作用,其他作用都用不上。 https://www.duozhutuan.com 目前放的是给搜索引擎提供搜索的原材料。没有做UI给人类浏览。所以看上去是粗糙的。 我并没有打算去做一个发microblog的 web客户端,那类的客户端太多了。 我觉得nostr社区需要解决的还是应用。如果仅仅是microblog 感觉有点够呛 幸运的是npub.pro 建站这样的,我觉得有点意思。 yakihonne 智能widget 也有意思 我做的TaskQ5 我自己在用了。分布式的任务系统,也挺好的。
@ 62033ff8:e4471203
2025-01-11 15:00:24收录的内容中 kind=1的部分,实话说 质量不高。 所以我增加了kind=30023 长文的article,但是更新的太少,多个relays 的服务器也没有多少长文。 所有搜索nostr如果需要产生价值,需要有高质量的文章和新闻。 而且现在有很多机器人的文章充满着浪费空间的作用,其他作用都用不上。 https://www.duozhutuan.com 目前放的是给搜索引擎提供搜索的原材料。没有做UI给人类浏览。所以看上去是粗糙的。 我并没有打算去做一个发microblog的 web客户端,那类的客户端太多了。 我觉得nostr社区需要解决的还是应用。如果仅仅是microblog 感觉有点够呛 幸运的是npub.pro 建站这样的,我觉得有点意思。 yakihonne 智能widget 也有意思 我做的TaskQ5 我自己在用了。分布式的任务系统,也挺好的。 @ 378562cd:a6fc6773
2025-01-10 16:37:38For many of us, reading isn’t just a pastime—it’s a deeply personal goal tied to self-growth, relaxation, and exploration. Yet, despite knowing its importance, we often struggle to make it happen. We start and stop, let books gather dust, and feel guilty for not finishing them. The truth? It’s not a time issue; it’s a mental barrier. This guide is designed to help you break through those barriers with a structured, rewarding framework that keeps you interested, engaged, and building momentum. Let’s turn reading into a habit you love—and can sustain. --- ### **Step 1: Understand the Real Problem** Before diving into action, take a moment to reflect. The issue isn’t that you don’t have time—it’s that you haven’t made reading a priority. Life pulls us in countless directions, but we always find time for what matters most. Reading deserves that place in your life because it nourishes your mind, brings you joy, and inspires growth. **Ask Yourself:** - Why do I want to read more? - How would my life improve if I prioritized reading? Write down your answers and keep them visible. Let your 'why' guide you forward. --- ### **Step 2: Start Where You Are (Small and Simple Wins)** Many people fail because they set huge, overwhelming goals like finishing a book every week. The secret to success? Start small. Commit to just **5 minutes a day** or a single page. Progress matters more than perfection. **Mini Challenge #1:** - Pick a book you’re genuinely excited about (not one you feel you *should* read). - Read for 5 minutes today. Just 5 minutes. When you complete this, check it off. That little win is the first step toward building momentum. --- ### **Step 3: Create a System That Fits Your Life** Habits thrive when they’re tied to something you already do. Look for natural openings in your day to read. - **Morning:** Read while sipping coffee or tea. - **Lunch Break:** Sneak in a few pages while eating. - **Evening:** Replace 10 minutes of scrolling with reading before bed. Make it impossible to forget by keeping books or an e-reader where you spend the most time: next to the bed, on the couch, or in your bag. **Mini Challenge #2:** - Set a specific time to read tomorrow. Write it down and stick to it. --- ### **Step 4: Make It Fun and Rewarding** Let’s face it—habits stick when they feel good. Build instant gratification into your reading routine. - **Gamify the Process:** Create a simple list of mini challenges (like the ones here) and cross them off as you go. - **Set Rewards:** For every milestone—like finishing a chapter or hitting a week of daily reading—treat yourself. It could be a fancy coffee, a cozy reading corner upgrade, or just the joy of marking progress. **Mini Challenge #3:** - Set a reward for finishing your first chapter or reading streak. Make it something exciting! --- ### **Step 5: Follow Your Interests, Not Rules** One of the biggest mental barriers is feeling like you *have to* finish every book you start. Forget that. Reading should be enjoyable, not a chore. If a book isn’t grabbing you, it’s okay to stop and try another. The key is to stay engaged, not stuck. **Mini Challenge #4:** - If you’re not loving a book after 50 pages, give yourself permission to move on. --- ### **Step 6: Build Momentum with Layered Challenges** To make reading exciting and natural, set challenges that grow progressively: 1. **Day 1–3:** Read 5 minutes daily. 2. **Day 4–7:** Extend to 10 minutes. 3. **Week 2:** Finish a chapter or two from a book you love. 4. **Week 3:** Try a new genre or author. Each challenge builds on the last, creating a sense of accomplishment. By the time you finish the third week, you’ll likely be hooked. --- ### **Step 7: Track and Celebrate Progress** Progress tracking is one of the simplest yet most effective ways to build a habit. Create a log to note what you’ve read, even if it’s just a chapter or a short story. Seeing your progress motivates you to keep going. **Ideas for Tracking:** - Use a journal or app to list books and dates you started/finished. - Jot down favorite quotes or lessons learned. - Share your progress with friends or join a book club for accountability. **Mini Challenge #5:** - Start a reading journal and write down what you love about the book you’re currently reading. --- ### **Step 8: Stay Flexible and Forgive Yourself** Life gets busy, and you might miss a day (or week). That’s okay. Habits are built over time, not overnight. The key is to keep coming back to your reading routine without guilt. Remember, even a little reading is better than none. --- ### **Final Thoughts** Reading is a gift you give yourself. It’s not about how fast you finish or how many books you complete—it’s about the joy, knowledge, and escape it brings. By breaking your mental barriers, starting small, and creating a system of rewards and challenges, you can make reading a natural and deeply fulfilling part of your life. So, grab a book, set a timer, and dive in. Your reading journey starts today.
@ 378562cd:a6fc6773
2025-01-10 16:37:38For many of us, reading isn’t just a pastime—it’s a deeply personal goal tied to self-growth, relaxation, and exploration. Yet, despite knowing its importance, we often struggle to make it happen. We start and stop, let books gather dust, and feel guilty for not finishing them. The truth? It’s not a time issue; it’s a mental barrier. This guide is designed to help you break through those barriers with a structured, rewarding framework that keeps you interested, engaged, and building momentum. Let’s turn reading into a habit you love—and can sustain. --- ### **Step 1: Understand the Real Problem** Before diving into action, take a moment to reflect. The issue isn’t that you don’t have time—it’s that you haven’t made reading a priority. Life pulls us in countless directions, but we always find time for what matters most. Reading deserves that place in your life because it nourishes your mind, brings you joy, and inspires growth. **Ask Yourself:** - Why do I want to read more? - How would my life improve if I prioritized reading? Write down your answers and keep them visible. Let your 'why' guide you forward. --- ### **Step 2: Start Where You Are (Small and Simple Wins)** Many people fail because they set huge, overwhelming goals like finishing a book every week. The secret to success? Start small. Commit to just **5 minutes a day** or a single page. Progress matters more than perfection. **Mini Challenge #1:** - Pick a book you’re genuinely excited about (not one you feel you *should* read). - Read for 5 minutes today. Just 5 minutes. When you complete this, check it off. That little win is the first step toward building momentum. --- ### **Step 3: Create a System That Fits Your Life** Habits thrive when they’re tied to something you already do. Look for natural openings in your day to read. - **Morning:** Read while sipping coffee or tea. - **Lunch Break:** Sneak in a few pages while eating. - **Evening:** Replace 10 minutes of scrolling with reading before bed. Make it impossible to forget by keeping books or an e-reader where you spend the most time: next to the bed, on the couch, or in your bag. **Mini Challenge #2:** - Set a specific time to read tomorrow. Write it down and stick to it. --- ### **Step 4: Make It Fun and Rewarding** Let’s face it—habits stick when they feel good. Build instant gratification into your reading routine. - **Gamify the Process:** Create a simple list of mini challenges (like the ones here) and cross them off as you go. - **Set Rewards:** For every milestone—like finishing a chapter or hitting a week of daily reading—treat yourself. It could be a fancy coffee, a cozy reading corner upgrade, or just the joy of marking progress. **Mini Challenge #3:** - Set a reward for finishing your first chapter or reading streak. Make it something exciting! --- ### **Step 5: Follow Your Interests, Not Rules** One of the biggest mental barriers is feeling like you *have to* finish every book you start. Forget that. Reading should be enjoyable, not a chore. If a book isn’t grabbing you, it’s okay to stop and try another. The key is to stay engaged, not stuck. **Mini Challenge #4:** - If you’re not loving a book after 50 pages, give yourself permission to move on. --- ### **Step 6: Build Momentum with Layered Challenges** To make reading exciting and natural, set challenges that grow progressively: 1. **Day 1–3:** Read 5 minutes daily. 2. **Day 4–7:** Extend to 10 minutes. 3. **Week 2:** Finish a chapter or two from a book you love. 4. **Week 3:** Try a new genre or author. Each challenge builds on the last, creating a sense of accomplishment. By the time you finish the third week, you’ll likely be hooked. --- ### **Step 7: Track and Celebrate Progress** Progress tracking is one of the simplest yet most effective ways to build a habit. Create a log to note what you’ve read, even if it’s just a chapter or a short story. Seeing your progress motivates you to keep going. **Ideas for Tracking:** - Use a journal or app to list books and dates you started/finished. - Jot down favorite quotes or lessons learned. - Share your progress with friends or join a book club for accountability. **Mini Challenge #5:** - Start a reading journal and write down what you love about the book you’re currently reading. --- ### **Step 8: Stay Flexible and Forgive Yourself** Life gets busy, and you might miss a day (or week). That’s okay. Habits are built over time, not overnight. The key is to keep coming back to your reading routine without guilt. Remember, even a little reading is better than none. --- ### **Final Thoughts** Reading is a gift you give yourself. It’s not about how fast you finish or how many books you complete—it’s about the joy, knowledge, and escape it brings. By breaking your mental barriers, starting small, and creating a system of rewards and challenges, you can make reading a natural and deeply fulfilling part of your life. So, grab a book, set a timer, and dive in. Your reading journey starts today. @ 228dde34:b5d0345e
2025-01-10 10:00:04##### By Glenda Chong ##### Editorial Admin ##### Hype Issue #60 ##### Join GLENDA CHONG as she experiences the magic of Korean indie band ADOY’s music and talks to the group about how they and the Korean indie scene have risen in prominence in the global music scene.  On New Year’s Eve, under a dark sky lit with twinkling city lights, I stood clinging onto a barricade with a friend before a modest yet commanding stage, littered with instruments that pulsed with the promise of what’s to come. We were at Music Day Out! - Magical Garden, a music event held at *SCAPE to celebrate the DIY ethos of independent musical acts from across Southeast Asia and to ring in the new year. It was just past 11pm, and with bated breath, I waited for the one act I had been keeping my eyes peeled for all night to take the stage. This musical artist was none other than ADOY, a South Korean band. The band, consisting of members Juhwan, Zee, Geunchang, and Dayoung, was slated to have the longest set time of the night. Undoubtedly, as the night’s most anticipated act, the crowd’s palpable, buzzing energy was at an all-time high. For me, however, the excitement ran much deeper: because before ADOY took the stage, tucked away in a rare moment of calm, I sat down with them to hear them outside of their melodies. Over the last few years, Korean indie bands have risen in prominence in the global music scene. While fellow musical genre, K-pop, from the same country has dominated global headlines with its intricate performances and infectious tunes, Korea’s indie music scene has been simmering just beneath the surface. But with the aid of social media and the internet providing opportunities for virality, Korean indie bands like ADOY and wave to earth are now carving a path of their own, one where their music resonates just as deeply with fans worldwide as their K-pop counterparts’ does.  *As the vocalist of ADOY, Juhwan’s voice is front and center in ADOY’s music. Photo by Glenda Chong.* When I asked the band what could be attributed to the growing success of Korean indie bands, member Juhwan pointed to how beyond the boom of K-pop, Korean pop culture in general, such as Korean shows like Squid Game, “is kind of helping the image as a whole”. He also mentioned that bands like themselves are “very energetic”. Although I cannot disagree with this, as experiencing live bands is an otherworldly experience, the music and messaging seem to be the key to being a gateway for global fans to enter the indie scene. If you take a peek at ADOY’s music, you will notice that they primarily sing in English; an artistic decision that was surprisingly intentional. When asked if their English lyrics help global fans connect with their fans further, this is what member Zee had to say: “That's one of the things we had in mind when we started making songs because it’s a global arena… so we wanted to include as many people as possible.” Funnily enough, even though the band have English lyrics in most of their music, the members (except for Zee who lived abroad in France, New Zealand, America, and Canada), are only somewhat fluent in English. So as a workaround, sometimes the band turns to translating from their native language to English. In a video interview with Front Row Live Ent. on YouTube, Zee shared that as the group’s English speaker, he would help translate Korean lyrics written by his members. Surprisingly, this does not pose as much of a challenge as I had assumed, as according to Zee, they find that they do not struggle with being lost in translation as they do write in English from the start at times. “I think it just comes naturally,” Zee stated. However, he acknowledged that at times, when attempting to express certain messages and feelings, the band “sometimes has to change a lot” as the two languages are different. “It’s quite difficult… but we do try as much as possible to retain the message”. But beyond the English lyrics, it is the feelings ADOY’s music evokes that are universal. Like many ADOY fans, the first ADOY song I was introduced to was one of their most popular tracks *Grace*, a slow tune filled with smooth vocals. Watching the YouTube video of them performing *Grace* on the show Yu Heeyeol’s Sketchbook for the first time was nothing short of magical. And just from reading the Korean comments, I finally understood what people meant when they said ADOY’s music transcends borders. Just like their domestic listeners, I too found myself transported to faraway places and nostalgic moments through their sound and lyrics. It was a connection that felt universal, yet deeply personal.  *ADOY jamming out at the start of their set at Music Day Out! Photo by Glenda Chong.* This universal appeal is part of why Korean indie bands like ADOY are finding such global recognition. With their rise, however, comes the inevitable question of what it means to remain ‘indie’, as the lines between ‘indie’ and ‘commercial’ can blur. Though for ADOY in particular, having dubbed themselves as “commercial indie”, they navigate this distinction with a unique balance. In a frank manner, member Zee explained that being “commercial indie” to them meant being able to “earn money” while doing music. “Being indie is just making your own stuff,” Zee said. “We wanted to earn money while doing this so we can do music for a professional career. That’s what we meant [when we said] we wanted to be commercial”. Judging from their journey, they have stuck to these principles closely. The band is independent from major record labels and has remained true to their sound and artistic essence, even while experimenting and fusing various genres. Their efforts have proven to be fruitful, as the global appetite for Korea’s diverse music scene is roaring louder than ever. Korean indie music has found its voice on the global stage, and ADOY has become one of its most compelling icons. Before we wrapped up our time together, I asked ADOY a very important question: which of their songs would they recommend to a first-timer of their music? Member Dayoung suggested the track *Don’t Stop* which appears on their first EP, *CATNIP*.  *Dayoung plays the bass and supports Juhwan with backing vocals in the team. Photo by Glenda Chong.* “*Don’t Stop* because it retains that energy of youth that I think it’s quite hard to describe song-wise, but I think that song has that good picture of youth in it,” Dayoung explained. With Dayoung’s words echoing in my mind, I eagerly wondered if the band would play this track during their set. And after close to an hour of immersing in ADOY’s dreamy soundscapes, I got my answer. Just minutes before the clock’s hands approached the new year, unlike the past hour where ADOY moved through each track seamlessly with little to no commentary, the energy shifted. Breaking their pattern of minimal commentary, Juhwan led the crowd to do a chant which I would soon learn to be the opening refrain of the anthemic *Don’t Stop*. And when the drums and the first few notes kicked in, Dayoung’s words sprang to life before my very eyes and ears.  *Juhwan “handing” his microphone to the crowd to encourage us to chant along to Don’t Stop’s hook. Photo by Glenda Chong.* *Dance away the whole night* *Play the song* *Here comes the waves, oh* *Don't stop me, I feel the ocean* *Don't stop me, we need no reason* *Don't stop me, this is the moment* *Keep me young and free, yeah* In that moment - headbanging to the lyrics furiously, the live instruments booming through my chest, it was a feeling no headphones or sound device could ever replicate and my efforts would forever be in vain. It can never compare to the indelible impression left behind by the raw, intensified energy of the crowd and ADOY’s unified symphony of shared emotion. As ADOY carried *Don’t Stop* in all its youthful defiance and boundless energy into 2025, it felt like more than a closing act; it was a moment of triumph. The night encapsulated the endless possibilities of the new year ahead, and for ADOY, the path is undeniably up.
@ 228dde34:b5d0345e
2025-01-10 10:00:04##### By Glenda Chong ##### Editorial Admin ##### Hype Issue #60 ##### Join GLENDA CHONG as she experiences the magic of Korean indie band ADOY’s music and talks to the group about how they and the Korean indie scene have risen in prominence in the global music scene.  On New Year’s Eve, under a dark sky lit with twinkling city lights, I stood clinging onto a barricade with a friend before a modest yet commanding stage, littered with instruments that pulsed with the promise of what’s to come. We were at Music Day Out! - Magical Garden, a music event held at *SCAPE to celebrate the DIY ethos of independent musical acts from across Southeast Asia and to ring in the new year. It was just past 11pm, and with bated breath, I waited for the one act I had been keeping my eyes peeled for all night to take the stage. This musical artist was none other than ADOY, a South Korean band. The band, consisting of members Juhwan, Zee, Geunchang, and Dayoung, was slated to have the longest set time of the night. Undoubtedly, as the night’s most anticipated act, the crowd’s palpable, buzzing energy was at an all-time high. For me, however, the excitement ran much deeper: because before ADOY took the stage, tucked away in a rare moment of calm, I sat down with them to hear them outside of their melodies. Over the last few years, Korean indie bands have risen in prominence in the global music scene. While fellow musical genre, K-pop, from the same country has dominated global headlines with its intricate performances and infectious tunes, Korea’s indie music scene has been simmering just beneath the surface. But with the aid of social media and the internet providing opportunities for virality, Korean indie bands like ADOY and wave to earth are now carving a path of their own, one where their music resonates just as deeply with fans worldwide as their K-pop counterparts’ does.  *As the vocalist of ADOY, Juhwan’s voice is front and center in ADOY’s music. Photo by Glenda Chong.* When I asked the band what could be attributed to the growing success of Korean indie bands, member Juhwan pointed to how beyond the boom of K-pop, Korean pop culture in general, such as Korean shows like Squid Game, “is kind of helping the image as a whole”. He also mentioned that bands like themselves are “very energetic”. Although I cannot disagree with this, as experiencing live bands is an otherworldly experience, the music and messaging seem to be the key to being a gateway for global fans to enter the indie scene. If you take a peek at ADOY’s music, you will notice that they primarily sing in English; an artistic decision that was surprisingly intentional. When asked if their English lyrics help global fans connect with their fans further, this is what member Zee had to say: “That's one of the things we had in mind when we started making songs because it’s a global arena… so we wanted to include as many people as possible.” Funnily enough, even though the band have English lyrics in most of their music, the members (except for Zee who lived abroad in France, New Zealand, America, and Canada), are only somewhat fluent in English. So as a workaround, sometimes the band turns to translating from their native language to English. In a video interview with Front Row Live Ent. on YouTube, Zee shared that as the group’s English speaker, he would help translate Korean lyrics written by his members. Surprisingly, this does not pose as much of a challenge as I had assumed, as according to Zee, they find that they do not struggle with being lost in translation as they do write in English from the start at times. “I think it just comes naturally,” Zee stated. However, he acknowledged that at times, when attempting to express certain messages and feelings, the band “sometimes has to change a lot” as the two languages are different. “It’s quite difficult… but we do try as much as possible to retain the message”. But beyond the English lyrics, it is the feelings ADOY’s music evokes that are universal. Like many ADOY fans, the first ADOY song I was introduced to was one of their most popular tracks *Grace*, a slow tune filled with smooth vocals. Watching the YouTube video of them performing *Grace* on the show Yu Heeyeol’s Sketchbook for the first time was nothing short of magical. And just from reading the Korean comments, I finally understood what people meant when they said ADOY’s music transcends borders. Just like their domestic listeners, I too found myself transported to faraway places and nostalgic moments through their sound and lyrics. It was a connection that felt universal, yet deeply personal.  *ADOY jamming out at the start of their set at Music Day Out! Photo by Glenda Chong.* This universal appeal is part of why Korean indie bands like ADOY are finding such global recognition. With their rise, however, comes the inevitable question of what it means to remain ‘indie’, as the lines between ‘indie’ and ‘commercial’ can blur. Though for ADOY in particular, having dubbed themselves as “commercial indie”, they navigate this distinction with a unique balance. In a frank manner, member Zee explained that being “commercial indie” to them meant being able to “earn money” while doing music. “Being indie is just making your own stuff,” Zee said. “We wanted to earn money while doing this so we can do music for a professional career. That’s what we meant [when we said] we wanted to be commercial”. Judging from their journey, they have stuck to these principles closely. The band is independent from major record labels and has remained true to their sound and artistic essence, even while experimenting and fusing various genres. Their efforts have proven to be fruitful, as the global appetite for Korea’s diverse music scene is roaring louder than ever. Korean indie music has found its voice on the global stage, and ADOY has become one of its most compelling icons. Before we wrapped up our time together, I asked ADOY a very important question: which of their songs would they recommend to a first-timer of their music? Member Dayoung suggested the track *Don’t Stop* which appears on their first EP, *CATNIP*.  *Dayoung plays the bass and supports Juhwan with backing vocals in the team. Photo by Glenda Chong.* “*Don’t Stop* because it retains that energy of youth that I think it’s quite hard to describe song-wise, but I think that song has that good picture of youth in it,” Dayoung explained. With Dayoung’s words echoing in my mind, I eagerly wondered if the band would play this track during their set. And after close to an hour of immersing in ADOY’s dreamy soundscapes, I got my answer. Just minutes before the clock’s hands approached the new year, unlike the past hour where ADOY moved through each track seamlessly with little to no commentary, the energy shifted. Breaking their pattern of minimal commentary, Juhwan led the crowd to do a chant which I would soon learn to be the opening refrain of the anthemic *Don’t Stop*. And when the drums and the first few notes kicked in, Dayoung’s words sprang to life before my very eyes and ears.  *Juhwan “handing” his microphone to the crowd to encourage us to chant along to Don’t Stop’s hook. Photo by Glenda Chong.* *Dance away the whole night* *Play the song* *Here comes the waves, oh* *Don't stop me, I feel the ocean* *Don't stop me, we need no reason* *Don't stop me, this is the moment* *Keep me young and free, yeah* In that moment - headbanging to the lyrics furiously, the live instruments booming through my chest, it was a feeling no headphones or sound device could ever replicate and my efforts would forever be in vain. It can never compare to the indelible impression left behind by the raw, intensified energy of the crowd and ADOY’s unified symphony of shared emotion. As ADOY carried *Don’t Stop* in all its youthful defiance and boundless energy into 2025, it felt like more than a closing act; it was a moment of triumph. The night encapsulated the endless possibilities of the new year ahead, and for ADOY, the path is undeniably up. @ f33c8a96:5ec6f741
2025-01-09 18:38:50<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><video style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" controls> <source src="https://plebdevs-bucket.nyc3.cdn.digitaloceanspaces.com/starter-lesson-5.mp4" type="video/mp4"/> <source src="https://plebdevs-bucket.nyc3.cdn.digitaloceanspaces.com/starter-lesson-5.webm" type="video/webm"/> </video></div> # JavaScript: Building Your First Interactive Web App ## Introduction In this lesson, we'll bring our web pages to life by adding dynamic functionality with JavaScript. We'll build a real-world application that displays and updates Bitcoin prices in real-time, teaching core JavaScript concepts along the way. ## Project Overview: Bitcoin Price Tracker We'll build a web application that: - Displays current Bitcoin price - Updates automatically every 3 seconds - Allows currency switching - Includes interactive controls - Shows current date/time ## Core JavaScript Concepts ### 1. Variables and Data Types ```javascript // Variables can be declared with let or const let currentCurrency = "USD"; // Can be changed const interval = 3000; // Cannot be changed // Basic data types const price = 45000; // Number const isVisible = true; // Boolean const currency = "USD"; // String ``` ### 2. DOM Manipulation ```javascript // Getting elements const priceElement = document.getElementById('price'); const button = document.getElementById('refresh-button'); // Modifying content priceElement.textContent = `${price} ${currency}`; // Changing styles priceElement.style.display = 'none'; ``` ### 3. Event Listeners ```javascript // Basic click handler button.addEventListener('click', () => { fetchBitcoinPrice(); }); // Change event for select elements selector.addEventListener('change', (event) => { handleCurrencyChange(event.value); }); ``` ### 4. Async Operations & Fetch API ```javascript async function fetchBitcoinPrice() { try { const response = await fetch(apiUrl); const data = await response.json(); updatePrice(data.price); } catch (error) { console.error('Error:', error); } } ``` ## Project Structure ### HTML Setup ```html <!DOCTYPE html> <html lang="en"> <head> <title>Bitcoin Price Tracker</title> <link rel="stylesheet" href="style.css"> <script src="index.js" defer></script> </head> <body> <h1>Current Bitcoin Price</h1> <p>The price is: <span id="price"></span></p> <!-- Additional elements --> </body> </html> ``` ### Core Functionality Implementation 1. **Setting Up the Timer** ```javascript // Update price every 3 seconds setInterval(fetchBitcoinPrice, 3000); // Update date/time every second setInterval(updateDateTime, 1000); ``` 2. **Currency Selection** ```javascript function handleCurrencyChange(newCurrency) { currentCurrency = newCurrency; fetchBitcoinPrice(); } ``` 3. **Toggle Visibility** ```javascript function togglePriceVisibility() { const price = document.getElementById('price'); price.style.display = price.style.display === 'none' ? 'inline' : 'none'; } ``` ## Best Practices ### 1. Error Handling - Always use try/catch with async operations - Provide meaningful error messages - Handle edge cases gracefully ### 2. Code Organization - Keep functions focused and small - Use meaningful variable names - Group related functionality - Add comments for clarity ### 3. Performance - Avoid unnecessary DOM updates - Use appropriate update intervals - Clean up intervals when not needed ## Common Challenges & Solutions ### 1. API Issues ```javascript // Handle API failures gracefully catch (error) { priceElement.textContent = 'Price unavailable'; console.error('API Error:', error); } ``` ### 2. Currency Formatting ```javascript function formatPrice(price, currency) { return new Intl.NumberFormat('en-US', { style: 'currency', currency: currency }).format(price); } ``` ### 3. Time Zones ```javascript function getLocalTime() { return new Date().toLocaleString(); } ``` ## Extending the Project Consider adding these features for practice: 1. Price change indicators (up/down arrows) 2. Historical price chart 3. Multiple cryptocurrency support 4. Price alerts 5. Local storage for settings ## Debugging Tips ### Using Console ```javascript console.log('Price fetched:', price); console.error('Error occurred:', error); console.table(priceHistory); ``` ### Chrome DevTools 1. Network tab for API calls 2. Console for errors 3. Elements for DOM inspection 4. Sources for debugging ## Additional Resources - MDN JavaScript Guide - JavaScript.info - CoinGecko API Documentation - Chrome DevTools Documentation ## Next Steps 1. Add styling with CSS 2. Implement additional features 3. Learn about React for more complex applications 4. Explore other APIs and cryptocurrencies Remember: The best way to learn is by doing. Don't be afraid to break things and experiment with the code. The developer console is your friend for debugging and understanding what's happening in your application. Happy coding! 🚀
@ f33c8a96:5ec6f741
2025-01-09 18:38:50<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;max-width:100%;"><video style="position:absolute;top:0;left:0;width:100%;height:100%;border:0;" controls> <source src="https://plebdevs-bucket.nyc3.cdn.digitaloceanspaces.com/starter-lesson-5.mp4" type="video/mp4"/> <source src="https://plebdevs-bucket.nyc3.cdn.digitaloceanspaces.com/starter-lesson-5.webm" type="video/webm"/> </video></div> # JavaScript: Building Your First Interactive Web App ## Introduction In this lesson, we'll bring our web pages to life by adding dynamic functionality with JavaScript. We'll build a real-world application that displays and updates Bitcoin prices in real-time, teaching core JavaScript concepts along the way. ## Project Overview: Bitcoin Price Tracker We'll build a web application that: - Displays current Bitcoin price - Updates automatically every 3 seconds - Allows currency switching - Includes interactive controls - Shows current date/time ## Core JavaScript Concepts ### 1. Variables and Data Types ```javascript // Variables can be declared with let or const let currentCurrency = "USD"; // Can be changed const interval = 3000; // Cannot be changed // Basic data types const price = 45000; // Number const isVisible = true; // Boolean const currency = "USD"; // String ``` ### 2. DOM Manipulation ```javascript // Getting elements const priceElement = document.getElementById('price'); const button = document.getElementById('refresh-button'); // Modifying content priceElement.textContent = `${price} ${currency}`; // Changing styles priceElement.style.display = 'none'; ``` ### 3. Event Listeners ```javascript // Basic click handler button.addEventListener('click', () => { fetchBitcoinPrice(); }); // Change event for select elements selector.addEventListener('change', (event) => { handleCurrencyChange(event.value); }); ``` ### 4. Async Operations & Fetch API ```javascript async function fetchBitcoinPrice() { try { const response = await fetch(apiUrl); const data = await response.json(); updatePrice(data.price); } catch (error) { console.error('Error:', error); } } ``` ## Project Structure ### HTML Setup ```html <!DOCTYPE html> <html lang="en"> <head> <title>Bitcoin Price Tracker</title> <link rel="stylesheet" href="style.css"> <script src="index.js" defer></script> </head> <body> <h1>Current Bitcoin Price</h1> <p>The price is: <span id="price"></span></p> <!-- Additional elements --> </body> </html> ``` ### Core Functionality Implementation 1. **Setting Up the Timer** ```javascript // Update price every 3 seconds setInterval(fetchBitcoinPrice, 3000); // Update date/time every second setInterval(updateDateTime, 1000); ``` 2. **Currency Selection** ```javascript function handleCurrencyChange(newCurrency) { currentCurrency = newCurrency; fetchBitcoinPrice(); } ``` 3. **Toggle Visibility** ```javascript function togglePriceVisibility() { const price = document.getElementById('price'); price.style.display = price.style.display === 'none' ? 'inline' : 'none'; } ``` ## Best Practices ### 1. Error Handling - Always use try/catch with async operations - Provide meaningful error messages - Handle edge cases gracefully ### 2. Code Organization - Keep functions focused and small - Use meaningful variable names - Group related functionality - Add comments for clarity ### 3. Performance - Avoid unnecessary DOM updates - Use appropriate update intervals - Clean up intervals when not needed ## Common Challenges & Solutions ### 1. API Issues ```javascript // Handle API failures gracefully catch (error) { priceElement.textContent = 'Price unavailable'; console.error('API Error:', error); } ``` ### 2. Currency Formatting ```javascript function formatPrice(price, currency) { return new Intl.NumberFormat('en-US', { style: 'currency', currency: currency }).format(price); } ``` ### 3. Time Zones ```javascript function getLocalTime() { return new Date().toLocaleString(); } ``` ## Extending the Project Consider adding these features for practice: 1. Price change indicators (up/down arrows) 2. Historical price chart 3. Multiple cryptocurrency support 4. Price alerts 5. Local storage for settings ## Debugging Tips ### Using Console ```javascript console.log('Price fetched:', price); console.error('Error occurred:', error); console.table(priceHistory); ``` ### Chrome DevTools 1. Network tab for API calls 2. Console for errors 3. Elements for DOM inspection 4. Sources for debugging ## Additional Resources - MDN JavaScript Guide - JavaScript.info - CoinGecko API Documentation - Chrome DevTools Documentation ## Next Steps 1. Add styling with CSS 2. Implement additional features 3. Learn about React for more complex applications 4. Explore other APIs and cryptocurrencies Remember: The best way to learn is by doing. Don't be afraid to break things and experiment with the code. The developer console is your friend for debugging and understanding what's happening in your application. Happy coding! 🚀 @ df173277:4ec96708
2025-01-09 17:13:20> Maple AI combines the best of both worlds – encryption and personal AI – to create a truly private AI experience. Discuss personal and company items with Maple, we can't read them even if we wanted to.\ > [Join the waitlist to get early access.](https://trymaple.ai) We are a culture of app users. Every day, we give our personal information to websites and apps, hoping they are safe. Location data, eating habits, financial details, and health information are just a few examples of what we entrust to third parties. People are now entering a new era of computing that promises next-level benefits when given even more personal data: AI. Should we sacrifice our privacy to unlock the productivity gains of AI? Should we hope our information won't be used in ways we disagree? We believe we can have the best of both worlds – privacy and personal AI – and have built a new project called Maple AI. Chat between you and an AI with full end-to-end encryption. We believe it's a game-changer for individuals seeking private and secure conversations. #### Building a Private Foundation Maple is built on our flagship product, [OpenSecret](https://opensecret.cloud), a backend platform for app developers that turns private encryption on by default. [The announcement post for OpenSecret explains our vision for an encrypted world and what the platform can do.](https://primal.net/e/naddr1qvzqqqr4gupzphchxfm3ste32hfhkvczzxapme9gz5qvqtget6tylyd7wa8vjecgqqe5jmn5wfhkgatrd9hxwt20wpjku5m9vdex2apdw35x2tt9de3hy7tsw3jkgttzv93kketwvskhgur5w9nx5h52tpj) We think both users and developers benefit when sensitive personal information is encrypted in a private vault; it's a win-win. #### The Power of Encrypted AI Chat AI chat is a personal and intimate experience. It's a place to share your thoughts, feelings, and desires without fear of judgment. The more you share with an AI chatbot, the more powerful it becomes. It can offer personalized insights, suggestions, and guidance tailored to your unique needs and perspectives. However, this intimacy requires trust, and that's where traditional AI chatbots often fall short. Traditional AI chats are designed to collect and analyze your data, often without your explicit consent. This data is used to improve the AI's performance, but it also creates a treasure trove of sensitive information that can be mined, sold, or even exploited by malicious actors. Maple AI takes a different approach. By using end-to-end encryption, we ensure that your conversations remain private and secure, even from us. #### Technical Overview So, how does Maple AI achieve this level of privacy and security? Here are some key technical aspects: - **Private Key:** Each user has a unique private key that is automatically managed for them. This key encrypts and decrypts conversations, ensuring that only the user can access their data. - **Secure Servers:** Our servers are designed with security in mind. We use secure enclaves to protect sensitive data and ensure that even our own team can't access your conversations. - **Encrypted Sync:** One of Maple's most significant benefits is its encrypted sync feature. Unlike traditional AI chatbots, which store conversations in local storage or on standard cloud servers, Maple syncs your chats across all your devices. The private key managed by our secure servers means you can pick up where you left off on any device without worrying about your data being compromised. - **Attestation and Open Code:** We publish our enclave code publicly. Using a process called attestation, users can verify that the code running on the enclave is the same as the code audited by the public. - **Open Source LLM:** Maple uses major open-source models to maximize the openness of responses. The chat box does not filter what you can talk about. This transparency ensures that our AI is trustworthy and unbiased. #### Personal and Work Use Maple is secure enough to handle your personal questions and work tasks. Because we can't see what you chat about, you are free to use AI as an assistant on sensitive company items. Use it for small tasks like writing an important email or large tasks like developing your organization's strategy. Feed it sensitive information; it's just you and AI in the room. Attestation provides cryptographic proof that your corporate secrets are safe. #### Local v Cloud Today's AI tools provide different levels of privacy. The main options are to trust a third party with your unencrypted data, hoping they don't do anything with it, or run your own AI locally on an underpowered machine. We created a third option. Maple gives you the power of cloud computing combined with the privacy and security of a machine running on your desk. It's the best of both worlds. #### Why the Maple name? Privacy isn't just a human value - it's a natural one exemplified by the Maple tree. These organisms communicate with each other through a network of underground fungal hyphae, sending messages and sharing resources in a way that's completely invisible to organisms above ground. This discreet communication system allows Maple trees to thrive in even the most challenging environments. Our goal is to provide a way for everyone to communicate with AI securely so they can thrive in any environment. #### Join the Waitlist Maple AI will launch in early 2025 with free and paid plans. We can't wait to share it with the world. [Join our waitlist today to be among the first to experience the power of private AI chat.](https://trymaple.ai) 
@ df173277:4ec96708
2025-01-09 17:13:20> Maple AI combines the best of both worlds – encryption and personal AI – to create a truly private AI experience. Discuss personal and company items with Maple, we can't read them even if we wanted to.\ > [Join the waitlist to get early access.](https://trymaple.ai) We are a culture of app users. Every day, we give our personal information to websites and apps, hoping they are safe. Location data, eating habits, financial details, and health information are just a few examples of what we entrust to third parties. People are now entering a new era of computing that promises next-level benefits when given even more personal data: AI. Should we sacrifice our privacy to unlock the productivity gains of AI? Should we hope our information won't be used in ways we disagree? We believe we can have the best of both worlds – privacy and personal AI – and have built a new project called Maple AI. Chat between you and an AI with full end-to-end encryption. We believe it's a game-changer for individuals seeking private and secure conversations. #### Building a Private Foundation Maple is built on our flagship product, [OpenSecret](https://opensecret.cloud), a backend platform for app developers that turns private encryption on by default. [The announcement post for OpenSecret explains our vision for an encrypted world and what the platform can do.](https://primal.net/e/naddr1qvzqqqr4gupzphchxfm3ste32hfhkvczzxapme9gz5qvqtget6tylyd7wa8vjecgqqe5jmn5wfhkgatrd9hxwt20wpjku5m9vdex2apdw35x2tt9de3hy7tsw3jkgttzv93kketwvskhgur5w9nx5h52tpj) We think both users and developers benefit when sensitive personal information is encrypted in a private vault; it's a win-win. #### The Power of Encrypted AI Chat AI chat is a personal and intimate experience. It's a place to share your thoughts, feelings, and desires without fear of judgment. The more you share with an AI chatbot, the more powerful it becomes. It can offer personalized insights, suggestions, and guidance tailored to your unique needs and perspectives. However, this intimacy requires trust, and that's where traditional AI chatbots often fall short. Traditional AI chats are designed to collect and analyze your data, often without your explicit consent. This data is used to improve the AI's performance, but it also creates a treasure trove of sensitive information that can be mined, sold, or even exploited by malicious actors. Maple AI takes a different approach. By using end-to-end encryption, we ensure that your conversations remain private and secure, even from us. #### Technical Overview So, how does Maple AI achieve this level of privacy and security? Here are some key technical aspects: - **Private Key:** Each user has a unique private key that is automatically managed for them. This key encrypts and decrypts conversations, ensuring that only the user can access their data. - **Secure Servers:** Our servers are designed with security in mind. We use secure enclaves to protect sensitive data and ensure that even our own team can't access your conversations. - **Encrypted Sync:** One of Maple's most significant benefits is its encrypted sync feature. Unlike traditional AI chatbots, which store conversations in local storage or on standard cloud servers, Maple syncs your chats across all your devices. The private key managed by our secure servers means you can pick up where you left off on any device without worrying about your data being compromised. - **Attestation and Open Code:** We publish our enclave code publicly. Using a process called attestation, users can verify that the code running on the enclave is the same as the code audited by the public. - **Open Source LLM:** Maple uses major open-source models to maximize the openness of responses. The chat box does not filter what you can talk about. This transparency ensures that our AI is trustworthy and unbiased. #### Personal and Work Use Maple is secure enough to handle your personal questions and work tasks. Because we can't see what you chat about, you are free to use AI as an assistant on sensitive company items. Use it for small tasks like writing an important email or large tasks like developing your organization's strategy. Feed it sensitive information; it's just you and AI in the room. Attestation provides cryptographic proof that your corporate secrets are safe. #### Local v Cloud Today's AI tools provide different levels of privacy. The main options are to trust a third party with your unencrypted data, hoping they don't do anything with it, or run your own AI locally on an underpowered machine. We created a third option. Maple gives you the power of cloud computing combined with the privacy and security of a machine running on your desk. It's the best of both worlds. #### Why the Maple name? Privacy isn't just a human value - it's a natural one exemplified by the Maple tree. These organisms communicate with each other through a network of underground fungal hyphae, sending messages and sharing resources in a way that's completely invisible to organisms above ground. This discreet communication system allows Maple trees to thrive in even the most challenging environments. Our goal is to provide a way for everyone to communicate with AI securely so they can thrive in any environment. #### Join the Waitlist Maple AI will launch in early 2025 with free and paid plans. We can't wait to share it with the world. [Join our waitlist today to be among the first to experience the power of private AI chat.](https://trymaple.ai)  @ df173277:4ec96708
2025-01-09 17:12:08> Maple AI combines the best of both worlds – encryption and personal AI – to create a truly private AI experience. Discuss personal and company items with Maple, we can't read them even if we wanted to.\ > [Join the waitlist to get early access.](https://trymaple.ai) We are a culture of app users. Every day, we give our personal information to websites and apps, hoping they are safe. Location data, eating habits, financial details, and health information are just a few examples of what we entrust to third parties. People are now entering a new era of computing that promises next-level benefits when given even more personal data: AI. Should we sacrifice our privacy to unlock the productivity gains of AI? Should we hope our information won't be used in ways we disagree? We believe we can have the best of both worlds – privacy and personal AI – and have built a new project called Maple AI. Chat between you and an AI with full end-to-end encryption. We believe it's a game-changer for individuals seeking private and secure conversations. #### Building a Private Foundation Maple is built on our flagship product, [OpenSecret](https://opensecret.cloud), a backend platform for app developers that turns private encryption on by default. [The announcement post for OpenSecret explains our vision for an encrypted world and what the platform can do.](nostr:naddr1qvzqqqr4gupzphchxfm3ste32hfhkvczzxapme9gz5qvqtget6tylyd7wa8vjecgqqe5jmn5wfhkgatrd9hxwt20wpjku5m9vdex2apdw35x2tt9de3hy7tsw3jkgttzv93kketwvskhgur5w9nx5h52tpj) We think both users and developers benefit when sensitive personal information is encrypted in a private vault; it's a win-win. #### The Power of Encrypted AI Chat AI chat is a personal and intimate experience. It's a place to share your thoughts, feelings, and desires without fear of judgment. The more you share with an AI chatbot, the more powerful it becomes. It can offer personalized insights, suggestions, and guidance tailored to your unique needs and perspectives. However, this intimacy requires trust, and that's where traditional AI chatbots often fall short. Traditional AI chats are designed to collect and analyze your data, often without your explicit consent. This data is used to improve the AI's performance, but it also creates a treasure trove of sensitive information that can be mined, sold, or even exploited by malicious actors. Maple AI takes a different approach. By using end-to-end encryption, we ensure that your conversations remain private and secure, even from us. #### Technical Overview So, how does Maple AI achieve this level of privacy and security? Here are some key technical aspects: - **Private Key:** Each user has a unique private key that is automatically managed for them. This key encrypts and decrypts conversations, ensuring that only the user can access their data. - **Secure Servers:** Our servers are designed with security in mind. We use secure enclaves to protect sensitive data and ensure that even our own team can't access your conversations. - **Encrypted Sync:** One of Maple's most significant benefits is its encrypted sync feature. Unlike traditional AI chatbots, which store conversations in local storage or on standard cloud servers, Maple syncs your chats across all your devices. The private key managed by our secure servers means you can pick up where you left off on any device without worrying about your data being compromised. - **Attestation and Open Code:** We publish our enclave code publicly. Using a process called attestation, users can verify that the code running on the enclave is the same as the code audited by the public. - **Open Source LLM:** Maple uses major open-source models to maximize the openness of responses. The chat box does not filter what you can talk about. This transparency ensures that our AI is trustworthy and unbiased. #### Personal and Work Use Maple is secure enough to handle your personal questions and work tasks. Because we can't see what you chat about, you are free to use AI as an assistant on sensitive company items. Use it for small tasks like writing an important email or large tasks like developing your organization's strategy. Feed it sensitive information; it's just you and AI in the room. Attestation provides cryptographic proof that your corporate secrets are safe. #### Local v Cloud Today's AI tools provide different levels of privacy. The main options are to trust a third party with your unencrypted data, hoping they don't do anything with it, or run your own AI locally on an underpowered machine. We created a third option. Maple gives you the power of cloud computing combined with the privacy and security of a machine running on your desk. It's the best of both worlds. #### Why the Maple name? Privacy isn't just a human value - it's a natural one exemplified by the Maple tree. These organisms communicate with each other through a network of underground fungal hyphae, sending messages and sharing resources in a way that's completely invisible to organisms above ground. This discreet communication system allows Maple trees to thrive in even the most challenging environments. Our goal is to provide a way for everyone to communicate with AI securely so they can thrive in any environment. #### Join the Waitlist Maple AI will launch in early 2025 with free and paid plans. We can't wait to share it with the world. [Join our waitlist today to be among the first to experience the power of private AI chat.](https://trymaple.ai) [](https://trymaple.ai/waitlist)
@ df173277:4ec96708
2025-01-09 17:12:08> Maple AI combines the best of both worlds – encryption and personal AI – to create a truly private AI experience. Discuss personal and company items with Maple, we can't read them even if we wanted to.\ > [Join the waitlist to get early access.](https://trymaple.ai) We are a culture of app users. Every day, we give our personal information to websites and apps, hoping they are safe. Location data, eating habits, financial details, and health information are just a few examples of what we entrust to third parties. People are now entering a new era of computing that promises next-level benefits when given even more personal data: AI. Should we sacrifice our privacy to unlock the productivity gains of AI? Should we hope our information won't be used in ways we disagree? We believe we can have the best of both worlds – privacy and personal AI – and have built a new project called Maple AI. Chat between you and an AI with full end-to-end encryption. We believe it's a game-changer for individuals seeking private and secure conversations. #### Building a Private Foundation Maple is built on our flagship product, [OpenSecret](https://opensecret.cloud), a backend platform for app developers that turns private encryption on by default. [The announcement post for OpenSecret explains our vision for an encrypted world and what the platform can do.](nostr:naddr1qvzqqqr4gupzphchxfm3ste32hfhkvczzxapme9gz5qvqtget6tylyd7wa8vjecgqqe5jmn5wfhkgatrd9hxwt20wpjku5m9vdex2apdw35x2tt9de3hy7tsw3jkgttzv93kketwvskhgur5w9nx5h52tpj) We think both users and developers benefit when sensitive personal information is encrypted in a private vault; it's a win-win. #### The Power of Encrypted AI Chat AI chat is a personal and intimate experience. It's a place to share your thoughts, feelings, and desires without fear of judgment. The more you share with an AI chatbot, the more powerful it becomes. It can offer personalized insights, suggestions, and guidance tailored to your unique needs and perspectives. However, this intimacy requires trust, and that's where traditional AI chatbots often fall short. Traditional AI chats are designed to collect and analyze your data, often without your explicit consent. This data is used to improve the AI's performance, but it also creates a treasure trove of sensitive information that can be mined, sold, or even exploited by malicious actors. Maple AI takes a different approach. By using end-to-end encryption, we ensure that your conversations remain private and secure, even from us. #### Technical Overview So, how does Maple AI achieve this level of privacy and security? Here are some key technical aspects: - **Private Key:** Each user has a unique private key that is automatically managed for them. This key encrypts and decrypts conversations, ensuring that only the user can access their data. - **Secure Servers:** Our servers are designed with security in mind. We use secure enclaves to protect sensitive data and ensure that even our own team can't access your conversations. - **Encrypted Sync:** One of Maple's most significant benefits is its encrypted sync feature. Unlike traditional AI chatbots, which store conversations in local storage or on standard cloud servers, Maple syncs your chats across all your devices. The private key managed by our secure servers means you can pick up where you left off on any device without worrying about your data being compromised. - **Attestation and Open Code:** We publish our enclave code publicly. Using a process called attestation, users can verify that the code running on the enclave is the same as the code audited by the public. - **Open Source LLM:** Maple uses major open-source models to maximize the openness of responses. The chat box does not filter what you can talk about. This transparency ensures that our AI is trustworthy and unbiased. #### Personal and Work Use Maple is secure enough to handle your personal questions and work tasks. Because we can't see what you chat about, you are free to use AI as an assistant on sensitive company items. Use it for small tasks like writing an important email or large tasks like developing your organization's strategy. Feed it sensitive information; it's just you and AI in the room. Attestation provides cryptographic proof that your corporate secrets are safe. #### Local v Cloud Today's AI tools provide different levels of privacy. The main options are to trust a third party with your unencrypted data, hoping they don't do anything with it, or run your own AI locally on an underpowered machine. We created a third option. Maple gives you the power of cloud computing combined with the privacy and security of a machine running on your desk. It's the best of both worlds. #### Why the Maple name? Privacy isn't just a human value - it's a natural one exemplified by the Maple tree. These organisms communicate with each other through a network of underground fungal hyphae, sending messages and sharing resources in a way that's completely invisible to organisms above ground. This discreet communication system allows Maple trees to thrive in even the most challenging environments. Our goal is to provide a way for everyone to communicate with AI securely so they can thrive in any environment. #### Join the Waitlist Maple AI will launch in early 2025 with free and paid plans. We can't wait to share it with the world. [Join our waitlist today to be among the first to experience the power of private AI chat.](https://trymaple.ai) [](https://trymaple.ai/waitlist) @ df173277:4ec96708
2025-01-09 17:02:52> OpenSecret is a backend for app developers that turns private encryption on by default. When sensitive data is readable only by the user, it protects both the user and the developer, creating a more free and open internet. We'll be launching in 2025. [Join our waitlist to get early access.](https://opensecret.cloud) In today's digital age, personal data is both an asset and a liability. With the rise of data breaches and cyber attacks, individuals and companies struggle to protect sensitive information. The consequences of a data breach can be devastating, resulting in financial losses, reputational damage, and compromised user trust. In 2023, the average data breach cost was $5 million, with some resulting in losses of over $1 billion. Meanwhile, individuals face problems related to identity theft, personal safety, and public embarrassment. Think about the apps on your phone, even the one you're using to read this. How much data have you trusted to other people, and how would it feel if that data were leaked online? Thankfully, some incredibly talented cypherpunks years ago gave the world cryptography. We can encrypt data, rendering it a secret between two people. So why then do we have data breaches? > Cryptography at scale is hard. #### The Cloud The cloud has revolutionized how we store and process data, but it has limitations. While cloud providers offer encryption, it mainly protects data in transit. Once data is stored in the cloud, it's often encrypted with a shared key, which can be accessed by employees, third-party vendors, or compromised by hackers. The solution is to generate a personal encryption password for each user, make sure they write it down, and, most importantly, hope they don't lose it. If the password is lost, the data is forever unreadable. That can be overwhelming, leading to low app usage. > Private key encryption needs a UX upgrade. ## Enter OpenSecret OpenSecret is a developer platform that enables encryption by default. Our platform provides a suite of security tools for app developers, including private key management, encrypted sync, private AI, and confidential compute. Every user has a private vault for their data, which means only they can read it. Developers are free to store less sensitive data in a shared manner because there is still a need to aggregate data across the system.  ### Private Key Management Private key management is the superpower that enables personal encryption per user. When each user has a unique private key, their data can be truly private. Typically, using a private key is a challenging experience for the user because they must write down a long autogenerated number or phrase of 12-24 words. If they lose it, their data is gone. OpenSecret uses secure enclaves to make private keys as easy as an everyday login experience that users are familiar with. Instead of managing a complicated key, the user logs in with an email address or a social media account. The developer doesn't have to manage private keys and can focus on the app's user experience. The user doesn't have to worry about losing a private key and can jump into using your app.  ### Encrypted Sync With user keys safely managed, we can synchronize user data to every device while maintaining privacy. The user does not need to do complicated things like scanning QR codes from one device to the next. Just log in and go. The user wins because the data is available on all their devices. The developer wins because only the user can read the data, so it isn't a liability to them. ### Private AI Artificial intelligence is here and making its way into everything. The true power of AI is unleashed when it can act on personal and company data. The current options are to run your own AI locally on an underpowered machine or to trust a third party with your data, hoping they don't read it or use it for anything. OpenSecret combines the power of cloud computing with the privacy and security of a machine running on your desk. **Check out Maple AI**\ Try private AI for yourself! We built an app built with this service called [Maple AI](https://trymaple.ai). It is an AI chat that is 100% private in a verifiable manner. Give it your innermost thoughts or embarrassing ideas; we can't judge you. We built Maple using OpenSecret, which means you have a private key that is automatically managed for you, and your chat history is synchronized to all your devices. [Learn more about Maple AI - Private chat in the announcement post.](https://blog.opensecret.cloud/maple-ai-private-encrypted-chat/)  ### Confidential Compute Confidential computing is a game-changer for data security. It's like the secure hardware that powers Apple Pay and Google Pay on your phone but in the cloud. Users can verify through a process called attestation that their data is handled appropriately. OpenSecret can help you run your own custom app backend code that would benefit from the security of an enclave. It's the new version of that lock on your web browser. When you see it, you know you're secure.  #### **But do we want our secrets to be open?** OpenSecret renders a data breach practically useless. If hackers get into the backend, they enter a virtual hallway of locked private vaults. The leaked data would be gibberish, a secret in the open that is unreadable. On the topic of openness, OpenSecret uses the power of open source to enable trust in the service. We publish our code in the open, and, using attestation, anyone can verify that private data is being handled as expected. This openness also provides developers with a backup option to safely and securely export their data. > Don't trust, verify. ### **Join the Movement** We're currently building out OpenSecret, and we invite you to join us on the journey. Our platform can work with your existing stack, and you can pick and choose the features you need. If you want to build apps with encryption enabled, [send us a message to get early access.](https://opensecret.cloud) Users and companies deserve better encryption and privacy.\ Together, let's make that a reality. [](https://opensecret.cloud)
@ df173277:4ec96708
2025-01-09 17:02:52> OpenSecret is a backend for app developers that turns private encryption on by default. When sensitive data is readable only by the user, it protects both the user and the developer, creating a more free and open internet. We'll be launching in 2025. [Join our waitlist to get early access.](https://opensecret.cloud) In today's digital age, personal data is both an asset and a liability. With the rise of data breaches and cyber attacks, individuals and companies struggle to protect sensitive information. The consequences of a data breach can be devastating, resulting in financial losses, reputational damage, and compromised user trust. In 2023, the average data breach cost was $5 million, with some resulting in losses of over $1 billion. Meanwhile, individuals face problems related to identity theft, personal safety, and public embarrassment. Think about the apps on your phone, even the one you're using to read this. How much data have you trusted to other people, and how would it feel if that data were leaked online? Thankfully, some incredibly talented cypherpunks years ago gave the world cryptography. We can encrypt data, rendering it a secret between two people. So why then do we have data breaches? > Cryptography at scale is hard. #### The Cloud The cloud has revolutionized how we store and process data, but it has limitations. While cloud providers offer encryption, it mainly protects data in transit. Once data is stored in the cloud, it's often encrypted with a shared key, which can be accessed by employees, third-party vendors, or compromised by hackers. The solution is to generate a personal encryption password for each user, make sure they write it down, and, most importantly, hope they don't lose it. If the password is lost, the data is forever unreadable. That can be overwhelming, leading to low app usage. > Private key encryption needs a UX upgrade. ## Enter OpenSecret OpenSecret is a developer platform that enables encryption by default. Our platform provides a suite of security tools for app developers, including private key management, encrypted sync, private AI, and confidential compute. Every user has a private vault for their data, which means only they can read it. Developers are free to store less sensitive data in a shared manner because there is still a need to aggregate data across the system.  ### Private Key Management Private key management is the superpower that enables personal encryption per user. When each user has a unique private key, their data can be truly private. Typically, using a private key is a challenging experience for the user because they must write down a long autogenerated number or phrase of 12-24 words. If they lose it, their data is gone. OpenSecret uses secure enclaves to make private keys as easy as an everyday login experience that users are familiar with. Instead of managing a complicated key, the user logs in with an email address or a social media account. The developer doesn't have to manage private keys and can focus on the app's user experience. The user doesn't have to worry about losing a private key and can jump into using your app.  ### Encrypted Sync With user keys safely managed, we can synchronize user data to every device while maintaining privacy. The user does not need to do complicated things like scanning QR codes from one device to the next. Just log in and go. The user wins because the data is available on all their devices. The developer wins because only the user can read the data, so it isn't a liability to them. ### Private AI Artificial intelligence is here and making its way into everything. The true power of AI is unleashed when it can act on personal and company data. The current options are to run your own AI locally on an underpowered machine or to trust a third party with your data, hoping they don't read it or use it for anything. OpenSecret combines the power of cloud computing with the privacy and security of a machine running on your desk. **Check out Maple AI**\ Try private AI for yourself! We built an app built with this service called [Maple AI](https://trymaple.ai). It is an AI chat that is 100% private in a verifiable manner. Give it your innermost thoughts or embarrassing ideas; we can't judge you. We built Maple using OpenSecret, which means you have a private key that is automatically managed for you, and your chat history is synchronized to all your devices. [Learn more about Maple AI - Private chat in the announcement post.](https://blog.opensecret.cloud/maple-ai-private-encrypted-chat/)  ### Confidential Compute Confidential computing is a game-changer for data security. It's like the secure hardware that powers Apple Pay and Google Pay on your phone but in the cloud. Users can verify through a process called attestation that their data is handled appropriately. OpenSecret can help you run your own custom app backend code that would benefit from the security of an enclave. It's the new version of that lock on your web browser. When you see it, you know you're secure.  #### **But do we want our secrets to be open?** OpenSecret renders a data breach practically useless. If hackers get into the backend, they enter a virtual hallway of locked private vaults. The leaked data would be gibberish, a secret in the open that is unreadable. On the topic of openness, OpenSecret uses the power of open source to enable trust in the service. We publish our code in the open, and, using attestation, anyone can verify that private data is being handled as expected. This openness also provides developers with a backup option to safely and securely export their data. > Don't trust, verify. ### **Join the Movement** We're currently building out OpenSecret, and we invite you to join us on the journey. Our platform can work with your existing stack, and you can pick and choose the features you need. If you want to build apps with encryption enabled, [send us a message to get early access.](https://opensecret.cloud) Users and companies deserve better encryption and privacy.\ Together, let's make that a reality. [](https://opensecret.cloud) @ e373ca41:b82abcc5
2025-01-09 13:28:41  Heute Abend um 19 Uhr sprechen Elon Musk und Alice Weidel auf X. Der alternative Radiosender Kontrafunk aus der Schweiz bringt eine Übersetzung davon im Stream. Da die Webseite des Kontrafunks gestern angegriffen wurde, ist hier der Stream unzensierbar aufrufbar, als kleines Back-up: <https://stream.kontrafunk.radio/listen/kontrafunk/radio.mp3> \ Im Nostr-Netzwerk dauerhauft auch u.a. **[hier](https://njump.me/naddr1qqxnzdenxc6rydejxymnwvfhqgswxu72gyq7ykjdfl9j556887jpzwu3mw3v9ez36quas55whq4te3grqsqqqa28qythwumn8ghj7urpwfjhgmewdehhxarjxyhxxmmdqvlg3v)** aufrufbar (falls wir angegriffen werden). *** Tonight at 7 pm (CET), Elon Musk and Alice Weidel will be speaking on X. The alternative radio station Kontrafunk from Switzerland will be streaming a translation. As the Kontrafunk website was attacked yesterday, the stream can be accessed uncensored here as a small backup: <https://stream.kontrafunk.radio/listen/kontrafunk/radio.mp3> In the Nostr network also permanently available **[here](https://njump.me/naddr1qqxnzdenxc6rydejxymnwvfhqgswxu72gyq7ykjdfl9j556887jpzwu3mw3v9ez36quas55whq4te3grqsqqqa28qythwumn8ghj7urpwfjhgmewdehhxarjxyhxxmmdqvlg3v)** (in case we are attacked). *** ADVERTISEMENT: *Looking for the easiest way to buy Bitcoin and store it yourself? The **[Relai app](https://relai.app/de/?af_xp=custom\&source_caller=ui\&pid=INFLUENCER\&is_retargeting=true\&af_click_lookback=7d\&shortlink=eo5zpzew\&af_channel=branded_url\&af_inactivity_window=30d\&c=Milosz%20Matuszek)** is the No. 1 crypto start-up and No. 2 of all fintech start-ups in Switzerland. **[Here you can buy Bitcoin](https://relai.app/de/?af_xp=custom\&source_caller=ui\&pid=INFLUENCER\&is_retargeting=true\&af_click_lookback=7d\&shortlink=eo5zpzew\&af_channel=branded_url\&af_inactivity_window=30d\&c=Milosz%20Matuszek)** in just a few steps and also set up savings plans. Nobody has access to your Bitcoin except you. With the referral code MILOSZ you save on fees (no financial advice). Disclaimer due to regulatory issues: The services of the Relai App are hereby only recommended to inhabitants of Switzerland or Italy.*  *Need more security? The **[Trezor wallets](https://trezor.io/trezor-safe-5-bitcoin-only?transaction_id=102e192a206d1585e56a2fddef6d83\&offer_id=238\&affiliate_id=35234)** are recommended and easy to use, others are available in the **[store](https://trezor.io/?transaction_id=102bc85bdca2733287749c7f879ebd\&offer_id=133\&affiliate_id=35234)**. Need more advice? Book an **[introductory meeting](https://trezor.io/trezor-expert-session?transaction_id=1020e18dad0aa4b1186289fd22e90f\&offer_id=241\&affiliate_id=35234)** with a wallet expert.* *** ***Join the marketplace of ideas!** We are building a publishing ecosystem on Nostr for citizen-journalism, starting with a client for blogging and newsletter distribution. Sound money and sound information should finally be in the hands of the people, right? Want to learn more about the [Pareto Project](https://pareto.space/en)? Zap me, if you want to contribute (all Zaps go to the project).* ***Update:** Since my last article on the [Pareto project](https://pareto.space/a/naddr1qqxnzdenxsenxdf5xgerwdfkqgswxu72gyq7ykjdfl9j556887jpzwu3mw3v9ez36quas55whq4te3grqsqqqa28qyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqf4hyum), we have received more than 50 messages from publications, journalists, authors, testers and supporters. Thank you very much, we are happy to help everyone become censorship-resistant! May just take a little time. Are you a publication and want to be part of it, test us, migrate your content to Nostr? Write to **<team@pareto.space>*** **Not yet on** **[Nostr](https://nostr.com/)** **and want the full experience?** Easy onboarding via **[Nosta.me.](https://nosta.me/create/welcome)** 
@ e373ca41:b82abcc5
2025-01-09 13:28:41  Heute Abend um 19 Uhr sprechen Elon Musk und Alice Weidel auf X. Der alternative Radiosender Kontrafunk aus der Schweiz bringt eine Übersetzung davon im Stream. Da die Webseite des Kontrafunks gestern angegriffen wurde, ist hier der Stream unzensierbar aufrufbar, als kleines Back-up: <https://stream.kontrafunk.radio/listen/kontrafunk/radio.mp3> \ Im Nostr-Netzwerk dauerhauft auch u.a. **[hier](https://njump.me/naddr1qqxnzdenxc6rydejxymnwvfhqgswxu72gyq7ykjdfl9j556887jpzwu3mw3v9ez36quas55whq4te3grqsqqqa28qythwumn8ghj7urpwfjhgmewdehhxarjxyhxxmmdqvlg3v)** aufrufbar (falls wir angegriffen werden). *** Tonight at 7 pm (CET), Elon Musk and Alice Weidel will be speaking on X. The alternative radio station Kontrafunk from Switzerland will be streaming a translation. As the Kontrafunk website was attacked yesterday, the stream can be accessed uncensored here as a small backup: <https://stream.kontrafunk.radio/listen/kontrafunk/radio.mp3> In the Nostr network also permanently available **[here](https://njump.me/naddr1qqxnzdenxc6rydejxymnwvfhqgswxu72gyq7ykjdfl9j556887jpzwu3mw3v9ez36quas55whq4te3grqsqqqa28qythwumn8ghj7urpwfjhgmewdehhxarjxyhxxmmdqvlg3v)** (in case we are attacked). *** ADVERTISEMENT: *Looking for the easiest way to buy Bitcoin and store it yourself? The **[Relai app](https://relai.app/de/?af_xp=custom\&source_caller=ui\&pid=INFLUENCER\&is_retargeting=true\&af_click_lookback=7d\&shortlink=eo5zpzew\&af_channel=branded_url\&af_inactivity_window=30d\&c=Milosz%20Matuszek)** is the No. 1 crypto start-up and No. 2 of all fintech start-ups in Switzerland. **[Here you can buy Bitcoin](https://relai.app/de/?af_xp=custom\&source_caller=ui\&pid=INFLUENCER\&is_retargeting=true\&af_click_lookback=7d\&shortlink=eo5zpzew\&af_channel=branded_url\&af_inactivity_window=30d\&c=Milosz%20Matuszek)** in just a few steps and also set up savings plans. Nobody has access to your Bitcoin except you. With the referral code MILOSZ you save on fees (no financial advice). Disclaimer due to regulatory issues: The services of the Relai App are hereby only recommended to inhabitants of Switzerland or Italy.*  *Need more security? The **[Trezor wallets](https://trezor.io/trezor-safe-5-bitcoin-only?transaction_id=102e192a206d1585e56a2fddef6d83\&offer_id=238\&affiliate_id=35234)** are recommended and easy to use, others are available in the **[store](https://trezor.io/?transaction_id=102bc85bdca2733287749c7f879ebd\&offer_id=133\&affiliate_id=35234)**. Need more advice? Book an **[introductory meeting](https://trezor.io/trezor-expert-session?transaction_id=1020e18dad0aa4b1186289fd22e90f\&offer_id=241\&affiliate_id=35234)** with a wallet expert.* *** ***Join the marketplace of ideas!** We are building a publishing ecosystem on Nostr for citizen-journalism, starting with a client for blogging and newsletter distribution. Sound money and sound information should finally be in the hands of the people, right? Want to learn more about the [Pareto Project](https://pareto.space/en)? Zap me, if you want to contribute (all Zaps go to the project).* ***Update:** Since my last article on the [Pareto project](https://pareto.space/a/naddr1qqxnzdenxsenxdf5xgerwdfkqgswxu72gyq7ykjdfl9j556887jpzwu3mw3v9ez36quas55whq4te3grqsqqqa28qyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqf4hyum), we have received more than 50 messages from publications, journalists, authors, testers and supporters. Thank you very much, we are happy to help everyone become censorship-resistant! May just take a little time. Are you a publication and want to be part of it, test us, migrate your content to Nostr? Write to **<team@pareto.space>*** **Not yet on** **[Nostr](https://nostr.com/)** **and want the full experience?** Easy onboarding via **[Nosta.me.](https://nosta.me/create/welcome)**  @ 30ceb64e:7f08bdf5
2025-01-08 20:14:45In a world dominated by surveillance banking and inflationary currencies, a new paradigm is emerging—one where individuals can operate sovereign, theft-resistant checking accounts using the world's hardest money. This isn't your grandfather's checking account; it's an entirely new financial operating system built on Bitcoin and Lightning technology. --- ## The Bitcoin Checking Account Revolution Traditional checking accounts are permission-based systems where banks maintain ultimate control over your money. In contrast, a sovereign Bitcoin checking account operates on a fundamentally different principle: you hold your own keys, control your own node, and maintain custody of your funds at all times. This architecture is built on several key components: - Self-hosted nodes providing direct network access - Lightning channels for instant settlement - Hardware wallets for secure key storage - Non-custodial software interfaces - Automated accounting and payment systems The concept of a Bitcoin checking account represents a paradigm shift in daily financial operations. Imagine getting a direct deposit sent to your lightning node and using NWC and a variety of plug and play solutions to handle things regarding accounting, bill pay, and daily POS transactions. We're starting to see these options emerge through services like Bitcoin Well, Albyhub, Strike, Clams and Cash App. ## Breaking Free from Financial Surveillance The current banking system tracks every transaction, creating a detailed financial surveillance network. Sovereign Bitcoin checking accounts offer a powerful alternative: - Private lightning channels for daily transactions - E-cash protocols for enhanced privacy - Peer-to-peer transactions without intermediaries - No account freezes or arbitrary limits - Freedom from traditional banking hours and restrictions Lightning and Cashu offer additional privacy and settlement speeds while enabling low cost transactions, and I believe these protocols will grow and exceed our expectations. The products and services for managing your bitcoin checking account will get more private and efficient as time moves forward. ## The Daily Operations Revolution Operating a sovereign checking account transforms everyday financial activities: 1. Income Reception - Direct deposit straight to Lightning - Instant availability of funds - No hold periods or bank delays - Multiple invoice routes for different income streams 2. Payment Management - Automated bill payments via Lightning - Instant merchant settlements - Cross-border transactions without fees - Dynamic fee management for optimal efficiency 3. Liquidity Control - Self-managed channel balances - Cold storage integration for savings - Automated rebalancing protocols - Real-time capital efficiency ## The Deflationary Advantage Perhaps the most revolutionary aspect is operating a checking account in deflationary money. This fundamentally changes spending psychology and financial planning: - Each sat potentially appreciates over time - Natural incentive for thoughtful spending - Built-in savings mechanism - Protection from currency debasement ## Global Market Integration This new financial infrastructure enables seamless participation in the global economy: - Borderless transactions - 24/7 market access - Direct international trade - No forex fees or exchange rate manipulation - Instant settlement across time zones ## Security and Resilience The system's security model represents a significant advancement: - Multi-signature protocols - Timelocked recovery options - Distributed backup systems - Attack-resistant architecture - No single points of failure ## The Future of Personal Banking As this technology matures, we're likely to see: - Simplified user interfaces - Enhanced privacy tools - Better integration with existing systems - More automated financial management - Increased merchant adoption In conclusion, sovereign Bitcoin checking accounts represent more than just a new way to bank—they're a fundamental reset of the relationship between individuals and their money. This system combines the security of cold storage with the utility of traditional checking accounts, all while leveraging the strength of deflationary sound money. As adoption grows, these accounts will likely become the standard for those seeking financial sovereignty in an increasingly digital world. --- The revolution isn't just about holding bitcoin—it's about using it in a way that maintains sovereignty while enabling practical daily finance. This is the future of money, and it's already here for those ready to embrace it.
@ 30ceb64e:7f08bdf5
2025-01-08 20:14:45In a world dominated by surveillance banking and inflationary currencies, a new paradigm is emerging—one where individuals can operate sovereign, theft-resistant checking accounts using the world's hardest money. This isn't your grandfather's checking account; it's an entirely new financial operating system built on Bitcoin and Lightning technology. --- ## The Bitcoin Checking Account Revolution Traditional checking accounts are permission-based systems where banks maintain ultimate control over your money. In contrast, a sovereign Bitcoin checking account operates on a fundamentally different principle: you hold your own keys, control your own node, and maintain custody of your funds at all times. This architecture is built on several key components: - Self-hosted nodes providing direct network access - Lightning channels for instant settlement - Hardware wallets for secure key storage - Non-custodial software interfaces - Automated accounting and payment systems The concept of a Bitcoin checking account represents a paradigm shift in daily financial operations. Imagine getting a direct deposit sent to your lightning node and using NWC and a variety of plug and play solutions to handle things regarding accounting, bill pay, and daily POS transactions. We're starting to see these options emerge through services like Bitcoin Well, Albyhub, Strike, Clams and Cash App. ## Breaking Free from Financial Surveillance The current banking system tracks every transaction, creating a detailed financial surveillance network. Sovereign Bitcoin checking accounts offer a powerful alternative: - Private lightning channels for daily transactions - E-cash protocols for enhanced privacy - Peer-to-peer transactions without intermediaries - No account freezes or arbitrary limits - Freedom from traditional banking hours and restrictions Lightning and Cashu offer additional privacy and settlement speeds while enabling low cost transactions, and I believe these protocols will grow and exceed our expectations. The products and services for managing your bitcoin checking account will get more private and efficient as time moves forward. ## The Daily Operations Revolution Operating a sovereign checking account transforms everyday financial activities: 1. Income Reception - Direct deposit straight to Lightning - Instant availability of funds - No hold periods or bank delays - Multiple invoice routes for different income streams 2. Payment Management - Automated bill payments via Lightning - Instant merchant settlements - Cross-border transactions without fees - Dynamic fee management for optimal efficiency 3. Liquidity Control - Self-managed channel balances - Cold storage integration for savings - Automated rebalancing protocols - Real-time capital efficiency ## The Deflationary Advantage Perhaps the most revolutionary aspect is operating a checking account in deflationary money. This fundamentally changes spending psychology and financial planning: - Each sat potentially appreciates over time - Natural incentive for thoughtful spending - Built-in savings mechanism - Protection from currency debasement ## Global Market Integration This new financial infrastructure enables seamless participation in the global economy: - Borderless transactions - 24/7 market access - Direct international trade - No forex fees or exchange rate manipulation - Instant settlement across time zones ## Security and Resilience The system's security model represents a significant advancement: - Multi-signature protocols - Timelocked recovery options - Distributed backup systems - Attack-resistant architecture - No single points of failure ## The Future of Personal Banking As this technology matures, we're likely to see: - Simplified user interfaces - Enhanced privacy tools - Better integration with existing systems - More automated financial management - Increased merchant adoption In conclusion, sovereign Bitcoin checking accounts represent more than just a new way to bank—they're a fundamental reset of the relationship between individuals and their money. This system combines the security of cold storage with the utility of traditional checking accounts, all while leveraging the strength of deflationary sound money. As adoption grows, these accounts will likely become the standard for those seeking financial sovereignty in an increasingly digital world. --- The revolution isn't just about holding bitcoin—it's about using it in a way that maintains sovereignty while enabling practical daily finance. This is the future of money, and it's already here for those ready to embrace it. @ bcea2b98:7ccef3c9
2025-01-08 18:22:00 originally posted at https://stacker.news/items/842405
@ bcea2b98:7ccef3c9
2025-01-08 18:22:00 originally posted at https://stacker.news/items/842405 @ 23b0e2f8:d8af76fc
2025-01-08 18:17:52## **Necessário** - Um Android que você não use mais (a câmera deve estar funcionando). - Um cartão microSD (opcional, usado apenas uma vez). - Um dispositivo para acompanhar seus fundos (provavelmente você já tem um). ## **Algumas coisas que você precisa saber** - O dispositivo servirá como um assinador. Qualquer movimentação só será efetuada após ser assinada por ele. - O cartão microSD será usado para transferir o APK do Electrum e garantir que o aparelho não terá contato com outras fontes de dados externas após sua formatação. Contudo, é possível usar um cabo USB para o mesmo propósito. - A ideia é deixar sua chave privada em um dispositivo offline, que ficará desligado em 99% do tempo. Você poderá acompanhar seus fundos em outro dispositivo conectado à internet, como seu celular ou computador pessoal. --- ## **O tutorial será dividido em dois módulos:** - Módulo 1 - Criando uma carteira fria/assinador. - Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador. --- ## **No final, teremos:** - Uma carteira fria que também servirá como assinador. - Um dispositivo para acompanhar os fundos da carteira.  --- ## **Módulo 1 - Criando uma carteira fria/assinador** 1. Baixe o APK do Electrum na aba de **downloads** em <https://electrum.org/>. Fique à vontade para [verificar as assinaturas](https://electrum.readthedocs.io/en/latest/gpg-check.html) do software, garantindo sua autenticidade. 2. Formate o cartão microSD e coloque o APK do Electrum nele. Caso não tenha um cartão microSD, pule este passo.  3. Retire os chips e acessórios do aparelho que será usado como assinador, formate-o e aguarde a inicialização.  4. Durante a inicialização, pule a etapa de conexão ao Wi-Fi e rejeite todas as solicitações de conexão. Após isso, você pode desinstalar aplicativos desnecessários, pois precisará apenas do Electrum. Certifique-se de que Wi-Fi, Bluetooth e dados móveis estejam desligados. Você também pode ativar o **modo avião**.\ *(Curiosidade: algumas pessoas optam por abrir o aparelho e danificar a antena do Wi-Fi/Bluetooth, impossibilitando essas funcionalidades.)*  5. Insira o cartão microSD com o APK do Electrum no dispositivo e instale-o. Será necessário permitir instalações de fontes não oficiais.  6. No Electrum, crie uma carteira padrão e gere suas palavras-chave (seed). Anote-as em um local seguro. Caso algo aconteça com seu assinador, essas palavras permitirão o acesso aos seus fundos novamente. *(Aqui entra seu método pessoal de backup.)*  --- ## **Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador.** 1. Criar uma carteira **somente leitura** em outro dispositivo, como seu celular ou computador pessoal, é uma etapa bastante simples. Para este tutorial, usaremos outro smartphone Android com Electrum. Instale o Electrum a partir da aba de downloads em <https://electrum.org/> ou da própria Play Store. *(ATENÇÃO: O Electrum não existe oficialmente para iPhone. Desconfie se encontrar algum.)* 2. Após instalar o Electrum, crie uma carteira padrão, mas desta vez escolha a opção **Usar uma chave mestra**.  3. Agora, no assinador que criamos no primeiro módulo, exporte sua chave pública: vá em **Carteira > Detalhes da carteira > Compartilhar chave mestra pública**.  4. Escaneie o QR gerado da chave pública com o dispositivo de consulta. Assim, ele poderá acompanhar seus fundos, mas sem permissão para movimentá-los. 5. Para receber fundos, envie Bitcoin para um dos endereços gerados pela sua carteira: **Carteira > Addresses/Coins**. 6. Para movimentar fundos, crie uma transação no dispositivo de consulta. Como ele não possui a chave privada, será necessário assiná-la com o dispositivo assinador.  7. No assinador, escaneie a transação não assinada, confirme os detalhes, assine e compartilhe. Será gerado outro QR, desta vez com a transação já assinada.  8. No dispositivo de consulta, escaneie o QR da transação assinada e transmita-a para a rede. --- ## **Conclusão** **Pontos positivos do setup:** - **Simplicidade:** Basta um dispositivo Android antigo. - **Flexibilidade:** Funciona como uma ótima carteira fria, ideal para holders. **Pontos negativos do setup:** - **Padronização:** Não utiliza seeds no padrão BIP-39, você sempre precisará usar o electrum. - **Interface:** A aparência do Electrum pode parecer antiquada para alguns usuários. Nesse ponto, temos uma carteira fria que também serve para assinar transações. O fluxo de assinar uma transação se torna: ***Gerar uma transação não assinada > Escanear o QR da transação não assinada > Conferir e assinar essa transação com o assinador > Gerar QR da transação assinada > Escanear a transação assinada com qualquer outro dispositivo que possa transmiti-la para a rede.*** Como alguns devem saber, uma transação assinada de Bitcoin é praticamente impossível de ser fraudada. Em um cenário catastrófico, você pode mesmo que sem internet, repassar essa transação assinada para alguém que tenha acesso à rede por qualquer meio de comunicação. Mesmo que não queiramos que isso aconteça um dia, esse setup acaba por tornar essa prática possível. ---
@ 23b0e2f8:d8af76fc
2025-01-08 18:17:52## **Necessário** - Um Android que você não use mais (a câmera deve estar funcionando). - Um cartão microSD (opcional, usado apenas uma vez). - Um dispositivo para acompanhar seus fundos (provavelmente você já tem um). ## **Algumas coisas que você precisa saber** - O dispositivo servirá como um assinador. Qualquer movimentação só será efetuada após ser assinada por ele. - O cartão microSD será usado para transferir o APK do Electrum e garantir que o aparelho não terá contato com outras fontes de dados externas após sua formatação. Contudo, é possível usar um cabo USB para o mesmo propósito. - A ideia é deixar sua chave privada em um dispositivo offline, que ficará desligado em 99% do tempo. Você poderá acompanhar seus fundos em outro dispositivo conectado à internet, como seu celular ou computador pessoal. --- ## **O tutorial será dividido em dois módulos:** - Módulo 1 - Criando uma carteira fria/assinador. - Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador. --- ## **No final, teremos:** - Uma carteira fria que também servirá como assinador. - Um dispositivo para acompanhar os fundos da carteira.  --- ## **Módulo 1 - Criando uma carteira fria/assinador** 1. Baixe o APK do Electrum na aba de **downloads** em <https://electrum.org/>. Fique à vontade para [verificar as assinaturas](https://electrum.readthedocs.io/en/latest/gpg-check.html) do software, garantindo sua autenticidade. 2. Formate o cartão microSD e coloque o APK do Electrum nele. Caso não tenha um cartão microSD, pule este passo.  3. Retire os chips e acessórios do aparelho que será usado como assinador, formate-o e aguarde a inicialização.  4. Durante a inicialização, pule a etapa de conexão ao Wi-Fi e rejeite todas as solicitações de conexão. Após isso, você pode desinstalar aplicativos desnecessários, pois precisará apenas do Electrum. Certifique-se de que Wi-Fi, Bluetooth e dados móveis estejam desligados. Você também pode ativar o **modo avião**.\ *(Curiosidade: algumas pessoas optam por abrir o aparelho e danificar a antena do Wi-Fi/Bluetooth, impossibilitando essas funcionalidades.)*  5. Insira o cartão microSD com o APK do Electrum no dispositivo e instale-o. Será necessário permitir instalações de fontes não oficiais.  6. No Electrum, crie uma carteira padrão e gere suas palavras-chave (seed). Anote-as em um local seguro. Caso algo aconteça com seu assinador, essas palavras permitirão o acesso aos seus fundos novamente. *(Aqui entra seu método pessoal de backup.)*  --- ## **Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador.** 1. Criar uma carteira **somente leitura** em outro dispositivo, como seu celular ou computador pessoal, é uma etapa bastante simples. Para este tutorial, usaremos outro smartphone Android com Electrum. Instale o Electrum a partir da aba de downloads em <https://electrum.org/> ou da própria Play Store. *(ATENÇÃO: O Electrum não existe oficialmente para iPhone. Desconfie se encontrar algum.)* 2. Após instalar o Electrum, crie uma carteira padrão, mas desta vez escolha a opção **Usar uma chave mestra**.  3. Agora, no assinador que criamos no primeiro módulo, exporte sua chave pública: vá em **Carteira > Detalhes da carteira > Compartilhar chave mestra pública**.  4. Escaneie o QR gerado da chave pública com o dispositivo de consulta. Assim, ele poderá acompanhar seus fundos, mas sem permissão para movimentá-los. 5. Para receber fundos, envie Bitcoin para um dos endereços gerados pela sua carteira: **Carteira > Addresses/Coins**. 6. Para movimentar fundos, crie uma transação no dispositivo de consulta. Como ele não possui a chave privada, será necessário assiná-la com o dispositivo assinador.  7. No assinador, escaneie a transação não assinada, confirme os detalhes, assine e compartilhe. Será gerado outro QR, desta vez com a transação já assinada.  8. No dispositivo de consulta, escaneie o QR da transação assinada e transmita-a para a rede. --- ## **Conclusão** **Pontos positivos do setup:** - **Simplicidade:** Basta um dispositivo Android antigo. - **Flexibilidade:** Funciona como uma ótima carteira fria, ideal para holders. **Pontos negativos do setup:** - **Padronização:** Não utiliza seeds no padrão BIP-39, você sempre precisará usar o electrum. - **Interface:** A aparência do Electrum pode parecer antiquada para alguns usuários. Nesse ponto, temos uma carteira fria que também serve para assinar transações. O fluxo de assinar uma transação se torna: ***Gerar uma transação não assinada > Escanear o QR da transação não assinada > Conferir e assinar essa transação com o assinador > Gerar QR da transação assinada > Escanear a transação assinada com qualquer outro dispositivo que possa transmiti-la para a rede.*** Como alguns devem saber, uma transação assinada de Bitcoin é praticamente impossível de ser fraudada. Em um cenário catastrófico, você pode mesmo que sem internet, repassar essa transação assinada para alguém que tenha acesso à rede por qualquer meio de comunicação. Mesmo que não queiramos que isso aconteça um dia, esse setup acaba por tornar essa prática possível. --- @ 207ad2a0:e7cca7b0
2025-01-07 03:46:04*Quick context: I wanted to check out Nostr's longform posts and this blog post seemed like a good one to try and mirror. It's originally from my [free to read/share attempt to write a novel](https://untitlednovel.dns7.top/contents/), but this post here is completely standalone - just describing how I used AI image generation to make a small piece of the work.* Hold on, put your pitchforks down - outside of using Grammerly & Emacs for grammatical corrections - not a single character was generated or modified by computers; a non-insignificant portion of my first draft originating on pen & paper. No AI is ~~weird and crazy~~ imaginative enough to write like I do. The only successful AI contribution you'll find is a single image, the map, which I heavily edited. This post will go over how I generated and modified an image using AI, which I believe brought some value to the work, and cover a few quick thoughts about AI towards the end. Let's be clear, I can't draw, but I wanted a map which I believed would improve the story I was working on. After getting abysmal results by prompting AI with text only I decided to use "Diffuse the Rest," a Stable Diffusion tool that allows you to provide a reference image + description to fine tune what you're looking for. I gave it this Microsoft Paint looking drawing:  and after a number of outputs, selected this one to work on:  The image is way better than the one I provided, but had I used it as is, I still feel it would have decreased the quality of my work instead of increasing it. After firing up Gimp I cropped out the top and bottom, expanded the ocean and separated the landmasses, then copied the top right corner of the large landmass to replace the bottom left that got cut off. Now we've got something that looks like concept art: not horrible, and gets the basic idea across, but it's still due for a lot more detail.  The next thing I did was add some texture to make it look more map like. I duplicated the layer in Gimp and applied the "Cartoon" filter to both for some texture. The top layer had a much lower effect strength to give it a more textured look, while the lower layer had a higher effect strength that looked a lot like mountains or other terrain features. Creating a layer mask allowed me to brush over spots to display the lower layer in certain areas, giving it some much needed features.  At this point I'd made it to where I felt it may improve the work instead of detracting from it - at least after labels and borders were added, but the colors seemed artificial and out of place. Luckily, however, this is when PhotoFunia could step in and apply a sketch effect to the image.  At this point I was pretty happy with how it was looking, it was close to what I envisioned and looked very visually appealing while still being a good way to portray information. All that was left was to make the white background transparent, add some minor details, and add the labels and borders. Below is the exact image I wound up using:  Overall, I'm very satisfied with how it turned out, and if you're working on a creative project, I'd recommend attempting something like this. It's not a central part of the work, but it improved the chapter a fair bit, and was doable despite lacking the talent and not intending to allocate a budget to my making of a free to read and share story. #### The AI Generated Elephant in the Room If you've read my non-fiction writing before, you'll know that I think AI will find its place around the skill floor as opposed to the skill ceiling. As you saw with my input, I have absolutely zero drawing talent, but with some elbow grease and an existing creative direction before and after generating an image I was able to get something well above what I could have otherwise accomplished. Outside of the lowest common denominators like stock photos for the sole purpose of a link preview being eye catching, however, I doubt AI will be wholesale replacing most creative works anytime soon. I can assure you that I tried numerous times to describe the map without providing a reference image, and if I used one of those outputs (or even just the unedited output after providing the reference image) it would have decreased the quality of my work instead of improving it. I'm going to go out on a limb and expect that AI image, text, and video is all going to find its place in slop & generic content (such as AI generated slop replacing article spinners and stock photos respectively) and otherwise be used in a supporting role for various creative endeavors. For people working on projects like I'm working on (e.g. intended budget $0) it's helpful to have an AI capable of doing legwork - enabling projects to exist or be improved in ways they otherwise wouldn't have. I'm also guessing it'll find its way into more professional settings for grunt work - think a picture frame or fake TV show that would exist in the background of an animated project - likely a detail most people probably wouldn't notice, but that would save the creators time and money and/or allow them to focus more on the essential aspects of said work. Beyond that, as I've predicted before: I expect plenty of emails will be generated from a short list of bullet points, only to be summarized by the recipient's AI back into bullet points. I will also make a prediction counter to what seems mainstream: AI is about to peak for a while. The start of AI image generation was with Google's DeepDream in 2015 - image recognition software that could be run in reverse to "recognize" patterns where there were none, effectively generating an image from digital noise or an unrelated image. While I'm not an expert by any means, I don't think we're too far off from that a decade later, just using very fine tuned tools that develop more coherent images. I guess that we're close to maxing out how efficiently we're able to generate images and video in that manner, and the hard caps on how much creative direction we can have when using AI - as well as the limits to how long we can keep it coherent (e.g. long videos or a chronologically consistent set of images) - will prevent AI from progressing too far beyond what it is currently unless/until another breakthrough occurs.
@ 207ad2a0:e7cca7b0
2025-01-07 03:46:04*Quick context: I wanted to check out Nostr's longform posts and this blog post seemed like a good one to try and mirror. It's originally from my [free to read/share attempt to write a novel](https://untitlednovel.dns7.top/contents/), but this post here is completely standalone - just describing how I used AI image generation to make a small piece of the work.* Hold on, put your pitchforks down - outside of using Grammerly & Emacs for grammatical corrections - not a single character was generated or modified by computers; a non-insignificant portion of my first draft originating on pen & paper. No AI is ~~weird and crazy~~ imaginative enough to write like I do. The only successful AI contribution you'll find is a single image, the map, which I heavily edited. This post will go over how I generated and modified an image using AI, which I believe brought some value to the work, and cover a few quick thoughts about AI towards the end. Let's be clear, I can't draw, but I wanted a map which I believed would improve the story I was working on. After getting abysmal results by prompting AI with text only I decided to use "Diffuse the Rest," a Stable Diffusion tool that allows you to provide a reference image + description to fine tune what you're looking for. I gave it this Microsoft Paint looking drawing:  and after a number of outputs, selected this one to work on:  The image is way better than the one I provided, but had I used it as is, I still feel it would have decreased the quality of my work instead of increasing it. After firing up Gimp I cropped out the top and bottom, expanded the ocean and separated the landmasses, then copied the top right corner of the large landmass to replace the bottom left that got cut off. Now we've got something that looks like concept art: not horrible, and gets the basic idea across, but it's still due for a lot more detail.  The next thing I did was add some texture to make it look more map like. I duplicated the layer in Gimp and applied the "Cartoon" filter to both for some texture. The top layer had a much lower effect strength to give it a more textured look, while the lower layer had a higher effect strength that looked a lot like mountains or other terrain features. Creating a layer mask allowed me to brush over spots to display the lower layer in certain areas, giving it some much needed features.  At this point I'd made it to where I felt it may improve the work instead of detracting from it - at least after labels and borders were added, but the colors seemed artificial and out of place. Luckily, however, this is when PhotoFunia could step in and apply a sketch effect to the image.  At this point I was pretty happy with how it was looking, it was close to what I envisioned and looked very visually appealing while still being a good way to portray information. All that was left was to make the white background transparent, add some minor details, and add the labels and borders. Below is the exact image I wound up using:  Overall, I'm very satisfied with how it turned out, and if you're working on a creative project, I'd recommend attempting something like this. It's not a central part of the work, but it improved the chapter a fair bit, and was doable despite lacking the talent and not intending to allocate a budget to my making of a free to read and share story. #### The AI Generated Elephant in the Room If you've read my non-fiction writing before, you'll know that I think AI will find its place around the skill floor as opposed to the skill ceiling. As you saw with my input, I have absolutely zero drawing talent, but with some elbow grease and an existing creative direction before and after generating an image I was able to get something well above what I could have otherwise accomplished. Outside of the lowest common denominators like stock photos for the sole purpose of a link preview being eye catching, however, I doubt AI will be wholesale replacing most creative works anytime soon. I can assure you that I tried numerous times to describe the map without providing a reference image, and if I used one of those outputs (or even just the unedited output after providing the reference image) it would have decreased the quality of my work instead of improving it. I'm going to go out on a limb and expect that AI image, text, and video is all going to find its place in slop & generic content (such as AI generated slop replacing article spinners and stock photos respectively) and otherwise be used in a supporting role for various creative endeavors. For people working on projects like I'm working on (e.g. intended budget $0) it's helpful to have an AI capable of doing legwork - enabling projects to exist or be improved in ways they otherwise wouldn't have. I'm also guessing it'll find its way into more professional settings for grunt work - think a picture frame or fake TV show that would exist in the background of an animated project - likely a detail most people probably wouldn't notice, but that would save the creators time and money and/or allow them to focus more on the essential aspects of said work. Beyond that, as I've predicted before: I expect plenty of emails will be generated from a short list of bullet points, only to be summarized by the recipient's AI back into bullet points. I will also make a prediction counter to what seems mainstream: AI is about to peak for a while. The start of AI image generation was with Google's DeepDream in 2015 - image recognition software that could be run in reverse to "recognize" patterns where there were none, effectively generating an image from digital noise or an unrelated image. While I'm not an expert by any means, I don't think we're too far off from that a decade later, just using very fine tuned tools that develop more coherent images. I guess that we're close to maxing out how efficiently we're able to generate images and video in that manner, and the hard caps on how much creative direction we can have when using AI - as well as the limits to how long we can keep it coherent (e.g. long videos or a chronologically consistent set of images) - will prevent AI from progressing too far beyond what it is currently unless/until another breakthrough occurs. @ 378562cd:a6fc6773
2025-01-06 19:57:44In our hyper-connected world, we are constantly bombarded with information — news of tragedies, celebrity gossip, and societal controversies — all delivered to us in real-time, whether we ask for it or not. **But here’s a profound truth: If you don’t know about it, it doesn’t matter to you. It’s almost like it doesn’t even happen!** This isn’t about apathy or ignoring the suffering of others. It’s about recognizing that our minds and hearts have limits. There’s only so much we can hold, care for, or act upon before it all becomes noise. And when we step back and filter out what truly matters to us, we find a liberating sense of peace. In our hyper-connected world, we are constantly bombarded with information — news of tragedies, celebrity gossip, and societal controversies — all delivered to us in real-time, whether we ask for it or not. # **When Knowing is a Burden** Consider this: if a bus full of strangers tragically ran off a cliff halfway around the world, it’s undeniably sad. But if you never heard about it, would it affect your day, your thoughts, or your actions? It wouldn’t. Not because you’re heartless but because it’s not within your sphere of influence or awareness. Similarly, when a celebrity you barely know goes through a messy divorce, why does that need to occupy your thoughts? If you never knew about it, it would make no difference in your life. And yet, the world shouts these details at us, demanding our attention for things that often have no real bearing on our existence. # **The Cost of Knowing Too Much** Knowing everything that happens everywhere comes with a cost: - **Emotional Overload**\ The human mind isn’t designed to process the pain, suffering, or drama of millions of people at once. Constant exposure to these stories can lead to anxiety, sadness, or even a sense of helplessness. - **Loss of Focus**\ The more attention we give to distant events or irrelevant gossip, the less energy we have for the people and moments that truly matter in our own lives. - **Manufactured Cravings**\ Advertisements and media feed us desires we didn’t have before. A new product, a luxurious vacation, or a perfect lifestyle — all things you might not have craved if you hadn’t been shown them. # **The Beauty of Not Knowing** When you step away from the constant influx of information, you create space to focus on what’s real and meaningful in your life. - **Your family and close friends.** Their joys and struggles are the ones you can genuinely care about and impact. - **Your passions and goals.** These deserve your full attention, free from unnecessary distractions. - **Your mental peace.** Without the noise, you can think clearly, feel deeply, and live authentically. # **What Truly Matters?** Not knowing isn’t about closing your eyes to the world. It’s about understanding the difference between what’s important and what’s irrelevant. It’s a practice of asking yourself: - Does this affect me or the people I love? - Can I do anything meaningful about this? - Will knowing this bring me peace, joy, or purpose? - Will BUYING this bring me peace, joy or purpose? If the answer is no, it’s okay to let it go. # **Living in Your Sphere of Influence** Focusing on what you can control and care for has immense power. Your energy has the most impact in your sphere of influence—the people, places, and things you interact with directly. By letting go of what lies outside that sphere, you free yourself from unnecessary burdens and find deeper joy in the things that truly matter. # **A New Year’s Challenge** This year, challenge yourself to embrace the art of *not knowing.* - **Curate your inputs:** Limit news consumption to what directly affects you. - **Mute the noise:** Avoid gossip, sensational headlines, and irrelevant drama. - **Stay present:** Focus on the people and moments around you. In doing so, you’ll find not only peace but also the clarity to live a life driven by your own values and priorities — not the ever-changing noise of the world. # **The Freedom of Letting Go** When you embrace the profound truth that *if you don’t know about it, it doesn’t matter to you,* you unlock a freedom that few ever experience. You stop carrying the weight of the world’s chaos and instead focus on the beauty, joy, and love within your own life. This year, let’s make peace with not knowing — and in doing so, rediscover what truly matters. # **Breaking Free from the Cycle of Consumerism** Consumerism isn’t just about buying things — it’s about the constant hunger for more. More stuff, more information, more experiences. It thrives on the idea that what you have and who you are isn’t enough, and it manipulates you into believing that fulfillment lies just one purchase or experience away. But here’s the truth: the cycle of consumerism isn’t designed to fulfill you — it’s designed to keep you chasing. If we want to find peace with not knowing, we must also confront the role consumerism plays in feeding our dissatisfaction and overstimulation. # **The Problem with Consumerism** Consumerism is fueled by two main forces: - **Artificial Wants:** Advertising and media don’t just sell products; they sell dissatisfaction. They show you a life that seems better than yours and make you believe that buying their product will bridge the gap. - **Overexposure:** The constant influx of social media, news, and targeted ads ensures you’re always aware of what you *don’t* have, subtly making you feel inadequate or left out. - The result? A world where happiness feels like it’s always just out of reach — an exhausting race that benefits corporations far more than individuals. # **The Cost of Consumerism** The cycle of consumerism doesn’t just drain your wallet; it also takes a toll on your mental, emotional, and spiritual well-being: - **Mental Overload:** Constant exposure to new products and ideas creates decision fatigue and anxiety. - **Emotional Burnout:** Comparing your life to idealized versions portrayed in ads or social media can lead to dissatisfaction and low self-esteem. - **Spiritual Disconnect:** Consumerism shifts your focus away from meaningful relationships, personal growth, and spiritual fulfillment, tethering your joy to material possessions. # **Combatting Consumerism: A Game Plan for Freedom** Breaking free from consumerism requires intentional effort, but it’s deeply rewarding. Here’s a game plan to start: ## **1. Detox Your Inputs** - **Unfollow Excess:** Reduce your exposure to ads and influencers who push a lifestyle of constant consumption. - **Limit Social Media:** Spend less time scrolling through content designed to spark envy or desire. - **Set Boundaries:** Avoid shopping as a pastime or browsing “just to look.” ## **2. Shift Your Mindset** - **Practice Gratitude:** Focus on what you already have, not what you lack. - **Redefine Success:** Measure your life by relationships, growth, and experiences, not possessions. - **Adopt Minimalism:** Learn to appreciate simplicity and find joy in having less. ## **3. Choose Quality Over Quantity** - **Invest in Essentials:** Buy fewer items, but prioritize durability and quality. - **Focus on Experiences:** Spend on memories, not material things. - **Be Mindful of Upgrades:** Don’t replace what’s working fine just because something new is available. ## **4. Build Intentional Habits** - **Wait Before Buying:** Give yourself 24 hours to think before making any purchase. - **Create a Wishlist:** Write down non-essential items you want. Review the list monthly to see if you still want them. - **Track Spending:** Be aware of where your money goes, and prioritize needs over wants. ## **5. Engage with Your Community** - **Support Local:** Choose local businesses and artisans over big corporations. - **Focus on Relationships:** Invest time in people, not possessions. - **Participate in Sharing Economies:** Borrow, lend, and swap items with neighbors or friends instead of buying. # **Living a Life of Intentional Simplicity** This is food for thought and I promise you it is a battle at this point. It will be difficult but you must gain back control of your own thoughts, desires etc… Take care and God bless!
@ 378562cd:a6fc6773
2025-01-06 19:57:44In our hyper-connected world, we are constantly bombarded with information — news of tragedies, celebrity gossip, and societal controversies — all delivered to us in real-time, whether we ask for it or not. **But here’s a profound truth: If you don’t know about it, it doesn’t matter to you. It’s almost like it doesn’t even happen!** This isn’t about apathy or ignoring the suffering of others. It’s about recognizing that our minds and hearts have limits. There’s only so much we can hold, care for, or act upon before it all becomes noise. And when we step back and filter out what truly matters to us, we find a liberating sense of peace. In our hyper-connected world, we are constantly bombarded with information — news of tragedies, celebrity gossip, and societal controversies — all delivered to us in real-time, whether we ask for it or not. # **When Knowing is a Burden** Consider this: if a bus full of strangers tragically ran off a cliff halfway around the world, it’s undeniably sad. But if you never heard about it, would it affect your day, your thoughts, or your actions? It wouldn’t. Not because you’re heartless but because it’s not within your sphere of influence or awareness. Similarly, when a celebrity you barely know goes through a messy divorce, why does that need to occupy your thoughts? If you never knew about it, it would make no difference in your life. And yet, the world shouts these details at us, demanding our attention for things that often have no real bearing on our existence. # **The Cost of Knowing Too Much** Knowing everything that happens everywhere comes with a cost: - **Emotional Overload**\ The human mind isn’t designed to process the pain, suffering, or drama of millions of people at once. Constant exposure to these stories can lead to anxiety, sadness, or even a sense of helplessness. - **Loss of Focus**\ The more attention we give to distant events or irrelevant gossip, the less energy we have for the people and moments that truly matter in our own lives. - **Manufactured Cravings**\ Advertisements and media feed us desires we didn’t have before. A new product, a luxurious vacation, or a perfect lifestyle — all things you might not have craved if you hadn’t been shown them. # **The Beauty of Not Knowing** When you step away from the constant influx of information, you create space to focus on what’s real and meaningful in your life. - **Your family and close friends.** Their joys and struggles are the ones you can genuinely care about and impact. - **Your passions and goals.** These deserve your full attention, free from unnecessary distractions. - **Your mental peace.** Without the noise, you can think clearly, feel deeply, and live authentically. # **What Truly Matters?** Not knowing isn’t about closing your eyes to the world. It’s about understanding the difference between what’s important and what’s irrelevant. It’s a practice of asking yourself: - Does this affect me or the people I love? - Can I do anything meaningful about this? - Will knowing this bring me peace, joy, or purpose? - Will BUYING this bring me peace, joy or purpose? If the answer is no, it’s okay to let it go. # **Living in Your Sphere of Influence** Focusing on what you can control and care for has immense power. Your energy has the most impact in your sphere of influence—the people, places, and things you interact with directly. By letting go of what lies outside that sphere, you free yourself from unnecessary burdens and find deeper joy in the things that truly matter. # **A New Year’s Challenge** This year, challenge yourself to embrace the art of *not knowing.* - **Curate your inputs:** Limit news consumption to what directly affects you. - **Mute the noise:** Avoid gossip, sensational headlines, and irrelevant drama. - **Stay present:** Focus on the people and moments around you. In doing so, you’ll find not only peace but also the clarity to live a life driven by your own values and priorities — not the ever-changing noise of the world. # **The Freedom of Letting Go** When you embrace the profound truth that *if you don’t know about it, it doesn’t matter to you,* you unlock a freedom that few ever experience. You stop carrying the weight of the world’s chaos and instead focus on the beauty, joy, and love within your own life. This year, let’s make peace with not knowing — and in doing so, rediscover what truly matters. # **Breaking Free from the Cycle of Consumerism** Consumerism isn’t just about buying things — it’s about the constant hunger for more. More stuff, more information, more experiences. It thrives on the idea that what you have and who you are isn’t enough, and it manipulates you into believing that fulfillment lies just one purchase or experience away. But here’s the truth: the cycle of consumerism isn’t designed to fulfill you — it’s designed to keep you chasing. If we want to find peace with not knowing, we must also confront the role consumerism plays in feeding our dissatisfaction and overstimulation. # **The Problem with Consumerism** Consumerism is fueled by two main forces: - **Artificial Wants:** Advertising and media don’t just sell products; they sell dissatisfaction. They show you a life that seems better than yours and make you believe that buying their product will bridge the gap. - **Overexposure:** The constant influx of social media, news, and targeted ads ensures you’re always aware of what you *don’t* have, subtly making you feel inadequate or left out. - The result? A world where happiness feels like it’s always just out of reach — an exhausting race that benefits corporations far more than individuals. # **The Cost of Consumerism** The cycle of consumerism doesn’t just drain your wallet; it also takes a toll on your mental, emotional, and spiritual well-being: - **Mental Overload:** Constant exposure to new products and ideas creates decision fatigue and anxiety. - **Emotional Burnout:** Comparing your life to idealized versions portrayed in ads or social media can lead to dissatisfaction and low self-esteem. - **Spiritual Disconnect:** Consumerism shifts your focus away from meaningful relationships, personal growth, and spiritual fulfillment, tethering your joy to material possessions. # **Combatting Consumerism: A Game Plan for Freedom** Breaking free from consumerism requires intentional effort, but it’s deeply rewarding. Here’s a game plan to start: ## **1. Detox Your Inputs** - **Unfollow Excess:** Reduce your exposure to ads and influencers who push a lifestyle of constant consumption. - **Limit Social Media:** Spend less time scrolling through content designed to spark envy or desire. - **Set Boundaries:** Avoid shopping as a pastime or browsing “just to look.” ## **2. Shift Your Mindset** - **Practice Gratitude:** Focus on what you already have, not what you lack. - **Redefine Success:** Measure your life by relationships, growth, and experiences, not possessions. - **Adopt Minimalism:** Learn to appreciate simplicity and find joy in having less. ## **3. Choose Quality Over Quantity** - **Invest in Essentials:** Buy fewer items, but prioritize durability and quality. - **Focus on Experiences:** Spend on memories, not material things. - **Be Mindful of Upgrades:** Don’t replace what’s working fine just because something new is available. ## **4. Build Intentional Habits** - **Wait Before Buying:** Give yourself 24 hours to think before making any purchase. - **Create a Wishlist:** Write down non-essential items you want. Review the list monthly to see if you still want them. - **Track Spending:** Be aware of where your money goes, and prioritize needs over wants. ## **5. Engage with Your Community** - **Support Local:** Choose local businesses and artisans over big corporations. - **Focus on Relationships:** Invest time in people, not possessions. - **Participate in Sharing Economies:** Borrow, lend, and swap items with neighbors or friends instead of buying. # **Living a Life of Intentional Simplicity** This is food for thought and I promise you it is a battle at this point. It will be difficult but you must gain back control of your own thoughts, desires etc… Take care and God bless! @ 3f770d65:7a745b24
2025-01-05 18:56:33New Year’s resolutions often feel boring and repetitive. Most revolve around getting in shape, eating healthier, or giving up alcohol. While the idea is interesting—using the start of a new calendar year as a catalyst for change—it also seems unnecessary. Why wait for a specific date to make a change? If you want to improve something in your life, you can just do it. You don’t need an excuse. That’s why I’ve never been drawn to the idea of making a list of resolutions. If I wanted a change, I’d make it happen, without worrying about the calendar. At least, that’s how I felt until now—when, for once, the timing actually gave me a real reason to embrace the idea of New Year’s resolutions. Enter [Olas](https://olas.app). If you're a visual creator, you've likely experienced the relentless grind of building a following on platforms like Instagram—endless doomscrolling, ever-changing algorithms, and the constant pressure to stay relevant. But what if there was a better way? Olas is a Nostr-powered alternative to Instagram that prioritizes community, creativity, and value-for-value exchanges. It's a game changer. Instagram’s failings are well-known. Its algorithm often dictates whose content gets seen, leaving creators frustrated and powerless. Monetization hurdles further alienate creators who are forced to meet arbitrary follower thresholds before earning anything. Additionally, the platform’s design fosters endless comparisons and exposure to negativity, which can take a significant toll on mental health. Instagram’s algorithms are notorious for keeping users hooked, often at the cost of their mental health. I've spoken about this extensively, most recently at Nostr Valley, explaining how legacy social media is bad for you. You might find yourself scrolling through content that leaves you feeling anxious or drained. Olas takes a fresh approach, replacing "doomscrolling" with "bloomscrolling." This is a common theme across the Nostr ecosystem. The lack of addictive rage algorithms allows the focus to shift to uplifting, positive content that inspires rather than exhausts. Monetization is another area where Olas will set itself apart. On Instagram, creators face arbitrary barriers to earning—needing thousands of followers and adhering to restrictive platform rules. Olas eliminates these hurdles by leveraging the Nostr protocol, enabling creators to earn directly through value-for-value exchanges. Fans can support their favorite artists instantly, with no delays or approvals required. The plan is to enable a brand new Olas account that can get paid instantly, with zero followers - that's wild. Olas addresses these issues head-on. Operating on the open Nostr protocol, it removes centralized control over one's content’s reach or one's ability to monetize. With transparent, configurable algorithms, and a community that thrives on mutual support, Olas creates an environment where creators can grow and succeed without unnecessary barriers. Join me on my New Year's resolution. Join me on Olas and take part in the [#Olas365](https://olas.app/search/olas365) challenge! It’s a simple yet exciting way to share your content. The challenge is straightforward: post at least one photo per day on Olas (though you’re welcome to share more!). [Download on iOS](https://testflight.apple.com/join/2FMVX2yM). [Download on Android](https://github.com/pablof7z/olas/releases/) or download via Zapstore. Let's make waves together.
@ 3f770d65:7a745b24
2025-01-05 18:56:33New Year’s resolutions often feel boring and repetitive. Most revolve around getting in shape, eating healthier, or giving up alcohol. While the idea is interesting—using the start of a new calendar year as a catalyst for change—it also seems unnecessary. Why wait for a specific date to make a change? If you want to improve something in your life, you can just do it. You don’t need an excuse. That’s why I’ve never been drawn to the idea of making a list of resolutions. If I wanted a change, I’d make it happen, without worrying about the calendar. At least, that’s how I felt until now—when, for once, the timing actually gave me a real reason to embrace the idea of New Year’s resolutions. Enter [Olas](https://olas.app). If you're a visual creator, you've likely experienced the relentless grind of building a following on platforms like Instagram—endless doomscrolling, ever-changing algorithms, and the constant pressure to stay relevant. But what if there was a better way? Olas is a Nostr-powered alternative to Instagram that prioritizes community, creativity, and value-for-value exchanges. It's a game changer. Instagram’s failings are well-known. Its algorithm often dictates whose content gets seen, leaving creators frustrated and powerless. Monetization hurdles further alienate creators who are forced to meet arbitrary follower thresholds before earning anything. Additionally, the platform’s design fosters endless comparisons and exposure to negativity, which can take a significant toll on mental health. Instagram’s algorithms are notorious for keeping users hooked, often at the cost of their mental health. I've spoken about this extensively, most recently at Nostr Valley, explaining how legacy social media is bad for you. You might find yourself scrolling through content that leaves you feeling anxious or drained. Olas takes a fresh approach, replacing "doomscrolling" with "bloomscrolling." This is a common theme across the Nostr ecosystem. The lack of addictive rage algorithms allows the focus to shift to uplifting, positive content that inspires rather than exhausts. Monetization is another area where Olas will set itself apart. On Instagram, creators face arbitrary barriers to earning—needing thousands of followers and adhering to restrictive platform rules. Olas eliminates these hurdles by leveraging the Nostr protocol, enabling creators to earn directly through value-for-value exchanges. Fans can support their favorite artists instantly, with no delays or approvals required. The plan is to enable a brand new Olas account that can get paid instantly, with zero followers - that's wild. Olas addresses these issues head-on. Operating on the open Nostr protocol, it removes centralized control over one's content’s reach or one's ability to monetize. With transparent, configurable algorithms, and a community that thrives on mutual support, Olas creates an environment where creators can grow and succeed without unnecessary barriers. Join me on my New Year's resolution. Join me on Olas and take part in the [#Olas365](https://olas.app/search/olas365) challenge! It’s a simple yet exciting way to share your content. The challenge is straightforward: post at least one photo per day on Olas (though you’re welcome to share more!). [Download on iOS](https://testflight.apple.com/join/2FMVX2yM). [Download on Android](https://github.com/pablof7z/olas/releases/) or download via Zapstore. Let's make waves together. @ 30ceb64e:7f08bdf5
2025-01-05 16:11:46Hey Freaks, Another round of songs I've been listening to lately. Un Sospiro slaps. Wind Tunnel hits me in the childhood. https://music.youtube.com/watch?v=50A-Mssm6w8&si=OFa8UA-0o71k4ETK https://music.youtube.com/watch?v=eMnxjdGTK4w&si=STFc4APblXLEp1Ig https://music.youtube.com/watch?v=RpsN6b95DAQ&si=ixMQY5ZnyuPeum2O https://music.youtube.com/watch?v=W91-jAQ2ijM&si=MhluAXuU1v_a86yW https://music.youtube.com/watch?v=LMAhXhRsRXA&si=jo-UPFILXvZd8pS7 https://music.youtube.com/watch?v=53FDkWb7Mv4&si=lp4ikhtx39UqHzSA https://music.youtube.com/watch?v=rrYMiAoGnVg&si=ya0qnGtbwCdyQ676 https://music.youtube.com/watch?v=Lk9Xwj0mnsI&si=OFMyBaXSO-Jyufxl https://music.youtube.com/watch?v=057A1RdssoU&si=4lueg4C8Y3ac3LCE https://music.youtube.com/watch?v=ghxzLw2wRis&si=wjgwjaPOJwo6-Cu2 https://music.youtube.com/playlist?list=PLmYfnnK_Qs5hOiZazXiwEoCdg1RiUvBBv&si=X4opO4goVt2K1T4D Thanks, Hustle originally posted at https://stacker.news/items/838006
@ 30ceb64e:7f08bdf5
2025-01-05 16:11:46Hey Freaks, Another round of songs I've been listening to lately. Un Sospiro slaps. Wind Tunnel hits me in the childhood. https://music.youtube.com/watch?v=50A-Mssm6w8&si=OFa8UA-0o71k4ETK https://music.youtube.com/watch?v=eMnxjdGTK4w&si=STFc4APblXLEp1Ig https://music.youtube.com/watch?v=RpsN6b95DAQ&si=ixMQY5ZnyuPeum2O https://music.youtube.com/watch?v=W91-jAQ2ijM&si=MhluAXuU1v_a86yW https://music.youtube.com/watch?v=LMAhXhRsRXA&si=jo-UPFILXvZd8pS7 https://music.youtube.com/watch?v=53FDkWb7Mv4&si=lp4ikhtx39UqHzSA https://music.youtube.com/watch?v=rrYMiAoGnVg&si=ya0qnGtbwCdyQ676 https://music.youtube.com/watch?v=Lk9Xwj0mnsI&si=OFMyBaXSO-Jyufxl https://music.youtube.com/watch?v=057A1RdssoU&si=4lueg4C8Y3ac3LCE https://music.youtube.com/watch?v=ghxzLw2wRis&si=wjgwjaPOJwo6-Cu2 https://music.youtube.com/playlist?list=PLmYfnnK_Qs5hOiZazXiwEoCdg1RiUvBBv&si=X4opO4goVt2K1T4D Thanks, Hustle originally posted at https://stacker.news/items/838006 @ e6817453:b0ac3c39
2025-01-05 14:29:17## The Rise of Graph RAGs and the Quest for Data Quality As we enter a new year, it’s impossible to ignore the boom of retrieval-augmented generation (RAG) systems, particularly those leveraging graph-based approaches. The previous year saw a surge in advancements and discussions about Graph RAGs, driven by their potential to enhance large language models (LLMs), reduce hallucinations, and deliver more reliable outputs. Let’s dive into the trends, challenges, and strategies for making the most of Graph RAGs in artificial intelligence. ## Booming Interest in Graph RAGs Graph RAGs have dominated the conversation in AI circles. With new research papers and innovations emerging weekly, it’s clear that this approach is reshaping the landscape. These systems, especially those developed by tech giants like Microsoft, demonstrate how graphs can: * **Enhance LLM Outputs:** By grounding responses in structured knowledge, graphs significantly reduce hallucinations. * **Support Complex Queries:** Graphs excel at managing linked and connected data, making them ideal for intricate problem-solving. Conferences on linked and connected data have increasingly focused on Graph RAGs, underscoring their central role in modern AI systems. However, the excitement around this technology has brought critical questions to the forefront: How do we ensure the quality of the graphs we’re building, and are they genuinely aligned with our needs? ## Data Quality: The Foundation of Effective Graphs A high-quality graph is the backbone of any successful RAG system. Constructing these graphs from unstructured data requires attention to detail and rigorous processes. Here’s why: * **Richness of Entities:** Effective retrieval depends on graphs populated with rich, detailed entities. * **Freedom from Hallucinations:** Poorly constructed graphs amplify inaccuracies rather than mitigating them. Without robust data quality, even the most sophisticated Graph RAGs become ineffective. As a result, the focus must shift to refining the graph construction process. Improving data strategy and ensuring meticulous data preparation is essential to unlock the full potential of Graph RAGs. ## Hybrid Graph RAGs and Variations While standard Graph RAGs are already transformative, hybrid models offer additional flexibility and power. Hybrid RAGs combine structured graph data with other retrieval mechanisms, creating systems that: * Handle diverse data sources with ease. * Offer improved adaptability to complex queries. Exploring these variations can open new avenues for AI systems, particularly in domains requiring structured and unstructured data processing. ## Ontology: The Key to Graph Construction Quality Ontology — defining how concepts relate within a knowledge domain — is critical for building effective graphs. While this might sound abstract, it’s a well-established field blending philosophy, engineering, and art. Ontology engineering provides the framework for: * **Defining Relationships:** Clarifying how concepts connect within a domain. * **Validating Graph Structures:** Ensuring constructed graphs are logically sound and align with domain-specific realities. Traditionally, ontologists — experts in this discipline — have been integral to large enterprises and research teams. However, not every team has access to dedicated ontologists, leading to a significant challenge: How can teams without such expertise ensure the quality of their graphs? ## How to Build Ontology Expertise in a Startup Team For startups and smaller teams, developing ontology expertise may seem daunting, but it is achievable with the right approach: 1. **Assign a Knowledge Champion:** Identify a team member with a strong analytical mindset and give them time and resources to learn ontology engineering. 2. **Provide Training:** Invest in courses, workshops, or certifications in knowledge graph and ontology creation. 3. **Leverage Partnerships:** Collaborate with academic institutions, domain experts, or consultants to build initial frameworks. 4. **Utilize Tools:** Introduce ontology development tools like Protégé, OWL, or SHACL to simplify the creation and validation process. 5. **Iterate with Feedback:** Continuously refine ontologies through collaboration with domain experts and iterative testing. So, it is not always affordable for a startup to have a dedicated oncologist or knowledge engineer in a team, but you could involve consulters or build barefoot experts. You could read about barefoot experts in my article : Even startups can achieve robust and domain-specific ontology frameworks by fostering in-house expertise. ## How to Find or Create Ontologies For teams venturing into Graph RAGs, several strategies can help address the ontology gap: 1. **Leverage Existing Ontologies:** Many industries and domains already have open ontologies. For instance: * **Public Knowledge Graphs:** Resources like Wikipedia’s graph offer a wealth of structured knowledge. * **Industry Standards:** Enterprises such as Siemens have invested in creating and sharing ontologies specific to their fields. * **Business Framework Ontology (BFO):** A valuable resource for enterprises looking to define business processes and structures. 1. **Build In-House Expertise:** If budgets allow, consider hiring knowledge engineers or providing team members with the resources and time to develop expertise in ontology creation. 2. **Utilize LLMs for Ontology Construction:** Interestingly, LLMs themselves can act as a starting point for ontology development: * **Prompt-Based Extraction:** LLMs can generate draft ontologies by leveraging their extensive training on graph data. * **Domain Expert Refinement:** Combine LLM-generated structures with insights from domain experts to create tailored ontologies. ## Parallel Ontology and Graph Extraction An emerging approach involves extracting ontologies and graphs in parallel. While this can streamline the process, it presents challenges such as: * **Detecting Hallucinations:** Differentiating between genuine insights and AI-generated inaccuracies. * **Ensuring Completeness:** Ensuring no critical concepts are overlooked during extraction. Teams must carefully validate outputs to ensure reliability and accuracy when employing this parallel method. ## LLMs as Ontologists While traditionally dependent on human expertise, ontology creation is increasingly supported by LLMs. These models, trained on vast amounts of data, possess inherent knowledge of many open ontologies and taxonomies. Teams can use LLMs to: * **Generate Skeleton Ontologies:** Prompt LLMs with domain-specific information to draft initial ontology structures. * **Validate and Refine Ontologies:** Collaborate with domain experts to refine these drafts, ensuring accuracy and relevance. However, for validation and graph construction, formal tools such as OWL, SHACL, and RDF should be prioritized over LLMs to minimize hallucinations and ensure robust outcomes. ## Final Thoughts: Unlocking the Power of Graph RAGs The rise of Graph RAGs underscores a simple but crucial correlation: improving graph construction and data quality directly enhances retrieval systems. To truly harness this power, teams must invest in understanding ontologies, building quality graphs, and leveraging both human expertise and advanced AI tools. As we move forward, the interplay between Graph RAGs and ontology engineering will continue to shape the future of AI. Whether through adopting existing frameworks or exploring innovative uses of LLMs, the path to success lies in a deep commitment to data quality and domain understanding. Have you explored these technologies in your work? Share your experiences and insights — and stay tuned for more discussions on ontology extraction and its role in AI advancements. Cheers to a year of innovation!
@ e6817453:b0ac3c39
2025-01-05 14:29:17## The Rise of Graph RAGs and the Quest for Data Quality As we enter a new year, it’s impossible to ignore the boom of retrieval-augmented generation (RAG) systems, particularly those leveraging graph-based approaches. The previous year saw a surge in advancements and discussions about Graph RAGs, driven by their potential to enhance large language models (LLMs), reduce hallucinations, and deliver more reliable outputs. Let’s dive into the trends, challenges, and strategies for making the most of Graph RAGs in artificial intelligence. ## Booming Interest in Graph RAGs Graph RAGs have dominated the conversation in AI circles. With new research papers and innovations emerging weekly, it’s clear that this approach is reshaping the landscape. These systems, especially those developed by tech giants like Microsoft, demonstrate how graphs can: * **Enhance LLM Outputs:** By grounding responses in structured knowledge, graphs significantly reduce hallucinations. * **Support Complex Queries:** Graphs excel at managing linked and connected data, making them ideal for intricate problem-solving. Conferences on linked and connected data have increasingly focused on Graph RAGs, underscoring their central role in modern AI systems. However, the excitement around this technology has brought critical questions to the forefront: How do we ensure the quality of the graphs we’re building, and are they genuinely aligned with our needs? ## Data Quality: The Foundation of Effective Graphs A high-quality graph is the backbone of any successful RAG system. Constructing these graphs from unstructured data requires attention to detail and rigorous processes. Here’s why: * **Richness of Entities:** Effective retrieval depends on graphs populated with rich, detailed entities. * **Freedom from Hallucinations:** Poorly constructed graphs amplify inaccuracies rather than mitigating them. Without robust data quality, even the most sophisticated Graph RAGs become ineffective. As a result, the focus must shift to refining the graph construction process. Improving data strategy and ensuring meticulous data preparation is essential to unlock the full potential of Graph RAGs. ## Hybrid Graph RAGs and Variations While standard Graph RAGs are already transformative, hybrid models offer additional flexibility and power. Hybrid RAGs combine structured graph data with other retrieval mechanisms, creating systems that: * Handle diverse data sources with ease. * Offer improved adaptability to complex queries. Exploring these variations can open new avenues for AI systems, particularly in domains requiring structured and unstructured data processing. ## Ontology: The Key to Graph Construction Quality Ontology — defining how concepts relate within a knowledge domain — is critical for building effective graphs. While this might sound abstract, it’s a well-established field blending philosophy, engineering, and art. Ontology engineering provides the framework for: * **Defining Relationships:** Clarifying how concepts connect within a domain. * **Validating Graph Structures:** Ensuring constructed graphs are logically sound and align with domain-specific realities. Traditionally, ontologists — experts in this discipline — have been integral to large enterprises and research teams. However, not every team has access to dedicated ontologists, leading to a significant challenge: How can teams without such expertise ensure the quality of their graphs? ## How to Build Ontology Expertise in a Startup Team For startups and smaller teams, developing ontology expertise may seem daunting, but it is achievable with the right approach: 1. **Assign a Knowledge Champion:** Identify a team member with a strong analytical mindset and give them time and resources to learn ontology engineering. 2. **Provide Training:** Invest in courses, workshops, or certifications in knowledge graph and ontology creation. 3. **Leverage Partnerships:** Collaborate with academic institutions, domain experts, or consultants to build initial frameworks. 4. **Utilize Tools:** Introduce ontology development tools like Protégé, OWL, or SHACL to simplify the creation and validation process. 5. **Iterate with Feedback:** Continuously refine ontologies through collaboration with domain experts and iterative testing. So, it is not always affordable for a startup to have a dedicated oncologist or knowledge engineer in a team, but you could involve consulters or build barefoot experts. You could read about barefoot experts in my article : Even startups can achieve robust and domain-specific ontology frameworks by fostering in-house expertise. ## How to Find or Create Ontologies For teams venturing into Graph RAGs, several strategies can help address the ontology gap: 1. **Leverage Existing Ontologies:** Many industries and domains already have open ontologies. For instance: * **Public Knowledge Graphs:** Resources like Wikipedia’s graph offer a wealth of structured knowledge. * **Industry Standards:** Enterprises such as Siemens have invested in creating and sharing ontologies specific to their fields. * **Business Framework Ontology (BFO):** A valuable resource for enterprises looking to define business processes and structures. 1. **Build In-House Expertise:** If budgets allow, consider hiring knowledge engineers or providing team members with the resources and time to develop expertise in ontology creation. 2. **Utilize LLMs for Ontology Construction:** Interestingly, LLMs themselves can act as a starting point for ontology development: * **Prompt-Based Extraction:** LLMs can generate draft ontologies by leveraging their extensive training on graph data. * **Domain Expert Refinement:** Combine LLM-generated structures with insights from domain experts to create tailored ontologies. ## Parallel Ontology and Graph Extraction An emerging approach involves extracting ontologies and graphs in parallel. While this can streamline the process, it presents challenges such as: * **Detecting Hallucinations:** Differentiating between genuine insights and AI-generated inaccuracies. * **Ensuring Completeness:** Ensuring no critical concepts are overlooked during extraction. Teams must carefully validate outputs to ensure reliability and accuracy when employing this parallel method. ## LLMs as Ontologists While traditionally dependent on human expertise, ontology creation is increasingly supported by LLMs. These models, trained on vast amounts of data, possess inherent knowledge of many open ontologies and taxonomies. Teams can use LLMs to: * **Generate Skeleton Ontologies:** Prompt LLMs with domain-specific information to draft initial ontology structures. * **Validate and Refine Ontologies:** Collaborate with domain experts to refine these drafts, ensuring accuracy and relevance. However, for validation and graph construction, formal tools such as OWL, SHACL, and RDF should be prioritized over LLMs to minimize hallucinations and ensure robust outcomes. ## Final Thoughts: Unlocking the Power of Graph RAGs The rise of Graph RAGs underscores a simple but crucial correlation: improving graph construction and data quality directly enhances retrieval systems. To truly harness this power, teams must invest in understanding ontologies, building quality graphs, and leveraging both human expertise and advanced AI tools. As we move forward, the interplay between Graph RAGs and ontology engineering will continue to shape the future of AI. Whether through adopting existing frameworks or exploring innovative uses of LLMs, the path to success lies in a deep commitment to data quality and domain understanding. Have you explored these technologies in your work? Share your experiences and insights — and stay tuned for more discussions on ontology extraction and its role in AI advancements. Cheers to a year of innovation! @ 6ad3e2a3:c90b7740
2025-01-05 14:26:34Maybe it’s because I watched [The Omen](https://www.youtube.com/watch?v=mDHisWRsE98) at way too young an age, or maybe it’s because the Book of Revelation’s “mark of the beast” allegory is playing out too literally for my tastes, but having already written about the [Second Coming](https://www.chrisliss.com/the_second_coming), it only follows I should speculate as to its counterpart. As I mentioned in [The Second Coming](https://www.chrisliss.com/the_second_coming), it’s dangerous to take the myths from our ancestors too literally. They used the symbols of their times, and we should be careful not to confuse the mental maps they had of their world with reality itself. That said, we should also not be dismissive — Mozart didn’t have fancy music editing software, but his genius using the modalities of the time was real. To the extent our forebears offered us their wisdom about the nature of man and forces within him we should endeavor to understand it. The technology and the symbols may have changed, but our essential nature is ever the same. Just as the second coming of Christ would free man from tyranny, the Antichrist would be its imposition. And just as I speculated that Jesus might not return in the form of a person, it’s likely neither would his counterpart. But if Satoshi, Bitcoin’s pseudonymous creator, can be the face, so to speak, representing the movement toward freedom and God, who and what would represent its antithesis? Let’s speculate. It would have to be someone charismatic, a person the multitudes would want to follow and in whom to look for reassurance. That eliminates villains du jour like Bill Gates, Klaus Schwab and Vladimir Putin. If that’s who Satan is sending, he’s not sending his best. What about Donald Trump? More charismatic, much more popular appeal. He’s a better choice than the first group, but while street-smart, he lacks refined intelligence and is too despised by wide swaths of the population. He’s also probably too old. For a while, I would have said Barack Obama was the best candidate, and even some hard-core right wingers agreed (it’s hilarious that this [claim was actually fact-checked](https://www.snopes.com/fact-check/anti-maim/)! — you can’t fact-check whether someone is the Antichrist!) Obama was relatively young, vital enough, popular, charismatic and intelligent. But he’s faded from view the last few years and has been a surprisingly inconsequential former president. That leaves one person of whom I can think with the qualities and societal position to fill the role. Regrettably it’s someone I like, but of course I would like the Antichrist! If he weren’t likable he wouldn’t be the Antichrist. That person is Elon Musk. Musk is the richest person in the world, among the most followed on Twitter, has a borderline worshipful fanbase and big plans for improving humanity. Musk is young enough, he’s probably a genius and considering a private takeover of arguably the world’s most important communications network. He’s also a big player in satellites, energy, transportation and [internet provision](https://twitter.com/elonmusk/status/1530234643219243009?s=20&t=olDDLEAUBFhreDIltCPkkQ). Musk says lots of sensible things with which I agree about free speech and rights. He is the perfect foil to the [out-of-central-casting](https://unlimitedhangout.com/2021/02/investigative-reports/schwab-family-values/) Schwab supervillain. As Edward Dowd speculated: But, you might object, if Musk is the foil to Schwab’s terrible ideas, isn’t that good for humanity? How could the Antichrist be for [free speech](https://twitter.com/elonmusk/status/1519036983137509376?s=20&t=olDDLEAUBFhreDIltCPkkQ), [renewable energy](https://twitter.com/elonmusk/status/1532030554778087424?s=20&t=olDDLEAUBFhreDIltCPkkQ), [population expansion](https://twitter.com/elonmusk/status/1529193812949614594?s=20&t=PIRRovWYIIUSQY5Uw7dFpw)? Again, of course, the Antichrist is going to have good, sensible ideas! But as Marshall McLuhan said, “[The medium is the message](https://www.brainyquote.com/quotes/marshall_mcluhan_157742).” Or, more aptly, the top-down messianic complex is the message. Musk has [long discussed saving humanity](https://twitter.com/elonmusk/status/1533410745429413888?s=20&t=gTsO-6ltAFVOs4SJP-VmpQ) via expansion into space and sustainable energy. But in order to save humanity, one must exert some control over it. While Musk’s Twitter takeover from the [ineffectual woke scolds](https://nypost.com/2022/05/18/good-riddance-to-the-ministry-of-truth-nina-jankowicz/) is getting most of the press, [this is also going on](https://finance.yahoo.com/news/elon-musk-says-neuralinks-brain-155733754.html): Klaus Schwab’s pitch to own nothing and eat bugs is weak, but Musk, via brain implant, could potentially create a more satisfying virtual experience than most could hope to achieve in reality. And what could be more tantamount to complete control than letting someone else get the keys to the very organ of perception itself?  Well don’t get the implant then. Just get in your Tesla and drive away. But electric cars don’t work that way — they are attached to the grid, trackable and capable of [being shut down remotely](https://tekdeeps.com/elon-musk-is-being-pressured-to-shut-down-tesla-cars-in-russia/). And that’s before we consider driverless cars in which there would be even less privacy and autonomy. Moreover, Teslas [track the driver’s movements](https://www.carscoops.com/2020/10/tesla-model-3s-interior-camera-tracking-eye-and-head-movement/) already to an extent combustion-engine cars do not, ostensibly to inform the developing AI, but uses for technology evolve over time — sending email and paying bills over the internet was commonplace in 2000, but now people are micro-tracked by Facebook and Google. One could object that Musk has, to-date, used his influence for good. But that makes it no less dangerous to entrust him with so much power: J.R.R. Tolkien understood this clearly: *“You are wise and powerful. Will you not take the Ring?”* *“No!” cried Gandalf, springing to his feet. “With that power I should have power too great and terrible. And over me the Ring would gain a power still greater and more deadly.” His eyes flashed and his face was lit as by a fire within. “Do not tempt me! For I do not wish to become like the Dark Lord himself. Yet the way of the Ring to my heart is by pity, pity for weakness and the desire of strength to do good. Do not tempt me! I dare not take it, not even to keep it safe, unused. The wish to wield it would be too great for my strength. I shall have such need of it. Great perils lie before me.”* *-- The Lord of the Rings* Beyond [Neuralink](https://neuralink.com/), Musk also seems to have a strong utilitarian bent: In this [paper](https://www.nickbostrom.com/astronomical/waste.html) Nick Bostrom makes the case that delaying technological advancement could cost humanity astronomical amounts of well-being because every moment we delay, stars are burning out, useful energy is being sucked into black holes, irreversible entropy is happening apace, depriving us of future potential. Bostrom translates it into potential human lives lost (or more aptly, never having been born) on account of this permanent loss. While Bostrom’s framework seems benign — who is against collective human happiness in the form of more worthwhile lives? — it’s actually a form of utilitarianism that tries to sum the totality of human happiness over the entire species rather than to consider, as Immanuel Kant would, [each individual as an end in himself](https://assets.cambridge.org/97811070/08519/frontmatter/9781107008519_frontmatter.pdf). This viewing of the collective good as the optimal outcome has been used to justify many of history’s worst atrocities. To create a master race, to make sure everyone gets the same amount, to protect the world from covid, we must do whatever it takes! If, per Bostrom’s math, one harnessed black hole were worth quadrillions of lives, it would, for example, seem an easy call to sacrifice a bunch of selfish losers on earth who stood in the way of creating the technology for doing so. Utilitarianism, ironically, winds up failing miserably by its own metric because (a) it can so easily be manipulated by whoever is maintaining the “greater good” spread sheet, which just happens to coincide with one’s ambitions; and (b) because it’s absurd to think you can calculate aggregate good for octillions of lives so far into an unknowable future. As such, while Musk’s pitch is more persuasive than Schwab’s or Gates’, it’s ultimately part of the same dangerous philosophy which is: “Let me optimize for total human happiness on your behalf.” Contrast Musk’s top-down humanity-saving endeavors with Bitcoin which is purely opt-in, works with simple incentives and imposes no value judgments on its users. It’s a [truth-recording clock](https://dergigi.com/2021/01/14/bitcoin-is-time/), impervious to fraud and cooption by the powerful. No matter how wealthy or powerful a person is, he cannot control the network or get treated with special privileges. Bitcoin’s finite supply means governments cannot print more of it, cannot finance unpopular wars or massive giveaways to the military and pharmaceutical industrial complexes. Instead of trusting any particular powerful person (the president, Elon Musk, Bill Gates) to be good, it simply removes the incentives toward and reduces the capacity for evil. *The supreme good is like water, which nourishes all things without trying to. It is content with the low places that people disdain. Thus it is like the Tao.* *From the [Tao Te Ching](http://albanycomplementaryhealth.com/wp-content/uploads/2016/07/TaoTeChing-LaoTzu-StephenMitchellTranslation-33p.pdf) (Lao Tse — translated by Stephen Mitchell)* We simply need the right conditions, the proper axioms on which to build. Just as the US Constitution created the framework for the most prosperous society in the history of the world, bitcoin will provide the axioms for peace, the harnessing of stranded energy and the [low-time preference](https://saifedean.com/podcast/84-hard-money-and-time-preference-lecture-at-the-property-freedom-society/) required for a more prosperous future. But it won’t be the future brought to you by Elon Musk, and ultimately I foresee a clash between the two. One tell is his otherwise inexplicable [promotion of Dogecoin](https://twitter.com/elonmusk/status/1530209049261658112?s=20&t=gTsO-6ltAFVOs4SJP-VmpQ) as a possible currency for Tesla purchases. Dogecoin was [literally a joke](https://thecryptobasic.com/2022/06/03/doge-founder-says-every-project-started-now-is-made-to-enrich-creators-at-the-expense-of-community/?utm_source=rss&utm_medium=rss&utm_campaign=doge-founder-says-every-project-started-now-is-made-to-enrich-creators-at-the-expense-of-community) from its creator and of course has none of the security, decentralization or censorship resistance of bitcoin. Musk is too smart not to know that — he put a couple billion dollars of Tesla’s balance sheet in bitcoin already and almost certainly understands the value proposition. That he still cites Doge seriously would be a clever way to muddy the waters about what bitcoin is vs what blockchain-based “crypto” is. And of course the Antichrist would avail himself of bitcoin, if only to obfuscate his real intentions and also to be able to crash the price by selling, if necessary, at an opportune time. The Klaus Schwab-Bill Gates-WEF set have already lost. They are widely despised, central banks are flailing, once-trusted institutions like the legacy media, major science and medical journals, the WHO, CDC and FDA are hemorrhaging influence. People are unhappy and looking for someone or something to trust. Elon Musk could fill that void, and if he does, he will be The Final Boss, the last false idol that needs to be discarded before humanity can, through its own efforts, enjoy a new era of prosperity, the [Second Coming](https://www.chrisliss.com/the_second_coming), so to speak. I actually suspect Musk is genuine in his desire to help humanity via his vision and am pretty sure he doesn’t have 666 embedded in his scalp — in any case even Damian in The Omen [neither knew who he was nor wanted to be](https://www.youtube.com/watch?v=QFNqkxFljvk) the Antichrist! But the most dangerous people for humanity are those with the biggest plans for it. Or put more succinctly: 
@ 6ad3e2a3:c90b7740
2025-01-05 14:26:34Maybe it’s because I watched [The Omen](https://www.youtube.com/watch?v=mDHisWRsE98) at way too young an age, or maybe it’s because the Book of Revelation’s “mark of the beast” allegory is playing out too literally for my tastes, but having already written about the [Second Coming](https://www.chrisliss.com/the_second_coming), it only follows I should speculate as to its counterpart. As I mentioned in [The Second Coming](https://www.chrisliss.com/the_second_coming), it’s dangerous to take the myths from our ancestors too literally. They used the symbols of their times, and we should be careful not to confuse the mental maps they had of their world with reality itself. That said, we should also not be dismissive — Mozart didn’t have fancy music editing software, but his genius using the modalities of the time was real. To the extent our forebears offered us their wisdom about the nature of man and forces within him we should endeavor to understand it. The technology and the symbols may have changed, but our essential nature is ever the same. Just as the second coming of Christ would free man from tyranny, the Antichrist would be its imposition. And just as I speculated that Jesus might not return in the form of a person, it’s likely neither would his counterpart. But if Satoshi, Bitcoin’s pseudonymous creator, can be the face, so to speak, representing the movement toward freedom and God, who and what would represent its antithesis? Let’s speculate. It would have to be someone charismatic, a person the multitudes would want to follow and in whom to look for reassurance. That eliminates villains du jour like Bill Gates, Klaus Schwab and Vladimir Putin. If that’s who Satan is sending, he’s not sending his best. What about Donald Trump? More charismatic, much more popular appeal. He’s a better choice than the first group, but while street-smart, he lacks refined intelligence and is too despised by wide swaths of the population. He’s also probably too old. For a while, I would have said Barack Obama was the best candidate, and even some hard-core right wingers agreed (it’s hilarious that this [claim was actually fact-checked](https://www.snopes.com/fact-check/anti-maim/)! — you can’t fact-check whether someone is the Antichrist!) Obama was relatively young, vital enough, popular, charismatic and intelligent. But he’s faded from view the last few years and has been a surprisingly inconsequential former president. That leaves one person of whom I can think with the qualities and societal position to fill the role. Regrettably it’s someone I like, but of course I would like the Antichrist! If he weren’t likable he wouldn’t be the Antichrist. That person is Elon Musk. Musk is the richest person in the world, among the most followed on Twitter, has a borderline worshipful fanbase and big plans for improving humanity. Musk is young enough, he’s probably a genius and considering a private takeover of arguably the world’s most important communications network. He’s also a big player in satellites, energy, transportation and [internet provision](https://twitter.com/elonmusk/status/1530234643219243009?s=20&t=olDDLEAUBFhreDIltCPkkQ). Musk says lots of sensible things with which I agree about free speech and rights. He is the perfect foil to the [out-of-central-casting](https://unlimitedhangout.com/2021/02/investigative-reports/schwab-family-values/) Schwab supervillain. As Edward Dowd speculated: But, you might object, if Musk is the foil to Schwab’s terrible ideas, isn’t that good for humanity? How could the Antichrist be for [free speech](https://twitter.com/elonmusk/status/1519036983137509376?s=20&t=olDDLEAUBFhreDIltCPkkQ), [renewable energy](https://twitter.com/elonmusk/status/1532030554778087424?s=20&t=olDDLEAUBFhreDIltCPkkQ), [population expansion](https://twitter.com/elonmusk/status/1529193812949614594?s=20&t=PIRRovWYIIUSQY5Uw7dFpw)? Again, of course, the Antichrist is going to have good, sensible ideas! But as Marshall McLuhan said, “[The medium is the message](https://www.brainyquote.com/quotes/marshall_mcluhan_157742).” Or, more aptly, the top-down messianic complex is the message. Musk has [long discussed saving humanity](https://twitter.com/elonmusk/status/1533410745429413888?s=20&t=gTsO-6ltAFVOs4SJP-VmpQ) via expansion into space and sustainable energy. But in order to save humanity, one must exert some control over it. While Musk’s Twitter takeover from the [ineffectual woke scolds](https://nypost.com/2022/05/18/good-riddance-to-the-ministry-of-truth-nina-jankowicz/) is getting most of the press, [this is also going on](https://finance.yahoo.com/news/elon-musk-says-neuralinks-brain-155733754.html): Klaus Schwab’s pitch to own nothing and eat bugs is weak, but Musk, via brain implant, could potentially create a more satisfying virtual experience than most could hope to achieve in reality. And what could be more tantamount to complete control than letting someone else get the keys to the very organ of perception itself?  Well don’t get the implant then. Just get in your Tesla and drive away. But electric cars don’t work that way — they are attached to the grid, trackable and capable of [being shut down remotely](https://tekdeeps.com/elon-musk-is-being-pressured-to-shut-down-tesla-cars-in-russia/). And that’s before we consider driverless cars in which there would be even less privacy and autonomy. Moreover, Teslas [track the driver’s movements](https://www.carscoops.com/2020/10/tesla-model-3s-interior-camera-tracking-eye-and-head-movement/) already to an extent combustion-engine cars do not, ostensibly to inform the developing AI, but uses for technology evolve over time — sending email and paying bills over the internet was commonplace in 2000, but now people are micro-tracked by Facebook and Google. One could object that Musk has, to-date, used his influence for good. But that makes it no less dangerous to entrust him with so much power: J.R.R. Tolkien understood this clearly: *“You are wise and powerful. Will you not take the Ring?”* *“No!” cried Gandalf, springing to his feet. “With that power I should have power too great and terrible. And over me the Ring would gain a power still greater and more deadly.” His eyes flashed and his face was lit as by a fire within. “Do not tempt me! For I do not wish to become like the Dark Lord himself. Yet the way of the Ring to my heart is by pity, pity for weakness and the desire of strength to do good. Do not tempt me! I dare not take it, not even to keep it safe, unused. The wish to wield it would be too great for my strength. I shall have such need of it. Great perils lie before me.”* *-- The Lord of the Rings* Beyond [Neuralink](https://neuralink.com/), Musk also seems to have a strong utilitarian bent: In this [paper](https://www.nickbostrom.com/astronomical/waste.html) Nick Bostrom makes the case that delaying technological advancement could cost humanity astronomical amounts of well-being because every moment we delay, stars are burning out, useful energy is being sucked into black holes, irreversible entropy is happening apace, depriving us of future potential. Bostrom translates it into potential human lives lost (or more aptly, never having been born) on account of this permanent loss. While Bostrom’s framework seems benign — who is against collective human happiness in the form of more worthwhile lives? — it’s actually a form of utilitarianism that tries to sum the totality of human happiness over the entire species rather than to consider, as Immanuel Kant would, [each individual as an end in himself](https://assets.cambridge.org/97811070/08519/frontmatter/9781107008519_frontmatter.pdf). This viewing of the collective good as the optimal outcome has been used to justify many of history’s worst atrocities. To create a master race, to make sure everyone gets the same amount, to protect the world from covid, we must do whatever it takes! If, per Bostrom’s math, one harnessed black hole were worth quadrillions of lives, it would, for example, seem an easy call to sacrifice a bunch of selfish losers on earth who stood in the way of creating the technology for doing so. Utilitarianism, ironically, winds up failing miserably by its own metric because (a) it can so easily be manipulated by whoever is maintaining the “greater good” spread sheet, which just happens to coincide with one’s ambitions; and (b) because it’s absurd to think you can calculate aggregate good for octillions of lives so far into an unknowable future. As such, while Musk’s pitch is more persuasive than Schwab’s or Gates’, it’s ultimately part of the same dangerous philosophy which is: “Let me optimize for total human happiness on your behalf.” Contrast Musk’s top-down humanity-saving endeavors with Bitcoin which is purely opt-in, works with simple incentives and imposes no value judgments on its users. It’s a [truth-recording clock](https://dergigi.com/2021/01/14/bitcoin-is-time/), impervious to fraud and cooption by the powerful. No matter how wealthy or powerful a person is, he cannot control the network or get treated with special privileges. Bitcoin’s finite supply means governments cannot print more of it, cannot finance unpopular wars or massive giveaways to the military and pharmaceutical industrial complexes. Instead of trusting any particular powerful person (the president, Elon Musk, Bill Gates) to be good, it simply removes the incentives toward and reduces the capacity for evil. *The supreme good is like water, which nourishes all things without trying to. It is content with the low places that people disdain. Thus it is like the Tao.* *From the [Tao Te Ching](http://albanycomplementaryhealth.com/wp-content/uploads/2016/07/TaoTeChing-LaoTzu-StephenMitchellTranslation-33p.pdf) (Lao Tse — translated by Stephen Mitchell)* We simply need the right conditions, the proper axioms on which to build. Just as the US Constitution created the framework for the most prosperous society in the history of the world, bitcoin will provide the axioms for peace, the harnessing of stranded energy and the [low-time preference](https://saifedean.com/podcast/84-hard-money-and-time-preference-lecture-at-the-property-freedom-society/) required for a more prosperous future. But it won’t be the future brought to you by Elon Musk, and ultimately I foresee a clash between the two. One tell is his otherwise inexplicable [promotion of Dogecoin](https://twitter.com/elonmusk/status/1530209049261658112?s=20&t=gTsO-6ltAFVOs4SJP-VmpQ) as a possible currency for Tesla purchases. Dogecoin was [literally a joke](https://thecryptobasic.com/2022/06/03/doge-founder-says-every-project-started-now-is-made-to-enrich-creators-at-the-expense-of-community/?utm_source=rss&utm_medium=rss&utm_campaign=doge-founder-says-every-project-started-now-is-made-to-enrich-creators-at-the-expense-of-community) from its creator and of course has none of the security, decentralization or censorship resistance of bitcoin. Musk is too smart not to know that — he put a couple billion dollars of Tesla’s balance sheet in bitcoin already and almost certainly understands the value proposition. That he still cites Doge seriously would be a clever way to muddy the waters about what bitcoin is vs what blockchain-based “crypto” is. And of course the Antichrist would avail himself of bitcoin, if only to obfuscate his real intentions and also to be able to crash the price by selling, if necessary, at an opportune time. The Klaus Schwab-Bill Gates-WEF set have already lost. They are widely despised, central banks are flailing, once-trusted institutions like the legacy media, major science and medical journals, the WHO, CDC and FDA are hemorrhaging influence. People are unhappy and looking for someone or something to trust. Elon Musk could fill that void, and if he does, he will be The Final Boss, the last false idol that needs to be discarded before humanity can, through its own efforts, enjoy a new era of prosperity, the [Second Coming](https://www.chrisliss.com/the_second_coming), so to speak. I actually suspect Musk is genuine in his desire to help humanity via his vision and am pretty sure he doesn’t have 666 embedded in his scalp — in any case even Damian in The Omen [neither knew who he was nor wanted to be](https://www.youtube.com/watch?v=QFNqkxFljvk) the Antichrist! But the most dangerous people for humanity are those with the biggest plans for it. Or put more succinctly:  @ 228dde34:b5d0345e
2025-01-05 10:30:04##### BY Joanna Hu ##### Editorial Admin ##### Hype Issue #60 ###### Join JOANNA HU as she delves into the world of Epic: The Musical, and explores the way it has brought an old tale into the hearts of new audiences.  *Photo from Jorge Rivera-Herrans’ YouTube page.* Over the past five years, Epic: The Musical has taken the internet by storm. Created by Puerto Rican artist Jorge Rivera-Herrans, known on social media as Jay Herrans, Epic is a sung-through retelling of Homer’s Odyssey. Blending influences from video games, anime, and manga, the musical is a nine-part series of audio-only concept albums. With a total of 40 songs across the nine sagas split into two acts, the story follows Odysseus – voiced by Rivera-Herrans himself – on his harrowing journey home after the Trojan War. With the latest release of the Ithaca Saga on December 25, 2024, the musical is finally complete, after two years of musical releases. Over its lifespan, Epic has garnered a massive and devoted fanbase, boasting millions of streams per song and over 100,000 members in its Discord community. So now, as the musical finally comes to a close, this breakthrough hit has left us asking: how exactly did Rivera-Herrans manage to captivate so many people with a story that has been around for over two thousand years?  *Jorge Rivera-Herrans, the creator of Epic: The Musical. Photo from Rivera-Herrans’ Facebook page (@JayHerrans).* ### Telling a story through music Like most musicals, Epic primarily tells its tale through music and its catchy, and sometimes humorous, lyrics. However, what really sets it apart from the crowd is the details in its intricate composition. Inspired by Peter and the Wolf, Sergei Prokofiev’s famous musical composition where different instruments are used to represent different characters, Rivera-Herrans takes a similar approach in Epic. Key characters are symbolized by distinct instruments — for example, Odysseus is embodied by a guitar, while Athena, his mentor, is characterized by the ticking of a metronome and running piano notes.  *Peter and the Wolf cover art from a 1959 Soviet vinyl. Photo taken from People’s World.* Recurring melodic motifs further enrich the listening experience, serving as callbacks to earlier moments, foreshadowing future events, or drawing parallels between different points in the story. These motifs add layers of depth; building tension and anticipation, and tugging on the heartstrings of fans who listen closely enough to notice them. Unlike traditional musicals, where stage or film visuals can be counted on to bring scenes to life, Epic has to rely almost entirely on sound. Although almost all the songs in the musical are conversation-based, it does not make the story any harder to follow. Beyond the instrumental and lyrical composition, Rivera-Herrans incorporates sound effects, like the roar of a monster or the twang of an arrow, directly into the music without it seeming out of place, immersing listeners in the world of the Odyssey without visual aids or scene descriptions. Combined with the motifs and lyrics, these audio cues make the narrative easy to follow, while also offering a treasure trove of Easter eggs for dedicated fans and musicians. ### The ‘TikTok musical’ and its digital fanbase Epic has sometimes been dubbed a ‘TikTok musical’, thanks to Rivera-Herrans’ extensive use of the platform throughout the project. In January 2021, when Epic was still in its early drafting stage, Rivera-Herrans shared a snippet of an early version of “Full Speed Ahead”, a song from the first saga, on TikTok. From there, he began posting clips of other song drafts, along with behind-the-scenes glimpses and explanations of his creative process. As such, Rivera-Herrans’ social media platforms have become a detailed documentation of Epic’s progress and evolution.  *Rivera-Herrans’ first post on TikTok about Epic: The Musical. Photo from TikTok.* Rivera-Herrans also used TikTok for casting calls, posting instrumental tracks for the characters’ main songs and inviting any and all interested candidates to audition by duetting his videos. This unconventional approach not only opened up opportunities for a wide range of talent but also boosted Epic's visibility, as auditioning candidates would share their videos with their own followers, further spreading awareness of the musical.  *Rivera-Herrans casting call on TikTok for the role of Calypso. Photo from TikTok.* ### Engaging the community Rivera-Herrans has fostered a strong sense of community among Epic fans. With each saga’s release, he hosts a livestream listening party, featuring animatics and artworks created by his fans with his input, bringing his vision to life. Not just that,he also frequently reposts fan art and animatics created independently after the official release of the sagas on his social media, crediting the artists and showing his appreciation. Rivera-Herrans also created the official Epic Discord server, providing fans with a dedicated space to discuss the musical and connect with one another, further deepening their engagement.  *Listening party on YouTube for the release of the Wisdom Saga. Photo from YouTube.* ### Taking creative liberties Like many modern adaptations of old stories, Epic takes some creative liberties with its source material. Some choices were intentional, aiming to humanise the characters and make them more relatable. Others, like a deviation in the timeline and the description of the Wind God Aeolus’ island, were unintentional, which Rivera-Herrans has openly acknowledged as a mistake on his part. As such, Epic is not a carbon copy of the Odyssey, and Rivera-Herrans has even encouraged fans to read the original tale for themselves. Nonetheless, the musical still serves as a gateway into the world of Greek mythology, and still maintains the spirit of the Odyssey in a way that appeals to the modern audience. ### What comes next for Epic: The Musical? With the release of the musical’s concluding chapter, the Ithaca saga, on December 25, 2024, the nine-part musical has now come to a close, leaving many fans speculating about the future of the series. Fortunately for fans of the show, several executive decisions in the musical’s past may leave the door open for future development in the world of Epic. In 2023, after disputes with his original licensing company, which had failed to pay royalties for the first two sagas, Rivera-Herrans founded his own company, Winion Entertainment LLC. Under this new banner, the cast re-recorded the entire first two sagas – the Troy and Cyclops sagas – releasing them alongside the Thunder Saga. With Winion Entertainment, Rivera-Herrans now has the potential to expand Epic into new business ventures which, as many fans hope, could include merchandise and future adaptations of the musical for film or stage. So, if you are a fan of Epic: The Musical, you might want to keep an eye out for any potential work from Rivera-Herrans in the future.  *‘Winions’ are Rivera-Herrans’ name for the Wind God Aeolus’ subjects, who appear as backing vocals in the song “Keeep Your Friends Close”. Photo from Epic: The Musical Wiki.*
@ 228dde34:b5d0345e
2025-01-05 10:30:04##### BY Joanna Hu ##### Editorial Admin ##### Hype Issue #60 ###### Join JOANNA HU as she delves into the world of Epic: The Musical, and explores the way it has brought an old tale into the hearts of new audiences.  *Photo from Jorge Rivera-Herrans’ YouTube page.* Over the past five years, Epic: The Musical has taken the internet by storm. Created by Puerto Rican artist Jorge Rivera-Herrans, known on social media as Jay Herrans, Epic is a sung-through retelling of Homer’s Odyssey. Blending influences from video games, anime, and manga, the musical is a nine-part series of audio-only concept albums. With a total of 40 songs across the nine sagas split into two acts, the story follows Odysseus – voiced by Rivera-Herrans himself – on his harrowing journey home after the Trojan War. With the latest release of the Ithaca Saga on December 25, 2024, the musical is finally complete, after two years of musical releases. Over its lifespan, Epic has garnered a massive and devoted fanbase, boasting millions of streams per song and over 100,000 members in its Discord community. So now, as the musical finally comes to a close, this breakthrough hit has left us asking: how exactly did Rivera-Herrans manage to captivate so many people with a story that has been around for over two thousand years?  *Jorge Rivera-Herrans, the creator of Epic: The Musical. Photo from Rivera-Herrans’ Facebook page (@JayHerrans).* ### Telling a story through music Like most musicals, Epic primarily tells its tale through music and its catchy, and sometimes humorous, lyrics. However, what really sets it apart from the crowd is the details in its intricate composition. Inspired by Peter and the Wolf, Sergei Prokofiev’s famous musical composition where different instruments are used to represent different characters, Rivera-Herrans takes a similar approach in Epic. Key characters are symbolized by distinct instruments — for example, Odysseus is embodied by a guitar, while Athena, his mentor, is characterized by the ticking of a metronome and running piano notes.  *Peter and the Wolf cover art from a 1959 Soviet vinyl. Photo taken from People’s World.* Recurring melodic motifs further enrich the listening experience, serving as callbacks to earlier moments, foreshadowing future events, or drawing parallels between different points in the story. These motifs add layers of depth; building tension and anticipation, and tugging on the heartstrings of fans who listen closely enough to notice them. Unlike traditional musicals, where stage or film visuals can be counted on to bring scenes to life, Epic has to rely almost entirely on sound. Although almost all the songs in the musical are conversation-based, it does not make the story any harder to follow. Beyond the instrumental and lyrical composition, Rivera-Herrans incorporates sound effects, like the roar of a monster or the twang of an arrow, directly into the music without it seeming out of place, immersing listeners in the world of the Odyssey without visual aids or scene descriptions. Combined with the motifs and lyrics, these audio cues make the narrative easy to follow, while also offering a treasure trove of Easter eggs for dedicated fans and musicians. ### The ‘TikTok musical’ and its digital fanbase Epic has sometimes been dubbed a ‘TikTok musical’, thanks to Rivera-Herrans’ extensive use of the platform throughout the project. In January 2021, when Epic was still in its early drafting stage, Rivera-Herrans shared a snippet of an early version of “Full Speed Ahead”, a song from the first saga, on TikTok. From there, he began posting clips of other song drafts, along with behind-the-scenes glimpses and explanations of his creative process. As such, Rivera-Herrans’ social media platforms have become a detailed documentation of Epic’s progress and evolution.  *Rivera-Herrans’ first post on TikTok about Epic: The Musical. Photo from TikTok.* Rivera-Herrans also used TikTok for casting calls, posting instrumental tracks for the characters’ main songs and inviting any and all interested candidates to audition by duetting his videos. This unconventional approach not only opened up opportunities for a wide range of talent but also boosted Epic's visibility, as auditioning candidates would share their videos with their own followers, further spreading awareness of the musical.  *Rivera-Herrans casting call on TikTok for the role of Calypso. Photo from TikTok.* ### Engaging the community Rivera-Herrans has fostered a strong sense of community among Epic fans. With each saga’s release, he hosts a livestream listening party, featuring animatics and artworks created by his fans with his input, bringing his vision to life. Not just that,he also frequently reposts fan art and animatics created independently after the official release of the sagas on his social media, crediting the artists and showing his appreciation. Rivera-Herrans also created the official Epic Discord server, providing fans with a dedicated space to discuss the musical and connect with one another, further deepening their engagement.  *Listening party on YouTube for the release of the Wisdom Saga. Photo from YouTube.* ### Taking creative liberties Like many modern adaptations of old stories, Epic takes some creative liberties with its source material. Some choices were intentional, aiming to humanise the characters and make them more relatable. Others, like a deviation in the timeline and the description of the Wind God Aeolus’ island, were unintentional, which Rivera-Herrans has openly acknowledged as a mistake on his part. As such, Epic is not a carbon copy of the Odyssey, and Rivera-Herrans has even encouraged fans to read the original tale for themselves. Nonetheless, the musical still serves as a gateway into the world of Greek mythology, and still maintains the spirit of the Odyssey in a way that appeals to the modern audience. ### What comes next for Epic: The Musical? With the release of the musical’s concluding chapter, the Ithaca saga, on December 25, 2024, the nine-part musical has now come to a close, leaving many fans speculating about the future of the series. Fortunately for fans of the show, several executive decisions in the musical’s past may leave the door open for future development in the world of Epic. In 2023, after disputes with his original licensing company, which had failed to pay royalties for the first two sagas, Rivera-Herrans founded his own company, Winion Entertainment LLC. Under this new banner, the cast re-recorded the entire first two sagas – the Troy and Cyclops sagas – releasing them alongside the Thunder Saga. With Winion Entertainment, Rivera-Herrans now has the potential to expand Epic into new business ventures which, as many fans hope, could include merchandise and future adaptations of the musical for film or stage. So, if you are a fan of Epic: The Musical, you might want to keep an eye out for any potential work from Rivera-Herrans in the future.  *‘Winions’ are Rivera-Herrans’ name for the Wind God Aeolus’ subjects, who appear as backing vocals in the song “Keeep Your Friends Close”. Photo from Epic: The Musical Wiki.* @ eac63075:b4988b48
2025-01-04 19:41:34Since its creation in 2009, Bitcoin has symbolized innovation and resilience. However, from time to time, alarmist narratives arise about emerging technologies that could "break" its security. Among these, quantum computing stands out as one of the most recurrent. But does quantum computing truly threaten Bitcoin? And more importantly, what is the community doing to ensure the protocol remains invulnerable? The answer, contrary to sensationalist headlines, is reassuring: Bitcoin is secure, and the community is already preparing for a future where quantum computing becomes a practical reality. Let’s dive into this topic to understand why the concerns are exaggerated and how the development of BIP-360 demonstrates that Bitcoin is one step ahead. --- ## What Is Quantum Computing, and Why Is Bitcoin Not Threatened? Quantum computing leverages principles of quantum mechanics to perform calculations that, in theory, could exponentially surpass classical computers—and it has nothing to do with what so-called “quantum coaches” teach to scam the uninformed. One of the concerns is that this technology could compromise two key aspects of Bitcoin’s security: 1. **Wallets**: These use elliptic curve algorithms (ECDSA) to protect private keys. A sufficiently powerful quantum computer could deduce a private key from its public key. 2. **Mining**: This is based on the SHA-256 algorithm, which secures the consensus process. A quantum attack could, in theory, compromise the proof-of-work mechanism. --- ## Understanding Quantum Computing’s Attack Priorities While quantum computing is often presented as a threat to Bitcoin, not all parts of the network are equally vulnerable. Theoretical attacks would be prioritized based on two main factors: ease of execution and potential reward. This creates two categories of attacks: ### 1. Attacks on Wallets Bitcoin wallets, secured by elliptic curve algorithms, would be the initial targets due to the relative vulnerability of their public keys, especially those already exposed on the blockchain. Two attack scenarios stand out: - **Short-term attacks**: These occur during the interval between sending a transaction and its inclusion in a block (approximately 10 minutes). A quantum computer could intercept the exposed public key and derive the corresponding private key to redirect funds by creating a transaction with higher fees. - **Long-term attacks**: These focus on old wallets whose public keys are permanently exposed. Wallets associated with Satoshi Nakamoto, for example, are especially vulnerable because they were created before the practice of using hashes to mask public keys. We can infer a priority order for how such attacks might occur based on urgency and importance. Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance) ### 2. Attacks on Mining Targeting the SHA-256 algorithm, which secures the mining process, would be the next objective. However, this is far more complex and requires a level of quantum computational power that is currently non-existent and far from realization. A successful attack would allow for the recalculation of all possible hashes to dominate the consensus process and potentially "mine" it instantly. --- Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin Attacks Recently, Narcelio asked me about a statement I made on Tubacast: https://x.com/eddieoz/status/1868371296683511969 If an attack became a reality **before Bitcoin was prepared**, it would be necessary to define the last block prior to the attack and proceed from there using a new hashing algorithm. The solution would resemble the response to the infamous 2013 bug. It’s a fact that this would cause market panic, and Bitcoin's price would drop significantly, creating a potential opportunity for the well-informed. Preferably, if developers could anticipate the threat and had time to work on a solution and build consensus before an attack, they would simply decide on a future block for the fork, which would then adopt the new algorithm. It might even rehash previous blocks (reaching consensus on them) to avoid potential reorganization through the re-mining of blocks using the old hash. (I often use the term "shielding" old transactions). --- ## How Can Users Protect Themselves? While quantum computing is still far from being a practical threat, some simple measures can already protect users against hypothetical scenarios: - **Avoid using exposed public keys**: Ensure funds sent to old wallets are transferred to new ones that use public key hashes. This reduces the risk of long-term attacks. - **Use modern wallets**: Opt for wallets compatible with SegWit or Taproot, which implement better security practices. - **Monitor security updates**: Stay informed about updates from the Bitcoin community, such as the implementation of BIP-360, which will introduce quantum-resistant addresses. - **Do not reuse addresses**: Every transaction should be associated with a new address to minimize the risk of repeated exposure of the same public key. - **Adopt secure backup practices**: Create offline backups of private keys and seeds in secure locations, protected from unauthorized access. --- ## BIP-360 and Bitcoin’s Preparation for the Future Even though quantum computing is still beyond practical reach, the Bitcoin community is not standing still. A concrete example is BIP-360, a proposal that establishes the technical framework to make wallets resistant to quantum attacks. BIP-360 addresses three main pillars: 1. **Introduction of quantum-resistant addresses**: A new address format starting with "BC1R" will be used. These addresses will be compatible with post-quantum algorithms, ensuring that stored funds are protected from future attacks. 2. **Compatibility with the current ecosystem**: The proposal allows users to transfer funds from old addresses to new ones without requiring drastic changes to the network infrastructure. 3. **Flexibility for future updates**: BIP-360 does not limit the choice of specific algorithms. Instead, it serves as a foundation for implementing new post-quantum algorithms as technology evolves. This proposal demonstrates how Bitcoin can adapt to emerging threats without compromising its decentralized structure. --- ## Post-Quantum Algorithms: The Future of Bitcoin Cryptography The community is exploring various algorithms to protect Bitcoin from quantum attacks. Among the most discussed are: - **Falcon**: A solution combining smaller public keys with compact digital signatures. Although it has been tested in limited scenarios, it still faces scalability and performance challenges. - **Sphincs**: Hash-based, this algorithm is renowned for its resilience, but its signatures can be extremely large, making it less efficient for networks like Bitcoin’s blockchain. - **Lamport**: Created in 1977, it’s considered one of the earliest post-quantum security solutions. Despite its reliability, its gigantic public keys (16,000 bytes) make it impractical and costly for Bitcoin. Two technologies show great promise and are well-regarded by the community: 1. **Lattice-Based Cryptography**: Considered one of the most promising, it uses complex mathematical structures to create systems nearly immune to quantum computing. Its implementation is still in its early stages, but the community is optimistic. 2. **Supersingular Elliptic Curve Isogeny**: These are very recent digital signature algorithms and require extensive study and testing before being ready for practical market use. The final choice of algorithm will depend on factors such as efficiency, cost, and integration capability with the current system. Additionally, it is preferable that these algorithms are standardized before implementation, a process that may take up to 10 years. --- ## Why Quantum Computing Is Far from Being a Threat The alarmist narrative about quantum computing overlooks the technical and practical challenges that still need to be overcome. Among them: - **Insufficient number of qubits**: Current quantum computers have only a few hundred qubits, whereas successful attacks would require millions. - **High error rate**: Quantum stability remains a barrier to reliable large-scale operations. - **High costs**: Building and operating large-scale quantum computers requires massive investments, limiting their use to scientific or specific applications. Moreover, even if quantum computers make significant advancements, Bitcoin is already adapting to ensure its infrastructure is prepared to respond. --- ## Conclusion: Bitcoin’s Secure Future Despite advancements in quantum computing, the reality is that Bitcoin is far from being threatened. Its security is ensured not only by its robust architecture but also by the community’s constant efforts to anticipate and mitigate challenges. The implementation of BIP-360 and the pursuit of post-quantum algorithms demonstrate that Bitcoin is not only resilient but also proactive. By adopting practical measures, such as using modern wallets and migrating to quantum-resistant addresses, users can further protect themselves against potential threats. Bitcoin’s future is not at risk—it is being carefully shaped to withstand any emerging technology, including quantum computing.
@ eac63075:b4988b48
2025-01-04 19:41:34Since its creation in 2009, Bitcoin has symbolized innovation and resilience. However, from time to time, alarmist narratives arise about emerging technologies that could "break" its security. Among these, quantum computing stands out as one of the most recurrent. But does quantum computing truly threaten Bitcoin? And more importantly, what is the community doing to ensure the protocol remains invulnerable? The answer, contrary to sensationalist headlines, is reassuring: Bitcoin is secure, and the community is already preparing for a future where quantum computing becomes a practical reality. Let’s dive into this topic to understand why the concerns are exaggerated and how the development of BIP-360 demonstrates that Bitcoin is one step ahead. --- ## What Is Quantum Computing, and Why Is Bitcoin Not Threatened? Quantum computing leverages principles of quantum mechanics to perform calculations that, in theory, could exponentially surpass classical computers—and it has nothing to do with what so-called “quantum coaches” teach to scam the uninformed. One of the concerns is that this technology could compromise two key aspects of Bitcoin’s security: 1. **Wallets**: These use elliptic curve algorithms (ECDSA) to protect private keys. A sufficiently powerful quantum computer could deduce a private key from its public key. 2. **Mining**: This is based on the SHA-256 algorithm, which secures the consensus process. A quantum attack could, in theory, compromise the proof-of-work mechanism. --- ## Understanding Quantum Computing’s Attack Priorities While quantum computing is often presented as a threat to Bitcoin, not all parts of the network are equally vulnerable. Theoretical attacks would be prioritized based on two main factors: ease of execution and potential reward. This creates two categories of attacks: ### 1. Attacks on Wallets Bitcoin wallets, secured by elliptic curve algorithms, would be the initial targets due to the relative vulnerability of their public keys, especially those already exposed on the blockchain. Two attack scenarios stand out: - **Short-term attacks**: These occur during the interval between sending a transaction and its inclusion in a block (approximately 10 minutes). A quantum computer could intercept the exposed public key and derive the corresponding private key to redirect funds by creating a transaction with higher fees. - **Long-term attacks**: These focus on old wallets whose public keys are permanently exposed. Wallets associated with Satoshi Nakamoto, for example, are especially vulnerable because they were created before the practice of using hashes to mask public keys. We can infer a priority order for how such attacks might occur based on urgency and importance. Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance) ### 2. Attacks on Mining Targeting the SHA-256 algorithm, which secures the mining process, would be the next objective. However, this is far more complex and requires a level of quantum computational power that is currently non-existent and far from realization. A successful attack would allow for the recalculation of all possible hashes to dominate the consensus process and potentially "mine" it instantly. --- Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin Attacks Recently, Narcelio asked me about a statement I made on Tubacast: https://x.com/eddieoz/status/1868371296683511969 If an attack became a reality **before Bitcoin was prepared**, it would be necessary to define the last block prior to the attack and proceed from there using a new hashing algorithm. The solution would resemble the response to the infamous 2013 bug. It’s a fact that this would cause market panic, and Bitcoin's price would drop significantly, creating a potential opportunity for the well-informed. Preferably, if developers could anticipate the threat and had time to work on a solution and build consensus before an attack, they would simply decide on a future block for the fork, which would then adopt the new algorithm. It might even rehash previous blocks (reaching consensus on them) to avoid potential reorganization through the re-mining of blocks using the old hash. (I often use the term "shielding" old transactions). --- ## How Can Users Protect Themselves? While quantum computing is still far from being a practical threat, some simple measures can already protect users against hypothetical scenarios: - **Avoid using exposed public keys**: Ensure funds sent to old wallets are transferred to new ones that use public key hashes. This reduces the risk of long-term attacks. - **Use modern wallets**: Opt for wallets compatible with SegWit or Taproot, which implement better security practices. - **Monitor security updates**: Stay informed about updates from the Bitcoin community, such as the implementation of BIP-360, which will introduce quantum-resistant addresses. - **Do not reuse addresses**: Every transaction should be associated with a new address to minimize the risk of repeated exposure of the same public key. - **Adopt secure backup practices**: Create offline backups of private keys and seeds in secure locations, protected from unauthorized access. --- ## BIP-360 and Bitcoin’s Preparation for the Future Even though quantum computing is still beyond practical reach, the Bitcoin community is not standing still. A concrete example is BIP-360, a proposal that establishes the technical framework to make wallets resistant to quantum attacks. BIP-360 addresses three main pillars: 1. **Introduction of quantum-resistant addresses**: A new address format starting with "BC1R" will be used. These addresses will be compatible with post-quantum algorithms, ensuring that stored funds are protected from future attacks. 2. **Compatibility with the current ecosystem**: The proposal allows users to transfer funds from old addresses to new ones without requiring drastic changes to the network infrastructure. 3. **Flexibility for future updates**: BIP-360 does not limit the choice of specific algorithms. Instead, it serves as a foundation for implementing new post-quantum algorithms as technology evolves. This proposal demonstrates how Bitcoin can adapt to emerging threats without compromising its decentralized structure. --- ## Post-Quantum Algorithms: The Future of Bitcoin Cryptography The community is exploring various algorithms to protect Bitcoin from quantum attacks. Among the most discussed are: - **Falcon**: A solution combining smaller public keys with compact digital signatures. Although it has been tested in limited scenarios, it still faces scalability and performance challenges. - **Sphincs**: Hash-based, this algorithm is renowned for its resilience, but its signatures can be extremely large, making it less efficient for networks like Bitcoin’s blockchain. - **Lamport**: Created in 1977, it’s considered one of the earliest post-quantum security solutions. Despite its reliability, its gigantic public keys (16,000 bytes) make it impractical and costly for Bitcoin. Two technologies show great promise and are well-regarded by the community: 1. **Lattice-Based Cryptography**: Considered one of the most promising, it uses complex mathematical structures to create systems nearly immune to quantum computing. Its implementation is still in its early stages, but the community is optimistic. 2. **Supersingular Elliptic Curve Isogeny**: These are very recent digital signature algorithms and require extensive study and testing before being ready for practical market use. The final choice of algorithm will depend on factors such as efficiency, cost, and integration capability with the current system. Additionally, it is preferable that these algorithms are standardized before implementation, a process that may take up to 10 years. --- ## Why Quantum Computing Is Far from Being a Threat The alarmist narrative about quantum computing overlooks the technical and practical challenges that still need to be overcome. Among them: - **Insufficient number of qubits**: Current quantum computers have only a few hundred qubits, whereas successful attacks would require millions. - **High error rate**: Quantum stability remains a barrier to reliable large-scale operations. - **High costs**: Building and operating large-scale quantum computers requires massive investments, limiting their use to scientific or specific applications. Moreover, even if quantum computers make significant advancements, Bitcoin is already adapting to ensure its infrastructure is prepared to respond. --- ## Conclusion: Bitcoin’s Secure Future Despite advancements in quantum computing, the reality is that Bitcoin is far from being threatened. Its security is ensured not only by its robust architecture but also by the community’s constant efforts to anticipate and mitigate challenges. The implementation of BIP-360 and the pursuit of post-quantum algorithms demonstrate that Bitcoin is not only resilient but also proactive. By adopting practical measures, such as using modern wallets and migrating to quantum-resistant addresses, users can further protect themselves against potential threats. Bitcoin’s future is not at risk—it is being carefully shaped to withstand any emerging technology, including quantum computing. @ 30ceb64e:7f08bdf5
2025-01-03 19:38:28Michael Saylor's recent assertion on Tom Bilyeu's podcast that Bitcoin offers a risk-free return sparked an interesting debate. While Tom struggled with the concept, the truth lies in understanding what "risk-free" truly means in our modern financial landscape. When you denominate your wealth in Bitcoin and store it properly in cold storage UTXOs, you're essentially protecting your work energy in perhaps the least risky way possible. https://m.primal.net/NQjb.png Traditional banking customers often consider their dollars in savings accounts to be risk-free, but this belief ignores fundamental realities. Bank failures are increasingly common, and FDIC insurance is merely a paper promise from the same entity responsible for systematic wealth destruction. The state has reached a point where repaying its debt within the current paradigm seems impossible. The paradox of taxation in a money-printing world raises profound questions. Why do we pay taxes when money can be created with the press of a button? The answer might lie in maintaining the illusion of government sustainability. We surrender roughly half our work energy to finance a system that can theoretically fund itself through money printing - a perplexing arrangement that defies logical explanation. Bitcoin represents hard money that doesn't require yield in the traditional sense. The real yield comes from humanity's natural progression toward efficiency and innovation. When your savings aren't being debased, technological advancement and human ingenuity naturally make your money more valuable over time. The world is inherently deflationary, but this truth becomes obscured when savings are denominated in infinitely printable currencies. This dynamic mirrors historical examples, like African communities saving in glass beads and shells, unaware that Europeans were mass-producing these "stores of value" in factories. Living in our current system is like existing in a deflationary world while being tricked into believing it's inflationary - a matrix-like illusion that drives the endless pursuit of "more" in a fundamentally broken system. The federal reserve is a glass bead manufacturer and some of us are the slaves that use it as money. https://m.primal.net/NQkA.webp Bitcoin's technical evolution continues to strengthen its position as sound money. Enhanced privacy features through initiatives like PayJoin, e-cash, and Lightning Network, combined with improved custody solutions and growing infrastructure, make it increasingly accessible and practical for everyday use. The ability to transact without permission or exploitative intermediaries, guided only by free market principles, represents a fundamental shift in financial sovereignty. The question of "enough" becomes central to the Bitcoin journey. While the technology offers a path to financial sovereignty, it's crucial to balance accumulation with life's other valuable resources - time with family, personal growth, and meaningful relationships. The timechain will judge our actions, but perhaps the most important consideration is whether our pursuit of satoshis comes at the cost of more precious aspects of life. We stand at a unique point in history where individual sovereignty is becoming truly possible. The pendulum swings toward a new paradigm that could secure prosperity for generations to come. While many haven't yet reached their personal "escape velocity," the path to financial freedom through Bitcoin becomes clearer with each passing day. The concept of risk-free extends beyond mere financial considerations. In a world where time is our most precious and finite resource, Bitcoin offers something unprecedented: the ability to store life energy in a system that appreciates with human progress, rather than depreciating with political whims. The risk isn't just about losing money - it's about losing life energy, family time, and personal freedom.
@ 30ceb64e:7f08bdf5
2025-01-03 19:38:28Michael Saylor's recent assertion on Tom Bilyeu's podcast that Bitcoin offers a risk-free return sparked an interesting debate. While Tom struggled with the concept, the truth lies in understanding what "risk-free" truly means in our modern financial landscape. When you denominate your wealth in Bitcoin and store it properly in cold storage UTXOs, you're essentially protecting your work energy in perhaps the least risky way possible. https://m.primal.net/NQjb.png Traditional banking customers often consider their dollars in savings accounts to be risk-free, but this belief ignores fundamental realities. Bank failures are increasingly common, and FDIC insurance is merely a paper promise from the same entity responsible for systematic wealth destruction. The state has reached a point where repaying its debt within the current paradigm seems impossible. The paradox of taxation in a money-printing world raises profound questions. Why do we pay taxes when money can be created with the press of a button? The answer might lie in maintaining the illusion of government sustainability. We surrender roughly half our work energy to finance a system that can theoretically fund itself through money printing - a perplexing arrangement that defies logical explanation. Bitcoin represents hard money that doesn't require yield in the traditional sense. The real yield comes from humanity's natural progression toward efficiency and innovation. When your savings aren't being debased, technological advancement and human ingenuity naturally make your money more valuable over time. The world is inherently deflationary, but this truth becomes obscured when savings are denominated in infinitely printable currencies. This dynamic mirrors historical examples, like African communities saving in glass beads and shells, unaware that Europeans were mass-producing these "stores of value" in factories. Living in our current system is like existing in a deflationary world while being tricked into believing it's inflationary - a matrix-like illusion that drives the endless pursuit of "more" in a fundamentally broken system. The federal reserve is a glass bead manufacturer and some of us are the slaves that use it as money. https://m.primal.net/NQkA.webp Bitcoin's technical evolution continues to strengthen its position as sound money. Enhanced privacy features through initiatives like PayJoin, e-cash, and Lightning Network, combined with improved custody solutions and growing infrastructure, make it increasingly accessible and practical for everyday use. The ability to transact without permission or exploitative intermediaries, guided only by free market principles, represents a fundamental shift in financial sovereignty. The question of "enough" becomes central to the Bitcoin journey. While the technology offers a path to financial sovereignty, it's crucial to balance accumulation with life's other valuable resources - time with family, personal growth, and meaningful relationships. The timechain will judge our actions, but perhaps the most important consideration is whether our pursuit of satoshis comes at the cost of more precious aspects of life. We stand at a unique point in history where individual sovereignty is becoming truly possible. The pendulum swings toward a new paradigm that could secure prosperity for generations to come. While many haven't yet reached their personal "escape velocity," the path to financial freedom through Bitcoin becomes clearer with each passing day. The concept of risk-free extends beyond mere financial considerations. In a world where time is our most precious and finite resource, Bitcoin offers something unprecedented: the ability to store life energy in a system that appreciates with human progress, rather than depreciating with political whims. The risk isn't just about losing money - it's about losing life energy, family time, and personal freedom. @ bd32f268:22b33966
2025-01-02 19:30:46Texto publicado por *Foundation Father @FoundationDads* e traduzido para português. Assumir responsabilidades numa época efeminada como a nossa é um superpoder. Algumas pessoas não sabem o que significa "assumir responsabilidades", no entanto, porque nunca tiveram um pai ou outra pessoa que as ama-se o suficiente para lhes ensinar. Então, aqui está como assumir responsabilidades. ## **Lembra-te que não és uma pessoa desamparada e incompetente.** As coisas não te acontecem simplesmente enquanto olhas fixamente com a boca aberta, usando todo o teu poder cerebral para te lembrares de como respirar. Tu tens poder de ação. ## Mantém estas perguntas em mente: "Que papel desempenhei eu nesta situação ou como ajudei a formar o sistema em que estou inserido?" "O que posso fazer agora mesmo para começar a corrigi-lo, por mais pequeno que seja?" Aqui estão alguns exemplos de como aplicar estas perguntas. *José Malhoa - Remédio* ## Saúde Estás com excesso de peso e cansado o tempo todo? Deprimido? Começa a caminhar 30 minutos por dia. De preferência ao ar livre. Pára de comer snacks. Marca uma consulta com um médico para fazer análises ao sangue. Todas estas coisas estão ao teu alcance. ## Finanças Estás a afogar-te em dívidas de cartão de crédito? Assumir responsabilidades significa reduzir drasticamente o teu consumo e iniciar um programa radical de pagamento do máximo de dívida que conseguires. Obtém uma aplicação de orçamento e começa a planear. Sentes-te preso no teu emprego sem futuro? Sentes que não ganhas o suficiente? Vai a entrevistas para vagas de emprego e descobre o teu verdadeiro valor no mercado. Reserva 1 hora todas as noites para melhorares. A menos que já estejas a trabalhar em dois empregos, toda a gente tem pelo menos 1 hora todas as noites. ## Arredores imediatos Se vês algo que precisa de ser feito, simplesmente faz. Não te queixes disso. Não resmungues baixinho. Não desejes que alguém tratasse disso. Simplesmente faz e não peças permissão. Guarda o carrinho de compras. Lava a caneca de café no lava-loiça. Arranca as ervas daninhas. Repara a parede. Se o quintal do teu vizinho estiver cheio de ervas, vai lá e corta a relva tu mesmo. Limpa a água do lava-loiça. Arruma a bancada. Leva o lixo para fora. Leva bom café para o escritório. ## Os teus filhos Muitos pais queixam-se do comportamento dos seus filhos como se não tivessem qualquer influência sobre o assunto. Mas os teus filhos farão o que tu os ensinaste a fazer. "Fizemos o melhor que pudemos." Não, não fizeram, e assumir responsabilidades significa admitir que foste permissivo e preguiçoso ou que querias sentir-te justo por não bater. Que pequena coisa podes fazer agora mesmo para começar? Escolhe um único comportamento que queres que eles parem, senta-os e explica as consequências do comportamento. Pede desculpa por teres deixado andar durante tanto tempo. Quando eles apresentarem o comportamento, aplica as consequências. Aconteça o que acontecer. ## Os teus relacionamentos Não tens amigos ou o teu grupo de amigos atual é uma má influência? Podes fazer novos amigos. Assumir responsabilidades significa admitir que a tua solidão é em grande parte auto-infligida. **O que podes fazer?** Começa a jogar ténis ou futebol. Existem ligas em todo o lado. Encontra uma boa igreja local e encontra maneiras de te envolver. Existem encontros para todo o tipo de atividade. Participa num que se alinhe com as tuas preferências. Quando estiveres em público, sorri mais e puxa conversa. Depois de conheceres algumas pessoas, estabelece uma cadência regular. Agenda almoços semanais ou mensais e alterna entre algumas pessoas. Ou talvez café de manhã. Não acontecerá da noite para o dia, mas dando pequenos passos consistentemente durante alguns meses e vais perceber que tens uma vida social. ## Os teus erros Se erraste, não te retires e escondas nem arranjes desculpas. Pede desculpa à pessoa que prejudicaste, diz-lhe porquê e oferece-te para compensar. Aceita as consequências com humildade. Vais descobrir que nada te conquista mais respeito do que assumir os teus erros. Esta é a principal. Se aprenderes a fazer isto bem, cobrirá uma infinidade de pecados porque cria hábito. Mesmo que tenhas apenas 1% de culpa na situação, assumir a responsabilidade e pedir desculpa pelo teu 1% está a construir um certo grupo de músculos. "Mas ele devia ter..." Pára com isso. Confiaste demasiado? Presumiste demasiado sem comunicar? Assume a responsabilidade por isso. Estes exemplos podiam continuar para sempre, então vou parar e terminar com este princípio: A tua resposta importa mais do que as tuas circunstâncias. Existem vítimas reais, algumas de tragédias horríveis. Mas mesmo que não te tenhas atirado para areias movediças, ainda podes assumir a responsabilidade por como reages e pelo que escolhes fazer a seguir. Às vezes, é agarrar numa corda de um transeunte e dizer: "Obrigado." Não te afogues nas areias movediças até que alguém te dê uma palmadinha nas costas por quão difícil é para ti, e não continues a apontar para o teu tempo nas areias movediças para desculpares os teus fracassos. Podes não ter escolhido uma batalha específica. Ainda podes assumir a responsabilidade por quão bem lutas a batalha. Num certo sentido, ninguém escolhe a principal batalha que enfrenta. Ninguém escolheu nascer. Ninguém escolheu a sua família. Ninguém escolheu as suas circunstâncias. O mundo nunca será perfeito. Tens de assumir a responsabilidade pela tua parte dele de qualquer maneira. Pode ser difícil. Pode ser doloroso. Não te foi prometida uma vida fácil e sem dor. Depois de começares a assumir responsabilidades, qual é o próximo passo? Altura de assumir mais responsabilidades. Por exemplo, se não tens problemas em fazer amigos e tens essa parte da tua vida resolvida, assume a responsabilidade por outra pessoa. Encontra um dos rapazes solitários na tua igreja que precisa de um amigo e adiciona-o à tua rotação de almoços. A recompensa por assumir responsabilidades é subir de nível e, como consequência, as coisas devem tornar-se mais desafiantes. Mas agora estás mais bem preparado para isso. Repete até morrer e, esperançosamente, a tua causa de morte será por viver e não por te queixares de não viver.
@ bd32f268:22b33966
2025-01-02 19:30:46Texto publicado por *Foundation Father @FoundationDads* e traduzido para português. Assumir responsabilidades numa época efeminada como a nossa é um superpoder. Algumas pessoas não sabem o que significa "assumir responsabilidades", no entanto, porque nunca tiveram um pai ou outra pessoa que as ama-se o suficiente para lhes ensinar. Então, aqui está como assumir responsabilidades. ## **Lembra-te que não és uma pessoa desamparada e incompetente.** As coisas não te acontecem simplesmente enquanto olhas fixamente com a boca aberta, usando todo o teu poder cerebral para te lembrares de como respirar. Tu tens poder de ação. ## Mantém estas perguntas em mente: "Que papel desempenhei eu nesta situação ou como ajudei a formar o sistema em que estou inserido?" "O que posso fazer agora mesmo para começar a corrigi-lo, por mais pequeno que seja?" Aqui estão alguns exemplos de como aplicar estas perguntas. *José Malhoa - Remédio* ## Saúde Estás com excesso de peso e cansado o tempo todo? Deprimido? Começa a caminhar 30 minutos por dia. De preferência ao ar livre. Pára de comer snacks. Marca uma consulta com um médico para fazer análises ao sangue. Todas estas coisas estão ao teu alcance. ## Finanças Estás a afogar-te em dívidas de cartão de crédito? Assumir responsabilidades significa reduzir drasticamente o teu consumo e iniciar um programa radical de pagamento do máximo de dívida que conseguires. Obtém uma aplicação de orçamento e começa a planear. Sentes-te preso no teu emprego sem futuro? Sentes que não ganhas o suficiente? Vai a entrevistas para vagas de emprego e descobre o teu verdadeiro valor no mercado. Reserva 1 hora todas as noites para melhorares. A menos que já estejas a trabalhar em dois empregos, toda a gente tem pelo menos 1 hora todas as noites. ## Arredores imediatos Se vês algo que precisa de ser feito, simplesmente faz. Não te queixes disso. Não resmungues baixinho. Não desejes que alguém tratasse disso. Simplesmente faz e não peças permissão. Guarda o carrinho de compras. Lava a caneca de café no lava-loiça. Arranca as ervas daninhas. Repara a parede. Se o quintal do teu vizinho estiver cheio de ervas, vai lá e corta a relva tu mesmo. Limpa a água do lava-loiça. Arruma a bancada. Leva o lixo para fora. Leva bom café para o escritório. ## Os teus filhos Muitos pais queixam-se do comportamento dos seus filhos como se não tivessem qualquer influência sobre o assunto. Mas os teus filhos farão o que tu os ensinaste a fazer. "Fizemos o melhor que pudemos." Não, não fizeram, e assumir responsabilidades significa admitir que foste permissivo e preguiçoso ou que querias sentir-te justo por não bater. Que pequena coisa podes fazer agora mesmo para começar? Escolhe um único comportamento que queres que eles parem, senta-os e explica as consequências do comportamento. Pede desculpa por teres deixado andar durante tanto tempo. Quando eles apresentarem o comportamento, aplica as consequências. Aconteça o que acontecer. ## Os teus relacionamentos Não tens amigos ou o teu grupo de amigos atual é uma má influência? Podes fazer novos amigos. Assumir responsabilidades significa admitir que a tua solidão é em grande parte auto-infligida. **O que podes fazer?** Começa a jogar ténis ou futebol. Existem ligas em todo o lado. Encontra uma boa igreja local e encontra maneiras de te envolver. Existem encontros para todo o tipo de atividade. Participa num que se alinhe com as tuas preferências. Quando estiveres em público, sorri mais e puxa conversa. Depois de conheceres algumas pessoas, estabelece uma cadência regular. Agenda almoços semanais ou mensais e alterna entre algumas pessoas. Ou talvez café de manhã. Não acontecerá da noite para o dia, mas dando pequenos passos consistentemente durante alguns meses e vais perceber que tens uma vida social. ## Os teus erros Se erraste, não te retires e escondas nem arranjes desculpas. Pede desculpa à pessoa que prejudicaste, diz-lhe porquê e oferece-te para compensar. Aceita as consequências com humildade. Vais descobrir que nada te conquista mais respeito do que assumir os teus erros. Esta é a principal. Se aprenderes a fazer isto bem, cobrirá uma infinidade de pecados porque cria hábito. Mesmo que tenhas apenas 1% de culpa na situação, assumir a responsabilidade e pedir desculpa pelo teu 1% está a construir um certo grupo de músculos. "Mas ele devia ter..." Pára com isso. Confiaste demasiado? Presumiste demasiado sem comunicar? Assume a responsabilidade por isso. Estes exemplos podiam continuar para sempre, então vou parar e terminar com este princípio: A tua resposta importa mais do que as tuas circunstâncias. Existem vítimas reais, algumas de tragédias horríveis. Mas mesmo que não te tenhas atirado para areias movediças, ainda podes assumir a responsabilidade por como reages e pelo que escolhes fazer a seguir. Às vezes, é agarrar numa corda de um transeunte e dizer: "Obrigado." Não te afogues nas areias movediças até que alguém te dê uma palmadinha nas costas por quão difícil é para ti, e não continues a apontar para o teu tempo nas areias movediças para desculpares os teus fracassos. Podes não ter escolhido uma batalha específica. Ainda podes assumir a responsabilidade por quão bem lutas a batalha. Num certo sentido, ninguém escolhe a principal batalha que enfrenta. Ninguém escolheu nascer. Ninguém escolheu a sua família. Ninguém escolheu as suas circunstâncias. O mundo nunca será perfeito. Tens de assumir a responsabilidade pela tua parte dele de qualquer maneira. Pode ser difícil. Pode ser doloroso. Não te foi prometida uma vida fácil e sem dor. Depois de começares a assumir responsabilidades, qual é o próximo passo? Altura de assumir mais responsabilidades. Por exemplo, se não tens problemas em fazer amigos e tens essa parte da tua vida resolvida, assume a responsabilidade por outra pessoa. Encontra um dos rapazes solitários na tua igreja que precisa de um amigo e adiciona-o à tua rotação de almoços. A recompensa por assumir responsabilidades é subir de nível e, como consequência, as coisas devem tornar-se mais desafiantes. Mas agora estás mais bem preparado para isso. Repete até morrer e, esperançosamente, a tua causa de morte será por viver e não por te queixares de não viver. @ a4a6b584:1e05b95b
2025-01-02 18:13:31## The Four-Layer Framework ### Layer 1: Zoom Out  Start by looking at the big picture. What’s the subject about, and why does it matter? Focus on the overarching ideas and how they fit together. Think of this as the 30,000-foot view—it’s about understanding the "why" and "how" before diving into the "what." **Example**: If you’re learning programming, start by understanding that it’s about giving logical instructions to computers to solve problems. - **Tip**: Keep it simple. Summarize the subject in one or two sentences and avoid getting bogged down in specifics at this stage. _Once you have the big picture in mind, it’s time to start breaking it down._ --- ### Layer 2: Categorize and Connect  Now it’s time to break the subject into categories—like creating branches on a tree. This helps your brain organize information logically and see connections between ideas. **Example**: Studying biology? Group concepts into categories like cells, genetics, and ecosystems. - **Tip**: Use headings or labels to group similar ideas. Jot these down in a list or simple diagram to keep track. _With your categories in place, you’re ready to dive into the details that bring them to life._ --- ### Layer 3: Master the Details  Once you’ve mapped out the main categories, you’re ready to dive deeper. This is where you learn the nuts and bolts—like formulas, specific techniques, or key terminology. These details make the subject practical and actionable. **Example**: In programming, this might mean learning the syntax for loops, conditionals, or functions in your chosen language. - **Tip**: Focus on details that clarify the categories from Layer 2. Skip anything that doesn’t add to your understanding. _Now that you’ve mastered the essentials, you can expand your knowledge to include extra material._ --- ### Layer 4: Expand Your Horizons  Finally, move on to the extra material—less critical facts, trivia, or edge cases. While these aren’t essential to mastering the subject, they can be useful in specialized discussions or exams. **Example**: Learn about rare programming quirks or historical trivia about a language’s development. - **Tip**: Spend minimal time here unless it’s necessary for your goals. It’s okay to skim if you’re short on time. --- ## Pro Tips for Better Learning ### 1. Use Active Recall and Spaced Repetition Test yourself without looking at notes. Review what you’ve learned at increasing intervals—like after a day, a week, and a month. This strengthens memory by forcing your brain to actively retrieve information. ### 2. Map It Out Create visual aids like [diagrams or concept maps](https://excalidraw.com/) to clarify relationships between ideas. These are particularly helpful for organizing categories in Layer 2. ### 3. Teach What You Learn Explain the subject to someone else as if they’re hearing it for the first time. Teaching **exposes any gaps** in your understanding and **helps reinforce** the material. ### 4. Engage with LLMs and Discuss Concepts Take advantage of tools like ChatGPT or similar large language models to **explore your topic** in greater depth. Use these tools to: - Ask specific questions to clarify confusing points. - Engage in discussions to simulate real-world applications of the subject. - Generate examples or analogies that deepen your understanding. **Tip**: Use LLMs as a study partner, but don’t rely solely on them. Combine these insights with your own critical thinking to develop a well-rounded perspective. --- ## Get Started Ready to try the Four-Layer Method? Take 15 minutes today to map out the big picture of a topic you’re curious about—what’s it all about, and why does it matter? By building your understanding step by step, you’ll master the subject with less stress and more confidence.
@ a4a6b584:1e05b95b
2025-01-02 18:13:31## The Four-Layer Framework ### Layer 1: Zoom Out  Start by looking at the big picture. What’s the subject about, and why does it matter? Focus on the overarching ideas and how they fit together. Think of this as the 30,000-foot view—it’s about understanding the "why" and "how" before diving into the "what." **Example**: If you’re learning programming, start by understanding that it’s about giving logical instructions to computers to solve problems. - **Tip**: Keep it simple. Summarize the subject in one or two sentences and avoid getting bogged down in specifics at this stage. _Once you have the big picture in mind, it’s time to start breaking it down._ --- ### Layer 2: Categorize and Connect  Now it’s time to break the subject into categories—like creating branches on a tree. This helps your brain organize information logically and see connections between ideas. **Example**: Studying biology? Group concepts into categories like cells, genetics, and ecosystems. - **Tip**: Use headings or labels to group similar ideas. Jot these down in a list or simple diagram to keep track. _With your categories in place, you’re ready to dive into the details that bring them to life._ --- ### Layer 3: Master the Details  Once you’ve mapped out the main categories, you’re ready to dive deeper. This is where you learn the nuts and bolts—like formulas, specific techniques, or key terminology. These details make the subject practical and actionable. **Example**: In programming, this might mean learning the syntax for loops, conditionals, or functions in your chosen language. - **Tip**: Focus on details that clarify the categories from Layer 2. Skip anything that doesn’t add to your understanding. _Now that you’ve mastered the essentials, you can expand your knowledge to include extra material._ --- ### Layer 4: Expand Your Horizons  Finally, move on to the extra material—less critical facts, trivia, or edge cases. While these aren’t essential to mastering the subject, they can be useful in specialized discussions or exams. **Example**: Learn about rare programming quirks or historical trivia about a language’s development. - **Tip**: Spend minimal time here unless it’s necessary for your goals. It’s okay to skim if you’re short on time. --- ## Pro Tips for Better Learning ### 1. Use Active Recall and Spaced Repetition Test yourself without looking at notes. Review what you’ve learned at increasing intervals—like after a day, a week, and a month. This strengthens memory by forcing your brain to actively retrieve information. ### 2. Map It Out Create visual aids like [diagrams or concept maps](https://excalidraw.com/) to clarify relationships between ideas. These are particularly helpful for organizing categories in Layer 2. ### 3. Teach What You Learn Explain the subject to someone else as if they’re hearing it for the first time. Teaching **exposes any gaps** in your understanding and **helps reinforce** the material. ### 4. Engage with LLMs and Discuss Concepts Take advantage of tools like ChatGPT or similar large language models to **explore your topic** in greater depth. Use these tools to: - Ask specific questions to clarify confusing points. - Engage in discussions to simulate real-world applications of the subject. - Generate examples or analogies that deepen your understanding. **Tip**: Use LLMs as a study partner, but don’t rely solely on them. Combine these insights with your own critical thinking to develop a well-rounded perspective. --- ## Get Started Ready to try the Four-Layer Method? Take 15 minutes today to map out the big picture of a topic you’re curious about—what’s it all about, and why does it matter? By building your understanding step by step, you’ll master the subject with less stress and more confidence. @ 5391098c:74403a0e
2025-01-02 16:50:29Ensaio em Prosa sobre Fotografia Analógica Tenho especial fascínio pela fotografia analógica. É que se trata dum processo artístico muito mais complexo que a fotografia digital, devemos entender todos os aspectos da fotografia para obter o resultado pretendido, desde aspectos mecânicos da câmera como abertura e tempo do obturador, foco, iluminação, até a sensibilidade do filme utilizado e o resultado, quando alcançado, é verdadeira obra de arte pintada, onde a tela é a película química. Importante dizer que meu fascínio pela fotografia analógica não me impede de reconhecer a importância da fotografia digital, não fosse essa você não estaria vendo minhas obras de arte que foram digitalizadas… Da mesma forma que meu fascínio pela máquina de escrever não me impede de ter essa e outras páginas na internet. Parte do meu livro FILOSOFIA FUNDAMENTAL foi escrito graças a inspiração da máquina de escrever, como ocorreu no capítulo sobre o que seria evolução, escrevi integralmente na minha Olivetti Studio 46, pois havia faltado luz: o que me fez refletir sobre se o computador realmente é a evolução da máquina de escrever. Outro exemplo foi a inspiração que as lindas formas arredondas de minha máquina de escrever da marca Érika me proporcionou, acabou resultando numa bela performance a qual dei nome de Paixão Erótika. Por isso, acredito que os equipamentos analógicos não ofuscam nossa criatividade e na fotografia não poderia deixar de ser diferente. No conjunto de fotografias analógicas abaixo utilizei uma Canon T50, objetiva de 50mm e filme Kodak Pro Image 100, a qual se encontra auto-fotografada em espelho, vamos ver: Na foto abaixo utilizei luz amarela indireta da direita superior para esquerda inferior, o desfoque ao redor foi proposital com o objetivo de parecer estar olhando o mundo através das lentes da câmera, nesse caso ela estava olhando para sí mesmo. Mesmo estando a parede e o espelho no mesmo plano, a profundidade de campo do espelho é diferente, por isso esse efeito foi possível. Destaque especial para o “olho” do diafragma, deve ter aberto até f5.6, pois a luz não era muito forte. Se a luz fosse mais forte o diafragma teria aberto o mínimo f16 o que aumentaria a profundidade de campo impedindo o desfoque pretendido. O resultado foi alcançado, ao mesmo tempo que a câmera aparece, essa fotografia transmite essa mensagem subliminar: https://image.nostr.build/a7cbfbe68a4bb89ae731c360c373ac8eff7599a5a100d13035eb234b5d788626.jpg PERFORMANCE Performance é o nome dado à mescla de mais de uma linguagem artística (arte visual, música, teatro, etc.) clicando em https://davipinheiro.com/id/performance/ você pode ver todas minhas performances. Nos exemplos abaixo a mescla se deu pela mistura de artes visuais criadas por mim e captadas pela fotografia analógica, vamos ver: A foto abaixo se trata dum terrário que criei num tronco de árvore, arte plástica. Para fotografar utilizei luz amarela superior, o desfoque foi para destacar o objeto, especial destaque para o reflexo da luz no vidro para dar noção tridimensional de algo transparente: https://image.nostr.build/e8026f9e99fa16631959954f8bb925af6f1764911f0a315ab0125bb413e3e89b.jpg Na foto abaixo o mesmo processo da foto anterior, também utilizando uma Canon T50 com filme Kodak Pro Image 100 e objetiva de 50mm, diferenciando o enquadramento e a luz direta frontal: https://image.nostr.build/4c44a0baf2b5ddaf63f83420952ab1b2e84f7df292f8e413a65f8134a2e7db58.jpg A foto abaixo retrata o processo de criação da obra. Ironicamente, nessa foto, meu galo Cara de Palhaço mesmo desfocado no fundo se destacou, parecendo estar em pé no tronco: https://image.nostr.build/d0d5e73ecbcdefa79ffd858d0143f41915c9deab7864d271d5ee724b3927f9bc.jpg A foto abaixo se trata do pisca-alerta original da minha super DT200R (viva os motores 2 tempos!) que caiu depois de uma trilha kkk. A Ideia nesta fotografia era fazer o sol parecer estar acendendo o alerta que deveria aparentar estar flutuando no céu. Infelizmente não fui bem sucedido, pois os fios que penduravam o objeto acabaram aparecendo. É impressionante a capacidade de cálculo da Canon T50 e a velocidade do seu obturador, a nitidez da objetiva e a resolução do filme Kodak Pro Image 100, cujo conjunto conseguiu captar até os pequenos fios de nylon transparentes. Eu imaginei que a foto ia estourar e os fios não apareceriam, ledo engano. Pelo menos o enquadramento ficou correto: objeto um pouco mais acima do centro para dar sensação de altitude e levemente de perfil para dar noção 3d. Quem sabe com uma câmera que seja possível ajustar a velocidade do obturador eu seja bem sucedido… https://image.nostr.build/808243d34b6dbeade25d38189163f9d58f6a12da9d00df17c85651d501e1bed8.jpg A foto abaixo se trata da minha performance favorita com a fotografia analógica, pois fotografei o primeiro quadro que pintei, o qual dei o nome de Elipsoíris sendo ele posteriormente capa do meu livro FILOSOFIA FUNDAMENTAL, então aí temos três linguagens artísticas profundas na mesma performance: O quadro que virou livro fotografado analogicamente. A ideia desta performance foi enquadrar o quadro desfocado, o qual somente pode ser desvendado com os olhos certos, por isso a lente. Utilizei luz natural e uma lente velha de óculos. Especial destaque para os dois pontos de luz que refletiram na lente parecendo dois olhos, isso não foi planejado e deu um toque especial para a fotografia, cabendo diversas interpretações, esse é o objeto da arte em geral. Fiquei muuuito contente com o resultado: https://image.nostr.build/6bb5b802b3ad1bb7262b925225fcfb0b8b00654fa0fec240be57f648c32245af.jpg Já na fotografia analógica abaixo considero uma performance porque não se trata duma fotografia comum de paisagem, flores, arquitetura, animais ou pessoas, visa passar uma mensagem. Utilizando apenas a luz natural, regulei o foco da Canon T50 para as lentes dos meus próprios óculos e escolhi um dia especialmente nublado e escuro para simbolizar as dificuldades pelas quais todos passamos no dia-a-dia, quando acreditamos por algum momento que as luzes estão apagadas para nós, até que com os óculos certos podemos enxergar com maior nitidez o horizonte, os óculos podem ser a palavra de Deus ou qualquer outra coisa que te ilumine e esclareça. Com certeza essa fotografia terá um bom uso em meus próximos escritos: https://image.nostr.build/b44b573bb39cdf5f2eb446e818bbf59d5dab9d3815ac6e917440b2f6b1ff431c.jpg DUPLA EXPOSIÇÃO Eis aqui um recurso nato da fotografia analógica: a dupla exposição. Se trata de fotografar mais de uma vez em cima do mesmo filme de modo que as imagens se sobreponham. Como esse método podemos simular movimento numa única fotografia, fazer montagens de disco voador kkkk, enfim a imaginação é o limite, vamos ver: Nessa fotografia analógica abaixo ocorreu uma quádrupla exposição, pois cliquei quatro enquadramentos diferentes sob o mesmo filme. Foi especialmente difícil fazer porque a Canon T50 não tem esse recurso, então tive que enganá-la pressionando o botão de rebobinar o filme ao mesmo tempo que disparava a câmera. Como eu estava usando o filme Kodak Pro Image que possui asa 100, também regulei a máquina como se estivesse usando um filme asa 25, então sabia que podia disparar quatro vezes sem queimar o filme. Pedi para a modelo (minha Mãe, kkk) ficar em três posições diferentes dando a impressão de movimento e não satisfeito no final ainda fotografei o sol. Adorei essa foto: https://image.nostr.build/5f8e2962e2ee94259d4dd5d3b777976a4d20ba293a5a4e68e81e30a0e1975543.jpg FOTOS EM MACRO OU CLOSE Acredito ser possível obter uma fotografia analógica em macro mesmo sem lente especial, tudo depende da pecinha que fica atrás da câmera: você, kkkk. Devemos tentar, se não obtivermos uma fotografia em macro, ao menos um close teremos, vamos ver: Na foto abaixo há um minúsculo cogumelo que cresceu num barranco qualquer, apareceu nitidamente no negativo, mesmo sem uso de lupa, por isso considero um macro, na verdade é apenas uma foto divertida: https://image.nostr.build/02aa4bbdc0cf54519b694c75237693fc2a6569fe4f3167220b05c7498757b822.jpg Já a foto abaixo é apenas um close, o ninho é especialmente profundo, por isso o leve desfoque nos ovos: para dar noção de profundidade. O foco dos quatro cantos da caixa está bem ajustada para dar noção tridimensional do objeto: https://image.nostr.build/24e5dcdd0e5a3560b341fe4f0d0d93b7d562f2d58054ac308a8e312c2707100c.jpg O PRIMEIRO QUADRO DO ROLO Na fotografia analógica cada rolo de filme nos dá pelo menos um tipo de fotografia artística bem específica. Se trata do primeiro quadro do rolo, onde ocorre uma parcial sobre-exposição. Isso se deve a incidência da luz diretamente no filme quando estamos carregando a máquina com o filme. A maioria das máquinas analógicas somente começa a contar os fotogramas após alguns disparos para evitar isso. Cabe ao fotógrafo saber aproveitar os fotogramas existentes antes do número 1, enquadrando a cena normalmente e disparando antes do número 1. Os resultados são quase imprevisíveis e geralmente interessantes. Abaixo uma fotografia analógica fantástica porque quase sempre a sobre-exposição do primeiro quadro do rolo ocorre nas extremidades da foto e nessa aí ocorreu no meio. Para conseguir esse efeito carreguei a máquina no escuro e acendi a luz no exato momento que estava fechando a tampa da câmera. Por uma fração de segundo o primeiro quadro do rolo foi exposto parcialmente a luz, sabia que iria ter uma fotografia diferente, jamais imaginei que a sobre-exposição iria sair no meio do fotograma, muito curioso: https://image.nostr.build/a2e08aab686af64df949e83b4ff3b0a00952698a7a138412f7753ebc0dd63d1f.jpg Na fotografia abaixo repeti o mesmo processo anterior. Como o tempo entre acender a luz e fechar da máquina foi diferente a sobre-exposição ficou bem visível na extremidade da foto. Especial destaque para sua incidência no lado direito, quando deveria incidir no lado esquerdo, pois na Canon T50 o filme roda da esquerda para direita. Essa aparente inversão de lados se deu porque fotografei com a máquina de cabeça para baixo: https://image.nostr.build/270681be8de71b6c833507dda6bfe4b5233c9b871aa97ea8fc2ebdcdd46a682a.jpg FOTOS DE AÇÃO Registrar uma ação com fotografia analógica é especialmente difícil se a máquina não calcula a abertura e tempo de exposição automaticamente, porque tudo acontece muito rápido e você não tem tempo de ficar pensando. Felizmente a Canon T50 é muito boa para esse tipo de fotografia, tive que me preocupar apenas com o foco. O que essa máquina me fez suar para fazer as duplas exposições acima, tirou de letra esse memorável momento, vamos ver: Na foto abaixo quando avistei esse grupo de corajosos saltando de paraglider corri pedir autorização para fotografá-los e rapidamente carreguei a máquina. Comecei a fotografar mesmo antes da máquina registrar o primeiro fotograma do rolo, tendo obtido esse lindo efeito de sobre-exposição de primeiro quadro do rolo: https://image.nostr.build/8e32e22d3bf7c897d7111e85555146e38bb139985c50b2795fe809b31880c7d8.jpg Já a foto abaixo foi a terceira do rolo. Tomei o cuidado de enquadrar tanto a alçada de vôo do paraglider quanto essa linda Veraneio, o que descreve em uma única foto o espírito aventureiro do pessoal. Reparem no sol refletindo sobre as nuvens, que lindo tudo: https://image.nostr.build/5bf0444e4621406d858ab70725c1ee2f6a7e39b87663e23a18085a32b9a06f6a.jpg Na foto abaixo tive que registrar mais uma dessa linda Veraneio, sou apaixonado por motores e mecânica, ela quase roubou a cena kkkk. Especial destaque para o detalhe do carro e da câmera que a fotografou serem da mesma época, sensível retorno ao passado. Verdadeira máquina do tempo essa foto. Se eu não dissesse que esta foto foi tirada no final do ano de 2020 daria para dizer que foi uma foto tirada de uma Veraneio Zero Km da época, segredinho nosso, kkk. https://image.nostr.build/f5284ff30986ad84d22f137e0a330067f91564907da8acf04c9eb93a991cbcf2.jpg Na foto abaixo voltando à cena, agora do Ângulo certo kkk. Esse foi a segunda foto, perceba ainda a presença do efeito de sobre-exposição do primeiro quadro. Aqui a máquina estava marcando o primeiro fotograma, tadinha kkk https://image.nostr.build/5c1d73f7d802fd1f730427e29f921c82e410c5dce3112a3133d6fce294d310c6.jpg Na foto abaixo a luz estava perfeita, o sol iluminava atrás de mim, incidindo frontalmente para o enquadramento da foto, linda essa: https://image.nostr.build/156fc878dd18257ad1f59d1b5d3fd719c7e773937356fad6ea09b0ce1f151f12.jpg Paraglider quase em posição de vôo, a foto ficou quase perfeita porque o momento em tela era a Hora de Ouro, momento do entardecer quando a posição do sol deixa o céu dourado, fenômeno muito querido pelos fotógrafos analógicos; até pelos digitais também. Mesmo assim eu não estava satisfeito, queria fotografar mais de perto. Dei zoom correndo para frente e o resultado você vê abaixo: https://image.nostr.build/b1f610695bd57db8abe7408df318978b6e69e85fe620a589b12fb9bcaae66156.jpg Abaixo a fotografia analógica simplesmente perfeita, sol na posição certa, hora de ouro, perfeito enquadramento e foco, tudo certo, universo conspirando à favor… ganhei o dia sem saber. Só descobri depois que revelei. O chão não foi cortado é que o piloto do paraglider já estava no desnível do chão pronto para saltar: https://image.nostr.build/93a7e416d11c996b65a32b019667a43124d96985109d34fd1a9b239ef365bbfe.jpg Abaixo O salto… tive que correr para o barranco para dar zoom, outra foto perfeita na hora de ouro: https://image.nostr.build/f254c2e71863a233816b517564dd5fb7fe85ee0bd927b02687fba43bde53dcd6.jpg FOTOGRAFIA ANALÓGICA DE ANIMAIS É especialmente difícil fazer um animal posar para gente, temos que ter um pouco de comida pra negociar kkk. Não fosse a Canon T50 calcular a exposição sozinha seria ainda mais difícil porque os momentos são muito rápidos e você não tem tempo para regular a abertura e tempo de exposição, tive que regular apenas o foco. Mais um ponto para essa notável máquina que me fez apanhar na dupla exposição acima. A fotografia analógica de animais também é um tipo de fotografia de ação, temos que ser rápidos no gatilho, vamos ver os resultados: Abaixo novamente dei zoom chegando bem perto, fotógrafo de verdade não tem medo, tudo pela arte! https://image.nostr.build/5f0af116b1fd81edb3f21dfd5d7cce6c534751ac8660bd5fb58ce08c652d8aaf.jpg Abaixo foco no segundo plano, acabei pegando os dois de perfil: https://image.nostr.build/fbd78fcf71749569444d3438e0d5283d321fc3f3350cacc6e4a3e9a0cdc914f5.jpg Abaixo foco no segundo plano. Aqui peguei os dois olhando para mim e dizendo xiiiis, kkk. https://image.nostr.build/3a1f50ee1e3c6213b337654e69ee23819ab60100c8a1a049ee0b2b66fac0d8f8.jpg Abaixo podemos comprovar que o fotômetro da Canon T50 é matricial e não pontual, porque o centro da foto tinha muito mais luz que os cantos: https://image.nostr.build/11a8a5a7ff14a661755f04f743d70d3dd1a9d11e412791ce42f5cbf1da1c6be2.jpg Abaixo linda foto: Cavalo da Montanha. Eu estava esperando a Hora de Ouro chegar, pena que quando chegou o modelo não quis mais ser fotografado kkk. https://image.nostr.build/83429975966cb4b0e71e5e089651d4585513d823fea404014b0b78b21e859302.jpg Abaixo lindo close de perfil com fundo totalmente desfocado. Preto absoluto, a fotometria esta certinha: https://image.nostr.build/f36aed8fa89b6ba81dd77c7d3b32c24424483e626a9634cbadb16baf91427d66.jpg Abaixo muita coisa acontecendo ao mesmo tempo: As galinhas comendo, o milho sendo jogado, a sombra do fotógrafo… Para obter essa foto joguei o milho para o alto e tive que ser tão rápido no gatilho quanto o Kid Morengueira. Você pode perceber na minha sombra que estou segurando apenas a câmera, o pote de milho já tinha voado longe kkk. Escolhi especialmente um dia ensolarado para que o fotômetro da Canon T50 usasse toda a velocidade possível no obturador, sendo possível congelar o milho no ar sem muito efeito borrão. https://image.nostr.build/d566e46a8a3cba8855e80295910e5addb0a8aa7735093c9f93f129cac2379472.jpg Abaixo galinha chocando numa roda de carro. Como amo animais e carros, para montar essa cena tive que forrar uma roda velha de carro para formar um ninho e esperar, esperar e esperar… No momento certo a Jurema se sentiu confiante para entrar na roda. Nem se incomodou com minha presença pois estava de papo cheio, pois é, também tive que negociar com a galinha, isso é a fotografia analógica de animais kkk. Percebam novamente que o fotômetro da Canon T50 é matricial, pois a maior parte da foto era com pouca luz e o raio de sol que entrava estourou a foto. Percebam ainda como eu estava perto da galinha, pois foquei em sua cabeça e o resto do corpo que estava um pouco mais distante saiu desfocado. Certamente a câmera estava com abertura máxima f1.8 e com uma velocidade bem lenta, o que explica a baixa profundidade de campo. Além disso se a Jurema tivesse mexido a cabeça na hora do disparo certamente teria saído um borrão por causa da baixa velocidade. Acabou saindo tudo certo e meus dias de espera por essa foto não foram em vão. https://image.nostr.build/d7484609c8ff9be05ee6d518def402f66484a02109dc96ef5c734b11216385bf.jpg FOTOGRAFIA ANALÓGICA DE ARQUITETURA Na fotografia analógica de arquitetura devemos conhecer os conceitos básicos de iluminação e preenchimento, trabalhamos apenas com luz natural e deve ser bem usada para termos a noção tridimensional da construção. Conforme ensina Fernando Bagnola, a tridimensionalidade do objeto depende da incidência da luz em três pontos diferentes e com intensidades diferentes, algo difícil de se obter apenas com a luz do sol, vamos ver: Abaixo se trata do Museu do Olho em Curitiba/PR. Como sua parte frontal é escura e o sol se posicionava atrás da construção tive de me posicional na sua lateral, assim consegui obter um resultado tridimensional, pois o sol iluminava a parte de cima, refletia na parte de baixo em menor intensidade e na parte frontal quase não havia luz. Se eu estivesse posicionando na frente da construção o efeito tridimensional seria impossível: https://image.nostr.build/6f74c1c7e606f7950eaf45007868b92e9a0288722b3d5e580ecaa4930700e3ea.jpg Abaixo para minha sorte, nesse exato momento um grupo de jovens contracultura (assim como eu) passavam pelo local, tornando a foto icônica pela presença de jovens modernos contracultura contrastando com arquitetura moderna da cultura tradicional. Minha posição em relação ao sol também favoreceu o sucesso desta fotografia, tendo iluminado corretamente todos os pontos de interesse: https://image.nostr.build/7c374205d7df21985a6a71c6c17e4f67ab29baf452f0cd406b869df94d68296c.jpg Abaixo esse aqui é um exemplo de fotografia analógica arquitetônica errada. O enquadramento foi frontal em razão do desejo de captar o reflexo dos edifícios nos vidros negros do “olho”: https://image.nostr.build/f9a0869a165bc7e634944c01e59085203347ab6c353610bdcaace30ee3ed8d8a.jpg Abaixo se trata do Panteon dos Heroes na Lapa/PR um monumento erguido para guardar os corpos dos soldados das forças republicanas que pereceram durante o chamado Cerco da Lapa, batalha da Revolução Federalista de 1894. Aqui o dia estava nublado, momento perfeito para fotografar uma arquitetura tão triste como essa. Não me importei com a questão tridimensional, pois era impossível, não havia sol. Quis retratar a tristeza na foto. O filme usado foi o mesmo (Kodak Pro Image 100). Aqui percebemos que a química desse filme é ajustada para a luz amarela do sol como branco absoluto, como o céu estava nublado, a luz natural estava com temperatura mais fria o que puxou o tom mais para o azul e o roxeado da foto devem ter sido os raios ultravioleta. Se eu estivesse usando um filtro ultravioleta provavelmente a foto sairia mais acinzentada. Me recordo que nesse dia estava tudo cinza. De qualquer forma adorei esse tom arroxeado da foto. Fica a dica: conseguimos o mesmo efeito de um filme Lomochrome Purple caríssimo com um filme baratinho, basta fotografar nessas condições: https://image.nostr.build/24f91369c12e83861f7eec38ff99f1869f08ae1eec06c798ccbe08af62263a2e.jpg Abaixo novamente o tom arrocheado com um filme barato. Para se ter uma ideia um Lomochrome Purple costuma custar seis vezes ou mais que um que o Kodak Pro Image 100 de R$ 30,00 à R$ 40,00 na data da publicação deste artigo em 09/04/21. Percebam que no momento desta foto as nuvens deram uma trégua e alguns raios de sol passaram dando uma leve noção tridimensional da arquitetura. O certo seria eu estar um pouco mais à esquerda para aproveitar bem a iluminação. Mesmo assim, me senti feliz com a triste foto kkk pois mesmo com a luz amarela do sol refletindo o efeito Lomo-Violeta ocorreu: https://image.nostr.build/099a1a4d7857325e59f5b35805c0ebb5c3fa55af45de2096236f1dfbadca4d4a.jpg Abaixo parece que a foto está mal enquadrada. E está mesmo. É que no lado direito havia um poste de energia elétrica muito feio, eu não queria que aparecesse. Me preocupei apenas com a iluminação e obtive sucesso com a noção de profundidade da arquitetura. A foto está puxando para o amarelo porque a Universidade Federal do Paraná em Curitiba é meio amarela mesmo. https://image.nostr.build/48a4d517488fc1656e027568ad314688bc0fd9995e67289003f832eb904e5260.jpg Abaixo para finalizar o conjunto de fotografias analógicas arquitetônicas nada melhor que um cemitério, afinal todos vamos morrer um dia, devemos sempre lembrar disso para fazer nossas vidas mundanas valerem a pena. Quando morremos não levamos nada a não ser nossas experiências evolucionais, nossas graças e pecados. Devemos deixar um legado, algo positivo para quem fica. Pois bem, foi nesse contexto a foto. Para mim a morte deve ser evitada. Quando ocorrer, se fizermos tudo certo vamos para luz, as trevas são aqui na terra mesmo. Portanto, ao contrário da maioria dos fotógrafos, escolhi um dia ensolarado para fotografar ali. Quis simbolizar a luz que nos aguarda após a morte. Então me posicionei dentro do cemitério para fotografar de dentro para fora. Esperei o sol se posicionar de forma que dos portões para fora houvesse pouca luz, tal como é o mundo, deixando toda a iluminação para dentro dos portões. Percebam como pequenos detalhes fazem toda a diferença numa fotografia analógica artística. Essa foto pode perfeitamente ser usada para ilustrar qualquer material que corrobore com esse pensamento. Se eu quisesse retratar que a vida é mil maravilhas e a morte um triste fim, deveria estar do lado de fora dos portões com tudo iluminado exceto o interior do cemitério. Interessante não… https://image.nostr.build/051592db1d3612c719621547a69bc8dfd0319d6b89656451d5b60582ae864e8e.jpg FOTOGRAFIA ANALÓGICA DE PESSOAS Basicamente se divide em dois tipos, a cena e o retrato. Na cena a pessoa posa para a foto sem contudo revelar sua personalidade, é uma cena criada artificialmente. Já o retrato, no conceito artístico da fotografia, ocorre quando conseguimos captar o interior da pessoa. Por exemplo: se for uma pessoa triste ela aparecerá com semblante triste, se for uma pessoa alegre com semblante alegre, não necessariamente sorrido. Se for uma pessoa sofrida suas rugas, desasseios e receios ficarão visíveis. Se for uma pessoa engraçada sentiremos vontade de rir ao ver seu retrato. O retrato é algo verdadeiro e espontâneo da pessoa. Se uma pessoa triste aparece sorrido não é um retrato e sim uma cena, vamos ver: Abaixo normalmente na fotografia analógica de pessoas o correto é deixar o segundo plano mais escuro e o primeiro plano mais claro. Ai quis fazer diferente. Pedi para o modelo (Meu Melhor Amigo) se posicionar de costas para o sol, pois já tinha avistado aquele arco-íris no fundo. Nesse caso foi um retrato pois meu amigo apareceu sorrindo sem eu pedir e sei que ele é uma pessoa feliz e engraçada, pois vive contando piadas e seu repertório é infinito. O interessante é que esse não é um retrato comum e sim um retrato artístico, pois inverti a iluminação dos planos e ainda captei uma arco-íris, foi uma cena construida para um retrato, ideia antagônica para fotografia analógica de pessoas. Como resultado obtive uma fotografia que parece uma montagem, onde a imagem do modelo ter-se-ia sido colada sobre a paisagem, tamanha foi a diferença de iluminação entre o primeiro e segundo plano. Contudo, um pequeno raio de sol que incidiu sobre o canteiro inferior esquerdo não me deixa mentir que a fotografia é autêntica. Além disso tendo os negativos que não mentem kkk. Essa foi minha fotografia preferida de pessoas, pela qualidade do resultado artístico e pela pessoa do modelo, um abração amigo! Vou chamar essa foto de “Meu Parça na Praça”: https://image.nostr.build/51db1df7741227dc2d86529bc9e7a93cf27365f0f2d7b591a4e84a9a05855dfb.jpg Abaixo sou eu. Se trata apenas de uma cena simples porque minha expressão não aparece e sequer minhas roupas traduziam minha personalidade. Regulei o foco da máquina para 5 metros, entreguei-a para meu amigo e contei alguns passos para trás. Não me preocupei muito em acertar minha posição em exatos 5 metros porque o dia estava bem ensolarado e sabia qua a Canon T50 iria abrir pouco o diafragma por causa disso, o que aumentou a profundidade de campo consideravelmente. Podemos perceber no fundo a Universidade Federal do Paraná sem qualquer desfoque por causa disso. O maldito poste que tentei evitar na foto arquitetônica da UFPR acima acabou aparecendo aqui, mesmo assim gostei da foto pelo tom de cores que só a fotografia analógica nos dá. https://image.nostr.build/ce8af555274333fa8a26375247373ca92315e87d7414bcc9ad7b5a4840cb3a21.jpg FOTOGRAFIA ANELÓGICA DE OBJETOS A fotografia analógica de objetos, assim como a arquitetônica, deve se obedecer os conceitos básicos de iluminação para obter noção tridimensional do objeto. Além disso, a cena montada deve combinar com o objeto para entrar em sintonia com o conceito natural de beleza, vamos ver: Abaixo queria fotografar um objeto qualquer, então peguei essa faca. Esse objeto combina muito bem com o ambiente rústico do campo, então a finquei-a num toco de árvore com vista para o campo, tomando cuidado para ela ficar levemente torcida e dar a noção tridimensional. Naturalmente a foto ornou porque o objeto esta em sintonia com a cena. Essa deve ser a combinação da fotografia analógica de objetos, por exemplo. A não ser que o fotógrafo busque justamente causar repudia invertendo a combinação do objeto com a cena. Por exemplo: para causar nojo pode-se fotografar barro em formato de cocô num prato. Merda e comida são coisas totalmente opostas e essa inversão naturalmente é perturbadora para qualquer ser humano. Existe uma lógica natural de combinação de objetos com a cena. Enfim, podemos inclusive combinar mais de um objeto secundário para criar uma cena ao objeto principal, como veremos mais abaixo com a xícara de café: https://image.nostr.build/6474901ce85d34aef3421ce5f720e258208c50aeb57e9893c8a750c6dc8fc1df.jpg Na foto abaixo o objeto principal é uma caneca de café. Para criar a cena utilizei outros três objetos. O palheiro que combina com café, a tampa da objetiva da minha Canon T50 que combina com o efeito da cafeína para pensar mais rápido sobre as cenas que irei montar, e o vazo de suculenta que remete a algo mais áspero e amargo como o café e o palheiro. Se o objeto principal fosse um copo de milkshake no lugar do palheiro haveriam balas coloridas, no lugar da tampa da máquina haveria um guardanapo e no lugar da suculenta haveria um flor fofa e cor de rosa. Falando em flor vou encerrar este ensaio com o tópico sobre fotografia analógica de flores para deixar todos felizes no final: https://image.nostr.build/8e95c6bae536cfea47e3c5d44aa63725ab8fe20eacd1c6d5eeaae1720dd0a9e5.jpg FOTOGRAFIA ANELÓGICA DE FLORES É um tipo de fotografia livre da fotografia analógica, sem muitas preocupações para o fotógrafo analógico, devemos atentar apenas para a vivacidade das cores e para isso o dia deve estar especialmente ensolarado. Se for fotografia interna de preferência usar luz quente (amarela), o resto é só diversão, vamos ver: https://image.nostr.build/fc8cf663300794761b0d8dc6f1a765e3a423c65a4ad4a85a7885b00716b46533.jpg https://image.nostr.build/dc4fbe15a7b46817d66bdbeb3d0e11851999b2c1292c576fd457956436e75c77.jpg https://image.nostr.build/73fa3b1b30a088954b342294e1b0aa555a693c3ad425dea9807d2238ec529747.jpg Viva a fotografia analógica! Se você deseja fazer um ensaio artístico com fotografia analógia comigo entre em contato e terei o prazer de agendar o serviço.
@ 5391098c:74403a0e
2025-01-02 16:50:29Ensaio em Prosa sobre Fotografia Analógica Tenho especial fascínio pela fotografia analógica. É que se trata dum processo artístico muito mais complexo que a fotografia digital, devemos entender todos os aspectos da fotografia para obter o resultado pretendido, desde aspectos mecânicos da câmera como abertura e tempo do obturador, foco, iluminação, até a sensibilidade do filme utilizado e o resultado, quando alcançado, é verdadeira obra de arte pintada, onde a tela é a película química. Importante dizer que meu fascínio pela fotografia analógica não me impede de reconhecer a importância da fotografia digital, não fosse essa você não estaria vendo minhas obras de arte que foram digitalizadas… Da mesma forma que meu fascínio pela máquina de escrever não me impede de ter essa e outras páginas na internet. Parte do meu livro FILOSOFIA FUNDAMENTAL foi escrito graças a inspiração da máquina de escrever, como ocorreu no capítulo sobre o que seria evolução, escrevi integralmente na minha Olivetti Studio 46, pois havia faltado luz: o que me fez refletir sobre se o computador realmente é a evolução da máquina de escrever. Outro exemplo foi a inspiração que as lindas formas arredondas de minha máquina de escrever da marca Érika me proporcionou, acabou resultando numa bela performance a qual dei nome de Paixão Erótika. Por isso, acredito que os equipamentos analógicos não ofuscam nossa criatividade e na fotografia não poderia deixar de ser diferente. No conjunto de fotografias analógicas abaixo utilizei uma Canon T50, objetiva de 50mm e filme Kodak Pro Image 100, a qual se encontra auto-fotografada em espelho, vamos ver: Na foto abaixo utilizei luz amarela indireta da direita superior para esquerda inferior, o desfoque ao redor foi proposital com o objetivo de parecer estar olhando o mundo através das lentes da câmera, nesse caso ela estava olhando para sí mesmo. Mesmo estando a parede e o espelho no mesmo plano, a profundidade de campo do espelho é diferente, por isso esse efeito foi possível. Destaque especial para o “olho” do diafragma, deve ter aberto até f5.6, pois a luz não era muito forte. Se a luz fosse mais forte o diafragma teria aberto o mínimo f16 o que aumentaria a profundidade de campo impedindo o desfoque pretendido. O resultado foi alcançado, ao mesmo tempo que a câmera aparece, essa fotografia transmite essa mensagem subliminar: https://image.nostr.build/a7cbfbe68a4bb89ae731c360c373ac8eff7599a5a100d13035eb234b5d788626.jpg PERFORMANCE Performance é o nome dado à mescla de mais de uma linguagem artística (arte visual, música, teatro, etc.) clicando em https://davipinheiro.com/id/performance/ você pode ver todas minhas performances. Nos exemplos abaixo a mescla se deu pela mistura de artes visuais criadas por mim e captadas pela fotografia analógica, vamos ver: A foto abaixo se trata dum terrário que criei num tronco de árvore, arte plástica. Para fotografar utilizei luz amarela superior, o desfoque foi para destacar o objeto, especial destaque para o reflexo da luz no vidro para dar noção tridimensional de algo transparente: https://image.nostr.build/e8026f9e99fa16631959954f8bb925af6f1764911f0a315ab0125bb413e3e89b.jpg Na foto abaixo o mesmo processo da foto anterior, também utilizando uma Canon T50 com filme Kodak Pro Image 100 e objetiva de 50mm, diferenciando o enquadramento e a luz direta frontal: https://image.nostr.build/4c44a0baf2b5ddaf63f83420952ab1b2e84f7df292f8e413a65f8134a2e7db58.jpg A foto abaixo retrata o processo de criação da obra. Ironicamente, nessa foto, meu galo Cara de Palhaço mesmo desfocado no fundo se destacou, parecendo estar em pé no tronco: https://image.nostr.build/d0d5e73ecbcdefa79ffd858d0143f41915c9deab7864d271d5ee724b3927f9bc.jpg A foto abaixo se trata do pisca-alerta original da minha super DT200R (viva os motores 2 tempos!) que caiu depois de uma trilha kkk. A Ideia nesta fotografia era fazer o sol parecer estar acendendo o alerta que deveria aparentar estar flutuando no céu. Infelizmente não fui bem sucedido, pois os fios que penduravam o objeto acabaram aparecendo. É impressionante a capacidade de cálculo da Canon T50 e a velocidade do seu obturador, a nitidez da objetiva e a resolução do filme Kodak Pro Image 100, cujo conjunto conseguiu captar até os pequenos fios de nylon transparentes. Eu imaginei que a foto ia estourar e os fios não apareceriam, ledo engano. Pelo menos o enquadramento ficou correto: objeto um pouco mais acima do centro para dar sensação de altitude e levemente de perfil para dar noção 3d. Quem sabe com uma câmera que seja possível ajustar a velocidade do obturador eu seja bem sucedido… https://image.nostr.build/808243d34b6dbeade25d38189163f9d58f6a12da9d00df17c85651d501e1bed8.jpg A foto abaixo se trata da minha performance favorita com a fotografia analógica, pois fotografei o primeiro quadro que pintei, o qual dei o nome de Elipsoíris sendo ele posteriormente capa do meu livro FILOSOFIA FUNDAMENTAL, então aí temos três linguagens artísticas profundas na mesma performance: O quadro que virou livro fotografado analogicamente. A ideia desta performance foi enquadrar o quadro desfocado, o qual somente pode ser desvendado com os olhos certos, por isso a lente. Utilizei luz natural e uma lente velha de óculos. Especial destaque para os dois pontos de luz que refletiram na lente parecendo dois olhos, isso não foi planejado e deu um toque especial para a fotografia, cabendo diversas interpretações, esse é o objeto da arte em geral. Fiquei muuuito contente com o resultado: https://image.nostr.build/6bb5b802b3ad1bb7262b925225fcfb0b8b00654fa0fec240be57f648c32245af.jpg Já na fotografia analógica abaixo considero uma performance porque não se trata duma fotografia comum de paisagem, flores, arquitetura, animais ou pessoas, visa passar uma mensagem. Utilizando apenas a luz natural, regulei o foco da Canon T50 para as lentes dos meus próprios óculos e escolhi um dia especialmente nublado e escuro para simbolizar as dificuldades pelas quais todos passamos no dia-a-dia, quando acreditamos por algum momento que as luzes estão apagadas para nós, até que com os óculos certos podemos enxergar com maior nitidez o horizonte, os óculos podem ser a palavra de Deus ou qualquer outra coisa que te ilumine e esclareça. Com certeza essa fotografia terá um bom uso em meus próximos escritos: https://image.nostr.build/b44b573bb39cdf5f2eb446e818bbf59d5dab9d3815ac6e917440b2f6b1ff431c.jpg DUPLA EXPOSIÇÃO Eis aqui um recurso nato da fotografia analógica: a dupla exposição. Se trata de fotografar mais de uma vez em cima do mesmo filme de modo que as imagens se sobreponham. Como esse método podemos simular movimento numa única fotografia, fazer montagens de disco voador kkkk, enfim a imaginação é o limite, vamos ver: Nessa fotografia analógica abaixo ocorreu uma quádrupla exposição, pois cliquei quatro enquadramentos diferentes sob o mesmo filme. Foi especialmente difícil fazer porque a Canon T50 não tem esse recurso, então tive que enganá-la pressionando o botão de rebobinar o filme ao mesmo tempo que disparava a câmera. Como eu estava usando o filme Kodak Pro Image que possui asa 100, também regulei a máquina como se estivesse usando um filme asa 25, então sabia que podia disparar quatro vezes sem queimar o filme. Pedi para a modelo (minha Mãe, kkk) ficar em três posições diferentes dando a impressão de movimento e não satisfeito no final ainda fotografei o sol. Adorei essa foto: https://image.nostr.build/5f8e2962e2ee94259d4dd5d3b777976a4d20ba293a5a4e68e81e30a0e1975543.jpg FOTOS EM MACRO OU CLOSE Acredito ser possível obter uma fotografia analógica em macro mesmo sem lente especial, tudo depende da pecinha que fica atrás da câmera: você, kkkk. Devemos tentar, se não obtivermos uma fotografia em macro, ao menos um close teremos, vamos ver: Na foto abaixo há um minúsculo cogumelo que cresceu num barranco qualquer, apareceu nitidamente no negativo, mesmo sem uso de lupa, por isso considero um macro, na verdade é apenas uma foto divertida: https://image.nostr.build/02aa4bbdc0cf54519b694c75237693fc2a6569fe4f3167220b05c7498757b822.jpg Já a foto abaixo é apenas um close, o ninho é especialmente profundo, por isso o leve desfoque nos ovos: para dar noção de profundidade. O foco dos quatro cantos da caixa está bem ajustada para dar noção tridimensional do objeto: https://image.nostr.build/24e5dcdd0e5a3560b341fe4f0d0d93b7d562f2d58054ac308a8e312c2707100c.jpg O PRIMEIRO QUADRO DO ROLO Na fotografia analógica cada rolo de filme nos dá pelo menos um tipo de fotografia artística bem específica. Se trata do primeiro quadro do rolo, onde ocorre uma parcial sobre-exposição. Isso se deve a incidência da luz diretamente no filme quando estamos carregando a máquina com o filme. A maioria das máquinas analógicas somente começa a contar os fotogramas após alguns disparos para evitar isso. Cabe ao fotógrafo saber aproveitar os fotogramas existentes antes do número 1, enquadrando a cena normalmente e disparando antes do número 1. Os resultados são quase imprevisíveis e geralmente interessantes. Abaixo uma fotografia analógica fantástica porque quase sempre a sobre-exposição do primeiro quadro do rolo ocorre nas extremidades da foto e nessa aí ocorreu no meio. Para conseguir esse efeito carreguei a máquina no escuro e acendi a luz no exato momento que estava fechando a tampa da câmera. Por uma fração de segundo o primeiro quadro do rolo foi exposto parcialmente a luz, sabia que iria ter uma fotografia diferente, jamais imaginei que a sobre-exposição iria sair no meio do fotograma, muito curioso: https://image.nostr.build/a2e08aab686af64df949e83b4ff3b0a00952698a7a138412f7753ebc0dd63d1f.jpg Na fotografia abaixo repeti o mesmo processo anterior. Como o tempo entre acender a luz e fechar da máquina foi diferente a sobre-exposição ficou bem visível na extremidade da foto. Especial destaque para sua incidência no lado direito, quando deveria incidir no lado esquerdo, pois na Canon T50 o filme roda da esquerda para direita. Essa aparente inversão de lados se deu porque fotografei com a máquina de cabeça para baixo: https://image.nostr.build/270681be8de71b6c833507dda6bfe4b5233c9b871aa97ea8fc2ebdcdd46a682a.jpg FOTOS DE AÇÃO Registrar uma ação com fotografia analógica é especialmente difícil se a máquina não calcula a abertura e tempo de exposição automaticamente, porque tudo acontece muito rápido e você não tem tempo de ficar pensando. Felizmente a Canon T50 é muito boa para esse tipo de fotografia, tive que me preocupar apenas com o foco. O que essa máquina me fez suar para fazer as duplas exposições acima, tirou de letra esse memorável momento, vamos ver: Na foto abaixo quando avistei esse grupo de corajosos saltando de paraglider corri pedir autorização para fotografá-los e rapidamente carreguei a máquina. Comecei a fotografar mesmo antes da máquina registrar o primeiro fotograma do rolo, tendo obtido esse lindo efeito de sobre-exposição de primeiro quadro do rolo: https://image.nostr.build/8e32e22d3bf7c897d7111e85555146e38bb139985c50b2795fe809b31880c7d8.jpg Já a foto abaixo foi a terceira do rolo. Tomei o cuidado de enquadrar tanto a alçada de vôo do paraglider quanto essa linda Veraneio, o que descreve em uma única foto o espírito aventureiro do pessoal. Reparem no sol refletindo sobre as nuvens, que lindo tudo: https://image.nostr.build/5bf0444e4621406d858ab70725c1ee2f6a7e39b87663e23a18085a32b9a06f6a.jpg Na foto abaixo tive que registrar mais uma dessa linda Veraneio, sou apaixonado por motores e mecânica, ela quase roubou a cena kkkk. Especial destaque para o detalhe do carro e da câmera que a fotografou serem da mesma época, sensível retorno ao passado. Verdadeira máquina do tempo essa foto. Se eu não dissesse que esta foto foi tirada no final do ano de 2020 daria para dizer que foi uma foto tirada de uma Veraneio Zero Km da época, segredinho nosso, kkk. https://image.nostr.build/f5284ff30986ad84d22f137e0a330067f91564907da8acf04c9eb93a991cbcf2.jpg Na foto abaixo voltando à cena, agora do Ângulo certo kkk. Esse foi a segunda foto, perceba ainda a presença do efeito de sobre-exposição do primeiro quadro. Aqui a máquina estava marcando o primeiro fotograma, tadinha kkk https://image.nostr.build/5c1d73f7d802fd1f730427e29f921c82e410c5dce3112a3133d6fce294d310c6.jpg Na foto abaixo a luz estava perfeita, o sol iluminava atrás de mim, incidindo frontalmente para o enquadramento da foto, linda essa: https://image.nostr.build/156fc878dd18257ad1f59d1b5d3fd719c7e773937356fad6ea09b0ce1f151f12.jpg Paraglider quase em posição de vôo, a foto ficou quase perfeita porque o momento em tela era a Hora de Ouro, momento do entardecer quando a posição do sol deixa o céu dourado, fenômeno muito querido pelos fotógrafos analógicos; até pelos digitais também. Mesmo assim eu não estava satisfeito, queria fotografar mais de perto. Dei zoom correndo para frente e o resultado você vê abaixo: https://image.nostr.build/b1f610695bd57db8abe7408df318978b6e69e85fe620a589b12fb9bcaae66156.jpg Abaixo a fotografia analógica simplesmente perfeita, sol na posição certa, hora de ouro, perfeito enquadramento e foco, tudo certo, universo conspirando à favor… ganhei o dia sem saber. Só descobri depois que revelei. O chão não foi cortado é que o piloto do paraglider já estava no desnível do chão pronto para saltar: https://image.nostr.build/93a7e416d11c996b65a32b019667a43124d96985109d34fd1a9b239ef365bbfe.jpg Abaixo O salto… tive que correr para o barranco para dar zoom, outra foto perfeita na hora de ouro: https://image.nostr.build/f254c2e71863a233816b517564dd5fb7fe85ee0bd927b02687fba43bde53dcd6.jpg FOTOGRAFIA ANALÓGICA DE ANIMAIS É especialmente difícil fazer um animal posar para gente, temos que ter um pouco de comida pra negociar kkk. Não fosse a Canon T50 calcular a exposição sozinha seria ainda mais difícil porque os momentos são muito rápidos e você não tem tempo para regular a abertura e tempo de exposição, tive que regular apenas o foco. Mais um ponto para essa notável máquina que me fez apanhar na dupla exposição acima. A fotografia analógica de animais também é um tipo de fotografia de ação, temos que ser rápidos no gatilho, vamos ver os resultados: Abaixo novamente dei zoom chegando bem perto, fotógrafo de verdade não tem medo, tudo pela arte! https://image.nostr.build/5f0af116b1fd81edb3f21dfd5d7cce6c534751ac8660bd5fb58ce08c652d8aaf.jpg Abaixo foco no segundo plano, acabei pegando os dois de perfil: https://image.nostr.build/fbd78fcf71749569444d3438e0d5283d321fc3f3350cacc6e4a3e9a0cdc914f5.jpg Abaixo foco no segundo plano. Aqui peguei os dois olhando para mim e dizendo xiiiis, kkk. https://image.nostr.build/3a1f50ee1e3c6213b337654e69ee23819ab60100c8a1a049ee0b2b66fac0d8f8.jpg Abaixo podemos comprovar que o fotômetro da Canon T50 é matricial e não pontual, porque o centro da foto tinha muito mais luz que os cantos: https://image.nostr.build/11a8a5a7ff14a661755f04f743d70d3dd1a9d11e412791ce42f5cbf1da1c6be2.jpg Abaixo linda foto: Cavalo da Montanha. Eu estava esperando a Hora de Ouro chegar, pena que quando chegou o modelo não quis mais ser fotografado kkk. https://image.nostr.build/83429975966cb4b0e71e5e089651d4585513d823fea404014b0b78b21e859302.jpg Abaixo lindo close de perfil com fundo totalmente desfocado. Preto absoluto, a fotometria esta certinha: https://image.nostr.build/f36aed8fa89b6ba81dd77c7d3b32c24424483e626a9634cbadb16baf91427d66.jpg Abaixo muita coisa acontecendo ao mesmo tempo: As galinhas comendo, o milho sendo jogado, a sombra do fotógrafo… Para obter essa foto joguei o milho para o alto e tive que ser tão rápido no gatilho quanto o Kid Morengueira. Você pode perceber na minha sombra que estou segurando apenas a câmera, o pote de milho já tinha voado longe kkk. Escolhi especialmente um dia ensolarado para que o fotômetro da Canon T50 usasse toda a velocidade possível no obturador, sendo possível congelar o milho no ar sem muito efeito borrão. https://image.nostr.build/d566e46a8a3cba8855e80295910e5addb0a8aa7735093c9f93f129cac2379472.jpg Abaixo galinha chocando numa roda de carro. Como amo animais e carros, para montar essa cena tive que forrar uma roda velha de carro para formar um ninho e esperar, esperar e esperar… No momento certo a Jurema se sentiu confiante para entrar na roda. Nem se incomodou com minha presença pois estava de papo cheio, pois é, também tive que negociar com a galinha, isso é a fotografia analógica de animais kkk. Percebam novamente que o fotômetro da Canon T50 é matricial, pois a maior parte da foto era com pouca luz e o raio de sol que entrava estourou a foto. Percebam ainda como eu estava perto da galinha, pois foquei em sua cabeça e o resto do corpo que estava um pouco mais distante saiu desfocado. Certamente a câmera estava com abertura máxima f1.8 e com uma velocidade bem lenta, o que explica a baixa profundidade de campo. Além disso se a Jurema tivesse mexido a cabeça na hora do disparo certamente teria saído um borrão por causa da baixa velocidade. Acabou saindo tudo certo e meus dias de espera por essa foto não foram em vão. https://image.nostr.build/d7484609c8ff9be05ee6d518def402f66484a02109dc96ef5c734b11216385bf.jpg FOTOGRAFIA ANALÓGICA DE ARQUITETURA Na fotografia analógica de arquitetura devemos conhecer os conceitos básicos de iluminação e preenchimento, trabalhamos apenas com luz natural e deve ser bem usada para termos a noção tridimensional da construção. Conforme ensina Fernando Bagnola, a tridimensionalidade do objeto depende da incidência da luz em três pontos diferentes e com intensidades diferentes, algo difícil de se obter apenas com a luz do sol, vamos ver: Abaixo se trata do Museu do Olho em Curitiba/PR. Como sua parte frontal é escura e o sol se posicionava atrás da construção tive de me posicional na sua lateral, assim consegui obter um resultado tridimensional, pois o sol iluminava a parte de cima, refletia na parte de baixo em menor intensidade e na parte frontal quase não havia luz. Se eu estivesse posicionando na frente da construção o efeito tridimensional seria impossível: https://image.nostr.build/6f74c1c7e606f7950eaf45007868b92e9a0288722b3d5e580ecaa4930700e3ea.jpg Abaixo para minha sorte, nesse exato momento um grupo de jovens contracultura (assim como eu) passavam pelo local, tornando a foto icônica pela presença de jovens modernos contracultura contrastando com arquitetura moderna da cultura tradicional. Minha posição em relação ao sol também favoreceu o sucesso desta fotografia, tendo iluminado corretamente todos os pontos de interesse: https://image.nostr.build/7c374205d7df21985a6a71c6c17e4f67ab29baf452f0cd406b869df94d68296c.jpg Abaixo esse aqui é um exemplo de fotografia analógica arquitetônica errada. O enquadramento foi frontal em razão do desejo de captar o reflexo dos edifícios nos vidros negros do “olho”: https://image.nostr.build/f9a0869a165bc7e634944c01e59085203347ab6c353610bdcaace30ee3ed8d8a.jpg Abaixo se trata do Panteon dos Heroes na Lapa/PR um monumento erguido para guardar os corpos dos soldados das forças republicanas que pereceram durante o chamado Cerco da Lapa, batalha da Revolução Federalista de 1894. Aqui o dia estava nublado, momento perfeito para fotografar uma arquitetura tão triste como essa. Não me importei com a questão tridimensional, pois era impossível, não havia sol. Quis retratar a tristeza na foto. O filme usado foi o mesmo (Kodak Pro Image 100). Aqui percebemos que a química desse filme é ajustada para a luz amarela do sol como branco absoluto, como o céu estava nublado, a luz natural estava com temperatura mais fria o que puxou o tom mais para o azul e o roxeado da foto devem ter sido os raios ultravioleta. Se eu estivesse usando um filtro ultravioleta provavelmente a foto sairia mais acinzentada. Me recordo que nesse dia estava tudo cinza. De qualquer forma adorei esse tom arroxeado da foto. Fica a dica: conseguimos o mesmo efeito de um filme Lomochrome Purple caríssimo com um filme baratinho, basta fotografar nessas condições: https://image.nostr.build/24f91369c12e83861f7eec38ff99f1869f08ae1eec06c798ccbe08af62263a2e.jpg Abaixo novamente o tom arrocheado com um filme barato. Para se ter uma ideia um Lomochrome Purple costuma custar seis vezes ou mais que um que o Kodak Pro Image 100 de R$ 30,00 à R$ 40,00 na data da publicação deste artigo em 09/04/21. Percebam que no momento desta foto as nuvens deram uma trégua e alguns raios de sol passaram dando uma leve noção tridimensional da arquitetura. O certo seria eu estar um pouco mais à esquerda para aproveitar bem a iluminação. Mesmo assim, me senti feliz com a triste foto kkk pois mesmo com a luz amarela do sol refletindo o efeito Lomo-Violeta ocorreu: https://image.nostr.build/099a1a4d7857325e59f5b35805c0ebb5c3fa55af45de2096236f1dfbadca4d4a.jpg Abaixo parece que a foto está mal enquadrada. E está mesmo. É que no lado direito havia um poste de energia elétrica muito feio, eu não queria que aparecesse. Me preocupei apenas com a iluminação e obtive sucesso com a noção de profundidade da arquitetura. A foto está puxando para o amarelo porque a Universidade Federal do Paraná em Curitiba é meio amarela mesmo. https://image.nostr.build/48a4d517488fc1656e027568ad314688bc0fd9995e67289003f832eb904e5260.jpg Abaixo para finalizar o conjunto de fotografias analógicas arquitetônicas nada melhor que um cemitério, afinal todos vamos morrer um dia, devemos sempre lembrar disso para fazer nossas vidas mundanas valerem a pena. Quando morremos não levamos nada a não ser nossas experiências evolucionais, nossas graças e pecados. Devemos deixar um legado, algo positivo para quem fica. Pois bem, foi nesse contexto a foto. Para mim a morte deve ser evitada. Quando ocorrer, se fizermos tudo certo vamos para luz, as trevas são aqui na terra mesmo. Portanto, ao contrário da maioria dos fotógrafos, escolhi um dia ensolarado para fotografar ali. Quis simbolizar a luz que nos aguarda após a morte. Então me posicionei dentro do cemitério para fotografar de dentro para fora. Esperei o sol se posicionar de forma que dos portões para fora houvesse pouca luz, tal como é o mundo, deixando toda a iluminação para dentro dos portões. Percebam como pequenos detalhes fazem toda a diferença numa fotografia analógica artística. Essa foto pode perfeitamente ser usada para ilustrar qualquer material que corrobore com esse pensamento. Se eu quisesse retratar que a vida é mil maravilhas e a morte um triste fim, deveria estar do lado de fora dos portões com tudo iluminado exceto o interior do cemitério. Interessante não… https://image.nostr.build/051592db1d3612c719621547a69bc8dfd0319d6b89656451d5b60582ae864e8e.jpg FOTOGRAFIA ANALÓGICA DE PESSOAS Basicamente se divide em dois tipos, a cena e o retrato. Na cena a pessoa posa para a foto sem contudo revelar sua personalidade, é uma cena criada artificialmente. Já o retrato, no conceito artístico da fotografia, ocorre quando conseguimos captar o interior da pessoa. Por exemplo: se for uma pessoa triste ela aparecerá com semblante triste, se for uma pessoa alegre com semblante alegre, não necessariamente sorrido. Se for uma pessoa sofrida suas rugas, desasseios e receios ficarão visíveis. Se for uma pessoa engraçada sentiremos vontade de rir ao ver seu retrato. O retrato é algo verdadeiro e espontâneo da pessoa. Se uma pessoa triste aparece sorrido não é um retrato e sim uma cena, vamos ver: Abaixo normalmente na fotografia analógica de pessoas o correto é deixar o segundo plano mais escuro e o primeiro plano mais claro. Ai quis fazer diferente. Pedi para o modelo (Meu Melhor Amigo) se posicionar de costas para o sol, pois já tinha avistado aquele arco-íris no fundo. Nesse caso foi um retrato pois meu amigo apareceu sorrindo sem eu pedir e sei que ele é uma pessoa feliz e engraçada, pois vive contando piadas e seu repertório é infinito. O interessante é que esse não é um retrato comum e sim um retrato artístico, pois inverti a iluminação dos planos e ainda captei uma arco-íris, foi uma cena construida para um retrato, ideia antagônica para fotografia analógica de pessoas. Como resultado obtive uma fotografia que parece uma montagem, onde a imagem do modelo ter-se-ia sido colada sobre a paisagem, tamanha foi a diferença de iluminação entre o primeiro e segundo plano. Contudo, um pequeno raio de sol que incidiu sobre o canteiro inferior esquerdo não me deixa mentir que a fotografia é autêntica. Além disso tendo os negativos que não mentem kkk. Essa foi minha fotografia preferida de pessoas, pela qualidade do resultado artístico e pela pessoa do modelo, um abração amigo! Vou chamar essa foto de “Meu Parça na Praça”: https://image.nostr.build/51db1df7741227dc2d86529bc9e7a93cf27365f0f2d7b591a4e84a9a05855dfb.jpg Abaixo sou eu. Se trata apenas de uma cena simples porque minha expressão não aparece e sequer minhas roupas traduziam minha personalidade. Regulei o foco da máquina para 5 metros, entreguei-a para meu amigo e contei alguns passos para trás. Não me preocupei muito em acertar minha posição em exatos 5 metros porque o dia estava bem ensolarado e sabia qua a Canon T50 iria abrir pouco o diafragma por causa disso, o que aumentou a profundidade de campo consideravelmente. Podemos perceber no fundo a Universidade Federal do Paraná sem qualquer desfoque por causa disso. O maldito poste que tentei evitar na foto arquitetônica da UFPR acima acabou aparecendo aqui, mesmo assim gostei da foto pelo tom de cores que só a fotografia analógica nos dá. https://image.nostr.build/ce8af555274333fa8a26375247373ca92315e87d7414bcc9ad7b5a4840cb3a21.jpg FOTOGRAFIA ANELÓGICA DE OBJETOS A fotografia analógica de objetos, assim como a arquitetônica, deve se obedecer os conceitos básicos de iluminação para obter noção tridimensional do objeto. Além disso, a cena montada deve combinar com o objeto para entrar em sintonia com o conceito natural de beleza, vamos ver: Abaixo queria fotografar um objeto qualquer, então peguei essa faca. Esse objeto combina muito bem com o ambiente rústico do campo, então a finquei-a num toco de árvore com vista para o campo, tomando cuidado para ela ficar levemente torcida e dar a noção tridimensional. Naturalmente a foto ornou porque o objeto esta em sintonia com a cena. Essa deve ser a combinação da fotografia analógica de objetos, por exemplo. A não ser que o fotógrafo busque justamente causar repudia invertendo a combinação do objeto com a cena. Por exemplo: para causar nojo pode-se fotografar barro em formato de cocô num prato. Merda e comida são coisas totalmente opostas e essa inversão naturalmente é perturbadora para qualquer ser humano. Existe uma lógica natural de combinação de objetos com a cena. Enfim, podemos inclusive combinar mais de um objeto secundário para criar uma cena ao objeto principal, como veremos mais abaixo com a xícara de café: https://image.nostr.build/6474901ce85d34aef3421ce5f720e258208c50aeb57e9893c8a750c6dc8fc1df.jpg Na foto abaixo o objeto principal é uma caneca de café. Para criar a cena utilizei outros três objetos. O palheiro que combina com café, a tampa da objetiva da minha Canon T50 que combina com o efeito da cafeína para pensar mais rápido sobre as cenas que irei montar, e o vazo de suculenta que remete a algo mais áspero e amargo como o café e o palheiro. Se o objeto principal fosse um copo de milkshake no lugar do palheiro haveriam balas coloridas, no lugar da tampa da máquina haveria um guardanapo e no lugar da suculenta haveria um flor fofa e cor de rosa. Falando em flor vou encerrar este ensaio com o tópico sobre fotografia analógica de flores para deixar todos felizes no final: https://image.nostr.build/8e95c6bae536cfea47e3c5d44aa63725ab8fe20eacd1c6d5eeaae1720dd0a9e5.jpg FOTOGRAFIA ANELÓGICA DE FLORES É um tipo de fotografia livre da fotografia analógica, sem muitas preocupações para o fotógrafo analógico, devemos atentar apenas para a vivacidade das cores e para isso o dia deve estar especialmente ensolarado. Se for fotografia interna de preferência usar luz quente (amarela), o resto é só diversão, vamos ver: https://image.nostr.build/fc8cf663300794761b0d8dc6f1a765e3a423c65a4ad4a85a7885b00716b46533.jpg https://image.nostr.build/dc4fbe15a7b46817d66bdbeb3d0e11851999b2c1292c576fd457956436e75c77.jpg https://image.nostr.build/73fa3b1b30a088954b342294e1b0aa555a693c3ad425dea9807d2238ec529747.jpg Viva a fotografia analógica! Se você deseja fazer um ensaio artístico com fotografia analógia comigo entre em contato e terei o prazer de agendar o serviço. @ 1bda7e1f:bb97c4d9
2025-01-02 05:19:08### Tldr - Nostr is an open and interoperable protocol - You can integrate it with workflow automation tools to augment your experience - n8n is a great low/no-code workflow automation tool which you can host yourself - Nostrobots allows you to integrate Nostr into n8n - In this blog I create some workflow automations for Nostr - A simple form to delegate posting notes - Push notifications for mentions on multiple accounts - Push notifications for your favourite accounts when they post a note - All workflows are provided as open source with MIT license for you to use ### Inter-op All The Things Nostr is a new open social protocol for the internet. This open nature exciting because of the opportunities for interoperability with other technologies. In [Using NFC Cards with Nostr]() I explored the `nostr:` URI to launch Nostr clients from a card tap. The interoperability of Nostr doesn't stop there. The internet has many super-powers, and Nostr is open to all of them. Simply, there's no one to stop it. There is no one in charge, there are no permissioned APIs, and there are no risks of being de-platformed. If you can imagine technologies that would work well with Nostr, then any and all of them can ride on or alongside Nostr rails. My mental model for why this is special is Google Wave ~2010. Google Wave was to be the next big platform. Lars was running it and had a big track record from Maps. I was excited for it. Then, Google pulled the plug. And, immediately all the time and capital invested in understanding and building on the platform was wasted. This cannot happen to Nostr, as there is no one to pull the plug, and maybe even no plug to pull. So long as users demand Nostr, Nostr will exist, and that is a pretty strong guarantee. It makes it worthwhile to invest in bringing Nostr into our other applications. All we need are simple ways to plug things together. ### Nostr and Workflow Automation Workflow automation is about helping people to streamline their work. As a user, the most common way I achieve this is by connecting disparate systems together. By setting up one system to trigger another or to move data between systems, I can solve for many different problems and become way more effective. #### n8n for workflow automation Many workflow automation tools exist. My favourite is [n8n](https://n8n.io/). n8n is a low/no-code workflow automation platform which allows you to build all kinds of workflows. You can use it for free, you can self-host it, it has a user-friendly UI and useful API. Vs Zapier it can be far more elaborate. Vs Make.com I find it to be more intuitive in how it abstracts away the right parts of the code, but still allows you to code when you need to. Most importantly you can plug anything into n8n: You have built-in nodes for specific applications. HTTP nodes for any other API-based service. And community nodes built by individual community members for any other purpose you can imagine. #### Eating my own dogfood It's very clear to me that there is a big design space here just demanding to be explored. If you could integrate Nostr with anything, what would you do? In my view the best way for anyone to start anything is by solving their own problem first (aka "scratching your own itch" and "eating your own dogfood"). As I get deeper into Nostr I find myself controlling multiple Npubs – to date I have a personal Npub, a brand Npub for a community I am helping, an AI assistant Npub, and various testing Npubs. I need ways to delegate access to those Npubs without handing over the keys, ways to know if they're mentioned, and ways to know if they're posting. I can build workflows with n8n to solve these issues for myself to start with, and keep expanding from there as new needs come up. ### Running n8n with Nostrobots I am mostly non-technical with a very helpful AI. To set up n8n to work with Nostr and operate these workflows should be possible for anyone with basic technology skills. - I have a cheap VPS which currently runs my [HAVEN Nostr Relay](https://rodbishop.npub.pro/post/8ca68889/) and [Albyhub Lightning Node](https://rodbishop.npub.pro/post/setting-up-payments-on-nostr-7o6ls7/) in Docker containers, - My objective was to set up n8n to run alongside these in a separate Docker container on the same server, install the required nodes, and then build and host my workflows. #### Installing n8n Self-hosting n8n could not be easier. I followed n8n's [Docker-Compose installation docs](https://docs.n8n.io/hosting/installation/server-setups/docker-compose/)– - Install Docker and Docker-Compose if you haven't already, - Create your ``docker-compose.yml`` and `.env` files from the docs, - Create your data folder `sudo docker volume create n8n_data`, - Start your container with `sudo docker compose up -d`, - Your n8n instance should be online at port `5678`. n8n is free to self-host but does require a license. Enter your credentials into n8n to get your free license key. You should now have access to the Workflow dashboard and can create and host any kind of workflows from there. #### Installing Nostrobots To integrate n8n nicely with Nostr, I used the [Nostrobots](https://github.com/ocknamo/n8n-nodes-nostrobots?tab=readme-ov-file) community node by [Ocknamo](nostr:npub1y6aja0kkc4fdvuxgqjcdv4fx0v7xv2epuqnddey2eyaxquznp9vq0tp75l). In n8n parlance a "node" enables certain functionality as a step in a workflow e.g. a "set" node sets a variable, a "send email" node sends an email. n8n comes with all kinds of "official" nodes installed by default, and Nostr is not amongst them. However, n8n also comes with a framework for community members to create their own "community" nodes, which is where Nostrobots comes in. You can only use a community node in a self-hosted n8n instance (which is what you have if you are running in Docker on your own server, but this limitation does prevent you from using n8n's own hosted alternative). To install a community node, [see n8n community node docs](https://docs.n8n.io/integrations/community-nodes/installation/gui-install/). From your workflow dashboard– - Click the "..." in the bottom left corner beside your username, and click "settings", - Cilck "community nodes" left sidebar, - Click "Install", - Enter the "npm Package Name" which is `n8n-nodes-nostrobots`, - Accept the risks and click "Install", - Nostrobots is now added to your n8n instance. #### Using Nostrobots Nostrobots gives you nodes to help you build Nostr-integrated workflows– - **Nostr Write** – for posting Notes to the Nostr network, - **Nostr Read** – for reading Notes from the Nostr network, and - **Nostr Utils** – for performing certain conversions you may need (e.g. from bech32 to hex). Nostrobots has [good documentation](https://github.com/ocknamo/n8n-nodes-nostrobots?tab=readme-ov-file) on each node which focuses on simple use cases. Each node has a "convenience mode" by default. For example, the "Read" Node by default will fetch Kind 1 notes by a simple filter, in Nostrobots parlance a "Strategy". For example, with Strategy set to "Mention" the node will accept a pubkey and fetch all Kind 1 notes that Mention the pubkey within a time period. This is very good for quick use. What wasn't clear to me initially (until Ocknamo helped me out) is that advanced use cases are also possible. Each node also has an advanced mode. For example, the "Read" Node can have "Strategy" set to "RawFilter(advanced)". Now the node will accept json (anything you like that complies with [NIP-01](https://github.com/nostr-protocol/nips/blob/master/01.md)). You can use this to query Notes (Kind 1) as above, and also Profiles (Kind 0), Follow Lists (Kind 3), Reactions (Kind 7), Zaps (Kind 9734/9735), and anything else you can think of. #### Creating and adding workflows With n8n and Nostrobots installed, you can now create or add any kind of Nostr Workflow Automation. - Click "Add workflow" to go to the workflow builder screen, - If you would like to build your own workflow, you can start with adding any node. Click "+" and see what is available. Type "Nostr" to explore the Nostrobots nodes you have added, - If you would like to add workflows that someone else has built, click "..." in the top right. Then click "import from URL" and paste in the URL of any workflow you would like to use (including the ones I share later in this article). ### Nostr Workflow Automations It's time to build some things! #### A simple form to post a note to Nostr I started very simply. I needed to delegate the ability to post to Npubs that I own in order that a (future) team can test things for me. I don't want to worry about managing or training those people on how to use keys, and I want to revoke access easily. I needed a basic form with credentials that posted a Note. For this I can use a very simple workflow– - **A n8n Form node** – Creates a form for users to enter the note they wish to post. Allows for the form to be protected by a username and password. This node is the workflow "trigger" so that the workflow runs each time the form is submitted. - **A Set node** – Allows me to set some variables, in this case I set the relays that I intend to use. I typically add a Set node immediately following the trigger node, and put all the variables I need in this. It helps to make the workflows easier to update and maintain. - **A Nostr Write node** (from Nostrobots) – Writes a Kind-1 note to the Nostr network. It accepts Nostr credentials, the output of the Form node, and the relays from the Set node, and posts the Note to those relays. Once the workflow is built, you can test it with the testing form URL, and set it to "Active" to use the production form URL. That's it. You can now give posting access to anyone for any Npub. To revoke access, simply change the credentials or set to workflow to "Inactive". It may also be the world's simplest Nostr client. You can find the [Nostr Form to Post a Note workflow here](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Form_to_Post_a_Note.json). #### Push notifications on mentions and new notes One of the things Nostr is not very good at is push notifications. Furthermore I have some unique itches to scratch. I want– - **To make sure I never miss a note addressed to any of my Npubs** – For this I want a push notification any time any Nostr user mentions any of my Npubs, - **To make sure I always see all notes from key accounts** – For this I need a push notification any time any of my Npubs post any Notes to the network, - **To get these notifications on all of my devices** – Not just my phone where my Nostr regular client lives, but also on each of my laptops to suit wherever I am working that day. I needed to build a Nostr push notifications solution. To build this workflow I had to string a few ideas together– - **Triggering the node on a schedule** – Nostrobots does not include a trigger node. As every workflow starts with a trigger we needed a different method. I elected to run the workflow on a schedule of every 10-minutes. Frequent enough to see Notes while they are hot, but infrequent enough to not burden public relays or get rate-limited, - **Storing a list of Npubs in a Nostr list** – I needed a way to store the list of Npubs that trigger my notifications. I initially used an array defined in the workflow, this worked fine. Then I decided to try Nostr lists ([NIP-51, kind 30000](https://github.com/nostr-protocol/nips/blob/master/51.md)). By defining my list of Npubs as a list published to Nostr I can control my list from within a Nostr client (e.g. [Listr.lol](https://listr.lol/npub1r0d8u8mnj6769500nypnm28a9hpk9qg8jr0ehe30tygr3wuhcnvs4rfsft) or [Nostrudel.ninja](https://nostrudel.ninja/#/lists)). Not only does this "just work", but because it's based on Nostr lists automagically Amethyst client allows me to browse that list as a Feed, and everyone I add gets notified in their Mentions, - **Using specific relays** – I needed to query the right relays, including my own HAVEN relay inbox for notes addressed to me, and wss://purplepag.es for Nostr profile metadata, - **Querying Nostr events** (with Nostrobots) – I needed to make use of many different Nostr queries and use quite a wide range of what Nostrobots can do– - I read the EventID of my Kind 30000 list, to return the desired pubkeys, - For notifications on mentions, I read all Kind 1 notes that mention that pubkey, - For notifications on new notes, I read all Kind 1 notes published by that pubkey, - Where there are notes, I read the Kind 0 profile metadata event of that pubkey to get the displayName of the relevant Npub, - I transform the EventID into a Nevent to help clients find it. - **Using the Nostr URI** – As I did with my NFC card article, I created a link with the `nostr:` URI prefix so that my phone's native client opens the link by default, - **Push notifications solution** – I needed a push notifications solution. I found many with n8n integrations and chose to go with [Pushover](https://pushover.net/) which supports all my devices, has a free trial, and is unfairly cheap with a $5-per-device perpetual license. Once the workflow was built, lists published, and Pushover installed on my phone, I was fully set up with push notifications on Nostr. I have used these workflows for several weeks now and made various tweaks as I went. They are feeling robust and I'd welcome you to give them a go. You can find the [Nostr Push Notification If Mentioned here](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Push_Notify_If_Mentioned.json) and [If Posts a Note here](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Push_Notify_If_Post_a_Note.json). In speaking with other Nostr users while I was building this, there are all kind of other needs for push notifications too – like on replies to a certain bookmarked note, or when a followed Npub starts streaming on zap.stream. These are all possible. #### Use my workflows I have open sourced all my workflows at my [Github](https://github.com/r0d8lsh0p/nostr-n8n) with MIT license and tried to write complete docs, so that you can import them into your n8n and configure them for your own use. To import any of my workflows– - Click on the workflow of your choice, e.g. "[Nostr_Push_Notify_If_Mentioned.json](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Push_Notify_If_Mentioned.json "Nostr_Push_Notify_If_Mentioned.json")", - Click on the "raw" button to view the raw JSON, ex any Github page layout, - Copy that URL, - Enter that URL in the "import from URL" dialog [mentioned above](#creating-and-adding-workflows). To configure them– - Prerequisites, credentials, and variables are all stated, - In general any variables required are entered into a Set Node that follows the trigger node, - Pushover has some extra setup but is very straightforward and documented in the workflow. ### What next? Over my first four blogs I explored creating a good Nostr setup with [Vanity Npub](https://rodbishop.npub.pro/post/mining-your-vanity-pubkey-4iupbf/), [Lightning Payments](https://rodbishop.npub.pro/post/setting-up-payments-on-nostr-7o6ls7/), [Nostr Addresses at Your Domain](https://rodbishop.npub.pro/post/ee8a46bc/), and [Personal Nostr Relay](https://rodbishop.npub.pro/post/8ca68889/). Then in my latest two blogs I explored different types of interoperability [with NFC cards](https://rodbishop.npub.pro/post/edde8387/) and now n8n Workflow Automation. Thinking ahead n8n can power any kind of interoperability between Nostr and any other legacy technology solution. On my mind as I write this: - Further enhancements to posting and delegating solutions and forms (enhanced UI or different note kinds), - Automated or scheduled posting (such as auto-liking everything [Lyn Alden](nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a) posts), - Further enhancements to push notifications, on new and different types of events (such as notifying me when I get a new follower, on replies to certain posts, or when a user starts streaming), - All kinds of bridges, such as bridging notes to and from Telegram, Slack, or Campfire. Or bridging RSS or other event feeds to Nostr, - All kinds of other automation (such as [BlackCoffee](nostr:npub1dqepr0g4t3ahvnjtnxazvws4rkqjpxl854n29wcew8wph0fmw90qlsmmgt) [controlling a coffee machine](https://primal.net/e/note16fzhh5yfc3u4kufx0mck63tsfperdrlpp96am2lmq066cnuqutds8retc3)), - All kinds of AI Assistants and Agents, In fact I have already released an open source workflow for an [AI Assistant](https://primal.net/p/npub1ahjpx53ewavp23g5zj9jgyfrpr8djmgjzg5mpe4xd0z69dqvq0kq2lf353), and will share more about that in my next blog. Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle. GM Nostr.
@ 1bda7e1f:bb97c4d9
2025-01-02 05:19:08### Tldr - Nostr is an open and interoperable protocol - You can integrate it with workflow automation tools to augment your experience - n8n is a great low/no-code workflow automation tool which you can host yourself - Nostrobots allows you to integrate Nostr into n8n - In this blog I create some workflow automations for Nostr - A simple form to delegate posting notes - Push notifications for mentions on multiple accounts - Push notifications for your favourite accounts when they post a note - All workflows are provided as open source with MIT license for you to use ### Inter-op All The Things Nostr is a new open social protocol for the internet. This open nature exciting because of the opportunities for interoperability with other technologies. In [Using NFC Cards with Nostr]() I explored the `nostr:` URI to launch Nostr clients from a card tap. The interoperability of Nostr doesn't stop there. The internet has many super-powers, and Nostr is open to all of them. Simply, there's no one to stop it. There is no one in charge, there are no permissioned APIs, and there are no risks of being de-platformed. If you can imagine technologies that would work well with Nostr, then any and all of them can ride on or alongside Nostr rails. My mental model for why this is special is Google Wave ~2010. Google Wave was to be the next big platform. Lars was running it and had a big track record from Maps. I was excited for it. Then, Google pulled the plug. And, immediately all the time and capital invested in understanding and building on the platform was wasted. This cannot happen to Nostr, as there is no one to pull the plug, and maybe even no plug to pull. So long as users demand Nostr, Nostr will exist, and that is a pretty strong guarantee. It makes it worthwhile to invest in bringing Nostr into our other applications. All we need are simple ways to plug things together. ### Nostr and Workflow Automation Workflow automation is about helping people to streamline their work. As a user, the most common way I achieve this is by connecting disparate systems together. By setting up one system to trigger another or to move data between systems, I can solve for many different problems and become way more effective. #### n8n for workflow automation Many workflow automation tools exist. My favourite is [n8n](https://n8n.io/). n8n is a low/no-code workflow automation platform which allows you to build all kinds of workflows. You can use it for free, you can self-host it, it has a user-friendly UI and useful API. Vs Zapier it can be far more elaborate. Vs Make.com I find it to be more intuitive in how it abstracts away the right parts of the code, but still allows you to code when you need to. Most importantly you can plug anything into n8n: You have built-in nodes for specific applications. HTTP nodes for any other API-based service. And community nodes built by individual community members for any other purpose you can imagine. #### Eating my own dogfood It's very clear to me that there is a big design space here just demanding to be explored. If you could integrate Nostr with anything, what would you do? In my view the best way for anyone to start anything is by solving their own problem first (aka "scratching your own itch" and "eating your own dogfood"). As I get deeper into Nostr I find myself controlling multiple Npubs – to date I have a personal Npub, a brand Npub for a community I am helping, an AI assistant Npub, and various testing Npubs. I need ways to delegate access to those Npubs without handing over the keys, ways to know if they're mentioned, and ways to know if they're posting. I can build workflows with n8n to solve these issues for myself to start with, and keep expanding from there as new needs come up. ### Running n8n with Nostrobots I am mostly non-technical with a very helpful AI. To set up n8n to work with Nostr and operate these workflows should be possible for anyone with basic technology skills. - I have a cheap VPS which currently runs my [HAVEN Nostr Relay](https://rodbishop.npub.pro/post/8ca68889/) and [Albyhub Lightning Node](https://rodbishop.npub.pro/post/setting-up-payments-on-nostr-7o6ls7/) in Docker containers, - My objective was to set up n8n to run alongside these in a separate Docker container on the same server, install the required nodes, and then build and host my workflows. #### Installing n8n Self-hosting n8n could not be easier. I followed n8n's [Docker-Compose installation docs](https://docs.n8n.io/hosting/installation/server-setups/docker-compose/)– - Install Docker and Docker-Compose if you haven't already, - Create your ``docker-compose.yml`` and `.env` files from the docs, - Create your data folder `sudo docker volume create n8n_data`, - Start your container with `sudo docker compose up -d`, - Your n8n instance should be online at port `5678`. n8n is free to self-host but does require a license. Enter your credentials into n8n to get your free license key. You should now have access to the Workflow dashboard and can create and host any kind of workflows from there. #### Installing Nostrobots To integrate n8n nicely with Nostr, I used the [Nostrobots](https://github.com/ocknamo/n8n-nodes-nostrobots?tab=readme-ov-file) community node by [Ocknamo](nostr:npub1y6aja0kkc4fdvuxgqjcdv4fx0v7xv2epuqnddey2eyaxquznp9vq0tp75l). In n8n parlance a "node" enables certain functionality as a step in a workflow e.g. a "set" node sets a variable, a "send email" node sends an email. n8n comes with all kinds of "official" nodes installed by default, and Nostr is not amongst them. However, n8n also comes with a framework for community members to create their own "community" nodes, which is where Nostrobots comes in. You can only use a community node in a self-hosted n8n instance (which is what you have if you are running in Docker on your own server, but this limitation does prevent you from using n8n's own hosted alternative). To install a community node, [see n8n community node docs](https://docs.n8n.io/integrations/community-nodes/installation/gui-install/). From your workflow dashboard– - Click the "..." in the bottom left corner beside your username, and click "settings", - Cilck "community nodes" left sidebar, - Click "Install", - Enter the "npm Package Name" which is `n8n-nodes-nostrobots`, - Accept the risks and click "Install", - Nostrobots is now added to your n8n instance. #### Using Nostrobots Nostrobots gives you nodes to help you build Nostr-integrated workflows– - **Nostr Write** – for posting Notes to the Nostr network, - **Nostr Read** – for reading Notes from the Nostr network, and - **Nostr Utils** – for performing certain conversions you may need (e.g. from bech32 to hex). Nostrobots has [good documentation](https://github.com/ocknamo/n8n-nodes-nostrobots?tab=readme-ov-file) on each node which focuses on simple use cases. Each node has a "convenience mode" by default. For example, the "Read" Node by default will fetch Kind 1 notes by a simple filter, in Nostrobots parlance a "Strategy". For example, with Strategy set to "Mention" the node will accept a pubkey and fetch all Kind 1 notes that Mention the pubkey within a time period. This is very good for quick use. What wasn't clear to me initially (until Ocknamo helped me out) is that advanced use cases are also possible. Each node also has an advanced mode. For example, the "Read" Node can have "Strategy" set to "RawFilter(advanced)". Now the node will accept json (anything you like that complies with [NIP-01](https://github.com/nostr-protocol/nips/blob/master/01.md)). You can use this to query Notes (Kind 1) as above, and also Profiles (Kind 0), Follow Lists (Kind 3), Reactions (Kind 7), Zaps (Kind 9734/9735), and anything else you can think of. #### Creating and adding workflows With n8n and Nostrobots installed, you can now create or add any kind of Nostr Workflow Automation. - Click "Add workflow" to go to the workflow builder screen, - If you would like to build your own workflow, you can start with adding any node. Click "+" and see what is available. Type "Nostr" to explore the Nostrobots nodes you have added, - If you would like to add workflows that someone else has built, click "..." in the top right. Then click "import from URL" and paste in the URL of any workflow you would like to use (including the ones I share later in this article). ### Nostr Workflow Automations It's time to build some things! #### A simple form to post a note to Nostr I started very simply. I needed to delegate the ability to post to Npubs that I own in order that a (future) team can test things for me. I don't want to worry about managing or training those people on how to use keys, and I want to revoke access easily. I needed a basic form with credentials that posted a Note. For this I can use a very simple workflow– - **A n8n Form node** – Creates a form for users to enter the note they wish to post. Allows for the form to be protected by a username and password. This node is the workflow "trigger" so that the workflow runs each time the form is submitted. - **A Set node** – Allows me to set some variables, in this case I set the relays that I intend to use. I typically add a Set node immediately following the trigger node, and put all the variables I need in this. It helps to make the workflows easier to update and maintain. - **A Nostr Write node** (from Nostrobots) – Writes a Kind-1 note to the Nostr network. It accepts Nostr credentials, the output of the Form node, and the relays from the Set node, and posts the Note to those relays. Once the workflow is built, you can test it with the testing form URL, and set it to "Active" to use the production form URL. That's it. You can now give posting access to anyone for any Npub. To revoke access, simply change the credentials or set to workflow to "Inactive". It may also be the world's simplest Nostr client. You can find the [Nostr Form to Post a Note workflow here](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Form_to_Post_a_Note.json). #### Push notifications on mentions and new notes One of the things Nostr is not very good at is push notifications. Furthermore I have some unique itches to scratch. I want– - **To make sure I never miss a note addressed to any of my Npubs** – For this I want a push notification any time any Nostr user mentions any of my Npubs, - **To make sure I always see all notes from key accounts** – For this I need a push notification any time any of my Npubs post any Notes to the network, - **To get these notifications on all of my devices** – Not just my phone where my Nostr regular client lives, but also on each of my laptops to suit wherever I am working that day. I needed to build a Nostr push notifications solution. To build this workflow I had to string a few ideas together– - **Triggering the node on a schedule** – Nostrobots does not include a trigger node. As every workflow starts with a trigger we needed a different method. I elected to run the workflow on a schedule of every 10-minutes. Frequent enough to see Notes while they are hot, but infrequent enough to not burden public relays or get rate-limited, - **Storing a list of Npubs in a Nostr list** – I needed a way to store the list of Npubs that trigger my notifications. I initially used an array defined in the workflow, this worked fine. Then I decided to try Nostr lists ([NIP-51, kind 30000](https://github.com/nostr-protocol/nips/blob/master/51.md)). By defining my list of Npubs as a list published to Nostr I can control my list from within a Nostr client (e.g. [Listr.lol](https://listr.lol/npub1r0d8u8mnj6769500nypnm28a9hpk9qg8jr0ehe30tygr3wuhcnvs4rfsft) or [Nostrudel.ninja](https://nostrudel.ninja/#/lists)). Not only does this "just work", but because it's based on Nostr lists automagically Amethyst client allows me to browse that list as a Feed, and everyone I add gets notified in their Mentions, - **Using specific relays** – I needed to query the right relays, including my own HAVEN relay inbox for notes addressed to me, and wss://purplepag.es for Nostr profile metadata, - **Querying Nostr events** (with Nostrobots) – I needed to make use of many different Nostr queries and use quite a wide range of what Nostrobots can do– - I read the EventID of my Kind 30000 list, to return the desired pubkeys, - For notifications on mentions, I read all Kind 1 notes that mention that pubkey, - For notifications on new notes, I read all Kind 1 notes published by that pubkey, - Where there are notes, I read the Kind 0 profile metadata event of that pubkey to get the displayName of the relevant Npub, - I transform the EventID into a Nevent to help clients find it. - **Using the Nostr URI** – As I did with my NFC card article, I created a link with the `nostr:` URI prefix so that my phone's native client opens the link by default, - **Push notifications solution** – I needed a push notifications solution. I found many with n8n integrations and chose to go with [Pushover](https://pushover.net/) which supports all my devices, has a free trial, and is unfairly cheap with a $5-per-device perpetual license. Once the workflow was built, lists published, and Pushover installed on my phone, I was fully set up with push notifications on Nostr. I have used these workflows for several weeks now and made various tweaks as I went. They are feeling robust and I'd welcome you to give them a go. You can find the [Nostr Push Notification If Mentioned here](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Push_Notify_If_Mentioned.json) and [If Posts a Note here](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Push_Notify_If_Post_a_Note.json). In speaking with other Nostr users while I was building this, there are all kind of other needs for push notifications too – like on replies to a certain bookmarked note, or when a followed Npub starts streaming on zap.stream. These are all possible. #### Use my workflows I have open sourced all my workflows at my [Github](https://github.com/r0d8lsh0p/nostr-n8n) with MIT license and tried to write complete docs, so that you can import them into your n8n and configure them for your own use. To import any of my workflows– - Click on the workflow of your choice, e.g. "[Nostr_Push_Notify_If_Mentioned.json](https://github.com/r0d8lsh0p/nostr-n8n/blob/main/Nostr_Push_Notify_If_Mentioned.json "Nostr_Push_Notify_If_Mentioned.json")", - Click on the "raw" button to view the raw JSON, ex any Github page layout, - Copy that URL, - Enter that URL in the "import from URL" dialog [mentioned above](#creating-and-adding-workflows). To configure them– - Prerequisites, credentials, and variables are all stated, - In general any variables required are entered into a Set Node that follows the trigger node, - Pushover has some extra setup but is very straightforward and documented in the workflow. ### What next? Over my first four blogs I explored creating a good Nostr setup with [Vanity Npub](https://rodbishop.npub.pro/post/mining-your-vanity-pubkey-4iupbf/), [Lightning Payments](https://rodbishop.npub.pro/post/setting-up-payments-on-nostr-7o6ls7/), [Nostr Addresses at Your Domain](https://rodbishop.npub.pro/post/ee8a46bc/), and [Personal Nostr Relay](https://rodbishop.npub.pro/post/8ca68889/). Then in my latest two blogs I explored different types of interoperability [with NFC cards](https://rodbishop.npub.pro/post/edde8387/) and now n8n Workflow Automation. Thinking ahead n8n can power any kind of interoperability between Nostr and any other legacy technology solution. On my mind as I write this: - Further enhancements to posting and delegating solutions and forms (enhanced UI or different note kinds), - Automated or scheduled posting (such as auto-liking everything [Lyn Alden](nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a) posts), - Further enhancements to push notifications, on new and different types of events (such as notifying me when I get a new follower, on replies to certain posts, or when a user starts streaming), - All kinds of bridges, such as bridging notes to and from Telegram, Slack, or Campfire. Or bridging RSS or other event feeds to Nostr, - All kinds of other automation (such as [BlackCoffee](nostr:npub1dqepr0g4t3ahvnjtnxazvws4rkqjpxl854n29wcew8wph0fmw90qlsmmgt) [controlling a coffee machine](https://primal.net/e/note16fzhh5yfc3u4kufx0mck63tsfperdrlpp96am2lmq066cnuqutds8retc3)), - All kinds of AI Assistants and Agents, In fact I have already released an open source workflow for an [AI Assistant](https://primal.net/p/npub1ahjpx53ewavp23g5zj9jgyfrpr8djmgjzg5mpe4xd0z69dqvq0kq2lf353), and will share more about that in my next blog. Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle. GM Nostr. @ a95c6243:d345522c
2025-01-01 17:39:51**Heute möchte ich ein Gedicht mit euch teilen.** Es handelt sich um eine Ballade des österreichischen Lyrikers Johann Gabriel Seidl aus dem 19. Jahrhundert. Mir sind diese Worte fest in Erinnerung, da meine Mutter sie perfekt rezitieren konnte, auch als die Kräfte schon langsam schwanden. **Dem originalen Titel «Die Uhr»** habe ich für mich immer das Wort «innere» hinzugefügt. Denn der Zeitmesser – hier vermutliche eine Taschenuhr – symbolisiert zwar in dem Kontext das damalige Zeitempfinden und die Umbrüche durch die industrielle Revolution, sozusagen den Zeitgeist und das moderne Leben. Aber der Autor setzt sich philosophisch mit der Zeit auseinander und gibt seinem Werk auch eine klar spirituelle Dimension. **Das Ticken der Uhr und die Momente des Glücks und der Trauer** stehen sinnbildlich für das unaufhaltsame Fortschreiten und die Vergänglichkeit des Lebens. Insofern könnte man bei der Uhr auch an eine Sonnenuhr denken. Der Rhythmus der Ereignisse passt uns vielleicht nicht immer in den Kram. **Was den Takt pocht, ist durchaus auch das Herz,** unser «inneres Uhrwerk». Wenn dieses Meisterwerk einmal stillsteht, ist es unweigerlich um uns geschehen. Hoffentlich können wir dann dankbar sagen: «Ich habe mein Bestes gegeben.» *Ich trage, wo ich gehe, stets eine Uhr bei mir;* \ *Wieviel es geschlagen habe, genau seh ich an ihr.* \ *Es ist ein großer Meister, der künstlich ihr Werk gefügt,* \ *Wenngleich ihr Gang nicht immer dem törichten Wunsche genügt.*   *Ich wollte, sie wäre rascher gegangen an manchem Tag;* *\ Ich wollte, sie hätte manchmal verzögert den raschen Schlag.* *\ In meinen Leiden und Freuden, in Sturm und in der Ruh,* *\ Was immer geschah im Leben, sie pochte den Takt dazu.*   *Sie schlug am Sarge des Vaters, sie schlug an des Freundes Bahr,* *\ Sie schlug am Morgen der Liebe, sie schlug am Traualtar.* *\ Sie schlug an der Wiege des Kindes, sie schlägt, will's Gott, noch oft,* *\ Wenn bessere Tage kommen, wie meine Seele es hofft.*   *Und ward sie auch einmal träger, und drohte zu stocken ihr Lauf,* *\ So zog der Meister immer großmütig sie wieder auf.* *\ Doch stände sie einmal stille, dann wär's um sie geschehn,* *\ Kein andrer, als der sie fügte, bringt die Zerstörte zum Gehn.*   *Dann müßt ich zum Meister wandern, der wohnt am Ende wohl weit,* *\ Wohl draußen, jenseits der Erde, wohl dort in der Ewigkeit!* *\ Dann gäb ich sie ihm zurücke mit dankbar kindlichem Flehn:* *\ Sieh, Herr, ich hab nichts verdorben, sie blieb von selber stehn.*   *Johann Gabriel Seidl (1804-1875)*
@ a95c6243:d345522c
2025-01-01 17:39:51**Heute möchte ich ein Gedicht mit euch teilen.** Es handelt sich um eine Ballade des österreichischen Lyrikers Johann Gabriel Seidl aus dem 19. Jahrhundert. Mir sind diese Worte fest in Erinnerung, da meine Mutter sie perfekt rezitieren konnte, auch als die Kräfte schon langsam schwanden. **Dem originalen Titel «Die Uhr»** habe ich für mich immer das Wort «innere» hinzugefügt. Denn der Zeitmesser – hier vermutliche eine Taschenuhr – symbolisiert zwar in dem Kontext das damalige Zeitempfinden und die Umbrüche durch die industrielle Revolution, sozusagen den Zeitgeist und das moderne Leben. Aber der Autor setzt sich philosophisch mit der Zeit auseinander und gibt seinem Werk auch eine klar spirituelle Dimension. **Das Ticken der Uhr und die Momente des Glücks und der Trauer** stehen sinnbildlich für das unaufhaltsame Fortschreiten und die Vergänglichkeit des Lebens. Insofern könnte man bei der Uhr auch an eine Sonnenuhr denken. Der Rhythmus der Ereignisse passt uns vielleicht nicht immer in den Kram. **Was den Takt pocht, ist durchaus auch das Herz,** unser «inneres Uhrwerk». Wenn dieses Meisterwerk einmal stillsteht, ist es unweigerlich um uns geschehen. Hoffentlich können wir dann dankbar sagen: «Ich habe mein Bestes gegeben.» *Ich trage, wo ich gehe, stets eine Uhr bei mir;* \ *Wieviel es geschlagen habe, genau seh ich an ihr.* \ *Es ist ein großer Meister, der künstlich ihr Werk gefügt,* \ *Wenngleich ihr Gang nicht immer dem törichten Wunsche genügt.*   *Ich wollte, sie wäre rascher gegangen an manchem Tag;* *\ Ich wollte, sie hätte manchmal verzögert den raschen Schlag.* *\ In meinen Leiden und Freuden, in Sturm und in der Ruh,* *\ Was immer geschah im Leben, sie pochte den Takt dazu.*   *Sie schlug am Sarge des Vaters, sie schlug an des Freundes Bahr,* *\ Sie schlug am Morgen der Liebe, sie schlug am Traualtar.* *\ Sie schlug an der Wiege des Kindes, sie schlägt, will's Gott, noch oft,* *\ Wenn bessere Tage kommen, wie meine Seele es hofft.*   *Und ward sie auch einmal träger, und drohte zu stocken ihr Lauf,* *\ So zog der Meister immer großmütig sie wieder auf.* *\ Doch stände sie einmal stille, dann wär's um sie geschehn,* *\ Kein andrer, als der sie fügte, bringt die Zerstörte zum Gehn.*   *Dann müßt ich zum Meister wandern, der wohnt am Ende wohl weit,* *\ Wohl draußen, jenseits der Erde, wohl dort in der Ewigkeit!* *\ Dann gäb ich sie ihm zurücke mit dankbar kindlichem Flehn:* *\ Sieh, Herr, ich hab nichts verdorben, sie blieb von selber stehn.*   *Johann Gabriel Seidl (1804-1875)* @ a10260a2:caa23e3e
2025-01-01 12:42:22I’d like to start off by saying that phoenixd has been a great experience so far. The install (on a Linux machine) was as easy as depicted on their [website](https://phoenix.acinq.co/server/get-started).  And the channel I opened via [auto liquidity](https://phoenix.acinq.co/server/auto-liquidity) was super simple. I didn’t have to pick an LSP and I won’t need to manage liquidity. Unfortunately, the machine I installed the software on started to freeze seconds after every boot. After posting about it [here](https://stacker.news/items/825060/r/thebullishbitcoiner) and getting an answer from nostr:npub1lxktpvp5cnq3wl5ctu2x88e30mc0ahh8v47qvzc5dmneqqjrzlkqpm5xlc, I was surprised at how easy the migration seemed. It really was just a matter of restoring the seed words on another phoenixd instance. Of course, making sure that the two instances don’t run at the same time. As easy as it was, I wanted to create this post to give a quick overview for those who might be less tech savvy. ### Step 1 Grab seed words from the `seed.dat` file in hidden`.phoenix` folder on the old machine.  ### Step 2 Install phoenixd on the new machine ``` $ wget https://github.com/ACINQ/phoenixd/releases/download/v0.4.2/phoenix-0.4.2-linux-x64.zip $ unzip -j phoenix-0.4.2-linux-x64.zip $ # run the daemon: that's it! $ ./phoenixd ``` ### Step 3 (This is the step that wasn’t super clear and why I wanted to spell it out in this post) In order to install the software, `./phoenixd` has to be run. This is going to generate a new seed phrase.  Now, all you need to do is replace the seed words in `seed.dat` with the ones from the original install. In retrospect, I think you can replace the seed words right after unzipping the zip file and before running `./phoenixd`. That will probably achieve the same result. ### Step 4 Once the seed words have been restored. Just run `./phoenixd` again and it’ll start up like nothing happened. Literally. There was no indication whatsoever that something had changed, so I ran `./phoenix-cli getinfo` and, voila, there was my 2M-sat channel. It was quite magical. originally posted at https://stacker.news/items/829411 ### Update (1/1/2025) Phoenix Support got back to me and confirmed that the migration can be even simpler. You can actually just copy the ~/.phoenix directory onto the new machine and run `./phoenix`! 
@ a10260a2:caa23e3e
2025-01-01 12:42:22I’d like to start off by saying that phoenixd has been a great experience so far. The install (on a Linux machine) was as easy as depicted on their [website](https://phoenix.acinq.co/server/get-started).  And the channel I opened via [auto liquidity](https://phoenix.acinq.co/server/auto-liquidity) was super simple. I didn’t have to pick an LSP and I won’t need to manage liquidity. Unfortunately, the machine I installed the software on started to freeze seconds after every boot. After posting about it [here](https://stacker.news/items/825060/r/thebullishbitcoiner) and getting an answer from nostr:npub1lxktpvp5cnq3wl5ctu2x88e30mc0ahh8v47qvzc5dmneqqjrzlkqpm5xlc, I was surprised at how easy the migration seemed. It really was just a matter of restoring the seed words on another phoenixd instance. Of course, making sure that the two instances don’t run at the same time. As easy as it was, I wanted to create this post to give a quick overview for those who might be less tech savvy. ### Step 1 Grab seed words from the `seed.dat` file in hidden`.phoenix` folder on the old machine.  ### Step 2 Install phoenixd on the new machine ``` $ wget https://github.com/ACINQ/phoenixd/releases/download/v0.4.2/phoenix-0.4.2-linux-x64.zip $ unzip -j phoenix-0.4.2-linux-x64.zip $ # run the daemon: that's it! $ ./phoenixd ``` ### Step 3 (This is the step that wasn’t super clear and why I wanted to spell it out in this post) In order to install the software, `./phoenixd` has to be run. This is going to generate a new seed phrase.  Now, all you need to do is replace the seed words in `seed.dat` with the ones from the original install. In retrospect, I think you can replace the seed words right after unzipping the zip file and before running `./phoenixd`. That will probably achieve the same result. ### Step 4 Once the seed words have been restored. Just run `./phoenixd` again and it’ll start up like nothing happened. Literally. There was no indication whatsoever that something had changed, so I ran `./phoenix-cli getinfo` and, voila, there was my 2M-sat channel. It was quite magical. originally posted at https://stacker.news/items/829411 ### Update (1/1/2025) Phoenix Support got back to me and confirmed that the migration can be even simpler. You can actually just copy the ~/.phoenix directory onto the new machine and run `./phoenix`!  @ 5188521b:008eb518
2025-01-01 10:47:04My experience of [daily posting on LinkedIn](https://www.linkedin.com/in/totallyhumanwriter/) started around three years ago, when I became more serious about my coaching business. In that time, I amassed 25,000 followers and garnered around 3 million impressions on my writing. It was a wild ride, but now it’s time to leave the theme park. # Reasons I Quit Posting on LinkedIn Here they are, in no particular order: 1. I went from coach to ghostwriter. 2024 threw up an unexpected career change. Since 2018, I've been a coach, moving from teaching English as a foreign language to working with groups of multilingual pro writers looking for better opportunities. Coaching is a tough industry (maybe I'll write about that someday). My idea was to write more meaningful words and less copy to market my coaching business. Ultimately, writing to develop the Bitcoin ecosystem is what I find meaningful, and writing for hire doesn't require as much copywriting as being a coach. With a solid portfolio, contacts, and profile, potential clients can see your results. You don't need to attract a ton of inbound leads by writing funny bits and wow-inducing educational posts on LinkedIn. 2. Time constraints Because of my own book marketing, new client work, and projects like [21 Futures](https://21futures.com/), I can't dedicate my creative efforts and several hours per week to writing on LinkedIn. That time works better for me elsewhere. 3. Worsening distribution 'Creators' (a.k.a. active posters with many followers) often say changes to the algorithm don't matter. 'Get on with it. Adapt and move forward.' I'd be lying if I said I'm happy seeing statistics for my posts plummet. In 2022 and 2023, a successful carousel might net 20,000 views with over 150 likes and 50+ comments. Now, an exceptional post for me attracts 5,000 views with 50 likes. I won't bore you with charts and statistics, but this is an average, based on hundreds of posts. It seems LinkedIn is reducing the reach of big accounts in favour of tighter networks and distributing the work of those with <5k followers. That's fine. Perhaps that will make the platform less showy, and less boastful, finally ridding us of fake stories, surprising hacks, and ultimate guides. Still, It makes creative types like me feel like failures. Does an 80% decrease in distribution seem fair for the three years of daily effort I've put in? Should I keep struggling for diminishing returns? No. Creative people must seek the best return on investment for their time. The lesson? Distribution is more important than follower numbers. I've also quit Medium, where I have 2,000 followers and regularly receive single-digit reads on my posts. 4. LinkedIn values machines over humans. Cost-cutting, extracting value, and planning for a robotic future. That's Microsoft's MO. Despite being a social network with over 1 billion users, LinkedIn seemingly relies on automated support to make decisions on which content, people, and ideas are allowed on the platform. Users' data is parsed without their express consent.\ LinkedIn seems desperate for us to use generative AI to express our 'insight'.\ We are constantly bombarded by LLM drivel and boring machine-made content. If you can't be bothered to write it, why should I bother to read it? As somebody who brands himself a human-centric writer, why would I offer up personal takes and stories writing for free in an AI-filled swamp? --- # What's next? So I'm giving up posting on LinkedIn. With that said, it can still produce a great benefit for its users, especially those in the bitcoin space. Why? The ability to search for potential connections, present your profile, and share your expertise can make a huge difference to your work - investment, partnership, and customers. If you have a smaller network and have the need to share personal takes, opinions, and expertise, posting on LinkedIn is worth it. So few are doing this in bitcoin, the opportunities in 2025 are mind-boggling. Next year, thousands of new startups and ventures will be vying for our attention. Those who can build trust and stay true to their message will win. And if LinkedIn stops working, you can always take your followers elsewhere. If you have read and enjoyed my words here on LinkedIn in the last three years, thank you. It has been a much-needed creative outlet and has brought me opportunities, laughs, knowledge, new colleagues, and friends. I'll still be stalking your posts and writing sarcastic comments. --- # Where can you find me: Bitcoin writing - [X](https://x.com/21Futures), [StackerNews](https://stacker.news/21futures) [21futures.com](https://21futures.com/)\ NOSTR - npub12xy9yxej6s9hgzsn3rfyfc3xgtdr29wqlvulquzhz2fhqqywk5vqnyvqut), [Totallyhumanwriter.com](https://totallyhumanwriter.com/) - website coming soon. [Maximum Freedom, Minimum Bullshit](https://maximumfreedom.substack.com/) on Substack. And you can reach me via email at philipcharterauthor@gmail.com I'm interested to know your thoughts and plans for 2025. Where will you be writing and why?
@ 5188521b:008eb518
2025-01-01 10:47:04My experience of [daily posting on LinkedIn](https://www.linkedin.com/in/totallyhumanwriter/) started around three years ago, when I became more serious about my coaching business. In that time, I amassed 25,000 followers and garnered around 3 million impressions on my writing. It was a wild ride, but now it’s time to leave the theme park. # Reasons I Quit Posting on LinkedIn Here they are, in no particular order: 1. I went from coach to ghostwriter. 2024 threw up an unexpected career change. Since 2018, I've been a coach, moving from teaching English as a foreign language to working with groups of multilingual pro writers looking for better opportunities. Coaching is a tough industry (maybe I'll write about that someday). My idea was to write more meaningful words and less copy to market my coaching business. Ultimately, writing to develop the Bitcoin ecosystem is what I find meaningful, and writing for hire doesn't require as much copywriting as being a coach. With a solid portfolio, contacts, and profile, potential clients can see your results. You don't need to attract a ton of inbound leads by writing funny bits and wow-inducing educational posts on LinkedIn. 2. Time constraints Because of my own book marketing, new client work, and projects like [21 Futures](https://21futures.com/), I can't dedicate my creative efforts and several hours per week to writing on LinkedIn. That time works better for me elsewhere. 3. Worsening distribution 'Creators' (a.k.a. active posters with many followers) often say changes to the algorithm don't matter. 'Get on with it. Adapt and move forward.' I'd be lying if I said I'm happy seeing statistics for my posts plummet. In 2022 and 2023, a successful carousel might net 20,000 views with over 150 likes and 50+ comments. Now, an exceptional post for me attracts 5,000 views with 50 likes. I won't bore you with charts and statistics, but this is an average, based on hundreds of posts. It seems LinkedIn is reducing the reach of big accounts in favour of tighter networks and distributing the work of those with <5k followers. That's fine. Perhaps that will make the platform less showy, and less boastful, finally ridding us of fake stories, surprising hacks, and ultimate guides. Still, It makes creative types like me feel like failures. Does an 80% decrease in distribution seem fair for the three years of daily effort I've put in? Should I keep struggling for diminishing returns? No. Creative people must seek the best return on investment for their time. The lesson? Distribution is more important than follower numbers. I've also quit Medium, where I have 2,000 followers and regularly receive single-digit reads on my posts. 4. LinkedIn values machines over humans. Cost-cutting, extracting value, and planning for a robotic future. That's Microsoft's MO. Despite being a social network with over 1 billion users, LinkedIn seemingly relies on automated support to make decisions on which content, people, and ideas are allowed on the platform. Users' data is parsed without their express consent.\ LinkedIn seems desperate for us to use generative AI to express our 'insight'.\ We are constantly bombarded by LLM drivel and boring machine-made content. If you can't be bothered to write it, why should I bother to read it? As somebody who brands himself a human-centric writer, why would I offer up personal takes and stories writing for free in an AI-filled swamp? --- # What's next? So I'm giving up posting on LinkedIn. With that said, it can still produce a great benefit for its users, especially those in the bitcoin space. Why? The ability to search for potential connections, present your profile, and share your expertise can make a huge difference to your work - investment, partnership, and customers. If you have a smaller network and have the need to share personal takes, opinions, and expertise, posting on LinkedIn is worth it. So few are doing this in bitcoin, the opportunities in 2025 are mind-boggling. Next year, thousands of new startups and ventures will be vying for our attention. Those who can build trust and stay true to their message will win. And if LinkedIn stops working, you can always take your followers elsewhere. If you have read and enjoyed my words here on LinkedIn in the last three years, thank you. It has been a much-needed creative outlet and has brought me opportunities, laughs, knowledge, new colleagues, and friends. I'll still be stalking your posts and writing sarcastic comments. --- # Where can you find me: Bitcoin writing - [X](https://x.com/21Futures), [StackerNews](https://stacker.news/21futures) [21futures.com](https://21futures.com/)\ NOSTR - npub12xy9yxej6s9hgzsn3rfyfc3xgtdr29wqlvulquzhz2fhqqywk5vqnyvqut), [Totallyhumanwriter.com](https://totallyhumanwriter.com/) - website coming soon. [Maximum Freedom, Minimum Bullshit](https://maximumfreedom.substack.com/) on Substack. And you can reach me via email at philipcharterauthor@gmail.com I'm interested to know your thoughts and plans for 2025. Where will you be writing and why? @ 3f770d65:7a745b24
2024-12-31 17:03:46Here are my predictions for Nostr in 2025: **Decentralization:** The outbox and inbox communication models, sometimes referred to as the Gossip model, will become the standard across the ecosystem. By the end of 2025, all major clients will support these models, providing seamless communication and enhanced decentralization. Clients that do not adopt outbox/inbox by then will be regarded as outdated or legacy systems. **Privacy Standards:** Major clients such as Damus and Primal will move away from NIP-04 DMs, adopting more secure protocol possibilities like NIP-17 or NIP-104. These upgrades will ensure enhanced encryption and metadata protection. Additionally, NIP-104 MLS tools will drive the development of new clients and features, providing users with unprecedented control over the privacy of their communications. **Interoperability:** Nostr's ecosystem will become even more interconnected. Platforms like the Olas image-sharing service will expand into prominent clients such as Primal, Damus, Coracle, and Snort, alongside existing integrations with Amethyst, Nostur, and Nostrudel. Similarly, audio and video tools like Nostr Nests and Zap.stream will gain seamless integration into major clients, enabling easy participation in live events across the ecosystem. **Adoption and Migration:** Inspired by early pioneers like Fountain and Orange Pill App, more platforms will adopt Nostr for authentication, login, and social systems. In 2025, a significant migration from a high-profile application platform with hundreds of thousands of users will transpire, doubling Nostr’s daily activity and establishing it as a cornerstone of decentralized technologies.
@ 3f770d65:7a745b24
2024-12-31 17:03:46Here are my predictions for Nostr in 2025: **Decentralization:** The outbox and inbox communication models, sometimes referred to as the Gossip model, will become the standard across the ecosystem. By the end of 2025, all major clients will support these models, providing seamless communication and enhanced decentralization. Clients that do not adopt outbox/inbox by then will be regarded as outdated or legacy systems. **Privacy Standards:** Major clients such as Damus and Primal will move away from NIP-04 DMs, adopting more secure protocol possibilities like NIP-17 or NIP-104. These upgrades will ensure enhanced encryption and metadata protection. Additionally, NIP-104 MLS tools will drive the development of new clients and features, providing users with unprecedented control over the privacy of their communications. **Interoperability:** Nostr's ecosystem will become even more interconnected. Platforms like the Olas image-sharing service will expand into prominent clients such as Primal, Damus, Coracle, and Snort, alongside existing integrations with Amethyst, Nostur, and Nostrudel. Similarly, audio and video tools like Nostr Nests and Zap.stream will gain seamless integration into major clients, enabling easy participation in live events across the ecosystem. **Adoption and Migration:** Inspired by early pioneers like Fountain and Orange Pill App, more platforms will adopt Nostr for authentication, login, and social systems. In 2025, a significant migration from a high-profile application platform with hundreds of thousands of users will transpire, doubling Nostr’s daily activity and establishing it as a cornerstone of decentralized technologies. @ e97aaffa:2ebd765d
2024-12-31 16:47:12Último dia do ano, momento para tirar o pó da bola de cristal, para fazer reflexões, previsões e desejos para o próximo ano e seguintes. Ano após ano, o Bitcoin evoluiu, foi ultrapassando etapas, tornou-se cada vez mais _mainstream_. Está cada vez mais difícil fazer previsões sobre o Bitcoin, já faltam poucas barreiras a serem ultrapassadas e as que faltam são altamente complexas ou tem um impacto profundo no sistema financeiro ou na sociedade. Estas alterações profundas tem que ser realizadas lentamente, porque uma alteração rápida poderia resultar em consequências terríveis, poderia provocar um retrocesso. # Código do Bitcoin No final de 2025, possivelmente vamos ter um _fork_, as discussões sobre os _covenants_ já estão avançadas, vão acelerar ainda mais. Já existe um consenso relativamente alto, a favor dos _covenants_, só falta decidir que modelo será escolhido. Penso que até ao final do ano será tudo decidido. Depois dos _covenants,_ o próximo foco será para a criptografia post-quantum, que será o maior desafio que o Bitcoin enfrenta. Criar uma criptografia segura e que não coloque a descentralização em causa. Espero muito de Ark, possivelmente a inovação do ano, gostaria de ver o Nostr a furar a bolha bitcoinheira e que o Cashu tivesse mais reconhecimento pelos _bitcoiners_. Espero que surjam avanços significativos no BitVM2 e BitVMX. Não sei o que esperar das layer 2 de Bitcoin, foram a maior desilusão de 2024. Surgiram com muita força, mas pouca coisa saiu do papel, foi uma mão cheia de nada. Uma parte dos projetos caiu na tentação da _shitcoinagem_, na criação de tokens, que tem um único objetivo, enriquecer os devs e os VCs. Se querem ser levados a sério, têm que ser sérios. > “À mulher de César não basta ser honesta, deve parecer honesta” Se querem ter o apoio dos _bitcoiners_, sigam o _ethos_ do Bitcoin. Neste ponto a atitude do pessoal da Ark é exemplar, em vez de andar a chorar no Twitter para mudar o código do Bitcoin, eles colocaram as mãos na massa e criaram o protocolo. É claro que agora está meio “coxo”, funciona com uma _multisig_ ou com os _covenants_ na Liquid. Mas eles estão a criar um produto, vão demonstrar ao mercado que o produto é bom e útil. Com a adoção, a comunidade vai perceber que o Ark necessita dos _covenants_ para melhorar a interoperabilidade e a soberania. É este o pensamento certo, que deveria ser seguido pelos restantes e futuros projetos. É seguir aquele pensamento do J.F. Kennedy: > “Não perguntem o que é que o vosso país pode fazer por vocês, perguntem o que é que vocês podem fazer pelo vosso país” Ou seja, não fiquem à espera que o bitcoin mude, criem primeiro as inovações/tecnologia, ganhem adoção e depois demonstrem que a alteração do código camada base pode melhorar ainda mais o vosso projeto. A necessidade é que vai levar a atualização do código. # Reservas Estratégicas de Bitcoin ## Bancos centrais Com a eleição de Trump, emergiu a ideia de uma Reserva Estratégia de Bitcoin, tornou este conceito _mainstream_. Foi um _pivot_, a partir desse momento, foram enumerados os políticos de todo o mundo a falar sobre o assunto. A Senadora Cynthia Lummis foi mais além e propôs um programa para adicionar 200 mil bitcoins à reserva ao ano, até 1 milhão de Bitcoin. Só que isto está a criar uma enorme expectativa na comunidade, só que pode resultar numa enorme desilusão. Porque no primeiro ano, o Trump em vez de comprar os 200 mil, pode apenas adicionar na reserva, os 198 mil que o Estado já tem em sua posse. Se isto acontecer, possivelmente vai resultar numa forte queda a curto prazo. Na minha opinião os bancos centrais deveriam seguir o exemplo de El Salvador, fazer um DCA diário. Mais que comprar bitcoin, para mim, o mais importante é a criação da Reserva, é colocar o Bitcoin ao mesmo nível do ouro, o impacto para o resto do mundo será tremendo, a teoria dos jogos na sua plenitude. Muitos outros bancos centrais vão ter que comprar, para não ficarem atrás, além disso, vai transmitir uma mensagem à generalidade da população, que o Bitcoin é “afinal é algo seguro, com valor”. Mas não foi Trump que iniciou esta teoria dos jogos, mas sim foi a primeira vítima dela. É o próprio Trump que o admite, que os EUA necessitam da reserva para não ficar atrás da China. Além disso, desde que os EUA utilizaram o dólar como uma arma, com sanção contra a Rússia, surgiram boatos de que a Rússia estaria a utilizar o Bitcoin para transações internacionais. Que foram confirmados recentemente, pelo próprio governo russo. Também há poucos dias, ainda antes deste reconhecimento público, Putin elogiou o Bitcoin, ao reconhecer que “Ninguém pode proibir o bitcoin”, defendendo como uma alternativa ao dólar. A narrativa está a mudar. Já existem alguns países com Bitcoin, mas apenas dois o fizeram conscientemente (El Salvador e Butão), os restantes têm devido a apreensões. Hoje são poucos, mas 2025 será o início de uma corrida pelos bancos centrais. Esta corrida era algo previsível, o que eu não esperava é que acontecesse tão rápido.  ## Empresas A criação de reservas estratégicas não vai ficar apenas pelos bancos centrais, também vai acelerar fortemente nas empresas em 2025.  Mas as empresas não vão seguir a estratégia do Saylor, vão comprar bitcoin sem alavancagem, utilizando apenas os tesouros das empresas, como uma proteção contra a inflação. Eu não sou grande admirador do Saylor, prefiro muito mais, uma estratégia conservadora, sem qualquer alavancagem. Penso que as empresas vão seguir a sugestão da BlackRock, que aconselha um alocações de 1% a 3%. Penso que 2025, ainda não será o ano da entrada das 6 magníficas (excepto Tesla), será sobretudo empresas de pequena e média dimensão. As magníficas ainda tem uma cota muito elevada de _shareholders_ com alguma idade, bastante conservadores, que têm dificuldade em compreender o Bitcoin, foi o que aconteceu recentemente com a Microsoft. Também ainda não será em 2025, talvez 2026, a inclusão nativamente de wallet Bitcoin nos sistema da Apple Pay e da Google Pay. Seria um passo gigante para a adoção a nível mundial. # ETFs Os ETFs para mim são uma incógnita, tenho demasiadas dúvidas, como será 2025. Este ano os _inflows_ foram superiores a 500 mil bitcoins, o IBIT foi o lançamento de ETF mais bem sucedido da história. O sucesso dos ETFs, deve-se a 2 situações que nunca mais se vão repetir. O mercado esteve 10 anos à espera pela aprovação dos ETFs, a procura estava reprimida, isso foi bem notório nos primeiros meses, os _inflows_ foram brutais. Também se beneficiou por ser um mercado novo, não existia _orderbook_ de vendas, não existia um mercado interno, praticamente era só _inflows_. Agora o mercado já estabilizou, a maioria das transações já são entre clientes dos próprios ETFs. Agora só uma pequena percentagem do volume das transações diárias vai resultar em _inflows_ ou _outflows_. Estes dois fenómenos nunca mais se vão repetir, eu não acredito que o número de _inflows_ em BTC supere os número de 2024, em dólares vai superar, mas em btc não acredito que vá superar. Mas em 2025 vão surgir uma infindável quantidade de novos produtos, derivativos, novos ETFs de cestos com outras criptos ou cestos com ativos tradicionais. O bitcoin será adicionado em produtos financeiros já existentes no mercado, as pessoas vão passar a deter bitcoin, sem o saberem. Com o fim da operação ChokePoint 2.0, vai surgir uma nova onda de adoção e de produtos financeiros. Possivelmente vamos ver bancos tradicionais a disponibilizar produtos ou serviços de custódia aos seus clientes. Eu adoraria ver o crescimento da adoção do bitcoin como moeda, só que a regulamentação não vai ajudar nesse processo. # Preço Eu acredito que o topo deste ciclo será alcançado no primeiro semestre, posteriormente haverá uma correção. Mas desta vez, eu acredito que a correção será muito menor que as anteriores, inferior a 50%, esta é a minha expectativa. Espero estar certo. # Stablecoins de dólar Agora saindo um pouco do universo do Bitcoin, acho importante destacar as _stablecoins_. No último ciclo, eu tenho dividido o tempo, entre continuar a estudar o Bitcoin e estudar o sistema financeiro, as suas dinâmicas e o comportamento humano. Isto tem sido o meu foco de reflexão, imaginar a transformação que o mundo vai sofrer devido ao padrão Bitcoin. É uma ilusão acreditar que a transição de um padrão FIAT para um padrão Bitcoin vai ser rápida, vai existir um processo transitório que pode demorar décadas. Com a re-entrada de Trump na Casa Branca, prometendo uma política altamente protecionista, vai provocar uma forte valorização do dólar, consequentemente as restantes moedas do mundo vão derreter. Provocando uma inflação generalizada, gerando uma corrida às _stablecoins_ de dólar nos países com moedas mais fracas. Trump vai ter uma política altamente expansionista, vai exportar dólares para todo o mundo, para financiar a sua própria dívida. A desigualdade entre os pobres e ricos irá crescer fortemente, aumentando a possibilidade de conflitos e revoltas. > “Casa onde não há pão, todos ralham e ninguém tem razão” Será mais lenha, para alimentar a fogueira, vai gravar os conflitos geopolíticos já existentes, ficando as sociedade ainda mais polarizadas. Eu acredito que 2025, vai haver um forte crescimento na adoção das _stablecoins_ de dólares, esse forte crescimento vai agravar o problema sistémico que são as _stablecoins_. Vai ser o início do fim das _stablecoins_, pelo menos, como nós conhecemos hoje em dia. ## Problema sistémico O sistema FIAT não nasceu de um dia para outro, foi algo que foi construído organicamente, ou seja, foi evoluindo ao longo dos anos, sempre que havia um problema/crise, eram criadas novas regras ou novas instituições para minimizar os problemas. Nestes quase 100 anos, desde os acordos de Bretton Woods, a evolução foram tantas, tornaram o sistema financeiro altamente complexo, burocrático e nada eficiente. Na prática é um castelo de cartas construído sobre outro castelo de cartas e que por sua vez, foi construído sobre outro castelo de cartas. As _stablecoins_ são um problema sistémico, devido às suas reservas em dólares e o sistema financeiro não está preparado para manter isso seguro. Com o crescimento das reservas ao longo dos anos, foi se agravando o problema. No início a Tether colocava as reservas em bancos comerciais, mas com o crescimento dos dólares sob gestão, criou um problema nos bancos comerciais, devido à reserva fracionária. Essas enormes reservas da Tether estavam a colocar em risco a própria estabilidade dos bancos. A Tether acabou por mudar de estratégia, optou por outros ativos, preferencialmente por títulos do tesouro/obrigações dos EUA. Só que a Tether continua a crescer e não dá sinais de abrandamento, pelo contrário. Até o próprio mundo cripto, menosprezava a gravidade do problema da Tether/_stablecoins_ para o resto do sistema financeiro, porque o _marketcap_ do cripto ainda é muito pequeno. É verdade que ainda é pequeno, mas a Tether não o é, está no top 20 dos maiores detentores de títulos do tesouros dos EUA e está ao nível dos maiores bancos centrais do mundo. Devido ao seu tamanho, está a preocupar os responsáveis/autoridades/reguladores dos EUA, pode colocar em causa a estabilidade do sistema financeiro global, que está assente nessas obrigações. Os títulos do tesouro dos EUA são o colateral mais utilizado no mundo, tanto por bancos centrais, como por empresas, é a charneira da estabilidade do sistema financeiro. Os títulos do tesouro são um assunto muito sensível. Na recente crise no Japão, do _carry trade_, o Banco Central do Japão tentou minimizar a desvalorização do iene através da venda de títulos dos EUA. Esta operação, obrigou a uma viagem de emergência, da Secretaria do Tesouro dos EUA, Janet Yellen ao Japão, onde disponibilizou liquidez para parar a venda de títulos por parte do Banco Central do Japão. Essa forte venda estava desestabilizando o mercado. Os principais detentores de títulos do tesouros são institucionais, bancos centrais, bancos comerciais, fundo de investimento e gestoras, tudo administrado por gestores altamente qualificados, racionais e que conhecem a complexidade do mercado de obrigações. O mundo cripto é seu oposto, é _naife_ com muita irracionalidade e uma forte pitada de loucura, na sua maioria nem faz a mínima ideia como funciona o sistema financeiro. Essa irracionalidade pode levar a uma “corrida bancária”, como aconteceu com o UST da Luna, que em poucas horas colapsou o projeto. Em termos de escala, a Luna ainda era muito pequena, por isso, o problema ficou circunscrito ao mundo cripto e a empresas ligadas diretamente ao cripto. Só que a Tether é muito diferente, caso exista algum FUD, que obrigue a Tether a desfazer-se de vários biliões ou dezenas de biliões de dólares em títulos num curto espaço de tempo, poderia provocar consequências terríveis em todo o sistema financeiro. A Tether é grande demais, é já um problema sistémico, que vai agravar-se com o crescimento em 2025. Não tenham dúvidas, se existir algum problema, o Tesouro dos EUA vai impedir a venda dos títulos que a Tether tem em sua posse, para salvar o sistema financeiro. O problema é, o que vai fazer a Tether, se ficar sem acesso às venda das reservas, como fará o _redeem_ dos dólares? Como o crescimento do Tether é inevitável, o Tesouro e o FED estão com um grande problema em mãos, o que fazer com o Tether? Mas o problema é que o atual sistema financeiro é como um curto cobertor: Quanto tapas a cabeça, destapas os pés; Ou quando tapas os pés, destapas a cabeça. Ou seja, para resolver o problema da guarda reservas da Tether, vai criar novos problemas, em outros locais do sistema financeiro e assim sucessivamente. ### Conta mestre Uma possível solução seria dar uma conta mestre à Tether, dando o acesso direto a uma conta no FED, semelhante à que todos os bancos comerciais têm. Com isto, a Tether deixaria de necessitar os títulos do tesouro, depositando o dinheiro diretamente no banco central. Só que isto iria criar dois novos problemas, com o Custodia Bank e com o restante sistema bancário. O Custodia Bank luta há vários anos contra o FED, nos tribunais pelo direito a ter licença bancária para um banco com _full-reserves_. O FED recusou sempre esse direito, com a justificativa que esse banco, colocaria em risco toda a estabilidade do sistema bancário existente, ou seja, todos os outros bancos poderiam colapsar. Perante a existência em simultâneo de bancos com reserva fracionária e com _full-reserves_, as pessoas e empresas iriam optar pelo mais seguro. Isso iria provocar uma corrida bancária, levando ao colapso de todos os bancos com reserva fracionária, porque no Custodia Bank, os fundos dos clientes estão 100% garantidos, para qualquer valor. Deixaria de ser necessário limites de fundos de Garantia de Depósitos. Eu concordo com o FED nesse ponto, que os bancos com _full-reserves_ são uma ameaça a existência dos restantes bancos. O que eu discordo do FED, é a origem do problema, o problema não está nos bancos _full-reserves_, mas sim nos que têm reserva fracionária. O FED ao conceder uma conta mestre ao Tether, abre um precedente, o Custodia Bank irá o aproveitar, reclamando pela igualdade de direitos nos tribunais e desta vez, possivelmente ganhará a sua licença. Ainda há um segundo problema, com os restantes bancos comerciais. A Tether passaria a ter direitos similares aos bancos comerciais, mas os deveres seriam muito diferentes. Isto levaria os bancos comerciais aos tribunais para exigir igualdade de tratamento, é uma concorrência desleal. Isto é o bom dos tribunais dos EUA, são independentes e funcionam, mesmo contra o estado. Os bancos comerciais têm custos exorbitantes devido às políticas de _compliance_, como o KYC e AML. Como o governo não vai querer aliviar as regras, logo seria a Tether, a ser obrigada a fazer o _compliance_ dos seus clientes. A obrigação do KYC para ter _stablecoins_ iriam provocar um terramoto no mundo cripto. Assim, é pouco provável que seja a solução para a Tether. ### FED Só resta uma hipótese, ser o próprio FED a controlar e a gerir diretamente as _stablecoins_ de dólar, nacionalizado ou absorvendo as existentes. Seria uma espécie de CBDC. Isto iria provocar um novo problema, um problema diplomático, porque as _stablecoins_ estão a colocar em causa a soberania monetária dos outros países. Atualmente as _stablecoins_ estão um pouco protegidas porque vivem num limbo jurídico, mas a partir do momento que estas são controladas pelo governo americano, tudo muda. Os países vão exigir às autoridades americanas medidas que limitem o uso nos seus respectivos países. Não existe uma solução boa, o sistema FIAT é um castelo de cartas, qualquer carta que se mova, vai provocar um desmoronamento noutro local. As autoridades não poderão adiar mais o problema, terão que o resolver de vez, senão, qualquer dia será tarde demais. Se houver algum problema, vão colocar a responsabilidade no cripto e no Bitcoin. Mas a verdade, a culpa é inteiramente dos políticos, da sua incompetência em resolver os problemas a tempo. Será algo para acompanhar futuramente, mas só para 2026, talvez… É curioso, há uns anos pensava-se que o Bitcoin seria a maior ameaça ao sistema ao FIAT, mas afinal, a maior ameaça aos sistema FIAT é o próprio FIAT(_stablecoins_). A ironia do destino. Isto é como uma corrida, o Bitcoin é aquele atleta que corre ao seu ritmo, umas vezes mais rápido, outras vezes mais lento, mas nunca pára. O FIAT é o atleta que dá tudo desde da partida, corre sempre em velocidade máxima. Só que a vida e o sistema financeiro não é uma prova de 100 metros, mas sim uma maratona. # Europa 2025 será um ano desafiante para todos europeus, sobretudo devido à entrada em vigor da regulamentação (MiCA). Vão começar a sentir na pele a regulamentação, vão agravar-se os problemas com os _compliance_, problemas para comprovar a origem de fundos e outras burocracias. Vai ser lindo. O _Travel Route_ passa a ser obrigatório, os europeus serão obrigados a fazer o KYC nas transações. A _Travel Route_ é uma suposta lei para criar mais transparência, mas prática, é uma lei de controle, de monitorização e para limitar as liberdades individuais dos cidadãos. O MiCA também está a colocar problemas nas _stablecoins_ de Euro, a Tether para já preferiu ficar de fora da europa. O mais ridículo é que as novas regras obrigam os emissores a colocar 30% das reservas em bancos comerciais. Os burocratas europeus não compreendem que isto coloca em risco a estabilidade e a solvência dos próprios bancos, ficam propensos a corridas bancárias. O MiCA vai obrigar a todas as exchanges a estar registadas em solo europeu, ficando vulnerável ao temperamento dos burocratas. Ainda não vai ser em 2025, mas a UE vai impor políticas de controle de capitais, é inevitável, as exchanges serão obrigadas a usar em exclusividade _stablecoins_ de euro, as restantes _stablecoins_ serão deslistadas. Todas estas novas regras do MiCA, são extremamente restritas, não é para garantir mais segurança aos cidadãos europeus, mas sim para garantir mais controle sobre a população. A UE está cada vez mais perto da autocracia, do que da democracia. A minha única esperança no horizonte, é que o sucesso das políticas cripto nos EUA, vai obrigar a UE a recuar e a aligeirar as regras, a teoria dos jogos é implacável. Mas esse recuo, nunca acontecerá em 2025, vai ser um longo período conturbado. # Recessão Os mercados estão todos em máximos históricos, isto não é sustentável por muito tempo, suspeito que no final de 2025 vai acontecer alguma correção nos mercados. A queda só não será maior, porque os bancos centrais vão imprimir dinheiro, muito dinheiro, como se não houvesse amanhã. Vão voltar a resolver os problemas com a injeção de liquidez na economia, é empurrar os problemas com a barriga, em de os resolver. Outra vez o efeito Cantillon. Será um ano muito desafiante a nível político, onde o papel dos políticos será fundamental. A crise política na França e na Alemanha, coloca a UE órfã, sem um comandante ao leme do navio. 2025 estará condicionado pelas eleições na Alemanha, sobretudo no resultado do AfD, que podem colocar em causa a propriedade UE e o euro. Possivelmente, só o fim da guerra poderia minimizar a crise, algo que é muito pouco provável acontecer. Em Portugal, a economia parece que está mais ou menos equilibrada, mas começam a aparecer alguns sinais preocupantes. Os jogos de sorte e azar estão em máximos históricos, batendo o recorde de 2014, época da grande crise, não é um bom sinal, possivelmente já existe algum desespero no ar. A Alemanha é o motor da Europa, quanto espirra, Portugal constipa-se. Além do problema da Alemanha, a Espanha também está à beira de uma crise, são os países que mais influenciam a economia portuguesa. Se existir uma recessão mundial, terá um forte impacto no turismo, que é hoje em dia o principal motor de Portugal. # Brasil Brasil é algo para acompanhar em 2025, sobretudo a nível macro e a nível político. Existe uma possibilidade de uma profunda crise no Brasil, sobretudo na sua moeda. O banco central já anda a queimar as reservas para minimizar a desvalorização do Real.  Sem mudanças profundas nas políticas fiscais, as reservas vão se esgotar. As políticas de controle de capitais são um cenário plausível, será interesse de acompanhar, como o governo irá proceder perante a existência do Bitcoin e _stablecoins_. No Brasil existe um forte adoção, será um bom _case study_, certamente irá repetir-se em outros países num futuro próximo. Os próximos tempos não serão fáceis para os brasileiros, especialmente para os que não têm Bitcoin. # Blockchain Em 2025, possivelmente vamos ver os primeiros passos da BlackRock para criar a primeira bolsa de valores, exclusivamente em _blockchain_. Eu acredito que a BlackRock vai criar uma própria _blockchain_, toda controlada por si, onde estarão os RWAs, para fazer concorrência às tradicionais bolsas de valores. Será algo interessante de acompanhar. ----------- Estas são as minhas previsões, eu escrevi isto muito em cima do joelho, certamente esqueci-me de algumas coisas, se for importante acrescentarei nos comentários. A maioria das previsões só acontecerá após 2025, mas fica aqui a minha opinião. Isto é apenas a minha opinião, **Don’t Trust, Verify**!
@ e97aaffa:2ebd765d
2024-12-31 16:47:12Último dia do ano, momento para tirar o pó da bola de cristal, para fazer reflexões, previsões e desejos para o próximo ano e seguintes. Ano após ano, o Bitcoin evoluiu, foi ultrapassando etapas, tornou-se cada vez mais _mainstream_. Está cada vez mais difícil fazer previsões sobre o Bitcoin, já faltam poucas barreiras a serem ultrapassadas e as que faltam são altamente complexas ou tem um impacto profundo no sistema financeiro ou na sociedade. Estas alterações profundas tem que ser realizadas lentamente, porque uma alteração rápida poderia resultar em consequências terríveis, poderia provocar um retrocesso. # Código do Bitcoin No final de 2025, possivelmente vamos ter um _fork_, as discussões sobre os _covenants_ já estão avançadas, vão acelerar ainda mais. Já existe um consenso relativamente alto, a favor dos _covenants_, só falta decidir que modelo será escolhido. Penso que até ao final do ano será tudo decidido. Depois dos _covenants,_ o próximo foco será para a criptografia post-quantum, que será o maior desafio que o Bitcoin enfrenta. Criar uma criptografia segura e que não coloque a descentralização em causa. Espero muito de Ark, possivelmente a inovação do ano, gostaria de ver o Nostr a furar a bolha bitcoinheira e que o Cashu tivesse mais reconhecimento pelos _bitcoiners_. Espero que surjam avanços significativos no BitVM2 e BitVMX. Não sei o que esperar das layer 2 de Bitcoin, foram a maior desilusão de 2024. Surgiram com muita força, mas pouca coisa saiu do papel, foi uma mão cheia de nada. Uma parte dos projetos caiu na tentação da _shitcoinagem_, na criação de tokens, que tem um único objetivo, enriquecer os devs e os VCs. Se querem ser levados a sério, têm que ser sérios. > “À mulher de César não basta ser honesta, deve parecer honesta” Se querem ter o apoio dos _bitcoiners_, sigam o _ethos_ do Bitcoin. Neste ponto a atitude do pessoal da Ark é exemplar, em vez de andar a chorar no Twitter para mudar o código do Bitcoin, eles colocaram as mãos na massa e criaram o protocolo. É claro que agora está meio “coxo”, funciona com uma _multisig_ ou com os _covenants_ na Liquid. Mas eles estão a criar um produto, vão demonstrar ao mercado que o produto é bom e útil. Com a adoção, a comunidade vai perceber que o Ark necessita dos _covenants_ para melhorar a interoperabilidade e a soberania. É este o pensamento certo, que deveria ser seguido pelos restantes e futuros projetos. É seguir aquele pensamento do J.F. Kennedy: > “Não perguntem o que é que o vosso país pode fazer por vocês, perguntem o que é que vocês podem fazer pelo vosso país” Ou seja, não fiquem à espera que o bitcoin mude, criem primeiro as inovações/tecnologia, ganhem adoção e depois demonstrem que a alteração do código camada base pode melhorar ainda mais o vosso projeto. A necessidade é que vai levar a atualização do código. # Reservas Estratégicas de Bitcoin ## Bancos centrais Com a eleição de Trump, emergiu a ideia de uma Reserva Estratégia de Bitcoin, tornou este conceito _mainstream_. Foi um _pivot_, a partir desse momento, foram enumerados os políticos de todo o mundo a falar sobre o assunto. A Senadora Cynthia Lummis foi mais além e propôs um programa para adicionar 200 mil bitcoins à reserva ao ano, até 1 milhão de Bitcoin. Só que isto está a criar uma enorme expectativa na comunidade, só que pode resultar numa enorme desilusão. Porque no primeiro ano, o Trump em vez de comprar os 200 mil, pode apenas adicionar na reserva, os 198 mil que o Estado já tem em sua posse. Se isto acontecer, possivelmente vai resultar numa forte queda a curto prazo. Na minha opinião os bancos centrais deveriam seguir o exemplo de El Salvador, fazer um DCA diário. Mais que comprar bitcoin, para mim, o mais importante é a criação da Reserva, é colocar o Bitcoin ao mesmo nível do ouro, o impacto para o resto do mundo será tremendo, a teoria dos jogos na sua plenitude. Muitos outros bancos centrais vão ter que comprar, para não ficarem atrás, além disso, vai transmitir uma mensagem à generalidade da população, que o Bitcoin é “afinal é algo seguro, com valor”. Mas não foi Trump que iniciou esta teoria dos jogos, mas sim foi a primeira vítima dela. É o próprio Trump que o admite, que os EUA necessitam da reserva para não ficar atrás da China. Além disso, desde que os EUA utilizaram o dólar como uma arma, com sanção contra a Rússia, surgiram boatos de que a Rússia estaria a utilizar o Bitcoin para transações internacionais. Que foram confirmados recentemente, pelo próprio governo russo. Também há poucos dias, ainda antes deste reconhecimento público, Putin elogiou o Bitcoin, ao reconhecer que “Ninguém pode proibir o bitcoin”, defendendo como uma alternativa ao dólar. A narrativa está a mudar. Já existem alguns países com Bitcoin, mas apenas dois o fizeram conscientemente (El Salvador e Butão), os restantes têm devido a apreensões. Hoje são poucos, mas 2025 será o início de uma corrida pelos bancos centrais. Esta corrida era algo previsível, o que eu não esperava é que acontecesse tão rápido.  ## Empresas A criação de reservas estratégicas não vai ficar apenas pelos bancos centrais, também vai acelerar fortemente nas empresas em 2025.  Mas as empresas não vão seguir a estratégia do Saylor, vão comprar bitcoin sem alavancagem, utilizando apenas os tesouros das empresas, como uma proteção contra a inflação. Eu não sou grande admirador do Saylor, prefiro muito mais, uma estratégia conservadora, sem qualquer alavancagem. Penso que as empresas vão seguir a sugestão da BlackRock, que aconselha um alocações de 1% a 3%. Penso que 2025, ainda não será o ano da entrada das 6 magníficas (excepto Tesla), será sobretudo empresas de pequena e média dimensão. As magníficas ainda tem uma cota muito elevada de _shareholders_ com alguma idade, bastante conservadores, que têm dificuldade em compreender o Bitcoin, foi o que aconteceu recentemente com a Microsoft. Também ainda não será em 2025, talvez 2026, a inclusão nativamente de wallet Bitcoin nos sistema da Apple Pay e da Google Pay. Seria um passo gigante para a adoção a nível mundial. # ETFs Os ETFs para mim são uma incógnita, tenho demasiadas dúvidas, como será 2025. Este ano os _inflows_ foram superiores a 500 mil bitcoins, o IBIT foi o lançamento de ETF mais bem sucedido da história. O sucesso dos ETFs, deve-se a 2 situações que nunca mais se vão repetir. O mercado esteve 10 anos à espera pela aprovação dos ETFs, a procura estava reprimida, isso foi bem notório nos primeiros meses, os _inflows_ foram brutais. Também se beneficiou por ser um mercado novo, não existia _orderbook_ de vendas, não existia um mercado interno, praticamente era só _inflows_. Agora o mercado já estabilizou, a maioria das transações já são entre clientes dos próprios ETFs. Agora só uma pequena percentagem do volume das transações diárias vai resultar em _inflows_ ou _outflows_. Estes dois fenómenos nunca mais se vão repetir, eu não acredito que o número de _inflows_ em BTC supere os número de 2024, em dólares vai superar, mas em btc não acredito que vá superar. Mas em 2025 vão surgir uma infindável quantidade de novos produtos, derivativos, novos ETFs de cestos com outras criptos ou cestos com ativos tradicionais. O bitcoin será adicionado em produtos financeiros já existentes no mercado, as pessoas vão passar a deter bitcoin, sem o saberem. Com o fim da operação ChokePoint 2.0, vai surgir uma nova onda de adoção e de produtos financeiros. Possivelmente vamos ver bancos tradicionais a disponibilizar produtos ou serviços de custódia aos seus clientes. Eu adoraria ver o crescimento da adoção do bitcoin como moeda, só que a regulamentação não vai ajudar nesse processo. # Preço Eu acredito que o topo deste ciclo será alcançado no primeiro semestre, posteriormente haverá uma correção. Mas desta vez, eu acredito que a correção será muito menor que as anteriores, inferior a 50%, esta é a minha expectativa. Espero estar certo. # Stablecoins de dólar Agora saindo um pouco do universo do Bitcoin, acho importante destacar as _stablecoins_. No último ciclo, eu tenho dividido o tempo, entre continuar a estudar o Bitcoin e estudar o sistema financeiro, as suas dinâmicas e o comportamento humano. Isto tem sido o meu foco de reflexão, imaginar a transformação que o mundo vai sofrer devido ao padrão Bitcoin. É uma ilusão acreditar que a transição de um padrão FIAT para um padrão Bitcoin vai ser rápida, vai existir um processo transitório que pode demorar décadas. Com a re-entrada de Trump na Casa Branca, prometendo uma política altamente protecionista, vai provocar uma forte valorização do dólar, consequentemente as restantes moedas do mundo vão derreter. Provocando uma inflação generalizada, gerando uma corrida às _stablecoins_ de dólar nos países com moedas mais fracas. Trump vai ter uma política altamente expansionista, vai exportar dólares para todo o mundo, para financiar a sua própria dívida. A desigualdade entre os pobres e ricos irá crescer fortemente, aumentando a possibilidade de conflitos e revoltas. > “Casa onde não há pão, todos ralham e ninguém tem razão” Será mais lenha, para alimentar a fogueira, vai gravar os conflitos geopolíticos já existentes, ficando as sociedade ainda mais polarizadas. Eu acredito que 2025, vai haver um forte crescimento na adoção das _stablecoins_ de dólares, esse forte crescimento vai agravar o problema sistémico que são as _stablecoins_. Vai ser o início do fim das _stablecoins_, pelo menos, como nós conhecemos hoje em dia. ## Problema sistémico O sistema FIAT não nasceu de um dia para outro, foi algo que foi construído organicamente, ou seja, foi evoluindo ao longo dos anos, sempre que havia um problema/crise, eram criadas novas regras ou novas instituições para minimizar os problemas. Nestes quase 100 anos, desde os acordos de Bretton Woods, a evolução foram tantas, tornaram o sistema financeiro altamente complexo, burocrático e nada eficiente. Na prática é um castelo de cartas construído sobre outro castelo de cartas e que por sua vez, foi construído sobre outro castelo de cartas. As _stablecoins_ são um problema sistémico, devido às suas reservas em dólares e o sistema financeiro não está preparado para manter isso seguro. Com o crescimento das reservas ao longo dos anos, foi se agravando o problema. No início a Tether colocava as reservas em bancos comerciais, mas com o crescimento dos dólares sob gestão, criou um problema nos bancos comerciais, devido à reserva fracionária. Essas enormes reservas da Tether estavam a colocar em risco a própria estabilidade dos bancos. A Tether acabou por mudar de estratégia, optou por outros ativos, preferencialmente por títulos do tesouro/obrigações dos EUA. Só que a Tether continua a crescer e não dá sinais de abrandamento, pelo contrário. Até o próprio mundo cripto, menosprezava a gravidade do problema da Tether/_stablecoins_ para o resto do sistema financeiro, porque o _marketcap_ do cripto ainda é muito pequeno. É verdade que ainda é pequeno, mas a Tether não o é, está no top 20 dos maiores detentores de títulos do tesouros dos EUA e está ao nível dos maiores bancos centrais do mundo. Devido ao seu tamanho, está a preocupar os responsáveis/autoridades/reguladores dos EUA, pode colocar em causa a estabilidade do sistema financeiro global, que está assente nessas obrigações. Os títulos do tesouro dos EUA são o colateral mais utilizado no mundo, tanto por bancos centrais, como por empresas, é a charneira da estabilidade do sistema financeiro. Os títulos do tesouro são um assunto muito sensível. Na recente crise no Japão, do _carry trade_, o Banco Central do Japão tentou minimizar a desvalorização do iene através da venda de títulos dos EUA. Esta operação, obrigou a uma viagem de emergência, da Secretaria do Tesouro dos EUA, Janet Yellen ao Japão, onde disponibilizou liquidez para parar a venda de títulos por parte do Banco Central do Japão. Essa forte venda estava desestabilizando o mercado. Os principais detentores de títulos do tesouros são institucionais, bancos centrais, bancos comerciais, fundo de investimento e gestoras, tudo administrado por gestores altamente qualificados, racionais e que conhecem a complexidade do mercado de obrigações. O mundo cripto é seu oposto, é _naife_ com muita irracionalidade e uma forte pitada de loucura, na sua maioria nem faz a mínima ideia como funciona o sistema financeiro. Essa irracionalidade pode levar a uma “corrida bancária”, como aconteceu com o UST da Luna, que em poucas horas colapsou o projeto. Em termos de escala, a Luna ainda era muito pequena, por isso, o problema ficou circunscrito ao mundo cripto e a empresas ligadas diretamente ao cripto. Só que a Tether é muito diferente, caso exista algum FUD, que obrigue a Tether a desfazer-se de vários biliões ou dezenas de biliões de dólares em títulos num curto espaço de tempo, poderia provocar consequências terríveis em todo o sistema financeiro. A Tether é grande demais, é já um problema sistémico, que vai agravar-se com o crescimento em 2025. Não tenham dúvidas, se existir algum problema, o Tesouro dos EUA vai impedir a venda dos títulos que a Tether tem em sua posse, para salvar o sistema financeiro. O problema é, o que vai fazer a Tether, se ficar sem acesso às venda das reservas, como fará o _redeem_ dos dólares? Como o crescimento do Tether é inevitável, o Tesouro e o FED estão com um grande problema em mãos, o que fazer com o Tether? Mas o problema é que o atual sistema financeiro é como um curto cobertor: Quanto tapas a cabeça, destapas os pés; Ou quando tapas os pés, destapas a cabeça. Ou seja, para resolver o problema da guarda reservas da Tether, vai criar novos problemas, em outros locais do sistema financeiro e assim sucessivamente. ### Conta mestre Uma possível solução seria dar uma conta mestre à Tether, dando o acesso direto a uma conta no FED, semelhante à que todos os bancos comerciais têm. Com isto, a Tether deixaria de necessitar os títulos do tesouro, depositando o dinheiro diretamente no banco central. Só que isto iria criar dois novos problemas, com o Custodia Bank e com o restante sistema bancário. O Custodia Bank luta há vários anos contra o FED, nos tribunais pelo direito a ter licença bancária para um banco com _full-reserves_. O FED recusou sempre esse direito, com a justificativa que esse banco, colocaria em risco toda a estabilidade do sistema bancário existente, ou seja, todos os outros bancos poderiam colapsar. Perante a existência em simultâneo de bancos com reserva fracionária e com _full-reserves_, as pessoas e empresas iriam optar pelo mais seguro. Isso iria provocar uma corrida bancária, levando ao colapso de todos os bancos com reserva fracionária, porque no Custodia Bank, os fundos dos clientes estão 100% garantidos, para qualquer valor. Deixaria de ser necessário limites de fundos de Garantia de Depósitos. Eu concordo com o FED nesse ponto, que os bancos com _full-reserves_ são uma ameaça a existência dos restantes bancos. O que eu discordo do FED, é a origem do problema, o problema não está nos bancos _full-reserves_, mas sim nos que têm reserva fracionária. O FED ao conceder uma conta mestre ao Tether, abre um precedente, o Custodia Bank irá o aproveitar, reclamando pela igualdade de direitos nos tribunais e desta vez, possivelmente ganhará a sua licença. Ainda há um segundo problema, com os restantes bancos comerciais. A Tether passaria a ter direitos similares aos bancos comerciais, mas os deveres seriam muito diferentes. Isto levaria os bancos comerciais aos tribunais para exigir igualdade de tratamento, é uma concorrência desleal. Isto é o bom dos tribunais dos EUA, são independentes e funcionam, mesmo contra o estado. Os bancos comerciais têm custos exorbitantes devido às políticas de _compliance_, como o KYC e AML. Como o governo não vai querer aliviar as regras, logo seria a Tether, a ser obrigada a fazer o _compliance_ dos seus clientes. A obrigação do KYC para ter _stablecoins_ iriam provocar um terramoto no mundo cripto. Assim, é pouco provável que seja a solução para a Tether. ### FED Só resta uma hipótese, ser o próprio FED a controlar e a gerir diretamente as _stablecoins_ de dólar, nacionalizado ou absorvendo as existentes. Seria uma espécie de CBDC. Isto iria provocar um novo problema, um problema diplomático, porque as _stablecoins_ estão a colocar em causa a soberania monetária dos outros países. Atualmente as _stablecoins_ estão um pouco protegidas porque vivem num limbo jurídico, mas a partir do momento que estas são controladas pelo governo americano, tudo muda. Os países vão exigir às autoridades americanas medidas que limitem o uso nos seus respectivos países. Não existe uma solução boa, o sistema FIAT é um castelo de cartas, qualquer carta que se mova, vai provocar um desmoronamento noutro local. As autoridades não poderão adiar mais o problema, terão que o resolver de vez, senão, qualquer dia será tarde demais. Se houver algum problema, vão colocar a responsabilidade no cripto e no Bitcoin. Mas a verdade, a culpa é inteiramente dos políticos, da sua incompetência em resolver os problemas a tempo. Será algo para acompanhar futuramente, mas só para 2026, talvez… É curioso, há uns anos pensava-se que o Bitcoin seria a maior ameaça ao sistema ao FIAT, mas afinal, a maior ameaça aos sistema FIAT é o próprio FIAT(_stablecoins_). A ironia do destino. Isto é como uma corrida, o Bitcoin é aquele atleta que corre ao seu ritmo, umas vezes mais rápido, outras vezes mais lento, mas nunca pára. O FIAT é o atleta que dá tudo desde da partida, corre sempre em velocidade máxima. Só que a vida e o sistema financeiro não é uma prova de 100 metros, mas sim uma maratona. # Europa 2025 será um ano desafiante para todos europeus, sobretudo devido à entrada em vigor da regulamentação (MiCA). Vão começar a sentir na pele a regulamentação, vão agravar-se os problemas com os _compliance_, problemas para comprovar a origem de fundos e outras burocracias. Vai ser lindo. O _Travel Route_ passa a ser obrigatório, os europeus serão obrigados a fazer o KYC nas transações. A _Travel Route_ é uma suposta lei para criar mais transparência, mas prática, é uma lei de controle, de monitorização e para limitar as liberdades individuais dos cidadãos. O MiCA também está a colocar problemas nas _stablecoins_ de Euro, a Tether para já preferiu ficar de fora da europa. O mais ridículo é que as novas regras obrigam os emissores a colocar 30% das reservas em bancos comerciais. Os burocratas europeus não compreendem que isto coloca em risco a estabilidade e a solvência dos próprios bancos, ficam propensos a corridas bancárias. O MiCA vai obrigar a todas as exchanges a estar registadas em solo europeu, ficando vulnerável ao temperamento dos burocratas. Ainda não vai ser em 2025, mas a UE vai impor políticas de controle de capitais, é inevitável, as exchanges serão obrigadas a usar em exclusividade _stablecoins_ de euro, as restantes _stablecoins_ serão deslistadas. Todas estas novas regras do MiCA, são extremamente restritas, não é para garantir mais segurança aos cidadãos europeus, mas sim para garantir mais controle sobre a população. A UE está cada vez mais perto da autocracia, do que da democracia. A minha única esperança no horizonte, é que o sucesso das políticas cripto nos EUA, vai obrigar a UE a recuar e a aligeirar as regras, a teoria dos jogos é implacável. Mas esse recuo, nunca acontecerá em 2025, vai ser um longo período conturbado. # Recessão Os mercados estão todos em máximos históricos, isto não é sustentável por muito tempo, suspeito que no final de 2025 vai acontecer alguma correção nos mercados. A queda só não será maior, porque os bancos centrais vão imprimir dinheiro, muito dinheiro, como se não houvesse amanhã. Vão voltar a resolver os problemas com a injeção de liquidez na economia, é empurrar os problemas com a barriga, em de os resolver. Outra vez o efeito Cantillon. Será um ano muito desafiante a nível político, onde o papel dos políticos será fundamental. A crise política na França e na Alemanha, coloca a UE órfã, sem um comandante ao leme do navio. 2025 estará condicionado pelas eleições na Alemanha, sobretudo no resultado do AfD, que podem colocar em causa a propriedade UE e o euro. Possivelmente, só o fim da guerra poderia minimizar a crise, algo que é muito pouco provável acontecer. Em Portugal, a economia parece que está mais ou menos equilibrada, mas começam a aparecer alguns sinais preocupantes. Os jogos de sorte e azar estão em máximos históricos, batendo o recorde de 2014, época da grande crise, não é um bom sinal, possivelmente já existe algum desespero no ar. A Alemanha é o motor da Europa, quanto espirra, Portugal constipa-se. Além do problema da Alemanha, a Espanha também está à beira de uma crise, são os países que mais influenciam a economia portuguesa. Se existir uma recessão mundial, terá um forte impacto no turismo, que é hoje em dia o principal motor de Portugal. # Brasil Brasil é algo para acompanhar em 2025, sobretudo a nível macro e a nível político. Existe uma possibilidade de uma profunda crise no Brasil, sobretudo na sua moeda. O banco central já anda a queimar as reservas para minimizar a desvalorização do Real.  Sem mudanças profundas nas políticas fiscais, as reservas vão se esgotar. As políticas de controle de capitais são um cenário plausível, será interesse de acompanhar, como o governo irá proceder perante a existência do Bitcoin e _stablecoins_. No Brasil existe um forte adoção, será um bom _case study_, certamente irá repetir-se em outros países num futuro próximo. Os próximos tempos não serão fáceis para os brasileiros, especialmente para os que não têm Bitcoin. # Blockchain Em 2025, possivelmente vamos ver os primeiros passos da BlackRock para criar a primeira bolsa de valores, exclusivamente em _blockchain_. Eu acredito que a BlackRock vai criar uma própria _blockchain_, toda controlada por si, onde estarão os RWAs, para fazer concorrência às tradicionais bolsas de valores. Será algo interessante de acompanhar. ----------- Estas são as minhas previsões, eu escrevi isto muito em cima do joelho, certamente esqueci-me de algumas coisas, se for importante acrescentarei nos comentários. A maioria das previsões só acontecerá após 2025, mas fica aqui a minha opinião. Isto é apenas a minha opinião, **Don’t Trust, Verify**! @ 472f440f:5669301e
2024-12-31 04:42:00I'm sure some of you are already tired of the discussion around the H-1B visa program that was started on Christmas Eve by Vivek Ramaswamy and escalated by Elon Musk and others as the "Silicon Valley MAGA" coalition began putting forth legal immigration policy proposals for the incoming Trump administration. Core to their policy is the expansion of the H-1B visa program so that America can "recruit the best talent in the world" to come build the American economy. Unfortunately, as it stands today - according to the Silicon Valley cognescenti, Americans are either a.) not smart enough to fulfill the roles necessary to enable the United States to maintain its lead as economic super power of the world or b.) expect too much in compensation for the available roles. At least this is my reading from the commentary I've seen over the last week. What seems abundantly clear to me is that the framing put forth by "Silicon Valley MAGA" crew is disingenuous and self-serving. It has been clear for awhile now that the H-1B visa program is being systematically abused to bring in cheap labor from other countries to help drive down labor costs for companies across the spectrum. Not just Silicon Valley tech companies. The system has a loophole in it and it is being exploited. Bring people to the US via H-1B visas to complete work for you at lower costs and your company's financials are likely to be better off (assuming the work being done is productive and a value add to the company). Now, this isn't to say that everyone who is in the US via an H-1B visa is here because these companies want to exploit the loophole that gives them the ability to spend less on head count. However, based off the data from the database of the H-1B visa program it is abundantly clear that the system is being taken advantage of. Egregiously and at the expense of American workers, who are most certainly not (all) "subtarded". Herein lies the crux of the problem; companies are abusing this program to get away from the problem of Americans demanding higher wages to maintain lives of dignity in a country run by a government that is chronically addicted to debt backed by a central bank that will print money ex-nihilo and at will to monetize that debt. Americans are then being scapegoated as either "lazy", "stupid" or "delusional about their worth in the work force". A classic straw man argument that avoids the root issue at hand; the money is broken and the broken money has created perverse incentives throughout the economy while also stripping Americans of the ability to properly save the value of their labor. We live in a high velocity trash economy that rewards grift and waste while disincentivizing hard work that is meaningful to the quality of life of the Common Man. Everything has been hyper-financialized to the point that one of the only ways to make it ahead is to speculate on the flow of capital into certain asset classes, which is often determined by the whims of central planners. Another is to build or speculate on tech "innovations" that typically materialize in the form of attention zapping apps and widgets that help people temporarily forget they live in a high-velocity trash economy. The mass of men lead lives of quiet desperation and it is because they don't see a way out of the nihilistic rat race created (unknowingly to most) by the money printer. The ability to print money out of nothing and throw it at everything creates misaligned incentives that result in the inability for the market to properly determine what is genuinely needed by the people instead of those who have learned how to game the broken system and its broken incentives. One last point, I would be remiss not to acknowledge that many individuals in America aren't intellectually equipped to do some of the cutting edge work that may be necessary to produce the technologies and companies that will push the country forward. The high-velocity trash economy run on money printed out of nothing has completely corrupted the education system. People in the United States are literally dumber than they were five decades ago. That is a fact. But it is not only the fault of the American people themselves, but the corrupt system they have been born into that destroyed the education system with perverse incentives. And the overwhelming majority of the blame is on the system, not the people. Even with that being said, the idea that we need to adopt a Tiger Mom mentality in the US - a culture of unrelenting devotion to studying STEM to the point that weekend sleepovers for kids are discouraged - is absolutely laughable and objectively un-American. There are plenty of incredibly intelligent, creative and driven young Americans who have contributed and will continue to contribute significantly to the American economy and they didn't need to shackle themselves to their desks to get that way. America isn't a country that was built by automatons. It's a country built by people who said, "Fuck you. Don't tell me what I can and cannot do. Watch this." Despite the fact that a system has been erected that actively works against the average American system the American spirit lives on in the souls of many across the country. Miraculously. The American spirit is something that cannot simply be imported. It is ingrained in our culture. It is certainly beginning to dwindle as hope for a better future becomes more and more dim for the masses as the system works against them despite all their best efforts to succeed. It is imperative that we stoke the coals of the American spirit while it is still alive in those who are too stubborn to give up. People need the ability to save their hard work in a money that cannot be debased. Opportunity cost needs to be reintroduced into the market so that things that actually add value and increase the quality of life for the Common Man are where hard money is allocated. And people need to start talking about the root of the problem more seriously instead of striking at branches with disingenuous straw man arguments. --- Final thought... Ready to go surfing.
@ 472f440f:5669301e
2024-12-31 04:42:00I'm sure some of you are already tired of the discussion around the H-1B visa program that was started on Christmas Eve by Vivek Ramaswamy and escalated by Elon Musk and others as the "Silicon Valley MAGA" coalition began putting forth legal immigration policy proposals for the incoming Trump administration. Core to their policy is the expansion of the H-1B visa program so that America can "recruit the best talent in the world" to come build the American economy. Unfortunately, as it stands today - according to the Silicon Valley cognescenti, Americans are either a.) not smart enough to fulfill the roles necessary to enable the United States to maintain its lead as economic super power of the world or b.) expect too much in compensation for the available roles. At least this is my reading from the commentary I've seen over the last week. What seems abundantly clear to me is that the framing put forth by "Silicon Valley MAGA" crew is disingenuous and self-serving. It has been clear for awhile now that the H-1B visa program is being systematically abused to bring in cheap labor from other countries to help drive down labor costs for companies across the spectrum. Not just Silicon Valley tech companies. The system has a loophole in it and it is being exploited. Bring people to the US via H-1B visas to complete work for you at lower costs and your company's financials are likely to be better off (assuming the work being done is productive and a value add to the company). Now, this isn't to say that everyone who is in the US via an H-1B visa is here because these companies want to exploit the loophole that gives them the ability to spend less on head count. However, based off the data from the database of the H-1B visa program it is abundantly clear that the system is being taken advantage of. Egregiously and at the expense of American workers, who are most certainly not (all) "subtarded". Herein lies the crux of the problem; companies are abusing this program to get away from the problem of Americans demanding higher wages to maintain lives of dignity in a country run by a government that is chronically addicted to debt backed by a central bank that will print money ex-nihilo and at will to monetize that debt. Americans are then being scapegoated as either "lazy", "stupid" or "delusional about their worth in the work force". A classic straw man argument that avoids the root issue at hand; the money is broken and the broken money has created perverse incentives throughout the economy while also stripping Americans of the ability to properly save the value of their labor. We live in a high velocity trash economy that rewards grift and waste while disincentivizing hard work that is meaningful to the quality of life of the Common Man. Everything has been hyper-financialized to the point that one of the only ways to make it ahead is to speculate on the flow of capital into certain asset classes, which is often determined by the whims of central planners. Another is to build or speculate on tech "innovations" that typically materialize in the form of attention zapping apps and widgets that help people temporarily forget they live in a high-velocity trash economy. The mass of men lead lives of quiet desperation and it is because they don't see a way out of the nihilistic rat race created (unknowingly to most) by the money printer. The ability to print money out of nothing and throw it at everything creates misaligned incentives that result in the inability for the market to properly determine what is genuinely needed by the people instead of those who have learned how to game the broken system and its broken incentives. One last point, I would be remiss not to acknowledge that many individuals in America aren't intellectually equipped to do some of the cutting edge work that may be necessary to produce the technologies and companies that will push the country forward. The high-velocity trash economy run on money printed out of nothing has completely corrupted the education system. People in the United States are literally dumber than they were five decades ago. That is a fact. But it is not only the fault of the American people themselves, but the corrupt system they have been born into that destroyed the education system with perverse incentives. And the overwhelming majority of the blame is on the system, not the people. Even with that being said, the idea that we need to adopt a Tiger Mom mentality in the US - a culture of unrelenting devotion to studying STEM to the point that weekend sleepovers for kids are discouraged - is absolutely laughable and objectively un-American. There are plenty of incredibly intelligent, creative and driven young Americans who have contributed and will continue to contribute significantly to the American economy and they didn't need to shackle themselves to their desks to get that way. America isn't a country that was built by automatons. It's a country built by people who said, "Fuck you. Don't tell me what I can and cannot do. Watch this." Despite the fact that a system has been erected that actively works against the average American system the American spirit lives on in the souls of many across the country. Miraculously. The American spirit is something that cannot simply be imported. It is ingrained in our culture. It is certainly beginning to dwindle as hope for a better future becomes more and more dim for the masses as the system works against them despite all their best efforts to succeed. It is imperative that we stoke the coals of the American spirit while it is still alive in those who are too stubborn to give up. People need the ability to save their hard work in a money that cannot be debased. Opportunity cost needs to be reintroduced into the market so that things that actually add value and increase the quality of life for the Common Man are where hard money is allocated. And people need to start talking about the root of the problem more seriously instead of striking at branches with disingenuous straw man arguments. --- Final thought... Ready to go surfing. @ 17538dc2:71ed77c4
2024-12-30 22:45:10Merry Christmas, and Happy New Year! Here's an overview of keeping tabs on interoperability on nostr. ## What is nostrability [Nostrability](https://github.com/nostrability/nostrability) is: -the practical documentation of broken things on nostr between two or more apps, and -a place to advocate for positive interoperability updates to apps ### Why does this matter? If the hop and/or interaction between apps sucks, then nostr users will not have an amazing and unique experience. Nostr will lose to well funded incumbents.  ### How did this start? Will was upset that he had to troubleshoot other dev's apps. ### What nostrability does *not* aim for All apps implement all NIPs. ### Where can I read in detail [https://github.com/nostrability/nostrability ](https://github.com/nostrability/nostrability ) ### Timeline Nov '23 Added placeholder to github. Jan '24 First issues documented. Jan '24 First nostrability two app bug is fixed [Coracle cannot send DMs to Damus](https://github.com/nostrability/nostrability/issues/1) (thank you Hodlbod!). '24 Gave [intro to nostrability talk at BBB](https://youtu.be/I3Qld_HXQuM). Presentation [link](https://slides.com/alltheseas/nostrability). Aug '24 Galaxy devs educated elsat at NostrCI discussion at Nostriga. (n.b. where's the video??) Oct '24 Humbled by and grateful for OpenSats acknowledgment and funding. Thank you to all nostr enjoyers & devs who gave me their precious time, and to my advocates & supporters - you know who you are 🙏. ### What are specific issues discussed? Over a hundred open [issues](https://github.com/nostrability/nostrability/issues), and a couple of dozen resolved issues. Many of these were reported by extremetly very normal nostr users, and devs. Example topics (too many to list in a single article) range from: -contact list wipes, mute list wipes (Kieran pls fix!!) -zaps not working between apps -[missing notes](https://github.com/nostrability/nostrability/issues/20) -broken profiles -old profile information -q tags, a tags, missing replies and/or parent notes etc.. -to [proposed onboarding best practices](https://github.com/nostrability/nostrability/issues/143) -[outbox tracker positive interop](https://github.com/nostrability/nostrability/issues/69) -[highlights](https://github.com/nostrability/nostrability/issues/61) -non-nostr interoperability: e.g. [bluesky bridgyfed profile info](https://github.com/nostrability/nostrability/issues/142) -spillover NIP/other controversy such as [edited notes](https://github.com/nostrability/nostrability/issues/118) -and [migrating to nostr best practices](https://github.com/nostrability/nostrability/issues/78) ### Learnings 1. Lone wolf, limited resource devs are the norm. Most devs focus on their one app, or their multiple apps. 2. Some devs are extremely generous with their time when it comes to interop. Proof of work is in the git repo. 3. There is a lot of space for building amazing interoperable experiences - this remains frontier territory on the design, product, and dev side. Which will be the first experience to blow people out of the water? Is it zaps, DVMs, or something not yet put together? 4. I empathize that without basic things "just working", and/or basic features missing it may be difficult to allocate resources to interoperability. 5. Even devs with teams may struggle to allocate resources to interoperability. 6. Bug reporting and crappy experience reporting matters! This is important for single apps, and even more so for multi-app interaction. Devs may not get around to fixing something right away. However, if nostriches don't share their negative experience, devs will have less impetus to improve an experience. ### 2025 plans 1. Continue documenting broken things. 2. Interview devs to better understand how I can suit nostrability to dev's single app workflows, as to more effectively close broken things, and better advocate for positive interoperability updates across apps. 3. Help test nostrCI automated interop testing methodology with galaxy dev of [nostr.watch](https://nostr.watch/) & NIP-66 Sandwich, so that nostrability can be automated per particular test cases. ### Dev and nostrich feedback Let me know how I can make nostrability more useful for yall. Tag me on nostr, create issues on nostrability 💪. !(image)[https://media.tenor.com/hF5RhwXuG_kAAAAC/arnold-schwarzenegger-terminator.gif]
@ 17538dc2:71ed77c4
2024-12-30 22:45:10Merry Christmas, and Happy New Year! Here's an overview of keeping tabs on interoperability on nostr. ## What is nostrability [Nostrability](https://github.com/nostrability/nostrability) is: -the practical documentation of broken things on nostr between two or more apps, and -a place to advocate for positive interoperability updates to apps ### Why does this matter? If the hop and/or interaction between apps sucks, then nostr users will not have an amazing and unique experience. Nostr will lose to well funded incumbents.  ### How did this start? Will was upset that he had to troubleshoot other dev's apps. ### What nostrability does *not* aim for All apps implement all NIPs. ### Where can I read in detail [https://github.com/nostrability/nostrability ](https://github.com/nostrability/nostrability ) ### Timeline Nov '23 Added placeholder to github. Jan '24 First issues documented. Jan '24 First nostrability two app bug is fixed [Coracle cannot send DMs to Damus](https://github.com/nostrability/nostrability/issues/1) (thank you Hodlbod!). '24 Gave [intro to nostrability talk at BBB](https://youtu.be/I3Qld_HXQuM). Presentation [link](https://slides.com/alltheseas/nostrability). Aug '24 Galaxy devs educated elsat at NostrCI discussion at Nostriga. (n.b. where's the video??) Oct '24 Humbled by and grateful for OpenSats acknowledgment and funding. Thank you to all nostr enjoyers & devs who gave me their precious time, and to my advocates & supporters - you know who you are 🙏. ### What are specific issues discussed? Over a hundred open [issues](https://github.com/nostrability/nostrability/issues), and a couple of dozen resolved issues. Many of these were reported by extremetly very normal nostr users, and devs. Example topics (too many to list in a single article) range from: -contact list wipes, mute list wipes (Kieran pls fix!!) -zaps not working between apps -[missing notes](https://github.com/nostrability/nostrability/issues/20) -broken profiles -old profile information -q tags, a tags, missing replies and/or parent notes etc.. -to [proposed onboarding best practices](https://github.com/nostrability/nostrability/issues/143) -[outbox tracker positive interop](https://github.com/nostrability/nostrability/issues/69) -[highlights](https://github.com/nostrability/nostrability/issues/61) -non-nostr interoperability: e.g. [bluesky bridgyfed profile info](https://github.com/nostrability/nostrability/issues/142) -spillover NIP/other controversy such as [edited notes](https://github.com/nostrability/nostrability/issues/118) -and [migrating to nostr best practices](https://github.com/nostrability/nostrability/issues/78) ### Learnings 1. Lone wolf, limited resource devs are the norm. Most devs focus on their one app, or their multiple apps. 2. Some devs are extremely generous with their time when it comes to interop. Proof of work is in the git repo. 3. There is a lot of space for building amazing interoperable experiences - this remains frontier territory on the design, product, and dev side. Which will be the first experience to blow people out of the water? Is it zaps, DVMs, or something not yet put together? 4. I empathize that without basic things "just working", and/or basic features missing it may be difficult to allocate resources to interoperability. 5. Even devs with teams may struggle to allocate resources to interoperability. 6. Bug reporting and crappy experience reporting matters! This is important for single apps, and even more so for multi-app interaction. Devs may not get around to fixing something right away. However, if nostriches don't share their negative experience, devs will have less impetus to improve an experience. ### 2025 plans 1. Continue documenting broken things. 2. Interview devs to better understand how I can suit nostrability to dev's single app workflows, as to more effectively close broken things, and better advocate for positive interoperability updates across apps. 3. Help test nostrCI automated interop testing methodology with galaxy dev of [nostr.watch](https://nostr.watch/) & NIP-66 Sandwich, so that nostrability can be automated per particular test cases. ### Dev and nostrich feedback Let me know how I can make nostrability more useful for yall. Tag me on nostr, create issues on nostrability 💪. !(image)[https://media.tenor.com/hF5RhwXuG_kAAAAC/arnold-schwarzenegger-terminator.gif] @ f9cf4e94:96abc355
2024-12-30 19:02:32Na era das grandes navegações, piratas ingleses eram autorizados pelo governo para roubar navios. A única coisa que diferenciava um pirata comum de um corsário é que o último possuía a “Carta do Corso”, que funcionava como um “Alvará para o roubo”, onde o governo Inglês legitimava o roubo de navios por parte dos corsários. É claro, que em troca ele exigia uma parte da espoliação. Bastante similar com a maneira que a Receita Federal atua, não? Na verdade, o caso é ainda pior, pois o governo fica com toda a riqueza espoliada, e apenas repassa um mísero salário para os corsários modernos, os agentes da receita federal. Porém eles “justificam” esse roubo ao chamá-lo de imposto, e isso parece acalmar os ânimos de grande parte da população, mas não de nós. Não é por acaso que 'imposto' é o particípio passado do verbo 'impor'. Ou seja, é aquilo que resulta do cumprimento obrigatório -- e não voluntário -- de todos os cidadãos. Se não for 'imposto' ninguém paga. Nem mesmo seus defensores. Isso mostra o quanto as pessoas realmente apreciam os serviços do estado. Apenas volte um pouco na história: os primeiros pagadores de impostos eram fazendeiros cujos territórios foram invadidos por nômades que pastoreavam seu gado. Esses invasores nômades forçavam os fazendeiros a lhes pagar uma fatia de sua renda em troca de "proteção". O fazendeiro que não concordasse era assassinado. Os nômades perceberam que era muito mais interessante e confortável apenas cobrar uma taxa de proteção em vez de matar o fazendeiro e assumir suas posses. Cobrando uma taxa, eles obtinham o que necessitavam. Já se matassem os fazendeiros, eles teriam de gerenciar por conta própria toda a produção da fazenda. Daí eles entenderam que, ao não assassinarem todos os fazendeiros que encontrassem pelo caminho, poderiam fazer desta prática um modo de vida. Assim nasceu o governo. Não assassinar pessoas foi o primeiro serviço que o governo forneceu. Como temos sorte em ter à nossa disposição esta instituição! Assim, não deixa de ser curioso que algumas pessoas digam que os impostos são pagos basicamente para impedir que aconteça exatamente aquilo que originou a existência do governo. O governo nasceu da extorsão. Os fazendeiros tinham de pagar um "arrego" para seu governo. Caso contrário, eram assassinados. Quem era a real ameaça? O governo. A máfia faz a mesma coisa. Mas existe uma forma de se proteger desses corsários modernos. Atualmente, existe uma propriedade privada que NINGUÉM pode tirar de você, ela é sua até mesmo depois da morte. É claro que estamos falando do Bitcoin. Fazendo as configurações certas, é impossível saber que você tem bitcoin. Nem mesmo o governo americano consegue saber. #brasil #bitcoinbrasil #nostrbrasil #grownostr #bitcoin
@ f9cf4e94:96abc355
2024-12-30 19:02:32Na era das grandes navegações, piratas ingleses eram autorizados pelo governo para roubar navios. A única coisa que diferenciava um pirata comum de um corsário é que o último possuía a “Carta do Corso”, que funcionava como um “Alvará para o roubo”, onde o governo Inglês legitimava o roubo de navios por parte dos corsários. É claro, que em troca ele exigia uma parte da espoliação. Bastante similar com a maneira que a Receita Federal atua, não? Na verdade, o caso é ainda pior, pois o governo fica com toda a riqueza espoliada, e apenas repassa um mísero salário para os corsários modernos, os agentes da receita federal. Porém eles “justificam” esse roubo ao chamá-lo de imposto, e isso parece acalmar os ânimos de grande parte da população, mas não de nós. Não é por acaso que 'imposto' é o particípio passado do verbo 'impor'. Ou seja, é aquilo que resulta do cumprimento obrigatório -- e não voluntário -- de todos os cidadãos. Se não for 'imposto' ninguém paga. Nem mesmo seus defensores. Isso mostra o quanto as pessoas realmente apreciam os serviços do estado. Apenas volte um pouco na história: os primeiros pagadores de impostos eram fazendeiros cujos territórios foram invadidos por nômades que pastoreavam seu gado. Esses invasores nômades forçavam os fazendeiros a lhes pagar uma fatia de sua renda em troca de "proteção". O fazendeiro que não concordasse era assassinado. Os nômades perceberam que era muito mais interessante e confortável apenas cobrar uma taxa de proteção em vez de matar o fazendeiro e assumir suas posses. Cobrando uma taxa, eles obtinham o que necessitavam. Já se matassem os fazendeiros, eles teriam de gerenciar por conta própria toda a produção da fazenda. Daí eles entenderam que, ao não assassinarem todos os fazendeiros que encontrassem pelo caminho, poderiam fazer desta prática um modo de vida. Assim nasceu o governo. Não assassinar pessoas foi o primeiro serviço que o governo forneceu. Como temos sorte em ter à nossa disposição esta instituição! Assim, não deixa de ser curioso que algumas pessoas digam que os impostos são pagos basicamente para impedir que aconteça exatamente aquilo que originou a existência do governo. O governo nasceu da extorsão. Os fazendeiros tinham de pagar um "arrego" para seu governo. Caso contrário, eram assassinados. Quem era a real ameaça? O governo. A máfia faz a mesma coisa. Mas existe uma forma de se proteger desses corsários modernos. Atualmente, existe uma propriedade privada que NINGUÉM pode tirar de você, ela é sua até mesmo depois da morte. É claro que estamos falando do Bitcoin. Fazendo as configurações certas, é impossível saber que você tem bitcoin. Nem mesmo o governo americano consegue saber. #brasil #bitcoinbrasil #nostrbrasil #grownostr #bitcoin @ 254f56d7:f2c38100
2024-12-30 07:38:27Vamos ver seu funcionamento 
@ 254f56d7:f2c38100
2024-12-30 07:38:27Vamos ver seu funcionamento  @ a012dc82:6458a70d
2024-12-30 05:51:11**Table Of Content** - The Influence of Global Oil Prices - Bitcoin's Roller Coaster Ride - Anticipation Surrounding the 2024 Halving Event - The Broader Crypto Landscape - Conclusions - FAQ In the ever-evolving world of cryptocurrencies, Bitcoin stands as a beacon, often dictating the mood of the entire crypto market. Its price fluctuations are closely watched by investors, analysts, and enthusiasts alike. Max Keiser, a prominent figure in the crypto space, recently shed light on some intriguing factors that might be influencing Bitcoin's current price trajectory. This article delves into Keiser's insights, exploring the broader implications of global events on Bitcoin's market performance. **The Influence of Global Oil Prices** Max Keiser, a renowned Bitcoin advocate and former trader, recently drew attention to the interplay between global oil prices and Bitcoin's market performance. Responding to a post by German economics expert, Holger Zschaepitz, Keiser highlighted the significance of Brent oil reaching $90 per barrel for the first time since the previous November. According to Keiser, the surge in oil prices, driven by Saudi Arabia's decision to extend its reduction in oil production for another three months, has had ripple effects in the financial world. One of these effects is the shift of investor interest towards higher interest deposit USD accounts. This diversion of investments is creating what Keiser terms as "a small headwind for Bitcoin," implying that as traditional markets like oil show promise, some investors might be reconsidering their cryptocurrency positions. **Bitcoin's Roller Coaster Ride** The cryptocurrency market, known for its volatility, witnessed Bitcoin's price undergoing significant fluctuations recently. A notable event that gave Bitcoin a temporary boost was Grayscale's triumph over the SEC in a legal battle concerning the conversion of its Bitcoin Trust into a spot ETF. This victory led to a rapid 7.88% spike in Bitcoin's price within a mere hour, pushing it from the $26,000 bracket to briefly touch the $28,000 threshold. However, this euphoria was short-lived. Over the subsequent week, the cryptocurrency saw its gains erode, settling in the $25,400 range. At the time the reference article was penned, Bitcoin was hovering around $25,688. **Anticipation Surrounding the 2024 Halving Event** The Bitcoin community is abuzz with anticipation for the next scheduled Bitcoin halving, projected to take place in April-May 2024. This event will see the rewards for Bitcoin miners being slashed by half, resulting in a decreased supply of Bitcoin entering the market. Historically, such halvings have acted as catalysts, propelling Bitcoin's price upwards. A case in point is the aftermath of the 2020 halving, post which Bitcoin soared to an all-time high of $69,000 in October 2021. However, some financial analysts argue that this surge was less about the halving and more a consequence of the extensive monetary measures adopted by institutions like the US Federal Reserve. These measures, taken in response to the pandemic and the ensuing lockdowns, flooded the market with cash, potentially driving up Bitcoin's price. **The Broader Crypto Landscape** While Bitcoin remains the most dominant and influential cryptocurrency, it's essential to consider its position within the broader crypto ecosystem. Other cryptocurrencies, often referred to as 'altcoins', also play a role in shaping investor sentiment and market dynamics. Factors such as technological advancements, regulatory changes, and global economic shifts not only impact Bitcoin but the entire crypto market. As investors diversify their portfolios and explore newer blockchain projects, Bitcoin's role as the market leader is continually tested. Yet, its pioneering status and proven resilience make it a focal point of discussions and analyses in the crypto world. **Conclusion** Bitcoin, the flagship cryptocurrency, has always been subject to a myriad of market forces and global events. While its inherent potential remains undeniable, the current market landscape, shaped by factors ranging from oil prices to global economic policies, presents challenges. Yet, with events like the 2024 halving on the horizon, there's an air of optimism among Bitcoin enthusiasts and investors about the future trajectory of this digital asset. **FAQ** **Who is Max Keiser?** Max Keiser is a prominent Bitcoin advocate, former trader, and well-known crypto podcaster. **What did Keiser say about Bitcoin's price?** Keiser pointed out that rising global oil prices and the allure of higher interest deposit USD accounts are creating a "small headwind" for Bitcoin. **How did Grayscale's legal victory affect Bitcoin?** Grayscale's win over the SEC led to a 7.88% spike in Bitcoin's price within an hour. **When is the next Bitcoin halving expected?** The next Bitcoin halving is projected to occur around April-May 2024. **Did the 2020 Bitcoin halving influence its price?** Yes, post the 2020 halving, Bitcoin reached an all-time high of $69,000 in October 2021. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: [@croxroadnews](https://x.com/croxroadnewsco)** **Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)** **Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** *DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.*
@ a012dc82:6458a70d
2024-12-30 05:51:11**Table Of Content** - The Influence of Global Oil Prices - Bitcoin's Roller Coaster Ride - Anticipation Surrounding the 2024 Halving Event - The Broader Crypto Landscape - Conclusions - FAQ In the ever-evolving world of cryptocurrencies, Bitcoin stands as a beacon, often dictating the mood of the entire crypto market. Its price fluctuations are closely watched by investors, analysts, and enthusiasts alike. Max Keiser, a prominent figure in the crypto space, recently shed light on some intriguing factors that might be influencing Bitcoin's current price trajectory. This article delves into Keiser's insights, exploring the broader implications of global events on Bitcoin's market performance. **The Influence of Global Oil Prices** Max Keiser, a renowned Bitcoin advocate and former trader, recently drew attention to the interplay between global oil prices and Bitcoin's market performance. Responding to a post by German economics expert, Holger Zschaepitz, Keiser highlighted the significance of Brent oil reaching $90 per barrel for the first time since the previous November. According to Keiser, the surge in oil prices, driven by Saudi Arabia's decision to extend its reduction in oil production for another three months, has had ripple effects in the financial world. One of these effects is the shift of investor interest towards higher interest deposit USD accounts. This diversion of investments is creating what Keiser terms as "a small headwind for Bitcoin," implying that as traditional markets like oil show promise, some investors might be reconsidering their cryptocurrency positions. **Bitcoin's Roller Coaster Ride** The cryptocurrency market, known for its volatility, witnessed Bitcoin's price undergoing significant fluctuations recently. A notable event that gave Bitcoin a temporary boost was Grayscale's triumph over the SEC in a legal battle concerning the conversion of its Bitcoin Trust into a spot ETF. This victory led to a rapid 7.88% spike in Bitcoin's price within a mere hour, pushing it from the $26,000 bracket to briefly touch the $28,000 threshold. However, this euphoria was short-lived. Over the subsequent week, the cryptocurrency saw its gains erode, settling in the $25,400 range. At the time the reference article was penned, Bitcoin was hovering around $25,688. **Anticipation Surrounding the 2024 Halving Event** The Bitcoin community is abuzz with anticipation for the next scheduled Bitcoin halving, projected to take place in April-May 2024. This event will see the rewards for Bitcoin miners being slashed by half, resulting in a decreased supply of Bitcoin entering the market. Historically, such halvings have acted as catalysts, propelling Bitcoin's price upwards. A case in point is the aftermath of the 2020 halving, post which Bitcoin soared to an all-time high of $69,000 in October 2021. However, some financial analysts argue that this surge was less about the halving and more a consequence of the extensive monetary measures adopted by institutions like the US Federal Reserve. These measures, taken in response to the pandemic and the ensuing lockdowns, flooded the market with cash, potentially driving up Bitcoin's price. **The Broader Crypto Landscape** While Bitcoin remains the most dominant and influential cryptocurrency, it's essential to consider its position within the broader crypto ecosystem. Other cryptocurrencies, often referred to as 'altcoins', also play a role in shaping investor sentiment and market dynamics. Factors such as technological advancements, regulatory changes, and global economic shifts not only impact Bitcoin but the entire crypto market. As investors diversify their portfolios and explore newer blockchain projects, Bitcoin's role as the market leader is continually tested. Yet, its pioneering status and proven resilience make it a focal point of discussions and analyses in the crypto world. **Conclusion** Bitcoin, the flagship cryptocurrency, has always been subject to a myriad of market forces and global events. While its inherent potential remains undeniable, the current market landscape, shaped by factors ranging from oil prices to global economic policies, presents challenges. Yet, with events like the 2024 halving on the horizon, there's an air of optimism among Bitcoin enthusiasts and investors about the future trajectory of this digital asset. **FAQ** **Who is Max Keiser?** Max Keiser is a prominent Bitcoin advocate, former trader, and well-known crypto podcaster. **What did Keiser say about Bitcoin's price?** Keiser pointed out that rising global oil prices and the allure of higher interest deposit USD accounts are creating a "small headwind" for Bitcoin. **How did Grayscale's legal victory affect Bitcoin?** Grayscale's win over the SEC led to a 7.88% spike in Bitcoin's price within an hour. **When is the next Bitcoin halving expected?** The next Bitcoin halving is projected to occur around April-May 2024. **Did the 2020 Bitcoin halving influence its price?** Yes, post the 2020 halving, Bitcoin reached an all-time high of $69,000 in October 2021. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: [@croxroadnews](https://x.com/croxroadnewsco)** **Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)** **Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** *DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.* @ 6be5cc06:5259daf0
2024-12-29 19:54:14Um dos padrões mais bem estabelecidos ao medir a opinião pública é que cada geração tende a seguir um caminho semelhante em termos de política e ideologia geral. Seus membros compartilham das mesmas experiências formativas, atingem os marcos importantes da vida ao mesmo tempo e convivem nos mesmos espaços. Então, como devemos entender os relatórios que mostram que a **Geração Z** é hiperprogressista em certos assuntos, mas surpreendentemente conservadora em outros? A resposta, nas palavras de **Alice Evans**, pesquisadora visitante na Universidade de Stanford e uma das principais estudiosas do tema, é que os jovens de hoje estão passando por um grande **divergência de gênero**, com as jovens mulheres do primeiro grupo e os jovens homens do segundo. A **Geração Z** representa duas gerações, e não apenas uma. Em países de todos os continentes, surgiu um **distanciamento ideológico** entre jovens homens e mulheres. Milhões de pessoas que compartilham das mesmas cidades, locais de trabalho, salas de aula e até casas, não veem mais as coisas da mesma maneira. Nos **Estados Unidos**, os dados da Gallup mostram que, após décadas em que os sexos estavam distribuídos de forma relativamente equilibrada entre visões políticas liberais e conservadoras, as mulheres entre **18 e 30 anos** são agora **30 pontos percentuais mais liberais** do que os homens dessa faixa etária. Essa diferença surgiu em apenas **seis anos**. A **Alemanha** também apresenta um distanciamento de 30 pontos entre homens jovens conservadores e mulheres jovens progressistas, e no **Reino Unido**, a diferença é de **25 pontos**. Na **Polônia**, no ano passado, quase metade dos homens entre **18 e 21 anos** apoiou o partido de extrema direita Confederation, em contraste com apenas um sexto das jovens mulheres dessa mesma idade.  Fora do Ocidente, há divisões ainda mais acentuadas. Na **Coreia do Sul**, há um enorme abismo entre homens e mulheres jovens, e a situação é semelhante na **China**. Na **África**, a **Tunísia** apresenta o mesmo padrão. Vale notar que em todos os países essa divisão drástica ocorre principalmente entre a **geração mais jovem**, sendo muito menos pronunciada entre homens e mulheres na faixa dos **30 anos** ou mais velhos. O movimento **# MeToo** foi o **principal estopim**, trazendo à tona valores feministas intensos entre jovens mulheres que se sentiram empoderadas para denunciar injustiças de longa data. Esse estopim encontrou especialmente terreno fértil na **Coreia do Sul**, onde a **desigualdade de gênero** é bastante visível e a **misoginia explícita** é comum. (palavras da Financial Times, eu só traduzi) Na eleição presidencial da **Coreia do Sul** em **2022**, enquanto homens e mulheres mais velhos votaram de forma unificada, os jovens homens apoiaram fortemente o partido de direita **People Power**, enquanto as jovens mulheres apoiaram o partido liberal **Democratic** em números quase iguais e opostos. A situação na **Coreia** é extrema, mas serve como um alerta para outros países sobre o que pode acontecer quando jovens homens e mulheres se distanciam. A sociedade está **dividida**, a taxa de casamento despencou e a taxa de natalidade caiu drasticamente, chegando a **0,78 filhos por mulher** em **2022**, o menor número no mundo todo. Sete anos após a explosão inicial do movimento **# MeToo**, a **divergência de gênero** em atitudes tornou-se autossustentável. Dados das pesquisas mostram que em muitos países, as diferenças ideológicas vão além dessa questão específica. A divisão progressista-conservadora sobre **assédio sexual** parece ter causado ou pelo menos faz parte de um **alinhamento mais amplo**, em que jovens homens e mulheres estão se organizando em grupos conservadores e liberais em outros assuntos. Nos **EUA**, **Reino Unido** e **Alemanha**, as jovens mulheres agora adotam posturas mais liberais sobre temas como **imigração** e **justiça racial**, enquanto grupos etários mais velhos permanecem equilibrados. A tendência na maioria dos países tem sido de **mulheres se inclinando mais para a esquerda**, enquanto os homens permanecem estáveis. No entanto, há sinais de que os jovens homens estão se **movendo para a direita** na **Alemanha**, tornando-se mais críticos em relação à imigração e se aproximando do partido de extrema direita **AfD** nos últimos anos. Seria fácil dizer que tudo isso é apenas uma **fase passageira**, mas os abismos ideológicos apenas crescem, e os dados mostram que as experiências políticas formativas das pessoas são difíceis de mudar. Tudo isso é agravado pelo fato de que o aumento dos smartphones e das redes sociais faz com que os jovens homens e mulheres agora **vivam em espaços separados** e tenham **culturas distintas**. As opiniões dos jovens frequentemente são ignoradas devido à **baixa participação política**, mas essa mudança pode deixar **consequências duradouras**, impactando muito mais do que apenas os resultados das eleições. Retirado de: https://www.ft.com/content/29fd9b5c-2f35-41bf-9d4c-994db4e12998
@ 6be5cc06:5259daf0
2024-12-29 19:54:14Um dos padrões mais bem estabelecidos ao medir a opinião pública é que cada geração tende a seguir um caminho semelhante em termos de política e ideologia geral. Seus membros compartilham das mesmas experiências formativas, atingem os marcos importantes da vida ao mesmo tempo e convivem nos mesmos espaços. Então, como devemos entender os relatórios que mostram que a **Geração Z** é hiperprogressista em certos assuntos, mas surpreendentemente conservadora em outros? A resposta, nas palavras de **Alice Evans**, pesquisadora visitante na Universidade de Stanford e uma das principais estudiosas do tema, é que os jovens de hoje estão passando por um grande **divergência de gênero**, com as jovens mulheres do primeiro grupo e os jovens homens do segundo. A **Geração Z** representa duas gerações, e não apenas uma. Em países de todos os continentes, surgiu um **distanciamento ideológico** entre jovens homens e mulheres. Milhões de pessoas que compartilham das mesmas cidades, locais de trabalho, salas de aula e até casas, não veem mais as coisas da mesma maneira. Nos **Estados Unidos**, os dados da Gallup mostram que, após décadas em que os sexos estavam distribuídos de forma relativamente equilibrada entre visões políticas liberais e conservadoras, as mulheres entre **18 e 30 anos** são agora **30 pontos percentuais mais liberais** do que os homens dessa faixa etária. Essa diferença surgiu em apenas **seis anos**. A **Alemanha** também apresenta um distanciamento de 30 pontos entre homens jovens conservadores e mulheres jovens progressistas, e no **Reino Unido**, a diferença é de **25 pontos**. Na **Polônia**, no ano passado, quase metade dos homens entre **18 e 21 anos** apoiou o partido de extrema direita Confederation, em contraste com apenas um sexto das jovens mulheres dessa mesma idade.  Fora do Ocidente, há divisões ainda mais acentuadas. Na **Coreia do Sul**, há um enorme abismo entre homens e mulheres jovens, e a situação é semelhante na **China**. Na **África**, a **Tunísia** apresenta o mesmo padrão. Vale notar que em todos os países essa divisão drástica ocorre principalmente entre a **geração mais jovem**, sendo muito menos pronunciada entre homens e mulheres na faixa dos **30 anos** ou mais velhos. O movimento **# MeToo** foi o **principal estopim**, trazendo à tona valores feministas intensos entre jovens mulheres que se sentiram empoderadas para denunciar injustiças de longa data. Esse estopim encontrou especialmente terreno fértil na **Coreia do Sul**, onde a **desigualdade de gênero** é bastante visível e a **misoginia explícita** é comum. (palavras da Financial Times, eu só traduzi) Na eleição presidencial da **Coreia do Sul** em **2022**, enquanto homens e mulheres mais velhos votaram de forma unificada, os jovens homens apoiaram fortemente o partido de direita **People Power**, enquanto as jovens mulheres apoiaram o partido liberal **Democratic** em números quase iguais e opostos. A situação na **Coreia** é extrema, mas serve como um alerta para outros países sobre o que pode acontecer quando jovens homens e mulheres se distanciam. A sociedade está **dividida**, a taxa de casamento despencou e a taxa de natalidade caiu drasticamente, chegando a **0,78 filhos por mulher** em **2022**, o menor número no mundo todo. Sete anos após a explosão inicial do movimento **# MeToo**, a **divergência de gênero** em atitudes tornou-se autossustentável. Dados das pesquisas mostram que em muitos países, as diferenças ideológicas vão além dessa questão específica. A divisão progressista-conservadora sobre **assédio sexual** parece ter causado ou pelo menos faz parte de um **alinhamento mais amplo**, em que jovens homens e mulheres estão se organizando em grupos conservadores e liberais em outros assuntos. Nos **EUA**, **Reino Unido** e **Alemanha**, as jovens mulheres agora adotam posturas mais liberais sobre temas como **imigração** e **justiça racial**, enquanto grupos etários mais velhos permanecem equilibrados. A tendência na maioria dos países tem sido de **mulheres se inclinando mais para a esquerda**, enquanto os homens permanecem estáveis. No entanto, há sinais de que os jovens homens estão se **movendo para a direita** na **Alemanha**, tornando-se mais críticos em relação à imigração e se aproximando do partido de extrema direita **AfD** nos últimos anos. Seria fácil dizer que tudo isso é apenas uma **fase passageira**, mas os abismos ideológicos apenas crescem, e os dados mostram que as experiências políticas formativas das pessoas são difíceis de mudar. Tudo isso é agravado pelo fato de que o aumento dos smartphones e das redes sociais faz com que os jovens homens e mulheres agora **vivam em espaços separados** e tenham **culturas distintas**. As opiniões dos jovens frequentemente são ignoradas devido à **baixa participação política**, mas essa mudança pode deixar **consequências duradouras**, impactando muito mais do que apenas os resultados das eleições. Retirado de: https://www.ft.com/content/29fd9b5c-2f35-41bf-9d4c-994db4e12998 @ 30ceb64e:7f08bdf5
2024-12-29 19:09:13I've been working 28 hours a week on the weekends as a Direct service professional, assisting adults with autism and intellectual disabilities. I've brought my laptop freaks. There's enough downtime for me to work on obtaining certifications online, posts to SN and Nostr, and work on my coding project Nostr Run Club. I work with 2 normies on saturday and sunday, and had the bright idea of pitching my app to them. Here is how the conversation went. Hustle: Hey do you guys want to see what i'm working on? Normie 1: Sure.... Normie 2: "Comes around to curiously investigate" ***The Pitch Hustle: Alright, so.....what social media do you use? Normie 1: Instagram. Hustle: Alright so....I'm making a running app. Imagine logging in with instagram, and seeing a feed of all of the runners and all of your friends. Now, what music streaming service do you use? Normie 1: Pandora Normie 2: Spotify Hustle: Cool, so imagine seeing your pandora and Spotify liked songs and playlists in the running app. So the app can track your run, its connected to your social media and streaming platform, and people can send you small donations congratulating you for the run. Normie 1 and 2: Ahh, that's cool. Normie 2: But why would people send you money? Oh? I think I've seen something like it where people send you a star and the star can be redeemed for like 99 cents, or they send you points and the app rewards you for points. Hustle: Nah. That parts already figured out, I'm just having trouble getting the music from "Spotify" to play, and then I'll release it into the wild, that's pretty much my hustle. And that was the conversation, it left me thinking about a few things. 1. V4V The concept is extremely familiar to me. I say good Morning I get 50 cents. I give 35 cents to other GM freaks and keep it pushing. Its normal. But for them the concept seemed so strange, they were looking for some solution or explanation on why people would just give someone else money for seemingly nothing. When the solution is already here, just not evenly distributed or promoted or adopted. Likely because the normies are still existing in the paradox of card companies and ravenous third party intermediaries imposing their cut. 2. The broken social media landscape of disconnected walled gardens I was thinking normie one would say Facebook, if asked normie 2 would've said snapchat, Tik Tok, Instagram etc. for music they could've said apple music, tidal, Youtube music etc. I see Nostr as a highway that connects all of these guys, and instead of buying multiple cars to travel on different streets, you have one car that you use to travel across the country. 3. The tact required to pitch ideas like Nostr and bitcoin I used to work at bank of America and was tasked to sell credit cards without saying the word credit card..... I would say "Hello, good sir/mam, have you thought about getting rewarded for your daily purchases??" I found myself in a familiar situation, introducing them to Nostr without using the word Nostr and introducing them to bitcoin without using the word inevitable. The experience was stranger for me than it was for them, they left thinking "Ahh, thats neat" I walked away from the conversation eager to get notify the freaks. In Conclusion, The interaction gave me a few interesting insights: 1. We'll need to bridge the conceptual gap between traditional and new payment paradigms. 2. The importance of focusing on user benefits rather than technical details 3. The market opportunity for solutions that unify fragmented digital services 4. The value of strategic communication that meets users where they are Successful adoption of new technologies like Nostr and Bitcoin requires careful attention to user education and communication, focusing on practical benefits rather than technical features. The positive reception to the core concept, even without understanding the underlying technology, shows huge potential for mainstream adoption when presented appropriately. Thanks, Hustle originally posted at https://stacker.news/items/829000
@ 30ceb64e:7f08bdf5
2024-12-29 19:09:13I've been working 28 hours a week on the weekends as a Direct service professional, assisting adults with autism and intellectual disabilities. I've brought my laptop freaks. There's enough downtime for me to work on obtaining certifications online, posts to SN and Nostr, and work on my coding project Nostr Run Club. I work with 2 normies on saturday and sunday, and had the bright idea of pitching my app to them. Here is how the conversation went. Hustle: Hey do you guys want to see what i'm working on? Normie 1: Sure.... Normie 2: "Comes around to curiously investigate" ***The Pitch Hustle: Alright, so.....what social media do you use? Normie 1: Instagram. Hustle: Alright so....I'm making a running app. Imagine logging in with instagram, and seeing a feed of all of the runners and all of your friends. Now, what music streaming service do you use? Normie 1: Pandora Normie 2: Spotify Hustle: Cool, so imagine seeing your pandora and Spotify liked songs and playlists in the running app. So the app can track your run, its connected to your social media and streaming platform, and people can send you small donations congratulating you for the run. Normie 1 and 2: Ahh, that's cool. Normie 2: But why would people send you money? Oh? I think I've seen something like it where people send you a star and the star can be redeemed for like 99 cents, or they send you points and the app rewards you for points. Hustle: Nah. That parts already figured out, I'm just having trouble getting the music from "Spotify" to play, and then I'll release it into the wild, that's pretty much my hustle. And that was the conversation, it left me thinking about a few things. 1. V4V The concept is extremely familiar to me. I say good Morning I get 50 cents. I give 35 cents to other GM freaks and keep it pushing. Its normal. But for them the concept seemed so strange, they were looking for some solution or explanation on why people would just give someone else money for seemingly nothing. When the solution is already here, just not evenly distributed or promoted or adopted. Likely because the normies are still existing in the paradox of card companies and ravenous third party intermediaries imposing their cut. 2. The broken social media landscape of disconnected walled gardens I was thinking normie one would say Facebook, if asked normie 2 would've said snapchat, Tik Tok, Instagram etc. for music they could've said apple music, tidal, Youtube music etc. I see Nostr as a highway that connects all of these guys, and instead of buying multiple cars to travel on different streets, you have one car that you use to travel across the country. 3. The tact required to pitch ideas like Nostr and bitcoin I used to work at bank of America and was tasked to sell credit cards without saying the word credit card..... I would say "Hello, good sir/mam, have you thought about getting rewarded for your daily purchases??" I found myself in a familiar situation, introducing them to Nostr without using the word Nostr and introducing them to bitcoin without using the word inevitable. The experience was stranger for me than it was for them, they left thinking "Ahh, thats neat" I walked away from the conversation eager to get notify the freaks. In Conclusion, The interaction gave me a few interesting insights: 1. We'll need to bridge the conceptual gap between traditional and new payment paradigms. 2. The importance of focusing on user benefits rather than technical details 3. The market opportunity for solutions that unify fragmented digital services 4. The value of strategic communication that meets users where they are Successful adoption of new technologies like Nostr and Bitcoin requires careful attention to user education and communication, focusing on practical benefits rather than technical features. The positive reception to the core concept, even without understanding the underlying technology, shows huge potential for mainstream adoption when presented appropriately. Thanks, Hustle originally posted at https://stacker.news/items/829000 @ f4d89779:2b522db9
2024-12-29 16:46:43In the game of Ultimate Frisbee, there is a beloved phrase that captures one of the best aspects of playing. Ultimate is about decision making. It is played on a rectangular field with seven players on each side. Much like football, the object of the game is to score with a throw into the end zone. To "HUCK", means to launch the disc down field in the hopes of scoring. You can probably guess what the "OR YOU'RE NOTHING" means but the spirit of it is that when the opportunity comes ... PUT THE DISC IN THE AIR <https://i.nostr.build/XyTpXdNOSpv5f8ZZ.jpg> Sorry, I had to channel my inner ODELL there for a second. These are all caps kind of moments. Time feels like it stops, the disc floats in the air, the receiver and defender are sprinting all out, you can hear the collective breath of anticipation from the audience and then you score. If you're good that is. You know what? You and I are civilized people, we use the NOSTR, so I won't limit myself to just words. Here are some of those moments: <https://v.nostr.build/zav5o04BK97FiNAt.mp4> During the course of play, teams get into a formation with a couple of the players doing the majority of the disc throwing. These players are called handlers. They handle the disc, they have the responsibility of moving the disc downfield, and handle most of the decision making. A good handler develops a sort of instinct for each of their receivers, can guess the capabilities of each defender, and knows himself well enough to know if he has the throw. They know who is good and reliable at short cuts. They know who has the top end speed to throw a long floating pass into the end zone. With each play they are judging all of the moving objects on the field and deciding on real time risk of each throw and where things will lead. Mistakes lead to turnovers and turnovers, like in many other sports, are death. Hopefully, you start to see how ultimate relates to life and Bitcoin. Life is a field and you have defenders and you have receivers. It is your disc and the decisions you make have a huge impact on whether you win or lose. Knowingly or not, you saw Bitcoin as a potential receiver and Governments, academics, shitcoiners, as defenders. In some ways those around you were also defenders. They whispered, or maybe still whisper the risk and probability of failure in your ear. Their fear weighed against what you know. With the btc/usd exchange rate at $94k, and companies fighting over the best ways to get sats I think we can say that you did not get lucky. They called you crazy, they said that throw won't work, they said your receiver sucked but you knew better. You saw that receiver leaving every defender in the dust and you HUCKED it and you are certainly not NOTHING.
@ f4d89779:2b522db9
2024-12-29 16:46:43In the game of Ultimate Frisbee, there is a beloved phrase that captures one of the best aspects of playing. Ultimate is about decision making. It is played on a rectangular field with seven players on each side. Much like football, the object of the game is to score with a throw into the end zone. To "HUCK", means to launch the disc down field in the hopes of scoring. You can probably guess what the "OR YOU'RE NOTHING" means but the spirit of it is that when the opportunity comes ... PUT THE DISC IN THE AIR <https://i.nostr.build/XyTpXdNOSpv5f8ZZ.jpg> Sorry, I had to channel my inner ODELL there for a second. These are all caps kind of moments. Time feels like it stops, the disc floats in the air, the receiver and defender are sprinting all out, you can hear the collective breath of anticipation from the audience and then you score. If you're good that is. You know what? You and I are civilized people, we use the NOSTR, so I won't limit myself to just words. Here are some of those moments: <https://v.nostr.build/zav5o04BK97FiNAt.mp4> During the course of play, teams get into a formation with a couple of the players doing the majority of the disc throwing. These players are called handlers. They handle the disc, they have the responsibility of moving the disc downfield, and handle most of the decision making. A good handler develops a sort of instinct for each of their receivers, can guess the capabilities of each defender, and knows himself well enough to know if he has the throw. They know who is good and reliable at short cuts. They know who has the top end speed to throw a long floating pass into the end zone. With each play they are judging all of the moving objects on the field and deciding on real time risk of each throw and where things will lead. Mistakes lead to turnovers and turnovers, like in many other sports, are death. Hopefully, you start to see how ultimate relates to life and Bitcoin. Life is a field and you have defenders and you have receivers. It is your disc and the decisions you make have a huge impact on whether you win or lose. Knowingly or not, you saw Bitcoin as a potential receiver and Governments, academics, shitcoiners, as defenders. In some ways those around you were also defenders. They whispered, or maybe still whisper the risk and probability of failure in your ear. Their fear weighed against what you know. With the btc/usd exchange rate at $94k, and companies fighting over the best ways to get sats I think we can say that you did not get lucky. They called you crazy, they said that throw won't work, they said your receiver sucked but you knew better. You saw that receiver leaving every defender in the dust and you HUCKED it and you are certainly not NOTHING. @ 30ceb64e:7f08bdf5
2024-12-28 18:14:28I've been listening to this small playlist over and over again this week. Ivy keeps getting me. I'm having fun making these things https://music.youtube.com/watch?v=yNPfvgFEXuk&si=HjUdZxXKkGfqabk8 https://music.youtube.com/watch?v=LyRJfs-Qn70&si=2ugksRTltXATqHVo https://music.youtube.com/watch?v=XkpAE8ZZ6bU&si=WwWopN-YMLGguFiB https://music.youtube.com/watch?v=VIcQreSskyM&si=Ewza3W6SOkRDWF1E https://music.youtube.com/watch?v=5xm8Q-1cOpU&si=GeQv3Kum_TV9H6KD https://music.youtube.com/watch?v=xYM-aZG9QbE&si=fwfzIFLAyVumnTs4 https://music.youtube.com/watch?v=r7JWHuGFUeI&si=MqoFBqvb0iI7pAAY https://music.youtube.com/watch?v=GjnjUHY8MiM&si=F_Aepjxc_g2SH7UG https://music.youtube.com/watch?v=sgjTb7UQe2A&si=04wik3m5LefpbGMV https://music.youtube.com/watch?v=SMOund_uFTk&si=v7sa3XxchH607d0Y https://music.youtube.com/playlist?list=PLmYfnnK_Qs5jpv5hKuBKFOEvMnPFl3vto&si=Dkudss84jFszdGmj Thanks Anon, Hustle originally posted at https://stacker.news/items/827883
@ 30ceb64e:7f08bdf5
2024-12-28 18:14:28I've been listening to this small playlist over and over again this week. Ivy keeps getting me. I'm having fun making these things https://music.youtube.com/watch?v=yNPfvgFEXuk&si=HjUdZxXKkGfqabk8 https://music.youtube.com/watch?v=LyRJfs-Qn70&si=2ugksRTltXATqHVo https://music.youtube.com/watch?v=XkpAE8ZZ6bU&si=WwWopN-YMLGguFiB https://music.youtube.com/watch?v=VIcQreSskyM&si=Ewza3W6SOkRDWF1E https://music.youtube.com/watch?v=5xm8Q-1cOpU&si=GeQv3Kum_TV9H6KD https://music.youtube.com/watch?v=xYM-aZG9QbE&si=fwfzIFLAyVumnTs4 https://music.youtube.com/watch?v=r7JWHuGFUeI&si=MqoFBqvb0iI7pAAY https://music.youtube.com/watch?v=GjnjUHY8MiM&si=F_Aepjxc_g2SH7UG https://music.youtube.com/watch?v=sgjTb7UQe2A&si=04wik3m5LefpbGMV https://music.youtube.com/watch?v=SMOund_uFTk&si=v7sa3XxchH607d0Y https://music.youtube.com/playlist?list=PLmYfnnK_Qs5jpv5hKuBKFOEvMnPFl3vto&si=Dkudss84jFszdGmj Thanks Anon, Hustle originally posted at https://stacker.news/items/827883 @ 30ceb64e:7f08bdf5
2024-12-28 17:47:48A recent conversation with fellow Bitcoiners prompted me to share this overview of Nostr tools. While you don't need to use everything, understanding the ecosystem helps paint a picture of where we're heading. I often hear people say "I'm posting to the void" or "My feed is boring" or "I'm not earning any bitcoin" or "It's too complicated." Let me address these concerns with a comprehensive overview. ### Core Clients and Features Primal and Amethyst are currently the best daily drivers. Theyre both valid twitter replacements with primal focusing on user friendliness and amethyst focusing on being more feature rich. Both apps feature an algorithm marketplace (we call them DVMs) where you can choose from various feed styles. Soon, anyone will be able to create and share their own algorithms. For additional feed customization, Listr.lol lets you curate lists of npubs to further refine your experience. ### Content and Rewards Stacker News (SN) integrates beautifully with Nostr. Cross-post your SN content to appear as longform notes on platforms like Highlighter, Yakihonne, and Habla.news. SN's rewards system pays out satoshis for quality content, bridging their closed platform with Nostr's open network. ### Payments and Zaps For zaps, I recommend CoinOS, or AlbyHub for a more sovereign alternative. CoinOS is non kyc and gives you a lightning address and NWC connection string to throw into your nostr clients. CoinOS supports e-cash and Bolt 12, Liquid, and can auto-withdraw earnings to cold storage. You can use coinOs as a PWA or input the connection string into Alby Go for a more minimal wallet alternative. ### Security and App Management Android users should use zap.store for downloading Nostr apps. It verifies app authenticity and implements Web of Trust features, showing which trusted npubs use each app. For managing multiple apps, Pokey provides a unified notification dashboard. Amber (Android) offers secure client login without exposing your nsec, while Citrine lets you run a relay on your phone for data backup. ### Creator Tools - Wavlake: Spotify alternative with open music graph - Fountain: Podcast app with Nostr integration - Zap.stream: Live streaming - Nostr.build: Media hosting - Cypher.space: Website creation with integrated marketplace - Olas: Instagram alternative - Gifbuddy.lol: Gif creation - memeamigo.lol: Meme creation - Zappadd: Promotional tools ### Making the Most of Nostr The key to Nostr is understanding that nothing is force-fed. You're responsible for: - Creating your desired feed - Choosing your client - Selecting your relays - Managing your wallet - Curating who you follow For best results, go all in: 1. Leave traditional social media 2. Use Primal and or Amethyst as your main client 3. Follow 1000 npubs 4. Set up CoinOS for payments 5. Engage daily with the community ### Future Outlook Some ask if Nostr is truly decentralized, censorship-resistant, or profitable. My response: the user experience will become so good that most internet users will naturally gravitate here. The only barrier will be ideological resistance. Nostr represents a new internet paradigm where users outpower platforms, identity persists across apps, and Bitcoin is the standard. We've practically already won. ### Crazy Ideas I'm thinking the age of of the super nostr app will come to a close. We're probably going to enter an era of a thousand micro apps and client templates, which allow users to build their own client in 30 seconds. Some templates will be impermanent, one time use clients, others will be more robust for building a daily driver. You'll be able to share your completed piece on nostr for other people to use, and they'll zap you for building it. A marketplace of user created apps supported by thousands of micro apps and relays and templates, probably a user experience holy grail, made possible by nostr's open social graph, smooth monetization processes from bitcoin. ### Growth Predictions Daily Active Users doubling yearly: 2024: 20k → 2029: 640k The beauty of Nostr isn't just in its decentralized nature or bitcoin integration – it's in the user experience that puts you in control. While traditional social media platforms force-feed you content through black-box algorithms, Nostr hands you the keys to your own digital kingdom. You choose your feed, your apps, your connections, and your level of engagement. Yes, there's a learning curve, but that's the price of digital sovereignty. Think of where Twitter was in 2006 or Bitcoin in 2013. Those who saw the potential and jumped in early didn't just benefit financially – they helped shape the future. Nostr is at that same inflection point. The tools are here, the infrastructure is growing, and the community is building. Whether you're a creator, developer, bitcoiner, or just someone tired of traditional social media, Nostr offers a glimpse of what the internet should have been all along. The question isn't if Nostr will win, but when. And when it does, you'll want to be able to say you were here when it all began. Thanks, Hustle originally posted at https://stacker.news/items/827860
@ 30ceb64e:7f08bdf5
2024-12-28 17:47:48A recent conversation with fellow Bitcoiners prompted me to share this overview of Nostr tools. While you don't need to use everything, understanding the ecosystem helps paint a picture of where we're heading. I often hear people say "I'm posting to the void" or "My feed is boring" or "I'm not earning any bitcoin" or "It's too complicated." Let me address these concerns with a comprehensive overview. ### Core Clients and Features Primal and Amethyst are currently the best daily drivers. Theyre both valid twitter replacements with primal focusing on user friendliness and amethyst focusing on being more feature rich. Both apps feature an algorithm marketplace (we call them DVMs) where you can choose from various feed styles. Soon, anyone will be able to create and share their own algorithms. For additional feed customization, Listr.lol lets you curate lists of npubs to further refine your experience. ### Content and Rewards Stacker News (SN) integrates beautifully with Nostr. Cross-post your SN content to appear as longform notes on platforms like Highlighter, Yakihonne, and Habla.news. SN's rewards system pays out satoshis for quality content, bridging their closed platform with Nostr's open network. ### Payments and Zaps For zaps, I recommend CoinOS, or AlbyHub for a more sovereign alternative. CoinOS is non kyc and gives you a lightning address and NWC connection string to throw into your nostr clients. CoinOS supports e-cash and Bolt 12, Liquid, and can auto-withdraw earnings to cold storage. You can use coinOs as a PWA or input the connection string into Alby Go for a more minimal wallet alternative. ### Security and App Management Android users should use zap.store for downloading Nostr apps. It verifies app authenticity and implements Web of Trust features, showing which trusted npubs use each app. For managing multiple apps, Pokey provides a unified notification dashboard. Amber (Android) offers secure client login without exposing your nsec, while Citrine lets you run a relay on your phone for data backup. ### Creator Tools - Wavlake: Spotify alternative with open music graph - Fountain: Podcast app with Nostr integration - Zap.stream: Live streaming - Nostr.build: Media hosting - Cypher.space: Website creation with integrated marketplace - Olas: Instagram alternative - Gifbuddy.lol: Gif creation - memeamigo.lol: Meme creation - Zappadd: Promotional tools ### Making the Most of Nostr The key to Nostr is understanding that nothing is force-fed. You're responsible for: - Creating your desired feed - Choosing your client - Selecting your relays - Managing your wallet - Curating who you follow For best results, go all in: 1. Leave traditional social media 2. Use Primal and or Amethyst as your main client 3. Follow 1000 npubs 4. Set up CoinOS for payments 5. Engage daily with the community ### Future Outlook Some ask if Nostr is truly decentralized, censorship-resistant, or profitable. My response: the user experience will become so good that most internet users will naturally gravitate here. The only barrier will be ideological resistance. Nostr represents a new internet paradigm where users outpower platforms, identity persists across apps, and Bitcoin is the standard. We've practically already won. ### Crazy Ideas I'm thinking the age of of the super nostr app will come to a close. We're probably going to enter an era of a thousand micro apps and client templates, which allow users to build their own client in 30 seconds. Some templates will be impermanent, one time use clients, others will be more robust for building a daily driver. You'll be able to share your completed piece on nostr for other people to use, and they'll zap you for building it. A marketplace of user created apps supported by thousands of micro apps and relays and templates, probably a user experience holy grail, made possible by nostr's open social graph, smooth monetization processes from bitcoin. ### Growth Predictions Daily Active Users doubling yearly: 2024: 20k → 2029: 640k The beauty of Nostr isn't just in its decentralized nature or bitcoin integration – it's in the user experience that puts you in control. While traditional social media platforms force-feed you content through black-box algorithms, Nostr hands you the keys to your own digital kingdom. You choose your feed, your apps, your connections, and your level of engagement. Yes, there's a learning curve, but that's the price of digital sovereignty. Think of where Twitter was in 2006 or Bitcoin in 2013. Those who saw the potential and jumped in early didn't just benefit financially – they helped shape the future. Nostr is at that same inflection point. The tools are here, the infrastructure is growing, and the community is building. Whether you're a creator, developer, bitcoiner, or just someone tired of traditional social media, Nostr offers a glimpse of what the internet should have been all along. The question isn't if Nostr will win, but when. And when it does, you'll want to be able to say you were here when it all began. Thanks, Hustle originally posted at https://stacker.news/items/827860 @ 228dde34:b5d0345e
2024-12-27 09:59:42##### BY Cheryl Nya, Glenda Chong, and Jonathan Tan ##### Hype Issue #60 ###### Join CHERYL NYA, GLENDA CHONG and JONATHAN TAN as they explore how Singaporean cafe owner, Sunshine Irene, celebrates Christmas through charity.  *Sunshine Irene, first row, third from the right, as Santarina, and her husband as Santa, with the youth volunteers at the 2023 NY Cafe Christmas carnival. Photo by Xaen.* On Christmas Day, a quiet cafe in the Upper Thompson neighbourhood is filled with many volunteers doing charity work and blessing others as festive lights, holiday music, and a cheerful buzz perfectly capture the true spirit of the Christmas holiday. Meet Irene, 51, the person behind this lively holiday cheer at NY Cafe’s annual Christmas carnival. Over the years, she has become a community pillar due to her charity work. She shares how this event got started, “So last year, we had the privilege of hosting a very fun [and] fulfilling charity Christmas event at NY cafe”. What has now become a festive tradition was once originated by a group of women and youths, alongside Irene, with a generous determination to give back to the community.“[Partnering with Community Chest, a charity organisation in Singapore], we put up a few events, carnivals, booths, workshops, and all funds that we collect one hundred percent go to charity,” Irene shares.  *Interactive storytelling by NY Cafe’s very own Santa was well-received by the crowd. Photo by NY Cafe.* The NY Cafe Christmas carnival was truly a dream. There were booths that offered fun activities like terrarium making, ornament painting and colouring, giving everyone the opportunity to unleash their creativity. Santa’s storytelling corner was a big hit with the kids, as was the ‘Decorate Your Own Cupcakes and Donuts’ booth. The caroling was a crowd favourite, with classic Christmas hits drawing smiles from all. The lucky draw, or ‘blessed draw’ as they called it, also treated the winners to delightful Christmas gifts to take home.   *A group of youths came down on Christmas day to volunteer at the NY Cafe Christmas carnival, where they facilitated the activities and engaged the guests. Photo by NY Cafe.* But Irene’s favourite part? All the activities were facilitated by youth volunteers. “They were like my hands and legs running the carnival,” she remembers fondly. Witnessing the smiles they brought to their audience and the joy reflected back on their own was the greatest gift of all. This year, however, the cafe’s carnival has been scaled back to more of a cosy hearth than a blazing bonfire. Why a smaller carnival? Irene explains that it has to do with the hurdles the cafe faced this year. “The main reason is because we lost the cafe… because the building was sold,” Irene says. This forced NY Cafe to close and with that, a venue to run any charity events was lost.   *Irene ran a small booth at One Sentosa Cove this year, to raise and donate funds to charity in the festive spirit of giving. Photo by Irene.* Despite such circumstances, instead of forfeiting a carnival completely, Irene scaled back on the festivities by hosting a mini pop-up store in One Sentosa Cove and one near Lentor, the neighbourhood NY Cafe had originated from as it was “for the neighbourhood community”. Another setback Irene faced was the lack of outreach resulting from having no resources and capacity. “Because we did not have the outreach… the [turnout] was not good enough to raise much funds. So I would say that the charity part may not be as successful as [it was in] previous years,” Irene admits. However, while the cafe may have faced shadows of unmet expectations and goals, they did not lose sight of the light. The carnival’s flame burned smaller this year, yet its warmth still reached the hearts of the neighbourhood. “We [could have done better] in [terms of reaching out]… but what we gain is awareness,” Irene says. “The neighbourhood knows that…there is this thing going on and they are very happy. They would be keen to be contributors [to the event] moving forward.” Ultimately, hosting this year’s Christmas charity had its share of problems and challenges; but it’s a tradition that Irene wants to uphold. “What sparks me to do this? It's a lot to do with [my desire] to spark joy in other people's lives, in any small ways that we can,” Irene shares. The emphasis on charity has always been one of Irene’s core values. “In my life, most decisions that I have made were led by growth and contributions, these two big values of my life; so doing charity has always been one of the big pillars of my life.” The joy that comes with seeing her impact on the lives of the less fortunate is a powerful motivator for Irene’s efforts. Moreover, Irene hopes that her dedication to helping others will encourage her children to do the same. “I also hope that my kids are able to be a contributor in someone's life as well,” Irene says. “Since they are very young, I have exposed them to do charity and create impact on others' lives as well.”  *The volunteers who step up to bless the less fortunate in the same spirit of giving make it all worth it. Photo by NY Cafe.* And so, over the years, Irene’s annual charity events have served as a reminder of the true meaning of Christmas. Year after year, volunteers step up and work together to bless the less fortunate on this very special day. “Witnessing the volunteers, the people stepping up, stepping forward to be a contributor, that really melts my heart,” Irene shares. “And regardless of what role they play, they actually contribute wholeheartedly, and they also immerse and enjoy themselves.” Every year as Christmas approaches, it’s easy to get caught up in the whirlwind of bright light, lavish gifts and extravagant festivities, losing sight of the true spirit of giving and kindness. Perhaps Irene’s commitment to spreading charity every year serves as a reminder to us of what Christmas should really be about. “It's a season to remember people who touched our lives, or people whose lives we want to touch, and give them a little gift to help them remember… there's love around, and there's warmth around everybody,” Irene says.
@ 228dde34:b5d0345e
2024-12-27 09:59:42##### BY Cheryl Nya, Glenda Chong, and Jonathan Tan ##### Hype Issue #60 ###### Join CHERYL NYA, GLENDA CHONG and JONATHAN TAN as they explore how Singaporean cafe owner, Sunshine Irene, celebrates Christmas through charity.  *Sunshine Irene, first row, third from the right, as Santarina, and her husband as Santa, with the youth volunteers at the 2023 NY Cafe Christmas carnival. Photo by Xaen.* On Christmas Day, a quiet cafe in the Upper Thompson neighbourhood is filled with many volunteers doing charity work and blessing others as festive lights, holiday music, and a cheerful buzz perfectly capture the true spirit of the Christmas holiday. Meet Irene, 51, the person behind this lively holiday cheer at NY Cafe’s annual Christmas carnival. Over the years, she has become a community pillar due to her charity work. She shares how this event got started, “So last year, we had the privilege of hosting a very fun [and] fulfilling charity Christmas event at NY cafe”. What has now become a festive tradition was once originated by a group of women and youths, alongside Irene, with a generous determination to give back to the community.“[Partnering with Community Chest, a charity organisation in Singapore], we put up a few events, carnivals, booths, workshops, and all funds that we collect one hundred percent go to charity,” Irene shares.  *Interactive storytelling by NY Cafe’s very own Santa was well-received by the crowd. Photo by NY Cafe.* The NY Cafe Christmas carnival was truly a dream. There were booths that offered fun activities like terrarium making, ornament painting and colouring, giving everyone the opportunity to unleash their creativity. Santa’s storytelling corner was a big hit with the kids, as was the ‘Decorate Your Own Cupcakes and Donuts’ booth. The caroling was a crowd favourite, with classic Christmas hits drawing smiles from all. The lucky draw, or ‘blessed draw’ as they called it, also treated the winners to delightful Christmas gifts to take home.   *A group of youths came down on Christmas day to volunteer at the NY Cafe Christmas carnival, where they facilitated the activities and engaged the guests. Photo by NY Cafe.* But Irene’s favourite part? All the activities were facilitated by youth volunteers. “They were like my hands and legs running the carnival,” she remembers fondly. Witnessing the smiles they brought to their audience and the joy reflected back on their own was the greatest gift of all. This year, however, the cafe’s carnival has been scaled back to more of a cosy hearth than a blazing bonfire. Why a smaller carnival? Irene explains that it has to do with the hurdles the cafe faced this year. “The main reason is because we lost the cafe… because the building was sold,” Irene says. This forced NY Cafe to close and with that, a venue to run any charity events was lost.   *Irene ran a small booth at One Sentosa Cove this year, to raise and donate funds to charity in the festive spirit of giving. Photo by Irene.* Despite such circumstances, instead of forfeiting a carnival completely, Irene scaled back on the festivities by hosting a mini pop-up store in One Sentosa Cove and one near Lentor, the neighbourhood NY Cafe had originated from as it was “for the neighbourhood community”. Another setback Irene faced was the lack of outreach resulting from having no resources and capacity. “Because we did not have the outreach… the [turnout] was not good enough to raise much funds. So I would say that the charity part may not be as successful as [it was in] previous years,” Irene admits. However, while the cafe may have faced shadows of unmet expectations and goals, they did not lose sight of the light. The carnival’s flame burned smaller this year, yet its warmth still reached the hearts of the neighbourhood. “We [could have done better] in [terms of reaching out]… but what we gain is awareness,” Irene says. “The neighbourhood knows that…there is this thing going on and they are very happy. They would be keen to be contributors [to the event] moving forward.” Ultimately, hosting this year’s Christmas charity had its share of problems and challenges; but it’s a tradition that Irene wants to uphold. “What sparks me to do this? It's a lot to do with [my desire] to spark joy in other people's lives, in any small ways that we can,” Irene shares. The emphasis on charity has always been one of Irene’s core values. “In my life, most decisions that I have made were led by growth and contributions, these two big values of my life; so doing charity has always been one of the big pillars of my life.” The joy that comes with seeing her impact on the lives of the less fortunate is a powerful motivator for Irene’s efforts. Moreover, Irene hopes that her dedication to helping others will encourage her children to do the same. “I also hope that my kids are able to be a contributor in someone's life as well,” Irene says. “Since they are very young, I have exposed them to do charity and create impact on others' lives as well.”  *The volunteers who step up to bless the less fortunate in the same spirit of giving make it all worth it. Photo by NY Cafe.* And so, over the years, Irene’s annual charity events have served as a reminder of the true meaning of Christmas. Year after year, volunteers step up and work together to bless the less fortunate on this very special day. “Witnessing the volunteers, the people stepping up, stepping forward to be a contributor, that really melts my heart,” Irene shares. “And regardless of what role they play, they actually contribute wholeheartedly, and they also immerse and enjoy themselves.” Every year as Christmas approaches, it’s easy to get caught up in the whirlwind of bright light, lavish gifts and extravagant festivities, losing sight of the true spirit of giving and kindness. Perhaps Irene’s commitment to spreading charity every year serves as a reminder to us of what Christmas should really be about. “It's a season to remember people who touched our lives, or people whose lives we want to touch, and give them a little gift to help them remember… there's love around, and there's warmth around everybody,” Irene says. @ 79a7270b:d61d9067
2024-12-26 09:16:59Fifteen years after its creation, Bitcoin continues to break paradigms and solidify its role in the global economic landscape. In 2021, El Salvador adopted it as legal tender, marking a significant turning point. Three years later, its acceptance has advanced considerably, with Wall Street embracing Bitcoin ETFs and U.S. political debates focusing on its adoption as a strategic reserve. With its portability, scarcity, accessibility, and liquidity in a 24/7 open market, Bitcoin distinguishes itself as an asset that transcends the limitations of traditional resources like gold and oil. Unlike these assets, which often face logistical challenges and market constraints, Bitcoin’s digital nature allows for seamless global transactions without physical barriers. Its scarcity mirrors that of gold, preserving its value over time, while its accessibility and round-the-clock liquidity make it an appealing choice for investors and policymakers alike. This unique combination of attributes positions Bitcoin as a versatile and strategic tool, increasingly relevant to advancing national interests in a rapidly digitizing world. The expansion of the BRICS block, whose combined GDP now surpasses that of the G7, has heightened pressures on Western hegemony. These countries are exploring Bitcoin as a neutral and government-independent currency. They are considering denominating international transactions in Bitcoin as part of their broader goal: to create a de-dollarized, independent financial system resilient to Western-imposed sanctions. Game theory sheds light on how Bitcoin adoption creates powerful incentives for nations. If the BRICS use Bitcoin as a strategic asset, Western nations would be compelled to accumulate it to influence the market and counteract sanctions circumvention, making Bitcoin critical for national security. In a scenario where major powers hold Bitcoin, it would be unfeasible to remain competitive without it. This logic extends to Bitcoin mining, the process that validates transactions. By deciding what is confirmed, nations dominating mining operations gain significant influence over transaction flows. Consequently, Bitcoin-accumulating countries will prioritize investing in domestic mining infrastructure, enhancing the network's decentralization and security. For instance, Russia reportedly funds regional initiatives to develop AI and Bitcoin mining infrastructure within the BRICS framework through its Sovereign Wealth Fund. This dynamic triggers a chain reaction: as one nation adopts Bitcoin, others are pressured to follow suit to avoid competitive disadvantages. This cycle embodies the essence of game theory, where each player's choices shape the strategies of others, positioning Bitcoin as a critical asset in the global geopolitical arena.
@ 79a7270b:d61d9067
2024-12-26 09:16:59Fifteen years after its creation, Bitcoin continues to break paradigms and solidify its role in the global economic landscape. In 2021, El Salvador adopted it as legal tender, marking a significant turning point. Three years later, its acceptance has advanced considerably, with Wall Street embracing Bitcoin ETFs and U.S. political debates focusing on its adoption as a strategic reserve. With its portability, scarcity, accessibility, and liquidity in a 24/7 open market, Bitcoin distinguishes itself as an asset that transcends the limitations of traditional resources like gold and oil. Unlike these assets, which often face logistical challenges and market constraints, Bitcoin’s digital nature allows for seamless global transactions without physical barriers. Its scarcity mirrors that of gold, preserving its value over time, while its accessibility and round-the-clock liquidity make it an appealing choice for investors and policymakers alike. This unique combination of attributes positions Bitcoin as a versatile and strategic tool, increasingly relevant to advancing national interests in a rapidly digitizing world. The expansion of the BRICS block, whose combined GDP now surpasses that of the G7, has heightened pressures on Western hegemony. These countries are exploring Bitcoin as a neutral and government-independent currency. They are considering denominating international transactions in Bitcoin as part of their broader goal: to create a de-dollarized, independent financial system resilient to Western-imposed sanctions. Game theory sheds light on how Bitcoin adoption creates powerful incentives for nations. If the BRICS use Bitcoin as a strategic asset, Western nations would be compelled to accumulate it to influence the market and counteract sanctions circumvention, making Bitcoin critical for national security. In a scenario where major powers hold Bitcoin, it would be unfeasible to remain competitive without it. This logic extends to Bitcoin mining, the process that validates transactions. By deciding what is confirmed, nations dominating mining operations gain significant influence over transaction flows. Consequently, Bitcoin-accumulating countries will prioritize investing in domestic mining infrastructure, enhancing the network's decentralization and security. For instance, Russia reportedly funds regional initiatives to develop AI and Bitcoin mining infrastructure within the BRICS framework through its Sovereign Wealth Fund. This dynamic triggers a chain reaction: as one nation adopts Bitcoin, others are pressured to follow suit to avoid competitive disadvantages. This cycle embodies the essence of game theory, where each player's choices shape the strategies of others, positioning Bitcoin as a critical asset in the global geopolitical arena. @ fd208ee8:0fd927c1
2024-12-26 07:02:59I just read this, and found it enlightening. > Jung... notes that intelligence can be seen as problem solving at an everyday level..., whereas creativity may represent problem solving for less common issues > Other studies have used metaphor creation as a creativity measure instead of divergent thinking and a spectrum of CHC components instead of just g and have found much higher relationships between creativity and intelligence than past studies https://www.mdpi.com/2079-3200/3/3/59 I'm unusually intelligent (Who isn't?), but I'm much more creative, than intelligent, and I think that confuses people. The ability to apply intelligence, to solve completely novel problems, on the fly, is something IQ tests don't even claim to measure. They just claim a correlation. Creativity requires taking wild, mental leaps out into nothingness; simply trusting that your brain will land you safely. And this is why I've been at the forefront of massive innovation, over and over, but never got rich off of it. *I'm a starving autist.* Zaps are the first time I've ever made money directly, for solving novel problems. Companies don't do this because there is a span of time between providing a solution and the solution being implemented, and the person building the implementation (or their boss) receives all the credit for the existence of the solution. At best, you can hope to get pawned off with a small bonus. Nobody can remember who came up with the solution, originally, and that person might not even be there, anymore, and probably never filed a patent, and may have no idea that their idea has even been built. They just run across it, later, in a tech magazine or museum, and say, "Well, will you look at that! Someone actually went and built it! Isn't that nice!" Universities at least had the idea of cementing novel solutions in academic papers, but that: 1) only works if you're an academic, and at a university, 2) is an incredibly slow process, not appropriate for a truly innovative field, 3) leads to manifestations of perverse incentives and biased research frameworks, coming from 'publish or perish' policies. But I think long-form notes and zaps solve for this problem. #Alexandria, especially, is being built to cater to this long-suffering class of chronic underachievers. It leaves a written, public, time-stamped record of *Clever Ideas We Have Had*. Because they are clever, the ideas. And we have had them.
@ fd208ee8:0fd927c1
2024-12-26 07:02:59I just read this, and found it enlightening. > Jung... notes that intelligence can be seen as problem solving at an everyday level..., whereas creativity may represent problem solving for less common issues > Other studies have used metaphor creation as a creativity measure instead of divergent thinking and a spectrum of CHC components instead of just g and have found much higher relationships between creativity and intelligence than past studies https://www.mdpi.com/2079-3200/3/3/59 I'm unusually intelligent (Who isn't?), but I'm much more creative, than intelligent, and I think that confuses people. The ability to apply intelligence, to solve completely novel problems, on the fly, is something IQ tests don't even claim to measure. They just claim a correlation. Creativity requires taking wild, mental leaps out into nothingness; simply trusting that your brain will land you safely. And this is why I've been at the forefront of massive innovation, over and over, but never got rich off of it. *I'm a starving autist.* Zaps are the first time I've ever made money directly, for solving novel problems. Companies don't do this because there is a span of time between providing a solution and the solution being implemented, and the person building the implementation (or their boss) receives all the credit for the existence of the solution. At best, you can hope to get pawned off with a small bonus. Nobody can remember who came up with the solution, originally, and that person might not even be there, anymore, and probably never filed a patent, and may have no idea that their idea has even been built. They just run across it, later, in a tech magazine or museum, and say, "Well, will you look at that! Someone actually went and built it! Isn't that nice!" Universities at least had the idea of cementing novel solutions in academic papers, but that: 1) only works if you're an academic, and at a university, 2) is an incredibly slow process, not appropriate for a truly innovative field, 3) leads to manifestations of perverse incentives and biased research frameworks, coming from 'publish or perish' policies. But I think long-form notes and zaps solve for this problem. #Alexandria, especially, is being built to cater to this long-suffering class of chronic underachievers. It leaves a written, public, time-stamped record of *Clever Ideas We Have Had*. Because they are clever, the ideas. And we have had them. @ 228dde34:b5d0345e
2024-12-25 09:35:38##### By Cheryl Nya ##### Deputy Editor ##### Hype Issue #60 ###### CHERYL NYA dives into the four attachment styles and discovers how they can be understood and used to strengthen our interpersonal relationships.  In the midst of a heated conflict, what is your first instinct? Would it be to apologise repeatedly, or to calmly suggest a solution? Or perhaps your first move would be to walk away from the issue. Could it be that you lash out emotionally only to withdraw suddenly out of guilt? Regardless of which of the four responses you resonate with, it all boils down to your own unique style of attachment; something that is different for everyone. Experts theorise that humans exhibit four different attachment styles which determine their patterns of closeness, trust, and dependency in relationships. Each style reflects the different ways people seek connection and express their emotional needs. Originated by British psychologist, John Bowlby, and expanded upon by Mary Ainsworth, the attachment theory suggests that humans are biologically wired to form attachments for survival, and the nature of these attachments shapes our development and experiences in relationships. At its core, the theory asserts that children naturally turn to a caregiver for comfort during times of distress or uncertainty. The bond formed in these moments establishes the foundation for secure or insecure attachments. As the child grows, this connection shapes how they approach future relationships and manage stress.  *The four attachment styles – each representing distinct ways people approach connections. Photo by The New York Times.* Now let’s dive into the four attachment styles: secure, anxious, avoidant and disorganised. **Secure Attachment** Individuals with the secure attachment style have a healthy balance of independence and reliance on others. They manage conflict well, being comfortable with healthy communication, and are confident in both giving and receiving affection. These people enjoy being with others, and aren’t anxious when apart. **Anxious Attachment** This group of individuals tend to be perceived as needy, and in most cases, excessively so. People with the anxious attachment style usually have low self-esteem and often need approval; they crave emotional intimacy and reassurance but worry that others might lose interest, or not want to be with them. Their significant fear of abandonment and rejection could lead them to face difficulty being alone. **Avoidant Attachment** Someone who’s avoidant may find it challenging to handle emotional intimacy. This group of individuals value their independence and freedom so much that intimacy and closeness can often make them uncomfortable. They tend to suppress or downplay their feelings to avoid situations where they have to be vulnerable or dependent on others. **Disorganised Attachment** This attachment style is marked by the deep desire for closeness coupled with an equally intense fear of getting hurt. The unpredictable behaviour of these people could look like: Being warm and affectionate one moment, and distant and withdrawn the next. Their struggle to regulate their emotions results in their contradictory actions. The disorganised attachment style exhibits both the traits of the anxious and the avoidant styles.  *Take a moment to understand why you can’t help but react a certain way; it might just be your attachment style. Photo taken from Pinterest.* To put attachment theory into context, let’s explore how individuals with different attachment styles would respond in the same situation. Scenario: You’ve made plans with a loved one but they cancel on you. Secure attachment style: “No worries, we can reschedule! Hope all’s well on your side!” Anxious attachment style: “Why don’t they want to see me? I’m not important enough…” Avoidant attachment style: “Nice, I have more time for myself now.” Disorganised attachment style: “Did I do something wrong? Whatever, I shouldn’t care.” Alongside popular concepts such as love languages and the Myers-Briggs Type Indicator (MBTI), attachment styles have also become part of the blueprint for modern relationships. Understanding attachment styles is important because it helps you identify your emotional triggers and behaviours in relationships. This awareness improves your ability to communicate your needs with your loved ones, particularly for those with insecure attachment styles (anxious, avoidant, disorganised). Enhanced communication could also help you interpret others’ actions without jumping to conclusions. This knowledge equips you to navigate conflicts between different attachment styles more effectively. Everyone has their own way of connecting with others, and when you understand why some people want constant approval, or why others actively seek solitude, you have the ability to adjust your approach to make your relationships smoother.   *Loving someone could look like two extremes: constant reassurance and giving them space. Nothing wrong with either, we just have different ways of wanting to feel loved. Photos taken from Pinterest.* For example, if you’re the secure type, you can step up and offer that extra reassurance when someone with an anxious attachment style is feeling uncertain. It’s not so much about smothering them, but just simply showing that you care and that you’re listening to their needs. Or when dealing with an avoidant friend, you can respect their need for space while trying not to take it too personally. They might not always be down for a real and deep conversation like you are, but that’s totally okay. By recognising the behaviours of different styles, you help to avoid misunderstandings and facilitate amicable relationships.  *Understanding each other’s different style of attachment and reaching a compromise could strengthen your relationship. Photo taken from Pinterest.* Conversely, if you’re the anxious type, you can try making an effort to seek less validation from others, and find your worth in yourself. Remind yourself that you’re worthy of love, just as you are. Likewise for people with the avoidant attachment style, try to gather courage to face your vulnerabilities and true feelings by talking it out with a trusted loved one. These efforts can also make a secure type friend feel heard when their need for a good balance between emotional closeness and independence is met. The best part is that learning about attachment styles helps you communicate in ways that fit each person’s needs. Your relationships aren’t the only things that will benefit from this knowledge: you grow into a more thoughtful and empathetic individual too. Be it the clingy friend, the ‘keep a distance’ type, the secure or the ‘can’t decide what I want to feel right now’ kind that you’re dealing with, knowing how to adjust your approach can effectively turn conflicts into growth. Now that you know a little more about attachment styles, why not take a moment to reflect on your own? Take a quick quiz online or chat with a partner about their attachment style. You might be surprised by how much it can change the way you connect with people in your life. So, the next time you’re trying to figure out why someone is acting a certain way, remember – it might just be their attachment style talking!
@ 228dde34:b5d0345e
2024-12-25 09:35:38##### By Cheryl Nya ##### Deputy Editor ##### Hype Issue #60 ###### CHERYL NYA dives into the four attachment styles and discovers how they can be understood and used to strengthen our interpersonal relationships.  In the midst of a heated conflict, what is your first instinct? Would it be to apologise repeatedly, or to calmly suggest a solution? Or perhaps your first move would be to walk away from the issue. Could it be that you lash out emotionally only to withdraw suddenly out of guilt? Regardless of which of the four responses you resonate with, it all boils down to your own unique style of attachment; something that is different for everyone. Experts theorise that humans exhibit four different attachment styles which determine their patterns of closeness, trust, and dependency in relationships. Each style reflects the different ways people seek connection and express their emotional needs. Originated by British psychologist, John Bowlby, and expanded upon by Mary Ainsworth, the attachment theory suggests that humans are biologically wired to form attachments for survival, and the nature of these attachments shapes our development and experiences in relationships. At its core, the theory asserts that children naturally turn to a caregiver for comfort during times of distress or uncertainty. The bond formed in these moments establishes the foundation for secure or insecure attachments. As the child grows, this connection shapes how they approach future relationships and manage stress.  *The four attachment styles – each representing distinct ways people approach connections. Photo by The New York Times.* Now let’s dive into the four attachment styles: secure, anxious, avoidant and disorganised. **Secure Attachment** Individuals with the secure attachment style have a healthy balance of independence and reliance on others. They manage conflict well, being comfortable with healthy communication, and are confident in both giving and receiving affection. These people enjoy being with others, and aren’t anxious when apart. **Anxious Attachment** This group of individuals tend to be perceived as needy, and in most cases, excessively so. People with the anxious attachment style usually have low self-esteem and often need approval; they crave emotional intimacy and reassurance but worry that others might lose interest, or not want to be with them. Their significant fear of abandonment and rejection could lead them to face difficulty being alone. **Avoidant Attachment** Someone who’s avoidant may find it challenging to handle emotional intimacy. This group of individuals value their independence and freedom so much that intimacy and closeness can often make them uncomfortable. They tend to suppress or downplay their feelings to avoid situations where they have to be vulnerable or dependent on others. **Disorganised Attachment** This attachment style is marked by the deep desire for closeness coupled with an equally intense fear of getting hurt. The unpredictable behaviour of these people could look like: Being warm and affectionate one moment, and distant and withdrawn the next. Their struggle to regulate their emotions results in their contradictory actions. The disorganised attachment style exhibits both the traits of the anxious and the avoidant styles.  *Take a moment to understand why you can’t help but react a certain way; it might just be your attachment style. Photo taken from Pinterest.* To put attachment theory into context, let’s explore how individuals with different attachment styles would respond in the same situation. Scenario: You’ve made plans with a loved one but they cancel on you. Secure attachment style: “No worries, we can reschedule! Hope all’s well on your side!” Anxious attachment style: “Why don’t they want to see me? I’m not important enough…” Avoidant attachment style: “Nice, I have more time for myself now.” Disorganised attachment style: “Did I do something wrong? Whatever, I shouldn’t care.” Alongside popular concepts such as love languages and the Myers-Briggs Type Indicator (MBTI), attachment styles have also become part of the blueprint for modern relationships. Understanding attachment styles is important because it helps you identify your emotional triggers and behaviours in relationships. This awareness improves your ability to communicate your needs with your loved ones, particularly for those with insecure attachment styles (anxious, avoidant, disorganised). Enhanced communication could also help you interpret others’ actions without jumping to conclusions. This knowledge equips you to navigate conflicts between different attachment styles more effectively. Everyone has their own way of connecting with others, and when you understand why some people want constant approval, or why others actively seek solitude, you have the ability to adjust your approach to make your relationships smoother.   *Loving someone could look like two extremes: constant reassurance and giving them space. Nothing wrong with either, we just have different ways of wanting to feel loved. Photos taken from Pinterest.* For example, if you’re the secure type, you can step up and offer that extra reassurance when someone with an anxious attachment style is feeling uncertain. It’s not so much about smothering them, but just simply showing that you care and that you’re listening to their needs. Or when dealing with an avoidant friend, you can respect their need for space while trying not to take it too personally. They might not always be down for a real and deep conversation like you are, but that’s totally okay. By recognising the behaviours of different styles, you help to avoid misunderstandings and facilitate amicable relationships.  *Understanding each other’s different style of attachment and reaching a compromise could strengthen your relationship. Photo taken from Pinterest.* Conversely, if you’re the anxious type, you can try making an effort to seek less validation from others, and find your worth in yourself. Remind yourself that you’re worthy of love, just as you are. Likewise for people with the avoidant attachment style, try to gather courage to face your vulnerabilities and true feelings by talking it out with a trusted loved one. These efforts can also make a secure type friend feel heard when their need for a good balance between emotional closeness and independence is met. The best part is that learning about attachment styles helps you communicate in ways that fit each person’s needs. Your relationships aren’t the only things that will benefit from this knowledge: you grow into a more thoughtful and empathetic individual too. Be it the clingy friend, the ‘keep a distance’ type, the secure or the ‘can’t decide what I want to feel right now’ kind that you’re dealing with, knowing how to adjust your approach can effectively turn conflicts into growth. Now that you know a little more about attachment styles, why not take a moment to reflect on your own? Take a quick quiz online or chat with a partner about their attachment style. You might be surprised by how much it can change the way you connect with people in your life. So, the next time you’re trying to figure out why someone is acting a certain way, remember – it might just be their attachment style talking! @ bcea2b98:7ccef3c9
2024-12-25 03:11:27It has been a fun year of learning and entertainment with you all. Merry Christmas! originally posted at https://stacker.news/items/823433
@ bcea2b98:7ccef3c9
2024-12-25 03:11:27It has been a fun year of learning and entertainment with you all. Merry Christmas! originally posted at https://stacker.news/items/823433 @ 2fc236af:455ba142
2024-12-24 19:40:20# 22 February 2025 • 10 a.m. to 2 p.m. • The Doddridge Centre (opposite Church's Shoes factory), St. James, Northampton • NN5 5LD Seedy Saturday is an community seed swap event held each February in Northampton, UK. We'll have a wide range of fruit, vegetable, herb and flower seeds to choose from, including some rare and unusual varieties you won't find in the catalogues. We'll also have a marketplace selling garden and eco-related goods, community groups, and a pop-up cafe serving a range of hot food, drinks and snacks. Whether you're a newly-minted gardener or a child of the soil, we're sure to have something for you! Click/tap here for a handy map and details of how to find us (opens in new tab / window). We bring together a vibrant community of local gardeners and growers of all ages and abilities; it's a great way to start the gardening season. If you've new to the idea of seed swaps, read on! ----------- ### What's a seed swap? A seed swap is a community event where gardeners can exchange their spare vegetable, flower, fruit and herb seeds—either own-grown or commercially produced—for other seeds they want to grow. Most seed swaps are run by gardeners for gardeners; you'll often find rare and interesting local varieties on offer. They're also a great place to meet and chat with other local growers. The seed table is the heart of any seed swap; here you'll find all sorts of garden seeds on offer. Though we can't guarantee to have everything you want, you're sure to find something interesting. At Northampton's Seedy Saturday you'll also find: •stalls selling local produce and garden-centric items; •seed potatoes; •community organisations that focus on food, gardening and the environment; •a pop-up cafe serving hot drinks and light snacks. ### How does our seed swap work? Pack your home-grown seeds into envelopes or self-sealing bags and label them with the plant's name (common or Latin), the variety's name, and the year it was grown. You can also add the place where it was grown, – for example; ""Tomato: Gardeners Delight, grown in Brixworth 2023"". Securely seal the packets. When you arrive, bring your spare seeds to the seed reception table, where our volunteers will check and sort them for display. Then, choose any seeds you want from the table; we'll exchange seeds on a pack-for-pack basis. Don't worry if you've no seeds to swap or want to take more than you've donated; you can take more seeds for a minimum donation of 50p per pack. ### What to bring: To make sure everyone's swapped seeds will grow and flourish, please follow these guidelines when choosing seeds to bring to the swap table. We welcome: •non-hybrid seeds you've grown and harvested yourself (though see below); and •unopened packs of commercially packed seeds that have been stored in cool, dry conditions and are no more than one year past their "sow by" date. What to leave at home: •part-used and opened packs of seeds where the inner pack has been opened; •seeds that are unpackaged, unlabelled or undated; •seeds from produce you haven't grown yourself (eg; shop-bought fruits and vegetables); •commercially packed seeds that are more than one year past their "sow by" date and home-grown seeds that are more than two years old; •seeds that have been stored in hot or damp conditions (eg; in a greenhouse or shed); •seeds that may have been cross-pollinated; •seeds from diseased or unhealthy plants; •seeds of patented varieties or genetically modified organisms (GMOs); •seeds of any plant that is illegal, restricted or regulated by UK law (eg; cannabis, invasive weeds etc). ### Want to know more about seed-saving? Click or tap [here](nostr:nevent1qvzqqqr4gupzqt7zx6he9d03g48cls83565lkqgfwpmj6pf7wzfqrma5jfz4hg2zqythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyghwumn8ghj7vf5xqhxvdm69e5k7tcpzamhxue69uhkyarr9e4kcetwv3sh5afwvdhk6tcpr4mhxue69uhkymmnw3ezucnfw33k76tww3ux76m09e3k7mf0qyw8wumn8ghj7cn4vd4k2apwvdhhyctrd3jjuum0vd5kzmp0qqsrfshynqaajprtzt4umj04hrxwuw353f27k9eh9pgs0062sn3g4fqzz09tg). Northampton's Seedy Saturday is organised by Fruitful Abundance, a group of volunteers who campaign for a fairer, more resilient and less-wasteful food system. We update this page as needed but our Facebook page [(link)](https://www.facebook.com/northamptonseedysaturday/) is often more up-to-date. You can contact us via our Facebook page. Please note we are unpaid volunteers with busy lives so you may not get an immediate response to your query.
@ 2fc236af:455ba142
2024-12-24 19:40:20# 22 February 2025 • 10 a.m. to 2 p.m. • The Doddridge Centre (opposite Church's Shoes factory), St. James, Northampton • NN5 5LD Seedy Saturday is an community seed swap event held each February in Northampton, UK. We'll have a wide range of fruit, vegetable, herb and flower seeds to choose from, including some rare and unusual varieties you won't find in the catalogues. We'll also have a marketplace selling garden and eco-related goods, community groups, and a pop-up cafe serving a range of hot food, drinks and snacks. Whether you're a newly-minted gardener or a child of the soil, we're sure to have something for you! Click/tap here for a handy map and details of how to find us (opens in new tab / window). We bring together a vibrant community of local gardeners and growers of all ages and abilities; it's a great way to start the gardening season. If you've new to the idea of seed swaps, read on! ----------- ### What's a seed swap? A seed swap is a community event where gardeners can exchange their spare vegetable, flower, fruit and herb seeds—either own-grown or commercially produced—for other seeds they want to grow. Most seed swaps are run by gardeners for gardeners; you'll often find rare and interesting local varieties on offer. They're also a great place to meet and chat with other local growers. The seed table is the heart of any seed swap; here you'll find all sorts of garden seeds on offer. Though we can't guarantee to have everything you want, you're sure to find something interesting. At Northampton's Seedy Saturday you'll also find: •stalls selling local produce and garden-centric items; •seed potatoes; •community organisations that focus on food, gardening and the environment; •a pop-up cafe serving hot drinks and light snacks. ### How does our seed swap work? Pack your home-grown seeds into envelopes or self-sealing bags and label them with the plant's name (common or Latin), the variety's name, and the year it was grown. You can also add the place where it was grown, – for example; ""Tomato: Gardeners Delight, grown in Brixworth 2023"". Securely seal the packets. When you arrive, bring your spare seeds to the seed reception table, where our volunteers will check and sort them for display. Then, choose any seeds you want from the table; we'll exchange seeds on a pack-for-pack basis. Don't worry if you've no seeds to swap or want to take more than you've donated; you can take more seeds for a minimum donation of 50p per pack. ### What to bring: To make sure everyone's swapped seeds will grow and flourish, please follow these guidelines when choosing seeds to bring to the swap table. We welcome: •non-hybrid seeds you've grown and harvested yourself (though see below); and •unopened packs of commercially packed seeds that have been stored in cool, dry conditions and are no more than one year past their "sow by" date. What to leave at home: •part-used and opened packs of seeds where the inner pack has been opened; •seeds that are unpackaged, unlabelled or undated; •seeds from produce you haven't grown yourself (eg; shop-bought fruits and vegetables); •commercially packed seeds that are more than one year past their "sow by" date and home-grown seeds that are more than two years old; •seeds that have been stored in hot or damp conditions (eg; in a greenhouse or shed); •seeds that may have been cross-pollinated; •seeds from diseased or unhealthy plants; •seeds of patented varieties or genetically modified organisms (GMOs); •seeds of any plant that is illegal, restricted or regulated by UK law (eg; cannabis, invasive weeds etc). ### Want to know more about seed-saving? Click or tap [here](nostr:nevent1qvzqqqr4gupzqt7zx6he9d03g48cls83565lkqgfwpmj6pf7wzfqrma5jfz4hg2zqythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyghwumn8ghj7vf5xqhxvdm69e5k7tcpzamhxue69uhkyarr9e4kcetwv3sh5afwvdhk6tcpr4mhxue69uhkymmnw3ezucnfw33k76tww3ux76m09e3k7mf0qyw8wumn8ghj7cn4vd4k2apwvdhhyctrd3jjuum0vd5kzmp0qqsrfshynqaajprtzt4umj04hrxwuw353f27k9eh9pgs0062sn3g4fqzz09tg). Northampton's Seedy Saturday is organised by Fruitful Abundance, a group of volunteers who campaign for a fairer, more resilient and less-wasteful food system. We update this page as needed but our Facebook page [(link)](https://www.facebook.com/northamptonseedysaturday/) is often more up-to-date. You can contact us via our Facebook page. Please note we are unpaid volunteers with busy lives so you may not get an immediate response to your query.