-
 @ 39f70015:9d4e378a
2025-04-07 17:28:03
@ 39f70015:9d4e378a
2025-04-07 17:28:03This is a copy of chapter four of Mastering Bitcoin Cash. I'm using it to test out creating long-form content on highlighter.com.
This is an edit after the original post. I want to test how editing long-form content works on Nostr.
4. Transactions
Introduction
Transactions are the most important part of the Bitcoin Cash system. Everything else in Bitcoin Cash is designed to ensure that transactions can be created, propagated on the network, validated, and finally added to the global ledger of transactions (the blockchain). Transactions are data structures that encode the transfer of value between participants in the Bitcoin Cash system. Each transaction is a public entry in Bitcoin Cash’s blockchain, the global double-entry bookkeeping ledger.
In this chapter we will examine all the various forms of transactions, what they contain, how to create them, how they are verified, and how they become part of the permanent record of all transactions.
Transaction Lifecycle
A transaction’s lifecycle starts with the transaction’s creation, also known as origination. The transaction is then signed with one or more signatures indicating the authorization to spend the funds referenced by the transaction. The transaction is then broadcast on the Bitcoin Cash network, where each network node (participant) validates and propagates the transaction until it reaches (almost) every node in the network. Finally, the transaction is verified by a mining node and included in a block of transactions that is recorded on the blockchain.
Once recorded on the blockchain and confirmed by sufficient subsequent blocks (confirmations), the transaction is a permanent part of the Bitcoin Cash ledger and is accepted as valid by all participants. The funds allocated to a new owner by the transaction can then be spent in a new transaction, extending the chain of ownership and beginning the lifecycle of a transaction again.
Creating Transactions
In some ways it helps to think of a transaction in the same way as a paper check. Like a check, a transaction is an instrument that expresses the intent to transfer money and is not visible to the financial system until it is submitted for execution. Like a check, the originator of the transaction does not have to be the one signing the transaction.
Transactions can be created online or offline by anyone, even if the person creating the transaction is not an authorized signer on the account. For example, an accounts payable clerk might process payable checks for signature by the CEO. Similarly, an accounts payable clerk can create Bitcoin Cash transactions and then have the CEO apply digital signatures to make them valid. Whereas a check references a specific account as the source of the funds, a Bitcoin Cash transaction references a specific previous transaction as its source, rather than an account.
Once a transaction has been created, it is signed by the owner (or owners) of the source funds. If it is properly formed and signed, the signed transaction is now valid and contains all the information needed to execute the transfer of funds. Finally, the valid transaction has to reach the Bitcoin Cash network so that it can be propagated until it reaches a miner for inclusion in the pubic ledger (the blockchain).
Broadcasting Transactions to the Bitcoin Cash Network
First, a transaction needs to be delivered to the Bitcoin Cash network so that it can be propagated and included in the blockchain. In essence, a Bitcoin Cash transaction is just 300 to 400 bytes of data and has to reach any one of tens of thousands of Bitcoin Cash nodes. The senders do not need to trust the nodes they use to broadcast the transaction, as long as they use more than one to ensure that it propagates. The nodes don’t need to trust the sender or establish the sender’s "identity." Because the transaction is signed and contains no confidential information, private keys, or credentials, it can be publicly broadcast using any underlying network transport that is convenient. Unlike credit card transactions, for example, which contain sensitive information and can only be transmitted on encrypted networks, a Bitcoin Cash transaction can be sent over any network. As long as the transaction can reach a Bitcoin Cash node that will propagate it into the Bitcoin Cash network, it doesn’t matter how it is transported to the first node.
Bitcoin Cash transactions can therefore be transmitted to the Bitcoin Cash network over insecure networks such as WiFi, Bluetooth, NFC, Chirp, barcodes, or by copying and pasting into a web form. In extreme cases, a Bitcoin Cash transaction could be transmitted over packet radio, satellite relay, or shortwave using burst transmission, spread spectrum, or frequency hopping to evade detection and jamming. A Bitcoin Cash transaction could even be encoded as smileys (emoticons) and posted in a public forum or sent as a text message or Skype chat message. Bitcoin Cash has turned money into a data structure, making it virtually impossible to stop anyone from creating and executing a Bitcoin Cash transaction.
Propagating Transactions on the Bitcoin Cash Network
Once a Bitcoin Cash transaction is sent to any node connected to the Bitcoin Cash network, the transaction will be validated by that node. If valid, that node will propagate it to the other nodes to which it is connected, and a success message will be returned synchronously to the originator. If the transaction is invalid, the node will reject it and synchronously return a rejection message to the originator.
The Bitcoin Cash network is a peer-to-peer network, meaning that each Bitcoin Cash node is connected to a few other Bitcoin Cash nodes that it discovers during startup through the peer-to-peer protocol. The entire network forms a loosely connected mesh without a fixed topology or any structure, making all nodes equal peers. Messages, including transactions and blocks, are propagated from each node to all the peers to which it is connected, a process called "flooding." A new validated transaction injected into any node on the network will be sent to all of the nodes connected to it (neighbors), each of which will send the transaction to all its neighbors, and so on. In this way, within a few seconds a valid transaction will propagate in an exponentially expanding ripple across the network until all nodes in the network have received it.
The Bitcoin Cash network is designed to propagate transactions and blocks to all nodes in an efficient and resilient manner that is resistant to attacks. To prevent spamming, denial-of-service attacks, or other nuisance attacks against the Bitcoin Cash system, every node independently validates every transaction before propagating it further. A malformed transaction will not get beyond one node.
Transaction Structure
A transaction is a data structure that encodes a transfer of value from a source of funds, called an input, to a destination, called an output. Transaction inputs and outputs are not related to accounts or identities. Instead, you should think of them as Bitcoin Cash amounts—chunks of Bitcoin Cash—being locked with a specific secret that only the owner, or person who knows the secret, can unlock. A transaction contains a number of fields, as shown in The structure of a transaction.
| Size | Field | Description | | --- | --- | --- | | 4 bytes | Version | Specifies which rules this transaction follows | | 1–9 bytes (VarInt) | Input Counter | How many inputs are included | | Variable | Inputs | One or more transaction inputs | | 1–9 bytes (VarInt) | Output Counter | How many outputs are included | | variable | Outputs | One or more transaction outputs | | 4 bytes | Locktime | A Unix timestamp or block number |
Table 1. The structure of a transaction
Transaction Locktime
Locktime, also known as nLockTime from the variable name used in the reference client, defines the earliest time that a transaction is valid and can be relayed on the network or added to the blockchain. It is set to zero in most transactions to indicate immediate propagation and execution. If locktime is nonzero and below 500 million, it is interpreted as a block height, meaning the transaction is not valid and is not relayed or included in the blockchain prior to the specified block height. If it is above 500 million, it is interpreted as a Unix Epoch timestamp (seconds since Jan-1-1970) and the transaction is not valid prior to the specified time. Transactions with locktime specifying a future block or time must be held by the originating system and transmitted to the Bitcoin Cash network only after they become valid. The use of locktime is equivalent to postdating a paper check.
Transaction Outputs and Inputs
The fundamental building block of a Bitcoin Cash transaction is an unspent transaction output, or UTXO. UTXO are indivisible chunks of Bitcoin Cash currency locked to a specific owner, recorded on the blockchain, and recognized as currency units by the entire network. The Bitcoin Cash network tracks all available (unspent) UTXO currently numbering in the millions. Whenever a user receives Bitcoin Cash, that amount is recorded within the blockchain as a UTXO. Thus, a user’s Bitcoin Cash might be scattered as UTXO amongst hundreds of transactions and hundreds of blocks. In effect, there is no such thing as a stored balance of a Bitcoin Cash address or account; there are only scattered UTXO, locked to specific owners. The concept of a user’s Bitcoin Cash balance is a derived construct created by the wallet application. The wallet calculates the user’s balance by scanning the blockchain and aggregating all UTXO belonging to that user.
There are no accounts or balances in Bitcoin Cash; there are only _unspent transaction outputs_ (UTXO) scattered in the blockchain.
A UTXO can have an arbitrary value denominated as a multiple of satoshis. Just like dollars can be divided down to two decimal places as cents, bitcoins can be divided down to eight decimal places as satoshis. Although UTXO can be any arbitrary value, once created it is indivisible just like a coin that cannot be cut in half. If a UTXO is larger than the desired value of a transaction, it must still be consumed in its entirety and change must be generated in the transaction. In other words, if you have a 20 Bitcoin Cash UTXO and want to pay 1 Bitcoin Cash, your transaction must consume the entire 20 Bitcoin Cash UTXO and produce two outputs: one paying 1 Bitcoin Cash to your desired recipient and another paying 19 Bitcoin Cash in change back to your wallet. As a result, most Bitcoin Cash transactions will generate change.
Imagine a shopper buying a $1.50 beverage, reaching into her wallet and trying to find a combination of coins and bank notes to cover the $1.50 cost. The shopper will choose exact change if available (a dollar bill and two quarters), or a combination of smaller denominations (six quarters), or if necessary, a larger unit such as a five dollar bank note. If she hands too much money, say $5, to the shop owner, she will expect $3.50 change, which she will return to her wallet and have available for future transactions.
Similarly, a Bitcoin Cash transaction must be created from a user’s UTXO in whatever denominations that user has available. Users cannot cut a UTXO in half any more than they can cut a dollar bill in half and use it as currency. The user’s wallet application will typically select from the user’s available UTXO various units to compose an amount greater than or equal to the desired transaction amount.
As with real life, the Bitcoin Cash application can use several strategies to satisfy the purchase amount: combining several smaller units, finding exact change, or using a single unit larger than the transaction value and making change. All of this complex assembly of spendable UTXO is done by the user’s wallet automatically and is invisible to users. It is only relevant if you are programmatically constructing raw transactions from UTXO.
The UTXO consumed by a transaction are called transaction inputs, and the UTXO created by a transaction are called transaction outputs. This way, chunks of Bitcoin Cash value move forward from owner to owner in a chain of transactions consuming and creating UTXO. Transactions consume UTXO by unlocking it with the signature of the current owner and create UTXO by locking it to the Bitcoin Cash address of the new owner.
The exception to the output and input chain is a special type of transaction called the coinbase transaction, which is the first transaction in each block. This transaction is placed there by the "winning" miner and creates brand-new Bitcoin Cash payable to that miner as a reward for mining. This is how Bitcoin Cash’s money supply is created during the mining process, as we will see in Mining and Consensus.
What comes first? Inputs or outputs, the chicken or the egg? Strictly speaking, outputs come first because coinbase transactions, which generate new Bitcoin Cash, have no inputs and create outputs from nothing.
Transaction Outputs
Every Bitcoin Cash transaction creates outputs, which are recorded on the Bitcoin Cash ledger. Almost all of these outputs, with one exception (see Data Output (OP_RETURN)) create spendable chunks of Bitcoin Cash called unspent transaction outputs or UTXO, which are then recognized by the whole network and available for the owner to spend in a future transaction. Sending someone Bitcoin Cash is creating an unspent transaction output (UTXO) registered to their address and available for them to spend.
UTXO are tracked by every full-node Bitcoin Cash client as a data set called the UTXO set or UTXO pool, held in a database. New transactions consume (spend) one or more of these outputs from the UTXO set.
Transaction outputs consist of two parts:
- An amount of Bitcoin Cash, denominated in satoshis, the smallest Bitcoin Cash unit
- A locking script, also known as an "encumbrance" that "locks" this amount by specifying the conditions that must be met to spend the output
The transaction scripting language, used in the locking script mentioned previously, is discussed in detail in Transaction Scripts and Script Language. The structure of a transaction output shows the structure of a transaction output.
| Size | Field | Description | | --- | --- | --- | | 8 bytes | Amount | Bitcoin Cash value in satoshis (108 Bitcoin Cash) | | 1–9 bytes (VarInt) | Locking-Script Size | Locking-Script length in bytes, to follow | | Variable | Locking-Script | A script defining the conditions needed to spend the output | | 1–9 bytes (VarInt) | Output Counter | How many outputs are included | | variable | Outputs | One or more transaction outputs | | 4 bytes | Locktime | A Unix timestamp or block number |
Table 2. The structure of a transaction output
In A script that calls
bitbox.Address.utxoto find the UTXO related to an address, we use thebitbox.Addressclass to find the unspent outputs (UTXO) of a specific address.Example 1. A script that calls
bitbox.Address.utxoto find the UTXO related to an address```javascript bitbox.Address.utxo('bitcoincash:qpcxf2sv9hjw08nvpgffpamfus9nmksm3chv5zqtnz').then((result) => { console.log(result); }, (err) => { console.log(err); });
Returns the following: [{ txid: 'cc27be8846276612dfce5924b7be96556212f0f0e62bd17641732175edb9911e', vout: 0, scriptPubKey: '76a9147064aa0c2de4e79e6c0a1290f769e40b3dda1b8e88ac', amount: 0.00007021, satoshis: 7021, height: 527155, confirmations: 11879, legacyAddress: '1BFHGm4HzqgXXyNX8n7DsQno5DAC4iLMRA', cashAddress: 'bitcoincash:qpcxf2sv9hjw08nvpgffpamfus9nmksm3chv5zqtnz' } ] ```
Running the script, we see an array of objects representing unspent transaction outputs which are available to this address.
Spending conditions (encumbrances)
Transaction outputs associate a specific amount (in satoshis) to a specific encumbrance or locking script that defines the condition that must be met to spend that amount. In most cases, the locking script will lock the output to a specific Bitcoin Cash address, thereby transferring ownership of that amount to the new owner. When Alice paid Bob’s Cafe for a cup of coffee, her transaction created a 0.00208507 Bitcoin Cash output encumbered or locked to the cafe’s Bitcoin Cash address. That 0.00208507 Bitcoin Cash output was recorded on the blockchain and became part of the Unspent Transaction Output set, meaning it showed in Bob’s wallet as part of the available balance. When Bob chooses to spend that amount, his transaction will release the encumbrance, unlocking the output by providing an unlocking script containing a signature from Bob’s private key.
Transaction Inputs
In simple terms, transaction inputs are pointers to UTXO. They point to a specific UTXO by reference to the transaction hash and sequence number where the UTXO is recorded in the blockchain. To spend UTXO, a transaction input also includes unlocking scripts that satisfy the spending conditions set by the UTXO. The unlocking script is usually a signature proving ownership of the Bitcoin Cash address that is in the locking script.
When users make a payment, their wallet constructs a transaction by selecting from the available UTXO. For example, to make a 0.00208507 Bitcoin Cash payment, the wallet app may select a 0.002 UTXO and a 0.00008507 UTXO, using them both to add up to the desired payment amount.
Once the UTXO is selected, the wallet then produces unlocking scripts containing signatures for each of the UTXO, thereby making them spendable by satisfying their locking script conditions. The wallet adds these UTXO references and unlocking scripts as inputs to the transaction. The structure of a transaction input shows the structure of a transaction input.
| Size | Field | Description | | --- | --- | --- | | 32 bytes | Transaction Hash | Pointer to the transaction containing the UTXO to be spent | | 4 bytes | Output Index | The index number of the UTXO to be spent; first one is 0 | | 1-9 bytes (VarInt) | Unlocking-Script Size | Unlocking-Script length in bytes, to follow | | Variable | Unlocking-Script | A script that fulfills the conditions of the UTXO locking script | | 4 bytes | Sequence Number | Currently disabled Tx-replacement feature, set to 0xFFFFFFFF |
Table 3. The structure of a transaction input
Transaction Fees
Most transactions include transaction fees, which compensate the Bitcoin Cash miners for securing the network. Mining and the fees and rewards collected by miners are discussed in more detail in Mining and Consensus. This section examines how transaction fees are included in a typical transaction. Most wallets calculate and include transaction fees automatically. However, if you are constructing transactions programmatically, or using a command-line interface, you must manually account for and include these fees.
Transaction fees serve as an incentive to include (mine) a transaction into the next block and also as a disincentive against "spam" transactions or any kind of abuse of the system, by imposing a small cost on every transaction. Transaction fees are collected by the miner who mines the block that records the transaction on the blockchain.
Transaction fees are calculated based on the size of the transaction in kilobytes, not the value of the transaction in Bitcoin Cash. Overall, transaction fees are set based on market forces within the Bitcoin Cash network. Miners prioritize transactions based on many different criteria, including fees, and might even process transactions for free under certain circumstances. Transaction fees affect the processing priority, meaning that a transaction with sufficient fees is likely to be included in the next-most–mined block, whereas a transaction with insufficient or no fees might be delayed, processed on a best-effort basis after a few blocks, or not processed at all. Transaction fees are not mandatory, and transactions without fees might be processed eventually; however, including transaction fees encourages priority processing.
The current algorithm used by miners to prioritize transactions for inclusion in a block based on their fees is examined in detail in Mining and Consensus.
Adding Fees to Transactions
The data structure of transactions does not have a field for fees. Instead, fees are implied as the difference between the sum of inputs and the sum of outputs. Any excess amount that remains after all outputs have been deducted from all inputs is the fee that is collected by the miners.
Transaction fees are implied, as the excess of inputs minus outputs:
Fees = Sum(Inputs) – Sum(Outputs)This is a somewhat confusing element of transactions and an important point to understand, because if you are constructing your own transactions you must ensure you do not inadvertently include a very large fee by underspending the inputs. That means that you must account for all inputs, if necessary by creating change, or you will end up giving the miners a very big tip!
For example, if you consume a 20-Bitcoin Cash UTXO to make a 1-Bitcoin Cash payment, you must include a 19-Bitcoin Cash change output back to your wallet. Otherwise, the 19-Bitcoin Cash "leftover" will be counted as a transaction fee and will be collected by the miner who mines your transaction in a block. Although you will receive priority processing and make a miner very happy, this is probably not what you intended.
If you forget to add a change output in a manually constructed transaction, you will be paying the change as a transaction fee. "Keep the change!" might not be what you intended.
Let’s see how this works in practice, by looking at Alice’s coffee purchase again. Alice wants to spend 0.00208507 Bitcoin Cash to pay for coffee. To ensure this transaction is processed promptly, she will want to include a transaction fee of 1 satoshi per byte. That will mean that the total cost of the transaction will be 0.00208750. Her wallet must therefore source a set of UTXO that adds up to 0.00208750 Bitcoin Cash or more and, if necessary, create change. Let’s say her wallet has a 0.00277257-Bitcoin Cash UTXO available. It will therefore need to consume this UTXO, create one output to Bob’s Cafe for 0.00208507, and a second output with 0.00068507 Bitcoin Cash in change back to her own wallet, leaving 0.00000243 Bitcoin Cash unallocated, as an implicit fee for the transaction.
Transaction Chaining and Orphan Transactions
As we have seen, transactions form a chain, whereby one transaction spends the outputs of the previous transaction (known as the parent) and creates outputs for a subsequent transaction (known as the child). Sometimes an entire chain of transactions depending on each other—say a parent, child, and grandchild transaction—are created at the same time, to fulfill a complex transactional workflow that requires valid children to be signed before the parent is signed.
When a chain of transactions is transmitted across the network, they don’t always arrive in the same order. Sometimes, the child might arrive before the parent. In that case, the nodes that see a child first can see that it references a parent transaction that is not yet known. Rather than reject the child, they put it in a temporary pool to await the arrival of its parent and propagate it to every other node. The pool of transactions without parents is known as the orphan transaction pool. Once the parent arrives, any orphans that reference the UTXO created by the parent are released from the pool, revalidated recursively, and then the entire chain of transactions can be included in the transaction pool, ready to be mined in a block. Transaction chains can be arbitrarily long, with any number of generations transmitted simultaneously. The mechanism of holding orphans in the orphan pool ensures that otherwise valid transactions will not be rejected just because their parent has been delayed and that eventually the chain they belong to is reconstructed in the correct order, regardless of the order of arrival.
There is a limit to the number of orphan transactions stored in memory, to prevent a denial-of-service attack against Bitcoin Cash nodes. The limit is defined as MAX_ORPHAN_TRANSACTIONS in the source code of the Bitcoin Cash reference client. If the number of orphan transactions in the pool exceeds MAX_ORPHAN_TRANSACTIONS, one or more randomly selected orphan transactions are evicted from the pool, until the pool size is back within limits.
Transaction Scripts and Script Language
Bitcoin Cash clients validate transactions by executing a script, written in a Forth-like scripting language. Both the locking script (encumbrance) placed on a UTXO and the unlocking script that usually contains a signature are written in this scripting language. When a transaction is validated, the unlocking script in each input is executed alongside the corresponding locking script to see if it satisfies the spending condition.
Today, most transactions processed through the Bitcoin Cash network have the form "Alice pays Bob" and are based on the same script called a Pay-to-Public-Key-Hash script. However, the use of scripts to lock outputs and unlock inputs means that through use of the programming language, transactions can contain an infinite number of conditions. Bitcoin Cash transactions are not limited to the "Alice pays Bob" form and pattern.
This is only the tip of the iceberg of possibilities that can be expressed with this scripting language. In this section, we will demonstrate the components of the Bitcoin Cash transaction scripting language and show how it can be used to express complex conditions for spending and how those conditions can be satisfied by unlocking scripts.
Bitcoin Cash transaction validation is not based on a static pattern, but instead is achieved through the execution of a scripting language. This language allows for a nearly infinite variety of conditions to be expressed. This is how Bitcoin Cash gets the power of "programmable money."
Script Construction (Lock + Unlock)
Bitcoin Cash’s transaction validation engine relies on two types of scripts to validate transactions: a locking script and an unlocking script.
A locking script is an encumbrance placed on an output, and it specifies the conditions that must be met to spend the output in the future. Historically, the locking script was called a scriptPubKey, because it usually contained a public key or Bitcoin Cash address. In this book we refer to it as a "locking script" to acknowledge the much broader range of possibilities of this scripting technology. In most Bitcoin Cash applications, what we refer to as a locking script will appear in the source code as scriptPubKey.
An unlocking script is a script that "solves," or satisfies, the conditions placed on an output by a locking script and allows the output to be spent. Unlocking scripts are part of every transaction input, and most of the time they contain a digital signature produced by the user’s wallet from his or her private key. Historically, the unlocking script is called scriptSig, because it usually contained a digital signature. In most Bitcoin Cash applications, the source code refers to the unlocking script as scriptSig. In this book, we refer to it as an "unlocking script" to acknowledge the much broader range of locking script requirements, because not all unlocking scripts must contain signatures.
Every Bitcoin Cash client will validate transactions by executing the locking and unlocking scripts together. For each input in the transaction, the validation software will first retrieve the UTXO referenced by the input. That UTXO contains a locking script defining the conditions required to spend it. The validation software will then take the unlocking script contained in the input that is attempting to spend this UTXO and execute the two scripts.
In the original Bitcoin Cash client, the unlocking and locking scripts were concatenated and executed in sequence. For security reasons, this was changed in 2010, because of a vulnerability that allowed a malformed unlocking script to push data onto the stack and corrupt the locking script. In the current implementation, the scripts are executed separately with the stack transferred between the two executions, as described next.
First, the unlocking script is executed, using the stack execution engine. If the unlocking script executed without errors (e.g., it has no "dangling" operators left over), the main stack (not the alternate stack) is copied and the locking script is executed. If the result of executing the locking script with the stack data copied from the unlocking script is "TRUE," the unlocking script has succeeded in resolving the conditions imposed by the locking script and, therefore, the input is a valid authorization to spend the UTXO. If any result other than "TRUE" remains after execution of the combined script, the input is invalid because it has failed to satisfy the spending conditions placed on the UTXO. Note that the UTXO is permanently recorded in the blockchain, and therefore is invariable and is unaffected by failed attempts to spend it by reference in a new transaction. Only a valid transaction that correctly satisfies the conditions of the UTXO results in the UTXO being marked as "spent" and removed from the set of available (unspent) UTXO.
Combining scriptSig and scriptPubKey to evaluate a transaction script is an example of the unlocking and locking scripts for the most common type of Bitcoin Cash transaction (a payment to a public key hash), showing the combined script resulting from the concatenation of the unlocking and locking scripts prior to script validation.
 Figure 1. Combining scriptSig and scriptPubKey to evaluate a transaction script
Figure 1. Combining scriptSig and scriptPubKey to evaluate a transaction scriptScripting Language
The Bitcoin Cash transaction script language, called Script, is a Forth-like reverse-polish notation stack-based execution language. If that sounds like gibberish, you probably haven’t studied 1960’s programming languages. Script is a very simple language that was designed to be limited in scope and executable on a range of hardware, perhaps as simple as an embedded device, such as a handheld calculator. It requires minimal processing and cannot do many of the fancy things modern programming languages can do. In the case of programmable money, that is a deliberate security feature.
Bitcoin Cash’s scripting language is called a stack-based language because it uses a data structure called a stack. A stack is a very simple data structure, which can be visualized as a stack of cards. A stack allows two operations: push and pop. Push adds an item on top of the stack. Pop removes the top item from the stack.
The scripting language executes the script by processing each item from left to right. Numbers (data constants) are pushed onto the stack. Operators push or pop one or more parameters from the stack, act on them, and might push a result onto the stack. For example, OP_ADD will pop two items from the stack, add them, and push the resulting sum onto the stack.
Conditional operators evaluate a condition, producing a boolean result of TRUE or FALSE. For example, OP_EQUAL pops two items from the stack and pushes TRUE (TRUE is represented by the number 1) if they are equal or FALSE (represented by zero) if they are not equal. Bitcoin Cash transaction scripts usually contain a conditional operator, so that they can produce the TRUE result that signifies a valid transaction.
In Bitcoin Cash’s script validation doing simple math, the script 2 3 OP_ADD 5 OP_EQUAL demonstrates the arithmetic addition operator OP_ADD, adding two numbers and putting the result on the stack, followed by the conditional operator OP_EQUAL, which checks that the resulting sum is equal to 5. For brevity, the OP_ prefix is omitted in the step-by-step example.
The following is a slightly more complex script, which calculates 2 + 7 – 3 + 1. Notice that when the script contains several operators in a row, the stack allows the results of one operator to be acted upon by the next operator:
2 7 OP_ADD 3 OP_SUB 1 OP_ADD 7 OP_EQUALTry validating the preceding script yourself using pencil and paper. When the script execution ends, you should be left with the value TRUE on the stack.
Although most locking scripts refer to a Bitcoin Cash address or public key, thereby requiring proof of ownership to spend the funds, the script does not have to be that complex. Any combination of locking and unlocking scripts that results in a TRUE value is valid. The simple arithmetic we used as an example of the scripting language is also a valid locking script that can be used to lock a transaction output.
Use part of the arithmetic example script as the locking script:
3 OP_ADD 5 OP_EQUALwhich can be satisfied by a transaction containing an input with the unlocking script:
2The validation software combines the locking and unlocking scripts and the resulting script is:
2 3 OP_ADD 5 OP_EQUALAs we saw in the step-by-step example in Bitcoin Cash’s script validation doing simple math, when this script is executed, the result is OP_TRUE, making the transaction valid. Not only is this a valid transaction output locking script, but the resulting UTXO could be spent by anyone with the arithmetic skills to know that the number 2 satisfies the script.
 Figure 2. Bitcoin Cash’s script validation doing simple math
Figure 2. Bitcoin Cash’s script validation doing simple mathTransactions are valid if the top result on the stack is TRUE (noted as {0x01}), any other non-zero value or if the stack is empty after script execution. Transactions are invalid if the top value on the stack is FALSE (a zero-length empty value, noted as {}) or if script execution is halted explicitly by an operator, such as OP_VERIFY, OP_RETURN, or a conditional terminator such as OP_ENDIF.
Turing Incompleteness
The Bitcoin Cash transaction script language contains many operators, but is deliberately limited in one important way—there are no loops or complex flow control capabilities other than conditional flow control. This ensures that the language is not Turing Complete, meaning that scripts have limited complexity and predictable execution times. Script is not a general-purpose language. These limitations ensure that the language cannot be used to create an infinite loop or other form of "logic bomb" that could be embedded in a transaction in a way that causes a denial-of-service attack against the Bitcoin Cash network. Remember, every transaction is validated by every full node on the Bitcoin Cash network. A limited language prevents the transaction validation mechanism from being used as a vulnerability.
Stateless Verification
The Bitcoin Cash transaction script language is stateless, in that there is no state prior to execution of the script, or state saved after execution of the script. Therefore, all the information needed to execute a script is contained within the script. A script will predictably execute the same way on any system. If your system verifies a script, you can be sure that every other system in the Bitcoin Cash network will also verify the script, meaning that a valid transaction is valid for everyone and everyone knows this. This predictability of outcomes is an essential benefit of the Bitcoin Cash system.
Standard Transactions
In the first few years of Bitcoin Cash’s development, the developers introduced some limitations in the types of scripts that could be processed by the reference client. These limitations are encoded in a function called isStandard(), which defines five types of "standard" transactions. These limitations are temporary and might be lifted by the time you read this. Until then, the five standard types of transaction scripts are the only ones that will be accepted by the reference client and most miners who run the reference client. Although it is possible to create a nonstandard transaction containing a script that is not one of the standard types, you must find a miner who does not follow these limitations to mine that transaction into a block.
Check the source code of the Bitcoin Core client (the reference implementation) to see what is currently allowed as a valid transaction script.
The five standard types of transaction scripts are pay-to-public-key-hash (P2PKH), public-key, multi-signature (limited to 15 keys), pay-to-script-hash (P2SH), and data output (OP_RETURN), which are described in more detail in the following sections.
Pay-to-Public-Key-Hash (P2PKH)
The vast majority of transactions processed on the Bitcoin Cash network are P2PKH transactions. These contain a locking script that encumbers the output with a public key hash, more commonly known as a Bitcoin Cash address. Transactions that pay a Bitcoin Cash address contain P2PKH scripts. An output locked by a P2PKH script can be unlocked (spent) by presenting a public key and a digital signature created by the corresponding private key.
For example, let’s look at Alice’s payment to Bob’s Cafe again. Alice made a payment of 0.00208507 Bitcoin Cash to the cafe’s Bitcoin Cash address. That transaction output would have a locking script of the form:
OP_DUP OP_HASH160 <Cafe Public Key Hash> OP_EQUAL OP_CHECKSIGThe Cafe Public Key Hash is equivalent to the Bitcoin Cash address of the cafe, without the Base58Check encoding. Most applications would show the public key hash in hexadecimal encoding and not the familiar Bitcoin Cash address Base58Check format that begins with a "1".
The preceding locking script can be satisfied with an unlocking script of the form:
<Cafe Signature> <Cafe Public Key>The two scripts together would form the following combined validation script:
<Cafe Signature> <Cafe Public Key> OP_DUP OP_HASH160 <Cafe Public Key Hash> OP_EQUAL OP_CHECKSIGWhen executed, this combined script will evaluate to TRUE if, and only if, the unlocking script matches the conditions set by the locking script. In other words, the result will be TRUE if the unlocking script has a valid signature from the cafe’s private key that corresponds to the public key hash set as an encumbrance.
Figures and show (in two parts) a step-by-step execution of the combined script, which will prove this is a valid transaction.
 Figure 3. Evaluating a script for a P2PKH transaction (Part 1 of 2)
Figure 3. Evaluating a script for a P2PKH transaction (Part 1 of 2)Pay-to-Public-Key
Pay-to-public-key is a simpler form of a Bitcoin Cash payment than pay-to-public-key-hash. With this script form, the public key itself is stored in the locking script, rather than a public-key-hash as with P2PKH earlier, which is much shorter. Pay-to-public-key-hash was invented by Satoshi to make Bitcoin Cash addresses shorter, for ease of use. Pay-to-public-key is now most often seen in coinbase transactions, generated by older mining software that has not been updated to use P2PKH.
A pay-to-public-key locking script looks like this:
<Public Key A> OP_CHECKSIGThe corresponding unlocking script that must be presented to unlock this type of output is a simple signature, like this:
<Signature from Private Key A>The combined script, which is validated by the transaction validation software, is:
<Signature from Private Key A> <Public Key A> OP_CHECKSIGThis script is a simple invocation of the CHECKSIG operator, which validates the signature as belonging to the correct key and returns TRUE on the stack.
 Figure 4. Evaluating a script for a P2PKH transaction (Part 2 of 2)
Figure 4. Evaluating a script for a P2PKH transaction (Part 2 of 2)Multi-Signature
Multi-signature scripts set a condition where N public keys are recorded in the script and at least M of those must provide signatures to release the encumbrance. This is also known as an M-of-N scheme, where N is the total number of keys and M is the threshold of signatures required for validation. For example, a 2-of-3 multi-signature is one where three public keys are listed as potential signers and at least two of those must be used to create signatures for a valid transaction to spend the funds. At this time, standard multi-signature scripts are limited to at most 15 listed public keys, meaning you can do anything from a 1-of-1 to a 15-of-15 multi-signature or any combination within that range. The limitation to 15 listed keys might be lifted by the time this book is published, so check the isStandard() function to see what is currently accepted by the network.
The general form of a locking script setting an M-of-N multi-signature condition is:
M <Public Key 1> <Public Key 2> ... <Public Key N> N OP_CHECKMULTISIGwhere N is the total number of listed public keys and M is the threshold of required signatures to spend the output.
A locking script setting a 2-of-3 multi-signature condition looks like this:
2 <Public Key A> <Public Key B> <Public Key C> 3 OP_CHECKMULTISIGThe preceding locking script can be satisfied with an unlocking script containing pairs of signatures and public keys:
OP_0 <Signature B> <Signature C>or any combination of two signatures from the private keys corresponding to the three listed public keys.
The prefix OP_0 is required because of a bug in the original implementation of CHECKMULTISIG where one item too many is popped off the stack. It is ignored by CHECKMULTISIG and is simply a placeholder.
The two scripts together would form the combined validation script:
OP_0 <Signature B> <Signature C> 2 <Public Key A> <Public Key B> <Public Key C> 3 OP_CHECKMULTISIGWhen executed, this combined script will evaluate to TRUE if, and only if, the unlocking script matches the conditions set by the locking script. In this case, the condition is whether the unlocking script has a valid signature from the two private keys that correspond to two of the three public keys set as an encumbrance.
Data Output (OP_RETURN)
Bitcoin Cash’s distributed and timestamped ledger, the blockchain, has potential uses far beyond payments. Many developers have tried to use the transaction scripting language to take advantage of the security and resilience of the system for applications such as digital notary services, stock certificates, and smart contracts. Early attempts to use Bitcoin Cash’s script language for these purposes involved creating transaction outputs that recorded data on the blockchain; for example, to record a digital fingerprint of a file in such a way that anyone could establish proof-of-existence of that file on a specific date by reference to that transaction.
The use of Bitcoin Cash’s blockchain to store data unrelated to Bitcoin Cash payments is a controversial subject. Many developers consider such use abusive and want to discourage it. Others view it as a demonstration of the powerful capabilities of blockchain technology and want to encourage such experimentation. Those who object to the inclusion of non-payment data argue that it causes "blockchain bloat," burdening those running full Bitcoin Cash nodes with carrying the cost of disk storage for data that the blockchain was not intended to carry. Moreover, such transactions create UTXO that cannot be spent, using the destination Bitcoin Cash address as a free-form 20-byte field. Because the address is used for data, it doesn’t correspond to a private key and the resulting UTXO can never be spent; it’s a fake payment. These transactions that can never be spent are therefore never removed from the UTXO set and cause the size of the UTXO database to forever increase, or "bloat."
A compromise was reached with the introduction of the OPRETURN operator. OP_RETURN allows developers to add 220 bytes of nonpayment data to a transaction output. However, unlike the use of "fake" UTXO, the OP_RETURN operator creates an explicitly _provably unspendable output, which does not need to be stored in the UTXO set. OP_RETURN outputs are recorded on the blockchain, so they consume disk space and contribute to the increase in the blockchain’s size, but they are not stored in the UTXO set and therefore do not bloat the UTXO memory pool and burden full nodes with the cost of more expensive RAM.
``` OP_RETURN scripts look like this:
OP_RETURN ```
The data portion is limited to 220 bytes and most often represents a hash, such as the output from the SHA256 algorithm (32 bytes). Many applications put a prefix in front of the data to help identify the application per the Terab 4-byte prefix guideline for OP_RETURN on Bitcoin Cash.
Keep in mind that there is no "unlocking script" that corresponds to OPRETURN that could possibly be used to "spend" an OP_RETURN output. The whole point of OP_RETURN is that you can’t spend the money locked in that output, and therefore it does not need to be held in the UTXO set as potentially spendable—OP_RETURN is _provably un-spendable. OP_RETURN is usually an output with a zero Bitcoin Cash amount, because any Bitcoin Cash assigned to such an output is effectively lost forever. If an OP_RETURN is encountered by the script validation software, it results immediately in halting the execution of the validation script and marking the transaction as invalid. Thus, if you accidentally reference an OP_RETURN output as an input in a transaction, that transaction is invalid.
A standard transaction (one that conforms to the isStandard() checks) can have only one OP_RETURN output. However, a single OP_RETURN output can be combined in a transaction with outputs of any other type.
OP_RETURN was initially proposed with a limit of 80 bytes, but the limit was raised to 220 bytes of data on the May 15th 2018 BCH network upgrade.
Pay-to-Script-Hash (P2SH)
Pay-to-script-hash (P2SH) was introduced in 2012 as a powerful new type of transaction that greatly simplifies the use of complex transaction scripts. To explain the need for P2SH, let’s look at a practical example.
In What is Bitcoin Cash we introduced Mohammed, an electronics importer based in Dubai. Mohammed’s company uses Bitcoin Cash’s multi-signature feature extensively for its corporate accounts. Multi-signature scripts are one of the most common uses of Bitcoin Cash’s advanced scripting capabilities and are a very powerful feature. Mohammed’s company uses a multi-signature script for all customer payments, known in accounting terms as "accounts receivable," or AR. With the multi-signature scheme, any payments made by customers are locked in such a way that they require at least two signatures to release, from Mohammed and one of his partners or from his attorney who has a backup key. A multi-signature scheme like that offers corporate governance controls and protects against theft, embezzlement, or loss.
The resulting script is quite long and looks like this:
2 <Mohammed's Public Key> 5 OP_CHECKMULTISIG
Although multi-signature scripts are a powerful feature, they are cumbersome to use. Given the preceding script, Mohammed would have to communicate this script to every customer prior to payment. Each customer would have to use special Bitcoin Cash wallet software with the ability to create custom transaction scripts, and each customer would have to understand how to create a transaction using custom scripts. Furthermore, the resulting transaction would be about five times larger than a simple payment transaction, because this script contains very long public keys. The burden of that extra-large transaction would be borne by the customer in the form of fees. Finally, a large transaction script like this would be carried in the UTXO set in RAM in every full node, until it was spent. All of these issues make using complex output scripts difficult in practice.
Pay-to-script-hash (P2SH) was developed to resolve these practical difficulties and to make the use of complex scripts as easy as a payment to a Bitcoin Cash address. With P2SH payments, the complex locking script is replaced with its digital fingerprint, a cryptographic hash. When a transaction attempting to spend the UTXO is presented later, it must contain the script that matches the hash, in addition to the unlocking script. In simple terms, P2SH means "pay to a script matching this hash, a script that will be presented later when this output is spent."
In P2SH transactions, the locking script that is replaced by a hash is referred to as the redeem script because it is presented to the system at redemption time rather than as a locking script. Complex script without P2SH shows the script without P2SH and Complex script as P2SH shows the same script encoded with P2SH.
Locking Script: 2 PubKey1 PubKey2 PubKey3 PubKey4 PubKey5 5 OP_CHECKMULTISIG Unlocking Script: Sig1 Sig2
Table 4. Complex script without P2SH
Redeem Script: 2 PubKey1 PubKey2 PubKey3 PubKey4 PubKey5 5 OP_CHECKMULTISIG Locking Script: OP_HASH160 <20-byte hash of redeem script> OP_EQUAL Unlocking Script: Sig1 Sig2 redeem script
Table 5. Complex script as P2SH
As you can see from the tables, with P2SH the complex script that details the conditions for spending the output (redeem script) is not presented in the locking script. Instead, only a hash of it is in the locking script and the redeem script itself is presented later, as part of the unlocking script when the output is spent. This shifts the burden in fees and complexity from the sender to the recipient (spender) of the transaction.
Let’s look at Mohammed’s company, the complex multi-signature script, and the resulting P2SH scripts.
First, the multi-signature script that Mohammed’s company uses for all incoming payments from customers:
2 <Mohammed's Public Key> <Partner1 Public Key> <Partner2 Public Key> <Partner3 Public Key> <Attorney Public Key> 5 OP_CHECKMULTISIGIf the placeholders are replaced by actual public keys (shown here as 520-bit numbers starting with 04) you can see that this script becomes very long:
2 04C16B8698A9ABF84250A7C3EA7EEDEF9897D1C8C6ADF47F06CF73370D74DCCA01CDCA79DCC5C395D7EEC6984D83F1F50C900A24DD47F569FD4193AF5DE762C58704A2192968D8655D6A935BEAF2CA23E3FB87A3495E7AF308EDF08DAC3C1FCBFC2C75B4B0F4D0B1B70CD2423657738C0C2B1D5CE65C97D78D0E34224858008E8B49047E63248B75DB7379BE9CDA8CE5751D16485F431E46117B9D0C1837C9D5737812F393DA7D4420D7E1A9162F0279CFC10F1E8E8F3020DECDBC3C0DD389D99779650421D65CBD7149B255382ED7F78E946580657EE6FDA162A187543A9D85BAAA93A4AB3A8F044DADA618D087227440645ABE8A35DA8C5B73997AD343BE5C2AFD94A5043752580AFA1ECED3C68D446BCAB69AC0BA7DF50D56231BE0AABF1FDEEC78A6A45E394BA29A1EDF518C022DD618DA774D207D137AAB59E0B000EB7ED238F4D800 5 OP_CHECKMULTISIGThis entire script can instead be represented by a 20-byte cryptographic hash, by first applying the SHA256 hashing algorithm and then applying the RIPEMD160 algorithm on the result. The 20-byte hash of the preceding script is:
54c557e07dde5bb6cb791c7a540e0a4796f5e97eA P2SH transaction locks the output to this hash instead of the longer script, using the locking script:
OP_HASH160 54c557e07dde5bb6cb791c7a540e0a4796f5e97e OP_EQUALwhich, as you can see, is much shorter. Instead of "pay to this 5-key multi-signature script," the P2SH equivalent transaction is "pay to a script with this hash." A customer making a payment to Mohammed’s company need only include this much shorter locking script in his payment. When Mohammed wants to spend this UTXO, they must present the original redeem script (the one whose hash locked the UTXO) and the signatures necessary to unlock it, like this:
<Sig1> <Sig2> <2 PK1 PK2 PK3 PK4 PK5 5 OP_CHECKMULTISIG>The two scripts are combined in two stages. First, the redeem script is checked against the locking script to make sure the hash matches:
<2 PK1 PK2 PK3 PK4 PK5 5 OP_CHECKMULTISIG> OP_HASH160 <redeem scriptHash> OP_EQUALIf the redeem script hash matches, the unlocking script is executed on its own, to unlock the redeem script:
<Sig1> <Sig2> 2 PK1 PK2 PK3 PK4 PK5 5 OP_CHECKMULTISIGPay-to-script-hash addresses
Another important part of the P2SH feature is the ability to encode a script hash as an address, as defined in BIP0013. P2SH addresses are Base58Check encodings of the 20-byte hash of a script, just like Bitcoin Cash addresses are Base58Check encodings of the 20-byte hash of a public key. P2SH addresses use the version prefix "5", which results in Base58Check-encoded addresses that start with a "3". For example, Mohammed’s complex script, hashed and Base58Check-encoded as a P2SH address becomes 39RF6JqABiHdYHkfChV6USGMe6Nsr66Gzw. Now, Mohammed can give this "address" to his customers and they can use almost any Bitcoin Cash wallet to make a simple payment, as if it were a Bitcoin Cash address. The 3 prefix gives them a hint that this is a special type of address, one corresponding to a script instead of a public key, but otherwise it works in exactly the same way as a payment to a Bitcoin Cash address.
P2SH addresses hide all of the complexity, so that the person making a payment does not see the script.
Benefits of pay-to-script-hash
The pay-to-script-hash feature offers the following benefits compared to the direct use of complex scripts in locking outputs:
- Complex scripts are replaced by shorter fingerprints in the transaction output, making the transaction smaller.
- Scripts can be coded as an address, so the sender and the sender’s wallet don’t need complex engineering to implement P2SH.
- P2SH shifts the burden of constructing the script to the recipient, not the sender.
- P2SH shifts the burden in data storage for the long script from the output (which is in the UTXO set) to the input (stored on the blockchain).
- P2SH shifts the burden in data storage for the long script from the present time (payment) to a future time (when it is spent).
- P2SH shifts the transaction fee cost of a long script from the sender to the recipient, who has to include the long redeem script to spend it.
Redeem script and isStandard validation
Prior to version 0.9.2, pay-to-script-hash was limited to the standard types of Bitcoin Cash transaction scripts, by the isStandard() function. That means that the redeem script presented in the spending transaction could only be one of the standard types: P2PK, P2PKH, or multi-sig nature, excluding OP_RETURN and P2SH itself.
As of version 0.9.2, P2SH transactions can contain any valid script, making the P2SH standard much more flexible and allowing for experimentation with many novel and complex types of transactions.
Note that you are not able to put a P2SH inside a P2SH redeem script, because the P2SH specification is not recursive. You are also still not able to use OP_RETURN in a redeem script because OP_RETURN cannot be redeemed by definition.
Note that because the redeem script is not presented to the network until you attempt to spend a P2SH output, if you lock an output with the hash of an invalid transaction it will be processed regardless. However, you will not be able to spend it because the spending transaction, which includes the redeem script, will not be accepted because it is an invalid script. This creates a risk, because you can lock Bitcoin Cash in a P2SH that cannot be spent later. The network will accept the P2SH encumbrance even if it corresponds to an invalid redeem script, because the script hash gives no indication of the script it represents.
P2SH locking scripts contain the hash of a redeem script, which gives no clues as to the content of the redeem script itself. The P2SH transaction will be considered valid and accepted even if the redeem script is invalid. You might accidentally lock Bitcoin Cash in such a way that it cannot later be spent.
-
 @ 3165b802:a9f51d37
2025-04-07 17:01:23
@ 3165b802:a9f51d37
2025-04-07 17:01:23Humanrights #Human #Rights
-
 @ 8f69ac99:4f92f5fd
2025-04-07 15:35:08
@ 8f69ac99:4f92f5fd
2025-04-07 15:35:08No dia 2 de Abril de 2025, o Presidente dos Estados Unidos, Donald Trump, anunciou um novo pacote abrangente de tarifas com o objectivo de combater os desequilíbrios comerciais e revitalizar as indústrias nacionais. Foi imposta uma tarifa geral de 10% sobre todas as importações, com taxas mais elevadas—34% para a China e 20% para a União Europeia—em preparação para entrar em vigor. O anúncio reacendeu debates antigos sobre proteccionismo, globalização e o futuro do dólar norte-americano.
Embora estas medidas possam parecer extremas, as tarifas são um instrumento tradicional da política comercial internacional. Países de todo o mundo, incluindo a União Europeia, utilizam-nas rotineiramente para proteger indústrias estratégicas, regular o comércio e gerar receitas. A UE, por exemplo, impõe há muito tempo taxas sobre produtos norte-americanos como bens agrícolas, maquinaria e têxteis. Em contrapartida, os EUA já taxaram importações da UE, como o aço, alumínio e aeronaves, em disputas comerciais.
O que distingue a proposta de Trump é a sua escala, ambição e o objectivo mais amplo: reestruturar a economia dos EUA. Por detrás desta estratégia está uma realidade económica mais profunda—moldada por décadas de défices comerciais, endividamento crescente e o papel do dólar como moeda de reserva mundial. Este artigo explora como estes factores se cruzam, por que razão os EUA se encontram numa posição precária, e se políticas como tarifas elevadas, taxas de juro baixas ou até o Bitcoin podem apontar o caminho a seguir.
As Raízes da Crise: Sobreconsumo e Desindustrialização nos EUA
Durante décadas, os Estados Unidos "viveram acima das suas possibilidades", acumulando um défice comercial que actualmente ultrapassa os 800 mil milhões de dólares por ano. Este desequilíbrio—em que o país compra mais do que vende ao exterior—é sintoma de um problema mais profundo. No pós-Segunda Guerra Mundial, os EUA eram uma potência industrial. Mas, a partir dos anos 70, e com maior intensidade nos anos 90, a globalização transferiu a produção para o estrangeiro. As empresas procuraram custos de mão de obra mais baixos e os mercados norte-americanos encheram-se de produtos fabricados fora.
Para sustentar este consumo, os EUA apoiaram-se na sua posição privilegiada: a emissão da moeda de reserva mundial. Isso gerou um ciclo de endividamento, com o país a pedir emprestado ao exterior para manter o nível de vida. O resultado? Desindustrialização. Fábricas fecharam e milhões de empregos na indústria desapareceram em estados como Ohio, Michigan e Pensilvânia.
Hoje, os EUA produzem muito menos—em proporção ao seu tamanho—do que há algumas décadas, mesmo mantendo um apetite crescente por importações. O défice comercial expõe uma fragilidade estrutural: um país cada vez mais incapaz de sustentar-se através da sua própria produção. Os dólares gastos fora regressam muitas vezes sob a forma de compras de dívida pública, perpetuando o ciclo.
À medida que os défices crescem e a economia depende cada vez mais de mecanismos financeiros do que da produção real, surge uma questão inevitável: até quando poderá a América continuar a comprar a crédito antes que o cartão seja recusado?
O Dilema de Triffin: Moeda Global vs. Potência Industrial
Imagine ser a única pessoa numa cidade com uma impressora de dinheiro que todos usam. Para satisfazer a procura, continua a imprimir e a enviar notas para o exterior—até que o seu próprio negócio local entra em decadência e se torna dependente dos outros. Esta é a essência do Dilema de Triffin, e a corda bamba que os EUA têm vindo a atravessar há gerações.
O dilema surge quando a moeda de um país é usada como padrão global. O dólar—utilizado mundialmente para transacções de petróleo, comércio e reservas—precisa de estar amplamente disponível. Essa abundância provém de défices comerciais persistentes por parte dos EUA.
Mas os défices têm um custo. Os dólares enviados para fora voltam como procura por bens estrangeiros, enfraquecendo a produção interna. Porque fabricar um produto em Detroit por 10 dólares, quando se pode importar por $2? Com o tempo, isto destrói a base industrial do país.
Esta não é uma preocupação teórica—é uma realidade histórica. O economista Robert Triffin advertiu nos anos 60 que um país não pode simultaneamente manter a sua moeda como padrão mundial e conservar uma base industrial sólida. Os EUA confirmaram essa previsão. Após a guerra, os dólares ajudaram a reconstruir a Europa e o Japão, mas esses mesmos países tornaram-se concorrentes industriais dos EUA em sectores como o aço e a indústria automóvel.
As fábricas abandonadas no Midwest e os teares silenciosos no sul são marcas visíveis desta troca. O domínio do dólar concedeu influência global à América, mas às custas da sua produção.
Espiral da Dívida: Obrigações Financeiras Crescentes dos EUA
Em 2025, a dívida federal dos EUA ultrapassa os 36 biliões de dólares ($36 000 000 000 000 000 000)—cerca de 108 mil dólares por cada americano, adultos, jovens, idosos. Durante anos, o acesso fácil ao crédito e a procura global por dívida americana mascararam os riscos. Agora, as fissuras estão à vista.
O problema não é apenas o montante—é o prazo e o custo de manter esta dívida. Grande parte dela é de curto prazo, exigindo refinanciamentos frequentes. Com o aumento das taxas de juro, os custos associados disparam. Só em 2024, os pagamentos de juros ultrapassaram 1 bilião de dólares—mais do que os orçamentos combinados de educação, transportes e habitação.
A “Lei de Ferguson”, proposta pelo historiador Niall Ferguson, afirma que quando os juros da dívida superam os gastos militares, o império está em declínio. Em 2025, os EUA gastam cerca de 900 mil milhões em defesa, e os encargos com juros já os ultrapassaram.
Este ponto de viragem trouxe problemas a impérios do passado—do Reino Unido após a Primeira Guerra Mundial até Roma no seu declínio. Hoje, cresce o cepticismo quanto à saúde fiscal dos EUA. Países como a China e a Rússia estão a reduzir as suas reservas em dívida americana, preferindo ouro, yuan ou outros activos.
Se mais nações seguirem o mesmo caminho, os EUA terão de escolher: continuar a endividar-se para sustentar o sistema ou aceitar um papel reduzido para o dólar na economia mundial.
Desdolarização: A Mudança Global Longe do Dólar
A desdolarização refere-se à tendência crescente de reduzir a dependência do dólar nas transacções comerciais, reservas e sistemas financeiros. Embora o dólar ainda domine, a sua supremacia está sob crescente pressão de novas potências económicas e tensões geopolíticas.
Porque Está o Mundo a Afastar-se do Dólar?
- Risco Económico: A volatilidade do dólar, agravada pela dívida e instabilidade política nos EUA, torna-o menos fiável como reserva de valor.
- Instrumento Geopolítico: O uso do dólar pelos EUA para impor sanções leva rivais a procurar alternativas.
Alternativas Emergentes
- Ouro: Bancos centrais estão a reforçar as reservas em ouro como protecção.
- Commodities: Petróleo e cereais começam a ser transaccionados em moedas alternativas—como vendas de petróleo em yuan pela Arábia Saudita.
- Criptomoedas: Bitcoin e outros activos digitais ganham terreno como reservas neutras e descentralizadas.
- Moedas Regionais: Os países dos BRICS desenvolvem sistemas de pagamento e discutem uma moeda comum para reduzir a dependência do dólar.
Um Declínio Lento, Mas Visível
A percentagem do dólar nas reservas cambiais mundiais caiu de 70% no ano 2000 para menos de 60% actualmente. O comércio em moedas não-dólar cresceu 25% desde 2020. O domínio do dólar persiste, mas o movimento de mudança é claro.
A Estratégia Económica de Trump em 3 Etapas
Em 2025, Trump apresentou uma estratégia económica audaciosa em três frentes:
1. Tarifas Elevadas para Revitalizar a Indústria
Uma tarifa de 10% sobre todas as importações, com taxas superiores para países com superavit comercial, visa incentivar a produção interna. Críticos alertam para o aumento de preços e inflação, mas apoiantes defendem que é necessário para reindustrializar.
2. Redução das Taxas de Juro para Gerir a Dívida
A administração pressiona a Reserva Federal para baixar as taxas, reduzindo os encargos da dívida pública. Isto levanta preocupações sobre a independência do banco central e a estabilidade monetária a longo prazo.
3. Bitcoin como Activo Estratégico de Reserva
Num passo histórico, Trump assinou uma ordem executiva para criar a Reserva Estratégica de Bitcoin e o Stock Nacional de Activos Digitais. O objectivo é diversificar as reservas e proteger contra a inflação.
Riscos e Compensações
A estratégia económica de Trump não está isenta de riscos:
- Inflação: Tarifas mais altas poderão aumentar o custo de vida.
- Polarização Política: Medidas controversas poderão acentuar divisões internas.
- Incerteza Económica: O proteccionismo pode afastar investimento e travar a inovação.
- Instabilidade Monetária: Um erro na gestão da dívida ou dos activos digitais poderá enfraquecer o dólar.
Estes riscos exigem gestão cuidadosa para evitar agravar os problemas existentes.
O Papel de Bitcoin: Protecção ou Último Recurso?
Integrar Bitcoin nas reservas nacionais é ousado—mas pode ser revolucionário, e a meu ver, inevitável!
Vantagens
- Escassez: Com oferta limitada a 21 milhões de unidades, Bitcoin é deflacionário.
- Descentralização: Resistente à censura e manipulação, reforça a soberania financeira.
- Alcance Global: Sem fronteiras, permite trocas neutras num mundo multipolar.
Desafios
- Volatilidade: As flutuações no curto prazo são ainda significativas, mas a adopção institucional pode estabilizar o preço.
- Regulação: O enquadramento legal está em evolução, mas tende para maior clareza.
- Adopção Técnica: Persistem desafios de escalabilidade, embora soluções como a Lightning Network estejam a amadurecer.
A Reserva Estratégica de Bitcoin pode revelar-se visionária—ou precipitada. Tudo dependerá da execução e da aceitação global.
Futuros Possíveis: Crise ou Reinvenção?
Os EUA estão perante uma encruzilhada histórica. Um caminho aponta para a renovação: revitalizar a indústria e adoptar activos digitais, como por exemplo as stablecoins para perpetuar a hegemonia do dólar, lastreado em Bitcoin. O outro conduz à crise—com inflação, instabilidade e perda de influência global.
Num cenário optimista, os EUA emergem como líderes industriais e digitais, com reservas diversificadas que incluem Bitcoin. A recente ordem executiva para adquirir Bitcoin de forma neutra ao orçamento é um sinal positivo.
Num cenário pessimista, menos provável com as medidas em curso, o país mergulha em dívidas, vê o dólar enfraquecer e perde coesão interna. Mas com visão estratégica e inovação económica, há margem para navegar os desafios com sucesso.
Conclusão
A América enfrenta uma oportunidade única de redefinir o seu destino económico. A estratégia de Trump—baseada em tarifas, taxas de juro baixas e Bitcoin—pode marcar o início de uma nova era de resiliência e recuperação industrial.
A inclusão de Bitcoin nas reservas nacionais mostra que os instrumentos tradicionais já não bastam. Ao abraçar os activos digitais e restaurar a produção nacional, os EUA podem recuperar a liderança económica mundial.
O caminho será difícil. Mas com ousadia e execução eficaz, os Estados Unidos não só podem recuperar—podem reinventar-se.
-
 @ f1577c25:de26ba14
2025-04-07 09:44:30
@ f1577c25:de26ba14
2025-04-07 09:44:30تنبيه مهم
أهلاً! قبل ما نبدأ، أنا مش مستشار مالي ولا خبير حاجة. أنا بس واحد قعد يتابع قنوات ويقرا عن الاستثمار الفترة اللي فاتت. مش مسؤول عن أي خسارة فلوس، بس كل اللي هاقوله هنا أنا بطبقه على نفسي الأول، فطبعاً مش هاضر نفسي (عن قصد على الأقل).
إيه اللي هنتكلم عنه
هاعمل سلسلة بوستات عن: - الأساسيات اللي لازم تعرفها عن الاستثمار والتداول - أفكار تساعدك تعمل محفظة استثمارية كويسة - تجربتي مع تطبيقات الاستثمار المختلفة - إجابة على الأسئلة اللي بتتسأل كتير
هاحدّث البوستات لو في معلومات جديدة وهاكتب تاريخ آخر تحديث. عايز تتواصل معايا؟ اكتب كومنت علي بوست ريديت اللي لاقيت فيه لينك المقالة دي.
الأساسيات
الغلطة الأولى: لازم يكون معاك فلوس كتير علشان تستثمر
دي فكرة غلط خالص. في الحقيقة، إنت بتستثمر علشان تجمع فلوس مش العكس. معظم الطرق اللي هاقولك عليها ممكن تبدأ بمبلغ صغير (حوالي 100 جنيه) وتزود عليه كل شهر. والحلو إن معظم الحاجات دي بتخليك تقدر تسحب فلوسك بسهولة لو احتجت.
أهمية التحويش
علشان تستثمر بجد، لازم تحوّش جزء من مرتبك كل شهر. المفروض تحوّش 25% من مرتبك، بس مع الغلا اللي احنا فيه دلوقتي، ابدأ بأي مبلغ تقدر عليه حتى لو 100 جنيه بس في الشهر. احسب مصاريفك لكام شهر وحط جنب مبلغ يكفيك 3-6 شهور للطوارئ.
طريقة تفكير المستثمر
الناس الناجحة مش بتصرف على المظاهر. قبل ما تشتري أي حاجة، اسأل نفسك: "هاستخدم الحاجة دي بعد 3 شهور؟" حدد احتياجاتك الحقيقية وبعدين دوّر على أحسن حاجة تناسبك. الاستثمار طريقة تفكير قبل ما يكون مجرد حتة تحط فيها فلوسك وخلاص.
بلاش تخلي مشاعرك تتحكم فيك
متخليش قلبك يتحكم في قرارات استثمارك. أكيد السوق ممكن ينزل شوية، بس على المدى البعيد بيطلع تاني. بص مثلاً على مؤشر S&P 500. في مقولة حلوة بتقول: "If in doubt, zoom out".
أهمية توزيع الفلوس
متحطش فلوسك كلها في مكان واحد. لو حطيت كل فلوسك في البورصة وحصل هبوط، هتخسر جامد. لكن لو حاطط جزء في البورصة وجزء في الدهب مثلاً، لما واحدة تنزل التانية ممكن تطلع. اختار استثماراتك على حسب هدفك: عايز تسيب فلوسك لمدة طويلة (دهب وبورصة)؟ ولا عايز دخل شهري (صناديق استثمار أو شهادات بنك)؟
صعب ما هتبقي غني علي المدي القصير
في ناس كتير لما بتسمع كلمة "استثمار" بتتخيل على طول عربيات فيراري وقصور. ولما تقولهم اشتروا دهب بيقولولك "لأ هستنى لما ينزل" (وهو أصلاً بيطلع).
الفكرة إنك متحاولش تحدد "الوقت المثالي للسوق" (Time the market) عشان تدخل، لأنه ببساطة صعب جداً تعرف إمتى الوقت ده. ناس كتير بتحاول تحقق عائد أعلى من المتوسط (اللي هو 10% سنوياً) وبينتهي بيهم الأمر خسرانين.
فمتحاولش تعمل ذكي أوي وتفضل مستني وتأجل. ابدأ على طول، والتزم بالاستثمار بانتظام.
مفيش حاجة كاملة
انا عارف شعور انك عايز كل حاجة وصدقني مش انت لوحدك، بس زي ما بيقولوا بالإنجليزي "you can't have your cake and eat it too"!
يعني مثلاً لو عايز ربح كتير هتلاقي مقابله مخاطرة عالية، أو لو عايز أمان لفلوسك هتلاقي العائد قليل. دايماً هتلاقي حاجة على حساب حاجة وانت بس اللي تقرر هتستحمل إيه.
أنا بالنسبة لي، بفضل حاجة بعائد صغير سنوي بس فيها أمان علشان مع الوقت يحصل تراكم للفوايد (compound interest) ويزيد المبلغ، بدل ما أخش في حاجة وأخسر كل حاجة.
بس زي ما قلت، دي بترجع من شخص لشخص. ممكن مثلاً لو حاسس إن قدامك فرصة حلوة، تجرب بنسبة صغيرة (زي 20% من فلوسك) كتجربة. بس دايماً دايماً دايماً متخليش الطمع يسوقك.
الوقت والعائد
معظم طرق الاستثمار الآمنة بتاخد وقت علشان تظهر نتايجها. زي ما قلت قبل كده: العائد السريع غالباً بيقابله مخاطرة عالية. أنا بقدملك هنا خيارات أكثر أماناً، لكن مقابل ده هتلاقي العائد مش هيبقى مبهر على المدى القصير. عشان كده لازم تفكر في الاستثمار على مدة متوسطة لطويلة (من 3 لـ 5 سنين) علشان تحصد ثمار استثمارك بشكل كويس وتشوف النتايج اللي بتتمناها.
مصادر للتعلم
قنوات يوتيوب
- بالمصري:
- عميد يستثمر
-
محمد محي الدين
-
بالإنجليزي:
- Two Cents
- The Money Guy Show
- Clear Value Tax
- The Plain Bagel
مواقع تفيدك
- بالإنجليزي:
- Investopedia
كمل قراية من هنا: nostr:naddr1qvzqqqr4gupzpu2h0sja0vmqdqjzq6e820jjjnuytzw2ksmemfnadhe0hm0zdws5qqxnzde5xvurqdp4xuunqd3sau2w7y
ادعمني (لو حابب)
- USDT (TRC20):
TKQ3Uwkq21ntiua2Zh9Hu376fdMdnRGWN6
آخر تحديث: 4 أبريل 2025
-
 @ e97aaffa:2ebd765d
2025-04-07 09:38:20
@ e97aaffa:2ebd765d
2025-04-07 09:38:20A electricidade ou os computadores ou a Internet foram revoluções que mudaram o mundo, mas a adoção e a evolução da tecnologia foi lenta, permitindo que as populações e as económicas se adaptassem.
Ao contrário, na AI, a evolução está a ser tão rápida, que as sociedades não vão conseguir acompanhar e adaptar a uma nova realidade.
A AI tem um potencial inacreditável, talvez seja a revolução tecnológica mais rápida de sempre, além disso é muito abrangente, quase todos os sectores económicos podem beneficiar, pode provocar um forte aumento na produtividade.
O potencial é tão elevado, como pode ser perigoso, sobretudo quando utilizado como uma arma contra a humanidade. Os governos ou empresas vão construir ferramentas com AI para monitorizar, manipular e controlar os cidadãos.
Muitas profissões vão desaparecer ou reduzir drasticamente o número de trabalhadores. Tal como aconteceu nas revoluções anteriores, muitas profissões acabaram, mas surgir outras novas profissões.
Ou seja, o problema não é a tecnologia, mas sim a maneira como se usa essa tecnologia. Os desafios para o futuro são tremendos.
E o cidadão comum, o que está a fazer e a pensar… a fazer desenhos, a fazer idiotices. https://image.nostr.build/326d506f0015c99d09e061094bf3552764c6f6334be2899c6f5359f0a809d8bc.jpg
Algo similar acontece com o Bitcoin, uma tecnologia revolucionária, em alguns casos particulares, as stablecoins poderão ser interessantes. Mas o povo prefere especulador em tokens absurdos e jogar no casino das memecoins.
Também acontece com a internet, é uma fonte acessível e inesgotável de conhecimento, mas as pessoas preferem passar horas sem fim, nas redes sociais a fazer swipe up, a consumir conteúdo degradante.
O mundo ocidental está a transformar os cidadãos em zumbis, facilmente manipuláveis, obedientes, viciados. Nós necessitamos é de pessoas curiosas, com espírito crítico, criativas. Essencialmente, que pensem pela sua própria cabeça.
-
 @ 7d33ba57:1b82db35
2025-04-07 09:17:04
@ 7d33ba57:1b82db35
2025-04-07 09:17:04Prague, the capital of the Czech Republic, is like stepping into a real-life fairy tale. With its Gothic towers, baroque churches, medieval streets, and a majestic castle watching over the city, it’s no surprise that it’s one of Europe’s most beloved destinations. Add in great beer, cozy cafés, and stunning river views, and you’ve got the perfect city break.
🌟 Top Things to Do in Prague
1️⃣ Prague Castle & St. Vitus Cathedral
- One of the largest castle complexes in the world
- Don’t miss St. Vitus Cathedral, the Old Royal Palace, and Golden Lane
- Climb the cathedral tower for epic city views

2️⃣ Charles Bridge (Karlův most)
- Iconic 14th-century bridge lined with 30 baroque statues
- Walk it at sunrise or late at night to avoid the crowds
- Great for photos, street musicians, and romantic vibes
3️⃣ Old Town Square & Astronomical Clock
- The heart of the city, with colorful buildings and Gothic spires
- Watch the Astronomical Clock chime on the hour (since 1410!)
- Check out Týn Church and the Old Town Hall Tower
4️⃣ Explore the Jewish Quarter (Josefov)
- Visit the Old Jewish Cemetery, synagogues, and the Jewish Museum
- Learn about centuries of Jewish heritage and resilience in Prague
5️⃣ Climb Up to Petřín Hill
- Take the funicular or walk to the top for gardens, a mirror maze, and a mini Eiffel Tower
- Fantastic place for picnics, sunsets, and panoramic views
🍽️ What to Eat & Drink in Prague
- Goulash with dumplings (guláš s knedlíky) – Hearty and satisfying
- Svíčková – Beef with creamy vegetable sauce and cranberry
- Trdelník – Tourist favorite sweet pastry (not traditionally Czech, but tasty!)
- Czech beer – World-famous for a reason (Pilsner Urquell, Kozel, Staropramen) 🍻
- Try a traditional pub or lokál for authentic Czech cuisine and great prices
🛶 Other Cool Experiences
✅ Take a Vltava River cruise – see Prague from the water
✅ Visit Letná Park for sweeping views and a beer garden
✅ Check out Kafka Museum for surreal vibes and literary history
✅ Explore Vyšehrad – lesser-known castle ruins with gorgeous views and peaceful paths
✅ Snap pics at the Lennon Wall, especially for street art fans 🎨🚇 Getting Around
- Very walkable, especially in the historic center
- Excellent public transport: trams, metro, and buses (get a 24 or 72-hour pass)
- Uber and Bolt are reliable if you need a ride
- Be cautious with exchange rates and ATMs—use official places or bank ATMs only
💡 Tips for Visiting Prague
🕰️ Wake up early to enjoy the city without crowds
🎟️ Book castle or tower tickets in advance during peak seasons
🌧️ Pack layers—it can be breezy even in spring
📷 Keep your camera ready—every corner is postcard-worthy -
 @ e5de992e:4a95ef85
2025-04-07 08:23:48
@ e5de992e:4a95ef85
2025-04-07 08:23:48Historical Rapid Declines in the S&P 500: Lessons from Major Market Crashes
The S&P 500 has experienced rapid declines of over 10% within short periods on several notable occasions, each linked to significant economic or geopolitical events. These instances underscore the market's vulnerability during times of crisis.
October 19-20, 1987 (Black Monday Crash)
-
Drop:
On October 19, 1987, the S&P 500 plummeted approximately 20.47%, marking the largest single-day percentage decline in its history. The following day saw further losses, culminating in a two-day drop exceeding 25%. -
Context:
Factors such as program trading, portfolio insurance strategies, and widespread panic selling contributed to this unprecedented crash.
November 19-20, 2008 (Global Financial Crisis)
-
Drop:
Amid the 2008 financial crisis, the S&P 500 declined roughly 10.8% over two days, reflecting the turmoil following the collapse of major financial institutions. -
Context:
The bankruptcy of Lehman Brothers and escalating fears of a global recession led to this significant market downturn.
March 11-12, 2020 (COVID-19 Pandemic Crash)
-
Drop:
The rapid spread of COVID-19 and ensuing economic shutdowns triggered a two-day decline of approximately 12.2% in the S&P 500. By March 16, the total decline over four days exceeded 20%. -
Context:
The pandemic's uncertainty and global impact led to one of the fastest descents into bear market territory.
April 3-4, 2025 (Trade War-Induced Crash)
-
Drop:
Recently, the S&P 500 experienced a sharp decline of 10.5% over two days, erasing approximately $5 trillion in market value. -
Context:
This downturn followed sweeping tariffs announced by President Donald Trump—a 10% baseline tariff on all imports, with higher rates on specific countries (e.g., China, the European Union). China's retaliatory tariffs intensified fears of a global trade war and a potential recession.
Observations
-
Frequency:
Such rapid declines are rare, occurring approximately once every 10-20 years, typically during periods of extreme market stress. -
Catalysts:
Each event was precipitated by unique factors: - Technological trading mechanisms in 1987
- Financial sector instability in 2008
- A global health crisis in 2020
-
Geopolitical trade tensions in 2025
-
Market Resilience:
Despite these significant setbacks, markets have historically demonstrated resilience, often rebounding and reaching new highs in subsequent years.
Conclusion
Understanding these historical instances provides valuable insights into market dynamics and the potential impact of external shocks on financial systems. Recognizing the catalysts and observing market resilience over time can help investors navigate future downturns with a more informed perspective.
-
-
 @ f1577c25:de26ba14
2025-04-07 07:32:22
@ f1577c25:de26ba14
2025-04-07 07:32:22احنا المرة اللي فاتت اتكلمنا عن طرق الاستثمار بشكل عام فا تعالي بقي ناخدهم واحدة واحدة بالمميزات و العيوب و اول حاجة هنبدا بيها هي البورصة الامريكية.
المنصات التداول:
المنصتين اللي انصح بيهم عن تجربة شخصية هما:
IBKR
- حلوة لو لسه جديد علشان شكل الموقع خفيف
- العمولات صغيرة
- عيبها إن طرق الايداع صعبة
Tastytrade
- حلوة علشان فية طرق ايداع عن طريق الكريبتو فا اسهل
- عيبها إن الشكل مش احسن حاجة كا تصميم للموقع
مميزات البورصة الأمريكية
- بالدولار الامريكي (هيساعد بالتضخم)
- الحد الادني 5 دولار لشراء جزء من السهم (علي حسب منصة التداول بس اغلبهم يعني)
- تقدر تخرج بأي وقت لو محتاج الفلوس
- مضمون و علي المدي الطويل العائد كان مضمون
عيوب البورصة الأمريكية
- لازم باسبور او بطاقة مترجمة من مكان معتمد
- طرق الايداع صعبة لو هتستخدم موقع زي IBKR مثلا
- علي المدي القصير ممكن تخسر فلوسك
- العمولات بتختلف من منصة للتاني بس في حدود ال11 سنت لو هتشتري جزء من السهم
ادعمني (اختياري)
- لو حابب تسجل عن طريق Tastytrade ممكن تستخدم رابط الاحاله بتاعي: https://open.tastytrade.com/signup?referralCode=FE3YFNRFJZ
- USDT (TRC20):
TKQ3Uwkq21ntiua2Zh9Hu376fdMdnRGWN6
شوف الكومنتات لو فيه أي تعديل أو بوستات جديدة.
-
 @ f1577c25:de26ba14
2025-04-07 07:32:02
@ f1577c25:de26ba14
2025-04-07 07:32:02المرة اللي فاتت اتكلمنا عن مميزات وعيوب العملات الرقمية والذهب العالمي. النهاردة هنتكلم عن طريقة استثمار مختلفة: ازاي تستثمر في العقارات برا مصر وانت قاعد في مكانك أونلاين!
مميزات وعيوب بشكل عام
المميزات
- استثمار في أصل حقيقي (عقار) فبتضمن فلوسك في حاجة ملموسة
- العقارات على المدى الطويل بتكسب كويس
- العائد بالدولار (9-10% سنوياً)
- الدخل بيتوزع أسبوعي أو شهري على حسب المنصة
- الحد الأدنى للاستثمار منخفض مقارنة بالاستثمار العقاري في مصر
العيوب
- المنصات أونلاين، فممكن في أي وقت يحصل مشكلة والموقع يقفل
- ممكن سعر العقار ينهار في المنطقة اللي اشتريت فيها
- ممكن يحصل مشاكل غير متوقعة للعقار (حريق، زلزال، إلخ)
- الاستثمار بيحتاج مدة طويلة (3-5 سنين) علشان يكون مجزي
المنصات
المنصات دي بتعمل شركة بتشتري العقار، وبعدين بتوزع أسهم الشركة على المستثمرين. يعني انت مش بتشتري العقار مباشرةً، لكن بتشتري حصة في شركة مالكة للعقار. ده بيخليك متدفعش ضرائب على العقار نفسه (على حد علمي، بس أسأل حد خبير للتأكيد).
منصة Realt
دي منصة بتتيح لك الاستثمار في عقارات بأمريكا وبنما. بتشتغل بنظام البلوكتشين والعملات الرقمية. كل توكن (token) بيمثل حصة في العقار (أو في الشركة المالكة للعقار).
مثلاً: لو التوكن الواحد بـ 50 دولار والربح المتوقع 5 دولار في السنة، يبقى العائد 10% سنوياً. العائد بيتوزع أسبوعياً من خلال عملة USDC، سواء على شبكة ETH (هتدفع رسوم gas fees) أو شبكة Gnosis (بدون رسوم).
فيها خدمة حلوة اسمها YAM (You and Me) وهي سوق P2P للعقارات. يعني تقدر تبيع عقارك لأفراد مش للموقع نفسه، وتحدد السعر اللي يناسبك، أو تشتري عقارات قديمة من مستثمرين تانيين.
مميزات Realt
- سهلة الاستخدام نسبياً
- الحد الأدنى صغير (حوالي 50 دولار)
- في محفظة داخل الموقع لو معندكش محفظة عملات رقمية
- تقدر تشتري بالفيزا أو بالعملات الرقمية
- العائد أسبوعي
- تقدر تبيع في أي وقت
عيوب Realt
- ممكن المنصة تقفل فجأة
- ممكن تحصل مشكلة بالشبكة
- لازم يكون معاك باسبور
منصة Stake
دي منصة بتتيح لك الاستثمار في أسواق السعودية والإمارات. مرخصة من البلدين، وتعتبر أسهل من Realt لأنها مفيهاش حوار العملات الرقمية.
هتدخل تسجل بالباسبور، وتختار العقار وتشتري أسهم فيه. الحد الأدنى 500 درهم (حوالي 135 دولار) للعقار. العائد شهري (مش متأكد 100%، لسه منتظر أول توزيع) وبيتحول على حسابك البنكي سواء برا أو جوا الإمارات وبأي عملة انت تختارها.
عشان تسحب فلوسك، في فترات محددة اسمها "exit window" بتكون مرتين في السنة. أو بعد 3 سنين، بيحصل تصويت بين أصحاب العقار لو عايزين يبيعوا قبل مدة الـ 5 سنين.
مميزات Stake
- سهلة الاستخدام
- واجهة ممتازة وبسيطة
- منصة مرخصة من السعودية والإمارات
عيوب Stake
- الخروج مش مرن (مرتين في السنة)
- ممكن المنصة تتعرض لمشاكل
- مخاطر العقارات العامة
ادعمني (اختياري)
- لو حابب تسجل عن طريق Realt ممكن تستخدم رابط الإحالة بتاعي: https://realt.co/ref/esmailelbob/
- لو حابب تسجل عن طريق Stake ممكن تستخدم رابط الإحالة بتاعي: https://app.getstake.com/rewards?c=ISMAEL182
- USDT (TRC20):
TKQ3Uwkq21ntiua2Zh9Hu376fdMdnRGWN6
شوف الكومنتات لو فيه أي تعديل أو بوستات جديدة.
-
 @ f1577c25:de26ba14
2025-04-07 07:31:44
@ f1577c25:de26ba14
2025-04-07 07:31:44النهاردة هنتكلم عن طريقة استثمار مختلفة: ازاي تستثمر في العقارات جوا مصر وانت قاعد في مكانك أونلاين!
مميزات وعيوب بشكل عام
المميزات
- استثمار في أصل حقيقي (عقار) فبتضمن فلوسك في حاجة ملموسة
- العقارات على المدى الطويل بتكسب كويس
- العائد بالجنية بس مربوط بالدولار (9-10% سنوياً) يعني لو الجنية اتعوم تاني العائد اللي بيجي ليك بالجنية هيزيد 500 بدل 300 مثلا.
- الدخل بيتوزع شهري
العيوب
- ممكن سعر العقار ينهار في مصر
- ممكن يحصل مشاكل غير متوقعة للعقار (حريق، زلزال، إلخ)
- الاستثمار بيحتاج مدة طويلة (3-5 سنين) علشان يكون مجزي
- الحد الادني كبير نسبيا يعني 50 الف جنية
- تدفع ضرائب عقارية
المنصات
هي منصة واحده (علي الاقل اللي جربتة) اسمها Safe هي تبع مدينه مصر و علي عكس الاستثمار العالمي هو انت فعلا بتشتري جزء من الشقة فا حلو لانه مشترك مباشر بس بالمقابل هتدفع ضرائب العقارية كل سنة لانه انت كدا مالك لعقار جوا مصر
منصة Safe
دي المنصة الوحيدة اللي اعرفها علي الاقل في مصر و هي الي حد ما حلوة يعني الستجيل بالبطاقة و بعدها بتختار العقار و تحط الفيزا سواء تدفع مره واحده او بالتقسيط (بفوائد) لحد سنة و بعد كدا باسبوع هيجي شخص تمضي معاه العقد و بعد شهر هيجي ليك اول عائد في حسابك البنكي اللي كاتبة في التطبيق
المميزات: - سهل - ينفع بالبطاقة العيوب: - الفلوس محجوزة لمده 6 شهور قبل ما تقدر تبيع وتسحب فلوسك - فيه شويه اخطاء تقنيه زي مثلا انا وصلي العائد في البنك بس لسه مسمعش في التطبيق لحد دلوقتي و في شويه عقارات بتظهر و تختفي (لما تكون اتملت) فا اللي هو حاسس في حاجات لسه يدوي و متوقع لان التطبيق جديد بس قصدي كان عندي امل يستنوا شويه اكتر الاول قبل ما يبدوا التطبيق
ادعمني (اختياري)
- USDT (TRC20):
TKQ3Uwkq21ntiua2Zh9Hu376fdMdnRGWN6
شوف الكومنتات لو فيه أي تعديل أو بوستات جديدة.
-
 @ f1577c25:de26ba14
2025-04-07 07:31:27
@ f1577c25:de26ba14
2025-04-07 07:31:27النهاردة هنتكلم عن شهادات البنك. وقبل ما أكمل، أنا مش شيخ ومش دوري أقولك الحلال والحرام. إنت تقدر تسأل أهل العلم أكتر على حسب دينك طبعاً.
أنا برشح شهادات البنك في حالتين: لو كانت بالدولار (مع إني في الحالة دي هقولك اعملهم عملات رقمية أحسن لأنه هيبقى سهل تحركهم برا البنك وقرفه)، أو شهادات بالجنيه علشان تصرف منهم (بس هنا برضه هقولك شوفلك فوري يومي أحسن شوية).
غير بقى لو إنت عايز الشهادات اللي العائد فيها أعلى، بمعنى حاجة زي 27% سنوي أو ال3 سنين تناقصي (أول سنة 30%، تاني سنة 28%، وتالت سنة 25% تقريباً) وساعتها العائد مش هيبقى شهري. بس لو دي خطتك، فساعتها بس هرشح ليك شهادات البنك. غير كدا مش شايف ليها لازمة، لأنه بكل بساطة عقبال ما الفلوس تتفك هيكون قيمتها قلت والعائد نفسه ملهوش قيمة أوي.
طبعاً هنا مش هقدر أتكلم كتير لأن كل بنك ليه سياسته، بس كل اللي أقدر أرشحه أي حاجة تكون أقرب من بيتك وشهاداتها عالية زي البنك الأهلي المصري أو بنك مصر. والحلو إنك تقدر تعمل شهادة أونلاين عن طريق التطبيق.
وإنت بتفتح حساب، أرشحلك تفتح وقت الشمول المالي لأنه بيبقى سهل، وتفعّل تطبيق البنك وتعمل شهادات براحتك. بس العيوب إنها بتختلف من بنك لبنك، والحساب بيبقى فيه حد أقصى للرصيد لو شمول مالي حوالي 100 ألف أو 200 ألف (مشاكل أغنياء برضه بس حبيت أوضحها). ده غير كل 3 شهور مصاريف الحساب برضه، وطبعاً إنك مش هتقدر تاخد الفلوس غير بعد المدة أو أول 6 شهور بس هتخسر جامد فيهم، فخلي بالك.
مع باقي حاجات البنك المعقدة دي بقى، اسأل البنك. وبرضه حابب أوضح: خلي بالك وإنت بتمضي، لأنه بسمع حالات كتير موظف البنك خلى الناس تمضي على كريدت كارد وتأمين للحياة وغيره كتير. فاقرأ إنه نت بنكي وفتح حساب وخلاص. وللأسف هنا الفرع بيفرق، فاختار الأقرب أو أنضف أقرب حاجة ليك (لو فيه فرع معروف إنه وحش يعني). ولو في أي مشاكل أنصحك تعمل بلاغ في البنك المركزي https://www.cbe.org.eg/ar/consumer-protection علشان تاخد حقك.
المميزات: - سهل نسبياً ومضمون - بطاقة بس لو حساب شمول مالي
العيوب: - مش هتاخد الفلوس غير بعد المدة سواء سنة أو 3 سنين - ممكن البنك يرخم عليك - مصاريف الحساب الدورية (غير لو كان بنك زي QNB مثلاً، بس في الوقت ده الشهادات العائد فيها قليل مقارنة بالباقي ومفيش شهادات بالعملات الأجنبية)
ادعمني (اختياري)
- USDT (TRC20):
TKQ3Uwkq21ntiua2Zh9Hu376fdMdnRGWN6
شوف الكومنتات لو فيه أي تعديل أو بوستات جديدة.
- USDT (TRC20):
-
 @ f1577c25:de26ba14
2025-04-07 07:31:09
@ f1577c25:de26ba14
2025-04-07 07:31:09النهاردة هنتكلم عن فوري يومي، تقريباً أكتر صندوق مقرب لقلبي وبرشحه لأي شخص بيدور على حاجة تطلع بيها عائد يصرف منه. العائد بتاعه حوالي 24% وبينزل يومي، فمقارنة بالعائد الشهري بتاع البنوك اللي هو 23% أو 23.5%، فيعتبر حلو جداً لأن العائد يومي زي ما قلت وبتقدر تسحب فلوسك فوري (عن طريق الكارت الأصفر) أو خلال يومين عمل لو تحويل بنكي. قصدي إنه مش بيتجمد زي البنك، بس فيه عيوب برضه زي إنك لازم تروح تمضي الورق من فرع فوري بلس، أو إن الحد الأقصى 100 ألف جنيه (مشاكل أغنياء عارف، بس لازم أقول كل العيوب)، غير لو هتقدم مصدر دخل وهكذا. هقولك بالتفصيل تحت عن مشكلة حصلت معايا عشان تاخد بالك منها وإنت بتقدم.
تطبيق ماي فوري
علشان تبدأ في الصندوق، لازم تروح الفرع ويبقى معاك تطبيق ماي فوري. وللصراحة، الموضوع سهل وبسيط: هو بطاقتك وتروح أي فرع، هتمضي على ورق وتتصور هناك (هما هيصوروك) وكام يوم وبس كدا هتتفعل.
أعتقد مش محتاج كارت فوري الأصفر، بس هو هيساعدك كتير وببلاش، فأنصحك تعمله مع الصندوق. بس خلي بالك ومهم جداً جداً: لأني تاني مرة لما كنت بعمل الكارت (كانت بعد حادثة تهكير فوري)، الراجل هناك قعد يحوّر ويقولي لازم تعمل محفظة على رقم التليفون وإلزامي وبتاع، وفي الآخر طلع بيكدب علشان ياخد بونص. وأنا مش بهاجمه، بس قصدي خلي بالك لأنه ممكن يستغلوك بالفرع ويمضيك على حاجات زيادة. فإنت اقرأ العقد بتاعك قبل ما تمضي، أو روح فرع نضيف. هو مش لازم أقرب فرع ليك، فخلي بالك من النقطة دي.
المميزات:
- سهل
- بطاقتك بس
- تقدر تسحب في أي وقت وسهولة الإيداع كمان
عيوب:
- كبداية في حد أقصى 100 ألف جنيه، بس ممكن تزودهم بعدين
- الإيداع بيقعد كام يوم عمل لحد ما يسمع
- العائد بينزل يومي ماعدا الجمعة والسبت والأحد تقريباً كمان
ادعمني (اختياري)
- USDT (TRC20):
TKQ3Uwkq21ntiua2Zh9Hu376fdMdnRGWN6
شوف الكومنتات لو فيه أي تعديل أو بوستات جديدة.
-
 @ f1577c25:de26ba14
2025-04-07 07:27:17
@ f1577c25:de26ba14
2025-04-07 07:27:17أهلاً! أفترض إنك قرأت أول كام بوست، ولو لأ فده لينك أول بوست علشان تتابع بالترتيب: <لينك أول بوست>
المرة اللي فاتت اتكلمنا عن مميزات وعيوب البورصة الأمريكية، زي إنك تقدر تستخدم الكريبتو كطريقة إيداع سهلة. النهاردة هنتكلم عن حاجتين مهمين: العملات الرقمية المستقرة والذهب العالمي.
العملات الرقمية المستقرة (Stablecoins):
لما بتكلم عن العملات الرقمية، مش قصدي تشتري بيتكوين وخلاص. أنا قصدي العملات المستقرة زي USDT وUSDC، لأن كل عملة منهم ليها ما يعادلها بالدولار أو أصول حقيقية. يعني لو بصيت على سعر البيتكوين هتلاقيه ممكن 80 ألف دولار للوحدة، لكن USDT أو USDC دايماً سعرها قريب من 1 دولار. دي حلوة جداً للتعامل الإلكتروني لأنها زي الدولار المشفر.
إحنا هنستخدمها في خدمة اسمها "Earn" وهي شبه شهادات البنك. بتروح على بينانس، تشتري عن طريق P2P، وبعدين تروح على صفحة الـ Earn: https://www.binance.me/en/earn/simple-earn
هناك هتلاقي خيار تعمل "stake" للعملات دي، يعني بتحجز فلوسك لمدة معينة على الموقع، والموقع بيستخدمها (يسلفها لحد تاني أو يستخدمها كسيولة). الحلو إن في Earn، مش لازم تقفل فلوسك لسنة أو 3 سنين زي البنك. في اختيار اسمه "Flexible" بتقدر تحط فلوسك وتسحبها في نفس اليوم، والعائد بينزل يومياً. العيب إن العائد بيتغير يومياً. ممكن تختار Flexible لو عايز تسحب في أي وقت، أو تختار مدة أسبوع أو 90 يوم بعائد ثابت (بس بيكون أقل من الـ Flexible شوية).
ممكن كمان تفعل "Auto-Subscribe" لأن العائد بينزل بنفس نوع العملة، فبدل ما العائد يفضل مركون، أو لما يبقى معاك عملات زيادة في المحفظة، هو بيشترك تلقائي في Earn، فبيبقى زي العائد المركب.
المميزات
- عائد دولاري ومش متأثر بالجنيه
- بينزل عائد يومي
- تقدر تسحب فلوسك في أي وقت
- الحد الأدنى صغير (حوالي 100 جنيه)
العيوب
- الأمان مش 100% لأنها منصة وممكن (لا قدر الله) تقفل حسابك
- العملات الرقمية غير قانونية في بعض البلدان فخلي بالك
- خلي بالك من محاولات النصب: زي لما حد يقولك نكمل المعاملة برا المنصة، أو يبعت رسالة من رقمه كأنها من إنستاباي أو فودافون كاش
- العائد متغير وممكن يقل (بس حالياً حوالين 10%)
- قيمة الدولار نفسها ممكن تتغير
ملحوظة: لو قلقان من بينانس، فيه منصات تانية زي Kraken (بس العائد أسبوعي ومش عالي) أو OKX اللي بتدي أول 180 يوم عائد 10% مضمون، وبعدين ممكن تحول لـ Binance أو Bybit.
الذهب العالمي (PAXG)
بالنسبة للذهب، نفس الخطوات السابقة بالظبط. الحلو إنه في خدمة Earn لـ PAXG - صحيح العائد أقل من 1% سنوياً، بس أحسن من مفيش!
هتشتري USDT من خلال P2P، بعدين تروح بينانس وتعمل تحويل من USDT إلى PAXG. كده بقى معاك ذهب بالسعر العالمي. أحب أطمنك إن PAXG من شركة موثوقة، وتقدر تقرا عنها هنا: https://www.paxos.com/pax-gold
فيه عملات تانية شبهها، بس دي من أفضلهم، خصوصاً إنهم بيعملوا تقييم للأصول بشكل دوري للتأكد من مصداقية الشركة.
المميزات
- ذهب سهل الوصول إليه
- الحد الأدنى قليل
- أمان نسبي ضد التضخم
- سهولة الشراء والبيع
العيوب
- نفس عيوب المنصات الرقمية
- قيمة الذهب نفسها ممكن تتغير
- العائد على الـ PAXG منخفض (أقل من 1%)
العملة موجودة كمان على Kraken، بس مش متأكد لو فيها خدمة Earn زي بينانس.
ادعمني (اختياري)
- لو حابب تسجل عن طريق Binance ممكن تستخدم رابط الإحالة بتاعي: https://www.binance.com/referral/earn-together/refertoearn2000usdc/claim?hl=en&ref=GRO_14352_5LGSE
- USDT (TRC20):
TKQ3Uwkq21ntiua2Zh9Hu376fdMdnRGWN6
شوف التعليقات لو في اي تعديل او بوستات جديدة.
-
 @ da0b9bc3:4e30a4a9
2025-04-07 06:15:43
@ da0b9bc3:4e30a4a9
2025-04-07 06:15:43Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/936802
-
 @ 57d1a264:69f1fee1
2025-04-07 06:04:14
@ 57d1a264:69f1fee1
2025-04-07 06:04:14It's so cool how AI is blending design and engineering together, making it easier for us all to be efforts creative in new ways!
Steve Jobs once said:
“The doers are the major thinkers. The people who really create the things that change this industry are both the thinker-doer in one person.”
— Steve JobsWould its words become truth? Or they already are?
originally posted at https://stacker.news/items/936796
-
 @ e5de992e:4a95ef85
2025-04-07 05:46:58
@ e5de992e:4a95ef85
2025-04-07 05:46:58The stock market is currently experiencing a significant downturn, with major indices such as the S&P 500 and the Dow Jones Industrial Average recording substantial losses. This decline is largely attributed to the recent implementation of sweeping tariffs by President Donald Trump, including a 10% levy on all imports and higher duties on exports from key trading partners like China, the European Union, Japan, and Vietnam. These measures have ignited fears of a global trade war, leading to a massive sell-off in the markets. Notably, the S&P 500 dropped 6%, the Nasdaq slid 5.8%, and the Dow Jones fell by 2,231 points—some of the steepest declines since the early days of the COVID-19 pandemic.
Everyday Patience Versus Irrational Trading
In everyday life, consumers often exhibit patience by waiting for prices to drop before making purchases:
- Seasonal Sales: Shoppers wait for discounts to buy clothing.
- Tech Promotions: Tech enthusiasts delay buying electronics until promotional events.
- Real Estate: Prospective homebuyers hold off during market slowdowns to secure better deals.
This common-sense approach maximizes value and minimizes expenditure.
In contrast, many stock market traders fall prey to irrational behaviors:
- Fear of Missing Out (FOMO): Investors buy stocks at high prices or the dip, worried they might miss potential gains.
- Herd Mentality: Individuals mimic the actions of the majority, often buying during market highs and selling during lows.
These emotional decisions often lead to poor outcomes, as they contradict the logical approach of waiting for favorable prices.
The Risks of Ignoring Rational Investment Principles
Irrational trading practices can result in significant financial losses. By purchasing stocks at inflated prices during market euphoria, investors expose themselves to sharp declines when corrections occur. Unlike unpredictable black swan events, these losses stem from market corrections that follow overvaluation periods. Ignoring fundamental investment principles can, therefore, be more damaging than unforeseen events.
A Balanced Approach to Investing
A more balanced approach involves:
-
Risk Management Strategies:
Diversify across asset classes to mitigate potential losses. -
Maintaining a Long-Term Perspective:
Adhere to disciplined investment plans to avoid impulsive decisions. -
Understanding Your Risk Tolerance:
Set stop-loss orders and know your limits to protect against downturns.
These strategies help investors avoid pitfalls driven by FOMO and herd mentality.
Conclusion
While the current market downturn presents challenges, it also serves as a reminder of the importance of rational investment behavior. By drawing parallels from everyday purchasing decisions, investors can appreciate the value of patience and strategic planning. Embracing risk management techniques and resisting psychological pitfalls like FOMO and herd mentality can lead to more resilient and successful investment outcomes.
-
 @ 57d1a264:69f1fee1
2025-04-07 05:22:14
@ 57d1a264:69f1fee1
2025-04-07 05:22:14This idea has been explored along the last decades. Nothing has never taken the van place in the BMW series. The most successful intent was the 80s' Vixer in the US. Too sporty for a van? Or too luxurious to cover that already saturated market?
Collected some pictures all around, most oof them are designs and prototypes. Tried to order chronologically below:
Now in 2025, this came out of Ai
https://www.youtube.com/watch?v=d7p9CGBmRAA
originally posted at https://stacker.news/items/936787
-
 @ fd78c37f:a0ec0833
2025-04-07 05:06:58
@ fd78c37f:a0ec0833
2025-04-07 05:06:58In this feature, we’re excited to welcome MadMunky, who shares insights on fostering a decentralized community of activists, artists, and musicians, and how Bitcoin and Nostr are empowering unfiltered expression.
YakiHonne: MadMunky, thank you for joining us! Before we dive into the interview, I’d like to briefly introduce YakiHonne. We’re a decentralized media platform built on the Nostr protocol—a technology designed to champion free speech. YakiHonne empowers creators to own their voices and assets, offering innovative features like smart widgets, verified notes, and support for long-form content. With that in mind, we’d love to hear more about you and your community.
MadMunky: Thanks for having me! I’m someone who thrives on staying active—dabbling in various projects and traveling whenever I can. These pursuits give me a sense of freedom, or perhaps the illusion of it. I see myself as a craftsman of sorts, woodworker, dj, chef constantly exploring free-market solutions. I firmly believe that activism, paired with a truly free market, can address many of the world’s challenges.
That belief gave birth to 2140 Collective about two years ago, a project I co-founded with Anon. Collective that enables our community to create and publish freely. Before this, no platform truly supported our vision without compromise—social media often demanded personal data in exchange for access. We’re a collective of activists, artists, and musicians who simply want to build our own space. Communities like ours are essential for mutual support among like-minded individuals. This is also why I champion Bitcoin. It’s not perfect, but it’s transparent and honest—a pillar of freedom. Bitcoin offers an escape from centralized control, and that’s a powerful force. It’s why we’re here today.
YakiHonne: What first drew you to Bitcoin, and what inspired you to build a community around it?
MadMunky: My journey into free tech stemmed from growing frustration with persistent privacy invasions. For me, the erosion of privacy is deeply unsettling. About a year and a half ago, I met Anon, a close friend who introduced me to this space. We started brainstorming ways to empower people like us to carve out our own creative and communal haven.
We didn’t want to limit ourselves to an online presence. Our goal was to bring the community into the physical world through exhibitions, gatherings, and eventually a parallel economy. Plans like high-end auctions are on the horizon, and all these initiatives will be showcased on https://2140.wtf . Through art and culture, we aim to drive Bitcoin adoption. Some argue adoption isn’t necessary, but I believe these mediums are powerful gateways to introduce Bitcoin’s message. It’s not just about display—it’s about embedding critical thinking. When people encounter Bitcoin-inspired art or music, the underlying ideas spark curiosity. That shift from passive consumption to active engagement is how adoption grows.
YakiHonne: How did your community take shape, and how did you attract members?
MadMunky: It wasn’t easy. We kicked things off after a Bitcoin birthday event in London, connecting with artists and musicians over platforms like Signal. We officially launched around last year’s Bitcoin birthday, creating a space on Telegram and experimenting with platforms like Console—billed as the “Discord of networks.” Back then, Nostr was still nascent, and Console, while promising, felt clunky and failed to draw people in. Building momentum was tough—people are busy, and convincing them to switch platforms is a challenge. It takes dedicated individuals willing to invest time and share knowledge.
We tried Twitter early on but found it stifling—its control over speech made it a dead end. Nostr, with its remarkable strides in the past year, became our home.
But we’re making progress. In London, we host “Nostrland,” a bi-weekly meetup focused on Nostr, Bitcoin, and freedom tech. It’s growing organically, with new attendees and venues each time. Our crew is behind Bitcoin Culture Festival / London , and contributing in many others across Europe.
YakiHonne: Beyond the lack of freedom on some platforms, what other hurdles have you faced?
MadMunky: Free speech has been on my mind a lot lately—it’s a cornerstone of true freedom. Many assume Bitcoin alone is enough, but it’s just one piece of the puzzle. For years, we lacked tools to express ourselves without censorship. Platforms like Twitter and Facebook track everything—our locations, connections, and words. I ditched Facebook years ago when I realized how invasive it was. These systems wield algorithms that can fracture social bonds and control narratives.
Now, though, we have solutions. Protocols like Nostr and platforms like YakiHonne let creators speak freely, without gatekeepers. That’s revolutionary. If we don’t address the chaos of our current monetary system, suffering will deepen. Activism—raising awareness and sharing tools like Bitcoin and Nostr—is vital. We’re still early in this movement, but the ability to connect and communicate freely is transformative. After two decades of being trapped, spreading ideas is finally within reach.
YakiHonne: Free speech is indeed fundamental. What does your community do with Bitcoin? Are you focused on the technical side or more on cultural aspects?
MadMunky: Our members hail from across Europe, with diverse backgrounds—anyone can join. We blend technical and cultural efforts. For instance, Anon explored LoRa mesh networks, which let us send Nostr messages via radio waves—a concept most people don’t even know exists. These innovations often come from volunteers with bold ideas, woven into protocols. It’s incredible.
I’m not a tech fanatic myself, but I see the value in spreading these concepts. It’s not just about discussing Nostr or Bitcoin’s freedom—it’s about understanding the tools we use. Privacy isn’t simple; it’s a journey. Even with a powerful message, if you’re on an iPhone or Android, you’re still tracked. Staying free takes effort. Our community ties technical workshops, art exhibitions, and music together—think Bitcoin-inspired food, culture or tech talks. These pieces form a broader solution to today’s monetary mess.
YakiHonne: What advice would you offer technically inclined individuals or organizations eager to contribute to Bitcoin’s ecosystem?
MadMunky: Support is key—not just financial, but active engagement. We don’t have all the answers or know every project, so we invite people to join our events, share ideas, and help organize. Collaboration matters. Many have brilliant concepts but lack time due to life’s demands. Companies with resources can pitch in—offering tools or testing grounds.
This Friday, for example, we’re hosting a workshop at Cyphermunk House in London, exploring privacy-focused solutions like Graphene OS. People are waking up to these issues, and interest is surging. It’s about devices, funding, and teamwork—embracing a cyberpunk ethos. If you find a great idea, back it. Open-source tools and protocols are how we reshape the world.
YakiHonne: How do you envision the Bitcoin community evolving in terms of scalability, privacy, and adaptability?
MadMunky: In my two years in this space, Bitcoin’s transparency and cyberpunk-like tech have blown me away. Soon, we’ll make payments without networks—Bitcoin as eCash flow is wild. The potential for Bitcoin, Nostr, and tools like YakiHonne is immense. A year ago, these ideas were unimaginable; now, they’re racing forward.
Governments will push back—regulating, taxing, targeting centralized platforms—but that’s fine. People are waking up, seeking privacy and freedom. Education is critical; the more who grasp these decentralized tools, the stronger we become. We reject a government-controlled future. Peer-to-peer, freedom, and decentralization—that’s the path. Let’s keep building.
YakiHonne: Thank you, MadMunky. This has been an enlightening and inspiring conversation. We’re grateful for your insights!
-
 @ e5de992e:4a95ef85
2025-04-07 04:04:42
@ e5de992e:4a95ef85
2025-04-07 04:04:42U.S. Financial Market Volatility Amid Trade Tensions and Policy Changes
The U.S. financial markets are experiencing significant volatility in response to recent policy decisions and escalating global trade tensions.
Major U.S. Stock Indices
-
S&P 500:
The SPDR S&P 500 ETF Trust (SPY) is currently priced at $505.28, reflecting a decline of approximately 5.75% from the previous close. -
Dow Jones Industrial Average:
The SPDR Dow Jones Industrial Average ETF (DIA) stands at $383.22, down about 5.42%. -
Nasdaq Composite:
The Invesco QQQ Trust Series 1 (QQQ) is at $422.67, showing a decrease of 6.09%. -
Russell 2000:
The iShares Russell 2000 ETF (IWM) is priced at $181.19, down 4.41%.
Advisor Perspectives
Key Factors Influencing Market Movements
-
Implementation of Sweeping Tariffs:
President Donald Trump's administration has imposed a baseline 10% tariff on all imports, with higher rates targeting specific countries—34% on Chinese imports and 20% on goods from the European Union. -
Global Retaliatory Measures:
In response, China has announced retaliatory tariffs of 34% on U.S. goods, intensifying fears of a global trade war and its potential impact on economic growth. -
Market Reactions and Investor Sentiment:
The announcement of these tariffs has triggered significant sell-offs. The S&P 500 and Nasdaq recorded their worst drops in years, with the Dow Jones falling over 9%, as investors react to the economic implications of escalating trade tensions.
Economic Indicators
- Oil Prices:
Crude oil prices have plunged to a four-year low. - Brent Crude: Trading at $63.01 per barrel.
-
West Texas Intermediate: At $60.63 per barrel.
-
Treasury Yields:
The yield on the 10-year U.S. Treasury note has declined to approximately 3.94%, indicating a shift toward safer assets amid market volatility.
Corporate Highlights
-
Tesla Inc. (TSLA):
Current stock price is $239.43, down 10.46% from the previous close. -
Apple Inc. (AAPL):
Stock stands at $188.38, reflecting a decrease of 7.27%. -
Boeing Co. (BA):
Shares are at $136.59, down 9.47%.
Global Market Impact
International markets have reacted variably to U.S. policy changes:
-
Japan's Nikkei 225:
Dropped nearly 8% amid concerns over U.S. tariffs affecting automakers like Toyota. -
South Korea's KOSPI and European Markets:
Both have experienced downturns as trade disputes add uncertainty. -
Hong Kong's Hang Seng:
Declined, reflecting broader concerns over trade uncertainties and impacts on Chinese tech stocks.
Outlook
The current market environment is marked by heightened volatility and uncertainty:
- Investors are advised to exercise caution and consider diversification strategies.
- Key developments such as trade negotiations and policy changes will be crucial in shaping future market dynamics.
- Monitoring evolving economic data and geopolitical events remains essential for navigating this complex landscape.
-
-
 @ 5d4b6c8d:8a1c1ee3
2025-04-06 23:58:21
@ 5d4b6c8d:8a1c1ee3
2025-04-06 23:58:21We have a winner! It was a very tight race and I want to once again thank each of the entrants for their great posts.
Q1 Top Post
Bitcoin and (Monetary) Economics—Properly (Bitcoin Policy Institute)
by @denlillaapan
29 Comments and 5k Sats
This post is a summary of and commentary on a video of several economics professors' talking about bitcoin. There are actually lots of academic economists who think about the things bitcoiners are obsessed with. The video is worth a watch and @denlillaapan's commentary is certainly worth a read.
This post is also the first nominee for Post of the Year.
Posts of the Month
- January: California Wild Fires: Perspective of a Native Californian by @kepford
- February: Bitcoin and (Monetary) Economics—Properly (Bitcoin Policy Institute) by @denlillaapan
- March: The Pleb Economist #5: Shitcoins are part of Bitcoin's Gartner Hype Cycle by @SimpleStacker
All of these posts will be honored in our end of year ceremony. Make sure to read any that you may have missed.
originally posted at https://stacker.news/items/936613
-
 @ 5d4b6c8d:8a1c1ee3
2025-04-06 23:26:53
@ 5d4b6c8d:8a1c1ee3
2025-04-06 23:26:53We had a nice sunny day and took advantage of it...by doing yardwork. Mowing, planting, and some light landscaping were a good workout and got me to almost 12k steps.
This was a great entry in Active April, which has generally been going pretty well.
Are all the other Stackers starting to get out into their yards?
originally posted at https://stacker.news/items/936592
-
 @ e516ecb8:1be0b167
2025-04-06 18:25:12
@ e516ecb8:1be0b167
2025-04-06 18:25:12Bitcoin ha recorrido un camino fascinante: de ser un experimento cypherpunk nacido en las sombras de la crisis de 2008 a convertirse en un activo que algunos estados, como El Salvador, consideran parte de sus reservas estratégicas, una especie de "oro digital". Hace apenas 15 años, era un código curioso que valía centavos; hoy, hay países apostando su futuro económico a él. Sin embargo, no hace falta haber leído Hijacking Bitcoin para sospechar que hay nubes en el horizonte. Y no, no hablo solo de la volatilidad, ese eterno fantasma que siempre se menciona. Sí, Bitcoin sube y baja como montaña rusa —en 2021 tocó los 69 mil dólares y luego cayó a 16 mil en 2022—, pero si hacemos un zoom out —como dicen los gringos—, la tendencia a largo plazo es al alza, mientras que las monedas fiduciarias, en palabras de Huerta de Soto, no son más que "papelitos coloreados" que tienden a valer cero. Pero dejemos la poesía de lado y miremos con lupa: ¿qué problemas podrían acechar el futuro de Bitcoin? Aquí van algunos puntos que me dan vueltas en la cabeza.
1. Bloques vacíos y el dilema del HODL
En marzo de 2025, se reportó que casi el 20% de los bloques de la blockchain estaban vacíos o con pocas transacciones. Esto encaja con una teoría: Bitcoin dejó de ser la moneda peer-to-peer que soñó Satoshi Nakamoto para transformarse en un depósito de valor. Hoy, la filosofía dominante es "HODL" (sujetar y no soltar), y figuras como Michael Saylor no esconden que les conviene que la gente pierda sus llaves privadas: menos bitcoins en circulación, mayor escasez, precio más alto. Imagina a Saylor frotándose las manos cada vez que alguien olvida su contraseña. Pero si todos acumulan y nadie gasta, ¿qué pasará con los mineros cuando las transacciones escaseen? Sin ellas, sus ingresos dependen de las recompensas por bloque, que algún día desaparecerán. Claro, ahora existen billeteras con opciones de herencia, pero si la idea es holdear hasta la tumba, ¿para qué acumular?
2. La red Lightning y el fantasma de los terceros
Para revivir la red, hacen falta más transacciones. Pero cuidado: el tamaño de los bloques es limitado a 1 MB (o un poco más con SegWit). Si el volumen crece demasiado —como en 2017, cuando las tarifas llegaron a 50 dólares por transacción—, la red se congestiona y adiós practicidad. ¿Aumentar el tamaño de los bloques? Ni lo menciones, eso sería darle la razón a los de Bitcoin Cash, un pecado mortal para cualquier bitcoinero Core. La solución, entonces, son las segundas capas como la red Lightning, que promete transacciones rápidas y baratas. El problema es que sigue pareciendo un eterno beta: hay fallos técnicos que no termino de entender (y sospecho que no soy el único). Pero lo que sí entiendo es que, al usarla, mucha gente termina dependiendo de terceros. Y si "no son tus llaves, no es tu dinero", esto choca de frente con la filosofía original de Bitcoin.
3. Computación cuántica: ¿el fin de la inviolabilidad?
Pasemos a un terreno más técnico. La computación cuántica podría, en teoría, descifrar las direcciones antiguas de Bitcoin, esas basadas en algoritmos vulnerables como ECDSA. Algunos proponen "quemar" esos bitcoins para proteger la red, pero imagina el golpe a la confianza: ¿qué tan "seguro" es un activo si de pronto desaparecen millones de unidades? Este riesgo no es exclusivo de Bitcoin —afecta a casi todas las criptos—, pero solo un puñado, como QRL o IOTA en sus inicios, usa algoritmos post-cuánticos, y ninguna es mainstream. Un tema que da para pensar.
4. Filosofía traicionada: del antisistema al lobby estatal
Bitcoin nació como un grito contra los bancos, los gobiernos y el sistema monetario tras la crisis de 2008. Entonces, ¿por qué vemos a sus principales voceros viajando por el mundo, haciendo lobby para que estados y gigantes como BlackRock lo adopten como reserva de valor? Podría ser solo una contradicción filosófica menor, pero hay más: si Bitcoin es tan libre y transfronterizo, ¿por qué los aranceles de Trump lograron tumbar su precio un 5% en diciembre pasado? Algo no cuadra en el discurso de la independencia absoluta.
5. El fin de la minería y la dependencia estatal
A largo plazo, cuando se mine el último bitcoin en 2140 (sí, falta mucho), los mineros dependerán exclusivamente de las tarifas por transacción. Pero si el modelo es "sujetar y no soltar", ¿quién pagará esas tarifas? Ya hemos visto momentos en que minar sale más caro que las ganancias —en 2018, muchos apagaron sus máquinas—, y aunque hasta ahora han sido excepciones, el futuro pinta complicado. Si los costos energéticos no bajan, ¿quién mantendrá la red? ¿Empresas dispuestas a perder dinero por un "bien mayor"? Suena a utopía, salvo que hablemos de empresas estatales. Y aquí volvemos al punto inicial: ¿Bitcoin dependiendo de los estados? ¿Pagando impuestos en dinero fiduciario para subsidiar mineros? ¿No era esto lo que queríamos evitar? El oro, una vez extraído, no necesita mineros para seguir existiendo; Bitcoin, por el contrario, sí.
6. El caso argentino: libertarismo con asterisco
Para rematar, esta semana salió la noticia de que el gobierno argentino —sí, el de Milei, abanderado del libertarismo— planea exigir que los residentes declaren sus billeteras de criptoactivos. No niego las reformas positivas de su gestión, como la desregulación económica, pero esto huele a Gran Hermano. ¿Qué tan libertario es un sistema que te vigila mientras predica libertad? Otra contradicción que suma ruido.
Después de ganarme el odio de los maximalistas de Bitcoin (esperaré comentarios tipo: "¡este tipo no entiende nada!"), y quizás de algún fan de Milei, quiero aclarar: no estoy en contra de Bitcoin. Lo que me molesta son las inconsistencias. Odio igual a los políticos que dicen una cosa y hacen otra que a los predicadores de un "antisistema" que termina dependiendo del sistema para sobrevivir. Me hace tanto ruido como esos malacatosos que rayan paredes con la "A" de anarquía mientras piden más Estado.
Dicho esto, no todo está perdido. Si Bitcoin quiere ser ese oro digital y cumplir su promesa libertaria, tal vez necesite ajustes: algoritmos más robustos contra la computación cuántica y algún método para pasar los bitcoins de direcciones antiguas a nuevas de forma transparente (ni idea si es técnicamente posible), una red Lightning que realmente funcione sin intermediarios, o una comunidad que priorice la utilidad sobre el HODL ciego. En resumen, apoyo a Bitcoin siempre que sus defensores sean coherentes. Si es libertad, que no se arrodille ante nadie. ¿Es mucho pedir?
-
 @ f7d424b5:618c51e8
2025-04-06 16:48:03
@ f7d424b5:618c51e8
2025-04-06 16:48:03The promised Nintendo direct has come and there is a LOT to say about it. If you ever wondered how such a reveal would be taken differently by a dad, a NEET, and a people programmer this is the episode for you! Also those SAG bootlickers are getting uppity again. All of that and more!
Sources cited:
- Nintendo Online subscribers get to upgrade the zelda games for free for some reason?
- Do Nintendo games ever actually go on sale?
- Kirby
- Metroid
- TOTK
- Pokeshit
- EOW
- there's literally 252 games on sale at VGP right now
- SAG agreement you can read for yourself
- SAG literally says on their website to go audition for non-union roles and then strongarm them into going union if they wanna keep you
Obligatory:
- Listen to the new episode here!
- Discuss this episode on OUR NEW FORUM
- Get the RSS and Subscribe (this is a new feed URL, but the old one redirects here too!)
- Get a modern podcast app to use that RSS feed on at newpodcastapps.com
- Or listen to the show on the forum using the embedded Podverse player!
- Send your complaints here
Reminder that this is a Value4Value podcast so any support you can give us via a modern podcasting app is greatly appreciated and we will never bow to corporate sponsors!
-
 @ 9358c676:9f2912fc
2025-04-06 16:33:35
@ 9358c676:9f2912fc
2025-04-06 16:33:35OBJECTIVE
Establish a comprehensive and standardized hospital framework for the diagnosis, treatment, and management of pulmonary embolism (PE), aiming to improve quality of care, optimize resources, and reduce morbidity and mortality associated with this condition in the hospital setting.
SCOPE
All hospitalized patients over 15 years of age in our institution.
RESPONSIBILITIES
Institution physicians. Nursing staff.
REFERENCES AND BIBLIOGRAPHY
- SATI Guidelines for the Management and Treatment of Acute Thromboembolic Disease. Revista Argentina de Terapia Intensiva 2019 - 36 No. 4.
- Farreras-Rozman. Internal Medicine. 16th Edition. El Sevier. 2010.
- SAC Consensus for the Diagnosis and Treatment of Venous Thromboembolic Disease. Argentine Journal of Cardiology. October 2024 Vol. 92 Suppl. 6 ISSN 0034-7000
- 2019 ESC Guidelines for the diagnosis and management of acute pulmonary embolism developed in collaboration with the European Respiratory Society (ERS). European Heart Journal (2020) 41, 543-603. doi:10.1093/eurheartj/ehz405
INTRODUCTION
Pulmonary embolism (PE) is a cardiovascular emergency caused by a blood clot, usually originating from the deep veins of the lower limbs, that travels to the lungs and obstructs the pulmonary arteries. This condition represents a significant cause of morbidity and mortality in hospitals. Timely diagnosis and treatment are essential to improve clinical outcomes.
The clinical presentation of PE is highly variable, ranging from mild symptoms to acute cardiovascular shock. Risk factors such as prolonged immobilization, recent surgery, and chronic illnesses complicate its identification and management.
PE has an annual incidence of 70 cases per 100,000 people. Prognosis varies from high-risk PE with high mortality to low-risk PE with minimal hemodynamic impact. Without thromboprophylaxis, deep vein thrombosis (DVT)—the main predisposing factor (90–95% of cases)—has variable incidence depending on the surgery type, and up to 25% of embolic events occur post-discharge.
PREDISPOSING FACTORS
Strong Risk Factors (OR >10): - Hip or leg fracture - Hip or knee prosthesis - Major general surgery - Major trauma - Spinal cord injury
Moderate Risk Factors (OR 2–9): - Arthroscopic knee surgery - Central venous catheters - Chemotherapy - Chronic heart or respiratory failure - Hormonal replacement therapy - Malignancy - Oral contraceptives - Stroke with paralysis - Pregnancy or postpartum - Prior VTE - Thrombophilia
Mild Risk Factors (OR <2): - Bed rest <3 days - Prolonged travel - Advanced age - Laparoscopic surgery - Obesity - Antepartum period - Varicose veins
CLINICAL MANIFESTATIONS AND BASIC COMPLEMENTARY STUDIES
Symptoms: Dyspnea, chest pain, cough, hemoptysis, bronchospasm, fever.
Signs: Tachycardia, desaturation, jugular vein distention, orthostatism, DVT signs, syncope, or shock.Basic Studies: - Chest X-ray (may show infarction or atelectasis) - ECG (T wave inversion, RV strain, S1Q3T3 pattern)
RISK ASSESSMENT SCORES
Wells Score: - >6 points: High probability - 2–6: Moderate - ≤2: Low - Modified: >4 = likely PE, ≤4 = unlikely PE
Geneva Score: - >10: High - 4–10: Intermediate - 0–3: Low
PERC Rule: If all criteria are negative and clinical suspicion is low, PE can be excluded without further testing.
DIAGNOSTIC STUDIES
- D-dimer: High sensitivity; used in low/moderate risk patients.
- CT Pulmonary Angiography (CTPA): First-line imaging; limited in pregnancy/renal failure.
- Lower limb Doppler ultrasound: Indirect evidence of PE when DVT is detected.
- V/Q scan: Alternative when CTPA is contraindicated.
- Transthoracic echocardiogram: Used to assess RV function, especially in shock.
- Pulmonary angiography: Gold standard; reserved for complex cases due to invasiveness.
RISK STRATIFICATION
High-risk PE (5%): Hemodynamic instability, mortality >15%. Requires urgent reperfusion.
Intermediate-risk PE (30–50%): Hemodynamically stable with signs of RV dysfunction or elevated biomarkers.
Low-risk PE: Mortality <1%, eligible for outpatient management.
PESI Score: - I (<65): Very low risk - II (65–85): Low - III (86–105): Intermediate - IV (106–125): High - V (>125): Very high
Simplified PESI: ≥1 point = high risk; 0 = low risk
TREATMENT
High-risk PE: - Systemic fibrinolysis with alteplase 100 mg over 2 h or 0.6 mg/kg (max 50 mg) IV bolus over 15 min. - Suspend UFH 30–60 min before lysis if already on treatment. - Resume anticoagulation (UFH or LMWH) when aPTT <2x normal. - Consider surgical embolectomy or catheter-directed therapy if fibrinolysis fails or is contraindicated. - Maintain SpO₂ >90%, CVP 8–12 mmHg, and use vasopressors/inotropes as needed. ECMO in select cases.
Contraindications to Fibrinolytics: - Absolute: Recent stroke, active bleeding, CNS tumors, recent major trauma or surgery. - Relative: Anticoagulant use, recent TIA, pregnancy, uncontrolled hypertension, liver disease.
Intermediate-risk PE: - Initiate anticoagulation (enoxaparin 1–1.5 mg/kg SC every 12 h, max 100 mg/dose). - Fibrinolysis is not routine; reserve for clinical deterioration. - Direct oral anticoagulants (DOACs) may be considered. - Consider IVC filter in absolute contraindication to anticoagulation or recurrence despite treatment.
RIETE Bleeding Risk Score: - >4 points: High risk - 1–4: Intermediate - 0: Low
INVASIVE TREATMENT
Consider catheter-directed therapy when: - High bleeding risk - Fibrinolysis contraindicated - Delayed symptom onset >14 days
Some centers use this as first-line therapy in high-risk PE.
QUALITY INDICATOR
Indicator: Proportion of PE cases with documented risk stratification in the medical record at initial evaluation.
Formula: (PE cases with documented stratification / total PE cases evaluated) × 100
Target: >85% of PE cases must have risk stratification recorded at the time of initial evaluation.
Autor
Kamo Weasel - MD Infectious Diseases - MD Internal Medicine - #DocChain Community npub1jdvvva54m8nchh3t708pav99qk24x6rkx2sh0e7jthh0l8efzt7q9y7jlj
-
 @ fe32b72c:14cfcb1e
2025-04-06 15:56:23
@ fe32b72c:14cfcb1e
2025-04-06 15:56:23Libertarian tariff controversy
GM. First long form note, so let's see how this goes.
Reading a lot of Libertarians complaining about tariffs on twitter this morning. And I get it — they're a tax on imports, and furthermore, a barrier to free trade. Not exactly something libertarians are fans of, lowercase "l" or doctrinaire capital "L" party members.
But there's something I've been pointing out to many. That is: being the issuer of the global reserve currency (which itself relies upon inflation, and thus is also a tax) necessarily creates trade deficits. I'm preaching to the choir on this one a bit I expect, but it's a key reason as to why given that we have this backdrop, and we can't simply overnight completely change the monetary system, it is not an unreasonable stance for a libertarian leaning person to hold the idea that using tariffs as a way to offset this trade deficit while moving away from a fiat currency is actually a sound idea. There are plenty of places for devils to hide in details of course, and by all means, I'm not a Trumpist, but speaking generally, this seems like a sound stance. It's all well and good to have an idea of where you want to go, but if you want to actually get there, charting a course is often harder than picking a destination.
Now, as for what I think we can expect
Tariffs will raise consumer prices. It's not inflation, because it's not about an expansion of the money supply, but it's also true that the cost has to be born by someone. However, tariffs will also decrease imports. Which will reduce dollar outflows into foreign nations, where, thanks to the mechanics of the Eurodollar system, will create a panic. The reality is, dollars outside of the US are not something that is created by the Federal Reserve, because foreign banks can't hold reserves. Rather, Eurodollar deposits are loaned into existence by private banks, and are generally settled by a variety of creative means, including offsetting liabilities, and sale of assets — most commonly, US Treasury securities. This means they need dollars to flow — it's not about getting wealthier, but rather, about covering their debts that they simply have no way to bail out. Reduced dollar outflow is a reduction in supply; as such, the price of the dollar goes up (or at least, goes down slower). That is, there's deflation, or at least disinflation. The end result is, those prices that went up thanks to tariffs start going back down to American consumers.
Meanwhile, dollars being more expensive than they were when liabilities were taken on likely leads to recessionary conditions — both domestically and internationally. However, companies importing goods into the US that can onshore their production will seek to do so, which will have an effect of offsetting that recessionary impulse domestically. In effect, "exporting" the recession.
As for what this means for the national debt
The national debt of course has been a sore point given that interest expense has been astronomical, and rolling the debt has been necessary thanks to Yellen's failure to term it out. Foreign parties will of course want more treasury assets, as a way to cover their dollar liabilities amid diminished dollar flow, but it doesn't take a doctorate to know that desires and needs are not the same thing as increased aggregate demand. Some may have good enough credit to borrow more dollars from American banks, and thus, buy treasuries, which would of course be good for bringing down interest rates, but I'm not sure I'd bet too much on that horse, especially amid an environment where recession is being exported. There is a fair bit of exposure to US equities abroad that may rotate into American sovereign debt, though the time to do that was probably before 10% of the value got evaporated off of that over the past week.
There may be increased domestic demand for treasuries, as all of this on-shoring means a lot of running in place, so to speak, by companies pivoting to domestic production, and thus under performance by equities. This is a place I'd be curious about the overall impact on the Treasury market, and am certainly not qualified to weigh in on it. But I'd love to see some sober analysis by those who recognize it as worth taking a closer look at.
Then there's the Fed, which is almost an afterthought for me, given that they're simply not going to do the levels of QE that it would take to actually bring interest rates on long term debt down, but it is worth pointing out that amid the churning deflation there will likely be at least a few rate cuts that come into play. Note, however, that rate cuts only help so much, as they directly affect the immediate end of the curve, with very little impact on the longer end where it's needed, regardless of what Greenspan would have you believe about "series of forward rates." That said, as inflation expectations come down, it may be that longer tenor rates come do down as well, because inflation expectations are an actual driver of rates, rather than Fed Funds policy rates, but that may take longer than the Treasury can wait for. That said, US10Y rates are already down 26 bps in a week, so things do seem to be starting out in the right direction. We'll see if that holds once issuance starts ramping up.
Where this all leaves us
There seem to me to be too many variables to really predict how this all plays out on the treasury market, which is hard enough to predict given that it's the largest asset class in the world. I'm inclined to think Bessent knows what he's doing (and that Trump is at least smart enough to listen to him, if not game it all out himself). What's clear is that he's trying something to address the bigger issue rather than simply kick the can down the road, which is more than we can say of policymakers for at least the past half century, and likely longer.
With any luck all of this turbulence will drive further adoption by Bitcoin, as foreign nations need to resort to something to get them out of their crushing dollar denominated liabilities. At the end of the day, being free of both taxes on imports and "invisible" taxes by deflation should be something we can all cheer for. In the meantime, hopefully this article has given a bit of perspective on what developments will be of interest in the bond market as this fourth turning plays out.
Finance #Tariffs #Bitcoin #NationalDebt #Libertarianism #FreeTrade
-
 @ 8d34bd24:414be32b
2025-04-06 14:34:37
@ 8d34bd24:414be32b
2025-04-06 14:34:37This weekend my pastor was preaching on this passage. Two words stood out when we were reading the passage, “but Jesus … .” This made me start searching for other instances of “but Jesus …” to see what we could learn.
And a woman who had a hemorrhage for twelve years, and could not be healed by anyone, came up behind Him and touched the fringe of His cloak, and immediately her hemorrhage stopped. And Jesus said, “Who is the one who touched Me?” And while they were all denying it, Peter said, “Master, the people are crowding and pressing in on You.” But Jesus said, “Someone did touch Me, for I was aware that power had gone out of Me.” (Luke 8:43-46) {emphasis mine}
In this passage people were crowding Jesus and fighting to get close to Him or even touch Him and in this dense crowd he asked, “Who is the one who touched Me?” Despite many people being pressed up beside Him, they all denied touching Him and Peter basically reprimanded Jesus that this was a ridiculous question because so many people were touching Him. “But Jesus …” knew that someone had touched Him and faith and that His power had healed that person. For the sake of the woman, the crowd, and His disciples, He wanted them to know what had happened and bless this woman that had suffered for more than a decade. He didn’t see the situation like everyone else. He saw things they did not see and like all of the best teachers, he asked His students questions to lead them to the truth. Despite the fact that he was on the way to helping Jairus’s dying daughter, Jesus stopped for this moment to bless this suffering woman and to teach the crowd the meaning of faith and the meaning of mercy.
How often do we ignore teaching moments or moments of service that could make a difference in a person’s life because we are busy and focused on something else? But Jesus did not miss the opportunity.
So often Jesus’s response to things are not like our own. “For as the heavens are higher than the earth, So are My ways higher than your ways And My thoughts than your thoughts.” (Isaiah 55:9)
But the news about Him was spreading even farther, and large crowds were gathering to hear Him and to be healed of their sicknesses. But Jesus Himself would often slip away to the wilderness and pray. (Luke 5:15-16) {emphasis mine}
Most of us, if we were bringing crowds through a blog or preaching or conferences would tend to continue working to reach more people, but Jesus took time to slip away from the crowd to pray. He prioritized prayer and fellowship with the Father knowing that ministry without the Father is no ministry at all. Jesus knew that there is more to sharing the Gospel than just drawing a crowd or growing a following. Jesus built the foundation before trying to build the church.
And some men were carrying on a bed a man who was paralyzed; and they were trying to bring him in and to set him down in front of Him. But not finding any way to bring him in because of the crowd, they went up on the roof and let him down through the tiles with his stretcher, into the middle of the crowd, in front of Jesus. Seeing their faith, He said, “Friend, your sins are forgiven you.” The scribes and the Pharisees began to reason, saying, “Who is this man who speaks blasphemies? Who can forgive sins, but God alone?” But Jesus, aware of their reasonings, answered and said to them, “Why are you reasoning in your hearts? Which is easier, to say, ‘Your sins have been forgiven you,’ or to say, ‘Get up and walk’? But, so that you may know that the Son of Man has authority on earth to forgive sins,”—He said to the paralytic—“I say to you, get up, and pick up your stretcher and go home.” (Luke 5:18-24) {emphasis mine}
This suffering man was paralyzed. His loving friends were trying to get him help by focusing on his physical needs, but Jesus saw the man’s most important need — his need for salvation. Instead of focusing on the obvious physical needs of the man, He dealt with the more important spiritual needs. He also knew that His critics were judging Him and denying His ability to wipe the man’s sins away. To prove that He could forgive the man’s sins, He also healed the man’s paralysis. After healing the man’s more important spiritual needs, He then healed the more obvious physical needs.
I know I catch myself spending lots of time praying for people’s physical needs. I pray asking for people to have healing from sickness and cancer. I pray for jobs and finances. I pray for relationships. I’ve noticed that I spend more time praying for physical needs that are problem today, but don’t matter eternally and not enough praying for salvation and guidance for people. I focus on what I can see, that although urgent, have little to no effect on the eternal well-being of the people. I should be more like Jesus and spend more time on praying for people’s spiritual needs that determine their eternal well-being.
Now when He was in Jerusalem at the Passover, during the feast, many believed in His name, observing His signs which He was doing. But Jesus, on His part, was not entrusting Himself to them, for He knew all men, and because He did not need anyone to testify concerning man, for He Himself knew what was in man. (John 2:23-25) {emphasis mine}
When we have people asking for us to share Jesus with them, we jump at the opportunity. We seek the crowds and the following. We seek the influence and prestige, but Jesus did not trust those seeking Him and knew they were looking for blessings without the submission or repentance.
I’ve noticed that I will have people asking questions about the Bible and Christianity. They ask me to defend everything in the Bible and what I believe. Because I have studied these things and studied apologetics, I tend to spend a large amount of time debating these topics, but it is frequently obvious from the beginning that these people are not truth seekers. They are people looking to throw “gotcha” questions at Christians in the hope of destroying their faith or making them look bad. I need to get better at asking questions of them and recognizing these situations as not interest and inquisitiveness, but attempts to destroy and not waste time on them. (Of course, sometimes there are watchers/listeners who can be helped by knowing there are answers to these questions.)
When it was evening, the disciples came to Him and said, “This place is desolate and the hour is already late; so send the crowds away, that they may go into the villages and buy food for themselves.” But Jesus said to them, “They do not need to go away; you give them something to eat!” They said to Him, “We have here only five loaves and two fish.” And He said, “Bring them here to Me.” Ordering the people to sit down on the grass, He took the five loaves and the two fish, and looking up toward heaven, He blessed the food, and breaking the loaves He gave them to the disciples, and the disciples gave them to the crowds, and they all ate and were satisfied. They picked up what was left over of the broken pieces, twelve full baskets. (Matthew 14:15-20) {emphasis mine}
We so often see the glass half empty. We see all of the things we can’t do, but Jesus knows what can be done and we should know that we can do all things in Christ who strengthens us. Instead of focusing on why we can’t, we need to trust God to enable us to do whatever He asks us to do.
Some Pharisees came up to Jesus, testing Him, and began to question Him whether it was lawful for a man to divorce a wife. And He answered and said to them, “What did Moses command you?” They said, “Moses permitted a man to write a certificate of divorce and send her away.” But Jesus said to them, “Because of your hardness of heart he wrote you this commandment. But from the beginning of creation, God made them male and female. For this reason a man shall leave his father and mother, and the two shall become one flesh; so they are no longer two, but one flesh. What therefore God has joined together, let no man separate.” (Mark 10:2-8) {emphasis mine}
How often do we look for a loophole in God’s word? The Pharisees were looking for an excuse to do what they wanted to do, but Jesus said that He had allowed for their evil ways (for the good of the woman they wanted to divorce) despite His perfect plan which they had rejected. “Then Peter came to Jesus and asked, “Lord, how many times shall I forgive my brother or sister who sins against me? Up to seven times?” Jesus answered, “I tell you, not seven times, but seventy-seven times. (Matthew 18:21-22)” Peter thought he was being generous forgiving someone seven times, but Jesus wanted him to forgive as He had forgiven Peter. (See the Lord’s Prayer “Forgive us our sins, for we also forgive everyone who sins against us.” Luke 11:4)**
And they sent their disciples to Him, along with the Herodians, saying, “Teacher, we know that You are truthful and teach the way of God in truth, and defer to no one; for You are not partial to any. Tell us then, what do You think? Is it lawful to give a poll-tax to Caesar, or not?” But Jesus perceived their malice, and said, “Why are you testing Me, you hypocrites? Show Me the coin used for the poll-tax.” And they brought Him a denarius. And He said to them, “Whose likeness and inscription is this?” They said to Him, “Caesar’s.” Then He said to them, “Then render to Caesar the things that are Caesar’s; and to God the things that are God’s.” And hearing this, they were amazed, and leaving Him, they went away. (Matthew 22:16-22) {emphasis mine}
Instead of directly answering the question that was asked, since it was not asked in good faith, He corrected their hypocrisy and showed them the truth. We are not nearly as wise and observant as Jesus, but we should still try to see what is truly being asked instead of just answering the obvious question. So often there is a need or motive behind the question that needs to be addressed. I’ve found that asking questions of the questioner can both uncover what is behind the question and also lead them to the truth. This method, also known as the Socratic Method, is taught well from a Christian perspective in the book “Tactics” by Gregory Koukl.
They brought the boy to Him. When he saw Him, immediately the spirit threw him into a convulsion, and falling to the ground, he began rolling around and foaming at the mouth. And He asked his father, “How long has this been happening to him?” And he said, “From childhood. It has often thrown him both into the fire and into the water to destroy him. But if You can do anything, take pity on us and help us!” And Jesus said to him, “ ‘If You can?’ All things are possible to him who believes.” Immediately the boy’s father cried out and said, “I do believe; help my unbelief.” When Jesus saw that a crowd was rapidly gathering, He rebuked the unclean spirit, saying to it, “You deaf and mute spirit, I command you, come out of him and do not enter him again.” After crying out and throwing him into terrible convulsions, it came out; and the boy became so much like a corpse that most of them said, “He is dead!” But Jesus took him by the hand and raised him; and he got up. (Mark 9:20-27) {emphasis mine}
Jesus sees things as they are. He honors belief. I love the boy’s father’s response to Jesus, “I do believe; help my unbelief.” I’ve felt like this before. Jesus never gives up and as long as we have Jesus, we should never give up on someone.
As soon as He was approaching, near the descent of the Mount of Olives, the whole crowd of the disciples began to praise God joyfully with a loud voice for all the miracles which they had seen, shouting:
“Blessed is the King who comes in the name of the Lord;\ Peace in heaven and glory in the highest!”
Some of the Pharisees in the crowd said to Him, “Teacher, rebuke Your disciples.” But Jesus answered, “I tell you, if these become silent, the stones will cry out!” (Luke 19:31-40) {emphasis mine}
The Pharisees saw a threat to their power and prestige, but Jesus saw reality as it was. Jesus saw the fulfillment of scripture and a small glimpse of the glory He deserved. They focused on what they disagreed with and what they didn’t like. Jesus focused on the fact that worship of God cannot be stopped. What do you focus on?
Therefore when Pilate heard this statement, he was even more afraid; and he entered into the Praetorium again and said to Jesus, “Where are You from?” But Jesus gave him no answer. So Pilate said to Him, “You do not speak to me? Do You not know that I have authority to release You, and I have authority to crucify You?” Jesus answered, “You would have no authority over Me, unless it had been given you from above; for this reason he who delivered Me to you has the greater sin.” (John 19:8-11) {emphasis mine}
Most innocent men would be continually speaking the truth of their innocence and trying to convince Pilate to listen, but Jesus had a purpose. He didn’t act like a normal innocent man, nor did He act like a normal guilty man. He was God incarnate living out His perfect plan. He knew Pilate didn’t have authority to kill or free Him, but that everything was going according to His perfect plan.
When we are following Jesus, we need to accept that God is in control. Not every hardship needs to be fixed. Sometimes it is part of God’s perfect plan. No one, man or spirit, has the authority to harm a believer unless God allows it and He only allows it if it furthers His perfect plan and is used for good. We need to know God and know His word. We need to listen to His leading through the Spirit, so we respond as Jesus did, “You would have no authority over Me, unless it had been given you from above.” This is as true of us today as it was about our savior on that fateful day. God is always in control.
Pilate questioned Him, “Are You the King of the Jews?” And He *answered him, “It is as you say.” The chief priests began to accuse Him harshly. Then Pilate questioned Him again, saying, “Do You not answer? See how many charges they bring against You!” But Jesus made no further answer; so Pilate was amazed. (Mark 15:2-5) {emphasis mine}
How often are people amazed because Jesus does not respond in the way a normal person would. Are there times that we should speak up and defend the word of God? Yes. Are there times that we should, like Jesus, make no further answer? Yes. We must ask God for guidance on the right response for each situation.
While He was still speaking, behold, a crowd came, and the one called Judas, one of the twelve, was preceding them; and he approached Jesus to kiss Him. But Jesus said to him, “Judas, are you betraying the Son of Man with a kiss?” When those who were around Him saw what was going to happen, they said, “Lord, shall we strike with the sword?” And one of them struck the slave of the high priest and cut off his right ear. But Jesus answered and said, “Stop! No more of this.” And He touched his ear and healed him. (Luke 22:47-51) {emphasis mine}
The common response to being mistreated is to mistreat back. We so often try to do to others at least as badly as they have done to us, but Jesus was different. When Judas betrayed Jesus, He mercifully responded, “Judas, are you betraying the Son of Man with a kiss?” When soldiers came to arrest Jesus for crimes He did not commit and one of His disciples struck a man with his sword, Jesus healed this man who had come to do Him harm. Jesus followed His own command to turn the other cheek. He gave love to those who were unloving. He gave mercy to those who showed no mercy. Do you seek revenge or do you seek to understand those who do you wrong and help them? Be loving and merciful just as Jesus is loving and merciful.
The best way to be a light for Jesus is to act like Jesus and acting like Jesus requires thinking like Jesus and responding in the most unimaginable ways. Jesus was not like a normal man and neither should we be.
Father God, help us to see other people and the world as you see it. Help us to respond as Jesus would. Help us to be different, so we can honor you with our differences.
Trust Jesus
-
 @ e97aaffa:2ebd765d
2025-04-06 14:06:32
@ e97aaffa:2ebd765d
2025-04-06 14:06:32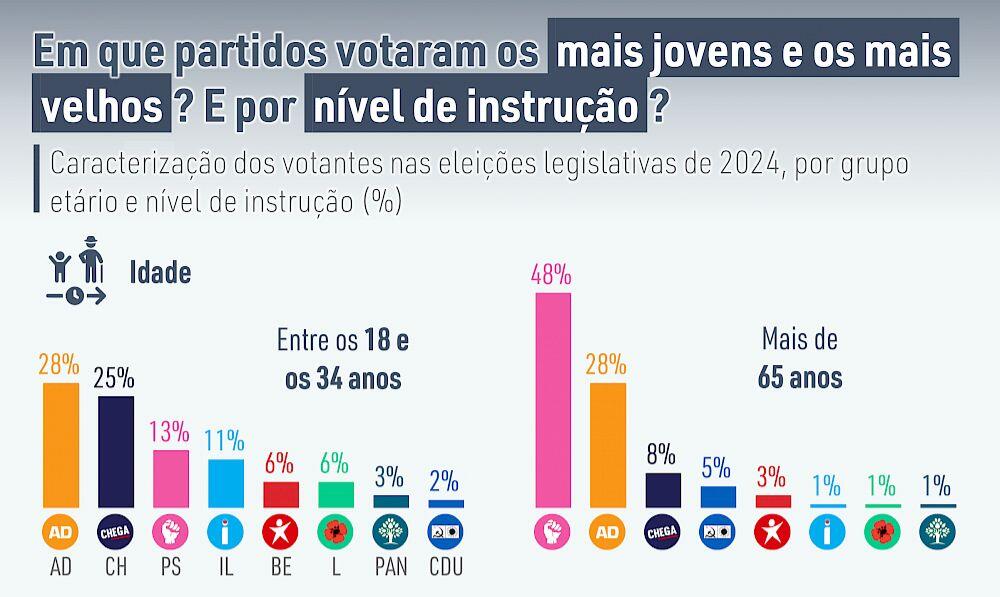
Este estudo é bem representativo da divergência geracional que existe em Portugal, sobretudo em quem foi votar nas legislativas de 2024.
Nos +65 anos, são 65% esquerda e 37% na direita. Mas entre os 18 e 34 anos, são 30% na esquerda e 64% na direita. A esquerda tem menos da metade. Ainda é muito o reflexo da herança do 25 de Abril, muitas pessoas votam em partidos, pelo que fizeram no passado e não pelo que fazem hoje em dia.
A maior discrepância é no PS, com 48% nos +65 anos, para apenas 13% dos mais novos. O Chega está no sentido oposto, 8% para 25%.
Nos “pequeninos”, a situação do PCP era previsível, mas o destaque vai para o Livre e o IL, ambos com 1% nos +65 anos, mas têm um crescimento nos mais jovens, com 6% e 11%, respectivamente.
O PS, nos últimos anos, virou muito para esquerda, afastando-se do centro, mas agora está numa encruzilhada, ou volta mais para o centro, ou poderá acontecer o mesmo que o PCP, tornar-se num partido insignificante, sobretudo com um público de pessoas idosas, sem prespetivas de futuro.
Quem tem +65 anos, quer governos mais de esquerda e os mais novos(18 a 34 anos) preferem um governo de direita. Isto é bem demonstrativo, o porquê dos políticos, de todos quadrantes, apostarem em políticas de aumento de pensões, subsídios, tudo para cativar os mais velhos. Muitas das políticas beneficiam mais os velhos em detrimento dos mais novos, isso provocou uma ruptura geracional, no pensamento político, os jovens demonstram um certo cansaço com as políticas socialistas.
E como Portugal é um país com envelhecimento acentuado e o abstencionismo é menor nos mais velhos, quem cativar esta parcela de pessoas, vencerá as eleições. Segundo o INE, existem 2.2 milhões(22%) com +65 anos e 1.8 milhões (18%) entre os 18 e os 34 anos.
Nível de Instrução
Nos níveis de instrução, as diferenças não são profundas mas existem, mas a direita tem um ligeira preferência pelos mais instruídos. A única excepção é o Chega, que é muito mais forte mas pessoas menos instruídas.
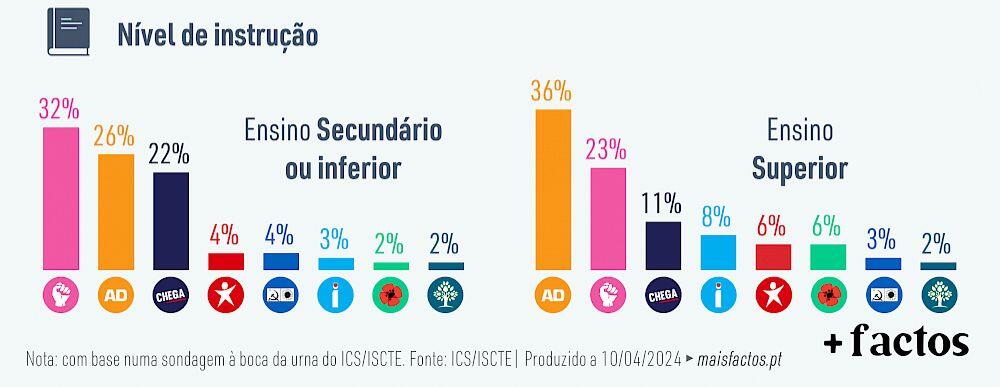
-
 @ 7d33ba57:1b82db35
2025-04-06 09:29:33
@ 7d33ba57:1b82db35
2025-04-06 09:29:33Istanbul is one of the world’s most mesmerizing cities, where East meets West—literally. Straddling Europe and Asia, it offers a rich blend of cultures, centuries-old architecture, vibrant bazaars, and world-class food. From the Byzantine wonders of the Old City to the buzzing energy of modern neighborhoods, Istanbul is a city of contrasts—and it's unforgettable.
🏛️ Top Things to See & Do in Istanbul
1️⃣ Hagia Sophia (Ayasofya)
- Once a church, then a mosque, then a museum—and now a mosque again
- A stunning symbol of Byzantine architecture with a vast domed ceiling
- Open to all visitors (entry to main floor is free)
2️⃣ Blue Mosque (Sultan Ahmed Mosque)
- Famous for its six minarets and beautiful blue Iznik tiles inside
- Still an active mosque—visitors are welcome outside of prayer times
- Dress modestly and bring a scarf if you're visiting as a woman
3️⃣ Topkapi Palace
- Former residence of the Ottoman sultans
- Visit the Imperial Harem, treasury with the Topkapi Dagger, and panoramic gardens overlooking the Bosphorus
4️⃣ Grand Bazaar & Spice Bazaar 🛍️
- One of the largest and oldest covered markets in the world
- Shop for lamps, ceramics, carpets, jewelry, spices, and teas
- Practice your bargaining skills—it’s part of the fun!
5️⃣ Bosphorus Cruise
- Sail between Europe and Asia for incredible views of palaces, mosques, and waterfront mansions
- Options range from 1-hour quick cruises to sunset or dinner cruises
6️⃣ Galata Tower & Karaköy
- Climb the medieval Galata Tower for 360° city views
- Explore Karaköy’s trendy cafés, street art, and boutique shops nearby
7️⃣ Sultanahmet Square & Hippodrome
- Historic heart of Istanbul—once the center of Byzantine Constantinople
- See the Obelisk of Theodosius, Serpent Column, and German Fountain
🍽️ What to Eat in Istanbul
- Simit – Turkish sesame bagel, best fresh in the morning
- Kebabs – From Adana to Iskender, every type has its own flavor
- Meze platters – Tasty small plates to share (like hummus, ezme, dolma)
- Balık Ekmek – Fish sandwich by the Galata Bridge
- Baklava & Turkish delight – Sweet, flaky, and irresistible
- Turkish tea (çay) & strong coffee – Always served with hospitality ☕
🕌 Local Experiences You Shouldn’t Miss
✅ Soak in a historic hammam (Turkish bath) – like Cemberlitas or Hurrem Sultan Hammam
✅ Watch the Whirling Dervishes ceremony for a glimpse into Sufi spirituality
✅ Get lost in Süleymaniye Mosque – peaceful and less crowded than the Blue Mosque
✅ Explore Balat & Fener – colorful, local neighborhoods with rich Jewish and Greek history
✅ Take a ferry to the Asian side (Kadıköy or Üsküdar) for a more local vibe and great food🚇 Getting Around Istanbul
- Use Istanbulkart for all public transport: trams, ferries, metro, and buses
- Traffic can be intense—trams and ferries are your best friend
- The city is very walkable in historical areas, but hilly in places
- Ferries between continents are not just scenic—they’re super efficient too!
💡 Tips for Visiting Istanbul
🕌 Mosques are free to visit, but check prayer times and dress respectfully
📸 Sunset at Galata Bridge or from a rooftop in Karaköy = magic
🛍️ Bargaining is expected in markets, but done with a smile
📅 Best times to visit: April–June or September–October for mild weather
🍽️ Eat like a local – some of the best food is found in tiny family-run spots
-
 @ f3328521:a00ee32a
2025-04-06 08:58:34
@ f3328521:a00ee32a
2025-04-06 08:58:34Notes from the Inaugural Muslim Bitcoin Summit Nostr Workshop.
04.06.25 Dallas, TX
What is Nostr?
“Notes and Other Stuff Transmitted by Relays” ~ fiatjaf
Nostr is an open protocol that is a censorship-resistant, global "social" network. It doesn't rely on any trusted central server (has resilient decentralization), and is based on cryptographic keys and signatures (so it is tamperproof).
The initial description of the idea can be found at https://fiatjaf.com/nostr.html.
Digital Sovereignty
“The first step towards establishing any type of Digital Sovereignty is to consider migration away from infrastructure and networks that are saturated with malevolent surveillance… there must be a simple recognition that anything sustainable from an Islamic perspective cannot be built on the platforms of Meta, Google or Amazon.” ~ Ibn Maghreb
Palestine has become the litmus test for censorship in social media:
- X (formerly Twitter) - Musk openly supports Zionism
- Meta (FB, IG, WhatsApp) - Project Lavender
- Google (YouTube) - Project Nimbus
- Microsoft (LI) - BDS “No Azure for Apartheid” campaign
These are just a few examples of the barrier for a muslim narrative in fiat social media. To build unstoppable resistance we must move away from the platform and address the issue at the protocol level.
Nostr Protocol Explained
- Relays: Backend servers that store and broadcast data. Anyone can run one. Currently over 1k relays across over 50 countries.
- Clients: Platforms built for graphical user interface with Nostr. Anyone can build these and most are interoperable.
- Key Cryptography: User public and private keys.
Simple video explaination: Nostr in less than 10 minutes!
Nostr's Key Features:
- No Ownership - No CEO, board of directors, foundation, etc.
- No Ads, No Big Data Collection - Users are not a product.
- No Algorithms - Less drama, less depressing content.
- Uncensorability - Not your keys, not your posts.
- SEO - clean
dofollowlinks for “Google Juice”. - Zaps! - BTC/Lightning integration.
“This is really really important in the age of AI where in a few years you are not going to know the difference between something that is real and something that is fake. We need technologies that you can actually sign and you have the authenticity to do so, and only you, to do that.” ~ Jack Dorsey
Getting Started On Nostr
Nostr 101: A Beginners Guide To Nostr
Top Recommended Client: Yakihonne
Other popular options: (web) Nostrudel (iOS) Damus (Android) Amethyst
Top Recommended Wallet: Coinos
Other popular options: Primal Wallet AlbyHub Zeus (pending NWC integration)
Highlights From The Nostr Ecosystem:
Other Clients: Olas (photos) Habla (blogging) Zap.Stream (video)
Shopping: Plebeian Market Shopstr
Podcasting 2.0: Fountain Wavlake
Workspace Tools: Listr Formstr Docstr Nostr.Build
Footnote
-
 @ ec9bd746:df11a9d0
2025-04-06 08:06:08
@ ec9bd746:df11a9d0
2025-04-06 08:06:08🌍 Time Window:
🕘 When: Every even week on Sunday at 9:00 PM CET
🗺️ Where: https://cornychat.com/eurocornStart: 21:00 CET (Prague, UTC+1)
End: approx. 02:00 CET (Prague, UTC+1, next day)
Duration: usually 5+ hours.| Region | Local Time Window | Convenience Level | |-----------------------------------------------------|--------------------------------------------|---------------------------------------------------------| | Europe (CET, Prague) 🇨🇿🇩🇪 | 21:00–02:00 CET | ✅ Very Good; evening & night | | East Coast North America (EST) 🇺🇸🇨🇦 | 15:00–20:00 EST | ✅ Very Good; afternoon & early evening | | West Coast North America (PST) 🇺🇸🇨🇦 | 12:00–17:00 PST | ✅ Very Good; midday & afternoon | | Central America (CST) 🇲🇽🇨🇷🇬🇹 | 14:00–19:00 CST | ✅ Very Good; afternoon & evening | | South America West (Peru/Colombia PET/COT) 🇵🇪🇨🇴 | 15:00–20:00 PET/COT | ✅ Very Good; afternoon & evening | | South America East (Brazil/Argentina/Chile, BRT/ART/CLST) 🇧🇷🇦🇷🇨🇱 | 17:00–22:00 BRT/ART/CLST | ✅ Very Good; early evening | | United Kingdom/Ireland (GMT) 🇬🇧🇮🇪 | 20:00–01:00 GMT | ✅ Very Good; evening hours (midnight convenient) | | Eastern Europe (EET) 🇷🇴🇬🇷🇺🇦 | 22:00–03:00 EET | ✅ Good; late evening & early night (slightly late) | | Africa (South Africa, SAST) 🇿🇦 | 22:00–03:00 SAST | ✅ Good; late evening & overnight (late-night common) | | New Zealand (NZDT) 🇳🇿 | 09:00–14:00 NZDT (next day) | ✅ Good; weekday morning & afternoon | | Australia (AEDT, Sydney) 🇦🇺 | 07:00–12:00 AEDT (next day) | ✅ Good; weekday morning to noon | | East Africa (Kenya, EAT) 🇰🇪 | 23:00–04:00 EAT | ⚠️ Slightly late (night hours; late night common) | | Russia (Moscow, MSK) 🇷🇺 | 23:00–04:00 MSK | ⚠️ Slightly late (join at start is fine, very late night) | | Middle East (UAE, GST) 🇦🇪🇴🇲 | 00:00–05:00 GST (next day) | ⚠️ Late night start (midnight & early morning, but shorter attendance plausible)| | Japan/Korea (JST/KST) 🇯🇵🇰🇷 | 05:00–10:00 JST/KST (next day) | ⚠️ Early; convenient joining from ~07:00 onwards possible | | China (Beijing, CST) 🇨🇳 | 04:00–09:00 CST (next day) | ❌ Challenging; very early morning start (better ~07:00 onwards) | | India (IST) 🇮🇳 | 01:30–06:30 IST (next day) | ❌ Very challenging; overnight timing typically difficult|
-
 @ e516ecb8:1be0b167
2025-04-05 23:09:31
@ e516ecb8:1be0b167
2025-04-05 23:09:31En el vasto universo de "Dune", Frank Herbert nos presenta un mundo donde el poder, la religión y la economía se entrelazan de manera fascinante. A primera vista, uno podría pensar que esta saga épica no tiene mucho que ofrecer a los libertarios. Sin embargo, al examinarla a través de la lente de la Escuela Austriaca y el anarcocapitalismo, emergen lecciones valiosas sobre la naturaleza del poder, la importancia del libre mercado y los peligros del intervencionismo estatal.
El Estado y el control de los recursos
En "Dune", el Estado, representado por el Imperio Corrino, ejerce un control férreo sobre el recurso más valioso del universo: la especia melange. Este monopolio estatal sofoca la innovación y el libre intercambio, creando una economía distorsionada y propensa a la corrupción. La lucha por el control de Arrakis, el único planeta donde se produce la especia, es un claro ejemplo de cómo el intervencionismo estatal genera conflictos y guerras.
El mesianismo y el peligro del liderazgo carismático
La figura de Paul Atreides, el mesías Muad'Dib, nos advierte sobre los peligros del liderazgo carismático y el culto a la personalidad. Su ascenso al poder, impulsado por la manipulación religiosa y el miedo, desemboca en una guerra santa que se extiende por el universo, cobrando millones de vidas. Esta tragedia nos recuerda que el poder, incluso cuando se ejerce con las mejores intenciones, tiende a corromper y a generar consecuencias imprevistas.
El libre mercado y la innovación
A pesar del control estatal, en "Dune" también encontramos ejemplos de libre mercado e innovación. Los fremen, habitantes del desierto de Arrakis, han desarrollado una cultura basada en la autosuficiencia y el ingenio, adaptándose a un entorno hostil y creando tecnologías únicas. Su capacidad para sobrevivir y prosperar en un mundo sin Estado es un testimonio del poder del libre mercado y la iniciativa individual.
Lecciones para el anarcocapitalismo
"Dune" nos ofrece valiosas lecciones para el anarcocapitalismo. Nos recuerda que el Estado, incluso en sus formas más benignas, tiende a sofocar la libertad y la prosperidad. Nos advierte sobre los peligros del liderazgo carismático y la importancia de la descentralización del poder. Y nos muestra que el libre mercado y la innovación son esenciales para la supervivencia y el progreso de la humanidad.
En un mundo donde el Estado y el poder centralizado siguen siendo la norma, "Dune" nos invita a imaginar un futuro donde la libertad y la cooperación voluntaria sean los pilares de la sociedad. Un futuro donde, como los fremen en el desierto, podamos construir un mundo mejor sin necesidad de amos ni señores.
-
 @ dbc27e2e:b1dd0b0b
2025-04-05 22:49:04
@ dbc27e2e:b1dd0b0b
2025-04-05 22:49:04Dose:
30g coffee (Fine-medium grind size) 500mL soft or bottled water (97°C / 206.6°F)Instructions:
- Rinse out your filter paper with hot water to remove the papery taste. This will also preheat the brewer.
- Add your grounds carefully to the center of the V60 and then create a well in the middle of the grounds.
- For the bloom, start to gently pour 60mL of water, making sure that all the coffee is wet in this initial phase.
- As soon as you’ve added your water, grab your V60 and begin to swirl in a circular motion. This will ensure the water and coffee are evenly mixed. Let this rest and bloom for up to 45 seconds.
- Pour the rest of the water in in 2 phases. You want to try and get 60% of your total water in, within 30 seconds.
- Pour until you reach 300mL total with a time at 1:15. Here you want to pour with a little agitation, but not so much that you have an uneven extraction.
- Once you hit 60% of your total brew weight, start to pour a little slower and more gently, keeping your V60 cone topped up. Aim to have 100% of your brew weight in within the next 30 seconds.
- Once you get to 500mL, with a spoon give the V60 a small stir in one direction, and then again in the other direction. This will release any grounds stuck to the side of the paper.
- Allow the V60 to drain some more, and then give it one final swirl. This will help keep the bed flat towards the end of the brew, giving you the most even possible extraction.
-
 @ fd208ee8:0fd927c1
2025-04-05 21:51:52
@ fd208ee8:0fd927c1
2025-04-05 21:51:52Markdown: Syntax
Note: This document is itself written using Markdown; you can see the source for it by adding '.text' to the URL.
Overview
Philosophy
Markdown is intended to be as easy-to-read and easy-to-write as is feasible.
Readability, however, is emphasized above all else. A Markdown-formatted document should be publishable as-is, as plain text, without looking like it's been marked up with tags or formatting instructions. While Markdown's syntax has been influenced by several existing text-to-HTML filters -- including Setext, atx, Textile, reStructuredText, Grutatext, and EtText -- the single biggest source of inspiration for Markdown's syntax is the format of plain text email.
Block Elements
Paragraphs and Line Breaks
A paragraph is simply one or more consecutive lines of text, separated by one or more blank lines. (A blank line is any line that looks like a blank line -- a line containing nothing but spaces or tabs is considered blank.) Normal paragraphs should not be indented with spaces or tabs.
The implication of the "one or more consecutive lines of text" rule is that Markdown supports "hard-wrapped" text paragraphs. This differs significantly from most other text-to-HTML formatters (including Movable Type's "Convert Line Breaks" option) which translate every line break character in a paragraph into a
<br />tag.When you do want to insert a
<br />break tag using Markdown, you end a line with two or more spaces, then type return.Headers
Markdown supports two styles of headers, [Setext] [1] and [atx] [2].
Optionally, you may "close" atx-style headers. This is purely cosmetic -- you can use this if you think it looks better. The closing hashes don't even need to match the number of hashes used to open the header. (The number of opening hashes determines the header level.)
Blockquotes
Markdown uses email-style
>characters for blockquoting. If you're familiar with quoting passages of text in an email message, then you know how to create a blockquote in Markdown. It looks best if you hard wrap the text and put a>before every line:This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
Markdown allows you to be lazy and only put the
>before the first line of a hard-wrapped paragraph:This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
Blockquotes can be nested (i.e. a blockquote-in-a-blockquote) by adding additional levels of
>:This is the first level of quoting.
This is nested blockquote.
Back to the first level.
Blockquotes can contain other Markdown elements, including headers, lists, and code blocks:
This is a header.
- This is the first list item.
- This is the second list item.
Here's some example code:
return shell_exec("echo $input | $markdown_script");Any decent text editor should make email-style quoting easy. For example, with BBEdit, you can make a selection and choose Increase Quote Level from the Text menu.
Lists
Markdown supports ordered (numbered) and unordered (bulleted) lists.
Unordered lists use asterisks, pluses, and hyphens -- interchangably -- as list markers:
- Red
- Green
- Blue
is equivalent to:
- Red
- Green
- Blue
and:
- Red
- Green
- Blue
Ordered lists use numbers followed by periods:
- Bird
- McHale
- Parish
It's important to note that the actual numbers you use to mark the list have no effect on the HTML output Markdown produces. The HTML Markdown produces from the above list is:
If you instead wrote the list in Markdown like this:
- Bird
- McHale
- Parish
or even:
- Bird
- McHale
- Parish
you'd get the exact same HTML output. The point is, if you want to, you can use ordinal numbers in your ordered Markdown lists, so that the numbers in your source match the numbers in your published HTML. But if you want to be lazy, you don't have to.
To make lists look nice, you can wrap items with hanging indents:
- Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
- Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
But if you want to be lazy, you don't have to:
- Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
- Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
List items may consist of multiple paragraphs. Each subsequent paragraph in a list item must be indented by either 4 spaces or one tab:
-
This is a list item with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus.
Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus. Donec sit amet nisl. Aliquam semper ipsum sit amet velit.
-
Suspendisse id sem consectetuer libero luctus adipiscing.
It looks nice if you indent every line of the subsequent paragraphs, but here again, Markdown will allow you to be lazy:
-
This is a list item with two paragraphs.
This is the second paragraph in the list item. You're only required to indent the first line. Lorem ipsum dolor sit amet, consectetuer adipiscing elit.
-
Another item in the same list.
To put a blockquote within a list item, the blockquote's
>delimiters need to be indented:-
A list item with a blockquote:
This is a blockquote inside a list item.
To put a code block within a list item, the code block needs to be indented twice -- 8 spaces or two tabs:
- A list item with a code block:
<code goes here>
Code Blocks
Pre-formatted code blocks are used for writing about programming or markup source code. Rather than forming normal paragraphs, the lines of a code block are interpreted literally. Markdown wraps a code block in both
<pre>and<code>tags.To produce a code block in Markdown, simply indent every line of the block by at least 4 spaces or 1 tab.
This is a normal paragraph:
This is a code block.Here is an example of AppleScript:
tell application "Foo" beep end tellA code block continues until it reaches a line that is not indented (or the end of the article).
Within a code block, ampersands (
&) and angle brackets (<and>) are automatically converted into HTML entities. This makes it very easy to include example HTML source code using Markdown -- just paste it and indent it, and Markdown will handle the hassle of encoding the ampersands and angle brackets. For example, this:<div class="footer"> © 2004 Foo Corporation </div>Regular Markdown syntax is not processed within code blocks. E.g., asterisks are just literal asterisks within a code block. This means it's also easy to use Markdown to write about Markdown's own syntax.
tell application "Foo" beep end tellSpan Elements
Links
Markdown supports two style of links: inline and reference.
In both styles, the link text is delimited by [square brackets].
To create an inline link, use a set of regular parentheses immediately after the link text's closing square bracket. Inside the parentheses, put the URL where you want the link to point, along with an optional title for the link, surrounded in quotes. For example:
This is an example inline link.
This link has no title attribute.
Emphasis
Markdown treats asterisks (
*) and underscores (_) as indicators of emphasis. Text wrapped with one*or_will be wrapped with an HTML<em>tag; double*'s or_'s will be wrapped with an HTML<strong>tag. E.g., this input:single asterisks
single underscores
double asterisks
double underscores
Code
To indicate a span of code, wrap it with backtick quotes (
`). Unlike a pre-formatted code block, a code span indicates code within a normal paragraph. For example:Use the
printf()function. -
 @ fd208ee8:0fd927c1
2025-04-05 21:36:33
@ fd208ee8:0fd927c1
2025-04-05 21:36:33Markdown: Syntax
Note: This document is itself written using Markdown; you can see the source for it by adding '.text' to the URL.
Overview
Philosophy
Markdown is intended to be as easy-to-read and easy-to-write as is feasible.
Readability, however, is emphasized above all else. A Markdown-formatted document should be publishable as-is, as plain text, without looking like it's been marked up with tags or formatting instructions. While Markdown's syntax has been influenced by several existing text-to-HTML filters -- including Setext, atx, Textile, reStructuredText, Grutatext, and EtText -- the single biggest source of inspiration for Markdown's syntax is the format of plain text email.
Block Elements
Paragraphs and Line Breaks
A paragraph is simply one or more consecutive lines of text, separated by one or more blank lines. (A blank line is any line that looks like a blank line -- a line containing nothing but spaces or tabs is considered blank.) Normal paragraphs should not be indented with spaces or tabs.
The implication of the "one or more consecutive lines of text" rule is that Markdown supports "hard-wrapped" text paragraphs. This differs significantly from most other text-to-HTML formatters (including Movable Type's "Convert Line Breaks" option) which translate every line break character in a paragraph into a
<br />tag.When you do want to insert a
<br />break tag using Markdown, you end a line with two or more spaces, then type return.Headers
Markdown supports two styles of headers, [Setext] [1] and [atx] [2].
Optionally, you may "close" atx-style headers. This is purely cosmetic -- you can use this if you think it looks better. The closing hashes don't even need to match the number of hashes used to open the header. (The number of opening hashes determines the header level.)
Blockquotes
Markdown uses email-style
>characters for blockquoting. If you're familiar with quoting passages of text in an email message, then you know how to create a blockquote in Markdown. It looks best if you hard wrap the text and put a>before every line:This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
Markdown allows you to be lazy and only put the
>before the first line of a hard-wrapped paragraph:This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
Blockquotes can be nested (i.e. a blockquote-in-a-blockquote) by adding additional levels of
>:This is the first level of quoting.
This is nested blockquote.
Back to the first level.
Blockquotes can contain other Markdown elements, including headers, lists, and code blocks:
This is a header.
- This is the first list item.
- This is the second list item.
Here's some example code:
return shell_exec("echo $input | $markdown_script");Any decent text editor should make email-style quoting easy. For example, with BBEdit, you can make a selection and choose Increase Quote Level from the Text menu.
Lists
Markdown supports ordered (numbered) and unordered (bulleted) lists.
Unordered lists use asterisks, pluses, and hyphens -- interchangably -- as list markers:
- Red
- Green
- Blue
is equivalent to:
- Red
- Green
- Blue
and:
- Red
- Green
- Blue
Ordered lists use numbers followed by periods:
- Bird
- McHale
- Parish
It's important to note that the actual numbers you use to mark the list have no effect on the HTML output Markdown produces. The HTML Markdown produces from the above list is:
If you instead wrote the list in Markdown like this:
- Bird
- McHale
- Parish
or even:
- Bird
- McHale
- Parish
you'd get the exact same HTML output. The point is, if you want to, you can use ordinal numbers in your ordered Markdown lists, so that the numbers in your source match the numbers in your published HTML. But if you want to be lazy, you don't have to.
To make lists look nice, you can wrap items with hanging indents:
- Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
- Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
But if you want to be lazy, you don't have to:
- Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
- Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
List items may consist of multiple paragraphs. Each subsequent paragraph in a list item must be indented by either 4 spaces or one tab:
-
This is a list item with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus.
Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus. Donec sit amet nisl. Aliquam semper ipsum sit amet velit.
-
Suspendisse id sem consectetuer libero luctus adipiscing.
It looks nice if you indent every line of the subsequent paragraphs, but here again, Markdown will allow you to be lazy:
-
This is a list item with two paragraphs.
This is the second paragraph in the list item. You're only required to indent the first line. Lorem ipsum dolor sit amet, consectetuer adipiscing elit.
-
Another item in the same list.
To put a blockquote within a list item, the blockquote's
>delimiters need to be indented:-
A list item with a blockquote:
This is a blockquote inside a list item.
To put a code block within a list item, the code block needs to be indented twice -- 8 spaces or two tabs:
- A list item with a code block:
<code goes here>
Code Blocks
Pre-formatted code blocks are used for writing about programming or markup source code. Rather than forming normal paragraphs, the lines of a code block are interpreted literally. Markdown wraps a code block in both
<pre>and<code>tags.To produce a code block in Markdown, simply indent every line of the block by at least 4 spaces or 1 tab.
This is a normal paragraph:
This is a code block.Here is an example of AppleScript:
tell application "Foo" beep end tellA code block continues until it reaches a line that is not indented (or the end of the article).
Within a code block, ampersands (
&) and angle brackets (<and>) are automatically converted into HTML entities. This makes it very easy to include example HTML source code using Markdown -- just paste it and indent it, and Markdown will handle the hassle of encoding the ampersands and angle brackets. For example, this:<div class="footer"> © 2004 Foo Corporation </div>Regular Markdown syntax is not processed within code blocks. E.g., asterisks are just literal asterisks within a code block. This means it's also easy to use Markdown to write about Markdown's own syntax.
tell application "Foo" beep end tellSpan Elements
Links
Markdown supports two style of links: inline and reference.
In both styles, the link text is delimited by [square brackets].
To create an inline link, use a set of regular parentheses immediately after the link text's closing square bracket. Inside the parentheses, put the URL where you want the link to point, along with an optional title for the link, surrounded in quotes. For example:
This is an example inline link.
This link has no title attribute.
Emphasis
Markdown treats asterisks (
*) and underscores (_) as indicators of emphasis. Text wrapped with one*or_will be wrapped with an HTML<em>tag; double*'s or_'s will be wrapped with an HTML<strong>tag. E.g., this input:single asterisks
single underscores
double asterisks
double underscores
Code
To indicate a span of code, wrap it with backtick quotes (
`). Unlike a pre-formatted code block, a code span indicates code within a normal paragraph. For example:Use the
printf()function. -
 @ e372d24b:e25df41f
2025-04-05 18:11:15
@ e372d24b:e25df41f
2025-04-05 18:11:15Unlocking Learning Potential: Why Student's Ideas Matter
Introduction
Recent research in mathematics education emphasizes the importance of valuing and building upon students' initial ideas and intuitive understanding. This approach, often referred to as "taking students' ideas seriously," has enhanced conceptual understanding, problem-solving skills, and overall mathematical achievement. This overview examines this approach's theoretical foundations, cognitive processes, and practical implications in mathematics classrooms.

FREE DOWNLOAD - Questions and Prompts
Theoretical Foundations
Taking students' ideas seriously is grounded in constructivist learning theory and research on how students develop mathematical understanding. Hiebert and Carpenter (1992) argue that "if children possessed internal networks constructed both in and out of school and if they recognized the connections between them, their understanding and performance in both settings would improve." This highlights the importance of connecting students' informal knowledge with formal mathematical concepts. Carpenter's work further emphasizes the value of students' intuitive knowledge: "Children come to school with a great deal of informal or intuitive knowledge of mathematics that can serve as the basis for developing much of the formal mathematics of the primary school curriculum." This suggests that taking students' initial ideas seriously can provide a strong foundation for developing a more sophisticated mathematical understanding.
Cognitive Processes
When students' ideas are taken seriously in mathematics classrooms, several cognitive processes are engaged:
-
Schema Formation: As students articulate and refine their ideas, they develop and modify mental frameworks or schemas that organize mathematical concepts.
-
Metacognition: Explaining their thinking engages students' metacognitive processes, promoting reflection on their own understanding and problem-solving strategies.
-
Elaborative Rehearsal: Verbalizing mathematical concepts helps move information from working memory to long-term memory, enhancing retention.
-
Cognitive Conflict: When students encounter differing viewpoints, it can create cognitive conflict, stimulating the reconciliation of new information with existing schemas.
Practical Implications
Eliciting and Valuing Student Ideas
Carpenter and Lehrer argue that for learning with understanding to occur, instruction needs to provide specific opportunities: "For learning with understanding to occur, instruction needs to provide students the opportunity to develop productive relationships, extend and apply their knowledge, reflect about their experiences, articulate what they know, and make knowledge their own." This emphasizes the need for instructional approaches that actively elicit and value student ideas.
Creating a Supportive Environment
To effectively take students' ideas seriously, teachers must foster a classroom environment where all contributions are respected. This involves:
-
Provide adequate thinking time for students to formulate their thoughts.
-
Using open-ended questions that encourage diverse thinking and approaches.
-
Implementing collaborative strategies like think-pair-share to build confidence in sharing ideas.
Connecting to Formal Mathematics
Hiebert advocates for teaching practices that promote understanding by focusing on "the inherent structure of the emerging mathematical ideas and addressing students' misconceptions as they arise" . This involves helping students connect their informal ideas to more formal mathematical concepts and procedures.
Impact on Student Learning
Research indicates that taking students' ideas seriously can significantly improve mathematical understanding and achievement. A study by Carpenter et al. (1998) found that when teachers based their instruction on students' thinking, students demonstrated greater problem-solving skills and conceptual understanding compared to control groups. Moreover, this approach has increased student engagement and motivation in mathematics. When students feel their ideas are valued, they are more likely to participate actively in mathematical discussions and take intellectual risks.
Challenges and Considerations
While the benefits of taking students' ideas seriously are well-documented, implementing this approach can present challenges:
-
Time Constraints: Allowing for extended student discussions and idea exploration can be time-consuming within the constraints of a typical school schedule.
-
Teacher Preparation: Effectively building on student ideas requires strong content knowledge and pedagogical skills from teachers.
-
Assessment Alignment: Traditional assessment methods may not adequately capture the depth of understanding developed through this approach, necessitating new forms of evaluation.
Conclusion
Taking students' ideas seriously in mathematics education represents a powerful approach to fostering deep conceptual understanding and problem-solving skills. By valuing students' initial thoughts and building upon their intuitive knowledge, educators can create more engaging and effective learning environments. While challenges exist in implementation, the potential benefits for student learning and mathematical achievement make this approach worthy of serious consideration and further research.
References
Ball, D. L., Thames, M. H., & Phelps, G. (2008). Content knowledge for teaching: What makes it special? Journal of Teacher Education, 59(5), 389-407.
Boaler, J. (2002). Experiencing school mathematics: Traditional and reform approaches to teaching and their impact on student learning. Routledge.
Boaler, J., & Brodie, K. (2004). The importance, nature and impact of teacher questions. In D. E. McDougall & J. A. Ross (Eds.), Proceedings of the 26th annual meeting of the North American Chapter of the International Group for the Psychology of Mathematics Education (Vol. 2, pp. 773-782). Toronto: OISE/UT. Carpenter, T. P., Fennema, E., & Franke, M. L. (1996). Cognitively guided instruction: A knowledge base for reform in primary mathematics instruction. The Elementary School Journal, 97(1), 3-20.
Carpenter, T. P., Fennema, E., Franke, M. L., Levi, L., & Empson, S. B. (1999). Children's mathematics: Cognitively guided instruction. Portsmouth, NH: Heinemann.
Carpenter, T. P., & Lehrer, R. (1999). Teaching and learning mathematics with understanding. In E. Fennema & T. A. Romberg (Eds.), Mathematics classrooms that promote understanding (pp. 19-32). Mahwah, NJ: Lawrence Erlbaum Associates.
Craik, F. I., & Lockhart, R. S. (1972). Levels of processing: A framework for memory research. Journal of Verbal Learning and Verbal Behavior, 11(6), 671-684.
Driscoll, M. P. (2005). Psychology of learning for instruction (3rd ed.). Boston: Allyn and Bacon.
Flavell, J. H. (1979). Metacognition and cognitive monitoring: A new area of cognitive-developmental inquiry. American Psychologist, 34(10), 906-911.
Hiebert, J., & Carpenter, T. P. (1992). Learning and teaching with understanding. In D. A. Grouws (Ed.), Handbook of research on mathematics teaching and learning (pp. 65-97). New York: Macmillan.
Hiebert, J., Carpenter, T. P., Fennema, E., Fuson, K. C., Wearne, D., Murray, H., ... & Human, P. (1997). Making sense: Teaching and learning mathematics with understanding. Portsmouth, NH: Heinemann.
Lyman, F. (1981). The responsive classroom discussion: The inclusion of all students. In A. S. Anderson (Ed.), Mainstreaming Digest (pp. 109-113). College Park: University of Maryland Press.
Piaget, J. (1952). The origins of intelligence in children. New York: International Universities Press.
Rowe, M. B. (1986). Wait time: Slowing down may be a way of speeding up! Journal of Teacher Education, 37(1), 43- 50.
Shepard, L. A. (2000). The role of assessment in a learning culture. Educational Researcher, 29(7), 4-14.
Smith, M. S., & Stein, M. K. (2011). 5 practices for orchestrating productive mathematics discussions. Reston, VA: National Council of Teachers of Mathematics.
Social Media.
Research in mathematics education highlights the significance of taking students' ideas seriously, demonstrating how this approach enhances conceptual understanding, problem-solving abilities, and overall mathematical achievement. Rooted in constructivist learning theory, this method engages crucial cognitive processes like schema formation, metacognition, and elaborative rehearsal. By connecting students’ informal knowledge with formal mathematical concepts, educators can establish a robust foundation for advanced mathematical thinking. Studies show that when instruction is based on students' thinking, learners exhibit superior problem-solving skills and a deeper conceptual grasp than traditional teaching methods.
Join us in exploring these powerful teaching approaches and their impact on mathematical thinking and achievement!
-
-
 @ 21c9f12c:75695e59
2025-04-05 18:11:02
@ 21c9f12c:75695e59
2025-04-05 18:11:02Details
- 🍳 Cook time: 1 hour and 15 minutes
Ingredients
- 1 cup dried red lentils
- (2) 25-ounce jars marinara sauce
- 1 cup raw cashews
- 14.5 ounce firm tofu (patted dry)
- ½ cup nutritional yeast
- 3 tablespoons fresh lemon juice (from about 2 lemons)
- 1 teaspoon salt
- 1 teaspoon dried basil
- 1 teaspoon oregano
- ½ teaspoon garlic powder
- 3 cups baby spinach
- 1 box lasagna noodles (about 12 noodles) (regular, gluten free or whole grain)
- Double recipe Easy Vegan Mozzarella Cheese (or 2-3 cups shredded vegan mozzarella)
Directions
- lentilsCook the red lentils . Add 1 cup dried red lentils and 3 cups of water to a medium pot. Bring to a boil, and then simmer for about 20 minutes. Drain the lentils in a fine strainer, and then add back to the pot and stir in the marinara sauce . Set aside.
- ovenPreheat the oven to 350 degrees .
- Make the Cashew-Tofu Ricotta: Add the cashews to a food processor and process until fine and crumbly. Then add the tofu in chunks, nutritional yeast , lemon juice , salt , basil , oregano and garlic powder to the food processor. Pulse until well combined and pretty smooth. If it's too thick, add a few tablespoons of water to blend. Set aside.
- LasagnaAssembling the lasagna: Add about 1 cup of lentil marinara to the bottom of a large 9x13 inch casserole dish. Spread it around evenly. Next add 4-5 lasagna noodles (uncooked). Spread half of the ricotta on top of the noodles . Top with half of the spinach . Add about 1 cup of the marinara sauce over the spinach , then place 4-5 lasagna noodles on top. Spread the rest of the ricotta over the noodles , then the rest of the spinach . Place 4-5 more noodles on top of the spinach , and then pour the rest of the sauce over the top, evenly.
- LasagnaCover tightly with foil and bake for 40 minutes.
- MozzarellaWhile the lasagna is cooking, make your Vegan Mozzarella Cheese , if using. Alternatively, use 2-3 cups store bought vegan mozzarella cheese .
- LasagnaAfter 40 minutes, remove the foil and spoon on the mozzarella (or sprinkle the cheese all over). Place the lasagna back in the oven and bake for 20 more minutes, uncovered. Remove from oven, let cool for at least 15 minutes and serve.
-
 @ c066aac5:6a41a034
2025-04-05 16:58:58
@ c066aac5:6a41a034
2025-04-05 16:58:58I’m drawn to extremities in art. The louder, the bolder, the more outrageous, the better. Bold art takes me out of the mundane into a whole new world where anything and everything is possible. Having grown up in the safety of the suburban midwest, I was a bit of a rebellious soul in search of the satiation that only came from the consumption of the outrageous. My inclination to find bold art draws me to NOSTR, because I believe NOSTR can be the place where the next generation of artistic pioneers go to express themselves. I also believe that as much as we are able, were should invite them to come create here.
My Background: A Small Side Story
My father was a professional gamer in the 80s, back when there was no money or glory in the avocation. He did get a bit of spotlight though after the fact: in the mid 2000’s there were a few parties making documentaries about that era of gaming as well as current arcade events (namely 2007’sChasing GhostsandThe King of Kong: A Fistful of Quarters). As a result of these documentaries, there was a revival in the arcade gaming scene. My family attended events related to the documentaries or arcade gaming and I became exposed to a lot of things I wouldn’t have been able to find. The producer ofThe King of Kong: A Fistful of Quarters had previously made a documentary calledNew York Dollwhich was centered around the life of bassist Arthur Kane. My 12 year old mind was blown: The New York Dolls were a glam-punk sensation dressed in drag. The music was from another planet. Johnny Thunders’ guitar playing was like Chuck Berry with more distortion and less filter. Later on I got to meet the Galaga record holder at the time, Phil Day, in Ottumwa Iowa. Phil is an Australian man of high intellect and good taste. He exposed me to great creators such as Nick Cave & The Bad Seeds, Shakespeare, Lou Reed, artists who created things that I had previously found inconceivable.
I believe this time period informed my current tastes and interests, but regrettably I think it also put coals on the fire of rebellion within. I stopped taking my parents and siblings seriously, the Christian faith of my family (which I now hold dearly to) seemed like a mundane sham, and I felt I couldn’t fit in with most people because of my avant-garde tastes. So I write this with the caveat that there should be a way to encourage these tastes in children without letting them walk down the wrong path. There is nothing inherently wrong with bold art, but I’d advise parents to carefully find ways to cultivate their children’s tastes without completely shutting them down and pushing them away as a result. My parents were very loving and patient during this time; I thank God for that.
With that out of the way, lets dive in to some bold artists:
Nicolas Cage: Actor
There is an excellent video by Wisecrack on Nicolas Cage that explains him better than I will, which I will linkhere. Nicolas Cage rejects the idea that good acting is tied to mere realism; all of his larger than life acting decisions are deliberate choices. When that clicked for me, I immediately realized the man is a genius. He borrows from Kabuki and German Expressionism, art forms that rely on exaggeration to get the message across. He has even created his own acting style, which he calls Nouveau Shamanic. He augments his imagination to go from acting to being. Rather than using the old hat of method acting, he transports himself to a new world mentally. The projects he chooses to partake in are based on his own interests or what he considers would be a challenge (making a bad script good for example). Thus it doesn’t matter how the end result comes out; he has already achieved his goal as an artist. Because of this and because certain directors don’t know how to use his talents, he has a noticeable amount of duds in his filmography. Dig around the duds, you’ll find some pure gold. I’d personally recommend the filmsPig, Joe, Renfield, and his Christmas film The Family Man.
Nick Cave: Songwriter
What a wild career this man has had! From the apocalyptic mayhem of his band The Birthday Party to the pensive atmosphere of his albumGhosteen, it seems like Nick Cave has tried everything. I think his secret sauce is that he’s always working. He maintains an excellent newsletter calledThe Red Hand Files, he has written screenplays such asLawless, he has written books, he has made great film scores such asThe Assassination of Jesse James by the Coward Robert Ford, the man is religiously prolific. I believe that one of the reasons he is prolific is that he’s not afraid to experiment. If he has an idea, he follows it through to completion. From the albumMurder Ballads(which is comprised of what the title suggests) to his rejected sequel toGladiator(Gladiator: Christ Killer), he doesn’t seem to be afraid to take anything on. This has led to some over the top works as well as some deeply personal works. Albums likeSkeleton TreeandGhosteenwere journeys through the grief of his son’s death. The Boatman’s Callis arguably a better break-up album than anything Taylor Swift has put out. He’s not afraid to be outrageous, he’s not afraid to offend, but most importantly he’s not afraid to be himself. Works I’d recommend include The Birthday Party’sLive 1981-82, Nick Cave & The Bad Seeds’The Boatman’s Call, and the filmLawless.
Jim Jarmusch: Director
I consider Jim’s films to be bold almost in an ironic sense: his works are bold in that they are, for the most part, anti-sensational. He has a rule that if his screenplays are criticized for a lack of action, he makes them even less eventful. Even with sensational settings his films feel very close to reality, and they demonstrate the beauty of everyday life. That's what is bold about his art to me: making the sensational grounded in reality while making everyday reality all the more special. Ghost Dog: The Way of the Samurai is about a modern-day African-American hitman who strictly follows the rules of the ancient Samurai, yet one can resonate with the humanity of a seemingly absurd character. Only Lovers Left Aliveis a vampire love story, but in the middle of a vampire romance one can see their their own relationships in a new deeply human light. Jim’s work reminds me that art reflects life, and that there is sacred beauty in seemingly mundane everyday life. I personally recommend his filmsPaterson,Down by Law, andCoffee and Cigarettes.
NOSTR: We Need Bold Art
NOSTR is in my opinion a path to a better future. In a world creeping slowly towards everything apps, I hope that the protocol where the individual owns their data wins over everything else. I love freedom and sovereignty. If NOSTR is going to win the race of everything apps, we need more than Bitcoin content. We need more than shirtless bros paying for bananas in foreign countries and exercising with girls who have seductive accents. Common people cannot see themselves in such a world. NOSTR needs to catch the attention of everyday people. I don’t believe that this can be accomplished merely by introducing more broadly relevant content; people are searching for content that speaks to them. I believe that NOSTR can and should attract artists of all kinds because NOSTR is one of the few places on the internet where artists can express themselves fearlessly. Getting zaps from NOSTR’s value-for-value ecosystem has far less friction than crowdfunding a creative project or pitching investors that will irreversibly modify an artist’s vision. Having a place where one can post their works without fear of censorship should be extremely enticing. Having a place where one can connect with fellow humans directly as opposed to a sea of bots should seem like the obvious solution. If NOSTR can become a safe haven for artists to express themselves and spread their work, I believe that everyday people will follow. The banker whose stressful job weighs on them will suddenly find joy with an original meme made by a great visual comedian. The programmer for a healthcare company who is drowning in hopeless mundanity could suddenly find a new lust for life by hearing the song of a musician who isn’t afraid to crowdfund their their next project by putting their lighting address on the streets of the internet. The excel guru who loves independent film may find that NOSTR is the best way to support non corporate movies. My closing statement: continue to encourage the artists in your life as I’m sure you have been, but while you’re at it give them the purple pill. You may very well be a part of building a better future.
-
 @ 8bad797a:8461b4bc
2025-04-05 14:49:13
@ 8bad797a:8461b4bc
2025-04-05 14:49:13Frank Palmer Purcell
I claim to be a Catholic American; even though I now follow the Russian Orthodox tradition, I do so in a small sui juris Church in communion with Rome, not Constantinople. When I was a little kid, knee high to a trilobite, some folks still had a problem with that, with being Catholic and American, I mean; Orthodoxy was beyond our horizon. My mother was one of those who had the problem. As long as I was a Catholic like my father (and her own mother, as a little girl in Ireland and on the lower East Side), I couldn't be a real American like her father, a bookbinder replaced by a machine, disowned by his family for marrying out of caste, who spent his days in the nearest tavern. "Pop" Palmer died at 78, and four years later I was born and named for him, or at least that was my mother's intention. The priest baptized me in Latin, as was the custom in those dark days, and pronounced "Frank" so that it sounded like the nickname ("Frenchy") of a (doubtless) dirty medieval Italian beggar baptized Giovanni.
My early spirituality, to use a ten dollar word for a fifty cent thing, was more American than Franciscan. Emerson and Thoreau, Melville and Whitman spoke and still speak to me as no European voice can, and when I came to study philosophy in a serious way I found the Americans, Josiah Royce, Rufus Jones and Ernest Hocking, C. I. (not C. S.) Lewis and Brand (not Paul) Blanshard, speaking a language that was my own, though by then the professoriate resonated to other tonalities. Though I fell in love with Schopenhauer and Kierkegaard, as every teenager who meets them must, and inhaled the sweet incense and felt the calming breeze of the shrines of the East, as my generation did, and was introduced to the mysteries of Thomas Aquinas by the subtle writings of Jacques Maritain, as we should all be, when I came to take hold of the great tradition of Western theology in a personal way, I found the distinctly American perspectives of Paul Tillich and Richard (not Reinhold) Niebuhr most helpful.
Back in 1963, in the New Jersey family television room, Joseph Campbell's urbane mythological sermons on Channel 13 (still a Newark station) touched something deep inside me an hour after Bishop Sheen's passionate exhortations on Channel 5 had left me (perhaps deplorably) cold. I would go up to my room and say my prayers after a fashion in time for the nightly racetrack bugle and exhilarating nostalgia of Arthur Fiedler's performance of the Bahnfrei Polka of Edouard Strauss, which introduced the nightly raconteurship of the incomparable Jean Shepherd, and, if I were still awake, the more outre world of Long John Nebel and his, ah, eccentric guests. You can't get more American than that. Or more New Jersey.
As the child of a mixed marriage and a pupil of the public schools I was not warmly welcome in the Catholic ghetto. Still, in those years of the civil rights revolution and the Vietnam War, with the polarized positions of right and left equally abstract and inhumane, I found my take on national affairs reflecting the distinctly Catholic perspectives of Dorothy Day and Thomas Merton on the one hand and Frederick Wilhelmsen and Erik Maria, Ritter von Kuehnelt-Leddihn on the other. And, though the writings of Rufus Jones, to which I even now frequently turn for inspiration, had led me to seek out a Quaker education, I found it was the Catholic scholars and pioneers of the spirit who were beginning the interreligious dialogue which was then and is now one of the pressing needs of humanity. In graduate school I became a devoted Americanist, that is, a scholar dedicated to using the tools of the historian of ideas to get some sense of what this place is all about, this gallimaufry of peoples who have somehow, in spite of all learned and astute prognostications, made themselves and each other into a kind of unity, a unity which it may take someone like the present [at the time of writing] Pope (and there isn't really anyone else very much like him) to discern.
I do not speak of Joseph Ratzinger, Benedict XVI, as a theologian nor even as a philosopher, but I must note that in New York and Washington in 2008 he revealed himself as an historian of ideas of astonishing and exquisite discernment. By this I mean, among other things, of course, that he strongly confirmed the discoveries and intimations of my own forty years of brooding in and on America. I was fortunate indeed to turn up at Columbia University's Teachers College when Douglas Sloan was putting the finishing touches on his groundbreaking study of the Scottish Enlightenment as the great inspiration of the American colonists, especially the intellectual elite, in the age of the War of Independence. Sloan's insights would eventually be popularized, without their scholarly context and qualifications, in Garry Wills' bestselling Inventing America, and it is now taken for granted that our Founding Father Across the Sea was not John Locke, but the Ulster Scot Francis Hutcheson (1694-1746).
Indeed, the Evangelical position seems to be that it was Hutcheson who corrupted American civilization at the root, turning us from the Calvinist faith once delivered to Jonathan Edwards (himself a notorious Lockean, but never mind). In fact, Oxford University Press recently published a six hundred page tract to that effect, authored at Wheaton. Hutcheson, and the Scottish school of Common Sense which he inspired, held that all human beings, Pagan and Christian, Protestant and Catholic, share a basic ability to come to an understanding of certain fundamental truths, and can come to agreement upon these with the aid of reason. Calvinism, especially the neoCalvinism which is the unquestioned (because unquestionable) paradigm of the Evangelical academy, holds that the elect have a unique and divinely sanctioned "world view" which stands in judgment of all others in all particulars. To these zealots the very idea that there can be any common human ground between believers and unbelievers is itself a damnable heresy. Still, it is the damnable heresy on which American society and civilization are built, and the Calvinism which so despises it is a near kin of those varieties of Islam that Benedict so boldly challenged at Regensburg in 2006.
When the same Benedict addressed the United Nations a year and a half later, he pointed out how the principles of that august body, and the Universal Declaration of Human Rights whose anniversary he was commemorating, grew out of the Natural Law philosophy of CounterReformation Scholasticism, particularly as formulated by Francisco de Vitoria (1492?–1546). Needless to say, the "Scottish Philosophy" of a later age grew out of this tradition as well, and many of the American founders were directly familiar with Natural Law theory as expounded by Catholic and Protestant Scholastics. On the same visit Benedict made ample use of the language of sacred architecture, as if in conscious homage to the fact that he was honoring a country founded by Freemasons, who used that language to teach the conformity of right living to the law of nature and nature's God. If he was giving a Catholic interpretation to this symbolism, so did the Catholic Jacobites who were prominent in the Craft before the Masonic movement became identified with indifferentism, anticlericalism, and finally (at least on the Continent) atheism. It was striking indeed that to one steeped in American tradition it was the Pope of Rome of all people who was speaking our own language in a familiar tone, and the neoCalvinist Evangelicals who jibbered and muttered in an outlandish and menacing jargon more Muslim than Christian. I sure wonder what Mommy would think.
Natural Law. What is that to us today; what was it to me in what we call the Vietnam era? In 2008 the issue was torture, and a President of the United States who took pleasure in his presumed power to order it, to physically degrade his enemies, to morally degrade our own soldiers. I am proud that when Mr. Bush asked our military for advice on the subject, they replied that he has no such power, that such actions are contrary to our laws and the traditions of our armed services, and, moreover, ineffectual. (The latter point is an important indication that powerful men order torture not to accomplish anything, but to pleasure themselves.) And I am ashamed that he chose to take the advice of Israeli advisors, who hold to another morality, one going back to ancient Assyria, and profoundly alien to our own Christian civilization.
In my youth the overriding issue was not torture, but terrorism. Not that torture didn't take place. At graduate school I knew a former naval officer who had interrogated captured Viet Minh and Viet Cong; the "extraordinary means" had been applied by our allies by the time he was introduced to his prisoners, and the specialists who had softened them up had already moved on or backed off. The issues before us then were atrocious acts of war against civilian populations in North and South Vietnam, in Laos and Cambodia, in Central and South America, even in Germany and Japan a generation before, not to mention the subversion and corruption of constitutional government in America by a regime that felt justified in using any means necessary to keep power away from the Communists and their sympathizers, the Democrats and liberal Republicans.
Nor was such evil a monopoly of the socalled right. A young antiwar activist formerly associated with Martin Luther King even went so far as to criticize the sainted Che Guevara for not being enough of a terrorist to tear the peasantry away from their conformity to a "fascist" state. (Two generations later the man was advising George Bush.) In my undergraduate days I had been a loyal member of the conservative movement, back when the Intercollegiate Studies Institute was still called the Intercollegiate Society of Individualists, some members of the Students for a Democratic Society still honored democracy, and Murray Rothbard and Carl Ogelsby were moving "beyond left and right." If I got nothing more from the conservatives, and in fact I got a great deal more, it was an ever deepening admiration for Edmund Burke. Burke was prized by the cold warriors because his Letters on a Regicide Peace could be used to justify a war of extermination against the Soviet Union, the Peoples Republic of China, and any other people so temerarious as not join the alliance against these forces of absolute evil and subordinate their interests to those of the United States. A superficial reading, I need hardly remark. But Burke was not only the acute critic of the French Revolution who predicted the Terror from its earliest signs, he also was a tireless advocate for Irish freedom, particularly freedom of conscience, and a loyal ally of the American colonies in Parliament. But Burke's finest hour came at the end of his long career, when he boldly fought against the depredations of Warren Hastings and the British East India Company. Anyone who wants to know what natural law meant to the men of the Eighteenth Century, including those who liberated the American colonies and forged their political constitution can get a good sense of it from the eighth day (!) of his impeachment of Hastings before the House of Lords, which, I warn you, I have quoted before and shall no doubt quote again:
No man can lawfully govern himself according to his own will—much less can one person be governed by the will of another. We are all born in subjection—all born equally, high and low, governors and governed, in subjection to one great, immutable, preexistent law, prior to all our devices, and prior to all our contrivances, paramount to all our ideas and to all our sensations, antecedent to our very existence, by which we are knit and connected in the eternal frame of the universe, out of which we can not stir. This great law does not arise from our conventions or compacts; on the contrary, it gives to our conventions and compacts all the force and sanction they can have: it does not arise from our vain institutions. Every good gift is of God, all power is of God; and He who has given the power, and from whom alone it originates, will never suffer the exercise of it to be practised upon any less solid foundation than the power itself. If, then, all dominion of man over man is the effect of the divine disposition, it is bound by the eternal laws of Him that gave it, with which no human authority can dispense; neither he that exercises it, nor even those who are subject to it; and, if they were mad enough to make an express compact, that should release their magistrate from 5 his duty, and should declare their lives, liberties and properties, dependent upon, not rules and laws, but his mere capricious will, that covenant would be void. This arbitrary power is not to be had by conquest. Nor can any sovereign have it by succession; for no man can succeed to fraud, rapine, and violence. Those who give and those who receive arbitrary power are alike criminal; and there is no man but is bound to resist it to the best of his power, wherever it shall show its face to the world.
Mr. Jefferson couldn't have put it better. Human rights are inalienable -- you can't give them away, and when they are taken away there is not only the right of rebellion, but the solemn duty to resist. The difficulty of natural law theory, of course, is in the details. Back in '68 Pope Paul VI had announced that artificial contraception was against the natural law, but this decision did not immediately commend itself to the common sense of many of those who were not subject to his religious authority. I don't mean he was wrong, or that he exceeded his authority, or even that his decision was inopportune. But when the Supreme Court, alarmed by the birthrate of blacks and an end to white domination of the nation and the world, soon mandated abortion on demand, it was all too easy to dismiss arguments in favor of the human being of the embryonic human as religious dogma rather than an honest attempt to think things through. Since then the concept of natural law is often dismissed by feminists and homosexualists (to use Mr. Vidal's eloquent term) as a mere excuse for oppression. It does seem to me, however, that the insistent denial of the very idea of human rights does nothing to advance the liberation of humanity or any part of it. But maybe that's just me.
In any case, I don't think America was ever anything like the sort of Catholic nation that, say, Portugal was under the late Dr. Salazar, or is very likely to get there any time soon, despite the best wishes and even efforts of some of my friends. I do think that for a good part of our history a great many people in public life would have said that the words of Burke I have quoted express their most basic political convictions and sentiments as well as anyone ever could, and this puts America right at the center of the great tradition of Western civilization. And this was true long after old Europe had gone down other ways, the ways of the French revolution, the reaction against it, and the nationalism that synthesized the worst of both. To be sure, we have had nationalists here, and have them today, and have preached our crusades to end slavery, make the world safe for democracy, eradicate the evil empire of the moment, but there is, if not always a ringing and uncontested affirmation of civilized values, by which I mean the values of our civilization, at least a powerful nostalgia for them, and a sincere wish that one could believe in them with a good conscience, a good conscience which postmodernist deconstructionism denies us. A good conscience which Joseph Ratzinger Benedict XVI, who has suffered modernity as few of us have and thought more deeply about it, was offering us back.
To be perfectly frank, it took the Catholic Church a good long time to recognize the Christian virtues of Enlightenment, even the Scottish one, and Revolution, even the American one. Better late than never. And despite the mantric invocation of John Courtney Murray, the Church in America has not always been on the side of the angels. The theology of the American Church has always been Jansenist, not Catholic, combining the worst of Pelagius and Calvin, making Boston Irish the kissing cousins of Cotton Mather. The American Church never permitted itself to be organized according to canon law because this would limit the despotism of prelates. The American Church refused to acknowledge the priesthood of Eastern Catholics ordained as married men, driving the Catholic Ruthenians into communion with the Patriarch of Moscow (the present Orthodox Church in America), and later blackmailing a bankrupt papacy into forbidding married priests throughout the Western hemisphere, driving a second group of Ruthenians into communion with the Ecumenical Patriarch of Constantinople (the present American CarpathoRussian Orthodox Diocese).
They American Cathholic Church wouldn't even allow American women to become real nuns, or foreign nuns to come to America without renouncing their vows. The vast majority of Catholic women called nuns are nothing of the sort, but religious sisters first organized as cheap labor at the beck and call of the clergy, and now loose cannons like the Papessas Mother Angelica and Sister Joan. Yes, one or two real abbeys for women were founded in the last century, but the American Church continues to hold the contemplative life in deepest contempt, even for women. Women religious lead the crusade against contemplative traditions, and now rail against the Church as an organ of worldly power from which they are unjustly excluded.
Deprived of traditional spiritual direction, a lamentable number of priests "demythologized" the Faith while looking to worldly culture for a way of salvation. Many found it in the gospel of orgasm, and undertook to liberate the young men in their care by sharing the only joy they thought worth having, with results we see today.
Catholic involvement in American public life has not been edifying either. The American bishops turned their backs on Benedict XV's attempt to end the slaughter in the trenches and refused to make any move to bring Woodrow Wilson over to the side of peace. As patriotic Americans, they in effect signed on to the WASP jihad to extirpate the Catholic powers of the Old World. A couple of generations later millions of Catholic schoolchildren were forced to write letters demanding that the Senate not censure that great American Joseph McCarthy, who was probably the Soviet Union's most valuable (presumably unwitting) asset in American public life, who had discredited all responsible criticism of Communism and its supporters by viciously slandering the United States Army, the Department of State, and the Protestant clergy as nests of traitors. Some years later Catholic activists succeeded in driving the voices of moderation out of the Republican Party, and the urban ethnic social conservatives out of the Democratic, and the forms of civility from the public square.
Americans can be forgiven for not rushing to enlist in the nearest Roman Catholic parish. There are other conversions needed, perhaps beginning with American Catholics themselves. Back in the days of Reagan a fellow named Alan Bloom made an almost persuasive case that the American Mind was closed to the Great Tradition of Western Civilization, and needed to be reopened. Alas, Bloom was a Neoconservative, a follower of their guru Leo Strauss, and a teacher of a a number of shady operatives of the Program for the New American Century type, as Saul Bellow's last novel so amusingly portrays him. Bloom's Great Tradition was something cobbled together by Machiavelli and others out of the misunderstood shards of ancient paganism; thinkers and writers tainted by the Christian gospel remained under embargo. (Mortimer Adler was less fearful, more intellectually curious, but look where he ended up.) It took a Bavarian Pope to remind us that the basic principles of our cherished hopes of international organization and human rights, and indeed of the American founding itself, go back to the Iberian scholastics of the Catholic Reformation. ("CounterReformation" is misleadingly negative.)
Benedict's reminder harmonized well with my own studies in the history of philosophy. I began some five decades ago with the riddle, the riddles, of Charles Sanders Peirce (1839 - 1914), our own and only philosopher to be ranked with the likes of Aristotle and Kant. What was this Common Sense he went on and on about? (The Scottish Philosophy was studiously ignored in the academy; it still is.) As I said, I was lucky to find out. Now John Deely has been showing that any postmodern philosophy worthy of the name, one founded on semeiology rather than Cartesian (or empiricist) methodologism, needs to go back to Peirce and with Peirce back to the very beginnings of the theory of signification as we find them in John Poinsot (1589 1644). Poinsot, as it happens, is part of the same Iberian Renaissance to which Benedict has now called our attention. Indeed, under another name (John of St. Thomas) Poinsot inspired the neo Thomism of Jacques Maritain which undergirded the Christian Humanism of Paul VI and many other Fathers of the Second Vatican Council. (His treatise on *The Gifts of the Holy Spirit, as interpreted by theologians often dismissed as too conservative, is behind the rather daring notion that all Christians are called to holiness in this life, and, indeed to the mystical path of acquired contemplation, and thus such more recent developments as Centering Prayer, the World Community for Christian Meditation, and the ommunion and Liberation movement.
As if all this were not enough, Murray Rothbard, no Christian he, though personally excommunicated and anathematized by Ayn Rand for not repudiating his openly Christian wife, has argued that the Austrian School of Economics, the Old Liberalism of von Mises and Hayek, goes back not so much to Adam Smith (who missed a few points), as to the scholastic philosophers of Spain and Portugal in the early modern period. Mention Iberian philosophy to the American of average education and he will look at you as though you had spoken of Uzbek grand opera or (indeed) the Scottish Enlightenment. He might even tell you that Spanish ignorance, superstition, and bigotry are precisely what God sent Englishmen into the New World to stamp out: the legenda negra. Needless to say, this is not a view of history a good many newcomers to the United States are likely to tolerate with equanimity, and it is just as well that it isn't true.
Once we retire that vulgar prejudice against Hispanidad we might just get a fair hearing for the work of Xavier Zubiri, the only European thinker of the last century who compares with Peirce for breadth of learning and depth of discernment as well as sheer unadulterated difficulty. If nothing else, the challenge of Catholicity invites Americans to break down the walls of the AngloSaxon ghetto, which do not serve us well now, if they ever did. But it may also provoke a new interest in our own Golden Age of (Protestant) theology. Let me set the stage for this with an extended quotation from Joseph Ratzinger's 1977 essay, "Is Faith Really Good News?" (Now translated in Principles of Catholic Theology:
Truth is not always comfortable for man, but it is only truth that makes him free and only freedom that brings him joy. Now, however, we must ask more precisely: What makes a man joyful? What robs him of joy? What puts him at odds with himself? What opens him to himself and to others? When we want to describe the most extreme form of being at odds with existence, we often say of an individual that he does not like himself. But whom or what is he to like who does not like himself? Something very importamt makes its appearance here: egoism, certainly, is natural to man and needs no encouragement; but this is not true of selfacceptance. The former must be overcome; the latter must be discovered, and it is assuredly one of the most dangerous errors of Christian teachers and moralists that they have all too often confused the two and, by exorcizing the affirmation of self, have enabled egoism to avenge such a betrayal by becoming all the more rampant this, ultimately, of what the French have labeled the maladie catholique: one who wants to live only on the supernatural level and to the exclusion of self will be, in the end, without a self but not, for that reason, selfless. (79)
Reading this a day or two after Ratzinger's papification I couldn't help thinking of our own Paul Tillich, whose seminal sermon "You are Accepted" baptized the human potential movement (as it was called), whose Courage to Be is a perennial best seller even after half a century, whose Systematic Theology Martin Luther King had asked for in his Georgia prison cell, and I myself poured over eagerly as an Earlham undergraduate. Of course the problematic goes back to Kierkegaard's penetrating analysis of despair, and, indeed to Luther's experience of divine wrath and mercy. Now it is all very well to say we must accept our acceptance, somehow (mysticism? art?) so ground ourselves in the very Ground of Being as to powerfully affirm our being against the powers of nonbeing. But is it true? That is the question haunting Tillich, Martin Luther King, and modern American culture down to our own time, which Ratzinger, challenged by Nietzsche and Camus, dared to speak aloud:
We come now to the allimportant question: Is it true, then, when someone says to me: "It is good that you exist"? Is it really good? Is it not possible that that person's love, which wills my existence, is just a tragic error? If the love that gives me courage to exist is not based on truth, then I must, in the end, come to curse the love that deceives me that maintains in existence something that were better destroyed. This dilemma could be 10 strikingly illustrated by reference to the interpretations of the contemporary experience of life in Sartre or Camus or in the attitudes of the new Left. Even without such evidence, it is obvious, however, that the apparently so simple act of liking myself, of being at one with myself, actually raises the question of the whole universe It raises the question of truth: Is it good that I exist? Is it good that anything at all exists? is the world good? How many persons today would dare to affirm this question from the heart to believe it is good that they exist? That is the source of the anxiety and despair that incessantly affect mankind. Love alone is of no avail. It serves no purpose if truth is not on its side. Only when truth and love are in harmony can man know joy. For it is truth that makes man free. (80)
And the question of truth won't leave us alone. For Tillich the Christian faith was perhaps a true myth, but, perhaps true only the way that other myths are true. He tended to sacramentalize modern art, leftish politics, and sexual liberation; the president of Union Seminary had to remind him that it looked bad for their most eminent theologian not to go to church. The tragedy of attempting to make a religion of art, politics, or sex is obvious by now, and it as a sad circumstance that the leadership of the American Catholic Church were seminarians at a time when Catholic theology looked to the Protestants for validation, and Tillich was at the height of his prestige in the liberal denominations. The painful story of Tillich's sexual obsessions is now well known enough from his wife's two memoirs, Dr. King's escapades have stained the memory of the civil rights movement as much as his infatuation with the Soviet power, and the sexual scandals of the American Church are unspeakably worse, blighting the lives of tens (hundreds?) of thousands of children. That is something Benedict, on his recent visit, would not allow us to forget for even a moment. But at least he offers a remedy in that confrontation with the truth of our being which liberal theology, Catholic and Protestant (though perhaps not Orthodox),attempted to evade:
The content of the Christian evangelium reads: God finds man so important that he himself has suffered for man. The Cross, which was for Nietzche the most detestable expression of the negative character of the Christian religion, is in truth the center of the evangelium, the glad tidings: "It is good that you exist" No, "It is necessary that you exist." The Cross is the approbation of our existence, not in words, but in an act so completely radical that it caused God to become flesh and pierced this flesh to the quick; that, to God, it was worth the death of his incarnate Son. One who is so loved that the other identifies his life with this love and no longer desires to live if he is deprived of it; one who is loved even unto death such a one knows that he is truly loved. But if God so loves, then we are loved in truth. Then love is truth, and truth is love. Then life is worth living. This is the evangelium. (81)
The whole idea of the Cross as God's affirmation of man will strike many an American as shocking, ludicrous even. It the caross not the stock in trade of a thousand "evangelists" as the ultimate proof of our total depravity, the ultimate refutation of all aspirations for human freedom and dignity? Surely Nietzsche got that from his preacher father, though it is hard to find any such slander of humanity in either the written scriptures or the teaching of the Fathers of the Church (except for Augustine, and that on a bad day he later repented). I am happy to note that Ratzinger's point of view, scriptural, patristic, and Benedictine in every sense of the term is very close to what some in the Evangelical churches are calling "gracious Christianity," for that is what it is. That movement is still a prophetic minority in the churches and the academy, and we still need to come to terms with the main stream of American spirituality as represented, for better and worse, by Tillich. And Ratzinger, even in his early days as a professor, has given us the means to do just that. Not everything in the American theological mainstream, and not everything in Tillich, needs to be discarded wholesale.
A follower of Ratiznger's good friend Don Liugi Giussani who studies Tillich's theology will find close analogies between Tillich's method of correlation and the principle of correspondence which Giussani urged on members of the Communion and Liberation movement he founded, a movement in which the Ratzinger Pope (to use the Catholic injargon) takes more than a passing interest he is said even now to take part in a weekly School of Community in which movement people use that method to explore the meaning of the Gospel in relation to their own day to day lives, and the meaning of their lives in relation to the Gospel, though his episcopal orders forbid his formal membership in the Fraternity. I do not mean to imply that Benedict is a follower of Giussani in matters of pure theology, but it seems clear that he recognizes Giussani's method as the best practical application of the theological principles both men learned from such masters of La Nouvelle Theologie as de Lubac, von Balthasar, and (with reservations) Rahner.
But before I move away from the idea of correspondence, the method of correlation, I should mention that this became the life work of two American philosophers, Ira Progoff, with whom and with whose students I was privileged to do postdoctoral work, and Eugene Gendlin, both known as psychologists for the contributions they have made to psychology, who offer what I can only describe as means of spiritual direction. The few folks who remember Tillich today often contrast him with Reinhold Niebuhr, his colleague at Union, who inspired the Cold war mainstream much as Tillich inspired the New Left, and whom Don Gius was fond of quoting.
But the man to rediscover is Reinhold's brother Richard, a theologian's theologian, that is, one whose writings were never taken up by the movers and shakers of middlebrow culture. His Meaning of Revelation shows the kind of emphasis the Catholic Church in Europe is coming around to, or coming back to, as it is very much in the spirit of the Fathers of the Church, the Eastern Fathers in particular. For many of us what may be most prophetic in his life work is his refusal of the temptation of neoconservatism to which Reinhold gave in to his fame and profit. Reinhold ostentatiously resigned from the Fellowship of Reconciliation in the early '30s in righteous indignation that some Christians did not demand that the government do something (what?) about the Japanese in China. Richard, on the other hand, had no hope for the efficacy of political, economic, and military power exercised by the United States against Japan. Sensing that Western Christendom was going the way of old Rome, he thought that the best Christian response was that pioneered by St. Benedict, from whom of course among others the last pontiff took his name. For him the issue was not Japan against China, or the United States against Japan, but, to cite the title of a 1935 book to which he contributed, The Church Against the World. A few years later Dietrich von Hildebrand, in his villa in Florence, was giving the retreats later published as Transformation in Christ to Christian activists who intended to remain behind in Nazi Germany to keep the light of Christian civilization burning in that dark time, and Dietrich Bonhoeffer would take refuge with the Benedictines in his own effort to do the same. A few pages before the long passage I have quoted, Ratzinger's Principles of Catholic Theology gives a lengthy exegesis of Hildebrand's text as the model for Christian repentance. I can't help wondering if this forbidden book is one that his father had hidden around the house, as Evangelicals might have concealed Bonhoeffer's Cost of Discipleship. Discipleship and transformation are not matters of effortful striving, but the response to a calling which is a revelation.
Richard is particularly enlightening on revelation as calling. He shows that it is not the communication of some kind of knowldege, however supernatural or esoteric, by possession of which we are justified, elevated from the companionship of our neighbors, saved from the world; that would be Gnosticism. Rather, revelation is participation in an ongoing event, a relationship with a person previously unknown, or at least unrecognized. Some words toward the end of The Meaning of Revelation put the matter thus:
Revelation means the moment in our history through which we know ourselves to be known from beginning to end, in which we are apprehended by the knower; it means the the selfdisclosure of the judge. Revelation means that we find ourselves to be valued rather than valuing and that all our values are transvaluated by the activity of a universal valuer. When a price is put upon our heads, which is not our price, when the unfairness of all the fair prices we have placed on things is shown up, when the great riches of God reduce our wealth to poverty, that is revelation. When we find out that we are no longer thinking him, but that he first thought us, that is revelation. Revelation is the emergence of the person on whose external garments and body we had looked as objects of our masterful and curious understanding. Revelation means that in our common history the fate that lowers over us as persons in our communities reveals itself to be a person in community with us. What this means for us cannot be expressed in the impersonal ways of creeds or other propositions but only in responsive acts of a personal character. we acknowledge revelation by no third person proposition, such as that there is a God, but only in the direct confession of the heart, "Thou art my God."... From this point forward we must listen for the remembered voice in all the sounds that assail our ears, and look for the remembered activity in all the actions of the world upon us. The God who reveals himself in Jesus Christ is now trusted and known in the contemporary God, revealing himself in every event, but we do not understand how we could tract his working in these happenings if he did not make himself known to us through the memory of Jesus Christ; nor do we know how we should be able to interpret all the words we read as words of God save by the aid of this Rosetta stone. (80 - 81)
Catholics who remember the discourses of the Pope Benedict will find the flavor of this passage very Benedictine in both senses of the term. Those who follow the way of Luigi Giussani find their spirit particularly familiar, for those of them who live in community, including the little band that managed Benedict's household and conduct the School of Community he attended, are known precisely as Memores Domini, those who strive to keep the Lord constantly in mind, and allow their own memory and mindfulness, personal and collective, painful and pleasing, on the surface of association or deeply hidden, to be transformed by their relationship with God in Christ, their participation in the ongoing incarnation of the Word of God: the God who is the author of our nature, and an incarnation that runs to meet the deepest desire of that nature with more that could have been imagined. What this means in the experience of living our life is well stated at the conclusion of Niebuhr's great work:
The God who reveals himself in Jesus Christ meets no unresponsive will but the living spirit of men in search of all good. And he fulfills our need. Here is the one for whose sake all life and every life is worth living, even lives that seem bereft of beauty, of truth and of goodness. The glimpse of his great glory in the face of Jesus Christ, its reflections in the darkened mirrors of the saints' adorations intimate a God who is good beyond all that is good and fair beyond all fairness. Yet the goodness that shines upon us through the moment of revelation is not the glory or the goodness we had expected in our thoughts about deity. The essential goodness of the Father of our Lord Jesus Christ is the simple everyday goodness of love the value which belongs to a person rather [than] the value we find in an idea or a pattern; it is the goodness which exists as pure activity. He fulfills our expectation of the intrinsic good and yet this adorable goodness differs from everything we had expected, and puts our expectations to shame. We sought a good to love and were found by a good that loved us. And therewith all our religious ambitions are brought low, all our desires to be ministers of God are humbled; he is our minister. By that revelation we are convicted of having corrupted our religious life through our unquenchable desire to keep ourselves with our love of our good in the center of the picture. Here is the goodness that empties itself, and makes itself of no reputation, a goodness that is all outgoing, reserving nothing for itself, yet having all things. So we must begin to rethink all our definitions of deity and convert all our worship and our prayers. Revelation is not the development and not the elimination of our natural religion; it is the revolution of the religious life. (98 - 99)
But what does all this mean to one who stands outside the light of revelation, who relies on the reason of Western Civilization, the common sense of the founding Fathers? If believers and unbelievers are to take part in one community, what do we have to say to each other? This is the point of Benedict's challenge to the Muslim world, the question of what could make the libertine Doctor Franklin and the evangelical President Witherspoon active participants in the same foundational dialog. Niebuhr has an answer, and it is the same answer as Benedict:
The pure reason does not need to be limited in order that room be made for faith, but faith emancipates the pure reason from the necessity of defending and guarding the interests of selves, which are now found to be established and guarded, not by nature, but by the God of revelation whose garment nature is. (91 - 92)
It is faith that liberates and, indeed, inspires us to invent, develop, explore, and test scientific understandings which would otherwise be too much for the vain imaginings of our all too human hearts:
To know the person is to lose all sense of shame because of kinship with the clod and the ape. The mind is freed to pursue its knowledge of the external world disinterestedly not by the conviction that nothing matters, but by the faith that nothing God has made is mean or unclean. Hence any failure of Christians to develop scientific knowledge of the world is not an indication of their loyalty to the revealed God but of their unbelief. (90 - 91)
Seven going on eight decades after these words were published, ministers of "religion" are still attempting to prevent the teaching of ascertained facts of human biology in order to retain the authority of their own stupidly selectively literalistic reading of the Bible; some of the more advanced institutions of Evangelical learning defiantly profess a form of Calvinism in which some sort of theology remains the queen of the sciences in an unconstitutional monarchy, with no other discipline permitted its own proper autonomy and integrity; while in more numerous groves of Academus, even the Roman Catholic plantations, men and women of faith are quickly brushed off as obvious enemies of intellect.
My own mother, as I have said already, doubted that you can be a good Catholic and a real American at the same time. Pope Benedict warned his flock that they will not be good Catholics until they are Americans to the extent of acknowledging the law of nature and of nations as developed by Victoria (among others, some of them Scots), and aspiring to live in local, regional national and international communities under that law, in which the freedom and dignity of the human person are given the first priority. On the other hand I do not see how we can be real Americans without realizing that the aspirations of 1776 and 1789 are grounded in that natural law, and grew up as the fruit of a civilization in which the reason of Greece and Rome reached full maturity in the care of Mother Church, a church whose members, including the hierarchy, were not always consistently faithful to it, calling forth reformations, enlightenments, and even revolutions. I think we must all be Catholic at least in the wider sense of loyalty to that civilization, and our best way may well be to reappropriate the riches of the golden age of American philosophy and theology, of which the work of H. Richard Niebuhr is a small but important part.
Sources quoted: Edmund Burke, Impeachment of Warren Hastings before the House of Lords (numerous editions), eighth day. Joseph Ratzinger, Principles of Catholic Theology. San Fransisco: Ignatius, 1987. H. Richard Niebuhr, The Meaning of Revelation [1941]. Louisville: Westminster John Knox Press, 2006.
© FP Purcell
-
 @ 5d4b6c8d:8a1c1ee3
2025-04-05 14:11:31
@ 5d4b6c8d:8a1c1ee3
2025-04-05 14:11:31Here's a fun little Rorschach Test for Stackers. Clearly there's a trend change during the pandemic, but when does it start and what is the most likely cause?
I'll reserve my commentary for the comment section.
originally posted at https://stacker.news/items/935188
-
 @ e5de992e:4a95ef85
2025-04-05 12:10:46
@ e5de992e:4a95ef85
2025-04-05 12:10:46In the labyrinth of stock market wisdom, tales of unconventional methods often provide the most enduring insights. One such narrative, shared by Houston reader Melvid Hogan, recounts his life-changing encounter with Mr. Womack—a farmer whose approach to investing defied conventional Wall Street wisdom. By equating the act of purchasing stocks to buying a truckload of pigs, Mr. Womack’s philosophy offers a vivid metaphor for value investing, discipline, and the timeless nature of market cycles.
A Glimpse into a Bygone Era
Emerging from the shadows of World War II, the post-war economic boom reshaped America’s financial landscape. Many investors, like Hogan, ventured into stock trading as a means of wealth creation, facing the typical challenges of an eager novice. Early experiments with technical and fundamental analysis often led to losses, mirroring the struggles of countless investors trying to decipher an evolving market.
Set against the backdrop of a bustling Merrill Lynch office in Houston, Hogan’s story reminds us that even in the midst of market excitement, seasoned professionals and unlikely mentors were quietly redefining investment strategies. In this era, when emotional trading and market rallies were the norm, Mr. Womack’s measured approach was a radical departure from impulsive trading strategies.
The Farmer’s Philosophy: Patience, Discipline, and Intrinsic Value
At the heart of Mr. Womack’s method is a profound respect for natural cycles—both in agriculture and the stock market. Just as a farmer plans for planting and harvesting seasons, Mr. Womack approached stock investing with patience and impeccable timing. His strategy was simple: buy stocks when they are as undervalued as a truckload of pigs. In other words, purchase when the price is so low that it leaves little room for error.
This metaphor goes beyond mere pricing. Mr. Womack believed that, much like pigs require ongoing care, stocks need nurturing—through dividends and reinvestment—to deliver long-term value. His focus on dividend-producing companies trading below $10 a share underscores his commitment to tangible, lasting value over speculative gains.
Moreover, his approach wasn’t about predicting market movements with pinpoint accuracy but understanding market cycles. In times of depression or stagnation, when fear prevails and trading volumes drop, Mr. Womack saw opportunity. He would aggregate undervalued stocks and hold them for several years until market conditions improved—a strategy that resonates with modern-day value investing.
Technical Analysis Versus Fundamental Insight
Mr. Womack’s story also serves as a critique of over-reliance on technical indicators. In today’s financial world, technical fads and complex derivatives often distract from what truly matters: the fundamental worth of a company. During turbulent times—the 1960s, or the dramatic downturn of 1970—Mr. Womack’s unwavering discipline allowed him to capitalize on opportunities that more impulsive traders missed.
His method of rebalancing his portfolio during market lows and adhering strictly to principles rooted in intrinsic value mirrors the strategies of today’s top investors, who prize steady, long-term growth over short-lived market euphoria.
Market Trends and the Enduring Relevance of Value Investing
In an era dominated by high-frequency trading and algorithm-driven strategies, traditional value investing can sometimes seem outdated. However, Mr. Womack’s insistence on buying stocks at a discount—comparable to purchasing pigs at an unbeatable price—reminds us that market cycles are cyclical for a reason.
During bullish phases, when optimism runs high, even a farmer might overestimate his yield during a bumper harvest. Conversely, in depressed markets, when trading volumes dwindle and fear takes hold, the disciplined investor recognizes that these moments offer the best buying opportunities. As Hogan’s experience shows, understanding the market’s rhythm and acting with measured conviction can transform potential losses into substantial long-term gains.
This approach also speaks to an essential truth about risk: if you maintain a cost position well below an asset’s intrinsic value, you’re positioned to succeed over the long haul—regardless of short-term market fluctuations.
Reflections on a Lifelong Investment Philosophy
The narrative of Mr. Womack—a humble farmer with a deep understanding of both agriculture and the stock market—offers a powerful metaphor for investors of all stripes. His story is a reminder that successful investing doesn’t always require complex formulas or cutting-edge technology; sometimes, it demands nothing more than discipline, a keen eye for value, and the patience to let time do its work.
In the broader context of financial history, Mr. Womack’s approach stands as a testament to the virtues of pragmatism and foresight. It challenges modern investors to rethink the allure of rapid gains and to embrace strategies that prioritize long-term wealth accumulation over fleeting market trends. Whether you’re a seasoned trader or a newcomer to finance, there is enduring wisdom in treating stocks not as volatile commodities but as valuable assets—each with the potential to yield substantial rewards if bought at the right price and nurtured with care.
Remember: As Mr. Womack might say, invest with the same care a farmer shows for his livestock. With patience and discipline, even the simplest strategies can lead to long-term prosperity.
-
 @ e97aaffa:2ebd765d
2025-04-05 10:47:37
@ e97aaffa:2ebd765d
2025-04-05 10:47:37Vamos analisar a volatilidade do Bitcoin em gráficos, são dados desde 2012 até à atualidade.
 4.2% dos dias, o Bitcoin tem uma variação diária de ~0%, enquanto no S&P500 é de ~7.7%.
4.2% dos dias, o Bitcoin tem uma variação diária de ~0%, enquanto no S&P500 é de ~7.7%.
83.5% dos dias, o S&P 500 teve variação entre o -1% e 1%, enquanto o bitcoin, foi apenas 39%, foram 1882 dias, desde 2012.

Agora com os dois mercados em simultâneo, a curva da distribuição do S&P500 é mais centralizada, o bitcoin é mais alargado, sinónimo de mais volatilidade.

-
 @ 7d33ba57:1b82db35
2025-04-05 09:35:14
@ 7d33ba57:1b82db35
2025-04-05 09:35:14Ljubljana (pronounced lyoo-blyah-nah) is the small but stunning capital of Slovenia, known for its laid-back vibe, green spaces, baroque architecture, and lively café culture along the emerald-green Ljubljanica River. With its pedestrian-friendly Old Town, castle-topped hill, and artsy, youthful spirit, Ljubljana is often called one of Europe’s most underrated cities**—and it’s easy to see why.
🌟 Top Things to See & Do in Ljubljana
1️⃣ Ljubljana Castle
- Perched above the city, this medieval castle offers spectacular views
- Visit the watchtower, interactive museum, or take the funicular up and walk down
- Great spot for sunset or evening drinks with a view
2️⃣ Wander the Old Town
- Explore the cobbled streets, baroque buildings, and colorful facades
- Visit Prešeren Square, the Triple Bridge, and Town Hall
- Don’t miss Robba Fountain and St. Nicholas Cathedral
3️⃣ Stroll Along the Ljubljanica River
- Lined with outdoor cafés, bridges, and market stalls
- Cross the famous Dragon Bridge and Butcher’s Bridge (filled with love locks)
- Ideal for a coffee, gelato, or evening drink by the water
4️⃣ Central Market & Open Kitchen (Odprta Kuhna)
- Fresh produce, local products, and street food stalls
- Open Kitchen (Fridays in warm months) brings chefs from all over Slovenia to cook in the open air – a foodie’s dream!
5️⃣ Metelkova Art Center 🎨
- A gritty, colorful alternative culture zone filled with street art, galleries, and live music venues
- Great for nightlife, or even just to wander through during the day
6️⃣ Tivoli Park
- Ljubljana’s largest green space, ideal for relaxing walks or picnics
- Home to manicured gardens, sculptures, and Jakopič Promenade’s open-air photo exhibitions
🍽️ What to Eat & Drink in Ljubljana
- Kranjska klobasa – Traditional Carniolan sausage
- Štruklji – Rolled dough dumplings with sweet or savory fillings
- Jota – Hearty stew with beans, sauerkraut, and potatoes
- Local wines & craft beer – Slovenia has excellent wineries and microbreweries 🍷🍺
- Try riverside restaurants or cozy spots like Druga Violina, Gostilna Sokol, or Slovenska Hiša
🚶♀️ Tips for Visiting Ljubljana
✅ It’s small and walkable – most attractions are in or near the Old Town
✅ Free walking tours are great for learning local history & legends
✅ Rent a bike or e-scooter for exploring parks and neighborhoods
✅ Day trip options include Lake Bled, Postojna Cave, and Triglav National Park
✅ Ljubljana is eco-friendly – the center is car-free, and tap water is clean and drinkable -
 @ 592295cf:413a0db9
2025-04-05 07:26:23
@ 592295cf:413a0db9
2025-04-05 07:26:23[Edit] I tried to get the slides and an audio file, from Constant's talk at NostRiga, about 8 months ago
1.
Nostr's adoption thesis
The less you define, the more you imply
by Wouter Constant
2.
Dutch Bitcoiner
AntiHashedPodcast
Writing Book about nostr
00:40
3.
What this presentation about
A protocols design includes initself a thesis
on protocol adoption, due to underlying assumptions
1:17
4.
Examples
Governments/Academic: Pubhubs (Matrix)
Bussiness: Bluesky
Foss: Nostr
1:58
5.
What constitutes minimal viability?
Pubhubs (Matrix): make is "safe" for user
Bluesky: liability and monetization
Foss: Simpel for developer
4:03
6.
The Point of Nostr
Capture network effects through interoperability
4:43
7.
Three assumptions
The direction is workable
Method is workable
Motivation and means are sufficient
5:27
8.
Assumption 1
The asymmetric cryptography paradigm is a good idea
6:16
9.
Nostr is a exponent of the key-pair paradigm.
And Basicly just that.
6.52
10.
Keys suck
Protect a secret that you are supposed use all the time.
7:37
11.
Assumption two
The unaddressed things will be figured out within a 'meta-design consensus'
8:11
12.
Nostr's base protocol is not minimally viable for anything, except own development.
8:25
13.
Complexity leads to capture;
i.e. free and open in the name,
controlled in pratice
9:54
14.
Meta-design consensus
Buildings things 'note centric' mantains interoperability.
11:51
15.
Assumption three
the nightmare is scary;
the cream is appealing.
12:41
16.
Get it minimally viable,
for whatever target,
such that it is not a waste of time.
13:23
17.
Summarize
We are in a nightmare.
Assume key/signature are the way out.
Assume we can Maintain an open stardand while manifesting the dream.
Assume we are motivated enought to bootstrap this to adulthood.
14:01
18.
We want this,
we can do this,
because we have to.
14:12
Thank you for contribuiting
[Edit] Note for audio presentation
nostr:nevent1qvzqqqqqqypzqkfzjh8jkzd8l9247sadku6vhm52snhgjtknlyeku6sfkeqn5rdeqyf8wumn8ghj7mn0wd68ytnvw5hxkef0qyg8wumn8ghj7mn0wd68ytnddakj7qpqqqq6fdnhvp95gqf4k3vxmljh87uvjezpepyt222jl2267q857uwqz7gcke
-
 @ 57d1a264:69f1fee1
2025-04-05 06:58:25
@ 57d1a264:69f1fee1
2025-04-05 06:58:25Summary We are looking for a Visual Designer with a strong focus on illustration and animation to help shape and refine our brand’s visual identity. You will create compelling assets for digital and print, including marketing materials, social media content, website illustrations, and motion graphics. Working closely with our marketing and product teams, you will play a key role in developing a consistent and recognizable visual style through thoughtful use of illustration, color, patterns, and animation. This role requires creativity, adaptability, and the ability to deliver high-quality work in a fast-paced, remote environment.
Responsibilities - Create high-quality, iconic illustrations, branding assets, and motion graphics that contribute to and refine our visual identity. - Develop digital assets for marketing, social media, website, and app. - Work within brand guidelines while exploring ways to evolve and strengthen our visual style.
Requirements - 2+ years of experience in graphic design, with a strong focus on illustration. - Ability to help define and develop a cohesive visual style for the brand. - Proficiency in Adobe products. - Experience with Figma is a plus. - Strong organizational skills—your layers and files should be neatly labeled. - Clear communication and collaboration skills to work effectively with the team. - Located in LATAM
Please attach a link to your portfolio to showcase your work when applying.
originally posted at https://stacker.news/items/935007
-
 @ 57d1a264:69f1fee1
2025-04-05 06:47:55
@ 57d1a264:69f1fee1
2025-04-05 06:47:55Location: Remote (Austria) Area: Graphics and communication design Pay: 37,500 € to 50,000 € / year
Hi! We are @21bitcoinApp - a Bitcoin-Only Investment app that aims to accelerate the transition to an economy driven by Bitcoin.
👋 About the role As a passionate graphic designer, you support our marketing team in creating graphics and designs for print documents, online advertising material and our website. You also support us in the area of social media and content management and can also contribute your skills in these subject areas.
tasks - Design and implementation of creative and congruent designs for social media channels, websites, templates and marketing materials - Creation of individual content (posts, stories, banners, ads) for social media - Planning and development of campaigns to strengthen the brand presence - Further development of the existing corporate design support in the area of content management (website, blog)
qualification - Completed training or studies in graphic design - At least 2 years of experience in graphic design, preferably with experience in the areas of social media and content management - Safe use of design tools such as Figma, Adobe Creative Suite - Experience in creating social media content and maintaining channels - Creativity, good communication skills and team spirit - Very good knowledge of German and English - Knowledge of Bitcoin is desirable
Benefits - Offsites with the team in exciting places - Flexible working hours in a company that relies on remote work - Help shape the future - to make the world a better place by helping to speed up Bitcoin's adaptation - Buy Bitcoin without fees! 21 Premium! - Gross annual salary & potential share options for outstanding performance / bonus payments
📝 Interview process
How do I apply? Please send us an email and add some information about you, your resume, examples of previous projects and a few key points about why you are interested in participating in 21bitcoin and what you expect.
By the way: CVs are important but don't forget to include your favorite Bitcoin meme in the application!
⁇ 京 Resume Review Portfolio of Work: Add a link to your portfolio / previous work or resume that we can review (LinkedIn, Github, Twitter, ...)
📞 Exploratory call We discuss what appeals to you about this role and ask you a few questions about your previous experiences
👬 On-Site Deep Dive During the deep dive session, we use a case study or extensive interview to discuss the specific skills required for the role.
👍 Time for a decision!
originally posted at https://stacker.news/items/935004
-
 @ 57d1a264:69f1fee1
2025-04-05 06:35:58
@ 57d1a264:69f1fee1
2025-04-05 06:35:58We’re looking for a Product Designer to join our team and take the lead in enhancing the experience of our mobile app. You’ll play a key role in evolving the app’s interface and interactions, ensuring that our solutions are intuitive, efficient, and aligned with both user needs and business goals.
Key Responsibilities: - Design and improve the @Bipa app experience, focusing on usability and measurable business impact. - Apply data-driven design, making decisions based on user research, metrics, and testing. - Lead and participate in usability tests and discovery processes to validate hypotheses and continuously improve the product. - Collaborate closely with Product Managers, developers, and other stakeholders to align design with product strategy. - Create wireframes, high-fidelity prototypes, and visual interfaces for new features and app optimizations. - Monitor the performance of delivered solutions, ensuring meaningful improvements for users and the business. - Contribute to the evolution and maintenance of our design system, ensuring consistency and scalability across the app.
Qualifications: - Previous experience as a Product Designer or UX/UI Designer, with a strong focus on mobile apps. - Solid understanding of user-centered design (UCD) principles and usability heuristics. - Hands-on experience with user research methods, including usability testing, interviews, and behavior analysis. - Ability to work with both quantitative and qualitative data to guide design decisions. - Familiarity with product metrics and how design impacts business outcomes (e.g. conversion, retention, engagement). - Proficiency in design tools like Figma (or similar). - Experience working with design systems and design tokens to ensure consistency. - Comfortable working in an agile, fast-paced, and iterative environment. - Strong communication skills and the ability to advocate for design decisions backed by research and data.
Benefits: 🏥 Health Insurance 💉 Dental Plan 🍽️ Meal Allowance (CAJU card) 💻 Home Office Stipend 📈 Stock Options from Day One
originally posted at https://stacker.news/items/935003
-
 @ 57d1a264:69f1fee1
2025-04-05 06:28:16
@ 57d1a264:69f1fee1
2025-04-05 06:28:16⚡️ About Us
@AdoptingBTC is the leading Bitcoin-only conference in El Salvador. For our 5th edition, we’re looking for a passionate Video Creator intern to help showcase Bitcoin’s future as MONEY.
⚡️ The Role
Create 30 short (3-minute or less) videos highlighting global circular economies, to be featured at AB25. We’ll provide all source material, direction, and inspiration—you’ll have full creative freedom, with feedback rounds to align with the conference’s vision.
⚡️ Responsibilities
Produce 30 short videos on circular economies. Incorporate subtitles as needed. Submit videos on a deliverables basis. Participate in check-ins and communicate with the AB team and circular economy communities.
⚡️ What We Offer
Free ticket to AB25. Networking with Bitcoiners and industry leaders. Letter of recommendation and LinkedIn endorsement upon completion. Mentorship and hands-on experience with a high-profile Bitcoin project.
⚡️ Skills & Qualifications
Passion for Bitcoin and circular economies. Basic to intermediate video editing skills (no specific software required). Creative independence with feedback. Portfolio or work samples preferred.
⚡️ Time Commitment
Flexible, project-based internship with check-ins and feedback rounds.
⚡️ How to Apply
Email kiki@adoptingbitcoin.org with subject “Circular Economy Video Creator Submission -
{NAME OR NYM}.” Include a brief background, your experience, why the project resonates with you, and a portfolio (if available).originally posted at https://stacker.news/items/935001
-
 @ a047a37c:dfcb432c
2025-04-05 01:09:09
@ a047a37c:dfcb432c
2025-04-05 01:09:09Chef's notes
Using only top quality dill pickles and juice is highly recommended. Do not cheap out on this ingredient. The better the pickle juice, the better your fried chicken will taste.
Do not let the chicken fry for too long. If the color is not a light golden brown and you let it fry too dark. Then it will not taste right!!!
Details
- ⏲️ Prep time: 20 min
- 🍳 Cook time: 25-30 min
- 🍽️ Servings: 3-4
Ingredients
- 1 1/2 Pounds Chicken Breasts
- 2 Chicken Eggs
- 2 Cups Dill Pickle Juice
- 1/2 Cup Water
- 1 Cup Buttermilk
- 1 Cup Unbleached Flour
- 3 Tablespoons Powdered Sugar
- 1 Teaspoon Paprika
- 1 Teaspoon Garlic Powder
- 1 Teaspoon Cayenne Pepper
- 1 Teaspoon Ground Black Pepper
- 1 Teaspoon Sea Salt
- 1/2 Teaspoon Baking Powder
- 3-4 Cups Peanut Oil
- 3-4 Toasted Brioche Buns (Chicken Sandwiches Only)
- 1 Tablespoon Orange Blossom Honey (Chicken Sandwiches Only)
- 1/4 Cup Sliced Dill Pickles (Chicken Sandwiches Only)
Directions
- There are 2 ways to make The Legendary CFA Fried Chicken. If you want to make it into nuggets then take the chicken breasts and cut them with a kitchen knife into 1 inch cubes. If you want to make it into chicken breast sandwiches, then ensure they are no bigger than 1-1.5 inches thick cut once down the middle. Once you have made your decision and cut them to size. Place the chicken in a large mixing bowl Pour the pickle juice into the bowl, cover it, and place it in the refrigerator to marinate for the next 24 hours.
- Take a large mixing bowl and add in the flour, powdered sugar, paprika, ground black pepper, cayenne pepper, sea salt, garlic powder, and baking powder. Whisk it all together until it is fully mixed and set aside.
- Take another large mixing bowl. Add in the chicken eggs and buttermilk. Then whisk together until it is fully blended and set aside.
- Add 3-4 cups of peanut oil to a large cast iron frying pan, or a deep fryer. Heat the oil to 350F degrees.
- Remove the marinated chicken from the refrigerator. Drain out all of the pickle juice.
- Dredge the chicken in the buttermilk egg mixture until it is fully coated. Coat the chicken in the flour mixture. Then immediately repeat these two steps so it is double coated to ensure maximum crispiness.
- Add the chicken into the peanut oil and allow it to cook evenly until it has reached a light golden brown color and is fully cooked inside.
- Remove the chicken from the pan and place it onto a paper towel to drain the excess oil off. If you made it into chicken nuggets then simply choose your favorite dipping sauce and serve. If you chose to make chicken sandwiches then lightly toast the brioche bun to a golden brown and drizzle on the honey on the inside of the top of the bun. Then add 1 piece of chicken breast per bun on the bottom half, top it off with sliced dill pickles. Complete the sandwich and serve immediately.
-
 @ da18e986:3a0d9851
2025-04-04 20:25:50
@ da18e986:3a0d9851
2025-04-04 20:25:50I'm making this tutorial for myself, as I plan to write many wiki pages describing DVM kinds, as a resource for DVMDash.
Wiki pages on Nostr are written using AsciiDoc. If you don't know ascii doc, get an LLM (like https://duck.ai) to help you format into the right syntax.
Here's the test wiki page I'm going to write:
``` = Simple AsciiDoc Demo
This is a simple demonstration of AsciiDoc syntax for testing purposes.
== Features
AsciiDoc offers many formatting options that are easy to use.
- Easy to learn
- Supports rich text formatting
- Can include code snippets
- Works great for documentation
[source,json]
{ "name": "Test", "version": "1.0", "active": true }
```
We're going to use nak to publish it
First, install
nakif you haven't alreadygo install github.com/fiatjaf/nak@latestNote: if you don't use Go a lot, you may need to first install it and then add it to your path so the
nakcommand is recognized by the terminal```
this is how to add it to your path on mac if using zsh
echo 'export PATH=$PATH:$(go env GOPATH)/bin' >> ~/.zshrc ```
And here's how to sign and publish this event with nak.
First, if you want to use your own nostr sec key, you can set the env variable to it and nak will use that if no secret key is specified
```
replace with your full secret key
export NOSTR_SECRET_KEY="nsec1zcdn..." ```
Now to sign and publish the event:
Note: inner double quotes need to be escaped with a
\before them in order to keep the formatting correct, because we're doing this in the terminalnak event -k 30818 -d "dvm-wiki-page-test" -t 'title=dvm wiki page test' -c "= Simple AsciiDoc Demo\n\nThis is a simple demonstration of AsciiDoc syntax for testing purposes. \n\n== Features\n\nAsciiDoc offers many formatting options that are easy to use. \n\n* Easy to learn \n* Supports rich text formatting \n* Can include code snippets \n* Works great for documentation \n\n[source,json] \n---- \n{ \"name\": \"Test\", \"version\": \"1.0\", \"active\": true } \n----" wss://relay.primal.net wss://relay.damus.io wss://relay.wikifreedia.xyzYou've now published your first wiki page! If done correctly, it will show up on wikistr.com, like mine did here: https://wikistr.com/dvm-wiki-page-test*da18e9860040f3bf493876fc16b1a912ae5a6f6fa8d5159c3de2b8233a0d9851
and on wikifreedia.xyz https://wikifreedia.xyz/dvm-wiki-page-test/dustind@dtdannen.github.io
-
 @ 000002de:c05780a7
2025-04-04 20:22:47
@ 000002de:c05780a7
2025-04-04 20:22:47We are fostering a lamb named Frank. He was left behind when his flock was moved to a new grazing area. He almost didn't make it.
I've learned that sheep are not as dumb as I thought they were. He seems to be pretty sharp and has quickly become spoiled. He follows us around like a puppy. We have had some cold nights so we made him a jacket.
He's about 3 weeks old now and seems to be doing well.
originally posted at https://stacker.news/items/934770
-
 @ c631e267:c2b78d3e
2025-04-04 18:47:27
@ c631e267:c2b78d3e
2025-04-04 18:47:27Zwei mal drei macht vier, \ widewidewitt und drei macht neune, \ ich mach mir die Welt, \ widewide wie sie mir gefällt. \ Pippi Langstrumpf
Egal, ob Koalitionsverhandlungen oder politischer Alltag: Die Kontroversen zwischen theoretisch verschiedenen Parteien verschwinden, wenn es um den Kampf gegen politische Gegner mit Rückenwind geht. Wer den Alteingesessenen die Pfründe ernsthaft streitig machen könnte, gegen den werden nicht nur «Brandmauern» errichtet, sondern der wird notfalls auch strafrechtlich verfolgt. Doppelstandards sind dabei selbstverständlich inklusive.
In Frankreich ist diese Woche Marine Le Pen wegen der Veruntreuung von EU-Geldern von einem Gericht verurteilt worden. Als Teil der Strafe wurde sie für fünf Jahre vom passiven Wahlrecht ausgeschlossen. Obwohl das Urteil nicht rechtskräftig ist – Le Pen kann in Berufung gehen –, haben die Richter das Verbot, bei Wahlen anzutreten, mit sofortiger Wirkung verhängt. Die Vorsitzende des rechtsnationalen Rassemblement National (RN) galt als aussichtsreiche Kandidatin für die Präsidentschaftswahl 2027.
Das ist in diesem Jahr bereits der zweite gravierende Fall von Wahlbeeinflussung durch die Justiz in einem EU-Staat. In Rumänien hatte Călin Georgescu im November die erste Runde der Präsidentenwahl überraschend gewonnen. Das Ergebnis wurde später annulliert, die behauptete «russische Wahlmanipulation» konnte jedoch nicht bewiesen werden. Die Kandidatur für die Wahlwiederholung im Mai wurde Georgescu kürzlich durch das Verfassungsgericht untersagt.
Die Veruntreuung öffentlicher Gelder muss untersucht und geahndet werden, das steht außer Frage. Diese Anforderung darf nicht selektiv angewendet werden. Hingegen mussten wir in der Vergangenheit bei ungleich schwerwiegenderen Fällen von (mutmaßlichem) Missbrauch ganz andere Vorgehensweisen erleben, etwa im Fall der heutigen EZB-Chefin Christine Lagarde oder im «Pfizergate»-Skandal um die Präsidentin der EU-Kommission Ursula von der Leyen.
Wenngleich derartige Angelegenheiten formal auf einer rechtsstaatlichen Grundlage beruhen mögen, so bleibt ein bitterer Beigeschmack. Es stellt sich die Frage, ob und inwieweit die Justiz politisch instrumentalisiert wird. Dies ist umso interessanter, als die Gewaltenteilung einen essenziellen Teil jeder demokratischen Ordnung darstellt, während die Bekämpfung des politischen Gegners mit juristischen Mitteln gerade bei den am lautesten rufenden Verteidigern «unserer Demokratie» populär zu sein scheint.
Die Delegationen von CDU/CSU und SPD haben bei ihren Verhandlungen über eine Regierungskoalition genau solche Maßnahmen diskutiert. «Im Namen der Wahrheit und der Demokratie» möchte man noch härter gegen «Desinformation» vorgehen und dafür zum Beispiel den Digital Services Act der EU erweitern. Auch soll der Tatbestand der Volksverhetzung verschärft werden – und im Entzug des passiven Wahlrechts münden können. Auf europäischer Ebene würde Friedrich Merz wohl gerne Ungarn das Stimmrecht entziehen.
Der Pegel an Unzufriedenheit und Frustration wächst in großen Teilen der Bevölkerung kontinuierlich. Arroganz, Machtmissbrauch und immer abstrusere Ausreden für offensichtlich willkürliche Maßnahmen werden kaum verhindern, dass den etablierten Parteien die Unterstützung entschwindet. In Deutschland sind die Umfrageergebnisse der AfD ein guter Gradmesser dafür.
[Vorlage Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 7d33ba57:1b82db35
2025-04-04 18:13:02
@ 7d33ba57:1b82db35
2025-04-04 18:13:02Edinburgh is a city where ancient history and modern culture meet in the most atmospheric way. From its dramatic castle perched on a volcanic rock to narrow medieval alleys, vibrant festivals, and cozy pubs, Scotland’s capital is a must-visit for travelers seeking both beauty and depth. It’s a city that feels like stepping into a storybook—with a few ghost tales thrown in for good measure.
🏛️ Top Things to See & Do in Edinburgh
1️⃣ Edinburgh Castle
- Iconic and steeped in royal history
- See the Crown Jewels, the Stone of Destiny, and sweeping views over the city
- Don’t miss the 1 o’clock cannon fire!
2️⃣ Walk the Royal Mile
- The main street running from Edinburgh Castle to Holyrood Palace
- Lined with shops, historic closes (alleyways), churches, and pubs
- Pop into St Giles’ Cathedral and explore the Writer’s Museum
3️⃣ Holyrood Palace & Arthur’s Seat
- The Queen’s official Scottish residence 👑
- Hike up Arthur’s Seat, an ancient volcano, for amazing panoramic views of Edinburgh and beyond
4️⃣ Explore the Old Town & New Town
- Old Town: Medieval, moody, atmospheric
- New Town: Elegant Georgian streets and great shopping on Princes Street
- Don’t miss Victoria Street – rumored inspiration for Harry Potter’s Diagon Alley ✨
5️⃣ Museums & Culture
- National Museum of Scotland – interactive and family-friendly
- Scottish National Gallery – features art by Turner, Van Gogh, and more
- Camera Obscura & World of Illusions – quirky and fun near the castle
6️⃣ Edinburgh’s Underground & Ghost Tours
- Explore the hidden vaults under the city
- Join a ghost tour or learn about Edinburgh’s dark past, including grave robbers and plague victims
7️⃣ Festivals Galore 🎭
- Edinburgh Festival Fringe (August) – The largest arts festival in the world
- Edinburgh International Festival, Book Festival, and Hogmanay (New Year) celebrations
🍽️ What to Eat in Edinburgh
- Haggis, neeps & tatties – A classic, surprisingly tasty Scottish dish
- Scottish salmon, Cullen skink (smoky fish soup)
- Afternoon tea or Scottish whisky tasting in a historic bar 🥃
- Try local spots like The Witchery, Makars Gourmet Mash Bar, or The Scran & Scallie
🚶♀️ Tips for Visiting Edinburgh
✅ Wear comfy shoes – cobblestones and hills are part of the charm
✅ Be ready for 4 seasons in a day – pack layers and a rain jacket ☁️☀️🌧️
✅ Book ahead in summer – especially during August festivals
✅ Take a day trip to Rosslyn Chapel, the Highlands, or Stirling Castle for more Scottish beauty
✅ Consider the Edinburgh City Pass if planning to visit many attractions -
 @ 9bcc5462:eb501d90
2025-04-04 16:02:14
@ 9bcc5462:eb501d90
2025-04-04 16:02:14The story you are about to read is one hundred percent true. It is also my first encounter with a supernatural force.
It was the summer of 2003 and I was visiting my auntie in Nashville as a 16-year-old, pimply-faced teenager. My younger cousins, Alex, Mikey, and Tony were also there. One afternoon, they were all sitting bored outside in the blazing heat, sheltered under the tree on the front lawn. It was a comical sight really, all of them sprawled out lifeless and silent, eaten alive by the unforgiving mosquitos. I ducked inside and asked my aunt if it was okay to borrow her RAV4 to take them to play basketball nearby at Pitts Park. Despite not having a license she handed me the keys and when I went outside to tell the boys we were going to shoot hoops, you’d have thought I said I was taking them to Disney World!
Off we went up and down the rollercoaster-like hills of Tennessee. Yes, I was speeding, and no, we were not wearing seatbelts. (Remember, sixteen, acne, angst, etc.) We arrived at the park and immediately I felt an eerie sensation. I had been there before with my other cousin Kim, but this time was undeniably different. It didn’t matter that the sun was shining above the bright blue sky, I sensed a darkness lingering. And it had nothing to do with the sticky Southern humidity. It was an overwhelming, odd, ineffable sensation. My eyes couldn’t help but focus on the trees behind the court. As if someone or something was watching us.
Nevertheless, after shooting for teams, we began a 2-on-2 immediately. When Mikey and I won, (I towered over them and Mikey was surprisingly pretty good) Tony wasn’t too happy about losing. In frustration, he bounced the basketball with both hands as hard as he could. The ball ended up on the other side of the fences surrounding the court and rolled into the bordering woods. None of the little squirts wanted to retrieve the ball, so as the big cuz I volunteered myself. Nothing to it right? Wrong!
As I walked towards the woods I couldn’t even locate the basketball. I stopped and scanned until I finally saw it, way deep among the trees. “How did it get all the way over there?” I mumbled beneath my breath. Then, while approaching the ball I heard a loud and distinct voice—“Hey!”—I turned around suddenly, but nothing was there. At first I wasn’t afraid, rather I was genuinely confused. It just made no damn sense, there was no one around. I swiveled my head in every direction and once again the deep, gravelly voice called out, “Hey!” This time I knew where it was coming from and crept towards the source until I spotted something in the bushes. I crouched and pushed some branches aside. And that’s when I noticed it. Buried under the shrubs was a tombstone! It stared back at me, weathered, cracked, moss-eaten. I picked my ass up, ran to the ball, scooped it and bolted back to the court.
Little Alex asked if we were going to play a rematch; I said, “Hell no”. After herding them back to the car, we left and never looked back. To this day I remember the voice. I recall the inexplicable feeling of the unknown energy, force, or spirit that was with us. I only recently shared this story with him and now, at 27, he asked why I didn’t tell him sooner. I thought hard about it and answered, “I guess I didn’t want you to get scared and piss yourself.”
-
 @ 7d33ba57:1b82db35
2025-04-04 14:35:00
@ 7d33ba57:1b82db35
2025-04-04 14:35:00Zlarin is a small, car-free island near Šibenik, known for its peaceful atmosphere, crystal-clear waters, and centuries-old coral tradition. It’s often called the “Golden Island” for its natural beauty, and it remains a hidden gem on the Adriatic coast—perfect for quiet beach days, cycling, and slow travel.
🌿 Why Visit Zlarin?
- No cars = pure tranquility – the whole island is pedestrian- and bike-friendly 🚲
- Rich in coral diving heritage – once the center of Croatia’s coral trade 🪸
- Beautiful stone houses, pine forests, and untouched coves
- Easy to reach via a short ferry ride from Šibenik ⛴️
🏖️ Things to Do on Zlarin
1️⃣ Swim & Relax on Secluded Beaches
- Veleš Beach – A pebbly beach surrounded by pines, great for families 🌲
- Magarna Bay – Quiet, wild beach perfect for those seeking solitude 🧘♀️
- Hidden coves – Wander the coast and find your own little swimming spot 🌅
2️⃣ Walk or Cycle the Island
- Well-marked trails through pine forests and olive groves
- Visit the hilltop viewpoint for a panoramic look at Šibenik and nearby islands
- Bring or rent a bike in Šibenik – bikes are ideal for exploring Zlarin 🚴♂️
3️⃣ Learn About Coral Traditions
- Visit the Zlarinka Museum dedicated to the island’s red coral harvesting history
- See traditional jewelry and tools, and learn about the craft’s cultural significance
4️⃣ Stroll Through the Village
- Picturesque stone streets, old chapels, and flower-filled gardens
- Enjoy a drink at a local konoba (tavern) with views of the sea 🍷
5️⃣ Take a Boat Tour or Kayak Trip
- Explore nearby Prvić, Kaprije, or Žirje islands
- Great area for kayaking or paddleboarding over glassy waters 🚣
🚢 How to Get to Zlarin
- Ferry from Šibenik (approx. 25 minutes, year-round service)
- No cars allowed, so park in Šibenik if needed
- Easy to visit for a day trip or stay overnight for peace and stargazing
💡 Tips for Visiting Zlarin
✅ Best time to visit? Late spring to early autumn for swimming and quiet vibes ☀️
✅ Bring cash – not all places accept cards 💶
✅ Pack snorkel gear and water shoes – the underwater world is beautiful 🐠
✅ Stay overnight for an unforgettable quiet island evening under the stars ✨ -
 @ 5d4b6c8d:8a1c1ee3
2025-04-04 14:17:31
@ 5d4b6c8d:8a1c1ee3
2025-04-04 14:17:31We're down to the Final Four in March Madness and not only am I running away with the Points Challenge, but I'll be running away with all of @grayruby's sats in the Predyx live Predyxion markets. Is it good that all of the top teams are still alive or do we miss the upsets?
In the NBA, the West is still all jumbled up. Seeds 2-9 are up for grabs. What matchups are likely in the playoffs and which ones are we hoping for?
Ovechkin is right on the cusp of the All-Time Goals Scored record. Will he get there by the end of the season?
@grayruby has some irresponsible, way too early, MLB takes.
The NFL Draft picture might be clearing up, but there are always surprises. We'll talk about our hopes for how our teams approach the first few rounds.
And, of course, we'll give updates on all the territory action.
Happy stacking, stackers!
originally posted at https://stacker.news/items/934354
-
 @ 5d4b6c8d:8a1c1ee3
2025-04-04 13:07:55
@ 5d4b6c8d:8a1c1ee3
2025-04-04 13:07:55https://primal.net/e/nevent1qvzqqqqqqypzqdtgwhlaw2dsdm45c8t6wzslw5qyt5r8waxjrs86llj272ledghgqqsdjv9nadd5dwgzg9w02qp4s4gzphcxj3t8640nw4xn7qgf2lyzxysk9lmtp
There are lots of possible issues with this chart, but it is pretty stark.
A few random thoughts: 1. It might not be the people eating unhealthy amounts of sugar who cut back on it. I was never obese and I radically cut back on my sugar intake. 2. Sugar may have been highly correlated with other similar substances that people didn't cut back on. I'm thinking about other refined carbs, primarily. 3. There may simply be a lag and obesity will start declining as a result of lower sugar consumption. 4. It does look like the rate of obesity increase decreased slightly (lower slope), so maybe the issue is just that sugar intake is still too high, but the relationship is correct.
What do you think explains this divergence?
originally posted at https://stacker.news/items/934292
-
 @ 96203d66:643a819c
2025-04-04 12:58:46
@ 96203d66:643a819c
2025-04-04 12:58:46nostr:nevent1qqs9j3aw7jrzrw6mtgs9w2znhpg7u0vvur4v69mc8xhw90lqahej74ccx749u nostr:nevent1qqsxrleatwc7v4jvpu4hk3k4s5xvvral0uvt6svyydwtqsz7tk2v03spph2jk nostr:nevent1qqsykq5q6gaa499nykagjaf6sav7ul4ve0ge9y22707gueuasdtr97qsnceys nostr:nevent1qqsvyhuwmnjglrk8hxdw8ye3lzy9f0ahf3ajfsn0wkf3pnztlx7dxxsq7jhlg nostr:nevent1qqs2mmqn2sr6a0ysfjyyuwx5gwy4rxre6pwnjqnzzdszzrgh2zgynlgvv59j3 nostr:nevent1qqswhdmpjhkqzp0nld0m23kgyesqmyacksu9zf8kefxtwzracn7efuqt825sd nostr:nevent1qqsdzsjfa2dmkue5hk5dr8ttl76l3kf649yx4lwslwnh238442jfmmsv4fzmd nostr:nevent1qqszun5jhc22du06rle5r0z8zhj2ezm9pmmrfsqx4843qhz57k3aqxg738uv6 nostr:nevent1qqs8sx9mc2yuldpm5edrtplnge8ckgcr4xj8x7af3zdac0r4rat377ga689un nostr:nevent1qqswe5auf0ym9lg78prwj9ppy0rvpdq92pwend96jmq6udh3d5r3mfqxlyl8j nostr:nevent1qqsqtwgpl0v6qf03r4e9r4tsnyly354req9am2u6s5gjrtefwtedpmc72v3jx nostr:nevent1qqsx2w65lvwmf23rutmnhzw3k2paftngssvfdzqmwle4f3m77hk4u8c6lgmrx nostr:nevent1qqsfz6zpaw2gkgxjxfvevgsww0rhw07swwg0hun23xc4mfuh8f7afrg875wcx nostr:nevent1qqs0eknqgzut0sv0undcps42pnw7an4wjt7a2rwjxd2zaqg6rqpjdwg56yeq7 nostr:nevent1qqsrg7yyaacetzugj8304krg5ne0xxu7kdnps8tlnd797myseqp97vs8r7tup nostr:nevent1qqs20ap690l97n8py0g44w22963jkze78ws2em6e0cl02vc65nexmsqw9ugcd
-
 @ e0ef3b4e:6fd74878
2025-04-04 12:55:14
@ e0ef3b4e:6fd74878
2025-04-04 12:55:14At a conference I sit in a quite area and observe and enjoy a coffee. It's bustling around and many are attending a speech at the main stage. Two people sit next to me on a sofa and begin a conversation. He's wearing a beige hoodie and seems to be builder in the space, she's wearing a green winter dress and they seem to be colleagues.
It seems they are now meeting for the first time in real life and exchanging advice, him advising her on how to store her Bitcoin. He’s been longer in the space it seems and she’s just started at the new start-up. I quickly introduce myself and ask them if I may listen in on the conversation since I am a researcher working in the space. They happily agree. She goes on to mention that she will be paid in Bitcoin and does not know how to store it. He goes on to advise her on using a hardware wallet, then takes out his phone and shows a video of the hardware wallet he is using.
She says "Wow, it looks so easy to use. I tried so many different hardware wallets but they are so difficult to use." I see the tension in her shoulders, which then relaxes a bit. He goes on to show her all the security and backup methods for this particular hardware wallet. "I'm sold." She's smiling now and one can see that a decision has been made.
These conversations are happening everyday across the world not only at conferences but in villages, cafes or during random conversation at co-working working spaces. While we strive for good marketing and adoption of Bitcoin, these simple conversations between two people are what is driving actual use.
Safety and trust is a cultural concept in many countries and viewed differently depending on where one has originated from. If one is to imagine that many people would benefit from storing BTC on a device or using an app for lighting transactions then they must trust the process. This need to trust is a basic primary human need.
They will only trust the process if:
-
Empowered: They feel as if they 100% know what they are doing when they are onboarded to the application/hardware device. If there is anything that creates doubt or friction in their minds, the trust to use it as a storage of BTC is gone. A person will window shop when deciding to use a wallet. On average when we interviewed people for various UX research initiatives one person had a minimum of two different Bitcoin wallets on their phone. Prior to that they had tested out quite a few wallets before settling on a decision.
-
Safe: Many are nervous that they will not be able to access their funds once they put it online/on a hardware device. However often receiving advice from someone they trust this will result in them feeling safe. They will likely use the very same device/application that is being used by their friend/colleague or person in a close inner circle.
While this story might seem overly simplified, it’s been repeated multiple times while observing the behavior of people at conferences, through usability tests, and through interviews.
If we understand that a person is tentatively stepping into a “home” (Bitcoin wallet/hardware device) and looking “around” (onboarding process). Once they step in, they will only leave their “bag” (BTC) on the table if specific criteria are met. If not, they will pick up their “bag” (BTC) and walk into the next “home.” (Bitcoin wallet/hardware device). During this process there are basic psychological principles are taking place.
This is where design comes in and creates an experience. The UX design could be equated to the “interior design” of the house. Every click, every interaction every visual that a person sees or experiences is driving them to trust or distrust the experience. We as builders have a unique role in this process and I fully believe that we will solve these challenges together.
If you've read all the way to the end, thank you. On another note, the last 3 weeks have been filled with a lot of strategic thinking, planning, and collaboration.
There are many balls in the air at the moment:
-
UX Research Africa strategy
If you've read all the way to the end, thank you for reading.
✌🏽Peace
-
-
 @ 6a6be47b:3e74e3e1
2025-04-04 12:41:11
@ 6a6be47b:3e74e3e1
2025-04-04 12:41:11⛅️ This week has been a bit hazy—I haven’t been feeling my best. And that’s okay. There are days like that. But this time, it felt like something deeper, as if something was off. Like I wasn’t enough.
🌞 Thankfully, as the days went by, I started to feel better. Today, I feel like myself again—like I’ve put my human suit back on and climbed back on the horse.
✏️ I picked up my pencil and started drawing again, just me and my iPad, without any expectations weighing me down. It felt good—peaceful even—to create for the sake of creating.
🦉 What I’ve realized is this: It’s not bad to have goals or aspirations. Those are important! But what becomes unhealthy is chasing perfectionism while trying to achieve those goals. For me, perfectionism turns into a spiral—not rainbows and butterflies but a storm cloud of self-doubt. I guess I just want to share this in case anyone out there needs to hear it: It’s okay to be imperfect. And most importantly, it’s okay to just be yourself.

🎨 As part of my journey back to myself this week, I decided to draw something simple and even try my hand at a little animation since it had been a while. Here’s what I came up with:
Imposter syndrome can be deceiving—it whispers lies about your worth and tries to steal your joy—but just like anything in life, this too shall pass.
🎢 The ebbs and flows are part of life’s natural rhythm; you’d think I’d have learned that by now! But life has its way of (re)teaching us lessons when we need them most.
✨ To anyone reading this who might be struggling: Be kind to yourself. You’re doing better than you think you are. And remember—you are enough.
Godspeed
-
 @ c1a9282b:75752c6d
2025-04-04 12:20:54
@ c1a9282b:75752c6d
2025-04-04 12:20:54«Rainha em trapos», chamavam-na. Antes andarilha, assentava-se agora em trono xexelento, lixo cenográfico de alguma companhia de teatro. A qualquer que passasse perto dela, encarando-a, concedia retribuir um sorriso condescendente e um aceno de mão, entendendo que a ela agradeciam algum favor.
Antes da aurora, levantava-se e ordenava ao sol que amanhecesse; antes do ocaso, o contrário: que anoitecesse. Em certa data, por capricho, decidiu que não haveria nem raiar nem cessar de raiar naquele dia, e ordenou ao Sol que nem ousasse despontar. Negou-se o Sol a obedecer simplesmente cumprindo seu diuturno trajeto.
— A esse rebelde, matem-no!
[revista gueto: 2017]
-
 @ 1aa9ff07:3cb793b5
2025-04-04 09:42:28
@ 1aa9ff07:3cb793b5
2025-04-04 09:42:28Artificial intelligence (AI) has gained significant momentum in recent years, and it is expected to bring revolutionary changes to our lives over the next five years. Today, AI plays a crucial role in automation, healthcare, education, and many other fields. In the near future, its impact will become even more profound. Here are some key transformations AI is expected to bring:
- Major Changes in the Business World
AI will automate repetitive tasks, allowing human workers to focus on more strategic areas. AI-powered assistants, data analytics, and customer service applications will become more widespread, shifting human efforts toward creative and problem-solving roles.
- Revolutionary Advances in Healthcare
AI in medicine will enable earlier disease diagnosis and personalized treatment plans. Thanks to advancements in image processing and genetic analysis, diseases such as cancer can be detected more quickly and accurately.
- Widespread Adoption of Autonomous Vehicles
Over the next five years, autonomous vehicle technologies will continue to evolve, becoming more common in urban transportation and logistics. This will lead to a reduction in traffic accidents, lower transportation costs, and significant changes in urban planning.
- AI-Powered Personalized Learning in Education
AI will enhance personalized education solutions, making learning processes more efficient. AI-assisted teachers and learning platforms will analyze students’ weaknesses and create customized study programs tailored to their needs.
- New Challenges in Security and Data Privacy
As AI technology advances, cybersecurity and data privacy will become even more critical. While AI-driven security systems can detect cyber threats proactively, malicious applications of AI may introduce new vulnerabilities.
- Creative Innovations in Art and Entertainment
AI-generated content will become more prevalent in fields such as art, music, and cinema. AI-assisted scripts, music compositions, and digital artwork may give rise to a new wave of artistic expression.
Conclusion
In the next five years, AI's influence will be felt in every aspect of life. From business and healthcare to transportation and the arts, various sectors will undergo transformative innovations. However, addressing ethical concerns, security challenges, and data privacy issues will be crucial to ensuring AI's positive impact. By harnessing AI’s potential responsibly, we can build a more efficient, secure, and sustainable future.
Artificial intelligence (AI) has gained significant momentum in recent years, and it is expected to bring revolutionary changes to our lives over the next five years. Today, AI plays a crucial role in automation, healthcare, education, and many other fields. In the near future, its impact will become even more profound. Here are some key transformations AI is expected to bring:
-
 @ 674473f6:f859eb3c
2025-04-04 08:42:17
@ 674473f6:f859eb3c
2025-04-04 08:42:17darkman คืออะไร
Darkman เป็นโปรแกรมที่ช่วยควบคุมการเปลี่ยนโหมดสีของเดสก์ท็อประหว่างโหมดมืดและโหมดสว่างบนระบบปฏิบัติการ Unix-like. โปรแกรมนี้จะทำงานในเบื้องหลัง(background process) และสามารถตั้งค่าให้เปลี่ยนไปใช้โหมดมืดเมื่อพระอาทิตย์ตก หรือเปลี่ยนกลับไปใช้โหมดสว่างเมื่อพระอาทิตย์ขึ้นได้
การทำงานของ Darkman
เรียกใช้ผ่าน systemd service หรือคำสั่ง
darkman runโดยตรงได้เลย- การตั้งค่าโหมด: Darkman สามารถตั้งค่าโหมดปัจจุบันเป็นโหมดมืดหรือโหมดสว่างได้ด้วยคำสั่ง
darkman set <light|dark>. - การตรวจสอบโหมดปัจจุบัน: สามารถตรวจสอบโหมดปัจจุบันได้ด้วยคำสั่ง
darkman get. - การสลับโหมด: สามารถสลับโหมดระหว่างโหมดมืดและโหมดสว่างได้ด้วยคำสั่ง
darkman toggle. - การทำงานอัตโนมัติ: Darkman จะทำงานอัตโนมัติโดยใช้ข้อมูลตำแหน่งที่ตั้งของระบบเพื่อกำหนดเวลาพระอาทิตย์ขึ้นและตก.
- การปรับแต่ง: สามารถเพิ่มสคริปต์เพื่อปรับแต่งการทำงานของโปรแกรมให้เข้ากับแอปพลิเคชันต่างๆ ได้.
การตั้งค่า darkman
- สร้างไฟล์
config.yamlในโฟลเดอร์~/.config/darkman/
yaml lat: 13.7563 lng: 100.5018 # ตำแหน่งกรุงเทพ usegeoclue: false dbusserver: true portal: true- การตั้งค่า portal สำหรับ Darkman
จะช่วยให้โปรแกรมสามารถเปลี่ยนโหมดสีของเดสก์ท็อปได้โดยใช้ XDG settings portal API.
2.1 สร้างไฟล์ portals.conf ในโฟลเดอร์ ~/.config/xdg-desktop-portal/
conf [preferred] org.freedesktop.impl.portal.Settings=darkman2.1 รีสตาร์ท service xdg-desktop-portal เพื่อให้การตั้งค่าใหม่มีผล:
bash systemctl --user restart xdg-desktop-portalการตั้งค่านี้จะช่วยให้แอปพลิเคชันต่างๆ บนเดสก์ท็อปสามารถอ่านค่าโหมดสีจาก Darkman และปรับเปลี่ยนตามที่กำหนด.
- Custom executables
ใน Darkman สามารถเพิ่มการทำงานเพิ่มเติมเมื่อมีการเปลี่ยนโหมดสีของเดสก์ท็อป โดยการวางสคริปต์หรือโปรแกรมที่ต้องการในไดเรกทอรีที่กำหนด
ไดเรกทอรีสำหรับ Custom executables:
$XDG_DATA_DIRS/dark-mode.d/: สำหรับสคริปต์ที่ต้องการรันเมื่อเปลี่ยนไปใช้โหมดมืด$XDG_DATA_DIRS/light-mode.d/: สำหรับสคริปต์ที่ต้องการรันเมื่อเปลี่ยนไปใช้โหมดสว่าง
ตัวอย่างการใช้งาน Custom executables:
- สร้างสคริปต์สำหรับโหมดมืด:
- สร้างไฟล์
set_dark_mode.shในไดเรกทอรี$XDG_DATA_DIRS/dark-mode.d/ - เพิ่มเนื้อหาดังนี้:
```bash
!/bin/bash
ตัวอย่างสคริปต์สำหรับโหมดมืด
gsettings set org.gnome.desktop.interface gtk-theme "Adwaita-dark" notify-send "Dark Mode Activated" ```
- สร้างสคริปต์สำหรับโหมดสว่าง:
- สร้างไฟล์
set_light_mode.shในไดเรกทอรี$XDG_DATA_DIRS/light-mode.d/ - เพิ่มเนื้อหาดังนี้:
```bash
!/bin/bash
ตัวอย่างสคริปต์สำหรับโหมดสว่าง
gsettings set org.gnome.desktop.interface gtk-theme "Adwaita" notify-send "Light Mode Activated" ```
- ตั้งค่าสิทธิ์การรันสคริปต์:
- ตั้งค่าสิทธิ์ให้สคริปต์สามารถรันได้:
bash chmod +x $XDG_DATA_DIRS/dark-mode.d/set_dark_mode.sh chmod +x $XDG_DATA_DIRS/light-mode.d/set_light_mode.shเมื่อ Darkman เปลี่ยนโหมด สคริปต์เหล่านี้จะถูกเรียกใช้งานตามที่กำหนด
การแก้ไขหากไม่พบ XDG_DATA_DIRS
หากไม่พบตัวแปร
XDG_DATA_DIRSคุณสามารถสร้างไดเรกทอรีที่จำเป็นเองได้ตามต้องการ โดยปกติแล้วXDG_DATA_DIRSจะประกอบด้วยไดเรกทอรีเหล่านี้:~/.local/share//usr/local/share//usr/share/
คุณสามารถสร้างไดเรกทอรีเหล่านี้และเพิ่มสคริปต์ของคุณได้ตามนี้:
- สร้างไดเรกทอรี:
- สร้างไดเรกทอรีสำหรับโหมดมืดและโหมดสว่าง:
bash mkdir -p ~/.local/share/dark-mode.d mkdir -p ~/.local/share/light-mode.d- ทำการ export XDG_DATA_DIRS:
โดยทั่วไปเราสามารถตั้งตัวแปร Environments ต่าง ๆ ได้ที่
~/.profileและตัวแปรทั้งหมดจะถูกโหลดหลังจากเรา Loginbash export XDG_DATA_DIRS=$HOME/.local/share:/usr/local/share:/usr/share:$XDG_DATA_DIRSSource: darkman
- การตั้งค่าโหมด: Darkman สามารถตั้งค่าโหมดปัจจุบันเป็นโหมดมืดหรือโหมดสว่างได้ด้วยคำสั่ง
-
 @ 3104fbbf:ac623068
2025-04-04 06:58:30
@ 3104fbbf:ac623068
2025-04-04 06:58:30
Introduction
If you have a functioning brain, it’s impossible to fully stand for any politician or align completely with any political party. The solutions we need are not found in the broken systems of power but in individual actions and local initiatives. Voting for someone may be your choice, but relying solely on elections every few years as a form of political activism is a losing strategy. People around the world have fallen into the trap of thinking that casting a ballot once every four years is enough, only to return to complacency as conditions worsen. Voting for the "lesser of two evils" has been the norm for decades, yet expecting different results from the same flawed system is naive at best.
The truth is, governments are too corrupt to save us. In times of crisis, they won’t come to your aid—instead, they will tighten their grip, imposing more surveillance, control, and wealth extraction to benefit the oligarch class. To break free from this cycle, we must first protect ourselves individually—financially, geographically, and digitally—alongside our families.
Then, we must organize and build resilient local communities. These are the only ways forward. History has shown us time and again that the masses are easily deceived by the political circus, falling for the illusion of a "savior" who will fix everything. But whether right, center, or left, the story remains the same: corruption, lies, and broken promises. If you possess a critical and investigative mind, you know better than to place your trust in politicians, parties, or self-proclaimed heroes. The real solution lies in free and sovereign individuals who reject the herd mentality and take responsibility for their own lives.
From the beginning of time, true progress has come from individuals who think for themselves and act independently. The nauseating web of politicians, billionaires, and oligarchs fighting for power and resources has never been—and will never be—the answer to our problems. In a world increasingly dominated by corrupted governments, NGOs, and elites, ordinary people must take proactive steps to protect themselves and their families.
1. Financial Protection: Reclaiming Sovereignty Through Bitcoin
Governments and central banks have long manipulated fiat currencies, eroding wealth through inflation and bailouts that transfer resources to the oligarch class. Bitcoin, as a decentralized, censorship-resistant, and finite currency, offers a way out. Here’s what individuals can do:
-
Adopt Bitcoin as a Savings Tool: Shift a portion of your savings into Bitcoin to protect against inflation and currency devaluation. Bitcoin’s fixed supply (21 million coins) ensures it cannot be debased like fiat money.
-
Learn Self-Custody: Store your Bitcoin in a hardware wallet or use open-source software wallets. Avoid centralized exchanges, which are vulnerable to government seizure or collapse.
-
Diversify Geographically: Hold assets in multiple jurisdictions to reduce the risk of confiscation or capital controls. Consider offshore accounts or trusts if feasible.
-
Barter and Local Economies: In times of crisis, local barter systems and community currencies can bypass failing national systems. Bitcoin can serve as a global medium of exchange in such scenarios.
2. Geographical Flexibility: Reducing Dependence on Oppressive Systems
Authoritarian regimes thrive on controlling populations within fixed borders. By increasing geographical flexibility, individuals can reduce their vulnerability:
-
Obtain Second Passports or Residencies: Invest in citizenship-by-investment programs or residency permits in countries with greater freedoms and lower surveillance.
-
Relocate to Freer Jurisdictions: Research and consider moving to regions with stronger property rights, lower taxes, and less government overreach.
-
Decentralize Your Life: Avoid keeping all your assets, family, or business operations in one location. Spread them across multiple regions to mitigate risks.
3. Digital Privacy: Fighting Surveillance with Advanced Tools
The rise of mass surveillance and data harvesting by governments and corporations threatens individual freedom. Here’s how to protect yourself:
-
Use Encryption: Encrypt all communications using tools like Signal or ProtonMail. Ensure your devices are secured with strong passwords and biometric locks.
-
Adopt Privacy-Focused Technologies: Use Tor for anonymous browsing, VPNs to mask your IP address, and open-source operating systems like Linux to avoid backdoors.
-
Reject Surveillance Tech: Avoid smart devices that spy on you (e.g., Alexa, Google Home). Opt for decentralized alternatives like Mastodon instead of Twitter, or PeerTube instead of YouTube.
-
Educate Yourself on Digital Privacy: Learn about tools and practices that enhance your online privacy and security.
4. Building Resilient Local Communities: The Foundation of a Free Future
While individual actions are crucial, collective resilience is equally important. Governments are too corrupt to save populations in times of crisis—history shows they will instead impose more control and transfer wealth to the elite.
To counter this, communities must organize locally:
-
Form Mutual Aid Networks: Create local groups that share resources, skills, and knowledge. These networks can provide food, medical supplies, and security during crises.
-
Promote Local Economies: Support local businesses, farmers, and artisans. Use local currencies or barter systems to reduce dependence on centralized financial systems.
-
Develop Off-Grid Infrastructure: Invest in renewable energy, water filtration, and food production to ensure self-sufficiency. Community gardens, solar panels, and rainwater harvesting are excellent starting points.
-
Educate and Empower: Host workshops on financial literacy, digital privacy, and sustainable living. Knowledge is the most powerful tool against authoritarianism.
5. The Bigger Picture: Rejecting the Illusion of Saviors
The deep corruption within governments, NGOs, and the billionaire class is evident. These entities will never act in the interest of ordinary people. Instead, they will exploit crises to expand surveillance, control, and wealth extraction. The idea of a political “savior” is a dangerous illusion. True freedom comes from individuals taking responsibility for their own lives and working together to build decentralized, resilient systems.
Conclusion: A Call to Action
The path to a genuinely free humanity begins with individual action. By adopting Bitcoin, securing digital privacy, increasing geographical flexibility, and building resilient local communities, ordinary people can protect themselves against authoritarianism. Governments will not save us—they are the problem. It is up to us to create a better future, free from the control of corrupt elites.
-
The tools for liberation already exist.
-
The question is: will we use them?
For those interested, I share ideas and solutions in my book « THE GATEWAY TO FREEDOM » https://blisshodlenglish.substack.com/p/the-gateway-to-freedom
⚡ The time to act is now. Freedom is not given—it is taken. ⚡
If you enjoyed this article, consider supporting it with a Zap!
My Substack ENGLISH = https://blisshodlenglish.substack.com/ My substack FRENCH = https://blisshodl.substack.com/
Get my Book « THE GATEWAY TO FREEDOM » here 🙏 => https://coinos.io/blisshodl
-
-
 @ da0b9bc3:4e30a4a9
2025-04-04 06:24:48
@ da0b9bc3:4e30a4a9
2025-04-04 06:24:48Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/934111
-
 @ bf95e1a4:ebdcc848
2025-04-04 06:11:18
@ bf95e1a4:ebdcc848
2025-04-04 06:11:18This is a part of the Bitcoin Infinity Academy course on Knut Svanholm's book Bitcoin: Sovereignty Through Mathematics. For more information, check out our Geyser page!
The Gullible Collective
We humans are biased by nature. Everything we think we know is distorted in one way or another by our cognitive shortcomings. The human brain has been forced to evolve and adapt to whatever environment it found itself in over millennia. Having a brain that is capable of setting aside personal aims for the sake of the collective has proven to be advantageous for the evolution of our species as a whole. The same is true for every other social life form. However, letting these parts of our brains guide our political judgment can lead to disastrous results in the long run — not because of bad intentions but because of the simple fact that a few individuals will always thrive by playing every political system for personal gain. From an evolutionary perspective, an army of ay-sayers and martyrs, regardless of whether we’re talking about an army of humans or an army of ants or bacteria, has an advantage over a less disciplined one. From an individual's evolutionary perspective though, it is better to appear like you’re a martyr but to run and hide when the actual battle happens. This at least partly explains the high percentage of sociopaths in leadership positions all over the world. If you can appear to act for the good of the collective but dupe your way into more and more power behind people’s backs, you’re more likely to succeed than someone playing a fair game.
The story of banking and fiat currency is a story about collective madness. Historically, rulers have tricked people into killing each other through the promise of an after-life. Through central banking, the rulers of the world wars could trick people into building armies for them by printing more money. This is seldom mentioned in history classes because it still goes on today on a massive scale. Inflation might no longer be paying tank factory workers, but it is the main mechanism that funnels wealth into the pockets of the super-rich and away from everyone else. Inflation is the mechanism that hinders us from transporting the value of our labor through time. It makes us avoid real long-term thinking. We hardly ever consider this a problem because none of us has ever experienced an alternative to it.
Money is still vastly misunderstood by the lion's share of the world’s population. In most parts of the world, banks do something called fractional reserve lending. This means that they lend out money that they don't have — conjuring up new money out of thin air and handing it out to their customers as loans. Loans that have to be paid back with interest. Interest that can’t be paid back with thin air but has to be paid with so-called real money. Real money, of which there isn’t enough around to pay back all the loans, so that a constant need for new credit becomes a crucial part of the entire system. Not to mention central banks, which do the same and worse for governments. We’re so used to it by now that every country is expected to have a national debt. All but a handful of ridiculously rich ones do. National debts are also loans that have to be paid back with interest backed by nothing. Think about that. Your taxes are paying someone else's interest. Your tax money is not paying for your grandmother's bypass operation, it is paying interest to a central bank.
When the ideas of the catholic church ruled Europe, people who didn’t believe in God were few and very seldomly outspoken. They had good reason for this since belief in God was virtually mandatory throughout society. Ever since 1971, when famously dishonest American president Richard Nixon cut the last string that tied the US Dollar to gold, our conception of what the world economy is and ought to be has been skewed by an utterly corrupt system. We’re led to believe that we’re all supposed to work longer and longer days in order to spend more and more money and bury ourselves in more and more debt to keep the machine running. We’re duped into thinking that buying a new car every other year is somehow good for the environment and that bringing a cotton bag to the grocery store will somehow save the planet. Stores manipulate us all the time through advertising and product placement, but we’re led to believe that if we can be “climate-smart,” we’re behaving responsibly. Somehow, our gross domestic product is supposed to increase indefinitely while politicians will save us from ourselves through carbon taxes. Fortunately for us, and unfortunately for them, there now exists a way for unbelievers of this narrative to opt out. Life finds a way, as Jeff Goldblum once so famously put it.
Collectivism has ruined many societies. Those of us fortunate enough to live in liberal democracies tend to forget that even democracy is an involuntary system. It’s often referred to as the “worst form of government except all others that have been tried,” but the system itself is very rarely criticized. We’re so used to being governed that not having a leader seems preposterous to most of us. Still, we pay our taxes, and an enormous cut of the fruit of our labor goes to a third party via inflation and the taxation of every good and service imaginable. Institutions, once in place, tend to always favor their own survival just as much as any other living thing does. People employed in the public sector are unlikely to vote against policies that threaten their livelihood. This is a bigger problem than we realize because it’s subtle and takes a long time, but every democracy is headed in the same direction. A bigger state, a more complicated system, and fewer individual freedoms. Long term, it seems that all of our systems tend to favor those who know how to play that system and not those who contribute the most value to their fellow man. Proponents of socialist policies often claim that failed socialist states “weren’t really socialist” or that “that wasn’t really socialism.” What most people fail to realize is that we’ve never tried real capitalism since we’ve always used more or less inflationary currencies. This might very well be the most skewed narrative of our era. We’re all experiencing real, albeit disguised, socialism every single day. True free market capitalism is what we haven’t experienced yet, and it might turn out to be a very different thing than what we’re told to believe that it is by almost all mainstream media.
The validity of the classic right-left scale describing political viewpoints has been debated a lot lately, and alternative scales, like GAL-TAN, the one with an additional Y-axis describing more or less authoritarian tendencies, are popping up in various contexts around the web. After the birth of Bitcoin, there’s a new way to see this. Imagine an origo, a zero point, and a vector pointing to the left of that. All politics are arguably on the left because all policies need to be funded by taxes, and taxation can be viewed as theft. Taxation can be viewed as theft because, at its core, it’s involuntary. If a person refuses to pay his taxes, there is a threat of violence lurking in the background. Not to mention inflation, which Milton Friedman so elegantly described as “taxation without legislation.” What you do with the portion of your wealth that you have in Bitcoin is another matter altogether. If you take sufficient precautionary privacy measures and you know what you’re doing, your business in Bitcoin is beyond politics altogether. With the introduction of the Lightning Network and other privacy-improving features, it is now impossible for any third party to confiscate your money or even know that you have it, for that matter. This changes the political landscape of every nation on Earth. Bitcoin is much less confiscatable than gold and other scarce assets, which makes it a much better tool for hedging against nation-states. In this sense, Bitcoin obsoletes borders. You can cross any border on Earth with any amount of Bitcoin in your head. Think about that! Your Bitcoin exists in every country simultaneously. Any imposed limit on how much money you can carry from one nation to the other is now made obsolete by beautiful mathematics. Bitcoin is sometimes referred to as a “virtual currency.” This is a very inaccurate description. Bitcoin is just mathematics, and mathematics is just about the most real thing there is. There’s nothing virtual about it. Counterintuitive to some, but real nonetheless.
The complexity of human societal hierarchies and power structures is described perfectly in a classic children's book, The Emperor’s New Clothes, by Hans Christian Andersen. See the world as the kid who points out that the king is naked in the tale, and everything starts to make sense. Everything in human society is man-made. Nations, leaders, laws, political systems. They’re all castles in the air with nothing but a lurking threat of violence to back them up. Bitcoin is a different beast altogether. It enables every individual to verify the validity of the system at all times. If you really think about it, morality is easy. Don’t hurt other people, and don’t steal other people’s stuff. That’s the basic premise. Humans have but two ways of resolving conflict, conversation and violence, and in this sense, to hurt someone can only mean physical violence. This is why free speech is so important and why you should defend people’s right to speak their minds above everything else. It’s not about being able to express yourself. It’s about your right to hear every side of every argument and thus not have to resort to violence should a conflict of interests occur. You can’t limit free speech with just more speech — there’s always a threat of violence behind the limitations. Code, which both Bitcoin and the Internet are entirely made up of, is speech. Any limitations or regulations that your government implements in regard to Bitcoin are not only a display of Bitcoin’s censorship resistance but also a test of your government's stance on freedom of expression. A restriction on Bitcoin use is a restriction on free speech.
Remember, the only alternative to speech that anyone has is violence. Code is a language, mathematics is a language, and money is a linguistic tool. A linguistic tool we use as a means of expressing value to each other and as a way to transport value through space and time. Any restrictions or regulations regarding how you can express value, for example, making it impossible to buy Bitcoin with your credit card, prove that the money you have in your bank account is not really yours. When people realize this, the demand for Bitcoin goes up, not down. If you know what you're doing, there’s no need to fear the regulators. They, on the other hand, have good reason to fear an invention that shamelessly breaks their spell.
About the Bitcoin Infinity Academy
The Bitcoin Infinity Academy is an educational project built around Knut Svanholm’s books about Bitcoin and Austrian Economics. Each week, a whole chapter from one of the books is released for free on Highlighter, accompanied by a video in which Knut and Luke de Wolf discuss that chapter’s ideas. You can join the discussions by signing up for one of the courses on our Geyser page. Signed books, monthly calls, and lots of other benefits are also available.
-
 @ 0edc2f47:730cff1b
2025-04-04 03:37:15
@ 0edc2f47:730cff1b
2025-04-04 03:37:15Chef's notes
This started as a spontaneous kitchen experiment—an amalgamation of recipes from old cookbooks and online finds. My younger daughter wanted to surprise her sister with something quick but fancy ("It's a vibe, Mom."), and this is what we came up with. It’s quickly established itself as a go-to favorite: simple, rich, and deeply satisfying. It serves 4 (or 1, depending on the day; I am not here to judge). Tightly wrapped, it will keep up to 3 days in the fridge, but I bet it won't last that long!
Details
- ⏲️ Prep time: 10 min
- 🍳 Cook time: 0 min
Ingredients
- 1 cup (240mL) heavy whipping cream
- 1/4 cup (24g) cocoa powder
- 5 tbsp (38g) Confectioners (powdered) sugar
- 1/4 tsp (1.25mL) vanilla extract (optional)
- Flaky sea salt (optional, but excellent)
Directions
-
- Whip the cream until frothy.
-
- Sift in cocoa and sugar, fold or gently mix (add vanilla if using).
-
- Whip to medium peaks (or stiff peaks, if that's more your thing). Chill and serve (topped with a touch of sea salt if you’re feeling fancy).
-
 @ 502ab02a:a2860397
2025-04-04 02:50:35
@ 502ab02a:a2860397
2025-04-04 02:50:35หลังจากที่เราเพิ่งเปิดเรื่องไฟโตสเตอรอลไปหมาด ๆ ถึงเวลาที่ต้องมาคุยกันเรื่อง oryzanol ซึ่งเป็นอีกหนึ่งสารที่ถูกอุตสาหกรรมผลักดันให้เรารู้สึกว่า “ต้องกิน” เหมือนเป็นไอเทมลับสำหรับสุขภาพหัวใจ แต่เดี๋ยวก่อนนะ ทำไมสิ่งที่มนุษย์ไม่เคยต้องการมาก่อนถึงกลายเป็นสิ่งจำเป็นไปได้ ?
Oryzanol หรือ gamma-oryzanol เป็นสารประกอบที่พบได้ในน้ำมันรำข้าว มีโครงสร้างเป็น sterol ester ของกรดเฟอรูลิก (Ferulic acid esters of sterols and triterpenes) ซึ่งหมายความว่ามันมีโครงสร้างคล้ายกับไฟโตสเตอรอล แต่มาพร้อมกับองค์ประกอบของสารต้านอนุมูลอิสระที่ได้จากกรดเฟอรูลิก นั่นทำให้มันถูกโฆษณาว่าเป็นสารที่ช่วยลดคอเลสเตอรอล มีฤทธิ์ต้านอนุมูลอิสระ และอาจช่วยลดความเสี่ยงโรคหัวใจ ฟังดูดีใช่ไหม ? แต่มันก็คล้ายกับไฟโตสเตอรอลเลย คือเป็นสารที่ แข่งขันกับคอเลสเตอรอลในการดูดซึม และแน่นอนว่าผลข้างเคียงก็ยังคงอยู่ นั่นคือ มันอาจลดการดูดซึมวิตามิน A, D, E, K ซึ่งเป็นวิตามินที่ละลายในไขมันและจำเป็นต่อร่างกาย นั่นหมายความว่า ในขณะที่มันช่วยลด LDL ในกระดาษ มันอาจทำให้ร่างกายขาดสารอาหารที่สำคัญไปด้วย
ปัญหาที่ใหญ่กว่าคือ oryzanol พบมากใน น้ำมันรำข้าว ซึ่งเป็นหนึ่งในน้ำมันพืชที่ผ่านการแปรรูปสูง และการบริโภคน้ำมันพืชมากเกินไปนั้นสัมพันธ์กับ ภาวะอักเสบเรื้อรัง (chronic inflammation), ภาวะต้านอินซูลิน (insulin resistance), และความเสี่ยงโรคหัวใจและหลอดเลือด การที่อุตสาหกรรมบอกให้เราเพิ่ม oryzanol ในอาหาร จึงเป็นเหมือนการผลักให้ผู้คนบริโภคน้ำมันพืชมากขึ้นโดยไม่รู้ตัว ทั้งที่น้ำมันพืชโดยเฉพาะที่ผ่านกรรมวิธีอย่างน้ำมันรำข้าวมีปริมาณโอเมก้า-6 สูง ซึ่งถ้ารับมากเกินไปจะไปกระตุ้นกระบวนการอักเสบในร่างกาย เคยสังเกตไหมครับว่า น้ำมันรำข้าวมักโชว์ตัวเลขเก๋ๆของ Oryzanol แต่กลับไม่โชว์สัดส่วน โอเมก้า 6 กับ โอเมก้า 3
เทียบง่ายๆครับ น้ำมันคาโนลา มีโอเมก้า 6 ราวๆ 2200 - 2800 ต่อน้ำมัน 15 มล. (หน่วยบริโภค) น้ำมันรำข้าว มีโอเมก้า 6 ราวๆ 4,140 - 5,520 มก. ต่อน้ำมัน 15 มล. (หน่วยบริโภค) ในขณะที่โอเมก้า 3 ราวๆ 138 - 276 มก.ต่อน้ำมัน 15 มล. (หน่วยบริโภค) นี่หมายถึงสัดส่วนสูงไปถึงได้ราวๆ 40:1 ทั้งๆที่เราเข้าใจแหละว่าโอเมก้า6 ร่างกายจำเป็น แต่แต่แต่ จำเป็นไม่ได้หมายความว่าจัดหนัก เพราะสิ่งที่เราต้องพึงสังวรคือ สัดส่วนที่สมดุลระหว่าง โอเมก้า3และโอเมก้า6 ดังนั้น 40:1 ไม่เรียกว่าสมดุล ซึ่งจะกระตุ้นการอักเสบเรื้อรัง ในร่างกาย และเกี่ยวข้องกับโรคหัวใจ เบาหวาน และปัญหาสุขภาพอื่นๆ พาเหรดกันมา แต่คุณจะไม่เห็นตัวเลขนี้บนฉลากครับ
ผู้ผลิตผิดไหม? จะไปผิดอะไรครับ หน่วยบริโภคแนะนำเขา 1 หน่วยบริโภคคือ 15 มิลลิลิตร หรือ 1 ช้อนโต๊ะ แค่นั้นเอง คำถามคือ มีใครใช้ตามนั้นบ้าง คุณเจียวไข่เจียวใช้เท่าไร ผัดข้าวผัดใช้เท่าไหร่ อ่ะ ผัดผักรวมมิตรก็ได้ เอาแบบเต็มเปี่ยมเลย รู้ไหมว่ามีหลายคนเอาไปทำน้ำสลัด OMG ผมถึงบอกอยู่ครับว่า คุณอย่าไปว่าผู้ผลิตเลย เขาปกป้องตัวเองไว้เรียบร้อยทุกมุมอยู่แล้วครับ ถ้าเรายังไม่อ่านฉลาก ซื้อเครื่องไฟฟ้าไม่เคยดูคู่มือ เซนต์สัญญาแบบไม่อ่านก่อน คุณจะว่าใครจริงไหมครับ
ที่น่าสนใจกว่านั้นคือเราเข้าใจกันแล้วใช่ไหมว่า oryzanol ไม่ได้มาจากการกินรำข้าวตรง ๆ แต่ต้องผ่านกระบวนการสกัดที่ซับซ้อนเพื่อได้น้ำมันมาใช้ และวิธีที่อุตสาหกรรมใช้มากที่สุดก็คือ การสกัดด้วยเฮกเซน (Hexane Extraction) ซึ่งเป็นตัวทำละลายเคมีที่อาจมีสารตกค้างในผลิตภัณฑ์สุดท้าย ถึงแม้จะมีวิธีอื่นที่ปลอดภัยกว่า เช่น การสกัดด้วยเอทานอล (Ethanol Extraction), การสกัดด้วยเอนไซม์ (Enzyme-Assisted Extraction), หรือการสกัดด้วยคาร์บอนไดออกไซด์เหนือวิกฤต (Supercritical CO₂ Extraction) แต่ทั้งหมดนี้มีต้นทุนสูงกว่า ทำให้ไม่เป็นที่นิยมในอุตสาหกรรม นั่นหมายความว่า ถ้าผลิตภัณฑ์ที่คุณซื้อไม่ได้ระบุว่าใช้วิธีอื่น ส่วนใหญ่ก็คือเฮกเซนแน่นอน
ข้อเสียของการบริโภค oryzanol มากเกินไปไม่ได้จบแค่การขัดขวางการดูดซึมวิตามิน เพราะการบริโภคในปริมาณสูงอาจส่งผลให้เกิด ความไม่สมดุลของฮอร์โมน เนื่องจาก oryzanol มีโครงสร้างคล้ายกับสเตอรอลในร่างกาย มันอาจไปรบกวนกระบวนการเผาผลาญของสเตอรอยด์ฮอร์โมน เช่น ฮอร์โมนเพศชาย (Testosterone) และฮอร์โมนความเครียด (Cortisol) ซึ่งในระยะยาวอาจส่งผลต่อระบบภูมิคุ้มกัน อารมณ์ และระดับพลังงานของร่างกาย
ประเด็นที่สำคัญคือ ในเมื่อเรามีอาหารจากธรรมชาติที่ช่วยบำรุงหัวใจได้โดยไม่ต้องมีผลข้างเคียง เช่น ไขมันสัตว์ดี ๆ ที่มีวิตามิน A, D, E, K ครบถ้วน ทำไมต้องพึ่งพาสารสกัดจากอุตสาหกรรม ? สิ่งที่ดูเหมือนดีจากงานวิจัยในแล็บ อาจไม่ได้ดีในระยะยาวเมื่ออยู่ในร่างกายมนุษย์จริง ๆ
ทีนี้เรามาดูจุดขายของ น้ำมันรำข้าวกัน - oryzanol เป็นสารธรรมชาติ ทนความร้อนสูง เอาไปใช้ทอดจะไม่เกิดการสลายตัว ทนความร้อนสูงนี่จริงเลยครับ โอริซานอลเป็นสารต้านอนุมูลอิสระในกลุ่ม Ferulic Acid Esters ซึ่งมีโครงสร้างเสถียรกว่าวิตามินอี (เทียบกับวิตามินอีเพราะ ต้านอนุมูลอิสระ และ การปกป้องไขมันจากการเกิดออกซิเดชัน ) มี จุดสลายตัวสูงกว่า 250°C ซึ่งทำให้ยังคงอยู่ได้ในอุณหภูมิที่ใช้ทอดอาหาร แล้วมันแปลว่าดีจริงไหม? ในขณะที่ น้ำมันรำข้าวมีโอเมก้า-6 สูงมาก (30-40%) ซึ่งไวต่อการเกิดออกซิเดชัน ถึงแม้โอริซานอลจะช่วยชะลอการเหม็นหืน แต่มันไม่ได้ช่วยลดการเกิด สารพิษจากไขมันไหม้ เช่น Aldehydes หรือ HNE (4-Hydroxy-2-nonenal) ที่มาจากโอเมก้า-6 หรือเปล่า??? มันคือการพูดให้เราไปโฟกัสจุดเดียวครับ "โอริซานอลทนร้อน ไม่ได้แปลว่า น้ำมันรำข้าวดีต่อสุขภาพ" เพราะโอเมก้า6 ที่ไวต่อการเกิดออกซิเดชัน รวมถึงวิตามินต่างๆ ก็ยังสูญสลายไปด้วยความร้อน นี่ยังไม่รวมถึงโทษของการกินโอริซานอลมากไปตามที่ให้ข้อมูลไว้ข้างบนด้วย
นอกจากนี้ยังมีคนตั้งคำถามไว้มากมายว่า หากโอริซานอลมีผลชัดเจนต่อสุขภาพเช่นเดียวกับที่โฆษณา ทำไมจึงไม่ได้รับการพัฒนาเป็นยาอย่างจริงจัง? หรือคำตอบคือ งานวิจัยที่สนับสนุนโอริซานอลยังไม่เพียงพอ และในหลายกรณี ผลของมันอาจเกิดจาก Placebo Effect (ผลจากความเชื่อว่ามันได้ผล มากกว่าผลจริงๆ ของสารนั้น) ซึ่งเป็นลักษณะเดียวกับ "ยาหลอก" ที่ไม่ได้มีฤทธิ์ทางชีวเคมีที่ส่งผลชัดเจน
-
มีไลโนเลอิกสูง ใช่ครับไม่ผิดเลยในจุดนี้ ไลโนเลอิก (Linoleic acid) เป็น กรดไขมันไม่อิ่มตัวชนิดหลายพันธะ (Polyunsaturated Fatty Acid, PUFA) ที่สำคัญและจำเป็นสำหรับร่างกาย โดยเฉพาะอย่างยิ่งในการช่วยบำรุงเซลล์และระบบต่างๆ ของร่างกาย ที่สำคัญคือ ไลโนเลอิกเป็นกรดไขมันในกลุ่ม โอเมก้า-6 เป็นสิ่งที่บอกกับเราชัดๆว่า โอเมก้า6 สูงนั่นเอง ถ้าจะดึงเฉพาะข้อดีมาคุยกันก็ไม่ผิดอะไรเลยครับ เพราะโอเมก้า6 สำคัญกับร่างกายจริงๆ แต่ แต่ แต่ การรับโอเมก้า-6 ในปริมาณสูงเกินไปอาจทำให้เกิดการอักเสบในร่างกาย ซึ่งเกี่ยวข้องกับโรคต่างๆ เช่น โรคหัวใจ โรคมะเร็ง และโรคเบาหวาน อย่างที่เรารู้กัน ดังนั้นที่บอกไว้ข้างบนครับ สัดส่วนโอเมก้า 6:3 คือ 40:1 หรือใน 1 ช้อนโต๊ะ มีโอเมก้า 6 สูงถึง ราวๆ 4,140 - 5,520 มก. เรียกว่าโฆษณาไม่ผิดเลยเรื่องปริมาณ แต่จริงๆแล้วเราควรรักษาสมดุล โอเมก้า 6:3 ให้ใกล้เคียง 1:1 มากที่สุดเท่าที่ทำได้ เราก็อาจต้องตั้งคำถามอีกทีว่า การมีไลโนเลอิกสูง มันดีจริงไหม
-
โทโคฟีรอล (Tocopherols) เป็นสารประกอบที่อยู่ในกลุ่ม วิตามินอี เป็นสารต้านอนุมูลอิสระในร่างกาย โดยช่วยปกป้องเซลล์จากความเสียหายจากอนุมูลอิสระและช่วยชะลอการเสื่อมของเซลล์ ถูกต้องตามโฆษณา จริงๆหน้าที่หลักคือปกป้องไขมันไม่ให้เกิดการออกซิเดชัน ซึ่งสามารถช่วยยืดอายุการใช้งานของน้ำมัน หรือไม่ให้เกิดการหืน นั่นเอง แต่การทอดหรือปรุงอาหารในอุณหภูมิสูงเกินไป ก็อาจทำให้น้ำมันเกิดการออกซิเดชันและเกิดสารพิษที่เป็นอันตรายต่อร่างกายได้ อย่าลืมนะครับว่าคำแนะนำในการใช้น้ำมันรำข้าว กลับชูการเหมาะกับอาหารทอดอุณหภูมิสูง
-
โทโคไทรอีนอล (Tocotrienols) เป็นส่วนหนึ่งของกลุ่ม วิตามินอี เช่นกัน การบริโภคมากเกินไป การรับประทาน โทโคไทรอีนอลในปริมาณมาก อาจมีผลข้างเคียงที่ไม่พึงประสงค์ เช่น ส่งผลกระทบต่อการดูดซึมวิตามินอื่นๆ ในร่างกายโดยเฉพาะวิตามิน K ซึ่งอาจทำให้เกิดปัญหาการแข็งตัวของเลือด, ทำให้ตับทำงานหนักขึ้นในการจัดการกับสารนี้ ซึ่งอาจส่งผลเสียต่อการทำงานของตับระยะยาว
สุดท้ายแล้ว เราต้องกลับมาตั้งคำถามว่า เราอยากให้สุขภาพของเราถูกกำหนดโดยการตลาดของอุตสาหกรรม หรือโดยสิ่งที่ธรรมชาติออกแบบมาให้เราตั้งแต่แรก ? ถ้าจะดูแลหัวใจจริง ๆ การกินอาหารที่มนุษย์วิวัฒนาการมากับมันมาตลอด เช่น เนื้อสัตว์ ไข่ ตับ และไขมันดี ๆ อาจเป็นคำตอบที่เรียบง่ายและมีเหตุผลมากกว่าการไล่ตามสารสกัดที่อุตสาหกรรมบอกว่าจำเป็น แต่ธรรมชาติอาจไม่เคยเห็นว่ามันสำคัญเลยก็ได้
#pirateketo #ฉลาก3รู้ #กูต้องรู้มั๊ย #ม้วนหางสิลูก
-
-
 @ c8adf82a:7265ee75
2025-04-04 01:58:49
@ c8adf82a:7265ee75
2025-04-04 01:58:49What is knowledge? Why do we need it?
Since we were small, our parents/guardian put us in school, worked their asses off to give us elective lessons, some get help until college, some even after college and after professional work. Why is this intelligence thing so sought after?
When you were born, you mostly just accepted what your parents said, they say go to school - you go to school, they say go learn the piano - you learn the piano. Of course with a lot of questions and denials, but you do it because you know your parents are doing it for your own good. You can feel the love so you disregard the 'why' and go on with faith
Everything starts with why, and for most people maybe the purpose of knowledge is to be smarter, to know more, just because. But for me this sounds utterly useless. One day I will die next to a man with half a brain and we would feel the same exact thing on the ground. Literally being smarter at the end does not matter at all
However, I am not saying to just be lazy and foolish. For me the purpose of knowledge is action. The more you learn, the more you know what to do, the more you can be sure you are doing the right thing, the more you can make progress on your own being, etc etc
Now, how can you properly learn? Imagine a water bottle. The water bottle's sole purpose is to contain water, but you cannot fill in the water bottle before you open the cap. To learn properly, make sure you open the cap and let all that water pour into you
If you are reading this, you are alive. Don't waste your time doing useless stuff and start to make a difference in your life
Seize the day
-
 @ 6389be64:ef439d32
2025-04-03 21:32:58
@ 6389be64:ef439d32
2025-04-03 21:32:58Brewing Biology
Episode 1068 of Bitcoin And . . . is LIVE!
This episode of Bitcoin And dives into Brewing Biology—a regenerative system combining compost tea, biochar, Bitcoin mining, and carbon credits—developed through a deep, idea-driven conversation with ChatGPT.
LISTEN HERE --> https://fountain.fm/episode/p0DmvPzxirDHh2l68zOX <-- LISTEN HERE
The future of Bitcoin isn’t just about code or money—it’s about soil. A groundbreaking fusion of biology, technology, and financial innovation might change the rules of agriculture, offering landowners a path to profitability while Healing our soils. At the heart of this revolution is biochar, a form of charcoal that supercharges soil health. When mixed with compost tea and microbial inoculants, this carbon-rich material becomes a game-changer.
Biochar’s porous structure acts as a microbial hotel, hosting fungi like arbuscular mycorrhizal fungi (AMF) and bacteria such as Bacillus subtilis. These organisms form symbiotic networks that boost nutrient absorption and secrete glomalin—a natural “glue” that binds soil, preventing erosion. But here’s the twist: this system doesn’t just heal the earth; it also generates revenue.
Biochar’s Hidden Superpower: Adsorption & Buffering Biochar’s porous structure acts as a molecular storage hub. Unlike absorption (soaking up water like a sponge), adsorption is a chemical process where water and nutrients cling to biochar’s surfaces. A single gram of biochar has the surface area of a basketball court, creating a lattice of microscopic nooks and crannies. This allows it to:
Lock in moisture: Biochar retains up to 10x its weight in water, acting like a “soil battery” that releases hydration slowly during droughts.
Hoard nutrients: It buffers nitrogen, phosphorus, potassium, and micronutrients in its pores, preventing leaching. Plants access these nutrients gradually, reducing fertilizer needs.
Stabilize pH: Biochar’s alkaline nature buffers acidic soils, creating a neutral environment where microbes and roots thrive.
This buffering effect means plants face fewer nutrient and water spikes or shortages, ensuring steady growth even in erratic climates.
The Carbon Math Every ton of biochar (which is ~85% carbon by weight) sequesters 3.12 tons of CO₂ (using the 1:3.67 carbon-to-CO₂ ratio). With carbon credits trading at $42–$60/ton, a 1,000-acre project applying 1 pound of biochar per linear foot (via a three-shank plow at 2-foot spacing) could sequester ~12,000 tons of CO₂ annually—generating $504,000–$720,000 in carbon credit revenue.
Tools for the Revolution The Keyline Plow fractures subsoil to inject biochar slurry 30–45cm deep, revitalizing compacted land. For smaller plots, the VOGT Geo Injector delivers pinpoint inoculations—think of it as a soil “injection gun” for lawns, golf courses, or urban gardens. These methods ensure biochar stays where it’s needed, turning even parched landscapes into carbon sinks.
Bitcoin’s Role in the Loop Biochar production generates syngas—a byproduct that fuels electric generators for Bitcoin mining. This closed-loop system turns agricultural waste into energy, creating dual revenue streams: carbon credits and mining income.
The Market Potential Farmers, ranchers, and eco-conscious landowners aren’t the only beneficiaries. Golf courses can slash water use and homeowners can boost lawn resilience.
Why This Matters This isn’t just farming—it’s a movement. By marrying soil science with economics, we can prove that healing the planet and profiting go hand in hand. Whether you’re a Bitcoin miner, a farmer, or an eco-entrepreneur, this system offers a blueprint for a future where every acre works for you—and the planet.
The takeaway? Regenerative agriculture isn’t a trend. It’s the next gold rush—except this time, the gold is carbon, soil, and sats.---
P.S. – If you’re ready to turn your land into a carbon credit powerhouse (and maybe mine some Bitcoin along the way), the soil is waiting.
You can read the full article, Brewing Biology HERE -> https://the-bitcoin-and-Podcast.ghost.io/ghost/#/editor/post/67e5922fa289aa00088da3c6
originally posted at https://stacker.news/items/933800
-
 @ 2ed3596e:98b4cc78
2025-04-03 21:20:27
@ 2ed3596e:98b4cc78
2025-04-03 21:20:27We’re giving you the chance to win even more sats through the Bitcoin (Wishing) Well—just for telling us what you love about Bitcoin Well.
Each month, when you leave a review for either the Bitcoin Well portal on Trustpilot (include your WellTag), or our Bitcoin ATMs and (include your transaction ID and email), you’ll be entered for a draw where you can win $210 in bitcoin just for sharing your experience!
Whether it’s our self-custody focus, fast Lightning purchases, Lightning referral payouts, private ATM transactions or our unbeatable customer support, we want to hear what makes Bitcoin Well your go-to place for buying, selling, and using bitcoin.
How to leave your Trustpilot review for our portal
- Head to our Trustpilot page
- Write a quick review sharing your favourite Bitcoin Well feature
- Include your WellTag (or transaction ID), in the review so we can add you to the prize draw
How to leave your google review for one of our ATMs
- Google the Bitcoin Well Bitcoin ATM you recently used
- Write a quick review sharing your favourite Bitcoin Well feature
- Include your transaction ID, in the review so we can add you to the prize draw
It’s that easy! Once your review is verified with your welltag or transaction ID, we’ll add your entry to our monthly draw for your chance to win $210 in bitcoin! We’ll announce the winner and the start of each month. Good luck and keep stacking sats!
What makes Bitcoin Well different
Bitcoin Well is on a mission to enable independence. We do this by making it easy to self custody bitcoin. By custodying their own money, our customers are free to do as they wish without begging for permission. By creating a full ecosystem to buy, sell and use your bitcoin to connect with the modern financial world, you are able to have your cake and eat it too - or have your bitcoin in self custody and easily spend it too 🎂.
Create your Bitcoin Well account now →
Invest in Bitcoin Well
We are publicly traded (and love it when our customers become shareholders!) and hold ourselves to a high standard of enabling life on a Bitcoin standard. If you want to learn more about Bitcoin Well, please visit our website.
-
 @ df67f9a7:2d4fc200
2025-04-03 19:54:29
@ df67f9a7:2d4fc200
2025-04-03 19:54:29More than just “follows follows” on Nostr, webs of trust algos will ingest increasingly MORE kinds of user generated content in order to map our interactions across the network. Webs of trust will power user discovery, content search, reviews and reccomendations, identity verification, and access to all corners of the Nostr network. Without relying on a central “trust authority” to recommend people and content for us, sovereign Nostr users will make use of “relative trust” scores generated by a wide range of independent apps and services. The problem is, Nostr doesn’t have an opensource library for performing WoT calculations and delivering NIP standard recommendations to users. In order for a “free market” ecosystem of really smart apps and services to thrive, independent developers will need access to extensible “middleware” such as this.
Project Description
I am building a library for independent developers to offer their own interoperable and configurable WoT services and clients. In addition, and as the primary use case, I am also developing a web client for “in person onboarding” to Nostr, which will make use of this library to provide webs of trust recommendations for “invited” users.
-
Meet Me On Nostr (onboarding client) : This is my first project on Nostr, which began a year ago with seed funding from @druid. This web client will leverage “in person” QR invites to generate WoT powered recommendations of follows, apps, and other stuff for new users at their first Nostr touchpoint. The functional MVP release (April ‘25) allows for “instant, anonymous, and fully encrypted” direct messaging and “move in ready” profile creation from a single QR scan.
-
GrapeRank Engine (developer library) : Working with @straycat last fall, I built an opensource and extensible library for Nostr developers to integrate “web of trust” powered reccomendations into their products and services. The real power behind GrapeRank is its “pluggable” interpreter, allowing any kind of content (not just “follows follows”) to be ingested for WoT scoring, and configurable easily by developers as well as end users. This library is currently in v0.1, “generating and storing usable scores”, and doesn’t yet produce NIP standard outputs for Nostr clients.
-
My Grapevine (algo dashboard) : In addition, I’ve just wrapped up the demo release of a web client by which users and developers can explore the power of the GrapeRank Engine.
Potential Impact
Webs of Trust is how Nostr scales. But so far, Nostr implementations have been ad-hoc and primarily client centered, with no consistency and little choice for end users. The “onboarding and discovery” tools I am developing promise to :
-
Establish sovereignty for webs of trust users (supporting a “free market” of algo choices), with opensource libraries by which any developer can easily implement WoT powered recommendations.
-
Accelerate the isolation of bots and bad actors (and improve the “trustiness” of Nostr for everyone else) by streamlining the onboarding of “real world” acquaintances directly into established webs of trust.
-
Improve “discoverability of users and content” for any user on any client (to consume and take advantage of WoT powered recommendations for any use case, even as the NIP standards for this are still in flux), by providing an algo engine with “pluggable” inputs and outputs.
-
Pave the way for “global Nostr adoption”, where WoT powered recommendations (and searches) are consistently available for every user across a wide variety of clients.
Timeline & Milestones
2025 roadmap for “Webs of Trust Onboarding and Discovery” :
-
Meet Me On Nostr (onboarding client) : MVP release : “scan my QR invite to private message me instantly with a ‘move in ready’ account on Nostr”. https://nostrmeet.me/
-
GrapeRank Engine (developer library) : 1.0 release : “expanded inputs and output WoT scores to Nostr NIPs and other stuff” for consumption by clients and relays. https://github.com/Pretty-Good-Freedom-Tech/graperank-nodejs
-
My Grapevine (algo dashboard) : 1.0 release : “algo usage and configuration webapp with API endpoints” for end users to setup GrapeRank scoring for consumption by their own clients and relays. https://grapevine.my/
-
Meet Me On Nostr (onboarding client) : 1.0 release : first GrapeRank integration, offering “follow and app recommendations for invited users”, customizable per-invite for Nostr advocates. https://nostrmeet.me/
Prior contributions
-
Last spring I hosted panel discussions and wrote articles on Nostr exploring how to build “sovereign webs of trust”, where end users can have control over which algorithms to use, and what defines “trust”.
-
I contributed gift wrap encryption to NDK.
-
I am also authoring gift wrapped direct messaging and chat room modules for NDK.
-
Last July, I attended The Bitcoin Conference on an OpenSource pass to raise funds for my onboarding client. I onboarded many Bitcoiners to Nostr, and made valuable connections at Bitcoin Park.
About Me
I discovered Nostr in September ‘23 as a freelance web developer, after years of looking for a “sovereignty respecting” social media on which to build apps. With this came my first purchase of Bitcoin. By December of that year, I was settled on “open source freedom tech” (Nostr and Bitcoin) as the new direction for my career.
As a web professional for 20+ years, I know the importance of “proof of work” and being connected. For the last 18 months, I have been establishing myself as a builder in this community. This pivot has not been easy, but it has been rewarding and necessary. After so many years building private tech for other people, I finally have a chance to build freedom tech for everyone. I have finally come home to my peeps and my purpose.
Thank you for considering this application for funding.
-
-
 @ 502ab02a:a2860397
2025-04-03 17:41:20
@ 502ab02a:a2860397
2025-04-03 17:41:20ไฟโตสเตอรอล (Phytosterols) เป็นสารประกอบที่พบในพืชและมีโครงสร้างคล้ายคลึงกับคลอเลสเตอรอล (Cholesterol) ของมนุษย์ แต่ไฟโตสเตอรอลไม่ได้ทำหน้าที่เหมือนคลอเลสเตอรอลในร่างกายครับ ไฟโตสเตอรอลมีบทบาทสำคัญในการลดการดูดซึมคลอเลสเตอรอลจากอาหารในระบบทางเดินอาหาร ทำให้ไฟโตสเตอรอลได้รับการส่งเสริมว่าเป็นสารที่ช่วยลดระดับคลอเลสเตอรอลในเลือดไปโดยปริยาย
อย่างไรก็ตาม สิ่งที่หลายคนไม่ได้ตั้งข้อสงสัยคือวิธีการโฆษณาและการตลาดนั้นจะแฝงไปด้วยข้อมูลที่บิดเบือนเกี่ยวกับไฟโตสเตอรอลซึ่งอาจนำไปสู่การเสพสารนี้ในปริมาณมากเกินไปจนทำให้เกิดปัญหาสุขภาพหรือเปล่า? เราลองมาค่อยๆตั้งคำถามกันครับ
ไฟโตสเตอรอลในธรรมชาติจะพบในปริมาณที่ค่อนข้างน้อยในพืชต่าง ๆ เช่น ธัญพืช ถั่ว เมล็ดพืช อย่างไรก็ตาม ปริมาณไฟโตสเตอรอลในธรรมชาติเป็นเม็ดเป็นผลจะอยู่ในระดับต่ำมาก เช่น ในเมล็ดแฟลกซีด (flaxseed) จะมีไฟโตสเตอรอลอยู่ประมาณ 1,000–2,000 ppm (parts per million) ขณะที่น้ำมันรำข้าวที่มักถูกโฆษณาว่ามีไฟโตสเตอรอลสูงถึงหลักหมื่น ๆ ppm เช่น 12,000 ppm หรือบางยี่ห้ออาจสูงกว่านั้น ซึ่งไม่ใช่แค่สูงจนน่าสรรเสริญ แต่ยังเป็นการขยายความสำคัญของไฟโตสเตอรอลในทางที่ตอบสนองต่อการตลาดได้ในวงกว้างเสียด้วย
กระบวนการผลิตน้ำมันรำข้าวนั้นเริ่มต้นจากการสกัดน้ำมันจากรำข้าว โดยมีการใช้เทคนิคการกลั่นน้ำมันที่สามารถช่วยให้ได้น้ำมันที่มีคุณภาพสูง น้ำมันรำข้าวเป็นน้ำมันที่มีไฟโตสเตอรอลสูงเพราะรำข้าว (bran) ซึ่งเป็นเปลือกที่หุ้มเมล็ดข้าวนั้น มีไฟโตสเตอรอลอยู่ในปริมาณสูงตามธรรมชาติอยุ่แล้ว ในกระบวนการสกัดน้ำมันนั้น ตัวไฟโตสเตอรอลจะถูกรักษาไว้ โดยไม่ต้องเติมเข้าไปใหม่ ดังนั้น เมื่อโฆษณาน้ำมันรำข้าวว่า "มีไฟโตสเตอรอลสูงถึง 12,000 ppm" สิ่งนี้ไม่ได้หมายความว่าเป็นการเติมสารเพิ่มเข้ามาหรอกครับ แต่เป็นการยืนยันถึงความ "เข้มข้น" ของไฟโตสเตอรอลที่มีอยู่ในน้ำมันรำข้าวตามธรรมชาตินั่นละครับว่ามันกลั่นมาเข้มข้นขนาดไหน มากกว่าการกินจากธรรมชาติขนาดไหนเพื่อให้เรากินกันนั่นเอง
ถึงแม้ว่าไฟโตสเตอรอลจะถูกส่งเสริมให้เป็นสารที่ช่วยลดระดับคลอเลสเตอรอลในเลือด แต่การโฆษณาและการตลาดเกี่ยวกับไฟโตสเตอรอลนั้นอาจทำให้คนเข้าใจผิดว่า ผลิตภัณฑ์ที่มีไฟโตสเตอรอลสูง จะช่วยทำให้สุขภาพดีขึ้นและลดความเสี่ยงจากโรคหัวใจและหลอดเลือด เพราะซึ่งสิ่งนี้ยังไม่ได้รับการสนับสนุนอย่างชัดเจนจากงานวิจัยที่สามารถยืนยันได้ในระยะยาว นอกจากนี้ยังมีผลการศึกษาบางชิ้นเช่นกันที่พบว่า การบริโภคไฟโตสเตอรอลในปริมาณสูงอาจ "ไม่ได้มีผล" ในการลดระดับคลอเลสเตอรอลที่น่ามหัศจรรย์หรือช่วยลดการเสี่ยงต่อโรคหัวใจได้ตามที่โฆษณาเอามาขยายความกัน ซึ่งแน่นอนหละครับว่า ถ้าจะทำสงครามวิจัย มันย่อมไม่จบสิ้นเพราะทุกฝ่ายมีการวิจัยสนับสนุนในแบบ peer review ทั้งนั้น ไม่ต้องไปเป็น member อะไรที่ไหน (ถ้าเราไม่คิดจะอ่านมันเอง)
ไฟโตสเตอรอลมีหลายประเภทที่พบในพืชและน้ำมันพืชแต่ละชนิด โดยแต่ละชนิดจะมีคุณสมบัติและผลกระทบต่อร่างกายที่แตกต่างกัน ซึ่งสามารถแบ่งออกเป็นหลายประเภทหลักที่พบได้บ่อยในธรรมชาติ แต่ละประเภทก็มีข้อดีและข้อเสียที่ควรพิจารณาก่อนการบริโภคตามประเภทมันไปครับ
-บีตาสติโรล (Beta-Sitosterol) เป็นไฟโตสเตอรอลที่พบมากในพืชหลายชนิด โดยเฉพาะในเมล็ดพืช ถั่ว และน้ำมันพืช บีตาสติโรลได้รับความนิยมในวงการสุขภาพเนื่องจากการศึกษาบางชิ้นพบว่ามันสามารถช่วยลดระดับคอเลสเตอรอลในเลือดได้ โดยการลดการดูดซึมคอเลสเตอรอลจากอาหารในระบบย่อยอาหาร แต่การบริโภคบีตาสติโรลในปริมาณสูงอาจส่งผลต่อการดูดซึมวิตามินที่ละลายในไขมัน เช่น วิตามิน A, D, E และ K ซึ่งอาจทำให้เกิดการขาดวิตามินเหล่านี้ในระยะยาวได้ นอกจากนี้ การบริโภคบีตาสติโรลในปริมาณที่มากเกินไปอาจส่งผลให้เกิดปัญหาด้านระบบฮอร์โมน โดยเฉพาะในผู้ที่มีปัญหาฮอร์โมนเพศหรือระบบสืบพันธุ์
-แคมป์สเตอรอล (Campesterol) เป็นอีกหนึ่งไฟโตสเตอรอลที่พบในพืชหลายชนิด โดยเฉพาะในน้ำมันพืชและผักผลไม้ แคมป์สเตอรอลมีโครงสร้างที่คล้ายกับคอเลสเตอรอลในร่างกาย และมันได้รับการศึกษาว่ามีคุณสมบัติช่วยลดระดับคอเลสเตอรอลในเลือดได้เช่นกัน อย่างไรก็ตาม การบริโภคแคมป์สเตอรอลมากเกินไปอาจทำให้เกิดผลกระทบต่อการดูดซึมสารอาหารบางประเภท เช่น วิตามินที่ละลายในไขมัน โดยเฉพาะในผู้ที่มีปัญหาทางเดินอาหาร หรือผู้ที่มีปัญหาการดูดซึมสารอาหาร อาจทำให้เกิดภาวะขาดสารอาหารหรือการดูดซึมสารอาหารไม่เต็มที่ได้ นอกจากนี้ การบริโภคแคมป์สเตอรอลในปริมาณสูงอาจส่งผลกระทบต่อการทำงานของฮอร์โมนเพศ เช่น การเปลี่ยนแปลงของฮอร์โมนในร่างกาย ซึ่งอาจเกิดผลเสียต่อสุขภาพในระยะยาว
-สแตกิโอรอล (Stigmasterol) เป็นไฟโตสเตอรอลชนิดหนึ่งที่พบมากในพืชบางชนิด เช่น ถั่วเหลือง และน้ำมันถั่วเหลือง สแตกิโอรอลได้รับการศึกษาในแง่ของการลดการอักเสบและการช่วยบำรุงสุขภาพหัวใจและหลอดเลือด แต่การบริโภคสแตกิโอรอลในปริมาณสูงอาจมีผลเสียต่อการทำงานของฮอร์โมนเพศได้เช่นกัน โดยเฉพาะในผู้ที่มีปัญหาฮอร์โมนไม่สมดุลหรือมีปัญหาเกี่ยวกับระบบสืบพันธุ์ การบริโภคไฟโตสเตอรอลชนิดนี้มากเกินไปอาจทำให้เกิดผลกระทบต่อการทำงานของระบบฮอร์โมนในร่างกาย ซึ่งอาจส่งผลให้เกิดอาการผิดปกติในระยะยาว รวมทั้งความเสี่ยงต่อการมีบุตรหรือสุขภาพที่ไม่ดีเกี่ยวกับระบบฮอร์โมน
ไฟโตสเตอรอลประเภทอื่น ๆ ที่พบในพืชและน้ำมันพืช ได้แก่ อะฟิตเตอร์ออล (Afitosterol) และซิตรัสเตอรอล (Citrusterol) ซึ่งมักพบในน้ำมันจากพืชต่าง ๆ เช่น น้ำมันเมล็ดองุ่น น้ำมันดอกทานตะวัน การบริโภคไฟโตสเตอรอลเหล่านี้ในปริมาณที่สูงเกินไปอาจทำให้เกิดปัญหาด้านระบบย่อยอาหาร หรือปัญหาการดูดซึมสารอาหารที่จำเป็นจากอาหารได้ นอกจากนี้ การบริโภคไฟโตสเตอรอลประเภทอื่น ๆ ในปริมาณสูงยังอาจส่งผลกระทบต่อระบบฮอร์โมนและการทำงานของร่างกายในระยะยาว เช่น การทำงานของระบบภูมิคุ้มกัน หรือการทำงานของตับ ที่อาจได้รับผลกระทบจากการบริโภคในปริมาณสูง ดังนั้น ควรระมัดระวังในการบริโภคไฟโตสเตอรอลจากแหล่งต่าง ๆ อย่างรอบคอบ เพื่อหลีกเลี่ยงผลเสียที่อาจเกิดขึ้นกับร่างกายในระยะยาว
สิ่งที่จริงแล้วอาจเป็นอันตรายมากกว่า คือ การที่ผู้บริโภคตัดสินใจบริโภคผลิตภัณฑ์ที่มีไฟโตสเตอรอลสูงในปริมาณมากเกินไป โดยไม่คำนึงถึงผลกระทบต่อร่างกายในระยะยาว อาจมีผลกระทบต่อการดูดซึมสารอาหารที่จำเป็น เช่น วิตามิน A, D, E, K ซึ่งเป็นวิตามินที่ละลายในไขมัน การดูดซึมของวิตามินเหล่านี้อาจถูกยับยั้งไป เนื่องจากไฟโตสเตอรอลสามารถแข่งขันกับคลอเลสเตอรอลในร่างกายในการดูดซึมสารอาหารเหล่านี้ นอกจากนี้ยังมีข้อกังวลเกี่ยวกับผลกระทบที่อาจเกิดขึ้นจากการบริโภคไฟโตสเตอรอลในปริมาณสูงที่อาจไปเพิ่มความเสี่ยงของการเกิดโรคบางอย่าง เช่น โรคมะเร็งต่อมลูกหมาก
ผลเสียจากการบริโภคไฟโตสเตอรอลมากเกินไปไม่ได้จำกัดเพียงแค่การแย่งสารอาหาร แต่ยังมีการศึกษาที่แสดงให้เห็นว่า การบริโภคไฟโตสเตอรอลในปริมาณสูงอาจกระทบต่อการทำงานของระบบภูมิคุ้มกันของร่างกาย ในบางกรณีไฟโตสเตอรอลอาจเข้าไปแทรกแซงกระบวนการทางชีวเคมีที่สำคัญ และอาจทำให้ร่างกายเกิดความผิดปกติในการตอบสนองต่อสารแปลกปลอมที่มีอยู่ในสิ่งแวดล้อม
ข้อโต้แย้งที่สำคัญคือลักษณะการโฆษณาของน้ำมันรำข้าวและผลิตภัณฑ์ที่มีไฟโตสเตอรอลสูงนั้น ไม่ได้สะท้อนความจริงในสิ่งที่เป็นประโยชน์ต่อสุขภาพจริง ๆ การใช้ไฟโตสเตอรอลในผลิตภัณฑ์ต่าง ๆ โดยเน้นที่ปริมาณที่สูงเกินจริงนั้น เป็นวิธีการตลาดที่ใช้บอกเป็นนัยกับผู้บริโภคให้เข้าใจว่าการบริโภคสารเหล่านี้จะช่วยลดระดับคลอเลสเตอรอลและช่วยให้สุขภาพหัวใจดีขึ้น ทั้งที่ในความเป็นจริง ไฟโตสเตอรอลไม่ได้ช่วยแก้ปัญหาสุขภาพพื้นฐานอย่างการอักเสบที่เป็นสาเหตุหลักของโรคหัวใจและหลอดเลือด แต่ทั้งนี้ทั้งนั้น การโฆษณาดังกล่าวก็อยู่ภายใต้กฎเกณฑ์ของประกาศและกฎหมายต่างๆอยู่ดี ผู้บริโภคจึงควรหาความรู้สนับสนุนการเลือกด้วยตัวเอง ว่าจะตัดสินใจอย่างไร
การที่ไฟโตสเตอรอลมีโครงสร้างที่คล้ายกับคอเลสเตอรอลในร่างกาย ทำให้มันสามารถแทรกซึมเข้าไปในเซลล์ได้คล้ายคลึงกับคอเลสเตอรอล แต่แตกต่างกันตรงที่ไฟโตสเตอรอลไม่สามารถทำหน้าที่ในการสร้างฮอร์โมนต่าง ๆ หรือทำหน้าที่ในระบบร่างกายได้เหมือนคอเลสเตอรอล การที่ไฟโตสเตอรอลแทรกซึมเข้าไปในเซลล์จึงเป็นแค่การสามารถช่วยป้องกันการดูดซึมคอเลสเตอรอลจากอาหารในระบบย่อยอาหารได้ ซึ่งจะทำให้นี่เป็นสาเหตุของการทำให้ ระดับคอเลสเตอรอลในเลือดลดลงได้ พูดง่ายๆคือมันไปแซงคลอเลสเตอรอล อะครับ
นอกจากนี้ ไฟโตสเตอรอลยังสามารถไปแข่งขันกับคอเลสเตอรอลในการเข้าเซลล์ผ่านตัวรับ LDL (low-density lipoprotein receptor) ซึ่งเป็นตัวรับที่ช่วยดูดซึมคอเลสเตอรอลเข้าสู่เซลล์ ดังนั้น เมื่อไฟโตสเตอรอลแทรกซึมเข้ามามากขึ้น ก็จะช่วยลดการดูดซึมคอเลสเตอรอล ที่มาจากอาหารลงไปได้ ทำให้ระดับคอเลสเตอรอลในเลือดลดลง โดยการลดการดูดซึมคอเลสเตอรอลจากทางเดินอาหารเข้าสู่กระแสเลือด แต่ไฟโตสเตอรอลไม่ได้มีผลโดยตรงในการลดคอเลสเตอรอลที่เซลล์ในร่างกายสร้างขึ้นเอง (endogenous cholesterol) เพราะไฟโตสเตอรอลไม่ได้เข้าไปแทรกซึมและทำงานที่จุดที่เซลล์ผลิตคอเลสเตอรอลในร่างกาย
ร่างกายสามารถผลิตคอเลสเตอรอลได้เอง ซึ่งเป็นกระบวนการที่ไฟโตสเตอรอลไม่สามารถไปขัดขวางหรือยับยั้งได้ นั่นหมายความว่า หากร่างกายผลิตคอเลสเตอรอลในระดับสูง ไฟโตสเตอรอลจะไม่สามารถลดระดับคอเลสเตอรอลที่มาจากการสร้างของร่างกายได้ ดังนั้น ไฟโตสเตอรอลมีประโยชน์ในการลดคอเลสเตอรอลจากอาหาร แต่ไม่ได้ช่วยในการลดคอเลสเตอรอลที่ร่างกายผลิตขึ้นเอง
การโฆษณาไม่ได้ให้ข้อมูลในด้านที่ว่า ผลกระทบระยะยาวจากการบริโภคไฟโตสเตอรอลในปริมาณสูงอาจทำให้เกิดปัญหาสุขภาพอื่น ๆ โดยเฉพาะในด้านการดูดซึมสารอาหารหรือความสามารถในการทำงานของระบบภูมิคุ้มกัน ซึ่งเป็นสิ่งที่ควรคำนึงถึงในการตัดสินใจเลือกผลิตภัณฑ์ที่จะนำมาใช้ในชีวิตประจำวัน ในความเห็นของผมนั้น สิ่งที่ควรให้ความสำคัญมากกว่าคือการเลือกบริโภคอาหารที่เป็นธรรมชาติ และหลีกเลี่ยงการพึ่งพาผลิตภัณฑ์ที่มีการผ่านกระบวนการต่าง ๆ เช่น ไฟโตสเตอรอลเข้มข้น หรือสารเติมแต่งอื่น ๆ ที่ไม่จำเป็นต่อร่างกาย การเลือกรับประทานอาหารที่มีคุณค่าทางโภชนาการครบถ้วนจะช่วยส่งเสริมสุขภาพโดยรวมได้ดีกว่าแทนที่จะพึ่งพาสิ่งที่โฆษณาบอกไว้ข้างขวด
ไฟโตสเตอรอลอาจมีคุณสมบัติในการลดการดูดซึมคลอเลสเตอรอลจากอาหารในทางทฤษฎี แต่การบริโภคในปริมาณมากเกินไปนั้นอาจส่งผลเสียต่อร่างกายในหลาย ๆ ด้าน ดังนั้นจึงควรหันมาใส่ใจในข้อมูลที่มีพื้นฐาน และตั้งคำถามกับสิ่งต่างๆ โดยเฉพาะอะไรที่การตลาดตะโกนดังๆว่า ไอ้นี่ดี อันโน้นเยี่ยมยอด อันนี้ที่สุดแห่งความซุปเปอร์ ต่อมเอ๊ะทำงานไว้ก่อน ผิดถูกไม่รู้หาข้อมูลมาโยงเส้นทางแล้วชวนคุยกัน
เช่นเราตั้งคำถามตั้งต้นก่อนไหมว่า จริงๆแล้ว คลอลเสเตอรอล มันต้องกลัวขนาดนั้นเลยหรือ ในเมื่อมันเป็นสารตั้งต้นของชีวิต และเป็นสิ่งจำเป็นในการซ่อมแซมเสริมสร้างร่ายกาย เราต้องลดการดูดซึมด้วยเหรอ
-
 @ 7d33ba57:1b82db35
2025-04-03 17:36:08
@ 7d33ba57:1b82db35
2025-04-03 17:36:08Zadar is a coastal city in northern Dalmatia, known for its rich Roman and Venetian history, stunning sunsets, and unique modern attractions like the Sea Organ and Sun Salutation. With ancient ruins, beautiful beaches, and a lively Old Town, Zadar offers a less crowded but equally charming alternative** to Split and Dubrovnik.
🏛️ Top Things to See & Do in Zadar
1️⃣ Explore Zadar Old Town 🏰
- Walk through narrow, stone-paved streets, surrounded by Roman and medieval architecture.
- Visit People’s Square (Narodni Trg) – The heart of Zadar’s Old Town, filled with lively cafés.
2️⃣ Visit the Sea Organ & Sun Salutation 🎶🌞
- Sea Organ – A one-of-a-kind musical instrument, where waves create natural melodies.
- Sun Salutation – A large solar-powered light display, best seen at sunset.
- Alfred Hitchcock once called Zadar’s sunset “the most beautiful in the world.” 🌅
3️⃣ Admire St. Donatus Church & Roman Forum ⛪
- St. Donatus (9th century) – A unique, round Byzantine-style church with great acoustics.
- Roman Forum – The remains of an ancient Roman marketplace, built in the 1st century BC.
4️⃣ Climb the Bell Tower of St. Anastasia’s Cathedral 🔔
- Enjoy spectacular views over Zadar’s rooftops and the Adriatic.
- One of the tallest church towers in Croatia.
5️⃣ Relax at Zadar’s Best Beaches 🏖️
- Kolovare Beach – The most popular city beach, just a short walk from the Old Town.
- Borik Beach – A sandy beach with shallow waters, ideal for families.
- Punta Bajlo – A more natural and peaceful spot, great for a quiet swim.
6️⃣ Take a Day Trip to Kornati National Park ⛵
- A beautiful archipelago of 89 islands, perfect for boating, swimming, and snorkeling.
- Join a boat tour from Zadar to explore the untouched nature of the Adriatic.
7️⃣ Try Dalmatian Cuisine 🍽️
- Black Risotto (Crni Rižot) – A delicious squid-ink seafood dish. 🦑
- Pag Cheese (Paški Sir) – A famous sheep’s milk cheese from Pag Island. 🧀
- Grilled Adriatic Fish – Freshly caught and served with olive oil & Dalmatian herbs. 🐟
🚗 How to Get to Zadar
✈️ By Air:
- Zadar Airport (ZAD) is just 15 minutes from the city center.
🚘 By Car:
- From Split: ~1.5 hours (160 km)
- From Zagreb: ~2.5 hours (285 km)
🚌 By Bus: Regular buses from Split, Zagreb, Dubrovnik, and Plitvice Lakes.
⛴️ By Ferry: Ferries connect Zadar to nearby islands like Ugljan, Dugi Otok, and Pašman.
💡 Tips for Visiting Zadar
✅ Best time to visit? May–October for warm weather & island trips ☀️
✅ Stay near the Old Town – Everything is within walking distance 🏡
✅ Catch the sunset at the Sea Organ – It’s a must-do experience 🌊🎶
✅ Take a ferry to Ugljan Island for a day of beaches & cycling 🚢🚴♂️
✅ Book Kornati boat tours in advance – They sell out fast in summer! ⛵ -
 @ 000002de:c05780a7
2025-04-03 17:27:03
@ 000002de:c05780a7
2025-04-03 17:27:03I score zero points. How about you?
https://m.primal.net/QDDi.jpg
I almost called this a boomer test but its more of a Gen X test.
Credit to Jack Spirko for sharing this on Twitter.
originally posted at https://stacker.news/items/933537
-
 @ 5708b1f6:208df3b8
2025-04-03 15:25:33
@ 5708b1f6:208df3b8
2025-04-03 15:25:33The role and significance of music naturally varies from person to person. For some, it is counted among the most important things in life. For others, it may be a superfluous additive of limited value. Due to this difference in perception relating to music, it may be difficult for some individuals to recognize the benefits of compiling a personalized music playlist.
However, the value of music as a therapeutic tool for people already suffering from advanced dementia has been repeatedly demonstrated, and sometimes with astounding, although temporary, results. The internet is full of studies and stories, and YouTube searches yield an abundance of video evidence ranging from clinical studies to anecdotal family recordings of elderly relatives.
All of these data and anecdotes point to a compelling suggestion and an exciting conclusion: music appreciation has tremendous potential as a supplemental activity for mental health maintenance. With insights gained from the study of neuroplasticity, the neurological benefits for musicians and performers are easy to see, but less clear is the fact that mere exposure to music as a casual listener can be of profound psychological importance, even for individuals who don’t consider themselves to be music lovers.
The transformative effect of music is on full display in many of the available videos on YouTube. We can simply search “dementia music,” or ‘Alzheimer’s music” for fast, relevant results. In video after video, we can see elderly subjects who may be slow to speak, detached, disoriented, barely-intelligible, or unresponsive. In care facilities and at gatherings with families, they are interviewed about their youth, and about their feelings related to music.
Many of the videos first show footage of the individual’s normal daily cognitive state, and them listening and responding to the questions, followed by a period of music listening, and then another brief, post-music discussion. The transformation of mental states tends to be very clear when we compare the quality of their cognitive performance before and after the introduction of music. People remark that “a light has been turned back on,” or “his personality returned,” or “it’s as if the person has woken up from sleep.”
Unfortunately, these positive responses are only temporary, and music does not have the power to permanently reverse the symptoms and pathology of advanced dementia and age-related cognitive decline. Also there is no guarantee it will work for every person, or to what degree. Nevertheless, it does not mean that music as therapy is completely without value. In fact, it can be quite the opposite.
When the response is positive, the event can have multiple benefits, and may even be a therapeutic experience for certain listeners. Faces once despondent or vacant become animated and radiant. Long lost smiles return from faraway times and places. Memories and associations from previous ages shake loose and rise to the surface. Many listeners were asked to recount their experiences related to the songs and the time in life with which they were primarily associated. Some of them were able to describe events, places, people, emotions, and reactions with a degree of clarity, dexterity, and articulation that was completely inconsistent with their medical diagnosis and their cognitive performance prior to hearing the music. The song quite literally revives the personality that makes the person, temporarily and superficially reversing the undoing of the mind. For a mind that is coming undone, music as therapy has potential to mitigate suffering and confusion, provide moments of joy and enthusiasm, and ease the transition into and experience of the end-of-life period that awaits all who are fortunate enough to “die of natural causes” in old age.
The benefits described above are specific to “treatment” recipients, but the merit of music as therapy cascades into the lives of everyone involved. Doctors and caretakers are uplifted and encouraged by success stories, which contributes to further proliferation and advancement of music as therapy. More critically, it can have a profound impact on families of dementia patients. In some cases, relatives get a chance to communicate with their loved ones again. Grandchildren have a window of opportunity to learn more, directly from their grandparents, about the youthful experiences and memories of past generations. It’s clear that generational bonds are also strengthened, which can positively impact the future prospects of the young generation as they in turn grow old, and lay new groundwork for generations that follow.
It is unfortunate that some elderly individuals seem to derive less cognitive benefit than others from music therapy. It is not entirely certain why this is so, because there are many factors to consider, but two of the clearest factors are a person’s degree of cognitive decline, and their degree of interest in and enthusiasm for music in general. While these are the most popular metrics by which to judge the potential effectiveness and suitability of music as therapy for a given individual, by far the most important consideration is relevance to each particular person’s life experiences.
This is the opportunity to finally state the obvious: It’s not possible to simply pick any song at random and expect it to have a beneficial effect on the cognitive function of every person who hears it. It’s not as if there’s a Britney Spears song that sparks joy in the heart of every soul on Earth. And the legend of Bill and Ted’s ultimate song that united the world could never be a true story (also because, as we finally learned in 2020, it was not two men and a song that united the world, but rather, the world uniting together to create that song.) However, everyone in the world can make their own playlist custom-tailored to their individual life, experiences, and memories, and some of those playlists might have a song or two by Britney Spears, or even some from one of the “Bill and Ted” soundtracks.
Throughout my decades of music appreciation, an ever-growing level of respect for the enduring spirit of music has overwhelmed me, and it’s clear that no song will ever be loved by all. But every song will be loved by some, certainly at least by someone, or it would cease to exist. This is why a personalized playlist is infinitely more valuable than randomly selected songs, and we can see the truth of this claim upon close examination of recorded interviews with the elderly subjects. The songs that triggered the greatest reactions were songs that interviewees felt strong connections to, based primarily on the song’s associations to the time and place, as well as the emotional context imprinted on the memory of the events surrounding the songs.
This simply means that songs for which we have emotional attachments and vivid memories are songs that invigorate our neural circuits, activating cognitive pathways and opening doors of memory similar to how olfactory sensations can trigger a memory or a sense of déjà vu. There are some exceptions, but a lot of these songs are from a person’s formative years, particularly early developmental years and their teenage period. This comes as no surprise to the discerning neuroplastician, because these are periods of life when neural plasticity is most fluid, neural development and refinement functions are most active and receptive, and the degree of exciting novelty in life tends to be highest when we are young and inexperienced.
Novelty and emotion are critical components of memory formation and whether a given experience will be memorable or not. Something completely new (novelty) can be memorable if it commands your attention, or derails you from your usual pattern of behavior. Similarly, the content of a tedious lecture may be harder to recall without taking notes, while that of an exciting, fun, and funny, interactive lesson has a greater chance of being memorable, and recalled with more clarity and detail (emotion).
When it comes to music, the connection to novelty and emotion is crystal clear. The first time you ever heard that song, it was new and your emotional response was strong. You might even remember the events of that first time you heard it, but not necessarily. Your emotional attachment to the song may have developed later on, when you heard it playing at a party, on one of the most memorable nights of your teenage life, for example. Perhaps it’s just a song (or songs) your parents played a lot when you were young, and it could be a song you yourself heard many times, and looking back realized it holds a special place in your heart, for whatever reason. There are also songs that are special to romantic couples (This song was playing when we…; This is our song; We were together the first time we heard this song; etc.) and these songs, for obvious reasons, can be added to a personalized music playlist at any time in life, as new and old songs take on added personal significance in various ways. There are a multitude of ways that novelty and emotion can combine to form experiences worth remembering, by which memories are made, and if these experiences are imprinted with a musical stamp, the song stamped onto the memory is likely to remain just as memorable as the event itself, and conversely, listening to the song has the potential to vivify the memories and feelings of nostalgia related to the song.
Therefore, as a preventative measure we can implement now, and an insurance policy we may benefit from later, it is advisable that each person should endeavor to compile their own personal, individualized cognitive reserve playlist. When speaking to someone about this idea, they responded, “But what’s the hurry? After all, you’re still quite young.” Just then, it spontaneously occurred to me that a traumatic head injury could befall me the following day or any day hence, and the simple point that “it’s never too early” was well taken.
To create your own cognitive reserve playlist, it is helpful to have a few guiding parameters. Most important of all is to keep an open mind without setting anything in stone. It’s not necessary to finalize the list immediately, if ever. This is a project that deserves your thoughtful consideration, so you deserve to be allowed to take your time. It’s better to get the list populated with your definite favorites, and as many others that come to mind, just to kick-start the process. Besides, due to the virtually infinite number of songs and compositions in existence, we will never be able to make the perfect list in one day, one month, or even one year. We can always revisit the list and make changes later, because our minds cannot retrieve all the data at once. We must go about our business of carrying on, and wait for it to come to us. (It’s guaranteed to be worth the wait, so never fret about it.) You may even find yourself removing one of those “definite favorites” from the list, which is welcome and fine, because it’s not merely a list of your favorite songs. Being a “favorite” is just one of multiple indicators that a song might be appropriate for a cognitive reserve playlist. “Memorable” is another key word.
There are still other factors that determine a song’s suitability for a personal playlist, such as a song that isn’t a personal favorite, but which nevertheless evokes a strong emotional response in some other way. This is best described as nostalgia, and nostalgic emotions are powerful anchors for memories. So any song that arouses some sense of nostalgia also has the power to arouse the memory of events, places, times, and other details tied to that nostalgia. To know what songs are nostalgic for you and add them to your list today, may help you if a time should come that you need music as therapy in order to trigger your memory and cognitive function.
It is because of nostalgia that many songs from our youth are good candidates for inclusion on the playlist. Songs that were popular on the radio or TV when we were children, theme songs from popular television programs that are unforgettable for us, and songs that acted as the soundtrack to our lives, so to speak, while growing into childhood, and then blossoming again from adolescence into adulthood. This period is rich with music of great significance to our personal center.
It is my sincere hope that all people earnestly endeavor to compile their own personalized cognitive reserve playlists, and encourage their loved ones to do the same. Maybe it can help those who suffer to better cope with the condition. Perhaps starting this project now, and focusing on mental health now can be a significant contributing factor to developing robust cognitive reserve in the first place, thereby heading off the worst of what this condition can throw at us, and delaying it until later. And of course, not only should we create the lists, but it’s highly recommended that we also play the songs frequently, and dance to them as well, preferably. It is in the interest of your future health, ability, mobility, enjoyment, and ease of living that I offer this potentially beneficial suggestion, and I am grateful that you have taken the time to hear me out regarding my passion about the restorative and healing properties of music, as they relate to the broader topic of neuroplasticity. So on that note, shall we press play and dance?
-
 @ 8671a6e5:f88194d1
2025-04-03 14:52:44
@ 8671a6e5:f88194d1
2025-04-03 14:52:44\~ The person came up to me from behind his merchandise stand and saw my Noderunners pin on my black t-shirt, then looked me dead in the eye and asked : “So… what do you sell?”
This is the eighth long-read in a series of twelve “food for thought” writings on Bitcoin. It was originally meant to be a few chapters in a book, but life’s too short for that.
Define
Let me start by saying there’s no single way to define or explain a “Bitcoin conference.” The experience can vary depending on a few factors: who’s organizing it (a long-time Bitcoiner or someone from traditional finance trying to grasp Bitcoin), where it’s being held (a sunny paradise like Madeira or a gloomy northern French town), and who’s speaking (technical experts or charismatic entertainers or people with little substance).
Despite these differences, there’s a shared culture that ties these conferences together: a mix of excitement, frustrations, and inevitable evolution. That’s what I explore.
This is just my take, based on what I’ve personally witnessed and what I hear from my surroundings. It’s not meant to be a blanket critique of all Bitcoin conferences as there are plenty I haven’t attended, though I hear about most of them. Even the good ones will evolve into something else over time. So, plan accordingly.
A bit of background on my perspective: at some point in my life, I hit a bump in the road that kept me tied to where I live — a bleak corner of Belgium, surrounded by fiat slaves, shitcoiners, and people who spend six hours a day consuming brain-numbing garbage television. Traveling is an exception for me, but for many Bitcoin conference attendees, it’s a ritual, a must-do event.
So, I view these events with a mix of fascination and grounded skepticism — something I’ve found lacking in many Bitcoiners. I’ve never been to a Bitcoin conference before 2023, despite receiving plenty of invites over the years. From what I heard and saw in photos from friends who attended (even the real early ones) these events seemed eerily similar to the dull hotel conference rooms I once endured in tech and telecom. I’ve had my fill of lukewarm, watery coffee and lifeless speakers droning on about firewalls. So I skipped that particular honor.
Up until around 2018, Bitcoin conferences were a soulless sea of chairs lined up under fluorescent tube lights, draining the life out of attendees—one telecom acronym at a time. Not exactly inviting. Yet, looking back from the perspective of 2025, those were the “pure” days. Back then, people like Roger Ver (before he pivoted to Bitcoin Cash), Andreas Antonopoulos, and encryption specialists spoke to small audiences, explaining Bitcoin in its raw form.
But, like any Bitcoiner, I try to improve myself. So, I made the effort to travel, visit other Bitcoiners, and attend Bitcoin conferences. The conferences I attended in 2023/2024 made me a bit wiser ; not necessarily from what was said on stage (with a few lucky exceptions who still try to bring original thoughts). Most of what I learned came from the long queues, the drama, and watching grifters operate in real time and the good characters floating around.
So, here’s what I’ve learned.

Chain of ticket
I quickly discovered that many Bitcoin conferences have their own “quest for tickets” dynamic, almost like an industry with its own inner circle. It’s a waterfall system: tickets start at lower prices to fill up the venue (usually right after the previous edition). That’s standard practice, both inside and outside of Bitcoin. But what’s strange is seeing organizations that only pop up when a conference needs promotion—somehow securing tickets for themselves and their friends (or for *making* friends) while shilling referral links for small discounts to their followers.
The real free tickets, though, are a hot topic in many local communities and make all the difference for some attendees. What’s particularly interesting is that most ticket prices can be paid in Bitcoin, adding a layer of calculation to the process.
If you paid 230500 sats for your ticket and later see the dollar price fluctuate, say from $180 to $270, or the other way around, by the time the conference starts, you realize you either bought too late or too early.\ It’s better to not have bought at all.
Some ticket holders end up paying less (in dollar terms) than others, making it a gamble. As the event date approaches, ticket prices tend to rise—unless you wait until the last minute, when they haven’t sold out, or just pay at the door. It’s a strange feeling knowing that not everyone paid the same amount (and as mentioned, a significant number get in for free) depending on their timing.
Many organizations and local community representatives show up primarily to be present; securing free tickets, which function more as a badge of recognition than a necessity.\ It’s similar to how a rock groupie sees backstage access: a status symbol, whether for an autograph or something more. Being seen standing next to big names is a huge deal for some, as they derive their own status from proximity.\ This also reinforces the “rockstar status” that conferences create around certain figures, once they come out to take a selfie with some nice people and young fans, then to quickly disappear back to the ‘whale room’ or backstage.
There’s often an entire insider network determining who gets these free tickets. In some cases, it’s naturally tied to the local community, but in others, the professionalism is laughably low. At certain events, you could probably just walk up to the entrance (if there’s even someone checking) and say, “I’m with the organization” to get in for free.
It gets even more absurd.\ At a conference near the French-Swiss border, I was probably one of the very few who actually paid for entry. The real spectacle wasn’t in the talk rooms — which remained eerily empty — but in the dining area, where half the town seemed to have shown up just for the free food. Around 200 people queued for a free lunch, while the presentation halls were at best one-third full throughout the day.
And beyond the ticket games, there are plenty of ways to slip in unnoticed. Carrying a random piece of equipment and mumbling\ “I need to put this crate in the back” can get you past security. Or you can just wait for the one security guard to get distracted by chatting up a girl or stepping out for a smoke, and you’re in. At one event, I walked in alongside someone carrying crates of wine for the VIP lounge. I blended in perfectly (I paid afterward).
So, to sum up: at nearly every conference I’ve been to, a big portion of attendees either walk in for free or hold compensation tickets they got through some connection. Sometimes that connection is uncomfortably close to the organizers. Other times, they just slap an “industry” label on themselves when, in reality, they’re nothing more than a social media bio with a few followers.
Local representatives of a podcast, community, influencer network, or fake marketing club also get in for free. And you? The regular guest, you and I are paying for them. There’s no real vetting process; with some organizers, anyone wearing a Bitcoin t-shirt and saying the magic words “I do community building” or “I know the local Bitcoin meetups” gets a free pass.
The ones who actually want to learn about Bitcoin — the ones who click the link and pay full price — are the ones covering the costs for everyone else and ultimately making these conferences profitable (or at least break even). The problem? They’re the ones left wondering: “Was it really worth my time and money?” only to never return again most of the time.
Because many of the people at these conferences aren’t there to learn. They’re part of the circus. And others? They’re the ones paying for the circus boss, the clowns, and the trapeze artists.
At that one conference with the massive free-lunch crowd, I saw one interesting talk. And I had plenty of valuable conversations and observations — conversations I could have just as easily had by visiting that place outside of a conference setting.
In the end, I realized the main reason I was there was to support a fellow Bitcoiner giving a presentation. And after that? They disappeared from my life. Because, just like in the fiat world, you’re only as good as your last few hours of usefulness to most people.
Which brings me to the next element of Bitcoin conferences...friends
Bitcoin “frens”
This might be the hardest lesson of all: you meet fellow Bitcoiners at these conferences. And some of them? They’re truly special characters. A few even made such a deep connection with not-so-well-traveled-me that I would’ve gladly traveled a full travel day just to spend time working and doing something meaningful together (which I actually did).
But most of these connections? They last only a moment. Few survive beyond the conference, mainly because of the vast distances— both in kilometers (or miles) and in the way we live our everyday lives. The Bitcoiners you meet at these events are, for the most part, just regular people trying to make ends meet in the fiat world while saving in Bitcoin. Or they’re chasing the Bitcoin dream or even find a job in the fata morgana of bitcoin jobs. They act like they belong, like a clown acting like he’s going to climb the trapeze.
I respect that. But over time, I realized that many of them operate in Bitcoin mode; a kind of facade. Behind that front, that mask, most are just testing the waters to see if they can make it. And most don’t.\ Treating Bitcoin as a lifestyle movement, a career shortcut, or an identity, has its limits. Eventually, the real person breaks through. And you have to face your own instincts and personality.\ I’ve tried to be an acrobat, and ride the lion, make the audience laugh, but I’m still the seal who’s brought back to the cage after he balanced a ball on his nose. The quote “I’m Jack’s wasted life.” came to mind often when standing somewhere at a conference space.
Self-doubting people stay self-doubting, owning Bitcoin or not. Emotional wrecks remain emotional wrecks — just with Bitcoin now. And when these masks slip off, you’ll see everything: the greed, the overconfidence, the longing for drama, the addictions, the narcissism, the energy-draining personalities, sleaziness usually with the ones who always say the right oneliners or wear the right Bitcoin merch to blend in.
And you can love people for that. Everyone has flaws. Everyone has a price as well.
But these Bitcoin “frens” can also hurt you badly. Because as Bitcoiners, we carry hopes. And hopes are like ants on a sidewalk, they’ll eventually get crushed.\ We long to meet people who see the same truth, the same vision of Bitcoin as we do. Some will act like they actually understand and do, they talk the talk for a while, as if they’re parroting a podcast.
If you stay in the shadows - like I did for years - you won’t have to deal with these things. If you never try, you’ll never be let down. But you still stay in the imaginary basement, letting yourself down. That’s not the bitcoin style. We router around problems. Even if we stand amidst the problems (like a conference).
But if you do? There’s a hefty price to pay — beyond just the money spent. It’s a cost paid in energy, emotions, and social interactions and above all: time.
And once in a while, you’ll meet a friend for life.
Just be prepared:
Bitcoin is a journey that few people you encounter at a conference can take for longer than four years, or even four hours of conversation actually.
And then, after navigating the social maze of Bitcoin conferences —the connections, the masks, the fleeting friendships, the smell of weed and regret — you find yourself facing an even greater challenge: the queue at a coffee stall.

## \ The Soviet LN Queue
It’s one of the most fascinating and frustrating aspects of every conference: the insanely long lines. Whether it’s for the toilets, a coffee booth, or some niche merchandise stall, you’ll see Bitcoiners waiting like it’s 1963 after a Soviet state bakery just got fresh deliveries.
waiting for coffee Seriously, aren’t we supposed to be the pinnacle of free-market efficiency? Instead, we’ve somehow perfected the art of the long food lines. I remember people waiting in line for like 35 minutes to order a cappuccino!
The usual culprit? A mix of payment chaos and the Bitcoin Orangepill mental issues in action.
A large portion insists on using Lightning (as in "their preferred lighting wallet"), which would be fine except they’re fumbling with some exotic, half-working wallet because using something that’s actually fast might get them sneered at for being “custodial.”
On top of that, vendors are juggling card payments, cash, various Lightning POS systems, and even the occasional cutting edge dudes trying to pay with an Apple Watch or worse, some newly released Lightning-enabled gadget that doesn’t work yet. And when it does work, it requires so much attention and Instagram footage that it takes five minutes just to hand someone a coffee while the guy pays with a lighting NFC ring on his finger, something you can't use ànywhere else ever. It’s cool. But not to anyone else than you.
So, here’s a tip for the regular people, the rats that pay for all of this : sneak out.
Then you find a small, locally owned café outside the conference, pay them in cash, and actually enjoy your food in a few seconds or minutes.
If (and only if) they accept Bitcoin, great! Tip them well. Otherwise, just relax and have a conversation with a local, all the while inside the conference venue there are Bitcoiners filming each other struggling to make a payment with the latest Lightning-enabled NFC card or making the staff uneasy.
Meanwhile, some poor 22-year-old café worker is trapped in an unsolicited podcast participation:
“Wait, you accept tips in Wallet of Satoshi? Who told you that? I’ll explain it to you!”
Or worse:
“Hold on, I just need to do a quick swap… It’s an on-chain transaction, the last block was 19 minutes ago, can’t be long now… wait… umm… do you take VISA?”
At this point, ordering a simple drink at a Bitcoin conference has become an unnecessarily complex, ego-driven performance. With long queues as a direct result. And don’t get me started on the story when 30+ bitcoiners walked in to a Portuguese restaurant without a reservation, and they all wanted to pay with different payment methods. It was like the Vietnam war.
Solution:
A tip for conference organizers and their catering : pick one Bitcoin point of sales system, set clear guidelines, and make everyone stick to them. Instruct people to adhere to the following :
Pay with a (bank) card, cash, or Lightning and PLEASE decide beforehand which method you’re using before ordering your stuff! We prefer lighting.
If you’re using Lightning, have enough balance on you wallet or get lost.
Use a compatible wallet. (Provide a tested “approved” list and train staff properly. Users who use other stuff get their order “cancelled” at the first sign of trouble. Your app‘s not scanning, or not compatible, or it has some technical mumbo-jumbo going on to your vpn LN node at home 2000 km away? Please get real and pay with a bank card or something.
No filming, duck-facing (like it's 2017) or stupid selfies with your payment. It’s been done a thousand times by now. There are people in line, waiting behind you, they want to order as well, while you have your little ego trip or marketing moment. Move on please!
“Our staff knows how bitcoin payments work, you don’t need to #orangesplain it to anyone.” We don’t care about your 200th LN app or the latest “but… this one is faster” thingy. Order your drinks, pay and get out of the way please.
Bitcoin fixes many things. But it hasn’t quite fixed this yet.
The bitcoin conference axiom
Going to a conference, versus keeping your bitcoin in your wallet is a tough choice for many.
If you pay nothing for tickets and lodging, while enjoying free meals and cocktails, your opportunity cost drops close to zero —yet your networking and social impact are maximized while you can also do business. That’s ideal. At least, for you. In such case, Bitcoin may only "win" over an extended timeline, but for you, it's essentially a free ride. You incur no real opportunity costs. You drink their milkshake.
On the other hand, if you’re a regular attendee, you pay full price: the ticket, overpriced drinks and food from the stands (losing even more if you generously pay for coffee in sats), plus extras like t-shirts and books (which you’ll never read). Your milkshake gets taken—at least half of it.
If you’re lucky, you might spend an evening in town with the event’s "stars"—those occasional luminaries who briefly grace the normies with their presence for a drink. Some can’t even hold their liquor. Year after year, the same 10 to 15 speakers or panelists appear, funded by your dime, traveling the world and enjoying the perks—some even cultivating fan bases and hosting exclusive parties.
The real opportunity cost hits hardest for regular attendees who come to learn, shelling out significant money while accumulating their fourth hardware wallet or yet another orange-themed t-shirt. They might even squeeze in a selfie with a former sportswear model turned Bitcoiner. For normies (as they’re often called), the financial and social scales rarely tip in their favor.
Calculating the conference opportunity cost
To determine the opportunity cost of attending a conference instead of investing in Bitcoin, over time follow these steps:
-
Calculate your total conference expenses, including tickets, travel, food, drinks, and lodging (merchandise and donations).
-
Estimate Bitcoin’s percentage gain over the conference period and the following year(s). (in order to not make you cry, I suggest nog going over 5 years)
-
Multiply your total conference cost by this percentage to determine the potential Bitcoin profit you forgo.
-
Assign a dollar value to the networking or business opportunities you expect to gain from the conference (if you’re not just in it for the laughs, meeting high-class consultants, friendships, self-proclaimed social media Bitcoiners, or the occasional gyrating on one of the musicians/artists/food stall staff members).
-
Subtract this “networking” value from the missed Bitcoin profit to find your net opportunity cost (this is rather personal,… with me it’s zero, but for someone selling t-shirts it’s probably much more).
If the result is negative over the chosen timeframe, the conference was financially worthwhile for you. If positive, holding or buying Bitcoin was the smarter move.
Unless you’re a recognized speaker in this traveling circus, your opportunity cost will likely be positive — meaning all the others lose hard money, while fumbling with your Lightning wallet.
The Conference Opportunity Cost Formula
Let:
CT = Total conference ticket & entrance cost (in dollars)
CR = Total related conference costs (travel, lodging, food, etc.)
C = CT + CR (Total cost)
G = Bitcoin’s % gain per year (as a decimal, e.g., 5% = 0.05)
N = Estimated fiat value of networking/business opportunities and knowledge gained.
OC = (C × G) − N
Where:
OC (Opportunity Cost) < 0 → The conference was worth attending.
OC (Opportunity Cost) > 0 → Holding/buying Bitcoin was the better move.
Some example calculations (I've left out examples before 2020, I don't want people crying or waking up at night thinking "Why did I go to Amsterdam in 2014?!")
example : Conference in April 2024 Entrance: $200 Lodging, t-shirt, and travel: $900 Bitcoin's estimated gain: 23% (0.23) No business / knowledge value gained OC = (200 + 900) × 0.23 - 0
- $253 OC (Bitcoin would have been the better choice.)
Conference in April 2020 (adjusted for historical Bitcoin growth) Entrance: $175 Lodging and travel: $700 Bitcoin's estimated gain: 1089% (10.89) No business / knowledge value gained OC = (175 + 700) × 10.89 - 0 OC = +$9,529 (Massive missed gains — Bitcoin was the clear winner.
--
So the first lesson in bitcoin should be: Only attend conferences if you get paid to do so and get a free ticket and free lodging, which kind of would kill that whole industry to begin with.
Energizing
At first, it’s energizing to meet like-minded bitcoiners, but after a while, you realize that a big chunk of them are just trying to sell you something or aren’t really bitcoin-focused at all. And some of them are just looking for their next way to kill time and boredom.
The drama that comes with attending these conference and the personal interaction can get pretty intense at times, since expectations often don’t match the personalities. Before you know, you’re walking around at night through some bad part of a town, while crying your eyes out because you thought you found your soulmate.
Future pure industry conferences will suffer less from this drama, because everyone there has the same goal — pushing their company or product— while the “other” grassroots conferences are more of a meeting spot for bitcoiners of all types and perspectives, bringing the usual drama and mess that comes with human interactions. Current conferences are a mix of both usually.
I think the current era of bitcoin conferences is coming to an end. Soon, probably by the end of 2025, we’ll see a clear split between industry-driven and human-driven (grassroots) smaller conferences, and it’ll be really important to keep these two separate.
I even had the idea to launch a sort of conference where there wouldn’t be any industry speakers or companies present. Just bitcoiners gathering at a certain place at a specific week and having a good time. I called it “club Sat” And you could just go there, and meet other bitcoiners, while acting there was a big venue and speakers,… but there aren’t any. Would be refreshing. No struggle for tickets, no backstage stuff, no boring talks and presentation,… just the surroundings and the drama lever you want and probably like.
On stage
The podium is usually left for the known names. Not every conference is like that, but most of them need these names, badly. These names know each other, they encounter one another in VIP rooms and “the industry” a lot of times anyway.
The same people you see in the bitcoin news, the same people having a cult following, and the very same people traveling, staying and drinking for free while spreading the same bitcoin wisdoms will be invited over and over again.
Or… they go rock around as they’re usually so bored they had to start a rock band to entertain themselves. Which is rather entertaining if you’re following up on who does what, but in the end it’s largely just for their own amusement and it shows. I get that. I would do the same. It’s fun and all.
It’s just a bit sad that there are only a small group of top-layer speakers, and then the sub-top that usually has more to say, or gets little opportunity. The reason for that is simple: the “normies” who pay in full for tickets, come there for the “big” names. They don’t know that much about bitcoin usually, so they’re not waiting on some unknown dude explaining something about an obscure niche subject. A debate can help remedie this, to mix it in with some lesser known names, but I have the feeling the current “line-up” of bitcoin conferences feels like a rock festival in 2025 putting the Stone temple pilots or Creed on the card.
Yes, they’ll attract an audience and do their playset well,… but it’s not exactly the pinnacle of the music industry at the moment, neither is Madonna by the way :)
Promoting anything
The people organizing these events usually aren’t Bitcoiners either — they’re promoters (few exceptions though).

They don’t care if they organize a symposium about a newly discovered STD, A three-day cheese tasting event, a Star Trek convention, or a Lucha Libre wrestling tournament featuring El HODLador, as long as they can sell tickets and make money from merchandise they're good. The last thing on the mind with some of them will be helping bitcoin adoption. There will be a time (soon) where people that know bitcoin, known bitcoiners and know how to organize events get their act together. It will be different than the early days, and it will be different than the boring going-through-the-motions conferences we have now. There shall be fun, social gatherings, life, excitement and culture, and not the “what do you sell?” atmosphere, neither the “this old dude on stage again”?
That’s why they’ll slap any semi-famous name on the poster to pull in a crowd - could be a washed-up Mexican wrestling star with strange legal issues, the cheese-tasting equivalent of Usain Bolt, or your neighborhood Bitcoin old-timer with a beard and a "best selling author" label.
It’s also why most of these conferences end up being more about shitcoins than anything else. And even if they're for the most part about bitcoin, the venue is usually infested with marketing budgets, useless organizations that wanted complimentary tickets (some of them do only one thing: popping up when a conference is nearby and then they’re gone again) ... along with some hawking consultant types you never see anywhere else.
They'll occasionally pay people but usually in fiat, or if you're a bigger name, you might get other deals. For artists or staff, it's all in fiat from what I heard.
Pure Bitcoin conferences, also rely on these big names. Whether it’s a well-known Bitcoiner, a CEO, president, or someone with real reveling knowledge to share with the audience (though that last type is getting rare).
Looking for love in all the wrong places
\ Let’s also address the fair share of “orange diggers” at Bitcoin conferences—because yes, they exist. And no, let’s not single out one particular gender here.
Some people treat a Bitcoin conference like a live-action dating app mixed with a financial vetting process for potential partners. It’s essentially an opportunity to inspect and assess the grab bag of fintech, crypto, and Bitcoin folks in real life.
And if you think this is exaggerated, just attend a few conferences—three is enough. You’ll start noticing the same people popping up, seemingly without any real Bitcoin knowledge, but with a very strong interest in dining, chatting, and generally being around—as long as you look and play the part. I can only imagine how dialed-up this effect must be at a shitcoin conference — probably like flies on a cowpie.
The trick is, in Bitcoin, these people try to blend in. Some even tag along with real Bitcoiners, while others just crash the party and try to get noticed. Their actual interest in Bitcoin? Close to zero. Their main target? Your wallet, or some fantasy thing about getting to know someone out of the ordinary.
And that’s a shame for the people who genuinely care about Bitcoin, who want to network, or who simply are looking for like-minded people. They often find themselves competing for attention with those who’ve turned “being noticed” into a sport, while the rest just wander around, lost in the shuffle. Talk to the quiet ones. Certainly if they look like they belong in a antiques shop.
My advice: Talk to people and be genuine. If you don’t know much about Bitcoin, that’s fine - nobody expects you to be a walking whitepaper and on top of that, most people you'll encounter don't know that much either. It’s bitcoin: we’re all rather average people that hold an extraordinary asset.
Just don’t be "that orange digger" looking for a partner with a loaded bag of bitcoin.
Because in the end, what’s the prize you win? You don’t know who’s under the mask. You don’t even know who’s under your own mask.
Finding a man or woman at a place where half the people are laser-focused on financial sovereignty, and the other half are busy arguing about seed phrase storage, UTXO management, and why your Lightning wallet sucks? But good luck with that. The judge of character usually comes when they find the next shiny object or ditched you standing in the rain at the entrance of a restaurant while dealing with a lightning watchtower or a funny cigarette or whatever.
If you’re truly looking for love, maybe stick to going to a normal bar. If you’re here to learn, connect, and be part of something of a grassroots movement, then be real yourself.
I've seen some rather nasty examples of people at Bitcoin conferences—of all kinds. And I've also seen some really cool examples of truly awesome people. This led me to believe that Bitcoin conferences simply let you meet… people, just dialed up a bit.
Future If you encounter rotten people, they’ll usually be even more rotten than in the fiat world. If you meet really cool people, they’ll be even more awesome than the cool people in the fiat world.
Our volatility is our freedom. So, I guess it’s normal. Doesn’t make it any easier, though.
Bitcoin sees through bullshit, and so do Bitcoiners (even if it takes 21,000 blocks)
Pretty soon, I reckon we’ll see conferences fork into two camps: grass roots, and the “industry” level ones. (human / corporate) I guess I’ll only attend the human part, for sure, but I can’t help but booking myself a single room in a hotel in a nice area in that case, so I don’t have to deal with class of 2022 hippies sharing referral links to their middleman service while asking me for a lighter 3 times in a row. The chances for me of meeting cool bitcoiners in a nearby cocktail bar are a lot higher.
In the meanwhile, I’ll look forward and see how the bitcoin conferences will evolve, fork in two “styles”. One corporate and one underground. Maybe there will be one more genre just for the fun of it.
I’ll stay away, as I don’t like this current mix of industry gigs and having the insiders and “the rest” of us all mingled together clamoring for tickets, attention and coffee. The game is rigged. Staying at home is the better option (for now).
written by AVB
If you like : tip here
-
-
 @ f1989a96:bcaaf2c1
2025-04-03 14:30:08
@ f1989a96:bcaaf2c1
2025-04-03 14:30:08Good morning, readers!
Georgian officials froze the bank accounts of five nonprofit organizations that provide financial and legal support to detained protesters. This follows rising public unrest as Georgia’s regime pushes new laws restricting free speech and assembly, introducing new fines and penalties, and expanding law enforcement powers. By eroding civil protections, the regime makes it more dangerous and costly for activists, dissenters, and everyday citizens to stand up against an increasingly repressive regime.\ \ Meanwhile, the Indian government introduced a new income tax bill that grants tax authorities sweeping surveillance power over anyone they “suspect” of tax evasion. If suspected, tax authorities are legally allowed to access Indians' email, social media, and bank accounts, raising obvious concerns over state overreach and invasions of individual financial privacy.\ \ In freedom tech news, HRF donated 1 billion satoshis to more than 20 projects worldwide, focusing on supporting human rights defenders and vulnerable communities under authoritarian regimes across Asia, Africa, and Latin America. These gifts advance censorship-resistant communications and transactions, bitcoin education, and privacy tools so that dissidents, nonprofits, and individuals may better protect their human rights and financial freedom. In this letter we also spotlight a new open-source mobile Bitcoin wallet called Cove. While still in beta, the wallet can be used with a hardware device or on its own as a hot wallet, offering a flexible self-custody setup for managing Bitcoin.
We end with a podcast in which HRF Chief Strategy Officer Alex Gladstein discusses the state of freedom tech and why Bitcoin stands as the most promising tool for financial liberation.
Now, let’s get right to it!
SUBSCRIBE HERE
GLOBAL NEWS
Georgia | Officials Freeze Accounts of Organizations Supporting Protesters
Georgian officials have frozen the bank accounts of five nonprofit organizations that provide financial and legal aid to dissenters. This comes in response to an uprising of protests over new controversial laws that restrict free expression and assembly, increase fines and detention periods, and expand law enforcement powers. Georgian officials justify the account freezes as part of an investigation into “sabotage,” yet they have provided no evidence. Amnesty International warns this financial assault could “kill the entire protest movement.” Bitcoin provides a way to circumvent these struggles. Its uncensorable and permissionless nature has helped sustain pro-democracy movements across Belarus and Nigeria, proving it is capable of addressing the immense financial restrictions dictators impose.
United Arab Emirates | Plans to Launch “Digital Durham” CBDC in 2025
The United Arab Emirates (UAE) will launch its central bank digital currency (CBDC), the “Digital Durham,” by the end of 2025. According to the central bank, the CBDC will be available through licensed financial institutions and operate via a government-run digital wallet. Every transaction will be recorded on a permissioned blockchain run by the government. The central bank further admitted the CBDC will replace cash and assist law enforcement “by leaving a digital trail for transactions involving illicit funds.” Officials claim this is to combat financial crime, but it also enables real-time surveillance and tracking of individual financial activity. In a country known for strict laws against dissent and extensive surveillance capabilities, it is not hard to see how a CBDC will erode the autonomy and rights of activists, dissenters, and others who oppose an increasingly authoritarian regime.
India | Grants Tax Authorities Access to Citizens’ Online Data
Starting in April 2026, the Indian government will grant tax authorities legal access to the private online data of any citizen “suspected” of tax evasion. This will include legal access to personal emails, social media, and bank accounts. The new law expands on the Income Tax Act of 1961, which previously limited officials to searching physical premises for financial documents. Now, officials can bypass digital security measures and access private data without consent — all under a legal framework. This dissipation of financial privacy sets an intrusive precedent and opens the door to state-level corruption and surveillance in a country where the Modi regime has already made it clear they are happy to use financial repression to further cement their power.
Myanmar | Bitcoin as a Tool Support Earthquake Disaster Relief
Last week, a 7.7 magnitude earthquake struck central Burma, with strong tremors reaching neighboring Thailand. The official death toll has surpassed 2700. And in Bangkok, a 33-story building under construction collapsed. Despite an already strenuous situation, Burma’s military junta continues its oppression. They are blocking rescue teams from reaching the Sagaing region — the epicenter of the earthquake and the heart of Burma’s pro-democracy movement — and instead channeling aid to regime-controlled cities like Naypyidaw and Mandalay. The junta is also continuing to conduct air strikes on civilians and restricting equipment and fuel for aid groups, leaving a million people in Sagaing to fend for themselves. In these repressive circumstances, Bitcoin can provide a censorship-resistant way to send funds directly to those affected.
Angola | Regime Jacks Price of Diesel
The Angolan regime raised diesel prices by 50% in the process of eliminating fuel subsidies. Diesel prices suddenly increased from 200 to 300 kwanza per liter, driving up transportation costs in a country where over half the population lives on less than $2 a day and inflation is over 42%. Previous fuel subsidy cuts in 2023 (where the price of diesel rose 80%) sparked protests between taxi drivers, nonprofit workers, and law enforcement. This recent price increase now raises fears of renewed crackdowns. The Angolan regime also introduced new civil society laws that Guilherme Neves, chairman of the human rights organization Associacao Maos Livres, describes as a “license to erase non-governmental organizations that are not government-compliant.” Angolans find themselves in increasingly precarious financial positions as the government erodes the civil safeguards protecting nonprofits and dissenters.
Nicaragua | Ortega’s Dismantling of Press Freedom
Since coming to power in 2007, Ortega has closed or seized 61 media outlets, imprisoned countless journalists, and forced over 280 journalists into exile. His assault on press freedom has unfolded in two phases: initial raids on local radio stations and TV channels between 2007 and 2017, followed by full-scale censorship in 2018 on independent media outlets like La Prensa and CONFIDENCIAL. Ortega then intensified attacks from 2019 to 2021 by closing Nicaragua’s second-oldest newspaper and passing laws to criminalize free expression. This is a deliberate strategy to eliminate dissent and independent voices. What’s happening in Nicaragua highlights the importance of open and decentralized protocols like nostr, which allow journalists to publish freely without getting censored. While still early, it is becoming essential for sharing information absent the fear of being blocked or silenced by autocratic leaders.
BITCOIN AND FREEDOM TECH NEWS
HRF | Gifts 1 Billion Satoshis to 20+ Open Source Projects Worldwide
HRF gifted 1 billion satoshis in its Q1 2025 round of Bitcoin Development Fund (BDF) grants, supporting more than 20 open-source projects around the world. These projects advance Bitcoin education, open-source software, mining decentralization, and privacy tools for activists contending with authoritarian regimes across Asia, Latin America, and Africa. Supporting permissionless financial tools and censorship-resistant technologies empowers dissidents, journalists, and civil society to organize, transact, and communicate without state suppression and interference. Learn more about the grantees and their work here.
Cove | New Open-Source and Permissionless Bitcoin Wallet
Cove is a new open-source and permissionless mobile Bitcoin wallet that aims to put users in full control of their Bitcoin. Users can connect their own hardware wallet (to manage Bitcoin offline) or use Cove as a hot wallet (to manage Bitcoin online). It also allows users to create multiple wallets from the app itself. In the future, Cove plans to add Unspent Transaction Output (UTXO) selection and coin control, giving users more independence over their transactions and the tools to better protect their financial privacy. While still in beta and only suitable for test funds, this wallet holds promise as a privacy tool to equip dissidents with self-custodied Bitcoin. You can try it here.
Second | New Ark Implementation Launches on Bitcoin Signet
Second, a company building on Ark, a protocol designed to help scale Bitcoin’s transaction throughput, launched “Bark.” Bark is a test implementation of the Ark protocol deployed on Bitcoin’s Signet network (where developers test software). More broadly, the Ark protocol helps make Bitcoin transactions more private, faster, and cheaper, supporting the network in handling more transactions and users with the tradeoff of being less trusted than the mainchain, as funds stored in a noncustodial way on Ark can expire if not used. While it is still in early development, the test release of Bark marks a step toward deployment on the main Bitcoin network. Scaling solutions like Ark could be important for activists and individuals. They might ensure Bitcoin remains accessible to all, even as block space demand increases and network fees rise. Learn about it here.
Braiins | Open Sources Bitcoin Control Board
Braiins, a company building tools for Bitcoin mining, open-sourced its BCB100 Bitcoin Control Board, giving miners using their products greater insight and control over their Bitcoin mining hardware and firmware. Sharing the design files and firmware openly helps strengthen Bitcoin’s decentralization, making it more resilient against corporate or state interference. Specifically, open-sourcing mining hardware ensures individual miners can operate independently, reducing censorship risks across the entire network. In turn, this preserves financial freedom by keeping Bitcoin accessible and usable by dissidents, nonprofits, and individuals who need it most.
African Bitcoiners | Publish Bitcoin Starter Guide
African Bitcoiners just published “Bitcoin: Africa’s Guide to Freedom Money,” a Bitcoin guide providing clear, practical insights into how Bitcoin can help people across the continent escape inflation, corrupt regimes, and failing financial systems. It covers essential topics to get started — from choosing a wallet to properly securing Bitcoin. In Africa, where some of the world’s longest-standing dictators restrict even basic financial activity, this guide is a powerful resource for human rights defenders, nonprofits, and everyday citizens. Read it here.
OpenSats | 10th Wave of Nostr Grants
OpenSats, a nonprofit that supports open-source software development, announced its tenth wave of grants for projects in the nostr ecosystem. Nostr is a decentralized protocol that enables digital identity and communications outside the reach of authoritarian states. The grant round provides support to nostr Epoxy, which enhances access to nostr by circumventing censorship through a network of paid proxies. This ensures activists and dissidents can continue to communicate even in restrictive environments. Additionally, Zapstore received a grant for providing a permissionless app store built on nostr that enables developers to distribute software without corporate gatekeepers. This provides an open-source alternative to centralized app stores that often comply with government censorship and restrict dissidents’ access to freedom tools.
RECOMMENDED CONTENT
Freedom Tech with Alex Gladstein
In this episode of The Gwart Show, Alex Gladstein, chief strategy officer at HRF, breaks down how and why Bitcoin serves as “money dictators can’t stop.” Drawing on more than 17 years of human rights work, he shares real-world examples of activists and citizens using Bitcoin to escape financial repression in authoritarian countries. Gladstein also explores privacy tools, cross-border payments, and why Bitcoin offers promising hope for financial freedom. Watch the full conversation here.
The State of Personal Online Security and Confidentiality with Meredith Whittaker
In this keynote for SXSW 2025, Signal CEO Meredith Whittaker shares her growing concerns around AI, personal data collection, and the erosion of privacy in today’s increasingly digital world. She emphasizes the need for more secure, uncensorable, and privacy-protecting technologies that shield users from surveillance and exploitation, especially in the context of authoritarian regimes. Watch the full discussion for a pragmatic view into the future of digital privacy and security.
If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report here.
Support the newsletter by donating bitcoin to HRF’s Financial Freedom program via BTCPay.\ Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ hrf.org
The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals here.
-
 @ 1aa9ff07:3cb793b5
2025-04-03 14:06:38
@ 1aa9ff07:3cb793b5
2025-04-03 14:06:38In an era where centralized platforms dominate the internet, concerns over censorship, privacy, and data ownership have led to the rise of decentralized alternatives. One such innovation is Nostr, a lightweight and resilient protocol designed to enable censorship-resistant and decentralized communication. In this article, we will explore what Nostr is, how it works, its advantages, and why it is gaining traction among privacy advocates and decentralized technology enthusiasts.
What is Nostr?
Nostr (Notes and Other Stuff Transmitted by Relays) is an open protocol designed for creating censorship-resistant social networks and communication platforms. Unlike traditional social media networks, which rely on centralized servers controlled by corporations, Nostr operates on a decentralized model using cryptographic keys and relays.
Nostr allows users to publish and receive messages without the need for a central authority. It is not tied to any single application but instead provides a foundation upon which developers can build various types of social and communication tools.
How Does Nostr Work?
Nostr consists of two main components:
- Clients – Applications that users interact with, such as social media platforms, chat applications, or blogging tools.
- Relays – Servers that distribute messages between clients without storing them permanently or acting as gatekeepers.
When a user wants to send a message or publish content, their client signs the data using their private key and broadcasts it to multiple relays. Other users who subscribe to those relays can receive and interact with the messages.
Nostr does not have a concept of user accounts managed by a central entity. Instead, identity is established using public and private cryptographic keys. The private key is used to sign messages, while the public key acts as the user’s identity across the network.
Advantages of Nostr
-
Censorship Resistance – Since Nostr does not rely on a central authority, it is much harder for governments or corporations to censor content. Users can publish messages freely, and if one relay refuses to distribute them, they can simply use another.
-
Privacy and Security – Messages are signed using cryptographic keys, ensuring authenticity and reducing the risk of impersonation. Users retain full control over their identities and content.
-
Interoperability – Nostr is not tied to a single platform or application. Developers can create different types of services using the protocol, from microblogging platforms to encrypted messaging apps.
-
Resilience – Since the network relies on multiple relays instead of a single centralized server, it is less susceptible to shutdowns or attacks.
Use Cases for Nostr
- Decentralized Social Media – Platforms like Twitter alternatives can be built on Nostr, allowing users to post updates without fear of censorship.
- Private Messaging – Secure and encrypted messaging applications can be developed using the protocol.
- Blogging and Content Publishing – Writers and journalists can publish articles in a censorship-resistant manner.
- Bitcoin and Cryptocurrency Communities – Many Bitcoin enthusiasts are adopting Nostr due to its decentralized nature and alignment with privacy-focused principles.
Challenges and Limitations
While Nostr is a promising technology, it is still in its early stages and faces several challenges:
- Adoption and Network Effects – Since Nostr is not as widely used as traditional social media platforms, building a strong user base is a challenge.
- Spam and Moderation – Without central moderation, handling spam and malicious content is more difficult, requiring innovative solutions such as reputation-based filtering.
- User Experience – Decentralized networks often have a steeper learning curve for new users compared to centralized platforms.
The Future of Nostr
Despite these challenges, Nostr is gaining momentum among privacy advocates, developers, and decentralized technology supporters. With continued development and improvements in usability, Nostr has the potential to reshape online communication by offering a truly decentralized and censorship-resistant platform.
As more developers create applications and services using Nostr, its ecosystem is likely to expand, providing a viable alternative to traditional social media networks. Whether you are a developer, a privacy-conscious user, or someone interested in the future of decentralized internet, Nostr is a technology worth exploring.
Conclusion
Nostr represents a significant step toward a more open and decentralized internet. By removing central points of control and enabling user-driven communication, it empowers individuals to interact freely without the risk of censorship or data exploitation. As the protocol matures and more applications emerge, it could play a crucial role in shaping the next generation of online communication.
If you are interested in experimenting with Nostr, you can start by exploring various Nostr-based applications, setting up your cryptographic keys, and connecting with the growing community of users and developers. The future of decentralized communication is just beginning, and Nostr is at the forefront of this movement.
Understanding Nostr: A Decentralized Social Network Protocol
In an era where centralized platforms dominate the internet, concerns over censorship, privacy, and data ownership have led to the rise of decentralized alternatives. One such innovation is Nostr, a lightweight and resilient protocol designed to enable censorship-resistant and decentralized communication. In this article, we will explore what Nostr is, how it works, its advantages, and why it is gaining traction among privacy advocates and decentralized technology enthusiasts.
What is Nostr?
Nostr (Notes and Other Stuff Transmitted by Relays) is an open protocol designed for creating censorship-resistant social networks and communication platforms. Unlike traditional social media networks, which rely on centralized servers controlled by corporations, Nostr operates on a decentralized model using cryptographic keys and relays.
Nostr allows users to publish and receive messages without the need for a central authority. It is not tied to any single application but instead provides a foundation upon which developers can build various types of social and communication tools.
How Does Nostr Work?
Nostr consists of two main components:
-
Clients – Applications that users interact with, such as social media platforms, chat applications, or blogging tools.
-
Relays – Servers that distribute messages between clients without storing them permanently or acting as gatekeepers.
When a user wants to send a message or publish content, their client signs the data using their private key and broadcasts it to multiple relays. Other users who subscribe to those relays can receive and interact with the messages.
Nostr does not have a concept of user accounts managed by a central entity. Instead, identity is established using public and private cryptographic keys. The private key is used to sign messages, while the public key acts as the user’s identity across the network.
Advantages of Nostr
-
Censorship Resistance – Since Nostr does not rely on a central authority, it is much harder for governments or corporations to censor content. Users can publish messages freely, and if one relay refuses to distribute them, they can simply use another.
-
Privacy and Security – Messages are signed using cryptographic keys, ensuring authenticity and reducing the risk of impersonation. Users retain full control over their identities and content.
-
Interoperability – Nostr is not tied to a single platform or application. Developers can create different types of services using the protocol, from microblogging platforms to encrypted messaging apps.
-
Resilience – Since the network relies on multiple relays instead of a single centralized server, it is less susceptible to shutdowns or attacks.
Use Cases for Nostr
-
Decentralized Social Media – Platforms like Twitter alternatives can be built on Nostr, allowing users to post updates without fear of censorship.
-
Private Messaging – Secure and encrypted messaging applications can be developed using the protocol.
-
Blogging and Content Publishing – Writers and journalists can publish articles in a censorship-resistant manner.
-
Bitcoin and Cryptocurrency Communities – Many Bitcoin enthusiasts are adopting Nostr due to its decentralized nature and alignment with privacy-focused principles.
Challenges and Limitations
While Nostr is a promising technology, it is still in its early stages and faces several challenges:
-
Adoption and Network Effects – Since Nostr is not as widely used as traditional social media platforms, building a strong user base is a challenge.
-
Spam and Moderation – Without central moderation, handling spam and malicious content is more difficult, requiring innovative solutions such as reputation-based filtering.
-
User Experience – Decentralized networks often have a steeper learning curve for new users compared to centralized platforms.
The Future of Nostr
Despite these challenges, Nostr is gaining momentum among privacy advocates, developers, and decentralized technology supporters. With continued development and improvements in usability, Nostr has the potential to reshape online communication by offering a truly decentralized and censorship-resistant platform.
As more developers create applications and services using Nostr, its ecosystem is likely to expand, providing a viable alternative to traditional social media networks. Whether you are a developer, a privacy-conscious user, or someone interested in the future of decentralized internet, Nostr is a technology worth exploring.
Conclusion
Nostr represents a significant step toward a more open and decentralized internet. By removing central points of control and enabling user-driven communication, it empowers individuals to interact freely without the risk of censorship or data exploitation. As the protocol matures and more applications emerge, it could play a crucial role in shaping the next generation of online communication.
If you are interested in experimenting with Nostr, you can start by exploring various Nostr-based applications, setting up your cryptographic keys, and connecting with the growing community of users and developers. The future of decentralized communication is just beginning, and Nostr is at the forefront of this movement.
-
 @ 502ab02a:a2860397
2025-04-03 08:31:07
@ 502ab02a:a2860397
2025-04-03 08:31:07ที่มาทำเพลง #ตัวหนังสือมีเสียง
วันนี้จะเล่าถึงเพลง ตรุษจีนครับ เป็นเพลงที่เขียนเสร็จภายในคืนเดียว คือไม่ใช่ว่าเก่งกาจอะไรครับ แต่เนื้อหามีในหัวตั้งนานแล้วตั้งใจจะทำนานแล้วแต่ภารกิจอื่นมีมากจน 24 ชั่วโมงมันรู้สึกน้อยเกินไป
เพลงนี้ความตั้งใจคือ หวังสูงเลยครับ หวังว่าสักวันหนึ่งเยาวราชจะเปิดเพลงนี้กันกระหึ่มในวันตรุษจีน ซึ่งรู้ตัวดีครับว่า ตัวเล็กๆ คงไม่ดังเปรี้ยงในรอบเดียว ผมคิดว่า จะอีก 5ปี 10ปี เพลงนี้มันปล่อยไปแล้วมันยังอยู่ไปเรื่อยๆครับ (เปิดตัวครั้งแรก มีคนเอาแผ่นเสียง tiktok ไปทำอวยพรกันราวๆ 185คลิป ผมดีใจมากแล้ว บางคนลิปซิงค์ด้วยแสดงว่าหัดร้อง โคตรดีใจเลยครับ)
ผมตั้งใจทำให้โทนออกมาเป็นเหมือนคนจีนร้อง แนวประมาณฮอทเป๊บเปอร์ โซเฟียลา อะไรประมาณนี้ ดังนั้นการออกเสียงจะเหมือนคนจีนพูดไทยไม่ชัดอะไรแบบนั้นครับ
เนื้อร้องนี่ผมตั้งใจเขียนแบบ เอาใจอาม่าเลย เราลองมาดูบางท่อนกันครับ
"ซินเจียยู่อี่ ซินนี้ฮวดไช้ วันตรุษจีนนี้ ขอพรจากใจ จะทำสิ่งใด ขอให้เฮงเฮง" เป็นท่อนย้ำแล้วย้ำอีก เพราะจงใจให้เป็นเพลงอวยพร ก็เลยทำเป็นแกนหลักของเพลงนี้ จากนั้นตัวรองก็จะเป็นคำอวยพรในแต่ละเรื่อง มาซ้อนอีกทีนึง
"ปีใหม่หวังได้สุขดี โรคภัยไม่มี แข็งแรงกว่าใคร เลือดลม กำลังภายใน เดินวิ่งยังไหว ได้เที่ยวทั้งปี" ท่อนนี้ผมนึกถึงอาม่าของผมครับ แกชอบดูหนังกำลังภายใน วีดีโอม้วนเป็นชุดๆ แล้วการได้ไปเที่ยวเรื่อยๆก็เป็นอีกความสุขนึงของคนแก่ ไม่ได้ต้องการอะไรมากไปกว่าร่างกายแข็งแรง เดินเหินไหว เที่ยวได้
"ไม่เพียงแค่ในปีนี้ แต่ขอให้ดี ทุกทุกปีไป ครอบครัวยิ้มได้ละไม ทุกคนสุขใจ เฮงเฮงดีดีดี" เป็นท่อนท้ายเพลงแล้ว ซึ่งก็ตบด้วยว่าไม่ได้เฉพาะปีนี้นะ ที่อวยพรกันขอให้ดีไปยาวๆ แล้วก็เล่นคำท้ายว่า "เฮงเฮงดีดีดี" คือ มันเป็นการรวมคำดีๆย้ำๆ ผมรู้สึกว่าพอตอนที่ทำเป็นเพลง มันจะเป็นท่อนที่คนยิ้มกว้างเลยหล่ะ
เนื้อเพลงเต็มๆผมลงไว้ให้ข้างล่าง ส่วนการรับฟัง สามารถเข้าได้หลายทางมากครับ youtube music https://music.youtube.com/watch?v=EBKTZv3VvGM&si=f_IMFbDhdEJ6wEcv
spotify https://open.spotify.com/track/3fCJyoQVAeWxdczfGbL3yT?si=vHV45hUTRPO6Mg9Pnh-w2w
apple music https://music.apple.com/th/album/%E0%B8%8B-%E0%B8%99%E0%B9%80%E0%B8%88-%E0%B8%A2%E0%B8%A2-%E0%B8%AD-%E0%B8%8B-%E0%B8%99%E0%B8%99-%E0%B8%AE%E0%B8%A7%E0%B8%94%E0%B9%84%E0%B8%8A/1789787248?i=1789787249
tiktok แผ่นเสียง https://vt.tiktok.com/ZSrk49SfL/
ส่วนเพลงอื่นๆ ฟังเต็มๆได้ทุก music plattform แล้วนะครับ ค้นหา heretong teera siri เพราะเพลงไม่ดังเลยต้องหาจากชื่อคนแทนครับ 55555
新正如意,新年发财 วันตรุษจีนนี้ขอพรจากใจ จะทำสิ่งใด ขอให้เฮงเฮง
ปีใหม่หวังได้สุขดี เป็นเศรษฐีมีเงินทองใช้ ร่ำรวย รุ่งเรืองไปไกล คิดสิ่งใด ได้สมฤดี
ซินเจียยู่อี่ ซินนี้ฮวดไช้ วันตรุษจีนนี้ขอพรจากใจ จะทำสิ่งใด ขอให้เฮงเฮง
ปีใหม่หวังได้สุขดี โรคภัยไม่มี แข็งแรงกว่าใคร เลือดลม กำลังภายใน เดินวิ่งยังไหว ได้เที่ยวทั้งปี
ซินเจียยู่อี่ ซินนี้ฮวดไช้ วันตรุษจีนนี้ขอพรจากใจ จะทำสิ่งใด ขอให้เฮงเฮง
ไม่เพียงหวังได้สุขดี โรคภัยไม่มี แข็งแรงกว่าใคร เลือดลม กำลังภายใน เดินวิ่งยังไหว ได้เที่ยวทั้งปี
ซินเจียยู่อี่ ซินนี้ฮวดไช้ วันตรุษจีนนี้ขอพรจากใจ จะทำสิ่งใด ขอให้เฮงเฮง
ไม่เพียงแค่ในปีนี้ แต่ขอให้ดี ทุกทุกปีไป ครอบครัวยิ้มได้ละไม ทุกคนสุขใจ เฮงเฮงดีดีดี
ซินเจียยู่อี่ ซินนี้ฮวดไช้ ขอจงมีความสุขใจ อวยพรนำชัย ให้ทั่วทุกคน ขอจงมีความสุขใจ อวยพรนำชัย ให้ทั่วทุกคน ขอจงมีความสุขใจ อวยพรนำชัย…ให้จงรุ่งเรือง
pirateketo #siripun #ตำรับเอ๋ #siamstr
-
 @ c13fd381:b46236ea
2025-04-03 07:55:31
@ c13fd381:b46236ea
2025-04-03 07:55:31Over the past few years, The School of Bitcoin (TSOBTC) has built a reputation as a decentralised, open-source educational initiative dedicated to financial sovereignty and digital literacy. Our faculty, contributors, and global community have worked tirelessly to create resources that embody the Free and Open-Source Software (FOSS) ethos, ensuring that knowledge remains accessible to all.
As part of our commitment to maintaining an open and transparent model, we are excited to announce that The School of Bitcoin is officially migrating to Consensus21.School. This transition is not just a rebranding--it marks the consolidation of all our initiatives, projects, and educational resources under the Consensus21.School banner. The School of Bitcoin will no longer exist as a separate entity.
This move comes as a response to growing confusion between our initiative and another entity operating under the domain schoolofbitcoin (SOB), which has taken a direction that does not align with our open-source philosophy. To reaffirm our dedication to FOSS and community-driven education, we are bringing everything--our courses, programs, and collaborations--into a singular, more focused ecosystem at Consensus21.School.
What Does This Mean for Our Community?
Rest assured, all the valuable content, courses, and educational materials that have been developed under TSOBTC will remain available. We continue to embrace a value-for-value model, ensuring that learners can access resources while supporting the ecosystem in a way that aligns with their means and values.
By consolidating under Consensus21.School, we are doubling down on the principles of decentralisation, self-sovereignty, and permissionless learning. This transition includes all of our key initiatives, including V4V Open Lessons, the Decentralised Autonomous Education System (DAES), and our involvement with the Plan B Network.
Full Migration of DAES and Plan B Network Collaboration
As part of this transition, the Decentralised Autonomous Education System (DAES) is now officially part of Consensus21.School and is fully reflected in the Consensus21.School Whitepaper. DAES will continue to provide a platform for aspiring learners to submit their Bitcoin project ideas for potential funding and mentorship, with active engagement in our Stacker News /~Education territory and Signal chat for collaboration. We invite contributors to support our learner fund and help bring innovative ideas to fruition within this new ecosystem.
Additionally, our collaboration with the Plan B Network will now operate under Consensus21.School. Through this partnership, we will continue teaching using the Plan B Network's curriculum to provide high-quality Bitcoin education and strengthen local Bitcoin communities. This global initiative remains a core part of our mission, now fully integrated within Consensus21.School.
Looking Ahead
With Consensus21.School, we will continue innovating in peer-to-peer learning, integrating cutting-edge developments in Bitcoin, Nostr, and decentralised technologies. We encourage our community to stay engaged, contribute, and help us build an even stronger foundation for the future of open education.
This is more than just a domain change--it is the next evolution of our mission. The School of Bitcoin as an entity is now retired, and all our efforts, including DAES and the Plan B Network collaboration, will move forward exclusively under Consensus21.School. We invite educators, students, and enthusiasts to join us in shaping this next phase of open financial education.
The journey continues, and we are thrilled to embark on this new chapter together
-
 @ 77c2969e:a33cfa50
2025-04-03 07:54:55
@ 77c2969e:a33cfa50
2025-04-03 07:54:55最近又开始折腾 Technitium DNS Server,发现之前记录的过程不太完善,于是更新一下。
安装acme.sh
curl https://get.acme.sh | sh -s email=youreMailAddress导入环境变量
export CF_Token="填API token" export CF_Zone_ID="填区域ID" export CF_Account_ID="填账户ID"- Cloudflare 的 API Token 是在 Cloudflare 网页右上角的👤头像--配置文件--API 令牌处创建
- 在 Cloudflare 主页点击你需要使用的域名,下滑到右下角可以看到区域 ID 和账户 ID
申请证书
acme.sh --issue --dns dns_cf -d dns.235421.xyz-d后面是你想使用的域名
安装证书
``` acme.sh --install-cert -d dns.235421.xyz \ --key-file /root/certs/key.pem \ --fullchain-file /root/certs/cert.pem \ --reloadcmd "cd /root/certs && openssl pkcs12 -export -out 'dns.pfx' -inkey 'key.pem' -in 'cert.pem' -password pass:1021"
```
reloadcmd是在申请证书之后执行的代码,以后自动更新时也会自动执行这个代码,所以第一次配置好就基本上不用管了。reloadcmd中的代码是将pem格式的证书和密钥转换成一个pfx格式的证书文件,-out后面是输出的pfx证书文件名,-inkey和-in分别是前一步acme.sh申请的密钥和证书文件。这里必须添加密码,也就是1021这个,如果不设密码执行命令的话,它会让你交互式输入,但是在自动脚本中就不行。我在前面加了先cd到证书目录,避免出现问题。
安装 Technitium DNS Server
-
在Technitium DNS Server 官网 获取安装脚本,也有提供 Docker 镜像以及 Windows 版本。
-
安装后在
公网IP:5380进入管理界面,首次进入需设置管理员密码,管理员账户默认是admin。 -
在
Settings–optional protocols处开启 DNS over HTTPS ,TLS Certificate File Path处填入转换好的pfx证书路径,TLS Certificate Password处填你设定的密码,就是我的1021。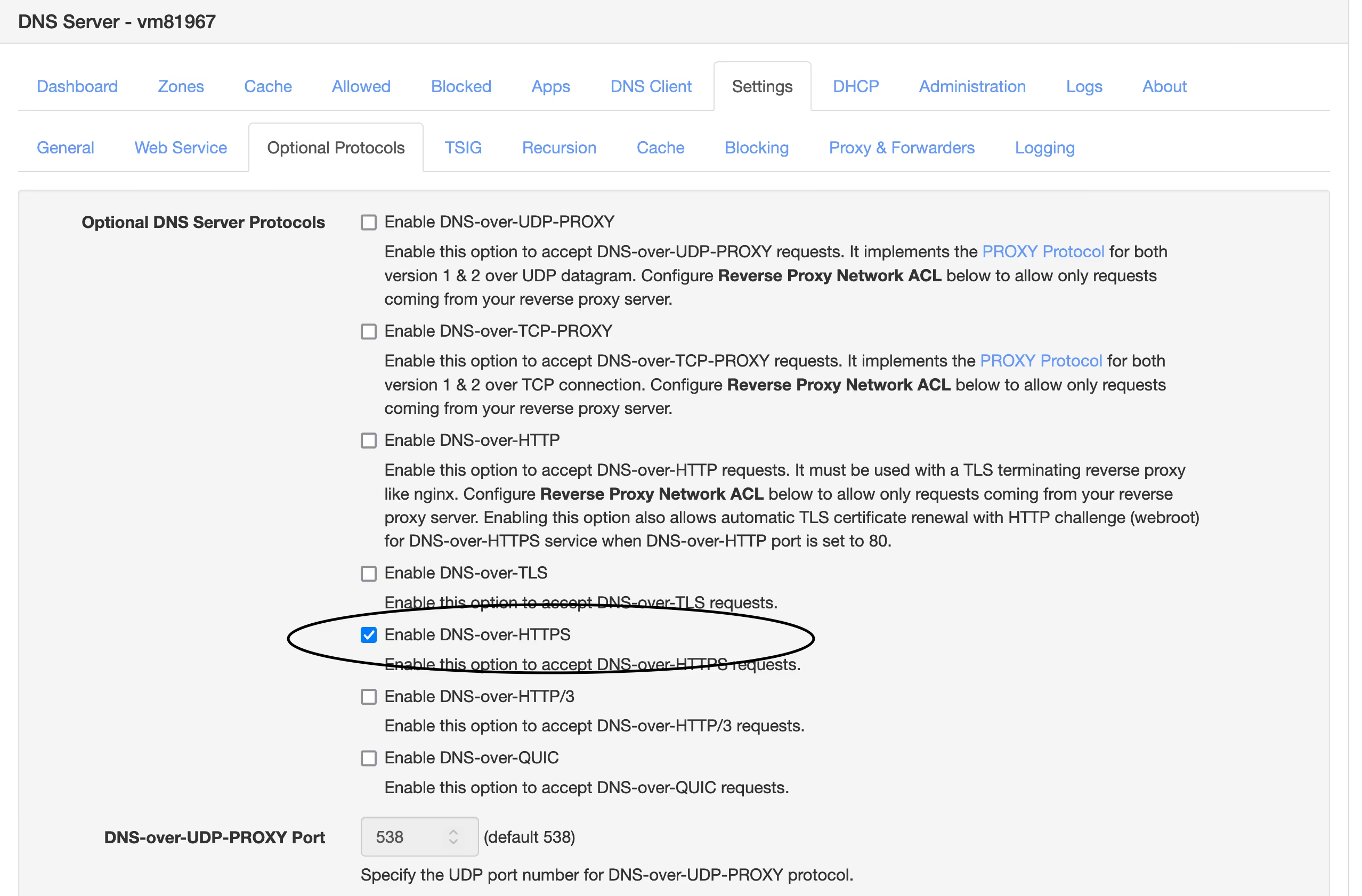
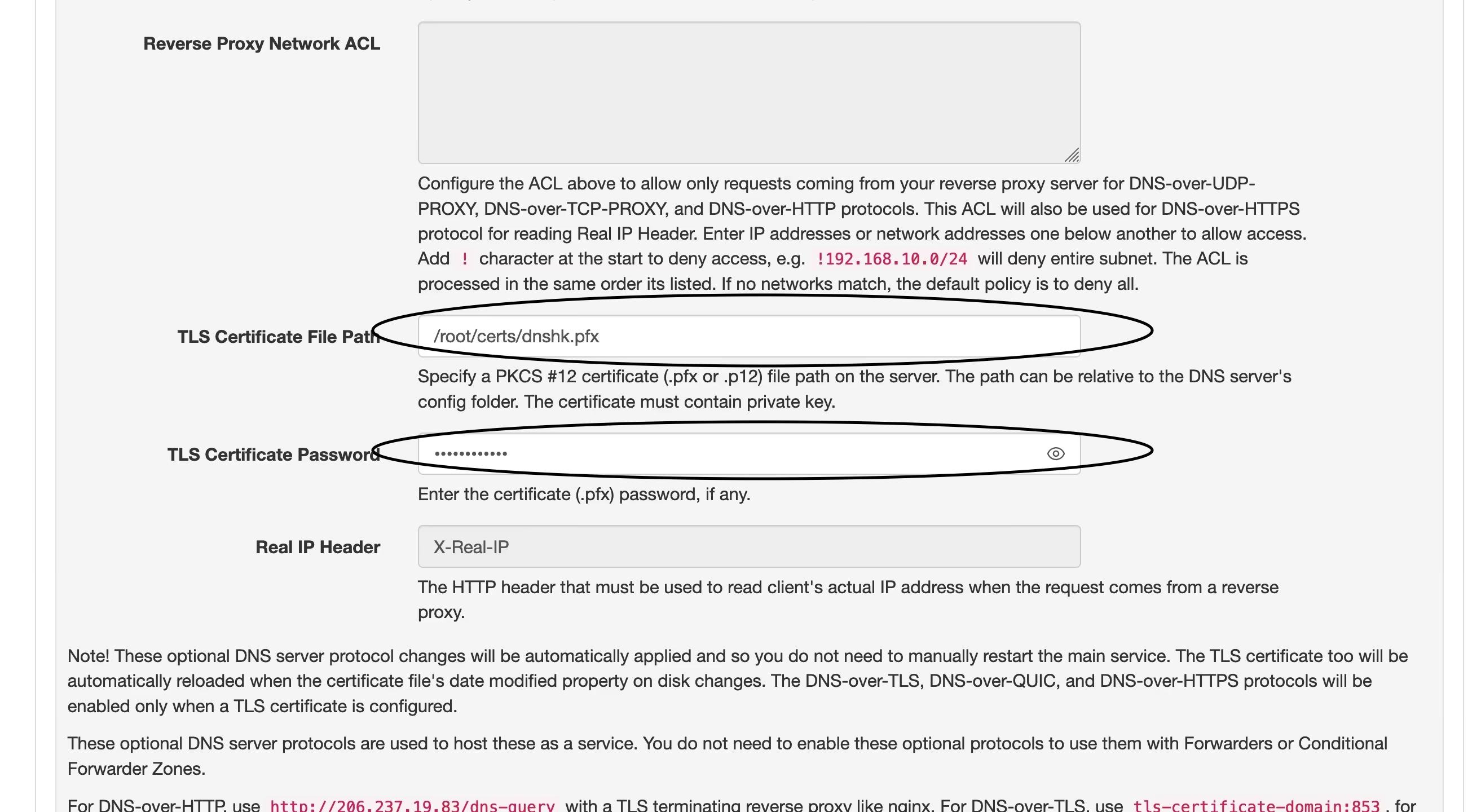
-
现在打开你的域名,看到如图这样就说明设定成功了,然后在需要设置 DoH 的地方填入
https://yourdomain.com/dns-query即可。
我在之前的文章中使用的是
DNS over HTTP并用 Nginx 反代来实现DNS over HTTPS的,现在直接用 DoH ,省去了配置 Nginx 的部分,只是多了一步证书格式转换,总体上更简单了。
我的设置
- 在
Settings–Recursion处打开Allow Recursion以允许递归解析。 - 在
Settings–Cache处将Cache Maximum Entries调大些,默认 10000 有点少了。 - 在
Settings–General处开启EDNS Client Subnet (ECS)。 - 在
Settings–Logging处开启Use Local Time。 - 在
Apps–App Store中安装Query Logs (Sqlite)以便在Logs–Query Logs处查看 DNS 查询日志。
以下设置可选
- 在
Settings–General处开启Prefer IPv6 - 在
Settings–Web Service处为后台管理页面开启 HTTPS,可使用与 DoH 相同的域名和证书,仅端口不同,这个默认 HTTPS 端口是53443。 - 在
Settings–Blocking处开启拦截功能(默认开启),下面Allow / Block List URLs可以配置规则,与 AdGuard Home 规则通用,白名单规则须在链接前加上英文叹号!。也可以是本地规则,填路径即可。 - 在
Settings–Proxy & Forwarders处可以设置上游DNSForwarders。
-
 @ c631e267:c2b78d3e
2025-04-03 07:42:25
@ c631e267:c2b78d3e
2025-04-03 07:42:25Spanien bleibt einer der Vorreiter im europäischen Prozess der totalen Überwachung per Digitalisierung. Seit Mittwoch ist dort der digitale Personalausweis verfügbar. Dabei handelt es sich um eine Regierungs-App, die auf dem Smartphone installiert werden muss und in den Stores von Google und Apple zu finden ist. Per Dekret von Regierungschef Pedro Sánchez und Zustimmung des Ministerrats ist diese Maßnahme jetzt in Kraft getreten.
Mit den üblichen Argumenten der Vereinfachung, des Komforts, der Effizienz und der Sicherheit preist das Innenministerium die «Innovation» an. Auch die Beteuerung, dass die digitale Variante parallel zum physischen Ausweis existieren wird und diesen nicht ersetzen soll, fehlt nicht. Während der ersten zwölf Monate wird «der Neue» noch nicht für alle Anwendungsfälle gültig sein, ab 2026 aber schon.
Dass die ganze Sache auch «Risiken und Nebenwirkungen» haben könnte, wird in den Mainstream-Medien eher selten thematisiert. Bestenfalls wird der Aspekt der Datensicherheit angesprochen, allerdings in der Regel direkt mit dem Regierungsvokabular von den «maximalen Sicherheitsgarantien» abgehandelt. Dennoch gibt es einige weitere Aspekte, die Bürger mit etwas Sinn für Privatsphäre bedenken sollten.
Um sich die digitale Version des nationalen Ausweises besorgen zu können (eine App mit dem Namen MiDNI), muss man sich vorab online registrieren. Dabei wird die Identität des Bürgers mit seiner mobilen Telefonnummer verknüpft. Diese obligatorische fixe Verdrahtung kennen wir von diversen anderen Apps und Diensten. Gleichzeitig ist das die Basis für eine perfekte Lokalisierbarkeit der Person.
Für jeden Vorgang der Identifikation in der Praxis wird später «eine Verbindung zu den Servern der Bundespolizei aufgebaut». Die Daten des Individuums werden «in Echtzeit» verifiziert und im Erfolgsfall von der Polizei signiert zurückgegeben. Das Ergebnis ist ein QR-Code mit zeitlich begrenzter Gültigkeit, der an Dritte weitergegeben werden kann.
Bei derartigen Szenarien sträuben sich einem halbwegs kritischen Staatsbürger die Nackenhaare. Allein diese minimale Funktionsbeschreibung lässt die totale Überwachung erkennen, die damit ermöglicht wird. Jede Benutzung des Ausweises wird künftig registriert, hinterlässt also Spuren. Und was ist, wenn die Server der Polizei einmal kein grünes Licht geben? Das wäre spätestens dann ein Problem, wenn der digitale doch irgendwann der einzig gültige Ausweis ist: Dann haben wir den abschaltbaren Bürger.
Dieser neue Vorstoß der Regierung von Pedro Sánchez ist ein weiterer Schritt in Richtung der «totalen Digitalisierung» des Landes, wie diese Politik in manchen Medien – nicht einmal kritisch, sondern sehr naiv – genannt wird. Ebenso verharmlosend wird auch erwähnt, dass sich das spanische Projekt des digitalen Ausweises nahtlos in die Initiativen der EU zu einer digitalen Identität für alle Bürger sowie des digitalen Euro einreiht.
In Zukunft könnte der neue Ausweis «auch in andere staatliche und private digitale Plattformen integriert werden», wie das Medienportal Cope ganz richtig bemerkt. Das ist die Perspektive.
[Titelbild: Pixabay]
Dazu passend:
Nur Abschied vom Alleinfahren? Monströse spanische Überwachungsprojekte gemäß EU-Norm
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 0f9da413:01bd07d7
2025-04-03 05:32:55
@ 0f9da413:01bd07d7
2025-04-03 05:32:55
หลังจากจบทริปเที่ยวพัทยาเรียบร้อยแล้วก็ได้เดินทางไปยังเกาะช้างโดยติดรถเจ้าหน้าที่ในที่ทำงานไปไปเกาะช้างครั้งแรกรู้สึกว่ามันไกลเหลือเกินไปค่อนข้างยากหากไม่มีรถส่วนตัว ถ้าให้ไปส่วนตัวก็คงต้องอยู่นานๆ หน่อยชักแบบอาทิตย์หนึ่ง ใช้ชีวิตแบบฝรั่งเที่ยวอยู่ง่ายๆ กินง่ายๆ จากที่ดูในแผนที่ btcmap แล้วพบว่าก็มีร้านที่ปักหมุดไว้อยู่ทั้งหมดสองร้านด้วยกันซึ่งระยะทางก็ค่อนข้างซันเหมือนกัน และมีเนินสูงต่ำสลับกันไป หากไม่มีรถส่วนตัวไปนี่ค่อนข้่างลำบากพอสมควร ต้องเช่ามอไซต์ไป อันนี้ก็เช่าไปเหมือนกัน โดยผมเช่ามอไซต์ 1 วันวันละ 200 บาท (แต่มัดจำ 3000 บาท) ก็เอาเรื่องเหมือนกัน และก็มาเริ่มต้นที่ร้านแรกเลยคือ
Mr. A Coffee

ร้านอาหารสไตล์บ้านๆ ที่ขายอาหาร น้ำ เครื่องดื่ม มีทั้งอาหารไทยและอาหารฝรั่ง ส่วนตัวก็ขับรถมอไซต์มายังสถานที่แห่งนี้ทางเข้าไปยังร้านเป็นหมู่บ้านเล็กๆ ไม่มีถนนเข้า แต่มอไซต์เข้าไปได้พอสมควร ตอนนั้นค่อนข้างเย็นมากแล้ว ได้มาสั่งอาหารมาคือ ข้าวเหนียวมะม่วงกับน้ำแก้วมังกรปั่นแบบไม่หวาน (ทั้งๆที่ตัวเองก็จะเตรียมไปกินบุ๊ปเฟ่อีกหนึ่งชั่วโมงข้างหน้า 555) ก็ได้สั่งไปแล้วก็ถามว่ารับ bitcoin ไหมครับ เจ้าของร้านก็บอกว่า รับๆ ผมกับเจ้าของร้านก็ได้พูดคุยกันเกือบประมาณครึ่งชั่วโมง ซึ่งหากผมมาเร็วกว่านี้หน่อยก็คงได้คุยกันยาวๆ แล้วละ ซึ่งเป็นการคุยที่สนุกมากซึ่งตัวเจ้าของร้านเองก็ได้เล่าถึงเหตุผลที่รับ bitcoin เหมือนกันว่าช่วง โควิดตอนปี 2020 ที่ผ่านมา บนเกาะช้างไม่มีอะไรเลยชาวบ้านก็ต้องไปหารากไม้ หาเห็ดตามป่าเขากัน แต่พี่เจ้าของร้านได้รู้จักกับฝรั่งคนหนึ่งเขาช่วยเหลือพี่เจ้าของร้านด้วยการบริจาคบิทคอยให้ และคนนี้ก็เป็นคนสอนให้เขารับบิทคอยโดยใช้ WOS และเจ้าของร้านก็เล่าให้ผมฟังเพิ่มเติม ณ ปัจจุบันว่า คนเราเองก็ยังต้องมีสภาพคล่องในการใช้งานอยู่ ตั้งมีเงิน fiat ไว้ส่วนหนึ่ง ส่วนบิทคอยที่ได้เขาได้ก็เก็บไว้เพื่อสร้างเป็นทรัพย์สินในอนาคตที่หากมีปัญหาช่วงไหนก็นำมาขายได้ ก็แลก P2P โดยตรง ซึ่งผมค่อนข้างตกใจเพราะเขาเรียนรู้จากการรับบิทคอยโดยนักท่องเที่ยวชาวต่างชาติที่ชวนเขาให้รับ เผื่อว่าจะมีฝรั่งมาใช้งานบิทคอย ณ สถานที่ร้านแห่งนี้

กึมมิคที่หลายท่านอาจจะต้องลุ้นหน่อยว่าหากมีโอกาสได้ไปเที่ยวและแวะที่ร้าน ก็คงต้่องลุ้นว่าคุณจะได้จ่ายด้วย bitcoin ไหม หากวันนั้นเจ้าของร้านไม่อยากรับเพราะว่าโคต้ารับบิทคอยวันนั้นเต็มแล้ว ฮ่าๆ รูปแบบระบบวาสนาร้านสูญของคุณมิกตอนเมื่อก่อน (เหมือนกันเลย) จริงๆ แล้วหากมีเวลามากพอก็คงได้พูดคุยกับพี่เจ้าของร้านสนุกๆกันไป ผมชอบความเรียบง่ายของร้านพี่เขา และมีอาหารหลากหลายอย่างเต็มไปหมด อีกเรื่องอย่างข้าวเหนียวมะม่วง ผมยังจำได้ว่าเมื่อก่อนมีแต่ช่วงฤดูเดียวที่สามารถกินมะม่วงสุกได้ หรือ อาหารแบบข้าวเหนียวมะม่วง แต่ปัจจุบันคือถ้าจะกิน ข้าวเหนียวมะม่วงแล้ว สามารถสั่งกินได้ตลอดทั้งปีกันเลยซึ่งก็โอเครพอสมควร แบบอยากไปทะเลตอนหน้าฝนแล้วอยากกินข้าวเหนียวมะม่วงของหน้าร้อนแบบนี้

ท้ายสุดร้าน Mr. A Coffee เป็นร้านที่ถ้านั่งชิวๆ แบบฝรั่งก็สามารถอยู่ได้ยาวๆ เลยนะจิบกาแฟ ทำงาน WFH ล้่อมรอบโดยธรรมชาติ แต่เส้นทางมาที่ร้านก็ลำบากหน่อยเหมาะกับคนที่ local จริงๆ low time ระดับหนึ่ง ท้ายสุดผมเองก็แจกสติกเกอร์ของพี่แชมป์เอาไปให้เจ้าของร้านแจกกันต่อไป
 งานนี้ทั้งข้าวเหนียวมะม่วงและน้ำแก้วมังกรปั่น เสีย sats ไปทั้งหมด 6,050 sats แต่สิ่งที่ได้คือการแลกเปลี่ยนมุมมองกับเจ้าของร้านกับจุดเริ่มต้นของการรับบิทคอยในพื้นที่เกาะช้างแห่งนี้ และหากมีโอกาสอาจจะไปพักอยู่แถวนั้นชักอาทิตย์และแวะมาอุดหนุนร้านนี้ตลอด เพราะวิวฝั่งใต้สุดของเกาะช้างก็ยังคงความสวยงามไม่แพ้กับฝั่งทิศตะวันตกที่ฝรั่งอยู่กัน แต่ฝั่งใต้โซนนี้ก็มีความที่เป็นบ้านไม้ เพิงง่ายๆ ที่ชาวต่างชาติชอบกันอยู่ :)
งานนี้ทั้งข้าวเหนียวมะม่วงและน้ำแก้วมังกรปั่น เสีย sats ไปทั้งหมด 6,050 sats แต่สิ่งที่ได้คือการแลกเปลี่ยนมุมมองกับเจ้าของร้านกับจุดเริ่มต้นของการรับบิทคอยในพื้นที่เกาะช้างแห่งนี้ และหากมีโอกาสอาจจะไปพักอยู่แถวนั้นชักอาทิตย์และแวะมาอุดหนุนร้านนี้ตลอด เพราะวิวฝั่งใต้สุดของเกาะช้างก็ยังคงความสวยงามไม่แพ้กับฝั่งทิศตะวันตกที่ฝรั่งอยู่กัน แต่ฝั่งใต้โซนนี้ก็มีความที่เป็นบ้านไม้ เพิงง่ายๆ ที่ชาวต่างชาติชอบกันอยู่ :)Google-map: https://maps.app.goo.gl/b45JGeTzL6Lwwi9i9
BTC-map: https://btcmap.org/merchant/node:12416107504
**Koh Chang Wine Gallery **

และเราก็ย้อนกลับมาอีกร้านหนึ่งในวันถัดไปและเป็นวันที่จะต้องออกจากเกาะช้างเช่นเดียวกัน และผมก็ไม่พลาดร้าน Koh Chang Wine Gallery ตั้งอยู่ในโซนหมู่บ้านแหล่งท่องเที่ยวเส้นทางถนนทางตะวันตก ร้านนี้ไม่ได้มีป้ายรับบิทคอย แต่รับชำระด้วยบิทคอยซึ่งเป็นฝรั่งท่านหนึ่งที่คาดว่าน่าจะแต่งงานกับภรรยาคนไทย เป็นร้านสไตล์แบบฝรั่งเลย ผมเองก็สั่งสเต็กเนื้อไป และน้ำมะม่วงปั่น (ไม่รู้เวลาไปเกาะทีไรติดใจกับน้ำมะม่วงปั่น) อาจจะไม่ได้พูดคุยอะไรมากมายนัก แต่ก็หมดไป 32,620 sats เป็นร้านอาหารเช้าและอาหารแนวฝรั่งตรงๆ ถือว่าค่อนข้างอร่อยใช้ได้ดีเลยทีเดียว แต่หากจะจ่ายด้วยบิทคอยก็ต้องแจ้งก่อนนะว่าขอจ่ายด้วยบิทคอยก่อน เหมือนพี่ฝรั่งที่เขารับตอนนี้ก็รับแต่เฉพาะ bitcoin อย่างเดียวเมื่อก่อนรับ xrp กับ doge ด้วยแต่ผมเองเวลาคุยกับฝรั่งก็เหงื่อแตกเหมือนกัน (รึว่าเพราะมันร้อน บนเกาะก็อบอ้าวใช้ได้ 555+)



Google-map: https://maps.app.goo.gl/6QbNgRbiV5Uao2Xz8
BTC-map: https://btcmap.org/merchant/node:11461720813
เส้นทางไปร้านค่อนข้างง่ายติดถนนในหมู่บ้าน ซึ่งหากมายังเกาะช้างแล้วหากขึ้นฝั่งมาแล้วเลี้ยวขวาก็จะขับรถหรือนั่งรถมาเส้นถนนฝั่งตะวันตกของเกาะก็จะพบกับร้านนี้ก่อน อันนี้แล้วแต่ความสะดวกแต่ละท่านเลยครับหากได้มีโอกาสแวะมาเกาะช้างและอยากใช้จ่าย bitcoin เราก็มีทางเลือกร้านในสองสไตล์กันเลย แบบวิถีฝรั่งตอนเช้าก็ร้าน Koh Chang Wine Gallery หรือ แบบ Local ก็ Mr. A Coffee หรือไปทังคู่เลยจะดีมากแต่ต้องบ้าหน่อย เพราะเส้นทางไปก็ค่อนข้างลำบากพอควรเหมือนกัน หมายถึงมีภูเขาชันมีทางขึ้นลงหักศอกนิดหน่อยก็เท่านั้นเอง
รวมๆ ทริปบนเกาะช้างนี้ก็หมดไปไม่เยอะมาก 38,670 sats ก็จะตัวลอยเบาๆ หน่อย (สำรวจเมื่อ มีนาคม 2025 อนาคตอาจจะมีการเปลี่ยนแปลงได้) สำหรับจากนี้จะเป็นการ ปสก. ส่วนตัวกับการใช้งาน Bitcoin Lightning ตามสถานที่ที่ได้เดินทาง Part 3 จะเป็นสถานที่ในพื้นที่หาดใหญ่ จังหวัดสงขลา และ เสริมประสบการณ์การเดินทางโดยรถไฟระยะเวลาเกือบ 18 ชั่วโมง พร้อมด้วยมิตรสหายในรังอย่างกัปตัน จะป่วนแค่ไหนก็รอติดตามกันครับ :)
-
 @ 5cf42f9d:4465eebf
2025-04-02 21:32:31
@ 5cf42f9d:4465eebf
2025-04-02 21:32:31 -
 @ 3c7dc2c5:805642a8
2025-04-02 21:15:55
@ 3c7dc2c5:805642a8
2025-04-02 21:15:55🧠Quote(s) of the week:
CBDC the digital euro - a centralized solution in search of a problem. While the ECB may see it as a way to 'modernize' finance, true innovation comes from empowering individuals, not consolidating control. CBDCs are just surveillance tools disguised as innovation. Bitcoin is the only true digital money—decentralized, scarce, and free. Stack sats, not CBDCs.
🧡Bitcoin news🧡
2025 https://i.ibb.co/vx988kT1/Gn-Ix-Dp-YWs-AASkiw.jpg
On the 24th of March:
➡️The Pakistan central bank is exploring mining Bitcoin with excess electricity.
➡️'MicroStrategy just added another 7,000 Bitcoin to their treasury. They're now holding over 506,000 BTC ($44 billion). Look at the corporate Bitcoin ownership breakdown: - MicroStrategy: 506,000+ BTC - Marathon: ~46,000 BTC (10x smaller) - Riot: ~19,000 BTC (26x smaller) That acquisition curve has gone parabolic since Q4 2024. Strategy's buying pace now rivals what we're seeing from the Bitcoin ETFs, a single public company absorbing supply at an institutional scale. Clear institutional conviction signal here.' -Ecoinometrics
➡️SQUARE CEO JACK DORSEY: "Bitcoin will make the current financial system feel as irrelevant as the fax machine."
On the 25th of March:
➡️'BITCOIN HASH-RIBBON FLASHES BUY SIGNAL
- This is one of the most reliable "buy" indicators.
- Significant price gains have followed 7 out of the last 7 times this indicator was triggered.' -Bitcoin Archive (foto) Bitcoin is always a buy. Just DCA.
➡️GameStop includes Bitcoin as a treasury reserve asset in its investment policy update. GameStop has $4.6 billion in cash to invest.
➡️Strategy’s sale of 8.5 million STRF shares closes today, unlocking $711 million in new capital to buy more Bitcoin.
➡️BBC News reports from a remote community of 15,000 people in the far north-western tip of Zambia relying on hydroelectric power, “The bitcoin mine now accounts for around 30% of the plant's revenue allowing them to keep the prices down for the local town” - Source: https://www.bbc.com/news/articles/cly4xe373p4o Gridless is doing a splendid job in Africa and showing through proof-of-work that if you aren't mining Bitcoin, you are wasting energy. It's time for such communities to appear more around the world.
Daniel Batten: 'They couldn't resist zooming out and implying this is an outlier (it isn't, the majority of off-grid bitcoin mining operations are renewably powered). In doing so BBC made three factually incorrect statements at the end about Bitcoin mining straining grids (multiple peer-reviewed studies show the opposite is true), and "Greenidge gas power plant in New York which was renovated to mine bitcoin" (it didn't, it re-opened to supply power back to the grid), and stating that Bitcoin mining needs artificial govt incentives or rules to do the right thing (It doesn't, it's become 56.7% sustainably powered without any govt incentives)
But let's shine the light on the positive - it has far fewer factually incorrect statements than previous reporting, and it is a step in the right direction in its gradual journey towards objective Bitcoin reporting for a media company that has until now only published negative news stories on Bitcoin.'
➡️Femke Halsema, Mayor of Amsterdam, wants a national ban on Bitcoin payments: "It undermines our civilization".
I rather believe the opposite.
Under Femke Halsema - Amsterdam
-
The number of civil servants increased by 50% (14K -> 20K)
-
Debt increased by 150% (4 billion -> approx. 10 billion)
Despite high revenues, Amsterdam has to borrow nearly half a billion euros every year. Local taxes continue to rise, whether it's water authority taxes or property taxes (OZB). But, above all, you should be concerned about those 0.3% criminal Bitcoin / Crypto transactions (worldwide). The audacity.
Even if the Netherlands were to legally ban Bitcoin payments, users could easily continue trading through foreign exchanges or peer-to-peer platforms. A ban might actually push Bitcoin usage further underground, making oversight of suspicious transactions worse rather than better.
➡️Mt. Gox moves 11.501 Bitcoin ($1B) for creditor repayment.
➡️BlackRock launched a European Bitcoin ETP today - Bloomberg
➡️North Carolina introduces a bill to invest 5% of state funds into Bitcoin.
On the 26th of March:
➡️NYDIG just became a big Bitcoin miner. Crusoe, the first to scale Bitcoin mining off flared gas (~200MW worth, across 425 data centers) has sold its entire Bitcoin mining business to NYDIG.
➡️Metaplanet has raised ~$55.2m (¥8.28b) of equity capital through three trading days this week while partially deleveraging with the redemption of $23.3m (¥3.5b) of 0% ordinary bonds.
➡️GameStop can service a loan of up to $100 BILLION for 4.6 years with its existing $4.6b cash balance at 1% interest. That's twice the amount of Bitcoin Michael Saylor's Strategy currently holds.
➡️New feature by Protonmail enables their 100 million users to send Bitcoin using their email addresses.
➡️The Blockchain Group confirms the acquisition of 580 BTC for ~€47.3 million, the holding of a total of 620 BTC, and a BTC Yield of 709.8% YTD.
→ Confirmation of the acquisition of 580 BTC for ~€47.3 million at ~€81,550 per bitcoin
→ Total group holdings of 620 BTC for ~€50.5 million at ~€81,480 per bitcoin
→ Adoption of ‘BTC Yield’, ‘BTC Gain’, and ‘BTC € Gain’ as KPIs, following the steps of Strategy and Metaplanet
This is a major step in our Bitcoin Treasury Company strategy focused on increasing Bitcoin per share over time.
Source: https://t.co/QDj61ZDe6O
The Blockchain Group is Europe's First Bitcoin Treasury Company!
On the 27th of March:
➡️'Bitcoin's 4-year Compound Annual Growth Rate (CAGR) is at historic lows.' -Pierre Rochard
➡️Daniel Batten: Yet another paper on Bitcoin and energy TL:DR: "The opportunities offered by bitcoin mining in reduction of the greenhouse gas emissions and renewable energy transition are greater than generally assumed" The journal has a (high) impact factor of 7.1."
Source: https://t.co/W3gytMgcpC
➡️A home miner with only 4 machines mined block 888737.
https://i.ibb.co/7xm91R4t/Gn-Ef-H9y-Ws-AA4jkn.jpg
Bitcoin proves anyone can participate and earn—true freedom!
➡️'Short-Term Holders have increased their Bitcoin holdings by 201,743 BTC to 5,750,076 BTC since January, remaining below previous cycle peaks. 200K BTC are currently held at an unrealized loss, representing about $17B.' -Bitcoin News
➡️Bitcoin mining hardware manufacturer Canaan signs a three-year colocation agreement with Mawson Infrastructure Group's Mawson Hosting LLC for facilities in Midland, Pennsylvania, and Edna, Texas. Most of the 4.7 EH/s hashrate is expected to be operational by Q2 2025.
On the 28th of March:
➡️If Saylor had bet on ETH instead of Bitcoin, Strategy would be down $9 billion, instead of up $9 billion like they are today. ETHBTC made fresh lows 0.02210. Ether is down 74% against Bitcoin since switching from proof of work to proof of stake. Yikes!
➡️Representative introduces a strategic Bitcoin reserve bill in South Carolina.
➡️A Russian company built a Bitcoin mine in the Arctic. Set in the frozen city of Norilsk, the facility taps into cheap excess energy from one of the world's most isolated industrial hubs.
➡️The price of bitcoin has nearly followed the same phases of volatility for 15 years, according to Fidelity.
https://i.ibb.co/LdQfrqG0/Gn-Ig-Skd-XMAAi-L3r.jpg
another great chart:
https://i.ibb.co/G4WmDjhd/Gn-JED1q-Xk-AAq-Kqk.jpg
On the 29th of March:
➡️Public miner MARA with a $2B common stock offering to buy more Bitcoin. https://i.ibb.co/PZZxXJ37/Gn-Kj-Vqza-EAEUG-V.png
➡️California has officially included Bitcoin Rights protections in its newly proposed digital asset bill. If passed, it will guarantee the right to self-custody for nearly 40M residents and prohibit discrimination against Bitcoin use.
➡️The number of addresses with more than one Bitcoin has fallen below 1 million, standing today at 995,207.
On the 31st of March:
➡️Larry Fink, Founder/CEO of BlackRock in his annual letter to shareholders: “If the U.S. doesn't get its debt under control, if deficits keep ballooning, America risks losing that position to digital assets like Bitcoin."
https://www.blackrock.com/corporate/literature/presentation/larry-fink-annual-chairmans-letter.pdf
➡️Strategy has acquired 22,048 BTC for ~$1.92 billion at ~$86,969 per bitcoin and has achieved a BTC Yield of 11.0% YTD 2025. As of 3/30/2025, Strategy holds 528,185 $BTC acquired for ~$35.63 billion at ~$67,458 per bitcoin.
➡️ The Bitcoin Policy Institute releases a framework for the USA to buy $200 billion worth of #Bitcoin using Bit Bonds.
➡️Is Indonesia the next Bitcoin Country? Bitcoin Indonesia mapped out the entire Bitcoin ecosystem.
A new map shows Bitcoin adoption EXPLODING across the Southeast Asian island nation of Indonesia. Check out all the communities, projects, and businesses embracing Bitcoin. The revolution is happening.
https://i.ibb.co/cXL8mC0x/Gnbdg-Lub-IAAdwcb.jpg
On the 1st of April:
➡️'Over 73,353 BTC were bought by corporations in Q1 2025. Only 40,500 BTC new Bitcoin was mined, but still no supply shock, for now... Which company do you want to see adopt BTC next?'
Here is the breakdown by Alec: https://x.com/Alec_Bitcoin/status/1907062290345783723
➡️After skeptics questioned Tether’s Bitcoin holdings, CEO Paolo Ardoino fired back, sharing the company’s BTC address with a confirmed balance of 92,646 BTC. On the same day Tether bought 8,888 Bitcoin worth $735 million as per on-chain data. They now hold over 100,000 BTC.
➡️'GameStop just raised $1.48B. They are expected to use that and possibly more of the now $6B+ on their balance sheet to buy Bitcoin. A master class on how to pivot from meme stock to capitalize on volatility in the ultimate store of value.' -James Lavish
➡️Texas' state house Democrats have proposed a bill that would authorize up to $250 million in state investment in Bitcoin and up to $10 million for each municipality and county.
➡️Human Rights Foundation donates 10 Bitcoins worth $830,000 to over 20 projects worldwide.
Alex Gladstein: '1 billion sats gifted carefully to a variety of stellar organizations and individuals to support BTC privacy, decentralization, education, and p2p use, aimed at folks working under authoritarianism.'
💸Traditional Finance / Macro:
On the 29th of March
👉🏽'From Wednesday to Friday, the S&P 500 lost -$100 billion PER trading hour for a total of -$2 TRILLION. Then, after the market closed on Friday, S&P 500 futures erased ANOTHER -$120 billion in minutes.' -TKL
🏦Banks:
👉🏽 no news
🌎Macro/Geopolitics:
On the 24th of March:
👉🏽Financelot: 'This is fascinating. The Dow Jones to Gold Ratio is about to cross a level only seen 4 times in history. Every time it crossed this level it marked the beginning of an 18-month recession/depression. 1929, 1973, 2008 & 2025' I don't think we won't see a depression. History rhymes but doesn't always mean it will repeat, although human behavior stays the same. For now, it means the market is overvalued, gold is undervalued, or both.
👉🏽US household wealth is falling: US household equity wealth is set to drop a whopping -$3 trillion this quarter, the most since the 2022 bear market, according to BofA estimates. By comparison, equity holdings rose +$9 trillion in 2024 to a record $56 trillion. In other words, one-third of last year's gains have likely been wiped out due to the recent market pullback.
Furthermore, the top 10% of the wealthiest Americans own 87% of US stocks. This, in turn, may negatively impact consumer spending as the top 10% reflect a record 50% of all consumer expenditures. Consumer spending is set to slow in Q2 2025.' -TKL
👉🏽Demolition of the Boiler House at Moorburg Power Plant in Hamburg. Germany is preparing for combat by dynamiting its own modern energy infrastructure down. This was the most advanced coal plant. 6 years old and cost three billion euros. The Netherlands is following a similar policy—they poured concrete into their gas drilling pipes.
BowTiedMara on Twitter: "In 2022, a girl tied herself to the net at Roland Garros in protest, and she wore a T-shirt that said: "We have 1,028 days left." Today, the 27th of March, marks those 1,028 days, and nothing happened. Climate doomers are like Aztecs who think the sun stops unless they cut out some organs."
👉🏽Starting in April, the 66,000 employees of the European institutions will receive their seventh salary increase in just three years! Normally, this happens at most once per year. The President of the European Commission, Ursula von der Leyen, will see the largest increase, with her monthly salary rising to €34,800—an increase of €2,700—according to a report by the German newspaper Bild-Zeitung today.
For the Dutch readers: https://ejbron.wordpress.com/2025/03/24/eu-bureaucraten-en-politici-krijgen-de-7e-salarisverhoging-sinds-2022/
They are compensating for the inflation they impose on the EU. Lucky them Fair to say we need a DOGE in Europe.
On the 25th of March:
👉🏽Dutch minister announces a huge increase in excise duties of 25.8 cents on gasoline. On top of that, the price of gasoline will rise by an additional 7 cents due to the blending requirement and 11 cents due to the ETS-2 regulation. In a free market, prices would not be announced by politicians but would emerge through supply and demand. How I love the EU....although it is a bit more nuanced. The temporary discount is ending. Unless the parliament decides to extend it, the price of gasoline will rise. The Dutch government should simply spend less and abolish all taxes, excise duties, and levies on food, fuel, and energy. Never gonna happen though.
👉🏽"Shell will be thoroughly reviewing all its chemical divisions worldwide in the coming period. In Europe, this could lead to the partial or complete closure of various chemical branches." As mentioned multiple times last month, major industrial companies sounded the alarm. They warned that high energy costs in the Netherlands put their future at risk. Additionally, sustainability efforts and unclear government policies are challenging the sector. Frans Everts, President-Director of Shell Netherlands, warned that the entire industry could collapse.
The Green Deal is moving full speed ahead—soon everyone will be relying on food banks…
For the Dutch readers: https://nos.nl/artikel/2561036-shell-kijkt-naar-gedeeltelijke-sluiting-van-chemie-onderdelen
On the 26th of March:
👉🏽EU countries will start using a digital driver’s license from 2030. This is the result of negotiations between the European Parliament and EU member states. In the Netherlands, the digital license will be valid for ten years and will be accessible via an app. And we all know which app that will be! The EU Digital Wallet must be filled, after all.
Not just your driver’s license—everything will soon be linked to your digital identity. It’s all right there on the EU’s website, and it’s been planned for a long time. The COVID pass was already part of the rollout. The fact that they present these as separate steps just shows that they know people wouldn’t accept it if they were fully aware of what’s happening.
On the 27th of March:
👉🏽Gold surpasses $3,100 for the first time in history. TKL: 'Gold prices have hit 50 all-time highs over the last 12 months, its best streak in 12 years. This is also the 3rd-longest streak on record after a historic run during the late 1970s. The 1970s came with a period of double-digit inflation, stagnant economic growth, and a high unemployment rate, also known as stagflation. As a result, gold prices recorded 4 consecutive yearly gains.'
On the 31st of March for the first time, gold blasted through $100,000/kilogram. This time, gold prices have rallied 39% over the last 12 months, are up 16% year-to-date, and are on track for the 3rd annual positive performance.'
👉🏽NATO Secretary General Rutte insists there will be no normalization of relations with Russia for decades to come.
On March 14, 2025, Bloomberg, Rutte says: "Once the war is over, relations with Russia will gradually be restored."
On March 26, 2025, Rutte said: "There will be no normalization of relations with Russia for decades, even after the war is over."
That is the Mark I know!
"Mark Rutte, the long-serving Dutch Prime Minister, earned the nickname “Pinokkio” (Dutch for Pinocchio) primarily because of perceived dishonesty or evasiveness in political debates and scandals. While some still view Rutte as a pragmatic and stable leader, the nickname “Pinokkio” reflects a broader public sentiment of distrust, especially among those who felt betrayed by his communication style or decisions.”
On the 28th of March:
👉🏽US consumers now expect 5.0%(!) inflation in the next twelve months. Inflation expectations have DOUBLED in just four months. That's huge! Long-term US inflation expectations have officially SURGED to 4.1%, the highest level since 1993. Tariff front-running has led to a $300+ BILLION trade deficit in 2 months, and consumer sentiment has collapsed.
Atlanta Fed is now projecting that Q1 GDP will be -2.8%… a large contraction. It’s negative even “gold adjusted”
4 weeks ago it was +2.3%
8 weeks ago it was +3.9%
Yikes!
👉🏽The State Department is officially shutting down USAID and has formally notified Congress of its closure. The remaining 900 employees are set to be terminated.
👉🏽Argentina’s Economy Grows 6.5% in January. Argentina’s Poverty Rate Drops from 52.9% to 38.1% in 15 Months Under Javier Milei
👉🏽Fix the money, fix the world:
DOGE “There is actually really only ONE BANK ACCOUNT that's used to disperse ALL monies that go out of the federal government” “It's a big one — A couple of weeks ago it had $800 billion in it, it's the treasury general account”
“We're serving 580+ agencies. And up until very recently, effectively they could say, make the payment and Treasury just sent it out as fast as possible. NO VERIFICATION”
“There's a $500 billion of fraud every year. There are hundreds of billion dollars of improper payments and we can't pass an audit. The consolidated financial report is produced by treasury and we cannot pass an audit”
Extremely fascinating interview by Bret Baier with the highly talented and competent DOGE team, which is rigorously streamlining the U.S. government bureaucracy. This work can only be done by competent (and motivated) outsiders with experience. Also urgently needed in the Netherlands, and in Europe.
On the 29th of March:
👉🏽'US debt has been "limited" by the $36.104 trillion debt ceiling since January but the liabilities don't stop rising. As of today, US debt is now ~$37 trillion. Treasury has burned through $560BN of its cash balance in the past month. Just $280BN left.' -ZeroHedge
On the 1st of April:
In recent weeks, I have shared my opinion on the latest Dutch pension fund drama. This week:
https://i.ibb.co/96ZhS0W/Gn-XEVQRXw-AM6b0-A.jpg
APG and pension funds refused to invest in Dutch housing (for political reasons). This involved 25 billion euros.
Currently we almost have a political scandal over a medal, but the fact that our pension system is being put at risk...no biggie!?
For our own housing market? “Too political.” For war and Brussels' military ambitions? €100,000,000,000—no problem.
They’re gambling with your pension while first-time buyers can’t afford a home and seniors struggle to make ends meet. Our money, their agenda.
Got Bitcoin?
I will end this Weekly Recap with a Stanley Druckenmiller quote:
"My favorite quote of all time is maybe Mark Twain: "Put all your eggs in one basket and watch the basket carefully."
"I tend to think that's what great investors do."
I know what I do and have. Bitcoin!
🎁If you have made it this far I would like to give you a little gift:
What Bitcoin Did: Peter Dunworth is the Director of a multi-family office and is the co-founder of The Bitcoin Adviser. In this episode, they discuss why Bitcoin is the only asset that can recapitalize the financial system, why Peter believes Bitcoin could become a $100 trillion asset within a decade, why credit markets are ultimately a collateral problem, and why financializing Bitcoin might be necessary to save Main Street from being collateral damage. They also get into Australia's property obsession, GameStop’s pivot to Bitcoin, the difference between Bitcoin derivatives and the asset itself, and MicroStrategy.
https://www.youtube.com/watch?v=_bSprc0IAow
Credit: I have used multiple sources!
My savings account: Bitcoin The tool I recommend for setting up a Bitcoin savings plan: PocketBitcoin especially suited for beginners or people who want to invest in Bitcoin with an automated investment plan once a week or monthly.
Use the code SE3997Get your Bitcoin out of exchanges. Save them on a hardware wallet, run your own node...be your own bank. Not your keys, not your coins. It's that simple. ⠀ ⠀
⠀⠀ ⠀ ⠀⠀⠀
Do you think this post is helpful to you? If so, please share it and support my work with a zap.
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
⭐ Many thanks⭐
Felipe - Bitcoin Friday!
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
-
 @ ef53426a:7e988851
2025-04-02 21:02:06
@ ef53426a:7e988851
2025-04-02 21:02:06Bartering and early money
\ Early societies bartered goods, but transactions were often complicated. The value of goods doesn’t always align.
Enter money. It’s used as an indirect exchange for any goods, so everyone wants it.
Early money wasn’t anything like what we use today. For example, the inhabitants of Yap Island (Micronesia) used large Rai stones for trade. New stones were dragged up a hill for everyone to see. The owner would then exchange part of the stone for goods and services.
As they were hard to quarry and move, Rai stones retained their value (salability). Then, an Irish-American captain started importing stones using modern technology. Soon enough, they became so common, they no longer worked as money.
Gold — the basis for sound money
\ Smelting made it possible to create highly salable and transportable coins. Gold was best because it’s virtually impossible to destroy and can’t be synthesized using other materials. It has a fairly limited supply, which grows slowly and predictably (due to the difficulty of mining).
Technologies like the telegraph and trains made it easier for both people and goods to get from point A to point B. That, in turn, justified forms of payment like checks, paper receipts, and bills. But paper is not worth much unless it’s backed by something.
Governments worldwide issued paper money backed by precious metals, which they stored in vaults. By 1900, around 50 countries had adopted the Gold Standard. This was sound money.
Currencies devalued
\ Roman emperor Julius Caesar issued the Aureus, an empire-standard coin containing 8 grams of gold. But as growth began to slow, rulers started ‘coin clipping’, reducing the quantity of precious metal in coins. This eventually triggered a series of economic crises that led to the downfall of the Roman Empire.
The gold standard had one major flaw: it had to be stored in bank vaults. This created a highly centralized system in which governments controlled the value of paper money. If they wanted to, they could always increase the supply of money without increasing the corresponding amount of gold.
In 1914, nearly every major European power decided to do this to fund their war operations. Rather than raising taxes, they simply printed new money with no extra gold. The standard had been abandoned.
Government-backed money
\ Governments chose to introduce fiat money – currency backed by decree rather than gold. The adoption of the fiat system led to an age of unsound money shaped by ever-greater intervention in the economy as governments scrambled to stabilize their currencies.
By 1944, the end of the Second World War was in sight, and the victors began planning the postwar economic order. The world’s currencies would be tied to the US dollar at a fixed exchange rate. The dollar would in turn be tied to the value of gold, again at a fixed rate.
The United States bent the rules and inflated its own currency compared to gold. Other nations inflated their currencies compared to the dollar. On August 15, 1971, President Nixon announced that dollars would no longer be convertible to gold.
Sound money = functioning economy
\ Sound money encourages people to save and invest, enabling sustainable, long-term growth. Why? Well, humans have a natural positive time preference: we prefer instant gratification over future gratification. Sound money prompts us to think more about the future.
The more capital accumulation there is, the greater the chance of stable, long-term economic growth. Unsound money distorts capital accumulation. When governments interfere with the money supply, they also interfere with prices. And prices give investors the information they need to make good decisions without having to learn every tiny detail about global events.
Recessions and debt arise from unsound money
\ Government interference takes the form of central planning. No single person, agency, or department ever has access to all the information necessary to understand the vast and complex economy. Interventions distort markets, creating boom and bust cycles.
According to Keynes and his followers, the best way to respond to recessions is to increase spending. You could lower taxes, but people don’t usually spend their extra money. Raising taxes is unpopular, so governments invariably decide to increase the money supply. Saving becomes less attractive, creating a culture of unwise spending and growing debt.
We need to return to sound money and a new gold standard. Enter bitcoin.
Bitcoin is scarce
\ Bitcoin has similar traits to gold. Its supply is literally fixed. Once there are 21 million bitcoins in circulation, no more will be issued.
The supply grows at a diminishing rate. Computers across the Bitcoin network pool their processing power to solve complex algorithmic problems. Once these puzzles have been cracked, the “miners” receive bitcoins as a reward.
Satoshi Nakamoto designed the system to avoid gold rushes. The algorithmic problems become more difficult to solve as the number of computers working on them rises, guaranteeing a steady and reliable supply. Also, the number of bitcoins issued is halved every four years, resulting in ever-smaller releases until 2140, after which no more coins will be released.
That makes bitcoin unique. It is the only good that is defined by absolute scarcity. No amount of time or resources can create more bitcoins than the programmed supply allows. The supply cannot be manipulated, making it a perfect store of value.
Bitcoin is secure
\ The bitcoin ledger uses the public blockchain. When mining computers crack an algorithmic puzzle, they create a block. The blocks on the ledger contain details about every blockchain transaction ever completed. Every network user can view this information.
Ownership of bitcoins is only valid once it’s been registered on the blockchain. This is only possible if the majority of network users approve it, so there’s no need for a central authority to oversee transactions. While verifying new blocks requires virtually no energy, creating a fraudulent block would cost a significant amount of processing power.
Even if a user decided to expend vast amounts of energy and successfully hacked a majority of all network nodes to approve a fraudulent block, they’d gain very little. Trust in bitcoin would be lost, leading to a drop in demand and value.
Challenges for adoption
\ Because bitcoin is new, demand has varied. The volatile price has, at times, undermined the currency’s status as an effective store of value.
Bitcoin’s transaction limit is currently set at 500,000 per day. That could be increased, but there will always be a daily cap. The more transactions that take place, the more nodes there’ll need to be. This increases transaction fees and the amount of processing power expended.
Bitcoin could be traded off the blockchain, meaning currencies will be backed by bitcoin. That would create a new standard, but it would also mean that new centralized institutions would need to manage this system.

This 5-minute summary did not use copyrighted material from the book. It aims simply to give readers a quick understanding of the book (which is well worth reading).
‘The Bitcoin Standard: The Decentralized Alternative to Central Banking’ was written by economist Saifedean Ammous in 2018.
Buy the book and many more titles at bitcoinbook.shop
-
 @ 7d33ba57:1b82db35
2025-04-02 19:47:25
@ 7d33ba57:1b82db35
2025-04-02 19:47:25Trogir is a UNESCO-listed coastal town just 30 minutes from Split, known for its well-preserved medieval architecture, charming waterfront, and rich history. Often called "The Little Venice of Dalmatia," Trogir is built on a small island connected to the mainland and Čiovo Island by bridges. Its cobblestone streets, Renaissance palaces, and lively cafés** make it a perfect stop for history lovers and travelers seeking authentic Dalmatian charm.
🏛️ Top Things to See & Do in Trogir
1️⃣ Explore Trogir Old Town (UNESCO) 🏡
- Wander through the labyrinth of narrow streets, filled with hidden courtyards and stone houses.
- Admire Venetian-style palaces, Romanesque churches, and medieval city walls.
- Visit St. Lawrence Cathedral, featuring the famous Radovan Portal, a masterpiece of medieval stone carving.
2️⃣ Climb the Bell Tower of St. Lawrence ⛪
- Offers stunning panoramic views over Trogir and the Adriatic.
- A bit of a steep climb, but totally worth it for the breathtaking scenery!
3️⃣ Visit Kamerlengo Fortress 🏰
- A 15th-century Venetian fortress with amazing sea views from the top.
- In summer, it hosts concerts and cultural events.
4️⃣ Stroll Along the Trogir Riva Promenade 🌊
- A lively waterfront filled with cafés, restaurants, and luxury yachts.
- Perfect for a relaxing evening walk while watching the sunset.
5️⃣ Relax on the Best Beaches Near Trogir 🏖️
- Okrug Gornji Beach (Copacabana Beach) – A long, lively beach with bars & water activities.
- Pantan Beach – A quieter spot with clear waters and pine tree shade.
- Kava Beach (Čiovo Island) – A more secluded and natural beach, ideal for relaxation.
6️⃣ Take a Boat Trip to the Blue Lagoon 🛥️
- A stunning turquoise bay, perfect for swimming and snorkeling.
- Just a short boat ride from Trogir.
7️⃣ Try Dalmatian Cuisine 🍽️
- Grilled fresh fish & seafood – Trogir’s specialty! 🐟
- Pašticada – Slow-cooked beef in a rich red wine sauce, served with gnocchi.
- Homemade Dalmatian prosciutto & cheese – Best paired with local Plavac Mali wine.
🚗 How to Get to Trogir
✈️ By Air:
- Split Airport (SPU) is just 10 minutes away! 🚕
🚘 By Car:
- From Split: ~30 minutes (27 km)
- From Zadar: ~1.5 hours (130 km)
🚌 By Bus: Frequent buses run between Split and Trogir.
⛵ By Boat: A seasonal boat line connects Trogir with Split and nearby islands.💡 Tips for Visiting Trogir
✅ Best time to visit? April–October for sunny weather & fewer crowds ☀️
✅ Stay for sunset – The views from the Riva & Kamerlengo Fortress are magical 🌅
✅ Wear comfy shoes – The old town’s stone streets can be slippery 👟
✅ Book Blue Lagoon trips in advance – It’s a popular excursion 🚤
✅ Try a wine tasting at a local konoba (traditional tavern) 🍷
-
 @ cbaa0c82:e9313245
2025-04-02 18:53:57
@ cbaa0c82:e9313245
2025-04-02 18:53:57TheWholeGrain - #March2025
March of 2025 was a standard month for Bread and Toast. However, it did include a the occasional five Sunday Singles which seems like hitting the jackpot! Talk about lucky!
Included with the five Sunday Singles was two more pages of the Adventure Series: Questline where we saw Bread, Toast, and End-Piece face off against their first adversary!
End-Piece made a first appearance for in Toast's Comic Collection under the title E: The Last Slice while the Concept Art piece was the original drawing of all three slices of bread together. And, last of all we updated the Bitcoin logo because why not!?
Sunday Singles - March 2025 2025-03-02 | Sunday Single 82 Title: Slingshot! Watch out! Toast is quite the sharpshooter! https://i.nostr.build/zHA9C7cOOZLOCl0o.png
2025-03-09 | Sunday Single 83 Title: Puzzles End-Piece just figured out the puzzle! https://i.nostr.build/u2EBdcsuwO2xo23P.png
2025-03-16 | Sunday Single 84 Title: Basketball Oh, the madness! https://i.nostr.build/8F1OFFVra7zQOIy6.png
2025-03-23 | Sunday Single 85 Title: Coffee The perfect way to start the day. https://i.nostr.build/aiGZOvOmow3igru6.png
2025-03-30 | Sunday Single 86 Title: Origami End-Piece has a way with paper. https://i.nostr.build/0ySzGwF9QnZxwLxD.png
Adventure Series: Questline The group is attacked by a crow with Bread being the target of the giant bird, but with a group of trusty friends any enemy can be defeated!
Artist: Dakota Jernigan (The Bitcoin Painter) Writer: Daniel David (dan 🍞)
2025-03-11 | Questline 005 - Under Attack Toast and End-Piece are able to escape the attack from the giant winged predator, but Bread being distracted by thoughts of the village is caught off guard. End-Piece immediately charges the attacker with a fury of mallet swings. Meanwhile, Toast loads up an arrow with intentions of piercing through the giant bird. https://i.nostr.build/F24sd7SFFbsW9WZY.png
2025-03-25 | Questline 006 - A Finished Battle End-Piece lands a series of blows to the winged beast. Toast finishes it off with a second arrow to the heart. Bread is only slightly injured, but is more upset about having been so vulnerable due to being so distracted. Moving forward Bread will have to be more vigilant. https://i.nostr.build/n5a7Jztq9MHxuGNf.png
Other Content Released in March 2025 2025-03-05 | Toast's Comic Collection Title: E: The Last Slice #11 A gluten-based pandemic has killed off all slices of bread that are not Toast except for one slice of bread that happens to be an end piece. https://i.nostr.build/aar20oHAAKmZOovD.png
2025-03-12 | Concept Art Title: Original Bread and Toast This was the first drawing of all three characters together. It was used a lot for branding when the project first started up in 2023. https://i.nostr.build/yqkmBuTiH8AKbCzI.png
2025-03-19 | Bitcoin Art Title: Bitcoin/Bread Block Height: 888566 Two things that just go together. https://i.nostr.build/MDPkzOPVEaOJVTFE.png
Thanks for checking out the seventh issue of The Whole Grain. The Whole Grain is released on the first of every month and covers all of the content released by Bread and Toast in the previous month. For all Bread and Toast content visit BreadandToast.com!
So long, March! Bread, Toast, and End-Piece
BreadandToast #SundaySingle #Questline #ToastsComicCollection #ConceptArt #BitcoinArt #Bread #Toast #EndPiece #Artstr #Comic #Cartoon #NostrOnly #🍞 #🖼️
List of nPubs Mentioned: The Bitcoin Painter: npub1tx5ccpregnm9afq0xaj42hh93xl4qd3lfa7u74v5cdvyhwcnlanqplhd8g
dan 🍞: npub16e3vzr7dk2uepjcnl85nfare3kdapxge08gr42s99n9kg7xs8xhs90y9v6
-
 @ 17538dc2:71ed77c4
2025-04-02 16:04:59
@ 17538dc2:71ed77c4
2025-04-02 16:04:59The MacOS security update summary is a reminder that laptops and desktops are incredibly compromised.
macOS Sequoia 15.4
Released March 31, 2025
Accessibility Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: A logging issue was addressed with improved data redaction.
CVE-2025-24202: Zhongcheng Li from IES Red Team of ByteDance
AccountPolicy Available for: macOS Sequoia
Impact: A malicious app may be able to gain root privileges
Description: This issue was addressed by removing the vulnerable code.
CVE-2025-24234: an anonymous researcher
AirDrop Available for: macOS Sequoia
Impact: An app may be able to read arbitrary file metadata
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-24097: Ron Masas of BREAKPOINT.SH
App Store Available for: macOS Sequoia
Impact: A malicious app may be able to access private information
Description: This issue was addressed by removing the vulnerable code.
CVE-2025-24276: an anonymous researcher
AppleMobileFileIntegrity Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: The issue was addressed with improved checks.
CVE-2025-24272: Mickey Jin (@patch1t)
AppleMobileFileIntegrity Available for: macOS Sequoia
Impact: An app may be able to access protected user data
Description: A downgrade issue was addressed with additional code-signing restrictions.
CVE-2025-24239: Wojciech Regula of SecuRing (wojciechregula.blog)
AppleMobileFileIntegrity Available for: macOS Sequoia
Impact: A malicious app may be able to read or write to protected files
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-24233: Claudio Bozzato and Francesco Benvenuto of Cisco Talos.
AppleMobileFileIntegrity Available for: macOS Sequoia
Impact: An app may be able to access user-sensitive data
Description: A privacy issue was addressed by removing the vulnerable code.
CVE-2025-30443: Bohdan Stasiuk (@bohdan_stasiuk)
Audio Available for: macOS Sequoia
Impact: Processing a maliciously crafted font may result in the disclosure of process memory
Description: The issue was addressed with improved memory handling.
CVE-2025-24244: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative
Audio Available for: macOS Sequoia
Impact: Processing a maliciously crafted file may lead to arbitrary code execution
Description: The issue was addressed with improved memory handling.
CVE-2025-24243: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative
Authentication Services Available for: macOS Sequoia
Impact: Password autofill may fill in passwords after failing authentication
Description: This issue was addressed through improved state management.
CVE-2025-30430: Dominik Rath
Authentication Services Available for: macOS Sequoia
Impact: A malicious website may be able to claim WebAuthn credentials from another website that shares a registrable suffix
Description: The issue was addressed with improved input validation.
CVE-2025-24180: Martin Kreichgauer of Google Chrome
Authentication Services Available for: macOS Sequoia
Impact: A malicious app may be able to access a user's saved passwords
Description: This issue was addressed by adding a delay between verification code attempts.
CVE-2025-24245: Ian Mckay (@iann0036)
Automator Available for: macOS Sequoia
Impact: An app may be able to access protected user data
Description: A permissions issue was addressed by removing vulnerable code and adding additional checks.
CVE-2025-30460: an anonymous researcher
BiometricKit Available for: macOS Sequoia
Impact: An app may be able to cause unexpected system termination
Description: A buffer overflow was addressed with improved bounds checking.
CVE-2025-24237: Yutong Xiu
Calendar Available for: macOS Sequoia
Impact: An app may be able to break out of its sandbox
Description: A path handling issue was addressed with improved validation.
CVE-2025-30429: Denis Tokarev (@illusionofcha0s)
Calendar Available for: macOS Sequoia
Impact: An app may be able to break out of its sandbox
Description: This issue was addressed with improved checks.
CVE-2025-24212: Denis Tokarev (@illusionofcha0s)
CloudKit Available for: macOS Sequoia
Impact: A malicious app may be able to access private information
Description: The issue was addressed with improved checks.
CVE-2025-24215: Kirin (@Pwnrin)
CoreAudio Available for: macOS Sequoia
Impact: Parsing a file may lead to an unexpected app termination
Description: The issue was addressed with improved checks.
CVE-2025-24163: Google Threat Analysis Group
CoreAudio Available for: macOS Sequoia
Impact: Playing a malicious audio file may lead to an unexpected app termination
Description: An out-of-bounds read issue was addressed with improved input validation.
CVE-2025-24230: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative
CoreMedia Available for: macOS Sequoia
Impact: Processing a maliciously crafted video file may lead to unexpected app termination or corrupt process memory
Description: This issue was addressed with improved memory handling.
CVE-2025-24211: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative
CoreMedia Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: An access issue was addressed with additional sandbox restrictions.
CVE-2025-24236: Csaba Fitzl (@theevilbit) and Nolan Astrein of Kandji
CoreMedia Available for: macOS Sequoia
Impact: Processing a maliciously crafted video file may lead to unexpected app termination or corrupt process memory
Description: The issue was addressed with improved memory handling.
CVE-2025-24190: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative
CoreMedia Playback Available for: macOS Sequoia
Impact: A malicious app may be able to access private information
Description: A path handling issue was addressed with improved validation.
CVE-2025-30454: pattern-f (@pattern_F_)
CoreServices Description: This issue was addressed through improved state management.
CVE-2025-31191: Jonathan Bar Or (@yo_yo_yo_jbo) of Microsoft, and an anonymous researcher Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
CoreText Available for: macOS Sequoia
Impact: Processing a maliciously crafted font may result in the disclosure of process memory
Description: An out-of-bounds read issue was addressed with improved input validation.
CVE-2025-24182: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative
Crash Reporter Available for: macOS Sequoia
Impact: An app may be able to gain root privileges
Description: A parsing issue in the handling of directory paths was addressed with improved path validation.
CVE-2025-24277: Csaba Fitzl (@theevilbit) of Kandji and Gergely Kalman (@gergely_kalman), and an anonymous researcher
curl Available for: macOS Sequoia
Impact: An input validation issue was addressed
Description: This is a vulnerability in open source code and Apple Software is among the affected projects. The CVE-ID was assigned by a third party. Learn more about the issue and CVE-ID at cve.org.
CVE-2024-9681
Disk Images Available for: macOS Sequoia
Impact: An app may be able to break out of its sandbox
Description: A file access issue was addressed with improved input validation.
CVE-2025-24255: an anonymous researcher
DiskArbitration Available for: macOS Sequoia
Impact: An app may be able to gain root privileges
Description: A parsing issue in the handling of directory paths was addressed with improved path validation.
CVE-2025-30456: Gergely Kalman (@gergely_kalman)
DiskArbitration Available for: macOS Sequoia
Impact: An app may be able to gain root privileges
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-24267: an anonymous researcher
Dock Available for: macOS Sequoia
Impact: A malicious app may be able to access private information
Description: The issue was addressed with improved checks.
CVE-2025-30455: Mickey Jin (@patch1t), and an anonymous researcher
Dock Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: This issue was addressed by removing the vulnerable code.
CVE-2025-31187: Rodolphe BRUNETTI (@eisw0lf) of Lupus Nova
dyld Available for: macOS Sequoia
Impact: Apps that appear to use App Sandbox may be able to launch without restrictions
Description: A library injection issue was addressed with additional restrictions.
CVE-2025-30462: Pietro Francesco Tirenna, Davide Silvetti, Abdel Adim Oisfi of Shielder (shielder.com)
FaceTime Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: This issue was addressed with improved redaction of sensitive information.
CVE-2025-30451: Kirin (@Pwnrin) and luckyu (@uuulucky)
FeedbackLogger Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: This issue was addressed with improved data protection.
CVE-2025-24281: Rodolphe BRUNETTI (@eisw0lf)
Focus Available for: macOS Sequoia
Impact: An attacker with physical access to a locked device may be able to view sensitive user information
Description: The issue was addressed with improved checks.
CVE-2025-30439: Andr.Ess
Focus Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: A logging issue was addressed with improved data redaction.
CVE-2025-24283: Kirin (@Pwnrin)
Foundation Available for: macOS Sequoia
Impact: An app may be able to access protected user data
Description: An access issue was addressed with additional sandbox restrictions on the system pasteboards.
CVE-2025-30461: an anonymous researcher
Foundation Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: The issue was resolved by sanitizing logging
CVE-2025-30447: LFY@secsys from Fudan University
Foundation Available for: macOS Sequoia
Impact: An app may be able to cause a denial-of-service
Description: An uncontrolled format string issue was addressed with improved input validation.
CVE-2025-24199: Manuel Fernandez (Stackhopper Security)
GPU Drivers Available for: macOS Sequoia
Impact: An app may be able to cause unexpected system termination or corrupt kernel memory
Description: An out-of-bounds write issue was addressed with improved bounds checking.
CVE-2025-30464: ABC Research s.r.o.
CVE-2025-24273: Wang Yu of Cyberserval
GPU Drivers Available for: macOS Sequoia
Impact: An app may be able to disclose kernel memory
Description: The issue was addressed with improved bounds checks.
CVE-2025-24256: Anonymous working with Trend Micro Zero Day Initiative, Murray Mike
Handoff Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: The issue was addressed with improved restriction of data container access.
CVE-2025-30463: mzzzz__
ImageIO Available for: macOS Sequoia
Impact: Parsing an image may lead to disclosure of user information
Description: A logic error was addressed with improved error handling.
CVE-2025-24210: Anonymous working with Trend Micro Zero Day Initiative
Installer Available for: macOS Sequoia
Impact: An app may be able to check the existence of an arbitrary path on the file system
Description: A permissions issue was addressed with additional sandbox restrictions.
CVE-2025-24249: YingQi Shi(@Mas0nShi) of DBAppSecurity's WeBin lab and Minghao Lin (@Y1nKoc)
Installer Available for: macOS Sequoia
Impact: A sandboxed app may be able to access sensitive user data
Description: A logic issue was addressed with improved checks.
CVE-2025-24229: an anonymous researcher
IOGPUFamily Available for: macOS Sequoia
Impact: An app may be able to cause unexpected system termination or write kernel memory
Description: An out-of-bounds write issue was addressed with improved input validation.
CVE-2025-24257: Wang Yu of Cyberserval
IOMobileFrameBuffer Available for: macOS Sequoia
Impact: An app may be able to corrupt coprocessor memory
Description: The issue was addressed with improved bounds checks.
CVE-2025-30437: Ye Zhang (@VAR10CK) of Baidu Security
Kerberos Helper Available for: macOS Sequoia
Impact: A remote attacker may be able to cause unexpected app termination or heap corruption
Description: A memory initialization issue was addressed with improved memory handling.
CVE-2025-24235: Dave G.
Kernel Available for: macOS Sequoia
Impact: An app may be able to access protected user data
Description: The issue was addressed with improved checks.
CVE-2025-24204: Koh M. Nakagawa (@tsunek0h) of FFRI Security, Inc.
Kernel Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: The issue was addressed with improved checks.
CVE-2025-24203: Ian Beer of Google Project Zero
Kernel Available for: macOS Sequoia
Impact: An attacker with user privileges may be able to read kernel memory
Description: A type confusion issue was addressed with improved memory handling.
CVE-2025-24196: Joseph Ravichandran (@0xjprx) of MIT CSAIL
LaunchServices Available for: macOS Sequoia
Impact: A malicious JAR file may bypass Gatekeeper checks
Description: This issue was addressed with improved handling of executable types.
CVE-2025-24148: Kenneth Chew
libarchive Available for: macOS Sequoia
Impact: An input validation issue was addressed
Description: This is a vulnerability in open source code and Apple Software is among the affected projects. The CVE-ID was assigned by a third party. Learn more about the issue and CVE-ID at cve.org.
CVE-2024-48958
Libinfo Available for: macOS Sequoia
Impact: A user may be able to elevate privileges
Description: An integer overflow was addressed with improved input validation.
CVE-2025-24195: Paweł Płatek (Trail of Bits)
libnetcore Available for: macOS Sequoia
Impact: Processing maliciously crafted web content may result in the disclosure of process memory
Description: A logic issue was addressed with improved checks.
CVE-2025-24194: an anonymous researcher
libxml2 Available for: macOS Sequoia
Impact: Parsing a file may lead to an unexpected app termination
Description: This is a vulnerability in open source code and Apple Software is among the affected projects. The CVE-ID was assigned by a third party. Learn more about the issue and CVE-ID at cve.org.
CVE-2025-27113
CVE-2024-56171
libxpc Available for: macOS Sequoia
Impact: An app may be able to break out of its sandbox
Description: This issue was addressed through improved state management.
CVE-2025-24178: an anonymous researcher
libxpc Available for: macOS Sequoia
Impact: An app may be able to delete files for which it does not have permission
Description: This issue was addressed with improved handling of symlinks.
CVE-2025-31182: Alex Radocea and Dave G. of Supernetworks, 风沐云烟(@binary_fmyy) and Minghao Lin(@Y1nKoc)
libxpc Available for: macOS Sequoia
Impact: An app may be able to gain elevated privileges
Description: A logic issue was addressed with improved checks.
CVE-2025-24238: an anonymous researcher
Mail Available for: macOS Sequoia
Impact: "Block All Remote Content" may not apply for all mail previews
Description: A permissions issue was addressed with additional sandbox restrictions.
CVE-2025-24172: an anonymous researcher
manpages Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: This issue was addressed with improved validation of symlinks.
CVE-2025-30450: Pwn2car
Maps Available for: macOS Sequoia
Impact: An app may be able to read sensitive location information
Description: A path handling issue was addressed with improved logic.
CVE-2025-30470: LFY@secsys from Fudan University
NetworkExtension Available for: macOS Sequoia
Impact: An app may be able to enumerate a user's installed apps
Description: This issue was addressed with additional entitlement checks.
CVE-2025-30426: Jimmy
Notes Available for: macOS Sequoia
Impact: A sandboxed app may be able to access sensitive user data in system logs
Description: A privacy issue was addressed with improved private data redaction for log entries.
CVE-2025-24262: LFY@secsys from Fudan University
NSDocument Available for: macOS Sequoia
Impact: A malicious app may be able to access arbitrary files
Description: This issue was addressed through improved state management.
CVE-2025-24232: an anonymous researcher
OpenSSH Available for: macOS Sequoia
Impact: An app may be able to access user-sensitive data
Description: An injection issue was addressed with improved validation.
CVE-2025-24246: Mickey Jin (@patch1t)
PackageKit Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: The issue was addressed with improved checks.
CVE-2025-24261: Mickey Jin (@patch1t)
PackageKit Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: A logic issue was addressed with improved checks.
CVE-2025-24164: Mickey Jin (@patch1t)
PackageKit Available for: macOS Sequoia
Impact: A malicious app with root privileges may be able to modify the contents of system files
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-30446: Pedro Tôrres (@t0rr3sp3dr0)
Parental Controls Available for: macOS Sequoia
Impact: An app may be able to retrieve Safari bookmarks without an entitlement check
Description: This issue was addressed with additional entitlement checks.
CVE-2025-24259: Noah Gregory (wts.dev)
Photos Storage Available for: macOS Sequoia
Impact: Deleting a conversation in Messages may expose user contact information in system logging
Description: A logging issue was addressed with improved data redaction.
CVE-2025-30424: an anonymous researcher
Power Services Available for: macOS Sequoia
Impact: An app may be able to break out of its sandbox
Description: This issue was addressed with additional entitlement checks.
CVE-2025-24173: Mickey Jin (@patch1t)
Python Available for: macOS Sequoia
Impact: A remote attacker may be able to bypass sender policy checks and deliver malicious content via email
Description: This is a vulnerability in open source code and Apple Software is among the affected projects. The CVE-ID was assigned by a third party. Learn more about the issue and CVE-ID at cve.org.
CVE-2023-27043
RPAC Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: The issue was addressed with improved validation of environment variables.
CVE-2025-24191: Claudio Bozzato and Francesco Benvenuto of Cisco Talos
Safari Available for: macOS Sequoia
Impact: Visiting a malicious website may lead to user interface spoofing
Description: The issue was addressed with improved UI.
CVE-2025-24113: @RenwaX23
Safari Available for: macOS Sequoia
Impact: Visiting a malicious website may lead to address bar spoofing
Description: The issue was addressed with improved checks.
CVE-2025-30467: @RenwaX23
Safari Available for: macOS Sequoia
Impact: A website may be able to access sensor information without user consent
Description: The issue was addressed with improved checks.
CVE-2025-31192: Jaydev Ahire
Safari Available for: macOS Sequoia
Impact: A download's origin may be incorrectly associated
Description: This issue was addressed through improved state management.
CVE-2025-24167: Syarif Muhammad Sajjad
Sandbox Available for: macOS Sequoia
Impact: An app may be able to access removable volumes without user consent
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-24093: Yiğit Can YILMAZ (@yilmazcanyigit)
Sandbox Available for: macOS Sequoia
Impact: An input validation issue was addressed
Description: The issue was addressed with improved checks.
CVE-2025-30452: an anonymous researcher
Sandbox Available for: macOS Sequoia
Impact: An app may be able to access protected user data
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-24181: Arsenii Kostromin (0x3c3e)
SceneKit Available for: macOS Sequoia
Impact: An app may be able to read files outside of its sandbox
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-30458: Mickey Jin (@patch1t)
Security Available for: macOS Sequoia
Impact: A remote user may be able to cause a denial-of-service
Description: A validation issue was addressed with improved logic.
CVE-2025-30471: Bing Shi, Wenchao Li, Xiaolong Bai of Alibaba Group, Luyi Xing of Indiana University Bloomington
Security Available for: macOS Sequoia
Impact: A malicious app acting as a HTTPS proxy could get access to sensitive user data
Description: This issue was addressed with improved access restrictions.
CVE-2025-24250: Wojciech Regula of SecuRing (wojciechregula.blog)
Share Sheet Available for: macOS Sequoia
Impact: A malicious app may be able to dismiss the system notification on the Lock Screen that a recording was started
Description: This issue was addressed with improved access restrictions.
CVE-2025-30438: Halle Winkler, Politepix theoffcuts.org
Shortcuts Available for: macOS Sequoia
Impact: A shortcut may be able to access files that are normally inaccessible to the Shortcuts app
Description: A permissions issue was addressed with improved validation.
CVE-2025-30465: an anonymous researcher
Shortcuts Available for: macOS Sequoia
Impact: An app may be able to access user-sensitive data
Description: An access issue was addressed with additional sandbox restrictions.
CVE-2025-24280: Kirin (@Pwnrin)
Shortcuts Available for: macOS Sequoia
Impact: A Shortcut may run with admin privileges without authentication
Description: An authentication issue was addressed with improved state management.
CVE-2025-31194: Dolf Hoegaerts
Shortcuts Available for: macOS Sequoia
Impact: A shortcut may be able to access files that are normally inaccessible to the Shortcuts app
Description: This issue was addressed with improved access restrictions.
CVE-2025-30433: Andrew James Gonzalez
Siri Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: The issue was addressed with improved restriction of data container access.
CVE-2025-31183: Kirin (@Pwnrin), Bohdan Stasiuk (@bohdan_stasiuk)
Siri Available for: macOS Sequoia
Impact: A sandboxed app may be able to access sensitive user data in system logs
Description: This issue was addressed with improved redaction of sensitive information.
CVE-2025-30435: K宝 (@Pwnrin) and luckyu (@uuulucky)
Siri Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: This issue was addressed with improved redaction of sensitive information.
CVE-2025-24217: Kirin (@Pwnrin)
Siri Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: A privacy issue was addressed by not logging contents of text fields.
CVE-2025-24214: Kirin (@Pwnrin)
Siri Available for: macOS Sequoia
Impact: An app may be able to enumerate devices that have signed into the user's Apple Account
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-24248: Minghao Lin (@Y1nKoc) and Tong Liu@Lyutoon_ and 风(binary_fmyy) and F00L
Siri Available for: macOS Sequoia
Impact: An app may be able to access user-sensitive data
Description: An authorization issue was addressed with improved state management.
CVE-2025-24205: YingQi Shi(@Mas0nShi) of DBAppSecurity's WeBin lab and Minghao Lin (@Y1nKoc)
Siri Available for: macOS Sequoia
Impact: An attacker with physical access may be able to use Siri to access sensitive user data
Description: This issue was addressed by restricting options offered on a locked device.
CVE-2025-24198: Richard Hyunho Im (@richeeta) with routezero.security
SMB Available for: macOS Sequoia
Impact: An app may be able to cause unexpected system termination
Description: The issue was addressed with improved memory handling.
CVE-2025-24269: Alex Radocea of Supernetworks
SMB Available for: macOS Sequoia
Impact: Mounting a maliciously crafted SMB network share may lead to system termination
Description: A race condition was addressed with improved locking.
CVE-2025-30444: Dave G.
SMB Available for: macOS Sequoia
Impact: An app may be able to execute arbitrary code with kernel privileges
Description: A buffer overflow issue was addressed with improved memory handling.
CVE-2025-24228: Joseph Ravichandran (@0xjprx) of MIT CSAIL
smbx Available for: macOS Sequoia
Impact: An attacker in a privileged position may be able to perform a denial-of-service
Description: The issue was addressed with improved memory handling.
CVE-2025-24260: zbleet of QI-ANXIN TianGong Team
Software Update Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: A library injection issue was addressed with additional restrictions.
CVE-2025-24282: Claudio Bozzato and Francesco Benvenuto of Cisco Talos
Software Update Available for: macOS Sequoia
Impact: A user may be able to elevate privileges
Description: This issue was addressed with improved validation of symlinks.
CVE-2025-24254: Arsenii Kostromin (0x3c3e)
Software Update Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: The issue was addressed with improved checks.
CVE-2025-24231: Claudio Bozzato and Francesco Benvenuto of Cisco Talos
StickerKit Available for: macOS Sequoia
Impact: An app may be able to observe unprotected user data
Description: A privacy issue was addressed by moving sensitive data to a protected location.
CVE-2025-24263: Cristian Dinca of "Tudor Vianu" National High School of Computer Science, Romania
Storage Management Available for: macOS Sequoia
Impact: An app may be able to enable iCloud storage features without user consent
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-24207: YingQi Shi (@Mas0nShi) of DBAppSecurity's WeBin lab, 风沐云烟 (binary_fmyy) and Minghao Lin (@Y1nKoc)
StorageKit Available for: macOS Sequoia
Impact: An app may be able to gain root privileges
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-30449: Arsenii Kostromin (0x3c3e), and an anonymous researcher
StorageKit Available for: macOS Sequoia
Impact: An app may be able to access protected user data
Description: This issue was addressed with improved handling of symlinks.
CVE-2025-24253: Mickey Jin (@patch1t), Csaba Fitzl (@theevilbit) of Kandji
StorageKit Available for: macOS Sequoia
Impact: An app may be able to access user-sensitive data
Description: A race condition was addressed with additional validation.
CVE-2025-24240: Mickey Jin (@patch1t)
StorageKit Available for: macOS Sequoia
Impact: An app may be able to bypass Privacy preferences
Description: A race condition was addressed with additional validation.
CVE-2025-31188: Mickey Jin (@patch1t)
Summarization Services Available for: macOS Sequoia
Impact: An app may be able to access information about a user's contacts
Description: A privacy issue was addressed with improved private data redaction for log entries.
CVE-2025-24218: Kirin and FlowerCode, Bohdan Stasiuk (@bohdan_stasiuk)
System Settings Available for: macOS Sequoia
Impact: An app may be able to access protected user data
Description: This issue was addressed with improved validation of symlinks.
CVE-2025-24278: Zhongquan Li (@Guluisacat)
System Settings Available for: macOS Sequoia
Impact: An app with root privileges may be able to access private information
Description: This issue was addressed with improved handling of symlinks.
CVE-2025-24242: Koh M. Nakagawa (@tsunek0h) of FFRI Security, Inc.
SystemMigration Available for: macOS Sequoia
Impact: A malicious app may be able to create symlinks to protected regions of the disk
Description: This issue was addressed with improved validation of symlinks.
CVE-2025-30457: Mickey Jin (@patch1t)
Voice Control Available for: macOS Sequoia
Impact: An app may be able to access contacts
Description: This issue was addressed with improved file handling.
CVE-2025-24279: Mickey Jin (@patch1t)
Web Extensions Available for: macOS Sequoia
Impact: An app may gain unauthorized access to Local Network
Description: This issue was addressed with improved permissions checking.
CVE-2025-31184: Alexander Heinrich (@Sn0wfreeze), SEEMOO, TU Darmstadt & Mathy Vanhoef (@vanhoefm) and Jeroen Robben (@RobbenJeroen), DistriNet, KU Leuven
Web Extensions Available for: macOS Sequoia
Impact: Visiting a website may leak sensitive data
Description: A script imports issue was addressed with improved isolation.
CVE-2025-24192: Vsevolod Kokorin (Slonser) of Solidlab
WebKit Available for: macOS Sequoia
Impact: Processing maliciously crafted web content may lead to an unexpected Safari crash
Description: The issue was addressed with improved memory handling.
WebKit Bugzilla: 285892
CVE-2025-24264: Gary Kwong, and an anonymous researcher
WebKit Bugzilla: 284055
CVE-2025-24216: Paul Bakker of ParagonERP
WebKit Available for: macOS Sequoia
Impact: A type confusion issue could lead to memory corruption
Description: This issue was addressed with improved handling of floats.
WebKit Bugzilla: 286694
CVE-2025-24213: Google V8 Security Team
WebKit Available for: macOS Sequoia
Impact: Processing maliciously crafted web content may lead to an unexpected process crash
Description: A buffer overflow issue was addressed with improved memory handling.
WebKit Bugzilla: 286462
CVE-2025-24209: Francisco Alonso (@revskills), and an anonymous researcher
WebKit Available for: macOS Sequoia
Impact: Processing maliciously crafted web content may lead to an unexpected Safari crash
Description: A use-after-free issue was addressed with improved memory management.
WebKit Bugzilla: 285643
CVE-2025-30427: rheza (@ginggilBesel)
WebKit Available for: macOS Sequoia
Impact: A malicious website may be able to track users in Safari private browsing mode
Description: This issue was addressed through improved state management.
WebKit Bugzilla: 286580
CVE-2025-30425: an anonymous researcher
WindowServer Available for: macOS Sequoia
Impact: An attacker may be able to cause unexpected app termination
Description: A type confusion issue was addressed with improved checks.
CVE-2025-24247: PixiePoint Security
WindowServer Available for: macOS Sequoia
Impact: An app may be able to trick a user into copying sensitive data to the pasteboard
Description: A configuration issue was addressed with additional restrictions.
CVE-2025-24241: Andreas Hegenberg (folivora.AI GmbH)
Xsan Available for: macOS Sequoia
Impact: An app may be able to cause unexpected system termination
Description: A buffer overflow was addressed with improved bounds checking.
CVE-2025-24266: an anonymous researcher
Xsan Available for: macOS Sequoia
Impact: An app may be able to cause unexpected system termination
Description: An out-of-bounds read was addressed with improved bounds checking.
CVE-2025-24265: an anonymous researcher
Xsan Available for: macOS Sequoia
Impact: An app may be able to cause unexpected system termination or corrupt kernel memory
Description: A buffer overflow issue was addressed with improved memory handling.
CVE-2025-24157: an anonymous researcher
-
 @ 8d34bd24:414be32b
2025-04-02 14:13:03
@ 8d34bd24:414be32b
2025-04-02 14:13:03I was reading this passage last night:
…from that time when one came to a grain heap of twenty measures, there would be only ten; and when one came to the wine vat to draw fifty measures, there would be only twenty. I smote you and every work of your hands with blasting wind, mildew and hail; yet you did not come back to Me,’ declares the Lord. ‘Do consider from this day onward, from the twenty-fourth day of the ninth month; from the day when the temple of the Lord was founded, consider: Is the seed still in the barn? Even including the vine, the fig tree, the pomegranate and the olive tree, it has not borne fruit. Yet from this day on I will bless you.’ ” (Haggai 2:16-19) {emphasis mine}
Why were bad things happening to the Israelites? Because they were not following God. Why did God allow these difficult situations to occur? Because God was calling them back to Himself.
This made me think of several times lately, when I had written about Christians going through hard times, that fellow believers had tried to kindly correct me implying that God would not allow these painful things to happen to believers. They were trying to defend God’s honor, but instead they were degrading God. If God is not in control of everything, then either God is unable to protect His own from harm because of sin or bad things happened accidentally and God ignored the injustice. Saying God was not in control of allowing every hardship is either saying God isn’t strong enough, isn’t smart enough, or isn’t loving enough. The God I serve is omniscient, omnipotent, omnipresent, and love incarnate. He also didn’t promise us easy, pleasant lives, but did promise that good would come out of every situation.
And we know that in all things God works for the good of those who love him, who have been called according to his purpose. (Romans 8:28)
When Jesus walked on earth and some people said they wanted to follow Him, His response was not what we would expect:
And He was saying to them all, “If anyone wishes to come after Me, he must deny himself, and take up his cross daily and follow Me. For whoever wishes to save his life will lose it, but whoever loses his life for My sake, he is the one who will save it. For what is a man profited if he gains the whole world, and loses or forfeits himself? For whoever is ashamed of Me and My words, the Son of Man will be ashamed of him when He comes in His glory, and the glory of the Father and of the holy angels. (Luke 9:23-26) {emphasis mine}
When one particular man said that he would follow Jesus anywhere, Jesus responded this way.
As they were going along the road, someone said to Him, “I will follow You wherever You go.” And Jesus said to him, “The foxes have holes and the birds of the air have nests, but the Son of Man has nowhere to lay His head.” (Luke 9:57-58) {emphasis mine}
Jesus was brutally honest that following Him would not be easy or comfortable. Following Jesus is more likely to lead to hardship and persecution that prosperity and comfort.
“Then they will deliver you to tribulation, and will kill you, and you will be hated by all nations because of My name. At that time many will fall away and will betray one another and hate one another. Many false prophets will arise and will mislead many. Because lawlessness is increased, most people’s love will grow cold. But the one who endures to the end, he will be saved. This gospel of the kingdom shall be preached in the whole world as a testimony to all the nations, and then the end will come. (Matthew 24:9-14) {emphasis mine}
Of course God isn’t putting us through hardship to torture us. He is putting us in situations to grow our faith and dependence on Him, i.e. Abraham. He is putting us in situations where we can minister to others, i.e. Joseph. He is using us as examples of faith to others, i.e. Job. Any hardship has an eternal purpose. Sometimes we can see it (at least eventually) if we are looking for God’s will and plan. Sometime we won’t see what He was accomplishing until we get to heaven. Still we need to trust God through it all, knowing His plan is perfect.
“For my thoughts are not your thoughts,\ neither are your ways my ways,”\ declares the Lord.
“As the heavens are higher than the earth,\ so are my ways higher than your ways\ and my thoughts than your thoughts.
As the rain and the snow\ come down from heaven,\ and do not return to it\ without watering the earth\ and making it bud and flourish,\ so that it yields seed for the sower and bread for the eater,\ so is my word that goes out from my mouth:\ It will not return to me empty,\ but will accomplish what I desire\ and achieve the purpose for which I sent it. (Isaiah 55:8-11) {emphasis mine}
God understands how hard it is to understand what He is accomplishing. We live in the here and now while He is outside time and space and therefore has a heavenly and eternal perspective that we will never truly have this side of heaven. He has told us how the story ends, so that we can have peace and trust Him through whatever circumstances He has blessed us.
Jesus answered them, “Do you now believe? Behold, an hour is coming, and has already come, for you to be scattered, each to his own home, and to leave Me alone; and yet I am not alone, because the Father is with Me. These things I have spoken to you, so that in Me you may have peace. In the world you have tribulation, but take courage; I have overcome the world.” (John 16:31-33) {emphasis mine}
In fact, Jesus made this so clear that His disciples rejoiced in persecution they received due to obeying Him and sharing His word.
They took his advice; and after calling the apostles in, they flogged them and ordered them not to speak in the name of Jesus, and then released them. So they went on their way from the presence of the Council, rejoicing that they had been considered worthy to suffer shame for His name. (Acts 5:40-41) {emphasis mine}
Peter specifically warns believers to expect trials and hardship.
Dear friends, do not be surprised at the fiery ordeal that has come on you to test you, as though something strange were happening to you. But rejoice inasmuch as you participate in the sufferings of Christ, so that you may be overjoyed when his glory is revealed. If you are insulted because of the name of Christ, you are blessed, for the Spirit of glory and of God rests on you. If you suffer, it should not be as a murderer or thief or any other kind of criminal, or even as a meddler. However, if you suffer as a Christian, do not be ashamed, but praise God that you bear that name. For it is time for judgment to begin with God’s household; and if it begins with us, what will the outcome be for those who do not obey the gospel of God? And,
“If it is hard for the righteous to be saved,\ what will become of the ungodly and the sinner?”
So then, those who suffer according to God’s will should commit themselves to their faithful Creator and continue to do good. (1 Peter 4:12-19) {emphasis mine}
Paul writes about begging God to take away a health issue. Eventually he accepted it as part of God’s plan for his life and boasted gladly in his hardship.
…Therefore, in order to keep me from becoming conceited, I was given a thorn in my flesh, a messenger of Satan, to torment me. Three times I pleaded with the Lord to take it away from me. But he said to me, “My grace is sufficient for you, for my power is made perfect in weakness.” Therefore I will boast all the more gladly about my weaknesses, so that Christ’s power may rest on me. That is why, for Christ’s sake, I delight in weaknesses, in insults, in hardships, in persecutions, in difficulties. For when I am weak, then I am strong. (2 Corinthians 12:7b-10) {emphasis mine}
No matter what hardships we experience in life, whether poverty or persecution or poor health or loss of a loved one or any other hardship, God is with us working everything for our good.
Who will separate us from the love of Christ? Will tribulation, or distress, or persecution, or famine, or nakedness, or peril, or sword? Just as it is written,
“For Your sake we are being put to death all day long;\ We were considered as sheep to be slaughtered.” **But in all these things we overwhelmingly conquer through Him who loved us. For I am convinced that neither death, nor life, nor angels, nor principalities, nor things present, nor things to come, nor powers, nor height, nor depth, nor any other created thing, will be able to separate us from the love of God, which is in Christ Jesus our Lord. (Romans 8:35-39) {emphasis mine}
I like to look at the story of Joseph as an example of God’s extraordinary plan in the life of a faithful believer. Joseph trusted and honored God. God had a plan for Joseph to be used to save the lives of his family and the people of the Middle East from famine, but God didn’t just instantly put Joseph in a position of power to help. He prepared Joseph and slowly moved him to where he needed to be.
First Josephs brothers wanted to kill him out of jealousy, but God used greed to get them to sell Joseph as a slave instead. He orchestrated the right slave traders to walk by at the right time so that Joseph would wind up in the house of Potiphar, the Pharaoh’s guard.
Then when Joseph acted honorably towards God, his master, and his master’s wife, Joseph was sent to jail for years. I’m sure Joseph was wondering why God would send him to prison for doing what was right, but it put him into the presence of the cupbearer of Pharaoh. A long time after correctly interpreting the cup bearer’s dream, Joseph was called up to interpret Pharaoh’s dream, put in charge of the famine preparation and became second in command after Pharaoh. Joseph, after years of slavery and jail time, was now the second most powerful man in the Middle East, if not the world. God had a plan, but it was hard to see until its completion.
In the same way, Job lost his wealth, his children, his health, and his reputation, but remember that Satan had to get God’s permission before anything could be done to hurt Job. So many people today are blessed by seeing Job’s response to hardship and loss, by seeing Job’s faith, his struggle, and his submission to God’s plan. In this case God even gives Job more after this time of testing than he had before.
When we experience hardship we need to know that God has a plan for our life. It may be something amazing here on Earth. It may be souls won for Christ. It may be to prepare us for heaven. Whatever the case, it is for our good.
We don’t need to be ashamed that God would allow hardship. We grow most when we experience hardship. Our light shines brightest in darkness.
Oh, the depth of the riches of the wisdom and knowledge of God!\ How unsearchable his judgments,\ and his paths beyond tracing out!\ “Who has known the mind of the Lord?\ Or who has been his counselor?”\ “Who has ever given to God,\ that God should repay them?”\ For from him and through him and for him are all things.\ To him be the glory forever! Amen. (Romans 11:33-36)
Trust Jesus
-
 @ f3873798:24b3f2f3
2025-04-02 13:50:17
@ f3873798:24b3f2f3
2025-04-02 13:50:17O Bitcoin e as criptomoedas surgiram como uma alternativa descentralizada ao sistema financeiro tradicional. No entanto, no Brasil, o Sistema Financeiro Nacional (SFN) tem adotado medidas para controlar e limitar a exposição de investidores e instituições a esses ativos. Neste artigo, exploraremos as principais resoluções e regulamentações que restringem o investimento em Bitcoin no país.
O Posicionamento do Banco Central do Brasil (Bacen)

O Banco Central do Brasil (Bacen) e outros órgãos reguladores, como a Comissão de Valores Mobiliários (CVM), têm adotado uma postura cautelosa em relação às criptomoedas.
Resolução Bacen nº 4.753/2021
- Proíbe que instituições financeiras ofereçam serviços de criptomoedas em suas carteiras sem autorização prévia.
- Restringe bancos e corretoras de operarem diretamente com criptoativos, limitando sua integração ao sistema financeiro tradicional.
Comunicado do Bacen sobre Riscos das Criptomoedas
- O Bacen já emitiu alertas sobre os riscos de volatilidade, fraudes e falta de garantias em investimentos em Bitcoin.
- Recomenda que investidores tratem criptomoedas como ativos de alto risco.
A CVM e as Restrições a Fundos de Investimento em Bitcoin
A CVM tem sido mais restritiva que o Bacen em relação a produtos financeiros baseados em criptomoedas.
Deliberação CVM nº 175/2022
- Proíbe fundos de investimento no exterior (FIE) de alocarem mais de 10% do patrimônio em criptomoedas.
- Impede que fundos multimercados brasileiros tenham exposição direta a Bitcoin e outras criptomoedas.
Instrução CVM nº 555/2021
- Estabelece que ETFs de Bitcoin não podem ser comercializados no Brasil sem aprovação expressa da CVM.
- Até hoje, nenhum ETF de criptomoeda foi aprovado no país.
Tributação e Controles da Receita Federal
Além das restrições do Bacen e da CVM, a Receita Federal impõe regras rígidas para transações em Bitcoin:
Instrução Normativa RFB nº 1.888/2019
- Obriga declaração de todas as operações em criptomoedas acima de R$ 35 mil por mês.
- Tributa ganhos de capital em criptomoedas em 15% a 22,5%, dependendo do valor.
O Bitcoin Sob Vigilância do SFN
O Sistema Financeiro Nacional tem adotado medidas para limitar a adoção em massa do Bitcoin, seja por meio de regulamentações rígidas, restrições a fundos ou alertas sobre riscos.
Enquanto o mercado de criptomoedas cresce globalmente, no Brasil ainda há um cenário de cautela e controle, com o SFN buscando evitar que criptomoedas desafiem a hegemonia do sistema financeiro tradicional.
-
 @ 06639a38:655f8f71
2025-04-02 13:47:57
@ 06639a38:655f8f71
2025-04-02 13:47:57You can follow the work in progress here in this pull request https://github.com/nostrver-se/nostr-php/pull/68 on Github.
Before my 3-month break (Dec/Jan/Feb) working on Nostr-PHP I started with the NIP-19 integration in October '24. Encoding and decoding the simple prefixes (
npub,nsecandnote) was already done in the first commits.Learn more about NIP-19 here: https://nips.nostr.com/19
TLV's
Things were getting more complicated with the other prefixes / identifiers defined in NIP-19:
neventnaddrnprofile
This is because these identifiers contain (optional) metadata called Type-Lenght-Value aka TLV's.
When sharing a profile or an event, an app may decide to include relay information and other metadata such that other apps can locate and display these entities more easily.
For these events, the contents are a binary-encoded list of_TLV_(type-length-value), with_T_and_L_being 1 byte each (_uint8_, i.e. a number in the range of 0-255), and_V_being a sequence of bytes of the size indicated by_L_.These possible standardized
TLVtypes are:0:special- depends on the bech32 prefix:
- for
nprofileit will be the 32 bytes of the profile public key - for
neventit will be the 32 bytes of the event id - for
naddr, it is the identifier (the"d"tag) of the event being referenced. For normal replaceable events use an empty string.
- for
- depends on the bech32 prefix:
1:relay- for
nprofile,neventandnaddr, optionally, a relay in which the entity (profile or event) is more likely to be found, encoded as ascii - this may be included multiple times
- for
2:author- for
naddr, the 32 bytes of the pubkey of the event - for
nevent, optionally, the 32 bytes of the pubkey of the event
- for
3:kind- for
naddr, the 32-bit unsigned integer of the kind, big-endian - for
nevent, optionally, the 32-bit unsigned integer of the kind, big-endian
- for
These identifiers are formatted as bech32 strings, but are much longer than the package
bitwasp/bech32(used in the library) for can handle for encoding and decoding. The bech32 strings handled bybitwasp/bech32are limited to a maximum length of 90 characters.Thanks to the effort of others (nostr:npub1636uujeewag8zv8593lcvdrwlymgqre6uax4anuq3y5qehqey05sl8qpl4 and nostr:npub1efz8l77esdtpw6l359sjvakm7azvyv6mkuxphjdk3vfzkgxkatrqlpf9s4) during my break, some contributions are made (modifiying the bech32 package supporting much longer strings, up to a max of 5000 characters). At this moment, I'm integrating this (mostly copy-pasting the stuff and refactoring the code):
So what's next?
- NIP-19 code housekeeping + refactoring
- Prepare a new release with NIP-19 integration
- Create documentation page how to use NIP-19 on https://nostr-php.dev
-
 @ 5d4b6c8d:8a1c1ee3
2025-04-02 13:15:30
@ 5d4b6c8d:8a1c1ee3
2025-04-02 13:15:30I've always loved Westbrook. He plays so hard and does things through sheer force of will that no one else has ever been able to do. He's also the last guy you want on the court at the end of close games.
No one has ever so reliably made poor choices in late game, or even just end of clock, situations. Here are some highlights from the epic Nuggets vs T-Wolves game, which Russ completely blew at the end.
https://youtu.be/rgtzQxRpH6c
I've said before that I think Russ' career +/- would be 4 points higher if coaches had never let him play at the ends of quarters. Translation for non-analytics nerds: Russ has blown virtually every final possession throughout his entire career. It's unbelievable.
Is there anyone I'm overlooking as a worse clutch performer?
originally posted at https://stacker.news/items/932077
-
 @ 7bdef7be:784a5805
2025-04-02 12:37:35
@ 7bdef7be:784a5805
2025-04-02 12:37:35The following script try, using nak, to find out the last ten people who have followed a
target_pubkey, sorted by the most recent. It's possibile to shortensearch_timerangeto speed up the search.```
!/usr/bin/env fish
Target pubkey we're looking for in the tags
set target_pubkey "6e468422dfb74a5738702a8823b9b28168abab8655faacb6853cd0ee15deee93"
set current_time (date +%s) set search_timerange (math $current_time - 600) # 24 hours = 86400 seconds
set pubkeys (nak req --kind 3 -s $search_timerange wss://relay.damus.io/ wss://nos.lol/ 2>/dev/null | \ jq -r --arg target "$target_pubkey" ' select(. != null and type == "object" and has("tags")) | select(.tags[] | select(.[0] == "p" and .[1] == $target)) | .pubkey ' | sort -u)
if test -z "$pubkeys" exit 1 end
set all_events "" set extended_search_timerange (math $current_time - 31536000) # One year
for pubkey in $pubkeys echo "Checking $pubkey" set events (nak req --author $pubkey -l 5 -k 3 -s $extended_search_timerange wss://relay.damus.io wss://nos.lol 2>/dev/null | \ jq -c --arg target "$target_pubkey" ' select(. != null and type == "object" and has("tags")) | select(.tags[][] == $target) ' 2>/dev/null)
set count (echo "$events" | jq -s 'length') if test "$count" -eq 1 set all_events $all_events $events endend
if test -n "$all_events" echo -e "Last people following $target_pubkey:" echo -e ""
set sorted_events (printf "%s\n" $all_events | jq -r -s ' unique_by(.id) | sort_by(-.created_at) | .[] | @json ') for event in $sorted_events set npub (echo $event | jq -r '.pubkey' | nak encode npub) set created_at (echo $event | jq -r '.created_at') if test (uname) = "Darwin" set follow_date (date -r "$created_at" "+%Y-%m-%d %H:%M") else set follow_date (date -d @"$created_at" "+%Y-%m-%d %H:%M") end echo "$follow_date - $npub" endend ```
-
 @ 7bdef7be:784a5805
2025-04-02 12:12:12
@ 7bdef7be:784a5805
2025-04-02 12:12:12We value sovereignty, privacy and security when accessing online content, using several tools to achieve this, like open protocols, open OSes, open software products, Tor and VPNs.
The problem
Talking about our social presence, we can manually build up our follower list (social graph), pick a Nostr client that is respectful of our preferences on what to show and how, but with the standard following mechanism, our main feed is public, so everyone can actually snoop what we are interested in, and what is supposable that we read daily.
The solution
Nostr has a simple solution for this necessity: encrypted lists. Lists are what they appear, a collection of people or interests (but they can also group much other stuff, see NIP-51). So we can create lists with contacts that we don't have in our main social graph; these lists can be used primarily to create dedicated feeds, but they could have other uses, for example, related to monitoring. The interesting thing about lists is that they can also be encrypted, so unlike the basic following list, which is always public, we can hide the lists' content from others. The implications are obvious: we can not only have a more organized way to browse content, but it is also really private one.
One might wonder what use can really be made of private lists; here are some examples:
- Browse “can't miss” content from users I consider a priority;
- Supervise competitors or adversarial parts;
- Monitor sensible topics (tags);
- Following someone without being publicly associated with them, as this may be undesirable;
The benefits in terms of privacy as usual are not only related to the casual, or programmatic, observer, but are also evident when we think of how many bots scan our actions to profile us.
The current state
Unfortunately, lists are not widely supported by Nostr clients, and encrypted support is a rarity. Often the excuse to not implement them is that they are harder to develop, since they require managing the encryption stuff (NIP-44). Nevertheless, developers have an easier option to start offering private lists: give the user the possibility to simply mark them as local-only, and never push them to the relays. Even if the user misses the sync feature, this is sufficient to create a private environment.
To date, as far as I know, the best client with list management is Gossip, which permits to manage both encrypted and local-only lists.
Beg your Nostr client to implement private lists!
-
 @ 04cb16e4:2ec3e5d5
2025-04-02 10:51:31
@ 04cb16e4:2ec3e5d5
2025-04-02 10:51:31Wenn irgendein weltpolitisches Thema auf den Tisch kommt, wird zumeist erst einmal gefragt, ob du dafür oder dagegen bist und auf welcher Seite du dich befindest. Das macht es einfacher, dich als Freund oder Feind einzusortieren. So wird das Leben übersichtlicher und man muss nicht in die Tiefe gehen und sich mit lästigen Details auseinandersetzen. Man muss auch nicht verreisen um sich ein Bild zu machen. Dafür gibt es ja die Tagesschau. Klassisches Beispiel: Ich war vor Kurzem mit einigen Freunden essen. Einer berichtete entsetzt: „Der Putin hat die Heimatstadt von Selenski angegriffen!“
Ich versuchte mir das bildlich vorzustellen und kam zu dem Schluss, das „der Putin“ wahrscheinlich Verstärkung dabei hatte. Und ausgerechnet nachdem Trump und dessen Flügelmann Vance den armen Wolodymyr rund gemacht hatten, greift der böse Imperator dessen Heimatstadt an. Das ist fies! Das macht „der Putin“ wahrscheinlich immer so, wenn er jemandem eins auswischen will. Die Heimatstadt angreifen! Ganz gleich, ob es strategisch gerade Sinn macht oder nicht. "Der Putin" ist halt ein Teufel.
Radio Berliner Morgenröte auf X
Ich denke viele gucken einfach zu viele qualitativ minderwertige Spielfilme und können Fiktion und Realität nicht mehr voneinander unterscheiden. Möglicherweise meinen sie auch, weil sie die Handlung eines Kriegsfilmes gerafft haben, verstehen sie einen Krieg.
https://www.eisbrenner.de/produkt-kategorie/buch/
Mein Gesprächspartner Tino Eisbrenner hat keine Sightseeing Tour durch Moskau gemacht, sondern ist in Land und Leute regelrecht eingetaucht. Außerdem kommt seine Schwiegermutter aus Russland. Da ist man dem ganzen auch menschlich viel näher und bekommt man ganz andere Einblicke als die, die einem von der Tagesschau gewährt werden. Tino ist als Friedensmusiker viel im Osten unterwegs, unter anderem auch in Georgien, Weißrussland und auf der Krim. Er spricht mit Politikern, Künstlern, Journalisten, Taxifahrern und Dissidenten. Und viele fragen ihn: „Was ist eigentlich mit den Deutschen los?“ Gute Frage! Was ist eigentlich mit uns los? Wir senden unsere Volksvertreter in die Welt hinaus, damit sie Staatsoberhäuptern aus Ländern - die um ein Vielfaches umfangreicher an Fläche und Einwohnerzahl sind und eine komplett andere Kulturgeschichte haben - damit sie denen erklären können wie man seinen Job macht. Wahrscheinlich in dem irrwitzigen Glauben, dass sie selbst ihren Job tadellos und vorbildlich ausführen.
Spenden nehmen wir entweder mit dem Paypal Button am Ende unserer Webseite https://radio-berliner-morgenroete.de/ oder per Überweisung aufs Bankkonto: DE93 1001 1001 2624 3740 74 entgegen.
Wir sind aber nicht nur verantwortlich für unsere politische Führung, sondern auch für unseren Umgang miteinander. Denn im „Großen“ gilt dasselbe wie im „Kleinen“! Man sollte erst mal bei sich selbst schauen wo es hakt und dann miteinander ins Gespräch gehen. Der Mangel an Realitätssinn und Konfliktfähigkeit zieht sich durch alle Schichten unserer Bevölkerung. Deswegen sagt Radio Berliner Morgenröte: „Wenn ihr Frieden wollt, fangt in Deutschland an und wenn ihr euch eine Meinung über Russland oder China bilden wollt, dann fahrt einfach mal dorthin und redet mit den Leuten, So wie Tino. Mir hat es riesig Spaß gemacht, ihm zuzuhören.
Weiterer Buchtipp – Ausgegendert
https://mcdn.podbean.com/mf/web/e5qbg23gz6mru9zz/Tino_Eisbrenner9tbpx.mp3
-
 @ d04ecf33:1d62aa90
2025-04-02 09:48:16
@ d04ecf33:1d62aa90
2025-04-02 09:48:16Physical prototyping
3D printers have evolved as useful tools for rapid prototyping of physical products for inspiration and demonstration purposes.
Nowadays people also use them for hobbyist endeavors. They create nice little items for pure enjoyment or very simple substitution parts that can be used regardless of industrial precision and material limitations.
Prototypers of Ideas
Similarly with LLMs, you can bounce ideas off them to better understand your own thinking and also let them generate variations of ideas. They provide inspiration, summaries, and proof-of-concept boilerplates. They are rapid prototypers for and of your ideas, creating a feedback loop.
However, to use LLMs successfully, people must understand that LLMs cannot and will never discover key insights. They are not creative in a human sense, just like 3D printers cannot produce a real car.
From engineering to art and business ideas, people use tools for almost all phases. The key innovation of LLMs is that they offer an effective tool to iterate faster in the ideation phase.
And yes, that's true of coding too. The code that LLMs generate is not production-ready, but it is a good starting point. Beware of using the prototype as the final product, as it will inevitably backfire. Use LLMs where their high-frequency but low-quality output is justified. Situations where low-quality boilerplate makes sense include experiments and other instances like code snippets, text summaries, sketches, demo videos, mockups, etc.
So, take your key idea and start the conversation. Apply critical thinking to identify where the answers lack important aspects and make mistakes, but most importantly, learn how to formulate your questions better.
Economic Impact
3D printers lower the barrier to entry in the manufacturing of physical products. LLMs, on the other hand, lower the barrier to generating useful ideas. That is to say, they lower the barrier to produce anything and everything because ideas are the basis of any product. This has a deflationary impact and, in my estimation, will further lower the need for mediocre, unimaginative people across the board. It's the bureaucrats' nightmare.
Another impactful aspect of LLMs is that they are very effective learning tools, just like 3D printers. Learning in a feedback loop used to be available only by hiring a human. Now that is one prompt and a few sats away.
Progress
LLMs need "quality data" to improve, i.e., more human insight and true creativity. Therefore, they feed on open-source. Closed-source proprietary information and "intellectual property" slow their progress, but not for long. Humans, overall, yearn for innovation more than they fear censorship and punishment. It's another Pandora's box, and the effects will never be reversed. People are essentially and foremost explainers of the world, creative innovators.
If you ask me, the human touch will be necessary at least until we have true AGI, and the path LLMs are on right now can never achieve that, not in a million years. I agree with David Deutsch's take on this: To produce real AGI, we must first crack serious concepts like how Meaning, Consciousness, Creativity, and Free Will work. We don't know how far we are from that, but it's not to be found along the path of what we call AI today.
If you are striving to become a better version of yourself and learn every day, rest assured: LLMs are your leverage. Otherwise, you will need some fiat authority, like the state today, to force others to value your work while it has an overall negative impact (90% in that category in my estimation). People like that need a shift of perspective or will suffer the consequences.
Keep printing ideas and execute on them! Learn and repeat. The path to success.
llm #ai #agi #3dp #programming
-
 @ a60e79e0:1e0e6813
2025-04-02 08:26:48
@ a60e79e0:1e0e6813
2025-04-02 08:26:48This is a long form note of a post that lives on my Nostr educational website Hello Nostr.
So you've got yourself started, you're up to speed with the latest Nostr jargon and you've learned the basics about the protocol, but you're left wanting more!? Well, look no further! This post contains a useful list of Nostr based utilities than can enhance your experience in and around the Nostr protocol.
Search and Discovery
Getting started with Nostr can sometimes feel like a lonely journey, particularly if you're the first of your friends and family to discover how awesome it can be! These tools can help you discover new content, connect with existing follows from other networks and just generally have a poke around at the different types of content Nostr has to offer.
Have a hobby or existing community elsewhere? Have a search for it here to find others with shared interests
- Nostr.Band - Search for people, posts, media and stats literally anything Nostr has to offer!
- Nostr.Directory - Find your Twitter follows on Nostr
- Awesome Nostr - Extensive list of Relay software
- Nostr View - Generic Nostr search
Relays
Relays might not be the sexiest of topics, particularly for newcomers to the network, but they are a crucial part of what makes Nostr great. As you become more competent, you'll want to customize your relay selection and maybe even run your own! Here are some great starting points.
Running a personal relay is a powerful way to improve the redundancy of your Nostr events.
- Nostr.Watch - Browse, test and research Nostr relays
- Nostrwat.ch - List of active Nostr relays
- Advanced Nostr Search - Targetted search with date ranges
- Nostr.Wine - Reliable paid Relay
NIP-05 Identity Services
Your nPub, or public key (that long string of letters and numbers) is your ‘official’ Nostr ID, but it’s not exactly catchy. NIP-05 identifiers are a human-readable and easily shareable way to have people find you on Nostr. They look like an email address, like qna@hellonostr.xyz. If you have your own domain and web server, you can easily create your own NIP-05 identifier in just a few minutes. If you don't, you'll want to leverage one of the many free or paid solutions.
Make yourself easier to find on Nostr with a NIP-05 identifier
- Bitcoiner.Chat - Free service operated by QnA
- Nostr Plebs - Paid service with extra features
- Alby - Lightning wallet with + NIP-05 solution
- Nostr Address - Paid service with extra features
- Zaps.Lol - Free service
Key Management
Your private key (or nsec) it the key to your Nostr world. It is what allows you to access and interact with your social graph from any client. It doesn't matter if that client is a micro-blogging app like Amethyst, a podcast app like Fountain, or a P2P marketplace like Plebeian Market, your nsec is paramount to those interactions. Should your nsec be lost, or fall into the wrong hands, whoever then holds a copy can access Nostr and pretend to be you, meaning that you'll need to start again with a new keypair. Not a nice situation to find yourself in, so treat your nsec VERY carefully.
Your private key IS your Nostr identity. Treat it with extreme care and do not share it.
- Alby - Browser extension enabling you to sign into web app without sharing the private key
- Nos2x - Another browser extension key manager
- Keys.Band - Another browser extension key manager
- Amber - Android app for safe nsec storage. Can talk to other clients on the same phone to log in and sign events
- Nostr Signing Device - Dedicated device to store your nsec
- Passport - Hardware wallet for offline and deterministic nsec generation and storage
Zap Tools
Zaps are one of the most fun parts of Nostr. Never before have we been able to send fractions of a penny, instantly to our friends because their meme made us laugh, or their blog post was very insightful. Zaps use Bitcoin’s Lightning Network, a faster and cheaper way to move Bitcoin around. To Zap someone, you need a Lightning wallet linked to your Nostr client. Some clients, like Primal, ship with their own custodial wallet to make getting started a breeze. Most clients also allow more advanced users to connect an existing Lightning Wallet to reduce reliance and trust in the client provider.
- Alby - Browser extension and self-custodial Lightning wallet
- LNBits - A Zap server running on your own Bitcoin node
- BTCPay Server - Another Zap server running on your own Bitcoin node
- Zeus - Zap compatible self-custodial mobile Lightning wallet
- Nostr Wallet Connect - Communication protocol between Lightning wallets and Nostr apps
- Ecash Wallets - Custodial Ecash based wallets that are interoperable with Lightning and Nostr (Funds may be at risk)
- Wallet of Satoshi - Custodial Lightning wallet (Funds may be at risk)
If you found this post useful, please share it with your peers and consider following and zapping me on Nostr. If you write to me and let me know that you found me via this post, I'll be sure to Zap you back! ⚡️
-
 @ 7d33ba57:1b82db35
2025-04-02 08:15:08
@ 7d33ba57:1b82db35
2025-04-02 08:15:08Supetar is the main town and ferry port on Brač Island, located just across the sea from Split. It’s a charming coastal town with historic streets, beautiful beaches, and a relaxed island vibe. As the main entry point to Brač, it’s the perfect base for exploring the island’s stunning beaches, olive groves, and cultural landmarks.
🏛️ Top Things to See & Do in Supetar
1️⃣ Explore the Supetar Old Town 🏡
- Stroll through narrow, stone-paved alleys, lined with historic buildings and seaside cafés.
- Visit St. Peter’s Church & Mausoleum, featuring intricate stone carvings.
- Admire the harbor filled with fishing boats, offering postcard-worthy views.
2️⃣ Relax on Supetar’s Beaches 🏖️
- Banj Beach – A family-friendly beach with crystal-clear water & soft pebbles.
- Acapulco Beach – A more secluded, rocky beach with turquoise waters.
- Vela Luka Bay – A beautiful bay surrounded by pine forests, perfect for relaxation.
3️⃣ Visit the Olive Oil Museum in Škrip 🫒
- Just 15 minutes from Supetar, this museum showcases Brač’s olive oil heritage.
- Try traditional Dalmatian olive oil tastings & local island delicacies.
4️⃣ Take a Boat Trip to the Famous Zlatni Rat Beach ⛵
- One of Croatia’s most iconic beaches, known for its shifting horn-shaped coastline.
- Located in Bol, just a short boat or car ride away from Supetar.
5️⃣ Hike or Drive to Vidova Gora 🌄
- The highest peak on the Adriatic islands (778m), offering breathtaking views over Brač, Hvar, and beyond.
- Accessible by hiking (moderate difficulty) or driving.
6️⃣ Try Dalmatian Cuisine 🍽️
- Vitalac – A unique Brač specialty, made from lamb offal and cooked over an open fire.
- Pašticada – A slow-cooked beef dish, traditionally served with gnocchi.
- Homemade Brač cheese & wine – Try local goat cheese paired with Plavac Mali wine.
🚗 How to Get to Supetar
⛴️ By Ferry (from Split):
- The Split-Supetar ferry is the main connection (50 min ride).
- Ferries run frequently (especially in summer).
🚘 By Car:
- Supetar is the best entry point for road trips across Brač.
- Car rentals are available in town or at the ferry port.💡 Tips for Visiting Supetar
✅ Best time to visit? May–September for warm weather & clear seas ☀️
✅ Stay at least a night – Supetar has a lovely evening atmosphere 🌙
✅ Rent a scooter or car to explore Brač’s hidden beaches & inland villages 🏍️
✅ Try local wines & olive oils – Brač is famous for both 🍷🫒
✅ Visit early in the morning for a peaceful experience before ferries get busy ⏳ -
 @ da0b9bc3:4e30a4a9
2025-04-02 05:35:30
@ da0b9bc3:4e30a4a9
2025-04-02 05:35:30Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/931908



















































