-
 @ fd06f542:8d6d54cd
2025-04-12 02:13:35
@ fd06f542:8d6d54cd
2025-04-12 02:13:35 -
 @ fd06f542:8d6d54cd
2025-04-12 01:32:38
@ fd06f542:8d6d54cd
2025-04-12 01:32:38使用nostrbook.com网站
登录和创建用户:
 登录按钮 ,可以粘贴 已有的 nsec....账号,完成登录。
登录按钮 ,可以粘贴 已有的 nsec....账号,完成登录。注册:
 可以点击红标位置 生成你的账户。 “确定” 完成注册。
可以点击红标位置 生成你的账户。 “确定” 完成注册。创建书籍
封面的上传
 创建书籍,可以用 微信截图 后直接 ctrl+v. 粘贴即可。
创建书籍,可以用 微信截图 后直接 ctrl+v. 粘贴即可。或者点击浏览 本地图片文件。
标题和作者
正常填写就可以。 书的作者和上传文件人没有一一绑定。
写书
 创建完成后就可以写书了,写书入口在 登录处 “我的书籍” 。点进去会出现你创建的书籍。选择一本就可以写书了。
创建完成后就可以写书了,写书入口在 登录处 “我的书籍” 。点进去会出现你创建的书籍。选择一本就可以写书了。列出你创建的所有的书籍

点击图标,就可以进入开始写作了。例如《nostrbook站点日记》

如图所示有4个部分
- (1)关闭按钮,点击就退出编辑,这时候他会提示你保存,如果不需要保存退出,点击 “不保存退出”
- (2)
大纲是编写 你书籍的大纲,这个参考 docsify文档 下面会有例子。时间排列是 你所有为本书写的章节。但是有些章节你可能废弃了,或者暂时不想展示,都会存在 时间排列里面,就是按照你编写的时间倒序排列的。草稿是你暂时存储的内容,没有上传到网络,存在你本地浏览器的缓存里面。 - (3)这个部分看到的就是你的章节列表,当让你第一次来的这个地方是空的。
新增章节下一次就会有内容了。 - (4)文件名,是我们存储章节的唯一标识。
readme.md和_sidebar.md是系统默认必须有的。因为docsify技术默认需要这2个。
如何编写大纲
如果你是第一次开始,大纲的界面是这样的。

- 点击
增加大纲 - 点击
查看样例 - 修改系统生成的例子,此时 readme.md是必须的readme 对应的名字你可以自己修改
- 点击提交 就可以完成大纲了。
第二次、点击
更新大纲按钮- [首页](/readme.md) - [国人开发者](/01.md) - [中文用户列表](/02.md)大纲例子,“[]” 内是标题,“()”内是 文件名; 标题是是显示在文章的右侧; 文件名的作用是匹配 ‘新增章节’ 里面的markdown的相匹配关联的。
如何编写一个章节,例如:readme.md
 * 点击
* 点击 新增章节* 填写标题 * 填写内容 * 关键是 填写文件名,需要和大纲里的名字对应 * 提交?> 如果你写的 章节 并没有在大纲里标识名字 ,用户在浏览的时候,左侧的章节并不会出现。
-
 @ fd06f542:8d6d54cd
2025-04-12 01:21:03
@ fd06f542:8d6d54cd
2025-04-12 01:21:03{"coverurl":"https://cdn.nostrcheck.me/fd06f542bc6c06a39881810de917e6c5d277dfb51689a568ad7b7a548d6d54cd/19105641454b483284cf76c42fbdde2ed3f47b1bb2a366a58eaa49630d385027.webp","title":"nostr-examples","author":"nostr-dev"}
-
 @ caa88a52:6c226a91
2025-04-11 22:58:40
@ caa88a52:6c226a91
2025-04-11 22:58:40Running Nestr!
-
 @ 378562cd:a6fc6773
2025-04-11 22:40:19
@ 378562cd:a6fc6773
2025-04-11 22:40:19Here in the country, we know a thing or two about focus. You can't fix a fence, milk a cow, or hoe a straight row if you're half-distracted or daydreaming about something else. The same applies to anything in life, whether it's trying to finish a project, have a meaningful conversation, or simply sit still long enough to pray. Concentration is a skill that, like all good things, requires a little grit and a lot of practice.
Here’s some practical, common-sense advice to help you buckle down and focus when your mind is spinning a bit too fast.
-
Clear the Mess Before You Start A messy space leads to a messy mind. You wouldn’t gut a deer on the kitchen table, and you shouldn’t expect to think clearly in a cluttered room. Clean up your work area. Put things away. Next, do the same with your mind and jot down everything swirling around in there. Get it out, set it aside, and focus completely on one task at a time.
-
Work Like a Farmer: in Spurts! A farmer doesn’t plow from sunup to sundown without stopping to catch his breath. He works steadily, confidently, but knows when to rest his bones, wipe his brow, and sip a cold drink. That’s the kind of rhythm that gets things done without wearing a man down. Try working in short, focused bursts for about twenty-five minutes, then take a five-minute breather. Stretch your legs, step outside, say a quick prayer, and return to your task. After a few rounds, take a longer break to let your mind cool off. You’ll accomplish more this way and won’t feel worn out by noon.
-
Stop Trying to Juggle Chickens Multitasking may seem impressive, but let’s face it: attempting to accomplish five tasks at once often results in none being done correctly. Concentrate on one task. Give it your all. Then move on. You’ll be more productive and less stressed.
-
Turn Down the Noise Distractions are like flies at a picnic - relentless and annoying. Shoo them away. Keep your phone out of reach. Use apps to block websites that drain your time. Turn off the TV. You cannot harvest peace and quiet if you’re watering weeds.
-
Feed Your Brain Like You Feed Your Livestock Your brain ain’t some spare part you can ignore and still expect to run strong. It needs proper tending, just like the rest of you. So drink plenty of water, not just coffee. Eat real food that grew in the ground or once walked on it, not something cooked up in a lab. Step outside and let the breeze hit your face. Soak up some sunshine and stretch your legs. Move a little; even a short walk can shake the cobwebs loose. It doesn’t take much, but you’ll be surprised what a difference it makes. A well-fed, well-rested mind is a sharp one, ready to do good work and hear what God’s saying through the noise.
-
Start Small, Grow Strong You don’t plant a tree and expect shade the next day. Same with focus. If you can only concentrate for ten minutes at first, that’s fine. Do that. Then, stretch it to fifteen, then thirty. It takes time and a little muscle, like splitting wood or learning to fish.
-
Know Your Why There’s a reason behind everything we do; remembering your reason helps you stay the course. Ask yourself: Why does this matter? Who am I doing this for? What good will come of it? Purpose gives power to your focus.
-
Rest Like It’s Part of the Job—Because It Is Hard work matters, and so does rest. Even the Lord took a day off. Sleep well, take breaks, go for a walk, and let your brain breathe. You don’t have to earn your rest; you just have to honor it. You’ll be sharper when you return.
Final Word from the Porch Concentration ain’t about being superhuman. It’s about making smart choices in small moments. Shut out the noise. Show up for your tasks. Give them your full attention. That’s how fences get mended, stories get written, and lives get changed.
Take it slow. Take it steady. And keep your eye on the prize.
-
-
 @ d0aa74cd:603d35cd
2025-04-11 20:24:40
@ d0aa74cd:603d35cd
2025-04-11 20:24:40Experimenting with cat package examples.
Gleam #Gleamlang #cat #Haskell
https://photonsphere.org/post/2025-04-11-gleam-cat/
-
 @ 2ed3596e:98b4cc78
2025-04-11 20:13:03
@ 2ed3596e:98b4cc78
2025-04-11 20:13:03Americans can now instantly sell bitcoin directly from their Lightning Wallets. The same auto conversion Bitcoin Well Customers are used for instantly and conveniently selling bitcoin from self-custody now has a Lightning option ready in the Sell bitcoin page of your Bitcoin Well account.
Adding the ability to sell bitcoin from the Lightning Network underscores our commitment to enabling you to get the most out of the freedom and independence Bitcoin has to offer. No longer must you rely on giving up custody of your bitcoin or navigate complicated trading interfaces for fast and convenient sales! Just send sats and receive dollars – Lightning fast.
Selling sats from the Lightning Network is quick and easy:
- From your Bitcoin Well account, go to Sell bitcoin and enter the amount of dollars you want
- Choose your bank, select “Lightning” and then generate a Lightning Invoice
- Pay the Lightning invoice and we’ll send dollars to your bank account
Here are detailed steps to guide you on how to sell sats from the Lightning Network 👇
Get your Lightning Invoice
Navigate to your Sell bitcoin page, enter the amount of dollars you wish to receive, set your destination bank account and select “Lightning”.
 Tap ‘Generate invoice’ to create a Lightning invoice. This Lightning invoice will be for the exact amount of sats you need to send for the amount of dollars you want to receive.
Tap ‘Generate invoice’ to create a Lightning invoice. This Lightning invoice will be for the exact amount of sats you need to send for the amount of dollars you want to receive.Send sats to your Lightning Invoice
To instantly sell bitcoin for dollars, simply pay the Lightning Invoice from your Lightning wallet. You can do this by scanning the QR code or by tapping the QR code to copy + paste the invoice into your Lightning wallet. Once received (basically instantly), we automatically convert received sats into dollars and send the dollars to your selected bank account. No waiting for confirmations, no mining fees and no complicated trading interfaces. Just sats in, dollars out. Lightning fast ⚡️
 ## What is the Lightning Network?
## What is the Lightning Network?The Lightning Network is a second-layer protocol built on top of Bitcoin. It enables fast, cheap, and private bitcoin payments, perfect for small transactions and daily use. Think of it like the relationship between the credit card network and the banking system. While Bitcoin’s base layer is optimized for security, Lightning is optimized for frequent or small, cheap and private payments for everyday transactions — instantly and without bloating the blockchain. The Lightning Network makes it much more convenient to use bitcoin in everyday life, bringing you closer to replacing your bank with bitcoin.
Currently, sats on the Lightning Network cannot be directly sent to an on-chain bitcoin wallet, and vice versa. However, that won’t remain true for Bitcoin Well accounts for long…
Why Does the Lightning Network Matter?
The Lightning Network helps bitcoin reach its full potential as everyday money. While Bitcoin’s base chain is perfect for storing value, it’s not always practical for everyday payments or quick, small transactions. Lightning fills that gap — it’s fast, inexpensive, and built for a world where people use bitcoin as easily as cash. Bitcoin is the future of money. Lightning makes it usable today. We love Lightning, and have some exciting additional products coming that will shock you!
Earn sats over the Lightning Network
Earn sats when you refer your friends! When you add your Lightning Payment address from your personal Lightning Wallet to your Referral page, every time someone you referred transacts on the portal, you get a kickback paid in sats! Of course, we never custody your bitcoin, even when you get a Lightning referral reward! All bitcoin is always sent straight to your wallet. ⚡\ \ Haven’t signed up with Bitcoin Well yet? Sign up here and embrace the Bitcoin Standard.
About Bitcoin Well
Bitcoin Well exists to enable independence. We do this by coupling the convenience of modern banking, with the benefits of bitcoin. In other words, we want to make it easy to use bitcoin in self-custody.
We are publicly traded (and love it when our customers become shareholders!) and hold ourselves to a high standard of enabling life on a Bitcoin standard. If you want to learn more about Bitcoin Well, please visit our website or reach out!
-
 @ e111a405:fa441558
2025-04-11 17:15:58
@ e111a405:fa441558
2025-04-11 17:15:58Meritocracy without equality is basically a ladder with missing steps, which only the fortunate few can climb. The rest is basically left at the ground to gaze up.
Furthermore, a pure focus on meritocracy can become a weakness if it’s a zero-sum game. While talents thrive in systems that value it, without fairness, you ultimately get exploitation, resentment, or fragility.
Ergo: meritocracy needs to be balanced with equality, and equality needs to be balanced with meritocracy.
In a meritocratic system, you basically need that the fortunate and the able are compassionate towards those less fortunate and able.
If you are more on the libertarian side, you need the fortunate individuals to compete as capitalists and then be socialists within their communities and families.
If you prefer a state, then the state must encourage meritocratic contribution of everyone that is able, to the best of their ability, while balancing it with a fair welfare system that nurtures and supports those less able and fortunate.
I think this is something Germany did historically quite well, but at one point we lost the balance: we lost the culture of merit by putting too much emphasis on equality – even to a point that Germany now cares for millions of non-citizens that never contributed, when it should instead demand these individuals to contribute to the best of their ability.
If we want to have a state, then we don’t want a welfare state, and – I think – we should also not want a pure capitalistic state. We need balance and thus a social meritocracy.
-
 @ c230edd3:8ad4a712
2025-04-11 16:02:15
@ c230edd3:8ad4a712
2025-04-11 16:02:15Chef's notes
Wildly enough, this is delicious. It's sweet and savory.
(I copied this recipe off of a commercial cheese maker's site, just FYI)
I hadn't fully froze the ice cream when I took the picture shown. This is fresh out of the churner.
Details
- ⏲️ Prep time: 15 min
- 🍳 Cook time: 30 min
- 🍽️ Servings: 4
Ingredients
- 12 oz blue cheese
- 3 Tbsp lemon juice
- 1 c sugar
- 1 tsp salt
- 1 qt heavy cream
- 3/4 c chopped dark chocolate
Directions
- Put the blue cheese, lemon juice, sugar, and salt into a bowl
- Bring heavy cream to a boil, stirring occasionally
- Pour heavy cream over the blue cheese mix and stir until melted
- Pour into prepared ice cream maker, follow unit instructions
- Add dark chocolate halfway through the churning cycle
- Freeze until firm. Enjoy.
-
 @ 2101a7ec:d9d8f2db
2025-04-11 14:50:45
@ 2101a7ec:d9d8f2db
2025-04-11 14:50:45Ghostty is terminal manager with GPU acceleration and great looks. It works mostly out of the box, but you might want to do some setups to tailor it to your particular needs.
Here is how I set it up.
Installation
I won't spend much time on installation details, I installed it using
brewthere are multiple installation options, surprisingly flatpack is not within the options at the moment. For further details please check ghostty installation instructions.Configuration
Config file is available on these locations
$HOME/Library/Application Support/com.mitchellh.ghostty/config$XDG_CONFIG_HOME/ghostty/configI use
$XDG_CONFIG_HOMEas I keep all my config there.Configuration reference is available on line. And can be generated from the command line doing
ghostty +show-config --default --docsAnd finally to list available themes
ghostty +list-themes.This is my config, it's available with my dotfiles
```config
~/.config/ghostty/config
to show the default configuration with documentation.
ghostty +show-config --default --docs
font-family = "JetBrains Mono"
font-size = 14
Run
ghostty +list-themesto browse available themes.theme = SynthwaveAlpha cursor-style = block
background-opacity = 0.96 background-blur-radius = 40
shell integration.
shell-integration = bash shell-integration-features = cursor, sudo, title
macos-titlebar-style = tabs
Auto-update Ghostty when a new release is available.
auto-update = download
mouse-hide-while-typing = true
keymaps
keybind = global:cmd+`=toggle_quick_terminal
keybind = cmd+left=previous_tab keybind = cmd+right=next_tab
byobu keybinds fix
macos-option-as-alt = left keybind = alt+left=unbind keybind = alt+right=unbind
quit-after-last-window-closed = true window-new-tab-position = end
```
I had some issues with SSH, so I added this to my
~/.ssh/configwhich fixed my issues.ssh Host * # ghostty https://ghostty.org/docs/help/terminfo SetEnv TERM=xterm-256color # end ghostty -
 @ 0b118e40:4edc09cb
2025-04-11 14:38:22
@ 0b118e40:4edc09cb
2025-04-11 14:38:22There’s an African proverb that says, “To get lost is to learn the way.”
Humans have always been explorers, searching for connection. To belong. To feel home. You can trace this instinct back to the start of our existence. Whether you start with Adam and Eve or the “Out of Africa” theory, the story is the same. We’ve always moved toward each other, building tribes and forming communities.
But somewhere along the way, something broke. With the rise of empires and organized control, religion and politics divided us into bubbles. We were sorted, labeled, and often pitted against one another. While technology advanced, something fundamental was lost. Our ability to truly connect started to fade.
Then came the internet, a modern-day Silk Road. It rekindled hope. Walls seemed to crumble, distances disappeared, and we dreamed of a truly connected world. For a time, it felt like the answer.
And then it wasn’t.
The history of Internet
The story began around 1830s when Charles Babbage started working on his computer prototype but without moolah he couldn't continue. A century later, after WW2 in the 1950s, the US Department of Defense funded what became known as modern computing.
Back then the military relied on systems like the Navajo Code Talkers. The indigenous code talkers were ingenious but operated under dangerous conditions, always on the frontlines.
In 1969, ARPANET made a revolutionary breakthrough as it connected four university computers for the first time. It was a big deal.
At that time, the internet was about openness. Researchers pushed for universal protocols. This gave rise to hacker culture that valued knowledge-sharing and keeping systems accessible to everyone.
In the 80s, NSFNET (National Science Foundation ) expanded these connections but kept it strictly for academic use only. That caused massive dissatisfaction.
Senator Al Gore pitched the concept of the “information superhighway,” to balance public access with private innovation. But by the 90s, the Clinton administration leaned into privatization. NSFNET’s infrastructure was completely handed off to private companies, and the internet grew into a commercial powerhouse.
The good news is that everyone has internet access now. Bad news is that what started as something free from government and commercial control became completely dominated by both.
Open source vs IP during the early internet days
This part of the story is about Bill Gates and Marc Andreessen.
Tim Berners-Lee invented the World Wide Web, but Marc saw the opportunity to make it user-friendly. He launched Netscape, an open-source browser. It drove the openness of internet culture. Netscape captured 90% of the market by giving its software away for free, and monetizing through other means.
Then came along Bill Gates. Microsoft back then was known for its aggressive tactics to monopolize industries. Gates licensed Mosaic’s code, created Internet Explorer, and bundled it for free with Windows 95. He wasn’t shy about playing dirty, even formed exclusive contracts with manufacturers to block competitors. Even the Department of Justice tried to file an antitrust lawsuit against Microsoft, but by then, it was too late. Netscape’s market share crumbled, and its position in the industry eroded.
Windows 95 brought the internet to the people globally, but it also closed it up.
Marc Andreeson started with open source ideologies, but is now funding altcoin projects.
The Californian ideology
Around this time, the term “Californian Ideology” started floating around. It was an unusual mix of libertarianism, techno-utopianism, and countercultural ideals. A marriage of cultural bohemianism (hippies) with high-tech entrepreneurship (yuppies). This ideology fused left-wing values like freedom of expression and direct democracy with right-wing beliefs in free markets and minimal government interference.
I absolutely love it.
Ironically, the term “Californian Ideology” wasn’t coined as a compliment. Richard Barbrook and Andy Cameron used it to piss on these visionaries for romanticizing the idea that the internet must remain a lawless, egalitarian space.
But many people loved and embraced the Californian ideology. Stewart Brand, who founded The Whole Earth Catalog, connected counterculture with early tech innovation. His work inspired people like Steve Jobs and Steve Wozniak. Steve Wozniak used to share Apple’s early schematics at the Homebrew Computer Club for feedback and collaboration.
EBay’s founder Pierre Omidyar envisioned eBay as a libertarian experiment. He believed the “invisible hand” of the market would ensure fairness. But as eBay grew, fraud, disputes, and dissatisfaction among users forced Omidyar to introduce governance which contradicted his goals.
And this story repeats itself over the years.
Platforms begin with libertarian visions, but as they scale, real-world challenges emerge. Governance (government, corporate charters, advertisers, and investors) is introduced to address safety and trust issues.
But they also chip away at the liberty the internet once promised.
Can Nostr be the solution ?
Yes.
But to appreciate Nostr, let’s first understand how the internet works today. (Note : I am no expert of this section but I'll try my best to explain)
The internet operates through four main layers:
- Application Layer (where apps like browsers, Google, or Zoom live)
- Transport Layer
- Internet Layer
- Network Access Layer
Let’s use a simple example of searching “Pink Panther” on Google.
Step 1: The Application Layer - You open your browser, type "Pink Panther," and hit search. This request is sent using HTTP/HTTPS (a protocol that formats the query and ensures it's secure).
Step 2: The Transport Layer - Think of your search query as a letter being sent. The Transport Layer breaks it into smaller packets (like splitting a long letter into multiple envelopes). TCP (Transmission Control Protocol) ensures all packets arrive and reassemble in the correct order.
Step 3: The Internet Layer - This layer acts like a postal service, assigning each device an address (IP address) to route the packets properly. Your device's IP (e.g., 192.168.1.10) and Google’s server IP (e.g., 142.250.72.238) help routers find the best path to deliver your packets.
Step 4: The Network Access Layer - Finally, the Network Access Layer physically delivers the packets. These travel as electrical signals (over cables), radio waves (Wi-Fi), or light pulses (fiber optics). This is the act of moving envelopes via trucks, planes, or postal workers, just much faster.
So how is data transmitted via Nostr ?
Nostr’s architecture of the Internet
Nostr reimagines the Application Layer while keeping the lower layers (Transport, Internet, and Network Access) largely unchanged.
In the traditional internet stack, the Application Layer is where platforms like Google or Twitter operate. It’s also where most censorship occurs due to single point of failure (centralised servers). Nostr flips this model on its head.
Technically, it’s like building a parallel internet that shares the same foundational layers but diverges at the top.
To borrow from Robert Frost:
"Two roads diverged in a wood, and I—
I took the one less traveled by,
And that has made all the difference."
For Nostr to fully realize its potential, it needs its own ecosystem of apps. Developers can build these tools within the Nostr protocol's framework
Let’s say there is a search engine on Nostr called Noogle.
Here’s how it works:
When you type "Pink Panther" on Noogle, your query is sent to multiple relays (servers) simultaneously. Each relay processes or forwards the query and returns results based on the data it holds.
As Nostr grows, the amount of information on relays will increase, giving Noogle more robust search results. But the biggest win is that compared to Google, Nostr's Noogle will have no ads, no surveillance, just pure, decentralized searching that respects your privacy.
For the transport layer, Nostr still relies on TCP/IP but enhances it with privacy and efficiency. Encrypted messages and simplified protocols enable faster real-time communication. The rest of the layer remains unchanged.
At its core, Nostr takes the internet back to its original ideals: open, uncensored, and decentralized.
Why Nostr matters ?
The internet we use today relies on centralized systems at the application layer. This creates a single point of failure where governments and corporations can control access, censor content, monitor activity, and even shut down entire platforms.
For example, the Malaysian government once proposed routing all web traffic through a centralized system, claiming it was for "security" reasons. In reality, this action allow those in power to block access to specific content or platforms that might threaten their positions.
Centralization weaponizes the internet.
It turns what was meant to be a tool for connection and freedom into a mechanism for control and oppression.
Let's look at DNS and ISPs as examples. DNS (Domain Name System) is like the phonebook of the internet. It helps translate website names (like example.com) into IP addresses so your browser can connect to them. ISPs (Internet Service Providers) are companies that give you access to the internet.
Both are controlled by centralized entities. If a government gains control of either, it can block specific websites or even shut down internet access entirely.
We've seen this happen repeatedly: * India’s internet shutdowns in regions like Kashmir * Turkey’s social media bans during political events * Ethiopia’s internet blackouts * China’s Great Firewall blocking major platforms like Google and Facebook * Even the US, where Edward Snowden revealed massive surveillance programs
This is where Nostr comes in, as the antidote to centralized control.
Instead of relying on centralized servers or platforms, Nostr creates a peer-to-peer network of independent relays. No single entity controls it. There is no central switch governments can flip to block access. If one relay is shut down, users simply connect to others in the network.
Nostr’s decentralized design makes it: * Resistant to censorship: Governments cannot easily block or filter content. * Privacy-preserving: Users can communicate anonymously, even in heavily surveilled environments. * Resilient: With no single point of failure, the network keeps running, even under attack.
And it gets better. Nostr can integrate with privacy tools like Tor to bypass restrictions entirely, making it nearly impossible for governments to stop.
The internet has become a battlefield for control, but Nostr provides a way to reclaim digital freedom. It empowers people to build, connect, and share without fear of being silenced.
How does Nostr overcome the "Californian Ideology" problems?
The Californian Ideology seemed like the blueprint for a utopian internet, libertarian ideals wrapped in Silicon Valley innovation. But as centralized platforms scaled, cracks started to show. Challenges like trust, safety, and accessibility forced governance teams to step in and decide “what’s best for the people.”
This resulted in platforms once built on ideals of freedom in becoming gatekeepers of control.
Nostr breaks this cycle. How?
1. Trust issues - With private keys, you control your identity and data. Moderation is decentralized. You can block or mute others at a personal level or through client tools, not by relying on a central authority. While this system needs refinement to be more user-friendly, it fundamentally shifts the power to users.
2. Funding Without Advertiser - Nostr’s integration of Bitcoin and the Lightning Network eliminates reliance on advertisers or corporate sponsors. Bitcoin enables anyone to contribute without gatekeeping. As more people join and apps mature, this model only gets stronger. For now, we have good souls like Jack seeding it.
3. Resisting Government Control - (refer to the above) Nostr avoids single points of attacks.
So what is Nostr ?
Nostr is internet
The new internet.
The open and free internet.
What can you build on Nostr?
Anything you have seen on the internet, you can recreate on Nostr. Anything you can imagine, you can bring to life here. It is a blank canvas for dreamers, builders, and changemakers.
But the best part is this. You have Bitcoin as its financial backbone. This changes the game entirely.
And with new games, comes new rules. New vibes. New ways.
The way people use this new internet will be different from the traditional internet as control falls back to the people. With Bitcoin as the underlying backbone, the business models will be different.
But there is more to it than just creating. There's that joy of creation, where we invite curiosity and inspire users to experience something new, something revolutionary.
Have you watched “The Last Lecture” by Randy Pausch?
He coined the term “head fake.” He taught his students programming, but not everyone was excited to learn programming. So he created fun projects and performances that pulled them in. The students had so much fun, they didn’t even realize they were learning to code.
What you build on Nostr is that head fake. The apps and projects you create draw people in with fun and utility, subtly reminding them they have a right to their own voice and thoughts.
The work you’re doing is so precious. When everything feels like doom and gloom, it’s these kinds of projects that give people hope.
Through Nostr, you’re making a difference. One project, one connection at a time.
The new Internet era
Centralized systems, like empires of the past, eventually crumble under the weight of their control. Decentralization provides a different path. It is a modern revival of our primal instincts to explore, connect, and build tribes.
By definition, Nostr is a protocol. I think more so, it's a philosophy. It challenges us to rethink how we share, communicate, and create. It is the internet as it was meant to be. Free, open, and governed by no one.
The beauty of Nostr lies in its simplicity. It does not rely on massive infrastructure, corporate giants, or government oversight. It thrives on community, much like the early tribes that defined humanity.
We have come full circle. From wandering continents to building roads, bridges, and networks, our journey has always been about connection and finding our tribe.
As the African proverb reminds us, 'To get lost is to learn the way.' There is finally a way now.
But at the end of the day, it’s entirely up to you what kind of world you want to be part of.
Find your tribe. Build the future. Love them hard.
More info :
On those who played a role in the history of internet and computers
https://hiddenheroes.netguru.com/ -
 @ 34ff86e0:dbb6b9fb
2025-04-11 14:35:59
@ 34ff86e0:dbb6b9fb
2025-04-11 14:35:59Lorem Ipsum is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry's standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book. It has survived not only five centuries, but also the leap into electronic typesetting, remaining essentially unchanged. It was popularised in the 1960s with the release of Letraset sheets containing Lorem Ipsum passages, and more recently with desktop publishing software like Aldus PageMaker including versions of Lorem Ipsum
-
 @ e17e9a18:66d67a6b
2025-04-11 14:00:27
@ e17e9a18:66d67a6b
2025-04-11 14:00:27We wrote this album to explain the inspiration behind Mutiny Brewing, and as a way to share the story of Bitcoin and freedom technologies like nostr. Through these songs, we’ve tried to capture every truth that we believe is essential to understand about money, freedom, trust, and human connection in the internet age. It’s our way of making these ideas real and relatable, and we hope it helps others see the power of taking control of their future through the systems we use.
01. "Tomorrow's Prices on Yesterday's Wage" explores the harsh reality of inflation. As central banks inflate the money supply, prices rise faster than wages, leaving us constantly falling behind. People, expecting prices to keep climbing, borrow more to buy sooner, pushing prices even higher in a vicious cycle. You're always a step behind, forced to pay tomorrow's inflated prices with yesterday's stagnant wages.
https://wavlake.com/track/76a6cd02-e876-4a37-b093-1fe919e9eabe
02. "Everybody Works For The Bank" exposes the hidden truth behind our fiat money system. When banks issue loans, they create new money from debt—but you must pay back both the principal and interest. That interest requires even more money, relying on others to borrow, creating an endless cycle of debt. If borrowing slows, the system falters and governments step in, printing more money to keep banks afloat. Ultimately, we’re all working to service debt, chained to the banks.
“Paying back what they create, working till I break” https://wavlake.com/track/4d94cb4b-ff3b-4423-be6a-03e0be8177d6
03. "Let My People Go" references Moses' demand for freedom but directly draws from Proverbs 6:1–5, exposing the danger of debt based money. Every dollar you hold is actually someone else's debt, making you personally liable—held in the hand of your debtor and at risk of their losses, which you ultimately pay for through inflation or higher taxes. As the song says, "The more you try to save it up, the deeper in you get." The wisdom of Proverbs urges immediate action, pleading urgently to escape this trap and free yourself, like a gazelle from a hunter.
https://wavlake.com/track/76214ff1-f8fd-45b0-a677-d9c285b1e7d6
04. "Mutiny Brewing" embodies Friedrich Hayek's insight: "I don't believe we shall ever have good money again before we take it out of the hands of government... we can't take it violently... all we can do is by some sly roundabout way introduce something they can't stop."
Inspired also by the Cypherpunk manifesto's rallying cry, "We will write the code", the song celebrates Bitcoin as exactly that unstoppable solution.
"Not here to break ya, just here to create our own little world where we determine our fate." https://wavlake.com/track/ba767fc8-6afc-4b0d-be64-259b340432f3
05. "Invisible Wealth" is inspired by The Sovereign Individual, a groundbreaking 1990s book that predicted the rise of digital money and explores how the return on violence shaped civilizations. The song references humanity's vulnerability since agriculture began—where stored wealth attracted violence, forcing reliance on larger governments for protection.
Today, digital privacy enabled by cryptography fundamentally changes this dynamic. When wealth is stored privately, secured by cryptographic keys, violence becomes ineffective. As the song emphasizes, "You can't bomb what you can't see." Cryptography dismantles traditional power structures, providing individuals true financial security, privacy, and freedom from exploitation.
“Violence is useless against cryptography” https://wavlake.com/track/648da3cc-d58c-4049-abe0-d22f9e61fef0
06. "Run A Node" is a rallying cry for Bitcoin's decentralisation. At its heart, it's about personal verification and choice: every node is a vote, every check’s a voice. By running the code yourself, you enforce the rules you choose to follow. This is true digital democracy. When everyone participates, there's no room for collusion, and authority comes directly from transparent code rather than blind trust.
"I verify, therefore I do." https://wavlake.com/track/ee11362b-2e84-4631-b05e-df6d8e6797f8
07. "Leverage is a Liar" warns against gambling with your wealth, but beneath the surface, it's a sharp critique of fractional reserve banking. Fractional reserves inflate asset prices, creating the illusion of wealth built on leverage. This system isn't sustainable and inevitably leads to collapse. Real wealth requires sound money, money that can't be inflated. Trying to gain more through leverage only feeds the lie.
"Watch it burn higher and higher—leverage is a liar." https://wavlake.com/track/67f9c39c-c5e1-4e15-b171-f1f5442f29a5
08. "Don't Get Rekt" serves as a stark warning about trusting custodians with your Bitcoin. Highlighting infamous collapses like Mt.Gox, Celsius, and FTX. These modern failures echo the 1933 Executive Order 6102, where the US government forcibly seized citizens' gold, banned its use, and then promptly devalued the currency exchanged for it. History shows clearly: trusting others with your wealth means risking losing it all.
"Your keys, your life, don't forget." https://wavlake.com/track/fbd9b46d-56fc-4496-bc4b-71dec2043705
09. "One Language" critiques the thousands of cryptocurrencies claiming to be revolutionary. Like languages, while anyone can invent one, getting people to actually use it is another story. Most of these cryptos are just affinity scams, centralized towers built on shaky foundations. Drawing from The Bitcoin Standard, the song argues money naturally gravitates toward a single unit, a universal language understood by all. When the dust settles, only genuine, decentralized currency remains.
"One voice speaking loud and clear, the rest will disappear." https://wavlake.com/track/22fb4705-9a01-4f65-9b68-7e8a77406a16
10. "Key To Life" is an anthem dedicated to nostr, the permissionless, unstoppable internet identity protocol. Unlike mainstream social media’s walled gardens, nostr places your identity securely in a cryptographic key, allowing you total control. Every message or action you sign proves authenticity, verifiable by anyone. This ensures censorship resistant communication, crucial for decentralised coordination around Bitcoin, keeping it free from centralised control.
"I got the key that sets me free—my truth is mine, authentically." https://wavlake.com/track/0d702284-88d2-4d3a-9059-960cc9286d3f
11. "Web Of Trust" celebrates genuine human connections built through protocols like nostr, free from corporate algorithms and their manipulative agendas. Instead of top down control, it champions grassroots sharing of information among trusted peers, ensuring truth and authenticity rise naturally. It's about reclaiming our digital lives, building real communities where trust isn't manufactured by machines, but created by people.
"My filter, my future, my choice to make, real connections no one can fake." https://wavlake.com/track/b383d4e2-feba-4d63-b9f6-10382683b54b
12. "Proof Of Work" is an anthem for fair value creation. In Bitcoin, new money is earned through real work, computing power and electricity spent to secure the network. No shortcuts, no favourites. It's a system grounded in natural law: you reap what you sow. Unlike fiat money, which rewards those closest to power and the printing press, Proof of Work ensures rewards flow to those who put in the effort. Paper castles built on easy money will crumble, but real work builds lasting worth.
"Real work makes real worth, that's the law of this earth." https://wavlake.com/track/01bb7327-0e77-490b-9985-b5ff4d4fdcfc
13. "Stay Humble" is a reminder that true wealth isn’t measured in coins or possessions. It’s grounded in the truth that a man’s life does not consist in the abundance of his possessions. Real wealth is the freedom to use your life and time for what is good and meaningful. When you let go of the obsession with numbers, you make room for gratitude, purpose, and peace. It's not about counting coins, it's about counting your blessings.
"Real wealth ain't what you own, it's gratitude that sets the tone." https://wavlake.com/track/3fdb2e9b-2f52-4def-a8c5-c6b3ee1cd194
-
 @ 1bc70a01:24f6a411
2025-04-11 13:50:38
@ 1bc70a01:24f6a411
2025-04-11 13:50:38The heading to be
Testing apps, a tireless quest, Click and swipe, then poke the rest. Crashing bugs and broken flows, Hidden deep where logic goes.
Specs in hand, we watch and trace, Each edge case in its hiding place. From flaky taps to loading spins, The war on regressions slowly wins.
Push the build, review the log, One more fix, then clear the fog. For in each test, truth will unfold— A quiet tale of stable code.
This has been a test. Thanks for tuning in.
- one
- two
- three
Listen a chillTranquility
And leisure
-
 @ bf95e1a4:ebdcc848
2025-04-11 11:21:48
@ bf95e1a4:ebdcc848
2025-04-11 11:21:48This is a part of the Bitcoin Infinity Academy course on Knut Svanholm's book Bitcoin: Sovereignty Through Mathematics. For more information, check out our Geyser page!
An Immaculate Conception
Some concepts in nature are harder for us humans to understand than others. How complex things can emerge out of simpler ones is one of those concepts. A termite colony, for instance, has a complex cooling system at its lower levels. No single termite knows how it works. Completely unaware of the end results, they build complex mounds and nests, shelter tubes to protect their paths, and networks of subterranean tunnels to connect their dirt cities. Everything seems organized and designed, but it is not. Evolution has equipped the termite with a pheromone receptor that tells the termite what task he ought to engage himself in by simply counting the number of neighboring termites doing the same thing. If there’s a surplus of workers in an area, nearby termites become warriors, and so on. Complex structures emerge from simple rules. The fractal patterns found all around nature are another example. Fractals look complex, but in reality, they’re not. They’re basically algorithms — the same pattern, repeated over and over again with a slightly modified starting point. The human brain is an excellent example of a complex thing that evolved out of simpler things, and we humans still have a hard time accepting that it wasn’t designed. Religions, which themselves are emergent systems spawned out of human interaction, have come up with a plethora of explanations for how we came to be. All sorts of wild origin stories have been more widely accepted than the simple explanation that our complexities just emerged out of simpler things following a set of rules that nature itself provided our world with.
Complex systems emerge out of human interactions all the time. The phone in your pocket is the result of a century of mostly free global market competition, and no single human could ever have come up with the entire thing. The device, together with its internet connection, is capable of a lot more than the sum of its individual parts. A pocket-sized gadget that can grant instant access to almost all of the world’s literature, music, and film, which fits in your pocket, was an unthinkable science fiction a mere twenty years ago. Bitcoin, first described in Satoshi Nakamoto’s whitepaper ten years before these words were written, was designed to be decentralized. Still, it wasn’t until years later that the network started to show actual proof of this. Sound money, or absolute digital scarcity, emerged out of the network not only because of its technical design. How Bitcoin’s first ten years actually unfolded played a huge part in how true decentralization could emerge, and this is also the main reason why the experiment cannot be replicated. Scarcity on the internet could only be invented once. Satoshi’s disappearance was Bitcoin’s first step towards true decentralization. No marketing whatsoever and the randomness of who hopped onto the train first were the steps that followed. Bitcoin truly had an immaculate conception.
The network has shown a remarkable resistance to change over the last few years especially, and its current state might be its last incarnation given the size of the network and the 95% agreement threshold in its consensus rules. It might never change again. In that case, an entirely new, complex life form will have emerged out of a simple set of rules. Even if small upgrades are implemented in the future, the 21 million coin supply cap is set in stone forever. Bitcoin is not for humans to have opinions about — it exists regardless of what anyone thinks about it, and it ought to be studied rather than discussed. We don’t know what true scarcity and a truly global, anonymous free market will do to our species yet, but we are about to find out. It is naïve to think otherwise. Various futurists and doomsday prophets have been focused on the dangers of the impending general artificial intelligence singularity lately, warning us about the point of no return, whereupon an artificial intelligence will be able to improve itself faster than any human could. Such a scenario could, as news anchor Ron Burgundy would have put it, escalate quickly. This may or may not be of real concern to us, but meanwhile, right under our noses, another type of unstoppable digital life has emerged, and it is already changing the behavior and preferences of millions of people around the globe. This is probably bad news for big corporations and governments but good news for the little guy looking for a little freedom. At least, that’s what those of us who lean towards the ideas of the Austrian school of economics believe. This time around, we will find out whether this is the case or not. No one knows what it will lead to and what new truths will emerge out of this new reality.
Unlike the termite, we humans are able to experience the grandeur of our progress. We can look in awe at the Sistine Chapel or the pyramids, and we can delve into the technicalities and brief history of Bitcoin and discover new ways of thinking about value along the way. Money is the language in which we express value to each other through space and time. Now, that language is spoken by computers. Value expressed in this language can’t be diluted through inflation or counterfeiting any longer. It is a language that is borderless, permissionless, peer-to-peer, anonymous (if you have the skills), unreplicable, completely scarce, non-dilutable, unchangeable, untouchable, undeniable, fungible, and free for everyone on Earth to use. It is a language for the future and it emerged out of a specific set of events in the past. All languages are examples of complex systems emerging out of simpler things, and Bitcoin evolved just as organically as any other human language did.
Decentralization is hard to achieve. Really hard. When it comes to claims of decentralization, a “don’t trust, verify” approach to the validity of such claims will help you filter out the noise. So, how can the validity of Bitcoin’s decentralization be verified? It’s a tricky question because decentralization is not a binary thing, like life or death, but rather a very difficult concept to define. However, the most fundamental concepts in Bitcoin, like the 21 million cap on coin issuance or the ten-minute block interval as a result of the difficulty adjustment and the Proof of Work algorithm, have not changed since very early on in the history of the network. This lack of change, which is arguably Bitcoin’s biggest strength, has been achieved through the consensus rules, which define what the blockchain is. Some special mechanisms (for example, BIP9) are sometimes used to deploy changes to the consensus rules. These mechanisms use a threshold when counting blocks that signal for a certain upgrade. For example, the upgrade “Segregated Witness” activated in a node when 95% or more of the blocks in a retarget period signaled support. Bitcoin has displayed a remarkable immutability through the years, and it is highly unlikely that this would have been the case if the game-theoretical mechanisms that enable its decentralized governance model hadn’t worked, given the many incentives to cheat that always seem to corrupt monetary systems. In other words, the longer the system seems to be working, the higher the likelihood that it actually does.
Satoshi set in stone the length of the halving period — a very important aspect of Bitcoin’s issuance schedule and initial distribution. During the first four years of Bitcoin’s existence, fifty new coins were issued every ten minutes up until the first block reward halving four years later. Every four years, this reward is halved so that the issuance rate goes down by fifty percent. This effectively means that half of all the Bitcoin that will ever exist was mined during the first four years of the network’s life, one fourth during its next four years, and so on. At the time of writing, we’re a little more than a year from the third halving. After that, only 6.25 Bitcoin will be minted every ten minutes as opposed to 50, which was the initial rate. What this seems to do is to create hype cycles for Bitcoin’s adoption. Every time the price of Bitcoin booms and then busts down to a level above where it started, a hype cycle takes place. Bitcoin had no marketing whatsoever, so awareness of it had to be spread through some other mechanism. When a bull run begins, people start talking about it, which leads to even more people buying due to fear of missing out (FOMO), which inevitably causes the price to rise even more rapidly. This leads to more FOMO, and on and on the bull market goes until it suddenly ends, and the price crashes down to somewhere around, or slightly above, the level it was at before the bull run started. Unlike what is true for most other assets, Bitcoin never really crashes all the way. Why? Because every time a hype cycle occurs, some more people learn about Bitcoin’s fundamentals and manage to resist the urge to sell, even when almost all hope seems lost. They understand that these bull markets are a reoccurring thing due to the nature of the protocol. These cycles create new waves of evangelists who start promoting Bitcoin simply because of what they stand to gain from a price increase. In a sense, the protocol itself pays for its own promotion in this way. This organic marketing creates a lot of noise and confusion, too, as a lot of people who don’t seem to understand how Bitcoin works are often very outspoken about it despite their lack of knowledge. Red herrings, such as altcoins and Bitcoin forks, are then weeded out naturally during bear markets. Every time a bull market happens, a new generation of Bitcoiners is born.
The four-year period between halvings seems to serve a deliberate purpose. Satoshi could just as well have programmed a smooth issuance curve into the Bitcoin protocol, but he didn’t. As events unfold, it seems that he had good reason for this since these hype cycles provide a very effective onboarding mechanism, and they seem to be linked to the halvings. They certainly make Bitcoin volatile, but remember that in this early stage, the volatility is needed in order for these hype cycles to happen. Later on, when Bitcoin’s stock-to-flow ratio is higher, the seas will calm, and its volatility level will go down. In truth, it already has. The latest almost 80% price drop was far from the worst we’ve seen in Bitcoin. This technology is still in its infancy, and it is very likely that we’ll see a lot more volatility before mainstream adoption, or hyperbitcoinization, truly happens.
About the Bitcoin Infinity Academy
The Bitcoin Infinity Academy is an educational project built around Knut Svanholm’s books about Bitcoin and Austrian Economics. Each week, a whole chapter from one of the books is released for free on Highlighter, accompanied by a video in which Knut and Luke de Wolf discuss that chapter’s ideas. You can join the discussions by signing up for one of the courses on our Geyser page. Signed books, monthly calls, and lots of other benefits are also available.
-
 @ bf95e1a4:ebdcc848
2025-04-11 11:18:42
@ bf95e1a4:ebdcc848
2025-04-11 11:18:42This is a part of the Bitcoin Infinity Academy course on Knut Svanholm's book Bitcoin: Sovereignty Through Mathematics. For more information, check out our Geyser page!
An Immaculate Conception
Some concepts in nature are harder for us humans to understand than others. How complex things can emerge out of simpler ones is one of those concepts. A termite colony, for instance, has a complex cooling system at its lower levels. No single termite knows how it works. Completely unaware of the end results, they build complex mounds and nests, shelter tubes to protect their paths, and networks of subterranean tunnels to connect their dirt cities. Everything seems organized and designed, but it is not. Evolution has equipped the termite with a pheromone receptor that tells the termite what task he ought to engage himself in by simply counting the number of neighboring termites doing the same thing. If there’s a surplus of workers in an area, nearby termites become warriors, and so on. Complex structures emerge from simple rules. The fractal patterns found all around nature are another example. Fractals look complex, but in reality, they’re not. They’re basically algorithms — the same pattern, repeated over and over again with a slightly modified starting point. The human brain is an excellent example of a complex thing that evolved out of simpler things, and we humans still have a hard time accepting that it wasn’t designed. Religions, which themselves are emergent systems spawned out of human interaction, have come up with a plethora of explanations for how we came to be. All sorts of wild origin stories have been more widely accepted than the simple explanation that our complexities just emerged out of simpler things following a set of rules that nature itself provided our world with.
Complex systems emerge out of human interactions all the time. The phone in your pocket is the result of a century of mostly free global market competition, and no single human could ever have come up with the entire thing. The device, together with its internet connection, is capable of a lot more than the sum of its individual parts. A pocket-sized gadget that can grant instant access to almost all of the world’s literature, music, and film, which fits in your pocket, was an unthinkable science fiction a mere twenty years ago. Bitcoin, first described in Satoshi Nakamoto’s whitepaper ten years before these words were written, was designed to be decentralized. Still, it wasn’t until years later that the network started to show actual proof of this. Sound money, or absolute digital scarcity, emerged out of the network not only because of its technical design. How Bitcoin’s first ten years actually unfolded played a huge part in how true decentralization could emerge, and this is also the main reason why the experiment cannot be replicated. Scarcity on the internet could only be invented once. Satoshi’s disappearance was Bitcoin’s first step towards true decentralization. No marketing whatsoever and the randomness of who hopped onto the train first were the steps that followed. Bitcoin truly had an immaculate conception.
The network has shown a remarkable resistance to change over the last few years especially, and its current state might be its last incarnation given the size of the network and the 95% agreement threshold in its consensus rules. It might never change again. In that case, an entirely new, complex life form will have emerged out of a simple set of rules. Even if small upgrades are implemented in the future, the 21 million coin supply cap is set in stone forever. Bitcoin is not for humans to have opinions about — it exists regardless of what anyone thinks about it, and it ought to be studied rather than discussed. We don’t know what true scarcity and a truly global, anonymous free market will do to our species yet, but we are about to find out. It is naïve to think otherwise. Various futurists and doomsday prophets have been focused on the dangers of the impending general artificial intelligence singularity lately, warning us about the point of no return, whereupon an artificial intelligence will be able to improve itself faster than any human could. Such a scenario could, as news anchor Ron Burgundy would have put it, escalate quickly. This may or may not be of real concern to us, but meanwhile, right under our noses, another type of unstoppable digital life has emerged, and it is already changing the behavior and preferences of millions of people around the globe. This is probably bad news for big corporations and governments but good news for the little guy looking for a little freedom. At least, that’s what those of us who lean towards the ideas of the Austrian school of economics believe. This time around, we will find out whether this is the case or not. No one knows what it will lead to and what new truths will emerge out of this new reality.
Unlike the termite, we humans are able to experience the grandeur of our progress. We can look in awe at the Sistine Chapel or the pyramids, and we can delve into the technicalities and brief history of Bitcoin and discover new ways of thinking about value along the way. Money is the language in which we express value to each other through space and time. Now, that language is spoken by computers. Value expressed in this language can’t be diluted through inflation or counterfeiting any longer. It is a language that is borderless, permissionless, peer-to-peer, anonymous (if you have the skills), unreplicable, completely scarce, non-dilutable, unchangeable, untouchable, undeniable, fungible, and free for everyone on Earth to use. It is a language for the future and it emerged out of a specific set of events in the past. All languages are examples of complex systems emerging out of simpler things, and Bitcoin evolved just as organically as any other human language did.
Decentralization is hard to achieve. Really hard. When it comes to claims of decentralization, a “don’t trust, verify” approach to the validity of such claims will help you filter out the noise. So, how can the validity of Bitcoin’s decentralization be verified? It’s a tricky question because decentralization is not a binary thing, like life or death, but rather a very difficult concept to define. However, the most fundamental concepts in Bitcoin, like the 21 million cap on coin issuance or the ten-minute block interval as a result of the difficulty adjustment and the Proof of Work algorithm, have not changed since very early on in the history of the network. This lack of change, which is arguably Bitcoin’s biggest strength, has been achieved through the consensus rules, which define what the blockchain is. Some special mechanisms (for example, BIP9) are sometimes used to deploy changes to the consensus rules. These mechanisms use a threshold when counting blocks that signal for a certain upgrade. For example, the upgrade “Segregated Witness” activated in a node when 95% or more of the blocks in a retarget period signaled support. Bitcoin has displayed a remarkable immutability through the years, and it is highly unlikely that this would have been the case if the game-theoretical mechanisms that enable its decentralized governance model hadn’t worked, given the many incentives to cheat that always seem to corrupt monetary systems. In other words, the longer the system seems to be working, the higher the likelihood that it actually does.
Satoshi set in stone the length of the halving period — a very important aspect of Bitcoin’s issuance schedule and initial distribution. During the first four years of Bitcoin’s existence, fifty new coins were issued every ten minutes up until the first block reward halving four years later. Every four years, this reward is halved so that the issuance rate goes down by fifty percent. This effectively means that half of all the Bitcoin that will ever exist was mined during the first four years of the network’s life, one fourth during its next four years, and so on. At the time of writing, we’re a little more than a year from the third halving. After that, only 6.25 Bitcoin will be minted every ten minutes as opposed to 50, which was the initial rate. What this seems to do is to create hype cycles for Bitcoin’s adoption. Every time the price of Bitcoin booms and then busts down to a level above where it started, a hype cycle takes place. Bitcoin had no marketing whatsoever, so awareness of it had to be spread through some other mechanism. When a bull run begins, people start talking about it, which leads to even more people buying due to fear of missing out (FOMO), which inevitably causes the price to rise even more rapidly. This leads to more FOMO, and on and on the bull market goes until it suddenly ends, and the price crashes down to somewhere around, or slightly above, the level it was at before the bull run started. Unlike what is true for most other assets, Bitcoin never really crashes all the way. Why? Because every time a hype cycle occurs, some more people learn about Bitcoin’s fundamentals and manage to resist the urge to sell, even when almost all hope seems lost. They understand that these bull markets are a reoccurring thing due to the nature of the protocol. These cycles create new waves of evangelists who start promoting Bitcoin simply because of what they stand to gain from a price increase. In a sense, the protocol itself pays for its own promotion in this way. This organic marketing creates a lot of noise and confusion, too, as a lot of people who don’t seem to understand how Bitcoin works are often very outspoken about it despite their lack of knowledge. Red herrings, such as altcoins and Bitcoin forks, are then weeded out naturally during bear markets. Every time a bull market happens, a new generation of Bitcoiners is born.
The four-year period between halvings seems to serve a deliberate purpose. Satoshi could just as well have programmed a smooth issuance curve into the Bitcoin protocol, but he didn’t. As events unfold, it seems that he had good reason for this since these hype cycles provide a very effective onboarding mechanism, and they seem to be linked to the halvings. They certainly make Bitcoin volatile, but remember that in this early stage, the volatility is needed in order for these hype cycles to happen. Later on, when Bitcoin’s stock-to-flow ratio is higher, the seas will calm, and its volatility level will go down. In truth, it already has. The latest almost 80% price drop was far from the worst we’ve seen in Bitcoin. This technology is still in its infancy, and it is very likely that we’ll see a lot more volatility before mainstream adoption, or hyperbitcoinization, truly happens.
About the Bitcoin Infinity Academy
The Bitcoin Infinity Academy is an educational project built around Knut Svanholm’s books about Bitcoin and Austrian Economics. Each week, a whole chapter from one of the books is released for free on Highlighter, accompanied by a video in which Knut and Luke de Wolf discuss that chapter’s ideas. You can join the discussions by signing up for one of the courses on our Geyser page. Signed books, monthly calls, and lots of other benefits are also available.
-
 @ fd06f542:8d6d54cd
2025-04-11 11:15:10
@ fd06f542:8d6d54cd
2025-04-11 11:15:10Warning
unrecommended: deprecated in favor of NIP-27NIP-08
Handling Mentions
finalunrecommendedoptionalThis document standardizes the treatment given by clients of inline mentions of other events and pubkeys inside the content of
text_notes.Clients that want to allow tagged mentions they MUST show an autocomplete component or something analogous to that whenever the user starts typing a special key (for example, "@") or presses some button to include a mention etc -- or these clients can come up with other ways to unambiguously differentiate between mentions and normal text.
Once a mention is identified, for example, the pubkey
27866e9d854c78ae625b867eefdfa9580434bc3e675be08d2acb526610d96fbe, the client MUST add that pubkey to the.tagswith the tagp, then replace its textual reference (inside.content) with the notation#[index]in which "index" is equal to the 0-based index of the related tag in the tags array.The same process applies for mentioning event IDs.
A client that receives a
text_noteevent with such#[index]mentions in its.contentCAN do a search-and-replace using the actual contents from the.tagsarray with the actual pubkey or event ID that is mentioned, doing any desired context augmentation (for example, linking to the pubkey or showing a preview of the mentioned event contents) it wants in the process.Where
#[index]has anindexthat is outside the range of the tags array or points to a tag that is not aneorptag or a tag otherwise declared to support this notation, the client MUST NOT perform such replacement or augmentation, but instead display it as normal text. -
 @ fd06f542:8d6d54cd
2025-04-11 11:14:36
@ fd06f542:8d6d54cd
2025-04-11 11:14:36- 第三章、NIP-03: OpenTimestamps Attestations for Events
- 第四章、NIP-04: Encrypted Direct Message
- 第五章、NIP-05: Mapping Nostr keys to DNS-based internet identifiers
- 第六章、NIP-06: Basic key derivation from mnemonic seed phrase
- 第七章、NIP-07: window.nostr capability for web browsers
- 第八章、NIP-08: Handling Mentions --- unrecommended: deprecated in favor of NIP-27
-
 @ 7d33ba57:1b82db35
2025-04-11 10:08:21
@ 7d33ba57:1b82db35
2025-04-11 10:08:21Rome isn’t just a city—it’s a living, breathing museum where ancient ruins, baroque fountains, and buzzing piazzas come together in beautiful, chaotic harmony. Every cobblestone has a story, every espresso has a punch, and every sunset behind the Colosseum feels like a scene from a movie. Whether it's your first visit or your fifth, Rome never gets old.
🏛️ Top Things to See & Do in Rome
1️⃣ The Colosseum & Roman Forum
- Step inside the iconic arena of gladiators
- Wander through the ruins of the Forum, once the heart of ancient Rome
- Don’t miss Palatine Hill for views over it all
2️⃣ Vatican City
- Home to St. Peter’s Basilica, the Sistine Chapel, and the Vatican Museums
- Climb to the top of the basilica dome for one of the best panoramas in Rome
- Book tickets ahead—it gets packed!
3️⃣ Trevi Fountain
- Toss in a coin to ensure your return to Rome 💧
- Visit early in the morning or late at night to beat the crowds and get that perfect photo
4️⃣ Pantheon
- One of the best-preserved Roman temples—free to enter, awe guaranteed
- Look up: the open oculus in the dome is engineering genius
- Step outside for a coffee in Piazza della Rotonda
5️⃣ Piazza Navona & Campo de’ Fiori
- Piazza Navona: Elegant fountains, artists, street performers
- Campo de’ Fiori: Bustling morning market and lively nightlife
- Great spots to grab an aperitivo or soak up atmosphere
🍕 What to Eat in Rome
- Cacio e Pepe – Pasta with pecorino and black pepper—simple, bold, and pure Rome
- Carbonara – No cream! Just egg, cheese, guanciale, and pepper
- Supplì – Deep-fried rice balls with melted mozzarella inside
- Roman-style pizza – Thin and crispy, often sold by weight
- Gelato – Try real artisan shops like Gelateria del Teatro or Otaleg
🌇 Bonus Rome Moments
- Watch sunset from Pincian Hill or Gianicolo Terrace
- Stroll across the Tiber River to the charming Trastevere neighborhood
- Visit the Jewish Ghetto for history, architecture, and amazing food (hello, fried artichokes!)
- Wander without a map—Rome loves surprising you
🛵 Tips for Visiting
✅ Wear comfy shoes—Rome’s cobbles are beautiful, but brutal on feet
✅ Book major attractions in advance to skip lines
✅ Tap water is fresh—refill from Rome’s historic fountains (nasoni)
✅ Don’t rush—Rome is best enjoyed slowly, with a gelato in hand -
 @ f57bac88:6045161e
2025-04-11 08:00:16
@ f57bac88:6045161e
2025-04-11 08:00:16مقدمه\ کتاب پول درهمشکسته نوشته لین الدن، یکی از برجستهترین آثار در زمینه اقتصاد و فناوری مالی است که در تابستان ۱۴۰۲ (۲۰۲۳ میلادی) منتشر شد. این کتاب با نگاهی عمیق به ریشههای پول، کاستیهای نظام مالی کنونی و ظرفیتهای فناوریهای نوین مانند بیتکوین، خوانندگان را به سفری فکری دعوت میکند. الدن با زبانی روان و دیدگاهی چندجانبه، پیچیدگیهای پول را به شکلی ساده اما پرمغز توضیح میدهد و به ما کمک میکند تا درک بهتری از چیستی پول، نقش آن در زندگی و آیندهاش به دست آوریم. این اثر ۵۳۸ صفحهای، با ساختاری جامع، گذشته، حال و آینده پول را در شش بخش اصلی بررسی میکند.
بخش اول: گذشته پول – از دفترهای قدیمی تا بانکداری نوین\ الدن داستان تکامل پول را در دو بخش ابتدایی کتاب روایت میکند. او پول را بهعنوان یک «دفتر حسابداری» معرفی میکند که از ابتدا برای ثبت بدهیها و طلبها در جوامع به کار میرفت. بخش اول به بررسی پولهای کالایی مانند صدف و فلزات گرانبها و ویژگیهای ایدهآل پول میپردازد. بخش دوم به ظهور خدمات بانکی اولیه و بانکداری گسترده اختصاص دارد و نشان میدهد که چگونه فناوریهایی مانند تلگراف در قرن نوزدهم تراکنشها را سریعتر کردند. اما این پیشرفتها، به گفته الدن، با متمرکز شدن کنترل پول در دست بانکهای مرکزی، اغلب به زیان مردم عادی تمام شدند و شکاف طبقاتی را عمیقتر کردند.
بخش دوم: حال پول – چرا سیستم مالی کنونی شکسته است؟\ در دو بخش بعدی، الدن به نقد نظام مالی کنونی میپردازد که بر پایه پول بیپشتوانه (فیات) بنا شده است. او استدلال میکند که این سیستم با مشکلاتی مانند تورم مداوم، نابرابری اقتصادی و سلطه بیشازحد نهادهای مالی دستبهگریبان است. بخش سوم به نظام مالی جهانی از اوایل قرن بیستم، از جمله نظام برتون وودز، میپردازد. بخش چهارم خلق پول مدرن و تأثیرات بدهیهای بیثباتکننده را تحلیل میکند. الدن معتقد است که پول بیپشتوانه بهگونهای طراحی شده که ارزش آن بهمرور کاهش مییابد و ثروت را از جیب مردم عادی بهسوی بانکها و شرکتهای بزرگ هدایت میکند. او با مثالهایی واقعی، مانند بحران اقتصادی لبنان در سال ۱۴۰۱ (۲۰۲۲) یا تورم افسارگسیخته در کشورهایی مانند ترکیه، آرژانتین و ایران، نشان میدهد که این مشکلات چگونه زندگی میلیونها نفر را تحت تأثیر قرار دادهاند.
بخش سوم: آینده پول – نقش نوآوریهای دیجیتال\ در دو بخش پایانی، الدن به بررسی فناوریهای نوین مالی، بهویژه بیتکوین و بلاکچین، میپردازد. بخش پنجم به نوآوریهای دیجیتال قرن بیستویکم، مانند بیتکوین، اختصاص دارد که الدن آن را یک دفتر حسابداری غیرمتمرکز میبیند. این فناوری میتواند قدرت را از نهادهای مرکزی خارج کرده و به افراد بازگرداند. بخش ششم به اخلاقیات پول و نقش رمزنگاری در شبکههای مالی میپردازد و آیندهای را تصور میکند که در آن افراد کنترل بیشتری بر داراییهای خود دارند. بااینحال، الدن به چالشهای بیتکوین، مانند نوسانات شدید قیمت، مصرف بالای انرژی و مشکلات مقیاسپذیری، نیز اشاره میکند. او همچنین به نمونههایی از استفاده بیتکوین در کشورهای درحالتوسعه، مانند السالوادور، اشاره دارد که این ارز بهعنوان ابزاری برای دور زدن محدودیتهای مالی به کار گرفته شده است.
نقاط قوت کتاب\ ۱. سادگی در عین عمق: الدن مفاهیم پیچیدهای مانند تورم، نظام بانکی و بلاکچین را با زبانی قابلفهم برای همگان توضیح میدهد، بدون آنکه از دقت علمی کاسته شود.\ ۲. دیدگاه چندرشتهای: او با ترکیب دانش مهندسی و تحلیل مالی، پول را بهعنوان یک فناوری بررسی میکند که با پیشرفتهای بشری تکامل مییابد.\ ۳. تمرکز بر انسانها: کتاب تنها به آمار و ارقام بسنده نمیکند؛ الدن نشان میدهد که نقصهای نظام مالی چگونه زندگی واقعی مردم را تحت تأثیر قرار داده است.\ ۴. بیطرفی نسبی: اگرچه الدن از طرفداران بیتکوین است، تلاش میکند با بررسی جنبههای مثبت و منفی هر سیستم، از یکجانبهگرایی پرهیز کند.
نقاط ضعف کتاب\ ۱. تمرکز بیشازحد بر بیتکوین: برخی معتقدند که الدن بیشازحد به بیتکوین خوشبین است و به دیگر فناوریهای مالی نوین، مانند اتریوم یا استیبلکوینها، کمتر پرداخته است.\ ۲. پیچیدگی برای تازهکارها: هرچند کتاب برای مخاطب عام نوشته شده، برخی بخشها ممکن است برای افرادی که هیچ آشنایی با اقتصاد یا ارزهای دیجیتال ندارند، دشوار باشد.\ ۳. کمبود راهحلهای عملی: الدن در شناسایی مشکلات موفق است، اما راهحلهای پیشنهادی او گاهی کلی و غیرملموس به نظر میرسند.
چرا این کتاب را بخوانیم؟\ پول درهمشکسته برای هرکسی که میخواهد بداند پول چیست، چرا ارزشش تغییر میکند و آیندهاش چه خواهد شد، یک راهنمای بینظیر است. این کتاب به ما کمک میکند تا به چیزهایی که بدیهی میپنداریم—مانند اسکناسی که هر روز خرج میکنیم—عمیقتر نگاه کنیم. برای خوانندگان ایرانی، که سالهاست با تورم، کاهش ارزش پول ملی و تحریمهای مالی دستوپنجه نرم میکنند، این کتاب پاسخهایی روشنگر به سؤالهایی مانند «چرا پول ما بیارزش میشود؟» یا «آیا راهی برای محافظت از داراییها وجود دارد؟» ارائه میدهد. ساختار ششبخشی کتاب، با پوشش جامع گذشته، حال و آینده، خواننده را به درک کاملی از پول و قدرت آن هدایت میکند.
جمعبندی\ پول درهمشکسته بیش از یک کتاب اقتصادی است؛ دعوتی است به تأمل و تغییر. لین الدن با دانش، دقت و نگاهی انسانی، ما را به سفری از گذشته پول تا آیندهاش میبرد و نشان میدهد که چگونه میتوانیم با آگاهی و انتخابهای درست، بهسوی سیستمی عادلانهتر حرکت کنیم. این کتاب برای هرکسی که به اقتصاد، فناوری یا عدالت اجتماعی علاقهمند است، اثری ضروری و الهامبخش به شمار میرود.
منابع و دسترسی به ترجمه\ بخشهایی از این کتاب به فارسی ترجمه شده و از طریق کانالهای تلگرامی مانند «ترجمهی مقالههای بیتکوین» در دسترس است. برای یافتن ترجمه، میتوانید عبارت «پول درهمشکسته» یا نام نویسنده را در این کانال جستجو کنید. همچنین، پیشنهاد میشود برای ادامه این مسیر و فرهنگ از مترجم و مدیر کانال ترجمه مقالات حمایت مالی کنید
-
 @ 34ff86e0:dbb6b9fb
2025-04-11 03:51:31
@ 34ff86e0:dbb6b9fb
2025-04-11 03:51:31test description 2 lang arabic
-
 @ 872982aa:8fb54cfe
2025-04-11 03:30:48
@ 872982aa:8fb54cfe
2025-04-11 03:30:48{"coverurl":"https://cdn.nostrcheck.me/872982aa37b864973a389d465bc6ed5045a78586496d104e05f39b8d8fb54cfe/e6d4161955877a472f69b7ed27230e8677da2a3f3fb8ae0b472816852111cb38.webp","title":"设计艺术和配色","author":"彩色盒子"}
-
 @ 872982aa:8fb54cfe
2025-04-11 03:20:33
@ 872982aa:8fb54cfe
2025-04-11 03:20:33{"coverurl":"https://cdn.nostrcheck.me/872982aa37b864973a389d465bc6ed5045a78586496d104e05f39b8d8fb54cfe/2d173d2aabda99d75f054da0ac0bf04e67c58b09af84ae0765dcf904516da75d.webp","title":"Nostr protocol4","author":"fiatjaf"}
-
 @ 872982aa:8fb54cfe
2025-04-11 02:37:15
@ 872982aa:8fb54cfe
2025-04-11 02:37:15{"coverurl":"https://cdn.nostrcheck.me/872982aa37b864973a389d465bc6ed5045a78586496d104e05f39b8d8fb54cfe/1c39bd6f09aca6e9f20f7399809a547950069d06a68b78f565fbfab4b14ec93c.webp","title":"竹林的声音2","author":"花花的作者"}
-
 @ 9a1adc34:9a9d705b
2025-04-11 01:59:19
@ 9a1adc34:9a9d705b
2025-04-11 01:59:19Testing the concept of using Nostr as a personal CMS.
-
 @ a7f85dfe:27305a2b
2025-04-11 00:41:45
@ a7f85dfe:27305a2b
2025-04-11 00:41:45 -
 @ a7f85dfe:27305a2b
2025-04-11 00:38:51
@ a7f85dfe:27305a2b
2025-04-11 00:38:511.更改bios,usb启动
根据自己电脑的要求进入bios,选择优先usb启动。
2.安装系统
傻瓜式,安装proxmox。网络设置部分,建议直接插线联网,系统会根据现有网络分配IP网关信息,方便服务器开始运行时可其他电脑可以通过IP地址访问。
3.挂载硬盘
安装成功后,通过其他电脑访问服务器IP,进入图形管理界面。可以看到这时将系统盘分为local 跟local-lvm。其他硬盘得先挂载才能进行pve管理。
1.列出可用硬盘及目录地址,如果硬盘有多个分区,需要删除分区的话
fdisk -lfdisk /dev/sda #你硬盘的地址 m #查看文档 d # 列出分区号码,选择删除的分区 n #创建分区 p #创建主分区 w #写入分区2. 格式化分区系统mkfs -t ext4 /dev/sda1- 挂载硬盘
mkdir /mnt/data mount -t ext4 /dev/sda1 /mnt/data
4.开机自动挂载
lsblk #查看硬盘和分区sudo blkid # 查看硬盘的uuidsudo vi /etc/fstab #打开fstab文件添加如下一行UUID=你的硬盘ID /mnt/data ext4 defaults 0 2测试挂载sudo mount -a #如果没有显示错误信息就是挂载正确 - 挂载硬盘
-
 @ 378562cd:a6fc6773
2025-04-11 00:02:38
@ 378562cd:a6fc6773
2025-04-11 00:02:38What Happens When You Wean Your Digital Life Way Back?
We’re swimming in screens. Notifications, news, and endless feeds are all designed to keep us plugged in, distracted, and running on digital fumes. But what happens when you stop feeding the machine?
What happens when you step back, shut it off, and just… live?
You might be amazed.
Step One: Wean Way Down
Start simple. No grand declarations, but just a quiet rebellion.
Fewer apps. Fewer tabs. Less time online. Maybe you only use the computer in the mornings. Maybe you can turn your phone off in the evening. Maybe Sunday will become a screen-free Sabbath.
The goal? Clear. Clean. Quiet.
At first, it might feel weird. Like quitting sugar or coffee, you’ll feel the pull. But then? Something shifts.
What Starts to Happen… 1. Your Mind Clears Up You stop bouncing from thought to thought. You breathe. You remember what it feels like to think deeply, uninterrupted. Your brain stops buffering and starts building again.
-
Time Slows Down You realize how much time was slipping through your fingers. Without the digital drag, you suddenly have space. You get stuff done. You notice the birds. You fix the fence. You write a letter. You rest. I've personally done these things. It IS AMAZING!
-
You Hear God More Clearly When the digital static dies down, the whisper of God gets louder. Scripture comes alive again. Prayer feels less like a chore and more like a lifeline. You hear Him in the quiet—and sometimes, even in yourself.
-
People Come Back into Focus You stop skimming people like headlines. You sit down, look up, listen, and be present. You find yourself reaching out more, talking longer, and remembering what a real connection feels like.
-
You Feel Alive Again You get energy back, your hands get busy with real work, your body moves, and your sleep deepens. You feel stronger, clearer, and more grounded like your soul has room to breathe again.
It’s Not About Losing—It’s About Gaining Less screen time isn’t about guilt or rules. It’s about freedom. It’s about trading mindless digital noise for something deeper, like clarity, creativity, peace, and presence.
Will you miss some stuff? Sure. But what you’ll gain is real life. Good life.
Try it. Wean way down. Scale Back! Watch what happens.
-
-
 @ 000002de:c05780a7
2025-04-10 22:22:41
@ 000002de:c05780a7
2025-04-10 22:22:41From time to time I will listen to a podcast called "The Dangerous History Podcast" and in the most recent episode he plays some "music" from the WW1 propaganda machine. Its wild how on the nose it is. I think people forget how in your face propaganda was in the past. Its more subtle today and people sometimes act as if news, media and entertainment were once reliable sources of information. When I hear people complaining about bias or propaganda in media today I usually push back and say, its better than it was in the past. At least now we have more choice as well as tools to check things for ourselves.
Don't forget, the state has always been about manipulating you. Sure, it changes its tactics but there really isn't some golden era where this wasn't happening. They have just become more sophisticated as the people get more keen on the old tactics.
originally posted at https://stacker.news/items/940221
-
 @ 88cc134b:5ae99079
2025-04-10 15:57:14
@ 88cc134b:5ae99079
2025-04-10 15:57:14article
-
 @ f1989a96:bcaaf2c1
2025-04-10 14:25:09
@ f1989a96:bcaaf2c1
2025-04-10 14:25:09Good morning, readers!
Today, HRF takes part in the launch of the Bitcoin Humanitarian Alliance in London, where a dozen human rights and aid groups will convene with policymakers, media, finance professionals, and technologists at the Frontline Club to explain how they are using Bitcoin in their work in the field.
Elsewhere, we bring news from Turkey, where large, pro-democracy protests erupted over President Recep Tayyip Erdogan’s increasing political repression and economic fallout. The Turkish regime has detained more than 2,000 protesters (and counting) as youth appear in droves demanding democracy, accountability, and economic reform.
In Eastern Africa, Tanzania’s government extended immense restrictions on foreign currency, effectively barring its use in day-to-day payments outside a few circumstances. In a poverty-stricken country where fuel prices have moved forcibly upward for two consecutive months, access to and usage of alternative currencies can be a financial lifeline.
In Bitcoin news, we spotlight Misty Breez, a new open-source Bitcoin wallet built by Lightning Network infrastructure company Breez. The wallet is a Lightning and Liquid Network hybrid wallet. It gives users control over their funds and abstracts away any complexities of payment channel management, but users must trust the Liquid Federation. In terms of functionality, Misty Breez supports a wide variety of address types, offering users flexibility across the fees, privacy, and censorship resistance of their payments. It may prove a helpful tool for dissidents and activists standing against tyranny.
We end with the latest edition of the HRF x Pubkey Freedom Tech Series, where HRF’s Ayelen Osorio joins Zimbabwean pastor-turned-activist Evan Mawarire, who recounts his inspiring journey of a peaceful uprising against Robert Mugabe’s dictatorship and the hyperinflation and repression he unleashed on the population. We also feature the live streams of the 2025 MIT Bitcoin Expo in collaboration with HRF. These videos highlight the speakers, panels, and activities led by HRF to raise awareness about financial repression and the tools being built to resist it.
Now, let’s jump right in!
SUBSCRIBE HERE
GLOBAL NEWS
Turkey | Government Detains Thousands of Pro-Democracy Protesters
The largest protests in over a decade erupted in Istanbul, Turkey, after President Recep Tayyip Erdoğan detained political opposition figure and Istanbul Mayor Ekrem Imamoglu. Turks of all walks of life find themselves united by common outrage at the regime’s ongoing political repression and tumultuous economic conditions. With inflation soaring above 39% and widespread unemployment among the nation’s youth, it’s no surprise Turks are flooding the streets and demanding change. In response to these demonstrations, law enforcement has since detained more than 2,000 demonstrators, and police blockades have met student protesters with water cannon trucks to suppress their dissent. Many young Turks feel their future is slipping away in a country where saving is futile, the currency is collapsing, and speaking out comes at a high personal cost. “This feels like our last chance,” one young protester said, adding, “If we don’t succeed, many of us will have to leave Turkey.”
Tanzania | Regime Enacts Restrictions on Foreign Currency
Tanzania’s regime is banning the use of foreign currency outside of a few circumstances (such as duty-free retailers and government membership fees). This means quoting prices in, accepting, or facilitating payments with foreign currency is now illegal, alongside declining to accept the official Tanzanian shilling (TZS). Losing the ability to transact with more stable currencies removes individuals’ ability to shield themselves from inflation and subjects them to local currency volatility. The mandate comes in addition to the Energy and Water Utilities Regulatory Authority raising the cost of fuel for a second consecutive month. Locals worry this could further increase the cost of living as the fuel price hike ripples through the economy. These policies mirror the tactics of authoritarians using financial control to limit dissent and restrict individual financial freedom.
China | Incorporates e-CNY CBDC into Financial Sector Guidelines
China is incorporating the e-CNY central bank digital currency (CBDC) into financial sector guidelines for the first time, signaling a strengthening commitment to fully roll out its CBDC. The e-CNY’s usage is reportedly expanding among Chinese citizens, with the Chinese Communist Party (CCP) claiming 800 million wallets and over 10.2 trillion CNY in transaction volume — though these numbers are both dubiously high and difficult to independently verify. As usage grows, so do concerns over financial and individual liberties. The CCP already uses the financial system to monitor and suppress dissent. For Uyghurs, a Muslim minority in the Uyghur Region grappling with ongoing cultural genocide, mass surveillance, and forced labor from the CCP, the e-CNY would allow the regime to restrict their financial autonomy and freedom completely. As it begins to roll out, it’s important to become aware of the dangers of the e-CNY here.
Burkina Faso | Arrests Three Journalists in Press Crackdown
Burkina Faso’s military junta arrested three journalists for reporting on regime-imposed press restrictions. Since seizing power in 2022, the military junta, under the leadership of Ibrahim Traoré, has targeted independent media by detaining reporters, forcing critics into exile, abusing emergency laws to suppress dissent, and using financial repression to disrupt independent funding. Journalists disappear under the guise of forced conscription, international coverage of military abuses is blocked, and outlets that report on crimes against humanity are eradicated. With press freedom in ashes, Burkinabés face an information blackout where state propaganda proliferates. In these contexts, open and uncensorable protocols like nostr can serve as a digital town square where information, value, and assembly flow undisturbed by the reach of oppressive regimes.
Tunisia | Saied Sacks Prime Minister as Economy Crumbles
Tunisian President Kais Saied dismissed Prime Minister Kamel Maddouri less than a year into his term and replaced him with Sara Zaafarani, Tunisia’s third prime minister in under two years. As Saied reshuffles his cabinet to best suit his interests and goals, Tunisia’s economy has reached a standstill. Growth is running below 1.5%, the cost of living continues to climb, and shortages of staple goods like rice, sugar, and coffee burden the everyday lives of Tunisians. After staging a coup, dissolving the government, and ruling by decree, Saied’s consolidation of power has come inch by inch with the erosion of democracy and financial stability.
BITCOIN AND FREEDOM TECH NEWS
Breez | Releases New Open-Source Bitcoin Wallet
Breez, a company helping build out the Bitcoin Lightning economy, released a new open-source Bitcoin wallet called “Misty Breez.” It is a hybrid Lightning and Liquid Network wallet built using the Nodeless Breez SDK. The wallet offers fast and private transactions without the complexities of payment channel management. The tradeoff? Trusting the Liquid Federation with custody of your Bitcoin. Still, Misty Breez supports many Bitcoin and Lightning features, including on-chain payments, Lightning addresses, BOLT 12 invoices, and offline receiving. So, while the wallet is a trust-minimized solution rather than fully custodial, users gain a wide range of use cases and features unique to this wallet. This could make Misty Breez useful for people facing financial surveillance, internet outages, or authoritarian-imposed financial restrictions. Learn more about the wallet here.
OpenCash | Bounty for Open Source Cashu x BTCPay Server Plugin
The OpenCash Association is offering a two million satoshi bounty for an open-source plugin allowing merchants to accept Cashu payments through BTCPay Server. Cashu is a Bitcoin-based ecash protocol designed to offer fast, low-cost, and very private transactions. For activists and dissidents, ecash enables payments without compromising financial privacy, but they must trust the mints (entities managing the system) to custody their funds. OpenCash specified that the Cashu plugin must integrate cleanly with BTCPay Server and include an input field for ecash redemption or a scannable Cashu payment request. If claimed, this bounty and subsequent integration will help advance Bitcoin’s medium of exchange capabilities and make private payments more accessible by integrating with self-hosted, independent Bitcoin payment infrastructure. Learn more about the bounty here.
Machankura | Adds Support for Offline Bitcoin Transactions in Uganda
Machankura, a custodial Bitcoin Lightning wallet that helps Africans access Bitcoin without the Internet, announced they expanded service to Uganda, enabling Ugandans to use Bitcoin without an Internet connection. To do so, Machankura leverages the Unstructured Supplementary Service Data (USSD) protocol for sending text messages. To use the service, users simply dial a designated number on a feature phone (or a smartphone without data) and can access the Bitcoin network in countries like Nigeria, Malawi, Zambia, and now Uganda. Machankura helps democratize Bitcoin access, expands censorship-resistant money across Africa, and offers a practical solution to financial inclusion. If you’re in Uganda or another supported country, try it here.
Zeus Wallet | Plans to Introduce Cashu Support
Zeus, a leading self-custodial mobile Lightning wallet, shared plans for a future Cashu integration. Cashu is an ecash protocol for Bitcoin. It enables practical everyday payments on Bitcoin that are private by design (but users must trust mints to manage their funds). By adding ecash support, Zeus can expand the accessibility of private Bitcoin payments and provide its users with greater flexibility over their financial activity. As part of its upcoming release, the wallet also introduces two new types of addresses: Zaplocker addresses for Lightning self-custody on mobile and Nostr Wallet Connect (NWC) addresses for remote node runners. While a little more technical, these integrations will improve individuals' ability to transact without exposing their financial history, reducing surveillance risks, especially for those living under authoritarian regimes or in jurisdictions with strict financial controls.
Bitcoin Thailand Festival | Half-Marathon to Challenge Financial Repression
The Thai city of Chiang Mai will host the nation’s inaugural Bitcoin Half Marathon and Bitcoin Thailand Festival from Nov. 1-2, 2025, under the theme “Run For Freedom.” The marathon’s theme contrasts Thailand’s increasing financial repression and long history of erasing dissent. Even still, the festival’s mission to advance financial freedom and financial literacy with participation from the local Bitcoin community comes at a pressing time. The Thai government is increasingly restricting financial freedoms through digital cash handouts, which, for all intents and purposes, function as a central bank digital currency that imposes spending restrictions and expiration dates on money. In these environments, Bitcoin education and awareness are more urgent than ever.
Btrust Builders | Announces Builders Pathways
Btrust Builders introduced Btrust Builders Pathways, a new program designed to equip African developers with the skills and experience needed to contribute to Bitcoin open-source software. The initiative offers five learning tracks, from beginner-friendly Bitcoin fundamentals to advanced Rust programming and Bitcoin Core development. Participants will gain hands-on experience, mentorship, and access to potential funding via Btrust Developer Grants. With this launch, Btrust Builders continues its mission to grow Africa’s Bitcoin development talent and strengthen the software’s ecosystem in a region where many suffer under dozens of authoritarian governments.
RECOMMENDED CONTENT
How Bitcoin Fights Corruption & Injustice with Evan Mawarire
In the latest edition of the HRF x Pubkey Freedom Tech Series, HRF’s Content & Research lead Ayelen Osorio sits down with Zimbabwean pastor-turned-activist Evan Mawarire to explore how Bitcoin can serve as a tool for fighting inflation, corruption, and injustice. Together, they unpack Mawarire’s personal journey of leading a peaceful uprising against the tyranny of Robert Mugabe and the hyperinflation he unleashed on his undeserving population. Mawarire details how Zimbabwe’s economic collapse became an orchestrated strategy to control and silence Zimbabweans. He further explains how the peaceful movement galvanized a generation, why financial repression is a central pillar of authoritarianism, and how Bitcoin offers ordinary citizens a way to resist and rebuild. Catch the full conversation here.
MIT Bitcoin Expo Livestream
Last week, software developers, human rights activists, students, and researchers gathered at the Massachusetts Institute of Technology (MIT) for the 12th annual MIT Bitcoin Expo — this year in partnership with HRF — to explore how Bitcoin and freedom technologies can defend civil liberties and empower individuals, especially under authoritarian regimes. Born from MIT’s 2014 Bitcoin Project, the expo has grown into a major forum for individual liberation, with panels, workshops, and hackathons centered on privacy, financial autonomy, and decentralized protocols. Tune into the livestream recording to catch the speakers, presentations, and panels that defined the event.
If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report here.
Support the newsletter by donating bitcoin to HRF’s Financial Freedom program via BTCPay.\ Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ hrf.org
The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals here.
-
 @ 7e538978:a5987ab6
2025-04-10 13:14:04
@ 7e538978:a5987ab6
2025-04-10 13:14:04After five years and over 6,000 commits, LNbits has reached a momentous milestone: Version 1.0.0 is here. LNbits is officially out of beta!
This release represents the five years relentless development, dedication, bug-hunting, feature-building, and community involvement. What started as a lightweight Lightning wallet application for Lightning Network payments has evolved into one of the most versatile, modular, and widely-used Bitcoin tools in the space.
We want to offer a heartfelt thank you to every contributor, developer, tester, and user—from those running LNbits for personal use to the communities and businesses who rely on it every day. Your feedback, bug reports, feature requests, and support have made LNbits what it is today.
🚀 Key Highlights in v1.0.0
- LNbits now at v1.0.0 – the software is stable, hardened, and production-ready.
- Vue 3 migration – a complete frontend overhaul for performance and long-term maintainability.
- WebSocket payments – faster and more efficient, replacing older SSE and long-polling methods.
- New lnbits.sh install script – simplifies setup and local deployment.
- Access Control Lists (ACL) – token-based permissions for powerful role and scope control.
- Admin tools:
- Admin payments overview
- Toggle outgoing payments
- View payments from deleted wallets
- NWC (Nostr Wallet Connect) support
- Login with Nostr or OAuth – expanding integration and authentication options
💱 Fiat & Exchange Upgrades
- Custom exchange providers
- Improved fiat precision
- Wallet-level fiat tracking and labels
- Support for Bitpay and Yadio fiat rate providers
🧑🎨 UI / UX Improvements New Login/Register interface
- Default theme for new users
- Custom background images
- Visual refresh with new themes (including neon and light/dark modes)
- Revamped Pay Invoice dialog and invoice creation
- Custom wallet icons/colours
- CSV export and in-wallet payment filtering
🛠️ Developer Tools & Internal Enhancements Migration to pyjwt, updated to breez-sdk 0.6.6, pyln-client 24.5
- Support for Python 3.10–3.13
- New nodemanager for managing Lightning channels
- Backend refactors, improved database handling, type hinting, and extension logic
- More robust testing and CI support
🩹 Maintenance & Fixes Persistent fix for admin removal bug
- Improved extension handling
- Bug fixes across wallet logic, funding sources, and legacy compatibility
- Dozens of improvements to reliability, performance, and developer experience
🎉 A Huge Thank You
To every developer, translator, tester, UX contributor, node runner, and user: thank you.
LNbits wouldn’t be what it is without your involvement. Whether you've written code, opened issues, translated labels, or simply used it and given feedback—this release is yours too.
Here's to the next chapter!
-
 @ 7d33ba57:1b82db35
2025-04-10 11:09:40
@ 7d33ba57:1b82db35
2025-04-10 11:09:40Tucked into Italy’s far northeastern corner, Trieste feels like a place where cultures meet and stories linger. With Austro-Hungarian architecture, Adriatic views, literary cafés, and a unique Central European flair, it’s Italy—but not quite like the Italy you know. Bordering Slovenia and once the seaport of an empire, Trieste is full of quiet charm and timeless elegance.
🌟 Top Things to Do in Trieste
1️⃣ Piazza Unità d’Italia
- One of Europe’s largest sea-facing squares
- Surrounded by grand buildings and open to the Adriatic—sunsets here are magical
- Great spot to sit at a café and people-watch
2️⃣ Castello di Miramare
- A fairy-tale white castle perched over the sea, built for Archduke Ferdinand Maximilian
- Explore the ornate interiors and stroll the surrounding park with sea views
- A short bus or bike ride from the city
3️⃣ Canal Grande & Borgo Teresiano
- A small Venetian-style canal lined with cafés, bridges, and boats
- At its end, you’ll find the neoclassical Sant’Antonio Nuovo church
- The area is perfect for evening walks and aperitivo
4️⃣ Caffè Culture & James Joyce Trail ☕📖
- Trieste has a legendary café scene—literary, elegant, and historic
- Visit Caffè San Marco or Caffè degli Specchi
- Follow the trail of James Joyce, who lived here for over a decade
5️⃣ Barcola Promenade
- A local favorite for seafront walks, swimming, and sunbathing
- Bring a towel, grab a gelato, and relax like a true Triestino
- Especially lively in summer
🏛️ Also Worth a Visit
- Teatro Romano – A well-preserved Roman theater right in the city center
- Castello di San Giusto & Cathedral – Hilltop views and Roman ruins nearby
- Risiera di San Sabba – A sobering WWII concentration camp memorial site
🍝 What to Eat in Trieste
- Jota – A hearty stew of sauerkraut, beans, and potatoes (Slavic roots!)
- Seafood everything – Fresh Adriatic catch, especially scampi and sardoni
- Strudel, goulash, and schnitzel – Trieste’s menu mixes Italian and Mitteleuropean
- Pair with local wines like Vitovska or a crisp Malvasia
🎯 Tips for Travelers
✅ Trieste is walkable and elegant—bring comfy shoes for those marble pavements
✅ Great base for day trips to Miramare Castle, Grotta Gigante, or even Ljubljana and Piran
✅ Try the osmize in the surrounding hills—rustic, family-run wine farms that open to the public
✅ Slovenian and Croatian borders are right nearby—Trieste is a crossroads city -
 @ 20986fb8:cdac21b3
2025-04-10 08:59:38
@ 20986fb8:cdac21b3
2025-04-10 08:59:38社交应用正迎来全新阶段:从传统的中心化平台迈向去中心化生态,用户对轻量级、智能化和隐私保护的应用需求与日俱增。在这一趋势下,Mini Apps 凭借其快速开发、灵活部署和去中心化的特性,正在成为社交应用的主流选择。加密货币支付的兴起进一步推动了这一趋势,其低成本、无国界和金融自由的优势,不仅大幅降低了交易门槛,还为 Mini Apps 的规模化发展注入了强劲动力。作为比特币生态 Nostr 协议上最受欢迎的去中心化社交支付客户端之一,YakiHonne 凭借卓越的用户体验和便捷的社交支付功能,覆盖全球 170 多个国家。如今,YakiHonne 即将推出可编程 Smart Widgets——一款支持 Mini Apps 的开发者组件。这款产品将重新定义用户在社交平台上的互动与消费方式,为链上应用生态和社交支付带来全新活力。
YakiHonne Smart Widgets:社交与消费的创新引擎
YakiHonne Smart Widgets 是一款融入社交动态的可编程微型应用,让用户在浏览内容时就能轻松完成链上支付、互动和操作。它不仅是一款工具,更是一个开放的去中心化应用市场,为用户和开发者带来无限创造力与灵活性。
Smart Widgets 提供三种简单易用的创建方式,满足不同用户的需求:
- 基础组件(Basic Widgets):任何用户都能通过直观编辑器快速创建,只需选择模板、输入内容,就能生成打赏、Mint 或投票等互动功能。用户在浏览动态时,点击按钮即可完成链上操作,体验快速、无需跳转。
- 动作组件(ActionWidgets):用户可通过嵌入应用链接快速创建,无需开发经验。普通用户点击动态中的按钮,就能直接在当前界面访问外部去中心化应用(如交易所),享受顺畅不中断的体验。
- 工具组件(Tool Widgets-Mini App):适合有开发能力的用户或开发者,通过 Smart Widgets SDK 打造功能更丰富的应用,支持复杂链上操作。用户在社交动态中即可完成数据查询、链上任务、游戏互动或即时支付,体验高度集成且流畅。
主要特性:
- 快速构建:开发者仅需数小时即可将创意变为现实,支持常用 Web 技术,打造接近原生应用的体验,无需繁琐的应用商店审核。
- 社交登录:用户无需账号密码即可进入 Mini Apps,直接使用 Nostr/YakiHonne 身份在动态中互动,流程简单,社交体验更紧密。
- 易于发现与留存:通过动态 feeds 一键发现新应用,内置裂变机制助力快速传播,Mini App 商店提供更多选择,用户可保存喜爱应用并通过通知随时回归。
- 即时互动与消费:Mini Apps 通过 YakiHonne 的社交支付功能基础设施实现无缝集成,用户无需离开动态即可完成支付、投票或游戏等操作。社交互动与链上行为自然融合,消费体验轻松融入每一次互动场景。
改变日常体验:Smart Widgets 的多场景应用
YakiHonne Smart Widgets 将社交互动与链上消费深度结合,为用户带来多样化的应用场景:
- 链上互动:用户在浏览动态时,可通过 Smart Widgets 参与链上投票或轻量游戏。例如,一键完成社区提案投票,或与好友挑战链上小游戏,互动即刻完成,无需跳转。
- 智能 Agent:用户可使用 Agent Widgets 自动创作并发布内容,例如生成个性化帖子或短视频,打造 AI 驱动的新型媒体体验。
- DAO 治理:基于aMACI创建匿名投票,结合 Agent 实现自主治理。用户直接在社交动态中参与 DAO 决策,推动去中心化社区发展。
- 社交支付:用户可通过动态发送即时支付或链上红包,例如分享一笔小额打赏,激发好友互动与消费转化。
- 订阅服务:支持内容创作者或应用的连续订阅,用户一键订阅喜爱的服务,享受无缝续费体验。
这些场景不仅提升了用户的参与感和便利性,还为创作者、开发者及社区提供了新的增长机会。
引领新趋势:Smart Widgets 的生态价值
YakiHonne Smart Widgets 的推出将为链上消费应用生态和社交支付带来深远影响。它为开发者提供了一个开放的舞台,任何人都可以通过 Widgets 快速部署创新应用,丰富 YakiHonne 的生态多样性。YakiHonne 的社交支付功能基础设施进一步为 Mini Apps 赋能,提供高效的支付支持,降低了开发者的支付集成成本,同时为用户带来安全、便捷的交易体验。这种支持不仅加速了 Mini Apps 的商业化进程,还推动了链上消费的规模化增长。
对于用户而言,Smart Widgets 将社交互动与消费行为融为一体,创造更具沉浸感和实用性的数字体验。对于内容创作者和社区,它则提供了一个低门槛的链上入口,助力其触达全球用户。这一产品不仅是对技术边界的探索,更是对未来去中心化生活方式的预演。YakiHonne 致力于通过 Smart Widgets 构建一个开放、活跃的社交与消费生态,让每一次互动都成为链上价值流动的起点。
立即体验:Smart Widgets 等你探索
YakiHonne 诚邀全球用户和开发者共同参与这一激动人心的旅程。开发者可申请加入 Smart Widgets SDK 测试计划,开发属于自己的 Mini Apps,与 YakiHonne 的全球用户群共享成果。用户则可关注 YakiHonne 官方渠道(X或下载YakiHonne iOS/Android),体验链上互动与社交支付的全新可能。
-
 @ 3b3a42d3:d192e325
2025-04-10 08:57:51
@ 3b3a42d3:d192e325
2025-04-10 08:57:51Atomic Signature Swaps (ASS) over Nostr is a protocol for atomically exchanging Schnorr signatures using Nostr events for orchestration. This new primitive enables multiple interesting applications like:
- Getting paid to publish specific Nostr events
- Issuing automatic payment receipts
- Contract signing in exchange for payment
- P2P asset exchanges
- Trading and enforcement of asset option contracts
- Payment in exchange for Nostr-based credentials or access tokens
- Exchanging GMs 🌞
It only requires that (i) the involved signatures be Schnorr signatures using the secp256k1 curve and that (ii) at least one of those signatures be accessible to both parties. These requirements are naturally met by Nostr events (published to relays), Taproot transactions (published to the mempool and later to the blockchain), and Cashu payments (using mints that support NUT-07, allowing any pair of these signatures to be swapped atomically.
How the Cryptographic Magic Works 🪄
This is a Schnorr signature
(Zₓ, s):s = z + H(Zₓ || P || m)⋅kIf you haven't seen it before, don't worry, neither did I until three weeks ago.
The signature scalar s is the the value a signer with private key
k(and public keyP = k⋅G) must calculate to prove his commitment over the messagemgiven a randomly generated noncez(Zₓis just the x-coordinate of the public pointZ = z⋅G).His a hash function (sha256 with the tag "BIP0340/challenge" when dealing with BIP340),||just means to concatenate andGis the generator point of the elliptic curve, used to derive public values from private ones.Now that you understand what this equation means, let's just rename
z = r + t. We can do that,zis just a randomly generated number that can be represented as the sum of two other numbers. It also follows thatz⋅G = r⋅G + t⋅G ⇔ Z = R + T. Putting it all back into the definition of a Schnorr signature we get:s = (r + t) + H((R + T)ₓ || P || m)⋅kWhich is the same as:
s = sₐ + twheresₐ = r + H((R + T)ₓ || P || m)⋅ksₐis what we call the adaptor signature scalar) and t is the secret.((R + T)ₓ, sₐ)is an incomplete signature that just becomes valid by add the secret t to thesₐ:s = sₐ + tWhat is also important for our purposes is that by getting access to the valid signature s, one can also extract t from it by just subtracting
sₐ:t = s - sₐThe specific value of
tdepends on our choice of the public pointT, sinceRis just a public point derived from a randomly generated noncer.So how do we choose
Tso that it requires the secret t to be the signature over a specific messagem'by an specific public keyP'? (without knowing the value oft)Let's start with the definition of t as a valid Schnorr signature by P' over m':
t = r' + H(R'ₓ || P' || m')⋅k' ⇔ t⋅G = r'⋅G + H(R'ₓ || P' || m')⋅k'⋅GThat is the same as:
T = R' + H(R'ₓ || P' || m')⋅P'Notice that in order to calculate the appropriate
Tthat requirestto be an specific signature scalar, we only need to know the public nonceR'used to generate that signature.In summary: in order to atomically swap Schnorr signatures, one party
P'must provide a public nonceR', while the other partyPmust provide an adaptor signature using that nonce:sₐ = r + H((R + T)ₓ || P || m)⋅kwhereT = R' + H(R'ₓ || P' || m')⋅P'P'(the nonce provider) can then add his own signature t to the adaptor signaturesₐin order to get a valid signature byP, i.e.s = sₐ + t. When he publishes this signature (as a Nostr event, Cashu transaction or Taproot transaction), it becomes accessible toPthat can now extract the signaturetbyP'and also make use of it.Important considerations
A signature may not be useful at the end of the swap if it unlocks funds that have already been spent, or that are vulnerable to fee bidding wars.
When a swap involves a Taproot UTXO, it must always use a 2-of-2 multisig timelock to avoid those issues.
Cashu tokens do not require this measure when its signature is revealed first, because the mint won't reveal the other signature if they can't be successfully claimed, but they also require a 2-of-2 multisig timelock when its signature is only revealed last (what is unavoidable in cashu for cashu swaps).
For Nostr events, whoever receives the signature first needs to publish it to at least one relay that is accessible by the other party. This is a reasonable expectation in most cases, but may be an issue if the event kind involved is meant to be used privately.
How to Orchestrate the Swap over Nostr?
Before going into the specific event kinds, it is important to recognize what are the requirements they must meet and what are the concerns they must address. There are mainly three requirements:
- Both parties must agree on the messages they are going to sign
- One party must provide a public nonce
- The other party must provide an adaptor signature using that nonce
There is also a fundamental asymmetry in the roles of both parties, resulting in the following significant downsides for the party that generates the adaptor signature:
- NIP-07 and remote signers do not currently support the generation of adaptor signatures, so he must either insert his nsec in the client or use a fork of another signer
- There is an overhead of retrieving the completed signature containing the secret, either from the blockchain, mint endpoint or finding the appropriate relay
- There is risk he may not get his side of the deal if the other party only uses his signature privately, as I have already mentioned
- There is risk of losing funds by not extracting or using the signature before its timelock expires. The other party has no risk since his own signature won't be exposed by just not using the signature he received.
The protocol must meet all those requirements, allowing for some kind of role negotiation and while trying to reduce the necessary hops needed to complete the swap.
Swap Proposal Event (kind:455)
This event enables a proposer and his counterparty to agree on the specific messages whose signatures they intend to exchange. The
contentfield is the following stringified JSON:{ "give": <signature spec (required)>, "take": <signature spec (required)>, "exp": <expiration timestamp (optional)>, "role": "<adaptor | nonce (optional)>", "description": "<Info about the proposal (optional)>", "nonce": "<Signature public nonce (optional)>", "enc_s": "<Encrypted signature scalar (optional)>" }The field
roleindicates what the proposer will provide during the swap, either the nonce or the adaptor. When this optional field is not provided, the counterparty may decide whether he will send a nonce back in a Swap Nonce event or a Swap Adaptor event using thenonce(optionally) provided by in the Swap Proposal in order to avoid one hop of interaction.The
enc_sfield may be used to store the encrypted scalar of the signature associated with thenonce, since this information is necessary later when completing the adaptor signature received from the other party.A
signature specspecifies thetypeand all necessary information for producing and verifying a given signature. In the case of signatures for Nostr events, it contain a template with all the fields, exceptpubkey,idandsig:{ "type": "nostr", "template": { "kind": "<kind>" "content": "<content>" "tags": [ … ], "created_at": "<created_at>" } }In the case of Cashu payments, a simplified
signature specjust needs to specify the payment amount and an array of mints trusted by the proposer:{ "type": "cashu", "amount": "<amount>", "mint": ["<acceptable mint_url>", …] }This works when the payer provides the adaptor signature, but it still needs to be extended to also work when the payer is the one receiving the adaptor signature. In the later case, the
signature specmust also include atimelockand the derived public keysYof each Cashu Proof, but for now let's just ignore this situation. It should be mentioned that the mint must be trusted by both parties and also support Token state check (NUT-07) for revealing the completed adaptor signature and P2PK spending conditions (NUT-11) for the cryptographic scheme to work.The
tagsare:"p", the proposal counterparty's public key (required)"a", akind:30455Swap Listing event or an application specific version of it (optional)
Forget about this Swap Listing event for now, I will get to it later...
Swap Nonce Event (kind:456) - Optional
This is an optional event for the Swap Proposal receiver to provide the public nonce of his signature when the proposal does not include a nonce or when he does not want to provide the adaptor signature due to the downsides previously mentioned. The
contentfield is the following stringified JSON:{ "nonce": "<Signature public nonce>", "enc_s": "<Encrypted signature scalar (optional)>" }And the
tagsmust contain:"e", akind:455Swap Proposal Event (required)"p", the counterparty's public key (required)
Swap Adaptor Event (kind:457)
The
contentfield is the following stringified JSON:{ "adaptors": [ { "sa": "<Adaptor signature scalar>", "R": "<Signer's public nonce (including parity byte)>", "T": "<Adaptor point (including parity byte)>", "Y": "<Cashu proof derived public key (if applicable)>", }, …], "cashu": "<Cashu V4 token (if applicable)>" }And the
tagsmust contain:"e", akind:455Swap Proposal Event (required)"p", the counterparty's public key (required)
Discoverability
The Swap Listing event previously mentioned as an optional tag in the Swap Proposal may be used to find an appropriate counterparty for a swap. It allows a user to announce what he wants to accomplish, what his requirements are and what is still open for negotiation.
Swap Listing Event (kind:30455)
The
contentfield is the following stringified JSON:{ "description": "<Information about the listing (required)>", "give": <partial signature spec (optional)>, "take": <partial signature spec (optional)>, "examples: [<take signature spec>], // optional "exp": <expiration timestamp (optional)>, "role": "<adaptor | nonce (optional)>" }The
descriptionfield describes the restrictions on counterparties and signatures the user is willing to accept.A
partial signature specis an incompletesignature specused in Swap Proposal eventskind:455where omitting fields signals that they are still open for negotiation.The
examplesfield is an array ofsignature specsthe user would be willing totake.The
tagsare:"d", a unique listing id (required)"s", the status of the listingdraft | open | closed(required)"t", topics related to this listing (optional)"p", public keys to notify about the proposal (optional)
Application Specific Swap Listings
Since Swap Listings are still fairly generic, it is expected that specific use cases define new event kinds based on the generic listing. Those application specific swap listing would be easier to filter by clients and may impose restrictions and add new fields and/or tags. The following are some examples under development:
Sponsored Events
This listing is designed for users looking to promote content on the Nostr network, as well as for those who want to monetize their accounts by sharing curated sponsored content with their existing audiences.
It follows the same format as the generic Swap Listing event, but uses the
kind:30456instead.The following new tags are included:
"k", event kind being sponsored (required)"title", campaign title (optional)
It is required that at least one
signature spec(giveand/ortake) must have"type": "nostr"and also contain the following tag["sponsor", "<pubkey>", "<attestation>"]with the sponsor's public key and his signature over the signature spec without the sponsor tag as his attestation. This last requirement enables clients to disclose and/or filter sponsored events.Asset Swaps
This listing is designed for users looking for counterparties to swap different assets that can be transferred using Schnorr signatures, like any unit of Cashu tokens, Bitcoin or other asset IOUs issued using Taproot.
It follows the same format as the generic Swap Listing event, but uses the
kind:30457instead.It requires the following additional tags:
"t", asset pair to be swapped (e.g."btcusd")"t", asset being offered (e.g."btc")"t", accepted payment method (e.g."cashu","taproot")
Swap Negotiation
From finding an appropriate Swap Listing to publishing a Swap Proposal, there may be some kind of negotiation between the involved parties, e.g. agreeing on the amount to be paid by one of the parties or the exact content of a Nostr event signed by the other party. There are many ways to accomplish that and clients may implement it as they see fit for their specific goals. Some suggestions are:
- Adding
kind:1111Comments to the Swap Listing or an existing Swap Proposal - Exchanging tentative Swap Proposals back and forth until an agreement is reached
- Simple exchanges of DMs
- Out of band communication (e.g. Signal)
Work to be done
I've been refining this specification as I develop some proof-of-concept clients to experience its flaws and trade-offs in practice. I left the signature spec for Taproot signatures out of the current document as I still have to experiment with it. I will probably find some important orchestration issues related to dealing with
2-of-2 multisig timelocks, which also affects Cashu transactions when spent last, that may require further adjustments to what was presented here.The main goal of this article is to find other people interested in this concept and willing to provide valuable feedback before a PR is opened in the NIPs repository for broader discussions.
References
- GM Swap- Nostr client for atomically exchanging GM notes. Live demo available here.
- Sig4Sats Script - A Typescript script demonstrating the swap of a Cashu payment for a signed Nostr event.
- Loudr- Nostr client under development for sponsoring the publication of Nostr events. Live demo available at loudr.me.
- Poelstra, A. (2017). Scriptless Scripts. Blockstream Research. https://github.com/BlockstreamResearch/scriptless-scripts
-
 @ 20986fb8:cdac21b3
2025-04-10 08:52:37
@ 20986fb8:cdac21b3
2025-04-10 08:52:37Social apps are entering a new era, evolving from traditional centralized platforms to decentralized ecosystems. Users increasingly demand lightweight, intelligent, and privacy-focused applications. In this shift, Mini Apps have emerged as a mainstream choice for social applications, thanks to their rapid development, flexible deployment, and decentralized nature. The rise of cryptocurrency payments has further fueled this trend, offering low-cost, borderless, and financially liberating solutions that significantly lower transaction barriers and drive the scalability of Mini Apps. As one of the most popular decentralized social payment clients on the Bitcoin ecosystem’s Nostr protocol, YakiHonne has earned a global reputation for its exceptional user experience and seamless social payment features, reaching over 170 countries. Now, YakiHonne is set to launch its programmable Smart Widgets—a developer toolkit for Mini Apps. This product will redefine how users interact and transact on social platforms, bringing fresh energy to the on-chain app ecosystem and social payments.
Smart Widgets: A Game-Changer for Social and On-Chain Consumption
YakiHonne Smart Widgets are programmable mini-apps embedded within social feeds, enabling users to effortlessly make on-chain payments, engage in interactions, and perform actions without leaving their content stream. More than just a tool, Smart Widgets serve as an open, decentralized app store, empowering both users and developers with unparalleled creativity and flexibility.
Smart Widgets come in three user-friendly formats to meet diverse needs:
- Basic Widgets: Anyone can create these using an intuitive editor—just pick a template, add content, and generate features like zap, minting, or voting. Users can interact with these actions directly in their feed with a single click, enjoying a fast, seamless experience.
- Action Widgets: Users can quickly create these by embedding app links, no coding required. With a single tap on a button in the feed, users can access external decentralized apps (like exchanges) right within the interface, ensuring a smooth, uninterrupted experience.
- Tool Widgets (Mini Apps): Designed for developers or users with coding skills, these are built using the Smart Widgets SDK to create more advanced apps with complex on-chain operations. Users can perform tasks like data queries, on-chain actions, gaming, or instant payments directly in their social feed, with a highly integrated and fluid experience.
Key Features:
- Rapid Development: Developers can turn ideas into reality in just hours, using familiar web technologies to create near-native app experiences—no lengthy app store reviews required.
- Social Login: Users can access Mini Apps without usernames or passwords, using their Nostr/YakiHonne identity to interact seamlessly within their social feed, making the experience more connected and effortless.
- Easy Discovery and Retention: With one-tap discovery through social feeds, built-in viral growth mechanics, and a Mini App store for more options, users can explore new apps effortlessly. They can save favorites and get notifications to return for more.
- Instant Interaction and Consumption: Mini Apps integrate seamlessly with YakiHonne’s social payment infrastructure, allowing users to pay, vote, or play games without leaving their feed. Social engagement and on-chain actions blend naturally, with consumption woven effortlessly into every interaction.
Transforming Daily Experiences: Smart Widgets in Action
YakiHonne Smart Widgets bridge social engagement and on-chain consumption, delivering a wide range of use cases: - On-Chain Interactions: While browsing their feed, users can join on-chain votes or play lightweight games through Smart Widgets—like casting a vote on a community proposal or challenging a friend to a quick game, all without leaving the app. - Smart Agents: Users can leverage Agent Widgets to auto-create and share content, such as personalized posts or short videos, powering an AI-driven media experience. - DAO Governance: Using aMACI for anonymous voting, combined with Agent Widgets for autonomous governance, users can participate in DAO decisions directly within their feed, fostering decentralized community growth. - Social Zap: Users can send small tips through their feed, like rewarding a friend’s post with an on-chain token, sparking more engagement and driving consumption. - Content Subscriptions: Support creators or apps with ongoing subscriptions—users can subscribe to their favorite services with one tap, enjoying a seamless renewal experience.
These scenarios not only boost user engagement and convenience but also open new growth opportunities for creators, developers, and communities.
Shaping the Future: The Ecosystem Impact of Smart Widgets
YakiHonne Smart Widgets are poised to transform the on-chain app ecosystem and social payments. They provide an open platform for developers, enabling anyone to deploy innovative apps quickly and enrich YakiHonne’s ecosystem. YakiHonne’s social payment infrastructure further empowers Mini Apps by offering efficient payment support, reducing integration costs for developers while ensuring a secure, seamless transaction experience for users. This support accelerates the commercialization of Mini Apps and fuels the growth of on-chain consumption.
For users, Smart Widgets seamlessly blend social interaction with consumption, creating an immersive and practical digital experience. For creators and communities, they offer a low-barrier entry to on-chain opportunities, helping them connect with a global audience. This product isn’t just a technological leap—it’s a glimpse into the future of decentralized lifestyles. YakiHonne is committed to building an open, vibrant social and consumption ecosystem through Smart Widgets, where every interaction sparks on-chain value.
Join the Future: Explore Smart Widgets Today
YakiHonne invites users and developers worldwide to join this exciting journey. Developers can apply to join the Smart Widgets SDK testing program, creating their own Mini Apps and tapping into YakiHonne’s global user base. Users can follow YakiHonne on official channels –X or download the YakiHonne iOS/Android app– to experience the next generation of on-chain interactions and social payments.
YakiHonne Programmable Smart Widgets are set to launch a new chapter for social and on-chain consumption. Let’s embrace this transformation together!
-
 @ c1e9ab3a:9cb56b43
2025-04-10 02:58:16
@ c1e9ab3a:9cb56b43
2025-04-10 02:58:16Assumptions
| Factor | Assumption | |--------|------------| | CO₂ | Not considered a pollutant or is captured/stored later | | Water Use | Regulated across all sources; cooling towers or dry cooling required | | Compliance Cost | Nuclear no longer burdened by long licensing and construction delays | | Coal Waste | Treated as valuable raw material (e.g., fly ash for cement, gypsum from scrubbers) | | Nuclear Tech | Gen IV SMRs in widespread use (e.g., 50–300 MWe units, modular build, passive safety) | | Grid Role | All three provide baseload or load-following power | | Fuel Pricing | Moderate and stable (no energy crisis or supply chain disruptions) |
Performance Comparison
| Category | Coal (IGCC + Scrubbers) | Natural Gas (CCGT) | Nuclear (Gen IV SMRs) | |---------|-----------------------------|------------------------|--------------------------| | Thermal Efficiency | 40–45% | 55–62% | 30–35% | | CAPEX ($/kW) | $3,500–5,000 | $900–1,300 | $4,000–7,000 (modularized) | | O&M Cost ($/MWh) | $30–50 | $10–20 | $10–25 | | Fuel Cost ($/MWh) | $15–25 | $25–35 | $6–10 | | Water Use (gal/MWh) | 300–500 (with cooling towers) | 100–250 | 300–600 | | Air Emissions | Very low (excluding CO₂) | Very low | None | | Waste | Usable (fly ash, FGD gypsum, slag) | Minimal | Compact, long-term storage required | | Ramp/Flexibility | Slow ramp (newer designs better) | Fast ramp | Medium (SMRs better than traditional) | | Footprint (Land & Supply) | Large (mining, transport) | Medium | Small | | Energy Density | Medium | Medium-high | Very high | | Build Time | 4–7 years | 2–4 years | 2–5 years (with factory builds) | | Lifecycle (years) | 40+ | 30+ | 60+ | | Grid Resilience | High | High | Very High (passive safety, long refuel) |
Strategic Role Summary
1. Coal (Clean & Integrated)
- Strengths: Long-term fuel security; byproduct reuse; high reliability; domestic resource.
- Drawbacks: Still low flexibility; moderate efficiency; large physical/logistical footprint.
- Strategic Role: Best suited for regions with abundant coal and industrial reuse markets.
2. Natural Gas (CCGT)
- Strengths: High efficiency, low CAPEX, grid agility, low emissions.
- Drawbacks: Still fossil-based; dependent on well infrastructure; less long-lived.
- Strategic Role: Excellent transitional and peaking solution; strong complement to renewables.
3. Nuclear (Gen IV SMRs)
- Strengths: Highest energy density; no air emissions or CO₂; long lifespan; modular & scalable.
- Drawbacks: Still needs safe waste handling; high upfront cost; novel tech in deployment stage.
- Strategic Role: Ideal for low-carbon baseload, remote areas, and national strategic assets.
Adjusted Levelized Cost of Electricity (LCOE)
| Source | LCOE ($/MWh) | Notes | |--------|------------------|-------| | Coal (IGCC w/scrubbers) | ~$75–95 | Lower with valuable waste | | Natural Gas (CCGT) | ~$45–70 | Highly competitive if fuel costs are stable | | Gen IV SMRs | ~$65–85 | Assuming factory production and streamlined permitting |
Final Verdict (Under Optimized Assumptions)
- Most Economical Short-Term: Natural Gas
- Most Strategic Long-Term: Gen IV SMRs
- Most Viable if Industrial Ecosystem Exists: Clean Coal
All three could coexist in a diversified, stable energy grid: - Coal filling a regional or industrial niche, - Gas providing flexibility and economy, - SMRs ensuring long-term sustainability and energy security.
-
 @ c1e9ab3a:9cb56b43
2025-04-10 02:55:11
@ c1e9ab3a:9cb56b43
2025-04-10 02:55:11The United States is on the cusp of a historic technological renaissance, often referred to as the Fourth Industrial Revolution. Artificial intelligence, automation, advanced robotics, quantum computing, biotechnology, and clean manufacturing are converging into a seismic shift that will redefine how we live, work, and relate to one another. But there's a critical catch: this transformation depends entirely on the availability of stable, abundant, and inexpensive electricity.
Why Electricity is the Keystone of Innovation
Let’s start with something basic but often overlooked. Every industrial revolution has had an energy driver:
- The First rode the steam engine, powered by coal.
- The Second was electrified through centralized power plants.
- The Third harnessed computing and the internet.
- The Fourth will demand energy on a scale and reliability never seen before.
Imagine a city where thousands of small factories run 24/7 with robotics and AI doing precision manufacturing. Imagine a national network of autonomous vehicles, delivery drones, urban vertical farms, and high-bandwidth communication systems. All of this requires uninterrupted and inexpensive power.
Without it? Costs balloon. Innovation stalls. Investment leaves. And America risks becoming a second-tier economic power in a multipolar world.
So here’s the thesis: If we want to lead the Fourth Industrial Revolution, we must first lead in energy. And nuclear — specifically Gen IV Small Modular Reactors (SMRs) — must be part of that leadership.
The Nuclear Case: Clean, Scalable, Strategic
Let’s debunk the myth: nuclear is not the boogeyman of the 1970s. It’s one of the safest, cleanest, and most energy-dense sources we have.
But traditional nuclear has problems:
- Too expensive to build.
- Too long to license.
- Too bespoke and complex.
Enter Gen IV SMRs:
- Factory-built and transportable.
- Passively safe with walk-away safety designs.
- Scalable in 50–300 MWe increments.
- Ideal for remote areas, industrial parks, and military bases.
But even SMRs will struggle under the current regulatory, economic, and manufacturing ecosystem. To unlock their potential, we need a new national approach.
The Argument for National Strategy
Let’s paint a vision:
SMRs deployed at military bases across the country, secured by trained personnel, powering critical infrastructure, and feeding clean, carbon-free power back into surrounding communities.
SMRs operated by public chartered utilities—not for Wall Street profits, but for stability, security, and public good.
SMRs manufactured by a competitive ecosystem of certified vendors, just like aircraft or medical devices, with standard parts and rapid regulatory approval.
This isn't science fiction. It's a plausible, powerful model. Here’s how we do it.
Step 1: Treat SMRs as a National Security Asset
Why does the Department of Defense spend billions to secure oil convoys and build fuel depots across the world, but not invest in nuclear microgrids that would make forward bases self-sufficient for decades?
Nuclear power is inherently a strategic asset:
- Immune to price shocks.
- Hard to sabotage.
- Decades of stable power from a small footprint.
It’s time to reframe SMRs from an energy project to a national security platform. That changes everything.
Step 2: Create Public-Chartered Operating Companies
We don’t need another corporate monopoly or Wall Street scheme. Instead, let’s charter SMR utilities the way we chartered the TVA or the Postal Service:
- Low-margin, mission-oriented.
- Publicly accountable.
- Able to sign long-term contracts with DOD, DOE, or regional utilities.
These organizations won’t chase quarterly profits. They’ll chase uptime, grid stability, and national resilience.
Step 3: Build a Competitive SMR Industry Like Aerospace
Imagine multiple manufacturers building SMRs to common, certified standards. Components sourced from a wide supplier base. Designs evolving year over year, with upgrades like software and avionics do.
This is how we build:
- Safer reactors
- Cheaper units
- Modular designs
- A real export industry
Airplanes are safe, affordable, and efficient because of scale and standardization. We can do the same with reactors.
Step 4: Anchor SMRs to the Coming Fourth Industrial Revolution
AI, robotics, and distributed manufacturing don’t need fossil fuels. They need cheap, clean, continuous electricity.
- AI datacenters
- Robotic agriculture
- Carbon-free steel and cement
- Direct air capture
- Electric industrial transport
SMRs enable this future. And they decentralize power, both literally and economically. That means jobs in every region, not just coastal tech hubs.
Step 5: Pair Energy Sovereignty with Economic Reform
Here’s the big leap: what if this new energy architecture was tied to a transparent, auditable, and sovereign monetary system?
- Public utilities priced in a new digital dollar.
- Trade policy balanced by low-carbon energy exports.
- Public accounting verified with open ledgers.
This is not just national security. It’s monetary resilience.
The world is moving to multi-polar trade systems. Energy exports and energy reliability will define economic influence. If America leads with SMRs, we lead the conversation.
Conclusion: A Moral and Strategic Imperative
We can either:
- Let outdated fears and bureaucracy stall the future, or...
- Build the infrastructure for clean, secure, and sovereign prosperity.
We have the designs.
We have the talent.
We have the need.What we need now is will.
The Fourth Industrial Revolution will either be powered by us—or by someone else. Let’s make sure America leads. And let’s do it with SMRs, public charter, competitive industry, and national purpose.
It’s time.
This is a call to engineers, legislators, veterans, economists, and every American who believes in building again. SMRs are not just about power. They are about sovereignty, security, and shared prosperity.
Further reading:
nostr:naddr1qqgrjv33xenx2drpve3kxvrp8quxgqgcwaehxw309anxjmr5v4ezumn0wd68ytnhd9hx2tczyrq7n2e62632km9yh6l5f6nykt76gzkxxy0gs6agddr9y95uk445xqcyqqq823cdzc99s
-
 @ c3e23eb5:03d7caa9
2025-04-10 00:41:12
@ c3e23eb5:03d7caa9
2025-04-10 00:41:12The issue I have with the term "mesh networks" is that it is associated with a flat network topology. While I love the idea of avoiding hierarchy, this simply doesn't scale.
Data Plane: How the Internet Scales
The internet on the scales because it has a tree like structure. As you can see in the diagram below, global (tier 1) ISPs branch out to national (tier 2) ISPs who in turn branch out to local (tier 3) ISPs. ``` ,-[ Tier 1 ISP (Global) ]─-───────[ Tier 1 ISP (Global) ] / |
/ ▼
[IXP (Global)]═══╦═══[IXP (Global)]
║
Tier 2 ISP (National)◄──────────╗
/ \ ║
▼ ▼ ║
[IXP (Regional)]════╬══[IXP (Regional)] ║
/ \ ║
▼ ▼ ║
Tier 3 ISP (Local) Tier 3 ISP (Local) ║
| | ║
▼ ▼ ▼
[User] [User] [Enterprise]▲ IXPs are physical switch fabrics - members peer directly ▲ Tier 1/2 ISPs provide transit through IXPs but don't control them ```
This structure also reflects in IP addresses, where regional traffic gets routed by regional tiers and global traffic keeps getting passed up through gateways till it reaches the root of the tree. The global ISP then routes the traffic into the correct branch so that it can trickle down to the destination IP at the bottom.
12.0.0.0/8 - Tier 1 manages routing (IANA-allocated) └─12.34.0.0/16 - Tier 2 allocated block (through RIR) └─12.34.56.0/24 - Tier 3 subnet via upstream provider ├─12.34.56.1 Public IP (CGNAT pool) └─192.168.1.1 Private IP (local NAT reuse)Balancing idealism with pragmatism
This approach to scaling is much less idealistic than a flat hierarchy, because it relies on an authority (IANA) to assign the IP ranges to ISPs through Regional Internet Registries (RIRs). Even if this authority wasn't required, the fact that many users rely on few Tier 1 ISPs means that the system is inherently susceptible to sabotage (see 2019 BGP leak incident).
Control Plane: the internet is still described as decentralised
The internet is still described as decentralised because there is a flat hierarchy between
tier 1ISPs at the root of the tree. ``` INTERNET CORE (Tier 1 ISPs)
AT&T (AS7018) <══════════> Deutsche Telekom (AS3320) ║ ╔════════════════════╗ ║ ║ ║ ║ ║ ╚══>║ NTT (AS2914) ║<══╝ ║ ║ ║ ║ ║ ║ ╚═══════> Lumen (AS3356) ║ ║ ╚════╩════════════> Telia (AS1299) ```
The border gateway protocol (BGP) is used to exchange routing information between autonomous systems (ISPs). Each autonomous system is a branch of the "internet tree" and each autonomous system advertises routes to downstream autonomous systems (branches). However, the autonomous systems at the root of the tree also maintain a record of their piers, so that they can forward traffic to the correct peer. Hence, the following is a more complete diagram of the internet:
INTERNET CORE (TIER 1 MESH) ╔══════════════╦═════════════╦════════╦═════════════╗ ║ ║ ║ ║ ║ AT&T (AS7018) <══╬══> Lumen (AS3356) <══╬══> NTT (AS2914) ║ ║ ║ ║ ║ ║ ║ ╚══> Telia (AS1299) <══╝ ║ ║ ╚═══════════════════════════════╝ ║ ║ ╚═> Deutsche Telekom (AS3320) <═╝ ║ TREE HIERARCHY BELOW - MESH ABOVE ║ ▼ [ Tier 1 ISP ]───────────────────┐ / | | / ▼ ▼ [IXP]═══╦═══[IXP] [IXP] ║ ║ ▼ ▼ Tier 2 ISP◄──────────╗ Tier 2 ISP◄───────╗ / \ ║ / \ ║ ▼ ▼ ║ ▼ ▼ ║ [IXP]═╦[IXP] ║ [IXP]═╦[IXP] ║ / \ ║ / \ ║ ▼ ▼ ▼ ▼ ▼ ▼ Tier 3 ISP User Tier 3 ISP EnterpriseSo its a mesh network - whats wrong with that?
In the example above, NTT can only send traffic to Deutsche Telekom via Lumen or AT&T. NTT relies on its peers to maintain a correct record of the IP range that they are responsible for, so that traffic that was intended for Deutsche Telekom doesn't end up in the wrong network. An intentional or even accidental error in an autonomous system's routing tables can be detrimental to the flow of traffic through the network.
Hence, mesh networks require: * Reliability: peers rely on each-other not to fail (e.g., 2019 AWS US-East-1 availability) * Trust: peers must be honest about address ranges (e.g., 2018 BGP hijacking incident) * Central planning: BGP traffic engineering determines which route a packet takes
Application Layer Innovations
Now that we have a rough overview of how the internet is broken, lets think about what can still be done. The flat hierarchy that we associate with mesh networks sounds beautiful, but it doesn't scale. However, the tree-like structure assumes that most participants in the network rely on an authority to give them an address or a range of addresses so that they can communicate.
Overlay networks
Fortunately all it takes to interact with someone on nostr is their public key. The recipients client will render your signed and/or encrypted event no matter how it reaches them. Whether your note reaches them over the internet, over some other network or via a carrier pigeon doesn't matter. nostr:npub1hw6amg8p24ne08c9gdq8hhpqx0t0pwanpae9z25crn7m9uy7yarse465gr is working on a NIP for that and I'm sure he will share an explanation of how it works.
Bitcoin Instead of a Routing Algorithm
Now that we have digital bearer assets (e-cash), users can pay their internet gateway (TollGate) for access to the internet even though they are still offline. Once the TollGate has redeemed the e-cash, it gives the user access to the internet.
Frictionless Switching between ISPs (TollGates)
Legacy internet service providers use KYC money (fiat) to transfer the cost of the infrastructure to their users. However, this means that they are able to identify which packet belongs to which user. The KYC nature of their interaction with the users also makes it difficult for users to switch ISPs when service providers undercut each-other. Internet users who are on e-cash rails can hop between ISPs frictionlessly since they buy small amounts of data frequently in a granular manner.
Users that have access to independent competing TollGates can switch between them freely, so its impossible for any one TollGate to prevent a user from connecting to the internet. The only thing a TollGate can do is attract traffic by providing cheaper and/or faster internet access.
Anyone can arbitrage connectivity
Now that users have non KYC internet, there is nothing stopping them from reselling access to their internet connection. Anyone who has a WiFi router and access to a cheap internet connection can act as a range extender by re-selling access to that gateway for people who aren't able to connect directly.
Now the route that the traffic takes through the network is determined dynamically by the markets. The individual TollGate operators select their gateways and set their prices when they create a business model. The customers select the route that best meets their needs by selecting a gateway for their next purchase.
-
 @ 0fa80bd3:ea7325de
2025-04-09 21:19:39
@ 0fa80bd3:ea7325de
2025-04-09 21:19:39DAOs promised decentralization. They offered a system where every member could influence a project's direction, where money and power were transparently distributed, and decisions were made through voting. All of it recorded immutably on the blockchain, free from middlemen.
But something didn’t work out. In practice, most DAOs haven’t evolved into living, self-organizing organisms. They became something else: clubs where participation is unevenly distributed. Leaders remained - only now without formal titles. They hold influence through control over communications, task framing, and community dynamics. Centralization still exists, just wrapped in a new package.
But there's a second, less obvious problem. Crowds can’t create strategy. In DAOs, people vote for what "feels right to the majority." But strategy isn’t about what feels good - it’s about what’s necessary. Difficult, unpopular, yet forward-looking decisions often fail when put to a vote. A founder’s vision is a risk. But in healthy teams, it’s that risk that drives progress. In DAOs, risk is almost always diluted until it becomes something safe and vague.
Instead of empowering leaders, DAOs often neutralize them. This is why many DAOs resemble consensus machines. Everyone talks, debates, and participates, but very little actually gets done. One person says, “Let’s jump,” and five others respond, “Let’s discuss that first.” This dynamic might work for open forums, but not for action.
Decentralization works when there’s trust and delegation, not just voting. Until DAOs develop effective systems for assigning roles, taking ownership, and acting with flexibility, they will keep losing ground to old-fashioned startups led by charismatic founders with a clear vision.
We’ve seen this in many real-world cases. Take MakerDAO, one of the most mature and technically sophisticated DAOs. Its governance token (MKR) holders vote on everything from interest rates to protocol upgrades. While this has allowed for transparency and community involvement, the process is often slow and bureaucratic. Complex proposals stall. Strategic pivots become hard to implement. And in 2023, a controversial proposal to allocate billions to real-world assets passed only narrowly, after months of infighting - highlighting how vision and execution can get stuck in the mud of distributed governance.
On the other hand, Uniswap DAO, responsible for the largest decentralized exchange, raised governance participation only after launching a delegation system where token holders could choose trusted representatives. Still, much of the activity is limited to a small group of active contributors. The vast majority of token holders remain passive. This raises the question: is it really community-led, or just a formalized power structure with lower transparency?
Then there’s ConstitutionDAO, an experiment that went viral. It raised over $40 million in days to try and buy a copy of the U.S. Constitution. But despite the hype, the DAO failed to win the auction. Afterwards, it struggled with refund logistics, communication breakdowns, and confusion over governance. It was a perfect example of collective enthusiasm without infrastructure or planning - proof that a DAO can raise capital fast but still lack cohesion.
Not all efforts have failed. Projects like Gitcoin DAO have made progress by incentivizing small, individual contributions. Their quadratic funding mechanism rewards projects based on the number of contributors, not just the size of donations, helping to elevate grassroots initiatives. But even here, long-term strategy often falls back on a core group of organizers rather than broad community consensus.
The pattern is clear: when the stakes are low or the tasks are modular, DAOs can coordinate well. But when bold moves are needed—when someone has to take responsibility and act under uncertainty DAOs often freeze. In the name of consensus, they lose momentum.
That’s why the organization of the future can’t rely purely on decentralization. It must encourage individual initiative and the ability to take calculated risks. People need to see their contribution not just as a vote, but as a role with clear actions and expected outcomes. When the situation demands, they should be empowered to act first and present the results to the community afterwards allowing for both autonomy and accountability. That’s not a flaw in the system. It’s how real progress happens.
-
 @ 7d33ba57:1b82db35
2025-04-09 21:01:07
@ 7d33ba57:1b82db35
2025-04-09 21:01:07Nestled along the Cassowary Coast in Far North Queensland, Mission Beach is a dreamy stretch of palm-fringed sand where the Great Barrier Reef meets the Wet Tropics rainforest. It's serene, scenic, and refreshingly uncrowded—a perfect escape if you’re chasing natural beauty, island vibes, and a bit of adventure.
🌟 Top Things to Do in Mission Beach
1️⃣ Walk the Endless Beach
- A stunning 14-kilometer stretch of golden sand
- Often you’ll feel like you have it all to yourself
- Lined with coconut palms and mountain backdrops—ideal for morning strolls or sunset walks
2️⃣ Dunk Island Adventures
- Just a 10-minute boat ride away, Dunk Island offers hiking trails, snorkeling, and tranquil beaches
- Go for a day trip or camp overnight for the real castaway feel
- You can kayak there if you're feeling adventurous 🚣♀️
3️⃣ Spot a Cassowary in the Wild
- Mission Beach is one of the best places to see the endangered cassowary, a striking and ancient-looking bird
- Keep your eyes peeled around Licuala Rainforest Walk or Bicentennial Trail
4️⃣ Skydiving with a Beach Landing 🪂
- One of the most iconic skydives in Australia
- Jump from 15,000 ft with views of the reef, rainforest, and islands—and land right on the sand!
5️⃣ Explore the Rainforest
- Walk in the Djiru National Park, home to lush jungle, creeks, and butterflies
- Or hike the Clump Mountain track for coastal views
🍉 Where to Eat & Chill
- The Garage Bar & Grill – Laid-back, good vibes, great burgers
- Baba Curry – Casual spot for Indian and tropical twists
- Mission Beach Tavern – Classic Aussie pub fare, cold beers, and often live music
- Spicy Thai Hut – Small, authentic, and big on flavor
🌺 Need-to-Know Tips
✅ Stinger season (Oct–May) means you should swim in designated netted areas or wear stinger suits
✅ Great base to explore the Atherton Tablelands, Tully Gorge, or Paronella Park
✅ Car rental is super handy—Mission Beach is spread out and public transport is limited
✅ It’s quiet here—perfect for relaxing, recharging, and going off-grid -
 @ 7d33ba57:1b82db35
2025-04-09 19:30:29
@ 7d33ba57:1b82db35
2025-04-09 19:30:29Havana (La Habana) is a city that grabs you with its vintage soul, vivid colors, and irresistible rhythm. Picture classic 1950s cars cruising past crumbling colonial mansions, locals dancing to live salsa in the streets, and the smell of strong Cuban coffee and cigars in the air. It’s not polished, but that’s part of the magic—Havana is alive.
🌟 Top Things to Do in Havana
1️⃣ Explore Old Havana (Habana Vieja)
- A UNESCO World Heritage Site with narrow streets, pastel facades, and grand plazas
- Must-see spots: Plaza Vieja, Plaza de la Catedral, Plaza de Armas, and El Capitolio
- Stop at a rooftop bar for mojitos and views over the city 🌆
2️⃣ Ride in a Classic American Car 🚗
- Take a guided tour in a vintage convertible—pink, red, or baby blue, your choice!
- Cruise along the Malecón, past the Hotel Nacional and through leafy neighborhoods like Vedado

3️⃣ Walk the Malecón
- Havana’s famous seaside promenade is the city’s open-air living room
- Best at sunset, when locals gather to fish, chat, play music, or just watch the waves crash
4️⃣ Visit the Museum of the Revolution
- Housed in Batista’s former palace, it tells the story of Cuba’s revolutionary history
- The building itself, with bullet holes and all, is part of the experience
5️⃣ Fábrica de Arte Cubano (FAC)
- A mix of gallery, nightclub, performance space, and bar
- Where Havana’s artsy and creative crowd hangs out—don’t miss it if you're into music or culture
🍹 What to Eat & Drink in Havana
- Ropa vieja – Shredded beef in tomato sauce, a Cuban classic
- Moros y Cristianos – Black beans and rice served with everything
- Tostones & yuca – Tasty fried plantains and cassava
- Mojitos & daiquiris – Best enjoyed where Hemingway drank them: La Bodeguita del Medio and El Floridita
- Cuban coffee – Small, strong, and sweet
🎵 Feel the Vibe
✅ Catch live music in every bar—from salsa and rumba to jazz and son cubano
✅ Watch a local dance show, or better yet, join a salsa class
✅ Visit Callejón de Hamel on Sundays for Afro-Cuban rhythms and street art🛺 Tips for Visiting Havana
🌞 Bring cash (euros or USD)—credit cards aren’t widely accepted
📶 Expect limited Wi-Fi—most people use Wi-Fi parks with pre-paid cards
💡 Embrace the slower pace—this is Cuba, not a rush
🚖 Use official taxis or pre-negotiate fares
💬 Learn a few Spanish basics—locals really appreciate it
💃 Talk to people—Cubans are warm, proud, and full of stories -
 @ 16f1a010:31b1074b
2025-04-09 19:23:44
@ 16f1a010:31b1074b
2025-04-09 19:23:44
Arceus was born from nothing, not even chaos.



Arceus soon made Dialga, Palkia, and then Giratina. Dialga created time, Palkia created space, and Giratina created anti-matter. And thus, the Universe was born.Dialga, Palkia, and Giratina began battling and as a result were banished to their individual realms by Arceus.
Arceus then created Groudon, Kyogre, and Rayquaza. Groudon formed the huge celestial bodies known as planets, and the trio chose one to inhabit with life. Arceus created the sun, then shot off across the universe to create all the many stars.


But he had learnt from experience, so he tasked Rayquaza as the peace-keeper.
The trio set to work, with Groudon raising land violently, creating volcanoes and mountains; Kyogre, creating the seas, where the land was not, and Rayquaza making an atmosphere full of 'air'.
Sure enough, Kyogre's waters started to corrode Groudon's land, and this angered him. The two battled, but Rayquaza broke it up, and sent Groudon deep underground, while Kyogre was sent deep into the oceans, before returning out into the ozone layer.
Soon, Arceus returned, and it tried to make life, but failed miserably. So it created Regigigas. Regigigas moved the continents with its bare hands, piecing them together like a puzzle.

When the final chunk of land was put into place, the world sprung to life, with grass and trees sprouting everywhere. Finally, the world was ready for life.
Arceus sent Regigigas into a coma until it was needed once more. It then created thousands of Pokémon to inhabit the world. These Pokémon belonged to one of five races.
Celebi
 Jirachi
Jirachi  Mew
Mew 
Manaphy
 or Victini
or Victini 
It also created Latios and Latias, its personal agents, whom it sent flying through the universe in search of a species with great intelligence to live in harmony with its creations, before leaving once more to regain energy.


After much searching, Latias found an intelligent alien species known as Deoxys. They were bacterial but advanced. They chose a few of them and brought them back to their world.

For a while, things were fine, and the Deoxys and natives lived together in harmony. Until the Deoxys discovered they could 'infect' the natives and use their bodies. Suddenly, they were all infecting a host, and then war broke out.The Mew, Jirachi, Manaphy, Celebi, and Victini battled their infected brethren to set them free, while the Deoxys sought total dominance.
The war raged on for many centuries, until there were but a handful left of each species. Arceus returned and destroyed the last of the Deoxys, but the damage was done. The population of the world was little more than 20.
The Celebi retreated to the forests, hiding amongst the trees and in time. The Manaphy retreated to the sea, the Jirachi fell asleep, only waking up every so often, and the Victini hid in far-off lands.
This left only the Mew.During the war, three Mew had hidden under lakes in search of enlightenment.



Leaving only a handful of Mew left to roam. They were alone.The war had left the land in ruins; some places were battle-scarred beyond repair. Instead of lush grass, there were harsh deserts. This angered Groudon, sending him into a rage. Volcanoes spurted and spewed lava everywhere.
One day, a Mew was floating along when a sudden flow of lava approached it. Thinking quickly, Mew unleashed energy inside it that even Arceus didn't know about. It morphed the lava into a form and gave it LIFE. The first Heatran was created.

Arceus sensed this and had an idea. Gathering all the able Mew, it channeled immense power through them, using their life-giving abilities to create more living creatures. These were crude and unfinished, prototypes of what was to come.
Aerodactyl filled the sky, while Lileep, Cranidos, and Shieldon roamed the land.




Anorith, Omanyte, and Kabuto populated the seas.



Arceus also bestowed upon most of these beings the power to 'evolve' into more powerful creatures if the correct environment was met.
Finally, Latias returned once more. They had been far more thorough in their searching than before. However, Arceus had told them to stop, but guilt kept them going. They were determined to complete their job.
They brought humans from another planet. Basic but intelligent beings who definitely lacked the ability to infect anything. The humans settled in quickly, initially living relatively separately from the animals.
But Arceus wasn't convinced; he felt the need to test them.
First, Arceus created Articuno, who he ordered to send the planet into an Ice Age.

Articuno froze the planet, killing many creatures, but giving birth to new ones like Mamoswine.

To Arceus' pleasure, the humans adapted, creating structures out of ice and snow. The severe drop in temperature awoke Regigigas, who rose high above the land and saw what was happening.
The humans instantly fell in love with Regigigas, worshipping the titan and creating statues of it from ice. Touched by this, Regigigas found one of the statues and breathed life into it before returning to sleep.

However, this scared the humans, and they locked it away in a cave.
Realizing that the Ice Age did not affect the humans, Arceus created another bird, Moltres, and ordered it to send the world into a drought. The ice melted, and the water evaporated as the temperature rose higher and higher.

While the humans continued to adapt, using the skills they had learned with the ice and applying them to rock, the creatures weren't as lucky. The Mamoswine and other creatures that adapted to the cold died off, but new ones such as huge insects like Yanmega became common.

Once again, the drought awoke Regigigas, who once again saw a statue of himself. Thinking the humans would have learned from last time, Regigigas gave it life. But rumors of the living statue had been passed down and exaggerated since last time, and once again, the scared humans locked away this second 'Regi'.

When the drought finally wore off, Arceus began the third and final test. He created one more legendary bird, Zapdos. Zapdos created powerful electrical storms all across the land.

The storms killed off the last of the prototype creatures, leaving only the humans and the few pets they brought from their home land. One extremely intelligent man managed to harness the power of electricity, creating the first electronic device.
Of course, Regigigas awoke one final time. He discovered that the humans were far more evolved than expected, able to harness metals and electricity, albeit at a somewhat primitive level. More out of tradition than anything else, Regigigas created the third Regi out of steel. The humans were no longer scared of this Regi, but they sealed it away with the other two nonetheless, knowing that one day someone powerful enough would tame them.

Arceus was baffled. The humans had passed all three tests of harsh weather. Zapdos calmed the storms, and the world became peaceful once again.
Arceus herded the Mew together for a second time. Having learned the strengths and weaknesses of his prototype beings, Arceus was ready to go farther.
Siphoning its huge power through the small pink beings, Arceus filled the world with hundreds of species of creatures that would become known as 'Pokémon'. They were more diverse than it had ever imagined, filling the skies, land, and sea.
The life energies even reacted with the sun rays and moonlight, creating Ho-oh and Lugia respectively.


Some radiated out of the planet's moon, creating a population of Clefairy, as well as Cresselia on the light side and Darkrai on the dark side of the moon.



Lugia befriended the three elemental birds, and they followed him like a leader. Meanwhile, humans started to get closer to these new creatures, using them as slaves, weapons, or pets. The term 'Pokémon' arose from strange travelers and stuck.
The first Pokéballs were created from Apricorns, and the bond between human and Pokémon was complete.


Ho-oh took residence at the top of the Bell Tower. It was jealous of Lugia's trio of birds and wanted one of its own. One day, three Kimono girls entered its tower with a Jolteon, Flareon, and Vaporeon.



Ho-oh burnt down the tower with its Sacred Fire. Most escaped, but the three Pokémon were trapped and perished in the flames. Ho-oh soon resurrected them as Entei, Raikou, and Suicune.



Humans continued to evolve and take over the land, and Pokémon continued to work alongside and for them for many, many years.
That is the story of the Pokémon World.
-
 @ 378562cd:a6fc6773
2025-04-09 17:11:25
@ 378562cd:a6fc6773
2025-04-09 17:11:25So, this is the way I see things...
Bitcoin’s rise is not merely a technological revolution—it serves as a masterclass in game theory unfolding in real time. At its core, game theory examines how individuals make decisions when outcomes rely on the choices of others. Bitcoin adoption adheres to this model precisely.
Imagine a global network where each new participant increases the value and security of the system. Early adopters take a risk, hoping others will follow. The incentive to join grows stronger as more people opt in—whether out of curiosity, conviction, or FOMO. No one wants to be last to the party, especially if that party rewrites financial history.
Here’s how the game theory of adoption plays out:
-
🧠 First movers take risks but gain the most—they enter when the price is low and the potential is high.
-
👀 Everyone watches everyone else—people, companies, and countries are scanning the field for the next move.
-
The network effect kicks in—the more players are in the game, the more valuable and secure the system becomes.
-
⏳ Waiting can cost you—as adoption grows, the price of entry rises, making hesitation expensive.
-
No one wants to be left behind—especially in a global economy battling inflation and instability.
Game theory tells us that smart players make decisions that bring them the most goodies. As Bitcoin gets more popular, it’s like a party that’s really heating up, and you don’t want to be the one left outside! In this thrilling game, the early bird doesn’t just get the worm—it lands a juicy opportunity in a brand-new way to spend money. So don’t dawdle; now’s the time to jump in and grab your piece of this financial fiesta!
-
-
 @ c253bd19:7911dadc
2025-04-09 16:52:54
@ c253bd19:7911dadc
2025-04-09 16:52:54Welcome to my overly technical green nook and follow me as I explore the possibility of becoming partially self reliant in terms of produce in an urban setting with only limited resources and effort. 🌱🌱
I was going to write a cool lengthy article explaining my motivation. Explaining how I got here and why I want to do what I want to do. I had all the punchy lines ready and I spend a decent amount of time on the first draft. Some parts were even pretty good. But then I realized that the audience of this content probably already knows that something is off. That some parts of our world are just broken. That we need to do something. We can feel it in our bones. The great uneasiness. I realized I'd be preaching to the choir for most part and I therefore decided to park my lengthy article. At least for now.
I am just going to lay out 3 quick thoughts for you to ponder and then I am going to jump straight in. Alright, here it goes:
-
I do software engineering for living. I used to love it for the freedom and creativity. I still like it but I feel like most of my projects have no meaning and add no real world value. You might say this is just a typical case of burnout. But I think that we might be interpreting burnout wrong. Maybe it's just our inner voice telling us to put our skills and efforts towards something meaningful. Maybe we should not fight it. Maybe we should listen.
-
I think our world has become overly complex. I think technology and complicated systems bring a lot of convenience and comfort but I also think that sometimes we go too far and we give up control of our lives. The complexity often hides poor design and occasionally even ill intentions - seeking profit no matter the cost. I think some things should remain small-scale, simple, transparent, and pure.
-
I value personal freedom but I also think we need to take responsibility for our actions, or lack of action. We use nebulous labels to transfer guilt and abstract problems away. The corporations are exploiting the poor countries. The corporations are killing the planet. It helps us sleep better at night. But in fact, the corporations are just groups of people. It's us exploiting each other. It's us destroying the plant. I think it's up to us to do something about it on the individual level. We don't need any grand plans, we just need to do something. Baby steps.
Loosely following the 3 points above, I set out to come up with a personal project that would be:
- technical and involve coding but at the same time has a very tangible final product
- has potential to improve my day-to-day life, is reproducible, and may inspire other people
- revolves around self-reliance, sustainability, and decreasing my environmental footprint
...and voila, I landed with microgreens. I've always had a green thumb and I have a ton of plants in my apartment. I also like to cook and I pay attention to my nutrition. Especially to the quality of the ingredients I use. Produce is a frequent flyer in my meals so naturally I was curious if I could maybe just grow some on my own. I wanted to see if I can opt out from the grocery industry for at least this little part of my nutritional intake. Baby steps, remember? Well, there's one catch. I am not exactly a farmer. Quite the opposite. I live in a tiny apartment in a big city and I don't have a garden (at least for now). That's why microgreens came into play. Being able to grow fresh greens indoors and within just a few days. With only limited supplies and space. That'd be pretty neat.
In my typical fashion, I jumped straight into it. I got some trays and some soil. I ordered some seeds and in just a couple days I successfully...made a huge mess. I hit all kinds of snags. There was soil everywhere. Majority of my crop went down with mold, and the few greens I actually harvested had soil all over them. Mmmm earthy. They were basically unusable. A great success!/s
I quickly realized that this is not the way to go. Sure, I could learn and make this work, but it was clear to me that this is not what I was looking for. I didn't exactly want to start a farm in my living room. I wanted to come up with a clever yet simple process. I wanted something that might take some effort initially but something that is a smooth sailing once set up. With that I went back to the drawing board.
My pilot attempt was a failure but I did learn a few things:
- soil = mess
- more variables means more things to go wrong
- precise and consistent watering is the key to success
For my next iteration I decided to go small and simple. I am going use my 3d printer to print a reusable tray suitable for bottom watering. I will use a coconut fiber mat as the growing medium in order to avoid all the soil mess. I am also thinking about using a simple grid laid on top of the mat to make the greens grow evenly and to make it easier to cut them once they are ready for harvest.
After a few (read countless) hours with Blender, I've got my prototype and the 3d printer warming up so stay tuned...

-
-
 @ 51307ca1:de21c861
2025-04-09 16:02:59
@ 51307ca1:de21c861
2025-04-09 16:02:59{"type": "canvas_creation", "canvas_id": "canvas_1qqs7793", "timestamp": "2025-04-09T09:02:59.945647"}
-
 @ 51307ca1:de21c861
2025-04-09 15:46:25
@ 51307ca1:de21c861
2025-04-09 15:46:25{"type": "canvas_creation", "canvas_id": "canvas_c06fd5f6", "timestamp": "2025-04-09T08:46:25.204352"}
-
 @ 51307ca1:de21c861
2025-04-09 15:05:48
@ 51307ca1:de21c861
2025-04-09 15:05:48{"version": "1.0", "type": "canvas", "description": "This is a test canvas that will evolve with zaps", "initial_state": {"width": 1024, "height": 1024, "background_color": "#FFFFFF"}}
-
 @ 8d34bd24:414be32b
2025-04-09 14:45:28
@ 8d34bd24:414be32b
2025-04-09 14:45:28I was listening to “Ultimately with R.C. Sproul.” He made the comment that “Sin is so common that we don’t think it is that concerning, but it is especially concerning because it is so common.” This is so true.
I used to really look down on Adam and Eve for eating the forbidden fruit. I thought, “How hard is it to obey a single command? We have so many to obey today from God, government, parents, etc.” One day I finally realized two truths. Adam and Eve were adults, but they had not been around very long (the Bible doesn’t say how long, but the implication is not very long, maybe even as short as days after being created.) They didn’t have life experience. They also had never been lied to before. They weren’t looking at the world with suspicion. They lived in a perfect environment with a perfect, loving God. It would’ve never crossed their mind that a person would lie, so they trusted the lie instead of God.
Today, we live in a sinful, fallen world. Everyone lies. Everyone steals. Everyone is unkind. Everyone has selfish motives. Yes, there is a difference in how often and how “bad” the lie, the theft, the motive, or the unkindness, but sin is everywhere. We get used to it and it seems normal. When we act the same way, it doesn’t seem that bad. We just took a pen home from work, nobody will miss it. We just told the person what they wanted to hear, so we won’t hurt their feelings. It is only a little white lie. Yes, I was unkind, but that person really deserved it because they were worse. We think this way and excuse our sins because we aren’t as bad as someone else.
I’ve noticed as I’ve grown older that the age when you become old keeps getting older and older. Old is always a little bit older than I am. When I was 10, a teenager was really old. When I was 16, an 18 year old was an adult and old. When I was 20, a 40 year old was old. When I was 50, a 65 year old was old. Old keeps getting older because my reference is myself. The truth is that I am getting older. I am on the downhill slide. I am closer to death than I am to birth. My arbitrary, moving reference doesn’t change this fact.
In the same way, when we look at sin, we have the same problem. We are always looking for someone who sins worse to make us look better and to excuse our sins. We compare ourselves to sinful men instead of our perfect, holy, sinless Savior.
In an earlier post, I made the comparison of the lights in the sky. If you go outside on a dark, moonless night, you will see the stars in the sky shining. They seem bright, but some are brighter than others. You can compare the brightness of the stars and call some brighter and others darker, but when the sun rises, you can’t see any light from the stars. Their light is drowned out by the light of the sun. The sun is so much brighter that it is as if the stars don’t produce any light at all.
In the same way, we may do some good things. When we compare our good deeds to others, we may look better, but when the true reference, the Son of God is our reference, our good works look like they don’t exist at all. The differences between the best person and the worst person are insignificant, just like the brightness of the brightest star and the dimmest star seems insignificant when compared with the brightness of the Sun.
The cool thing is that there is another light in the sky, the moon. The moon doesn’t have any light of its own, but it is the second brightest light in the sky. Why? Because it reflects the light of the sun. We should be the same way. We will never measure up if we seek to be good and sinless. We will never meet the standard that Jesus set for us with His perfect, sinless, sacrificial life, but we can reflect the glory of Jesus in our lives.
Yes, when we sin, we can hurt others, but who are we really sinning against? David knows.
Be gracious to me, O God, according to Your lovingkindness;\ According to the greatness of Your compassion blot out my transgressions.\ Wash me thoroughly from my iniquity\ And cleanse me from my sin.\ For I know my transgressions,\ And my sin is ever before me.\ **Against You, You only, I have sinned\ And done what is evil in Your sight,\ So that You are justified when You speak\ And blameless when You judge.\ Behold, I was brought forth in iniquity,\ And in sin my mother conceived me.\ Behold, You desire truth in the innermost being,\ And in the hidden part You will make me know wisdom. (Psalm 51:1-6) {emphasis mine}
Yes, our sins can hurt other people and do, but the true damage is to the glory of our generous Creator God. We must confess our sins to God first and then to anyone we have hurt. We must accept that we deserve any judgement God gives us because He created us and everyone and everything with which we interact. Our allegiance, submission, and worship is due to our Creator God.
Because we can never fully understand how abhorrent sin is to God, I thought I’d share how a godly man, the priest and prophet, Ezra, reacted to sin among his brethren.
When I heard about this matter, I tore my garment and my robe, and pulled some of the hair from my head and my beard, and sat down appalled. Then everyone who trembled at the words of the God of Israel on account of the unfaithfulness of the exiles gathered to me, and I sat appalled until the evening offering.
But at the evening offering I arose from my humiliation, even with my garment and my robe torn, and I fell on my knees and stretched out my hands to the Lord my God; and I said, “O my God, I am ashamed and embarrassed to lift up my face to You, my God, for our iniquities have risen above our heads and our guilt has grown even to the heavens. Since the days of our fathers to this day we have been in great guilt, and on account of our iniquities we, our kings and our priests have been given into the hand of the kings of the lands, to the sword, to captivity and to plunder and to open shame, as it is this day. But now for a brief moment grace has been shown from the Lord our God, to leave us an escaped remnant and to give us a peg in His holy place, that our God may enlighten our eyes and grant us a little reviving in our bondage. (Ezra 9:3-8) {emphasis mine}
Ezra sees sin, shreds his clothes, pulls out his hair, and sits appalled. Do we feel even a fraction of the horror at guilt that Ezra showed? When faced with some Israelites marrying non-Israelite (many from the banned people groups), Ezra admits that “our iniquities have risen above our heads and our guilt has grown even to the heavens.” How many of us would think that was only a little sin or that since it was only a few people, it wasn’t that important? Ezra, instead of saying, “Why did you send us into exile for 70 years and why are you not blessing us now?” said, “But now for a brief moment grace has been shown from the Lord our God.” Instead of accusing God of not being good enough or kind enough, thanks God for His grace which was completely undeserved. If only we could look at sin in this way.
After all that has come upon us for our evil deeds and our great guilt, since You our God have requited us less than our iniquities deserve, and have given us an escaped remnant as this, (Ezra 9:13) {emphasis mine}
Ezra understood that we all deserve only judgment. Every good thing we receive is only due to God’s grace. Instead of asking why God would allow a bad thing to happen to us, we should be asking why God is so gracious to give us good things in our lives and not give us nothing but punishment.
Jesus also talked about our sins. Although it is good, when we are tempted to sin, to choose to not sin, even evil thoughts are sins. They mean our minds and hearts are not fully submitted to God.
“You have heard that the ancients were told, ‘You shall not commit murder’ and ‘Whoever commits murder shall be liable to the court.’ But I say to you that everyone who is angry with his brother shall be guilty before the court; and whoever says to his brother, ‘You good-for-nothing,’ shall be guilty before the supreme court; and whoever says, ‘You fool,’ shall be guilty enough to go into the fiery hell. Therefore if you are presenting your offering at the altar, and there remember that your brother has something against you, leave your offering there before the altar and go; first be reconciled to your brother, and then come and present your offering. Make friends quickly with your opponent at law while you are with him on the way, so that your opponent may not hand you over to the judge, and the judge to the officer, and you be thrown into prison. Truly I say to you, you will not come out of there until you have paid up the last cent.
“You have heard that it was said, ‘You shall not commit adultery’; but I say to you that everyone who looks at a woman with lust for her has already committed adultery with her in his heart. If your right eye makes you stumble, tear it out and throw it from you; for it is better for you to lose one of the parts of your body, than for your whole body to be thrown into hell. If your right hand makes you stumble, cut it off and throw it from you; for it is better for you to lose one of the parts of your body, than for your whole body to go into hell.
“It was said, ‘Whoever sends his wife away, let him give her a certificate of divorce’; but I say to you that everyone who divorces his wife, except for the reason of unchastity, makes her commit adultery; and whoever marries a divorced woman commits adultery.
“Again, you have heard that the ancients were told, ‘You shall not make false vows, but shall fulfill your vows to the Lord.’ But I say to you, make no oath at all, either by heaven, for it is the throne of God, or by the earth, for it is the footstool of His feet, or by Jerusalem, for it is the city of the great King. Nor shall you make an oath by your head, for you cannot make one hair white or black. But let your statement be, ‘Yes, yes’ or ‘No, no’; anything beyond these is of evil.
“You have heard that it was said, ‘An eye for an eye, and a tooth for a tooth.’ But I say to you, do not resist an evil person; but whoever slaps you on your right cheek, turn the other to him also. If anyone wants to sue you and take your shirt, let him have your coat also. Whoever forces you to go one mile, go with him two. Give to him who asks of you, and do not turn away from him who wants to borrow from you.
“You have heard that it was said, ‘You shall love your neighbor and hate your enemy.’ But I say to you, love your enemies and pray for those who persecute you, so that you may be sons of your Father who is in heaven; for He causes His sun to rise on the evil and the good, and sends rain on the righteous and the unrighteous. For if you love those who love you, what reward do you have? Do not even the tax collectors do the same? If you greet only your brothers, what more are you doing than others? Do not even the Gentiles do the same? Therefore you are to be perfect, as your heavenly Father is perfect. (Matthew 5:21-48) {emphasis mine}
Many people say that as New Testament believers, we are not under the Old Covenant and the Old Testament laws do not apply to us. While that may be true of the ceremonial laws, the truth is that Jesus made the laws stricter. It is still true that we are not to commit murder, but we are also not to hate another. It is still true that we are not to commit adultery, but we are also not to lust after another. We are also not to fight against those who mistreat us and we are to love those who hate us. Jesus expects more, not less, maybe because we now have the guidance and power of the Holy Spirit within us.
If we have the mind of Christ, we should despise the things God hates. If we have the heart of Christ, we should love even those who hate us and we should seek their eternal good. We should see with the eyes of Christ and see the hurt behind the hate and dishonesty. How do we do this? We need to fill our minds with the word of God. We need to obey Paul’s command to those in Philippi:
Finally, brethren, whatever is true, whatever is honorable, whatever is right, whatever is pure, whatever is lovely, whatever is of good repute, if there is any excellence and if anything worthy of praise, dwell on these things. (Philippians 4:8)
We need to so fill our mind with God’s word that God’s goodness overflows into our lives.
God of heaven, please change our hearts and minds and make them fully aligned with your heart and mind. Help us to see sin as you see sin and to see people as you see people. Help us to see the hurt instead of the lashing out, so we can have a merciful heart towards those who are unkind to us. Help us to fill our minds with your goodness and your word, so there is no room for evil in us. Make us more like you.
Trust Jesus
FYI, there are many people who can’t see their own sin and who discount the severity of sin. I am writing for these people. There are also people who have no trouble seeing their own sin. Their problem is not accepting the forgiveness of God. Never doubt that God has forgiven you if you have confessed your sins and trusted Jesus as Savior. Jesus has covered your sins and the Father sees only the holiness of Jesus. Your relationship with the Godhead is fully reconciled. You should do right out of thankfulness and love of God, but there is nothing else you need to do to be saved and have a right relationship with God.
-
 @ 7bc05901:8c26d22b
2025-04-09 14:15:31
@ 7bc05901:8c26d22b
2025-04-09 14:15:31My wife (girlfriend at the time) and I were heading back from Nashville after celebrating the opening of Bitcoin Park in Nashville. My boy Ryan had, once again, drug me to a Bitcoin event in the waning days of my stubborn shitcoinery. This event was the nail in the coffin for those days, and I'm happy to say the "stay humble stack sats" message finally permeated.
My wife is a dedicated reseller, her family has been flipping garage sale finds and auction grabs for years, so we rarely see a flea market or antique mall that we pass up. Somewhere between Missouri and Nashville we pulled off the highway to check out a spot in a dying but (if you squint your eyes and imagine it is 50 years in the past) a picturesque little town.
We were in my little Scion FRS, a two door sports car, so when I came across an old newspaper vending machine, I had to do a lot of geometry to figure out if I could shove this thing in the Scion. I concluded that my girlfriend would have to ride in the backseat for the remaining three hour drive if I really wanted to scoop up this vending machine, because it was too wide to slide into the trunk. Even though she knew I had an infatuation for retro newspaper things and was encouraging me to buy it, I declined. Probably the right call, but I still think about that thing -- the price was right.
I don't know what I would have done with it, but I have for years produced various hobbyist newspaper zines focusing on local political issues that I distributed from the coffeeshop that I worked at in my small town. The idea was hitting so hard when the social media censorship conversation was at a fever pitch after 2016 -- You can't censor a copy machine, I kept thinking. Analog zines, I was convinced, were the future.
I hadn't thought through decentralized social media protocols, but I did get really tired of distributing zines that nobody was excited to pay me for. Copying, organizing, stapling. I should have known I didn't have the patience to maintain that, or the finances.
Even established local news corporations, especially in my town, are struggling to justify a print version. This wasn't the case a quarter of a century ago.
My dad would stop at the Casey's convenience story every morning on the way into town, as he took us to school. If you brought your own travel mug, it was only fifty cents to fill up your cup of coffee. Nearly everyday, he would also come out with a copy of the local newspaper: The Daily Journal. The price was right around a dollar for the paper. It might have even been cheaper, like fifty or seventy-five cents.
The idea I am inching towards in this post, is that if every person valued the distribution of local (and global) news to the tune of a buck or a buck fifty, we could see the re-emergence sustaining news ecosystems. A buck fifty is almost two thousand sats today -- imagine if each appreciator of local news set aside just a thousand sats a day to zap news distributors. If there was a bias for following and amplifying local news events in each user's town, which tend to get a lot of attention on the centralized social media platforms, I think an entirely new value-4-value journalism enterprise model could emerge.
It may be important to start tinkering on a client that is built specifically for newspapers. I am not sure which features would be critical, but as the normies trickle over to the uncensorable social media protocol -- let's be ready.
-
 @ 04c195f1:3329a1da
2025-04-09 10:54:43
@ 04c195f1:3329a1da
2025-04-09 10:54:43The old world order is crumbling. What was once considered stable and unshakable—the American-led global framework established after World War II—is now rapidly disintegrating. From the fraying fabric of NATO to the self-serving protectionism of Trump’s renewed presidency, the signals are clear: the empire that once held the Western world together is retreating. And in the vacuum it leaves behind, a new power must emerge.
The question is: will Europe finally seize this moment?
For decades, Europe has relied on the illusion of safety under an American umbrella. This dependency allowed us to indulge in what can only be described as “luxury politics.” Instead of strengthening our core institutions—defense, infrastructure, energy independence—we poured our energy into ideological experiments: value-based governance, multiculturalism, aggressive climate goals, and endless layers of bureaucracy.
We let ourselves believe history had ended. That war, scarcity, and geopolitical struggle were things of the past. That our greatest challenges would be inclusivity, carbon credits, and data protection regulations.
But history, as always, had other plans.
Trump, Nationalist Hope and Hard Reality
Across Europe, many nationalists and conservatives initially welcomed Donald Trump. He rejected the tenets of liberal globalism, called out the absurdities of woke ideology, and promised a return to realism. In a world saturated by progressive conformity, he seemed like a disruptive breath of fresh air.
And to a certain extent, he was.
But history will likely remember his presidency not for culture wars or conservative rhetoric—but for something far more consequential: the dismantling of the American empire.
What we are witnessing under Trump is the accelerated withdrawal of the United States from its role as global enforcer. Whether by design or incompetence, the result is the same. American institutions are retracting, its alliances are fraying, and its strategic grip on Europe is loosening.
For Americans, this may seem like decline. For Europe, it is an opportunity—an uncomfortable, painful, but necessary opportunity.
This is our chance to break free from the American yoke and step into the world as a sovereign power in our own right.
The End of Illusions
Europe is not a weak continent. We have a population larger than the United States, an economy that outpaces Russia’s many times over, and centuries of civilizational strength behind us. But we have been kept fragmented, distracted, and dependent—by design.
Both Washington and Moscow have an interest in a divided, impotent Europe. American strategists see us as junior partners at best, liabilities at worst. Russian elites, like Sergey Karaganov, openly admit their goal is to push Europe off the global stage. China, for its part, eyes our markets while quietly maneuvering to undermine our autonomy.
But something is changing.
In Brussels, even the ideologically captured technocrats are beginning to see the writing on the wall. Overbearing regulations like GDPR are being reconsidered. The long-pushed Equal Treatment Directive—a pan-European anti-discrimination law—may finally be scrapped. These are small signs, but signs nonetheless. Europe is waking up.
From Fracture to Foundation
To build something new, the old must first fall. That collapse is now well underway.
The collapse of American hegemony does not mean the rise of chaos—it means the opening of a path. Europe has a choice: continue to drift, clinging to broken institutions and obsolete alliances, or embrace the challenge of becoming a serious actor in a multipolar world.
This does not mean copying the imperial ambitions of others. Europe’s strength will not come from domination, but from independence, coherence, and confidence. A strong Europe is not one ruled from Brussels, but one composed of strong, rooted nations acting together in strategic alignment. Not a federation, not an empire in the classical sense—but a civilization asserting its right to survive and thrive on its own terms.
At the same time, we must not fall into the trap of romantic isolationism. Some nationalists still cling to the idea that their nation alone can stand firm on the global stage, detached from continental collaboration. That vision no longer matches the geopolitical reality. The world has changed, and so must our strategy. In key areas—such as defense, border security, trade policy, and technological sovereignty—Europe must act with unity and purpose. This does not require dissolving national identities; it requires mature cooperation among free nations. To retreat into purely national silos would be to condemn Europe to irrelevance. Strengthening the right kind of European cooperation—while returning power in other areas to the national level—is not a betrayal of nationalism, but its necessary evolution.
A Third Position: Beyond East and West
As the American empire stumbles and Russia attempts to fill the void, Europe must not become a pawn in someone else’s game. Our task is not to shift allegiance from one master to another—but to step into sovereignty. This is not about trading Washington for Moscow, or Beijing. It is about rejecting all external domination and asserting our own geopolitical will.
A truly pro-European nationalism must recognize that our civilizational future lies not in nostalgia or subservience, but in strategic clarity. We must build a third position—a pole of stability and power that stands apart from the decaying empires of the past.
That requires sacrifice, but it also promises freedom.
Hope Through Action
There is a romantic notion among some European nationalists that decline is inevitable—that we are simply passengers on a sinking ship. But fatalism is not tradition. It is surrender.
Our ancestors did not build cathedrals, repel invaders, or chart the globe by giving in to despair. They acted—often against impossible odds—because they believed in a Europe worth fighting for.
We must now rediscover that spirit.
This is not a call for uniformity, but for unity. Not for empire, but for sovereignty. Not for nostalgia, but for renewal. Across the continent, a new consciousness is stirring. From the Alps to the Baltic, from Lisbon to Helsinki, there are voices calling for something more than submission to global markets and American whims.
They are calling for Europe.
The Hour Has Come
There may not be a second chance. The tide of history is turning, and the next ten years will determine whether Europe reclaims its role in the world—or becomes a museum piece, mourned by tourists and remembered by none.
This is not the end.
It is our beginning—if we are brave enough to seize it.
■
-
 @ 7d33ba57:1b82db35
2025-04-09 08:25:02
@ 7d33ba57:1b82db35
2025-04-09 08:25:02Sagres, perched on the dramatic cliffs of Portugal’s Algarve, feels like the end of the world—and in the best way. It's a small, laid-back town with a surfer vibe, windswept beaches, and rugged coastal views that are simply breathtaking. If you’re into nature, chill vibes, and jaw-dropping sunsets, Sagres is your spot.
🌟 Top Things to See & Do in Sagres
1️⃣ Cabo de São Vicente (Cape St. Vincent)
- The southwesternmost point of mainland Europe
- Home to a dramatic cliffside lighthouse and epic sunsets
- Once thought to be the "end of the world" in ancient times
2️⃣ Fortaleza de Sagres
- A 15th-century fortress with a giant stone compass, sea views, and a coastal walking path
- Linked to Henry the Navigator and Portugal’s Age of Discoveries
- Simple, scenic, and full of history
3️⃣ Surf the Waves 🌊
- Some of the best surfing beaches in Europe
- Try Praia do Tonel or Praia do Beliche—great for both beginners and pros
- Tons of surf schools and rental shops around town
4️⃣ Chill on the Beaches
- Praia da Mareta – calm and central, perfect for swimming
- Praia do Beliche – surrounded by cliffs, more secluded
- Praia do Martinhal – family-friendly with shallow water
5️⃣ Coastal Hiking & Cliffs
- Walk along the Rota Vicentina trails for raw Atlantic views, wildflowers, and sea breeze
- Bring water and a camera—it's a nature-lover’s dream
🍽️ What to Eat in Sagres
- Fresh seafood – grilled sardines, octopus salad, and cataplana
- Percebes (goose barnacles) – a local delicacy from the rocks
- Pastéis de nata – always a good idea ☕
- Pair it all with a cold Super Bock or a glass of vinho verde
Try beachside spots or cozy taverns in town—nothing too fancy, just simple, tasty, and fresh.
🏄 Vibe & Tips
✅ Sagres is quiet, remote, and windswept—perfect if you're looking to unwind
✅ Great for vanlifers, surfers, hikers, and sunset chasers
✅ Bring layers—it can be windy, even in summer
✅ Sunsets at Cabo de São Vicente are legendary—get there early for a good spot
✅ A car helps to explore the nearby coastlines and hidden beaches -
 @ 39cc53c9:27168656
2025-04-09 07:59:35
@ 39cc53c9:27168656
2025-04-09 07:59:35The new website is finally live! I put in a lot of hard work over the past months on it. I'm proud to say that it's out now and it looks pretty cool, at least to me!
Why rewrite it all?
The old kycnot.me site was built using Python with Flask about two years ago. Since then, I've gained a lot more experience with Golang and coding in general. Trying to update that old codebase, which had a lot of design flaws, would have been a bad idea. It would have been like building on an unstable foundation.
That's why I made the decision to rewrite the entire application. Initially, I chose to use SvelteKit with JavaScript. I did manage to create a stable site that looked similar to the new one, but it required Jav aScript to work. As I kept coding, I started feeling like I was repeating "the Python mistake". I was writing the app in a language I wasn't very familiar with (just like when I was learning Python at that mom ent), and I wasn't happy with the code. It felt like spaghetti code all the time.
So, I made a complete U-turn and started over, this time using Golang. While I'm not as proficient in Golang as I am in Python now, I find it to be a very enjoyable language to code with. Most aof my recent pr ojects have been written in Golang, and I'm getting the hang of it. I tried to make the best decisions I could and structure the code as well as possible. Of course, there's still room for improvement, which I'll address in future updates.
Now I have a more maintainable website that can scale much better. It uses a real database instead of a JSON file like the old site, and I can add many more features. Since I chose to go with Golang, I mad e the "tradeoff" of not using JavaScript at all, so all the rendering load falls on the server. But I believe it's a tradeoff that's worth it.
What's new
- UI/UX - I've designed a new logo and color palette for kycnot.me. I think it looks pretty cool and cypherpunk. I am not a graphic designer, but I think I did a decent work and I put a lot of thinking on it to make it pleasant!
- Point system - The new point system provides more detailed information about the listings, and can be expanded to cover additional features across all services. Anyone can request a new point!
- ToS Scrapper: I've implemented a powerful automated terms-of-service scrapper that collects all the ToS pages from the listings. It saves you from the hassle of reading the ToS by listing the lines that are suspiciously related to KYC/AML practices. This is still in development and it will improve for sure, but it works pretty fine right now!
- Search bar - The new search bar allows you to easily filter services. It performs a full-text search on the Title, Description, Category, and Tags of all the services. Looking for VPN services? Just search for "vpn"!
- Transparency - To be more transparent, all discussions about services now take place publicly on GitLab. I won't be answering any e-mails (an auto-reply will prompt to write to the corresponding Gitlab issue). This ensures that all service-related matters are publicly accessible and recorded. Additionally, there's a real-time audits page that displays database changes.
- Listing Requests - I have upgraded the request system. The new form allows you to directly request services or points without any extra steps. In the future, I plan to enable requests for specific changes to parts of the website.
- Lightweight and fast - The new site is lighter and faster than its predecessor!
- Tor and I2P - At last! kycnot.me is now officially on Tor and I2P!
How?
This rewrite has been a labor of love, in the end, I've been working on this for more than 3 months now. I don't have a team, so I work by myself on my free time, but I find great joy in helping people on their private journey with cryptocurrencies. Making it easier for individuals to use cryptocurrencies without KYC is a goal I am proud of!
If you appreciate my work, you can support me through the methods listed here. Alternatively, feel free to send me an email with a kind message!
Technical details
All the code is written in Golang, the website makes use of the chi router for the routing part. I also make use of BigCache for caching database requests. There is 0 JavaScript, so all the rendering load falls on the server, this means it needed to be efficient enough to not drawn with a few users since the old site was reporting about 2M requests per month on average (note that this are not unique users).
The database is running with mariadb, using gorm as the ORM. This is more than enough for this project. I started working with an
sqlitedatabase, but I ended up migrating to mariadb since it works better with JSON.The scraper is using chromedp combined with a series of keywords, regex and other logic. It runs every 24h and scraps all the services. You can find the scraper code here.
The frontend is written using Golang Templates for the HTML, and TailwindCSS plus DaisyUI for the CSS classes framework. I also use some plain CSS, but it's minimal.
The requests forms is the only part of the project that requires JavaScript to be enabled. It is needed for parsing some from fields that are a bit complex and for the "captcha", which is a simple Proof of Work that runs on your browser, destinated to avoid spam. For this, I use mCaptcha.
-
 @ 39cc53c9:27168656
2025-04-09 07:59:33
@ 39cc53c9:27168656
2025-04-09 07:59:33Know Your Customer is a regulation that requires companies of all sizes to verify the identity, suitability, and risks involved with maintaining a business relationship with a customer. Such procedures fit within the broader scope of anti-money laundering (AML) and counterterrorism financing (CTF) regulations.
Banks, exchanges, online business, mail providers, domain registrars... Everyone wants to know who you are before you can even opt for their service. Your personal information is flowing around the internet in the hands of "god-knows-who" and secured by "trust-me-bro military-grade encryption". Once your account is linked to your personal (and verified) identity, tracking you is just as easy as keeping logs on all these platforms.
Rights for Illusions
KYC processes aim to combat terrorist financing, money laundering, and other illicit activities. On the surface, KYC seems like a commendable initiative. I mean, who wouldn't want to halt terrorists and criminals in their tracks?
The logic behind KYC is: "If we mandate every financial service provider to identify their users, it becomes easier to pinpoint and apprehend the malicious actors."
However, terrorists and criminals are not precisely lining up to be identified. They're crafty. They may adopt false identities or find alternative strategies to continue their operations. Far from being outwitted, many times they're several steps ahead of regulations. Realistically, KYC might deter a small fraction – let's say about 1% ^1 – of these malefactors. Yet, the cost? All of us are saddled with the inconvenient process of identification just to use a service.
Under the rhetoric of "ensuring our safety", governments and institutions enact regulations that seem more out of a dystopian novel, gradually taking away our right to privacy.
To illustrate, consider a city where the mayor has rolled out facial recognition cameras in every nook and cranny. A band of criminals, intent on robbing a local store, rolls in with a stolen car, their faces obscured by masks and their bodies cloaked in all-black clothes. Once they've committed the crime and exited the city's boundaries, they switch vehicles and clothes out of the cameras' watchful eyes. The high-tech surveillance? It didn’t manage to identify or trace them. Yet, for every law-abiding citizen who merely wants to drive through the city or do some shopping, their movements and identities are constantly logged. The irony? This invasive tracking impacts all of us, just to catch the 1% ^1 of less-than-careful criminals.
KYC? Not you.
KYC creates barriers to participation in normal economic activity, to supposedly stop criminals. ^2
KYC puts barriers between many users and businesses. One of these comes from the fact that the process often requires multiple forms of identification, proof of address, and sometimes even financial records. For individuals in areas with poor record-keeping, non-recognized legal documents, or those who are unbanked, homeless or transient, obtaining these documents can be challenging, if not impossible.
For people who are not skilled with technology or just don't have access to it, there's also a barrier since KYC procedures are mostly online, leaving them inadvertently excluded.
Another barrier goes for the casual or one-time user, where they might not see the value in undergoing a rigorous KYC process, and these requirements can deter them from using the service altogether.
It also wipes some businesses out of the equation, since for smaller businesses, the costs associated with complying with KYC norms—from the actual process of gathering and submitting documents to potential delays in operations—can be prohibitive in economical and/or technical terms.
You're not welcome
Imagine a swanky new club in town with a strict "members only" sign. You hear the music, you see the lights, and you want in. You step up, ready to join, but suddenly there's a long list of criteria you must meet. After some time, you are finally checking all the boxes. But then the club rejects your membership with no clear reason why. You just weren't accepted. Frustrating, right?
This club scenario isn't too different from the fact that KYC is being used by many businesses as a convenient gatekeeping tool. A perfect excuse based on a "legal" procedure they are obliged to.
Even some exchanges may randomly use this to freeze and block funds from users, claiming these were "flagged" by a cryptic system that inspects the transactions. You are left hostage to their arbitrary decision to let you successfully pass the KYC procedure. If you choose to sidestep their invasive process, they might just hold onto your funds indefinitely.
Your identity has been stolen
KYC data has been found to be for sale on many dark net markets^3. Exchanges may have leaks or hacks, and such leaks contain very sensitive data. We're talking about the full monty: passport or ID scans, proof of address, and even those awkward selfies where you're holding up your ID next to your face. All this data is being left to the mercy of the (mostly) "trust-me-bro" security systems of such companies. Quite scary, isn't it?
As cheap as $10 for 100 documents, with discounts applying for those who buy in bulk, the personal identities of innocent users who passed KYC procedures are for sale. ^3
In short, if you have ever passed the KYC/AML process of a crypto exchange, your privacy is at risk of being compromised, or it might even have already been compromised.
(they) Know Your Coins
You may already know that Bitcoin and most cryptocurrencies have a transparent public blockchain, meaning that all data is shown unencrypted for everyone to see and recorded forever. If you link an address you own to your identity through KYC, for example, by sending an amount from a KYC exchange to it, your Bitcoin is no longer pseudonymous and can then be traced.
If, for instance, you send Bitcoin from such an identified address to another KYC'ed address (say, from a friend), everyone having access to that address-identity link information (exchanges, governments, hackers, etc.) will be able to associate that transaction and know who you are transacting with.
Conclusions
To sum up, KYC does not protect individuals; rather, it's a threat to our privacy, freedom, security and integrity. Sensible information flowing through the internet is thrown into chaos by dubious security measures. It puts borders between many potential customers and businesses, and it helps governments and companies track innocent users. That's the chaos KYC has stirred.
The criminals are using stolen identities from companies that gathered them thanks to these very same regulations that were supposed to combat them. Criminals always know how to circumvent such regulations. In the end, normal people are the most affected by these policies.
The threat that KYC poses to individuals in terms of privacy, security and freedom is not to be neglected. And if we don’t start challenging these systems and questioning their efficacy, we are just one step closer to the dystopian future that is now foreseeable.
Edited 20/03/2024 * Add reference to the 1% statement on Rights for Illusions section to an article where Chainalysis found that only 0.34% of the transaction volume with cryptocurrencies in 2023 was attributable to criminal activity ^1
-
 @ 39cc53c9:27168656
2025-04-09 07:59:32
@ 39cc53c9:27168656
2025-04-09 07:59:32Over the past few months, I've dedicated my time to a complete rewrite of the kycnot.me website. The technology stack remains unchanged; Golang paired with TailwindCSS. However, I've made some design choices in this iteration that I believe significantly enhance the site. Particularly to backend code.
UI Improvements
You'll notice a refreshed UI that retains the original concept but has some notable enhancements. The service list view is now more visually engaging, it displays additional information in a more aesthetically pleasing manner. Both filtering and searching functionalities have been optimized for speed and user experience.
Service pages have been also redesigned to highlight key information at the top, with the KYC Level box always accessible. The display of service attributes is now more visually intuitive.
The request form, especially the Captcha, has undergone substantial improvements. The new self-made Captcha is robust, addressing the reliability issues encountered with the previous version.
Terms of Service Summarizer
A significant upgrade is the Terms of Service summarizer/reviewer, now powered by AI (GPT-4-turbo). It efficiently condenses each service's ToS, extracting and presenting critical points, including any warnings. Summaries are updated monthly, processing over 40 ToS pages via the OpenAI API using a self-crafted and thoroughly tested prompt.
Nostr Comments
I've integrated a comment section for each service using Nostr. For guidance on using this feature, visit the dedicated how-to page.
Database
The backend database has transitioned to pocketbase, an open-source Golang backend that has been a pleasure to work with. I maintain an updated fork of the Golang SDK for pocketbase at pluja/pocketbase.
Scoring
The scoring algorithm has also been refined to be more fair. Despite I had considered its removal due to the complexity it adds (it is very difficult to design a fair scoring system), some users highlighted its value, so I kept it. The updated algorithm is available open source.
Listings
Each listing has been re-evaluated, and the ones that were no longer operational were removed. New additions are included, and the backlog of pending services will be addressed progressively, since I still have access to the old database.
API
The API now offers more comprehensive data. For more details, check here.
About Page
The About page has been restructured for brevity and clarity.
Other Changes
Extensive changes have been implemented in the server-side logic, since the whole code base was re-written from the ground up. I may discuss these in a future post, but for now, I consider the current version to be just a bit beyond beta, and additional updates are planned in the coming weeks.
-
 @ 39cc53c9:27168656
2025-04-09 07:59:30
@ 39cc53c9:27168656
2025-04-09 07:59:30I'm launching a new service review section on this blog in collaboration with OrangeFren. These reviews are sponsored, yet the sponsorship does not influence the outcome of the evaluations. Reviews are done in advance, then, the service provider has the discretion to approve publication without modifications.
Sponsored reviews are independent from the kycnot.me list, being only part of the blog. The reviews have no impact on the scores of the listings or their continued presence on the list. Should any issues arise, I will not hesitate to remove any listing.
The review
WizardSwap is an instant exchange centred around privacy coins. It was launched in 2020 making it old enough to have weathered the 2021 bull run and the subsequent bearish year.
| Pros | Cons | |------|------| | Tor-friendly | Limited liquidity | | Guarantee of no KYC | Overly simplistic design | | Earn by providing liquidity | |
Rating: ★★★★★ Service Website: wizardswap.io
Liquidity
Right off the bat, we'll start off by pointing out that WizardSwap relies on its own liquidity reserves, meaning they aren't just a reseller of Binance or another exchange. They're also committed to a no-KYC policy, when asking them, they even promised they would rather refund a user their original coins, than force them to undergo any sort of verification.
On the one hand, full control over all their infrastructure gives users the most privacy and conviction about the KYC policies remaining in place.
On the other hand, this means the liquidity available for swapping isn't huge. At the time of testing we could only purchase at most about 0.73 BTC with XMR.
It's clear the team behind WizardSwap is aware of this shortfall and so they've come up with a solution unique among instant exchanges. They let you, the user, deposit any of the currencies they support into your account and earn a profit on the trades made using your liquidity.
Trading
Fees on WizardSwap are middle-of-the-pack. The normal fee is 2.2%. That's more than some exchanges that reserve the right to suddenly demand you undergo verification, yet less than half the fees on some other privacy-first exchanges. However as we mentioned in the section above you can earn almost all of that fee (2%) if you provide liquidity to WizardSwap.
It's good that with the current Bitcoin fee market their fees are constant regardless of how much, or how little, you send. This is in stark contrast with some of the alternative swap providers that will charge you a massive premium when attempting to swap small amounts of BTC away.
Test trades
Test trades are always performed without previous notice to the service provider.
During our testing we performed a few test trades and found that every single time WizardSwap immediately detected the incoming transaction and the amount we received was exactly what was quoted before depositing. The fees were inline with what WizardSwap advertises.

- Monero payment proof
- Bitcoin received
- Wizardswap TX link - it's possible that this link may cease to be valid at some point in the future.
ToS and KYC
WizardSwap does not have a Terms of Service or a Privacy Policy page, at least none that can be found by users. Instead, they offer a FAQ section where they addresses some basic questions.
The site does not mention any KYC or AML practices. It also does not specify how refunds are handled in case of failure. However, based on the FAQ section "What if I send funds after the offer expires?" it can be inferred that contacting support is necessary and network fees will be deducted from any refund.
UI & Tor
WizardSwap can be visited both via your usual browser and Tor Browser. Should you decide on the latter you'll find that the website works even with the most strict settings available in the Tor Browser (meaning no JavaScript).
However, when disabling Javascript you'll miss the live support chat, as well as automatic refreshing of the trade page. The lack of the first means that you will have no way to contact support from the trade page if anything goes wrong during your swap, although you can do so by mail.
One important thing to have in mind is that if you were to accidentally close the browser during the swap, and you did not save the swap ID or your browser history is disabled, you'll have no easy way to return to the trade. For this reason we suggest when you begin a trade to copy the url or ID to someplace safe, before sending any coins to WizardSwap.
The UI you'll be greeted by is simple, minimalist, and easy to navigate. It works well not just across browsers, but also across devices. You won't have any issues using this exchange on your phone.
Getting in touch
The team behind WizardSwap appears to be most active on X (formerly Twitter): https://twitter.com/WizardSwap_io
If you have any comments or suggestions about the exchange make sure to reach out to them. In the past they've been very receptive to user feedback, for instance a few months back WizardSwap was planning on removing DeepOnion, but the community behind that project got together ^1 and after reaching out WizardSwap reversed their decision ^2.
You can also contact them via email at:
support @ wizardswap . ioDisclaimer
None of the above should be understood as investment or financial advice. The views are our own only and constitute a faithful representation of our experience in using and investigating this exchange. This review is not a guarantee of any kind on the services rendered by the exchange. Do your own research before using any service.
-
 @ 39cc53c9:27168656
2025-04-09 07:59:28
@ 39cc53c9:27168656
2025-04-09 07:59:28Bitcoin enthusiasts frequently and correctly remark how much value it adds to Bitcoin not to have a face, a leader, or a central authority behind it. This particularity means there isn't a single person to exert control over, or a single human point of failure who could become corrupt or harmful to the project.
Because of this, it is said that no other coin can be equally valuable as Bitcoin in terms of decentralization and trustworthiness. Bitcoin is unique not just for being first, but also because of how the events behind its inception developed. This implies that, from Bitcoin onwards, any coin created would have been created by someone, consequently having an authority behind it. For this and some other reasons, some people refer to Bitcoin as "The Immaculate Conception".
While other coins may have their own unique features and advantages, they may not be able to replicate Bitcoin's community-driven nature. However, one other cryptocurrency shares a similar story of mystery behind its creation: Monero.
History of Monero
Bytecoin and CryptoNote
In March 2014, a Bitcointalk thread titled "Bytecoin. Secure, private, untraceable since 2012" was initiated by a user under the nickname "DStrange"^1^. DStrange presented Bytecoin (BCN) as a unique cryptocurrency, in operation since July 2012. Unlike Bitcoin, it employed a new algorithm known as CryptoNote.
DStrange apparently stumbled upon the Bytecoin website by chance while mining a dying bitcoin fork, and decided to create a thread on Bitcointalk^1^. This sparked curiosity among some users, who wondered how could Bytecoin remain unnoticed since its alleged launch in 2012 until then^2^.
Some time after, a user brought up the "CryptoNote v2.0" whitepaper for the first time, underlining its innovative features^4^. Authored by the pseudonymous Nicolas van Saberhagen in October 2013, the CryptoNote v2 whitepaper^5^ highlighted the traceability and privacy problems in Bitcoin. Saberhagen argued that these flaws could not be quickly fixed, suggesting it would be more efficient to start a new project rather than trying to patch the original^5^, an statement simmilar to the one from Satoshi Nakamoto^6^.
Checking with Saberhagen's digital signature, the release date of the whitepaper seemed correct, which would mean that Cryptonote (v1) was created in 2012^7^, although there's an important detail: "Signing time is from the clock on the signer's computer" ^9^.
Moreover, the whitepaper v1 contains a footnote link to a Bitcointalk post dated May 5, 2013^10^, making it impossible for the whitepaper to have been signed and released on December 12, 2012.
As the narrative developed, users discovered that a significant 80% portion of Bytecoin had been pre-mined^11^ and blockchain dates seemed to be faked to make it look like it had been operating since 2012, leading to controversy surrounding the project.
The origins of CryptoNote and Bytecoin remain mysterious, leaving suspicions of a possible scam attempt, although the whitepaper had a good amount of work and thought on it.
The fork
In April 2014, the Bitcointalk user
thankful_for_today, who had also participated in the Bytecoin thread^12^, announced plans to launch a Bytecoin fork named Bitmonero^13^.The primary motivation behind this fork was "Because there is a number of technical and marketing issues I wanted to do differently. And also because I like ideas and technology and I want it to succeed"^14^. This time Bitmonero did things different from Bytecoin: there was no premine or instamine, and no portion of the block reward went to development.
However, thankful_for_today proposed controversial changes that the community disagreed with. Johnny Mnemonic relates the events surrounding Bitmonero and thankful_for_today in a Bitcointalk comment^15^:
When thankful_for_today launched BitMonero [...] he ignored everything that was discussed and just did what he wanted. The block reward was considerably steeper than what everyone was expecting. He also moved forward with 1-minute block times despite everyone's concerns about the increase of orphan blocks. He also didn't address the tail emission concern that should've (in my opinion) been in the code at launch time. Basically, he messed everything up. Then, he disappeared.
After disappearing for a while, thankful_for_today returned to find that the community had taken over the project. Johnny Mnemonic continues:
I, and others, started working on new forks that were closer to what everyone else was hoping for. [...] it was decided that the BitMonero project should just be taken over. There were like 9 or 10 interested parties at the time if my memory is correct. We voted on IRC to drop the "bit" from BitMonero and move forward with the project. Thankful_for_today suddenly resurfaced, and wasn't happy to learn the community had assumed control of the coin. He attempted to maintain his own fork (still calling it "BitMonero") for a while, but that quickly fell into obscurity.
The unfolding of these events show us the roots of Monero. Much like Satoshi Nakamoto, the creators behind CryptoNote/Bytecoin and thankful_for_today remain a mystery^17^, having disappeared without a trace. This enigma only adds to Monero's value.
Since community took over development, believing in the project's potential and its ability to be guided in a better direction, Monero was given one of Bitcoin's most important qualities: a leaderless nature. With no single face or entity directing its path, Monero is safe from potential corruption or harm from a "central authority".
The community continued developing Monero until today. Since then, Monero has undergone a lot of technological improvements, migrations and achievements such as RingCT and RandomX. It also has developed its own Community Crowdfundinc System, conferences such as MoneroKon and Monerotopia are taking place every year, and has a very active community around it.
Monero continues to develop with goals of privacy and security first, ease of use and efficiency second. ^16^
This stands as a testament to the power of a dedicated community operating without a central figure of authority. This decentralized approach aligns with the original ethos of cryptocurrency, making Monero a prime example of community-driven innovation. For this, I thank all the people involved in Monero, that lead it to where it is today.
If you find any information that seems incorrect, unclear or any missing important events, please contact me and I will make the necessary changes.
Sources of interest
- https://forum.getmonero.org/20/general-discussion/211/history-of-monero
- https://monero.stackexchange.com/questions/852/what-is-the-origin-of-monero-and-its-relationship-to-bytecoin
- https://en.wikipedia.org/wiki/Monero
- https://bitcointalk.org/index.php?topic=583449.0
- https://bitcointalk.org/index.php?topic=563821.0
- https://bitcointalk.org/index.php?action=profile;u=233561
- https://bitcointalk.org/index.php?topic=512747.0
- https://bitcointalk.org/index.php?topic=740112.0
- https://monero.stackexchange.com/a/1024
- https://inspec2t-project.eu/cryptocurrency-with-a-focus-on-anonymity-these-facts-are-known-about-monero/
- https://medium.com/coin-story/coin-perspective-13-riccardo-spagni-69ef82907bd1
- https://www.getmonero.org/resources/about/
- https://www.wired.com/2017/01/monero-drug-dealers-cryptocurrency-choice-fire/
- https://www.monero.how/why-monero-vs-bitcoin
- https://old.reddit.com/r/Monero/comments/u8e5yr/satoshi_nakamoto_talked_about_privacy_features/
-
 @ 39cc53c9:27168656
2025-04-09 07:59:27
@ 39cc53c9:27168656
2025-04-09 07:59:27I've been thinking about how to improve my seed backup in a cheap and cool way, mostly for fun. Until now, I had the seed written on a piece of paper in a desk drawer, and I wanted something more durable and fire-proof.
After searching online, I found two options I liked the most: the Cryptosteel Capsule and the Trezor Keep. These products are nice but quite expensive, and I didn't want to spend that much on my seed backup. Privacy is also important, and sharing details like a shipping address makes me uncomfortable. This concern has grown since the Ledger incident^1. A $5 wrench attack^2 seems too cheap, even if you only hold a few sats.
Upon seeing the design of Cryptosteel, I considered creating something similar at home. Although it may not be as cool as their device, it could offer almost the same in terms of robustness and durability.
Step 1: Get the materials and tools
When choosing the materials, you will want to go with stainless steel. It is durable, resistant to fire, water, and corrosion, very robust, and does not rust. Also, its price point is just right; it's not the cheapest, but it's cheap for the value you get.

I went to a material store and bought:
- Two bolts
- Two hex nuts and head nuts for the bolts
- A bag of 30 washers
All items were made of stainless steel. The total price was around €6. This is enough for making two seed backups.
You will also need:
- A set of metal letter stamps (I bought a 2mm-size letter kit since my washers were small, 6mm in diameter)
- You can find these in local stores or online marketplaces. The set I bought cost me €13.
- A good hammer
- A solid surface to stamp on
Total spent: 19€ for two backups
Step 2: Stamp and store
Once you have all the materials, you can start stamping your words. There are many videos on the internet that use fancy 3D-printed tools to get the letters nicely aligned, but I went with the free-hand option. The results were pretty decent.

I only stamped the first 4 letters for each word since the BIP-39 wordlist allows for this. Because my stamping kit did not include numbers, I used alphabet letters to define the order. This way, if all the washers were to fall off, I could still reassemble the seed correctly.
The final result
So this is the final result. I added two smaller washers as protection and also put the top washer reversed so the letters are not visible:

Compared to the Cryptosteel or the Trezor Keep, its size is much more compact. This makes for an easier-to-hide backup, in case you ever need to hide it inside your human body.
Some ideas
Tamper-evident seal
To enhance the security this backup, you can consider using a tamper-evident seal. This can be easily achieved by printing a unique image or using a specific day's newspaper page (just note somewhere what day it was).
Apply a thin layer of glue to the washer's surface and place the seal over it. If someone attempts to access the seed, they will be forced to destroy the seal, which will serve as an evident sign of tampering.
This simple measure will provide an additional layer of protection and allow you to quickly identify any unauthorized access attempts.
Note that this method is not resistant to outright theft. The tamper-evident seal won't stop a determined thief but it will prevent them from accessing your seed without leaving any trace.
Redundancy
Make sure to add redundancy. Make several copies of this cheap backup, and store them in separate locations.
Unique wordset
Another layer of security could be to implement your own custom mnemonic dictionary. However, this approach has the risk of permanently losing access to your funds if not implemented correctly.
If done properly, you could potentially end up with a highly secure backup, as no one else would be able to derive the seed phrase from it. To create your custom dictionary, assign a unique number from 1 to 2048 to a word of your choice. Maybe you could use a book, and index the first 2048 unique words that appear. Make sure to store this book and even get a couple copies of it (digitally and phisically).
This self-curated set of words will serve as your personal BIP-39 dictionary. When you need to translate between your custom dictionary and the official BIP-39 wordlist, simply use the index number to find the corresponding word in either list.
Never write the idex or words on your computer (Do not use
Ctr+F) -
 @ 39cc53c9:27168656
2025-04-09 07:59:25
@ 39cc53c9:27168656
2025-04-09 07:59:25kycnot.me features a somewhat hidden tool that some users may not be aware of. Every month, an automated job crawls every listed service's Terms of Service (ToS) and FAQ pages and conducts an AI-driven analysis, generating a comprehensive overview that highlights key points related to KYC and user privacy.
Here's an example: Changenow's Tos Review

Why?
ToS pages typically contain a lot of complicated text. Since the first versions of kycnot.me, I have tried to provide users a comprehensive overview of what can be found in such documents. This automated method keeps the information up-to-date every month, which was one of the main challenges with manual updates.
A significant part of the time I invest in investigating a service for kycnot.me involves reading the ToS and looking for any clauses that might indicate aggressive KYC practices or privacy concerns. For the past four years, I performed this task manually. However, with advancements in language models, this process can now be somewhat automated. I still manually review the ToS for a quick check and regularly verify the AI’s findings. However, over the past three months, this automated method has proven to be quite reliable.
Having a quick ToS overview section allows users to avoid reading the entire ToS page. Instead, you can quickly read the important points that are grouped, summarized, and referenced, making it easier and faster to understand the key information.
Limitations
This method has a key limitation: JS-generated pages. For this reason, I was using Playwright in my crawler implementation. I plan to make a release addressing this issue in the future. There are also sites that don't have ToS/FAQ pages, but these sites already include a warning in that section.
Another issue is false positives. Although not very common, sometimes the AI might incorrectly interpret something harmless as harmful. Such errors become apparent upon reading; it's clear when something marked as bad should not be categorized as such. I manually review these cases regularly, checking for anything that seems off and then removing any inaccuracies.
Overall, the automation provides great results.
How?
There have been several iterations of this tool. Initially, I started with GPT-3.5, but the results were not good in any way. It made up many things, and important thigs were lost on large ToS pages. I then switched to GPT-4 Turbo, but it was expensive. Eventually, I settled on Claude 3 Sonnet, which provides a quality compromise between GPT-3.5 and GPT-4 Turbo at a more reasonable price, while allowing a generous 200K token context window.
I designed a prompt, which is open source^1, that has been tweaked many times and will surely be adjusted further in the future.
For the ToS scraping part, I initially wrote a scraper API using Playwright^2, but I replaced it with Jina AI Reader^3, which works quite well and is designed for this task.
Non-conflictive ToS
All services have a dropdown in the ToS section called "Non-conflictive ToS Reviews." These are the reviews that the AI flagged as not needing a user warning. I still provide these because I think they may be interesting to read.
Feedback and contributing
You can give me feedback on this tool, or share any inaccuraties by either opening an issue on Codeberg^4 or by contacting me ^5.
You can contribute with pull requests, which are always welcome, or you can support this project with any of the listed ways.
-
 @ 39cc53c9:27168656
2025-04-09 07:59:24
@ 39cc53c9:27168656
2025-04-09 07:59:24These reviews are sponsored, yet the sponsorship does not influence the outcome of the evaluations. Sponsored reviews are independent from the kycnot.me list, being only part of the blog. The reviews have no impact on the scores of the listings or their continued presence on the list. Should any issues arise, I will not hesitate to remove any listing. Reviews are in collaboration with Orangefren.
The review
Swapter.io is an all-purpose instant exchange. They entered the scene in the depths of the bear market about 2 years ago in June of 2022.
| Pros | Cons | | --------------- | ---------------------------------- | | Low fees | Shotgun KYC with opaque triggers | | Large liquidity | Relies on 3rd party liquidity | | Works over Tor | Front-end not synced with back-end | | Pretty UI | |
Rating: ★★★☆☆ Service Website: swapter.io
⚠️ There is an ongoing issue with this service: read more on Reddit.
Test Trades
During our testing we performed a trade from XMR to LTC, and then back to XMR.
Our first trade had the ID of:
mpUitpGemhN8jjNAjQuo6EvQ. We were promised 0.8 LTC for sending 0.5 XMR, before we sent the Monero. When the Monero arrived we were sent 0.799 LTC.On the return journey we performed trade with ID:
yaCRb5pYcRKAZcBqg0AzEGYg. This time we were promised 0.4815 XMR for sending 0.799 LTC. After Litecoin arrived we were sent 0.4765 XMR.As such we saw a discrepancy of
~0.1%in the first trade and~1%in the second trade. Considering those trades were floating we determine the estimates presented in the UI to be highly accurate and honest.Of course Swapter could've been imposing a large fee on their estimates, but we checked their estimates against CoinGecko and found the difference to be equivalent to a fee of just over
0.5%. Perfectly in line with other swapping services.Trading
Swapter supports BTC, LTC, XMR and well over a thousand other coins. Sadly they don't support the Lightning Network. For the myriad of currencies they deal with they provide massive upper limits. You could exchange tens, or even hundreds, of thousands of dollars worth of cryptocurrency in a single trade (although we wouldn't recommend it).
The flip side to this is that Swapter relies on 3rd party liquidity. Aside from the large liqudity this also benefits the user insofar as it allows for very low fees. However, it also comes with a negative - the 3rd party gets to see all your trades. Unfortunately Swapter opted not to share where they source their liquidity in their Privacy Policy or Terms of Service.
KYC & AML policies
Swapter reserves the right to require its users to provide their full name, their date of birth, their address and government-issued ID. A practice known as "shotgun KYC". This should not happen often - in our testing it never did - however it's not clear when exactly it could happen. The AML & KYC policy provided on Swapter's website simply states they will put your trade on hold if their "risk scoring system [deems it] as suspicious".
Worse yet, if they determine that "any of the information [the] customer provided is incorrect, false, outdated, or incomplete" then Swapter may decide to terminate all of the services they provide to the user. What exactly would happen to their funds in such a case remains unclear.
The only clarity we get is that the Swapter policy outlines a designated 3rd party that will verify the information provided by the user. The third party's name is Sum & Substance Ltd, also simply known as samsub and available at sumsub.com
It's understandable that some exchanges will decide on a policy of this sort, especially when they rely on external liquidity, but we would prefer more clarity be given. When exactly is a trade suspicious?
Tor
We were pleased to discover Swapter works over Tor. However, they do not provide a Tor mirror, nor do they work without JavaScript. Additionally, we found that some small features, such as the live chat, did not work over Tor. Fortunately, other means of contacting their support are still available.
UI
We have found the Swapter UI to be very modern, straightforward and simple to use. It's available in 4 languages (English, French, Dutch and Russian), although we're unable to vouch for the quality of some of those, the ones that we used seemed perfectly serviceable.
Our only issue with the UI was that it claims the funds have been sent following the trade, when in reality it seems to take the backend a minute or so to actually broadcast the transaction.
Getting in touch
Swapter's team has a chat on their website, a support email address and a support Telegram. Their social media presence in most active on Telegram and X (formerly Twitter).
Disclaimer
None of the above should be understood as investment or financial advice. The views are our own only and constitute a faithful representation of our experience in using and investigating this exchange. This review is not a guarantee of any kind on the services rendered by the exchange. Do your own research before using any service.
-
 @ 39cc53c9:27168656
2025-04-09 07:59:22
@ 39cc53c9:27168656
2025-04-09 07:59:22“The future is there... staring back at us. Trying to make sense of the fiction we will have become.” — William Gibson.
This month is the 4th anniversary of kycnot.me. Thank you for being here.
Fifteen years ago, Satoshi Nakamoto introduced Bitcoin, a peer-to-peer electronic cash system: a decentralized currency free from government and institutional control. Nakamoto's whitepaper showed a vision for a financial system based on trustless transactions, secured by cryptography. Some time forward and KYC (Know Your Customer), AML (Anti-Money Laundering), and CTF (Counter-Terrorism Financing) regulations started to come into play.
What a paradox: to engage with a system designed for decentralization, privacy, and independence, we are forced to give away our personal details. Using Bitcoin in the economy requires revealing your identity, not just to the party you interact with, but also to third parties who must track and report the interaction. You are forced to give sensitive data to entities you don't, can't, and shouldn't trust. Information can never be kept 100% safe; there's always a risk. Information is power, who knows about you has control over you.
Information asymmetry creates imbalances of power. When entities have detailed knowledge about individuals, they can manipulate, influence, or exploit this information to their advantage. The accumulation of personal data by corporations and governments enables extensive surveillances.
Such practices, moreover, exclude individuals from traditional economic systems if their documentation doesn't meet arbitrary standards, reinforcing a dystopian divide. Small businesses are similarly burdened by the costs of implementing these regulations, hindering free market competition^1:

How will they keep this information safe? Why do they need my identity? Why do they force businesses to enforce such regulations? It's always for your safety, to protect you from the "bad". Your life is perpetually in danger: terrorists, money launderers, villains... so the government steps in to save us.
‟Hush now, baby, baby, don't you cry Mamma's gonna make all of your nightmares come true Mamma's gonna put all of her fears into you Mamma's gonna keep you right here, under her wing She won't let you fly, but she might let you sing Mamma's gonna keep baby cosy and warm” — Mother, Pink Floyd
We must resist any attack on our privacy and freedom. To do this, we must collaborate.
If you have a service, refuse to ask for KYC; find a way. Accept cryptocurrencies like Bitcoin and Monero. Commit to circular economies. Remove the need to go through the FIAT system. People need fiat money to use most services, but we can change that.
If you're a user, donate to and prefer using services that accept such currencies. Encourage your friends to accept cryptocurrencies as well. Boycott FIAT system to the greatest extent you possibly can.
This may sound utopian, but it can be achieved. This movement can't be stopped. Go kick the hornet's nest.
“We must defend our own privacy if we expect to have any. We must come together and create systems which allow anonymous transactions to take place. People have been defending their own privacy for centuries with whispers, darkness, envelopes, closed doors, secret handshakes, and couriers. The technologies of the past did not allow for strong privacy, but electronic technologies do.” — Eric Hughes, A Cypherpunk's Manifesto
The anniversary
Four years ago, I began exploring ways to use crypto without KYC. I bookmarked a few favorite services and thought sharing them to the world might be useful. That was the first version of kycnot.me — a simple list of about 15 services. Since then, I've added services, rewritten it three times, and improved it to what it is now.
kycnot.me has remained 100% independent and 100% open source^2 all these years. I've received offers to buy the site, all of which I have declined and will continue to decline. It has been DDoS attacked many times, but we made it through. I have also rewritten the whole site almost once per year (three times in four years).
The code and scoring algorithm are open source (contributions are welcome) and I can't arbitrarly change a service's score without adding or removing attributes, making any arbitrary alterations obvious if they were fake. You can even see the score summary for any service's score.
I'm a one-person team, dedicating my free time to this project. I hope to keep doing so for many more years. Again, thank you for being part of this.
-
 @ a367f9eb:0633efea
2025-04-09 07:28:49
@ a367f9eb:0633efea
2025-04-09 07:28:49WIEN – Diese Woche enthüllte Innenminister Gerhard Karner von der ÖVP, dass er einen Gesetzesentwurf "schnell" durchsetzen möchte, der der Regierung die Befugnis geben würde, verschlüsselte Kommunikation in Nachrichten-Apps zu überwachen.
Obwohl Karner betont hat, dass die neuen Befugnisse nur sehr gezielt eingesetzt würden, ist unklar, ob die Entwickler und Anbieter von Nachrichten-Apps gezwungen werden sollen, die Verschlüsselung zu brechen, um die Anordnungen durchzuführen.
Wie der stellvertretende Direktor des Consumer Choice Center, Yaël Ossowski, erklärte, würde diese Befugnis bedeuten, die Verschlüsselung für Millionen von österreichischen Verbrauchern zu untergraben und zu brechen.
„Jeder Versuch, die Verschlüsselung für einige ausgewählte Personen zu brechen, gefährdet gleichzeitig die Privatsphäre von Millionen von Österreichern. Dies ist weniger eine Frage der angemessenen Polizeibefugnisse als vielmehr eine Frage der technischen und sicherheitsrelevanten Aspekte. Schwächere Verschlüsselung macht österreichische Nutzer weniger sicher“ sagte Ossowski.
„Verschlüsselungsstandards von Apps wie Signal, WhatsApp und sogar iMessage aufzuheben, würde der österreichischen Regierung außergewöhnliche Befugnisse einräumen, die das Risiko bergen, jede und alle Kommunikation zu kompromittieren, nicht nur die von Verdächtigen oder Terroristen.
„Um gegen kriminelle Akteure vorzugehen, sollte die Koalition das bestehende Justizsystem nutzen, um Haftbefehle auf Grundlage eines begründeten Verdachts durchzusetzen, anstatt Messaging-Dienste und Apps dazu zu zwingen, diese Aufgabe für sie zu übernehmen“ erklärte Ossowski.
Das Consumer Choice Center weist darauf hin, dass ähnliche Versuche, die Verschlüsselung mit polizeilicher Gewalt zu brechen, bereits im Vereinigten Königreich und in Frankreich unternommen wurden, wo sie von Bürgerrechtsgruppen abgelehnt wurden.
###
Das Consumer Choice Center ist eine unabhängige, parteiunabhängige Verbraucherorganisation, die die Vorteile von Wahlfreiheit, Innovation und Wachstum im Alltagsleben für Verbraucher in über 100 Ländern fördert. Wir interessieren uns insbesondere für regulatorische Trends in Washington, Brüssel, Wien, Berlin, Ottawa, Brasília, London und Genf genau.
Erfahren Sie mehr auf consumerchoicecenter.org
-
 @ 872982aa:8fb54cfe
2025-04-09 05:41:40
@ 872982aa:8fb54cfe
2025-04-09 05:41:40茶业
-
 @ 872982aa:8fb54cfe
2025-04-09 05:40:27
@ 872982aa:8fb54cfe
2025-04-09 05:40:27432143214321412
-
 @ df67f9a7:2d4fc200
2025-04-09 04:42:34
@ df67f9a7:2d4fc200
2025-04-09 04:42:34Businesses want Nostr, but Nostr is not ready for business. What can be done?
- Businesses want reliable SEO and socials to put their brands in front of users, rather than arbitrary gate keepers, censoring the marketplace on a whim.
- Businesses want open access to harvest public data for free on a soveregnty respecting network, rather than paying gate keepers for access to user data of questionalble origin.
- Businesses want the freedom to NOT take ownership of certain user data collected by their apps, rather than being liabile for moderation and safe handling on their private infrastructure.
- Busineses want a single open protocol on which to build their apps, with unlimited potential and a diversity of shared users from other apps, rather than multiple siloed networks with difering APIs and demographics.
- Businesses want to own the technology they build and to use it as they wish, rather than submit their code for approval and control by arbitrary gate keepers.
But Nostr is not ready for business.
- Businesses DON'T want proprietary app data stored publicly as signed Nostr events on user specified relays.
- Businesses DON'T want to have to specify, or be constrained by, or even navigate the complexity of Nostr NIP standards for every novel kind of content that their apps generate.
- Businesses DON'T want to "open source" their entire suite of native apps JUST to assure end users that Nostr private keys are being safely handled.
- Businesses DON'T want to have to "rewrite" their entire app backend just to accomodate the Nostr way of "users sign events but dont actually login to your server" auth architecture.
- Businesses DONT want to suffer DDOS from bots and bad actors, or to expose their users to unwanted content, or even to have their own content disappear a sea of spam and misinformation.
Here is some of what can be done.
- More tools and services for private business apps to coexist with freedom tech, and even thrive together, on the Nostr network.
- Extensible Webs of Trust algos for discovery and reach into any audience or demographic of trusted users.
- WoT powered standard APIs for exposing content to Nostr (and other business apps) from within a “black box” business app.
- HTTP AUTH (NIP 98) integration for business apps, allowing users to create local content WITHOUT needing discrete signatures or “linked” user accounts.
- Frost compatible “login“ for business apps, allowing users to paste “disposable” nsecs into proprietary clients without fear of their “cold” nsec being compromised.
- Support for “incremental” (and voluntary) adoption of freedom tech into existing business apps, with easy off-ramps for businesses to transfer more and more siloed data onto the “public” network.
Thoughts so far…
-
 @ 872982aa:8fb54cfe
2025-04-09 03:47:17
@ 872982aa:8fb54cfe
2025-04-09 03:47:17 -
 @ f7f4e308:b44d67f4
2025-04-09 02:12:18
@ f7f4e308:b44d67f4
2025-04-09 02:12:18https://sns-video-hw.xhscdn.com/stream/1/110/258/01e7ec7be81a85850103700195f3c4ba45_258.mp4
-
 @ c230edd3:8ad4a712
2025-04-09 00:33:31
@ c230edd3:8ad4a712
2025-04-09 00:33:31Chef's notes
I found this recipe a couple years ago and have been addicted to it since. Its incredibly easy, and cheap to prep. Freeze the sausage in flat, single serving portions. That way it can be cooked from frozen for a fast, flavorful, and healthy lunch or dinner. I took inspiration from the video that contained this recipe, and almost always pan fry the frozen sausage with some baby broccoli. The steam cooks the broccoli and the fats from the sausage help it to sear, while infusing the vibrant flavors. Serve with some rice, if desired. I often use serrano peppers, due to limited produce availability. They work well for a little heat and nice flavor that is not overpowering.
Details
- ⏲️ Prep time: 25 min
- 🍳 Cook time: 15 min (only needed if cooking at time of prep)
- 🍽️ Servings: 10
Ingredients
- 4 lbs ground pork
- 12-15 cloves garlic, minced
- 6 Thai or Serrano peppers, rough chopped
- 1/4 c. lime juice
- 4 Tbsp fish sauce
- 1 Tbsp brown sugar
- 1/2 c. chopped cilantro
Directions
- Mix all ingredients in a large bowl.
- Portion and freeze, as desired.
- Sautè frozen portions in hot frying pan, with broccoli or other fresh veggies.
- Serve with rice or alone.
-
 @ 4d41a7cb:7d3633cc
2025-04-08 20:45:34
@ 4d41a7cb:7d3633cc
2025-04-08 20:45:34The most interesting relation that a lawyer holds to the community, outside of his technical occupation, is that of a legislator. Lawyers were the chief authors of the Constitution of the United States and of all the state constitutions.
It seems natural that lawyers should predominate in the government. They framed the former instrument. They both make and interpret the law.
Every time the text is in italics, it is a direct quote from the book.
Lawyers control every branch of the republican form of government: legislative, executive, and judicial. The influence of the lawyers is enormous, for good or for evil.

The lawyer has the supreme power of direction in the general exercise, commencement, and conduct of litigated or other legal matters. It lies with him to suggest and to direct. There is no arbiter over him but his conscience.
The duty of a lawyer is threefold: to the state, as an officer and citizen; to the court, as an officer and adviser; and to his client, as a fiduciary.
The crude sentiments of the people must be filtered through the lawyers, first as politicians, then as legislators, and afterwards as lawyers and judges.
Since lawyers are in charge of every government branch as ‘elected officials’ in representation of the people, education about morality and their duties and responsibilities is fundamental since in their hands lies the monopoly of violence held by the government.
Without contingent arrangements with lawyers, their power would become oppressive and tyrannical.
THE PROBLEM
“Permit me to issue and control the currency of a nation, and I care not who makes its laws.” Mayer Amschel Rothschild (1744-1812)
- Money was placed above rightness, truth, and justice. The incentive structure is inverted, and it's detrimental. Society is morally bankrupt above and below. Institutions are no better than the individuals who compose them.
- Common law was replaced by commercial code (encryption). Adding complexity, inefficiencies, costs, and capacity to trick and twist the law. The incentive structure is broken. Cheating pays more than playing clean; we have more lawyers but less justice.
- The lawyer is not educated about the spirit of the profession, his duty, and the form of government he’s supposed to protect. The interest of the client is put above the interest of the court and the nation. Jurisprudence is taught instead of elementary law.
INSTITUTIONS CANNOT BE BETTER THAN THE MEMBERS OF WHICH THEY ARE COMPOSED. THE GOVERNMENT IS NO DIFFERENT.
The combined acts of a body of lawyers, oft repeated, like an army of worms, silently and secretly gnawing at the foundation of a great and magnificent structure, will gradually but surely cause it to give way and tumble into ruins. It is perhaps not going too far to assert that the lawyers, as a class, are largely answerable for the minimum of respect and obedience that the public has for the law.
1. Money was placed above rightness, truth, and justice.
Commercialism and materialism have placed money above everything else, including the human. This has completely demoralized society in every aspect, from government and justice to education, architecture, medicine, nutrition, and so on.
This has a common denominator: the quality of the currency. As the quality of the currency evaporates, so does the values of the people. But money and currency are inanimate and dead objects; the real actors are the humans trading and using that money.
The ‘fiat money’ we use these days is a result of codified law, a legal fiction for money, a commercial contract paper to exchange goods and services, and a creature of the codified public and private law.
This fiat currency has enabled its possessors to buy, or secure, political and social positions, which should be attained only by real merit, refinement, and learning.
Today judicial systems do not provide justice, newspapers and mainstream media do not provide the truth, today banks do not protect your money, today medical treatment does not cure you, etc. Profit is placed above everything else.
It was evident that materialism completely controlled the economic structure, the ultimate goal of which was for the individual to become part of a system that provided him with economic security at the expense of his soul, mind, and body.
Manly P. Hall, 1988
Society was morally bankrupted by materialistic ideologies and human institutions that are no better than the individuals who compose them.
No judicial action can be put in motion without the sanction of some lawyer.
The lawyer appears everywhere and in all stages of business transactions but also in family and other private and delicate matters as the trusted advisor and friend of his client.
There is a moral corruption, equally as bad in its results upon the judges, the bar, and the community.
2. The incentive structure is inverted, and it's detrimental.
Moral relativism justifies every wrongdoing since ‘there’s no objective difference between right and wrong.’ How can you have justice if you can justify every wrongdoing and there’s no moral compass?
But if being a member of a club or friends with the judge gives you an edge, how can you have excellence, meritocracy, and justice? The incentive is to short-cup your way, to cheat, to manipulate the game and law to your advantage to get economic stability.
If you want to have justice and great institutions, you need to educate their members in a high level of morality, ethics, and purpose…
The commercial code replaced common law. The difference between a common-law lawyer and the practitioner under the Code is the difference between a surgeon and a butcher.
Codification has produced more material to aid dishonest clients than the common law supplied. The lawyers as a body are morally worse than their professional ancestors. The lawyers of the past believed the constitution was adaptable; those of the present regard it as elastic.
Laws have accumulated really fast, creating inextricable confusion and doubt. Making justice was turned into a thing of doubt and change.
Instead of seeking the truth, the courts and the bar are engaged in the pursuit of technicality and form.
A precedent can be found on any side of any subject that anyone chooses to espouse.
The ratio of lawyers has multiplied four times since the law was codified and its complexity increased. The code was adopted in New York in 1848. Argentina's Commercial Code was first adopted by the Province of Buenos Aires in 1859 and later as the national code in 1862. In 1850 there was 1 lawyer per 1000 citizens in the United States. Now there is 1 in 256.
The excessive number of lawyers is detrimental, both to the community and the morale of the profession.
It creates, encourages, and continues illegal, unfounded, and fraudulent practices, demands, and litigations, because necessarily many of the lawyers depend not upon professional knowledge and accomplishments but upon sharpness and cunning. In the effort to sustain themselves, much unnecessary and unfounded litigation is inaugurated, and many disgraceful practices are engendered.
Let anyone consider the effect of the forty or fifty thousand legal agents spending their lives distorting and prostituting the forms of justice, misapplying and perverting its principles, and undermining the constitution and laws, and they can make a fairly accurate calculation as to the longevity of the system of government under which they exist and thrive.
Cunning and trickery have replaced real knowledge and ethics.
The modern code lawyer knows little of elementary law, but he carries, as a soldier would a knapsack, a memory filled with sections of codes and adjudicated cases.
Sheltered in the grip of his office, the lawyer can always, insidiously and secretly, deflect the course of justice and defraud the law. It is difficult to detect him; he is representing another’s interest and is not responsible for his client’s morals or frauds.
To say nothing of the extra cost and expenses, the manifold delays and intricacies of legal procedure, the attempt to simplify has been to muddle, confound, and destroy—to produce a race of pygmy lawyers, chattering and quarreling over the meaning of words in the Code.
The ones who benefit from codification are the same ones who benefit from fiat currencies and central banks. They have used the same strategy in both cases: create a problem, manipulate public opinion and make them demand the ‘solution’ they have already prepared—codification of law, central banks, etc. Time has shown that the public was manipulated and that the solutions that was sold to them only increased the size of the problem they were ‘trying’ to fix.
Picture the lawyers training themselves in a school of dishonesty, trickery, and chicanery, diverting and stopping the machinery of the law, prostituting the forms of justice for gain, selling their knowledge, ability, experience, and such talent as they may possess to the client who pays most for the service, and resorting to every device of cunning and deceit to gain their end! Do such lawyers exist? Do such practices prevail? Unfortunately, yes. In the first rank of the profession can be found many lawyers whose services are sought only to enable guilty men to escape punishment; only to open a door for others to avoid the consequences of the civil law and of their contracts; only to defeat and evade the legislative will and public policy; only to show their clients how to cheat, defraud, vilify, and defame without penalty or damage.
His profession consists of thwarting the law instead of enforcing it. The modern idea of a great lawyer is one who can most successfully manipulate the law and the facts. The public no longer calls them “great” but “successful” lawyers. Not a great jurist or profound student, but a successful practitioner.
The more desperate the case he wins, the greater his reputation.
It is the common belief, inside and outside of the profession, that the most brilliant and learned of the lawyers are employed to defeat or strangle justice.
In this view, every lawyer might be regarded as an intellectual prostitute whose mind, time, experience, knowledge, and influence can be hired and occupied by any stranger who desires to comply with his terms as to fees.
There is nothing secret or underhand about this part of the lawyer’s business. It has the approval of the people everywhere.
In fact, the community looks with perfect complacency and composure upon a transaction in which the leading lawyer sells his talent, his knowledge, his time, and his influence to the most corrupt or infamous individual in the land.
The lawyer is deliberately made an instrument to thwart the law and justice—and he knows it.
He uses the machinery of the law to accomplish results contrary to justice, truth, and right.
When the laws can be easily thwarted, the moral sense of the whole community is deadened. The incentive for justice was inverted and destroyed.
3. The lawyer is not educated about the spirit of the profession.
The lawyer’s power arises from the necessity of political organization; he is the official and authorized agent that puts in motion the machinery of the law.
In the commencement of suits, the lawyer has need, therefore, of honesty, learning, prudence, and patriotism. It rests with him to preserve the purity of the legal system; to separate the chaff of fraud, exaggeration, and doubt from the wheat of fact and truth.
The government exists for the people, not the people for the government.
American governments were organized by the people to provide the people a peaceful way of resolving conflicts and trading peacefully, providing justice and the protection of private property and equality under the law. The public is taxed for the general expenses of the courts, among other things.
Here’s the secret, -the cornerstone- of all legislation.
The goal is to have an easy and understandable set of rules that everyone can understand: to make as few laws as possible; for, in all normal and sound conditions of society, that country is best governed which is least governed. But codification has done the opposite: add complexity and create thousands of codified laws.
Here’s the secret, -the cornerstone- of all legislation.
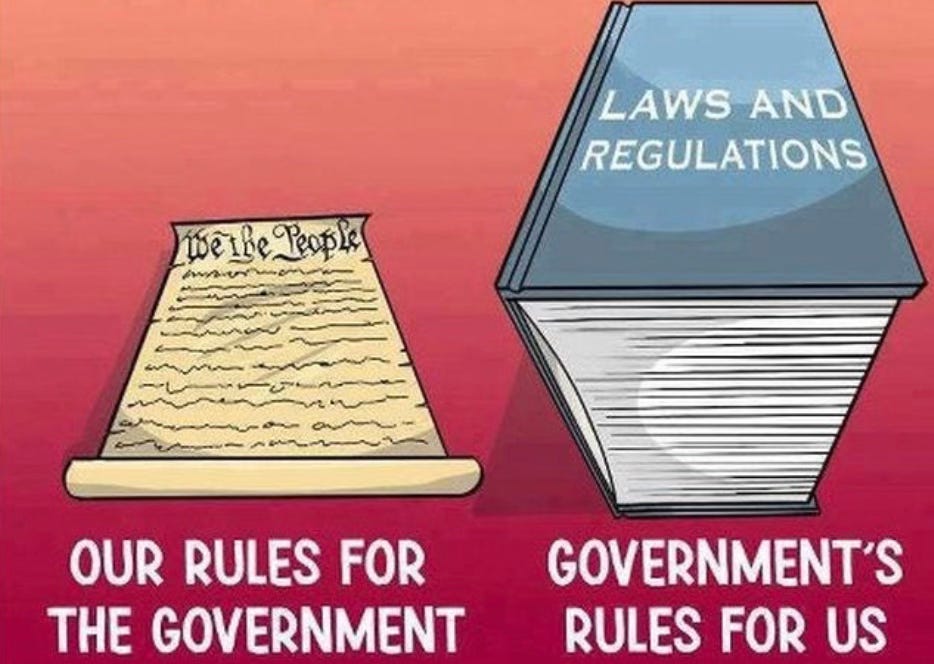 The legislator should, therefore, be a man who understands the origin and nature of society- familiar with past and existing laws and history- with such practical and discriminating judgment as enables him to comprehend the wants and necessities of his fellow men.
The legislator should, therefore, be a man who understands the origin and nature of society- familiar with past and existing laws and history- with such practical and discriminating judgment as enables him to comprehend the wants and necessities of his fellow men.Still, none of the formal oaths defines the duties of the lawyer.
Everything is now left to the moral perception of the lawyer.
THE LOYALTY TO ITS CLIENT (THE HAND THAT FEEDS HIS MOUTH) IS PLACED ABOVE THE ALLIANCE TO THE STATE (THE HAND THAT FEEDS THE JUDICIAL SYSTEM).
It is not the exception, but the rule, for the lawyer to surrender his whole mental, intellectual, and physical power to his client’s cause.
REMEDY
To produce lawyers who can perform their duties, they should be taught to cultivate a moral sense; the nature and object of law; the nature and duties of citizenship; the nature and duties of a legislator; but above and beyond everything else, they should be taught the real mission of the lawyer - which includes professional ethics. These fundamental requisites to the making of a full lawyer are almost entirely overlooked in all of the courses of education followed in law offices, law schools, and academies or colleges. Lawyers are made up to be mere instruments for their clients, without any attention being paid to their duties to the State. The fact is extraordinary, nay, incredible. But it is true. The curriculum of legal study is based upon codification. O means the sentiment of codification., pervades and influences all legal education.
If the moral sense of the community, which is another name for public opinion, should be maintained to the highest possible degree, an educated Bar, and a free, pure and intelligent Press, are the factors which can do much to accomplish all these results.
But this conscience, which should guide the lawyer, comes from training and education.
Trained in the knowledge of human nature, when he enters the field of jurisprudence and politics, his acts and opinions should be of the greatest value to the people. I would build up a race of pure lawyers, as far removed from commercialism as possible.
The country needs such a class more than ever.
-
 @ 7d33ba57:1b82db35
2025-04-08 14:34:59
@ 7d33ba57:1b82db35
2025-04-08 14:34:59Barcelona is a city that sizzles with creativity, blends beach life with bold architecture, and radiates Mediterranean energy. From Gaudí’s surreal masterpieces to the lively buzz of La Rambla and the golden sands of Barceloneta Beach, it's a place where every street feels like a gallery—and every evening invites a fiesta.
🌟 Top Things to Do in Barcelona
1️⃣ Sagrada Família
- Gaudí’s unfinished masterpiece and Barcelona’s iconic landmark
- A kaleidoscope of colorful stained glass, soaring columns, and symbolism
- Book tickets in advance—it gets busy for a reason
2️⃣ Park Güell
- A whimsical hilltop park filled with mosaics, dragons, and curves
- Explore the Monumental Zone and enjoy views over the city
- Like stepping into a dream—or a fairytale!

3️⃣ Stroll La Rambla & Explore the Gothic Quarter
- A lively pedestrian street with flower stalls, performers, and markets
- Wander into the Gothic Quarter (Barri Gòtic) for narrow alleys, Roman ruins, and hidden plazas
- Visit Plaça Reial for tapas and a good vibe
4️⃣ Casa Batlló & Casa Milà (La Pedrera)
- Two of Gaudí’s iconic modernist buildings on Passeig de Gràcia
- Casa Batlló looks like it’s made of bones and sea waves 🌊
- La Pedrera is all flowing stone and rooftop sculptures
5️⃣ Magic Fountain of Montjuïc
- Evening light & music shows (check schedule!)
- Combine it with a walk up Montjuïc for museums, parks, and castle views
6️⃣ Barceloneta Beach & Port Vell
- Chill on the beach or bike along the palm-lined promenade
- Great area for seafood, sangria, or sunset cocktails
- Stroll the harbor and check out the yachts at Port Vell

🍴 What to Eat in Barcelona
- Tapas – Patatas bravas, croquetas, pan con tomate
- Paella – Best enjoyed seaside, with seafood or mixed options
- Calçots (in season) – Grilled green onions with romesco sauce
- Crema catalana – Like crème brûlée, but with a Catalan twist
- Vermouth – A pre-lunch drink that's become trendy again 🍸
Try local markets like La Boqueria or cozy taverns in El Born for the full flavor.
🚇 Getting Around
- Metro & buses are fast and efficient – get a T-Casual card or Hola BCN pass
- Walk or rent a bike—many areas are super pedestrian-friendly
- Taxis & ride apps like Free Now are widely available
🎉 Extra Tips & Local Vibes
✅ Time your meals late – locals eat lunch at 2–3pm and dinner after 9pm
✅ Watch a Flamenco show, but choose authentic venues, not tourist traps
✅ Visit Bunkers del Carmel for one of the best panoramic sunset spots in the city
✅ Be aware of pickpockets in crowded areas (especially on La Rambla)
✅ If you love art: check out Museu Picasso and MACBA (modern art)

-
 @ 5188521b:008eb518
2025-04-08 13:33:42
@ 5188521b:008eb518
2025-04-08 13:33:42Ecology
When my father died, an entire ecosystem system of beneficiaries withered. Moussa Ag El Khir funded scholarships and community projects, paying thousands of Dinars monthly to stop the oasis town of In Salah from burning up. The few families we knew operating outside the oil-field economy would be forced to flee to the Mediterranean coast, along with just about every other Berber.
It wasn’t unexpected. My father had cystic fibrosis for all sixty-one years of his life. So far, that’s the only legacy he’s passed on to his children. My brothers are just carriers, but me, his precious daughter ended up like him in more ways than one.
We sat there in the lawyer’s office in Algiers, my brothers and I, staring at the ledger which contained payment for his life’s work.
“And he only left one word in his will?” asked Ibrahim for the third time. Ecology.
The lawyer said Moussa was very clear. He chose each of the keys himself. The contents of the ledger would belong to whoever could decode his life — those who understood the real meaning. Then he cut all communications and walked into the Sahara. The Tuareg caravan on the road to Akabli found his body a week later, reddened by sand burn.
Earth
We made an agreement that day. To share each word we discovered. We could break the code together. Of course, Ibrahim and Hama didn’t share anything. We barely speak. That’s what happens when one child follows their father into science, and her two brothers move to France the minute they get rich enough to buy a wife. I bet they spent longer looking into legal loopholes to get their hands on my father’s assets than they did trying to identify the keys.
That day was the start of my second life, and I went from research assistant at a regional university to private-key detective. 2048 words and few clues where to start. Although I was 27, I was virtually a grandmother according to the In Salah wives. But of course, I could never be a grandmother, or even a mother. Every night, I scoured photos in the family archive. An initial sweep of his digital footprint returned no out-of-place instances of any keywords.
It took me a year to find the GPS tag he’d added to one photo — an eighteen-year-old daughter standing next to a father proud of his first infinite solar prototype. The panel has long-since been torn out by the oil corp, but the base is still there. I drove the three kilometres from the town limit and shone the high beams at the spot. When I got out, the air was cool but still thick with sand. A few more steps through sinking dunes, and I saw it. He’d scratched a little globe into the blistered metal, and for a moment, my mucus-laden lungs tasted clear air.
Trigger
The next word took three years. Friends, contacts, professors, biographers — visits to anyone with whom he might have left a clue. But it was in the In Salah hospital, where, upon a routine CF checkup with Jerome Devailier, a French doctor, ‘trigger’ appeared. The government might stack everything against the desert peoples, but they hadn’t taken away healthcare. I’d been living off the kindness of neighbours while finishing my thesis on the very solar technology my father developed. How could he have known the ‘buyer’ was just a tendril of the very oil company he sought to defeat.
Dr Devalier went through the list of carcinogens and allergens to avoid with my new drugs. Over forty triggers which could be my downfall. If I was lucky, I’d live as long as my father did.
By then, my research stipend was long gone. I existed on toughened bread and soup, which always carried the taste of the scorched city air. Yet, I stayed. The public library, disconnected from the grid by the oil corp, was where I finished my manuscript. They would fight its publication. Since father’s money no longer flowed into the town, many had deserted me. There were those who said he killed an entire people by selling his solar patent to the wrong buyers. Others in In Salah worshipped his name, but eventually, they all trudged north to the cities. My brothers sold the family home from under me, forcing me to follow.
When I returned from the hospital, I dug out my father’s medical documents. On every page, the word ‘trigger’ was underlined. That was the moment I knew my life’s work would be unlocking the ledger, not publishing studies on long-dead solar panel technology. That battle was lost.
They
All we need is a simple document, but here, it is the administrators’ job to send people away. Physical copies are only issued in extreme circumstances. Citizens’ Registry screens played endless repetitions of how to apply for digital documents. The shrill voices of family members desperate for the original copy of a pirated document drowned the TV messaging. Women removed headscarves and revealed thick black hair; teenagers paced. The atmosphere thickened with sweat. And hours passed. Each appointment required a reset of digital protocol, biometric tests, and identity cards from legal descendents. Through counterfeit identities, our Dinars leak into the hands of criminals, but still the government denies the need for bitcoin. They just print more money. They is the word my father used for the government that fought his patent so hard.
After a four-hour wait, I discovered that the physical death certificate included an ‘identifying mark’ on the deceased’s body. The ink was fresh — etched into the shoulder blade of a man who wished to turn his back on the government that ignored its people. The tattoo read aqqalan, the Tamasheq word for they.
Scheme
It took two trips to his cluttered Marseille office to convince him I was serious. Two visas, two flights, and the small amount from the sale of the family house. But few detectives wanted to work for a promise.
The ledger could not legally be owned in Algeria, and Laurent Mercier was the only serious professional who entertained a percentage of what was on there. The solar tech patent and documents from my father were enough to start Laurent on the trail. ‘Preliminary,’ he said, until I had the ledger in my possession.
“Flying is not easy with my condition,” I said.
He lowered his sunglasses. “Working is not easy without money.”
Contact with my brother through the lawyer in Algiers was achingly slow, but eventually they agreed to give me possession. What was 33% of nothing anyway? Years had gone by.
So, when I sat for the second time, in the sweaty office in Marseille, I gave Laurent the ledger, and he handed me a surprise. In all his business affairs, my father used little English, but the word ‘scheme’ appeared in all three company names he incorporated in the last three years of his life. We had our fifth word, and I finally had someone on my side.
Make
Some days, I could barely walk to the public library. I became lethargic and mostly sat in the cool dark of my room in the shelter. The government refused to provide housing outside of Algiers, but a Tuareg organisation from Mali opened a shelter in In Salah. Bulging eyes and faded clothes stared back in the mirror each day. How long had it been since I’d been to a wedding, or celebrated a friend’s child? Occupants came and went, and all that was left was a barren room and one meal per day.
As the sun punished the city with every ray of Allah’s untapped gift, streets grew thick with dust, and the local government fell, seat by seat, to oil execs. The only transport running was to and from the oil fields, which belched the remnants of the land into the sky. And still they worked. Still they sat on my father’s patent and refused to supply the world with efficient solar power.
With little else to cling onto, I harboured thoughts of how I could spend the ledger money. Fixing the town and replanting lost gardens. Bringing people back. That all took a back seat to decoding the message my father was sending. Laurent and I began to believe that the keys he chose formed some sort of instruction for his legacy.
Ten years to the day after his death, I was in the public library, looking for clues in an English history book. On my exit, the librarian stopped me.
“We have a gift for you, Kana.”
I waited while he fetched a package.
“Your father instructed me to give this to you. But not before this date.”
My hands tore open the package. More books, technical manuals, and hand-written notes. Amongst the papers was a tasselled leather bookmark embossed with the four letters that comprised one of the seven missing words. Make.
Citizen
It’s hard for a father in Algeria to admit to his daughter that she is his spirit — the heir to his life’s work. Of course he felt terrible guilt after our mother’s passing. That was when the letters started.
Moussa wrote to himself really, trying to come to terms with bringing a protégé into the world with a bright scientific mind and lungs that would snap her life expectancy. We communicated by letter for the last few years of his life — sharing the breakthroughs of his findings and what it might mean for our decaying oasis town. Analogue writing was the only real privacy, he said. His letters always ran to the same length, as if they were one lesson divided into equal chunks. We even exchanged letters during his last hospitalisation in Algiers. Those words were the only real strength I gained.
It was Laurent who analysed the letters with a new text scanning tool. For me, my father’s last letters were advice, regret, pain, and love, but to Laurent, they were simply a puzzle to solve to get one step closer.
Our letters gave Laurent the idea to communicate via physical mail. The process was painful, with letters sent from outlying towns before being shipped across the Alboran Sea and up into France. Muatin was one name my father called me. Like him, I dreamed of helping many through science. This was one of the few Arabic words in the French letters he wrote. It was also the only keyword included in any of the letters. Citizen.
When
Years of quiet followed. In Salah became unlivable after they co-opted the city reservoir for cooling drilling rigs. Each study that proved the field was still viable funnelled funds away from the locals who clung on. Resettlement benefits went up, and all but the semi-nomadic Tuaregs left. I followed. My health could not take much more desert. In the cooler coastal plains, I recovered strength, and subsidies for new medications helped me survive on a meagre teaching salary.
With no further clues, my Marseillais detective lost interest. His last letter, sent years ago, stated with unusual brevity that he was resigning the case. No payment was due.
I had lost my health, my father, his work, my money, our house, the town, and I spent each week delivering science and English classes to teenagers. They had no more hope for our country than I had. Algerians had already lost the Sahara. A one-degree temperature shift each decade of my life had shrunk Africa and sent its peoples northwards.
My father’s word puzzle occupied my thoughts. The combinations and permutations of letters and characters had millions of possible meanings but only one correct answer. Yet simple linguistic logic provided the next word. The headteacher was a linguist — a profession long lost to the higher-powered text analysers and language AI. He spoke little English but asked about the categorisations of grammatical terms in the 2048 key words.
“Why do you ask?”
“Because,” he said, “for a sentence of twelve words, at least one conjunction is necessary to form a second clause.”
He was right. I had been focussing on lists and complex codes to build my father’s motto. When I got home, I furiously searched my list of terms for conjunctions. I found only one. ‘When.’
Can
The permutations were still huge. Even eliminating some of the more conceptual words did not help. Millions of sentences existed in my dead father’s mind. Millions of meanings, all lost to the need for more energy to fund the world’s great thirst for energy. Still, the panels in most of the ‘dead middle’ (as the space between the tropics became known) melted at over 50 degrees.
I was back in Paris for CF treatment. As a young woman, I would have been pleased to make fifty years. But the realities of daily visits and the sickness brought on by medication stung. I wanted things to end, even when I discovered the next key.
It had been years since I had dreamed of the freedoms my father’s fortune could bring. Parts of Asia held out against bitcoin, but the cost of countries doing business off-network had become prohibitive. Eventually, the fossil conglomerates would give in to the need for solar mining and the provision of universal energy.
It was in a Parisian hospital bed that I discovered ‘can.’ My wardmate, a rough labourer from Oran, found a biography in the hospital library that made me sit up straight. ‘Can’ was repeated in almost every description of my father in his one-time business partner’s book. And it was this Arabian ‘businessman,’ Abdulkarim Rahman, who brokered the deal that robbed the world of infinite solar power. Each page mocked my father as believing only physical impossibilities are impossible. He branded him the ‘can man.’
Drastic
During my recuperation, I spent the final two weeks of my visa stay in Marseille. My days passed with endless algorithm tweaks to reject or accept word orders for the elusive twelve-word sentence my father once wrote.
Food lost its taste, and friends and colleagues in academia had scattered. In-person meetings were often contained to the night hours, but Marseille was not a place to go out after dark. The latest protests had gotten violent, and the government looked likely to topple. My people had always been resilient, but when the option to move and operate a caravan was removed by General Hafiz, part of my spirit died. I resolved to spend my final years in In Salah, however uncomfortable they would be.
My final port of call before returning was Laurent’s office. The eTaxi cast me out into the dusty street, and I wheezed as I climbed the three flights of stairs to his tiny door on Rue Marché. We hadn’t spoken in years, but I was surprised to find a different name about the door. Pascale Dupont, Investigateur.
The assistant I remembered was quite the opposite to Laurent — slow and methodical, short and heavy set.
“Madame,” he said. “I have difficult news.”
Their business had always straddled the law, but I never imagined an ex-officer of the law could be convicted of treason.
“A closed-door trial,” said Pascale. Then he handed over an air-gapped 3D storage file. “Laurent knew you would come for this.”
My mind cast forward to the reams of information he must have built on my father. The patents and technical diagrams he illegally acquired and other clues. I instantly recognised the brand of storage file as a keyword. Drastic.
“How can I thank him?”
“He is dead, madame.” Pascale hung his head. “He survived prison for only two weeks.”
Must
My final years brought me home. In Salah had gained fame for its one group of Tuaregs who refused to leave. The Lakzis owned a house in a desperate condition, not dissimilar to my failing body. By the age of fifty-two, I could no longer walk, but they welcomed me. I pooled my disability allowance and some money I’d gained from selling my father’s watch. We waited for the world to mourn the death of a once great city. We would keep it alive by refusing to move, by refusing to permit its rebranding as an ‘industrial area.’ Now the oil fields were finally drying up, they wanted to dig under the town.
We had managed to eliminate half of the remaining words. Just under 1,000 possible selections for the final two words, but little idea of an order.
The problem was that I was the only English speaker among them, and it took great energy to attempt to teach the meaning of the words and possible grammatical constructions for my father’s sentence.
But soon, patterns began to emerge. Fragments of word pairings and groups. ‘Trigger drastic scheme’ appeared again and again in the permutations. ‘They can’ and ‘When they can’ gave a tantalising glimpse. We ranked sentences in terms of likelihood to form the full key and categorised them by the most likely remaining words. Due to the need for a modal verb, ‘must’ scored highest by our calculations.
In this race to unlock the ledger before In Salah’s destruction, we nosed ahead.
Yet the day of that discovery was my final day in the desert. An air ambulance transported my feeble body to Algiers, and I would never return.
They messaged me — so close. They would unlock the ledger with the final word after my operation. The bitcoin could undo the wrongs of the past, and my father’s sentence would live on.
End
The phrase which began the global revolution first appeared on the wall of a much-disputed oil refinery in the desert outside In Salah, Algeria.
When they can make ecology end, citizen earth must trigger drastic scheme
Soon, the graffiti marked government buildings in Algiers. Activists took to the streets. Governments crumbled and currencies collapsed. Climate groups received massive donations said to come from ‘the one,’ a ledger with a huge stack written off by financiers the world over. The codebreaker credited with unlocking the ledger was unable to witness the transfer of 10,000 coins to the Global Climate Fund due to her death, aged 52, from a congenital condition.
The words of Moussa Ag El Khir now mark each of the millions of panels, which line the ‘dead middle.’ They contribute over 80% of the Earth’s power supply.
To mark the fiftieth anniversary of his death, the World Climate Forum will be held in the town of his birth, In Salah, Algeria. This story, compiled from the diaries of his daughter, Kana Ult El Khir, will be read as the opening address of the conference.
This story was originally published in 21 Futures: Tales From the Timechain
To continue the story of the real-world treasure (sats) use the address (it's real).\ Who knows, maybe some zaps will find their way into the wallet...

-
 @ e4950c93:1b99eccd
2025-04-08 13:11:01
@ e4950c93:1b99eccd
2025-04-08 13:11:01Vous avez trouvé un produit naturel ? Partagez-le ici en commentant cette page !
Ce site référence uniquement des produits et objets à usage durable. Les consommables (aliments, cosmétiques, combustibles, etc.) ne sont pas inclus.
Pour être référencé, le produit doit être composé de matières naturelles. 👉 En savoir plus sur les matières
Chaque information ajoutée (nom, matière, lien, zone de livraison pour un lien, etc.) et validée est considérée comme une contribution. 👉 En savoir plus sur les contributions
Chaque contribution validée est comptabilisée et donne lieu à une rétribution. 👉 En savoir plus sur les rétributions
Copiez-collez le modèle ci-dessous et remplissez les informations dont vous disposez. D’autres contribut-eur-rice-s pourront compléter les éléments manquants.
Nouveau produit
- Nom du produit :
- Image du produit (lien) :
- Description courte :
- Catégories :
- Marque ou fabricant :
- Composition (matériaux utilisés, y compris les éléments inconnus) :
- Liens pour l’acheter (et zone de livraison) :
- Zone de livraison pour les
- Autres infos utiles (lieu de fabrication, labels, etc.) :
Cet article est publié sur origine-nature.com 🌐 See this article in English
-
 @ e4950c93:1b99eccd
2025-04-08 13:08:56
@ e4950c93:1b99eccd
2025-04-08 13:08:56Vous connaissez une marque proposant des alternatives naturelles ? Partagez-la ici en commentant cette page !
Pour être référencée, la marque doit proposer une partie au moins de ses produits en matières naturelles. 👉 En savoir plus sur les matières
Chaque information ajoutée (nom, lien, catégorie, etc.) et validée est considérée comme une contribution. 👉 En savoir plus sur les contributions
Chaque contribution validée est comptabilisée et donne lieu à une rétribution. 👉 En savoir plus sur les rétributions
Copiez-collez le modèle ci-dessous et remplissez les informations que vous avez. D’autres contribut-eur-rice-s pourront compléter les éléments manquants.
Nouvelle marque ou fabricant
- Nom de la marque :
- Image représentant des produits de la marque (lien, idéalement depuis le site de la marque) :
- Courte description :
- Catégories de produits proposées :
- Matières utilisées pour ses produits :
- Site internet de la marque :
- Autres informations (lieu de production, labels…) :
Cet article est publié sur origine-nature.com 🌐 See this article in English
-
 @ e4950c93:1b99eccd
2025-04-08 12:58:34
@ e4950c93:1b99eccd
2025-04-08 12:58:34
Cet article est publié sur origine-nature.com 🌐 See this article in English
-
 @ 4bc0bea1:29b9f2aa
2025-04-08 12:27:36
@ 4bc0bea1:29b9f2aa
2025-04-08 12:27:36How I’m Training Around An Elbow Injury
My right elbow is a mess.
I hurt it wrestling with a friend on a wooden deck.
It's easy to avoid injuries in wrestling...if you only wrestle on the mat. I guess I don't like it easy.
To take it a step further, I made it much worse by doing straight arm ring exercises.
C'mon Jordan!
Straight arm ring exercises while your elbow already hurts...pure buffoonery.
Alas, here I am.
I could sit out from jiujitsu, but instead, I’m adjusting how I train so I don’t lose progress.
Injuries are part of the game, but how you adapt defines your progress.
Most people see injuries as setbacks. But they're actually opportunities to refine your game.
These opportunities force you to find ways to keep improving even when things aren’t perfect.
Things don't need to be perfect if you have some G.R.I.T.
Let's break this approach down.
G – Grapple (Smart)
Don't stop training. Modify it. Drill with a dummy, watch tape, or do technique you can handle. Buy a brace if need be. Stay in the game.
There's nothing worse than forgetting everything you worked hard to learn. So don't let it happen.
Keep rolling. Do what you can without pain. Buy a brace if you think it will help. I wear Anaconda's Elbow Brace when I roll to make sure my elbow stays safe and pain-free.
I stop if I experience pain and don't allow myself to go 100%. Ignore your ego and give your body the pain-free work that it needs.
On days when it's fatigued, I drill with my dummy and watch instructionals so I can improve my technique.
Don't sit around. Grapple. But do it smart.
R – Restore Movement
Move the injured part pain-free to get blood flowing. Restore function over time.
If you sit around and don't move your injured body part, it will heal slower.
Healing requires the nutrients that blood brings. And blood won't bring as much of the goods if it's not recruited.
Rehab your injury to give it the blood boost it needs.
I diagnosed myself with Olecranon (Elbow) Bursitis. I've been doing exercises recommended here to help it heal faster.
I only do the exercises that are pain-free for me right now. And I'm moving on to more difficult ones as my elbow condition improves.
Waiting for an injury to heal is a slow, frustrating process.
Be patient and stay consistent with your rehab.
I – Integrate Strength
Once pain-free, begin light strengthening. Train around the injury, not through it.
Instagram recently sniped me with an ad for something called The Torque Bar.
The benefits from using it are endless:
- It's a single tool that targets forearms, wrists, elbows, biceps, triceps, and shoulders.
- It has a thick knurled handle that enhances grip strength and forearm activation.
- It improves rotational strength (supination/pronation) for sports.
- It helps with tennis elbow, golfer’s elbow, wrist tendinitis, and rotator cuff issues.
- It strengthens stabilizing muscles to reduce joint hyperextension and strain risks.
So of course I had to buy it.
A couple weeks of these torque bar exercises and I'm hooked. It's strengthening my neglected arm muscles and my elbow without any pain.
It's a key piece of my routine going forward and I highly recommend it for others.
The best part is that it doesn't agitate my injury and it's helping me get stronger.
That's the goal here.
T – Thrive with Nutrition & Sleep
Eat clean to recover faster. Sleep well. Don’t waste healing energy on processed junk.
This is the number one lever to pull in your healing journey. And also a great way to live.
Eat Clean
I eat healthy foods like ground beef, wild caught salmon, fruit, and more whole foods 80% of the time.
The days I eat clean are the days my elbow feels it best.
The other 20% of the time – when I eat some processed, junk food – my elbow aches. It makes me feel like I'm back at square one. The consequences of junk food are astounding.
I've put the 80/20 rule on hold and changed it to 95/5 to help this injury heal faster.
Sleep Well
My sleep has been horrible.
My daughter was born 3 weeks ago and she's been fussy. I'm getting 3-6hrs of sleep a night. It's definitely not helping my elbow.
Sleep is the most important piece of the human equation.
Bad sleep can result in
- Low energy levels
- Increased risk of injury
- Poor eating habits
- Lack of productivity
It sets the tone for each day.
If you take anything away from this, let it be that you need to optimize for sleep.
If you're in a situation like me, control what you can control.
I have more control over my food than my sleep so that's why I'm being more disciplined with it.
Once my sleep improves, I expect everything to be firing on all cylinders.
The Bottom Line
Injuries are opportunities to refine your game.
But you need to have some G.R.I.T. to do it.
- G – Grapple (Smart): Don’t stop training. Change it. Drill with a dummy, watch tape, or do technique you can handle. Stay in the game.
- R – Restore Movement: Move the injured part pain-free to get blood flowing. Restore function over time.
- I – Integrate Strength: Once pain-free, begin light strengthening. Train around the injury, not through it.
- T – Thrive with Nutrition & Sleep: Eat clean to recover faster. Sleep well. Don’t waste healing energy on processed junk.
Do the above and you'll be back better than before.
Injured and not sure what you can still train? Send me a message – happy to help however I can.
Original post is here
-
 @ e31e84c4:77bbabc0
2025-04-08 11:53:57
@ e31e84c4:77bbabc0
2025-04-08 11:53:57The third annual edition of Bitcoin FilmFest returns to Warsaw this May. From its niche beginnings in 2023 to today’s global stage, BFF has become a catalyst for authentic storytelling—merging independent cinema, permissionless art, and Bitcoin’s ethos.
“Where centralized scripts end, new narratives begin — explore the uncharted stories beyond the frame.”
May 22-25, 2025, Poland: This year’s theme, “Beyond the Frame,” BFF25 expands the focus on creative expression—featuring narrative films, fiction, Bitcoin ads, and even a touch of AI, while keeping its genuine, community-driven vibe.
Key Highlights of Bitcoin FilmFest 2025
-
Pizza Day: The biggest European gathering to celebrate the first real-world Bitcoin transaction.
-
Exclusive Screenings: Feature films, documentaries, animations and shorts—including, for example: UNBANKABLE, SATOSHI THE MOVIE, REVOLUCIÓN BITCOIN, THE MAN WHO WOULDN’T CRY, HOTEL BITCOIN —all followed by face-to-face discussions with creators.
-
Golden Rabbits: Cinematic awards in categories like Best Movie, Best Story, Audience Choice.
-
Movie Pitch Contest: A platform for creators to turn Bitcoin-themed ideas into cinematic reality.
-
Generative Cinema: A special segment exploring AI’s role in filmmaking, including screenings and dynamic debates.
-
BFF PoWies: A dedicated show with Bitcoin-themed advertising, concluding with its own award ceremony (categories: GRAND PRIX / freestyle, VISUAL / video ad + out of home, IDENTITY / brand creative + campaigns).
-
Workshops & Networking: Thematic sessions on filmmaking, art, philosophy, spirituality, and beyond.
-
Memorable Experiences: Inspiring conversations in intimate circles, live music (concerts and DJ sets), stand-up comedy, and dozens of site activities—from bitcoin-only marketplaces, though yoga to self-defense.
\ Details, Tickets, Discounts.
For more visit the official event site: bitcoinfilmfest.com/bff25/
Follow the project's official feed on social media to stay up-to-date:
X: @bitcoinfilmfest | Nostr: Bitcoin FilmFest | LinkedIn: Bitcoin FilmFest
Use the discount code BITESIZE to get 10% off on tickets.
-
-
 @ c11cf5f8:4928464d
2025-04-08 11:31:37
@ c11cf5f8:4928464d
2025-04-08 11:31:37Here we are again with our monthly Magnificent Seven, the summary giving you a hit of what you missed in the ~AGORA territory. This month, new ideas came to us to trying increase engagement within the marketplace. Thanks to all for sharing your ideas and needs.
Auctions OPEN! First of all, @AGORA made a comprehensive research analyzing all the various types of auctions and discovering which one could be the most suitable for stackers. Published a guide that help define a first experimental auction for Satoshi Nakamoto 50th ₿DAY Commemorative Poster.
Build your own Shopfront Second, we discovered that AGORA could enable shopfronts to simply showcase and link external products, one per comment. This allows, for example, @SN to have its own to showcase and collect all the past and future editions of the SNZ weekly zine, check it out here. Isn't that fantastic? We found a new use case, just leveraging current functionalities! We might try to highlight the details with a how-to guide soon.
Now let's check our top performing post Ads!
Top-Performing Ads
This month, the most engaging ones are:
01[SELL] SNZ serialized inaugural issue, 3k sats (shipping to US) by @plebpoet congrats on launching this great initiative! Look forward to seeing ext one coming out!02Easy self-hosting of a basic ecommerce store that accepts bitcoin? by @k00b that apparently opted in for @zaprite, as he was unable to find a better solution to self-host and sell zines and other products sovereignly.03[SELL] Art piece "Reborn" by Von Bitcoin Art - Brekkie⚒️ @BVBTC (30k) by @Design_r promoting @BVBTC wonderful art masterpieces!04[OFFER] BOLT12 Day: 12K sats for an item from the “Bullish X Alby” collection by @thebullishbitcoiner together with few other offers.05Sats with 10% discount where @purpurato was trying to have someone pay a VPS service with PayPal and refund in sats. Glad to kow this deal has been completed successfully!06[GIVEAWAY] Only a few hours left to post a meme to win free 21 Futures paperback by @realBitcoinDog how it went? Keep us posted!07(SELL) Fine Art Black and White for sale by @Diego a photographer taking timeless shots. I look forward to seeing more of them framed and sold around here.
We also had so many other posts this month by @3a42879d5f, @kurszusz, @catoshi, @Coinsreporter, @BitFlio, @zapsammy and last but not the least, @whiteyfrauds, that actually posted a full list of interesting books and hacking software programs he is currently selling. Thank you all! Let's keep these trades coming and grow the Bitcoin circular economy!
Lost & Found in SN' Wild West Web
Stay with me, we're not done yet! I found plenty of other deals and offers in other territories too..
- Bitaxe 10% off code @stack_harder shared to buy within Europe.
- @plebpoet questioning What has Craigslist done for you?
- Costa Rica based Web Hosting and VPS for Bitcoin & Lightning shared by @hyperfree
- @Darthcoin remind us that there is an extensive set of options out there if you want to buy stuff with your precious sats https://stacker.news/items/775324/r/AG?commentId=776759
Wow, such an exciting month!
Active Professional Services accepting Bitcoin in the AGORA
Let us know if we miss any, here below the most memorable ones: - https://stacker.news/items/900208/r/AG @unschooled offering Language Tutoring - https://stacker.news/items/813013/r/AG @gpvansat's [OFFER][Graphic Design] From the paste editions (It's important to keep these offers available) - https://stacker.news/items/775383/r/AG @TinstrMedia - Color Grading (Styling) Your Pictures as a Service - https://stacker.news/items/773557/r/AG @MamaHodl, MATHS TUTOR 50K SATS/hour English global - https://stacker.news/items/684163/r/AG @BTCLNAT's OFFER HEALTH COUNSELING [21 SAT/ consultation - https://stacker.news/items/689268/r/AG @mathswithtess [SELL] MATHS TUTOR ONILINE, 90k sats per hour. Global but English only.
In case you missed
Here some interesting post, opening conversations and free speech about markets and business on the bitcoin circular economy:
- https://stacker.news/items/917679/r/AG Mundus Sine Caesaribus - A World Without Caesars Shirts by @k00b
- https://stacker.news/items/934100/r/AG 🛍️ Kartapio, a decentralized marketplace connecting businesses with customers. by @supratic
- https://stacker.news/items/924694/r/AG 🐢 4get is an open source search engine without data collection by @isolabellart
- https://stacker.news/items/914570/r/AG Sans is a library which supports ios/android/windows/macos/linux by @profullstack
BUYing or SELLing Cowboys Credits?
BUY or SELL them in the ~AGORA marketplace
Here's what stackers have to offers: - [SWAP] SN Cowboy credits by @DarthCoin - https://stacker.news/items/758411/r/AG by @SimpleStacker that also shares a CCs market analysis. - [BUY] 100 cowboy credits for one satoshi by @ek - Will Pay Sats For Cowboy Credits by @siggy47 - 📢 CCs to Sats Exchange Megathread recently started by @holonite, not sure why in ~bitcoin. Consider the ~AGORA next time ;)
🏷️ Spending Sunday and Selling weekly?
Share your most recent Bitcoin purchases of just check what other stackers are buying with their sats! All series available here: Or read the latest one from https://stacker.news/items/935969/r/AG
We also kickstarted a new weekly series titled What have you sold for Bitcoin this week?. It has been, and will be, going out every Thursday. Subscribe to our @AG0RA
botto don't miss the reminders!
Create your Ads now!
Looking to start something new? Hit one of the links below to free your mind:
- 💬 TOPIC for conversation,
- [⚖️ SELL] anything! or,
- if you're looking for something, hit the [🛒 BUY]!
- [🧑💻 HIRE] any bitcoiner skill or stuff from bitcoiners
- [🖇 OFFER] any product or service and stack more sats
- [🧑⚖️ AUCTION] to let stackers decide a fair price for your item
- [🤝 SWAP] if you're looking to exchange anything with anything else
- [🆓 FREE] your space, make a gift!
- Start your own [SHOPFRONT] or simply...
- [⭐ REVIEW] any bitcoin product or LN service you recently bought or subscribed to.
Or contact @AGORA team on nostr DM, and we can help you publish a personalized post.
.
#nostr#bitcoin#stuff4sats#sell#buy#plebchain#grownostr#asknostr#market#businessoriginally posted at https://stacker.news/items/937858
-
 @ edeb837b:ac664163
2025-04-08 11:24:58
@ edeb837b:ac664163
2025-04-08 11:24:58In today’s fast-paced, hyper-connected world, investing is no longer a solo sport.
The rise of social investing has transformed the way people trade, learn, and grow their wealth. Whether you're a seasoned trader or just getting started, chances are you've already encountered social investors—on Twitter, Discord, Reddit, or even in group chats. But who exactly are they? And why is NVSTly the go-to platform for this new wave of investors?
Let’s break it down.
What is a Social Investor?
A social investor is someone who engages in trading or investing with a strong focus on community, transparency, and collaboration.
They're not just buying and selling behind closed doors. They're:
- Sharing trades and strategies in real time
- Following top traders to learn from their wins (and losses)
- Collaborating with others in Discord servers, Telegram groups, and social media threads
- Using data-driven insights from the crowd to sharpen their own edge
Social investors believe that trading is better together—and they’re not wrong.
What Do Social Investors Do?
Social investors operate at the intersection of finance and social media. Here's what their day-to-day might look like:
✅ Share Trades Publicly
They log and post their trades for the community to see—building trust, accountability, and transparency.
✅ Follow Traders They Trust
They find top-performing traders or those with a style that resonates, then follow their moves to learn, mirror, or improve their own game.
✅ Collaborate & Discuss
Social investors thrive on conversation—sharing opinions, chart analysis, market sentiment, and more.
✅ Track Performance Over Time
Many use dashboards to measure their win rates, gain/loss ratios, and trade history to keep improving.
So… How Does Social Investing Actually Work?
At its core, social investing works like this:
-
Connect with the Community
Whether it’s a Discord server, app, or forum—start engaging. -
Log & Share Trades
Share your trade ideas, entries/exits, or even link your brokerage to auto-share your trades in real-time. -
Follow & Learn from Others
Use leaderboards, performance stats, and trade insights to follow top traders or promising new ones. -
Analyze and Improve
Get real-time feedback, stats, and charts to refine your strategy and grow your edge.
That’s where NVSTly comes in.
Why NVSTly is the Best Platform for Social Investors
NVSTly wasn’t just built for social investors—it was built by them.
Whether you're day trading crypto, swinging options, or investing long-term in stocks, NVSTly gives you everything you need to track, share, analyze, and grow—together.
Here’s what makes NVSTly stand out:
-
🚀 Real-Time Trade Sharing
Trades post instantly—on the app, and even in Discord—so your followers are always in the loop. -
📈 POV Charts
Our unique Point-of-View Chart shows the exact candlestick where a trader made a move. No more guessing—you see the strategy play out visually. -
🧠 Advanced Trade Insights
Dive into trade performance with key stats like win rate, average gain/loss, long vs short ratio, and even drawdowns. -
🌎 Global Leaderboards
See who’s crushing it across the platform, by day, week, month, or all-time. Filter by asset class, strategy, and more. -
🔗 Broker & Exchange Integration
Automatically track your trades from brokerages like Webull (with more on the way). No more manual input—just connect and go. -
📲 Multi-Platform Access
Use NVSTly on Web, iOS, Android—and even directly inside Discord via the NVSTly Bot. (Telegram support coming soon!) -
📣 Instant Social Sharing
Auto-post your trades to Discord, X (Twitter), and other platforms the moment they happen. Build your brand while you trade.
Social Investing is the Future. NVSTly is the Hub.
Whether you’re looking to grow your audience, follow expert traders, or just become more disciplined in your own trading, NVSTly is where social investors thrive.
Join 50,000+ traders who believe that sharing trades isn’t just about clout—it’s about accountability, growth, and community.
Ready to Social Trade?
Create your free account today and become part of the fastest-growing social trading platform in the game.
👉 Start Trading with NVSTly on the web, iOS, Android, or through the Discord app/bot.
-
 @ f683e870:557f5ef2
2025-04-08 11:13:27
@ f683e870:557f5ef2
2025-04-08 11:13:27When it comes to the Nostr Web of Trust, several NIPs have been proposed, but the one that seemed to gather the most traction was Trusted Assertion by Vitor Pamplona.
The idea is to have
kind:30382represent assertions made about an entity, which could be a pubkey, for example. The NIP also specifies a tag calledrank, which can be used to build some basic WoT primitives.Example event:
{ "kind": 30382, "tags": [ ["d", "e88a6...50411"], ["rank", "89"], ["zap_amt_sent", "1000000"], ], "content": "", //... }However, we quickly realized that this NIP was too limiting for what we wanted to accomplish: real-time, personalized ranking.
To illustrate our different approaches, we will show how to replicate our Verify Reputation with trusted assertions.
Verify Reputation
Verify Reputation returns:
- the rank, follow count and followers count of the given
target - its top followers by rank.
All ranks are personalized to the given
source.This “batteries included” solution helps users avoid impersonation and fraud with a single request, no matter what application they are using, be it a kind:1 client, chat app, wallet, marketplace, or more.
To get the same result with trusted assertions, you would have to
- Get all contact lists that contain the
target(as aptag) - Build the target’s
followerlist from those event authors - Get the trusted assertions for the target and each of the followers
- Sort them by the rank provided by the trusted assertions
This operation is computationally expensive, especially on mobile devices. It is clear that if the user is willing to verify and process a large number of events (potentially +100k), he can compute some (rudimentary) ranking directly on the device, without the need to trust a third party.
More generally, trusted assertions are very hard to use when one doesn’t know the pubkeys of the people he’s looking for. This goes fundamentally against our approach of Web of Trust, as a powerful mechanism for discovery.
Are you looking to add Web of Trust capabilities to your app or project?
- the rank, follow count and followers count of the given
-
 @ ef53426a:7e988851
2025-04-08 10:30:14
@ ef53426a:7e988851
2025-04-08 10:30:14Lead generation experts, growth hackers, and ‘battle-tested’ copywriters — this is the makeup of a 2025 LinkedIn feed.
The platform has grown to nearly 1 billion users and has successfully rebranded itself from an online CV database to a playground for entrepreneurs and content creators. With this comes great opportunity, but it also attracts sycophants and narcissists in their droves.
I’ve been writing on the platform since 2021. As a coach for multilingual writing pros, I post tips and thoughts about the English language, writing craft, and the state of the industry. Overall, it’s been a positive creative outlet, as well as a genuine source for clients. What they say really is true — your network is your net worth.
Yet, in recent months, I’ve become more frustrated with the swathes of ‘experts’ adding their voices to a sea of posts about content marketing. Most of those billion users aren’t active, and very few actually post and comment. LinkedIn is full of lurkers, too scared to let their bosses see the meme they liked. So why are all of these creative minnows so keen to reach them?

Why people write on LinkedIn
Unlike other social platforms, LinkedIn pays content creators 0. It doesn’t matter how many followers you acquire or how many eyeballs you drive to the platform, LinkedIn will pay you 0. In fact, creators often pay for LinkedIn premium accounts in order to access more powerful search functions and understand who is viewing their profile.
In 2022, the social network gained $13.8 billion in revenue, with the majority coming from premium accounts and B2B data sales, rather than ad revenue. For Microsoft (the owner of LinkedIn), advertising is a mere side hustle.
Searchable data is what makes LinkedIn an attractive place for freelancers and founders, as well as big businesses. Imagine you are a freelance web designer who helps Yoga teachers with their online presence. Or maybe you’re a communication coach who works with Japanese executives living in the US. You can find your ideal clients through search, publish useful content just for them, and start conversations by direct message.
Building your network in this way can lead to corporate clients, long-term relationships, and high-ticket sales. All this instead of a few measly dollars of ad revenue.
Of course, you have to learn a lot about marketing and sales, and all of this does not happen over night. Essentially, LinkedIn is a slower game, with a bigger payoff.
What top creators write about
LinkedIn is a business platform, so it’s not surprising that remote work, career growth, technology, and diversity comprise the staple topics of many of the articles, posts and videos shared.
But it’s not all leadership gurus. Whereas the route to LinkedIn gold used to be about selling non-fiction books and booking speaking engagements (a la Simon Sinek or Adam Grant) things look very different in 2023. Entrepreneurship, marketing and personal branding have become more than trending topics — they have stolen the show. Just check your LinkedIn feed, and you’ll see what I mean.
With an army of new creators looking for clients and customers, creators tend to build big followings by telling others how to grow their LinkedIn business. Being a LinkedIn coach would have seemed like a joke in 2019, but hundreds (or even thousands) are making serious money doing so.
These experts sell the dream of becoming a successful entrepreneur, just like them. They sell courses or run paid communities based on copywriting, social media growth, side hustles, and marketing.
For me, most of these ‘top voices’ blend into one. It all seems so insular, and all those likes and shares get kicked up the chain. In fact, it’s not dissimilar to how a pyramid scheme operates:
Step 1: sell a course on how to make money on LinkedIn
Step 2: the original clients learn how to do the same and find other ambitious digital entrepreneurs
Step 3: after several levels of resale, the buck stops with those who want to target clients in other industries, who are less driven by the ‘earn a six-figure income in 30 days’ type headlines.

How the algorithm fuels the fire
First of all, personal networks are much smaller than audiences on other social sites. Most LinkedIn accounts have an audience comprising mostly those they have ‘connected’ with (allowing reciprocal DMs). The maximum number of connections permitted is 30,000, so with a few followers added in, accounts can gain a huge amount of influence on LinkedIn.
Post reach is determined by how many in your network like, share or comment on your posts (similar to other social sites). But here’s the difference, the comments of your connections show up in your feed too.
This means the ultimate goal of smaller accounts is to get bigger creators to comment on their posts. If a big account interacts with your post, you could gain hundreds of followers or connect with other industry players who follow them. So, whatever they post, the top accounts are showered with love. “Great post :)”, “Totally agree”, “You nailed it!!!”.
Once a creator reaches a higher number of followers, they can post insipid quotes and obvious advice and still receive a torrent of engagement. It causes the top 1% to form strong bonds and collaborate on content in order to cement their position as experts and remain at the top. Newer writers tend to parrot the same half-baked marketing advice to try and appear as successful as the ‘Top Voices’ without realising that THEY are the product. Of course, all they have to do to get to the next level is buy a course. Simple.
I say this not to judge or complain. I’m involved in it all in some way. Although I never claim I’ll double clients’ income or make them a star on social media, I do sell coaching courses on writing effectively. Some days, I’m grateful for the positivity and interaction my writing receives on LinkedIn; others, I write sarcastic slideshows about the ridiculous promises, fake gurus and bad advice I see daily on the platform. My question is why are so few others recognising that creators are trapped in a bondage scheme, with all the wealth travelling up to the top 1%?
Is the creator economy a pyramid scheme?
What’s happening with writers on LinkedIn can be seen on other creative platforms too. On YouTube, Patreon, Podcasts, Substack and more, a low percentage of creators are making it work. Those who do best often tell others how to grow and make money. Let’s be honest, it’s a never-ending source of Medium articles too.
However, Medium seems more equitable. If you build a relationship by reading and commenting on others’ posts, they’ll probably return the favour. Our writing does not succeed or fail on whether we paid a designer to make it look beautiful. And many of the most-followed writers on the platform were early adopters, brought an audience from elsewhere, or have logged thousands of hours curating a publication.
As ever, the life of a writer is never easy, and the quandary of how to make money doing it remains. Despite what I’ve said, I do recommend writing on LinkedIn. It is a place where you can build genuine connections and read insightful pieces.
Just remember, if you see a headline like “How I got 34 clients to pay me over $2,000 each last month” or “You are positioning your personal brand TERRIBLY. Do this instead!!!”, beware. Don’t fall into the trap of the pyramid scheme; make your own way as best you can.
-
 @ 866e0139:6a9334e5
2025-04-08 08:52:09
@ 866e0139:6a9334e5
2025-04-08 08:52:09
Autor: Lionne Douce. (Bild: Florian Simon Eiler). Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier.**

LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt. (Vorerst an alle, da wir den Mailversand testen, später ca. drei Mails pro Woche.).
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: milosz@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 000002de:c05780a7
2025-04-08 01:24:25
@ 000002de:c05780a7
2025-04-08 01:24:25Trump is trying to sell a victim narrative and I don't buy it.
Trump repeats a troupe that I find hard to swallow. The US is getting ripped off. When he says this, as far as I can tell he's not referring to the people. He's referring the US government getting ripped off by other nations. This is so absurd I'm surprised I don't hear more people push back on it.
The US is the most powerful government in the history of the planet. No nation has the firepower or wealth of the US. The US has manipulated the governments and policies of much of the world since WW2. The idea that the US government is getting ripped off is absurd.
Trump and I agree that NATO is obsolete. It was created to counter a government that dissolved in the 90s. This should be an example to everyone that governments do not behave like businesses. They do not respond to market forces. They will always seek to increase their power and influence and always resist any efforts to reduce their size and scope. But back to Trump. He says that the US is getting ripped off by the other NATO countries. I would say the US people are in indeed being ripped off by their own government. But the US government is NOT getting ripped off.
The US military power in Europe is a massive influence on geopolitics in the region. US military companies benefit massively as well. The US military has bases all over the globe and if you don't think that is a factor in "diplomatic" negotiations you are being naive. The US uses this "defensive" shield to keep the "leaders" of Europe in line. The US isn't being ripped off. This is just a marketing tactic Trump is using to sell downsizing the US military deployments.
Trump also loves to point out how other countries are imposing tariffs on the US. We are being ripped off! I mean, he has a point there. But if tariffs aren't a tax as many in his admin like to claim, how exactly are "we" being ripped off? We are being told that Trump's tariff policy isn't a tax and that expecting prices to increase is oversimplifying things. The talk about tariffs is frankly frustrating.
On the one hand the left is saying tariffs are a tax and is going to drive up prices. Yet these same people pretend to not understand that corporate tax increases don't have the same effect. The right claims to understand tax policy and often oppose corporate taxes. They will tell you that those taxes just get passed down to consumers in the form of price increases. Now they are pretending to not get this in relation to tariffs.
I've read and listened to the pro tariff people and they aren't all dumb. They may be right about tariffs not effecting all products and nations equally. I guess we will find out. But, can we be honest? The US is not getting ripped off.
Someone is getting ripped off, but it isn't the US federal government. Its the people of the world. First, the people of the world live under the thumb of the US fiat dollar standard. We in the US complain about 3+% inflation but most people in the world would kill for that level of inflation. Most of the world gets none of supposed benefits from government spending. They only get the debasement of their own currencies.
Moving away from economics, the entire globe is affected by the elections in the US. The US is the top dog government and its decisions effect people everywhere. The US deep state has manipulated many elections across the globe and continues to do so. Meanwhile we are told that Russia is manipulating our elections. So who exactly is getting ripped off here? I think the nation (the people) are being subjected to massive mismanagement at best. I can support that argument.
Don't get me wrong... I know we in the US are getting ripped off. We are being ruled by people that do not represent us and do not answer to us. The politicians that claim to represent us are being paid and influenced by foreign groups ranging from Israeli political groups, to any number of other groups domestic and foreign. We are getting ripped off, but I firmly believe the people in the US have it better than most of the world. Trump is trying to sell a victim narrative and I don't buy it.
originally posted at https://stacker.news/items/937482
-
 @ 4d41a7cb:7d3633cc
2025-04-08 01:17:39
@ 4d41a7cb:7d3633cc
2025-04-08 01:17:39Satoshi Nakamoto, the pseudonymous creator of Bitcoin, registered his birthday as April 5, 1975, on his P2P Foundation profile. Many think that he chose this date because on that same day in 1933, the United States government confiscated the gold of the American people. Whether this was on purpose or not, what happened in this day is very important to understand how do we ended up here.
In 1933, as expressed in Roosevelt’s Executive Orders 6073, 6102, and 6260, the United States first declared bankruptcy. The bankrupt U.S. went into receivership in 1933. America was turned over via receivership and reorganization in favor of its creditors. These creditors, the International Bankers, from the beginning stated their intent, which was to plunder, bankrupt, conquer and enslave America and return it to its colonial status.1
As one of his first acts as President, Franklin Delano Roosevelt declared a “Banking Emergency” to bail out the Federal Reserve Bank, which had embezzled this country’s gold supply. The Congress gave the President dictatorial powers under the “War Powers Act of 1917” (amended 1933), written, by the way, by the Board of Governors of the Federal Reserve Bank of New York.2
This day marked the official abandonment of the American Constitution, law and real money. Today, 92 years after this event, most of the people living today have never had any real money or paid for anything using real money; unless they used Bitcoin...
There could be no bankruptcy if there was not a private central bank lending paper currency to the government at interest, so we must start from 1913, when the Federal Reserve was created: a non-federal private bank with no reserves and the monopoly of issuing debt based paper currency in unlimited amounts and lending it to the government at interest by buying treasury bills. The fact that this currency is lent into existence at interest makes the debt mathematically impossible to be repaid; it can only be refinanced or defaulted.
Between 1929 and 1933, the Federal Reserve Bank reduced the currency supply by 33%, thereby creating the Great Depression, bankrupting the US government, stealing the Americans’ gold supply, and officially ending the gold standard. Since then the US dollar (money) was replaced with Federal Reserve Notes (debt). This was also the end of the Republican form of government and the beginning of a socialist mob rule democracy (Fascism).
“Fascism should more properly be called corporatism because it is the merger of state and corporate power.” — Benito Mussolini
The United States government has been bankrupt since 1933, since it defaulted on its gold bonds. This type of bond existed until 1933, when the U.S. monetary system abandoned the gold standard. 3 From this year the government has been totally controlled by the International bankers and used as a tool to spread and maintain their power worldwide.
Many people think that the gold standard was abandoned in 1971, but this is not true; in fact, this happened in 1933 when the US dollar was replaced by Federal Reserve Notes that are 100% debt-based fiat paper currency.
The year 1933 in the United States marked:
- The end of the Republican form of government and the beginning of American Fascism
- The end of the United States dollar and its replacement by Federal Reserve Notes
- The abandonment of common law and replacement with military admiralty law
- The takeover of the United States government by International bankers
- A massive gold theft and the end of the US gold standard
- The exchange of rights with privileges and licenses
- The United States government bankruptcy
The next shameful event in our history which still plagues us to this day was the “War Powers Act of 1933.” This Act permitted President Roosevelt to make law in the form of Executive Order, bypass Congress and create his socialist state. We (citizens of this country) were ever after to be considered enemies of the United States who must be licensed to engage in any commercial activity. With the aid of the Federal Reserve (the same people who created the Depression), the President confiscated our gold and silver coin and replaced it with worthless pieces of paper and a debt system that will eventually destroy this great country. Our land and our labor were pledged to the Federal Reserve Bank, Inc., as collateral for a debt system that could never be paid.4
“Emergency Powers” means any form of military style government, martial law, or martial rule. Martial law and martial rule are not the same.
United States Congressional Record March 17, 1993 Vol. #33, page H- 1303, Congressman James Traficant, Jr. (Ohio) addressing the House:
“Mr. Speaker, we are here now in chapter 11. Members of Congress are official trustees presiding over the greatest reorganization of any Bankrupt entity in world history, the U.S. Government. We are setting forth, hopefully, a blueprint for our future”
“There are some who say it is a coroner’s report that will lead to our demise. It is an established fact that the United States Federal Government has been dissolved by the Emergency Banking Act, March 9, 1933, 48 Stat. 1, Public Law 89-719; dered by President Roosevelt, being bankrupt and insolvent. H.J.R. 192, 73rd Congress in session June 5, 1933 – Joint Resolution To Suspend The Gold Standard and Abrogate the Gold Clause dissolved the Sovereign Authority of the United States and the official capacities of all United States Governmental Offices, Officers, and Departments and is further evidence that the United States Federal Government exists today in name only” **“The receivers of the United States Bankruptcy are the International Bankers, via the United Nations, the World Bank and the International Monetary Fund”
“All United States Offices, Officials, and Departments are now operating within a de facto status in name only under Emergency War Powers. With the Constitutional Republican form of Government now dissolved, the receivers of the Bankruptcy have adopted a new form of government for the United States. This new form of government is known as a Democracy, being an established Socialist/Communist order under a new governor for America. This act was instituted and established by transferring and/or placing the Office of the Secretary of Treasury to that of the Governor of the International Monetary Fund. Public Law 94-564, page 8, Section H.R. 13955 read in part:”
“The U.S. Secretary of Treasury receives no compensation for representing the United States.”
The American Spirit
The intention of the founding fathers of the United States was to create a constitutional republic to protect natural human rights and escape from the tyrannical English monarchy and its usurious Bank of England's monetary system. They created an honest monetary system based on gold and silver (United State Dollar) and got rid of nobility titles, creating equality under the law.
Section 10 of the American Constitution says:
No State shall enter into any Treaty, Alliance, or Confederation; grant Letters of Marque and Reprisal; coin Money; emit Bills of Credit; make anything but gold and silver Coin a tender in payment of debts; pass any bill of attainder, ex post facto law, or law impairing the obligation of contracts; or grant any title of nobility.
The United States Dollar (1792-1933)
A dollar is a measure of weight defined by the Coinage Act of 1792 and 1900, which specifies a certain quantity—24.8 grains of gold or 371.25 grains of silver (from 1792 to 1900) when the American dollar was based on a bimetallic standard.
The Gold Standard Act of 1900 formally placed the United States on the gold standard, setting the value of one dollar at 25.8 grams of 90% pure gold, which fixed the price of gold at $20.67 per troy ounce. This standard was totally abandoned in 1933.
Gold and silver were such powerful money during the founding of the United States of America that the founding fathers declared that only gold or silver coins could be “money” in America.
But since the greedy bankers cannot profit from honest money they cannot print, they replaced the money with paper debt instruments. And by doing this, they have effectively enslaved the American people until today. My definition of modern slavery is working for a currency that someone else can create at no cost or effort. What's worse is that they even demand to be paid back and with interest!
Federal Reserve Notes (1913-present)
Federal Reserve Notes are not real money. Money that has metallic or other intrinsic value, as distinguished from paper currency, checks, and drafts.
Federal Reserve Notes (FRNs) are a legal fiction. An assumption that something is true even though it may be untrue. 5 The assumption that they are money, when in fact they are the opposite of money: debt or paper currency.
Paper money. Paper documents that circulate as currency; bills drawn by a government against its own credit. 6 Like Goldsmiths' notes. Hist. Bankers' cash notes: promissory notes given by bankers to customers as acknowledgments of the receipt of money. • This term derives from the London banking business, which originally was transacted by goldsmiths.7
These notes were scientifically designed to bankrupt the government and slave the American people, as Alfred Owen Crozier warned one year before the bill for the creation of the FED was passed through Congress (1912):
If Congress yields and authorizes a private central bank as proposed by the pending bill, the end when the bubble bursts will be universal ruin and national bankruptcy.
Unfortunately, the bill was passed in 1913, and this private bank started printing a new currency different from the US dollar creating the great depression and effectible bankrupting the government like Alfred warned 20 years before.
Alfred also warned:
Thus the way is opened for an unlimited inflation of corporate paper currency issued by a mere private corporation with relatively small net assets and no government guarantee, every dollar supposed to be redeemable in gold, but with not a single dollar of gold necessarily held in the reserves of such corporation to accomplish such redemption.
Differently from what's commonly believed Federal Reserve Notes (FRNs) were never really “backed” by gold; they were never supposed to be hard currency. Currency backed by reserves, esp. gold and silver reserves.
The United States government defaulted on its gold clauses, calling for payment in gold. This marked the end of the gold standard. A monetary system in which currency is convertible into its legal equivalent in gold or gold coin.
Since then we have been under a paper standard, where we use fake money as tender for payments. Paper standard. A monetary system based entirely on paper; a system of currency that is not convertible into gold or other precious metal.
People traded their coupons as money or “currency.” Currency is not money but a money substitute. Redeemable currency must promise to pay a dollar equivalent in gold or silver money. Federal Reserve Notes (FRNs) make no such promises and are not “money.” A Federal Reserve Note is a debt obligation of the federal United States government, not “money.” The federal United States government and the U.S. Congress were not and have never been authorized by the Constitution of the United States of America to issue currency of any kind, but only lawful money—gold and silver coin.8
A bona fide note can be used in a financial transaction to discharge the debt only because it is an unconditional promise to pay by the issuer to the bearer. Is a Federal Reserve Note a contract note, an unconditional promise to pay? At one time the Federal Reserve issued bona fide contractual notes and certificates, redeemable in gold and silver coin. Most people never saw or comprehended the contract. It went largely unread because the Federal Reserve very cunningly hid the contract on the face of the note by breaking it up into five separate lines of text with a significantly different typeface for each line and placing the president’s picture right in the middle of it. They even used the old attorney’s ruse of obscuring the most important text in fine print! Over time, the terms and conditions of the contract were diluted until eventually they literally became an I.O.U. for nothing.
FEDERAL RESERVE NOTE
-
THIS NOTE IS LEGAL TENDER FOR ALL DEBT, PUBLIC AND PRIVATE, AND IT IS REDEEMABLE IN LAWFUL MONEY AT THE UNITED STATES TREASURY OR ANY FEDERAL RESERVE BANK.
-
DATE: SERIES OF 1934
-
WILL PAY TO THE BEARER ON DEMAND: ONE HUNDRED DOLLARS
-
TREASURER OF THE UNITED STATES SIGNATURE
-
SECRETARY OF THE TREASURY SIGNATURE

Nowadays FRNs say "This note is legal tender for all debts public and private" it tender debt but it does not pay the bearer on demand. It value was stolen by a counterfeiting technique commonly know as inflation.
One hundred dollars (SERIES OF 1934) will be 2480 grains of gold, or 159.4 grams, or 5.1249 troy ounces. Today one troy ounce is priced around $3,000 federal reserve notes. 5.1249 X 3,000 = $15,375 actual FRNs.
A $100 FRN bill today will buy 0.65% of a real gold $100 dollar certificate. That’s a -99.35% loss of purchasing power in the last 91 years.
FRNs savers have been rugged pulled!
Gold bugs where the winners...
But Bitcoin is even better...
Happy birthday Satoshi! April 5 will be forever remembered.
Satoshi... The man, the myth, the Legend...
-
 @ d9a329af:bef580d7
2025-04-08 01:08:42
@ d9a329af:bef580d7
2025-04-08 01:08:42Everyone who sees it knows at this point that the matrix of control comes from the overdependence of proprietary software to do our everyday tasks. You can think of this like us being the cling wrap that will just not let go of these pieces of garbage software that don't allow you to see what is in their source code, and how they work. This will tend to lead to the unlawful collection of data (violating the most basic of privacy laws, despite unenforceable contracts that are enforced regardless), bad OPSEC that sees you being stalked and harassed over nothing significant. In the worst of cases, if you speak your mind where you aren't necessarily supposed to be able to do that, and you get doxxed, the worst cases could be far worse than one could imagine.
The solution to this, on the other hand, is using almost exclusively free/libre open-source software and GNU/Linux operation systems. If you're using certain proprietary software, hardening it to give as little data as possible to the entity responsible for it will also work, as long as you know which ones to use. This is a hard pass for a lot of people, but if you want to escape the control matrix of proprietary software, Winblows, HackOS, iHackOS, iBloatOS and stock Google AI Fever Dream, then researching which Free Software (notice the spelling) to use is your first bet. I had already done this for the past four and a half years, and will continue to do it as long as I live, seeing what new Free Software compliant applications and libraries come into the spotlight once things get locked down into walled gardens like what HackOS, iHackOS and BlindnessOS do on a regular basis.
Each of these pieces of software will be in a categorized list with a brief description of what the software is used for. There is a lot to take in, so research this yourself and see if these are right for you. These are the applications I personally use on a regular day-to-day basis, and they work for my needs.
- Operating Systems (the core to your device)
- GNU/Linux operating systems (for PCs) or GrapheneOS (for de-googled Android phones) To be fair on this one, GNU/Linux is the combination of the Linux kernel with the GNU toolchain, which in turn allows any developer to make an operating system that is FOSS, not necessarily Free Software, especially with the Linux Kernel's proprietary bits of code. The Linux kernel is also used in the Android Open-Source Project (AOSP), and is used as the base of operating systems for Android phones such as GrapheneOS, the only AOSP custom ROM I would recommend based upon the research I had done on this (even if very little).
My recommendations on the Linux side of things are almost any Arch-based distribution (with the exception of Manjaro), Debian-based distributions like Linux Mint Debian edition, regular Debian, AntiX or Devuan, or a Fedora/RedHat-based distribution like Nobara Project (if you're a gamer), OpenSUSE (if set up properly) or even Bluefin if you want an atomic desktop (I wouldn't recommend Bluefin if you want to monkey with your operating system and DIY on many aspects of it). Once you learn how to set these up securely, privately and properly, you're on your way to starting your journey into digital liberation, but there's far more to go on this front.
- Web Browsers (How you surf the internet)
-
Firefox Forks This one is self-explanatory. I harden all the Firefox forks I use (LibreWolf, Waterfox, Cachy Browser, Floorp and Zen as some examples) to the nines, despite being unable to do anything about my fingerprint. This is why I use multiple browsers for specific purposes to counteract the fingerprint spying due to weaponized JavaScript. There are ways to circumvent the fingerprint-based espionage, and make sure the site fingerprint.com doesn't know that one's lying about what their user agent is, though it's not very easy to fool that site, as it's used by 6,000 companies.
-
Brave Browser This is the only Chromium-based browser I would recommend, as it's better when hardened against all the other Chromium-based browsers, including Ungoogled Chromium, which is almost impossible to harden due to security vulnerabilities. Despite that, Brave has some of the best features for a Chromium-based browser one can feel comfortable using, even though you'll have similar issues with Firefox-based browsers that aren't actually Firefox (and Firefox has its own issues regarding espionage from Mozilla)
-
Office Suites (If you need to do professional office documents)
-
LibreOffice A fork of Apache's OpenOffice, made better with many features missing from even OnlyOffice and OpenOffice, this suite of applications is the go-to Free Software office suite for many people looking to switch from the proprietary software nether to the diamonds of free/libre open-source software. Though one may need to perform some extra steps to set up compatibility with G-Suite and Microsoft Office past 2015 potentially, it's still a good thing that people trust LibreOffice as their one-stop shop for office documents, despite being completely different from your standard office suite fare.
-
OnlyOffice The competitor to LibreOffice with the ease of Microsoft Office and G-Suite compatibility, OnlyOffice is another office suite that can be good for those who need it, especially since anybody who had used Microsoft Office in particular will be familiar with its layout, if not for a slight learning curve. As someone who's used G-Suite more (due to schooling that stunk worse than a decomposing rat in New York City), that's part of the reason why I switched to LibreOffice, though I tried some others, including OnlyOffice and Abiword (since I use a word processor a lot). This one is another solid option for those who need it.
-
Wordgrinder For those who like to use a terminal emulator like I do, Wordgrinder is a word processor with a terminal user interface (TUI) designed with just focusing on typing without distractions in mind. .wg is the file extension for documents made using Wordgrinder, especially since nowadays most word processors are cloud based. For those who live in a terminal, this is a good option to your terminal UI-based toolbox
-
Text editors
-
Vi, Vim, Neovim and other Vim-like editors The classic VI Improved (Vim), a fork of the TUI modal editor, vi, with keybinds that will be confusing at first, but with practice and patience, bring about muscle memory to stay on the keyboard, and not necessarily touch the mouse, keypad on the right hand side, or even the arrow keys. These keybind skills will stay with one for the rest of their life once they learn how the modes in vi, Vim or vi-based editors work. It's a classic for those working in the terminal, and a staple in FLOSS text editing and coding tools once customized potentially to the nines to your particular style.
-
VSCodium The Free Software fork of Code OSS by Microsoft, but made to be similar in function to VSCode without Microsoft's espionage baked into it. It has almost exactly the same features as VSCode that one would need, and even any VSIX files from VSCode will work in VSCodium. This one is an easy switch from VSCode for those who use it, but don't want the forced telemetry.
-
Emacs The competitor to Vim, Emacs is an editor that is FLOSS in every way imaginable. It is one of the most customizable editors anybody could have ever conceived, though the programming language used in Emacs is a dialect of Lisp the developers had made themselves. There are more keybinds to memorize compared to Vim, though Vim keybinds can be added using the Evil Mode package in any Emacs package manager to get the best of both worlds in Emacs. Once one gets a handle of the steep learning curve for Emacs, it's customizable in every imaginable way almost.
These four categories will get you started on your privacy journey, though I covered things a developer might want. I have plans on more lists to compile once I get my ducks in a row on what I want to cover here on Nostr in a longform format. Feel free to let me know if you have recommendations for me to write about, and I can do some digging on that if it isn't a rabbit hole.
-
 @ a7f85dfe:27305a2b
2025-04-07 23:56:34
@ a7f85dfe:27305a2b
2025-04-07 23:56:34在收到二手mini pc之前,先制作USB起动器。
首先,官网下载最新安装器的iso文件,下载地址:
https://www.proxmox.com/en/downloads
第二步,linux系统下使用dd命令制作USB起动器
查找usb路径
lsblkdd命令直接烧录 ``` sudo dd if=/path/to/iso_file.iso of=/dev/sdX bs=4M status=progress```
-
 @ a7f85dfe:27305a2b
2025-04-07 23:47:06
@ a7f85dfe:27305a2b
2025-04-07 23:47:06记录proxmox安装过程。
-
 @ a396e36e:ec991f1c
2025-04-07 23:46:01
@ a396e36e:ec991f1c
2025-04-07 23:46:01Introduction
In recent years, the term "the new normal" has been used to describe a world reshaped by pandemic policies, inflationary economic measures, rising surveillance, and growing cultural compliance. For many, this phrase signals safety and adaptation. But for others, it marks an era of overreach and loss of personal autonomy. At the heart of the digital resistance to this new order stands an unlikely champion: Bitcoin.
More than a volatile investment or tech novelty, Bitcoin has become a tool of protest, a lifeline for dissidents, and a vehicle for economic sovereignty. As governments expand control over currencies, transactions, and narratives, Bitcoin's decentralized, censorship-resistant architecture offers a parallel path. This post explores how Bitcoin is used to challenge the core pillars of the new normal.
- Pandemic-Era Restrictions and Bitcoin as a Lifeline
During the COVID-19 pandemic, governments worldwide implemented measures ranging from lockdowns to vaccine passports and mass surveillance. For many protestors, these policies were seen not as safety measures, but as infringements on civil liberties.
In Nigeria, during the #EndSARS protests against police brutality, bank accounts of organizers were frozen. Bitcoin became the fallback. Donations poured in through decentralized wallets, bypassing government censors. Similarly, in Canada’s 2022 Freedom Convoy, traditional fundraising platforms were blocked. Activists turned to Bitcoin, distributing funds peer-to-peer using QR codes, out of reach from centralized authority.
These examples underscore Bitcoin’s core strength: permissionless value transfer. No bank account, no ID, no government approval required. It provided activists with the means to continue their work even under financial siege.
- Economic Collapse and the Return to Sound Money
The economic fallout from pandemic stimulus measures has been immense. In the U.S. alone, over $5 trillion in stimulus spending contributed to record-breaking inflation, eroding the purchasing power of fiat currencies. Central banks worldwide flooded markets with newly created money, leading to a global crisis of confidence in fiat.
Bitcoin offered an escape route. With its capped supply of 21 million coins and transparent monetary policy, it attracted investors, corporations, and citizens looking to hedge against inflation and financial mismanagement. In countries like Turkey, Argentina, and Venezuela, where national currencies collapsed, Bitcoin emerged as a digital safe haven.
More than a hedge, Bitcoin became a symbol of protest. Where governments printed wealth out of thin air, Bitcoiners opted out. For them, stacking sats (satoshis) wasn't just financial planning—it was civil disobedience against fiat excess.
- CBDCs, Programmable Money, and the Case for Financial Autonomy
Central Bank Digital Currencies (CBDCs) are on the rise. Promoted as modern, efficient alternatives to cash, they also raise alarms for privacy advocates. Programmable money, expiration dates on stimulus funds, restrictions on purchases—these aren’t speculative fears. They’re openly discussed features.
Bitcoin offers the inverse: a financial system without surveillance, control, or gatekeeping. Unlike CBDCs, it is neutral, global, and governed by code, not political whim. Where CBDCs threaten to tether money to state approval, Bitcoin affirms the right to transact freely.
In this context, adopting Bitcoin is more than a tech choice. It’s a rejection of programmable compliance in favor of financial autonomy.
- Censorship, Compliance Culture, and the Sovereign Individual
Beyond economics and health, the new normal is marked by growing censorship and behavioral control. From deplatforming to frozen bank accounts, those who dissent often find their financial access cut off.
Bitcoin resists this. It doesn’t care who you are, what you believe, or where you live. As long as you control your private keys, your funds are yours.
This neutrality makes Bitcoin a sanctuary for the politically persecuted, the economically excluded, and the privacy-conscious. It’s not about hiding—it’s about freedom by design. In a time when expressing the wrong opinion can cost you your livelihood, Bitcoin offers a parallel economy where your rights don’t expire when you disagree.
Conclusion
Bitcoin is not a panacea. It doesn’t guarantee utopia, and it's not immune to misuse. But in the context of expanding state power, algorithmic governance, and compliant culture, it stands out as one of the few tools that empowers individuals to say "no."
To use Bitcoin today is to engage in a subtle form of protest. It is to opt out of a system many see as rigged, to reclaim privacy, and to assert control over one’s economic life. For those resisting the new normal—not with slogans, but with actions—Bitcoin is not just code. It’s civil disobedience made digital.
-
 @ a7f85dfe:27305a2b
2025-04-07 23:26:25
@ a7f85dfe:27305a2b
2025-04-07 23:26:25{"coverurl":"https://cdn.nostrcheck.me/a7f85dfe651aaa0b47d69659266f434479e40558a640a308a8f6769627305a2b/e9801593f2ea4560c55a6a2651788620cfe6c587c17c08f0e8023f06e7ffaf31.webp","title":"proxmox安装记录","author":"npub15lu"}
-
 @ 39f70015:9d4e378a
2025-04-07 17:28:03
@ 39f70015:9d4e378a
2025-04-07 17:28:03This is a copy of chapter four of Mastering Bitcoin Cash. I'm using it to test out creating long-form content on highlighter.com.
This is an edit after the original post. I want to test how editing long-form content works on Nostr.
4. Transactions
Introduction
Transactions are the most important part of the Bitcoin Cash system. Everything else in Bitcoin Cash is designed to ensure that transactions can be created, propagated on the network, validated, and finally added to the global ledger of transactions (the blockchain). Transactions are data structures that encode the transfer of value between participants in the Bitcoin Cash system. Each transaction is a public entry in Bitcoin Cash’s blockchain, the global double-entry bookkeeping ledger.
In this chapter we will examine all the various forms of transactions, what they contain, how to create them, how they are verified, and how they become part of the permanent record of all transactions.
Transaction Lifecycle
A transaction’s lifecycle starts with the transaction’s creation, also known as origination. The transaction is then signed with one or more signatures indicating the authorization to spend the funds referenced by the transaction. The transaction is then broadcast on the Bitcoin Cash network, where each network node (participant) validates and propagates the transaction until it reaches (almost) every node in the network. Finally, the transaction is verified by a mining node and included in a block of transactions that is recorded on the blockchain.
Once recorded on the blockchain and confirmed by sufficient subsequent blocks (confirmations), the transaction is a permanent part of the Bitcoin Cash ledger and is accepted as valid by all participants. The funds allocated to a new owner by the transaction can then be spent in a new transaction, extending the chain of ownership and beginning the lifecycle of a transaction again.
Creating Transactions
In some ways it helps to think of a transaction in the same way as a paper check. Like a check, a transaction is an instrument that expresses the intent to transfer money and is not visible to the financial system until it is submitted for execution. Like a check, the originator of the transaction does not have to be the one signing the transaction.
Transactions can be created online or offline by anyone, even if the person creating the transaction is not an authorized signer on the account. For example, an accounts payable clerk might process payable checks for signature by the CEO. Similarly, an accounts payable clerk can create Bitcoin Cash transactions and then have the CEO apply digital signatures to make them valid. Whereas a check references a specific account as the source of the funds, a Bitcoin Cash transaction references a specific previous transaction as its source, rather than an account.
Once a transaction has been created, it is signed by the owner (or owners) of the source funds. If it is properly formed and signed, the signed transaction is now valid and contains all the information needed to execute the transfer of funds. Finally, the valid transaction has to reach the Bitcoin Cash network so that it can be propagated until it reaches a miner for inclusion in the pubic ledger (the blockchain).
Broadcasting Transactions to the Bitcoin Cash Network
First, a transaction needs to be delivered to the Bitcoin Cash network so that it can be propagated and included in the blockchain. In essence, a Bitcoin Cash transaction is just 300 to 400 bytes of data and has to reach any one of tens of thousands of Bitcoin Cash nodes. The senders do not need to trust the nodes they use to broadcast the transaction, as long as they use more than one to ensure that it propagates. The nodes don’t need to trust the sender or establish the sender’s "identity." Because the transaction is signed and contains no confidential information, private keys, or credentials, it can be publicly broadcast using any underlying network transport that is convenient. Unlike credit card transactions, for example, which contain sensitive information and can only be transmitted on encrypted networks, a Bitcoin Cash transaction can be sent over any network. As long as the transaction can reach a Bitcoin Cash node that will propagate it into the Bitcoin Cash network, it doesn’t matter how it is transported to the first node.
Bitcoin Cash transactions can therefore be transmitted to the Bitcoin Cash network over insecure networks such as WiFi, Bluetooth, NFC, Chirp, barcodes, or by copying and pasting into a web form. In extreme cases, a Bitcoin Cash transaction could be transmitted over packet radio, satellite relay, or shortwave using burst transmission, spread spectrum, or frequency hopping to evade detection and jamming. A Bitcoin Cash transaction could even be encoded as smileys (emoticons) and posted in a public forum or sent as a text message or Skype chat message. Bitcoin Cash has turned money into a data structure, making it virtually impossible to stop anyone from creating and executing a Bitcoin Cash transaction.
Propagating Transactions on the Bitcoin Cash Network
Once a Bitcoin Cash transaction is sent to any node connected to the Bitcoin Cash network, the transaction will be validated by that node. If valid, that node will propagate it to the other nodes to which it is connected, and a success message will be returned synchronously to the originator. If the transaction is invalid, the node will reject it and synchronously return a rejection message to the originator.
The Bitcoin Cash network is a peer-to-peer network, meaning that each Bitcoin Cash node is connected to a few other Bitcoin Cash nodes that it discovers during startup through the peer-to-peer protocol. The entire network forms a loosely connected mesh without a fixed topology or any structure, making all nodes equal peers. Messages, including transactions and blocks, are propagated from each node to all the peers to which it is connected, a process called "flooding." A new validated transaction injected into any node on the network will be sent to all of the nodes connected to it (neighbors), each of which will send the transaction to all its neighbors, and so on. In this way, within a few seconds a valid transaction will propagate in an exponentially expanding ripple across the network until all nodes in the network have received it.
The Bitcoin Cash network is designed to propagate transactions and blocks to all nodes in an efficient and resilient manner that is resistant to attacks. To prevent spamming, denial-of-service attacks, or other nuisance attacks against the Bitcoin Cash system, every node independently validates every transaction before propagating it further. A malformed transaction will not get beyond one node.
Transaction Structure
A transaction is a data structure that encodes a transfer of value from a source of funds, called an input, to a destination, called an output. Transaction inputs and outputs are not related to accounts or identities. Instead, you should think of them as Bitcoin Cash amounts—chunks of Bitcoin Cash—being locked with a specific secret that only the owner, or person who knows the secret, can unlock. A transaction contains a number of fields, as shown in The structure of a transaction.
| Size | Field | Description | | --- | --- | --- | | 4 bytes | Version | Specifies which rules this transaction follows | | 1–9 bytes (VarInt) | Input Counter | How many inputs are included | | Variable | Inputs | One or more transaction inputs | | 1–9 bytes (VarInt) | Output Counter | How many outputs are included | | variable | Outputs | One or more transaction outputs | | 4 bytes | Locktime | A Unix timestamp or block number |
Table 1. The structure of a transaction
Transaction Locktime
Locktime, also known as nLockTime from the variable name used in the reference client, defines the earliest time that a transaction is valid and can be relayed on the network or added to the blockchain. It is set to zero in most transactions to indicate immediate propagation and execution. If locktime is nonzero and below 500 million, it is interpreted as a block height, meaning the transaction is not valid and is not relayed or included in the blockchain prior to the specified block height. If it is above 500 million, it is interpreted as a Unix Epoch timestamp (seconds since Jan-1-1970) and the transaction is not valid prior to the specified time. Transactions with locktime specifying a future block or time must be held by the originating system and transmitted to the Bitcoin Cash network only after they become valid. The use of locktime is equivalent to postdating a paper check.
Transaction Outputs and Inputs
The fundamental building block of a Bitcoin Cash transaction is an unspent transaction output, or UTXO. UTXO are indivisible chunks of Bitcoin Cash currency locked to a specific owner, recorded on the blockchain, and recognized as currency units by the entire network. The Bitcoin Cash network tracks all available (unspent) UTXO currently numbering in the millions. Whenever a user receives Bitcoin Cash, that amount is recorded within the blockchain as a UTXO. Thus, a user’s Bitcoin Cash might be scattered as UTXO amongst hundreds of transactions and hundreds of blocks. In effect, there is no such thing as a stored balance of a Bitcoin Cash address or account; there are only scattered UTXO, locked to specific owners. The concept of a user’s Bitcoin Cash balance is a derived construct created by the wallet application. The wallet calculates the user’s balance by scanning the blockchain and aggregating all UTXO belonging to that user.
There are no accounts or balances in Bitcoin Cash; there are only _unspent transaction outputs_ (UTXO) scattered in the blockchain.
A UTXO can have an arbitrary value denominated as a multiple of satoshis. Just like dollars can be divided down to two decimal places as cents, bitcoins can be divided down to eight decimal places as satoshis. Although UTXO can be any arbitrary value, once created it is indivisible just like a coin that cannot be cut in half. If a UTXO is larger than the desired value of a transaction, it must still be consumed in its entirety and change must be generated in the transaction. In other words, if you have a 20 Bitcoin Cash UTXO and want to pay 1 Bitcoin Cash, your transaction must consume the entire 20 Bitcoin Cash UTXO and produce two outputs: one paying 1 Bitcoin Cash to your desired recipient and another paying 19 Bitcoin Cash in change back to your wallet. As a result, most Bitcoin Cash transactions will generate change.
Imagine a shopper buying a $1.50 beverage, reaching into her wallet and trying to find a combination of coins and bank notes to cover the $1.50 cost. The shopper will choose exact change if available (a dollar bill and two quarters), or a combination of smaller denominations (six quarters), or if necessary, a larger unit such as a five dollar bank note. If she hands too much money, say $5, to the shop owner, she will expect $3.50 change, which she will return to her wallet and have available for future transactions.
Similarly, a Bitcoin Cash transaction must be created from a user’s UTXO in whatever denominations that user has available. Users cannot cut a UTXO in half any more than they can cut a dollar bill in half and use it as currency. The user’s wallet application will typically select from the user’s available UTXO various units to compose an amount greater than or equal to the desired transaction amount.
As with real life, the Bitcoin Cash application can use several strategies to satisfy the purchase amount: combining several smaller units, finding exact change, or using a single unit larger than the transaction value and making change. All of this complex assembly of spendable UTXO is done by the user’s wallet automatically and is invisible to users. It is only relevant if you are programmatically constructing raw transactions from UTXO.
The UTXO consumed by a transaction are called transaction inputs, and the UTXO created by a transaction are called transaction outputs. This way, chunks of Bitcoin Cash value move forward from owner to owner in a chain of transactions consuming and creating UTXO. Transactions consume UTXO by unlocking it with the signature of the current owner and create UTXO by locking it to the Bitcoin Cash address of the new owner.
The exception to the output and input chain is a special type of transaction called the coinbase transaction, which is the first transaction in each block. This transaction is placed there by the "winning" miner and creates brand-new Bitcoin Cash payable to that miner as a reward for mining. This is how Bitcoin Cash’s money supply is created during the mining process, as we will see in Mining and Consensus.
What comes first? Inputs or outputs, the chicken or the egg? Strictly speaking, outputs come first because coinbase transactions, which generate new Bitcoin Cash, have no inputs and create outputs from nothing.
Transaction Outputs
Every Bitcoin Cash transaction creates outputs, which are recorded on the Bitcoin Cash ledger. Almost all of these outputs, with one exception (see Data Output (OP_RETURN)) create spendable chunks of Bitcoin Cash called unspent transaction outputs or UTXO, which are then recognized by the whole network and available for the owner to spend in a future transaction. Sending someone Bitcoin Cash is creating an unspent transaction output (UTXO) registered to their address and available for them to spend.
UTXO are tracked by every full-node Bitcoin Cash client as a data set called the UTXO set or UTXO pool, held in a database. New transactions consume (spend) one or more of these outputs from the UTXO set.
Transaction outputs consist of two parts:
- An amount of Bitcoin Cash, denominated in satoshis, the smallest Bitcoin Cash unit
- A locking script, also known as an "encumbrance" that "locks" this amount by specifying the conditions that must be met to spend the output
The transaction scripting language, used in the locking script mentioned previously, is discussed in detail in Transaction Scripts and Script Language. The structure of a transaction output shows the structure of a transaction output.
| Size | Field | Description | | --- | --- | --- | | 8 bytes | Amount | Bitcoin Cash value in satoshis (108 Bitcoin Cash) | | 1–9 bytes (VarInt) | Locking-Script Size | Locking-Script length in bytes, to follow | | Variable | Locking-Script | A script defining the conditions needed to spend the output | | 1–9 bytes (VarInt) | Output Counter | How many outputs are included | | variable | Outputs | One or more transaction outputs | | 4 bytes | Locktime | A Unix timestamp or block number |
Table 2. The structure of a transaction output
In A script that calls
bitbox.Address.utxoto find the UTXO related to an address, we use thebitbox.Addressclass to find the unspent outputs (UTXO) of a specific address.Example 1. A script that calls
bitbox.Address.utxoto find the UTXO related to an address```javascript bitbox.Address.utxo('bitcoincash:qpcxf2sv9hjw08nvpgffpamfus9nmksm3chv5zqtnz').then((result) => { console.log(result); }, (err) => { console.log(err); });
Returns the following: [{ txid: 'cc27be8846276612dfce5924b7be96556212f0f0e62bd17641732175edb9911e', vout: 0, scriptPubKey: '76a9147064aa0c2de4e79e6c0a1290f769e40b3dda1b8e88ac', amount: 0.00007021, satoshis: 7021, height: 527155, confirmations: 11879, legacyAddress: '1BFHGm4HzqgXXyNX8n7DsQno5DAC4iLMRA', cashAddress: 'bitcoincash:qpcxf2sv9hjw08nvpgffpamfus9nmksm3chv5zqtnz' } ] ```
Running the script, we see an array of objects representing unspent transaction outputs which are available to this address.
Spending conditions (encumbrances)
Transaction outputs associate a specific amount (in satoshis) to a specific encumbrance or locking script that defines the condition that must be met to spend that amount. In most cases, the locking script will lock the output to a specific Bitcoin Cash address, thereby transferring ownership of that amount to the new owner. When Alice paid Bob’s Cafe for a cup of coffee, her transaction created a 0.00208507 Bitcoin Cash output encumbered or locked to the cafe’s Bitcoin Cash address. That 0.00208507 Bitcoin Cash output was recorded on the blockchain and became part of the Unspent Transaction Output set, meaning it showed in Bob’s wallet as part of the available balance. When Bob chooses to spend that amount, his transaction will release the encumbrance, unlocking the output by providing an unlocking script containing a signature from Bob’s private key.
Transaction Inputs
In simple terms, transaction inputs are pointers to UTXO. They point to a specific UTXO by reference to the transaction hash and sequence number where the UTXO is recorded in the blockchain. To spend UTXO, a transaction input also includes unlocking scripts that satisfy the spending conditions set by the UTXO. The unlocking script is usually a signature proving ownership of the Bitcoin Cash address that is in the locking script.
When users make a payment, their wallet constructs a transaction by selecting from the available UTXO. For example, to make a 0.00208507 Bitcoin Cash payment, the wallet app may select a 0.002 UTXO and a 0.00008507 UTXO, using them both to add up to the desired payment amount.
Once the UTXO is selected, the wallet then produces unlocking scripts containing signatures for each of the UTXO, thereby making them spendable by satisfying their locking script conditions. The wallet adds these UTXO references and unlocking scripts as inputs to the transaction. The structure of a transaction input shows the structure of a transaction input.
| Size | Field | Description | | --- | --- | --- | | 32 bytes | Transaction Hash | Pointer to the transaction containing the UTXO to be spent | | 4 bytes | Output Index | The index number of the UTXO to be spent; first one is 0 | | 1-9 bytes (VarInt) | Unlocking-Script Size | Unlocking-Script length in bytes, to follow | | Variable | Unlocking-Script | A script that fulfills the conditions of the UTXO locking script | | 4 bytes | Sequence Number | Currently disabled Tx-replacement feature, set to 0xFFFFFFFF |
Table 3. The structure of a transaction input
Transaction Fees
Most transactions include transaction fees, which compensate the Bitcoin Cash miners for securing the network. Mining and the fees and rewards collected by miners are discussed in more detail in Mining and Consensus. This section examines how transaction fees are included in a typical transaction. Most wallets calculate and include transaction fees automatically. However, if you are constructing transactions programmatically, or using a command-line interface, you must manually account for and include these fees.
Transaction fees serve as an incentive to include (mine) a transaction into the next block and also as a disincentive against "spam" transactions or any kind of abuse of the system, by imposing a small cost on every transaction. Transaction fees are collected by the miner who mines the block that records the transaction on the blockchain.
Transaction fees are calculated based on the size of the transaction in kilobytes, not the value of the transaction in Bitcoin Cash. Overall, transaction fees are set based on market forces within the Bitcoin Cash network. Miners prioritize transactions based on many different criteria, including fees, and might even process transactions for free under certain circumstances. Transaction fees affect the processing priority, meaning that a transaction with sufficient fees is likely to be included in the next-most–mined block, whereas a transaction with insufficient or no fees might be delayed, processed on a best-effort basis after a few blocks, or not processed at all. Transaction fees are not mandatory, and transactions without fees might be processed eventually; however, including transaction fees encourages priority processing.
The current algorithm used by miners to prioritize transactions for inclusion in a block based on their fees is examined in detail in Mining and Consensus.
Adding Fees to Transactions
The data structure of transactions does not have a field for fees. Instead, fees are implied as the difference between the sum of inputs and the sum of outputs. Any excess amount that remains after all outputs have been deducted from all inputs is the fee that is collected by the miners.
Transaction fees are implied, as the excess of inputs minus outputs:
Fees = Sum(Inputs) – Sum(Outputs)This is a somewhat confusing element of transactions and an important point to understand, because if you are constructing your own transactions you must ensure you do not inadvertently include a very large fee by underspending the inputs. That means that you must account for all inputs, if necessary by creating change, or you will end up giving the miners a very big tip!
For example, if you consume a 20-Bitcoin Cash UTXO to make a 1-Bitcoin Cash payment, you must include a 19-Bitcoin Cash change output back to your wallet. Otherwise, the 19-Bitcoin Cash "leftover" will be counted as a transaction fee and will be collected by the miner who mines your transaction in a block. Although you will receive priority processing and make a miner very happy, this is probably not what you intended.
If you forget to add a change output in a manually constructed transaction, you will be paying the change as a transaction fee. "Keep the change!" might not be what you intended.
Let’s see how this works in practice, by looking at Alice’s coffee purchase again. Alice wants to spend 0.00208507 Bitcoin Cash to pay for coffee. To ensure this transaction is processed promptly, she will want to include a transaction fee of 1 satoshi per byte. That will mean that the total cost of the transaction will be 0.00208750. Her wallet must therefore source a set of UTXO that adds up to 0.00208750 Bitcoin Cash or more and, if necessary, create change. Let’s say her wallet has a 0.00277257-Bitcoin Cash UTXO available. It will therefore need to consume this UTXO, create one output to Bob’s Cafe for 0.00208507, and a second output with 0.00068507 Bitcoin Cash in change back to her own wallet, leaving 0.00000243 Bitcoin Cash unallocated, as an implicit fee for the transaction.
Transaction Chaining and Orphan Transactions
As we have seen, transactions form a chain, whereby one transaction spends the outputs of the previous transaction (known as the parent) and creates outputs for a subsequent transaction (known as the child). Sometimes an entire chain of transactions depending on each other—say a parent, child, and grandchild transaction—are created at the same time, to fulfill a complex transactional workflow that requires valid children to be signed before the parent is signed.
When a chain of transactions is transmitted across the network, they don’t always arrive in the same order. Sometimes, the child might arrive before the parent. In that case, the nodes that see a child first can see that it references a parent transaction that is not yet known. Rather than reject the child, they put it in a temporary pool to await the arrival of its parent and propagate it to every other node. The pool of transactions without parents is known as the orphan transaction pool. Once the parent arrives, any orphans that reference the UTXO created by the parent are released from the pool, revalidated recursively, and then the entire chain of transactions can be included in the transaction pool, ready to be mined in a block. Transaction chains can be arbitrarily long, with any number of generations transmitted simultaneously. The mechanism of holding orphans in the orphan pool ensures that otherwise valid transactions will not be rejected just because their parent has been delayed and that eventually the chain they belong to is reconstructed in the correct order, regardless of the order of arrival.
There is a limit to the number of orphan transactions stored in memory, to prevent a denial-of-service attack against Bitcoin Cash nodes. The limit is defined as MAX_ORPHAN_TRANSACTIONS in the source code of the Bitcoin Cash reference client. If the number of orphan transactions in the pool exceeds MAX_ORPHAN_TRANSACTIONS, one or more randomly selected orphan transactions are evicted from the pool, until the pool size is back within limits.
Transaction Scripts and Script Language
Bitcoin Cash clients validate transactions by executing a script, written in a Forth-like scripting language. Both the locking script (encumbrance) placed on a UTXO and the unlocking script that usually contains a signature are written in this scripting language. When a transaction is validated, the unlocking script in each input is executed alongside the corresponding locking script to see if it satisfies the spending condition.
Today, most transactions processed through the Bitcoin Cash network have the form "Alice pays Bob" and are based on the same script called a Pay-to-Public-Key-Hash script. However, the use of scripts to lock outputs and unlock inputs means that through use of the programming language, transactions can contain an infinite number of conditions. Bitcoin Cash transactions are not limited to the "Alice pays Bob" form and pattern.
This is only the tip of the iceberg of possibilities that can be expressed with this scripting language. In this section, we will demonstrate the components of the Bitcoin Cash transaction scripting language and show how it can be used to express complex conditions for spending and how those conditions can be satisfied by unlocking scripts.
Bitcoin Cash transaction validation is not based on a static pattern, but instead is achieved through the execution of a scripting language. This language allows for a nearly infinite variety of conditions to be expressed. This is how Bitcoin Cash gets the power of "programmable money."
Script Construction (Lock + Unlock)
Bitcoin Cash’s transaction validation engine relies on two types of scripts to validate transactions: a locking script and an unlocking script.
A locking script is an encumbrance placed on an output, and it specifies the conditions that must be met to spend the output in the future. Historically, the locking script was called a scriptPubKey, because it usually contained a public key or Bitcoin Cash address. In this book we refer to it as a "locking script" to acknowledge the much broader range of possibilities of this scripting technology. In most Bitcoin Cash applications, what we refer to as a locking script will appear in the source code as scriptPubKey.
An unlocking script is a script that "solves," or satisfies, the conditions placed on an output by a locking script and allows the output to be spent. Unlocking scripts are part of every transaction input, and most of the time they contain a digital signature produced by the user’s wallet from his or her private key. Historically, the unlocking script is called scriptSig, because it usually contained a digital signature. In most Bitcoin Cash applications, the source code refers to the unlocking script as scriptSig. In this book, we refer to it as an "unlocking script" to acknowledge the much broader range of locking script requirements, because not all unlocking scripts must contain signatures.
Every Bitcoin Cash client will validate transactions by executing the locking and unlocking scripts together. For each input in the transaction, the validation software will first retrieve the UTXO referenced by the input. That UTXO contains a locking script defining the conditions required to spend it. The validation software will then take the unlocking script contained in the input that is attempting to spend this UTXO and execute the two scripts.
In the original Bitcoin Cash client, the unlocking and locking scripts were concatenated and executed in sequence. For security reasons, this was changed in 2010, because of a vulnerability that allowed a malformed unlocking script to push data onto the stack and corrupt the locking script. In the current implementation, the scripts are executed separately with the stack transferred between the two executions, as described next.
First, the unlocking script is executed, using the stack execution engine. If the unlocking script executed without errors (e.g., it has no "dangling" operators left over), the main stack (not the alternate stack) is copied and the locking script is executed. If the result of executing the locking script with the stack data copied from the unlocking script is "TRUE," the unlocking script has succeeded in resolving the conditions imposed by the locking script and, therefore, the input is a valid authorization to spend the UTXO. If any result other than "TRUE" remains after execution of the combined script, the input is invalid because it has failed to satisfy the spending conditions placed on the UTXO. Note that the UTXO is permanently recorded in the blockchain, and therefore is invariable and is unaffected by failed attempts to spend it by reference in a new transaction. Only a valid transaction that correctly satisfies the conditions of the UTXO results in the UTXO being marked as "spent" and removed from the set of available (unspent) UTXO.
Combining scriptSig and scriptPubKey to evaluate a transaction script is an example of the unlocking and locking scripts for the most common type of Bitcoin Cash transaction (a payment to a public key hash), showing the combined script resulting from the concatenation of the unlocking and locking scripts prior to script validation.
 Figure 1. Combining scriptSig and scriptPubKey to evaluate a transaction script
Figure 1. Combining scriptSig and scriptPubKey to evaluate a transaction scriptScripting Language
The Bitcoin Cash transaction script language, called Script, is a Forth-like reverse-polish notation stack-based execution language. If that sounds like gibberish, you probably haven’t studied 1960’s programming languages. Script is a very simple language that was designed to be limited in scope and executable on a range of hardware, perhaps as simple as an embedded device, such as a handheld calculator. It requires minimal processing and cannot do many of the fancy things modern programming languages can do. In the case of programmable money, that is a deliberate security feature.
Bitcoin Cash’s scripting language is called a stack-based language because it uses a data structure called a stack. A stack is a very simple data structure, which can be visualized as a stack of cards. A stack allows two operations: push and pop. Push adds an item on top of the stack. Pop removes the top item from the stack.
The scripting language executes the script by processing each item from left to right. Numbers (data constants) are pushed onto the stack. Operators push or pop one or more parameters from the stack, act on them, and might push a result onto the stack. For example, OP_ADD will pop two items from the stack, add them, and push the resulting sum onto the stack.
Conditional operators evaluate a condition, producing a boolean result of TRUE or FALSE. For example, OP_EQUAL pops two items from the stack and pushes TRUE (TRUE is represented by the number 1) if they are equal or FALSE (represented by zero) if they are not equal. Bitcoin Cash transaction scripts usually contain a conditional operator, so that they can produce the TRUE result that signifies a valid transaction.
In Bitcoin Cash’s script validation doing simple math, the script 2 3 OP_ADD 5 OP_EQUAL demonstrates the arithmetic addition operator OP_ADD, adding two numbers and putting the result on the stack, followed by the conditional operator OP_EQUAL, which checks that the resulting sum is equal to 5. For brevity, the OP_ prefix is omitted in the step-by-step example.
The following is a slightly more complex script, which calculates 2 + 7 – 3 + 1. Notice that when the script contains several operators in a row, the stack allows the results of one operator to be acted upon by the next operator:
2 7 OP_ADD 3 OP_SUB 1 OP_ADD 7 OP_EQUALTry validating the preceding script yourself using pencil and paper. When the script execution ends, you should be left with the value TRUE on the stack.
Although most locking scripts refer to a Bitcoin Cash address or public key, thereby requiring proof of ownership to spend the funds, the script does not have to be that complex. Any combination of locking and unlocking scripts that results in a TRUE value is valid. The simple arithmetic we used as an example of the scripting language is also a valid locking script that can be used to lock a transaction output.
Use part of the arithmetic example script as the locking script:
3 OP_ADD 5 OP_EQUALwhich can be satisfied by a transaction containing an input with the unlocking script:
2The validation software combines the locking and unlocking scripts and the resulting script is:
2 3 OP_ADD 5 OP_EQUALAs we saw in the step-by-step example in Bitcoin Cash’s script validation doing simple math, when this script is executed, the result is OP_TRUE, making the transaction valid. Not only is this a valid transaction output locking script, but the resulting UTXO could be spent by anyone with the arithmetic skills to know that the number 2 satisfies the script.
 Figure 2. Bitcoin Cash’s script validation doing simple math
Figure 2. Bitcoin Cash’s script validation doing simple mathTransactions are valid if the top result on the stack is TRUE (noted as {0x01}), any other non-zero value or if the stack is empty after script execution. Transactions are invalid if the top value on the stack is FALSE (a zero-length empty value, noted as {}) or if script execution is halted explicitly by an operator, such as OP_VERIFY, OP_RETURN, or a conditional terminator such as OP_ENDIF.
Turing Incompleteness
The Bitcoin Cash transaction script language contains many operators, but is deliberately limited in one important way—there are no loops or complex flow control capabilities other than conditional flow control. This ensures that the language is not Turing Complete, meaning that scripts have limited complexity and predictable execution times. Script is not a general-purpose language. These limitations ensure that the language cannot be used to create an infinite loop or other form of "logic bomb" that could be embedded in a transaction in a way that causes a denial-of-service attack against the Bitcoin Cash network. Remember, every transaction is validated by every full node on the Bitcoin Cash network. A limited language prevents the transaction validation mechanism from being used as a vulnerability.
Stateless Verification
The Bitcoin Cash transaction script language is stateless, in that there is no state prior to execution of the script, or state saved after execution of the script. Therefore, all the information needed to execute a script is contained within the script. A script will predictably execute the same way on any system. If your system verifies a script, you can be sure that every other system in the Bitcoin Cash network will also verify the script, meaning that a valid transaction is valid for everyone and everyone knows this. This predictability of outcomes is an essential benefit of the Bitcoin Cash system.
Standard Transactions
In the first few years of Bitcoin Cash’s development, the developers introduced some limitations in the types of scripts that could be processed by the reference client. These limitations are encoded in a function called isStandard(), which defines five types of "standard" transactions. These limitations are temporary and might be lifted by the time you read this. Until then, the five standard types of transaction scripts are the only ones that will be accepted by the reference client and most miners who run the reference client. Although it is possible to create a nonstandard transaction containing a script that is not one of the standard types, you must find a miner who does not follow these limitations to mine that transaction into a block.
Check the source code of the Bitcoin Core client (the reference implementation) to see what is currently allowed as a valid transaction script.
The five standard types of transaction scripts are pay-to-public-key-hash (P2PKH), public-key, multi-signature (limited to 15 keys), pay-to-script-hash (P2SH), and data output (OP_RETURN), which are described in more detail in the following sections.
Pay-to-Public-Key-Hash (P2PKH)
The vast majority of transactions processed on the Bitcoin Cash network are P2PKH transactions. These contain a locking script that encumbers the output with a public key hash, more commonly known as a Bitcoin Cash address. Transactions that pay a Bitcoin Cash address contain P2PKH scripts. An output locked by a P2PKH script can be unlocked (spent) by presenting a public key and a digital signature created by the corresponding private key.
For example, let’s look at Alice’s payment to Bob’s Cafe again. Alice made a payment of 0.00208507 Bitcoin Cash to the cafe’s Bitcoin Cash address. That transaction output would have a locking script of the form:
OP_DUP OP_HASH160 <Cafe Public Key Hash> OP_EQUAL OP_CHECKSIGThe Cafe Public Key Hash is equivalent to the Bitcoin Cash address of the cafe, without the Base58Check encoding. Most applications would show the public key hash in hexadecimal encoding and not the familiar Bitcoin Cash address Base58Check format that begins with a "1".
The preceding locking script can be satisfied with an unlocking script of the form:
<Cafe Signature> <Cafe Public Key>The two scripts together would form the following combined validation script:
<Cafe Signature> <Cafe Public Key> OP_DUP OP_HASH160 <Cafe Public Key Hash> OP_EQUAL OP_CHECKSIGWhen executed, this combined script will evaluate to TRUE if, and only if, the unlocking script matches the conditions set by the locking script. In other words, the result will be TRUE if the unlocking script has a valid signature from the cafe’s private key that corresponds to the public key hash set as an encumbrance.
Figures and show (in two parts) a step-by-step execution of the combined script, which will prove this is a valid transaction.
 Figure 3. Evaluating a script for a P2PKH transaction (Part 1 of 2)
Figure 3. Evaluating a script for a P2PKH transaction (Part 1 of 2)Pay-to-Public-Key
Pay-to-public-key is a simpler form of a Bitcoin Cash payment than pay-to-public-key-hash. With this script form, the public key itself is stored in the locking script, rather than a public-key-hash as with P2PKH earlier, which is much shorter. Pay-to-public-key-hash was invented by Satoshi to make Bitcoin Cash addresses shorter, for ease of use. Pay-to-public-key is now most often seen in coinbase transactions, generated by older mining software that has not been updated to use P2PKH.
A pay-to-public-key locking script looks like this:
<Public Key A> OP_CHECKSIGThe corresponding unlocking script that must be presented to unlock this type of output is a simple signature, like this:
<Signature from Private Key A>The combined script, which is validated by the transaction validation software, is:
<Signature from Private Key A> <Public Key A> OP_CHECKSIGThis script is a simple invocation of the CHECKSIG operator, which validates the signature as belonging to the correct key and returns TRUE on the stack.
 Figure 4. Evaluating a script for a P2PKH transaction (Part 2 of 2)
Figure 4. Evaluating a script for a P2PKH transaction (Part 2 of 2)Multi-Signature
Multi-signature scripts set a condition where N public keys are recorded in the script and at least M of those must provide signatures to release the encumbrance. This is also known as an M-of-N scheme, where N is the total number of keys and M is the threshold of signatures required for validation. For example, a 2-of-3 multi-signature is one where three public keys are listed as potential signers and at least two of those must be used to create signatures for a valid transaction to spend the funds. At this time, standard multi-signature scripts are limited to at most 15 listed public keys, meaning you can do anything from a 1-of-1 to a 15-of-15 multi-signature or any combination within that range. The limitation to 15 listed keys might be lifted by the time this book is published, so check the isStandard() function to see what is currently accepted by the network.
The general form of a locking script setting an M-of-N multi-signature condition is:
M <Public Key 1> <Public Key 2> ... <Public Key N> N OP_CHECKMULTISIGwhere N is the total number of listed public keys and M is the threshold of required signatures to spend the output.
A locking script setting a 2-of-3 multi-signature condition looks like this:
2 <Public Key A> <Public Key B> <Public Key C> 3 OP_CHECKMULTISIGThe preceding locking script can be satisfied with an unlocking script containing pairs of signatures and public keys:
OP_0 <Signature B> <Signature C>or any combination of two signatures from the private keys corresponding to the three listed public keys.
The prefix OP_0 is required because of a bug in the original implementation of CHECKMULTISIG where one item too many is popped off the stack. It is ignored by CHECKMULTISIG and is simply a placeholder.
The two scripts together would form the combined validation script:
OP_0 <Signature B> <Signature C> 2 <Public Key A> <Public Key B> <Public Key C> 3 OP_CHECKMULTISIGWhen executed, this combined script will evaluate to TRUE if, and only if, the unlocking script matches the conditions set by the locking script. In this case, the condition is whether the unlocking script has a valid signature from the two private keys that correspond to two of the three public keys set as an encumbrance.
Data Output (OP_RETURN)
Bitcoin Cash’s distributed and timestamped ledger, the blockchain, has potential uses far beyond payments. Many developers have tried to use the transaction scripting language to take advantage of the security and resilience of the system for applications such as digital notary services, stock certificates, and smart contracts. Early attempts to use Bitcoin Cash’s script language for these purposes involved creating transaction outputs that recorded data on the blockchain; for example, to record a digital fingerprint of a file in such a way that anyone could establish proof-of-existence of that file on a specific date by reference to that transaction.
The use of Bitcoin Cash’s blockchain to store data unrelated to Bitcoin Cash payments is a controversial subject. Many developers consider such use abusive and want to discourage it. Others view it as a demonstration of the powerful capabilities of blockchain technology and want to encourage such experimentation. Those who object to the inclusion of non-payment data argue that it causes "blockchain bloat," burdening those running full Bitcoin Cash nodes with carrying the cost of disk storage for data that the blockchain was not intended to carry. Moreover, such transactions create UTXO that cannot be spent, using the destination Bitcoin Cash address as a free-form 20-byte field. Because the address is used for data, it doesn’t correspond to a private key and the resulting UTXO can never be spent; it’s a fake payment. These transactions that can never be spent are therefore never removed from the UTXO set and cause the size of the UTXO database to forever increase, or "bloat."
A compromise was reached with the introduction of the OPRETURN operator. OP_RETURN allows developers to add 220 bytes of nonpayment data to a transaction output. However, unlike the use of "fake" UTXO, the OP_RETURN operator creates an explicitly _provably unspendable output, which does not need to be stored in the UTXO set. OP_RETURN outputs are recorded on the blockchain, so they consume disk space and contribute to the increase in the blockchain’s size, but they are not stored in the UTXO set and therefore do not bloat the UTXO memory pool and burden full nodes with the cost of more expensive RAM.
``` OP_RETURN scripts look like this:
OP_RETURN ```
The data portion is limited to 220 bytes and most often represents a hash, such as the output from the SHA256 algorithm (32 bytes). Many applications put a prefix in front of the data to help identify the application per the Terab 4-byte prefix guideline for OP_RETURN on Bitcoin Cash.
Keep in mind that there is no "unlocking script" that corresponds to OPRETURN that could possibly be used to "spend" an OP_RETURN output. The whole point of OP_RETURN is that you can’t spend the money locked in that output, and therefore it does not need to be held in the UTXO set as potentially spendable—OP_RETURN is _provably un-spendable. OP_RETURN is usually an output with a zero Bitcoin Cash amount, because any Bitcoin Cash assigned to such an output is effectively lost forever. If an OP_RETURN is encountered by the script validation software, it results immediately in halting the execution of the validation script and marking the transaction as invalid. Thus, if you accidentally reference an OP_RETURN output as an input in a transaction, that transaction is invalid.
A standard transaction (one that conforms to the isStandard() checks) can have only one OP_RETURN output. However, a single OP_RETURN output can be combined in a transaction with outputs of any other type.
OP_RETURN was initially proposed with a limit of 80 bytes, but the limit was raised to 220 bytes of data on the May 15th 2018 BCH network upgrade.
Pay-to-Script-Hash (P2SH)
Pay-to-script-hash (P2SH) was introduced in 2012 as a powerful new type of transaction that greatly simplifies the use of complex transaction scripts. To explain the need for P2SH, let’s look at a practical example.
In What is Bitcoin Cash we introduced Mohammed, an electronics importer based in Dubai. Mohammed’s company uses Bitcoin Cash’s multi-signature feature extensively for its corporate accounts. Multi-signature scripts are one of the most common uses of Bitcoin Cash’s advanced scripting capabilities and are a very powerful feature. Mohammed’s company uses a multi-signature script for all customer payments, known in accounting terms as "accounts receivable," or AR. With the multi-signature scheme, any payments made by customers are locked in such a way that they require at least two signatures to release, from Mohammed and one of his partners or from his attorney who has a backup key. A multi-signature scheme like that offers corporate governance controls and protects against theft, embezzlement, or loss.
The resulting script is quite long and looks like this:
2 <Mohammed's Public Key> 5 OP_CHECKMULTISIG
Although multi-signature scripts are a powerful feature, they are cumbersome to use. Given the preceding script, Mohammed would have to communicate this script to every customer prior to payment. Each customer would have to use special Bitcoin Cash wallet software with the ability to create custom transaction scripts, and each customer would have to understand how to create a transaction using custom scripts. Furthermore, the resulting transaction would be about five times larger than a simple payment transaction, because this script contains very long public keys. The burden of that extra-large transaction would be borne by the customer in the form of fees. Finally, a large transaction script like this would be carried in the UTXO set in RAM in every full node, until it was spent. All of these issues make using complex output scripts difficult in practice.
Pay-to-script-hash (P2SH) was developed to resolve these practical difficulties and to make the use of complex scripts as easy as a payment to a Bitcoin Cash address. With P2SH payments, the complex locking script is replaced with its digital fingerprint, a cryptographic hash. When a transaction attempting to spend the UTXO is presented later, it must contain the script that matches the hash, in addition to the unlocking script. In simple terms, P2SH means "pay to a script matching this hash, a script that will be presented later when this output is spent."
In P2SH transactions, the locking script that is replaced by a hash is referred to as the redeem script because it is presented to the system at redemption time rather than as a locking script. Complex script without P2SH shows the script without P2SH and Complex script as P2SH shows the same script encoded with P2SH.
Locking Script: 2 PubKey1 PubKey2 PubKey3 PubKey4 PubKey5 5 OP_CHECKMULTISIG Unlocking Script: Sig1 Sig2
Table 4. Complex script without P2SH
Redeem Script: 2 PubKey1 PubKey2 PubKey3 PubKey4 PubKey5 5 OP_CHECKMULTISIG Locking Script: OP_HASH160 <20-byte hash of redeem script> OP_EQUAL Unlocking Script: Sig1 Sig2 redeem script
Table 5. Complex script as P2SH
As you can see from the tables, with P2SH the complex script that details the conditions for spending the output (redeem script) is not presented in the locking script. Instead, only a hash of it is in the locking script and the redeem script itself is presented later, as part of the unlocking script when the output is spent. This shifts the burden in fees and complexity from the sender to the recipient (spender) of the transaction.
Let’s look at Mohammed’s company, the complex multi-signature script, and the resulting P2SH scripts.
First, the multi-signature script that Mohammed’s company uses for all incoming payments from customers:
2 <Mohammed's Public Key> <Partner1 Public Key> <Partner2 Public Key> <Partner3 Public Key> <Attorney Public Key> 5 OP_CHECKMULTISIGIf the placeholders are replaced by actual public keys (shown here as 520-bit numbers starting with 04) you can see that this script becomes very long:
2 04C16B8698A9ABF84250A7C3EA7EEDEF9897D1C8C6ADF47F06CF73370D74DCCA01CDCA79DCC5C395D7EEC6984D83F1F50C900A24DD47F569FD4193AF5DE762C58704A2192968D8655D6A935BEAF2CA23E3FB87A3495E7AF308EDF08DAC3C1FCBFC2C75B4B0F4D0B1B70CD2423657738C0C2B1D5CE65C97D78D0E34224858008E8B49047E63248B75DB7379BE9CDA8CE5751D16485F431E46117B9D0C1837C9D5737812F393DA7D4420D7E1A9162F0279CFC10F1E8E8F3020DECDBC3C0DD389D99779650421D65CBD7149B255382ED7F78E946580657EE6FDA162A187543A9D85BAAA93A4AB3A8F044DADA618D087227440645ABE8A35DA8C5B73997AD343BE5C2AFD94A5043752580AFA1ECED3C68D446BCAB69AC0BA7DF50D56231BE0AABF1FDEEC78A6A45E394BA29A1EDF518C022DD618DA774D207D137AAB59E0B000EB7ED238F4D800 5 OP_CHECKMULTISIGThis entire script can instead be represented by a 20-byte cryptographic hash, by first applying the SHA256 hashing algorithm and then applying the RIPEMD160 algorithm on the result. The 20-byte hash of the preceding script is:
54c557e07dde5bb6cb791c7a540e0a4796f5e97eA P2SH transaction locks the output to this hash instead of the longer script, using the locking script:
OP_HASH160 54c557e07dde5bb6cb791c7a540e0a4796f5e97e OP_EQUALwhich, as you can see, is much shorter. Instead of "pay to this 5-key multi-signature script," the P2SH equivalent transaction is "pay to a script with this hash." A customer making a payment to Mohammed’s company need only include this much shorter locking script in his payment. When Mohammed wants to spend this UTXO, they must present the original redeem script (the one whose hash locked the UTXO) and the signatures necessary to unlock it, like this:
<Sig1> <Sig2> <2 PK1 PK2 PK3 PK4 PK5 5 OP_CHECKMULTISIG>The two scripts are combined in two stages. First, the redeem script is checked against the locking script to make sure the hash matches:
<2 PK1 PK2 PK3 PK4 PK5 5 OP_CHECKMULTISIG> OP_HASH160 <redeem scriptHash> OP_EQUALIf the redeem script hash matches, the unlocking script is executed on its own, to unlock the redeem script:
<Sig1> <Sig2> 2 PK1 PK2 PK3 PK4 PK5 5 OP_CHECKMULTISIGPay-to-script-hash addresses
Another important part of the P2SH feature is the ability to encode a script hash as an address, as defined in BIP0013. P2SH addresses are Base58Check encodings of the 20-byte hash of a script, just like Bitcoin Cash addresses are Base58Check encodings of the 20-byte hash of a public key. P2SH addresses use the version prefix "5", which results in Base58Check-encoded addresses that start with a "3". For example, Mohammed’s complex script, hashed and Base58Check-encoded as a P2SH address becomes 39RF6JqABiHdYHkfChV6USGMe6Nsr66Gzw. Now, Mohammed can give this "address" to his customers and they can use almost any Bitcoin Cash wallet to make a simple payment, as if it were a Bitcoin Cash address. The 3 prefix gives them a hint that this is a special type of address, one corresponding to a script instead of a public key, but otherwise it works in exactly the same way as a payment to a Bitcoin Cash address.
P2SH addresses hide all of the complexity, so that the person making a payment does not see the script.
Benefits of pay-to-script-hash
The pay-to-script-hash feature offers the following benefits compared to the direct use of complex scripts in locking outputs:
- Complex scripts are replaced by shorter fingerprints in the transaction output, making the transaction smaller.
- Scripts can be coded as an address, so the sender and the sender’s wallet don’t need complex engineering to implement P2SH.
- P2SH shifts the burden of constructing the script to the recipient, not the sender.
- P2SH shifts the burden in data storage for the long script from the output (which is in the UTXO set) to the input (stored on the blockchain).
- P2SH shifts the burden in data storage for the long script from the present time (payment) to a future time (when it is spent).
- P2SH shifts the transaction fee cost of a long script from the sender to the recipient, who has to include the long redeem script to spend it.
Redeem script and isStandard validation
Prior to version 0.9.2, pay-to-script-hash was limited to the standard types of Bitcoin Cash transaction scripts, by the isStandard() function. That means that the redeem script presented in the spending transaction could only be one of the standard types: P2PK, P2PKH, or multi-sig nature, excluding OP_RETURN and P2SH itself.
As of version 0.9.2, P2SH transactions can contain any valid script, making the P2SH standard much more flexible and allowing for experimentation with many novel and complex types of transactions.
Note that you are not able to put a P2SH inside a P2SH redeem script, because the P2SH specification is not recursive. You are also still not able to use OP_RETURN in a redeem script because OP_RETURN cannot be redeemed by definition.
Note that because the redeem script is not presented to the network until you attempt to spend a P2SH output, if you lock an output with the hash of an invalid transaction it will be processed regardless. However, you will not be able to spend it because the spending transaction, which includes the redeem script, will not be accepted because it is an invalid script. This creates a risk, because you can lock Bitcoin Cash in a P2SH that cannot be spent later. The network will accept the P2SH encumbrance even if it corresponds to an invalid redeem script, because the script hash gives no indication of the script it represents.
P2SH locking scripts contain the hash of a redeem script, which gives no clues as to the content of the redeem script itself. The P2SH transaction will be considered valid and accepted even if the redeem script is invalid. You might accidentally lock Bitcoin Cash in such a way that it cannot later be spent.
-
 @ 3165b802:a9f51d37
2025-04-07 17:01:23
@ 3165b802:a9f51d37
2025-04-07 17:01:23Humanrights #Human #Rights
-
 @ ef53426a:7e988851
2025-04-07 15:25:58
@ ef53426a:7e988851
2025-04-07 15:25:58Bitcoin and stories are much alike.
They can be described in powerful simplicity or astonishing complexity. Both are unique developments in human history and feed our well-being. Bitcoin and stories are forces for good, but they must be used wisely.
By removing himself from the equation, Satoshi Nakamoto left it to us to write the future of bitcoin. It’s not surprising that we have been tentative to propose a narrative. Stories have never been decentralized before.
Think of the pyramids, the invention of the printing press, or the release of the iPhone 1. Instead of the technology itself, we focus on the people who made it possible and how its invention affected society. But in relity, the story of the pyramids survives in every tourist’s photograph; the joy of reading touches a higher percentage of the world’s population every year; the garage-to-keynote-speaker tale of Apple’s late CEO inspires would-be entrepreneurs worldwide.
To unite interest in bitcoin, we need to be better at telling its stories. Only stories have the power to stop us, to wake us, to make us feel rather than think.
In late 2022, Konsensus Network, the Freedom Publishing House, announced a call for submissions for the world’s first bitcoin fiction anthology. The book seeks to link the emotive power of stories with the possible effects and ramifications of a hyperbitcoinized world.
For most people, great change doesn’t arrive from binary logic and a working knowledge of code. Understanding grows through narrative. It is stories that bring change.
Here’s https://www.youtube.com/embed/vIQ41B8jFPI?si=pN2kr44P-Th3bug4 for the book with some of the original artwork which accompanies the 21 stories.
21 Futures: Tales from the Timechain
Political dissidents scramble to cross the threshold to freedom. A decades-long hunt for keys incites a change in world order. A clear-blood dares to question the oppression of noderoids. A cryo-frozen oligarch wakes into his worst nightmare.
A lowly space station miner buys a planet.
In this book of diverse stories planted firmly in the bitcoin-verse, reality fractures into 21 futures. Some are wonderful, others terrifying.
You are not prepared.
[https://21futures.com] (21 Futures) is now an imprint of Konsensus Network, publishing a variety of freedom fiction stories and books.
In my next blog, I'll go into some of the many developments in the bitcoin fiction space in the last few years.
For now, let's keep sharing stories.
-
 @ e4950c93:1b99eccd
2025-04-07 14:34:11
@ e4950c93:1b99eccd
2025-04-07 14:34:11Équipe Cœur
L'équipe Cœur porte le projet et valide les contenus.
- Jean-David Bar : https://njump.me/npub1qr4p7uamcpawv7cr8z9nlhmd60lylukf7lvmtlnpe7r4juwxudzq3hrnll
Pour démarrer, je gère le projet en solo en partageant mes favoris pour éviter le plastique sur nous et sur nos enfants. Contactez-moi si vous souhaitez rejoindre l'aventure !
Enrichisseu-r-se-s de contenus
Les contribut-eur-rice-s rendent ce site vivant et intéressant.
A venir.
👉 En savoir plus sur les contributions
Cet article est publié sur origine-nature.com 🌐 See this article in English
-
 @ e4950c93:1b99eccd
2025-04-07 13:46:05
@ e4950c93:1b99eccd
2025-04-07 13:46:05Trouver des produits 100% naturels, sans plastique, est bien plus compliqué que je ne le pensais… Alors j’ai commencé à collectionner des marque-pages. Et puis je me suis dit : « Et si on partageait ?! »
Aidez-moi à dénicher les meilleures alternatives naturelles pour s’habiller et s’équiper sans plastique !
Ce projet repose sur le partage : la moitié des revenus éventuels du site est reversée aux contribut-eur-rice-s. Une petite expérimentation de partage de la valeur sur Internet. :-)
Questions-réponses
Pourquoi se focaliser sur les matières naturelles ?
Les matières synthétiques sont essentiellement des plastiques (polyester, polyamide…). Problème ? Oui ! Ils finissent par nous contaminer :
- Microplastiques absorbés par la peau,
- Particules diffusées à chaque lavage, se retrouvant dans l’eau que nous buvons et les aliments que nous consommons,
- Enjeux majeurs liés au recyclage des déchets plastiques.
C'est quoi, au juste, des matières naturelles ?
Ce sont des matières non synthétiques, dont les composants existent à l’état naturel, sans modification de leur structure moléculaire. Mais ce qui nous intéresse avant tout, c’est leur biodégradabilité et leur absence de toxicité.
Certaines matières feront sûrement débat sur leur acceptabilité ici.
👉 En savoir plus sur les matières
Quelle différence avec d'autres sites de mode ou de shopping éthiques ?
Il existe déjà de nombreux sites proposant des produits éthiques et durables, mais j’ai constaté qu’ils incluaient souvent des matières synthétiques. Je devais vérifier produit par produit. Certains mettent en avant les fibres en plastique recyclé comme démarche environnementale, mais je préfère éviter d’en porter sur ma peau ou d'en mettre sur mes enfants.
Comment contribuer ?
Si vous trouvez ce projet utile ou intéressant, voici comment le soutenir :
-
📝 En contribuant : suggérez des modifications en commentant les fiches existantes ou proposez de nouvelles références de produits ou de marque. 👉 En savoir plus sur les contributions
-
⚡ En faisant un don : pour faire vivre le projet et remercier les contribut-eur-ice-s. 👉 En savoir plus sur les dons
-
📢 En le partageant : faites connaître le site sur les réseaux sociaux, votre blog…
Comment recevoir une partie des revenus du site ?
Il suffit d’avoir un compte NOSTR et une adresse Bitcoin Lightning.
👉 En savoir plus sur les rétributions
C'est quoi NOSTR ?
C’est un protocole décentralisé pour Internet, encore en phase expérimentale. Il permet :
- De publier et consulter du contenu sans dépendre d’une plateforme centralisée.
- De se connecter à plusieurs services en conservant le contrôle total de ses données.
- D’intégrer le réseau Bitcoin Lightning pour des paiements instantanés et décentralisés.
Et la confidentialité de mes données ?
- Aucune publicité, aucun traçage personnalisé.
- Les commentaires NOSTR sont publics, mais vous pouvez utiliser un pseudonyme.
- Vous conservez la propriété de vos contributions sur le protocole NOSTR.
Qui porte ce projet ?
👉 Voir les contribut-eur-rice-s
Nous utilisons des outils et services open source :
- NOSTR pour la publication des contenus et la vérification des contributions,
- npub.pro pour la visualisation des contenus,
- Coinos.io pour la gestion des paiements.
Cet article est publié sur origine-nature.com 🌐 See this article in English
-
 @ 9223d2fa:b57e3de7
2025-04-07 11:17:18
@ 9223d2fa:b57e3de7
2025-04-07 11:17:182,241 steps
-
 @ e97aaffa:2ebd765d
2025-04-07 09:38:20
@ e97aaffa:2ebd765d
2025-04-07 09:38:20A electricidade ou os computadores ou a Internet foram revoluções que mudaram o mundo, mas a adoção e a evolução da tecnologia foi lenta, permitindo que as populações e as económicas se adaptassem.
Ao contrário, na AI, a evolução está a ser tão rápida, que as sociedades não vão conseguir acompanhar e adaptar a uma nova realidade.
A AI tem um potencial inacreditável, talvez seja a revolução tecnológica mais rápida de sempre, além disso é muito abrangente, quase todos os sectores económicos podem beneficiar, pode provocar um forte aumento na produtividade.
O potencial é tão elevado, como pode ser perigoso, sobretudo quando utilizado como uma arma contra a humanidade. Os governos ou empresas vão construir ferramentas com AI para monitorizar, manipular e controlar os cidadãos.
Muitas profissões vão desaparecer ou reduzir drasticamente o número de trabalhadores. Tal como aconteceu nas revoluções anteriores, muitas profissões acabaram, mas surgir outras novas profissões.
Ou seja, o problema não é a tecnologia, mas sim a maneira como se usa essa tecnologia. Os desafios para o futuro são tremendos.
E o cidadão comum, o que está a fazer e a pensar… a fazer desenhos, a fazer idiotices. https://image.nostr.build/326d506f0015c99d09e061094bf3552764c6f6334be2899c6f5359f0a809d8bc.jpg
Algo similar acontece com o Bitcoin, uma tecnologia revolucionária, em alguns casos particulares, as stablecoins poderão ser interessantes. Mas o povo prefere especulador em tokens absurdos e jogar no casino das memecoins.
Também acontece com a internet, é uma fonte acessível e inesgotável de conhecimento, mas as pessoas preferem passar horas sem fim, nas redes sociais a fazer swipe up, a consumir conteúdo degradante.
O mundo ocidental está a transformar os cidadãos em zumbis, facilmente manipuláveis, obedientes, viciados. Nós necessitamos é de pessoas curiosas, com espírito crítico, criativas. Essencialmente, que pensem pela sua própria cabeça.
-
 @ 7d33ba57:1b82db35
2025-04-07 09:17:04
@ 7d33ba57:1b82db35
2025-04-07 09:17:04Prague, the capital of the Czech Republic, is like stepping into a real-life fairy tale. With its Gothic towers, baroque churches, medieval streets, and a majestic castle watching over the city, it’s no surprise that it’s one of Europe’s most beloved destinations. Add in great beer, cozy cafés, and stunning river views, and you’ve got the perfect city break.
🌟 Top Things to Do in Prague
1️⃣ Prague Castle & St. Vitus Cathedral
- One of the largest castle complexes in the world
- Don’t miss St. Vitus Cathedral, the Old Royal Palace, and Golden Lane
- Climb the cathedral tower for epic city views

2️⃣ Charles Bridge (Karlův most)
- Iconic 14th-century bridge lined with 30 baroque statues
- Walk it at sunrise or late at night to avoid the crowds
- Great for photos, street musicians, and romantic vibes
3️⃣ Old Town Square & Astronomical Clock
- The heart of the city, with colorful buildings and Gothic spires
- Watch the Astronomical Clock chime on the hour (since 1410!)
- Check out Týn Church and the Old Town Hall Tower
4️⃣ Explore the Jewish Quarter (Josefov)
- Visit the Old Jewish Cemetery, synagogues, and the Jewish Museum
- Learn about centuries of Jewish heritage and resilience in Prague
5️⃣ Climb Up to Petřín Hill
- Take the funicular or walk to the top for gardens, a mirror maze, and a mini Eiffel Tower
- Fantastic place for picnics, sunsets, and panoramic views
🍽️ What to Eat & Drink in Prague
- Goulash with dumplings (guláš s knedlíky) – Hearty and satisfying
- Svíčková – Beef with creamy vegetable sauce and cranberry
- Trdelník – Tourist favorite sweet pastry (not traditionally Czech, but tasty!)
- Czech beer – World-famous for a reason (Pilsner Urquell, Kozel, Staropramen) 🍻
- Try a traditional pub or lokál for authentic Czech cuisine and great prices
🛶 Other Cool Experiences
✅ Take a Vltava River cruise – see Prague from the water
✅ Visit Letná Park for sweeping views and a beer garden
✅ Check out Kafka Museum for surreal vibes and literary history
✅ Explore Vyšehrad – lesser-known castle ruins with gorgeous views and peaceful paths
✅ Snap pics at the Lennon Wall, especially for street art fans 🎨🚇 Getting Around
- Very walkable, especially in the historic center
- Excellent public transport: trams, metro, and buses (get a 24 or 72-hour pass)
- Uber and Bolt are reliable if you need a ride
- Be cautious with exchange rates and ATMs—use official places or bank ATMs only
💡 Tips for Visiting Prague
🕰️ Wake up early to enjoy the city without crowds
🎟️ Book castle or tower tickets in advance during peak seasons
🌧️ Pack layers—it can be breezy even in spring
📷 Keep your camera ready—every corner is postcard-worthy -
 @ 0fa50ac1:13162495
2025-04-06 23:56:52
@ 0fa50ac1:13162495
2025-04-06 23:56:52You say, “Bitcoin has no intrinsic value.”
But brother, I say to you—nothing does.
❧
Gold, wheat, steel, water, art—
none possess value in themselves.
A thing is not valuable.
A person finds value in a thing.
❧
Value is not a substance.
It is not discovered in the dirt,
nor stamped into metal.
It is born in the mind
of the one who chooses,
who compares,
who prefers.
❧
This is the truth they will not teach you.
Because once you know it,
you cannot be controlled.
❧
To say value is “intrinsic”
is to say it is knowable, measurable,
assignable from above.
And if it can be known,
then it can be fixed.
And if it can be fixed,
then the planners will fix it.
And if the planners fix it,
freedom dies.
❧
Only subjective value
lets prices breathe.
Only subjective value
lets the game go on,
as tastes shift,
as time moves,
as each man finds joy in what others overlook.
❧
It is this truth
that makes room for artists,
for inventors,
for those with strange passions
and quiet genius.
❧
And Bitcoin—
it breaks the frame.
It’s not a commodity.
It’s not a company.
It’s not backed by force.
❧
So they say,
“It has no value.”
❧
And we reply,
“No—you place no value on it.
But others do.
And the market has spoken.”
❧
Transparent. Scarce. Borderless. Unstoppable.
Valued by those who need it most.
Valued by those who understand it best.
❧
It rises not because it was declared valuable,
but because someone, somewhere
was willing to trade for it.
❧
And so the price rose.
And so the signal spread.
And so the economy moved,
as it always has,
not by decree,
but by the ever-motivated
force of desire.
❧
You don’t have to value Bitcoin.
But you do have to accept this:
All value exists only and entirely
in the mind of the economizing human.
 You say, “Bitcoin has no intrinsic value.”
You say, “Bitcoin has no intrinsic value.”But brother, I say to you—nothing does.
❧
Gold, wheat, steel, water, art—
none possess value in themselves.
A thing is not valuable.
A person finds value in a thing.
❧
Value is not a substance.
It is not discovered in the dirt,
nor stamped into metal.
It is born in the mind
of the one who chooses,
who compares,
who prefers.
❧
This is the truth they will not teach you.
Because once you know it,
you cannot be controlled.
❧
To say value is “intrinsic”
is to say it is knowable, measurable,
assignable from above.
And if it can be known,
then it can be fixed.
And if it can be fixed,
then the planners will fix it.
And if the planners fix it,
freedom dies.
❧
Only subjective value
lets prices breathe.
Only subjective value
lets the game go on,
as tastes shift,
as time moves,
as each man finds joy in what others overlook.
❧
It is this truth
that makes room for artists,
for inventors,
for those with strange passions
and quiet genius.
❧
And Bitcoin—
it breaks the frame.
It’s not a commodity.
It’s not a company.
It’s not backed by force.
❧
So they say,
“It has no value.”
❧
And we reply,
“No—you place no value on it.
But others do.
And the market has spoken.”
❧
Transparent. Scarce. Borderless. Unstoppable.
Valued by those who need it most.
Valued by those who understand it best.
❧
It rises not because it was declared valuable,
but because someone, somewhere
was willing to trade for it.
❧
And so the price rose.
And so the signal spread.
And so the economy moved,
as it always has,
not by decree,
but by the ever-motivated
force of desire.
❧
You don’t have to value Bitcoin.
But you do have to accept this:
All value exists only and entirely
in the mind of the economizing human.
-
 @ 878dff7c:037d18bc
2025-04-06 23:35:54
@ 878dff7c:037d18bc
2025-04-06 23:35:54Australia Highlights Critical Minerals in Trade Discussions with U.S.
Summary:
In an effort to avoid renegotiation of its subsidized prescription-drug system, Australia is emphasizing its vast reserves of essential minerals like lithium and rare earths during trade talks with the U.S. Treasurer Jim Chalmers underscored that these resources serve as a strategic advantage, proposing the creation of a strategic reserve for these minerals. This move aligns with President Trump's initiatives to secure mineral access and reflects Australia's intent to leverage its mineral wealth in international negotiations.
Source: The Wall Street Journal - April 7, 2025
ASX Braces for Significant Losses Amid Global Tariff Tensions
Summary:
The Australian Securities Exchange (ASX) is poised for a substantial downturn, with projections indicating a potential loss of approximately $115 billion. This anticipated decline follows the implementation of new tariffs by U.S. President Donald Trump, ranging from 10% to 50% on foreign imports, which have sparked fears of a global trade war. The Australian dollar has also been affected, dropping below 60 US cents for the first time since the COVID-19 pandemic. Analysts warn that these developments could have far-reaching implications for the Australian economy, including increased inflation and potential interest rate cuts.
Sources: News.com.au - April 7, 2025, The Australian - April 7, 2025, ABC News - April 7, 2025
U.S. Department of Energy Considers Cuts to Clean Energy Projects
Summary:
The U.S. Department of Energy is reviewing potential funding cuts exceeding $1.5 billion for various clean energy projects, including those focused on energy storage and carbon capture. Affected initiatives span multiple states and involve technologies crucial for integrating renewable energy into the power grid and reducing carbon emissions. Industry stakeholders and lawmakers have expressed concern, emphasizing the strategic importance of these technologies for energy resilience and environmental objectives.
Source: Reuters - April 5, 2025
Hazardous Materials Incident in South Australia's Mount Lofty Ranges
Summary:
The Country Fire Service (CFS) is responding to an ammonia gas leak at Plummer Road near Lenswood and Lobethal in the Mount Lofty Ranges, South Australia. Residents are advised to stay clear of the area as firefighters work to contain the leak. CFS
Sources: CFS - April 6, 2025
Coalition Reverses Work-From-Home Policy Amid Backlash
Summary:
Opposition Leader Peter Dutton has reversed the Coalition's policy to mandate full-time office attendance for public servants, acknowledging it was a "mistake" that fueled concerns about opposition to flexible working arrangements, particularly among women. Initially, the plan required Australian Public Service employees to work from the office five days a week, but after criticism from unions and advocacy groups, Dutton amended the policy to apply only to Canberra-based workers. Further backlash led to a complete withdrawal of the mandate, with Dutton apologizing for the confusion and stating that existing flexible work arrangements would remain intact. Labor leaders criticized the policy's inconsistency and potential economic impact on families.
Sources: The Guardian - April 7, 2025, News.com.au - April 7, 2025, The Guardian - April 7, 2025
Chevron Australia Warns of Investment Risks Due to Policy Uncertainty
Summary:
Chevron Australia Managing Director Mark Hatfield has expressed concerns over increasing policy uncertainty affecting investment confidence in Australia's energy sector. He highlighted recent policy shifts, such as changes to the petroleum resource rent tax and proposed domestic gas reservation mandates, as factors creating instability and deterring future investment. Hatfield emphasized the need for a balanced energy transition that prioritizes reliability, affordability, and environmental goals. The Australian
Source: The Australian - April 7, 2025
Australia Calls for Independent Investigation into Aid Worker Deaths in Gaza
Summary:
Australia has joined international calls for an independent investigation into the deaths of aid workers in Gaza, including a United Nations employee and eight Palestinian Red Crescent Society medics, who were found in a mass grave on March 27. Senator Penny Wong emphasized the need for a thorough inquiry to ensure accountability and adherence to international humanitarian law, which mandates the protection of humanitarian workers. Israel's military has launched an internal investigation, but international actors are urging for an independent probe, especially in light of newly emerged video evidence that contradicts Israel’s official explanation for the killings.
Sources: News.com.au - April 7, 2025
Recall Issued for Popular Fitbit Smartwatches Due to Burn Risk
Summary:
Fitbit has issued a recall for its Sense and Versa 3 smartwatches after discovering that the battery may overheat, posing a risk of burns to users. The Australian Competition and Consumer Commission (ACCC) has advised consumers to update their devices with the latest firmware to mitigate this risk. Users are encouraged to check their devices and follow the manufacturer's instructions to ensure safety.
Sources: News.com.au - April 2, 2025, The Australian - April 2, 2025
Keir Starmer Declares 'Globalisation is Over' Amid Tariff Disputes
Summary:
UK Prime Minister Keir Starmer has announced the end of globalisation, acknowledging its failure to benefit many voters. This declaration comes in response to significant global economic disruptions caused by new U.S. tariffs imposed by President Trump. Starmer advocates for accelerated supply-side reforms to boost UK growth and plans to introduce pro-growth measures, including easing regulations for electric vehicle manufacturers. He also aims to advance the UK's industrial strategy and pursue trade talks with India and Australia. While opposing tariffs, Starmer recognizes the appeal of Trump's economic nationalism to disaffected voters.
Sources: The Times - April 7, 2025, The Australian - April 7, 2025
Rainbow Lorikeet Tops Australia's Annual Bird Count
Summary:
The rainbow lorikeet has been identified as the most frequently recorded bird in BirdLife Australia's annual Aussie Bird Count, maintaining its top position since the event's inception in 2014. In the 2024 count, over 57,000 participants recorded more than 4.1 million birds, with the noisy miner and Australian magpie following in second and third places, respectively. The count highlights regional diversity in bird populations and provides critical data on environmental trends. Despite concerns about health threats affecting some species, no significant population declines were reported.
Sources: The Guardian - April 7, 2025
In episode #463 of the Lex Fridman Podcast, Lex engages with Douglas Murray, a British author and political commentator, to discuss a range of pressing geopolitical topics.
Key Discussion Points and Insights:
-
Russia-Ukraine Conflict: Murray provides his perspective on Vladimir Putin's motivations and the broader implications of Russia's actions in Ukraine. He delves into the resilience and leadership of President Volodymyr Zelenskyy amidst the ongoing conflict.
-
U.S. Political Landscape: The conversation shifts to former President Donald Trump, examining his influence on both domestic and international politics. Murray offers insights into the polarization within the United States and the potential trajectory of its political future.
-
Middle East Dynamics: An in-depth analysis of Israel's political environment is presented, focusing on Prime Minister Benjamin Netanyahu's leadership. The discussion extends to the complexities of the Israeli-Palestinian conflict, with particular attention to the roles of Hamas and the situation in Gaza.
Throughout the episode, Murray emphasizes the importance of understanding historical contexts to fully grasp current geopolitical events. He advocates for nuanced perspectives, cautioning against oversimplified narratives that often dominate media discourse.
Listeners can gain a comprehensive understanding of these intricate issues, benefiting from Murray's extensive experience and thoughtful analysis.
Sources: Lex Fridman Podcast Episode #463
-
-
 @ e111a405:fa441558
2025-04-06 18:09:31
@ e111a405:fa441558
2025-04-06 18:09:31Running in circles is an expression that is often used to express when no matter what we do, nothing changes. We run in a circle, always ending up where we started.
Imagine the circle lines as boundaries, not physical boundaries, but mental barriers. In our life, we often run within our circle of possibilities. Anything outside our circle seem impossible. Outside the circle is anything that seems unattainable.
For some, healing a chronic disease may seem unattainable, for others it is a nice house, finding one’s soulmate, or merely financial abundance.
Over our lifetime, through our upbringing, we have defined our circle of possibilities. We have defined what is within our possibility and what is outside our possibility.
But this is just a line we drew. It is a mental barrier that does not exist outside our mind. In order to attain what seems unattainable, we have to expand our circle of possibilities. We have to pull what is outside our circle inside.
Imagine it like this: anything that is within our circle is easy and comes effortless. For example, making a coffee, driving a car are within our circle of effortless possibilities.
Other things seem out of reach. They are outside our circle of possibilities. They look extremely hard and impossible to reach.
What we need to do is reframe our understanding of what is within and what is without our circle. We pull seemingly impossible things inside our circle, and thereby we are expanding the size of our circle exponentially. We do this by following our excitement.
Not everything can be pulled inside our circle. But anything we are absolutely excited and passionate about can be pulled inside and made attainable.
You might think that you want to be the founder and CEO of a large, successful company. But if this is merely a desire that comes from mimesis – in other words, a desire that we have because we see other people have or desire it – not from our true inner being.
We will try forever to pull this inauthentic desire inside our circle, but we will fail because it is against our nature. Listening to our true excitement is key. We have to follow what is truly authentic to us — what we are truly excited about from our whole heart – and pull it inside our circle.
You may find true excitement and joy playing the piano or researching a certain subject. But true mastery of the piano or earning a livelihood with it may seem like an impossibility. Don’t let this hold you back. If this is what excites you the most, make the decision to pull it into your circle, define it is easily attainable, possible.
Inside our circle, doing and attaining our desires is as natural and easy as making a cup of coffee. Our inner circle represents our current reality. It is both endless and limiting. Endless in terms of repetition and confinement of boundaries.
Think again of walking in a circle, you always end up in the same spot, never really advancing. We try to improve the conditions within our circles, but improvements within our circles is like improving a prison cell.
True freedom comes from expanding that circle. Or stepping out of that circle into an entirely new one. That is difficult because we are like fish in an aquarium, unaware of the world behind. We only see what is familiar, what is within our circle, and everything beyond that feels alien or unattainable even though we desire it.
The real truth is that it takes the same energy to live and operate within our current circle as it takes to live within a much larger circle or to step. It takes the same effort to be in our current circle as it takes to be in a completely different, much larger circle.
First, you need to identify that you are inside a circle. What are your current habits and goals? What is your current reality?
Once you are aware, the next step is to identify what is outside your circle. What is it that you desire but looks unattainable, impossible?
Now we define a new circle. In this new circle, our goals, our habits are aligned with our authentic aspirations, our true excitement. We create a new reality.
Stepping out of this circle requires risk. It means breaking free from the familiar, and pursing something that may seem uncomfortable or unattainable.
We leave our circle, we leave our comfort zone.
We can do this in small, consistent steps, or we can make a sharp turn–an instant shift in our approach to living, like flipping from being chased to becoming the one who chases.
The real key to escaping our limiting circle is focus.
Where we focus our mental energy on determines the reality we will experience. By only focusing on improving our current reality, we remain locked in. But by expanding our vision to something outside our current circle, outside our current reality, we open up the possibilities of stepping into a new, much larger circle of possibilities.
What seems impossible now, becomes as effortless as making a cup of coffee.
The decision to break free starts with the realization that we are contained in a circle and the decision that we are ready to stop running in circles.
-
 @ f7d424b5:618c51e8
2025-04-06 16:48:03
@ f7d424b5:618c51e8
2025-04-06 16:48:03The promised Nintendo direct has come and there is a LOT to say about it. If you ever wondered how such a reveal would be taken differently by a dad, a NEET, and a people programmer this is the episode for you! Also those SAG bootlickers are getting uppity again. All of that and more!
Sources cited:
- Nintendo Online subscribers get to upgrade the zelda games for free for some reason?
- Do Nintendo games ever actually go on sale?
- Kirby
- Metroid
- TOTK
- Pokeshit
- EOW
- there's literally 252 games on sale at VGP right now
- SAG agreement you can read for yourself
- SAG literally says on their website to go audition for non-union roles and then strongarm them into going union if they wanna keep you
Obligatory:
- Listen to the new episode here!
- Discuss this episode on OUR NEW FORUM
- Get the RSS and Subscribe (this is a new feed URL, but the old one redirects here too!)
- Get a modern podcast app to use that RSS feed on at newpodcastapps.com
- Or listen to the show on the forum using the embedded Podverse player!
- Send your complaints here
Reminder that this is a Value4Value podcast so any support you can give us via a modern podcasting app is greatly appreciated and we will never bow to corporate sponsors!













































