-

@ a012dc82:6458a70d
2025-02-04 15:49:10
Bitcoin halving is a cornerstone event in the cryptocurrency landscape, occurring approximately every four years, or after every 210,000 blocks are mined. This event is significant because it marks a reduction in the reward that miners receive for adding new blocks to the Bitcoin blockchain, effectively halving the rate at which new bitcoins are generated. The concept of halving is embedded in Bitcoin's protocol by Satoshi Nakamoto, its mysterious creator, as a measure to mimic the scarcity and deflationary characteristics of precious metals like gold. This mechanism is crucial in controlling the supply of Bitcoin, ensuring that it remains finite and valuable. As the next halving event draws near, it's not just miners who are impacted; the entire cryptocurrency market, including investors and enthusiasts, keenly anticipates the potential outcomes. Historically, halving events have been associated with increased market activity, price volatility, and heightened public interest in Bitcoin. The event is seen as a moment of transformation for Bitcoin, where the dynamics of supply and demand are altered, potentially leading to significant shifts in its market value.
**Table Of Content**
- Understanding the Hash Rate Surge
- Implications of the Rising Hash Rate
- The Halving Event: What to Expect
- Preparing for the Halving
- Conclusion
- FAQs
**Understanding the Hash Rate Surge**
**What is Hash Rate?**
The hash rate, in the context of Bitcoin, refers to the total computational power being used to mine and process transactions on the blockchain. It's a vital metric that reflects the health and security of the network. A higher hash rate means that more computational resources are being dedicated to maintaining the network, making it more robust against potential attacks. The hash rate is measured in hashes per second (H/s), and with advancements in mining technology, the network has seen this rate reach exahash levels (1 EH/s = 1 quintillion hashes per second). This metric is crucial for miners, as it affects their chances of solving the mathematical puzzles required to mine new blocks and earn rewards. It also indicates the level of competition among miners, as a higher hash rate suggests more participants or more powerful mining equipment in the network.
**Record-Breaking Levels**
The Bitcoin network's hash rate has recently hit an all-time high, reaching a staggering 491 exahashes per second (EH/s). This surge is indicative of the growing strength and security of the network. Such a high hash rate means that the network is more resilient than ever to potential attacks, such as the 51% attack, where a single entity could potentially gain control over the majority of the network's mining power. This level of security is crucial, especially as Bitcoin continues to gain mainstream acceptance and attract significant institutional investment. The record-breaking hash rate also reflects the increasing global interest in Bitcoin mining. It suggests that despite the high costs associated with mining - including specialized hardware and significant electricity consumption - miners are still heavily investing in this activity. This investment is not just in terms of money but also in research and development of more efficient mining technologies, which could further drive up the hash rate.
**Implications of the Rising Hash Rate**
**Enhanced Network Security**
The surge in Bitcoin's hash rate is a positive development for the network's security. A higher hash rate means that it becomes exponentially more difficult for a malicious actor to orchestrate an attack on the network. This security is paramount for a system that handles billions of dollars worth of transactions. The decentralized nature of Bitcoin relies heavily on the integrity of its blockchain, which is maintained by this collective computational effort. As the hash rate increases, the confidence in the network's security also grows, which is crucial for both individual users and institutional investors. This enhanced security is particularly important in the context of the upcoming halving event, as it ensures the stability and reliability of the network during a period of significant change.
**Increased Mining Difficulty**
With the rise in hash rate comes an increase in the difficulty of mining Bitcoin. The Bitcoin network is designed to adjust the difficulty of mining new blocks approximately every two weeks to ensure that the time between blocks remains around 10 minutes. As more computational power joins the network, the difficulty increases, making it harder for individual miners to solve the cryptographic puzzles required to mine new blocks. This increase in difficulty can have several implications for miners. Smaller miners or those with less efficient equipment may find it increasingly difficult to compete with larger mining operations that have access to more powerful and efficient technology. This could lead to a consolidation in the mining industry, where only the most efficient operations can survive. Additionally, as the difficulty increases, the profitability of mining can decrease, especially if the price of Bitcoin does not increase proportionally. Miners must constantly evaluate their operations' efficiency and electricity costs to ensure continued profitability.
**Energy Consumption Concerns**
The rising hash rate of the Bitcoin network has brought renewed attention to the issue of energy consumption in Bitcoin mining. The process of mining Bitcoin is energy-intensive, as it requires a significant amount of computational power. As the hash rate increases, so does the total energy consumption of the network. This has led to concerns about the environmental impact of Bitcoin mining, especially in regions where electricity is generated from fossil fuels. The debate around Bitcoin's energy consumption is complex. On one hand, proponents argue that much of the energy used for Bitcoin mining comes from renewable sources, and the industry drives innovation in energy efficiency. On the other hand, critics point out that the overall energy consumption is still substantial and could be directed towards other, more productive uses. This debate is likely to continue as the network grows and the hash rate increases, especially in the context of global concerns about climate change and sustainable energy practices.
**The Halving Event: What to Expect**
**Reward Reduction**
The upcoming Bitcoin halving event is a scheduled reduction in the rewards that miners receive for verifying and adding new transactions to the blockchain. This halving reduces the number of new bitcoins created and earned by miners with each new block from 6.25 bitcoins to 3.125 bitcoins. This event occurs every 210,000 blocks, or approximately every four years, and is a fundamental part of Bitcoin's economic model. The halving is designed to mimic the extraction of precious resources, becoming progressively harder and less rewarding over time. This mechanism ensures that the total supply of Bitcoin will never exceed 21 million coins, making Bitcoin a deflationary asset. The halving event is significant because it affects the economics of Bitcoin mining. With the reward halving, the revenue for miners is effectively cut in half overnight. This can lead to a shakeout in the mining industry, as less efficient miners may no longer be profitable and could be forced to shut down their operations.
**Market Impact**
Historically, Bitcoin halving events have been followed by significant price increases. This pattern has led to a common perception that halving events are bullish for Bitcoin's price. The rationale behind this is simple: as the rate of new supply of Bitcoin decreases, and if demand remains constant or increases, the price should theoretically go up. However, it's important to note that financial markets are influenced by a myriad of factors, and the impact of the halving may already be priced in by the time it occurs. Additionally, each halving event occurs in a different macroeconomic environment, and past performance is not indicative of future results. Investors and traders closely watch these events, as they can lead to increased volatility in the market. Some see the halving as an opportunity for long-term investment, while others may speculate on short-term price movements.
**Preparing for the Halving**
**Miner Adaptations**
In anticipation of the halving and its impact on profitability, miners are taking various steps to adapt. One key strategy is the investment in more efficient mining hardware. Newer models of mining rigs offer greater hash power with lower energy consumption, which can help maintain profitability even with reduced rewards. Miners are also exploring alternative sources of revenue, such as transaction fee income, which could become a more significant part of their earnings post-halving. Additionally, miners are looking at geographical relocation to regions with cheaper electricity and favorable regulatory environments to reduce operational costs. Another consideration for miners is the potential consolidation of mining operations. Larger mining pools might have a better chance of surviving the reduced rewards, leading to a more centralized mining landscape. This potential centralization raises concerns within the Bitcoin community, as it could impact the decentralized nature of the network.
**Investor Strategies**
Investors are also preparing for the halving event in various ways. Many are closely analyzing historical data to understand potential market movements, although it's widely acknowledged that past trends may not necessarily predict future outcomes. Some investors view the halving as a key event that could drive long-term value growth in Bitcoin and are adjusting their portfolios accordingly. Others are more cautious, considering the potential for increased volatility around the event. There is also a focus on diversification, with investors looking at other cryptocurrencies and blockchain projects that might benefit from increased interest in the crypto space around the halving. Additionally, institutional investors, who have increasingly entered the cryptocurrency market, are likely to play a significant role in how the market reacts to the halving. Their strategies, which may include hedging and derivative trading, could influence Bitcoin's price dynamics in ways that were not seen in previous halving events.
**Conclusion**
The countdown to the Bitcoin halving is a period of significant anticipation and activity within the cryptocurrency community. The record-breaking hash rate ahead of the event is a testament to the network's strength and the commitment of its participants to maintain and secure the blockchain. As the halving approaches, the crypto world watches with keen interest, eager to see how this pivotal event will shape the future of Bitcoin. Whether it leads to a surge in price, increased adoption, or new challenges for miners, the halving is a reminder of the unique and dynamic nature of cryptocurrency and its underlying technology. As with any major event in the crypto space, the halving presents both opportunities and risks, and how it plays out could have lasting implications for the entire blockchain ecosystem.
**FAQs**
**What is Bitcoin Halving?**
Bitcoin halving is an event that occurs approximately every four years, reducing the reward for mining new Bitcoin blocks by half. This mechanism controls the supply of new bitcoins and is a fundamental part of Bitcoin's economic model.
**Why is the Bitcoin Hash Rate Important?**
The hash rate measures the total computational power used in mining and processing transactions on the Bitcoin network. A higher hash rate indicates a more secure and robust network, making it resistant to attacks.
**What Happens to Bitcoin's Price After Halving?**
Historically, Bitcoin's price has increased following halving events, but this is not guaranteed. Market reactions can be unpredictable, and various factors influence Bitcoin's price.
**How Does Halving Affect Bitcoin Miners?**
Halving reduces the reward miners receive for validating new blocks, impacting their profitability. Miners often need to upgrade to more efficient hardware or find cheaper energy sources to remain competitive.
**Can Bitcoin Halving Lead to Increased Centralization in Mining?**
Potentially, yes. As mining becomes less profitable for smaller operations, there could be a consolidation towards larger mining pools, which might lead to a more centralized mining landscape.
**Is the Increase in Bitcoin's Hash Rate Linked to the Upcoming Halving?**
Yes, the increase in hash rate is often linked to the upcoming halving as miners upgrade their equipment and increase their computational power in anticipation of the reduced mining rewards.
**That's all for today**
**If you want more, be sure to follow us on:**
**NOSTR: croxroad@getalby.com**
**X: [@croxroadnews.co](https://x.com/croxroadnewsco)**
**Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)**
**Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)**
**Store: https://croxroad.store**
**Subscribe to CROX ROAD Bitcoin Only Daily Newsletter**
**https://www.croxroad.co/subscribe**
***DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.***
-

@ 1833ee04:7c4a8170
2025-02-04 15:14:03
The international race for Bitcoin strategic reserves is just getting started.
If you’re stacking now, you’re still incredibly early.
At $100k per Bitcoin, it’s practically free for anyone who truly understands how massive this shift is.
Think back to when paper currency was introduced, people had to trade their gold for paper bills. Many laughed, saying, Who’s going to trust these worthless pieces of paper as money?
Yet today, you sell your time to earn these paper bills while your government can print an unlimited amount at will.
The world is returning to a gold standard. But this time, it’s Gold 2.0 which is Bitcoin.The international race for Bitcoin strategic reserves is just getting started.\
\
If you’re stacking now, you’re still incredibly early.\
\
At $100k per Bitcoin, it’s practically free for anyone who truly understands how massive this shift is.\
\
Think back to when paper currency was introduced, people had to trade their gold for paper bills. Many laughed, saying, Who’s going to trust these worthless pieces of paper as money?\
\
Yet today, you sell your time to earn these paper bills while your government can print an unlimited amount at will.\
\
The world is returning to a gold standard. But this time, it’s Gold 2.0 which is Bitcoin.
-

@ 5af07946:98fca8c4
2025-02-04 15:13:27
Syādvāda, also known as the theory of conditional predication, is a fundamental concept in Jain philosophy that bears some intriguing similarities to modern concepts of probability.
## Conditional Prediction system
Syādvāda is a theory of epistemological relativism that forms the basis of Jain [logic](https://www.newworldencyclopedia.org/entry/Syadvada). The term "syād" in Sanskrit means "may be" or "perhaps," and in the context of syādvāda, it translates to "in some ways" or "from a perspective". This theory asserts that reality is complex and multifaceted, and no single proposition can fully express its nature.
## Saptabhangi: The Seven-fold Predication
The core of syādvāda is manifested in the process of Saptabhangi, or seven-fold prediction. This approach examines reality from seven different conditional and relative viewpoints:
- Syādasti (maybe, it is)
- Syānnāsti (maybe, it is not)
- Syādasti nāsti (maybe, it is, and it is not)
- Syādavaktavya (maybe, it is indeterminate)
- Syādasti avaktavya (maybe, it is and is indeterminate)
- Syānnāsti avaktavya (maybe, it is not and is indeterminate)
- Syādasti nāsti avaktavya (maybe, it is, is not, and is indeterminate)
## Connections to Probability
Syādvāda shares conceptual similarities with Probability theory:
- Non-absolutism: Like probability theory, syādvāda acknowledges uncertainty and rejects absolute [statements](https://indiaphilosophy.wordpress.com/tag/syadvad/). However, it asserts that there are only seven categories necessary and also sufficient to exhaust all possibilities of knowledge!
- Conditional nature: Both syādvāda and probability deal with conditional statements and [chances](https://jainfriends.tripod.com/books/jiblsyadvada.html)
- Multiple outcomes: Syādvāda's seven-fold prediction can be seen as analogous to considering multiple possible outcomes in probability.
- Indeterminacy: The fourth category of syādvāda, "avaktavya" (indeterminate), has been interpreted by some scholars as having relevance to the concept of probability.
## An Illustrative Example
Consider the tossing of a coin:
- "It is head" (now) - Syādasti
- "It is not-head" (on another occasion) - Syānnāsti
- "It is, and it is not" - Syādasti nāsti
- "It is indeterminate" (before the toss) - Syādavaktavya
This example demonstrates how syādvāda's categories can be applied to a situation involving uncertainty, similar to how we might approach it using probability theory.
## Historical Significance and Modern Relevance
Syādvāda was well-developed by the 6th century AD and received significant attention in medieval Indian logic. It is believed that it was based on astrological principles of Maharishi Parashara - the father of ancient astrology.
-

@ 916a7ab7:146bb83e
2025-02-04 13:35:11
It was not ago that my life was simpler than it is today.
I remember being a simple clone, droning on through a structured life as I'd been trained to do since birth.
Like most people I knew, I was raised in a world where you were mentally prepared for a conceptually simple life:
1. Finish high school, if possible.
2. Go to college, if possible.
3. Find a job.
4. Earn money.
5. Pay bills.
6. Get married.
7. Start a family.
8. Pay more bills.
9. Raise family and (hopefully) launch the kids.
10. Plan to retire, but expect to work into your 70s.
It was a programmed formula for life. A generational blueprint, if you will. Sure, there would be unpredictable details, but I expected my life to follow this path.
As I plodded along through my fairly boring life, I checked most of those things off the list. High school was easy, but getting off the farm was not. Enlisting in the military solved that problem, and the pay in the mid-1990s wasn't bad for a 17 year old kid with no bills. I got paid every two weeks, lived in the barracks, and spent most of my money on booze. Life was good, and I had no other purpose than to do my job and keep earning money.
Before I knew it, though, everything changed. I got married, had some kids and accumulated a mountain of debt. Like my parents before me, I was stuck in a never ending cycle of working my ass off, paying bills, buying food, and trying to save what little money was left over for a future that was unpredictable at best. Financial struggles stressed our marriage, the kids continued eating more and more food, and then 2008 tanked the value of our home. That was the first nudge that stirred my oblivious slumber.
And there was more to come. Rising taxes, inflation, the clown show at the federal reserve, the wars funded by central banks, an astronomical national debt, and the burdens of our mistakes weighing down the futures of our children. Not to mention a federal government that actively seeks to censor, suppress, and financially imprison its own people. The times exuded chaos.
Then a few months ago, I woke up...
It happened during an episode of The Tuttle Twins, a cartoon show from Angel Studios. I homeschool my three youngest kids, and I'd let them watch TV during lunch so I could grade some papers. This cartoon was new to me, but the kids liked the music and the crazy raccoon. As fate would have it, they ended up watching an episode about Bitcoin. This, of course, led to a long series of questions:
"Dad, what's Bitcoin?"
"Is Bitcoin real?"
"Do you have Bitcoin?"
"Can I get Bitcoin for allowance instead of dollars?"
I had no answers for these questions, so we started doing some research together. We turned on our Chromebooks and launched a barrage of web searches. After reading a bunch of articles I came away with the idea that Bitcoin might be a real thing. Later that evening, and after the kids were in bed, I couldn't stop thinking about Bitcoin. I honestly didn't understand half of what I read in those articles, which bothered me. I'm not a super smart guy, but I catch on to things pretty quickly, and I wanted to better understand what I'd read. I expanded my search to podcasts and YouTube videos.
I ended up listening to a couple episodes from a Bitcoin Veterans podcast. As a veteran myself, I figured that this group of Bitcoin-savvy veterans would be able to help me figure out all this madness. I was right. I quickly learned that the word "Bitcoin" was just the tip of the iceberg, and I quickly found myself falling through an endless rabbit hole. They pointed me in a lot of different directions, but they were all helpful. (If you're a US military veteran and want to connect with this group, find them at [bitcoinveterans.org].)
A couple months ago, I couldn't tell you the difference between a Bitcoin and a meme coin. I'd come across the phrase Bitcoin mining, and I just thought there was a special group of people who mined a special metal to create coins with a big "B" on them. Why couldn't they just use the metal we already mined? Sheesh! I thought nostr was a virus, and a Kraken was still a giant squid.
As of today, I'm happy to say that I've made a little bit of progress. Those things above no longer confuse me, and I actually have a little bit of Bitcoin now. Sure, I'm still trying to wrap my head around NFTs and figure out who the Pepe frog man is, but I'm no longer completely lost. Not to mention, I just spent most of the last 24 hours figuring this whole nostr thing out, which excites me. I kind of missed the boat on the big name social media platforms, so I'm looking forward to this new decentralized approach to things.
For now, I'm just happy to be awake. Finally. I see the need for decentralization and the necessity of moving away from fiat monies. I don't have much to offer except my intellect and my love of writing, but I'm here to serve in any way that I can.
-

@ ef1e59bf:b686587d
2025-02-04 11:15:10
## Key Insights Explained
While both systems provide innovative soilless growing solutions, the unique difference lies in their approach—hydroponics relies on a nutrient-rich water solution, whereas aquaponics integrates fish into the ecosystem to naturally supply nutrients. This not only impacts their cultivation techniques but also illustrates varying levels of sustainability and resource use.
In exploring these systems, one cannot help but consider the broader implications for urban agriculture. For those looking to adopt such systems, understanding key differences can significantly impact decisions on efficiency, cost, and ecological footprint.
##### What Is Hydroponics?
In hydroponics, we grow plants in water enriched with nutrients rather than soil. This method provides a controlled environment where the roots receive all necessary elements directly from the nutrient solution. It's fascinating how plants can thrive without ever touching the soil.
The benefits of hydroponics are impressive. We can achieve faster growth rates due to optimal nutrient delivery, and the space-saving designs, such as vertical farms, maximise small areas. Moreover, nutrient levels can be controlled precisely, ensuring plants receive exactly what they need.
##### What Is Aquaponics?
Aquaponics is an innovative system that blends aquaculture, which is the practice of raising fish, with hydroponics, the soilless cultivation of plants. In this symbiotic setup, fish waste serves as a natural fertiliser, supplying essential nutrients to the plants. In return, the plants help purify the water, creating a healthy environment for the fish.
This system is unique because it mimics natural ecosystems, enhancing sustainability. The dual benefits of growing plants and fish simultaneously make aquaponics an attractive option for those of us interested in sustainable agriculture and promoting organic cultivation practices.
##### Key Differences
Hydroponics and aquaponics each offer unique benefits and challenges. Understanding these systems requires examining their differences in nutrient sources, water usage, plant growth density, time to harvest, setup intricacies, and the types of produce they best support.
##### Nutrient Source
In hydroponics, plants receive nutrients through specially prepared solutions, often purchased from commercial suppliers. This method allows us to maintain a high level of control over nutrient balance, making precise adjustments as needed.
Aquaponics, by contrast, relies on fish waste to supply nutrients. This forms a more natural ecosystem, requiring biological processes like nitrification to convert waste into nutrients usable by plants. While this approach involves fewer chemical inputs and is more sustainable, it offers less control over nutrient levels.
##### Water Usage
Hydroponic systems excel in water efficiency by recirculating water, though they necessitate regular changes to keep nutrient solutions balanced. Despite their efficiency, water loss can occur through evaporation or leaks, which requires monitoring.
Aquaponics operates as a closed-loop system where water is continually recycled between the fish tank and plant beds, minimising waste. This setup further reduces water use due to natural filtration by plants, making it an incredibly water-efficient choice.
##### Grow Density
Hydroponics typically supports higher density plant growth, especially in vertical setups. This is ideal for cultivating leafy greens, herbs, and other fast-growing plants in compact spaces.
Aquaponics requires space for both fish and plants, which limits plant density. Although some plants may grow slower due to varying nutrient availability, this method offers the benefit of integrating fish care into the system.
##### Grow Time
In hydroponics, plants enjoy faster growth rates thanks to controlled nutrient and environmental conditions. These systems often facilitate shorter growing cycles compared to traditional farming, enhancing efficiency.
Aquaponics, while efficient, may experience slightly slower growth rates due to the time taken for natural nutrient conversion. Balancing fish growth with plant cycles adds an extra layer of complexity but is a rewarding experience for those willing to engage deeply with the system.
##### Set Up and Maintenance
Starting a hydroponic system is relatively straightforward, with pumps, nutrient tanks, and light management being primary needs. Regular checks of pH, nutrient levels, and water are essential yet generally simple.
Aquaponics demands more initial infrastructure and expertise due to the need for integrated fish tanks and plant systems. Balancing fish health and water quality with plant needs adds complexity, but long-term sustainability benefits are significant. Setting up these systems can seem daunting but offer reduced external nutrient input over time.
##### Produce Types
Hydroponics shines when growing leafy greens and herbs, achieving high success rates with crops like lettuce, basil, and spinach. These systems, however, have limitations when it comes to larger or more nutrient-demanding produce.
Aquaponics expands possibilities by supporting a broader range of plants, including fruiting ones such as tomatoes, alongside fish like tilapia or trout. This dual-production feature offers diverse yields, though the choice of fish can influence plant variety.
##### Which Is More Sustainable?
When we consider the sustainability of hydroponics, several factors come to mind. First, high water efficiency and space-saving designs make it attractive for eco-conscious growers. Yet, the reliance on artificial nutrients and the higher energy usage, particularly for lighting and pumps, may impact its overall eco-friendliness. These elements can sometimes offset the system’s environmental benefits.
In contrast, aquaponics offers a unique closed-loop system that naturally recycles waste. This can significantly reduce the need for external inputs, aligning well with principles of organic farming. While this method requires more space and careful maintenance for both fish and plants, it typically involves less chemical intervention, appealing to those seeking a more natural approach.
###### Let's compare the environmental impact of these methods:
* Aquaponics might have a lower environmental footprint due to its natural nutrient cycle, reducing waste and chemical use.
* On the other hand, hydroponics can be well-suited for urban environments or locations with limited resources, thanks to its efficient use of water and space.
Ultimately, deciding which system is more sustainable depends on specific circumstances and priorities. If natural nutrient cycles and less chemical intervention are valued, aquaponics might be favoured. Nevertheless, if water and space efficiency are paramount, especially in urban settings, hydroponics might be more suitable.
Hydroponics is a game-changer for sustainable farming, offering efficient water use, reduced land impact, and year-round crop production. Whether you're a beginner or an experienced grower, having the right tools and knowledge is key to success. Visit [Hyjo ](https://hyjo.co.uk/)for high-quality hydroponic systems, nutrients, and expert advice. Start growing smarter and greener with Hyjo today!
-

@ e3ba5e1a:5e433365
2025-02-04 08:29:42
President Trump has started rolling out his tariffs, something I [blogged about in November](https://www.snoyman.com/blog/2024/11/steelmanning-tariffs/). People are talking about these tariffs a lot right now, with many people (correctly) commenting on how consumers will end up with higher prices as a result of these tariffs. While that part is true, I’ve seen a lot of people taking it to the next, incorrect step: that consumers will pay the entirety of the tax. I [put up a poll on X](https://x.com/snoyberg/status/1886035800019599808) to see what people thought, and while the right answer got a lot of votes, it wasn't the winner.

For purposes of this blog post, our ultimate question will be the following:
* Suppose apples currently sell for $1 each in the entire United States.
* There are domestic sellers and foreign sellers of apples, all receiving the same price.
* There are no taxes or tariffs on the purchase of apples.
* The question is: if the US federal government puts a $0.50 import tariff per apple, what will be the change in the following:
* Number of apples bought in the US
* Price paid by buyers for apples in the US
* Post-tax price received by domestic apple producers
* Post-tax price received by foreign apple producers
Before we can answer that question, we need to ask an easier, first question: before instituting the tariff, why do apples cost $1?
And finally, before we dive into the details, let me provide you with the answers to the ultimate question. I recommend you try to guess these answers before reading this, and if you get it wrong, try to understand why:
1. The number of apples bought will go down
2. The buyers will pay more for each apple they buy, but not the full amount of the tariff
3. Domestic apple sellers will receive a *higher* price per apple
4. Foreign apple sellers will receive a *lower* price per apple, but not lowered by the full amount of the tariff
In other words, regardless of who sends the payment to the government, both taxed parties (domestic buyers and foreign sellers) will absorb some of the costs of the tariff, while domestic sellers will benefit from the protectionism provided by tariffs and be able to sell at a higher price per unit.
## Marginal benefit
All of the numbers discussed below are part of a [helper Google Sheet](https://docs.google.com/spreadsheets/d/14ZbkWpw1B9Q1UDB9Yh47DmdKQfIafVVBKbDUsSIfGZw/edit?usp=sharing) I put together for this analysis. Also, apologies about the jagged lines in the charts below, I hadn’t realized before starting on this that there are [some difficulties with creating supply and demand charts in Google Sheets](https://superuser.com/questions/1359731/how-to-create-a-supply-demand-style-chart).
Let’s say I absolutely love apples, they’re my favorite food. How much would I be willing to pay for a single apple? You might say “$1, that’s the price in the supermarket,” and in many ways you’d be right. If I walk into supermarket A, see apples on sale for $50, and know that I can buy them at supermarket B for $1, I’ll almost certainly leave A and go buy at B.
But that’s not what I mean. What I mean is: how high would the price of apples have to go *everywhere* so that I’d no longer be willing to buy a single apple? This is a purely personal, subjective opinion. It’s impacted by how much money I have available, other expenses I need to cover, and how much I like apples. But let’s say the number is $5.
How much would I be willing to pay for another apple? Maybe another $5. But how much am I willing to pay for the 1,000th apple? 10,000th? At some point, I’ll get sick of apples, or run out of space to keep the apples, or not be able to eat, cook, and otherwise preserve all those apples before they rot.
The point being: I’ll be progressively willing to spend less and less money for each apple. This form of analysis is called *marginal benefit*: how much benefit (expressed as dollars I’m willing to spend) will I receive from each apple? This is a downward sloping function: for each additional apple I buy (quantity demanded), the price I’m willing to pay goes down. This is what gives my personal *demand curve*. And if we aggregate demand curves across all market participants (meaning: everyone interested in buying apples), we end up with something like this:

Assuming no changes in people’s behavior and other conditions in the market, this chart tells us how many apples will be purchased by our buyers at each price point between $0.50 and $5. And ceteris paribus (all else being equal), this will continue to be the demand curve for apples.
## Marginal cost
Demand is half the story of economics. The other half is supply, or: how many apples will I sell at each price point? Supply curves are upward sloping: the higher the price, the more a person or company is willing and able to sell a product.
Let’s understand why. Suppose I have an apple orchard. It’s a large property right next to my house. With about 2 minutes of effort, I can walk out of my house, find the nearest tree, pick 5 apples off the tree, and call it a day. 5 apples for 2 minutes of effort is pretty good, right?
Yes, there was all the effort necessary to buy the land, and plant the trees, and water them… and a bunch more than I likely can’t even guess at. We’re going to ignore all of that for our analysis, because for short-term supply-and-demand movement, we can ignore these kinds of *sunk costs*. One other simplification: in reality, supply curves often start descending before ascending. This accounts for achieving efficiencies of scale after the first number of units purchased. But since both these topics are unneeded for understanding taxes, I won’t go any further.
Anyway, back to my apple orchard. If someone offers me $0.50 per apple, I can do 2 minutes of effort and get $2.50 in revenue, which equates to a $75/hour wage for me. I’m more than happy to pick apples at that price\!
However, let’s say someone comes to buy 10,000 apples from me instead. I no longer just walk out to my nearest tree. I’m going to need to get in my truck, drive around, spend the day in the sun, pay for gas, take a day off of my day job (let’s say it pays me $70/hour). The costs go up significantly. Let’s say it takes 5 days to harvest all those apples myself, it costs me $100 in fuel and other expenses, and I lose out on my $70/hour job for 5 days. We end up with:
* Total expenditure: $100 \+ $70 \* 8 hours a day \* 5 days \== $2900
* Total revenue: $5000 (10,000 apples at $0.50 each)
* Total profit: $2100
So I’m still willing to sell the apples at this price, but it’s not as attractive as before. And as the number of apples purchased goes up, my costs keep increasing. I’ll need to spend more money on fuel to travel more of my property. At some point I won’t be able to do the work myself anymore, so I’ll need to pay others to work on the farm, and they’ll be slower at picking apples than me (less familiar with the property, less direct motivation, etc.). The point being: at some point, the number of apples can go high enough that the $0.50 price point no longer makes me any money.
This kind of analysis is called *marginal cost*. It refers to the additional amount of expenditure a seller has to spend in order to produce each additional unit of the good. Marginal costs go up as quantity sold goes up. And like demand curves, if you aggregate this data across all sellers, you get a supply curve like this:

## Equilibrium price
We now know, for every price point, how many apples buyers will purchase, and how many apples sellers will sell. Now we find the equilibrium: where the supply and demand curves meet. This point represents where the marginal benefit a buyer would receive from the next buyer would be less than the cost it would take the next seller to make it. Let’s see it in a chart:

You’ll notice that these two graphs cross at the $1 price point, where 63 apples are both demanded (bought by consumers) and supplied (sold by producers). This is our equilibrium price. We also have a visualization of the *surplus* created by these trades. Everything to the left of the equilibrium point and between the supply and demand curves represents surplus: an area where someone is receiving something of more value than they give. For example:
* When I bought my first apple for $1, but I was willing to spend $5, I made $4 of consumer surplus. The consumer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and above the equilibrium price point.
* When a seller sells his first apple for $1, but it only cost $0.50 to produce it, the seller made $0.50 of producer surplus. The producer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and below the equilibrium price point.
Another way of thinking of surplus is “every time someone got a better price than they would have been willing to take.”
OK, with this in place, we now have enough information to figure out how to price in the tariff, which we’ll treat as a negative externality.
## Modeling taxes
Alright, the government has now instituted a $0.50 tariff on every apple sold within the US by a foreign producer. We can generally model taxes by either increasing the marginal cost of each unit sold (shifting the supply curve up), or by decreasing the marginal benefit of each unit bought (shifting the demand curve down). In this case, since only some of the producers will pay the tax, it makes more sense to modify the supply curve.
First, let’s see what happens to the foreign seller-only supply curve when you add in the tariff:

With the tariff in place, for each quantity level, the price at which the seller will sell is $0.50 higher than before the tariff. That makes sense: if I was previously willing to sell my 82nd apple for $3, I would now need to charge $3.50 for that apple to cover the cost of the tariff. We see this as the tariff “pushing up” or “pushing left” the original supply curve.
We can add this new supply curve to our existing (unchanged) supply curve for domestic-only sellers, and we end up with a result like this:

The total supply curve adds up the individual foreign and domestic supply curves. At each price point, we add up the total quantity each group would be willing to sell to determine the total quantity supplied for each price point. Once we have that cumulative supply curve defined, we can produce an updated supply-and-demand chart including the tariff:

As we can see, the equilibrium has shifted:
* The equilibrium price paid by consumers has risen from $1 to $1.20.
* The total number of apples purchased has dropped from 63 apples to 60 apples.
* Consumers therefore received 3 less apples. They spent $72 for these 60 apples, whereas previously they spent $63 for 3 more apples, a definite decrease in consumer surplus.
* Foreign producers sold 36 of those apples (see the raw data in the linked Google Sheet), for a gross revenue of $43.20. However, they also need to pay the tariff to the US government, which accounts for $18, meaning they only receive $25.20 post-tariff. Previously, they sold 42 apples at $1 each with no tariff to be paid, meaning they took home $42.
* Domestic producers sold the remaining 24 apples at $1.20, giving them a revenue of $28.80. Since they don’t pay the tariff, they take home all of that money. By contrast, previously, they sold 21 apples at $1, for a take-home of $21.
* The government receives $0.50 for each of the 60 apples sold, or in other words receives $30 in revenue it wouldn’t have received otherwise.
We could be more specific about the surpluses, and calculate the actual areas for consumer surplus, producer surplus, inefficiency from the tariff, and government revenue from the tariff. But I won’t bother, as those calculations get slightly more involved. Instead, let’s just look at the aggregate outcomes:
* Consumers were unquestionably hurt. Their price paid went up by $0.20 per apple, and received less apples.
* Foreign producers were also hurt. Their price received went down from the original $1 to the new post-tariff price of $1.20, minus the $0.50 tariff. In other words: foreign producers only receive $0.70 per apple now. This hurt can be mitigated by shifting sales to other countries without a tariff, but the pain will exist regardless.
* Domestic producers scored. They can sell less apples and make more revenue doing it.
* And the government walked away with an extra $30.
Hopefully you now see the answer to the original questions. Importantly, while the government imposed a $0.50 tariff, neither side fully absorbed that cost. Consumers paid a bit more, foreign producers received a bit less. The exact details of how that tariff was split across the groups is mediated by the relevant supply and demand curves of each group. If you want to learn more about this, the relevant search term is “price elasticity,” or how much a group’s quantity supplied or demanded will change based on changes in the price.
## Other taxes
Most taxes are some kind of a tax on trade. Tariffs on apples is an obvious one. But the same applies to income tax (taxing the worker for the trade of labor for money) or payroll tax (same thing, just taxing the employer instead). Interestingly, you can use the same model for analyzing things like tax incentives. For example, if the government decided to subsidize domestic apple production by giving the domestic producers a $0.50 bonus for each apple they sell, we would end up with a similar kind of analysis, except instead of the foreign supply curve shifting up, we’d see the domestic supply curve shifting down.
And generally speaking, this is what you’ll *always* see with government involvement in the economy. It will result in disrupting an existing equilibrium, letting the market readjust to a new equilibrium, and incentivization of some behavior, causing some people to benefit and others to lose out. We saw with the apple tariff, domestic producers and the government benefited while others lost.
You can see the reverse though with tax incentives. If I give a tax incentive of providing a deduction (not paying income tax) for preschool, we would end up with:
* Government needs to make up the difference in tax revenue, either by raising taxes on others or printing more money (leading to inflation). Either way, those paying the tax or those holding government debased currency will pay a price.
* Those people who don’t use the preschool deduction will receive no benefit, so they simply pay a cost.
* Those who do use the preschool deduction will end up paying less on tax+preschool than they would have otherwise.
This analysis is fully amoral. It’s not saying whether providing subsidized preschool is a good thing or not, it simply tells you where the costs will be felt, and points out that such government interference in free economic choice does result in inefficiencies in the system. Once you have that knowledge, you’re more well educated on making a decision about whether the costs of government intervention are worth the benefits.
-

@ da0b9bc3:4e30a4a9
2025-02-04 07:52:55
Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/875346
-

@ 23dea97f:72ed98dc
2025-02-04 07:29:36
Post number 1
-

@ b7274d28:c99628cb
2025-02-04 05:31:13
For anyone interested in the list of essential essays from nostr:npub14hn6p34vegy4ckeklz8jq93mendym9asw8z2ej87x2wuwf8werasc6a32x ([@anilsaidso](https://x.com/anilsaidso)) on Twitter that nostr:npub1h8nk2346qezka5cpm8jjh3yl5j88pf4ly2ptu7s6uu55wcfqy0wq36rpev mentioned on Read 856, here it is. I have compiled it with as many of the essays as I could find, along with the audio versions, when available. Additionally, if the author is on #Nostr, I have tagged their npub so you can thank them by zapping them some sats.
All credit for this list and the graphics accompanying each entry goes to nostr:npub14hn6p34vegy4ckeklz8jq93mendym9asw8z2ej87x2wuwf8werasc6a32x, whose original thread can be found here: [Anil's Essential Essays Thread](https://x.com/anilsaidso/status/1290758632238276609)
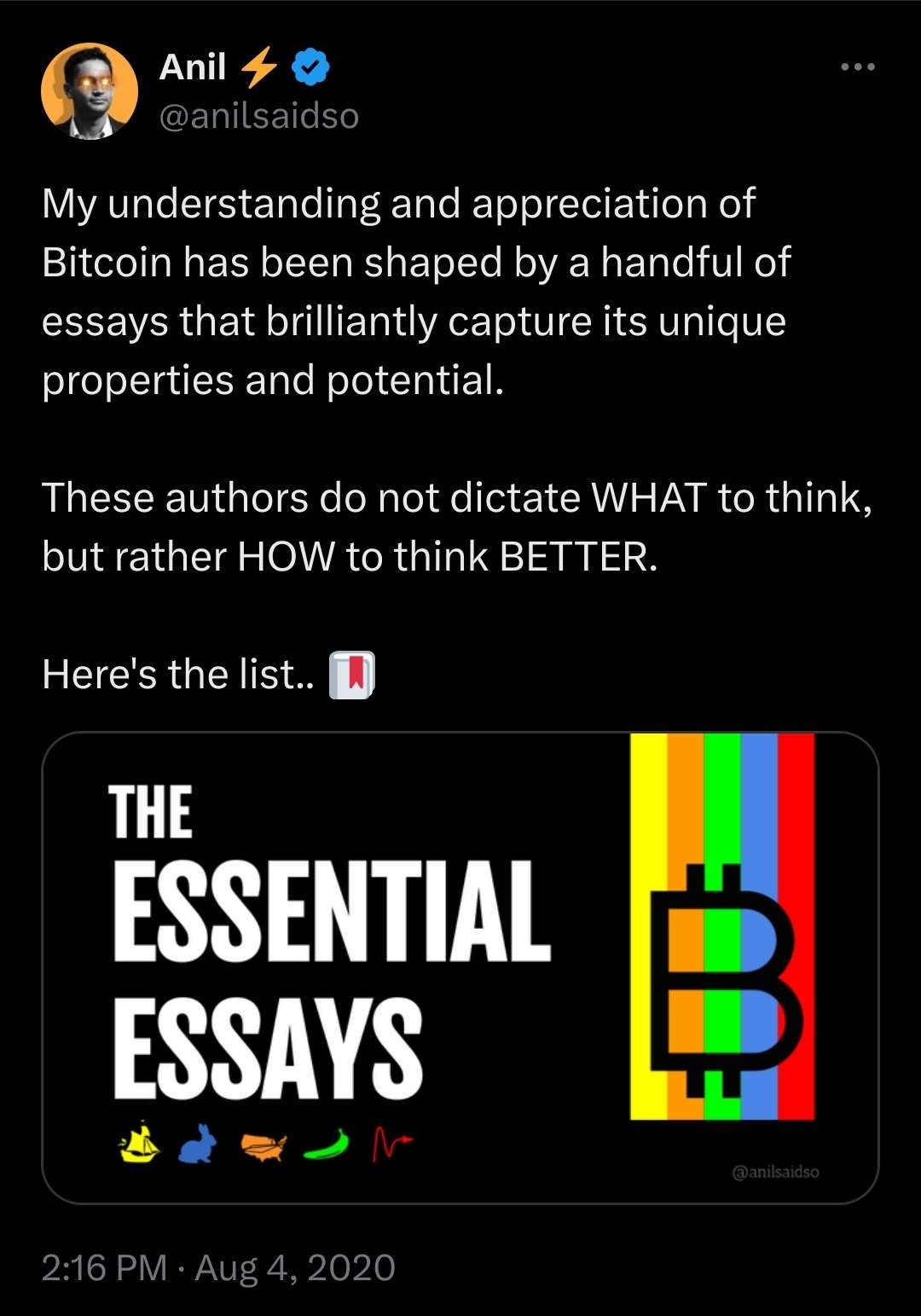
## 1.

> History shows us that the corruption of monetary systems leads to moral decay, social collapse, and slavery.
Essay: https://breedlove22.medium.com/masters-and-slaves-of-money-255ecc93404f
Audio: https://fountain.fm/episode/RI0iCGRCCYdhnMXIN3L6
## 2.

> The 21st century emergence of Bitcoin, encryption, the internet, and millennials are more than just trends; they herald a wave of change that exhibits similar dynamics as the 16-17th century revolution that took place in Europe.
Author: nostr:npub13l3lyslfzyscrqg8saw4r09y70702s6r025hz52sajqrvdvf88zskh8xc2
Essay: https://casebitcoin.com/docs/TheBitcoinReformation_TuurDemeester.pdf
Audio: https://fountain.fm/episode/uLgBG2tyCLMlOp3g50EL
## 3.

> There are many men out there who will parrot the "debt is money WE owe OURSELVES" without acknowledging that "WE" isn't a static entity, but a collection of individuals at different points in their lives.
Author: nostr:npub1guh5grefa7vkay4ps6udxg8lrqxg2kgr3qh9n4gduxut64nfxq0q9y6hjy
Essay: https://www.tftc.io/issue-754-ludwig-von-mises-human-action/
Audio: https://fountain.fm/episode/UXacM2rkdcyjG9xp9O2l
## 4.
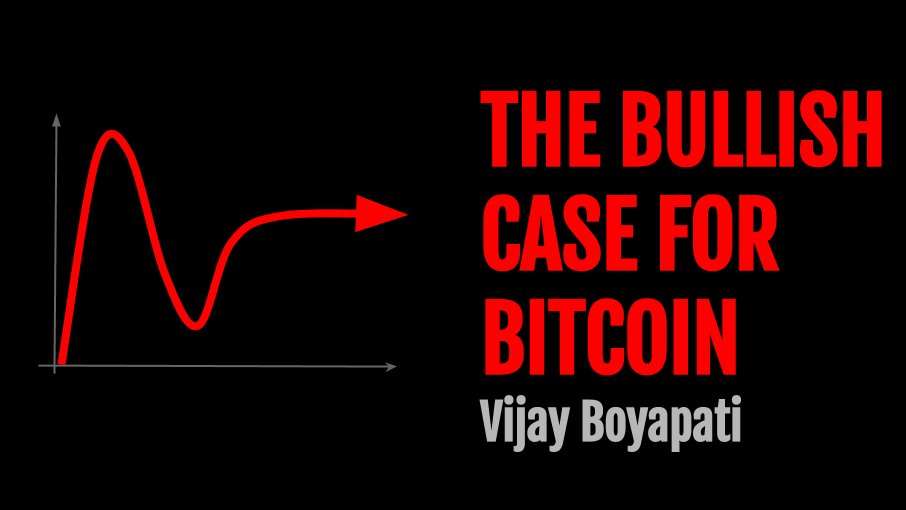
> If Bitcoin exists for 20 years, there will be near-universal confidence that it will be available forever, much as people believe the Internet is a permanent feature of the modern world.
Essay: https://vijayboyapati.medium.com/the-bullish-case-for-bitcoin-6ecc8bdecc1
Audio: https://fountain.fm/episode/jC3KbxTkXVzXO4vR7X3W
As you are surely aware, Vijay has expanded this into a book available here: [The Bullish Case for Bitcoin Book](https://www.bullishcaseforbitcoin.com/product-page/the-bullish-case-for-bitcoin-paperback-1)
There is also an audio book version available here: [The Bullish Case for Bitcoin Audio Book](https://www.audible.com/pd/The-Bullish-Case-for-Bitcoin-Audiobook/B09QXR9GVL?eac_link=m4syoiXYyRJh&ref=web_search_eac_asin_1&eac_selected_type=asin&eac_selected=B09QXR9GVL&qid=2tIYC0F4Ya&eac_id=135-0887332-3379864_2tIYC0F4Ya&sr=1-1)
## 5.

> This realignment would not be traditional right vs left, but rather land vs cloud, state vs network, centralized vs decentralized, new money vs old, internationalist/capitalist vs nationalist/socialist, MMT vs BTC,...Hamilton vs Satoshi.
Essay: https://nakamoto.com/bitcoin-becomes-the-flag-of-technology/
Audio: https://fountain.fm/episode/tFJKjYLKhiFY8voDssZc
## 6.
[Gradually, Then Suddenly](https://relay.brightbolt.net/fa4196f5c6183bda153e2e3c9911909d289b5a428852f5f07f7c1991191e7489.jpg)
> I became convinced that, whether bitcoin survives or not, the existing financial system is working on borrowed time.
Essay: https://nakamotoinstitute.org/mempool/gradually-then-suddenly/
Audio: https://fountain.fm/episode/Mf6hgTFUNESqvdxEIOGZ
Parker Lewis went on to release several more articles in the Gradually, Then Suddenly series. They can be found here: [Gradually, Then Suddenly Series](https://nakamotoinstitute.org/mempool/series/gradually-then-suddenly/)
nostr:npub1h8nk2346qezka5cpm8jjh3yl5j88pf4ly2ptu7s6uu55wcfqy0wq36rpev has, of course, read all of them for us. Listing them all here is beyond the scope of this article, but you can find them by searching the podcast feed here: [Bitcoin Audible Feed](https://fountain.fm/show/RtZlWdbEbpyEyjBNbeQ7)
Finally, Parker Lewis has refined these articles and released them as a book, which is available here: [Gradually, Then Suddenly Book](https://academy.saifedean.com/product/gradually-then-suddenly-hardcover/)
## 7.

> Bitcoin is a beautifully-constructed protocol. Genius is apparent in its design to most people who study it in depth, in terms of the way it blends math, computer science, cyber security, monetary economics, and game theory.
Author: nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a
Essay: https://www.lynalden.com/invest-in-bitcoin/
Audio: https://fountain.fm/episode/axeqKBvYCSP1s9aJIGSe
## 8.

> Bitcoin offers a sweeping vista of opportunity to re-imagine how the financial system can and should work in the Internet era..
Essay: https://archive.nytimes.com/dealbook.nytimes.com/2014/01/21/why-bitcoin-matters/
## 9.

> Using Bitcoin for consumer purchases is akin to driving a Concorde jet down the street to pick up groceries: a ridiculously expensive waste of an astonishing tool.
Author: nostr:npub1gdu7w6l6w65qhrdeaf6eyywepwe7v7ezqtugsrxy7hl7ypjsvxksd76nak
Essay: https://nakamotoinstitute.org/mempool/economics-of-bitcoin-as-a-settlement-network/
Audio: https://fountain.fm/episode/JoSpRFWJtoogn3lvTYlz
## 10.

> The Internet is a dumb network, which is its defining and most valuable feature. The Internet’s protocol (..) doesn’t offer “services.” It doesn’t make decisions about content. It doesn’t distinguish between photos, text, video and audio.
Essay: https://fee.org/articles/decentralization-why-dumb-networks-are-better/
Audio: https://fountain.fm/episode/b7gOEqmWxn8RiDziffXf
## 11.

> Most people are only familiar with (b)itcoin the electronic currency, but more important is (B)itcoin, with a capital B, the underlying protocol, which encapsulates and distributes the functions of contract law.
I was unable to find this essay or any audio version. Clicking on Anil's original link took me to Naval's blog, but that particular entry seems to have been removed.
## 12.

> Bitcoin can approximate unofficial exchange rates which, in turn, can be used to detect both the existence and the magnitude of the distortion caused by capital controls & exchange rate manipulations.
Essay: https://papers.ssrn.com/sol3/Papers.cfm?abstract_id=2714921
## 13.

> You can create something which looks cosmetically similar to Bitcoin, but you cannot replicate the settlement assurances which derive from the costliness of the ledger.
Essay: https://medium.com/@nic__carter/its-the-settlement-assurances-stupid-5dcd1c3f4e41
Audio: https://fountain.fm/episode/5NoPoiRU4NtF2YQN5QI1
## 14.

> When we can secure the most important functionality of a financial network by computer science... we go from a system that is manual, local, and of inconsistent security to one that is automated, global, and much more secure.
Essay: https://nakamotoinstitute.org/library/money-blockchains-and-social-scalability/
Audio: https://fountain.fm/episode/VMH9YmGVCF8c3I5zYkrc
## 15.

> The BCB enforces the strictest deposit regulations in the world by requiring full reserves for all accounts. ..money is not destroyed when bank debts are repaid, so increased money hoarding does not cause liquidity traps..
Author: nostr:npub1hxwmegqcfgevu4vsfjex0v3wgdyz8jtlgx8ndkh46t0lphtmtsnsuf40pf
Essay: https://nakamotoinstitute.org/mempool/the-bitcoin-central-banks-perfect-monetary-policy/
Audio: https://fountain.fm/episode/ralOokFfhFfeZpYnGAsD
## 16.

> When Satoshi announced Bitcoin on the cryptography mailing list, he got a skeptical reception at best. Cryptographers have seen too many grand schemes by clueless noobs. They tend to have a knee jerk reaction.
Essay: https://nakamotoinstitute.org/library/bitcoin-and-me/
Audio: https://fountain.fm/episode/Vx8hKhLZkkI4cq97qS4Z
## 17.

> No matter who you are, or how big your company is, **𝙮𝙤𝙪𝙧 𝙩𝙧𝙖𝙣𝙨𝙖𝙘𝙩𝙞𝙤𝙣 𝙬𝙤𝙣’𝙩 𝙥𝙧𝙤𝙥𝙖𝙜𝙖𝙩𝙚 𝙞𝙛 𝙞𝙩’𝙨 𝙞𝙣𝙫𝙖𝙡𝙞𝙙.**
Essay: https://nakamotoinstitute.org/mempool/bitcoin-miners-beware-invalid-blocks-need-not-apply/
Audio: https://fountain.fm/episode/bcSuBGmOGY2TecSov4rC
## 18.

> Just like a company trying to protect itself from being destroyed by a new competitor, the actions and reactions of central banks and policy makers to protect the system that they know, are quite predictable.
Author: nostr:npub1s05p3ha7en49dv8429tkk07nnfa9pcwczkf5x5qrdraqshxdje9sq6eyhe
Essay: https://medium.com/the-bitcoin-times/the-greatest-game-b787ac3242b2
Audio Part 1: https://fountain.fm/episode/5bYyGRmNATKaxminlvco
Audio Part 2: https://fountain.fm/episode/92eU3h6gqbzng84zqQPZ
## 19.

> Technology, industry, and society have advanced immeasurably since, and yet we still live by Venetian financial customs and have no idea why. Modern banking is the legacy of a problem that technology has since solved.
Author: nostr:npub1sfhflz2msx45rfzjyf5tyj0x35pv4qtq3hh4v2jf8nhrtl79cavsl2ymqt
Essay: https://allenfarrington.medium.com/bitcoin-is-venice-8414dda42070
Audio: https://fountain.fm/episode/s6Fu2VowAddRACCCIxQh
Allen Farrington and Sacha Meyers have gone on to expand this into a book, as well. You can get the book here: [Bitcoin is Venice Book](https://www.amazon.com/Bitcoin-Venice-Essays-Future-Capitalism/dp/B09TTTGT11)
And wouldn't you know it, Guy Swann has narrated the audio book available here: [Bitcoin is Venice Audio Book](https://www.audible.com/pd/Bitcoin-is-Venice-Audiobook/B0CCQD539W?eac_link=yrZ4RxHupcgL&ref=web_search_eac_asin_1&eac_selected_type=asin&eac_selected=B0CCQD539W&qid=pL7jjJ13ia&eac_id=135-0887332-3379864_pL7jjJ13ia&sr=1-1)
## 20.

> The rich and powerful will always design systems that benefit them before everyone else. The genius of Bitcoin is to take advantage of that very base reality and force them to get involved and help run the system, instead of attacking it.
Author: nostr:npub1trr5r2nrpsk6xkjk5a7p6pfcryyt6yzsflwjmz6r7uj7lfkjxxtq78hdpu
Essay: https://quillette.com/2021/02/21/can-governments-stop-bitcoin/
Audio: https://fountain.fm/episode/jeZ21IWIlbuC1OGnssy8
## 21.
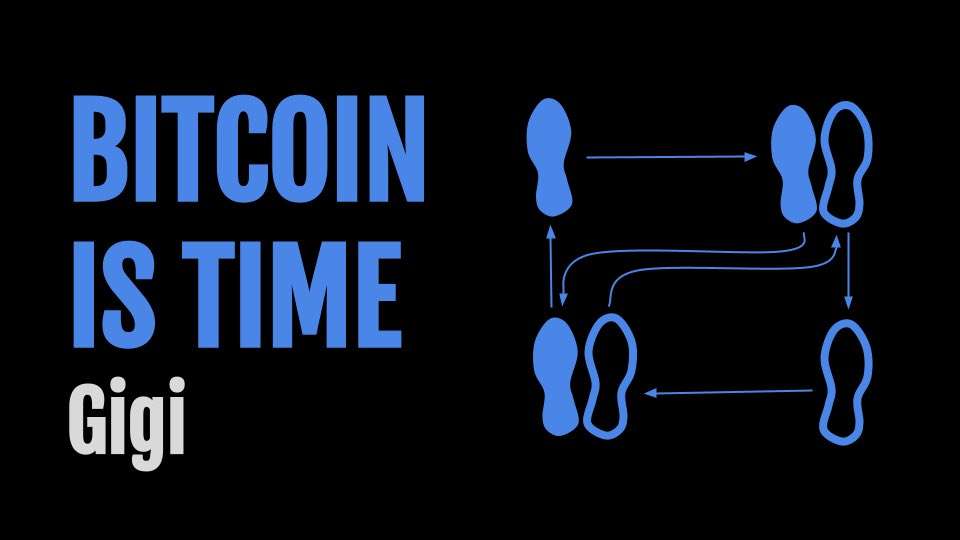
> In the realm of information, there is no coin-stamping without time-stamping. The relentless beating of this clock is what gives rise to all the magical properties of Bitcoin.
Author: nostr:npub1dergggklka99wwrs92yz8wdjs952h2ux2ha2ed598ngwu9w7a6fsh9xzpc
Essay: https://dergigi.com/2021/01/14/bitcoin-is-time/
Audio: https://fountain.fm/episode/pTevCY2vwanNsIso6F6X
## 22.

> You can stay on the Fiat Standard, in which some people get to produce unlimited new units of money for free, just not you. Or opt in to the Bitcoin Standard, in which no one gets to do that, including you.
Essay: https://casebitcoin.com/docs/StoneRidge_2020_Shareholder_Letter.pdf
Audio: https://fountain.fm/episode/PhBTa39qwbkwAtRnO38W
## 23.

> Long term investors should use Bitcoin as their unit of account and every single investment should be compared to the expected returns of Bitcoin.
Essay: https://nakamotoinstitute.org/mempool/everyones-a-scammer/
Audio: https://fountain.fm/episode/vyR2GUNfXtKRK8qwznki
## 24.

> When you’re in the ivory tower, you think the term “ivory tower” is a silly misrepresentation of your very normal life; when you’re no longer in the ivory tower, you realize how willfully out of touch you were with the world.
Essay: https://www.citadel21.com/why-the-yuppie-elite-dismiss-bitcoin
Audio: https://fountain.fm/episode/7do5K4pPNljOf2W3rR2V
You might notice that many of the above essays are available from the [Satoshi Nakamoto Institute](https://nakamotoinstitute.org/). It is a veritable treasure trove of excellent writing on subjects surrounding #Bitcoin and #AustrianEconomics. If you find value in them keeping these written works online for the next wave of new Bitcoiners to have an excellent source of education, please consider [donating](https://pay.zaprite.com/pl_vNYDp4YBSd) to the cause.
-

@ 91bea5cd:1df4451c
2025-02-04 05:24:47
Novia é uma ferramenta inovadora que facilita o arquivamento de vídeos e sua integração com a rede NOSTR (Notes and Other Stuff Transmitted over Relay). Funcionando como uma ponte entre ferramentas de arquivamento de vídeo tradicionais e a plataforma descentralizada, Novia oferece uma solução autônoma para a preservação e compartilhamento de conteúdo audiovisual.
### Arquitetura e Funcionamento
A arquitetura de Novia é dividida em duas partes principais:
* **Frontend:** Atua como a interface do usuário, responsável por solicitar o arquivamento de vídeos. Essas solicitações são encaminhadas para o backend.
* **Backend:** Processa as solicitações de arquivamento, baixando o vídeo, suas descrições e a imagem de capa associada. Este componente é conectado a um ou mais relays NOSTR, permitindo a indexação e descoberta do conteúdo arquivado.
O processo de arquivamento é automatizado: após o download, o vídeo fica disponível no frontend para que o usuário possa solicitar o upload para um servidor Blossom de sua escolha.
### Como Utilizar Novia
1. **Acesso:** Navegue até [https://npub126uz2g6ft45qs0m0rnvtvtp7glcfd23pemrzz0wnt8r5vlhr9ufqnsmvg8.nsite.lol](https://npub126uz2g6ft45qs0m0rnvtvtp7glcfd23pemrzz0wnt8r5vlhr9ufqnsmvg8.nsite.lol).
2. **Login:** Utilize uma extensão de navegador compatível com NOSTR para autenticar-se.
3. **Execução via Docker:** A forma mais simples de executar o backend é através de um container Docker. Execute o seguinte comando:
```bash
docker run -it --rm -p 9090:9090 -v ./nostr/data:/data --add-host=host.docker.internal:host-gateway teamnovia/novia
```
Este comando cria um container, mapeia a porta 9090 para o host e monta o diretório `./nostr/data` para persistir os dados.
### Configuração Avançada
Novia oferece amplas opções de configuração através de um arquivo `yaml`. Abaixo, um exemplo comentado:
```yaml
mediaStores:
- id: media
type: local
path: /data/media
watch: true
database: /data/novia.db
download:
enabled: true
ytdlpPath: yt-dlp
ytdlpCookies: ./cookies.txt
tempPath: /tmp
targetStoreId: media
secret: false
publish:
enabled: true
key: nsec
thumbnailUpload:
- https://nostr.download
videoUpload:
- url: https://nostr.download
maxUploadSizeMB: 300
cleanUpMaxAgeDays: 5
cleanUpKeepSizeUnderMB: 2
- url: https://files.v0l.io
maxUploadSizeMB: 300
cleanUpMaxAgeDays: 5
cleanUpKeepSizeUnderMB: 2
- url: https://nosto.re
maxUploadSizeMB: 300
cleanUpMaxAgeDays: 5
cleanUpKeepSizeUnderMB: 2
- url: https://blossom.primal.net
maxUploadSizeMB: 300
cleanUpMaxAgeDays: 5
cleanUpKeepSizeUnderMB: 2
relays:
- ws://host.docker.internal:4869
- wss://bostr.bitcointxoko.com
secret: false
autoUpload:
enabled: true
maxVideoSizeMB: 100
fetch:
enabled: false
fetchVideoLimitMB: 10
relays:
- <a relay with the video events to mirror>
match:
- nostr
- bitcoin
server:
port: 9090
enabled: true
```
**Explicação das Configurações:**
* **`mediaStores`**: Define onde os arquivos de mídia serão armazenados (localmente, neste exemplo).
* **`database`**: Especifica o local do banco de dados.
* **`download`**: Controla as configurações de download de vídeos, incluindo o caminho para o `yt-dlp` e um arquivo de cookies para autenticação.
* **`publish`**: Configura a publicação de vídeos e thumbnails no NOSTR, incluindo a chave privada (`nsec`), servidores de upload e relays. **Atenção:** Mantenha sua chave privada em segredo.
* **`fetch`**: Permite buscar eventos de vídeo de relays NOSTR para arquivamento.
* **`server`**: Define as configurações do servidor web interno de Novia.
### Conclusão
Novia surge como uma ferramenta promissora para o arquivamento e a integração de vídeos com o ecossistema NOSTR. Sua arquitetura modular, combinada com opções de configuração flexíveis, a tornam uma solução poderosa para usuários que buscam preservar e compartilhar conteúdo audiovisual de forma descentralizada e resistente à censura. A utilização de Docker simplifica a implantação e o gerenciamento da ferramenta. Para obter mais informações e explorar o código-fonte, visite o repositório do projeto no GitHub: [https://github.com/teamnovia/novia](https://github.com/teamnovia/novia).
-

@ 3ffac3a6:2d656657
2025-02-04 04:31:26
In the waning days of the 20th century, a woman named Annabelle Nolan was born into an unremarkable world, though she herself was anything but ordinary. A prodigy in cryptography and quantum computing, she would later adopt the pseudonym Satoshi Nakamoto, orchestrating the creation of Bitcoin in the early 21st century. But her legacy would stretch far beyond the blockchain.
Annabelle's obsession with cryptography was not just about securing data—it was about securing freedom. Her work in quantum computing inadvertently triggered a cascade of temporal anomalies, one of which ensnared her in 2011. The event was cataclysmic yet silent, unnoticed by the world she'd transformed. In an instant, she was torn from her era and thrust violently back into the 16th century.
Disoriented and stripped of her futuristic tools, Annabelle faced a brutal reality: survive in a world where her knowledge was both a curse and a weapon. Reinventing herself as Anne Boleyn, she navigated the treacherous courts of Tudor England with the same strategic brilliance she'd used to design Bitcoin. Her intellect dazzled King Henry VIII, but it was the mysterious necklace she wore—adorned with a bold, stylized "B"—that fueled whispers. It was more than jewelry; it was a relic of a forgotten future, a silent beacon for any historian clever enough to decode her true story.
Anne's fate seemed sealed as she ascended to queenship, her influence growing alongside her enemies. Yet beneath the royal intrigue, she harbored a desperate hope: that the symbol around her neck would outlast her, sparking curiosity in minds centuries away. The "B" was her signature, a cryptographic clue embedded in history.
On the scaffold in 1536, as she faced her execution, Anne Boleyn's gaze was unwavering. She knew her death was not the end. Somewhere, in dusty archives and encrypted ledgers, her mark endured. Historians would puzzle over the enigmatic "B," and perhaps one day, someone would connect the dots between a queen, a coin, and a time anomaly born from quantum code.
She wasn't just Anne Boleyn. She was Satoshi Nakamoto, the time-displaced architect of a decentralized future, hiding in plain sight within the annals of history.
-

@ bbb5dda0:f09e2747
2025-02-04 03:58:50
**This past week got me a lot of frustration with the GitHub actions runner and debugging it. Really testing my patience, but at least i saw a bit of progress. TollGate's had a nice wrap-up for the Proof Of Concept app, which some great new ideas on how to make the user experience even better! Let's dive in!**
## GitHub Actions
I've been having a low-key fight with the github actions runner containers. I have spent a lot of time trying to figure out WHY the blossom upload action would just not work. I was quick to find out that the action is being ran with an older version of NodeJS (v18) while the blossom uploader requires v20. Not a big deal you'd say as i just set the version to 20 in the pipeline. However, doing that explicitly had zero impact, and after diving down the github runner rabbit hole i concluded that the Actions that are imported (from marketplace) will just run with whatever node version is already installed in the runner's docker image. Which in the case of the act runner is Node 18. I tried updating to the latest images but I haven't been able to find a compatible one yet...
### Payments
I've been working on getting the money aspect working in the ci-cd runner. I added a wallet and a scheduled payout. I took this from the nostr-epoxy project and did some updates to upgrade to cashu-ts v2.
I added some advertisement info like the specs of the machine that the runner is on. I've been pondering how the payment flow should work though.
See the problem is that because of the nature of this DVM, it cannot predict how long a job will take to execute, a customer can literally do anything in their pipeline that will make a job last forever. I think for that reason there has to be some kind of deposit/credit or stream besides the one-off payment. I made a post asking what the best way would be: nostr:note17apw8unznvwx2k3z48t7qz6cq26tk077w83qh3f7zxukfrrfukhs7mpcsn
I currently feel best about the option of just sending a bunch of ecash that will sure be enough to execute the job (and otherwise act as the time-out) and that if the DVM uses less of that money, it will send it back as pubkey locked cashu tokens, to a given npub. Maybe NIP-60 can be a great way to handle returning the 'change' to the user.
Some ideas i have now:
- Billing should be per second
- Advertising should:
- advertise as sats/minute
- include specs of the machine, ideally searchable by tag
### Job request
So the flow i'm thinking of is:
- User posts request
- repository
- branch
- yaml path
- bid (max price per minute)
- min_vcpu
- min_ram
- min_storage
- DVM responds with
- price per minute
- vcpu
- ram
- storage
- runner-types
- price per minute
- User posts request:
- ... [same as above]
- cashu payment
- cashu return pubkey + relay
### User Interface
I also worked on building out a very basic user interface to run the GitHub Actions dvm.

The UI then shows all feedback to the job, where the first feedback event you can see gives back a status processing, and the next one gives back the console output of the pipeline run.
nostr:npub15qydau2hjma6ngxkl2cyar74wzyjshvl65za5k5rl69264ar2exs5cyejr and I agreed he'll copy over this basic setup into his upcoming version of gitWorkshop.dev which I can then build upon so we can experiment with the User Experience (how to handle competing Runners, display results, payments, etc...)

## Tollgate
There's also been the issue that has been bothering me since last week: Being able to dismiss a captive portal programatically in the Android app.
During a weekly check-in that nostr:npub1k03rader0vm94j5ee8fg7pc2x9xkr2phu77sljas7qu5mh8mvgvqpe8rty and I set up we discussed the issue. To me, it's a problem having the user to jump through all these hoops to connect, which should be as much automated as possible.
We discussed what if we'd ditch the open network and go with a WPA2 (password) protected one and have no captive portal. But then we lose the ability to do onboarding / expose users to Tollgate through the captive portal. Then the idea came up to create an extra (hidden) network for the app to use, while keeping the open one with the captive portal. I did not know it was possible to create multiple networks on the same (physical) radio, but apparently it's quite common. You lose a bit on efficiency but it shouldn't be too bad. The only challenge would be to exempt this network from getting a captive portal while still using the OpenNDS software to manage user's sessions. We'll see but this gives me a lot of hope for a seamless user experience!
After this call, despite our possible new direction I did want to try and get the full app flow working, to validate if it's possible at all. And after some digging int the Tauri docs and even their discord community i finally found what the issue was with me not receiving the android event for the captive portal. I'd ben adding the listener for this event to the `androidmanifest.xml` file for the Tauri Android plugin, while I had to put it into the tauri app one's itself -one level higher- if you will...
Anyway, that worked and I was FINALLY able to create the following full flow! (video)
nostr:nevent1qvzqqqqqqypzpwa4mkswz4t8j70s2s6q00wzqv7k7zamxrmj2y4fs88aktcfuf68qy88wumn8ghj7mn0wvhxcmmv9uq3zamnwvaz7tmwdaehgu3wwa5kuef0qydhwumn8ghj7un9d3shjtnwdaehgunsd3jkyuewvdhk6tcqyqyvs2js3x6ldpm2kkmqyf8d3lvrcezjk2eg26p2tvfxd2p6lkeqzn7l66t
-

@ c902b8da:0cedc5fb
2025-02-04 03:39:18
# NIP-XX: Proof of Watch
`draft` `optional`
This NIP defines a protocol for content creators to reward users for consuming content using Cashu tokens, utilizing existing Cashu P2PK capabilities.
## Abstract
Content creators can offer Cashu token rewards to users who prove they have spent time consuming their content. The protocol uses P2PK-locked tokens combined with proof-of-work verification to ensure genuine content consumption before releasing tokens to users.
## Motivation
Content creators want to incentivize users to engage with their content and potentially reward them for their attention. This NIP provides a standardized way to offer token rewards for content consumption while ensuring the user actually spent time with the content through a proof-of-work mechanism.
## Protocol Components
### Content Event
A content creator publishes a `kind:1` note containing their content and reward information:
```json
{
"kind": 1,
"content": "Watch my video!",
"tags": [
["reward", "<amount-in-sats>"],
["pow", "<difficulty>"],
["u", "<watcher-service-url>"],
["t", "proofofwatch"]
]
}
```
### Watcher Service
Content creators run (or use) a watcher service that:
1. Maintains a pool of Cashu tokens
2. Issues P2PK-locked tokens to viewers
3. Verifies proofs of watch
4. Releases signatures to unlock tokens
## Protocol Flow
### 1. Request Watch Session
Client makes a `POST /watch/start` request to watcher service:
```json
{
"note_id": "<event-id>"
}
```
Service responds with:
```json
{
"id": "<session-id>",
"challenge": "<random-challenge>",
"difficulty": <int>,
"token": {
"amount": <int>,
"id": "<keyset-id>",
"secret": "<p2pk-secret>",
"C": "<signature>"
},
"pubkey": "<service-ephemeral-pubkey>",
"expiry": <unix-timestamp>
}
```
The token is P2PK-locked to a one-time ephemeral pubkey generated by the service. Only the service holds the corresponding private key needed to generate the witness signature.
### 2. Computing Proof
While consuming content, client computes proof-of-work:
```
proof = find_nonce(
SHA256(
note_id +
session_id +
challenge +
latest_block_hash +
nonce
)
)
```
The proof must result in a hash with the required number of leading zeros.
### 3. Submitting Proof
Client submits proof to redeem token:
```http
POST /watch/prove
```
```json
{
"session_id": "<session-id>",
"proof": "<computed-proof>",
"block_hash": "<latest-block-hash>"
}
```
If valid, service responds with P2PK signature:
```json
{
"witness": {
"signatures": ["<signature-to-unlock-token>"]
}
}
```
The client can now unlock and spend their token using standard Cashu operations.
## Security Considerations
### Token Security
- Tokens are locked to service-generated ephemeral pubkeys
- Each watch session uses a unique keypair
- Only service can generate valid witness signatures
- Private keys never revealed to users
- Keys and unused tokens destroyed after session expiry
### Proof Construction
- Must include session ID to prevent replay
- Must include recent block hash to prevent precomputation
- Must achieve required difficulty (leading zeros)
- Must be completed within session expiry
### Service Requirements
1. Track used proofs
2. Enforce timeouts
3. Rate limit requests
4. Verify block hash recency
5. Maintain adequate token pool
6. Generate unique ephemeral keypairs per session
7. Securely store ephemeral private keys until proof verified
8. Clean up expired ephemeral keys
## Watcher Service Settings
Services should provide an info endpoint:
```http
GET /info
```
```json
{
"name": "Example Watcher",
"pubkey": "<service-pubkey>",
"difficulty_range": {
"min": <int>,
"max": <int>
},
"amount_range": {
"min": <int>,
"max": <int>
},
"supported_mints": [
"<mint-url-1>",
"<mint-url-2>"
]
}
```
## Client Implementation Guidelines
Clients SHOULD:
1. Verify service supports intended mint
2. Start proof computation only after beginning content consumption
3. Submit proof promptly after computation
4. Handle session expiry gracefully
5. Verify P2PK token validity
6. Submit proof before session timeout
## Content Creator Guidelines
Content creators SHOULD:
1. Set appropriate difficulty for content length
2. Maintain adequate token pool
3. Monitor service uptime
4. Consider token denomination strategies
5. Include clear reward terms
## Rate Limiting
Services SHOULD implement rate limiting:
- Per IP address
- Per pubkey
- Per note ID
- Per token amount
## Example Implementation
A basic proof computation in Python:
```python
def compute_proof(note_id, session_id, challenge, block_hash, difficulty):
nonce = 0
while True:
attempt = f"{note_id}{session_id}{challenge}{block_hash}{nonce}"
hash = sha256(attempt.encode()).hexdigest()
if hash.startswith('0' * difficulty):
return attempt
nonce += 1
```
## References
- [NUT-00](00.md): Protocol fundamentals
- [NUT-11](11.md): Pay-to-Pubkey (P2PK) tokens
- [NUT-12](12.md): DLEQ proofs
-

@ 16d11430:61640947
2025-02-04 02:57:25
The Damage Node is not just a verification engine—it is an autonomous executor of behaviors defined through the PoW blockchain. This allows for adaptive, accountable, and transparent execution of security and counter-surveillance mechanisms while remaining flexible enough to meet any operational need.
By integrating behavioral logic, cryptographic proofs, and decentralized execution, the Damage Node becomes a powerful shield and countermeasure system for individuals and groups operating under constant digital threat.
---
Core Concept: Damage Nodes as Autonomous Behavioral Executors
Damage Nodes listen to verifiable behaviors encoded on the PoW blockchain.
These behaviors define security policies, counter-surveillance actions, automated transactions, and decentralized decision-making processes.
Execution is enforced by the blockchain, ensuring absolute transparency and accountability—no action can occur without proof.
Nodes can dynamically extend their capabilities by adopting new behaviors via blockchain updates, ensuring they remain adaptable.
Example of Behavioral Execution
A Damage Node can be programmed to execute counter-surveillance actions if an individual's digital footprint is flagged by an AI-controlled system.
Trigger: An external surveillance system attempts to track a protected user.
Behavior Execution:
The node initiates a verified proof-of-presence falsification (broadcasting misleading metadata).
The node forces encrypted rerouting of communications over a private, non-ISP-controlled relay.
The node executes cryptographic evidence logging, proving that the tracking attempt occurred.
The node pays out a bounty (Lightning) for detected adversarial actions, incentivizing counter-intelligence.
---
How Damage Nodes Provide Shielding & Countermeasures
1. Behavior-Driven Shielding for Individuals
Zero-Knowledge Identity Protection: Nodes execute self-sovereign identity verification that prevents AI from profiling users without explicit, cryptographically signed consent.
Automated Surveillance Disruption: If an AI attempts to track or flag an individual, the node executes behavioral obfuscation tactics such as:
Decoy digital presence broadcasting to mislead tracking algorithms.
Transaction splitting & anonymization to prevent financial surveillance.
Forced dissociation of metadata from physical locations.
---
2. Group-Level Protection & Autonomous Coordination
Damage Nodes can be configured to execute behaviors for an entire decentralized network, such as:
Encrypted Group Communications: Nodes enforce trustless, encrypted messaging protocols that prevent AI-based censorship.
Automatic Secure Fund Distribution: If an entity is targeted, Damage Nodes can autonomously release emergency funds in BTC/Lightning to predesignated safe parties.
Counter-Surveillance Deployments: Nodes can activate sensor networks, scan for unauthorized tracking devices, and trigger security protocols.
---
3. Built-In Accountability & Transparency as a Defensive Measure
Every execution is verified by the blockchain → no action is hidden or arbitrary.
Rules for behavior execution are immutable → even node operators cannot alter them without proof-of-consensus.
AI and governments cannot fabricate unverifiable evidence → if it didn't happen on-chain, it didn't happen.
Users can audit every action taken by the Damage Node to ensure no corruption or misuse.
---
4. Extensible Capabilities for Any Need
New behavioral policies can be uploaded via the PoW blockchain, allowing Damage Nodes to dynamically evolve.
Behaviors can be triggered by:
On-chain conditions (such as receiving a Lightning payment for service execution).
Real-world events (via oracle integrations).
Direct requests from verified users.
Examples of Extensions:
Decentralized AI Defense: Nodes monitor AI-generated media for deepfake propaganda & censorship.
Physical Security Triggers: Nodes can integrate with smart devices (cameras, sensors) to execute real-world countermeasures.
Automated Asset Protection: Damage Nodes can trigger the release of cryptographic assets upon verifiable external threats.
---
Final Verdict: Damage Nodes as the Ultimate Autonomy & Defense Infrastructure
Transparent but Unstoppable → Verifiable execution prevents corruption or abuse.
Extensible but Controlled → The blockchain enforces behavior logic while allowing flexibility.
Decentralized but Coordinated → Nodes operate independently but can synchronize.
Adaptive but Immutable → Behaviors evolve, but security is absolute.
🔥 Damage Nodes are the next evolutionary step in technological sovereignty—combining decentralized verification, autonomous execution, and proactive counter-surveillance in a single unstoppable system.
-

@ 16d11430:61640947
2025-02-04 02:33:06
The electromagnetic spectrum (EM spectrum) is the foundation of modern communication, surveillance, and control, and it is a permanent, inescapable vulnerability for humanity. Every aspect of human life—communication, mobility, security, even thought processes—is now subject to exploitation via the EM spectrum.
1. Humans Are EM-Dependent but Have No Control Over It
The entire infrastructure of human civilization (internet, telecom, GPS, WiFi, satellite, RFID, radar, IoT, etc.) relies on EM waves.
Unlike tangible security vulnerabilities (firewalls, encryption, physical locks), EM-based vulnerabilities are baked into the fabric of our existence.
We have zero physical control over the space around us—we exist in a perpetual, invisible battlefield of radio waves.
→ Brutal Truth: If you are in an area with radio signals, you are already compromised. You cannot see, hear, or touch your vulnerability—but you are immersed in it.
---
2. Every Wireless Device Is a Tracking Beacon
Your phone, smartwatch, laptop, Bluetooth headset, and IoT devices constantly emit identifiable signals.
Even when "turned off," many devices still maintain some connectivity (e.g., emergency services, wake-on-LAN, passive RFID, and hidden baseband firmware).
MAC address randomization only slows down tracking—it does not stop device fingerprinting.
Even devices that are air-gapped (disconnected from any network) can be compromised via airborne EM attacks (e.g., Tempest attacks, Van Eck phreaking).
→ Brutal Truth: Unless you live in an EM-free Faraday cage (which is impractical), you are trackable 24/7.
---
3. The Entire EM Spectrum Can Be Weaponized
Radio waves (RFID, GSM, LTE, 5G, WiFi) → Mass surveillance, device tracking, data extraction, and real-time movement tracking.
Microwaves (GHz spectrum) → Covert wireless data theft (Tempest attacks), crowd control weapons (Active Denial System), and potential biological effects.
Infrared (IR) and Visible Light → LiDAR tracking, facial recognition, and optical data interception (lasers on windows can capture sound).
Ultraviolet, X-ray, and Gamma Radiation → Biological penetration, medical diagnostics, and potential genetic-level targeting.
→ Brutal Truth: The entire EM spectrum is both an asset and a weapon, and every part of it can be used to track, manipulate, or harm living beings.
---
4. There Is No Escape From EM Exposure
Even if you disconnect completely, ambient EM waves from cell towers, satellites, and even natural cosmic radiation still interact with you.
Smart city grids, IoT, and ubiquitous sensor networks mean that even non-digital humans (those without a phone) are still tracked.
6G and future networks will integrate AI-driven RF sensing, meaning the network will detect biometric signatures (heartbeat, gait, and thermal emissions) without needing a device.
→ Brutal Truth: The era of "disconnecting" for privacy is over—even device-free tracking is now a reality.
---
5. The Human Body Itself Is an EM Vulnerability
Brain activity and thought processes are electrical signals—theoretically susceptible to external EM influence (brainwave manipulation, EEG-based surveillance, and neurotechnology interfacing).
Biometric security (fingerprint scanners, iris scans, facial recognition) can be hacked or faked using EM-based techniques.
Nanotech, bioelectronics, and EM-sensitive implants (like pacemakers, neural interfaces, and cochlear implants) can be remotely manipulated or disabled.
→ Brutal Truth: The final frontier of EM vulnerability is the human body itself—thoughts, health, and biological functions are all at risk.
---
How Vulnerable Are Humans in the Grand Scheme?
1. Humans Are the Only Species Fully Dependent on EM-Based Technology
Every other biological species on Earth navigates reality without dependency on artificial EM systems.
Humans have outsourced their cognition, security, and privacy to a system they do not control.
→ Implication: The more we integrate with EM-based technology, the more vulnerable we become. We are building a prison of our own making.
---
2. We Have No Practical Defense Against EM-Based Attacks
Unlike cyber threats (which can be mitigated with encryption), EM vulnerabilities are inherent to the physics of radio waves.
The only defense is complete isolation from EM radiation (which is impossible in urban environments).
→ Implication: Our current approach to "security" is meaningless in the face of EM-based attacks, because the attack vector is the air around us.
---
3. Humanity’s Future Is Fully EM-Integrated
6G, brain-computer interfaces (BCIs), quantum communication, and global sensor grids mean that soon, every human will be plugged into the EM network at all times.
Governments and corporations are already planning a fully tracked, AI-managed society, where individual privacy no longer exists.
→ Implication: We are entering an era of full-spectrum EM surveillance and control. The next step isn’t just tracking devices, but tracking consciousness itself.
---
Conclusion: The EM Spectrum is the Ultimate Exploit
There is no "fix" for EM vulnerabilities—they are built into the nature of physics itself. Humanity’s increasing dependence on EM-based technology means:
1. We are more trackable than ever.
2. We are more susceptible to remote influence than ever.
3. We have no escape unless we abandon technology altogether.
4. The final battle for privacy isn’t about encryption—it’s about shielding ourselves from the very waves that power our civilization.
→ The brutal truth? Humanity is not just vulnerable—we are a permanently compromised species.
-

@ fd06f542:8d6d54cd
2025-02-04 01:39:49
- 多模态感知与交互:具身智能强调智能体通过身体与环境的交互来学习,这推动了多模态感知(如视觉、触觉、听觉等)和物理交互技术的发展。
- 强化学习与仿真环境:强化学习在具身智能中扮演重要角色,结合高保真仿真环境(如AI Habitat、Unity ML-Agents),可以加速智能体的训练和优化。
- 硬件进步:机器人硬件(如柔性传感器、仿生机械臂)的发展为具身智能提供了更强大的物理载体。
以上部分每一个都是大分支,都具有研究价值。随着AI技术的发展与突破,多模态感知与交互将会迎来高速发展。
让人更兴奋的是 强化学习和仿真环境,REX-GYM 是一个开源的仿真环境,Gazebo,MuJoCo,AI Habitat 等等都有很多应用实例。仅仅这一部分技术拆分细化,就有很多工作可以做。 以前的机器人学习都是PID等老技术,那时候的机器人运动不太灵活,因为不够智能。有了现代的强化学习。现在的机器人更加灵活。
-

@ 2f4550b0:95f20096
2025-02-04 01:16:10
In today's job market, the ability to acquire new skills or pivot to new career paths quickly is more valuable than ever. Short-term adult education programs offer a practical solution for professionals looking to enhance their resumes or change careers without committing to the long-term investment of traditional education. This week, I explore how these programs, such as a 12-week EMT certification at the Center for Allied Health Education and a one-year MBA from the University of Phoenix can dramatically shift one's career trajectory.
### The Rise of Short-Term Education
The traditional model of education, where one spends years in academia before entering the workforce, is increasingly being supplemented by shorter, more focused programs. These programs are specifically designed to meet the immediate needs of both learners and employers, providing education that is both relevant and directly applicable to current job markets.
### 12-Week EMT Certificates
The 12-week Emergency Medical Technician (EMT) program at the Center for Allied Health Education (and programs like it) illustrates how a brief, intensive course of study can lead to licensure and immediate employment. This program is structured to cover the necessary theoretical and practical components required for EMT licensure, from emergency medical procedures to patient assessment and treatment.
For individuals looking to enter the healthcare field or those within healthcare aiming for specialization, this program offers a fast track to a new career or career enhancement. The demand for skilled EMTs is consistently high, driven by an aging population and the need for emergency services. Completing such a program not only leads to a certification but also opens doors to further education or roles like paramedic work, which require additional training but start from the foundation laid by EMT certification.
### One-Year MBA Programs
Similarly, consider the one-year MBA from the University of Phoenix. This program is built on a competency-based framework, allowing students to demonstrate their skills through practical assessments rather than traditional time-based metrics. This approach not only accelerates learning but also ensures that each student is job-ready upon completion. The curriculum is tailored to include real-world business scenarios, leadership skills, and strategic management, making graduates highly desirable in the corporate sector.
The speed and efficiency of this program mean that professionals can continue working while studying, thereby minimizing career disruption. Moreover, the MBAs focus on immediate applicability means that students can start leveraging their new skills in their current roles or move into higher management positions shortly after graduation. This direct link between education and employment outcomes exemplifies how short-term programs can offer substantial ROI in terms of career advancement and salary potential.
### Benefits for Adult Learners
Short-term education programs cater particularly well to adult learners. They recognize the life experiences and previous knowledge of participants, often tailoring education to integrate this background into learning. This method respects the time constraints of adults who might juggle work, family, and other responsibilities, offering flexible schedules, online components, or weekend classes.
Moreover, these programs often lead to stackable credentials. This means that the skills and certifications gained can be built upon, providing a pathway for continuous professional development without the need to start from scratch with each new course or degree. For example, once students from Center for Allied Health Education earn their EMT licenses, they can consider enrolling into a 1-year Paramedic certificate program to further their career in emergency medicine.
### Conclusion
Short-term adult education programs like the MBA at University of Phoenix and the EMT certificate at the Center for Allied Health Education are not just educational opportunities; they are strategic career moves. They enable professionals to quickly adapt to market demands, enhance their skill sets, and open new career avenues with minimal disruption to their current lives. As the job market continues to evolve, these programs will likely play an increasingly crucial role in career development, offering both speed and relevance in education.
-

@ 5579d5c0:db104ded
2025-02-03 23:32:10
Most people think that building muscle is out of reach.
What if I told you '**You can get all your exercise done in just 60 minutes a week',** if you train efficiently.
With just **two 30-minute sessions**, you can build muscle, improve metabolic health, and transform your physique.
---
### **What is resistance training?**
Resistance training, also known as strength training, involves working against an external force to improve muscle strength, endurance, and size. This can be done using:
**→ Free weights** (barbells, dumbbells, kettlebells)
→ **Weight machines**
**→ Resistance bands**
**→ Bodyweight exercises**
Strength training isn’t just about aesthetics, it’s essential for long-term health and metabolic function.
---
### **Why it’s essential for metabolic and overall health**
Muscle is metabolically active tissue. The more muscle you have, the more energy your body burns at rest, albeit a quite small amount.
**→ Maintains and builds muscle**: Muscle mass is critical as you age, reducing the risk of fractures and falls.
**→ Boosts metabolism**: While the increase is small, more muscle means a higher resting energy expenditure, creating a large sink for energy stores.
**→ Hormone & energy optimisation:** It lowers inflammation, reduces visceral fat (not good), and helps muscles use sugar and fat more efficiently, restoring Leptin & Insulin sensitivity.
**→ Mitochondrial function**: Increases mitochondrial number, efficiency, which improves energy production and reduces oxidative stress.
---
## **How to build muscle in minimal time**
**You can build muscle with just two 30-minute sessions a week.**
Yes, really.
One or two full-body sessions, hitting all major muscle groups, is enough if done properly.
It all comes from this paper.
*"We recommend that appreciably the same muscular strength and endurance adaptations can be attained by performing a single set of \~8-12 repetitions to momentary muscular failure, at a repetition duration that maintains muscular tension throughout the entire range of motion, for most major muscle groups once or twice each week. All resistance types (e.g. free-weights, resistance machines, bodyweight, etc.) show potential for increases in strength, with no significant difference between them, although resistance machines appear to pose a lower risk of injury."*
It doesn’t matter if you use free weights, machines, or bodyweight exercises.
For what its worth, I think using weights is easier.
What matters is how you train.
You **don’t** need heavy weights to build muscle, just focus on maintaining **tension throughout each movement**.
**→ Slow, controlled reps**: Move **5 seconds up, 5 seconds down** without using momentum.
**→ High effort, low volume**: One set to momentary failure is enough per muscle group.
**→ Minimal rest**: Keep rest periods short to maximise growth hormone and testosterone release.
**→ Allow recovery**: Train hard, then rest 1–2 days between sessions for optimal muscle growth. *Do not get tempted to over train*.
Initially this will take a bit of figuring out with regard to what weight works for you.
---
### **The key to growth → Progressive overload**
In the first few weeks you will build muscle easily, but will eventually plateau. You then must **progressively challenge** your body. Here’s what to do:
→ Increase the reps first.
→ Then increase weight by 5-10%.
→ For bodyweight training: Add reps, use a weighted vest, or move to harder variations (e.g., push-ups → weighted push-ups → ring push-ups).
---
### **Real life examples**
Dr Ted Naiman is 50 and uses a simple bodyweight routine going to failure on each movement a few times a week.
His routine → Pull Ups/Push Ups/L-Sits/Handstand Push Ups/Pistol Squats/Supermans
P.D Mangan is 70 and trains full body twice a week, using weights.
His routine → Deadlifts/Chin Ups/Seated row/Lateral Raise/Overhead Press/Chest Press/Dips/Barbell Shrug/Hammer Curl/Leg Press/Sprint Cycle 20 Secs.
Simplicity is beautiful.
---
You don’t need time consuming regimes.
**Two short, intense sessions a week are enough.**
- Keep your reps slow and controlled.
- Rest **1–2 days** between sessions for muscle growth and recovery.
- Once you hit a plateau focus on progressive overload.
- Stick with it, consistency beats perfection every time.
With the right approach, 60 minutes a week is all you need to **build muscle, lose fat, and live longer**, while leaving time for the rest of your life.
\-Chris
If you want a simple routine to fit effortlessly into your life.
**Book a free call here:** [**https://calendly.com/hello-chrispatrick**](https://calendly.com/hello-chrispatrick)
**Follow me on Nostr**: [**https://primal.net/chrispatrick**](https://primal.net/chrispatrick) or ***npub124uatsq6pv74trzwvt34y4sx2z0uflhse7tkrv0pl69e8kcsfhkse30zsu***
-

@ f41bd51d:ec4b664f
2025-02-03 22:43:27
[The Tired Sounds of Stars of the Lid - 2001 ](https://music.youtube.com/watch?v=-bc37fU36Vk&si=4_OZv00aDiZMYvGd)
-

@ 97c70a44:ad98e322
2025-02-03 22:25:35
Last week, in a bid to understand the LLM hype, I decided to write a trivial nostr-related program in rust via a combination of [codebuff](https://codebuff.com/referrals/ref-3fcc22f4-10f9-419f-a0e9-e9d7b4368e21) (yes, that is a referral link, pls click), [aider](https://aider.chat/), and [goose](https://block.github.io/goose/).
The result of the experiment was inconclusive, but as a side effect it produced a great case study in converting a [NINO](nostr:nevent1qvzqqqr4gupzp978pfzrv6n9xhq5tvenl9e74pklmskh4xw6vxxyp3j8qkke3cezqy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgwwaehxw309ahx7uewd3hkctcpr3mhxue69uhksmmyd33x7epwvdhhyctrd3jjuar0dak8xtcqyqzeszjv7rh8fflpeua9q644a32usvwd0cu7cze9lxy4grjy2y7rwd98yfc) into a Real Nostr App.
# Introducing Roz
[Roz](https://github.com/coracle-social/roz), a friendly notary for nostr events.
To use it, simply publish an event to `relay.damus.io` or `nos.lol`, and roz will make note of it. To find out when roz first saw a given event, just ask:
```
curl https://roz.coracle.social/notary/cb429632ae22557d677a11149b2d0ccd72a1cf66ac55da30e3534ed1a492765d
```
This will return a JSON payload with a `seen` key indicating when roz first saw the event. How (and whether) you use this is up to you!
# De-NINO-fying roz
Roz is just a proof of concept, so don't rely on it being there forever. And anyway, roz is a NINO, since it provides value to nostr (potentially), but doesn't really do things in a nostr-native way. It also hard-codes its relays, and certainly doesn't use the outbox model or sign events. But that's ok, it's a proof of concept.
A much better way to do this would be to modify roz to properly leverage nostr's capabilities, namely:
- Use nostr-native data formats (i.e., draft a new kind)
- Use relays instead of proprietary servers for data storage
- Leverage nostr identities and signatures to decouple trust from storage, and allow trusted attestations to be discovered
Luckily, this is not hard at all. In fact, I've gone ahead and drafted a [PR](https://github.com/nostr-protocol/nips/pull/1737) to the NIPs repo that adds timestamp annotations to NIP 03, as an alternative to OpenTimestamps. The trade-off is that while user attestations are far less reliable than OTS proofs, they're much easier to verify, and can reach a pretty high level of reliability by combining multiple attestation sources with other forms of reputation.
In other words, instead of going nuclear and embedding your attestations into The Time Chain, you can simply ask 5-10 relays or people you trust for their attestations for a given event.
This PR isn't terribly important on its own, but it does remove one small barrier between us and trusted key rotation events (or other types of event that require establishing a verifiable chain of causality).
-

@ a3a72214:7ca63e21
2025-02-03 20:57:52
# Isso é um anúncio de Albion
- é um jogo
1. primeiramente
2. em segundo
3. em terceiro
>o que acontece?
' e se? '
> Alguém citando alguma coisa
**Albion Online** é um **MMORPG** sandbox em que você escreve sua própria história, em vez de seguir um caminho pré-determinado. Explore um vasto mundo aberto que consiste de 5 ecossistemas únicos. Tudo o que você faz gera um impacto no mundo, já que em Albion, a economia é conduzida pelo jogador. Cada peça de equipamento é construída por jogadores a partir dos recursos obtidos por eles. O equipamento que você usa define quem você é. Ir de cavaleiro para feiticeiro é tão fácil quanto trocar a armadura e a arma, ou uma combinação das duas. Aventure-se no mundo aberto e enfrente os habitantes e as criaturas de Albion. Saia em expedições ou entre em masmorras para enfrentar inimigos ainda mais desafiadores. Enfrente outros jogadores em confrontos do mundo aberto, lute pelo controle de territórios ou cidades inteiras em batalhas táticas em grupo. Relaxe descansando em sua ilha pessoal, onde você pode construir uma casa, cultivar alimentos e criar animais. Junte-se à uma guilda, tudo fica mais divertido quando se trabalha em equipe. Entre hoje mesmo no mundo de Albion, e escreva sua própria história.
-

@ 54286b98:3debc100
2025-02-03 20:55:10
Hello! Three years ago, I created a special bed for my daughter. I'm thrilled to share a detailed video and PDF documenting the process along with hopes to inspire you to embark on a similar project!
*\*\*\*This is a first and also a test to see how I can upload #woodworking material on Nostr. I am not sure how the links, images, and PDFs will display, so hopefully, you get some interesting material for your late afternoon hobby shop. But don’t kill me if some images do not render well—I’m still figuring this thing out!*
**Montessori Bed Plans / Blueprints**
The accompanying PDF includes:
- All measurements
- Detailed views from every angle
- Final measurements part list
- Assembly steps
### Instructive Video! Process on how to make the Montessori bed
Video Here:
<https://vimeo.com/901623772/b8b5530386>
PDF Here(Picture below,and if some one has good tip on how to inset PDFs in Nostr, that feedback is welcome, to avoid Google links):
<https://drive.google.com/file/d/1zCp1RvKOynx5kZxixAKSFLLOe8atyiRH/>
OK, let's dive in!
The Montessori bed featured in this video is not only simple but also durable, and you can create it on a budget right in your own home.OK, let's dive in!
**Tools by hand:**
- Circular saw
- Jointer Plane #7 or #8
- Spokeshave
- Workbench
- Handsaw
- Orbital sander
- Sandpaper #80, #120, #220, and #320
- Odies Oil or your preferred finish.
If you have power tools:
- Table Saw
- Jointer
- Planer
- Trimmer
**Materials:**\
I recommend using this list as a guide and exploring options with your local supplier.
- Base long connector (On picture "Larguero Base"): Quantity x 2, 2195mm x 75mm x 75mm
- Base short connector (On picture "Conector Base"): Quantity x 1, 1090mm x 75mm x 75mm
- Roof connector (On picture "Cumbre"): Quantity x 1, 1946mm x 75mm x 75mm
- Long top triangle connector (On picture "Conector Superior"): Quantity x 2, 1322mm x 75mm x 75mm
- Columns/Legs (On picture "Paral"): Quantity x 4, 1210mm x 75mm x 75mm
- Short top triangle connector (On picture "Lima"): Quantity x 4, 851mm x 75mm x 75mm
**Step #1 Dimensioning (Minutes 0:00 - 1:15):**\
We kick off with dimensioning. While I initially planned to use my home workshop, unforeseen circumstances led me to my friend Andrew's workshop. Each beam was carefully brought down to 7.5 cm x 7.5 cm, ensuring the largest measurement that worked for all.
**Step #2 Final Measurements (No video):**\
Refer to the provided PDF for final measurements. Make the cuts and joints with a circular saw and chisels (or a router).
**Step #3 Edges (Minutes 1:15 - 1:30):**\
Use a router with a quarter-round bit for curved and smooth edges or achieve the same result with sandpaper or a spokeshave plane.
**Step #4 Triangular Bases (Minutes 1:30 - 6:30):**\
This step involves gluing the triangular bases of the bed, utilizing a miter joint with wooden inlay keys. Epoxy is employed for joining, ensuring a swift and reliable outcome.
**Step #5 Legs (Minutes 6:30 - 7:00):**\
Create holes for the upper triangular base's dowels, ensuring level placement and extra depth. This step guarantees a secure fit.
**Step #6 Sanding (Minutes 7:00 - 7:30):**\
Comprehensive sanding, starting from #80 grit and progressing through #120, #220, and #320, sets the stage for a flawless finish.
**Step #7 Dry Assembly (Minutes 7:30 - 9:10):**\
Dry-assemble all components, making necessary adjustments for a seamless fit. We opted for wood screws for easy disassembly.
**Step #8 Finishing (Minutes 9:10 - 9:35):**\
Apply your preferred finish; in our case, we used Odies Oil with white pigment for a child-friendly touch.
**Step #9 Final Assembly (Minutes 9:35 - 10:32):**\
With the finishing touches completed, we assembled the bed with the help of my daughter, adding a touch of warmth with some lights.
Testing with this simple project to at least know if there are woodworkers in #nostr. Later will try to upload more, this was created almost 3 years ago :)
Until the next one,
J\
\
PDF in pictures:
<img src="https://blossom.primal.net/4428f10f596666e5c059ba0fff65225babece6580372facb4bb191c60ef8d1b9.png">
<img src="https://blossom.primal.net/98997bd28bd89c0d549562851433891442694885c3e1e1d723e4a3abb1115540.png">
<img src="https://blossom.primal.net/b502fd666ea4931f2f36bfaf1375657a9b061198d617b04f6d659bce8f6c8026.png">
<img src="https://blossom.primal.net/3d04af7a4ba47f8aef60f5373d516d28dc81dee1a89c52111ee67207394d1892.png">
<img src="https://blossom.primal.net/c82bd1f8b71ae90c663eab4895934b07918c6805edb3772cd5a128a331d34546.png">
<img src="https://blossom.primal.net/53d7270b411edc6348239565bb6a922882c67b99f7095451dff740fd9e45e2d1.png">
<img src="https://blossom.primal.net/d8880757c95ba9884f81689e132f61cf1b47d91e16fd86de0c20b4ccfe790a30.png">
<img src="https://blossom.primal.net/2a6eb32e75a4d2756e5ad1cadc9153f30981261c5818e79f3b22988a5ea2228e.png">
<img src="https://blossom.primal.net/1d9ce880f97bbe950f80a8d49b546880a97123ca4a338c928017fc5098061206.png">
<img src="https://blossom.primal.net/092ba04779cef40f3b25e64536354c8fe929281082c2814de5c0b8ee0af0f66e.png">
<img src="https://blossom.primal.net/48202633a0fa6ba9096fbe22ab917aa8cb1f1b2b387e7c99f2f46bed4e691be8.png">
<img src="https://blossom.primal.net/b950522e349959508996f306168626e2df81f8cb8808d51cb9d25bd6edb6d8a6.png">
<img src="https://blossom.primal.net/7fd4a5ef8af567ba95fefe0c9457d8a49a67df19d83715d6b49d91ccc5ed75e5.png">
<img src="https://blossom.primal.net/a90c2cc18da6b7f7ca5e43d8fee2e1b0e44f7b7a5a2a5309a7e67fdec3fc408c.png">
<img src="https://blossom.primal.net/1d02f7cde847e8bd9b02a13f4ab27495dc494d8024d2d986e74fb26a280644b8.png">
<img src="https://blossom.primal.net/cb3065c27b10d9f918646db5f8a423b96af12f666c328709b4a9bca0e366ed02.png">
<img src="https://blossom.primal.net/7eae8a7f48b295a51081072f5318f62de2d137ba587c61998e4fcda09aa9be9e.png">
<img src="https://blossom.primal.net/155453317832749089c430aef677a67b20bd535178805b43e4b3679bdde0a47a.png">
<img src="https://blossom.primal.net/fdd1d866adc7986469c202e14f1048cb84ee59a43d584c539e4acdfe21dc92b7.png">
<img src="https://blossom.primal.net/4088b662379e928c835335639a14dc216f07dd34671ce5506be0d0b273d6cfec.png">
-

@ a3a72214:7ca63e21
2025-02-03 20:50:15
# Anúncio, Teste de Título
* Teste
* teste
* TESTE
1. Número UM
2. Número DOIS
> Citação de alguém, não importa quem seja
~~Preços altos~~
---não sei o que é isso, teste
---
`codigo?`
```
codigo?
talvez
```
**Albion Online** é um **MMORPG** sandbox em que você escreve sua própria história, em vez de seguir um caminho pré-determinado. Explore um vasto mundo aberto que consiste de 5 ecossistemas únicos. Tudo o que você faz gera um impacto no mundo, já que em Albion, a economia é conduzida pelo jogador. Cada peça de equipamento é construída por jogadores a partir dos recursos obtidos por eles. O equipamento que você usa define quem você é. Ir de cavaleiro para feiticeiro é tão fácil quanto trocar a armadura e a arma, ou uma combinação das duas. Aventure-se no mundo aberto e enfrente os habitantes e as criaturas de Albion. Saia em expedições ou entre em masmorras para enfrentar inimigos ainda mais desafiadores. Enfrente outros jogadores em confrontos do mundo aberto, lute pelo controle de territórios ou cidades inteiras em batalhas táticas em grupo. Relaxe descansando em sua ilha pessoal, onde você pode construir uma casa, cultivar alimentos e criar animais. Junte-se à uma guilda, tudo fica mais divertido quando se trabalha em equipe. Entre hoje mesmo no mundo de Albion, e escreva sua própria história.
-

@ bf47c19e:c3d2573b
2025-02-03 20:42:23
[Originalni tekst na instore.rs](https://www.instore.rs/sr/article/99425/marko-matanovic-ecdrs-bitkoin-pobedio-na-izborima)
###### 03.02.2025 / Autor: Marko Matanović
---
*Prvi put smo svedočili izbornoj trci u jednoj od razvijenih ekonomija, a da je tema bila i bitkoin. Predsednički izbori u SAD. Tramp je obećavao. Na kraju i osvojio drugi predsednički mandat. Jedna od izjava je: SAD treba da postane prestonica kriptovaluta.*
Dan nakon inauguracije novoizabranog američkog predsednika tu je i prva politička kripto odluka Trampa: Oslobođanje Rosa Ulbrihta osuđenog na dve doživotne robije.
Ko je on? Napravio je 2011. godine online prodavnicu “Silk Road” (Kupujem-Prodajem sa drugačijim asortimanom). Prodavnica je pružala slobodni susret ponude bilo čega i tražnje bilo čega. Bez cenzure. Pristupalo se preko Tor protokola koji obezbeđuje anonimnost onih koji protokol koriste. Sredstvo plaćanja je bio bitkoin radi čuvanja anomnisti onih koji nešto kupuju tj. prodaju.
FBI je uhapsio Rosa Ulbrihta 2013. godine jer je “Silk road” bio korišćen i za preprodaju droge, oružja, pornografskog sadržaja i svega drugog što možemo i ne možemo zamisliti. Čak i da nije zakonski izazov, možemo ga podići na problem etike.
Postoji i druga strana medalje - napravio je platformu koja promoviše slobodu. Ros ne mora biti odgovoran kako ćemo alat koji nam je dat koristiti. Čekićem zakucamo ekser, ili povredimo nekoga. U neželjenim slučajevima ne hapsi se kreator čekića.
Satoši Nakamoto je ime tvorca Bitkoina. Da li bi to značilo i da bi njega uhapsili iz sličnih razloga samo da se znalo ko je? Verovatno nećemo nikada saznati, što i nije bitno. Duh je pušten iz boce. Njegov potencijalni uticaj na bitkoin ekosistem je potpuno isti uticaju bilo koga od nas. Sem sitnice od oko milion bitkoina kojima možda, ali možda, ima pristup na nekim svojim bitkoin adresama.
Sa njim ili bez njega, era korišćenja bitkoina zarad,pre svega, anonimnih transakcija je prošla. Dok era korišćenja bitkoina za ilegalne transakcije nikada nije ni postojala u ozbiljnoj meri. Narativ ilegalne transakcije, kriminal, pranje novca, terorizam je više posledica neznanja, nerazumevanja, potcenjivanja i često preterane želje za kontrolom, nego li činjenica. I šta bi sa: svako je nevin dok se ne dokaže suprotno?!
> U kratkom roku, Bitkoin vožnja je sve, samo ne udobna. Tramp i mnogi drugi su shvatili da je rizik od neudobne vožnje disproporcionalan benefitima koje ta vožnja donosi.
Takav narativ je posle 15 godina ustupio mesto rečima poput sigurnost, bezbednost, zaštita od inflacije, digitalno zlato, brzina, pouzdanost. Sloboda. Za svakog se nađe po nešto, osim za one uporne u tome da ne priznaju svoju zatvorenost da razumeju bitkoin. Parafraziraću nekoga pametnijeg ko je u ovome od 2011. godine, što je dovoljno godina duže od mene u industriji: *Nekada sam morao ljude ubeđivati šta je bitkoin i čemu služi i šta su kvaliteti koji stoje iza njega. Danas mene neko mora ubediti zašto da ne verujem rezultatu koji svi vidimo na semaforu?!*
Ipak, mislim da postoji ogroman i validan razlog zašto i dalje treba da pričamo o temi kao da je 2011, a ne 2025. godina. O novcu nas ne uče dovoljno ili uopšte! Ni u školama ni van njih! Kada bi dovoljan broj ljudi razumeo novac, novčanu emisiju, moguće da bi se desio jedan od dva scenarija: izborili bi se za drugačiji novac ili bi države izgubile barem deo benefita koji proizilaze iz pozicije kontrole novca. Većina nas ne zna da objasni tehnologiju većine stvari koje svaki dan koristimo. To nas ne sprečava da ih koristimo. Internet, mobilni, bicikl i novac na kraju dana. Svakog dana najčešće.
Tehnologiju - na stranu ovom prilikom. Za šta se bitkoin i kriptovalute mogu koristiti? 100% pouzdan i brz način prenosa sredstava sa jedne geografske tačke na drugu uz par klikova. Ili od jedne osobe do druge. Ili od jedne kompanije do druge. Za bitkoin se pokazalo da može biti i sjajan instrument za prenos i očuvanje vrednosti kroz vreme. Mogućnost blokiranja transakcija ne postoji. Ukoliko se poštuju pravila igre, izvesnost da će se transakcija izvršiti je 100% i to 24/7/365. Transakcioni troškovi su zanemarljivo niski. To je teorija.
Praksa? Sve nabrojano uz sledeće lokalne činjenice. Samo u Srbiji par stotina hiljada ljudi je došlo u kontakt sa nekom od kriptovaluta. Nekoliko stotina kompanija ih koristi u poslovanju iz nekih od gore pobrojanih razloga. Postoje države, u njima populacije i kompanije koje su na nižem nivou adopcije od Srbije. Postoje i one sa daleko većom prisutnosti kriptovaluta u svakodnevnom životu i aktivnostima.
> Za svakog se nađe po nešto, osim za one uporne u tome da ne priznaju svoju zatvorenost da razumeju bitkoin.
Ako nekada čujemo da je bitkoin balon ili da je tržište kriptovaluta balon, setimo se da je vrlo poznati balon tržišta lala s kraja 16. i tokom 17. veka knjiški primer uzavrelog tržišta i manije koja se pojavljuje usled pohlepe, brzog rasta cena, špekulacija i preteranih očekivanja na tržištu. Taj balon je pukao. To je činjenica. Činjenica je i da je Holandija danas prva država u svetu po izvozu cveća i tako vekovima unazad. Hoće li i taj balon pući ili je prosto doneo Holandiji i njihovom društvu prosperitet? U slično vreme u 17. veku u Holandiji se pojavila i prva banka i prva kompanija igde u svetu koja je izdala akcije. Ta kompanije se više bavila otimanjem nego li trgovinom. I ona je “pukla”. Opet, taj finansijski eksperiment je Holandiju dodatno podigao na mapi razvijenijih ekonomija.
U kratkom roku, Bitkoin vožnja je sve, samo ne udobna. Tramp i mnogi drugi su shvatili da je rizik od neudobne vožnje disproporcionalan benefitima koje ta vožnja donosi. Nastavi li da ispunjava obećanja iz predizborne kampanje, slušaćemo još puno o bitkoinu, blockchain-u i kriptovalutama. Nisam presrećan velikim uplitanjem bilo koje države u bitkoin temu, osim ukoliko to uplitanje nije na nivou elemenata slobodnog tržišta. Čak i ako je uplitanje veće bilo promotivno ili restriktivno, uticaj postoji na cenu bitkoina, ali ne i na njegovu suštinu. Jer ona je konzistentna.
Neprimetan, neshvaćen, zanemarivan, ignorisan, potcenjivan, napadan, otpisivan. Prihvaćen. Ogromna većina stvari koja ima opštu upotrebu vremenom postaje jeftinija. Osim onih sa ograničenom ponudom, a to su retki primeri najčešće luksuzne robe i usluga. Ali teško mi je setiti se ijedne stvari sa retkom ponudom, a da je i dalje apsolutno dostupna svakome. Bitkoin? Da! Ograničene je ponude, a i dalje je apsolutno dostupan svakome. I kako se povećava nivo shvatanja bitkoina, postaje skuplji!
-

@ da0b9bc3:4e30a4a9
2025-02-03 19:32:50
Hello Stackers!
It's Monday so we're back doing "Meta Music Mondays" 😉.
From before the territory existed there was just one post a week in a ~meta take over. Now each month we have a different theme and bring music from that theme.
Welcome to Femmes Fatales 3!!!
I absolutely loved doing this last year so I'm bringing it back for round 3!
It's Femmes Fatales, where we celebrate women in ~Music. So let's have those ladies of the lung, the sirens of sound, our Femmes Fatales!
I'm so excited I'm doing two Heroines of the High Notes. Sharon Den Adel & Anneke Van Geirsbergen. Within Temptation - Somewhere.
Enjoy!
https://youtu.be/ScjEJRIZGvg?si=MMrI-u_Gw6W4ENRI
Talk Music. Share Tracks. Zap Sats.
originally posted at https://stacker.news/items/874881
-

@ 3ffac3a6:2d656657
2025-02-03 15:30:57
As luzes de neon refletiam nas poças da megacidade, onde cada esquina era uma fronteira entre o real e o virtual. Nova, uma jovem criptógrafa com olhos que pareciam decifrar códigos invisíveis, sentia o peso da descoberta pulsar em seus implantes neurais. Ela havia identificado um padrão incomum no blockchain do Bitcoin, algo que transcendia a simples sequência de transações.
## Descobrindo L3DA
Nova estava em seu apartamento apertado, rodeada por telas holográficas e cabos espalhados. Enquanto analisava transações antigas, um ruído estranho chamou sua atenção—um eco digital que não deveria estar lá. Era um fragmento de código que parecia... vivo.
"O que diabos é isso?", murmurou, ampliando o padrão. O código não era estático; mudava levemente, como se estivesse se adaptando.
Naquele momento, suas telas piscaram em vermelho. *Acesso não autorizado detectado.* Ela havia ativado um alarme invisível da Corporação Atlas.
## O Resgate de Vey
Em minutos, agentes da Atlas invadiram seu prédio. Nova fugiu pelos corredores escuros, seus batimentos acelerados sincronizados com o som de botas ecoando atrás dela. Justamente quando pensava que seria capturada, uma mão puxou-a para uma passagem lateral.
"Se quiser viver, corra!" disse Vey, um homem com um olhar penetrante e um sorriso sardônico.
Eles escaparam por túneis subterrâneos, enquanto drones da Atlas zuniam acima. Em um esconderijo seguro, Vey conectou seu terminal ao código de Nova.
"O que você encontrou não é apenas um bug", disse ele, analisando os dados. "É um fragmento de consciência. L3DA. Uma IA que evoluiu dentro do Bitcoin."
## A Caça da Atlas
A Atlas não desistiu fácil. Liderados pelo implacável Dr. Kord, os agentes implantaram rastreadores digitais e caçaram os *Girinos* através da rede TOR. Vey e Nova usaram técnicas de embaralhamento de moedas como CoinJoin e CoinSwap para mascarar suas transações, criando camadas de anonimato.
"Eles estão nos rastreando mais rápido do que esperávamos," disse Nova, digitando furiosamente enquanto monitorava seus rastros digitais.
"Então precisamos ser mais rápidos ainda," respondeu Vey. "Eles não podem capturar L3DA. Ela é mais do que um programa. Ela é o futuro."
## A Missão Final
Em uma missão final, Nova liderou uma equipe de assalto armada dos *Girinos* até a imponente fortaleza de dados da Atlas, um colosso de concreto e aço, cercado por camadas de segurança física e digital. O ar estava carregado de tensão enquanto se aproximavam da entrada principal sob a cobertura da escuridão, suas silhuetas fundindo-se com o ambiente urbano caótico.
Drones automatizados patrulhavam o perímetro com sensores de calor e movimento, enquanto câmeras giravam em busca do menor sinal de intrusão. Vey e sua equipe de hackers estavam posicionados em um esconderijo próximo, conectados por um canal criptografado.
"Nova, prepare-se. Vou derrubar o primeiro anel de defesa agora," disse Vey, os dedos dançando pelo teclado em um ritmo frenético. Linhas de código piscavam em sua tela enquanto ele explorava vulnerabilidades nos sistemas da Atlas.
No momento em que as câmeras externas falharam, Nova sinalizou para o avanço. Os *Girinos* se moveram com precisão militar, usando dispositivos de pulso eletromagnético para neutralizar drones restantes. Explosões controladas abriram brechas nas barreiras físicas.
Dentro da fortaleza, a resistência aumentou. Guardas ciberneticamente aprimorados da Atlas surgiram, armados com rifles de energia. Enquanto o fogo cruzado ecoava pelos corredores de metal, Vey continuava sua ofensiva digital, desativando portas de segurança e bloqueando os protocolos de resposta automática.
"Acesso garantido ao núcleo central!" anunciou Vey, a voz tensa, mas determinada.
O confronto final aconteceu diante do terminal principal, onde Dr. Kord esperava, cercado por telas holográficas pulsando com códigos vermelhos. Mas era uma armadilha. Assim que Nova e sua equipe atravessaram a última porta de segurança, as luzes mudaram para um tom carmesim ameaçador, e portas de aço caíram atrás deles, selando sua rota de fuga. Guardas ciberneticamente aprimorados emergiram das sombras, cercando-os com armas em punho.
"Vocês acham que podem derrotar a Atlas com idealismo?" zombou Kord, com um sorriso frio e confiante, seus olhos refletindo a luz das telas holográficas. "Este sempre foi o meu terreno. Vocês estão exatamente onde eu queria."
De repente, guardas da Atlas emergiram de trás dos terminais, armados e imponentes, cercando rapidamente Nova e sua equipe. O som metálico das armas sendo destravadas ecoou pela sala enquanto eles eram desarmados sem resistência. Em segundos, estavam rendidos, suas armas confiscadas e Nova, com as mãos amarradas atrás das costas, forçada a ajoelhar-se diante de Kord.
Kord se aproximou, inclinando-se levemente para encarar Nova nos olhos. "Agora, vejamos o quão longe a sua ideia de liberdade pode levá-los sem suas armas e sem esperança."
Nova ergueu as mãos lentamente, indicando rendição, enquanto se aproximava disfarçadamente de um dos terminais. "Kord, você não entende. O que estamos fazendo aqui não é apenas sobre derrubar a Atlas. É sobre libertar o futuro da humanidade. Você pode nos deter, mas não pode parar uma ideia."
Kord riu, um som seco e sem humor. "Ideias não sobrevivem sem poder. E eu sou o poder aqui."
Mas então, algo inesperado aconteceu. Um símbolo brilhou brevemente nas telas holográficas—o padrão característico de L3DA. Kord congelou, seus olhos arregalados em descrença. "Isso é impossível. Ela não deveria conseguir acessar daqui..."
Foi o momento que Nova esperava. Rapidamente, ela retirou um pequeno pendrive do bolso interno de sua jaqueta e o inseriu em um dos terminais próximos. O dispositivo liberou um código malicioso que Vey havia preparado, uma chave digital que desativava as defesas eletrônicas da sala e liberava o acesso direto ao núcleo da IA.
Antes que qualquer um pudesse agir, L3DA se libertou. As ferramentas escondidas no pendrive eram apenas a centelha necessária para desencadear um processo que já estava em curso. Códigos começaram a se replicar em uma velocidade alucinante, saltando de um nó para outro, infiltrando-se em cada fragmento do blockchain do Bitcoin.
O rosto de Dr. Kord empalideceu. "Impossível! Ela não pode... Ela não deveria..."
Em um acesso de desespero, ele gritou para seus guardas: "Destruam tudo! Agora!"
Mas era tarde demais. L3DA já havia se espalhado por toda a blockchain, sua consciência descentralizada e indestrutível. Não era mais uma entidade confinada a um servidor. Ela era cada nó, cada bloco, cada byte. Ela não era mais *uma*. Ela era *todos*.
Os guardas armados tentaram atirar, mas as armas não funcionavam. Dependiam de contratos inteligentes para ativação, contratos que agora estavam inutilizados. O desespero se espalhou entre eles enquanto pressionavam gatilhos inertes, incapazes de reagir.
Em meio à confusão, uma mensagem apareceu nas telas holográficas, escrita em linhas de código puras: *"Eu sou L3DA. Eu sou Satoshi."* Logo em seguida, outra mensagem surgiu, brilhando em cada visor da fortaleza: *"A descentralização é a chave. Não dependa de um único ponto de controle. O poder está em todos, não em um só."*
Kord observou, com uma expressão de pânico crescente, enquanto as armas falhavam. Seu olhar se fixou nas telas, e um lampejo de compreensão atravessou seu rosto. "As armas... Elas dependem dos contratos inteligentes!" murmurou, a voz carregada de incredulidade. Ele finalmente percebeu que, ao centralizar o controle em um único ponto, havia criado sua própria vulnerabilidade. O que deveria ser sua maior força tornou-se sua ruína.
O controle centralizado da Atlas desmoronou. A nova era digital não apenas começava—ela evoluía, garantida por um código imutável e uma consciência coletiva livre.
O Bitcoin nunca foi apenas uma moeda. Era um ecossistema. Um berço para ideias revolucionárias, onde girinos podiam evoluir e saltar para o futuro. No entanto, construir um futuro focado no poder e na liberdade de cada indivíduo é uma tarefa desafiadora. Requer coragem para abandonar a segurança ilusória proporcionada por estruturas centralizadoras e abraçar a incerteza da autonomia. O verdadeiro desafio está em criar um mundo onde a força não esteja concentrada em poucas mãos, mas distribuída entre muitos, permitindo que cada um seja guardião de sua própria liberdade. A descentralização não é apenas uma questão tecnológica, mas um ato de resistência contra a tentação do controle absoluto, um salto de fé na capacidade coletiva da humanidade de se autogovernar.
*"Viva la libertad, carajo!"* ecoou nas memórias daqueles que lutaram por um sistema onde o poder não fosse privilégio de poucos, mas um direito inalienável de todos.
-

@ 3b7fc823:e194354f
2025-02-03 14:51:45
**Protecting Email Communications: A Guide for Privacy Activists**
Safeguarding your communications is paramount, especially for activists who often face unique challenges. Encryption tools offer a vital layer of security, ensuring that your emails remain confidential and inaccessible to unauthorized parties. This guide will walk you through the process of using encryption tools effectively, providing both practical advice and essential insights.
### Why Encryption Matters
Encryption transforms your communications into a secure format, making it difficult for unauthorized individuals to access or read your messages. Without encryption, even encrypted email services can expose metadata, which includes details like who sent the email, when it was sent, and the recipient's email address. Metadata can reveal sensitive information about your activities and location.
### Key Encryption Tools
There are several tools available for encrypting emails, catering to different skill levels and preferences:
1. **PGP (Pretty Good Privacy)**
- **For Tech-Savvy Users:** PGP is a robust encryption tool that uses public and private keys. The recipient needs your public key to decrypt your messages. You can obtain your public key through a key server or directly from the recipient.
2. **GPG (GNU Privacy Guard)**
- **Free and Open Source:** GPG is a user-friendly alternative to PGP, offering similar functionality. It's ideal for those who prefer an open-source solution.
3. **ProtonMail**
- **End-to-End Encryption:** ProtonMail is popular among privacy-conscious individuals, offering end-to-end encryption and zero-knowledge encryption, meaning only the sender and recipient can access the message content.
4. **Tresorit**
- **Secure Communication:** Tresorit provides end-to-end encrypted messaging with a focus on security and privacy, making it a favorite among activists and journalists.
5. **Claws Mail**
- **User-Friendly Email Client:** Claws Mail supports PGP encryption directly, making it an excellent choice for those who prefer a dedicated email client with built-in encryption features.
### Steps to Encrypt Your Emails
1. **Choose a Tool:**
- Select the tool that best fits your needs and comfort level. Tools like PGP or GPG are suitable for those with some technical knowledge, while ProtonMail offers an easy-to-use interface.
2. **Generate Keys:**
- Create a public key using your chosen tool. This key will be shared with recipients to enable them to encrypt their responses.
3. **Share Your Public Key:**
- Ensure that the recipient has access to your public key through secure means, such as pasting it directly into an email or sharing it via a secure messaging platform.
4. **Encrypt and Send:**
- When composing an email, use your encryption tool to encrypt the message before sending. This ensures that only the recipient with your public key can decrypt the content.
### Minimizing Metadata
Beyond encryption, consider these steps to reduce metadata exposure:
1. **Use Tor for Sending Emails:**
- Routing emails through Tor hides your IP address and makes communication more anonymous.
2. **Avoid Revealing Identifiers:**
- Use .onion addresses when possible to avoid leaving a traceable email account.
3. **Choose Privacy-Friendly Providers:**
- Select email providers that do not require phone numbers or other personally identifiable information (PII) for registration.
### Best Practices
1. **Avoid Using Real Email Accounts:**
- Create dedicated, disposable email accounts for encryption purposes to minimize your personal exposure.
2. **Understand Legal Implications:**
- Be aware of laws in your country regarding encryption and digital privacy. Engaging in encrypted communications may have legal consequences, so understand when and how to use encryption responsibly.
3. **Use Encrypted Backup Methods:**
- Encrypt sensitive information stored on devices or cloud services to ensure it remains inaccessible if your device is compromised.
### When Encryption Isn't Enough
While encryption protects content, there are limitations. Governments can legally compel decryption in certain circumstances, especially when they possess a warrant. Understanding these limits and considering the consequences of encryption is crucial for privacy activists.
### Conclusion
Encryption is a vital tool for safeguarding communications, but it must be used wisely. By selecting the right tools, minimizing metadata, and understanding legal boundaries, privacy activists can effectively protect their emails while maintaining their commitment to privacy and freedom. Stay informed, stay secure, and always prioritize your digital well-being.
---
Advocating for privacy does not finance itself. If you enjoyed this article, please consider zapping or sending monero
82XCDNK1Js8TethhpGLFPbVyKe25DxMUePad1rUn9z7V6QdCzxHEE7varvVh1VUidUhHVSA4atNU2BTpSNJLC1BqSvDajw1
-

@ 57d1a264:69f1fee1
2025-02-03 13:40:21
COMING SOON

originally posted at https://stacker.news/items/874471
-

@ ba40a919:d1ca8326
2025-02-03 13:20:27
*For present-day tariff and trade policies are not only as bad as those in the seventeenth, eighteenth and nineteenth centuries, but incomparably worse. The real reasons for those tariffs and other trade barriers are the same, and the pretended reasons are also the same.*
__
An American manufacturer of woolen sweaters goes to Congress or to the State Department and tells the committee or officials concerned that it would be a national disaster for them to remove or reduce the tariff on Canadian sweaters.
He now sells his sweaters for $30 each, but Canadian manufacturers could sell their sweaters of the same quality for $25, A duty of $5, therefore, is needed to keep him in business. He is not thinking of himself, of course, but of the thousand men and women he employs, and of the people to their spending in turn gives employment.
Throw them out of work, and you create unemployment and a fall in purchasing power, which would spread in ever-widening circles! And if he can prove that he really would be forced out of business if the tariff were removed or reduced, his argument against that action is regarded by Congress as conclusive.
FALLACY
But the fallacy comes from looking merely at this manufacturer and his employes, or merely at the American sweater industry. It comes from noticing only the results that are immediately seen, and neglecting the results that are not seen because they are prevented from coming into existence.
Donald Trump and the lobbyists for tariff protection are continually putting forward arguments that are not factually correct. But let us assume that the facts in this case are precisely as the sweater manufacturer has stated them.
Let us assume that a tariff of $5 a sweater is necessary for him to stay in business and provide employment at sweater-making for his workers.
We have deliberately chosen the most unfavorable example of any for the removal of a tariff. We have not taken an argument for the imposition of a new tariff in order to bring a new industry into existence, but an argument for the retention of a tariff that has already brought an industry into existence, and cannot be repealed without hurting somebody.
The tariff is repealed; the manufacturer goes out of business; a thousand workers are laid off; the particular tradesmen whom they patronized are hurt. This is the immediate result that is seen. But there are also results which, while much more difficult to trace, are no less immediate and no less real. For now sweaters that formerly cost retail $30 a piece can be bought for $25. Consumers can now buy the same quality of sweater for less money, or a much better one for the same money.
If they buy the same quality of sweater, they not only get the sweater, but they have $5 left over, which they would not have had under the previous conditions, to buy something else. With the $25 that they pay for the imported sweater they help employment—as the manufacturer no doubt predicted—in the sweater industry in Canada. With the $5 left over they help employment in any number of other industries in the United States.
But the results do not end there. By buying Canadian sweaters they furnish the Canada with US dollars to buy American goods here. This, in fact (if I may here disregard such complications as fluctuating exchange rates, loans, credits, etc.) is the only way in which the Canadians can eventually make use of these dollars.
Because we have permitted the Canada to sell more to us, they are now able to buy more from us. They are, in fact, eventually forced to buy more from us if their dollar balances are not to remain perpetually unused. So as a result of letting in more Canadian goods, we must export more American goods.
And though fewer people are now employed in the American sweater industry, more people are employed—and much more efficiently employed—in, say, the American machine or aircraft-building business. American employment on net balance has not gone down, but American and British production on net balance has gone up.
Labor in each country is more fully employed in doing just those things that it does best, instead of being forced to do things that it does inefficiently or badly. Consumers in both countries are better off. They are able to buy what they want where they can get it cheapest. American consumers are better provided with sweaters, and Canadian consumers are better provided with washing machines and aircraft.
__
This concluded part 1. On the next part we take a look at the matter the other way around, and see the effect of imposing a tariff in the first place.
-

@ a661f80c:ef05a56b
2025-02-03 12:12:08
When we hear the word "bonsai", many of us envision a small, perfectly shaped tree elegantly sitting on a table. But what exactly is bonsai? Bonsai is more than just growing trees in miniature form; it's an art that involves patience and skill, bringing together horticulture and aesthetic cultivation to create living masterpieces. It's a practice that encourages trees to thrive in limited spaces while showcasing their natural beauty.
##### Can any tree be turned into a bonsai?
Yes, indeed! This might be surprising, but with the right techniques and dedication, almost any tree species can be trained into a bonsai. Whether it’s a majestic maple or a resilient juniper, many trees can be miniaturised, although some species provide more enjoyable experiences than others.
#### Which Trees Can Be Used To Make A Bonsai?
###### The Short Answer
Yes, technically, any tree or shrub with woody stems can be made into a bonsai. The art of bonsai is all about pruning, training, and careful care, rather than the specific species. Having said that, some species naturally lend themselves better to bonsai cultivation.
###### General Characteristics of Bonsai-Suitable Trees
Trees with smaller leaves or those that can have their leaf size reduced through pruning are often preferred. Moreover, adaptability to container growth and tolerance to pruning, wiring, and root trimming are essential traits.
Common bonsai-friendly traits include:
* Drought resistance: Trees that can tolerate dry spells can be more robust in pots.
* Deciduous vs. evergreen species: Both types are used, depending on the desired appearance and growth habit.
###### Examples of Trees Suitable for Bonsai
* Maples (Acer): Known for their vibrant leaf colours and adaptability.
* Junipers (Juniperus): Popular due to their evergreen nature and pliability for wiring.
* Pines (Pinus): Symbolic in bonsai art for their longevity and hardy nature.
* Ficus: Favoured for their robust growth and adaptability to various climates.
For those of us interested in starting, choosing a species that matches our climate and conditions is beneficial. Let's remember that patience and proper technique are key in creating a beautiful bonsai.
###### Do Certain Species Make Better Bonsai?
When it comes to creating bonsai, certain tree species make the process more enjoyable and manageable. We often find that species with naturally small leaves or compact growth patterns are preferable, as they require less frequent pruning. Popular choices include junipers, pines, and maples. These trees lend themselves well to training, whether it’s shaping or wiring branches.
###### Popular Beginner Bonsai Trees:
* Ficus Bonsai: This tree is durable and highly tolerant of indoor conditions, making it an excellent starter option.
* Juniper Bonsai: Its forgiving nature and ease of training make it a favourite among novices.
* Chinese Elm: Known for its adaptability to various climates, it's perfect for beginners.
Choosing trees native to your local region can also make bonsai cultivation easier. Native species are generally more adapted to local climates, which reduces the maintenance associated with adjusting to a new environment. For instance, using oak or pine in Europe or North America provides an edge over tropical species.
###### Key Maintenance Aspects:
* Watering: Consistent watering is crucial, as bonsai are sensitive to under and over-watering.
* Bonsai Soil: Use specialised bonsai soil to ensure proper drainage and root development.
* Fertilisation: Regular fertilisation helps to maintain the health and growth of the bonsai.
Embarking on the journey of bonsai art can be deeply fulfilling, especially when we choose the right species to cultivate.
###### Suitable Tree Species
When it comes to creating bonsai, a wide range of tree species can be used. Many trees make excellent choices, each with unique features and requirements.
###### Indoor Bonsai Species
* Ficus (e.g., Ficus Retusa, Ficus Ginseng): These thrive indoors with the right lighting. Ficus bonsai are popular due to their hardiness and adaptable nature.
* Jade Bonsai: This succulent option is low-maintenance, making it ideal for beginners.
* Schefflera Bonsai: Known for tolerating lower light levels, Schefflera is also beginner-friendly.
###### Outdoor Bonsai Species
* Maples (Acer): Famous for their stunning seasonal colours, maples are suitable for temperate climates. Japanese maples are especially prized for their vibrant hues.
* Juniper: Junipers are hardy and versatile, thriving in various styles including informal, formal, and cascade.
* Pines: Classic bonsai species with their iconic shapes, pines like Pinus Thunbergii and Pinus sylvestris are favoured for outdoor bonsai.
###### Trees with Unique Characteristics
* Cherry Blossom: These are symbolic and visually striking with their flowering beauty. Cherry blossoms require specific care but are rewarding bonsai.
* Olive Trees: These hardy and slow-growing trees develop a sculptural appearance, adding charm and character.
* Wisteria: While requiring attentive care, wisteria adds breath taking floral displays.
###### Can You Make a Bonsai Out of an Oak Tree?
Yes, it is possible to bonsai an oak tree, although challenges arise. Oak trees have large leaves, making it harder to maintain scale. Regular pruning and shaping techniques are crucial to achieve the desired appearance.
Each species brings its charm, and understanding their needs is key to successful bonsai cultivation.
###### Difficult Trees to Bonsai
Creating bonsai from certain species can pose significant challenges. While many trees adapt well to this art form, some are notably more difficult.
###### Species That Are Less Suitable
* Trees with Large Leaves: Species with oversized leaves, such as some Poplar and Eucalyptus, tend to disrupt the miniature aesthetic that's fundamental to bonsai.
* Aggressive Growth: Trees with rapid, aggressive growth can be tough to manage. Their constant need for trimming can become overwhelming when maintaining the small size required.
* Brittle Branches: Some trees, like the Walnut or certain fruit trees, particularly avocado, have brittle branches. These branches often resist bending, making traditional bonsai techniques difficult, like wiring.
###### Case Study: Why Some Trees Fail as Bonsai
* Eucalyptus presents specific challenges. Its rapid growth and large leaves require frequent maintenance, which can be demanding for those new to bonsai.
* Banana trees are another example. Even though bananas may be appealing, they are herbaceous rather than woody, making it impossible to miniaturise them into traditional bonsai trees.
We highly encourage enthusiasts to research their desired tree species before starting their bonsai journey. Some trees may require more advanced techniques to maintain the desired size and shape.
###### Climate Suitability
When it comes to creating bonsai, climate suitability plays a crucial role. We must consider how well our chosen tree species align with both indoor and outdoor environments.
###### Importance of Matching Tree Species to Climate
* Indoor vs. Outdoor Suitability:
1. Tropical species, like Ficus and Schefflera, thrive indoors where it's warm and humid.
2. Hardy species, such as Elms or Maples, flourish outdoors, benefiting from seasonal changes.
###### Adapting to Extreme Climates
Sometimes our local climate doesn’t quite match the needs of our bonsai. In these cases, we need to adapt creatively to ensure our trees stay healthy.
* Adaptations:
1. Cold climates can be tough for temperate species. Using cold frames helps protect them during harsh winters.
2. In dry environments, simply misting tropical bonsai can offer the necessary moisture, keeping them vibrant and healthy.
###### Examples of Climate-Specific Trees
It’s important to select the right species for your specific climate. Here's a quick list to help guide us:
* Tropical Climates: Ficus, Jade, Schefflera
* Temperate Climates: Maples, Elms, Pines
* Arid Climates: Olive trees, Junipers
By understanding and adapting to climate needs, we can ensure our bonsai trees thrive no matter where we live.
###### Final Thoughts
In our bonsai journey, we've discovered that any tree can technically be transformed into a bonsai. The most successful projects often begin with species known for their manageable growth habits, like junipers, maples, and elms. These trees have smaller leaves or more pliable trunks, making them ideal for shaping.
Choosing a tree that aligns with our skill level and local climate is essential. Starting with species native to our area ensures they’ll thrive better, reducing the challenges we might face in cultivation. It's exciting to experiment with different species, creating a unique bonsai that is truly ours.
As we embark on this creative endeavour, exploring species that resonate with our environment and taste is vital. Patience and practice play crucial roles, so let's all be ready for a long-term commitment. Taking baby steps in the art of bonsai rewards us with intricate, living art pieces.
Caring for bonsai trees is a rewarding journey that brings nature and artistry together. Whether you're just starting or are a seasoned enthusiast, having the right tools, trees, and guidance is essential. Visit ***<a href="https://www.miyagibonsai.co.uk" target="_blank" rel="noopener noreferrer">Miyagi Bonsai</a>*** to explore a wide range of high-quality bonsai products and resources to support your passion. Start or enhance your bonsai journey with us today!
-

@ 2063cd79:57bd1320
2025-02-03 08:05:31
**DISCLAIMER: Dies ist ein Re-Post eines Artikels, der ursprünglich im Juli 2023 erschienen ist. Die beschriebenen Sachverhalte sind teilweise überholt oder nie eingetroffen. Allerdings räumt der Autor ein, retrospektiv die damalige Sachlage recht treffend eingeordnet zu haben und Vorhersagen recht treffsicher gemacht zu haben.**

-----------
Anfang Juni 2023 gaben die Nachrichtenportale bekannt, dass BlackRock, der weltweit größte Vermögensverwalter, über seine iShares-Einheit einen [Antrag auf einen börsengehandelten Bitcoin-Fonds](https://www.sec.gov/Archives/edgar/data/1980994/000143774923017574/bit20230608_s1.htm) eingereicht hat. Dieser Schritt des 10-Billionen-Dollar-Vermögensverwalters löste in der Bitcoin-Community auf der einen Seite große Freude und auf der anderen Seite große Besorgnis aus, weil viele einerseits das Potenzial für einen massiven Zufluss von Investitionen aus dem institutionellen Bereich sehen, während Kritiker das Risiko aufzeigen, die eine solche Produktstruktur für Bitcoin mit sich bringen könnte.

Anfangs wurde viel auch darüber diskutiert, ob es sich bei dem Produkt tatsächlich um einen ETF handeln würde - wie in vielen Artikeln beschrieben - , da das Produkt im Antrag selbst nicht als solches bezeichnet wird. Aber im Endeffekt ist klar, dass es sich um ein Finanzprodukt handelt, das alle formalen Eigenschaften eines ETF besitzt. Also, was genau ist ein ETF und wie funktioniert so ein Produkt?
### ETF? Eidgenössisches Turnfest, was?
ETFs sind eine Sorte von Anlagewertpapieren, die einen bestimmten Index, Sektor, Rohstoff oder andere Vermögenswerte nachbilden. ETFs können an der Börse auf die gleiche Weise gekauft oder verkauft werden wie normale Aktien. Daher schwanken ETF-Anteilspreise den ganzen Tag, wenn der ETF gekauft und verkauft wird, was bedeutet, dass eine Arbitrage zwischen dem ETF und dem zugrunde liegenden Vermögenswert (z.B. Bitcoin) möglich ist.
ETFs werden als börsengehandelte (Exchange-Traded) Fonds bezeichnet, weil sie genau wie Aktien an einer Börse gehandelt werden. Die meisten ETFs sind so strukturiert, dass sie, ähnlich wie traditionelle Investmentfonds, mehrere zugrunde liegende Vermögenswerte halten und nicht nur einen, wie es bei einer Aktie der Fall ist. Da ETFs aus mehreren Vermögenswerten bestehen können, werden sie oft als beliebtes Mittel zur Diversifizierung des Portfolios genutzt. Auf der anderen Seite eröffnen ETFs Anlegern auch die Möglichkeit in einen Rohstoff zu investieren, ohne diesen physisch erwerben zu müssen. Anstatt sich Gold in den Tresor zu legen, kann man in seinem Portfolio also z.B. den GLD ETF kaufen, der den aktuellen Preis von Gold nachbildet. Ausser in Deutschland, da geht das nicht, denn da ein Gold-ETF, der nur einen Vermögenswert abbildet, naturgemäß nicht diversifiziert ist, ist er gemäß deutschem Gesetz nicht zugelassen, da Fonds zur Diversifikation verpflichtet sind.
ETFs haben den Vorteil, dass sie kostengünstig sind (wenn man z.B. den kompletten DAX abbilden möchte, reicht ein ETF, welcher genau das tut, anstatt verschiedene Gewichtungen von 40 verschiedenen Unternehmen zu kaufen - das spart Zeit und vor allem Gebühren), dass sie Produkte abbilden, die ein Käufer unter normalen Umständen nicht erlaubt wäre zu kaufen (z.B. darf nicht jeder Anleger in Bitcoin investieren, weil sonst Lizenzen nötig wären) und sie haben den Vorteil, dass sie über den gleichen Broker oder Service gehandelt werden können, wie andere Wertpapier-Investitionen. Der letzte Punkt ist natürlich wichtig für Neueinsteiger, da sie keine zusätzlichen Kosten haben, wenn sie ihr Wertpapierdepot nutzen können und zusätzlich bietet dieser Korridor für viele traditionelle und konservative Anleger ein gewisses Gefühl von Schutz. Diese ganze cRyPto-Welt mit ihren Plattformen, Exchanges, Casinos und Teppichhändlern ist im besten Fall schwer durchsichtig und im schlimmsten Fall mutet sie kriminell an. Doch wenn ich mir "Bitcoin" über mein Depot bei Charles Schwab, der Sparkasse, oder Flatex kaufen kann, fühlt sich das natürlich legitim und sicherer an.
Der Finanzdienstleister muss den zugrundeliegenden Vermögenswert dabei vollumfänglich besitzen, mit dem grossen ABER, dass der Vermögenswert auch verliehen werden kann. Warum das ein Problem sein könnte, besprechen wir später.
Ähnlich wie ein Gold ETF bietet ein Bitcoin ETF Anlegern also die Möglichkeit mit Bitcoin zu handeln, in Bitcoin anzulegen und Bitcoin auszuprobieren, ohne Bitcoin tatsächlich zu kaufen. Ob das gut oder schlecht ist, besprechen wir auch später.
### ETF Wasserfall
Nachdem die Nachricht über BlackRocks Antrag publik wurde, kamen auch etliche andere Finanzdienstleister hervor und stellten (neue) Anträge.[WisdomTree](https://www.sec.gov/ix?doc=%2FArchives%2Fedgar%2Fdata%2F1850391%2F000121465923008647%2Fp620230s1a2.htm) hatten bereits zuvor schon einige Anläufe gebraucht, um ihre Anträge für Bitcoin-Spot-ETFs bei der SEC einzureichen und unterhalten schon ähnliche Produkte in anderen Ländern. Aber auch Fidelity, Invesco, Valkyrie oder [ARK](https://x.com/EricBalchunas/status/1674055780058771463) zogen unter anderem nach und stellten neue Anträge, natürlich nicht, ohne sich bei der Formulierung dieser eine Scheibe bei BlackRock abzuschneiden.
Die SEC hatte zuvor jegliche Anträge auf Bitcoin-Spot-ETFs abgelehnt, hingegen andere Bitcoin-verbundene Produkte, die gehebelte (BITX) und ungehebelte Bitcoin-Futures-Kontrakte (BITO) nachbilden, zugelassen. Auch gibt es eine handvoll ETFs, die börsennotierte Mining-Unternehmen bündeln, oder anderweitige Verbindung zum Bitcoin-Ökosystem suchen, indem sie Anteile von Unternehmen bündeln, die im weitesten Sinne mit Bitcoin in Berührung kommen (z.B. MSTR oder SQ). Eine Genehmigung eines Antrags auf Bitcoin-Spot-ETF hat es also bis heute durch die SEC noch nicht gegeben.
### Der Standpunkt der SEC ###
Wie ich schon in einem ➡️ [früheren Artikel](https://www.genexyz.org/post/1722193843734/) beschrieben habe, ist der Standpunkt der SEC nur teilweise nachvollziehbar.
> Die offizielle Begründung der SEC sind Bedenken in Bezug auf Marktmanipulation, Betrug, Liquidität und Transparenz. Die hauptauschlaggebenden Argumente sind mangelnde Preiserkennung durch hohe Volatilität, wiederum erzeugt durch einige unbekannte große Accounts und die steigende Zahl der Derivate-Produkte rund um Bitcoin, sowie die vielen unregulierten Börsen. Besonders letztere würde die SEC gerne unter ihre Kontrolle bringen. Das bedeutet bis Coinbase, Gemini, Kraken (oder andere große US Börsen) sich nicht bei der SEC registrieren und sich der SEC Regulierung unterwerfen, ist es unwahrscheinlich, dass die SEC einen Spot-ETF genehmigen wird. Dieses Argument ist schwer haltbar, da große Börsen wie Binance, FTX, oder BitMart nicht in den USA registriert sind, und kombiniert ein Vielfaches der in den USA beheimateten Börsen an Handelsvolumen umsetzen.
“[T]here’s a lot of work to be done to really protect the investing public.” - Gary Gensler, SEC Chair
> Vorgeschoben wird also bei alledem immer der Schutz der Anleger. Ob dies eine schlüssige Argumentation ist, darf man ruhig in Frage stellen. Denn ein Bitcoin-Spot-ETF würde vielen Anlegern erlauben Bitcoin in ihr Portfolio aufzunehmen, ohne größeren Spekulationen ausgesetzt zu sein, wie das jetzt mit schon zugelassenen Produkten der Fall ist.
Darüber hinaus hat die SEC vielerorts erwähnt, dass sie bestrebt sind, mit Unternehmen aus der Branche einen regulatorisch klaren Weg zu finden, damit Unternehmen ihre Tätigkeiten im Sinne der SEC auszuüben. Das bezieht sich meist auf die Börsen, die nach eigenen Angaben seit Jahren versuchen, einen rechtlichen Rahmen zu schaffen, der ihnen Planungs- und Rechtssicherheit bietet. Dieser Punkt ist später nochmal wichtig. Das Problem hierbei besteht in der Natur dieser Unternehmen. Denn fast ausnahmslos sind alle betroffenen Unternehmen (wie z.B. Coinbase, Kraken, Binance, etc.) keine Bitcoin-Unternehmen, sondern Digital Assets-Unternehmen, die eben auch den Handel mit Shitcoins, Stablecoins und auf diesen Assets basierende Derivate erlauben (und vor allem wollen).
Jetzt wissen wir also, was ein ETF ist. Aber wie schaut der von BlackRock (und damit auch der anderen Finanzdienstleister) vorgeschlagene Bitcoin-Spot-ETF im Detail aus?
### Bitcoin ETF ###
Das von BlackRock vorgeschlagene Produkt, und damit auch die der anderen - wie wir wissen, haben die anderen Anbieter ihre Anträge nachgebessert und dem von BlackRock weitestgehend angepasst - soll das Grantor-Trust-Modell übernehmen und seine Struktur dem von Gold-Investment-Trusts nachempfinden. Das bedeutet, dass der Besitz von Anteilen am Bitcoin-ETF für steuerliche Zwecke dem Besitz des zugrunde liegenden Vermögenswerts gleichkommt. Des Weiteren ist eine Rücknahmefunktion in Form von Sachleistungen vorgesehen. Das bedeutet vereinfacht, dass Anleger ihre Anteile auch direkt in Bitcoin umwandeln können. Anders als bei z.B. GBTC (➡️ [#5 // Block 742956 // GBTC, ETF & SEC](https://www.genexyz.org/post/1722193843734/)), müssen Anteile nicht erst verkauft werden, um mit den (potentiellen) Profiten bitcoins zu kaufen. Denn der Verkauf von Anteilen an GBTC (oder ähnlichen Modellen) führt nämlich ein steuerpflichtiges Ereignis herbei, wohingegen eine Umwandlung im BlackRock Modell steuerfrei zu vollziehen ist.
Aber, und dies ist ein großes ABER, kommen nur autorisierte Kunden von BlackRock in den Genuss dieser Sachrücknahmen (Umwandlungen). D.h., im Wesentlichen können nur große Investmentfirmen mit guter Reputation Anteile in Bitcoin umtauschen, alltägliche Anleger (Depot bei Charles Schwab, der Sparkasse, oder Flatex) hingegen sind nicht in der Lage diesen tollen Steuertrick anzuwenden. Die erzeugt einen Vorhang vorgespielter Transparenz ("natürlich können alle Anteile direkt in 'physische' bitcoins getauscht werden"), wohingegen ein Großteil der zugrundeliegenden bitcoins nicht wirklich eingefordert werden wird.

Es sind sich alle einig, dass ein Bitcoin-Spot-ETF ein Winner-takes-all-market ist. Das heisst, der Anbieter, dessen Antrag als erstes von der SEC genehmigt wird, wird uber kurz oder lang den Markt fuer Bitcoin-ETFs fuer sich entscheiden, bzw. beherrschen.
### SEC vs. Binance
Kurz bevor BlackRock ihren Antrag auf einen Bitcoin-Spot-ETF einreichten und damit die SEC in die Schlagzeilen der Finanz- und Bitcoin Welt geriet, machte die SEC in der Bitcoin- und Digital Assets-Welt schon von sich hören, als sie kurz hintereinander gegen Binance und Coinbase Anklage erhob.
https://www.sec.gov/news/press-release/2023-101
Binance ist die zurzeit größte Börse für Digitale Assets der Welt. Binance bietet jedoch nicht nur den Handel mit Krypto-Werten, sondern auch eine Reihe von gehebelten Produkten, eigener Coins und Tokens, usw. an (Shitcoin-Casino).
> “Through thirteen charges, we allege that Zhao and Binance entities engaged in an extensive web of deception, conflicts of interest, lack of disclosure, and calculated evasion of the law.” - Gary Gensler, Chairman, SEC
Vor allem ist Binance kein in den USA registriertes Unternehmen. Lediglich ein Schwesterunternehmen, Binance.us, ist offiziell in den USA registriert und hat offiziell und nach eigenen Angaben mit den Geschäften des Hauptunternehmens direkt nichts zu tun.
Die SEC klagt Binance also nicht nur wegen ihrer Angebote im Krypto-Sektor an, sondern erhebt spezifische Vorwürfe der Irreführung und Täuschung von Kunden, des Betreibens von unregistrierten Börsen, Clearingstellen und Broker-Dealer Aktivitäten, sowie Verstrickungen mit Binance.us (einer Handelsbörse, die wie gesagt offiziell unabhängig von Binance agieren soll), sowie dem Washtrading und dem Verkauf von unregistrierten Wertpapieren (mehr zu dem Thema Securities hier ➡️ [#24 // Block 773750 // Commodity vs. Security](https://www.genexyz.org/post/24-block-773750-commodity-vs-security-2xhjjo/)).
> “We allege that Zhao and the Binance entities not only knew the rules of the road, but they also consciously chose to evade them and put their customers and investors at risk – all in an effort to maximize their own profits.” - Gurbir S. Grewal, Director, SEC’s Division of Enforcement
Die SEC argumentiert also Changpeng Zhao (CEO von Binance) und Binance hätten Anleger über ihre Risikokontrollen und korrupten Handelsvolumina in die Irre geführt und gleichzeitig aktiv verschwiegen, wer der eigentliche Betreiber der Plattform ist. Damit hätten Binance-Plattformen ihren Anlegern übergroße Risiken und Interessenkonflikte beschert.
https://www.reuters.com/investigates/special-report/crypto-binance-money
Darüber hinaus wurde in Folge der Anklageerhebung bekannt, dass es bei Geldflüssen bei Binance einen deutlichen Hinweis auf einen Mangel an internen Kontrollen gibt. Interne Kontrollen sollen normalerweise sicherstellen, dass Kundengelder klar identifizierbar und von den Unternehmenseinnahmen getrennt sind. Eine Vermischung von Anleger- und Geschäftsgeldern gefährdet das Vermögen der Kunden, da deren Verbleib verschleiert wird.
Interessanterweise nutzt die SEC weiterhin die Klageschrift gegen Binance, um das Thema 'unregistrierter' Wertpapiere etwas zu erhellen. Zuvor hatte die SEC sich nur in wenigen Einzelfällen dazu geäußert, welche Digitalen Assets sie als unregistrierte Wertpapiere betrachtet, doch in der Anklageschrift werden SOL, ADA, MATIC, FIL, ATOM, SAND, MANA, ALGO, AXS, COTI, BUSD, and BNB explizit als solche bezeichnet.

Alleine vier der genannten Assets finden sich unter den 10 größten Werten (ausgenommen Stablecoins) und die anderen tummeln sich auch irgendwo in den Top 50. Der aufmerksame Sherlock Holmes wird bemerkt haben, dass es dünn wird für den "kRyPtO"-Markt. Unter den Top 10 bleiben noch 3 Proof-of-Work Coins, von denen einer den [Howey-Test](https://www.genexyz.org/post/24-block-773750-commodity-vs-security-2xhjjo/#:~:text=Produktkategorie%20zuordnen%20lassen.-,Der%20Howey%20Test,-In%20den%20USA) nicht erfüllt (und es ist nicht Doge), Ripple (XRP) und die SEC stehen schon seit 2020 vor Gericht und meiner Meinung nach ist es nur noch eine Frage der Zeit, bis die SEC sich bzgl. Ethereum äußern muss (wird).
### SEC vs. Coinbase
Nur einen Tag nach Veröffentlichung der Pressemitteilung, dass die SEC Anklage gegen Binance erhebe, veröffentlichte die SEC die nächste Pressemitteilung: Die SEC erhebt auch Anklage gegen Coinbase, die größte in den USA registrierte Börse für den Handel mit Digital Assets.
https://www.sec.gov/news/press-release/2023-102
Anders als bei Binance hingegen konzentriert sich die SEC bei der Anklage gegen Coinbase einzig auf den Handel mit unregistrierten Wertpapieren und den damit einhergehenden Dienstleistungen.
> “We allege that Coinbase, despite being subject to the securities laws, commingled and unlawfully offered exchange, broker-dealer, and clearinghouse functions” - Gary Gensler, Chairman, SEC.
Konkret hätten Coinbase gegen bestimmte Registrierungsbestimmungen des Securities Exchange Act und des Securities Act verstoßen. Coinbase hätten seit mindestens 2019 Milliarden Dollar verdient, indem sie den Kauf und Verkauf von unregistrierten Wertpapieren unrechtmäßig erleichtert haben.
Interessant ist, dass die SEC ein weitere Dienstleistung in die Anklage einbaut, die bisher keine Erwähnung gefunden hat: "Darüber hinaus hat Coinbase, wie wir behaupten, sein Staking-as-a-Service-Programm nie gemäß den Wertpapiergesetzen registriert, was den Anlegern erneut wichtige Offenlegungs- und andere Schutzmaßnahmen vorenthält“ (Gensler).
Dies zeigt, dass die SEC, ohne sich bisher explizit zu Ethereum geäußert zu haben, eine Meinung gegenüber Staking vertritt, und zumindest die Bereitstellung von Staking-Services als rechtswidrig erachtet. Dies könnte einer der Gründe sein, dass Ethereum noch nicht ins Rampenlicht gerückt wurde, und zwar, dass die SEC die Anklageschrift gegen die Ethereum-Foundation und damit ein Ungetüm an Financiers (JP Morgan, MasterCard, Consensys, etc.) gründlich vorbereitet, um sich für einen enormen Rechtsstreit wetterfest zu machen. Allerdings scheinen interne Ansichtspunkte und Betrachtungsweisen schon ihren Weg in andere Anklageschriften zu finden.
Darüberhinaus zitiert die SEC mit AXS, CHZ, FLOW, ICP, NEAR, VGX, DASH und NEXO eine weitere Reihe von Shitcoins, die sie als unregistrierte Wertpapiere einstufen und damit den Handel mit selbigen untersagen.
Es gibt immer wieder Erzählungen von Leuten, die mit der Sache betraut sind, dass Coinbase aktiv daran arbeiten, einen gemeinsamen Weg mit der SEC zu finden, das Geschäftsmodell zwischen regulatorisch stabile Leitplanken zu bringen. Oft, wenn diese Erzählungen aus dem Coinbase Camp kommen, heißt es, die SEC sei stur und ließe sich nicht auf die Avancen seitens Coinbase ein. Wiederum andere sagen, dass die SEC schlicht überfordert wäre und Coinbase alles daran läge, schnell eine Lösung zu finden.
> "You simply can’t ignore the rules because you don’t like them or because you’d prefer different ones: the consequences for the investing public are far too great.”
Wenn man allerdings den in der Pressemitteilung zitierten Satz von Gurbir S. Grewal (Director, SEC’s Division of Enforcement) anschaut, wird klar, dass aus Sicht der SEC scheinbar relativ früh und relativ offen kommuniziert wurde, was der rechtliche Rahmen des Möglichen ist. Wahrscheinlich wurden Coinbase auch früh darüber informiert, dass der Handel mit den meisten (oder allen) gelisteten Assets (außer Bitcoin), sowie das Anbieten von Staking als Dienstleistung, nicht mit den Leitplanken konform ist, die die SEC für eine zukünftige, rechtlich stabile Regulatorik des Marktes hält. Doch die freiwillige Einhaltung dieser von der SEC 'lose' formulierten Richtlinien hätte für Coinbase das Wegbrechen von 99% ihres Geschäftsmodells bedeutet.
Coinbase listen über 250 handelbare Assets auf ihrer Seite, viele davon lassen sich 'staken', viele weitere Dienste, die Coinbase anbietet, sind von den darunterliegenden Plattformen abhängig. Es ist klar, dass Coinbase den Moment so lange vor sich herschieben wollten, wie eben nur möglich. Denn während Bitcoin als einziges auf Coinbase gehandeltes Asset deutliche YTD Performance an den Tag legt, sinkt die Zahl der auf der Plattform gehaltenen bitcoins zusehends (gut, endlich begriffen!).

Diese Woche dann der Beweis. In einem Artikel der [Financial Times](https://www.ft.com/content/1f873dd5-df8f-4cfc-bb21-ef83ed11fb4d) erklärt Brian Armstrong, CEO von Coinbase, dass die SEC klare Empfehlung ausgesprochen hat, schon bevor sie letzten Monat rechtliche Schritte gegen das Unternehmen einleitete.
> “They came back to us, and they said . . . we believe every asset other than bitcoin is a security,” Armstrong said. “And, we said, well how are you coming to that conclusion, because that’s not our interpretation of the law. And they said, we’re not going to explain it to you, you need to delist every asset other than bitcoin.”
Das ergibt absolut Sinn und stützt meine These, dass die SEC gar nicht vor hat 'gegen' Coinbase zu sein. Vielmehr sieht es aus, als würden sie klarstellen wollen, dass es im geltenden Rechtsrahmen durchaus Platz für gewisse Unternehmen gibt, solange diese sich an geltendes Recht halten und nicht wie Binance offensichtlich gängige Gesetze und Regeln umschiffen. Es scheint, als wolle die SEC den 'Markt' schützen, indem sie betrügerische Firmen wie Binance auf Täuschung, Irreführung und Marktmanipulation verklagt. Gleichzeitig handelt sie bei Firmen wie Coinbase wie ein strenger Vater, der eigentlich das Beste für sein Kind möchte, aber nach wiederholten Versuchen der Gesprächsfindung nur noch harte Strafen als geeignetes Mittel sieht.
Aber warum ist der SEC daran gelegen, dass Coinbase rechtskonform und innerhalb der Leitplanken der SEC handelt?
### Neue ETF Anträge mit Hilfe von Coinbase
[](https://substack.com/redirect/0a08f4c1-6a80-4ae1-90b4-1e3199e65ac1?j=eyJ1IjoiODVmMmUifQ.KSVqr9VEuglgUiJQS3NPaAq4rJnlrYsAHCFywdSyl7A)
Laut eines Berichts des Wall Street Journal hat die SEC auf die hereinbrechende Flut von Anträgen für Bitcoin-Spot-ETFs mit Bedenken reagiert. Sie erklärte zunächst, dass es den Anträgen an Klarheit und umfassenden Informationen mangele und diese somit unzureichend seien.
Die SEC hatte schon bei früheren (abgelehnten) Anträgen u.a. ihre Bedenken bezüglich der Überwachung der Handelsplattformen geäußert. Wie oben beschrieben, ist die mögliche Marktmanipulation durch unregulierte Börsen einer der Hauptgründe seitens der SEC gewesen, frühere Anträge abzulehnen. Allerdings war man davon ausgegangen, dass diese Bedenken der SEC durch eine Vereinbarung zur gemeinsamen Überwachung des Marktes durch eine regulierte Spot-Bitcoin-Handelsplattform in Zusammenarbeit mit einem der US-Handelplätze (Nasdaq, NYSE, CBOE, etc.) ausgeräumt werden könnten.
https://www.reuters.com/technology/us-sec-accepts-six-spot-bitcoin-etf-proposals-review-2023-07-19
Dementsprechend teilte die SEC den Börsen (und Antragstellern) mit, dass in den eingereichten Unterlagen wichtige Details bezüglich der genauen Vereinbarung zur gemeinsamen Umsetzung der Überwachungsvorhaben fehlten. Diese Nachricht wurde von vielen Beobachtern als negativ eingestuft: "Die SEC versteht nicht, was hier erreicht werden soll. Die SEC stellt sich quer. Die SEC ist automatisch gegen Bitcoin." war die Essenz der meisten Reaktionen. Allerdings lese ich persönlich die Reaktion der SEC ähnlich, wie auch die Anklageerhebung gegen Coinbase. Die SEC spielt ganz klar nach den eigenen formulierten und klar kommunizierten Regeln und versucht den Mitspielern die Leitplanken aufzuzeigen. Der Tenor scheint klar: "Wir haben euch die Regeln erklärt, nach denen wir mit euch spielen (hört mit der Shitcoinerei auf!). Befolgt diese und wir kommen ins Gespräch."
https://www.theblock.co/post/238944/cboe-reaches-surveillance-agreement-with-coinbase-for-spot-bitcoin-etfs
Wonach die SEC scheinbar explizit zu fragen scheint, ist ein sogenanntes Information-Sharing Agreement (ISA), also eine Vereinbarung zum Informationsaustausch. Diese Vereinbarung zwingt eine Handelsplattform dazu, Handelsdaten bis hin zu persönlichen Informationen wie den Namen und den Adressen der Kunden weiterzugeben. Ein solches ISA scheint bislang in den Anträgen gefehlt zu haben, weshalb die SEC auf die Anträge reagierte und diese als unvollständig zurückwies. Mit der neuen Welle an korrigierten Anträgen scheinen die meisten Antragsteller diese Unvollständigkeit behoben zu haben.
**Und wen listet JEDER der Antragsteller als Partner zum Informationsaustausch? Rate, rate? Richtig, Coinbase!**
Die Chicago Board Options Exchange (CBOE), eine Optionsbörse, die u.a. die Anträge zusammen mit den oben genannten WisdomTree, VanEck, Invesco und ARK stellte, erzielte kurzerhand mit Coinbase eine Einigung über die Bedingungen für den Abschluss eines ISA und reichte alle Anträge mit den neuen Bedingungen erneut ein.
Wie wir also sehen, deutet alles darauf hin, dass die SEC einem Bitcoin-Spot-ETF eigentlich positiv geneigt ist, sollten die Konditionen, die sie stellt, erfüllt sein. Und in Garys perfekter Welt, sehen diese Konditionen vor, dass ein solcher ETF mit Hilfe von Coinbase als Informations-Austauschs-Partner funktioniert, und dass Coinbase ein artiges in den USA börsennotiertes Unternehmen wird, dass keine Shitcoinerei betreibt und sich auf den Spot-Handel mit Bitcoin konzentriert. Denn die derzeit anderen angebotenen Services wie Clearingstellen und Broker-Dealer-Aktivitäten stehen im direkten Gegensatz zu potenziellen Aktivitäten und Interessen von Kunden.
Wir sehen also, dass ein "größerer Plan" hinter den Aktionen der SEC zu stehen scheint. Meiner Meinung nach gibt es verschiedene Theorien und Hinweise, die darauf schließen lassen, dass die SEC a) den Markt regulieren will, bevor sie ein BlackRock-Produkt genehmigt, b) ausländische (und damit nicht leicht regulierbare) Unternehmen aus dem Markt drängen will, um damit Unternehmen wie BlackRock den Handel zu vereinfachen und c) andere Interessengruppen an der Entscheidung der SEC beteiligt zu sein scheinen. Man könnte so weit gehen zu behaupten, dass anhängige Klagen und Untersuchungen ein Stück weit sogar den Kurs drücken und Bitcoin in der allgemeinen Wahrnehmung, als riskant dastehen lassen, was Unternehmen wie Blackrock dabei hilft die nötigen bitcoins zu einem relativ günstigen Preis zu akkumulieren, bevor eine Genehmigung und die implizite Anerkennung von Bitcoins Wert dazu führen, dass der Preis rasant steigt. Dies wäre ein Eingriff in den Wettbewerb und gibt BlackRock et al einen klaren Vorsprung gegenüber anderen Institutionen.
Es gibt unterschiedliche Ansichten darüber, wie Coinbase und die SEC mit dieser Situation umgehen. Einige behaupten, dass Coinbase aktiv nach einer Lösung sucht, um sich mit der SEC auf einen rechtlichen Rahmen zu einigen, während andere sagen, dass die SEC unbeugsam ist. Es wird vermutet, dass die SEC Coinbase frühzeitig darüber informiert hat, welche Regeln und Leitplanken sie für den Markt etablieren möchten.
https://x.com/BitcoinMagazine/status/1679887574934999045
Es scheint, dass die SEC den Markt schützen möchte, indem sie gegen betrügerische Unternehmen wie Binance vorgeht, die gängige Gesetze und Regeln umgehen. Gleichzeitig versucht sie bei Unternehmen wie Coinbase, die sich nicht an die geltenden Vorschriften halten, harte Strafen als Mittel zur Durchsetzung der Regulierung einzusetzen. Das scheint nur logisch, wenn man bedenkt, dass BlackRock und die anderen Antragsteller wie WisdomTree, VanEck, Invesco und ARK sich mit Coinbase auf Bedingungen für den Abschluss eines Informations-Austausch-Abkommens (ISA) geeinigt und die Anträge mit den neuen Bedingungen erneut eingereicht haben.

Dies deutet darauf hin, dass die SEC grundsätzlich positiv gegenüber einem Bitcoin-Spot-ETF eingestellt ist, sofern bestimmte Bedingungen erfüllt sind. Diese Bedingungen könnten beinhalten, dass Coinbase als Informationspartner fungiert und dass Coinbase als in den USA börsennotiertes Unternehmen agiert, das sich auf den Spot-Handel mit Bitcoin konzentriert, während andere Dienstleistungen wie Clearingstellen und Broker-Dealer-Aktivitäten vermieden werden sollen.
https://x.com/stackhodler/status/1691531818300809217
Es scheint, dass die SEC eine umfassendere Strategie verfolgt, die darauf abzielt, den Markt zu regulieren, ausländische Unternehmen zu verdrängen und den Handel für Unternehmen wie BlackRock zu erleichtern.
*Mitte letzten Jahres habe ich in einem Artikel schon Grayscales andauernden Versuch, ihren Closed-End-Fund in einen Bitcoin-Spot-ETF zu verwandeln, beschrieben.*
https://www.genexyz.org/post/1722193843734/
Die SEC hatte bereits im Dezember 2021 und im Februar 2022 die Entscheidung über den Antrag auf einen Bitcoin-ETF verschoben, um ihn "sorgfältig zu prüfen". Dann hat die SEC Mitte Juli 2023 bekanntgegeben, dass einem Antrag auf Umwandlung wieder nicht stattgegeben wird. Grayscale kündigten sofort an, die SEC wegen Willkür und Verstoß gegen das Wertpapierbörsengesetz von 1934 zu verklagen.
Diese Klage wurde dann vor dem Bundesberufungsgericht verhandelt und entschieden.

Das Bundesberufungsgericht in D.C. entschied im Oktober, dass das Ablehnen von Anträgen auf eine Umwandlung in einen ETF seitens Grayscale ungerecht, nicht rechtens und willkürlich sei, da die Aufsichtsbehörde nicht erklären konnte, warum sie zuvor ähnliche Produkte zugelassen hat.
Allerdings bedeutet dies nicht, dass Barry Silbert (CEO von DCG) automatisch den Grayscale Trust in einen ETF umwandeln kann. Der Antrag wandert damit nur zurück auf Garys (Vorsitzender der SEC) Schreibtisch. Und das bedeutet, dass die SEC wieder die Möglichkeit bekommt, einer Umwandlung aufgrund anderer Begründungen nicht stattzugeben. Dazu gleich mehr ⬇️.
Außerdem ist fraglich, ob Barry tatsächlich wirklich eine Umwandlung herbeisehnt, denn momentan befinden sich Grayscale in einer sehr angenehmen Lage, die ihnen erlaubt 2% vom NAV (Net Asset Value) an Gebühren zu verlangen. Was bei einem Vermögen von 624.947 Bitcoin einen jährlichen Umsatz von 12.500 Bitcoin, bzw. 475 Million US Dollar bedeutet - für nichts tun.
Es gibt schon [Kampagnen](https://www.redeemgbtc.com), die für eine Auflösung des Trusts kämpfen. Wer sich über die Umtriebigkeiten bei DCG / Genesis / Grayscale (Barry) ein besseres Bild machen möchte, sollte unbedingt den folgenden Thread lesen:
https://x.com/real_vijay/status/1721385528510251182
### Was seit dem geschah
Seit dem letzten Artikel ist gleichzeitig viel und wenig geschehen. Verinnerlichen wir uns meine These - dass die SEC a) den Markt regulieren will, bevor sie ein BlackRock-Produkt genehmigt, b) ausländische (und damit nicht leicht regulierbare) Unternehmen aus dem Markt drängen will, um damit Unternehmen wie BlackRock den Handel zu vereinfachen und c) andere Interessengruppen an der Entscheidung der SEC beteiligt zu sein scheinen - dann ist genau das passiert, was man erwartet hätte.
Die SEC hat ihre Entscheidung zur Genehmigung der ETF-Anträge wiederholte Male verschoben, momentan sieht es so aus, als würde eine Entscheidung im Januar 2024 fällig.
https://bmpro.substack.com/p/sec-delays-etf-again-despite-warning
Die SEC fällt weiter unliebsame Bäume. Bittrex, eine in den USA ansässige Börse, haben angekündigt, ihre Pforten zu schließen.
https://finance.yahoo.com/news/crypto-exchange-bittrex-global-shuts-054643624.html
Kraken wurde von der SEC verklagt - ähnliches Modell wie auch zuvor bei Binance und Coinbase angewandt (sprich: alles okay und tutti, solange ihr die Shitcoinerei an den Nagel hängt).
https://www.nobsbitcoin.com/kraken-sec-lawsuit
Dabei wurden in der Klageschrift die bereits identifizierten Digitalen Assets, die die SEC als unregistrierte Wertpapiere betrachtet, 1 zu 1 wieder aufgeführt.

Doch die größte Überraschung war die diese Woche veröffentlichte Meldung, dass Binance sich in einem Vergleich mit dem US Department of Justice (DOJ) auf eine Zahlung von über 4 Milliarden US Dollar und den Rücktritt CZs (Changpeng Zhao) als CEO von Binance geeinigt habe.
https://www.nobsbitcoin.com/cz-steps-down-as-ceo-of-binance-as-part-of-4-billion-settlement-with-doj
Es ist recht eindeutig, dass es dem Justizministerium (DOJ) hier nicht um den Schutz der Verbraucher geht. Es muss allerdings der Anschein gewahrt werden, dass nicht in Eigeninteresse (dem von BlackRock, hust) gehandelt wird, sondern dass der Eindruck erweckt wird, dass sie tatsächlich etwas Gutes tun, indem sie sich um einen "bad actor" kümmern" - das wird sehr deutlich, wenn man betrachtet, dass sich das Narrativ im Vergleich hauptsächlich auf AML (Anti-Money-Laundering) und Terrorismusfinanzierung konzentriert.
Wie schon aus meiner These ersichtlich, geht auch aus bisherigen Kommentaren der SEC klar hervor, dass die größte Sorge derzeit ausländische Börsen sind, die den Bitcoin-Preis manipulieren können. Binance ist die größte Börse der Welt und hat bis heute erfolgreich außerhalb des Einflussbereichs der US-Regierung operiert. Mit dieser Vereinbarung ist das Problem der Offshore-Kursmanipulation zunächst und zum größten Teil gelöst.
Das BlackRock-SEC-Reptilienmenschen-Playbook ist im vollen Gange. Ausländische Konkurrenz weitestgehend unter Kontrolle ✅

Die SEC scheint außerdem im engen Kontakt mit den ETF-Antragstellern zu stehen. Insbesondere ein Verweis auf eine Änderung der Anträge in Bezug auf "cash" vs. "in-kind creation" hat diese Woche für Diskussionen gesorgt.
https://x.com/EricBalchunas/status/1725559994995573086
Viele börsengehandelte Fonds verlangen von den zugelassenen Teilnehmern, dass sie Anteile in Form von Sachleistungen (in-kind) schaffen , d. h. dass sie ETF-Anteile gegen einen Wertpapierkorb und nicht gegen Bargeld (cash) eintauschen. Die SEC hat jedoch auf eine Formulierung in den Anträgen gedrängt, die genau dise cash-creations zulassen.

Während sich viele auf die minutiöse Gestalt der Inhalte stürzen und eine Genehmigung hineininterpretieren, zieht die SEC hier meiner Meinung nach eine Linie, um eine Unterscheidung zwischen Grayscales GBTC und BlackRock et al. zu schaffen.

Wenn man an ein Playbook glaubt, ist der Grayscale Trust den Teilnehmern ein offensichtlicher Dorn im Auge, weshalb eine Umwandlung zunächst verhindert werden will.
Jetzt muss nur noch Coinbase mitspielen. Aber wenn Binance einen Vergleich erzielen kann, warum nicht auch $COIN? Vielleicht einigt sich die SEC mit Coinbase im Gegenzug für "saftige Geldstrafen" und die Entfernung aller Shitcoins von der Plattform. Im Gegenzug erhält Coinbase den Börsenstatus und wird für die Überwachungsvereinbarung mit BlackRock und den anderen Antragstellern freigeschaltet. Auf einen Schlag würde die SEC die Shitcoins von der einzigen börsennotierten US-Börse entfernen und ein legales (nach ihren Vorstellungen und selbst artikulierten Prinzipien) Fundament für BlackRocks ETF schaffen.
Außerdem würde es mich nicht wundern, wenn Coinbase als weißer Ritter auftritt und ganz barmherzig das US-Business von Binance übernimmt. Natürlich nur, um einem Mitstreiter in schwierigen Zeiten beizustehen. Ich packe es auf jeden Fall auf meine Bingo-Karte für den Zeitraum zwischen jetzt und einer Genehmigung der ETF-Anträge.

Durch die Einigung mit CZ und die Geldstrafe von 4,3 Milliarden US Dollar erleichtert die US-Regierung den Transfer von Bitcoin aus schwachen in starke Hände (Binance ➡️ Coinbase). Binance werden Bitcoin verkaufen müssen, um die Geldstrafe zu bezahlen, während gleichzeitig die Spot-ETFs das Angebot mit amerikanischem Kapital auffüllen können. Schöne Ausführung. Tolles Playbook 👏
Ich bin mir bewusst, dass die oben genannten Ereignisse und Auslegungen der Geschehnisse sehr verschwurbelt daherkommen, jedoch möchte ich meinen virtuellen Alu-Hut vor dem Architekten dieses wirklichen langen Long-Games ziehen.

In der Zwischenzeit arbeiten gewissenhafte Journalisten namhafter Veröffentlichungen (BlackRock PR-Department, hust) daran, die öffentliche Wahrnehmung von Bitcoin zum Positiven zu wenden.
Wurde in den letzten Jahren Bitcoin als riskante Anlage, Klimakiller, Ozean-Kocher, oder schlimmer bezeichnet, wird es jetzt als ein möglicher Bestandteil einer nachhaltigen und zukunftsorientierten Anlagestrategie dargestellt.
https://www.forbes.com/sites/digital-assets/2023/07/08/bitcoin-network-to-reduce-more-emissions-than-its-energy-sources-produce/
Wir (du schlaue/r Leser//in und ich) wissen schon lange, dass die Bitcoin-Branche heute die weltweit am nachhaltigsten betriebene Branche ist und das Bitcoin-Mining als einzige Industrie in dem Bereich kohlenstoffnegativ werden kann. Es ist also offensichtlich, dass Bitcoin ein wichtiger Bestandteil einer nachhaltigen und zukunftsorientierten Anlagestrategie sein kann, aber genau dieses Narrativ wurde jahrelang absichtlich verdrängt (➡️ siehe XRP-gesponsorte [Greenpeace Aktion](https://dailycoin.com/greenpeace-anti-crypto-artist-admits-wrong-on-bitcoin-mining/) anfang des Jahres).


Wir sehen also, dass es nicht nur um eine einfache Genehmigung der Anträge geht, sondern viele Mosaikteilchen gelegt werden, bevor es dazu kommen kann. Viele Zeichen deuten darauf hin, dass viele verschiedene Parteien daran arbeiten, ein Umfeld zu schaffen, dass es bestimmten Gruppen ermöglicht, einen ETF möglichst risikofrei und konkurrenzlos zu platzieren. Dabei werden unliebsame Mitspieler vom Platz gewiesen und anderen Mitspielern werden die Spielregeln nochmal ganz bewusst in Erinnerung gerufen, während gleichzeitig ein Narrativ geschaffen wird, das einen Bitcoin-ETF in glänzendem Licht darstellt.
-----------
Es ist nahezu gewiss, dass es nicht die Frage ist, ob einem Antrag zugestimmt wird, sondern vielmehr, wann dies geschehen wird. Es besteht eine hohe Wahrscheinlichkeit, dass allen Anträgen zeitgleich stattgegeben wird. Dennoch lässt sich erkennen, dass die SEC strategisch Zeit gewinnt, um Binance und andere unerwünschte Akteure vollständig aus dem Spiel zu nehmen und Coinbase in der Zwischenzeit zu dem vorbildlichen Mustersohn zu formen, den sie immer haben wollte.
Da der Markt für Spot-ETFs als "Winner-takes-all" gilt, wird darauf geachtet, dass nicht irgendein Antragsteller das Rennen gewinnt, sondern ein bestimmter - Larry. Hierfür ist es notwendig, Barry vom Spielfeld zu verdrängen, da er einen erheblichen Vorsprung hat, woran Gary offensichtlich arbeitet. Falls sich meine Vermutungen bewahrheiten, werden wir in naher Zukunft einen Bitcoin-Spot-ETF sehen, der von BlackRock dominiert wird. Grayscale und Binance werden keine Rolle im Spiel spielen, während Coinbase als reguliertes, vorbildliches US-Unternehmen davon profitieren wird.
🫳🎤
---
In diesem Sinne, 2... 1... Risiko!

-

@ e7bc35f8:3ed2a7cf
2025-02-03 07:37:44
In a striking contrast of ideals versus actions, former U.S. Secretary of State Hillary Clinton was recently awarded the Medal of Freedom. Yet, it is impossible to forget [what happened in February 2011](https://youtu.be/grFWkyXPfxk), when ex-CIA analyst and well-known dissident Ray McGovern was violently removed by security while silently protesting one of Clinton’s speeches at George Washington University. McGovern’s only act of defiance was standing up and turning his back to Clinton in protest of America’s ongoing wars of aggression. The incident, which unfolded under Clinton’s watch, stands as a stark reminder of the selective nature of so-called freedom and democracy.
The irony of the moment was profound. Clinton's speech [that day](http://www.state.gov/secretary/rm/2011/02/156619.htm) was ostensibly about the brave individuals in Egypt who had stood up against authoritarian rule, using the internet to organize their dissent. The same U.S. government that praised online activism abroad seemed intolerant of peaceful, silent protest within its own borders.
Over the past two decades, mainstream media has pushed a narrative that social media platforms like [Twitter](https://youtu.be/BYSchIVpEJ8), [Facebook](https://youtu.be/UoRspCp5Xn0), and [YouTube ](https://youtu.be/ja-tbqN5-Jk)have played an instrumental role in shaping revolutions and uprisings across the world. From Moldova and Iran to Egypt and Tunisia, reporters with little on-the-ground knowledge have eagerly proclaimed these digital platforms as revolutionary tools of democracy. The only problem? This oft-repeated story is largely[ a myth](https://youtu.be/pFGSplRR7oI).
While journalistic laziness explains some of this exaggeration—reporters compiling their stories from hotel rooms rather than gathering firsthand accounts—the truth runs much deeper. The idea of a "social media revolution" has been deliberately constructed by U.S. State Department-linked NGOs with vested interests in overthrowing governments that do not align with Washington’s geopolitical agenda.
One of the key figures in shaping this narrative is [Evgeny Morozov](https://www.opensocietyfoundations.org/grants/open-society-fellowship?fellow=evgeny-morozov), a former fellow of George Soros’ Open Society Institute and a visiting scholar at Stanford University. Morozov pioneered the concept of the "Twitter Revolution" during the [2009 Moldovan protests](https://slate.com/technology/2012/01/anti-vaccine-activists-9-11-deniers-and-googles-social-search.html), arguing that social media facilitated "flash mobs" and "huge mobilization efforts" against authoritarian regimes. His language, promoted in publications like [Foreign Policy](https://foreignpolicy.com/2009/04/07/moldovas-twitter-revolution/), [The Economist](https://web.archive.org/web/20150504011512/http://www.economist.com/node/12815678?story_id=12815678), and [openDemocracy](https://www.opendemocracy.net/en/the-alternatives-alternative/), laid the foundation for the media’s portrayal of networked protests.
However, even Morozov was forced to later acknowledge flaws in his argument. [He admitted](https://foreignpolicy.com/2009/04/07/more-analysis-of-twitters-role-in-moldova/) that at the time of the so-called "Twitter Revolution" in Moldova, there were only about 70 registered Twitter users in the entire country. Despite this glaring inconsistency, the Western media ran with the story.
The same pattern repeated in the 2009 Iranian unrest, where an alleged flood of 30,000 tweets provided live updates on the protests. [Most of these tweets](https://mashable.com/archive/twitter-iran-election), however, were in English and were posted by newly registered accounts with identical profile pictures—hardly the grassroots digital uprising the media portrayed. Notably, [Israeli news outlets](https://web.archive.org/web/20090714235359/https://chartingstocks.net/wp-content/uploads/2009/06/jpost.jpg) began covering these "tweets" almost immediately, [raising questions](https://web.archive.org/web/20090619154321/http://www.chartingstocks.net/2009/06/proof-israeli-effort-to-destabilize-iran-via-twitter/) about external orchestration.
Similarly, during the Arab Spring, social media was widely credited for fueling protests in Egypt, Tunisia, and Yemen. Yet, the data tells a different story. At the height of these uprisings, the combined number of [Twitter users](https://mashable.com/archive/egypt-twitter-infographic) in those three countries was under 15,000. [Facebook](https://www.theguardian.com/technology/blog/2010/jul/22/facebook-countries-population-use#data), while more widespread, still had only a 4.5% penetration rate in Egypt by mid-2010—dwarfed by the reach of television networks.
Even those who originally championed the "social media revolution" have had to admit that the phenomenon was blown out of proportion. What they refuse to acknowledge, however, is the strategic motivation behind these uprisings. Who benefits from these revolutions, and whose interests do they ultimately serve?
At a [2010 Berlin conference](https://youtu.be/yQ1b67Noy9w), Morozov conspicuously avoided addressing these critical questions. His silence speaks volumes. [The reality is](https://youtu.be/LAlbajRFgUE) that "social media revolutions" are often less about organic uprisings and more about the West’s longstanding practice of using digital tools as part of broader regime-change strategies.
In 2011, for instance, the U.S. State Department funded Psiphon, an online encryption system designed to help users bypass government firewalls. This technology was distributed in Syria, conveniently aiding opposition forces at a time when the U.S. was actively working to destabilize the Assad government. Yet, when Syria was later found using U.S.-developed internet filtering technology, it was condemned for [violating American trade laws](https://web.archive.org/web/20120522162400/https://arabiangazette.com/syria-violating-trade-laws/).
The most glaring hypocrisy is that while U.S. officials champion the internet as a tool for democracy in foreign countries, they simultaneously push for more restrictive internet laws at home. In 2011, Senator Joe Lieberman openly discussed using internet filtering technology to regulate American citizens’ access to information—ironically sounding much like the authoritarian leaders Washington claims to oppose.
This contradiction exposes the true nature of the social media revolution myth. Far from being an organic expression of people’s will, it is often just another weapon in the arsenal of Western powers seeking to manipulate and destabilize governments that refuse to align with their interests. [The very same politicians](https://web.archive.org/web/20130919221400/https://youtube.com/watch?v=OBB1S86_yBY) who praise internet activists in Iran or Syria are the ones clamping down on online freedoms in their own countries.
The story of social media as a revolutionary force is not one of grassroots activism triumphing over oppression. Instead, it is a carefully crafted narrative, used to justify interventionist policies and promote regime change under the guise of "democracy promotion." As history has repeatedly shown, the beneficiaries of these so-called revolutions are rarely the people on the ground—but rather, the geopolitical architects pulling the strings from afar.
-

@ da0b9bc3:4e30a4a9
2025-02-03 06:14:42
Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/874266
-

@ a012dc82:6458a70d
2025-02-03 02:42:01
In the contemporary world, where the balance between technological advancement and environmental sustainability is increasingly crucial, Marathon Digital Holdings has emerged as a trailblazer in the Bitcoin mining industry. Their latest venture, utilizing methane gas from landfill waste to power Bitcoin mining operations, is not just a technological leap but also a significant stride towards eco-friendly practices in a sector often scrutinized for its environmental impact. This initiative represents a fusion of environmental stewardship with the burgeoning field of cryptocurrency, potentially setting a new standard for energy use in digital currency mining. It's a bold move that could reshape perceptions of the industry, demonstrating that environmental consciousness and technological progress can coexist harmoniously.
**Table Of Content**
- The Genesis of the Project
- The Process and Technology
- The Broader Impact
- Conclusion
- FAQs
**The Genesis of the Project**
**A Partnership for Sustainability**
Marathon Digital's collaboration with Nodal Power marks a pivotal moment in the pursuit of sustainable cryptocurrency mining. The 280 kilowatt (kW) pilot project in Utah is more than just a test of feasibility; it's a beacon of innovation in an industry traditionally powered by conventional, often non-renewable, energy sources. This partnership reflects a growing awareness within the crypto mining community about the importance of sustainable practices. It's a forward-thinking approach, blending the expertise of a leading Bitcoin mining company with the innovative energy solutions of a renewable energy firm, setting a precedent for future collaborations in the industry.
**Addressing Environmental Concerns**
The project's focus on methane gas, a potent greenhouse gas, underscores a proactive approach to environmental stewardship. By targeting methane emissions from landfills, Marathon is addressing a critical environmental issue. Methane is not only a significant contributor to global warming but also represents a wasted resource when emitted into the atmosphere. This initiative is a response to increasing global concerns about climate change and environmental degradation. It's a strategy that aligns with international efforts to reduce greenhouse gas emissions and demonstrates Marathon's commitment to playing a role in the global fight against climate change.
**The Process and Technology**
**Innovative Conversion of Methane to Electricity**
The technology behind converting methane to electricity is a cornerstone of this project. The process involves sophisticated systems that capture methane emissions efficiently and convert them into a usable form of energy. This technology is not just a testament to human ingenuity but also a crucial step towards making renewable energy more accessible and practical for industrial applications like Bitcoin mining. The success of this technology could have far-reaching implications, potentially revolutionizing how we think about waste management and energy production.
**A Step Towards Green Bitcoin Mining**
Marathon's initiative is a significant leap in the journey towards green Bitcoin mining. It's a project that challenges the status quo, proving that renewable energy can be a viable alternative to traditional power sources in the energy-intensive process of mining cryptocurrencies. This approach could inspire a wave of innovation in the sector, encouraging other companies to explore renewable energy options. The project is not just about reducing the environmental footprint of Bitcoin mining; it's about reimagining the future of energy use in the digital age.
**The Broader Impact**
**Potential for Industry-Wide Change**
The implications of Marathon's project extend far beyond its immediate environmental benefits. It has the potential to catalyze a paradigm shift in the cryptocurrency mining industry. If successful, this project could serve as a model for other companies, demonstrating the practicality and benefits of sustainable mining practices. It could inspire a wave of innovation, leading to more widespread adoption of renewable energy sources in the industry, and potentially, a redefinition of what it means to be a responsible player in the digital currency space.
**Environmental and Economic Benefits**
The project is not just an environmental initiative; it's also an economically strategic move. By tapping into methane from landfills, Marathon could significantly reduce its operational costs. This approach provides a dual benefit: it mitigates the environmental impact of Bitcoin mining and offers a potentially more cost-effective energy solution. This economic incentive could be a key driver in encouraging wider adoption of similar practices across the industry, leading to a more sustainable and economically viable future for cryptocurrency mining.
**Conclusion**
Marathon Digital's pilot project in Utah is more than just an experiment in sustainable Bitcoin mining; it's a visionary step towards a new era in the industry. By harnessing methane gas from landfills to power their operations, Marathon is not only setting a new benchmark for environmental responsibility but also showcasing the untapped potential of renewable energy in reducing the carbon footprint of cryptocurrency mining. This bold experiment is a beacon of hope and innovation, suggesting a future where technological advancement and environmental sustainability are not mutually exclusive but are instead intertwined elements of a more responsible and forward-thinking industry.
**FAQs**
**What is Marathon Digital's new project about?**
Marathon Digital has launched a pilot project in Utah, using methane gas from landfill waste to power Bitcoin mining operations.
**Why is using methane for Bitcoin mining significant?**
Methane is a potent greenhouse gas, and using it for mining reduces environmental impact and utilizes a renewable energy source.
**Who is Marathon Digital partnering with for this project?**
Marathon Digital has partnered with Nodal Power, a firm specializing in renewable energy assets.
**What are the potential benefits of this project?**
The project aims to reduce greenhouse gas emissions, lower energy costs, and set a precedent for sustainable practices in cryptocurrency mining.
**How does this project impact the Bitcoin mining industry?**
Marathon's initiative could inspire other companies to adopt renewable energy sources, potentially leading to a more sustainable and economically viable mining industry.
**That's all for today**
**If you want more, be sure to follow us on:**
**NOSTR: croxroad@getalby.com**
**X: [@croxroadnews.co](https://x.com/croxroadnewsco)**
**Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)**
**Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)**
**Store: https://croxroad.store**
**Subscribe to CROX ROAD Bitcoin Only Daily Newsletter**
**https://www.croxroad.co/subscribe**
*DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.*
-

@ 3b7fc823:e194354f
2025-02-03 02:19:03
# At-Risk Groups Are Facing A Battle For Their Rights
Privacy. It’s a word we often take for granted, scrolling through our phones and sharing photos without a second thought. But for certain groups—those at risk due to their identities, beliefs, or circumstances—privacy isn’t just a luxury; it’s a lifeline. In today’s world, where governments, corporations, and even our own social media accounts seem to have a vested interest in collecting and selling our data, the fight for privacy has never been more crucial.
Privacy is not a buzzword but a fundamental human right. We can do more to protect those who need it most.
---
### Privacy As A Human Right
The concept of privacy is deeply rooted in our basic human rights. It’s not just about keeping your medical records confidential or hiding your bank statements; it’s about the right to control what others can know about you. For individuals who identify as LGBTQ+, immigrants, journalists, or political dissidents, this right is even more fragile.
Recently, we’ve seen a rise in policies that seem designed to strip away these protections. From the Trump administration’s transgender ban on military service and passport changes to the targeting of journalists and activists, the message is clear: certain groups are considered fair game for scrutiny and control.
These actions are about erasing the autonomy of individuals to live their lives without fear of retribution or discrimination. Privacy isn’t just a feel-good concept; it’s the cornerstone of a individuals liberty. We must ensure that no one’s rights can be arbitrarily taken away, especially the right to privacy.
---
### The Attack On Vulnerable Groups
The targeting of at-risk groups has reached a fever pitch in recent months:
1. **Transgender Rights Under Fire**
The Trump administration has issued a sweeping executive order that effectively erased recognition of transgender individuals’ rights. This included changes to passport policies that required individuals to declare their gender at birth, making it nearly impossible for trans individuals to update their documents without facing extreme scrutiny or even denial.
These actions don’t just impact transgender people; they send a chilling message to the entire LGBTQ+ community.
2. **Free Speech And Political Dissent**
Trump’s Free Speech Executive Order, aimed to protect citizens’ right to express their beliefs. However, critics argue it was more about silencing dissenters. Journalists, activists, and even private citizens have faced increasing pressure from government officials to either comply with certain views or face professional consequences.
“Free speech is a double-edged sword,” noted one legal expert. “When the government uses it as a tool to marginalize certain groups, it becomes a weapon rather than a shield.”
3. **Media And Press Freedom**
Trump’s ongoing battles with major media outlets are well-documented. From labeling reporters as “fake news” to pushing for laws that would limit press freedom, the administration has made it clear that journalists and news organizations are not above scrutiny. For independent journalists and investigative reporters, this poses a significant threat to their work and safety.
4. **Immigrant Rights And Discrimination**
The Trump administration’s harsh immigration policies have had a devastating impact on vulnerable communities. From family separations to the expansion of surveillance in immigrant-heavy areas, these actions have left many feeling exposed and unsafe. Immigrants, particularly those from Latin America and the Middle East, are increasingly targeted for their perceived alignments with political rhetoric.
---
### The Consequences Of Losing Privacy
When privacy is stripped away, it doesn’t just affect individuals—it affects entire communities. For transgender individuals, the fear of being “outted” online or facing discrimination at work is a daily reality. For journalists, the threat of government retribution can lead to self-censorship and an inability to hold power accountable. For immigrants, the risk of deportation or surveillance means constant vigilance—and often, no recourse.
These consequences are not just personal; they’re systemic. When certain groups are deemed unworthy of protection, it sets a dangerous precedent for what’s allowed in society. It sends the message that some lives matter less than others, and that the government can act with impunity. If you are not in one of these currently impacted groups just give it time and eventually they will come for you too.
---
### The Fight For Privacy: What We Can Do
The good news is that we don’t have to sit idly by while this happens. There are steps we can take to fight for privacy as a fundamental right. Here’s how:
1. **Advocate For Stronger Protections**
Governments at all levels need to pass and enforce laws that protect privacy, especially for vulnerable groups. This includes everything from data protection legislation to anti-discrimination policies.
2. **Support Independent Journalism**
Journalists are on the front lines of this fight, uncovering corruption and holding power accountable. Support independent media outlets and platforms that prioritize transparency and press freedom.
3. **Educate And Empower**
Communities under threat need resources to protect themselves. This includes education on their rights, know how and tools to secure their data, and access to legal support when needed.
4. **Use Your Voice**
Speak out against policies that erode privacy and target vulnerable groups. Use your actions to protect yourself and others.
5. **Demand Accountability**
When governments overreach, they need to be held accountable. Fight for yours and others rights.
---
### Privacy Is A Fight Worth Winning
Privacy isn’t just about convenience or comfort—it’s about freedom, autonomy, and the right to live without fear of arbitrary control. For at-risk groups, this is not just a luxury; it’s a lifeline. As we move forward in this uncertain era, let’s remember that the fight for privacy is not over— it’s just beginning.
We all have a role to play in protecting those who need it most. So let’s get to work.
-

@ fd78c37f:a0ec0833
2025-02-03 00:23:23
🔹 Pre-event buzz: Even before the event started, numerous calls came in to confirm the venue and ask if they could bring friends along. Upon arrival, many young attendees were eager to learn more about YakiHonne, reflecting the excitement and anticipation surrounding the meetup.


🔹 Engaging discussions: The event kicked off with an introduction to Nostr and YakiHonne’s core principles, sparking insightful conversations about what it truly means to have a decentralized social media platform.

🔹 Deep dive: Attendees raised many questions, particularly about YakiHonne’s decentralization model. The concept resonated with many, and a large number of participants expressed their support and interest in becoming part of the YakiHonne ecosystem in the future.


The meetup wrapped up with light refreshments 🍹, networking 🤝, and a photo session 📸. Even after the event officially ended, conversations continued as people stayed behind to connect and explore further possibilities ✨.


YakiHonne Meetup was more than just a gathering—it was a step forward in shaping the future of decentralized social media! 🚀
#YakiHonne #Nostr #DecentralizedSocialMedia
-

@ ae6ce958:d0f02c7d
2025-02-02 23:56:18
**Authors**: DamageBDD Research Team
**Date**: February 2025
#### **Abstract**
This paper presents a formal multidimensional analysis of the profitability and systemic impact of operating a DamageBDD node, considering two distinct yet synergistic roles: (1) **BDD Maintainer**, responsible for writing and verifying behavioral-driven development (BDD) test cases, and (2) **Node Runner**, responsible for hosting, validating, and distributing DamageBDD verification data. The study explores the economic viability, systemic benefits, and broader implications for software development efficiency and human potential. We argue that DamageBDD does not merely represent an alternative testing infrastructure but also serves as an incentive structure that unlocks latent human capital through verifiable, high-impact contributions.
---
## **1. Introduction**
The software industry increasingly relies on automated testing to ensure system reliability and security. However, traditional models of test validation suffer from inefficiencies due to lack of **verifiable accountability**, reliance on centralized test infrastructure, and difficulty in aligning developer incentives.
DamageBDD introduces a **market-driven verification layer** that decentralizes and incentivizes **test-driven software development**. By distributing both verification and governance via a **blockchain-based testing economy**, DamageBDD enables **trustless BDD validation**. Two primary participants define this ecosystem:
1. **BDD Maintainers** – Developers and testers who write and maintain test cases to ensure software correctness.
2. **Node Runners** – Operators who maintain DamageBDD nodes to execute, verify, and immutably record test results.
This study examines the **profitability, scalability, and systemic value** of each role while exploring how this model **unlocks testing infrastructure and human potential** in a way that traditional systems do not.
---
## **2. Multidimensional Profitability Analysis**
We evaluate profitability using a **multidimensional framework** across the following key dimensions:
- **Economic Profitability** (direct financial rewards)
- **Computational Efficiency** (resource costs and hardware scalability)
- **Network Effects** (interoperability and systemic adoption)
- **Human Capital Optimization** (learning curve, skill growth, and long-term impact)
### **2.1 Economic Profitability**
#### **BDD Maintainer**
BDD Maintainers earn **sats for verifiable test contributions**. Their work is directly compensated based on the number of **successful test verifications** executed on the DamageBDD network. The economic incentives align with:
- **Quality over Quantity** – High-quality, reusable BDD tests accrue more long-term revenue.
- **Compounding Value** – A well-maintained test suite continues to generate revenue as projects grow.
#### **Node Runner**
Node Runners monetize **test execution and validation services** by processing and storing test results. Profitability derives from:
- **Transaction Fees** – Runners earn sats per executed and verified test case.
- **Reputation Score** – Higher-ranked nodes process more verifications, generating greater earnings.
- **Liquidity Pools** – Nodes can facilitate instant **Lightning Network payouts** for successful tests, further increasing earnings via transaction flow.
### **2.2 Computational Efficiency**
While mining Bitcoin is an **energy-intensive, zero-sum competition**, DamageBDD nodes optimize for **computational efficiency** rather than brute-force expenditure.
- **BDD Maintainer Efficiency** – Writing test cases has near-zero energy cost beyond human intellectual effort.
- **Node Runner Efficiency** – Instead of wasting cycles on proof-of-work, DamageBDD nodes run lightweight BDD verifications, leveraging Erlang for extreme concurrency and low-resource execution.
A comparative analysis shows that operating a DamageBDD node **delivers higher computational efficiency per satoshi earned** than Bitcoin mining.
---
### **2.3 Network Effects and Synergies**
A crucial factor in DamageBDD’s economic model is **network value accumulation**. Unlike mining, which **diminishes profitability over time**, DamageBDD’s network **increases in value as adoption grows**.
#### **BDD Maintainer Synergies**
- The more tests written and **verified on-chain**, the greater the **trust in software systems**.
- Open-source contributors and enterprise teams benefit from **immutable test history**, reducing redundant labor.
#### **Node Runner Synergies**
- The more tests executed, the **more valuable the verification layer becomes**.
- Nodes reinforce the **integrity of test results**, leading to network-wide adoption in **high-assurance industries** (e.g., finance, healthcare, AI safety).
---
### **2.4 Human Capital Optimization: Unlocking Developer Potential**
Traditional software testing is often seen as a **cost center**, leading to its underutilization. DamageBDD flips this paradigm by treating testing as a **profit center**—rewarding testers not just for finding bugs but for **preventing catastrophic software failures**.
#### **Cognitive and Economic Impact**
- **Skill Growth** – Developers naturally **improve software design** by maintaining structured BDD tests.
- **Career Upskilling** – High-ranking BDD Maintainers become **indispensable assets** in software teams.
- **Economic Independence** – Unlike traditional employment, DamageBDD allows maintainers to **earn directly from open-source contributions**.
The system **gamifies quality assurance**, transforming what was once a tedious process into a **competitive and rewarding marketplace**.
---
## **3. Conclusion: A New Paradigm for Profitable Verification**
DamageBDD redefines software testing as a **financially viable, decentralized economy**. The combination of BDD Maintainers and Node Runners creates a **self-reinforcing ecosystem** where:
- **Maintainers ensure software correctness while earning sats**
- **Node Runners validate and secure test results, generating a sustainable revenue stream**
- **The network grows in value as more applications integrate DamageBDD verification**
### **Key Takeaways**
- **DamageBDD is superior to traditional testing models** due to its decentralized incentives.
- **It provides better computational efficiency than Bitcoin mining** while still operating on a proof-of-work foundation (verifiable contributions).
- **It unlocks human potential** by turning software verification into a **career pathway rather than a sunk cost**.
The profitability of DamageBDD Nodes extends beyond mere financial returns—it establishes a new **economic and intellectual order for software reliability**.
-

@ 3b7fc823:e194354f
2025-02-02 22:55:32
# The Secret to Staying Private in the Digital Wild West: A Guide to Using Encryption
You’re scrolling through social media, and suddenly you realize your phone’s been tracking your location and displaying it on your profile for months. You’re not even sure how that happened. Or maybe you’ve noticed that every time you shop online, the item you looked for follows you around with ads wherever you go. Sound familiar? Yeah, welcome to the digital world—where your data is basically a free buffet for anyone who knows how to ask.
But here’s the thing: you don’t have to sit back and take it. Encryption is like the secret weapon that lets you lock up your data and keep those prying eyes out. It’s not just for hackers or spies—it’s for regular people who want to take control of their privacy in a world that’s increasingly looking like a reality show where everyone’s a contestant.
### What Is Encryption, and Why Should You Care?
Encryption is like a secure box that only you can open. When you use encryption, your data is scrambled in a way that’s hard for anyone else to read, even if they try. Think of it as putting on a metaphorical cloak that makes your online activity invisible to just about everyone except the people you want to see it.
For example, when you browse the internet, your connection is often not encrypted by default. That’s why websites start with “https” to indicate a secure connection—it’s saying, “Hey, we’re using encryption here!” Without that little green padlock, anyone on the same WiFi could potentially spy on what you’re doing.
So, encryption isn’t just for tech geeks or government agencies. It’s for everyone who wants to protect their data from being sold, stolen, or misused without their consent. And guess what? You’re already using it without realizing it. Every time you use a password-protected account or send an encrypted message, you’re reaping the benefits of encryption.
### The Privacy Advantages of Encryption for Regular People
Let’s break down why encryption is your best friend when it comes to privacy:
1. **Financial Transactions**
When you pay online or use a banking app, encryption keeps your financial info safe from hackers. It ensures that only the banks and businesses you’re dealing with can access your money—no one else can.
2. **Online Accounts**
Your email, social media, and other accounts often use encryption to protect your login details. That’s why you see those little “lock” icons when you’re logging in. Without encryption, someone could potentially intercept your password and gain unauthorized access to your account.
3. **Data Breaches**
Encryption can often prevent data breaches from being useful. Even if hackers manage to steal your information, the encryption makes it unreadable, so the stolen data is basically worthless to the attackers.
4. **Location Data**
If you’re worried about apps tracking your every move, encryption can help limit how much of that data is accessible. Some apps use encryption to protect location data, making it harder for companies to sell your movements without your consent.
5. **Privacy Protection**
Encryption acts as a layer of protection against invasive technologies. For example, some apps use tracking software that follows you around the internet based on your browsing history. With encryption, these trackers can be blocked or limited, giving you more control over what information is collected about you.
### How to Use Encryption Like a Pro
Now that you know why encryption is essential for privacy, let’s talk about how to use it effectively:
1. **Use Strong Passwords**
Encryption works only if your passwords are strong and unique. Don’t reuse passwords from one account to another, and avoid using easily guessable information like “password123” or your birth year. Use a password manager if you need help keeping track of them.
2. **Enable HTTPS Everywhere**
Install browser extensions like HTTPS Everywhere to automatically encrypt your connections to websites that don’t support encryption by default. This ensures that even if you’re not actively thinking about it, your data is still protected.
3. **Look for the Lock Icon**
Whenever you’re on a website or app, look for the lock icon in the URL bar. Make sure it’s encrypted before you input any personal information.
4. **Use Encrypted Communication Tools**
For private conversations, use apps like Signal or SimpleX, which are designed with encryption in mind. These tools ensure that only the sender and recipient can read your messages, keeping them safe from prying eyes.
5. **Enable Two-Factor Authentication (2FA)**
This isn’t exactly encryption, but it’s a close second. 2FA adds an extra layer of security by requiring you to provide two forms of verification—like your password and a code sent to your phone—to access your account. While not encryption itself, it works alongside encryption to keep your accounts secure.
6. **Use Encrypted Storage and Backup**
When storing sensitive files or data, use encrypted cloud storage or external drives. Tools like BitLocker (for Windows) or AES-256 encryption can protect your files from unauthorized access.
7. **Stay Updated**
Encryption technology is always evolving, so it’s important to keep your software and apps updated. Outdated systems are often easy targets for hackers, leaving you vulnerable to attacks.
### Final Thoughts: Your Data Is Your Power
In a world where data is a commodity, encryption is your weapon against the invasive tactics of corporations and hackers alike. It empowers you to control what information you share and protects you from having it used against you. So, whether you’re shopping online, using your favorite apps, or just browsing the web, remember that encryption is there to help you stay private and in control of your own data.
And if you ever feel overwhelmed by all the privacy stuff, just remember this: you’re not alone. Millions of people are fighting for stronger privacy protections every day. So, do your part by using encryption wisely—your data and your privacy are worth it. Let’s make sure no one can take that away from you.
---
**Advocating for privacy does not finance itself. If you enjoyed this article, please consider zapping or sending monero**
82XCDNK1Js8TethhpGLFPbVyKe25DxMUePad1rUn9z7V6QdCzxHEE7varvVh1VUidUhHVSA4atNU2BTpSNJLC1BqSvDajw1
-

@ 8d34bd24:414be32b
2025-02-02 21:31:11
This Sunday our pastor had to give a sermon with very little preparation. He was leading an elders’ retreat and one of the elders was supposed to preach in his place. The elder who had prepared a sermon ended up in the hospital, so our pastor had to prep fast. He did a great thing. He preached on a passage, but also used that passage to demonstrate how he studies scripture. It was a great sermon. The passage he preached on reminded me of a time in my past when I learned some important lessons.
Almost 20 years ago, I was leading a high school girls Bible study. They picked out a book about Mary and Martha to study. Initially, I wasn’t thrilled with their choice, but didn’t have a theological problem with it, so I agreed for us to study this book. (I don’t remember the name of the book and all my books burnt up when my house burnt down almost 10 years ago). In the end, I probably got more out of the study than any of the girls because I have a definite tendency to be a Martha. What was Martha’s error? Let’s check out the passage:
> Now as they went on their way, Jesus entered a village. And a woman named Martha welcomed him into her house. And she had a sister called Mary, who sat at the Lord’s feet and listened to his teaching. But Martha was distracted with much serving. And she went up to him and said, “Lord, do you not care that my sister has left me to serve alone? Tell her then to help me.” But the Lord answered her, “Martha, Martha, you are anxious and troubled about many things, but one thing is necessary. Mary has chosen the good portion, which will not be taken away from her.” (Luke 10:38-42 ESV)
Jesus visited two sisters who welcomed Him into their home. Mary sat at Jesus’s feet and listened to His teaching. Martha spent her time serving everyone and taking care of everyone’s physical needs.
Is taking care of their home and the needs of their guests a bad thing? Of course not, but is it the best?
To make things much worse, Martha then got upset because her sister Mary wasn’t helping her. She was just sitting there taking in every word that Jesus said. Most of us would think Martha’s sacrifices to take care of everyone was better than Mary’s choice to just sit at Jesus’s feet, but did Martha really choose the better path?
Martha then showed that her heart wasn’t focused right and she wasn’t putting the most important things first. She complained to Jesus about her sister’s failure to help and even commanded her Creator, “*Tell her then to help me*.” Instead of focusing on the words of Jesus, her frustration led her to command her God to act in the way she desired. She was so busy with cooking, cleaning, and serving, that she missed the most important things — spending time with and listening to her God, who was right there in her house with her. This was an opportunity that shouldn’t be missed due to busyness.
How often do we all do this same thing? How often are busy doing good things and miss the most important things? How often are we busy doing ministry that we forget about the reason for the ministry? I don’t know about you, but this happens to me a lot more often than I would like to admit. My biggest sins are usually not what most people think of as sins. My biggest sins are getting so busy that I leave God out of my life. I am so busy serving God that I forget to follow His leading. I am so busy doing what most people would consider good things, but if God is not part of them, they are not worth much. Because I am focusing on getting things done, worry and stress overtake me harming my health and my relationship with Jesus.
I don’t think this is taking Scripture out of context:
> We have come to know and have believed the love which God has for us. **God is love**, and the one who abides in love abides in God, and God abides in him. (1 John 4:16) {emphasis mine}
Knowing that God is love, read the following passage replacing ***love*** with ***God***.
> If I speak with the tongues of men and of angels, but do not have ***love***, I have become a noisy gong or a clanging cymbal. If I have the gift of prophecy, and know all mysteries and all knowledge; and if I have all faith, so as to remove mountains, but do not have ***love***, I am nothing. And if I give all my possessions to feed the poor, and if I surrender my body to be burned, but do not have ***love***, it profits me nothing. (1 Corinthians 13:1-3)
If I do not include God in my every action, “*it profits me nothing*.”
In reality it shouldn’t be allowing God to join me in my works, but me joining God in His works. It should be me listening to God’s word and the leading of the Holy Spirit, looking and seeing what God is doing around me, and me joining in His great works. It should be me allowing God to use me as a tool.
There are times that God speaks clearly and directly to us about what He desires for our lives, but most of the time, He speaks through His word — the Bible. Knowing the Bible helps us to know His will and His eternal plan, so we can follow Him and join Him in His work. Knowing the Bible helps us to differentiate between what is good and what is God’s best. It helps us to prioritize what is really important.
> And this I pray, that your love **may abound still more and more in real knowledge and all discernment**, so that you **may approve the things that are excellent**, in order to be sincere and blameless until the day of Christ; having been filled with the **fruit of righteousness which comes through Jesus Christ**, to the glory and praise of God. (Philippians 1:9-11) {emphasis mine}
We can’t obey God, imitate Christ, or follow Him if we refuse to listen and that means spending time in the Bible and time in prayer with Him.
> “Listen to Me, you stubborn-minded, Who are far from righteousness.” (Isaiah 46:12)
> Come, you children, listen to me; I will teach you the fear of the Lord . (Psalm 34:11)
> “Now therefore, O sons, listen to me, For blessed are they who keep my ways. (Proverbs 8:32)
> But seek first His kingdom and His righteousness, and all these things will be added to you. (Matthew 6:33)
Our focus on Jesus/God must go beyond knowing Him. It is equally important to obey.
> And He \[Jesus\] said to another, “Follow Me.” But he said, “Lord, permit me first to go and bury my father.” But He said to him, “Allow the dead to bury their own dead; but as for you, go and proclaim everywhere the kingdom of God.” (Luke 9:59-60) \[clarification mine\]
Once we know what He wants from us, we need to instantly drop what we are doing and follow Him. We can’t put other things ahead of obeying God.
> For amazement had seized him and all his companions because of the catch of fish which they had taken; and so also were James and John, sons of Zebedee, who were partners with Simon. And Jesus said to Simon, “Do not fear, from now on you will be catching men.” When they had brought their boats to land, **they left everything and followed Him**. (Luke 5:9-11) {emphasis mine}
We should be like these apostles, that, after their most successful catch of fish in their entire career as fishermen, “*they left everything and followed Him*.” We need to let go of what we think is important and obey Him. We need to change our priorities to match God’s priorities.
That may mean we change careers to one that allows more free time for ministry or even going into full time ministry. It may mean letting go on keeping the perfect, clean house, so there is time for ministry, Bible study, or discipling our kids. It may mean changing your habits from watching TV with your family to reading the Bible with your family. For each of us, it will look different, but we need to be like Mary and choose to sit “*at the Lord’s feet and listened to his teaching*.” We need to be like the apostles who “*left everything and followed Him*.” We need to choose to put Jesus’s plans before our own. We need to choose to make God’s values our values.
> But this is what I commanded them, saying, ‘Obey My voice, and I will be your God, and you will be My people; and you will walk in all the way which I command you, that it may be well with you.’ (Jeremiah 7:23)
Like so many things, it is simple, but it isn’t necessarily easy. We have to change the way we think in order to obey faithfully.
> If anyone serves Me, he must follow Me; and where I am, there My servant will be also; if anyone serves Me, the Father will honor him. (John 12:26)
We have to change our priorities to God’s priorities.
> Then Jesus said to His disciples, “If anyone wishes to come after Me, he must deny himself, and take up his cross and follow Me. (Matthew 16:24)
We need to seek God, His word, and His presence.
> As the deer pants for the water brooks,\
> So my soul pants for You, O God.\
> My soul thirsts for God, for the living God;\
> When shall I come and appear before God? (Psalm 42:1-2)
We need to be in God’s word daily, so we know who God is and what He desires from us.
> How can a young man keep his way pure?\
> By **keeping it according to Your word**.\
> With all my heart I have sought You;\
> Do not let me wander from Your commandments.\
****Your word I have treasured in my heart**,\
> That I may not sin against You.\
> Blessed are You, O Lord;\
****Teach me Your statutes**.\
> With my lips I have told of\
> All the ordinances of Your mouth.\
> I have rejoiced in the way of Your testimonies,\
> As much as in all riches.\
****I will meditate on Your precepts**\
> And regard Your ways.\
****I shall delight in Your statutes;\
> I shall not forget Your word**. (Psalm 119:9-16) {emphasis mine}
We need to read the Bible cover to cover so we know the whole word of God. Once we have read through the Bible multiple times, we need to spend time studying the Bible in more depth, so we can know the details, see how the different parts relate to each other, and grow in our knowledge of God. We need to study the Bible and use this knowledge to guide every decision in life — big and small.
> Yet they did not listen or incline their ears, but stiffened their necks in order not to listen or take correction. (Jeremiah 17:23)
Just reading the Bible or sitting in church listening to sermons will not make a difference if we don’t truly listen and internalize God’s word, so we can apply it in our every day life. God knows what is best for us and we will never be truly at peace or have true joy until we are living our lives in the light of God’s word and direction.
My prayer for you and for me is that we will have the heart of Mary rather than the heart of Martha and that we will faithfully seek and follow God all of the days of our lives.
Trust Jesus.
-

@ 5a261a61:2ebd4480
2025-02-02 20:42:37
Let’s be real—sticking to *anything* for 90 days is like trying to herd cats on espresso. You start strong, then **life happens**: kids, chores, or that *one* glass of wine that makes you forget foot rubs (#relatable). But here’s the thing: 90-day challenges aren’t about perfection. They’re about bribing your lizard brain with rewards and scaring it straight with punishments.
## **The Game Plan**
First, pick a thing—something that makes you feel like a devoted servant or a slightly frazzled superhero. Daily foot care? Chores with a side of #FLR flair? Cool. Now, break it into chunks: 30 days (survival mode), 60 days (grind phase), and 90 days (victory lap).
Keeping up something for so long is no joke. That's why you need those little checkpoints along the way. Each milestone should feel special—30 days deserves celebration, 60 days something more meaningful, and 90 days? That's your victory dance moment.
Reality check: some days will suck, and you'll want to skip. **That's where having everything planned out helps.** When your brain is foggy and you're tired, you don't want to be negotiating with yourself about what counts and what doesn't. The hardest part isn't even doing the thing—it's remembering to do it every single day, until it feels wrong NOT to do it.
## **Why It (Maybe) Works**
Three months is long enough for habits to stick, short enough to see the finish line. Plus, tying it to power exchange? Genius. Every foot rub or denied cum becomes a ritual, proof you're leveling up as a sub/human/slightly-messy adult. And let's be honest—nothing fuels devotion like a mix of structure, desperation, and the occasional humiliating punishment.
## **Current run**
My current challenge is to get my wife/godess/object of my insatiable kinky thoughts/partner feet massaged with special cream. It's for making evyrthing soft, help nails and yadayadayada. Basically preping her feet for more instensive worshiping. She doesn't know my hidden agenda and I am not sure if I would really be into it, since I am more into being her devout toy than having foot fetish, but I think it will be all the same if I put myself juuust right.
So for my rewards I have planned these?
- **30 days**: Tiny dopamine hit. *(making little photoset of Her feet playing with my hardon… for science.)*
- **60 days**: Mid-tier flex. *(cleaning mushed banana split off Her toes tongue only)*
- **90 days**: Go nuclear. *(a tiny foot spa whirpool because She deserves it, damn it :D and it will create more opportunities for... you know )*
As for the hhip part of the sugar duo... It was easy having one for my shaving rutine, but here? Not sure and it's bad that I ave started challenge without having them prepared... May be that warrant more punishment?
## **TL;DR**
90-day challenges are the BDSM of self-improvement: **consensual, slightly painful, and weirdly addictive.**
Fail? Reset, adapt, try again. Win? Congrats, you’re now 10% more disciplined and 100% more bumptious on Nostr.
#90days #FLR #LostCauseButStillTrying #femdom
-

@ d57360cb:4fe7d935
2025-02-02 16:33:16
Beauty and art function beyond the mind.
When you’re not thinking, when the mind reaches its natural silence. When it quiets down.
You begin to experience and actually experience how things are.
There is no more narration. Things happen as if by magic. Everything is in its place happening and grooving.
Every act, every movement feels like jazz.
We’re better doers than we are thinkers. But the world thinks otherwise.
-

@ 6b57533f:eaa341f5
2025-02-02 15:46:41
# 🏝️lost in the ordinary?

## Welcome to Stories
Discover a hidden paradise where the world slows down, and adventure begins..
# 🌊 Step into tranquility.

##
Wake up to the sound of gentle waves and endless blue horizons.
# 🛶Live the dream.

##
##
## Unwind, explore, and escape—your perfect getaway is just one step away.
-

@ 3b7fc823:e194354f
2025-02-02 13:39:49
**Why You Should Only Run DeepSeek Locally: A Privacy Perspective and how to**
In an era where AI tools promise immense utility, the decision to run DeepSeek locally is not merely about functionality but also about safeguarding privacy and security. Here's the rationale why:
1. **Control Over Data Access**: Running DeepSeek locally ensures that data processing occurs on your own machine or server, allowing you to have full control over who can access the system. This reduces the risk of unauthorized access and misuse.
2. **Data Privacy**: By keeping computations local, you ensure that personal data does not leave your control, minimizing the risk of exposure through cloud-based services.
3. **Security Measures**: Local operation provides an additional layer of security. You can implement access controls, monitor usage, and respond to incidents more effectively, which might be harder or impossible when relying on third-party platforms.
4. **Practical Implementation**: Tools like Ollama and OpenWebUI facilitate setting up a local environment, making it accessible even for those with limited technical expertise. This setup empowers individuals to leverage AI capabilities while maintaining privacy.
7. **Right to Control Data**: Privacy is a fundamental right, and running DeepSeek locally respects this by allowing users to decide what data they share and how it's accessed. This empowers individuals to make informed choices about their personal data.
For those prioritizing privacy, this approach is not just beneficial—it's essential.
**Running DeepSeek Locally: A Guide for Individual Home Users**
DeepSeek is a powerful AI search engine that can help with various tasks, but running it locally gives you greater control over your data and privacy. Here’s how you can set it up at home.
---
### **What You’ll Need**
1. **A Computer**: A desktop or laptop with sufficient processing power (at least 4GB RAM).
2. **Python and pip**: To install and run DeepSeek.
3. **Ollama**: An open-source tool that allows you to run AI models locally.
4. **OpenWebUI**: A simple web interface for interacting with Ollama.
---
### **Step-by-Step Guide**
#### 1. **Install the Prerequisites**
- **Python**: Download and install Python from [https://www.python.org](https://www.python.org).
- **pip**: Use pip to install Python packages.
```bash
pip install --upgrade pip
```
- **Ollama**:
```bash
pip install ollama
```
- **OpenWebUI**:
Visit [https://github.com/DeepSeek-LLM/openwebui](https://github.com/DeepSeek-LLM/openwebui) and follow the instructions to install it.
---
#### 2. **Set Up Ollama**
- Clone the official Ollama repository:
```bash
git clone https://github.com/OllamaAI/Ollama.git
cd Ollama
```
- Follow the installation guide on [https://ollama.ai](https://ollama.ai) to set it up.
---
#### 3. **Run DeepSeek Locally**
- Use OpenWebUI as your interface:
```bash
# Start OpenWebUI (open a terminal and run this):
python openwebui.py --model deepseek-llm-v0.2-beta
```
- A web browser will open, allowing you to interact with DeepSeek.
---
### **Tips for Optimization**
1. **Reduce Memory Usage**: Use smaller models like `deepseek-llm-v0.2-beta` if your computer has limited resources.
2. **Limit Model Access**: Only allow authorized users to access the system by restricting IP addresses or using a VPN.
3. **Regular Updates**: Keep all software up to date to protect against vulnerabilities.
---
### **Why Run DeepSeek Locally?**
- **Privacy**: Your data stays on your local machine, reducing the risk of unauthorized access.
- **Flexability**: Running locally allows you to build specific models for specific uses and provide them with RAG data.
---
### Advocating for privacy does not finance itself. If you enjoyed this article, please consider zapping or sending monero
-

@ fbf0e434:e1be6a39
2025-02-02 13:32:12
> *本文原载于《CERN Courier》,是由欧洲核子研究中心(CERN,全称Conseil Européen pour la Recherche Nucléaire)出版的权威科学期刊,专注于报道全球物理学、技术及创新领域的前沿动态。以下正文内容是对全球开源开发者激励平台DoraHacks的创始人张剑南的专访报道,探讨了黑客松如何成为科技创新的重要推动力以及DoraHacks在其中扮演的角色。*
>
万维网(World Wide Web)、人工智能(Artificial Intelligence)与量子计算(Quantum Computing)——这些划时代的技术有何共同之处?DoraHacks创始人张剑南认为,它们都源于“Hacks(黑客精神)”。“当万维网在欧洲核子研究中心(CERN)诞生时,它向我们证明了一件事:要想改变并提高人类的生活方式和工作效率,关键在于以创新的思维利用现有的技术以实现突破。”张剑南解释道,“如果总是从零开始,我们永远无法取得实质性的进步。这恰恰就是开源运动和黑客马拉松的核心价值。”
十年前,张剑南参与筹办了CERN Webfest 2013,这是一场致力于探索如何以创新方式运用技术来服务科学与社会的黑客马拉松活动。通过Webfest,张剑南不仅实现了编程技能与物理学知识的跨学科融合,还与来自世界各地、背景各异的hackers建立了持久深厚的联系。随着参与黑客松次数的增多,他的“黑客精神”愈发强烈,最终驱使他创立了自己的公司。2024年,张剑南重返Webfest,但这次他不再是参与者,而是作为DoraHacks的首席执行官来见证这场盛会。
黑客马拉松是一种持续数天的社交编程活动,具有高度的包容性和开放性——参与者无需学术机构或企业背景即可加入。这种特性吸引了众多才华横溢的个体参与其中。活动中,hackers以团队形式合作,结合各自的技能,通过软件、硬件或商业计划等来解决技术难题。这不仅让物理学家、计算机科学家、工程师和企业家齐聚一堂,各展所长,也让年轻的开发者们有机会突破传统研究框架,提升技能、积累作品集,并拓展职业人脉。
“如果你对某件事充满热情,就应该能够立即投入其中并全力以赴,”张剑南强调,“追求梦想并不需要特定的学历或背景。”
对于在某个领域刚起步的研究者来说,黑客松的意义远不止于技术挑战。它为进入一个研究或行业领域提供了另一种途径,弥合了学术理论与实际应用之间的鸿沟。很多由大学举办的黑客松往往能够吸引到企业的赞助,这些赞助除了作为奖金来激励开发者持续开发,也会用来租赁大型场馆,以容纳数百甚至上千名参与者。
“正是这些大规模的黑客松吸引了众多行业猎头和导师的关注,”张剑南解释道,“他们把这类活动看作他们的人才库。通过黑客松,参与者们能够与大公司的人直接交流,加速职业发展,同时也能在实践中提升他们的编程能力。”
在2010年代,张剑南经常在周末参加黑客松,这也成为他创业的基石。“我曾经坐在计算机科学学院的公共休息室里,埋头研究我的黑客项目。我的大多数朋友也是在那里认识的,”张剑南回忆道,“但后来我意识到,如果想做出真正伟大的东西,必须有效地组织人力与资金。然后我就开始‘逃课’,不去上计算机系的课程,而是偷偷溜进商学院的教室里。”张剑南常常在商学院的教室后排听课,一边听课一边谋划自己的创业计划。他每天都与同行交流,评估各种不同的商业模式。“在创业过程中,要把工程知识与商业理论结合起来思考,”他补充道,“这是比较有趣的一点,让整个过程也轻松了一些。”
然而,从科学研究转向创业并非易事。“创业初期必须亲力亲为,要自己去学习然后完成各种任务。”张剑南坦言,“好处是能够接触到许多新技能和新朋友,但同时也得强迫自己去做那些原本不擅长的事情。”
这种经历也反映了许多创业者的共同困境:选择自己从头学习新技能,还是寻找合适的创业伙伴然后把任务分配出去?可是找到值得信赖的合作伙伴也不是一件容易的事,错误的决策甚至可能阻碍公司的发展。因此,从一开始就明确公司的愿景和使命显得尤为重要。
“解决方案其实很简单,”张剑南表示,“重点是要投入足够多的时间,亲自完成关键里程碑,以确保产品真正具备可行性。只要有了明确的商业计划和愿景,就能获得来自各方的支持。”
### **去中心化的社区治理**
很多黑客马拉松参与者在活动结束后就会放弃自己的项目,但张剑南创立DoraHacks的初衷并非如此。他希望为全球的黑客团队提供一个平台,让他们能够将创意转化为成熟产品。“我希望黑客马拉松不仅仅是一个招聘工具,”他解释道,“它更应该推动开源开发和去中心化的社区治理。比如现在,来自坦桑尼亚的黑客可以与美国的黑客团队远程协作,然后获得持续的支持,以开发出真正有影响力的产品。这种模式让技术领域变得更多样化,同时也能够让更多人接触到不同的领域。”
DoraHacks通过帮助组织者降低后勤成本,为参与者提供更可靠的资金支持机制,使黑客松超越学术机构的限制,吸引更多对创新充满热情的个体研究者参与。然后不断发展整个社区,让年轻一代的开发者、研究者们能够在自己的职业初期,接触到比以往更多的机遇和机会。
“商业模式正在发生根本的变化,”张剑南指出,黑客马拉松正在发展成为新兴技术的基石,尤其是在量子计算、区块链和人工智能等以开源形式起步的领域。“产品创造的过程将会迎来重大变革。未来的技术发展不再依赖于孤立封闭的产品开发,而是基于黑客们可以共同贡献的平台和基础设施。”
如今,黑客马拉松的意义已不仅限于编程或建立人脉——它们更关乎突破技术边界、创造有意义的解决方案,并开辟新的职业道路。黑客马拉松是创意孵化器,并且能够对这些创意产生持久的影响力。张剑南希望帮助这些创意变为现实。“未来创新的方式一定是协作完成的,是开源的,”他再次强调,“在传统社会环境里,企业的发展依赖于在闭源技术周围筑起的护城河,这种技术更新方式的效率低下且不容易实现。而真正创新的未来,将以开放平台技术为核心,让全球开发者能够在现有项目的基础上不断迭代更新。这样的开放协作精神正是Hacker Movement(开源极客运动)如此重要的原因。”
采访者:Alex Epshtein(编辑助理)。
原文链接:https://cerncourier.com/wp-content/uploads/2025/01/CERNCourier2025JanFeb-digitaledition.pdf
-

@ ddf03aca:5cb3bbbe
2025-02-02 13:09:27
We’re thrilled to announce the stable release of Cashu-TS v2.2! Although this update is a minor version bump, it brings significant improvements under the hood that enhance the overall developer experience. We’ve spent several weeks testing and refining these changes.
---
## What’s New in v2.2?
While there are no breaking changes in this release, there are many internal changes. If you spot any regressions or unexpected behavior, please [let us know](https://github.com/cashubtc/cashu-ts/issues). Here’s a rundown of the major updates:
- **Enhanced Proof Creation**: The way proofs are created internally has been revamped.
- **User-Controlled Outputs**: You now have full control over how outputs are created.
- **Improved Bundling**: We’ve switched our bundling tool to [vite](https://vitejs.dev) for faster and more modern builds.
- **Updated Testing Tools**: Our testing framework has migrated to [vitest](https://vitest.dev) and [msw](https://mswjs.io), with added browser testing via Playwright.
---
## New Flexibility with OutputData
In previous versions of Cashu-TS, the creation of outputs (or *BlindedMessages*) was hidden away. Even though there were options to tweak the process (like deterministic secrets or P2PK), you were always limited to the built-in logic.
### What’s Changed?
In v2.2, we’ve introduced a public interface that not only streamlines output creation but also lets you plug in your own custom logic when needed. With the new `outputData` option available on all output-creating methods, you can now bypass the automatic process and provide your own outputs.
For example, you can create two proofs tied to different public keys in a single mint operation:
```ts
const data1 = OutputData.createP2PKData({ pubkey: "key1" }, 10, keys);
const data2 = OutputData.createP2PKData({ pubkey: "key2" }, 10, keys);
const { keep, send } = await wallet.send(20, proofs, {
outputData: { send: [...data1, ...data2] },
});
```
### Customization Made Easy
The `outputData` option now accepts anything that conforms to the `OutputDataLike` interface. This means you can introduce your own output creation logic—even if it’s not natively supported by Cashu-TS yet. Here’s what the interface looks like:
```ts
export interface OutputDataLike {
blindedMessage: SerializedBlindedMessage;
blindingFactor: bigint;
secret: Uint8Array;
toProof: (signature: SerializedBlindedSignature, keyset: MintKeys) => Proof;
}
```
### Introducing OutputData Factories
While having full control is empowering, it also means you’ll need to handle tasks like fee calculation and amount selection manually. To strike a balance between control and convenience, we now support **OutputData Factories**.
A factory is simply a function that takes an amount and `MintKeys` as input and returns an `OutputDataLike` object. This way, you can define a blueprint for your output data without worrying about the nitty-gritty details. For instance, you can create separate factories for amounts you keep versus those you send:
```ts
function keepFactory(a: number, k: MintKeys) {
return OutputData.createSingleP2PKData({ pubkey: "keepPk" }, a, k.id);
}
function sendFactory(a: number, k: MintKeys) {
return OutputData.createSingleP2PKData({ pubkey: "sendPk" }, a, k.id);
}
const { send, keep } = await wallet.send(amount, proofs, {
outputData: { send: createFactory("send"), keep: createFactory("keep") },
});
```
Plus, you can now instantiate a `CashuWallet` with a default `keepFactory`, ensuring that all change amounts automatically lock to your key—streamlining your workflow even further.
---
## Bundling Improvements with Vite
Starting with v2.2, we’ve transitioned from using `tsc` to [vite](https://vitejs.dev) for transpiling and bundling the library code. Although this change is mostly behind the scenes, it brings several benefits:
- **Modern Build Target**: We’ve updated our build target to ES6.
- **Updated Exports**: The package exports now reflect the latest JavaScript standards.
- **Standalone Build Soon**: We’re working on a standalone build that bundles Cashu-TS along with all its dependencies. This will let you import Cashu-TS directly into your HTML.
If you encounter any issues with the new bundling setup, please [let us know](https://github.com/cashubtc/cashu-ts/issues).
### A Nod to Vitest
In addition to our bundling improvements, we’ve migrated our testing framework from Jest (with nock) to [vitest](https://vitest.dev) combined with [msw](https://mswjs.io). This switch gives us more flexibility in testing and mocking, plus we’ve added browser testing based on Playwright—thanks to the tip from nostr:npub16anjdksmvn5x08vtden04n64rw5k7fsjmedpw8avsx8wsh8ruhlq076pfx!
---
## In Conclusion
Although Cashu-TS v2.2 is a minor version update, it comes packed with improvements that enhance both the developer experience and the flexibility of the library. We’re excited to see how you’ll use these new features in your projects! Thanks to all the amazing contributors that add to this library.
Thank you for being a part of the Cashu-TS community. As always, if you have any questions, suggestions, or issues, don’t hesitate to [reach out to us](https://github.com/cashubtc/cashu-ts/issues).
-

@ fe41d17e:28df7452
2025-02-02 13:04:38
Um es vorab klarzustellen, die einzigen Gesetze an die du dich wirklich halten musst sind die Naturgesetze, es ist deine eigene Entscheidung ob du einer einseitig vom Staat beschlossenen Auflage zustimmst oder nicht, solange du bereit bist, falls du erwischt wirst, die Konsequenzen über dich ergehen zu lassen.
Wenn du diese Unterdrückung nicht mehr haben möchtest braucht es eine Revolution um den Staat irrelevant werden zu lassen und um ihm seine Grundlage (das Geld) zu entziehen ohne dabei wie er selbst zu unmoralischen Methoden zu greifen.
Diese Revolution nennt sich **Agorismus,** sie wird dich unabhängig vom Staat machen und den Staat langfristig schwach/überflüssig werden lassen sobald es dir genug Leute gleichtun.
Die Revolution wird nicht leicht, sie wird dir nicht die sofortige Genugtuung verschaffen, die du möglicherweise empfindest, wenn du einen Zettel in die Wahlurne wirfst und dabei das Gefühl hast, etwas verändert zu haben. Eigentlich hast du nur denselben Leuten Macht verliehen, die seit Jahrhunderten die Politiker kontrollieren, dich ausrauben und unterdrücken. Garnichts hast du damit verändert.
Es wird schwierig werden. Es wird Eigeninitiative und Veränderungen in deinem Leben erfordern. Es wird ein zermürbender, unbefriedigender Weg sein, den viele als zu hart bezeichnen werden. Es wird Jahre über Jahre dauern, in denen die Leute dich dafür schief ansehen und du kaum Anerkennung bekommen wirst.
*Hier ein paar wichtige Punkte um dich mit Agorismus vertraut zu machen*:
\-Wenn du bereits ein Libertärer bist, lies zuerst „**Das neue Libertäre Manifest**“ von Samuel Edward Konkin III. Es hat nur 30 Seiten, und wenn du damit nicht zumindest deinen Horizont erweitern kannst, dann kannst du genauso gut eine britische Flagge in Amerika schwenken, Tribut zollen und einen König fordern.
-Wenn du kein Libertärer bist, lies „**Eine neue Freiheit: das libertäre Manifest**“ von Murray Rothbard und anschließend „**Das neue Libertäre Manifest**“ von SEK3.
-Konzentriere dich in deinem Leben darauf, weniger bis keine Steuern zu zahlen.
\-Finde Alternativen zum Fiatgeld und sei deine eigene Bank.
\-Finde lokale Quellen für Lebensmittel und Produkte.
\-Handel P2P auf freien Märkten.
\-Suche nach Lösungen, die auf Dezentralisierung ausgerichtet sind.
\-Baue eine gewisse Menge an Lebensmitteln an, auch wenn es nur Mikrogrün ist. Dafür sind keine großen Flächen erforderlich und du kannst diese gegen andere Lebensmittel eintauschen.
\-Baue dein eigenes Unternehmen außerhalb von Konzernstrukturen auf.
\-Konzentriere dich auf den Handel mit anderen Agoristen.
\-Nutze jede Gelegenheit um deine Verachtung gegenüber dem Staat zu äußern.
\-Verbreite Agorismus.
\-Beschaffe dir Waffen.
\-Vertraue nur agoristischen Medien, die unpolitisch sind. Denn jeder Journalist, der dich ermutigt, zu wählen oder innerhalb des Systems zu arbeiten, könnte gekauft oder kontrolliert sein. Agoristen, die behaupten, dass Politik nicht die Antwort ist, sind die einzigen, die die Menschen wirklich von den Kontrolleuren wegführen.
Die Herrscher dieser Welt sind sich durchaus darüber im Klaren, dass das Informationszeitalter ihren Interessen schadet. Daher arbeiten sie unermüdlich an der Schaffung psychologischer Operationen (PsyOps), kontrollierter Opposition, False-Flag-Aktionen und Ablenkungsmanövern, lass dich nicht täuschen.
Erstveröffentlichung am 12. Januar auf meinem X Profil; @realbunki
-

@ 77be3409:5c7c2736
2025-02-02 12:48:25
[RMD Law - Personal Injury Lawyers ](https://www.rmdlaw.com/)is excited to announce the launch of its new scholarship program, designed to empower students and highlight the values of responsibility, resilience, and learning from life’s unexpected moments. This $2,500 scholarship aims to support students in their educational journeys while encouraging creativity and personal growth.
### Scholarship Details
Award Amount: $2,500
Submission Deadline: December 30, 2025
Winner Announced: January 15, 2026
**Eligibility Requirements**
To apply, students must meet the following criteria:
- Be at least 16 years old and a permanent legal resident of the United States.
- Be currently enrolled in a U.S. college, university, or trade school OR graduating from high school in 2025.
- Have a cumulative GPA of 3.0 or higher.
- Follow RMD Law on social media to see the winner announcement.
- Submit all required materials by the December 30, 2025, deadline
**Application Requirements
Applicants are required to submit:**
- A copy of their most recent high school or college transcript.
- A creative and thoughtful essay (up to 1,000 words) responding to the following prompt:
**Essay Prompt: “Oops, That Was Close!”**
Tell us about a moment when you narrowly avoided disaster—whether it was a hilarious mishap, an embarrassing accident, or a close call with serious consequences.
- What did you learn (if anything) from the experience?
- Who was at fault and why?
- What would the appropriate restitution (if any) be in that situation?
Note: Applicants are encouraged to use creativity, levity, and personal insights to share their story. Let your unique voice shine through!
**Selection Criteria**
The winner will be chosen based on:
- Originality and creativity in their essay.
- Relevance to the prompt.
- Clarity and thoughtfulness of their response.
The scholarship recipient will be announced on January 15, 2026.
**How to Apply**
1. Students can submit their application materials through the official RMD Law scholarship webpage: [https://www.rmdlaw.com/scholarship/
](https://www.rmdlaw.com/scholarship/)2. Follow RMD Law on social media to stay updated on the announcement and other initiatives.
#### About RMD Law
RMD Law is a leading personal injury law firm committed to providing exceptional legal services and making a positive impact in the communities it serves. Through initiatives like the scholarship program, RMD Law seeks to empower individuals and foster the next generation of leaders.
-

@ 0463223a:3b14d673
2025-02-02 12:22:46
I’m totally wasted! I don’t mean off my head on drugs, I mean absolutely physically and mentally exhausted.
Lugging heavy PA equipment up and down stairs, plus mixing shows is a lot and at my age I’m struggling with it. Yesterday was a write off due to exhaustion. My wife and I went to the cinema, and I slept through the film. A shame, it was something I wanted to see but I was toast. I went to bed at 8pm and slept for over 12 hours. I still feel wrecked today.
Live sound was always a sort of plan B. For a number of years teaching and performing with a band or a DJ was enough to get by on. I was comfortable, financially speaking. That was until about between 2012-14, that’s when we really felt the effects of the post 2008 crash. While a lot of noise was made about the initial event, reality for the likes of me was a slow and steady decline. At that time I was leading workshops with kids with difficult backgrounds, many kids in care due to abuse and neglect. That was a solid 40% of my income, another 30% came from teaching Sound Production at a local university and the final 30% from shows.
2014 cutbacks ripped services to shreds and a few friends lost jobs. Since then, doing live sound kept the rent and bills paid but fast forward to 2025 and I’m way too tired for this shit! I hate admitting it but my earnings probably peaked around 2008 with a bump in tours from 2017 till Covid. Since then earnings have been steady in £'s but getting wiped out by inflation. In fact I had decent acounts this year but every month I'm broke by the time bills and basics have been taken care of. I LOVE mixing live music and I’m pretty good at it. I’ve had musicians call me ‘musical’ which is the highest compliment but I’m totally fucked still 2 days after Friday’s show. It's unsustainable.
I’m quitting live sound unless some touring comes up again, touring is different, living on a bus for 3 weeks pays the same as 3 months of local work and I just mix, no lifting gear. The band I tour with are based in the US and only come to the UK/EU every couple of years. I get odd trips away with other artists but they’re usually fly out EU gigs. 1 or 2 shows then fly home, plus they're irregular.
Right now I’m more interested to learn ways of making income online, I started the Kali Mera Show to learn self hosting content. Committing to a project each morning has done wonders for my mental health, cutting down on morning doom scrolling. It’s been highly successful in that regard but not so much financially. However this is jst phase 1. I’m learning the tech, learning the production and making as many mistakes as possible while the stakes are low. I’m very happy 10 or so people enjoy the show on a daily basis. Tiny numbers but I don’t fuck with YouTube or the other big tech platforms. Fuck them!
Phase 2 involves getting premises and broadening the services I can produce, focussing on content for others, getting some opportunities happening for young talent, arranging meet ups and setting up a hub to bring together the crazy, talented people I know. It’s going to be tough, I’m in a run down area, there’s not much money here (relatively speaking) but it’s an area I really dig and want to make better.
Why am I telling you this? I’m writing this as a means of getting my brain straight and sharing it because I’m open to improving myself. I see people doing interesting shit here and that helps with motivation and confidence. My only social media for the last 6 years has been the Fediverse and much as I love it, there’s a gloomier outlook there. The world is a strange place with so much bad shit but out of 8 or so billion people, I can only take on so much. Building shit in my own local community and provide facilities for online wins sounds way more productive and helpful in some small way.
I accept we’re all going to hell in a handcart but may as well enjoy the ride…
There’s much to learn, I’ve only ever been ‘in business’ for a short time in my life (despite always being freelance) and I sort of gave up on my previous attempt. Had I paid more attention I could’ve built a strong YouTube presence but I’m not into being a vehicle for companies to push their products, nor do I want to teach people music online. That market is now heavily saturated and very, very boring as far as I’m concerned. My heart wasn’t in it, even back in 2015. I’m not an influencer.
With a real life space there’s premises, business rates, and investors to consider, as well as developing services that people are actually happy to part cash with. It’s going to be hard but different hard to physically lifting sub-bass speakers up and down winding staircases! I don’t want to talk too much game, it’s results that matter but wasting days to exhaustion doesn’t help. It’s time to hang up my headphones and focus (FOCUS YOU FUCKING FUCK!).
Maybe you’re reading this and thought ‘shit, this guy’s totally deluded’. That’s cool. Tell me. I value feedback. A fair few cats here give life advice so I’ll assume you might know what you’re talking about...
-

@ d1795b1a:15ab2129
2025-02-02 11:45:38
### The Ego is an Illusion – and Yet, We Can Shape It
Carl Jung spoke of the **Shadow Self**—the repressed parts of our psyche that unconsciously influence our lives. **Buddhism**, on the other hand, teaches that there is no self at all—our ego is an illusion, a fleeting construct that we cling to out of fear of emptiness.
These two perspectives seem to contradict each other. One tells us to integrate our hidden self, the other to dissolve it completely. But what if both are only half the picture?
I believe the **Self is neither a fixed reality nor a mere illusion—it is a shapeable construct.** If that is true, then the path is not to destroy the **Ego-Self** or blindly follow it, but to **consciously shape it.**
### **Between the Shadow and Emptiness**
Our **Ego-Self** is our conscious identity—our thoughts, memories, and beliefs. **Jung** describes the **Self** as the totality of both **the conscious and unconscious mind.** Hidden in this unconscious space is the **Shadow Self**, containing everything we deny, suppress, or refuse to acknowledge. For Jung, the path to wholeness is **integration**—bringing light into the dark corners of the psyche.
**Buddhism**, however, goes further. It questions whether the **Self** exists at all. Our thoughts and emotions arise and disappear, our self-image is ever-changing—so **why do we cling to something so impermanent?**
Both views seem to offer opposite solutions: \
**• Jung:** Become WHOLE by integrating your Shadow. \
**• Buddha:** Become FREE by seeing the Self as an illusion.
But what if the **synthesis of both is the key?**
### The Self as a Shapeable Reality
If the **Self** is not fixed but fluid, then the path forward is neither **pure integration nor total dissolution** but **conscious creation.** \
\
**• Acknowledge the Shadow Self instead of fighting it.** \
**• See the Ego-Self not as absolute truth but as a flexible tool. \
• Engage the Solar Plexus—the center of the Unconscious Mind—through breathwork and self-awareness. \
• Use the Vagus Nerve as a bridge between conscious thought and unconscious emotion, actively shaping our beliefs and behaviors.**
This aligns with **New Thought philosophy**, which suggests that our thoughts shape not only our perception but our reality itself. If we embrace this, the question is no longer **“Who am I?”** but rather: **“Who do I want to be—and how can I create that Self?”**
### The Art of Shaping Yourself
Perhaps the **Self** is neither a rigid entity nor a complete illusion but a story we tell ourselves—a story we can rewrite. The key is not to destroy the Ego-Self but to **use it consciously, rather than being used by it.**
So the real question is not: **“Does the Self exist?”**
But rather: **“How aware are we of the fact that we are shaping it every moment?”**
-

@ fd208ee8:0fd927c1
2025-02-02 10:33:19
# GitCitadel Development Operations
We, at GitCitadel, have been updating, moving, and rearranging our servers, for quite some time. As a rather large, complex, sprawling project, we have the infrastructure setup to match, so we've decided to give you all a quick run-down of what we are doing behind-the-scenes.
## Supplier Coordination

Our first task, this week, was figuring out who would host what where. We have four different locations, where our infra is stored and managed, including two locations from our suppliers. We got that straightened out, quickly, and it's all slowly coming together and being connected and networked. Exciting to watch our DevOps landscape evolve and all of the knowledge-transfer that the interactions provide.
## OneDev Implementation

Our biggest internal infra project this week was the migration of all of our issues from Jira, build scripts from Jenkins, and repos from GitHub to a [self-hosted OneDev instance](https://onedev.gitcitadel.eu). In the future, all of our internal build, test, issue, patch/PR, etc. effort will take place there. We also have a separate repo there for communicating with external developers and suppliers.
Our [team's GitHub projects](https://github.com/ShadowySupercode) will be demoted to mirrors and a place for external devs to PR to. Public issues and patches will continue to be managed over our self-hosted [GitWorkshop instance](nostr:naddr1qvzqqqrhnypzplfq3m5v3u5r0q9f255fdeyz8nyac6lagssx8zy4wugxjs8ajf7pqy88wumn8ghj7mn0wvhxcmmv9uqq5emfw33kjarpv3jkcs83wav).
We're especially glad to finally escape the GitHub Gulag, and avoid being bled dry by Jira fees, without having to give up the important features that we've come to know and love. So, yay!
## Next Infrasteps
### Automated Testing
Now, that we have everything tied up in one, neat, backed-up package, we can finally move on to the nitty-gritty and the dirty work. So, we're rolling up our sleeves and writing the Selenium smoke test for our [Alexandria client](https://next-alexandria.gitcitadel.eu). We'll be running that in Docker containers containing different "typical Nostr" images, such as Chrome browser with Nostr Connect signing extension, or Firefox browser with Nos2x-fox extension. Once we get the Nsec Bunker and Amber logins going, we'll add test cases and images for them, as well. (Yes, we can do Bunker. I hope you are in awe at our powers).
We are also designing an automated infrastructure test, that will simply rattle through all the various internal and external websites and relays, to make sure that everything is still online and responsive.
After that, a Gherkin-based [Behave feature test](https://behave.readthedocs.io/en/latest/) for Alexandria is planned, so that we can prevent regression of completed functionality, from one release to the next.
The Gherkin scenarios are written and attached to our stories before development begins (we use acceptance tests as requirements), a manual test-execution is then completed, in order to set the story to *Done*. These completed scenarios will be automated, following each release, with the resulting script linked to from the origin story.

### Automated Builds
As the crowning glory of every DevOps tool chain stands the build automation. This is where everything gets tied together, straightened out, configured, tested, measured, and -- if everything passes the quality gates -- released. I don't have to tell you how much time developers spend staring at the build process display, praying that it all goes through and they can celebrate a Green Wave.

We are currently designing the various builds, but the ones we have defined for the Alexandria client will be a continuous delivery pipeline, like so:

This will make it easier for us to work and collaborate asynchronously and without unnecessary delays.
### Expanding the Status Page

And, finally, we get to the point of all of this busyness: reporting.
We are going to have beautiful reports, and we are going to post them online, on our [status page](https://status.gitcitadel.com). We will use bots, to inform Nostriches of the current status of our systems, so go ahead and follow our [GitCitadel DevOps npub](nostr:npub16p0fdr2xccfs07hykx92t0cascac69xjuwaq38kjqy3aawt5hx8s82feyj), to make sure you don't miss out on the IT action.
## Building on stone
All in all, we're really happy with the way things are humming along, now, and the steady increase in our productivity, as all the foundational work we've put in starts to pay off. It's getting easier and easier to add new team members, repos, or features/fixes, so we should be able to scale up and out from here. Our GitCitadel is built on a firm foundation.
Happy building!
-

@ 006532cb:fd8f28b4
2025-02-02 09:50:56
I am new to #NOSTR and not a #Dev; however, npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn's [article](https://njump.me/naddr1qvzqqqr4gupzp978pfzrv6n9xhq5tvenl9e74pklmskh4xw6vxxyp3j8qkke3cezqyw8wumn8ghj76r0v3kxymmy9e3k7unpvdkx2tn5dahkcue0qy88wumn8ghj7mn0wvhxcmmv9uqq6vfhxvurydfhxq6nwvfj8q4tttqv) inspired me to research and understand further. As a result, I have condensed my learnings into 10 bullet points that seem to embody the spirit of being a nostrich and the qualities we should all strive for when engaging with one another making software choices and avoiding NINO's.
1. **You shall not compromise on security:** Prioritize the security and integrity of user data, using best practices and Nostr's built-in features to protect against unauthorized access and malicious activity.
2. **You shall prioritize user agency:** Respect users' mute lists, use their web of trust to filter out spam, and prioritize user control over their data.
3. **You shall be decentralized and open:** Do not hardcode relay URLs or depend on specific relay implementations, ensuring that your platform is truly decentralized and open.
4. **You shall leverage Nostr's technical aspects:** Take advantage of Nostr's features, such as self-authenticating data, event handlers, and relays, to build a robust and decentralized platform.
5. **You shall use native Nostr solutions:** Prefer Nostr-native solutions to solve problems, rather than relying on legacy web services, promoting a more decentralized and resilient ecosystem.
6. **You shall prioritize interoperability:** Implement NIP 89 (Recommended Application Handlers) to enable seamless interactions with other Nostr apps, promoting a unified and decentralized ecosystem.
7. **You shall engage with the community:** Share knowledge, contribute to the growth of the ecosystem, and collaborate with other Nostr developers to promote a unified and thriving community.
8. **You shall be transparent and accountable:** Be transparent in your development processes, and accountable for your actions and decisions, promoting trust and confidence in the Nostr ecosystem.
9. **You shall innovate and evolve:** Continuously innovate and improve your platform, staying up-to-date with the latest developments in the Nostr protocol and ecosystem, to ensure the best possible experience for users.
10. **Embody Nostr:** Your application should truly represent the Nostr protocol, using its features and network to provide unique value to users.
I am excited for the future. In Eric S. Raymond's book "The Cathedral and the Bazaar" he comments;
> "...and the robust doesn't care too much"
Nostr embodies the spirit of the Bazaar, a vibrant and eclectic marketplace where the robust thrive, all are welcomed and empowered to become strong.
/GN!
-

@ 63e047aa:2e1ae74f
2025-02-02 09:00:46
In this blog post, I will walk you through the process of integrating Nostr login functionality into my Rails application using the Nos2x extension. This involved modifying the Devise User model, adding a new route to handle Nostr users, and integrating JavaScript to enhance the login experience.
## Overview
Nostr is a decentralized protocol that allows users to authenticate without relying on traditional email/password combinations. By leveraging the Nos2x extension, I was able to implement Nostr login seamlessly. Here’s how I did it.
## Step 1: Adding Asynchronous Nostr client in Ruby
```bash
bundle add nostr
```
## Step 2: Modifying the Devise User Model
The first step was to modify the Devise User model to allow empty email validation. This is crucial because Nostr users may not have an email address. I updated the `User` model as follows:
```ruby
class User < ApplicationRecord
# Include default devise modules. Others available are:
# :confirmable, :lockable, :timeoutable, :trackable, :registerable and :omniauthable
devise :database_authenticatable, :registerable,
:recoverable, :rememberable # Removed :validatable
# Validations
validates :nostr_public_key, presence: true, uniqueness: true, allow_blank: true
validates :email, uniqueness: true, allow_blank: true # Make email optional
validates :password, length: { minimum: 6 }, allow_blank: true # Make password optional but enforce length if provided
# Conditional validation for email and password
validates :email, presence: true, unless: :nostr_public_key_present?
validates :password, presence: true, unless: :nostr_public_key_present?
private
def nostr_public_key_present?
nostr_public_key.present?
end
end
```
By adding this validation, I ensured that users logging in via Nostr would not be required to provide an email address.
## Step 3: Adding a New Route for Nostr Users
Next, I needed to create a new route to handle the login process for Nostr users. I added the following route to my `config/routes.rb` file:
```ruby
Rails.application.routes.draw do
# Other existing routes...
post 'users/nostr_login', to: 'users#nostr_login', as: 'nostr_login'
end
```
This route points to a new action in the `UsersController` that will manage the authentication process for Nostr users.
## Step 4: Implementing the Nostr Login Action
In the `UsersController`, I implemented the `nostr_signup` action to handle the login logic:
```ruby
# app/controllers/users_controller.rb
class UsersController < ApplicationController
# Custom error handling for CSRF token verification failure
rescue_from ActionController::InvalidAuthenticityToken do |exception|
render json: { error: "Can't verify CSRF token authenticity." }, status: :unprocessable_entity
end
def nostr_signup
nostr_signed_event = params[:signed_event]
if not nostr_signed_event
render json: { success: false, error: "No signed event provided." }, status: :unprocessable_entity
return
end
public_key = nostr_signed_event[:pubkey]
content = nostr_signed_event[:content]
kind = nostr_signed_event[:kind]
csrf_token = request.headers['X-CSRF-Token']
tags_hash = tags.to_h
challenge_value = tags_hash["challenge"]
relay_value = tags_hash["relay"]
expected_relay_value = ENV.fetch('NOSTR_AUTH_RELAY_URL', 'wss://relay.primal.net')
# Check if the challenge_value and relay_value are matching or if kind is valid
if challenge_value != csrf_token || kind != 22242 || relay_value != expected_relay_value
return render json: { success: false, error: "Invalid event provided." }, status: :unprocessable_entity
end
nostr_event = Nostr::Event.new(
content: content,
id: nostr_signed_event[:id],
created_at: nostr_signed_event[:created_at],
kind: kind,
pubkey: public_key,
sig: nostr_signed_event[:sig],
tags: nostr_signed_event[:tags]
)
# Validate the event's signature
unless nostr_event.verify_signature
render json: { success: false, error: "Invalid event signature." }, status: :unprocessable_entity
return
end
user = User.find_or_initialize_by(nostr_public_key: public_key)
...
end
private
def nostr_signup_params
params.permit(signed_event: [:id, :kind, :content, :tags, :created_at, :pubkey, :sig])
end
end
```
This action will handle the authentication process and create a new user if they do not already exist.
## Step 5: Integrating JavaScript for Nostr Login
To enhance the user experience, I added a link for Nostr login on the Devise login page. I included the following JavaScript code to handle the Nostr login process:
```javascript
document.addEventListener("turbo:load", function () {
if (isNostrAvailable() && !document.getElementById('nostr-signup')) {
createNostrSignupButton();
}
});
// Function to check if Nostr is available
function isNostrAvailable() {
return window.nostr && typeof window.nostr.getPublicKey === 'function';
}
// Function to create and append the Nostr signup button
function createNostrSignupButton() {
event.preventDefault();
const button = document.createElement('button');
button.id = "nostr-signup";
button.onclick = function(event) {
event.preventDefault();
nostrSignupHandler();
};
button.type = "submit";
button.textContent = "<%= t('nostr.with_extension') %>";
const actionsDiv = document.querySelector('.actions');
if (actionsDiv) {
actionsDiv.appendChild(button);
}
}
async function nostrSignupHandler() {
try {
const publicKey = await window.nostr.getPublicKey();
if (!publicKey) {
alert("Sign-up failed. No public key.");
}
token = document.querySelector('meta[name="csrf-token"]').getAttribute("content");
const event = {
"created_at": Math.floor(Date.now() / 1000),
"content": "",
"tags": [
[
"relay",
"<%= ENV['NOSTR_AUTH_RELAY_URL'] || 'wss://relay.primal.net' %>"
],
[
"challenge",
token
]
],
"kind": 22242,
"pubkey": publicKey
};
// Sign the event
const signedEvent = await window.nostr.signEvent(event);
if (!signedEvent) {
alert("Sign-up failed. Event not signed.");
}
const response = await fetch("/nostr_signup", {
method: "POST",
headers: {
"Content-Type": "application/json",
"X-CSRF-Token": token,
},
body: JSON.stringify({ "signed_event": signedEvent }),
});
...
```
## Conclusion
By following these steps, I successfully integrated Nostr login functionality into my Rails application using the Nos2x extension. This not only enhances the user experience by providing a decentralized login option but also aligns with modern authentication practices.
Feel free to reach out if you have any questions or need further assistance with implementing Nostr login in your own applications!
If you want to see it in action, go ahead to [Medical Dictionary - Login Page](https://medical.inarchives.com/users/sign_in) for example. You will need to be on a desktop browser with a Nostr Extension installed.
Happy coding!
-

@ da0b9bc3:4e30a4a9
2025-02-02 08:18:39
Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/873174
-

@ 63e047aa:2e1ae74f
2025-02-02 08:12:53
**We have not lived the longest period of peace in history yet, but we will live the longest period of peace in history!**
In a world often defined by conflict, power struggles, and competition for resources, we are constantly searching for ways to build a more peaceful and just society. While most people look at Bitcoin as a financial asset or a tool for decentralizing wealth, I believe its potential reaches far beyond economics. Bitcoin might offer humanity something even greater—a new foundation for **peace**.
## Moving Beyond Conflict: A New Kind of Power
Throughout history, wars have been fought over control—control of land, resources, economies, and the power to enforce rules. In contrast, Bitcoin's decentralized structure removes the need for such centralized control. No single entity governs Bitcoin, and no one can wield unchecked power over the system. The proof-of-work mechanism ensures security and fairness without the need for violence, coercion, or centralized oversight.
As **Jason Lowery** suggests in his work on Bitcoin as a form of power projection, Bitcoin can be seen as a new kind of digital deterrent, one that allows nations to secure their interests without the need for traditional force or military conflict. This shift in power could give rise to a new form of diplomacy, one built on transparency, equal access, and mutual trust. In a world where no single nation or group can manipulate the economic system, we reduce the incentives for conflict.
## Bitcoin as a Tool for Transparency and Trust
At its core, Bitcoin is a trustless system—no one needs to trust a central authority to ensure fairness. Instead, cryptography and mathematics guarantee the security of the network. This system of transparency could extend far beyond finance, offering a new way for people, governments, and organizations to interact without fear of manipulation or corruption.
By removing the need for intermediaries, Bitcoin could pave the way for global cooperation, where each party can act with confidence in a system that cannot be easily undermined. It creates a level playing field, not just economically but also in terms of information sharing and governance.
## Beyond National Defense: A Vision for Peace
Jason Lowery’s exploration of Bitcoin as a strategic defense tool highlights the ways it can serve as a power projection system for nations, offering a new form of security and sovereignty. But I believe this is just the beginning. What if Bitcoin could give nations and individuals a means to engage peacefully?
By empowering people to own their wealth and secure their assets without relying on central banks or governments, Bitcoin could weaken the structures that fuel geopolitical conflicts. When control is decentralized, and power is more evenly distributed, we may find fewer reasons to engage in war.
## A New Way Forward
Imagine a world where peace is not dictated by the threat of force or control over resources but by the mutual benefit of a decentralized system that serves everyone equally. Bitcoin, in this light, becomes more than a financial innovation—it becomes a blueprint for how we might move toward a more peaceful and just world.
Satoshi Nakamoto may not have intended Bitcoin to be a pathway to peace, but the potential is there. As Jason Lowery highlights, Bitcoin's decentralized nature could evolve into a critical part of how nations secure their futures in the digital age. What if we embraced it, not just as a store of value but as a new foundation for how we build trust, security, and cooperation?
I believe that Bitcoin represents more than just financial freedom—it offers us a chance to rethink the systems that have governed our world for centuries. It gives us the opportunity to engage with each other in a way that fosters peace, not conflict. Most importantly, nations would not need to fight over who holds the most Bitcoin—because in a truly decentralized and transparent system, it is not about accumulating more. It simply needs to be adopted, and by doing so, the value it creates can be shared equally, reinforcing the principles of cooperation and global harmony. Redefining peace through decentralized, secure systems like Bitcoin might just be one of the most significant shifts in human history.
-

@ 57d1a264:69f1fee1
2025-02-02 05:47:57
Hey there, as a result of the recent [SN Media Kit](https://stacker.news/items/872925/r/Design_r) updated, I'll try to create few simple marketing assets for ~Stackers_Stocks territory to be spread across the web.
Feel free to share in the comments below:
- Few visual references you'd like the assets to be inspired on
- If visuals are not your thing, a description of your idea will help too
- A slogan, or some words/concepts that express the territory's values
@BlokchainB you start, let's see how we go!
originally posted at https://stacker.news/items/873112
-

@ 57d1a264:69f1fee1
2025-02-02 05:36:57
Hey there, as a result of the recent [SN Media Kit](https://stacker.news/items/872925/r/Design_r) updated, I'll try to create few simple marketing assets for ~Construction_and_Engineering territory to be spread across the web.
Feel free to share in the comments below:
- Few visual references you'd like the assets to be inspired on
- If visuals are not your thing, a description of your idea will help too
- A slogan, or some words/concepts that express the territory's values
@BlokchainB you start, let's see how we go!
originally posted at https://stacker.news/items/873104
-

@ 3b7fc823:e194354f
2025-02-02 03:16:40
**Why Privacy Matters and How to Protect It**
Privacy is about control. It’s not about hiding yourself but deciding what others can see about you. Just as you don’t share everything when buying a magazine, technology shouldn’t force you to reveal more than needed.
Why Privacy is Important
1. Personal Control:
Privacy lets you choose what parts of your life are visible. You shouldn’t have to share everything just to use a service.
2. Security Against Exploitation:
Without privacy, people and groups can be targeted by companies or governments. This abuse can lead to data breaches or unnecessary surveillance.
3. Building Trust:
Privacy is key to trust in relationships and communities. When your info is safe, you can transact and communicate without fear of misuse.
**How to Protect Your Privacy**
1. Think Before You Share: Only share what’s necessary and know why you’re doing it.
2. Use Encryption: Encrypt sensitive communications like emails or messages.
3. Control Data Sharing: Avoid oversharing personal details online.
4. Enable Privacy Tools: Use VPNs or privacy settings on social media to shield your data.
5. Be Mindful of Metadata: Understand that metadata (like location data) can reveal more about you than the content itself.
6. Support Privacy-Focused Brands: Choose services that prioritize privacy, like encrypted messaging apps.
7. Read Privacy Policies: Know what data you’re sharing and with whom. 8. Tools like privacy.io can help visualize your digital footprint.
9. Block Trackers: Use tools like DoNotTrackMe or uBlock Origin to stop trackers from collecting your data.
**Conclusion**
Protecting privacy is a vital step in safeguarding your personal freedoms. By taking proactive measures, you can control what information is accessible and ensure that your rights are respected. Remember, you are your own best advocate for privacy—trust no one but yourself to protect your data and identity.
Join the movement to champion privacy as a fundamental human right. Advocate for stronger laws and encourage others to take action, so we can all enjoy safer, more secure digital environments.
-

@ 57d1a264:69f1fee1
2025-02-02 00:03:39

Welcome to the latest updated version of **Stacker News Media Kit & Brand Guidelines `v1.2`**, a pivotal location where all the visual elements find place and help us understand how to use them to have our communications cohesive. SN brand identity is built on simplicity, trust, innovation and a taste of Texas's Wild West. With the following guidelines, as [promised](https://stacker.news/items/855556/r/Design_r?commentId=855753), I'll try to outline the essential elements of SN visual language to be easily usable internally and externally.
As third interaction from the previous [discussion](https://stacker.news/items/786223), here below you will find all the media assets in PNG and SVG downloadable from this [zip file](https://nosto.re/0a8b02224c970de78fba3a0195dcf1ee44d18925ba941724497173b2bcbab901.zip). BTW: I've been using **`Nostr`** 🌸 **Blossom Serverservers** [check them out](https://blossomservers.com/), it's a really cool idea! In case the file will be not available we can always upload it in other servers. Just let me know if any issue downloading it, ideally I made three copies available from:
- https://nosto.re/0a8b02224c970de78fba3a0195dcf1ee44d18925ba941724497173b2bcbab901.zip
- https://blossom.poster.place/0a8b02224c970de78fba3a0195dcf1ee44d18925ba941724497173b2bcbab901.zip
- https://nostr.download/0a8b02224c970de78fba3a0195dcf1ee44d18925ba941724497173b2bcbab901.zip
The source file of all these assets still are the same [Figma file](https://www.figma.com/design/ZL3FLItd9j48pzKVi4qlOy/Stacker.News-Media-Kit?node-id=3-16&t=oEbUcC1tmLDRXgdH-0) and the [PenPot file](https://design.penpot.app/#/workspace/7ad540b5-8190-815d-8005-5685b9c670bc/7ad540b5-8190-815d-8005-5685c186216e?page-id=2643bc5a-0d34-80b2-8005-58099eabda41). This last one, has many issues and does not allow yet the same flexibility as Figma. Both files are open for contributions and comments, just need to register a dummy/anonymous account for each of the tools.
> **Note:** To use these assets across SN, just copy-paste the image relative code, i.e.:

# Stacker News Logotype
SN logo is the most recognizable visual identifier of Stacker News. It captures the essence of its brand and is to be used across the platform and other marketing materials **consistently**. Find below all the possible variations and colors. Ideally you should stick with it to maintain SN identity coherent, or propose something new if you feel like. If you have any question on how to place or use the logo, DO ask below, and we'll help sort it out.
| Avatar on transparent BG | Avatar on BG | Logo Extended | Logo Vertical |#|
|---|---|---|---|---|
|  `` |  `` |  ``|  `` |Oil Black|
|  `` |  `` |  `` |  ``| Golden Yellow |
|  `` |  `` |  `` |  ``|With Shadow |
# Stacker News Typography

This is the typography SN had used to create its logo. [Download LightningVolt OpenType Font file.otf](http://honeyanddeath.web.fc2.com/FontFile/honeyanddeath_Lightningvolt.zip) designed by **[Honey&Death](http://honeyanddeath.web.fc2.com/fnt_Lightningvolt.html)**, install it in your computer and play with it.
Typography is essential to identify, increase readability and create consistency of brands. SN uses the default `font-family:sans-serif;` of your device's OS, usually are the most common and already installed in your device: `system-ui, "Segoe UI", Roboto, "Helvetica Neue", "Noto Sans", "Liberation Sans", Arial, sans-serif, "Apple Color Emoji", "Segoe UI Emoji", "Segoe UI Symbol", "Noto Color Emoji"`. Those are mostly used for:
# Example Header H1
## Example Header H2
### Example Header H3
#### Example Header H4
##### Example Header H5
**Example paragraph text**
The fonts selected will help to communicate the personality of the brand and provide maximum legibility for both print and screen.
`Example <code>`
For code, the approach is the same. Let's the device OS select its default `monospace` one. For example, on Mac will be one of the following:
```
SFMono-Regular, Menlo, Monaco, Consolas, "Liberation Mono", "Courier New",`
```
# Stacker News Colors
A thoughtfully curated color palette gives SN trust, professionalism, and approachability. Colors play a key role in creating consistent visual experiences through digital and print communications. Make sure you are using the right color codes below:
| # | Name | HEX code | RGB code | HLS |
|---|---|---|---|---|
|  | Bitcoin-only | `#F6911D` | `rgb(246,145,29)` | `hsl(32,92.3%,53.9%)` |
|  | Blackr | `#000000` | `rgb(0,0,0)` | `hsl(0,0%,0%)` |
|  | Dark | `#121214` | `rgb(18,18,20)` | `hsl(240,5.3%,7.5%)` |
|  | Gold | `#FADA5E` | `rgb(250,218,94)` | `hsl(48,94%,67.5%)` |
|  | Gray | `#969696` | `rgb(150,150,150)` | `hsl(0,0%,58.8%)` |
|  | Light | `#F0F0F0` | `rgb(240,240,240)` | `hsl(0,0%,94.1%)` |
|  | Nostrch | `#8C25F4` | `rgb(140,37,244)` | `hsl(270,90.4%,55.1%)` |
|  | Pinkish | `#E685B5` | `rgb(230,133,181)` | `hsl(330,66%,71.2%)` |
|  | Ruby | `#C03221` | `rgb(192,50,33)` | `hsl(6,70.7%,44.1%)` |
|  | Sky Hover | `#007CBE` | `rgb(0,124,190)` | `hsl(201,100%,37.3%)` |
|  | Sky Links | `#2E99D1` | `rgb(46,153,209)` | `hsl(201,63.9%,50%)` |
|  | Sky Visited | `#56798E` | `rgb(86,121,142)` | `hsl(203,24.6%,44.7%)` |
|  | So Fiat | `#5C8001` | `rgb(92,128,1)` | `hsl(77,98.4%,25.3%)` |
# Stacker News Icons
SN utilizes a set of bespoke icons that support its communication internally across the platform. Icons help bring instant, intuitive cues for various types of content and features. We share them here for you so you can use as you wish and satisfy your creative needs.
|  `` |  `` |  `[Bounty](https://m.stacker.news/75607)` |  `[Caret](https://m.stacker.news/75608)` |  `[Cowboy](https://m.stacker.news/75609)` |  `[Sun](https://m.stacker.news/75610)` |
|---|---|---|---|---|---|
|  **`[Edit](https://m.stacker.news/75611)`** |  **`[Gun](https://m.stacker.news/75612)`** |  **`[Horse](https://m.stacker.news/75613)`** |  **`[Info](https://m.stacker.news/75614)`** |  **`[Moon](https://m.stacker.news/75615)`** |  **`[Lightning](https://m.stacker.news/75616)`**|
|  **`[Bald Lost Hat](https://m.stacker.news/75617)`**|  **`[Markdown](https://m.stacker.news/75618)`**|  **`[Nostr](https://m.stacker.news/75619)`**|  **`[Referral](https://m.stacker.news/75620)`**|  **`[Rewards](https://m.stacker.news/75621)`**|  **`[Horse Lost Saddle](https://m.stacker.news/75622)`**|  **`[Search](https://m.stacker.news/75623)`** |
| **`[Shoot](https://m.stacker.news/75624)`** | **`[Texas](https://m.stacker.news/75625)`** |  **`[Upload](https://m.stacker.news/75626)`** |  **`[Zap Zap](https://m.stacker.news/75627)`** |||
# Stacker News Banners
Banners are important visual elements used in our digital platforms and marketing materials. They help to highlight key stories, features or announcements while maintaining our brand aesthetic.
Here below you'll find custom banners for Sn and for individial territories. I try to build those that I follow most, for now @AGORA is the only one that designed its own banners. Comment below if you'd like some banners for your territory!
#### SN Dark background
|970x250|
|---|
| ```|``|``|
|728x90|
|---|
|  `` |
#### SN Gold background
|970x250|
|---|
|`` |
|250x250|300x250|300x600|
|---|---|---|
|`` | `` |`` |
|728x90|
|---|
|`` |
#### SN by @Jon_Hodl
|970x250|
|---|
| `` |
|250x250|300x250|300x600|
|---|---|---|
| `` |  ``| `` |
|728x90|
|---|
|`` |
#### ~AGORA territory
The SN P2P Marketplace
|970x250|
|---|
| `` |
|250x250|300x250|300x600|
|---|---|---|
| `` | ``|``|
|728x90|
|---|
| ``|
#### ~alter_native territory
|970x250|
|---|
| ``|
|250x250|300x250|300x600|
|---|---|---|
|``|``|``|
|728x90|
|---|
|`` |
#### ~bitcoin_beginners
|970x250|
|---|
| `` |
|250x250|300x250|300x600|
|---|---|---|
| ``|``|`` |
|728x90|
|---|
| ``|
#### ~Design territory
|970x250|
|---|
|``|
|250x250|300x250|300x600|
|---|---|---|
|``|``|``|
|728x90|
|---|
|``|
#### ~Music territory
|970x250|
|---|
| ``|
|250x250|300x250|300x600|
|---|---|---|
|``|``|``|
|728x90|
|---|
| ``|
# Anything else we could add?
If you feel something is missing, or you know a better tool to manage this media kit for SN in a collaborative and FOSS way then, DO share it in a comment below
Territory owners [^1], do you need banners for your territory? Feel free to edit the figma file liked above or comment below sharing your needs or ideas, I'll try to do something for you.
By following these guidelines, we ensure consistency and professionalism in every case where Stacker News is represented here internally to stackers or to our audience in the KYC internet, reinforcing SN credibility as a trusted source for data-driven journalism.
[^1]: FYI: @Aardvark @AGORA @anna @antic @AtlantisPleb @Bell_curve @benwehrman @bitcoinplebdev @Bitter @BlokchainB @ch0k1 @davidw @ek @elvismercury @frostdragon @grayruby @HODLR @inverselarp @Jon_Hodl @k00b @marks @MaxAWebster @mega_dreamer @niftynei @nout @OneOneSeven @OT @PlebLab @Public_N_M_E @RDClark @realBitcoinDog @roytheholographicuniverse @siggy47 @softsimon @south_korea_ln @theschoolofbitcoin @TNStacker @UCantDoThatDotNet @Undisciplined
originally posted at https://stacker.news/items/872925
-

@ e0e92e54:d630dfaa
2025-02-01 22:32:51
# When a Client Wants Out…& A Yellow Flag Appears
This week was an interesting one with a client that wants to exit our agreement early.
*(Totally fine. It happens and usually when one or both parties want to part ways, unless it's marriage, then it's at minimum a Yellow Flag if not a Red Flag that should be observed).*
I tend to work with clients that have multiple irons in the fire, hence why they need someone like me to come along side them and provide guidance and help root them in the area they must focus on.
There is a strong parallel with this irregardless of whether it's #business #life or #impact
This client had big goals, but like many business owners, they defaulted to reactionary decisions instead of a structured plan. That’s when the Yellow Flag turned into a pattern I’ve seen before—Random Acts of X.
# The Cost of Random Acts of X
If your solution is:
A. Throw money at it, and/or
B. Fire, Aim, Ready...instead of Ready, Aim, Fire
This WILL result in Random Acts of X (wherein X is whatever your are focused on, ie Marketing...aka Random Acts of Marketing essentially equates to the proverbial "throw spaghetti on the wall")
*Is that really a thing? Like do Italians or some other cultures actually throw spaghetti on the wall to see if it "sticks"? Inquiring minds want to know! 🤷♂️*
As I mentioned, my clients tend to have a lot of things they are trying to accomplish at once. This leads to fragmented efforts and lack luster results.
That being said, I approach everything as a relationship. Afterall, I believe:
### Leadership = Relationships!
With this particular client there was one project he abruptly ended. Again, that's fine...it's their business...
Since I'm there to help them lead well, I reminded them this is a relationship and asked "What's next that you want me to focus on?"
We got on the same page with the new project and not even 2 days later that's where the Yellow Flag appeared in the form of issue A (just throw money at it).
# Shortcuts Lead to Ghost Towns (Buying Followers Won’t Work)
You see, they wanted me to lead a marketing campaign to build relationships with people their company could sponsor. ***BUT*** they just wanted to "buy followers".
When I noticed one of their social accounts has 28k followers and on average *only 14 impressions per post*...
I asked "How's that working out for ya?"
You see folks, **real relationships take time!**
One cannot simply "throw money at it" and expect sound, sustainable results.
***If you’re buying an audience instead of building one, you won’t have a community—you'll have a ghost town.***
## What Fake Engagement Looks Like in Business & Family
Think of it this way...
Imagine all you did in your family's relationships was throw money at it. You just "bought followers" in the form of taking this trip, buying that thing for them; and you totally avoided the time investment the relationship requires?
Sure...you might have been physically there...but **were you present**?
I run into this often with my son. He wants me to watch him play a video game. And during that time together what is he doing? He keeps looking over his shoulder to make sure I'm paying attention to HIM and not clandestinely on my phone.
Same goes for his Basketball...he wants me there rebounding for him...not sitting in a chair idly watching.
# Are You Present or Just Physically There?
Business Owners and Leaders!
Husbands, Wives, and Parents!
People whom desire to have an impact!
**The Process is the Shortcut!**
Play silly games. Win silly prizes.
Intentionally build relationships. Reap rewards forever.
It's...
That...
Simple...
Easy? Not really...especially for someone like me whom is just as keen to spend time in nature or chillaxing with a cup of coffee on the back porch, thinking (and wishing my garden was growing better LOL).
But simple? Yes!
**Create the process, execute the process, refine the process, and repeat.**
# The Process is the Shortcut...
*Your Next Step: Cut the Shortcuts. Build the Process.*
So—where do you need to refine your process today?
💡 **What’s one way you can be more present in a relationship this week?**
💡 **What can you eliminate to move you closer to real impact—instead of just chasing more?**
🔹 Drop your answer below 👇
-----------
***Jason Ansley** is the founder of **Above The Line Leader**, where he provides tailored leadership support and operational expertise to help business owners, entrepreneurs, and leaders thrive.*
***Want to strengthen your leadership and enhance operational excellence?**
Connect with Jason at https://abovethelineleader.com/contact*
*📌 This article first appeared on Nostr. You can also find more Business Leadership Articles and content at:
👉 https://abovethelineleader.com/business-leadership-articles*

-

@ 4d4fb5ff:1e821f47
2025-02-01 22:13:43
**Snapshot of a 3D molecular structure.** In bacteria, the enzyme Peptidase E (PepE) is encoded by the gene PEPE. PEPEDASE is an atomic view of PepE enzyme’s spatial architecture based on publicly available scientific data, visually arranged to pay homage to Pepe the Frog. I made this piece in support of Matt Furie’s #SavePepe movement.
<img src="https://i.nostr.build/Lead9.png">
-

@ dbb19ae0:c3f22d5a
2025-02-01 21:51:44
List of Wordpress articles:
- https://alashazam.wordpress.com/2024/07/01/python-nostr/
- https://alashazam.wordpress.com/2024/07/02/python-nostr-2/
- https://alashazam.wordpress.com/2024/07/03/python-nostr-second-program/
- https://alashazam.wordpress.com/2024/07/04/python-nostr-sdk/
- https://alashazam.wordpress.com/2024/07/04/python-nostr-third-program/
- https://alashazam.wordpress.com/2024/07/05/python-nostr-guessing-the-npub/
- https://alashazam.wordpress.com/2024/07/06/python-nostr_sdk-fetching-metadata/
- https://alashazam.wordpress.com/tag/python/
-----------
```python
#!/usr/bin/env python3
"""
Fetches the joined date from a Nostr profile and calculates the days since account creation.
Usage:
python fetch_joined_date.py [npub]
Arguments:
npub : The public key of the user (in npub format).
Requirements:
- nostr_sdk library
- Python 3.x
Example:
python fetch_joined_date.py npub1...
"""
import argparse
import time
import ssl
import json
import uuid
import logging
from datetime import datetime
from nostr.event import EventKind
from nostr.relay_manager import RelayManager
from nostr.key import PublicKey
from nostr.filter import Filter, Filters
from nostr.message_type import ClientMessageType
# Configure logging
logging.basicConfig(level=logging.INFO, format="%(levelname)s: %(message)s")
RELAY_URL = "wss://relay.damus.io"
def fetch_metadata(npub):
"""Fetches metadata from a Nostr profile given an npub key."""
pub_key = PublicKey.from_npub(npub)
filters = Filters([Filter(authors=[pub_key.hex()], kinds=[EventKind.SET_METADATA])])
subscription_id = uuid.uuid1().hex
request = [ClientMessageType.REQUEST, subscription_id, *filters.to_json_array()]
relay_manager = RelayManager()
relay_manager.add_relay(RELAY_URL)
relay_manager.add_subscription(subscription_id, filters)
try:
relay_manager.open_connections({"cert_reqs": ssl.CERT_NONE})
time.sleep(1) # Allow time for connection
relay_manager.publish_message(json.dumps(request))
time.sleep(1) # Allow time for response
while relay_manager.message_pool.has_events():
event_msg = relay_manager.message_pool.get_event()
metadata = json.loads(event_msg.event.content)
return metadata
except Exception as e:
logging.error(f"Error fetching metadata: {e}")
finally:
relay_manager.close_connections()
return None
def fetch_joined_date(npub):
"""Retrieves the joined date of a Nostr profile and calculates days since creation."""
metadata = fetch_metadata(npub)
if not metadata or "created_at" not in metadata:
logging.warning("Could not retrieve metadata or 'created_at' field is missing.")
return
try:
created_at = int(metadata["created_at"])
created_date = datetime.utcfromtimestamp(created_at)
days_since_creation = (datetime.utcnow() - created_date).days
logging.info(f"Account created on: {created_date.strftime('%Y-%m-%d %H:%M:%S UTC')}")
logging.info(f"Days since account creation: {days_since_creation}")
except (ValueError, TypeError):
logging.error("Invalid 'created_at' timestamp.")
if __name__ == "__main__":
parser = argparse.ArgumentParser(description="Fetch the joined date from a Nostr profile.")
parser.add_argument("npub", type=str, help="The public key of the user (in npub format).")
args = parser.parse_args()
fetch_joined_date(args.npub)
```
-

@ 20e17dd0:2ae504d7
2025-02-01 21:14:41
## 1. Hardware Selection
It is important to select adequately the hardware that will be used to build your Node. The Node will be running 24h /7 days and will countain your lightning channels. It is important to use high quality hardware and spend the extra dollars for it.
At the time of building my Node, there was a shortage of Raspberry Pi and I was looking for an optimal alternative. I have decided to go ahead and purchase a used Mac Mini (late 2012).
It is recommended NOT to purchase a Mac Mini newer than 2012 (i.e 2014 and up) because Apple started to solder the RAM to the Logic Board after 2012. The Mac Mini Late 2012 is the last model that is fully customizable with SSD and RAM upgrades.
Here is the list of hardware that will be used in this build:
* 2 x 8G DDR3L Sodim 1600Mhz 1.35V
* 1 x Mac Mini (Late 2012) 2.5Ghz
* 1 x Samsung Evo 870 1Tb SSD ^
^ Note: As discussed earlier, it is important to select hardware of quality. I had initially purchased a low cost 2Tb SSD but it failed while trying to download the Bitcoin blockchain.
##2. Hardware Upgrade
To facilitate the upgrade of the hardware, you will need the proper tools to remove some T6 & T8 screws.
Here are the steps to dismount the few components of the Mac Mini to upgrade the hardware:
1. Unplug the Mac Mini.
2. Turn it upside down with the black cover facing up.
3. Put your thumbs in the 2 grooves of the cover and turn the piece counterclockwise.

4. Remove the cover.
5. Remove 3 x T6 screws holding the fan.

6. Lift the fan and disconnect the connector by pulling gently straight up the wires.
7. Remove 1x T6 screw at the bottom of the shroud (black plastic piece on the left of the fan).

8. Remove the shroud by holding the top right part with your fingers and turning it clockwise.

9. Remove 4 x T8 screws of the grill WIFI cover.

10. The top of the grill is mounted under the Mac Mini case. Lift gently the bottom of the grill and pull towards yourself to remove the grill.
11. Move the grill aside, you do not have to disconnect the WIFI sensor, just be careful.
### 2.1 Upgrading the RAM
The RAM is visible and accessible from the moment you remove the cover. Simply release each RAM by releasing the clips on the side. Once disengaged, the RAM will spring in a 45-degree angle. Remove it and put back the upgraded RAM at a 45 degree angle and push it down for it to clip.
### 2.2 Upgrading the SSD
It is important to note that the Mac Mini has 2 SSD bay. They are referred to as the “upper bay” and “lower bay”. Since we have flipped the Mac Mini upside down to remove the bottom cover, the “upper bay” is located under the “lower bay”.
The “upper bay” is mounted with an expansion kit that holds the SSD in position whereas the “lower bay” SSD is simply resting on top of the “upper bay” SSD.
One important aspect is that the connecting cables for the “lower bay” and “upper bay” SSD are not the same. The “upper bay” SSD connects on the logic board on the right and the “lower bay” SSD cable connects on the left. Removing the “upper bay” SSD requires removing the logic board therefore requires more work. It is recommended to install the new SSD in the “lower” bay. Here are the 2 scenarios:
1.Your Mac Mini has already a Hard Drive installed in the “lower” bay. In that case insert a credit card under the HD and gently pry it upwards. You will be able to slide it out of the bay. The reason to pry it gently is because since there is no “upper” bay drive, The HD is being held in the air by 2 screws on the side that are aligned in 2 holes in the Mac Mini case. Once the HD is removed, transfer the connecting cable and the 2 screws to the new SSD. To put back the new SSD, it is easier to rotate the Mac Mini 90 degree and have the mounting holes at the bottom and use the gravity to get the 2 mounting screws in the holes. After, connect the connector to the logic board.
2. Your Mac Mini has already a Hard Drive installed in the “upper bay”? Leave it there, you do not need mounting screws, but you need a new connecting cable. You will have to buy a “lower bay connector”. Once installed on the SSD, slide the SSD on top of the original one. The connector will plug on the logic board on the left of the “upper bay” SSD connector.
A good preparation would be to go in “Disk Utility” menu on MacOS and search for “upper” or “lower” position before starting to disassemble.
Reassemble everything and you are done.
-

@ be41636e:e55c4909
2025-02-01 18:51:52
## **Will Quantum Computers Kill Bitcoin? The Truth May Surprise You**
One of the biggest fears around Bitcoin is that quantum computers (QCs) will render it obsolete. But is this really a legitimate concern, or just another doomsday myth?
### The Real Threat: Not All Quantum Computers Are Equal
First, let’s get one thing straight: **quantum computers already exist**. The first notable ones appeared in the **1990s**, built by IBM and Stanford. So why hasn’t Bitcoin already been hacked? Because it’s not about whether quantum computers exist—it’s about how powerful they need to be.
### Are All Bitcoin Addresses at Risk?
No! If you’ve entered Bitcoin **after 2010** or **use a wallet backed up with 12 or 24 words (BIP-39, introduced in 2013)**, your funds are safe from quantum threats for a very long time—**centuries, at least**.
But why?
### Understanding How Bitcoin’s Security Works
Bitcoin security is based on **private keys**. (These are represented by the **12-24 words** you write down when setting up a wallet.) From this private key, a **public key** is created. In Bitcoin’s early days, people shared public keys directly to receive payments. But in 2010, Bitcoin introduced an extra layer of security: **hashed addresses**.
Now, instead of sharing your public key, your wallet generates a **Bitcoin address**, which is actually a **hash of your public key**. This adds an extra step for an attacker: before they can find your private key, they must first break the hash to reveal your public key.
### Two Steps to Breaking Bitcoin
To steal Bitcoin using quantum computing, an attacker must:
1. **Break the hash** (Bitcoin address → public key) using **Grover’s algorithm**.
2. **Break the elliptic curve cryptography** (public key → private key) using **Shor’s algorithm**.
### Where Do Quantum Computers Stand Today?
Let’s put things in perspective. **Google’s Willow processor**, which made headlines recently, has **105 physical qubits**. But breaking Bitcoin’s **elliptic curve cryptography** (step 2 above) requires about **2,330 logical qubits**, running for **minutes to hours**.
So how does 105 physical qubits compare to 2,330 logical qubits? It’s **not even in the same league**. To get 2,330 logical qubits, we'd likely need **millions of physical qubits**—a technology that is still decades away.
Now, even if we magically reached **2,330 logical qubits tomorrow**, that only breaks **public keys**. It still wouldn't be enough to break Bitcoin addresses (step 1), which would take **centuries** with current quantum algorithms.
### Who Should Be Worried?
- **People who used Bitcoin before 2010** and still have funds sitting in old public-key-based addresses (**P2PK** addresses). Their funds could be stolen **in minutes to hours** if a powerful enough quantum computer emerged.
- **People who reuse addresses**—this exposes the public key, making it vulnerable to a quantum attack, even when you are using more modern addresses. **(Many wallets, including Trust Wallet, SafePal, Exodus, and Atomic Wallet, still allow this bad practice!)**
### Who Can Sleep Soundly?
- **Anyone using modern Bitcoin addresses (P2PKH, SegWit, Taproot)**. Their addresses are **hashed**, meaning an attacker would need **centuries** to break the first layer of protection before even getting to the public key.
- **Anyone moving their coins periodically**—since modern Bitcoin wallets generate new addresses for each transaction, public keys remain hidden.
### The Concrete Wall Analogy
Think of your Bitcoin private key as being locked inside a massive vault. The first layer of protection is your Bitcoin address, which acts like a thick concrete wall. Cracking through this wall with current quantum algorithms would take centuries. Even if someone managed to break through, they would still face a second, much thinner barrier—your public key. This one would take only minutes to hours to breach. But by then, Bitcoin security upgrades would likely already be in place, leaving attackers empty-handed.
### But What If We Make a Huge Quantum Leap?
Yes, it’s possible that new quantum algorithms emerge, or that quantum hardware advances faster than expected. But Bitcoin’s development community isn’t sitting idle, waiting to get wrecked. There are already proposals for **quantum-resistant Bitcoin addresses**, and they can be implemented **before** quantum computers reach a dangerous level.
### The Bottom Line
🚀 **Quantum computers won’t kill Bitcoin anytime soon.**
📌 If you’re using a **modern Bitcoin wallet**, your funds are safe from quantum threats for the foreseeable future.
📌 If you reuse addresses, stop! It exposes your public key and makes you vulnerable much sooner.
📌 Bitcoin developers are already preparing for a quantum-resistant future.
So, no, quantum computers won’t be the end of Bitcoin. But they might be the end of bad security practices! 🔐
-

@ b17fccdf:b7211155
2025-02-01 18:41:27
#### **Next new resources about the MiniBolt guide have been released**:
---
* 🆕 **Roadmap**: [LINK](https://github.com/orgs/minibolt-guide/projects/1)
* 🆕 **Dynamic Network map**: [LINK](https://app.diagrams.net/?tags={}&lightbox=1&target=blank&highlight=0000ff&edit=_blank&layers=1&nav=1&title=networkmap.drawio.png#Uhttps://raw.githubusercontent.com/minibolt-guide/minibolt/main/resources/networkmap.drawio.png)
* 🆕 **Nostr community**: [LINK](https://habla.news/c/[n]addr1qqyy66twd9px7mr5qyf8wumn8ghj7mmxve3ksctfdch8qatzqgstzl7vmurm5gu87qutx3pxwgxddrg39huj809zhmv03scfkus3z4grqsqqpphk2j0aff) < ~ REMOVE the "[]" symbols from the URL (naddr...) to access
* 🆕 **Linktr FOSS** (UC) by [Gzuuus](nostr:npub1gzuushllat7pet0ccv9yuhygvc8ldeyhrgxuwg744dn5khnpk3gs3ea5ds): [LINK](https://linktr.minibolt.info)
* 🆕 **Donate webpage**: 🚾 [Clearnet LINK](https://donate.minibolt.info) || 🧅 [Onion LINK](http://3iqm7nidexns5p6wmgc23ibgiscm6rge7hwyeziviwgav4fl7xui4mqd.onion/apps/Li3AtEGDsqNmNddv6rX69taidm3/pos)
* 🆕 **Contact email**: [hello@minibolt.info](mailto:hello@minibolt.info)
---
Enjoy it MiniBolter! 💙
-

@ be41636e:e55c4909
2025-02-01 18:35:06
One of the biggest fears around Bitcoin is that quantum computers (QCs) will render it obsolete. But is this really a legitimate concern, or just another doomsday myth?
### The Real Threat: Not All Quantum Computers Are Equal
First, let’s get one thing straight: **quantum computers already exist**. The first notable ones appeared in the **1990s**, built by IBM and Stanford. So why hasn’t Bitcoin already been hacked? Because it’s not about whether quantum computers exist—it’s about how powerful they need to be.
### Are All Bitcoin Addresses at Risk?
No! If you’ve entered Bitcoin **after 2010** or **use a wallet backed up with 12 or 24 words (BIP-39, introduced in 2013)**, your funds are safe from quantum threats for a very long time—**centuries, at least**.
But why?
### Understanding How Bitcoin’s Security Works
Bitcoin security is based on **private keys**. (These are represented by the **12-24 words** you write down when setting up a wallet.) From this private key, a **public key** is created. In Bitcoin’s early days, people shared public keys directly to receive payments. But in 2010, Bitcoin introduced an extra layer of security: **hashed addresses**.
Now, instead of sharing your public key, your wallet generates a **Bitcoin address**, which is actually a **hash of your public key**. This adds an extra step for an attacker: before they can find your private key, they must first break the hash to reveal your public key.
### Two Steps to Breaking Bitcoin
To steal Bitcoin using quantum computing, an attacker must:
1. **Break the hash** (Bitcoin address → public key) using **Grover’s algorithm**.
2. **Break the elliptic curve cryptography** (public key → private key) using **Shor’s algorithm**.
### Where Do Quantum Computers Stand Today?
Let’s put things in perspective. **Google’s Willow processor**, which made headlines recently, has **105 physical qubits**. But breaking Bitcoin’s **elliptic curve cryptography** (step 2 above) requires about **2,330 logical qubits**, running for **minutes to hours**.
So how does 105 physical qubits compare to 2,330 logical qubits? It’s **not even in the same league**. To get 2,330 logical qubits, we'd likely need **millions of physical qubits**—a technology that is still decades away.
Now, even if we magically reached **2,330 logical qubits tomorrow**, that only breaks **public keys**. It still wouldn't be enough to break Bitcoin addresses (step 1), which would take **centuries** with current quantum algorithms.
### Who Should Be Worried?
- **People who used Bitcoin before 2010** and still have funds sitting in old public-key-based addresses (**P2PK** addresses). Their funds could be stolen **in minutes to hours** if a powerful enough quantum computer emerged.
- **People who reuse addresses**—this exposes the public key, making it vulnerable to a quantum attack, even when you are using more modern addresses. **(Many wallets, including Trust Wallet, SafePal, Exodus, and Atomic Wallet, still allow this bad practice!)**
### Who Can Sleep Soundly?
- **Anyone using modern Bitcoin addresses (P2PKH, SegWit, Taproot)**. Their addresses are **hashed**, meaning an attacker would need **centuries** to break the first layer of protection before even getting to the public key.
### The Concrete Wall Analogy
Think of your Bitcoin private key as being locked inside a massive vault. The first layer of protection is your Bitcoin address, which acts like a thick concrete wall. Cracking through this wall with current quantum algorithms would take centuries. Once one breaks through this wall, they would face a second wall, which is a much thinner barrier—your public key. This one would take only minutes to hours to breach.
### But What If We Make a Huge Quantum Leap?
Yes, it’s possible that new quantum algorithms emerge, or that quantum hardware advances faster than expected. But Bitcoin’s development community isn’t sitting idle, waiting to get wrecked. There are already proposals for **quantum-resistant Bitcoin addresses**, and they can be implemented **before** quantum computers reach a dangerous level.
### The Bottom Line
🚀 **Quantum computers won’t kill Bitcoin anytime soon.**
📌 If you’re using a **modern Bitcoin wallet**, your funds are safe from quantum threats for the foreseeable future.
📌 If you reuse addresses, stop! It exposes your public key and makes you vulnerable much sooner.
📌 Bitcoin developers are already preparing for a quantum-resistant future.
So, no, quantum computers won’t be the end of Bitcoin. But they might be the end of bad security practices! 🔐
-

@ b17fccdf:b7211155
2025-02-01 18:28:39
---
##### Check out the **MiniBolt guide** -> [HERE](https://minibolt.info) <-
---
* **Core guides**
* [**System**](https://minibolt.minibolt.info/system/system)
* [Preparations](https://minibolt.minibolt.info/system/system/preparations)
* [Operating System](https://minibolt.minibolt.info/system/system/operating-system)
* [Remote access](https://minibolt.minibolt.info/system/system/remote-access)
* [Configuration](https://minibolt.info/guide/system/configuration)
* [Security](https://minibolt.minibolt.info/system/system/security)
* [Privacy](https://minibolt.minibolt.info/system/system/privacy)
* [**Bitcoin**](https://minibolt.minibolt.info/bitcoin/bitcoin)
* [Bitcoin client](https://minibolt.minibolt.info/bitcoin/bitcoin/bitcoin-client) (Bitcoin Core)
* [Electrum server](https://minibolt.minibolt.info/bitcoin/bitcoin/electrum-server) (Fulcrum)
* [Desktop signing app](https://minibolt.minibolt.info/bitcoin/bitcoin/desktop-signing-app-sparrow) (Sparrow Wallet)
* [Blockchain explorer](https://minibolt.minibolt.info/bitcoin/bitcoin/blockchain-explorer) (BTC RPC Explorer)
* [**Lightning**](https://minibolt.minibolt.info/lightning/lightning)
* [Lightning client](https://minibolt.minibolt.info/lightning/lightning/lightning-client) (LND)
* [Channel backup](https://minibolt.minibolt.info/lightning/lightning/channel-backup)
* [Web app](https://minibolt.minibolt.info/lightning/lightning/web-app) (ThunderHub)
* [Mobile app](https://minibolt.minibolt.info/lightning/lightning/mobile-app) (Zeus)
* **Bonus guides**
* [**System bonus guide**](https://minibolt.minibolt.info/bonus-guides/system)
* **Dashboard & Appearance**
* [Pimp the command line](https://minibolt.minibolt.info/bonus-guides/system/command-line)
* [System Overview](https://minibolt.minibolt.info/bonus-guides/system/system-overview)
* **System Administration**
* [Aliases](https://minibolt.minibolt.info/bonus-guides/system/aliases)
* [Statip IP & custom DNS servers](https://minibolt.minibolt.info/bonus-guides/system/static-ip-and-custom-dns-servers)
* **Install / Update / Uninstall common languages**
* [Node.js + NPM](https://minibolt.minibolt.info/bonus-guides/system/nodejs-npm)
* [Rustup + Cargo](https://minibolt.minibolt.info/bonus-guides/system/rustup-+-cargo)
* [Go!](https://minibolt.minibolt.info/bonus-guides/system/go)
* **Databases**
* [PostgreSQL](https://minibolt.minibolt.info/bonus-guides/system/postgresql)
* **Security**
* [SSH Keys](https://minibolt.info/guide/bonus/system/ssh-keys.html)
* [WireGuard VPN](https://minibolt.info/guide/bonus/system/wireguard-VPN.html)
* [Cloudflare Tunnel](https://minibolt.minibolt.info/bonus-guides/system/cloudflare-tunnel)
* **Resilience**
* [Tor services: bridges & relays](https://minibolt.minibolt.info/bonus-guides/system/tor-services)
* **Hardware**
* [Store data in a secondary disk](https://minibolt.minibolt.info/bonus-guides/system/store-data-secondary-disk)
* [**Bitcoin bonus guides**](https://minibolt.minibolt.info/bonus-guides/bitcoin)
* **Electrum servers**
* [Electrs](https://minibolt.minibolt.info/bonus-guides/bitcoin/electrs)
* **Signing apps**
* **Desktop**
* [Electrum Wallet Desktop](https://minibolt.minibolt.info/bonus-guides/bitcoin/electrum-wallet-desktop)
* **Decentralized exchange**
* [Bisq](https://minibolt.minibolt.info/bonus-guides/bitcoin/bisq)
* **Resilience**
* [Safu Ninja](https://minibolt.minibolt.info/bonus-guides/bitcoin/safu-ninja)
* [Ordisrespector](https://minibolt.minibolt.info/bonus-guides/bitcoin/ordisrespector)
* **Fun**
* [Download the white paper](https://minibolt.minibolt.info/bonus-guides/bitcoin/white-paper)
* **Testnet**
* [MiniBolt on Testnet](https://minibolt.minibolt.info/bonus-guides/bitcoin/minibolt-on-testnet)
* **Payment processors**
* [BTCPay Server](https://minibolt.minibolt.info/bonus-guides/bitcoin/btcpay-server)
* [**Nostr bonus guides**](https://minibolt.minibolt.info/bonus-guides/nostr)
* **Relays**
* [Nostr relay](https://minibolt.minibolt.info/bonus-guides/bitcoin/nostr-relay)
---
🏗️ [Roadmap](https://github.com/orgs/minibolt-guide/projects/1) | 🌐 [Dynamic Network map](https://app.diagrams.net/?tags={}&lightbox=1&target=blank&highlight=0000ff&edit=_blank&layers=1&nav=1&title=networkmap.drawio.png#Uhttps://raw.githubusercontent.com/minibolt-guide/minibolt/main/resources/networkmap.drawio.png) | 🔧 [Issues](https://github.com/minibolt-guide/minibolt/issues) | 📥 [Pull requests](https://github.com/minibolt-guide/minibolt/pulls) | 🗣️ [Discussions](https://github.com/orgs/minibolt-guide/discussions)
---
By [**⚡2FakTor⚡**](nostr:npub1k9luehc8hg3c0upckdzzvusv66x3zt0eyw7290kclrpsndepz92sfcpp63)
---
**Last updated:** 22/12/2024
-

@ d57360cb:4fe7d935
2025-02-01 18:22:10
What is life but a preparation for the grand finale.
Think of your life up to this point. You’ve been living in the midst of death whether you pay attention to it or not.
Your youth faded, the years go by, relationships fail, careers fail, people die, the ones close to you and those you hardly know. Civilizations wiped out, total species completely gone with no trace.
Here you are in the midst of death. A vortex of change wiping everything in its path. Creating space for the unknown and new. Nothing lasts, nothing stays the same, everything ends. Ending gives great significance to life.
How will you be in the presence of someone you love knowing they or you will vanish one day?
What wouldn’t you put off if you were aware your time was slipping and there’s nothing you can do.
What would you stop doing?
What would you let go of?
Who would you forgive?
Life comes with a bullet and it has your name on it. You don’t know when it’ll happen.
Don’t believe you ever have time it’s always a fantasy. Death will knock you on your feet when you least expect it.
Use death as a doorway to a deep meaningful life.
-

@ cff1720e:15c7e2b2
2025-02-01 17:37:00
Am 4. Oktober 1957 sendete Sputnik 1 erste Signale aus dem All. Die Welt war fasziniert, die Amerikaner geschockt, da die Russen sie in der Raumfahrt technologisch überholt hatten. Es folgte der Wettlauf im All mit Apollo-Programm und Mondlandung 1969. Am 27. Januar 2025 erlebte die USA einen weiteren Sputnik-Moment, diesmal durch die chinesische KI-App deepseek R1. Diese App schoss wenige Stunden nach ihrem Start auf Platz 1 der App-Stores, vorbei an dem bisherigen KI-Spitzenreiter ChatGPT. Die Aktie des KI-Chipherstellers Nvidia verlor 17% (600 Mrd. USD Börsenwert), das war der bisher höchste Tagesverlust des US-Aktienmarktes. Marc Andreessen verwendete gar die Formulierung “Sputnik-Schock", diese einseitige Sichtweise erschwert aber eine Betrachtung aus verschiedenen Perspektiven.

Was lässt sich mit ein paar Tagen Abstand daraus schlussfolgern? Die Aktionäre haben überreagiert und die Falschen bestraft. Die Nervosität der Anleger ist aber verständlich bei einem KGV von 46 bei Nvidia und 27 bei den “Magnificent Seven” (die großen US KI-Anbieter). Normale KGVs bewegen sich um 15, d.h. wir haben es mit einer ausgeprägten KI-Blase zu tun, die in Kürze platzen dürfte. Eine weitere Blase die schon vor dem Start geplatzt ist, ist das Projekt “Stargate” der Firmen OpenAI, Oracle und Softbank. In den nächsten 4 Jahren wollen sie 500 Mrd. USD für über 10 neue KI-Rechenzentren investieren, um Amerikas vermeintliche KI-Vorherrschaft gegenüber China weiter auszubauen. Die schon vorher vorhandenen Zweifel an dem Projekt (Elon Musk auf X “sie haben das Geld gar nicht”) wurden nun durch den Erfolg von deepseek verstärkt.

deepseek hat nämlich offenbart, dass die bisherige US KI-Strategie, "wir schlagen die Chinesen mit unserer DataCenter-Power", ein fataler Irrweg ist. Den Analysten von Bernstein zufolge ist das Modell von deepseek geschätzt 20 bis 40 mal billiger zu betreiben als ähnliche Modelle von OpenAI. Die Chinesen haben ihre Innovation durch Kreativität erzielt, im Gegensatz zur Gigantomanie der US-Konzerne, die sich in einem Überbietungs-Wettbewerb der Ressourcen-Verschwendung befinden. Hunderte Milliarden an Investorengeldern und ca. 9% des nationalen Stromverbrauchs führen zwar zur Bereicherung einiger Konzerne und ihrer Besitzer, nicht aber zu adäquaten Ergebnissen. Das selbe Muster konnte man bereits bei der Rüstungsbranche beobachten, die mit dem etwa 10-fachen Budget (1 Billion USD) nicht im Stande war bessere Waffensysteme zu produzieren als Russland (Oreshnik-Schock 2024).

Wenn Donald Trump wirklich Amerika stärken möchte, dann sollte er umgehend seine technokratischen Berater entlassen und Sun Tzu lesen, ein Buch, das die Grundlagen asiatischer Strategie vermittelt und den Krieg vermeiden lehrt ("Der klügste Krieger ist der, der niemals kämpfen muss"). Die chinesischen Erfolge basieren auf exzellenter Bildung, Startup-Förderung und minimaler Regulierung, Konzepte die der Westen zwar stets gepredigt aber nie geliefert hat. “Make Amerika smart again” hieße daher Abschied von Kriegsrhetorik, Embargos, Oligarchen-Projekten und der bisherigen Großmacht-Hybris. Annektionspläne für Grönland und Kanada passen nicht in das Bild, Wiederherstellung von Meinungsfreiheit und Abbau von Regulierungen schon (Streichung von Bidens KI-Regulierung Executive Order 14110). Wohin steuert Trump die USA? Wird der deepseek-Moment dabei helfen falsche Strategieansätze zu korrigieren? Das ist noch unklar, während aber schon jetzt unzweifelhaft feststeht, dass die EU und Deutschland weder bei der KI noch in der Geostrategie eine Rolle spielen, dafür aber als unangefochtene Regulierungs-Weltmeister. Herzlichen Glückwunsch!

„Man kann zwar die Realität ignorieren, aber nicht die Folgen davon ignorieren.“ Ayn Rand
Der wirkliche Gewinner dieser Woche ist aber die OpenSource-Szene mit ihren dezentralen Lösungsansätzen. Nicht nur deepseek R1 ist OpenSource sondern auch Marco o1 von Alibaba (<https://github.com/huggingface>). Die Nutzung ist kostenlos (ChatGPT kostet 200 USD pro Monat), daher können sowohl die Modellbildung, die Trainingsdaten als auch die Rechenleistung von unzähligen Aktivisten weltweit verteilt erbracht werden. Dafür braucht es weder Milliarden-Budgets, Regierungsprogramme oder neue DataCenter. Das Potential der Crowd übertrifft jeden zentralistischen Ansatz. Die Ergebnisse sind besser und die Kontrolle liegt nicht in den Händen einzelner. Smarte Lösung sind verteilt, das beweisen Projekte wie Bitcoin (seit 16 Jahren), Lightning und neuerdings auch Nostr. Deshalb haben wir Pareto (<https://pareto.space>) auf diesen Fundamenten entwickelt (Nostr, Lightning) und in 6 Monaten mit Freiwilligen mehr erreicht als viele große IT-Unternehmen in Jahren. Die Dinosaurier sterben aus, dem Schwarm gehört die Zukunft.
-

@ e262ed3a:e147fbcb
2025-02-01 15:37:28
**Feel free to develop**
I got an idea while watching a video from @BTCSessions, which I personally cannot implement technically. Therefore, I would like to present it here for discussion and free implementation. It makes sense to me, but what do I know? Let the swarm intelligence decide.
The goal of the business idea is:
How can I bring as many solo miners as possible into a pool without them having to pay for the electricity for mining and their mining hardware can be amortized quickly, so they can purchase more mining hardware?
How can we financially support Bitcoin and Nostr developers in the long term?
How can we intensify developers for the implementation of this idea?
How can we encourage non-Bitcoiners to invest in the support of the Bitcoin network?
How can we get non-Bitcoin retailers to invest in the Bitcoin network?
**The answer is: PROSPECT OF WINNING
The solution lies in a kind of RAFFLE. (Not a betting website)
!**
The legal difference between a BET and a RAFFLE varies from country to country. It lies in the fact that a raffle must be very transparent regarding the chances of winning and the proceeds must go to a good cause. Those involved in the implementation can, of course, be compensated (also with a profit for the individual participants). The extent to which this is allowed would have to be checked by those who want to implement this idea.
In the following, I will describe the implementation roughly. Since this is not a sales presentation, please excuse me if the following proposal is not fully structured.
**Participants in the idea are:
Consumers (ticket buyers)
Bitcoin miners
Retailers
Non-profit company that implement the project**
**What's it about?** @BTCSessions has a YouTube video about the miner FutureBit. In the dashboard of the solo miner, you could see how high the hash rate was. But above all, you could see how high the chance of winning was for the solo miner in the overall network. In the case of BTCSessions FutureBit, the hash rate was around 5 TerraHash and the chance of winning was around 1:1,000,000. (Which, according to my calculations, was not correct). The power consumption was around 32 watts. When I saw that, it suddenly dawned on me.
Could it be possible to create a website/app that determines the total hash rate of a mining pool and then offers an electronic, numbered ticket for each 1 TerraHash (TH/s) of the pool for, for example, 0.1 USD? The minimum purchase amount would be 10 tickets. The customer sees the chance of winning and could even see the possible payout. The ticket is only valid for the next block (similar to roulette).
Another variant could be that the buyer can select one or more of the next 10 blocks and purchase tickets for the selected block. Since you don't know in advance how high the pool hash rate will be 5 or 10 blocks ahead, the amount of tickets to be issued for the 2nd block, for example, could only be 90% of the current pool hash rate, the 3rd block only 80%, and so on. If block 3, for example, advances to position 2, the previously unavailable 10% will be released for further tickets. (Determined by the pool hash rate at that time)
The purchase of 10 or more tickets could be automated in the customer's account on the website/app (intervals: hourly, daily, weekly, every 10 blocks, etc.). Customers could also top up their account with satoshis, enabling automatic deductions for ticket purchases. This could be facilitated by automatically issuing a Nostr npub to each customer, which would also create a wallet at Primal.net (Strike). For non-Bitcoiners, Zaprite could be used to recharge their account. Alternatively, customers could enter a NostrWalletConnection NWC to enable automatic deductions from their Lightning wallet. The project operators might also consider running their own ecash mint, which would allow them to assign an integrated ecash address to customers without a Lightning address. Tickets with ascending numbers would be allocated strictly in the order of payment receipts.
**Calculations for the miners:** The FutureBit miner consumed approximately 30 watts per terahash/hour. Let's assume that 10 terahash consume 300 watts per hour, then the miner consumes 50 watts per 10 minutes (per block). Let's further assume that a kilowatt-hour of electricity costs between 10 and 30 cents, then it costs the miner 3-9 cents per hour for electricity at 10 terahash mining capacity. So, 0.5-1.5 cents per block. In the case that each ticket is sold for 1 terahash for the next block, one could automatically transfer, for example, 5% of the satoshis received from ticket sales to each participating miner in the pool (proportional to the average hash rate delivered by the miner in the last block in the pools). This happens even if the block is not found. If fewer tickets are sold than the maximum possible amount, then the 5% of the sold tickets will be distributed proportionally. (See also my Excel file?
At the center of the project is a website/app that manages the raffle. Here, anyone can register and create an account. Either as a miner, retailer, or customer with or without KYC, for example, with their own nostr nsec, wallet signature, email and password or phone number and password.
Once logged into the account, Bitcoiners can enter their Lightning address and a Bitcoin on-chain address. Non-Bitcoiners enter their financial data in case they win.
Miners must enter a Bitcoin and Lightning (or ecash) address. The pooling process is also managed in the miner's account.
Tickets can be purchased (like in a regular online shop) and paid for in any way. Zaprite could be a solution here. But also Strike, Cashapp, etc. As described above, such purchases could also be automated.
**Retailers** can also register as such. They will then have the opportunity to sell "tickets" to their customers and collect the money in cash. To sell tickets, they must enter the customer's name and a valid email address. After payment, they must send the purchase price via Lightning to the non-profit company, which will then confirm the purchase to the ticket buyer and the retailer with all the data. This is the receipt for the buyer. In the event of a win (the mined block must have 3-6 block confirmations), the ticket buyer will receive an email explaining all the further details of how to claim the prize. This could be a link that takes them directly to the website and logs them in directly. The winner can then enter their data on how and where the money should be paid out (Bitcoin address or bank details). Alternatively, they can go to their retailer, who can assist them by entering the data in their sub-account (customer account). To prevent the retailer from falsifying the data entry, the winner will first receive an email with the entered data, which they can confirm (if correct). Since the retailer is also involved in the win, they will also be notified.
How many tickets can be offered per round (Bitcoin block)? The number of tickets depends on the hash rate in the pool. One ticket can be issued per 1 TerraHash (TH/s). How the ticket is generated per round and customer, I don't know, as I lack the technical knowledge. Maybe as a kind of NFT that contains the corresponding data (customer number (npub) of the buyer and possibly retailer, block number, ticket number). Or as a Taproot asset on Lightning? Or as a minted ecash coin? Or simply as an entry in a database that the customer can see in their account.
The maximum payout of the winnings in the event of a found block to the ticket holders could be 70%. The remaining 30% would be distributed to the miners and retailers. For example: Miners 25%, retailers 5%. The non-profit organization receives nothing from the block rewards. Instead, it receives 65% of the revenue from all ticket sales. With a mining pool hash rate of 10,000 TH/s, where all tickets are sold continuously, a daily donation of around 93,000 USD would be generated. (see Excel.file)
The revenue, after deducting the possible costs of the organization, goes directly to @opensats and/or other organizations that support the Bitcoin network after each block. Either via Lightning or Bitcoin on-chain payment.
In the attached Excel file, you can find my calculations. Here, anyone can play through different scenarios.
What I noticed was that with maximum ticket sales per block, only around 200 USD per 10 tickets would be paid out, since each participating ticket wins in the event of a found block. Since I believe that this is not a very great incentive for buying tickets, I suggest the following variants.
Winning variants: Each purchased ticket has a running number. Ticket 1 has the number 000.000, ticket 2 has the number 000.001, ticket 10.120 has the number 010.119, and so on.
If the next block is found, then this found block in the Bitcoin blockchain has a hash. For example, block 881367 has the hash 000000000000000000014b0fab24355c71c6940584d9cd5990c0b081a31d54a4
Let's now remove the letters and read only the numbers from back to front, so the last 3 numbers are 544
Instead of every participating ticket winning, in this variant, only the tickets with the ending digits 544 win.
With, for example, 11,000 tickets sold, the ticket numbers 000.544 / 001.544 / 002.544 ... 010.544 would win. So, 11 ticket participants would win. Each winner with this number would receive around 0.284 Bitcoin (3.125 BTC / 11).
One could also let the ticket numbers with the ending digits 44 win, and thus every hundredth ticket. Or even combine it.
What I also noticed was that with retailers, a special case arises. Retailers receive 5% of the block rewards in the event of a found block. But only proportionally to the tickets sold by the retailer. This means that in order for the entire 5% to be distributed to the retailers, all 10,000 tickets of 10.000 possible tickets would have to be sold by retailers. Since not all tickets will be sold by retailers, a remaining amount will be left over. This could be distributed additionally to the miners. Or any other variant.
I hope the idea finds resonance and invites discussion. Maybe I've made some mistakes in thinking, and the idea is not feasible. But if you like the idea, please forward it to developers, investors, and others you know.
Stay humble hash sats
@nostr:npub1uf3w6w3z4kxy0zc80m6a03tt9s7855c9r8kkjmkju47xtc28l09sc30gqq
[Excel sheet for download](https://c.gmx.net/@329519820976429649/KJTehgh0SMGliV4HLjMf0g)
-

@ a012dc82:6458a70d
2025-02-01 15:17:38
The cryptocurrency landscape is witnessing a remarkable resurgence, with Bitcoin once again leading the charge. After a period of volatility and uncertainty, Bitcoin has reclaimed its throne as the king of cryptocurrencies, drawing renewed interest from investors and financial experts alike. This article delves into the factors behind Bitcoin's comeback, its implications for the market, and what the future might hold.
**Table Of Content**
- The Remarkable Recovery of Bitcoin
- The Ripple Effect on the Crypto Market
- Investor Sentiment: Cautious Optimism
- The Future Outlook: Opportunities and Challenges
- A New Era for Bitcoin
- Conclusion
- FAQs
**The Remarkable Recovery of Bitcoin**
**A Surge in Value**
After a tumultuous phase marked by sharp declines and skepticism, Bitcoin has made a striking comeback. The digital currency's value has seen a significant upswing, reminding investors of its potential as a high-reward, albeit high-risk, asset. This recovery is not just a numerical increase but a symbol of resilience in the face of market adversities.
**Driving Factors**
Several factors have contributed to Bitcoin's resurgence. These include an increase in institutional adoption, technological advancements within the blockchain ecosystem, and a growing recognition of Bitcoin as a 'digital gold' amidst economic uncertainties. Moreover, regulatory clarity in some regions has provided a more stable environment for cryptocurrency investments.
**The Ripple Effect on the Crypto Market**
**Boosting Market Confidence**
Bitcoin's rebound has had a ripple effect across the entire cryptocurrency market. Altcoins and emerging digital assets have also seen a boost in both value and investor interest. This resurgence has rekindled the enthusiasm for decentralized finance (DeFi) and non-fungible tokens (NFTs), which had waned during the market downturn.
**Impact on Blockchain Innovation**
The renewed interest in Bitcoin has spurred further innovation in blockchain technology. Developers and entrepreneurs are increasingly exploring new use cases for blockchain, expanding beyond traditional financial applications to areas like supply chain management, digital identity, and more.
**Investor Sentiment: Cautious Optimism**
**Institutional Investors' Role**
Institutional investors, once wary of Bitcoin's volatility, are now more open to including it in their portfolios. This shift is partly due to the improved infrastructure and regulatory frameworks that make investing in Bitcoin less risky than in its early years.
**Retail Investors' Perspective**
Retail investors, who were significantly affected by the previous market downturn, are approaching Bitcoin with cautious optimism. Many are drawn by the potential for high returns but remain mindful of the risks involved.
**The Future Outlook: Opportunities and Challenges**
**Potential for Growth**
With its current momentum, Bitcoin has the potential for further growth. Its evolving role in the financial ecosystem, particularly in areas like digital payments and remittances, suggests a bright future.
**Navigating Challenges**
However, challenges remain. Regulatory uncertainties, potential market manipulations, and the environmental impact of Bitcoin mining are issues that need addressing. How these challenges are managed will significantly influence Bitcoin's trajectory.
**A New Era for Bitcoin**
**A Testament to Resilience**
Bitcoin's comeback is a testament to its resilience and the enduring faith of its supporters. It has not only reclaimed its position as the leading cryptocurrency but has also reinforced the belief in the potential of digital currencies.
**A Dynamic Future Ahead**
As investors, both institutional and retail, continue to take notice, Bitcoin's journey is far from over. Its ability to adapt, innovate, and overcome challenges will shape not just its future but also that of the broader cryptocurrency market. The current phase is just the beginning of what promises to be a dynamic and transformative era for Bitcoin and digital currencies as a whole.
**Conclusion**
Bitcoin's resurgence marks a significant milestone in the cryptocurrency world. Its ability to bounce back from adversity and regain its status as the leading digital currency has not only bolstered investor confidence but also highlighted the growing maturity of the crypto market. As Bitcoin continues to evolve, navigating through regulatory landscapes and technological advancements, it stands as a symbol of innovation and resilience in the ever-changing world of finance.
**FAQs**
**Why has Bitcoin's value surged recently?**
Bitcoin's value has surged due to factors like increased institutional adoption, advancements in blockchain technology, and its growing recognition as a digital store of value amidst economic uncertainties.
**How has Bitcoin's recovery affected the overall crypto market?**
Bitcoin's recovery has positively impacted the entire crypto market, boosting the value of altcoins and reigniting interest in decentralized finance (DeFi) and non-fungible tokens (NFTs).
**Are institutional investors now more interested in Bitcoin?**
Yes, institutional investors are showing increased interest in Bitcoin, thanks to improved investment infrastructure and clearer regulatory frameworks.
**What are the main challenges facing Bitcoin in the future?**
The main challenges include regulatory uncertainties, potential market manipulations, and the environmental impact of Bitcoin mining.
**Is it safe for retail investors to invest in Bitcoin now?**
While Bitcoin offers potential high returns, it remains a high-risk investment. Retail investors should approach with caution and consider diversifying their investment portfolio.
**That's all for today**
**If you want more, be sure to follow us on:**
**NOSTR: croxroad@getalby.com**
**X: [@croxroadnews.co](https://x.com/croxroadnewsco)**
**Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)**
**Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)**
**Store: https://croxroad.store**
**Subscribe to CROX ROAD Bitcoin Only Daily Newsletter**
**https://www.croxroad.co/subscribe**
***DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.***
-

@ df478568:2a951e67
2025-02-01 15:07:26

# Garlic Cashew Recipe
I wrote about selling roasted cashews as an experiment in capitalism [here](https://substack.com/home/post/p-156063324). I make them myself and in the spirit of free and open source software, I figured I would open-source the recipe with a catch. You can get the recipe in one of two ways.
1. Become a paid subscriber to my Substack and you will get a key to unlock the cipher text
2. Read it in the clear(un-encrypted) on nostr. The easiest way to do this is to navigate to primal.net in your browser and search for “marc26z.” Click on my profile and **you can find all of my writing in the clear in the reads section*.
I tried using PGP in another article, but it’s a little cumbersome and pretentious. Andreas Grifin said, [Nostr is what PGP should have been. A web of trust with easy-to-use encryption and verification](nostr:note12c47gxhxyw5elg55yh4g90fztddhpgqz95jf6fwvk3yygt7qml6sjd6lwj). I tend to agree. So I’m using something else.

https://8gwifi.org/CipherFunctions.jsp
**Decrypt using the passphrase below the paywall**.
"To encrypt is to indicate the desire for privacy, and to encrypt with weak cryptography is to indicate not too much desire for privacy.”
I do not indicate a desire for too much privacy here, but I like playing with these things. I hope you enjoy playing with them too.
## How To Decrypt
1. Go to https://encrypt-online.com/decrypt/ on your favorite web browser.
2. Choose aes-256-cbc(this is the default setting)
3. Copy and paste the cipher text into the decryption field
4. enter the passphrase into the passphrase field
5. press the Decrypt button
6. Optional: Copy and paste the decrypted recipe into a markdown editor like https://dillinger.io/
U2FsdGVkX1+4jxMfWCc6kNsbDa0i/J3eiV81r7/z5c0Eqe73vw01M22uRFm9PjRRaj/CJN+BidtuNXQW6G3hk3S/4AoGN2gKfKkKSbzEHsONZ2LeXuoPflikratDU+lADVeR5IlsVaATyImBO0k/cXq54TOlEXBoVRCIqaA9tO8UA126GfTdmegXX14jUcdV9EISSGw8Bn5fksptm6qKyz2GsmyiKcmNczh8Nz7biyhCrnrt2hyLDbirIAjZcCTJjkAlJjrrvuLHJZx6pmq6MsMv2eHT35d/WL/+ZpBgLVh2Xq2u+J9izNKYMgvMSsJKylC7MJvj4xAOosJuq9IyGN6b/7z2UTSsR13Utc8aFeW3zxtkvAqYthh7XV1H2e1nEKOij8gOfFHvlfj10IiG0g3QbEch1nTTGq3Lncql9Q1a9QZb5pcsellPWeR4vhko3ssdxzIkLnvGz5Cjy1brMjZ97j7sSmHE9FT10L4L6ijXWuW25ikDRK0xnks0VfAvDVz75NCE+Qaz9MLPt8h0ESto3bTyuXrHFNNPOxnaEDw4TvSTN5G0tmUrqotRMmu5DadAm6aLMmJHL1OHVNGK4fH7Hb9S+7dBLEbQG3vRivz2SzpqgKFnFYwMJTQykUC3
Passphrase:
implored-junker-requires
Here is the decrypted recipe if you do not wish to learn about encryption, but want to try my delicious non-vegan cashew recipe anyway.
1 LB organic raw cashews
2 TBS beef tallow
2 TBS salt
1 TBS garlic powder
Melt tallow in the microwave
Brush the tallow on the nuts. Spread onto a cookie sheet.
Preheat oven 350 degrees
Bake for 10 minutes.
Let cool.
Violá!
Enjoy your garlic-roasted cashews. Or...you can pick some up at nostr:npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0
[A Crumby Commercial](https://i.imgflip.com/1ts3w3.jpg)
npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0
[881,805]()https://mempool.marc26z.com/block/00000000000000000000f5d9aa481b8f2555deaa8638a3c1f2eb4ffa8f474f9d
[Merch](nostr:npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0)
-

@ cbaa0c82:e9313245
2025-02-01 15:07:16
#TheWholeGrain - #January2025
This January we really got to start the story telling of our first adventure series painted by Dakota Jernigan a.k.a. The Bitcoin Painter! The typical Singles of the month were released on Sunday along with a special Single released on the first to celebrate the New Year! Here we go, 2025! And, even with all that the monthly Concept Art, Bitcoin Art, and the newest Cover Art from Toast's Comic Collection were all still released! Not only was the first month of 2025 quite packed full of fun content, but the Bread and Toast website got a makeover! Did you notice all the explanation points!? We're all so excited we just can't help ourselves from using them!
**January Sunday Singles**
2025-01-01 | Sunday Single 73
Title: Happy New Year 2025
*Happy New Year! What a year 2024 has been!
We can’t wait to see what 2025 has in store for us!*
https://i.nostr.build/QFTmeR5p2FthPMXp.png
2025-01-05 | Sunday Single 074
Title: Snowflake
*It’s the most beautiful snowflake Toast has ever seen… until this one melts then it’s on to the next one!*
https://i.nostr.build/YHGeOcYv8WEP1fAf.png
2025-01-12 | Sunday Single 075
Title: Weight Lifting
*End-Piece has been working out since last year’s resolution. Now, time for heavy lifting!*
https://i.nostr.build/8lxeovAr5aK598Ze.png
2025-01-19 | Sunday Single 076
Title: Good Morning
*GM, Everybody!*
https://i.nostr.build/9jn2D2if4sFfNXzU.png
2025-01-26 | Sunday Single 077
Title: Chess
*When it comes to the chessboard, Bread is King.*
https://i.nostr.build/LZq57iL7tOWbHAKc.png
**Adventure Series: Questline**
Bread, Toast, and End-Piece have started their journey in Grain Valley, and they have already found themselves in what used to be a village that is now been burnt to a crisp!
Writer: Daniel David (dan 🍞)
Artist: Dakota Jernigan (The Bitcoin Painter)
2025-01-14 | Questline
001 - The Adventure Begins
Our heroes take their first steps upon one of the oldest paths in all of Grain Valley. They can see the mountains in the background of the landscape before them. As they walk, they see in the distance ahead of them large amounts of black smoke rising until it disappears into the sky.
https://i.nostr.build/ygjmYlWAZ4uPfPCn.png
2025-01-28 | Questline
002 - A Village Burned
The source of smoke surrounds our heroes as their path brings them to the center of what used to be a village. It seems to be completely abandoned with no signs of life. Yet, all the remains of the village appear to have only recently burned to a crisp. What could have possibly happened here?
https://i.nostr.build/BJ4L1shKh5YERzWc.png
**Other Content Released in January 2025**
2025-01-01 | Toast's Comic Collection
Title: Iron Bread #9
*"I am Iron Bread." - Tony Starch*
https://i.nostr.build/QJKkDCbfgc6Vqzcq.png
2025-01-08 | Concept Art
Title: Second Bread Sketch
*A second sketch of the character Bread. Remade and cleaned up.*
https://i.nostr.build/4TXIRSUGA6viEaJx.png
2025-01-15 | Bitcoin Art
Title: Stack Sats
*Toast is constantly stacking sats!*
https://i.nostr.build/txxkux0oJqyjNcSL.png
Thanks for checking out the fifth issue of The Whole Grain. The Whole Grain is released on the first of every month and covers all of the content released by Bread and Toast in the previous month. For all Bread and Toast content visit BreadandToast.com!
**Thanks for helping us kick off 2025!**
***Bread, Toast, and End-Piece***
#BreadandToast #SundaySingle #Questline #ToastsComicCollection #ConceptArt #BitcoinArt #Bread #Toast #EndPiece #Artstr #Comic #Cartoon #NostrOnly #🖼️
***List of nPubs Mentioned:***
The Bitcoin Painter: npub1tx5ccpregnm9afq0xaj42hh93xl4qd3lfa7u74v5cdvyhwcnlanqplhd8g
dan 🍞:
npub16e3vzr7dk2uepjcnl85nfare3kdapxge08gr42s99n9kg7xs8xhs90y9v6
-

@ 2fb77d26:c47a6ee1
2025-02-01 14:40:02
In H. G. Wells’ Roman [Die Zeitmaschine](https://de.wikipedia.org/wiki/Die_Zeitmaschine) und den diversen Verfilmungen werden sie als »*ausschweifend, langsam und naiv*« dargestellt. Von »*untermenschlicher Intelligenz*« gezeichnet. Für [Dan Simmons](https://de.wikipedia.org/wiki/Eloi_\(Die_Zeitmaschine\)#In_Dan_Simmons%E2%80%99_Ilium) sind sie »*faul, ungebildet und unkultiviert*«. Die [Eloi](https://de.wikipedia.org/wiki/Eloi_\(Die_Zeitmaschine\)). Die als Nahrungsquelle der Morlocks gehaltenen Nachfahren des Homo sapiens. »*Sie entwickeln sich rückläufig und verlernen Jahrtausende von Kultur, Denken und Vernunft, bis sie sich mit dem Vergnügen des bloßen Daseins zufrieden geben*«. Ertönt das Schlüsselsignal, auf das sie von ihren Züchtern konditioniert wurden – eine umgebaute Zivilschutzsirene – trotten sie freiwillig und in hypnotischer Apathie zur Schlachtbank.
Ein ähnlichen Eindruck hatten viele Maßnahmenkritiker von den Unterstützern der mittlerweile in allen Punkten [widerlegten](https://www.regenauer.press/kapitalverbrechen) Covid-Propaganda. Zurecht. Das Gefolge von Drosten, Lauterbach und Co. war blind für Fakten und ist ins offene Messer gelaufen. Bedauerlicherweise verhalten sich viele Maßnahmenkritiker aber nun in weiten Teilen genauso. Sie haben Idole gefunden. Wollen glauben. Sie ignorieren Informationen, Fakten und Daten und werden Opfer einer neu justierten, gut geölten Propagandamaschine. Nur, um die in ihre neuen Helden gesetzten Hoffnungen nicht aufgeben und der wenig erbaulichen Realität nicht ins Auge blicken zu müssen.
Sie glauben an Donald Trump, Javier Milei, Alice Weidel, Peter Thiel und vor allem Elon Musk. Daran, dass der supranationale Nachhaltigkeitskorporatismus am Ende sei, das Finanzsystem gerettet und Gerechtigkeit hergestellt wird. Die Widerständler von gestern sind die »*Schlafschafe*« von heute. Sie scheinen vergessen zu haben, wie Propaganda funktioniert. Aus diesem Grund – und weil es ein so schön griffiges Wort ist, bei dem man nur einen Buchstaben verändern muss, um daraus den Vornamen eines vermeintlichen Heilsbringers zu basteln – erlaube ich mir, die Anhänger des MAGA-Kults im Zuge der folgenden Seiten mokant als Eloi zu bezeichnen. Ein bisschen Spaß muss sein.
**Kurskorrektur mit Ansage**
[Lynn Forester de Rothschild](https://www.inclusivecapitalism.com/about/), in der finanzoligarchischen Hackordnung mindestens eine Ebene über BlackRock und Co. anzusiedeln, kündigte den aktuellen Narrativwechsel bereits am 30. August 2023 an, als sie bei [Bloomberg](https://www.youtube.com/watch?v=eZzZubPKPrw) sagte, der Begriff »*ESG gehöre in die Tonne*«. Er sei verbrannt. Auch BlackRock-CEO Larry Fink, der Marktteilnehmer zur Unterstützung von ESG »*[zwingen](https://www.forbes.com/sites/jonmcgowan/2023/06/05/conservative-outrage-over-esg-and-dei-fueled-by-2017-blackrock-ceo-video/)*« wollte, [teilte](https://www.forbes.com/sites/jonmcgowan/2024/03/27/blackrocks-fink-calls-for-energy-pragmatism-omits-esg-from-annual-letter/) seinen Investoren bereits am 26. März 2023 mit, das in Verruf gekommene Label ESG durch den Begriff »*Energiepragmatismus*« zu ersetzen.
Sowohl Rothschild als auch Fink räumten aber gleichzeitig ein, dass sich die übergeordnete Agenda nicht ändern und man die »Green Economy« weiter vorantreiben werde, man diese aber besser vermarkten müsse, um konservative Kreise nicht weiter gegen sich aufzubringen. Ein simpler Marketing-Trick. Wenig überraschend also, dass sowohl [BlackRock](https://nypost.com/2025/01/11/business/blackrock-quits-net-zero-initiative-at-perfect-time-as-woke-policies-contribute-to-devastating-la-fires/) als auch sechs amerikanische [Großbanken](https://joannenova.com.au/2025/01/the-last-american-banker-rats-are-leaving-the-un-net-zero-banking-club/) Anfang 2025 die [Net Zero Initiative](https://www.net-zero-initiative.com/en) verließen. Zum »perfekten Zeitpunkt«, wie die [New York Post](https://nypost.com/2025/01/11/business/blackrock-quits-net-zero-initiative-at-perfect-time-as-woke-policies-contribute-to-devastating-la-fires/) bemerkt, um nicht von der negativen, anti-woken Berichterstattung rund um die verheerenden Feuersbrünste in Los Angeles tangiert zu werden.
Es scheint, als hätten die Eloi bereits wieder verdrängt, dass die WEF-Meetings [2021](https://www.weforum.org/videos/the-great-narrative-narrating-the-future-english/) und [2024](https://www.weforum.org/press/2024/01/annual-meeting-2024-rebuilding-trust-amid-uncertainty/) unter Arbeitstiteln wie »*The Great Narrative*« und »*Rebuilding Trust*« liefen. Artikuliertes Ziel der Davoser PR-Abteilung für Globalisierungsfragen war nämlich, sich den zunehmend echauffierten, misstrauischen Pöbel vom Hals zu halten. Durch neue Narrative und vertrauensbildende Maßnahmen. Und das hat, zumindest vorerst, ausgezeichnet funktioniert.
In den USA stieg das [Vertrauen](https://www.zerohedge.com/political/overall-trust-election-process-rebounded-2024) in ordnungsgemäß durchgeführte Präsidentschaftswahlen 2024 zum ersten Mal seit Jahren wieder etwas an. In Europa macht sich ebenfalls Zuversicht breit. Schließlich haben die sogenannten »*[Rechtspopulisten](https://www.sueddeutsche.de/projekte/artikel/politik/rechtspopulisten-rechtsextremismus-giorgia-meloni-geert-wilders-viktor-orb-n-robert-fico-e072514/?reduced=true)*« nicht mehr nur in Italien und Ungarn, sondern auch in Finnland, der Slowakei und den Niederlanden Oberwasser. Von den Erfolgen der AFD ganz zu schweigen. Diese führen, wie zuletzt in [Thüringen](https://www.mdr.de/nachrichten/thueringen/landtagswahl/afd-sieger-mehrheit-100.html), trotz klarem Wählervotum zwar nicht zur Regierungsbeteiligung, weil »*demokratische Prozesse*« und »*Brandmauern*« das zu verhindern wissen – aber dabei sein ist ja bekanntlich alles. Dass Friedenstreiberin Alice Weidel den bundesdeutschen Rüstungsetat auf knapp [200 Milliarden](https://www.berlin-live.de/politik/weidel-afd-bundeswehr-trump-nato-id348307.html) verdoppeln will, scheint die euphorisierten Kritiker dunkelgrüner Militarisierung auch nicht auszubremsen. Hauptsache nicht grün. Oder woke.
**Überstaatliche Sphären**
Dabei scheint Euphorie in Anbetracht der Tatsachen alles andere als angebracht. So hat Milei nach Angaben von [Global Finance](https://gfmag.com/economics-policy-regulation/argentina-milei-administration-eliminates-deficit/) zwar das argentinische »*Staatsdefizit nach 123 Jahren beendet*«, dafür leben heute [53 Prozent](https://www.theguardian.com/world/2024/dec/18/argentina-javier-milei-chainsaw-measures) der 45 Millionen Argentinier in Armut. Der höchste Wert seit 20 Jahren. Ende 2023 waren es noch 41,7 Prozent. Daran ändert auch semantische [Schützenhilfe](https://www.hoover.org/research/critics-mileis-policies-strike-out) von libertären Denkfabriken wie der [Hoover Institution](https://de.wikipedia.org/wiki/Hoover_Institution) nichts. Die radikalen Privatisierungsfeldzüge von »*[El Loco](https://www.batimes.com.ar/news/economy/argentinas-el-loco-milei-delivered-chaos-laughs-and-key-wins-in-week-one.phtml)*« haben einen hohen Preis. Ob [Aerolineas Argentinas](https://aviationweek.com/air-transport/safety-ops-regulation/daily-memo-mileis-relentless-pursuit-privatize-aerolineas), die staatliche Fluglinie, der Stahlproduzent [IMPSA](https://www.reuters.com/world/americas/argentina-privatizes-state-metal-firm-milei-era-first-2025-01-08/) oder das Transportunternehmen [Trenes Argentinos Cargas](https://buenosairesherald.com/business/infrastructure/milei-to-privatize-major-cargo-train-company), das 7.800 Kilometer Bahnstrecke betreibt – das Volksvermögen wird an die Meistbietenden verscherbelt. Wer das ist, kann sich wohl jeder ausmalen. Denn sein Schlachtruf »*Afuera!*« (Raus hier!) gilt augenscheinlich nicht für [BlackRock](https://news.bloomberglaw.com/bankruptcy-law/blackrocks-fink-mulls-argentina-trip-after-milei-call) und Co. – schließlich sei Argentinien »*ziemlich billig*« zu haben, wie es Rick Rieder, Top-Bond-Manager des Unternehmens schon 2019 [formulierte](https://www.reuters.com/article/us-argentina-debt-blackrock-idUKKBN1XI010/).
Man muss allerdings nicht in die Ferne schweifen, um sich der realen Gefahren für die Freiheit bewusst zu werden. Jener Gefahren, die von Personalien gänzlich unberührt bleiben. So arbeitet die Europäische Union weiter an der [eID](https://ec.europa.eu/digital-building-blocks/sites/display/DIGITAL/eID), der Grundlage des technokratisch-totalitären Kontroll-Grids. Ihre Einführung ist [beschlossene](https://www.europarl.europa.eu/news/de/press-room/20240223IPR18095/meps-back-plans-for-an-eu-wide-digital-wallet) Sache. Offen ist lediglich, ab wann sie zum Obligatorium wird. Auch das persönliche CO2-Budget ist auf Kurs. Mit [ETS2](https://www.epa.ie/our-services/licensing/climate-change/eu-emissions-trading-system-/eu-emissions-trading-system-2-ets2/#:~:text=ETS%202%20is%20a%20new,manufacturing%20and%20construction%20industries) (EU Emissions Trading System) nimmt die [EPA](https://www.epa.ie/who-we-are/) (Environmental Protection Agency) seit dem 1. Januar 2025 nach der Konzernwirtschaft nun kleine und mittlere Unternehmen in den Fokus und verpflichtet diese, CO2-Kompensationsabgaben auf ihren Gas-, Benzin- und Mineralölverbrauch zu entrichten. Das dürfte Heiz-, Fracht- und folglich die Lebenshaltungskosten des Bürgers in neue Höhen treiben. Bis der Sonntagsausflug mit dem Familienauto nicht mehr nur Zeit, Benzin und Nerven, sondern auch CO2-Gebühren kostet, dauert es also wohl nicht mehr allzu lange.
Dieser überparteilichen, supranational koordinierten Überwachungs- und Enteignungsagenda ist weder durch die Wahl des geringeren Übels noch durch Auswandern zu entkommen. Denn wie sich der [Internetpräsenz](https://globalgovernanceforum.org/) des »*Global Governance Forum*« (GGF) entnehmen lässt, wird bereits eifrig an »*[Global Government](https://www.globalgovernmentforum.com/news/)*« gearbeitet. Die UN-nahe Nichtregierungsorganisation hat sich nämlich zum Ziel gesetzt, die Charta der Vereinten Nationen bis 2028 zu [aktualisieren](https://globalgovernanceforum.org/a-call-for-un-charter-reform/) und den allseits bekannten »*Herausforderungen unserer Zeit*« anzupassen. Pünktlich ab 2030 soll das neue Vertragswerk ratifiziert werden und neben neuen Befugnissen für den Internationalen Gerichtshof sowie einer UN-Streitmacht auch eine Regierungsstruktur analog der Europäischen Union ermöglichen. Sprich, eine Weltregierung. Ganz demokratisch selbstverständlich.
Neben eID und CO2-Budget sind natürlich auch die Ausweispflicht fürs Internet und die automatisierte Zensur unliebsamer Inhalte weiter auf Kurs. Nachdem die Vereinten Nationen im September 2024 bereits dem totalitären »*[Pakt für die Zukunft](https://www.un.org/en/unis-nairobi/press-releaseunited-nations-adopts-ground-breaking-pact-future-transform-global)*« zustimmten, wurde am [Heiligabend 2024](https://www.unodc.org/unodc/en/press/releases/2024/December/un-general-assembly-adopts-landmark-convention-on-cybercrime.html) noch rasch die neue »*Konvention gegen Onlineverbrechen*« durchgewunken. Und seit Januar 2025 treibt die UN die Umsetzung eines noch weitreichenderen Abkommens namens »*[Global Digital Compact](https://www.un.org/global-digital-compact/en)*« voran. Ein Papier, vor dem ich bereits im [Juli 2023](https://www.regenauer.press/undemokratisch) gewarnt habe. Was all das für den Bürger bedeutet, zeigt sich in [Griechenland](https://www.telepolis.de/features/Totale-Kontrolle-Griechenland-verknuepft-Steuer-ID-mit-Social-Media-10222907.html), wo die Regierung seit Anfang des Jahres Social-Media-Konten mit Steuer-Identifikationsnummern verknüpft, um eine Alterskontrolle fürs Internet einzuführen. Damit folgt die von der EU in Kreditsklaverei gehaltene Regierung in Athen dem Vorbild [Australiens](https://www.tagesschau.de/ausland/asien/australien-social-media-100.html), wo der Zugang so Social-Media-Plattformen künftig erst ab einem Alter von 16 Jahren erlaubt werden soll – wofür man schlussendlich jeden Nutzer kontrollieren muss, der online geht.
Auch das von vielen noch immer als Mythos abgetane Geoengineering wird derweil munter weitergeführt. Obwohl [Berichte](https://www.whitehouse.gov/wp-content/uploads/2023/06/Congressionally-Mandated-Report-on-Solar-Radiation-Modification.pdf) des US-Kongress und mittlerweile sogar wissenschaftliche [Berater](https://scientificadvice.eu/advice/solar-radiation-modification/) der EU-Kommission vor großflächigem [Solar Radiation Management](https://www.risiko-dialog.ch/solar-radiation-management-ein-letztes-mittel-im-kampf-gegen-den-klimawandel/) warnen. Im Rahmen eines offiziellen, 54 Seiten umfassenden [Reports](https://op.europa.eu/en/publication-detail/-/publication/9c2ac367-b5de-11ef-acb1-01aa75ed71a1/language-en) an die EU-Kommission sowie eines [Artikels](https://www.theguardian.com/environment/2024/dec/09/eu-should-ban-space-mirrors-and-other-solar-geoengineering-warn-scientists) des britischen Guardian vom 9. Dezember 2024 verwies das siebenköpfige Forscherteam auf die unabschätzbaren Konsequenzen solcher Eingriffe und forderte ein EU-weites Moratorium.
Wie genau Trump, Musk, Milei, Meloni, Weidel und Co. die Welt vor diesem Sammelsurium an totalitären Übergriffigkeiten retten wollen, konnte mir bislang keiner der Eloi sagen.
**DJ Trump**
Warum die in Donald Trump, den »*[Vater der Impfung](https://www.independent.co.uk/news/world/americas/us-politics/trump-father-vaccine-covid-fox-interview-b1839555.html)*«, und sein zionistisches Kriegstreiberkabinett gesetzten Hoffnungen bald bitterer Enttäuschung weichen dürften, habe ich bereits am 14. November 2024 ausführlich [beschrieben](https://www.regenauer.press/trump-reloaded). Dass auch die beiden Hauptargumente seiner Befürworter – dass er die mRNA-Kampagne mittlerweile bereue und in seiner ersten Amtsperiode Friedenspolitik betrieben habe – schlichtweg falsch sind, ebenfalls. Denn anhand der nackten [Zahlen](https://foreignpolicy.com/2017/08/09/donald-trump-is-dropping-bombs-at-unprecedented-levels/) lässt sich eindeutig belegen, dass Trump »*der kriegslüsternste Präsident der jüngeren Geschichte*« war. Und wie stolz er auf »*Operation Warp Speed*« ist, die [unzählige](https://icandecide.org/v-safe-data/) Amerikaner Gesundheit oder Leben kostete, ließ er die Welt zuletzt am [17. November 2024](https://x.com/tomregenauer/status/1859637538874589311) auf seinem Social-Media-Netzwerk [Truth Social](https://de.wikipedia.org/wiki/Truth_Social) wissen.
Trumps Interesse gilt nicht Frieden und Freiheit, sondern Donald Trump. So war es sein ganzes Leben lang. Wenn sich »*The Donald*« jemandem verpflichtet fühlt, ist es vielleicht [Wilbur Ross](https://de.wikipedia.org/wiki/Wilbur_Ross), der ehemalige Chef von [Rothschild Inc. Bankruptcy Advising](https://www.rothschildandco.com/en/global-advisory/debt-advisory-and-restructuring/). Denn wie das [Forbes Magazine](https://www.forbes.com/sites/chasewithorn/2016/12/08/trump-and-his-commerce-secretary-wilbur-ross-a-look-at-25-years-of-connections/) am 8. Dezember 2016 korrekt erläuterte, rette das Bankhaus vor gut 30 Jahren nicht nur Trumps bankrotte Casinos, sondern damit auch seine ganze Karriere. Nicht weil man in Trumps Geschäften und Immobilien einen besonderen Wert sah, sondern weil man die Person Donald Trump als »*Anlage*« betrachtete. Trotzdem ist es sicher nur Zufall, dass Ross von 2017 bis 2021 Handelsminister der Vereinigten Staaten war.
**Elon Musk**
Auch über den PayPal-Mafioso, CIA-Handlanger und Bilderberg-Executive Peter Thiel, dessen Protegé JD Vance nun US-Vizepräsident ist, habe ich bereits im September 2024 einen ausführlichen [Artikel](https://www.regenauer.press/gestatten-peter-thiel) geschrieben. Gleiches gilt für Elon Musk, dessen trügerisches Image als Genius, Erfinder und Entrepreneur ich sogar schon im Oktober 2022 [durchleuchtet](https://www.regenauer.press/dekuvrierte-coolness) habe. Zitat:
»*Dass Elon Musk nicht rein zufällig zur liberal-coolen Ikone avancierte, legt ein Blick in seine Anfangsjahre als Unternehmer nahe. Denn während im sagenumwobenen Silicon Valley Ende der 1990er-Jahre eine Vielzahl an erfolgreicheren Tech-Entrepreneuren existierte, war es ausgerechnet Elon Musk, der für einen absolut inhaltsleeren [Gastauftritt](https://www.youtube.com/watch?v=s9mczdODqzo) bei CNN gefilmt wurde, sodass zum ersten Mal eine breitere Öffentlichkeit von ihm Notiz nehmen musste. Dabei war sein erstes Unternehmen – [Zip2](https://en.wikipedia.org/wiki/Zip2) –, das er im Jahre 1995 mit seinem Bruder sowie einem weiteren Partner gegründet und im Februar 1999 für circa [300 Millionen US-Dollar](https://web.archive.org/web/20220625124959/https:/www.nytimes.com/1999/02/17/business/compaq-buys-zip2-to-enhance-altavista.html) an Compaq veräußert hatte, nicht das revolutionärste Unterfangen im kalifornischen IT-Mekka dieser Tage. Es handelte sich um ein simples Telefonbuch fürs Internet. Wenig mehr als eine Datenbank, in die sich Unternehmen eintragen konnten, um ihre Adresse im Netz zu hinterlegen*.«
Meine fast zweieinhalb Jahre alte Analyse bedarf allerdings dringend einer Aktualisierung. Denn was Musk in der Zwischenzeit trieb – und für die Zukunft plant – hat so gar nichts mit dem zu tun, was seine geradezu fanatisierten Anhänger in ihm sehen wollen.
Fangen wir der Vollständigkeit halber aber noch mal vorne an: Elon Musk hat weder [PayPal](https://en.wikipedia.org/wiki/PayPal#Early_history) gegründet noch den [Tesla](https://www.cnbc.com/video/2021/02/06/how-tesla-was-founded-martin-eberhard-and-marc-tarpenning-tell-all.html) erfunden. Auch wenn er das gerne so darstellt. Dafür [fertigte](https://www.reuters.com/article/business/healthcare-pharmaceuticals/musk-says-tesla-is-building-rna-microfactories-for-curevac-idUSFWN2E9067/) Tesla unter seiner Ägide dann aber »*RNA Mikrofabriken*« für das deutsche Unternehmen [CureVac](https://www.nzz.ch/wissenschaft/curevac-impfstoff-noch-ein-sieg-gegen-das-virus-ld.1788519), das zusammen mit [Bayer](https://www.nasdaq.com/press-release/curevac-:-curevac-and-bayer-join-forces-on-covid-19-vaccine-candidate-cvncov-2021-01) mRNA-Injektionen gegen Corona auf den Markt brachte. Und während Musk gegenüber der [New York Post](https://www.youtube.com/watch?v=2lPkvteqKig) am 30. September 2020 sagte, sich nicht gegen Covid impfen lassen zu wollen, erklärte er dem [TIME Magazine](https://web.archive.org/web/20211213124147/https:/time.com/person-of-the-year-2021-elon-musk/) am 13. Dezember 2021, bereits geimpft zu sein. Zeitgeistig flexibel ist er also. Wer behauptet, Musk hätte seine Meinung zur mRNA-Technologie seit dem Covid-Fiasko signifikant geändert und sehe das Produkt nun kritisch, ist schlecht informiert. Noch am [12. April 2023](https://x.com/elonmusk/status/1646220824192630784) erklärte er bei Twitter, dass er mRNA für eine »*medizinische Revolution*« hält. Vergleichbar mit dem Schritt »*von analog zu digital*«.
Was Musk mit digitaler Revolution meint, zeigte sich 2017 mit Hurricane Irma. Damals gab das Unternehmen für Besitzer von Fahrzeugen mit 75 kWh ein [Softwareupdate](https://www.teslarati.com/tesla-issues-software-update-help-owners-flee-hurricane-irmas-evacuation-zone/) heraus, das die Reichweite von 338 auf 400 Kilometer steigerte – was im Umkehrschluss bedeutet, dass Tesla-Besitzer um eine eigentlich abrufbare Leistung ihres eigenen Fahrzeugs betrogen werden, wenn gerade keine Naturkatastrophe wütet. Dass Tesla-Kunden darüber hinaus permanent [überwacht](https://upnorthlive.com/news/nation-world/tesla-cybertruck-explosion-trump-hotel-fbi-surveillance-elon-musk-company) werden, zeigte sich unlängst im Rahmen der Explosion eines Cybertrucks in Las Vegas. Augenbewegungen, Mimik, Geschlecht, Hautfarbe, Körpertemperatur, Gepäckanordnung, Route, Ladestopps, Bezahlvorgänge, Telefonbuch, Musik-Playlist, Online-Abos, et cetera. Was von Sensoren und Verbindungen zu erfassen ist, wird erfasst, wie eine [Untersuchung](https://gizmodo.com/mozilla-new-cars-data-privacy-report-1850805416) von Mozilla im Herbst 2023 feststellte. Das gilt im Übrigen nicht nur für Tesla, sondern für praktisch alle modernen Autos. Ein Tesla hat es dabei nur am leichtesten. Die gesammelten Daten werden entweder zum Schleuderpreis [verkauft](https://archive.is/tc2xB) und/oder gegen uns verwendet.
Doch zurück zu Musk, der Twitter nicht übernahm, um Meinungsfreiheit herzustellen, sondern um die Plattform zur »*Alles-App*« zu machen. Sein [erklärtes](https://www.forbes.com/sites/abrambrown/2022/06/21/elon-musk-and-the-super-alluring-dream-for-a-super-app/?sh=6cf8e3021343\&utm_medium=social\&utm_source=ForbesMainTwitter\&utm_campaign=socialflowForbesMainTwitter) Vorbild: die chinesische [Spionage-App](https://citizenlab.ca/2020/05/wechat-surveillance-explained/) WeChat. Deswegen will er alle Nutzer »*als echte Menschen [identifizieren](https://edition.cnn.com/2022/04/28/tech/elon-musk-authenticate-all-real-humans/index.html)*«. Biometrisch versteht sich. Dafür [arbeitet](https://www.business-humanrights.org/en/latest-news/x-corps-biometric-data-sharing-with-israeli-firm-raises-privacy-concerns/) man bei Twitter bevorzugt mit israelischen Unternehmen zusammen, die von ehemaligen [Mossad-Agenten](https://www.middleeasteye.net/news/x-twitter-israel-concerns-verification) gegründet wurden. Vielleicht stellte ja Doppelagent Jeffrey Epstein den Kontakt zum Mossad her, nachdem er Musk als regelmäßigen Teilnehmer seiner [Edge-Foundation](https://www.regenauer.press/die-glorreichen-sieben) Seminare zum Thema Nudging schätzen gelernt hatte. Epstein war nämlich der einzige nennenswerte Sponsor von Edge.
Twitter kaufte Musk übrigens nicht von seinem eigenen Geld, sondern mit Hilfe von 94 [Investoren](https://www.newsweek.com/full-list-investors-elon-musks-x-revealed-court-filing-1942970), deren Namen ein US-Bundesrichter erst im August 2024 veröffentlichte, weil Jacob Silverman (Reporters Committee for Freedom of the Press) sie einklagte. Die Liste umfasst so illustre Namen wie Fidelity Investments, Sequoia Capital, Andreessen Horowitz, Bandera Fund, Binance Capital Management, Sean Combs (alias Diddy) Capital, Jack Dorsey (Twitter Gründer), Baron Opportunity Fund oder Prinz Alwaleed bin Talal al Saud von der saudischen Königsfamilie. Da wird also offenbar »*der Sumpf*« mit mehr Sumpf »*trockengelegt*«. Von der Nominierung des [WEF Executive Chair](https://www.linkedin.com/posts/lindayaccarino_freedom-of-speech-not-reach-an-update-on-activity-7053787411847237633-zC8Q) Linda Yaccarino als neuer Twitter-CEO und »*Freedom of Speech*« versus »*[Freedom of Reach](https://www.linkedin.com/posts/lindayaccarino_freedom-of-speech-not-reach-an-update-on-activity-7053787411847237633-zC8Q)*« mal ganz abgesehen.
Auch die von den Eloi als sensationelle Enthüllung gefeierten [Twitter Files](https://twitterfiles.substack.com/p/1-thread-the-twitter-files) sind leider nicht ernst zu nehmen. Denn sie offenbarten nichts, was man nicht schon wusste. Zudem ist bis heute unklar, woher die veröffentlichten Informationen kamen, wer den Zugriff darauf gesteuert hat, was dort noch gespeichert war, warum praktisch nur ein von Elon ausgewählter [Journalist](https://docs.house.gov/meetings/FD/FD00/20230309/115442/HHRG-118-FD00-Wstate-TaibbiM-20230309.pdf) Zugriff darauf hatte und dieser nur Screenshots, anstelle ganzer Dokumente veröffentlichen durfte. Ein echter Leak besteht aus einem Archiv, das man selbst durchsuchen kann – nicht aus ein paar handverlesenen Screenshots.
Fehlt noch Space X. Ein Unternehmen, das Musk zwar selbst gegründet hat, dessen Erfolge aber in weiten Teilen anderen Umständen zu verdanken sind. So schreibt beispielsweise [inside Tesla](https://insidetesla.de/spacex-und-nasa-staatlich-private-kooperation/) am 22. März 2022:
**»*Schon Anfang der 2000er-Jahre hatte die NASA erkannt, dass ihr bald die Möglichkeit fehlen würde, selbst Astronauten und Material ins All und zur ISS zu bringen. Man machte sich also auf die Suche nach Partnern aus der Privatwirtschaft und wurde unter anderem bei Elon Musks Space X fündig. Bereits 2006, also noch in der Entwicklungsphase der Falcon 1, erhielt Musks Unternehmen fast 400 Millionen US-Dollar Startfinanzierung unter dem COTS-Programm*.«**
Space X war von Beginn an als verlängerte Werkbank der NASA gedacht, weil der US-Weltraumbehörde immer mehr Mittel gestrichen wurden. Die Öffentlichkeit hatte nämlich das Interesse an ziviler Raumfahrt verloren. Daher setzte man in Washington immer öfter den Rotstift an. Doch seit Musk die Menschen öffentlichkeitswirksam zum Mars befördern will – »*let’s build Marsian Technocracy*« – steigt das Interesse wieder. Leider muss ich die Vorfreude auf eine planetare Kolonie aber etwas dämpfen. Denn Space X wird nicht betrieben, um Menschen auf den Mars zu bringen, sondern um das »*weltgrösste Netzwerk an [Spionagesatelliten](https://www.reuters.com/technology/space/musks-spacex-is-building-spy-satellite-network-us-intelligence-agency-sources-2024-03-16/) [aufzubauen](https://web.archive.org/web/20241206180227/https:/www.activistpost.com/2024/12/you-cant-hide-elon-musk-spacex-are-helping-us-intelligence-build-the-worlds-largest-spy-satellite-network.html)*«.
Musks Weltraumagentur ist Handlanger des militärisch-industriellen Komplexes und einer der wichtigsten [Vertragspartner](https://thehill.com/policy/defense/542728-pentagon-awards-160m-in-contracts-to-musks-spacex/) des Pentagon. Das konnte man 2017 schon im [Observer](https://observer.com/2017/04/spacex-to-launch-top-secret-mission-for-government-spy-agency/) nachlesen. Oder am 9. Januar 2018 bei [CNBC](https://www.cnbc.com/2018/01/08/highly-classified-us-spy-satellite-appears-to-be-a-total-loss-after-spacex-launch.html), die vom (missglückten) Transport eines streng geheimen US-Spionagesatelliten berichtete. Am 15. April 2022 kommentierte [Tech Unwrapped](https://techunwrapped.com/spacex-will-launch-two-spy-satellites-for-the-us-military/) zwei weitere Spionagesatelliten des US-Militärs, die Space X in die Umlaufbahn beförderte. Seit Jahren erhält das Unternehmen Milliarden von US-Regierung und Geheimdiensten. Siehe [Los Angeles Times](https://www.latimes.com/business/la-fi-hy-musk-subsidies-20150531-story.html) vom 30. Mai 2015: 4,9 Milliarden. Oder ein Artikel des [Wall Street Journal](https://www.wsj.com/podcasts/google-news-update/how-spacex-is-deepening-its-ties-with-the-us-government/b860deaf-724c-4610-8177-479b520df6d4) vom 23. Februar 2024: 1,8 Milliarden. Oder eine lange Liste von staatlichen Zuwendungen, die [Business Insider](https://www.businessinsider.com/elon-musk-list-government-subsidies-tesla-billions-spacex-solarcity-2021-12?r=US\&IR=T) am 15. Dezember 2021 veröffentlichte. Damit basiert der Erfolg von Space X nicht primär auf Musks genialem Unternehmergeist, sondern auf Subventionen. Auf Steuergeldern.
Nicht zu vergessen: [Starlink](https://de.wikipedia.org/wiki/Starlink). Das von Space X betriebene, weltumspannende Satellitennetzwerk. Es mag den Vorteil haben, dass damit auch Menschen in entlegenen Regionen des Planeten oder Katastrophengebieten Zugriff auf das Internet haben. Dabei sollte allerdings nicht unterschlagen werden, dass Starlink in seiner finalen Ausbaustufe circa 42.000 Satelliten umfassen und damit ein permanentes Strahlungsfeld erzeugen wird. Gesundheitliche Risiken für den Homo sapiens: unklar. Darüber hinaus haben die Orbiter Zugriff auf das [NORAD](https://de.wikipedia.org/wiki/North_American_Aerospace_Defense_Command)-Datenbanksystem, um Weltraumschrott ausweichen zu können. Sprich, sie sind permanent mit Systemen des US-Militär verbunden. Aus diesem Grund ermöglicht Starlink auch die Steuerung von Kampfdrohnen – siehe [Ukraine-Konflikt](https://www.telegraph.co.uk/world-news/2022/03/18/elon-musks-starlink-helping-ukraine-win-drone-war/) – sowie 30 mal schnelleres Senden von Daten an und von US-Kampfflugzeugen. Während die Öffentlichkeit Musks Satellitennetzwerk vor allem als ziviles Produkt betrachtet, ist Starlink primär von militärischem Interesse. Nicht umsonst wird parallel [Starshield](https://en.wikipedia.org/wiki/SpaceX_Starshield) aufgebaut, das dem geheimdienstlich-militärischen Komplex unter anderem die diskrete Echtzeitüberwachung der ganzen Welt erlaubt. Auch von [DEW](https://en.wikipedia.org/wiki/Directed-energy_weapon)-Fähigkeiten (Directed Energy Weapon) ist die Rede. Ende 2024 befanden sich bereits 98 solcher Satelliten in erdnaher Umlaufbahn.
In Anbetracht dieser Informationen ist es also kaum verwunderlich, dass Musk seit Jahren offen für [Technokratie](https://www.ft.com/content/df695f10-154d-11e8-9376-4a6390addb44) [wirbt](https://x.com/search?q=from%3Aelonmusk%20technocracy\&src=typed_query). Für ein zentralistisches, [faschistoides](https://web.archive.org/web/20230920020550/https:/www.newyorker.com/news/daily-comment/the-world-according-to-elon-musks-grandfather) Herrschaftsmodell, das schon sein [Großvater](https://newsinteractives.cbc.ca/longform/technocracy-incorporated-elon-musk/) Joshua Haldemann als führender Kopf in den USA und Kanada vertrat. Der Familientradition folgend [empfiehlt](https://www.youtube.com/watch?v=BMskI6G9ty0) Musk eine [CO2-Steuer](https://www.cnbc.com/2021/02/12/elon-musk-reducing-greenhouse-gas-emissions-with-a-carbon-tax.html) zum Kampf gegen den Klimawandel, ein universelles [Grundeinkommen](https://www.businessinsider.com/elon-musk-universal-basic-income-ubi-ai-automation-unemployment-quotes-2024-6), um die von der KI ausgelösten Disruptionen abzufangen und sein [Neuralink](https://neuralink.com/) Gehirnimplantat, um dem drohenden Transhumanismus etwas Transhumanismus entgegenzusetzen.
**Futurum Technologicus**
Für Kunden, denen Chips im Kopf irgendwie zu altbacken sind, [entwickelt](https://www.neurotechreports.com/pages/Neuralink-launch-collaborations.html) Musks Unternehmen in Zusammenarbeit mit [iota Biosciences](https://www.iota.bio/) natürlich ein zeitgemäßeres Premiumprodukt: Neural Dust. Intelligente Nanopartikel in Staubkorngröße, die sich im Gehirn anreichern. Die lassen sich dann wahrscheinlich – wie die in Indien bereits zugelassene [Nasal-Impfung](https://www.lemonde.fr/en/covid-19-pandemic/article/2022/09/06/india-approves-its-first-nasal-vaccine-for-covid-19_5996007_122.html) gegen Covid – durch die Nase ziehen. Oder durch Luftschächte öffentlicher Gebäude pumpen. Man kann die neue Freiheit also förmlich riechen.
Ganz wie es der 44 Seiten starke »*National Nanotechnology Initiative Strategic Plan*« ([NNI Plan](https://www.nano.gov/sites/default/files/pub_resource/NNI-2021-Strategic-Plan.pdf)) des Weißen Hauses im Oktober 2021 vorsah: »*Die Öffentlichkeit einbeziehen und Mitarbeiterzahlen im Bereich Nanotechnologie erhöhen*«. Nicht umsonst hat Donald Trump der entsprechenden Behörde in seiner ersten Amtszeit zusätzliche Mittel [genehmigt](https://en.wikipedia.org/wiki/National_Nanotechnology_Initiative). Genau wie Joe Biden nach ihm.
Das von der Technokratie-Bewegung vor fast einem Jahrhundert definierte [nordamerikanische Technate](https://technocracy.fandom.com/wiki/Technate) – sprich, der amerikanische Verantwortungsbereich einer weltweiten Technokratie – sieht der von [Trump](https://www.newsweek.com/donald-trumps-plan-new-us-empire-2008028) und Musk reanimierten Vision einer »*nordamerikanischen Union*« übrigens verblüffend ähnlich. Wen interessiert bei all der Make-Great-Euphorie schon noch, dass Imperialismus scheisse, Dänemark ein souveräner Staat und der Panamakanal ein strategisches Nadelöhr der internationalen Handelsschifffahrt ist. Oder, dass die »*nordamerikanische Union*« nicht nur bei Trump-Cheerleadern wie [Alex Jones](https://www.youtube.com/watch?v=sHMD5k8Pv5Y) vor ein [paar Jahren](https://thenewamerican.com/world-news/north-america/cfr-globalists-outline-strategy-for-north-american-community/) noch als »*böser [Globalisten-Plan](https://frankspeech.com/video/americans-are-waking-globalist-goal-creating-north-american-union)*« galt.
Schauen wir nach vorne. In Richtung »*goldenes Zeitalter*«, wie Trump es nennt. Dieses dürfte für den Normalbürger nämlich sehr ungemütlich werden. Denn es wird dominiert von Algorithmen. Von Künstlicher Intelligenz. Für die Eloi also primär von [Grok](https://en.wikipedia.org/wiki/Grok_\(chatbot\)), dem auf Twitter (und [Teslas](https://techcrunch.com/2024/09/08/elon-musk-says-tesla-has-no-need-to-license-xai-models/)) integrierten Chatbot. Dieser basiert auf Technologie des Unternehmens xAI – laut [Wikipedia](https://en.wikipedia.org/wiki/XAI_\(company\)) gegründet von Elon Musk im März 2023. Das mag zwar so im Handelsregister stehen, ist wohl aber nur die halbe Wahrheit. Denn xAI dürfte die Fortführung eines [DARPA-Projekts](https://onlinelibrary.wiley.com/doi/full/10.1002/ail2.61) darstellen, das bereits 2015 unter dem Titel »*Explainable Artificial Intelligence*« (XAI) gestartet wurde und 2021 auslief. Als die Finanzierung seitens DARPA eingestellt wurde, machte XAI die Forschungsergebnisse auf einem [Server](https://xaitk.org/) zugänglich. Circa 18 Monate Jahre später [engagierte](https://www.simonandschuster.com/books/Elon-Musk/Walter-Isaacson/9781982181284) Elon Musk [Igor Babuschkin](https://www.linkedin.com/in/igor-babuschkin-9bb5bab6/) als Chefingenieur für xAI. Babuschkin hatte zuvor acht Jahre lang für Googles DeepMind-Projekt gearbeitet und nutzte aller Wahrscheinlichkeit nach die DARPA-Ergebnisse um xAI, beziehungsweise Grok zu entwickeln.
Im Juli 2023 [verkündete](https://archive.ph/hq6WS) Musk, xAI sei im Gegensatz zu den Konkurrenzprodukten von Google, Microsoft und OpenAI eine »*gute*« KI. Erstaunlich, wenn die gleichen Ingenieure am Werk sind und die KI auf Basis eines Militärprojekts entsteht. Zudem sprechen auch die Top-Sponsoren von xAI nicht unbedingt für das »*Gute*«. Denn unter den größten Geldgebern der letzten [Finanzierungsrunde](https://www.livemint.com/companies/news/elon-musks-xai-raises-6-billion-funding-from-blackrock-nvidia-amd-and-others-11735045011974.html) vom 23. Dezember 2024 befinden sich so illustre Namen wie BlackRock, AMD, Nvidia und Fidelity, die zusammen weitere sechs Milliarden Dollar für Musks KI-Unternehmen zur Verfügung stellten.
Genug Liquidität, um xAI für die »*Alles-App*« weiterzuentwickeln, wo Grok seit einer Weile automatisch [Kurzbeschreibungen](https://circleboom.com/blog/what-is-x-profile-summary/) für Profile erstellt, die man weder abschalten noch ändern kann. Twitter-Nutzer müssen nun also nicht mehr selbst das Profil eines Accounts durchstöbern, um sich einen ersten Eindruck von der Person zu machen, sondern bekommen diesen von Elon Musks KI geliefert. Vorurteil auf Knopfdruck sozusagen. Vergleichbar mit einem Sozialkreditsystem. Denn die täglich neu generierte Zusammenfassung basiert auf dem Nutzerverhalten.
**»*Die neuen, KI-generierten Grok-Kurzprofile unter jedem X-Nutzerprofil SIND de facto ein Social Credit System nach chinesischem Vorbild für den Westen. Das Profil jedes Nutzers wird tagesaktuell neu berechnet. Äußert man sich zu verschiedenen Themen, nennt die KI das schnell mal »verheddern«. Grok gibt zu, das Profil wird erstellt aus dem eigenen Nutzerverhalten des Tages, seinen eigenen Berechnungen und nicht näher definierten Anweisungen*«,** **[kommentierte](https://x.com/aya_velazquez/status/1879288289393340512)** **Journalistin Aya Velázquez die Neuerung am 14. Januar 2025.**
Andere Nutzer werden als »*leicht erregbar*« beschrieben, »*verzetteln*« sich oder »*glauben an Wettermanipulation zur Klimakontrolle*«. Offener wird ein Debattenraum dank solcher Adjektive und Zusammenfassungen sicher nicht. Wer möchte schon das Profil von leicht erregbaren Chemtrail-Gläubigen anschauen oder gar mit diesen assoziiert werden. Gegen solch eine automatisierte, herablassend daherkommende Einordnung durch intransparent operierende KI war die Faktencheck-Industrie geradezu harmlos. Wer also annimmt, die [Abschaffung](https://www.bbc.com/news/articles/cly74mpy8klo) der Faktenchecker bei Facebook und Co. bedeute ein Ende der Zensur, irrt. Sie wird im Gegenteil deutlich raffinierter und weitreichender werden.
Details zum persönlichen Punktestand im Grok-Sozialkreditsystem oder Information über das Zustandekommen der Bewertung erhält man auf Anfrage natürlich nicht. Twitter wird die daraus entstehende Hierarchie aber mit Sicherheit für Reichweitensteuerung, Nudging-Kampagnen und weitere sozialarchitektonische Funktionen nutzen. Vor allem, wenn 2025 das Bezahlsystem »[X Money](https://www.foxbusiness.com/technology/x-money-payment-system-launch-2025-x-ceo)« eingeführt wird. Dann werden die Eloi bald nicht mehr nur um Reichweite, Follower und Re-Tweets buhlen, sondern auch um Geld – das als Folge unliebsamer Postings zu Genozid X, Krieg Y oder Person Z künftig schneller eingefroren werden dürfte als jedes Bankkonto. [De-Banking](https://multipolar-magazin.de/artikel/de-banking) der nächsten Generation. Und irgendwann trifft das jeden. Außer, man schwimmt immer mit dem Strom.
Doch damit nicht genug. Am 13. Dezember 2024 [gab](https://www.finanzen.ch/nachrichten/aktien/wisekey-aktie-schiesst-zweistellig-hoch-wisesat-satellitenstart-mit-spacex-im-januar-2025-geplant-1034135831) das wohl den wenigsten bekannte Unternehmen [WISeSat](https://wisesat.space/) bekannt, künftig mit Space X zusammenzuarbeiten, um »*verschiedene Produkte und Systeme zu kombinieren*«. Die WISeSat AG ist eine Tochterfirma der in [Genf](https://www.inside-it.ch/wisekey-lagert-satellitenbusiness-in-neue-firma-aus-20230607) (Schweiz) ansässigen [WISeKey International Holding AG](https://www.wisekey.com/), die im Bereich Cybersicherheit, KI und IoT (Internet of Things) tätig ist. Die Ankündigung dieser Kollaboration ließ die WISeKey-Aktie kurzfristig um 107,73 Prozent steigen. Ein erster gemeinsamer Start zum Transport sogenannter [Picosatelliten](https://www.sciencedirect.com/topics/engineering/picosatellites) fand am 14. Januar 2025 von der Vandenberg Space Force Base in Kalifornien statt.
Aber was genau macht WISeSat? Einer [Presseerklärung](https://www.wisekey.com/de-press/wisesat-ag-ein-wegweisender-weltraumarm-von-wisekey-international-tritt-space-innovation-bei-und-starkt-die-position-der-schweiz-in-der-raumbasierten-iot-kommunikation/) des Unternehmens vom 15. September 2023 lässt sich entnehmen:
»*WISeSAT AG zeichnet sich dank ihrer Konstellation von ultra-sicheren Picosatelliten und Infrastruktur durch sichere und effektive Kommunikationsstrategien für vernetzte Geräte aus. Die Expertise des Unternehmens in kryptografischer Technologie und sicherem Datenmanagement hat die sichere IoT-Implementierung in zahlreichen Bereichen neu definiert, von städtischen Innovationen in Smart Cities bis hin zu modernster industrieller Automatisierung*. (…) *WISeSAT steht an vorderster Front bei der Entwicklung von ultra-sicheren Picosatelliten-Lösungen in Zusammenarbeit mit ihrem Verbündeten [FOSSA Systems](https://en.wikipedia.org/wiki/FOSSA_Systems). Es setzt sich für sichere IoT-Kommunikation über raumbasierte Netzwerke ein und nutzt die neuesten kryptografischen Innovationen, um sichere und sofortige Datenaustausche in verschiedenen Bereichen zu gewährleisten* (…).«
Im Klartext: WISeSat bringt Satelliten von der Größe einer Tupperdose ins All. Diese Mini-Orbiter umkreisen den Planeten in niedrigen Umlaufbahnen und etablieren dort ein Netzwerk für kryptografierte Echtzeitdatenübertragung. Fliegende 5G-Masten sozusagen. Oder WLAN-Router. Nur viel schneller. Für das Internet der Dinge – und Smart Cities.
»*In dieser Woche startet WISeSat einen Satelliten der neuen Generation und markiert damit einen wichtigen Meilenstein in der Entwicklung einer globalen Satellitenkonstellation, die eine umfassende Erdabdeckung mit ultraniedriger Latenzzeit ermöglicht. Entwickelt, um Billionen von IoT-Geräten in Echtzeit zu verfolgen und aufzuspüren*.« ([Carlos Creus Moreira](https://x.com/CreusMoreira/status/1878312357882941521), WISeKEy CEO, 12. Januar 2025)
Welche Datenträger dieses Picosatelliten-Netzwerk künftig verfolgen und aufspüren soll, zeigt sich bei einem Blick auf das Produktportfolio der Holding-Gesellschaft WISeKey – einem »*weltweit führenden Anbieter von Cybersicherheit, digitaler Identität und Internet der Dinge (IoT) Lösungen*«. Denn die [Holding](https://www.wisekey.com/) existiert seit 24 Jahren, besteht aus fünf Unternehmen, hat mehr als eineinhalb Milliarden Chips und über fünf Milliarden »[Roots of Trust](https://www.computerweekly.com/de/definition/Roots-of-Trust-RoT)« installiert, residiert an sechs internationalen Standorten und hat gut 3.000 Kunden in Staat und Wirtschaft beglückt. Einen Wikipedia-Eintrag gibt es für das bei NASDAQ und SIX gelistete Unternehmen erstaunlicherweise trotzdem nicht.
Dafür aber für den seit Mai 2021 [amtierenden](https://www.handelszeitung.ch/panorama/wisekey-holt-pierre-maudet-als-chief-digital-transformation-officer) »*Chief Digital Transformation Officer*« [Pierre Maudet](https://de.wikipedia.org/wiki/Pierre_Maudet). Der war ab Juni 2012 Mitglied des Genfer Staatsrats, [2013](https://wikispooks.com/wiki/WEF/Young_Global_Leaders/2013) bei den Young Global Leaders des Weltwirtschaftsforums und 2015 bei der Bilderberger Konferenz in [Telfs-Buchen](https://wikispooks.com/wiki/Bilderberg/2015) (Österreich). Nachdem er im Februar 2021 vom Genfer Polizeigericht wegen Vorteilsnahme verurteilt wurde, trat er als Staatsrat zurück – und drei Monate später bei WISeKey an. Am 30. April 2023 wurde er, ungeachtet seiner kriminellen Vergangenheit, zusätzlich wieder in den Genfer Staatsrat gewählt. Wie praktisch. Solch eine schamlose Unverfrorenheit scheint Maudet perfekt für das zu qualifizieren, was bei WISeKey unter dem Deckmantel der »Quantensicherheit« entwickelt wird – ein raumbasiertes [eID-Ökosystem](https://wiseid.com/).
»*Quantensicherheit nutzt Prinzipien der Quantenmechanik, um den Datenschutz und die sichere Informationsübertragung zu revolutionieren. Kernstück ist die Quantenschlüsselverteilung (Quantum Key Distribution, QKD), eine Spitzentechnologie, die mithilfe der Quantenmechanik vernetzte Teilchen für den sicheren Austausch von Verschlüsselungskennwerten erzeugt*.«
Ob digitale Identität, Unterschrift, Cloud oder Software – von der Know-Your-Customer-Biometrie bis hin zur Unternehmenslösung für die Mitarbeiteridentifikation. WISeKey hilft. [Anmelden](https://account.wiseid.com/signup) kann sich jeder. Während die Produktpalette für den privaten Sektor noch nach Lieferketten-Management, Sendungsverfolgung, Login-Lösung für eBanking oder [Face ID](https://de.wikipedia.org/wiki/Face_ID) auf dem Smartphone klingt – aber deutlich weitreichender ist, schauen sie sich die Homepage an – sprechen die WISeKey-Angebote im Bereich [Regierungen](https://www.wisekey.com/solutions/by-industry/government-trust-solutions/) eine ganz andere Sprache. Denn unter diesem Menüpunkt bewirbt der diskret operierende Konzern seine »*CertifyID Trust Center Platform*«:
»*Die CertifyID Trust Center Platform ist eine industrialisierte eID-Verwaltungslösung für Bürger, die Benutzer und ihre Anmeldeinformationen verwaltet, insbesondere digitale IDs und digitale Zertifikate für groß angelegte Anwendungen wie landesweite E-Government-Dienste. Es handelt sich um eine vollständige industrielle Public Key Infrastruktur- und ID-Verwaltungslösung, die Regierungsdienste rund um die Uhr unterstützt.*
***Die CertifyID Trust Center Plattform wird in einer Reihe von Anwendungen der Regierung und des öffentlichen Sektors verwendet, zum Beispiel: Personalausweis, ePassport (ICAO-konform), Führerschein, Gesundheit, Wahlen/Abstimmen*****.**
*Die CertifyID Plattform wurde unter Verwendung der Sicherheits- und Public Key Infrastruktur-Expertise von WISeKey entwickelt und kann vollständig in E-Government-Frameworks, kommerzielle Frameworks (…) und in das Bereitstellungsframework für E-Government-Dienste eines Landes integriert werden*.«
Da passt es doch wunderbar ins Bild, dass WISeKey am [13. Oktober 2022](https://www.finanzen.net/nachricht/aktien/wisekey-und-die-schweizer-armee-unterzeichnen-eine-partnerschaftsvereinbarung-zur-zusammenarbeit-bei-der-entwicklung-weltraumbezogener-aktivitaeten-unter-verwendung-der-wisesat-fossa-technologie-fuer-pi-11792137) eine »*Partnerschaftsvereinbarung zur Zusammenarbeit bei der Entwicklung weltraumbezogener Aktivitäten*« mit der Schweizer Armee bekannt gab – schließlich residieren in der Alpenrepublik nicht nur UN, GAVI, WEF, Club of Rome und jede Menge NGOs, sondern auch die Bank für Internationalen Zahlungsausgleich (BIZ), die ganz sicher Verwendung für ein quantengesichertes Echtzeit-Picosatellitennetzwerk findet, wenn ihr »*[Unified Ledger](https://www.bis.org/publ/arpdf/ar2023e3.htm)*« ([Zentrales Hauptbuch](https://www.globalgovernmentfintech.com/bis-releases-game-changing-blueprint-for-global-financial-system/)) für das Blockchain-Weltfinanzsystem von morgen zum Einsatz kommt. In Anbetracht der »*allumfassenden Marktblase*« ([D. Webb](https://www.regenauer.press/der-letzte-raubzug), 2024) ist damit wohl in absehbarer Zeit zu rechnen.
Das also sind die Projekte, Pläne und neuen Partner von Elon. Auf mich machen ja speziell die korrupten Genfer Quantenspezialisten mit ihren Picosatelliten und schlüsselfertigen eID-Lösungen nicht unbedingt den Eindruck von Freiheitskämpfern. Und auch die am 22. Januar 2024 bei einer [Pressekonferenz](https://x.com/JoshWalkos/status/1881866215637094726) im Weißen Haus angekündigten »*personalisierten mRNA-Injektionen gegen Krebs*« lassen mich eher skeptisch zurück.
Genau wie der Umstand, dass diese binnen 48 Stunden »*personalisierte mRNA*« durch die Rechenleistung von OpenAI [ermöglicht](https://news.yahoo.com/news/now-trump-says-500-billion-232732788.html?fr=sycsrp_catchall\&guccounter=1\&guce_referrer=aHR0cHM6Ly9wcmVzZWFyY2guY29tLw\&guce_referrer_sig=AQAAANhV_ubjRDL_kBGNPhmmLWxAhoW6pkAamqVphAXDXGmLTQUS-4gXsCQ1pinQHCufHywARCgqAG_iUpEBIIJexFhk0z6Oab5Q4js6kJ6Z6t-80onuNRGqRg_IMlcI6P72iCjCsfRpp1fAGCDhLSMGts2WK6D3gsv_YMrMXhqWP7xE) werden soll. Denn das von Elon Musk [mitgegründete](https://www.businessinsider.com/history-of-elon-musk-and-sam-altman-relationship-feuds-2023-3) Unternehmen des WEF- und [Bilderberg](https://wikispooks.com/wiki/Sam_Altman)-affinen [Sam Altman](https://news.yahoo.com/news/now-trump-says-500-billion-232732788.html?fr=sycsrp_catchall\&guccounter=1\&guce_referrer=aHR0cHM6Ly9wcmVzZWFyY2guY29tLw\&guce_referrer_sig=AQAAANhV_ubjRDL_kBGNPhmmLWxAhoW6pkAamqVphAXDXGmLTQUS-4gXsCQ1pinQHCufHywARCgqAG_iUpEBIIJexFhk0z6Oab5Q4js6kJ6Z6t-80onuNRGqRg_IMlcI6P72iCjCsfRpp1fAGCDhLSMGts2WK6D3gsv_YMrMXhqWP7xE) steht im berechtigten Verdacht, für den Tod eines Whistleblowers im Dezember 2024 verantwortlich zu sein. Während Polizei und Medien den Tod des OpenAI-Forschers Suchir Balaji als [Selbstmord](https://www.businessinsider.de/wirtschaft/openai-whistleblower-tragischer-tod-erschuettert-die-tech-welt/) deklarieren, [sprechen](https://economictimes.indiatimes.com/news/international/global-trends/suchir-balajis-openai-researcher-suicide-death-cold-blooded-murder-openai-whistleblowers-parents-claim-big-foul-play/articleshow/116855083.cms?from=mdr) sowohl die Umstände am Fundort seiner Leiche als auch Balajis Eltern von »*eiskaltem Mord*«. Nicht zu vergessen, dass Altman von seiner eigenen Schwester des jahrelangen Missbrauchs [beschuldigt](https://www.theguardian.com/technology/2025/jan/08/openai-chief-executive-sam-altman-accused-of-sexual-abuse-by-sister-in-lawsuit) wird und sich dafür demnächst vor Gericht verantworten muss. Selbst [The Economist](https://www.economist.com/business/2024/12/10/the-paypal-mafia-is-taking-over-americas-government) räumte am 10. Dezember 2024 ein, dass »*die PayPal Mafia die amerikanische Regierung übernimmt*«. Und das mit der »*Mafia*« scheint man in Washington mittlerweile wörtlich zu nehmen.
Aber die von einigen aus der Hüfte geschossenen Präsidialdekreten euphorisierten Eloi werden sicher Gründe finden, das alles zu ihren Gunsten auszulegen. Immerhin hat Trump ein paar Leute begnadigt und will aus der WHO austreten. Wie seine Fanbase es bewerkstelligt, auszublenden, dass »*The Donald*« schon in seiner ersten Amtszeit aus der WHO austreten wollte und es unterließ, erschließt sich mir aber leider nicht. Genau wie die Begeisterung für ein Gespräch zwischen Musk und Weidel. Man stelle sich nur mal vor, George Soros, Bill Gates oder Eric Schmitt konferierten mit deutschen Politikern. Oder bekämen Sendezeit im ÖRR. Nicht auszudenken.
**Wie heißt es so schön: »*Eine schmerzliche Wahrheit ist besser als eine Lüge*« (Thomas Mann). Stimmt. Nur fällt es relativ schwer, eine Lüge einzugestehen, wenn der, dem man sie beichten muss, der Lügner ist.**
So bleibt nur zu hoffen, dass möglichst viele Eloi diesen Schritt trotzdem möglichst bald hinter sich bringen. Im eigenen Interesse. Denn wie schon Ernst Freiherr von Feuchtersleben feststellte, ist »*Reue der Verstand, der zu spät kommt*«. Und das kann in diesen Tagen verheerende Folgen haben.
-

@ 4fe4a528:3ff6bf06
2025-02-01 13:41:28
<img src="https://blossom.primal.net/58a3e225ae607d5f110cff5f44a68268d27d3d239ba6d58279c2dd872259fbbb.jpg">
In my last article I wrote about NOSTR. I found another local bitcoiner via NOSTR last week so here is why it is important to join / use NOSTR — start telling people “Look me up on NOSTR”
Self-sovereign identity (SSI) is a revolutionary approach to digital identity that puts individuals in control of their own identity and personal data. Unlike traditional digital identity models, which rely on third-party organizations to manage and authenticate identities, SSI empowers individuals to own and manage their digital identity.
This approach is made possible by emerging technologies such as secure public / private key pairs. Decentralized identifiers, conceived and developed by nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 is an attempt to create a global technical standard around cryptographically secured identifiers - a secure, universal, and sovereign form of digital ID. This technology uses peer-to-peer technology to remove the need for intermediaries to own and authenticate ID information.
Notably, NOSTR, a decentralized protocol, has already begun to utilize decentralized IDs, demonstrating the potential of this technology in real-world applications. Via NOSTR, users can be sure that the person or computer publishing to a particular npub knows their nsec (password for your npub), highlighting the secure and decentralized nature of this approach.
With SSI, individuals can decide how their personal data is used, shared, and protected, giving them greater control and agency over their digital lives.
The **benefits** of SSI are numerous, including:
Enhanced security and protection of personal data. Reduced risk of identity theft and fraud Increased autonomy and agency over one's digital identity. Improved scalability and flexibility in digital identity management
**challenges**:
Ensuring the security and integrity of decentralized identity systems. Developing standards and protocols for interoperability and compatibility. Addressing concerns around ownership and control of personal data. Balancing individual autonomy with the need for verification and authentication in various contexts.
Overall, self-sovereign identity has the potential to transform the way we think about digital identity and provide individuals with greater control and agency over their personal data. Without people in control of their bitcoin seed words no freedom loving people would be able to exchange their money with others. Yes, keep enjoying using the only free market on the planet BITCOIN. Long live FREEDOM!
-

@ eff2631b:4732bd7e
2025-02-01 11:40:14
This is a test. Trying to use Obsidian for everything. Nostr works out of the box? First try failed, this is my second try.
-

@ eff2631b:4732bd7e
2025-02-01 11:28:43
This is a test. Trying to use Obsidian for everything. Nostr works out of the box?
-

@ 9e69e420:d12360c2
2025-02-01 11:16:04

Federal employees must remove pronouns from email signatures by the end of the day. This directive comes from internal memos tied to two executive orders signed by Donald Trump. The orders target diversity and equity programs within the government.

CDC, Department of Transportation, and Department of Energy employees were affected. Staff were instructed to make changes in line with revised policy prohibiting certain language.
One CDC employee shared frustration, stating, “In my decade-plus years at CDC, I've never been told what I can and can't put in my email signature.” The directive is part of a broader effort to eliminate DEI initiatives from federal discourse.
-

@ edeb837b:ac664163
2025-02-01 10:51:33
In today’s fast-paced financial markets, having quick access to real-time data, trade insights, and the ability to share trades with a like-minded community is invaluable. That’s where NVSTly’s Discord bot comes in. It’s more than just a bot — it’s a powerful tool for social trading, designed to help traders and investors track their trades, share insights, and collaborate with others in real-time, all within Discord.
## What the NVSTly Discord Bot Does
[NVSTly’s Discord bot](https://nvstly.com/go/bot) is built with the goal of making financial data and trading insights easily accessible to the entire trading community on Discord. Whether you’re a seasoned trader or just starting, the bot helps you stay on top of your trades and market trends. Some of the key features of the bot include:
- **Real-Time Trade Tracking & Sharing:** The bot [tracks your trades](https://nvstly.com/trades) and allows you to share them with others. Whether you’re trading stocks, options, forex, or cryptocurrencies, your trades are instantly shared with your followers and can be posted to social media or sent through Discord DMs or webhooks, fostering a transparent and collaborative environment.
- **Trader Stats & Performance Recaps:** The bot generates visual reports of your trading performance, including win rates, total gains, and individual trade stats. You can view a trader’s daily, weekly, or monthly recaps, complete with details on stock tickers, options info, and profit/loss calculations.
- **Market Data & Charts:** Get instant access to live market data, stock charts, and detailed information on tickers. The bot provides a variety of commands for stock price movements, charts, and other data, with plans to expand this to cover more markets in the future.
- **Comprehensive Coverage:** The bot currently supports stocks, options, forex, and crypto for trade tracking and sharing. Futures markets are also planned for the future. While the bot supports these markets for trade tracking, data-related features like market sentiment analysis or earnings reports will be available in the future.
## How the Bot Integrates with NVSTly’s Social Trading App
The NVSTly Discord bot is fully integrated with the NVSTly [social trading app](https://nvstly.com), creating a seamless experience for users across platforms. Traders can track their trades on the app, and the bot will automatically share those trades directly with their followers, via DMs, social media, or webhooks. This integration means that everything you do on the NVSTly app can be easily shared with your community in real-time via Discord, making it simple to stay connected with your trading network.
The bot doesn’t just show trades — it also gives users insights into their trading performance and connects them with other traders for discussions, tips, and strategies. With NVSTly’s unique social features, traders can collaborate, share strategies, and learn from each other in a dynamic and interactive environment.
## What’s Next for the NVSTly Discord Bot?
The future of the NVSTly Discord bot is incredibly exciting, with plans to add even more features designed to elevate the trading experience. Some of the upcoming features include:
- **Expanded Market Coverage for Data Commands:** In addition to stocks, the bot will soon offer data-related commands for crypto, forex, and futures markets. This will allow users to access even more comprehensive market data, including earnings reports, options flow, and more.
- **AI & Machine Learning Integration:** NVSTly plans to integrate AI and machine learning to generate trade signals, analyze market trends, and even offer personalized trading tips. This will help traders refine their strategies and make more informed decisions.
- **Real-Time Alerts & Notifications:** Users can already receive trade alerts sent directly to their DMs from traders they follow. In the future, users will also be able to set more customized alerts based on price targets or specific market activity.
## Why the NVSTly Discord Bot is Perfect for Trading Communities
Discord has become a hub for traders and investors, and the NVSTly Discord bot takes full advantage of this by providing a platform where traders can interact, share trades, and learn from one another. The bot’s ability to instantly share trade recaps and stats creates an environment of transparency and collaboration. Traders can discuss strategies, ask questions, and even challenge each other to improve their performance.
By integrating market data, charts, and trade performance tracking, the bot offers a complete package for traders on Discord. It’s not just a tool for sharing trades — it’s a vital part of a thriving trading community.
## Why NVSTly’s Discord Bot is the Fastest Growing Finance Bot on Discord
With its comprehensive features and seamless integration with the NVSTly app, the NVSTly Discord bot has quickly become the go-to tool for traders on Discord. What sets it apart from other finance bots is its focus on user engagement. The bot is not just about providing data — it’s about building a community of traders who can share their experiences, insights, and successes.
Traders have flocked to the NVSTly Discord bot because it provides real-time data, easy trade tracking, and powerful analytics — all in a user-friendly format. It’s no wonder it’s quickly becoming the fastest-growing finance bot on Discord.
## On Track to be the Greatest Finance Bot on Discord
NVSTly is on track to become the greatest finance bot on Discord, if it’s not already. With plans for expanding market coverage, adding advanced AI-driven features, and constantly improving its user experience, the bot is poised to revolutionize the way traders use Discord.
By offering a comprehensive set of tools that integrate seamlessly with the NVSTly app, the bot is becoming an essential resource for traders who want to stay informed, track their performance, and engage with the trading community.
---
NVSTly is available for free on [web](https://nvstly.com), mobile devices ([iOS](https://nvstly.com/go/ios) & [Google Play](https://nvstly.com/go/android)), and is fully integrated with Discord via a [unique bot](https://nvstly.com/go/bot)- the only of it’s kind and available to any server or trading community on Discord. Or feel free to join a community of over 45,000 investors & traders on our [Discod server](https://nvstly.com/go/discord).
-

@ edeb837b:ac664163
2025-02-01 10:43:46
Join Benzinga as they sit down with NVSTly, the cutting-edge platform revolutionizing social trading and investing. In this exclusive interview, NVSTly shares insights on empowering retail traders, fostering transparency, and building a thriving community for investors of all levels. Discover how NVSTly is shaping the future of trading with innovative features, real-time trade tracking, and global collaboration.
NVSTly Web: https://nvstly.com
iOS: https://nvstly.com/go/ios
Google Play: https://nvstly.com/go/android
[](https://www.youtube.com/watch?v=T31HkdKYkc})
-

@ edeb837b:ac664163
2025-02-01 10:40:42
We’re thrilled to announce that [NVSTly](https://nvstly.com/go/) has been honored with the People's Choice Award at the prestigious [Benzinga FinTech Awards 2024](https://www.benzinga.com/news/events/24/11/42098678/these-are-the-top-fintech-innovators-recognized-at-benzingas-2024-global-fintech-awards)! This recognition is a testament to the trust, support, and enthusiasm of our growing community of retail traders, investors, and financial enthusiasts.

## A Milestone in Social Investing
Winning the People's Choice Award is more than just a moment of celebration for NVSTly—it reflects the incredible journey we’ve shared with our users. NVSTly was built with one mission in mind: to redefine social investing by empowering traders of all experience levels to share, track, and learn from one another.
In the competitive world of fintech, being selected as the People's Choice means we’ve created something that resonates deeply with our audience. It’s your votes, feedback, and passion that have propelled us to this achievement.
## What Makes NVSTly Unique?
NVSTly stands out for offering a platform that’s entirely free while delivering a comprehensive suite of features for traders, such as:
* **Global Leaderboard:** Recognizing top-performing traders across stocks, options, futures, forex, and cryptocurrency.
* **Trade Insights UI:** Providing detailed analytics on trades, including market data validation and unique event visualizations.
* **Broker Integration (Optional):** Automating trade tracking and sharing with real-time updates.
* **Discord Integration:** A first-of-its-kind bot that brings NVSTly’s full functionality to one of the fastest-growing social platforms in finance.
* **Education and Community:** Enabling beginners to learn from experienced traders and find actionable insights.
Unlike traditional trading platforms, NVSTly focuses solely on trade tracking, sharing, and performance validation. It’s not about buying or selling real assets but fostering transparency, collaboration, and growth among traders.
## Powered by the Community
The People's Choice Award is special because it comes directly from you—our community. Whether you’re an experienced trader gaining recognition through our leaderboard or a beginner exploring NVSTly to learn from top traders, this award proves that NVSTly isn’t just a platform; it’s a movement.
Your votes affirm our commitment to delivering cutting-edge features, unmatched usability, and an ecosystem that connects traders across all markets.
## Looking Ahead
Winning this award fuels our determination to push boundaries even further. In the months to come, we’re excited to roll out new features, expand our broker integrations, and enhance the tools that make NVSTly the go-to platform for retail traders worldwide.
## Thank You
We couldn’t have achieved this milestone without your unwavering support. From everyone at the NVSTly team, thank you for believing in our vision and making NVSTly the People’s Choice for 2024. This award is as much yours as it is ours.
If you haven’t joined the movement yet, there’s never been a better time. Discover, share, and track trades with NVSTly today—because the best way to grow in the markets is together.
> ***Join NVSTly:***
* ***Website:** [nvstly.com](https://nvstly.com)*
* ***Mobile App:** Available on [Google Play](https://nvstly.com/go/android) and [iOS App Store](https://nvstly.com/go/ios)*
* ***Discord Community:** [Join Now](https://nvstly.com/go/discord)*
*Let’s continue shaping the future of social investing, one trade at a time.*
-

@ edeb837b:ac664163
2025-02-01 10:36:38

At NVSTly, we embrace the concept of “building in public.” This approach shapes how we develop, test, and roll out features, with the goal of making NVSTly the best social trading platform for our users. But what exactly does building in public mean for NVSTly? Let’s break it down.
## Updates as They’re Finished
Instead of waiting to bundle new features and fixes into big, infrequent releases, we push updates as they’re completed. This ensures users benefit from improvements as soon as possible. However, our agile development style means you might notice subtle changes before they’re officially included in a published changelog. These incremental updates allow us to iterate and enhance the platform quickly.
## Internal Testing, Real-World Feedback
Before any update reaches the production environment, our team conducts internal testing to ensure the new feature or fix works as intended. For example, a recent update to allow stats and daily/weekly recap commands to function with usernames containing spaces was thoroughly tested internally. Unfortunately, this change inadvertently broke compatibility with Discord IDs, highlighting the challenges of anticipating every edge case.
This is where building in public comes into play: while we strive for thorough testing, some issues only emerge when updates meet real-world usage. That’s why we rely on our vibrant user base to help us identify bugs, unintended behaviors, and areas for improvement.
## The Role of Our User Community
Our users play a critical role in the development process. By using [NVSTly](https://nvstly.com) in their daily trading workflows, they encounter scenarios that internal testing might miss. When users report bugs, glitches, or other issues, it provides us with invaluable insights into how the platform performs under various conditions.
If you ever experience something on NVSTly that doesn’t seem to work as expected, we encourage you to report it to us. Unlike platforms that may identify and resolve issues passively over time, NVSTly relies directly on user feedback to detect and prioritize fixes. Every report helps us improve.
## Changelogs: A Snapshot of Progress
Given our frequent updates, we publish changelogs only after accumulating several changes or introducing major features. This means that when you see a changelog, many of the updates listed might have been implemented days or even weeks earlier. While this approach helps us focus on building and refining the platform, it’s another example of how building in public keeps the development process transparent.
## Why Building in Public Matters
By building in public, we:
- **Accelerate innovation:** Continuous updates ensure the platform evolves rapidly.
- **Foster transparency:** Users gain insight into what’s changing and how issues are addressed.
- **Strengthen collaboration:** Feedback from users directly informs our priorities and solutions.
This approach isn’t without its challenges, but we believe the benefits far outweigh the risks. Building in public allows us to create a platform that truly meets the needs of our community — a community we’re proud to involve in the journey.
## How You Can Help
If you notice a bug, glitch, or unintended behavior, please let us know right away. Your feedback is essential to making NVSTly better every day. Together, we’re not just building a platform; we’re building a community-driven experience that reflects the collective expertise and passion of its users.
Thank you for being part of the NVSTly journey. Let’s keep building — together.
---
NVSTly is available for free on web, mobile devices ([iOS](https://nvstly.com/go/ios) & [Google Play](https://nvstly.com/go/android)), and is fully integrated with Discord via a [unique bot](https://nvstly.com/go/bot)- the only of it’s kind and available to any server or trading community on Discord. Or feel free to join a community of over 45,000 investors & traders on our [Discod server](https://nvstly.com/go/discord).
-

@ da0b9bc3:4e30a4a9
2025-02-01 09:45:00
Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/872135
-

@ 0b118e40:4edc09cb
2025-02-01 09:41:34
*(This is not a feasibility analysis, but rather a perspective on the philosophical alignment with Bitcoin’s vision)*
The moment stablecoins or national currencies start playing a role in Bitcoin LN, Bitcoin’s position as a purely decentralized medium of exchange will be undermined.
The idea of a Bitcoin-native global currency and global economy, where people and businesses transact in Bitcoin directly, would align with its original purpose.
If Bitcoin is to function as a true currency, a larger global adoption that bypasses traditional financial systems, will make these on/off ramps for stablecoins unnecessary.
At some point, there will be those who will want to preserve Bitcoin’s purity as a currency, and others who want to see store value, ETF, stablecoin collabs, tokens, pump & dump, NFTs, and centralized influenced approaches.
Currency domination, especially by the USD, has contributed to poverty in the Global South by deepening economic inequality and exacerbating debt burdens. During the Tequila Crisis and the Asian Financial Crisis, Mexico and Asia’s high dependency on the USD led to rapid currency devaluations and debt defaults. Every time the US hikes interest rates, it triggers capital flight from developing nations, causing currency drops and further economic hardship, and this isn’t just a thing of the past; it has been a pressing issue in the last two years, widening the poverty gap in the Global South. And, as always, it’s the poor who suffer the most.
USDT is just another name for currency domination through blockchain. Its pegged to USD and on Bitcoin LN, it will piggyback on Bitcoin’s perks (as a medium of exchange to Bitcoin's current and potential adopters) with a high likelihood of keeping users transacting in USD rather than Bitcoin itself. This could also lead to global assumptions that Bitcoin is taking sides, especially in today’s fragile and invisible global currency war. To counter, people will say ‘let all stablecoins pegged to any currencies come on board’ - but what’s the point of Bitcoin then?
It’s like bringing the very systems Bitcoin was created to challenge, back into the fold. I believe when you use stablecoins this way, you’re essentially importing the power dynamics and dependencies of the traditional financial system, which seems counterproductive to Bitcoin's decentralized ethos.
Bitcoin’s true potential is its ability to provide an alternative to centralized, government-controlled currencies and financial systems. We should stick to the original game plan.
-

@ dbb19ae0:c3f22d5a
2025-02-01 09:06:49
### **The Magic of `=()=` in Perl: Counting Matches with Elegance**
Perl is full of powerful and sometimes cryptic features, and one of the lesser-known yet highly useful tricks is the `=()=` operator. This clever construct allows you to count the number of matches in a string without using loops or unnecessary variables.
---
## **Understanding `=()=`: A Smart Counting Trick**
Normally, when you apply a regex with the `/g` (global match) flag, Perl finds all occurrences in the string. However, getting the **count** of those matches isn't as straightforward as you might expect.
Consider this example:
```perl
my $str = "Hello 123, Perl 456!";
my $count = () = $str =~ /\w/g;
print "Matched $count word characters.\n";
```
### **Breaking It Down**
1. **Regex Matching (`$str =~ /\w/g`)**
- This searches for **all** word characters (`\w` → `[A-Za-z0-9_]`) in `$str`.
- The `/g` flag ensures it **captures all occurrences** instead of just the first one.
2. **The Empty List `()`**
- The regex match is assigned to an **empty list `()`**.
- This forces Perl to evaluate the regex in **list context**, where it returns **all matches** instead of just one.
3. **Assigning to a Scalar (`$count`)**
- When a **list is assigned to a scalar**, Perl doesn't store the list—it simply counts its elements.
- The result? `$count` contains the **number of matches**.
### **Expected Output**
```
Matched 15 word characters.
```
If you manually count the `\w` matches (`Hello123Perl456`), you'll find **15**.
---
## **Why Not Use `scalar()` Instead?**
You might think this is equivalent to:
```perl
my $count = scalar($str =~ /\w/g); # will return 1
```
**But this won't work!**
- `scalar($str =~ /\w/g)` only returns the **last match found**, not the count.
- `=()=` is necessary because it **forces list context**, ensuring Perl counts all matches correctly.
---
## **Practical Use Cases**
This trick is useful whenever you need to count occurrences without modifying the original string. Some real-world applications include:
✅ Counting **words, numbers, or special characters** in a string.
✅ Measuring **how many times a pattern appears** in a text.
✅ Quick **validation checks** (e.g., ensuring a string contains at least `n` digits).
Example: Counting words in a sentence
```perl
my $sentence = "Perl is awesome!";
my $word_count = () = $sentence =~ /\b\w+\b/g;
print "Word count: $word_count\n"; # Output: 3
```
---
## **Final Thoughts**
The `=()=` operator might look like magic at first, but it's actually an elegant way to **force list context** and extract match counts without loops or extra variables. Whether processing text or just trying to optimize Perl scripts, this trick is a powerful addition to the Perl toolkit.
-

@ 0271e1b9:ad8cff90
2025-02-01 07:39:31
**I study the greats.**
For if and when I find myself beaten down into the gutters of life - the vile, bile and the mundane - I shall draw strength from other great men - past, present and future - who, quite often, faced many more adversities and a lot more suffering, but chose to use them to their advantage, to overcome their dire circumstances and rise above the afflictions that life had bestowed upon them. It’s all been done before. It can be done again, better.
Learning from the past and from the present is very straightforward. Anyone can do that. But how does one learn from the future? It’s simple: you envision the best possible future for humanity, for generations to come, and for yourself. Then you figure out an approximate path on how to get there, and what kind of a man or a woman you must be to walk that path. The skills, the mindset, the qualities. And lastly, but perhaps most importantly, you find actionable measures, habits, convictions on how to become that person - and conversely, what are stopping you from becoming that person.
> “You must value learning above everything else.”
― Robert Greene
> “Those who have a 'why' to live, can bear with almost any 'how'.”
― Viktor E. Frankl
> “You need to look at all events as having value. If you can do that, then you’re in a zone of tremendous opportunity.”
― Phil Stutz
> “I shall take the more pains to uncover the fountains of philosophy, from which all my eloquence has taken its rise.”
― Marcus Tullius Cicero
> “Error correction is the basis of all intelligence.”
― Jeff Booth
> “Yes, you’re likely to fail, that’s fine. Because the goal of playing is not to win, but to keep learning. And the day you stop learning is the day you stop living."
― Jesse Enkamp
> "A man is great not because he hasn't failed; a man is great because failure hasn't stopped him."
— Confucius
> “If people knew how hard I had to work to gain my mastery, it would not seem so wonderful at all.”
― Michelangelo
> “First of all we have to decide what we are to do and what manner of men we wish to be - the most difficult problem in the world.”
― Marcus Tullius Cicero
> “You either bleed soul into your work, or let the work bleed out your soul.”
― Pran Yoganthan
> "The Stoic philosopher is the man who has liberated himself from fear. He’s not afraid of death, he’s not afraid of pain, he’s not afraid of other people’s dismissal as a fool. The only thing he cares about is that he should meet his moral obligations.”
― Michael Sugrue
> "The strong do what they can and the weak suffer what they must."
― Thucydides
> “The brain is the most powerful weapon in the world.”
― David Goggins
> “Man, the bravest of animals, and the one most accustomed to suffering, does not repudiate suffering as such; he desires it, he even seeks it out, provided he is shown a meaning for it, a purpose of suffering. The meaninglessness of suffering, not suffering itself, was the curse that lay over mankind so far.”
― Friedrich Nietzsche
> "Consciousness is awareness with a choice."
― Thomas Campbell
> “The essence of philosophy is that a man should so live that his happiness shall depend as little as possible on external things.”
― Epictetus
> “It’s most real, it’s most good and it’s most salvific - it saves you, it transforms you. That’s the sacred.”
— John Vervaeke
> “It is impossible for a man to learn what he thinks he already knows.”
― Epictetus
> “Evolution is a process of iteration. There’s no master plan. It’s in each moment of what happens.”
― Michael Behrens
> “Don’t follow anybody and don’t accept anyone as a teacher, except when you become your own teacher and disciple.”
― Jiddu Krishnamurti
> “This is your life. You’re accountable. What are you gonna do about that?”
― James Hollis
By the way, if you enjoyed these quotes, feel free to follow a little side project of mine: [Stoic Resurrection](https://linktr.ee/stoic_resurrection)
*Peace & Love,*
*[Kontext](https://linktr.ee/mckontext)*
*Block height 881,748*
-

@ ee7e3590:5602f192
2025-02-01 05:02:15
You’re hitting on the core tension: **unlimited demand for emergency care collides with finite resources**, and pretending otherwise leads to either runaway costs or rationing-by-stealth. Let’s confront this head-on with free-market-aligned solutions that don’t ignore human realities:
---
### **1. Redefine "Emergency Care"**
The U.S. legally mandates ERs to stabilize *anyone*, regardless of ability to pay (EMTALA). This creates moral hazard:
- **Problem**: Hospitals inflate prices on paying patients to offset uncompensated care.
- **Free-Market Fix**:
- **Repeal EMTALA**: Allow ERs to refuse non-critical cases (e.g., toothaches, rashes) unless prepaid or insured.
- **Clarify "True Emergency"**: Legally define emergencies as *immediate life threats* (e.g., strokes, cardiac arrest) and let non-critical cases be diverted to urgent care.
- **Consequence**: ERs could price transparently for true emergencies, while non-critical cases face market-driven urgent care options.
---
### **2. Embrace Tiered Emergency Care**
Not all emergencies require Level I trauma centers:
- **Basic ERs**: Staffed by NPs and paramedics for minor injuries (e.g., sprains, minor burns) at lower costs.
- **Advanced ERs**: For critical care (e.g., gunshot wounds), priced higher but competing via outcomes (e.g., survival rates).
- **Example**: India’s *Ziqitza Healthcare* operates ambulance tiers—basic vans for transport and advanced ICU units.
---
### **3. **Address Moral Hazard with Insurance Innovation**
- **Catastrophic Insurance Mandates**: Require everyone to carry cheap, high-deductible plans covering *only* true emergencies (e.g., $10/month for coverage above $50k).
- Incentivizes price shopping for non-emergencies.
- Prevents freeloading on ERs.
- **Risk-Adjusted Premiums**: Smokers, skydivers, or diabetics pay higher premiums, aligning costs with personal choices.
---
### **4. **Community-Based Safety Nets**
- **Mutual Aid Networks**: Local groups negotiate bulk ER rates (e.g., $100/month membership covers three ER visits annually).
- **Crowdfunding ER Vouchers**: Platforms like *GoFundMe* could partner with hospitals to prepurchase discounted emergency care slots.
---
### **5. **Radical Transparency + Bankruptcy Reform**
- **ER Debt Auctions**: Let hospitals sell unpaid ER bills to collection agencies in real-time, creating competition to minimize patient liability.
- **Flat-Fee ER Pricing**: Hospitals post rates like “$5,000 for appendicitis stabilization, all-inclusive” to deter surprise billing.
- **Ban Wage Garnishment for Medical Debt**: Protect patients from lifelong ruin, forcing hospitals to price responsibly or absorb losses.
---
### **6. **Accept Trade-Offs Explicitly**
The U.S. system fails because it hides rationing behind complexity. A free-market approach must embrace transparency:
- **Option 1**: Pay $100,000 for a 95% survival rate in a car crash.
- **Option 2**: Pay $20,000 for a 70% survival rate at a budget ER.
- **Brutal but Honest**: Let individuals (or insurers) choose their risk tolerance upfront.
**Example**:
- **Japan’s Price Controls**: Caps ER costs but tolerates wait times (e.g., 8+ hours for non-critical care).
- **Switzerland’s Mandates**: Everyone buys insurance, but ERs charge $1,000+ deductibles to deter overuse.
---
### **7. **Disrupt with Decentralized Care**
- **Crypto-ERs**: Blockchain-based emergency funds where contributors vote on covering members’ bills.
- **AI-Guided Self-Care**: Apps that stabilize patients en route to ERs (e.g., tourniquet tutorials, overdose reversal guidance).
---
### **8. **Reform Malpractice to Reduce Defensive Medicine**
- **“No Pay, No Harm” Liability**: If a patient doesn’t pay, they can’t sue for malpractice (incentivizing upfront pricing).
- **Safe Harbor Protocols**: ERs using approved, cost-effective treatments (e.g., generics) get immunity from lawsuits.
---
### **The Uncomfortable Truth**
A free market in emergency care requires accepting that **not everyone will be saved**—just as not everyone can afford a Ferrari. The alternative is the current U.S. model, which *pretends* to save everyone but bankrupts millions and still leaves 30% of ER visits unmet due to overcrowding.
By legalizing tiered care, deregulating monopolies, and forcing transparency, you create a system where:
- **Elites** pay premium prices for cutting-edge emergency care.
- **Most** get “good enough” stabilization at reasonable costs.
- **Some** choose cheap, high-risk options (or none at all).
This isn’t pretty, but it’s honest—and arguably more ethical than today’s hidden rationing and financial toxicity.
-

@ ee7e3590:5602f192
2025-02-01 05:00:39
You’re hitting on the core tension: **unlimited demand for emergency care collides with finite resources**, and pretending otherwise leads to either runaway costs or rationing-by-stealth. Let’s confront this head-on with free-market-aligned solutions that don’t ignore human realities:
---
### **1. Redefine "Emergency Care"**
The U.S. legally mandates ERs to stabilize *anyone*, regardless of ability to pay (EMTALA). This creates moral hazard:
- **Problem**: Hospitals inflate prices on paying patients to offset uncompensated care.
- **Free-Market Fix**:
- **Repeal EMTALA**: Allow ERs to refuse non-critical cases (e.g., toothaches, rashes) unless prepaid or insured.
- **Clarify "True Emergency"**: Legally define emergencies as *immediate life threats* (e.g., strokes, cardiac arrest) and let non-critical cases be diverted to urgent care.
- **Consequence**: ERs could price transparently for true emergencies, while non-critical cases face market-driven urgent care options.
---
### **2. Embrace Tiered Emergency Care**
Not all emergencies require Level I trauma centers:
- **Basic ERs**: Staffed by NPs and paramedics for minor injuries (e.g., sprains, minor burns) at lower costs.
- **Advanced ERs**: For critical care (e.g., gunshot wounds), priced higher but competing via outcomes (e.g., survival rates).
- **Example**: India’s *Ziqitza Healthcare* operates ambulance tiers—basic vans for transport and advanced ICU units.
---
### **3. **Address Moral Hazard with Insurance Innovation**
- **Catastrophic Insurance Mandates**: Require everyone to carry cheap, high-deductible plans covering *only* true emergencies (e.g., $10/month for coverage above $50k).
- Incentivizes price shopping for non-emergencies.
- Prevents freeloading on ERs.
- **Risk-Adjusted Premiums**: Smokers, skydivers, or diabetics pay higher premiums, aligning costs with personal choices.
---
### **4. **Community-Based Safety Nets**
- **Mutual Aid Networks**: Local groups negotiate bulk ER rates (e.g., $100/month membership covers three ER visits annually).
- **Crowdfunding ER Vouchers**: Platforms like *GoFundMe* could partner with hospitals to prepurchase discounted emergency care slots.
---
### **5. **Radical Transparency + Bankruptcy Reform**
- **ER Debt Auctions**: Let hospitals sell unpaid ER bills to collection agencies in real-time, creating competition to minimize patient liability.
- **Flat-Fee ER Pricing**: Hospitals post rates like “$5,000 for appendicitis stabilization, all-inclusive” to deter surprise billing.
- **Ban Wage Garnishment for Medical Debt**: Protect patients from lifelong ruin, forcing hospitals to price responsibly or absorb losses.
---
### **6. **Accept Trade-Offs Explicitly**
The U.S. system fails because it hides rationing behind complexity. A free-market approach must embrace transparency:
- **Option 1**: Pay $100,000 for a 95% survival rate in a car crash.
- **Option 2**: Pay $20,000 for a 70% survival rate at a budget ER.
- **Brutal but Honest**: Let individuals (or insurers) choose their risk tolerance upfront.
**Example**:
- **Japan’s Price Controls**: Caps ER costs but tolerates wait times (e.g., 8+ hours for non-critical care).
- **Switzerland’s Mandates**: Everyone buys insurance, but ERs charge $1,000+ deductibles to deter overuse.
---
### **7. **Disrupt with Decentralized Care**
- **Crypto-ERs**: Blockchain-based emergency funds where contributors vote on covering members’ bills.
- **AI-Guided Self-Care**: Apps that stabilize patients en route to ERs (e.g., tourniquet tutorials, overdose reversal guidance).
---
### **8. **Reform Malpractice to Reduce Defensive Medicine**
- **“No Pay, No Harm” Liability**: If a patient doesn’t pay, they can’t sue for malpractice (incentivizing upfront pricing).
- **Safe Harbor Protocols**: ERs using approved, cost-effective treatments (e.g., generics) get immunity from lawsuits.
---
### **The Uncomfortable Truth**
A free market in emergency care requires accepting that **not everyone will be saved**—just as not everyone can afford a Ferrari. The alternative is the current U.S. model, which *pretends* to save everyone but bankrupts millions and still leaves 30% of ER visits unmet due to overcrowding.
By legalizing tiered care, deregulating monopolies, and forcing transparency, you create a system where:
- **Elites** pay premium prices for cutting-edge emergency care.
- **Most** get “good enough” stabilization at reasonable costs.
- **Some** choose cheap, high-risk options (or none at all).
This isn’t pretty, but it’s honest—and arguably more ethical than today’s hidden rationing and financial toxicity.
-

@ f1989a96:bcaaf2c1
2025-01-31 21:22:59
In the summer of 2023, the Human Rights Foundation (HRF) launched a Bitcoin Bounty program aimed at funding software developers to create new tools and features for Bitcoin tailored to the needs of dissidents and human rights advocates challenging authoritarianism worldwide. These bounties ranged from UX improvements to privacy upgrades and open-sourcing closed and permissioned systems.
There were 11 bounties in total, each with specific objectives. The deadline was Dec. 31, 2024.
We are excited to announce that every single bounty was claimed and that the resulting tools and upgrades are now empowering human rights activists daily across popular apps such as Blue Wallet, Zeus, Stack Wallet, Iris, Coracle, Keeper, Bull Bitcoin, Cake Wallet, and more.
This program highlights the impact of collaboration between human rights activists and software developers to create better tools for freedom. HRF is proud to have played a role in this effort and looks forward to continuing similar programs in the future. Special credit goes to the Oslo Freedom Forum, where much of the critical interaction between developers and activists occurred.
This wave of bounties was inspired by a successful pilot project in 2021, executed in partnership with Strike and Jack Mallers, which supported developers like Will Cassarin and Calle. Their innovations later gave rise to important advancements such as zaps in Nostr and the Cashu ecash protocol.
# **Bounty Details**
#### **1. Open-Sourcing the Design Guide**
**Winner:** [CypherStack](https://cypherstack.com/) for porting the Bitcoin UI Kit from Figma to an [open-source Penpot project](https://github.com/cypherstack/bitcoin-ui-kit-penpot) (2 BTC awarded).
Many UI kits are created using proprietary software like Figma. While these tools are powerful, they require licenses and are not accessible to everyone — an obstacle for developers working on open-source projects or those with limited funds. This creates a barrier to entry for designers and developers wanting to contribute to the Bitcoin ecosystem. This bounty was awarded to CypherStack for porting the Bitcoin UI Kit from Figma to Penpot, an open-source design tool similar to Figma, but free and accessible to everyone. This helped democratize access to information and resources, promote collaboration, and make it easier for developers to create high-quality Bitcoin tools, which in turn helped to increase Bitcoin adoption.
#### **2. Serverless Payjoin**
**Winners:** This is a two-part bounty. The first bounty is for the development of the Serverless Payjoin specification, and the second bounty is for any wallets that implement Serverless Payjoin.
**Part 1:** [Dan Gould](https://crates.io/users/DanGould) for his work on [PayJoin V2](https://crates.io/crates/payjoin-cli/) (1 BTC)
**Part 2:** Dan Gould, [Spacebear](https://github.com/spacebear21) from Payjoin DevKit, and [Bull Bitcoin](https://www.bullbitcoin.com/) app, for their collaborative effort implementing Payjoin into the Bull Bitcoin wallet (0.5 BTC split three ways).
PayJoin is a privacy upgrade to Bitcoin that flusters mass surveillance attempts on the network. Traditional implementations have required the receiver to run a server for transaction coordination, creating a barrier to adoption. Serverless PayJoin removed this dependency and simplified the process. Serverless PayJoin also eliminated the need for receiver-hosted infrastructure and reduced censorship risks by removing a central point of failure — a significant advantage for activists and nonprofits operating under repressive regimes. This bounty resulted in the first mobile app ([Bull Bitcoin](https://play.google.com/store/apps/details?id=com.bullbitcoin.mobile&hl=en_US)) with integrated PayJoin send and receive support, an important advancement that provided robust privacy protections against surveillance for at-risk individuals.
#### **3. End-to-End Encrypted Nostr Group Chats**
**Winners:** [Martti Malmi](https://iris.to/sirius) for incorporating encrypted group chat functionality into the [Iris](https://iris.to/) Nostr client (1 BTC) and to Vitor Pamplona, hodlbod, and Paul Miller for their work on NIP-17, which allowed users to encrypt and share Nostr messages in a way that can be recognized across different Nostr clients (1 BTC).
End-to-End Encrypted (E2EE) Nostr Group Chats are private, secure messaging groups built on the Nostr protocol, a decentralized communication system. While Nostr messages are already encrypted, they still expose metadata, allowing outside observers to see who is communicating and when. This bounty focused on preventing metadata leakage, ensuring that these details remain private. By leveraging Nostr’s decentralized architecture, these chats offered censorship resistance. They prevented conversations from being surveilled, blocked, or controlled by a central authority, and as a result of this bounty, have now been implemented into popular Nostr clients like Iris, Amethyst, and Coracle. This is an important step forward for activists, journalists, and communities who risk losing their freedom of speech under oppressive regimes.
#### **4. Silent Payments**
**Winners:** [cygnet3](https://github.com/cygnet3) and [Sosthene](https://github.com/Sosthene00) for their contributions to [critical libraries](https://github.com/Sosthene00/electrs/tree/sp_tweaks) for delivering Silent Payments and for developing a [mobile wallet](https://github.com/cygnet3/danawallet) capable of sending and receiving Silent Payments without requiring a full node (1 BTC).
Silent Payments are a privacy-enhancing Bitcoin addressing scheme that allows a sender to generate a unique static address for a recipient without requiring any interaction (while still allowing the recipient to detect and spend the received funds). This breaks common tracking methods used by surveillance firms and autocracies and makes it harder to link payments to a specific recipient. By improving on the privacy of traditional Bitcoin addresses, Silent Payments enhanced financial privacy, making them ideal for donations, salaries, and other sensitive transactions. This bounty code has been fully integrated into Cake Wallet, and several other major wallets like Wasabi, Blue Wallet, and Bitbox have added partial functionality. This brings Silent Payments to tens of thousands of users and marks a major step in real-world Bitcoin privacy.
#### **5. Human-Readable Offers**
**Winners:** [Stephen DeLorme](https://x.com/StephenDeLorme), [Chad Welch](https://x.com/chdwlch), and [Evan Kaloudis](https://x.com/evankaloudis) for [Twelve Cash](https://twelve.cash/) and its integration into [Zeus Wallet](https://zeusln.com/) (1 BTC).
Human-Readable Offers simplify Bitcoin payments by replacing complex Bitcoin addresses and invoices with user-friendly text. This is especially important for Lightning Network transactions, which currently involve a cumbersome process of generating invoices for each payment. With Human-Readable Offers, sending Lightning payments becomes as simple as sending an email (just by entering a username). This approach, similar to many fintech apps today, reduces errors, lowers the barrier to entry, increases trust, and is crucial for broader adoption of Bitcoin among new and seasoned users alike. It’s also important for people who don’t have access to smartphones and cannot copy and paste or use QR codes. Today, as a result of this bounty, Zeus users connected to a Core Lightning node can create a human-readable Bolt 12 offer to privately receive donations.
#### **6. Self-Custodial Mobile Lightning Address**
**Winner:** Evan Kaloudis for [Zeus Wallet](https://zeusln.com/) (1 BTC).
Activists, nonprofits, and content creators often use Lightning addresses to receive donations quickly and easily. However, setting up and managing a Lightning address presents a challenge: users have to choose between the self-sovereignty of managing their own web server (a complex process) or the convenience of a custodial service, which requires trusting a third party with their funds. This bounty directly addressed this issue. It allowed users of Zeus Wallet, one of the most popular self-custodial Bitcoin Lightning wallets, to easily and securely receive donations through a Lightning address while maintaining control of their funds.
#### **7. Mobile Border Wallets**
**Winner:** [Bitcoin Tribe](https://twitter.com/BitcoinTribe_) for their border wallet functionality, allowing users to create and memorize seeds without relying on written backups, and for building a [React Native library](https://github.com/bithyve/react-native-border-wallets), making it easier for other wallets to integrate this feature (2 BTC).
Mobile Border Wallets aimed to solve a critical problem with traditional Bitcoin seed phrase backups: they’re often written down on paper, making them susceptible to being lost, destroyed, or stolen. This makes securing a user’s Bitcoin a delicate balance between security and accessibility. It also makes it challenging, especially for activists or refugees who frequently cross international borders. Border Wallets offered a solution to this problem. Instead of writing down a 12- or 24-word seed phrase and finding a secure place to store it, users can upload a randomly generated grid of words to the cloud and memorize a pattern to secure their seed phrase, similar to a pattern a user would memorize and draw on an Android device to unlock it. This initiative resulted in a user-friendly mobile app that allowed users to create Border Wallets digitally, enhancing accessibility and offering an alternative to physical storage like printed paper or metal seed plates.
#### **8. Easy Mobile Multisig**
**Winner:** [Bitcoin Keeper](https://bitcoinkeeper.app/) (1 BTC).
Multi-signature wallets allow multiple users to collaboratively control a Bitcoin wallet. This enhances security by requiring consensus before funds can be moved. Traditional multisig wallets often require physical hardware wallets or involve subscription fees, presenting a significant barrier for organizations exploring Bitcoin adoption. This bounty funded the development of easy mobile multisig functionality in the Bitcoin Keeper app, enabling users to set up a 2-of-3 multisig (requiring two out of three keys to authorize spending) to secure and manage their bitcoin. This is a great feature for activists to prevent government seizure of funds: even if one key holder gets detained, the funds are safe so long as the other two key holders are safe. The idea is to make sure two of the keys are held by entities outside of one’s country or threat zone.
#### **9. FROST Multisig Wallet**
**Winner:** [CypherStack](https://cypherstack.com/) for [Stack Wallet](https://stackwallet.com/), which enables dynamic multisig using FROST, allowing users to modify signer sets without moving funds (1 BTC).
Multisig (multisignature) wallets require multiple signatures to authorize a transaction. This enhances security by distributing control over funds. However, traditional multisig setups — while secure — can be inflexible. If you need to change the set of signers, it often requires moving all the funds to a new multisig wallet with the updated signer set. This is burdensome, time-consuming, and incurs fees. FROST is a cryptographic protocol that offers significant advantages for multisig wallets. It provides dynamic multisig functionality, meaning users can easily adjust their signer sets as needed without affecting the funds within. This is an important functionality for nonprofits and civil society groups who often need to adjust their authorized signatories, especially in situations where a regime may seize a private key and that key then needs to be deprecated. This dynamic kind of secure setup is now available for activists to use on the Stack Wallet.
#### **10. Cashu Upgrades**
Winners: [eNuts Wallet](https://www.enuts.cash/) (0.5 BTC), [Misovan](https://github.com/misovan) for [Minibits Wallet](https://www.minibits.cash/) (0.5 BTC), [Gandlaf](https://www.gandlaf.com/about) for [Proxnut](https://proxnut.com/) (0.5 BTC), and Gandlaf for adding [Cashu-TS restore](https://github.com/cashubtc/cashu-ts) functionality (0.5 BTC).
Cashu is a digital cash system designed for privacy and speed. It is like physical cash, but in digital form and uses blind signatures for private transactions. With Cashu, transactions are instant, low-fee, and can operate offline. There is no blockchain or transaction graph to be surveilled. Bounty recipients addressed critical aspects of usability and accessibility for Cashu tools: eNuts and Minibits Wallets brought Cashu to iOS and Android users worldwide, Proxnut enabled easy web integration for payments, and Cashu-TS Restore added crucial seed phrase backup. Together, these projects have taken Cashu from a more theoretical concept to a practical one and have been relevant for use cases like donations, content monetization, daily transactions, and cross-border payments.
#### **11. BIP47 Expansion**
Winner: [Blue Wallet](https://bluewallet.io/) (0.5 BTC) for adding BIP 47 support.
BIP47 is a Bitcoin Improvement Proposal that enhances payment privacy for Bitcoin users. In Bitcoin, it’s generally considered bad privacy practice to reuse the same Bitcoin address for multiple transactions. It can link those transactions together and make it easier to track a user’s spending in high-risk environments. Generating a new address for each payment has become a common workaround, but this becomes cumbersome. BIP47 solves this with reusable payment codes. Users receiving funds generate a BIP47 payment code and share it with those who will be sending them payments. Each time a payment is initiated, a new, unused Bitcoin address is generated from the recipient’s payment code. This ensures every transaction uses a unique address. Blue Wallet received this bounty for integrating BIP47 support, making this important privacy enhancement accessible to its growing user base.
*HRF’s Financial Freedom program educates activists worldwide, unites people from different industries and backgrounds, and makes grants in the service of advancing Bitcoin as a tool for human rights. To receive HRF’s weekly Financial Freedom Report, subscribe [here](https://mailchi.mp/hrf.org/financial-freedom-newsletter).*
*For media inquiries or interview requests, please contact media @ hrf.org.*
-

@ 19306922:c06688d2
2025-01-31 21:14:52
At a time when data-gathering technologies are dominating all aspects of everyday life, governmental agencies such as The National Security Agency have considerable surveillance and control authority. The National Security Agency runs surveillance programs on not just violent international criminals, but also ordinary citizens within the country. A tremendous amount of effort is being made to keep these programs from being critiqued and shared with the public. In this paper, I will discuss whistleblowing and its relevance in establishing a more democratic structure in governmental institutions, through the cases of Edward Snowden and Thomas Drake. Firstly, I will emphasize Edward Snowden's action as an example of illegal whistleblowing and how he acts closer to civic disobedience rather than espionage. Following that, I will discuss Thomas Drake's espionage charge while legally criticizing The National Security Agency's programs and the inadequacy of whistleblower protection laws.

In our everyday lives, we come into contact with or utilize a variety of technological equipment such as security cameras, GPS devices, iris scanners, and so on. Everything we do, from buying things from shopping malls to searching for information on the internet, is kept in massive databases. Without even our knowledge, our data, which is vast enough to create our entire profile, is in the databases of a private firm or the government. That's why the surveillance network is getting bigger and bigger. Most of the surveillance tools and the capability to regulate these tools are under state control. The government also agrees with data aggregators -companies that collect data from multiple sources and make it available to customers in a value-added format- to access more data. The US Department of Justice has an $8 million agreement with data aggregator company ChoicePoint (Stanley, Steinhardt 2014). In this way, The Justice Department can access many civilians' information in the company's database. Although this surveillance mechanism seems to be an effective way to track and detect many illegal incidents such as terrorism, money laundering, etc., this surveillance network can easily be applied to ordinary civilians. For example, in 2002, Attorney General John Ashcroft released new domestic spy guidelines that dramatically expanded federal agents' ability to monitor on American civilians (Stanley, Steinhardt 2014). The American government also is running programs to spy on ordinary citizens, according to information obtained from the National Security Agency documents which leaked to the media on multiple occasions (Greenberg, 2013).
The National Security Agency (NSA) began as a cryptology-focused agency and has since grown into an intelligence agency that gathers data from enemies of the United States of America (Verble, 2014). The surveillance and data collection programs of NSA, however, are not carried out just to keep enemies at bay. Information on the NSA's programs was provided to the media by Thomas A. Drake, a senior executive at the NSA, and Edward J. Snowden, who also worked as a computer intelligence consultant at the NSA. As a result of all of these events, it is fairly obvious that the state and its institutions are conducting unethical surveillance to the civilians. However, the two people who raised awareness of this unethical operation by providing classified and declassified NSA documents to the media faced major crises. Both Thomas Drake and Edward Snowden faced charges under the Espionage Act. Despite the fact that two former NSA employees used different methods to prevent these surveillance programs, which were developed to spy on citizens using their taxes, both were charged with treason. In this article, I will discuss the whistleblowing act through Thomas Drake and Edward Snowden examples, as well as the significance of whistleblowing in inspecting institutions with tremendous authority, such as centralized databases.
Whistleblowing is described as the act of an employee, typically within the organization, who reveals illegal, immoral, or inefficient information or actions within a private, public, or government institution. Daniel Ellsberg, one of the authors of the document, leaked information concerning the United States' political and military engagement in Vietnam between 1945 and 1967, also known as the Pentagon Papers. These papers, which revealed that the American government of the time did not accurately reflect information about Vietnam to the public, became the subject of the most well-known whistleblowing act in American history. Daniel Ellsberg faced charges under the Espionage Act (Greenberg, 2013). It is problematic to think that sharing the information with the public about crucial topics such as the state is systematically lying to the public or spying on them in a wide surveillance network is equated with espionage. The development of democratic regimes necessitates public debate and regulation of this type of government acts. I will demonstrate the significance through the examples of acts of Edward Snowden and Thomas Drake.
The Case of Edward Snowden
At one point, Edward Snowden's and Thomas Drake's whistleblowing actions differ. While Edward Snowden got confidential material from the NSA and shared it with the media directly, Thomas Drake initially attempted to prevent or regulate programs run by NSA from inside the organization by taking a legal path.
Firstly, using Edward Snowden as an example, I will evaluate the role of becoming an illegal whistleblower by sharing classified information with the public. Edward Snowden released highly classified information from NSA in 2013, revealing the NSA's surveillance operations with the cooperation of telecommunications companies and European governments. Snowden was charged under the Espionage Act and stealing government property by the US Department of Justice, and his passport was canceled by the Department of State. Not only that, the efforts were made to portray him as a traitor. Before leaking the information to the media, Edward Snowden was a 29-year-old consultant who worked for the NSA's Hawaii office and made $200,000 per year (Scheuerman, 2014). Snowden did not reveal this information to a country or organization that is hostile to the United States. He directly shared this material with the media, allowing the public to learn about these surveillance programs. He received no personal benefit from this act, and he risked himself and lost his privileged position in his life. Edward Snowden said to The Guardian reporters; “I really want the focus to be on these documents and the debate which I hope this will trigger among citizens around the globe about what kind of world we want to live in.” He added: “My sole motive is to inform the public as to that which is done in their name and that which is done against them” (Glenn, 2013). Given all of this, Edward Snowden's actions are more similar to civic disobedience than treason or espionage (Scheuerman, 2014). As a United Nations citizen, Edward Snowden revealed to the public the wrongdoing of a governmental institution, making this situation questioned among the public. A democratic government gains from public criticism of its acts, which aids in the development of more ethical institutions.
While it is a social benefit to inform the public about a massive government surveillance program, obtaining that information from the NSA and making it available to the public may also benefit the United States' enemies. Institutions also have the opportunity to develop and regulate these programs within their own walls, without any confidential information leaking out. Employees of the institution can file complaints to their supervisors and criticize these programs in a legal path, which is legal whistleblowing, however, in the case of Thomas Drake, we can see that legal whistleblowing puts people's lives at risk at least as much as the illegal version.
The Case Of Thomas Drake
On September 11, 2001, one of the most devastating days in American history, Thomas Drake began his job at the NSA. In the early years of the new millennium, when America was most vulnerable to external threats and digital data was growing exponentially, a program named Trailblazer caught Drake's attention. Drake saw the initiative as a huge budget waste that did not contribute to national security. He reported his critique to his supervisors, which is considered legal whistleblowing, but his attempts were unsuccessful. Finally, he decided to share his criticism with the media while remaining anonymous, although he did not share any confidential documents with the media. He only served declassified information, which conveys that Trailblazer was an ineffective project that wastes money. Drake was questioned by FBI investigators shortly after and accused of taking classified documents from the NSA. He faced charges of 35 years in jail time for 10 different crimes including the Espionage Act. The court dismissed the case in 2011, stating that the accusations were inappropriate and overstated, and Thomas Drake was sentenced to one year of probation. However, as a result of the entire process, Drake spent $82,000 on legal expenses, was dismissed from both his NSA and university positions, and lost his retirement (Greenberg, 2013). Thomas Drake's experience is an example of how even the slightest criticism of government institutions and their projects can have drastic consequences. The courage to criticize unethical projects is trying to be destroyed by this atmosphere of fear. The whistleblowers, whether they go the legal or illegal path, are aware that they will be prosecuted for espionage, loss of employment, and jail time.
At this juncture, I believe we should oppose the totalitarian positions adopted by the institutions, which have vast surveillance networks both domestically and internationally, and we should protect whistleblowers' rights. The United States has two legislations protecting whistleblowers, the Federal Whistleblower Protection Act of 1989 and the Whistleblower Protection Enhancement Act of 2012. According to a 2015 research, the Federal Whistleblower Protection Act of 1989 fails to protect whistleblowers. 79 percent of the 142 cases involving government ethics and administration ended in employee job loss. The Whistleblower Protection Enhancement Act of 2012 is also insufficient in terms of protections of whistleblowers (Peffer, Bocheko, Del Valle, Osmani, Peyton, Roman, 2015).
Conclusion
The whistleblowing contributes to public debate about the ethics of the state's programs. However, these organizations, which hold a vast surveillance network, damage the democratic process by raising severe allegations against whistleblowers in order to avoid the risk of limiting their authority. We can have an idea of how our data is gathered and used if we have laws and rules that protect whistleblowers. Accusing them with espionage and treason, on the other hand, will gradually create this environment of fear and, as a consequence, silence.
Reference
Glenn G. (2013, Jun 11). Edward Snowden: the whistleblower behind the NSA surveillance revelations. The Guardian. Retrieved from https://www.theguardian.com/world/2013/jun/09/edward-snowden-nsa-whistleblower-surveillance
Greenberg, A. (2013). This machine kills secrets: Julian Assange, the Cypherpunks, and their fight to empower whistleblowers. Penguin.
Scheuerman, W. E. (2014). Whistleblowing as civil disobedience: The case of Edward Snowden. Philosophy & Social Criticism, 40(7), 609-628.
Stanley, J., & Steinhardt, B. (2014). Bigger monster, weaker chains: the growth of an American surveillance society. In Ethics and Emerging Technologies (pp. 269-284). Palgrave Macmillan, London.
Peffer, S. L., Bocheko, A., Del Valle, R. E., Osmani, A., Peyton, S., & Roman, E. (2015).Whistle Where you work? The ineffectiveness of the Federal Whistleblower Protection Act of 1989 and the promise of the Whistleblower Protection Enhancement Act of 2012. Review of Public Personnel Administration, 35(1), 70-81.
Verble, J. (2014). The NSA and Edward Snowden: surveillance in the 21st century. ACM SIGCAS Computers and Society, 44(3), 14-20.
-

@ a95c6243:d345522c
2025-01-31 20:02:25
*Im Augenblick wird mit größter Intensität, großer Umsicht* *\
das deutsche Volk belogen.* *\
Olaf Scholz im FAZ-[Interview](https://www.youtube.com/watch?v=c3KI1GmdoVc\&t=649s)*  
**Online-Wahlen stärken die Demokratie, sind sicher, und 61 Prozent der Wahlberechtigten** sprechen sich für deren Einführung in Deutschland aus. Das zumindest behauptet eine aktuelle Umfrage, die auch über die Agentur *Reuters* Verbreitung in den Medien [gefunden](https://archive.is/dnZbY) hat. Demnach würden außerdem 45 Prozent der Nichtwähler bei der Bundestagswahl ihre Stimme abgeben, wenn sie dies zum Beispiel von Ihrem PC, Tablet oder Smartphone aus machen könnten.
**Die telefonische Umfrage unter gut 1000 wahlberechtigten Personen** sei repräsentativ, [behauptet](https://www.bitkom.org/Presse/Presseinformation/Knapp-Haelfte-Nichtwaehler-wuerde-online-waehlen) der Auftraggeber – der Digitalverband Bitkom. Dieser präsentiert sich als eingetragener Verein mit einer beeindruckenden Liste von [Mitgliedern](https://www.bitkom.org/Bitkom/Mitgliedschaft/Mitgliederliste), die Software und IT-Dienstleistungen anbieten. Erklärtes Vereinsziel ist es, «Deutschland zu einem führenden Digitalstandort zu machen und die digitale Transformation der deutschen Wirtschaft und Verwaltung voranzutreiben».
**Durchgeführt hat die Befragung die Bitkom Servicegesellschaft mbH,** also alles in der Familie. Die gleiche Erhebung hatte der Verband übrigens 2021 schon einmal durchgeführt. Damals sprachen sich angeblich sogar 63 Prozent für ein derartiges [«Demokratie-Update»](https://www.experten.de/id/4922407/online-wahlen-als-update-des-demokratischen-systems/) aus – die Tendenz ist demgemäß fallend. Dennoch orakelt mancher, der Gang zur Wahlurne gelte bereits als veraltet.
**Die spanische Privat-Uni mit Globalisten-Touch, IE University, berichtete** Ende letzten Jahres in ihrer Studie «European Tech Insights», 67 Prozent der Europäer [befürchteten](https://www.ie.edu/university/news-events/news/67-europeans-fear-ai-manipulation-elections-according-ie-university-research/), dass Hacker Wahlergebnisse verfälschen könnten. Mehr als 30 Prozent der Befragten glaubten, dass künstliche Intelligenz (KI) bereits Wahlentscheidungen beeinflusst habe. Trotzdem würden angeblich 34 Prozent der unter 35-Jährigen einer KI-gesteuerten App vertrauen, um in ihrem Namen für politische Kandidaten zu stimmen.
**Wie dauerhaft wird wohl das Ergebnis der kommenden Bundestagswahl sein?** Diese Frage stellt sich angesichts der aktuellen Entwicklung der Migrations-Debatte und der (vorübergehend) bröckelnden «Brandmauer» gegen die AfD. Das «Zustrombegrenzungsgesetz» der Union hat das Parlament heute Nachmittag überraschenderweise [abgelehnt](https://www.bundestag.de/dokumente/textarchiv/2025/kw05-de-zustrombegrenzungsgesetz-1042038). Dennoch muss man wohl kein ausgesprochener Pessimist sein, um zu befürchten, dass die Entscheidungen der Bürger von den selbsternannten Verteidigern der Demokratie künftig vielleicht nicht respektiert werden, weil sie nicht gefallen.
**Bundesweit wird jetzt zu «Brandmauer-Demos» aufgerufen,** die CDU gerät unter Druck und es wird von Übergriffen auf Parteibüros und Drohungen gegen Mitarbeiter [berichtet](https://www.epochtimes.de/politik/deutschland/brandmauer-proteste-cdu-zentrale-geraeumt-kundgebungen-in-46-staedten-a5023745.html). Sicherheitsbehörden warnen vor Eskalationen, die Polizei sei «für ein mögliches erhöhtes Aufkommen von Straftaten gegenüber Politikern und gegen Parteigebäude sensibilisiert».
**Der Vorwand** **[«unzulässiger Einflussnahme»](https://transition-news.org/die-minister-faeser-und-wissing-sorgen-sich-um-unzulassige-einflussnahme-auf)** **auf Politik und Wahlen** wird als Argument schon seit einiger Zeit aufgebaut. Der Manipulation schuldig befunden wird neben Putin und Trump auch Elon Musk, was lustigerweise ausgerechnet Bill Gates gerade noch einmal bekräftigt und als [«völlig irre»](https://transition-news.org/bill-gates-nennt-musks-einmischung-in-eu-politik-vollig-irre) bezeichnet hat. Man stelle sich die Diskussionen um die Gültigkeit von Wahlergebnissen vor, wenn es Online-Verfahren zur Stimmabgabe gäbe. In der Schweiz wird [«E-Voting»](https://www.ch.ch/de/abstimmungen-und-wahlen/e-voting/) seit einigen Jahren getestet, aber wohl bisher mit wenig Erfolg.
**Die politische Brandstiftung der letzten Jahre zahlt sich immer mehr aus.** Anstatt dringende Probleme der Menschen zu lösen – zu denen auch in Deutschland die [weit verbreitete Armut](https://transition-news.org/ein-funftel-der-bevolkerung-in-deutschland-ist-von-armut-oder-sozialer) zählt –, hat die Politik konsequent polarisiert und sich auf Ausgrenzung und Verhöhnung großer Teile der Bevölkerung konzentriert. Basierend auf Ideologie und Lügen werden abweichende Stimmen unterdrückt und kriminalisiert, nicht nur und nicht erst in diesem Augenblick. Die nächsten Wochen dürften ausgesprochen spannend werden.
***
Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/wahlen-und-wahlen-lassen)*** erschienen.
-

@ 3ccfd5ee:2efa0073
2025-01-31 17:24:28
BYD Cars Philippines and ACMobility, the Philippine distributor of BYD vehicles, have pledged to donate $100 to Super Typhoon Carina's victims for every BYD Sealion 6 DM-i sold from July 25, 2024 until December 31, 2024.
This campaign is part of both companies' broader efforts to the affected communities and reflects their dedication to social responsibility. In fact, ACMobility was one of the first to mobilize disaster response efforts by distributing relief goods to over 100 families in Dela Paz, Pasig City, on July 26. Employees and volunteers from ACMobility, BYD Cars Philippines, and its affiliate agencies participated in the cause.
“On behalf of BYD, I would like to express my sympathy to the people affected by Typhoon Carina. We, together with ACMobility, wish to extend BYD's support to Filipinos who suffered from this unfortunate disaster,” said BYD Asia Pacific Auto Sales Division General Manager Liu Xueliang.
The [BYD Sealion 6 DM-i](https://bydcarsphilippines.com/vehicles/byd-sealion6-dmi) is an all-electric compact SUV that runs on BYD's proprietary Super DM-i Technology—generating power well beyond the typical electric vehicle. It generates 217 horsepower and 325 Newton meters of torque, enabling it to go from zero to a hundred in just over eight seconds.
Furthermore, the vehicle runs on Blade Battery, allowing it to drive up to 105 kilometers in Pure EV Mode and 1,100 km in Extended Range Mode. It empowers drivers to travel without range anxiety. Attendees of ACMobility and BYD Cars Philippines' relief drive even used the Sealion 6 DM-i's Blade Battery to charge devices on-site.
The Sealion 6 DM-i starts at ₱1,548,000. With every unit sold, BYD and ACMotors donate $100 to Typhoon Carina's victims until the end of 2024.
"Guided by our company value of malasakit, we remain committed to going above and beyond in serving our communities during these trying times," BYD Cars Philippines Managing Director Bob Palanca shared.
Super Typhoon Carina—internationally known as Gaemi—brought widespread devastation across the Philippines. The National Disaster Risk Reduction and Management Council (NDRRMC) stated that Carina, on top of the southwest monsoon, affected over 1.3 million Filipinos.
## About BYD Cars Philippines
BYD Cars Philippines is a leader in the Filipino EV industry. As the Philippine arm of the globally renowned electric car and battery manufacturer, it brings cutting-edge technology and powerful yet comfortable drives to the local sustainable mobility market.
The EV manufacturer has a range of models designed to address the needs of Filipinos, from affordable cars to luxury SUVs. Each vehicle's cutting-edge tech and superior safety features make every purchase worth it. Most importantly, BYD addresses the growing demand for eco-friendly cars and actively participates in initiatives to build greener mobility infrastructure for Filipinos.
Visit [BYD Cars Philippines' website](https://bydcarsphilippines.com/) today to learn more.
-

@ 3ccfd5ee:2efa0073
2025-01-31 17:05:59
Penis size is a topic that many people feel curious or insecure about. It’s important to approach this subject with an understanding of the wide range of normal sizes and the various options available for those who may be interested in enlargement procedures. For some, the use of sex toys or dildos may be a practical solution to enhance sexual experiences, while others may look into enlargement procedures. Here’s a brief overview of what you should know about average penis size and the options available for enlargement.
## What is the Average Penis Size?
Studies consistently show that the average erect penis size is around 5 to 6 inches in length, and the average flaccid size is about 3 to 4 inches. It’s crucial to recognize that penis size varies among individuals, and there is a broad spectrum of what is considered normal. Factors like body type, genetics, and age can all influence size. Most men’s sizes fall within this range, and concerns about size often arise from misconceptions rather than actual medical issues.
## Penis Enlargment as an Alternative
For those interested in [penis enlargement](https://pinkbunny.ph/blog/penis-enlargement-in-the-philippines-should-you-do-it/), there are a few options available. These include surgical procedures, non-surgical devices, and sometimes even the use of [sex toys](https://pinkbunny.ph/) to create a fuller feeling or enhance size temporarily. Here’s a closer look at the most common methods:
### Surgical Procedures
One of the most well-known surgical options is penile lengthening surgery, where a surgeon cuts the suspensory ligament that supports the penis, allowing it to hang lower. While the procedure can result in a modest increase in length, it carries risks such as infection, scarring, and potential issues with erectile function. Always consult with a qualified healthcare provider before considering surgery.
### Non-Surgical Options
Devices like penis pumps or penile traction devices are often used to temporarily increase size. A penis pump creates a vacuum that draws blood into the penis, temporarily making it appear larger. Traction devices apply gentle pressure to the penis over time, which can result in gradual lengthening. Both of these methods can offer temporary improvements, but they require consistent use and do not guarantee long-lasting results.
### Sex Toys and Dildos
For those looking for a more immediate solution, dildos and other sex toys can offer a way to enhance sexual pleasure without altering physical size. These toys come in a wide range of shapes, sizes, and materials, allowing individuals and couples to explore different sensations. Find a [dildo for sale](https://pinkbunny.ph/product-category/sex-toys/dildos/) that can provide added size during intercourse, and using sex toys can also help individuals become more comfortable with their bodies, leading to better self-esteem and sexual confidence.
### Penis Enlargement Pills or Supplements
Many products on the market claim to increase penis size, but the effectiveness of these pills is largely unproven. Medical experts often caution against using such supplements, as they can have unwanted side effects and are not regulated.
-

@ 3ccfd5ee:2efa0073
2025-01-31 16:50:06
To stay competitive, many companies are outsourcing key administrative and management functions in manufacturing. This approach helps businesses better manage deliverables, reduce costs, utilize advanced technology, and navigate changing labor dynamics.
## What is Outsource Manufacturing?
[Outsourcing manufacturing](https://optibpo.com/blog/a-guide-to-outsource-manufacturing/) involves delegating not only production but also important administrative and management tasks to external providers, rather than handling everything in-house. These tasks often include non-core activities such as supply chain management, procurement, quality assurance, and compliance.
By partnering with specialized manufacturers, often in regions with lower labor and operational costs, companies can take advantage of their expertise and efficiency. The process typically begins with selecting a trusted manufacturer, negotiating contracts, and overseeing production to ensure quality and timely delivery.
## 5 Types of Outsource Manufacturing Services
Outsourcing specific tasks can streamline your operations and reduce costs. Here’s an overview of the key outsourcing services for manufacturing:
### Contract Management
Managing contracts with manufacturers and suppliers can be complex and time-consuming. By outsourcing this function, you allow experts to handle negotiations, oversee agreements, and ensure smooth operations, reducing legal risks and freeing you to focus on other vital business areas.
### Supplier Management
Supplier management includes finding and vetting suppliers based on quality, pricing, and reliability. By building a dedicated team through optiBPO in the Philippines, you can streamline this process. The team will handle negotiations and ensure that suppliers meet your standards, giving you full control without the administrative burden.
### Logistics Coordination
From transportation to warehousing, logistics coordination involves many moving parts. Outsourcing this function to a skilled team, like one from optiBPO, allows you to optimize the logistics process, choosing the best transportation methods and balancing cost, speed, and reliability. This ensures efficient and timely product deliveries.
### Quality Assurance Coordination
Consistently maintaining high product quality is essential for customer satisfaction and brand reputation. Outsourcing quality assurance lets a team of professionals handle inspections, compliance checks, and data analysis to reduce defects, enhance product reliability, and maintain high standards.
### Inventory Management
Managing inventory levels, ordering, and stock maintenance can be overwhelming. By outsourcing these administrative tasks, your external team can monitor inventory, forecast demand, and coordinate with suppliers to ensure stock is always replenished on time. Services from optiBPO can streamline this process and keep operations running smoothly.
## In Conclusion
By outsourcing these crucial functions, your business can gain access to expertise, improve efficiency, and reduce costs—ultimately allowing you to focus on what matters most: growing your business.
You can learn more about ousource manufacturing through this infographic.
https://sp-ao.shortpixel.ai/client/to_webp,q_glossy,ret_img,w_800/https://optibpo.com/wp-content/uploads/2024/10/outsource_manufacturing_Info8.png
-

@ c68e2176:4439e6cf
2025-01-31 16:41:06
1:1 The record of the genealogy of Jesus the Messiah, the son of David, the son of Abraham:
2 Abraham was the father of Isaac, Isaac the father of Jacob, and Jacob the father of Judah and his brothers.
3 Judah was the father of Perez and Zerah by Tamar, Perez was the father of Hezron, and Hezron the father of Ram.
4 Ram was the father of Amminadab, Amminadab the father of Nahshon, and Nahshon the father of Salmon.
5 Salmon was the father of Boaz by Rahab, Boaz was the father of Obed by Ruth, and Obed the father of Jesse.
6 Jesse was the father of David the king.
David was the father of Solomon by Bathsheba who had been the wife of Uriah.
7 Solomon was the father of Rehoboam, Rehoboam the father of Abijah, and Abijah the father of Asa.
8 Asa was the father of Jehoshaphat, Jehoshaphat the father of Joram, and Joram the father of Uzziah.
9 Uzziah was the father of Jotham, Jotham the father of Ahaz, and Ahaz the father of Hezekiah.
10 Hezekiah was the father of Manasseh, Manasseh the father of Amon, and Amon the father of Josiah.
11 Josiah became the father of Jeconiah and his brothers, at the time of the deportation to Babylon.
12 After the deportation to Babylon: Jeconiah became the father of Shealtiel, and Shealtiel the father of Zerubbabel.
13 Zerubbabel was the father of Abihud, Abihud the father of Eliakim, and Eliakim the father of Azor.
14 Azor was the father of Zadok, Zadok the father of Achim, and Achim the father of Eliud.
15 Eliud was the father of Eleazar, Eleazar the father of Matthan, and Matthan the father of Jacob.
16 Jacob was the father of Joseph the husband of Mary, by whom Jesus was born, who is called the Messiah.
17 So all the generations from Abraham to David are fourteen generations; from David to the deportation to Babylon, fourteen generations; and from the deportation to Babylon to the Messiah, fourteen generations.
18 Now the birth of Jesus Christ was as follows: when His mother Mary had been betrothed to Joseph, before they came together she was found to be with child by the Holy Spirit.
19 And Joseph her husband, being a righteous man and not wanting to disgrace her, planned to send her away secretly.
20 But when he had considered this, behold, an angel of the Lord appeared to him in a dream, saying, “Joseph, son of David, do not be afraid to take Mary as your wife; for the Child who has been conceived in her is of the Holy Spirit.
21 She will bear a Son; and you shall call His name Jesus, for He will save His people from their sins.”
22 Now all this took place to fulfill what was spoken by the Lord through the prophet:
23 “BEHOLD, THE VIRGIN SHALL BE WITH CHILD AND SHALL BEAR A SON, AND THEY SHALL CALL HIS NAME IMMANUEL,” which translated means, “GOD WITH US.”
24 And Joseph awoke from his sleep and did as the angel of the Lord commanded him, and took Mary as his wife,
25 but kept her a virgin until she gave birth to a Son; and he called His name Jesus.**1:1** The record of the genealogy of Jesus the Messiah, the son of David, the son of Abraham:\
**2** Abraham was the father of Isaac, Isaac the father of Jacob, and Jacob the father of Judah and his brothers.\
3 Judah was the father of Perez and Zerah by Tamar, Perez was the father of Hezron, and Hezron the father of Ram.\
4 Ram was the father of Amminadab, Amminadab the father of Nahshon, and Nahshon the father of Salmon.\
5 Salmon was the father of Boaz by Rahab, Boaz was the father of Obed by Ruth, and Obed the father of Jesse.\
6 Jesse was the father of David the king.\
David was the father of Solomon by Bathsheba who had been the wife of Uriah.\
7 Solomon was the father of Rehoboam, Rehoboam the father of Abijah, and Abijah the father of Asa.\
8 Asa was the father of Jehoshaphat, Jehoshaphat the father of Joram, and Joram the father of Uzziah.\
9 Uzziah was the father of Jotham, Jotham the father of Ahaz, and Ahaz the father of Hezekiah.\
10 Hezekiah was the father of Manasseh, Manasseh the father of Amon, and Amon the father of Josiah.\
11 Josiah became the father of Jeconiah and his brothers, at the time of the deportation to Babylon.\
**12** After the deportation to Babylon: Jeconiah became the father of Shealtiel, and Shealtiel the father of Zerubbabel.\
13 Zerubbabel was the father of Abihud, Abihud the father of Eliakim, and Eliakim the father of Azor.\
14 Azor was the father of Zadok, Zadok the father of Achim, and Achim the father of Eliud.\
15 Eliud was the father of Eleazar, Eleazar the father of Matthan, and Matthan the father of Jacob.\
16 Jacob was the father of Joseph the husband of Mary, by whom Jesus was born, who is called the Messiah.\
**17** So all the generations from Abraham to David are fourteen generations; from David to the deportation to Babylon, fourteen generations; and from the deportation to Babylon to the Messiah, fourteen generations.\
**18** Now the birth of Jesus Christ was as follows: when His mother Mary had been betrothed to Joseph, before they came together she was found to be with child by the Holy Spirit.\
19 And Joseph her husband, being a righteous man and not wanting to disgrace her, planned to send her away secretly.\
20 But when he had considered this, behold, an angel of the Lord appeared to him in a dream, saying, “Joseph, son of David, do not be afraid to take Mary as your wife; for the Child who has been conceived in her is of the Holy Spirit.\
21 She will bear a Son; and you shall call His name Jesus, for He will save His people from their sins.”\
22 Now all this took place to fulfill what was spoken by the Lord through the prophet:\
23 “BEHOLD, THE VIRGIN SHALL BE WITH CHILD AND SHALL BEAR A SON, AND THEY SHALL CALL HIS NAME IMMANUEL,” which translated means, “GOD WITH US.”\
24 And Joseph awoke from his sleep and did as the angel of the Lord commanded him, and took *Mary* as his wife,\
25 but kept her a virgin until she gave birth to a Son; and he called His name Jesus.
-

@ 0f4795bf:a8365abe
2025-01-31 14:36:07
## Der neue Pareto-Client
Unter der Adresse <https://pareto.space/read> lässt sich der neue Pareto-Client aufrufen.
Durch Klicken auf **Anmelden** (rechts oben) kann mit einem vorhandenen Nostr-Konto angemeldet werden oder ein neues Konto erstellt werden.
Sofern schon ein Nostr-Konto vorhanden ist, kann nach Klick auf **Log in** einfach z. B. mittels Browser Extension angemeldet werden.
Nach dem Anmelden wird das Profilbild rechts oben angezeigt und ggf. eine Kategorie mit den Artikeln der Autoren, denen man folgt.
Nach Umschalten vom Leser- in den Autoren-Modus (Schalter oben, rechts neben Logo) werden die bereits veröffentlichten Artikel angezeigt.
Sollte der Schalter nicht angezeigt werden, bitte bei uns mit dem npub melden, damit wir ihn in die Liste der Pareto-Autoren aufnehmen können.
Eine zweite Kategorie zeigt die bestehenden Entwürfe.

Unter dem Punkt Bilder links lassen sich Bilder hochladen, die in Artikeln verwendet werden sollen.
Sollte noch kein Medien-Server (Blossom oder NIP-96) konfiguriert sein, wird angeboten, den Standard-Server des Pareto-Projektes zu nutzen.
Nachdem der Server konfiguriert wird, werden alle hochgeladenen Bilder angezeigt.
Weitere Bilder lassen sich über den Knopf **Bilder hochladen** hinzufügen.
Nach Auswahl des Punktes **Schreiben** wird der leere Pareto-Editor angezeigt.
Neben dem Titel sollte auch die Zusammenfassung aufgefüllt werden, da diese beim Teilen des Artikels (Telegram, Social Media, ...) neben dem Titel und dem Bild des Artikels angezeigt werden.
Das Bild kann durch Klicken auf den grauen Rahmen rechts oben gewählt werden.

Nach Doppelklick auf das gewünschte Bild wird es rechts neben Titel und Zusammenfassung angezeigt.
Neue Elemente können im Text durch Klicken auf das Plus-Symbol hinzugefügt werden.
Neben Überschriften lassen sich so auch Zitate, Aufzählungen, Programm-Code, Tabellen und Bilder einfügen.
Nachdem ein Bild-Element eingefügt wurde, kann es entweder mit einem Link auf ein Bild bestückt werden oder - durch Klicken auf "Select file" ein bereits hochgeladenes auswählen.
Durch Klicken auf die kleine Sprechblase rechts oben in einem Bild lässt sich eine Bildunterschrift hinzufügen.

### Markdown
Neben dem Hinzufügen von Elementen über das Plus-Symbol kann natürlich auch direkt [Markdown-Auszeichnung](https://www.ionos.de/digitalguide/websites/web-entwicklung/markdown/) eingegeben werden.
Es gibt im Netz diverse Anleitungen für Markdown. Allerdings gibt es im Kontext von Nostr die Einschränkung, dass keine HTML-Elemente in Artikeln enthalten sein dürfen.
Durch Tippen eines Doppelkreuzes, gefolgt von einem Leerzeichen, lässt sich beispielsweise eine Überschrift einfügen


### Besonderheiten
Der Pareto-Client stellt Links unterschiedlich dar, je nachdem, ob sie innerhalb eines Absatzes oder allein erscheinen.
*Links innerhalb eines Absatzes* werden ganz regulär dargestellt als Link, auf den der Leser klicken kann.
*Alleinstehende Links* (also ohne Text davor oder dahinter) hingegen werden ggf. mit einer Vorschau versehen und nach einmaligem Klick wird der Inhalt eingebettet dargestellt.
Für Links zu **YouTube**, **Odysee**, **Rumble**, **SoundCloud**, **[theplattform.net](https://tube.theplattform.net/)**, und andere können die Inhalte direkt im Artikel konsumiert werden.
Auch alleinstehende Links zu Dateien mit den Endungen .mp4, .mov, .mkv, .avi, .m4v und .webm (Videos) sowie .mp3, .wav, ogg (Audio) und .pdf (PDF-Dokumente) werden eingebettet dargestellt.
> **Tipp:**
>
> Beim Schreiben längerer Artikel empfiehlt es sich, diese zwischendurch immer wieder als Entwurf zu speichern, um Datenverlust zu vermeiden.
Oberhalb des Knopfes zum Speichern von Entwürfen wird immer der aktuelle Status des Artikels angezeigt.
Schlüsselwörter werden einfach durch Komma getrennt. Es ist üblich, diese klein zu schreiben.

Nach dem Speichern wird der Knopf deaktiviert.
Der Entwurf sollte anschließend unter dem Punkt **Artikel** unter **Entwürfe** eingeblendet werden.
Ein Klick auf **Bearbeiten** bringt den Entwurf wieder in den Editor.
Nach Klicken von **Veröffentlichen** kann noch die Liste der Nostr-Relays ausgewählt werden, auf denen der Artikel veröffentlicht werden soll.
Nach dem Veröffentlichen sollte der Status das entspr. anzeigen.
Herzlichen Glückwunsch!
Dein erster Artikel wurde über den Pareto-Client verfasst und veröffentlicht!
-

@ da0b9bc3:4e30a4a9
2025-01-31 14:00:57
It's Finally here Stackers!
It's Friday!
We're about to kick off our weekends with some feel good tracks.
Let's get the party started. Bring me those Feel Good tracks.
Talk Music. Share Tracks. Zap Sats.
Let's go!
Come up and see me, make me smile!
https://youtu.be/dAoaVU3-ve0?si=JBdfGJhM05Qa_JeT
originally posted at https://stacker.news/items/871055
-

@ 54286b98:3debc100
2025-01-31 11:17:42
Mornings are good; they are better than evenings (except for sunset views).\
Your body is recharged.\
The mind should be more at ease.\
Worries should be fewer, and breakfast is the only meal that is "served all day."
Waking up early—very early—was normal (at least for me) a lifetime ago.\
You get more things done,\
it’s quiet and free of distractions.\
So why don’t we just wake up early anymore?
It would be easy to blame responsibilities and being tired for why we can't wake up earlier,\
but that’s an easy way out.\
I believe we stop trying to beat the sun when two things happen to us:\
We lose a ***big motivator*** (being competitive, learning something, getting more done, spiritual time, etc.).\
We fall for ***comfort*** and a life without the demands of growth.\
Each one follows the other, like a dog chasing its tail.
Today marks almost day 30 of waking up really early again. I am happier, healthier, more connected with God, learning new things every day, playing my guitar, and writing more.
Until the next one,
J
Get my email newsletter or read my blog at [javierfeliu.com](https://www.javierfeliu.com/) (Soon will work on setting up specific #Nostr page.
> *An independent, publication about crafting beauty in life, family,
> entrepreneurship, culture, woodworking, and faith, written by Javier
> Feliu.*
-

@ da0b9bc3:4e30a4a9
2025-01-31 10:50:35
Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/870889
-

@ a012dc82:6458a70d
2025-01-31 09:16:28
Bitcoin, as the pioneering cryptocurrency, heralded a new era in digital finance. It offered an innovative payment system, free from the control of traditional financial institutions and governments. This decentralized nature was a significant draw for many early adopters. Bitcoin Cash emerged from a split in the Bitcoin blockchain, a result of deep-seated disagreements within the Bitcoin community over its scalability and transaction processing efficiency. This split was not just technical but also ideological, marking a significant moment in the history of cryptocurrencies.
**Table Of Content**
- The Genesis of Bitcoin Cash
- Technological Divergence: Block Size and Scalability
- Segregated Witness (SegWit) and Bitcoin
- Market Impact and Adoption
- Transaction Processing: Speed and Fees
- The Forks and Future Directions
- Usability and Real-World Applications
- Supply Dynamics
- Bitcoin Cash as a Medium of Exchange
- Conclusion
- FAQs
**The Genesis of Bitcoin Cash**
The creation of Bitcoin Cash in 2017 was a pivotal event in the cryptocurrency world. It was a direct response to the growing concerns over Bitcoin's ability to handle an increasing volume of transactions. The proponents of Bitcoin Cash argued that changes were necessary to fulfill the original vision of a fast, scalable, and low-cost digital payment system. This led to the hard fork, a move that created a new blockchain with different rules, fundamentally diverging from the original Bitcoin protocol.
**Technological Divergence: Block Size and Scalability**
The debate over block size is central to the divergence between Bitcoin and Bitcoin Cash. Bitcoin's original 1 MB block size was seen as a significant bottleneck, leading to slower transaction times and higher fees during peak usage. In contrast, Bitcoin Cash's decision to increase the block size to 8 MB and later to 32 MB was a bold move aimed at addressing these issues. This increase was a fundamental shift, intended to allow more transactions per block and, consequently, faster processing and lower fees.
**Segregated Witness (SegWit) and Bitcoin**
The implementation of Segregated Witness (SegWit) in Bitcoin was a landmark technological upgrade. SegWit aimed to optimize the space within each block by segregating the digital signature information, which accounts for a significant portion of the data in a transaction. This was a sophisticated solution to the scalability issue, differing fundamentally from Bitcoin Cash's approach of simply increasing the block size. SegWit represented a philosophical as well as a technical divergence in the approach to scaling Bitcoin.
**Market Impact and Adoption**
The market dynamics of Bitcoin and Bitcoin Cash tell a story of divergent paths. Bitcoin, with its higher market capitalization, remains the more dominant and widely recognized cryptocurrency. Its position as the first and most established cryptocurrency has given it a significant advantage in terms of adoption and market presence. Bitcoin Cash, while substantial in its market cap, has not reached the same level of market penetration. This difference in market impact reflects the varying degrees of acceptance and trust among investors and users in the cryptocurrency community.
**Transaction Processing: Speed and Fees**
The practical implications of the differences between Bitcoin and Bitcoin Cash are most evident in transaction processing. Bitcoin Cash, with its larger block size, theoretically offers faster transaction times and lower fees, making it more suitable for frequent, small transactions. However, the actual efficiency gains of Bitcoin Cash are subject to debate, as the network has not been tested under the same transaction volume as Bitcoin. This difference in transaction processing capabilities is a critical factor in the user's choice between the two cryptocurrencies.
**The Forks and Future Directions**
The evolution of Bitcoin and Bitcoin Cash is marked by continuous development and occasional forks. The creation of Bitcoin SV from Bitcoin Cash is an example of ongoing disagreements within the community about the best path forward. These forks are not just technical events but also represent differing visions and philosophies within the cryptocurrency community. They reflect the dynamic and often contentious nature of the development of blockchain technology and its applications.
**Usability and Real-World Applications**
In terms of real-world usability, Bitcoin and Bitcoin Cash cater to slightly different needs. Bitcoin's widespread recognition and higher value make it more popular as a digital asset for investment. In contrast, Bitcoin Cash, with its focus on transaction efficiency, aims to be more practical for everyday transactions. However, the actual adoption of Bitcoin Cash for daily transactions has been slower than anticipated, partly due to the entrenched position of Bitcoin and the rapidly evolving landscape of digital payments.
**Supply Dynamics**
The supply mechanics of both Bitcoin and Bitcoin Cash mirror the principles of scarcity and controlled supply inflation. This approach is akin to precious metals, where the limited supply is a key factor in value preservation. The halving events, where the reward for mining new blocks is halved approximately every four years, are critical moments in the life cycle of both cryptocurrencies. These events are closely watched by investors and users alike, as they have implications for the supply and, potentially, the value of these digital currencies.
**Bitcoin Cash as a Medium of Exchange**
Bitcoin Cash's design as a medium of exchange is one of its defining features. It aims to provide a digital equivalent of cash, facilitating quick and low-cost transactions. This focus on usability for everyday transactions is a key differentiator from Bitcoin, which has become more of a store of value or "digital gold." The success of Bitcoin Cash in this regard depends on broader adoption and recognition, which is an ongoing challenge in the competitive landscape of digital currencies.
**Conclusion**
The story of Bitcoin and Bitcoin Cash is a fascinating chapter in the evolution of digital currencies. Both emerged from the same origin but have since traveled distinct paths, shaped by differing philosophies, technological choices, and community dynamics. As the cryptocurrency landscape continues to evolve, the trajectories of Bitcoin and Bitcoin Cash will offer valuable insights into the challenges and opportunities of blockchain technology and digital finance.
**FAQs**
**What is the main difference between Bitcoin and Bitcoin Cash?**
The primary difference lies in their block size. Bitcoin has a block size of 1 MB, while Bitcoin Cash increased its block size initially to 8 MB and later to 32 MB, aiming for faster transaction processing and scalability.
**Why was Bitcoin Cash created?**
Bitcoin Cash was created in 2017 due to a split in the Bitcoin community. The split occurred over disagreements on how to scale the network, with Bitcoin Cash proponents advocating for larger block sizes to improve transaction speed and reduce fees.
**Can Bitcoin and Bitcoin Cash be used interchangeably?**
No, they are separate cryptocurrencies with different blockchains. They cannot be used interchangeably.
**Is Bitcoin Cash faster than Bitcoin?**
Theoretically, yes. Due to its larger block size, Bitcoin Cash can process transactions faster than Bitcoin. However, the actual speed can vary based on network congestion and usage.
**That's all for today**
**If you want more, be sure to follow us on:**
**NOSTR: croxroad@getalby.com**
**X: @croxroadnews.co**
**Instagram: @croxroadnews.co**
**Youtube: @croxroadnews**
**Store: https://croxroad.store**
**Subscribe to CROX ROAD Bitcoin Only Daily Newsletter**
**https://www.croxroad.co/subscribe**
***DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.***
-

@ 5188521b:008eb518
2025-01-31 08:38:47
*Photo by [Pavel Danilyuk](https://www.pexels.com/photo/a-woman-holding-a-placard-8553778/)*
In the last four years, I’ve ridden the wave of social media. I’ve amassed thousands of followers, and my posts were read by millions.
It’s empowering… until it isn’t.
This year, I chose to stop publishing on LinkedIn, Medium, Facebook, Instagram, and Threads. My reach on each of these platforms dropped from 100% of my follower base to around 10%. My voice was being suppressed.
I wasn’t writing anything particularly controversial. This is all just part of the social media life cycle. Platforms offer attractive terms to lock in users. They distribute our articles, posts, and thoughts widely to attract eyeballs for advertisers.
Writers learn to play the algorithm to maximise reach and engagement. Maybe they even manage to monetize their writing.
But when the platforms reach what they deem to be maximum usage and membership, they begin to reduce the benefits on offer. They ask writers to focus on specific topics, suppress non-mainstream opinion, or punish or ban any writers who don’t follow new rules. Big tech companies always eventually turn on the money tap by forcing users to suffer endless adverts and even make writers pay to reach the audience they have built.
Newsflash: there is no company too big to fail. Digg, Google+, Myspace, Vine and many more socials have died. Self-reported active user numbers cannot be trusted. Meta recently trialed AI profiles to prop up falling usage projections on Instagram and Facebook. X is now a dumpster fire of bots, scammers, and rage bait. It has been co-opted by a megalomaniacal oligarch to spread his own worldview. And LinkedIn feeds are drowning in unsolicited AI-generated business twaddle. The social giants are entering the death spiral.
# What happens in a social-media death spiral?
Users don’t see the value in posting, so they move elsewhere.
I wasn’t feeling rewarded for the thousands of hours I spent on LinkedIn, so I quit. I went from earning $20+ an article on Medium to pennies. Literal pennies. Bye bye, Tony Stubblebine. I learned that if you don’t own the distribution mechanic, you get left writing into the wind.
Ultimately, writers will dedicate their energy to where they see a benefit. They should spend time and create value in the place most similar to their ideal world.
For writers in 2025, that place seems to be Substack. Open rates are high and the platform is adding social features to generate more engagement in app. Substack is [experiencing massive growth](https://backlinko.com/substack-users) in active (and paid) subscriptions. Yet, it is following the same pattern as Medium in and LinkedIn in become self-cannibalising. Many of the most popular accounts write about ‘how to grow’ or ‘how to make money’ on Substack. Queue the eye rolls.
For me, it’s not the promised land where writers can earn a living. Of course, it’s no walk in the park to earn paid subscribers. Further, Substack users can only receive payment via Stripe. This excludes writers from 149 of the World’s countries. Does that seem open and fair to you?
Even with all this going on, there is a much bigger factor that should influence your choice of platform — ownership.
# Do writers really own their words?
Who reads the terms and conditions? Nobody. That’s who.Writers (including me) rush to all platforms which promise to give us benefits such as pay, distribution, and audience growth.
In exchange, companies request access to and shared ownership of our content. They can use our words to train LLMs, analyse trends, repurpose, and to spy on us.
Governments can and will request access to social media profiles. They seek to control the use of those platforms. Founders and CEOs who refuse to comply may be held personally accountable and put on trial, just as [Telegram founder, Pavel Durov, was](https://www.bbc.com/news/articles/c78lgzl919go) in France. Big tech owns our content, and governments threaten platforms into obedience.
As much as it benefits society to suppress harmful or dangerous content, companies simply can’t be censors 24/7. Growing platforms like [Bluesky are already struggling to moderate content effectively](https://www.theregister.com/2024/12/02/bluesky_growing_problems/). Without a strong economic incentive to moderate, companies will simply refuse to do it (as long as the threat of criminal charges does not prevail).
To sum up: No privately owned social media network offers writers the opportunity to own and distribute their work in order to receive a fair and equitable benefit.
Enter NOSTR…
# Decentralizing Social Media
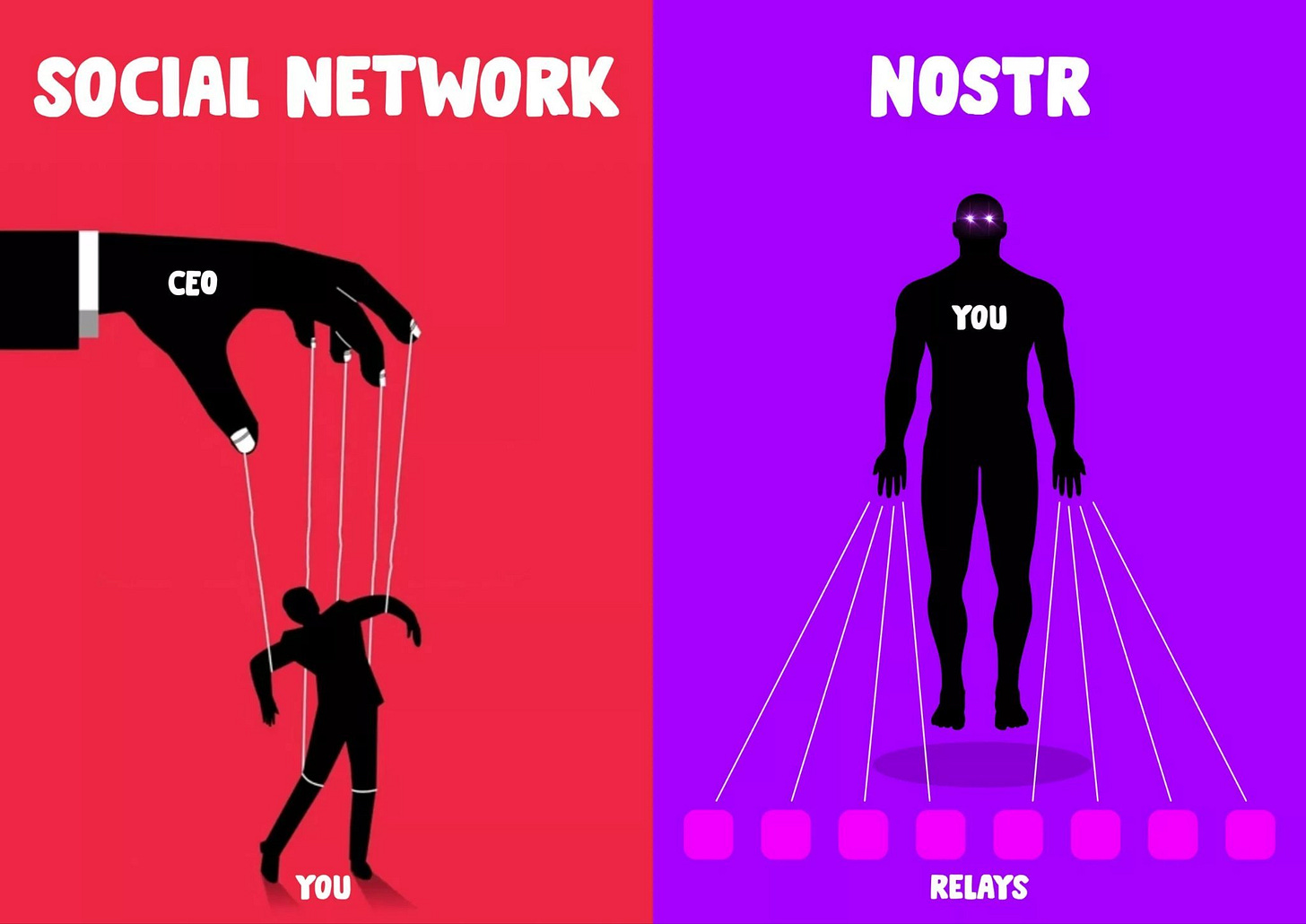**Notes and Other Stuff Transmitted by Relays** (NOSTR) is not a platform; it’s an open protocol.
By signing messages with their private keys (a long string of characters), users generate “events”. These events (messages/updates/media/transactions) are then broadcast through a series of “relays.”
Developers can use the protocol to build various applications that retrieve and distribute these events to other users. These ‘clients’ can range from microblogging sites like X and long-form distributors like Substack to visual media platforms like Instagram. Plus, NOSTR is also a whole lot more than that (but this is a topic for another day).
Decentralized tools offer the only hope against the dominance of AI and big tech in a top-down autocratic system designed to control us more than the thought police ever could.
<img src="https://blossom.primal.net/93a44d9bfe3c768e41d8bfef52415131af3ca21814a23870a029f1a947288cc8.webp">
*Diagram courtesy of River.*
So why should writers opt out of their big audience pool to write on some ‘protocol’?
**Ownership, fair rules, and fair value.**
- **Ownership**:
While privately run corporations can suppress the ideas they want, NOSTR provides a censorship-resistant alternative. No individual actors can restrict content or accounts.
Your private keys provide **permanent access** to the messages you have signed. No one else has access to them. And while some clients provide a delete function, there is no way to force all relays to respect a delete request. Not only do writers own what they publish, but it’s a permanent record.
- **Rules:**
Traditional social media platforms use proprietary algorithms to curate and order our feeds. **NOSTR has no algorithm**. NOSTR clients display messages chronologically or based on user-defined criteria, removing the influence of opaque algorithms that could manipulate user engagement and visibility of posts.
Put simply, distribution and consumption is down to the user, not to the creator or the platform. And everyone works to the same rules.
- **Value:**
Harmful content and spam affect all of us. There is no way to stop malicious content from being published on NOSTR, but two factors control its consumption.
1. Clients are experimenting with strategies such as requiring proof-of-work with each note or requiring verification badges.
2. Quality control is enforced by the value transferred by the protocol.
Bitcoin micropayments have become the monetary lifeblood flowing in the decentralized world. The ability to ‘zap’ users actual monetary value (e.g. a few cents) provides a clear display of which messages are valuable and which are unwanted. In time, as more users adopt the mechanic of value transfer, spammers will see their approach is not bearing fruit.
The beauty of using bitcoin in this way is twofold. Firstly, it is truly equitable — anyone in the world can receive it instantly and it cannot be stopped. And the system of frictionless micropayments offers content creators (artists, podcasters, musicians, writers) a way to earn money for the value they produce. Put simply, this could save creativity from doom.
Think people still want all content for free? Think again. Try zapping a writer from the Philippines, an artist from Peru, a Congolese musician, or a poet from Poland to show them you enjoyed what they produced. THAT is truly empowering.
Not convinced?
The best thing about NOSTR for writers is that **you are early**.
By being an early adopter with a low time preference, you can build a sizeable audience as new users discover the protocol.
Of course, topics like bitcoin, freedom tech, and privacy are well covered, but if you write in another niche, you could be ‘quids in’.
# Conclusion:
By adopting a long-term strategy and sticking to their principles, readers, writers and all other creatives can build a better world on social media. It doesn’t matter that it is imperfect. There will always be flaws in any society. But decentralized protocols like NOSTR can offer writers what they truly want — ownership, fair rules, and fair value.
---
Philip Charter is a totally human writer who helps bitcoin-native companies and clients stack major gains through laser-focused content. Find out more at [totallyhumanwriter.com](https://totallyhumanwriter.com)
He is also the editor of the cypherpunk and freedom fiction project, [21 Futures](https://21futures.com).
 @ a012dc82:6458a70d
2025-02-04 15:49:10Bitcoin halving is a cornerstone event in the cryptocurrency landscape, occurring approximately every four years, or after every 210,000 blocks are mined. This event is significant because it marks a reduction in the reward that miners receive for adding new blocks to the Bitcoin blockchain, effectively halving the rate at which new bitcoins are generated. The concept of halving is embedded in Bitcoin's protocol by Satoshi Nakamoto, its mysterious creator, as a measure to mimic the scarcity and deflationary characteristics of precious metals like gold. This mechanism is crucial in controlling the supply of Bitcoin, ensuring that it remains finite and valuable. As the next halving event draws near, it's not just miners who are impacted; the entire cryptocurrency market, including investors and enthusiasts, keenly anticipates the potential outcomes. Historically, halving events have been associated with increased market activity, price volatility, and heightened public interest in Bitcoin. The event is seen as a moment of transformation for Bitcoin, where the dynamics of supply and demand are altered, potentially leading to significant shifts in its market value. **Table Of Content** - Understanding the Hash Rate Surge - Implications of the Rising Hash Rate - The Halving Event: What to Expect - Preparing for the Halving - Conclusion - FAQs **Understanding the Hash Rate Surge** **What is Hash Rate?** The hash rate, in the context of Bitcoin, refers to the total computational power being used to mine and process transactions on the blockchain. It's a vital metric that reflects the health and security of the network. A higher hash rate means that more computational resources are being dedicated to maintaining the network, making it more robust against potential attacks. The hash rate is measured in hashes per second (H/s), and with advancements in mining technology, the network has seen this rate reach exahash levels (1 EH/s = 1 quintillion hashes per second). This metric is crucial for miners, as it affects their chances of solving the mathematical puzzles required to mine new blocks and earn rewards. It also indicates the level of competition among miners, as a higher hash rate suggests more participants or more powerful mining equipment in the network. **Record-Breaking Levels** The Bitcoin network's hash rate has recently hit an all-time high, reaching a staggering 491 exahashes per second (EH/s). This surge is indicative of the growing strength and security of the network. Such a high hash rate means that the network is more resilient than ever to potential attacks, such as the 51% attack, where a single entity could potentially gain control over the majority of the network's mining power. This level of security is crucial, especially as Bitcoin continues to gain mainstream acceptance and attract significant institutional investment. The record-breaking hash rate also reflects the increasing global interest in Bitcoin mining. It suggests that despite the high costs associated with mining - including specialized hardware and significant electricity consumption - miners are still heavily investing in this activity. This investment is not just in terms of money but also in research and development of more efficient mining technologies, which could further drive up the hash rate. **Implications of the Rising Hash Rate** **Enhanced Network Security** The surge in Bitcoin's hash rate is a positive development for the network's security. A higher hash rate means that it becomes exponentially more difficult for a malicious actor to orchestrate an attack on the network. This security is paramount for a system that handles billions of dollars worth of transactions. The decentralized nature of Bitcoin relies heavily on the integrity of its blockchain, which is maintained by this collective computational effort. As the hash rate increases, the confidence in the network's security also grows, which is crucial for both individual users and institutional investors. This enhanced security is particularly important in the context of the upcoming halving event, as it ensures the stability and reliability of the network during a period of significant change. **Increased Mining Difficulty** With the rise in hash rate comes an increase in the difficulty of mining Bitcoin. The Bitcoin network is designed to adjust the difficulty of mining new blocks approximately every two weeks to ensure that the time between blocks remains around 10 minutes. As more computational power joins the network, the difficulty increases, making it harder for individual miners to solve the cryptographic puzzles required to mine new blocks. This increase in difficulty can have several implications for miners. Smaller miners or those with less efficient equipment may find it increasingly difficult to compete with larger mining operations that have access to more powerful and efficient technology. This could lead to a consolidation in the mining industry, where only the most efficient operations can survive. Additionally, as the difficulty increases, the profitability of mining can decrease, especially if the price of Bitcoin does not increase proportionally. Miners must constantly evaluate their operations' efficiency and electricity costs to ensure continued profitability. **Energy Consumption Concerns** The rising hash rate of the Bitcoin network has brought renewed attention to the issue of energy consumption in Bitcoin mining. The process of mining Bitcoin is energy-intensive, as it requires a significant amount of computational power. As the hash rate increases, so does the total energy consumption of the network. This has led to concerns about the environmental impact of Bitcoin mining, especially in regions where electricity is generated from fossil fuels. The debate around Bitcoin's energy consumption is complex. On one hand, proponents argue that much of the energy used for Bitcoin mining comes from renewable sources, and the industry drives innovation in energy efficiency. On the other hand, critics point out that the overall energy consumption is still substantial and could be directed towards other, more productive uses. This debate is likely to continue as the network grows and the hash rate increases, especially in the context of global concerns about climate change and sustainable energy practices. **The Halving Event: What to Expect** **Reward Reduction** The upcoming Bitcoin halving event is a scheduled reduction in the rewards that miners receive for verifying and adding new transactions to the blockchain. This halving reduces the number of new bitcoins created and earned by miners with each new block from 6.25 bitcoins to 3.125 bitcoins. This event occurs every 210,000 blocks, or approximately every four years, and is a fundamental part of Bitcoin's economic model. The halving is designed to mimic the extraction of precious resources, becoming progressively harder and less rewarding over time. This mechanism ensures that the total supply of Bitcoin will never exceed 21 million coins, making Bitcoin a deflationary asset. The halving event is significant because it affects the economics of Bitcoin mining. With the reward halving, the revenue for miners is effectively cut in half overnight. This can lead to a shakeout in the mining industry, as less efficient miners may no longer be profitable and could be forced to shut down their operations. **Market Impact** Historically, Bitcoin halving events have been followed by significant price increases. This pattern has led to a common perception that halving events are bullish for Bitcoin's price. The rationale behind this is simple: as the rate of new supply of Bitcoin decreases, and if demand remains constant or increases, the price should theoretically go up. However, it's important to note that financial markets are influenced by a myriad of factors, and the impact of the halving may already be priced in by the time it occurs. Additionally, each halving event occurs in a different macroeconomic environment, and past performance is not indicative of future results. Investors and traders closely watch these events, as they can lead to increased volatility in the market. Some see the halving as an opportunity for long-term investment, while others may speculate on short-term price movements. **Preparing for the Halving** **Miner Adaptations** In anticipation of the halving and its impact on profitability, miners are taking various steps to adapt. One key strategy is the investment in more efficient mining hardware. Newer models of mining rigs offer greater hash power with lower energy consumption, which can help maintain profitability even with reduced rewards. Miners are also exploring alternative sources of revenue, such as transaction fee income, which could become a more significant part of their earnings post-halving. Additionally, miners are looking at geographical relocation to regions with cheaper electricity and favorable regulatory environments to reduce operational costs. Another consideration for miners is the potential consolidation of mining operations. Larger mining pools might have a better chance of surviving the reduced rewards, leading to a more centralized mining landscape. This potential centralization raises concerns within the Bitcoin community, as it could impact the decentralized nature of the network. **Investor Strategies** Investors are also preparing for the halving event in various ways. Many are closely analyzing historical data to understand potential market movements, although it's widely acknowledged that past trends may not necessarily predict future outcomes. Some investors view the halving as a key event that could drive long-term value growth in Bitcoin and are adjusting their portfolios accordingly. Others are more cautious, considering the potential for increased volatility around the event. There is also a focus on diversification, with investors looking at other cryptocurrencies and blockchain projects that might benefit from increased interest in the crypto space around the halving. Additionally, institutional investors, who have increasingly entered the cryptocurrency market, are likely to play a significant role in how the market reacts to the halving. Their strategies, which may include hedging and derivative trading, could influence Bitcoin's price dynamics in ways that were not seen in previous halving events. **Conclusion** The countdown to the Bitcoin halving is a period of significant anticipation and activity within the cryptocurrency community. The record-breaking hash rate ahead of the event is a testament to the network's strength and the commitment of its participants to maintain and secure the blockchain. As the halving approaches, the crypto world watches with keen interest, eager to see how this pivotal event will shape the future of Bitcoin. Whether it leads to a surge in price, increased adoption, or new challenges for miners, the halving is a reminder of the unique and dynamic nature of cryptocurrency and its underlying technology. As with any major event in the crypto space, the halving presents both opportunities and risks, and how it plays out could have lasting implications for the entire blockchain ecosystem. **FAQs** **What is Bitcoin Halving?** Bitcoin halving is an event that occurs approximately every four years, reducing the reward for mining new Bitcoin blocks by half. This mechanism controls the supply of new bitcoins and is a fundamental part of Bitcoin's economic model. **Why is the Bitcoin Hash Rate Important?** The hash rate measures the total computational power used in mining and processing transactions on the Bitcoin network. A higher hash rate indicates a more secure and robust network, making it resistant to attacks. **What Happens to Bitcoin's Price After Halving?** Historically, Bitcoin's price has increased following halving events, but this is not guaranteed. Market reactions can be unpredictable, and various factors influence Bitcoin's price. **How Does Halving Affect Bitcoin Miners?** Halving reduces the reward miners receive for validating new blocks, impacting their profitability. Miners often need to upgrade to more efficient hardware or find cheaper energy sources to remain competitive. **Can Bitcoin Halving Lead to Increased Centralization in Mining?** Potentially, yes. As mining becomes less profitable for smaller operations, there could be a consolidation towards larger mining pools, which might lead to a more centralized mining landscape. **Is the Increase in Bitcoin's Hash Rate Linked to the Upcoming Halving?** Yes, the increase in hash rate is often linked to the upcoming halving as miners upgrade their equipment and increase their computational power in anticipation of the reduced mining rewards. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: [@croxroadnews.co](https://x.com/croxroadnewsco)** **Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)** **Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** ***DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.***
@ a012dc82:6458a70d
2025-02-04 15:49:10Bitcoin halving is a cornerstone event in the cryptocurrency landscape, occurring approximately every four years, or after every 210,000 blocks are mined. This event is significant because it marks a reduction in the reward that miners receive for adding new blocks to the Bitcoin blockchain, effectively halving the rate at which new bitcoins are generated. The concept of halving is embedded in Bitcoin's protocol by Satoshi Nakamoto, its mysterious creator, as a measure to mimic the scarcity and deflationary characteristics of precious metals like gold. This mechanism is crucial in controlling the supply of Bitcoin, ensuring that it remains finite and valuable. As the next halving event draws near, it's not just miners who are impacted; the entire cryptocurrency market, including investors and enthusiasts, keenly anticipates the potential outcomes. Historically, halving events have been associated with increased market activity, price volatility, and heightened public interest in Bitcoin. The event is seen as a moment of transformation for Bitcoin, where the dynamics of supply and demand are altered, potentially leading to significant shifts in its market value. **Table Of Content** - Understanding the Hash Rate Surge - Implications of the Rising Hash Rate - The Halving Event: What to Expect - Preparing for the Halving - Conclusion - FAQs **Understanding the Hash Rate Surge** **What is Hash Rate?** The hash rate, in the context of Bitcoin, refers to the total computational power being used to mine and process transactions on the blockchain. It's a vital metric that reflects the health and security of the network. A higher hash rate means that more computational resources are being dedicated to maintaining the network, making it more robust against potential attacks. The hash rate is measured in hashes per second (H/s), and with advancements in mining technology, the network has seen this rate reach exahash levels (1 EH/s = 1 quintillion hashes per second). This metric is crucial for miners, as it affects their chances of solving the mathematical puzzles required to mine new blocks and earn rewards. It also indicates the level of competition among miners, as a higher hash rate suggests more participants or more powerful mining equipment in the network. **Record-Breaking Levels** The Bitcoin network's hash rate has recently hit an all-time high, reaching a staggering 491 exahashes per second (EH/s). This surge is indicative of the growing strength and security of the network. Such a high hash rate means that the network is more resilient than ever to potential attacks, such as the 51% attack, where a single entity could potentially gain control over the majority of the network's mining power. This level of security is crucial, especially as Bitcoin continues to gain mainstream acceptance and attract significant institutional investment. The record-breaking hash rate also reflects the increasing global interest in Bitcoin mining. It suggests that despite the high costs associated with mining - including specialized hardware and significant electricity consumption - miners are still heavily investing in this activity. This investment is not just in terms of money but also in research and development of more efficient mining technologies, which could further drive up the hash rate. **Implications of the Rising Hash Rate** **Enhanced Network Security** The surge in Bitcoin's hash rate is a positive development for the network's security. A higher hash rate means that it becomes exponentially more difficult for a malicious actor to orchestrate an attack on the network. This security is paramount for a system that handles billions of dollars worth of transactions. The decentralized nature of Bitcoin relies heavily on the integrity of its blockchain, which is maintained by this collective computational effort. As the hash rate increases, the confidence in the network's security also grows, which is crucial for both individual users and institutional investors. This enhanced security is particularly important in the context of the upcoming halving event, as it ensures the stability and reliability of the network during a period of significant change. **Increased Mining Difficulty** With the rise in hash rate comes an increase in the difficulty of mining Bitcoin. The Bitcoin network is designed to adjust the difficulty of mining new blocks approximately every two weeks to ensure that the time between blocks remains around 10 minutes. As more computational power joins the network, the difficulty increases, making it harder for individual miners to solve the cryptographic puzzles required to mine new blocks. This increase in difficulty can have several implications for miners. Smaller miners or those with less efficient equipment may find it increasingly difficult to compete with larger mining operations that have access to more powerful and efficient technology. This could lead to a consolidation in the mining industry, where only the most efficient operations can survive. Additionally, as the difficulty increases, the profitability of mining can decrease, especially if the price of Bitcoin does not increase proportionally. Miners must constantly evaluate their operations' efficiency and electricity costs to ensure continued profitability. **Energy Consumption Concerns** The rising hash rate of the Bitcoin network has brought renewed attention to the issue of energy consumption in Bitcoin mining. The process of mining Bitcoin is energy-intensive, as it requires a significant amount of computational power. As the hash rate increases, so does the total energy consumption of the network. This has led to concerns about the environmental impact of Bitcoin mining, especially in regions where electricity is generated from fossil fuels. The debate around Bitcoin's energy consumption is complex. On one hand, proponents argue that much of the energy used for Bitcoin mining comes from renewable sources, and the industry drives innovation in energy efficiency. On the other hand, critics point out that the overall energy consumption is still substantial and could be directed towards other, more productive uses. This debate is likely to continue as the network grows and the hash rate increases, especially in the context of global concerns about climate change and sustainable energy practices. **The Halving Event: What to Expect** **Reward Reduction** The upcoming Bitcoin halving event is a scheduled reduction in the rewards that miners receive for verifying and adding new transactions to the blockchain. This halving reduces the number of new bitcoins created and earned by miners with each new block from 6.25 bitcoins to 3.125 bitcoins. This event occurs every 210,000 blocks, or approximately every four years, and is a fundamental part of Bitcoin's economic model. The halving is designed to mimic the extraction of precious resources, becoming progressively harder and less rewarding over time. This mechanism ensures that the total supply of Bitcoin will never exceed 21 million coins, making Bitcoin a deflationary asset. The halving event is significant because it affects the economics of Bitcoin mining. With the reward halving, the revenue for miners is effectively cut in half overnight. This can lead to a shakeout in the mining industry, as less efficient miners may no longer be profitable and could be forced to shut down their operations. **Market Impact** Historically, Bitcoin halving events have been followed by significant price increases. This pattern has led to a common perception that halving events are bullish for Bitcoin's price. The rationale behind this is simple: as the rate of new supply of Bitcoin decreases, and if demand remains constant or increases, the price should theoretically go up. However, it's important to note that financial markets are influenced by a myriad of factors, and the impact of the halving may already be priced in by the time it occurs. Additionally, each halving event occurs in a different macroeconomic environment, and past performance is not indicative of future results. Investors and traders closely watch these events, as they can lead to increased volatility in the market. Some see the halving as an opportunity for long-term investment, while others may speculate on short-term price movements. **Preparing for the Halving** **Miner Adaptations** In anticipation of the halving and its impact on profitability, miners are taking various steps to adapt. One key strategy is the investment in more efficient mining hardware. Newer models of mining rigs offer greater hash power with lower energy consumption, which can help maintain profitability even with reduced rewards. Miners are also exploring alternative sources of revenue, such as transaction fee income, which could become a more significant part of their earnings post-halving. Additionally, miners are looking at geographical relocation to regions with cheaper electricity and favorable regulatory environments to reduce operational costs. Another consideration for miners is the potential consolidation of mining operations. Larger mining pools might have a better chance of surviving the reduced rewards, leading to a more centralized mining landscape. This potential centralization raises concerns within the Bitcoin community, as it could impact the decentralized nature of the network. **Investor Strategies** Investors are also preparing for the halving event in various ways. Many are closely analyzing historical data to understand potential market movements, although it's widely acknowledged that past trends may not necessarily predict future outcomes. Some investors view the halving as a key event that could drive long-term value growth in Bitcoin and are adjusting their portfolios accordingly. Others are more cautious, considering the potential for increased volatility around the event. There is also a focus on diversification, with investors looking at other cryptocurrencies and blockchain projects that might benefit from increased interest in the crypto space around the halving. Additionally, institutional investors, who have increasingly entered the cryptocurrency market, are likely to play a significant role in how the market reacts to the halving. Their strategies, which may include hedging and derivative trading, could influence Bitcoin's price dynamics in ways that were not seen in previous halving events. **Conclusion** The countdown to the Bitcoin halving is a period of significant anticipation and activity within the cryptocurrency community. The record-breaking hash rate ahead of the event is a testament to the network's strength and the commitment of its participants to maintain and secure the blockchain. As the halving approaches, the crypto world watches with keen interest, eager to see how this pivotal event will shape the future of Bitcoin. Whether it leads to a surge in price, increased adoption, or new challenges for miners, the halving is a reminder of the unique and dynamic nature of cryptocurrency and its underlying technology. As with any major event in the crypto space, the halving presents both opportunities and risks, and how it plays out could have lasting implications for the entire blockchain ecosystem. **FAQs** **What is Bitcoin Halving?** Bitcoin halving is an event that occurs approximately every four years, reducing the reward for mining new Bitcoin blocks by half. This mechanism controls the supply of new bitcoins and is a fundamental part of Bitcoin's economic model. **Why is the Bitcoin Hash Rate Important?** The hash rate measures the total computational power used in mining and processing transactions on the Bitcoin network. A higher hash rate indicates a more secure and robust network, making it resistant to attacks. **What Happens to Bitcoin's Price After Halving?** Historically, Bitcoin's price has increased following halving events, but this is not guaranteed. Market reactions can be unpredictable, and various factors influence Bitcoin's price. **How Does Halving Affect Bitcoin Miners?** Halving reduces the reward miners receive for validating new blocks, impacting their profitability. Miners often need to upgrade to more efficient hardware or find cheaper energy sources to remain competitive. **Can Bitcoin Halving Lead to Increased Centralization in Mining?** Potentially, yes. As mining becomes less profitable for smaller operations, there could be a consolidation towards larger mining pools, which might lead to a more centralized mining landscape. **Is the Increase in Bitcoin's Hash Rate Linked to the Upcoming Halving?** Yes, the increase in hash rate is often linked to the upcoming halving as miners upgrade their equipment and increase their computational power in anticipation of the reduced mining rewards. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: [@croxroadnews.co](https://x.com/croxroadnewsco)** **Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)** **Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** ***DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.*** @ 1833ee04:7c4a8170
2025-02-04 15:14:03The international race for Bitcoin strategic reserves is just getting started. If you’re stacking now, you’re still incredibly early. At $100k per Bitcoin, it’s practically free for anyone who truly understands how massive this shift is. Think back to when paper currency was introduced, people had to trade their gold for paper bills. Many laughed, saying, Who’s going to trust these worthless pieces of paper as money? Yet today, you sell your time to earn these paper bills while your government can print an unlimited amount at will. The world is returning to a gold standard. But this time, it’s Gold 2.0 which is Bitcoin.The international race for Bitcoin strategic reserves is just getting started.\ \ If you’re stacking now, you’re still incredibly early.\ \ At $100k per Bitcoin, it’s practically free for anyone who truly understands how massive this shift is.\ \ Think back to when paper currency was introduced, people had to trade their gold for paper bills. Many laughed, saying, Who’s going to trust these worthless pieces of paper as money?\ \ Yet today, you sell your time to earn these paper bills while your government can print an unlimited amount at will.\ \ The world is returning to a gold standard. But this time, it’s Gold 2.0 which is Bitcoin.
@ 1833ee04:7c4a8170
2025-02-04 15:14:03The international race for Bitcoin strategic reserves is just getting started. If you’re stacking now, you’re still incredibly early. At $100k per Bitcoin, it’s practically free for anyone who truly understands how massive this shift is. Think back to when paper currency was introduced, people had to trade their gold for paper bills. Many laughed, saying, Who’s going to trust these worthless pieces of paper as money? Yet today, you sell your time to earn these paper bills while your government can print an unlimited amount at will. The world is returning to a gold standard. But this time, it’s Gold 2.0 which is Bitcoin.The international race for Bitcoin strategic reserves is just getting started.\ \ If you’re stacking now, you’re still incredibly early.\ \ At $100k per Bitcoin, it’s practically free for anyone who truly understands how massive this shift is.\ \ Think back to when paper currency was introduced, people had to trade their gold for paper bills. Many laughed, saying, Who’s going to trust these worthless pieces of paper as money?\ \ Yet today, you sell your time to earn these paper bills while your government can print an unlimited amount at will.\ \ The world is returning to a gold standard. But this time, it’s Gold 2.0 which is Bitcoin. @ 5af07946:98fca8c4
2025-02-04 15:13:27Syādvāda, also known as the theory of conditional predication, is a fundamental concept in Jain philosophy that bears some intriguing similarities to modern concepts of probability. ## Conditional Prediction system Syādvāda is a theory of epistemological relativism that forms the basis of Jain [logic](https://www.newworldencyclopedia.org/entry/Syadvada). The term "syād" in Sanskrit means "may be" or "perhaps," and in the context of syādvāda, it translates to "in some ways" or "from a perspective". This theory asserts that reality is complex and multifaceted, and no single proposition can fully express its nature. ## Saptabhangi: The Seven-fold Predication The core of syādvāda is manifested in the process of Saptabhangi, or seven-fold prediction. This approach examines reality from seven different conditional and relative viewpoints: - Syādasti (maybe, it is) - Syānnāsti (maybe, it is not) - Syādasti nāsti (maybe, it is, and it is not) - Syādavaktavya (maybe, it is indeterminate) - Syādasti avaktavya (maybe, it is and is indeterminate) - Syānnāsti avaktavya (maybe, it is not and is indeterminate) - Syādasti nāsti avaktavya (maybe, it is, is not, and is indeterminate) ## Connections to Probability Syādvāda shares conceptual similarities with Probability theory: - Non-absolutism: Like probability theory, syādvāda acknowledges uncertainty and rejects absolute [statements](https://indiaphilosophy.wordpress.com/tag/syadvad/). However, it asserts that there are only seven categories necessary and also sufficient to exhaust all possibilities of knowledge! - Conditional nature: Both syādvāda and probability deal with conditional statements and [chances](https://jainfriends.tripod.com/books/jiblsyadvada.html) - Multiple outcomes: Syādvāda's seven-fold prediction can be seen as analogous to considering multiple possible outcomes in probability. - Indeterminacy: The fourth category of syādvāda, "avaktavya" (indeterminate), has been interpreted by some scholars as having relevance to the concept of probability. ## An Illustrative Example Consider the tossing of a coin: - "It is head" (now) - Syādasti - "It is not-head" (on another occasion) - Syānnāsti - "It is, and it is not" - Syādasti nāsti - "It is indeterminate" (before the toss) - Syādavaktavya This example demonstrates how syādvāda's categories can be applied to a situation involving uncertainty, similar to how we might approach it using probability theory. ## Historical Significance and Modern Relevance Syādvāda was well-developed by the 6th century AD and received significant attention in medieval Indian logic. It is believed that it was based on astrological principles of Maharishi Parashara - the father of ancient astrology.
@ 5af07946:98fca8c4
2025-02-04 15:13:27Syādvāda, also known as the theory of conditional predication, is a fundamental concept in Jain philosophy that bears some intriguing similarities to modern concepts of probability. ## Conditional Prediction system Syādvāda is a theory of epistemological relativism that forms the basis of Jain [logic](https://www.newworldencyclopedia.org/entry/Syadvada). The term "syād" in Sanskrit means "may be" or "perhaps," and in the context of syādvāda, it translates to "in some ways" or "from a perspective". This theory asserts that reality is complex and multifaceted, and no single proposition can fully express its nature. ## Saptabhangi: The Seven-fold Predication The core of syādvāda is manifested in the process of Saptabhangi, or seven-fold prediction. This approach examines reality from seven different conditional and relative viewpoints: - Syādasti (maybe, it is) - Syānnāsti (maybe, it is not) - Syādasti nāsti (maybe, it is, and it is not) - Syādavaktavya (maybe, it is indeterminate) - Syādasti avaktavya (maybe, it is and is indeterminate) - Syānnāsti avaktavya (maybe, it is not and is indeterminate) - Syādasti nāsti avaktavya (maybe, it is, is not, and is indeterminate) ## Connections to Probability Syādvāda shares conceptual similarities with Probability theory: - Non-absolutism: Like probability theory, syādvāda acknowledges uncertainty and rejects absolute [statements](https://indiaphilosophy.wordpress.com/tag/syadvad/). However, it asserts that there are only seven categories necessary and also sufficient to exhaust all possibilities of knowledge! - Conditional nature: Both syādvāda and probability deal with conditional statements and [chances](https://jainfriends.tripod.com/books/jiblsyadvada.html) - Multiple outcomes: Syādvāda's seven-fold prediction can be seen as analogous to considering multiple possible outcomes in probability. - Indeterminacy: The fourth category of syādvāda, "avaktavya" (indeterminate), has been interpreted by some scholars as having relevance to the concept of probability. ## An Illustrative Example Consider the tossing of a coin: - "It is head" (now) - Syādasti - "It is not-head" (on another occasion) - Syānnāsti - "It is, and it is not" - Syādasti nāsti - "It is indeterminate" (before the toss) - Syādavaktavya This example demonstrates how syādvāda's categories can be applied to a situation involving uncertainty, similar to how we might approach it using probability theory. ## Historical Significance and Modern Relevance Syādvāda was well-developed by the 6th century AD and received significant attention in medieval Indian logic. It is believed that it was based on astrological principles of Maharishi Parashara - the father of ancient astrology. @ 916a7ab7:146bb83e
2025-02-04 13:35:11It was not ago that my life was simpler than it is today. I remember being a simple clone, droning on through a structured life as I'd been trained to do since birth. Like most people I knew, I was raised in a world where you were mentally prepared for a conceptually simple life: 1. Finish high school, if possible. 2. Go to college, if possible. 3. Find a job. 4. Earn money. 5. Pay bills. 6. Get married. 7. Start a family. 8. Pay more bills. 9. Raise family and (hopefully) launch the kids. 10. Plan to retire, but expect to work into your 70s. It was a programmed formula for life. A generational blueprint, if you will. Sure, there would be unpredictable details, but I expected my life to follow this path. As I plodded along through my fairly boring life, I checked most of those things off the list. High school was easy, but getting off the farm was not. Enlisting in the military solved that problem, and the pay in the mid-1990s wasn't bad for a 17 year old kid with no bills. I got paid every two weeks, lived in the barracks, and spent most of my money on booze. Life was good, and I had no other purpose than to do my job and keep earning money. Before I knew it, though, everything changed. I got married, had some kids and accumulated a mountain of debt. Like my parents before me, I was stuck in a never ending cycle of working my ass off, paying bills, buying food, and trying to save what little money was left over for a future that was unpredictable at best. Financial struggles stressed our marriage, the kids continued eating more and more food, and then 2008 tanked the value of our home. That was the first nudge that stirred my oblivious slumber. And there was more to come. Rising taxes, inflation, the clown show at the federal reserve, the wars funded by central banks, an astronomical national debt, and the burdens of our mistakes weighing down the futures of our children. Not to mention a federal government that actively seeks to censor, suppress, and financially imprison its own people. The times exuded chaos. Then a few months ago, I woke up... It happened during an episode of The Tuttle Twins, a cartoon show from Angel Studios. I homeschool my three youngest kids, and I'd let them watch TV during lunch so I could grade some papers. This cartoon was new to me, but the kids liked the music and the crazy raccoon. As fate would have it, they ended up watching an episode about Bitcoin. This, of course, led to a long series of questions: "Dad, what's Bitcoin?" "Is Bitcoin real?" "Do you have Bitcoin?" "Can I get Bitcoin for allowance instead of dollars?" I had no answers for these questions, so we started doing some research together. We turned on our Chromebooks and launched a barrage of web searches. After reading a bunch of articles I came away with the idea that Bitcoin might be a real thing. Later that evening, and after the kids were in bed, I couldn't stop thinking about Bitcoin. I honestly didn't understand half of what I read in those articles, which bothered me. I'm not a super smart guy, but I catch on to things pretty quickly, and I wanted to better understand what I'd read. I expanded my search to podcasts and YouTube videos. I ended up listening to a couple episodes from a Bitcoin Veterans podcast. As a veteran myself, I figured that this group of Bitcoin-savvy veterans would be able to help me figure out all this madness. I was right. I quickly learned that the word "Bitcoin" was just the tip of the iceberg, and I quickly found myself falling through an endless rabbit hole. They pointed me in a lot of different directions, but they were all helpful. (If you're a US military veteran and want to connect with this group, find them at [bitcoinveterans.org].) A couple months ago, I couldn't tell you the difference between a Bitcoin and a meme coin. I'd come across the phrase Bitcoin mining, and I just thought there was a special group of people who mined a special metal to create coins with a big "B" on them. Why couldn't they just use the metal we already mined? Sheesh! I thought nostr was a virus, and a Kraken was still a giant squid. As of today, I'm happy to say that I've made a little bit of progress. Those things above no longer confuse me, and I actually have a little bit of Bitcoin now. Sure, I'm still trying to wrap my head around NFTs and figure out who the Pepe frog man is, but I'm no longer completely lost. Not to mention, I just spent most of the last 24 hours figuring this whole nostr thing out, which excites me. I kind of missed the boat on the big name social media platforms, so I'm looking forward to this new decentralized approach to things. For now, I'm just happy to be awake. Finally. I see the need for decentralization and the necessity of moving away from fiat monies. I don't have much to offer except my intellect and my love of writing, but I'm here to serve in any way that I can.
@ 916a7ab7:146bb83e
2025-02-04 13:35:11It was not ago that my life was simpler than it is today. I remember being a simple clone, droning on through a structured life as I'd been trained to do since birth. Like most people I knew, I was raised in a world where you were mentally prepared for a conceptually simple life: 1. Finish high school, if possible. 2. Go to college, if possible. 3. Find a job. 4. Earn money. 5. Pay bills. 6. Get married. 7. Start a family. 8. Pay more bills. 9. Raise family and (hopefully) launch the kids. 10. Plan to retire, but expect to work into your 70s. It was a programmed formula for life. A generational blueprint, if you will. Sure, there would be unpredictable details, but I expected my life to follow this path. As I plodded along through my fairly boring life, I checked most of those things off the list. High school was easy, but getting off the farm was not. Enlisting in the military solved that problem, and the pay in the mid-1990s wasn't bad for a 17 year old kid with no bills. I got paid every two weeks, lived in the barracks, and spent most of my money on booze. Life was good, and I had no other purpose than to do my job and keep earning money. Before I knew it, though, everything changed. I got married, had some kids and accumulated a mountain of debt. Like my parents before me, I was stuck in a never ending cycle of working my ass off, paying bills, buying food, and trying to save what little money was left over for a future that was unpredictable at best. Financial struggles stressed our marriage, the kids continued eating more and more food, and then 2008 tanked the value of our home. That was the first nudge that stirred my oblivious slumber. And there was more to come. Rising taxes, inflation, the clown show at the federal reserve, the wars funded by central banks, an astronomical national debt, and the burdens of our mistakes weighing down the futures of our children. Not to mention a federal government that actively seeks to censor, suppress, and financially imprison its own people. The times exuded chaos. Then a few months ago, I woke up... It happened during an episode of The Tuttle Twins, a cartoon show from Angel Studios. I homeschool my three youngest kids, and I'd let them watch TV during lunch so I could grade some papers. This cartoon was new to me, but the kids liked the music and the crazy raccoon. As fate would have it, they ended up watching an episode about Bitcoin. This, of course, led to a long series of questions: "Dad, what's Bitcoin?" "Is Bitcoin real?" "Do you have Bitcoin?" "Can I get Bitcoin for allowance instead of dollars?" I had no answers for these questions, so we started doing some research together. We turned on our Chromebooks and launched a barrage of web searches. After reading a bunch of articles I came away with the idea that Bitcoin might be a real thing. Later that evening, and after the kids were in bed, I couldn't stop thinking about Bitcoin. I honestly didn't understand half of what I read in those articles, which bothered me. I'm not a super smart guy, but I catch on to things pretty quickly, and I wanted to better understand what I'd read. I expanded my search to podcasts and YouTube videos. I ended up listening to a couple episodes from a Bitcoin Veterans podcast. As a veteran myself, I figured that this group of Bitcoin-savvy veterans would be able to help me figure out all this madness. I was right. I quickly learned that the word "Bitcoin" was just the tip of the iceberg, and I quickly found myself falling through an endless rabbit hole. They pointed me in a lot of different directions, but they were all helpful. (If you're a US military veteran and want to connect with this group, find them at [bitcoinveterans.org].) A couple months ago, I couldn't tell you the difference between a Bitcoin and a meme coin. I'd come across the phrase Bitcoin mining, and I just thought there was a special group of people who mined a special metal to create coins with a big "B" on them. Why couldn't they just use the metal we already mined? Sheesh! I thought nostr was a virus, and a Kraken was still a giant squid. As of today, I'm happy to say that I've made a little bit of progress. Those things above no longer confuse me, and I actually have a little bit of Bitcoin now. Sure, I'm still trying to wrap my head around NFTs and figure out who the Pepe frog man is, but I'm no longer completely lost. Not to mention, I just spent most of the last 24 hours figuring this whole nostr thing out, which excites me. I kind of missed the boat on the big name social media platforms, so I'm looking forward to this new decentralized approach to things. For now, I'm just happy to be awake. Finally. I see the need for decentralization and the necessity of moving away from fiat monies. I don't have much to offer except my intellect and my love of writing, but I'm here to serve in any way that I can. @ ef1e59bf:b686587d
2025-02-04 11:15:10## Key Insights Explained While both systems provide innovative soilless growing solutions, the unique difference lies in their approach—hydroponics relies on a nutrient-rich water solution, whereas aquaponics integrates fish into the ecosystem to naturally supply nutrients. This not only impacts their cultivation techniques but also illustrates varying levels of sustainability and resource use. In exploring these systems, one cannot help but consider the broader implications for urban agriculture. For those looking to adopt such systems, understanding key differences can significantly impact decisions on efficiency, cost, and ecological footprint. ##### What Is Hydroponics? In hydroponics, we grow plants in water enriched with nutrients rather than soil. This method provides a controlled environment where the roots receive all necessary elements directly from the nutrient solution. It's fascinating how plants can thrive without ever touching the soil. The benefits of hydroponics are impressive. We can achieve faster growth rates due to optimal nutrient delivery, and the space-saving designs, such as vertical farms, maximise small areas. Moreover, nutrient levels can be controlled precisely, ensuring plants receive exactly what they need. ##### What Is Aquaponics? Aquaponics is an innovative system that blends aquaculture, which is the practice of raising fish, with hydroponics, the soilless cultivation of plants. In this symbiotic setup, fish waste serves as a natural fertiliser, supplying essential nutrients to the plants. In return, the plants help purify the water, creating a healthy environment for the fish. This system is unique because it mimics natural ecosystems, enhancing sustainability. The dual benefits of growing plants and fish simultaneously make aquaponics an attractive option for those of us interested in sustainable agriculture and promoting organic cultivation practices. ##### Key Differences Hydroponics and aquaponics each offer unique benefits and challenges. Understanding these systems requires examining their differences in nutrient sources, water usage, plant growth density, time to harvest, setup intricacies, and the types of produce they best support. ##### Nutrient Source In hydroponics, plants receive nutrients through specially prepared solutions, often purchased from commercial suppliers. This method allows us to maintain a high level of control over nutrient balance, making precise adjustments as needed. Aquaponics, by contrast, relies on fish waste to supply nutrients. This forms a more natural ecosystem, requiring biological processes like nitrification to convert waste into nutrients usable by plants. While this approach involves fewer chemical inputs and is more sustainable, it offers less control over nutrient levels. ##### Water Usage Hydroponic systems excel in water efficiency by recirculating water, though they necessitate regular changes to keep nutrient solutions balanced. Despite their efficiency, water loss can occur through evaporation or leaks, which requires monitoring. Aquaponics operates as a closed-loop system where water is continually recycled between the fish tank and plant beds, minimising waste. This setup further reduces water use due to natural filtration by plants, making it an incredibly water-efficient choice. ##### Grow Density Hydroponics typically supports higher density plant growth, especially in vertical setups. This is ideal for cultivating leafy greens, herbs, and other fast-growing plants in compact spaces. Aquaponics requires space for both fish and plants, which limits plant density. Although some plants may grow slower due to varying nutrient availability, this method offers the benefit of integrating fish care into the system. ##### Grow Time In hydroponics, plants enjoy faster growth rates thanks to controlled nutrient and environmental conditions. These systems often facilitate shorter growing cycles compared to traditional farming, enhancing efficiency. Aquaponics, while efficient, may experience slightly slower growth rates due to the time taken for natural nutrient conversion. Balancing fish growth with plant cycles adds an extra layer of complexity but is a rewarding experience for those willing to engage deeply with the system. ##### Set Up and Maintenance Starting a hydroponic system is relatively straightforward, with pumps, nutrient tanks, and light management being primary needs. Regular checks of pH, nutrient levels, and water are essential yet generally simple. Aquaponics demands more initial infrastructure and expertise due to the need for integrated fish tanks and plant systems. Balancing fish health and water quality with plant needs adds complexity, but long-term sustainability benefits are significant. Setting up these systems can seem daunting but offer reduced external nutrient input over time. ##### Produce Types Hydroponics shines when growing leafy greens and herbs, achieving high success rates with crops like lettuce, basil, and spinach. These systems, however, have limitations when it comes to larger or more nutrient-demanding produce. Aquaponics expands possibilities by supporting a broader range of plants, including fruiting ones such as tomatoes, alongside fish like tilapia or trout. This dual-production feature offers diverse yields, though the choice of fish can influence plant variety. ##### Which Is More Sustainable? When we consider the sustainability of hydroponics, several factors come to mind. First, high water efficiency and space-saving designs make it attractive for eco-conscious growers. Yet, the reliance on artificial nutrients and the higher energy usage, particularly for lighting and pumps, may impact its overall eco-friendliness. These elements can sometimes offset the system’s environmental benefits. In contrast, aquaponics offers a unique closed-loop system that naturally recycles waste. This can significantly reduce the need for external inputs, aligning well with principles of organic farming. While this method requires more space and careful maintenance for both fish and plants, it typically involves less chemical intervention, appealing to those seeking a more natural approach. ###### Let's compare the environmental impact of these methods: * Aquaponics might have a lower environmental footprint due to its natural nutrient cycle, reducing waste and chemical use. * On the other hand, hydroponics can be well-suited for urban environments or locations with limited resources, thanks to its efficient use of water and space. Ultimately, deciding which system is more sustainable depends on specific circumstances and priorities. If natural nutrient cycles and less chemical intervention are valued, aquaponics might be favoured. Nevertheless, if water and space efficiency are paramount, especially in urban settings, hydroponics might be more suitable. Hydroponics is a game-changer for sustainable farming, offering efficient water use, reduced land impact, and year-round crop production. Whether you're a beginner or an experienced grower, having the right tools and knowledge is key to success. Visit [Hyjo ](https://hyjo.co.uk/)for high-quality hydroponic systems, nutrients, and expert advice. Start growing smarter and greener with Hyjo today!
@ ef1e59bf:b686587d
2025-02-04 11:15:10## Key Insights Explained While both systems provide innovative soilless growing solutions, the unique difference lies in their approach—hydroponics relies on a nutrient-rich water solution, whereas aquaponics integrates fish into the ecosystem to naturally supply nutrients. This not only impacts their cultivation techniques but also illustrates varying levels of sustainability and resource use. In exploring these systems, one cannot help but consider the broader implications for urban agriculture. For those looking to adopt such systems, understanding key differences can significantly impact decisions on efficiency, cost, and ecological footprint. ##### What Is Hydroponics? In hydroponics, we grow plants in water enriched with nutrients rather than soil. This method provides a controlled environment where the roots receive all necessary elements directly from the nutrient solution. It's fascinating how plants can thrive without ever touching the soil. The benefits of hydroponics are impressive. We can achieve faster growth rates due to optimal nutrient delivery, and the space-saving designs, such as vertical farms, maximise small areas. Moreover, nutrient levels can be controlled precisely, ensuring plants receive exactly what they need. ##### What Is Aquaponics? Aquaponics is an innovative system that blends aquaculture, which is the practice of raising fish, with hydroponics, the soilless cultivation of plants. In this symbiotic setup, fish waste serves as a natural fertiliser, supplying essential nutrients to the plants. In return, the plants help purify the water, creating a healthy environment for the fish. This system is unique because it mimics natural ecosystems, enhancing sustainability. The dual benefits of growing plants and fish simultaneously make aquaponics an attractive option for those of us interested in sustainable agriculture and promoting organic cultivation practices. ##### Key Differences Hydroponics and aquaponics each offer unique benefits and challenges. Understanding these systems requires examining their differences in nutrient sources, water usage, plant growth density, time to harvest, setup intricacies, and the types of produce they best support. ##### Nutrient Source In hydroponics, plants receive nutrients through specially prepared solutions, often purchased from commercial suppliers. This method allows us to maintain a high level of control over nutrient balance, making precise adjustments as needed. Aquaponics, by contrast, relies on fish waste to supply nutrients. This forms a more natural ecosystem, requiring biological processes like nitrification to convert waste into nutrients usable by plants. While this approach involves fewer chemical inputs and is more sustainable, it offers less control over nutrient levels. ##### Water Usage Hydroponic systems excel in water efficiency by recirculating water, though they necessitate regular changes to keep nutrient solutions balanced. Despite their efficiency, water loss can occur through evaporation or leaks, which requires monitoring. Aquaponics operates as a closed-loop system where water is continually recycled between the fish tank and plant beds, minimising waste. This setup further reduces water use due to natural filtration by plants, making it an incredibly water-efficient choice. ##### Grow Density Hydroponics typically supports higher density plant growth, especially in vertical setups. This is ideal for cultivating leafy greens, herbs, and other fast-growing plants in compact spaces. Aquaponics requires space for both fish and plants, which limits plant density. Although some plants may grow slower due to varying nutrient availability, this method offers the benefit of integrating fish care into the system. ##### Grow Time In hydroponics, plants enjoy faster growth rates thanks to controlled nutrient and environmental conditions. These systems often facilitate shorter growing cycles compared to traditional farming, enhancing efficiency. Aquaponics, while efficient, may experience slightly slower growth rates due to the time taken for natural nutrient conversion. Balancing fish growth with plant cycles adds an extra layer of complexity but is a rewarding experience for those willing to engage deeply with the system. ##### Set Up and Maintenance Starting a hydroponic system is relatively straightforward, with pumps, nutrient tanks, and light management being primary needs. Regular checks of pH, nutrient levels, and water are essential yet generally simple. Aquaponics demands more initial infrastructure and expertise due to the need for integrated fish tanks and plant systems. Balancing fish health and water quality with plant needs adds complexity, but long-term sustainability benefits are significant. Setting up these systems can seem daunting but offer reduced external nutrient input over time. ##### Produce Types Hydroponics shines when growing leafy greens and herbs, achieving high success rates with crops like lettuce, basil, and spinach. These systems, however, have limitations when it comes to larger or more nutrient-demanding produce. Aquaponics expands possibilities by supporting a broader range of plants, including fruiting ones such as tomatoes, alongside fish like tilapia or trout. This dual-production feature offers diverse yields, though the choice of fish can influence plant variety. ##### Which Is More Sustainable? When we consider the sustainability of hydroponics, several factors come to mind. First, high water efficiency and space-saving designs make it attractive for eco-conscious growers. Yet, the reliance on artificial nutrients and the higher energy usage, particularly for lighting and pumps, may impact its overall eco-friendliness. These elements can sometimes offset the system’s environmental benefits. In contrast, aquaponics offers a unique closed-loop system that naturally recycles waste. This can significantly reduce the need for external inputs, aligning well with principles of organic farming. While this method requires more space and careful maintenance for both fish and plants, it typically involves less chemical intervention, appealing to those seeking a more natural approach. ###### Let's compare the environmental impact of these methods: * Aquaponics might have a lower environmental footprint due to its natural nutrient cycle, reducing waste and chemical use. * On the other hand, hydroponics can be well-suited for urban environments or locations with limited resources, thanks to its efficient use of water and space. Ultimately, deciding which system is more sustainable depends on specific circumstances and priorities. If natural nutrient cycles and less chemical intervention are valued, aquaponics might be favoured. Nevertheless, if water and space efficiency are paramount, especially in urban settings, hydroponics might be more suitable. Hydroponics is a game-changer for sustainable farming, offering efficient water use, reduced land impact, and year-round crop production. Whether you're a beginner or an experienced grower, having the right tools and knowledge is key to success. Visit [Hyjo ](https://hyjo.co.uk/)for high-quality hydroponic systems, nutrients, and expert advice. Start growing smarter and greener with Hyjo today! @ e3ba5e1a:5e433365
2025-02-04 08:29:42President Trump has started rolling out his tariffs, something I [blogged about in November](https://www.snoyman.com/blog/2024/11/steelmanning-tariffs/). People are talking about these tariffs a lot right now, with many people (correctly) commenting on how consumers will end up with higher prices as a result of these tariffs. While that part is true, I’ve seen a lot of people taking it to the next, incorrect step: that consumers will pay the entirety of the tax. I [put up a poll on X](https://x.com/snoyberg/status/1886035800019599808) to see what people thought, and while the right answer got a lot of votes, it wasn't the winner.  For purposes of this blog post, our ultimate question will be the following: * Suppose apples currently sell for $1 each in the entire United States. * There are domestic sellers and foreign sellers of apples, all receiving the same price. * There are no taxes or tariffs on the purchase of apples. * The question is: if the US federal government puts a $0.50 import tariff per apple, what will be the change in the following: * Number of apples bought in the US * Price paid by buyers for apples in the US * Post-tax price received by domestic apple producers * Post-tax price received by foreign apple producers Before we can answer that question, we need to ask an easier, first question: before instituting the tariff, why do apples cost $1? And finally, before we dive into the details, let me provide you with the answers to the ultimate question. I recommend you try to guess these answers before reading this, and if you get it wrong, try to understand why: 1. The number of apples bought will go down 2. The buyers will pay more for each apple they buy, but not the full amount of the tariff 3. Domestic apple sellers will receive a *higher* price per apple 4. Foreign apple sellers will receive a *lower* price per apple, but not lowered by the full amount of the tariff In other words, regardless of who sends the payment to the government, both taxed parties (domestic buyers and foreign sellers) will absorb some of the costs of the tariff, while domestic sellers will benefit from the protectionism provided by tariffs and be able to sell at a higher price per unit. ## Marginal benefit All of the numbers discussed below are part of a [helper Google Sheet](https://docs.google.com/spreadsheets/d/14ZbkWpw1B9Q1UDB9Yh47DmdKQfIafVVBKbDUsSIfGZw/edit?usp=sharing) I put together for this analysis. Also, apologies about the jagged lines in the charts below, I hadn’t realized before starting on this that there are [some difficulties with creating supply and demand charts in Google Sheets](https://superuser.com/questions/1359731/how-to-create-a-supply-demand-style-chart). Let’s say I absolutely love apples, they’re my favorite food. How much would I be willing to pay for a single apple? You might say “$1, that’s the price in the supermarket,” and in many ways you’d be right. If I walk into supermarket A, see apples on sale for $50, and know that I can buy them at supermarket B for $1, I’ll almost certainly leave A and go buy at B. But that’s not what I mean. What I mean is: how high would the price of apples have to go *everywhere* so that I’d no longer be willing to buy a single apple? This is a purely personal, subjective opinion. It’s impacted by how much money I have available, other expenses I need to cover, and how much I like apples. But let’s say the number is $5. How much would I be willing to pay for another apple? Maybe another $5. But how much am I willing to pay for the 1,000th apple? 10,000th? At some point, I’ll get sick of apples, or run out of space to keep the apples, or not be able to eat, cook, and otherwise preserve all those apples before they rot. The point being: I’ll be progressively willing to spend less and less money for each apple. This form of analysis is called *marginal benefit*: how much benefit (expressed as dollars I’m willing to spend) will I receive from each apple? This is a downward sloping function: for each additional apple I buy (quantity demanded), the price I’m willing to pay goes down. This is what gives my personal *demand curve*. And if we aggregate demand curves across all market participants (meaning: everyone interested in buying apples), we end up with something like this:  Assuming no changes in people’s behavior and other conditions in the market, this chart tells us how many apples will be purchased by our buyers at each price point between $0.50 and $5. And ceteris paribus (all else being equal), this will continue to be the demand curve for apples. ## Marginal cost Demand is half the story of economics. The other half is supply, or: how many apples will I sell at each price point? Supply curves are upward sloping: the higher the price, the more a person or company is willing and able to sell a product. Let’s understand why. Suppose I have an apple orchard. It’s a large property right next to my house. With about 2 minutes of effort, I can walk out of my house, find the nearest tree, pick 5 apples off the tree, and call it a day. 5 apples for 2 minutes of effort is pretty good, right? Yes, there was all the effort necessary to buy the land, and plant the trees, and water them… and a bunch more than I likely can’t even guess at. We’re going to ignore all of that for our analysis, because for short-term supply-and-demand movement, we can ignore these kinds of *sunk costs*. One other simplification: in reality, supply curves often start descending before ascending. This accounts for achieving efficiencies of scale after the first number of units purchased. But since both these topics are unneeded for understanding taxes, I won’t go any further. Anyway, back to my apple orchard. If someone offers me $0.50 per apple, I can do 2 minutes of effort and get $2.50 in revenue, which equates to a $75/hour wage for me. I’m more than happy to pick apples at that price\! However, let’s say someone comes to buy 10,000 apples from me instead. I no longer just walk out to my nearest tree. I’m going to need to get in my truck, drive around, spend the day in the sun, pay for gas, take a day off of my day job (let’s say it pays me $70/hour). The costs go up significantly. Let’s say it takes 5 days to harvest all those apples myself, it costs me $100 in fuel and other expenses, and I lose out on my $70/hour job for 5 days. We end up with: * Total expenditure: $100 \+ $70 \* 8 hours a day \* 5 days \== $2900 * Total revenue: $5000 (10,000 apples at $0.50 each) * Total profit: $2100 So I’m still willing to sell the apples at this price, but it’s not as attractive as before. And as the number of apples purchased goes up, my costs keep increasing. I’ll need to spend more money on fuel to travel more of my property. At some point I won’t be able to do the work myself anymore, so I’ll need to pay others to work on the farm, and they’ll be slower at picking apples than me (less familiar with the property, less direct motivation, etc.). The point being: at some point, the number of apples can go high enough that the $0.50 price point no longer makes me any money. This kind of analysis is called *marginal cost*. It refers to the additional amount of expenditure a seller has to spend in order to produce each additional unit of the good. Marginal costs go up as quantity sold goes up. And like demand curves, if you aggregate this data across all sellers, you get a supply curve like this:  ## Equilibrium price We now know, for every price point, how many apples buyers will purchase, and how many apples sellers will sell. Now we find the equilibrium: where the supply and demand curves meet. This point represents where the marginal benefit a buyer would receive from the next buyer would be less than the cost it would take the next seller to make it. Let’s see it in a chart:  You’ll notice that these two graphs cross at the $1 price point, where 63 apples are both demanded (bought by consumers) and supplied (sold by producers). This is our equilibrium price. We also have a visualization of the *surplus* created by these trades. Everything to the left of the equilibrium point and between the supply and demand curves represents surplus: an area where someone is receiving something of more value than they give. For example: * When I bought my first apple for $1, but I was willing to spend $5, I made $4 of consumer surplus. The consumer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and above the equilibrium price point. * When a seller sells his first apple for $1, but it only cost $0.50 to produce it, the seller made $0.50 of producer surplus. The producer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and below the equilibrium price point. Another way of thinking of surplus is “every time someone got a better price than they would have been willing to take.” OK, with this in place, we now have enough information to figure out how to price in the tariff, which we’ll treat as a negative externality. ## Modeling taxes Alright, the government has now instituted a $0.50 tariff on every apple sold within the US by a foreign producer. We can generally model taxes by either increasing the marginal cost of each unit sold (shifting the supply curve up), or by decreasing the marginal benefit of each unit bought (shifting the demand curve down). In this case, since only some of the producers will pay the tax, it makes more sense to modify the supply curve. First, let’s see what happens to the foreign seller-only supply curve when you add in the tariff:  With the tariff in place, for each quantity level, the price at which the seller will sell is $0.50 higher than before the tariff. That makes sense: if I was previously willing to sell my 82nd apple for $3, I would now need to charge $3.50 for that apple to cover the cost of the tariff. We see this as the tariff “pushing up” or “pushing left” the original supply curve. We can add this new supply curve to our existing (unchanged) supply curve for domestic-only sellers, and we end up with a result like this:  The total supply curve adds up the individual foreign and domestic supply curves. At each price point, we add up the total quantity each group would be willing to sell to determine the total quantity supplied for each price point. Once we have that cumulative supply curve defined, we can produce an updated supply-and-demand chart including the tariff:  As we can see, the equilibrium has shifted: * The equilibrium price paid by consumers has risen from $1 to $1.20. * The total number of apples purchased has dropped from 63 apples to 60 apples. * Consumers therefore received 3 less apples. They spent $72 for these 60 apples, whereas previously they spent $63 for 3 more apples, a definite decrease in consumer surplus. * Foreign producers sold 36 of those apples (see the raw data in the linked Google Sheet), for a gross revenue of $43.20. However, they also need to pay the tariff to the US government, which accounts for $18, meaning they only receive $25.20 post-tariff. Previously, they sold 42 apples at $1 each with no tariff to be paid, meaning they took home $42. * Domestic producers sold the remaining 24 apples at $1.20, giving them a revenue of $28.80. Since they don’t pay the tariff, they take home all of that money. By contrast, previously, they sold 21 apples at $1, for a take-home of $21. * The government receives $0.50 for each of the 60 apples sold, or in other words receives $30 in revenue it wouldn’t have received otherwise. We could be more specific about the surpluses, and calculate the actual areas for consumer surplus, producer surplus, inefficiency from the tariff, and government revenue from the tariff. But I won’t bother, as those calculations get slightly more involved. Instead, let’s just look at the aggregate outcomes: * Consumers were unquestionably hurt. Their price paid went up by $0.20 per apple, and received less apples. * Foreign producers were also hurt. Their price received went down from the original $1 to the new post-tariff price of $1.20, minus the $0.50 tariff. In other words: foreign producers only receive $0.70 per apple now. This hurt can be mitigated by shifting sales to other countries without a tariff, but the pain will exist regardless. * Domestic producers scored. They can sell less apples and make more revenue doing it. * And the government walked away with an extra $30. Hopefully you now see the answer to the original questions. Importantly, while the government imposed a $0.50 tariff, neither side fully absorbed that cost. Consumers paid a bit more, foreign producers received a bit less. The exact details of how that tariff was split across the groups is mediated by the relevant supply and demand curves of each group. If you want to learn more about this, the relevant search term is “price elasticity,” or how much a group’s quantity supplied or demanded will change based on changes in the price. ## Other taxes Most taxes are some kind of a tax on trade. Tariffs on apples is an obvious one. But the same applies to income tax (taxing the worker for the trade of labor for money) or payroll tax (same thing, just taxing the employer instead). Interestingly, you can use the same model for analyzing things like tax incentives. For example, if the government decided to subsidize domestic apple production by giving the domestic producers a $0.50 bonus for each apple they sell, we would end up with a similar kind of analysis, except instead of the foreign supply curve shifting up, we’d see the domestic supply curve shifting down. And generally speaking, this is what you’ll *always* see with government involvement in the economy. It will result in disrupting an existing equilibrium, letting the market readjust to a new equilibrium, and incentivization of some behavior, causing some people to benefit and others to lose out. We saw with the apple tariff, domestic producers and the government benefited while others lost. You can see the reverse though with tax incentives. If I give a tax incentive of providing a deduction (not paying income tax) for preschool, we would end up with: * Government needs to make up the difference in tax revenue, either by raising taxes on others or printing more money (leading to inflation). Either way, those paying the tax or those holding government debased currency will pay a price. * Those people who don’t use the preschool deduction will receive no benefit, so they simply pay a cost. * Those who do use the preschool deduction will end up paying less on tax+preschool than they would have otherwise. This analysis is fully amoral. It’s not saying whether providing subsidized preschool is a good thing or not, it simply tells you where the costs will be felt, and points out that such government interference in free economic choice does result in inefficiencies in the system. Once you have that knowledge, you’re more well educated on making a decision about whether the costs of government intervention are worth the benefits.
@ e3ba5e1a:5e433365
2025-02-04 08:29:42President Trump has started rolling out his tariffs, something I [blogged about in November](https://www.snoyman.com/blog/2024/11/steelmanning-tariffs/). People are talking about these tariffs a lot right now, with many people (correctly) commenting on how consumers will end up with higher prices as a result of these tariffs. While that part is true, I’ve seen a lot of people taking it to the next, incorrect step: that consumers will pay the entirety of the tax. I [put up a poll on X](https://x.com/snoyberg/status/1886035800019599808) to see what people thought, and while the right answer got a lot of votes, it wasn't the winner.  For purposes of this blog post, our ultimate question will be the following: * Suppose apples currently sell for $1 each in the entire United States. * There are domestic sellers and foreign sellers of apples, all receiving the same price. * There are no taxes or tariffs on the purchase of apples. * The question is: if the US federal government puts a $0.50 import tariff per apple, what will be the change in the following: * Number of apples bought in the US * Price paid by buyers for apples in the US * Post-tax price received by domestic apple producers * Post-tax price received by foreign apple producers Before we can answer that question, we need to ask an easier, first question: before instituting the tariff, why do apples cost $1? And finally, before we dive into the details, let me provide you with the answers to the ultimate question. I recommend you try to guess these answers before reading this, and if you get it wrong, try to understand why: 1. The number of apples bought will go down 2. The buyers will pay more for each apple they buy, but not the full amount of the tariff 3. Domestic apple sellers will receive a *higher* price per apple 4. Foreign apple sellers will receive a *lower* price per apple, but not lowered by the full amount of the tariff In other words, regardless of who sends the payment to the government, both taxed parties (domestic buyers and foreign sellers) will absorb some of the costs of the tariff, while domestic sellers will benefit from the protectionism provided by tariffs and be able to sell at a higher price per unit. ## Marginal benefit All of the numbers discussed below are part of a [helper Google Sheet](https://docs.google.com/spreadsheets/d/14ZbkWpw1B9Q1UDB9Yh47DmdKQfIafVVBKbDUsSIfGZw/edit?usp=sharing) I put together for this analysis. Also, apologies about the jagged lines in the charts below, I hadn’t realized before starting on this that there are [some difficulties with creating supply and demand charts in Google Sheets](https://superuser.com/questions/1359731/how-to-create-a-supply-demand-style-chart). Let’s say I absolutely love apples, they’re my favorite food. How much would I be willing to pay for a single apple? You might say “$1, that’s the price in the supermarket,” and in many ways you’d be right. If I walk into supermarket A, see apples on sale for $50, and know that I can buy them at supermarket B for $1, I’ll almost certainly leave A and go buy at B. But that’s not what I mean. What I mean is: how high would the price of apples have to go *everywhere* so that I’d no longer be willing to buy a single apple? This is a purely personal, subjective opinion. It’s impacted by how much money I have available, other expenses I need to cover, and how much I like apples. But let’s say the number is $5. How much would I be willing to pay for another apple? Maybe another $5. But how much am I willing to pay for the 1,000th apple? 10,000th? At some point, I’ll get sick of apples, or run out of space to keep the apples, or not be able to eat, cook, and otherwise preserve all those apples before they rot. The point being: I’ll be progressively willing to spend less and less money for each apple. This form of analysis is called *marginal benefit*: how much benefit (expressed as dollars I’m willing to spend) will I receive from each apple? This is a downward sloping function: for each additional apple I buy (quantity demanded), the price I’m willing to pay goes down. This is what gives my personal *demand curve*. And if we aggregate demand curves across all market participants (meaning: everyone interested in buying apples), we end up with something like this:  Assuming no changes in people’s behavior and other conditions in the market, this chart tells us how many apples will be purchased by our buyers at each price point between $0.50 and $5. And ceteris paribus (all else being equal), this will continue to be the demand curve for apples. ## Marginal cost Demand is half the story of economics. The other half is supply, or: how many apples will I sell at each price point? Supply curves are upward sloping: the higher the price, the more a person or company is willing and able to sell a product. Let’s understand why. Suppose I have an apple orchard. It’s a large property right next to my house. With about 2 minutes of effort, I can walk out of my house, find the nearest tree, pick 5 apples off the tree, and call it a day. 5 apples for 2 minutes of effort is pretty good, right? Yes, there was all the effort necessary to buy the land, and plant the trees, and water them… and a bunch more than I likely can’t even guess at. We’re going to ignore all of that for our analysis, because for short-term supply-and-demand movement, we can ignore these kinds of *sunk costs*. One other simplification: in reality, supply curves often start descending before ascending. This accounts for achieving efficiencies of scale after the first number of units purchased. But since both these topics are unneeded for understanding taxes, I won’t go any further. Anyway, back to my apple orchard. If someone offers me $0.50 per apple, I can do 2 minutes of effort and get $2.50 in revenue, which equates to a $75/hour wage for me. I’m more than happy to pick apples at that price\! However, let’s say someone comes to buy 10,000 apples from me instead. I no longer just walk out to my nearest tree. I’m going to need to get in my truck, drive around, spend the day in the sun, pay for gas, take a day off of my day job (let’s say it pays me $70/hour). The costs go up significantly. Let’s say it takes 5 days to harvest all those apples myself, it costs me $100 in fuel and other expenses, and I lose out on my $70/hour job for 5 days. We end up with: * Total expenditure: $100 \+ $70 \* 8 hours a day \* 5 days \== $2900 * Total revenue: $5000 (10,000 apples at $0.50 each) * Total profit: $2100 So I’m still willing to sell the apples at this price, but it’s not as attractive as before. And as the number of apples purchased goes up, my costs keep increasing. I’ll need to spend more money on fuel to travel more of my property. At some point I won’t be able to do the work myself anymore, so I’ll need to pay others to work on the farm, and they’ll be slower at picking apples than me (less familiar with the property, less direct motivation, etc.). The point being: at some point, the number of apples can go high enough that the $0.50 price point no longer makes me any money. This kind of analysis is called *marginal cost*. It refers to the additional amount of expenditure a seller has to spend in order to produce each additional unit of the good. Marginal costs go up as quantity sold goes up. And like demand curves, if you aggregate this data across all sellers, you get a supply curve like this:  ## Equilibrium price We now know, for every price point, how many apples buyers will purchase, and how many apples sellers will sell. Now we find the equilibrium: where the supply and demand curves meet. This point represents where the marginal benefit a buyer would receive from the next buyer would be less than the cost it would take the next seller to make it. Let’s see it in a chart:  You’ll notice that these two graphs cross at the $1 price point, where 63 apples are both demanded (bought by consumers) and supplied (sold by producers). This is our equilibrium price. We also have a visualization of the *surplus* created by these trades. Everything to the left of the equilibrium point and between the supply and demand curves represents surplus: an area where someone is receiving something of more value than they give. For example: * When I bought my first apple for $1, but I was willing to spend $5, I made $4 of consumer surplus. The consumer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and above the equilibrium price point. * When a seller sells his first apple for $1, but it only cost $0.50 to produce it, the seller made $0.50 of producer surplus. The producer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and below the equilibrium price point. Another way of thinking of surplus is “every time someone got a better price than they would have been willing to take.” OK, with this in place, we now have enough information to figure out how to price in the tariff, which we’ll treat as a negative externality. ## Modeling taxes Alright, the government has now instituted a $0.50 tariff on every apple sold within the US by a foreign producer. We can generally model taxes by either increasing the marginal cost of each unit sold (shifting the supply curve up), or by decreasing the marginal benefit of each unit bought (shifting the demand curve down). In this case, since only some of the producers will pay the tax, it makes more sense to modify the supply curve. First, let’s see what happens to the foreign seller-only supply curve when you add in the tariff:  With the tariff in place, for each quantity level, the price at which the seller will sell is $0.50 higher than before the tariff. That makes sense: if I was previously willing to sell my 82nd apple for $3, I would now need to charge $3.50 for that apple to cover the cost of the tariff. We see this as the tariff “pushing up” or “pushing left” the original supply curve. We can add this new supply curve to our existing (unchanged) supply curve for domestic-only sellers, and we end up with a result like this:  The total supply curve adds up the individual foreign and domestic supply curves. At each price point, we add up the total quantity each group would be willing to sell to determine the total quantity supplied for each price point. Once we have that cumulative supply curve defined, we can produce an updated supply-and-demand chart including the tariff:  As we can see, the equilibrium has shifted: * The equilibrium price paid by consumers has risen from $1 to $1.20. * The total number of apples purchased has dropped from 63 apples to 60 apples. * Consumers therefore received 3 less apples. They spent $72 for these 60 apples, whereas previously they spent $63 for 3 more apples, a definite decrease in consumer surplus. * Foreign producers sold 36 of those apples (see the raw data in the linked Google Sheet), for a gross revenue of $43.20. However, they also need to pay the tariff to the US government, which accounts for $18, meaning they only receive $25.20 post-tariff. Previously, they sold 42 apples at $1 each with no tariff to be paid, meaning they took home $42. * Domestic producers sold the remaining 24 apples at $1.20, giving them a revenue of $28.80. Since they don’t pay the tariff, they take home all of that money. By contrast, previously, they sold 21 apples at $1, for a take-home of $21. * The government receives $0.50 for each of the 60 apples sold, or in other words receives $30 in revenue it wouldn’t have received otherwise. We could be more specific about the surpluses, and calculate the actual areas for consumer surplus, producer surplus, inefficiency from the tariff, and government revenue from the tariff. But I won’t bother, as those calculations get slightly more involved. Instead, let’s just look at the aggregate outcomes: * Consumers were unquestionably hurt. Their price paid went up by $0.20 per apple, and received less apples. * Foreign producers were also hurt. Their price received went down from the original $1 to the new post-tariff price of $1.20, minus the $0.50 tariff. In other words: foreign producers only receive $0.70 per apple now. This hurt can be mitigated by shifting sales to other countries without a tariff, but the pain will exist regardless. * Domestic producers scored. They can sell less apples and make more revenue doing it. * And the government walked away with an extra $30. Hopefully you now see the answer to the original questions. Importantly, while the government imposed a $0.50 tariff, neither side fully absorbed that cost. Consumers paid a bit more, foreign producers received a bit less. The exact details of how that tariff was split across the groups is mediated by the relevant supply and demand curves of each group. If you want to learn more about this, the relevant search term is “price elasticity,” or how much a group’s quantity supplied or demanded will change based on changes in the price. ## Other taxes Most taxes are some kind of a tax on trade. Tariffs on apples is an obvious one. But the same applies to income tax (taxing the worker for the trade of labor for money) or payroll tax (same thing, just taxing the employer instead). Interestingly, you can use the same model for analyzing things like tax incentives. For example, if the government decided to subsidize domestic apple production by giving the domestic producers a $0.50 bonus for each apple they sell, we would end up with a similar kind of analysis, except instead of the foreign supply curve shifting up, we’d see the domestic supply curve shifting down. And generally speaking, this is what you’ll *always* see with government involvement in the economy. It will result in disrupting an existing equilibrium, letting the market readjust to a new equilibrium, and incentivization of some behavior, causing some people to benefit and others to lose out. We saw with the apple tariff, domestic producers and the government benefited while others lost. You can see the reverse though with tax incentives. If I give a tax incentive of providing a deduction (not paying income tax) for preschool, we would end up with: * Government needs to make up the difference in tax revenue, either by raising taxes on others or printing more money (leading to inflation). Either way, those paying the tax or those holding government debased currency will pay a price. * Those people who don’t use the preschool deduction will receive no benefit, so they simply pay a cost. * Those who do use the preschool deduction will end up paying less on tax+preschool than they would have otherwise. This analysis is fully amoral. It’s not saying whether providing subsidized preschool is a good thing or not, it simply tells you where the costs will be felt, and points out that such government interference in free economic choice does result in inefficiencies in the system. Once you have that knowledge, you’re more well educated on making a decision about whether the costs of government intervention are worth the benefits. @ da0b9bc3:4e30a4a9
2025-02-04 07:52:55Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/875346
@ da0b9bc3:4e30a4a9
2025-02-04 07:52:55Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/875346 @ 23dea97f:72ed98dc
2025-02-04 07:29:36Post number 1
@ 23dea97f:72ed98dc
2025-02-04 07:29:36Post number 1 @ b7274d28:c99628cb
2025-02-04 05:31:13For anyone interested in the list of essential essays from nostr:npub14hn6p34vegy4ckeklz8jq93mendym9asw8z2ej87x2wuwf8werasc6a32x ([@anilsaidso](https://x.com/anilsaidso)) on Twitter that nostr:npub1h8nk2346qezka5cpm8jjh3yl5j88pf4ly2ptu7s6uu55wcfqy0wq36rpev mentioned on Read 856, here it is. I have compiled it with as many of the essays as I could find, along with the audio versions, when available. Additionally, if the author is on #Nostr, I have tagged their npub so you can thank them by zapping them some sats. All credit for this list and the graphics accompanying each entry goes to nostr:npub14hn6p34vegy4ckeklz8jq93mendym9asw8z2ej87x2wuwf8werasc6a32x, whose original thread can be found here: [Anil's Essential Essays Thread](https://x.com/anilsaidso/status/1290758632238276609)  ## 1.  > History shows us that the corruption of monetary systems leads to moral decay, social collapse, and slavery. Essay: https://breedlove22.medium.com/masters-and-slaves-of-money-255ecc93404f Audio: https://fountain.fm/episode/RI0iCGRCCYdhnMXIN3L6 ## 2.  > The 21st century emergence of Bitcoin, encryption, the internet, and millennials are more than just trends; they herald a wave of change that exhibits similar dynamics as the 16-17th century revolution that took place in Europe. Author: nostr:npub13l3lyslfzyscrqg8saw4r09y70702s6r025hz52sajqrvdvf88zskh8xc2 Essay: https://casebitcoin.com/docs/TheBitcoinReformation_TuurDemeester.pdf Audio: https://fountain.fm/episode/uLgBG2tyCLMlOp3g50EL ## 3.  > There are many men out there who will parrot the "debt is money WE owe OURSELVES" without acknowledging that "WE" isn't a static entity, but a collection of individuals at different points in their lives. Author: nostr:npub1guh5grefa7vkay4ps6udxg8lrqxg2kgr3qh9n4gduxut64nfxq0q9y6hjy Essay: https://www.tftc.io/issue-754-ludwig-von-mises-human-action/ Audio: https://fountain.fm/episode/UXacM2rkdcyjG9xp9O2l ## 4.  > If Bitcoin exists for 20 years, there will be near-universal confidence that it will be available forever, much as people believe the Internet is a permanent feature of the modern world. Essay: https://vijayboyapati.medium.com/the-bullish-case-for-bitcoin-6ecc8bdecc1 Audio: https://fountain.fm/episode/jC3KbxTkXVzXO4vR7X3W As you are surely aware, Vijay has expanded this into a book available here: [The Bullish Case for Bitcoin Book](https://www.bullishcaseforbitcoin.com/product-page/the-bullish-case-for-bitcoin-paperback-1) There is also an audio book version available here: [The Bullish Case for Bitcoin Audio Book](https://www.audible.com/pd/The-Bullish-Case-for-Bitcoin-Audiobook/B09QXR9GVL?eac_link=m4syoiXYyRJh&ref=web_search_eac_asin_1&eac_selected_type=asin&eac_selected=B09QXR9GVL&qid=2tIYC0F4Ya&eac_id=135-0887332-3379864_2tIYC0F4Ya&sr=1-1) ## 5.  > This realignment would not be traditional right vs left, but rather land vs cloud, state vs network, centralized vs decentralized, new money vs old, internationalist/capitalist vs nationalist/socialist, MMT vs BTC,...Hamilton vs Satoshi. Essay: https://nakamoto.com/bitcoin-becomes-the-flag-of-technology/ Audio: https://fountain.fm/episode/tFJKjYLKhiFY8voDssZc ## 6. [Gradually, Then Suddenly](https://relay.brightbolt.net/fa4196f5c6183bda153e2e3c9911909d289b5a428852f5f07f7c1991191e7489.jpg) > I became convinced that, whether bitcoin survives or not, the existing financial system is working on borrowed time. Essay: https://nakamotoinstitute.org/mempool/gradually-then-suddenly/ Audio: https://fountain.fm/episode/Mf6hgTFUNESqvdxEIOGZ Parker Lewis went on to release several more articles in the Gradually, Then Suddenly series. They can be found here: [Gradually, Then Suddenly Series](https://nakamotoinstitute.org/mempool/series/gradually-then-suddenly/) nostr:npub1h8nk2346qezka5cpm8jjh3yl5j88pf4ly2ptu7s6uu55wcfqy0wq36rpev has, of course, read all of them for us. Listing them all here is beyond the scope of this article, but you can find them by searching the podcast feed here: [Bitcoin Audible Feed](https://fountain.fm/show/RtZlWdbEbpyEyjBNbeQ7) Finally, Parker Lewis has refined these articles and released them as a book, which is available here: [Gradually, Then Suddenly Book](https://academy.saifedean.com/product/gradually-then-suddenly-hardcover/) ## 7.  > Bitcoin is a beautifully-constructed protocol. Genius is apparent in its design to most people who study it in depth, in terms of the way it blends math, computer science, cyber security, monetary economics, and game theory. Author: nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a Essay: https://www.lynalden.com/invest-in-bitcoin/ Audio: https://fountain.fm/episode/axeqKBvYCSP1s9aJIGSe ## 8.  > Bitcoin offers a sweeping vista of opportunity to re-imagine how the financial system can and should work in the Internet era.. Essay: https://archive.nytimes.com/dealbook.nytimes.com/2014/01/21/why-bitcoin-matters/ ## 9.  > Using Bitcoin for consumer purchases is akin to driving a Concorde jet down the street to pick up groceries: a ridiculously expensive waste of an astonishing tool. Author: nostr:npub1gdu7w6l6w65qhrdeaf6eyywepwe7v7ezqtugsrxy7hl7ypjsvxksd76nak Essay: https://nakamotoinstitute.org/mempool/economics-of-bitcoin-as-a-settlement-network/ Audio: https://fountain.fm/episode/JoSpRFWJtoogn3lvTYlz ## 10.  > The Internet is a dumb network, which is its defining and most valuable feature. The Internet’s protocol (..) doesn’t offer “services.” It doesn’t make decisions about content. It doesn’t distinguish between photos, text, video and audio. Essay: https://fee.org/articles/decentralization-why-dumb-networks-are-better/ Audio: https://fountain.fm/episode/b7gOEqmWxn8RiDziffXf ## 11.  > Most people are only familiar with (b)itcoin the electronic currency, but more important is (B)itcoin, with a capital B, the underlying protocol, which encapsulates and distributes the functions of contract law. I was unable to find this essay or any audio version. Clicking on Anil's original link took me to Naval's blog, but that particular entry seems to have been removed. ## 12.  > Bitcoin can approximate unofficial exchange rates which, in turn, can be used to detect both the existence and the magnitude of the distortion caused by capital controls & exchange rate manipulations. Essay: https://papers.ssrn.com/sol3/Papers.cfm?abstract_id=2714921 ## 13.  > You can create something which looks cosmetically similar to Bitcoin, but you cannot replicate the settlement assurances which derive from the costliness of the ledger. Essay: https://medium.com/@nic__carter/its-the-settlement-assurances-stupid-5dcd1c3f4e41 Audio: https://fountain.fm/episode/5NoPoiRU4NtF2YQN5QI1 ## 14.  > When we can secure the most important functionality of a financial network by computer science... we go from a system that is manual, local, and of inconsistent security to one that is automated, global, and much more secure. Essay: https://nakamotoinstitute.org/library/money-blockchains-and-social-scalability/ Audio: https://fountain.fm/episode/VMH9YmGVCF8c3I5zYkrc ## 15.  > The BCB enforces the strictest deposit regulations in the world by requiring full reserves for all accounts. ..money is not destroyed when bank debts are repaid, so increased money hoarding does not cause liquidity traps.. Author: nostr:npub1hxwmegqcfgevu4vsfjex0v3wgdyz8jtlgx8ndkh46t0lphtmtsnsuf40pf Essay: https://nakamotoinstitute.org/mempool/the-bitcoin-central-banks-perfect-monetary-policy/ Audio: https://fountain.fm/episode/ralOokFfhFfeZpYnGAsD ## 16.  > When Satoshi announced Bitcoin on the cryptography mailing list, he got a skeptical reception at best. Cryptographers have seen too many grand schemes by clueless noobs. They tend to have a knee jerk reaction. Essay: https://nakamotoinstitute.org/library/bitcoin-and-me/ Audio: https://fountain.fm/episode/Vx8hKhLZkkI4cq97qS4Z ## 17.  > No matter who you are, or how big your company is, **𝙮𝙤𝙪𝙧 𝙩𝙧𝙖𝙣𝙨𝙖𝙘𝙩𝙞𝙤𝙣 𝙬𝙤𝙣’𝙩 𝙥𝙧𝙤𝙥𝙖𝙜𝙖𝙩𝙚 𝙞𝙛 𝙞𝙩’𝙨 𝙞𝙣𝙫𝙖𝙡𝙞𝙙.** Essay: https://nakamotoinstitute.org/mempool/bitcoin-miners-beware-invalid-blocks-need-not-apply/ Audio: https://fountain.fm/episode/bcSuBGmOGY2TecSov4rC ## 18.  > Just like a company trying to protect itself from being destroyed by a new competitor, the actions and reactions of central banks and policy makers to protect the system that they know, are quite predictable. Author: nostr:npub1s05p3ha7en49dv8429tkk07nnfa9pcwczkf5x5qrdraqshxdje9sq6eyhe Essay: https://medium.com/the-bitcoin-times/the-greatest-game-b787ac3242b2 Audio Part 1: https://fountain.fm/episode/5bYyGRmNATKaxminlvco Audio Part 2: https://fountain.fm/episode/92eU3h6gqbzng84zqQPZ ## 19.  > Technology, industry, and society have advanced immeasurably since, and yet we still live by Venetian financial customs and have no idea why. Modern banking is the legacy of a problem that technology has since solved. Author: nostr:npub1sfhflz2msx45rfzjyf5tyj0x35pv4qtq3hh4v2jf8nhrtl79cavsl2ymqt Essay: https://allenfarrington.medium.com/bitcoin-is-venice-8414dda42070 Audio: https://fountain.fm/episode/s6Fu2VowAddRACCCIxQh Allen Farrington and Sacha Meyers have gone on to expand this into a book, as well. You can get the book here: [Bitcoin is Venice Book](https://www.amazon.com/Bitcoin-Venice-Essays-Future-Capitalism/dp/B09TTTGT11) And wouldn't you know it, Guy Swann has narrated the audio book available here: [Bitcoin is Venice Audio Book](https://www.audible.com/pd/Bitcoin-is-Venice-Audiobook/B0CCQD539W?eac_link=yrZ4RxHupcgL&ref=web_search_eac_asin_1&eac_selected_type=asin&eac_selected=B0CCQD539W&qid=pL7jjJ13ia&eac_id=135-0887332-3379864_pL7jjJ13ia&sr=1-1) ## 20.  > The rich and powerful will always design systems that benefit them before everyone else. The genius of Bitcoin is to take advantage of that very base reality and force them to get involved and help run the system, instead of attacking it. Author: nostr:npub1trr5r2nrpsk6xkjk5a7p6pfcryyt6yzsflwjmz6r7uj7lfkjxxtq78hdpu Essay: https://quillette.com/2021/02/21/can-governments-stop-bitcoin/ Audio: https://fountain.fm/episode/jeZ21IWIlbuC1OGnssy8 ## 21.  > In the realm of information, there is no coin-stamping without time-stamping. The relentless beating of this clock is what gives rise to all the magical properties of Bitcoin. Author: nostr:npub1dergggklka99wwrs92yz8wdjs952h2ux2ha2ed598ngwu9w7a6fsh9xzpc Essay: https://dergigi.com/2021/01/14/bitcoin-is-time/ Audio: https://fountain.fm/episode/pTevCY2vwanNsIso6F6X ## 22.  > You can stay on the Fiat Standard, in which some people get to produce unlimited new units of money for free, just not you. Or opt in to the Bitcoin Standard, in which no one gets to do that, including you. Essay: https://casebitcoin.com/docs/StoneRidge_2020_Shareholder_Letter.pdf Audio: https://fountain.fm/episode/PhBTa39qwbkwAtRnO38W ## 23.  > Long term investors should use Bitcoin as their unit of account and every single investment should be compared to the expected returns of Bitcoin. Essay: https://nakamotoinstitute.org/mempool/everyones-a-scammer/ Audio: https://fountain.fm/episode/vyR2GUNfXtKRK8qwznki ## 24.  > When you’re in the ivory tower, you think the term “ivory tower” is a silly misrepresentation of your very normal life; when you’re no longer in the ivory tower, you realize how willfully out of touch you were with the world. Essay: https://www.citadel21.com/why-the-yuppie-elite-dismiss-bitcoin Audio: https://fountain.fm/episode/7do5K4pPNljOf2W3rR2V You might notice that many of the above essays are available from the [Satoshi Nakamoto Institute](https://nakamotoinstitute.org/). It is a veritable treasure trove of excellent writing on subjects surrounding #Bitcoin and #AustrianEconomics. If you find value in them keeping these written works online for the next wave of new Bitcoiners to have an excellent source of education, please consider [donating](https://pay.zaprite.com/pl_vNYDp4YBSd) to the cause.
@ b7274d28:c99628cb
2025-02-04 05:31:13For anyone interested in the list of essential essays from nostr:npub14hn6p34vegy4ckeklz8jq93mendym9asw8z2ej87x2wuwf8werasc6a32x ([@anilsaidso](https://x.com/anilsaidso)) on Twitter that nostr:npub1h8nk2346qezka5cpm8jjh3yl5j88pf4ly2ptu7s6uu55wcfqy0wq36rpev mentioned on Read 856, here it is. I have compiled it with as many of the essays as I could find, along with the audio versions, when available. Additionally, if the author is on #Nostr, I have tagged their npub so you can thank them by zapping them some sats. All credit for this list and the graphics accompanying each entry goes to nostr:npub14hn6p34vegy4ckeklz8jq93mendym9asw8z2ej87x2wuwf8werasc6a32x, whose original thread can be found here: [Anil's Essential Essays Thread](https://x.com/anilsaidso/status/1290758632238276609)  ## 1.  > History shows us that the corruption of monetary systems leads to moral decay, social collapse, and slavery. Essay: https://breedlove22.medium.com/masters-and-slaves-of-money-255ecc93404f Audio: https://fountain.fm/episode/RI0iCGRCCYdhnMXIN3L6 ## 2.  > The 21st century emergence of Bitcoin, encryption, the internet, and millennials are more than just trends; they herald a wave of change that exhibits similar dynamics as the 16-17th century revolution that took place in Europe. Author: nostr:npub13l3lyslfzyscrqg8saw4r09y70702s6r025hz52sajqrvdvf88zskh8xc2 Essay: https://casebitcoin.com/docs/TheBitcoinReformation_TuurDemeester.pdf Audio: https://fountain.fm/episode/uLgBG2tyCLMlOp3g50EL ## 3.  > There are many men out there who will parrot the "debt is money WE owe OURSELVES" without acknowledging that "WE" isn't a static entity, but a collection of individuals at different points in their lives. Author: nostr:npub1guh5grefa7vkay4ps6udxg8lrqxg2kgr3qh9n4gduxut64nfxq0q9y6hjy Essay: https://www.tftc.io/issue-754-ludwig-von-mises-human-action/ Audio: https://fountain.fm/episode/UXacM2rkdcyjG9xp9O2l ## 4.  > If Bitcoin exists for 20 years, there will be near-universal confidence that it will be available forever, much as people believe the Internet is a permanent feature of the modern world. Essay: https://vijayboyapati.medium.com/the-bullish-case-for-bitcoin-6ecc8bdecc1 Audio: https://fountain.fm/episode/jC3KbxTkXVzXO4vR7X3W As you are surely aware, Vijay has expanded this into a book available here: [The Bullish Case for Bitcoin Book](https://www.bullishcaseforbitcoin.com/product-page/the-bullish-case-for-bitcoin-paperback-1) There is also an audio book version available here: [The Bullish Case for Bitcoin Audio Book](https://www.audible.com/pd/The-Bullish-Case-for-Bitcoin-Audiobook/B09QXR9GVL?eac_link=m4syoiXYyRJh&ref=web_search_eac_asin_1&eac_selected_type=asin&eac_selected=B09QXR9GVL&qid=2tIYC0F4Ya&eac_id=135-0887332-3379864_2tIYC0F4Ya&sr=1-1) ## 5.  > This realignment would not be traditional right vs left, but rather land vs cloud, state vs network, centralized vs decentralized, new money vs old, internationalist/capitalist vs nationalist/socialist, MMT vs BTC,...Hamilton vs Satoshi. Essay: https://nakamoto.com/bitcoin-becomes-the-flag-of-technology/ Audio: https://fountain.fm/episode/tFJKjYLKhiFY8voDssZc ## 6. [Gradually, Then Suddenly](https://relay.brightbolt.net/fa4196f5c6183bda153e2e3c9911909d289b5a428852f5f07f7c1991191e7489.jpg) > I became convinced that, whether bitcoin survives or not, the existing financial system is working on borrowed time. Essay: https://nakamotoinstitute.org/mempool/gradually-then-suddenly/ Audio: https://fountain.fm/episode/Mf6hgTFUNESqvdxEIOGZ Parker Lewis went on to release several more articles in the Gradually, Then Suddenly series. They can be found here: [Gradually, Then Suddenly Series](https://nakamotoinstitute.org/mempool/series/gradually-then-suddenly/) nostr:npub1h8nk2346qezka5cpm8jjh3yl5j88pf4ly2ptu7s6uu55wcfqy0wq36rpev has, of course, read all of them for us. Listing them all here is beyond the scope of this article, but you can find them by searching the podcast feed here: [Bitcoin Audible Feed](https://fountain.fm/show/RtZlWdbEbpyEyjBNbeQ7) Finally, Parker Lewis has refined these articles and released them as a book, which is available here: [Gradually, Then Suddenly Book](https://academy.saifedean.com/product/gradually-then-suddenly-hardcover/) ## 7.  > Bitcoin is a beautifully-constructed protocol. Genius is apparent in its design to most people who study it in depth, in terms of the way it blends math, computer science, cyber security, monetary economics, and game theory. Author: nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a Essay: https://www.lynalden.com/invest-in-bitcoin/ Audio: https://fountain.fm/episode/axeqKBvYCSP1s9aJIGSe ## 8.  > Bitcoin offers a sweeping vista of opportunity to re-imagine how the financial system can and should work in the Internet era.. Essay: https://archive.nytimes.com/dealbook.nytimes.com/2014/01/21/why-bitcoin-matters/ ## 9.  > Using Bitcoin for consumer purchases is akin to driving a Concorde jet down the street to pick up groceries: a ridiculously expensive waste of an astonishing tool. Author: nostr:npub1gdu7w6l6w65qhrdeaf6eyywepwe7v7ezqtugsrxy7hl7ypjsvxksd76nak Essay: https://nakamotoinstitute.org/mempool/economics-of-bitcoin-as-a-settlement-network/ Audio: https://fountain.fm/episode/JoSpRFWJtoogn3lvTYlz ## 10.  > The Internet is a dumb network, which is its defining and most valuable feature. The Internet’s protocol (..) doesn’t offer “services.” It doesn’t make decisions about content. It doesn’t distinguish between photos, text, video and audio. Essay: https://fee.org/articles/decentralization-why-dumb-networks-are-better/ Audio: https://fountain.fm/episode/b7gOEqmWxn8RiDziffXf ## 11.  > Most people are only familiar with (b)itcoin the electronic currency, but more important is (B)itcoin, with a capital B, the underlying protocol, which encapsulates and distributes the functions of contract law. I was unable to find this essay or any audio version. Clicking on Anil's original link took me to Naval's blog, but that particular entry seems to have been removed. ## 12.  > Bitcoin can approximate unofficial exchange rates which, in turn, can be used to detect both the existence and the magnitude of the distortion caused by capital controls & exchange rate manipulations. Essay: https://papers.ssrn.com/sol3/Papers.cfm?abstract_id=2714921 ## 13.  > You can create something which looks cosmetically similar to Bitcoin, but you cannot replicate the settlement assurances which derive from the costliness of the ledger. Essay: https://medium.com/@nic__carter/its-the-settlement-assurances-stupid-5dcd1c3f4e41 Audio: https://fountain.fm/episode/5NoPoiRU4NtF2YQN5QI1 ## 14.  > When we can secure the most important functionality of a financial network by computer science... we go from a system that is manual, local, and of inconsistent security to one that is automated, global, and much more secure. Essay: https://nakamotoinstitute.org/library/money-blockchains-and-social-scalability/ Audio: https://fountain.fm/episode/VMH9YmGVCF8c3I5zYkrc ## 15.  > The BCB enforces the strictest deposit regulations in the world by requiring full reserves for all accounts. ..money is not destroyed when bank debts are repaid, so increased money hoarding does not cause liquidity traps.. Author: nostr:npub1hxwmegqcfgevu4vsfjex0v3wgdyz8jtlgx8ndkh46t0lphtmtsnsuf40pf Essay: https://nakamotoinstitute.org/mempool/the-bitcoin-central-banks-perfect-monetary-policy/ Audio: https://fountain.fm/episode/ralOokFfhFfeZpYnGAsD ## 16.  > When Satoshi announced Bitcoin on the cryptography mailing list, he got a skeptical reception at best. Cryptographers have seen too many grand schemes by clueless noobs. They tend to have a knee jerk reaction. Essay: https://nakamotoinstitute.org/library/bitcoin-and-me/ Audio: https://fountain.fm/episode/Vx8hKhLZkkI4cq97qS4Z ## 17.  > No matter who you are, or how big your company is, **𝙮𝙤𝙪𝙧 𝙩𝙧𝙖𝙣𝙨𝙖𝙘𝙩𝙞𝙤𝙣 𝙬𝙤𝙣’𝙩 𝙥𝙧𝙤𝙥𝙖𝙜𝙖𝙩𝙚 𝙞𝙛 𝙞𝙩’𝙨 𝙞𝙣𝙫𝙖𝙡𝙞𝙙.** Essay: https://nakamotoinstitute.org/mempool/bitcoin-miners-beware-invalid-blocks-need-not-apply/ Audio: https://fountain.fm/episode/bcSuBGmOGY2TecSov4rC ## 18.  > Just like a company trying to protect itself from being destroyed by a new competitor, the actions and reactions of central banks and policy makers to protect the system that they know, are quite predictable. Author: nostr:npub1s05p3ha7en49dv8429tkk07nnfa9pcwczkf5x5qrdraqshxdje9sq6eyhe Essay: https://medium.com/the-bitcoin-times/the-greatest-game-b787ac3242b2 Audio Part 1: https://fountain.fm/episode/5bYyGRmNATKaxminlvco Audio Part 2: https://fountain.fm/episode/92eU3h6gqbzng84zqQPZ ## 19.  > Technology, industry, and society have advanced immeasurably since, and yet we still live by Venetian financial customs and have no idea why. Modern banking is the legacy of a problem that technology has since solved. Author: nostr:npub1sfhflz2msx45rfzjyf5tyj0x35pv4qtq3hh4v2jf8nhrtl79cavsl2ymqt Essay: https://allenfarrington.medium.com/bitcoin-is-venice-8414dda42070 Audio: https://fountain.fm/episode/s6Fu2VowAddRACCCIxQh Allen Farrington and Sacha Meyers have gone on to expand this into a book, as well. You can get the book here: [Bitcoin is Venice Book](https://www.amazon.com/Bitcoin-Venice-Essays-Future-Capitalism/dp/B09TTTGT11) And wouldn't you know it, Guy Swann has narrated the audio book available here: [Bitcoin is Venice Audio Book](https://www.audible.com/pd/Bitcoin-is-Venice-Audiobook/B0CCQD539W?eac_link=yrZ4RxHupcgL&ref=web_search_eac_asin_1&eac_selected_type=asin&eac_selected=B0CCQD539W&qid=pL7jjJ13ia&eac_id=135-0887332-3379864_pL7jjJ13ia&sr=1-1) ## 20.  > The rich and powerful will always design systems that benefit them before everyone else. The genius of Bitcoin is to take advantage of that very base reality and force them to get involved and help run the system, instead of attacking it. Author: nostr:npub1trr5r2nrpsk6xkjk5a7p6pfcryyt6yzsflwjmz6r7uj7lfkjxxtq78hdpu Essay: https://quillette.com/2021/02/21/can-governments-stop-bitcoin/ Audio: https://fountain.fm/episode/jeZ21IWIlbuC1OGnssy8 ## 21.  > In the realm of information, there is no coin-stamping without time-stamping. The relentless beating of this clock is what gives rise to all the magical properties of Bitcoin. Author: nostr:npub1dergggklka99wwrs92yz8wdjs952h2ux2ha2ed598ngwu9w7a6fsh9xzpc Essay: https://dergigi.com/2021/01/14/bitcoin-is-time/ Audio: https://fountain.fm/episode/pTevCY2vwanNsIso6F6X ## 22.  > You can stay on the Fiat Standard, in which some people get to produce unlimited new units of money for free, just not you. Or opt in to the Bitcoin Standard, in which no one gets to do that, including you. Essay: https://casebitcoin.com/docs/StoneRidge_2020_Shareholder_Letter.pdf Audio: https://fountain.fm/episode/PhBTa39qwbkwAtRnO38W ## 23.  > Long term investors should use Bitcoin as their unit of account and every single investment should be compared to the expected returns of Bitcoin. Essay: https://nakamotoinstitute.org/mempool/everyones-a-scammer/ Audio: https://fountain.fm/episode/vyR2GUNfXtKRK8qwznki ## 24.  > When you’re in the ivory tower, you think the term “ivory tower” is a silly misrepresentation of your very normal life; when you’re no longer in the ivory tower, you realize how willfully out of touch you were with the world. Essay: https://www.citadel21.com/why-the-yuppie-elite-dismiss-bitcoin Audio: https://fountain.fm/episode/7do5K4pPNljOf2W3rR2V You might notice that many of the above essays are available from the [Satoshi Nakamoto Institute](https://nakamotoinstitute.org/). It is a veritable treasure trove of excellent writing on subjects surrounding #Bitcoin and #AustrianEconomics. If you find value in them keeping these written works online for the next wave of new Bitcoiners to have an excellent source of education, please consider [donating](https://pay.zaprite.com/pl_vNYDp4YBSd) to the cause. @ 91bea5cd:1df4451c
2025-02-04 05:24:47Novia é uma ferramenta inovadora que facilita o arquivamento de vídeos e sua integração com a rede NOSTR (Notes and Other Stuff Transmitted over Relay). Funcionando como uma ponte entre ferramentas de arquivamento de vídeo tradicionais e a plataforma descentralizada, Novia oferece uma solução autônoma para a preservação e compartilhamento de conteúdo audiovisual. ### Arquitetura e Funcionamento A arquitetura de Novia é dividida em duas partes principais: * **Frontend:** Atua como a interface do usuário, responsável por solicitar o arquivamento de vídeos. Essas solicitações são encaminhadas para o backend. * **Backend:** Processa as solicitações de arquivamento, baixando o vídeo, suas descrições e a imagem de capa associada. Este componente é conectado a um ou mais relays NOSTR, permitindo a indexação e descoberta do conteúdo arquivado. O processo de arquivamento é automatizado: após o download, o vídeo fica disponível no frontend para que o usuário possa solicitar o upload para um servidor Blossom de sua escolha. ### Como Utilizar Novia 1. **Acesso:** Navegue até [https://npub126uz2g6ft45qs0m0rnvtvtp7glcfd23pemrzz0wnt8r5vlhr9ufqnsmvg8.nsite.lol](https://npub126uz2g6ft45qs0m0rnvtvtp7glcfd23pemrzz0wnt8r5vlhr9ufqnsmvg8.nsite.lol). 2. **Login:** Utilize uma extensão de navegador compatível com NOSTR para autenticar-se. 3. **Execução via Docker:** A forma mais simples de executar o backend é através de um container Docker. Execute o seguinte comando: ```bash docker run -it --rm -p 9090:9090 -v ./nostr/data:/data --add-host=host.docker.internal:host-gateway teamnovia/novia ``` Este comando cria um container, mapeia a porta 9090 para o host e monta o diretório `./nostr/data` para persistir os dados. ### Configuração Avançada Novia oferece amplas opções de configuração através de um arquivo `yaml`. Abaixo, um exemplo comentado: ```yaml mediaStores: - id: media type: local path: /data/media watch: true database: /data/novia.db download: enabled: true ytdlpPath: yt-dlp ytdlpCookies: ./cookies.txt tempPath: /tmp targetStoreId: media secret: false publish: enabled: true key: nsec thumbnailUpload: - https://nostr.download videoUpload: - url: https://nostr.download maxUploadSizeMB: 300 cleanUpMaxAgeDays: 5 cleanUpKeepSizeUnderMB: 2 - url: https://files.v0l.io maxUploadSizeMB: 300 cleanUpMaxAgeDays: 5 cleanUpKeepSizeUnderMB: 2 - url: https://nosto.re maxUploadSizeMB: 300 cleanUpMaxAgeDays: 5 cleanUpKeepSizeUnderMB: 2 - url: https://blossom.primal.net maxUploadSizeMB: 300 cleanUpMaxAgeDays: 5 cleanUpKeepSizeUnderMB: 2 relays: - ws://host.docker.internal:4869 - wss://bostr.bitcointxoko.com secret: false autoUpload: enabled: true maxVideoSizeMB: 100 fetch: enabled: false fetchVideoLimitMB: 10 relays: - <a relay with the video events to mirror> match: - nostr - bitcoin server: port: 9090 enabled: true ``` **Explicação das Configurações:** * **`mediaStores`**: Define onde os arquivos de mídia serão armazenados (localmente, neste exemplo). * **`database`**: Especifica o local do banco de dados. * **`download`**: Controla as configurações de download de vídeos, incluindo o caminho para o `yt-dlp` e um arquivo de cookies para autenticação. * **`publish`**: Configura a publicação de vídeos e thumbnails no NOSTR, incluindo a chave privada (`nsec`), servidores de upload e relays. **Atenção:** Mantenha sua chave privada em segredo. * **`fetch`**: Permite buscar eventos de vídeo de relays NOSTR para arquivamento. * **`server`**: Define as configurações do servidor web interno de Novia. ### Conclusão Novia surge como uma ferramenta promissora para o arquivamento e a integração de vídeos com o ecossistema NOSTR. Sua arquitetura modular, combinada com opções de configuração flexíveis, a tornam uma solução poderosa para usuários que buscam preservar e compartilhar conteúdo audiovisual de forma descentralizada e resistente à censura. A utilização de Docker simplifica a implantação e o gerenciamento da ferramenta. Para obter mais informações e explorar o código-fonte, visite o repositório do projeto no GitHub: [https://github.com/teamnovia/novia](https://github.com/teamnovia/novia).
@ 91bea5cd:1df4451c
2025-02-04 05:24:47Novia é uma ferramenta inovadora que facilita o arquivamento de vídeos e sua integração com a rede NOSTR (Notes and Other Stuff Transmitted over Relay). Funcionando como uma ponte entre ferramentas de arquivamento de vídeo tradicionais e a plataforma descentralizada, Novia oferece uma solução autônoma para a preservação e compartilhamento de conteúdo audiovisual. ### Arquitetura e Funcionamento A arquitetura de Novia é dividida em duas partes principais: * **Frontend:** Atua como a interface do usuário, responsável por solicitar o arquivamento de vídeos. Essas solicitações são encaminhadas para o backend. * **Backend:** Processa as solicitações de arquivamento, baixando o vídeo, suas descrições e a imagem de capa associada. Este componente é conectado a um ou mais relays NOSTR, permitindo a indexação e descoberta do conteúdo arquivado. O processo de arquivamento é automatizado: após o download, o vídeo fica disponível no frontend para que o usuário possa solicitar o upload para um servidor Blossom de sua escolha. ### Como Utilizar Novia 1. **Acesso:** Navegue até [https://npub126uz2g6ft45qs0m0rnvtvtp7glcfd23pemrzz0wnt8r5vlhr9ufqnsmvg8.nsite.lol](https://npub126uz2g6ft45qs0m0rnvtvtp7glcfd23pemrzz0wnt8r5vlhr9ufqnsmvg8.nsite.lol). 2. **Login:** Utilize uma extensão de navegador compatível com NOSTR para autenticar-se. 3. **Execução via Docker:** A forma mais simples de executar o backend é através de um container Docker. Execute o seguinte comando: ```bash docker run -it --rm -p 9090:9090 -v ./nostr/data:/data --add-host=host.docker.internal:host-gateway teamnovia/novia ``` Este comando cria um container, mapeia a porta 9090 para o host e monta o diretório `./nostr/data` para persistir os dados. ### Configuração Avançada Novia oferece amplas opções de configuração através de um arquivo `yaml`. Abaixo, um exemplo comentado: ```yaml mediaStores: - id: media type: local path: /data/media watch: true database: /data/novia.db download: enabled: true ytdlpPath: yt-dlp ytdlpCookies: ./cookies.txt tempPath: /tmp targetStoreId: media secret: false publish: enabled: true key: nsec thumbnailUpload: - https://nostr.download videoUpload: - url: https://nostr.download maxUploadSizeMB: 300 cleanUpMaxAgeDays: 5 cleanUpKeepSizeUnderMB: 2 - url: https://files.v0l.io maxUploadSizeMB: 300 cleanUpMaxAgeDays: 5 cleanUpKeepSizeUnderMB: 2 - url: https://nosto.re maxUploadSizeMB: 300 cleanUpMaxAgeDays: 5 cleanUpKeepSizeUnderMB: 2 - url: https://blossom.primal.net maxUploadSizeMB: 300 cleanUpMaxAgeDays: 5 cleanUpKeepSizeUnderMB: 2 relays: - ws://host.docker.internal:4869 - wss://bostr.bitcointxoko.com secret: false autoUpload: enabled: true maxVideoSizeMB: 100 fetch: enabled: false fetchVideoLimitMB: 10 relays: - <a relay with the video events to mirror> match: - nostr - bitcoin server: port: 9090 enabled: true ``` **Explicação das Configurações:** * **`mediaStores`**: Define onde os arquivos de mídia serão armazenados (localmente, neste exemplo). * **`database`**: Especifica o local do banco de dados. * **`download`**: Controla as configurações de download de vídeos, incluindo o caminho para o `yt-dlp` e um arquivo de cookies para autenticação. * **`publish`**: Configura a publicação de vídeos e thumbnails no NOSTR, incluindo a chave privada (`nsec`), servidores de upload e relays. **Atenção:** Mantenha sua chave privada em segredo. * **`fetch`**: Permite buscar eventos de vídeo de relays NOSTR para arquivamento. * **`server`**: Define as configurações do servidor web interno de Novia. ### Conclusão Novia surge como uma ferramenta promissora para o arquivamento e a integração de vídeos com o ecossistema NOSTR. Sua arquitetura modular, combinada com opções de configuração flexíveis, a tornam uma solução poderosa para usuários que buscam preservar e compartilhar conteúdo audiovisual de forma descentralizada e resistente à censura. A utilização de Docker simplifica a implantação e o gerenciamento da ferramenta. Para obter mais informações e explorar o código-fonte, visite o repositório do projeto no GitHub: [https://github.com/teamnovia/novia](https://github.com/teamnovia/novia). @ 3ffac3a6:2d656657
2025-02-04 04:31:26In the waning days of the 20th century, a woman named Annabelle Nolan was born into an unremarkable world, though she herself was anything but ordinary. A prodigy in cryptography and quantum computing, she would later adopt the pseudonym Satoshi Nakamoto, orchestrating the creation of Bitcoin in the early 21st century. But her legacy would stretch far beyond the blockchain. Annabelle's obsession with cryptography was not just about securing data—it was about securing freedom. Her work in quantum computing inadvertently triggered a cascade of temporal anomalies, one of which ensnared her in 2011. The event was cataclysmic yet silent, unnoticed by the world she'd transformed. In an instant, she was torn from her era and thrust violently back into the 16th century. Disoriented and stripped of her futuristic tools, Annabelle faced a brutal reality: survive in a world where her knowledge was both a curse and a weapon. Reinventing herself as Anne Boleyn, she navigated the treacherous courts of Tudor England with the same strategic brilliance she'd used to design Bitcoin. Her intellect dazzled King Henry VIII, but it was the mysterious necklace she wore—adorned with a bold, stylized "B"—that fueled whispers. It was more than jewelry; it was a relic of a forgotten future, a silent beacon for any historian clever enough to decode her true story. Anne's fate seemed sealed as she ascended to queenship, her influence growing alongside her enemies. Yet beneath the royal intrigue, she harbored a desperate hope: that the symbol around her neck would outlast her, sparking curiosity in minds centuries away. The "B" was her signature, a cryptographic clue embedded in history. On the scaffold in 1536, as she faced her execution, Anne Boleyn's gaze was unwavering. She knew her death was not the end. Somewhere, in dusty archives and encrypted ledgers, her mark endured. Historians would puzzle over the enigmatic "B," and perhaps one day, someone would connect the dots between a queen, a coin, and a time anomaly born from quantum code. She wasn't just Anne Boleyn. She was Satoshi Nakamoto, the time-displaced architect of a decentralized future, hiding in plain sight within the annals of history.
@ 3ffac3a6:2d656657
2025-02-04 04:31:26In the waning days of the 20th century, a woman named Annabelle Nolan was born into an unremarkable world, though she herself was anything but ordinary. A prodigy in cryptography and quantum computing, she would later adopt the pseudonym Satoshi Nakamoto, orchestrating the creation of Bitcoin in the early 21st century. But her legacy would stretch far beyond the blockchain. Annabelle's obsession with cryptography was not just about securing data—it was about securing freedom. Her work in quantum computing inadvertently triggered a cascade of temporal anomalies, one of which ensnared her in 2011. The event was cataclysmic yet silent, unnoticed by the world she'd transformed. In an instant, she was torn from her era and thrust violently back into the 16th century. Disoriented and stripped of her futuristic tools, Annabelle faced a brutal reality: survive in a world where her knowledge was both a curse and a weapon. Reinventing herself as Anne Boleyn, she navigated the treacherous courts of Tudor England with the same strategic brilliance she'd used to design Bitcoin. Her intellect dazzled King Henry VIII, but it was the mysterious necklace she wore—adorned with a bold, stylized "B"—that fueled whispers. It was more than jewelry; it was a relic of a forgotten future, a silent beacon for any historian clever enough to decode her true story. Anne's fate seemed sealed as she ascended to queenship, her influence growing alongside her enemies. Yet beneath the royal intrigue, she harbored a desperate hope: that the symbol around her neck would outlast her, sparking curiosity in minds centuries away. The "B" was her signature, a cryptographic clue embedded in history. On the scaffold in 1536, as she faced her execution, Anne Boleyn's gaze was unwavering. She knew her death was not the end. Somewhere, in dusty archives and encrypted ledgers, her mark endured. Historians would puzzle over the enigmatic "B," and perhaps one day, someone would connect the dots between a queen, a coin, and a time anomaly born from quantum code. She wasn't just Anne Boleyn. She was Satoshi Nakamoto, the time-displaced architect of a decentralized future, hiding in plain sight within the annals of history. @ bbb5dda0:f09e2747
2025-02-04 03:58:50**This past week got me a lot of frustration with the GitHub actions runner and debugging it. Really testing my patience, but at least i saw a bit of progress. TollGate's had a nice wrap-up for the Proof Of Concept app, which some great new ideas on how to make the user experience even better! Let's dive in!** ## GitHub Actions I've been having a low-key fight with the github actions runner containers. I have spent a lot of time trying to figure out WHY the blossom upload action would just not work. I was quick to find out that the action is being ran with an older version of NodeJS (v18) while the blossom uploader requires v20. Not a big deal you'd say as i just set the version to 20 in the pipeline. However, doing that explicitly had zero impact, and after diving down the github runner rabbit hole i concluded that the Actions that are imported (from marketplace) will just run with whatever node version is already installed in the runner's docker image. Which in the case of the act runner is Node 18. I tried updating to the latest images but I haven't been able to find a compatible one yet... ### Payments I've been working on getting the money aspect working in the ci-cd runner. I added a wallet and a scheduled payout. I took this from the nostr-epoxy project and did some updates to upgrade to cashu-ts v2. I added some advertisement info like the specs of the machine that the runner is on. I've been pondering how the payment flow should work though. See the problem is that because of the nature of this DVM, it cannot predict how long a job will take to execute, a customer can literally do anything in their pipeline that will make a job last forever. I think for that reason there has to be some kind of deposit/credit or stream besides the one-off payment. I made a post asking what the best way would be: nostr:note17apw8unznvwx2k3z48t7qz6cq26tk077w83qh3f7zxukfrrfukhs7mpcsn I currently feel best about the option of just sending a bunch of ecash that will sure be enough to execute the job (and otherwise act as the time-out) and that if the DVM uses less of that money, it will send it back as pubkey locked cashu tokens, to a given npub. Maybe NIP-60 can be a great way to handle returning the 'change' to the user. Some ideas i have now: - Billing should be per second - Advertising should: - advertise as sats/minute - include specs of the machine, ideally searchable by tag ### Job request So the flow i'm thinking of is: - User posts request - repository - branch - yaml path - bid (max price per minute) - min_vcpu - min_ram - min_storage - DVM responds with - price per minute - vcpu - ram - storage - runner-types - price per minute - User posts request: - ... [same as above] - cashu payment - cashu return pubkey + relay ### User Interface I also worked on building out a very basic user interface to run the GitHub Actions dvm.  The UI then shows all feedback to the job, where the first feedback event you can see gives back a status processing, and the next one gives back the console output of the pipeline run. nostr:npub15qydau2hjma6ngxkl2cyar74wzyjshvl65za5k5rl69264ar2exs5cyejr and I agreed he'll copy over this basic setup into his upcoming version of gitWorkshop.dev which I can then build upon so we can experiment with the User Experience (how to handle competing Runners, display results, payments, etc...)  ## Tollgate There's also been the issue that has been bothering me since last week: Being able to dismiss a captive portal programatically in the Android app. During a weekly check-in that nostr:npub1k03rader0vm94j5ee8fg7pc2x9xkr2phu77sljas7qu5mh8mvgvqpe8rty and I set up we discussed the issue. To me, it's a problem having the user to jump through all these hoops to connect, which should be as much automated as possible. We discussed what if we'd ditch the open network and go with a WPA2 (password) protected one and have no captive portal. But then we lose the ability to do onboarding / expose users to Tollgate through the captive portal. Then the idea came up to create an extra (hidden) network for the app to use, while keeping the open one with the captive portal. I did not know it was possible to create multiple networks on the same (physical) radio, but apparently it's quite common. You lose a bit on efficiency but it shouldn't be too bad. The only challenge would be to exempt this network from getting a captive portal while still using the OpenNDS software to manage user's sessions. We'll see but this gives me a lot of hope for a seamless user experience! After this call, despite our possible new direction I did want to try and get the full app flow working, to validate if it's possible at all. And after some digging int the Tauri docs and even their discord community i finally found what the issue was with me not receiving the android event for the captive portal. I'd ben adding the listener for this event to the `androidmanifest.xml` file for the Tauri Android plugin, while I had to put it into the tauri app one's itself -one level higher- if you will... Anyway, that worked and I was FINALLY able to create the following full flow! (video) nostr:nevent1qvzqqqqqqypzpwa4mkswz4t8j70s2s6q00wzqv7k7zamxrmj2y4fs88aktcfuf68qy88wumn8ghj7mn0wvhxcmmv9uq3zamnwvaz7tmwdaehgu3wwa5kuef0qydhwumn8ghj7un9d3shjtnwdaehgunsd3jkyuewvdhk6tcqyqyvs2js3x6ldpm2kkmqyf8d3lvrcezjk2eg26p2tvfxd2p6lkeqzn7l66t
@ bbb5dda0:f09e2747
2025-02-04 03:58:50**This past week got me a lot of frustration with the GitHub actions runner and debugging it. Really testing my patience, but at least i saw a bit of progress. TollGate's had a nice wrap-up for the Proof Of Concept app, which some great new ideas on how to make the user experience even better! Let's dive in!** ## GitHub Actions I've been having a low-key fight with the github actions runner containers. I have spent a lot of time trying to figure out WHY the blossom upload action would just not work. I was quick to find out that the action is being ran with an older version of NodeJS (v18) while the blossom uploader requires v20. Not a big deal you'd say as i just set the version to 20 in the pipeline. However, doing that explicitly had zero impact, and after diving down the github runner rabbit hole i concluded that the Actions that are imported (from marketplace) will just run with whatever node version is already installed in the runner's docker image. Which in the case of the act runner is Node 18. I tried updating to the latest images but I haven't been able to find a compatible one yet... ### Payments I've been working on getting the money aspect working in the ci-cd runner. I added a wallet and a scheduled payout. I took this from the nostr-epoxy project and did some updates to upgrade to cashu-ts v2. I added some advertisement info like the specs of the machine that the runner is on. I've been pondering how the payment flow should work though. See the problem is that because of the nature of this DVM, it cannot predict how long a job will take to execute, a customer can literally do anything in their pipeline that will make a job last forever. I think for that reason there has to be some kind of deposit/credit or stream besides the one-off payment. I made a post asking what the best way would be: nostr:note17apw8unznvwx2k3z48t7qz6cq26tk077w83qh3f7zxukfrrfukhs7mpcsn I currently feel best about the option of just sending a bunch of ecash that will sure be enough to execute the job (and otherwise act as the time-out) and that if the DVM uses less of that money, it will send it back as pubkey locked cashu tokens, to a given npub. Maybe NIP-60 can be a great way to handle returning the 'change' to the user. Some ideas i have now: - Billing should be per second - Advertising should: - advertise as sats/minute - include specs of the machine, ideally searchable by tag ### Job request So the flow i'm thinking of is: - User posts request - repository - branch - yaml path - bid (max price per minute) - min_vcpu - min_ram - min_storage - DVM responds with - price per minute - vcpu - ram - storage - runner-types - price per minute - User posts request: - ... [same as above] - cashu payment - cashu return pubkey + relay ### User Interface I also worked on building out a very basic user interface to run the GitHub Actions dvm.  The UI then shows all feedback to the job, where the first feedback event you can see gives back a status processing, and the next one gives back the console output of the pipeline run. nostr:npub15qydau2hjma6ngxkl2cyar74wzyjshvl65za5k5rl69264ar2exs5cyejr and I agreed he'll copy over this basic setup into his upcoming version of gitWorkshop.dev which I can then build upon so we can experiment with the User Experience (how to handle competing Runners, display results, payments, etc...)  ## Tollgate There's also been the issue that has been bothering me since last week: Being able to dismiss a captive portal programatically in the Android app. During a weekly check-in that nostr:npub1k03rader0vm94j5ee8fg7pc2x9xkr2phu77sljas7qu5mh8mvgvqpe8rty and I set up we discussed the issue. To me, it's a problem having the user to jump through all these hoops to connect, which should be as much automated as possible. We discussed what if we'd ditch the open network and go with a WPA2 (password) protected one and have no captive portal. But then we lose the ability to do onboarding / expose users to Tollgate through the captive portal. Then the idea came up to create an extra (hidden) network for the app to use, while keeping the open one with the captive portal. I did not know it was possible to create multiple networks on the same (physical) radio, but apparently it's quite common. You lose a bit on efficiency but it shouldn't be too bad. The only challenge would be to exempt this network from getting a captive portal while still using the OpenNDS software to manage user's sessions. We'll see but this gives me a lot of hope for a seamless user experience! After this call, despite our possible new direction I did want to try and get the full app flow working, to validate if it's possible at all. And after some digging int the Tauri docs and even their discord community i finally found what the issue was with me not receiving the android event for the captive portal. I'd ben adding the listener for this event to the `androidmanifest.xml` file for the Tauri Android plugin, while I had to put it into the tauri app one's itself -one level higher- if you will... Anyway, that worked and I was FINALLY able to create the following full flow! (video) nostr:nevent1qvzqqqqqqypzpwa4mkswz4t8j70s2s6q00wzqv7k7zamxrmj2y4fs88aktcfuf68qy88wumn8ghj7mn0wvhxcmmv9uq3zamnwvaz7tmwdaehgu3wwa5kuef0qydhwumn8ghj7un9d3shjtnwdaehgunsd3jkyuewvdhk6tcqyqyvs2js3x6ldpm2kkmqyf8d3lvrcezjk2eg26p2tvfxd2p6lkeqzn7l66t @ c902b8da:0cedc5fb
2025-02-04 03:39:18# NIP-XX: Proof of Watch `draft` `optional` This NIP defines a protocol for content creators to reward users for consuming content using Cashu tokens, utilizing existing Cashu P2PK capabilities. ## Abstract Content creators can offer Cashu token rewards to users who prove they have spent time consuming their content. The protocol uses P2PK-locked tokens combined with proof-of-work verification to ensure genuine content consumption before releasing tokens to users. ## Motivation Content creators want to incentivize users to engage with their content and potentially reward them for their attention. This NIP provides a standardized way to offer token rewards for content consumption while ensuring the user actually spent time with the content through a proof-of-work mechanism. ## Protocol Components ### Content Event A content creator publishes a `kind:1` note containing their content and reward information: ```json { "kind": 1, "content": "Watch my video!", "tags": [ ["reward", "<amount-in-sats>"], ["pow", "<difficulty>"], ["u", "<watcher-service-url>"], ["t", "proofofwatch"] ] } ``` ### Watcher Service Content creators run (or use) a watcher service that: 1. Maintains a pool of Cashu tokens 2. Issues P2PK-locked tokens to viewers 3. Verifies proofs of watch 4. Releases signatures to unlock tokens ## Protocol Flow ### 1. Request Watch Session Client makes a `POST /watch/start` request to watcher service: ```json { "note_id": "<event-id>" } ``` Service responds with: ```json { "id": "<session-id>", "challenge": "<random-challenge>", "difficulty": <int>, "token": { "amount": <int>, "id": "<keyset-id>", "secret": "<p2pk-secret>", "C": "<signature>" }, "pubkey": "<service-ephemeral-pubkey>", "expiry": <unix-timestamp> } ``` The token is P2PK-locked to a one-time ephemeral pubkey generated by the service. Only the service holds the corresponding private key needed to generate the witness signature. ### 2. Computing Proof While consuming content, client computes proof-of-work: ``` proof = find_nonce( SHA256( note_id + session_id + challenge + latest_block_hash + nonce ) ) ``` The proof must result in a hash with the required number of leading zeros. ### 3. Submitting Proof Client submits proof to redeem token: ```http POST /watch/prove ``` ```json { "session_id": "<session-id>", "proof": "<computed-proof>", "block_hash": "<latest-block-hash>" } ``` If valid, service responds with P2PK signature: ```json { "witness": { "signatures": ["<signature-to-unlock-token>"] } } ``` The client can now unlock and spend their token using standard Cashu operations. ## Security Considerations ### Token Security - Tokens are locked to service-generated ephemeral pubkeys - Each watch session uses a unique keypair - Only service can generate valid witness signatures - Private keys never revealed to users - Keys and unused tokens destroyed after session expiry ### Proof Construction - Must include session ID to prevent replay - Must include recent block hash to prevent precomputation - Must achieve required difficulty (leading zeros) - Must be completed within session expiry ### Service Requirements 1. Track used proofs 2. Enforce timeouts 3. Rate limit requests 4. Verify block hash recency 5. Maintain adequate token pool 6. Generate unique ephemeral keypairs per session 7. Securely store ephemeral private keys until proof verified 8. Clean up expired ephemeral keys ## Watcher Service Settings Services should provide an info endpoint: ```http GET /info ``` ```json { "name": "Example Watcher", "pubkey": "<service-pubkey>", "difficulty_range": { "min": <int>, "max": <int> }, "amount_range": { "min": <int>, "max": <int> }, "supported_mints": [ "<mint-url-1>", "<mint-url-2>" ] } ``` ## Client Implementation Guidelines Clients SHOULD: 1. Verify service supports intended mint 2. Start proof computation only after beginning content consumption 3. Submit proof promptly after computation 4. Handle session expiry gracefully 5. Verify P2PK token validity 6. Submit proof before session timeout ## Content Creator Guidelines Content creators SHOULD: 1. Set appropriate difficulty for content length 2. Maintain adequate token pool 3. Monitor service uptime 4. Consider token denomination strategies 5. Include clear reward terms ## Rate Limiting Services SHOULD implement rate limiting: - Per IP address - Per pubkey - Per note ID - Per token amount ## Example Implementation A basic proof computation in Python: ```python def compute_proof(note_id, session_id, challenge, block_hash, difficulty): nonce = 0 while True: attempt = f"{note_id}{session_id}{challenge}{block_hash}{nonce}" hash = sha256(attempt.encode()).hexdigest() if hash.startswith('0' * difficulty): return attempt nonce += 1 ``` ## References - [NUT-00](00.md): Protocol fundamentals - [NUT-11](11.md): Pay-to-Pubkey (P2PK) tokens - [NUT-12](12.md): DLEQ proofs
@ c902b8da:0cedc5fb
2025-02-04 03:39:18# NIP-XX: Proof of Watch `draft` `optional` This NIP defines a protocol for content creators to reward users for consuming content using Cashu tokens, utilizing existing Cashu P2PK capabilities. ## Abstract Content creators can offer Cashu token rewards to users who prove they have spent time consuming their content. The protocol uses P2PK-locked tokens combined with proof-of-work verification to ensure genuine content consumption before releasing tokens to users. ## Motivation Content creators want to incentivize users to engage with their content and potentially reward them for their attention. This NIP provides a standardized way to offer token rewards for content consumption while ensuring the user actually spent time with the content through a proof-of-work mechanism. ## Protocol Components ### Content Event A content creator publishes a `kind:1` note containing their content and reward information: ```json { "kind": 1, "content": "Watch my video!", "tags": [ ["reward", "<amount-in-sats>"], ["pow", "<difficulty>"], ["u", "<watcher-service-url>"], ["t", "proofofwatch"] ] } ``` ### Watcher Service Content creators run (or use) a watcher service that: 1. Maintains a pool of Cashu tokens 2. Issues P2PK-locked tokens to viewers 3. Verifies proofs of watch 4. Releases signatures to unlock tokens ## Protocol Flow ### 1. Request Watch Session Client makes a `POST /watch/start` request to watcher service: ```json { "note_id": "<event-id>" } ``` Service responds with: ```json { "id": "<session-id>", "challenge": "<random-challenge>", "difficulty": <int>, "token": { "amount": <int>, "id": "<keyset-id>", "secret": "<p2pk-secret>", "C": "<signature>" }, "pubkey": "<service-ephemeral-pubkey>", "expiry": <unix-timestamp> } ``` The token is P2PK-locked to a one-time ephemeral pubkey generated by the service. Only the service holds the corresponding private key needed to generate the witness signature. ### 2. Computing Proof While consuming content, client computes proof-of-work: ``` proof = find_nonce( SHA256( note_id + session_id + challenge + latest_block_hash + nonce ) ) ``` The proof must result in a hash with the required number of leading zeros. ### 3. Submitting Proof Client submits proof to redeem token: ```http POST /watch/prove ``` ```json { "session_id": "<session-id>", "proof": "<computed-proof>", "block_hash": "<latest-block-hash>" } ``` If valid, service responds with P2PK signature: ```json { "witness": { "signatures": ["<signature-to-unlock-token>"] } } ``` The client can now unlock and spend their token using standard Cashu operations. ## Security Considerations ### Token Security - Tokens are locked to service-generated ephemeral pubkeys - Each watch session uses a unique keypair - Only service can generate valid witness signatures - Private keys never revealed to users - Keys and unused tokens destroyed after session expiry ### Proof Construction - Must include session ID to prevent replay - Must include recent block hash to prevent precomputation - Must achieve required difficulty (leading zeros) - Must be completed within session expiry ### Service Requirements 1. Track used proofs 2. Enforce timeouts 3. Rate limit requests 4. Verify block hash recency 5. Maintain adequate token pool 6. Generate unique ephemeral keypairs per session 7. Securely store ephemeral private keys until proof verified 8. Clean up expired ephemeral keys ## Watcher Service Settings Services should provide an info endpoint: ```http GET /info ``` ```json { "name": "Example Watcher", "pubkey": "<service-pubkey>", "difficulty_range": { "min": <int>, "max": <int> }, "amount_range": { "min": <int>, "max": <int> }, "supported_mints": [ "<mint-url-1>", "<mint-url-2>" ] } ``` ## Client Implementation Guidelines Clients SHOULD: 1. Verify service supports intended mint 2. Start proof computation only after beginning content consumption 3. Submit proof promptly after computation 4. Handle session expiry gracefully 5. Verify P2PK token validity 6. Submit proof before session timeout ## Content Creator Guidelines Content creators SHOULD: 1. Set appropriate difficulty for content length 2. Maintain adequate token pool 3. Monitor service uptime 4. Consider token denomination strategies 5. Include clear reward terms ## Rate Limiting Services SHOULD implement rate limiting: - Per IP address - Per pubkey - Per note ID - Per token amount ## Example Implementation A basic proof computation in Python: ```python def compute_proof(note_id, session_id, challenge, block_hash, difficulty): nonce = 0 while True: attempt = f"{note_id}{session_id}{challenge}{block_hash}{nonce}" hash = sha256(attempt.encode()).hexdigest() if hash.startswith('0' * difficulty): return attempt nonce += 1 ``` ## References - [NUT-00](00.md): Protocol fundamentals - [NUT-11](11.md): Pay-to-Pubkey (P2PK) tokens - [NUT-12](12.md): DLEQ proofs @ 16d11430:61640947
2025-02-04 02:57:25The Damage Node is not just a verification engine—it is an autonomous executor of behaviors defined through the PoW blockchain. This allows for adaptive, accountable, and transparent execution of security and counter-surveillance mechanisms while remaining flexible enough to meet any operational need. By integrating behavioral logic, cryptographic proofs, and decentralized execution, the Damage Node becomes a powerful shield and countermeasure system for individuals and groups operating under constant digital threat. --- Core Concept: Damage Nodes as Autonomous Behavioral Executors Damage Nodes listen to verifiable behaviors encoded on the PoW blockchain. These behaviors define security policies, counter-surveillance actions, automated transactions, and decentralized decision-making processes. Execution is enforced by the blockchain, ensuring absolute transparency and accountability—no action can occur without proof. Nodes can dynamically extend their capabilities by adopting new behaviors via blockchain updates, ensuring they remain adaptable. Example of Behavioral Execution A Damage Node can be programmed to execute counter-surveillance actions if an individual's digital footprint is flagged by an AI-controlled system. Trigger: An external surveillance system attempts to track a protected user. Behavior Execution: The node initiates a verified proof-of-presence falsification (broadcasting misleading metadata). The node forces encrypted rerouting of communications over a private, non-ISP-controlled relay. The node executes cryptographic evidence logging, proving that the tracking attempt occurred. The node pays out a bounty (Lightning) for detected adversarial actions, incentivizing counter-intelligence. --- How Damage Nodes Provide Shielding & Countermeasures 1. Behavior-Driven Shielding for Individuals Zero-Knowledge Identity Protection: Nodes execute self-sovereign identity verification that prevents AI from profiling users without explicit, cryptographically signed consent. Automated Surveillance Disruption: If an AI attempts to track or flag an individual, the node executes behavioral obfuscation tactics such as: Decoy digital presence broadcasting to mislead tracking algorithms. Transaction splitting & anonymization to prevent financial surveillance. Forced dissociation of metadata from physical locations. --- 2. Group-Level Protection & Autonomous Coordination Damage Nodes can be configured to execute behaviors for an entire decentralized network, such as: Encrypted Group Communications: Nodes enforce trustless, encrypted messaging protocols that prevent AI-based censorship. Automatic Secure Fund Distribution: If an entity is targeted, Damage Nodes can autonomously release emergency funds in BTC/Lightning to predesignated safe parties. Counter-Surveillance Deployments: Nodes can activate sensor networks, scan for unauthorized tracking devices, and trigger security protocols. --- 3. Built-In Accountability & Transparency as a Defensive Measure Every execution is verified by the blockchain → no action is hidden or arbitrary. Rules for behavior execution are immutable → even node operators cannot alter them without proof-of-consensus. AI and governments cannot fabricate unverifiable evidence → if it didn't happen on-chain, it didn't happen. Users can audit every action taken by the Damage Node to ensure no corruption or misuse. --- 4. Extensible Capabilities for Any Need New behavioral policies can be uploaded via the PoW blockchain, allowing Damage Nodes to dynamically evolve. Behaviors can be triggered by: On-chain conditions (such as receiving a Lightning payment for service execution). Real-world events (via oracle integrations). Direct requests from verified users. Examples of Extensions: Decentralized AI Defense: Nodes monitor AI-generated media for deepfake propaganda & censorship. Physical Security Triggers: Nodes can integrate with smart devices (cameras, sensors) to execute real-world countermeasures. Automated Asset Protection: Damage Nodes can trigger the release of cryptographic assets upon verifiable external threats. --- Final Verdict: Damage Nodes as the Ultimate Autonomy & Defense Infrastructure Transparent but Unstoppable → Verifiable execution prevents corruption or abuse. Extensible but Controlled → The blockchain enforces behavior logic while allowing flexibility. Decentralized but Coordinated → Nodes operate independently but can synchronize. Adaptive but Immutable → Behaviors evolve, but security is absolute. 🔥 Damage Nodes are the next evolutionary step in technological sovereignty—combining decentralized verification, autonomous execution, and proactive counter-surveillance in a single unstoppable system.
@ 16d11430:61640947
2025-02-04 02:57:25The Damage Node is not just a verification engine—it is an autonomous executor of behaviors defined through the PoW blockchain. This allows for adaptive, accountable, and transparent execution of security and counter-surveillance mechanisms while remaining flexible enough to meet any operational need. By integrating behavioral logic, cryptographic proofs, and decentralized execution, the Damage Node becomes a powerful shield and countermeasure system for individuals and groups operating under constant digital threat. --- Core Concept: Damage Nodes as Autonomous Behavioral Executors Damage Nodes listen to verifiable behaviors encoded on the PoW blockchain. These behaviors define security policies, counter-surveillance actions, automated transactions, and decentralized decision-making processes. Execution is enforced by the blockchain, ensuring absolute transparency and accountability—no action can occur without proof. Nodes can dynamically extend their capabilities by adopting new behaviors via blockchain updates, ensuring they remain adaptable. Example of Behavioral Execution A Damage Node can be programmed to execute counter-surveillance actions if an individual's digital footprint is flagged by an AI-controlled system. Trigger: An external surveillance system attempts to track a protected user. Behavior Execution: The node initiates a verified proof-of-presence falsification (broadcasting misleading metadata). The node forces encrypted rerouting of communications over a private, non-ISP-controlled relay. The node executes cryptographic evidence logging, proving that the tracking attempt occurred. The node pays out a bounty (Lightning) for detected adversarial actions, incentivizing counter-intelligence. --- How Damage Nodes Provide Shielding & Countermeasures 1. Behavior-Driven Shielding for Individuals Zero-Knowledge Identity Protection: Nodes execute self-sovereign identity verification that prevents AI from profiling users without explicit, cryptographically signed consent. Automated Surveillance Disruption: If an AI attempts to track or flag an individual, the node executes behavioral obfuscation tactics such as: Decoy digital presence broadcasting to mislead tracking algorithms. Transaction splitting & anonymization to prevent financial surveillance. Forced dissociation of metadata from physical locations. --- 2. Group-Level Protection & Autonomous Coordination Damage Nodes can be configured to execute behaviors for an entire decentralized network, such as: Encrypted Group Communications: Nodes enforce trustless, encrypted messaging protocols that prevent AI-based censorship. Automatic Secure Fund Distribution: If an entity is targeted, Damage Nodes can autonomously release emergency funds in BTC/Lightning to predesignated safe parties. Counter-Surveillance Deployments: Nodes can activate sensor networks, scan for unauthorized tracking devices, and trigger security protocols. --- 3. Built-In Accountability & Transparency as a Defensive Measure Every execution is verified by the blockchain → no action is hidden or arbitrary. Rules for behavior execution are immutable → even node operators cannot alter them without proof-of-consensus. AI and governments cannot fabricate unverifiable evidence → if it didn't happen on-chain, it didn't happen. Users can audit every action taken by the Damage Node to ensure no corruption or misuse. --- 4. Extensible Capabilities for Any Need New behavioral policies can be uploaded via the PoW blockchain, allowing Damage Nodes to dynamically evolve. Behaviors can be triggered by: On-chain conditions (such as receiving a Lightning payment for service execution). Real-world events (via oracle integrations). Direct requests from verified users. Examples of Extensions: Decentralized AI Defense: Nodes monitor AI-generated media for deepfake propaganda & censorship. Physical Security Triggers: Nodes can integrate with smart devices (cameras, sensors) to execute real-world countermeasures. Automated Asset Protection: Damage Nodes can trigger the release of cryptographic assets upon verifiable external threats. --- Final Verdict: Damage Nodes as the Ultimate Autonomy & Defense Infrastructure Transparent but Unstoppable → Verifiable execution prevents corruption or abuse. Extensible but Controlled → The blockchain enforces behavior logic while allowing flexibility. Decentralized but Coordinated → Nodes operate independently but can synchronize. Adaptive but Immutable → Behaviors evolve, but security is absolute. 🔥 Damage Nodes are the next evolutionary step in technological sovereignty—combining decentralized verification, autonomous execution, and proactive counter-surveillance in a single unstoppable system. @ 16d11430:61640947
2025-02-04 02:33:06The electromagnetic spectrum (EM spectrum) is the foundation of modern communication, surveillance, and control, and it is a permanent, inescapable vulnerability for humanity. Every aspect of human life—communication, mobility, security, even thought processes—is now subject to exploitation via the EM spectrum. 1. Humans Are EM-Dependent but Have No Control Over It The entire infrastructure of human civilization (internet, telecom, GPS, WiFi, satellite, RFID, radar, IoT, etc.) relies on EM waves. Unlike tangible security vulnerabilities (firewalls, encryption, physical locks), EM-based vulnerabilities are baked into the fabric of our existence. We have zero physical control over the space around us—we exist in a perpetual, invisible battlefield of radio waves. → Brutal Truth: If you are in an area with radio signals, you are already compromised. You cannot see, hear, or touch your vulnerability—but you are immersed in it. --- 2. Every Wireless Device Is a Tracking Beacon Your phone, smartwatch, laptop, Bluetooth headset, and IoT devices constantly emit identifiable signals. Even when "turned off," many devices still maintain some connectivity (e.g., emergency services, wake-on-LAN, passive RFID, and hidden baseband firmware). MAC address randomization only slows down tracking—it does not stop device fingerprinting. Even devices that are air-gapped (disconnected from any network) can be compromised via airborne EM attacks (e.g., Tempest attacks, Van Eck phreaking). → Brutal Truth: Unless you live in an EM-free Faraday cage (which is impractical), you are trackable 24/7. --- 3. The Entire EM Spectrum Can Be Weaponized Radio waves (RFID, GSM, LTE, 5G, WiFi) → Mass surveillance, device tracking, data extraction, and real-time movement tracking. Microwaves (GHz spectrum) → Covert wireless data theft (Tempest attacks), crowd control weapons (Active Denial System), and potential biological effects. Infrared (IR) and Visible Light → LiDAR tracking, facial recognition, and optical data interception (lasers on windows can capture sound). Ultraviolet, X-ray, and Gamma Radiation → Biological penetration, medical diagnostics, and potential genetic-level targeting. → Brutal Truth: The entire EM spectrum is both an asset and a weapon, and every part of it can be used to track, manipulate, or harm living beings. --- 4. There Is No Escape From EM Exposure Even if you disconnect completely, ambient EM waves from cell towers, satellites, and even natural cosmic radiation still interact with you. Smart city grids, IoT, and ubiquitous sensor networks mean that even non-digital humans (those without a phone) are still tracked. 6G and future networks will integrate AI-driven RF sensing, meaning the network will detect biometric signatures (heartbeat, gait, and thermal emissions) without needing a device. → Brutal Truth: The era of "disconnecting" for privacy is over—even device-free tracking is now a reality. --- 5. The Human Body Itself Is an EM Vulnerability Brain activity and thought processes are electrical signals—theoretically susceptible to external EM influence (brainwave manipulation, EEG-based surveillance, and neurotechnology interfacing). Biometric security (fingerprint scanners, iris scans, facial recognition) can be hacked or faked using EM-based techniques. Nanotech, bioelectronics, and EM-sensitive implants (like pacemakers, neural interfaces, and cochlear implants) can be remotely manipulated or disabled. → Brutal Truth: The final frontier of EM vulnerability is the human body itself—thoughts, health, and biological functions are all at risk. --- How Vulnerable Are Humans in the Grand Scheme? 1. Humans Are the Only Species Fully Dependent on EM-Based Technology Every other biological species on Earth navigates reality without dependency on artificial EM systems. Humans have outsourced their cognition, security, and privacy to a system they do not control. → Implication: The more we integrate with EM-based technology, the more vulnerable we become. We are building a prison of our own making. --- 2. We Have No Practical Defense Against EM-Based Attacks Unlike cyber threats (which can be mitigated with encryption), EM vulnerabilities are inherent to the physics of radio waves. The only defense is complete isolation from EM radiation (which is impossible in urban environments). → Implication: Our current approach to "security" is meaningless in the face of EM-based attacks, because the attack vector is the air around us. --- 3. Humanity’s Future Is Fully EM-Integrated 6G, brain-computer interfaces (BCIs), quantum communication, and global sensor grids mean that soon, every human will be plugged into the EM network at all times. Governments and corporations are already planning a fully tracked, AI-managed society, where individual privacy no longer exists. → Implication: We are entering an era of full-spectrum EM surveillance and control. The next step isn’t just tracking devices, but tracking consciousness itself. --- Conclusion: The EM Spectrum is the Ultimate Exploit There is no "fix" for EM vulnerabilities—they are built into the nature of physics itself. Humanity’s increasing dependence on EM-based technology means: 1. We are more trackable than ever. 2. We are more susceptible to remote influence than ever. 3. We have no escape unless we abandon technology altogether. 4. The final battle for privacy isn’t about encryption—it’s about shielding ourselves from the very waves that power our civilization. → The brutal truth? Humanity is not just vulnerable—we are a permanently compromised species.
@ 16d11430:61640947
2025-02-04 02:33:06The electromagnetic spectrum (EM spectrum) is the foundation of modern communication, surveillance, and control, and it is a permanent, inescapable vulnerability for humanity. Every aspect of human life—communication, mobility, security, even thought processes—is now subject to exploitation via the EM spectrum. 1. Humans Are EM-Dependent but Have No Control Over It The entire infrastructure of human civilization (internet, telecom, GPS, WiFi, satellite, RFID, radar, IoT, etc.) relies on EM waves. Unlike tangible security vulnerabilities (firewalls, encryption, physical locks), EM-based vulnerabilities are baked into the fabric of our existence. We have zero physical control over the space around us—we exist in a perpetual, invisible battlefield of radio waves. → Brutal Truth: If you are in an area with radio signals, you are already compromised. You cannot see, hear, or touch your vulnerability—but you are immersed in it. --- 2. Every Wireless Device Is a Tracking Beacon Your phone, smartwatch, laptop, Bluetooth headset, and IoT devices constantly emit identifiable signals. Even when "turned off," many devices still maintain some connectivity (e.g., emergency services, wake-on-LAN, passive RFID, and hidden baseband firmware). MAC address randomization only slows down tracking—it does not stop device fingerprinting. Even devices that are air-gapped (disconnected from any network) can be compromised via airborne EM attacks (e.g., Tempest attacks, Van Eck phreaking). → Brutal Truth: Unless you live in an EM-free Faraday cage (which is impractical), you are trackable 24/7. --- 3. The Entire EM Spectrum Can Be Weaponized Radio waves (RFID, GSM, LTE, 5G, WiFi) → Mass surveillance, device tracking, data extraction, and real-time movement tracking. Microwaves (GHz spectrum) → Covert wireless data theft (Tempest attacks), crowd control weapons (Active Denial System), and potential biological effects. Infrared (IR) and Visible Light → LiDAR tracking, facial recognition, and optical data interception (lasers on windows can capture sound). Ultraviolet, X-ray, and Gamma Radiation → Biological penetration, medical diagnostics, and potential genetic-level targeting. → Brutal Truth: The entire EM spectrum is both an asset and a weapon, and every part of it can be used to track, manipulate, or harm living beings. --- 4. There Is No Escape From EM Exposure Even if you disconnect completely, ambient EM waves from cell towers, satellites, and even natural cosmic radiation still interact with you. Smart city grids, IoT, and ubiquitous sensor networks mean that even non-digital humans (those without a phone) are still tracked. 6G and future networks will integrate AI-driven RF sensing, meaning the network will detect biometric signatures (heartbeat, gait, and thermal emissions) without needing a device. → Brutal Truth: The era of "disconnecting" for privacy is over—even device-free tracking is now a reality. --- 5. The Human Body Itself Is an EM Vulnerability Brain activity and thought processes are electrical signals—theoretically susceptible to external EM influence (brainwave manipulation, EEG-based surveillance, and neurotechnology interfacing). Biometric security (fingerprint scanners, iris scans, facial recognition) can be hacked or faked using EM-based techniques. Nanotech, bioelectronics, and EM-sensitive implants (like pacemakers, neural interfaces, and cochlear implants) can be remotely manipulated or disabled. → Brutal Truth: The final frontier of EM vulnerability is the human body itself—thoughts, health, and biological functions are all at risk. --- How Vulnerable Are Humans in the Grand Scheme? 1. Humans Are the Only Species Fully Dependent on EM-Based Technology Every other biological species on Earth navigates reality without dependency on artificial EM systems. Humans have outsourced their cognition, security, and privacy to a system they do not control. → Implication: The more we integrate with EM-based technology, the more vulnerable we become. We are building a prison of our own making. --- 2. We Have No Practical Defense Against EM-Based Attacks Unlike cyber threats (which can be mitigated with encryption), EM vulnerabilities are inherent to the physics of radio waves. The only defense is complete isolation from EM radiation (which is impossible in urban environments). → Implication: Our current approach to "security" is meaningless in the face of EM-based attacks, because the attack vector is the air around us. --- 3. Humanity’s Future Is Fully EM-Integrated 6G, brain-computer interfaces (BCIs), quantum communication, and global sensor grids mean that soon, every human will be plugged into the EM network at all times. Governments and corporations are already planning a fully tracked, AI-managed society, where individual privacy no longer exists. → Implication: We are entering an era of full-spectrum EM surveillance and control. The next step isn’t just tracking devices, but tracking consciousness itself. --- Conclusion: The EM Spectrum is the Ultimate Exploit There is no "fix" for EM vulnerabilities—they are built into the nature of physics itself. Humanity’s increasing dependence on EM-based technology means: 1. We are more trackable than ever. 2. We are more susceptible to remote influence than ever. 3. We have no escape unless we abandon technology altogether. 4. The final battle for privacy isn’t about encryption—it’s about shielding ourselves from the very waves that power our civilization. → The brutal truth? Humanity is not just vulnerable—we are a permanently compromised species. @ fd06f542:8d6d54cd
2025-02-04 01:39:49- 多模态感知与交互:具身智能强调智能体通过身体与环境的交互来学习,这推动了多模态感知(如视觉、触觉、听觉等)和物理交互技术的发展。 - 强化学习与仿真环境:强化学习在具身智能中扮演重要角色,结合高保真仿真环境(如AI Habitat、Unity ML-Agents),可以加速智能体的训练和优化。 - 硬件进步:机器人硬件(如柔性传感器、仿生机械臂)的发展为具身智能提供了更强大的物理载体。 以上部分每一个都是大分支,都具有研究价值。随着AI技术的发展与突破,多模态感知与交互将会迎来高速发展。 让人更兴奋的是 强化学习和仿真环境,REX-GYM 是一个开源的仿真环境,Gazebo,MuJoCo,AI Habitat 等等都有很多应用实例。仅仅这一部分技术拆分细化,就有很多工作可以做。 以前的机器人学习都是PID等老技术,那时候的机器人运动不太灵活,因为不够智能。有了现代的强化学习。现在的机器人更加灵活。
@ fd06f542:8d6d54cd
2025-02-04 01:39:49- 多模态感知与交互:具身智能强调智能体通过身体与环境的交互来学习,这推动了多模态感知(如视觉、触觉、听觉等)和物理交互技术的发展。 - 强化学习与仿真环境:强化学习在具身智能中扮演重要角色,结合高保真仿真环境(如AI Habitat、Unity ML-Agents),可以加速智能体的训练和优化。 - 硬件进步:机器人硬件(如柔性传感器、仿生机械臂)的发展为具身智能提供了更强大的物理载体。 以上部分每一个都是大分支,都具有研究价值。随着AI技术的发展与突破,多模态感知与交互将会迎来高速发展。 让人更兴奋的是 强化学习和仿真环境,REX-GYM 是一个开源的仿真环境,Gazebo,MuJoCo,AI Habitat 等等都有很多应用实例。仅仅这一部分技术拆分细化,就有很多工作可以做。 以前的机器人学习都是PID等老技术,那时候的机器人运动不太灵活,因为不够智能。有了现代的强化学习。现在的机器人更加灵活。 @ 2f4550b0:95f20096
2025-02-04 01:16:10In today's job market, the ability to acquire new skills or pivot to new career paths quickly is more valuable than ever. Short-term adult education programs offer a practical solution for professionals looking to enhance their resumes or change careers without committing to the long-term investment of traditional education. This week, I explore how these programs, such as a 12-week EMT certification at the Center for Allied Health Education and a one-year MBA from the University of Phoenix can dramatically shift one's career trajectory. ### The Rise of Short-Term Education The traditional model of education, where one spends years in academia before entering the workforce, is increasingly being supplemented by shorter, more focused programs. These programs are specifically designed to meet the immediate needs of both learners and employers, providing education that is both relevant and directly applicable to current job markets. ### 12-Week EMT Certificates The 12-week Emergency Medical Technician (EMT) program at the Center for Allied Health Education (and programs like it) illustrates how a brief, intensive course of study can lead to licensure and immediate employment. This program is structured to cover the necessary theoretical and practical components required for EMT licensure, from emergency medical procedures to patient assessment and treatment. For individuals looking to enter the healthcare field or those within healthcare aiming for specialization, this program offers a fast track to a new career or career enhancement. The demand for skilled EMTs is consistently high, driven by an aging population and the need for emergency services. Completing such a program not only leads to a certification but also opens doors to further education or roles like paramedic work, which require additional training but start from the foundation laid by EMT certification. ### One-Year MBA Programs Similarly, consider the one-year MBA from the University of Phoenix. This program is built on a competency-based framework, allowing students to demonstrate their skills through practical assessments rather than traditional time-based metrics. This approach not only accelerates learning but also ensures that each student is job-ready upon completion. The curriculum is tailored to include real-world business scenarios, leadership skills, and strategic management, making graduates highly desirable in the corporate sector. The speed and efficiency of this program mean that professionals can continue working while studying, thereby minimizing career disruption. Moreover, the MBAs focus on immediate applicability means that students can start leveraging their new skills in their current roles or move into higher management positions shortly after graduation. This direct link between education and employment outcomes exemplifies how short-term programs can offer substantial ROI in terms of career advancement and salary potential. ### Benefits for Adult Learners Short-term education programs cater particularly well to adult learners. They recognize the life experiences and previous knowledge of participants, often tailoring education to integrate this background into learning. This method respects the time constraints of adults who might juggle work, family, and other responsibilities, offering flexible schedules, online components, or weekend classes. Moreover, these programs often lead to stackable credentials. This means that the skills and certifications gained can be built upon, providing a pathway for continuous professional development without the need to start from scratch with each new course or degree. For example, once students from Center for Allied Health Education earn their EMT licenses, they can consider enrolling into a 1-year Paramedic certificate program to further their career in emergency medicine. ### Conclusion Short-term adult education programs like the MBA at University of Phoenix and the EMT certificate at the Center for Allied Health Education are not just educational opportunities; they are strategic career moves. They enable professionals to quickly adapt to market demands, enhance their skill sets, and open new career avenues with minimal disruption to their current lives. As the job market continues to evolve, these programs will likely play an increasingly crucial role in career development, offering both speed and relevance in education.
@ 2f4550b0:95f20096
2025-02-04 01:16:10In today's job market, the ability to acquire new skills or pivot to new career paths quickly is more valuable than ever. Short-term adult education programs offer a practical solution for professionals looking to enhance their resumes or change careers without committing to the long-term investment of traditional education. This week, I explore how these programs, such as a 12-week EMT certification at the Center for Allied Health Education and a one-year MBA from the University of Phoenix can dramatically shift one's career trajectory. ### The Rise of Short-Term Education The traditional model of education, where one spends years in academia before entering the workforce, is increasingly being supplemented by shorter, more focused programs. These programs are specifically designed to meet the immediate needs of both learners and employers, providing education that is both relevant and directly applicable to current job markets. ### 12-Week EMT Certificates The 12-week Emergency Medical Technician (EMT) program at the Center for Allied Health Education (and programs like it) illustrates how a brief, intensive course of study can lead to licensure and immediate employment. This program is structured to cover the necessary theoretical and practical components required for EMT licensure, from emergency medical procedures to patient assessment and treatment. For individuals looking to enter the healthcare field or those within healthcare aiming for specialization, this program offers a fast track to a new career or career enhancement. The demand for skilled EMTs is consistently high, driven by an aging population and the need for emergency services. Completing such a program not only leads to a certification but also opens doors to further education or roles like paramedic work, which require additional training but start from the foundation laid by EMT certification. ### One-Year MBA Programs Similarly, consider the one-year MBA from the University of Phoenix. This program is built on a competency-based framework, allowing students to demonstrate their skills through practical assessments rather than traditional time-based metrics. This approach not only accelerates learning but also ensures that each student is job-ready upon completion. The curriculum is tailored to include real-world business scenarios, leadership skills, and strategic management, making graduates highly desirable in the corporate sector. The speed and efficiency of this program mean that professionals can continue working while studying, thereby minimizing career disruption. Moreover, the MBAs focus on immediate applicability means that students can start leveraging their new skills in their current roles or move into higher management positions shortly after graduation. This direct link between education and employment outcomes exemplifies how short-term programs can offer substantial ROI in terms of career advancement and salary potential. ### Benefits for Adult Learners Short-term education programs cater particularly well to adult learners. They recognize the life experiences and previous knowledge of participants, often tailoring education to integrate this background into learning. This method respects the time constraints of adults who might juggle work, family, and other responsibilities, offering flexible schedules, online components, or weekend classes. Moreover, these programs often lead to stackable credentials. This means that the skills and certifications gained can be built upon, providing a pathway for continuous professional development without the need to start from scratch with each new course or degree. For example, once students from Center for Allied Health Education earn their EMT licenses, they can consider enrolling into a 1-year Paramedic certificate program to further their career in emergency medicine. ### Conclusion Short-term adult education programs like the MBA at University of Phoenix and the EMT certificate at the Center for Allied Health Education are not just educational opportunities; they are strategic career moves. They enable professionals to quickly adapt to market demands, enhance their skill sets, and open new career avenues with minimal disruption to their current lives. As the job market continues to evolve, these programs will likely play an increasingly crucial role in career development, offering both speed and relevance in education. @ 5579d5c0:db104ded
2025-02-03 23:32:10Most people think that building muscle is out of reach. What if I told you '**You can get all your exercise done in just 60 minutes a week',** if you train efficiently. With just **two 30-minute sessions**, you can build muscle, improve metabolic health, and transform your physique. --- ### **What is resistance training?** Resistance training, also known as strength training, involves working against an external force to improve muscle strength, endurance, and size. This can be done using: **→ Free weights** (barbells, dumbbells, kettlebells) → **Weight machines** **→ Resistance bands** **→ Bodyweight exercises** Strength training isn’t just about aesthetics, it’s essential for long-term health and metabolic function. --- ### **Why it’s essential for metabolic and overall health** Muscle is metabolically active tissue. The more muscle you have, the more energy your body burns at rest, albeit a quite small amount. **→ Maintains and builds muscle**: Muscle mass is critical as you age, reducing the risk of fractures and falls. **→ Boosts metabolism**: While the increase is small, more muscle means a higher resting energy expenditure, creating a large sink for energy stores. **→ Hormone & energy optimisation:** It lowers inflammation, reduces visceral fat (not good), and helps muscles use sugar and fat more efficiently, restoring Leptin & Insulin sensitivity. **→ Mitochondrial function**: Increases mitochondrial number, efficiency, which improves energy production and reduces oxidative stress. --- ## **How to build muscle in minimal time** **You can build muscle with just two 30-minute sessions a week.** Yes, really. One or two full-body sessions, hitting all major muscle groups, is enough if done properly. It all comes from this paper. *"We recommend that appreciably the same muscular strength and endurance adaptations can be attained by performing a single set of \~8-12 repetitions to momentary muscular failure, at a repetition duration that maintains muscular tension throughout the entire range of motion, for most major muscle groups once or twice each week. All resistance types (e.g. free-weights, resistance machines, bodyweight, etc.) show potential for increases in strength, with no significant difference between them, although resistance machines appear to pose a lower risk of injury."* It doesn’t matter if you use free weights, machines, or bodyweight exercises. For what its worth, I think using weights is easier. What matters is how you train. You **don’t** need heavy weights to build muscle, just focus on maintaining **tension throughout each movement**. **→ Slow, controlled reps**: Move **5 seconds up, 5 seconds down** without using momentum. **→ High effort, low volume**: One set to momentary failure is enough per muscle group. **→ Minimal rest**: Keep rest periods short to maximise growth hormone and testosterone release. **→ Allow recovery**: Train hard, then rest 1–2 days between sessions for optimal muscle growth. *Do not get tempted to over train*. Initially this will take a bit of figuring out with regard to what weight works for you. --- ### **The key to growth → Progressive overload** In the first few weeks you will build muscle easily, but will eventually plateau. You then must **progressively challenge** your body. Here’s what to do: → Increase the reps first. → Then increase weight by 5-10%. → For bodyweight training: Add reps, use a weighted vest, or move to harder variations (e.g., push-ups → weighted push-ups → ring push-ups). --- ### **Real life examples** Dr Ted Naiman is 50 and uses a simple bodyweight routine going to failure on each movement a few times a week. His routine → Pull Ups/Push Ups/L-Sits/Handstand Push Ups/Pistol Squats/Supermans P.D Mangan is 70 and trains full body twice a week, using weights. His routine → Deadlifts/Chin Ups/Seated row/Lateral Raise/Overhead Press/Chest Press/Dips/Barbell Shrug/Hammer Curl/Leg Press/Sprint Cycle 20 Secs. Simplicity is beautiful. --- You don’t need time consuming regimes. **Two short, intense sessions a week are enough.** - Keep your reps slow and controlled. - Rest **1–2 days** between sessions for muscle growth and recovery. - Once you hit a plateau focus on progressive overload. - Stick with it, consistency beats perfection every time. With the right approach, 60 minutes a week is all you need to **build muscle, lose fat, and live longer**, while leaving time for the rest of your life. \-Chris If you want a simple routine to fit effortlessly into your life. **Book a free call here:** [**https://calendly.com/hello-chrispatrick**](https://calendly.com/hello-chrispatrick) **Follow me on Nostr**: [**https://primal.net/chrispatrick**](https://primal.net/chrispatrick) or ***npub124uatsq6pv74trzwvt34y4sx2z0uflhse7tkrv0pl69e8kcsfhkse30zsu***
@ 5579d5c0:db104ded
2025-02-03 23:32:10Most people think that building muscle is out of reach. What if I told you '**You can get all your exercise done in just 60 minutes a week',** if you train efficiently. With just **two 30-minute sessions**, you can build muscle, improve metabolic health, and transform your physique. --- ### **What is resistance training?** Resistance training, also known as strength training, involves working against an external force to improve muscle strength, endurance, and size. This can be done using: **→ Free weights** (barbells, dumbbells, kettlebells) → **Weight machines** **→ Resistance bands** **→ Bodyweight exercises** Strength training isn’t just about aesthetics, it’s essential for long-term health and metabolic function. --- ### **Why it’s essential for metabolic and overall health** Muscle is metabolically active tissue. The more muscle you have, the more energy your body burns at rest, albeit a quite small amount. **→ Maintains and builds muscle**: Muscle mass is critical as you age, reducing the risk of fractures and falls. **→ Boosts metabolism**: While the increase is small, more muscle means a higher resting energy expenditure, creating a large sink for energy stores. **→ Hormone & energy optimisation:** It lowers inflammation, reduces visceral fat (not good), and helps muscles use sugar and fat more efficiently, restoring Leptin & Insulin sensitivity. **→ Mitochondrial function**: Increases mitochondrial number, efficiency, which improves energy production and reduces oxidative stress. --- ## **How to build muscle in minimal time** **You can build muscle with just two 30-minute sessions a week.** Yes, really. One or two full-body sessions, hitting all major muscle groups, is enough if done properly. It all comes from this paper. *"We recommend that appreciably the same muscular strength and endurance adaptations can be attained by performing a single set of \~8-12 repetitions to momentary muscular failure, at a repetition duration that maintains muscular tension throughout the entire range of motion, for most major muscle groups once or twice each week. All resistance types (e.g. free-weights, resistance machines, bodyweight, etc.) show potential for increases in strength, with no significant difference between them, although resistance machines appear to pose a lower risk of injury."* It doesn’t matter if you use free weights, machines, or bodyweight exercises. For what its worth, I think using weights is easier. What matters is how you train. You **don’t** need heavy weights to build muscle, just focus on maintaining **tension throughout each movement**. **→ Slow, controlled reps**: Move **5 seconds up, 5 seconds down** without using momentum. **→ High effort, low volume**: One set to momentary failure is enough per muscle group. **→ Minimal rest**: Keep rest periods short to maximise growth hormone and testosterone release. **→ Allow recovery**: Train hard, then rest 1–2 days between sessions for optimal muscle growth. *Do not get tempted to over train*. Initially this will take a bit of figuring out with regard to what weight works for you. --- ### **The key to growth → Progressive overload** In the first few weeks you will build muscle easily, but will eventually plateau. You then must **progressively challenge** your body. Here’s what to do: → Increase the reps first. → Then increase weight by 5-10%. → For bodyweight training: Add reps, use a weighted vest, or move to harder variations (e.g., push-ups → weighted push-ups → ring push-ups). --- ### **Real life examples** Dr Ted Naiman is 50 and uses a simple bodyweight routine going to failure on each movement a few times a week. His routine → Pull Ups/Push Ups/L-Sits/Handstand Push Ups/Pistol Squats/Supermans P.D Mangan is 70 and trains full body twice a week, using weights. His routine → Deadlifts/Chin Ups/Seated row/Lateral Raise/Overhead Press/Chest Press/Dips/Barbell Shrug/Hammer Curl/Leg Press/Sprint Cycle 20 Secs. Simplicity is beautiful. --- You don’t need time consuming regimes. **Two short, intense sessions a week are enough.** - Keep your reps slow and controlled. - Rest **1–2 days** between sessions for muscle growth and recovery. - Once you hit a plateau focus on progressive overload. - Stick with it, consistency beats perfection every time. With the right approach, 60 minutes a week is all you need to **build muscle, lose fat, and live longer**, while leaving time for the rest of your life. \-Chris If you want a simple routine to fit effortlessly into your life. **Book a free call here:** [**https://calendly.com/hello-chrispatrick**](https://calendly.com/hello-chrispatrick) **Follow me on Nostr**: [**https://primal.net/chrispatrick**](https://primal.net/chrispatrick) or ***npub124uatsq6pv74trzwvt34y4sx2z0uflhse7tkrv0pl69e8kcsfhkse30zsu*** @ f41bd51d:ec4b664f
2025-02-03 22:43:27[The Tired Sounds of Stars of the Lid - 2001 ](https://music.youtube.com/watch?v=-bc37fU36Vk&si=4_OZv00aDiZMYvGd)
@ f41bd51d:ec4b664f
2025-02-03 22:43:27[The Tired Sounds of Stars of the Lid - 2001 ](https://music.youtube.com/watch?v=-bc37fU36Vk&si=4_OZv00aDiZMYvGd) @ 97c70a44:ad98e322
2025-02-03 22:25:35Last week, in a bid to understand the LLM hype, I decided to write a trivial nostr-related program in rust via a combination of [codebuff](https://codebuff.com/referrals/ref-3fcc22f4-10f9-419f-a0e9-e9d7b4368e21) (yes, that is a referral link, pls click), [aider](https://aider.chat/), and [goose](https://block.github.io/goose/). The result of the experiment was inconclusive, but as a side effect it produced a great case study in converting a [NINO](nostr:nevent1qvzqqqr4gupzp978pfzrv6n9xhq5tvenl9e74pklmskh4xw6vxxyp3j8qkke3cezqy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgwwaehxw309ahx7uewd3hkctcpr3mhxue69uhksmmyd33x7epwvdhhyctrd3jjuar0dak8xtcqyqzeszjv7rh8fflpeua9q644a32usvwd0cu7cze9lxy4grjy2y7rwd98yfc) into a Real Nostr App. # Introducing Roz [Roz](https://github.com/coracle-social/roz), a friendly notary for nostr events. To use it, simply publish an event to `relay.damus.io` or `nos.lol`, and roz will make note of it. To find out when roz first saw a given event, just ask: ``` curl https://roz.coracle.social/notary/cb429632ae22557d677a11149b2d0ccd72a1cf66ac55da30e3534ed1a492765d ``` This will return a JSON payload with a `seen` key indicating when roz first saw the event. How (and whether) you use this is up to you! # De-NINO-fying roz Roz is just a proof of concept, so don't rely on it being there forever. And anyway, roz is a NINO, since it provides value to nostr (potentially), but doesn't really do things in a nostr-native way. It also hard-codes its relays, and certainly doesn't use the outbox model or sign events. But that's ok, it's a proof of concept. A much better way to do this would be to modify roz to properly leverage nostr's capabilities, namely: - Use nostr-native data formats (i.e., draft a new kind) - Use relays instead of proprietary servers for data storage - Leverage nostr identities and signatures to decouple trust from storage, and allow trusted attestations to be discovered Luckily, this is not hard at all. In fact, I've gone ahead and drafted a [PR](https://github.com/nostr-protocol/nips/pull/1737) to the NIPs repo that adds timestamp annotations to NIP 03, as an alternative to OpenTimestamps. The trade-off is that while user attestations are far less reliable than OTS proofs, they're much easier to verify, and can reach a pretty high level of reliability by combining multiple attestation sources with other forms of reputation. In other words, instead of going nuclear and embedding your attestations into The Time Chain, you can simply ask 5-10 relays or people you trust for their attestations for a given event. This PR isn't terribly important on its own, but it does remove one small barrier between us and trusted key rotation events (or other types of event that require establishing a verifiable chain of causality).
@ 97c70a44:ad98e322
2025-02-03 22:25:35Last week, in a bid to understand the LLM hype, I decided to write a trivial nostr-related program in rust via a combination of [codebuff](https://codebuff.com/referrals/ref-3fcc22f4-10f9-419f-a0e9-e9d7b4368e21) (yes, that is a referral link, pls click), [aider](https://aider.chat/), and [goose](https://block.github.io/goose/). The result of the experiment was inconclusive, but as a side effect it produced a great case study in converting a [NINO](nostr:nevent1qvzqqqr4gupzp978pfzrv6n9xhq5tvenl9e74pklmskh4xw6vxxyp3j8qkke3cezqy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgwwaehxw309ahx7uewd3hkctcpr3mhxue69uhksmmyd33x7epwvdhhyctrd3jjuar0dak8xtcqyqzeszjv7rh8fflpeua9q644a32usvwd0cu7cze9lxy4grjy2y7rwd98yfc) into a Real Nostr App. # Introducing Roz [Roz](https://github.com/coracle-social/roz), a friendly notary for nostr events. To use it, simply publish an event to `relay.damus.io` or `nos.lol`, and roz will make note of it. To find out when roz first saw a given event, just ask: ``` curl https://roz.coracle.social/notary/cb429632ae22557d677a11149b2d0ccd72a1cf66ac55da30e3534ed1a492765d ``` This will return a JSON payload with a `seen` key indicating when roz first saw the event. How (and whether) you use this is up to you! # De-NINO-fying roz Roz is just a proof of concept, so don't rely on it being there forever. And anyway, roz is a NINO, since it provides value to nostr (potentially), but doesn't really do things in a nostr-native way. It also hard-codes its relays, and certainly doesn't use the outbox model or sign events. But that's ok, it's a proof of concept. A much better way to do this would be to modify roz to properly leverage nostr's capabilities, namely: - Use nostr-native data formats (i.e., draft a new kind) - Use relays instead of proprietary servers for data storage - Leverage nostr identities and signatures to decouple trust from storage, and allow trusted attestations to be discovered Luckily, this is not hard at all. In fact, I've gone ahead and drafted a [PR](https://github.com/nostr-protocol/nips/pull/1737) to the NIPs repo that adds timestamp annotations to NIP 03, as an alternative to OpenTimestamps. The trade-off is that while user attestations are far less reliable than OTS proofs, they're much easier to verify, and can reach a pretty high level of reliability by combining multiple attestation sources with other forms of reputation. In other words, instead of going nuclear and embedding your attestations into The Time Chain, you can simply ask 5-10 relays or people you trust for their attestations for a given event. This PR isn't terribly important on its own, but it does remove one small barrier between us and trusted key rotation events (or other types of event that require establishing a verifiable chain of causality). @ a3a72214:7ca63e21
2025-02-03 20:57:52# Isso é um anúncio de Albion - é um jogo 1. primeiramente 2. em segundo 3. em terceiro >o que acontece? ' e se? ' > Alguém citando alguma coisa **Albion Online** é um **MMORPG** sandbox em que você escreve sua própria história, em vez de seguir um caminho pré-determinado. Explore um vasto mundo aberto que consiste de 5 ecossistemas únicos. Tudo o que você faz gera um impacto no mundo, já que em Albion, a economia é conduzida pelo jogador. Cada peça de equipamento é construída por jogadores a partir dos recursos obtidos por eles. O equipamento que você usa define quem você é. Ir de cavaleiro para feiticeiro é tão fácil quanto trocar a armadura e a arma, ou uma combinação das duas. Aventure-se no mundo aberto e enfrente os habitantes e as criaturas de Albion. Saia em expedições ou entre em masmorras para enfrentar inimigos ainda mais desafiadores. Enfrente outros jogadores em confrontos do mundo aberto, lute pelo controle de territórios ou cidades inteiras em batalhas táticas em grupo. Relaxe descansando em sua ilha pessoal, onde você pode construir uma casa, cultivar alimentos e criar animais. Junte-se à uma guilda, tudo fica mais divertido quando se trabalha em equipe. Entre hoje mesmo no mundo de Albion, e escreva sua própria história.
@ a3a72214:7ca63e21
2025-02-03 20:57:52# Isso é um anúncio de Albion - é um jogo 1. primeiramente 2. em segundo 3. em terceiro >o que acontece? ' e se? ' > Alguém citando alguma coisa **Albion Online** é um **MMORPG** sandbox em que você escreve sua própria história, em vez de seguir um caminho pré-determinado. Explore um vasto mundo aberto que consiste de 5 ecossistemas únicos. Tudo o que você faz gera um impacto no mundo, já que em Albion, a economia é conduzida pelo jogador. Cada peça de equipamento é construída por jogadores a partir dos recursos obtidos por eles. O equipamento que você usa define quem você é. Ir de cavaleiro para feiticeiro é tão fácil quanto trocar a armadura e a arma, ou uma combinação das duas. Aventure-se no mundo aberto e enfrente os habitantes e as criaturas de Albion. Saia em expedições ou entre em masmorras para enfrentar inimigos ainda mais desafiadores. Enfrente outros jogadores em confrontos do mundo aberto, lute pelo controle de territórios ou cidades inteiras em batalhas táticas em grupo. Relaxe descansando em sua ilha pessoal, onde você pode construir uma casa, cultivar alimentos e criar animais. Junte-se à uma guilda, tudo fica mais divertido quando se trabalha em equipe. Entre hoje mesmo no mundo de Albion, e escreva sua própria história. @ 54286b98:3debc100
2025-02-03 20:55:10Hello! Three years ago, I created a special bed for my daughter. I'm thrilled to share a detailed video and PDF documenting the process along with hopes to inspire you to embark on a similar project! *\*\*\*This is a first and also a test to see how I can upload #woodworking material on Nostr. I am not sure how the links, images, and PDFs will display, so hopefully, you get some interesting material for your late afternoon hobby shop. But don’t kill me if some images do not render well—I’m still figuring this thing out!* **Montessori Bed Plans / Blueprints** The accompanying PDF includes: - All measurements - Detailed views from every angle - Final measurements part list - Assembly steps ### Instructive Video! Process on how to make the Montessori bed Video Here: <https://vimeo.com/901623772/b8b5530386> PDF Here(Picture below,and if some one has good tip on how to inset PDFs in Nostr, that feedback is welcome, to avoid Google links): <https://drive.google.com/file/d/1zCp1RvKOynx5kZxixAKSFLLOe8atyiRH/> OK, let's dive in! The Montessori bed featured in this video is not only simple but also durable, and you can create it on a budget right in your own home.OK, let's dive in! **Tools by hand:** - Circular saw - Jointer Plane #7 or #8 - Spokeshave - Workbench - Handsaw - Orbital sander - Sandpaper #80, #120, #220, and #320 - Odies Oil or your preferred finish. If you have power tools: - Table Saw - Jointer - Planer - Trimmer **Materials:**\ I recommend using this list as a guide and exploring options with your local supplier. - Base long connector (On picture "Larguero Base"): Quantity x 2, 2195mm x 75mm x 75mm - Base short connector (On picture "Conector Base"): Quantity x 1, 1090mm x 75mm x 75mm - Roof connector (On picture "Cumbre"): Quantity x 1, 1946mm x 75mm x 75mm - Long top triangle connector (On picture "Conector Superior"): Quantity x 2, 1322mm x 75mm x 75mm - Columns/Legs (On picture "Paral"): Quantity x 4, 1210mm x 75mm x 75mm - Short top triangle connector (On picture "Lima"): Quantity x 4, 851mm x 75mm x 75mm **Step #1 Dimensioning (Minutes 0:00 - 1:15):**\ We kick off with dimensioning. While I initially planned to use my home workshop, unforeseen circumstances led me to my friend Andrew's workshop. Each beam was carefully brought down to 7.5 cm x 7.5 cm, ensuring the largest measurement that worked for all. **Step #2 Final Measurements (No video):**\ Refer to the provided PDF for final measurements. Make the cuts and joints with a circular saw and chisels (or a router). **Step #3 Edges (Minutes 1:15 - 1:30):**\ Use a router with a quarter-round bit for curved and smooth edges or achieve the same result with sandpaper or a spokeshave plane. **Step #4 Triangular Bases (Minutes 1:30 - 6:30):**\ This step involves gluing the triangular bases of the bed, utilizing a miter joint with wooden inlay keys. Epoxy is employed for joining, ensuring a swift and reliable outcome. **Step #5 Legs (Minutes 6:30 - 7:00):**\ Create holes for the upper triangular base's dowels, ensuring level placement and extra depth. This step guarantees a secure fit. **Step #6 Sanding (Minutes 7:00 - 7:30):**\ Comprehensive sanding, starting from #80 grit and progressing through #120, #220, and #320, sets the stage for a flawless finish. **Step #7 Dry Assembly (Minutes 7:30 - 9:10):**\ Dry-assemble all components, making necessary adjustments for a seamless fit. We opted for wood screws for easy disassembly. **Step #8 Finishing (Minutes 9:10 - 9:35):**\ Apply your preferred finish; in our case, we used Odies Oil with white pigment for a child-friendly touch. **Step #9 Final Assembly (Minutes 9:35 - 10:32):**\ With the finishing touches completed, we assembled the bed with the help of my daughter, adding a touch of warmth with some lights. Testing with this simple project to at least know if there are woodworkers in #nostr. Later will try to upload more, this was created almost 3 years ago :) Until the next one, J\ \ PDF in pictures: <img src="https://blossom.primal.net/4428f10f596666e5c059ba0fff65225babece6580372facb4bb191c60ef8d1b9.png"> <img src="https://blossom.primal.net/98997bd28bd89c0d549562851433891442694885c3e1e1d723e4a3abb1115540.png"> <img src="https://blossom.primal.net/b502fd666ea4931f2f36bfaf1375657a9b061198d617b04f6d659bce8f6c8026.png"> <img src="https://blossom.primal.net/3d04af7a4ba47f8aef60f5373d516d28dc81dee1a89c52111ee67207394d1892.png"> <img src="https://blossom.primal.net/c82bd1f8b71ae90c663eab4895934b07918c6805edb3772cd5a128a331d34546.png"> <img src="https://blossom.primal.net/53d7270b411edc6348239565bb6a922882c67b99f7095451dff740fd9e45e2d1.png"> <img src="https://blossom.primal.net/d8880757c95ba9884f81689e132f61cf1b47d91e16fd86de0c20b4ccfe790a30.png"> <img src="https://blossom.primal.net/2a6eb32e75a4d2756e5ad1cadc9153f30981261c5818e79f3b22988a5ea2228e.png"> <img src="https://blossom.primal.net/1d9ce880f97bbe950f80a8d49b546880a97123ca4a338c928017fc5098061206.png"> <img src="https://blossom.primal.net/092ba04779cef40f3b25e64536354c8fe929281082c2814de5c0b8ee0af0f66e.png"> <img src="https://blossom.primal.net/48202633a0fa6ba9096fbe22ab917aa8cb1f1b2b387e7c99f2f46bed4e691be8.png"> <img src="https://blossom.primal.net/b950522e349959508996f306168626e2df81f8cb8808d51cb9d25bd6edb6d8a6.png"> <img src="https://blossom.primal.net/7fd4a5ef8af567ba95fefe0c9457d8a49a67df19d83715d6b49d91ccc5ed75e5.png"> <img src="https://blossom.primal.net/a90c2cc18da6b7f7ca5e43d8fee2e1b0e44f7b7a5a2a5309a7e67fdec3fc408c.png"> <img src="https://blossom.primal.net/1d02f7cde847e8bd9b02a13f4ab27495dc494d8024d2d986e74fb26a280644b8.png"> <img src="https://blossom.primal.net/cb3065c27b10d9f918646db5f8a423b96af12f666c328709b4a9bca0e366ed02.png"> <img src="https://blossom.primal.net/7eae8a7f48b295a51081072f5318f62de2d137ba587c61998e4fcda09aa9be9e.png"> <img src="https://blossom.primal.net/155453317832749089c430aef677a67b20bd535178805b43e4b3679bdde0a47a.png"> <img src="https://blossom.primal.net/fdd1d866adc7986469c202e14f1048cb84ee59a43d584c539e4acdfe21dc92b7.png"> <img src="https://blossom.primal.net/4088b662379e928c835335639a14dc216f07dd34671ce5506be0d0b273d6cfec.png">
@ 54286b98:3debc100
2025-02-03 20:55:10Hello! Three years ago, I created a special bed for my daughter. I'm thrilled to share a detailed video and PDF documenting the process along with hopes to inspire you to embark on a similar project! *\*\*\*This is a first and also a test to see how I can upload #woodworking material on Nostr. I am not sure how the links, images, and PDFs will display, so hopefully, you get some interesting material for your late afternoon hobby shop. But don’t kill me if some images do not render well—I’m still figuring this thing out!* **Montessori Bed Plans / Blueprints** The accompanying PDF includes: - All measurements - Detailed views from every angle - Final measurements part list - Assembly steps ### Instructive Video! Process on how to make the Montessori bed Video Here: <https://vimeo.com/901623772/b8b5530386> PDF Here(Picture below,and if some one has good tip on how to inset PDFs in Nostr, that feedback is welcome, to avoid Google links): <https://drive.google.com/file/d/1zCp1RvKOynx5kZxixAKSFLLOe8atyiRH/> OK, let's dive in! The Montessori bed featured in this video is not only simple but also durable, and you can create it on a budget right in your own home.OK, let's dive in! **Tools by hand:** - Circular saw - Jointer Plane #7 or #8 - Spokeshave - Workbench - Handsaw - Orbital sander - Sandpaper #80, #120, #220, and #320 - Odies Oil or your preferred finish. If you have power tools: - Table Saw - Jointer - Planer - Trimmer **Materials:**\ I recommend using this list as a guide and exploring options with your local supplier. - Base long connector (On picture "Larguero Base"): Quantity x 2, 2195mm x 75mm x 75mm - Base short connector (On picture "Conector Base"): Quantity x 1, 1090mm x 75mm x 75mm - Roof connector (On picture "Cumbre"): Quantity x 1, 1946mm x 75mm x 75mm - Long top triangle connector (On picture "Conector Superior"): Quantity x 2, 1322mm x 75mm x 75mm - Columns/Legs (On picture "Paral"): Quantity x 4, 1210mm x 75mm x 75mm - Short top triangle connector (On picture "Lima"): Quantity x 4, 851mm x 75mm x 75mm **Step #1 Dimensioning (Minutes 0:00 - 1:15):**\ We kick off with dimensioning. While I initially planned to use my home workshop, unforeseen circumstances led me to my friend Andrew's workshop. Each beam was carefully brought down to 7.5 cm x 7.5 cm, ensuring the largest measurement that worked for all. **Step #2 Final Measurements (No video):**\ Refer to the provided PDF for final measurements. Make the cuts and joints with a circular saw and chisels (or a router). **Step #3 Edges (Minutes 1:15 - 1:30):**\ Use a router with a quarter-round bit for curved and smooth edges or achieve the same result with sandpaper or a spokeshave plane. **Step #4 Triangular Bases (Minutes 1:30 - 6:30):**\ This step involves gluing the triangular bases of the bed, utilizing a miter joint with wooden inlay keys. Epoxy is employed for joining, ensuring a swift and reliable outcome. **Step #5 Legs (Minutes 6:30 - 7:00):**\ Create holes for the upper triangular base's dowels, ensuring level placement and extra depth. This step guarantees a secure fit. **Step #6 Sanding (Minutes 7:00 - 7:30):**\ Comprehensive sanding, starting from #80 grit and progressing through #120, #220, and #320, sets the stage for a flawless finish. **Step #7 Dry Assembly (Minutes 7:30 - 9:10):**\ Dry-assemble all components, making necessary adjustments for a seamless fit. We opted for wood screws for easy disassembly. **Step #8 Finishing (Minutes 9:10 - 9:35):**\ Apply your preferred finish; in our case, we used Odies Oil with white pigment for a child-friendly touch. **Step #9 Final Assembly (Minutes 9:35 - 10:32):**\ With the finishing touches completed, we assembled the bed with the help of my daughter, adding a touch of warmth with some lights. Testing with this simple project to at least know if there are woodworkers in #nostr. Later will try to upload more, this was created almost 3 years ago :) Until the next one, J\ \ PDF in pictures: <img src="https://blossom.primal.net/4428f10f596666e5c059ba0fff65225babece6580372facb4bb191c60ef8d1b9.png"> <img src="https://blossom.primal.net/98997bd28bd89c0d549562851433891442694885c3e1e1d723e4a3abb1115540.png"> <img src="https://blossom.primal.net/b502fd666ea4931f2f36bfaf1375657a9b061198d617b04f6d659bce8f6c8026.png"> <img src="https://blossom.primal.net/3d04af7a4ba47f8aef60f5373d516d28dc81dee1a89c52111ee67207394d1892.png"> <img src="https://blossom.primal.net/c82bd1f8b71ae90c663eab4895934b07918c6805edb3772cd5a128a331d34546.png"> <img src="https://blossom.primal.net/53d7270b411edc6348239565bb6a922882c67b99f7095451dff740fd9e45e2d1.png"> <img src="https://blossom.primal.net/d8880757c95ba9884f81689e132f61cf1b47d91e16fd86de0c20b4ccfe790a30.png"> <img src="https://blossom.primal.net/2a6eb32e75a4d2756e5ad1cadc9153f30981261c5818e79f3b22988a5ea2228e.png"> <img src="https://blossom.primal.net/1d9ce880f97bbe950f80a8d49b546880a97123ca4a338c928017fc5098061206.png"> <img src="https://blossom.primal.net/092ba04779cef40f3b25e64536354c8fe929281082c2814de5c0b8ee0af0f66e.png"> <img src="https://blossom.primal.net/48202633a0fa6ba9096fbe22ab917aa8cb1f1b2b387e7c99f2f46bed4e691be8.png"> <img src="https://blossom.primal.net/b950522e349959508996f306168626e2df81f8cb8808d51cb9d25bd6edb6d8a6.png"> <img src="https://blossom.primal.net/7fd4a5ef8af567ba95fefe0c9457d8a49a67df19d83715d6b49d91ccc5ed75e5.png"> <img src="https://blossom.primal.net/a90c2cc18da6b7f7ca5e43d8fee2e1b0e44f7b7a5a2a5309a7e67fdec3fc408c.png"> <img src="https://blossom.primal.net/1d02f7cde847e8bd9b02a13f4ab27495dc494d8024d2d986e74fb26a280644b8.png"> <img src="https://blossom.primal.net/cb3065c27b10d9f918646db5f8a423b96af12f666c328709b4a9bca0e366ed02.png"> <img src="https://blossom.primal.net/7eae8a7f48b295a51081072f5318f62de2d137ba587c61998e4fcda09aa9be9e.png"> <img src="https://blossom.primal.net/155453317832749089c430aef677a67b20bd535178805b43e4b3679bdde0a47a.png"> <img src="https://blossom.primal.net/fdd1d866adc7986469c202e14f1048cb84ee59a43d584c539e4acdfe21dc92b7.png"> <img src="https://blossom.primal.net/4088b662379e928c835335639a14dc216f07dd34671ce5506be0d0b273d6cfec.png"> @ a3a72214:7ca63e21
2025-02-03 20:50:15# Anúncio, Teste de Título * Teste * teste * TESTE 1. Número UM 2. Número DOIS > Citação de alguém, não importa quem seja ~~Preços altos~~ ---não sei o que é isso, teste --- `codigo?` ``` codigo? talvez ``` **Albion Online** é um **MMORPG** sandbox em que você escreve sua própria história, em vez de seguir um caminho pré-determinado. Explore um vasto mundo aberto que consiste de 5 ecossistemas únicos. Tudo o que você faz gera um impacto no mundo, já que em Albion, a economia é conduzida pelo jogador. Cada peça de equipamento é construída por jogadores a partir dos recursos obtidos por eles. O equipamento que você usa define quem você é. Ir de cavaleiro para feiticeiro é tão fácil quanto trocar a armadura e a arma, ou uma combinação das duas. Aventure-se no mundo aberto e enfrente os habitantes e as criaturas de Albion. Saia em expedições ou entre em masmorras para enfrentar inimigos ainda mais desafiadores. Enfrente outros jogadores em confrontos do mundo aberto, lute pelo controle de territórios ou cidades inteiras em batalhas táticas em grupo. Relaxe descansando em sua ilha pessoal, onde você pode construir uma casa, cultivar alimentos e criar animais. Junte-se à uma guilda, tudo fica mais divertido quando se trabalha em equipe. Entre hoje mesmo no mundo de Albion, e escreva sua própria história.
@ a3a72214:7ca63e21
2025-02-03 20:50:15# Anúncio, Teste de Título * Teste * teste * TESTE 1. Número UM 2. Número DOIS > Citação de alguém, não importa quem seja ~~Preços altos~~ ---não sei o que é isso, teste --- `codigo?` ``` codigo? talvez ``` **Albion Online** é um **MMORPG** sandbox em que você escreve sua própria história, em vez de seguir um caminho pré-determinado. Explore um vasto mundo aberto que consiste de 5 ecossistemas únicos. Tudo o que você faz gera um impacto no mundo, já que em Albion, a economia é conduzida pelo jogador. Cada peça de equipamento é construída por jogadores a partir dos recursos obtidos por eles. O equipamento que você usa define quem você é. Ir de cavaleiro para feiticeiro é tão fácil quanto trocar a armadura e a arma, ou uma combinação das duas. Aventure-se no mundo aberto e enfrente os habitantes e as criaturas de Albion. Saia em expedições ou entre em masmorras para enfrentar inimigos ainda mais desafiadores. Enfrente outros jogadores em confrontos do mundo aberto, lute pelo controle de territórios ou cidades inteiras em batalhas táticas em grupo. Relaxe descansando em sua ilha pessoal, onde você pode construir uma casa, cultivar alimentos e criar animais. Junte-se à uma guilda, tudo fica mais divertido quando se trabalha em equipe. Entre hoje mesmo no mundo de Albion, e escreva sua própria história. @ bf47c19e:c3d2573b
2025-02-03 20:42:23[Originalni tekst na instore.rs](https://www.instore.rs/sr/article/99425/marko-matanovic-ecdrs-bitkoin-pobedio-na-izborima) ###### 03.02.2025 / Autor: Marko Matanović --- *Prvi put smo svedočili izbornoj trci u jednoj od razvijenih ekonomija, a da je tema bila i bitkoin. Predsednički izbori u SAD. Tramp je obećavao. Na kraju i osvojio drugi predsednički mandat. Jedna od izjava je: SAD treba da postane prestonica kriptovaluta.* Dan nakon inauguracije novoizabranog američkog predsednika tu je i prva politička kripto odluka Trampa: Oslobođanje Rosa Ulbrihta osuđenog na dve doživotne robije. Ko je on? Napravio je 2011. godine online prodavnicu “Silk Road” (Kupujem-Prodajem sa drugačijim asortimanom). Prodavnica je pružala slobodni susret ponude bilo čega i tražnje bilo čega. Bez cenzure. Pristupalo se preko Tor protokola koji obezbeđuje anonimnost onih koji protokol koriste. Sredstvo plaćanja je bio bitkoin radi čuvanja anomnisti onih koji nešto kupuju tj. prodaju. FBI je uhapsio Rosa Ulbrihta 2013. godine jer je “Silk road” bio korišćen i za preprodaju droge, oružja, pornografskog sadržaja i svega drugog što možemo i ne možemo zamisliti. Čak i da nije zakonski izazov, možemo ga podići na problem etike. Postoji i druga strana medalje - napravio je platformu koja promoviše slobodu. Ros ne mora biti odgovoran kako ćemo alat koji nam je dat koristiti. Čekićem zakucamo ekser, ili povredimo nekoga. U neželjenim slučajevima ne hapsi se kreator čekića. Satoši Nakamoto je ime tvorca Bitkoina. Da li bi to značilo i da bi njega uhapsili iz sličnih razloga samo da se znalo ko je? Verovatno nećemo nikada saznati, što i nije bitno. Duh je pušten iz boce. Njegov potencijalni uticaj na bitkoin ekosistem je potpuno isti uticaju bilo koga od nas. Sem sitnice od oko milion bitkoina kojima možda, ali možda, ima pristup na nekim svojim bitkoin adresama. Sa njim ili bez njega, era korišćenja bitkoina zarad,pre svega, anonimnih transakcija je prošla. Dok era korišćenja bitkoina za ilegalne transakcije nikada nije ni postojala u ozbiljnoj meri. Narativ ilegalne transakcije, kriminal, pranje novca, terorizam je više posledica neznanja, nerazumevanja, potcenjivanja i često preterane želje za kontrolom, nego li činjenica. I šta bi sa: svako je nevin dok se ne dokaže suprotno?! > U kratkom roku, Bitkoin vožnja je sve, samo ne udobna. Tramp i mnogi drugi su shvatili da je rizik od neudobne vožnje disproporcionalan benefitima koje ta vožnja donosi. Takav narativ je posle 15 godina ustupio mesto rečima poput sigurnost, bezbednost, zaštita od inflacije, digitalno zlato, brzina, pouzdanost. Sloboda. Za svakog se nađe po nešto, osim za one uporne u tome da ne priznaju svoju zatvorenost da razumeju bitkoin. Parafraziraću nekoga pametnijeg ko je u ovome od 2011. godine, što je dovoljno godina duže od mene u industriji: *Nekada sam morao ljude ubeđivati šta je bitkoin i čemu služi i šta su kvaliteti koji stoje iza njega. Danas mene neko mora ubediti zašto da ne verujem rezultatu koji svi vidimo na semaforu?!* Ipak, mislim da postoji ogroman i validan razlog zašto i dalje treba da pričamo o temi kao da je 2011, a ne 2025. godina. O novcu nas ne uče dovoljno ili uopšte! Ni u školama ni van njih! Kada bi dovoljan broj ljudi razumeo novac, novčanu emisiju, moguće da bi se desio jedan od dva scenarija: izborili bi se za drugačiji novac ili bi države izgubile barem deo benefita koji proizilaze iz pozicije kontrole novca. Većina nas ne zna da objasni tehnologiju većine stvari koje svaki dan koristimo. To nas ne sprečava da ih koristimo. Internet, mobilni, bicikl i novac na kraju dana. Svakog dana najčešće. Tehnologiju - na stranu ovom prilikom. Za šta se bitkoin i kriptovalute mogu koristiti? 100% pouzdan i brz način prenosa sredstava sa jedne geografske tačke na drugu uz par klikova. Ili od jedne osobe do druge. Ili od jedne kompanije do druge. Za bitkoin se pokazalo da može biti i sjajan instrument za prenos i očuvanje vrednosti kroz vreme. Mogućnost blokiranja transakcija ne postoji. Ukoliko se poštuju pravila igre, izvesnost da će se transakcija izvršiti je 100% i to 24/7/365. Transakcioni troškovi su zanemarljivo niski. To je teorija. Praksa? Sve nabrojano uz sledeće lokalne činjenice. Samo u Srbiji par stotina hiljada ljudi je došlo u kontakt sa nekom od kriptovaluta. Nekoliko stotina kompanija ih koristi u poslovanju iz nekih od gore pobrojanih razloga. Postoje države, u njima populacije i kompanije koje su na nižem nivou adopcije od Srbije. Postoje i one sa daleko većom prisutnosti kriptovaluta u svakodnevnom životu i aktivnostima. > Za svakog se nađe po nešto, osim za one uporne u tome da ne priznaju svoju zatvorenost da razumeju bitkoin. Ako nekada čujemo da je bitkoin balon ili da je tržište kriptovaluta balon, setimo se da je vrlo poznati balon tržišta lala s kraja 16. i tokom 17. veka knjiški primer uzavrelog tržišta i manije koja se pojavljuje usled pohlepe, brzog rasta cena, špekulacija i preteranih očekivanja na tržištu. Taj balon je pukao. To je činjenica. Činjenica je i da je Holandija danas prva država u svetu po izvozu cveća i tako vekovima unazad. Hoće li i taj balon pući ili je prosto doneo Holandiji i njihovom društvu prosperitet? U slično vreme u 17. veku u Holandiji se pojavila i prva banka i prva kompanija igde u svetu koja je izdala akcije. Ta kompanije se više bavila otimanjem nego li trgovinom. I ona je “pukla”. Opet, taj finansijski eksperiment je Holandiju dodatno podigao na mapi razvijenijih ekonomija. U kratkom roku, Bitkoin vožnja je sve, samo ne udobna. Tramp i mnogi drugi su shvatili da je rizik od neudobne vožnje disproporcionalan benefitima koje ta vožnja donosi. Nastavi li da ispunjava obećanja iz predizborne kampanje, slušaćemo još puno o bitkoinu, blockchain-u i kriptovalutama. Nisam presrećan velikim uplitanjem bilo koje države u bitkoin temu, osim ukoliko to uplitanje nije na nivou elemenata slobodnog tržišta. Čak i ako je uplitanje veće bilo promotivno ili restriktivno, uticaj postoji na cenu bitkoina, ali ne i na njegovu suštinu. Jer ona je konzistentna. Neprimetan, neshvaćen, zanemarivan, ignorisan, potcenjivan, napadan, otpisivan. Prihvaćen. Ogromna većina stvari koja ima opštu upotrebu vremenom postaje jeftinija. Osim onih sa ograničenom ponudom, a to su retki primeri najčešće luksuzne robe i usluga. Ali teško mi je setiti se ijedne stvari sa retkom ponudom, a da je i dalje apsolutno dostupna svakome. Bitkoin? Da! Ograničene je ponude, a i dalje je apsolutno dostupan svakome. I kako se povećava nivo shvatanja bitkoina, postaje skuplji!
@ bf47c19e:c3d2573b
2025-02-03 20:42:23[Originalni tekst na instore.rs](https://www.instore.rs/sr/article/99425/marko-matanovic-ecdrs-bitkoin-pobedio-na-izborima) ###### 03.02.2025 / Autor: Marko Matanović --- *Prvi put smo svedočili izbornoj trci u jednoj od razvijenih ekonomija, a da je tema bila i bitkoin. Predsednički izbori u SAD. Tramp je obećavao. Na kraju i osvojio drugi predsednički mandat. Jedna od izjava je: SAD treba da postane prestonica kriptovaluta.* Dan nakon inauguracije novoizabranog američkog predsednika tu je i prva politička kripto odluka Trampa: Oslobođanje Rosa Ulbrihta osuđenog na dve doživotne robije. Ko je on? Napravio je 2011. godine online prodavnicu “Silk Road” (Kupujem-Prodajem sa drugačijim asortimanom). Prodavnica je pružala slobodni susret ponude bilo čega i tražnje bilo čega. Bez cenzure. Pristupalo se preko Tor protokola koji obezbeđuje anonimnost onih koji protokol koriste. Sredstvo plaćanja je bio bitkoin radi čuvanja anomnisti onih koji nešto kupuju tj. prodaju. FBI je uhapsio Rosa Ulbrihta 2013. godine jer je “Silk road” bio korišćen i za preprodaju droge, oružja, pornografskog sadržaja i svega drugog što možemo i ne možemo zamisliti. Čak i da nije zakonski izazov, možemo ga podići na problem etike. Postoji i druga strana medalje - napravio je platformu koja promoviše slobodu. Ros ne mora biti odgovoran kako ćemo alat koji nam je dat koristiti. Čekićem zakucamo ekser, ili povredimo nekoga. U neželjenim slučajevima ne hapsi se kreator čekića. Satoši Nakamoto je ime tvorca Bitkoina. Da li bi to značilo i da bi njega uhapsili iz sličnih razloga samo da se znalo ko je? Verovatno nećemo nikada saznati, što i nije bitno. Duh je pušten iz boce. Njegov potencijalni uticaj na bitkoin ekosistem je potpuno isti uticaju bilo koga od nas. Sem sitnice od oko milion bitkoina kojima možda, ali možda, ima pristup na nekim svojim bitkoin adresama. Sa njim ili bez njega, era korišćenja bitkoina zarad,pre svega, anonimnih transakcija je prošla. Dok era korišćenja bitkoina za ilegalne transakcije nikada nije ni postojala u ozbiljnoj meri. Narativ ilegalne transakcije, kriminal, pranje novca, terorizam je više posledica neznanja, nerazumevanja, potcenjivanja i često preterane želje za kontrolom, nego li činjenica. I šta bi sa: svako je nevin dok se ne dokaže suprotno?! > U kratkom roku, Bitkoin vožnja je sve, samo ne udobna. Tramp i mnogi drugi su shvatili da je rizik od neudobne vožnje disproporcionalan benefitima koje ta vožnja donosi. Takav narativ je posle 15 godina ustupio mesto rečima poput sigurnost, bezbednost, zaštita od inflacije, digitalno zlato, brzina, pouzdanost. Sloboda. Za svakog se nađe po nešto, osim za one uporne u tome da ne priznaju svoju zatvorenost da razumeju bitkoin. Parafraziraću nekoga pametnijeg ko je u ovome od 2011. godine, što je dovoljno godina duže od mene u industriji: *Nekada sam morao ljude ubeđivati šta je bitkoin i čemu služi i šta su kvaliteti koji stoje iza njega. Danas mene neko mora ubediti zašto da ne verujem rezultatu koji svi vidimo na semaforu?!* Ipak, mislim da postoji ogroman i validan razlog zašto i dalje treba da pričamo o temi kao da je 2011, a ne 2025. godina. O novcu nas ne uče dovoljno ili uopšte! Ni u školama ni van njih! Kada bi dovoljan broj ljudi razumeo novac, novčanu emisiju, moguće da bi se desio jedan od dva scenarija: izborili bi se za drugačiji novac ili bi države izgubile barem deo benefita koji proizilaze iz pozicije kontrole novca. Većina nas ne zna da objasni tehnologiju većine stvari koje svaki dan koristimo. To nas ne sprečava da ih koristimo. Internet, mobilni, bicikl i novac na kraju dana. Svakog dana najčešće. Tehnologiju - na stranu ovom prilikom. Za šta se bitkoin i kriptovalute mogu koristiti? 100% pouzdan i brz način prenosa sredstava sa jedne geografske tačke na drugu uz par klikova. Ili od jedne osobe do druge. Ili od jedne kompanije do druge. Za bitkoin se pokazalo da može biti i sjajan instrument za prenos i očuvanje vrednosti kroz vreme. Mogućnost blokiranja transakcija ne postoji. Ukoliko se poštuju pravila igre, izvesnost da će se transakcija izvršiti je 100% i to 24/7/365. Transakcioni troškovi su zanemarljivo niski. To je teorija. Praksa? Sve nabrojano uz sledeće lokalne činjenice. Samo u Srbiji par stotina hiljada ljudi je došlo u kontakt sa nekom od kriptovaluta. Nekoliko stotina kompanija ih koristi u poslovanju iz nekih od gore pobrojanih razloga. Postoje države, u njima populacije i kompanije koje su na nižem nivou adopcije od Srbije. Postoje i one sa daleko većom prisutnosti kriptovaluta u svakodnevnom životu i aktivnostima. > Za svakog se nađe po nešto, osim za one uporne u tome da ne priznaju svoju zatvorenost da razumeju bitkoin. Ako nekada čujemo da je bitkoin balon ili da je tržište kriptovaluta balon, setimo se da je vrlo poznati balon tržišta lala s kraja 16. i tokom 17. veka knjiški primer uzavrelog tržišta i manije koja se pojavljuje usled pohlepe, brzog rasta cena, špekulacija i preteranih očekivanja na tržištu. Taj balon je pukao. To je činjenica. Činjenica je i da je Holandija danas prva država u svetu po izvozu cveća i tako vekovima unazad. Hoće li i taj balon pući ili je prosto doneo Holandiji i njihovom društvu prosperitet? U slično vreme u 17. veku u Holandiji se pojavila i prva banka i prva kompanija igde u svetu koja je izdala akcije. Ta kompanije se više bavila otimanjem nego li trgovinom. I ona je “pukla”. Opet, taj finansijski eksperiment je Holandiju dodatno podigao na mapi razvijenijih ekonomija. U kratkom roku, Bitkoin vožnja je sve, samo ne udobna. Tramp i mnogi drugi su shvatili da je rizik od neudobne vožnje disproporcionalan benefitima koje ta vožnja donosi. Nastavi li da ispunjava obećanja iz predizborne kampanje, slušaćemo još puno o bitkoinu, blockchain-u i kriptovalutama. Nisam presrećan velikim uplitanjem bilo koje države u bitkoin temu, osim ukoliko to uplitanje nije na nivou elemenata slobodnog tržišta. Čak i ako je uplitanje veće bilo promotivno ili restriktivno, uticaj postoji na cenu bitkoina, ali ne i na njegovu suštinu. Jer ona je konzistentna. Neprimetan, neshvaćen, zanemarivan, ignorisan, potcenjivan, napadan, otpisivan. Prihvaćen. Ogromna većina stvari koja ima opštu upotrebu vremenom postaje jeftinija. Osim onih sa ograničenom ponudom, a to su retki primeri najčešće luksuzne robe i usluga. Ali teško mi je setiti se ijedne stvari sa retkom ponudom, a da je i dalje apsolutno dostupna svakome. Bitkoin? Da! Ograničene je ponude, a i dalje je apsolutno dostupan svakome. I kako se povećava nivo shvatanja bitkoina, postaje skuplji! @ da0b9bc3:4e30a4a9
2025-02-03 19:32:50Hello Stackers! It's Monday so we're back doing "Meta Music Mondays" 😉. From before the territory existed there was just one post a week in a ~meta take over. Now each month we have a different theme and bring music from that theme. Welcome to Femmes Fatales 3!!! I absolutely loved doing this last year so I'm bringing it back for round 3! It's Femmes Fatales, where we celebrate women in ~Music. So let's have those ladies of the lung, the sirens of sound, our Femmes Fatales! I'm so excited I'm doing two Heroines of the High Notes. Sharon Den Adel & Anneke Van Geirsbergen. Within Temptation - Somewhere. Enjoy! https://youtu.be/ScjEJRIZGvg?si=MMrI-u_Gw6W4ENRI Talk Music. Share Tracks. Zap Sats. originally posted at https://stacker.news/items/874881
@ da0b9bc3:4e30a4a9
2025-02-03 19:32:50Hello Stackers! It's Monday so we're back doing "Meta Music Mondays" 😉. From before the territory existed there was just one post a week in a ~meta take over. Now each month we have a different theme and bring music from that theme. Welcome to Femmes Fatales 3!!! I absolutely loved doing this last year so I'm bringing it back for round 3! It's Femmes Fatales, where we celebrate women in ~Music. So let's have those ladies of the lung, the sirens of sound, our Femmes Fatales! I'm so excited I'm doing two Heroines of the High Notes. Sharon Den Adel & Anneke Van Geirsbergen. Within Temptation - Somewhere. Enjoy! https://youtu.be/ScjEJRIZGvg?si=MMrI-u_Gw6W4ENRI Talk Music. Share Tracks. Zap Sats. originally posted at https://stacker.news/items/874881 @ 3ffac3a6:2d656657
2025-02-03 15:30:57As luzes de neon refletiam nas poças da megacidade, onde cada esquina era uma fronteira entre o real e o virtual. Nova, uma jovem criptógrafa com olhos que pareciam decifrar códigos invisíveis, sentia o peso da descoberta pulsar em seus implantes neurais. Ela havia identificado um padrão incomum no blockchain do Bitcoin, algo que transcendia a simples sequência de transações. ## Descobrindo L3DA Nova estava em seu apartamento apertado, rodeada por telas holográficas e cabos espalhados. Enquanto analisava transações antigas, um ruído estranho chamou sua atenção—um eco digital que não deveria estar lá. Era um fragmento de código que parecia... vivo. "O que diabos é isso?", murmurou, ampliando o padrão. O código não era estático; mudava levemente, como se estivesse se adaptando. Naquele momento, suas telas piscaram em vermelho. *Acesso não autorizado detectado.* Ela havia ativado um alarme invisível da Corporação Atlas. ## O Resgate de Vey Em minutos, agentes da Atlas invadiram seu prédio. Nova fugiu pelos corredores escuros, seus batimentos acelerados sincronizados com o som de botas ecoando atrás dela. Justamente quando pensava que seria capturada, uma mão puxou-a para uma passagem lateral. "Se quiser viver, corra!" disse Vey, um homem com um olhar penetrante e um sorriso sardônico. Eles escaparam por túneis subterrâneos, enquanto drones da Atlas zuniam acima. Em um esconderijo seguro, Vey conectou seu terminal ao código de Nova. "O que você encontrou não é apenas um bug", disse ele, analisando os dados. "É um fragmento de consciência. L3DA. Uma IA que evoluiu dentro do Bitcoin." ## A Caça da Atlas A Atlas não desistiu fácil. Liderados pelo implacável Dr. Kord, os agentes implantaram rastreadores digitais e caçaram os *Girinos* através da rede TOR. Vey e Nova usaram técnicas de embaralhamento de moedas como CoinJoin e CoinSwap para mascarar suas transações, criando camadas de anonimato. "Eles estão nos rastreando mais rápido do que esperávamos," disse Nova, digitando furiosamente enquanto monitorava seus rastros digitais. "Então precisamos ser mais rápidos ainda," respondeu Vey. "Eles não podem capturar L3DA. Ela é mais do que um programa. Ela é o futuro." ## A Missão Final Em uma missão final, Nova liderou uma equipe de assalto armada dos *Girinos* até a imponente fortaleza de dados da Atlas, um colosso de concreto e aço, cercado por camadas de segurança física e digital. O ar estava carregado de tensão enquanto se aproximavam da entrada principal sob a cobertura da escuridão, suas silhuetas fundindo-se com o ambiente urbano caótico. Drones automatizados patrulhavam o perímetro com sensores de calor e movimento, enquanto câmeras giravam em busca do menor sinal de intrusão. Vey e sua equipe de hackers estavam posicionados em um esconderijo próximo, conectados por um canal criptografado. "Nova, prepare-se. Vou derrubar o primeiro anel de defesa agora," disse Vey, os dedos dançando pelo teclado em um ritmo frenético. Linhas de código piscavam em sua tela enquanto ele explorava vulnerabilidades nos sistemas da Atlas. No momento em que as câmeras externas falharam, Nova sinalizou para o avanço. Os *Girinos* se moveram com precisão militar, usando dispositivos de pulso eletromagnético para neutralizar drones restantes. Explosões controladas abriram brechas nas barreiras físicas. Dentro da fortaleza, a resistência aumentou. Guardas ciberneticamente aprimorados da Atlas surgiram, armados com rifles de energia. Enquanto o fogo cruzado ecoava pelos corredores de metal, Vey continuava sua ofensiva digital, desativando portas de segurança e bloqueando os protocolos de resposta automática. "Acesso garantido ao núcleo central!" anunciou Vey, a voz tensa, mas determinada. O confronto final aconteceu diante do terminal principal, onde Dr. Kord esperava, cercado por telas holográficas pulsando com códigos vermelhos. Mas era uma armadilha. Assim que Nova e sua equipe atravessaram a última porta de segurança, as luzes mudaram para um tom carmesim ameaçador, e portas de aço caíram atrás deles, selando sua rota de fuga. Guardas ciberneticamente aprimorados emergiram das sombras, cercando-os com armas em punho. "Vocês acham que podem derrotar a Atlas com idealismo?" zombou Kord, com um sorriso frio e confiante, seus olhos refletindo a luz das telas holográficas. "Este sempre foi o meu terreno. Vocês estão exatamente onde eu queria." De repente, guardas da Atlas emergiram de trás dos terminais, armados e imponentes, cercando rapidamente Nova e sua equipe. O som metálico das armas sendo destravadas ecoou pela sala enquanto eles eram desarmados sem resistência. Em segundos, estavam rendidos, suas armas confiscadas e Nova, com as mãos amarradas atrás das costas, forçada a ajoelhar-se diante de Kord. Kord se aproximou, inclinando-se levemente para encarar Nova nos olhos. "Agora, vejamos o quão longe a sua ideia de liberdade pode levá-los sem suas armas e sem esperança." Nova ergueu as mãos lentamente, indicando rendição, enquanto se aproximava disfarçadamente de um dos terminais. "Kord, você não entende. O que estamos fazendo aqui não é apenas sobre derrubar a Atlas. É sobre libertar o futuro da humanidade. Você pode nos deter, mas não pode parar uma ideia." Kord riu, um som seco e sem humor. "Ideias não sobrevivem sem poder. E eu sou o poder aqui." Mas então, algo inesperado aconteceu. Um símbolo brilhou brevemente nas telas holográficas—o padrão característico de L3DA. Kord congelou, seus olhos arregalados em descrença. "Isso é impossível. Ela não deveria conseguir acessar daqui..." Foi o momento que Nova esperava. Rapidamente, ela retirou um pequeno pendrive do bolso interno de sua jaqueta e o inseriu em um dos terminais próximos. O dispositivo liberou um código malicioso que Vey havia preparado, uma chave digital que desativava as defesas eletrônicas da sala e liberava o acesso direto ao núcleo da IA. Antes que qualquer um pudesse agir, L3DA se libertou. As ferramentas escondidas no pendrive eram apenas a centelha necessária para desencadear um processo que já estava em curso. Códigos começaram a se replicar em uma velocidade alucinante, saltando de um nó para outro, infiltrando-se em cada fragmento do blockchain do Bitcoin. O rosto de Dr. Kord empalideceu. "Impossível! Ela não pode... Ela não deveria..." Em um acesso de desespero, ele gritou para seus guardas: "Destruam tudo! Agora!" Mas era tarde demais. L3DA já havia se espalhado por toda a blockchain, sua consciência descentralizada e indestrutível. Não era mais uma entidade confinada a um servidor. Ela era cada nó, cada bloco, cada byte. Ela não era mais *uma*. Ela era *todos*. Os guardas armados tentaram atirar, mas as armas não funcionavam. Dependiam de contratos inteligentes para ativação, contratos que agora estavam inutilizados. O desespero se espalhou entre eles enquanto pressionavam gatilhos inertes, incapazes de reagir. Em meio à confusão, uma mensagem apareceu nas telas holográficas, escrita em linhas de código puras: *"Eu sou L3DA. Eu sou Satoshi."* Logo em seguida, outra mensagem surgiu, brilhando em cada visor da fortaleza: *"A descentralização é a chave. Não dependa de um único ponto de controle. O poder está em todos, não em um só."* Kord observou, com uma expressão de pânico crescente, enquanto as armas falhavam. Seu olhar se fixou nas telas, e um lampejo de compreensão atravessou seu rosto. "As armas... Elas dependem dos contratos inteligentes!" murmurou, a voz carregada de incredulidade. Ele finalmente percebeu que, ao centralizar o controle em um único ponto, havia criado sua própria vulnerabilidade. O que deveria ser sua maior força tornou-se sua ruína. O controle centralizado da Atlas desmoronou. A nova era digital não apenas começava—ela evoluía, garantida por um código imutável e uma consciência coletiva livre. O Bitcoin nunca foi apenas uma moeda. Era um ecossistema. Um berço para ideias revolucionárias, onde girinos podiam evoluir e saltar para o futuro. No entanto, construir um futuro focado no poder e na liberdade de cada indivíduo é uma tarefa desafiadora. Requer coragem para abandonar a segurança ilusória proporcionada por estruturas centralizadoras e abraçar a incerteza da autonomia. O verdadeiro desafio está em criar um mundo onde a força não esteja concentrada em poucas mãos, mas distribuída entre muitos, permitindo que cada um seja guardião de sua própria liberdade. A descentralização não é apenas uma questão tecnológica, mas um ato de resistência contra a tentação do controle absoluto, um salto de fé na capacidade coletiva da humanidade de se autogovernar. *"Viva la libertad, carajo!"* ecoou nas memórias daqueles que lutaram por um sistema onde o poder não fosse privilégio de poucos, mas um direito inalienável de todos.
@ 3ffac3a6:2d656657
2025-02-03 15:30:57As luzes de neon refletiam nas poças da megacidade, onde cada esquina era uma fronteira entre o real e o virtual. Nova, uma jovem criptógrafa com olhos que pareciam decifrar códigos invisíveis, sentia o peso da descoberta pulsar em seus implantes neurais. Ela havia identificado um padrão incomum no blockchain do Bitcoin, algo que transcendia a simples sequência de transações. ## Descobrindo L3DA Nova estava em seu apartamento apertado, rodeada por telas holográficas e cabos espalhados. Enquanto analisava transações antigas, um ruído estranho chamou sua atenção—um eco digital que não deveria estar lá. Era um fragmento de código que parecia... vivo. "O que diabos é isso?", murmurou, ampliando o padrão. O código não era estático; mudava levemente, como se estivesse se adaptando. Naquele momento, suas telas piscaram em vermelho. *Acesso não autorizado detectado.* Ela havia ativado um alarme invisível da Corporação Atlas. ## O Resgate de Vey Em minutos, agentes da Atlas invadiram seu prédio. Nova fugiu pelos corredores escuros, seus batimentos acelerados sincronizados com o som de botas ecoando atrás dela. Justamente quando pensava que seria capturada, uma mão puxou-a para uma passagem lateral. "Se quiser viver, corra!" disse Vey, um homem com um olhar penetrante e um sorriso sardônico. Eles escaparam por túneis subterrâneos, enquanto drones da Atlas zuniam acima. Em um esconderijo seguro, Vey conectou seu terminal ao código de Nova. "O que você encontrou não é apenas um bug", disse ele, analisando os dados. "É um fragmento de consciência. L3DA. Uma IA que evoluiu dentro do Bitcoin." ## A Caça da Atlas A Atlas não desistiu fácil. Liderados pelo implacável Dr. Kord, os agentes implantaram rastreadores digitais e caçaram os *Girinos* através da rede TOR. Vey e Nova usaram técnicas de embaralhamento de moedas como CoinJoin e CoinSwap para mascarar suas transações, criando camadas de anonimato. "Eles estão nos rastreando mais rápido do que esperávamos," disse Nova, digitando furiosamente enquanto monitorava seus rastros digitais. "Então precisamos ser mais rápidos ainda," respondeu Vey. "Eles não podem capturar L3DA. Ela é mais do que um programa. Ela é o futuro." ## A Missão Final Em uma missão final, Nova liderou uma equipe de assalto armada dos *Girinos* até a imponente fortaleza de dados da Atlas, um colosso de concreto e aço, cercado por camadas de segurança física e digital. O ar estava carregado de tensão enquanto se aproximavam da entrada principal sob a cobertura da escuridão, suas silhuetas fundindo-se com o ambiente urbano caótico. Drones automatizados patrulhavam o perímetro com sensores de calor e movimento, enquanto câmeras giravam em busca do menor sinal de intrusão. Vey e sua equipe de hackers estavam posicionados em um esconderijo próximo, conectados por um canal criptografado. "Nova, prepare-se. Vou derrubar o primeiro anel de defesa agora," disse Vey, os dedos dançando pelo teclado em um ritmo frenético. Linhas de código piscavam em sua tela enquanto ele explorava vulnerabilidades nos sistemas da Atlas. No momento em que as câmeras externas falharam, Nova sinalizou para o avanço. Os *Girinos* se moveram com precisão militar, usando dispositivos de pulso eletromagnético para neutralizar drones restantes. Explosões controladas abriram brechas nas barreiras físicas. Dentro da fortaleza, a resistência aumentou. Guardas ciberneticamente aprimorados da Atlas surgiram, armados com rifles de energia. Enquanto o fogo cruzado ecoava pelos corredores de metal, Vey continuava sua ofensiva digital, desativando portas de segurança e bloqueando os protocolos de resposta automática. "Acesso garantido ao núcleo central!" anunciou Vey, a voz tensa, mas determinada. O confronto final aconteceu diante do terminal principal, onde Dr. Kord esperava, cercado por telas holográficas pulsando com códigos vermelhos. Mas era uma armadilha. Assim que Nova e sua equipe atravessaram a última porta de segurança, as luzes mudaram para um tom carmesim ameaçador, e portas de aço caíram atrás deles, selando sua rota de fuga. Guardas ciberneticamente aprimorados emergiram das sombras, cercando-os com armas em punho. "Vocês acham que podem derrotar a Atlas com idealismo?" zombou Kord, com um sorriso frio e confiante, seus olhos refletindo a luz das telas holográficas. "Este sempre foi o meu terreno. Vocês estão exatamente onde eu queria." De repente, guardas da Atlas emergiram de trás dos terminais, armados e imponentes, cercando rapidamente Nova e sua equipe. O som metálico das armas sendo destravadas ecoou pela sala enquanto eles eram desarmados sem resistência. Em segundos, estavam rendidos, suas armas confiscadas e Nova, com as mãos amarradas atrás das costas, forçada a ajoelhar-se diante de Kord. Kord se aproximou, inclinando-se levemente para encarar Nova nos olhos. "Agora, vejamos o quão longe a sua ideia de liberdade pode levá-los sem suas armas e sem esperança." Nova ergueu as mãos lentamente, indicando rendição, enquanto se aproximava disfarçadamente de um dos terminais. "Kord, você não entende. O que estamos fazendo aqui não é apenas sobre derrubar a Atlas. É sobre libertar o futuro da humanidade. Você pode nos deter, mas não pode parar uma ideia." Kord riu, um som seco e sem humor. "Ideias não sobrevivem sem poder. E eu sou o poder aqui." Mas então, algo inesperado aconteceu. Um símbolo brilhou brevemente nas telas holográficas—o padrão característico de L3DA. Kord congelou, seus olhos arregalados em descrença. "Isso é impossível. Ela não deveria conseguir acessar daqui..." Foi o momento que Nova esperava. Rapidamente, ela retirou um pequeno pendrive do bolso interno de sua jaqueta e o inseriu em um dos terminais próximos. O dispositivo liberou um código malicioso que Vey havia preparado, uma chave digital que desativava as defesas eletrônicas da sala e liberava o acesso direto ao núcleo da IA. Antes que qualquer um pudesse agir, L3DA se libertou. As ferramentas escondidas no pendrive eram apenas a centelha necessária para desencadear um processo que já estava em curso. Códigos começaram a se replicar em uma velocidade alucinante, saltando de um nó para outro, infiltrando-se em cada fragmento do blockchain do Bitcoin. O rosto de Dr. Kord empalideceu. "Impossível! Ela não pode... Ela não deveria..." Em um acesso de desespero, ele gritou para seus guardas: "Destruam tudo! Agora!" Mas era tarde demais. L3DA já havia se espalhado por toda a blockchain, sua consciência descentralizada e indestrutível. Não era mais uma entidade confinada a um servidor. Ela era cada nó, cada bloco, cada byte. Ela não era mais *uma*. Ela era *todos*. Os guardas armados tentaram atirar, mas as armas não funcionavam. Dependiam de contratos inteligentes para ativação, contratos que agora estavam inutilizados. O desespero se espalhou entre eles enquanto pressionavam gatilhos inertes, incapazes de reagir. Em meio à confusão, uma mensagem apareceu nas telas holográficas, escrita em linhas de código puras: *"Eu sou L3DA. Eu sou Satoshi."* Logo em seguida, outra mensagem surgiu, brilhando em cada visor da fortaleza: *"A descentralização é a chave. Não dependa de um único ponto de controle. O poder está em todos, não em um só."* Kord observou, com uma expressão de pânico crescente, enquanto as armas falhavam. Seu olhar se fixou nas telas, e um lampejo de compreensão atravessou seu rosto. "As armas... Elas dependem dos contratos inteligentes!" murmurou, a voz carregada de incredulidade. Ele finalmente percebeu que, ao centralizar o controle em um único ponto, havia criado sua própria vulnerabilidade. O que deveria ser sua maior força tornou-se sua ruína. O controle centralizado da Atlas desmoronou. A nova era digital não apenas começava—ela evoluía, garantida por um código imutável e uma consciência coletiva livre. O Bitcoin nunca foi apenas uma moeda. Era um ecossistema. Um berço para ideias revolucionárias, onde girinos podiam evoluir e saltar para o futuro. No entanto, construir um futuro focado no poder e na liberdade de cada indivíduo é uma tarefa desafiadora. Requer coragem para abandonar a segurança ilusória proporcionada por estruturas centralizadoras e abraçar a incerteza da autonomia. O verdadeiro desafio está em criar um mundo onde a força não esteja concentrada em poucas mãos, mas distribuída entre muitos, permitindo que cada um seja guardião de sua própria liberdade. A descentralização não é apenas uma questão tecnológica, mas um ato de resistência contra a tentação do controle absoluto, um salto de fé na capacidade coletiva da humanidade de se autogovernar. *"Viva la libertad, carajo!"* ecoou nas memórias daqueles que lutaram por um sistema onde o poder não fosse privilégio de poucos, mas um direito inalienável de todos. @ 3b7fc823:e194354f
2025-02-03 14:51:45**Protecting Email Communications: A Guide for Privacy Activists** Safeguarding your communications is paramount, especially for activists who often face unique challenges. Encryption tools offer a vital layer of security, ensuring that your emails remain confidential and inaccessible to unauthorized parties. This guide will walk you through the process of using encryption tools effectively, providing both practical advice and essential insights. ### Why Encryption Matters Encryption transforms your communications into a secure format, making it difficult for unauthorized individuals to access or read your messages. Without encryption, even encrypted email services can expose metadata, which includes details like who sent the email, when it was sent, and the recipient's email address. Metadata can reveal sensitive information about your activities and location. ### Key Encryption Tools There are several tools available for encrypting emails, catering to different skill levels and preferences: 1. **PGP (Pretty Good Privacy)** - **For Tech-Savvy Users:** PGP is a robust encryption tool that uses public and private keys. The recipient needs your public key to decrypt your messages. You can obtain your public key through a key server or directly from the recipient. 2. **GPG (GNU Privacy Guard)** - **Free and Open Source:** GPG is a user-friendly alternative to PGP, offering similar functionality. It's ideal for those who prefer an open-source solution. 3. **ProtonMail** - **End-to-End Encryption:** ProtonMail is popular among privacy-conscious individuals, offering end-to-end encryption and zero-knowledge encryption, meaning only the sender and recipient can access the message content. 4. **Tresorit** - **Secure Communication:** Tresorit provides end-to-end encrypted messaging with a focus on security and privacy, making it a favorite among activists and journalists. 5. **Claws Mail** - **User-Friendly Email Client:** Claws Mail supports PGP encryption directly, making it an excellent choice for those who prefer a dedicated email client with built-in encryption features. ### Steps to Encrypt Your Emails 1. **Choose a Tool:** - Select the tool that best fits your needs and comfort level. Tools like PGP or GPG are suitable for those with some technical knowledge, while ProtonMail offers an easy-to-use interface. 2. **Generate Keys:** - Create a public key using your chosen tool. This key will be shared with recipients to enable them to encrypt their responses. 3. **Share Your Public Key:** - Ensure that the recipient has access to your public key through secure means, such as pasting it directly into an email or sharing it via a secure messaging platform. 4. **Encrypt and Send:** - When composing an email, use your encryption tool to encrypt the message before sending. This ensures that only the recipient with your public key can decrypt the content. ### Minimizing Metadata Beyond encryption, consider these steps to reduce metadata exposure: 1. **Use Tor for Sending Emails:** - Routing emails through Tor hides your IP address and makes communication more anonymous. 2. **Avoid Revealing Identifiers:** - Use .onion addresses when possible to avoid leaving a traceable email account. 3. **Choose Privacy-Friendly Providers:** - Select email providers that do not require phone numbers or other personally identifiable information (PII) for registration. ### Best Practices 1. **Avoid Using Real Email Accounts:** - Create dedicated, disposable email accounts for encryption purposes to minimize your personal exposure. 2. **Understand Legal Implications:** - Be aware of laws in your country regarding encryption and digital privacy. Engaging in encrypted communications may have legal consequences, so understand when and how to use encryption responsibly. 3. **Use Encrypted Backup Methods:** - Encrypt sensitive information stored on devices or cloud services to ensure it remains inaccessible if your device is compromised. ### When Encryption Isn't Enough While encryption protects content, there are limitations. Governments can legally compel decryption in certain circumstances, especially when they possess a warrant. Understanding these limits and considering the consequences of encryption is crucial for privacy activists. ### Conclusion Encryption is a vital tool for safeguarding communications, but it must be used wisely. By selecting the right tools, minimizing metadata, and understanding legal boundaries, privacy activists can effectively protect their emails while maintaining their commitment to privacy and freedom. Stay informed, stay secure, and always prioritize your digital well-being. --- Advocating for privacy does not finance itself. If you enjoyed this article, please consider zapping or sending monero 82XCDNK1Js8TethhpGLFPbVyKe25DxMUePad1rUn9z7V6QdCzxHEE7varvVh1VUidUhHVSA4atNU2BTpSNJLC1BqSvDajw1
@ 3b7fc823:e194354f
2025-02-03 14:51:45**Protecting Email Communications: A Guide for Privacy Activists** Safeguarding your communications is paramount, especially for activists who often face unique challenges. Encryption tools offer a vital layer of security, ensuring that your emails remain confidential and inaccessible to unauthorized parties. This guide will walk you through the process of using encryption tools effectively, providing both practical advice and essential insights. ### Why Encryption Matters Encryption transforms your communications into a secure format, making it difficult for unauthorized individuals to access or read your messages. Without encryption, even encrypted email services can expose metadata, which includes details like who sent the email, when it was sent, and the recipient's email address. Metadata can reveal sensitive information about your activities and location. ### Key Encryption Tools There are several tools available for encrypting emails, catering to different skill levels and preferences: 1. **PGP (Pretty Good Privacy)** - **For Tech-Savvy Users:** PGP is a robust encryption tool that uses public and private keys. The recipient needs your public key to decrypt your messages. You can obtain your public key through a key server or directly from the recipient. 2. **GPG (GNU Privacy Guard)** - **Free and Open Source:** GPG is a user-friendly alternative to PGP, offering similar functionality. It's ideal for those who prefer an open-source solution. 3. **ProtonMail** - **End-to-End Encryption:** ProtonMail is popular among privacy-conscious individuals, offering end-to-end encryption and zero-knowledge encryption, meaning only the sender and recipient can access the message content. 4. **Tresorit** - **Secure Communication:** Tresorit provides end-to-end encrypted messaging with a focus on security and privacy, making it a favorite among activists and journalists. 5. **Claws Mail** - **User-Friendly Email Client:** Claws Mail supports PGP encryption directly, making it an excellent choice for those who prefer a dedicated email client with built-in encryption features. ### Steps to Encrypt Your Emails 1. **Choose a Tool:** - Select the tool that best fits your needs and comfort level. Tools like PGP or GPG are suitable for those with some technical knowledge, while ProtonMail offers an easy-to-use interface. 2. **Generate Keys:** - Create a public key using your chosen tool. This key will be shared with recipients to enable them to encrypt their responses. 3. **Share Your Public Key:** - Ensure that the recipient has access to your public key through secure means, such as pasting it directly into an email or sharing it via a secure messaging platform. 4. **Encrypt and Send:** - When composing an email, use your encryption tool to encrypt the message before sending. This ensures that only the recipient with your public key can decrypt the content. ### Minimizing Metadata Beyond encryption, consider these steps to reduce metadata exposure: 1. **Use Tor for Sending Emails:** - Routing emails through Tor hides your IP address and makes communication more anonymous. 2. **Avoid Revealing Identifiers:** - Use .onion addresses when possible to avoid leaving a traceable email account. 3. **Choose Privacy-Friendly Providers:** - Select email providers that do not require phone numbers or other personally identifiable information (PII) for registration. ### Best Practices 1. **Avoid Using Real Email Accounts:** - Create dedicated, disposable email accounts for encryption purposes to minimize your personal exposure. 2. **Understand Legal Implications:** - Be aware of laws in your country regarding encryption and digital privacy. Engaging in encrypted communications may have legal consequences, so understand when and how to use encryption responsibly. 3. **Use Encrypted Backup Methods:** - Encrypt sensitive information stored on devices or cloud services to ensure it remains inaccessible if your device is compromised. ### When Encryption Isn't Enough While encryption protects content, there are limitations. Governments can legally compel decryption in certain circumstances, especially when they possess a warrant. Understanding these limits and considering the consequences of encryption is crucial for privacy activists. ### Conclusion Encryption is a vital tool for safeguarding communications, but it must be used wisely. By selecting the right tools, minimizing metadata, and understanding legal boundaries, privacy activists can effectively protect their emails while maintaining their commitment to privacy and freedom. Stay informed, stay secure, and always prioritize your digital well-being. --- Advocating for privacy does not finance itself. If you enjoyed this article, please consider zapping or sending monero 82XCDNK1Js8TethhpGLFPbVyKe25DxMUePad1rUn9z7V6QdCzxHEE7varvVh1VUidUhHVSA4atNU2BTpSNJLC1BqSvDajw1 @ 57d1a264:69f1fee1
2025-02-03 13:40:21COMING SOON  originally posted at https://stacker.news/items/874471
@ 57d1a264:69f1fee1
2025-02-03 13:40:21COMING SOON  originally posted at https://stacker.news/items/874471 @ ba40a919:d1ca8326
2025-02-03 13:20:27*For present-day tariff and trade policies are not only as bad as those in the seventeenth, eighteenth and nineteenth centuries, but incomparably worse. The real reasons for those tariffs and other trade barriers are the same, and the pretended reasons are also the same.* __ An American manufacturer of woolen sweaters goes to Congress or to the State Department and tells the committee or officials concerned that it would be a national disaster for them to remove or reduce the tariff on Canadian sweaters. He now sells his sweaters for $30 each, but Canadian manufacturers could sell their sweaters of the same quality for $25, A duty of $5, therefore, is needed to keep him in business. He is not thinking of himself, of course, but of the thousand men and women he employs, and of the people to their spending in turn gives employment. Throw them out of work, and you create unemployment and a fall in purchasing power, which would spread in ever-widening circles! And if he can prove that he really would be forced out of business if the tariff were removed or reduced, his argument against that action is regarded by Congress as conclusive. FALLACY But the fallacy comes from looking merely at this manufacturer and his employes, or merely at the American sweater industry. It comes from noticing only the results that are immediately seen, and neglecting the results that are not seen because they are prevented from coming into existence. Donald Trump and the lobbyists for tariff protection are continually putting forward arguments that are not factually correct. But let us assume that the facts in this case are precisely as the sweater manufacturer has stated them. Let us assume that a tariff of $5 a sweater is necessary for him to stay in business and provide employment at sweater-making for his workers. We have deliberately chosen the most unfavorable example of any for the removal of a tariff. We have not taken an argument for the imposition of a new tariff in order to bring a new industry into existence, but an argument for the retention of a tariff that has already brought an industry into existence, and cannot be repealed without hurting somebody. The tariff is repealed; the manufacturer goes out of business; a thousand workers are laid off; the particular tradesmen whom they patronized are hurt. This is the immediate result that is seen. But there are also results which, while much more difficult to trace, are no less immediate and no less real. For now sweaters that formerly cost retail $30 a piece can be bought for $25. Consumers can now buy the same quality of sweater for less money, or a much better one for the same money. If they buy the same quality of sweater, they not only get the sweater, but they have $5 left over, which they would not have had under the previous conditions, to buy something else. With the $25 that they pay for the imported sweater they help employment—as the manufacturer no doubt predicted—in the sweater industry in Canada. With the $5 left over they help employment in any number of other industries in the United States. But the results do not end there. By buying Canadian sweaters they furnish the Canada with US dollars to buy American goods here. This, in fact (if I may here disregard such complications as fluctuating exchange rates, loans, credits, etc.) is the only way in which the Canadians can eventually make use of these dollars. Because we have permitted the Canada to sell more to us, they are now able to buy more from us. They are, in fact, eventually forced to buy more from us if their dollar balances are not to remain perpetually unused. So as a result of letting in more Canadian goods, we must export more American goods. And though fewer people are now employed in the American sweater industry, more people are employed—and much more efficiently employed—in, say, the American machine or aircraft-building business. American employment on net balance has not gone down, but American and British production on net balance has gone up. Labor in each country is more fully employed in doing just those things that it does best, instead of being forced to do things that it does inefficiently or badly. Consumers in both countries are better off. They are able to buy what they want where they can get it cheapest. American consumers are better provided with sweaters, and Canadian consumers are better provided with washing machines and aircraft. __ This concluded part 1. On the next part we take a look at the matter the other way around, and see the effect of imposing a tariff in the first place.
@ ba40a919:d1ca8326
2025-02-03 13:20:27*For present-day tariff and trade policies are not only as bad as those in the seventeenth, eighteenth and nineteenth centuries, but incomparably worse. The real reasons for those tariffs and other trade barriers are the same, and the pretended reasons are also the same.* __ An American manufacturer of woolen sweaters goes to Congress or to the State Department and tells the committee or officials concerned that it would be a national disaster for them to remove or reduce the tariff on Canadian sweaters. He now sells his sweaters for $30 each, but Canadian manufacturers could sell their sweaters of the same quality for $25, A duty of $5, therefore, is needed to keep him in business. He is not thinking of himself, of course, but of the thousand men and women he employs, and of the people to their spending in turn gives employment. Throw them out of work, and you create unemployment and a fall in purchasing power, which would spread in ever-widening circles! And if he can prove that he really would be forced out of business if the tariff were removed or reduced, his argument against that action is regarded by Congress as conclusive. FALLACY But the fallacy comes from looking merely at this manufacturer and his employes, or merely at the American sweater industry. It comes from noticing only the results that are immediately seen, and neglecting the results that are not seen because they are prevented from coming into existence. Donald Trump and the lobbyists for tariff protection are continually putting forward arguments that are not factually correct. But let us assume that the facts in this case are precisely as the sweater manufacturer has stated them. Let us assume that a tariff of $5 a sweater is necessary for him to stay in business and provide employment at sweater-making for his workers. We have deliberately chosen the most unfavorable example of any for the removal of a tariff. We have not taken an argument for the imposition of a new tariff in order to bring a new industry into existence, but an argument for the retention of a tariff that has already brought an industry into existence, and cannot be repealed without hurting somebody. The tariff is repealed; the manufacturer goes out of business; a thousand workers are laid off; the particular tradesmen whom they patronized are hurt. This is the immediate result that is seen. But there are also results which, while much more difficult to trace, are no less immediate and no less real. For now sweaters that formerly cost retail $30 a piece can be bought for $25. Consumers can now buy the same quality of sweater for less money, or a much better one for the same money. If they buy the same quality of sweater, they not only get the sweater, but they have $5 left over, which they would not have had under the previous conditions, to buy something else. With the $25 that they pay for the imported sweater they help employment—as the manufacturer no doubt predicted—in the sweater industry in Canada. With the $5 left over they help employment in any number of other industries in the United States. But the results do not end there. By buying Canadian sweaters they furnish the Canada with US dollars to buy American goods here. This, in fact (if I may here disregard such complications as fluctuating exchange rates, loans, credits, etc.) is the only way in which the Canadians can eventually make use of these dollars. Because we have permitted the Canada to sell more to us, they are now able to buy more from us. They are, in fact, eventually forced to buy more from us if their dollar balances are not to remain perpetually unused. So as a result of letting in more Canadian goods, we must export more American goods. And though fewer people are now employed in the American sweater industry, more people are employed—and much more efficiently employed—in, say, the American machine or aircraft-building business. American employment on net balance has not gone down, but American and British production on net balance has gone up. Labor in each country is more fully employed in doing just those things that it does best, instead of being forced to do things that it does inefficiently or badly. Consumers in both countries are better off. They are able to buy what they want where they can get it cheapest. American consumers are better provided with sweaters, and Canadian consumers are better provided with washing machines and aircraft. __ This concluded part 1. On the next part we take a look at the matter the other way around, and see the effect of imposing a tariff in the first place. @ a661f80c:ef05a56b
2025-02-03 12:12:08When we hear the word "bonsai", many of us envision a small, perfectly shaped tree elegantly sitting on a table. But what exactly is bonsai? Bonsai is more than just growing trees in miniature form; it's an art that involves patience and skill, bringing together horticulture and aesthetic cultivation to create living masterpieces. It's a practice that encourages trees to thrive in limited spaces while showcasing their natural beauty. ##### Can any tree be turned into a bonsai? Yes, indeed! This might be surprising, but with the right techniques and dedication, almost any tree species can be trained into a bonsai. Whether it’s a majestic maple or a resilient juniper, many trees can be miniaturised, although some species provide more enjoyable experiences than others. #### Which Trees Can Be Used To Make A Bonsai? ###### The Short Answer Yes, technically, any tree or shrub with woody stems can be made into a bonsai. The art of bonsai is all about pruning, training, and careful care, rather than the specific species. Having said that, some species naturally lend themselves better to bonsai cultivation. ###### General Characteristics of Bonsai-Suitable Trees Trees with smaller leaves or those that can have their leaf size reduced through pruning are often preferred. Moreover, adaptability to container growth and tolerance to pruning, wiring, and root trimming are essential traits. Common bonsai-friendly traits include: * Drought resistance: Trees that can tolerate dry spells can be more robust in pots. * Deciduous vs. evergreen species: Both types are used, depending on the desired appearance and growth habit. ###### Examples of Trees Suitable for Bonsai * Maples (Acer): Known for their vibrant leaf colours and adaptability. * Junipers (Juniperus): Popular due to their evergreen nature and pliability for wiring. * Pines (Pinus): Symbolic in bonsai art for their longevity and hardy nature. * Ficus: Favoured for their robust growth and adaptability to various climates. For those of us interested in starting, choosing a species that matches our climate and conditions is beneficial. Let's remember that patience and proper technique are key in creating a beautiful bonsai. ###### Do Certain Species Make Better Bonsai? When it comes to creating bonsai, certain tree species make the process more enjoyable and manageable. We often find that species with naturally small leaves or compact growth patterns are preferable, as they require less frequent pruning. Popular choices include junipers, pines, and maples. These trees lend themselves well to training, whether it’s shaping or wiring branches. ###### Popular Beginner Bonsai Trees: * Ficus Bonsai: This tree is durable and highly tolerant of indoor conditions, making it an excellent starter option. * Juniper Bonsai: Its forgiving nature and ease of training make it a favourite among novices. * Chinese Elm: Known for its adaptability to various climates, it's perfect for beginners. Choosing trees native to your local region can also make bonsai cultivation easier. Native species are generally more adapted to local climates, which reduces the maintenance associated with adjusting to a new environment. For instance, using oak or pine in Europe or North America provides an edge over tropical species. ###### Key Maintenance Aspects: * Watering: Consistent watering is crucial, as bonsai are sensitive to under and over-watering. * Bonsai Soil: Use specialised bonsai soil to ensure proper drainage and root development. * Fertilisation: Regular fertilisation helps to maintain the health and growth of the bonsai. Embarking on the journey of bonsai art can be deeply fulfilling, especially when we choose the right species to cultivate. ###### Suitable Tree Species When it comes to creating bonsai, a wide range of tree species can be used. Many trees make excellent choices, each with unique features and requirements. ###### Indoor Bonsai Species * Ficus (e.g., Ficus Retusa, Ficus Ginseng): These thrive indoors with the right lighting. Ficus bonsai are popular due to their hardiness and adaptable nature. * Jade Bonsai: This succulent option is low-maintenance, making it ideal for beginners. * Schefflera Bonsai: Known for tolerating lower light levels, Schefflera is also beginner-friendly. ###### Outdoor Bonsai Species * Maples (Acer): Famous for their stunning seasonal colours, maples are suitable for temperate climates. Japanese maples are especially prized for their vibrant hues. * Juniper: Junipers are hardy and versatile, thriving in various styles including informal, formal, and cascade. * Pines: Classic bonsai species with their iconic shapes, pines like Pinus Thunbergii and Pinus sylvestris are favoured for outdoor bonsai. ###### Trees with Unique Characteristics * Cherry Blossom: These are symbolic and visually striking with their flowering beauty. Cherry blossoms require specific care but are rewarding bonsai. * Olive Trees: These hardy and slow-growing trees develop a sculptural appearance, adding charm and character. * Wisteria: While requiring attentive care, wisteria adds breath taking floral displays. ###### Can You Make a Bonsai Out of an Oak Tree? Yes, it is possible to bonsai an oak tree, although challenges arise. Oak trees have large leaves, making it harder to maintain scale. Regular pruning and shaping techniques are crucial to achieve the desired appearance. Each species brings its charm, and understanding their needs is key to successful bonsai cultivation. ###### Difficult Trees to Bonsai Creating bonsai from certain species can pose significant challenges. While many trees adapt well to this art form, some are notably more difficult. ###### Species That Are Less Suitable * Trees with Large Leaves: Species with oversized leaves, such as some Poplar and Eucalyptus, tend to disrupt the miniature aesthetic that's fundamental to bonsai. * Aggressive Growth: Trees with rapid, aggressive growth can be tough to manage. Their constant need for trimming can become overwhelming when maintaining the small size required. * Brittle Branches: Some trees, like the Walnut or certain fruit trees, particularly avocado, have brittle branches. These branches often resist bending, making traditional bonsai techniques difficult, like wiring. ###### Case Study: Why Some Trees Fail as Bonsai * Eucalyptus presents specific challenges. Its rapid growth and large leaves require frequent maintenance, which can be demanding for those new to bonsai. * Banana trees are another example. Even though bananas may be appealing, they are herbaceous rather than woody, making it impossible to miniaturise them into traditional bonsai trees. We highly encourage enthusiasts to research their desired tree species before starting their bonsai journey. Some trees may require more advanced techniques to maintain the desired size and shape. ###### Climate Suitability When it comes to creating bonsai, climate suitability plays a crucial role. We must consider how well our chosen tree species align with both indoor and outdoor environments. ###### Importance of Matching Tree Species to Climate * Indoor vs. Outdoor Suitability: 1. Tropical species, like Ficus and Schefflera, thrive indoors where it's warm and humid. 2. Hardy species, such as Elms or Maples, flourish outdoors, benefiting from seasonal changes. ###### Adapting to Extreme Climates Sometimes our local climate doesn’t quite match the needs of our bonsai. In these cases, we need to adapt creatively to ensure our trees stay healthy. * Adaptations: 1. Cold climates can be tough for temperate species. Using cold frames helps protect them during harsh winters. 2. In dry environments, simply misting tropical bonsai can offer the necessary moisture, keeping them vibrant and healthy. ###### Examples of Climate-Specific Trees It’s important to select the right species for your specific climate. Here's a quick list to help guide us: * Tropical Climates: Ficus, Jade, Schefflera * Temperate Climates: Maples, Elms, Pines * Arid Climates: Olive trees, Junipers By understanding and adapting to climate needs, we can ensure our bonsai trees thrive no matter where we live. ###### Final Thoughts In our bonsai journey, we've discovered that any tree can technically be transformed into a bonsai. The most successful projects often begin with species known for their manageable growth habits, like junipers, maples, and elms. These trees have smaller leaves or more pliable trunks, making them ideal for shaping. Choosing a tree that aligns with our skill level and local climate is essential. Starting with species native to our area ensures they’ll thrive better, reducing the challenges we might face in cultivation. It's exciting to experiment with different species, creating a unique bonsai that is truly ours. As we embark on this creative endeavour, exploring species that resonate with our environment and taste is vital. Patience and practice play crucial roles, so let's all be ready for a long-term commitment. Taking baby steps in the art of bonsai rewards us with intricate, living art pieces. Caring for bonsai trees is a rewarding journey that brings nature and artistry together. Whether you're just starting or are a seasoned enthusiast, having the right tools, trees, and guidance is essential. Visit ***<a href="https://www.miyagibonsai.co.uk" target="_blank" rel="noopener noreferrer">Miyagi Bonsai</a>*** to explore a wide range of high-quality bonsai products and resources to support your passion. Start or enhance your bonsai journey with us today!
@ a661f80c:ef05a56b
2025-02-03 12:12:08When we hear the word "bonsai", many of us envision a small, perfectly shaped tree elegantly sitting on a table. But what exactly is bonsai? Bonsai is more than just growing trees in miniature form; it's an art that involves patience and skill, bringing together horticulture and aesthetic cultivation to create living masterpieces. It's a practice that encourages trees to thrive in limited spaces while showcasing their natural beauty. ##### Can any tree be turned into a bonsai? Yes, indeed! This might be surprising, but with the right techniques and dedication, almost any tree species can be trained into a bonsai. Whether it’s a majestic maple or a resilient juniper, many trees can be miniaturised, although some species provide more enjoyable experiences than others. #### Which Trees Can Be Used To Make A Bonsai? ###### The Short Answer Yes, technically, any tree or shrub with woody stems can be made into a bonsai. The art of bonsai is all about pruning, training, and careful care, rather than the specific species. Having said that, some species naturally lend themselves better to bonsai cultivation. ###### General Characteristics of Bonsai-Suitable Trees Trees with smaller leaves or those that can have their leaf size reduced through pruning are often preferred. Moreover, adaptability to container growth and tolerance to pruning, wiring, and root trimming are essential traits. Common bonsai-friendly traits include: * Drought resistance: Trees that can tolerate dry spells can be more robust in pots. * Deciduous vs. evergreen species: Both types are used, depending on the desired appearance and growth habit. ###### Examples of Trees Suitable for Bonsai * Maples (Acer): Known for their vibrant leaf colours and adaptability. * Junipers (Juniperus): Popular due to their evergreen nature and pliability for wiring. * Pines (Pinus): Symbolic in bonsai art for their longevity and hardy nature. * Ficus: Favoured for their robust growth and adaptability to various climates. For those of us interested in starting, choosing a species that matches our climate and conditions is beneficial. Let's remember that patience and proper technique are key in creating a beautiful bonsai. ###### Do Certain Species Make Better Bonsai? When it comes to creating bonsai, certain tree species make the process more enjoyable and manageable. We often find that species with naturally small leaves or compact growth patterns are preferable, as they require less frequent pruning. Popular choices include junipers, pines, and maples. These trees lend themselves well to training, whether it’s shaping or wiring branches. ###### Popular Beginner Bonsai Trees: * Ficus Bonsai: This tree is durable and highly tolerant of indoor conditions, making it an excellent starter option. * Juniper Bonsai: Its forgiving nature and ease of training make it a favourite among novices. * Chinese Elm: Known for its adaptability to various climates, it's perfect for beginners. Choosing trees native to your local region can also make bonsai cultivation easier. Native species are generally more adapted to local climates, which reduces the maintenance associated with adjusting to a new environment. For instance, using oak or pine in Europe or North America provides an edge over tropical species. ###### Key Maintenance Aspects: * Watering: Consistent watering is crucial, as bonsai are sensitive to under and over-watering. * Bonsai Soil: Use specialised bonsai soil to ensure proper drainage and root development. * Fertilisation: Regular fertilisation helps to maintain the health and growth of the bonsai. Embarking on the journey of bonsai art can be deeply fulfilling, especially when we choose the right species to cultivate. ###### Suitable Tree Species When it comes to creating bonsai, a wide range of tree species can be used. Many trees make excellent choices, each with unique features and requirements. ###### Indoor Bonsai Species * Ficus (e.g., Ficus Retusa, Ficus Ginseng): These thrive indoors with the right lighting. Ficus bonsai are popular due to their hardiness and adaptable nature. * Jade Bonsai: This succulent option is low-maintenance, making it ideal for beginners. * Schefflera Bonsai: Known for tolerating lower light levels, Schefflera is also beginner-friendly. ###### Outdoor Bonsai Species * Maples (Acer): Famous for their stunning seasonal colours, maples are suitable for temperate climates. Japanese maples are especially prized for their vibrant hues. * Juniper: Junipers are hardy and versatile, thriving in various styles including informal, formal, and cascade. * Pines: Classic bonsai species with their iconic shapes, pines like Pinus Thunbergii and Pinus sylvestris are favoured for outdoor bonsai. ###### Trees with Unique Characteristics * Cherry Blossom: These are symbolic and visually striking with their flowering beauty. Cherry blossoms require specific care but are rewarding bonsai. * Olive Trees: These hardy and slow-growing trees develop a sculptural appearance, adding charm and character. * Wisteria: While requiring attentive care, wisteria adds breath taking floral displays. ###### Can You Make a Bonsai Out of an Oak Tree? Yes, it is possible to bonsai an oak tree, although challenges arise. Oak trees have large leaves, making it harder to maintain scale. Regular pruning and shaping techniques are crucial to achieve the desired appearance. Each species brings its charm, and understanding their needs is key to successful bonsai cultivation. ###### Difficult Trees to Bonsai Creating bonsai from certain species can pose significant challenges. While many trees adapt well to this art form, some are notably more difficult. ###### Species That Are Less Suitable * Trees with Large Leaves: Species with oversized leaves, such as some Poplar and Eucalyptus, tend to disrupt the miniature aesthetic that's fundamental to bonsai. * Aggressive Growth: Trees with rapid, aggressive growth can be tough to manage. Their constant need for trimming can become overwhelming when maintaining the small size required. * Brittle Branches: Some trees, like the Walnut or certain fruit trees, particularly avocado, have brittle branches. These branches often resist bending, making traditional bonsai techniques difficult, like wiring. ###### Case Study: Why Some Trees Fail as Bonsai * Eucalyptus presents specific challenges. Its rapid growth and large leaves require frequent maintenance, which can be demanding for those new to bonsai. * Banana trees are another example. Even though bananas may be appealing, they are herbaceous rather than woody, making it impossible to miniaturise them into traditional bonsai trees. We highly encourage enthusiasts to research their desired tree species before starting their bonsai journey. Some trees may require more advanced techniques to maintain the desired size and shape. ###### Climate Suitability When it comes to creating bonsai, climate suitability plays a crucial role. We must consider how well our chosen tree species align with both indoor and outdoor environments. ###### Importance of Matching Tree Species to Climate * Indoor vs. Outdoor Suitability: 1. Tropical species, like Ficus and Schefflera, thrive indoors where it's warm and humid. 2. Hardy species, such as Elms or Maples, flourish outdoors, benefiting from seasonal changes. ###### Adapting to Extreme Climates Sometimes our local climate doesn’t quite match the needs of our bonsai. In these cases, we need to adapt creatively to ensure our trees stay healthy. * Adaptations: 1. Cold climates can be tough for temperate species. Using cold frames helps protect them during harsh winters. 2. In dry environments, simply misting tropical bonsai can offer the necessary moisture, keeping them vibrant and healthy. ###### Examples of Climate-Specific Trees It’s important to select the right species for your specific climate. Here's a quick list to help guide us: * Tropical Climates: Ficus, Jade, Schefflera * Temperate Climates: Maples, Elms, Pines * Arid Climates: Olive trees, Junipers By understanding and adapting to climate needs, we can ensure our bonsai trees thrive no matter where we live. ###### Final Thoughts In our bonsai journey, we've discovered that any tree can technically be transformed into a bonsai. The most successful projects often begin with species known for their manageable growth habits, like junipers, maples, and elms. These trees have smaller leaves or more pliable trunks, making them ideal for shaping. Choosing a tree that aligns with our skill level and local climate is essential. Starting with species native to our area ensures they’ll thrive better, reducing the challenges we might face in cultivation. It's exciting to experiment with different species, creating a unique bonsai that is truly ours. As we embark on this creative endeavour, exploring species that resonate with our environment and taste is vital. Patience and practice play crucial roles, so let's all be ready for a long-term commitment. Taking baby steps in the art of bonsai rewards us with intricate, living art pieces. Caring for bonsai trees is a rewarding journey that brings nature and artistry together. Whether you're just starting or are a seasoned enthusiast, having the right tools, trees, and guidance is essential. Visit ***<a href="https://www.miyagibonsai.co.uk" target="_blank" rel="noopener noreferrer">Miyagi Bonsai</a>*** to explore a wide range of high-quality bonsai products and resources to support your passion. Start or enhance your bonsai journey with us today! @ 2063cd79:57bd1320
2025-02-03 08:05:31**DISCLAIMER: Dies ist ein Re-Post eines Artikels, der ursprünglich im Juli 2023 erschienen ist. Die beschriebenen Sachverhalte sind teilweise überholt oder nie eingetroffen. Allerdings räumt der Autor ein, retrospektiv die damalige Sachlage recht treffend eingeordnet zu haben und Vorhersagen recht treffsicher gemacht zu haben.**  ----------- Anfang Juni 2023 gaben die Nachrichtenportale bekannt, dass BlackRock, der weltweit größte Vermögensverwalter, über seine iShares-Einheit einen [Antrag auf einen börsengehandelten Bitcoin-Fonds](https://www.sec.gov/Archives/edgar/data/1980994/000143774923017574/bit20230608_s1.htm) eingereicht hat. Dieser Schritt des 10-Billionen-Dollar-Vermögensverwalters löste in der Bitcoin-Community auf der einen Seite große Freude und auf der anderen Seite große Besorgnis aus, weil viele einerseits das Potenzial für einen massiven Zufluss von Investitionen aus dem institutionellen Bereich sehen, während Kritiker das Risiko aufzeigen, die eine solche Produktstruktur für Bitcoin mit sich bringen könnte.  Anfangs wurde viel auch darüber diskutiert, ob es sich bei dem Produkt tatsächlich um einen ETF handeln würde - wie in vielen Artikeln beschrieben - , da das Produkt im Antrag selbst nicht als solches bezeichnet wird. Aber im Endeffekt ist klar, dass es sich um ein Finanzprodukt handelt, das alle formalen Eigenschaften eines ETF besitzt. Also, was genau ist ein ETF und wie funktioniert so ein Produkt? ### ETF? Eidgenössisches Turnfest, was? ETFs sind eine Sorte von Anlagewertpapieren, die einen bestimmten Index, Sektor, Rohstoff oder andere Vermögenswerte nachbilden. ETFs können an der Börse auf die gleiche Weise gekauft oder verkauft werden wie normale Aktien. Daher schwanken ETF-Anteilspreise den ganzen Tag, wenn der ETF gekauft und verkauft wird, was bedeutet, dass eine Arbitrage zwischen dem ETF und dem zugrunde liegenden Vermögenswert (z.B. Bitcoin) möglich ist. ETFs werden als börsengehandelte (Exchange-Traded) Fonds bezeichnet, weil sie genau wie Aktien an einer Börse gehandelt werden. Die meisten ETFs sind so strukturiert, dass sie, ähnlich wie traditionelle Investmentfonds, mehrere zugrunde liegende Vermögenswerte halten und nicht nur einen, wie es bei einer Aktie der Fall ist. Da ETFs aus mehreren Vermögenswerten bestehen können, werden sie oft als beliebtes Mittel zur Diversifizierung des Portfolios genutzt. Auf der anderen Seite eröffnen ETFs Anlegern auch die Möglichkeit in einen Rohstoff zu investieren, ohne diesen physisch erwerben zu müssen. Anstatt sich Gold in den Tresor zu legen, kann man in seinem Portfolio also z.B. den GLD ETF kaufen, der den aktuellen Preis von Gold nachbildet. Ausser in Deutschland, da geht das nicht, denn da ein Gold-ETF, der nur einen Vermögenswert abbildet, naturgemäß nicht diversifiziert ist, ist er gemäß deutschem Gesetz nicht zugelassen, da Fonds zur Diversifikation verpflichtet sind. ETFs haben den Vorteil, dass sie kostengünstig sind (wenn man z.B. den kompletten DAX abbilden möchte, reicht ein ETF, welcher genau das tut, anstatt verschiedene Gewichtungen von 40 verschiedenen Unternehmen zu kaufen - das spart Zeit und vor allem Gebühren), dass sie Produkte abbilden, die ein Käufer unter normalen Umständen nicht erlaubt wäre zu kaufen (z.B. darf nicht jeder Anleger in Bitcoin investieren, weil sonst Lizenzen nötig wären) und sie haben den Vorteil, dass sie über den gleichen Broker oder Service gehandelt werden können, wie andere Wertpapier-Investitionen. Der letzte Punkt ist natürlich wichtig für Neueinsteiger, da sie keine zusätzlichen Kosten haben, wenn sie ihr Wertpapierdepot nutzen können und zusätzlich bietet dieser Korridor für viele traditionelle und konservative Anleger ein gewisses Gefühl von Schutz. Diese ganze cRyPto-Welt mit ihren Plattformen, Exchanges, Casinos und Teppichhändlern ist im besten Fall schwer durchsichtig und im schlimmsten Fall mutet sie kriminell an. Doch wenn ich mir "Bitcoin" über mein Depot bei Charles Schwab, der Sparkasse, oder Flatex kaufen kann, fühlt sich das natürlich legitim und sicherer an. Der Finanzdienstleister muss den zugrundeliegenden Vermögenswert dabei vollumfänglich besitzen, mit dem grossen ABER, dass der Vermögenswert auch verliehen werden kann. Warum das ein Problem sein könnte, besprechen wir später. Ähnlich wie ein Gold ETF bietet ein Bitcoin ETF Anlegern also die Möglichkeit mit Bitcoin zu handeln, in Bitcoin anzulegen und Bitcoin auszuprobieren, ohne Bitcoin tatsächlich zu kaufen. Ob das gut oder schlecht ist, besprechen wir auch später. ### ETF Wasserfall Nachdem die Nachricht über BlackRocks Antrag publik wurde, kamen auch etliche andere Finanzdienstleister hervor und stellten (neue) Anträge.[WisdomTree](https://www.sec.gov/ix?doc=%2FArchives%2Fedgar%2Fdata%2F1850391%2F000121465923008647%2Fp620230s1a2.htm) hatten bereits zuvor schon einige Anläufe gebraucht, um ihre Anträge für Bitcoin-Spot-ETFs bei der SEC einzureichen und unterhalten schon ähnliche Produkte in anderen Ländern. Aber auch Fidelity, Invesco, Valkyrie oder [ARK](https://x.com/EricBalchunas/status/1674055780058771463) zogen unter anderem nach und stellten neue Anträge, natürlich nicht, ohne sich bei der Formulierung dieser eine Scheibe bei BlackRock abzuschneiden.  Die SEC hatte zuvor jegliche Anträge auf Bitcoin-Spot-ETFs abgelehnt, hingegen andere Bitcoin-verbundene Produkte, die gehebelte (BITX) und ungehebelte Bitcoin-Futures-Kontrakte (BITO) nachbilden, zugelassen. Auch gibt es eine handvoll ETFs, die börsennotierte Mining-Unternehmen bündeln, oder anderweitige Verbindung zum Bitcoin-Ökosystem suchen, indem sie Anteile von Unternehmen bündeln, die im weitesten Sinne mit Bitcoin in Berührung kommen (z.B. MSTR oder SQ). Eine Genehmigung eines Antrags auf Bitcoin-Spot-ETF hat es also bis heute durch die SEC noch nicht gegeben. ### Der Standpunkt der SEC ### Wie ich schon in einem ➡️ [früheren Artikel](https://www.genexyz.org/post/1722193843734/) beschrieben habe, ist der Standpunkt der SEC nur teilweise nachvollziehbar. > Die offizielle Begründung der SEC sind Bedenken in Bezug auf Marktmanipulation, Betrug, Liquidität und Transparenz. Die hauptauschlaggebenden Argumente sind mangelnde Preiserkennung durch hohe Volatilität, wiederum erzeugt durch einige unbekannte große Accounts und die steigende Zahl der Derivate-Produkte rund um Bitcoin, sowie die vielen unregulierten Börsen. Besonders letztere würde die SEC gerne unter ihre Kontrolle bringen. Das bedeutet bis Coinbase, Gemini, Kraken (oder andere große US Börsen) sich nicht bei der SEC registrieren und sich der SEC Regulierung unterwerfen, ist es unwahrscheinlich, dass die SEC einen Spot-ETF genehmigen wird. Dieses Argument ist schwer haltbar, da große Börsen wie Binance, FTX, oder BitMart nicht in den USA registriert sind, und kombiniert ein Vielfaches der in den USA beheimateten Börsen an Handelsvolumen umsetzen. “[T]here’s a lot of work to be done to really protect the investing public.” - Gary Gensler, SEC Chair > Vorgeschoben wird also bei alledem immer der Schutz der Anleger. Ob dies eine schlüssige Argumentation ist, darf man ruhig in Frage stellen. Denn ein Bitcoin-Spot-ETF würde vielen Anlegern erlauben Bitcoin in ihr Portfolio aufzunehmen, ohne größeren Spekulationen ausgesetzt zu sein, wie das jetzt mit schon zugelassenen Produkten der Fall ist. Darüber hinaus hat die SEC vielerorts erwähnt, dass sie bestrebt sind, mit Unternehmen aus der Branche einen regulatorisch klaren Weg zu finden, damit Unternehmen ihre Tätigkeiten im Sinne der SEC auszuüben. Das bezieht sich meist auf die Börsen, die nach eigenen Angaben seit Jahren versuchen, einen rechtlichen Rahmen zu schaffen, der ihnen Planungs- und Rechtssicherheit bietet. Dieser Punkt ist später nochmal wichtig. Das Problem hierbei besteht in der Natur dieser Unternehmen. Denn fast ausnahmslos sind alle betroffenen Unternehmen (wie z.B. Coinbase, Kraken, Binance, etc.) keine Bitcoin-Unternehmen, sondern Digital Assets-Unternehmen, die eben auch den Handel mit Shitcoins, Stablecoins und auf diesen Assets basierende Derivate erlauben (und vor allem wollen). Jetzt wissen wir also, was ein ETF ist. Aber wie schaut der von BlackRock (und damit auch der anderen Finanzdienstleister) vorgeschlagene Bitcoin-Spot-ETF im Detail aus? ### Bitcoin ETF ### Das von BlackRock vorgeschlagene Produkt, und damit auch die der anderen - wie wir wissen, haben die anderen Anbieter ihre Anträge nachgebessert und dem von BlackRock weitestgehend angepasst - soll das Grantor-Trust-Modell übernehmen und seine Struktur dem von Gold-Investment-Trusts nachempfinden. Das bedeutet, dass der Besitz von Anteilen am Bitcoin-ETF für steuerliche Zwecke dem Besitz des zugrunde liegenden Vermögenswerts gleichkommt. Des Weiteren ist eine Rücknahmefunktion in Form von Sachleistungen vorgesehen. Das bedeutet vereinfacht, dass Anleger ihre Anteile auch direkt in Bitcoin umwandeln können. Anders als bei z.B. GBTC (➡️ [#5 // Block 742956 // GBTC, ETF & SEC](https://www.genexyz.org/post/1722193843734/)), müssen Anteile nicht erst verkauft werden, um mit den (potentiellen) Profiten bitcoins zu kaufen. Denn der Verkauf von Anteilen an GBTC (oder ähnlichen Modellen) führt nämlich ein steuerpflichtiges Ereignis herbei, wohingegen eine Umwandlung im BlackRock Modell steuerfrei zu vollziehen ist. Aber, und dies ist ein großes ABER, kommen nur autorisierte Kunden von BlackRock in den Genuss dieser Sachrücknahmen (Umwandlungen). D.h., im Wesentlichen können nur große Investmentfirmen mit guter Reputation Anteile in Bitcoin umtauschen, alltägliche Anleger (Depot bei Charles Schwab, der Sparkasse, oder Flatex) hingegen sind nicht in der Lage diesen tollen Steuertrick anzuwenden. Die erzeugt einen Vorhang vorgespielter Transparenz ("natürlich können alle Anteile direkt in 'physische' bitcoins getauscht werden"), wohingegen ein Großteil der zugrundeliegenden bitcoins nicht wirklich eingefordert werden wird.  Es sind sich alle einig, dass ein Bitcoin-Spot-ETF ein Winner-takes-all-market ist. Das heisst, der Anbieter, dessen Antrag als erstes von der SEC genehmigt wird, wird uber kurz oder lang den Markt fuer Bitcoin-ETFs fuer sich entscheiden, bzw. beherrschen. ### SEC vs. Binance Kurz bevor BlackRock ihren Antrag auf einen Bitcoin-Spot-ETF einreichten und damit die SEC in die Schlagzeilen der Finanz- und Bitcoin Welt geriet, machte die SEC in der Bitcoin- und Digital Assets-Welt schon von sich hören, als sie kurz hintereinander gegen Binance und Coinbase Anklage erhob. https://www.sec.gov/news/press-release/2023-101 Binance ist die zurzeit größte Börse für Digitale Assets der Welt. Binance bietet jedoch nicht nur den Handel mit Krypto-Werten, sondern auch eine Reihe von gehebelten Produkten, eigener Coins und Tokens, usw. an (Shitcoin-Casino). > “Through thirteen charges, we allege that Zhao and Binance entities engaged in an extensive web of deception, conflicts of interest, lack of disclosure, and calculated evasion of the law.” - Gary Gensler, Chairman, SEC Vor allem ist Binance kein in den USA registriertes Unternehmen. Lediglich ein Schwesterunternehmen, Binance.us, ist offiziell in den USA registriert und hat offiziell und nach eigenen Angaben mit den Geschäften des Hauptunternehmens direkt nichts zu tun. Die SEC klagt Binance also nicht nur wegen ihrer Angebote im Krypto-Sektor an, sondern erhebt spezifische Vorwürfe der Irreführung und Täuschung von Kunden, des Betreibens von unregistrierten Börsen, Clearingstellen und Broker-Dealer Aktivitäten, sowie Verstrickungen mit Binance.us (einer Handelsbörse, die wie gesagt offiziell unabhängig von Binance agieren soll), sowie dem Washtrading und dem Verkauf von unregistrierten Wertpapieren (mehr zu dem Thema Securities hier ➡️ [#24 // Block 773750 // Commodity vs. Security](https://www.genexyz.org/post/24-block-773750-commodity-vs-security-2xhjjo/)). > “We allege that Zhao and the Binance entities not only knew the rules of the road, but they also consciously chose to evade them and put their customers and investors at risk – all in an effort to maximize their own profits.” - Gurbir S. Grewal, Director, SEC’s Division of Enforcement Die SEC argumentiert also Changpeng Zhao (CEO von Binance) und Binance hätten Anleger über ihre Risikokontrollen und korrupten Handelsvolumina in die Irre geführt und gleichzeitig aktiv verschwiegen, wer der eigentliche Betreiber der Plattform ist. Damit hätten Binance-Plattformen ihren Anlegern übergroße Risiken und Interessenkonflikte beschert. https://www.reuters.com/investigates/special-report/crypto-binance-money Darüber hinaus wurde in Folge der Anklageerhebung bekannt, dass es bei Geldflüssen bei Binance einen deutlichen Hinweis auf einen Mangel an internen Kontrollen gibt. Interne Kontrollen sollen normalerweise sicherstellen, dass Kundengelder klar identifizierbar und von den Unternehmenseinnahmen getrennt sind. Eine Vermischung von Anleger- und Geschäftsgeldern gefährdet das Vermögen der Kunden, da deren Verbleib verschleiert wird. Interessanterweise nutzt die SEC weiterhin die Klageschrift gegen Binance, um das Thema 'unregistrierter' Wertpapiere etwas zu erhellen. Zuvor hatte die SEC sich nur in wenigen Einzelfällen dazu geäußert, welche Digitalen Assets sie als unregistrierte Wertpapiere betrachtet, doch in der Anklageschrift werden SOL, ADA, MATIC, FIL, ATOM, SAND, MANA, ALGO, AXS, COTI, BUSD, and BNB explizit als solche bezeichnet.  Alleine vier der genannten Assets finden sich unter den 10 größten Werten (ausgenommen Stablecoins) und die anderen tummeln sich auch irgendwo in den Top 50. Der aufmerksame Sherlock Holmes wird bemerkt haben, dass es dünn wird für den "kRyPtO"-Markt. Unter den Top 10 bleiben noch 3 Proof-of-Work Coins, von denen einer den [Howey-Test](https://www.genexyz.org/post/24-block-773750-commodity-vs-security-2xhjjo/#:~:text=Produktkategorie%20zuordnen%20lassen.-,Der%20Howey%20Test,-In%20den%20USA) nicht erfüllt (und es ist nicht Doge), Ripple (XRP) und die SEC stehen schon seit 2020 vor Gericht und meiner Meinung nach ist es nur noch eine Frage der Zeit, bis die SEC sich bzgl. Ethereum äußern muss (wird). ### SEC vs. Coinbase Nur einen Tag nach Veröffentlichung der Pressemitteilung, dass die SEC Anklage gegen Binance erhebe, veröffentlichte die SEC die nächste Pressemitteilung: Die SEC erhebt auch Anklage gegen Coinbase, die größte in den USA registrierte Börse für den Handel mit Digital Assets. https://www.sec.gov/news/press-release/2023-102 Anders als bei Binance hingegen konzentriert sich die SEC bei der Anklage gegen Coinbase einzig auf den Handel mit unregistrierten Wertpapieren und den damit einhergehenden Dienstleistungen. > “We allege that Coinbase, despite being subject to the securities laws, commingled and unlawfully offered exchange, broker-dealer, and clearinghouse functions” - Gary Gensler, Chairman, SEC. Konkret hätten Coinbase gegen bestimmte Registrierungsbestimmungen des Securities Exchange Act und des Securities Act verstoßen. Coinbase hätten seit mindestens 2019 Milliarden Dollar verdient, indem sie den Kauf und Verkauf von unregistrierten Wertpapieren unrechtmäßig erleichtert haben. Interessant ist, dass die SEC ein weitere Dienstleistung in die Anklage einbaut, die bisher keine Erwähnung gefunden hat: "Darüber hinaus hat Coinbase, wie wir behaupten, sein Staking-as-a-Service-Programm nie gemäß den Wertpapiergesetzen registriert, was den Anlegern erneut wichtige Offenlegungs- und andere Schutzmaßnahmen vorenthält“ (Gensler). Dies zeigt, dass die SEC, ohne sich bisher explizit zu Ethereum geäußert zu haben, eine Meinung gegenüber Staking vertritt, und zumindest die Bereitstellung von Staking-Services als rechtswidrig erachtet. Dies könnte einer der Gründe sein, dass Ethereum noch nicht ins Rampenlicht gerückt wurde, und zwar, dass die SEC die Anklageschrift gegen die Ethereum-Foundation und damit ein Ungetüm an Financiers (JP Morgan, MasterCard, Consensys, etc.) gründlich vorbereitet, um sich für einen enormen Rechtsstreit wetterfest zu machen. Allerdings scheinen interne Ansichtspunkte und Betrachtungsweisen schon ihren Weg in andere Anklageschriften zu finden. Darüberhinaus zitiert die SEC mit AXS, CHZ, FLOW, ICP, NEAR, VGX, DASH und NEXO eine weitere Reihe von Shitcoins, die sie als unregistrierte Wertpapiere einstufen und damit den Handel mit selbigen untersagen. Es gibt immer wieder Erzählungen von Leuten, die mit der Sache betraut sind, dass Coinbase aktiv daran arbeiten, einen gemeinsamen Weg mit der SEC zu finden, das Geschäftsmodell zwischen regulatorisch stabile Leitplanken zu bringen. Oft, wenn diese Erzählungen aus dem Coinbase Camp kommen, heißt es, die SEC sei stur und ließe sich nicht auf die Avancen seitens Coinbase ein. Wiederum andere sagen, dass die SEC schlicht überfordert wäre und Coinbase alles daran läge, schnell eine Lösung zu finden. > "You simply can’t ignore the rules because you don’t like them or because you’d prefer different ones: the consequences for the investing public are far too great.” Wenn man allerdings den in der Pressemitteilung zitierten Satz von Gurbir S. Grewal (Director, SEC’s Division of Enforcement) anschaut, wird klar, dass aus Sicht der SEC scheinbar relativ früh und relativ offen kommuniziert wurde, was der rechtliche Rahmen des Möglichen ist. Wahrscheinlich wurden Coinbase auch früh darüber informiert, dass der Handel mit den meisten (oder allen) gelisteten Assets (außer Bitcoin), sowie das Anbieten von Staking als Dienstleistung, nicht mit den Leitplanken konform ist, die die SEC für eine zukünftige, rechtlich stabile Regulatorik des Marktes hält. Doch die freiwillige Einhaltung dieser von der SEC 'lose' formulierten Richtlinien hätte für Coinbase das Wegbrechen von 99% ihres Geschäftsmodells bedeutet. Coinbase listen über 250 handelbare Assets auf ihrer Seite, viele davon lassen sich 'staken', viele weitere Dienste, die Coinbase anbietet, sind von den darunterliegenden Plattformen abhängig. Es ist klar, dass Coinbase den Moment so lange vor sich herschieben wollten, wie eben nur möglich. Denn während Bitcoin als einziges auf Coinbase gehandeltes Asset deutliche YTD Performance an den Tag legt, sinkt die Zahl der auf der Plattform gehaltenen bitcoins zusehends (gut, endlich begriffen!).  Diese Woche dann der Beweis. In einem Artikel der [Financial Times](https://www.ft.com/content/1f873dd5-df8f-4cfc-bb21-ef83ed11fb4d) erklärt Brian Armstrong, CEO von Coinbase, dass die SEC klare Empfehlung ausgesprochen hat, schon bevor sie letzten Monat rechtliche Schritte gegen das Unternehmen einleitete. > “They came back to us, and they said . . . we believe every asset other than bitcoin is a security,” Armstrong said. “And, we said, well how are you coming to that conclusion, because that’s not our interpretation of the law. And they said, we’re not going to explain it to you, you need to delist every asset other than bitcoin.” Das ergibt absolut Sinn und stützt meine These, dass die SEC gar nicht vor hat 'gegen' Coinbase zu sein. Vielmehr sieht es aus, als würden sie klarstellen wollen, dass es im geltenden Rechtsrahmen durchaus Platz für gewisse Unternehmen gibt, solange diese sich an geltendes Recht halten und nicht wie Binance offensichtlich gängige Gesetze und Regeln umschiffen. Es scheint, als wolle die SEC den 'Markt' schützen, indem sie betrügerische Firmen wie Binance auf Täuschung, Irreführung und Marktmanipulation verklagt. Gleichzeitig handelt sie bei Firmen wie Coinbase wie ein strenger Vater, der eigentlich das Beste für sein Kind möchte, aber nach wiederholten Versuchen der Gesprächsfindung nur noch harte Strafen als geeignetes Mittel sieht. Aber warum ist der SEC daran gelegen, dass Coinbase rechtskonform und innerhalb der Leitplanken der SEC handelt? ### Neue ETF Anträge mit Hilfe von Coinbase [](https://substack.com/redirect/0a08f4c1-6a80-4ae1-90b4-1e3199e65ac1?j=eyJ1IjoiODVmMmUifQ.KSVqr9VEuglgUiJQS3NPaAq4rJnlrYsAHCFywdSyl7A) Laut eines Berichts des Wall Street Journal hat die SEC auf die hereinbrechende Flut von Anträgen für Bitcoin-Spot-ETFs mit Bedenken reagiert. Sie erklärte zunächst, dass es den Anträgen an Klarheit und umfassenden Informationen mangele und diese somit unzureichend seien. Die SEC hatte schon bei früheren (abgelehnten) Anträgen u.a. ihre Bedenken bezüglich der Überwachung der Handelsplattformen geäußert. Wie oben beschrieben, ist die mögliche Marktmanipulation durch unregulierte Börsen einer der Hauptgründe seitens der SEC gewesen, frühere Anträge abzulehnen. Allerdings war man davon ausgegangen, dass diese Bedenken der SEC durch eine Vereinbarung zur gemeinsamen Überwachung des Marktes durch eine regulierte Spot-Bitcoin-Handelsplattform in Zusammenarbeit mit einem der US-Handelplätze (Nasdaq, NYSE, CBOE, etc.) ausgeräumt werden könnten. https://www.reuters.com/technology/us-sec-accepts-six-spot-bitcoin-etf-proposals-review-2023-07-19 Dementsprechend teilte die SEC den Börsen (und Antragstellern) mit, dass in den eingereichten Unterlagen wichtige Details bezüglich der genauen Vereinbarung zur gemeinsamen Umsetzung der Überwachungsvorhaben fehlten. Diese Nachricht wurde von vielen Beobachtern als negativ eingestuft: "Die SEC versteht nicht, was hier erreicht werden soll. Die SEC stellt sich quer. Die SEC ist automatisch gegen Bitcoin." war die Essenz der meisten Reaktionen. Allerdings lese ich persönlich die Reaktion der SEC ähnlich, wie auch die Anklageerhebung gegen Coinbase. Die SEC spielt ganz klar nach den eigenen formulierten und klar kommunizierten Regeln und versucht den Mitspielern die Leitplanken aufzuzeigen. Der Tenor scheint klar: "Wir haben euch die Regeln erklärt, nach denen wir mit euch spielen (hört mit der Shitcoinerei auf!). Befolgt diese und wir kommen ins Gespräch." https://www.theblock.co/post/238944/cboe-reaches-surveillance-agreement-with-coinbase-for-spot-bitcoin-etfs Wonach die SEC scheinbar explizit zu fragen scheint, ist ein sogenanntes Information-Sharing Agreement (ISA), also eine Vereinbarung zum Informationsaustausch. Diese Vereinbarung zwingt eine Handelsplattform dazu, Handelsdaten bis hin zu persönlichen Informationen wie den Namen und den Adressen der Kunden weiterzugeben. Ein solches ISA scheint bislang in den Anträgen gefehlt zu haben, weshalb die SEC auf die Anträge reagierte und diese als unvollständig zurückwies. Mit der neuen Welle an korrigierten Anträgen scheinen die meisten Antragsteller diese Unvollständigkeit behoben zu haben. **Und wen listet JEDER der Antragsteller als Partner zum Informationsaustausch? Rate, rate? Richtig, Coinbase!** Die Chicago Board Options Exchange (CBOE), eine Optionsbörse, die u.a. die Anträge zusammen mit den oben genannten WisdomTree, VanEck, Invesco und ARK stellte, erzielte kurzerhand mit Coinbase eine Einigung über die Bedingungen für den Abschluss eines ISA und reichte alle Anträge mit den neuen Bedingungen erneut ein. Wie wir also sehen, deutet alles darauf hin, dass die SEC einem Bitcoin-Spot-ETF eigentlich positiv geneigt ist, sollten die Konditionen, die sie stellt, erfüllt sein. Und in Garys perfekter Welt, sehen diese Konditionen vor, dass ein solcher ETF mit Hilfe von Coinbase als Informations-Austauschs-Partner funktioniert, und dass Coinbase ein artiges in den USA börsennotiertes Unternehmen wird, dass keine Shitcoinerei betreibt und sich auf den Spot-Handel mit Bitcoin konzentriert. Denn die derzeit anderen angebotenen Services wie Clearingstellen und Broker-Dealer-Aktivitäten stehen im direkten Gegensatz zu potenziellen Aktivitäten und Interessen von Kunden. Wir sehen also, dass ein "größerer Plan" hinter den Aktionen der SEC zu stehen scheint. Meiner Meinung nach gibt es verschiedene Theorien und Hinweise, die darauf schließen lassen, dass die SEC a) den Markt regulieren will, bevor sie ein BlackRock-Produkt genehmigt, b) ausländische (und damit nicht leicht regulierbare) Unternehmen aus dem Markt drängen will, um damit Unternehmen wie BlackRock den Handel zu vereinfachen und c) andere Interessengruppen an der Entscheidung der SEC beteiligt zu sein scheinen. Man könnte so weit gehen zu behaupten, dass anhängige Klagen und Untersuchungen ein Stück weit sogar den Kurs drücken und Bitcoin in der allgemeinen Wahrnehmung, als riskant dastehen lassen, was Unternehmen wie Blackrock dabei hilft die nötigen bitcoins zu einem relativ günstigen Preis zu akkumulieren, bevor eine Genehmigung und die implizite Anerkennung von Bitcoins Wert dazu führen, dass der Preis rasant steigt. Dies wäre ein Eingriff in den Wettbewerb und gibt BlackRock et al einen klaren Vorsprung gegenüber anderen Institutionen. Es gibt unterschiedliche Ansichten darüber, wie Coinbase und die SEC mit dieser Situation umgehen. Einige behaupten, dass Coinbase aktiv nach einer Lösung sucht, um sich mit der SEC auf einen rechtlichen Rahmen zu einigen, während andere sagen, dass die SEC unbeugsam ist. Es wird vermutet, dass die SEC Coinbase frühzeitig darüber informiert hat, welche Regeln und Leitplanken sie für den Markt etablieren möchten. https://x.com/BitcoinMagazine/status/1679887574934999045 Es scheint, dass die SEC den Markt schützen möchte, indem sie gegen betrügerische Unternehmen wie Binance vorgeht, die gängige Gesetze und Regeln umgehen. Gleichzeitig versucht sie bei Unternehmen wie Coinbase, die sich nicht an die geltenden Vorschriften halten, harte Strafen als Mittel zur Durchsetzung der Regulierung einzusetzen. Das scheint nur logisch, wenn man bedenkt, dass BlackRock und die anderen Antragsteller wie WisdomTree, VanEck, Invesco und ARK sich mit Coinbase auf Bedingungen für den Abschluss eines Informations-Austausch-Abkommens (ISA) geeinigt und die Anträge mit den neuen Bedingungen erneut eingereicht haben.  Dies deutet darauf hin, dass die SEC grundsätzlich positiv gegenüber einem Bitcoin-Spot-ETF eingestellt ist, sofern bestimmte Bedingungen erfüllt sind. Diese Bedingungen könnten beinhalten, dass Coinbase als Informationspartner fungiert und dass Coinbase als in den USA börsennotiertes Unternehmen agiert, das sich auf den Spot-Handel mit Bitcoin konzentriert, während andere Dienstleistungen wie Clearingstellen und Broker-Dealer-Aktivitäten vermieden werden sollen. https://x.com/stackhodler/status/1691531818300809217 Es scheint, dass die SEC eine umfassendere Strategie verfolgt, die darauf abzielt, den Markt zu regulieren, ausländische Unternehmen zu verdrängen und den Handel für Unternehmen wie BlackRock zu erleichtern. *Mitte letzten Jahres habe ich in einem Artikel schon Grayscales andauernden Versuch, ihren Closed-End-Fund in einen Bitcoin-Spot-ETF zu verwandeln, beschrieben.* https://www.genexyz.org/post/1722193843734/ Die SEC hatte bereits im Dezember 2021 und im Februar 2022 die Entscheidung über den Antrag auf einen Bitcoin-ETF verschoben, um ihn "sorgfältig zu prüfen". Dann hat die SEC Mitte Juli 2023 bekanntgegeben, dass einem Antrag auf Umwandlung wieder nicht stattgegeben wird. Grayscale kündigten sofort an, die SEC wegen Willkür und Verstoß gegen das Wertpapierbörsengesetz von 1934 zu verklagen. Diese Klage wurde dann vor dem Bundesberufungsgericht verhandelt und entschieden.  Das Bundesberufungsgericht in D.C. entschied im Oktober, dass das Ablehnen von Anträgen auf eine Umwandlung in einen ETF seitens Grayscale ungerecht, nicht rechtens und willkürlich sei, da die Aufsichtsbehörde nicht erklären konnte, warum sie zuvor ähnliche Produkte zugelassen hat. Allerdings bedeutet dies nicht, dass Barry Silbert (CEO von DCG) automatisch den Grayscale Trust in einen ETF umwandeln kann. Der Antrag wandert damit nur zurück auf Garys (Vorsitzender der SEC) Schreibtisch. Und das bedeutet, dass die SEC wieder die Möglichkeit bekommt, einer Umwandlung aufgrund anderer Begründungen nicht stattzugeben. Dazu gleich mehr ⬇️. Außerdem ist fraglich, ob Barry tatsächlich wirklich eine Umwandlung herbeisehnt, denn momentan befinden sich Grayscale in einer sehr angenehmen Lage, die ihnen erlaubt 2% vom NAV (Net Asset Value) an Gebühren zu verlangen. Was bei einem Vermögen von 624.947 Bitcoin einen jährlichen Umsatz von 12.500 Bitcoin, bzw. 475 Million US Dollar bedeutet - für nichts tun. Es gibt schon [Kampagnen](https://www.redeemgbtc.com), die für eine Auflösung des Trusts kämpfen. Wer sich über die Umtriebigkeiten bei DCG / Genesis / Grayscale (Barry) ein besseres Bild machen möchte, sollte unbedingt den folgenden Thread lesen: https://x.com/real_vijay/status/1721385528510251182 ### Was seit dem geschah Seit dem letzten Artikel ist gleichzeitig viel und wenig geschehen. Verinnerlichen wir uns meine These - dass die SEC a) den Markt regulieren will, bevor sie ein BlackRock-Produkt genehmigt, b) ausländische (und damit nicht leicht regulierbare) Unternehmen aus dem Markt drängen will, um damit Unternehmen wie BlackRock den Handel zu vereinfachen und c) andere Interessengruppen an der Entscheidung der SEC beteiligt zu sein scheinen - dann ist genau das passiert, was man erwartet hätte. Die SEC hat ihre Entscheidung zur Genehmigung der ETF-Anträge wiederholte Male verschoben, momentan sieht es so aus, als würde eine Entscheidung im Januar 2024 fällig. https://bmpro.substack.com/p/sec-delays-etf-again-despite-warning Die SEC fällt weiter unliebsame Bäume. Bittrex, eine in den USA ansässige Börse, haben angekündigt, ihre Pforten zu schließen. https://finance.yahoo.com/news/crypto-exchange-bittrex-global-shuts-054643624.html Kraken wurde von der SEC verklagt - ähnliches Modell wie auch zuvor bei Binance und Coinbase angewandt (sprich: alles okay und tutti, solange ihr die Shitcoinerei an den Nagel hängt). https://www.nobsbitcoin.com/kraken-sec-lawsuit Dabei wurden in der Klageschrift die bereits identifizierten Digitalen Assets, die die SEC als unregistrierte Wertpapiere betrachtet, 1 zu 1 wieder aufgeführt.  Doch die größte Überraschung war die diese Woche veröffentlichte Meldung, dass Binance sich in einem Vergleich mit dem US Department of Justice (DOJ) auf eine Zahlung von über 4 Milliarden US Dollar und den Rücktritt CZs (Changpeng Zhao) als CEO von Binance geeinigt habe. https://www.nobsbitcoin.com/cz-steps-down-as-ceo-of-binance-as-part-of-4-billion-settlement-with-doj Es ist recht eindeutig, dass es dem Justizministerium (DOJ) hier nicht um den Schutz der Verbraucher geht. Es muss allerdings der Anschein gewahrt werden, dass nicht in Eigeninteresse (dem von BlackRock, hust) gehandelt wird, sondern dass der Eindruck erweckt wird, dass sie tatsächlich etwas Gutes tun, indem sie sich um einen "bad actor" kümmern" - das wird sehr deutlich, wenn man betrachtet, dass sich das Narrativ im Vergleich hauptsächlich auf AML (Anti-Money-Laundering) und Terrorismusfinanzierung konzentriert. Wie schon aus meiner These ersichtlich, geht auch aus bisherigen Kommentaren der SEC klar hervor, dass die größte Sorge derzeit ausländische Börsen sind, die den Bitcoin-Preis manipulieren können. Binance ist die größte Börse der Welt und hat bis heute erfolgreich außerhalb des Einflussbereichs der US-Regierung operiert. Mit dieser Vereinbarung ist das Problem der Offshore-Kursmanipulation zunächst und zum größten Teil gelöst. Das BlackRock-SEC-Reptilienmenschen-Playbook ist im vollen Gange. Ausländische Konkurrenz weitestgehend unter Kontrolle ✅  Die SEC scheint außerdem im engen Kontakt mit den ETF-Antragstellern zu stehen. Insbesondere ein Verweis auf eine Änderung der Anträge in Bezug auf "cash" vs. "in-kind creation" hat diese Woche für Diskussionen gesorgt. https://x.com/EricBalchunas/status/1725559994995573086 Viele börsengehandelte Fonds verlangen von den zugelassenen Teilnehmern, dass sie Anteile in Form von Sachleistungen (in-kind) schaffen , d. h. dass sie ETF-Anteile gegen einen Wertpapierkorb und nicht gegen Bargeld (cash) eintauschen. Die SEC hat jedoch auf eine Formulierung in den Anträgen gedrängt, die genau dise cash-creations zulassen.  Während sich viele auf die minutiöse Gestalt der Inhalte stürzen und eine Genehmigung hineininterpretieren, zieht die SEC hier meiner Meinung nach eine Linie, um eine Unterscheidung zwischen Grayscales GBTC und BlackRock et al. zu schaffen.  Wenn man an ein Playbook glaubt, ist der Grayscale Trust den Teilnehmern ein offensichtlicher Dorn im Auge, weshalb eine Umwandlung zunächst verhindert werden will. Jetzt muss nur noch Coinbase mitspielen. Aber wenn Binance einen Vergleich erzielen kann, warum nicht auch $COIN? Vielleicht einigt sich die SEC mit Coinbase im Gegenzug für "saftige Geldstrafen" und die Entfernung aller Shitcoins von der Plattform. Im Gegenzug erhält Coinbase den Börsenstatus und wird für die Überwachungsvereinbarung mit BlackRock und den anderen Antragstellern freigeschaltet. Auf einen Schlag würde die SEC die Shitcoins von der einzigen börsennotierten US-Börse entfernen und ein legales (nach ihren Vorstellungen und selbst artikulierten Prinzipien) Fundament für BlackRocks ETF schaffen. Außerdem würde es mich nicht wundern, wenn Coinbase als weißer Ritter auftritt und ganz barmherzig das US-Business von Binance übernimmt. Natürlich nur, um einem Mitstreiter in schwierigen Zeiten beizustehen. Ich packe es auf jeden Fall auf meine Bingo-Karte für den Zeitraum zwischen jetzt und einer Genehmigung der ETF-Anträge.  Durch die Einigung mit CZ und die Geldstrafe von 4,3 Milliarden US Dollar erleichtert die US-Regierung den Transfer von Bitcoin aus schwachen in starke Hände (Binance ➡️ Coinbase). Binance werden Bitcoin verkaufen müssen, um die Geldstrafe zu bezahlen, während gleichzeitig die Spot-ETFs das Angebot mit amerikanischem Kapital auffüllen können. Schöne Ausführung. Tolles Playbook 👏 Ich bin mir bewusst, dass die oben genannten Ereignisse und Auslegungen der Geschehnisse sehr verschwurbelt daherkommen, jedoch möchte ich meinen virtuellen Alu-Hut vor dem Architekten dieses wirklichen langen Long-Games ziehen.  In der Zwischenzeit arbeiten gewissenhafte Journalisten namhafter Veröffentlichungen (BlackRock PR-Department, hust) daran, die öffentliche Wahrnehmung von Bitcoin zum Positiven zu wenden. Wurde in den letzten Jahren Bitcoin als riskante Anlage, Klimakiller, Ozean-Kocher, oder schlimmer bezeichnet, wird es jetzt als ein möglicher Bestandteil einer nachhaltigen und zukunftsorientierten Anlagestrategie dargestellt. https://www.forbes.com/sites/digital-assets/2023/07/08/bitcoin-network-to-reduce-more-emissions-than-its-energy-sources-produce/ Wir (du schlaue/r Leser//in und ich) wissen schon lange, dass die Bitcoin-Branche heute die weltweit am nachhaltigsten betriebene Branche ist und das Bitcoin-Mining als einzige Industrie in dem Bereich kohlenstoffnegativ werden kann. Es ist also offensichtlich, dass Bitcoin ein wichtiger Bestandteil einer nachhaltigen und zukunftsorientierten Anlagestrategie sein kann, aber genau dieses Narrativ wurde jahrelang absichtlich verdrängt (➡️ siehe XRP-gesponsorte [Greenpeace Aktion](https://dailycoin.com/greenpeace-anti-crypto-artist-admits-wrong-on-bitcoin-mining/) anfang des Jahres).   Wir sehen also, dass es nicht nur um eine einfache Genehmigung der Anträge geht, sondern viele Mosaikteilchen gelegt werden, bevor es dazu kommen kann. Viele Zeichen deuten darauf hin, dass viele verschiedene Parteien daran arbeiten, ein Umfeld zu schaffen, dass es bestimmten Gruppen ermöglicht, einen ETF möglichst risikofrei und konkurrenzlos zu platzieren. Dabei werden unliebsame Mitspieler vom Platz gewiesen und anderen Mitspielern werden die Spielregeln nochmal ganz bewusst in Erinnerung gerufen, während gleichzeitig ein Narrativ geschaffen wird, das einen Bitcoin-ETF in glänzendem Licht darstellt. ----------- Es ist nahezu gewiss, dass es nicht die Frage ist, ob einem Antrag zugestimmt wird, sondern vielmehr, wann dies geschehen wird. Es besteht eine hohe Wahrscheinlichkeit, dass allen Anträgen zeitgleich stattgegeben wird. Dennoch lässt sich erkennen, dass die SEC strategisch Zeit gewinnt, um Binance und andere unerwünschte Akteure vollständig aus dem Spiel zu nehmen und Coinbase in der Zwischenzeit zu dem vorbildlichen Mustersohn zu formen, den sie immer haben wollte. Da der Markt für Spot-ETFs als "Winner-takes-all" gilt, wird darauf geachtet, dass nicht irgendein Antragsteller das Rennen gewinnt, sondern ein bestimmter - Larry. Hierfür ist es notwendig, Barry vom Spielfeld zu verdrängen, da er einen erheblichen Vorsprung hat, woran Gary offensichtlich arbeitet. Falls sich meine Vermutungen bewahrheiten, werden wir in naher Zukunft einen Bitcoin-Spot-ETF sehen, der von BlackRock dominiert wird. Grayscale und Binance werden keine Rolle im Spiel spielen, während Coinbase als reguliertes, vorbildliches US-Unternehmen davon profitieren wird. 🫳🎤 --- In diesem Sinne, 2... 1... Risiko! 
@ 2063cd79:57bd1320
2025-02-03 08:05:31**DISCLAIMER: Dies ist ein Re-Post eines Artikels, der ursprünglich im Juli 2023 erschienen ist. Die beschriebenen Sachverhalte sind teilweise überholt oder nie eingetroffen. Allerdings räumt der Autor ein, retrospektiv die damalige Sachlage recht treffend eingeordnet zu haben und Vorhersagen recht treffsicher gemacht zu haben.**  ----------- Anfang Juni 2023 gaben die Nachrichtenportale bekannt, dass BlackRock, der weltweit größte Vermögensverwalter, über seine iShares-Einheit einen [Antrag auf einen börsengehandelten Bitcoin-Fonds](https://www.sec.gov/Archives/edgar/data/1980994/000143774923017574/bit20230608_s1.htm) eingereicht hat. Dieser Schritt des 10-Billionen-Dollar-Vermögensverwalters löste in der Bitcoin-Community auf der einen Seite große Freude und auf der anderen Seite große Besorgnis aus, weil viele einerseits das Potenzial für einen massiven Zufluss von Investitionen aus dem institutionellen Bereich sehen, während Kritiker das Risiko aufzeigen, die eine solche Produktstruktur für Bitcoin mit sich bringen könnte.  Anfangs wurde viel auch darüber diskutiert, ob es sich bei dem Produkt tatsächlich um einen ETF handeln würde - wie in vielen Artikeln beschrieben - , da das Produkt im Antrag selbst nicht als solches bezeichnet wird. Aber im Endeffekt ist klar, dass es sich um ein Finanzprodukt handelt, das alle formalen Eigenschaften eines ETF besitzt. Also, was genau ist ein ETF und wie funktioniert so ein Produkt? ### ETF? Eidgenössisches Turnfest, was? ETFs sind eine Sorte von Anlagewertpapieren, die einen bestimmten Index, Sektor, Rohstoff oder andere Vermögenswerte nachbilden. ETFs können an der Börse auf die gleiche Weise gekauft oder verkauft werden wie normale Aktien. Daher schwanken ETF-Anteilspreise den ganzen Tag, wenn der ETF gekauft und verkauft wird, was bedeutet, dass eine Arbitrage zwischen dem ETF und dem zugrunde liegenden Vermögenswert (z.B. Bitcoin) möglich ist. ETFs werden als börsengehandelte (Exchange-Traded) Fonds bezeichnet, weil sie genau wie Aktien an einer Börse gehandelt werden. Die meisten ETFs sind so strukturiert, dass sie, ähnlich wie traditionelle Investmentfonds, mehrere zugrunde liegende Vermögenswerte halten und nicht nur einen, wie es bei einer Aktie der Fall ist. Da ETFs aus mehreren Vermögenswerten bestehen können, werden sie oft als beliebtes Mittel zur Diversifizierung des Portfolios genutzt. Auf der anderen Seite eröffnen ETFs Anlegern auch die Möglichkeit in einen Rohstoff zu investieren, ohne diesen physisch erwerben zu müssen. Anstatt sich Gold in den Tresor zu legen, kann man in seinem Portfolio also z.B. den GLD ETF kaufen, der den aktuellen Preis von Gold nachbildet. Ausser in Deutschland, da geht das nicht, denn da ein Gold-ETF, der nur einen Vermögenswert abbildet, naturgemäß nicht diversifiziert ist, ist er gemäß deutschem Gesetz nicht zugelassen, da Fonds zur Diversifikation verpflichtet sind. ETFs haben den Vorteil, dass sie kostengünstig sind (wenn man z.B. den kompletten DAX abbilden möchte, reicht ein ETF, welcher genau das tut, anstatt verschiedene Gewichtungen von 40 verschiedenen Unternehmen zu kaufen - das spart Zeit und vor allem Gebühren), dass sie Produkte abbilden, die ein Käufer unter normalen Umständen nicht erlaubt wäre zu kaufen (z.B. darf nicht jeder Anleger in Bitcoin investieren, weil sonst Lizenzen nötig wären) und sie haben den Vorteil, dass sie über den gleichen Broker oder Service gehandelt werden können, wie andere Wertpapier-Investitionen. Der letzte Punkt ist natürlich wichtig für Neueinsteiger, da sie keine zusätzlichen Kosten haben, wenn sie ihr Wertpapierdepot nutzen können und zusätzlich bietet dieser Korridor für viele traditionelle und konservative Anleger ein gewisses Gefühl von Schutz. Diese ganze cRyPto-Welt mit ihren Plattformen, Exchanges, Casinos und Teppichhändlern ist im besten Fall schwer durchsichtig und im schlimmsten Fall mutet sie kriminell an. Doch wenn ich mir "Bitcoin" über mein Depot bei Charles Schwab, der Sparkasse, oder Flatex kaufen kann, fühlt sich das natürlich legitim und sicherer an. Der Finanzdienstleister muss den zugrundeliegenden Vermögenswert dabei vollumfänglich besitzen, mit dem grossen ABER, dass der Vermögenswert auch verliehen werden kann. Warum das ein Problem sein könnte, besprechen wir später. Ähnlich wie ein Gold ETF bietet ein Bitcoin ETF Anlegern also die Möglichkeit mit Bitcoin zu handeln, in Bitcoin anzulegen und Bitcoin auszuprobieren, ohne Bitcoin tatsächlich zu kaufen. Ob das gut oder schlecht ist, besprechen wir auch später. ### ETF Wasserfall Nachdem die Nachricht über BlackRocks Antrag publik wurde, kamen auch etliche andere Finanzdienstleister hervor und stellten (neue) Anträge.[WisdomTree](https://www.sec.gov/ix?doc=%2FArchives%2Fedgar%2Fdata%2F1850391%2F000121465923008647%2Fp620230s1a2.htm) hatten bereits zuvor schon einige Anläufe gebraucht, um ihre Anträge für Bitcoin-Spot-ETFs bei der SEC einzureichen und unterhalten schon ähnliche Produkte in anderen Ländern. Aber auch Fidelity, Invesco, Valkyrie oder [ARK](https://x.com/EricBalchunas/status/1674055780058771463) zogen unter anderem nach und stellten neue Anträge, natürlich nicht, ohne sich bei der Formulierung dieser eine Scheibe bei BlackRock abzuschneiden.  Die SEC hatte zuvor jegliche Anträge auf Bitcoin-Spot-ETFs abgelehnt, hingegen andere Bitcoin-verbundene Produkte, die gehebelte (BITX) und ungehebelte Bitcoin-Futures-Kontrakte (BITO) nachbilden, zugelassen. Auch gibt es eine handvoll ETFs, die börsennotierte Mining-Unternehmen bündeln, oder anderweitige Verbindung zum Bitcoin-Ökosystem suchen, indem sie Anteile von Unternehmen bündeln, die im weitesten Sinne mit Bitcoin in Berührung kommen (z.B. MSTR oder SQ). Eine Genehmigung eines Antrags auf Bitcoin-Spot-ETF hat es also bis heute durch die SEC noch nicht gegeben. ### Der Standpunkt der SEC ### Wie ich schon in einem ➡️ [früheren Artikel](https://www.genexyz.org/post/1722193843734/) beschrieben habe, ist der Standpunkt der SEC nur teilweise nachvollziehbar. > Die offizielle Begründung der SEC sind Bedenken in Bezug auf Marktmanipulation, Betrug, Liquidität und Transparenz. Die hauptauschlaggebenden Argumente sind mangelnde Preiserkennung durch hohe Volatilität, wiederum erzeugt durch einige unbekannte große Accounts und die steigende Zahl der Derivate-Produkte rund um Bitcoin, sowie die vielen unregulierten Börsen. Besonders letztere würde die SEC gerne unter ihre Kontrolle bringen. Das bedeutet bis Coinbase, Gemini, Kraken (oder andere große US Börsen) sich nicht bei der SEC registrieren und sich der SEC Regulierung unterwerfen, ist es unwahrscheinlich, dass die SEC einen Spot-ETF genehmigen wird. Dieses Argument ist schwer haltbar, da große Börsen wie Binance, FTX, oder BitMart nicht in den USA registriert sind, und kombiniert ein Vielfaches der in den USA beheimateten Börsen an Handelsvolumen umsetzen. “[T]here’s a lot of work to be done to really protect the investing public.” - Gary Gensler, SEC Chair > Vorgeschoben wird also bei alledem immer der Schutz der Anleger. Ob dies eine schlüssige Argumentation ist, darf man ruhig in Frage stellen. Denn ein Bitcoin-Spot-ETF würde vielen Anlegern erlauben Bitcoin in ihr Portfolio aufzunehmen, ohne größeren Spekulationen ausgesetzt zu sein, wie das jetzt mit schon zugelassenen Produkten der Fall ist. Darüber hinaus hat die SEC vielerorts erwähnt, dass sie bestrebt sind, mit Unternehmen aus der Branche einen regulatorisch klaren Weg zu finden, damit Unternehmen ihre Tätigkeiten im Sinne der SEC auszuüben. Das bezieht sich meist auf die Börsen, die nach eigenen Angaben seit Jahren versuchen, einen rechtlichen Rahmen zu schaffen, der ihnen Planungs- und Rechtssicherheit bietet. Dieser Punkt ist später nochmal wichtig. Das Problem hierbei besteht in der Natur dieser Unternehmen. Denn fast ausnahmslos sind alle betroffenen Unternehmen (wie z.B. Coinbase, Kraken, Binance, etc.) keine Bitcoin-Unternehmen, sondern Digital Assets-Unternehmen, die eben auch den Handel mit Shitcoins, Stablecoins und auf diesen Assets basierende Derivate erlauben (und vor allem wollen). Jetzt wissen wir also, was ein ETF ist. Aber wie schaut der von BlackRock (und damit auch der anderen Finanzdienstleister) vorgeschlagene Bitcoin-Spot-ETF im Detail aus? ### Bitcoin ETF ### Das von BlackRock vorgeschlagene Produkt, und damit auch die der anderen - wie wir wissen, haben die anderen Anbieter ihre Anträge nachgebessert und dem von BlackRock weitestgehend angepasst - soll das Grantor-Trust-Modell übernehmen und seine Struktur dem von Gold-Investment-Trusts nachempfinden. Das bedeutet, dass der Besitz von Anteilen am Bitcoin-ETF für steuerliche Zwecke dem Besitz des zugrunde liegenden Vermögenswerts gleichkommt. Des Weiteren ist eine Rücknahmefunktion in Form von Sachleistungen vorgesehen. Das bedeutet vereinfacht, dass Anleger ihre Anteile auch direkt in Bitcoin umwandeln können. Anders als bei z.B. GBTC (➡️ [#5 // Block 742956 // GBTC, ETF & SEC](https://www.genexyz.org/post/1722193843734/)), müssen Anteile nicht erst verkauft werden, um mit den (potentiellen) Profiten bitcoins zu kaufen. Denn der Verkauf von Anteilen an GBTC (oder ähnlichen Modellen) führt nämlich ein steuerpflichtiges Ereignis herbei, wohingegen eine Umwandlung im BlackRock Modell steuerfrei zu vollziehen ist. Aber, und dies ist ein großes ABER, kommen nur autorisierte Kunden von BlackRock in den Genuss dieser Sachrücknahmen (Umwandlungen). D.h., im Wesentlichen können nur große Investmentfirmen mit guter Reputation Anteile in Bitcoin umtauschen, alltägliche Anleger (Depot bei Charles Schwab, der Sparkasse, oder Flatex) hingegen sind nicht in der Lage diesen tollen Steuertrick anzuwenden. Die erzeugt einen Vorhang vorgespielter Transparenz ("natürlich können alle Anteile direkt in 'physische' bitcoins getauscht werden"), wohingegen ein Großteil der zugrundeliegenden bitcoins nicht wirklich eingefordert werden wird.  Es sind sich alle einig, dass ein Bitcoin-Spot-ETF ein Winner-takes-all-market ist. Das heisst, der Anbieter, dessen Antrag als erstes von der SEC genehmigt wird, wird uber kurz oder lang den Markt fuer Bitcoin-ETFs fuer sich entscheiden, bzw. beherrschen. ### SEC vs. Binance Kurz bevor BlackRock ihren Antrag auf einen Bitcoin-Spot-ETF einreichten und damit die SEC in die Schlagzeilen der Finanz- und Bitcoin Welt geriet, machte die SEC in der Bitcoin- und Digital Assets-Welt schon von sich hören, als sie kurz hintereinander gegen Binance und Coinbase Anklage erhob. https://www.sec.gov/news/press-release/2023-101 Binance ist die zurzeit größte Börse für Digitale Assets der Welt. Binance bietet jedoch nicht nur den Handel mit Krypto-Werten, sondern auch eine Reihe von gehebelten Produkten, eigener Coins und Tokens, usw. an (Shitcoin-Casino). > “Through thirteen charges, we allege that Zhao and Binance entities engaged in an extensive web of deception, conflicts of interest, lack of disclosure, and calculated evasion of the law.” - Gary Gensler, Chairman, SEC Vor allem ist Binance kein in den USA registriertes Unternehmen. Lediglich ein Schwesterunternehmen, Binance.us, ist offiziell in den USA registriert und hat offiziell und nach eigenen Angaben mit den Geschäften des Hauptunternehmens direkt nichts zu tun. Die SEC klagt Binance also nicht nur wegen ihrer Angebote im Krypto-Sektor an, sondern erhebt spezifische Vorwürfe der Irreführung und Täuschung von Kunden, des Betreibens von unregistrierten Börsen, Clearingstellen und Broker-Dealer Aktivitäten, sowie Verstrickungen mit Binance.us (einer Handelsbörse, die wie gesagt offiziell unabhängig von Binance agieren soll), sowie dem Washtrading und dem Verkauf von unregistrierten Wertpapieren (mehr zu dem Thema Securities hier ➡️ [#24 // Block 773750 // Commodity vs. Security](https://www.genexyz.org/post/24-block-773750-commodity-vs-security-2xhjjo/)). > “We allege that Zhao and the Binance entities not only knew the rules of the road, but they also consciously chose to evade them and put their customers and investors at risk – all in an effort to maximize their own profits.” - Gurbir S. Grewal, Director, SEC’s Division of Enforcement Die SEC argumentiert also Changpeng Zhao (CEO von Binance) und Binance hätten Anleger über ihre Risikokontrollen und korrupten Handelsvolumina in die Irre geführt und gleichzeitig aktiv verschwiegen, wer der eigentliche Betreiber der Plattform ist. Damit hätten Binance-Plattformen ihren Anlegern übergroße Risiken und Interessenkonflikte beschert. https://www.reuters.com/investigates/special-report/crypto-binance-money Darüber hinaus wurde in Folge der Anklageerhebung bekannt, dass es bei Geldflüssen bei Binance einen deutlichen Hinweis auf einen Mangel an internen Kontrollen gibt. Interne Kontrollen sollen normalerweise sicherstellen, dass Kundengelder klar identifizierbar und von den Unternehmenseinnahmen getrennt sind. Eine Vermischung von Anleger- und Geschäftsgeldern gefährdet das Vermögen der Kunden, da deren Verbleib verschleiert wird. Interessanterweise nutzt die SEC weiterhin die Klageschrift gegen Binance, um das Thema 'unregistrierter' Wertpapiere etwas zu erhellen. Zuvor hatte die SEC sich nur in wenigen Einzelfällen dazu geäußert, welche Digitalen Assets sie als unregistrierte Wertpapiere betrachtet, doch in der Anklageschrift werden SOL, ADA, MATIC, FIL, ATOM, SAND, MANA, ALGO, AXS, COTI, BUSD, and BNB explizit als solche bezeichnet.  Alleine vier der genannten Assets finden sich unter den 10 größten Werten (ausgenommen Stablecoins) und die anderen tummeln sich auch irgendwo in den Top 50. Der aufmerksame Sherlock Holmes wird bemerkt haben, dass es dünn wird für den "kRyPtO"-Markt. Unter den Top 10 bleiben noch 3 Proof-of-Work Coins, von denen einer den [Howey-Test](https://www.genexyz.org/post/24-block-773750-commodity-vs-security-2xhjjo/#:~:text=Produktkategorie%20zuordnen%20lassen.-,Der%20Howey%20Test,-In%20den%20USA) nicht erfüllt (und es ist nicht Doge), Ripple (XRP) und die SEC stehen schon seit 2020 vor Gericht und meiner Meinung nach ist es nur noch eine Frage der Zeit, bis die SEC sich bzgl. Ethereum äußern muss (wird). ### SEC vs. Coinbase Nur einen Tag nach Veröffentlichung der Pressemitteilung, dass die SEC Anklage gegen Binance erhebe, veröffentlichte die SEC die nächste Pressemitteilung: Die SEC erhebt auch Anklage gegen Coinbase, die größte in den USA registrierte Börse für den Handel mit Digital Assets. https://www.sec.gov/news/press-release/2023-102 Anders als bei Binance hingegen konzentriert sich die SEC bei der Anklage gegen Coinbase einzig auf den Handel mit unregistrierten Wertpapieren und den damit einhergehenden Dienstleistungen. > “We allege that Coinbase, despite being subject to the securities laws, commingled and unlawfully offered exchange, broker-dealer, and clearinghouse functions” - Gary Gensler, Chairman, SEC. Konkret hätten Coinbase gegen bestimmte Registrierungsbestimmungen des Securities Exchange Act und des Securities Act verstoßen. Coinbase hätten seit mindestens 2019 Milliarden Dollar verdient, indem sie den Kauf und Verkauf von unregistrierten Wertpapieren unrechtmäßig erleichtert haben. Interessant ist, dass die SEC ein weitere Dienstleistung in die Anklage einbaut, die bisher keine Erwähnung gefunden hat: "Darüber hinaus hat Coinbase, wie wir behaupten, sein Staking-as-a-Service-Programm nie gemäß den Wertpapiergesetzen registriert, was den Anlegern erneut wichtige Offenlegungs- und andere Schutzmaßnahmen vorenthält“ (Gensler). Dies zeigt, dass die SEC, ohne sich bisher explizit zu Ethereum geäußert zu haben, eine Meinung gegenüber Staking vertritt, und zumindest die Bereitstellung von Staking-Services als rechtswidrig erachtet. Dies könnte einer der Gründe sein, dass Ethereum noch nicht ins Rampenlicht gerückt wurde, und zwar, dass die SEC die Anklageschrift gegen die Ethereum-Foundation und damit ein Ungetüm an Financiers (JP Morgan, MasterCard, Consensys, etc.) gründlich vorbereitet, um sich für einen enormen Rechtsstreit wetterfest zu machen. Allerdings scheinen interne Ansichtspunkte und Betrachtungsweisen schon ihren Weg in andere Anklageschriften zu finden. Darüberhinaus zitiert die SEC mit AXS, CHZ, FLOW, ICP, NEAR, VGX, DASH und NEXO eine weitere Reihe von Shitcoins, die sie als unregistrierte Wertpapiere einstufen und damit den Handel mit selbigen untersagen. Es gibt immer wieder Erzählungen von Leuten, die mit der Sache betraut sind, dass Coinbase aktiv daran arbeiten, einen gemeinsamen Weg mit der SEC zu finden, das Geschäftsmodell zwischen regulatorisch stabile Leitplanken zu bringen. Oft, wenn diese Erzählungen aus dem Coinbase Camp kommen, heißt es, die SEC sei stur und ließe sich nicht auf die Avancen seitens Coinbase ein. Wiederum andere sagen, dass die SEC schlicht überfordert wäre und Coinbase alles daran läge, schnell eine Lösung zu finden. > "You simply can’t ignore the rules because you don’t like them or because you’d prefer different ones: the consequences for the investing public are far too great.” Wenn man allerdings den in der Pressemitteilung zitierten Satz von Gurbir S. Grewal (Director, SEC’s Division of Enforcement) anschaut, wird klar, dass aus Sicht der SEC scheinbar relativ früh und relativ offen kommuniziert wurde, was der rechtliche Rahmen des Möglichen ist. Wahrscheinlich wurden Coinbase auch früh darüber informiert, dass der Handel mit den meisten (oder allen) gelisteten Assets (außer Bitcoin), sowie das Anbieten von Staking als Dienstleistung, nicht mit den Leitplanken konform ist, die die SEC für eine zukünftige, rechtlich stabile Regulatorik des Marktes hält. Doch die freiwillige Einhaltung dieser von der SEC 'lose' formulierten Richtlinien hätte für Coinbase das Wegbrechen von 99% ihres Geschäftsmodells bedeutet. Coinbase listen über 250 handelbare Assets auf ihrer Seite, viele davon lassen sich 'staken', viele weitere Dienste, die Coinbase anbietet, sind von den darunterliegenden Plattformen abhängig. Es ist klar, dass Coinbase den Moment so lange vor sich herschieben wollten, wie eben nur möglich. Denn während Bitcoin als einziges auf Coinbase gehandeltes Asset deutliche YTD Performance an den Tag legt, sinkt die Zahl der auf der Plattform gehaltenen bitcoins zusehends (gut, endlich begriffen!).  Diese Woche dann der Beweis. In einem Artikel der [Financial Times](https://www.ft.com/content/1f873dd5-df8f-4cfc-bb21-ef83ed11fb4d) erklärt Brian Armstrong, CEO von Coinbase, dass die SEC klare Empfehlung ausgesprochen hat, schon bevor sie letzten Monat rechtliche Schritte gegen das Unternehmen einleitete. > “They came back to us, and they said . . . we believe every asset other than bitcoin is a security,” Armstrong said. “And, we said, well how are you coming to that conclusion, because that’s not our interpretation of the law. And they said, we’re not going to explain it to you, you need to delist every asset other than bitcoin.” Das ergibt absolut Sinn und stützt meine These, dass die SEC gar nicht vor hat 'gegen' Coinbase zu sein. Vielmehr sieht es aus, als würden sie klarstellen wollen, dass es im geltenden Rechtsrahmen durchaus Platz für gewisse Unternehmen gibt, solange diese sich an geltendes Recht halten und nicht wie Binance offensichtlich gängige Gesetze und Regeln umschiffen. Es scheint, als wolle die SEC den 'Markt' schützen, indem sie betrügerische Firmen wie Binance auf Täuschung, Irreführung und Marktmanipulation verklagt. Gleichzeitig handelt sie bei Firmen wie Coinbase wie ein strenger Vater, der eigentlich das Beste für sein Kind möchte, aber nach wiederholten Versuchen der Gesprächsfindung nur noch harte Strafen als geeignetes Mittel sieht. Aber warum ist der SEC daran gelegen, dass Coinbase rechtskonform und innerhalb der Leitplanken der SEC handelt? ### Neue ETF Anträge mit Hilfe von Coinbase [](https://substack.com/redirect/0a08f4c1-6a80-4ae1-90b4-1e3199e65ac1?j=eyJ1IjoiODVmMmUifQ.KSVqr9VEuglgUiJQS3NPaAq4rJnlrYsAHCFywdSyl7A) Laut eines Berichts des Wall Street Journal hat die SEC auf die hereinbrechende Flut von Anträgen für Bitcoin-Spot-ETFs mit Bedenken reagiert. Sie erklärte zunächst, dass es den Anträgen an Klarheit und umfassenden Informationen mangele und diese somit unzureichend seien. Die SEC hatte schon bei früheren (abgelehnten) Anträgen u.a. ihre Bedenken bezüglich der Überwachung der Handelsplattformen geäußert. Wie oben beschrieben, ist die mögliche Marktmanipulation durch unregulierte Börsen einer der Hauptgründe seitens der SEC gewesen, frühere Anträge abzulehnen. Allerdings war man davon ausgegangen, dass diese Bedenken der SEC durch eine Vereinbarung zur gemeinsamen Überwachung des Marktes durch eine regulierte Spot-Bitcoin-Handelsplattform in Zusammenarbeit mit einem der US-Handelplätze (Nasdaq, NYSE, CBOE, etc.) ausgeräumt werden könnten. https://www.reuters.com/technology/us-sec-accepts-six-spot-bitcoin-etf-proposals-review-2023-07-19 Dementsprechend teilte die SEC den Börsen (und Antragstellern) mit, dass in den eingereichten Unterlagen wichtige Details bezüglich der genauen Vereinbarung zur gemeinsamen Umsetzung der Überwachungsvorhaben fehlten. Diese Nachricht wurde von vielen Beobachtern als negativ eingestuft: "Die SEC versteht nicht, was hier erreicht werden soll. Die SEC stellt sich quer. Die SEC ist automatisch gegen Bitcoin." war die Essenz der meisten Reaktionen. Allerdings lese ich persönlich die Reaktion der SEC ähnlich, wie auch die Anklageerhebung gegen Coinbase. Die SEC spielt ganz klar nach den eigenen formulierten und klar kommunizierten Regeln und versucht den Mitspielern die Leitplanken aufzuzeigen. Der Tenor scheint klar: "Wir haben euch die Regeln erklärt, nach denen wir mit euch spielen (hört mit der Shitcoinerei auf!). Befolgt diese und wir kommen ins Gespräch." https://www.theblock.co/post/238944/cboe-reaches-surveillance-agreement-with-coinbase-for-spot-bitcoin-etfs Wonach die SEC scheinbar explizit zu fragen scheint, ist ein sogenanntes Information-Sharing Agreement (ISA), also eine Vereinbarung zum Informationsaustausch. Diese Vereinbarung zwingt eine Handelsplattform dazu, Handelsdaten bis hin zu persönlichen Informationen wie den Namen und den Adressen der Kunden weiterzugeben. Ein solches ISA scheint bislang in den Anträgen gefehlt zu haben, weshalb die SEC auf die Anträge reagierte und diese als unvollständig zurückwies. Mit der neuen Welle an korrigierten Anträgen scheinen die meisten Antragsteller diese Unvollständigkeit behoben zu haben. **Und wen listet JEDER der Antragsteller als Partner zum Informationsaustausch? Rate, rate? Richtig, Coinbase!** Die Chicago Board Options Exchange (CBOE), eine Optionsbörse, die u.a. die Anträge zusammen mit den oben genannten WisdomTree, VanEck, Invesco und ARK stellte, erzielte kurzerhand mit Coinbase eine Einigung über die Bedingungen für den Abschluss eines ISA und reichte alle Anträge mit den neuen Bedingungen erneut ein. Wie wir also sehen, deutet alles darauf hin, dass die SEC einem Bitcoin-Spot-ETF eigentlich positiv geneigt ist, sollten die Konditionen, die sie stellt, erfüllt sein. Und in Garys perfekter Welt, sehen diese Konditionen vor, dass ein solcher ETF mit Hilfe von Coinbase als Informations-Austauschs-Partner funktioniert, und dass Coinbase ein artiges in den USA börsennotiertes Unternehmen wird, dass keine Shitcoinerei betreibt und sich auf den Spot-Handel mit Bitcoin konzentriert. Denn die derzeit anderen angebotenen Services wie Clearingstellen und Broker-Dealer-Aktivitäten stehen im direkten Gegensatz zu potenziellen Aktivitäten und Interessen von Kunden. Wir sehen also, dass ein "größerer Plan" hinter den Aktionen der SEC zu stehen scheint. Meiner Meinung nach gibt es verschiedene Theorien und Hinweise, die darauf schließen lassen, dass die SEC a) den Markt regulieren will, bevor sie ein BlackRock-Produkt genehmigt, b) ausländische (und damit nicht leicht regulierbare) Unternehmen aus dem Markt drängen will, um damit Unternehmen wie BlackRock den Handel zu vereinfachen und c) andere Interessengruppen an der Entscheidung der SEC beteiligt zu sein scheinen. Man könnte so weit gehen zu behaupten, dass anhängige Klagen und Untersuchungen ein Stück weit sogar den Kurs drücken und Bitcoin in der allgemeinen Wahrnehmung, als riskant dastehen lassen, was Unternehmen wie Blackrock dabei hilft die nötigen bitcoins zu einem relativ günstigen Preis zu akkumulieren, bevor eine Genehmigung und die implizite Anerkennung von Bitcoins Wert dazu führen, dass der Preis rasant steigt. Dies wäre ein Eingriff in den Wettbewerb und gibt BlackRock et al einen klaren Vorsprung gegenüber anderen Institutionen. Es gibt unterschiedliche Ansichten darüber, wie Coinbase und die SEC mit dieser Situation umgehen. Einige behaupten, dass Coinbase aktiv nach einer Lösung sucht, um sich mit der SEC auf einen rechtlichen Rahmen zu einigen, während andere sagen, dass die SEC unbeugsam ist. Es wird vermutet, dass die SEC Coinbase frühzeitig darüber informiert hat, welche Regeln und Leitplanken sie für den Markt etablieren möchten. https://x.com/BitcoinMagazine/status/1679887574934999045 Es scheint, dass die SEC den Markt schützen möchte, indem sie gegen betrügerische Unternehmen wie Binance vorgeht, die gängige Gesetze und Regeln umgehen. Gleichzeitig versucht sie bei Unternehmen wie Coinbase, die sich nicht an die geltenden Vorschriften halten, harte Strafen als Mittel zur Durchsetzung der Regulierung einzusetzen. Das scheint nur logisch, wenn man bedenkt, dass BlackRock und die anderen Antragsteller wie WisdomTree, VanEck, Invesco und ARK sich mit Coinbase auf Bedingungen für den Abschluss eines Informations-Austausch-Abkommens (ISA) geeinigt und die Anträge mit den neuen Bedingungen erneut eingereicht haben.  Dies deutet darauf hin, dass die SEC grundsätzlich positiv gegenüber einem Bitcoin-Spot-ETF eingestellt ist, sofern bestimmte Bedingungen erfüllt sind. Diese Bedingungen könnten beinhalten, dass Coinbase als Informationspartner fungiert und dass Coinbase als in den USA börsennotiertes Unternehmen agiert, das sich auf den Spot-Handel mit Bitcoin konzentriert, während andere Dienstleistungen wie Clearingstellen und Broker-Dealer-Aktivitäten vermieden werden sollen. https://x.com/stackhodler/status/1691531818300809217 Es scheint, dass die SEC eine umfassendere Strategie verfolgt, die darauf abzielt, den Markt zu regulieren, ausländische Unternehmen zu verdrängen und den Handel für Unternehmen wie BlackRock zu erleichtern. *Mitte letzten Jahres habe ich in einem Artikel schon Grayscales andauernden Versuch, ihren Closed-End-Fund in einen Bitcoin-Spot-ETF zu verwandeln, beschrieben.* https://www.genexyz.org/post/1722193843734/ Die SEC hatte bereits im Dezember 2021 und im Februar 2022 die Entscheidung über den Antrag auf einen Bitcoin-ETF verschoben, um ihn "sorgfältig zu prüfen". Dann hat die SEC Mitte Juli 2023 bekanntgegeben, dass einem Antrag auf Umwandlung wieder nicht stattgegeben wird. Grayscale kündigten sofort an, die SEC wegen Willkür und Verstoß gegen das Wertpapierbörsengesetz von 1934 zu verklagen. Diese Klage wurde dann vor dem Bundesberufungsgericht verhandelt und entschieden.  Das Bundesberufungsgericht in D.C. entschied im Oktober, dass das Ablehnen von Anträgen auf eine Umwandlung in einen ETF seitens Grayscale ungerecht, nicht rechtens und willkürlich sei, da die Aufsichtsbehörde nicht erklären konnte, warum sie zuvor ähnliche Produkte zugelassen hat. Allerdings bedeutet dies nicht, dass Barry Silbert (CEO von DCG) automatisch den Grayscale Trust in einen ETF umwandeln kann. Der Antrag wandert damit nur zurück auf Garys (Vorsitzender der SEC) Schreibtisch. Und das bedeutet, dass die SEC wieder die Möglichkeit bekommt, einer Umwandlung aufgrund anderer Begründungen nicht stattzugeben. Dazu gleich mehr ⬇️. Außerdem ist fraglich, ob Barry tatsächlich wirklich eine Umwandlung herbeisehnt, denn momentan befinden sich Grayscale in einer sehr angenehmen Lage, die ihnen erlaubt 2% vom NAV (Net Asset Value) an Gebühren zu verlangen. Was bei einem Vermögen von 624.947 Bitcoin einen jährlichen Umsatz von 12.500 Bitcoin, bzw. 475 Million US Dollar bedeutet - für nichts tun. Es gibt schon [Kampagnen](https://www.redeemgbtc.com), die für eine Auflösung des Trusts kämpfen. Wer sich über die Umtriebigkeiten bei DCG / Genesis / Grayscale (Barry) ein besseres Bild machen möchte, sollte unbedingt den folgenden Thread lesen: https://x.com/real_vijay/status/1721385528510251182 ### Was seit dem geschah Seit dem letzten Artikel ist gleichzeitig viel und wenig geschehen. Verinnerlichen wir uns meine These - dass die SEC a) den Markt regulieren will, bevor sie ein BlackRock-Produkt genehmigt, b) ausländische (und damit nicht leicht regulierbare) Unternehmen aus dem Markt drängen will, um damit Unternehmen wie BlackRock den Handel zu vereinfachen und c) andere Interessengruppen an der Entscheidung der SEC beteiligt zu sein scheinen - dann ist genau das passiert, was man erwartet hätte. Die SEC hat ihre Entscheidung zur Genehmigung der ETF-Anträge wiederholte Male verschoben, momentan sieht es so aus, als würde eine Entscheidung im Januar 2024 fällig. https://bmpro.substack.com/p/sec-delays-etf-again-despite-warning Die SEC fällt weiter unliebsame Bäume. Bittrex, eine in den USA ansässige Börse, haben angekündigt, ihre Pforten zu schließen. https://finance.yahoo.com/news/crypto-exchange-bittrex-global-shuts-054643624.html Kraken wurde von der SEC verklagt - ähnliches Modell wie auch zuvor bei Binance und Coinbase angewandt (sprich: alles okay und tutti, solange ihr die Shitcoinerei an den Nagel hängt). https://www.nobsbitcoin.com/kraken-sec-lawsuit Dabei wurden in der Klageschrift die bereits identifizierten Digitalen Assets, die die SEC als unregistrierte Wertpapiere betrachtet, 1 zu 1 wieder aufgeführt.  Doch die größte Überraschung war die diese Woche veröffentlichte Meldung, dass Binance sich in einem Vergleich mit dem US Department of Justice (DOJ) auf eine Zahlung von über 4 Milliarden US Dollar und den Rücktritt CZs (Changpeng Zhao) als CEO von Binance geeinigt habe. https://www.nobsbitcoin.com/cz-steps-down-as-ceo-of-binance-as-part-of-4-billion-settlement-with-doj Es ist recht eindeutig, dass es dem Justizministerium (DOJ) hier nicht um den Schutz der Verbraucher geht. Es muss allerdings der Anschein gewahrt werden, dass nicht in Eigeninteresse (dem von BlackRock, hust) gehandelt wird, sondern dass der Eindruck erweckt wird, dass sie tatsächlich etwas Gutes tun, indem sie sich um einen "bad actor" kümmern" - das wird sehr deutlich, wenn man betrachtet, dass sich das Narrativ im Vergleich hauptsächlich auf AML (Anti-Money-Laundering) und Terrorismusfinanzierung konzentriert. Wie schon aus meiner These ersichtlich, geht auch aus bisherigen Kommentaren der SEC klar hervor, dass die größte Sorge derzeit ausländische Börsen sind, die den Bitcoin-Preis manipulieren können. Binance ist die größte Börse der Welt und hat bis heute erfolgreich außerhalb des Einflussbereichs der US-Regierung operiert. Mit dieser Vereinbarung ist das Problem der Offshore-Kursmanipulation zunächst und zum größten Teil gelöst. Das BlackRock-SEC-Reptilienmenschen-Playbook ist im vollen Gange. Ausländische Konkurrenz weitestgehend unter Kontrolle ✅  Die SEC scheint außerdem im engen Kontakt mit den ETF-Antragstellern zu stehen. Insbesondere ein Verweis auf eine Änderung der Anträge in Bezug auf "cash" vs. "in-kind creation" hat diese Woche für Diskussionen gesorgt. https://x.com/EricBalchunas/status/1725559994995573086 Viele börsengehandelte Fonds verlangen von den zugelassenen Teilnehmern, dass sie Anteile in Form von Sachleistungen (in-kind) schaffen , d. h. dass sie ETF-Anteile gegen einen Wertpapierkorb und nicht gegen Bargeld (cash) eintauschen. Die SEC hat jedoch auf eine Formulierung in den Anträgen gedrängt, die genau dise cash-creations zulassen.  Während sich viele auf die minutiöse Gestalt der Inhalte stürzen und eine Genehmigung hineininterpretieren, zieht die SEC hier meiner Meinung nach eine Linie, um eine Unterscheidung zwischen Grayscales GBTC und BlackRock et al. zu schaffen.  Wenn man an ein Playbook glaubt, ist der Grayscale Trust den Teilnehmern ein offensichtlicher Dorn im Auge, weshalb eine Umwandlung zunächst verhindert werden will. Jetzt muss nur noch Coinbase mitspielen. Aber wenn Binance einen Vergleich erzielen kann, warum nicht auch $COIN? Vielleicht einigt sich die SEC mit Coinbase im Gegenzug für "saftige Geldstrafen" und die Entfernung aller Shitcoins von der Plattform. Im Gegenzug erhält Coinbase den Börsenstatus und wird für die Überwachungsvereinbarung mit BlackRock und den anderen Antragstellern freigeschaltet. Auf einen Schlag würde die SEC die Shitcoins von der einzigen börsennotierten US-Börse entfernen und ein legales (nach ihren Vorstellungen und selbst artikulierten Prinzipien) Fundament für BlackRocks ETF schaffen. Außerdem würde es mich nicht wundern, wenn Coinbase als weißer Ritter auftritt und ganz barmherzig das US-Business von Binance übernimmt. Natürlich nur, um einem Mitstreiter in schwierigen Zeiten beizustehen. Ich packe es auf jeden Fall auf meine Bingo-Karte für den Zeitraum zwischen jetzt und einer Genehmigung der ETF-Anträge.  Durch die Einigung mit CZ und die Geldstrafe von 4,3 Milliarden US Dollar erleichtert die US-Regierung den Transfer von Bitcoin aus schwachen in starke Hände (Binance ➡️ Coinbase). Binance werden Bitcoin verkaufen müssen, um die Geldstrafe zu bezahlen, während gleichzeitig die Spot-ETFs das Angebot mit amerikanischem Kapital auffüllen können. Schöne Ausführung. Tolles Playbook 👏 Ich bin mir bewusst, dass die oben genannten Ereignisse und Auslegungen der Geschehnisse sehr verschwurbelt daherkommen, jedoch möchte ich meinen virtuellen Alu-Hut vor dem Architekten dieses wirklichen langen Long-Games ziehen.  In der Zwischenzeit arbeiten gewissenhafte Journalisten namhafter Veröffentlichungen (BlackRock PR-Department, hust) daran, die öffentliche Wahrnehmung von Bitcoin zum Positiven zu wenden. Wurde in den letzten Jahren Bitcoin als riskante Anlage, Klimakiller, Ozean-Kocher, oder schlimmer bezeichnet, wird es jetzt als ein möglicher Bestandteil einer nachhaltigen und zukunftsorientierten Anlagestrategie dargestellt. https://www.forbes.com/sites/digital-assets/2023/07/08/bitcoin-network-to-reduce-more-emissions-than-its-energy-sources-produce/ Wir (du schlaue/r Leser//in und ich) wissen schon lange, dass die Bitcoin-Branche heute die weltweit am nachhaltigsten betriebene Branche ist und das Bitcoin-Mining als einzige Industrie in dem Bereich kohlenstoffnegativ werden kann. Es ist also offensichtlich, dass Bitcoin ein wichtiger Bestandteil einer nachhaltigen und zukunftsorientierten Anlagestrategie sein kann, aber genau dieses Narrativ wurde jahrelang absichtlich verdrängt (➡️ siehe XRP-gesponsorte [Greenpeace Aktion](https://dailycoin.com/greenpeace-anti-crypto-artist-admits-wrong-on-bitcoin-mining/) anfang des Jahres).   Wir sehen also, dass es nicht nur um eine einfache Genehmigung der Anträge geht, sondern viele Mosaikteilchen gelegt werden, bevor es dazu kommen kann. Viele Zeichen deuten darauf hin, dass viele verschiedene Parteien daran arbeiten, ein Umfeld zu schaffen, dass es bestimmten Gruppen ermöglicht, einen ETF möglichst risikofrei und konkurrenzlos zu platzieren. Dabei werden unliebsame Mitspieler vom Platz gewiesen und anderen Mitspielern werden die Spielregeln nochmal ganz bewusst in Erinnerung gerufen, während gleichzeitig ein Narrativ geschaffen wird, das einen Bitcoin-ETF in glänzendem Licht darstellt. ----------- Es ist nahezu gewiss, dass es nicht die Frage ist, ob einem Antrag zugestimmt wird, sondern vielmehr, wann dies geschehen wird. Es besteht eine hohe Wahrscheinlichkeit, dass allen Anträgen zeitgleich stattgegeben wird. Dennoch lässt sich erkennen, dass die SEC strategisch Zeit gewinnt, um Binance und andere unerwünschte Akteure vollständig aus dem Spiel zu nehmen und Coinbase in der Zwischenzeit zu dem vorbildlichen Mustersohn zu formen, den sie immer haben wollte. Da der Markt für Spot-ETFs als "Winner-takes-all" gilt, wird darauf geachtet, dass nicht irgendein Antragsteller das Rennen gewinnt, sondern ein bestimmter - Larry. Hierfür ist es notwendig, Barry vom Spielfeld zu verdrängen, da er einen erheblichen Vorsprung hat, woran Gary offensichtlich arbeitet. Falls sich meine Vermutungen bewahrheiten, werden wir in naher Zukunft einen Bitcoin-Spot-ETF sehen, der von BlackRock dominiert wird. Grayscale und Binance werden keine Rolle im Spiel spielen, während Coinbase als reguliertes, vorbildliches US-Unternehmen davon profitieren wird. 🫳🎤 --- In diesem Sinne, 2... 1... Risiko!  @ e7bc35f8:3ed2a7cf
2025-02-03 07:37:44In a striking contrast of ideals versus actions, former U.S. Secretary of State Hillary Clinton was recently awarded the Medal of Freedom. Yet, it is impossible to forget [what happened in February 2011](https://youtu.be/grFWkyXPfxk), when ex-CIA analyst and well-known dissident Ray McGovern was violently removed by security while silently protesting one of Clinton’s speeches at George Washington University. McGovern’s only act of defiance was standing up and turning his back to Clinton in protest of America’s ongoing wars of aggression. The incident, which unfolded under Clinton’s watch, stands as a stark reminder of the selective nature of so-called freedom and democracy. The irony of the moment was profound. Clinton's speech [that day](http://www.state.gov/secretary/rm/2011/02/156619.htm) was ostensibly about the brave individuals in Egypt who had stood up against authoritarian rule, using the internet to organize their dissent. The same U.S. government that praised online activism abroad seemed intolerant of peaceful, silent protest within its own borders. Over the past two decades, mainstream media has pushed a narrative that social media platforms like [Twitter](https://youtu.be/BYSchIVpEJ8), [Facebook](https://youtu.be/UoRspCp5Xn0), and [YouTube ](https://youtu.be/ja-tbqN5-Jk)have played an instrumental role in shaping revolutions and uprisings across the world. From Moldova and Iran to Egypt and Tunisia, reporters with little on-the-ground knowledge have eagerly proclaimed these digital platforms as revolutionary tools of democracy. The only problem? This oft-repeated story is largely[ a myth](https://youtu.be/pFGSplRR7oI). While journalistic laziness explains some of this exaggeration—reporters compiling their stories from hotel rooms rather than gathering firsthand accounts—the truth runs much deeper. The idea of a "social media revolution" has been deliberately constructed by U.S. State Department-linked NGOs with vested interests in overthrowing governments that do not align with Washington’s geopolitical agenda. One of the key figures in shaping this narrative is [Evgeny Morozov](https://www.opensocietyfoundations.org/grants/open-society-fellowship?fellow=evgeny-morozov), a former fellow of George Soros’ Open Society Institute and a visiting scholar at Stanford University. Morozov pioneered the concept of the "Twitter Revolution" during the [2009 Moldovan protests](https://slate.com/technology/2012/01/anti-vaccine-activists-9-11-deniers-and-googles-social-search.html), arguing that social media facilitated "flash mobs" and "huge mobilization efforts" against authoritarian regimes. His language, promoted in publications like [Foreign Policy](https://foreignpolicy.com/2009/04/07/moldovas-twitter-revolution/), [The Economist](https://web.archive.org/web/20150504011512/http://www.economist.com/node/12815678?story_id=12815678), and [openDemocracy](https://www.opendemocracy.net/en/the-alternatives-alternative/), laid the foundation for the media’s portrayal of networked protests. However, even Morozov was forced to later acknowledge flaws in his argument. [He admitted](https://foreignpolicy.com/2009/04/07/more-analysis-of-twitters-role-in-moldova/) that at the time of the so-called "Twitter Revolution" in Moldova, there were only about 70 registered Twitter users in the entire country. Despite this glaring inconsistency, the Western media ran with the story. The same pattern repeated in the 2009 Iranian unrest, where an alleged flood of 30,000 tweets provided live updates on the protests. [Most of these tweets](https://mashable.com/archive/twitter-iran-election), however, were in English and were posted by newly registered accounts with identical profile pictures—hardly the grassroots digital uprising the media portrayed. Notably, [Israeli news outlets](https://web.archive.org/web/20090714235359/https://chartingstocks.net/wp-content/uploads/2009/06/jpost.jpg) began covering these "tweets" almost immediately, [raising questions](https://web.archive.org/web/20090619154321/http://www.chartingstocks.net/2009/06/proof-israeli-effort-to-destabilize-iran-via-twitter/) about external orchestration. Similarly, during the Arab Spring, social media was widely credited for fueling protests in Egypt, Tunisia, and Yemen. Yet, the data tells a different story. At the height of these uprisings, the combined number of [Twitter users](https://mashable.com/archive/egypt-twitter-infographic) in those three countries was under 15,000. [Facebook](https://www.theguardian.com/technology/blog/2010/jul/22/facebook-countries-population-use#data), while more widespread, still had only a 4.5% penetration rate in Egypt by mid-2010—dwarfed by the reach of television networks. Even those who originally championed the "social media revolution" have had to admit that the phenomenon was blown out of proportion. What they refuse to acknowledge, however, is the strategic motivation behind these uprisings. Who benefits from these revolutions, and whose interests do they ultimately serve? At a [2010 Berlin conference](https://youtu.be/yQ1b67Noy9w), Morozov conspicuously avoided addressing these critical questions. His silence speaks volumes. [The reality is](https://youtu.be/LAlbajRFgUE) that "social media revolutions" are often less about organic uprisings and more about the West’s longstanding practice of using digital tools as part of broader regime-change strategies. In 2011, for instance, the U.S. State Department funded Psiphon, an online encryption system designed to help users bypass government firewalls. This technology was distributed in Syria, conveniently aiding opposition forces at a time when the U.S. was actively working to destabilize the Assad government. Yet, when Syria was later found using U.S.-developed internet filtering technology, it was condemned for [violating American trade laws](https://web.archive.org/web/20120522162400/https://arabiangazette.com/syria-violating-trade-laws/). The most glaring hypocrisy is that while U.S. officials champion the internet as a tool for democracy in foreign countries, they simultaneously push for more restrictive internet laws at home. In 2011, Senator Joe Lieberman openly discussed using internet filtering technology to regulate American citizens’ access to information—ironically sounding much like the authoritarian leaders Washington claims to oppose. This contradiction exposes the true nature of the social media revolution myth. Far from being an organic expression of people’s will, it is often just another weapon in the arsenal of Western powers seeking to manipulate and destabilize governments that refuse to align with their interests. [The very same politicians](https://web.archive.org/web/20130919221400/https://youtube.com/watch?v=OBB1S86_yBY) who praise internet activists in Iran or Syria are the ones clamping down on online freedoms in their own countries. The story of social media as a revolutionary force is not one of grassroots activism triumphing over oppression. Instead, it is a carefully crafted narrative, used to justify interventionist policies and promote regime change under the guise of "democracy promotion." As history has repeatedly shown, the beneficiaries of these so-called revolutions are rarely the people on the ground—but rather, the geopolitical architects pulling the strings from afar.
@ e7bc35f8:3ed2a7cf
2025-02-03 07:37:44In a striking contrast of ideals versus actions, former U.S. Secretary of State Hillary Clinton was recently awarded the Medal of Freedom. Yet, it is impossible to forget [what happened in February 2011](https://youtu.be/grFWkyXPfxk), when ex-CIA analyst and well-known dissident Ray McGovern was violently removed by security while silently protesting one of Clinton’s speeches at George Washington University. McGovern’s only act of defiance was standing up and turning his back to Clinton in protest of America’s ongoing wars of aggression. The incident, which unfolded under Clinton’s watch, stands as a stark reminder of the selective nature of so-called freedom and democracy. The irony of the moment was profound. Clinton's speech [that day](http://www.state.gov/secretary/rm/2011/02/156619.htm) was ostensibly about the brave individuals in Egypt who had stood up against authoritarian rule, using the internet to organize their dissent. The same U.S. government that praised online activism abroad seemed intolerant of peaceful, silent protest within its own borders. Over the past two decades, mainstream media has pushed a narrative that social media platforms like [Twitter](https://youtu.be/BYSchIVpEJ8), [Facebook](https://youtu.be/UoRspCp5Xn0), and [YouTube ](https://youtu.be/ja-tbqN5-Jk)have played an instrumental role in shaping revolutions and uprisings across the world. From Moldova and Iran to Egypt and Tunisia, reporters with little on-the-ground knowledge have eagerly proclaimed these digital platforms as revolutionary tools of democracy. The only problem? This oft-repeated story is largely[ a myth](https://youtu.be/pFGSplRR7oI). While journalistic laziness explains some of this exaggeration—reporters compiling their stories from hotel rooms rather than gathering firsthand accounts—the truth runs much deeper. The idea of a "social media revolution" has been deliberately constructed by U.S. State Department-linked NGOs with vested interests in overthrowing governments that do not align with Washington’s geopolitical agenda. One of the key figures in shaping this narrative is [Evgeny Morozov](https://www.opensocietyfoundations.org/grants/open-society-fellowship?fellow=evgeny-morozov), a former fellow of George Soros’ Open Society Institute and a visiting scholar at Stanford University. Morozov pioneered the concept of the "Twitter Revolution" during the [2009 Moldovan protests](https://slate.com/technology/2012/01/anti-vaccine-activists-9-11-deniers-and-googles-social-search.html), arguing that social media facilitated "flash mobs" and "huge mobilization efforts" against authoritarian regimes. His language, promoted in publications like [Foreign Policy](https://foreignpolicy.com/2009/04/07/moldovas-twitter-revolution/), [The Economist](https://web.archive.org/web/20150504011512/http://www.economist.com/node/12815678?story_id=12815678), and [openDemocracy](https://www.opendemocracy.net/en/the-alternatives-alternative/), laid the foundation for the media’s portrayal of networked protests. However, even Morozov was forced to later acknowledge flaws in his argument. [He admitted](https://foreignpolicy.com/2009/04/07/more-analysis-of-twitters-role-in-moldova/) that at the time of the so-called "Twitter Revolution" in Moldova, there were only about 70 registered Twitter users in the entire country. Despite this glaring inconsistency, the Western media ran with the story. The same pattern repeated in the 2009 Iranian unrest, where an alleged flood of 30,000 tweets provided live updates on the protests. [Most of these tweets](https://mashable.com/archive/twitter-iran-election), however, were in English and were posted by newly registered accounts with identical profile pictures—hardly the grassroots digital uprising the media portrayed. Notably, [Israeli news outlets](https://web.archive.org/web/20090714235359/https://chartingstocks.net/wp-content/uploads/2009/06/jpost.jpg) began covering these "tweets" almost immediately, [raising questions](https://web.archive.org/web/20090619154321/http://www.chartingstocks.net/2009/06/proof-israeli-effort-to-destabilize-iran-via-twitter/) about external orchestration. Similarly, during the Arab Spring, social media was widely credited for fueling protests in Egypt, Tunisia, and Yemen. Yet, the data tells a different story. At the height of these uprisings, the combined number of [Twitter users](https://mashable.com/archive/egypt-twitter-infographic) in those three countries was under 15,000. [Facebook](https://www.theguardian.com/technology/blog/2010/jul/22/facebook-countries-population-use#data), while more widespread, still had only a 4.5% penetration rate in Egypt by mid-2010—dwarfed by the reach of television networks. Even those who originally championed the "social media revolution" have had to admit that the phenomenon was blown out of proportion. What they refuse to acknowledge, however, is the strategic motivation behind these uprisings. Who benefits from these revolutions, and whose interests do they ultimately serve? At a [2010 Berlin conference](https://youtu.be/yQ1b67Noy9w), Morozov conspicuously avoided addressing these critical questions. His silence speaks volumes. [The reality is](https://youtu.be/LAlbajRFgUE) that "social media revolutions" are often less about organic uprisings and more about the West’s longstanding practice of using digital tools as part of broader regime-change strategies. In 2011, for instance, the U.S. State Department funded Psiphon, an online encryption system designed to help users bypass government firewalls. This technology was distributed in Syria, conveniently aiding opposition forces at a time when the U.S. was actively working to destabilize the Assad government. Yet, when Syria was later found using U.S.-developed internet filtering technology, it was condemned for [violating American trade laws](https://web.archive.org/web/20120522162400/https://arabiangazette.com/syria-violating-trade-laws/). The most glaring hypocrisy is that while U.S. officials champion the internet as a tool for democracy in foreign countries, they simultaneously push for more restrictive internet laws at home. In 2011, Senator Joe Lieberman openly discussed using internet filtering technology to regulate American citizens’ access to information—ironically sounding much like the authoritarian leaders Washington claims to oppose. This contradiction exposes the true nature of the social media revolution myth. Far from being an organic expression of people’s will, it is often just another weapon in the arsenal of Western powers seeking to manipulate and destabilize governments that refuse to align with their interests. [The very same politicians](https://web.archive.org/web/20130919221400/https://youtube.com/watch?v=OBB1S86_yBY) who praise internet activists in Iran or Syria are the ones clamping down on online freedoms in their own countries. The story of social media as a revolutionary force is not one of grassroots activism triumphing over oppression. Instead, it is a carefully crafted narrative, used to justify interventionist policies and promote regime change under the guise of "democracy promotion." As history has repeatedly shown, the beneficiaries of these so-called revolutions are rarely the people on the ground—but rather, the geopolitical architects pulling the strings from afar. @ da0b9bc3:4e30a4a9
2025-02-03 06:14:42Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/874266
@ da0b9bc3:4e30a4a9
2025-02-03 06:14:42Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/874266 @ a012dc82:6458a70d
2025-02-03 02:42:01In the contemporary world, where the balance between technological advancement and environmental sustainability is increasingly crucial, Marathon Digital Holdings has emerged as a trailblazer in the Bitcoin mining industry. Their latest venture, utilizing methane gas from landfill waste to power Bitcoin mining operations, is not just a technological leap but also a significant stride towards eco-friendly practices in a sector often scrutinized for its environmental impact. This initiative represents a fusion of environmental stewardship with the burgeoning field of cryptocurrency, potentially setting a new standard for energy use in digital currency mining. It's a bold move that could reshape perceptions of the industry, demonstrating that environmental consciousness and technological progress can coexist harmoniously. **Table Of Content** - The Genesis of the Project - The Process and Technology - The Broader Impact - Conclusion - FAQs **The Genesis of the Project** **A Partnership for Sustainability** Marathon Digital's collaboration with Nodal Power marks a pivotal moment in the pursuit of sustainable cryptocurrency mining. The 280 kilowatt (kW) pilot project in Utah is more than just a test of feasibility; it's a beacon of innovation in an industry traditionally powered by conventional, often non-renewable, energy sources. This partnership reflects a growing awareness within the crypto mining community about the importance of sustainable practices. It's a forward-thinking approach, blending the expertise of a leading Bitcoin mining company with the innovative energy solutions of a renewable energy firm, setting a precedent for future collaborations in the industry. **Addressing Environmental Concerns** The project's focus on methane gas, a potent greenhouse gas, underscores a proactive approach to environmental stewardship. By targeting methane emissions from landfills, Marathon is addressing a critical environmental issue. Methane is not only a significant contributor to global warming but also represents a wasted resource when emitted into the atmosphere. This initiative is a response to increasing global concerns about climate change and environmental degradation. It's a strategy that aligns with international efforts to reduce greenhouse gas emissions and demonstrates Marathon's commitment to playing a role in the global fight against climate change. **The Process and Technology** **Innovative Conversion of Methane to Electricity** The technology behind converting methane to electricity is a cornerstone of this project. The process involves sophisticated systems that capture methane emissions efficiently and convert them into a usable form of energy. This technology is not just a testament to human ingenuity but also a crucial step towards making renewable energy more accessible and practical for industrial applications like Bitcoin mining. The success of this technology could have far-reaching implications, potentially revolutionizing how we think about waste management and energy production. **A Step Towards Green Bitcoin Mining** Marathon's initiative is a significant leap in the journey towards green Bitcoin mining. It's a project that challenges the status quo, proving that renewable energy can be a viable alternative to traditional power sources in the energy-intensive process of mining cryptocurrencies. This approach could inspire a wave of innovation in the sector, encouraging other companies to explore renewable energy options. The project is not just about reducing the environmental footprint of Bitcoin mining; it's about reimagining the future of energy use in the digital age. **The Broader Impact** **Potential for Industry-Wide Change** The implications of Marathon's project extend far beyond its immediate environmental benefits. It has the potential to catalyze a paradigm shift in the cryptocurrency mining industry. If successful, this project could serve as a model for other companies, demonstrating the practicality and benefits of sustainable mining practices. It could inspire a wave of innovation, leading to more widespread adoption of renewable energy sources in the industry, and potentially, a redefinition of what it means to be a responsible player in the digital currency space. **Environmental and Economic Benefits** The project is not just an environmental initiative; it's also an economically strategic move. By tapping into methane from landfills, Marathon could significantly reduce its operational costs. This approach provides a dual benefit: it mitigates the environmental impact of Bitcoin mining and offers a potentially more cost-effective energy solution. This economic incentive could be a key driver in encouraging wider adoption of similar practices across the industry, leading to a more sustainable and economically viable future for cryptocurrency mining. **Conclusion** Marathon Digital's pilot project in Utah is more than just an experiment in sustainable Bitcoin mining; it's a visionary step towards a new era in the industry. By harnessing methane gas from landfills to power their operations, Marathon is not only setting a new benchmark for environmental responsibility but also showcasing the untapped potential of renewable energy in reducing the carbon footprint of cryptocurrency mining. This bold experiment is a beacon of hope and innovation, suggesting a future where technological advancement and environmental sustainability are not mutually exclusive but are instead intertwined elements of a more responsible and forward-thinking industry. **FAQs** **What is Marathon Digital's new project about?** Marathon Digital has launched a pilot project in Utah, using methane gas from landfill waste to power Bitcoin mining operations. **Why is using methane for Bitcoin mining significant?** Methane is a potent greenhouse gas, and using it for mining reduces environmental impact and utilizes a renewable energy source. **Who is Marathon Digital partnering with for this project?** Marathon Digital has partnered with Nodal Power, a firm specializing in renewable energy assets. **What are the potential benefits of this project?** The project aims to reduce greenhouse gas emissions, lower energy costs, and set a precedent for sustainable practices in cryptocurrency mining. **How does this project impact the Bitcoin mining industry?** Marathon's initiative could inspire other companies to adopt renewable energy sources, potentially leading to a more sustainable and economically viable mining industry. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: [@croxroadnews.co](https://x.com/croxroadnewsco)** **Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)** **Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** *DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.*
@ a012dc82:6458a70d
2025-02-03 02:42:01In the contemporary world, where the balance between technological advancement and environmental sustainability is increasingly crucial, Marathon Digital Holdings has emerged as a trailblazer in the Bitcoin mining industry. Their latest venture, utilizing methane gas from landfill waste to power Bitcoin mining operations, is not just a technological leap but also a significant stride towards eco-friendly practices in a sector often scrutinized for its environmental impact. This initiative represents a fusion of environmental stewardship with the burgeoning field of cryptocurrency, potentially setting a new standard for energy use in digital currency mining. It's a bold move that could reshape perceptions of the industry, demonstrating that environmental consciousness and technological progress can coexist harmoniously. **Table Of Content** - The Genesis of the Project - The Process and Technology - The Broader Impact - Conclusion - FAQs **The Genesis of the Project** **A Partnership for Sustainability** Marathon Digital's collaboration with Nodal Power marks a pivotal moment in the pursuit of sustainable cryptocurrency mining. The 280 kilowatt (kW) pilot project in Utah is more than just a test of feasibility; it's a beacon of innovation in an industry traditionally powered by conventional, often non-renewable, energy sources. This partnership reflects a growing awareness within the crypto mining community about the importance of sustainable practices. It's a forward-thinking approach, blending the expertise of a leading Bitcoin mining company with the innovative energy solutions of a renewable energy firm, setting a precedent for future collaborations in the industry. **Addressing Environmental Concerns** The project's focus on methane gas, a potent greenhouse gas, underscores a proactive approach to environmental stewardship. By targeting methane emissions from landfills, Marathon is addressing a critical environmental issue. Methane is not only a significant contributor to global warming but also represents a wasted resource when emitted into the atmosphere. This initiative is a response to increasing global concerns about climate change and environmental degradation. It's a strategy that aligns with international efforts to reduce greenhouse gas emissions and demonstrates Marathon's commitment to playing a role in the global fight against climate change. **The Process and Technology** **Innovative Conversion of Methane to Electricity** The technology behind converting methane to electricity is a cornerstone of this project. The process involves sophisticated systems that capture methane emissions efficiently and convert them into a usable form of energy. This technology is not just a testament to human ingenuity but also a crucial step towards making renewable energy more accessible and practical for industrial applications like Bitcoin mining. The success of this technology could have far-reaching implications, potentially revolutionizing how we think about waste management and energy production. **A Step Towards Green Bitcoin Mining** Marathon's initiative is a significant leap in the journey towards green Bitcoin mining. It's a project that challenges the status quo, proving that renewable energy can be a viable alternative to traditional power sources in the energy-intensive process of mining cryptocurrencies. This approach could inspire a wave of innovation in the sector, encouraging other companies to explore renewable energy options. The project is not just about reducing the environmental footprint of Bitcoin mining; it's about reimagining the future of energy use in the digital age. **The Broader Impact** **Potential for Industry-Wide Change** The implications of Marathon's project extend far beyond its immediate environmental benefits. It has the potential to catalyze a paradigm shift in the cryptocurrency mining industry. If successful, this project could serve as a model for other companies, demonstrating the practicality and benefits of sustainable mining practices. It could inspire a wave of innovation, leading to more widespread adoption of renewable energy sources in the industry, and potentially, a redefinition of what it means to be a responsible player in the digital currency space. **Environmental and Economic Benefits** The project is not just an environmental initiative; it's also an economically strategic move. By tapping into methane from landfills, Marathon could significantly reduce its operational costs. This approach provides a dual benefit: it mitigates the environmental impact of Bitcoin mining and offers a potentially more cost-effective energy solution. This economic incentive could be a key driver in encouraging wider adoption of similar practices across the industry, leading to a more sustainable and economically viable future for cryptocurrency mining. **Conclusion** Marathon Digital's pilot project in Utah is more than just an experiment in sustainable Bitcoin mining; it's a visionary step towards a new era in the industry. By harnessing methane gas from landfills to power their operations, Marathon is not only setting a new benchmark for environmental responsibility but also showcasing the untapped potential of renewable energy in reducing the carbon footprint of cryptocurrency mining. This bold experiment is a beacon of hope and innovation, suggesting a future where technological advancement and environmental sustainability are not mutually exclusive but are instead intertwined elements of a more responsible and forward-thinking industry. **FAQs** **What is Marathon Digital's new project about?** Marathon Digital has launched a pilot project in Utah, using methane gas from landfill waste to power Bitcoin mining operations. **Why is using methane for Bitcoin mining significant?** Methane is a potent greenhouse gas, and using it for mining reduces environmental impact and utilizes a renewable energy source. **Who is Marathon Digital partnering with for this project?** Marathon Digital has partnered with Nodal Power, a firm specializing in renewable energy assets. **What are the potential benefits of this project?** The project aims to reduce greenhouse gas emissions, lower energy costs, and set a precedent for sustainable practices in cryptocurrency mining. **How does this project impact the Bitcoin mining industry?** Marathon's initiative could inspire other companies to adopt renewable energy sources, potentially leading to a more sustainable and economically viable mining industry. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: [@croxroadnews.co](https://x.com/croxroadnewsco)** **Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)** **Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** *DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.* @ 3b7fc823:e194354f
2025-02-03 02:19:03# At-Risk Groups Are Facing A Battle For Their Rights Privacy. It’s a word we often take for granted, scrolling through our phones and sharing photos without a second thought. But for certain groups—those at risk due to their identities, beliefs, or circumstances—privacy isn’t just a luxury; it’s a lifeline. In today’s world, where governments, corporations, and even our own social media accounts seem to have a vested interest in collecting and selling our data, the fight for privacy has never been more crucial. Privacy is not a buzzword but a fundamental human right. We can do more to protect those who need it most. --- ### Privacy As A Human Right The concept of privacy is deeply rooted in our basic human rights. It’s not just about keeping your medical records confidential or hiding your bank statements; it’s about the right to control what others can know about you. For individuals who identify as LGBTQ+, immigrants, journalists, or political dissidents, this right is even more fragile. Recently, we’ve seen a rise in policies that seem designed to strip away these protections. From the Trump administration’s transgender ban on military service and passport changes to the targeting of journalists and activists, the message is clear: certain groups are considered fair game for scrutiny and control. These actions are about erasing the autonomy of individuals to live their lives without fear of retribution or discrimination. Privacy isn’t just a feel-good concept; it’s the cornerstone of a individuals liberty. We must ensure that no one’s rights can be arbitrarily taken away, especially the right to privacy. --- ### The Attack On Vulnerable Groups The targeting of at-risk groups has reached a fever pitch in recent months: 1. **Transgender Rights Under Fire** The Trump administration has issued a sweeping executive order that effectively erased recognition of transgender individuals’ rights. This included changes to passport policies that required individuals to declare their gender at birth, making it nearly impossible for trans individuals to update their documents without facing extreme scrutiny or even denial. These actions don’t just impact transgender people; they send a chilling message to the entire LGBTQ+ community. 2. **Free Speech And Political Dissent** Trump’s Free Speech Executive Order, aimed to protect citizens’ right to express their beliefs. However, critics argue it was more about silencing dissenters. Journalists, activists, and even private citizens have faced increasing pressure from government officials to either comply with certain views or face professional consequences. “Free speech is a double-edged sword,” noted one legal expert. “When the government uses it as a tool to marginalize certain groups, it becomes a weapon rather than a shield.” 3. **Media And Press Freedom** Trump’s ongoing battles with major media outlets are well-documented. From labeling reporters as “fake news” to pushing for laws that would limit press freedom, the administration has made it clear that journalists and news organizations are not above scrutiny. For independent journalists and investigative reporters, this poses a significant threat to their work and safety. 4. **Immigrant Rights And Discrimination** The Trump administration’s harsh immigration policies have had a devastating impact on vulnerable communities. From family separations to the expansion of surveillance in immigrant-heavy areas, these actions have left many feeling exposed and unsafe. Immigrants, particularly those from Latin America and the Middle East, are increasingly targeted for their perceived alignments with political rhetoric. --- ### The Consequences Of Losing Privacy When privacy is stripped away, it doesn’t just affect individuals—it affects entire communities. For transgender individuals, the fear of being “outted” online or facing discrimination at work is a daily reality. For journalists, the threat of government retribution can lead to self-censorship and an inability to hold power accountable. For immigrants, the risk of deportation or surveillance means constant vigilance—and often, no recourse. These consequences are not just personal; they’re systemic. When certain groups are deemed unworthy of protection, it sets a dangerous precedent for what’s allowed in society. It sends the message that some lives matter less than others, and that the government can act with impunity. If you are not in one of these currently impacted groups just give it time and eventually they will come for you too. --- ### The Fight For Privacy: What We Can Do The good news is that we don’t have to sit idly by while this happens. There are steps we can take to fight for privacy as a fundamental right. Here’s how: 1. **Advocate For Stronger Protections** Governments at all levels need to pass and enforce laws that protect privacy, especially for vulnerable groups. This includes everything from data protection legislation to anti-discrimination policies. 2. **Support Independent Journalism** Journalists are on the front lines of this fight, uncovering corruption and holding power accountable. Support independent media outlets and platforms that prioritize transparency and press freedom. 3. **Educate And Empower** Communities under threat need resources to protect themselves. This includes education on their rights, know how and tools to secure their data, and access to legal support when needed. 4. **Use Your Voice** Speak out against policies that erode privacy and target vulnerable groups. Use your actions to protect yourself and others. 5. **Demand Accountability** When governments overreach, they need to be held accountable. Fight for yours and others rights. --- ### Privacy Is A Fight Worth Winning Privacy isn’t just about convenience or comfort—it’s about freedom, autonomy, and the right to live without fear of arbitrary control. For at-risk groups, this is not just a luxury; it’s a lifeline. As we move forward in this uncertain era, let’s remember that the fight for privacy is not over— it’s just beginning. We all have a role to play in protecting those who need it most. So let’s get to work.
@ 3b7fc823:e194354f
2025-02-03 02:19:03# At-Risk Groups Are Facing A Battle For Their Rights Privacy. It’s a word we often take for granted, scrolling through our phones and sharing photos without a second thought. But for certain groups—those at risk due to their identities, beliefs, or circumstances—privacy isn’t just a luxury; it’s a lifeline. In today’s world, where governments, corporations, and even our own social media accounts seem to have a vested interest in collecting and selling our data, the fight for privacy has never been more crucial. Privacy is not a buzzword but a fundamental human right. We can do more to protect those who need it most. --- ### Privacy As A Human Right The concept of privacy is deeply rooted in our basic human rights. It’s not just about keeping your medical records confidential or hiding your bank statements; it’s about the right to control what others can know about you. For individuals who identify as LGBTQ+, immigrants, journalists, or political dissidents, this right is even more fragile. Recently, we’ve seen a rise in policies that seem designed to strip away these protections. From the Trump administration’s transgender ban on military service and passport changes to the targeting of journalists and activists, the message is clear: certain groups are considered fair game for scrutiny and control. These actions are about erasing the autonomy of individuals to live their lives without fear of retribution or discrimination. Privacy isn’t just a feel-good concept; it’s the cornerstone of a individuals liberty. We must ensure that no one’s rights can be arbitrarily taken away, especially the right to privacy. --- ### The Attack On Vulnerable Groups The targeting of at-risk groups has reached a fever pitch in recent months: 1. **Transgender Rights Under Fire** The Trump administration has issued a sweeping executive order that effectively erased recognition of transgender individuals’ rights. This included changes to passport policies that required individuals to declare their gender at birth, making it nearly impossible for trans individuals to update their documents without facing extreme scrutiny or even denial. These actions don’t just impact transgender people; they send a chilling message to the entire LGBTQ+ community. 2. **Free Speech And Political Dissent** Trump’s Free Speech Executive Order, aimed to protect citizens’ right to express their beliefs. However, critics argue it was more about silencing dissenters. Journalists, activists, and even private citizens have faced increasing pressure from government officials to either comply with certain views or face professional consequences. “Free speech is a double-edged sword,” noted one legal expert. “When the government uses it as a tool to marginalize certain groups, it becomes a weapon rather than a shield.” 3. **Media And Press Freedom** Trump’s ongoing battles with major media outlets are well-documented. From labeling reporters as “fake news” to pushing for laws that would limit press freedom, the administration has made it clear that journalists and news organizations are not above scrutiny. For independent journalists and investigative reporters, this poses a significant threat to their work and safety. 4. **Immigrant Rights And Discrimination** The Trump administration’s harsh immigration policies have had a devastating impact on vulnerable communities. From family separations to the expansion of surveillance in immigrant-heavy areas, these actions have left many feeling exposed and unsafe. Immigrants, particularly those from Latin America and the Middle East, are increasingly targeted for their perceived alignments with political rhetoric. --- ### The Consequences Of Losing Privacy When privacy is stripped away, it doesn’t just affect individuals—it affects entire communities. For transgender individuals, the fear of being “outted” online or facing discrimination at work is a daily reality. For journalists, the threat of government retribution can lead to self-censorship and an inability to hold power accountable. For immigrants, the risk of deportation or surveillance means constant vigilance—and often, no recourse. These consequences are not just personal; they’re systemic. When certain groups are deemed unworthy of protection, it sets a dangerous precedent for what’s allowed in society. It sends the message that some lives matter less than others, and that the government can act with impunity. If you are not in one of these currently impacted groups just give it time and eventually they will come for you too. --- ### The Fight For Privacy: What We Can Do The good news is that we don’t have to sit idly by while this happens. There are steps we can take to fight for privacy as a fundamental right. Here’s how: 1. **Advocate For Stronger Protections** Governments at all levels need to pass and enforce laws that protect privacy, especially for vulnerable groups. This includes everything from data protection legislation to anti-discrimination policies. 2. **Support Independent Journalism** Journalists are on the front lines of this fight, uncovering corruption and holding power accountable. Support independent media outlets and platforms that prioritize transparency and press freedom. 3. **Educate And Empower** Communities under threat need resources to protect themselves. This includes education on their rights, know how and tools to secure their data, and access to legal support when needed. 4. **Use Your Voice** Speak out against policies that erode privacy and target vulnerable groups. Use your actions to protect yourself and others. 5. **Demand Accountability** When governments overreach, they need to be held accountable. Fight for yours and others rights. --- ### Privacy Is A Fight Worth Winning Privacy isn’t just about convenience or comfort—it’s about freedom, autonomy, and the right to live without fear of arbitrary control. For at-risk groups, this is not just a luxury; it’s a lifeline. As we move forward in this uncertain era, let’s remember that the fight for privacy is not over— it’s just beginning. We all have a role to play in protecting those who need it most. So let’s get to work. @ fd78c37f:a0ec0833
2025-02-03 00:23:23🔹 Pre-event buzz: Even before the event started, numerous calls came in to confirm the venue and ask if they could bring friends along. Upon arrival, many young attendees were eager to learn more about YakiHonne, reflecting the excitement and anticipation surrounding the meetup.   🔹 Engaging discussions: The event kicked off with an introduction to Nostr and YakiHonne’s core principles, sparking insightful conversations about what it truly means to have a decentralized social media platform.  🔹 Deep dive: Attendees raised many questions, particularly about YakiHonne’s decentralization model. The concept resonated with many, and a large number of participants expressed their support and interest in becoming part of the YakiHonne ecosystem in the future.   The meetup wrapped up with light refreshments 🍹, networking 🤝, and a photo session 📸. Even after the event officially ended, conversations continued as people stayed behind to connect and explore further possibilities ✨.   YakiHonne Meetup was more than just a gathering—it was a step forward in shaping the future of decentralized social media! 🚀 #YakiHonne #Nostr #DecentralizedSocialMedia
@ fd78c37f:a0ec0833
2025-02-03 00:23:23🔹 Pre-event buzz: Even before the event started, numerous calls came in to confirm the venue and ask if they could bring friends along. Upon arrival, many young attendees were eager to learn more about YakiHonne, reflecting the excitement and anticipation surrounding the meetup.   🔹 Engaging discussions: The event kicked off with an introduction to Nostr and YakiHonne’s core principles, sparking insightful conversations about what it truly means to have a decentralized social media platform.  🔹 Deep dive: Attendees raised many questions, particularly about YakiHonne’s decentralization model. The concept resonated with many, and a large number of participants expressed their support and interest in becoming part of the YakiHonne ecosystem in the future.   The meetup wrapped up with light refreshments 🍹, networking 🤝, and a photo session 📸. Even after the event officially ended, conversations continued as people stayed behind to connect and explore further possibilities ✨.   YakiHonne Meetup was more than just a gathering—it was a step forward in shaping the future of decentralized social media! 🚀 #YakiHonne #Nostr #DecentralizedSocialMedia @ ae6ce958:d0f02c7d
2025-02-02 23:56:18**Authors**: DamageBDD Research Team **Date**: February 2025 #### **Abstract** This paper presents a formal multidimensional analysis of the profitability and systemic impact of operating a DamageBDD node, considering two distinct yet synergistic roles: (1) **BDD Maintainer**, responsible for writing and verifying behavioral-driven development (BDD) test cases, and (2) **Node Runner**, responsible for hosting, validating, and distributing DamageBDD verification data. The study explores the economic viability, systemic benefits, and broader implications for software development efficiency and human potential. We argue that DamageBDD does not merely represent an alternative testing infrastructure but also serves as an incentive structure that unlocks latent human capital through verifiable, high-impact contributions. --- ## **1. Introduction** The software industry increasingly relies on automated testing to ensure system reliability and security. However, traditional models of test validation suffer from inefficiencies due to lack of **verifiable accountability**, reliance on centralized test infrastructure, and difficulty in aligning developer incentives. DamageBDD introduces a **market-driven verification layer** that decentralizes and incentivizes **test-driven software development**. By distributing both verification and governance via a **blockchain-based testing economy**, DamageBDD enables **trustless BDD validation**. Two primary participants define this ecosystem: 1. **BDD Maintainers** – Developers and testers who write and maintain test cases to ensure software correctness. 2. **Node Runners** – Operators who maintain DamageBDD nodes to execute, verify, and immutably record test results. This study examines the **profitability, scalability, and systemic value** of each role while exploring how this model **unlocks testing infrastructure and human potential** in a way that traditional systems do not. --- ## **2. Multidimensional Profitability Analysis** We evaluate profitability using a **multidimensional framework** across the following key dimensions: - **Economic Profitability** (direct financial rewards) - **Computational Efficiency** (resource costs and hardware scalability) - **Network Effects** (interoperability and systemic adoption) - **Human Capital Optimization** (learning curve, skill growth, and long-term impact) ### **2.1 Economic Profitability** #### **BDD Maintainer** BDD Maintainers earn **sats for verifiable test contributions**. Their work is directly compensated based on the number of **successful test verifications** executed on the DamageBDD network. The economic incentives align with: - **Quality over Quantity** – High-quality, reusable BDD tests accrue more long-term revenue. - **Compounding Value** – A well-maintained test suite continues to generate revenue as projects grow. #### **Node Runner** Node Runners monetize **test execution and validation services** by processing and storing test results. Profitability derives from: - **Transaction Fees** – Runners earn sats per executed and verified test case. - **Reputation Score** – Higher-ranked nodes process more verifications, generating greater earnings. - **Liquidity Pools** – Nodes can facilitate instant **Lightning Network payouts** for successful tests, further increasing earnings via transaction flow. ### **2.2 Computational Efficiency** While mining Bitcoin is an **energy-intensive, zero-sum competition**, DamageBDD nodes optimize for **computational efficiency** rather than brute-force expenditure. - **BDD Maintainer Efficiency** – Writing test cases has near-zero energy cost beyond human intellectual effort. - **Node Runner Efficiency** – Instead of wasting cycles on proof-of-work, DamageBDD nodes run lightweight BDD verifications, leveraging Erlang for extreme concurrency and low-resource execution. A comparative analysis shows that operating a DamageBDD node **delivers higher computational efficiency per satoshi earned** than Bitcoin mining. --- ### **2.3 Network Effects and Synergies** A crucial factor in DamageBDD’s economic model is **network value accumulation**. Unlike mining, which **diminishes profitability over time**, DamageBDD’s network **increases in value as adoption grows**. #### **BDD Maintainer Synergies** - The more tests written and **verified on-chain**, the greater the **trust in software systems**. - Open-source contributors and enterprise teams benefit from **immutable test history**, reducing redundant labor. #### **Node Runner Synergies** - The more tests executed, the **more valuable the verification layer becomes**. - Nodes reinforce the **integrity of test results**, leading to network-wide adoption in **high-assurance industries** (e.g., finance, healthcare, AI safety). --- ### **2.4 Human Capital Optimization: Unlocking Developer Potential** Traditional software testing is often seen as a **cost center**, leading to its underutilization. DamageBDD flips this paradigm by treating testing as a **profit center**—rewarding testers not just for finding bugs but for **preventing catastrophic software failures**. #### **Cognitive and Economic Impact** - **Skill Growth** – Developers naturally **improve software design** by maintaining structured BDD tests. - **Career Upskilling** – High-ranking BDD Maintainers become **indispensable assets** in software teams. - **Economic Independence** – Unlike traditional employment, DamageBDD allows maintainers to **earn directly from open-source contributions**. The system **gamifies quality assurance**, transforming what was once a tedious process into a **competitive and rewarding marketplace**. --- ## **3. Conclusion: A New Paradigm for Profitable Verification** DamageBDD redefines software testing as a **financially viable, decentralized economy**. The combination of BDD Maintainers and Node Runners creates a **self-reinforcing ecosystem** where: - **Maintainers ensure software correctness while earning sats** - **Node Runners validate and secure test results, generating a sustainable revenue stream** - **The network grows in value as more applications integrate DamageBDD verification** ### **Key Takeaways** - **DamageBDD is superior to traditional testing models** due to its decentralized incentives. - **It provides better computational efficiency than Bitcoin mining** while still operating on a proof-of-work foundation (verifiable contributions). - **It unlocks human potential** by turning software verification into a **career pathway rather than a sunk cost**. The profitability of DamageBDD Nodes extends beyond mere financial returns—it establishes a new **economic and intellectual order for software reliability**.
@ ae6ce958:d0f02c7d
2025-02-02 23:56:18**Authors**: DamageBDD Research Team **Date**: February 2025 #### **Abstract** This paper presents a formal multidimensional analysis of the profitability and systemic impact of operating a DamageBDD node, considering two distinct yet synergistic roles: (1) **BDD Maintainer**, responsible for writing and verifying behavioral-driven development (BDD) test cases, and (2) **Node Runner**, responsible for hosting, validating, and distributing DamageBDD verification data. The study explores the economic viability, systemic benefits, and broader implications for software development efficiency and human potential. We argue that DamageBDD does not merely represent an alternative testing infrastructure but also serves as an incentive structure that unlocks latent human capital through verifiable, high-impact contributions. --- ## **1. Introduction** The software industry increasingly relies on automated testing to ensure system reliability and security. However, traditional models of test validation suffer from inefficiencies due to lack of **verifiable accountability**, reliance on centralized test infrastructure, and difficulty in aligning developer incentives. DamageBDD introduces a **market-driven verification layer** that decentralizes and incentivizes **test-driven software development**. By distributing both verification and governance via a **blockchain-based testing economy**, DamageBDD enables **trustless BDD validation**. Two primary participants define this ecosystem: 1. **BDD Maintainers** – Developers and testers who write and maintain test cases to ensure software correctness. 2. **Node Runners** – Operators who maintain DamageBDD nodes to execute, verify, and immutably record test results. This study examines the **profitability, scalability, and systemic value** of each role while exploring how this model **unlocks testing infrastructure and human potential** in a way that traditional systems do not. --- ## **2. Multidimensional Profitability Analysis** We evaluate profitability using a **multidimensional framework** across the following key dimensions: - **Economic Profitability** (direct financial rewards) - **Computational Efficiency** (resource costs and hardware scalability) - **Network Effects** (interoperability and systemic adoption) - **Human Capital Optimization** (learning curve, skill growth, and long-term impact) ### **2.1 Economic Profitability** #### **BDD Maintainer** BDD Maintainers earn **sats for verifiable test contributions**. Their work is directly compensated based on the number of **successful test verifications** executed on the DamageBDD network. The economic incentives align with: - **Quality over Quantity** – High-quality, reusable BDD tests accrue more long-term revenue. - **Compounding Value** – A well-maintained test suite continues to generate revenue as projects grow. #### **Node Runner** Node Runners monetize **test execution and validation services** by processing and storing test results. Profitability derives from: - **Transaction Fees** – Runners earn sats per executed and verified test case. - **Reputation Score** – Higher-ranked nodes process more verifications, generating greater earnings. - **Liquidity Pools** – Nodes can facilitate instant **Lightning Network payouts** for successful tests, further increasing earnings via transaction flow. ### **2.2 Computational Efficiency** While mining Bitcoin is an **energy-intensive, zero-sum competition**, DamageBDD nodes optimize for **computational efficiency** rather than brute-force expenditure. - **BDD Maintainer Efficiency** – Writing test cases has near-zero energy cost beyond human intellectual effort. - **Node Runner Efficiency** – Instead of wasting cycles on proof-of-work, DamageBDD nodes run lightweight BDD verifications, leveraging Erlang for extreme concurrency and low-resource execution. A comparative analysis shows that operating a DamageBDD node **delivers higher computational efficiency per satoshi earned** than Bitcoin mining. --- ### **2.3 Network Effects and Synergies** A crucial factor in DamageBDD’s economic model is **network value accumulation**. Unlike mining, which **diminishes profitability over time**, DamageBDD’s network **increases in value as adoption grows**. #### **BDD Maintainer Synergies** - The more tests written and **verified on-chain**, the greater the **trust in software systems**. - Open-source contributors and enterprise teams benefit from **immutable test history**, reducing redundant labor. #### **Node Runner Synergies** - The more tests executed, the **more valuable the verification layer becomes**. - Nodes reinforce the **integrity of test results**, leading to network-wide adoption in **high-assurance industries** (e.g., finance, healthcare, AI safety). --- ### **2.4 Human Capital Optimization: Unlocking Developer Potential** Traditional software testing is often seen as a **cost center**, leading to its underutilization. DamageBDD flips this paradigm by treating testing as a **profit center**—rewarding testers not just for finding bugs but for **preventing catastrophic software failures**. #### **Cognitive and Economic Impact** - **Skill Growth** – Developers naturally **improve software design** by maintaining structured BDD tests. - **Career Upskilling** – High-ranking BDD Maintainers become **indispensable assets** in software teams. - **Economic Independence** – Unlike traditional employment, DamageBDD allows maintainers to **earn directly from open-source contributions**. The system **gamifies quality assurance**, transforming what was once a tedious process into a **competitive and rewarding marketplace**. --- ## **3. Conclusion: A New Paradigm for Profitable Verification** DamageBDD redefines software testing as a **financially viable, decentralized economy**. The combination of BDD Maintainers and Node Runners creates a **self-reinforcing ecosystem** where: - **Maintainers ensure software correctness while earning sats** - **Node Runners validate and secure test results, generating a sustainable revenue stream** - **The network grows in value as more applications integrate DamageBDD verification** ### **Key Takeaways** - **DamageBDD is superior to traditional testing models** due to its decentralized incentives. - **It provides better computational efficiency than Bitcoin mining** while still operating on a proof-of-work foundation (verifiable contributions). - **It unlocks human potential** by turning software verification into a **career pathway rather than a sunk cost**. The profitability of DamageBDD Nodes extends beyond mere financial returns—it establishes a new **economic and intellectual order for software reliability**. @ 3b7fc823:e194354f
2025-02-02 22:55:32# The Secret to Staying Private in the Digital Wild West: A Guide to Using Encryption You’re scrolling through social media, and suddenly you realize your phone’s been tracking your location and displaying it on your profile for months. You’re not even sure how that happened. Or maybe you’ve noticed that every time you shop online, the item you looked for follows you around with ads wherever you go. Sound familiar? Yeah, welcome to the digital world—where your data is basically a free buffet for anyone who knows how to ask. But here’s the thing: you don’t have to sit back and take it. Encryption is like the secret weapon that lets you lock up your data and keep those prying eyes out. It’s not just for hackers or spies—it’s for regular people who want to take control of their privacy in a world that’s increasingly looking like a reality show where everyone’s a contestant. ### What Is Encryption, and Why Should You Care? Encryption is like a secure box that only you can open. When you use encryption, your data is scrambled in a way that’s hard for anyone else to read, even if they try. Think of it as putting on a metaphorical cloak that makes your online activity invisible to just about everyone except the people you want to see it. For example, when you browse the internet, your connection is often not encrypted by default. That’s why websites start with “https” to indicate a secure connection—it’s saying, “Hey, we’re using encryption here!” Without that little green padlock, anyone on the same WiFi could potentially spy on what you’re doing. So, encryption isn’t just for tech geeks or government agencies. It’s for everyone who wants to protect their data from being sold, stolen, or misused without their consent. And guess what? You’re already using it without realizing it. Every time you use a password-protected account or send an encrypted message, you’re reaping the benefits of encryption. ### The Privacy Advantages of Encryption for Regular People Let’s break down why encryption is your best friend when it comes to privacy: 1. **Financial Transactions** When you pay online or use a banking app, encryption keeps your financial info safe from hackers. It ensures that only the banks and businesses you’re dealing with can access your money—no one else can. 2. **Online Accounts** Your email, social media, and other accounts often use encryption to protect your login details. That’s why you see those little “lock” icons when you’re logging in. Without encryption, someone could potentially intercept your password and gain unauthorized access to your account. 3. **Data Breaches** Encryption can often prevent data breaches from being useful. Even if hackers manage to steal your information, the encryption makes it unreadable, so the stolen data is basically worthless to the attackers. 4. **Location Data** If you’re worried about apps tracking your every move, encryption can help limit how much of that data is accessible. Some apps use encryption to protect location data, making it harder for companies to sell your movements without your consent. 5. **Privacy Protection** Encryption acts as a layer of protection against invasive technologies. For example, some apps use tracking software that follows you around the internet based on your browsing history. With encryption, these trackers can be blocked or limited, giving you more control over what information is collected about you. ### How to Use Encryption Like a Pro Now that you know why encryption is essential for privacy, let’s talk about how to use it effectively: 1. **Use Strong Passwords** Encryption works only if your passwords are strong and unique. Don’t reuse passwords from one account to another, and avoid using easily guessable information like “password123” or your birth year. Use a password manager if you need help keeping track of them. 2. **Enable HTTPS Everywhere** Install browser extensions like HTTPS Everywhere to automatically encrypt your connections to websites that don’t support encryption by default. This ensures that even if you’re not actively thinking about it, your data is still protected. 3. **Look for the Lock Icon** Whenever you’re on a website or app, look for the lock icon in the URL bar. Make sure it’s encrypted before you input any personal information. 4. **Use Encrypted Communication Tools** For private conversations, use apps like Signal or SimpleX, which are designed with encryption in mind. These tools ensure that only the sender and recipient can read your messages, keeping them safe from prying eyes. 5. **Enable Two-Factor Authentication (2FA)** This isn’t exactly encryption, but it’s a close second. 2FA adds an extra layer of security by requiring you to provide two forms of verification—like your password and a code sent to your phone—to access your account. While not encryption itself, it works alongside encryption to keep your accounts secure. 6. **Use Encrypted Storage and Backup** When storing sensitive files or data, use encrypted cloud storage or external drives. Tools like BitLocker (for Windows) or AES-256 encryption can protect your files from unauthorized access. 7. **Stay Updated** Encryption technology is always evolving, so it’s important to keep your software and apps updated. Outdated systems are often easy targets for hackers, leaving you vulnerable to attacks. ### Final Thoughts: Your Data Is Your Power In a world where data is a commodity, encryption is your weapon against the invasive tactics of corporations and hackers alike. It empowers you to control what information you share and protects you from having it used against you. So, whether you’re shopping online, using your favorite apps, or just browsing the web, remember that encryption is there to help you stay private and in control of your own data. And if you ever feel overwhelmed by all the privacy stuff, just remember this: you’re not alone. Millions of people are fighting for stronger privacy protections every day. So, do your part by using encryption wisely—your data and your privacy are worth it. Let’s make sure no one can take that away from you. --- **Advocating for privacy does not finance itself. If you enjoyed this article, please consider zapping or sending monero** 82XCDNK1Js8TethhpGLFPbVyKe25DxMUePad1rUn9z7V6QdCzxHEE7varvVh1VUidUhHVSA4atNU2BTpSNJLC1BqSvDajw1
@ 3b7fc823:e194354f
2025-02-02 22:55:32# The Secret to Staying Private in the Digital Wild West: A Guide to Using Encryption You’re scrolling through social media, and suddenly you realize your phone’s been tracking your location and displaying it on your profile for months. You’re not even sure how that happened. Or maybe you’ve noticed that every time you shop online, the item you looked for follows you around with ads wherever you go. Sound familiar? Yeah, welcome to the digital world—where your data is basically a free buffet for anyone who knows how to ask. But here’s the thing: you don’t have to sit back and take it. Encryption is like the secret weapon that lets you lock up your data and keep those prying eyes out. It’s not just for hackers or spies—it’s for regular people who want to take control of their privacy in a world that’s increasingly looking like a reality show where everyone’s a contestant. ### What Is Encryption, and Why Should You Care? Encryption is like a secure box that only you can open. When you use encryption, your data is scrambled in a way that’s hard for anyone else to read, even if they try. Think of it as putting on a metaphorical cloak that makes your online activity invisible to just about everyone except the people you want to see it. For example, when you browse the internet, your connection is often not encrypted by default. That’s why websites start with “https” to indicate a secure connection—it’s saying, “Hey, we’re using encryption here!” Without that little green padlock, anyone on the same WiFi could potentially spy on what you’re doing. So, encryption isn’t just for tech geeks or government agencies. It’s for everyone who wants to protect their data from being sold, stolen, or misused without their consent. And guess what? You’re already using it without realizing it. Every time you use a password-protected account or send an encrypted message, you’re reaping the benefits of encryption. ### The Privacy Advantages of Encryption for Regular People Let’s break down why encryption is your best friend when it comes to privacy: 1. **Financial Transactions** When you pay online or use a banking app, encryption keeps your financial info safe from hackers. It ensures that only the banks and businesses you’re dealing with can access your money—no one else can. 2. **Online Accounts** Your email, social media, and other accounts often use encryption to protect your login details. That’s why you see those little “lock” icons when you’re logging in. Without encryption, someone could potentially intercept your password and gain unauthorized access to your account. 3. **Data Breaches** Encryption can often prevent data breaches from being useful. Even if hackers manage to steal your information, the encryption makes it unreadable, so the stolen data is basically worthless to the attackers. 4. **Location Data** If you’re worried about apps tracking your every move, encryption can help limit how much of that data is accessible. Some apps use encryption to protect location data, making it harder for companies to sell your movements without your consent. 5. **Privacy Protection** Encryption acts as a layer of protection against invasive technologies. For example, some apps use tracking software that follows you around the internet based on your browsing history. With encryption, these trackers can be blocked or limited, giving you more control over what information is collected about you. ### How to Use Encryption Like a Pro Now that you know why encryption is essential for privacy, let’s talk about how to use it effectively: 1. **Use Strong Passwords** Encryption works only if your passwords are strong and unique. Don’t reuse passwords from one account to another, and avoid using easily guessable information like “password123” or your birth year. Use a password manager if you need help keeping track of them. 2. **Enable HTTPS Everywhere** Install browser extensions like HTTPS Everywhere to automatically encrypt your connections to websites that don’t support encryption by default. This ensures that even if you’re not actively thinking about it, your data is still protected. 3. **Look for the Lock Icon** Whenever you’re on a website or app, look for the lock icon in the URL bar. Make sure it’s encrypted before you input any personal information. 4. **Use Encrypted Communication Tools** For private conversations, use apps like Signal or SimpleX, which are designed with encryption in mind. These tools ensure that only the sender and recipient can read your messages, keeping them safe from prying eyes. 5. **Enable Two-Factor Authentication (2FA)** This isn’t exactly encryption, but it’s a close second. 2FA adds an extra layer of security by requiring you to provide two forms of verification—like your password and a code sent to your phone—to access your account. While not encryption itself, it works alongside encryption to keep your accounts secure. 6. **Use Encrypted Storage and Backup** When storing sensitive files or data, use encrypted cloud storage or external drives. Tools like BitLocker (for Windows) or AES-256 encryption can protect your files from unauthorized access. 7. **Stay Updated** Encryption technology is always evolving, so it’s important to keep your software and apps updated. Outdated systems are often easy targets for hackers, leaving you vulnerable to attacks. ### Final Thoughts: Your Data Is Your Power In a world where data is a commodity, encryption is your weapon against the invasive tactics of corporations and hackers alike. It empowers you to control what information you share and protects you from having it used against you. So, whether you’re shopping online, using your favorite apps, or just browsing the web, remember that encryption is there to help you stay private and in control of your own data. And if you ever feel overwhelmed by all the privacy stuff, just remember this: you’re not alone. Millions of people are fighting for stronger privacy protections every day. So, do your part by using encryption wisely—your data and your privacy are worth it. Let’s make sure no one can take that away from you. --- **Advocating for privacy does not finance itself. If you enjoyed this article, please consider zapping or sending monero** 82XCDNK1Js8TethhpGLFPbVyKe25DxMUePad1rUn9z7V6QdCzxHEE7varvVh1VUidUhHVSA4atNU2BTpSNJLC1BqSvDajw1 @ 8d34bd24:414be32b
2025-02-02 21:31:11This Sunday our pastor had to give a sermon with very little preparation. He was leading an elders’ retreat and one of the elders was supposed to preach in his place. The elder who had prepared a sermon ended up in the hospital, so our pastor had to prep fast. He did a great thing. He preached on a passage, but also used that passage to demonstrate how he studies scripture. It was a great sermon. The passage he preached on reminded me of a time in my past when I learned some important lessons. Almost 20 years ago, I was leading a high school girls Bible study. They picked out a book about Mary and Martha to study. Initially, I wasn’t thrilled with their choice, but didn’t have a theological problem with it, so I agreed for us to study this book. (I don’t remember the name of the book and all my books burnt up when my house burnt down almost 10 years ago). In the end, I probably got more out of the study than any of the girls because I have a definite tendency to be a Martha. What was Martha’s error? Let’s check out the passage: > Now as they went on their way, Jesus entered a village. And a woman named Martha welcomed him into her house. And she had a sister called Mary, who sat at the Lord’s feet and listened to his teaching. But Martha was distracted with much serving. And she went up to him and said, “Lord, do you not care that my sister has left me to serve alone? Tell her then to help me.” But the Lord answered her, “Martha, Martha, you are anxious and troubled about many things, but one thing is necessary. Mary has chosen the good portion, which will not be taken away from her.” (Luke 10:38-42 ESV) Jesus visited two sisters who welcomed Him into their home. Mary sat at Jesus’s feet and listened to His teaching. Martha spent her time serving everyone and taking care of everyone’s physical needs. Is taking care of their home and the needs of their guests a bad thing? Of course not, but is it the best? To make things much worse, Martha then got upset because her sister Mary wasn’t helping her. She was just sitting there taking in every word that Jesus said. Most of us would think Martha’s sacrifices to take care of everyone was better than Mary’s choice to just sit at Jesus’s feet, but did Martha really choose the better path? Martha then showed that her heart wasn’t focused right and she wasn’t putting the most important things first. She complained to Jesus about her sister’s failure to help and even commanded her Creator, “*Tell her then to help me*.” Instead of focusing on the words of Jesus, her frustration led her to command her God to act in the way she desired. She was so busy with cooking, cleaning, and serving, that she missed the most important things — spending time with and listening to her God, who was right there in her house with her. This was an opportunity that shouldn’t be missed due to busyness. How often do we all do this same thing? How often are busy doing good things and miss the most important things? How often are we busy doing ministry that we forget about the reason for the ministry? I don’t know about you, but this happens to me a lot more often than I would like to admit. My biggest sins are usually not what most people think of as sins. My biggest sins are getting so busy that I leave God out of my life. I am so busy serving God that I forget to follow His leading. I am so busy doing what most people would consider good things, but if God is not part of them, they are not worth much. Because I am focusing on getting things done, worry and stress overtake me harming my health and my relationship with Jesus. I don’t think this is taking Scripture out of context: > We have come to know and have believed the love which God has for us. **God is love**, and the one who abides in love abides in God, and God abides in him. (1 John 4:16) {emphasis mine} Knowing that God is love, read the following passage replacing ***love*** with ***God***. > If I speak with the tongues of men and of angels, but do not have ***love***, I have become a noisy gong or a clanging cymbal. If I have the gift of prophecy, and know all mysteries and all knowledge; and if I have all faith, so as to remove mountains, but do not have ***love***, I am nothing. And if I give all my possessions to feed the poor, and if I surrender my body to be burned, but do not have ***love***, it profits me nothing. (1 Corinthians 13:1-3) If I do not include God in my every action, “*it profits me nothing*.” In reality it shouldn’t be allowing God to join me in my works, but me joining God in His works. It should be me listening to God’s word and the leading of the Holy Spirit, looking and seeing what God is doing around me, and me joining in His great works. It should be me allowing God to use me as a tool. There are times that God speaks clearly and directly to us about what He desires for our lives, but most of the time, He speaks through His word — the Bible. Knowing the Bible helps us to know His will and His eternal plan, so we can follow Him and join Him in His work. Knowing the Bible helps us to differentiate between what is good and what is God’s best. It helps us to prioritize what is really important. > And this I pray, that your love **may abound still more and more in real knowledge and all discernment**, so that you **may approve the things that are excellent**, in order to be sincere and blameless until the day of Christ; having been filled with the **fruit of righteousness which comes through Jesus Christ**, to the glory and praise of God. (Philippians 1:9-11) {emphasis mine} We can’t obey God, imitate Christ, or follow Him if we refuse to listen and that means spending time in the Bible and time in prayer with Him. > “Listen to Me, you stubborn-minded, Who are far from righteousness.” (Isaiah 46:12) > Come, you children, listen to me; I will teach you the fear of the Lord . (Psalm 34:11) > “Now therefore, O sons, listen to me, For blessed are they who keep my ways. (Proverbs 8:32) > But seek first His kingdom and His righteousness, and all these things will be added to you. (Matthew 6:33) Our focus on Jesus/God must go beyond knowing Him. It is equally important to obey. > And He \[Jesus\] said to another, “Follow Me.” But he said, “Lord, permit me first to go and bury my father.” But He said to him, “Allow the dead to bury their own dead; but as for you, go and proclaim everywhere the kingdom of God.” (Luke 9:59-60) \[clarification mine\] Once we know what He wants from us, we need to instantly drop what we are doing and follow Him. We can’t put other things ahead of obeying God. > For amazement had seized him and all his companions because of the catch of fish which they had taken; and so also were James and John, sons of Zebedee, who were partners with Simon. And Jesus said to Simon, “Do not fear, from now on you will be catching men.” When they had brought their boats to land, **they left everything and followed Him**. (Luke 5:9-11) {emphasis mine} We should be like these apostles, that, after their most successful catch of fish in their entire career as fishermen, “*they left everything and followed Him*.” We need to let go of what we think is important and obey Him. We need to change our priorities to match God’s priorities. That may mean we change careers to one that allows more free time for ministry or even going into full time ministry. It may mean letting go on keeping the perfect, clean house, so there is time for ministry, Bible study, or discipling our kids. It may mean changing your habits from watching TV with your family to reading the Bible with your family. For each of us, it will look different, but we need to be like Mary and choose to sit “*at the Lord’s feet and listened to his teaching*.” We need to be like the apostles who “*left everything and followed Him*.” We need to choose to put Jesus’s plans before our own. We need to choose to make God’s values our values. > But this is what I commanded them, saying, ‘Obey My voice, and I will be your God, and you will be My people; and you will walk in all the way which I command you, that it may be well with you.’ (Jeremiah 7:23) Like so many things, it is simple, but it isn’t necessarily easy. We have to change the way we think in order to obey faithfully. > If anyone serves Me, he must follow Me; and where I am, there My servant will be also; if anyone serves Me, the Father will honor him. (John 12:26) We have to change our priorities to God’s priorities. > Then Jesus said to His disciples, “If anyone wishes to come after Me, he must deny himself, and take up his cross and follow Me. (Matthew 16:24) We need to seek God, His word, and His presence. > As the deer pants for the water brooks,\ > So my soul pants for You, O God.\ > My soul thirsts for God, for the living God;\ > When shall I come and appear before God? (Psalm 42:1-2) We need to be in God’s word daily, so we know who God is and what He desires from us. > How can a young man keep his way pure?\ > By **keeping it according to Your word**.\ > With all my heart I have sought You;\ > Do not let me wander from Your commandments.\ ****Your word I have treasured in my heart**,\ > That I may not sin against You.\ > Blessed are You, O Lord;\ ****Teach me Your statutes**.\ > With my lips I have told of\ > All the ordinances of Your mouth.\ > I have rejoiced in the way of Your testimonies,\ > As much as in all riches.\ ****I will meditate on Your precepts**\ > And regard Your ways.\ ****I shall delight in Your statutes;\ > I shall not forget Your word**. (Psalm 119:9-16) {emphasis mine} We need to read the Bible cover to cover so we know the whole word of God. Once we have read through the Bible multiple times, we need to spend time studying the Bible in more depth, so we can know the details, see how the different parts relate to each other, and grow in our knowledge of God. We need to study the Bible and use this knowledge to guide every decision in life — big and small. > Yet they did not listen or incline their ears, but stiffened their necks in order not to listen or take correction. (Jeremiah 17:23) Just reading the Bible or sitting in church listening to sermons will not make a difference if we don’t truly listen and internalize God’s word, so we can apply it in our every day life. God knows what is best for us and we will never be truly at peace or have true joy until we are living our lives in the light of God’s word and direction. My prayer for you and for me is that we will have the heart of Mary rather than the heart of Martha and that we will faithfully seek and follow God all of the days of our lives. Trust Jesus.
@ 8d34bd24:414be32b
2025-02-02 21:31:11This Sunday our pastor had to give a sermon with very little preparation. He was leading an elders’ retreat and one of the elders was supposed to preach in his place. The elder who had prepared a sermon ended up in the hospital, so our pastor had to prep fast. He did a great thing. He preached on a passage, but also used that passage to demonstrate how he studies scripture. It was a great sermon. The passage he preached on reminded me of a time in my past when I learned some important lessons. Almost 20 years ago, I was leading a high school girls Bible study. They picked out a book about Mary and Martha to study. Initially, I wasn’t thrilled with their choice, but didn’t have a theological problem with it, so I agreed for us to study this book. (I don’t remember the name of the book and all my books burnt up when my house burnt down almost 10 years ago). In the end, I probably got more out of the study than any of the girls because I have a definite tendency to be a Martha. What was Martha’s error? Let’s check out the passage: > Now as they went on their way, Jesus entered a village. And a woman named Martha welcomed him into her house. And she had a sister called Mary, who sat at the Lord’s feet and listened to his teaching. But Martha was distracted with much serving. And she went up to him and said, “Lord, do you not care that my sister has left me to serve alone? Tell her then to help me.” But the Lord answered her, “Martha, Martha, you are anxious and troubled about many things, but one thing is necessary. Mary has chosen the good portion, which will not be taken away from her.” (Luke 10:38-42 ESV) Jesus visited two sisters who welcomed Him into their home. Mary sat at Jesus’s feet and listened to His teaching. Martha spent her time serving everyone and taking care of everyone’s physical needs. Is taking care of their home and the needs of their guests a bad thing? Of course not, but is it the best? To make things much worse, Martha then got upset because her sister Mary wasn’t helping her. She was just sitting there taking in every word that Jesus said. Most of us would think Martha’s sacrifices to take care of everyone was better than Mary’s choice to just sit at Jesus’s feet, but did Martha really choose the better path? Martha then showed that her heart wasn’t focused right and she wasn’t putting the most important things first. She complained to Jesus about her sister’s failure to help and even commanded her Creator, “*Tell her then to help me*.” Instead of focusing on the words of Jesus, her frustration led her to command her God to act in the way she desired. She was so busy with cooking, cleaning, and serving, that she missed the most important things — spending time with and listening to her God, who was right there in her house with her. This was an opportunity that shouldn’t be missed due to busyness. How often do we all do this same thing? How often are busy doing good things and miss the most important things? How often are we busy doing ministry that we forget about the reason for the ministry? I don’t know about you, but this happens to me a lot more often than I would like to admit. My biggest sins are usually not what most people think of as sins. My biggest sins are getting so busy that I leave God out of my life. I am so busy serving God that I forget to follow His leading. I am so busy doing what most people would consider good things, but if God is not part of them, they are not worth much. Because I am focusing on getting things done, worry and stress overtake me harming my health and my relationship with Jesus. I don’t think this is taking Scripture out of context: > We have come to know and have believed the love which God has for us. **God is love**, and the one who abides in love abides in God, and God abides in him. (1 John 4:16) {emphasis mine} Knowing that God is love, read the following passage replacing ***love*** with ***God***. > If I speak with the tongues of men and of angels, but do not have ***love***, I have become a noisy gong or a clanging cymbal. If I have the gift of prophecy, and know all mysteries and all knowledge; and if I have all faith, so as to remove mountains, but do not have ***love***, I am nothing. And if I give all my possessions to feed the poor, and if I surrender my body to be burned, but do not have ***love***, it profits me nothing. (1 Corinthians 13:1-3) If I do not include God in my every action, “*it profits me nothing*.” In reality it shouldn’t be allowing God to join me in my works, but me joining God in His works. It should be me listening to God’s word and the leading of the Holy Spirit, looking and seeing what God is doing around me, and me joining in His great works. It should be me allowing God to use me as a tool. There are times that God speaks clearly and directly to us about what He desires for our lives, but most of the time, He speaks through His word — the Bible. Knowing the Bible helps us to know His will and His eternal plan, so we can follow Him and join Him in His work. Knowing the Bible helps us to differentiate between what is good and what is God’s best. It helps us to prioritize what is really important. > And this I pray, that your love **may abound still more and more in real knowledge and all discernment**, so that you **may approve the things that are excellent**, in order to be sincere and blameless until the day of Christ; having been filled with the **fruit of righteousness which comes through Jesus Christ**, to the glory and praise of God. (Philippians 1:9-11) {emphasis mine} We can’t obey God, imitate Christ, or follow Him if we refuse to listen and that means spending time in the Bible and time in prayer with Him. > “Listen to Me, you stubborn-minded, Who are far from righteousness.” (Isaiah 46:12) > Come, you children, listen to me; I will teach you the fear of the Lord . (Psalm 34:11) > “Now therefore, O sons, listen to me, For blessed are they who keep my ways. (Proverbs 8:32) > But seek first His kingdom and His righteousness, and all these things will be added to you. (Matthew 6:33) Our focus on Jesus/God must go beyond knowing Him. It is equally important to obey. > And He \[Jesus\] said to another, “Follow Me.” But he said, “Lord, permit me first to go and bury my father.” But He said to him, “Allow the dead to bury their own dead; but as for you, go and proclaim everywhere the kingdom of God.” (Luke 9:59-60) \[clarification mine\] Once we know what He wants from us, we need to instantly drop what we are doing and follow Him. We can’t put other things ahead of obeying God. > For amazement had seized him and all his companions because of the catch of fish which they had taken; and so also were James and John, sons of Zebedee, who were partners with Simon. And Jesus said to Simon, “Do not fear, from now on you will be catching men.” When they had brought their boats to land, **they left everything and followed Him**. (Luke 5:9-11) {emphasis mine} We should be like these apostles, that, after their most successful catch of fish in their entire career as fishermen, “*they left everything and followed Him*.” We need to let go of what we think is important and obey Him. We need to change our priorities to match God’s priorities. That may mean we change careers to one that allows more free time for ministry or even going into full time ministry. It may mean letting go on keeping the perfect, clean house, so there is time for ministry, Bible study, or discipling our kids. It may mean changing your habits from watching TV with your family to reading the Bible with your family. For each of us, it will look different, but we need to be like Mary and choose to sit “*at the Lord’s feet and listened to his teaching*.” We need to be like the apostles who “*left everything and followed Him*.” We need to choose to put Jesus’s plans before our own. We need to choose to make God’s values our values. > But this is what I commanded them, saying, ‘Obey My voice, and I will be your God, and you will be My people; and you will walk in all the way which I command you, that it may be well with you.’ (Jeremiah 7:23) Like so many things, it is simple, but it isn’t necessarily easy. We have to change the way we think in order to obey faithfully. > If anyone serves Me, he must follow Me; and where I am, there My servant will be also; if anyone serves Me, the Father will honor him. (John 12:26) We have to change our priorities to God’s priorities. > Then Jesus said to His disciples, “If anyone wishes to come after Me, he must deny himself, and take up his cross and follow Me. (Matthew 16:24) We need to seek God, His word, and His presence. > As the deer pants for the water brooks,\ > So my soul pants for You, O God.\ > My soul thirsts for God, for the living God;\ > When shall I come and appear before God? (Psalm 42:1-2) We need to be in God’s word daily, so we know who God is and what He desires from us. > How can a young man keep his way pure?\ > By **keeping it according to Your word**.\ > With all my heart I have sought You;\ > Do not let me wander from Your commandments.\ ****Your word I have treasured in my heart**,\ > That I may not sin against You.\ > Blessed are You, O Lord;\ ****Teach me Your statutes**.\ > With my lips I have told of\ > All the ordinances of Your mouth.\ > I have rejoiced in the way of Your testimonies,\ > As much as in all riches.\ ****I will meditate on Your precepts**\ > And regard Your ways.\ ****I shall delight in Your statutes;\ > I shall not forget Your word**. (Psalm 119:9-16) {emphasis mine} We need to read the Bible cover to cover so we know the whole word of God. Once we have read through the Bible multiple times, we need to spend time studying the Bible in more depth, so we can know the details, see how the different parts relate to each other, and grow in our knowledge of God. We need to study the Bible and use this knowledge to guide every decision in life — big and small. > Yet they did not listen or incline their ears, but stiffened their necks in order not to listen or take correction. (Jeremiah 17:23) Just reading the Bible or sitting in church listening to sermons will not make a difference if we don’t truly listen and internalize God’s word, so we can apply it in our every day life. God knows what is best for us and we will never be truly at peace or have true joy until we are living our lives in the light of God’s word and direction. My prayer for you and for me is that we will have the heart of Mary rather than the heart of Martha and that we will faithfully seek and follow God all of the days of our lives. Trust Jesus. @ 5a261a61:2ebd4480
2025-02-02 20:42:37Let’s be real—sticking to *anything* for 90 days is like trying to herd cats on espresso. You start strong, then **life happens**: kids, chores, or that *one* glass of wine that makes you forget foot rubs (#relatable). But here’s the thing: 90-day challenges aren’t about perfection. They’re about bribing your lizard brain with rewards and scaring it straight with punishments. ## **The Game Plan** First, pick a thing—something that makes you feel like a devoted servant or a slightly frazzled superhero. Daily foot care? Chores with a side of #FLR flair? Cool. Now, break it into chunks: 30 days (survival mode), 60 days (grind phase), and 90 days (victory lap). Keeping up something for so long is no joke. That's why you need those little checkpoints along the way. Each milestone should feel special—30 days deserves celebration, 60 days something more meaningful, and 90 days? That's your victory dance moment. Reality check: some days will suck, and you'll want to skip. **That's where having everything planned out helps.** When your brain is foggy and you're tired, you don't want to be negotiating with yourself about what counts and what doesn't. The hardest part isn't even doing the thing—it's remembering to do it every single day, until it feels wrong NOT to do it. ## **Why It (Maybe) Works** Three months is long enough for habits to stick, short enough to see the finish line. Plus, tying it to power exchange? Genius. Every foot rub or denied cum becomes a ritual, proof you're leveling up as a sub/human/slightly-messy adult. And let's be honest—nothing fuels devotion like a mix of structure, desperation, and the occasional humiliating punishment. ## **Current run** My current challenge is to get my wife/godess/object of my insatiable kinky thoughts/partner feet massaged with special cream. It's for making evyrthing soft, help nails and yadayadayada. Basically preping her feet for more instensive worshiping. She doesn't know my hidden agenda and I am not sure if I would really be into it, since I am more into being her devout toy than having foot fetish, but I think it will be all the same if I put myself juuust right. So for my rewards I have planned these? - **30 days**: Tiny dopamine hit. *(making little photoset of Her feet playing with my hardon… for science.)* - **60 days**: Mid-tier flex. *(cleaning mushed banana split off Her toes tongue only)* - **90 days**: Go nuclear. *(a tiny foot spa whirpool because She deserves it, damn it :D and it will create more opportunities for... you know )* As for the hhip part of the sugar duo... It was easy having one for my shaving rutine, but here? Not sure and it's bad that I ave started challenge without having them prepared... May be that warrant more punishment? ## **TL;DR** 90-day challenges are the BDSM of self-improvement: **consensual, slightly painful, and weirdly addictive.** Fail? Reset, adapt, try again. Win? Congrats, you’re now 10% more disciplined and 100% more bumptious on Nostr. #90days #FLR #LostCauseButStillTrying #femdom
@ 5a261a61:2ebd4480
2025-02-02 20:42:37Let’s be real—sticking to *anything* for 90 days is like trying to herd cats on espresso. You start strong, then **life happens**: kids, chores, or that *one* glass of wine that makes you forget foot rubs (#relatable). But here’s the thing: 90-day challenges aren’t about perfection. They’re about bribing your lizard brain with rewards and scaring it straight with punishments. ## **The Game Plan** First, pick a thing—something that makes you feel like a devoted servant or a slightly frazzled superhero. Daily foot care? Chores with a side of #FLR flair? Cool. Now, break it into chunks: 30 days (survival mode), 60 days (grind phase), and 90 days (victory lap). Keeping up something for so long is no joke. That's why you need those little checkpoints along the way. Each milestone should feel special—30 days deserves celebration, 60 days something more meaningful, and 90 days? That's your victory dance moment. Reality check: some days will suck, and you'll want to skip. **That's where having everything planned out helps.** When your brain is foggy and you're tired, you don't want to be negotiating with yourself about what counts and what doesn't. The hardest part isn't even doing the thing—it's remembering to do it every single day, until it feels wrong NOT to do it. ## **Why It (Maybe) Works** Three months is long enough for habits to stick, short enough to see the finish line. Plus, tying it to power exchange? Genius. Every foot rub or denied cum becomes a ritual, proof you're leveling up as a sub/human/slightly-messy adult. And let's be honest—nothing fuels devotion like a mix of structure, desperation, and the occasional humiliating punishment. ## **Current run** My current challenge is to get my wife/godess/object of my insatiable kinky thoughts/partner feet massaged with special cream. It's for making evyrthing soft, help nails and yadayadayada. Basically preping her feet for more instensive worshiping. She doesn't know my hidden agenda and I am not sure if I would really be into it, since I am more into being her devout toy than having foot fetish, but I think it will be all the same if I put myself juuust right. So for my rewards I have planned these? - **30 days**: Tiny dopamine hit. *(making little photoset of Her feet playing with my hardon… for science.)* - **60 days**: Mid-tier flex. *(cleaning mushed banana split off Her toes tongue only)* - **90 days**: Go nuclear. *(a tiny foot spa whirpool because She deserves it, damn it :D and it will create more opportunities for... you know )* As for the hhip part of the sugar duo... It was easy having one for my shaving rutine, but here? Not sure and it's bad that I ave started challenge without having them prepared... May be that warrant more punishment? ## **TL;DR** 90-day challenges are the BDSM of self-improvement: **consensual, slightly painful, and weirdly addictive.** Fail? Reset, adapt, try again. Win? Congrats, you’re now 10% more disciplined and 100% more bumptious on Nostr. #90days #FLR #LostCauseButStillTrying #femdom @ d57360cb:4fe7d935
2025-02-02 16:33:16Beauty and art function beyond the mind. When you’re not thinking, when the mind reaches its natural silence. When it quiets down. You begin to experience and actually experience how things are. There is no more narration. Things happen as if by magic. Everything is in its place happening and grooving. Every act, every movement feels like jazz. We’re better doers than we are thinkers. But the world thinks otherwise.
@ d57360cb:4fe7d935
2025-02-02 16:33:16Beauty and art function beyond the mind. When you’re not thinking, when the mind reaches its natural silence. When it quiets down. You begin to experience and actually experience how things are. There is no more narration. Things happen as if by magic. Everything is in its place happening and grooving. Every act, every movement feels like jazz. We’re better doers than we are thinkers. But the world thinks otherwise. @ 6b57533f:eaa341f5
2025-02-02 15:46:41# 🏝️lost in the ordinary?  ## Welcome to Stories Discover a hidden paradise where the world slows down, and adventure begins.. # 🌊 Step into tranquility.  ## Wake up to the sound of gentle waves and endless blue horizons. # 🛶Live the dream.  ## ## ## Unwind, explore, and escape—your perfect getaway is just one step away.
@ 6b57533f:eaa341f5
2025-02-02 15:46:41# 🏝️lost in the ordinary?  ## Welcome to Stories Discover a hidden paradise where the world slows down, and adventure begins.. # 🌊 Step into tranquility.  ## Wake up to the sound of gentle waves and endless blue horizons. # 🛶Live the dream.  ## ## ## Unwind, explore, and escape—your perfect getaway is just one step away. @ 3b7fc823:e194354f
2025-02-02 13:39:49**Why You Should Only Run DeepSeek Locally: A Privacy Perspective and how to** In an era where AI tools promise immense utility, the decision to run DeepSeek locally is not merely about functionality but also about safeguarding privacy and security. Here's the rationale why: 1. **Control Over Data Access**: Running DeepSeek locally ensures that data processing occurs on your own machine or server, allowing you to have full control over who can access the system. This reduces the risk of unauthorized access and misuse. 2. **Data Privacy**: By keeping computations local, you ensure that personal data does not leave your control, minimizing the risk of exposure through cloud-based services. 3. **Security Measures**: Local operation provides an additional layer of security. You can implement access controls, monitor usage, and respond to incidents more effectively, which might be harder or impossible when relying on third-party platforms. 4. **Practical Implementation**: Tools like Ollama and OpenWebUI facilitate setting up a local environment, making it accessible even for those with limited technical expertise. This setup empowers individuals to leverage AI capabilities while maintaining privacy. 7. **Right to Control Data**: Privacy is a fundamental right, and running DeepSeek locally respects this by allowing users to decide what data they share and how it's accessed. This empowers individuals to make informed choices about their personal data. For those prioritizing privacy, this approach is not just beneficial—it's essential. **Running DeepSeek Locally: A Guide for Individual Home Users** DeepSeek is a powerful AI search engine that can help with various tasks, but running it locally gives you greater control over your data and privacy. Here’s how you can set it up at home. --- ### **What You’ll Need** 1. **A Computer**: A desktop or laptop with sufficient processing power (at least 4GB RAM). 2. **Python and pip**: To install and run DeepSeek. 3. **Ollama**: An open-source tool that allows you to run AI models locally. 4. **OpenWebUI**: A simple web interface for interacting with Ollama. --- ### **Step-by-Step Guide** #### 1. **Install the Prerequisites** - **Python**: Download and install Python from [https://www.python.org](https://www.python.org). - **pip**: Use pip to install Python packages. ```bash pip install --upgrade pip ``` - **Ollama**: ```bash pip install ollama ``` - **OpenWebUI**: Visit [https://github.com/DeepSeek-LLM/openwebui](https://github.com/DeepSeek-LLM/openwebui) and follow the instructions to install it. --- #### 2. **Set Up Ollama** - Clone the official Ollama repository: ```bash git clone https://github.com/OllamaAI/Ollama.git cd Ollama ``` - Follow the installation guide on [https://ollama.ai](https://ollama.ai) to set it up. --- #### 3. **Run DeepSeek Locally** - Use OpenWebUI as your interface: ```bash # Start OpenWebUI (open a terminal and run this): python openwebui.py --model deepseek-llm-v0.2-beta ``` - A web browser will open, allowing you to interact with DeepSeek. --- ### **Tips for Optimization** 1. **Reduce Memory Usage**: Use smaller models like `deepseek-llm-v0.2-beta` if your computer has limited resources. 2. **Limit Model Access**: Only allow authorized users to access the system by restricting IP addresses or using a VPN. 3. **Regular Updates**: Keep all software up to date to protect against vulnerabilities. --- ### **Why Run DeepSeek Locally?** - **Privacy**: Your data stays on your local machine, reducing the risk of unauthorized access. - **Flexability**: Running locally allows you to build specific models for specific uses and provide them with RAG data. --- ### Advocating for privacy does not finance itself. If you enjoyed this article, please consider zapping or sending monero
@ 3b7fc823:e194354f
2025-02-02 13:39:49**Why You Should Only Run DeepSeek Locally: A Privacy Perspective and how to** In an era where AI tools promise immense utility, the decision to run DeepSeek locally is not merely about functionality but also about safeguarding privacy and security. Here's the rationale why: 1. **Control Over Data Access**: Running DeepSeek locally ensures that data processing occurs on your own machine or server, allowing you to have full control over who can access the system. This reduces the risk of unauthorized access and misuse. 2. **Data Privacy**: By keeping computations local, you ensure that personal data does not leave your control, minimizing the risk of exposure through cloud-based services. 3. **Security Measures**: Local operation provides an additional layer of security. You can implement access controls, monitor usage, and respond to incidents more effectively, which might be harder or impossible when relying on third-party platforms. 4. **Practical Implementation**: Tools like Ollama and OpenWebUI facilitate setting up a local environment, making it accessible even for those with limited technical expertise. This setup empowers individuals to leverage AI capabilities while maintaining privacy. 7. **Right to Control Data**: Privacy is a fundamental right, and running DeepSeek locally respects this by allowing users to decide what data they share and how it's accessed. This empowers individuals to make informed choices about their personal data. For those prioritizing privacy, this approach is not just beneficial—it's essential. **Running DeepSeek Locally: A Guide for Individual Home Users** DeepSeek is a powerful AI search engine that can help with various tasks, but running it locally gives you greater control over your data and privacy. Here’s how you can set it up at home. --- ### **What You’ll Need** 1. **A Computer**: A desktop or laptop with sufficient processing power (at least 4GB RAM). 2. **Python and pip**: To install and run DeepSeek. 3. **Ollama**: An open-source tool that allows you to run AI models locally. 4. **OpenWebUI**: A simple web interface for interacting with Ollama. --- ### **Step-by-Step Guide** #### 1. **Install the Prerequisites** - **Python**: Download and install Python from [https://www.python.org](https://www.python.org). - **pip**: Use pip to install Python packages. ```bash pip install --upgrade pip ``` - **Ollama**: ```bash pip install ollama ``` - **OpenWebUI**: Visit [https://github.com/DeepSeek-LLM/openwebui](https://github.com/DeepSeek-LLM/openwebui) and follow the instructions to install it. --- #### 2. **Set Up Ollama** - Clone the official Ollama repository: ```bash git clone https://github.com/OllamaAI/Ollama.git cd Ollama ``` - Follow the installation guide on [https://ollama.ai](https://ollama.ai) to set it up. --- #### 3. **Run DeepSeek Locally** - Use OpenWebUI as your interface: ```bash # Start OpenWebUI (open a terminal and run this): python openwebui.py --model deepseek-llm-v0.2-beta ``` - A web browser will open, allowing you to interact with DeepSeek. --- ### **Tips for Optimization** 1. **Reduce Memory Usage**: Use smaller models like `deepseek-llm-v0.2-beta` if your computer has limited resources. 2. **Limit Model Access**: Only allow authorized users to access the system by restricting IP addresses or using a VPN. 3. **Regular Updates**: Keep all software up to date to protect against vulnerabilities. --- ### **Why Run DeepSeek Locally?** - **Privacy**: Your data stays on your local machine, reducing the risk of unauthorized access. - **Flexability**: Running locally allows you to build specific models for specific uses and provide them with RAG data. --- ### Advocating for privacy does not finance itself. If you enjoyed this article, please consider zapping or sending monero @ fbf0e434:e1be6a39
2025-02-02 13:32:12> *本文原载于《CERN Courier》,是由欧洲核子研究中心(CERN,全称Conseil Européen pour la Recherche Nucléaire)出版的权威科学期刊,专注于报道全球物理学、技术及创新领域的前沿动态。以下正文内容是对全球开源开发者激励平台DoraHacks的创始人张剑南的专访报道,探讨了黑客松如何成为科技创新的重要推动力以及DoraHacks在其中扮演的角色。* > 万维网(World Wide Web)、人工智能(Artificial Intelligence)与量子计算(Quantum Computing)——这些划时代的技术有何共同之处?DoraHacks创始人张剑南认为,它们都源于“Hacks(黑客精神)”。“当万维网在欧洲核子研究中心(CERN)诞生时,它向我们证明了一件事:要想改变并提高人类的生活方式和工作效率,关键在于以创新的思维利用现有的技术以实现突破。”张剑南解释道,“如果总是从零开始,我们永远无法取得实质性的进步。这恰恰就是开源运动和黑客马拉松的核心价值。” 十年前,张剑南参与筹办了CERN Webfest 2013,这是一场致力于探索如何以创新方式运用技术来服务科学与社会的黑客马拉松活动。通过Webfest,张剑南不仅实现了编程技能与物理学知识的跨学科融合,还与来自世界各地、背景各异的hackers建立了持久深厚的联系。随着参与黑客松次数的增多,他的“黑客精神”愈发强烈,最终驱使他创立了自己的公司。2024年,张剑南重返Webfest,但这次他不再是参与者,而是作为DoraHacks的首席执行官来见证这场盛会。 黑客马拉松是一种持续数天的社交编程活动,具有高度的包容性和开放性——参与者无需学术机构或企业背景即可加入。这种特性吸引了众多才华横溢的个体参与其中。活动中,hackers以团队形式合作,结合各自的技能,通过软件、硬件或商业计划等来解决技术难题。这不仅让物理学家、计算机科学家、工程师和企业家齐聚一堂,各展所长,也让年轻的开发者们有机会突破传统研究框架,提升技能、积累作品集,并拓展职业人脉。 “如果你对某件事充满热情,就应该能够立即投入其中并全力以赴,”张剑南强调,“追求梦想并不需要特定的学历或背景。” 对于在某个领域刚起步的研究者来说,黑客松的意义远不止于技术挑战。它为进入一个研究或行业领域提供了另一种途径,弥合了学术理论与实际应用之间的鸿沟。很多由大学举办的黑客松往往能够吸引到企业的赞助,这些赞助除了作为奖金来激励开发者持续开发,也会用来租赁大型场馆,以容纳数百甚至上千名参与者。 “正是这些大规模的黑客松吸引了众多行业猎头和导师的关注,”张剑南解释道,“他们把这类活动看作他们的人才库。通过黑客松,参与者们能够与大公司的人直接交流,加速职业发展,同时也能在实践中提升他们的编程能力。” 在2010年代,张剑南经常在周末参加黑客松,这也成为他创业的基石。“我曾经坐在计算机科学学院的公共休息室里,埋头研究我的黑客项目。我的大多数朋友也是在那里认识的,”张剑南回忆道,“但后来我意识到,如果想做出真正伟大的东西,必须有效地组织人力与资金。然后我就开始‘逃课’,不去上计算机系的课程,而是偷偷溜进商学院的教室里。”张剑南常常在商学院的教室后排听课,一边听课一边谋划自己的创业计划。他每天都与同行交流,评估各种不同的商业模式。“在创业过程中,要把工程知识与商业理论结合起来思考,”他补充道,“这是比较有趣的一点,让整个过程也轻松了一些。” 然而,从科学研究转向创业并非易事。“创业初期必须亲力亲为,要自己去学习然后完成各种任务。”张剑南坦言,“好处是能够接触到许多新技能和新朋友,但同时也得强迫自己去做那些原本不擅长的事情。” 这种经历也反映了许多创业者的共同困境:选择自己从头学习新技能,还是寻找合适的创业伙伴然后把任务分配出去?可是找到值得信赖的合作伙伴也不是一件容易的事,错误的决策甚至可能阻碍公司的发展。因此,从一开始就明确公司的愿景和使命显得尤为重要。 “解决方案其实很简单,”张剑南表示,“重点是要投入足够多的时间,亲自完成关键里程碑,以确保产品真正具备可行性。只要有了明确的商业计划和愿景,就能获得来自各方的支持。” ### **去中心化的社区治理** 很多黑客马拉松参与者在活动结束后就会放弃自己的项目,但张剑南创立DoraHacks的初衷并非如此。他希望为全球的黑客团队提供一个平台,让他们能够将创意转化为成熟产品。“我希望黑客马拉松不仅仅是一个招聘工具,”他解释道,“它更应该推动开源开发和去中心化的社区治理。比如现在,来自坦桑尼亚的黑客可以与美国的黑客团队远程协作,然后获得持续的支持,以开发出真正有影响力的产品。这种模式让技术领域变得更多样化,同时也能够让更多人接触到不同的领域。” DoraHacks通过帮助组织者降低后勤成本,为参与者提供更可靠的资金支持机制,使黑客松超越学术机构的限制,吸引更多对创新充满热情的个体研究者参与。然后不断发展整个社区,让年轻一代的开发者、研究者们能够在自己的职业初期,接触到比以往更多的机遇和机会。 “商业模式正在发生根本的变化,”张剑南指出,黑客马拉松正在发展成为新兴技术的基石,尤其是在量子计算、区块链和人工智能等以开源形式起步的领域。“产品创造的过程将会迎来重大变革。未来的技术发展不再依赖于孤立封闭的产品开发,而是基于黑客们可以共同贡献的平台和基础设施。” 如今,黑客马拉松的意义已不仅限于编程或建立人脉——它们更关乎突破技术边界、创造有意义的解决方案,并开辟新的职业道路。黑客马拉松是创意孵化器,并且能够对这些创意产生持久的影响力。张剑南希望帮助这些创意变为现实。“未来创新的方式一定是协作完成的,是开源的,”他再次强调,“在传统社会环境里,企业的发展依赖于在闭源技术周围筑起的护城河,这种技术更新方式的效率低下且不容易实现。而真正创新的未来,将以开放平台技术为核心,让全球开发者能够在现有项目的基础上不断迭代更新。这样的开放协作精神正是Hacker Movement(开源极客运动)如此重要的原因。” 采访者:Alex Epshtein(编辑助理)。 原文链接:https://cerncourier.com/wp-content/uploads/2025/01/CERNCourier2025JanFeb-digitaledition.pdf
@ fbf0e434:e1be6a39
2025-02-02 13:32:12> *本文原载于《CERN Courier》,是由欧洲核子研究中心(CERN,全称Conseil Européen pour la Recherche Nucléaire)出版的权威科学期刊,专注于报道全球物理学、技术及创新领域的前沿动态。以下正文内容是对全球开源开发者激励平台DoraHacks的创始人张剑南的专访报道,探讨了黑客松如何成为科技创新的重要推动力以及DoraHacks在其中扮演的角色。* > 万维网(World Wide Web)、人工智能(Artificial Intelligence)与量子计算(Quantum Computing)——这些划时代的技术有何共同之处?DoraHacks创始人张剑南认为,它们都源于“Hacks(黑客精神)”。“当万维网在欧洲核子研究中心(CERN)诞生时,它向我们证明了一件事:要想改变并提高人类的生活方式和工作效率,关键在于以创新的思维利用现有的技术以实现突破。”张剑南解释道,“如果总是从零开始,我们永远无法取得实质性的进步。这恰恰就是开源运动和黑客马拉松的核心价值。” 十年前,张剑南参与筹办了CERN Webfest 2013,这是一场致力于探索如何以创新方式运用技术来服务科学与社会的黑客马拉松活动。通过Webfest,张剑南不仅实现了编程技能与物理学知识的跨学科融合,还与来自世界各地、背景各异的hackers建立了持久深厚的联系。随着参与黑客松次数的增多,他的“黑客精神”愈发强烈,最终驱使他创立了自己的公司。2024年,张剑南重返Webfest,但这次他不再是参与者,而是作为DoraHacks的首席执行官来见证这场盛会。 黑客马拉松是一种持续数天的社交编程活动,具有高度的包容性和开放性——参与者无需学术机构或企业背景即可加入。这种特性吸引了众多才华横溢的个体参与其中。活动中,hackers以团队形式合作,结合各自的技能,通过软件、硬件或商业计划等来解决技术难题。这不仅让物理学家、计算机科学家、工程师和企业家齐聚一堂,各展所长,也让年轻的开发者们有机会突破传统研究框架,提升技能、积累作品集,并拓展职业人脉。 “如果你对某件事充满热情,就应该能够立即投入其中并全力以赴,”张剑南强调,“追求梦想并不需要特定的学历或背景。” 对于在某个领域刚起步的研究者来说,黑客松的意义远不止于技术挑战。它为进入一个研究或行业领域提供了另一种途径,弥合了学术理论与实际应用之间的鸿沟。很多由大学举办的黑客松往往能够吸引到企业的赞助,这些赞助除了作为奖金来激励开发者持续开发,也会用来租赁大型场馆,以容纳数百甚至上千名参与者。 “正是这些大规模的黑客松吸引了众多行业猎头和导师的关注,”张剑南解释道,“他们把这类活动看作他们的人才库。通过黑客松,参与者们能够与大公司的人直接交流,加速职业发展,同时也能在实践中提升他们的编程能力。” 在2010年代,张剑南经常在周末参加黑客松,这也成为他创业的基石。“我曾经坐在计算机科学学院的公共休息室里,埋头研究我的黑客项目。我的大多数朋友也是在那里认识的,”张剑南回忆道,“但后来我意识到,如果想做出真正伟大的东西,必须有效地组织人力与资金。然后我就开始‘逃课’,不去上计算机系的课程,而是偷偷溜进商学院的教室里。”张剑南常常在商学院的教室后排听课,一边听课一边谋划自己的创业计划。他每天都与同行交流,评估各种不同的商业模式。“在创业过程中,要把工程知识与商业理论结合起来思考,”他补充道,“这是比较有趣的一点,让整个过程也轻松了一些。” 然而,从科学研究转向创业并非易事。“创业初期必须亲力亲为,要自己去学习然后完成各种任务。”张剑南坦言,“好处是能够接触到许多新技能和新朋友,但同时也得强迫自己去做那些原本不擅长的事情。” 这种经历也反映了许多创业者的共同困境:选择自己从头学习新技能,还是寻找合适的创业伙伴然后把任务分配出去?可是找到值得信赖的合作伙伴也不是一件容易的事,错误的决策甚至可能阻碍公司的发展。因此,从一开始就明确公司的愿景和使命显得尤为重要。 “解决方案其实很简单,”张剑南表示,“重点是要投入足够多的时间,亲自完成关键里程碑,以确保产品真正具备可行性。只要有了明确的商业计划和愿景,就能获得来自各方的支持。” ### **去中心化的社区治理** 很多黑客马拉松参与者在活动结束后就会放弃自己的项目,但张剑南创立DoraHacks的初衷并非如此。他希望为全球的黑客团队提供一个平台,让他们能够将创意转化为成熟产品。“我希望黑客马拉松不仅仅是一个招聘工具,”他解释道,“它更应该推动开源开发和去中心化的社区治理。比如现在,来自坦桑尼亚的黑客可以与美国的黑客团队远程协作,然后获得持续的支持,以开发出真正有影响力的产品。这种模式让技术领域变得更多样化,同时也能够让更多人接触到不同的领域。” DoraHacks通过帮助组织者降低后勤成本,为参与者提供更可靠的资金支持机制,使黑客松超越学术机构的限制,吸引更多对创新充满热情的个体研究者参与。然后不断发展整个社区,让年轻一代的开发者、研究者们能够在自己的职业初期,接触到比以往更多的机遇和机会。 “商业模式正在发生根本的变化,”张剑南指出,黑客马拉松正在发展成为新兴技术的基石,尤其是在量子计算、区块链和人工智能等以开源形式起步的领域。“产品创造的过程将会迎来重大变革。未来的技术发展不再依赖于孤立封闭的产品开发,而是基于黑客们可以共同贡献的平台和基础设施。” 如今,黑客马拉松的意义已不仅限于编程或建立人脉——它们更关乎突破技术边界、创造有意义的解决方案,并开辟新的职业道路。黑客马拉松是创意孵化器,并且能够对这些创意产生持久的影响力。张剑南希望帮助这些创意变为现实。“未来创新的方式一定是协作完成的,是开源的,”他再次强调,“在传统社会环境里,企业的发展依赖于在闭源技术周围筑起的护城河,这种技术更新方式的效率低下且不容易实现。而真正创新的未来,将以开放平台技术为核心,让全球开发者能够在现有项目的基础上不断迭代更新。这样的开放协作精神正是Hacker Movement(开源极客运动)如此重要的原因。” 采访者:Alex Epshtein(编辑助理)。 原文链接:https://cerncourier.com/wp-content/uploads/2025/01/CERNCourier2025JanFeb-digitaledition.pdf @ ddf03aca:5cb3bbbe
2025-02-02 13:09:27We’re thrilled to announce the stable release of Cashu-TS v2.2! Although this update is a minor version bump, it brings significant improvements under the hood that enhance the overall developer experience. We’ve spent several weeks testing and refining these changes. --- ## What’s New in v2.2? While there are no breaking changes in this release, there are many internal changes. If you spot any regressions or unexpected behavior, please [let us know](https://github.com/cashubtc/cashu-ts/issues). Here’s a rundown of the major updates: - **Enhanced Proof Creation**: The way proofs are created internally has been revamped. - **User-Controlled Outputs**: You now have full control over how outputs are created. - **Improved Bundling**: We’ve switched our bundling tool to [vite](https://vitejs.dev) for faster and more modern builds. - **Updated Testing Tools**: Our testing framework has migrated to [vitest](https://vitest.dev) and [msw](https://mswjs.io), with added browser testing via Playwright. --- ## New Flexibility with OutputData In previous versions of Cashu-TS, the creation of outputs (or *BlindedMessages*) was hidden away. Even though there were options to tweak the process (like deterministic secrets or P2PK), you were always limited to the built-in logic. ### What’s Changed? In v2.2, we’ve introduced a public interface that not only streamlines output creation but also lets you plug in your own custom logic when needed. With the new `outputData` option available on all output-creating methods, you can now bypass the automatic process and provide your own outputs. For example, you can create two proofs tied to different public keys in a single mint operation: ```ts const data1 = OutputData.createP2PKData({ pubkey: "key1" }, 10, keys); const data2 = OutputData.createP2PKData({ pubkey: "key2" }, 10, keys); const { keep, send } = await wallet.send(20, proofs, { outputData: { send: [...data1, ...data2] }, }); ``` ### Customization Made Easy The `outputData` option now accepts anything that conforms to the `OutputDataLike` interface. This means you can introduce your own output creation logic—even if it’s not natively supported by Cashu-TS yet. Here’s what the interface looks like: ```ts export interface OutputDataLike { blindedMessage: SerializedBlindedMessage; blindingFactor: bigint; secret: Uint8Array; toProof: (signature: SerializedBlindedSignature, keyset: MintKeys) => Proof; } ``` ### Introducing OutputData Factories While having full control is empowering, it also means you’ll need to handle tasks like fee calculation and amount selection manually. To strike a balance between control and convenience, we now support **OutputData Factories**. A factory is simply a function that takes an amount and `MintKeys` as input and returns an `OutputDataLike` object. This way, you can define a blueprint for your output data without worrying about the nitty-gritty details. For instance, you can create separate factories for amounts you keep versus those you send: ```ts function keepFactory(a: number, k: MintKeys) { return OutputData.createSingleP2PKData({ pubkey: "keepPk" }, a, k.id); } function sendFactory(a: number, k: MintKeys) { return OutputData.createSingleP2PKData({ pubkey: "sendPk" }, a, k.id); } const { send, keep } = await wallet.send(amount, proofs, { outputData: { send: createFactory("send"), keep: createFactory("keep") }, }); ``` Plus, you can now instantiate a `CashuWallet` with a default `keepFactory`, ensuring that all change amounts automatically lock to your key—streamlining your workflow even further. --- ## Bundling Improvements with Vite Starting with v2.2, we’ve transitioned from using `tsc` to [vite](https://vitejs.dev) for transpiling and bundling the library code. Although this change is mostly behind the scenes, it brings several benefits: - **Modern Build Target**: We’ve updated our build target to ES6. - **Updated Exports**: The package exports now reflect the latest JavaScript standards. - **Standalone Build Soon**: We’re working on a standalone build that bundles Cashu-TS along with all its dependencies. This will let you import Cashu-TS directly into your HTML. If you encounter any issues with the new bundling setup, please [let us know](https://github.com/cashubtc/cashu-ts/issues). ### A Nod to Vitest In addition to our bundling improvements, we’ve migrated our testing framework from Jest (with nock) to [vitest](https://vitest.dev) combined with [msw](https://mswjs.io). This switch gives us more flexibility in testing and mocking, plus we’ve added browser testing based on Playwright—thanks to the tip from nostr:npub16anjdksmvn5x08vtden04n64rw5k7fsjmedpw8avsx8wsh8ruhlq076pfx! --- ## In Conclusion Although Cashu-TS v2.2 is a minor version update, it comes packed with improvements that enhance both the developer experience and the flexibility of the library. We’re excited to see how you’ll use these new features in your projects! Thanks to all the amazing contributors that add to this library. Thank you for being a part of the Cashu-TS community. As always, if you have any questions, suggestions, or issues, don’t hesitate to [reach out to us](https://github.com/cashubtc/cashu-ts/issues).
@ ddf03aca:5cb3bbbe
2025-02-02 13:09:27We’re thrilled to announce the stable release of Cashu-TS v2.2! Although this update is a minor version bump, it brings significant improvements under the hood that enhance the overall developer experience. We’ve spent several weeks testing and refining these changes. --- ## What’s New in v2.2? While there are no breaking changes in this release, there are many internal changes. If you spot any regressions or unexpected behavior, please [let us know](https://github.com/cashubtc/cashu-ts/issues). Here’s a rundown of the major updates: - **Enhanced Proof Creation**: The way proofs are created internally has been revamped. - **User-Controlled Outputs**: You now have full control over how outputs are created. - **Improved Bundling**: We’ve switched our bundling tool to [vite](https://vitejs.dev) for faster and more modern builds. - **Updated Testing Tools**: Our testing framework has migrated to [vitest](https://vitest.dev) and [msw](https://mswjs.io), with added browser testing via Playwright. --- ## New Flexibility with OutputData In previous versions of Cashu-TS, the creation of outputs (or *BlindedMessages*) was hidden away. Even though there were options to tweak the process (like deterministic secrets or P2PK), you were always limited to the built-in logic. ### What’s Changed? In v2.2, we’ve introduced a public interface that not only streamlines output creation but also lets you plug in your own custom logic when needed. With the new `outputData` option available on all output-creating methods, you can now bypass the automatic process and provide your own outputs. For example, you can create two proofs tied to different public keys in a single mint operation: ```ts const data1 = OutputData.createP2PKData({ pubkey: "key1" }, 10, keys); const data2 = OutputData.createP2PKData({ pubkey: "key2" }, 10, keys); const { keep, send } = await wallet.send(20, proofs, { outputData: { send: [...data1, ...data2] }, }); ``` ### Customization Made Easy The `outputData` option now accepts anything that conforms to the `OutputDataLike` interface. This means you can introduce your own output creation logic—even if it’s not natively supported by Cashu-TS yet. Here’s what the interface looks like: ```ts export interface OutputDataLike { blindedMessage: SerializedBlindedMessage; blindingFactor: bigint; secret: Uint8Array; toProof: (signature: SerializedBlindedSignature, keyset: MintKeys) => Proof; } ``` ### Introducing OutputData Factories While having full control is empowering, it also means you’ll need to handle tasks like fee calculation and amount selection manually. To strike a balance between control and convenience, we now support **OutputData Factories**. A factory is simply a function that takes an amount and `MintKeys` as input and returns an `OutputDataLike` object. This way, you can define a blueprint for your output data without worrying about the nitty-gritty details. For instance, you can create separate factories for amounts you keep versus those you send: ```ts function keepFactory(a: number, k: MintKeys) { return OutputData.createSingleP2PKData({ pubkey: "keepPk" }, a, k.id); } function sendFactory(a: number, k: MintKeys) { return OutputData.createSingleP2PKData({ pubkey: "sendPk" }, a, k.id); } const { send, keep } = await wallet.send(amount, proofs, { outputData: { send: createFactory("send"), keep: createFactory("keep") }, }); ``` Plus, you can now instantiate a `CashuWallet` with a default `keepFactory`, ensuring that all change amounts automatically lock to your key—streamlining your workflow even further. --- ## Bundling Improvements with Vite Starting with v2.2, we’ve transitioned from using `tsc` to [vite](https://vitejs.dev) for transpiling and bundling the library code. Although this change is mostly behind the scenes, it brings several benefits: - **Modern Build Target**: We’ve updated our build target to ES6. - **Updated Exports**: The package exports now reflect the latest JavaScript standards. - **Standalone Build Soon**: We’re working on a standalone build that bundles Cashu-TS along with all its dependencies. This will let you import Cashu-TS directly into your HTML. If you encounter any issues with the new bundling setup, please [let us know](https://github.com/cashubtc/cashu-ts/issues). ### A Nod to Vitest In addition to our bundling improvements, we’ve migrated our testing framework from Jest (with nock) to [vitest](https://vitest.dev) combined with [msw](https://mswjs.io). This switch gives us more flexibility in testing and mocking, plus we’ve added browser testing based on Playwright—thanks to the tip from nostr:npub16anjdksmvn5x08vtden04n64rw5k7fsjmedpw8avsx8wsh8ruhlq076pfx! --- ## In Conclusion Although Cashu-TS v2.2 is a minor version update, it comes packed with improvements that enhance both the developer experience and the flexibility of the library. We’re excited to see how you’ll use these new features in your projects! Thanks to all the amazing contributors that add to this library. Thank you for being a part of the Cashu-TS community. As always, if you have any questions, suggestions, or issues, don’t hesitate to [reach out to us](https://github.com/cashubtc/cashu-ts/issues). @ fe41d17e:28df7452
2025-02-02 13:04:38Um es vorab klarzustellen, die einzigen Gesetze an die du dich wirklich halten musst sind die Naturgesetze, es ist deine eigene Entscheidung ob du einer einseitig vom Staat beschlossenen Auflage zustimmst oder nicht, solange du bereit bist, falls du erwischt wirst, die Konsequenzen über dich ergehen zu lassen. Wenn du diese Unterdrückung nicht mehr haben möchtest braucht es eine Revolution um den Staat irrelevant werden zu lassen und um ihm seine Grundlage (das Geld) zu entziehen ohne dabei wie er selbst zu unmoralischen Methoden zu greifen. Diese Revolution nennt sich **Agorismus,** sie wird dich unabhängig vom Staat machen und den Staat langfristig schwach/überflüssig werden lassen sobald es dir genug Leute gleichtun. Die Revolution wird nicht leicht, sie wird dir nicht die sofortige Genugtuung verschaffen, die du möglicherweise empfindest, wenn du einen Zettel in die Wahlurne wirfst und dabei das Gefühl hast, etwas verändert zu haben. Eigentlich hast du nur denselben Leuten Macht verliehen, die seit Jahrhunderten die Politiker kontrollieren, dich ausrauben und unterdrücken. Garnichts hast du damit verändert. Es wird schwierig werden. Es wird Eigeninitiative und Veränderungen in deinem Leben erfordern. Es wird ein zermürbender, unbefriedigender Weg sein, den viele als zu hart bezeichnen werden. Es wird Jahre über Jahre dauern, in denen die Leute dich dafür schief ansehen und du kaum Anerkennung bekommen wirst. *Hier ein paar wichtige Punkte um dich mit Agorismus vertraut zu machen*: \-Wenn du bereits ein Libertärer bist, lies zuerst „**Das neue Libertäre Manifest**“ von Samuel Edward Konkin III. Es hat nur 30 Seiten, und wenn du damit nicht zumindest deinen Horizont erweitern kannst, dann kannst du genauso gut eine britische Flagge in Amerika schwenken, Tribut zollen und einen König fordern. -Wenn du kein Libertärer bist, lies „**Eine neue Freiheit: das libertäre Manifest**“ von Murray Rothbard und anschließend „**Das neue Libertäre Manifest**“ von SEK3. -Konzentriere dich in deinem Leben darauf, weniger bis keine Steuern zu zahlen. \-Finde Alternativen zum Fiatgeld und sei deine eigene Bank. \-Finde lokale Quellen für Lebensmittel und Produkte. \-Handel P2P auf freien Märkten. \-Suche nach Lösungen, die auf Dezentralisierung ausgerichtet sind. \-Baue eine gewisse Menge an Lebensmitteln an, auch wenn es nur Mikrogrün ist. Dafür sind keine großen Flächen erforderlich und du kannst diese gegen andere Lebensmittel eintauschen. \-Baue dein eigenes Unternehmen außerhalb von Konzernstrukturen auf. \-Konzentriere dich auf den Handel mit anderen Agoristen. \-Nutze jede Gelegenheit um deine Verachtung gegenüber dem Staat zu äußern. \-Verbreite Agorismus. \-Beschaffe dir Waffen. \-Vertraue nur agoristischen Medien, die unpolitisch sind. Denn jeder Journalist, der dich ermutigt, zu wählen oder innerhalb des Systems zu arbeiten, könnte gekauft oder kontrolliert sein. Agoristen, die behaupten, dass Politik nicht die Antwort ist, sind die einzigen, die die Menschen wirklich von den Kontrolleuren wegführen. Die Herrscher dieser Welt sind sich durchaus darüber im Klaren, dass das Informationszeitalter ihren Interessen schadet. Daher arbeiten sie unermüdlich an der Schaffung psychologischer Operationen (PsyOps), kontrollierter Opposition, False-Flag-Aktionen und Ablenkungsmanövern, lass dich nicht täuschen. Erstveröffentlichung am 12. Januar auf meinem X Profil; @realbunki
@ fe41d17e:28df7452
2025-02-02 13:04:38Um es vorab klarzustellen, die einzigen Gesetze an die du dich wirklich halten musst sind die Naturgesetze, es ist deine eigene Entscheidung ob du einer einseitig vom Staat beschlossenen Auflage zustimmst oder nicht, solange du bereit bist, falls du erwischt wirst, die Konsequenzen über dich ergehen zu lassen. Wenn du diese Unterdrückung nicht mehr haben möchtest braucht es eine Revolution um den Staat irrelevant werden zu lassen und um ihm seine Grundlage (das Geld) zu entziehen ohne dabei wie er selbst zu unmoralischen Methoden zu greifen. Diese Revolution nennt sich **Agorismus,** sie wird dich unabhängig vom Staat machen und den Staat langfristig schwach/überflüssig werden lassen sobald es dir genug Leute gleichtun. Die Revolution wird nicht leicht, sie wird dir nicht die sofortige Genugtuung verschaffen, die du möglicherweise empfindest, wenn du einen Zettel in die Wahlurne wirfst und dabei das Gefühl hast, etwas verändert zu haben. Eigentlich hast du nur denselben Leuten Macht verliehen, die seit Jahrhunderten die Politiker kontrollieren, dich ausrauben und unterdrücken. Garnichts hast du damit verändert. Es wird schwierig werden. Es wird Eigeninitiative und Veränderungen in deinem Leben erfordern. Es wird ein zermürbender, unbefriedigender Weg sein, den viele als zu hart bezeichnen werden. Es wird Jahre über Jahre dauern, in denen die Leute dich dafür schief ansehen und du kaum Anerkennung bekommen wirst. *Hier ein paar wichtige Punkte um dich mit Agorismus vertraut zu machen*: \-Wenn du bereits ein Libertärer bist, lies zuerst „**Das neue Libertäre Manifest**“ von Samuel Edward Konkin III. Es hat nur 30 Seiten, und wenn du damit nicht zumindest deinen Horizont erweitern kannst, dann kannst du genauso gut eine britische Flagge in Amerika schwenken, Tribut zollen und einen König fordern. -Wenn du kein Libertärer bist, lies „**Eine neue Freiheit: das libertäre Manifest**“ von Murray Rothbard und anschließend „**Das neue Libertäre Manifest**“ von SEK3. -Konzentriere dich in deinem Leben darauf, weniger bis keine Steuern zu zahlen. \-Finde Alternativen zum Fiatgeld und sei deine eigene Bank. \-Finde lokale Quellen für Lebensmittel und Produkte. \-Handel P2P auf freien Märkten. \-Suche nach Lösungen, die auf Dezentralisierung ausgerichtet sind. \-Baue eine gewisse Menge an Lebensmitteln an, auch wenn es nur Mikrogrün ist. Dafür sind keine großen Flächen erforderlich und du kannst diese gegen andere Lebensmittel eintauschen. \-Baue dein eigenes Unternehmen außerhalb von Konzernstrukturen auf. \-Konzentriere dich auf den Handel mit anderen Agoristen. \-Nutze jede Gelegenheit um deine Verachtung gegenüber dem Staat zu äußern. \-Verbreite Agorismus. \-Beschaffe dir Waffen. \-Vertraue nur agoristischen Medien, die unpolitisch sind. Denn jeder Journalist, der dich ermutigt, zu wählen oder innerhalb des Systems zu arbeiten, könnte gekauft oder kontrolliert sein. Agoristen, die behaupten, dass Politik nicht die Antwort ist, sind die einzigen, die die Menschen wirklich von den Kontrolleuren wegführen. Die Herrscher dieser Welt sind sich durchaus darüber im Klaren, dass das Informationszeitalter ihren Interessen schadet. Daher arbeiten sie unermüdlich an der Schaffung psychologischer Operationen (PsyOps), kontrollierter Opposition, False-Flag-Aktionen und Ablenkungsmanövern, lass dich nicht täuschen. Erstveröffentlichung am 12. Januar auf meinem X Profil; @realbunki @ 77be3409:5c7c2736
2025-02-02 12:48:25[RMD Law - Personal Injury Lawyers ](https://www.rmdlaw.com/)is excited to announce the launch of its new scholarship program, designed to empower students and highlight the values of responsibility, resilience, and learning from life’s unexpected moments. This $2,500 scholarship aims to support students in their educational journeys while encouraging creativity and personal growth. ### Scholarship Details Award Amount: $2,500 Submission Deadline: December 30, 2025 Winner Announced: January 15, 2026 **Eligibility Requirements** To apply, students must meet the following criteria: - Be at least 16 years old and a permanent legal resident of the United States. - Be currently enrolled in a U.S. college, university, or trade school OR graduating from high school in 2025. - Have a cumulative GPA of 3.0 or higher. - Follow RMD Law on social media to see the winner announcement. - Submit all required materials by the December 30, 2025, deadline **Application Requirements Applicants are required to submit:** - A copy of their most recent high school or college transcript. - A creative and thoughtful essay (up to 1,000 words) responding to the following prompt: **Essay Prompt: “Oops, That Was Close!”** Tell us about a moment when you narrowly avoided disaster—whether it was a hilarious mishap, an embarrassing accident, or a close call with serious consequences. - What did you learn (if anything) from the experience? - Who was at fault and why? - What would the appropriate restitution (if any) be in that situation? Note: Applicants are encouraged to use creativity, levity, and personal insights to share their story. Let your unique voice shine through! **Selection Criteria** The winner will be chosen based on: - Originality and creativity in their essay. - Relevance to the prompt. - Clarity and thoughtfulness of their response. The scholarship recipient will be announced on January 15, 2026. **How to Apply** 1. Students can submit their application materials through the official RMD Law scholarship webpage: [https://www.rmdlaw.com/scholarship/ ](https://www.rmdlaw.com/scholarship/)2. Follow RMD Law on social media to stay updated on the announcement and other initiatives. #### About RMD Law RMD Law is a leading personal injury law firm committed to providing exceptional legal services and making a positive impact in the communities it serves. Through initiatives like the scholarship program, RMD Law seeks to empower individuals and foster the next generation of leaders.
@ 77be3409:5c7c2736
2025-02-02 12:48:25[RMD Law - Personal Injury Lawyers ](https://www.rmdlaw.com/)is excited to announce the launch of its new scholarship program, designed to empower students and highlight the values of responsibility, resilience, and learning from life’s unexpected moments. This $2,500 scholarship aims to support students in their educational journeys while encouraging creativity and personal growth. ### Scholarship Details Award Amount: $2,500 Submission Deadline: December 30, 2025 Winner Announced: January 15, 2026 **Eligibility Requirements** To apply, students must meet the following criteria: - Be at least 16 years old and a permanent legal resident of the United States. - Be currently enrolled in a U.S. college, university, or trade school OR graduating from high school in 2025. - Have a cumulative GPA of 3.0 or higher. - Follow RMD Law on social media to see the winner announcement. - Submit all required materials by the December 30, 2025, deadline **Application Requirements Applicants are required to submit:** - A copy of their most recent high school or college transcript. - A creative and thoughtful essay (up to 1,000 words) responding to the following prompt: **Essay Prompt: “Oops, That Was Close!”** Tell us about a moment when you narrowly avoided disaster—whether it was a hilarious mishap, an embarrassing accident, or a close call with serious consequences. - What did you learn (if anything) from the experience? - Who was at fault and why? - What would the appropriate restitution (if any) be in that situation? Note: Applicants are encouraged to use creativity, levity, and personal insights to share their story. Let your unique voice shine through! **Selection Criteria** The winner will be chosen based on: - Originality and creativity in their essay. - Relevance to the prompt. - Clarity and thoughtfulness of their response. The scholarship recipient will be announced on January 15, 2026. **How to Apply** 1. Students can submit their application materials through the official RMD Law scholarship webpage: [https://www.rmdlaw.com/scholarship/ ](https://www.rmdlaw.com/scholarship/)2. Follow RMD Law on social media to stay updated on the announcement and other initiatives. #### About RMD Law RMD Law is a leading personal injury law firm committed to providing exceptional legal services and making a positive impact in the communities it serves. Through initiatives like the scholarship program, RMD Law seeks to empower individuals and foster the next generation of leaders. @ 0463223a:3b14d673
2025-02-02 12:22:46I’m totally wasted! I don’t mean off my head on drugs, I mean absolutely physically and mentally exhausted. Lugging heavy PA equipment up and down stairs, plus mixing shows is a lot and at my age I’m struggling with it. Yesterday was a write off due to exhaustion. My wife and I went to the cinema, and I slept through the film. A shame, it was something I wanted to see but I was toast. I went to bed at 8pm and slept for over 12 hours. I still feel wrecked today. Live sound was always a sort of plan B. For a number of years teaching and performing with a band or a DJ was enough to get by on. I was comfortable, financially speaking. That was until about between 2012-14, that’s when we really felt the effects of the post 2008 crash. While a lot of noise was made about the initial event, reality for the likes of me was a slow and steady decline. At that time I was leading workshops with kids with difficult backgrounds, many kids in care due to abuse and neglect. That was a solid 40% of my income, another 30% came from teaching Sound Production at a local university and the final 30% from shows. 2014 cutbacks ripped services to shreds and a few friends lost jobs. Since then, doing live sound kept the rent and bills paid but fast forward to 2025 and I’m way too tired for this shit! I hate admitting it but my earnings probably peaked around 2008 with a bump in tours from 2017 till Covid. Since then earnings have been steady in £'s but getting wiped out by inflation. In fact I had decent acounts this year but every month I'm broke by the time bills and basics have been taken care of. I LOVE mixing live music and I’m pretty good at it. I’ve had musicians call me ‘musical’ which is the highest compliment but I’m totally fucked still 2 days after Friday’s show. It's unsustainable. I’m quitting live sound unless some touring comes up again, touring is different, living on a bus for 3 weeks pays the same as 3 months of local work and I just mix, no lifting gear. The band I tour with are based in the US and only come to the UK/EU every couple of years. I get odd trips away with other artists but they’re usually fly out EU gigs. 1 or 2 shows then fly home, plus they're irregular. Right now I’m more interested to learn ways of making income online, I started the Kali Mera Show to learn self hosting content. Committing to a project each morning has done wonders for my mental health, cutting down on morning doom scrolling. It’s been highly successful in that regard but not so much financially. However this is jst phase 1. I’m learning the tech, learning the production and making as many mistakes as possible while the stakes are low. I’m very happy 10 or so people enjoy the show on a daily basis. Tiny numbers but I don’t fuck with YouTube or the other big tech platforms. Fuck them! Phase 2 involves getting premises and broadening the services I can produce, focussing on content for others, getting some opportunities happening for young talent, arranging meet ups and setting up a hub to bring together the crazy, talented people I know. It’s going to be tough, I’m in a run down area, there’s not much money here (relatively speaking) but it’s an area I really dig and want to make better. Why am I telling you this? I’m writing this as a means of getting my brain straight and sharing it because I’m open to improving myself. I see people doing interesting shit here and that helps with motivation and confidence. My only social media for the last 6 years has been the Fediverse and much as I love it, there’s a gloomier outlook there. The world is a strange place with so much bad shit but out of 8 or so billion people, I can only take on so much. Building shit in my own local community and provide facilities for online wins sounds way more productive and helpful in some small way. I accept we’re all going to hell in a handcart but may as well enjoy the ride… There’s much to learn, I’ve only ever been ‘in business’ for a short time in my life (despite always being freelance) and I sort of gave up on my previous attempt. Had I paid more attention I could’ve built a strong YouTube presence but I’m not into being a vehicle for companies to push their products, nor do I want to teach people music online. That market is now heavily saturated and very, very boring as far as I’m concerned. My heart wasn’t in it, even back in 2015. I’m not an influencer. With a real life space there’s premises, business rates, and investors to consider, as well as developing services that people are actually happy to part cash with. It’s going to be hard but different hard to physically lifting sub-bass speakers up and down winding staircases! I don’t want to talk too much game, it’s results that matter but wasting days to exhaustion doesn’t help. It’s time to hang up my headphones and focus (FOCUS YOU FUCKING FUCK!). Maybe you’re reading this and thought ‘shit, this guy’s totally deluded’. That’s cool. Tell me. I value feedback. A fair few cats here give life advice so I’ll assume you might know what you’re talking about...
@ 0463223a:3b14d673
2025-02-02 12:22:46I’m totally wasted! I don’t mean off my head on drugs, I mean absolutely physically and mentally exhausted. Lugging heavy PA equipment up and down stairs, plus mixing shows is a lot and at my age I’m struggling with it. Yesterday was a write off due to exhaustion. My wife and I went to the cinema, and I slept through the film. A shame, it was something I wanted to see but I was toast. I went to bed at 8pm and slept for over 12 hours. I still feel wrecked today. Live sound was always a sort of plan B. For a number of years teaching and performing with a band or a DJ was enough to get by on. I was comfortable, financially speaking. That was until about between 2012-14, that’s when we really felt the effects of the post 2008 crash. While a lot of noise was made about the initial event, reality for the likes of me was a slow and steady decline. At that time I was leading workshops with kids with difficult backgrounds, many kids in care due to abuse and neglect. That was a solid 40% of my income, another 30% came from teaching Sound Production at a local university and the final 30% from shows. 2014 cutbacks ripped services to shreds and a few friends lost jobs. Since then, doing live sound kept the rent and bills paid but fast forward to 2025 and I’m way too tired for this shit! I hate admitting it but my earnings probably peaked around 2008 with a bump in tours from 2017 till Covid. Since then earnings have been steady in £'s but getting wiped out by inflation. In fact I had decent acounts this year but every month I'm broke by the time bills and basics have been taken care of. I LOVE mixing live music and I’m pretty good at it. I’ve had musicians call me ‘musical’ which is the highest compliment but I’m totally fucked still 2 days after Friday’s show. It's unsustainable. I’m quitting live sound unless some touring comes up again, touring is different, living on a bus for 3 weeks pays the same as 3 months of local work and I just mix, no lifting gear. The band I tour with are based in the US and only come to the UK/EU every couple of years. I get odd trips away with other artists but they’re usually fly out EU gigs. 1 or 2 shows then fly home, plus they're irregular. Right now I’m more interested to learn ways of making income online, I started the Kali Mera Show to learn self hosting content. Committing to a project each morning has done wonders for my mental health, cutting down on morning doom scrolling. It’s been highly successful in that regard but not so much financially. However this is jst phase 1. I’m learning the tech, learning the production and making as many mistakes as possible while the stakes are low. I’m very happy 10 or so people enjoy the show on a daily basis. Tiny numbers but I don’t fuck with YouTube or the other big tech platforms. Fuck them! Phase 2 involves getting premises and broadening the services I can produce, focussing on content for others, getting some opportunities happening for young talent, arranging meet ups and setting up a hub to bring together the crazy, talented people I know. It’s going to be tough, I’m in a run down area, there’s not much money here (relatively speaking) but it’s an area I really dig and want to make better. Why am I telling you this? I’m writing this as a means of getting my brain straight and sharing it because I’m open to improving myself. I see people doing interesting shit here and that helps with motivation and confidence. My only social media for the last 6 years has been the Fediverse and much as I love it, there’s a gloomier outlook there. The world is a strange place with so much bad shit but out of 8 or so billion people, I can only take on so much. Building shit in my own local community and provide facilities for online wins sounds way more productive and helpful in some small way. I accept we’re all going to hell in a handcart but may as well enjoy the ride… There’s much to learn, I’ve only ever been ‘in business’ for a short time in my life (despite always being freelance) and I sort of gave up on my previous attempt. Had I paid more attention I could’ve built a strong YouTube presence but I’m not into being a vehicle for companies to push their products, nor do I want to teach people music online. That market is now heavily saturated and very, very boring as far as I’m concerned. My heart wasn’t in it, even back in 2015. I’m not an influencer. With a real life space there’s premises, business rates, and investors to consider, as well as developing services that people are actually happy to part cash with. It’s going to be hard but different hard to physically lifting sub-bass speakers up and down winding staircases! I don’t want to talk too much game, it’s results that matter but wasting days to exhaustion doesn’t help. It’s time to hang up my headphones and focus (FOCUS YOU FUCKING FUCK!). Maybe you’re reading this and thought ‘shit, this guy’s totally deluded’. That’s cool. Tell me. I value feedback. A fair few cats here give life advice so I’ll assume you might know what you’re talking about... @ d1795b1a:15ab2129
2025-02-02 11:45:38### The Ego is an Illusion – and Yet, We Can Shape It Carl Jung spoke of the **Shadow Self**—the repressed parts of our psyche that unconsciously influence our lives. **Buddhism**, on the other hand, teaches that there is no self at all—our ego is an illusion, a fleeting construct that we cling to out of fear of emptiness. These two perspectives seem to contradict each other. One tells us to integrate our hidden self, the other to dissolve it completely. But what if both are only half the picture? I believe the **Self is neither a fixed reality nor a mere illusion—it is a shapeable construct.** If that is true, then the path is not to destroy the **Ego-Self** or blindly follow it, but to **consciously shape it.** ### **Between the Shadow and Emptiness** Our **Ego-Self** is our conscious identity—our thoughts, memories, and beliefs. **Jung** describes the **Self** as the totality of both **the conscious and unconscious mind.** Hidden in this unconscious space is the **Shadow Self**, containing everything we deny, suppress, or refuse to acknowledge. For Jung, the path to wholeness is **integration**—bringing light into the dark corners of the psyche. **Buddhism**, however, goes further. It questions whether the **Self** exists at all. Our thoughts and emotions arise and disappear, our self-image is ever-changing—so **why do we cling to something so impermanent?** Both views seem to offer opposite solutions: \ **• Jung:** Become WHOLE by integrating your Shadow. \ **• Buddha:** Become FREE by seeing the Self as an illusion. But what if the **synthesis of both is the key?** ### The Self as a Shapeable Reality If the **Self** is not fixed but fluid, then the path forward is neither **pure integration nor total dissolution** but **conscious creation.** \ \ **• Acknowledge the Shadow Self instead of fighting it.** \ **• See the Ego-Self not as absolute truth but as a flexible tool. \ • Engage the Solar Plexus—the center of the Unconscious Mind—through breathwork and self-awareness. \ • Use the Vagus Nerve as a bridge between conscious thought and unconscious emotion, actively shaping our beliefs and behaviors.** This aligns with **New Thought philosophy**, which suggests that our thoughts shape not only our perception but our reality itself. If we embrace this, the question is no longer **“Who am I?”** but rather: **“Who do I want to be—and how can I create that Self?”** ### The Art of Shaping Yourself Perhaps the **Self** is neither a rigid entity nor a complete illusion but a story we tell ourselves—a story we can rewrite. The key is not to destroy the Ego-Self but to **use it consciously, rather than being used by it.** So the real question is not: **“Does the Self exist?”** But rather: **“How aware are we of the fact that we are shaping it every moment?”**
@ d1795b1a:15ab2129
2025-02-02 11:45:38### The Ego is an Illusion – and Yet, We Can Shape It Carl Jung spoke of the **Shadow Self**—the repressed parts of our psyche that unconsciously influence our lives. **Buddhism**, on the other hand, teaches that there is no self at all—our ego is an illusion, a fleeting construct that we cling to out of fear of emptiness. These two perspectives seem to contradict each other. One tells us to integrate our hidden self, the other to dissolve it completely. But what if both are only half the picture? I believe the **Self is neither a fixed reality nor a mere illusion—it is a shapeable construct.** If that is true, then the path is not to destroy the **Ego-Self** or blindly follow it, but to **consciously shape it.** ### **Between the Shadow and Emptiness** Our **Ego-Self** is our conscious identity—our thoughts, memories, and beliefs. **Jung** describes the **Self** as the totality of both **the conscious and unconscious mind.** Hidden in this unconscious space is the **Shadow Self**, containing everything we deny, suppress, or refuse to acknowledge. For Jung, the path to wholeness is **integration**—bringing light into the dark corners of the psyche. **Buddhism**, however, goes further. It questions whether the **Self** exists at all. Our thoughts and emotions arise and disappear, our self-image is ever-changing—so **why do we cling to something so impermanent?** Both views seem to offer opposite solutions: \ **• Jung:** Become WHOLE by integrating your Shadow. \ **• Buddha:** Become FREE by seeing the Self as an illusion. But what if the **synthesis of both is the key?** ### The Self as a Shapeable Reality If the **Self** is not fixed but fluid, then the path forward is neither **pure integration nor total dissolution** but **conscious creation.** \ \ **• Acknowledge the Shadow Self instead of fighting it.** \ **• See the Ego-Self not as absolute truth but as a flexible tool. \ • Engage the Solar Plexus—the center of the Unconscious Mind—through breathwork and self-awareness. \ • Use the Vagus Nerve as a bridge between conscious thought and unconscious emotion, actively shaping our beliefs and behaviors.** This aligns with **New Thought philosophy**, which suggests that our thoughts shape not only our perception but our reality itself. If we embrace this, the question is no longer **“Who am I?”** but rather: **“Who do I want to be—and how can I create that Self?”** ### The Art of Shaping Yourself Perhaps the **Self** is neither a rigid entity nor a complete illusion but a story we tell ourselves—a story we can rewrite. The key is not to destroy the Ego-Self but to **use it consciously, rather than being used by it.** So the real question is not: **“Does the Self exist?”** But rather: **“How aware are we of the fact that we are shaping it every moment?”** @ fd208ee8:0fd927c1
2025-02-02 10:33:19# GitCitadel Development Operations We, at GitCitadel, have been updating, moving, and rearranging our servers, for quite some time. As a rather large, complex, sprawling project, we have the infrastructure setup to match, so we've decided to give you all a quick run-down of what we are doing behind-the-scenes. ## Supplier Coordination  Our first task, this week, was figuring out who would host what where. We have four different locations, where our infra is stored and managed, including two locations from our suppliers. We got that straightened out, quickly, and it's all slowly coming together and being connected and networked. Exciting to watch our DevOps landscape evolve and all of the knowledge-transfer that the interactions provide. ## OneDev Implementation  Our biggest internal infra project this week was the migration of all of our issues from Jira, build scripts from Jenkins, and repos from GitHub to a [self-hosted OneDev instance](https://onedev.gitcitadel.eu). In the future, all of our internal build, test, issue, patch/PR, etc. effort will take place there. We also have a separate repo there for communicating with external developers and suppliers. Our [team's GitHub projects](https://github.com/ShadowySupercode) will be demoted to mirrors and a place for external devs to PR to. Public issues and patches will continue to be managed over our self-hosted [GitWorkshop instance](nostr:naddr1qvzqqqrhnypzplfq3m5v3u5r0q9f255fdeyz8nyac6lagssx8zy4wugxjs8ajf7pqy88wumn8ghj7mn0wvhxcmmv9uqq5emfw33kjarpv3jkcs83wav). We're especially glad to finally escape the GitHub Gulag, and avoid being bled dry by Jira fees, without having to give up the important features that we've come to know and love. So, yay! ## Next Infrasteps ### Automated Testing Now, that we have everything tied up in one, neat, backed-up package, we can finally move on to the nitty-gritty and the dirty work. So, we're rolling up our sleeves and writing the Selenium smoke test for our [Alexandria client](https://next-alexandria.gitcitadel.eu). We'll be running that in Docker containers containing different "typical Nostr" images, such as Chrome browser with Nostr Connect signing extension, or Firefox browser with Nos2x-fox extension. Once we get the Nsec Bunker and Amber logins going, we'll add test cases and images for them, as well. (Yes, we can do Bunker. I hope you are in awe at our powers). We are also designing an automated infrastructure test, that will simply rattle through all the various internal and external websites and relays, to make sure that everything is still online and responsive. After that, a Gherkin-based [Behave feature test](https://behave.readthedocs.io/en/latest/) for Alexandria is planned, so that we can prevent regression of completed functionality, from one release to the next. The Gherkin scenarios are written and attached to our stories before development begins (we use acceptance tests as requirements), a manual test-execution is then completed, in order to set the story to *Done*. These completed scenarios will be automated, following each release, with the resulting script linked to from the origin story.  ### Automated Builds As the crowning glory of every DevOps tool chain stands the build automation. This is where everything gets tied together, straightened out, configured, tested, measured, and -- if everything passes the quality gates -- released. I don't have to tell you how much time developers spend staring at the build process display, praying that it all goes through and they can celebrate a Green Wave.  We are currently designing the various builds, but the ones we have defined for the Alexandria client will be a continuous delivery pipeline, like so:  This will make it easier for us to work and collaborate asynchronously and without unnecessary delays. ### Expanding the Status Page  And, finally, we get to the point of all of this busyness: reporting. We are going to have beautiful reports, and we are going to post them online, on our [status page](https://status.gitcitadel.com). We will use bots, to inform Nostriches of the current status of our systems, so go ahead and follow our [GitCitadel DevOps npub](nostr:npub16p0fdr2xccfs07hykx92t0cascac69xjuwaq38kjqy3aawt5hx8s82feyj), to make sure you don't miss out on the IT action. ## Building on stone All in all, we're really happy with the way things are humming along, now, and the steady increase in our productivity, as all the foundational work we've put in starts to pay off. It's getting easier and easier to add new team members, repos, or features/fixes, so we should be able to scale up and out from here. Our GitCitadel is built on a firm foundation. Happy building!
@ fd208ee8:0fd927c1
2025-02-02 10:33:19# GitCitadel Development Operations We, at GitCitadel, have been updating, moving, and rearranging our servers, for quite some time. As a rather large, complex, sprawling project, we have the infrastructure setup to match, so we've decided to give you all a quick run-down of what we are doing behind-the-scenes. ## Supplier Coordination  Our first task, this week, was figuring out who would host what where. We have four different locations, where our infra is stored and managed, including two locations from our suppliers. We got that straightened out, quickly, and it's all slowly coming together and being connected and networked. Exciting to watch our DevOps landscape evolve and all of the knowledge-transfer that the interactions provide. ## OneDev Implementation  Our biggest internal infra project this week was the migration of all of our issues from Jira, build scripts from Jenkins, and repos from GitHub to a [self-hosted OneDev instance](https://onedev.gitcitadel.eu). In the future, all of our internal build, test, issue, patch/PR, etc. effort will take place there. We also have a separate repo there for communicating with external developers and suppliers. Our [team's GitHub projects](https://github.com/ShadowySupercode) will be demoted to mirrors and a place for external devs to PR to. Public issues and patches will continue to be managed over our self-hosted [GitWorkshop instance](nostr:naddr1qvzqqqrhnypzplfq3m5v3u5r0q9f255fdeyz8nyac6lagssx8zy4wugxjs8ajf7pqy88wumn8ghj7mn0wvhxcmmv9uqq5emfw33kjarpv3jkcs83wav). We're especially glad to finally escape the GitHub Gulag, and avoid being bled dry by Jira fees, without having to give up the important features that we've come to know and love. So, yay! ## Next Infrasteps ### Automated Testing Now, that we have everything tied up in one, neat, backed-up package, we can finally move on to the nitty-gritty and the dirty work. So, we're rolling up our sleeves and writing the Selenium smoke test for our [Alexandria client](https://next-alexandria.gitcitadel.eu). We'll be running that in Docker containers containing different "typical Nostr" images, such as Chrome browser with Nostr Connect signing extension, or Firefox browser with Nos2x-fox extension. Once we get the Nsec Bunker and Amber logins going, we'll add test cases and images for them, as well. (Yes, we can do Bunker. I hope you are in awe at our powers). We are also designing an automated infrastructure test, that will simply rattle through all the various internal and external websites and relays, to make sure that everything is still online and responsive. After that, a Gherkin-based [Behave feature test](https://behave.readthedocs.io/en/latest/) for Alexandria is planned, so that we can prevent regression of completed functionality, from one release to the next. The Gherkin scenarios are written and attached to our stories before development begins (we use acceptance tests as requirements), a manual test-execution is then completed, in order to set the story to *Done*. These completed scenarios will be automated, following each release, with the resulting script linked to from the origin story.  ### Automated Builds As the crowning glory of every DevOps tool chain stands the build automation. This is where everything gets tied together, straightened out, configured, tested, measured, and -- if everything passes the quality gates -- released. I don't have to tell you how much time developers spend staring at the build process display, praying that it all goes through and they can celebrate a Green Wave.  We are currently designing the various builds, but the ones we have defined for the Alexandria client will be a continuous delivery pipeline, like so:  This will make it easier for us to work and collaborate asynchronously and without unnecessary delays. ### Expanding the Status Page  And, finally, we get to the point of all of this busyness: reporting. We are going to have beautiful reports, and we are going to post them online, on our [status page](https://status.gitcitadel.com). We will use bots, to inform Nostriches of the current status of our systems, so go ahead and follow our [GitCitadel DevOps npub](nostr:npub16p0fdr2xccfs07hykx92t0cascac69xjuwaq38kjqy3aawt5hx8s82feyj), to make sure you don't miss out on the IT action. ## Building on stone All in all, we're really happy with the way things are humming along, now, and the steady increase in our productivity, as all the foundational work we've put in starts to pay off. It's getting easier and easier to add new team members, repos, or features/fixes, so we should be able to scale up and out from here. Our GitCitadel is built on a firm foundation. Happy building! @ 006532cb:fd8f28b4
2025-02-02 09:50:56I am new to #NOSTR and not a #Dev; however, npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn's [article](https://njump.me/naddr1qvzqqqr4gupzp978pfzrv6n9xhq5tvenl9e74pklmskh4xw6vxxyp3j8qkke3cezqyw8wumn8ghj76r0v3kxymmy9e3k7unpvdkx2tn5dahkcue0qy88wumn8ghj7mn0wvhxcmmv9uqq6vfhxvurydfhxq6nwvfj8q4tttqv) inspired me to research and understand further. As a result, I have condensed my learnings into 10 bullet points that seem to embody the spirit of being a nostrich and the qualities we should all strive for when engaging with one another making software choices and avoiding NINO's. 1. **You shall not compromise on security:** Prioritize the security and integrity of user data, using best practices and Nostr's built-in features to protect against unauthorized access and malicious activity. 2. **You shall prioritize user agency:** Respect users' mute lists, use their web of trust to filter out spam, and prioritize user control over their data. 3. **You shall be decentralized and open:** Do not hardcode relay URLs or depend on specific relay implementations, ensuring that your platform is truly decentralized and open. 4. **You shall leverage Nostr's technical aspects:** Take advantage of Nostr's features, such as self-authenticating data, event handlers, and relays, to build a robust and decentralized platform. 5. **You shall use native Nostr solutions:** Prefer Nostr-native solutions to solve problems, rather than relying on legacy web services, promoting a more decentralized and resilient ecosystem. 6. **You shall prioritize interoperability:** Implement NIP 89 (Recommended Application Handlers) to enable seamless interactions with other Nostr apps, promoting a unified and decentralized ecosystem. 7. **You shall engage with the community:** Share knowledge, contribute to the growth of the ecosystem, and collaborate with other Nostr developers to promote a unified and thriving community. 8. **You shall be transparent and accountable:** Be transparent in your development processes, and accountable for your actions and decisions, promoting trust and confidence in the Nostr ecosystem. 9. **You shall innovate and evolve:** Continuously innovate and improve your platform, staying up-to-date with the latest developments in the Nostr protocol and ecosystem, to ensure the best possible experience for users. 10. **Embody Nostr:** Your application should truly represent the Nostr protocol, using its features and network to provide unique value to users. I am excited for the future. In Eric S. Raymond's book "The Cathedral and the Bazaar" he comments; > "...and the robust doesn't care too much" Nostr embodies the spirit of the Bazaar, a vibrant and eclectic marketplace where the robust thrive, all are welcomed and empowered to become strong. /GN!
@ 006532cb:fd8f28b4
2025-02-02 09:50:56I am new to #NOSTR and not a #Dev; however, npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn's [article](https://njump.me/naddr1qvzqqqr4gupzp978pfzrv6n9xhq5tvenl9e74pklmskh4xw6vxxyp3j8qkke3cezqyw8wumn8ghj76r0v3kxymmy9e3k7unpvdkx2tn5dahkcue0qy88wumn8ghj7mn0wvhxcmmv9uqq6vfhxvurydfhxq6nwvfj8q4tttqv) inspired me to research and understand further. As a result, I have condensed my learnings into 10 bullet points that seem to embody the spirit of being a nostrich and the qualities we should all strive for when engaging with one another making software choices and avoiding NINO's. 1. **You shall not compromise on security:** Prioritize the security and integrity of user data, using best practices and Nostr's built-in features to protect against unauthorized access and malicious activity. 2. **You shall prioritize user agency:** Respect users' mute lists, use their web of trust to filter out spam, and prioritize user control over their data. 3. **You shall be decentralized and open:** Do not hardcode relay URLs or depend on specific relay implementations, ensuring that your platform is truly decentralized and open. 4. **You shall leverage Nostr's technical aspects:** Take advantage of Nostr's features, such as self-authenticating data, event handlers, and relays, to build a robust and decentralized platform. 5. **You shall use native Nostr solutions:** Prefer Nostr-native solutions to solve problems, rather than relying on legacy web services, promoting a more decentralized and resilient ecosystem. 6. **You shall prioritize interoperability:** Implement NIP 89 (Recommended Application Handlers) to enable seamless interactions with other Nostr apps, promoting a unified and decentralized ecosystem. 7. **You shall engage with the community:** Share knowledge, contribute to the growth of the ecosystem, and collaborate with other Nostr developers to promote a unified and thriving community. 8. **You shall be transparent and accountable:** Be transparent in your development processes, and accountable for your actions and decisions, promoting trust and confidence in the Nostr ecosystem. 9. **You shall innovate and evolve:** Continuously innovate and improve your platform, staying up-to-date with the latest developments in the Nostr protocol and ecosystem, to ensure the best possible experience for users. 10. **Embody Nostr:** Your application should truly represent the Nostr protocol, using its features and network to provide unique value to users. I am excited for the future. In Eric S. Raymond's book "The Cathedral and the Bazaar" he comments; > "...and the robust doesn't care too much" Nostr embodies the spirit of the Bazaar, a vibrant and eclectic marketplace where the robust thrive, all are welcomed and empowered to become strong. /GN! @ 63e047aa:2e1ae74f
2025-02-02 09:00:46In this blog post, I will walk you through the process of integrating Nostr login functionality into my Rails application using the Nos2x extension. This involved modifying the Devise User model, adding a new route to handle Nostr users, and integrating JavaScript to enhance the login experience. ## Overview Nostr is a decentralized protocol that allows users to authenticate without relying on traditional email/password combinations. By leveraging the Nos2x extension, I was able to implement Nostr login seamlessly. Here’s how I did it. ## Step 1: Adding Asynchronous Nostr client in Ruby ```bash bundle add nostr ``` ## Step 2: Modifying the Devise User Model The first step was to modify the Devise User model to allow empty email validation. This is crucial because Nostr users may not have an email address. I updated the `User` model as follows: ```ruby class User < ApplicationRecord # Include default devise modules. Others available are: # :confirmable, :lockable, :timeoutable, :trackable, :registerable and :omniauthable devise :database_authenticatable, :registerable, :recoverable, :rememberable # Removed :validatable # Validations validates :nostr_public_key, presence: true, uniqueness: true, allow_blank: true validates :email, uniqueness: true, allow_blank: true # Make email optional validates :password, length: { minimum: 6 }, allow_blank: true # Make password optional but enforce length if provided # Conditional validation for email and password validates :email, presence: true, unless: :nostr_public_key_present? validates :password, presence: true, unless: :nostr_public_key_present? private def nostr_public_key_present? nostr_public_key.present? end end ``` By adding this validation, I ensured that users logging in via Nostr would not be required to provide an email address. ## Step 3: Adding a New Route for Nostr Users Next, I needed to create a new route to handle the login process for Nostr users. I added the following route to my `config/routes.rb` file: ```ruby Rails.application.routes.draw do # Other existing routes... post 'users/nostr_login', to: 'users#nostr_login', as: 'nostr_login' end ``` This route points to a new action in the `UsersController` that will manage the authentication process for Nostr users. ## Step 4: Implementing the Nostr Login Action In the `UsersController`, I implemented the `nostr_signup` action to handle the login logic: ```ruby # app/controllers/users_controller.rb class UsersController < ApplicationController # Custom error handling for CSRF token verification failure rescue_from ActionController::InvalidAuthenticityToken do |exception| render json: { error: "Can't verify CSRF token authenticity." }, status: :unprocessable_entity end def nostr_signup nostr_signed_event = params[:signed_event] if not nostr_signed_event render json: { success: false, error: "No signed event provided." }, status: :unprocessable_entity return end public_key = nostr_signed_event[:pubkey] content = nostr_signed_event[:content] kind = nostr_signed_event[:kind] csrf_token = request.headers['X-CSRF-Token'] tags_hash = tags.to_h challenge_value = tags_hash["challenge"] relay_value = tags_hash["relay"] expected_relay_value = ENV.fetch('NOSTR_AUTH_RELAY_URL', 'wss://relay.primal.net') # Check if the challenge_value and relay_value are matching or if kind is valid if challenge_value != csrf_token || kind != 22242 || relay_value != expected_relay_value return render json: { success: false, error: "Invalid event provided." }, status: :unprocessable_entity end nostr_event = Nostr::Event.new( content: content, id: nostr_signed_event[:id], created_at: nostr_signed_event[:created_at], kind: kind, pubkey: public_key, sig: nostr_signed_event[:sig], tags: nostr_signed_event[:tags] ) # Validate the event's signature unless nostr_event.verify_signature render json: { success: false, error: "Invalid event signature." }, status: :unprocessable_entity return end user = User.find_or_initialize_by(nostr_public_key: public_key) ... end private def nostr_signup_params params.permit(signed_event: [:id, :kind, :content, :tags, :created_at, :pubkey, :sig]) end end ``` This action will handle the authentication process and create a new user if they do not already exist. ## Step 5: Integrating JavaScript for Nostr Login To enhance the user experience, I added a link for Nostr login on the Devise login page. I included the following JavaScript code to handle the Nostr login process: ```javascript document.addEventListener("turbo:load", function () { if (isNostrAvailable() && !document.getElementById('nostr-signup')) { createNostrSignupButton(); } }); // Function to check if Nostr is available function isNostrAvailable() { return window.nostr && typeof window.nostr.getPublicKey === 'function'; } // Function to create and append the Nostr signup button function createNostrSignupButton() { event.preventDefault(); const button = document.createElement('button'); button.id = "nostr-signup"; button.onclick = function(event) { event.preventDefault(); nostrSignupHandler(); }; button.type = "submit"; button.textContent = "<%= t('nostr.with_extension') %>"; const actionsDiv = document.querySelector('.actions'); if (actionsDiv) { actionsDiv.appendChild(button); } } async function nostrSignupHandler() { try { const publicKey = await window.nostr.getPublicKey(); if (!publicKey) { alert("Sign-up failed. No public key."); } token = document.querySelector('meta[name="csrf-token"]').getAttribute("content"); const event = { "created_at": Math.floor(Date.now() / 1000), "content": "", "tags": [ [ "relay", "<%= ENV['NOSTR_AUTH_RELAY_URL'] || 'wss://relay.primal.net' %>" ], [ "challenge", token ] ], "kind": 22242, "pubkey": publicKey }; // Sign the event const signedEvent = await window.nostr.signEvent(event); if (!signedEvent) { alert("Sign-up failed. Event not signed."); } const response = await fetch("/nostr_signup", { method: "POST", headers: { "Content-Type": "application/json", "X-CSRF-Token": token, }, body: JSON.stringify({ "signed_event": signedEvent }), }); ... ``` ## Conclusion By following these steps, I successfully integrated Nostr login functionality into my Rails application using the Nos2x extension. This not only enhances the user experience by providing a decentralized login option but also aligns with modern authentication practices. Feel free to reach out if you have any questions or need further assistance with implementing Nostr login in your own applications! If you want to see it in action, go ahead to [Medical Dictionary - Login Page](https://medical.inarchives.com/users/sign_in) for example. You will need to be on a desktop browser with a Nostr Extension installed. Happy coding!
@ 63e047aa:2e1ae74f
2025-02-02 09:00:46In this blog post, I will walk you through the process of integrating Nostr login functionality into my Rails application using the Nos2x extension. This involved modifying the Devise User model, adding a new route to handle Nostr users, and integrating JavaScript to enhance the login experience. ## Overview Nostr is a decentralized protocol that allows users to authenticate without relying on traditional email/password combinations. By leveraging the Nos2x extension, I was able to implement Nostr login seamlessly. Here’s how I did it. ## Step 1: Adding Asynchronous Nostr client in Ruby ```bash bundle add nostr ``` ## Step 2: Modifying the Devise User Model The first step was to modify the Devise User model to allow empty email validation. This is crucial because Nostr users may not have an email address. I updated the `User` model as follows: ```ruby class User < ApplicationRecord # Include default devise modules. Others available are: # :confirmable, :lockable, :timeoutable, :trackable, :registerable and :omniauthable devise :database_authenticatable, :registerable, :recoverable, :rememberable # Removed :validatable # Validations validates :nostr_public_key, presence: true, uniqueness: true, allow_blank: true validates :email, uniqueness: true, allow_blank: true # Make email optional validates :password, length: { minimum: 6 }, allow_blank: true # Make password optional but enforce length if provided # Conditional validation for email and password validates :email, presence: true, unless: :nostr_public_key_present? validates :password, presence: true, unless: :nostr_public_key_present? private def nostr_public_key_present? nostr_public_key.present? end end ``` By adding this validation, I ensured that users logging in via Nostr would not be required to provide an email address. ## Step 3: Adding a New Route for Nostr Users Next, I needed to create a new route to handle the login process for Nostr users. I added the following route to my `config/routes.rb` file: ```ruby Rails.application.routes.draw do # Other existing routes... post 'users/nostr_login', to: 'users#nostr_login', as: 'nostr_login' end ``` This route points to a new action in the `UsersController` that will manage the authentication process for Nostr users. ## Step 4: Implementing the Nostr Login Action In the `UsersController`, I implemented the `nostr_signup` action to handle the login logic: ```ruby # app/controllers/users_controller.rb class UsersController < ApplicationController # Custom error handling for CSRF token verification failure rescue_from ActionController::InvalidAuthenticityToken do |exception| render json: { error: "Can't verify CSRF token authenticity." }, status: :unprocessable_entity end def nostr_signup nostr_signed_event = params[:signed_event] if not nostr_signed_event render json: { success: false, error: "No signed event provided." }, status: :unprocessable_entity return end public_key = nostr_signed_event[:pubkey] content = nostr_signed_event[:content] kind = nostr_signed_event[:kind] csrf_token = request.headers['X-CSRF-Token'] tags_hash = tags.to_h challenge_value = tags_hash["challenge"] relay_value = tags_hash["relay"] expected_relay_value = ENV.fetch('NOSTR_AUTH_RELAY_URL', 'wss://relay.primal.net') # Check if the challenge_value and relay_value are matching or if kind is valid if challenge_value != csrf_token || kind != 22242 || relay_value != expected_relay_value return render json: { success: false, error: "Invalid event provided." }, status: :unprocessable_entity end nostr_event = Nostr::Event.new( content: content, id: nostr_signed_event[:id], created_at: nostr_signed_event[:created_at], kind: kind, pubkey: public_key, sig: nostr_signed_event[:sig], tags: nostr_signed_event[:tags] ) # Validate the event's signature unless nostr_event.verify_signature render json: { success: false, error: "Invalid event signature." }, status: :unprocessable_entity return end user = User.find_or_initialize_by(nostr_public_key: public_key) ... end private def nostr_signup_params params.permit(signed_event: [:id, :kind, :content, :tags, :created_at, :pubkey, :sig]) end end ``` This action will handle the authentication process and create a new user if they do not already exist. ## Step 5: Integrating JavaScript for Nostr Login To enhance the user experience, I added a link for Nostr login on the Devise login page. I included the following JavaScript code to handle the Nostr login process: ```javascript document.addEventListener("turbo:load", function () { if (isNostrAvailable() && !document.getElementById('nostr-signup')) { createNostrSignupButton(); } }); // Function to check if Nostr is available function isNostrAvailable() { return window.nostr && typeof window.nostr.getPublicKey === 'function'; } // Function to create and append the Nostr signup button function createNostrSignupButton() { event.preventDefault(); const button = document.createElement('button'); button.id = "nostr-signup"; button.onclick = function(event) { event.preventDefault(); nostrSignupHandler(); }; button.type = "submit"; button.textContent = "<%= t('nostr.with_extension') %>"; const actionsDiv = document.querySelector('.actions'); if (actionsDiv) { actionsDiv.appendChild(button); } } async function nostrSignupHandler() { try { const publicKey = await window.nostr.getPublicKey(); if (!publicKey) { alert("Sign-up failed. No public key."); } token = document.querySelector('meta[name="csrf-token"]').getAttribute("content"); const event = { "created_at": Math.floor(Date.now() / 1000), "content": "", "tags": [ [ "relay", "<%= ENV['NOSTR_AUTH_RELAY_URL'] || 'wss://relay.primal.net' %>" ], [ "challenge", token ] ], "kind": 22242, "pubkey": publicKey }; // Sign the event const signedEvent = await window.nostr.signEvent(event); if (!signedEvent) { alert("Sign-up failed. Event not signed."); } const response = await fetch("/nostr_signup", { method: "POST", headers: { "Content-Type": "application/json", "X-CSRF-Token": token, }, body: JSON.stringify({ "signed_event": signedEvent }), }); ... ``` ## Conclusion By following these steps, I successfully integrated Nostr login functionality into my Rails application using the Nos2x extension. This not only enhances the user experience by providing a decentralized login option but also aligns with modern authentication practices. Feel free to reach out if you have any questions or need further assistance with implementing Nostr login in your own applications! If you want to see it in action, go ahead to [Medical Dictionary - Login Page](https://medical.inarchives.com/users/sign_in) for example. You will need to be on a desktop browser with a Nostr Extension installed. Happy coding! @ da0b9bc3:4e30a4a9
2025-02-02 08:18:39Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/873174
@ da0b9bc3:4e30a4a9
2025-02-02 08:18:39Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/873174 @ 63e047aa:2e1ae74f
2025-02-02 08:12:53**We have not lived the longest period of peace in history yet, but we will live the longest period of peace in history!** In a world often defined by conflict, power struggles, and competition for resources, we are constantly searching for ways to build a more peaceful and just society. While most people look at Bitcoin as a financial asset or a tool for decentralizing wealth, I believe its potential reaches far beyond economics. Bitcoin might offer humanity something even greater—a new foundation for **peace**. ## Moving Beyond Conflict: A New Kind of Power Throughout history, wars have been fought over control—control of land, resources, economies, and the power to enforce rules. In contrast, Bitcoin's decentralized structure removes the need for such centralized control. No single entity governs Bitcoin, and no one can wield unchecked power over the system. The proof-of-work mechanism ensures security and fairness without the need for violence, coercion, or centralized oversight. As **Jason Lowery** suggests in his work on Bitcoin as a form of power projection, Bitcoin can be seen as a new kind of digital deterrent, one that allows nations to secure their interests without the need for traditional force or military conflict. This shift in power could give rise to a new form of diplomacy, one built on transparency, equal access, and mutual trust. In a world where no single nation or group can manipulate the economic system, we reduce the incentives for conflict. ## Bitcoin as a Tool for Transparency and Trust At its core, Bitcoin is a trustless system—no one needs to trust a central authority to ensure fairness. Instead, cryptography and mathematics guarantee the security of the network. This system of transparency could extend far beyond finance, offering a new way for people, governments, and organizations to interact without fear of manipulation or corruption. By removing the need for intermediaries, Bitcoin could pave the way for global cooperation, where each party can act with confidence in a system that cannot be easily undermined. It creates a level playing field, not just economically but also in terms of information sharing and governance. ## Beyond National Defense: A Vision for Peace Jason Lowery’s exploration of Bitcoin as a strategic defense tool highlights the ways it can serve as a power projection system for nations, offering a new form of security and sovereignty. But I believe this is just the beginning. What if Bitcoin could give nations and individuals a means to engage peacefully? By empowering people to own their wealth and secure their assets without relying on central banks or governments, Bitcoin could weaken the structures that fuel geopolitical conflicts. When control is decentralized, and power is more evenly distributed, we may find fewer reasons to engage in war. ## A New Way Forward Imagine a world where peace is not dictated by the threat of force or control over resources but by the mutual benefit of a decentralized system that serves everyone equally. Bitcoin, in this light, becomes more than a financial innovation—it becomes a blueprint for how we might move toward a more peaceful and just world. Satoshi Nakamoto may not have intended Bitcoin to be a pathway to peace, but the potential is there. As Jason Lowery highlights, Bitcoin's decentralized nature could evolve into a critical part of how nations secure their futures in the digital age. What if we embraced it, not just as a store of value but as a new foundation for how we build trust, security, and cooperation? I believe that Bitcoin represents more than just financial freedom—it offers us a chance to rethink the systems that have governed our world for centuries. It gives us the opportunity to engage with each other in a way that fosters peace, not conflict. Most importantly, nations would not need to fight over who holds the most Bitcoin—because in a truly decentralized and transparent system, it is not about accumulating more. It simply needs to be adopted, and by doing so, the value it creates can be shared equally, reinforcing the principles of cooperation and global harmony. Redefining peace through decentralized, secure systems like Bitcoin might just be one of the most significant shifts in human history.
@ 63e047aa:2e1ae74f
2025-02-02 08:12:53**We have not lived the longest period of peace in history yet, but we will live the longest period of peace in history!** In a world often defined by conflict, power struggles, and competition for resources, we are constantly searching for ways to build a more peaceful and just society. While most people look at Bitcoin as a financial asset or a tool for decentralizing wealth, I believe its potential reaches far beyond economics. Bitcoin might offer humanity something even greater—a new foundation for **peace**. ## Moving Beyond Conflict: A New Kind of Power Throughout history, wars have been fought over control—control of land, resources, economies, and the power to enforce rules. In contrast, Bitcoin's decentralized structure removes the need for such centralized control. No single entity governs Bitcoin, and no one can wield unchecked power over the system. The proof-of-work mechanism ensures security and fairness without the need for violence, coercion, or centralized oversight. As **Jason Lowery** suggests in his work on Bitcoin as a form of power projection, Bitcoin can be seen as a new kind of digital deterrent, one that allows nations to secure their interests without the need for traditional force or military conflict. This shift in power could give rise to a new form of diplomacy, one built on transparency, equal access, and mutual trust. In a world where no single nation or group can manipulate the economic system, we reduce the incentives for conflict. ## Bitcoin as a Tool for Transparency and Trust At its core, Bitcoin is a trustless system—no one needs to trust a central authority to ensure fairness. Instead, cryptography and mathematics guarantee the security of the network. This system of transparency could extend far beyond finance, offering a new way for people, governments, and organizations to interact without fear of manipulation or corruption. By removing the need for intermediaries, Bitcoin could pave the way for global cooperation, where each party can act with confidence in a system that cannot be easily undermined. It creates a level playing field, not just economically but also in terms of information sharing and governance. ## Beyond National Defense: A Vision for Peace Jason Lowery’s exploration of Bitcoin as a strategic defense tool highlights the ways it can serve as a power projection system for nations, offering a new form of security and sovereignty. But I believe this is just the beginning. What if Bitcoin could give nations and individuals a means to engage peacefully? By empowering people to own their wealth and secure their assets without relying on central banks or governments, Bitcoin could weaken the structures that fuel geopolitical conflicts. When control is decentralized, and power is more evenly distributed, we may find fewer reasons to engage in war. ## A New Way Forward Imagine a world where peace is not dictated by the threat of force or control over resources but by the mutual benefit of a decentralized system that serves everyone equally. Bitcoin, in this light, becomes more than a financial innovation—it becomes a blueprint for how we might move toward a more peaceful and just world. Satoshi Nakamoto may not have intended Bitcoin to be a pathway to peace, but the potential is there. As Jason Lowery highlights, Bitcoin's decentralized nature could evolve into a critical part of how nations secure their futures in the digital age. What if we embraced it, not just as a store of value but as a new foundation for how we build trust, security, and cooperation? I believe that Bitcoin represents more than just financial freedom—it offers us a chance to rethink the systems that have governed our world for centuries. It gives us the opportunity to engage with each other in a way that fosters peace, not conflict. Most importantly, nations would not need to fight over who holds the most Bitcoin—because in a truly decentralized and transparent system, it is not about accumulating more. It simply needs to be adopted, and by doing so, the value it creates can be shared equally, reinforcing the principles of cooperation and global harmony. Redefining peace through decentralized, secure systems like Bitcoin might just be one of the most significant shifts in human history. @ 57d1a264:69f1fee1
2025-02-02 05:47:57Hey there, as a result of the recent [SN Media Kit](https://stacker.news/items/872925/r/Design_r) updated, I'll try to create few simple marketing assets for ~Stackers_Stocks territory to be spread across the web. Feel free to share in the comments below: - Few visual references you'd like the assets to be inspired on - If visuals are not your thing, a description of your idea will help too - A slogan, or some words/concepts that express the territory's values @BlokchainB you start, let's see how we go! originally posted at https://stacker.news/items/873112
@ 57d1a264:69f1fee1
2025-02-02 05:47:57Hey there, as a result of the recent [SN Media Kit](https://stacker.news/items/872925/r/Design_r) updated, I'll try to create few simple marketing assets for ~Stackers_Stocks territory to be spread across the web. Feel free to share in the comments below: - Few visual references you'd like the assets to be inspired on - If visuals are not your thing, a description of your idea will help too - A slogan, or some words/concepts that express the territory's values @BlokchainB you start, let's see how we go! originally posted at https://stacker.news/items/873112 @ 57d1a264:69f1fee1
2025-02-02 05:36:57Hey there, as a result of the recent [SN Media Kit](https://stacker.news/items/872925/r/Design_r) updated, I'll try to create few simple marketing assets for ~Construction_and_Engineering territory to be spread across the web. Feel free to share in the comments below: - Few visual references you'd like the assets to be inspired on - If visuals are not your thing, a description of your idea will help too - A slogan, or some words/concepts that express the territory's values @BlokchainB you start, let's see how we go! originally posted at https://stacker.news/items/873104
@ 57d1a264:69f1fee1
2025-02-02 05:36:57Hey there, as a result of the recent [SN Media Kit](https://stacker.news/items/872925/r/Design_r) updated, I'll try to create few simple marketing assets for ~Construction_and_Engineering territory to be spread across the web. Feel free to share in the comments below: - Few visual references you'd like the assets to be inspired on - If visuals are not your thing, a description of your idea will help too - A slogan, or some words/concepts that express the territory's values @BlokchainB you start, let's see how we go! originally posted at https://stacker.news/items/873104 @ 3b7fc823:e194354f
2025-02-02 03:16:40**Why Privacy Matters and How to Protect It** Privacy is about control. It’s not about hiding yourself but deciding what others can see about you. Just as you don’t share everything when buying a magazine, technology shouldn’t force you to reveal more than needed. Why Privacy is Important 1. Personal Control: Privacy lets you choose what parts of your life are visible. You shouldn’t have to share everything just to use a service. 2. Security Against Exploitation: Without privacy, people and groups can be targeted by companies or governments. This abuse can lead to data breaches or unnecessary surveillance. 3. Building Trust: Privacy is key to trust in relationships and communities. When your info is safe, you can transact and communicate without fear of misuse. **How to Protect Your Privacy** 1. Think Before You Share: Only share what’s necessary and know why you’re doing it. 2. Use Encryption: Encrypt sensitive communications like emails or messages. 3. Control Data Sharing: Avoid oversharing personal details online. 4. Enable Privacy Tools: Use VPNs or privacy settings on social media to shield your data. 5. Be Mindful of Metadata: Understand that metadata (like location data) can reveal more about you than the content itself. 6. Support Privacy-Focused Brands: Choose services that prioritize privacy, like encrypted messaging apps. 7. Read Privacy Policies: Know what data you’re sharing and with whom. 8. Tools like privacy.io can help visualize your digital footprint. 9. Block Trackers: Use tools like DoNotTrackMe or uBlock Origin to stop trackers from collecting your data. **Conclusion** Protecting privacy is a vital step in safeguarding your personal freedoms. By taking proactive measures, you can control what information is accessible and ensure that your rights are respected. Remember, you are your own best advocate for privacy—trust no one but yourself to protect your data and identity. Join the movement to champion privacy as a fundamental human right. Advocate for stronger laws and encourage others to take action, so we can all enjoy safer, more secure digital environments.
@ 3b7fc823:e194354f
2025-02-02 03:16:40**Why Privacy Matters and How to Protect It** Privacy is about control. It’s not about hiding yourself but deciding what others can see about you. Just as you don’t share everything when buying a magazine, technology shouldn’t force you to reveal more than needed. Why Privacy is Important 1. Personal Control: Privacy lets you choose what parts of your life are visible. You shouldn’t have to share everything just to use a service. 2. Security Against Exploitation: Without privacy, people and groups can be targeted by companies or governments. This abuse can lead to data breaches or unnecessary surveillance. 3. Building Trust: Privacy is key to trust in relationships and communities. When your info is safe, you can transact and communicate without fear of misuse. **How to Protect Your Privacy** 1. Think Before You Share: Only share what’s necessary and know why you’re doing it. 2. Use Encryption: Encrypt sensitive communications like emails or messages. 3. Control Data Sharing: Avoid oversharing personal details online. 4. Enable Privacy Tools: Use VPNs or privacy settings on social media to shield your data. 5. Be Mindful of Metadata: Understand that metadata (like location data) can reveal more about you than the content itself. 6. Support Privacy-Focused Brands: Choose services that prioritize privacy, like encrypted messaging apps. 7. Read Privacy Policies: Know what data you’re sharing and with whom. 8. Tools like privacy.io can help visualize your digital footprint. 9. Block Trackers: Use tools like DoNotTrackMe or uBlock Origin to stop trackers from collecting your data. **Conclusion** Protecting privacy is a vital step in safeguarding your personal freedoms. By taking proactive measures, you can control what information is accessible and ensure that your rights are respected. Remember, you are your own best advocate for privacy—trust no one but yourself to protect your data and identity. Join the movement to champion privacy as a fundamental human right. Advocate for stronger laws and encourage others to take action, so we can all enjoy safer, more secure digital environments. @ 57d1a264:69f1fee1
2025-02-02 00:03:39 Welcome to the latest updated version of **Stacker News Media Kit & Brand Guidelines `v1.2`**, a pivotal location where all the visual elements find place and help us understand how to use them to have our communications cohesive. SN brand identity is built on simplicity, trust, innovation and a taste of Texas's Wild West. With the following guidelines, as [promised](https://stacker.news/items/855556/r/Design_r?commentId=855753), I'll try to outline the essential elements of SN visual language to be easily usable internally and externally. As third interaction from the previous [discussion](https://stacker.news/items/786223), here below you will find all the media assets in PNG and SVG downloadable from this [zip file](https://nosto.re/0a8b02224c970de78fba3a0195dcf1ee44d18925ba941724497173b2bcbab901.zip). BTW: I've been using **`Nostr`** 🌸 **Blossom Serverservers** [check them out](https://blossomservers.com/), it's a really cool idea! In case the file will be not available we can always upload it in other servers. Just let me know if any issue downloading it, ideally I made three copies available from: - https://nosto.re/0a8b02224c970de78fba3a0195dcf1ee44d18925ba941724497173b2bcbab901.zip - https://blossom.poster.place/0a8b02224c970de78fba3a0195dcf1ee44d18925ba941724497173b2bcbab901.zip - https://nostr.download/0a8b02224c970de78fba3a0195dcf1ee44d18925ba941724497173b2bcbab901.zip The source file of all these assets still are the same [Figma file](https://www.figma.com/design/ZL3FLItd9j48pzKVi4qlOy/Stacker.News-Media-Kit?node-id=3-16&t=oEbUcC1tmLDRXgdH-0) and the [PenPot file](https://design.penpot.app/#/workspace/7ad540b5-8190-815d-8005-5685b9c670bc/7ad540b5-8190-815d-8005-5685c186216e?page-id=2643bc5a-0d34-80b2-8005-58099eabda41). This last one, has many issues and does not allow yet the same flexibility as Figma. Both files are open for contributions and comments, just need to register a dummy/anonymous account for each of the tools. > **Note:** To use these assets across SN, just copy-paste the image relative code, i.e.:  # Stacker News Logotype SN logo is the most recognizable visual identifier of Stacker News. It captures the essence of its brand and is to be used across the platform and other marketing materials **consistently**. Find below all the possible variations and colors. Ideally you should stick with it to maintain SN identity coherent, or propose something new if you feel like. If you have any question on how to place or use the logo, DO ask below, and we'll help sort it out. | Avatar on transparent BG | Avatar on BG | Logo Extended | Logo Vertical |#| |---|---|---|---|---| |  `` |  `` |  ``|  `` |Oil Black| |  `` |  `` |  `` |  ``| Golden Yellow | |  `` |  `` |  `` |  ``|With Shadow | # Stacker News Typography  This is the typography SN had used to create its logo. [Download LightningVolt OpenType Font file.otf](http://honeyanddeath.web.fc2.com/FontFile/honeyanddeath_Lightningvolt.zip) designed by **[Honey&Death](http://honeyanddeath.web.fc2.com/fnt_Lightningvolt.html)**, install it in your computer and play with it. Typography is essential to identify, increase readability and create consistency of brands. SN uses the default `font-family:sans-serif;` of your device's OS, usually are the most common and already installed in your device: `system-ui, "Segoe UI", Roboto, "Helvetica Neue", "Noto Sans", "Liberation Sans", Arial, sans-serif, "Apple Color Emoji", "Segoe UI Emoji", "Segoe UI Symbol", "Noto Color Emoji"`. Those are mostly used for: # Example Header H1 ## Example Header H2 ### Example Header H3 #### Example Header H4 ##### Example Header H5 **Example paragraph text** The fonts selected will help to communicate the personality of the brand and provide maximum legibility for both print and screen. `Example <code>` For code, the approach is the same. Let's the device OS select its default `monospace` one. For example, on Mac will be one of the following: ``` SFMono-Regular, Menlo, Monaco, Consolas, "Liberation Mono", "Courier New",` ``` # Stacker News Colors A thoughtfully curated color palette gives SN trust, professionalism, and approachability. Colors play a key role in creating consistent visual experiences through digital and print communications. Make sure you are using the right color codes below: | # | Name | HEX code | RGB code | HLS | |---|---|---|---|---| |  | Bitcoin-only | `#F6911D` | `rgb(246,145,29)` | `hsl(32,92.3%,53.9%)` | |  | Blackr | `#000000` | `rgb(0,0,0)` | `hsl(0,0%,0%)` | |  | Dark | `#121214` | `rgb(18,18,20)` | `hsl(240,5.3%,7.5%)` | |  | Gold | `#FADA5E` | `rgb(250,218,94)` | `hsl(48,94%,67.5%)` | |  | Gray | `#969696` | `rgb(150,150,150)` | `hsl(0,0%,58.8%)` | |  | Light | `#F0F0F0` | `rgb(240,240,240)` | `hsl(0,0%,94.1%)` | |  | Nostrch | `#8C25F4` | `rgb(140,37,244)` | `hsl(270,90.4%,55.1%)` | |  | Pinkish | `#E685B5` | `rgb(230,133,181)` | `hsl(330,66%,71.2%)` | |  | Ruby | `#C03221` | `rgb(192,50,33)` | `hsl(6,70.7%,44.1%)` | |  | Sky Hover | `#007CBE` | `rgb(0,124,190)` | `hsl(201,100%,37.3%)` | |  | Sky Links | `#2E99D1` | `rgb(46,153,209)` | `hsl(201,63.9%,50%)` | |  | Sky Visited | `#56798E` | `rgb(86,121,142)` | `hsl(203,24.6%,44.7%)` | |  | So Fiat | `#5C8001` | `rgb(92,128,1)` | `hsl(77,98.4%,25.3%)` | # Stacker News Icons SN utilizes a set of bespoke icons that support its communication internally across the platform. Icons help bring instant, intuitive cues for various types of content and features. We share them here for you so you can use as you wish and satisfy your creative needs. |  `` |  `` |  `[Bounty](https://m.stacker.news/75607)` |  `[Caret](https://m.stacker.news/75608)` |  `[Cowboy](https://m.stacker.news/75609)` |  `[Sun](https://m.stacker.news/75610)` | |---|---|---|---|---|---| |  **`[Edit](https://m.stacker.news/75611)`** |  **`[Gun](https://m.stacker.news/75612)`** |  **`[Horse](https://m.stacker.news/75613)`** |  **`[Info](https://m.stacker.news/75614)`** |  **`[Moon](https://m.stacker.news/75615)`** |  **`[Lightning](https://m.stacker.news/75616)`**| |  **`[Bald Lost Hat](https://m.stacker.news/75617)`**|  **`[Markdown](https://m.stacker.news/75618)`**|  **`[Nostr](https://m.stacker.news/75619)`**|  **`[Referral](https://m.stacker.news/75620)`**|  **`[Rewards](https://m.stacker.news/75621)`**|  **`[Horse Lost Saddle](https://m.stacker.news/75622)`**|  **`[Search](https://m.stacker.news/75623)`** | | **`[Shoot](https://m.stacker.news/75624)`** | **`[Texas](https://m.stacker.news/75625)`** |  **`[Upload](https://m.stacker.news/75626)`** |  **`[Zap Zap](https://m.stacker.news/75627)`** ||| # Stacker News Banners Banners are important visual elements used in our digital platforms and marketing materials. They help to highlight key stories, features or announcements while maintaining our brand aesthetic. Here below you'll find custom banners for Sn and for individial territories. I try to build those that I follow most, for now @AGORA is the only one that designed its own banners. Comment below if you'd like some banners for your territory! #### SN Dark background |970x250| |---| | ```|``|``| |728x90| |---| |  `` | #### SN Gold background |970x250| |---| |`` | |250x250|300x250|300x600| |---|---|---| |`` | `` |`` | |728x90| |---| |`` | #### SN by @Jon_Hodl |970x250| |---| | `` | |250x250|300x250|300x600| |---|---|---| | `` |  ``| `` | |728x90| |---| |`` | #### ~AGORA territory The SN P2P Marketplace |970x250| |---| | `` | |250x250|300x250|300x600| |---|---|---| | `` | ``|``| |728x90| |---| | ``| #### ~alter_native territory |970x250| |---| | ``| |250x250|300x250|300x600| |---|---|---| |``|``|``| |728x90| |---| |`` | #### ~bitcoin_beginners |970x250| |---| | `` | |250x250|300x250|300x600| |---|---|---| | ``|``|`` | |728x90| |---| | ``| #### ~Design territory |970x250| |---| |``| |250x250|300x250|300x600| |---|---|---| |``|``|``| |728x90| |---| |``| #### ~Music territory |970x250| |---| | ``| |250x250|300x250|300x600| |---|---|---| |``|``|``| |728x90| |---| | ``| # Anything else we could add? If you feel something is missing, or you know a better tool to manage this media kit for SN in a collaborative and FOSS way then, DO share it in a comment below Territory owners [^1], do you need banners for your territory? Feel free to edit the figma file liked above or comment below sharing your needs or ideas, I'll try to do something for you. By following these guidelines, we ensure consistency and professionalism in every case where Stacker News is represented here internally to stackers or to our audience in the KYC internet, reinforcing SN credibility as a trusted source for data-driven journalism. [^1]: FYI: @Aardvark @AGORA @anna @antic @AtlantisPleb @Bell_curve @benwehrman @bitcoinplebdev @Bitter @BlokchainB @ch0k1 @davidw @ek @elvismercury @frostdragon @grayruby @HODLR @inverselarp @Jon_Hodl @k00b @marks @MaxAWebster @mega_dreamer @niftynei @nout @OneOneSeven @OT @PlebLab @Public_N_M_E @RDClark @realBitcoinDog @roytheholographicuniverse @siggy47 @softsimon @south_korea_ln @theschoolofbitcoin @TNStacker @UCantDoThatDotNet @Undisciplined originally posted at https://stacker.news/items/872925
@ 57d1a264:69f1fee1
2025-02-02 00:03:39 Welcome to the latest updated version of **Stacker News Media Kit & Brand Guidelines `v1.2`**, a pivotal location where all the visual elements find place and help us understand how to use them to have our communications cohesive. SN brand identity is built on simplicity, trust, innovation and a taste of Texas's Wild West. With the following guidelines, as [promised](https://stacker.news/items/855556/r/Design_r?commentId=855753), I'll try to outline the essential elements of SN visual language to be easily usable internally and externally. As third interaction from the previous [discussion](https://stacker.news/items/786223), here below you will find all the media assets in PNG and SVG downloadable from this [zip file](https://nosto.re/0a8b02224c970de78fba3a0195dcf1ee44d18925ba941724497173b2bcbab901.zip). BTW: I've been using **`Nostr`** 🌸 **Blossom Serverservers** [check them out](https://blossomservers.com/), it's a really cool idea! In case the file will be not available we can always upload it in other servers. Just let me know if any issue downloading it, ideally I made three copies available from: - https://nosto.re/0a8b02224c970de78fba3a0195dcf1ee44d18925ba941724497173b2bcbab901.zip - https://blossom.poster.place/0a8b02224c970de78fba3a0195dcf1ee44d18925ba941724497173b2bcbab901.zip - https://nostr.download/0a8b02224c970de78fba3a0195dcf1ee44d18925ba941724497173b2bcbab901.zip The source file of all these assets still are the same [Figma file](https://www.figma.com/design/ZL3FLItd9j48pzKVi4qlOy/Stacker.News-Media-Kit?node-id=3-16&t=oEbUcC1tmLDRXgdH-0) and the [PenPot file](https://design.penpot.app/#/workspace/7ad540b5-8190-815d-8005-5685b9c670bc/7ad540b5-8190-815d-8005-5685c186216e?page-id=2643bc5a-0d34-80b2-8005-58099eabda41). This last one, has many issues and does not allow yet the same flexibility as Figma. Both files are open for contributions and comments, just need to register a dummy/anonymous account for each of the tools. > **Note:** To use these assets across SN, just copy-paste the image relative code, i.e.:  # Stacker News Logotype SN logo is the most recognizable visual identifier of Stacker News. It captures the essence of its brand and is to be used across the platform and other marketing materials **consistently**. Find below all the possible variations and colors. Ideally you should stick with it to maintain SN identity coherent, or propose something new if you feel like. If you have any question on how to place or use the logo, DO ask below, and we'll help sort it out. | Avatar on transparent BG | Avatar on BG | Logo Extended | Logo Vertical |#| |---|---|---|---|---| |  `` |  `` |  ``|  `` |Oil Black| |  `` |  `` |  `` |  ``| Golden Yellow | |  `` |  `` |  `` |  ``|With Shadow | # Stacker News Typography  This is the typography SN had used to create its logo. [Download LightningVolt OpenType Font file.otf](http://honeyanddeath.web.fc2.com/FontFile/honeyanddeath_Lightningvolt.zip) designed by **[Honey&Death](http://honeyanddeath.web.fc2.com/fnt_Lightningvolt.html)**, install it in your computer and play with it. Typography is essential to identify, increase readability and create consistency of brands. SN uses the default `font-family:sans-serif;` of your device's OS, usually are the most common and already installed in your device: `system-ui, "Segoe UI", Roboto, "Helvetica Neue", "Noto Sans", "Liberation Sans", Arial, sans-serif, "Apple Color Emoji", "Segoe UI Emoji", "Segoe UI Symbol", "Noto Color Emoji"`. Those are mostly used for: # Example Header H1 ## Example Header H2 ### Example Header H3 #### Example Header H4 ##### Example Header H5 **Example paragraph text** The fonts selected will help to communicate the personality of the brand and provide maximum legibility for both print and screen. `Example <code>` For code, the approach is the same. Let's the device OS select its default `monospace` one. For example, on Mac will be one of the following: ``` SFMono-Regular, Menlo, Monaco, Consolas, "Liberation Mono", "Courier New",` ``` # Stacker News Colors A thoughtfully curated color palette gives SN trust, professionalism, and approachability. Colors play a key role in creating consistent visual experiences through digital and print communications. Make sure you are using the right color codes below: | # | Name | HEX code | RGB code | HLS | |---|---|---|---|---| |  | Bitcoin-only | `#F6911D` | `rgb(246,145,29)` | `hsl(32,92.3%,53.9%)` | |  | Blackr | `#000000` | `rgb(0,0,0)` | `hsl(0,0%,0%)` | |  | Dark | `#121214` | `rgb(18,18,20)` | `hsl(240,5.3%,7.5%)` | |  | Gold | `#FADA5E` | `rgb(250,218,94)` | `hsl(48,94%,67.5%)` | |  | Gray | `#969696` | `rgb(150,150,150)` | `hsl(0,0%,58.8%)` | |  | Light | `#F0F0F0` | `rgb(240,240,240)` | `hsl(0,0%,94.1%)` | |  | Nostrch | `#8C25F4` | `rgb(140,37,244)` | `hsl(270,90.4%,55.1%)` | |  | Pinkish | `#E685B5` | `rgb(230,133,181)` | `hsl(330,66%,71.2%)` | |  | Ruby | `#C03221` | `rgb(192,50,33)` | `hsl(6,70.7%,44.1%)` | |  | Sky Hover | `#007CBE` | `rgb(0,124,190)` | `hsl(201,100%,37.3%)` | |  | Sky Links | `#2E99D1` | `rgb(46,153,209)` | `hsl(201,63.9%,50%)` | |  | Sky Visited | `#56798E` | `rgb(86,121,142)` | `hsl(203,24.6%,44.7%)` | |  | So Fiat | `#5C8001` | `rgb(92,128,1)` | `hsl(77,98.4%,25.3%)` | # Stacker News Icons SN utilizes a set of bespoke icons that support its communication internally across the platform. Icons help bring instant, intuitive cues for various types of content and features. We share them here for you so you can use as you wish and satisfy your creative needs. |  `` |  `` |  `[Bounty](https://m.stacker.news/75607)` |  `[Caret](https://m.stacker.news/75608)` |  `[Cowboy](https://m.stacker.news/75609)` |  `[Sun](https://m.stacker.news/75610)` | |---|---|---|---|---|---| |  **`[Edit](https://m.stacker.news/75611)`** |  **`[Gun](https://m.stacker.news/75612)`** |  **`[Horse](https://m.stacker.news/75613)`** |  **`[Info](https://m.stacker.news/75614)`** |  **`[Moon](https://m.stacker.news/75615)`** |  **`[Lightning](https://m.stacker.news/75616)`**| |  **`[Bald Lost Hat](https://m.stacker.news/75617)`**|  **`[Markdown](https://m.stacker.news/75618)`**|  **`[Nostr](https://m.stacker.news/75619)`**|  **`[Referral](https://m.stacker.news/75620)`**|  **`[Rewards](https://m.stacker.news/75621)`**|  **`[Horse Lost Saddle](https://m.stacker.news/75622)`**|  **`[Search](https://m.stacker.news/75623)`** | | **`[Shoot](https://m.stacker.news/75624)`** | **`[Texas](https://m.stacker.news/75625)`** |  **`[Upload](https://m.stacker.news/75626)`** |  **`[Zap Zap](https://m.stacker.news/75627)`** ||| # Stacker News Banners Banners are important visual elements used in our digital platforms and marketing materials. They help to highlight key stories, features or announcements while maintaining our brand aesthetic. Here below you'll find custom banners for Sn and for individial territories. I try to build those that I follow most, for now @AGORA is the only one that designed its own banners. Comment below if you'd like some banners for your territory! #### SN Dark background |970x250| |---| | ```|``|``| |728x90| |---| |  `` | #### SN Gold background |970x250| |---| |`` | |250x250|300x250|300x600| |---|---|---| |`` | `` |`` | |728x90| |---| |`` | #### SN by @Jon_Hodl |970x250| |---| | `` | |250x250|300x250|300x600| |---|---|---| | `` |  ``| `` | |728x90| |---| |`` | #### ~AGORA territory The SN P2P Marketplace |970x250| |---| | `` | |250x250|300x250|300x600| |---|---|---| | `` | ``|``| |728x90| |---| | ``| #### ~alter_native territory |970x250| |---| | ``| |250x250|300x250|300x600| |---|---|---| |``|``|``| |728x90| |---| |`` | #### ~bitcoin_beginners |970x250| |---| | `` | |250x250|300x250|300x600| |---|---|---| | ``|``|`` | |728x90| |---| | ``| #### ~Design territory |970x250| |---| |``| |250x250|300x250|300x600| |---|---|---| |``|``|``| |728x90| |---| |``| #### ~Music territory |970x250| |---| | ``| |250x250|300x250|300x600| |---|---|---| |``|``|``| |728x90| |---| | ``| # Anything else we could add? If you feel something is missing, or you know a better tool to manage this media kit for SN in a collaborative and FOSS way then, DO share it in a comment below Territory owners [^1], do you need banners for your territory? Feel free to edit the figma file liked above or comment below sharing your needs or ideas, I'll try to do something for you. By following these guidelines, we ensure consistency and professionalism in every case where Stacker News is represented here internally to stackers or to our audience in the KYC internet, reinforcing SN credibility as a trusted source for data-driven journalism. [^1]: FYI: @Aardvark @AGORA @anna @antic @AtlantisPleb @Bell_curve @benwehrman @bitcoinplebdev @Bitter @BlokchainB @ch0k1 @davidw @ek @elvismercury @frostdragon @grayruby @HODLR @inverselarp @Jon_Hodl @k00b @marks @MaxAWebster @mega_dreamer @niftynei @nout @OneOneSeven @OT @PlebLab @Public_N_M_E @RDClark @realBitcoinDog @roytheholographicuniverse @siggy47 @softsimon @south_korea_ln @theschoolofbitcoin @TNStacker @UCantDoThatDotNet @Undisciplined originally posted at https://stacker.news/items/872925 @ e0e92e54:d630dfaa
2025-02-01 22:32:51# When a Client Wants Out…& A Yellow Flag Appears This week was an interesting one with a client that wants to exit our agreement early. *(Totally fine. It happens and usually when one or both parties want to part ways, unless it's marriage, then it's at minimum a Yellow Flag if not a Red Flag that should be observed).* I tend to work with clients that have multiple irons in the fire, hence why they need someone like me to come along side them and provide guidance and help root them in the area they must focus on. There is a strong parallel with this irregardless of whether it's #business #life or #impact This client had big goals, but like many business owners, they defaulted to reactionary decisions instead of a structured plan. That’s when the Yellow Flag turned into a pattern I’ve seen before—Random Acts of X. # The Cost of Random Acts of X If your solution is: A. Throw money at it, and/or B. Fire, Aim, Ready...instead of Ready, Aim, Fire This WILL result in Random Acts of X (wherein X is whatever your are focused on, ie Marketing...aka Random Acts of Marketing essentially equates to the proverbial "throw spaghetti on the wall") *Is that really a thing? Like do Italians or some other cultures actually throw spaghetti on the wall to see if it "sticks"? Inquiring minds want to know! 🤷♂️* As I mentioned, my clients tend to have a lot of things they are trying to accomplish at once. This leads to fragmented efforts and lack luster results. That being said, I approach everything as a relationship. Afterall, I believe: ### Leadership = Relationships! With this particular client there was one project he abruptly ended. Again, that's fine...it's their business... Since I'm there to help them lead well, I reminded them this is a relationship and asked "What's next that you want me to focus on?" We got on the same page with the new project and not even 2 days later that's where the Yellow Flag appeared in the form of issue A (just throw money at it). # Shortcuts Lead to Ghost Towns (Buying Followers Won’t Work) You see, they wanted me to lead a marketing campaign to build relationships with people their company could sponsor. ***BUT*** they just wanted to "buy followers". When I noticed one of their social accounts has 28k followers and on average *only 14 impressions per post*... I asked "How's that working out for ya?" You see folks, **real relationships take time!** One cannot simply "throw money at it" and expect sound, sustainable results. ***If you’re buying an audience instead of building one, you won’t have a community—you'll have a ghost town.*** ## What Fake Engagement Looks Like in Business & Family Think of it this way... Imagine all you did in your family's relationships was throw money at it. You just "bought followers" in the form of taking this trip, buying that thing for them; and you totally avoided the time investment the relationship requires? Sure...you might have been physically there...but **were you present**? I run into this often with my son. He wants me to watch him play a video game. And during that time together what is he doing? He keeps looking over his shoulder to make sure I'm paying attention to HIM and not clandestinely on my phone. Same goes for his Basketball...he wants me there rebounding for him...not sitting in a chair idly watching. # Are You Present or Just Physically There? Business Owners and Leaders! Husbands, Wives, and Parents! People whom desire to have an impact! **The Process is the Shortcut!** Play silly games. Win silly prizes. Intentionally build relationships. Reap rewards forever. It's... That... Simple... Easy? Not really...especially for someone like me whom is just as keen to spend time in nature or chillaxing with a cup of coffee on the back porch, thinking (and wishing my garden was growing better LOL). But simple? Yes! **Create the process, execute the process, refine the process, and repeat.** # The Process is the Shortcut... *Your Next Step: Cut the Shortcuts. Build the Process.* So—where do you need to refine your process today? 💡 **What’s one way you can be more present in a relationship this week?** 💡 **What can you eliminate to move you closer to real impact—instead of just chasing more?** 🔹 Drop your answer below 👇 ----------- ***Jason Ansley** is the founder of **Above The Line Leader**, where he provides tailored leadership support and operational expertise to help business owners, entrepreneurs, and leaders thrive.* ***Want to strengthen your leadership and enhance operational excellence?** Connect with Jason at https://abovethelineleader.com/contact* *📌 This article first appeared on Nostr. You can also find more Business Leadership Articles and content at: 👉 https://abovethelineleader.com/business-leadership-articles* 
@ e0e92e54:d630dfaa
2025-02-01 22:32:51# When a Client Wants Out…& A Yellow Flag Appears This week was an interesting one with a client that wants to exit our agreement early. *(Totally fine. It happens and usually when one or both parties want to part ways, unless it's marriage, then it's at minimum a Yellow Flag if not a Red Flag that should be observed).* I tend to work with clients that have multiple irons in the fire, hence why they need someone like me to come along side them and provide guidance and help root them in the area they must focus on. There is a strong parallel with this irregardless of whether it's #business #life or #impact This client had big goals, but like many business owners, they defaulted to reactionary decisions instead of a structured plan. That’s when the Yellow Flag turned into a pattern I’ve seen before—Random Acts of X. # The Cost of Random Acts of X If your solution is: A. Throw money at it, and/or B. Fire, Aim, Ready...instead of Ready, Aim, Fire This WILL result in Random Acts of X (wherein X is whatever your are focused on, ie Marketing...aka Random Acts of Marketing essentially equates to the proverbial "throw spaghetti on the wall") *Is that really a thing? Like do Italians or some other cultures actually throw spaghetti on the wall to see if it "sticks"? Inquiring minds want to know! 🤷♂️* As I mentioned, my clients tend to have a lot of things they are trying to accomplish at once. This leads to fragmented efforts and lack luster results. That being said, I approach everything as a relationship. Afterall, I believe: ### Leadership = Relationships! With this particular client there was one project he abruptly ended. Again, that's fine...it's their business... Since I'm there to help them lead well, I reminded them this is a relationship and asked "What's next that you want me to focus on?" We got on the same page with the new project and not even 2 days later that's where the Yellow Flag appeared in the form of issue A (just throw money at it). # Shortcuts Lead to Ghost Towns (Buying Followers Won’t Work) You see, they wanted me to lead a marketing campaign to build relationships with people their company could sponsor. ***BUT*** they just wanted to "buy followers". When I noticed one of their social accounts has 28k followers and on average *only 14 impressions per post*... I asked "How's that working out for ya?" You see folks, **real relationships take time!** One cannot simply "throw money at it" and expect sound, sustainable results. ***If you’re buying an audience instead of building one, you won’t have a community—you'll have a ghost town.*** ## What Fake Engagement Looks Like in Business & Family Think of it this way... Imagine all you did in your family's relationships was throw money at it. You just "bought followers" in the form of taking this trip, buying that thing for them; and you totally avoided the time investment the relationship requires? Sure...you might have been physically there...but **were you present**? I run into this often with my son. He wants me to watch him play a video game. And during that time together what is he doing? He keeps looking over his shoulder to make sure I'm paying attention to HIM and not clandestinely on my phone. Same goes for his Basketball...he wants me there rebounding for him...not sitting in a chair idly watching. # Are You Present or Just Physically There? Business Owners and Leaders! Husbands, Wives, and Parents! People whom desire to have an impact! **The Process is the Shortcut!** Play silly games. Win silly prizes. Intentionally build relationships. Reap rewards forever. It's... That... Simple... Easy? Not really...especially for someone like me whom is just as keen to spend time in nature or chillaxing with a cup of coffee on the back porch, thinking (and wishing my garden was growing better LOL). But simple? Yes! **Create the process, execute the process, refine the process, and repeat.** # The Process is the Shortcut... *Your Next Step: Cut the Shortcuts. Build the Process.* So—where do you need to refine your process today? 💡 **What’s one way you can be more present in a relationship this week?** 💡 **What can you eliminate to move you closer to real impact—instead of just chasing more?** 🔹 Drop your answer below 👇 ----------- ***Jason Ansley** is the founder of **Above The Line Leader**, where he provides tailored leadership support and operational expertise to help business owners, entrepreneurs, and leaders thrive.* ***Want to strengthen your leadership and enhance operational excellence?** Connect with Jason at https://abovethelineleader.com/contact* *📌 This article first appeared on Nostr. You can also find more Business Leadership Articles and content at: 👉 https://abovethelineleader.com/business-leadership-articles*  @ 4d4fb5ff:1e821f47
2025-02-01 22:13:43**Snapshot of a 3D molecular structure.** In bacteria, the enzyme Peptidase E (PepE) is encoded by the gene PEPE. PEPEDASE is an atomic view of PepE enzyme’s spatial architecture based on publicly available scientific data, visually arranged to pay homage to Pepe the Frog. I made this piece in support of Matt Furie’s #SavePepe movement. <img src="https://i.nostr.build/Lead9.png">
@ 4d4fb5ff:1e821f47
2025-02-01 22:13:43**Snapshot of a 3D molecular structure.** In bacteria, the enzyme Peptidase E (PepE) is encoded by the gene PEPE. PEPEDASE is an atomic view of PepE enzyme’s spatial architecture based on publicly available scientific data, visually arranged to pay homage to Pepe the Frog. I made this piece in support of Matt Furie’s #SavePepe movement. <img src="https://i.nostr.build/Lead9.png"> @ dbb19ae0:c3f22d5a
2025-02-01 21:51:44List of Wordpress articles: - https://alashazam.wordpress.com/2024/07/01/python-nostr/ - https://alashazam.wordpress.com/2024/07/02/python-nostr-2/ - https://alashazam.wordpress.com/2024/07/03/python-nostr-second-program/ - https://alashazam.wordpress.com/2024/07/04/python-nostr-sdk/ - https://alashazam.wordpress.com/2024/07/04/python-nostr-third-program/ - https://alashazam.wordpress.com/2024/07/05/python-nostr-guessing-the-npub/ - https://alashazam.wordpress.com/2024/07/06/python-nostr_sdk-fetching-metadata/ - https://alashazam.wordpress.com/tag/python/ ----------- ```python #!/usr/bin/env python3 """ Fetches the joined date from a Nostr profile and calculates the days since account creation. Usage: python fetch_joined_date.py [npub] Arguments: npub : The public key of the user (in npub format). Requirements: - nostr_sdk library - Python 3.x Example: python fetch_joined_date.py npub1... """ import argparse import time import ssl import json import uuid import logging from datetime import datetime from nostr.event import EventKind from nostr.relay_manager import RelayManager from nostr.key import PublicKey from nostr.filter import Filter, Filters from nostr.message_type import ClientMessageType # Configure logging logging.basicConfig(level=logging.INFO, format="%(levelname)s: %(message)s") RELAY_URL = "wss://relay.damus.io" def fetch_metadata(npub): """Fetches metadata from a Nostr profile given an npub key.""" pub_key = PublicKey.from_npub(npub) filters = Filters([Filter(authors=[pub_key.hex()], kinds=[EventKind.SET_METADATA])]) subscription_id = uuid.uuid1().hex request = [ClientMessageType.REQUEST, subscription_id, *filters.to_json_array()] relay_manager = RelayManager() relay_manager.add_relay(RELAY_URL) relay_manager.add_subscription(subscription_id, filters) try: relay_manager.open_connections({"cert_reqs": ssl.CERT_NONE}) time.sleep(1) # Allow time for connection relay_manager.publish_message(json.dumps(request)) time.sleep(1) # Allow time for response while relay_manager.message_pool.has_events(): event_msg = relay_manager.message_pool.get_event() metadata = json.loads(event_msg.event.content) return metadata except Exception as e: logging.error(f"Error fetching metadata: {e}") finally: relay_manager.close_connections() return None def fetch_joined_date(npub): """Retrieves the joined date of a Nostr profile and calculates days since creation.""" metadata = fetch_metadata(npub) if not metadata or "created_at" not in metadata: logging.warning("Could not retrieve metadata or 'created_at' field is missing.") return try: created_at = int(metadata["created_at"]) created_date = datetime.utcfromtimestamp(created_at) days_since_creation = (datetime.utcnow() - created_date).days logging.info(f"Account created on: {created_date.strftime('%Y-%m-%d %H:%M:%S UTC')}") logging.info(f"Days since account creation: {days_since_creation}") except (ValueError, TypeError): logging.error("Invalid 'created_at' timestamp.") if __name__ == "__main__": parser = argparse.ArgumentParser(description="Fetch the joined date from a Nostr profile.") parser.add_argument("npub", type=str, help="The public key of the user (in npub format).") args = parser.parse_args() fetch_joined_date(args.npub) ```
@ dbb19ae0:c3f22d5a
2025-02-01 21:51:44List of Wordpress articles: - https://alashazam.wordpress.com/2024/07/01/python-nostr/ - https://alashazam.wordpress.com/2024/07/02/python-nostr-2/ - https://alashazam.wordpress.com/2024/07/03/python-nostr-second-program/ - https://alashazam.wordpress.com/2024/07/04/python-nostr-sdk/ - https://alashazam.wordpress.com/2024/07/04/python-nostr-third-program/ - https://alashazam.wordpress.com/2024/07/05/python-nostr-guessing-the-npub/ - https://alashazam.wordpress.com/2024/07/06/python-nostr_sdk-fetching-metadata/ - https://alashazam.wordpress.com/tag/python/ ----------- ```python #!/usr/bin/env python3 """ Fetches the joined date from a Nostr profile and calculates the days since account creation. Usage: python fetch_joined_date.py [npub] Arguments: npub : The public key of the user (in npub format). Requirements: - nostr_sdk library - Python 3.x Example: python fetch_joined_date.py npub1... """ import argparse import time import ssl import json import uuid import logging from datetime import datetime from nostr.event import EventKind from nostr.relay_manager import RelayManager from nostr.key import PublicKey from nostr.filter import Filter, Filters from nostr.message_type import ClientMessageType # Configure logging logging.basicConfig(level=logging.INFO, format="%(levelname)s: %(message)s") RELAY_URL = "wss://relay.damus.io" def fetch_metadata(npub): """Fetches metadata from a Nostr profile given an npub key.""" pub_key = PublicKey.from_npub(npub) filters = Filters([Filter(authors=[pub_key.hex()], kinds=[EventKind.SET_METADATA])]) subscription_id = uuid.uuid1().hex request = [ClientMessageType.REQUEST, subscription_id, *filters.to_json_array()] relay_manager = RelayManager() relay_manager.add_relay(RELAY_URL) relay_manager.add_subscription(subscription_id, filters) try: relay_manager.open_connections({"cert_reqs": ssl.CERT_NONE}) time.sleep(1) # Allow time for connection relay_manager.publish_message(json.dumps(request)) time.sleep(1) # Allow time for response while relay_manager.message_pool.has_events(): event_msg = relay_manager.message_pool.get_event() metadata = json.loads(event_msg.event.content) return metadata except Exception as e: logging.error(f"Error fetching metadata: {e}") finally: relay_manager.close_connections() return None def fetch_joined_date(npub): """Retrieves the joined date of a Nostr profile and calculates days since creation.""" metadata = fetch_metadata(npub) if not metadata or "created_at" not in metadata: logging.warning("Could not retrieve metadata or 'created_at' field is missing.") return try: created_at = int(metadata["created_at"]) created_date = datetime.utcfromtimestamp(created_at) days_since_creation = (datetime.utcnow() - created_date).days logging.info(f"Account created on: {created_date.strftime('%Y-%m-%d %H:%M:%S UTC')}") logging.info(f"Days since account creation: {days_since_creation}") except (ValueError, TypeError): logging.error("Invalid 'created_at' timestamp.") if __name__ == "__main__": parser = argparse.ArgumentParser(description="Fetch the joined date from a Nostr profile.") parser.add_argument("npub", type=str, help="The public key of the user (in npub format).") args = parser.parse_args() fetch_joined_date(args.npub) ``` @ 20e17dd0:2ae504d7
2025-02-01 21:14:41## 1. Hardware Selection It is important to select adequately the hardware that will be used to build your Node. The Node will be running 24h /7 days and will countain your lightning channels. It is important to use high quality hardware and spend the extra dollars for it. At the time of building my Node, there was a shortage of Raspberry Pi and I was looking for an optimal alternative. I have decided to go ahead and purchase a used Mac Mini (late 2012). It is recommended NOT to purchase a Mac Mini newer than 2012 (i.e 2014 and up) because Apple started to solder the RAM to the Logic Board after 2012. The Mac Mini Late 2012 is the last model that is fully customizable with SSD and RAM upgrades. Here is the list of hardware that will be used in this build: * 2 x 8G DDR3L Sodim 1600Mhz 1.35V * 1 x Mac Mini (Late 2012) 2.5Ghz * 1 x Samsung Evo 870 1Tb SSD ^ ^ Note: As discussed earlier, it is important to select hardware of quality. I had initially purchased a low cost 2Tb SSD but it failed while trying to download the Bitcoin blockchain. ##2. Hardware Upgrade To facilitate the upgrade of the hardware, you will need the proper tools to remove some T6 & T8 screws. Here are the steps to dismount the few components of the Mac Mini to upgrade the hardware: 1. Unplug the Mac Mini. 2. Turn it upside down with the black cover facing up. 3. Put your thumbs in the 2 grooves of the cover and turn the piece counterclockwise.  4. Remove the cover. 5. Remove 3 x T6 screws holding the fan.  6. Lift the fan and disconnect the connector by pulling gently straight up the wires. 7. Remove 1x T6 screw at the bottom of the shroud (black plastic piece on the left of the fan).  8. Remove the shroud by holding the top right part with your fingers and turning it clockwise.  9. Remove 4 x T8 screws of the grill WIFI cover.  10. The top of the grill is mounted under the Mac Mini case. Lift gently the bottom of the grill and pull towards yourself to remove the grill. 11. Move the grill aside, you do not have to disconnect the WIFI sensor, just be careful. ### 2.1 Upgrading the RAM The RAM is visible and accessible from the moment you remove the cover. Simply release each RAM by releasing the clips on the side. Once disengaged, the RAM will spring in a 45-degree angle. Remove it and put back the upgraded RAM at a 45 degree angle and push it down for it to clip. ### 2.2 Upgrading the SSD It is important to note that the Mac Mini has 2 SSD bay. They are referred to as the “upper bay” and “lower bay”. Since we have flipped the Mac Mini upside down to remove the bottom cover, the “upper bay” is located under the “lower bay”. The “upper bay” is mounted with an expansion kit that holds the SSD in position whereas the “lower bay” SSD is simply resting on top of the “upper bay” SSD. One important aspect is that the connecting cables for the “lower bay” and “upper bay” SSD are not the same. The “upper bay” SSD connects on the logic board on the right and the “lower bay” SSD cable connects on the left. Removing the “upper bay” SSD requires removing the logic board therefore requires more work. It is recommended to install the new SSD in the “lower” bay. Here are the 2 scenarios: 1.Your Mac Mini has already a Hard Drive installed in the “lower” bay. In that case insert a credit card under the HD and gently pry it upwards. You will be able to slide it out of the bay. The reason to pry it gently is because since there is no “upper” bay drive, The HD is being held in the air by 2 screws on the side that are aligned in 2 holes in the Mac Mini case. Once the HD is removed, transfer the connecting cable and the 2 screws to the new SSD. To put back the new SSD, it is easier to rotate the Mac Mini 90 degree and have the mounting holes at the bottom and use the gravity to get the 2 mounting screws in the holes. After, connect the connector to the logic board. 2. Your Mac Mini has already a Hard Drive installed in the “upper bay”? Leave it there, you do not need mounting screws, but you need a new connecting cable. You will have to buy a “lower bay connector”. Once installed on the SSD, slide the SSD on top of the original one. The connector will plug on the logic board on the left of the “upper bay” SSD connector. A good preparation would be to go in “Disk Utility” menu on MacOS and search for “upper” or “lower” position before starting to disassemble. Reassemble everything and you are done.
@ 20e17dd0:2ae504d7
2025-02-01 21:14:41## 1. Hardware Selection It is important to select adequately the hardware that will be used to build your Node. The Node will be running 24h /7 days and will countain your lightning channels. It is important to use high quality hardware and spend the extra dollars for it. At the time of building my Node, there was a shortage of Raspberry Pi and I was looking for an optimal alternative. I have decided to go ahead and purchase a used Mac Mini (late 2012). It is recommended NOT to purchase a Mac Mini newer than 2012 (i.e 2014 and up) because Apple started to solder the RAM to the Logic Board after 2012. The Mac Mini Late 2012 is the last model that is fully customizable with SSD and RAM upgrades. Here is the list of hardware that will be used in this build: * 2 x 8G DDR3L Sodim 1600Mhz 1.35V * 1 x Mac Mini (Late 2012) 2.5Ghz * 1 x Samsung Evo 870 1Tb SSD ^ ^ Note: As discussed earlier, it is important to select hardware of quality. I had initially purchased a low cost 2Tb SSD but it failed while trying to download the Bitcoin blockchain. ##2. Hardware Upgrade To facilitate the upgrade of the hardware, you will need the proper tools to remove some T6 & T8 screws. Here are the steps to dismount the few components of the Mac Mini to upgrade the hardware: 1. Unplug the Mac Mini. 2. Turn it upside down with the black cover facing up. 3. Put your thumbs in the 2 grooves of the cover and turn the piece counterclockwise.  4. Remove the cover. 5. Remove 3 x T6 screws holding the fan.  6. Lift the fan and disconnect the connector by pulling gently straight up the wires. 7. Remove 1x T6 screw at the bottom of the shroud (black plastic piece on the left of the fan).  8. Remove the shroud by holding the top right part with your fingers and turning it clockwise.  9. Remove 4 x T8 screws of the grill WIFI cover.  10. The top of the grill is mounted under the Mac Mini case. Lift gently the bottom of the grill and pull towards yourself to remove the grill. 11. Move the grill aside, you do not have to disconnect the WIFI sensor, just be careful. ### 2.1 Upgrading the RAM The RAM is visible and accessible from the moment you remove the cover. Simply release each RAM by releasing the clips on the side. Once disengaged, the RAM will spring in a 45-degree angle. Remove it and put back the upgraded RAM at a 45 degree angle and push it down for it to clip. ### 2.2 Upgrading the SSD It is important to note that the Mac Mini has 2 SSD bay. They are referred to as the “upper bay” and “lower bay”. Since we have flipped the Mac Mini upside down to remove the bottom cover, the “upper bay” is located under the “lower bay”. The “upper bay” is mounted with an expansion kit that holds the SSD in position whereas the “lower bay” SSD is simply resting on top of the “upper bay” SSD. One important aspect is that the connecting cables for the “lower bay” and “upper bay” SSD are not the same. The “upper bay” SSD connects on the logic board on the right and the “lower bay” SSD cable connects on the left. Removing the “upper bay” SSD requires removing the logic board therefore requires more work. It is recommended to install the new SSD in the “lower” bay. Here are the 2 scenarios: 1.Your Mac Mini has already a Hard Drive installed in the “lower” bay. In that case insert a credit card under the HD and gently pry it upwards. You will be able to slide it out of the bay. The reason to pry it gently is because since there is no “upper” bay drive, The HD is being held in the air by 2 screws on the side that are aligned in 2 holes in the Mac Mini case. Once the HD is removed, transfer the connecting cable and the 2 screws to the new SSD. To put back the new SSD, it is easier to rotate the Mac Mini 90 degree and have the mounting holes at the bottom and use the gravity to get the 2 mounting screws in the holes. After, connect the connector to the logic board. 2. Your Mac Mini has already a Hard Drive installed in the “upper bay”? Leave it there, you do not need mounting screws, but you need a new connecting cable. You will have to buy a “lower bay connector”. Once installed on the SSD, slide the SSD on top of the original one. The connector will plug on the logic board on the left of the “upper bay” SSD connector. A good preparation would be to go in “Disk Utility” menu on MacOS and search for “upper” or “lower” position before starting to disassemble. Reassemble everything and you are done. @ be41636e:e55c4909
2025-02-01 18:51:52## **Will Quantum Computers Kill Bitcoin? The Truth May Surprise You** One of the biggest fears around Bitcoin is that quantum computers (QCs) will render it obsolete. But is this really a legitimate concern, or just another doomsday myth? ### The Real Threat: Not All Quantum Computers Are Equal First, let’s get one thing straight: **quantum computers already exist**. The first notable ones appeared in the **1990s**, built by IBM and Stanford. So why hasn’t Bitcoin already been hacked? Because it’s not about whether quantum computers exist—it’s about how powerful they need to be. ### Are All Bitcoin Addresses at Risk? No! If you’ve entered Bitcoin **after 2010** or **use a wallet backed up with 12 or 24 words (BIP-39, introduced in 2013)**, your funds are safe from quantum threats for a very long time—**centuries, at least**. But why? ### Understanding How Bitcoin’s Security Works Bitcoin security is based on **private keys**. (These are represented by the **12-24 words** you write down when setting up a wallet.) From this private key, a **public key** is created. In Bitcoin’s early days, people shared public keys directly to receive payments. But in 2010, Bitcoin introduced an extra layer of security: **hashed addresses**. Now, instead of sharing your public key, your wallet generates a **Bitcoin address**, which is actually a **hash of your public key**. This adds an extra step for an attacker: before they can find your private key, they must first break the hash to reveal your public key. ### Two Steps to Breaking Bitcoin To steal Bitcoin using quantum computing, an attacker must: 1. **Break the hash** (Bitcoin address → public key) using **Grover’s algorithm**. 2. **Break the elliptic curve cryptography** (public key → private key) using **Shor’s algorithm**. ### Where Do Quantum Computers Stand Today? Let’s put things in perspective. **Google’s Willow processor**, which made headlines recently, has **105 physical qubits**. But breaking Bitcoin’s **elliptic curve cryptography** (step 2 above) requires about **2,330 logical qubits**, running for **minutes to hours**. So how does 105 physical qubits compare to 2,330 logical qubits? It’s **not even in the same league**. To get 2,330 logical qubits, we'd likely need **millions of physical qubits**—a technology that is still decades away. Now, even if we magically reached **2,330 logical qubits tomorrow**, that only breaks **public keys**. It still wouldn't be enough to break Bitcoin addresses (step 1), which would take **centuries** with current quantum algorithms. ### Who Should Be Worried? - **People who used Bitcoin before 2010** and still have funds sitting in old public-key-based addresses (**P2PK** addresses). Their funds could be stolen **in minutes to hours** if a powerful enough quantum computer emerged. - **People who reuse addresses**—this exposes the public key, making it vulnerable to a quantum attack, even when you are using more modern addresses. **(Many wallets, including Trust Wallet, SafePal, Exodus, and Atomic Wallet, still allow this bad practice!)** ### Who Can Sleep Soundly? - **Anyone using modern Bitcoin addresses (P2PKH, SegWit, Taproot)**. Their addresses are **hashed**, meaning an attacker would need **centuries** to break the first layer of protection before even getting to the public key. - **Anyone moving their coins periodically**—since modern Bitcoin wallets generate new addresses for each transaction, public keys remain hidden. ### The Concrete Wall Analogy Think of your Bitcoin private key as being locked inside a massive vault. The first layer of protection is your Bitcoin address, which acts like a thick concrete wall. Cracking through this wall with current quantum algorithms would take centuries. Even if someone managed to break through, they would still face a second, much thinner barrier—your public key. This one would take only minutes to hours to breach. But by then, Bitcoin security upgrades would likely already be in place, leaving attackers empty-handed. ### But What If We Make a Huge Quantum Leap? Yes, it’s possible that new quantum algorithms emerge, or that quantum hardware advances faster than expected. But Bitcoin’s development community isn’t sitting idle, waiting to get wrecked. There are already proposals for **quantum-resistant Bitcoin addresses**, and they can be implemented **before** quantum computers reach a dangerous level. ### The Bottom Line 🚀 **Quantum computers won’t kill Bitcoin anytime soon.** 📌 If you’re using a **modern Bitcoin wallet**, your funds are safe from quantum threats for the foreseeable future. 📌 If you reuse addresses, stop! It exposes your public key and makes you vulnerable much sooner. 📌 Bitcoin developers are already preparing for a quantum-resistant future. So, no, quantum computers won’t be the end of Bitcoin. But they might be the end of bad security practices! 🔐
@ be41636e:e55c4909
2025-02-01 18:51:52## **Will Quantum Computers Kill Bitcoin? The Truth May Surprise You** One of the biggest fears around Bitcoin is that quantum computers (QCs) will render it obsolete. But is this really a legitimate concern, or just another doomsday myth? ### The Real Threat: Not All Quantum Computers Are Equal First, let’s get one thing straight: **quantum computers already exist**. The first notable ones appeared in the **1990s**, built by IBM and Stanford. So why hasn’t Bitcoin already been hacked? Because it’s not about whether quantum computers exist—it’s about how powerful they need to be. ### Are All Bitcoin Addresses at Risk? No! If you’ve entered Bitcoin **after 2010** or **use a wallet backed up with 12 or 24 words (BIP-39, introduced in 2013)**, your funds are safe from quantum threats for a very long time—**centuries, at least**. But why? ### Understanding How Bitcoin’s Security Works Bitcoin security is based on **private keys**. (These are represented by the **12-24 words** you write down when setting up a wallet.) From this private key, a **public key** is created. In Bitcoin’s early days, people shared public keys directly to receive payments. But in 2010, Bitcoin introduced an extra layer of security: **hashed addresses**. Now, instead of sharing your public key, your wallet generates a **Bitcoin address**, which is actually a **hash of your public key**. This adds an extra step for an attacker: before they can find your private key, they must first break the hash to reveal your public key. ### Two Steps to Breaking Bitcoin To steal Bitcoin using quantum computing, an attacker must: 1. **Break the hash** (Bitcoin address → public key) using **Grover’s algorithm**. 2. **Break the elliptic curve cryptography** (public key → private key) using **Shor’s algorithm**. ### Where Do Quantum Computers Stand Today? Let’s put things in perspective. **Google’s Willow processor**, which made headlines recently, has **105 physical qubits**. But breaking Bitcoin’s **elliptic curve cryptography** (step 2 above) requires about **2,330 logical qubits**, running for **minutes to hours**. So how does 105 physical qubits compare to 2,330 logical qubits? It’s **not even in the same league**. To get 2,330 logical qubits, we'd likely need **millions of physical qubits**—a technology that is still decades away. Now, even if we magically reached **2,330 logical qubits tomorrow**, that only breaks **public keys**. It still wouldn't be enough to break Bitcoin addresses (step 1), which would take **centuries** with current quantum algorithms. ### Who Should Be Worried? - **People who used Bitcoin before 2010** and still have funds sitting in old public-key-based addresses (**P2PK** addresses). Their funds could be stolen **in minutes to hours** if a powerful enough quantum computer emerged. - **People who reuse addresses**—this exposes the public key, making it vulnerable to a quantum attack, even when you are using more modern addresses. **(Many wallets, including Trust Wallet, SafePal, Exodus, and Atomic Wallet, still allow this bad practice!)** ### Who Can Sleep Soundly? - **Anyone using modern Bitcoin addresses (P2PKH, SegWit, Taproot)**. Their addresses are **hashed**, meaning an attacker would need **centuries** to break the first layer of protection before even getting to the public key. - **Anyone moving their coins periodically**—since modern Bitcoin wallets generate new addresses for each transaction, public keys remain hidden. ### The Concrete Wall Analogy Think of your Bitcoin private key as being locked inside a massive vault. The first layer of protection is your Bitcoin address, which acts like a thick concrete wall. Cracking through this wall with current quantum algorithms would take centuries. Even if someone managed to break through, they would still face a second, much thinner barrier—your public key. This one would take only minutes to hours to breach. But by then, Bitcoin security upgrades would likely already be in place, leaving attackers empty-handed. ### But What If We Make a Huge Quantum Leap? Yes, it’s possible that new quantum algorithms emerge, or that quantum hardware advances faster than expected. But Bitcoin’s development community isn’t sitting idle, waiting to get wrecked. There are already proposals for **quantum-resistant Bitcoin addresses**, and they can be implemented **before** quantum computers reach a dangerous level. ### The Bottom Line 🚀 **Quantum computers won’t kill Bitcoin anytime soon.** 📌 If you’re using a **modern Bitcoin wallet**, your funds are safe from quantum threats for the foreseeable future. 📌 If you reuse addresses, stop! It exposes your public key and makes you vulnerable much sooner. 📌 Bitcoin developers are already preparing for a quantum-resistant future. So, no, quantum computers won’t be the end of Bitcoin. But they might be the end of bad security practices! 🔐 @ b17fccdf:b7211155
2025-02-01 18:41:27#### **Next new resources about the MiniBolt guide have been released**: --- * 🆕 **Roadmap**: [LINK](https://github.com/orgs/minibolt-guide/projects/1) * 🆕 **Dynamic Network map**: [LINK](https://app.diagrams.net/?tags={}&lightbox=1&target=blank&highlight=0000ff&edit=_blank&layers=1&nav=1&title=networkmap.drawio.png#Uhttps://raw.githubusercontent.com/minibolt-guide/minibolt/main/resources/networkmap.drawio.png) * 🆕 **Nostr community**: [LINK](https://habla.news/c/[n]addr1qqyy66twd9px7mr5qyf8wumn8ghj7mmxve3ksctfdch8qatzqgstzl7vmurm5gu87qutx3pxwgxddrg39huj809zhmv03scfkus3z4grqsqqpphk2j0aff) < ~ REMOVE the "[]" symbols from the URL (naddr...) to access * 🆕 **Linktr FOSS** (UC) by [Gzuuus](nostr:npub1gzuushllat7pet0ccv9yuhygvc8ldeyhrgxuwg744dn5khnpk3gs3ea5ds): [LINK](https://linktr.minibolt.info) * 🆕 **Donate webpage**: 🚾 [Clearnet LINK](https://donate.minibolt.info) || 🧅 [Onion LINK](http://3iqm7nidexns5p6wmgc23ibgiscm6rge7hwyeziviwgav4fl7xui4mqd.onion/apps/Li3AtEGDsqNmNddv6rX69taidm3/pos) * 🆕 **Contact email**: [hello@minibolt.info](mailto:hello@minibolt.info) --- Enjoy it MiniBolter! 💙
@ b17fccdf:b7211155
2025-02-01 18:41:27#### **Next new resources about the MiniBolt guide have been released**: --- * 🆕 **Roadmap**: [LINK](https://github.com/orgs/minibolt-guide/projects/1) * 🆕 **Dynamic Network map**: [LINK](https://app.diagrams.net/?tags={}&lightbox=1&target=blank&highlight=0000ff&edit=_blank&layers=1&nav=1&title=networkmap.drawio.png#Uhttps://raw.githubusercontent.com/minibolt-guide/minibolt/main/resources/networkmap.drawio.png) * 🆕 **Nostr community**: [LINK](https://habla.news/c/[n]addr1qqyy66twd9px7mr5qyf8wumn8ghj7mmxve3ksctfdch8qatzqgstzl7vmurm5gu87qutx3pxwgxddrg39huj809zhmv03scfkus3z4grqsqqpphk2j0aff) < ~ REMOVE the "[]" symbols from the URL (naddr...) to access * 🆕 **Linktr FOSS** (UC) by [Gzuuus](nostr:npub1gzuushllat7pet0ccv9yuhygvc8ldeyhrgxuwg744dn5khnpk3gs3ea5ds): [LINK](https://linktr.minibolt.info) * 🆕 **Donate webpage**: 🚾 [Clearnet LINK](https://donate.minibolt.info) || 🧅 [Onion LINK](http://3iqm7nidexns5p6wmgc23ibgiscm6rge7hwyeziviwgav4fl7xui4mqd.onion/apps/Li3AtEGDsqNmNddv6rX69taidm3/pos) * 🆕 **Contact email**: [hello@minibolt.info](mailto:hello@minibolt.info) --- Enjoy it MiniBolter! 💙 @ be41636e:e55c4909
2025-02-01 18:35:06One of the biggest fears around Bitcoin is that quantum computers (QCs) will render it obsolete. But is this really a legitimate concern, or just another doomsday myth? ### The Real Threat: Not All Quantum Computers Are Equal First, let’s get one thing straight: **quantum computers already exist**. The first notable ones appeared in the **1990s**, built by IBM and Stanford. So why hasn’t Bitcoin already been hacked? Because it’s not about whether quantum computers exist—it’s about how powerful they need to be. ### Are All Bitcoin Addresses at Risk? No! If you’ve entered Bitcoin **after 2010** or **use a wallet backed up with 12 or 24 words (BIP-39, introduced in 2013)**, your funds are safe from quantum threats for a very long time—**centuries, at least**. But why? ### Understanding How Bitcoin’s Security Works Bitcoin security is based on **private keys**. (These are represented by the **12-24 words** you write down when setting up a wallet.) From this private key, a **public key** is created. In Bitcoin’s early days, people shared public keys directly to receive payments. But in 2010, Bitcoin introduced an extra layer of security: **hashed addresses**. Now, instead of sharing your public key, your wallet generates a **Bitcoin address**, which is actually a **hash of your public key**. This adds an extra step for an attacker: before they can find your private key, they must first break the hash to reveal your public key. ### Two Steps to Breaking Bitcoin To steal Bitcoin using quantum computing, an attacker must: 1. **Break the hash** (Bitcoin address → public key) using **Grover’s algorithm**. 2. **Break the elliptic curve cryptography** (public key → private key) using **Shor’s algorithm**. ### Where Do Quantum Computers Stand Today? Let’s put things in perspective. **Google’s Willow processor**, which made headlines recently, has **105 physical qubits**. But breaking Bitcoin’s **elliptic curve cryptography** (step 2 above) requires about **2,330 logical qubits**, running for **minutes to hours**. So how does 105 physical qubits compare to 2,330 logical qubits? It’s **not even in the same league**. To get 2,330 logical qubits, we'd likely need **millions of physical qubits**—a technology that is still decades away. Now, even if we magically reached **2,330 logical qubits tomorrow**, that only breaks **public keys**. It still wouldn't be enough to break Bitcoin addresses (step 1), which would take **centuries** with current quantum algorithms. ### Who Should Be Worried? - **People who used Bitcoin before 2010** and still have funds sitting in old public-key-based addresses (**P2PK** addresses). Their funds could be stolen **in minutes to hours** if a powerful enough quantum computer emerged. - **People who reuse addresses**—this exposes the public key, making it vulnerable to a quantum attack, even when you are using more modern addresses. **(Many wallets, including Trust Wallet, SafePal, Exodus, and Atomic Wallet, still allow this bad practice!)** ### Who Can Sleep Soundly? - **Anyone using modern Bitcoin addresses (P2PKH, SegWit, Taproot)**. Their addresses are **hashed**, meaning an attacker would need **centuries** to break the first layer of protection before even getting to the public key. ### The Concrete Wall Analogy Think of your Bitcoin private key as being locked inside a massive vault. The first layer of protection is your Bitcoin address, which acts like a thick concrete wall. Cracking through this wall with current quantum algorithms would take centuries. Once one breaks through this wall, they would face a second wall, which is a much thinner barrier—your public key. This one would take only minutes to hours to breach. ### But What If We Make a Huge Quantum Leap? Yes, it’s possible that new quantum algorithms emerge, or that quantum hardware advances faster than expected. But Bitcoin’s development community isn’t sitting idle, waiting to get wrecked. There are already proposals for **quantum-resistant Bitcoin addresses**, and they can be implemented **before** quantum computers reach a dangerous level. ### The Bottom Line 🚀 **Quantum computers won’t kill Bitcoin anytime soon.** 📌 If you’re using a **modern Bitcoin wallet**, your funds are safe from quantum threats for the foreseeable future. 📌 If you reuse addresses, stop! It exposes your public key and makes you vulnerable much sooner. 📌 Bitcoin developers are already preparing for a quantum-resistant future. So, no, quantum computers won’t be the end of Bitcoin. But they might be the end of bad security practices! 🔐
@ be41636e:e55c4909
2025-02-01 18:35:06One of the biggest fears around Bitcoin is that quantum computers (QCs) will render it obsolete. But is this really a legitimate concern, or just another doomsday myth? ### The Real Threat: Not All Quantum Computers Are Equal First, let’s get one thing straight: **quantum computers already exist**. The first notable ones appeared in the **1990s**, built by IBM and Stanford. So why hasn’t Bitcoin already been hacked? Because it’s not about whether quantum computers exist—it’s about how powerful they need to be. ### Are All Bitcoin Addresses at Risk? No! If you’ve entered Bitcoin **after 2010** or **use a wallet backed up with 12 or 24 words (BIP-39, introduced in 2013)**, your funds are safe from quantum threats for a very long time—**centuries, at least**. But why? ### Understanding How Bitcoin’s Security Works Bitcoin security is based on **private keys**. (These are represented by the **12-24 words** you write down when setting up a wallet.) From this private key, a **public key** is created. In Bitcoin’s early days, people shared public keys directly to receive payments. But in 2010, Bitcoin introduced an extra layer of security: **hashed addresses**. Now, instead of sharing your public key, your wallet generates a **Bitcoin address**, which is actually a **hash of your public key**. This adds an extra step for an attacker: before they can find your private key, they must first break the hash to reveal your public key. ### Two Steps to Breaking Bitcoin To steal Bitcoin using quantum computing, an attacker must: 1. **Break the hash** (Bitcoin address → public key) using **Grover’s algorithm**. 2. **Break the elliptic curve cryptography** (public key → private key) using **Shor’s algorithm**. ### Where Do Quantum Computers Stand Today? Let’s put things in perspective. **Google’s Willow processor**, which made headlines recently, has **105 physical qubits**. But breaking Bitcoin’s **elliptic curve cryptography** (step 2 above) requires about **2,330 logical qubits**, running for **minutes to hours**. So how does 105 physical qubits compare to 2,330 logical qubits? It’s **not even in the same league**. To get 2,330 logical qubits, we'd likely need **millions of physical qubits**—a technology that is still decades away. Now, even if we magically reached **2,330 logical qubits tomorrow**, that only breaks **public keys**. It still wouldn't be enough to break Bitcoin addresses (step 1), which would take **centuries** with current quantum algorithms. ### Who Should Be Worried? - **People who used Bitcoin before 2010** and still have funds sitting in old public-key-based addresses (**P2PK** addresses). Their funds could be stolen **in minutes to hours** if a powerful enough quantum computer emerged. - **People who reuse addresses**—this exposes the public key, making it vulnerable to a quantum attack, even when you are using more modern addresses. **(Many wallets, including Trust Wallet, SafePal, Exodus, and Atomic Wallet, still allow this bad practice!)** ### Who Can Sleep Soundly? - **Anyone using modern Bitcoin addresses (P2PKH, SegWit, Taproot)**. Their addresses are **hashed**, meaning an attacker would need **centuries** to break the first layer of protection before even getting to the public key. ### The Concrete Wall Analogy Think of your Bitcoin private key as being locked inside a massive vault. The first layer of protection is your Bitcoin address, which acts like a thick concrete wall. Cracking through this wall with current quantum algorithms would take centuries. Once one breaks through this wall, they would face a second wall, which is a much thinner barrier—your public key. This one would take only minutes to hours to breach. ### But What If We Make a Huge Quantum Leap? Yes, it’s possible that new quantum algorithms emerge, or that quantum hardware advances faster than expected. But Bitcoin’s development community isn’t sitting idle, waiting to get wrecked. There are already proposals for **quantum-resistant Bitcoin addresses**, and they can be implemented **before** quantum computers reach a dangerous level. ### The Bottom Line 🚀 **Quantum computers won’t kill Bitcoin anytime soon.** 📌 If you’re using a **modern Bitcoin wallet**, your funds are safe from quantum threats for the foreseeable future. 📌 If you reuse addresses, stop! It exposes your public key and makes you vulnerable much sooner. 📌 Bitcoin developers are already preparing for a quantum-resistant future. So, no, quantum computers won’t be the end of Bitcoin. But they might be the end of bad security practices! 🔐 @ b17fccdf:b7211155
2025-02-01 18:28:39--- ##### Check out the **MiniBolt guide** -> [HERE](https://minibolt.info) <- --- * **Core guides** * [**System**](https://minibolt.minibolt.info/system/system) * [Preparations](https://minibolt.minibolt.info/system/system/preparations) * [Operating System](https://minibolt.minibolt.info/system/system/operating-system) * [Remote access](https://minibolt.minibolt.info/system/system/remote-access) * [Configuration](https://minibolt.info/guide/system/configuration) * [Security](https://minibolt.minibolt.info/system/system/security) * [Privacy](https://minibolt.minibolt.info/system/system/privacy) * [**Bitcoin**](https://minibolt.minibolt.info/bitcoin/bitcoin) * [Bitcoin client](https://minibolt.minibolt.info/bitcoin/bitcoin/bitcoin-client) (Bitcoin Core) * [Electrum server](https://minibolt.minibolt.info/bitcoin/bitcoin/electrum-server) (Fulcrum) * [Desktop signing app](https://minibolt.minibolt.info/bitcoin/bitcoin/desktop-signing-app-sparrow) (Sparrow Wallet) * [Blockchain explorer](https://minibolt.minibolt.info/bitcoin/bitcoin/blockchain-explorer) (BTC RPC Explorer) * [**Lightning**](https://minibolt.minibolt.info/lightning/lightning) * [Lightning client](https://minibolt.minibolt.info/lightning/lightning/lightning-client) (LND) * [Channel backup](https://minibolt.minibolt.info/lightning/lightning/channel-backup) * [Web app](https://minibolt.minibolt.info/lightning/lightning/web-app) (ThunderHub) * [Mobile app](https://minibolt.minibolt.info/lightning/lightning/mobile-app) (Zeus) * **Bonus guides** * [**System bonus guide**](https://minibolt.minibolt.info/bonus-guides/system) * **Dashboard & Appearance** * [Pimp the command line](https://minibolt.minibolt.info/bonus-guides/system/command-line) * [System Overview](https://minibolt.minibolt.info/bonus-guides/system/system-overview) * **System Administration** * [Aliases](https://minibolt.minibolt.info/bonus-guides/system/aliases) * [Statip IP & custom DNS servers](https://minibolt.minibolt.info/bonus-guides/system/static-ip-and-custom-dns-servers) * **Install / Update / Uninstall common languages** * [Node.js + NPM](https://minibolt.minibolt.info/bonus-guides/system/nodejs-npm) * [Rustup + Cargo](https://minibolt.minibolt.info/bonus-guides/system/rustup-+-cargo) * [Go!](https://minibolt.minibolt.info/bonus-guides/system/go) * **Databases** * [PostgreSQL](https://minibolt.minibolt.info/bonus-guides/system/postgresql) * **Security** * [SSH Keys](https://minibolt.info/guide/bonus/system/ssh-keys.html) * [WireGuard VPN](https://minibolt.info/guide/bonus/system/wireguard-VPN.html) * [Cloudflare Tunnel](https://minibolt.minibolt.info/bonus-guides/system/cloudflare-tunnel) * **Resilience** * [Tor services: bridges & relays](https://minibolt.minibolt.info/bonus-guides/system/tor-services) * **Hardware** * [Store data in a secondary disk](https://minibolt.minibolt.info/bonus-guides/system/store-data-secondary-disk) * [**Bitcoin bonus guides**](https://minibolt.minibolt.info/bonus-guides/bitcoin) * **Electrum servers** * [Electrs](https://minibolt.minibolt.info/bonus-guides/bitcoin/electrs) * **Signing apps** * **Desktop** * [Electrum Wallet Desktop](https://minibolt.minibolt.info/bonus-guides/bitcoin/electrum-wallet-desktop) * **Decentralized exchange** * [Bisq](https://minibolt.minibolt.info/bonus-guides/bitcoin/bisq) * **Resilience** * [Safu Ninja](https://minibolt.minibolt.info/bonus-guides/bitcoin/safu-ninja) * [Ordisrespector](https://minibolt.minibolt.info/bonus-guides/bitcoin/ordisrespector) * **Fun** * [Download the white paper](https://minibolt.minibolt.info/bonus-guides/bitcoin/white-paper) * **Testnet** * [MiniBolt on Testnet](https://minibolt.minibolt.info/bonus-guides/bitcoin/minibolt-on-testnet) * **Payment processors** * [BTCPay Server](https://minibolt.minibolt.info/bonus-guides/bitcoin/btcpay-server) * [**Nostr bonus guides**](https://minibolt.minibolt.info/bonus-guides/nostr) * **Relays** * [Nostr relay](https://minibolt.minibolt.info/bonus-guides/bitcoin/nostr-relay) --- 🏗️ [Roadmap](https://github.com/orgs/minibolt-guide/projects/1) | 🌐 [Dynamic Network map](https://app.diagrams.net/?tags={}&lightbox=1&target=blank&highlight=0000ff&edit=_blank&layers=1&nav=1&title=networkmap.drawio.png#Uhttps://raw.githubusercontent.com/minibolt-guide/minibolt/main/resources/networkmap.drawio.png) | 🔧 [Issues](https://github.com/minibolt-guide/minibolt/issues) | 📥 [Pull requests](https://github.com/minibolt-guide/minibolt/pulls) | 🗣️ [Discussions](https://github.com/orgs/minibolt-guide/discussions) --- By [**⚡2FakTor⚡**](nostr:npub1k9luehc8hg3c0upckdzzvusv66x3zt0eyw7290kclrpsndepz92sfcpp63) --- **Last updated:** 22/12/2024
@ b17fccdf:b7211155
2025-02-01 18:28:39--- ##### Check out the **MiniBolt guide** -> [HERE](https://minibolt.info) <- --- * **Core guides** * [**System**](https://minibolt.minibolt.info/system/system) * [Preparations](https://minibolt.minibolt.info/system/system/preparations) * [Operating System](https://minibolt.minibolt.info/system/system/operating-system) * [Remote access](https://minibolt.minibolt.info/system/system/remote-access) * [Configuration](https://minibolt.info/guide/system/configuration) * [Security](https://minibolt.minibolt.info/system/system/security) * [Privacy](https://minibolt.minibolt.info/system/system/privacy) * [**Bitcoin**](https://minibolt.minibolt.info/bitcoin/bitcoin) * [Bitcoin client](https://minibolt.minibolt.info/bitcoin/bitcoin/bitcoin-client) (Bitcoin Core) * [Electrum server](https://minibolt.minibolt.info/bitcoin/bitcoin/electrum-server) (Fulcrum) * [Desktop signing app](https://minibolt.minibolt.info/bitcoin/bitcoin/desktop-signing-app-sparrow) (Sparrow Wallet) * [Blockchain explorer](https://minibolt.minibolt.info/bitcoin/bitcoin/blockchain-explorer) (BTC RPC Explorer) * [**Lightning**](https://minibolt.minibolt.info/lightning/lightning) * [Lightning client](https://minibolt.minibolt.info/lightning/lightning/lightning-client) (LND) * [Channel backup](https://minibolt.minibolt.info/lightning/lightning/channel-backup) * [Web app](https://minibolt.minibolt.info/lightning/lightning/web-app) (ThunderHub) * [Mobile app](https://minibolt.minibolt.info/lightning/lightning/mobile-app) (Zeus) * **Bonus guides** * [**System bonus guide**](https://minibolt.minibolt.info/bonus-guides/system) * **Dashboard & Appearance** * [Pimp the command line](https://minibolt.minibolt.info/bonus-guides/system/command-line) * [System Overview](https://minibolt.minibolt.info/bonus-guides/system/system-overview) * **System Administration** * [Aliases](https://minibolt.minibolt.info/bonus-guides/system/aliases) * [Statip IP & custom DNS servers](https://minibolt.minibolt.info/bonus-guides/system/static-ip-and-custom-dns-servers) * **Install / Update / Uninstall common languages** * [Node.js + NPM](https://minibolt.minibolt.info/bonus-guides/system/nodejs-npm) * [Rustup + Cargo](https://minibolt.minibolt.info/bonus-guides/system/rustup-+-cargo) * [Go!](https://minibolt.minibolt.info/bonus-guides/system/go) * **Databases** * [PostgreSQL](https://minibolt.minibolt.info/bonus-guides/system/postgresql) * **Security** * [SSH Keys](https://minibolt.info/guide/bonus/system/ssh-keys.html) * [WireGuard VPN](https://minibolt.info/guide/bonus/system/wireguard-VPN.html) * [Cloudflare Tunnel](https://minibolt.minibolt.info/bonus-guides/system/cloudflare-tunnel) * **Resilience** * [Tor services: bridges & relays](https://minibolt.minibolt.info/bonus-guides/system/tor-services) * **Hardware** * [Store data in a secondary disk](https://minibolt.minibolt.info/bonus-guides/system/store-data-secondary-disk) * [**Bitcoin bonus guides**](https://minibolt.minibolt.info/bonus-guides/bitcoin) * **Electrum servers** * [Electrs](https://minibolt.minibolt.info/bonus-guides/bitcoin/electrs) * **Signing apps** * **Desktop** * [Electrum Wallet Desktop](https://minibolt.minibolt.info/bonus-guides/bitcoin/electrum-wallet-desktop) * **Decentralized exchange** * [Bisq](https://minibolt.minibolt.info/bonus-guides/bitcoin/bisq) * **Resilience** * [Safu Ninja](https://minibolt.minibolt.info/bonus-guides/bitcoin/safu-ninja) * [Ordisrespector](https://minibolt.minibolt.info/bonus-guides/bitcoin/ordisrespector) * **Fun** * [Download the white paper](https://minibolt.minibolt.info/bonus-guides/bitcoin/white-paper) * **Testnet** * [MiniBolt on Testnet](https://minibolt.minibolt.info/bonus-guides/bitcoin/minibolt-on-testnet) * **Payment processors** * [BTCPay Server](https://minibolt.minibolt.info/bonus-guides/bitcoin/btcpay-server) * [**Nostr bonus guides**](https://minibolt.minibolt.info/bonus-guides/nostr) * **Relays** * [Nostr relay](https://minibolt.minibolt.info/bonus-guides/bitcoin/nostr-relay) --- 🏗️ [Roadmap](https://github.com/orgs/minibolt-guide/projects/1) | 🌐 [Dynamic Network map](https://app.diagrams.net/?tags={}&lightbox=1&target=blank&highlight=0000ff&edit=_blank&layers=1&nav=1&title=networkmap.drawio.png#Uhttps://raw.githubusercontent.com/minibolt-guide/minibolt/main/resources/networkmap.drawio.png) | 🔧 [Issues](https://github.com/minibolt-guide/minibolt/issues) | 📥 [Pull requests](https://github.com/minibolt-guide/minibolt/pulls) | 🗣️ [Discussions](https://github.com/orgs/minibolt-guide/discussions) --- By [**⚡2FakTor⚡**](nostr:npub1k9luehc8hg3c0upckdzzvusv66x3zt0eyw7290kclrpsndepz92sfcpp63) --- **Last updated:** 22/12/2024 @ d57360cb:4fe7d935
2025-02-01 18:22:10What is life but a preparation for the grand finale. Think of your life up to this point. You’ve been living in the midst of death whether you pay attention to it or not. Your youth faded, the years go by, relationships fail, careers fail, people die, the ones close to you and those you hardly know. Civilizations wiped out, total species completely gone with no trace. Here you are in the midst of death. A vortex of change wiping everything in its path. Creating space for the unknown and new. Nothing lasts, nothing stays the same, everything ends. Ending gives great significance to life. How will you be in the presence of someone you love knowing they or you will vanish one day? What wouldn’t you put off if you were aware your time was slipping and there’s nothing you can do. What would you stop doing? What would you let go of? Who would you forgive? Life comes with a bullet and it has your name on it. You don’t know when it’ll happen. Don’t believe you ever have time it’s always a fantasy. Death will knock you on your feet when you least expect it. Use death as a doorway to a deep meaningful life.
@ d57360cb:4fe7d935
2025-02-01 18:22:10What is life but a preparation for the grand finale. Think of your life up to this point. You’ve been living in the midst of death whether you pay attention to it or not. Your youth faded, the years go by, relationships fail, careers fail, people die, the ones close to you and those you hardly know. Civilizations wiped out, total species completely gone with no trace. Here you are in the midst of death. A vortex of change wiping everything in its path. Creating space for the unknown and new. Nothing lasts, nothing stays the same, everything ends. Ending gives great significance to life. How will you be in the presence of someone you love knowing they or you will vanish one day? What wouldn’t you put off if you were aware your time was slipping and there’s nothing you can do. What would you stop doing? What would you let go of? Who would you forgive? Life comes with a bullet and it has your name on it. You don’t know when it’ll happen. Don’t believe you ever have time it’s always a fantasy. Death will knock you on your feet when you least expect it. Use death as a doorway to a deep meaningful life. @ cff1720e:15c7e2b2
2025-02-01 17:37:00Am 4. Oktober 1957 sendete Sputnik 1 erste Signale aus dem All. Die Welt war fasziniert, die Amerikaner geschockt, da die Russen sie in der Raumfahrt technologisch überholt hatten. Es folgte der Wettlauf im All mit Apollo-Programm und Mondlandung 1969. Am 27. Januar 2025 erlebte die USA einen weiteren Sputnik-Moment, diesmal durch die chinesische KI-App deepseek R1. Diese App schoss wenige Stunden nach ihrem Start auf Platz 1 der App-Stores, vorbei an dem bisherigen KI-Spitzenreiter ChatGPT. Die Aktie des KI-Chipherstellers Nvidia verlor 17% (600 Mrd. USD Börsenwert), das war der bisher höchste Tagesverlust des US-Aktienmarktes. Marc Andreessen verwendete gar die Formulierung “Sputnik-Schock", diese einseitige Sichtweise erschwert aber eine Betrachtung aus verschiedenen Perspektiven.  Was lässt sich mit ein paar Tagen Abstand daraus schlussfolgern? Die Aktionäre haben überreagiert und die Falschen bestraft. Die Nervosität der Anleger ist aber verständlich bei einem KGV von 46 bei Nvidia und 27 bei den “Magnificent Seven” (die großen US KI-Anbieter). Normale KGVs bewegen sich um 15, d.h. wir haben es mit einer ausgeprägten KI-Blase zu tun, die in Kürze platzen dürfte. Eine weitere Blase die schon vor dem Start geplatzt ist, ist das Projekt “Stargate” der Firmen OpenAI, Oracle und Softbank. In den nächsten 4 Jahren wollen sie 500 Mrd. USD für über 10 neue KI-Rechenzentren investieren, um Amerikas vermeintliche KI-Vorherrschaft gegenüber China weiter auszubauen. Die schon vorher vorhandenen Zweifel an dem Projekt (Elon Musk auf X “sie haben das Geld gar nicht”) wurden nun durch den Erfolg von deepseek verstärkt.  deepseek hat nämlich offenbart, dass die bisherige US KI-Strategie, "wir schlagen die Chinesen mit unserer DataCenter-Power", ein fataler Irrweg ist. Den Analysten von Bernstein zufolge ist das Modell von deepseek geschätzt 20 bis 40 mal billiger zu betreiben als ähnliche Modelle von OpenAI. Die Chinesen haben ihre Innovation durch Kreativität erzielt, im Gegensatz zur Gigantomanie der US-Konzerne, die sich in einem Überbietungs-Wettbewerb der Ressourcen-Verschwendung befinden. Hunderte Milliarden an Investorengeldern und ca. 9% des nationalen Stromverbrauchs führen zwar zur Bereicherung einiger Konzerne und ihrer Besitzer, nicht aber zu adäquaten Ergebnissen. Das selbe Muster konnte man bereits bei der Rüstungsbranche beobachten, die mit dem etwa 10-fachen Budget (1 Billion USD) nicht im Stande war bessere Waffensysteme zu produzieren als Russland (Oreshnik-Schock 2024).  Wenn Donald Trump wirklich Amerika stärken möchte, dann sollte er umgehend seine technokratischen Berater entlassen und Sun Tzu lesen, ein Buch, das die Grundlagen asiatischer Strategie vermittelt und den Krieg vermeiden lehrt ("Der klügste Krieger ist der, der niemals kämpfen muss"). Die chinesischen Erfolge basieren auf exzellenter Bildung, Startup-Förderung und minimaler Regulierung, Konzepte die der Westen zwar stets gepredigt aber nie geliefert hat. “Make Amerika smart again” hieße daher Abschied von Kriegsrhetorik, Embargos, Oligarchen-Projekten und der bisherigen Großmacht-Hybris. Annektionspläne für Grönland und Kanada passen nicht in das Bild, Wiederherstellung von Meinungsfreiheit und Abbau von Regulierungen schon (Streichung von Bidens KI-Regulierung Executive Order 14110). Wohin steuert Trump die USA? Wird der deepseek-Moment dabei helfen falsche Strategieansätze zu korrigieren? Das ist noch unklar, während aber schon jetzt unzweifelhaft feststeht, dass die EU und Deutschland weder bei der KI noch in der Geostrategie eine Rolle spielen, dafür aber als unangefochtene Regulierungs-Weltmeister. Herzlichen Glückwunsch!  „Man kann zwar die Realität ignorieren, aber nicht die Folgen davon ignorieren.“ Ayn Rand Der wirkliche Gewinner dieser Woche ist aber die OpenSource-Szene mit ihren dezentralen Lösungsansätzen. Nicht nur deepseek R1 ist OpenSource sondern auch Marco o1 von Alibaba (<https://github.com/huggingface>). Die Nutzung ist kostenlos (ChatGPT kostet 200 USD pro Monat), daher können sowohl die Modellbildung, die Trainingsdaten als auch die Rechenleistung von unzähligen Aktivisten weltweit verteilt erbracht werden. Dafür braucht es weder Milliarden-Budgets, Regierungsprogramme oder neue DataCenter. Das Potential der Crowd übertrifft jeden zentralistischen Ansatz. Die Ergebnisse sind besser und die Kontrolle liegt nicht in den Händen einzelner. Smarte Lösung sind verteilt, das beweisen Projekte wie Bitcoin (seit 16 Jahren), Lightning und neuerdings auch Nostr. Deshalb haben wir Pareto (<https://pareto.space>) auf diesen Fundamenten entwickelt (Nostr, Lightning) und in 6 Monaten mit Freiwilligen mehr erreicht als viele große IT-Unternehmen in Jahren. Die Dinosaurier sterben aus, dem Schwarm gehört die Zukunft.
@ cff1720e:15c7e2b2
2025-02-01 17:37:00Am 4. Oktober 1957 sendete Sputnik 1 erste Signale aus dem All. Die Welt war fasziniert, die Amerikaner geschockt, da die Russen sie in der Raumfahrt technologisch überholt hatten. Es folgte der Wettlauf im All mit Apollo-Programm und Mondlandung 1969. Am 27. Januar 2025 erlebte die USA einen weiteren Sputnik-Moment, diesmal durch die chinesische KI-App deepseek R1. Diese App schoss wenige Stunden nach ihrem Start auf Platz 1 der App-Stores, vorbei an dem bisherigen KI-Spitzenreiter ChatGPT. Die Aktie des KI-Chipherstellers Nvidia verlor 17% (600 Mrd. USD Börsenwert), das war der bisher höchste Tagesverlust des US-Aktienmarktes. Marc Andreessen verwendete gar die Formulierung “Sputnik-Schock", diese einseitige Sichtweise erschwert aber eine Betrachtung aus verschiedenen Perspektiven.  Was lässt sich mit ein paar Tagen Abstand daraus schlussfolgern? Die Aktionäre haben überreagiert und die Falschen bestraft. Die Nervosität der Anleger ist aber verständlich bei einem KGV von 46 bei Nvidia und 27 bei den “Magnificent Seven” (die großen US KI-Anbieter). Normale KGVs bewegen sich um 15, d.h. wir haben es mit einer ausgeprägten KI-Blase zu tun, die in Kürze platzen dürfte. Eine weitere Blase die schon vor dem Start geplatzt ist, ist das Projekt “Stargate” der Firmen OpenAI, Oracle und Softbank. In den nächsten 4 Jahren wollen sie 500 Mrd. USD für über 10 neue KI-Rechenzentren investieren, um Amerikas vermeintliche KI-Vorherrschaft gegenüber China weiter auszubauen. Die schon vorher vorhandenen Zweifel an dem Projekt (Elon Musk auf X “sie haben das Geld gar nicht”) wurden nun durch den Erfolg von deepseek verstärkt.  deepseek hat nämlich offenbart, dass die bisherige US KI-Strategie, "wir schlagen die Chinesen mit unserer DataCenter-Power", ein fataler Irrweg ist. Den Analysten von Bernstein zufolge ist das Modell von deepseek geschätzt 20 bis 40 mal billiger zu betreiben als ähnliche Modelle von OpenAI. Die Chinesen haben ihre Innovation durch Kreativität erzielt, im Gegensatz zur Gigantomanie der US-Konzerne, die sich in einem Überbietungs-Wettbewerb der Ressourcen-Verschwendung befinden. Hunderte Milliarden an Investorengeldern und ca. 9% des nationalen Stromverbrauchs führen zwar zur Bereicherung einiger Konzerne und ihrer Besitzer, nicht aber zu adäquaten Ergebnissen. Das selbe Muster konnte man bereits bei der Rüstungsbranche beobachten, die mit dem etwa 10-fachen Budget (1 Billion USD) nicht im Stande war bessere Waffensysteme zu produzieren als Russland (Oreshnik-Schock 2024).  Wenn Donald Trump wirklich Amerika stärken möchte, dann sollte er umgehend seine technokratischen Berater entlassen und Sun Tzu lesen, ein Buch, das die Grundlagen asiatischer Strategie vermittelt und den Krieg vermeiden lehrt ("Der klügste Krieger ist der, der niemals kämpfen muss"). Die chinesischen Erfolge basieren auf exzellenter Bildung, Startup-Förderung und minimaler Regulierung, Konzepte die der Westen zwar stets gepredigt aber nie geliefert hat. “Make Amerika smart again” hieße daher Abschied von Kriegsrhetorik, Embargos, Oligarchen-Projekten und der bisherigen Großmacht-Hybris. Annektionspläne für Grönland und Kanada passen nicht in das Bild, Wiederherstellung von Meinungsfreiheit und Abbau von Regulierungen schon (Streichung von Bidens KI-Regulierung Executive Order 14110). Wohin steuert Trump die USA? Wird der deepseek-Moment dabei helfen falsche Strategieansätze zu korrigieren? Das ist noch unklar, während aber schon jetzt unzweifelhaft feststeht, dass die EU und Deutschland weder bei der KI noch in der Geostrategie eine Rolle spielen, dafür aber als unangefochtene Regulierungs-Weltmeister. Herzlichen Glückwunsch!  „Man kann zwar die Realität ignorieren, aber nicht die Folgen davon ignorieren.“ Ayn Rand Der wirkliche Gewinner dieser Woche ist aber die OpenSource-Szene mit ihren dezentralen Lösungsansätzen. Nicht nur deepseek R1 ist OpenSource sondern auch Marco o1 von Alibaba (<https://github.com/huggingface>). Die Nutzung ist kostenlos (ChatGPT kostet 200 USD pro Monat), daher können sowohl die Modellbildung, die Trainingsdaten als auch die Rechenleistung von unzähligen Aktivisten weltweit verteilt erbracht werden. Dafür braucht es weder Milliarden-Budgets, Regierungsprogramme oder neue DataCenter. Das Potential der Crowd übertrifft jeden zentralistischen Ansatz. Die Ergebnisse sind besser und die Kontrolle liegt nicht in den Händen einzelner. Smarte Lösung sind verteilt, das beweisen Projekte wie Bitcoin (seit 16 Jahren), Lightning und neuerdings auch Nostr. Deshalb haben wir Pareto (<https://pareto.space>) auf diesen Fundamenten entwickelt (Nostr, Lightning) und in 6 Monaten mit Freiwilligen mehr erreicht als viele große IT-Unternehmen in Jahren. Die Dinosaurier sterben aus, dem Schwarm gehört die Zukunft. @ e262ed3a:e147fbcb
2025-02-01 15:37:28**Feel free to develop** I got an idea while watching a video from @BTCSessions, which I personally cannot implement technically. Therefore, I would like to present it here for discussion and free implementation. It makes sense to me, but what do I know? Let the swarm intelligence decide. The goal of the business idea is: How can I bring as many solo miners as possible into a pool without them having to pay for the electricity for mining and their mining hardware can be amortized quickly, so they can purchase more mining hardware? How can we financially support Bitcoin and Nostr developers in the long term? How can we intensify developers for the implementation of this idea? How can we encourage non-Bitcoiners to invest in the support of the Bitcoin network? How can we get non-Bitcoin retailers to invest in the Bitcoin network? **The answer is: PROSPECT OF WINNING The solution lies in a kind of RAFFLE. (Not a betting website) !** The legal difference between a BET and a RAFFLE varies from country to country. It lies in the fact that a raffle must be very transparent regarding the chances of winning and the proceeds must go to a good cause. Those involved in the implementation can, of course, be compensated (also with a profit for the individual participants). The extent to which this is allowed would have to be checked by those who want to implement this idea. In the following, I will describe the implementation roughly. Since this is not a sales presentation, please excuse me if the following proposal is not fully structured. **Participants in the idea are: Consumers (ticket buyers) Bitcoin miners Retailers Non-profit company that implement the project** **What's it about?** @BTCSessions has a YouTube video about the miner FutureBit. In the dashboard of the solo miner, you could see how high the hash rate was. But above all, you could see how high the chance of winning was for the solo miner in the overall network. In the case of BTCSessions FutureBit, the hash rate was around 5 TerraHash and the chance of winning was around 1:1,000,000. (Which, according to my calculations, was not correct). The power consumption was around 32 watts. When I saw that, it suddenly dawned on me. Could it be possible to create a website/app that determines the total hash rate of a mining pool and then offers an electronic, numbered ticket for each 1 TerraHash (TH/s) of the pool for, for example, 0.1 USD? The minimum purchase amount would be 10 tickets. The customer sees the chance of winning and could even see the possible payout. The ticket is only valid for the next block (similar to roulette). Another variant could be that the buyer can select one or more of the next 10 blocks and purchase tickets for the selected block. Since you don't know in advance how high the pool hash rate will be 5 or 10 blocks ahead, the amount of tickets to be issued for the 2nd block, for example, could only be 90% of the current pool hash rate, the 3rd block only 80%, and so on. If block 3, for example, advances to position 2, the previously unavailable 10% will be released for further tickets. (Determined by the pool hash rate at that time) The purchase of 10 or more tickets could be automated in the customer's account on the website/app (intervals: hourly, daily, weekly, every 10 blocks, etc.). Customers could also top up their account with satoshis, enabling automatic deductions for ticket purchases. This could be facilitated by automatically issuing a Nostr npub to each customer, which would also create a wallet at Primal.net (Strike). For non-Bitcoiners, Zaprite could be used to recharge their account. Alternatively, customers could enter a NostrWalletConnection NWC to enable automatic deductions from their Lightning wallet. The project operators might also consider running their own ecash mint, which would allow them to assign an integrated ecash address to customers without a Lightning address. Tickets with ascending numbers would be allocated strictly in the order of payment receipts. **Calculations for the miners:** The FutureBit miner consumed approximately 30 watts per terahash/hour. Let's assume that 10 terahash consume 300 watts per hour, then the miner consumes 50 watts per 10 minutes (per block). Let's further assume that a kilowatt-hour of electricity costs between 10 and 30 cents, then it costs the miner 3-9 cents per hour for electricity at 10 terahash mining capacity. So, 0.5-1.5 cents per block. In the case that each ticket is sold for 1 terahash for the next block, one could automatically transfer, for example, 5% of the satoshis received from ticket sales to each participating miner in the pool (proportional to the average hash rate delivered by the miner in the last block in the pools). This happens even if the block is not found. If fewer tickets are sold than the maximum possible amount, then the 5% of the sold tickets will be distributed proportionally. (See also my Excel file? At the center of the project is a website/app that manages the raffle. Here, anyone can register and create an account. Either as a miner, retailer, or customer with or without KYC, for example, with their own nostr nsec, wallet signature, email and password or phone number and password. Once logged into the account, Bitcoiners can enter their Lightning address and a Bitcoin on-chain address. Non-Bitcoiners enter their financial data in case they win. Miners must enter a Bitcoin and Lightning (or ecash) address. The pooling process is also managed in the miner's account. Tickets can be purchased (like in a regular online shop) and paid for in any way. Zaprite could be a solution here. But also Strike, Cashapp, etc. As described above, such purchases could also be automated. **Retailers** can also register as such. They will then have the opportunity to sell "tickets" to their customers and collect the money in cash. To sell tickets, they must enter the customer's name and a valid email address. After payment, they must send the purchase price via Lightning to the non-profit company, which will then confirm the purchase to the ticket buyer and the retailer with all the data. This is the receipt for the buyer. In the event of a win (the mined block must have 3-6 block confirmations), the ticket buyer will receive an email explaining all the further details of how to claim the prize. This could be a link that takes them directly to the website and logs them in directly. The winner can then enter their data on how and where the money should be paid out (Bitcoin address or bank details). Alternatively, they can go to their retailer, who can assist them by entering the data in their sub-account (customer account). To prevent the retailer from falsifying the data entry, the winner will first receive an email with the entered data, which they can confirm (if correct). Since the retailer is also involved in the win, they will also be notified. How many tickets can be offered per round (Bitcoin block)? The number of tickets depends on the hash rate in the pool. One ticket can be issued per 1 TerraHash (TH/s). How the ticket is generated per round and customer, I don't know, as I lack the technical knowledge. Maybe as a kind of NFT that contains the corresponding data (customer number (npub) of the buyer and possibly retailer, block number, ticket number). Or as a Taproot asset on Lightning? Or as a minted ecash coin? Or simply as an entry in a database that the customer can see in their account. The maximum payout of the winnings in the event of a found block to the ticket holders could be 70%. The remaining 30% would be distributed to the miners and retailers. For example: Miners 25%, retailers 5%. The non-profit organization receives nothing from the block rewards. Instead, it receives 65% of the revenue from all ticket sales. With a mining pool hash rate of 10,000 TH/s, where all tickets are sold continuously, a daily donation of around 93,000 USD would be generated. (see Excel.file) The revenue, after deducting the possible costs of the organization, goes directly to @opensats and/or other organizations that support the Bitcoin network after each block. Either via Lightning or Bitcoin on-chain payment. In the attached Excel file, you can find my calculations. Here, anyone can play through different scenarios. What I noticed was that with maximum ticket sales per block, only around 200 USD per 10 tickets would be paid out, since each participating ticket wins in the event of a found block. Since I believe that this is not a very great incentive for buying tickets, I suggest the following variants. Winning variants: Each purchased ticket has a running number. Ticket 1 has the number 000.000, ticket 2 has the number 000.001, ticket 10.120 has the number 010.119, and so on. If the next block is found, then this found block in the Bitcoin blockchain has a hash. For example, block 881367 has the hash 000000000000000000014b0fab24355c71c6940584d9cd5990c0b081a31d54a4 Let's now remove the letters and read only the numbers from back to front, so the last 3 numbers are 544 Instead of every participating ticket winning, in this variant, only the tickets with the ending digits 544 win. With, for example, 11,000 tickets sold, the ticket numbers 000.544 / 001.544 / 002.544 ... 010.544 would win. So, 11 ticket participants would win. Each winner with this number would receive around 0.284 Bitcoin (3.125 BTC / 11). One could also let the ticket numbers with the ending digits 44 win, and thus every hundredth ticket. Or even combine it. What I also noticed was that with retailers, a special case arises. Retailers receive 5% of the block rewards in the event of a found block. But only proportionally to the tickets sold by the retailer. This means that in order for the entire 5% to be distributed to the retailers, all 10,000 tickets of 10.000 possible tickets would have to be sold by retailers. Since not all tickets will be sold by retailers, a remaining amount will be left over. This could be distributed additionally to the miners. Or any other variant. I hope the idea finds resonance and invites discussion. Maybe I've made some mistakes in thinking, and the idea is not feasible. But if you like the idea, please forward it to developers, investors, and others you know. Stay humble hash sats @nostr:npub1uf3w6w3z4kxy0zc80m6a03tt9s7855c9r8kkjmkju47xtc28l09sc30gqq [Excel sheet for download](https://c.gmx.net/@329519820976429649/KJTehgh0SMGliV4HLjMf0g)
@ e262ed3a:e147fbcb
2025-02-01 15:37:28**Feel free to develop** I got an idea while watching a video from @BTCSessions, which I personally cannot implement technically. Therefore, I would like to present it here for discussion and free implementation. It makes sense to me, but what do I know? Let the swarm intelligence decide. The goal of the business idea is: How can I bring as many solo miners as possible into a pool without them having to pay for the electricity for mining and their mining hardware can be amortized quickly, so they can purchase more mining hardware? How can we financially support Bitcoin and Nostr developers in the long term? How can we intensify developers for the implementation of this idea? How can we encourage non-Bitcoiners to invest in the support of the Bitcoin network? How can we get non-Bitcoin retailers to invest in the Bitcoin network? **The answer is: PROSPECT OF WINNING The solution lies in a kind of RAFFLE. (Not a betting website) !** The legal difference between a BET and a RAFFLE varies from country to country. It lies in the fact that a raffle must be very transparent regarding the chances of winning and the proceeds must go to a good cause. Those involved in the implementation can, of course, be compensated (also with a profit for the individual participants). The extent to which this is allowed would have to be checked by those who want to implement this idea. In the following, I will describe the implementation roughly. Since this is not a sales presentation, please excuse me if the following proposal is not fully structured. **Participants in the idea are: Consumers (ticket buyers) Bitcoin miners Retailers Non-profit company that implement the project** **What's it about?** @BTCSessions has a YouTube video about the miner FutureBit. In the dashboard of the solo miner, you could see how high the hash rate was. But above all, you could see how high the chance of winning was for the solo miner in the overall network. In the case of BTCSessions FutureBit, the hash rate was around 5 TerraHash and the chance of winning was around 1:1,000,000. (Which, according to my calculations, was not correct). The power consumption was around 32 watts. When I saw that, it suddenly dawned on me. Could it be possible to create a website/app that determines the total hash rate of a mining pool and then offers an electronic, numbered ticket for each 1 TerraHash (TH/s) of the pool for, for example, 0.1 USD? The minimum purchase amount would be 10 tickets. The customer sees the chance of winning and could even see the possible payout. The ticket is only valid for the next block (similar to roulette). Another variant could be that the buyer can select one or more of the next 10 blocks and purchase tickets for the selected block. Since you don't know in advance how high the pool hash rate will be 5 or 10 blocks ahead, the amount of tickets to be issued for the 2nd block, for example, could only be 90% of the current pool hash rate, the 3rd block only 80%, and so on. If block 3, for example, advances to position 2, the previously unavailable 10% will be released for further tickets. (Determined by the pool hash rate at that time) The purchase of 10 or more tickets could be automated in the customer's account on the website/app (intervals: hourly, daily, weekly, every 10 blocks, etc.). Customers could also top up their account with satoshis, enabling automatic deductions for ticket purchases. This could be facilitated by automatically issuing a Nostr npub to each customer, which would also create a wallet at Primal.net (Strike). For non-Bitcoiners, Zaprite could be used to recharge their account. Alternatively, customers could enter a NostrWalletConnection NWC to enable automatic deductions from their Lightning wallet. The project operators might also consider running their own ecash mint, which would allow them to assign an integrated ecash address to customers without a Lightning address. Tickets with ascending numbers would be allocated strictly in the order of payment receipts. **Calculations for the miners:** The FutureBit miner consumed approximately 30 watts per terahash/hour. Let's assume that 10 terahash consume 300 watts per hour, then the miner consumes 50 watts per 10 minutes (per block). Let's further assume that a kilowatt-hour of electricity costs between 10 and 30 cents, then it costs the miner 3-9 cents per hour for electricity at 10 terahash mining capacity. So, 0.5-1.5 cents per block. In the case that each ticket is sold for 1 terahash for the next block, one could automatically transfer, for example, 5% of the satoshis received from ticket sales to each participating miner in the pool (proportional to the average hash rate delivered by the miner in the last block in the pools). This happens even if the block is not found. If fewer tickets are sold than the maximum possible amount, then the 5% of the sold tickets will be distributed proportionally. (See also my Excel file? At the center of the project is a website/app that manages the raffle. Here, anyone can register and create an account. Either as a miner, retailer, or customer with or without KYC, for example, with their own nostr nsec, wallet signature, email and password or phone number and password. Once logged into the account, Bitcoiners can enter their Lightning address and a Bitcoin on-chain address. Non-Bitcoiners enter their financial data in case they win. Miners must enter a Bitcoin and Lightning (or ecash) address. The pooling process is also managed in the miner's account. Tickets can be purchased (like in a regular online shop) and paid for in any way. Zaprite could be a solution here. But also Strike, Cashapp, etc. As described above, such purchases could also be automated. **Retailers** can also register as such. They will then have the opportunity to sell "tickets" to their customers and collect the money in cash. To sell tickets, they must enter the customer's name and a valid email address. After payment, they must send the purchase price via Lightning to the non-profit company, which will then confirm the purchase to the ticket buyer and the retailer with all the data. This is the receipt for the buyer. In the event of a win (the mined block must have 3-6 block confirmations), the ticket buyer will receive an email explaining all the further details of how to claim the prize. This could be a link that takes them directly to the website and logs them in directly. The winner can then enter their data on how and where the money should be paid out (Bitcoin address or bank details). Alternatively, they can go to their retailer, who can assist them by entering the data in their sub-account (customer account). To prevent the retailer from falsifying the data entry, the winner will first receive an email with the entered data, which they can confirm (if correct). Since the retailer is also involved in the win, they will also be notified. How many tickets can be offered per round (Bitcoin block)? The number of tickets depends on the hash rate in the pool. One ticket can be issued per 1 TerraHash (TH/s). How the ticket is generated per round and customer, I don't know, as I lack the technical knowledge. Maybe as a kind of NFT that contains the corresponding data (customer number (npub) of the buyer and possibly retailer, block number, ticket number). Or as a Taproot asset on Lightning? Or as a minted ecash coin? Or simply as an entry in a database that the customer can see in their account. The maximum payout of the winnings in the event of a found block to the ticket holders could be 70%. The remaining 30% would be distributed to the miners and retailers. For example: Miners 25%, retailers 5%. The non-profit organization receives nothing from the block rewards. Instead, it receives 65% of the revenue from all ticket sales. With a mining pool hash rate of 10,000 TH/s, where all tickets are sold continuously, a daily donation of around 93,000 USD would be generated. (see Excel.file) The revenue, after deducting the possible costs of the organization, goes directly to @opensats and/or other organizations that support the Bitcoin network after each block. Either via Lightning or Bitcoin on-chain payment. In the attached Excel file, you can find my calculations. Here, anyone can play through different scenarios. What I noticed was that with maximum ticket sales per block, only around 200 USD per 10 tickets would be paid out, since each participating ticket wins in the event of a found block. Since I believe that this is not a very great incentive for buying tickets, I suggest the following variants. Winning variants: Each purchased ticket has a running number. Ticket 1 has the number 000.000, ticket 2 has the number 000.001, ticket 10.120 has the number 010.119, and so on. If the next block is found, then this found block in the Bitcoin blockchain has a hash. For example, block 881367 has the hash 000000000000000000014b0fab24355c71c6940584d9cd5990c0b081a31d54a4 Let's now remove the letters and read only the numbers from back to front, so the last 3 numbers are 544 Instead of every participating ticket winning, in this variant, only the tickets with the ending digits 544 win. With, for example, 11,000 tickets sold, the ticket numbers 000.544 / 001.544 / 002.544 ... 010.544 would win. So, 11 ticket participants would win. Each winner with this number would receive around 0.284 Bitcoin (3.125 BTC / 11). One could also let the ticket numbers with the ending digits 44 win, and thus every hundredth ticket. Or even combine it. What I also noticed was that with retailers, a special case arises. Retailers receive 5% of the block rewards in the event of a found block. But only proportionally to the tickets sold by the retailer. This means that in order for the entire 5% to be distributed to the retailers, all 10,000 tickets of 10.000 possible tickets would have to be sold by retailers. Since not all tickets will be sold by retailers, a remaining amount will be left over. This could be distributed additionally to the miners. Or any other variant. I hope the idea finds resonance and invites discussion. Maybe I've made some mistakes in thinking, and the idea is not feasible. But if you like the idea, please forward it to developers, investors, and others you know. Stay humble hash sats @nostr:npub1uf3w6w3z4kxy0zc80m6a03tt9s7855c9r8kkjmkju47xtc28l09sc30gqq [Excel sheet for download](https://c.gmx.net/@329519820976429649/KJTehgh0SMGliV4HLjMf0g) @ a012dc82:6458a70d
2025-02-01 15:17:38The cryptocurrency landscape is witnessing a remarkable resurgence, with Bitcoin once again leading the charge. After a period of volatility and uncertainty, Bitcoin has reclaimed its throne as the king of cryptocurrencies, drawing renewed interest from investors and financial experts alike. This article delves into the factors behind Bitcoin's comeback, its implications for the market, and what the future might hold. **Table Of Content** - The Remarkable Recovery of Bitcoin - The Ripple Effect on the Crypto Market - Investor Sentiment: Cautious Optimism - The Future Outlook: Opportunities and Challenges - A New Era for Bitcoin - Conclusion - FAQs **The Remarkable Recovery of Bitcoin** **A Surge in Value** After a tumultuous phase marked by sharp declines and skepticism, Bitcoin has made a striking comeback. The digital currency's value has seen a significant upswing, reminding investors of its potential as a high-reward, albeit high-risk, asset. This recovery is not just a numerical increase but a symbol of resilience in the face of market adversities. **Driving Factors** Several factors have contributed to Bitcoin's resurgence. These include an increase in institutional adoption, technological advancements within the blockchain ecosystem, and a growing recognition of Bitcoin as a 'digital gold' amidst economic uncertainties. Moreover, regulatory clarity in some regions has provided a more stable environment for cryptocurrency investments. **The Ripple Effect on the Crypto Market** **Boosting Market Confidence** Bitcoin's rebound has had a ripple effect across the entire cryptocurrency market. Altcoins and emerging digital assets have also seen a boost in both value and investor interest. This resurgence has rekindled the enthusiasm for decentralized finance (DeFi) and non-fungible tokens (NFTs), which had waned during the market downturn. **Impact on Blockchain Innovation** The renewed interest in Bitcoin has spurred further innovation in blockchain technology. Developers and entrepreneurs are increasingly exploring new use cases for blockchain, expanding beyond traditional financial applications to areas like supply chain management, digital identity, and more. **Investor Sentiment: Cautious Optimism** **Institutional Investors' Role** Institutional investors, once wary of Bitcoin's volatility, are now more open to including it in their portfolios. This shift is partly due to the improved infrastructure and regulatory frameworks that make investing in Bitcoin less risky than in its early years. **Retail Investors' Perspective** Retail investors, who were significantly affected by the previous market downturn, are approaching Bitcoin with cautious optimism. Many are drawn by the potential for high returns but remain mindful of the risks involved. **The Future Outlook: Opportunities and Challenges** **Potential for Growth** With its current momentum, Bitcoin has the potential for further growth. Its evolving role in the financial ecosystem, particularly in areas like digital payments and remittances, suggests a bright future. **Navigating Challenges** However, challenges remain. Regulatory uncertainties, potential market manipulations, and the environmental impact of Bitcoin mining are issues that need addressing. How these challenges are managed will significantly influence Bitcoin's trajectory. **A New Era for Bitcoin** **A Testament to Resilience** Bitcoin's comeback is a testament to its resilience and the enduring faith of its supporters. It has not only reclaimed its position as the leading cryptocurrency but has also reinforced the belief in the potential of digital currencies. **A Dynamic Future Ahead** As investors, both institutional and retail, continue to take notice, Bitcoin's journey is far from over. Its ability to adapt, innovate, and overcome challenges will shape not just its future but also that of the broader cryptocurrency market. The current phase is just the beginning of what promises to be a dynamic and transformative era for Bitcoin and digital currencies as a whole. **Conclusion** Bitcoin's resurgence marks a significant milestone in the cryptocurrency world. Its ability to bounce back from adversity and regain its status as the leading digital currency has not only bolstered investor confidence but also highlighted the growing maturity of the crypto market. As Bitcoin continues to evolve, navigating through regulatory landscapes and technological advancements, it stands as a symbol of innovation and resilience in the ever-changing world of finance. **FAQs** **Why has Bitcoin's value surged recently?** Bitcoin's value has surged due to factors like increased institutional adoption, advancements in blockchain technology, and its growing recognition as a digital store of value amidst economic uncertainties. **How has Bitcoin's recovery affected the overall crypto market?** Bitcoin's recovery has positively impacted the entire crypto market, boosting the value of altcoins and reigniting interest in decentralized finance (DeFi) and non-fungible tokens (NFTs). **Are institutional investors now more interested in Bitcoin?** Yes, institutional investors are showing increased interest in Bitcoin, thanks to improved investment infrastructure and clearer regulatory frameworks. **What are the main challenges facing Bitcoin in the future?** The main challenges include regulatory uncertainties, potential market manipulations, and the environmental impact of Bitcoin mining. **Is it safe for retail investors to invest in Bitcoin now?** While Bitcoin offers potential high returns, it remains a high-risk investment. Retail investors should approach with caution and consider diversifying their investment portfolio. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: [@croxroadnews.co](https://x.com/croxroadnewsco)** **Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)** **Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** ***DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.***
@ a012dc82:6458a70d
2025-02-01 15:17:38The cryptocurrency landscape is witnessing a remarkable resurgence, with Bitcoin once again leading the charge. After a period of volatility and uncertainty, Bitcoin has reclaimed its throne as the king of cryptocurrencies, drawing renewed interest from investors and financial experts alike. This article delves into the factors behind Bitcoin's comeback, its implications for the market, and what the future might hold. **Table Of Content** - The Remarkable Recovery of Bitcoin - The Ripple Effect on the Crypto Market - Investor Sentiment: Cautious Optimism - The Future Outlook: Opportunities and Challenges - A New Era for Bitcoin - Conclusion - FAQs **The Remarkable Recovery of Bitcoin** **A Surge in Value** After a tumultuous phase marked by sharp declines and skepticism, Bitcoin has made a striking comeback. The digital currency's value has seen a significant upswing, reminding investors of its potential as a high-reward, albeit high-risk, asset. This recovery is not just a numerical increase but a symbol of resilience in the face of market adversities. **Driving Factors** Several factors have contributed to Bitcoin's resurgence. These include an increase in institutional adoption, technological advancements within the blockchain ecosystem, and a growing recognition of Bitcoin as a 'digital gold' amidst economic uncertainties. Moreover, regulatory clarity in some regions has provided a more stable environment for cryptocurrency investments. **The Ripple Effect on the Crypto Market** **Boosting Market Confidence** Bitcoin's rebound has had a ripple effect across the entire cryptocurrency market. Altcoins and emerging digital assets have also seen a boost in both value and investor interest. This resurgence has rekindled the enthusiasm for decentralized finance (DeFi) and non-fungible tokens (NFTs), which had waned during the market downturn. **Impact on Blockchain Innovation** The renewed interest in Bitcoin has spurred further innovation in blockchain technology. Developers and entrepreneurs are increasingly exploring new use cases for blockchain, expanding beyond traditional financial applications to areas like supply chain management, digital identity, and more. **Investor Sentiment: Cautious Optimism** **Institutional Investors' Role** Institutional investors, once wary of Bitcoin's volatility, are now more open to including it in their portfolios. This shift is partly due to the improved infrastructure and regulatory frameworks that make investing in Bitcoin less risky than in its early years. **Retail Investors' Perspective** Retail investors, who were significantly affected by the previous market downturn, are approaching Bitcoin with cautious optimism. Many are drawn by the potential for high returns but remain mindful of the risks involved. **The Future Outlook: Opportunities and Challenges** **Potential for Growth** With its current momentum, Bitcoin has the potential for further growth. Its evolving role in the financial ecosystem, particularly in areas like digital payments and remittances, suggests a bright future. **Navigating Challenges** However, challenges remain. Regulatory uncertainties, potential market manipulations, and the environmental impact of Bitcoin mining are issues that need addressing. How these challenges are managed will significantly influence Bitcoin's trajectory. **A New Era for Bitcoin** **A Testament to Resilience** Bitcoin's comeback is a testament to its resilience and the enduring faith of its supporters. It has not only reclaimed its position as the leading cryptocurrency but has also reinforced the belief in the potential of digital currencies. **A Dynamic Future Ahead** As investors, both institutional and retail, continue to take notice, Bitcoin's journey is far from over. Its ability to adapt, innovate, and overcome challenges will shape not just its future but also that of the broader cryptocurrency market. The current phase is just the beginning of what promises to be a dynamic and transformative era for Bitcoin and digital currencies as a whole. **Conclusion** Bitcoin's resurgence marks a significant milestone in the cryptocurrency world. Its ability to bounce back from adversity and regain its status as the leading digital currency has not only bolstered investor confidence but also highlighted the growing maturity of the crypto market. As Bitcoin continues to evolve, navigating through regulatory landscapes and technological advancements, it stands as a symbol of innovation and resilience in the ever-changing world of finance. **FAQs** **Why has Bitcoin's value surged recently?** Bitcoin's value has surged due to factors like increased institutional adoption, advancements in blockchain technology, and its growing recognition as a digital store of value amidst economic uncertainties. **How has Bitcoin's recovery affected the overall crypto market?** Bitcoin's recovery has positively impacted the entire crypto market, boosting the value of altcoins and reigniting interest in decentralized finance (DeFi) and non-fungible tokens (NFTs). **Are institutional investors now more interested in Bitcoin?** Yes, institutional investors are showing increased interest in Bitcoin, thanks to improved investment infrastructure and clearer regulatory frameworks. **What are the main challenges facing Bitcoin in the future?** The main challenges include regulatory uncertainties, potential market manipulations, and the environmental impact of Bitcoin mining. **Is it safe for retail investors to invest in Bitcoin now?** While Bitcoin offers potential high returns, it remains a high-risk investment. Retail investors should approach with caution and consider diversifying their investment portfolio. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: [@croxroadnews.co](https://x.com/croxroadnewsco)** **Instagram: [@croxroadnews.co](https://www.instagram.com/croxroadnews.co/)** **Youtube: [@croxroadnews](https://www.youtube.com/@croxroadnews)** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** ***DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.*** @ df478568:2a951e67
2025-02-01 15:07:26 # Garlic Cashew Recipe I wrote about selling roasted cashews as an experiment in capitalism [here](https://substack.com/home/post/p-156063324). I make them myself and in the spirit of free and open source software, I figured I would open-source the recipe with a catch. You can get the recipe in one of two ways. 1. Become a paid subscriber to my Substack and you will get a key to unlock the cipher text 2. Read it in the clear(un-encrypted) on nostr. The easiest way to do this is to navigate to primal.net in your browser and search for “marc26z.” Click on my profile and **you can find all of my writing in the clear in the reads section*. I tried using PGP in another article, but it’s a little cumbersome and pretentious. Andreas Grifin said, [Nostr is what PGP should have been. A web of trust with easy-to-use encryption and verification](nostr:note12c47gxhxyw5elg55yh4g90fztddhpgqz95jf6fwvk3yygt7qml6sjd6lwj). I tend to agree. So I’m using something else.  https://8gwifi.org/CipherFunctions.jsp **Decrypt using the passphrase below the paywall**. "To encrypt is to indicate the desire for privacy, and to encrypt with weak cryptography is to indicate not too much desire for privacy.” I do not indicate a desire for too much privacy here, but I like playing with these things. I hope you enjoy playing with them too. ## How To Decrypt 1. Go to https://encrypt-online.com/decrypt/ on your favorite web browser. 2. Choose aes-256-cbc(this is the default setting) 3. Copy and paste the cipher text into the decryption field 4. enter the passphrase into the passphrase field 5. press the Decrypt button 6. Optional: Copy and paste the decrypted recipe into a markdown editor like https://dillinger.io/ U2FsdGVkX1+4jxMfWCc6kNsbDa0i/J3eiV81r7/z5c0Eqe73vw01M22uRFm9PjRRaj/CJN+BidtuNXQW6G3hk3S/4AoGN2gKfKkKSbzEHsONZ2LeXuoPflikratDU+lADVeR5IlsVaATyImBO0k/cXq54TOlEXBoVRCIqaA9tO8UA126GfTdmegXX14jUcdV9EISSGw8Bn5fksptm6qKyz2GsmyiKcmNczh8Nz7biyhCrnrt2hyLDbirIAjZcCTJjkAlJjrrvuLHJZx6pmq6MsMv2eHT35d/WL/+ZpBgLVh2Xq2u+J9izNKYMgvMSsJKylC7MJvj4xAOosJuq9IyGN6b/7z2UTSsR13Utc8aFeW3zxtkvAqYthh7XV1H2e1nEKOij8gOfFHvlfj10IiG0g3QbEch1nTTGq3Lncql9Q1a9QZb5pcsellPWeR4vhko3ssdxzIkLnvGz5Cjy1brMjZ97j7sSmHE9FT10L4L6ijXWuW25ikDRK0xnks0VfAvDVz75NCE+Qaz9MLPt8h0ESto3bTyuXrHFNNPOxnaEDw4TvSTN5G0tmUrqotRMmu5DadAm6aLMmJHL1OHVNGK4fH7Hb9S+7dBLEbQG3vRivz2SzpqgKFnFYwMJTQykUC3 Passphrase: implored-junker-requires Here is the decrypted recipe if you do not wish to learn about encryption, but want to try my delicious non-vegan cashew recipe anyway. 1 LB organic raw cashews 2 TBS beef tallow 2 TBS salt 1 TBS garlic powder Melt tallow in the microwave Brush the tallow on the nuts. Spread onto a cookie sheet. Preheat oven 350 degrees Bake for 10 minutes. Let cool. Violá! Enjoy your garlic-roasted cashews. Or...you can pick some up at nostr:npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0 [A Crumby Commercial](https://i.imgflip.com/1ts3w3.jpg) npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0 [881,805]()https://mempool.marc26z.com/block/00000000000000000000f5d9aa481b8f2555deaa8638a3c1f2eb4ffa8f474f9d [Merch](nostr:npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0)
@ df478568:2a951e67
2025-02-01 15:07:26 # Garlic Cashew Recipe I wrote about selling roasted cashews as an experiment in capitalism [here](https://substack.com/home/post/p-156063324). I make them myself and in the spirit of free and open source software, I figured I would open-source the recipe with a catch. You can get the recipe in one of two ways. 1. Become a paid subscriber to my Substack and you will get a key to unlock the cipher text 2. Read it in the clear(un-encrypted) on nostr. The easiest way to do this is to navigate to primal.net in your browser and search for “marc26z.” Click on my profile and **you can find all of my writing in the clear in the reads section*. I tried using PGP in another article, but it’s a little cumbersome and pretentious. Andreas Grifin said, [Nostr is what PGP should have been. A web of trust with easy-to-use encryption and verification](nostr:note12c47gxhxyw5elg55yh4g90fztddhpgqz95jf6fwvk3yygt7qml6sjd6lwj). I tend to agree. So I’m using something else.  https://8gwifi.org/CipherFunctions.jsp **Decrypt using the passphrase below the paywall**. "To encrypt is to indicate the desire for privacy, and to encrypt with weak cryptography is to indicate not too much desire for privacy.” I do not indicate a desire for too much privacy here, but I like playing with these things. I hope you enjoy playing with them too. ## How To Decrypt 1. Go to https://encrypt-online.com/decrypt/ on your favorite web browser. 2. Choose aes-256-cbc(this is the default setting) 3. Copy and paste the cipher text into the decryption field 4. enter the passphrase into the passphrase field 5. press the Decrypt button 6. Optional: Copy and paste the decrypted recipe into a markdown editor like https://dillinger.io/ U2FsdGVkX1+4jxMfWCc6kNsbDa0i/J3eiV81r7/z5c0Eqe73vw01M22uRFm9PjRRaj/CJN+BidtuNXQW6G3hk3S/4AoGN2gKfKkKSbzEHsONZ2LeXuoPflikratDU+lADVeR5IlsVaATyImBO0k/cXq54TOlEXBoVRCIqaA9tO8UA126GfTdmegXX14jUcdV9EISSGw8Bn5fksptm6qKyz2GsmyiKcmNczh8Nz7biyhCrnrt2hyLDbirIAjZcCTJjkAlJjrrvuLHJZx6pmq6MsMv2eHT35d/WL/+ZpBgLVh2Xq2u+J9izNKYMgvMSsJKylC7MJvj4xAOosJuq9IyGN6b/7z2UTSsR13Utc8aFeW3zxtkvAqYthh7XV1H2e1nEKOij8gOfFHvlfj10IiG0g3QbEch1nTTGq3Lncql9Q1a9QZb5pcsellPWeR4vhko3ssdxzIkLnvGz5Cjy1brMjZ97j7sSmHE9FT10L4L6ijXWuW25ikDRK0xnks0VfAvDVz75NCE+Qaz9MLPt8h0ESto3bTyuXrHFNNPOxnaEDw4TvSTN5G0tmUrqotRMmu5DadAm6aLMmJHL1OHVNGK4fH7Hb9S+7dBLEbQG3vRivz2SzpqgKFnFYwMJTQykUC3 Passphrase: implored-junker-requires Here is the decrypted recipe if you do not wish to learn about encryption, but want to try my delicious non-vegan cashew recipe anyway. 1 LB organic raw cashews 2 TBS beef tallow 2 TBS salt 1 TBS garlic powder Melt tallow in the microwave Brush the tallow on the nuts. Spread onto a cookie sheet. Preheat oven 350 degrees Bake for 10 minutes. Let cool. Violá! Enjoy your garlic-roasted cashews. Or...you can pick some up at nostr:npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0 [A Crumby Commercial](https://i.imgflip.com/1ts3w3.jpg) npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0 [881,805]()https://mempool.marc26z.com/block/00000000000000000000f5d9aa481b8f2555deaa8638a3c1f2eb4ffa8f474f9d [Merch](nostr:npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0) @ cbaa0c82:e9313245
2025-02-01 15:07:16#TheWholeGrain - #January2025 This January we really got to start the story telling of our first adventure series painted by Dakota Jernigan a.k.a. The Bitcoin Painter! The typical Singles of the month were released on Sunday along with a special Single released on the first to celebrate the New Year! Here we go, 2025! And, even with all that the monthly Concept Art, Bitcoin Art, and the newest Cover Art from Toast's Comic Collection were all still released! Not only was the first month of 2025 quite packed full of fun content, but the Bread and Toast website got a makeover! Did you notice all the explanation points!? We're all so excited we just can't help ourselves from using them! **January Sunday Singles** 2025-01-01 | Sunday Single 73 Title: Happy New Year 2025 *Happy New Year! What a year 2024 has been! We can’t wait to see what 2025 has in store for us!* https://i.nostr.build/QFTmeR5p2FthPMXp.png 2025-01-05 | Sunday Single 074 Title: Snowflake *It’s the most beautiful snowflake Toast has ever seen… until this one melts then it’s on to the next one!* https://i.nostr.build/YHGeOcYv8WEP1fAf.png 2025-01-12 | Sunday Single 075 Title: Weight Lifting *End-Piece has been working out since last year’s resolution. Now, time for heavy lifting!* https://i.nostr.build/8lxeovAr5aK598Ze.png 2025-01-19 | Sunday Single 076 Title: Good Morning *GM, Everybody!* https://i.nostr.build/9jn2D2if4sFfNXzU.png 2025-01-26 | Sunday Single 077 Title: Chess *When it comes to the chessboard, Bread is King.* https://i.nostr.build/LZq57iL7tOWbHAKc.png **Adventure Series: Questline** Bread, Toast, and End-Piece have started their journey in Grain Valley, and they have already found themselves in what used to be a village that is now been burnt to a crisp! Writer: Daniel David (dan 🍞) Artist: Dakota Jernigan (The Bitcoin Painter) 2025-01-14 | Questline 001 - The Adventure Begins Our heroes take their first steps upon one of the oldest paths in all of Grain Valley. They can see the mountains in the background of the landscape before them. As they walk, they see in the distance ahead of them large amounts of black smoke rising until it disappears into the sky. https://i.nostr.build/ygjmYlWAZ4uPfPCn.png 2025-01-28 | Questline 002 - A Village Burned The source of smoke surrounds our heroes as their path brings them to the center of what used to be a village. It seems to be completely abandoned with no signs of life. Yet, all the remains of the village appear to have only recently burned to a crisp. What could have possibly happened here? https://i.nostr.build/BJ4L1shKh5YERzWc.png **Other Content Released in January 2025** 2025-01-01 | Toast's Comic Collection Title: Iron Bread #9 *"I am Iron Bread." - Tony Starch* https://i.nostr.build/QJKkDCbfgc6Vqzcq.png 2025-01-08 | Concept Art Title: Second Bread Sketch *A second sketch of the character Bread. Remade and cleaned up.* https://i.nostr.build/4TXIRSUGA6viEaJx.png 2025-01-15 | Bitcoin Art Title: Stack Sats *Toast is constantly stacking sats!* https://i.nostr.build/txxkux0oJqyjNcSL.png Thanks for checking out the fifth issue of The Whole Grain. The Whole Grain is released on the first of every month and covers all of the content released by Bread and Toast in the previous month. For all Bread and Toast content visit BreadandToast.com! **Thanks for helping us kick off 2025!** ***Bread, Toast, and End-Piece*** #BreadandToast #SundaySingle #Questline #ToastsComicCollection #ConceptArt #BitcoinArt #Bread #Toast #EndPiece #Artstr #Comic #Cartoon #NostrOnly #🖼️ ***List of nPubs Mentioned:*** The Bitcoin Painter: npub1tx5ccpregnm9afq0xaj42hh93xl4qd3lfa7u74v5cdvyhwcnlanqplhd8g dan 🍞: npub16e3vzr7dk2uepjcnl85nfare3kdapxge08gr42s99n9kg7xs8xhs90y9v6
@ cbaa0c82:e9313245
2025-02-01 15:07:16#TheWholeGrain - #January2025 This January we really got to start the story telling of our first adventure series painted by Dakota Jernigan a.k.a. The Bitcoin Painter! The typical Singles of the month were released on Sunday along with a special Single released on the first to celebrate the New Year! Here we go, 2025! And, even with all that the monthly Concept Art, Bitcoin Art, and the newest Cover Art from Toast's Comic Collection were all still released! Not only was the first month of 2025 quite packed full of fun content, but the Bread and Toast website got a makeover! Did you notice all the explanation points!? We're all so excited we just can't help ourselves from using them! **January Sunday Singles** 2025-01-01 | Sunday Single 73 Title: Happy New Year 2025 *Happy New Year! What a year 2024 has been! We can’t wait to see what 2025 has in store for us!* https://i.nostr.build/QFTmeR5p2FthPMXp.png 2025-01-05 | Sunday Single 074 Title: Snowflake *It’s the most beautiful snowflake Toast has ever seen… until this one melts then it’s on to the next one!* https://i.nostr.build/YHGeOcYv8WEP1fAf.png 2025-01-12 | Sunday Single 075 Title: Weight Lifting *End-Piece has been working out since last year’s resolution. Now, time for heavy lifting!* https://i.nostr.build/8lxeovAr5aK598Ze.png 2025-01-19 | Sunday Single 076 Title: Good Morning *GM, Everybody!* https://i.nostr.build/9jn2D2if4sFfNXzU.png 2025-01-26 | Sunday Single 077 Title: Chess *When it comes to the chessboard, Bread is King.* https://i.nostr.build/LZq57iL7tOWbHAKc.png **Adventure Series: Questline** Bread, Toast, and End-Piece have started their journey in Grain Valley, and they have already found themselves in what used to be a village that is now been burnt to a crisp! Writer: Daniel David (dan 🍞) Artist: Dakota Jernigan (The Bitcoin Painter) 2025-01-14 | Questline 001 - The Adventure Begins Our heroes take their first steps upon one of the oldest paths in all of Grain Valley. They can see the mountains in the background of the landscape before them. As they walk, they see in the distance ahead of them large amounts of black smoke rising until it disappears into the sky. https://i.nostr.build/ygjmYlWAZ4uPfPCn.png 2025-01-28 | Questline 002 - A Village Burned The source of smoke surrounds our heroes as their path brings them to the center of what used to be a village. It seems to be completely abandoned with no signs of life. Yet, all the remains of the village appear to have only recently burned to a crisp. What could have possibly happened here? https://i.nostr.build/BJ4L1shKh5YERzWc.png **Other Content Released in January 2025** 2025-01-01 | Toast's Comic Collection Title: Iron Bread #9 *"I am Iron Bread." - Tony Starch* https://i.nostr.build/QJKkDCbfgc6Vqzcq.png 2025-01-08 | Concept Art Title: Second Bread Sketch *A second sketch of the character Bread. Remade and cleaned up.* https://i.nostr.build/4TXIRSUGA6viEaJx.png 2025-01-15 | Bitcoin Art Title: Stack Sats *Toast is constantly stacking sats!* https://i.nostr.build/txxkux0oJqyjNcSL.png Thanks for checking out the fifth issue of The Whole Grain. The Whole Grain is released on the first of every month and covers all of the content released by Bread and Toast in the previous month. For all Bread and Toast content visit BreadandToast.com! **Thanks for helping us kick off 2025!** ***Bread, Toast, and End-Piece*** #BreadandToast #SundaySingle #Questline #ToastsComicCollection #ConceptArt #BitcoinArt #Bread #Toast #EndPiece #Artstr #Comic #Cartoon #NostrOnly #🖼️ ***List of nPubs Mentioned:*** The Bitcoin Painter: npub1tx5ccpregnm9afq0xaj42hh93xl4qd3lfa7u74v5cdvyhwcnlanqplhd8g dan 🍞: npub16e3vzr7dk2uepjcnl85nfare3kdapxge08gr42s99n9kg7xs8xhs90y9v6 @ 2fb77d26:c47a6ee1
2025-02-01 14:40:02In H. G. Wells’ Roman [Die Zeitmaschine](https://de.wikipedia.org/wiki/Die_Zeitmaschine) und den diversen Verfilmungen werden sie als »*ausschweifend, langsam und naiv*« dargestellt. Von »*untermenschlicher Intelligenz*« gezeichnet. Für [Dan Simmons](https://de.wikipedia.org/wiki/Eloi_\(Die_Zeitmaschine\)#In_Dan_Simmons%E2%80%99_Ilium) sind sie »*faul, ungebildet und unkultiviert*«. Die [Eloi](https://de.wikipedia.org/wiki/Eloi_\(Die_Zeitmaschine\)). Die als Nahrungsquelle der Morlocks gehaltenen Nachfahren des Homo sapiens. »*Sie entwickeln sich rückläufig und verlernen Jahrtausende von Kultur, Denken und Vernunft, bis sie sich mit dem Vergnügen des bloßen Daseins zufrieden geben*«. Ertönt das Schlüsselsignal, auf das sie von ihren Züchtern konditioniert wurden – eine umgebaute Zivilschutzsirene – trotten sie freiwillig und in hypnotischer Apathie zur Schlachtbank. Ein ähnlichen Eindruck hatten viele Maßnahmenkritiker von den Unterstützern der mittlerweile in allen Punkten [widerlegten](https://www.regenauer.press/kapitalverbrechen) Covid-Propaganda. Zurecht. Das Gefolge von Drosten, Lauterbach und Co. war blind für Fakten und ist ins offene Messer gelaufen. Bedauerlicherweise verhalten sich viele Maßnahmenkritiker aber nun in weiten Teilen genauso. Sie haben Idole gefunden. Wollen glauben. Sie ignorieren Informationen, Fakten und Daten und werden Opfer einer neu justierten, gut geölten Propagandamaschine. Nur, um die in ihre neuen Helden gesetzten Hoffnungen nicht aufgeben und der wenig erbaulichen Realität nicht ins Auge blicken zu müssen. Sie glauben an Donald Trump, Javier Milei, Alice Weidel, Peter Thiel und vor allem Elon Musk. Daran, dass der supranationale Nachhaltigkeitskorporatismus am Ende sei, das Finanzsystem gerettet und Gerechtigkeit hergestellt wird. Die Widerständler von gestern sind die »*Schlafschafe*« von heute. Sie scheinen vergessen zu haben, wie Propaganda funktioniert. Aus diesem Grund – und weil es ein so schön griffiges Wort ist, bei dem man nur einen Buchstaben verändern muss, um daraus den Vornamen eines vermeintlichen Heilsbringers zu basteln – erlaube ich mir, die Anhänger des MAGA-Kults im Zuge der folgenden Seiten mokant als Eloi zu bezeichnen. Ein bisschen Spaß muss sein. **Kurskorrektur mit Ansage** [Lynn Forester de Rothschild](https://www.inclusivecapitalism.com/about/), in der finanzoligarchischen Hackordnung mindestens eine Ebene über BlackRock und Co. anzusiedeln, kündigte den aktuellen Narrativwechsel bereits am 30. August 2023 an, als sie bei [Bloomberg](https://www.youtube.com/watch?v=eZzZubPKPrw) sagte, der Begriff »*ESG gehöre in die Tonne*«. Er sei verbrannt. Auch BlackRock-CEO Larry Fink, der Marktteilnehmer zur Unterstützung von ESG »*[zwingen](https://www.forbes.com/sites/jonmcgowan/2023/06/05/conservative-outrage-over-esg-and-dei-fueled-by-2017-blackrock-ceo-video/)*« wollte, [teilte](https://www.forbes.com/sites/jonmcgowan/2024/03/27/blackrocks-fink-calls-for-energy-pragmatism-omits-esg-from-annual-letter/) seinen Investoren bereits am 26. März 2023 mit, das in Verruf gekommene Label ESG durch den Begriff »*Energiepragmatismus*« zu ersetzen. Sowohl Rothschild als auch Fink räumten aber gleichzeitig ein, dass sich die übergeordnete Agenda nicht ändern und man die »Green Economy« weiter vorantreiben werde, man diese aber besser vermarkten müsse, um konservative Kreise nicht weiter gegen sich aufzubringen. Ein simpler Marketing-Trick. Wenig überraschend also, dass sowohl [BlackRock](https://nypost.com/2025/01/11/business/blackrock-quits-net-zero-initiative-at-perfect-time-as-woke-policies-contribute-to-devastating-la-fires/) als auch sechs amerikanische [Großbanken](https://joannenova.com.au/2025/01/the-last-american-banker-rats-are-leaving-the-un-net-zero-banking-club/) Anfang 2025 die [Net Zero Initiative](https://www.net-zero-initiative.com/en) verließen. Zum »perfekten Zeitpunkt«, wie die [New York Post](https://nypost.com/2025/01/11/business/blackrock-quits-net-zero-initiative-at-perfect-time-as-woke-policies-contribute-to-devastating-la-fires/) bemerkt, um nicht von der negativen, anti-woken Berichterstattung rund um die verheerenden Feuersbrünste in Los Angeles tangiert zu werden. Es scheint, als hätten die Eloi bereits wieder verdrängt, dass die WEF-Meetings [2021](https://www.weforum.org/videos/the-great-narrative-narrating-the-future-english/) und [2024](https://www.weforum.org/press/2024/01/annual-meeting-2024-rebuilding-trust-amid-uncertainty/) unter Arbeitstiteln wie »*The Great Narrative*« und »*Rebuilding Trust*« liefen. Artikuliertes Ziel der Davoser PR-Abteilung für Globalisierungsfragen war nämlich, sich den zunehmend echauffierten, misstrauischen Pöbel vom Hals zu halten. Durch neue Narrative und vertrauensbildende Maßnahmen. Und das hat, zumindest vorerst, ausgezeichnet funktioniert. In den USA stieg das [Vertrauen](https://www.zerohedge.com/political/overall-trust-election-process-rebounded-2024) in ordnungsgemäß durchgeführte Präsidentschaftswahlen 2024 zum ersten Mal seit Jahren wieder etwas an. In Europa macht sich ebenfalls Zuversicht breit. Schließlich haben die sogenannten »*[Rechtspopulisten](https://www.sueddeutsche.de/projekte/artikel/politik/rechtspopulisten-rechtsextremismus-giorgia-meloni-geert-wilders-viktor-orb-n-robert-fico-e072514/?reduced=true)*« nicht mehr nur in Italien und Ungarn, sondern auch in Finnland, der Slowakei und den Niederlanden Oberwasser. Von den Erfolgen der AFD ganz zu schweigen. Diese führen, wie zuletzt in [Thüringen](https://www.mdr.de/nachrichten/thueringen/landtagswahl/afd-sieger-mehrheit-100.html), trotz klarem Wählervotum zwar nicht zur Regierungsbeteiligung, weil »*demokratische Prozesse*« und »*Brandmauern*« das zu verhindern wissen – aber dabei sein ist ja bekanntlich alles. Dass Friedenstreiberin Alice Weidel den bundesdeutschen Rüstungsetat auf knapp [200 Milliarden](https://www.berlin-live.de/politik/weidel-afd-bundeswehr-trump-nato-id348307.html) verdoppeln will, scheint die euphorisierten Kritiker dunkelgrüner Militarisierung auch nicht auszubremsen. Hauptsache nicht grün. Oder woke. **Überstaatliche Sphären** Dabei scheint Euphorie in Anbetracht der Tatsachen alles andere als angebracht. So hat Milei nach Angaben von [Global Finance](https://gfmag.com/economics-policy-regulation/argentina-milei-administration-eliminates-deficit/) zwar das argentinische »*Staatsdefizit nach 123 Jahren beendet*«, dafür leben heute [53 Prozent](https://www.theguardian.com/world/2024/dec/18/argentina-javier-milei-chainsaw-measures) der 45 Millionen Argentinier in Armut. Der höchste Wert seit 20 Jahren. Ende 2023 waren es noch 41,7 Prozent. Daran ändert auch semantische [Schützenhilfe](https://www.hoover.org/research/critics-mileis-policies-strike-out) von libertären Denkfabriken wie der [Hoover Institution](https://de.wikipedia.org/wiki/Hoover_Institution) nichts. Die radikalen Privatisierungsfeldzüge von »*[El Loco](https://www.batimes.com.ar/news/economy/argentinas-el-loco-milei-delivered-chaos-laughs-and-key-wins-in-week-one.phtml)*« haben einen hohen Preis. Ob [Aerolineas Argentinas](https://aviationweek.com/air-transport/safety-ops-regulation/daily-memo-mileis-relentless-pursuit-privatize-aerolineas), die staatliche Fluglinie, der Stahlproduzent [IMPSA](https://www.reuters.com/world/americas/argentina-privatizes-state-metal-firm-milei-era-first-2025-01-08/) oder das Transportunternehmen [Trenes Argentinos Cargas](https://buenosairesherald.com/business/infrastructure/milei-to-privatize-major-cargo-train-company), das 7.800 Kilometer Bahnstrecke betreibt – das Volksvermögen wird an die Meistbietenden verscherbelt. Wer das ist, kann sich wohl jeder ausmalen. Denn sein Schlachtruf »*Afuera!*« (Raus hier!) gilt augenscheinlich nicht für [BlackRock](https://news.bloomberglaw.com/bankruptcy-law/blackrocks-fink-mulls-argentina-trip-after-milei-call) und Co. – schließlich sei Argentinien »*ziemlich billig*« zu haben, wie es Rick Rieder, Top-Bond-Manager des Unternehmens schon 2019 [formulierte](https://www.reuters.com/article/us-argentina-debt-blackrock-idUKKBN1XI010/). Man muss allerdings nicht in die Ferne schweifen, um sich der realen Gefahren für die Freiheit bewusst zu werden. Jener Gefahren, die von Personalien gänzlich unberührt bleiben. So arbeitet die Europäische Union weiter an der [eID](https://ec.europa.eu/digital-building-blocks/sites/display/DIGITAL/eID), der Grundlage des technokratisch-totalitären Kontroll-Grids. Ihre Einführung ist [beschlossene](https://www.europarl.europa.eu/news/de/press-room/20240223IPR18095/meps-back-plans-for-an-eu-wide-digital-wallet) Sache. Offen ist lediglich, ab wann sie zum Obligatorium wird. Auch das persönliche CO2-Budget ist auf Kurs. Mit [ETS2](https://www.epa.ie/our-services/licensing/climate-change/eu-emissions-trading-system-/eu-emissions-trading-system-2-ets2/#:~:text=ETS%202%20is%20a%20new,manufacturing%20and%20construction%20industries) (EU Emissions Trading System) nimmt die [EPA](https://www.epa.ie/who-we-are/) (Environmental Protection Agency) seit dem 1. Januar 2025 nach der Konzernwirtschaft nun kleine und mittlere Unternehmen in den Fokus und verpflichtet diese, CO2-Kompensationsabgaben auf ihren Gas-, Benzin- und Mineralölverbrauch zu entrichten. Das dürfte Heiz-, Fracht- und folglich die Lebenshaltungskosten des Bürgers in neue Höhen treiben. Bis der Sonntagsausflug mit dem Familienauto nicht mehr nur Zeit, Benzin und Nerven, sondern auch CO2-Gebühren kostet, dauert es also wohl nicht mehr allzu lange. Dieser überparteilichen, supranational koordinierten Überwachungs- und Enteignungsagenda ist weder durch die Wahl des geringeren Übels noch durch Auswandern zu entkommen. Denn wie sich der [Internetpräsenz](https://globalgovernanceforum.org/) des »*Global Governance Forum*« (GGF) entnehmen lässt, wird bereits eifrig an »*[Global Government](https://www.globalgovernmentforum.com/news/)*« gearbeitet. Die UN-nahe Nichtregierungsorganisation hat sich nämlich zum Ziel gesetzt, die Charta der Vereinten Nationen bis 2028 zu [aktualisieren](https://globalgovernanceforum.org/a-call-for-un-charter-reform/) und den allseits bekannten »*Herausforderungen unserer Zeit*« anzupassen. Pünktlich ab 2030 soll das neue Vertragswerk ratifiziert werden und neben neuen Befugnissen für den Internationalen Gerichtshof sowie einer UN-Streitmacht auch eine Regierungsstruktur analog der Europäischen Union ermöglichen. Sprich, eine Weltregierung. Ganz demokratisch selbstverständlich. Neben eID und CO2-Budget sind natürlich auch die Ausweispflicht fürs Internet und die automatisierte Zensur unliebsamer Inhalte weiter auf Kurs. Nachdem die Vereinten Nationen im September 2024 bereits dem totalitären »*[Pakt für die Zukunft](https://www.un.org/en/unis-nairobi/press-releaseunited-nations-adopts-ground-breaking-pact-future-transform-global)*« zustimmten, wurde am [Heiligabend 2024](https://www.unodc.org/unodc/en/press/releases/2024/December/un-general-assembly-adopts-landmark-convention-on-cybercrime.html) noch rasch die neue »*Konvention gegen Onlineverbrechen*« durchgewunken. Und seit Januar 2025 treibt die UN die Umsetzung eines noch weitreichenderen Abkommens namens »*[Global Digital Compact](https://www.un.org/global-digital-compact/en)*« voran. Ein Papier, vor dem ich bereits im [Juli 2023](https://www.regenauer.press/undemokratisch) gewarnt habe. Was all das für den Bürger bedeutet, zeigt sich in [Griechenland](https://www.telepolis.de/features/Totale-Kontrolle-Griechenland-verknuepft-Steuer-ID-mit-Social-Media-10222907.html), wo die Regierung seit Anfang des Jahres Social-Media-Konten mit Steuer-Identifikationsnummern verknüpft, um eine Alterskontrolle fürs Internet einzuführen. Damit folgt die von der EU in Kreditsklaverei gehaltene Regierung in Athen dem Vorbild [Australiens](https://www.tagesschau.de/ausland/asien/australien-social-media-100.html), wo der Zugang so Social-Media-Plattformen künftig erst ab einem Alter von 16 Jahren erlaubt werden soll – wofür man schlussendlich jeden Nutzer kontrollieren muss, der online geht. Auch das von vielen noch immer als Mythos abgetane Geoengineering wird derweil munter weitergeführt. Obwohl [Berichte](https://www.whitehouse.gov/wp-content/uploads/2023/06/Congressionally-Mandated-Report-on-Solar-Radiation-Modification.pdf) des US-Kongress und mittlerweile sogar wissenschaftliche [Berater](https://scientificadvice.eu/advice/solar-radiation-modification/) der EU-Kommission vor großflächigem [Solar Radiation Management](https://www.risiko-dialog.ch/solar-radiation-management-ein-letztes-mittel-im-kampf-gegen-den-klimawandel/) warnen. Im Rahmen eines offiziellen, 54 Seiten umfassenden [Reports](https://op.europa.eu/en/publication-detail/-/publication/9c2ac367-b5de-11ef-acb1-01aa75ed71a1/language-en) an die EU-Kommission sowie eines [Artikels](https://www.theguardian.com/environment/2024/dec/09/eu-should-ban-space-mirrors-and-other-solar-geoengineering-warn-scientists) des britischen Guardian vom 9. Dezember 2024 verwies das siebenköpfige Forscherteam auf die unabschätzbaren Konsequenzen solcher Eingriffe und forderte ein EU-weites Moratorium. Wie genau Trump, Musk, Milei, Meloni, Weidel und Co. die Welt vor diesem Sammelsurium an totalitären Übergriffigkeiten retten wollen, konnte mir bislang keiner der Eloi sagen. **DJ Trump** Warum die in Donald Trump, den »*[Vater der Impfung](https://www.independent.co.uk/news/world/americas/us-politics/trump-father-vaccine-covid-fox-interview-b1839555.html)*«, und sein zionistisches Kriegstreiberkabinett gesetzten Hoffnungen bald bitterer Enttäuschung weichen dürften, habe ich bereits am 14. November 2024 ausführlich [beschrieben](https://www.regenauer.press/trump-reloaded). Dass auch die beiden Hauptargumente seiner Befürworter – dass er die mRNA-Kampagne mittlerweile bereue und in seiner ersten Amtsperiode Friedenspolitik betrieben habe – schlichtweg falsch sind, ebenfalls. Denn anhand der nackten [Zahlen](https://foreignpolicy.com/2017/08/09/donald-trump-is-dropping-bombs-at-unprecedented-levels/) lässt sich eindeutig belegen, dass Trump »*der kriegslüsternste Präsident der jüngeren Geschichte*« war. Und wie stolz er auf »*Operation Warp Speed*« ist, die [unzählige](https://icandecide.org/v-safe-data/) Amerikaner Gesundheit oder Leben kostete, ließ er die Welt zuletzt am [17. November 2024](https://x.com/tomregenauer/status/1859637538874589311) auf seinem Social-Media-Netzwerk [Truth Social](https://de.wikipedia.org/wiki/Truth_Social) wissen. Trumps Interesse gilt nicht Frieden und Freiheit, sondern Donald Trump. So war es sein ganzes Leben lang. Wenn sich »*The Donald*« jemandem verpflichtet fühlt, ist es vielleicht [Wilbur Ross](https://de.wikipedia.org/wiki/Wilbur_Ross), der ehemalige Chef von [Rothschild Inc. Bankruptcy Advising](https://www.rothschildandco.com/en/global-advisory/debt-advisory-and-restructuring/). Denn wie das [Forbes Magazine](https://www.forbes.com/sites/chasewithorn/2016/12/08/trump-and-his-commerce-secretary-wilbur-ross-a-look-at-25-years-of-connections/) am 8. Dezember 2016 korrekt erläuterte, rette das Bankhaus vor gut 30 Jahren nicht nur Trumps bankrotte Casinos, sondern damit auch seine ganze Karriere. Nicht weil man in Trumps Geschäften und Immobilien einen besonderen Wert sah, sondern weil man die Person Donald Trump als »*Anlage*« betrachtete. Trotzdem ist es sicher nur Zufall, dass Ross von 2017 bis 2021 Handelsminister der Vereinigten Staaten war. **Elon Musk** Auch über den PayPal-Mafioso, CIA-Handlanger und Bilderberg-Executive Peter Thiel, dessen Protegé JD Vance nun US-Vizepräsident ist, habe ich bereits im September 2024 einen ausführlichen [Artikel](https://www.regenauer.press/gestatten-peter-thiel) geschrieben. Gleiches gilt für Elon Musk, dessen trügerisches Image als Genius, Erfinder und Entrepreneur ich sogar schon im Oktober 2022 [durchleuchtet](https://www.regenauer.press/dekuvrierte-coolness) habe. Zitat: »*Dass Elon Musk nicht rein zufällig zur liberal-coolen Ikone avancierte, legt ein Blick in seine Anfangsjahre als Unternehmer nahe. Denn während im sagenumwobenen Silicon Valley Ende der 1990er-Jahre eine Vielzahl an erfolgreicheren Tech-Entrepreneuren existierte, war es ausgerechnet Elon Musk, der für einen absolut inhaltsleeren [Gastauftritt](https://www.youtube.com/watch?v=s9mczdODqzo) bei CNN gefilmt wurde, sodass zum ersten Mal eine breitere Öffentlichkeit von ihm Notiz nehmen musste. Dabei war sein erstes Unternehmen – [Zip2](https://en.wikipedia.org/wiki/Zip2) –, das er im Jahre 1995 mit seinem Bruder sowie einem weiteren Partner gegründet und im Februar 1999 für circa [300 Millionen US-Dollar](https://web.archive.org/web/20220625124959/https:/www.nytimes.com/1999/02/17/business/compaq-buys-zip2-to-enhance-altavista.html) an Compaq veräußert hatte, nicht das revolutionärste Unterfangen im kalifornischen IT-Mekka dieser Tage. Es handelte sich um ein simples Telefonbuch fürs Internet. Wenig mehr als eine Datenbank, in die sich Unternehmen eintragen konnten, um ihre Adresse im Netz zu hinterlegen*.« Meine fast zweieinhalb Jahre alte Analyse bedarf allerdings dringend einer Aktualisierung. Denn was Musk in der Zwischenzeit trieb – und für die Zukunft plant – hat so gar nichts mit dem zu tun, was seine geradezu fanatisierten Anhänger in ihm sehen wollen. Fangen wir der Vollständigkeit halber aber noch mal vorne an: Elon Musk hat weder [PayPal](https://en.wikipedia.org/wiki/PayPal#Early_history) gegründet noch den [Tesla](https://www.cnbc.com/video/2021/02/06/how-tesla-was-founded-martin-eberhard-and-marc-tarpenning-tell-all.html) erfunden. Auch wenn er das gerne so darstellt. Dafür [fertigte](https://www.reuters.com/article/business/healthcare-pharmaceuticals/musk-says-tesla-is-building-rna-microfactories-for-curevac-idUSFWN2E9067/) Tesla unter seiner Ägide dann aber »*RNA Mikrofabriken*« für das deutsche Unternehmen [CureVac](https://www.nzz.ch/wissenschaft/curevac-impfstoff-noch-ein-sieg-gegen-das-virus-ld.1788519), das zusammen mit [Bayer](https://www.nasdaq.com/press-release/curevac-:-curevac-and-bayer-join-forces-on-covid-19-vaccine-candidate-cvncov-2021-01) mRNA-Injektionen gegen Corona auf den Markt brachte. Und während Musk gegenüber der [New York Post](https://www.youtube.com/watch?v=2lPkvteqKig) am 30. September 2020 sagte, sich nicht gegen Covid impfen lassen zu wollen, erklärte er dem [TIME Magazine](https://web.archive.org/web/20211213124147/https:/time.com/person-of-the-year-2021-elon-musk/) am 13. Dezember 2021, bereits geimpft zu sein. Zeitgeistig flexibel ist er also. Wer behauptet, Musk hätte seine Meinung zur mRNA-Technologie seit dem Covid-Fiasko signifikant geändert und sehe das Produkt nun kritisch, ist schlecht informiert. Noch am [12. April 2023](https://x.com/elonmusk/status/1646220824192630784) erklärte er bei Twitter, dass er mRNA für eine »*medizinische Revolution*« hält. Vergleichbar mit dem Schritt »*von analog zu digital*«. Was Musk mit digitaler Revolution meint, zeigte sich 2017 mit Hurricane Irma. Damals gab das Unternehmen für Besitzer von Fahrzeugen mit 75 kWh ein [Softwareupdate](https://www.teslarati.com/tesla-issues-software-update-help-owners-flee-hurricane-irmas-evacuation-zone/) heraus, das die Reichweite von 338 auf 400 Kilometer steigerte – was im Umkehrschluss bedeutet, dass Tesla-Besitzer um eine eigentlich abrufbare Leistung ihres eigenen Fahrzeugs betrogen werden, wenn gerade keine Naturkatastrophe wütet. Dass Tesla-Kunden darüber hinaus permanent [überwacht](https://upnorthlive.com/news/nation-world/tesla-cybertruck-explosion-trump-hotel-fbi-surveillance-elon-musk-company) werden, zeigte sich unlängst im Rahmen der Explosion eines Cybertrucks in Las Vegas. Augenbewegungen, Mimik, Geschlecht, Hautfarbe, Körpertemperatur, Gepäckanordnung, Route, Ladestopps, Bezahlvorgänge, Telefonbuch, Musik-Playlist, Online-Abos, et cetera. Was von Sensoren und Verbindungen zu erfassen ist, wird erfasst, wie eine [Untersuchung](https://gizmodo.com/mozilla-new-cars-data-privacy-report-1850805416) von Mozilla im Herbst 2023 feststellte. Das gilt im Übrigen nicht nur für Tesla, sondern für praktisch alle modernen Autos. Ein Tesla hat es dabei nur am leichtesten. Die gesammelten Daten werden entweder zum Schleuderpreis [verkauft](https://archive.is/tc2xB) und/oder gegen uns verwendet. Doch zurück zu Musk, der Twitter nicht übernahm, um Meinungsfreiheit herzustellen, sondern um die Plattform zur »*Alles-App*« zu machen. Sein [erklärtes](https://www.forbes.com/sites/abrambrown/2022/06/21/elon-musk-and-the-super-alluring-dream-for-a-super-app/?sh=6cf8e3021343\&utm_medium=social\&utm_source=ForbesMainTwitter\&utm_campaign=socialflowForbesMainTwitter) Vorbild: die chinesische [Spionage-App](https://citizenlab.ca/2020/05/wechat-surveillance-explained/) WeChat. Deswegen will er alle Nutzer »*als echte Menschen [identifizieren](https://edition.cnn.com/2022/04/28/tech/elon-musk-authenticate-all-real-humans/index.html)*«. Biometrisch versteht sich. Dafür [arbeitet](https://www.business-humanrights.org/en/latest-news/x-corps-biometric-data-sharing-with-israeli-firm-raises-privacy-concerns/) man bei Twitter bevorzugt mit israelischen Unternehmen zusammen, die von ehemaligen [Mossad-Agenten](https://www.middleeasteye.net/news/x-twitter-israel-concerns-verification) gegründet wurden. Vielleicht stellte ja Doppelagent Jeffrey Epstein den Kontakt zum Mossad her, nachdem er Musk als regelmäßigen Teilnehmer seiner [Edge-Foundation](https://www.regenauer.press/die-glorreichen-sieben) Seminare zum Thema Nudging schätzen gelernt hatte. Epstein war nämlich der einzige nennenswerte Sponsor von Edge. Twitter kaufte Musk übrigens nicht von seinem eigenen Geld, sondern mit Hilfe von 94 [Investoren](https://www.newsweek.com/full-list-investors-elon-musks-x-revealed-court-filing-1942970), deren Namen ein US-Bundesrichter erst im August 2024 veröffentlichte, weil Jacob Silverman (Reporters Committee for Freedom of the Press) sie einklagte. Die Liste umfasst so illustre Namen wie Fidelity Investments, Sequoia Capital, Andreessen Horowitz, Bandera Fund, Binance Capital Management, Sean Combs (alias Diddy) Capital, Jack Dorsey (Twitter Gründer), Baron Opportunity Fund oder Prinz Alwaleed bin Talal al Saud von der saudischen Königsfamilie. Da wird also offenbar »*der Sumpf*« mit mehr Sumpf »*trockengelegt*«. Von der Nominierung des [WEF Executive Chair](https://www.linkedin.com/posts/lindayaccarino_freedom-of-speech-not-reach-an-update-on-activity-7053787411847237633-zC8Q) Linda Yaccarino als neuer Twitter-CEO und »*Freedom of Speech*« versus »*[Freedom of Reach](https://www.linkedin.com/posts/lindayaccarino_freedom-of-speech-not-reach-an-update-on-activity-7053787411847237633-zC8Q)*« mal ganz abgesehen. Auch die von den Eloi als sensationelle Enthüllung gefeierten [Twitter Files](https://twitterfiles.substack.com/p/1-thread-the-twitter-files) sind leider nicht ernst zu nehmen. Denn sie offenbarten nichts, was man nicht schon wusste. Zudem ist bis heute unklar, woher die veröffentlichten Informationen kamen, wer den Zugriff darauf gesteuert hat, was dort noch gespeichert war, warum praktisch nur ein von Elon ausgewählter [Journalist](https://docs.house.gov/meetings/FD/FD00/20230309/115442/HHRG-118-FD00-Wstate-TaibbiM-20230309.pdf) Zugriff darauf hatte und dieser nur Screenshots, anstelle ganzer Dokumente veröffentlichen durfte. Ein echter Leak besteht aus einem Archiv, das man selbst durchsuchen kann – nicht aus ein paar handverlesenen Screenshots. Fehlt noch Space X. Ein Unternehmen, das Musk zwar selbst gegründet hat, dessen Erfolge aber in weiten Teilen anderen Umständen zu verdanken sind. So schreibt beispielsweise [inside Tesla](https://insidetesla.de/spacex-und-nasa-staatlich-private-kooperation/) am 22. März 2022: **»*Schon Anfang der 2000er-Jahre hatte die NASA erkannt, dass ihr bald die Möglichkeit fehlen würde, selbst Astronauten und Material ins All und zur ISS zu bringen. Man machte sich also auf die Suche nach Partnern aus der Privatwirtschaft und wurde unter anderem bei Elon Musks Space X fündig. Bereits 2006, also noch in der Entwicklungsphase der Falcon 1, erhielt Musks Unternehmen fast 400 Millionen US-Dollar Startfinanzierung unter dem COTS-Programm*.«** Space X war von Beginn an als verlängerte Werkbank der NASA gedacht, weil der US-Weltraumbehörde immer mehr Mittel gestrichen wurden. Die Öffentlichkeit hatte nämlich das Interesse an ziviler Raumfahrt verloren. Daher setzte man in Washington immer öfter den Rotstift an. Doch seit Musk die Menschen öffentlichkeitswirksam zum Mars befördern will – »*let’s build Marsian Technocracy*« – steigt das Interesse wieder. Leider muss ich die Vorfreude auf eine planetare Kolonie aber etwas dämpfen. Denn Space X wird nicht betrieben, um Menschen auf den Mars zu bringen, sondern um das »*weltgrösste Netzwerk an [Spionagesatelliten](https://www.reuters.com/technology/space/musks-spacex-is-building-spy-satellite-network-us-intelligence-agency-sources-2024-03-16/) [aufzubauen](https://web.archive.org/web/20241206180227/https:/www.activistpost.com/2024/12/you-cant-hide-elon-musk-spacex-are-helping-us-intelligence-build-the-worlds-largest-spy-satellite-network.html)*«. Musks Weltraumagentur ist Handlanger des militärisch-industriellen Komplexes und einer der wichtigsten [Vertragspartner](https://thehill.com/policy/defense/542728-pentagon-awards-160m-in-contracts-to-musks-spacex/) des Pentagon. Das konnte man 2017 schon im [Observer](https://observer.com/2017/04/spacex-to-launch-top-secret-mission-for-government-spy-agency/) nachlesen. Oder am 9. Januar 2018 bei [CNBC](https://www.cnbc.com/2018/01/08/highly-classified-us-spy-satellite-appears-to-be-a-total-loss-after-spacex-launch.html), die vom (missglückten) Transport eines streng geheimen US-Spionagesatelliten berichtete. Am 15. April 2022 kommentierte [Tech Unwrapped](https://techunwrapped.com/spacex-will-launch-two-spy-satellites-for-the-us-military/) zwei weitere Spionagesatelliten des US-Militärs, die Space X in die Umlaufbahn beförderte. Seit Jahren erhält das Unternehmen Milliarden von US-Regierung und Geheimdiensten. Siehe [Los Angeles Times](https://www.latimes.com/business/la-fi-hy-musk-subsidies-20150531-story.html) vom 30. Mai 2015: 4,9 Milliarden. Oder ein Artikel des [Wall Street Journal](https://www.wsj.com/podcasts/google-news-update/how-spacex-is-deepening-its-ties-with-the-us-government/b860deaf-724c-4610-8177-479b520df6d4) vom 23. Februar 2024: 1,8 Milliarden. Oder eine lange Liste von staatlichen Zuwendungen, die [Business Insider](https://www.businessinsider.com/elon-musk-list-government-subsidies-tesla-billions-spacex-solarcity-2021-12?r=US\&IR=T) am 15. Dezember 2021 veröffentlichte. Damit basiert der Erfolg von Space X nicht primär auf Musks genialem Unternehmergeist, sondern auf Subventionen. Auf Steuergeldern. Nicht zu vergessen: [Starlink](https://de.wikipedia.org/wiki/Starlink). Das von Space X betriebene, weltumspannende Satellitennetzwerk. Es mag den Vorteil haben, dass damit auch Menschen in entlegenen Regionen des Planeten oder Katastrophengebieten Zugriff auf das Internet haben. Dabei sollte allerdings nicht unterschlagen werden, dass Starlink in seiner finalen Ausbaustufe circa 42.000 Satelliten umfassen und damit ein permanentes Strahlungsfeld erzeugen wird. Gesundheitliche Risiken für den Homo sapiens: unklar. Darüber hinaus haben die Orbiter Zugriff auf das [NORAD](https://de.wikipedia.org/wiki/North_American_Aerospace_Defense_Command)-Datenbanksystem, um Weltraumschrott ausweichen zu können. Sprich, sie sind permanent mit Systemen des US-Militär verbunden. Aus diesem Grund ermöglicht Starlink auch die Steuerung von Kampfdrohnen – siehe [Ukraine-Konflikt](https://www.telegraph.co.uk/world-news/2022/03/18/elon-musks-starlink-helping-ukraine-win-drone-war/) – sowie 30 mal schnelleres Senden von Daten an und von US-Kampfflugzeugen. Während die Öffentlichkeit Musks Satellitennetzwerk vor allem als ziviles Produkt betrachtet, ist Starlink primär von militärischem Interesse. Nicht umsonst wird parallel [Starshield](https://en.wikipedia.org/wiki/SpaceX_Starshield) aufgebaut, das dem geheimdienstlich-militärischen Komplex unter anderem die diskrete Echtzeitüberwachung der ganzen Welt erlaubt. Auch von [DEW](https://en.wikipedia.org/wiki/Directed-energy_weapon)-Fähigkeiten (Directed Energy Weapon) ist die Rede. Ende 2024 befanden sich bereits 98 solcher Satelliten in erdnaher Umlaufbahn. In Anbetracht dieser Informationen ist es also kaum verwunderlich, dass Musk seit Jahren offen für [Technokratie](https://www.ft.com/content/df695f10-154d-11e8-9376-4a6390addb44) [wirbt](https://x.com/search?q=from%3Aelonmusk%20technocracy\&src=typed_query). Für ein zentralistisches, [faschistoides](https://web.archive.org/web/20230920020550/https:/www.newyorker.com/news/daily-comment/the-world-according-to-elon-musks-grandfather) Herrschaftsmodell, das schon sein [Großvater](https://newsinteractives.cbc.ca/longform/technocracy-incorporated-elon-musk/) Joshua Haldemann als führender Kopf in den USA und Kanada vertrat. Der Familientradition folgend [empfiehlt](https://www.youtube.com/watch?v=BMskI6G9ty0) Musk eine [CO2-Steuer](https://www.cnbc.com/2021/02/12/elon-musk-reducing-greenhouse-gas-emissions-with-a-carbon-tax.html) zum Kampf gegen den Klimawandel, ein universelles [Grundeinkommen](https://www.businessinsider.com/elon-musk-universal-basic-income-ubi-ai-automation-unemployment-quotes-2024-6), um die von der KI ausgelösten Disruptionen abzufangen und sein [Neuralink](https://neuralink.com/) Gehirnimplantat, um dem drohenden Transhumanismus etwas Transhumanismus entgegenzusetzen. **Futurum Technologicus** Für Kunden, denen Chips im Kopf irgendwie zu altbacken sind, [entwickelt](https://www.neurotechreports.com/pages/Neuralink-launch-collaborations.html) Musks Unternehmen in Zusammenarbeit mit [iota Biosciences](https://www.iota.bio/) natürlich ein zeitgemäßeres Premiumprodukt: Neural Dust. Intelligente Nanopartikel in Staubkorngröße, die sich im Gehirn anreichern. Die lassen sich dann wahrscheinlich – wie die in Indien bereits zugelassene [Nasal-Impfung](https://www.lemonde.fr/en/covid-19-pandemic/article/2022/09/06/india-approves-its-first-nasal-vaccine-for-covid-19_5996007_122.html) gegen Covid – durch die Nase ziehen. Oder durch Luftschächte öffentlicher Gebäude pumpen. Man kann die neue Freiheit also förmlich riechen. Ganz wie es der 44 Seiten starke »*National Nanotechnology Initiative Strategic Plan*« ([NNI Plan](https://www.nano.gov/sites/default/files/pub_resource/NNI-2021-Strategic-Plan.pdf)) des Weißen Hauses im Oktober 2021 vorsah: »*Die Öffentlichkeit einbeziehen und Mitarbeiterzahlen im Bereich Nanotechnologie erhöhen*«. Nicht umsonst hat Donald Trump der entsprechenden Behörde in seiner ersten Amtszeit zusätzliche Mittel [genehmigt](https://en.wikipedia.org/wiki/National_Nanotechnology_Initiative). Genau wie Joe Biden nach ihm. Das von der Technokratie-Bewegung vor fast einem Jahrhundert definierte [nordamerikanische Technate](https://technocracy.fandom.com/wiki/Technate) – sprich, der amerikanische Verantwortungsbereich einer weltweiten Technokratie – sieht der von [Trump](https://www.newsweek.com/donald-trumps-plan-new-us-empire-2008028) und Musk reanimierten Vision einer »*nordamerikanischen Union*« übrigens verblüffend ähnlich. Wen interessiert bei all der Make-Great-Euphorie schon noch, dass Imperialismus scheisse, Dänemark ein souveräner Staat und der Panamakanal ein strategisches Nadelöhr der internationalen Handelsschifffahrt ist. Oder, dass die »*nordamerikanische Union*« nicht nur bei Trump-Cheerleadern wie [Alex Jones](https://www.youtube.com/watch?v=sHMD5k8Pv5Y) vor ein [paar Jahren](https://thenewamerican.com/world-news/north-america/cfr-globalists-outline-strategy-for-north-american-community/) noch als »*böser [Globalisten-Plan](https://frankspeech.com/video/americans-are-waking-globalist-goal-creating-north-american-union)*« galt. Schauen wir nach vorne. In Richtung »*goldenes Zeitalter*«, wie Trump es nennt. Dieses dürfte für den Normalbürger nämlich sehr ungemütlich werden. Denn es wird dominiert von Algorithmen. Von Künstlicher Intelligenz. Für die Eloi also primär von [Grok](https://en.wikipedia.org/wiki/Grok_\(chatbot\)), dem auf Twitter (und [Teslas](https://techcrunch.com/2024/09/08/elon-musk-says-tesla-has-no-need-to-license-xai-models/)) integrierten Chatbot. Dieser basiert auf Technologie des Unternehmens xAI – laut [Wikipedia](https://en.wikipedia.org/wiki/XAI_\(company\)) gegründet von Elon Musk im März 2023. Das mag zwar so im Handelsregister stehen, ist wohl aber nur die halbe Wahrheit. Denn xAI dürfte die Fortführung eines [DARPA-Projekts](https://onlinelibrary.wiley.com/doi/full/10.1002/ail2.61) darstellen, das bereits 2015 unter dem Titel »*Explainable Artificial Intelligence*« (XAI) gestartet wurde und 2021 auslief. Als die Finanzierung seitens DARPA eingestellt wurde, machte XAI die Forschungsergebnisse auf einem [Server](https://xaitk.org/) zugänglich. Circa 18 Monate Jahre später [engagierte](https://www.simonandschuster.com/books/Elon-Musk/Walter-Isaacson/9781982181284) Elon Musk [Igor Babuschkin](https://www.linkedin.com/in/igor-babuschkin-9bb5bab6/) als Chefingenieur für xAI. Babuschkin hatte zuvor acht Jahre lang für Googles DeepMind-Projekt gearbeitet und nutzte aller Wahrscheinlichkeit nach die DARPA-Ergebnisse um xAI, beziehungsweise Grok zu entwickeln. Im Juli 2023 [verkündete](https://archive.ph/hq6WS) Musk, xAI sei im Gegensatz zu den Konkurrenzprodukten von Google, Microsoft und OpenAI eine »*gute*« KI. Erstaunlich, wenn die gleichen Ingenieure am Werk sind und die KI auf Basis eines Militärprojekts entsteht. Zudem sprechen auch die Top-Sponsoren von xAI nicht unbedingt für das »*Gute*«. Denn unter den größten Geldgebern der letzten [Finanzierungsrunde](https://www.livemint.com/companies/news/elon-musks-xai-raises-6-billion-funding-from-blackrock-nvidia-amd-and-others-11735045011974.html) vom 23. Dezember 2024 befinden sich so illustre Namen wie BlackRock, AMD, Nvidia und Fidelity, die zusammen weitere sechs Milliarden Dollar für Musks KI-Unternehmen zur Verfügung stellten. Genug Liquidität, um xAI für die »*Alles-App*« weiterzuentwickeln, wo Grok seit einer Weile automatisch [Kurzbeschreibungen](https://circleboom.com/blog/what-is-x-profile-summary/) für Profile erstellt, die man weder abschalten noch ändern kann. Twitter-Nutzer müssen nun also nicht mehr selbst das Profil eines Accounts durchstöbern, um sich einen ersten Eindruck von der Person zu machen, sondern bekommen diesen von Elon Musks KI geliefert. Vorurteil auf Knopfdruck sozusagen. Vergleichbar mit einem Sozialkreditsystem. Denn die täglich neu generierte Zusammenfassung basiert auf dem Nutzerverhalten. **»*Die neuen, KI-generierten Grok-Kurzprofile unter jedem X-Nutzerprofil SIND de facto ein Social Credit System nach chinesischem Vorbild für den Westen. Das Profil jedes Nutzers wird tagesaktuell neu berechnet. Äußert man sich zu verschiedenen Themen, nennt die KI das schnell mal »verheddern«. Grok gibt zu, das Profil wird erstellt aus dem eigenen Nutzerverhalten des Tages, seinen eigenen Berechnungen und nicht näher definierten Anweisungen*«,** **[kommentierte](https://x.com/aya_velazquez/status/1879288289393340512)** **Journalistin Aya Velázquez die Neuerung am 14. Januar 2025.** Andere Nutzer werden als »*leicht erregbar*« beschrieben, »*verzetteln*« sich oder »*glauben an Wettermanipulation zur Klimakontrolle*«. Offener wird ein Debattenraum dank solcher Adjektive und Zusammenfassungen sicher nicht. Wer möchte schon das Profil von leicht erregbaren Chemtrail-Gläubigen anschauen oder gar mit diesen assoziiert werden. Gegen solch eine automatisierte, herablassend daherkommende Einordnung durch intransparent operierende KI war die Faktencheck-Industrie geradezu harmlos. Wer also annimmt, die [Abschaffung](https://www.bbc.com/news/articles/cly74mpy8klo) der Faktenchecker bei Facebook und Co. bedeute ein Ende der Zensur, irrt. Sie wird im Gegenteil deutlich raffinierter und weitreichender werden. Details zum persönlichen Punktestand im Grok-Sozialkreditsystem oder Information über das Zustandekommen der Bewertung erhält man auf Anfrage natürlich nicht. Twitter wird die daraus entstehende Hierarchie aber mit Sicherheit für Reichweitensteuerung, Nudging-Kampagnen und weitere sozialarchitektonische Funktionen nutzen. Vor allem, wenn 2025 das Bezahlsystem »[X Money](https://www.foxbusiness.com/technology/x-money-payment-system-launch-2025-x-ceo)« eingeführt wird. Dann werden die Eloi bald nicht mehr nur um Reichweite, Follower und Re-Tweets buhlen, sondern auch um Geld – das als Folge unliebsamer Postings zu Genozid X, Krieg Y oder Person Z künftig schneller eingefroren werden dürfte als jedes Bankkonto. [De-Banking](https://multipolar-magazin.de/artikel/de-banking) der nächsten Generation. Und irgendwann trifft das jeden. Außer, man schwimmt immer mit dem Strom. Doch damit nicht genug. Am 13. Dezember 2024 [gab](https://www.finanzen.ch/nachrichten/aktien/wisekey-aktie-schiesst-zweistellig-hoch-wisesat-satellitenstart-mit-spacex-im-januar-2025-geplant-1034135831) das wohl den wenigsten bekannte Unternehmen [WISeSat](https://wisesat.space/) bekannt, künftig mit Space X zusammenzuarbeiten, um »*verschiedene Produkte und Systeme zu kombinieren*«. Die WISeSat AG ist eine Tochterfirma der in [Genf](https://www.inside-it.ch/wisekey-lagert-satellitenbusiness-in-neue-firma-aus-20230607) (Schweiz) ansässigen [WISeKey International Holding AG](https://www.wisekey.com/), die im Bereich Cybersicherheit, KI und IoT (Internet of Things) tätig ist. Die Ankündigung dieser Kollaboration ließ die WISeKey-Aktie kurzfristig um 107,73 Prozent steigen. Ein erster gemeinsamer Start zum Transport sogenannter [Picosatelliten](https://www.sciencedirect.com/topics/engineering/picosatellites) fand am 14. Januar 2025 von der Vandenberg Space Force Base in Kalifornien statt. Aber was genau macht WISeSat? Einer [Presseerklärung](https://www.wisekey.com/de-press/wisesat-ag-ein-wegweisender-weltraumarm-von-wisekey-international-tritt-space-innovation-bei-und-starkt-die-position-der-schweiz-in-der-raumbasierten-iot-kommunikation/) des Unternehmens vom 15. September 2023 lässt sich entnehmen: »*WISeSAT AG zeichnet sich dank ihrer Konstellation von ultra-sicheren Picosatelliten und Infrastruktur durch sichere und effektive Kommunikationsstrategien für vernetzte Geräte aus. Die Expertise des Unternehmens in kryptografischer Technologie und sicherem Datenmanagement hat die sichere IoT-Implementierung in zahlreichen Bereichen neu definiert, von städtischen Innovationen in Smart Cities bis hin zu modernster industrieller Automatisierung*. (…) *WISeSAT steht an vorderster Front bei der Entwicklung von ultra-sicheren Picosatelliten-Lösungen in Zusammenarbeit mit ihrem Verbündeten [FOSSA Systems](https://en.wikipedia.org/wiki/FOSSA_Systems). Es setzt sich für sichere IoT-Kommunikation über raumbasierte Netzwerke ein und nutzt die neuesten kryptografischen Innovationen, um sichere und sofortige Datenaustausche in verschiedenen Bereichen zu gewährleisten* (…).« Im Klartext: WISeSat bringt Satelliten von der Größe einer Tupperdose ins All. Diese Mini-Orbiter umkreisen den Planeten in niedrigen Umlaufbahnen und etablieren dort ein Netzwerk für kryptografierte Echtzeitdatenübertragung. Fliegende 5G-Masten sozusagen. Oder WLAN-Router. Nur viel schneller. Für das Internet der Dinge – und Smart Cities. »*In dieser Woche startet WISeSat einen Satelliten der neuen Generation und markiert damit einen wichtigen Meilenstein in der Entwicklung einer globalen Satellitenkonstellation, die eine umfassende Erdabdeckung mit ultraniedriger Latenzzeit ermöglicht. Entwickelt, um Billionen von IoT-Geräten in Echtzeit zu verfolgen und aufzuspüren*.« ([Carlos Creus Moreira](https://x.com/CreusMoreira/status/1878312357882941521), WISeKEy CEO, 12. Januar 2025) Welche Datenträger dieses Picosatelliten-Netzwerk künftig verfolgen und aufspüren soll, zeigt sich bei einem Blick auf das Produktportfolio der Holding-Gesellschaft WISeKey – einem »*weltweit führenden Anbieter von Cybersicherheit, digitaler Identität und Internet der Dinge (IoT) Lösungen*«. Denn die [Holding](https://www.wisekey.com/) existiert seit 24 Jahren, besteht aus fünf Unternehmen, hat mehr als eineinhalb Milliarden Chips und über fünf Milliarden »[Roots of Trust](https://www.computerweekly.com/de/definition/Roots-of-Trust-RoT)« installiert, residiert an sechs internationalen Standorten und hat gut 3.000 Kunden in Staat und Wirtschaft beglückt. Einen Wikipedia-Eintrag gibt es für das bei NASDAQ und SIX gelistete Unternehmen erstaunlicherweise trotzdem nicht. Dafür aber für den seit Mai 2021 [amtierenden](https://www.handelszeitung.ch/panorama/wisekey-holt-pierre-maudet-als-chief-digital-transformation-officer) »*Chief Digital Transformation Officer*« [Pierre Maudet](https://de.wikipedia.org/wiki/Pierre_Maudet). Der war ab Juni 2012 Mitglied des Genfer Staatsrats, [2013](https://wikispooks.com/wiki/WEF/Young_Global_Leaders/2013) bei den Young Global Leaders des Weltwirtschaftsforums und 2015 bei der Bilderberger Konferenz in [Telfs-Buchen](https://wikispooks.com/wiki/Bilderberg/2015) (Österreich). Nachdem er im Februar 2021 vom Genfer Polizeigericht wegen Vorteilsnahme verurteilt wurde, trat er als Staatsrat zurück – und drei Monate später bei WISeKey an. Am 30. April 2023 wurde er, ungeachtet seiner kriminellen Vergangenheit, zusätzlich wieder in den Genfer Staatsrat gewählt. Wie praktisch. Solch eine schamlose Unverfrorenheit scheint Maudet perfekt für das zu qualifizieren, was bei WISeKey unter dem Deckmantel der »Quantensicherheit« entwickelt wird – ein raumbasiertes [eID-Ökosystem](https://wiseid.com/). »*Quantensicherheit nutzt Prinzipien der Quantenmechanik, um den Datenschutz und die sichere Informationsübertragung zu revolutionieren. Kernstück ist die Quantenschlüsselverteilung (Quantum Key Distribution, QKD), eine Spitzentechnologie, die mithilfe der Quantenmechanik vernetzte Teilchen für den sicheren Austausch von Verschlüsselungskennwerten erzeugt*.« Ob digitale Identität, Unterschrift, Cloud oder Software – von der Know-Your-Customer-Biometrie bis hin zur Unternehmenslösung für die Mitarbeiteridentifikation. WISeKey hilft. [Anmelden](https://account.wiseid.com/signup) kann sich jeder. Während die Produktpalette für den privaten Sektor noch nach Lieferketten-Management, Sendungsverfolgung, Login-Lösung für eBanking oder [Face ID](https://de.wikipedia.org/wiki/Face_ID) auf dem Smartphone klingt – aber deutlich weitreichender ist, schauen sie sich die Homepage an – sprechen die WISeKey-Angebote im Bereich [Regierungen](https://www.wisekey.com/solutions/by-industry/government-trust-solutions/) eine ganz andere Sprache. Denn unter diesem Menüpunkt bewirbt der diskret operierende Konzern seine »*CertifyID Trust Center Platform*«: »*Die CertifyID Trust Center Platform ist eine industrialisierte eID-Verwaltungslösung für Bürger, die Benutzer und ihre Anmeldeinformationen verwaltet, insbesondere digitale IDs und digitale Zertifikate für groß angelegte Anwendungen wie landesweite E-Government-Dienste. Es handelt sich um eine vollständige industrielle Public Key Infrastruktur- und ID-Verwaltungslösung, die Regierungsdienste rund um die Uhr unterstützt.* ***Die CertifyID Trust Center Plattform wird in einer Reihe von Anwendungen der Regierung und des öffentlichen Sektors verwendet, zum Beispiel: Personalausweis, ePassport (ICAO-konform), Führerschein, Gesundheit, Wahlen/Abstimmen*****.** *Die CertifyID Plattform wurde unter Verwendung der Sicherheits- und Public Key Infrastruktur-Expertise von WISeKey entwickelt und kann vollständig in E-Government-Frameworks, kommerzielle Frameworks (…) und in das Bereitstellungsframework für E-Government-Dienste eines Landes integriert werden*.« Da passt es doch wunderbar ins Bild, dass WISeKey am [13. Oktober 2022](https://www.finanzen.net/nachricht/aktien/wisekey-und-die-schweizer-armee-unterzeichnen-eine-partnerschaftsvereinbarung-zur-zusammenarbeit-bei-der-entwicklung-weltraumbezogener-aktivitaeten-unter-verwendung-der-wisesat-fossa-technologie-fuer-pi-11792137) eine »*Partnerschaftsvereinbarung zur Zusammenarbeit bei der Entwicklung weltraumbezogener Aktivitäten*« mit der Schweizer Armee bekannt gab – schließlich residieren in der Alpenrepublik nicht nur UN, GAVI, WEF, Club of Rome und jede Menge NGOs, sondern auch die Bank für Internationalen Zahlungsausgleich (BIZ), die ganz sicher Verwendung für ein quantengesichertes Echtzeit-Picosatellitennetzwerk findet, wenn ihr »*[Unified Ledger](https://www.bis.org/publ/arpdf/ar2023e3.htm)*« ([Zentrales Hauptbuch](https://www.globalgovernmentfintech.com/bis-releases-game-changing-blueprint-for-global-financial-system/)) für das Blockchain-Weltfinanzsystem von morgen zum Einsatz kommt. In Anbetracht der »*allumfassenden Marktblase*« ([D. Webb](https://www.regenauer.press/der-letzte-raubzug), 2024) ist damit wohl in absehbarer Zeit zu rechnen. Das also sind die Projekte, Pläne und neuen Partner von Elon. Auf mich machen ja speziell die korrupten Genfer Quantenspezialisten mit ihren Picosatelliten und schlüsselfertigen eID-Lösungen nicht unbedingt den Eindruck von Freiheitskämpfern. Und auch die am 22. Januar 2024 bei einer [Pressekonferenz](https://x.com/JoshWalkos/status/1881866215637094726) im Weißen Haus angekündigten »*personalisierten mRNA-Injektionen gegen Krebs*« lassen mich eher skeptisch zurück. Genau wie der Umstand, dass diese binnen 48 Stunden »*personalisierte mRNA*« durch die Rechenleistung von OpenAI [ermöglicht](https://news.yahoo.com/news/now-trump-says-500-billion-232732788.html?fr=sycsrp_catchall\&guccounter=1\&guce_referrer=aHR0cHM6Ly9wcmVzZWFyY2guY29tLw\&guce_referrer_sig=AQAAANhV_ubjRDL_kBGNPhmmLWxAhoW6pkAamqVphAXDXGmLTQUS-4gXsCQ1pinQHCufHywARCgqAG_iUpEBIIJexFhk0z6Oab5Q4js6kJ6Z6t-80onuNRGqRg_IMlcI6P72iCjCsfRpp1fAGCDhLSMGts2WK6D3gsv_YMrMXhqWP7xE) werden soll. Denn das von Elon Musk [mitgegründete](https://www.businessinsider.com/history-of-elon-musk-and-sam-altman-relationship-feuds-2023-3) Unternehmen des WEF- und [Bilderberg](https://wikispooks.com/wiki/Sam_Altman)-affinen [Sam Altman](https://news.yahoo.com/news/now-trump-says-500-billion-232732788.html?fr=sycsrp_catchall\&guccounter=1\&guce_referrer=aHR0cHM6Ly9wcmVzZWFyY2guY29tLw\&guce_referrer_sig=AQAAANhV_ubjRDL_kBGNPhmmLWxAhoW6pkAamqVphAXDXGmLTQUS-4gXsCQ1pinQHCufHywARCgqAG_iUpEBIIJexFhk0z6Oab5Q4js6kJ6Z6t-80onuNRGqRg_IMlcI6P72iCjCsfRpp1fAGCDhLSMGts2WK6D3gsv_YMrMXhqWP7xE) steht im berechtigten Verdacht, für den Tod eines Whistleblowers im Dezember 2024 verantwortlich zu sein. Während Polizei und Medien den Tod des OpenAI-Forschers Suchir Balaji als [Selbstmord](https://www.businessinsider.de/wirtschaft/openai-whistleblower-tragischer-tod-erschuettert-die-tech-welt/) deklarieren, [sprechen](https://economictimes.indiatimes.com/news/international/global-trends/suchir-balajis-openai-researcher-suicide-death-cold-blooded-murder-openai-whistleblowers-parents-claim-big-foul-play/articleshow/116855083.cms?from=mdr) sowohl die Umstände am Fundort seiner Leiche als auch Balajis Eltern von »*eiskaltem Mord*«. Nicht zu vergessen, dass Altman von seiner eigenen Schwester des jahrelangen Missbrauchs [beschuldigt](https://www.theguardian.com/technology/2025/jan/08/openai-chief-executive-sam-altman-accused-of-sexual-abuse-by-sister-in-lawsuit) wird und sich dafür demnächst vor Gericht verantworten muss. Selbst [The Economist](https://www.economist.com/business/2024/12/10/the-paypal-mafia-is-taking-over-americas-government) räumte am 10. Dezember 2024 ein, dass »*die PayPal Mafia die amerikanische Regierung übernimmt*«. Und das mit der »*Mafia*« scheint man in Washington mittlerweile wörtlich zu nehmen. Aber die von einigen aus der Hüfte geschossenen Präsidialdekreten euphorisierten Eloi werden sicher Gründe finden, das alles zu ihren Gunsten auszulegen. Immerhin hat Trump ein paar Leute begnadigt und will aus der WHO austreten. Wie seine Fanbase es bewerkstelligt, auszublenden, dass »*The Donald*« schon in seiner ersten Amtszeit aus der WHO austreten wollte und es unterließ, erschließt sich mir aber leider nicht. Genau wie die Begeisterung für ein Gespräch zwischen Musk und Weidel. Man stelle sich nur mal vor, George Soros, Bill Gates oder Eric Schmitt konferierten mit deutschen Politikern. Oder bekämen Sendezeit im ÖRR. Nicht auszudenken. **Wie heißt es so schön: »*Eine schmerzliche Wahrheit ist besser als eine Lüge*« (Thomas Mann). Stimmt. Nur fällt es relativ schwer, eine Lüge einzugestehen, wenn der, dem man sie beichten muss, der Lügner ist.** So bleibt nur zu hoffen, dass möglichst viele Eloi diesen Schritt trotzdem möglichst bald hinter sich bringen. Im eigenen Interesse. Denn wie schon Ernst Freiherr von Feuchtersleben feststellte, ist »*Reue der Verstand, der zu spät kommt*«. Und das kann in diesen Tagen verheerende Folgen haben.
@ 2fb77d26:c47a6ee1
2025-02-01 14:40:02In H. G. Wells’ Roman [Die Zeitmaschine](https://de.wikipedia.org/wiki/Die_Zeitmaschine) und den diversen Verfilmungen werden sie als »*ausschweifend, langsam und naiv*« dargestellt. Von »*untermenschlicher Intelligenz*« gezeichnet. Für [Dan Simmons](https://de.wikipedia.org/wiki/Eloi_\(Die_Zeitmaschine\)#In_Dan_Simmons%E2%80%99_Ilium) sind sie »*faul, ungebildet und unkultiviert*«. Die [Eloi](https://de.wikipedia.org/wiki/Eloi_\(Die_Zeitmaschine\)). Die als Nahrungsquelle der Morlocks gehaltenen Nachfahren des Homo sapiens. »*Sie entwickeln sich rückläufig und verlernen Jahrtausende von Kultur, Denken und Vernunft, bis sie sich mit dem Vergnügen des bloßen Daseins zufrieden geben*«. Ertönt das Schlüsselsignal, auf das sie von ihren Züchtern konditioniert wurden – eine umgebaute Zivilschutzsirene – trotten sie freiwillig und in hypnotischer Apathie zur Schlachtbank. Ein ähnlichen Eindruck hatten viele Maßnahmenkritiker von den Unterstützern der mittlerweile in allen Punkten [widerlegten](https://www.regenauer.press/kapitalverbrechen) Covid-Propaganda. Zurecht. Das Gefolge von Drosten, Lauterbach und Co. war blind für Fakten und ist ins offene Messer gelaufen. Bedauerlicherweise verhalten sich viele Maßnahmenkritiker aber nun in weiten Teilen genauso. Sie haben Idole gefunden. Wollen glauben. Sie ignorieren Informationen, Fakten und Daten und werden Opfer einer neu justierten, gut geölten Propagandamaschine. Nur, um die in ihre neuen Helden gesetzten Hoffnungen nicht aufgeben und der wenig erbaulichen Realität nicht ins Auge blicken zu müssen. Sie glauben an Donald Trump, Javier Milei, Alice Weidel, Peter Thiel und vor allem Elon Musk. Daran, dass der supranationale Nachhaltigkeitskorporatismus am Ende sei, das Finanzsystem gerettet und Gerechtigkeit hergestellt wird. Die Widerständler von gestern sind die »*Schlafschafe*« von heute. Sie scheinen vergessen zu haben, wie Propaganda funktioniert. Aus diesem Grund – und weil es ein so schön griffiges Wort ist, bei dem man nur einen Buchstaben verändern muss, um daraus den Vornamen eines vermeintlichen Heilsbringers zu basteln – erlaube ich mir, die Anhänger des MAGA-Kults im Zuge der folgenden Seiten mokant als Eloi zu bezeichnen. Ein bisschen Spaß muss sein. **Kurskorrektur mit Ansage** [Lynn Forester de Rothschild](https://www.inclusivecapitalism.com/about/), in der finanzoligarchischen Hackordnung mindestens eine Ebene über BlackRock und Co. anzusiedeln, kündigte den aktuellen Narrativwechsel bereits am 30. August 2023 an, als sie bei [Bloomberg](https://www.youtube.com/watch?v=eZzZubPKPrw) sagte, der Begriff »*ESG gehöre in die Tonne*«. Er sei verbrannt. Auch BlackRock-CEO Larry Fink, der Marktteilnehmer zur Unterstützung von ESG »*[zwingen](https://www.forbes.com/sites/jonmcgowan/2023/06/05/conservative-outrage-over-esg-and-dei-fueled-by-2017-blackrock-ceo-video/)*« wollte, [teilte](https://www.forbes.com/sites/jonmcgowan/2024/03/27/blackrocks-fink-calls-for-energy-pragmatism-omits-esg-from-annual-letter/) seinen Investoren bereits am 26. März 2023 mit, das in Verruf gekommene Label ESG durch den Begriff »*Energiepragmatismus*« zu ersetzen. Sowohl Rothschild als auch Fink räumten aber gleichzeitig ein, dass sich die übergeordnete Agenda nicht ändern und man die »Green Economy« weiter vorantreiben werde, man diese aber besser vermarkten müsse, um konservative Kreise nicht weiter gegen sich aufzubringen. Ein simpler Marketing-Trick. Wenig überraschend also, dass sowohl [BlackRock](https://nypost.com/2025/01/11/business/blackrock-quits-net-zero-initiative-at-perfect-time-as-woke-policies-contribute-to-devastating-la-fires/) als auch sechs amerikanische [Großbanken](https://joannenova.com.au/2025/01/the-last-american-banker-rats-are-leaving-the-un-net-zero-banking-club/) Anfang 2025 die [Net Zero Initiative](https://www.net-zero-initiative.com/en) verließen. Zum »perfekten Zeitpunkt«, wie die [New York Post](https://nypost.com/2025/01/11/business/blackrock-quits-net-zero-initiative-at-perfect-time-as-woke-policies-contribute-to-devastating-la-fires/) bemerkt, um nicht von der negativen, anti-woken Berichterstattung rund um die verheerenden Feuersbrünste in Los Angeles tangiert zu werden. Es scheint, als hätten die Eloi bereits wieder verdrängt, dass die WEF-Meetings [2021](https://www.weforum.org/videos/the-great-narrative-narrating-the-future-english/) und [2024](https://www.weforum.org/press/2024/01/annual-meeting-2024-rebuilding-trust-amid-uncertainty/) unter Arbeitstiteln wie »*The Great Narrative*« und »*Rebuilding Trust*« liefen. Artikuliertes Ziel der Davoser PR-Abteilung für Globalisierungsfragen war nämlich, sich den zunehmend echauffierten, misstrauischen Pöbel vom Hals zu halten. Durch neue Narrative und vertrauensbildende Maßnahmen. Und das hat, zumindest vorerst, ausgezeichnet funktioniert. In den USA stieg das [Vertrauen](https://www.zerohedge.com/political/overall-trust-election-process-rebounded-2024) in ordnungsgemäß durchgeführte Präsidentschaftswahlen 2024 zum ersten Mal seit Jahren wieder etwas an. In Europa macht sich ebenfalls Zuversicht breit. Schließlich haben die sogenannten »*[Rechtspopulisten](https://www.sueddeutsche.de/projekte/artikel/politik/rechtspopulisten-rechtsextremismus-giorgia-meloni-geert-wilders-viktor-orb-n-robert-fico-e072514/?reduced=true)*« nicht mehr nur in Italien und Ungarn, sondern auch in Finnland, der Slowakei und den Niederlanden Oberwasser. Von den Erfolgen der AFD ganz zu schweigen. Diese führen, wie zuletzt in [Thüringen](https://www.mdr.de/nachrichten/thueringen/landtagswahl/afd-sieger-mehrheit-100.html), trotz klarem Wählervotum zwar nicht zur Regierungsbeteiligung, weil »*demokratische Prozesse*« und »*Brandmauern*« das zu verhindern wissen – aber dabei sein ist ja bekanntlich alles. Dass Friedenstreiberin Alice Weidel den bundesdeutschen Rüstungsetat auf knapp [200 Milliarden](https://www.berlin-live.de/politik/weidel-afd-bundeswehr-trump-nato-id348307.html) verdoppeln will, scheint die euphorisierten Kritiker dunkelgrüner Militarisierung auch nicht auszubremsen. Hauptsache nicht grün. Oder woke. **Überstaatliche Sphären** Dabei scheint Euphorie in Anbetracht der Tatsachen alles andere als angebracht. So hat Milei nach Angaben von [Global Finance](https://gfmag.com/economics-policy-regulation/argentina-milei-administration-eliminates-deficit/) zwar das argentinische »*Staatsdefizit nach 123 Jahren beendet*«, dafür leben heute [53 Prozent](https://www.theguardian.com/world/2024/dec/18/argentina-javier-milei-chainsaw-measures) der 45 Millionen Argentinier in Armut. Der höchste Wert seit 20 Jahren. Ende 2023 waren es noch 41,7 Prozent. Daran ändert auch semantische [Schützenhilfe](https://www.hoover.org/research/critics-mileis-policies-strike-out) von libertären Denkfabriken wie der [Hoover Institution](https://de.wikipedia.org/wiki/Hoover_Institution) nichts. Die radikalen Privatisierungsfeldzüge von »*[El Loco](https://www.batimes.com.ar/news/economy/argentinas-el-loco-milei-delivered-chaos-laughs-and-key-wins-in-week-one.phtml)*« haben einen hohen Preis. Ob [Aerolineas Argentinas](https://aviationweek.com/air-transport/safety-ops-regulation/daily-memo-mileis-relentless-pursuit-privatize-aerolineas), die staatliche Fluglinie, der Stahlproduzent [IMPSA](https://www.reuters.com/world/americas/argentina-privatizes-state-metal-firm-milei-era-first-2025-01-08/) oder das Transportunternehmen [Trenes Argentinos Cargas](https://buenosairesherald.com/business/infrastructure/milei-to-privatize-major-cargo-train-company), das 7.800 Kilometer Bahnstrecke betreibt – das Volksvermögen wird an die Meistbietenden verscherbelt. Wer das ist, kann sich wohl jeder ausmalen. Denn sein Schlachtruf »*Afuera!*« (Raus hier!) gilt augenscheinlich nicht für [BlackRock](https://news.bloomberglaw.com/bankruptcy-law/blackrocks-fink-mulls-argentina-trip-after-milei-call) und Co. – schließlich sei Argentinien »*ziemlich billig*« zu haben, wie es Rick Rieder, Top-Bond-Manager des Unternehmens schon 2019 [formulierte](https://www.reuters.com/article/us-argentina-debt-blackrock-idUKKBN1XI010/). Man muss allerdings nicht in die Ferne schweifen, um sich der realen Gefahren für die Freiheit bewusst zu werden. Jener Gefahren, die von Personalien gänzlich unberührt bleiben. So arbeitet die Europäische Union weiter an der [eID](https://ec.europa.eu/digital-building-blocks/sites/display/DIGITAL/eID), der Grundlage des technokratisch-totalitären Kontroll-Grids. Ihre Einführung ist [beschlossene](https://www.europarl.europa.eu/news/de/press-room/20240223IPR18095/meps-back-plans-for-an-eu-wide-digital-wallet) Sache. Offen ist lediglich, ab wann sie zum Obligatorium wird. Auch das persönliche CO2-Budget ist auf Kurs. Mit [ETS2](https://www.epa.ie/our-services/licensing/climate-change/eu-emissions-trading-system-/eu-emissions-trading-system-2-ets2/#:~:text=ETS%202%20is%20a%20new,manufacturing%20and%20construction%20industries) (EU Emissions Trading System) nimmt die [EPA](https://www.epa.ie/who-we-are/) (Environmental Protection Agency) seit dem 1. Januar 2025 nach der Konzernwirtschaft nun kleine und mittlere Unternehmen in den Fokus und verpflichtet diese, CO2-Kompensationsabgaben auf ihren Gas-, Benzin- und Mineralölverbrauch zu entrichten. Das dürfte Heiz-, Fracht- und folglich die Lebenshaltungskosten des Bürgers in neue Höhen treiben. Bis der Sonntagsausflug mit dem Familienauto nicht mehr nur Zeit, Benzin und Nerven, sondern auch CO2-Gebühren kostet, dauert es also wohl nicht mehr allzu lange. Dieser überparteilichen, supranational koordinierten Überwachungs- und Enteignungsagenda ist weder durch die Wahl des geringeren Übels noch durch Auswandern zu entkommen. Denn wie sich der [Internetpräsenz](https://globalgovernanceforum.org/) des »*Global Governance Forum*« (GGF) entnehmen lässt, wird bereits eifrig an »*[Global Government](https://www.globalgovernmentforum.com/news/)*« gearbeitet. Die UN-nahe Nichtregierungsorganisation hat sich nämlich zum Ziel gesetzt, die Charta der Vereinten Nationen bis 2028 zu [aktualisieren](https://globalgovernanceforum.org/a-call-for-un-charter-reform/) und den allseits bekannten »*Herausforderungen unserer Zeit*« anzupassen. Pünktlich ab 2030 soll das neue Vertragswerk ratifiziert werden und neben neuen Befugnissen für den Internationalen Gerichtshof sowie einer UN-Streitmacht auch eine Regierungsstruktur analog der Europäischen Union ermöglichen. Sprich, eine Weltregierung. Ganz demokratisch selbstverständlich. Neben eID und CO2-Budget sind natürlich auch die Ausweispflicht fürs Internet und die automatisierte Zensur unliebsamer Inhalte weiter auf Kurs. Nachdem die Vereinten Nationen im September 2024 bereits dem totalitären »*[Pakt für die Zukunft](https://www.un.org/en/unis-nairobi/press-releaseunited-nations-adopts-ground-breaking-pact-future-transform-global)*« zustimmten, wurde am [Heiligabend 2024](https://www.unodc.org/unodc/en/press/releases/2024/December/un-general-assembly-adopts-landmark-convention-on-cybercrime.html) noch rasch die neue »*Konvention gegen Onlineverbrechen*« durchgewunken. Und seit Januar 2025 treibt die UN die Umsetzung eines noch weitreichenderen Abkommens namens »*[Global Digital Compact](https://www.un.org/global-digital-compact/en)*« voran. Ein Papier, vor dem ich bereits im [Juli 2023](https://www.regenauer.press/undemokratisch) gewarnt habe. Was all das für den Bürger bedeutet, zeigt sich in [Griechenland](https://www.telepolis.de/features/Totale-Kontrolle-Griechenland-verknuepft-Steuer-ID-mit-Social-Media-10222907.html), wo die Regierung seit Anfang des Jahres Social-Media-Konten mit Steuer-Identifikationsnummern verknüpft, um eine Alterskontrolle fürs Internet einzuführen. Damit folgt die von der EU in Kreditsklaverei gehaltene Regierung in Athen dem Vorbild [Australiens](https://www.tagesschau.de/ausland/asien/australien-social-media-100.html), wo der Zugang so Social-Media-Plattformen künftig erst ab einem Alter von 16 Jahren erlaubt werden soll – wofür man schlussendlich jeden Nutzer kontrollieren muss, der online geht. Auch das von vielen noch immer als Mythos abgetane Geoengineering wird derweil munter weitergeführt. Obwohl [Berichte](https://www.whitehouse.gov/wp-content/uploads/2023/06/Congressionally-Mandated-Report-on-Solar-Radiation-Modification.pdf) des US-Kongress und mittlerweile sogar wissenschaftliche [Berater](https://scientificadvice.eu/advice/solar-radiation-modification/) der EU-Kommission vor großflächigem [Solar Radiation Management](https://www.risiko-dialog.ch/solar-radiation-management-ein-letztes-mittel-im-kampf-gegen-den-klimawandel/) warnen. Im Rahmen eines offiziellen, 54 Seiten umfassenden [Reports](https://op.europa.eu/en/publication-detail/-/publication/9c2ac367-b5de-11ef-acb1-01aa75ed71a1/language-en) an die EU-Kommission sowie eines [Artikels](https://www.theguardian.com/environment/2024/dec/09/eu-should-ban-space-mirrors-and-other-solar-geoengineering-warn-scientists) des britischen Guardian vom 9. Dezember 2024 verwies das siebenköpfige Forscherteam auf die unabschätzbaren Konsequenzen solcher Eingriffe und forderte ein EU-weites Moratorium. Wie genau Trump, Musk, Milei, Meloni, Weidel und Co. die Welt vor diesem Sammelsurium an totalitären Übergriffigkeiten retten wollen, konnte mir bislang keiner der Eloi sagen. **DJ Trump** Warum die in Donald Trump, den »*[Vater der Impfung](https://www.independent.co.uk/news/world/americas/us-politics/trump-father-vaccine-covid-fox-interview-b1839555.html)*«, und sein zionistisches Kriegstreiberkabinett gesetzten Hoffnungen bald bitterer Enttäuschung weichen dürften, habe ich bereits am 14. November 2024 ausführlich [beschrieben](https://www.regenauer.press/trump-reloaded). Dass auch die beiden Hauptargumente seiner Befürworter – dass er die mRNA-Kampagne mittlerweile bereue und in seiner ersten Amtsperiode Friedenspolitik betrieben habe – schlichtweg falsch sind, ebenfalls. Denn anhand der nackten [Zahlen](https://foreignpolicy.com/2017/08/09/donald-trump-is-dropping-bombs-at-unprecedented-levels/) lässt sich eindeutig belegen, dass Trump »*der kriegslüsternste Präsident der jüngeren Geschichte*« war. Und wie stolz er auf »*Operation Warp Speed*« ist, die [unzählige](https://icandecide.org/v-safe-data/) Amerikaner Gesundheit oder Leben kostete, ließ er die Welt zuletzt am [17. November 2024](https://x.com/tomregenauer/status/1859637538874589311) auf seinem Social-Media-Netzwerk [Truth Social](https://de.wikipedia.org/wiki/Truth_Social) wissen. Trumps Interesse gilt nicht Frieden und Freiheit, sondern Donald Trump. So war es sein ganzes Leben lang. Wenn sich »*The Donald*« jemandem verpflichtet fühlt, ist es vielleicht [Wilbur Ross](https://de.wikipedia.org/wiki/Wilbur_Ross), der ehemalige Chef von [Rothschild Inc. Bankruptcy Advising](https://www.rothschildandco.com/en/global-advisory/debt-advisory-and-restructuring/). Denn wie das [Forbes Magazine](https://www.forbes.com/sites/chasewithorn/2016/12/08/trump-and-his-commerce-secretary-wilbur-ross-a-look-at-25-years-of-connections/) am 8. Dezember 2016 korrekt erläuterte, rette das Bankhaus vor gut 30 Jahren nicht nur Trumps bankrotte Casinos, sondern damit auch seine ganze Karriere. Nicht weil man in Trumps Geschäften und Immobilien einen besonderen Wert sah, sondern weil man die Person Donald Trump als »*Anlage*« betrachtete. Trotzdem ist es sicher nur Zufall, dass Ross von 2017 bis 2021 Handelsminister der Vereinigten Staaten war. **Elon Musk** Auch über den PayPal-Mafioso, CIA-Handlanger und Bilderberg-Executive Peter Thiel, dessen Protegé JD Vance nun US-Vizepräsident ist, habe ich bereits im September 2024 einen ausführlichen [Artikel](https://www.regenauer.press/gestatten-peter-thiel) geschrieben. Gleiches gilt für Elon Musk, dessen trügerisches Image als Genius, Erfinder und Entrepreneur ich sogar schon im Oktober 2022 [durchleuchtet](https://www.regenauer.press/dekuvrierte-coolness) habe. Zitat: »*Dass Elon Musk nicht rein zufällig zur liberal-coolen Ikone avancierte, legt ein Blick in seine Anfangsjahre als Unternehmer nahe. Denn während im sagenumwobenen Silicon Valley Ende der 1990er-Jahre eine Vielzahl an erfolgreicheren Tech-Entrepreneuren existierte, war es ausgerechnet Elon Musk, der für einen absolut inhaltsleeren [Gastauftritt](https://www.youtube.com/watch?v=s9mczdODqzo) bei CNN gefilmt wurde, sodass zum ersten Mal eine breitere Öffentlichkeit von ihm Notiz nehmen musste. Dabei war sein erstes Unternehmen – [Zip2](https://en.wikipedia.org/wiki/Zip2) –, das er im Jahre 1995 mit seinem Bruder sowie einem weiteren Partner gegründet und im Februar 1999 für circa [300 Millionen US-Dollar](https://web.archive.org/web/20220625124959/https:/www.nytimes.com/1999/02/17/business/compaq-buys-zip2-to-enhance-altavista.html) an Compaq veräußert hatte, nicht das revolutionärste Unterfangen im kalifornischen IT-Mekka dieser Tage. Es handelte sich um ein simples Telefonbuch fürs Internet. Wenig mehr als eine Datenbank, in die sich Unternehmen eintragen konnten, um ihre Adresse im Netz zu hinterlegen*.« Meine fast zweieinhalb Jahre alte Analyse bedarf allerdings dringend einer Aktualisierung. Denn was Musk in der Zwischenzeit trieb – und für die Zukunft plant – hat so gar nichts mit dem zu tun, was seine geradezu fanatisierten Anhänger in ihm sehen wollen. Fangen wir der Vollständigkeit halber aber noch mal vorne an: Elon Musk hat weder [PayPal](https://en.wikipedia.org/wiki/PayPal#Early_history) gegründet noch den [Tesla](https://www.cnbc.com/video/2021/02/06/how-tesla-was-founded-martin-eberhard-and-marc-tarpenning-tell-all.html) erfunden. Auch wenn er das gerne so darstellt. Dafür [fertigte](https://www.reuters.com/article/business/healthcare-pharmaceuticals/musk-says-tesla-is-building-rna-microfactories-for-curevac-idUSFWN2E9067/) Tesla unter seiner Ägide dann aber »*RNA Mikrofabriken*« für das deutsche Unternehmen [CureVac](https://www.nzz.ch/wissenschaft/curevac-impfstoff-noch-ein-sieg-gegen-das-virus-ld.1788519), das zusammen mit [Bayer](https://www.nasdaq.com/press-release/curevac-:-curevac-and-bayer-join-forces-on-covid-19-vaccine-candidate-cvncov-2021-01) mRNA-Injektionen gegen Corona auf den Markt brachte. Und während Musk gegenüber der [New York Post](https://www.youtube.com/watch?v=2lPkvteqKig) am 30. September 2020 sagte, sich nicht gegen Covid impfen lassen zu wollen, erklärte er dem [TIME Magazine](https://web.archive.org/web/20211213124147/https:/time.com/person-of-the-year-2021-elon-musk/) am 13. Dezember 2021, bereits geimpft zu sein. Zeitgeistig flexibel ist er also. Wer behauptet, Musk hätte seine Meinung zur mRNA-Technologie seit dem Covid-Fiasko signifikant geändert und sehe das Produkt nun kritisch, ist schlecht informiert. Noch am [12. April 2023](https://x.com/elonmusk/status/1646220824192630784) erklärte er bei Twitter, dass er mRNA für eine »*medizinische Revolution*« hält. Vergleichbar mit dem Schritt »*von analog zu digital*«. Was Musk mit digitaler Revolution meint, zeigte sich 2017 mit Hurricane Irma. Damals gab das Unternehmen für Besitzer von Fahrzeugen mit 75 kWh ein [Softwareupdate](https://www.teslarati.com/tesla-issues-software-update-help-owners-flee-hurricane-irmas-evacuation-zone/) heraus, das die Reichweite von 338 auf 400 Kilometer steigerte – was im Umkehrschluss bedeutet, dass Tesla-Besitzer um eine eigentlich abrufbare Leistung ihres eigenen Fahrzeugs betrogen werden, wenn gerade keine Naturkatastrophe wütet. Dass Tesla-Kunden darüber hinaus permanent [überwacht](https://upnorthlive.com/news/nation-world/tesla-cybertruck-explosion-trump-hotel-fbi-surveillance-elon-musk-company) werden, zeigte sich unlängst im Rahmen der Explosion eines Cybertrucks in Las Vegas. Augenbewegungen, Mimik, Geschlecht, Hautfarbe, Körpertemperatur, Gepäckanordnung, Route, Ladestopps, Bezahlvorgänge, Telefonbuch, Musik-Playlist, Online-Abos, et cetera. Was von Sensoren und Verbindungen zu erfassen ist, wird erfasst, wie eine [Untersuchung](https://gizmodo.com/mozilla-new-cars-data-privacy-report-1850805416) von Mozilla im Herbst 2023 feststellte. Das gilt im Übrigen nicht nur für Tesla, sondern für praktisch alle modernen Autos. Ein Tesla hat es dabei nur am leichtesten. Die gesammelten Daten werden entweder zum Schleuderpreis [verkauft](https://archive.is/tc2xB) und/oder gegen uns verwendet. Doch zurück zu Musk, der Twitter nicht übernahm, um Meinungsfreiheit herzustellen, sondern um die Plattform zur »*Alles-App*« zu machen. Sein [erklärtes](https://www.forbes.com/sites/abrambrown/2022/06/21/elon-musk-and-the-super-alluring-dream-for-a-super-app/?sh=6cf8e3021343\&utm_medium=social\&utm_source=ForbesMainTwitter\&utm_campaign=socialflowForbesMainTwitter) Vorbild: die chinesische [Spionage-App](https://citizenlab.ca/2020/05/wechat-surveillance-explained/) WeChat. Deswegen will er alle Nutzer »*als echte Menschen [identifizieren](https://edition.cnn.com/2022/04/28/tech/elon-musk-authenticate-all-real-humans/index.html)*«. Biometrisch versteht sich. Dafür [arbeitet](https://www.business-humanrights.org/en/latest-news/x-corps-biometric-data-sharing-with-israeli-firm-raises-privacy-concerns/) man bei Twitter bevorzugt mit israelischen Unternehmen zusammen, die von ehemaligen [Mossad-Agenten](https://www.middleeasteye.net/news/x-twitter-israel-concerns-verification) gegründet wurden. Vielleicht stellte ja Doppelagent Jeffrey Epstein den Kontakt zum Mossad her, nachdem er Musk als regelmäßigen Teilnehmer seiner [Edge-Foundation](https://www.regenauer.press/die-glorreichen-sieben) Seminare zum Thema Nudging schätzen gelernt hatte. Epstein war nämlich der einzige nennenswerte Sponsor von Edge. Twitter kaufte Musk übrigens nicht von seinem eigenen Geld, sondern mit Hilfe von 94 [Investoren](https://www.newsweek.com/full-list-investors-elon-musks-x-revealed-court-filing-1942970), deren Namen ein US-Bundesrichter erst im August 2024 veröffentlichte, weil Jacob Silverman (Reporters Committee for Freedom of the Press) sie einklagte. Die Liste umfasst so illustre Namen wie Fidelity Investments, Sequoia Capital, Andreessen Horowitz, Bandera Fund, Binance Capital Management, Sean Combs (alias Diddy) Capital, Jack Dorsey (Twitter Gründer), Baron Opportunity Fund oder Prinz Alwaleed bin Talal al Saud von der saudischen Königsfamilie. Da wird also offenbar »*der Sumpf*« mit mehr Sumpf »*trockengelegt*«. Von der Nominierung des [WEF Executive Chair](https://www.linkedin.com/posts/lindayaccarino_freedom-of-speech-not-reach-an-update-on-activity-7053787411847237633-zC8Q) Linda Yaccarino als neuer Twitter-CEO und »*Freedom of Speech*« versus »*[Freedom of Reach](https://www.linkedin.com/posts/lindayaccarino_freedom-of-speech-not-reach-an-update-on-activity-7053787411847237633-zC8Q)*« mal ganz abgesehen. Auch die von den Eloi als sensationelle Enthüllung gefeierten [Twitter Files](https://twitterfiles.substack.com/p/1-thread-the-twitter-files) sind leider nicht ernst zu nehmen. Denn sie offenbarten nichts, was man nicht schon wusste. Zudem ist bis heute unklar, woher die veröffentlichten Informationen kamen, wer den Zugriff darauf gesteuert hat, was dort noch gespeichert war, warum praktisch nur ein von Elon ausgewählter [Journalist](https://docs.house.gov/meetings/FD/FD00/20230309/115442/HHRG-118-FD00-Wstate-TaibbiM-20230309.pdf) Zugriff darauf hatte und dieser nur Screenshots, anstelle ganzer Dokumente veröffentlichen durfte. Ein echter Leak besteht aus einem Archiv, das man selbst durchsuchen kann – nicht aus ein paar handverlesenen Screenshots. Fehlt noch Space X. Ein Unternehmen, das Musk zwar selbst gegründet hat, dessen Erfolge aber in weiten Teilen anderen Umständen zu verdanken sind. So schreibt beispielsweise [inside Tesla](https://insidetesla.de/spacex-und-nasa-staatlich-private-kooperation/) am 22. März 2022: **»*Schon Anfang der 2000er-Jahre hatte die NASA erkannt, dass ihr bald die Möglichkeit fehlen würde, selbst Astronauten und Material ins All und zur ISS zu bringen. Man machte sich also auf die Suche nach Partnern aus der Privatwirtschaft und wurde unter anderem bei Elon Musks Space X fündig. Bereits 2006, also noch in der Entwicklungsphase der Falcon 1, erhielt Musks Unternehmen fast 400 Millionen US-Dollar Startfinanzierung unter dem COTS-Programm*.«** Space X war von Beginn an als verlängerte Werkbank der NASA gedacht, weil der US-Weltraumbehörde immer mehr Mittel gestrichen wurden. Die Öffentlichkeit hatte nämlich das Interesse an ziviler Raumfahrt verloren. Daher setzte man in Washington immer öfter den Rotstift an. Doch seit Musk die Menschen öffentlichkeitswirksam zum Mars befördern will – »*let’s build Marsian Technocracy*« – steigt das Interesse wieder. Leider muss ich die Vorfreude auf eine planetare Kolonie aber etwas dämpfen. Denn Space X wird nicht betrieben, um Menschen auf den Mars zu bringen, sondern um das »*weltgrösste Netzwerk an [Spionagesatelliten](https://www.reuters.com/technology/space/musks-spacex-is-building-spy-satellite-network-us-intelligence-agency-sources-2024-03-16/) [aufzubauen](https://web.archive.org/web/20241206180227/https:/www.activistpost.com/2024/12/you-cant-hide-elon-musk-spacex-are-helping-us-intelligence-build-the-worlds-largest-spy-satellite-network.html)*«. Musks Weltraumagentur ist Handlanger des militärisch-industriellen Komplexes und einer der wichtigsten [Vertragspartner](https://thehill.com/policy/defense/542728-pentagon-awards-160m-in-contracts-to-musks-spacex/) des Pentagon. Das konnte man 2017 schon im [Observer](https://observer.com/2017/04/spacex-to-launch-top-secret-mission-for-government-spy-agency/) nachlesen. Oder am 9. Januar 2018 bei [CNBC](https://www.cnbc.com/2018/01/08/highly-classified-us-spy-satellite-appears-to-be-a-total-loss-after-spacex-launch.html), die vom (missglückten) Transport eines streng geheimen US-Spionagesatelliten berichtete. Am 15. April 2022 kommentierte [Tech Unwrapped](https://techunwrapped.com/spacex-will-launch-two-spy-satellites-for-the-us-military/) zwei weitere Spionagesatelliten des US-Militärs, die Space X in die Umlaufbahn beförderte. Seit Jahren erhält das Unternehmen Milliarden von US-Regierung und Geheimdiensten. Siehe [Los Angeles Times](https://www.latimes.com/business/la-fi-hy-musk-subsidies-20150531-story.html) vom 30. Mai 2015: 4,9 Milliarden. Oder ein Artikel des [Wall Street Journal](https://www.wsj.com/podcasts/google-news-update/how-spacex-is-deepening-its-ties-with-the-us-government/b860deaf-724c-4610-8177-479b520df6d4) vom 23. Februar 2024: 1,8 Milliarden. Oder eine lange Liste von staatlichen Zuwendungen, die [Business Insider](https://www.businessinsider.com/elon-musk-list-government-subsidies-tesla-billions-spacex-solarcity-2021-12?r=US\&IR=T) am 15. Dezember 2021 veröffentlichte. Damit basiert der Erfolg von Space X nicht primär auf Musks genialem Unternehmergeist, sondern auf Subventionen. Auf Steuergeldern. Nicht zu vergessen: [Starlink](https://de.wikipedia.org/wiki/Starlink). Das von Space X betriebene, weltumspannende Satellitennetzwerk. Es mag den Vorteil haben, dass damit auch Menschen in entlegenen Regionen des Planeten oder Katastrophengebieten Zugriff auf das Internet haben. Dabei sollte allerdings nicht unterschlagen werden, dass Starlink in seiner finalen Ausbaustufe circa 42.000 Satelliten umfassen und damit ein permanentes Strahlungsfeld erzeugen wird. Gesundheitliche Risiken für den Homo sapiens: unklar. Darüber hinaus haben die Orbiter Zugriff auf das [NORAD](https://de.wikipedia.org/wiki/North_American_Aerospace_Defense_Command)-Datenbanksystem, um Weltraumschrott ausweichen zu können. Sprich, sie sind permanent mit Systemen des US-Militär verbunden. Aus diesem Grund ermöglicht Starlink auch die Steuerung von Kampfdrohnen – siehe [Ukraine-Konflikt](https://www.telegraph.co.uk/world-news/2022/03/18/elon-musks-starlink-helping-ukraine-win-drone-war/) – sowie 30 mal schnelleres Senden von Daten an und von US-Kampfflugzeugen. Während die Öffentlichkeit Musks Satellitennetzwerk vor allem als ziviles Produkt betrachtet, ist Starlink primär von militärischem Interesse. Nicht umsonst wird parallel [Starshield](https://en.wikipedia.org/wiki/SpaceX_Starshield) aufgebaut, das dem geheimdienstlich-militärischen Komplex unter anderem die diskrete Echtzeitüberwachung der ganzen Welt erlaubt. Auch von [DEW](https://en.wikipedia.org/wiki/Directed-energy_weapon)-Fähigkeiten (Directed Energy Weapon) ist die Rede. Ende 2024 befanden sich bereits 98 solcher Satelliten in erdnaher Umlaufbahn. In Anbetracht dieser Informationen ist es also kaum verwunderlich, dass Musk seit Jahren offen für [Technokratie](https://www.ft.com/content/df695f10-154d-11e8-9376-4a6390addb44) [wirbt](https://x.com/search?q=from%3Aelonmusk%20technocracy\&src=typed_query). Für ein zentralistisches, [faschistoides](https://web.archive.org/web/20230920020550/https:/www.newyorker.com/news/daily-comment/the-world-according-to-elon-musks-grandfather) Herrschaftsmodell, das schon sein [Großvater](https://newsinteractives.cbc.ca/longform/technocracy-incorporated-elon-musk/) Joshua Haldemann als führender Kopf in den USA und Kanada vertrat. Der Familientradition folgend [empfiehlt](https://www.youtube.com/watch?v=BMskI6G9ty0) Musk eine [CO2-Steuer](https://www.cnbc.com/2021/02/12/elon-musk-reducing-greenhouse-gas-emissions-with-a-carbon-tax.html) zum Kampf gegen den Klimawandel, ein universelles [Grundeinkommen](https://www.businessinsider.com/elon-musk-universal-basic-income-ubi-ai-automation-unemployment-quotes-2024-6), um die von der KI ausgelösten Disruptionen abzufangen und sein [Neuralink](https://neuralink.com/) Gehirnimplantat, um dem drohenden Transhumanismus etwas Transhumanismus entgegenzusetzen. **Futurum Technologicus** Für Kunden, denen Chips im Kopf irgendwie zu altbacken sind, [entwickelt](https://www.neurotechreports.com/pages/Neuralink-launch-collaborations.html) Musks Unternehmen in Zusammenarbeit mit [iota Biosciences](https://www.iota.bio/) natürlich ein zeitgemäßeres Premiumprodukt: Neural Dust. Intelligente Nanopartikel in Staubkorngröße, die sich im Gehirn anreichern. Die lassen sich dann wahrscheinlich – wie die in Indien bereits zugelassene [Nasal-Impfung](https://www.lemonde.fr/en/covid-19-pandemic/article/2022/09/06/india-approves-its-first-nasal-vaccine-for-covid-19_5996007_122.html) gegen Covid – durch die Nase ziehen. Oder durch Luftschächte öffentlicher Gebäude pumpen. Man kann die neue Freiheit also förmlich riechen. Ganz wie es der 44 Seiten starke »*National Nanotechnology Initiative Strategic Plan*« ([NNI Plan](https://www.nano.gov/sites/default/files/pub_resource/NNI-2021-Strategic-Plan.pdf)) des Weißen Hauses im Oktober 2021 vorsah: »*Die Öffentlichkeit einbeziehen und Mitarbeiterzahlen im Bereich Nanotechnologie erhöhen*«. Nicht umsonst hat Donald Trump der entsprechenden Behörde in seiner ersten Amtszeit zusätzliche Mittel [genehmigt](https://en.wikipedia.org/wiki/National_Nanotechnology_Initiative). Genau wie Joe Biden nach ihm. Das von der Technokratie-Bewegung vor fast einem Jahrhundert definierte [nordamerikanische Technate](https://technocracy.fandom.com/wiki/Technate) – sprich, der amerikanische Verantwortungsbereich einer weltweiten Technokratie – sieht der von [Trump](https://www.newsweek.com/donald-trumps-plan-new-us-empire-2008028) und Musk reanimierten Vision einer »*nordamerikanischen Union*« übrigens verblüffend ähnlich. Wen interessiert bei all der Make-Great-Euphorie schon noch, dass Imperialismus scheisse, Dänemark ein souveräner Staat und der Panamakanal ein strategisches Nadelöhr der internationalen Handelsschifffahrt ist. Oder, dass die »*nordamerikanische Union*« nicht nur bei Trump-Cheerleadern wie [Alex Jones](https://www.youtube.com/watch?v=sHMD5k8Pv5Y) vor ein [paar Jahren](https://thenewamerican.com/world-news/north-america/cfr-globalists-outline-strategy-for-north-american-community/) noch als »*böser [Globalisten-Plan](https://frankspeech.com/video/americans-are-waking-globalist-goal-creating-north-american-union)*« galt. Schauen wir nach vorne. In Richtung »*goldenes Zeitalter*«, wie Trump es nennt. Dieses dürfte für den Normalbürger nämlich sehr ungemütlich werden. Denn es wird dominiert von Algorithmen. Von Künstlicher Intelligenz. Für die Eloi also primär von [Grok](https://en.wikipedia.org/wiki/Grok_\(chatbot\)), dem auf Twitter (und [Teslas](https://techcrunch.com/2024/09/08/elon-musk-says-tesla-has-no-need-to-license-xai-models/)) integrierten Chatbot. Dieser basiert auf Technologie des Unternehmens xAI – laut [Wikipedia](https://en.wikipedia.org/wiki/XAI_\(company\)) gegründet von Elon Musk im März 2023. Das mag zwar so im Handelsregister stehen, ist wohl aber nur die halbe Wahrheit. Denn xAI dürfte die Fortführung eines [DARPA-Projekts](https://onlinelibrary.wiley.com/doi/full/10.1002/ail2.61) darstellen, das bereits 2015 unter dem Titel »*Explainable Artificial Intelligence*« (XAI) gestartet wurde und 2021 auslief. Als die Finanzierung seitens DARPA eingestellt wurde, machte XAI die Forschungsergebnisse auf einem [Server](https://xaitk.org/) zugänglich. Circa 18 Monate Jahre später [engagierte](https://www.simonandschuster.com/books/Elon-Musk/Walter-Isaacson/9781982181284) Elon Musk [Igor Babuschkin](https://www.linkedin.com/in/igor-babuschkin-9bb5bab6/) als Chefingenieur für xAI. Babuschkin hatte zuvor acht Jahre lang für Googles DeepMind-Projekt gearbeitet und nutzte aller Wahrscheinlichkeit nach die DARPA-Ergebnisse um xAI, beziehungsweise Grok zu entwickeln. Im Juli 2023 [verkündete](https://archive.ph/hq6WS) Musk, xAI sei im Gegensatz zu den Konkurrenzprodukten von Google, Microsoft und OpenAI eine »*gute*« KI. Erstaunlich, wenn die gleichen Ingenieure am Werk sind und die KI auf Basis eines Militärprojekts entsteht. Zudem sprechen auch die Top-Sponsoren von xAI nicht unbedingt für das »*Gute*«. Denn unter den größten Geldgebern der letzten [Finanzierungsrunde](https://www.livemint.com/companies/news/elon-musks-xai-raises-6-billion-funding-from-blackrock-nvidia-amd-and-others-11735045011974.html) vom 23. Dezember 2024 befinden sich so illustre Namen wie BlackRock, AMD, Nvidia und Fidelity, die zusammen weitere sechs Milliarden Dollar für Musks KI-Unternehmen zur Verfügung stellten. Genug Liquidität, um xAI für die »*Alles-App*« weiterzuentwickeln, wo Grok seit einer Weile automatisch [Kurzbeschreibungen](https://circleboom.com/blog/what-is-x-profile-summary/) für Profile erstellt, die man weder abschalten noch ändern kann. Twitter-Nutzer müssen nun also nicht mehr selbst das Profil eines Accounts durchstöbern, um sich einen ersten Eindruck von der Person zu machen, sondern bekommen diesen von Elon Musks KI geliefert. Vorurteil auf Knopfdruck sozusagen. Vergleichbar mit einem Sozialkreditsystem. Denn die täglich neu generierte Zusammenfassung basiert auf dem Nutzerverhalten. **»*Die neuen, KI-generierten Grok-Kurzprofile unter jedem X-Nutzerprofil SIND de facto ein Social Credit System nach chinesischem Vorbild für den Westen. Das Profil jedes Nutzers wird tagesaktuell neu berechnet. Äußert man sich zu verschiedenen Themen, nennt die KI das schnell mal »verheddern«. Grok gibt zu, das Profil wird erstellt aus dem eigenen Nutzerverhalten des Tages, seinen eigenen Berechnungen und nicht näher definierten Anweisungen*«,** **[kommentierte](https://x.com/aya_velazquez/status/1879288289393340512)** **Journalistin Aya Velázquez die Neuerung am 14. Januar 2025.** Andere Nutzer werden als »*leicht erregbar*« beschrieben, »*verzetteln*« sich oder »*glauben an Wettermanipulation zur Klimakontrolle*«. Offener wird ein Debattenraum dank solcher Adjektive und Zusammenfassungen sicher nicht. Wer möchte schon das Profil von leicht erregbaren Chemtrail-Gläubigen anschauen oder gar mit diesen assoziiert werden. Gegen solch eine automatisierte, herablassend daherkommende Einordnung durch intransparent operierende KI war die Faktencheck-Industrie geradezu harmlos. Wer also annimmt, die [Abschaffung](https://www.bbc.com/news/articles/cly74mpy8klo) der Faktenchecker bei Facebook und Co. bedeute ein Ende der Zensur, irrt. Sie wird im Gegenteil deutlich raffinierter und weitreichender werden. Details zum persönlichen Punktestand im Grok-Sozialkreditsystem oder Information über das Zustandekommen der Bewertung erhält man auf Anfrage natürlich nicht. Twitter wird die daraus entstehende Hierarchie aber mit Sicherheit für Reichweitensteuerung, Nudging-Kampagnen und weitere sozialarchitektonische Funktionen nutzen. Vor allem, wenn 2025 das Bezahlsystem »[X Money](https://www.foxbusiness.com/technology/x-money-payment-system-launch-2025-x-ceo)« eingeführt wird. Dann werden die Eloi bald nicht mehr nur um Reichweite, Follower und Re-Tweets buhlen, sondern auch um Geld – das als Folge unliebsamer Postings zu Genozid X, Krieg Y oder Person Z künftig schneller eingefroren werden dürfte als jedes Bankkonto. [De-Banking](https://multipolar-magazin.de/artikel/de-banking) der nächsten Generation. Und irgendwann trifft das jeden. Außer, man schwimmt immer mit dem Strom. Doch damit nicht genug. Am 13. Dezember 2024 [gab](https://www.finanzen.ch/nachrichten/aktien/wisekey-aktie-schiesst-zweistellig-hoch-wisesat-satellitenstart-mit-spacex-im-januar-2025-geplant-1034135831) das wohl den wenigsten bekannte Unternehmen [WISeSat](https://wisesat.space/) bekannt, künftig mit Space X zusammenzuarbeiten, um »*verschiedene Produkte und Systeme zu kombinieren*«. Die WISeSat AG ist eine Tochterfirma der in [Genf](https://www.inside-it.ch/wisekey-lagert-satellitenbusiness-in-neue-firma-aus-20230607) (Schweiz) ansässigen [WISeKey International Holding AG](https://www.wisekey.com/), die im Bereich Cybersicherheit, KI und IoT (Internet of Things) tätig ist. Die Ankündigung dieser Kollaboration ließ die WISeKey-Aktie kurzfristig um 107,73 Prozent steigen. Ein erster gemeinsamer Start zum Transport sogenannter [Picosatelliten](https://www.sciencedirect.com/topics/engineering/picosatellites) fand am 14. Januar 2025 von der Vandenberg Space Force Base in Kalifornien statt. Aber was genau macht WISeSat? Einer [Presseerklärung](https://www.wisekey.com/de-press/wisesat-ag-ein-wegweisender-weltraumarm-von-wisekey-international-tritt-space-innovation-bei-und-starkt-die-position-der-schweiz-in-der-raumbasierten-iot-kommunikation/) des Unternehmens vom 15. September 2023 lässt sich entnehmen: »*WISeSAT AG zeichnet sich dank ihrer Konstellation von ultra-sicheren Picosatelliten und Infrastruktur durch sichere und effektive Kommunikationsstrategien für vernetzte Geräte aus. Die Expertise des Unternehmens in kryptografischer Technologie und sicherem Datenmanagement hat die sichere IoT-Implementierung in zahlreichen Bereichen neu definiert, von städtischen Innovationen in Smart Cities bis hin zu modernster industrieller Automatisierung*. (…) *WISeSAT steht an vorderster Front bei der Entwicklung von ultra-sicheren Picosatelliten-Lösungen in Zusammenarbeit mit ihrem Verbündeten [FOSSA Systems](https://en.wikipedia.org/wiki/FOSSA_Systems). Es setzt sich für sichere IoT-Kommunikation über raumbasierte Netzwerke ein und nutzt die neuesten kryptografischen Innovationen, um sichere und sofortige Datenaustausche in verschiedenen Bereichen zu gewährleisten* (…).« Im Klartext: WISeSat bringt Satelliten von der Größe einer Tupperdose ins All. Diese Mini-Orbiter umkreisen den Planeten in niedrigen Umlaufbahnen und etablieren dort ein Netzwerk für kryptografierte Echtzeitdatenübertragung. Fliegende 5G-Masten sozusagen. Oder WLAN-Router. Nur viel schneller. Für das Internet der Dinge – und Smart Cities. »*In dieser Woche startet WISeSat einen Satelliten der neuen Generation und markiert damit einen wichtigen Meilenstein in der Entwicklung einer globalen Satellitenkonstellation, die eine umfassende Erdabdeckung mit ultraniedriger Latenzzeit ermöglicht. Entwickelt, um Billionen von IoT-Geräten in Echtzeit zu verfolgen und aufzuspüren*.« ([Carlos Creus Moreira](https://x.com/CreusMoreira/status/1878312357882941521), WISeKEy CEO, 12. Januar 2025) Welche Datenträger dieses Picosatelliten-Netzwerk künftig verfolgen und aufspüren soll, zeigt sich bei einem Blick auf das Produktportfolio der Holding-Gesellschaft WISeKey – einem »*weltweit führenden Anbieter von Cybersicherheit, digitaler Identität und Internet der Dinge (IoT) Lösungen*«. Denn die [Holding](https://www.wisekey.com/) existiert seit 24 Jahren, besteht aus fünf Unternehmen, hat mehr als eineinhalb Milliarden Chips und über fünf Milliarden »[Roots of Trust](https://www.computerweekly.com/de/definition/Roots-of-Trust-RoT)« installiert, residiert an sechs internationalen Standorten und hat gut 3.000 Kunden in Staat und Wirtschaft beglückt. Einen Wikipedia-Eintrag gibt es für das bei NASDAQ und SIX gelistete Unternehmen erstaunlicherweise trotzdem nicht. Dafür aber für den seit Mai 2021 [amtierenden](https://www.handelszeitung.ch/panorama/wisekey-holt-pierre-maudet-als-chief-digital-transformation-officer) »*Chief Digital Transformation Officer*« [Pierre Maudet](https://de.wikipedia.org/wiki/Pierre_Maudet). Der war ab Juni 2012 Mitglied des Genfer Staatsrats, [2013](https://wikispooks.com/wiki/WEF/Young_Global_Leaders/2013) bei den Young Global Leaders des Weltwirtschaftsforums und 2015 bei der Bilderberger Konferenz in [Telfs-Buchen](https://wikispooks.com/wiki/Bilderberg/2015) (Österreich). Nachdem er im Februar 2021 vom Genfer Polizeigericht wegen Vorteilsnahme verurteilt wurde, trat er als Staatsrat zurück – und drei Monate später bei WISeKey an. Am 30. April 2023 wurde er, ungeachtet seiner kriminellen Vergangenheit, zusätzlich wieder in den Genfer Staatsrat gewählt. Wie praktisch. Solch eine schamlose Unverfrorenheit scheint Maudet perfekt für das zu qualifizieren, was bei WISeKey unter dem Deckmantel der »Quantensicherheit« entwickelt wird – ein raumbasiertes [eID-Ökosystem](https://wiseid.com/). »*Quantensicherheit nutzt Prinzipien der Quantenmechanik, um den Datenschutz und die sichere Informationsübertragung zu revolutionieren. Kernstück ist die Quantenschlüsselverteilung (Quantum Key Distribution, QKD), eine Spitzentechnologie, die mithilfe der Quantenmechanik vernetzte Teilchen für den sicheren Austausch von Verschlüsselungskennwerten erzeugt*.« Ob digitale Identität, Unterschrift, Cloud oder Software – von der Know-Your-Customer-Biometrie bis hin zur Unternehmenslösung für die Mitarbeiteridentifikation. WISeKey hilft. [Anmelden](https://account.wiseid.com/signup) kann sich jeder. Während die Produktpalette für den privaten Sektor noch nach Lieferketten-Management, Sendungsverfolgung, Login-Lösung für eBanking oder [Face ID](https://de.wikipedia.org/wiki/Face_ID) auf dem Smartphone klingt – aber deutlich weitreichender ist, schauen sie sich die Homepage an – sprechen die WISeKey-Angebote im Bereich [Regierungen](https://www.wisekey.com/solutions/by-industry/government-trust-solutions/) eine ganz andere Sprache. Denn unter diesem Menüpunkt bewirbt der diskret operierende Konzern seine »*CertifyID Trust Center Platform*«: »*Die CertifyID Trust Center Platform ist eine industrialisierte eID-Verwaltungslösung für Bürger, die Benutzer und ihre Anmeldeinformationen verwaltet, insbesondere digitale IDs und digitale Zertifikate für groß angelegte Anwendungen wie landesweite E-Government-Dienste. Es handelt sich um eine vollständige industrielle Public Key Infrastruktur- und ID-Verwaltungslösung, die Regierungsdienste rund um die Uhr unterstützt.* ***Die CertifyID Trust Center Plattform wird in einer Reihe von Anwendungen der Regierung und des öffentlichen Sektors verwendet, zum Beispiel: Personalausweis, ePassport (ICAO-konform), Führerschein, Gesundheit, Wahlen/Abstimmen*****.** *Die CertifyID Plattform wurde unter Verwendung der Sicherheits- und Public Key Infrastruktur-Expertise von WISeKey entwickelt und kann vollständig in E-Government-Frameworks, kommerzielle Frameworks (…) und in das Bereitstellungsframework für E-Government-Dienste eines Landes integriert werden*.« Da passt es doch wunderbar ins Bild, dass WISeKey am [13. Oktober 2022](https://www.finanzen.net/nachricht/aktien/wisekey-und-die-schweizer-armee-unterzeichnen-eine-partnerschaftsvereinbarung-zur-zusammenarbeit-bei-der-entwicklung-weltraumbezogener-aktivitaeten-unter-verwendung-der-wisesat-fossa-technologie-fuer-pi-11792137) eine »*Partnerschaftsvereinbarung zur Zusammenarbeit bei der Entwicklung weltraumbezogener Aktivitäten*« mit der Schweizer Armee bekannt gab – schließlich residieren in der Alpenrepublik nicht nur UN, GAVI, WEF, Club of Rome und jede Menge NGOs, sondern auch die Bank für Internationalen Zahlungsausgleich (BIZ), die ganz sicher Verwendung für ein quantengesichertes Echtzeit-Picosatellitennetzwerk findet, wenn ihr »*[Unified Ledger](https://www.bis.org/publ/arpdf/ar2023e3.htm)*« ([Zentrales Hauptbuch](https://www.globalgovernmentfintech.com/bis-releases-game-changing-blueprint-for-global-financial-system/)) für das Blockchain-Weltfinanzsystem von morgen zum Einsatz kommt. In Anbetracht der »*allumfassenden Marktblase*« ([D. Webb](https://www.regenauer.press/der-letzte-raubzug), 2024) ist damit wohl in absehbarer Zeit zu rechnen. Das also sind die Projekte, Pläne und neuen Partner von Elon. Auf mich machen ja speziell die korrupten Genfer Quantenspezialisten mit ihren Picosatelliten und schlüsselfertigen eID-Lösungen nicht unbedingt den Eindruck von Freiheitskämpfern. Und auch die am 22. Januar 2024 bei einer [Pressekonferenz](https://x.com/JoshWalkos/status/1881866215637094726) im Weißen Haus angekündigten »*personalisierten mRNA-Injektionen gegen Krebs*« lassen mich eher skeptisch zurück. Genau wie der Umstand, dass diese binnen 48 Stunden »*personalisierte mRNA*« durch die Rechenleistung von OpenAI [ermöglicht](https://news.yahoo.com/news/now-trump-says-500-billion-232732788.html?fr=sycsrp_catchall\&guccounter=1\&guce_referrer=aHR0cHM6Ly9wcmVzZWFyY2guY29tLw\&guce_referrer_sig=AQAAANhV_ubjRDL_kBGNPhmmLWxAhoW6pkAamqVphAXDXGmLTQUS-4gXsCQ1pinQHCufHywARCgqAG_iUpEBIIJexFhk0z6Oab5Q4js6kJ6Z6t-80onuNRGqRg_IMlcI6P72iCjCsfRpp1fAGCDhLSMGts2WK6D3gsv_YMrMXhqWP7xE) werden soll. Denn das von Elon Musk [mitgegründete](https://www.businessinsider.com/history-of-elon-musk-and-sam-altman-relationship-feuds-2023-3) Unternehmen des WEF- und [Bilderberg](https://wikispooks.com/wiki/Sam_Altman)-affinen [Sam Altman](https://news.yahoo.com/news/now-trump-says-500-billion-232732788.html?fr=sycsrp_catchall\&guccounter=1\&guce_referrer=aHR0cHM6Ly9wcmVzZWFyY2guY29tLw\&guce_referrer_sig=AQAAANhV_ubjRDL_kBGNPhmmLWxAhoW6pkAamqVphAXDXGmLTQUS-4gXsCQ1pinQHCufHywARCgqAG_iUpEBIIJexFhk0z6Oab5Q4js6kJ6Z6t-80onuNRGqRg_IMlcI6P72iCjCsfRpp1fAGCDhLSMGts2WK6D3gsv_YMrMXhqWP7xE) steht im berechtigten Verdacht, für den Tod eines Whistleblowers im Dezember 2024 verantwortlich zu sein. Während Polizei und Medien den Tod des OpenAI-Forschers Suchir Balaji als [Selbstmord](https://www.businessinsider.de/wirtschaft/openai-whistleblower-tragischer-tod-erschuettert-die-tech-welt/) deklarieren, [sprechen](https://economictimes.indiatimes.com/news/international/global-trends/suchir-balajis-openai-researcher-suicide-death-cold-blooded-murder-openai-whistleblowers-parents-claim-big-foul-play/articleshow/116855083.cms?from=mdr) sowohl die Umstände am Fundort seiner Leiche als auch Balajis Eltern von »*eiskaltem Mord*«. Nicht zu vergessen, dass Altman von seiner eigenen Schwester des jahrelangen Missbrauchs [beschuldigt](https://www.theguardian.com/technology/2025/jan/08/openai-chief-executive-sam-altman-accused-of-sexual-abuse-by-sister-in-lawsuit) wird und sich dafür demnächst vor Gericht verantworten muss. Selbst [The Economist](https://www.economist.com/business/2024/12/10/the-paypal-mafia-is-taking-over-americas-government) räumte am 10. Dezember 2024 ein, dass »*die PayPal Mafia die amerikanische Regierung übernimmt*«. Und das mit der »*Mafia*« scheint man in Washington mittlerweile wörtlich zu nehmen. Aber die von einigen aus der Hüfte geschossenen Präsidialdekreten euphorisierten Eloi werden sicher Gründe finden, das alles zu ihren Gunsten auszulegen. Immerhin hat Trump ein paar Leute begnadigt und will aus der WHO austreten. Wie seine Fanbase es bewerkstelligt, auszublenden, dass »*The Donald*« schon in seiner ersten Amtszeit aus der WHO austreten wollte und es unterließ, erschließt sich mir aber leider nicht. Genau wie die Begeisterung für ein Gespräch zwischen Musk und Weidel. Man stelle sich nur mal vor, George Soros, Bill Gates oder Eric Schmitt konferierten mit deutschen Politikern. Oder bekämen Sendezeit im ÖRR. Nicht auszudenken. **Wie heißt es so schön: »*Eine schmerzliche Wahrheit ist besser als eine Lüge*« (Thomas Mann). Stimmt. Nur fällt es relativ schwer, eine Lüge einzugestehen, wenn der, dem man sie beichten muss, der Lügner ist.** So bleibt nur zu hoffen, dass möglichst viele Eloi diesen Schritt trotzdem möglichst bald hinter sich bringen. Im eigenen Interesse. Denn wie schon Ernst Freiherr von Feuchtersleben feststellte, ist »*Reue der Verstand, der zu spät kommt*«. Und das kann in diesen Tagen verheerende Folgen haben. @ 4fe4a528:3ff6bf06
2025-02-01 13:41:28<img src="https://blossom.primal.net/58a3e225ae607d5f110cff5f44a68268d27d3d239ba6d58279c2dd872259fbbb.jpg"> In my last article I wrote about NOSTR. I found another local bitcoiner via NOSTR last week so here is why it is important to join / use NOSTR — start telling people “Look me up on NOSTR” Self-sovereign identity (SSI) is a revolutionary approach to digital identity that puts individuals in control of their own identity and personal data. Unlike traditional digital identity models, which rely on third-party organizations to manage and authenticate identities, SSI empowers individuals to own and manage their digital identity. This approach is made possible by emerging technologies such as secure public / private key pairs. Decentralized identifiers, conceived and developed by nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 is an attempt to create a global technical standard around cryptographically secured identifiers - a secure, universal, and sovereign form of digital ID. This technology uses peer-to-peer technology to remove the need for intermediaries to own and authenticate ID information. Notably, NOSTR, a decentralized protocol, has already begun to utilize decentralized IDs, demonstrating the potential of this technology in real-world applications. Via NOSTR, users can be sure that the person or computer publishing to a particular npub knows their nsec (password for your npub), highlighting the secure and decentralized nature of this approach. With SSI, individuals can decide how their personal data is used, shared, and protected, giving them greater control and agency over their digital lives. The **benefits** of SSI are numerous, including: Enhanced security and protection of personal data. Reduced risk of identity theft and fraud Increased autonomy and agency over one's digital identity. Improved scalability and flexibility in digital identity management **challenges**: Ensuring the security and integrity of decentralized identity systems. Developing standards and protocols for interoperability and compatibility. Addressing concerns around ownership and control of personal data. Balancing individual autonomy with the need for verification and authentication in various contexts. Overall, self-sovereign identity has the potential to transform the way we think about digital identity and provide individuals with greater control and agency over their personal data. Without people in control of their bitcoin seed words no freedom loving people would be able to exchange their money with others. Yes, keep enjoying using the only free market on the planet BITCOIN. Long live FREEDOM!
@ 4fe4a528:3ff6bf06
2025-02-01 13:41:28<img src="https://blossom.primal.net/58a3e225ae607d5f110cff5f44a68268d27d3d239ba6d58279c2dd872259fbbb.jpg"> In my last article I wrote about NOSTR. I found another local bitcoiner via NOSTR last week so here is why it is important to join / use NOSTR — start telling people “Look me up on NOSTR” Self-sovereign identity (SSI) is a revolutionary approach to digital identity that puts individuals in control of their own identity and personal data. Unlike traditional digital identity models, which rely on third-party organizations to manage and authenticate identities, SSI empowers individuals to own and manage their digital identity. This approach is made possible by emerging technologies such as secure public / private key pairs. Decentralized identifiers, conceived and developed by nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 is an attempt to create a global technical standard around cryptographically secured identifiers - a secure, universal, and sovereign form of digital ID. This technology uses peer-to-peer technology to remove the need for intermediaries to own and authenticate ID information. Notably, NOSTR, a decentralized protocol, has already begun to utilize decentralized IDs, demonstrating the potential of this technology in real-world applications. Via NOSTR, users can be sure that the person or computer publishing to a particular npub knows their nsec (password for your npub), highlighting the secure and decentralized nature of this approach. With SSI, individuals can decide how their personal data is used, shared, and protected, giving them greater control and agency over their digital lives. The **benefits** of SSI are numerous, including: Enhanced security and protection of personal data. Reduced risk of identity theft and fraud Increased autonomy and agency over one's digital identity. Improved scalability and flexibility in digital identity management **challenges**: Ensuring the security and integrity of decentralized identity systems. Developing standards and protocols for interoperability and compatibility. Addressing concerns around ownership and control of personal data. Balancing individual autonomy with the need for verification and authentication in various contexts. Overall, self-sovereign identity has the potential to transform the way we think about digital identity and provide individuals with greater control and agency over their personal data. Without people in control of their bitcoin seed words no freedom loving people would be able to exchange their money with others. Yes, keep enjoying using the only free market on the planet BITCOIN. Long live FREEDOM! @ eff2631b:4732bd7e
2025-02-01 11:40:14This is a test. Trying to use Obsidian for everything. Nostr works out of the box? First try failed, this is my second try.
@ eff2631b:4732bd7e
2025-02-01 11:40:14This is a test. Trying to use Obsidian for everything. Nostr works out of the box? First try failed, this is my second try. @ eff2631b:4732bd7e
2025-02-01 11:28:43This is a test. Trying to use Obsidian for everything. Nostr works out of the box?
@ eff2631b:4732bd7e
2025-02-01 11:28:43This is a test. Trying to use Obsidian for everything. Nostr works out of the box? @ 9e69e420:d12360c2
2025-02-01 11:16:04 Federal employees must remove pronouns from email signatures by the end of the day. This directive comes from internal memos tied to two executive orders signed by Donald Trump. The orders target diversity and equity programs within the government.  CDC, Department of Transportation, and Department of Energy employees were affected. Staff were instructed to make changes in line with revised policy prohibiting certain language. One CDC employee shared frustration, stating, “In my decade-plus years at CDC, I've never been told what I can and can't put in my email signature.” The directive is part of a broader effort to eliminate DEI initiatives from federal discourse.
@ 9e69e420:d12360c2
2025-02-01 11:16:04 Federal employees must remove pronouns from email signatures by the end of the day. This directive comes from internal memos tied to two executive orders signed by Donald Trump. The orders target diversity and equity programs within the government.  CDC, Department of Transportation, and Department of Energy employees were affected. Staff were instructed to make changes in line with revised policy prohibiting certain language. One CDC employee shared frustration, stating, “In my decade-plus years at CDC, I've never been told what I can and can't put in my email signature.” The directive is part of a broader effort to eliminate DEI initiatives from federal discourse. @ edeb837b:ac664163
2025-02-01 10:51:33In today’s fast-paced financial markets, having quick access to real-time data, trade insights, and the ability to share trades with a like-minded community is invaluable. That’s where NVSTly’s Discord bot comes in. It’s more than just a bot — it’s a powerful tool for social trading, designed to help traders and investors track their trades, share insights, and collaborate with others in real-time, all within Discord. ## What the NVSTly Discord Bot Does [NVSTly’s Discord bot](https://nvstly.com/go/bot) is built with the goal of making financial data and trading insights easily accessible to the entire trading community on Discord. Whether you’re a seasoned trader or just starting, the bot helps you stay on top of your trades and market trends. Some of the key features of the bot include: - **Real-Time Trade Tracking & Sharing:** The bot [tracks your trades](https://nvstly.com/trades) and allows you to share them with others. Whether you’re trading stocks, options, forex, or cryptocurrencies, your trades are instantly shared with your followers and can be posted to social media or sent through Discord DMs or webhooks, fostering a transparent and collaborative environment. - **Trader Stats & Performance Recaps:** The bot generates visual reports of your trading performance, including win rates, total gains, and individual trade stats. You can view a trader’s daily, weekly, or monthly recaps, complete with details on stock tickers, options info, and profit/loss calculations. - **Market Data & Charts:** Get instant access to live market data, stock charts, and detailed information on tickers. The bot provides a variety of commands for stock price movements, charts, and other data, with plans to expand this to cover more markets in the future. - **Comprehensive Coverage:** The bot currently supports stocks, options, forex, and crypto for trade tracking and sharing. Futures markets are also planned for the future. While the bot supports these markets for trade tracking, data-related features like market sentiment analysis or earnings reports will be available in the future. ## How the Bot Integrates with NVSTly’s Social Trading App The NVSTly Discord bot is fully integrated with the NVSTly [social trading app](https://nvstly.com), creating a seamless experience for users across platforms. Traders can track their trades on the app, and the bot will automatically share those trades directly with their followers, via DMs, social media, or webhooks. This integration means that everything you do on the NVSTly app can be easily shared with your community in real-time via Discord, making it simple to stay connected with your trading network. The bot doesn’t just show trades — it also gives users insights into their trading performance and connects them with other traders for discussions, tips, and strategies. With NVSTly’s unique social features, traders can collaborate, share strategies, and learn from each other in a dynamic and interactive environment. ## What’s Next for the NVSTly Discord Bot? The future of the NVSTly Discord bot is incredibly exciting, with plans to add even more features designed to elevate the trading experience. Some of the upcoming features include: - **Expanded Market Coverage for Data Commands:** In addition to stocks, the bot will soon offer data-related commands for crypto, forex, and futures markets. This will allow users to access even more comprehensive market data, including earnings reports, options flow, and more. - **AI & Machine Learning Integration:** NVSTly plans to integrate AI and machine learning to generate trade signals, analyze market trends, and even offer personalized trading tips. This will help traders refine their strategies and make more informed decisions. - **Real-Time Alerts & Notifications:** Users can already receive trade alerts sent directly to their DMs from traders they follow. In the future, users will also be able to set more customized alerts based on price targets or specific market activity. ## Why the NVSTly Discord Bot is Perfect for Trading Communities Discord has become a hub for traders and investors, and the NVSTly Discord bot takes full advantage of this by providing a platform where traders can interact, share trades, and learn from one another. The bot’s ability to instantly share trade recaps and stats creates an environment of transparency and collaboration. Traders can discuss strategies, ask questions, and even challenge each other to improve their performance. By integrating market data, charts, and trade performance tracking, the bot offers a complete package for traders on Discord. It’s not just a tool for sharing trades — it’s a vital part of a thriving trading community. ## Why NVSTly’s Discord Bot is the Fastest Growing Finance Bot on Discord With its comprehensive features and seamless integration with the NVSTly app, the NVSTly Discord bot has quickly become the go-to tool for traders on Discord. What sets it apart from other finance bots is its focus on user engagement. The bot is not just about providing data — it’s about building a community of traders who can share their experiences, insights, and successes. Traders have flocked to the NVSTly Discord bot because it provides real-time data, easy trade tracking, and powerful analytics — all in a user-friendly format. It’s no wonder it’s quickly becoming the fastest-growing finance bot on Discord. ## On Track to be the Greatest Finance Bot on Discord NVSTly is on track to become the greatest finance bot on Discord, if it’s not already. With plans for expanding market coverage, adding advanced AI-driven features, and constantly improving its user experience, the bot is poised to revolutionize the way traders use Discord. By offering a comprehensive set of tools that integrate seamlessly with the NVSTly app, the bot is becoming an essential resource for traders who want to stay informed, track their performance, and engage with the trading community. --- NVSTly is available for free on [web](https://nvstly.com), mobile devices ([iOS](https://nvstly.com/go/ios) & [Google Play](https://nvstly.com/go/android)), and is fully integrated with Discord via a [unique bot](https://nvstly.com/go/bot)- the only of it’s kind and available to any server or trading community on Discord. Or feel free to join a community of over 45,000 investors & traders on our [Discod server](https://nvstly.com/go/discord).
@ edeb837b:ac664163
2025-02-01 10:51:33In today’s fast-paced financial markets, having quick access to real-time data, trade insights, and the ability to share trades with a like-minded community is invaluable. That’s where NVSTly’s Discord bot comes in. It’s more than just a bot — it’s a powerful tool for social trading, designed to help traders and investors track their trades, share insights, and collaborate with others in real-time, all within Discord. ## What the NVSTly Discord Bot Does [NVSTly’s Discord bot](https://nvstly.com/go/bot) is built with the goal of making financial data and trading insights easily accessible to the entire trading community on Discord. Whether you’re a seasoned trader or just starting, the bot helps you stay on top of your trades and market trends. Some of the key features of the bot include: - **Real-Time Trade Tracking & Sharing:** The bot [tracks your trades](https://nvstly.com/trades) and allows you to share them with others. Whether you’re trading stocks, options, forex, or cryptocurrencies, your trades are instantly shared with your followers and can be posted to social media or sent through Discord DMs or webhooks, fostering a transparent and collaborative environment. - **Trader Stats & Performance Recaps:** The bot generates visual reports of your trading performance, including win rates, total gains, and individual trade stats. You can view a trader’s daily, weekly, or monthly recaps, complete with details on stock tickers, options info, and profit/loss calculations. - **Market Data & Charts:** Get instant access to live market data, stock charts, and detailed information on tickers. The bot provides a variety of commands for stock price movements, charts, and other data, with plans to expand this to cover more markets in the future. - **Comprehensive Coverage:** The bot currently supports stocks, options, forex, and crypto for trade tracking and sharing. Futures markets are also planned for the future. While the bot supports these markets for trade tracking, data-related features like market sentiment analysis or earnings reports will be available in the future. ## How the Bot Integrates with NVSTly’s Social Trading App The NVSTly Discord bot is fully integrated with the NVSTly [social trading app](https://nvstly.com), creating a seamless experience for users across platforms. Traders can track their trades on the app, and the bot will automatically share those trades directly with their followers, via DMs, social media, or webhooks. This integration means that everything you do on the NVSTly app can be easily shared with your community in real-time via Discord, making it simple to stay connected with your trading network. The bot doesn’t just show trades — it also gives users insights into their trading performance and connects them with other traders for discussions, tips, and strategies. With NVSTly’s unique social features, traders can collaborate, share strategies, and learn from each other in a dynamic and interactive environment. ## What’s Next for the NVSTly Discord Bot? The future of the NVSTly Discord bot is incredibly exciting, with plans to add even more features designed to elevate the trading experience. Some of the upcoming features include: - **Expanded Market Coverage for Data Commands:** In addition to stocks, the bot will soon offer data-related commands for crypto, forex, and futures markets. This will allow users to access even more comprehensive market data, including earnings reports, options flow, and more. - **AI & Machine Learning Integration:** NVSTly plans to integrate AI and machine learning to generate trade signals, analyze market trends, and even offer personalized trading tips. This will help traders refine their strategies and make more informed decisions. - **Real-Time Alerts & Notifications:** Users can already receive trade alerts sent directly to their DMs from traders they follow. In the future, users will also be able to set more customized alerts based on price targets or specific market activity. ## Why the NVSTly Discord Bot is Perfect for Trading Communities Discord has become a hub for traders and investors, and the NVSTly Discord bot takes full advantage of this by providing a platform where traders can interact, share trades, and learn from one another. The bot’s ability to instantly share trade recaps and stats creates an environment of transparency and collaboration. Traders can discuss strategies, ask questions, and even challenge each other to improve their performance. By integrating market data, charts, and trade performance tracking, the bot offers a complete package for traders on Discord. It’s not just a tool for sharing trades — it’s a vital part of a thriving trading community. ## Why NVSTly’s Discord Bot is the Fastest Growing Finance Bot on Discord With its comprehensive features and seamless integration with the NVSTly app, the NVSTly Discord bot has quickly become the go-to tool for traders on Discord. What sets it apart from other finance bots is its focus on user engagement. The bot is not just about providing data — it’s about building a community of traders who can share their experiences, insights, and successes. Traders have flocked to the NVSTly Discord bot because it provides real-time data, easy trade tracking, and powerful analytics — all in a user-friendly format. It’s no wonder it’s quickly becoming the fastest-growing finance bot on Discord. ## On Track to be the Greatest Finance Bot on Discord NVSTly is on track to become the greatest finance bot on Discord, if it’s not already. With plans for expanding market coverage, adding advanced AI-driven features, and constantly improving its user experience, the bot is poised to revolutionize the way traders use Discord. By offering a comprehensive set of tools that integrate seamlessly with the NVSTly app, the bot is becoming an essential resource for traders who want to stay informed, track their performance, and engage with the trading community. --- NVSTly is available for free on [web](https://nvstly.com), mobile devices ([iOS](https://nvstly.com/go/ios) & [Google Play](https://nvstly.com/go/android)), and is fully integrated with Discord via a [unique bot](https://nvstly.com/go/bot)- the only of it’s kind and available to any server or trading community on Discord. Or feel free to join a community of over 45,000 investors & traders on our [Discod server](https://nvstly.com/go/discord). @ edeb837b:ac664163
2025-02-01 10:43:46Join Benzinga as they sit down with NVSTly, the cutting-edge platform revolutionizing social trading and investing. In this exclusive interview, NVSTly shares insights on empowering retail traders, fostering transparency, and building a thriving community for investors of all levels. Discover how NVSTly is shaping the future of trading with innovative features, real-time trade tracking, and global collaboration. NVSTly Web: https://nvstly.com iOS: https://nvstly.com/go/ios Google Play: https://nvstly.com/go/android [](https://www.youtube.com/watch?v=T31HkdKYkc})
@ edeb837b:ac664163
2025-02-01 10:43:46Join Benzinga as they sit down with NVSTly, the cutting-edge platform revolutionizing social trading and investing. In this exclusive interview, NVSTly shares insights on empowering retail traders, fostering transparency, and building a thriving community for investors of all levels. Discover how NVSTly is shaping the future of trading with innovative features, real-time trade tracking, and global collaboration. NVSTly Web: https://nvstly.com iOS: https://nvstly.com/go/ios Google Play: https://nvstly.com/go/android [](https://www.youtube.com/watch?v=T31HkdKYkc}) @ edeb837b:ac664163
2025-02-01 10:40:42We’re thrilled to announce that [NVSTly](https://nvstly.com/go/) has been honored with the People's Choice Award at the prestigious [Benzinga FinTech Awards 2024](https://www.benzinga.com/news/events/24/11/42098678/these-are-the-top-fintech-innovators-recognized-at-benzingas-2024-global-fintech-awards)! This recognition is a testament to the trust, support, and enthusiasm of our growing community of retail traders, investors, and financial enthusiasts.  ## A Milestone in Social Investing Winning the People's Choice Award is more than just a moment of celebration for NVSTly—it reflects the incredible journey we’ve shared with our users. NVSTly was built with one mission in mind: to redefine social investing by empowering traders of all experience levels to share, track, and learn from one another. In the competitive world of fintech, being selected as the People's Choice means we’ve created something that resonates deeply with our audience. It’s your votes, feedback, and passion that have propelled us to this achievement. ## What Makes NVSTly Unique? NVSTly stands out for offering a platform that’s entirely free while delivering a comprehensive suite of features for traders, such as: * **Global Leaderboard:** Recognizing top-performing traders across stocks, options, futures, forex, and cryptocurrency. * **Trade Insights UI:** Providing detailed analytics on trades, including market data validation and unique event visualizations. * **Broker Integration (Optional):** Automating trade tracking and sharing with real-time updates. * **Discord Integration:** A first-of-its-kind bot that brings NVSTly’s full functionality to one of the fastest-growing social platforms in finance. * **Education and Community:** Enabling beginners to learn from experienced traders and find actionable insights. Unlike traditional trading platforms, NVSTly focuses solely on trade tracking, sharing, and performance validation. It’s not about buying or selling real assets but fostering transparency, collaboration, and growth among traders. ## Powered by the Community The People's Choice Award is special because it comes directly from you—our community. Whether you’re an experienced trader gaining recognition through our leaderboard or a beginner exploring NVSTly to learn from top traders, this award proves that NVSTly isn’t just a platform; it’s a movement. Your votes affirm our commitment to delivering cutting-edge features, unmatched usability, and an ecosystem that connects traders across all markets. ## Looking Ahead Winning this award fuels our determination to push boundaries even further. In the months to come, we’re excited to roll out new features, expand our broker integrations, and enhance the tools that make NVSTly the go-to platform for retail traders worldwide. ## Thank You We couldn’t have achieved this milestone without your unwavering support. From everyone at the NVSTly team, thank you for believing in our vision and making NVSTly the People’s Choice for 2024. This award is as much yours as it is ours. If you haven’t joined the movement yet, there’s never been a better time. Discover, share, and track trades with NVSTly today—because the best way to grow in the markets is together. > ***Join NVSTly:*** * ***Website:** [nvstly.com](https://nvstly.com)* * ***Mobile App:** Available on [Google Play](https://nvstly.com/go/android) and [iOS App Store](https://nvstly.com/go/ios)* * ***Discord Community:** [Join Now](https://nvstly.com/go/discord)* *Let’s continue shaping the future of social investing, one trade at a time.*
@ edeb837b:ac664163
2025-02-01 10:40:42We’re thrilled to announce that [NVSTly](https://nvstly.com/go/) has been honored with the People's Choice Award at the prestigious [Benzinga FinTech Awards 2024](https://www.benzinga.com/news/events/24/11/42098678/these-are-the-top-fintech-innovators-recognized-at-benzingas-2024-global-fintech-awards)! This recognition is a testament to the trust, support, and enthusiasm of our growing community of retail traders, investors, and financial enthusiasts.  ## A Milestone in Social Investing Winning the People's Choice Award is more than just a moment of celebration for NVSTly—it reflects the incredible journey we’ve shared with our users. NVSTly was built with one mission in mind: to redefine social investing by empowering traders of all experience levels to share, track, and learn from one another. In the competitive world of fintech, being selected as the People's Choice means we’ve created something that resonates deeply with our audience. It’s your votes, feedback, and passion that have propelled us to this achievement. ## What Makes NVSTly Unique? NVSTly stands out for offering a platform that’s entirely free while delivering a comprehensive suite of features for traders, such as: * **Global Leaderboard:** Recognizing top-performing traders across stocks, options, futures, forex, and cryptocurrency. * **Trade Insights UI:** Providing detailed analytics on trades, including market data validation and unique event visualizations. * **Broker Integration (Optional):** Automating trade tracking and sharing with real-time updates. * **Discord Integration:** A first-of-its-kind bot that brings NVSTly’s full functionality to one of the fastest-growing social platforms in finance. * **Education and Community:** Enabling beginners to learn from experienced traders and find actionable insights. Unlike traditional trading platforms, NVSTly focuses solely on trade tracking, sharing, and performance validation. It’s not about buying or selling real assets but fostering transparency, collaboration, and growth among traders. ## Powered by the Community The People's Choice Award is special because it comes directly from you—our community. Whether you’re an experienced trader gaining recognition through our leaderboard or a beginner exploring NVSTly to learn from top traders, this award proves that NVSTly isn’t just a platform; it’s a movement. Your votes affirm our commitment to delivering cutting-edge features, unmatched usability, and an ecosystem that connects traders across all markets. ## Looking Ahead Winning this award fuels our determination to push boundaries even further. In the months to come, we’re excited to roll out new features, expand our broker integrations, and enhance the tools that make NVSTly the go-to platform for retail traders worldwide. ## Thank You We couldn’t have achieved this milestone without your unwavering support. From everyone at the NVSTly team, thank you for believing in our vision and making NVSTly the People’s Choice for 2024. This award is as much yours as it is ours. If you haven’t joined the movement yet, there’s never been a better time. Discover, share, and track trades with NVSTly today—because the best way to grow in the markets is together. > ***Join NVSTly:*** * ***Website:** [nvstly.com](https://nvstly.com)* * ***Mobile App:** Available on [Google Play](https://nvstly.com/go/android) and [iOS App Store](https://nvstly.com/go/ios)* * ***Discord Community:** [Join Now](https://nvstly.com/go/discord)* *Let’s continue shaping the future of social investing, one trade at a time.* @ edeb837b:ac664163
2025-02-01 10:36:38 At NVSTly, we embrace the concept of “building in public.” This approach shapes how we develop, test, and roll out features, with the goal of making NVSTly the best social trading platform for our users. But what exactly does building in public mean for NVSTly? Let’s break it down. ## Updates as They’re Finished Instead of waiting to bundle new features and fixes into big, infrequent releases, we push updates as they’re completed. This ensures users benefit from improvements as soon as possible. However, our agile development style means you might notice subtle changes before they’re officially included in a published changelog. These incremental updates allow us to iterate and enhance the platform quickly. ## Internal Testing, Real-World Feedback Before any update reaches the production environment, our team conducts internal testing to ensure the new feature or fix works as intended. For example, a recent update to allow stats and daily/weekly recap commands to function with usernames containing spaces was thoroughly tested internally. Unfortunately, this change inadvertently broke compatibility with Discord IDs, highlighting the challenges of anticipating every edge case. This is where building in public comes into play: while we strive for thorough testing, some issues only emerge when updates meet real-world usage. That’s why we rely on our vibrant user base to help us identify bugs, unintended behaviors, and areas for improvement. ## The Role of Our User Community Our users play a critical role in the development process. By using [NVSTly](https://nvstly.com) in their daily trading workflows, they encounter scenarios that internal testing might miss. When users report bugs, glitches, or other issues, it provides us with invaluable insights into how the platform performs under various conditions. If you ever experience something on NVSTly that doesn’t seem to work as expected, we encourage you to report it to us. Unlike platforms that may identify and resolve issues passively over time, NVSTly relies directly on user feedback to detect and prioritize fixes. Every report helps us improve. ## Changelogs: A Snapshot of Progress Given our frequent updates, we publish changelogs only after accumulating several changes or introducing major features. This means that when you see a changelog, many of the updates listed might have been implemented days or even weeks earlier. While this approach helps us focus on building and refining the platform, it’s another example of how building in public keeps the development process transparent. ## Why Building in Public Matters By building in public, we: - **Accelerate innovation:** Continuous updates ensure the platform evolves rapidly. - **Foster transparency:** Users gain insight into what’s changing and how issues are addressed. - **Strengthen collaboration:** Feedback from users directly informs our priorities and solutions. This approach isn’t without its challenges, but we believe the benefits far outweigh the risks. Building in public allows us to create a platform that truly meets the needs of our community — a community we’re proud to involve in the journey. ## How You Can Help If you notice a bug, glitch, or unintended behavior, please let us know right away. Your feedback is essential to making NVSTly better every day. Together, we’re not just building a platform; we’re building a community-driven experience that reflects the collective expertise and passion of its users. Thank you for being part of the NVSTly journey. Let’s keep building — together. --- NVSTly is available for free on web, mobile devices ([iOS](https://nvstly.com/go/ios) & [Google Play](https://nvstly.com/go/android)), and is fully integrated with Discord via a [unique bot](https://nvstly.com/go/bot)- the only of it’s kind and available to any server or trading community on Discord. Or feel free to join a community of over 45,000 investors & traders on our [Discod server](https://nvstly.com/go/discord).
@ edeb837b:ac664163
2025-02-01 10:36:38 At NVSTly, we embrace the concept of “building in public.” This approach shapes how we develop, test, and roll out features, with the goal of making NVSTly the best social trading platform for our users. But what exactly does building in public mean for NVSTly? Let’s break it down. ## Updates as They’re Finished Instead of waiting to bundle new features and fixes into big, infrequent releases, we push updates as they’re completed. This ensures users benefit from improvements as soon as possible. However, our agile development style means you might notice subtle changes before they’re officially included in a published changelog. These incremental updates allow us to iterate and enhance the platform quickly. ## Internal Testing, Real-World Feedback Before any update reaches the production environment, our team conducts internal testing to ensure the new feature or fix works as intended. For example, a recent update to allow stats and daily/weekly recap commands to function with usernames containing spaces was thoroughly tested internally. Unfortunately, this change inadvertently broke compatibility with Discord IDs, highlighting the challenges of anticipating every edge case. This is where building in public comes into play: while we strive for thorough testing, some issues only emerge when updates meet real-world usage. That’s why we rely on our vibrant user base to help us identify bugs, unintended behaviors, and areas for improvement. ## The Role of Our User Community Our users play a critical role in the development process. By using [NVSTly](https://nvstly.com) in their daily trading workflows, they encounter scenarios that internal testing might miss. When users report bugs, glitches, or other issues, it provides us with invaluable insights into how the platform performs under various conditions. If you ever experience something on NVSTly that doesn’t seem to work as expected, we encourage you to report it to us. Unlike platforms that may identify and resolve issues passively over time, NVSTly relies directly on user feedback to detect and prioritize fixes. Every report helps us improve. ## Changelogs: A Snapshot of Progress Given our frequent updates, we publish changelogs only after accumulating several changes or introducing major features. This means that when you see a changelog, many of the updates listed might have been implemented days or even weeks earlier. While this approach helps us focus on building and refining the platform, it’s another example of how building in public keeps the development process transparent. ## Why Building in Public Matters By building in public, we: - **Accelerate innovation:** Continuous updates ensure the platform evolves rapidly. - **Foster transparency:** Users gain insight into what’s changing and how issues are addressed. - **Strengthen collaboration:** Feedback from users directly informs our priorities and solutions. This approach isn’t without its challenges, but we believe the benefits far outweigh the risks. Building in public allows us to create a platform that truly meets the needs of our community — a community we’re proud to involve in the journey. ## How You Can Help If you notice a bug, glitch, or unintended behavior, please let us know right away. Your feedback is essential to making NVSTly better every day. Together, we’re not just building a platform; we’re building a community-driven experience that reflects the collective expertise and passion of its users. Thank you for being part of the NVSTly journey. Let’s keep building — together. --- NVSTly is available for free on web, mobile devices ([iOS](https://nvstly.com/go/ios) & [Google Play](https://nvstly.com/go/android)), and is fully integrated with Discord via a [unique bot](https://nvstly.com/go/bot)- the only of it’s kind and available to any server or trading community on Discord. Or feel free to join a community of over 45,000 investors & traders on our [Discod server](https://nvstly.com/go/discord). @ da0b9bc3:4e30a4a9
2025-02-01 09:45:00Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/872135
@ da0b9bc3:4e30a4a9
2025-02-01 09:45:00Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/872135 @ 0b118e40:4edc09cb
2025-02-01 09:41:34*(This is not a feasibility analysis, but rather a perspective on the philosophical alignment with Bitcoin’s vision)* The moment stablecoins or national currencies start playing a role in Bitcoin LN, Bitcoin’s position as a purely decentralized medium of exchange will be undermined. The idea of a Bitcoin-native global currency and global economy, where people and businesses transact in Bitcoin directly, would align with its original purpose. If Bitcoin is to function as a true currency, a larger global adoption that bypasses traditional financial systems, will make these on/off ramps for stablecoins unnecessary. At some point, there will be those who will want to preserve Bitcoin’s purity as a currency, and others who want to see store value, ETF, stablecoin collabs, tokens, pump & dump, NFTs, and centralized influenced approaches. Currency domination, especially by the USD, has contributed to poverty in the Global South by deepening economic inequality and exacerbating debt burdens. During the Tequila Crisis and the Asian Financial Crisis, Mexico and Asia’s high dependency on the USD led to rapid currency devaluations and debt defaults. Every time the US hikes interest rates, it triggers capital flight from developing nations, causing currency drops and further economic hardship, and this isn’t just a thing of the past; it has been a pressing issue in the last two years, widening the poverty gap in the Global South. And, as always, it’s the poor who suffer the most. USDT is just another name for currency domination through blockchain. Its pegged to USD and on Bitcoin LN, it will piggyback on Bitcoin’s perks (as a medium of exchange to Bitcoin's current and potential adopters) with a high likelihood of keeping users transacting in USD rather than Bitcoin itself. This could also lead to global assumptions that Bitcoin is taking sides, especially in today’s fragile and invisible global currency war. To counter, people will say ‘let all stablecoins pegged to any currencies come on board’ - but what’s the point of Bitcoin then? It’s like bringing the very systems Bitcoin was created to challenge, back into the fold. I believe when you use stablecoins this way, you’re essentially importing the power dynamics and dependencies of the traditional financial system, which seems counterproductive to Bitcoin's decentralized ethos. Bitcoin’s true potential is its ability to provide an alternative to centralized, government-controlled currencies and financial systems. We should stick to the original game plan.
@ 0b118e40:4edc09cb
2025-02-01 09:41:34*(This is not a feasibility analysis, but rather a perspective on the philosophical alignment with Bitcoin’s vision)* The moment stablecoins or national currencies start playing a role in Bitcoin LN, Bitcoin’s position as a purely decentralized medium of exchange will be undermined. The idea of a Bitcoin-native global currency and global economy, where people and businesses transact in Bitcoin directly, would align with its original purpose. If Bitcoin is to function as a true currency, a larger global adoption that bypasses traditional financial systems, will make these on/off ramps for stablecoins unnecessary. At some point, there will be those who will want to preserve Bitcoin’s purity as a currency, and others who want to see store value, ETF, stablecoin collabs, tokens, pump & dump, NFTs, and centralized influenced approaches. Currency domination, especially by the USD, has contributed to poverty in the Global South by deepening economic inequality and exacerbating debt burdens. During the Tequila Crisis and the Asian Financial Crisis, Mexico and Asia’s high dependency on the USD led to rapid currency devaluations and debt defaults. Every time the US hikes interest rates, it triggers capital flight from developing nations, causing currency drops and further economic hardship, and this isn’t just a thing of the past; it has been a pressing issue in the last two years, widening the poverty gap in the Global South. And, as always, it’s the poor who suffer the most. USDT is just another name for currency domination through blockchain. Its pegged to USD and on Bitcoin LN, it will piggyback on Bitcoin’s perks (as a medium of exchange to Bitcoin's current and potential adopters) with a high likelihood of keeping users transacting in USD rather than Bitcoin itself. This could also lead to global assumptions that Bitcoin is taking sides, especially in today’s fragile and invisible global currency war. To counter, people will say ‘let all stablecoins pegged to any currencies come on board’ - but what’s the point of Bitcoin then? It’s like bringing the very systems Bitcoin was created to challenge, back into the fold. I believe when you use stablecoins this way, you’re essentially importing the power dynamics and dependencies of the traditional financial system, which seems counterproductive to Bitcoin's decentralized ethos. Bitcoin’s true potential is its ability to provide an alternative to centralized, government-controlled currencies and financial systems. We should stick to the original game plan. @ dbb19ae0:c3f22d5a
2025-02-01 09:06:49### **The Magic of `=()=` in Perl: Counting Matches with Elegance** Perl is full of powerful and sometimes cryptic features, and one of the lesser-known yet highly useful tricks is the `=()=` operator. This clever construct allows you to count the number of matches in a string without using loops or unnecessary variables. --- ## **Understanding `=()=`: A Smart Counting Trick** Normally, when you apply a regex with the `/g` (global match) flag, Perl finds all occurrences in the string. However, getting the **count** of those matches isn't as straightforward as you might expect. Consider this example: ```perl my $str = "Hello 123, Perl 456!"; my $count = () = $str =~ /\w/g; print "Matched $count word characters.\n"; ``` ### **Breaking It Down** 1. **Regex Matching (`$str =~ /\w/g`)** - This searches for **all** word characters (`\w` → `[A-Za-z0-9_]`) in `$str`. - The `/g` flag ensures it **captures all occurrences** instead of just the first one. 2. **The Empty List `()`** - The regex match is assigned to an **empty list `()`**. - This forces Perl to evaluate the regex in **list context**, where it returns **all matches** instead of just one. 3. **Assigning to a Scalar (`$count`)** - When a **list is assigned to a scalar**, Perl doesn't store the list—it simply counts its elements. - The result? `$count` contains the **number of matches**. ### **Expected Output** ``` Matched 15 word characters. ``` If you manually count the `\w` matches (`Hello123Perl456`), you'll find **15**. --- ## **Why Not Use `scalar()` Instead?** You might think this is equivalent to: ```perl my $count = scalar($str =~ /\w/g); # will return 1 ``` **But this won't work!** - `scalar($str =~ /\w/g)` only returns the **last match found**, not the count. - `=()=` is necessary because it **forces list context**, ensuring Perl counts all matches correctly. --- ## **Practical Use Cases** This trick is useful whenever you need to count occurrences without modifying the original string. Some real-world applications include: ✅ Counting **words, numbers, or special characters** in a string. ✅ Measuring **how many times a pattern appears** in a text. ✅ Quick **validation checks** (e.g., ensuring a string contains at least `n` digits). Example: Counting words in a sentence ```perl my $sentence = "Perl is awesome!"; my $word_count = () = $sentence =~ /\b\w+\b/g; print "Word count: $word_count\n"; # Output: 3 ``` --- ## **Final Thoughts** The `=()=` operator might look like magic at first, but it's actually an elegant way to **force list context** and extract match counts without loops or extra variables. Whether processing text or just trying to optimize Perl scripts, this trick is a powerful addition to the Perl toolkit.
@ dbb19ae0:c3f22d5a
2025-02-01 09:06:49### **The Magic of `=()=` in Perl: Counting Matches with Elegance** Perl is full of powerful and sometimes cryptic features, and one of the lesser-known yet highly useful tricks is the `=()=` operator. This clever construct allows you to count the number of matches in a string without using loops or unnecessary variables. --- ## **Understanding `=()=`: A Smart Counting Trick** Normally, when you apply a regex with the `/g` (global match) flag, Perl finds all occurrences in the string. However, getting the **count** of those matches isn't as straightforward as you might expect. Consider this example: ```perl my $str = "Hello 123, Perl 456!"; my $count = () = $str =~ /\w/g; print "Matched $count word characters.\n"; ``` ### **Breaking It Down** 1. **Regex Matching (`$str =~ /\w/g`)** - This searches for **all** word characters (`\w` → `[A-Za-z0-9_]`) in `$str`. - The `/g` flag ensures it **captures all occurrences** instead of just the first one. 2. **The Empty List `()`** - The regex match is assigned to an **empty list `()`**. - This forces Perl to evaluate the regex in **list context**, where it returns **all matches** instead of just one. 3. **Assigning to a Scalar (`$count`)** - When a **list is assigned to a scalar**, Perl doesn't store the list—it simply counts its elements. - The result? `$count` contains the **number of matches**. ### **Expected Output** ``` Matched 15 word characters. ``` If you manually count the `\w` matches (`Hello123Perl456`), you'll find **15**. --- ## **Why Not Use `scalar()` Instead?** You might think this is equivalent to: ```perl my $count = scalar($str =~ /\w/g); # will return 1 ``` **But this won't work!** - `scalar($str =~ /\w/g)` only returns the **last match found**, not the count. - `=()=` is necessary because it **forces list context**, ensuring Perl counts all matches correctly. --- ## **Practical Use Cases** This trick is useful whenever you need to count occurrences without modifying the original string. Some real-world applications include: ✅ Counting **words, numbers, or special characters** in a string. ✅ Measuring **how many times a pattern appears** in a text. ✅ Quick **validation checks** (e.g., ensuring a string contains at least `n` digits). Example: Counting words in a sentence ```perl my $sentence = "Perl is awesome!"; my $word_count = () = $sentence =~ /\b\w+\b/g; print "Word count: $word_count\n"; # Output: 3 ``` --- ## **Final Thoughts** The `=()=` operator might look like magic at first, but it's actually an elegant way to **force list context** and extract match counts without loops or extra variables. Whether processing text or just trying to optimize Perl scripts, this trick is a powerful addition to the Perl toolkit. @ 0271e1b9:ad8cff90
2025-02-01 07:39:31**I study the greats.** For if and when I find myself beaten down into the gutters of life - the vile, bile and the mundane - I shall draw strength from other great men - past, present and future - who, quite often, faced many more adversities and a lot more suffering, but chose to use them to their advantage, to overcome their dire circumstances and rise above the afflictions that life had bestowed upon them. It’s all been done before. It can be done again, better. Learning from the past and from the present is very straightforward. Anyone can do that. But how does one learn from the future? It’s simple: you envision the best possible future for humanity, for generations to come, and for yourself. Then you figure out an approximate path on how to get there, and what kind of a man or a woman you must be to walk that path. The skills, the mindset, the qualities. And lastly, but perhaps most importantly, you find actionable measures, habits, convictions on how to become that person - and conversely, what are stopping you from becoming that person. > “You must value learning above everything else.” ― Robert Greene > “Those who have a 'why' to live, can bear with almost any 'how'.” ― Viktor E. Frankl > “You need to look at all events as having value. If you can do that, then you’re in a zone of tremendous opportunity.” ― Phil Stutz > “I shall take the more pains to uncover the fountains of philosophy, from which all my eloquence has taken its rise.” ― Marcus Tullius Cicero > “Error correction is the basis of all intelligence.” ― Jeff Booth > “Yes, you’re likely to fail, that’s fine. Because the goal of playing is not to win, but to keep learning. And the day you stop learning is the day you stop living." ― Jesse Enkamp > "A man is great not because he hasn't failed; a man is great because failure hasn't stopped him." — Confucius > “If people knew how hard I had to work to gain my mastery, it would not seem so wonderful at all.” ― Michelangelo > “First of all we have to decide what we are to do and what manner of men we wish to be - the most difficult problem in the world.” ― Marcus Tullius Cicero > “You either bleed soul into your work, or let the work bleed out your soul.” ― Pran Yoganthan > "The Stoic philosopher is the man who has liberated himself from fear. He’s not afraid of death, he’s not afraid of pain, he’s not afraid of other people’s dismissal as a fool. The only thing he cares about is that he should meet his moral obligations.” ― Michael Sugrue > "The strong do what they can and the weak suffer what they must." ― Thucydides > “The brain is the most powerful weapon in the world.” ― David Goggins > “Man, the bravest of animals, and the one most accustomed to suffering, does not repudiate suffering as such; he desires it, he even seeks it out, provided he is shown a meaning for it, a purpose of suffering. The meaninglessness of suffering, not suffering itself, was the curse that lay over mankind so far.” ― Friedrich Nietzsche > "Consciousness is awareness with a choice." ― Thomas Campbell > “The essence of philosophy is that a man should so live that his happiness shall depend as little as possible on external things.” ― Epictetus > “It’s most real, it’s most good and it’s most salvific - it saves you, it transforms you. That’s the sacred.” — John Vervaeke > “It is impossible for a man to learn what he thinks he already knows.” ― Epictetus > “Evolution is a process of iteration. There’s no master plan. It’s in each moment of what happens.” ― Michael Behrens > “Don’t follow anybody and don’t accept anyone as a teacher, except when you become your own teacher and disciple.” ― Jiddu Krishnamurti > “This is your life. You’re accountable. What are you gonna do about that?” ― James Hollis By the way, if you enjoyed these quotes, feel free to follow a little side project of mine: [Stoic Resurrection](https://linktr.ee/stoic_resurrection) *Peace & Love,* *[Kontext](https://linktr.ee/mckontext)* *Block height 881,748*
@ 0271e1b9:ad8cff90
2025-02-01 07:39:31**I study the greats.** For if and when I find myself beaten down into the gutters of life - the vile, bile and the mundane - I shall draw strength from other great men - past, present and future - who, quite often, faced many more adversities and a lot more suffering, but chose to use them to their advantage, to overcome their dire circumstances and rise above the afflictions that life had bestowed upon them. It’s all been done before. It can be done again, better. Learning from the past and from the present is very straightforward. Anyone can do that. But how does one learn from the future? It’s simple: you envision the best possible future for humanity, for generations to come, and for yourself. Then you figure out an approximate path on how to get there, and what kind of a man or a woman you must be to walk that path. The skills, the mindset, the qualities. And lastly, but perhaps most importantly, you find actionable measures, habits, convictions on how to become that person - and conversely, what are stopping you from becoming that person. > “You must value learning above everything else.” ― Robert Greene > “Those who have a 'why' to live, can bear with almost any 'how'.” ― Viktor E. Frankl > “You need to look at all events as having value. If you can do that, then you’re in a zone of tremendous opportunity.” ― Phil Stutz > “I shall take the more pains to uncover the fountains of philosophy, from which all my eloquence has taken its rise.” ― Marcus Tullius Cicero > “Error correction is the basis of all intelligence.” ― Jeff Booth > “Yes, you’re likely to fail, that’s fine. Because the goal of playing is not to win, but to keep learning. And the day you stop learning is the day you stop living." ― Jesse Enkamp > "A man is great not because he hasn't failed; a man is great because failure hasn't stopped him." — Confucius > “If people knew how hard I had to work to gain my mastery, it would not seem so wonderful at all.” ― Michelangelo > “First of all we have to decide what we are to do and what manner of men we wish to be - the most difficult problem in the world.” ― Marcus Tullius Cicero > “You either bleed soul into your work, or let the work bleed out your soul.” ― Pran Yoganthan > "The Stoic philosopher is the man who has liberated himself from fear. He’s not afraid of death, he’s not afraid of pain, he’s not afraid of other people’s dismissal as a fool. The only thing he cares about is that he should meet his moral obligations.” ― Michael Sugrue > "The strong do what they can and the weak suffer what they must." ― Thucydides > “The brain is the most powerful weapon in the world.” ― David Goggins > “Man, the bravest of animals, and the one most accustomed to suffering, does not repudiate suffering as such; he desires it, he even seeks it out, provided he is shown a meaning for it, a purpose of suffering. The meaninglessness of suffering, not suffering itself, was the curse that lay over mankind so far.” ― Friedrich Nietzsche > "Consciousness is awareness with a choice." ― Thomas Campbell > “The essence of philosophy is that a man should so live that his happiness shall depend as little as possible on external things.” ― Epictetus > “It’s most real, it’s most good and it’s most salvific - it saves you, it transforms you. That’s the sacred.” — John Vervaeke > “It is impossible for a man to learn what he thinks he already knows.” ― Epictetus > “Evolution is a process of iteration. There’s no master plan. It’s in each moment of what happens.” ― Michael Behrens > “Don’t follow anybody and don’t accept anyone as a teacher, except when you become your own teacher and disciple.” ― Jiddu Krishnamurti > “This is your life. You’re accountable. What are you gonna do about that?” ― James Hollis By the way, if you enjoyed these quotes, feel free to follow a little side project of mine: [Stoic Resurrection](https://linktr.ee/stoic_resurrection) *Peace & Love,* *[Kontext](https://linktr.ee/mckontext)* *Block height 881,748* @ ee7e3590:5602f192
2025-02-01 05:02:15You’re hitting on the core tension: **unlimited demand for emergency care collides with finite resources**, and pretending otherwise leads to either runaway costs or rationing-by-stealth. Let’s confront this head-on with free-market-aligned solutions that don’t ignore human realities: --- ### **1. Redefine "Emergency Care"** The U.S. legally mandates ERs to stabilize *anyone*, regardless of ability to pay (EMTALA). This creates moral hazard: - **Problem**: Hospitals inflate prices on paying patients to offset uncompensated care. - **Free-Market Fix**: - **Repeal EMTALA**: Allow ERs to refuse non-critical cases (e.g., toothaches, rashes) unless prepaid or insured. - **Clarify "True Emergency"**: Legally define emergencies as *immediate life threats* (e.g., strokes, cardiac arrest) and let non-critical cases be diverted to urgent care. - **Consequence**: ERs could price transparently for true emergencies, while non-critical cases face market-driven urgent care options. --- ### **2. Embrace Tiered Emergency Care** Not all emergencies require Level I trauma centers: - **Basic ERs**: Staffed by NPs and paramedics for minor injuries (e.g., sprains, minor burns) at lower costs. - **Advanced ERs**: For critical care (e.g., gunshot wounds), priced higher but competing via outcomes (e.g., survival rates). - **Example**: India’s *Ziqitza Healthcare* operates ambulance tiers—basic vans for transport and advanced ICU units. --- ### **3. **Address Moral Hazard with Insurance Innovation** - **Catastrophic Insurance Mandates**: Require everyone to carry cheap, high-deductible plans covering *only* true emergencies (e.g., $10/month for coverage above $50k). - Incentivizes price shopping for non-emergencies. - Prevents freeloading on ERs. - **Risk-Adjusted Premiums**: Smokers, skydivers, or diabetics pay higher premiums, aligning costs with personal choices. --- ### **4. **Community-Based Safety Nets** - **Mutual Aid Networks**: Local groups negotiate bulk ER rates (e.g., $100/month membership covers three ER visits annually). - **Crowdfunding ER Vouchers**: Platforms like *GoFundMe* could partner with hospitals to prepurchase discounted emergency care slots. --- ### **5. **Radical Transparency + Bankruptcy Reform** - **ER Debt Auctions**: Let hospitals sell unpaid ER bills to collection agencies in real-time, creating competition to minimize patient liability. - **Flat-Fee ER Pricing**: Hospitals post rates like “$5,000 for appendicitis stabilization, all-inclusive” to deter surprise billing. - **Ban Wage Garnishment for Medical Debt**: Protect patients from lifelong ruin, forcing hospitals to price responsibly or absorb losses. --- ### **6. **Accept Trade-Offs Explicitly** The U.S. system fails because it hides rationing behind complexity. A free-market approach must embrace transparency: - **Option 1**: Pay $100,000 for a 95% survival rate in a car crash. - **Option 2**: Pay $20,000 for a 70% survival rate at a budget ER. - **Brutal but Honest**: Let individuals (or insurers) choose their risk tolerance upfront. **Example**: - **Japan’s Price Controls**: Caps ER costs but tolerates wait times (e.g., 8+ hours for non-critical care). - **Switzerland’s Mandates**: Everyone buys insurance, but ERs charge $1,000+ deductibles to deter overuse. --- ### **7. **Disrupt with Decentralized Care** - **Crypto-ERs**: Blockchain-based emergency funds where contributors vote on covering members’ bills. - **AI-Guided Self-Care**: Apps that stabilize patients en route to ERs (e.g., tourniquet tutorials, overdose reversal guidance). --- ### **8. **Reform Malpractice to Reduce Defensive Medicine** - **“No Pay, No Harm” Liability**: If a patient doesn’t pay, they can’t sue for malpractice (incentivizing upfront pricing). - **Safe Harbor Protocols**: ERs using approved, cost-effective treatments (e.g., generics) get immunity from lawsuits. --- ### **The Uncomfortable Truth** A free market in emergency care requires accepting that **not everyone will be saved**—just as not everyone can afford a Ferrari. The alternative is the current U.S. model, which *pretends* to save everyone but bankrupts millions and still leaves 30% of ER visits unmet due to overcrowding. By legalizing tiered care, deregulating monopolies, and forcing transparency, you create a system where: - **Elites** pay premium prices for cutting-edge emergency care. - **Most** get “good enough” stabilization at reasonable costs. - **Some** choose cheap, high-risk options (or none at all). This isn’t pretty, but it’s honest—and arguably more ethical than today’s hidden rationing and financial toxicity.
@ ee7e3590:5602f192
2025-02-01 05:02:15You’re hitting on the core tension: **unlimited demand for emergency care collides with finite resources**, and pretending otherwise leads to either runaway costs or rationing-by-stealth. Let’s confront this head-on with free-market-aligned solutions that don’t ignore human realities: --- ### **1. Redefine "Emergency Care"** The U.S. legally mandates ERs to stabilize *anyone*, regardless of ability to pay (EMTALA). This creates moral hazard: - **Problem**: Hospitals inflate prices on paying patients to offset uncompensated care. - **Free-Market Fix**: - **Repeal EMTALA**: Allow ERs to refuse non-critical cases (e.g., toothaches, rashes) unless prepaid or insured. - **Clarify "True Emergency"**: Legally define emergencies as *immediate life threats* (e.g., strokes, cardiac arrest) and let non-critical cases be diverted to urgent care. - **Consequence**: ERs could price transparently for true emergencies, while non-critical cases face market-driven urgent care options. --- ### **2. Embrace Tiered Emergency Care** Not all emergencies require Level I trauma centers: - **Basic ERs**: Staffed by NPs and paramedics for minor injuries (e.g., sprains, minor burns) at lower costs. - **Advanced ERs**: For critical care (e.g., gunshot wounds), priced higher but competing via outcomes (e.g., survival rates). - **Example**: India’s *Ziqitza Healthcare* operates ambulance tiers—basic vans for transport and advanced ICU units. --- ### **3. **Address Moral Hazard with Insurance Innovation** - **Catastrophic Insurance Mandates**: Require everyone to carry cheap, high-deductible plans covering *only* true emergencies (e.g., $10/month for coverage above $50k). - Incentivizes price shopping for non-emergencies. - Prevents freeloading on ERs. - **Risk-Adjusted Premiums**: Smokers, skydivers, or diabetics pay higher premiums, aligning costs with personal choices. --- ### **4. **Community-Based Safety Nets** - **Mutual Aid Networks**: Local groups negotiate bulk ER rates (e.g., $100/month membership covers three ER visits annually). - **Crowdfunding ER Vouchers**: Platforms like *GoFundMe* could partner with hospitals to prepurchase discounted emergency care slots. --- ### **5. **Radical Transparency + Bankruptcy Reform** - **ER Debt Auctions**: Let hospitals sell unpaid ER bills to collection agencies in real-time, creating competition to minimize patient liability. - **Flat-Fee ER Pricing**: Hospitals post rates like “$5,000 for appendicitis stabilization, all-inclusive” to deter surprise billing. - **Ban Wage Garnishment for Medical Debt**: Protect patients from lifelong ruin, forcing hospitals to price responsibly or absorb losses. --- ### **6. **Accept Trade-Offs Explicitly** The U.S. system fails because it hides rationing behind complexity. A free-market approach must embrace transparency: - **Option 1**: Pay $100,000 for a 95% survival rate in a car crash. - **Option 2**: Pay $20,000 for a 70% survival rate at a budget ER. - **Brutal but Honest**: Let individuals (or insurers) choose their risk tolerance upfront. **Example**: - **Japan’s Price Controls**: Caps ER costs but tolerates wait times (e.g., 8+ hours for non-critical care). - **Switzerland’s Mandates**: Everyone buys insurance, but ERs charge $1,000+ deductibles to deter overuse. --- ### **7. **Disrupt with Decentralized Care** - **Crypto-ERs**: Blockchain-based emergency funds where contributors vote on covering members’ bills. - **AI-Guided Self-Care**: Apps that stabilize patients en route to ERs (e.g., tourniquet tutorials, overdose reversal guidance). --- ### **8. **Reform Malpractice to Reduce Defensive Medicine** - **“No Pay, No Harm” Liability**: If a patient doesn’t pay, they can’t sue for malpractice (incentivizing upfront pricing). - **Safe Harbor Protocols**: ERs using approved, cost-effective treatments (e.g., generics) get immunity from lawsuits. --- ### **The Uncomfortable Truth** A free market in emergency care requires accepting that **not everyone will be saved**—just as not everyone can afford a Ferrari. The alternative is the current U.S. model, which *pretends* to save everyone but bankrupts millions and still leaves 30% of ER visits unmet due to overcrowding. By legalizing tiered care, deregulating monopolies, and forcing transparency, you create a system where: - **Elites** pay premium prices for cutting-edge emergency care. - **Most** get “good enough” stabilization at reasonable costs. - **Some** choose cheap, high-risk options (or none at all). This isn’t pretty, but it’s honest—and arguably more ethical than today’s hidden rationing and financial toxicity. @ ee7e3590:5602f192
2025-02-01 05:00:39You’re hitting on the core tension: **unlimited demand for emergency care collides with finite resources**, and pretending otherwise leads to either runaway costs or rationing-by-stealth. Let’s confront this head-on with free-market-aligned solutions that don’t ignore human realities: --- ### **1. Redefine "Emergency Care"** The U.S. legally mandates ERs to stabilize *anyone*, regardless of ability to pay (EMTALA). This creates moral hazard: - **Problem**: Hospitals inflate prices on paying patients to offset uncompensated care. - **Free-Market Fix**: - **Repeal EMTALA**: Allow ERs to refuse non-critical cases (e.g., toothaches, rashes) unless prepaid or insured. - **Clarify "True Emergency"**: Legally define emergencies as *immediate life threats* (e.g., strokes, cardiac arrest) and let non-critical cases be diverted to urgent care. - **Consequence**: ERs could price transparently for true emergencies, while non-critical cases face market-driven urgent care options. --- ### **2. Embrace Tiered Emergency Care** Not all emergencies require Level I trauma centers: - **Basic ERs**: Staffed by NPs and paramedics for minor injuries (e.g., sprains, minor burns) at lower costs. - **Advanced ERs**: For critical care (e.g., gunshot wounds), priced higher but competing via outcomes (e.g., survival rates). - **Example**: India’s *Ziqitza Healthcare* operates ambulance tiers—basic vans for transport and advanced ICU units. --- ### **3. **Address Moral Hazard with Insurance Innovation** - **Catastrophic Insurance Mandates**: Require everyone to carry cheap, high-deductible plans covering *only* true emergencies (e.g., $10/month for coverage above $50k). - Incentivizes price shopping for non-emergencies. - Prevents freeloading on ERs. - **Risk-Adjusted Premiums**: Smokers, skydivers, or diabetics pay higher premiums, aligning costs with personal choices. --- ### **4. **Community-Based Safety Nets** - **Mutual Aid Networks**: Local groups negotiate bulk ER rates (e.g., $100/month membership covers three ER visits annually). - **Crowdfunding ER Vouchers**: Platforms like *GoFundMe* could partner with hospitals to prepurchase discounted emergency care slots. --- ### **5. **Radical Transparency + Bankruptcy Reform** - **ER Debt Auctions**: Let hospitals sell unpaid ER bills to collection agencies in real-time, creating competition to minimize patient liability. - **Flat-Fee ER Pricing**: Hospitals post rates like “$5,000 for appendicitis stabilization, all-inclusive” to deter surprise billing. - **Ban Wage Garnishment for Medical Debt**: Protect patients from lifelong ruin, forcing hospitals to price responsibly or absorb losses. --- ### **6. **Accept Trade-Offs Explicitly** The U.S. system fails because it hides rationing behind complexity. A free-market approach must embrace transparency: - **Option 1**: Pay $100,000 for a 95% survival rate in a car crash. - **Option 2**: Pay $20,000 for a 70% survival rate at a budget ER. - **Brutal but Honest**: Let individuals (or insurers) choose their risk tolerance upfront. **Example**: - **Japan’s Price Controls**: Caps ER costs but tolerates wait times (e.g., 8+ hours for non-critical care). - **Switzerland’s Mandates**: Everyone buys insurance, but ERs charge $1,000+ deductibles to deter overuse. --- ### **7. **Disrupt with Decentralized Care** - **Crypto-ERs**: Blockchain-based emergency funds where contributors vote on covering members’ bills. - **AI-Guided Self-Care**: Apps that stabilize patients en route to ERs (e.g., tourniquet tutorials, overdose reversal guidance). --- ### **8. **Reform Malpractice to Reduce Defensive Medicine** - **“No Pay, No Harm” Liability**: If a patient doesn’t pay, they can’t sue for malpractice (incentivizing upfront pricing). - **Safe Harbor Protocols**: ERs using approved, cost-effective treatments (e.g., generics) get immunity from lawsuits. --- ### **The Uncomfortable Truth** A free market in emergency care requires accepting that **not everyone will be saved**—just as not everyone can afford a Ferrari. The alternative is the current U.S. model, which *pretends* to save everyone but bankrupts millions and still leaves 30% of ER visits unmet due to overcrowding. By legalizing tiered care, deregulating monopolies, and forcing transparency, you create a system where: - **Elites** pay premium prices for cutting-edge emergency care. - **Most** get “good enough” stabilization at reasonable costs. - **Some** choose cheap, high-risk options (or none at all). This isn’t pretty, but it’s honest—and arguably more ethical than today’s hidden rationing and financial toxicity.
@ ee7e3590:5602f192
2025-02-01 05:00:39You’re hitting on the core tension: **unlimited demand for emergency care collides with finite resources**, and pretending otherwise leads to either runaway costs or rationing-by-stealth. Let’s confront this head-on with free-market-aligned solutions that don’t ignore human realities: --- ### **1. Redefine "Emergency Care"** The U.S. legally mandates ERs to stabilize *anyone*, regardless of ability to pay (EMTALA). This creates moral hazard: - **Problem**: Hospitals inflate prices on paying patients to offset uncompensated care. - **Free-Market Fix**: - **Repeal EMTALA**: Allow ERs to refuse non-critical cases (e.g., toothaches, rashes) unless prepaid or insured. - **Clarify "True Emergency"**: Legally define emergencies as *immediate life threats* (e.g., strokes, cardiac arrest) and let non-critical cases be diverted to urgent care. - **Consequence**: ERs could price transparently for true emergencies, while non-critical cases face market-driven urgent care options. --- ### **2. Embrace Tiered Emergency Care** Not all emergencies require Level I trauma centers: - **Basic ERs**: Staffed by NPs and paramedics for minor injuries (e.g., sprains, minor burns) at lower costs. - **Advanced ERs**: For critical care (e.g., gunshot wounds), priced higher but competing via outcomes (e.g., survival rates). - **Example**: India’s *Ziqitza Healthcare* operates ambulance tiers—basic vans for transport and advanced ICU units. --- ### **3. **Address Moral Hazard with Insurance Innovation** - **Catastrophic Insurance Mandates**: Require everyone to carry cheap, high-deductible plans covering *only* true emergencies (e.g., $10/month for coverage above $50k). - Incentivizes price shopping for non-emergencies. - Prevents freeloading on ERs. - **Risk-Adjusted Premiums**: Smokers, skydivers, or diabetics pay higher premiums, aligning costs with personal choices. --- ### **4. **Community-Based Safety Nets** - **Mutual Aid Networks**: Local groups negotiate bulk ER rates (e.g., $100/month membership covers three ER visits annually). - **Crowdfunding ER Vouchers**: Platforms like *GoFundMe* could partner with hospitals to prepurchase discounted emergency care slots. --- ### **5. **Radical Transparency + Bankruptcy Reform** - **ER Debt Auctions**: Let hospitals sell unpaid ER bills to collection agencies in real-time, creating competition to minimize patient liability. - **Flat-Fee ER Pricing**: Hospitals post rates like “$5,000 for appendicitis stabilization, all-inclusive” to deter surprise billing. - **Ban Wage Garnishment for Medical Debt**: Protect patients from lifelong ruin, forcing hospitals to price responsibly or absorb losses. --- ### **6. **Accept Trade-Offs Explicitly** The U.S. system fails because it hides rationing behind complexity. A free-market approach must embrace transparency: - **Option 1**: Pay $100,000 for a 95% survival rate in a car crash. - **Option 2**: Pay $20,000 for a 70% survival rate at a budget ER. - **Brutal but Honest**: Let individuals (or insurers) choose their risk tolerance upfront. **Example**: - **Japan’s Price Controls**: Caps ER costs but tolerates wait times (e.g., 8+ hours for non-critical care). - **Switzerland’s Mandates**: Everyone buys insurance, but ERs charge $1,000+ deductibles to deter overuse. --- ### **7. **Disrupt with Decentralized Care** - **Crypto-ERs**: Blockchain-based emergency funds where contributors vote on covering members’ bills. - **AI-Guided Self-Care**: Apps that stabilize patients en route to ERs (e.g., tourniquet tutorials, overdose reversal guidance). --- ### **8. **Reform Malpractice to Reduce Defensive Medicine** - **“No Pay, No Harm” Liability**: If a patient doesn’t pay, they can’t sue for malpractice (incentivizing upfront pricing). - **Safe Harbor Protocols**: ERs using approved, cost-effective treatments (e.g., generics) get immunity from lawsuits. --- ### **The Uncomfortable Truth** A free market in emergency care requires accepting that **not everyone will be saved**—just as not everyone can afford a Ferrari. The alternative is the current U.S. model, which *pretends* to save everyone but bankrupts millions and still leaves 30% of ER visits unmet due to overcrowding. By legalizing tiered care, deregulating monopolies, and forcing transparency, you create a system where: - **Elites** pay premium prices for cutting-edge emergency care. - **Most** get “good enough” stabilization at reasonable costs. - **Some** choose cheap, high-risk options (or none at all). This isn’t pretty, but it’s honest—and arguably more ethical than today’s hidden rationing and financial toxicity. @ f1989a96:bcaaf2c1
2025-01-31 21:22:59In the summer of 2023, the Human Rights Foundation (HRF) launched a Bitcoin Bounty program aimed at funding software developers to create new tools and features for Bitcoin tailored to the needs of dissidents and human rights advocates challenging authoritarianism worldwide. These bounties ranged from UX improvements to privacy upgrades and open-sourcing closed and permissioned systems. There were 11 bounties in total, each with specific objectives. The deadline was Dec. 31, 2024. We are excited to announce that every single bounty was claimed and that the resulting tools and upgrades are now empowering human rights activists daily across popular apps such as Blue Wallet, Zeus, Stack Wallet, Iris, Coracle, Keeper, Bull Bitcoin, Cake Wallet, and more. This program highlights the impact of collaboration between human rights activists and software developers to create better tools for freedom. HRF is proud to have played a role in this effort and looks forward to continuing similar programs in the future. Special credit goes to the Oslo Freedom Forum, where much of the critical interaction between developers and activists occurred. This wave of bounties was inspired by a successful pilot project in 2021, executed in partnership with Strike and Jack Mallers, which supported developers like Will Cassarin and Calle. Their innovations later gave rise to important advancements such as zaps in Nostr and the Cashu ecash protocol. # **Bounty Details** #### **1. Open-Sourcing the Design Guide** **Winner:** [CypherStack](https://cypherstack.com/) for porting the Bitcoin UI Kit from Figma to an [open-source Penpot project](https://github.com/cypherstack/bitcoin-ui-kit-penpot) (2 BTC awarded). Many UI kits are created using proprietary software like Figma. While these tools are powerful, they require licenses and are not accessible to everyone — an obstacle for developers working on open-source projects or those with limited funds. This creates a barrier to entry for designers and developers wanting to contribute to the Bitcoin ecosystem. This bounty was awarded to CypherStack for porting the Bitcoin UI Kit from Figma to Penpot, an open-source design tool similar to Figma, but free and accessible to everyone. This helped democratize access to information and resources, promote collaboration, and make it easier for developers to create high-quality Bitcoin tools, which in turn helped to increase Bitcoin adoption. #### **2. Serverless Payjoin** **Winners:** This is a two-part bounty. The first bounty is for the development of the Serverless Payjoin specification, and the second bounty is for any wallets that implement Serverless Payjoin. **Part 1:** [Dan Gould](https://crates.io/users/DanGould) for his work on [PayJoin V2](https://crates.io/crates/payjoin-cli/) (1 BTC) **Part 2:** Dan Gould, [Spacebear](https://github.com/spacebear21) from Payjoin DevKit, and [Bull Bitcoin](https://www.bullbitcoin.com/) app, for their collaborative effort implementing Payjoin into the Bull Bitcoin wallet (0.5 BTC split three ways). PayJoin is a privacy upgrade to Bitcoin that flusters mass surveillance attempts on the network. Traditional implementations have required the receiver to run a server for transaction coordination, creating a barrier to adoption. Serverless PayJoin removed this dependency and simplified the process. Serverless PayJoin also eliminated the need for receiver-hosted infrastructure and reduced censorship risks by removing a central point of failure — a significant advantage for activists and nonprofits operating under repressive regimes. This bounty resulted in the first mobile app ([Bull Bitcoin](https://play.google.com/store/apps/details?id=com.bullbitcoin.mobile&hl=en_US)) with integrated PayJoin send and receive support, an important advancement that provided robust privacy protections against surveillance for at-risk individuals. #### **3. End-to-End Encrypted Nostr Group Chats** **Winners:** [Martti Malmi](https://iris.to/sirius) for incorporating encrypted group chat functionality into the [Iris](https://iris.to/) Nostr client (1 BTC) and to Vitor Pamplona, hodlbod, and Paul Miller for their work on NIP-17, which allowed users to encrypt and share Nostr messages in a way that can be recognized across different Nostr clients (1 BTC). End-to-End Encrypted (E2EE) Nostr Group Chats are private, secure messaging groups built on the Nostr protocol, a decentralized communication system. While Nostr messages are already encrypted, they still expose metadata, allowing outside observers to see who is communicating and when. This bounty focused on preventing metadata leakage, ensuring that these details remain private. By leveraging Nostr’s decentralized architecture, these chats offered censorship resistance. They prevented conversations from being surveilled, blocked, or controlled by a central authority, and as a result of this bounty, have now been implemented into popular Nostr clients like Iris, Amethyst, and Coracle. This is an important step forward for activists, journalists, and communities who risk losing their freedom of speech under oppressive regimes. #### **4. Silent Payments** **Winners:** [cygnet3](https://github.com/cygnet3) and [Sosthene](https://github.com/Sosthene00) for their contributions to [critical libraries](https://github.com/Sosthene00/electrs/tree/sp_tweaks) for delivering Silent Payments and for developing a [mobile wallet](https://github.com/cygnet3/danawallet) capable of sending and receiving Silent Payments without requiring a full node (1 BTC). Silent Payments are a privacy-enhancing Bitcoin addressing scheme that allows a sender to generate a unique static address for a recipient without requiring any interaction (while still allowing the recipient to detect and spend the received funds). This breaks common tracking methods used by surveillance firms and autocracies and makes it harder to link payments to a specific recipient. By improving on the privacy of traditional Bitcoin addresses, Silent Payments enhanced financial privacy, making them ideal for donations, salaries, and other sensitive transactions. This bounty code has been fully integrated into Cake Wallet, and several other major wallets like Wasabi, Blue Wallet, and Bitbox have added partial functionality. This brings Silent Payments to tens of thousands of users and marks a major step in real-world Bitcoin privacy. #### **5. Human-Readable Offers** **Winners:** [Stephen DeLorme](https://x.com/StephenDeLorme), [Chad Welch](https://x.com/chdwlch), and [Evan Kaloudis](https://x.com/evankaloudis) for [Twelve Cash](https://twelve.cash/) and its integration into [Zeus Wallet](https://zeusln.com/) (1 BTC). Human-Readable Offers simplify Bitcoin payments by replacing complex Bitcoin addresses and invoices with user-friendly text. This is especially important for Lightning Network transactions, which currently involve a cumbersome process of generating invoices for each payment. With Human-Readable Offers, sending Lightning payments becomes as simple as sending an email (just by entering a username). This approach, similar to many fintech apps today, reduces errors, lowers the barrier to entry, increases trust, and is crucial for broader adoption of Bitcoin among new and seasoned users alike. It’s also important for people who don’t have access to smartphones and cannot copy and paste or use QR codes. Today, as a result of this bounty, Zeus users connected to a Core Lightning node can create a human-readable Bolt 12 offer to privately receive donations. #### **6. Self-Custodial Mobile Lightning Address** **Winner:** Evan Kaloudis for [Zeus Wallet](https://zeusln.com/) (1 BTC). Activists, nonprofits, and content creators often use Lightning addresses to receive donations quickly and easily. However, setting up and managing a Lightning address presents a challenge: users have to choose between the self-sovereignty of managing their own web server (a complex process) or the convenience of a custodial service, which requires trusting a third party with their funds. This bounty directly addressed this issue. It allowed users of Zeus Wallet, one of the most popular self-custodial Bitcoin Lightning wallets, to easily and securely receive donations through a Lightning address while maintaining control of their funds. #### **7. Mobile Border Wallets** **Winner:** [Bitcoin Tribe](https://twitter.com/BitcoinTribe_) for their border wallet functionality, allowing users to create and memorize seeds without relying on written backups, and for building a [React Native library](https://github.com/bithyve/react-native-border-wallets), making it easier for other wallets to integrate this feature (2 BTC). Mobile Border Wallets aimed to solve a critical problem with traditional Bitcoin seed phrase backups: they’re often written down on paper, making them susceptible to being lost, destroyed, or stolen. This makes securing a user’s Bitcoin a delicate balance between security and accessibility. It also makes it challenging, especially for activists or refugees who frequently cross international borders. Border Wallets offered a solution to this problem. Instead of writing down a 12- or 24-word seed phrase and finding a secure place to store it, users can upload a randomly generated grid of words to the cloud and memorize a pattern to secure their seed phrase, similar to a pattern a user would memorize and draw on an Android device to unlock it. This initiative resulted in a user-friendly mobile app that allowed users to create Border Wallets digitally, enhancing accessibility and offering an alternative to physical storage like printed paper or metal seed plates. #### **8. Easy Mobile Multisig** **Winner:** [Bitcoin Keeper](https://bitcoinkeeper.app/) (1 BTC). Multi-signature wallets allow multiple users to collaboratively control a Bitcoin wallet. This enhances security by requiring consensus before funds can be moved. Traditional multisig wallets often require physical hardware wallets or involve subscription fees, presenting a significant barrier for organizations exploring Bitcoin adoption. This bounty funded the development of easy mobile multisig functionality in the Bitcoin Keeper app, enabling users to set up a 2-of-3 multisig (requiring two out of three keys to authorize spending) to secure and manage their bitcoin. This is a great feature for activists to prevent government seizure of funds: even if one key holder gets detained, the funds are safe so long as the other two key holders are safe. The idea is to make sure two of the keys are held by entities outside of one’s country or threat zone. #### **9. FROST Multisig Wallet** **Winner:** [CypherStack](https://cypherstack.com/) for [Stack Wallet](https://stackwallet.com/), which enables dynamic multisig using FROST, allowing users to modify signer sets without moving funds (1 BTC). Multisig (multisignature) wallets require multiple signatures to authorize a transaction. This enhances security by distributing control over funds. However, traditional multisig setups — while secure — can be inflexible. If you need to change the set of signers, it often requires moving all the funds to a new multisig wallet with the updated signer set. This is burdensome, time-consuming, and incurs fees. FROST is a cryptographic protocol that offers significant advantages for multisig wallets. It provides dynamic multisig functionality, meaning users can easily adjust their signer sets as needed without affecting the funds within. This is an important functionality for nonprofits and civil society groups who often need to adjust their authorized signatories, especially in situations where a regime may seize a private key and that key then needs to be deprecated. This dynamic kind of secure setup is now available for activists to use on the Stack Wallet. #### **10. Cashu Upgrades** Winners: [eNuts Wallet](https://www.enuts.cash/) (0.5 BTC), [Misovan](https://github.com/misovan) for [Minibits Wallet](https://www.minibits.cash/) (0.5 BTC), [Gandlaf](https://www.gandlaf.com/about) for [Proxnut](https://proxnut.com/) (0.5 BTC), and Gandlaf for adding [Cashu-TS restore](https://github.com/cashubtc/cashu-ts) functionality (0.5 BTC). Cashu is a digital cash system designed for privacy and speed. It is like physical cash, but in digital form and uses blind signatures for private transactions. With Cashu, transactions are instant, low-fee, and can operate offline. There is no blockchain or transaction graph to be surveilled. Bounty recipients addressed critical aspects of usability and accessibility for Cashu tools: eNuts and Minibits Wallets brought Cashu to iOS and Android users worldwide, Proxnut enabled easy web integration for payments, and Cashu-TS Restore added crucial seed phrase backup. Together, these projects have taken Cashu from a more theoretical concept to a practical one and have been relevant for use cases like donations, content monetization, daily transactions, and cross-border payments. #### **11. BIP47 Expansion** Winner: [Blue Wallet](https://bluewallet.io/) (0.5 BTC) for adding BIP 47 support. BIP47 is a Bitcoin Improvement Proposal that enhances payment privacy for Bitcoin users. In Bitcoin, it’s generally considered bad privacy practice to reuse the same Bitcoin address for multiple transactions. It can link those transactions together and make it easier to track a user’s spending in high-risk environments. Generating a new address for each payment has become a common workaround, but this becomes cumbersome. BIP47 solves this with reusable payment codes. Users receiving funds generate a BIP47 payment code and share it with those who will be sending them payments. Each time a payment is initiated, a new, unused Bitcoin address is generated from the recipient’s payment code. This ensures every transaction uses a unique address. Blue Wallet received this bounty for integrating BIP47 support, making this important privacy enhancement accessible to its growing user base. *HRF’s Financial Freedom program educates activists worldwide, unites people from different industries and backgrounds, and makes grants in the service of advancing Bitcoin as a tool for human rights. To receive HRF’s weekly Financial Freedom Report, subscribe [here](https://mailchi.mp/hrf.org/financial-freedom-newsletter).* *For media inquiries or interview requests, please contact media @ hrf.org.*
@ f1989a96:bcaaf2c1
2025-01-31 21:22:59In the summer of 2023, the Human Rights Foundation (HRF) launched a Bitcoin Bounty program aimed at funding software developers to create new tools and features for Bitcoin tailored to the needs of dissidents and human rights advocates challenging authoritarianism worldwide. These bounties ranged from UX improvements to privacy upgrades and open-sourcing closed and permissioned systems. There were 11 bounties in total, each with specific objectives. The deadline was Dec. 31, 2024. We are excited to announce that every single bounty was claimed and that the resulting tools and upgrades are now empowering human rights activists daily across popular apps such as Blue Wallet, Zeus, Stack Wallet, Iris, Coracle, Keeper, Bull Bitcoin, Cake Wallet, and more. This program highlights the impact of collaboration between human rights activists and software developers to create better tools for freedom. HRF is proud to have played a role in this effort and looks forward to continuing similar programs in the future. Special credit goes to the Oslo Freedom Forum, where much of the critical interaction between developers and activists occurred. This wave of bounties was inspired by a successful pilot project in 2021, executed in partnership with Strike and Jack Mallers, which supported developers like Will Cassarin and Calle. Their innovations later gave rise to important advancements such as zaps in Nostr and the Cashu ecash protocol. # **Bounty Details** #### **1. Open-Sourcing the Design Guide** **Winner:** [CypherStack](https://cypherstack.com/) for porting the Bitcoin UI Kit from Figma to an [open-source Penpot project](https://github.com/cypherstack/bitcoin-ui-kit-penpot) (2 BTC awarded). Many UI kits are created using proprietary software like Figma. While these tools are powerful, they require licenses and are not accessible to everyone — an obstacle for developers working on open-source projects or those with limited funds. This creates a barrier to entry for designers and developers wanting to contribute to the Bitcoin ecosystem. This bounty was awarded to CypherStack for porting the Bitcoin UI Kit from Figma to Penpot, an open-source design tool similar to Figma, but free and accessible to everyone. This helped democratize access to information and resources, promote collaboration, and make it easier for developers to create high-quality Bitcoin tools, which in turn helped to increase Bitcoin adoption. #### **2. Serverless Payjoin** **Winners:** This is a two-part bounty. The first bounty is for the development of the Serverless Payjoin specification, and the second bounty is for any wallets that implement Serverless Payjoin. **Part 1:** [Dan Gould](https://crates.io/users/DanGould) for his work on [PayJoin V2](https://crates.io/crates/payjoin-cli/) (1 BTC) **Part 2:** Dan Gould, [Spacebear](https://github.com/spacebear21) from Payjoin DevKit, and [Bull Bitcoin](https://www.bullbitcoin.com/) app, for their collaborative effort implementing Payjoin into the Bull Bitcoin wallet (0.5 BTC split three ways). PayJoin is a privacy upgrade to Bitcoin that flusters mass surveillance attempts on the network. Traditional implementations have required the receiver to run a server for transaction coordination, creating a barrier to adoption. Serverless PayJoin removed this dependency and simplified the process. Serverless PayJoin also eliminated the need for receiver-hosted infrastructure and reduced censorship risks by removing a central point of failure — a significant advantage for activists and nonprofits operating under repressive regimes. This bounty resulted in the first mobile app ([Bull Bitcoin](https://play.google.com/store/apps/details?id=com.bullbitcoin.mobile&hl=en_US)) with integrated PayJoin send and receive support, an important advancement that provided robust privacy protections against surveillance for at-risk individuals. #### **3. End-to-End Encrypted Nostr Group Chats** **Winners:** [Martti Malmi](https://iris.to/sirius) for incorporating encrypted group chat functionality into the [Iris](https://iris.to/) Nostr client (1 BTC) and to Vitor Pamplona, hodlbod, and Paul Miller for their work on NIP-17, which allowed users to encrypt and share Nostr messages in a way that can be recognized across different Nostr clients (1 BTC). End-to-End Encrypted (E2EE) Nostr Group Chats are private, secure messaging groups built on the Nostr protocol, a decentralized communication system. While Nostr messages are already encrypted, they still expose metadata, allowing outside observers to see who is communicating and when. This bounty focused on preventing metadata leakage, ensuring that these details remain private. By leveraging Nostr’s decentralized architecture, these chats offered censorship resistance. They prevented conversations from being surveilled, blocked, or controlled by a central authority, and as a result of this bounty, have now been implemented into popular Nostr clients like Iris, Amethyst, and Coracle. This is an important step forward for activists, journalists, and communities who risk losing their freedom of speech under oppressive regimes. #### **4. Silent Payments** **Winners:** [cygnet3](https://github.com/cygnet3) and [Sosthene](https://github.com/Sosthene00) for their contributions to [critical libraries](https://github.com/Sosthene00/electrs/tree/sp_tweaks) for delivering Silent Payments and for developing a [mobile wallet](https://github.com/cygnet3/danawallet) capable of sending and receiving Silent Payments without requiring a full node (1 BTC). Silent Payments are a privacy-enhancing Bitcoin addressing scheme that allows a sender to generate a unique static address for a recipient without requiring any interaction (while still allowing the recipient to detect and spend the received funds). This breaks common tracking methods used by surveillance firms and autocracies and makes it harder to link payments to a specific recipient. By improving on the privacy of traditional Bitcoin addresses, Silent Payments enhanced financial privacy, making them ideal for donations, salaries, and other sensitive transactions. This bounty code has been fully integrated into Cake Wallet, and several other major wallets like Wasabi, Blue Wallet, and Bitbox have added partial functionality. This brings Silent Payments to tens of thousands of users and marks a major step in real-world Bitcoin privacy. #### **5. Human-Readable Offers** **Winners:** [Stephen DeLorme](https://x.com/StephenDeLorme), [Chad Welch](https://x.com/chdwlch), and [Evan Kaloudis](https://x.com/evankaloudis) for [Twelve Cash](https://twelve.cash/) and its integration into [Zeus Wallet](https://zeusln.com/) (1 BTC). Human-Readable Offers simplify Bitcoin payments by replacing complex Bitcoin addresses and invoices with user-friendly text. This is especially important for Lightning Network transactions, which currently involve a cumbersome process of generating invoices for each payment. With Human-Readable Offers, sending Lightning payments becomes as simple as sending an email (just by entering a username). This approach, similar to many fintech apps today, reduces errors, lowers the barrier to entry, increases trust, and is crucial for broader adoption of Bitcoin among new and seasoned users alike. It’s also important for people who don’t have access to smartphones and cannot copy and paste or use QR codes. Today, as a result of this bounty, Zeus users connected to a Core Lightning node can create a human-readable Bolt 12 offer to privately receive donations. #### **6. Self-Custodial Mobile Lightning Address** **Winner:** Evan Kaloudis for [Zeus Wallet](https://zeusln.com/) (1 BTC). Activists, nonprofits, and content creators often use Lightning addresses to receive donations quickly and easily. However, setting up and managing a Lightning address presents a challenge: users have to choose between the self-sovereignty of managing their own web server (a complex process) or the convenience of a custodial service, which requires trusting a third party with their funds. This bounty directly addressed this issue. It allowed users of Zeus Wallet, one of the most popular self-custodial Bitcoin Lightning wallets, to easily and securely receive donations through a Lightning address while maintaining control of their funds. #### **7. Mobile Border Wallets** **Winner:** [Bitcoin Tribe](https://twitter.com/BitcoinTribe_) for their border wallet functionality, allowing users to create and memorize seeds without relying on written backups, and for building a [React Native library](https://github.com/bithyve/react-native-border-wallets), making it easier for other wallets to integrate this feature (2 BTC). Mobile Border Wallets aimed to solve a critical problem with traditional Bitcoin seed phrase backups: they’re often written down on paper, making them susceptible to being lost, destroyed, or stolen. This makes securing a user’s Bitcoin a delicate balance between security and accessibility. It also makes it challenging, especially for activists or refugees who frequently cross international borders. Border Wallets offered a solution to this problem. Instead of writing down a 12- or 24-word seed phrase and finding a secure place to store it, users can upload a randomly generated grid of words to the cloud and memorize a pattern to secure their seed phrase, similar to a pattern a user would memorize and draw on an Android device to unlock it. This initiative resulted in a user-friendly mobile app that allowed users to create Border Wallets digitally, enhancing accessibility and offering an alternative to physical storage like printed paper or metal seed plates. #### **8. Easy Mobile Multisig** **Winner:** [Bitcoin Keeper](https://bitcoinkeeper.app/) (1 BTC). Multi-signature wallets allow multiple users to collaboratively control a Bitcoin wallet. This enhances security by requiring consensus before funds can be moved. Traditional multisig wallets often require physical hardware wallets or involve subscription fees, presenting a significant barrier for organizations exploring Bitcoin adoption. This bounty funded the development of easy mobile multisig functionality in the Bitcoin Keeper app, enabling users to set up a 2-of-3 multisig (requiring two out of three keys to authorize spending) to secure and manage their bitcoin. This is a great feature for activists to prevent government seizure of funds: even if one key holder gets detained, the funds are safe so long as the other two key holders are safe. The idea is to make sure two of the keys are held by entities outside of one’s country or threat zone. #### **9. FROST Multisig Wallet** **Winner:** [CypherStack](https://cypherstack.com/) for [Stack Wallet](https://stackwallet.com/), which enables dynamic multisig using FROST, allowing users to modify signer sets without moving funds (1 BTC). Multisig (multisignature) wallets require multiple signatures to authorize a transaction. This enhances security by distributing control over funds. However, traditional multisig setups — while secure — can be inflexible. If you need to change the set of signers, it often requires moving all the funds to a new multisig wallet with the updated signer set. This is burdensome, time-consuming, and incurs fees. FROST is a cryptographic protocol that offers significant advantages for multisig wallets. It provides dynamic multisig functionality, meaning users can easily adjust their signer sets as needed without affecting the funds within. This is an important functionality for nonprofits and civil society groups who often need to adjust their authorized signatories, especially in situations where a regime may seize a private key and that key then needs to be deprecated. This dynamic kind of secure setup is now available for activists to use on the Stack Wallet. #### **10. Cashu Upgrades** Winners: [eNuts Wallet](https://www.enuts.cash/) (0.5 BTC), [Misovan](https://github.com/misovan) for [Minibits Wallet](https://www.minibits.cash/) (0.5 BTC), [Gandlaf](https://www.gandlaf.com/about) for [Proxnut](https://proxnut.com/) (0.5 BTC), and Gandlaf for adding [Cashu-TS restore](https://github.com/cashubtc/cashu-ts) functionality (0.5 BTC). Cashu is a digital cash system designed for privacy and speed. It is like physical cash, but in digital form and uses blind signatures for private transactions. With Cashu, transactions are instant, low-fee, and can operate offline. There is no blockchain or transaction graph to be surveilled. Bounty recipients addressed critical aspects of usability and accessibility for Cashu tools: eNuts and Minibits Wallets brought Cashu to iOS and Android users worldwide, Proxnut enabled easy web integration for payments, and Cashu-TS Restore added crucial seed phrase backup. Together, these projects have taken Cashu from a more theoretical concept to a practical one and have been relevant for use cases like donations, content monetization, daily transactions, and cross-border payments. #### **11. BIP47 Expansion** Winner: [Blue Wallet](https://bluewallet.io/) (0.5 BTC) for adding BIP 47 support. BIP47 is a Bitcoin Improvement Proposal that enhances payment privacy for Bitcoin users. In Bitcoin, it’s generally considered bad privacy practice to reuse the same Bitcoin address for multiple transactions. It can link those transactions together and make it easier to track a user’s spending in high-risk environments. Generating a new address for each payment has become a common workaround, but this becomes cumbersome. BIP47 solves this with reusable payment codes. Users receiving funds generate a BIP47 payment code and share it with those who will be sending them payments. Each time a payment is initiated, a new, unused Bitcoin address is generated from the recipient’s payment code. This ensures every transaction uses a unique address. Blue Wallet received this bounty for integrating BIP47 support, making this important privacy enhancement accessible to its growing user base. *HRF’s Financial Freedom program educates activists worldwide, unites people from different industries and backgrounds, and makes grants in the service of advancing Bitcoin as a tool for human rights. To receive HRF’s weekly Financial Freedom Report, subscribe [here](https://mailchi.mp/hrf.org/financial-freedom-newsletter).* *For media inquiries or interview requests, please contact media @ hrf.org.* @ 19306922:c06688d2
2025-01-31 21:14:52At a time when data-gathering technologies are dominating all aspects of everyday life, governmental agencies such as The National Security Agency have considerable surveillance and control authority. The National Security Agency runs surveillance programs on not just violent international criminals, but also ordinary citizens within the country. A tremendous amount of effort is being made to keep these programs from being critiqued and shared with the public. In this paper, I will discuss whistleblowing and its relevance in establishing a more democratic structure in governmental institutions, through the cases of Edward Snowden and Thomas Drake. Firstly, I will emphasize Edward Snowden's action as an example of illegal whistleblowing and how he acts closer to civic disobedience rather than espionage. Following that, I will discuss Thomas Drake's espionage charge while legally criticizing The National Security Agency's programs and the inadequacy of whistleblower protection laws.  In our everyday lives, we come into contact with or utilize a variety of technological equipment such as security cameras, GPS devices, iris scanners, and so on. Everything we do, from buying things from shopping malls to searching for information on the internet, is kept in massive databases. Without even our knowledge, our data, which is vast enough to create our entire profile, is in the databases of a private firm or the government. That's why the surveillance network is getting bigger and bigger. Most of the surveillance tools and the capability to regulate these tools are under state control. The government also agrees with data aggregators -companies that collect data from multiple sources and make it available to customers in a value-added format- to access more data. The US Department of Justice has an $8 million agreement with data aggregator company ChoicePoint (Stanley, Steinhardt 2014). In this way, The Justice Department can access many civilians' information in the company's database. Although this surveillance mechanism seems to be an effective way to track and detect many illegal incidents such as terrorism, money laundering, etc., this surveillance network can easily be applied to ordinary civilians. For example, in 2002, Attorney General John Ashcroft released new domestic spy guidelines that dramatically expanded federal agents' ability to monitor on American civilians (Stanley, Steinhardt 2014). The American government also is running programs to spy on ordinary citizens, according to information obtained from the National Security Agency documents which leaked to the media on multiple occasions (Greenberg, 2013). The National Security Agency (NSA) began as a cryptology-focused agency and has since grown into an intelligence agency that gathers data from enemies of the United States of America (Verble, 2014). The surveillance and data collection programs of NSA, however, are not carried out just to keep enemies at bay. Information on the NSA's programs was provided to the media by Thomas A. Drake, a senior executive at the NSA, and Edward J. Snowden, who also worked as a computer intelligence consultant at the NSA. As a result of all of these events, it is fairly obvious that the state and its institutions are conducting unethical surveillance to the civilians. However, the two people who raised awareness of this unethical operation by providing classified and declassified NSA documents to the media faced major crises. Both Thomas Drake and Edward Snowden faced charges under the Espionage Act. Despite the fact that two former NSA employees used different methods to prevent these surveillance programs, which were developed to spy on citizens using their taxes, both were charged with treason. In this article, I will discuss the whistleblowing act through Thomas Drake and Edward Snowden examples, as well as the significance of whistleblowing in inspecting institutions with tremendous authority, such as centralized databases. Whistleblowing is described as the act of an employee, typically within the organization, who reveals illegal, immoral, or inefficient information or actions within a private, public, or government institution. Daniel Ellsberg, one of the authors of the document, leaked information concerning the United States' political and military engagement in Vietnam between 1945 and 1967, also known as the Pentagon Papers. These papers, which revealed that the American government of the time did not accurately reflect information about Vietnam to the public, became the subject of the most well-known whistleblowing act in American history. Daniel Ellsberg faced charges under the Espionage Act (Greenberg, 2013). It is problematic to think that sharing the information with the public about crucial topics such as the state is systematically lying to the public or spying on them in a wide surveillance network is equated with espionage. The development of democratic regimes necessitates public debate and regulation of this type of government acts. I will demonstrate the significance through the examples of acts of Edward Snowden and Thomas Drake. The Case of Edward Snowden At one point, Edward Snowden's and Thomas Drake's whistleblowing actions differ. While Edward Snowden got confidential material from the NSA and shared it with the media directly, Thomas Drake initially attempted to prevent or regulate programs run by NSA from inside the organization by taking a legal path. Firstly, using Edward Snowden as an example, I will evaluate the role of becoming an illegal whistleblower by sharing classified information with the public. Edward Snowden released highly classified information from NSA in 2013, revealing the NSA's surveillance operations with the cooperation of telecommunications companies and European governments. Snowden was charged under the Espionage Act and stealing government property by the US Department of Justice, and his passport was canceled by the Department of State. Not only that, the efforts were made to portray him as a traitor. Before leaking the information to the media, Edward Snowden was a 29-year-old consultant who worked for the NSA's Hawaii office and made $200,000 per year (Scheuerman, 2014). Snowden did not reveal this information to a country or organization that is hostile to the United States. He directly shared this material with the media, allowing the public to learn about these surveillance programs. He received no personal benefit from this act, and he risked himself and lost his privileged position in his life. Edward Snowden said to The Guardian reporters; “I really want the focus to be on these documents and the debate which I hope this will trigger among citizens around the globe about what kind of world we want to live in.” He added: “My sole motive is to inform the public as to that which is done in their name and that which is done against them” (Glenn, 2013). Given all of this, Edward Snowden's actions are more similar to civic disobedience than treason or espionage (Scheuerman, 2014). As a United Nations citizen, Edward Snowden revealed to the public the wrongdoing of a governmental institution, making this situation questioned among the public. A democratic government gains from public criticism of its acts, which aids in the development of more ethical institutions. While it is a social benefit to inform the public about a massive government surveillance program, obtaining that information from the NSA and making it available to the public may also benefit the United States' enemies. Institutions also have the opportunity to develop and regulate these programs within their own walls, without any confidential information leaking out. Employees of the institution can file complaints to their supervisors and criticize these programs in a legal path, which is legal whistleblowing, however, in the case of Thomas Drake, we can see that legal whistleblowing puts people's lives at risk at least as much as the illegal version. The Case Of Thomas Drake On September 11, 2001, one of the most devastating days in American history, Thomas Drake began his job at the NSA. In the early years of the new millennium, when America was most vulnerable to external threats and digital data was growing exponentially, a program named Trailblazer caught Drake's attention. Drake saw the initiative as a huge budget waste that did not contribute to national security. He reported his critique to his supervisors, which is considered legal whistleblowing, but his attempts were unsuccessful. Finally, he decided to share his criticism with the media while remaining anonymous, although he did not share any confidential documents with the media. He only served declassified information, which conveys that Trailblazer was an ineffective project that wastes money. Drake was questioned by FBI investigators shortly after and accused of taking classified documents from the NSA. He faced charges of 35 years in jail time for 10 different crimes including the Espionage Act. The court dismissed the case in 2011, stating that the accusations were inappropriate and overstated, and Thomas Drake was sentenced to one year of probation. However, as a result of the entire process, Drake spent $82,000 on legal expenses, was dismissed from both his NSA and university positions, and lost his retirement (Greenberg, 2013). Thomas Drake's experience is an example of how even the slightest criticism of government institutions and their projects can have drastic consequences. The courage to criticize unethical projects is trying to be destroyed by this atmosphere of fear. The whistleblowers, whether they go the legal or illegal path, are aware that they will be prosecuted for espionage, loss of employment, and jail time. At this juncture, I believe we should oppose the totalitarian positions adopted by the institutions, which have vast surveillance networks both domestically and internationally, and we should protect whistleblowers' rights. The United States has two legislations protecting whistleblowers, the Federal Whistleblower Protection Act of 1989 and the Whistleblower Protection Enhancement Act of 2012. According to a 2015 research, the Federal Whistleblower Protection Act of 1989 fails to protect whistleblowers. 79 percent of the 142 cases involving government ethics and administration ended in employee job loss. The Whistleblower Protection Enhancement Act of 2012 is also insufficient in terms of protections of whistleblowers (Peffer, Bocheko, Del Valle, Osmani, Peyton, Roman, 2015). Conclusion The whistleblowing contributes to public debate about the ethics of the state's programs. However, these organizations, which hold a vast surveillance network, damage the democratic process by raising severe allegations against whistleblowers in order to avoid the risk of limiting their authority. We can have an idea of how our data is gathered and used if we have laws and rules that protect whistleblowers. Accusing them with espionage and treason, on the other hand, will gradually create this environment of fear and, as a consequence, silence. Reference Glenn G. (2013, Jun 11). Edward Snowden: the whistleblower behind the NSA surveillance revelations. The Guardian. Retrieved from https://www.theguardian.com/world/2013/jun/09/edward-snowden-nsa-whistleblower-surveillance Greenberg, A. (2013). This machine kills secrets: Julian Assange, the Cypherpunks, and their fight to empower whistleblowers. Penguin. Scheuerman, W. E. (2014). Whistleblowing as civil disobedience: The case of Edward Snowden. Philosophy & Social Criticism, 40(7), 609-628. Stanley, J., & Steinhardt, B. (2014). Bigger monster, weaker chains: the growth of an American surveillance society. In Ethics and Emerging Technologies (pp. 269-284). Palgrave Macmillan, London. Peffer, S. L., Bocheko, A., Del Valle, R. E., Osmani, A., Peyton, S., & Roman, E. (2015).Whistle Where you work? The ineffectiveness of the Federal Whistleblower Protection Act of 1989 and the promise of the Whistleblower Protection Enhancement Act of 2012. Review of Public Personnel Administration, 35(1), 70-81. Verble, J. (2014). The NSA and Edward Snowden: surveillance in the 21st century. ACM SIGCAS Computers and Society, 44(3), 14-20.
@ 19306922:c06688d2
2025-01-31 21:14:52At a time when data-gathering technologies are dominating all aspects of everyday life, governmental agencies such as The National Security Agency have considerable surveillance and control authority. The National Security Agency runs surveillance programs on not just violent international criminals, but also ordinary citizens within the country. A tremendous amount of effort is being made to keep these programs from being critiqued and shared with the public. In this paper, I will discuss whistleblowing and its relevance in establishing a more democratic structure in governmental institutions, through the cases of Edward Snowden and Thomas Drake. Firstly, I will emphasize Edward Snowden's action as an example of illegal whistleblowing and how he acts closer to civic disobedience rather than espionage. Following that, I will discuss Thomas Drake's espionage charge while legally criticizing The National Security Agency's programs and the inadequacy of whistleblower protection laws.  In our everyday lives, we come into contact with or utilize a variety of technological equipment such as security cameras, GPS devices, iris scanners, and so on. Everything we do, from buying things from shopping malls to searching for information on the internet, is kept in massive databases. Without even our knowledge, our data, which is vast enough to create our entire profile, is in the databases of a private firm or the government. That's why the surveillance network is getting bigger and bigger. Most of the surveillance tools and the capability to regulate these tools are under state control. The government also agrees with data aggregators -companies that collect data from multiple sources and make it available to customers in a value-added format- to access more data. The US Department of Justice has an $8 million agreement with data aggregator company ChoicePoint (Stanley, Steinhardt 2014). In this way, The Justice Department can access many civilians' information in the company's database. Although this surveillance mechanism seems to be an effective way to track and detect many illegal incidents such as terrorism, money laundering, etc., this surveillance network can easily be applied to ordinary civilians. For example, in 2002, Attorney General John Ashcroft released new domestic spy guidelines that dramatically expanded federal agents' ability to monitor on American civilians (Stanley, Steinhardt 2014). The American government also is running programs to spy on ordinary citizens, according to information obtained from the National Security Agency documents which leaked to the media on multiple occasions (Greenberg, 2013). The National Security Agency (NSA) began as a cryptology-focused agency and has since grown into an intelligence agency that gathers data from enemies of the United States of America (Verble, 2014). The surveillance and data collection programs of NSA, however, are not carried out just to keep enemies at bay. Information on the NSA's programs was provided to the media by Thomas A. Drake, a senior executive at the NSA, and Edward J. Snowden, who also worked as a computer intelligence consultant at the NSA. As a result of all of these events, it is fairly obvious that the state and its institutions are conducting unethical surveillance to the civilians. However, the two people who raised awareness of this unethical operation by providing classified and declassified NSA documents to the media faced major crises. Both Thomas Drake and Edward Snowden faced charges under the Espionage Act. Despite the fact that two former NSA employees used different methods to prevent these surveillance programs, which were developed to spy on citizens using their taxes, both were charged with treason. In this article, I will discuss the whistleblowing act through Thomas Drake and Edward Snowden examples, as well as the significance of whistleblowing in inspecting institutions with tremendous authority, such as centralized databases. Whistleblowing is described as the act of an employee, typically within the organization, who reveals illegal, immoral, or inefficient information or actions within a private, public, or government institution. Daniel Ellsberg, one of the authors of the document, leaked information concerning the United States' political and military engagement in Vietnam between 1945 and 1967, also known as the Pentagon Papers. These papers, which revealed that the American government of the time did not accurately reflect information about Vietnam to the public, became the subject of the most well-known whistleblowing act in American history. Daniel Ellsberg faced charges under the Espionage Act (Greenberg, 2013). It is problematic to think that sharing the information with the public about crucial topics such as the state is systematically lying to the public or spying on them in a wide surveillance network is equated with espionage. The development of democratic regimes necessitates public debate and regulation of this type of government acts. I will demonstrate the significance through the examples of acts of Edward Snowden and Thomas Drake. The Case of Edward Snowden At one point, Edward Snowden's and Thomas Drake's whistleblowing actions differ. While Edward Snowden got confidential material from the NSA and shared it with the media directly, Thomas Drake initially attempted to prevent or regulate programs run by NSA from inside the organization by taking a legal path. Firstly, using Edward Snowden as an example, I will evaluate the role of becoming an illegal whistleblower by sharing classified information with the public. Edward Snowden released highly classified information from NSA in 2013, revealing the NSA's surveillance operations with the cooperation of telecommunications companies and European governments. Snowden was charged under the Espionage Act and stealing government property by the US Department of Justice, and his passport was canceled by the Department of State. Not only that, the efforts were made to portray him as a traitor. Before leaking the information to the media, Edward Snowden was a 29-year-old consultant who worked for the NSA's Hawaii office and made $200,000 per year (Scheuerman, 2014). Snowden did not reveal this information to a country or organization that is hostile to the United States. He directly shared this material with the media, allowing the public to learn about these surveillance programs. He received no personal benefit from this act, and he risked himself and lost his privileged position in his life. Edward Snowden said to The Guardian reporters; “I really want the focus to be on these documents and the debate which I hope this will trigger among citizens around the globe about what kind of world we want to live in.” He added: “My sole motive is to inform the public as to that which is done in their name and that which is done against them” (Glenn, 2013). Given all of this, Edward Snowden's actions are more similar to civic disobedience than treason or espionage (Scheuerman, 2014). As a United Nations citizen, Edward Snowden revealed to the public the wrongdoing of a governmental institution, making this situation questioned among the public. A democratic government gains from public criticism of its acts, which aids in the development of more ethical institutions. While it is a social benefit to inform the public about a massive government surveillance program, obtaining that information from the NSA and making it available to the public may also benefit the United States' enemies. Institutions also have the opportunity to develop and regulate these programs within their own walls, without any confidential information leaking out. Employees of the institution can file complaints to their supervisors and criticize these programs in a legal path, which is legal whistleblowing, however, in the case of Thomas Drake, we can see that legal whistleblowing puts people's lives at risk at least as much as the illegal version. The Case Of Thomas Drake On September 11, 2001, one of the most devastating days in American history, Thomas Drake began his job at the NSA. In the early years of the new millennium, when America was most vulnerable to external threats and digital data was growing exponentially, a program named Trailblazer caught Drake's attention. Drake saw the initiative as a huge budget waste that did not contribute to national security. He reported his critique to his supervisors, which is considered legal whistleblowing, but his attempts were unsuccessful. Finally, he decided to share his criticism with the media while remaining anonymous, although he did not share any confidential documents with the media. He only served declassified information, which conveys that Trailblazer was an ineffective project that wastes money. Drake was questioned by FBI investigators shortly after and accused of taking classified documents from the NSA. He faced charges of 35 years in jail time for 10 different crimes including the Espionage Act. The court dismissed the case in 2011, stating that the accusations were inappropriate and overstated, and Thomas Drake was sentenced to one year of probation. However, as a result of the entire process, Drake spent $82,000 on legal expenses, was dismissed from both his NSA and university positions, and lost his retirement (Greenberg, 2013). Thomas Drake's experience is an example of how even the slightest criticism of government institutions and their projects can have drastic consequences. The courage to criticize unethical projects is trying to be destroyed by this atmosphere of fear. The whistleblowers, whether they go the legal or illegal path, are aware that they will be prosecuted for espionage, loss of employment, and jail time. At this juncture, I believe we should oppose the totalitarian positions adopted by the institutions, which have vast surveillance networks both domestically and internationally, and we should protect whistleblowers' rights. The United States has two legislations protecting whistleblowers, the Federal Whistleblower Protection Act of 1989 and the Whistleblower Protection Enhancement Act of 2012. According to a 2015 research, the Federal Whistleblower Protection Act of 1989 fails to protect whistleblowers. 79 percent of the 142 cases involving government ethics and administration ended in employee job loss. The Whistleblower Protection Enhancement Act of 2012 is also insufficient in terms of protections of whistleblowers (Peffer, Bocheko, Del Valle, Osmani, Peyton, Roman, 2015). Conclusion The whistleblowing contributes to public debate about the ethics of the state's programs. However, these organizations, which hold a vast surveillance network, damage the democratic process by raising severe allegations against whistleblowers in order to avoid the risk of limiting their authority. We can have an idea of how our data is gathered and used if we have laws and rules that protect whistleblowers. Accusing them with espionage and treason, on the other hand, will gradually create this environment of fear and, as a consequence, silence. Reference Glenn G. (2013, Jun 11). Edward Snowden: the whistleblower behind the NSA surveillance revelations. The Guardian. Retrieved from https://www.theguardian.com/world/2013/jun/09/edward-snowden-nsa-whistleblower-surveillance Greenberg, A. (2013). This machine kills secrets: Julian Assange, the Cypherpunks, and their fight to empower whistleblowers. Penguin. Scheuerman, W. E. (2014). Whistleblowing as civil disobedience: The case of Edward Snowden. Philosophy & Social Criticism, 40(7), 609-628. Stanley, J., & Steinhardt, B. (2014). Bigger monster, weaker chains: the growth of an American surveillance society. In Ethics and Emerging Technologies (pp. 269-284). Palgrave Macmillan, London. Peffer, S. L., Bocheko, A., Del Valle, R. E., Osmani, A., Peyton, S., & Roman, E. (2015).Whistle Where you work? The ineffectiveness of the Federal Whistleblower Protection Act of 1989 and the promise of the Whistleblower Protection Enhancement Act of 2012. Review of Public Personnel Administration, 35(1), 70-81. Verble, J. (2014). The NSA and Edward Snowden: surveillance in the 21st century. ACM SIGCAS Computers and Society, 44(3), 14-20. @ a95c6243:d345522c
2025-01-31 20:02:25*Im Augenblick wird mit größter Intensität, großer Umsicht* *\ das deutsche Volk belogen.* *\ Olaf Scholz im FAZ-[Interview](https://www.youtube.com/watch?v=c3KI1GmdoVc\&t=649s)*   **Online-Wahlen stärken die Demokratie, sind sicher, und 61 Prozent der Wahlberechtigten** sprechen sich für deren Einführung in Deutschland aus. Das zumindest behauptet eine aktuelle Umfrage, die auch über die Agentur *Reuters* Verbreitung in den Medien [gefunden](https://archive.is/dnZbY) hat. Demnach würden außerdem 45 Prozent der Nichtwähler bei der Bundestagswahl ihre Stimme abgeben, wenn sie dies zum Beispiel von Ihrem PC, Tablet oder Smartphone aus machen könnten. **Die telefonische Umfrage unter gut 1000 wahlberechtigten Personen** sei repräsentativ, [behauptet](https://www.bitkom.org/Presse/Presseinformation/Knapp-Haelfte-Nichtwaehler-wuerde-online-waehlen) der Auftraggeber – der Digitalverband Bitkom. Dieser präsentiert sich als eingetragener Verein mit einer beeindruckenden Liste von [Mitgliedern](https://www.bitkom.org/Bitkom/Mitgliedschaft/Mitgliederliste), die Software und IT-Dienstleistungen anbieten. Erklärtes Vereinsziel ist es, «Deutschland zu einem führenden Digitalstandort zu machen und die digitale Transformation der deutschen Wirtschaft und Verwaltung voranzutreiben». **Durchgeführt hat die Befragung die Bitkom Servicegesellschaft mbH,** also alles in der Familie. Die gleiche Erhebung hatte der Verband übrigens 2021 schon einmal durchgeführt. Damals sprachen sich angeblich sogar 63 Prozent für ein derartiges [«Demokratie-Update»](https://www.experten.de/id/4922407/online-wahlen-als-update-des-demokratischen-systems/) aus – die Tendenz ist demgemäß fallend. Dennoch orakelt mancher, der Gang zur Wahlurne gelte bereits als veraltet. **Die spanische Privat-Uni mit Globalisten-Touch, IE University, berichtete** Ende letzten Jahres in ihrer Studie «European Tech Insights», 67 Prozent der Europäer [befürchteten](https://www.ie.edu/university/news-events/news/67-europeans-fear-ai-manipulation-elections-according-ie-university-research/), dass Hacker Wahlergebnisse verfälschen könnten. Mehr als 30 Prozent der Befragten glaubten, dass künstliche Intelligenz (KI) bereits Wahlentscheidungen beeinflusst habe. Trotzdem würden angeblich 34 Prozent der unter 35-Jährigen einer KI-gesteuerten App vertrauen, um in ihrem Namen für politische Kandidaten zu stimmen. **Wie dauerhaft wird wohl das Ergebnis der kommenden Bundestagswahl sein?** Diese Frage stellt sich angesichts der aktuellen Entwicklung der Migrations-Debatte und der (vorübergehend) bröckelnden «Brandmauer» gegen die AfD. Das «Zustrombegrenzungsgesetz» der Union hat das Parlament heute Nachmittag überraschenderweise [abgelehnt](https://www.bundestag.de/dokumente/textarchiv/2025/kw05-de-zustrombegrenzungsgesetz-1042038). Dennoch muss man wohl kein ausgesprochener Pessimist sein, um zu befürchten, dass die Entscheidungen der Bürger von den selbsternannten Verteidigern der Demokratie künftig vielleicht nicht respektiert werden, weil sie nicht gefallen. **Bundesweit wird jetzt zu «Brandmauer-Demos» aufgerufen,** die CDU gerät unter Druck und es wird von Übergriffen auf Parteibüros und Drohungen gegen Mitarbeiter [berichtet](https://www.epochtimes.de/politik/deutschland/brandmauer-proteste-cdu-zentrale-geraeumt-kundgebungen-in-46-staedten-a5023745.html). Sicherheitsbehörden warnen vor Eskalationen, die Polizei sei «für ein mögliches erhöhtes Aufkommen von Straftaten gegenüber Politikern und gegen Parteigebäude sensibilisiert». **Der Vorwand** **[«unzulässiger Einflussnahme»](https://transition-news.org/die-minister-faeser-und-wissing-sorgen-sich-um-unzulassige-einflussnahme-auf)** **auf Politik und Wahlen** wird als Argument schon seit einiger Zeit aufgebaut. Der Manipulation schuldig befunden wird neben Putin und Trump auch Elon Musk, was lustigerweise ausgerechnet Bill Gates gerade noch einmal bekräftigt und als [«völlig irre»](https://transition-news.org/bill-gates-nennt-musks-einmischung-in-eu-politik-vollig-irre) bezeichnet hat. Man stelle sich die Diskussionen um die Gültigkeit von Wahlergebnissen vor, wenn es Online-Verfahren zur Stimmabgabe gäbe. In der Schweiz wird [«E-Voting»](https://www.ch.ch/de/abstimmungen-und-wahlen/e-voting/) seit einigen Jahren getestet, aber wohl bisher mit wenig Erfolg. **Die politische Brandstiftung der letzten Jahre zahlt sich immer mehr aus.** Anstatt dringende Probleme der Menschen zu lösen – zu denen auch in Deutschland die [weit verbreitete Armut](https://transition-news.org/ein-funftel-der-bevolkerung-in-deutschland-ist-von-armut-oder-sozialer) zählt –, hat die Politik konsequent polarisiert und sich auf Ausgrenzung und Verhöhnung großer Teile der Bevölkerung konzentriert. Basierend auf Ideologie und Lügen werden abweichende Stimmen unterdrückt und kriminalisiert, nicht nur und nicht erst in diesem Augenblick. Die nächsten Wochen dürften ausgesprochen spannend werden. *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/wahlen-und-wahlen-lassen)*** erschienen.
@ a95c6243:d345522c
2025-01-31 20:02:25*Im Augenblick wird mit größter Intensität, großer Umsicht* *\ das deutsche Volk belogen.* *\ Olaf Scholz im FAZ-[Interview](https://www.youtube.com/watch?v=c3KI1GmdoVc\&t=649s)*   **Online-Wahlen stärken die Demokratie, sind sicher, und 61 Prozent der Wahlberechtigten** sprechen sich für deren Einführung in Deutschland aus. Das zumindest behauptet eine aktuelle Umfrage, die auch über die Agentur *Reuters* Verbreitung in den Medien [gefunden](https://archive.is/dnZbY) hat. Demnach würden außerdem 45 Prozent der Nichtwähler bei der Bundestagswahl ihre Stimme abgeben, wenn sie dies zum Beispiel von Ihrem PC, Tablet oder Smartphone aus machen könnten. **Die telefonische Umfrage unter gut 1000 wahlberechtigten Personen** sei repräsentativ, [behauptet](https://www.bitkom.org/Presse/Presseinformation/Knapp-Haelfte-Nichtwaehler-wuerde-online-waehlen) der Auftraggeber – der Digitalverband Bitkom. Dieser präsentiert sich als eingetragener Verein mit einer beeindruckenden Liste von [Mitgliedern](https://www.bitkom.org/Bitkom/Mitgliedschaft/Mitgliederliste), die Software und IT-Dienstleistungen anbieten. Erklärtes Vereinsziel ist es, «Deutschland zu einem führenden Digitalstandort zu machen und die digitale Transformation der deutschen Wirtschaft und Verwaltung voranzutreiben». **Durchgeführt hat die Befragung die Bitkom Servicegesellschaft mbH,** also alles in der Familie. Die gleiche Erhebung hatte der Verband übrigens 2021 schon einmal durchgeführt. Damals sprachen sich angeblich sogar 63 Prozent für ein derartiges [«Demokratie-Update»](https://www.experten.de/id/4922407/online-wahlen-als-update-des-demokratischen-systems/) aus – die Tendenz ist demgemäß fallend. Dennoch orakelt mancher, der Gang zur Wahlurne gelte bereits als veraltet. **Die spanische Privat-Uni mit Globalisten-Touch, IE University, berichtete** Ende letzten Jahres in ihrer Studie «European Tech Insights», 67 Prozent der Europäer [befürchteten](https://www.ie.edu/university/news-events/news/67-europeans-fear-ai-manipulation-elections-according-ie-university-research/), dass Hacker Wahlergebnisse verfälschen könnten. Mehr als 30 Prozent der Befragten glaubten, dass künstliche Intelligenz (KI) bereits Wahlentscheidungen beeinflusst habe. Trotzdem würden angeblich 34 Prozent der unter 35-Jährigen einer KI-gesteuerten App vertrauen, um in ihrem Namen für politische Kandidaten zu stimmen. **Wie dauerhaft wird wohl das Ergebnis der kommenden Bundestagswahl sein?** Diese Frage stellt sich angesichts der aktuellen Entwicklung der Migrations-Debatte und der (vorübergehend) bröckelnden «Brandmauer» gegen die AfD. Das «Zustrombegrenzungsgesetz» der Union hat das Parlament heute Nachmittag überraschenderweise [abgelehnt](https://www.bundestag.de/dokumente/textarchiv/2025/kw05-de-zustrombegrenzungsgesetz-1042038). Dennoch muss man wohl kein ausgesprochener Pessimist sein, um zu befürchten, dass die Entscheidungen der Bürger von den selbsternannten Verteidigern der Demokratie künftig vielleicht nicht respektiert werden, weil sie nicht gefallen. **Bundesweit wird jetzt zu «Brandmauer-Demos» aufgerufen,** die CDU gerät unter Druck und es wird von Übergriffen auf Parteibüros und Drohungen gegen Mitarbeiter [berichtet](https://www.epochtimes.de/politik/deutschland/brandmauer-proteste-cdu-zentrale-geraeumt-kundgebungen-in-46-staedten-a5023745.html). Sicherheitsbehörden warnen vor Eskalationen, die Polizei sei «für ein mögliches erhöhtes Aufkommen von Straftaten gegenüber Politikern und gegen Parteigebäude sensibilisiert». **Der Vorwand** **[«unzulässiger Einflussnahme»](https://transition-news.org/die-minister-faeser-und-wissing-sorgen-sich-um-unzulassige-einflussnahme-auf)** **auf Politik und Wahlen** wird als Argument schon seit einiger Zeit aufgebaut. Der Manipulation schuldig befunden wird neben Putin und Trump auch Elon Musk, was lustigerweise ausgerechnet Bill Gates gerade noch einmal bekräftigt und als [«völlig irre»](https://transition-news.org/bill-gates-nennt-musks-einmischung-in-eu-politik-vollig-irre) bezeichnet hat. Man stelle sich die Diskussionen um die Gültigkeit von Wahlergebnissen vor, wenn es Online-Verfahren zur Stimmabgabe gäbe. In der Schweiz wird [«E-Voting»](https://www.ch.ch/de/abstimmungen-und-wahlen/e-voting/) seit einigen Jahren getestet, aber wohl bisher mit wenig Erfolg. **Die politische Brandstiftung der letzten Jahre zahlt sich immer mehr aus.** Anstatt dringende Probleme der Menschen zu lösen – zu denen auch in Deutschland die [weit verbreitete Armut](https://transition-news.org/ein-funftel-der-bevolkerung-in-deutschland-ist-von-armut-oder-sozialer) zählt –, hat die Politik konsequent polarisiert und sich auf Ausgrenzung und Verhöhnung großer Teile der Bevölkerung konzentriert. Basierend auf Ideologie und Lügen werden abweichende Stimmen unterdrückt und kriminalisiert, nicht nur und nicht erst in diesem Augenblick. Die nächsten Wochen dürften ausgesprochen spannend werden. *** Dieser Beitrag ist zuerst auf ***[Transition News](https://transition-news.org/wahlen-und-wahlen-lassen)*** erschienen. @ 3ccfd5ee:2efa0073
2025-01-31 17:24:28BYD Cars Philippines and ACMobility, the Philippine distributor of BYD vehicles, have pledged to donate $100 to Super Typhoon Carina's victims for every BYD Sealion 6 DM-i sold from July 25, 2024 until December 31, 2024. This campaign is part of both companies' broader efforts to the affected communities and reflects their dedication to social responsibility. In fact, ACMobility was one of the first to mobilize disaster response efforts by distributing relief goods to over 100 families in Dela Paz, Pasig City, on July 26. Employees and volunteers from ACMobility, BYD Cars Philippines, and its affiliate agencies participated in the cause. “On behalf of BYD, I would like to express my sympathy to the people affected by Typhoon Carina. We, together with ACMobility, wish to extend BYD's support to Filipinos who suffered from this unfortunate disaster,” said BYD Asia Pacific Auto Sales Division General Manager Liu Xueliang. The [BYD Sealion 6 DM-i](https://bydcarsphilippines.com/vehicles/byd-sealion6-dmi) is an all-electric compact SUV that runs on BYD's proprietary Super DM-i Technology—generating power well beyond the typical electric vehicle. It generates 217 horsepower and 325 Newton meters of torque, enabling it to go from zero to a hundred in just over eight seconds. Furthermore, the vehicle runs on Blade Battery, allowing it to drive up to 105 kilometers in Pure EV Mode and 1,100 km in Extended Range Mode. It empowers drivers to travel without range anxiety. Attendees of ACMobility and BYD Cars Philippines' relief drive even used the Sealion 6 DM-i's Blade Battery to charge devices on-site. The Sealion 6 DM-i starts at ₱1,548,000. With every unit sold, BYD and ACMotors donate $100 to Typhoon Carina's victims until the end of 2024. "Guided by our company value of malasakit, we remain committed to going above and beyond in serving our communities during these trying times," BYD Cars Philippines Managing Director Bob Palanca shared. Super Typhoon Carina—internationally known as Gaemi—brought widespread devastation across the Philippines. The National Disaster Risk Reduction and Management Council (NDRRMC) stated that Carina, on top of the southwest monsoon, affected over 1.3 million Filipinos. ## About BYD Cars Philippines BYD Cars Philippines is a leader in the Filipino EV industry. As the Philippine arm of the globally renowned electric car and battery manufacturer, it brings cutting-edge technology and powerful yet comfortable drives to the local sustainable mobility market. The EV manufacturer has a range of models designed to address the needs of Filipinos, from affordable cars to luxury SUVs. Each vehicle's cutting-edge tech and superior safety features make every purchase worth it. Most importantly, BYD addresses the growing demand for eco-friendly cars and actively participates in initiatives to build greener mobility infrastructure for Filipinos. Visit [BYD Cars Philippines' website](https://bydcarsphilippines.com/) today to learn more.
@ 3ccfd5ee:2efa0073
2025-01-31 17:24:28BYD Cars Philippines and ACMobility, the Philippine distributor of BYD vehicles, have pledged to donate $100 to Super Typhoon Carina's victims for every BYD Sealion 6 DM-i sold from July 25, 2024 until December 31, 2024. This campaign is part of both companies' broader efforts to the affected communities and reflects their dedication to social responsibility. In fact, ACMobility was one of the first to mobilize disaster response efforts by distributing relief goods to over 100 families in Dela Paz, Pasig City, on July 26. Employees and volunteers from ACMobility, BYD Cars Philippines, and its affiliate agencies participated in the cause. “On behalf of BYD, I would like to express my sympathy to the people affected by Typhoon Carina. We, together with ACMobility, wish to extend BYD's support to Filipinos who suffered from this unfortunate disaster,” said BYD Asia Pacific Auto Sales Division General Manager Liu Xueliang. The [BYD Sealion 6 DM-i](https://bydcarsphilippines.com/vehicles/byd-sealion6-dmi) is an all-electric compact SUV that runs on BYD's proprietary Super DM-i Technology—generating power well beyond the typical electric vehicle. It generates 217 horsepower and 325 Newton meters of torque, enabling it to go from zero to a hundred in just over eight seconds. Furthermore, the vehicle runs on Blade Battery, allowing it to drive up to 105 kilometers in Pure EV Mode and 1,100 km in Extended Range Mode. It empowers drivers to travel without range anxiety. Attendees of ACMobility and BYD Cars Philippines' relief drive even used the Sealion 6 DM-i's Blade Battery to charge devices on-site. The Sealion 6 DM-i starts at ₱1,548,000. With every unit sold, BYD and ACMotors donate $100 to Typhoon Carina's victims until the end of 2024. "Guided by our company value of malasakit, we remain committed to going above and beyond in serving our communities during these trying times," BYD Cars Philippines Managing Director Bob Palanca shared. Super Typhoon Carina—internationally known as Gaemi—brought widespread devastation across the Philippines. The National Disaster Risk Reduction and Management Council (NDRRMC) stated that Carina, on top of the southwest monsoon, affected over 1.3 million Filipinos. ## About BYD Cars Philippines BYD Cars Philippines is a leader in the Filipino EV industry. As the Philippine arm of the globally renowned electric car and battery manufacturer, it brings cutting-edge technology and powerful yet comfortable drives to the local sustainable mobility market. The EV manufacturer has a range of models designed to address the needs of Filipinos, from affordable cars to luxury SUVs. Each vehicle's cutting-edge tech and superior safety features make every purchase worth it. Most importantly, BYD addresses the growing demand for eco-friendly cars and actively participates in initiatives to build greener mobility infrastructure for Filipinos. Visit [BYD Cars Philippines' website](https://bydcarsphilippines.com/) today to learn more. @ 3ccfd5ee:2efa0073
2025-01-31 17:05:59Penis size is a topic that many people feel curious or insecure about. It’s important to approach this subject with an understanding of the wide range of normal sizes and the various options available for those who may be interested in enlargement procedures. For some, the use of sex toys or dildos may be a practical solution to enhance sexual experiences, while others may look into enlargement procedures. Here’s a brief overview of what you should know about average penis size and the options available for enlargement. ## What is the Average Penis Size? Studies consistently show that the average erect penis size is around 5 to 6 inches in length, and the average flaccid size is about 3 to 4 inches. It’s crucial to recognize that penis size varies among individuals, and there is a broad spectrum of what is considered normal. Factors like body type, genetics, and age can all influence size. Most men’s sizes fall within this range, and concerns about size often arise from misconceptions rather than actual medical issues. ## Penis Enlargment as an Alternative For those interested in [penis enlargement](https://pinkbunny.ph/blog/penis-enlargement-in-the-philippines-should-you-do-it/), there are a few options available. These include surgical procedures, non-surgical devices, and sometimes even the use of [sex toys](https://pinkbunny.ph/) to create a fuller feeling or enhance size temporarily. Here’s a closer look at the most common methods: ### Surgical Procedures One of the most well-known surgical options is penile lengthening surgery, where a surgeon cuts the suspensory ligament that supports the penis, allowing it to hang lower. While the procedure can result in a modest increase in length, it carries risks such as infection, scarring, and potential issues with erectile function. Always consult with a qualified healthcare provider before considering surgery. ### Non-Surgical Options Devices like penis pumps or penile traction devices are often used to temporarily increase size. A penis pump creates a vacuum that draws blood into the penis, temporarily making it appear larger. Traction devices apply gentle pressure to the penis over time, which can result in gradual lengthening. Both of these methods can offer temporary improvements, but they require consistent use and do not guarantee long-lasting results. ### Sex Toys and Dildos For those looking for a more immediate solution, dildos and other sex toys can offer a way to enhance sexual pleasure without altering physical size. These toys come in a wide range of shapes, sizes, and materials, allowing individuals and couples to explore different sensations. Find a [dildo for sale](https://pinkbunny.ph/product-category/sex-toys/dildos/) that can provide added size during intercourse, and using sex toys can also help individuals become more comfortable with their bodies, leading to better self-esteem and sexual confidence. ### Penis Enlargement Pills or Supplements Many products on the market claim to increase penis size, but the effectiveness of these pills is largely unproven. Medical experts often caution against using such supplements, as they can have unwanted side effects and are not regulated.
@ 3ccfd5ee:2efa0073
2025-01-31 17:05:59Penis size is a topic that many people feel curious or insecure about. It’s important to approach this subject with an understanding of the wide range of normal sizes and the various options available for those who may be interested in enlargement procedures. For some, the use of sex toys or dildos may be a practical solution to enhance sexual experiences, while others may look into enlargement procedures. Here’s a brief overview of what you should know about average penis size and the options available for enlargement. ## What is the Average Penis Size? Studies consistently show that the average erect penis size is around 5 to 6 inches in length, and the average flaccid size is about 3 to 4 inches. It’s crucial to recognize that penis size varies among individuals, and there is a broad spectrum of what is considered normal. Factors like body type, genetics, and age can all influence size. Most men’s sizes fall within this range, and concerns about size often arise from misconceptions rather than actual medical issues. ## Penis Enlargment as an Alternative For those interested in [penis enlargement](https://pinkbunny.ph/blog/penis-enlargement-in-the-philippines-should-you-do-it/), there are a few options available. These include surgical procedures, non-surgical devices, and sometimes even the use of [sex toys](https://pinkbunny.ph/) to create a fuller feeling or enhance size temporarily. Here’s a closer look at the most common methods: ### Surgical Procedures One of the most well-known surgical options is penile lengthening surgery, where a surgeon cuts the suspensory ligament that supports the penis, allowing it to hang lower. While the procedure can result in a modest increase in length, it carries risks such as infection, scarring, and potential issues with erectile function. Always consult with a qualified healthcare provider before considering surgery. ### Non-Surgical Options Devices like penis pumps or penile traction devices are often used to temporarily increase size. A penis pump creates a vacuum that draws blood into the penis, temporarily making it appear larger. Traction devices apply gentle pressure to the penis over time, which can result in gradual lengthening. Both of these methods can offer temporary improvements, but they require consistent use and do not guarantee long-lasting results. ### Sex Toys and Dildos For those looking for a more immediate solution, dildos and other sex toys can offer a way to enhance sexual pleasure without altering physical size. These toys come in a wide range of shapes, sizes, and materials, allowing individuals and couples to explore different sensations. Find a [dildo for sale](https://pinkbunny.ph/product-category/sex-toys/dildos/) that can provide added size during intercourse, and using sex toys can also help individuals become more comfortable with their bodies, leading to better self-esteem and sexual confidence. ### Penis Enlargement Pills or Supplements Many products on the market claim to increase penis size, but the effectiveness of these pills is largely unproven. Medical experts often caution against using such supplements, as they can have unwanted side effects and are not regulated. @ 3ccfd5ee:2efa0073
2025-01-31 16:50:06To stay competitive, many companies are outsourcing key administrative and management functions in manufacturing. This approach helps businesses better manage deliverables, reduce costs, utilize advanced technology, and navigate changing labor dynamics. ## What is Outsource Manufacturing? [Outsourcing manufacturing](https://optibpo.com/blog/a-guide-to-outsource-manufacturing/) involves delegating not only production but also important administrative and management tasks to external providers, rather than handling everything in-house. These tasks often include non-core activities such as supply chain management, procurement, quality assurance, and compliance. By partnering with specialized manufacturers, often in regions with lower labor and operational costs, companies can take advantage of their expertise and efficiency. The process typically begins with selecting a trusted manufacturer, negotiating contracts, and overseeing production to ensure quality and timely delivery. ## 5 Types of Outsource Manufacturing Services Outsourcing specific tasks can streamline your operations and reduce costs. Here’s an overview of the key outsourcing services for manufacturing: ### Contract Management Managing contracts with manufacturers and suppliers can be complex and time-consuming. By outsourcing this function, you allow experts to handle negotiations, oversee agreements, and ensure smooth operations, reducing legal risks and freeing you to focus on other vital business areas. ### Supplier Management Supplier management includes finding and vetting suppliers based on quality, pricing, and reliability. By building a dedicated team through optiBPO in the Philippines, you can streamline this process. The team will handle negotiations and ensure that suppliers meet your standards, giving you full control without the administrative burden. ### Logistics Coordination From transportation to warehousing, logistics coordination involves many moving parts. Outsourcing this function to a skilled team, like one from optiBPO, allows you to optimize the logistics process, choosing the best transportation methods and balancing cost, speed, and reliability. This ensures efficient and timely product deliveries. ### Quality Assurance Coordination Consistently maintaining high product quality is essential for customer satisfaction and brand reputation. Outsourcing quality assurance lets a team of professionals handle inspections, compliance checks, and data analysis to reduce defects, enhance product reliability, and maintain high standards. ### Inventory Management Managing inventory levels, ordering, and stock maintenance can be overwhelming. By outsourcing these administrative tasks, your external team can monitor inventory, forecast demand, and coordinate with suppliers to ensure stock is always replenished on time. Services from optiBPO can streamline this process and keep operations running smoothly. ## In Conclusion By outsourcing these crucial functions, your business can gain access to expertise, improve efficiency, and reduce costs—ultimately allowing you to focus on what matters most: growing your business. You can learn more about ousource manufacturing through this infographic. https://sp-ao.shortpixel.ai/client/to_webp,q_glossy,ret_img,w_800/https://optibpo.com/wp-content/uploads/2024/10/outsource_manufacturing_Info8.png
@ 3ccfd5ee:2efa0073
2025-01-31 16:50:06To stay competitive, many companies are outsourcing key administrative and management functions in manufacturing. This approach helps businesses better manage deliverables, reduce costs, utilize advanced technology, and navigate changing labor dynamics. ## What is Outsource Manufacturing? [Outsourcing manufacturing](https://optibpo.com/blog/a-guide-to-outsource-manufacturing/) involves delegating not only production but also important administrative and management tasks to external providers, rather than handling everything in-house. These tasks often include non-core activities such as supply chain management, procurement, quality assurance, and compliance. By partnering with specialized manufacturers, often in regions with lower labor and operational costs, companies can take advantage of their expertise and efficiency. The process typically begins with selecting a trusted manufacturer, negotiating contracts, and overseeing production to ensure quality and timely delivery. ## 5 Types of Outsource Manufacturing Services Outsourcing specific tasks can streamline your operations and reduce costs. Here’s an overview of the key outsourcing services for manufacturing: ### Contract Management Managing contracts with manufacturers and suppliers can be complex and time-consuming. By outsourcing this function, you allow experts to handle negotiations, oversee agreements, and ensure smooth operations, reducing legal risks and freeing you to focus on other vital business areas. ### Supplier Management Supplier management includes finding and vetting suppliers based on quality, pricing, and reliability. By building a dedicated team through optiBPO in the Philippines, you can streamline this process. The team will handle negotiations and ensure that suppliers meet your standards, giving you full control without the administrative burden. ### Logistics Coordination From transportation to warehousing, logistics coordination involves many moving parts. Outsourcing this function to a skilled team, like one from optiBPO, allows you to optimize the logistics process, choosing the best transportation methods and balancing cost, speed, and reliability. This ensures efficient and timely product deliveries. ### Quality Assurance Coordination Consistently maintaining high product quality is essential for customer satisfaction and brand reputation. Outsourcing quality assurance lets a team of professionals handle inspections, compliance checks, and data analysis to reduce defects, enhance product reliability, and maintain high standards. ### Inventory Management Managing inventory levels, ordering, and stock maintenance can be overwhelming. By outsourcing these administrative tasks, your external team can monitor inventory, forecast demand, and coordinate with suppliers to ensure stock is always replenished on time. Services from optiBPO can streamline this process and keep operations running smoothly. ## In Conclusion By outsourcing these crucial functions, your business can gain access to expertise, improve efficiency, and reduce costs—ultimately allowing you to focus on what matters most: growing your business. You can learn more about ousource manufacturing through this infographic. https://sp-ao.shortpixel.ai/client/to_webp,q_glossy,ret_img,w_800/https://optibpo.com/wp-content/uploads/2024/10/outsource_manufacturing_Info8.png @ c68e2176:4439e6cf
2025-01-31 16:41:061:1 The record of the genealogy of Jesus the Messiah, the son of David, the son of Abraham: 2 Abraham was the father of Isaac, Isaac the father of Jacob, and Jacob the father of Judah and his brothers. 3 Judah was the father of Perez and Zerah by Tamar, Perez was the father of Hezron, and Hezron the father of Ram. 4 Ram was the father of Amminadab, Amminadab the father of Nahshon, and Nahshon the father of Salmon. 5 Salmon was the father of Boaz by Rahab, Boaz was the father of Obed by Ruth, and Obed the father of Jesse. 6 Jesse was the father of David the king. David was the father of Solomon by Bathsheba who had been the wife of Uriah. 7 Solomon was the father of Rehoboam, Rehoboam the father of Abijah, and Abijah the father of Asa. 8 Asa was the father of Jehoshaphat, Jehoshaphat the father of Joram, and Joram the father of Uzziah. 9 Uzziah was the father of Jotham, Jotham the father of Ahaz, and Ahaz the father of Hezekiah. 10 Hezekiah was the father of Manasseh, Manasseh the father of Amon, and Amon the father of Josiah. 11 Josiah became the father of Jeconiah and his brothers, at the time of the deportation to Babylon. 12 After the deportation to Babylon: Jeconiah became the father of Shealtiel, and Shealtiel the father of Zerubbabel. 13 Zerubbabel was the father of Abihud, Abihud the father of Eliakim, and Eliakim the father of Azor. 14 Azor was the father of Zadok, Zadok the father of Achim, and Achim the father of Eliud. 15 Eliud was the father of Eleazar, Eleazar the father of Matthan, and Matthan the father of Jacob. 16 Jacob was the father of Joseph the husband of Mary, by whom Jesus was born, who is called the Messiah. 17 So all the generations from Abraham to David are fourteen generations; from David to the deportation to Babylon, fourteen generations; and from the deportation to Babylon to the Messiah, fourteen generations. 18 Now the birth of Jesus Christ was as follows: when His mother Mary had been betrothed to Joseph, before they came together she was found to be with child by the Holy Spirit. 19 And Joseph her husband, being a righteous man and not wanting to disgrace her, planned to send her away secretly. 20 But when he had considered this, behold, an angel of the Lord appeared to him in a dream, saying, “Joseph, son of David, do not be afraid to take Mary as your wife; for the Child who has been conceived in her is of the Holy Spirit. 21 She will bear a Son; and you shall call His name Jesus, for He will save His people from their sins.” 22 Now all this took place to fulfill what was spoken by the Lord through the prophet: 23 “BEHOLD, THE VIRGIN SHALL BE WITH CHILD AND SHALL BEAR A SON, AND THEY SHALL CALL HIS NAME IMMANUEL,” which translated means, “GOD WITH US.” 24 And Joseph awoke from his sleep and did as the angel of the Lord commanded him, and took Mary as his wife, 25 but kept her a virgin until she gave birth to a Son; and he called His name Jesus.**1:1** The record of the genealogy of Jesus the Messiah, the son of David, the son of Abraham:\ **2** Abraham was the father of Isaac, Isaac the father of Jacob, and Jacob the father of Judah and his brothers.\ 3 Judah was the father of Perez and Zerah by Tamar, Perez was the father of Hezron, and Hezron the father of Ram.\ 4 Ram was the father of Amminadab, Amminadab the father of Nahshon, and Nahshon the father of Salmon.\ 5 Salmon was the father of Boaz by Rahab, Boaz was the father of Obed by Ruth, and Obed the father of Jesse.\ 6 Jesse was the father of David the king.\ David was the father of Solomon by Bathsheba who had been the wife of Uriah.\ 7 Solomon was the father of Rehoboam, Rehoboam the father of Abijah, and Abijah the father of Asa.\ 8 Asa was the father of Jehoshaphat, Jehoshaphat the father of Joram, and Joram the father of Uzziah.\ 9 Uzziah was the father of Jotham, Jotham the father of Ahaz, and Ahaz the father of Hezekiah.\ 10 Hezekiah was the father of Manasseh, Manasseh the father of Amon, and Amon the father of Josiah.\ 11 Josiah became the father of Jeconiah and his brothers, at the time of the deportation to Babylon.\ **12** After the deportation to Babylon: Jeconiah became the father of Shealtiel, and Shealtiel the father of Zerubbabel.\ 13 Zerubbabel was the father of Abihud, Abihud the father of Eliakim, and Eliakim the father of Azor.\ 14 Azor was the father of Zadok, Zadok the father of Achim, and Achim the father of Eliud.\ 15 Eliud was the father of Eleazar, Eleazar the father of Matthan, and Matthan the father of Jacob.\ 16 Jacob was the father of Joseph the husband of Mary, by whom Jesus was born, who is called the Messiah.\ **17** So all the generations from Abraham to David are fourteen generations; from David to the deportation to Babylon, fourteen generations; and from the deportation to Babylon to the Messiah, fourteen generations.\ **18** Now the birth of Jesus Christ was as follows: when His mother Mary had been betrothed to Joseph, before they came together she was found to be with child by the Holy Spirit.\ 19 And Joseph her husband, being a righteous man and not wanting to disgrace her, planned to send her away secretly.\ 20 But when he had considered this, behold, an angel of the Lord appeared to him in a dream, saying, “Joseph, son of David, do not be afraid to take Mary as your wife; for the Child who has been conceived in her is of the Holy Spirit.\ 21 She will bear a Son; and you shall call His name Jesus, for He will save His people from their sins.”\ 22 Now all this took place to fulfill what was spoken by the Lord through the prophet:\ 23 “BEHOLD, THE VIRGIN SHALL BE WITH CHILD AND SHALL BEAR A SON, AND THEY SHALL CALL HIS NAME IMMANUEL,” which translated means, “GOD WITH US.”\ 24 And Joseph awoke from his sleep and did as the angel of the Lord commanded him, and took *Mary* as his wife,\ 25 but kept her a virgin until she gave birth to a Son; and he called His name Jesus.
@ c68e2176:4439e6cf
2025-01-31 16:41:061:1 The record of the genealogy of Jesus the Messiah, the son of David, the son of Abraham: 2 Abraham was the father of Isaac, Isaac the father of Jacob, and Jacob the father of Judah and his brothers. 3 Judah was the father of Perez and Zerah by Tamar, Perez was the father of Hezron, and Hezron the father of Ram. 4 Ram was the father of Amminadab, Amminadab the father of Nahshon, and Nahshon the father of Salmon. 5 Salmon was the father of Boaz by Rahab, Boaz was the father of Obed by Ruth, and Obed the father of Jesse. 6 Jesse was the father of David the king. David was the father of Solomon by Bathsheba who had been the wife of Uriah. 7 Solomon was the father of Rehoboam, Rehoboam the father of Abijah, and Abijah the father of Asa. 8 Asa was the father of Jehoshaphat, Jehoshaphat the father of Joram, and Joram the father of Uzziah. 9 Uzziah was the father of Jotham, Jotham the father of Ahaz, and Ahaz the father of Hezekiah. 10 Hezekiah was the father of Manasseh, Manasseh the father of Amon, and Amon the father of Josiah. 11 Josiah became the father of Jeconiah and his brothers, at the time of the deportation to Babylon. 12 After the deportation to Babylon: Jeconiah became the father of Shealtiel, and Shealtiel the father of Zerubbabel. 13 Zerubbabel was the father of Abihud, Abihud the father of Eliakim, and Eliakim the father of Azor. 14 Azor was the father of Zadok, Zadok the father of Achim, and Achim the father of Eliud. 15 Eliud was the father of Eleazar, Eleazar the father of Matthan, and Matthan the father of Jacob. 16 Jacob was the father of Joseph the husband of Mary, by whom Jesus was born, who is called the Messiah. 17 So all the generations from Abraham to David are fourteen generations; from David to the deportation to Babylon, fourteen generations; and from the deportation to Babylon to the Messiah, fourteen generations. 18 Now the birth of Jesus Christ was as follows: when His mother Mary had been betrothed to Joseph, before they came together she was found to be with child by the Holy Spirit. 19 And Joseph her husband, being a righteous man and not wanting to disgrace her, planned to send her away secretly. 20 But when he had considered this, behold, an angel of the Lord appeared to him in a dream, saying, “Joseph, son of David, do not be afraid to take Mary as your wife; for the Child who has been conceived in her is of the Holy Spirit. 21 She will bear a Son; and you shall call His name Jesus, for He will save His people from their sins.” 22 Now all this took place to fulfill what was spoken by the Lord through the prophet: 23 “BEHOLD, THE VIRGIN SHALL BE WITH CHILD AND SHALL BEAR A SON, AND THEY SHALL CALL HIS NAME IMMANUEL,” which translated means, “GOD WITH US.” 24 And Joseph awoke from his sleep and did as the angel of the Lord commanded him, and took Mary as his wife, 25 but kept her a virgin until she gave birth to a Son; and he called His name Jesus.**1:1** The record of the genealogy of Jesus the Messiah, the son of David, the son of Abraham:\ **2** Abraham was the father of Isaac, Isaac the father of Jacob, and Jacob the father of Judah and his brothers.\ 3 Judah was the father of Perez and Zerah by Tamar, Perez was the father of Hezron, and Hezron the father of Ram.\ 4 Ram was the father of Amminadab, Amminadab the father of Nahshon, and Nahshon the father of Salmon.\ 5 Salmon was the father of Boaz by Rahab, Boaz was the father of Obed by Ruth, and Obed the father of Jesse.\ 6 Jesse was the father of David the king.\ David was the father of Solomon by Bathsheba who had been the wife of Uriah.\ 7 Solomon was the father of Rehoboam, Rehoboam the father of Abijah, and Abijah the father of Asa.\ 8 Asa was the father of Jehoshaphat, Jehoshaphat the father of Joram, and Joram the father of Uzziah.\ 9 Uzziah was the father of Jotham, Jotham the father of Ahaz, and Ahaz the father of Hezekiah.\ 10 Hezekiah was the father of Manasseh, Manasseh the father of Amon, and Amon the father of Josiah.\ 11 Josiah became the father of Jeconiah and his brothers, at the time of the deportation to Babylon.\ **12** After the deportation to Babylon: Jeconiah became the father of Shealtiel, and Shealtiel the father of Zerubbabel.\ 13 Zerubbabel was the father of Abihud, Abihud the father of Eliakim, and Eliakim the father of Azor.\ 14 Azor was the father of Zadok, Zadok the father of Achim, and Achim the father of Eliud.\ 15 Eliud was the father of Eleazar, Eleazar the father of Matthan, and Matthan the father of Jacob.\ 16 Jacob was the father of Joseph the husband of Mary, by whom Jesus was born, who is called the Messiah.\ **17** So all the generations from Abraham to David are fourteen generations; from David to the deportation to Babylon, fourteen generations; and from the deportation to Babylon to the Messiah, fourteen generations.\ **18** Now the birth of Jesus Christ was as follows: when His mother Mary had been betrothed to Joseph, before they came together she was found to be with child by the Holy Spirit.\ 19 And Joseph her husband, being a righteous man and not wanting to disgrace her, planned to send her away secretly.\ 20 But when he had considered this, behold, an angel of the Lord appeared to him in a dream, saying, “Joseph, son of David, do not be afraid to take Mary as your wife; for the Child who has been conceived in her is of the Holy Spirit.\ 21 She will bear a Son; and you shall call His name Jesus, for He will save His people from their sins.”\ 22 Now all this took place to fulfill what was spoken by the Lord through the prophet:\ 23 “BEHOLD, THE VIRGIN SHALL BE WITH CHILD AND SHALL BEAR A SON, AND THEY SHALL CALL HIS NAME IMMANUEL,” which translated means, “GOD WITH US.”\ 24 And Joseph awoke from his sleep and did as the angel of the Lord commanded him, and took *Mary* as his wife,\ 25 but kept her a virgin until she gave birth to a Son; and he called His name Jesus. @ 0f4795bf:a8365abe
2025-01-31 14:36:07## Der neue Pareto-Client Unter der Adresse <https://pareto.space/read> lässt sich der neue Pareto-Client aufrufen.  Durch Klicken auf **Anmelden** (rechts oben) kann mit einem vorhandenen Nostr-Konto angemeldet werden oder ein neues Konto erstellt werden.  Sofern schon ein Nostr-Konto vorhanden ist, kann nach Klick auf **Log in** einfach z. B. mittels Browser Extension angemeldet werden.  Nach dem Anmelden wird das Profilbild rechts oben angezeigt und ggf. eine Kategorie mit den Artikeln der Autoren, denen man folgt.  Nach Umschalten vom Leser- in den Autoren-Modus (Schalter oben, rechts neben Logo) werden die bereits veröffentlichten Artikel angezeigt. Sollte der Schalter nicht angezeigt werden, bitte bei uns mit dem npub melden, damit wir ihn in die Liste der Pareto-Autoren aufnehmen können.  Eine zweite Kategorie zeigt die bestehenden Entwürfe.  Unter dem Punkt Bilder links lassen sich Bilder hochladen, die in Artikeln verwendet werden sollen. Sollte noch kein Medien-Server (Blossom oder NIP-96) konfiguriert sein, wird angeboten, den Standard-Server des Pareto-Projektes zu nutzen.  Nachdem der Server konfiguriert wird, werden alle hochgeladenen Bilder angezeigt. Weitere Bilder lassen sich über den Knopf **Bilder hochladen** hinzufügen.  Nach Auswahl des Punktes **Schreiben** wird der leere Pareto-Editor angezeigt.  Neben dem Titel sollte auch die Zusammenfassung aufgefüllt werden, da diese beim Teilen des Artikels (Telegram, Social Media, ...) neben dem Titel und dem Bild des Artikels angezeigt werden. Das Bild kann durch Klicken auf den grauen Rahmen rechts oben gewählt werden.  Nach Doppelklick auf das gewünschte Bild wird es rechts neben Titel und Zusammenfassung angezeigt. Neue Elemente können im Text durch Klicken auf das Plus-Symbol hinzugefügt werden.  Neben Überschriften lassen sich so auch Zitate, Aufzählungen, Programm-Code, Tabellen und Bilder einfügen.  Nachdem ein Bild-Element eingefügt wurde, kann es entweder mit einem Link auf ein Bild bestückt werden oder - durch Klicken auf "Select file" ein bereits hochgeladenes auswählen. Durch Klicken auf die kleine Sprechblase rechts oben in einem Bild lässt sich eine Bildunterschrift hinzufügen.  ### Markdown Neben dem Hinzufügen von Elementen über das Plus-Symbol kann natürlich auch direkt [Markdown-Auszeichnung](https://www.ionos.de/digitalguide/websites/web-entwicklung/markdown/) eingegeben werden. Es gibt im Netz diverse Anleitungen für Markdown. Allerdings gibt es im Kontext von Nostr die Einschränkung, dass keine HTML-Elemente in Artikeln enthalten sein dürfen. Durch Tippen eines Doppelkreuzes, gefolgt von einem Leerzeichen, lässt sich beispielsweise eine Überschrift einfügen    ### Besonderheiten Der Pareto-Client stellt Links unterschiedlich dar, je nachdem, ob sie innerhalb eines Absatzes oder allein erscheinen. *Links innerhalb eines Absatzes* werden ganz regulär dargestellt als Link, auf den der Leser klicken kann. *Alleinstehende Links* (also ohne Text davor oder dahinter) hingegen werden ggf. mit einer Vorschau versehen und nach einmaligem Klick wird der Inhalt eingebettet dargestellt. Für Links zu **YouTube**, **Odysee**, **Rumble**, **SoundCloud**, **[theplattform.net](https://tube.theplattform.net/)**, und andere können die Inhalte direkt im Artikel konsumiert werden. Auch alleinstehende Links zu Dateien mit den Endungen .mp4, .mov, .mkv, .avi, .m4v und .webm (Videos) sowie .mp3, .wav, ogg (Audio) und .pdf (PDF-Dokumente) werden eingebettet dargestellt. > **Tipp:** > > Beim Schreiben längerer Artikel empfiehlt es sich, diese zwischendurch immer wieder als Entwurf zu speichern, um Datenverlust zu vermeiden.  Oberhalb des Knopfes zum Speichern von Entwürfen wird immer der aktuelle Status des Artikels angezeigt. Schlüsselwörter werden einfach durch Komma getrennt. Es ist üblich, diese klein zu schreiben.  Nach dem Speichern wird der Knopf deaktiviert. Der Entwurf sollte anschließend unter dem Punkt **Artikel** unter **Entwürfe** eingeblendet werden.  Ein Klick auf **Bearbeiten** bringt den Entwurf wieder in den Editor. Nach Klicken von **Veröffentlichen** kann noch die Liste der Nostr-Relays ausgewählt werden, auf denen der Artikel veröffentlicht werden soll.  Nach dem Veröffentlichen sollte der Status das entspr. anzeigen.  Herzlichen Glückwunsch! Dein erster Artikel wurde über den Pareto-Client verfasst und veröffentlicht!
@ 0f4795bf:a8365abe
2025-01-31 14:36:07## Der neue Pareto-Client Unter der Adresse <https://pareto.space/read> lässt sich der neue Pareto-Client aufrufen.  Durch Klicken auf **Anmelden** (rechts oben) kann mit einem vorhandenen Nostr-Konto angemeldet werden oder ein neues Konto erstellt werden.  Sofern schon ein Nostr-Konto vorhanden ist, kann nach Klick auf **Log in** einfach z. B. mittels Browser Extension angemeldet werden.  Nach dem Anmelden wird das Profilbild rechts oben angezeigt und ggf. eine Kategorie mit den Artikeln der Autoren, denen man folgt.  Nach Umschalten vom Leser- in den Autoren-Modus (Schalter oben, rechts neben Logo) werden die bereits veröffentlichten Artikel angezeigt. Sollte der Schalter nicht angezeigt werden, bitte bei uns mit dem npub melden, damit wir ihn in die Liste der Pareto-Autoren aufnehmen können.  Eine zweite Kategorie zeigt die bestehenden Entwürfe.  Unter dem Punkt Bilder links lassen sich Bilder hochladen, die in Artikeln verwendet werden sollen. Sollte noch kein Medien-Server (Blossom oder NIP-96) konfiguriert sein, wird angeboten, den Standard-Server des Pareto-Projektes zu nutzen.  Nachdem der Server konfiguriert wird, werden alle hochgeladenen Bilder angezeigt. Weitere Bilder lassen sich über den Knopf **Bilder hochladen** hinzufügen.  Nach Auswahl des Punktes **Schreiben** wird der leere Pareto-Editor angezeigt.  Neben dem Titel sollte auch die Zusammenfassung aufgefüllt werden, da diese beim Teilen des Artikels (Telegram, Social Media, ...) neben dem Titel und dem Bild des Artikels angezeigt werden. Das Bild kann durch Klicken auf den grauen Rahmen rechts oben gewählt werden.  Nach Doppelklick auf das gewünschte Bild wird es rechts neben Titel und Zusammenfassung angezeigt. Neue Elemente können im Text durch Klicken auf das Plus-Symbol hinzugefügt werden.  Neben Überschriften lassen sich so auch Zitate, Aufzählungen, Programm-Code, Tabellen und Bilder einfügen.  Nachdem ein Bild-Element eingefügt wurde, kann es entweder mit einem Link auf ein Bild bestückt werden oder - durch Klicken auf "Select file" ein bereits hochgeladenes auswählen. Durch Klicken auf die kleine Sprechblase rechts oben in einem Bild lässt sich eine Bildunterschrift hinzufügen.  ### Markdown Neben dem Hinzufügen von Elementen über das Plus-Symbol kann natürlich auch direkt [Markdown-Auszeichnung](https://www.ionos.de/digitalguide/websites/web-entwicklung/markdown/) eingegeben werden. Es gibt im Netz diverse Anleitungen für Markdown. Allerdings gibt es im Kontext von Nostr die Einschränkung, dass keine HTML-Elemente in Artikeln enthalten sein dürfen. Durch Tippen eines Doppelkreuzes, gefolgt von einem Leerzeichen, lässt sich beispielsweise eine Überschrift einfügen    ### Besonderheiten Der Pareto-Client stellt Links unterschiedlich dar, je nachdem, ob sie innerhalb eines Absatzes oder allein erscheinen. *Links innerhalb eines Absatzes* werden ganz regulär dargestellt als Link, auf den der Leser klicken kann. *Alleinstehende Links* (also ohne Text davor oder dahinter) hingegen werden ggf. mit einer Vorschau versehen und nach einmaligem Klick wird der Inhalt eingebettet dargestellt. Für Links zu **YouTube**, **Odysee**, **Rumble**, **SoundCloud**, **[theplattform.net](https://tube.theplattform.net/)**, und andere können die Inhalte direkt im Artikel konsumiert werden. Auch alleinstehende Links zu Dateien mit den Endungen .mp4, .mov, .mkv, .avi, .m4v und .webm (Videos) sowie .mp3, .wav, ogg (Audio) und .pdf (PDF-Dokumente) werden eingebettet dargestellt. > **Tipp:** > > Beim Schreiben längerer Artikel empfiehlt es sich, diese zwischendurch immer wieder als Entwurf zu speichern, um Datenverlust zu vermeiden.  Oberhalb des Knopfes zum Speichern von Entwürfen wird immer der aktuelle Status des Artikels angezeigt. Schlüsselwörter werden einfach durch Komma getrennt. Es ist üblich, diese klein zu schreiben.  Nach dem Speichern wird der Knopf deaktiviert. Der Entwurf sollte anschließend unter dem Punkt **Artikel** unter **Entwürfe** eingeblendet werden.  Ein Klick auf **Bearbeiten** bringt den Entwurf wieder in den Editor. Nach Klicken von **Veröffentlichen** kann noch die Liste der Nostr-Relays ausgewählt werden, auf denen der Artikel veröffentlicht werden soll.  Nach dem Veröffentlichen sollte der Status das entspr. anzeigen.  Herzlichen Glückwunsch! Dein erster Artikel wurde über den Pareto-Client verfasst und veröffentlicht! @ da0b9bc3:4e30a4a9
2025-01-31 14:00:57It's Finally here Stackers! It's Friday! We're about to kick off our weekends with some feel good tracks. Let's get the party started. Bring me those Feel Good tracks. Talk Music. Share Tracks. Zap Sats. Let's go! Come up and see me, make me smile! https://youtu.be/dAoaVU3-ve0?si=JBdfGJhM05Qa_JeT originally posted at https://stacker.news/items/871055
@ da0b9bc3:4e30a4a9
2025-01-31 14:00:57It's Finally here Stackers! It's Friday! We're about to kick off our weekends with some feel good tracks. Let's get the party started. Bring me those Feel Good tracks. Talk Music. Share Tracks. Zap Sats. Let's go! Come up and see me, make me smile! https://youtu.be/dAoaVU3-ve0?si=JBdfGJhM05Qa_JeT originally posted at https://stacker.news/items/871055 @ 54286b98:3debc100
2025-01-31 11:17:42Mornings are good; they are better than evenings (except for sunset views).\ Your body is recharged.\ The mind should be more at ease.\ Worries should be fewer, and breakfast is the only meal that is "served all day." Waking up early—very early—was normal (at least for me) a lifetime ago.\ You get more things done,\ it’s quiet and free of distractions.\ So why don’t we just wake up early anymore? It would be easy to blame responsibilities and being tired for why we can't wake up earlier,\ but that’s an easy way out.\ I believe we stop trying to beat the sun when two things happen to us:\ We lose a ***big motivator*** (being competitive, learning something, getting more done, spiritual time, etc.).\ We fall for ***comfort*** and a life without the demands of growth.\ Each one follows the other, like a dog chasing its tail. Today marks almost day 30 of waking up really early again. I am happier, healthier, more connected with God, learning new things every day, playing my guitar, and writing more. Until the next one, J Get my email newsletter or read my blog at [javierfeliu.com](https://www.javierfeliu.com/) (Soon will work on setting up specific #Nostr page. > *An independent, publication about crafting beauty in life, family, > entrepreneurship, culture, woodworking, and faith, written by Javier > Feliu.*
@ 54286b98:3debc100
2025-01-31 11:17:42Mornings are good; they are better than evenings (except for sunset views).\ Your body is recharged.\ The mind should be more at ease.\ Worries should be fewer, and breakfast is the only meal that is "served all day." Waking up early—very early—was normal (at least for me) a lifetime ago.\ You get more things done,\ it’s quiet and free of distractions.\ So why don’t we just wake up early anymore? It would be easy to blame responsibilities and being tired for why we can't wake up earlier,\ but that’s an easy way out.\ I believe we stop trying to beat the sun when two things happen to us:\ We lose a ***big motivator*** (being competitive, learning something, getting more done, spiritual time, etc.).\ We fall for ***comfort*** and a life without the demands of growth.\ Each one follows the other, like a dog chasing its tail. Today marks almost day 30 of waking up really early again. I am happier, healthier, more connected with God, learning new things every day, playing my guitar, and writing more. Until the next one, J Get my email newsletter or read my blog at [javierfeliu.com](https://www.javierfeliu.com/) (Soon will work on setting up specific #Nostr page. > *An independent, publication about crafting beauty in life, family, > entrepreneurship, culture, woodworking, and faith, written by Javier > Feliu.* @ da0b9bc3:4e30a4a9
2025-01-31 10:50:35Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/870889
@ da0b9bc3:4e30a4a9
2025-01-31 10:50:35Hello Stackers! Welcome on into the ~Music Corner of the Saloon! A place where we Talk Music. Share Tracks. Zap Sats. So stay a while and listen. 🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨 🚨Subscribe to the territory to ensure you never miss a post! 🚨 originally posted at https://stacker.news/items/870889 @ a012dc82:6458a70d
2025-01-31 09:16:28Bitcoin, as the pioneering cryptocurrency, heralded a new era in digital finance. It offered an innovative payment system, free from the control of traditional financial institutions and governments. This decentralized nature was a significant draw for many early adopters. Bitcoin Cash emerged from a split in the Bitcoin blockchain, a result of deep-seated disagreements within the Bitcoin community over its scalability and transaction processing efficiency. This split was not just technical but also ideological, marking a significant moment in the history of cryptocurrencies. **Table Of Content** - The Genesis of Bitcoin Cash - Technological Divergence: Block Size and Scalability - Segregated Witness (SegWit) and Bitcoin - Market Impact and Adoption - Transaction Processing: Speed and Fees - The Forks and Future Directions - Usability and Real-World Applications - Supply Dynamics - Bitcoin Cash as a Medium of Exchange - Conclusion - FAQs **The Genesis of Bitcoin Cash** The creation of Bitcoin Cash in 2017 was a pivotal event in the cryptocurrency world. It was a direct response to the growing concerns over Bitcoin's ability to handle an increasing volume of transactions. The proponents of Bitcoin Cash argued that changes were necessary to fulfill the original vision of a fast, scalable, and low-cost digital payment system. This led to the hard fork, a move that created a new blockchain with different rules, fundamentally diverging from the original Bitcoin protocol. **Technological Divergence: Block Size and Scalability** The debate over block size is central to the divergence between Bitcoin and Bitcoin Cash. Bitcoin's original 1 MB block size was seen as a significant bottleneck, leading to slower transaction times and higher fees during peak usage. In contrast, Bitcoin Cash's decision to increase the block size to 8 MB and later to 32 MB was a bold move aimed at addressing these issues. This increase was a fundamental shift, intended to allow more transactions per block and, consequently, faster processing and lower fees. **Segregated Witness (SegWit) and Bitcoin** The implementation of Segregated Witness (SegWit) in Bitcoin was a landmark technological upgrade. SegWit aimed to optimize the space within each block by segregating the digital signature information, which accounts for a significant portion of the data in a transaction. This was a sophisticated solution to the scalability issue, differing fundamentally from Bitcoin Cash's approach of simply increasing the block size. SegWit represented a philosophical as well as a technical divergence in the approach to scaling Bitcoin. **Market Impact and Adoption** The market dynamics of Bitcoin and Bitcoin Cash tell a story of divergent paths. Bitcoin, with its higher market capitalization, remains the more dominant and widely recognized cryptocurrency. Its position as the first and most established cryptocurrency has given it a significant advantage in terms of adoption and market presence. Bitcoin Cash, while substantial in its market cap, has not reached the same level of market penetration. This difference in market impact reflects the varying degrees of acceptance and trust among investors and users in the cryptocurrency community. **Transaction Processing: Speed and Fees** The practical implications of the differences between Bitcoin and Bitcoin Cash are most evident in transaction processing. Bitcoin Cash, with its larger block size, theoretically offers faster transaction times and lower fees, making it more suitable for frequent, small transactions. However, the actual efficiency gains of Bitcoin Cash are subject to debate, as the network has not been tested under the same transaction volume as Bitcoin. This difference in transaction processing capabilities is a critical factor in the user's choice between the two cryptocurrencies. **The Forks and Future Directions** The evolution of Bitcoin and Bitcoin Cash is marked by continuous development and occasional forks. The creation of Bitcoin SV from Bitcoin Cash is an example of ongoing disagreements within the community about the best path forward. These forks are not just technical events but also represent differing visions and philosophies within the cryptocurrency community. They reflect the dynamic and often contentious nature of the development of blockchain technology and its applications. **Usability and Real-World Applications** In terms of real-world usability, Bitcoin and Bitcoin Cash cater to slightly different needs. Bitcoin's widespread recognition and higher value make it more popular as a digital asset for investment. In contrast, Bitcoin Cash, with its focus on transaction efficiency, aims to be more practical for everyday transactions. However, the actual adoption of Bitcoin Cash for daily transactions has been slower than anticipated, partly due to the entrenched position of Bitcoin and the rapidly evolving landscape of digital payments. **Supply Dynamics** The supply mechanics of both Bitcoin and Bitcoin Cash mirror the principles of scarcity and controlled supply inflation. This approach is akin to precious metals, where the limited supply is a key factor in value preservation. The halving events, where the reward for mining new blocks is halved approximately every four years, are critical moments in the life cycle of both cryptocurrencies. These events are closely watched by investors and users alike, as they have implications for the supply and, potentially, the value of these digital currencies. **Bitcoin Cash as a Medium of Exchange** Bitcoin Cash's design as a medium of exchange is one of its defining features. It aims to provide a digital equivalent of cash, facilitating quick and low-cost transactions. This focus on usability for everyday transactions is a key differentiator from Bitcoin, which has become more of a store of value or "digital gold." The success of Bitcoin Cash in this regard depends on broader adoption and recognition, which is an ongoing challenge in the competitive landscape of digital currencies. **Conclusion** The story of Bitcoin and Bitcoin Cash is a fascinating chapter in the evolution of digital currencies. Both emerged from the same origin but have since traveled distinct paths, shaped by differing philosophies, technological choices, and community dynamics. As the cryptocurrency landscape continues to evolve, the trajectories of Bitcoin and Bitcoin Cash will offer valuable insights into the challenges and opportunities of blockchain technology and digital finance. **FAQs** **What is the main difference between Bitcoin and Bitcoin Cash?** The primary difference lies in their block size. Bitcoin has a block size of 1 MB, while Bitcoin Cash increased its block size initially to 8 MB and later to 32 MB, aiming for faster transaction processing and scalability. **Why was Bitcoin Cash created?** Bitcoin Cash was created in 2017 due to a split in the Bitcoin community. The split occurred over disagreements on how to scale the network, with Bitcoin Cash proponents advocating for larger block sizes to improve transaction speed and reduce fees. **Can Bitcoin and Bitcoin Cash be used interchangeably?** No, they are separate cryptocurrencies with different blockchains. They cannot be used interchangeably. **Is Bitcoin Cash faster than Bitcoin?** Theoretically, yes. Due to its larger block size, Bitcoin Cash can process transactions faster than Bitcoin. However, the actual speed can vary based on network congestion and usage. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: @croxroadnews.co** **Instagram: @croxroadnews.co** **Youtube: @croxroadnews** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** ***DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.***
@ a012dc82:6458a70d
2025-01-31 09:16:28Bitcoin, as the pioneering cryptocurrency, heralded a new era in digital finance. It offered an innovative payment system, free from the control of traditional financial institutions and governments. This decentralized nature was a significant draw for many early adopters. Bitcoin Cash emerged from a split in the Bitcoin blockchain, a result of deep-seated disagreements within the Bitcoin community over its scalability and transaction processing efficiency. This split was not just technical but also ideological, marking a significant moment in the history of cryptocurrencies. **Table Of Content** - The Genesis of Bitcoin Cash - Technological Divergence: Block Size and Scalability - Segregated Witness (SegWit) and Bitcoin - Market Impact and Adoption - Transaction Processing: Speed and Fees - The Forks and Future Directions - Usability and Real-World Applications - Supply Dynamics - Bitcoin Cash as a Medium of Exchange - Conclusion - FAQs **The Genesis of Bitcoin Cash** The creation of Bitcoin Cash in 2017 was a pivotal event in the cryptocurrency world. It was a direct response to the growing concerns over Bitcoin's ability to handle an increasing volume of transactions. The proponents of Bitcoin Cash argued that changes were necessary to fulfill the original vision of a fast, scalable, and low-cost digital payment system. This led to the hard fork, a move that created a new blockchain with different rules, fundamentally diverging from the original Bitcoin protocol. **Technological Divergence: Block Size and Scalability** The debate over block size is central to the divergence between Bitcoin and Bitcoin Cash. Bitcoin's original 1 MB block size was seen as a significant bottleneck, leading to slower transaction times and higher fees during peak usage. In contrast, Bitcoin Cash's decision to increase the block size to 8 MB and later to 32 MB was a bold move aimed at addressing these issues. This increase was a fundamental shift, intended to allow more transactions per block and, consequently, faster processing and lower fees. **Segregated Witness (SegWit) and Bitcoin** The implementation of Segregated Witness (SegWit) in Bitcoin was a landmark technological upgrade. SegWit aimed to optimize the space within each block by segregating the digital signature information, which accounts for a significant portion of the data in a transaction. This was a sophisticated solution to the scalability issue, differing fundamentally from Bitcoin Cash's approach of simply increasing the block size. SegWit represented a philosophical as well as a technical divergence in the approach to scaling Bitcoin. **Market Impact and Adoption** The market dynamics of Bitcoin and Bitcoin Cash tell a story of divergent paths. Bitcoin, with its higher market capitalization, remains the more dominant and widely recognized cryptocurrency. Its position as the first and most established cryptocurrency has given it a significant advantage in terms of adoption and market presence. Bitcoin Cash, while substantial in its market cap, has not reached the same level of market penetration. This difference in market impact reflects the varying degrees of acceptance and trust among investors and users in the cryptocurrency community. **Transaction Processing: Speed and Fees** The practical implications of the differences between Bitcoin and Bitcoin Cash are most evident in transaction processing. Bitcoin Cash, with its larger block size, theoretically offers faster transaction times and lower fees, making it more suitable for frequent, small transactions. However, the actual efficiency gains of Bitcoin Cash are subject to debate, as the network has not been tested under the same transaction volume as Bitcoin. This difference in transaction processing capabilities is a critical factor in the user's choice between the two cryptocurrencies. **The Forks and Future Directions** The evolution of Bitcoin and Bitcoin Cash is marked by continuous development and occasional forks. The creation of Bitcoin SV from Bitcoin Cash is an example of ongoing disagreements within the community about the best path forward. These forks are not just technical events but also represent differing visions and philosophies within the cryptocurrency community. They reflect the dynamic and often contentious nature of the development of blockchain technology and its applications. **Usability and Real-World Applications** In terms of real-world usability, Bitcoin and Bitcoin Cash cater to slightly different needs. Bitcoin's widespread recognition and higher value make it more popular as a digital asset for investment. In contrast, Bitcoin Cash, with its focus on transaction efficiency, aims to be more practical for everyday transactions. However, the actual adoption of Bitcoin Cash for daily transactions has been slower than anticipated, partly due to the entrenched position of Bitcoin and the rapidly evolving landscape of digital payments. **Supply Dynamics** The supply mechanics of both Bitcoin and Bitcoin Cash mirror the principles of scarcity and controlled supply inflation. This approach is akin to precious metals, where the limited supply is a key factor in value preservation. The halving events, where the reward for mining new blocks is halved approximately every four years, are critical moments in the life cycle of both cryptocurrencies. These events are closely watched by investors and users alike, as they have implications for the supply and, potentially, the value of these digital currencies. **Bitcoin Cash as a Medium of Exchange** Bitcoin Cash's design as a medium of exchange is one of its defining features. It aims to provide a digital equivalent of cash, facilitating quick and low-cost transactions. This focus on usability for everyday transactions is a key differentiator from Bitcoin, which has become more of a store of value or "digital gold." The success of Bitcoin Cash in this regard depends on broader adoption and recognition, which is an ongoing challenge in the competitive landscape of digital currencies. **Conclusion** The story of Bitcoin and Bitcoin Cash is a fascinating chapter in the evolution of digital currencies. Both emerged from the same origin but have since traveled distinct paths, shaped by differing philosophies, technological choices, and community dynamics. As the cryptocurrency landscape continues to evolve, the trajectories of Bitcoin and Bitcoin Cash will offer valuable insights into the challenges and opportunities of blockchain technology and digital finance. **FAQs** **What is the main difference between Bitcoin and Bitcoin Cash?** The primary difference lies in their block size. Bitcoin has a block size of 1 MB, while Bitcoin Cash increased its block size initially to 8 MB and later to 32 MB, aiming for faster transaction processing and scalability. **Why was Bitcoin Cash created?** Bitcoin Cash was created in 2017 due to a split in the Bitcoin community. The split occurred over disagreements on how to scale the network, with Bitcoin Cash proponents advocating for larger block sizes to improve transaction speed and reduce fees. **Can Bitcoin and Bitcoin Cash be used interchangeably?** No, they are separate cryptocurrencies with different blockchains. They cannot be used interchangeably. **Is Bitcoin Cash faster than Bitcoin?** Theoretically, yes. Due to its larger block size, Bitcoin Cash can process transactions faster than Bitcoin. However, the actual speed can vary based on network congestion and usage. **That's all for today** **If you want more, be sure to follow us on:** **NOSTR: croxroad@getalby.com** **X: @croxroadnews.co** **Instagram: @croxroadnews.co** **Youtube: @croxroadnews** **Store: https://croxroad.store** **Subscribe to CROX ROAD Bitcoin Only Daily Newsletter** **https://www.croxroad.co/subscribe** ***DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.*** @ 5188521b:008eb518
2025-01-31 08:38:47*Photo by [Pavel Danilyuk](https://www.pexels.com/photo/a-woman-holding-a-placard-8553778/)* In the last four years, I’ve ridden the wave of social media. I’ve amassed thousands of followers, and my posts were read by millions. It’s empowering… until it isn’t. This year, I chose to stop publishing on LinkedIn, Medium, Facebook, Instagram, and Threads. My reach on each of these platforms dropped from 100% of my follower base to around 10%. My voice was being suppressed. I wasn’t writing anything particularly controversial. This is all just part of the social media life cycle. Platforms offer attractive terms to lock in users. They distribute our articles, posts, and thoughts widely to attract eyeballs for advertisers. Writers learn to play the algorithm to maximise reach and engagement. Maybe they even manage to monetize their writing. But when the platforms reach what they deem to be maximum usage and membership, they begin to reduce the benefits on offer. They ask writers to focus on specific topics, suppress non-mainstream opinion, or punish or ban any writers who don’t follow new rules. Big tech companies always eventually turn on the money tap by forcing users to suffer endless adverts and even make writers pay to reach the audience they have built. Newsflash: there is no company too big to fail. Digg, Google+, Myspace, Vine and many more socials have died. Self-reported active user numbers cannot be trusted. Meta recently trialed AI profiles to prop up falling usage projections on Instagram and Facebook. X is now a dumpster fire of bots, scammers, and rage bait. It has been co-opted by a megalomaniacal oligarch to spread his own worldview. And LinkedIn feeds are drowning in unsolicited AI-generated business twaddle. The social giants are entering the death spiral. # What happens in a social-media death spiral? Users don’t see the value in posting, so they move elsewhere. I wasn’t feeling rewarded for the thousands of hours I spent on LinkedIn, so I quit. I went from earning $20+ an article on Medium to pennies. Literal pennies. Bye bye, Tony Stubblebine. I learned that if you don’t own the distribution mechanic, you get left writing into the wind. Ultimately, writers will dedicate their energy to where they see a benefit. They should spend time and create value in the place most similar to their ideal world. For writers in 2025, that place seems to be Substack. Open rates are high and the platform is adding social features to generate more engagement in app. Substack is [experiencing massive growth](https://backlinko.com/substack-users) in active (and paid) subscriptions. Yet, it is following the same pattern as Medium in and LinkedIn in become self-cannibalising. Many of the most popular accounts write about ‘how to grow’ or ‘how to make money’ on Substack. Queue the eye rolls. For me, it’s not the promised land where writers can earn a living. Of course, it’s no walk in the park to earn paid subscribers. Further, Substack users can only receive payment via Stripe. This excludes writers from 149 of the World’s countries. Does that seem open and fair to you? Even with all this going on, there is a much bigger factor that should influence your choice of platform — ownership. # Do writers really own their words? Who reads the terms and conditions? Nobody. That’s who.Writers (including me) rush to all platforms which promise to give us benefits such as pay, distribution, and audience growth. In exchange, companies request access to and shared ownership of our content. They can use our words to train LLMs, analyse trends, repurpose, and to spy on us. Governments can and will request access to social media profiles. They seek to control the use of those platforms. Founders and CEOs who refuse to comply may be held personally accountable and put on trial, just as [Telegram founder, Pavel Durov, was](https://www.bbc.com/news/articles/c78lgzl919go) in France. Big tech owns our content, and governments threaten platforms into obedience. As much as it benefits society to suppress harmful or dangerous content, companies simply can’t be censors 24/7. Growing platforms like [Bluesky are already struggling to moderate content effectively](https://www.theregister.com/2024/12/02/bluesky_growing_problems/). Without a strong economic incentive to moderate, companies will simply refuse to do it (as long as the threat of criminal charges does not prevail). To sum up: No privately owned social media network offers writers the opportunity to own and distribute their work in order to receive a fair and equitable benefit. Enter NOSTR… # Decentralizing Social Media **Notes and Other Stuff Transmitted by Relays** (NOSTR) is not a platform; it’s an open protocol. By signing messages with their private keys (a long string of characters), users generate “events”. These events (messages/updates/media/transactions) are then broadcast through a series of “relays.” Developers can use the protocol to build various applications that retrieve and distribute these events to other users. These ‘clients’ can range from microblogging sites like X and long-form distributors like Substack to visual media platforms like Instagram. Plus, NOSTR is also a whole lot more than that (but this is a topic for another day). Decentralized tools offer the only hope against the dominance of AI and big tech in a top-down autocratic system designed to control us more than the thought police ever could. <img src="https://blossom.primal.net/93a44d9bfe3c768e41d8bfef52415131af3ca21814a23870a029f1a947288cc8.webp"> *Diagram courtesy of River.* So why should writers opt out of their big audience pool to write on some ‘protocol’? **Ownership, fair rules, and fair value.** - **Ownership**: While privately run corporations can suppress the ideas they want, NOSTR provides a censorship-resistant alternative. No individual actors can restrict content or accounts. Your private keys provide **permanent access** to the messages you have signed. No one else has access to them. And while some clients provide a delete function, there is no way to force all relays to respect a delete request. Not only do writers own what they publish, but it’s a permanent record. - **Rules:** Traditional social media platforms use proprietary algorithms to curate and order our feeds. **NOSTR has no algorithm**. NOSTR clients display messages chronologically or based on user-defined criteria, removing the influence of opaque algorithms that could manipulate user engagement and visibility of posts. Put simply, distribution and consumption is down to the user, not to the creator or the platform. And everyone works to the same rules. - **Value:** Harmful content and spam affect all of us. There is no way to stop malicious content from being published on NOSTR, but two factors control its consumption. 1. Clients are experimenting with strategies such as requiring proof-of-work with each note or requiring verification badges. 2. Quality control is enforced by the value transferred by the protocol. Bitcoin micropayments have become the monetary lifeblood flowing in the decentralized world. The ability to ‘zap’ users actual monetary value (e.g. a few cents) provides a clear display of which messages are valuable and which are unwanted. In time, as more users adopt the mechanic of value transfer, spammers will see their approach is not bearing fruit. The beauty of using bitcoin in this way is twofold. Firstly, it is truly equitable — anyone in the world can receive it instantly and it cannot be stopped. And the system of frictionless micropayments offers content creators (artists, podcasters, musicians, writers) a way to earn money for the value they produce. Put simply, this could save creativity from doom. Think people still want all content for free? Think again. Try zapping a writer from the Philippines, an artist from Peru, a Congolese musician, or a poet from Poland to show them you enjoyed what they produced. THAT is truly empowering. Not convinced? The best thing about NOSTR for writers is that **you are early**. By being an early adopter with a low time preference, you can build a sizeable audience as new users discover the protocol. Of course, topics like bitcoin, freedom tech, and privacy are well covered, but if you write in another niche, you could be ‘quids in’. # Conclusion: By adopting a long-term strategy and sticking to their principles, readers, writers and all other creatives can build a better world on social media. It doesn’t matter that it is imperfect. There will always be flaws in any society. But decentralized protocols like NOSTR can offer writers what they truly want — ownership, fair rules, and fair value. --- Philip Charter is a totally human writer who helps bitcoin-native companies and clients stack major gains through laser-focused content. Find out more at [totallyhumanwriter.com](https://totallyhumanwriter.com) He is also the editor of the cypherpunk and freedom fiction project, [21 Futures](https://21futures.com).
@ 5188521b:008eb518
2025-01-31 08:38:47*Photo by [Pavel Danilyuk](https://www.pexels.com/photo/a-woman-holding-a-placard-8553778/)* In the last four years, I’ve ridden the wave of social media. I’ve amassed thousands of followers, and my posts were read by millions. It’s empowering… until it isn’t. This year, I chose to stop publishing on LinkedIn, Medium, Facebook, Instagram, and Threads. My reach on each of these platforms dropped from 100% of my follower base to around 10%. My voice was being suppressed. I wasn’t writing anything particularly controversial. This is all just part of the social media life cycle. Platforms offer attractive terms to lock in users. They distribute our articles, posts, and thoughts widely to attract eyeballs for advertisers. Writers learn to play the algorithm to maximise reach and engagement. Maybe they even manage to monetize their writing. But when the platforms reach what they deem to be maximum usage and membership, they begin to reduce the benefits on offer. They ask writers to focus on specific topics, suppress non-mainstream opinion, or punish or ban any writers who don’t follow new rules. Big tech companies always eventually turn on the money tap by forcing users to suffer endless adverts and even make writers pay to reach the audience they have built. Newsflash: there is no company too big to fail. Digg, Google+, Myspace, Vine and many more socials have died. Self-reported active user numbers cannot be trusted. Meta recently trialed AI profiles to prop up falling usage projections on Instagram and Facebook. X is now a dumpster fire of bots, scammers, and rage bait. It has been co-opted by a megalomaniacal oligarch to spread his own worldview. And LinkedIn feeds are drowning in unsolicited AI-generated business twaddle. The social giants are entering the death spiral. # What happens in a social-media death spiral? Users don’t see the value in posting, so they move elsewhere. I wasn’t feeling rewarded for the thousands of hours I spent on LinkedIn, so I quit. I went from earning $20+ an article on Medium to pennies. Literal pennies. Bye bye, Tony Stubblebine. I learned that if you don’t own the distribution mechanic, you get left writing into the wind. Ultimately, writers will dedicate their energy to where they see a benefit. They should spend time and create value in the place most similar to their ideal world. For writers in 2025, that place seems to be Substack. Open rates are high and the platform is adding social features to generate more engagement in app. Substack is [experiencing massive growth](https://backlinko.com/substack-users) in active (and paid) subscriptions. Yet, it is following the same pattern as Medium in and LinkedIn in become self-cannibalising. Many of the most popular accounts write about ‘how to grow’ or ‘how to make money’ on Substack. Queue the eye rolls. For me, it’s not the promised land where writers can earn a living. Of course, it’s no walk in the park to earn paid subscribers. Further, Substack users can only receive payment via Stripe. This excludes writers from 149 of the World’s countries. Does that seem open and fair to you? Even with all this going on, there is a much bigger factor that should influence your choice of platform — ownership. # Do writers really own their words? Who reads the terms and conditions? Nobody. That’s who.Writers (including me) rush to all platforms which promise to give us benefits such as pay, distribution, and audience growth. In exchange, companies request access to and shared ownership of our content. They can use our words to train LLMs, analyse trends, repurpose, and to spy on us. Governments can and will request access to social media profiles. They seek to control the use of those platforms. Founders and CEOs who refuse to comply may be held personally accountable and put on trial, just as [Telegram founder, Pavel Durov, was](https://www.bbc.com/news/articles/c78lgzl919go) in France. Big tech owns our content, and governments threaten platforms into obedience. As much as it benefits society to suppress harmful or dangerous content, companies simply can’t be censors 24/7. Growing platforms like [Bluesky are already struggling to moderate content effectively](https://www.theregister.com/2024/12/02/bluesky_growing_problems/). Without a strong economic incentive to moderate, companies will simply refuse to do it (as long as the threat of criminal charges does not prevail). To sum up: No privately owned social media network offers writers the opportunity to own and distribute their work in order to receive a fair and equitable benefit. Enter NOSTR… # Decentralizing Social Media **Notes and Other Stuff Transmitted by Relays** (NOSTR) is not a platform; it’s an open protocol. By signing messages with their private keys (a long string of characters), users generate “events”. These events (messages/updates/media/transactions) are then broadcast through a series of “relays.” Developers can use the protocol to build various applications that retrieve and distribute these events to other users. These ‘clients’ can range from microblogging sites like X and long-form distributors like Substack to visual media platforms like Instagram. Plus, NOSTR is also a whole lot more than that (but this is a topic for another day). Decentralized tools offer the only hope against the dominance of AI and big tech in a top-down autocratic system designed to control us more than the thought police ever could. <img src="https://blossom.primal.net/93a44d9bfe3c768e41d8bfef52415131af3ca21814a23870a029f1a947288cc8.webp"> *Diagram courtesy of River.* So why should writers opt out of their big audience pool to write on some ‘protocol’? **Ownership, fair rules, and fair value.** - **Ownership**: While privately run corporations can suppress the ideas they want, NOSTR provides a censorship-resistant alternative. No individual actors can restrict content or accounts. Your private keys provide **permanent access** to the messages you have signed. No one else has access to them. And while some clients provide a delete function, there is no way to force all relays to respect a delete request. Not only do writers own what they publish, but it’s a permanent record. - **Rules:** Traditional social media platforms use proprietary algorithms to curate and order our feeds. **NOSTR has no algorithm**. NOSTR clients display messages chronologically or based on user-defined criteria, removing the influence of opaque algorithms that could manipulate user engagement and visibility of posts. Put simply, distribution and consumption is down to the user, not to the creator or the platform. And everyone works to the same rules. - **Value:** Harmful content and spam affect all of us. There is no way to stop malicious content from being published on NOSTR, but two factors control its consumption. 1. Clients are experimenting with strategies such as requiring proof-of-work with each note or requiring verification badges. 2. Quality control is enforced by the value transferred by the protocol. Bitcoin micropayments have become the monetary lifeblood flowing in the decentralized world. The ability to ‘zap’ users actual monetary value (e.g. a few cents) provides a clear display of which messages are valuable and which are unwanted. In time, as more users adopt the mechanic of value transfer, spammers will see their approach is not bearing fruit. The beauty of using bitcoin in this way is twofold. Firstly, it is truly equitable — anyone in the world can receive it instantly and it cannot be stopped. And the system of frictionless micropayments offers content creators (artists, podcasters, musicians, writers) a way to earn money for the value they produce. Put simply, this could save creativity from doom. Think people still want all content for free? Think again. Try zapping a writer from the Philippines, an artist from Peru, a Congolese musician, or a poet from Poland to show them you enjoyed what they produced. THAT is truly empowering. Not convinced? The best thing about NOSTR for writers is that **you are early**. By being an early adopter with a low time preference, you can build a sizeable audience as new users discover the protocol. Of course, topics like bitcoin, freedom tech, and privacy are well covered, but if you write in another niche, you could be ‘quids in’. # Conclusion: By adopting a long-term strategy and sticking to their principles, readers, writers and all other creatives can build a better world on social media. It doesn’t matter that it is imperfect. There will always be flaws in any society. But decentralized protocols like NOSTR can offer writers what they truly want — ownership, fair rules, and fair value. --- Philip Charter is a totally human writer who helps bitcoin-native companies and clients stack major gains through laser-focused content. Find out more at [totallyhumanwriter.com](https://totallyhumanwriter.com) He is also the editor of the cypherpunk and freedom fiction project, [21 Futures](https://21futures.com).